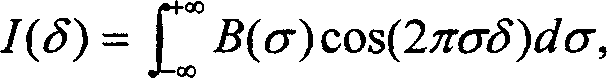Patents
Literature
55results about How to "Facilitate identification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
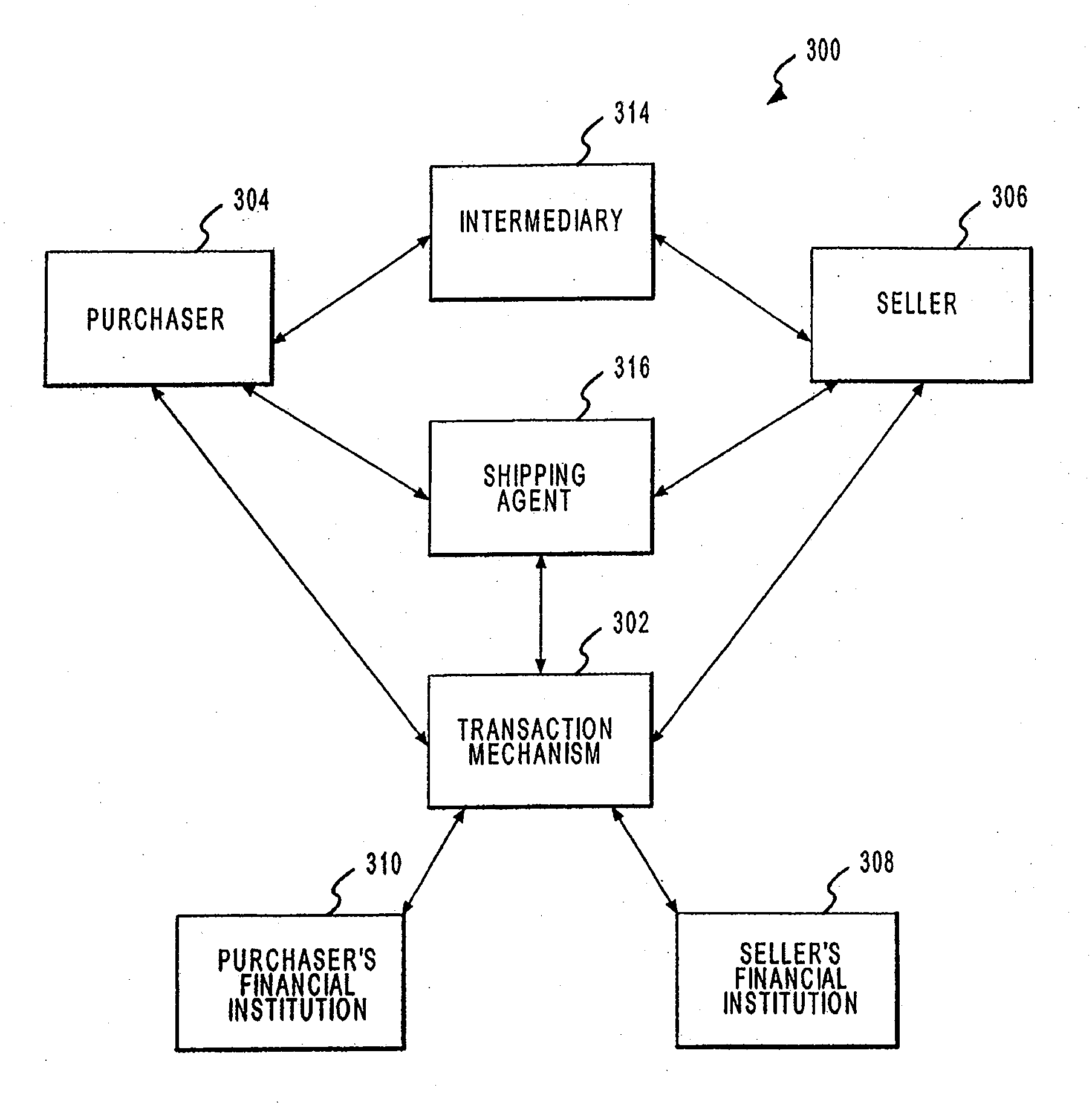
Systems for Locating a Payment System Utilizing a Point of Sale Device
InactiveUS20090164331A1Facilitates calculationFacilitate identificationHand manipulated computer devicesFinanceThird partyAuthorization
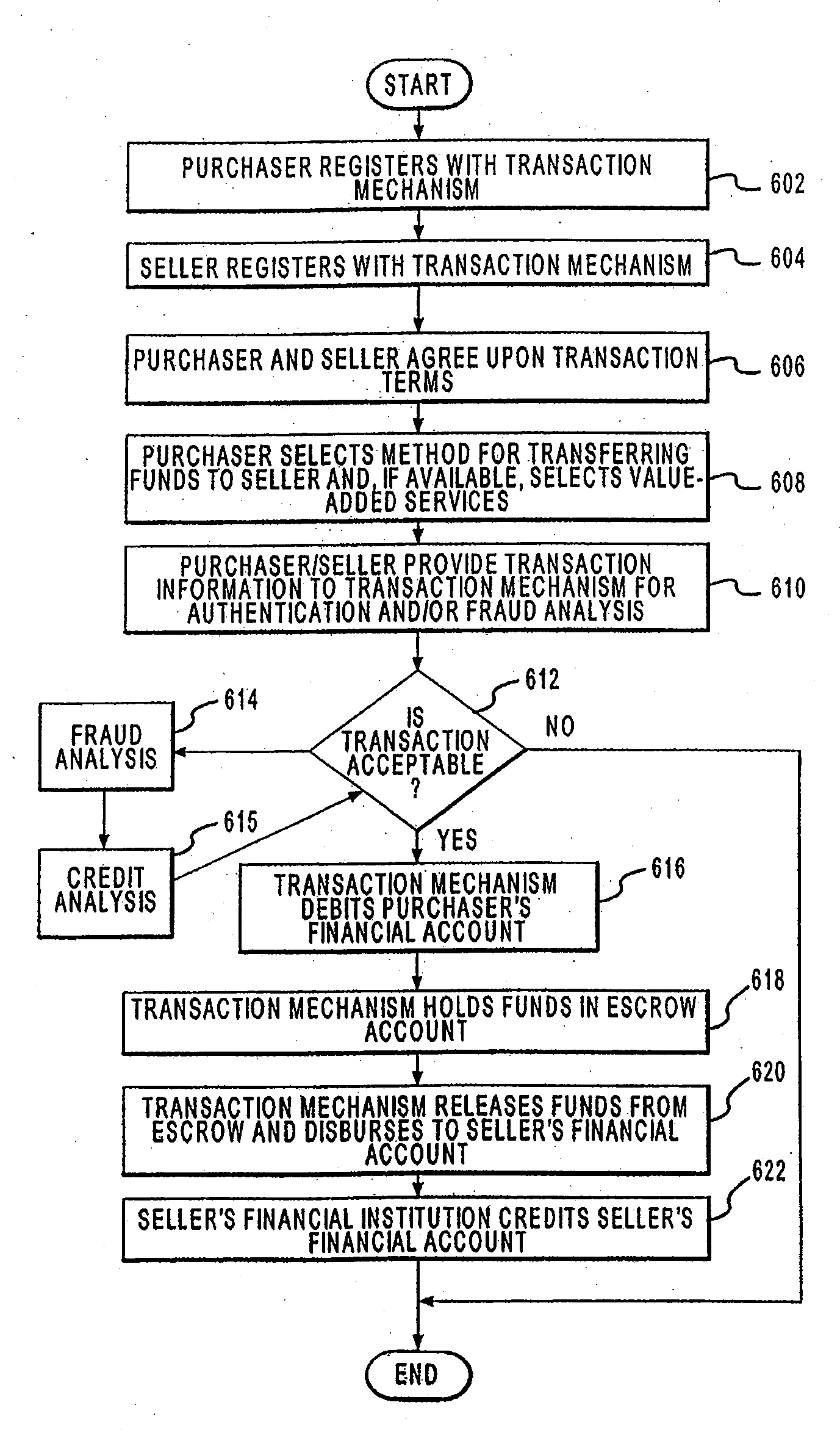
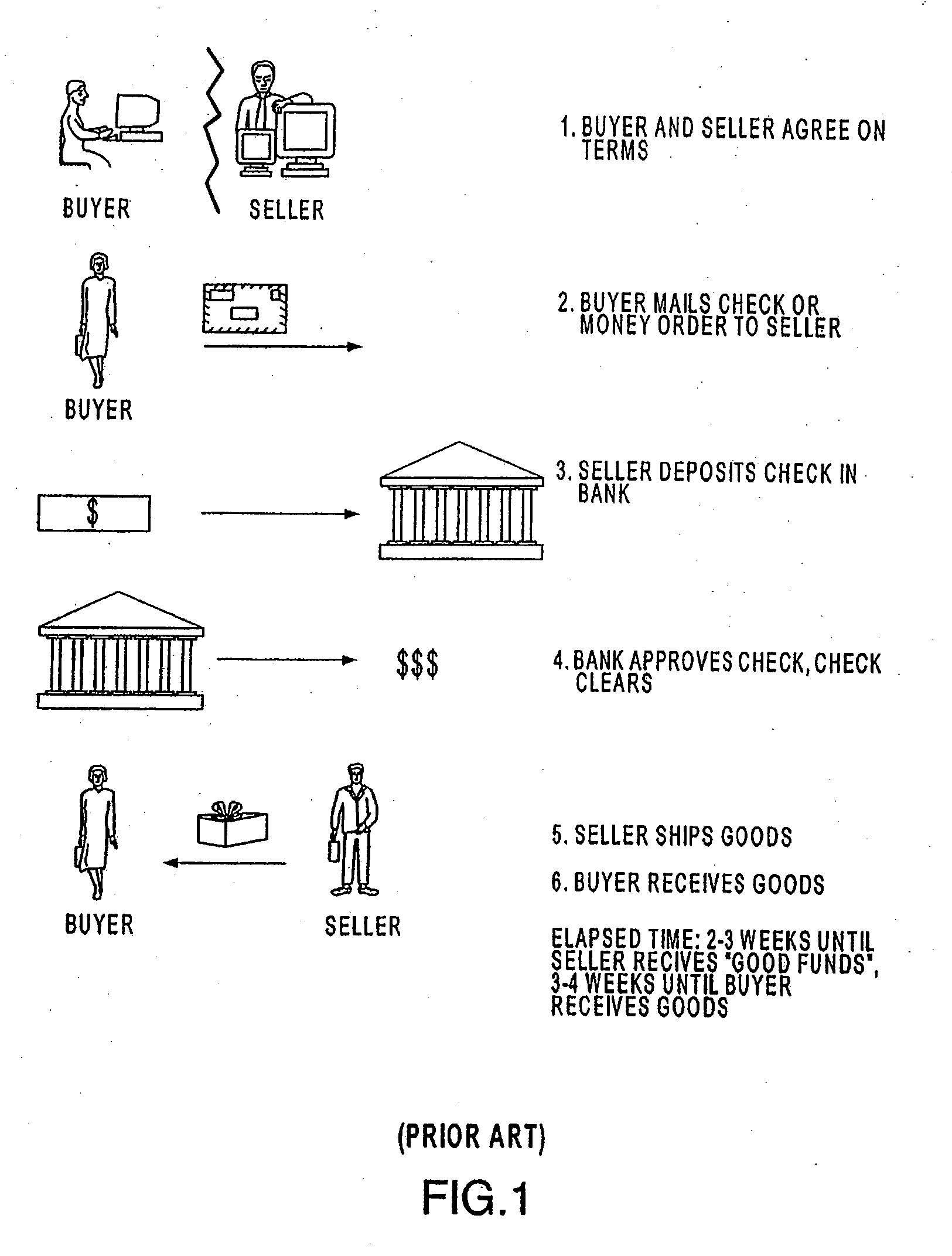
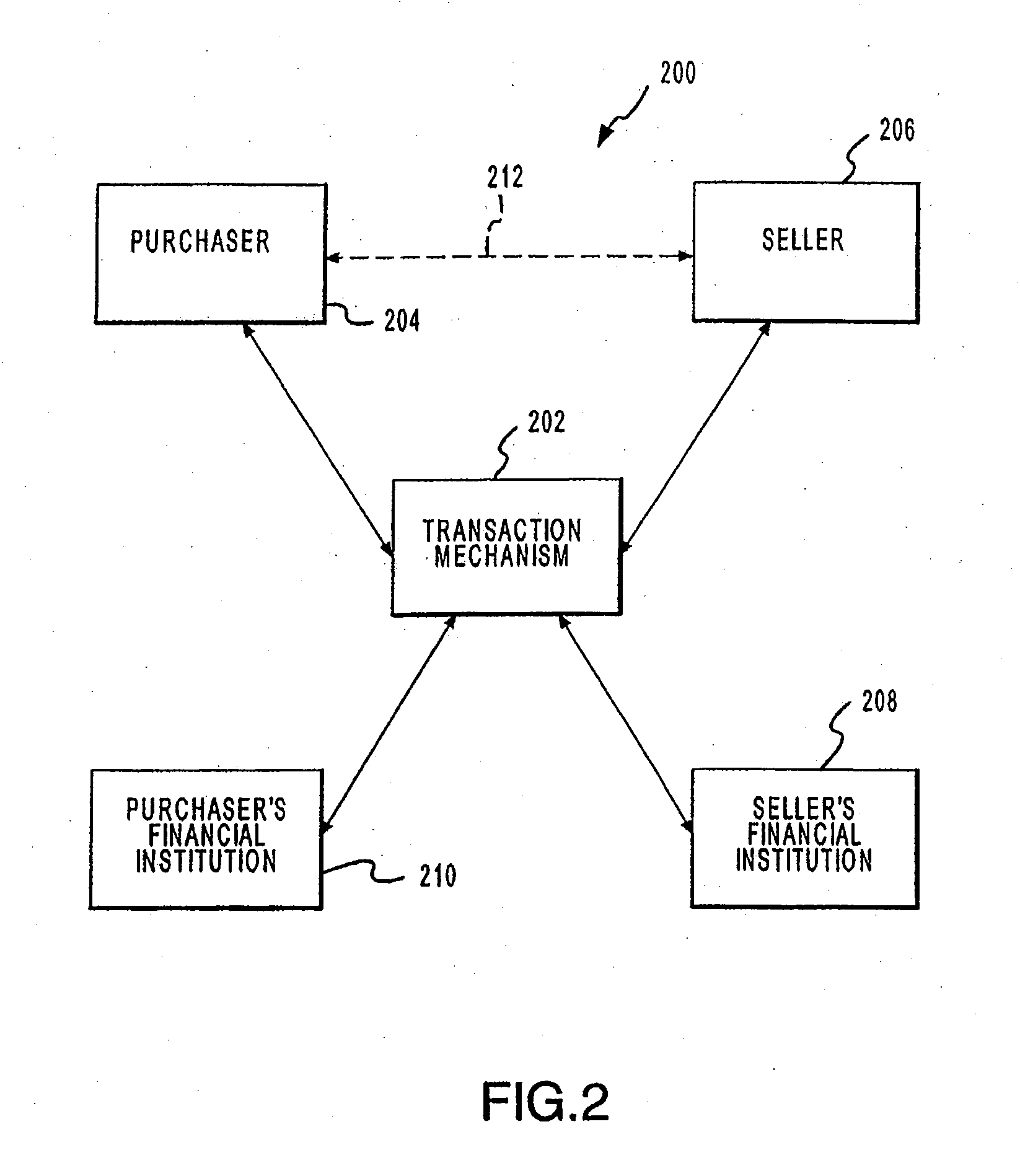
A point of sale (POS) device may be configured to locate a payment system and transmit a payment authorization request from a remote location to a payment system, either directly, or via a payment system directory and / or a SSL Gateway. The invention also includes inserting third party account information into an encrypted portion of the payment request, so the payment request appears as a normal request to the issuing bank, but the third party account information may be used by the third party to bill the customer. The payment system directory is further configured to determine one or more payment processors to direct a payment authorization request, such that a single transaction may me allocated among multiple payment processors for authorization. Moreover, the payment system directory is able to format alternative payment methods into a format that is able to be processed over existing payment networks.
Owner:LIBERTY PEAK VENTURES LLC +1
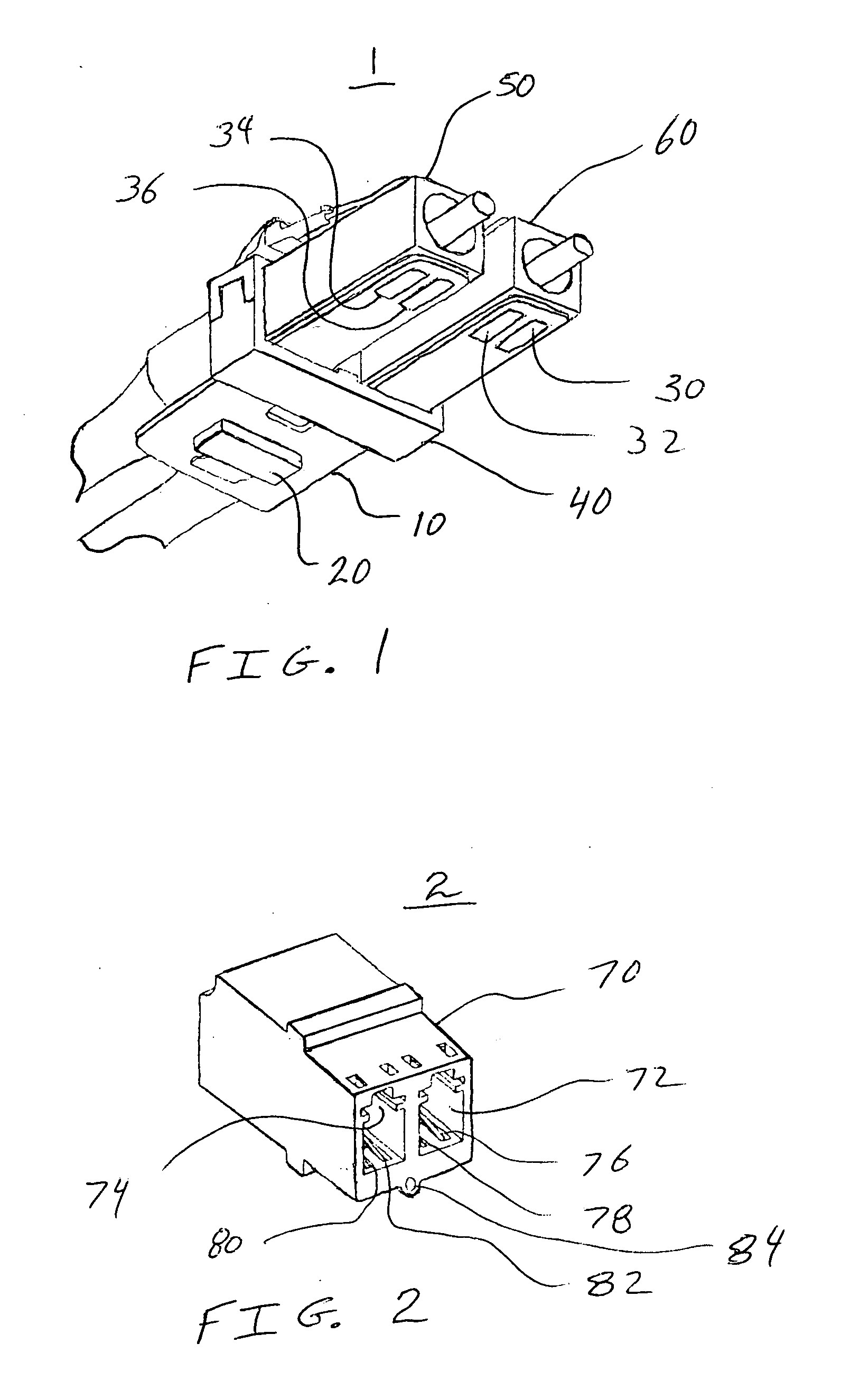
Transceiver/fiber optic connector adaptor with patch cord id reading capability
InactiveUS20070116411A1Facilitate identificationRetrieve informationCoupling light guidesOptical fiber connectorTransceiver
The device includes a first optical connector, a second optical connector, a flexible substrate, a first electrical connector, a second electrical connector, a memory chip, and a clip. The first electrical connector is attached to the flexible substrate. The second electrical connector is attached to the flexible substrate. The memory chip is attached to the flexible substrate. A clip retains the first optical connector and the second optical connector adjacent to the flexible substrate.
Owner:STRATOS INT
VEGF-C or VEGF-D materials and methods for treatment of neuropathologies
InactiveUS20070082848A1Facilitate identificationSuperior therapyOrganic active ingredientsAnimal cellsNeural stem cellCell biology
The present invention relates to VEGF-C or VEGF-D materials and methods for promoting growth and differentiation of neural stem cells and materials and methods for administering said cells to inhibit neuropathology.
Owner:VEGENICS PTY LTD
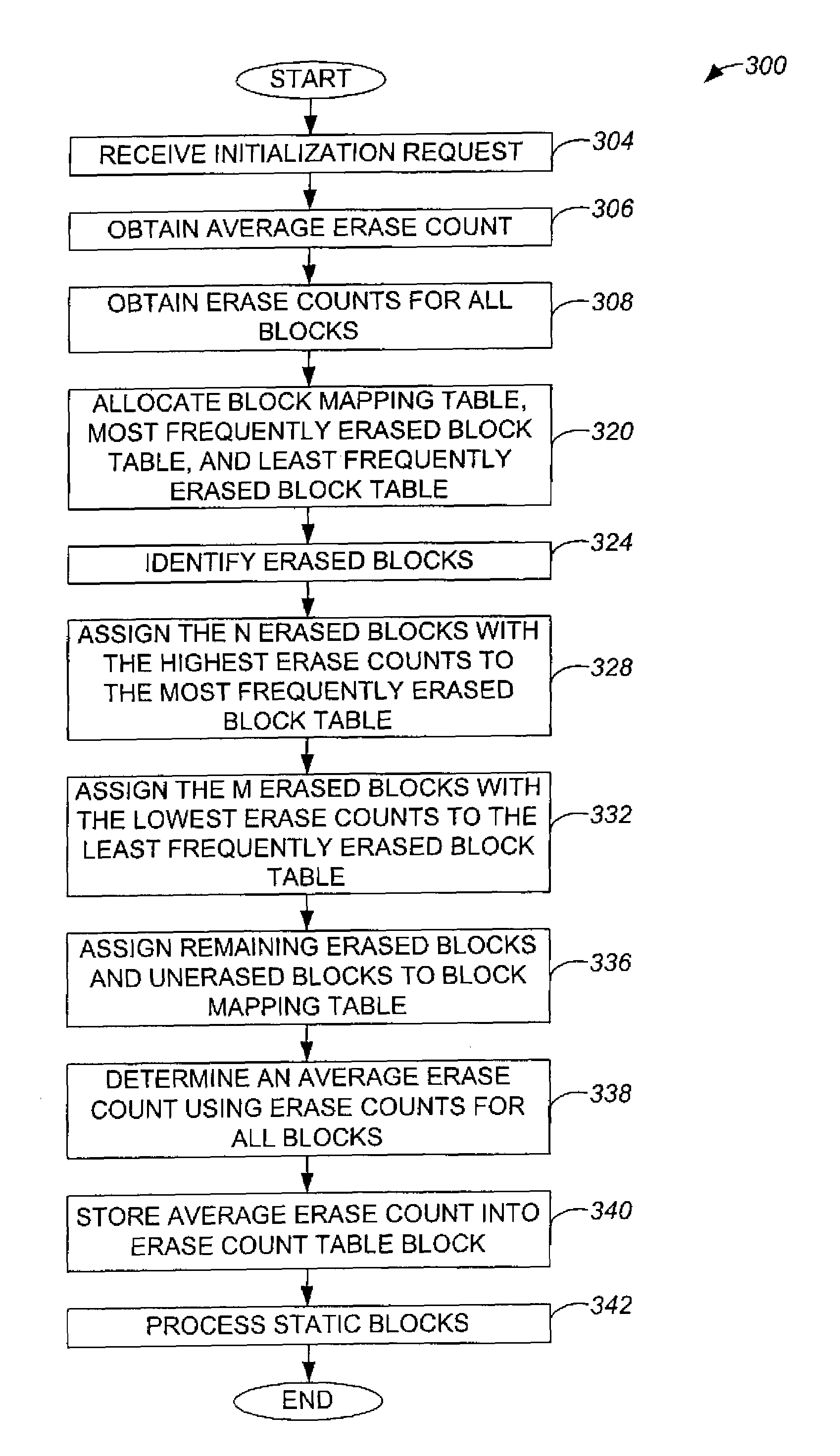
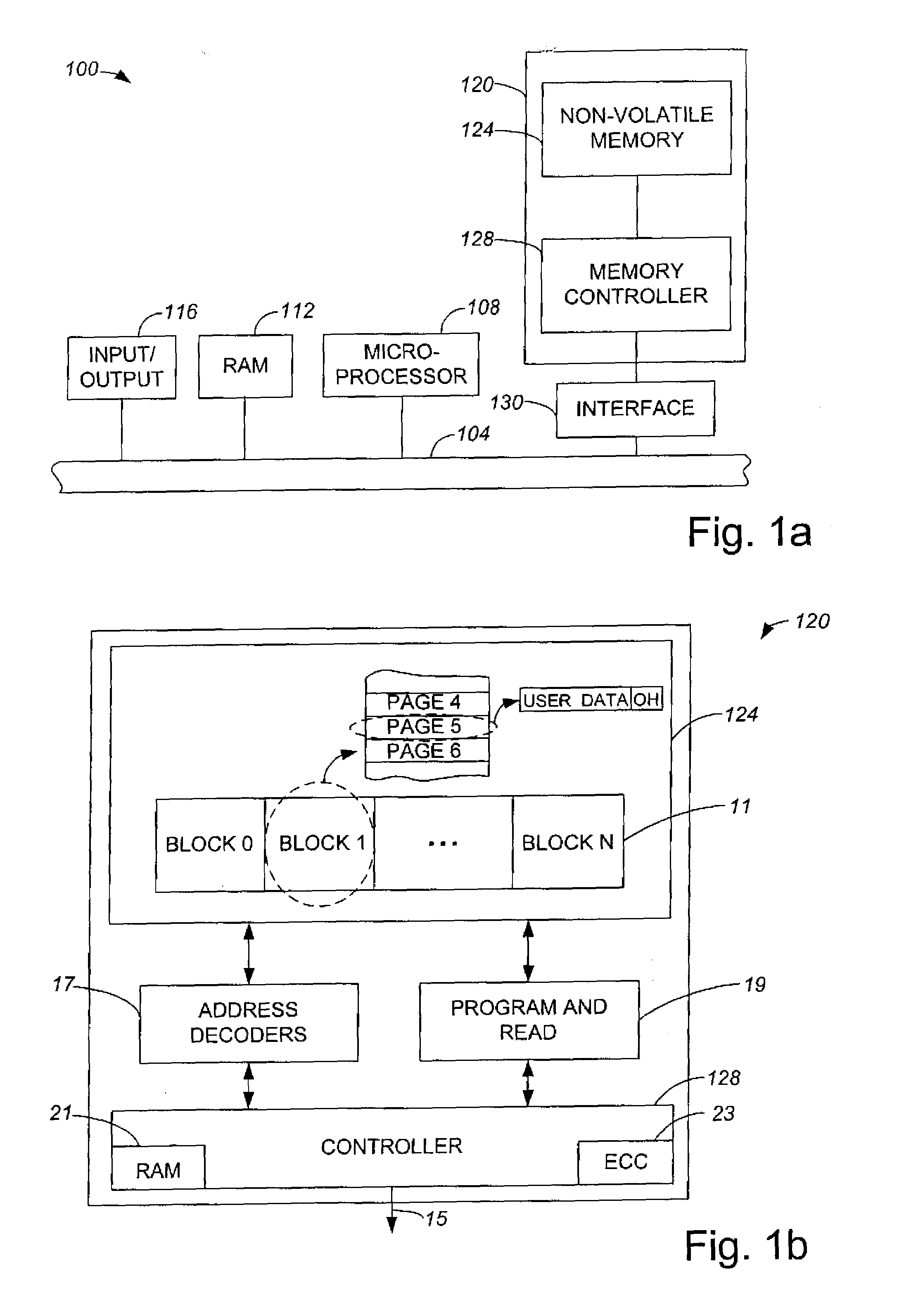
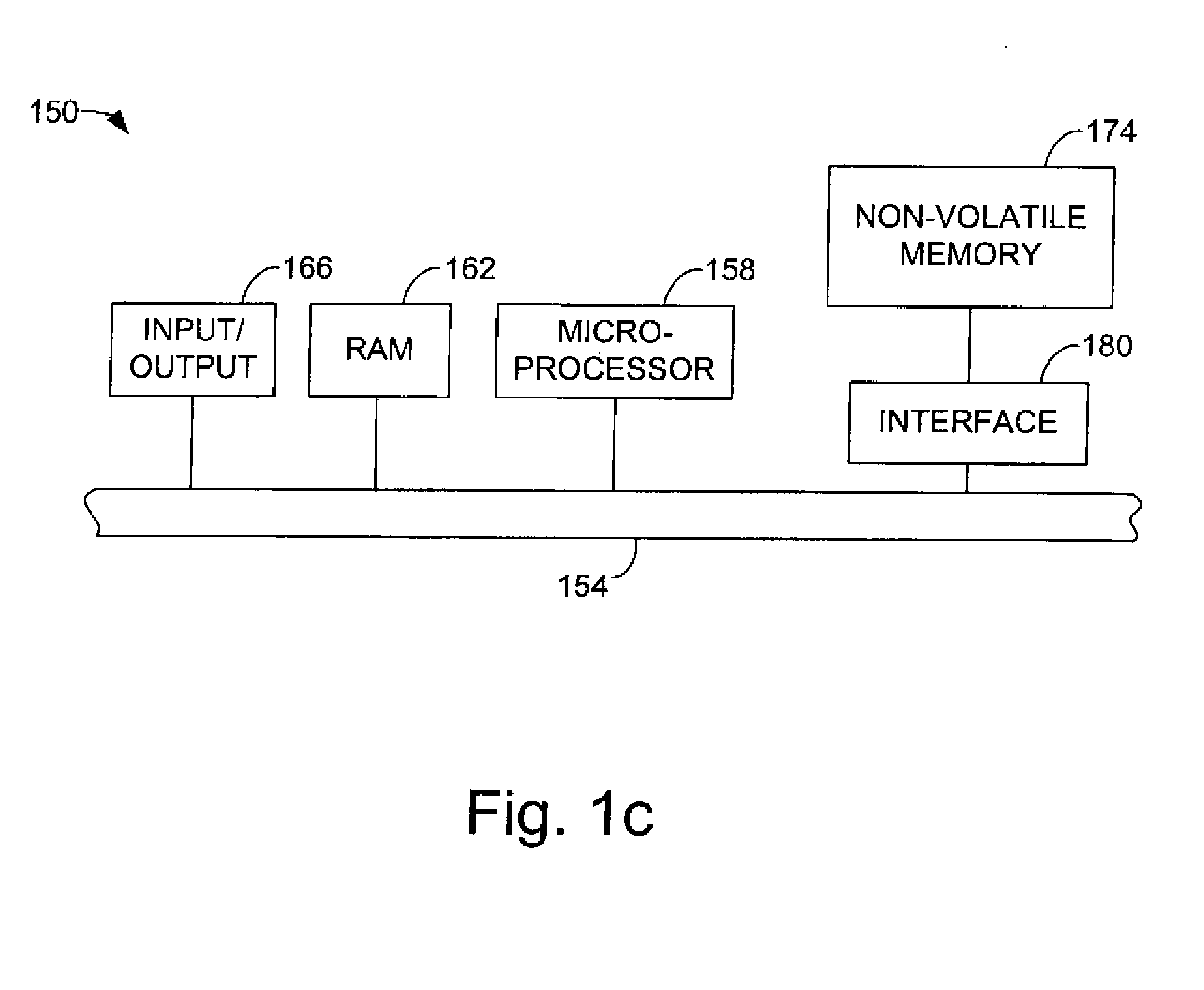
Method and apparatus for managing an erase count block
ActiveUS7103732B1Facilitate identificationReadily identifyMemory architecture accessing/allocationMemory adressing/allocation/relocationBlock methodOperating system
Methods and apparatus for managing erase counts in a non-volatile memory system. According to one aspect of the present invention, a method for initializing an erase count block in a system memory of a non-volatile memory system, the non-volatile memory system which includes a non-volatile memory involves allocating a plurality of pages within the system memory that are divided into a plurality of entries. Each entry of the plurality of entries has an associated block in the non-volatile memory. The method also includes identifying usable blocks which are suitable for use in accepting user data, and storing values in each entry which is associated with a usable block. Storing the values in each entry which is associated with a usable block substantially identifies the usable block as being usable.
Owner:SANDISK TECH LLC
Online service monitoring
InactiveUS20070027974A1Facilitate identificationFacilitate analysisDigital computer detailsTransmissionLoggingDistributed computing
A status notification method and facility is provided for use with a service chain processing a request for a service. The service chain can include multiple computer nodes, and the method includes dynamically creating the service chain for processing the request, and guaranteeing agreement, on at least two of the nodes of the service chain, about the status of the processing of the request. The method can also include saving detailed operational data logs in response to determining that a failure in processing the request has occurred. When a given node in the service chain determines that failure has occurred, agreement about the failure can be propagated throughout the service chain. Also, conditional logging of detailed operational data can minimize the amount of operational data transmitted over a network and saved to a data repository.
Owner:MICROSOFT TECH LICENSING LLC
Device for Allocating a Payment Authorization Request to a Payment Processor
InactiveUS20090157519A1Facilitates calculationFacilitate identificationHand manipulated computer devicesBuying/selling/leasing transactionsThird partyAuthorization
A point of sale (POS) device may be configured to locate a payment system and transmit a payment authorization request from a remote location to a payment system, either directly, or via a payment system directory and / or a SSL Gateway. The invention also includes inserting third party account information into an encrypted portion of the payment request, so the payment request appears as a normal request to the issuing bank, but the third party account information may be used by the third party to bill the customer. The payment system directory is further configured to determine one or more payment processors to direct a payment authorization request, such that a single transaction may me allocated among multiple payment processors for authorization. Moreover, the payment system directory is able to format alternative payment methods into a format that is able to be processed over existing payment networks.
Owner:LIBERTY PEAK VENTURES LLC
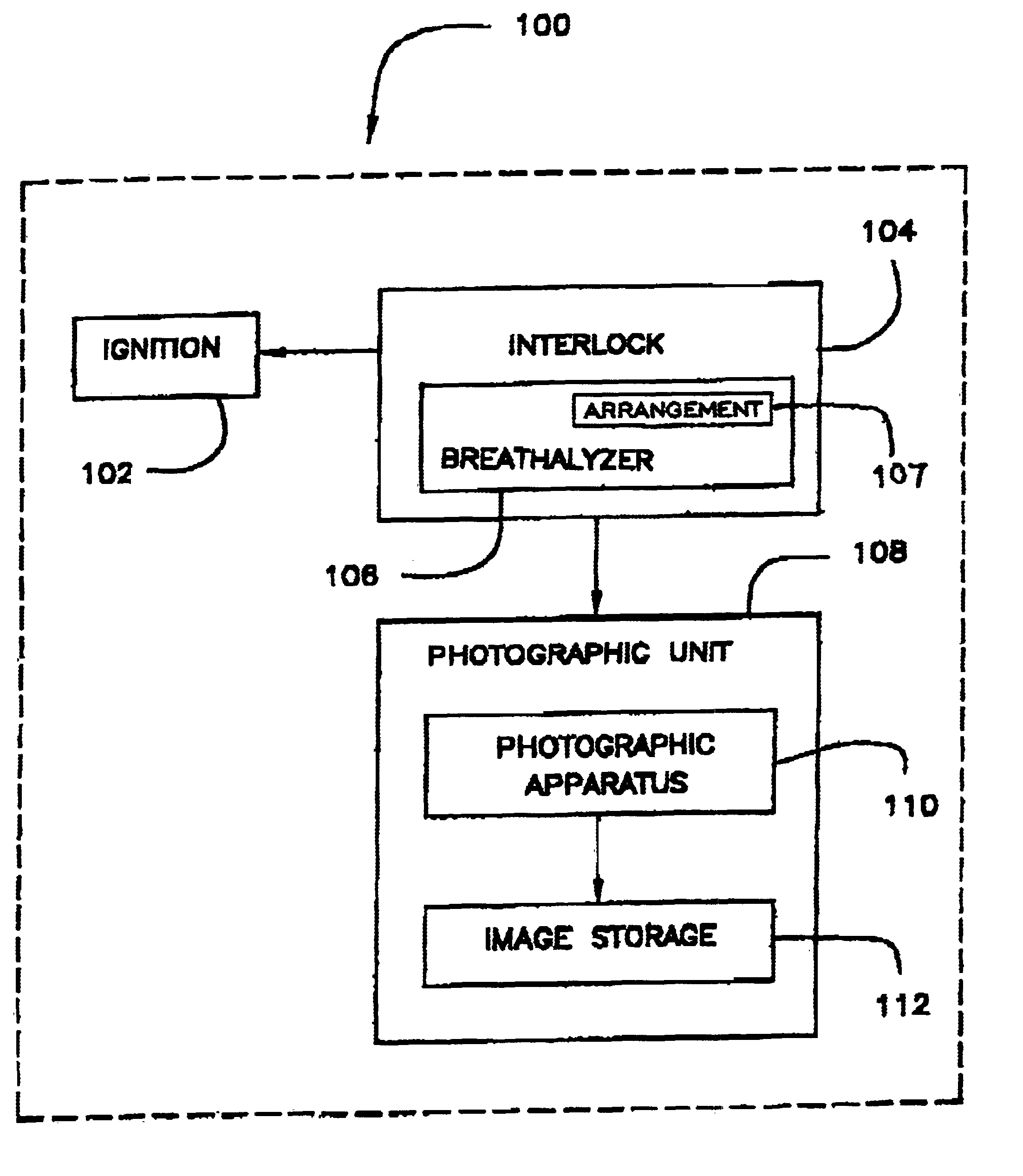
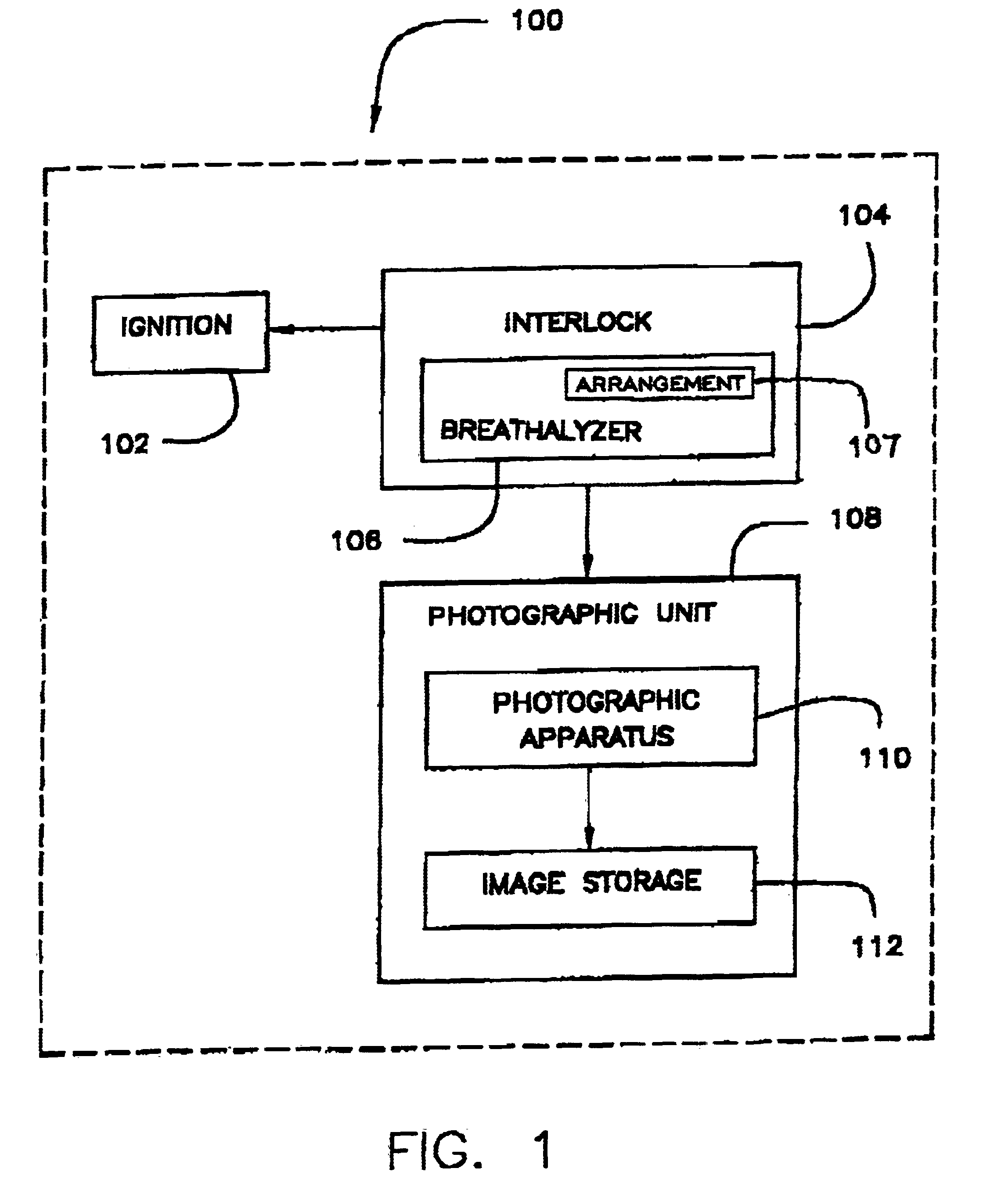
Substance testing devices with photo identification
InactiveUS6956484B2Facilitate identificationFacilitate photographic identificationElectric devicesAutomatic initiationsAmount of substanceIgnition interlock device
Owner:1A SMART START LLC
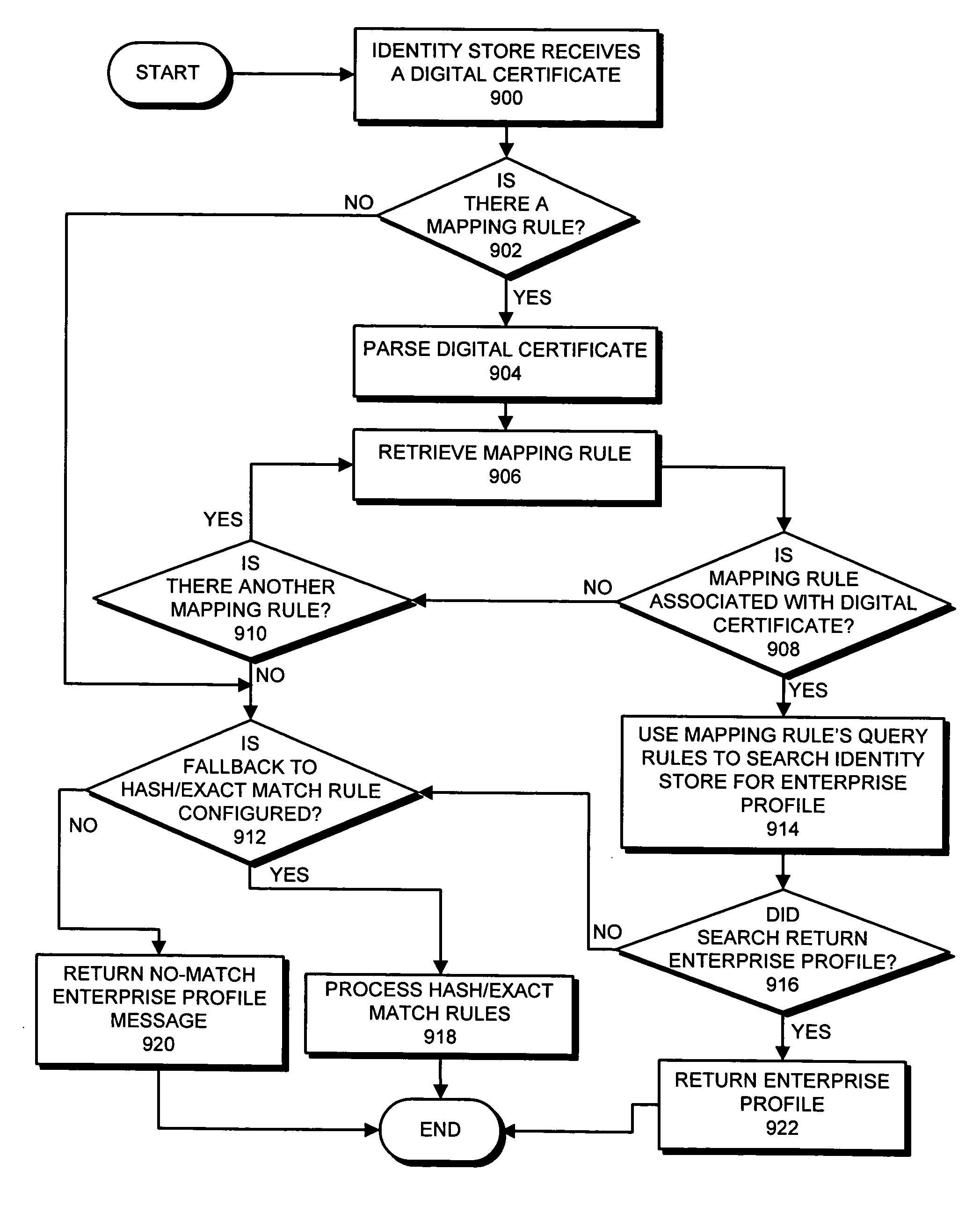
Method and apparatus for associating a digital certificate with an enterprise profile
ActiveUS20070118892A1Facilitates in associating/mappingFacilitate identificationDigital data processing detailsUser identity/authority verificationClient-sideBusiness enterprise
One embodiment of the present invention provides a system that associates a digital certificate with an enterprise profile. During operation, an identity store receives a digital certificate from a client. Next, the identity store searches for a mapping rule which determines if an enterprise profile is associated with the digital certificate, wherein the enterprise profile facilitates in identifying user capabilities. If a mapping rule is found, the identity store executes the mapping rule to determine if an enterprise profile is associated with the digital certificate. If so, the enterprise profile, which is associated with the digital certificate, is returned to the client.
Owner:ORACLE INT CORP
Method for developing and using an image reconstruction algorithm for multipath scattering
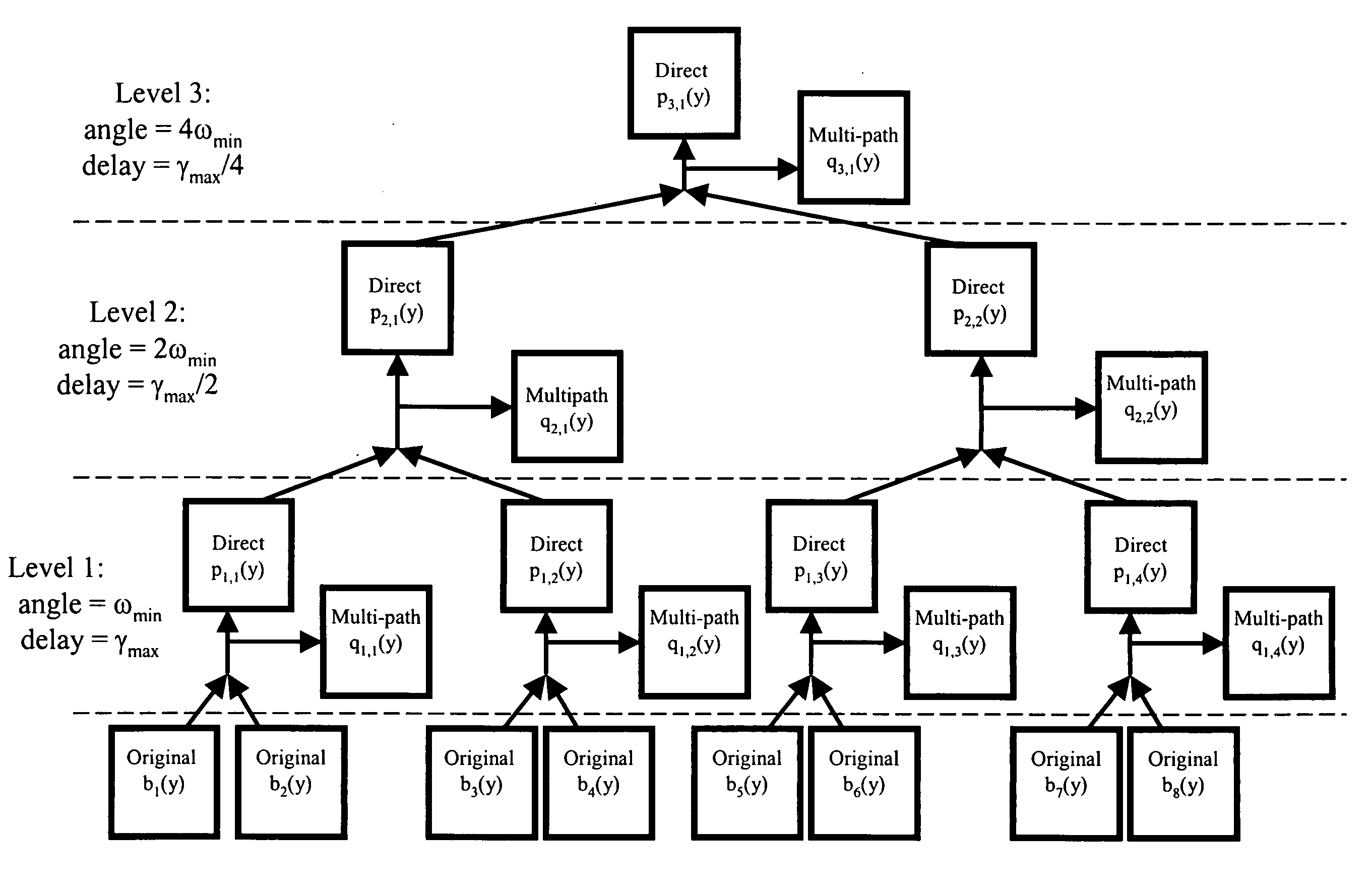
ActiveUS7259715B1Facilitate identificationEliminate effectsRadio wave reradiation/reflectionImage reconstruction algorithmImage resolution
Described herein is an implementation of the IRAMS processing based upon a multi-delay-resolution framework applied to SAR image data measured at different aspect angles. The power of this new embodiment of IRAMS is that it produces a good separation of immediate response scatterer and delayed response scatterer data for the case of anisotropic scattering events, i.e., those in which the scattering intensity depends upon the aspect angle. Two sources of delayed response scattering include multiple reflection scattering events and delayed responses arising from the physical material composition of the scatterer. That is, this multi-delay-resolution IRAMS processing separates immediate response and delayed response scattering for cases in which there exist delayed response scattering data in the original SAR image data at some aspect angles, but the intensity of these delayed response scattering data is weak or non-existent at different aspect angles. Thus, this IRAMS embodiment provides the additional information of the particular aspect angles at which delayed response scattering effects are most important, thereby improving both the estimates of the delayed response scattering data and the immediate response scattering data.
Owner:LEIDOS
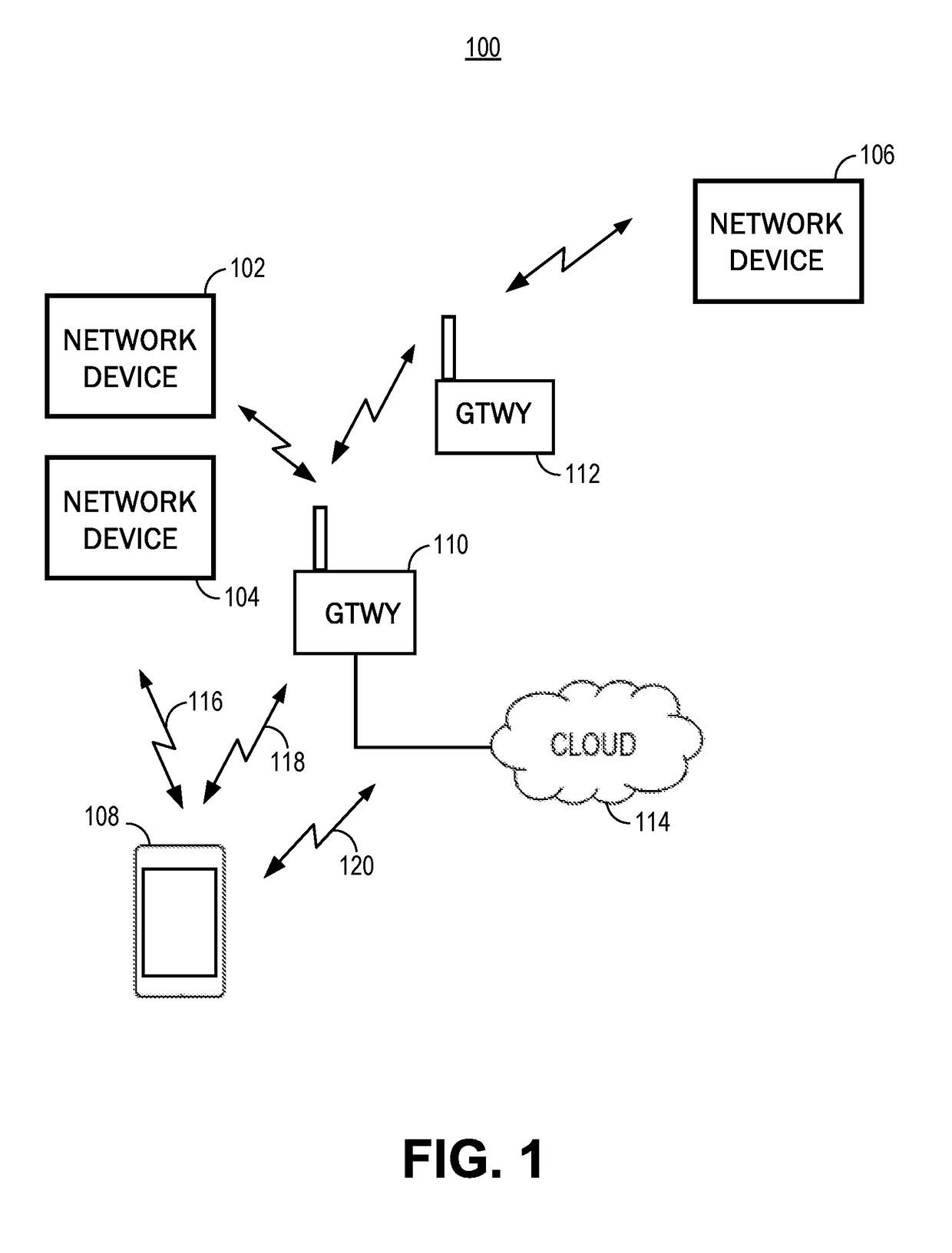
Associating devices and users with a local area network using network identifiers
ActiveUS20170079079A1Facilitate identificationEasy to identifyAssess restrictionNetwork topologiesUnique identifierLocal area network
Techniques for associating devices and users with a local area network using network identifiers are provided. For example, a method, system, and computer-program product for associating network devices with a local area network using a network identifier are provided. For example, a method may include receiving, at a computing device, a communication including a unique identifier for a network device connected to a network. The method may further include using the unique identifier to determine properties of the network device and generating a network identifier for the network, wherein the network identifier includes an indication of a time at which the network identifier is generated, an indication of the computing device, and an indication of the network device properties. The method can also include transmitting the network identifier, wherein when the network identifier is received, the network identifier facilitates identifying the network and associating the network device with the network.
Owner:BELKIN INT
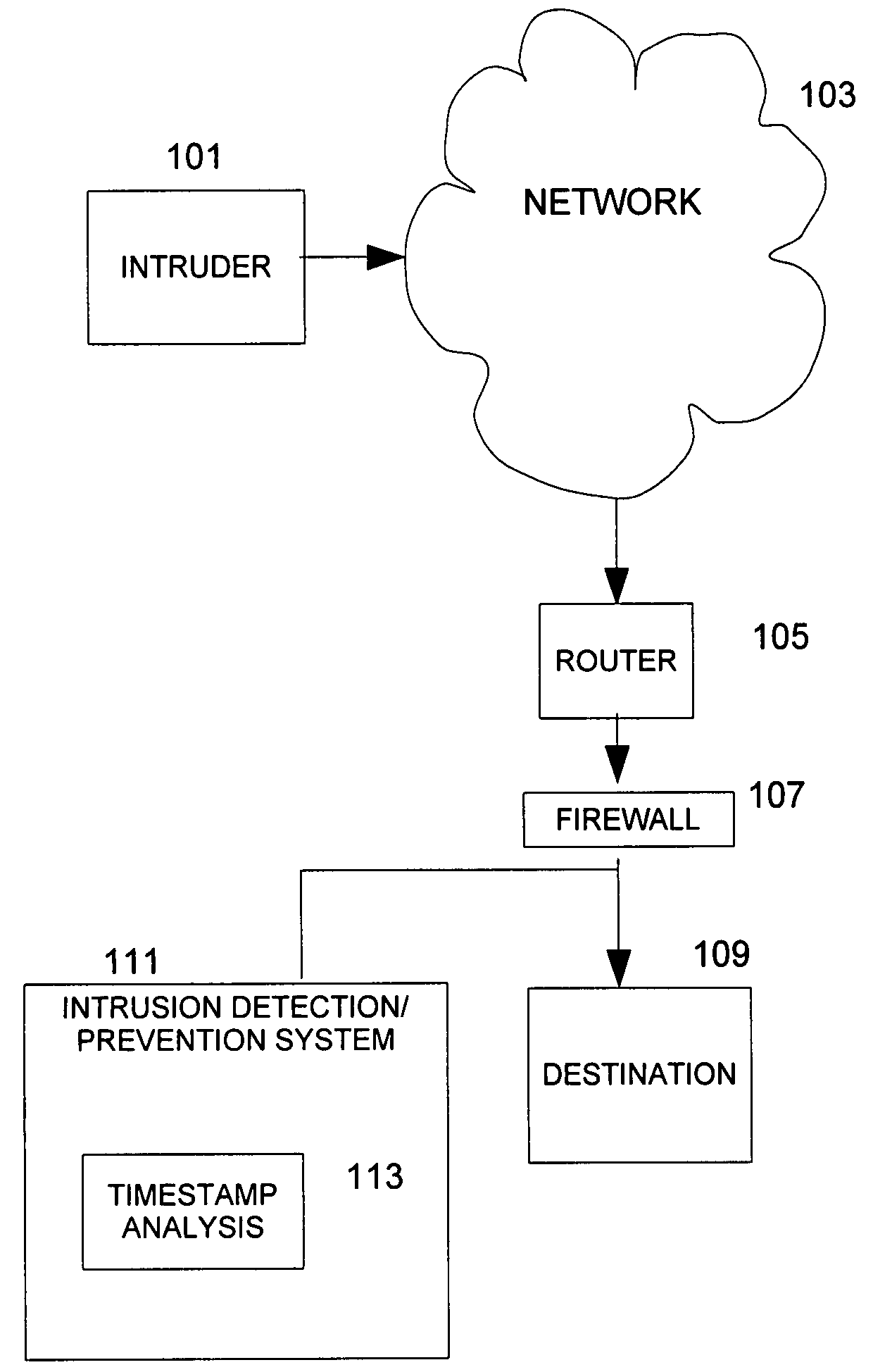
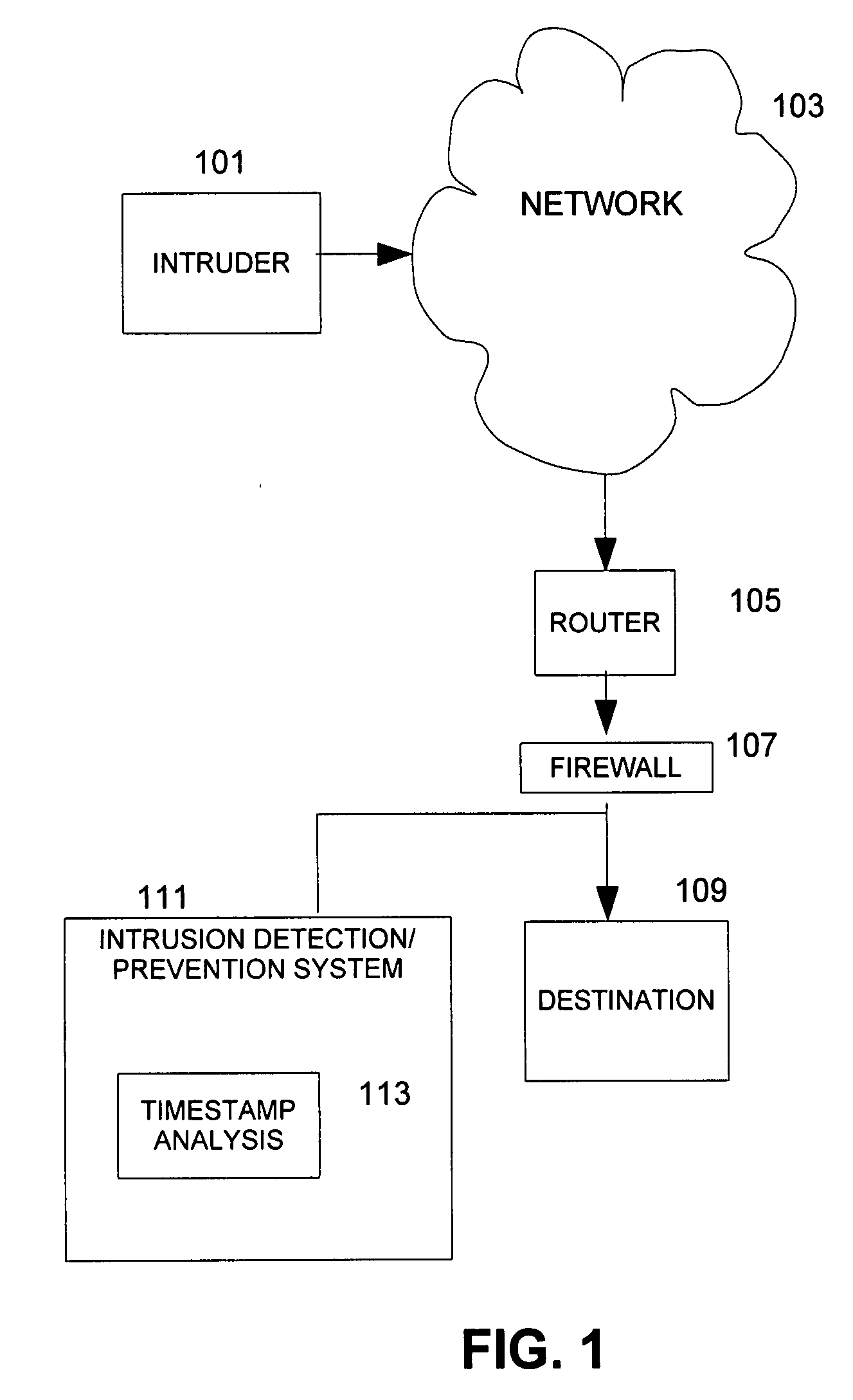
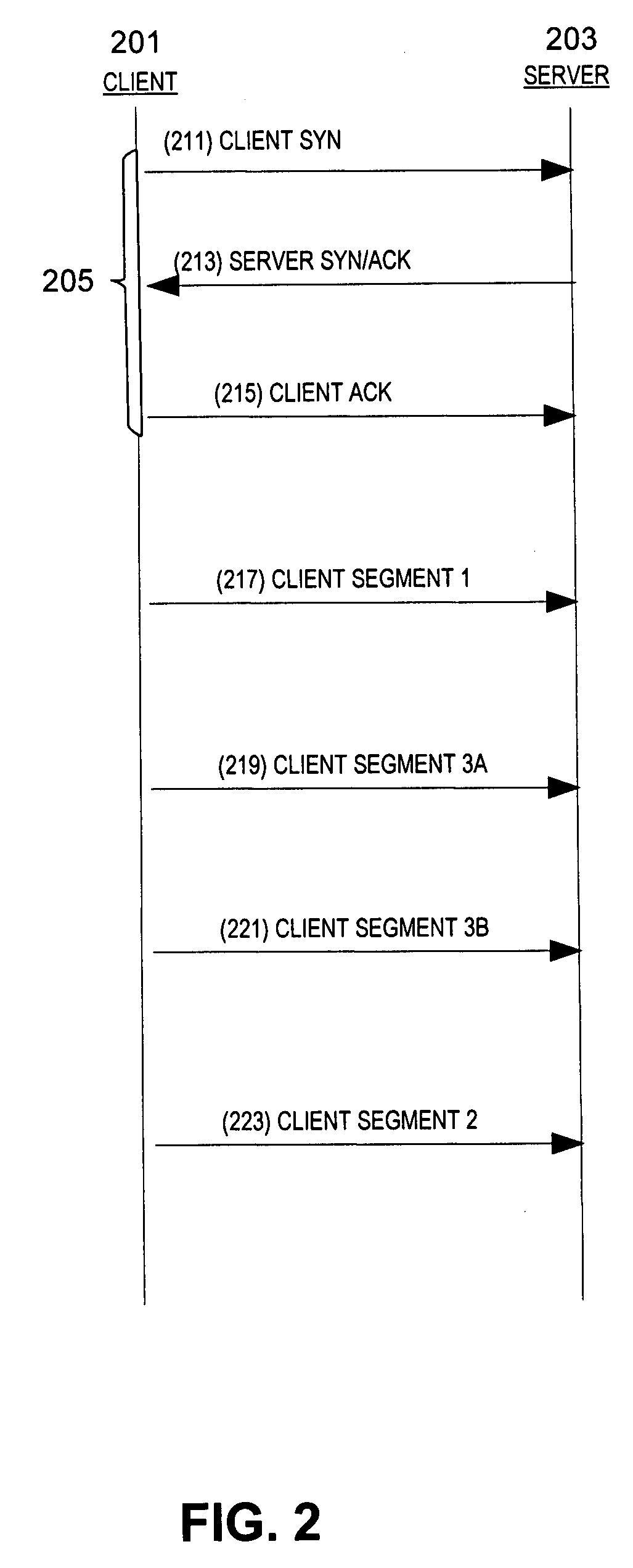
Device, system and method for timestamp analysis of segments in a transmission control protocol (TCP) session
ActiveUS20080209518A1Facilitate determiningFacilitate identificationDigital data processing detailsError detection/correctionTimestampHandshake
A method performed in an intrusion detection / prevention system, a system or a device for determining whether a transmission control protocol (TCP) segment in a TCP connection in a communication network is acceptable. The TCP connection can include TCP segments beginning with a three way handshake. A TCP segment can include a field for a timestamp. A timestamp policy of plural timestamp policies is identified, the timestamp policy corresponding to a target associated with the segments in a TCP connection. A baseline timestamp is identified based on a three way handshake in the TCP connection. Segments in the TCP connection are monitored. The segments in the TCP connection are filtered as indicated in the timestamp policy corresponding to the target, the timestamp policy indicating whether the segments are to be filtered out or forwarded to the target by comparing the timestamp of the segments to the baseline timestamp.
Owner:CISCO TECH INC
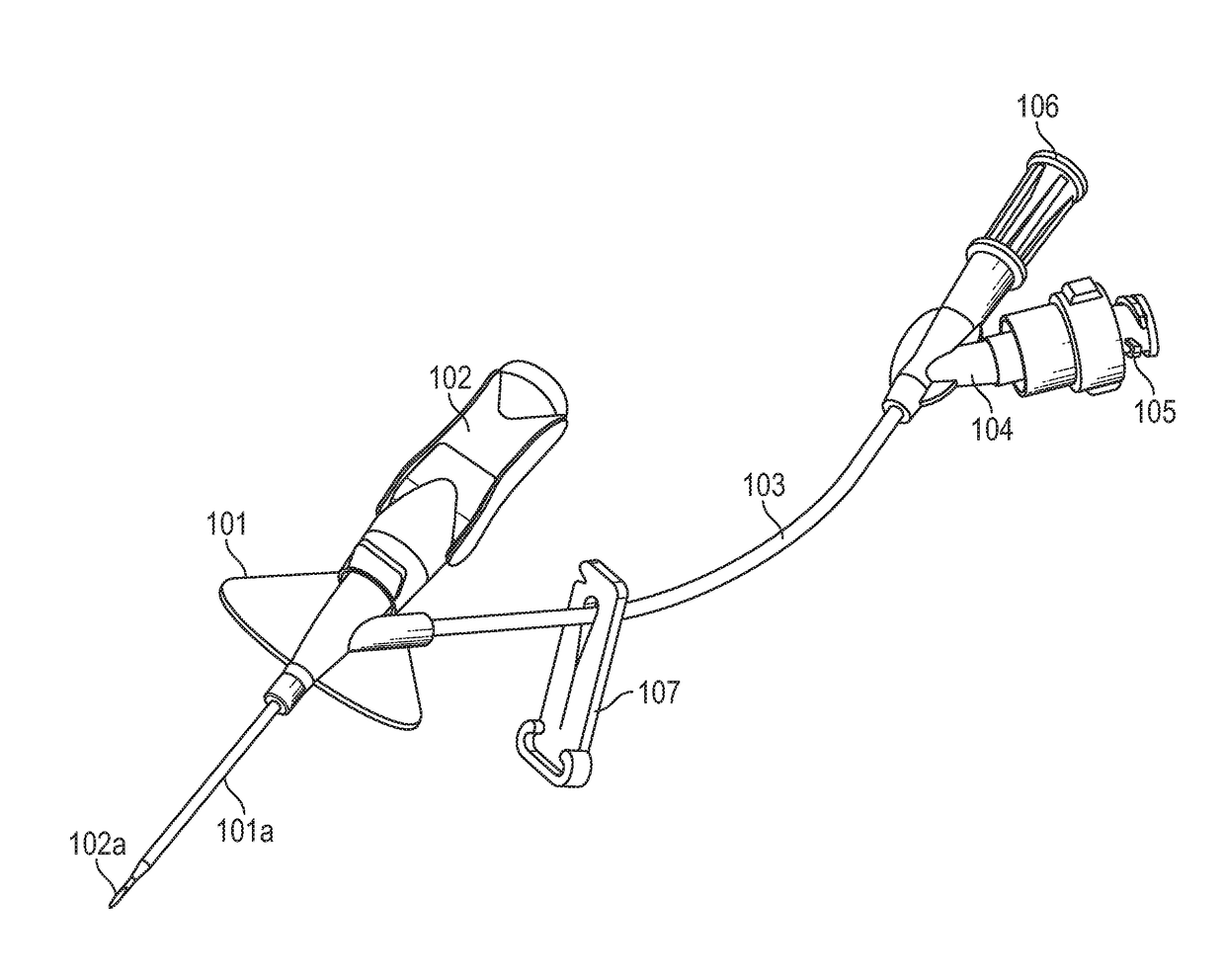
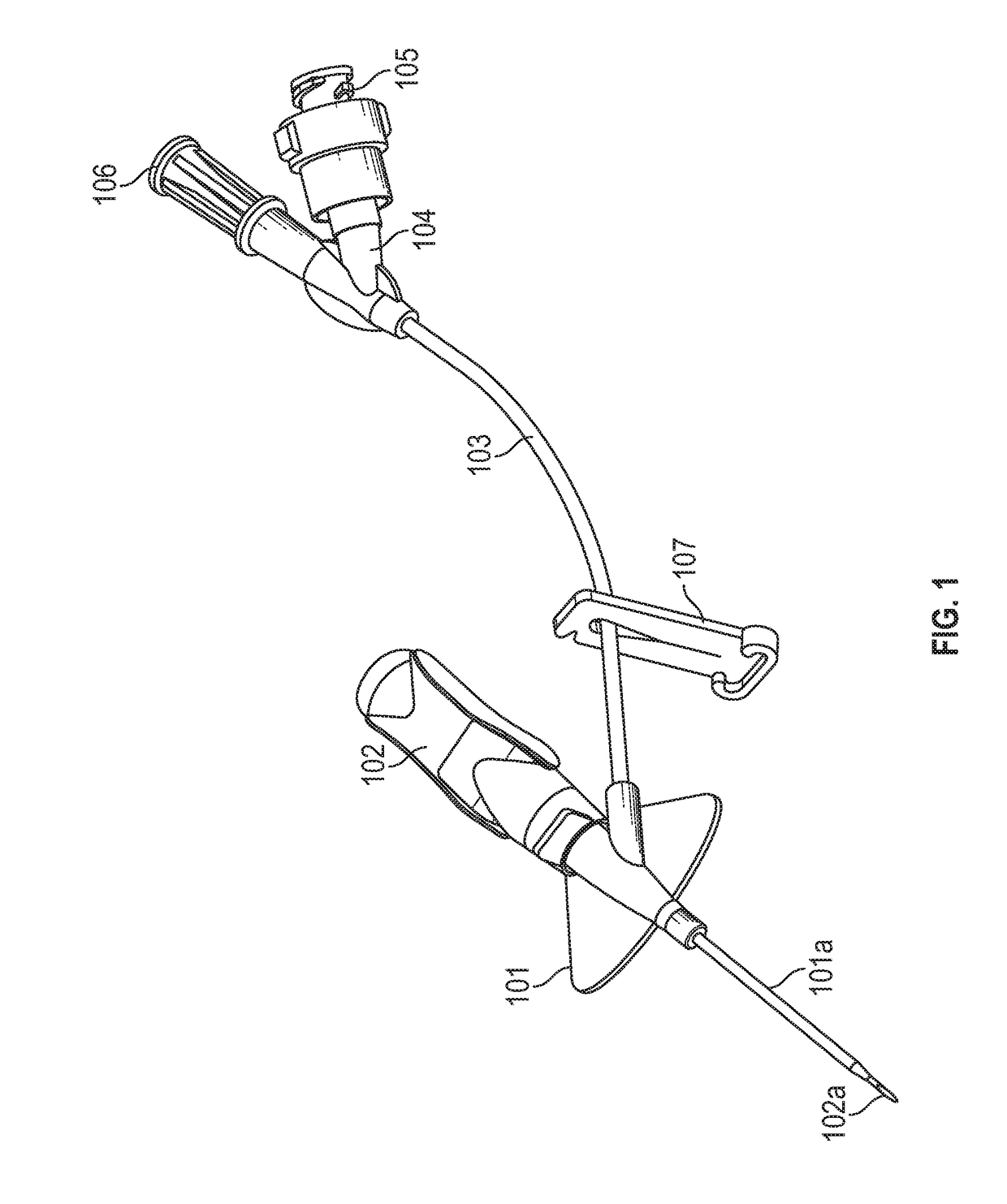
Closed iv access device with paddle grip needle hub and flash chamber
ActiveUS20170120017A1Facilitate identificationFacilitate insertion of catheterGuide needlesInfusion needlesVeinCatheter placement
An IV access device can include a needle hub that incorporates a flash chamber. The flash chamber can be used to provide visual confirmation of proper catheter placement within a vein. The flash chamber can include a path-defining structure to facilitate identifying whether blood is continually flowing into the flash chamber. The flash chamber may also be removable from the needle hub. In some cases, the needle hub may include a paddle grip that facilitates insertion of the catheter and separation of the needle hub from the catheter adapter.
Owner:BECTON DICKINSON & CO
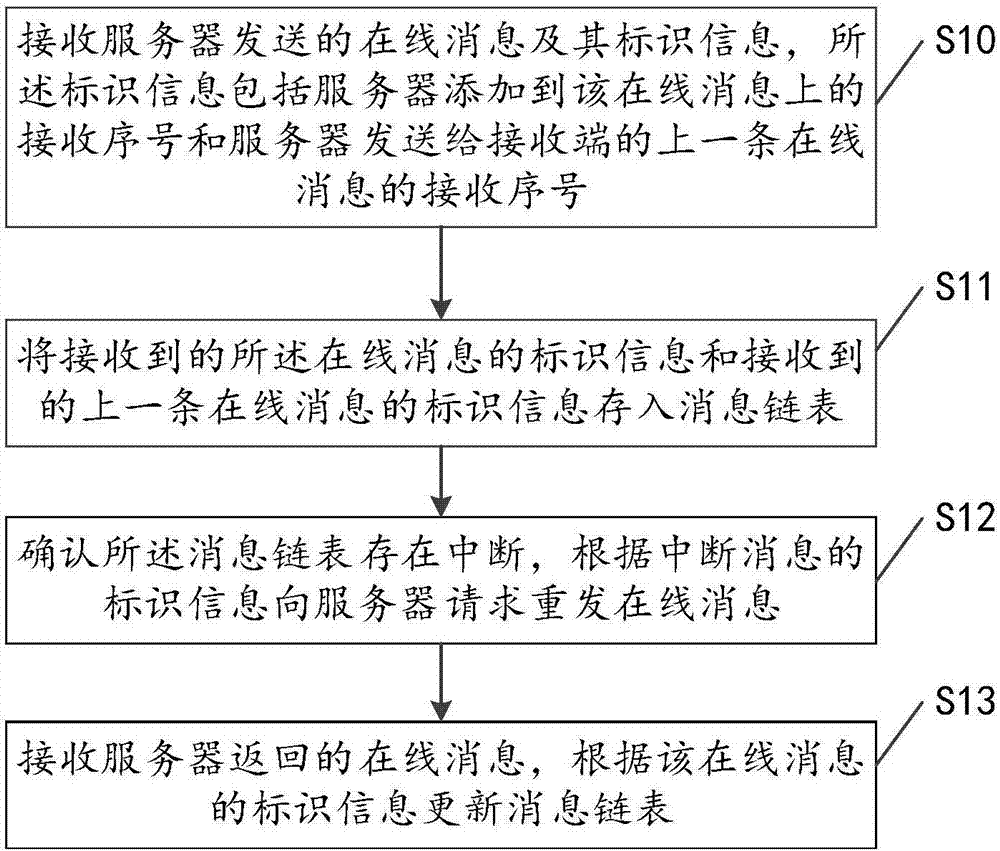
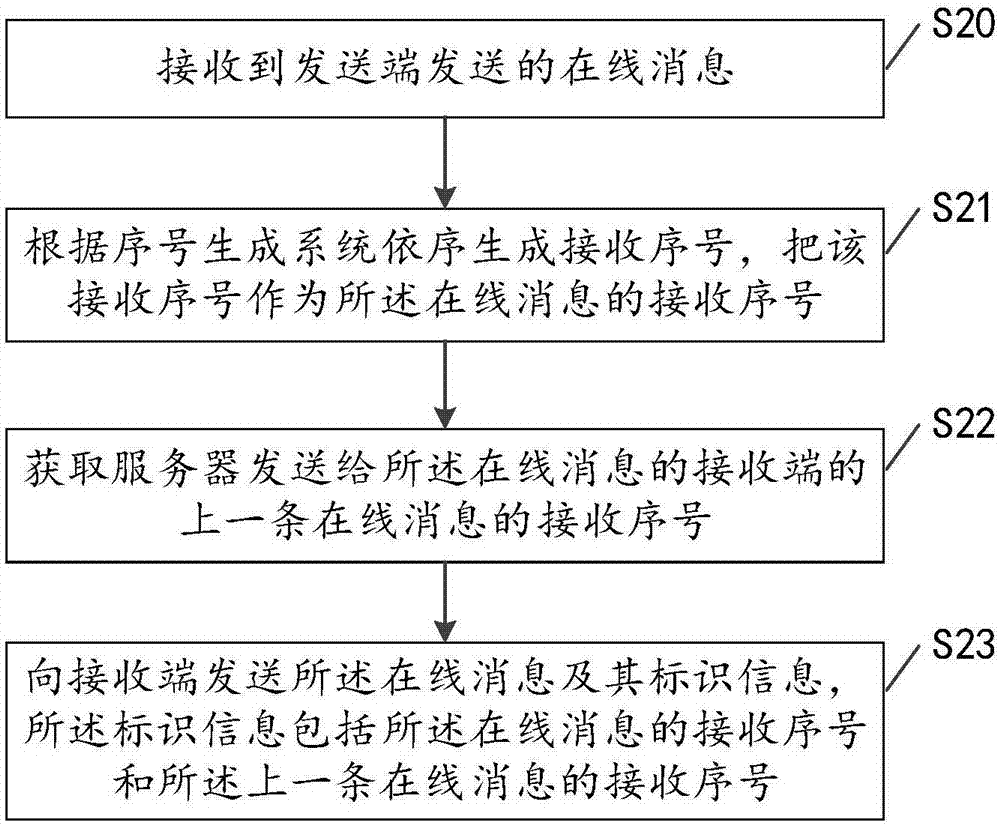
Message processing method based on serial number, terminal equipment and server
InactiveCN107491356AGood for timely deliveryMultiple coding methodsInterprogram communicationData switching networksTerminal equipmentComputer terminal
The invention discloses a message processing method based on a serial number. The message processing method comprises the steps of receiving an on-line message sent by a server and identification information of the on-line massage, wherein the identification information comprises a receiving serial number added to the on-line massage by the server and a receiving serial number of the last on-line message sent to the receiving side by the server; storing identification information of the received on-line message and the identification information of the received last on-line message into a message chain table; if it is determined that the message chain table is interrupted, requesting to resend the on-line message to the server according to the identification information of the interrupted massage; receiving the on-line message returned by the server, and updating the message chain table according to the identification information of the on-line message. The invention further provides terminal equipment and the server for achieving the method. Through the message processing method based on the serial number, the terminal equipment and the server, the lost message can be timely found out and accurately and completely retrieved.
Owner:GUANGZHOU BAIGUOYUAN INFORMATION TECH CO LTD
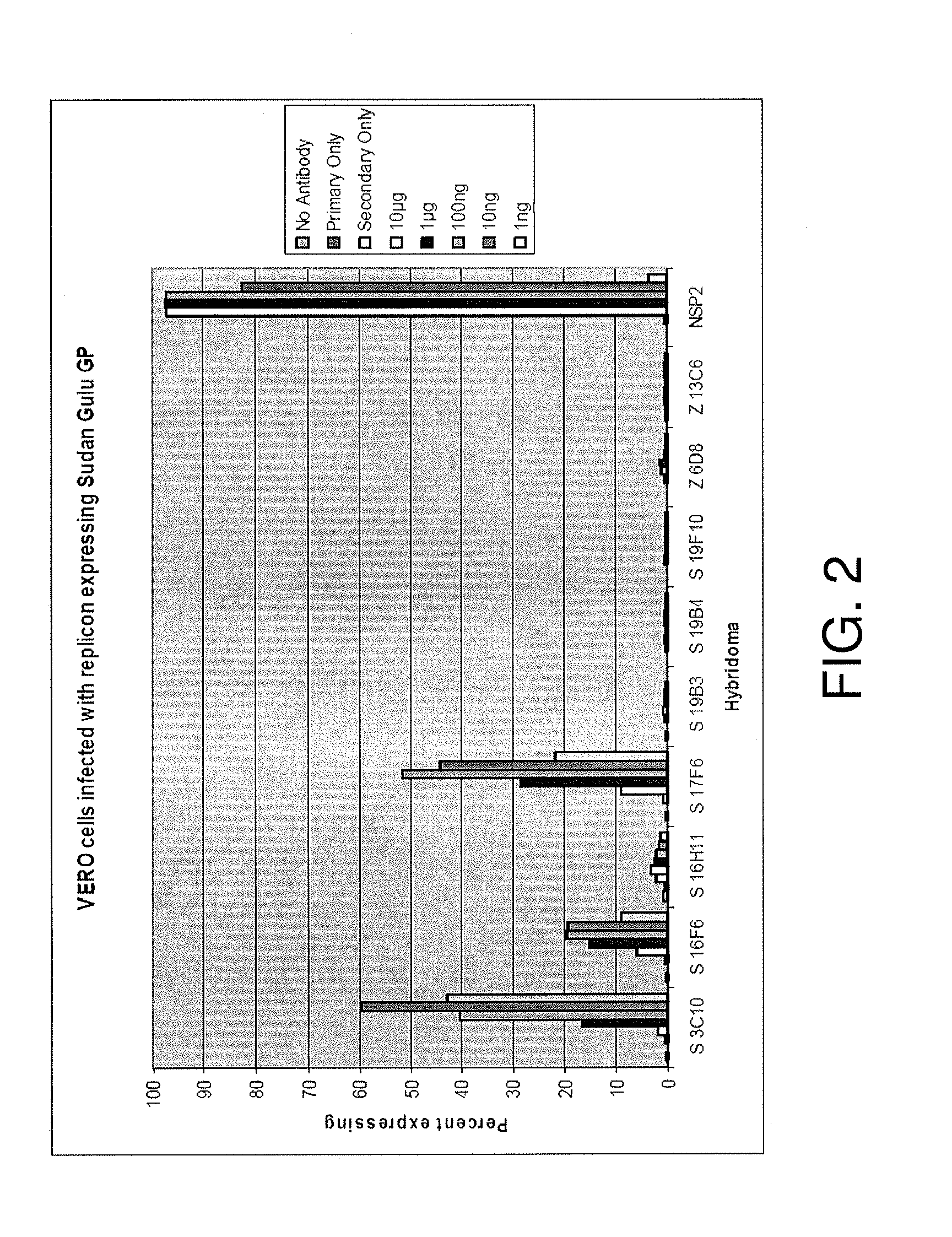
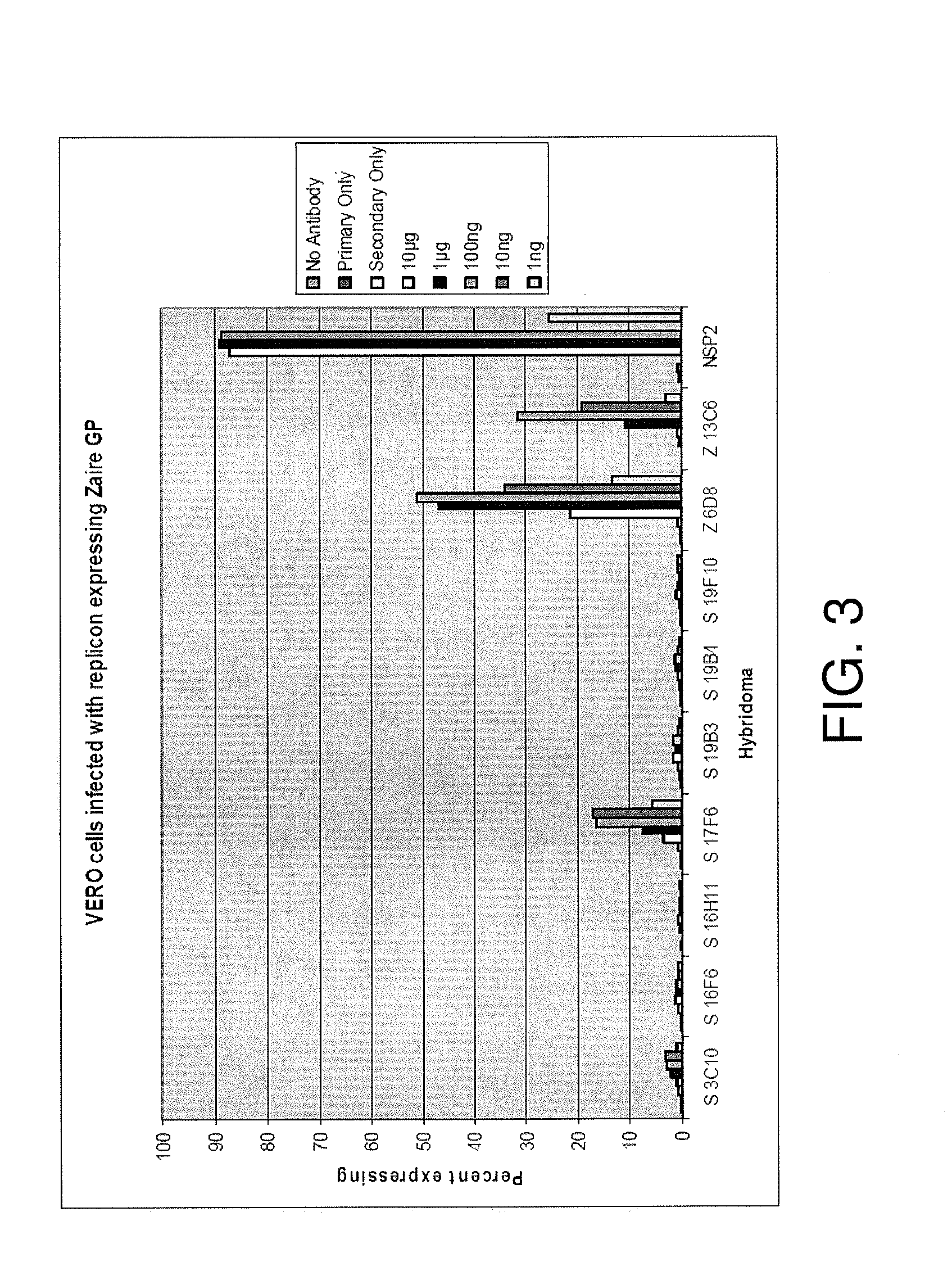
Monoclonal antibodies against glycoprotein of ebola sudan boniface virus
ActiveUS20120164153A1Facilitate identificationSsRNA viruses negative-senseGenetic material ingredientsGlycoproteinTherapeutic treatment
We disclose Ebola Sudan Boniface virus GP Monoclonal antibodies, epitopes recognized by these monoclonal antibodies, and the sequences of the variable regions of some of these antibodies. Also provided are mixtures of antibodies of the present invention, as well as methods of using individual antibodies or mixtures thereof for the detection, prevention, and / or therapeutic treatment of Ebola Sudan Boniface virus infections in vitro and in vivo.
Owner:THE US SEC THE ARMY ON BEHALF OF USAMRMC
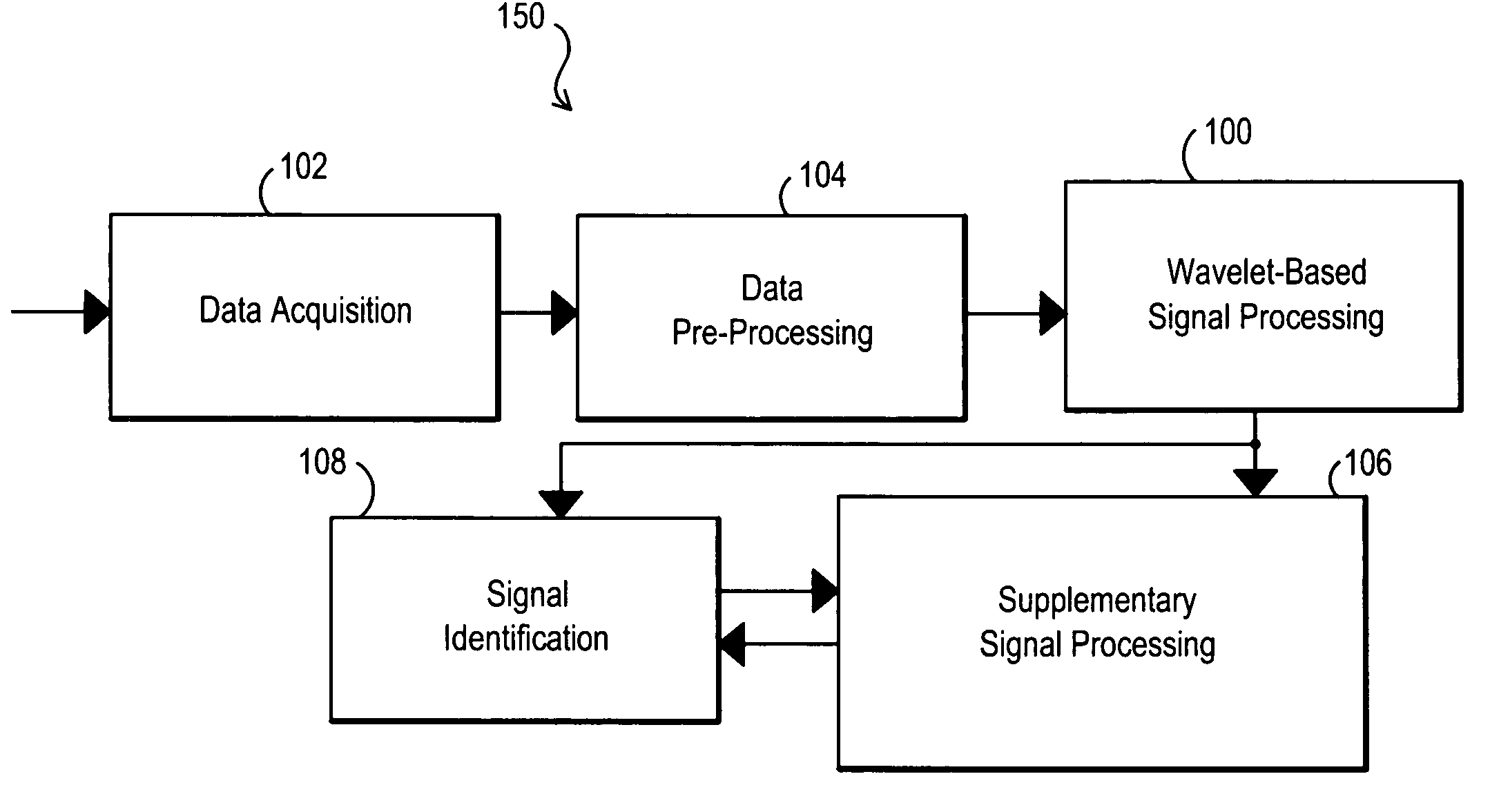
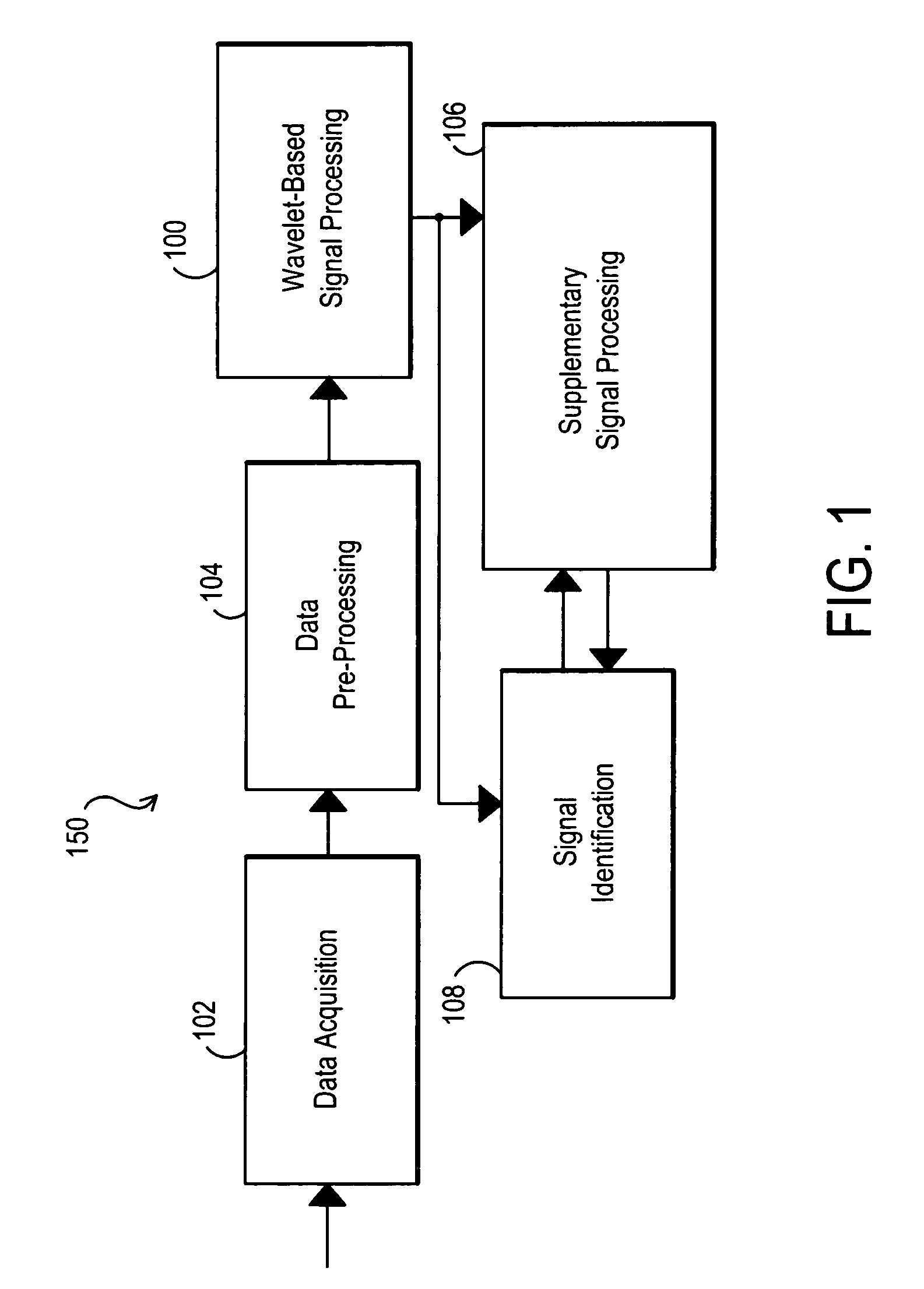
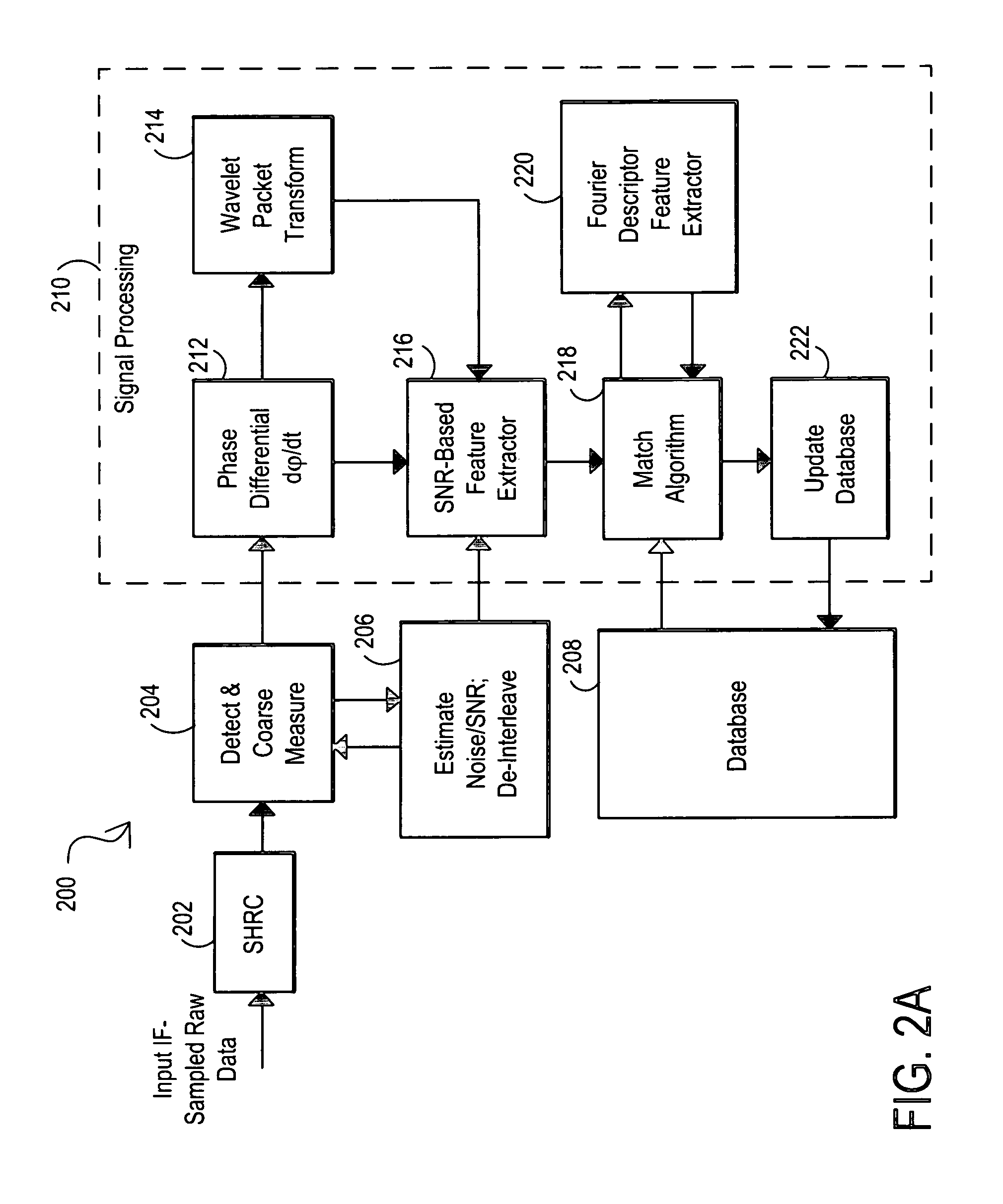
Signal source identification utilizing wavelet-based signal processing and associated method
InactiveUS7120562B1Facilitate identificationEnhance accuracyCircuit-breaking switches for excess currentsAmplifier modifications to reduce noise influenceFingerprintPacket processing
A signal source identification system and associated method are disclosed that utilize wavelet-based signal processing to facilitate signal source identification. In particular, the wavelet-based signal processing enables the extraction of fingerprint type signatures for signal sources using wavelet packet processing, and supplementary signal processing can be used to further enhance the accuracy of the system. This signal source identification system can be used for identifying signal sources within a received data signal, used for providing security features by verifying the identify of a transmitting device, and / or used in other environments where it is desirable to identify or differentiate among signal sources. Other features and variations can be implemented, if desired.
Owner:L 3 COMM INTEGRATED SYST
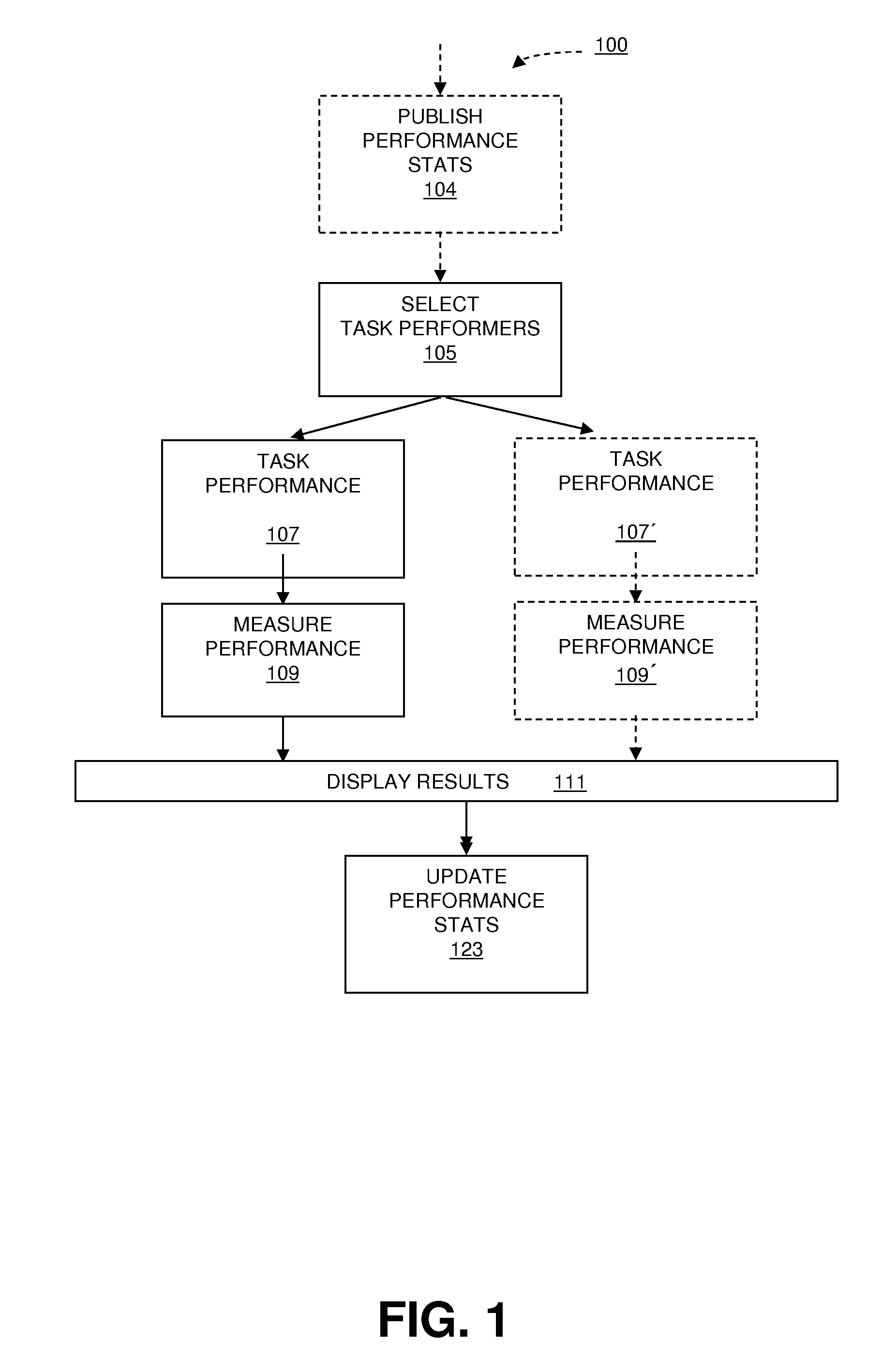
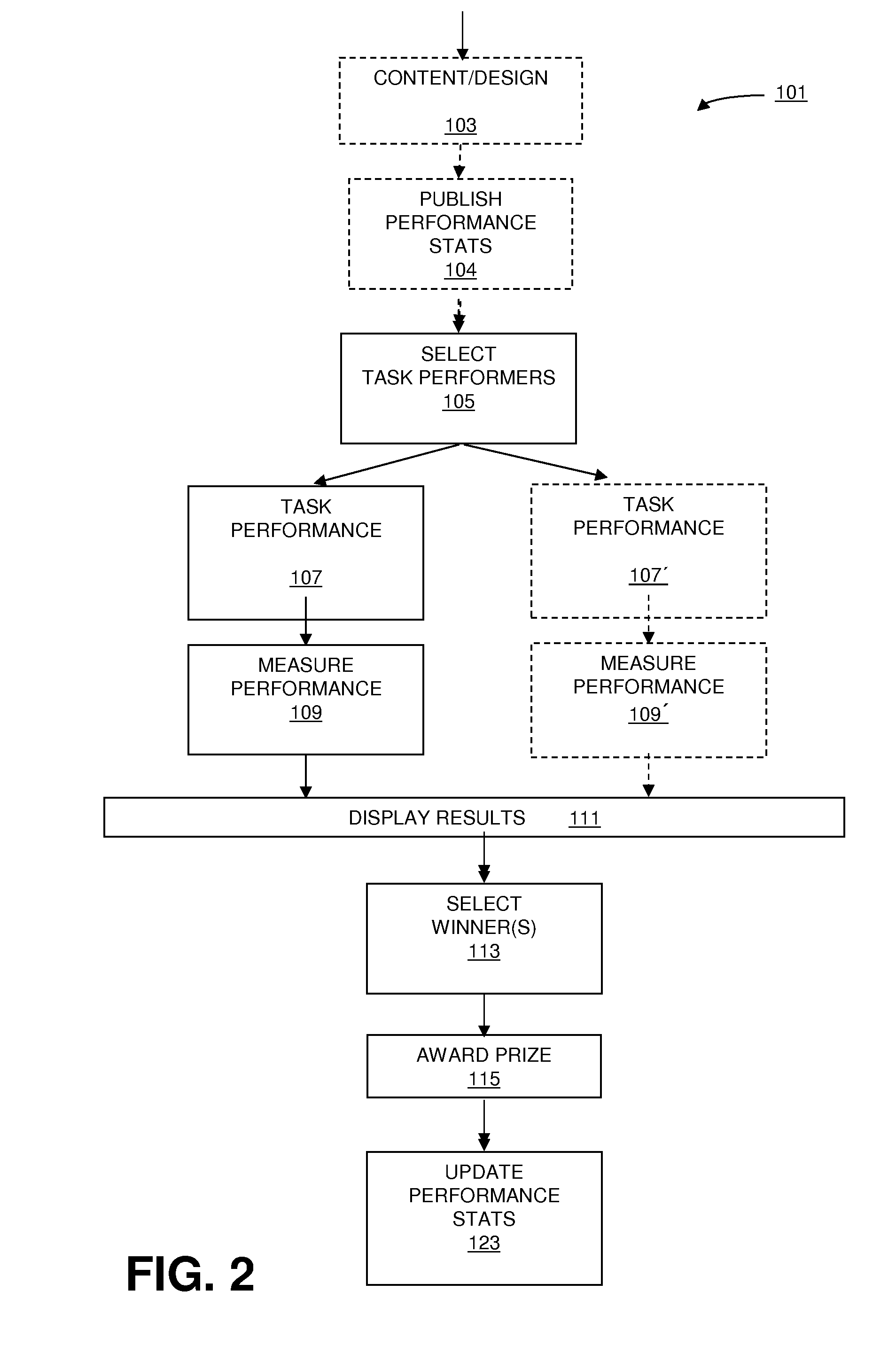
System and Method for Advertising Placement and/or Web Site Optimization
InactiveUS20100174603A1Facilitate identificationFacilitate selectionInput/output for user-computer interactionMultiple digital computer combinationsWeb siteWorld Wide Web
In general, in one aspect, a method for web site optimization includes publishing performance statistics of task performers, facilitating selection of task performers for participation in a competition based on the published performance statistics, facilitating optimization by each selected competitors, collecting response to the optimization of each selected competitor, updating the published performance statistics based on the response; and compensating the task performers based on the published performance statistics. In some embodiments, a prize is awarded to the task performer with the best performance. In some embodiments, a competition is conducted for the design of web site content to be optimized.
Owner:TOPCODER
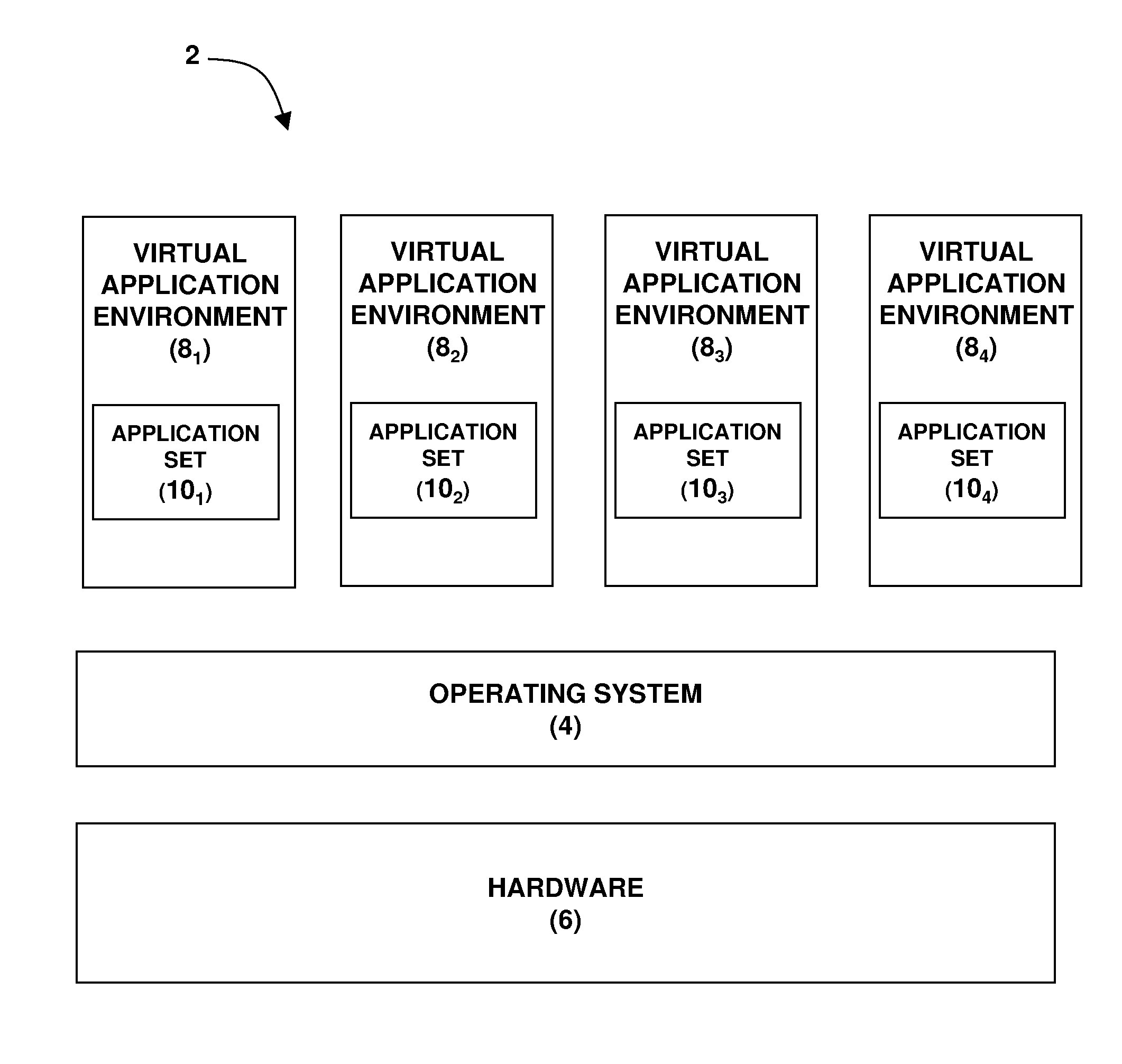
Fair memory resource control for mapped memory
InactiveUS20090037685A1Facilitate identificationMemory architecture accessing/allocationMemory systemsData transmissionApplication software
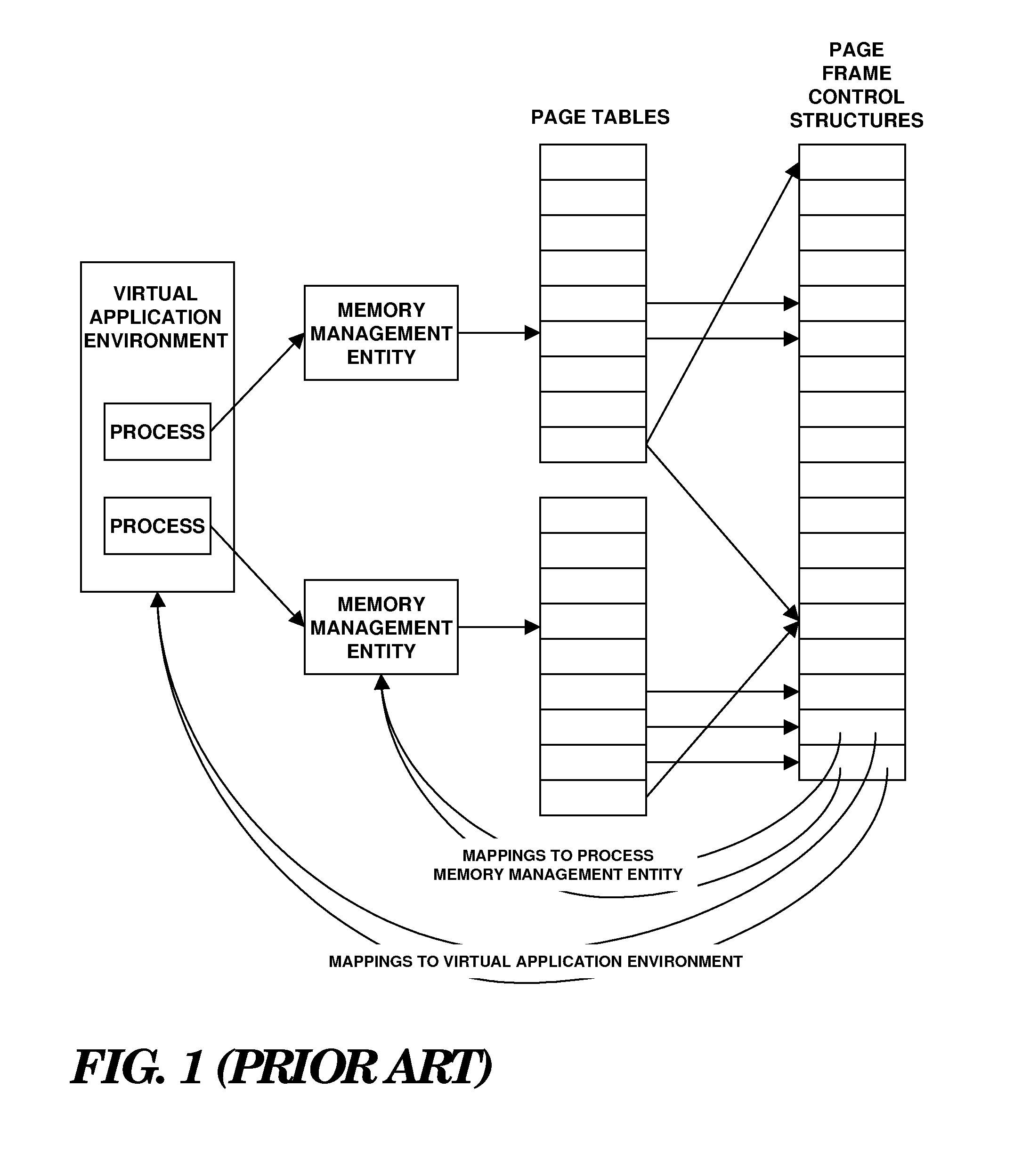
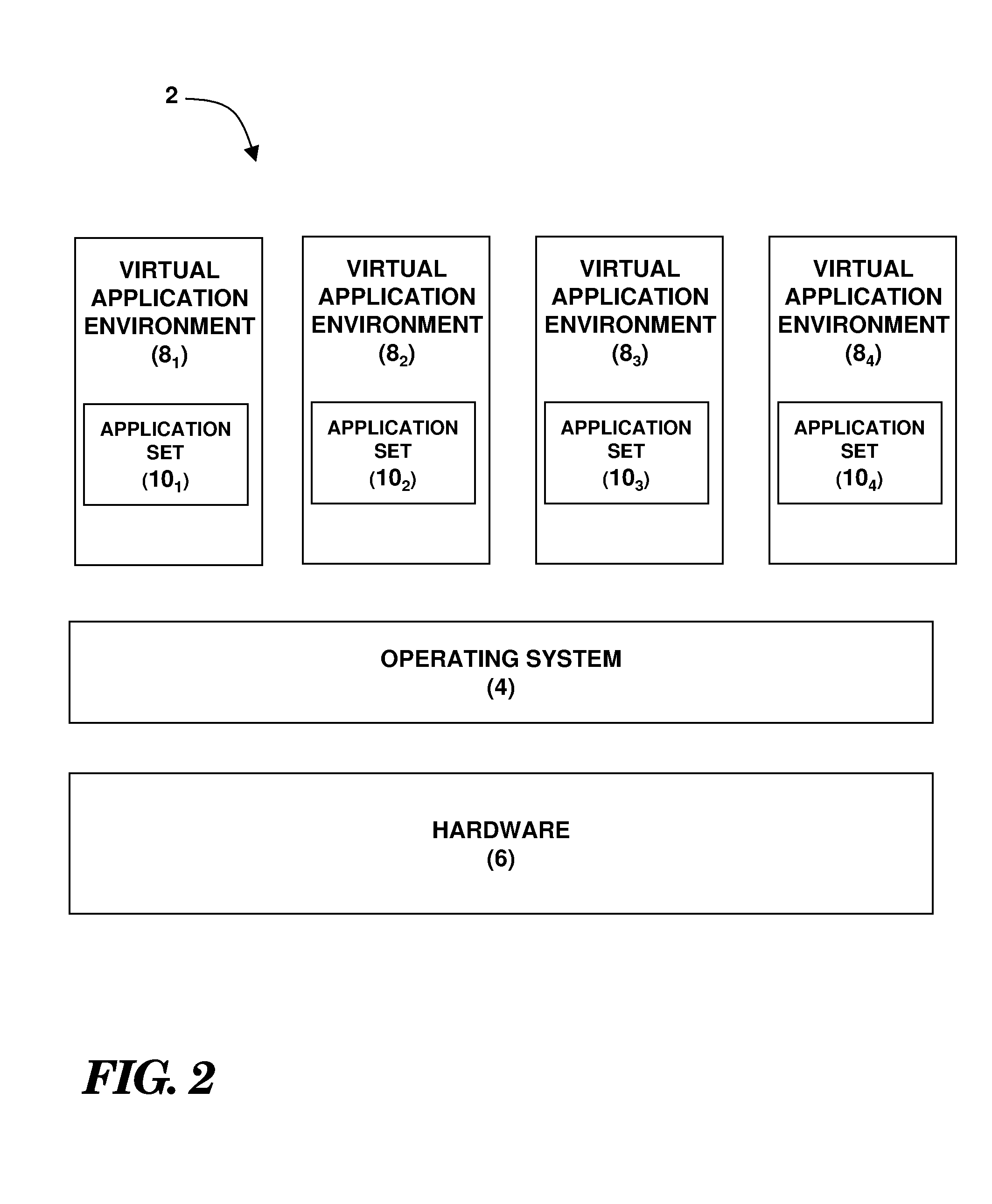
A method system and computer program product for managing memory allocation among plural virtual application environments supported by a common operating system. The technique may include establishing a mapping between a virtual application environment (or processes therein) and a mapping proxy that is reachable via a reverse mapping pathway adapted to facilitate identification of virtual addresses associated with a memory page frame. The virtual application environment (or processes therein) may be identified as an allocation recipient of the memory page frame by traversing the reversing mapping pathway to the mapping proxy. The memory page frame may be reclaimed for allocation to another virtual application environment by invalidating data therein or transferring the data to a storage resource based upon memory usage by the identified virtual application environment.
Owner:LINKEDIN
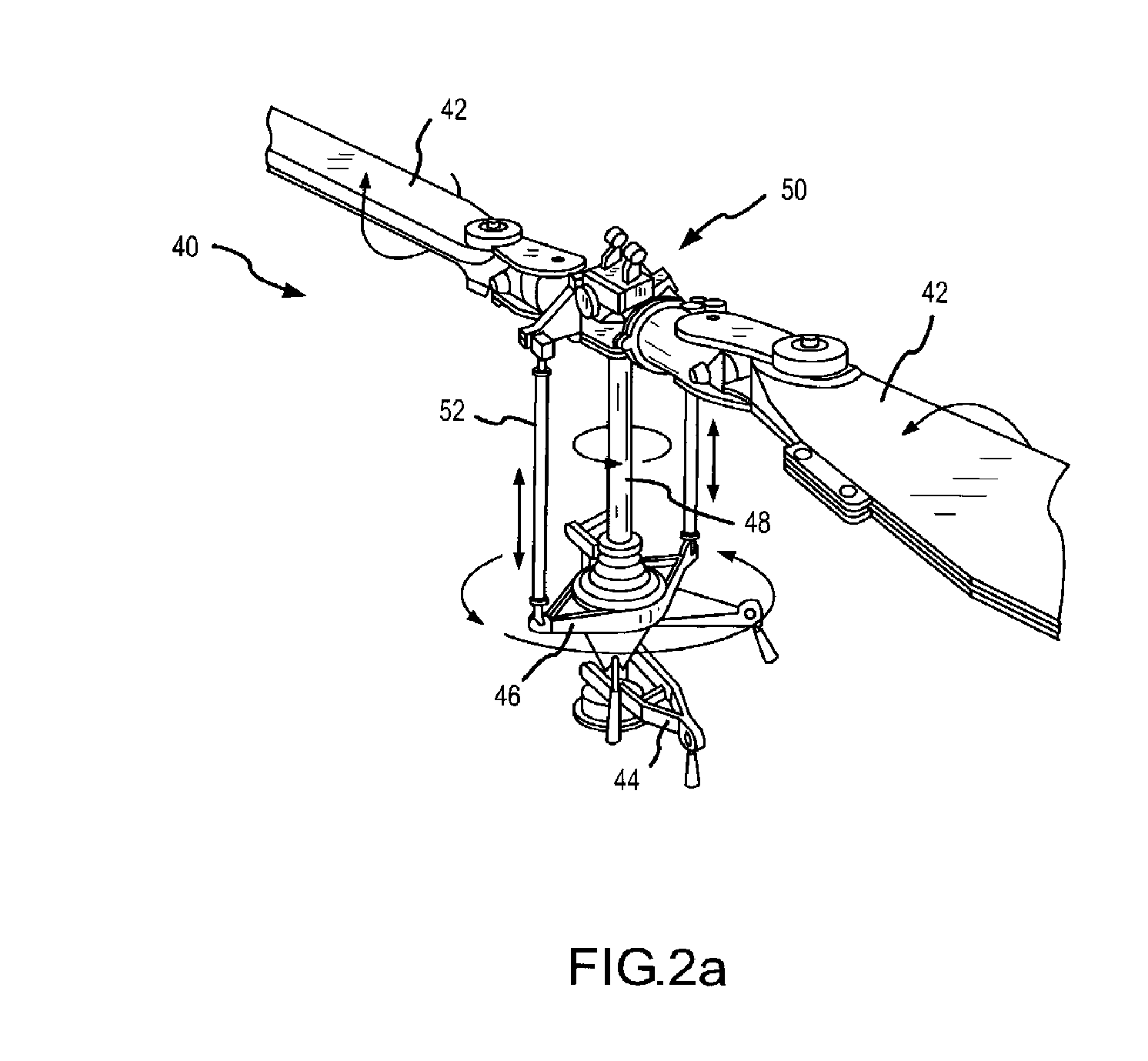
Airborne Look-Down Doppler Radar Tracking of Hovering Helicopters using Rotor Features
ActiveUS20070285303A1Facilitate identificationHigh rateRadio wave reradiation/reflectionDirection controllersMissileEnvironmental geology
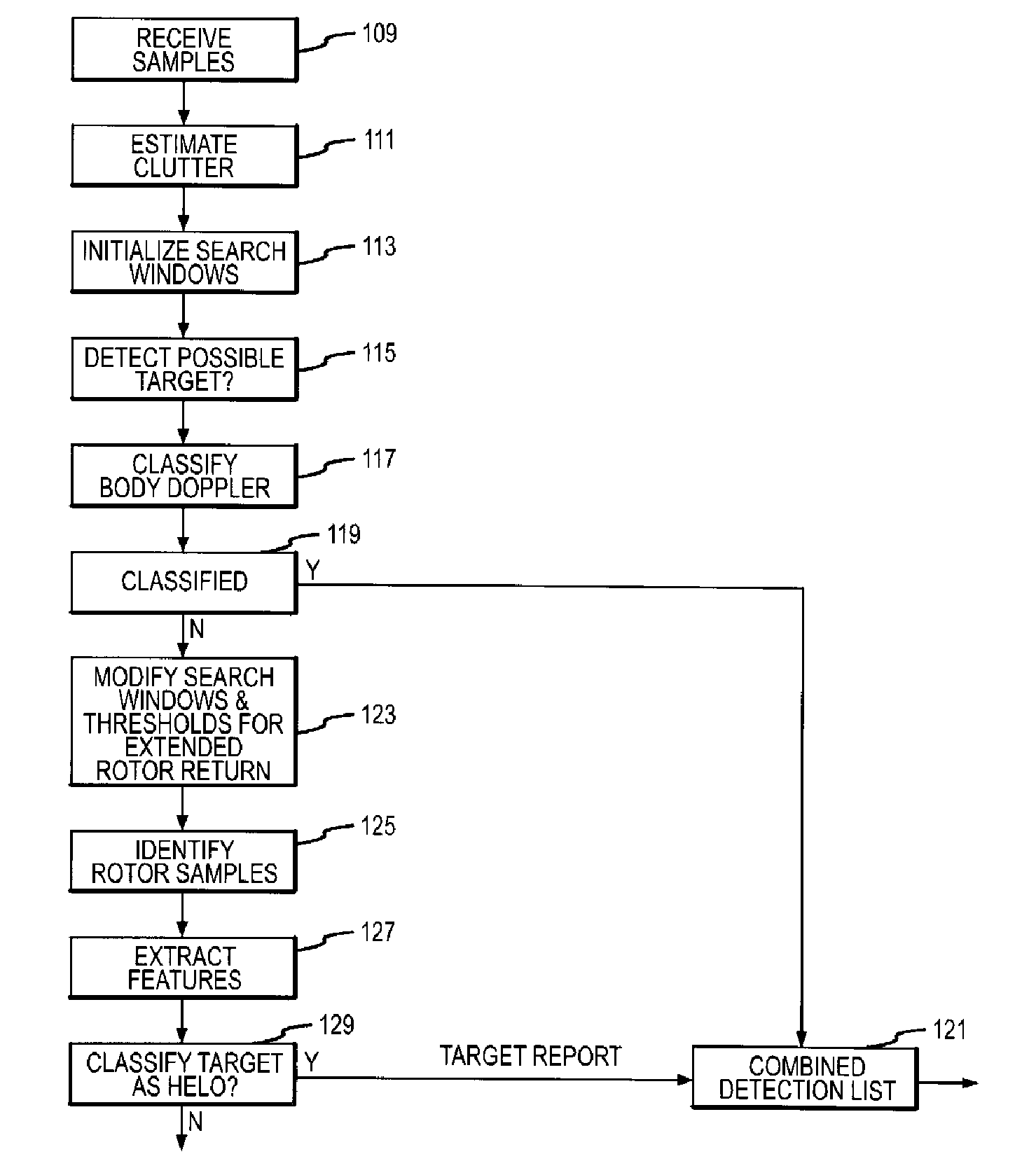
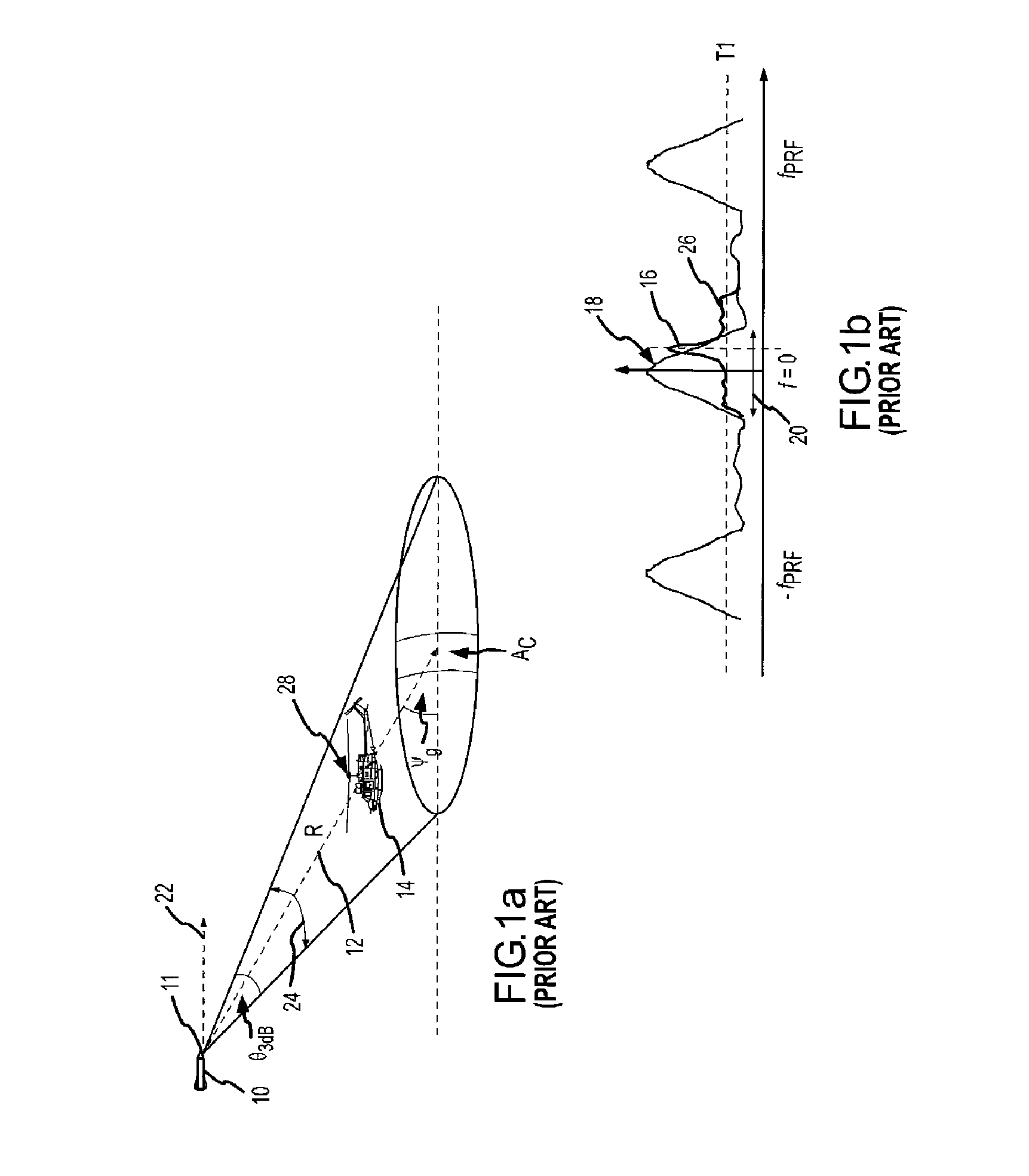
A system and method is presented for detecting and classifying slow-moving and hovering helicopters from a missile's took-down Doppler radar that is compatible with the existing base of Doppler radars. This approach uses definable attributes of a helicopter rotor assembly and its extended Doppler rotor return to differentiate “rotor samples” from other samples (steps 123, 125), extract features such as bandwidth, activity, angle, and shape from the rotor samples (step 127), and classify a potential target as a helicopter or other based on the extracted rotor features and the known attributes of the helicopter rotor assembly (step 129). A target report including a classification target, range, range-rate, and angle of the extended rotor return is suitably passed to a tracking processor (step 121).
Owner:RAYTHEON CO
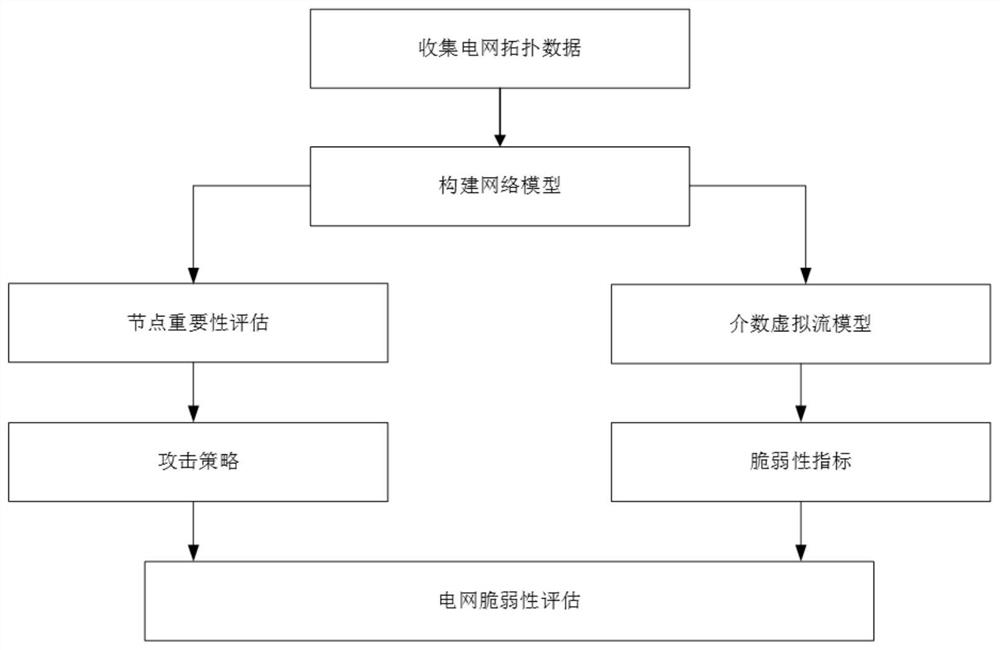
Power network vulnerability evaluation method based on multiple attack strategies
InactiveCN111950153AFacilitate identificationFeatures at the functional levelDesign optimisation/simulationResourcesElectric power systemAttack
The invention discloses a power system vulnerability evaluation method based on multiple attack strategies. The method comprises the following steps: 1) constructing a power grid model; 2) evaluatingthe importance of nodes in the network from four aspects of node degree, betweenness, local centrality and node fault loss, and completing the formulation of an attack strategy according to the importance of the network nodes; 3) establishing a betweenness virtual flow model to simulate a cascade fault propagation process in a power system; and 4) establishing a vulnerability index based on the betweenness virtual flow model, simulating a network attack by adopting a plurality of attack strategies, and evaluating the vulnerability of the IEEE300 power system network according to the change ofthe vulnerability index. Aiming at the vulnerability of the power network under the condition of various attack strategies, the betweenness virtual flow model and the various attack strategies are established to analyze the performance change of the power grid under the cascade failure. The importance of nodes in a power network can be identified, and decision support is provided for maintenance work of power system managers and power system fault prevention of designers.
Owner:XUZHOU NORMAL UNIVERSITY
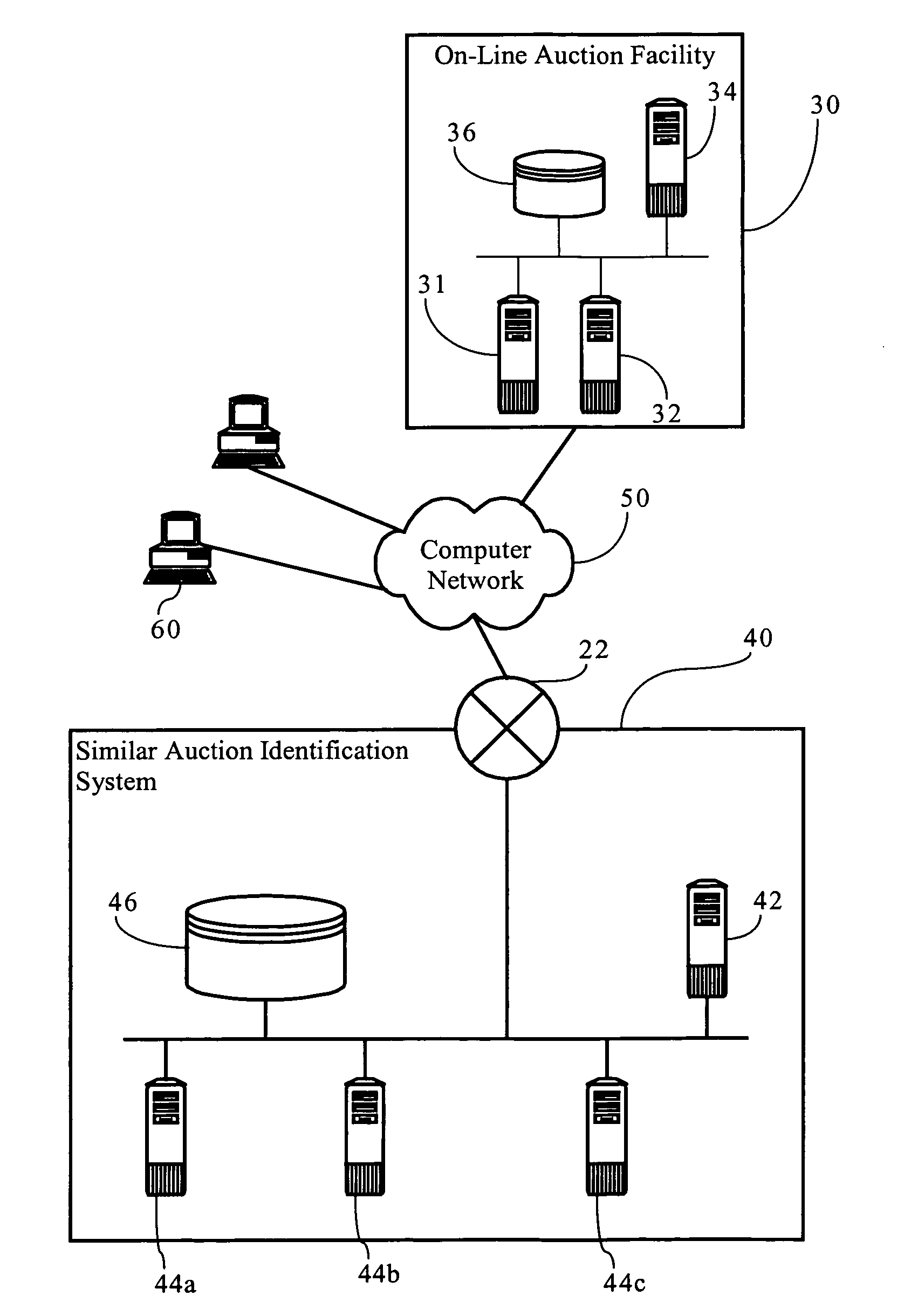
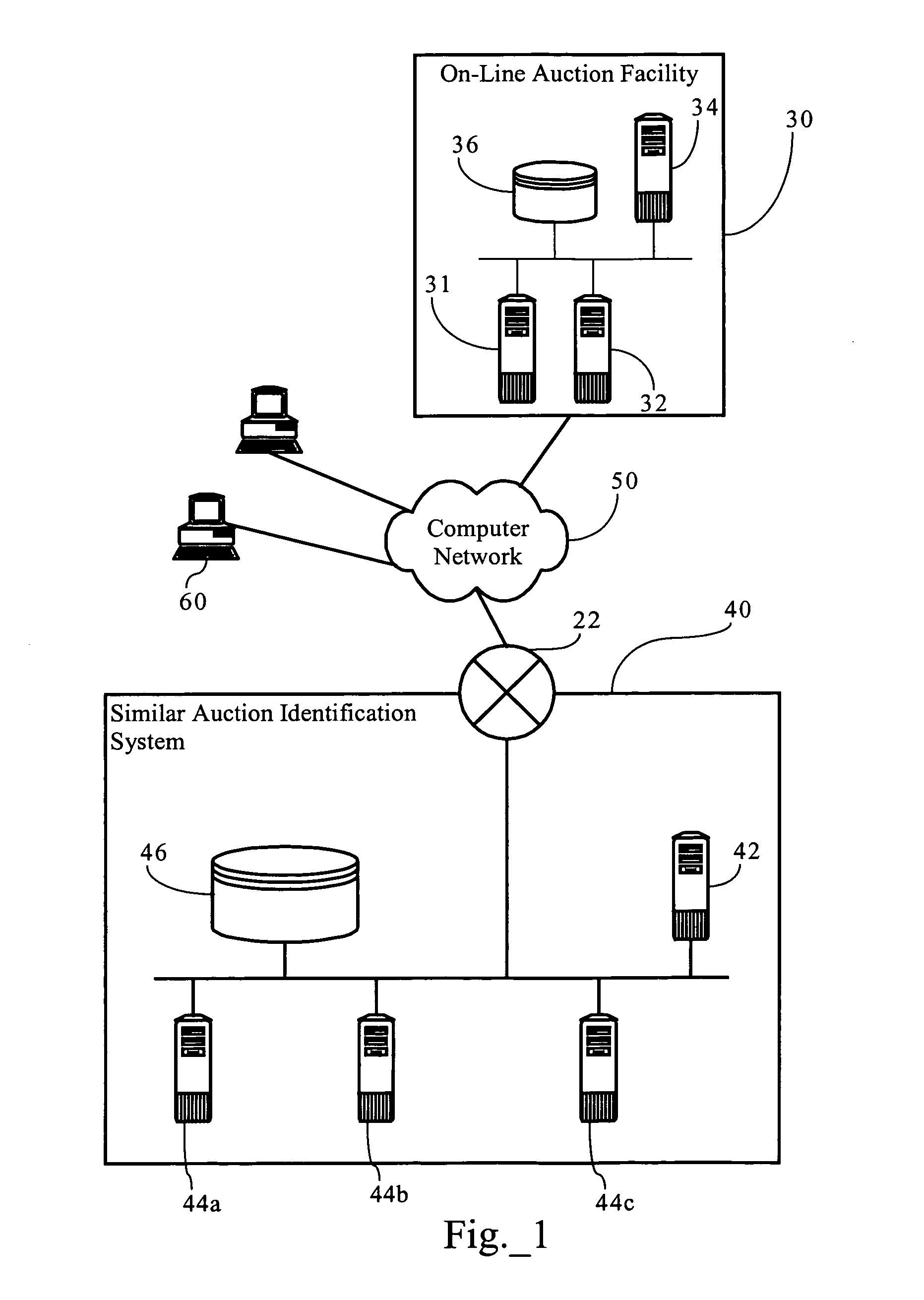
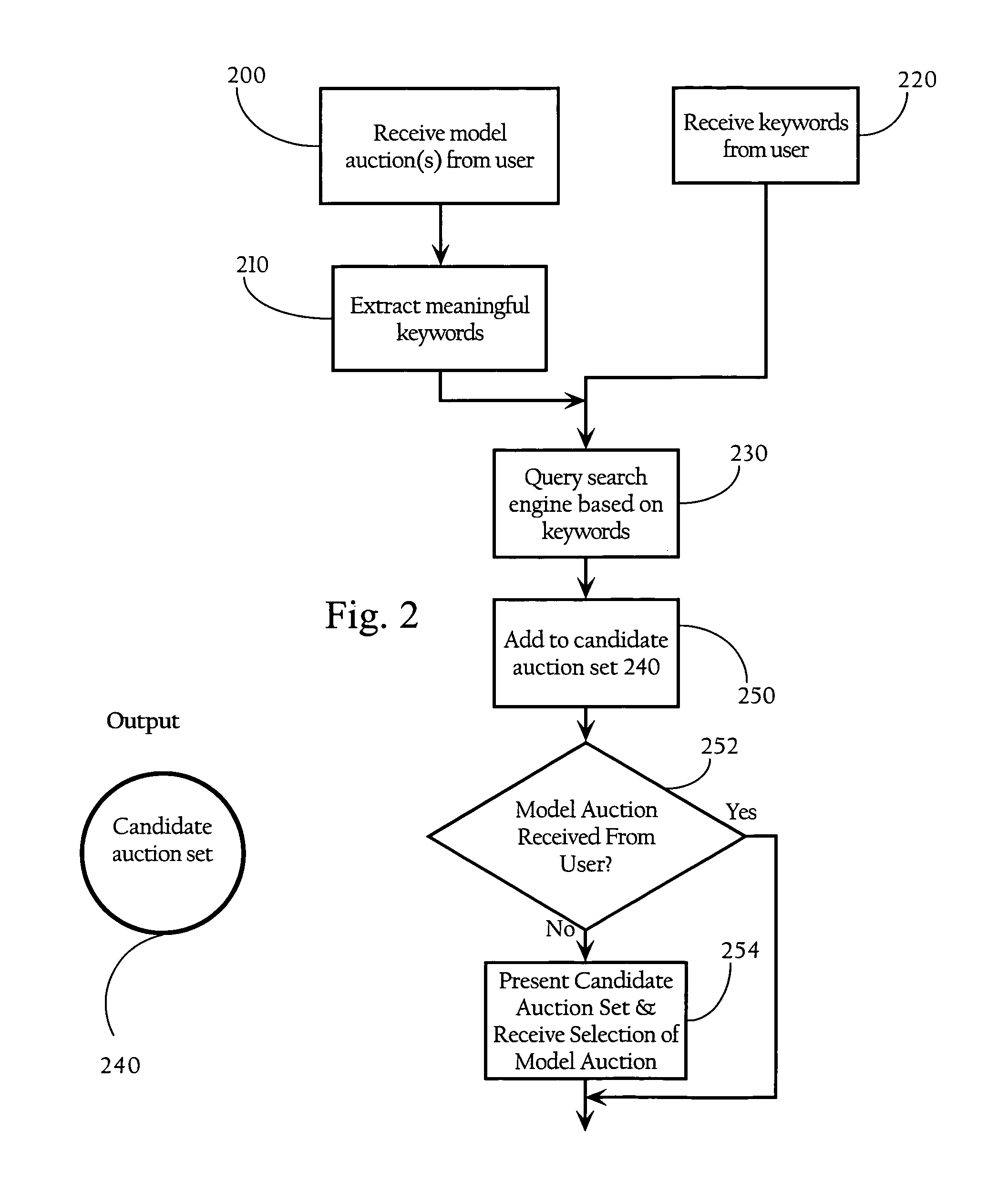
Method, medium, and apparatus for identifying similar auctions
InactiveUS7493273B1Facilitate identificationEfficient analysisAcutation objectsCommerceResult setOptimization system
Methods, apparatuses and systems directed to the identification of a set of auctions which are similar, or relevant, to a contemplated or model auction. In one embodiment, the similar auction identification system uses a model auction, including keywords and other information contained in a data structure that characterize attributes of the auction, as input data to identify a set of auctions that are similar or analytically relevant to the model auction. In one implementation, the resulting set of identified auctions allows a user to efficiently analyze the auctions in assessing the starting parameters of a contemplated auction, or for assessing the latest bid price in a currently pending auction. In one implementation, the set of identified auctions can be used as an input to an auction optimization system that, for example, computes a set of suggested auction parameters for a contemplated auction, and / or computes one or more predicted behavioral attributes for a contemplated auction.
Owner:EARTHTRAX
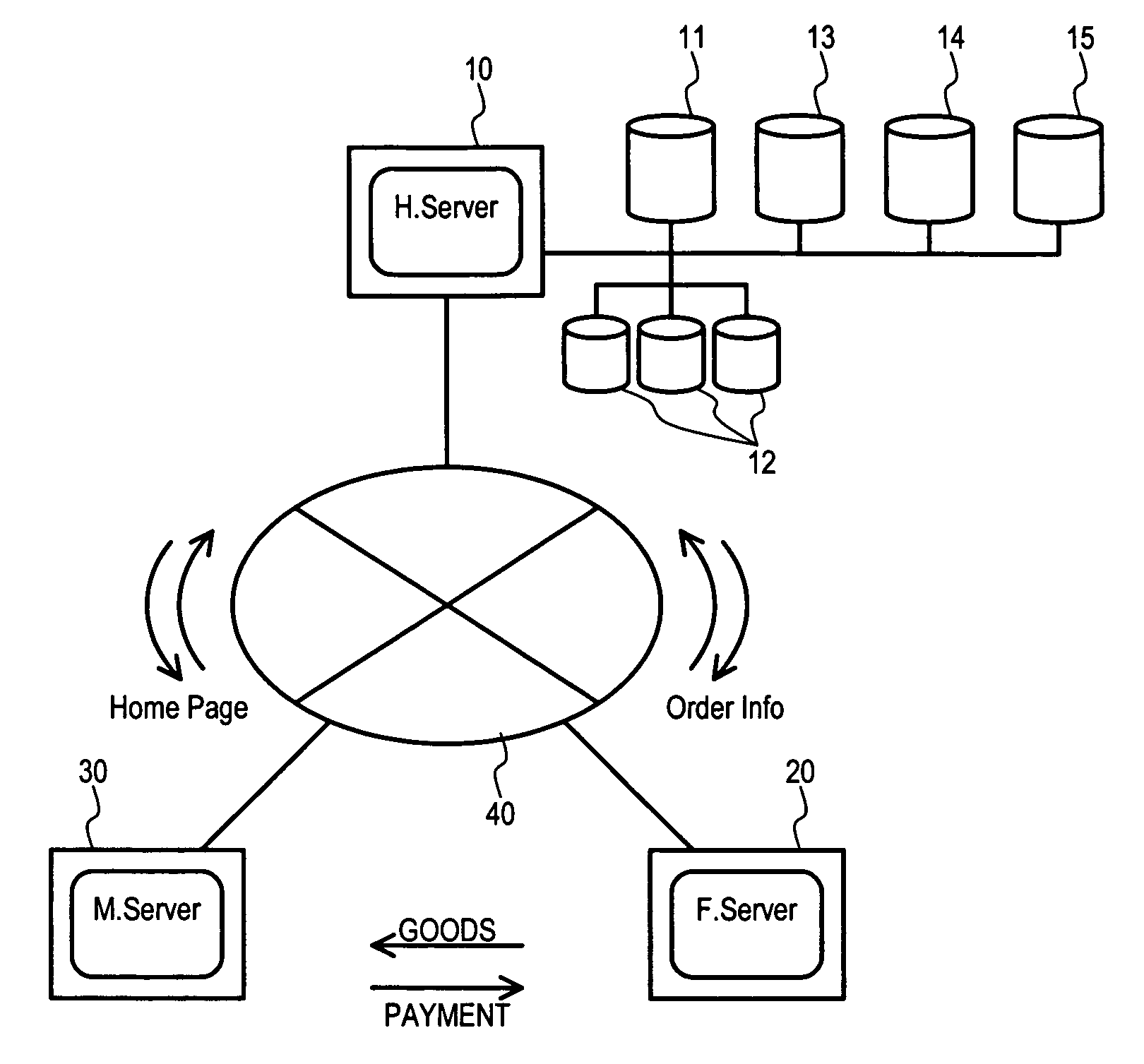
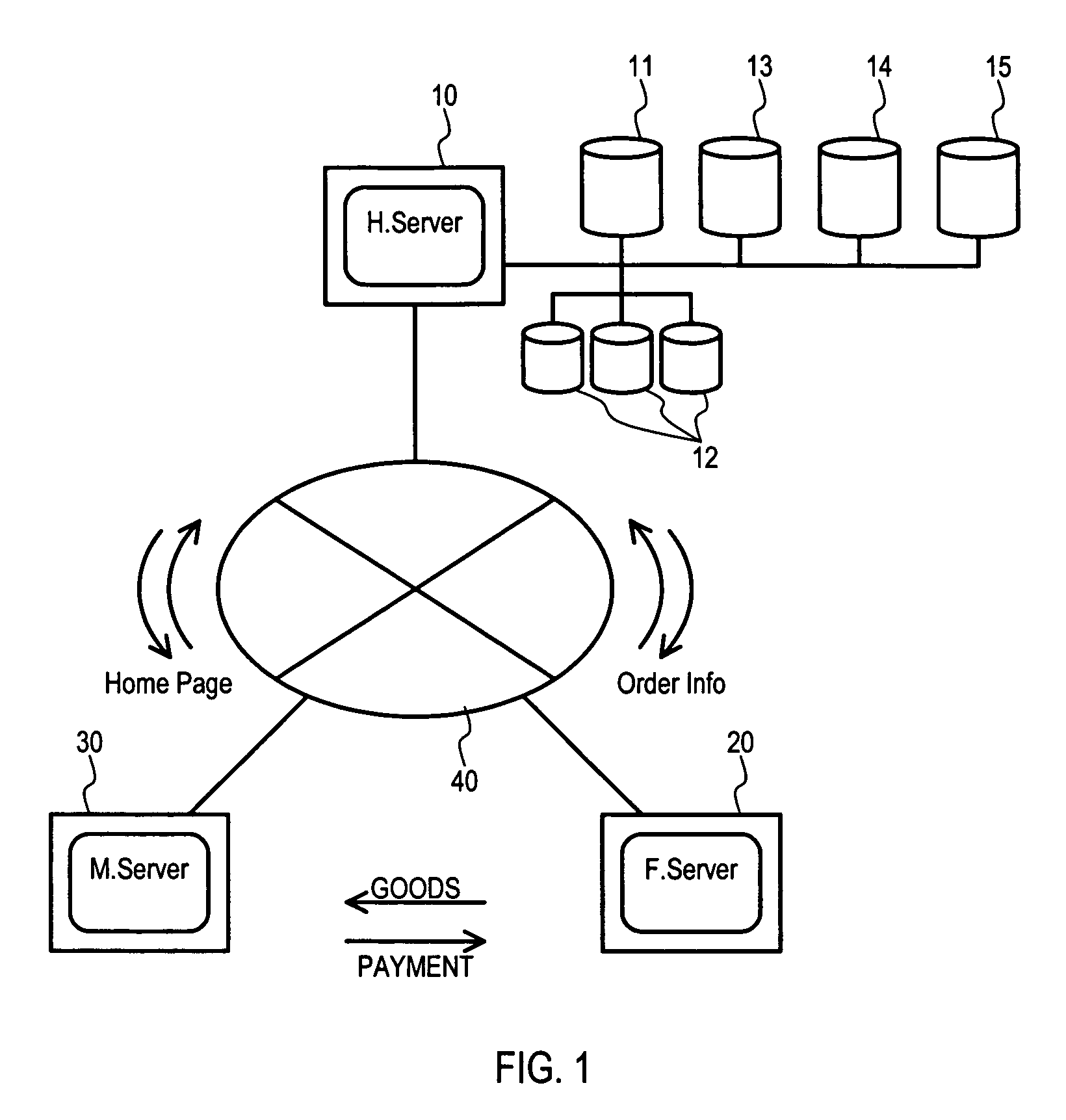
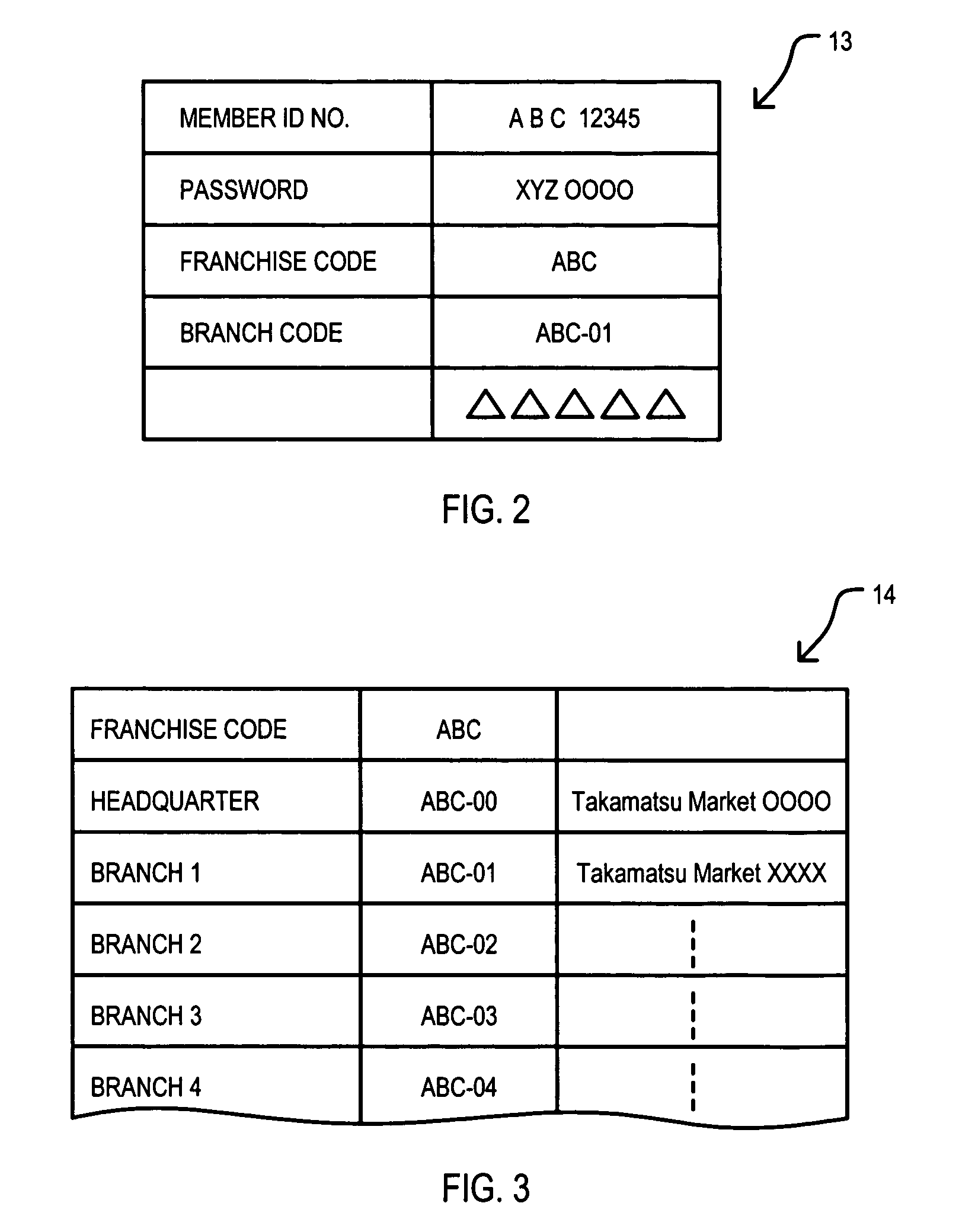
Network based franchise business system and method
A System (1) provides electronic commerce for franchise stores over the Internet without such franchise stores creating / maintaining / controlling their own home pages and by reducing the transaction cost for goods sold. The System (1) may include a headquarter server (H.Server) (10) that is connected to franchise store servers (F.Server) (20) and member servers (30), used by members collected by franchise stores, via Internet (40). Moreover, the H.Server (10) can store merchandise (goods) information, goods inventory data, inform franchise stores when their members have accessed, and receive orders from Members or non-Members placed through home page corresponding to particular franchise stores.
Owner:YOSHIOKA TETSURO
Method and system for tracking workers at worksites
ActiveUS20190108392A1Facilitate identificationEasy to identifyImage enhancementImage analysisComputer visionPixel based
Owner:CATERPILLAR INC
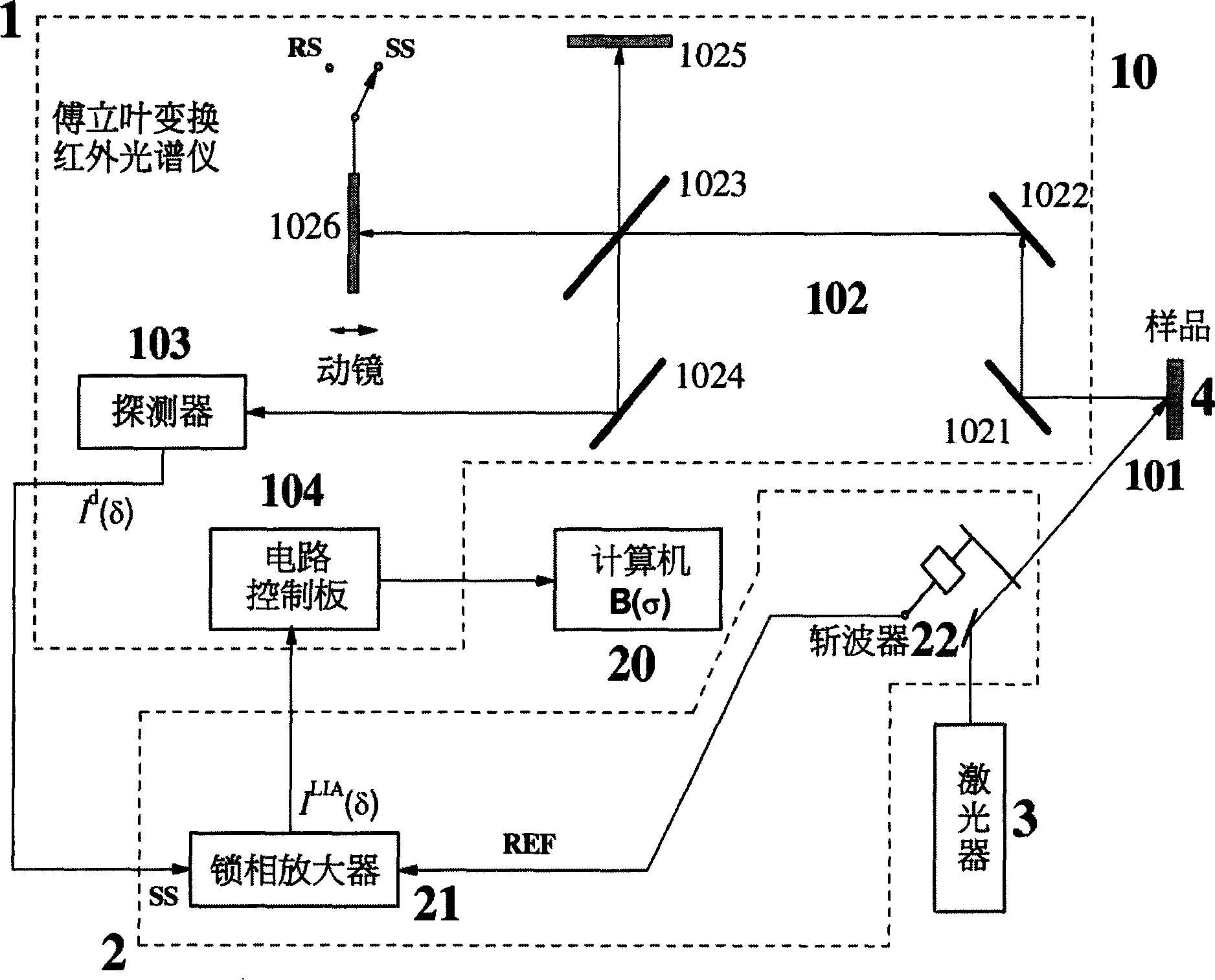
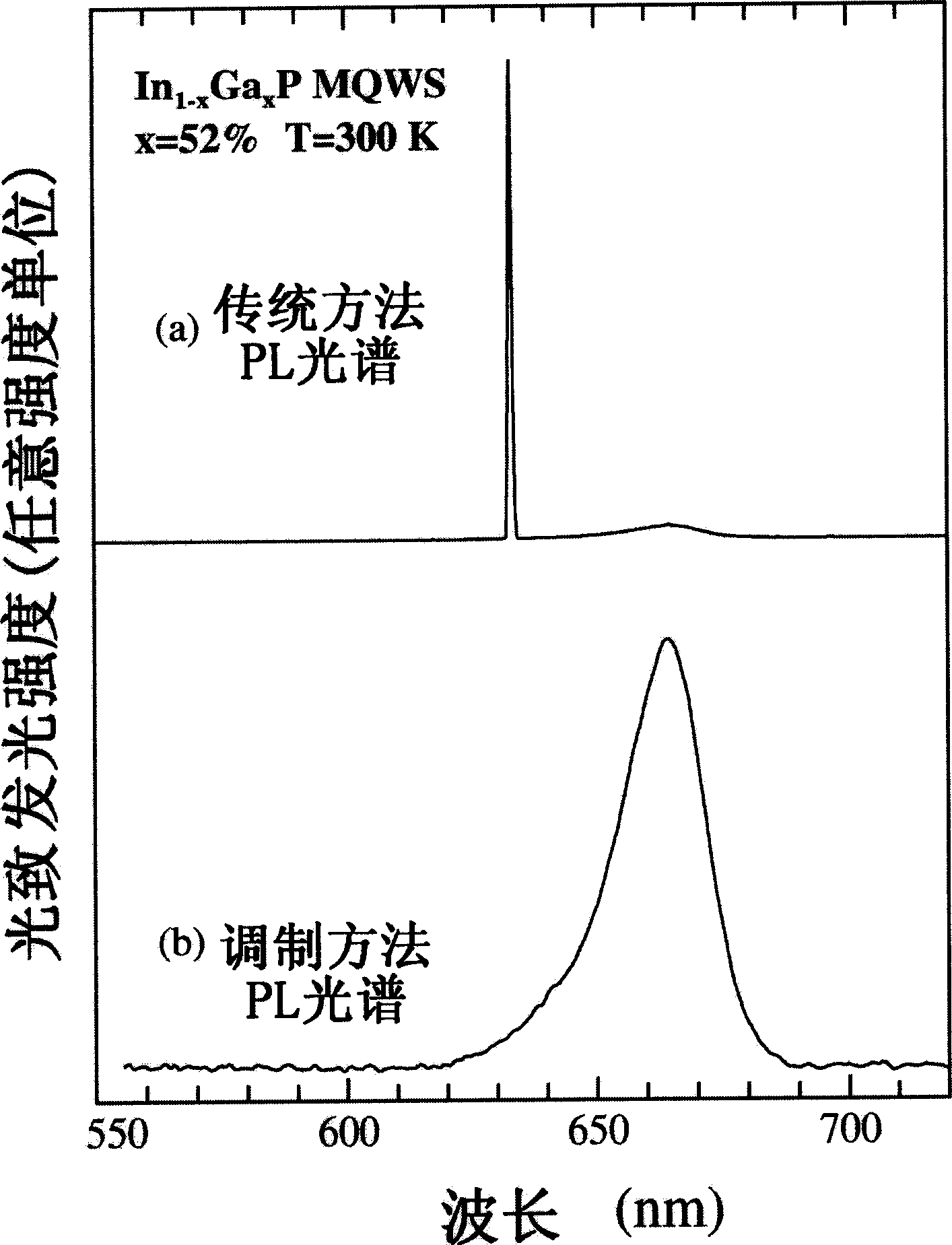
600-700nm band fourier transform infrared photoluminescence spectrum measuring method and apparatus
ActiveCN1804592AEliminate frequencyLoosening of strict restrictionsColor/spectral properties measurementsFluorescence/phosphorescenceSemiconductor materialsPhotoluminescence
The invention discloses a method and apparatus of 600-700nm wave range Fourier transform photo-induced luminous spectrum. The apparatus comprises a Fourier transform infrared spectrograph measuring system, a laser used as active light source, a lock-in amplifier which connects the Fourier transform infrared spectrograph detector and the circuit controlling plate and a circuit-breaker on the light path between the sample and the laser, so that it can transfer the constant active light into the modulated active light and feedback it in the reference end of the lock-in amplifier to control the lock-in.
Owner:SHANGHAI INST OF TECHNICAL PHYSICS - CHINESE ACAD OF SCI
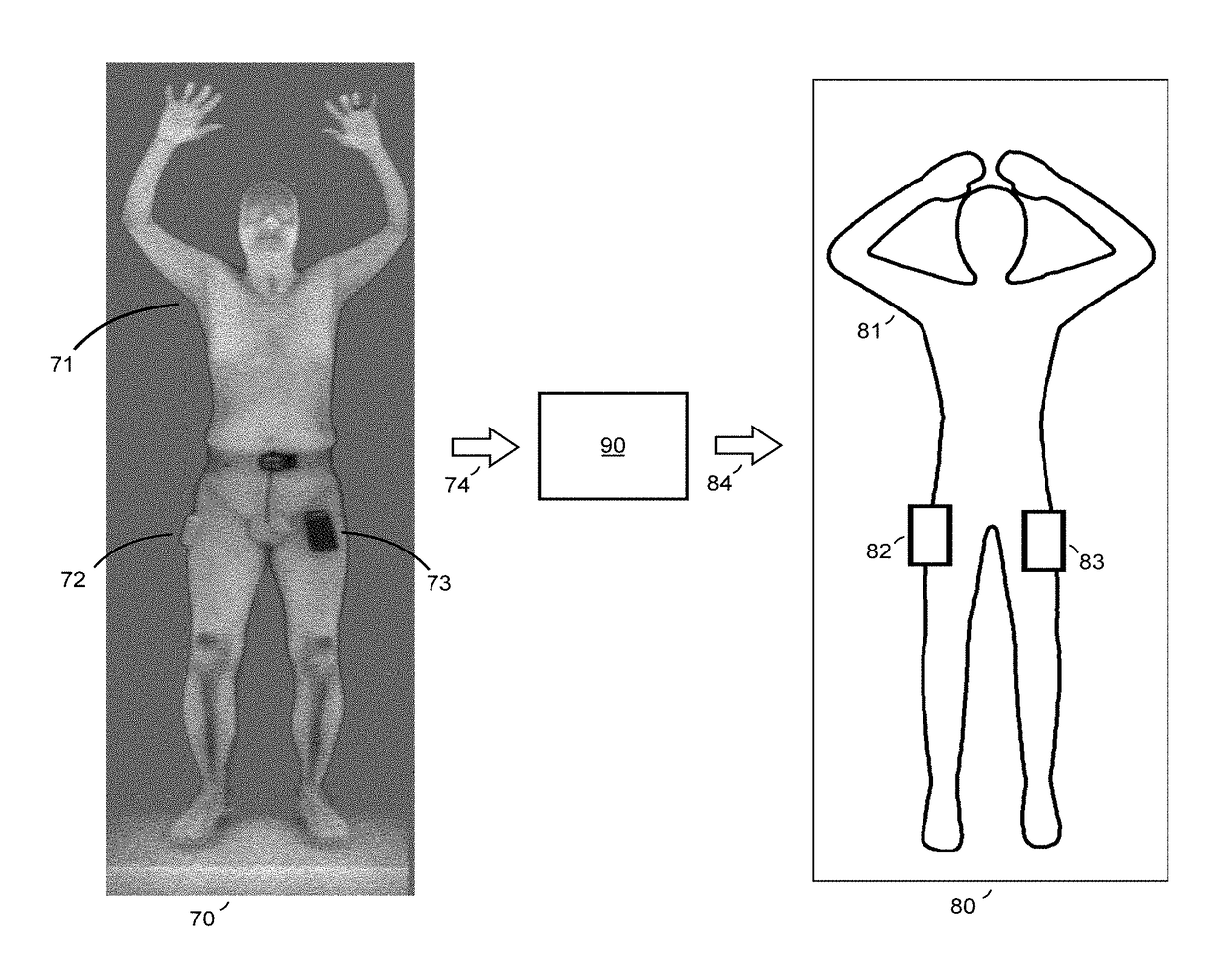
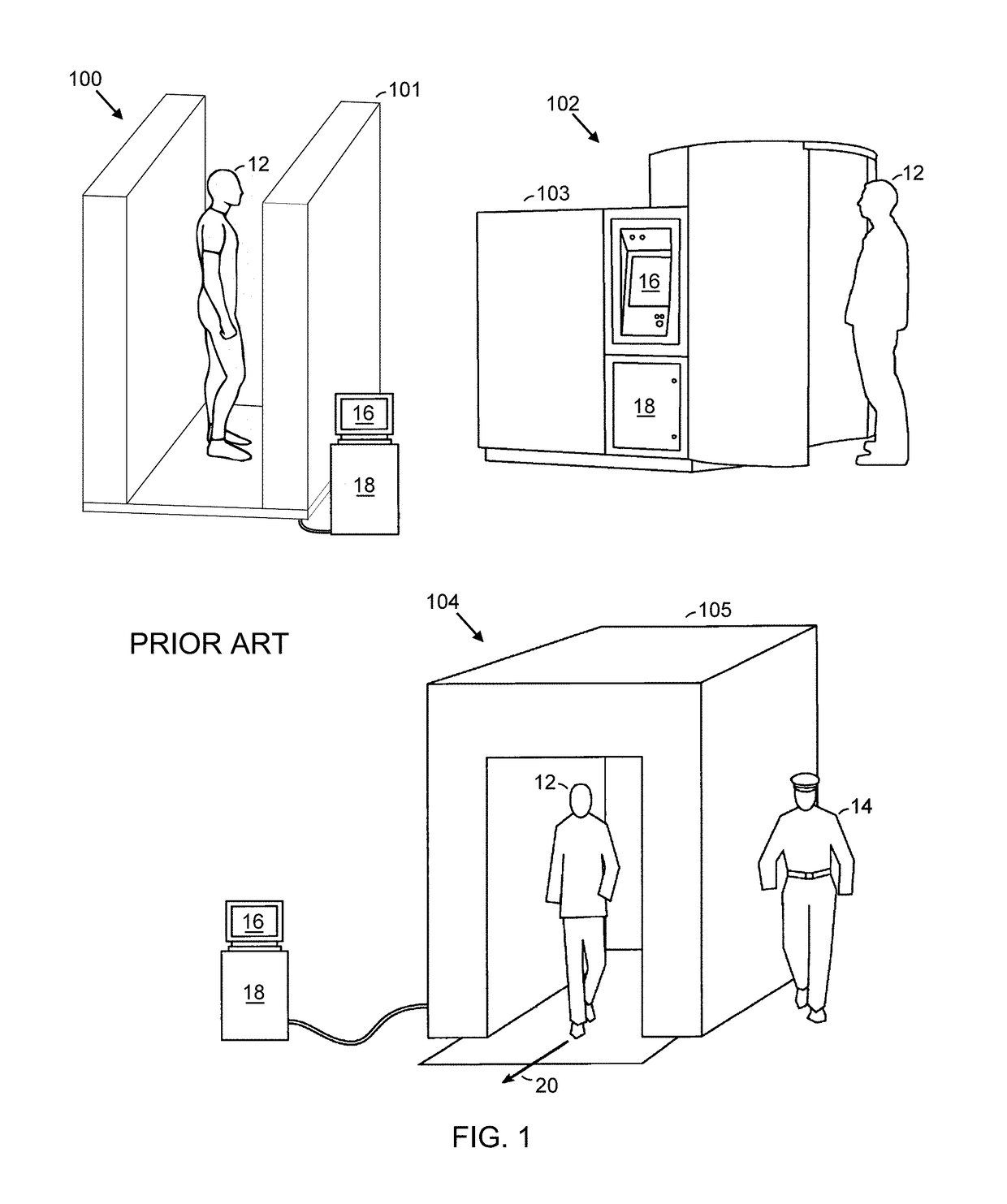
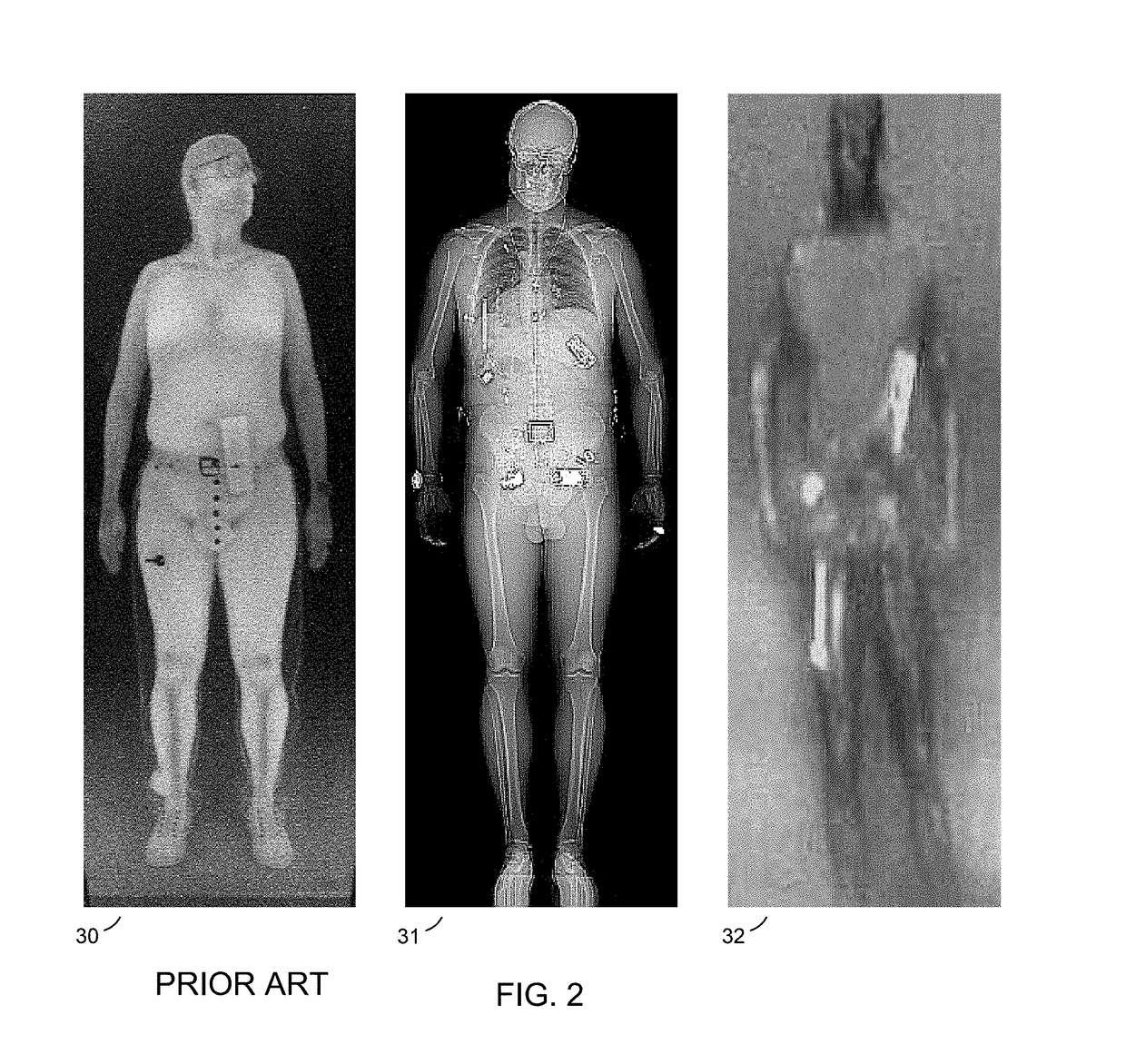
Body Scanner with Automated Target Recognition
ActiveUS20170337447A1Facilitate identificationImprove performanceImage enhancementImage analysisHuman anatomyImaging Feature
This Invention is directed at the automated analysis of body scanner images. Body scanners are used in airports and other secured facilities to detect weapons, explosives, and other security threats hidden under persons' clothing. These devices use x-rays, millimeter waves and other radiant energy to produce an electronic image of the person's body and any concealed objects. Examination of these images by human analysts is slow, expensive, and subject to privacy concerns. The Invention provides automated analysis of body scanner images by recognizing that human anatomy is bilaterally symmetric to a high degree, while concealed objects are asymmetric. Digital techniques are used to separate the scanned image into its symmetric and asymmetric parts, thereby effectively separating anatomic from non-anatomic image features.
Owner:TEK84 INC
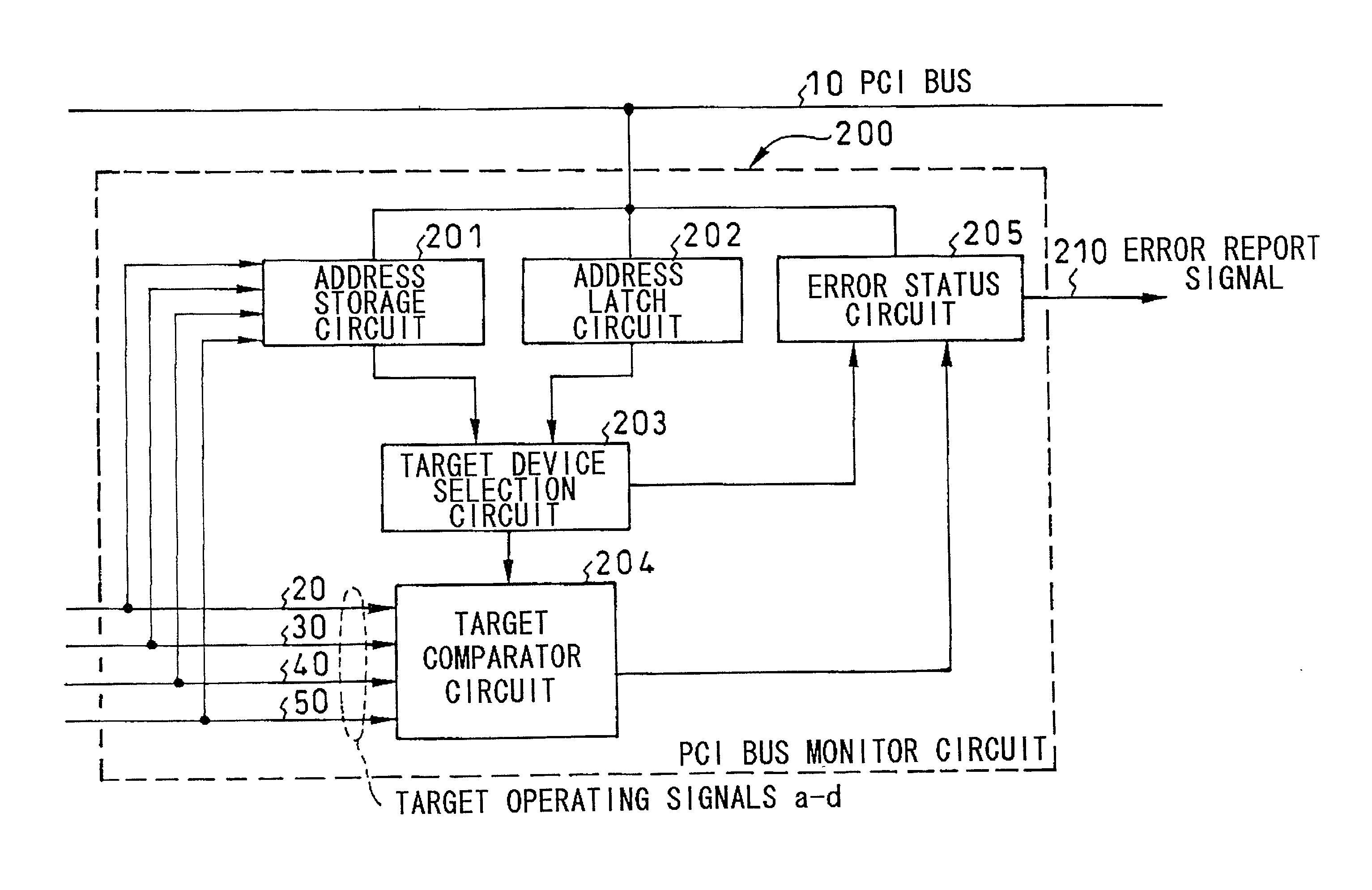
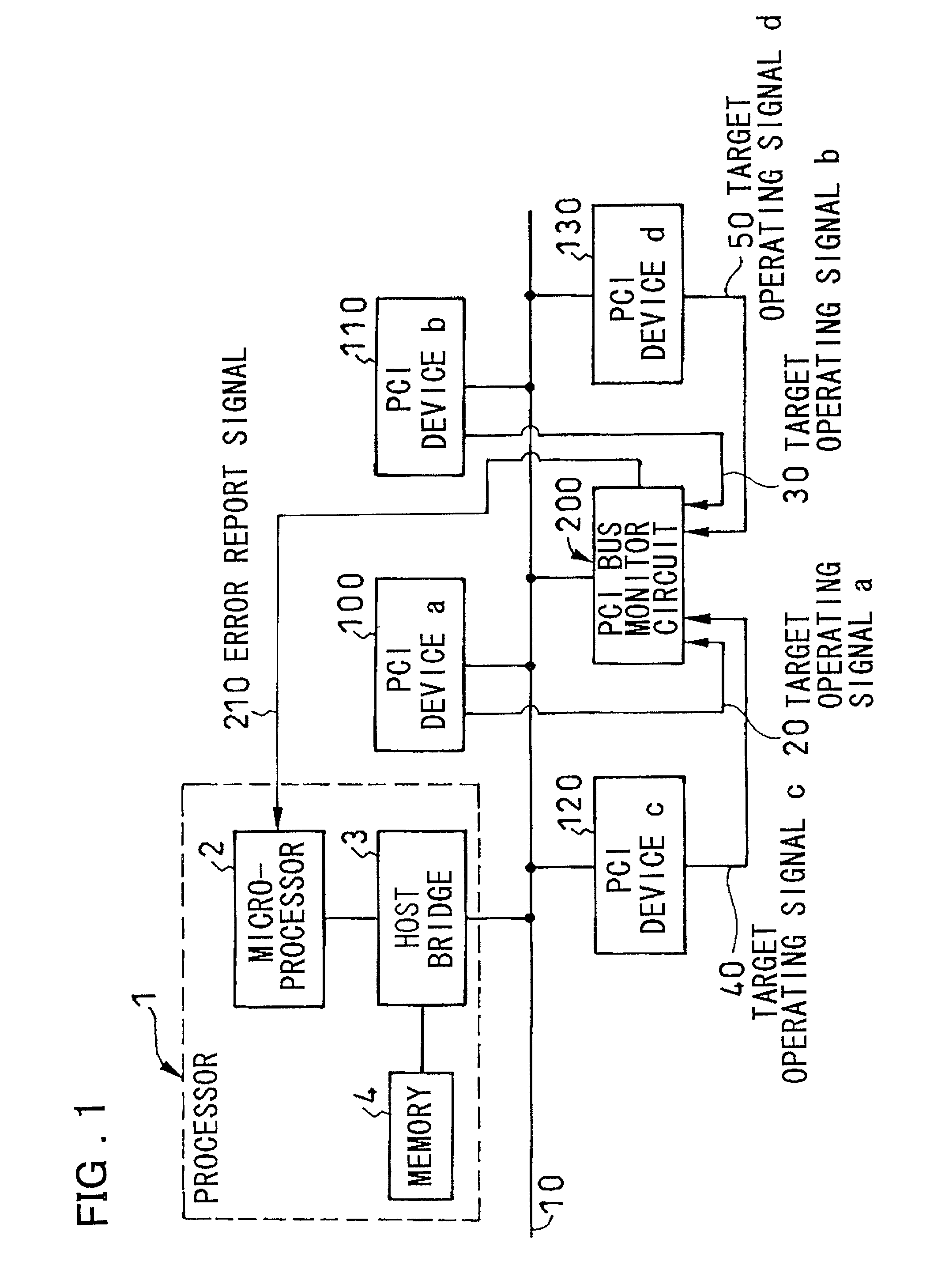
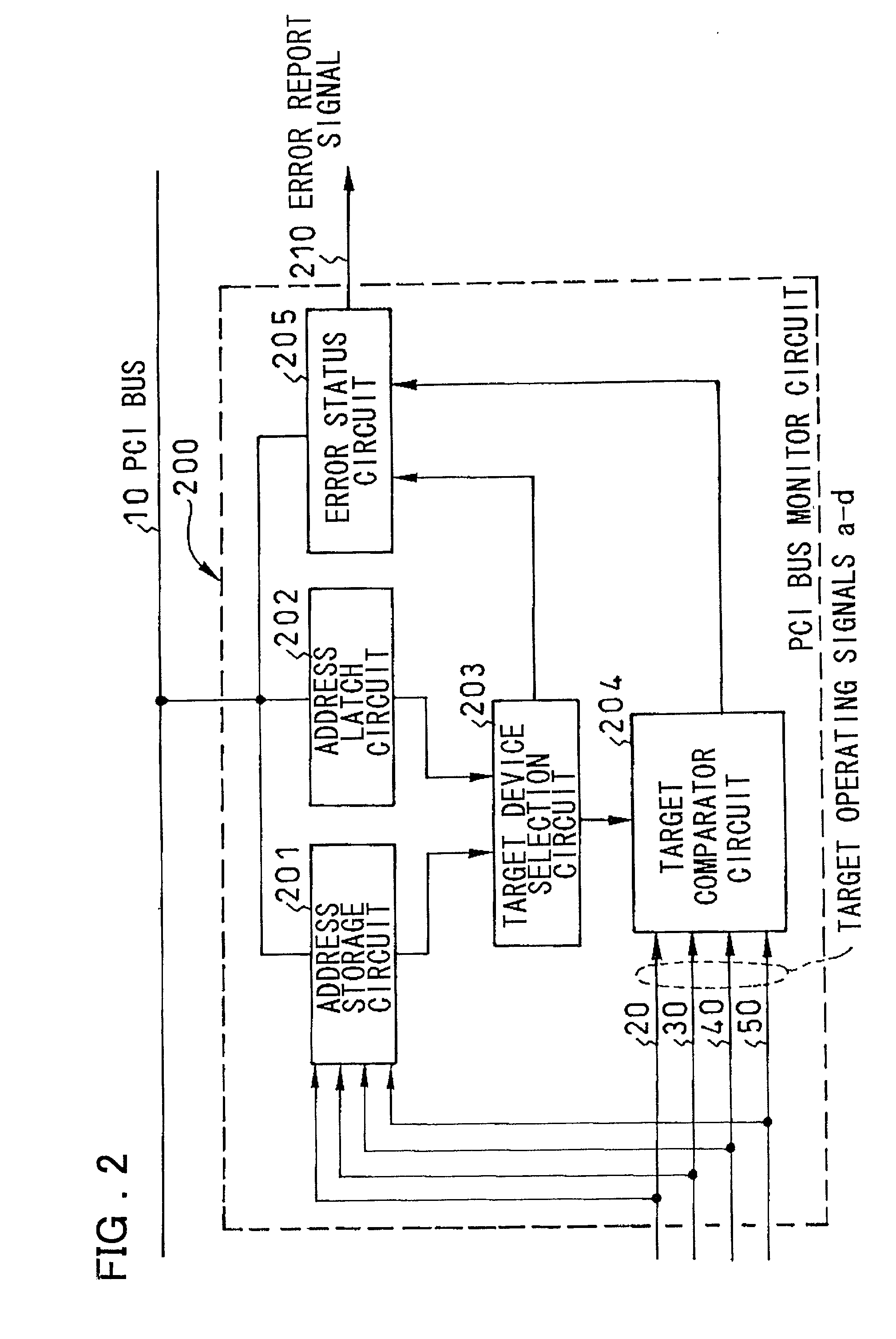
System for facilitated analysis of PCI bus malfuntion
InactiveUS20020124207A1Facilitate identificationFacilitate analysisHardware monitoringNon-redundant fault processingComputer hardwareComputerized system
In a computer system, which makes an error detectable in case plural PCI target devices respond in one PCI cycle and the PCI protocol has become illicit, a processor 1 is connected over a PCI bus 10 to plural PCI devices a 100 to d 130, each of which activates corresponding target operating signal a 20 to d 50 respectively when operating as a PCI target device. The PCI bus monitor circuit 200 monitors the target address of a command executed on the PCI bus 10 and the target operating signals a 20 to d 50 from the plural PCI devices a 100 to d 130. If plural PCI target devices have responded for one PCI cycle, the PCI bus monitor circuit 200 sends an error report signal 210 to the processor unit 1.
Owner:NEC CORP
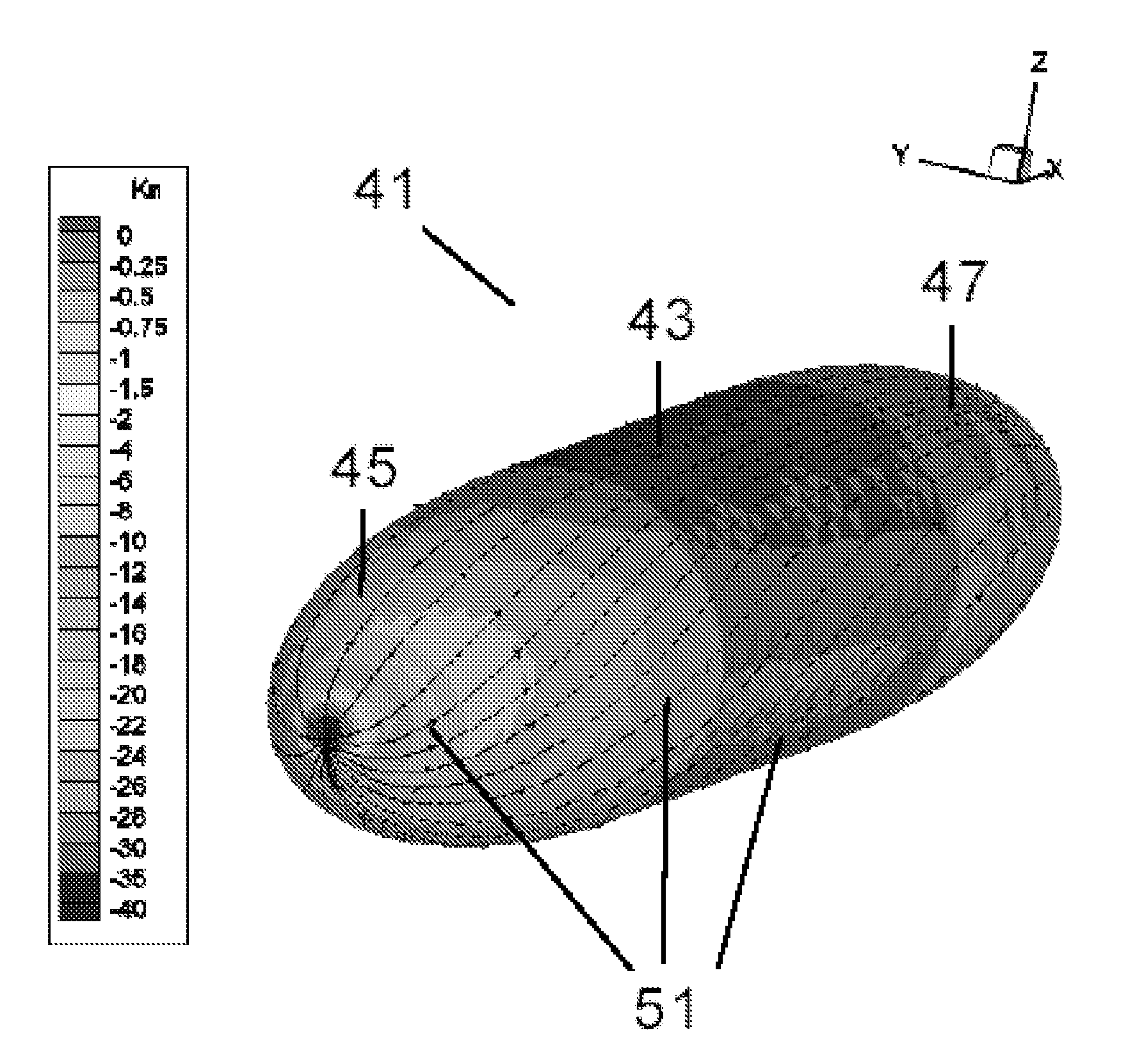
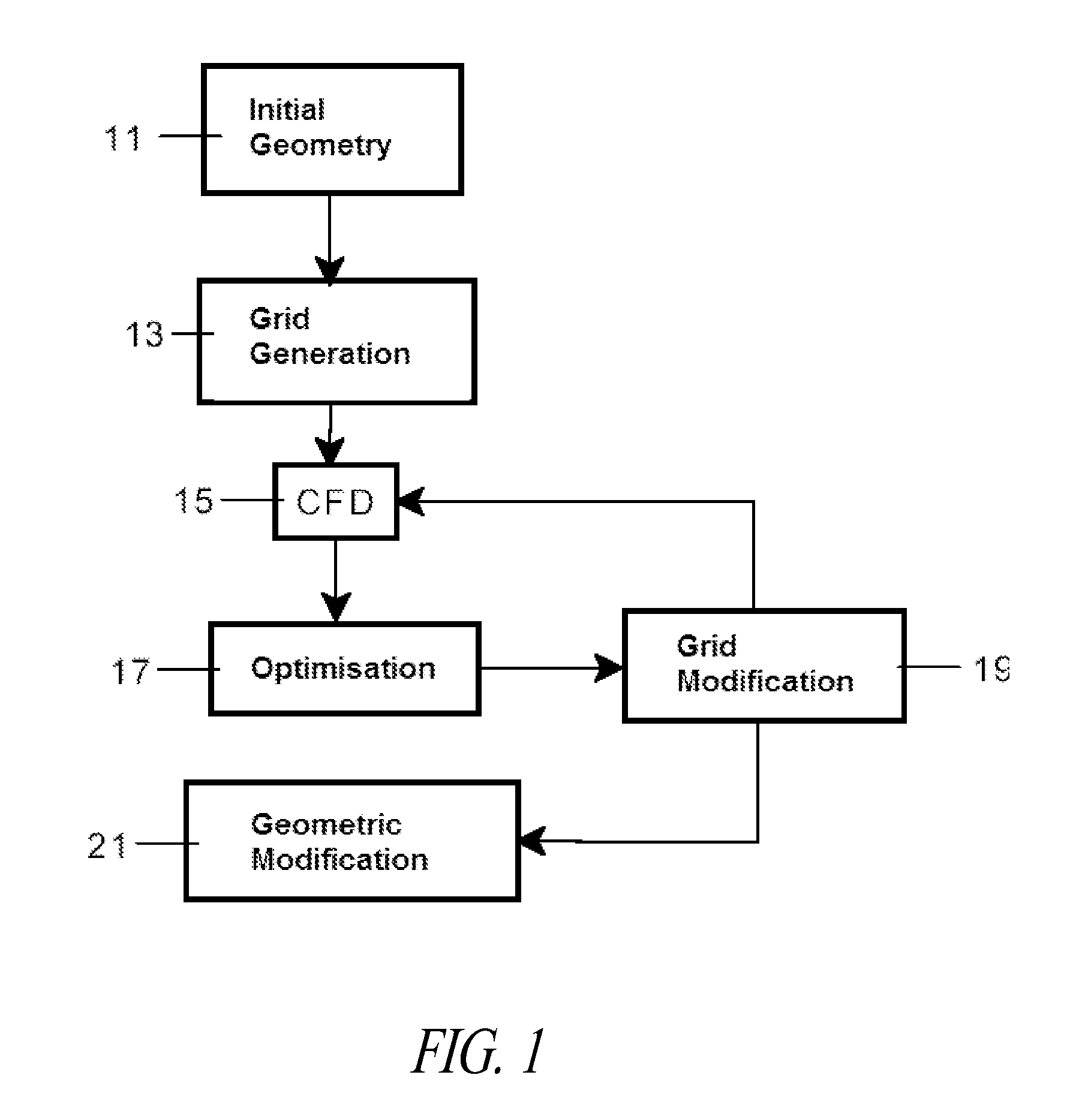
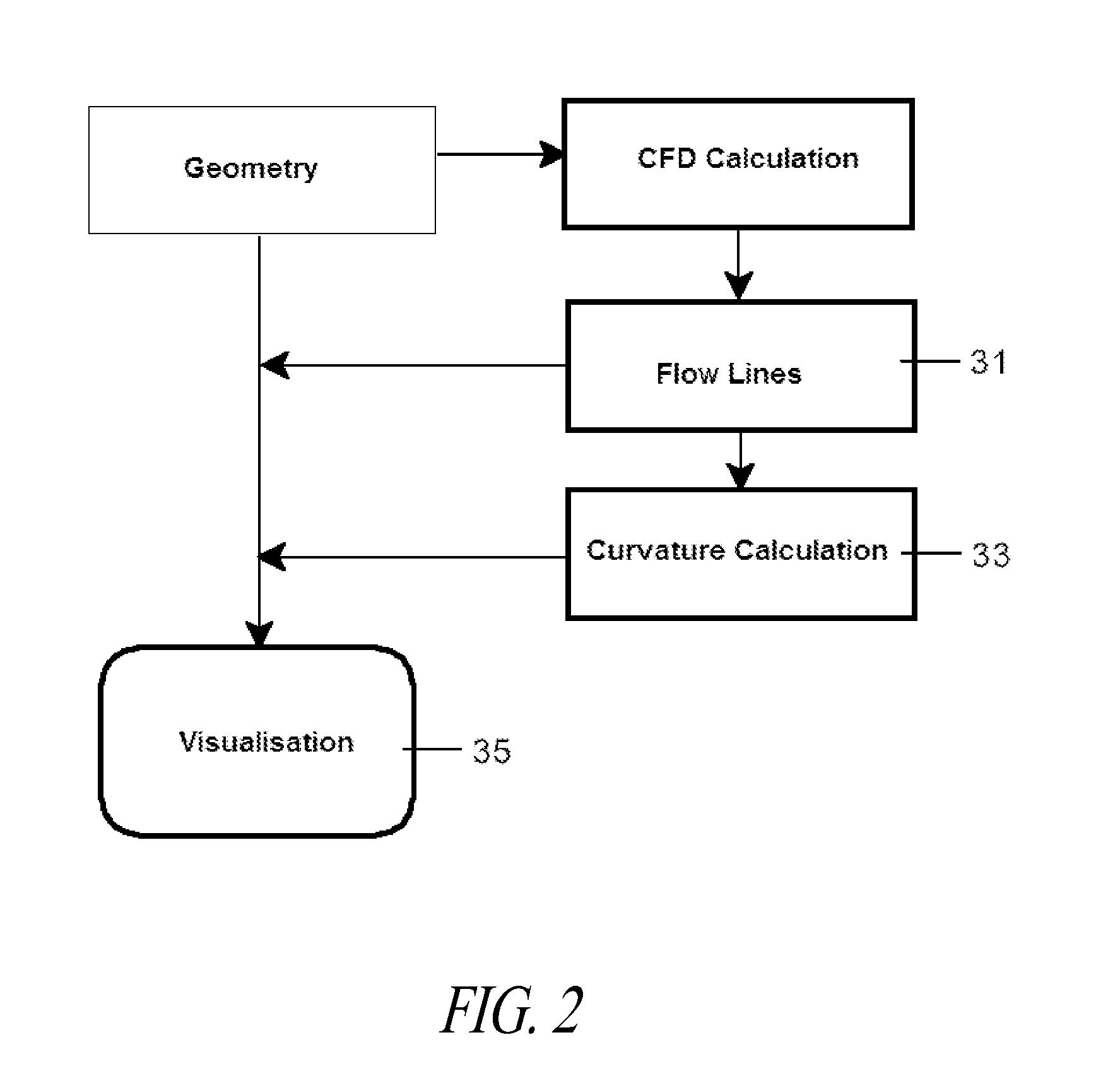
Methods and systems for optimising the design of aerodynamic surfaces
ActiveUS20110161057A1Facilitate identificationOptimise surfaceGeometric CADSustainable transportationImage resolutionAerodynamics
Methods and systems for optimising the design of aerodynamic surfaces. They include in the design process of the aerodynamic surface of a body (41) which moves through a flow field, the following steps: a) preparation of a CFD simulation of said body (41); b) resolution of the CFD calculation for specific conditions of the flow field and for obtaining the flow lines (51) of the flow on said surface; c) calculation of at least one geometrical variable of the surface such as the normal curvature, according to the direction of said flow lines (51) and additionally at least one relevant variable of the aerodynamic flow, such as the pressure gradient; d) simultaneous visualisation of the surface of said body (41) and of at least one geometric variable and, additionally, said at least one variable of the aerodynamic flow.
Owner:AIRBUS OPERATIONS SL
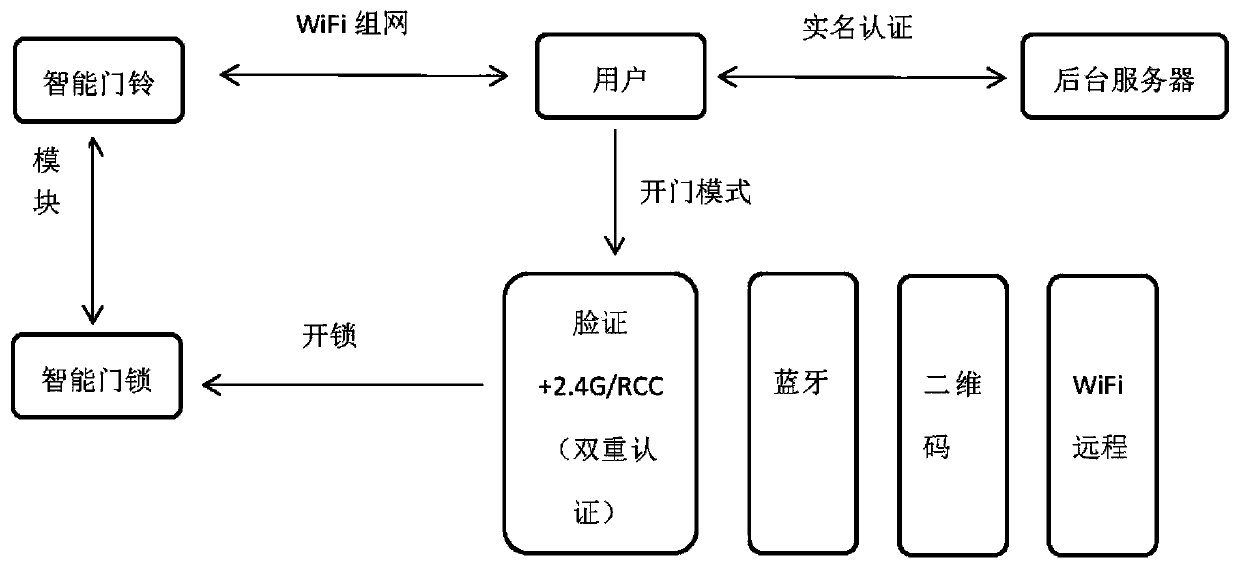
WIFI intelligent doorbell unlocking system and method based on face recognition
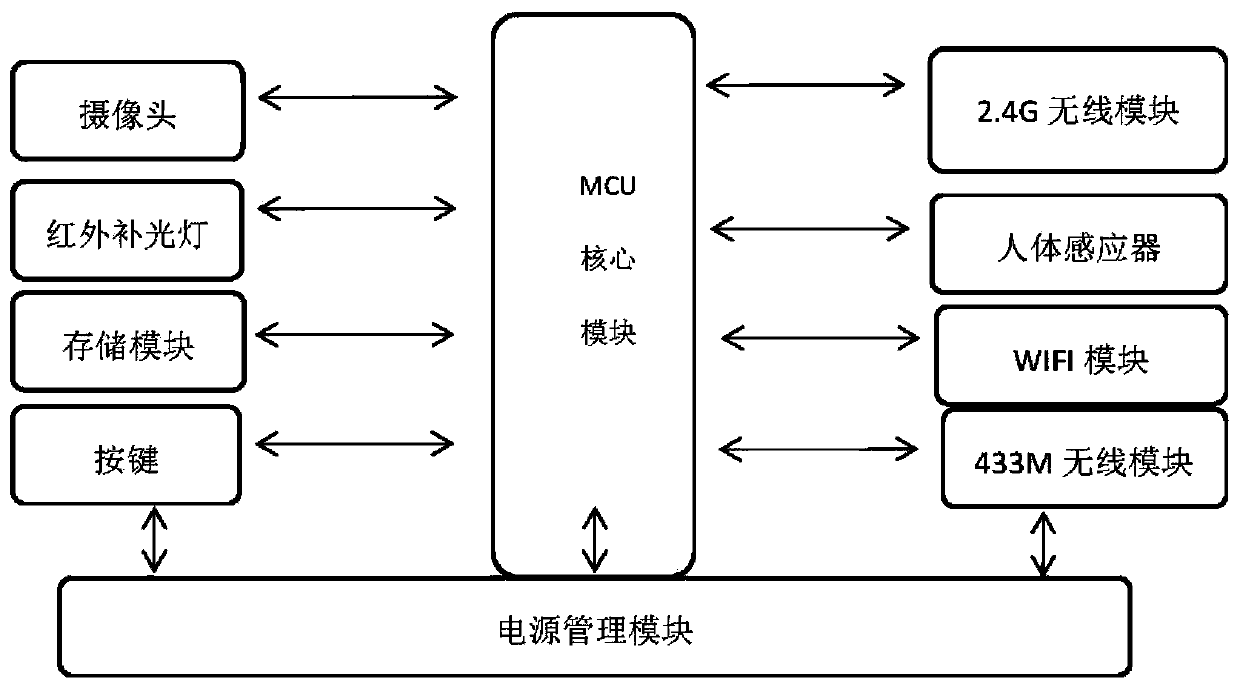
PendingCN110009792ATo meet the various needs of different applicable occasionsMeet the needs of frequent accessIndividual entry/exit registersDoorbellData interchange
The invention discloses a WIFI intelligent doorbell unlocking system based on face recognition. The WIFI intelligent doorbell unlocking system includes an intelligent doorbell, an intelligent door lock, and a backstage administration module. The intelligent doorbell includes an MCU core module, a 2.4 G wireless module, a 433 M wireless module, a WiFi module, and a power source management module. The intelligent doorbell is connected with the intelligent door lock in a wireless communication mode through the 433 M wireless module. The backstage administration module is connected with the MCU core module of the intelligent doorbell through the WiFimodule. The 2.4 G wireless module is used for data exchanging communication between the intelligent doorbell and mobile phone APPs of users. The MCU core module is used for intelligent control overall the parts. The power source management module provides working power sources for all the parts. The WIFI intelligent doorbell unlocking system aims at the broad prospects of intelligent home application, real name authentication is applied to intelligent home, and safety is also improved while convenience is brought to the users The WIFI intelligent doorbell unlocking system has the advantages of convenient and quick use, real name authentication, safety and reliability.
Owner:广州国联智慧信息技术有限公司
Product identification system for persons with limited vision
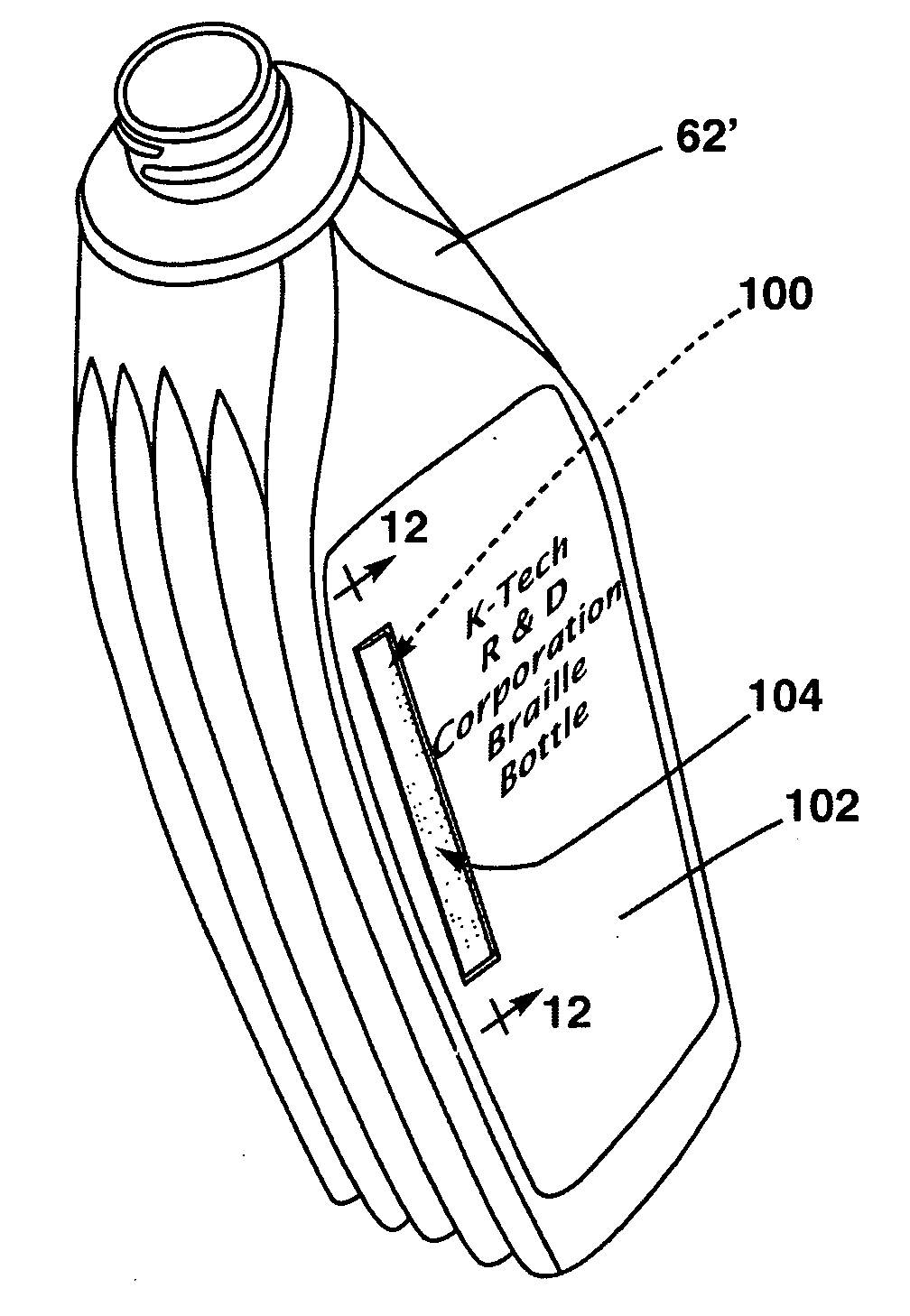
InactiveUS20100200449A1Facilitate identificationReadily determineStampsMachine supportsEngineeringProduct identification
A method of facilitating the identification of portable consumer articles at a point of purchase display, the method including the steps of: providing a plurality of portable consumer articles each with tactilely sensible information thereon that identifies at least one of: a) a general nature of the article and / or its contents; and b) a provider of the article; and displaying the plurality of articles at the point of purchase display in a manner that allows potential consumers to lift and handle each of the plurality of articles so as to thereby readily determine through tactile sensing of the information at least one of: a) the general nature of the handled article and / or its contents; and b) the provider of the handled article.
Owner:KASBOSKE GEORGE
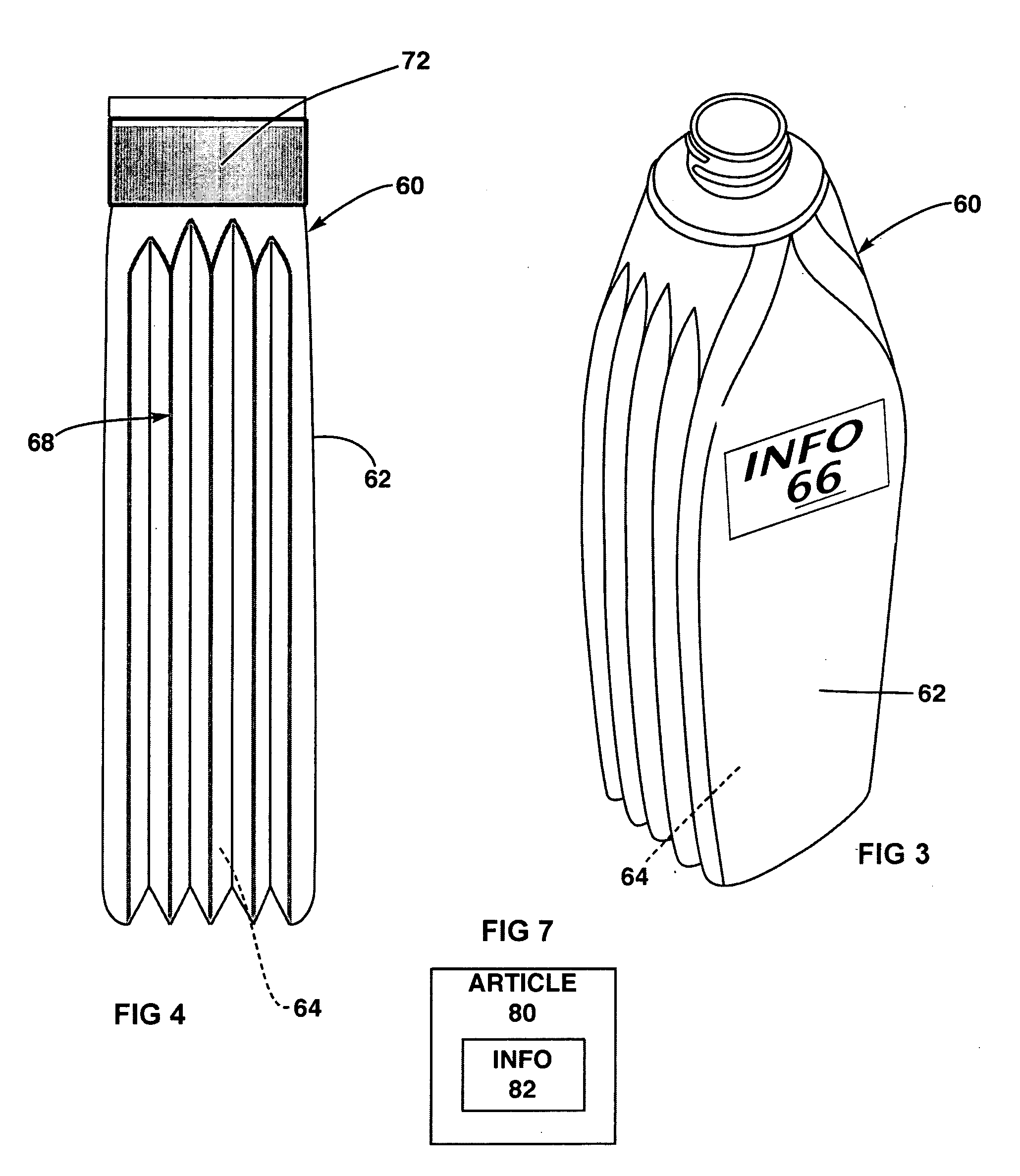
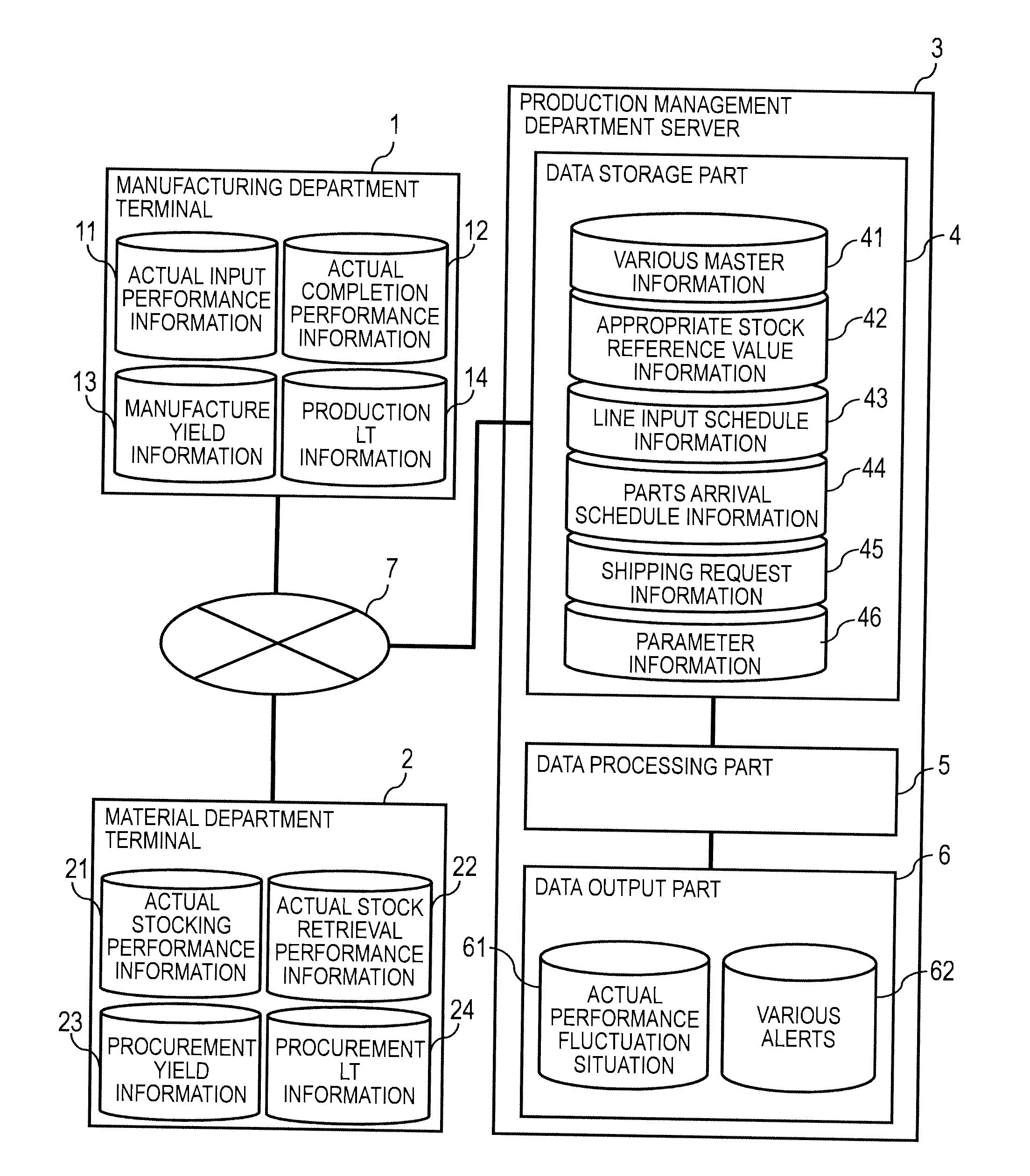
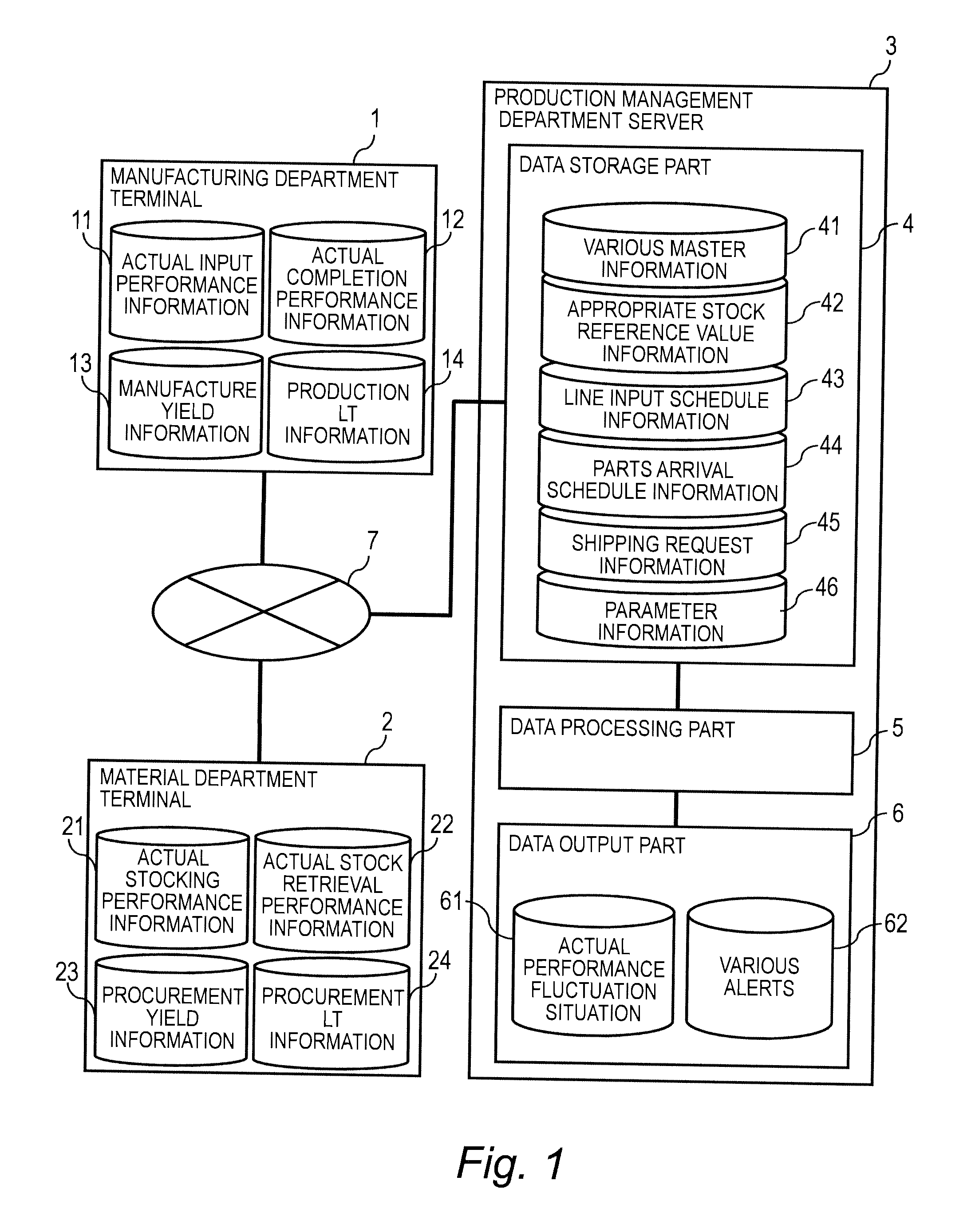
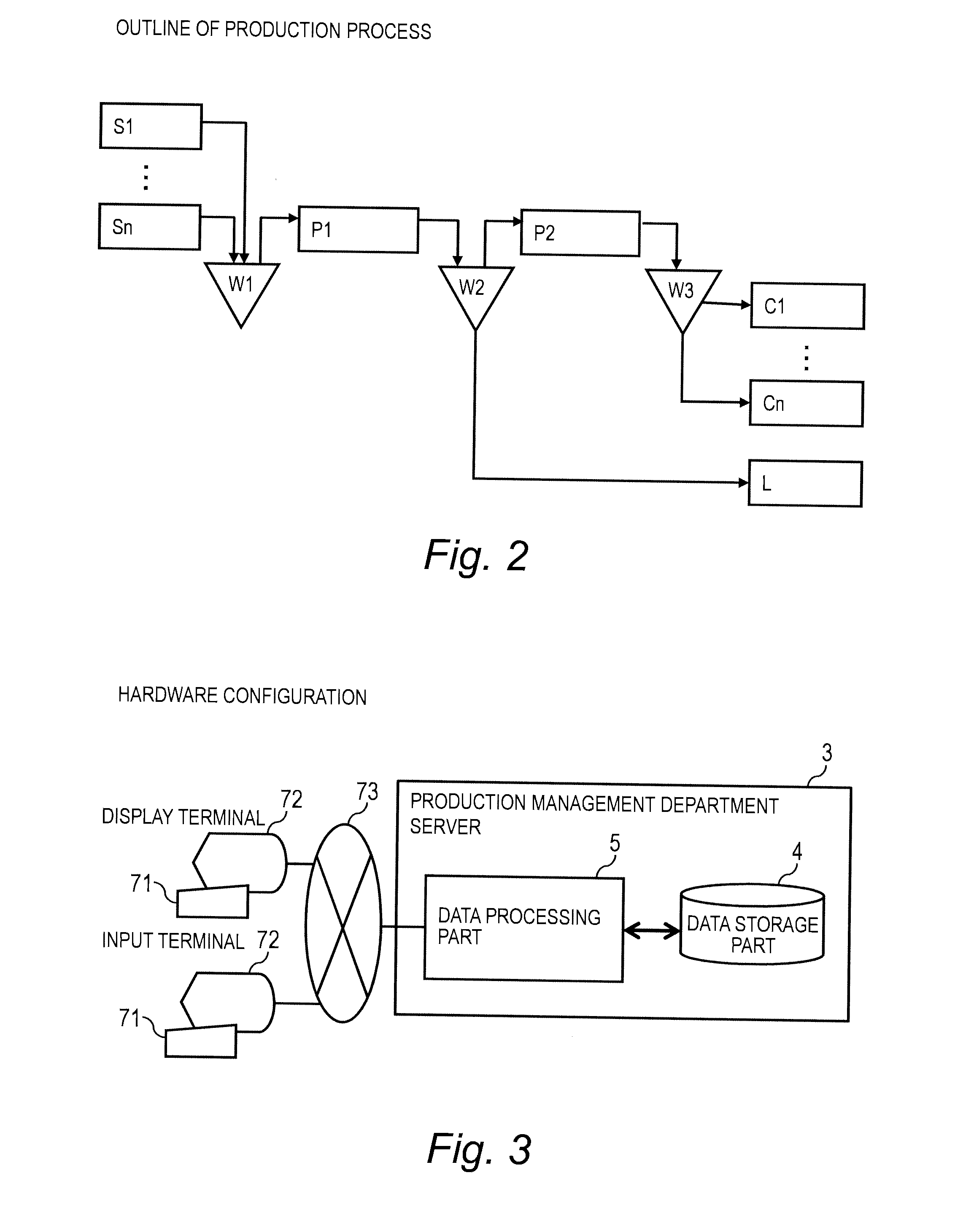
Production management system and management method
InactiveUS20140297374A1Facilitate identificationEasy to identifyResourcesComputer scienceComputer terminal
A production management system for managing at least one process for producing a product, has a terminal and a management computer. The management computer obtains actual performance information from the terminal, and calculates a discrepancy of the actual performance value of the process from the reference value. In a case where the calculated discrepancy is outside a threshold, the management computer displays an alert display screen. In a case where one of the processes is selected on the alert display screen, the management computer displays a details displaying screen that includes, for each product, an actual performance value in the selected process.
Owner:HITACHI LTD
Medicament tray inventory system and method
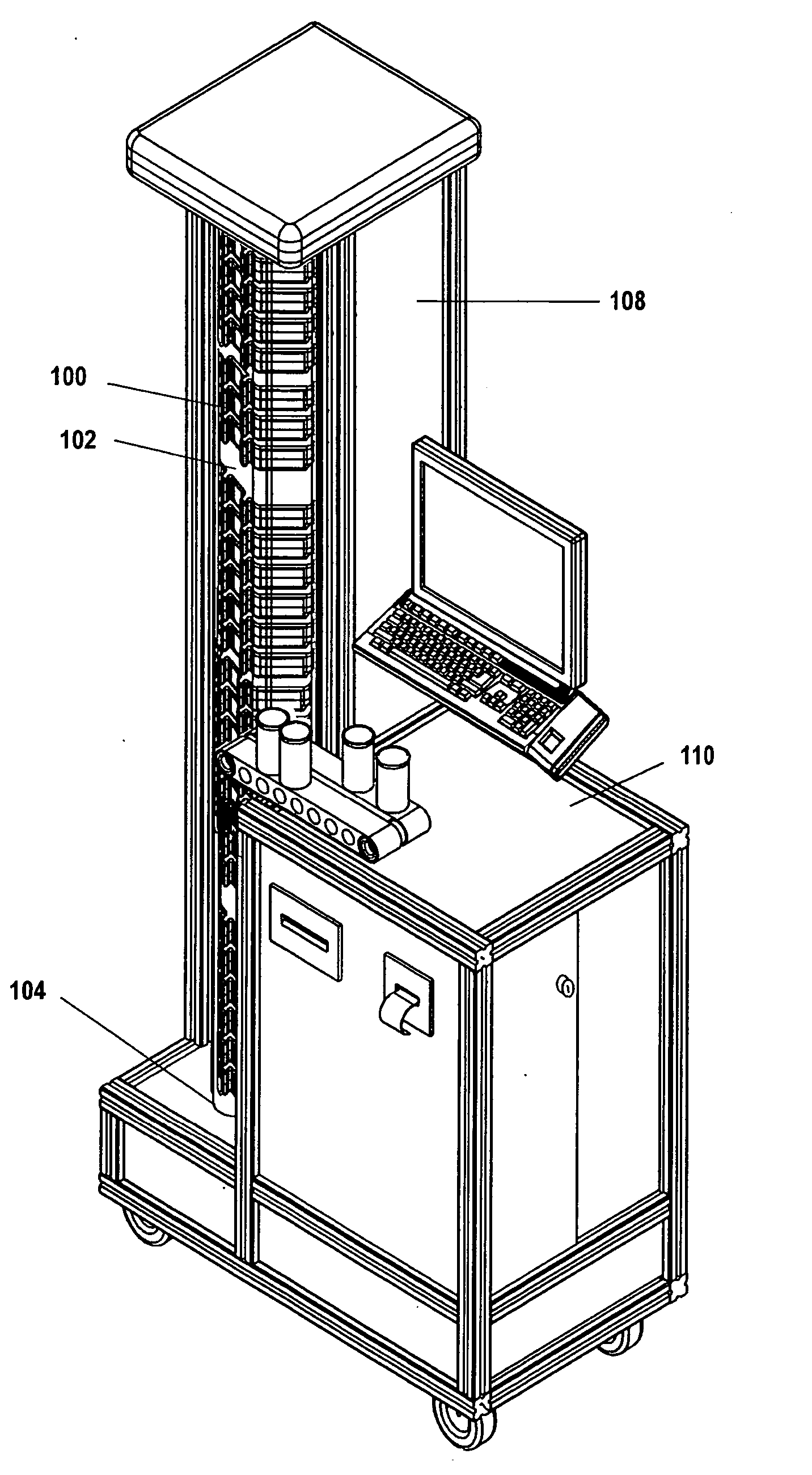
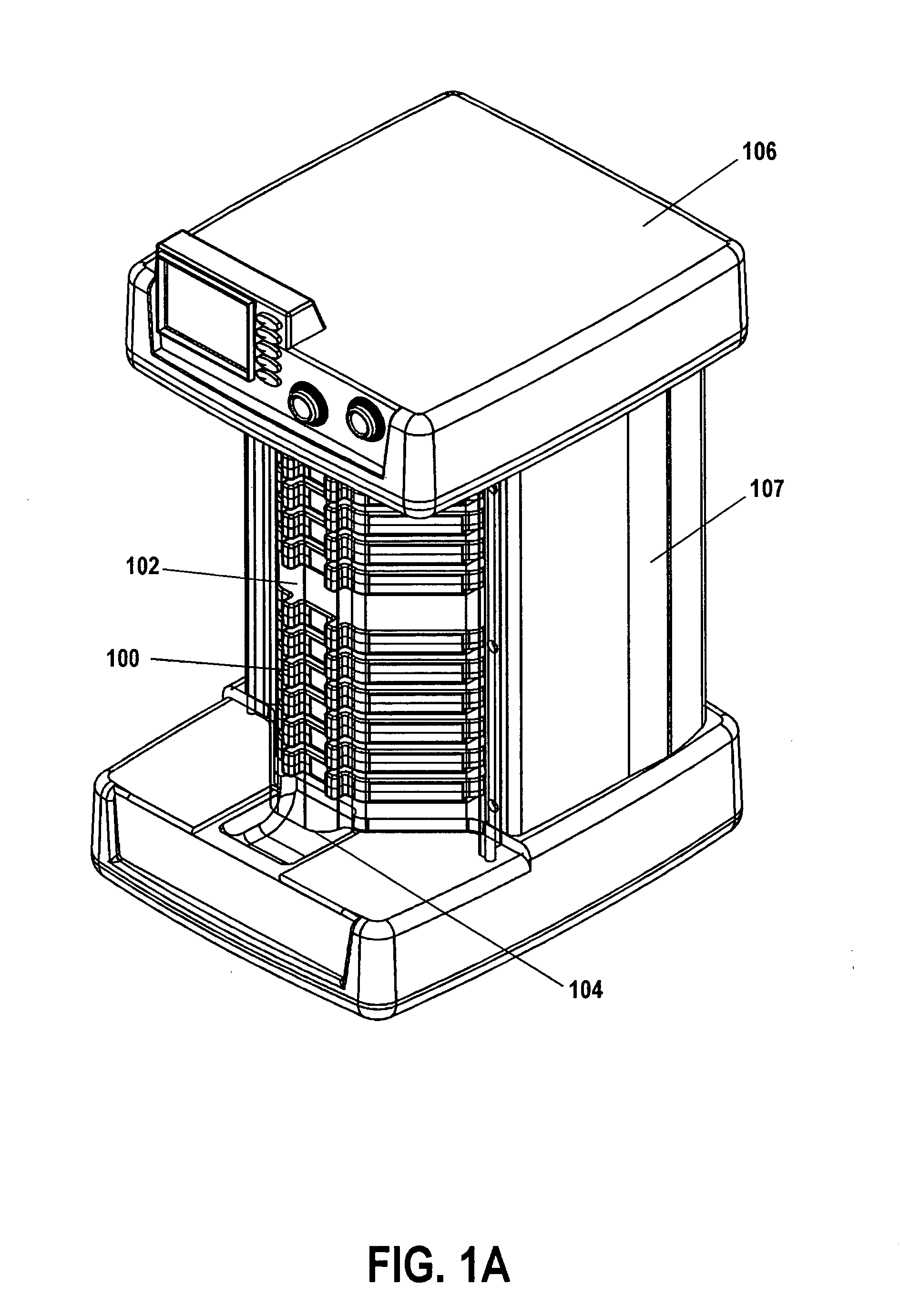
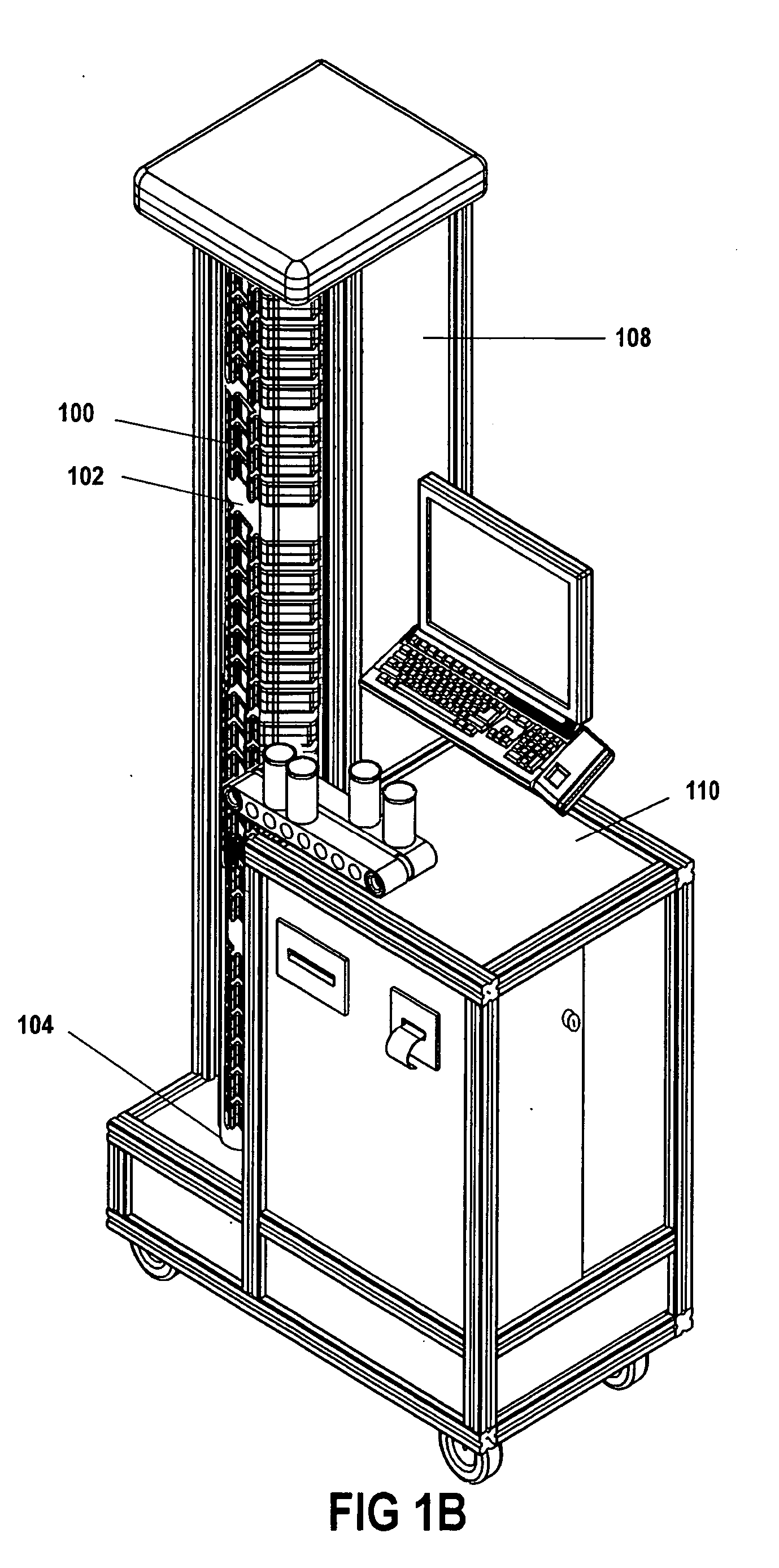
InactiveUS20060058726A1Facilitate identificationElectrotherapyDrug and medicationsDrugBiomedical engineering
The invention relates to a method and system that utilizes one or more cassettes or trays, which hold one or more types of medicaments, the cassettes or trays being configured for intelligent dispensing of the medicaments. In one embodiment, a smart tray for dispensing medicaments includes:
Owner:ANIMATRONICS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com