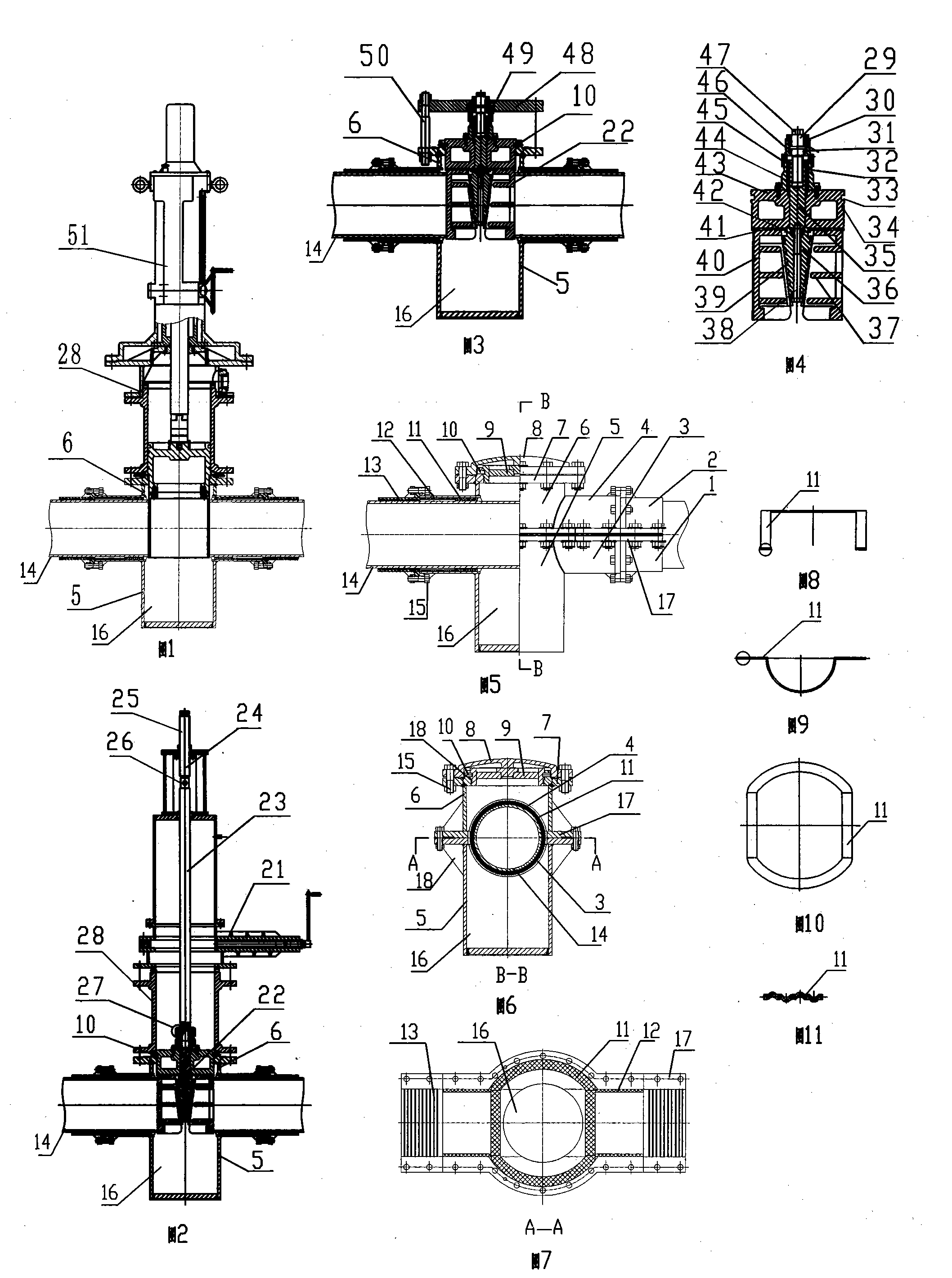
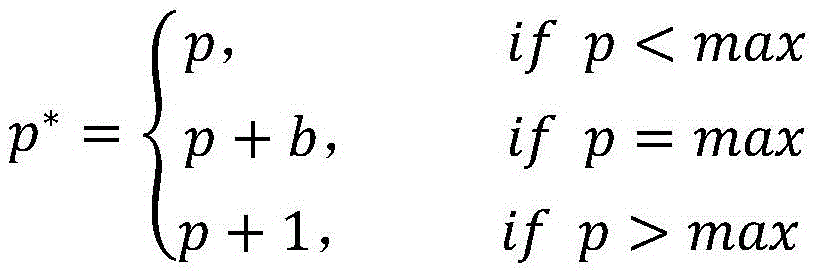Patents
Literature
408 results about "Block method" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The block method is not the only way of writing a comparison and contrast essay. In the point-by-point method, each paragraph gives a point (or idea) and its similarities and contrasts. In the combination method, you combine the point-by-point method with the block method.
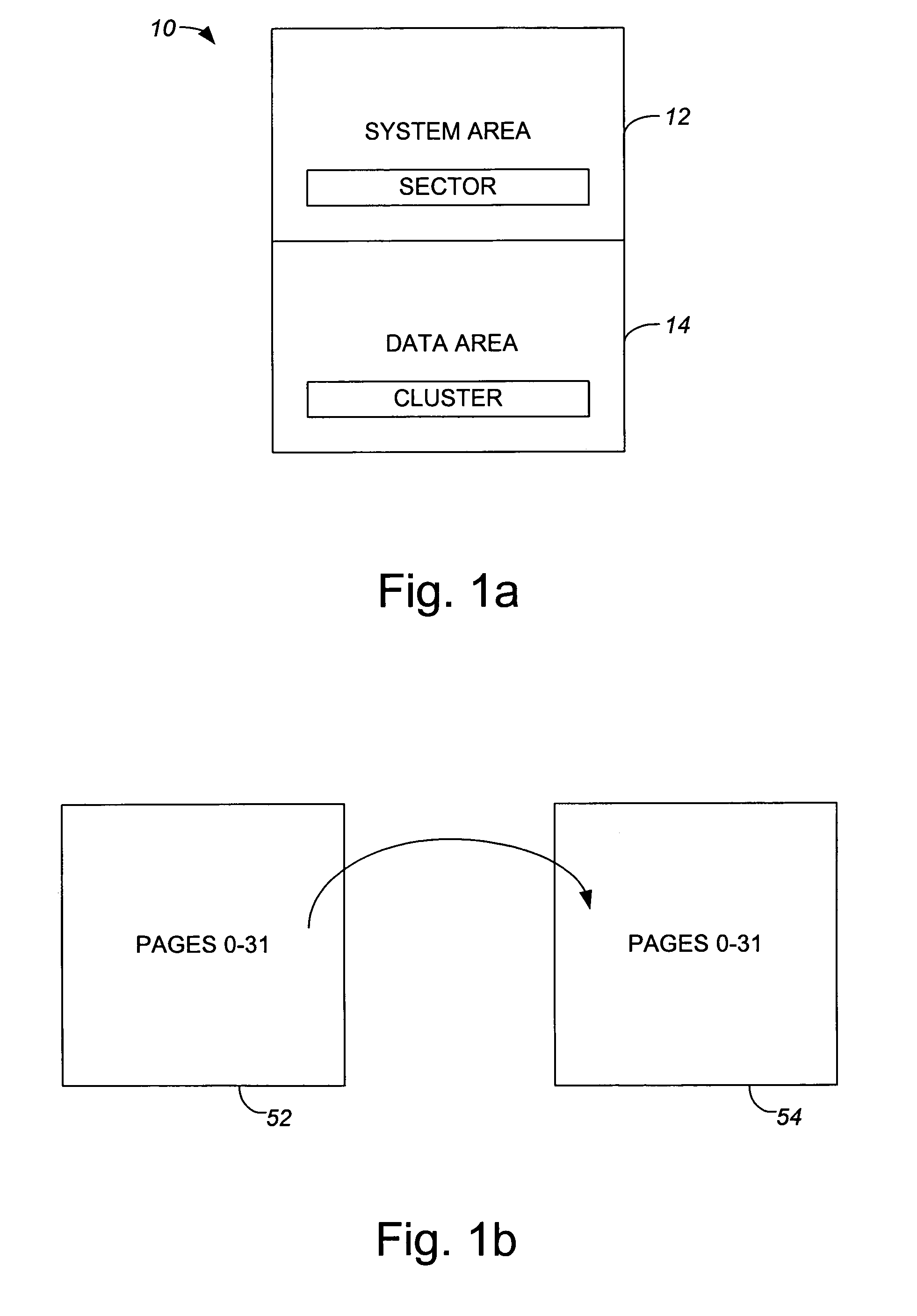
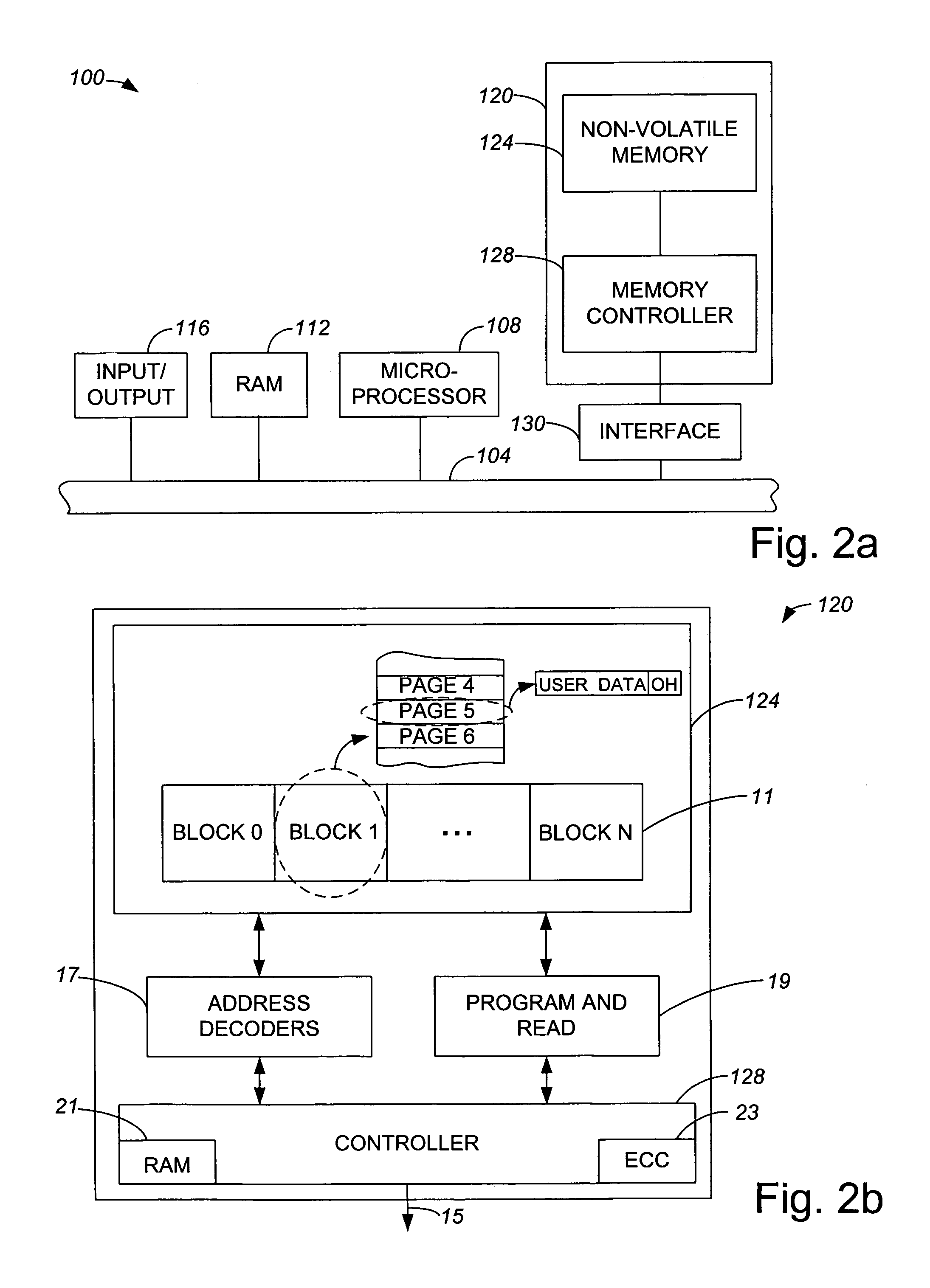
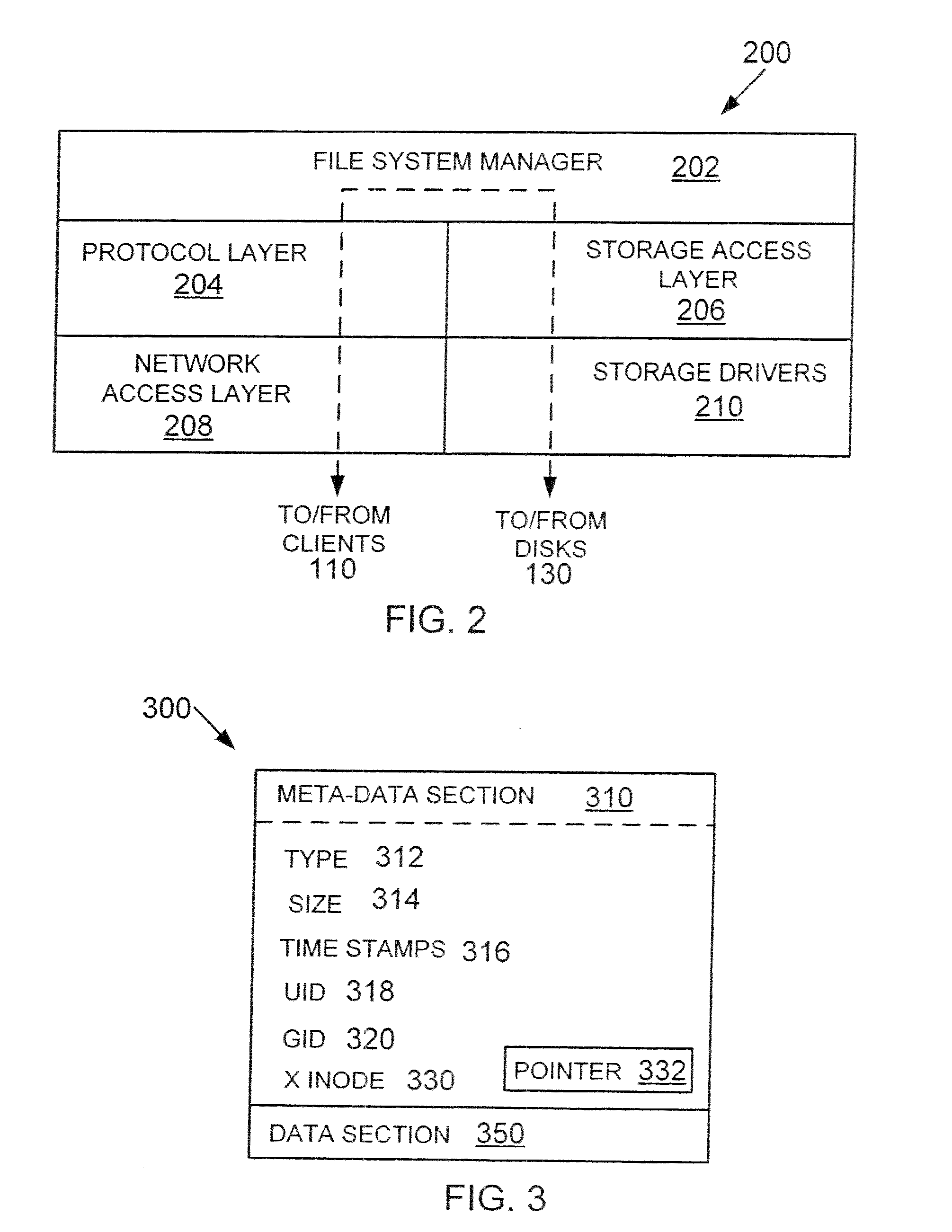
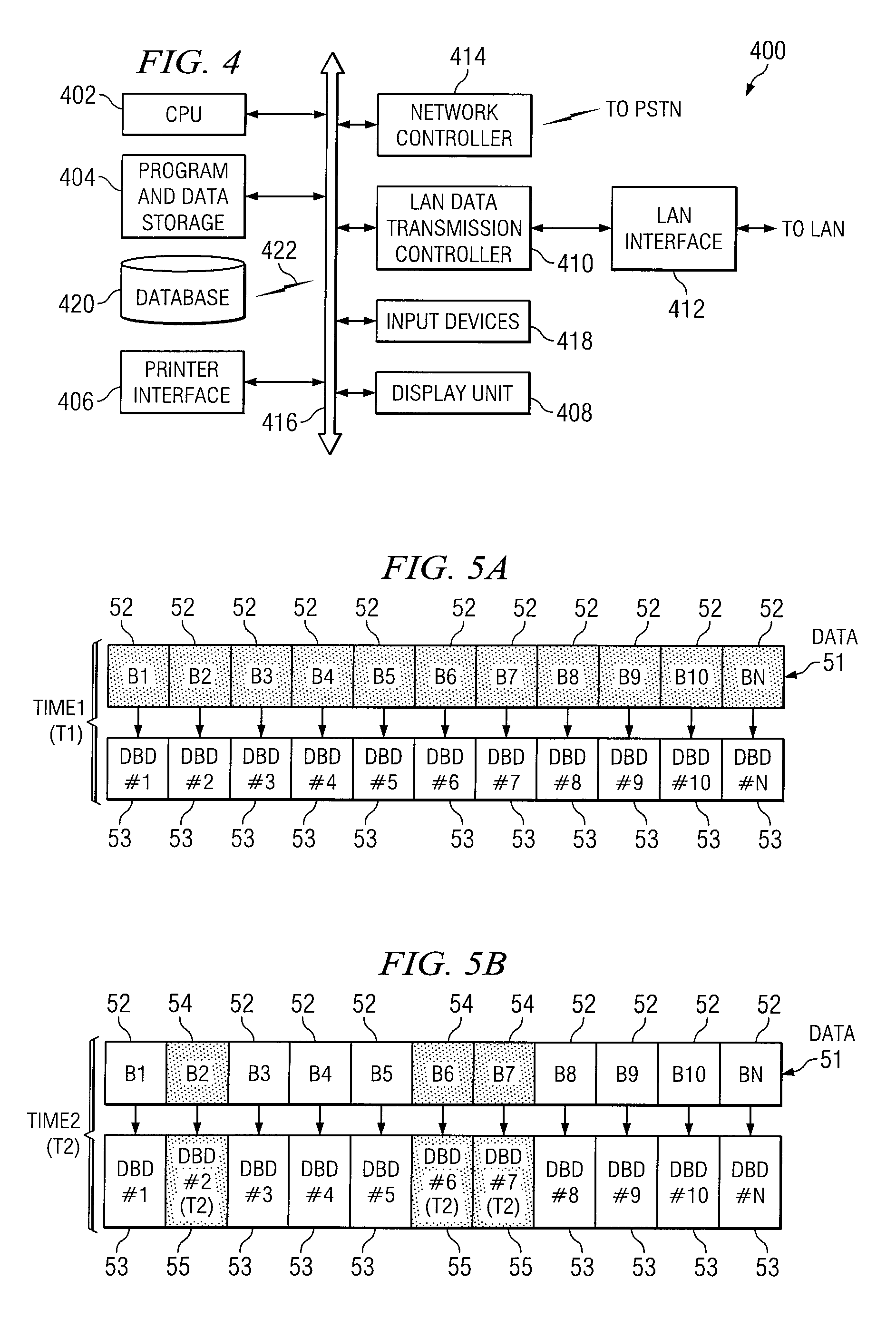
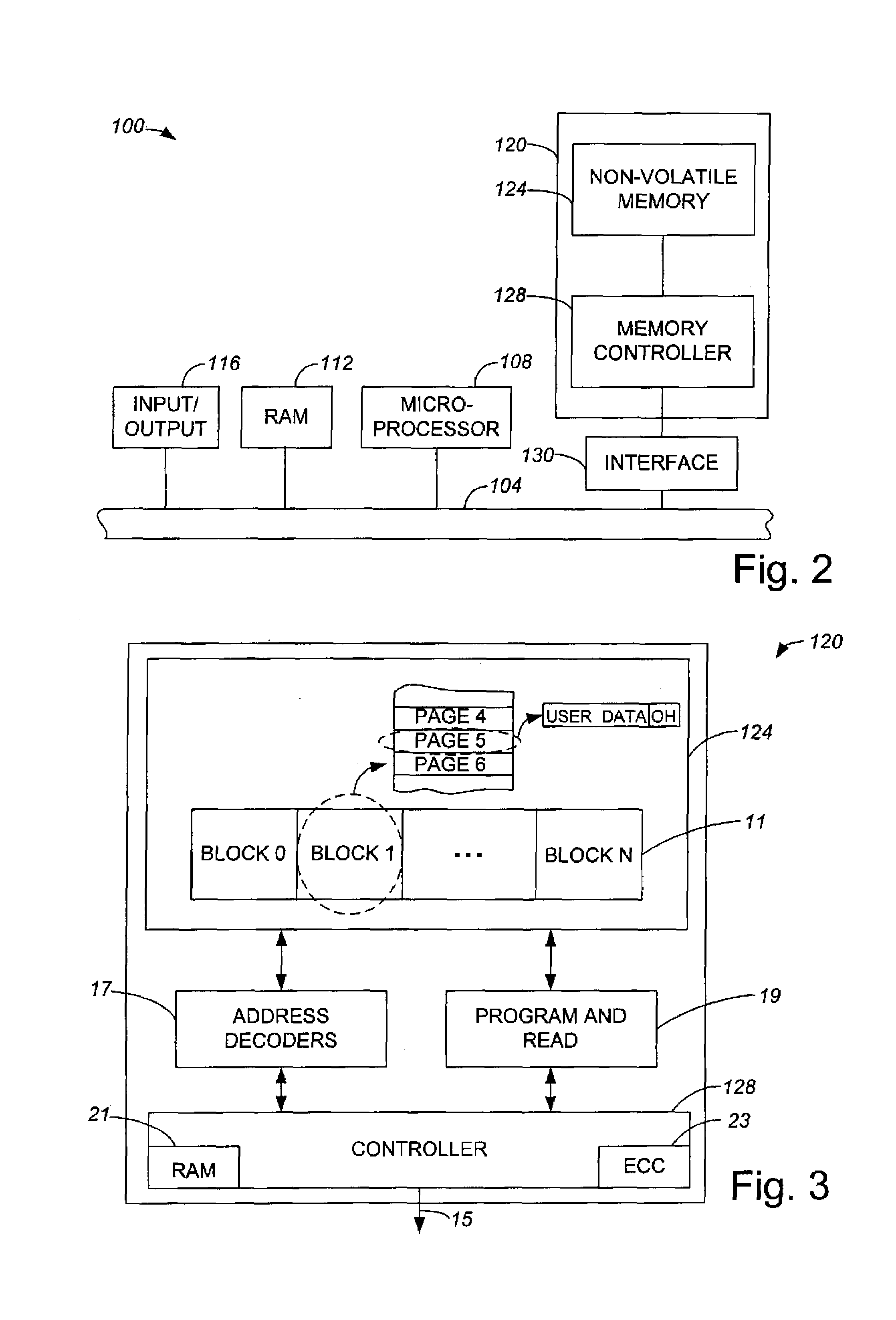
Method and apparatus for grouping pages within a block
InactiveUS7254668B1Improve efficiencyReduce dataMemory adressing/allocation/relocationRead-only memoriesBlock methodDatabase
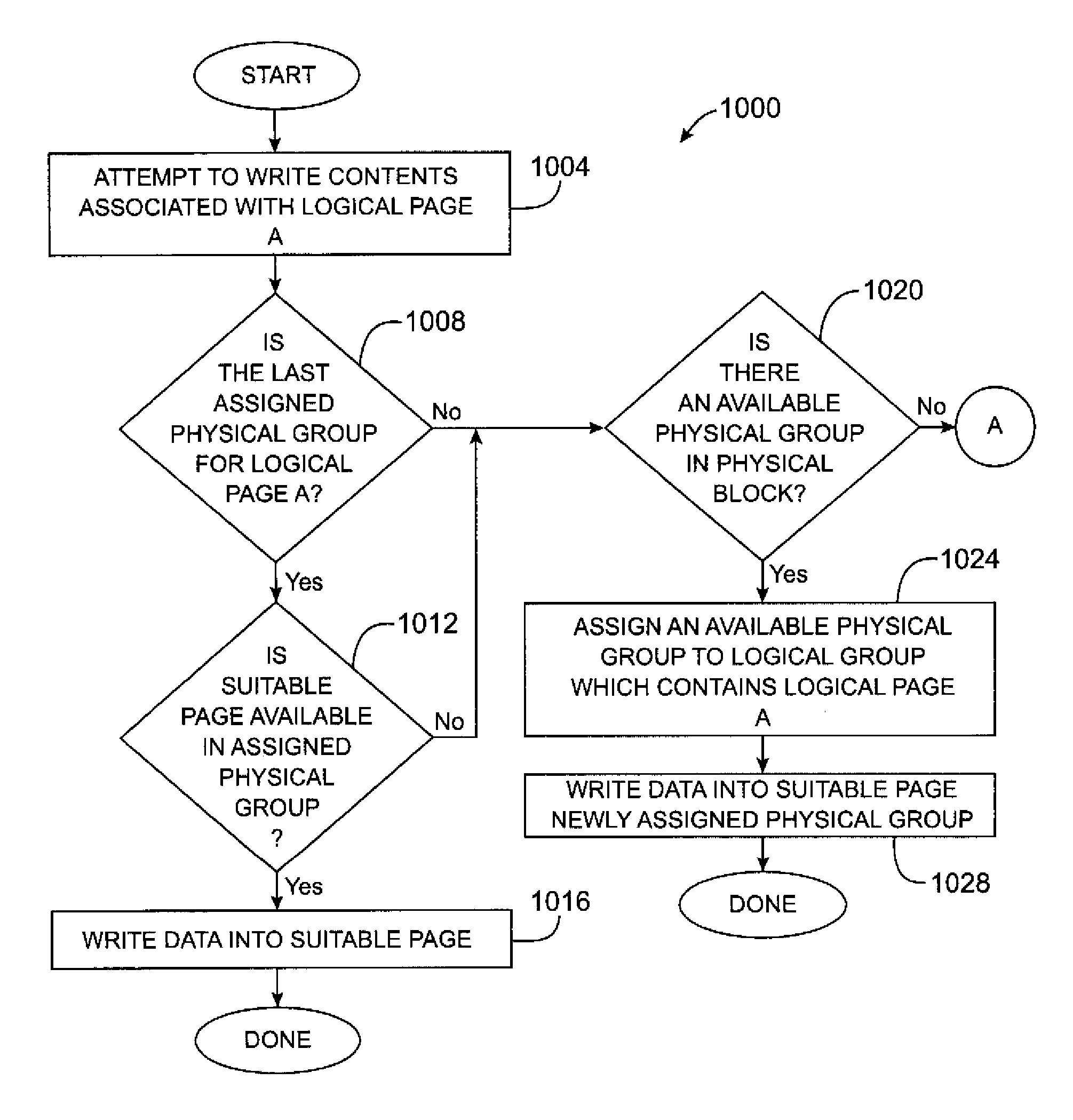
Methods and apparatus for efficiently enabling pages within a block to be accessed are disclosed. According to one aspect of the present invention, a method for writing data into a first block in a non-volatile memory which includes pages that are grouped into groups which each include two or more pages involves determining when a first group is available to receive the data. When it is determined that the first group is available to receive the data, the data is written into a first page included in the first group. The method also includes determining when a second group is available to receive the data if it is determined that the first group is not available to receive the data, and writing the data into a second page included in the second group when it is determined that the second group is available to receive the data.
Owner:SANDISK TECH LLC
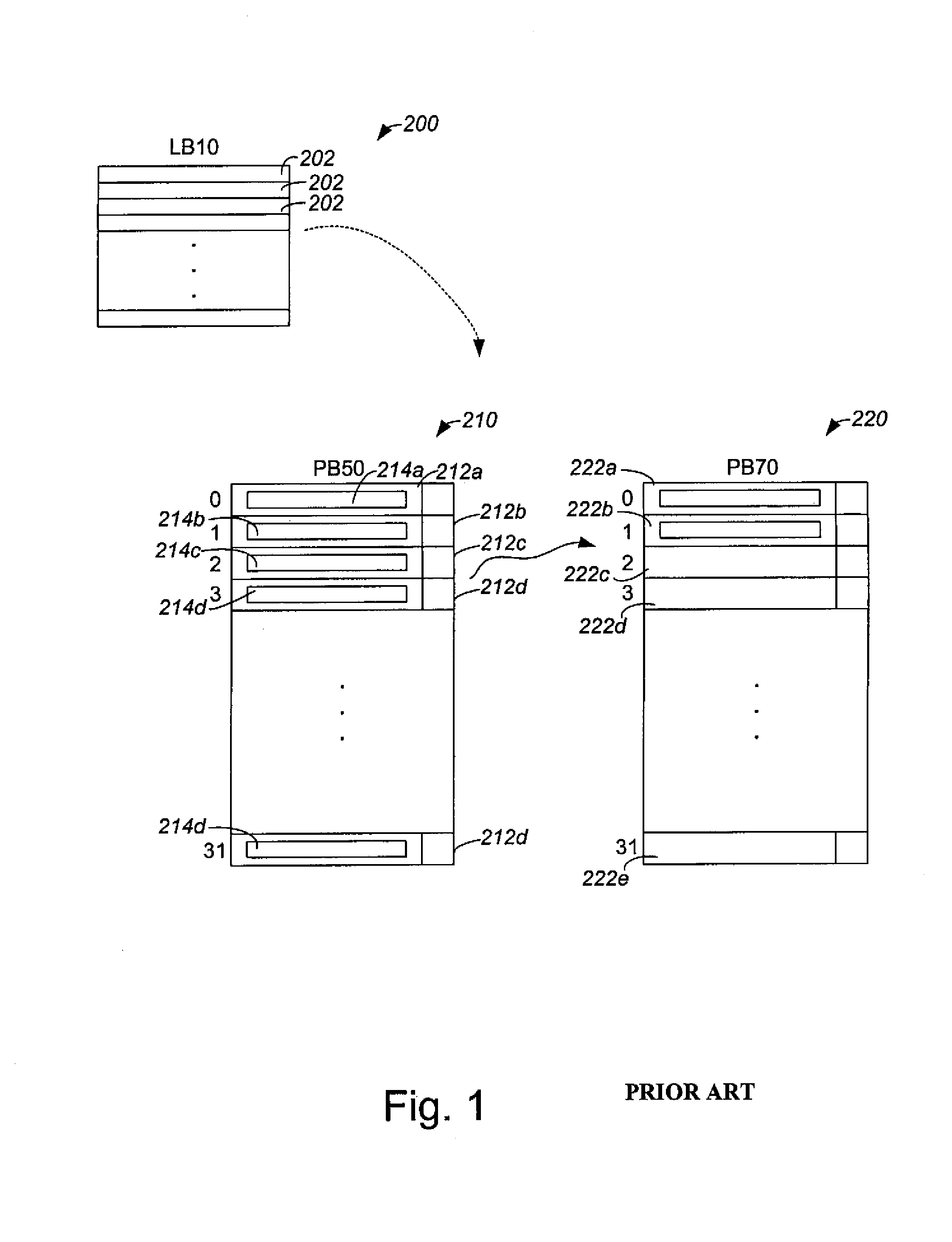
Method and apparatus for splitting a logical block
InactiveUS7039788B1Improve performanceReduce needMemory architecture accessing/allocationMemory adressing/allocation/relocationBlock methodNon-volatile memory
Methods and apparatus for splitting a single logical block into two or more physical blocks are disclosed. According to one aspect of the present invention, a method for associating a plurality of physical blocks of a non-volatile memory with a logical block that includes of logical block elements involves grouping the logical block elements into at least a first logical set and a second logical set. Data associated with the first logical set is provided to a first physical block, and data associated with the second logical set is provided to a second physical block.
Owner:SANDISK TECH LLC
Hard rock tunnel non-blasting digging blocking method and construction method
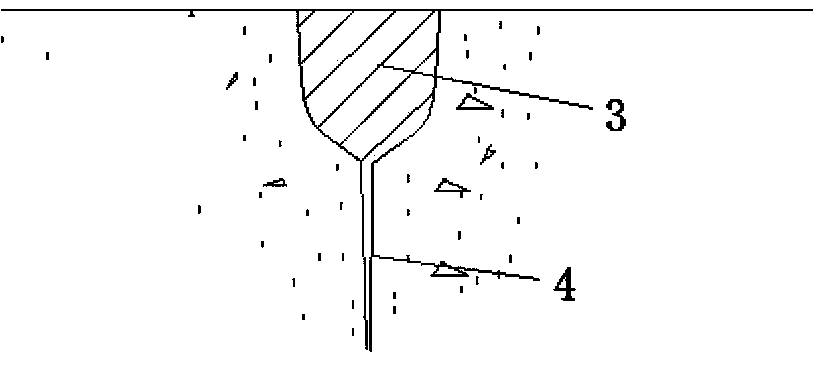
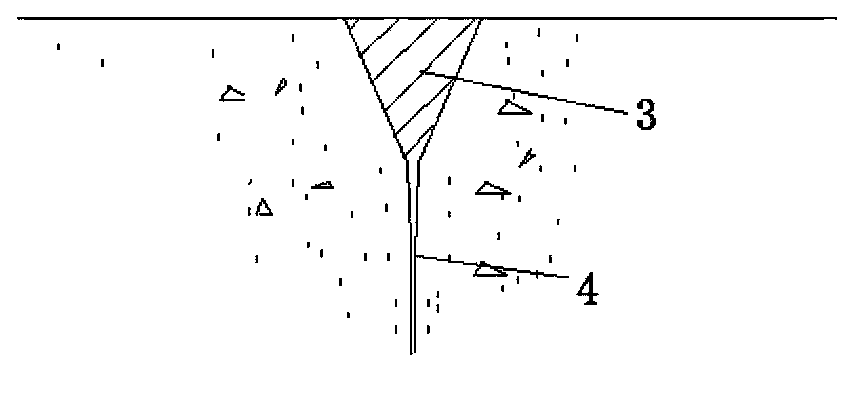
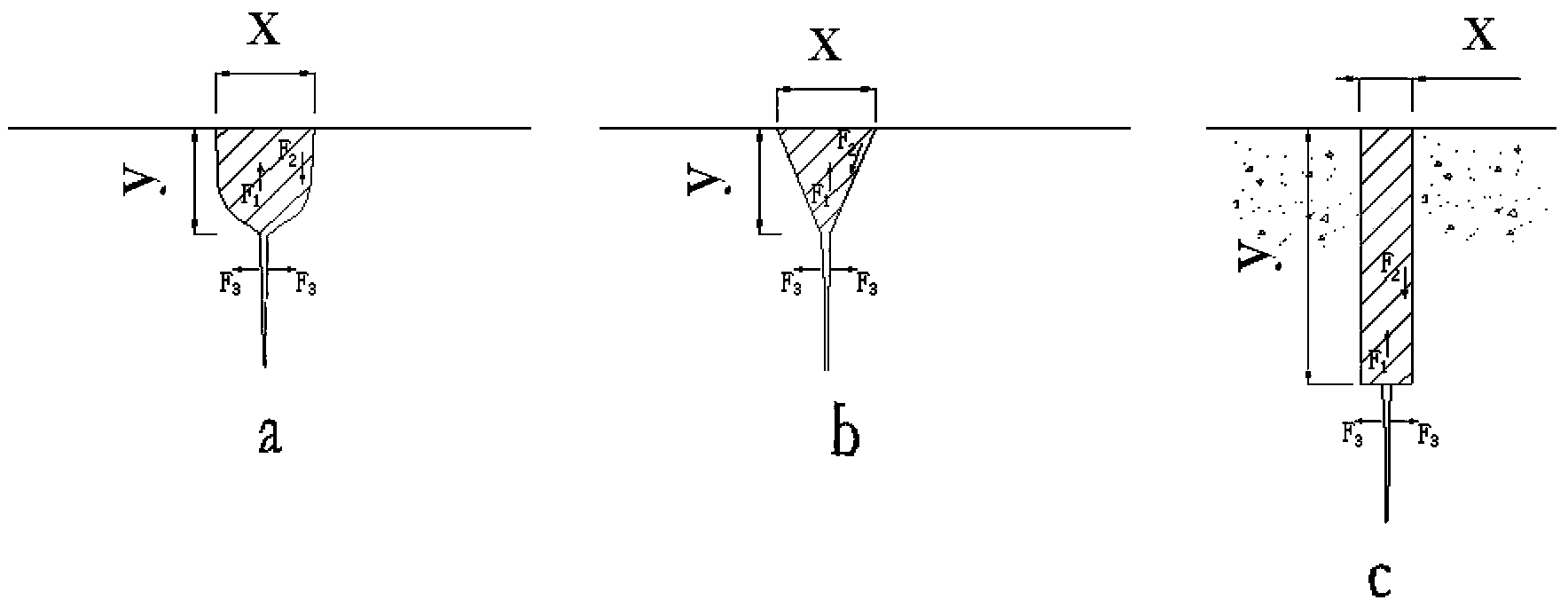
The invention relates to a hard rock tunnel non-blasting digging blocking method and a construction method. According to the method, a hole drilling core taking technology is utilized, mutually engaged cutting peripheral holes are formed along a tunnel digging contour line, so that a hole wall-shaped digging free face is formed on the periphery of a tunnel face; a hydraulic splitting machine splitting technology is used, in addition, the characteristic that the tensile intensity and the shearing-resistant intensity of rock are much smaller than the pressure-resistant intensity is utilized, the tunnel face digging blocking is firstly carried out, in each digging block, the synchronous splitting digging splitting surfaces do not exceed two, in addition, the two splitting surfaces are in large-angle obtuse angle intersection, in addition, at least one digging free face vertical to the tunnel face is included, then, the digging construction sequence from the lower side to the upper side and from the periphery to the middle is adopted, and the smaller splitting force is used for carrying out rock pulling cracking and shearing cutting splitting digging on the tunnel face along the splitting surface. The hard rock tunnel non-blasting digging blocking method has the advantages that the adverse influence of vibration, noise and dust in the hard rock digging construction can be eliminated, and the utilization rate of tunnel hole slag as building stone materials can be improved.
Owner:FUZHOU PLANNING DESIGN & RES INST
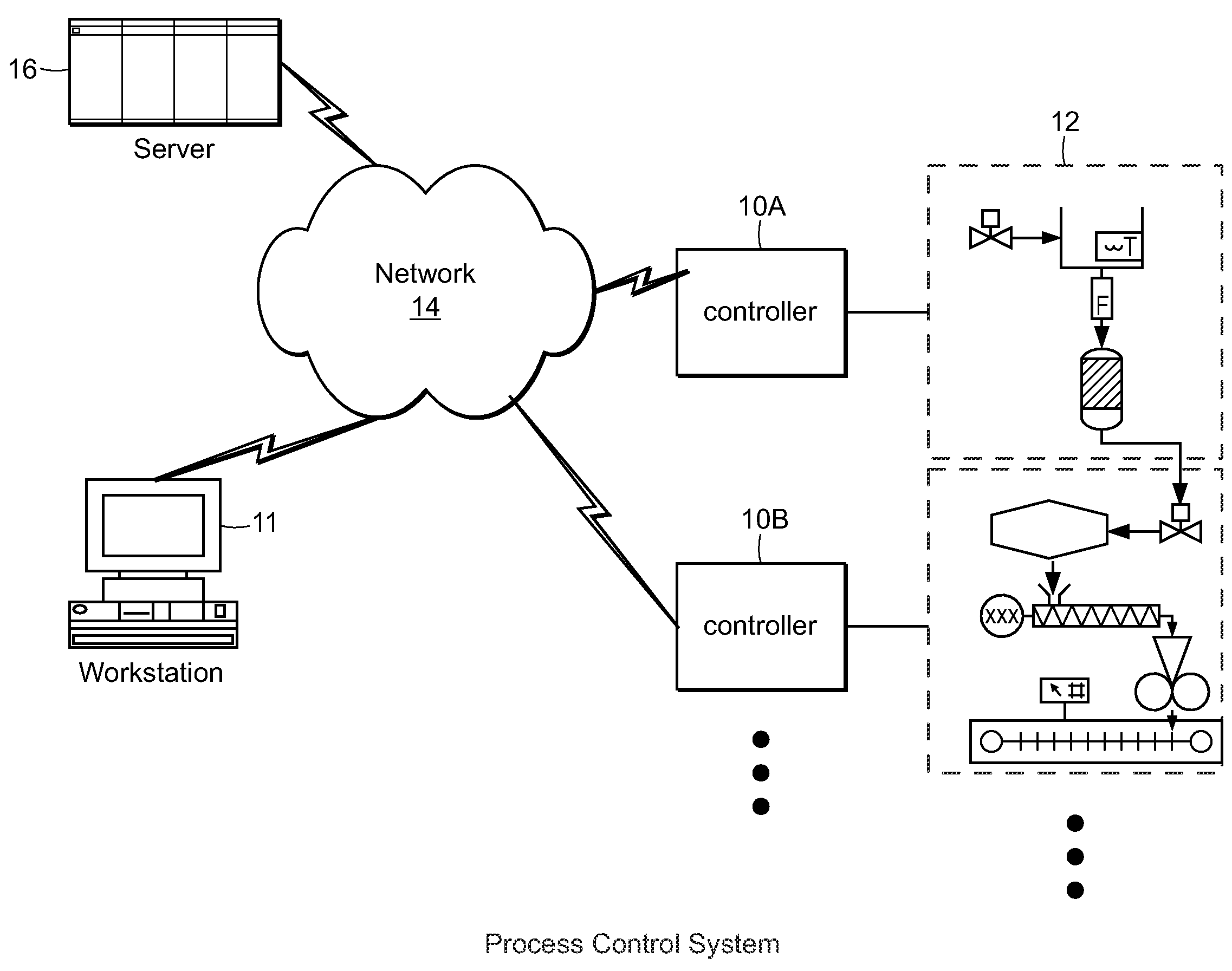
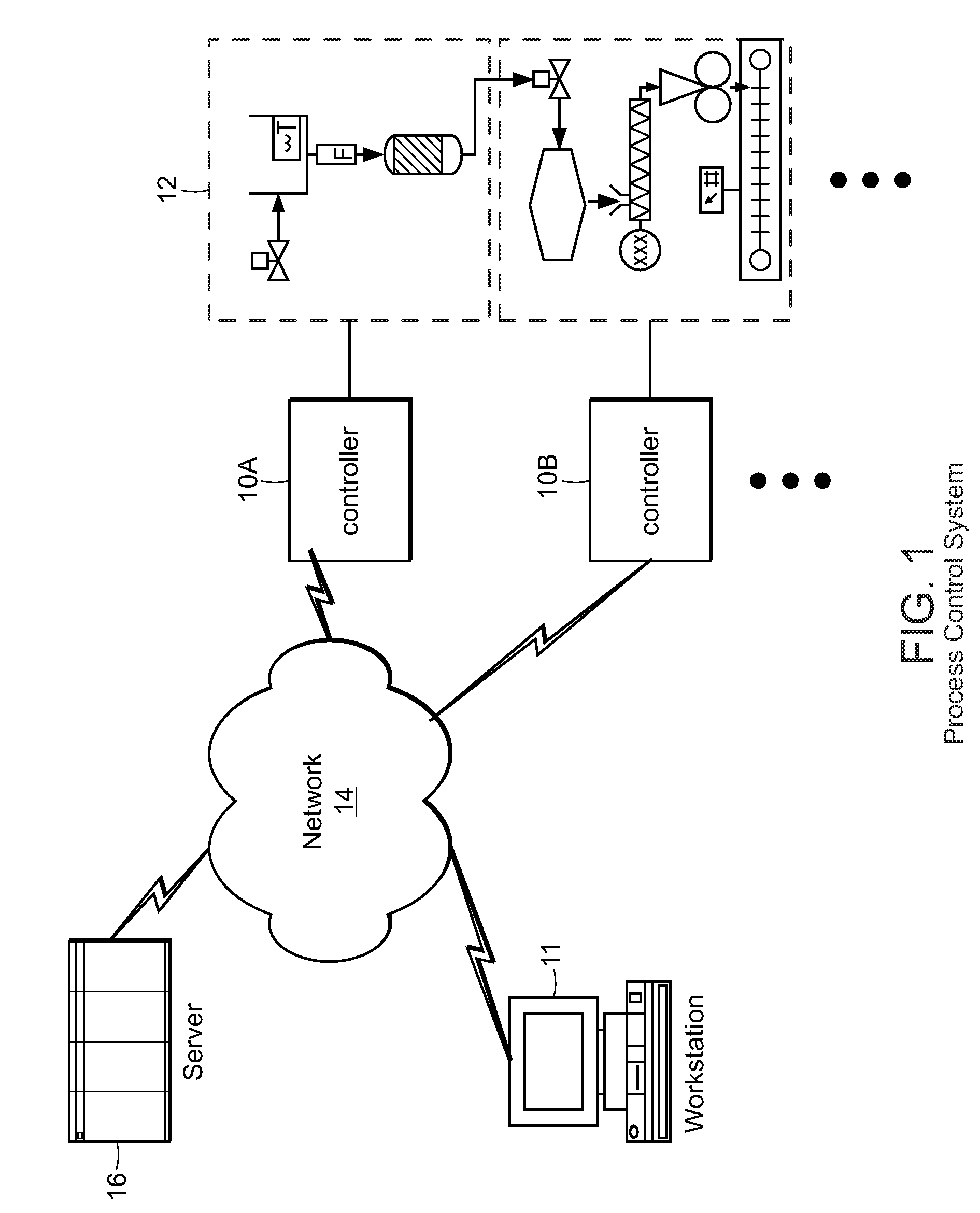
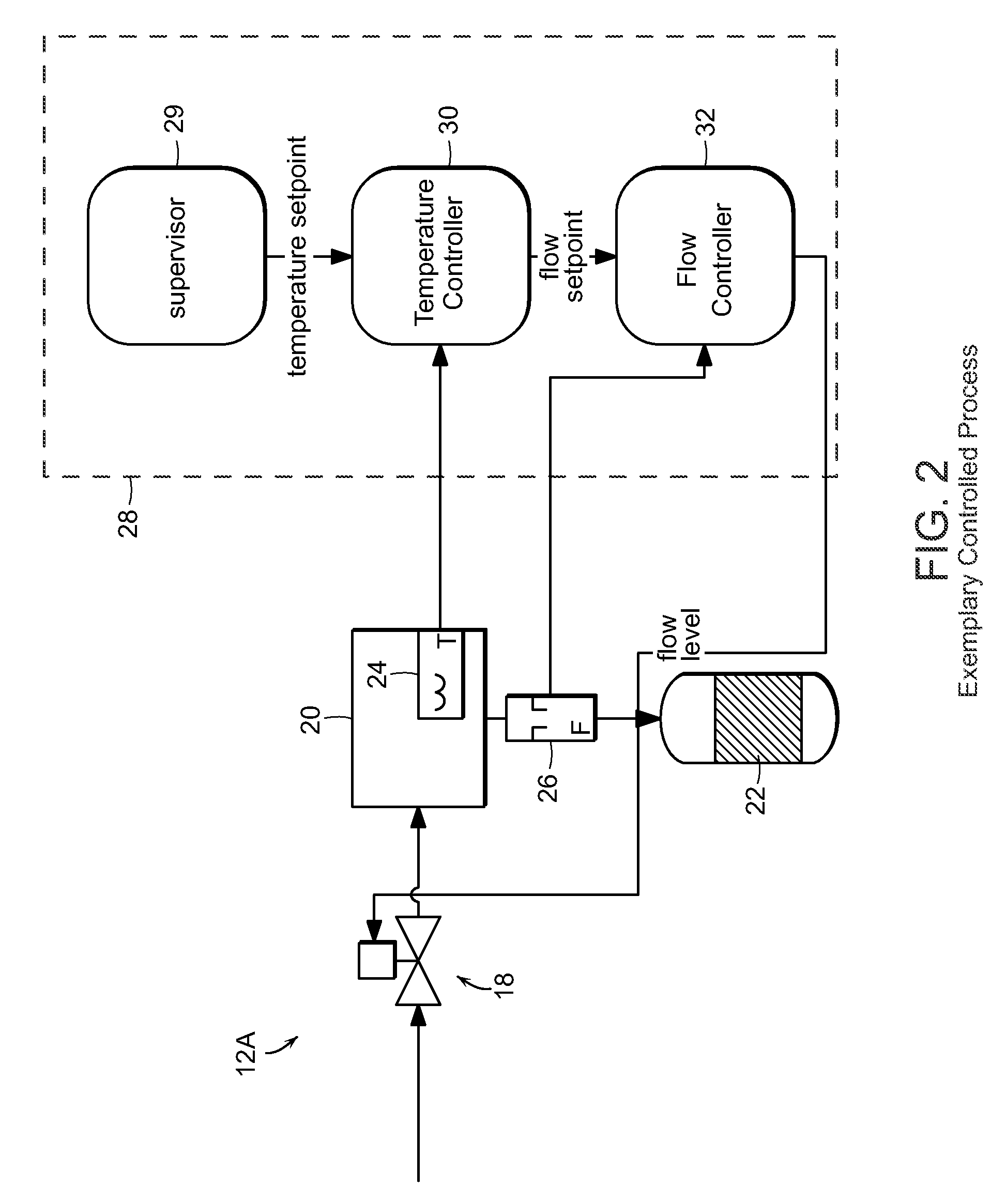
Control systems and methods with smart blocks
InactiveUS20090118846A1OptimizationOptimize system configurationData processing applicationsComputer controlGraphicsGraphical user interface
Methods and apparatus for configuring process, environmental, industrial and other control systems generate and / or utilize models representing configurations of control systems and / or the systems controlled by them. Records of changes to the models or the configurations represented by them are maintained, thereby, for example, providing bases for determining current states, prior states and histories of changes. Objects in the model have characteristics, such as an object type characteristic and an area characteristic. Users can have corresponding permissions. A security mechanism apparatus controls access by users to the objects. Composite objects are defined by definition objects and are displayed in encapsulated or expanded formats. Objects can include an edit control type identifier that determines how they are presented for editing. Functionality responds to user commands by transferring characteristics of a first object depicted by the graphical user interface to a second object. Configuration-time formulas contained objects are evaluated to constants prior to downloading to the control system.
Owner:SCHNEIDER ELECTRIC SYST USA INC
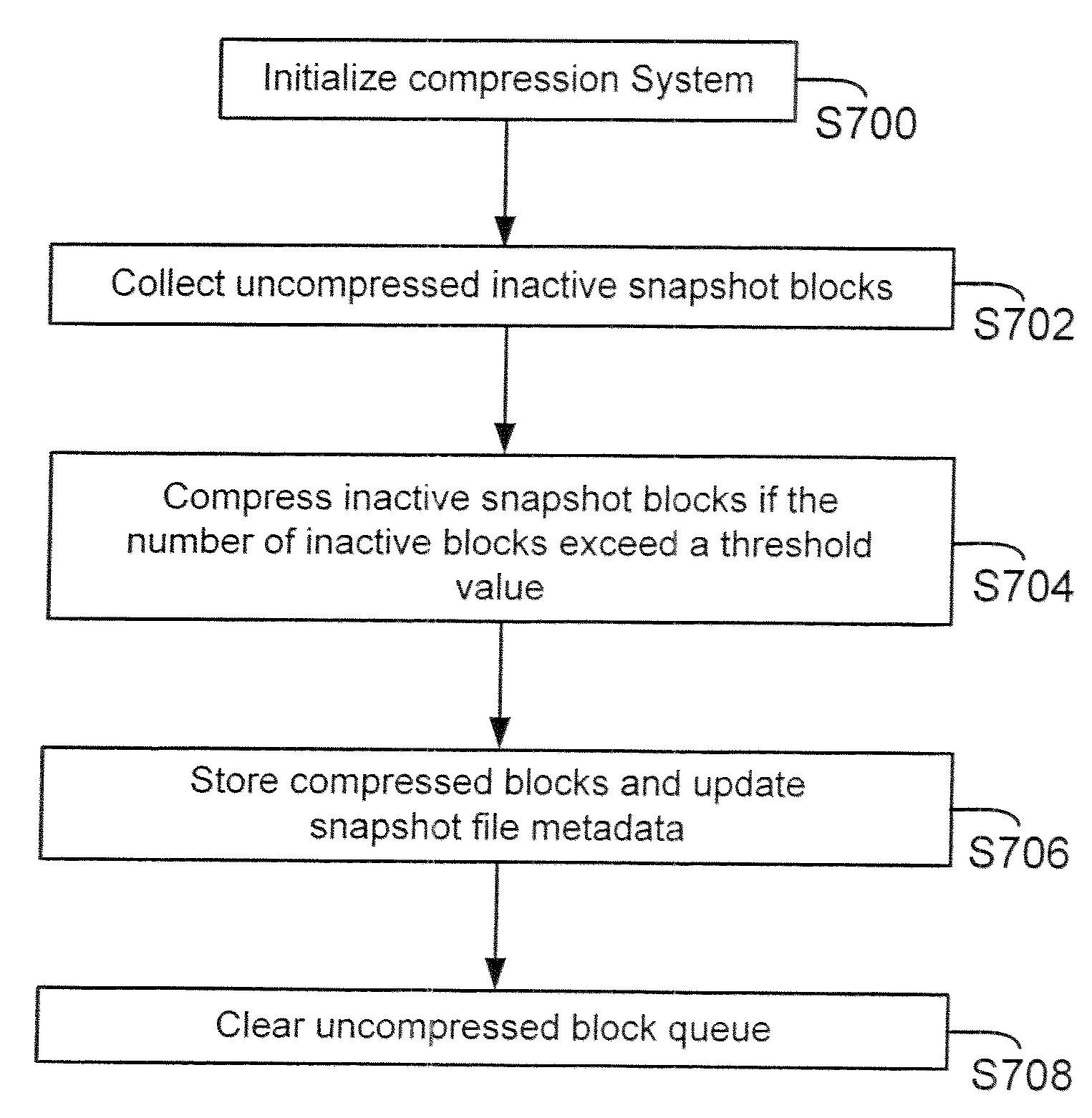
Method and system for managing inactive snapshot blocks
ActiveUS20090265516A1Save storage spaceMemory systemsInput/output processes for data processingBlock methodComputer science
Method and system are provided for managing inactive snapshot blocks. Information regarding inactive blocks is collected and placed in a queue. After the queue reaches a threshold number of inactive blocks, the inactive blocks are compressed and stored as a compressed segment. The compressed segment may include inactive blocks for different snapshot data structures. A compression map structure stores information regarding a plurality of compressed segments, including identifiers identifying different snapshot files which may point to one or more inactive blocks. For each compressed segment, a compression information map identifies the location of each inactive block within the compressed segment and the compression state for each inactive block.
Owner:NETWORK APPLIANCE INC
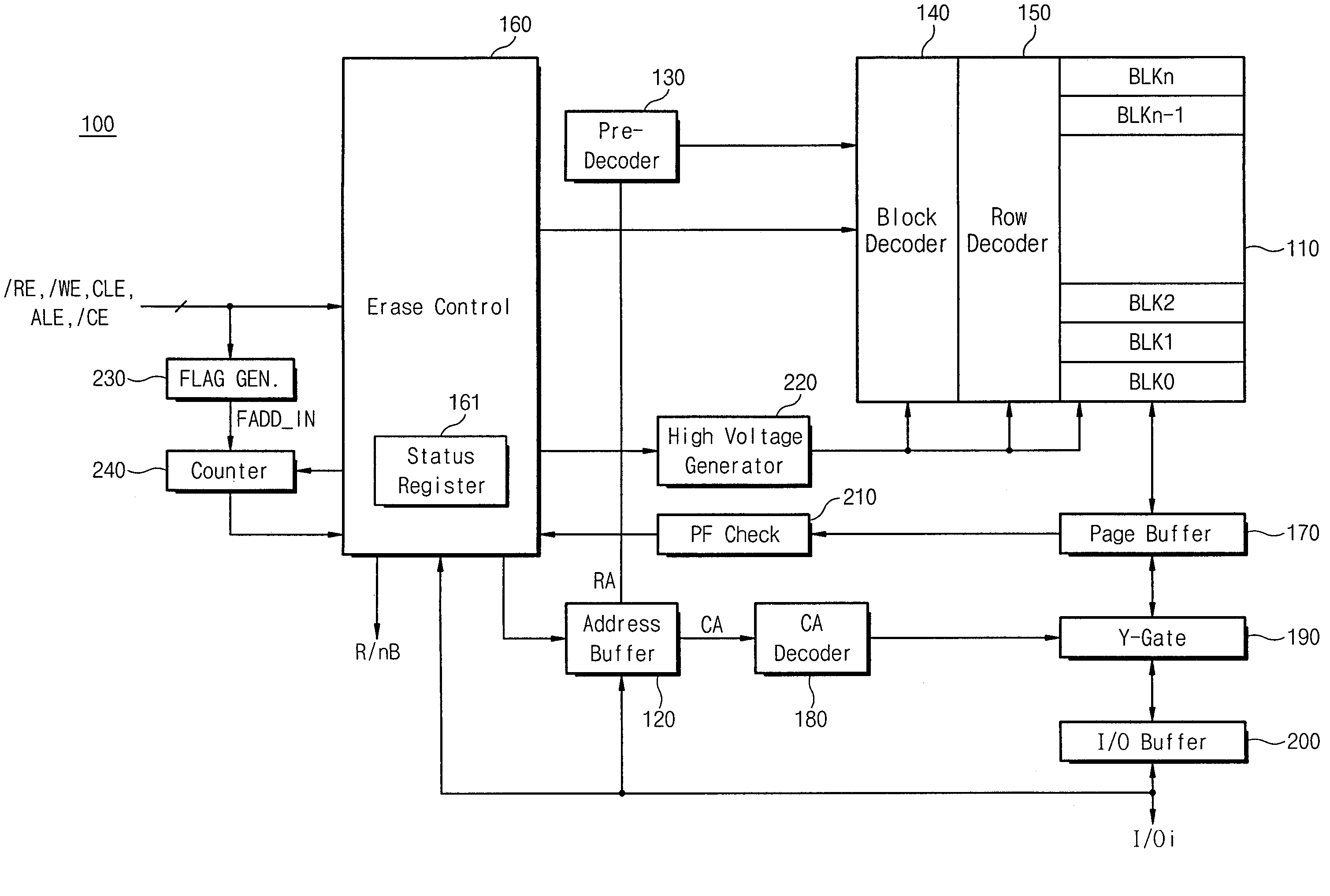
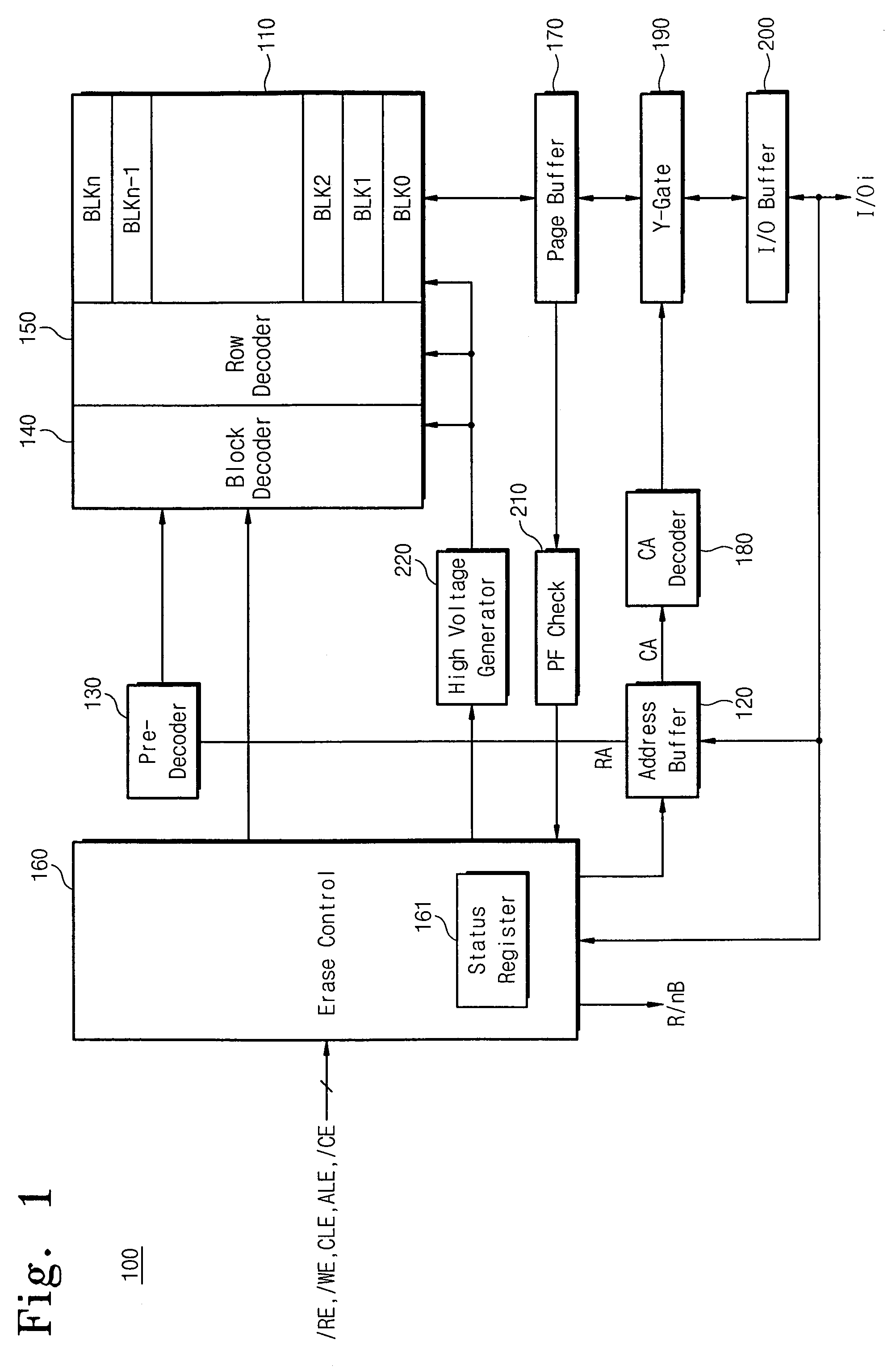
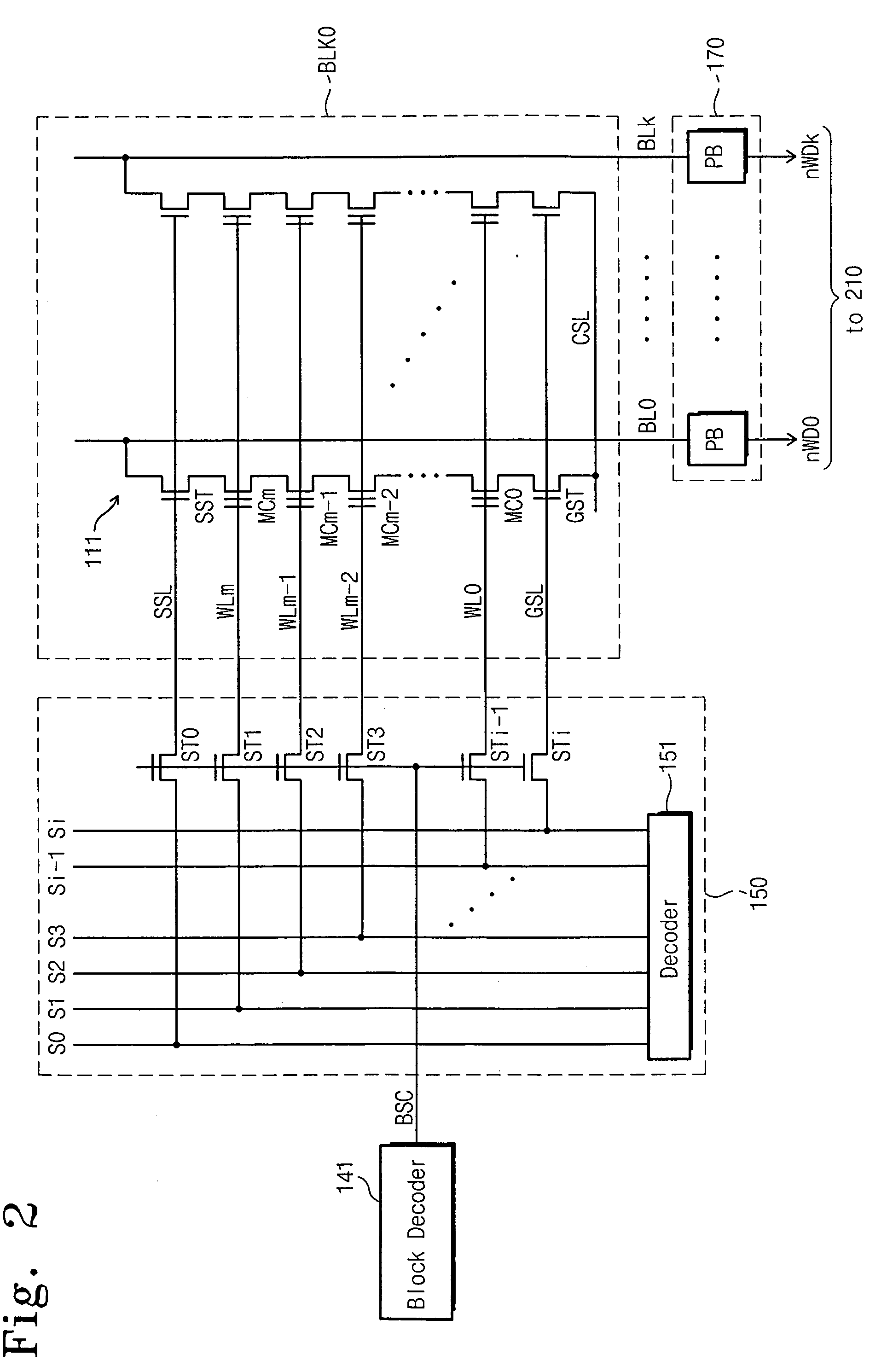
Non-volatile semiconductor memory device and multi-block erase method thereof
A non-volatile semiconductor memory device includes memory blocks and an erase controller configured to control a multi-block erase operation where at least two of the memory blocks are simultaneously erased. According to some embodiments, after selecting and simultaneously erasing the selected memory blocks, an erase verify operation for each of the erased memory blocks is performed according to an externally provided erase verify command and block address. According to some embodiments, if a suspend command is received by the memory device while selected memory blocks are being erased, the erase operation ceases and another operation, such as a read operation, begins. When a resume command is received by the memory device, the erase operation resumes. Other embodiments are described and claimed.
Owner:SAMSUNG ELECTRONICS CO LTD
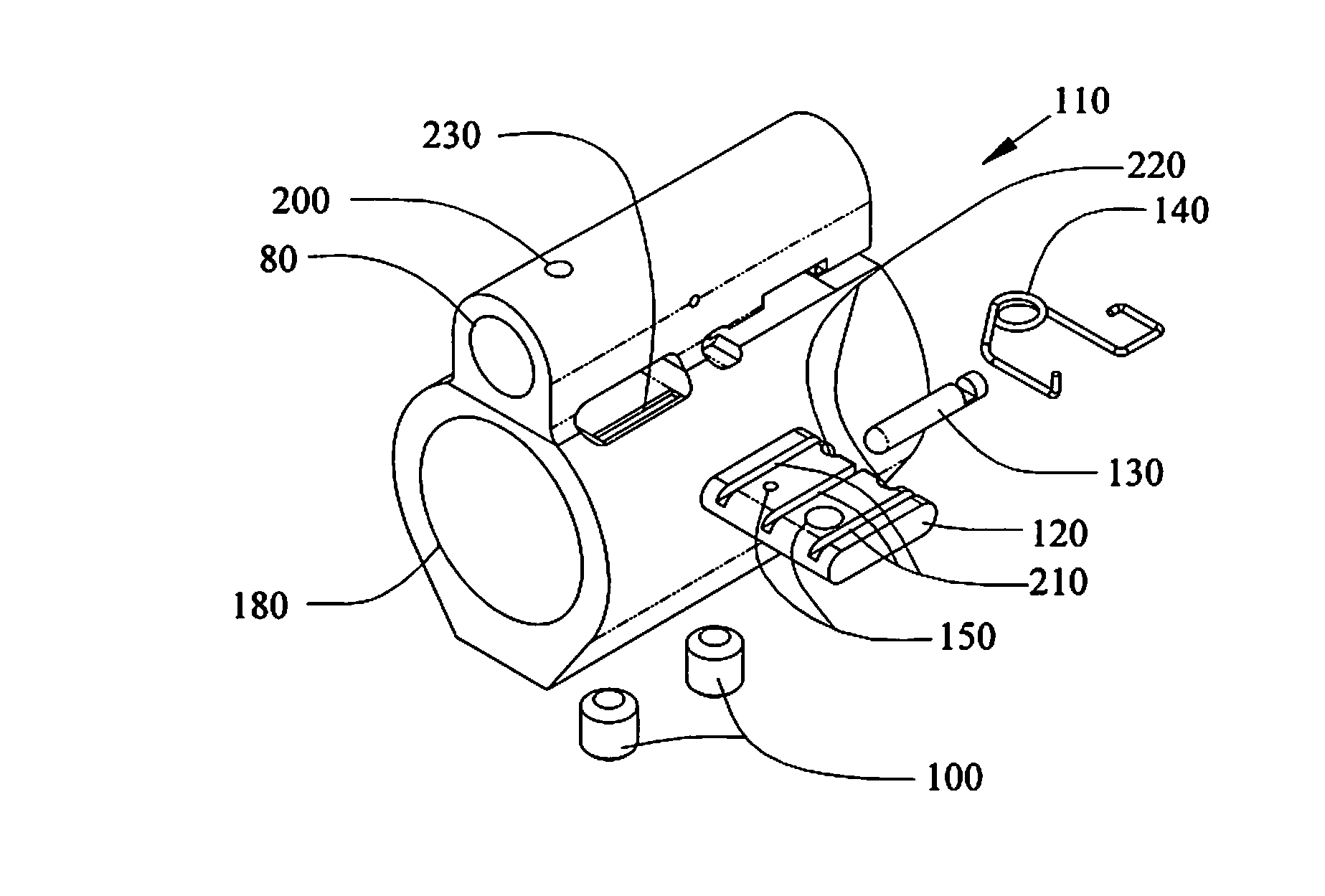
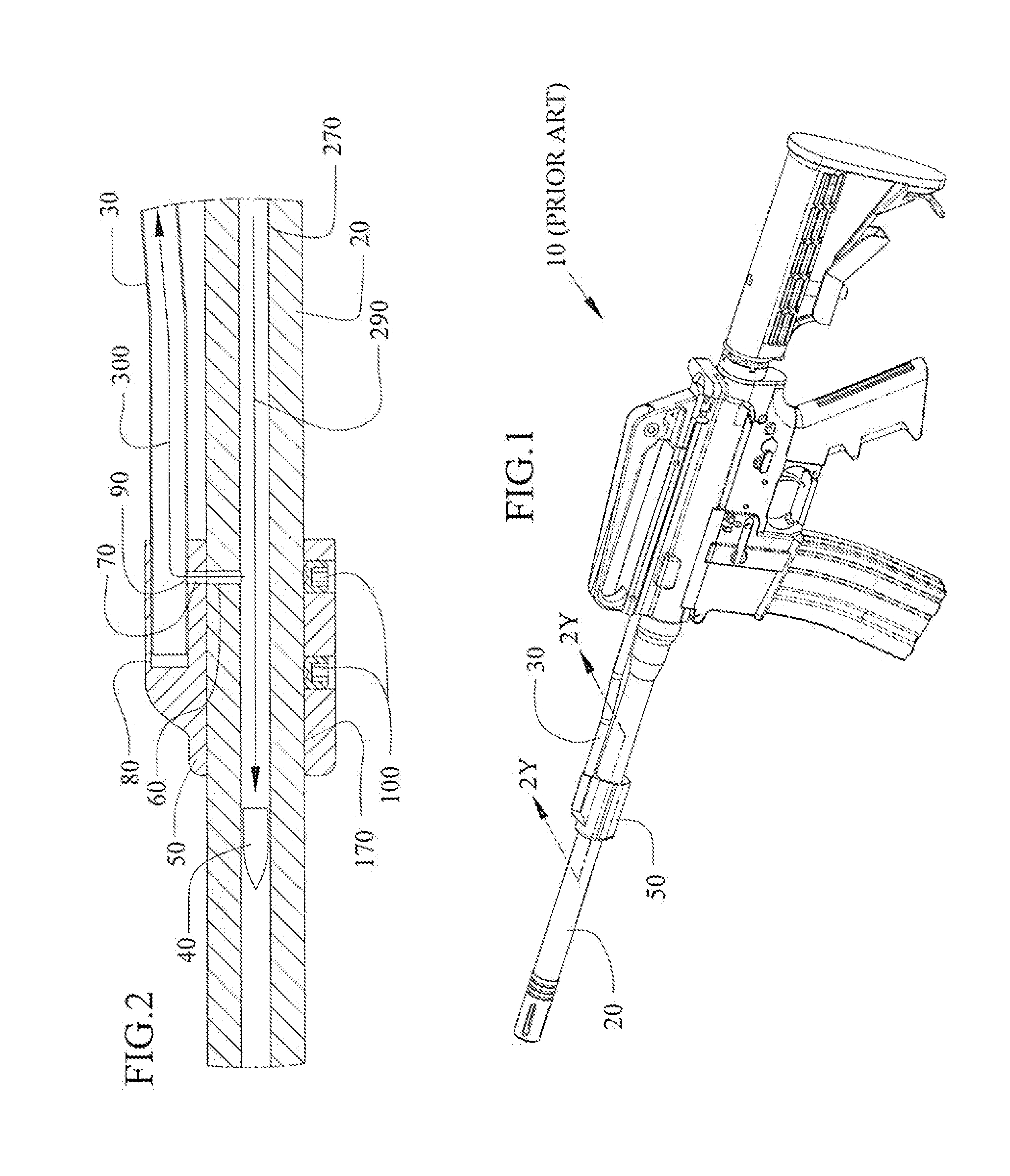
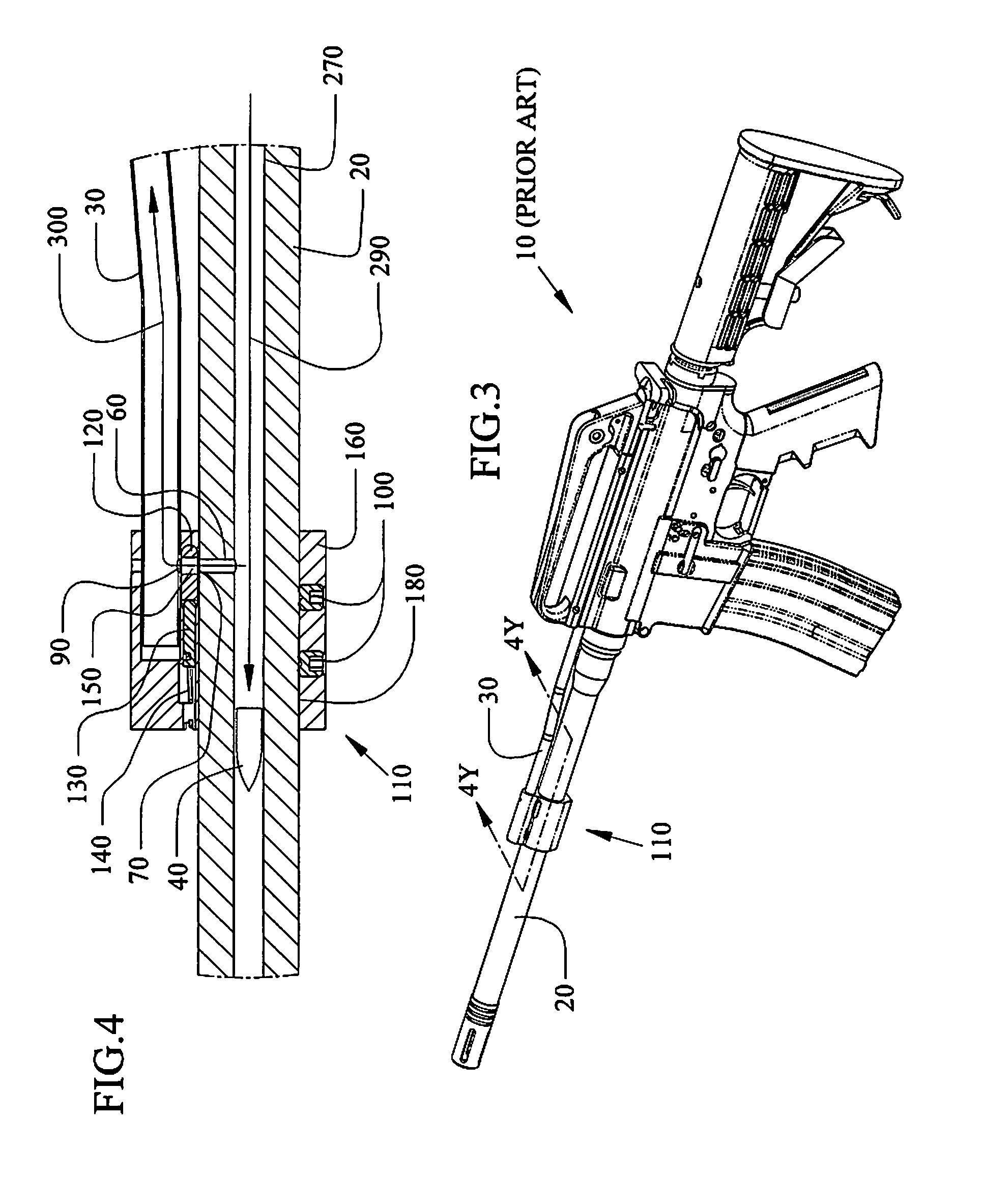
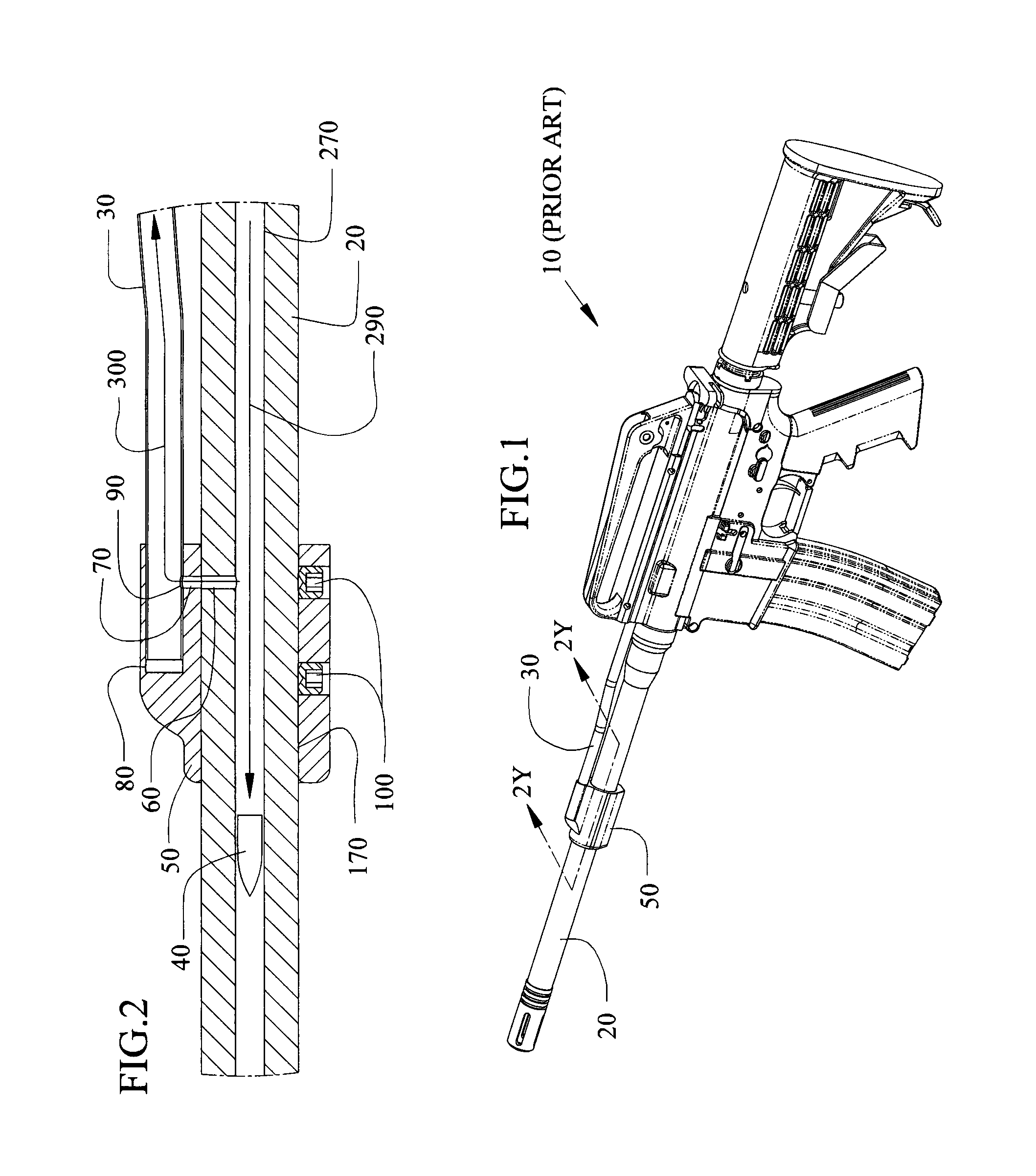
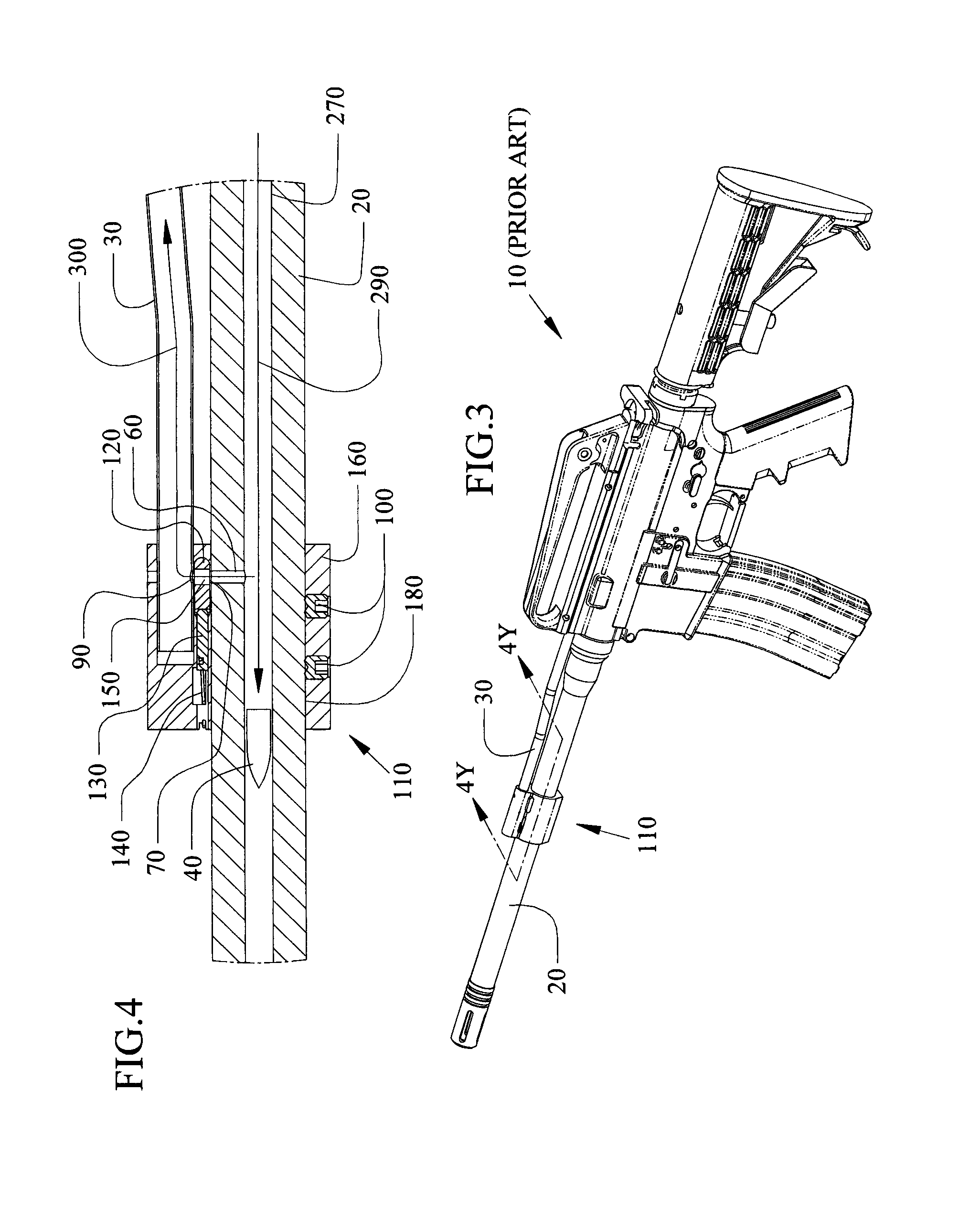
Adjustable gas block method, system and device for a gas operation firearm
Methods, systems and devices for an adjustable gas block with variable gas port dimensions to control the amount of gas in the gas block before the gas enters into the gas tube. The adjustable gas block includes a gas block barrel bore to slide the block over a barrel and a gas tube bore to mate with the firearm gas tube, a gas port between the barrel bore and the gas tube bore, a sliding adjustment plate with different adjustment gas ports to slide one of the gas ports into alignment with the block gas port and the barrel gas port, and a spring to hold the sliding gas port in alignment with the barrel gas port. An alignment hole in the gas tube bore can align the block gas port with the barrel gas port.
Owner:SPC IP LLC
Real-time repetition removal and transmission method for data in network file system
InactiveCN101917396ASave storage spaceImprove reliabilityTransmissionSpecial data processing applicationsNetwork File SystemBlock method
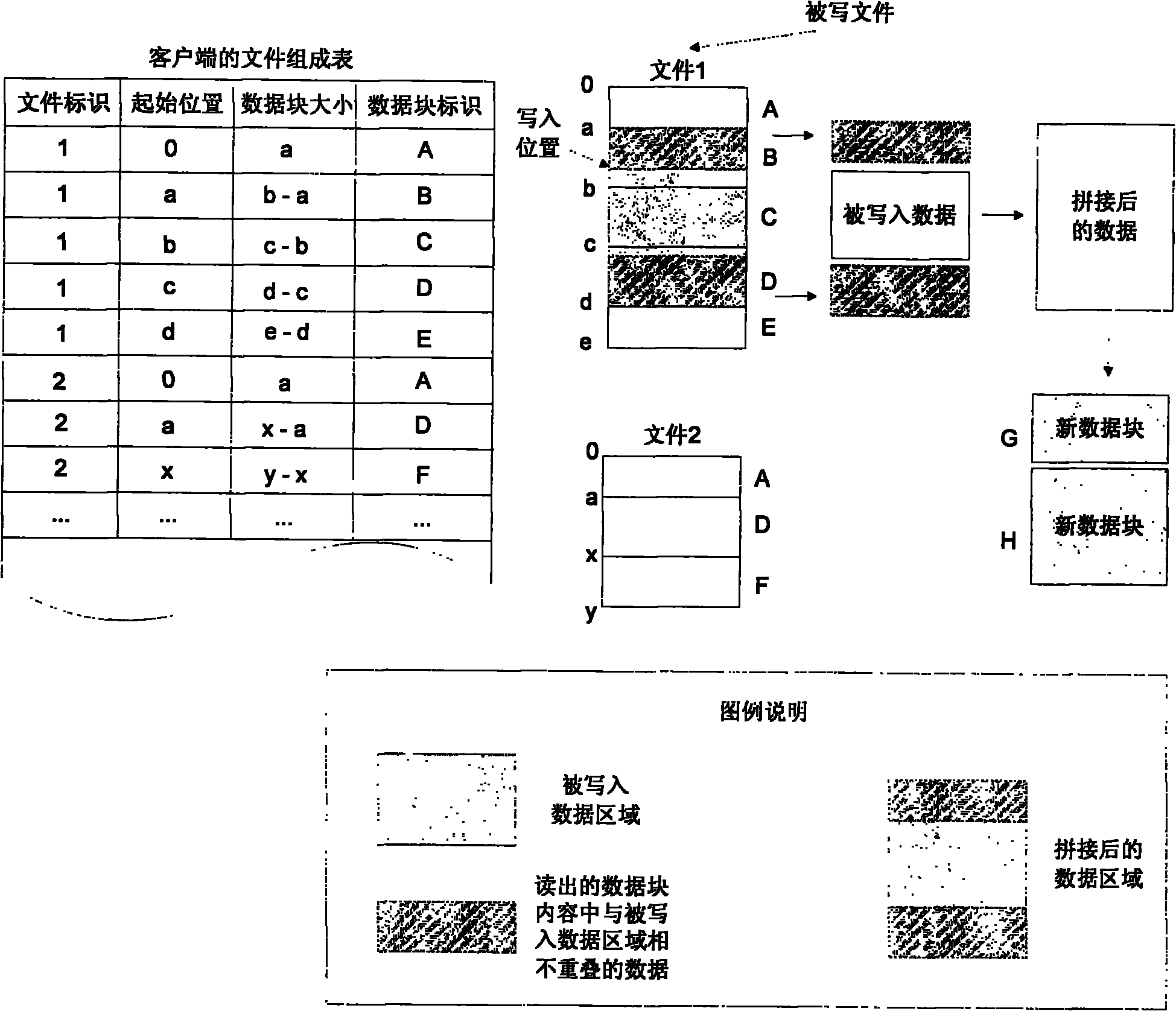
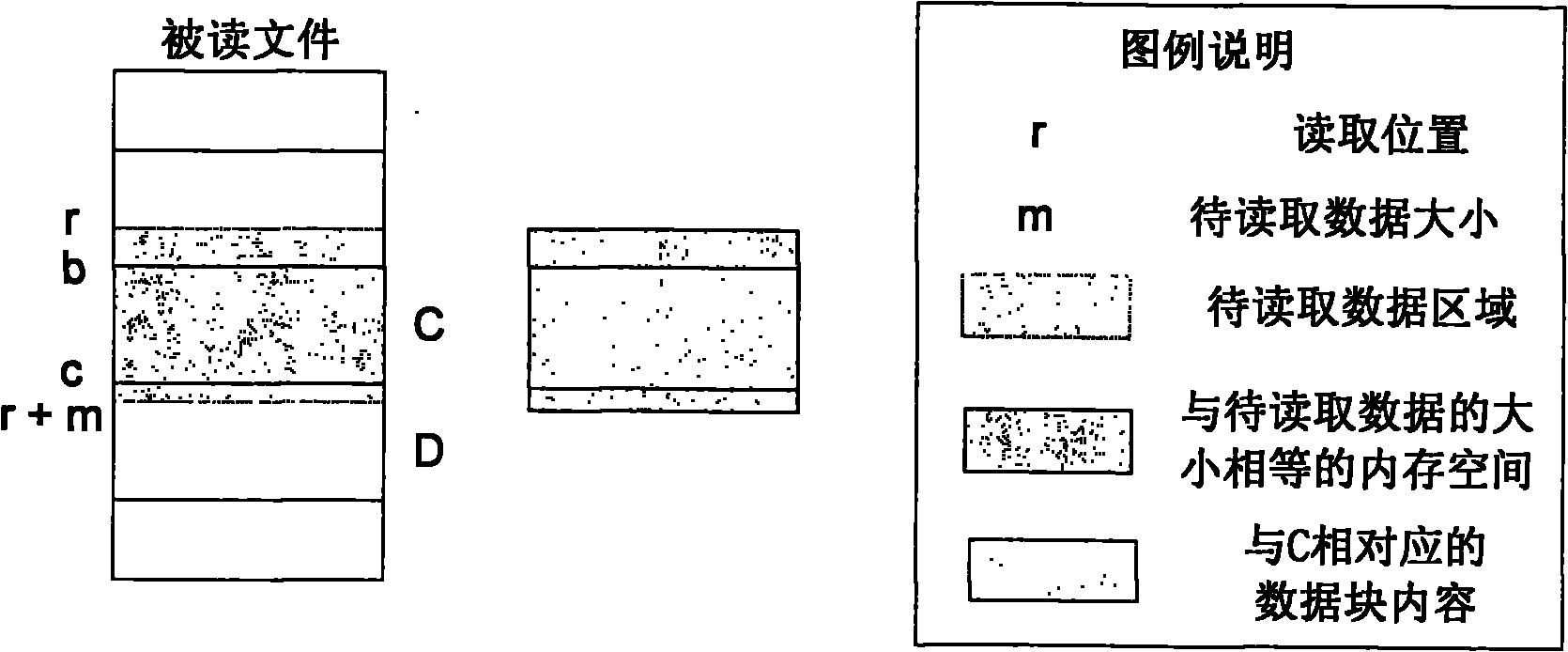
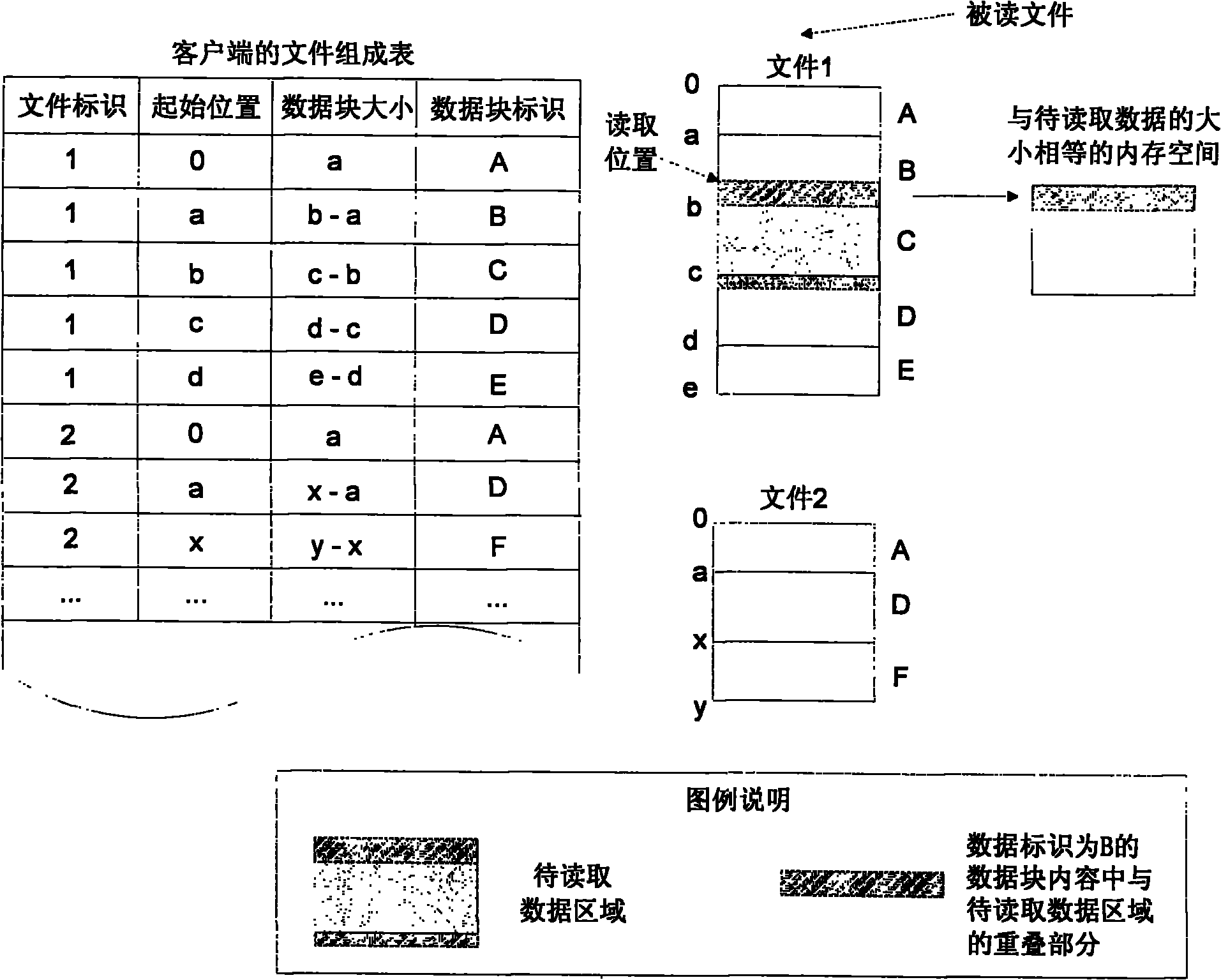
The invention relates to a real-time repetition removal and transmission method for data in a network file system, and belongs to the technical field of computer data storage. The method comprises the following steps of: setting a file metadata table, a data block index table and a file composition table in a client and a server respectively, and setting a to-be-transmitted message queue for storing data and updating message in the client; receiving and responding an operating command initiated to the network file system by a client application program through a file system drive by the client, wherein the operating command comprises the operation of creating a new file, writing data into an existing file, reading the data from the existing file and deleting the existing file; and settinga network service interface for uploading and downloading data block contents and receiving and answering client message in the server. The method can delete the repeated data so as to save the storage space, avoid transmitting the existing data of the opposite side between the client and the server and reduce the overhead of network bandwidth; meanwhile, the method supports a file blocking method of fixed length and unfixed length so as to improve the utilization rate of the storage space.
Owner:TSINGHUA UNIV
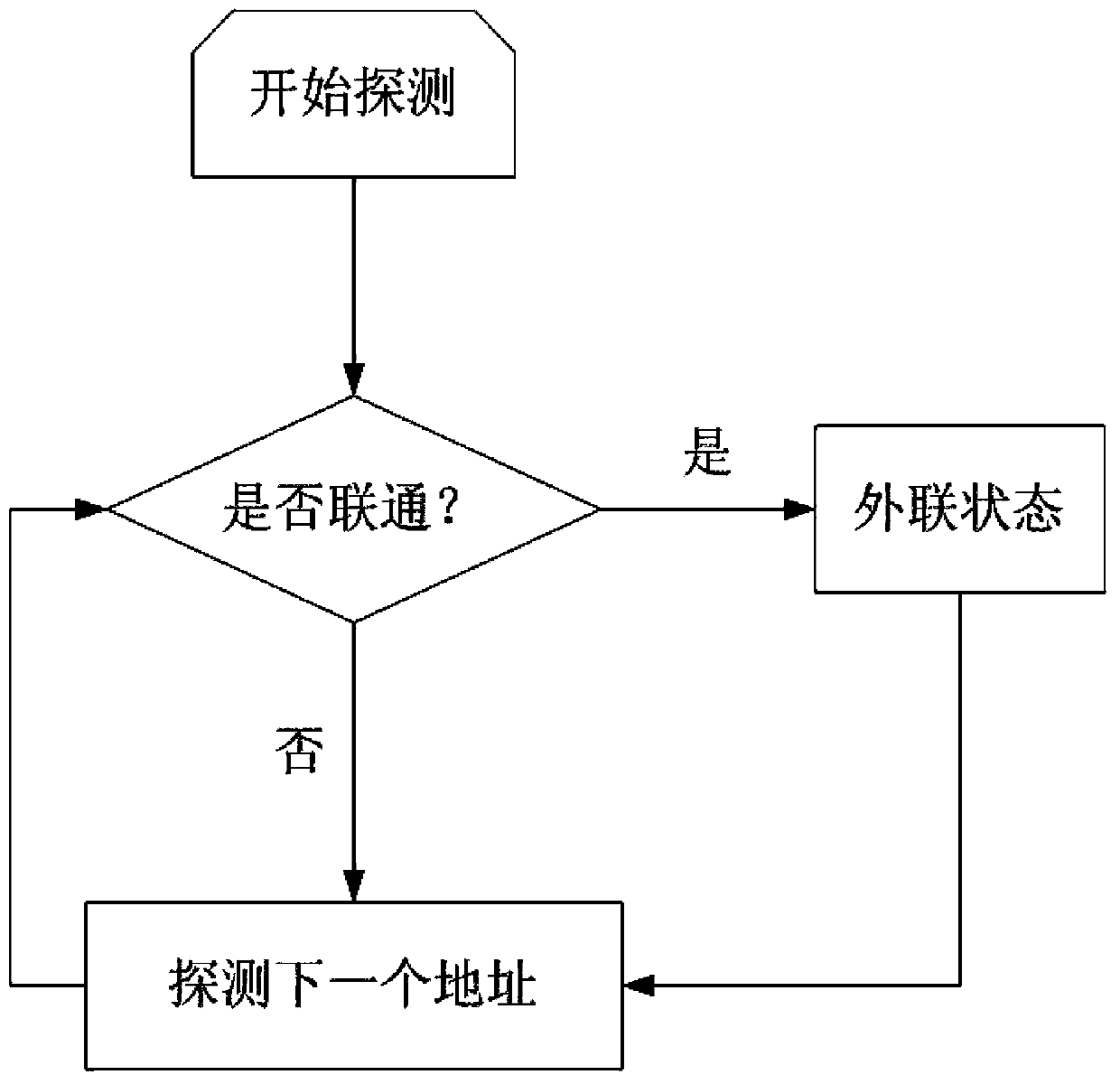
Alarm and blocking method for illegal external connections
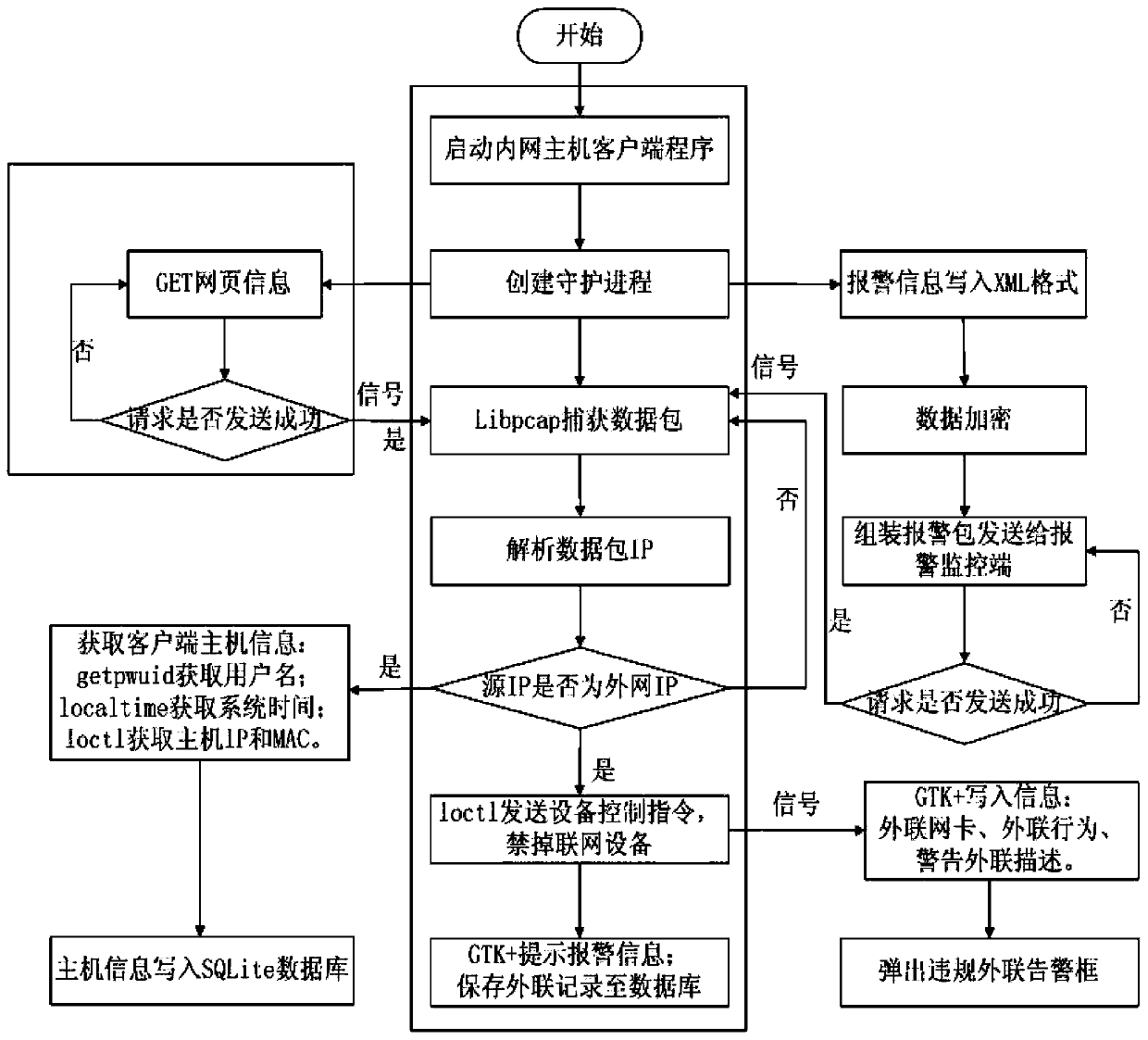
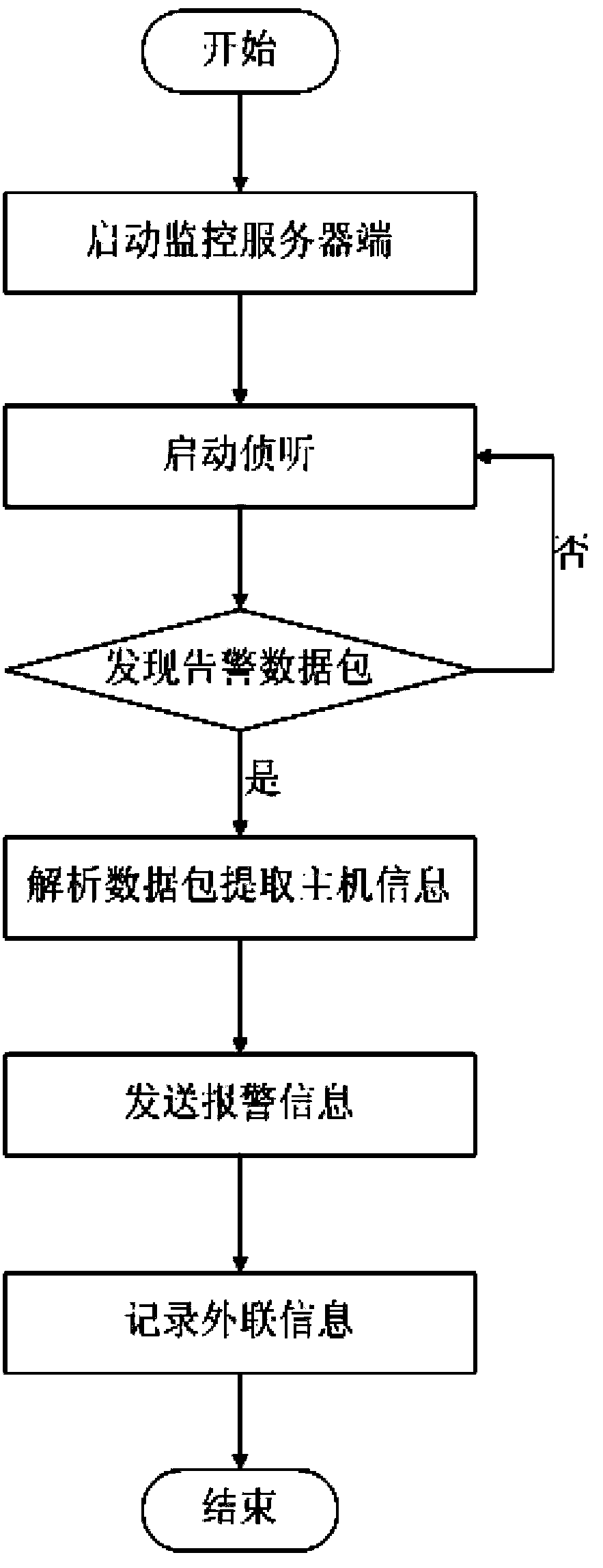
ActiveCN103391216AEasy to deployHas practical valueData switching networksNetwork packetBlock method
The invention relates to an alarm and blocking method for illegal external connections. The alarm and blocking method comprises that 1), an intranet host client monitors networking behaviors of intranet computers in real time according to a plurality of external connection modes; 2), the intranet host client initiatively sends an encrypted alarm data packet to an external connection alarm monitoring terminal by using a Libnet function library to detect whether the intranet computers have external connection behaviors and gives an alarm for illegal external connection behaviors; 3), the intranet host client performs bottom layer packet capture on alarmed intranet hosts to obtain all data packets passing through network cards of the hosts to judge the illegal external connection behaviors; 4), blocking the network cards of the hosts having the illegal external connection behaviors through judgment. The alarm and blocking method is high in timeliness and good in monitoring performance in the aspect of illegal external connection monitoring. By means of the alarm and blocking method, the safety and the transmission efficiency of the alarm data packets in systems are improved, leaking risks caused by stealing of alarm information are effectively avoided, meanwhile, the safety of software is improved, and the software has anti-shielding and anti-unloading capacities.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
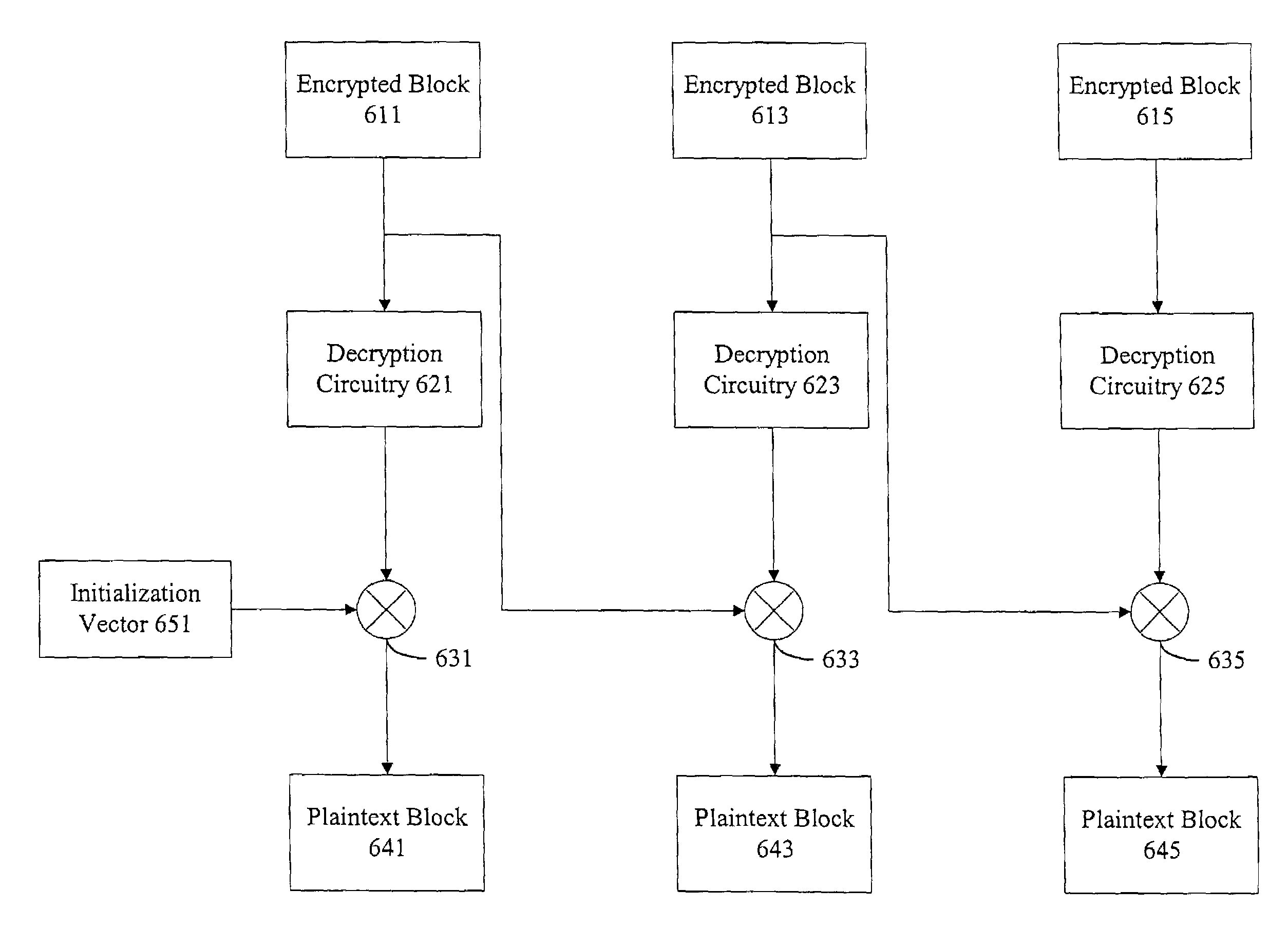
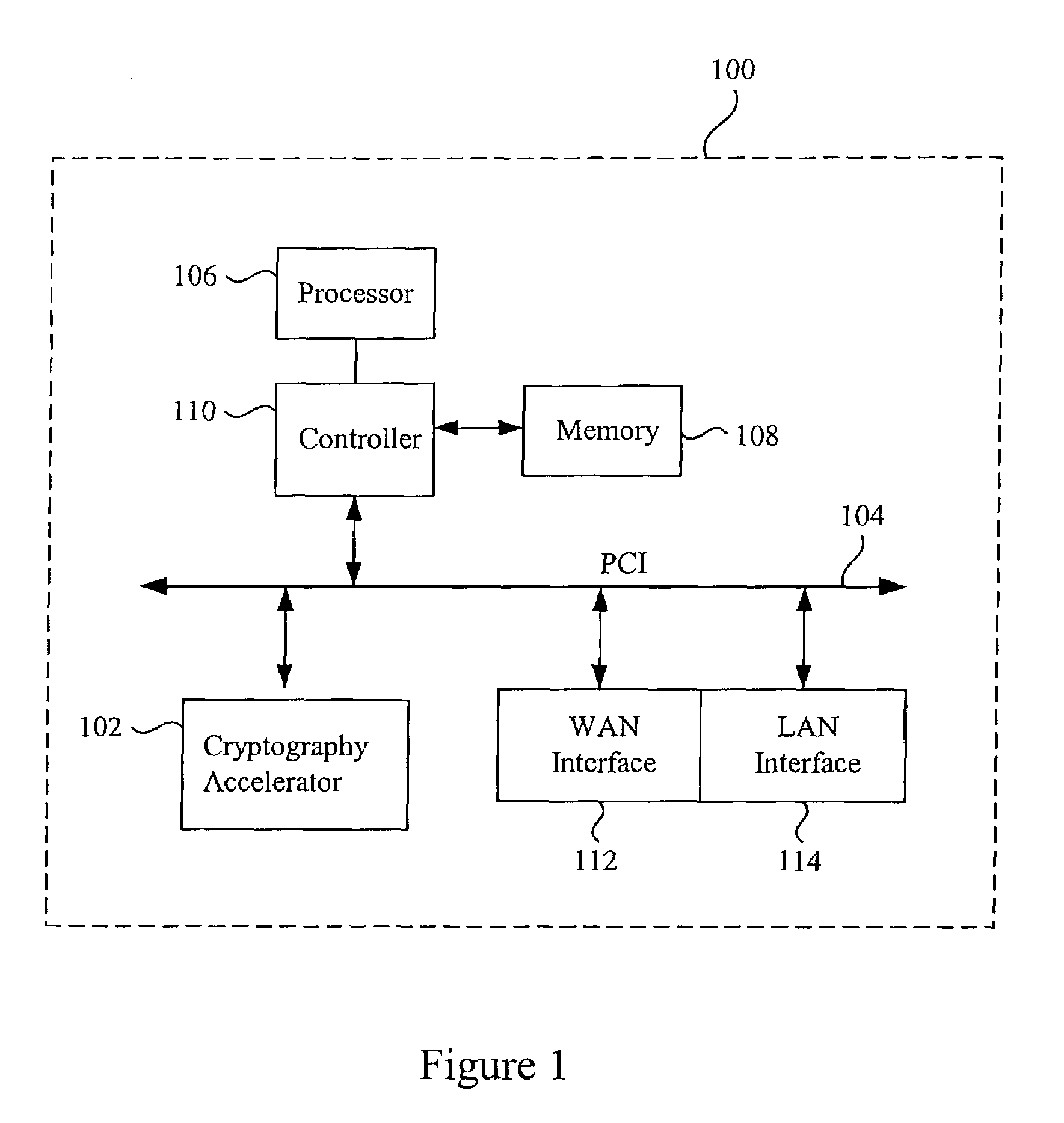
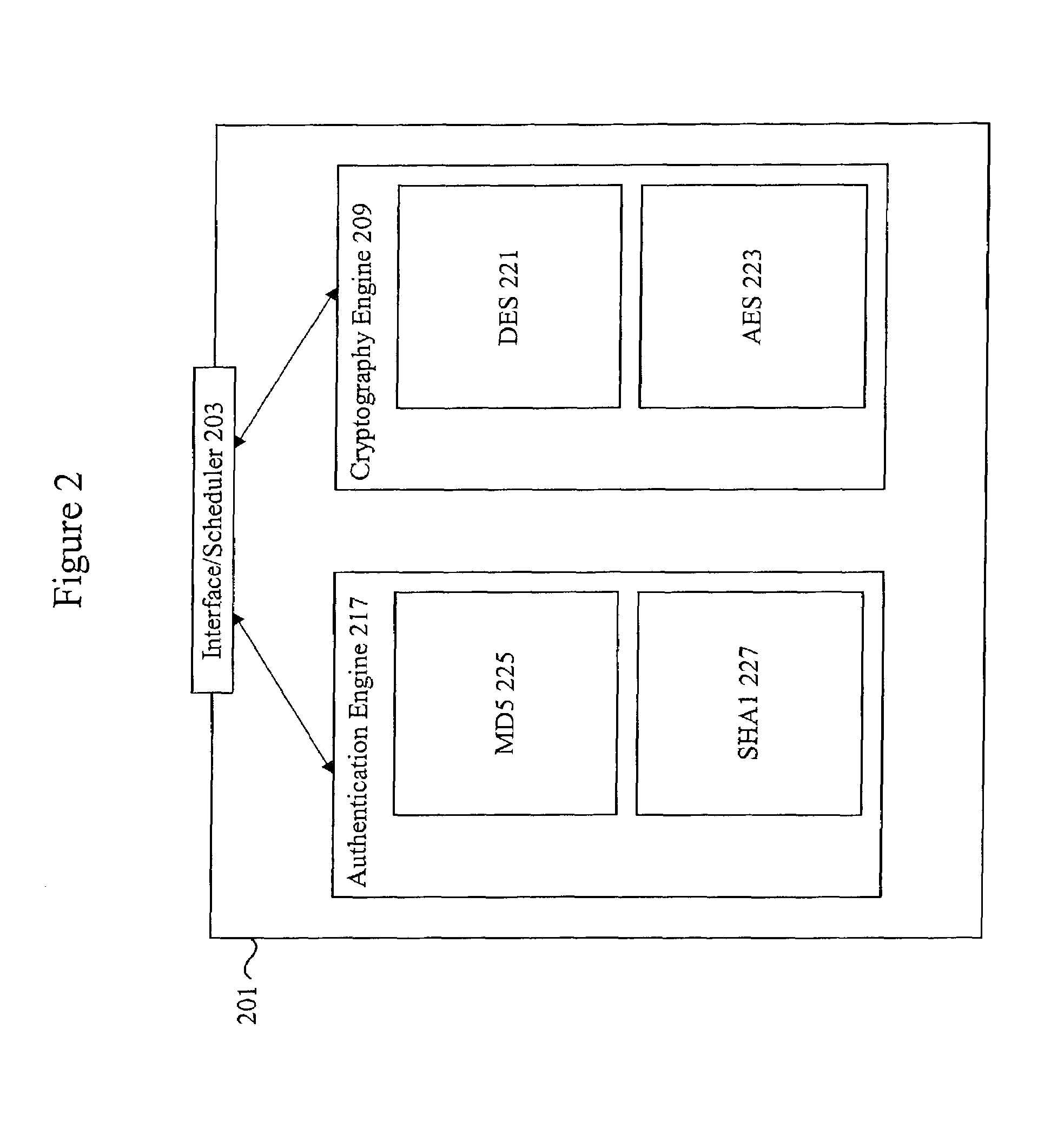
Method and apparatus for performing accelerated authentication and decryption using data blocks
ActiveUS7082534B2User identity/authority verificationSecret communicationComputer hardwareBlock method
Methods and apparatus are provided for performing authentication and decryption operations. A record including multiple encrypted blocks is received. An encrypted block in the record is extracted and decrypted first in order to obtain context information for performing authentication operations. Each remaining block is then decrypted and authenticated by using the available context information. Authentication operations can be performed without having to wait for the decryption of all of the blocks in the record.
Owner:AVAGO TECH INT SALES PTE LTD
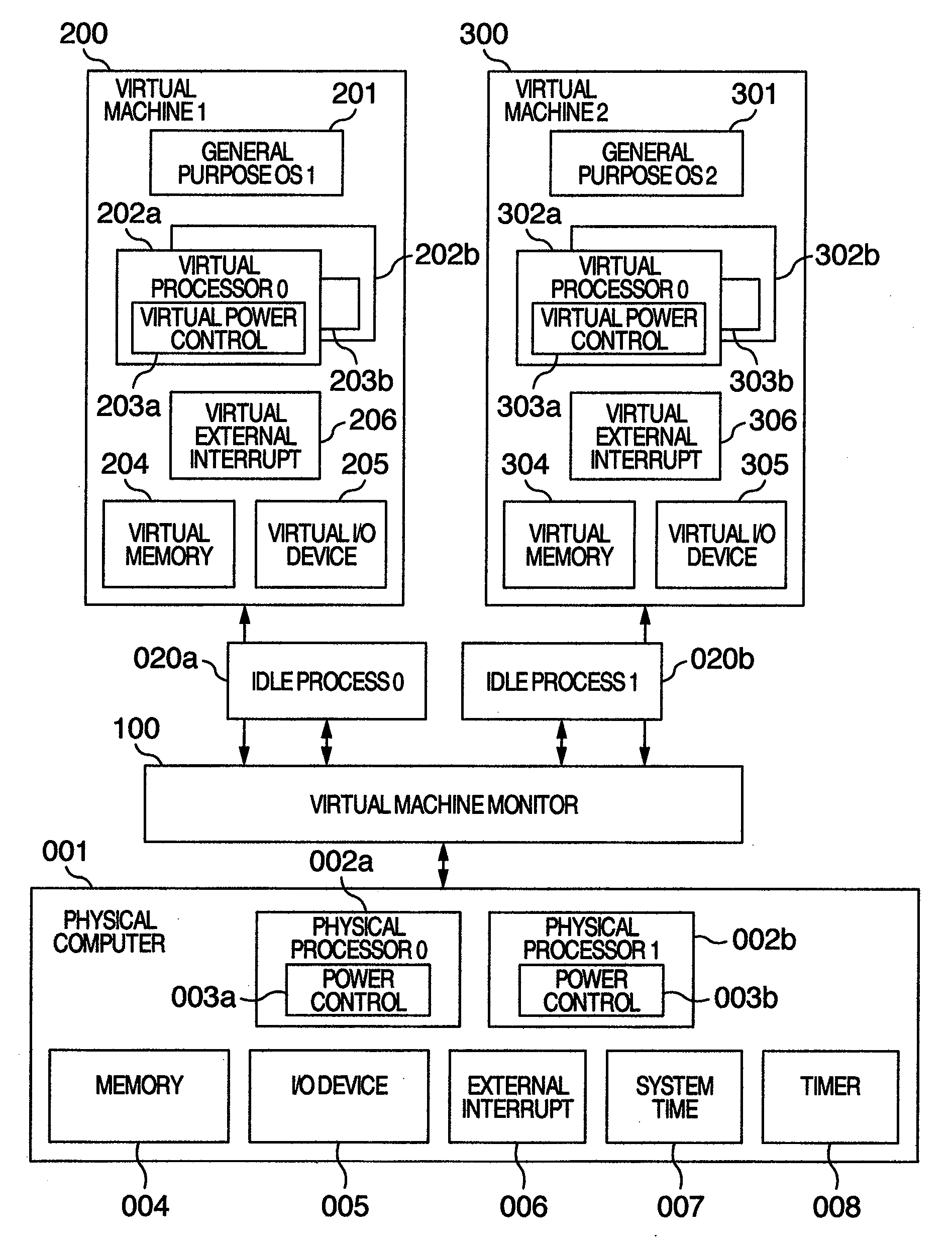
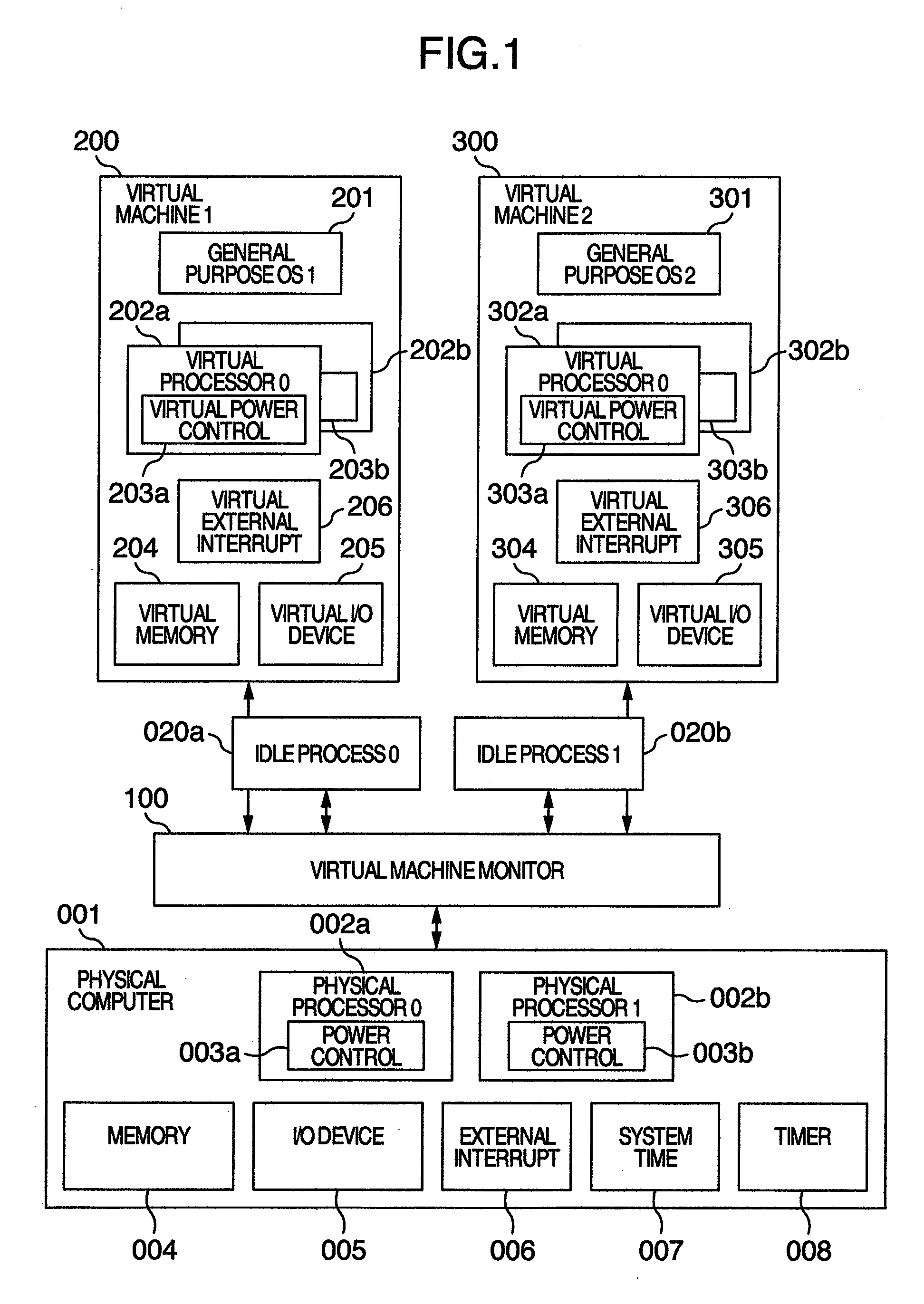
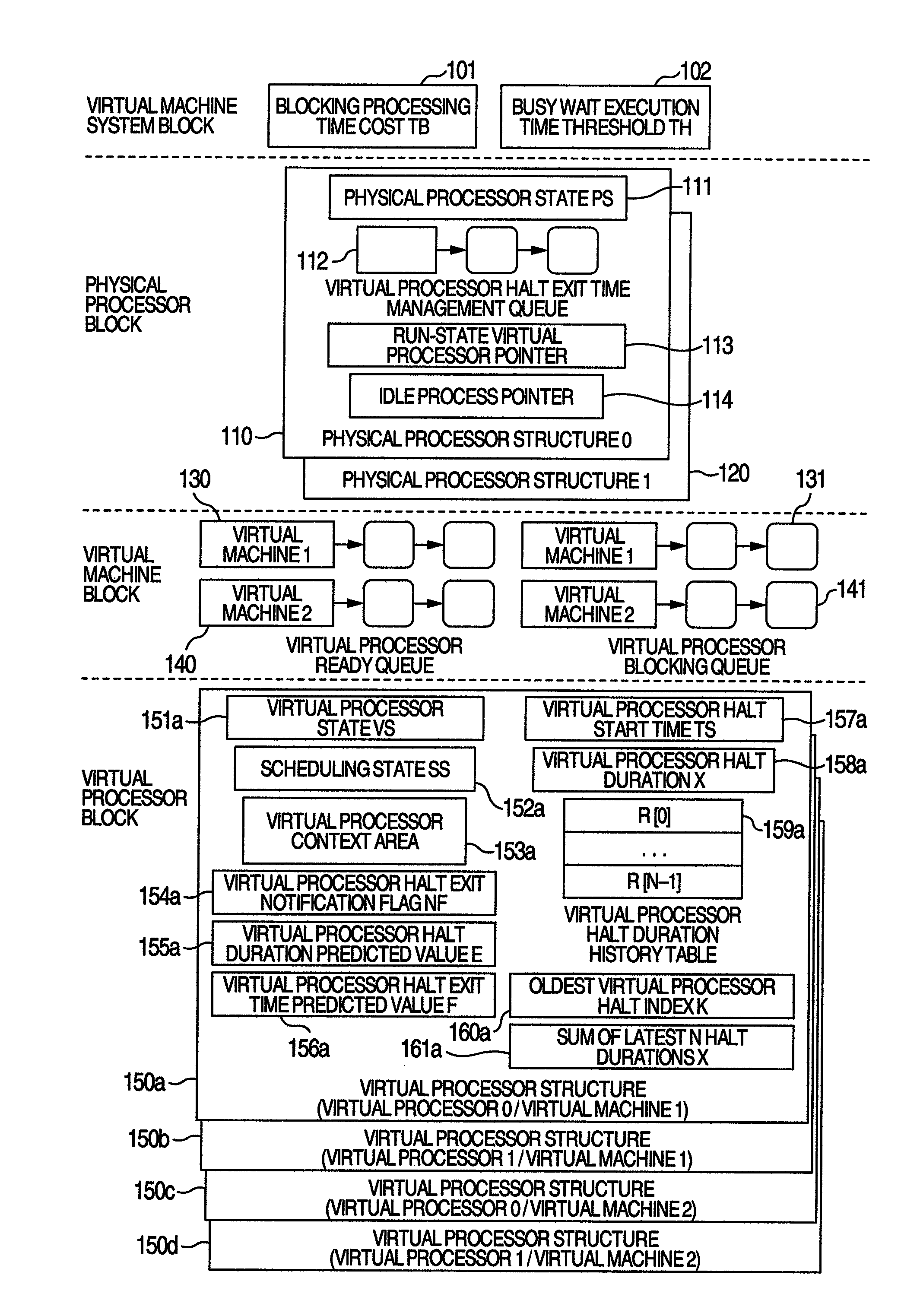
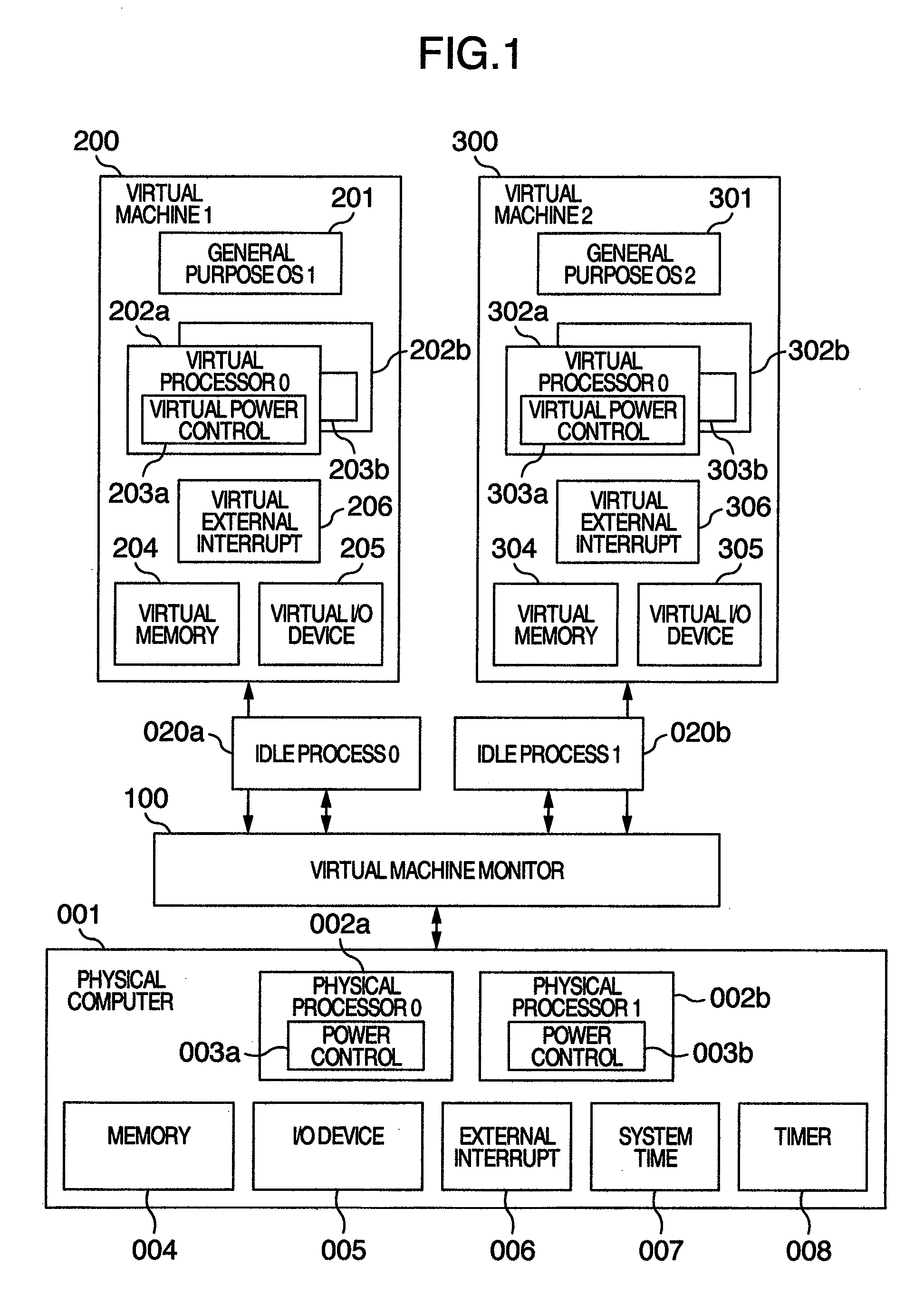
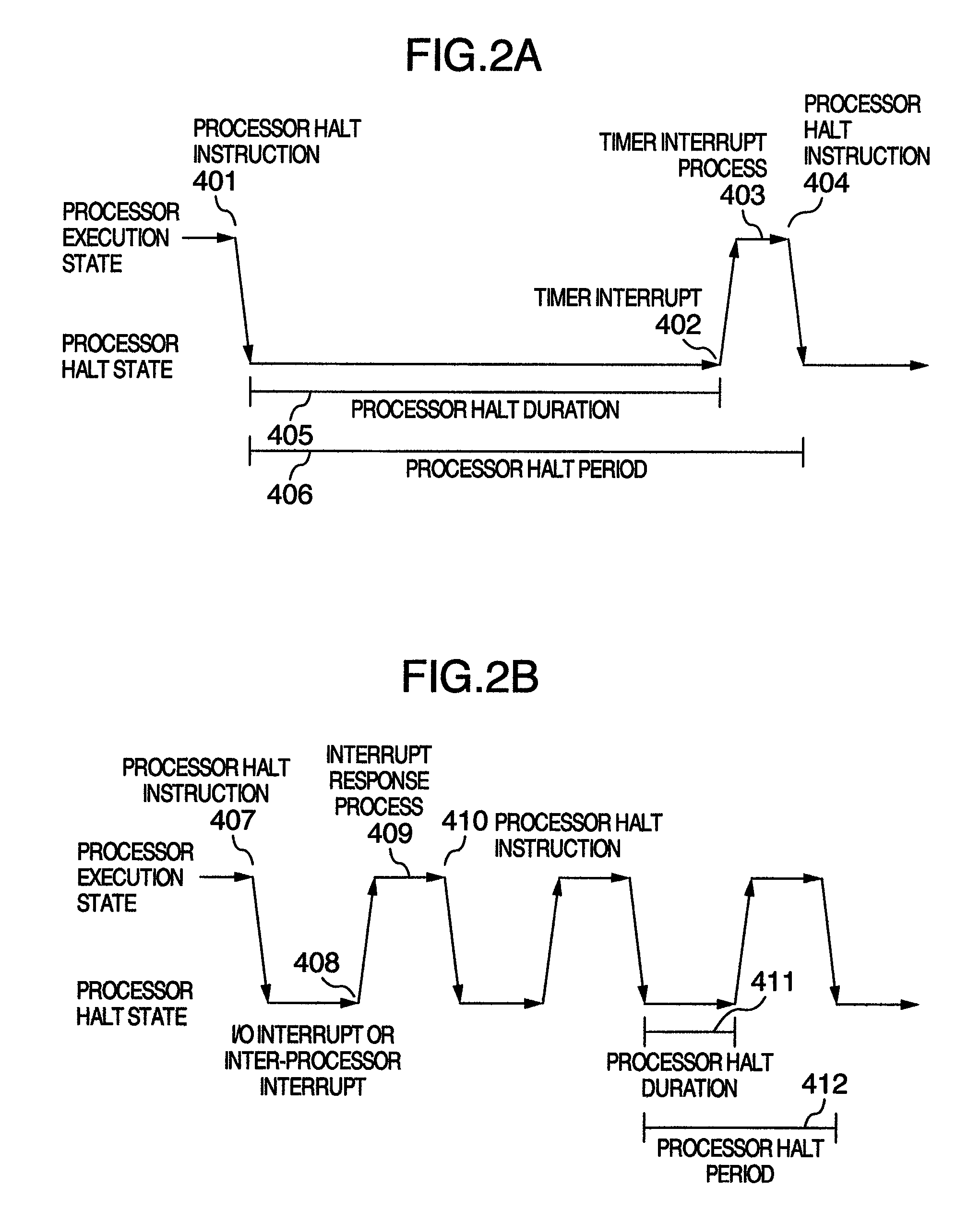
Computer system, virtual machine monitor and scheduling method for virtual machine monitor
ActiveUS20110010713A1Reduce power consumptionReduce processing timeEnergy efficient ICTMultiprogramming arrangementsComputerized systemPhysics processing unit
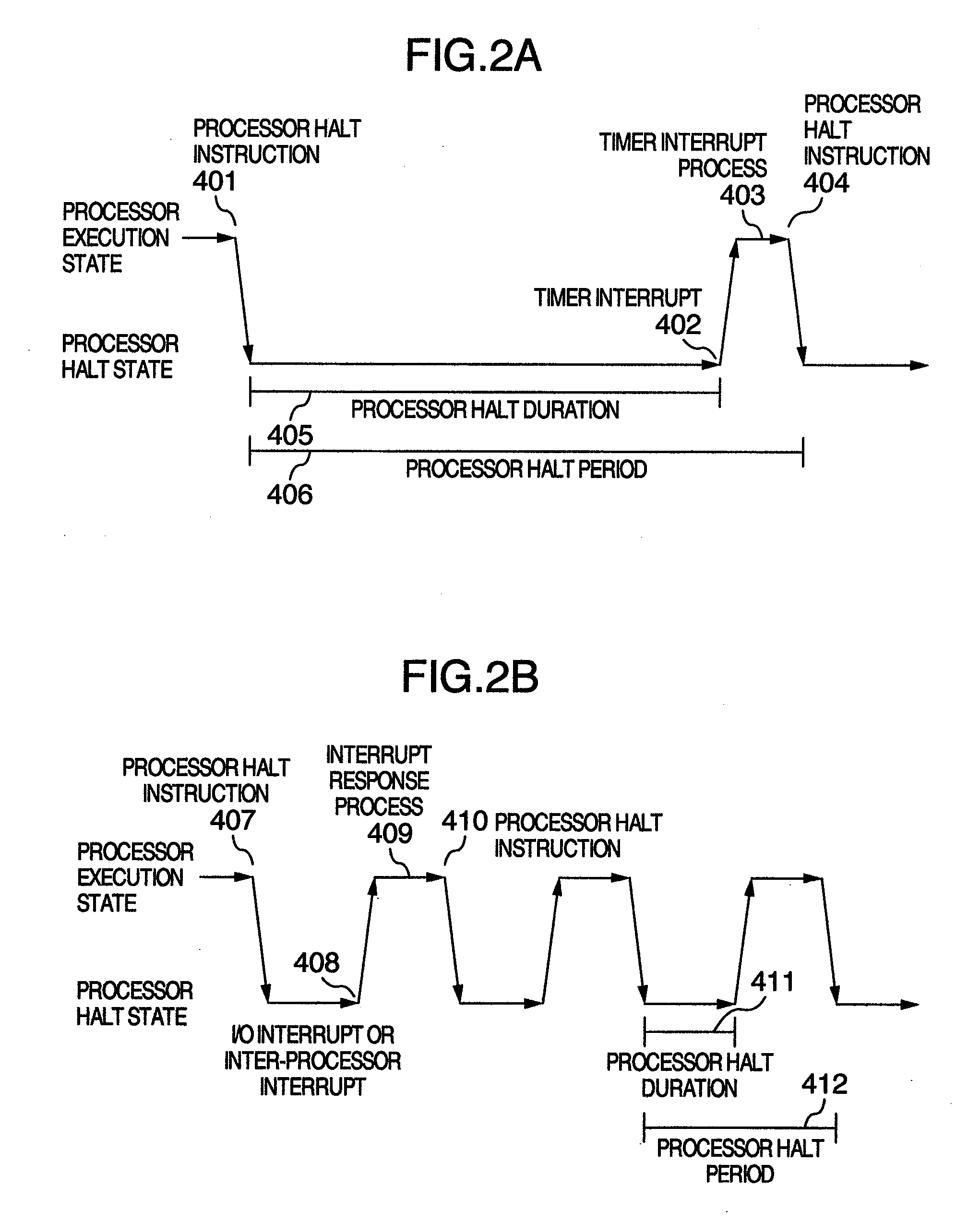
In a computer system according to the background art, when a request to halt a virtual processor was detected, the virtual processor was blocked. In the blocking method, latency of virtual halt exit of the virtual processor was so long that a problem of performance was caused. A virtual machine monitor selects either of a busy wait method for making repeatedly examination until the virtual halt state exits while the virtual processor stays on the physical processor and a blocking method for stopping execution of the virtual processor and scheduling other virtual processors on the physical processor while yielding the operating physical processor and checking off scheduling of the virtual processor to the physical processor, based on a virtual processor halt duration predicted value of the virtual processor which is an average value of latest N virtual processor halt durations of the virtual processor.
Owner:HITACHI LTD
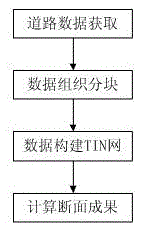
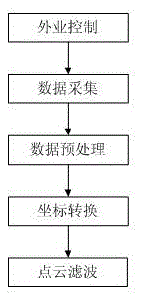
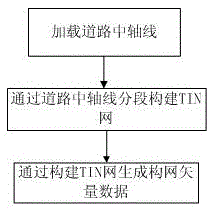
Road longitudinal and lateral section obtaining method based on LiDAR point cloud
InactiveCN106887020ASolve the problem that large data cannot be read uniformlyReliable and finer designImage enhancementImage analysisPoint cloudLidar point cloud
The invention discloses a road longitudinal and lateral section obtaining method based on a LiDAR point cloud, and relates to the technical field of measurement. The method comprises the following steps: road data obtaining: generating filtered road surface point cloud data through the steps of field control, data collection, data preprocessing, coordinate conversion and point cloud filtering; data organization blocking: carrying out the block management of point cloud data according to a proper distance grid; TIN network construction through data: carrying out the buffering and constructing a TIN network according to an existing road central axis and a specific distance; section accomplishment calculation: generating a longitudinal and lateral section file according to a mileage file. The method is advantageous in that the method organizes the point cloud data through an engineering file, manages the point cloud data through the engineering file, carries out the automatic call of ground point cloud data in a corresponding range of the central axis of a road, and enables the data to be used for constructing the TIN network after format conversion. The seamless blocking method ingeniously solves a problem that point cloud data cannot be read in a unified manner because the size of the point cloud data is large.
Owner:星际空间(天津)科技发展有限公司
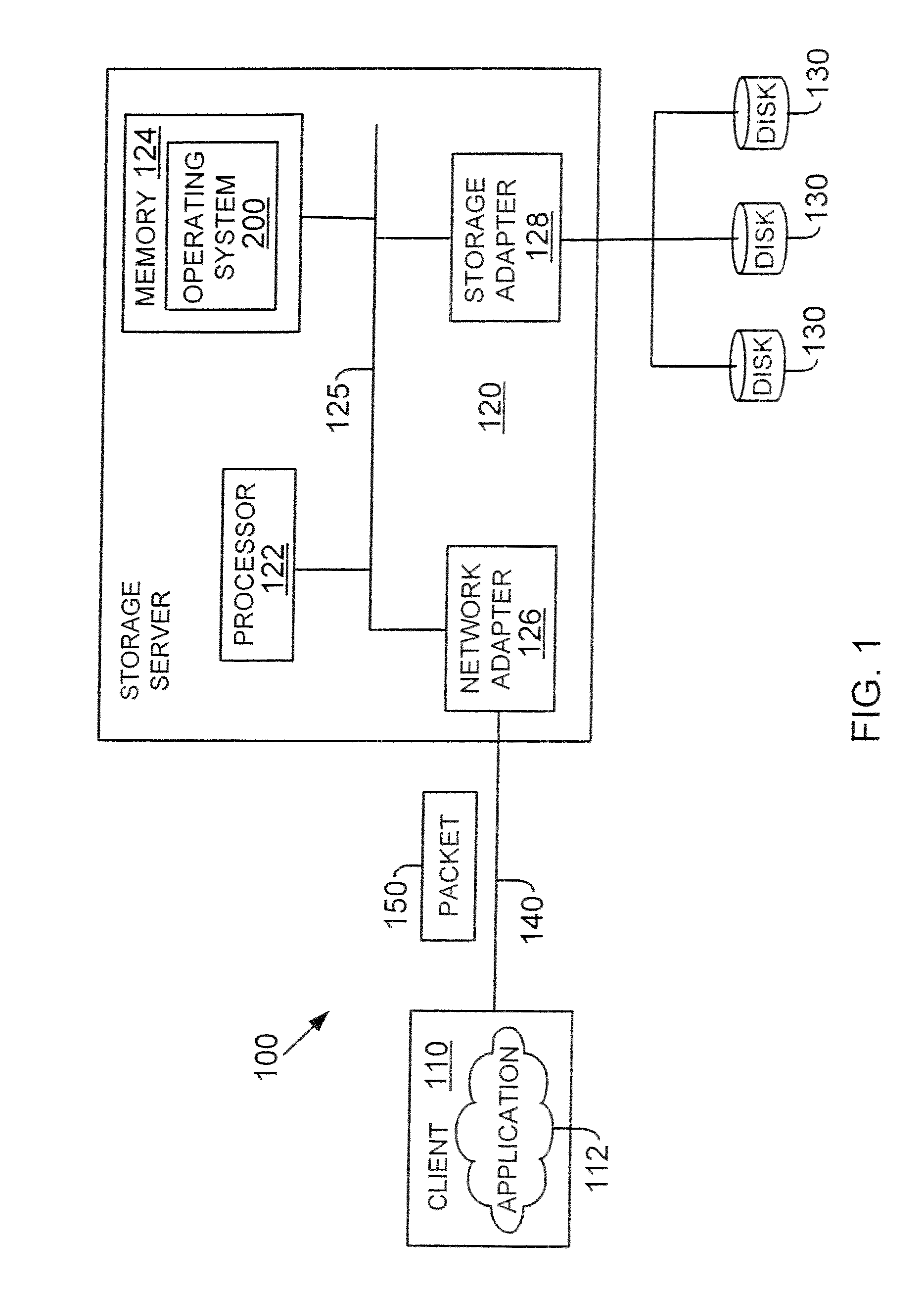
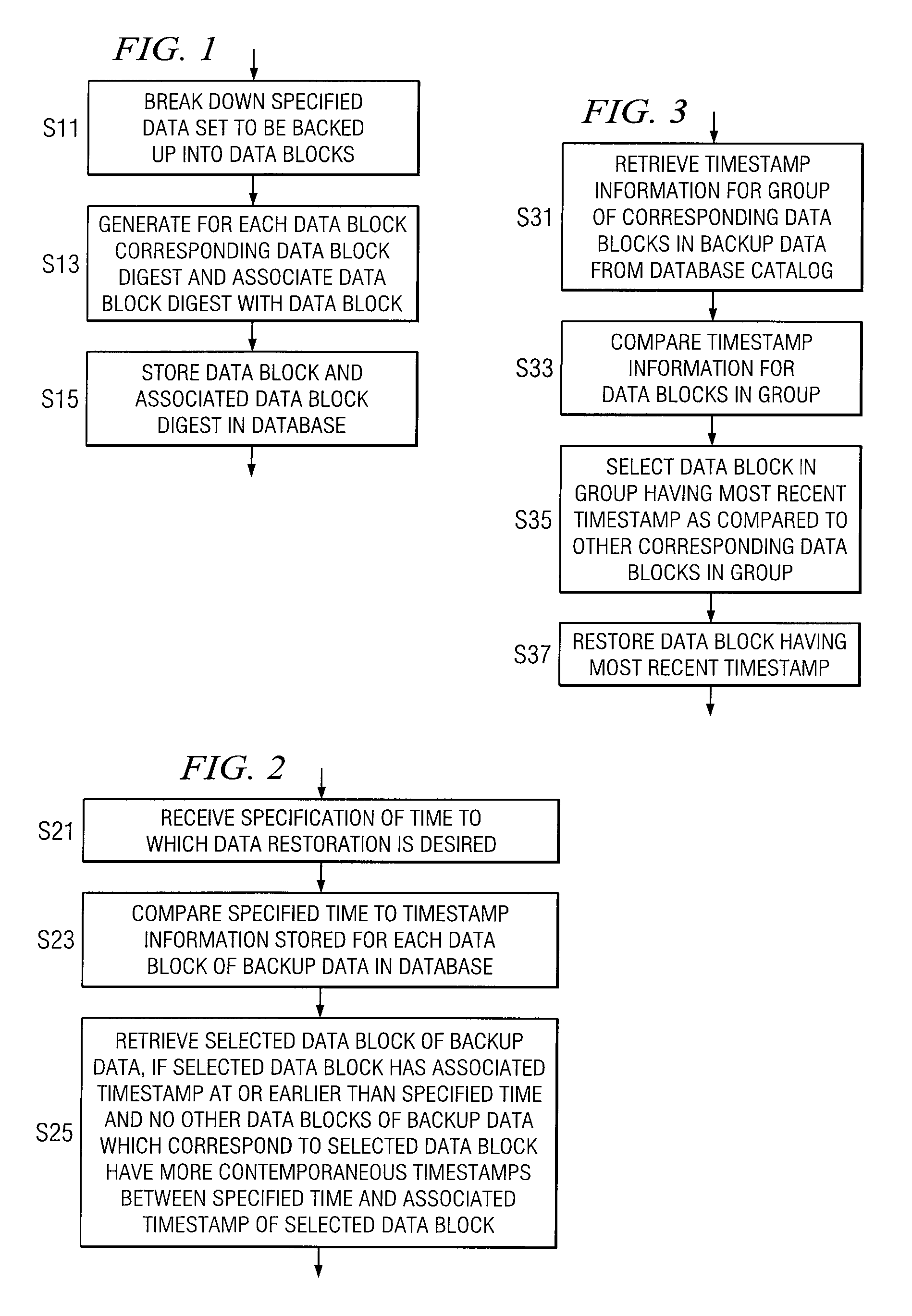
Method and apparatus for data backup using data blocks
Methods and apparatuses for backing up data to a database are provided. A specified data set to be backed up is broken down into a plurality of data blocks, each data block is associated with a data block digest, and the data blocks and associated data block digests are stored in the database. When one or more data blocks are subsequently changed, an update to the backup may be performed by adding to the backup data only the data blocks that have changed since the initial backup. Methods and apparatuses for restoring backup data from a database are also provided. Timestamp information associated with the data blocks in the database is used to select the data blocks to be restored.
Owner:COMP ASSOC THINK INC
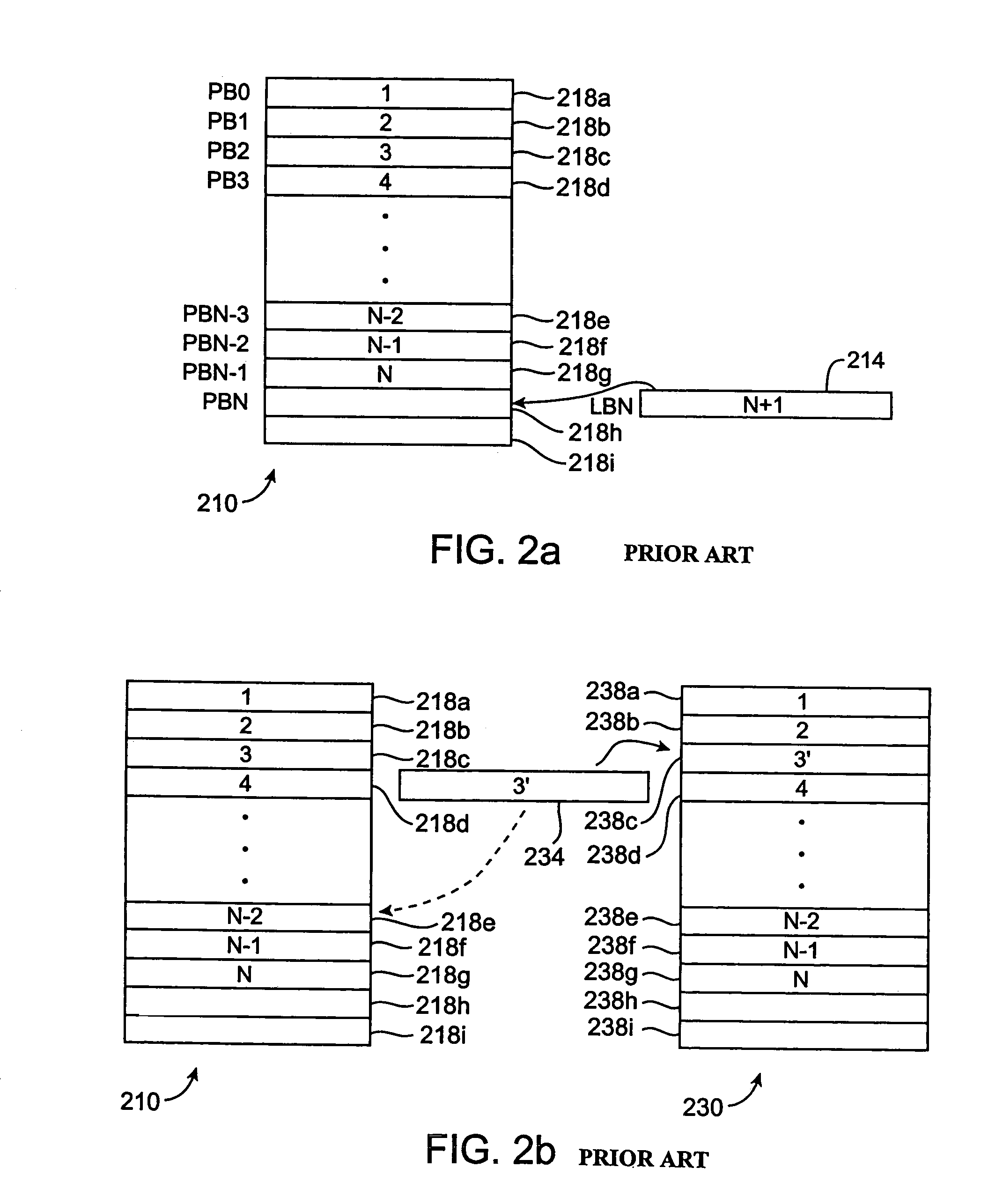
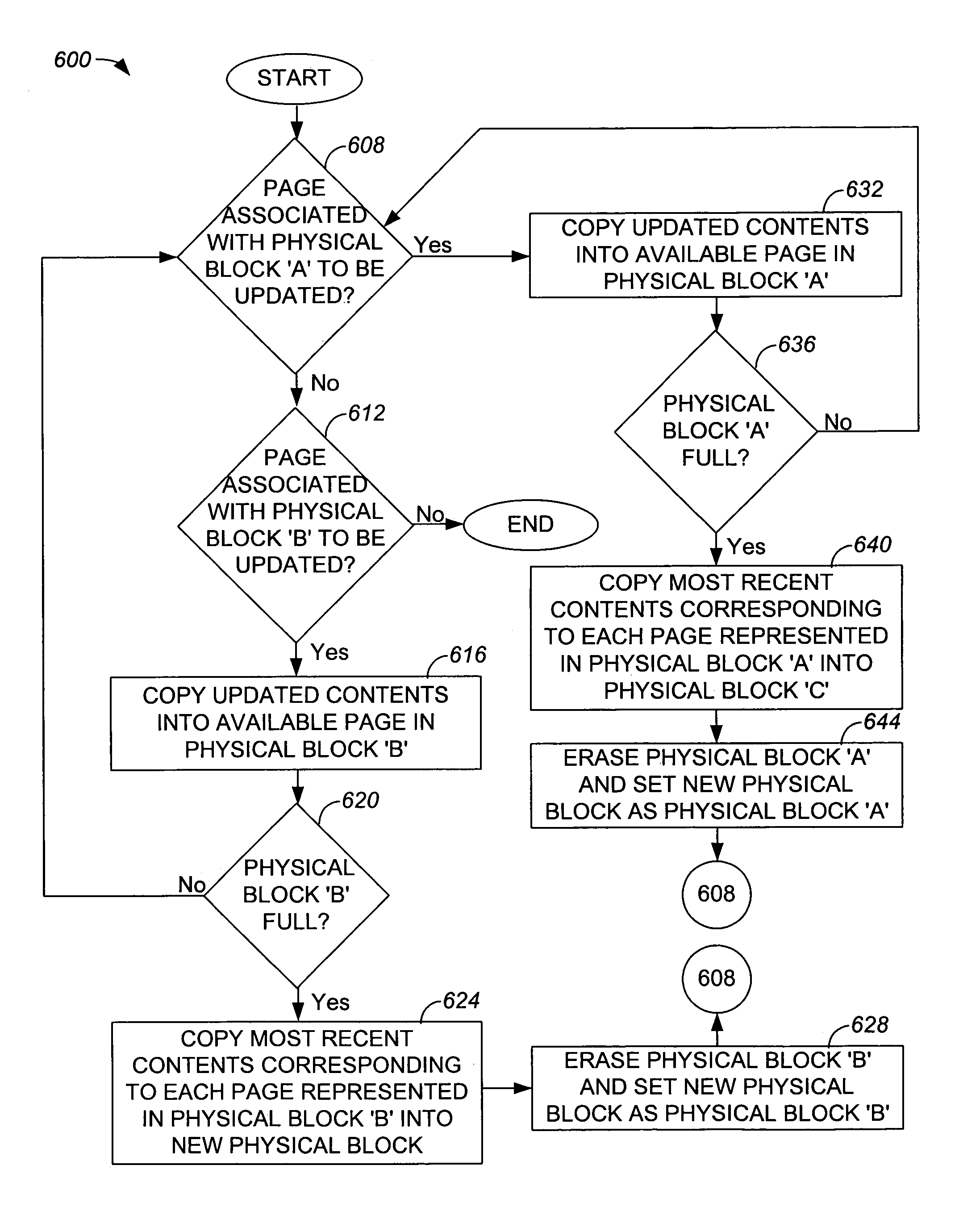
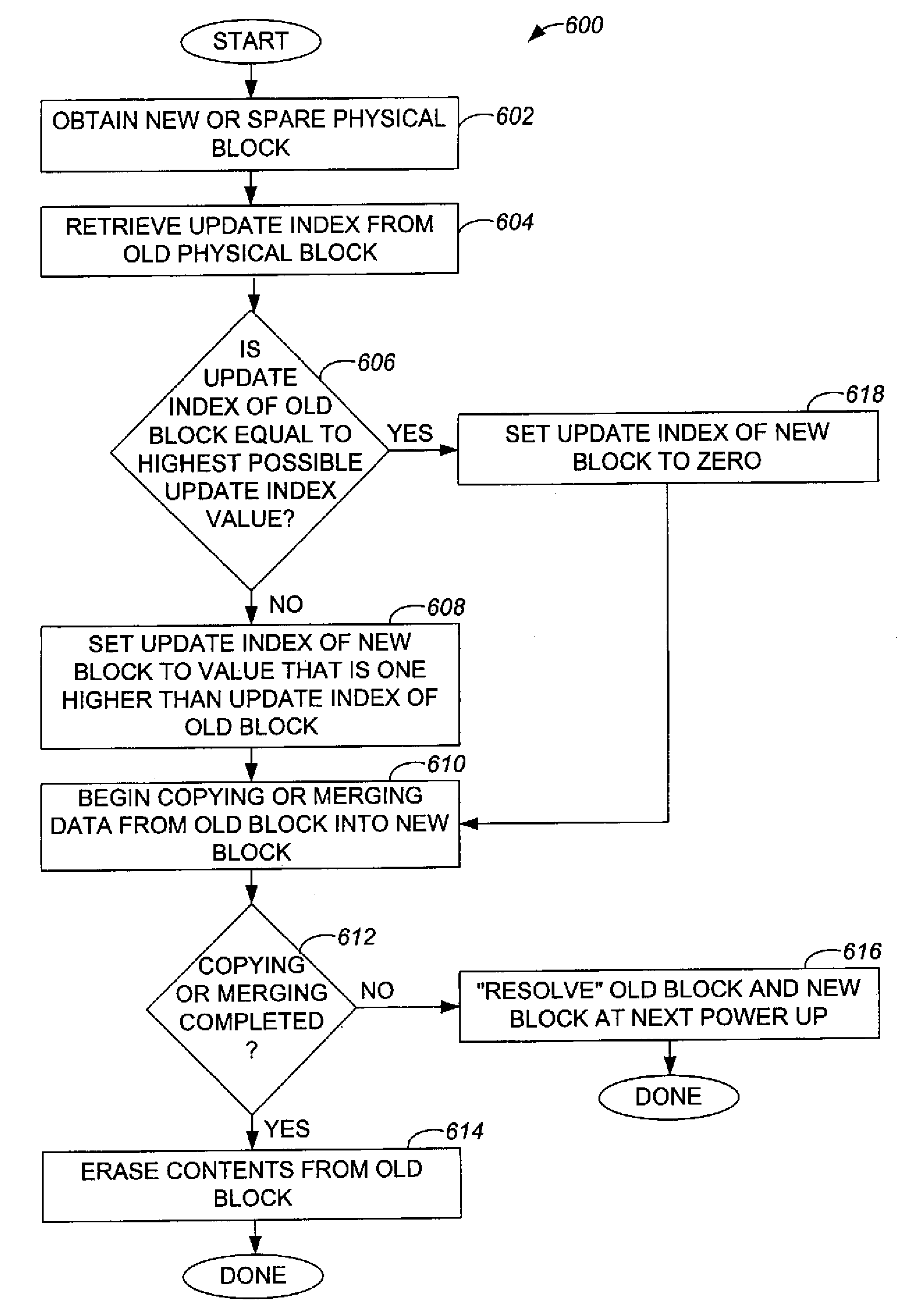
Method and apparatus for resolving physical blocks associated with a common logical block
InactiveUS7234036B1Readily and efficiently be determinedPower Loss MinimizationInput/output to record carriersMemory adressing/allocation/relocationBlock methodOperating system
Methods and apparatus for determining which of a plurality of physical blocks associated with a logical block is more recently associated with the logical block are disclosed. According to one aspect of the present invention, a method for resolving associations of a first physical block and a second physical block to a logical block associated with a non-volatile memory system includes obtaining a first identifier associated with the first physical block and obtaining a second identifier associated with the second physical block. The identifiers are compared to ascertain whether the first identifier indicates that the first physical block is more recently associated with the logical block. The method also includes completing an operation arranged to provide contents associated with the logical block to the first physical block when it is determined that the first identifier indicates that the first physical block is more newly associated with the logical block.
Owner:SANDISK TECH LLC
Automatic identification and blocking method of spam cell
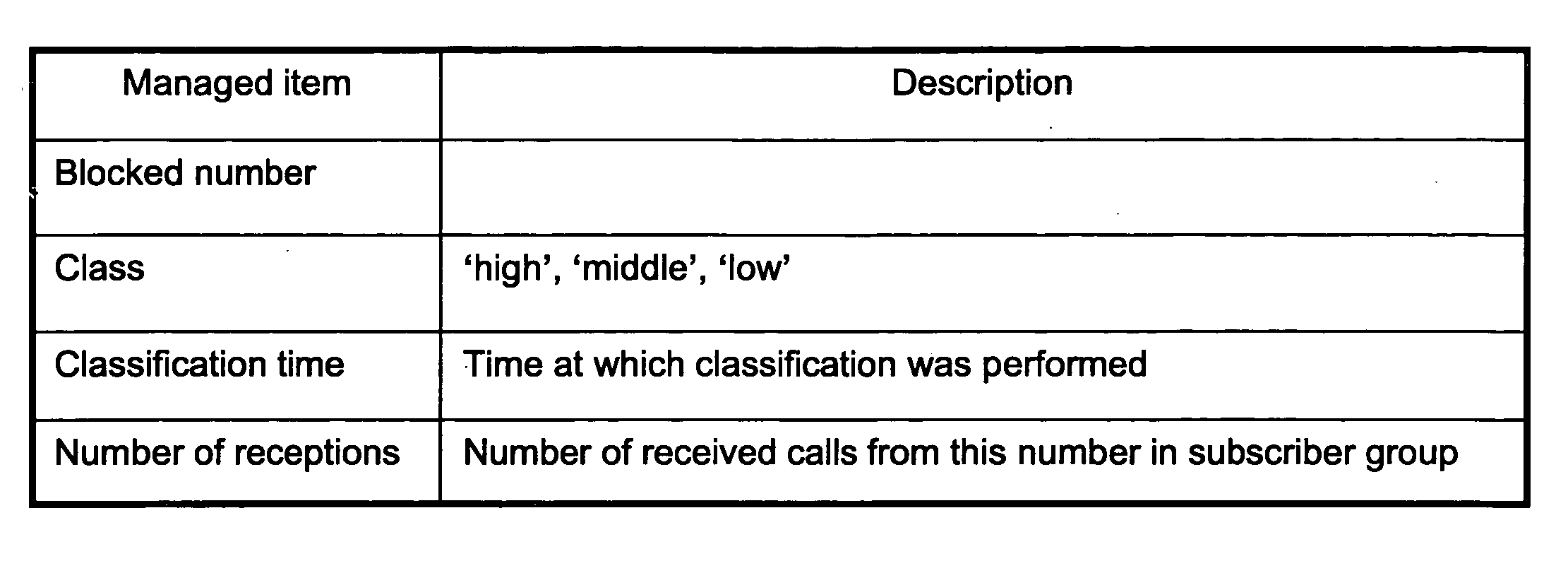
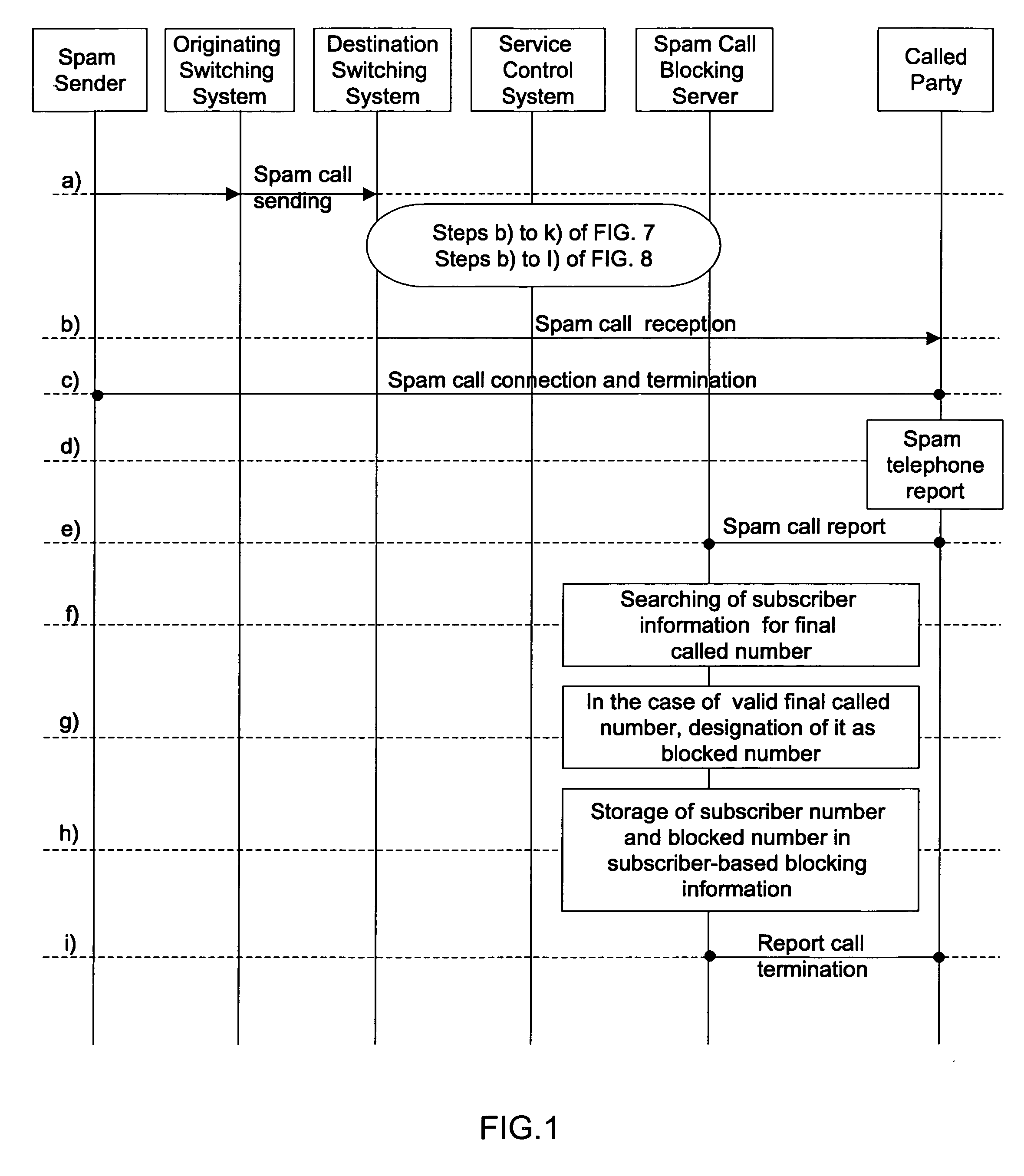
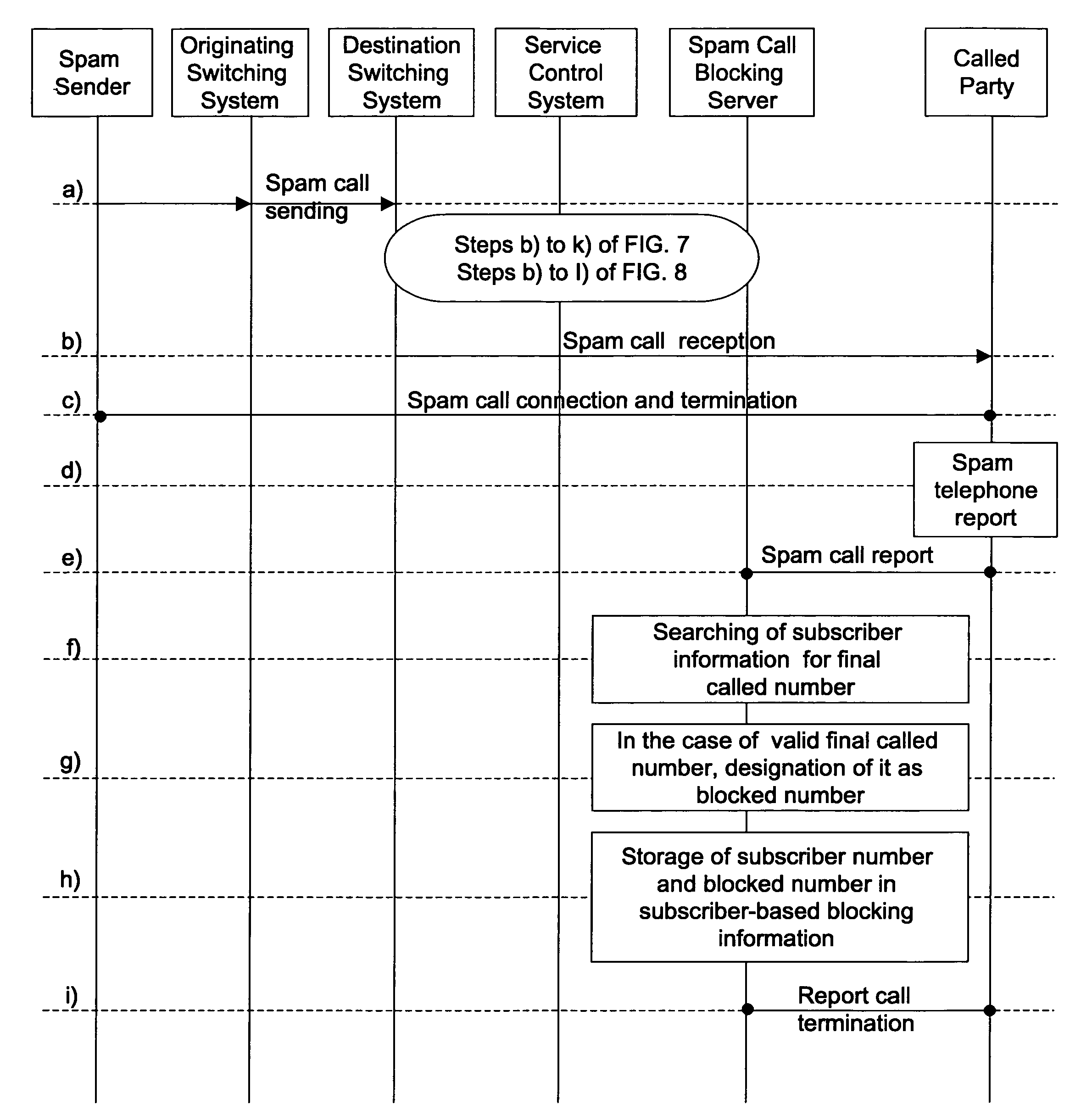
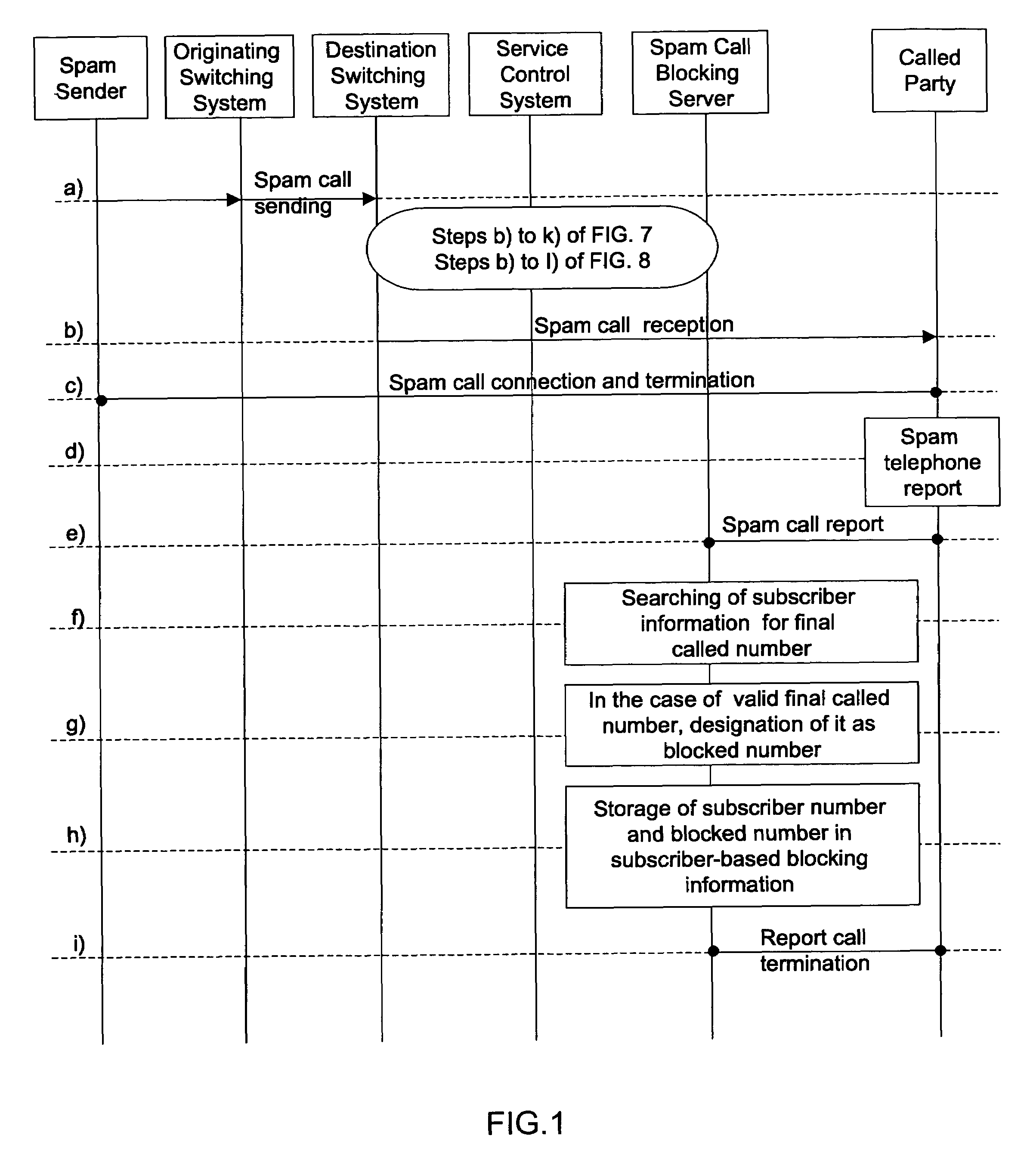
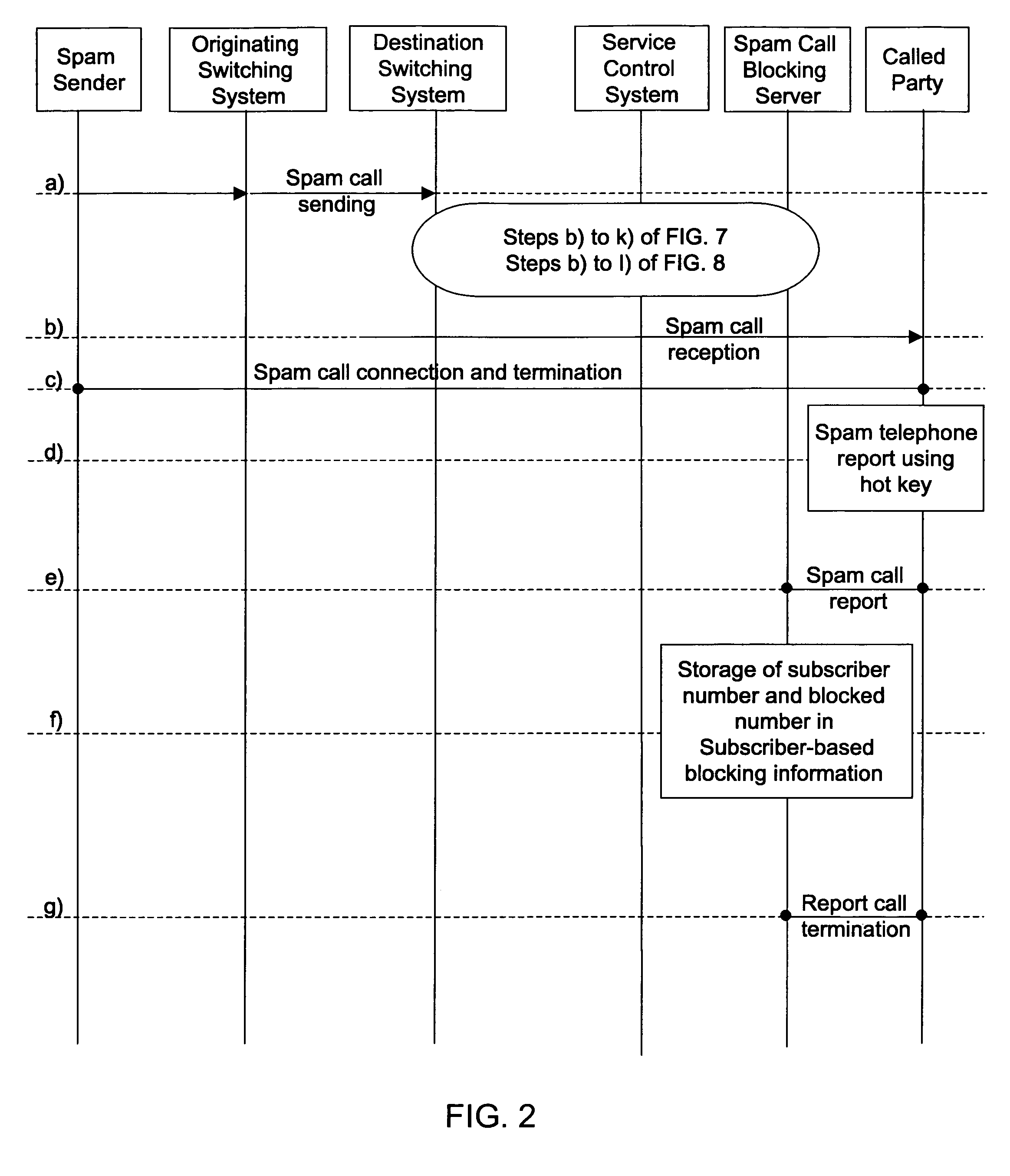
InactiveUS20070283006A1Easy to reportEasy and rapid registrationSpecial service for subscribersDigital computer detailsAuditory displayControl system
Disclosed herein is a method of visually or auditorily indicating spam status or a spam class for a calling number through a called terminal. The method includes the steps of the destination switching system requesting service from a spam call blocking server by delivering the calling number and a called number to the spam call blocking server; the spam call blocking server inquiring about spam status or a spam class for the calling number; if the spam status is ‘blocked’, or if the spam status is ‘blocked’ and the spam class is equal to or higher than a predetermined class, the spam call blocking server transmitting the spam status or spam class; the service control system activating caller identification service of a called party; the service control system including information about the spam status or spam class in caller identification information for the caller identification service; the service control system transmitting call connection information and the caller identification information to a destination switching system and, thus, the destination switching system making a call with a called terminal; and the destination switching system delivering the caller identification information to the destination terminal and, thus, providing visual or auditory display through the called terminal.
Owner:UANGEL CORP
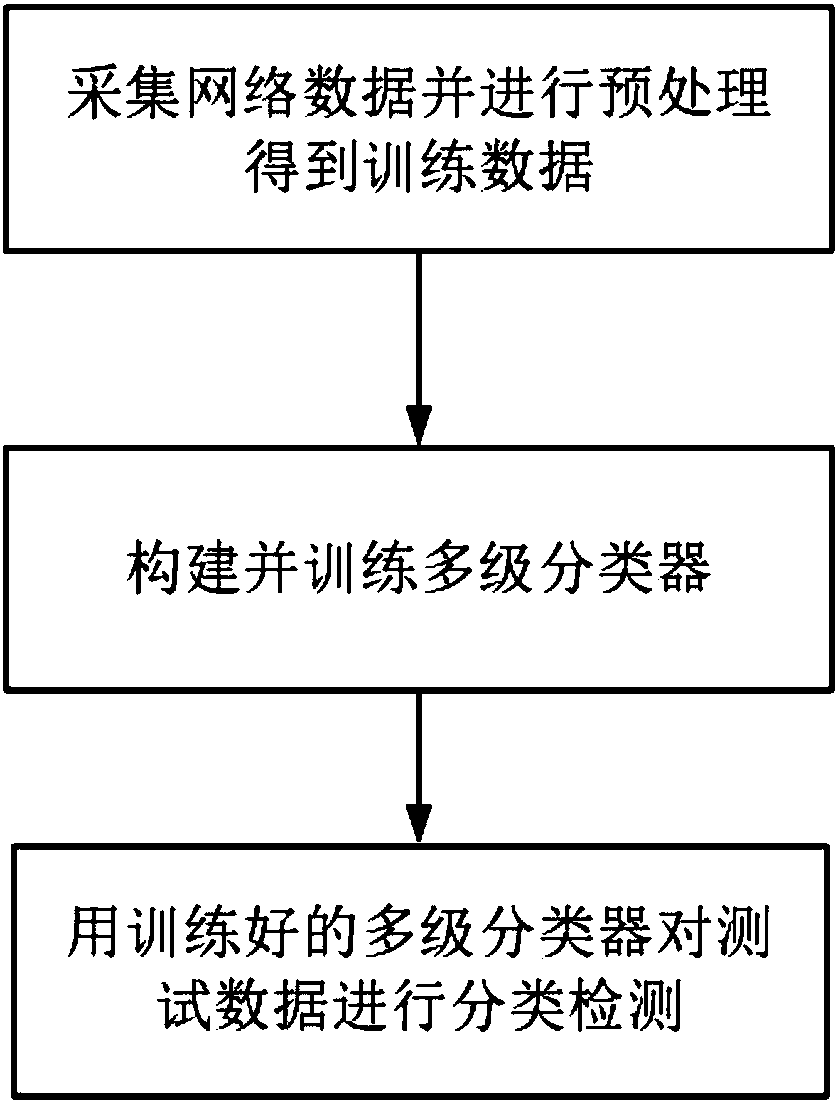
Method for carrying out classification detection on network attack behaviors through utilization of machine learning technology
InactiveCN108540451ASmall scaleImprove efficiencyCharacter and pattern recognitionTransmissionPretreatment methodParallel algorithm
The invention relates to a method for carrying out classification detection on network attack behaviors through utilization of a machine learning technology and belongs to the technical field of information. The method comprises the steps of 1, collecting network data and carrying out preprocessing to obtain training data; 2, establishing and training a multilevel classifier; and carrying out classification detection on test data through utilization of the trained multilevel classifier. Compared with the prior art, the method provided by the invention has the advantages that 1, through utilization of a preprocessing method for the collection data, the data scale can be reduced, moreover, partial unrelated data is removed, and the integrated efficiency is improved; 2, through utilization ofthe multilevel classifier and an integrated learning thought, the problem that a single classifier is low in fitting precision is solved, and the detection precision of the system is greatly improved; and 3, through design of a data blocking method based on an improved random forest algorithm, different types of attach behavior detection can be realized as parallel algorithms, so the integrated detection speed of the system is improved.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Gas pipe under-pressure leakage-plugging method
The invention discloses a plugging method for fuel gas pipeline under pressure during fuel gas leaking. The steps are that 1, a concrete leakage point is found out according to the geographic position where the leakage point happens; packing materials around the leakage point are tore up; 2, after the leakage point are tore up, the leakage point performs the preliminary leakage blocking process; 3, rotproof substances, iron rusts and contaminant on the surface of the pipeline around the leakage point are cleaned up; 4, a patch block is pressed on the leakage point, and an apply force applied on the patch block is adjusted to make the fire resistant cushioning layer on the inner side of the patch block be completely blocked the leakage point; 5, the patch block is welded on the pipeline; 6, the leak detecting and the brush treatment are performed. The leakage blocking method of the invention can perform leakage blocking under the condition that air is not cut off, and can effectively block the leakage point; can avoid the deficiencies that the time consumed by the air cutting leakage blocking method is long, the natural gas resource is wasted, air is polluted, great losses and potential safety hazard are caused, thereby having the evident economic benefit and social benefit.
Owner:CHONGQING GAS GRP CORP LTD
Concrete crack surface cut groove sealing and blocking structure and method
InactiveCN103437432AGuaranteed Appearance RequirementsChange stress conditionsBuilding material handlingSocial benefitsEconomic benefits
The invention discloses a concrete crack surface cut groove sealing and blocking structure and a concrete crack surface cut groove sealing and blocking method. Through adopting the small-width-to-depth-ratio cut groove sealing and blocking technology, concrete cracks can be effectively repaired or reinforced. Firstly, a proper handheld angle grinding machine is adopted, a matched and proper angle grinding machine is selected for grinding sheets, the concrete is cut into a plurality of end-to-end fold lines along the cracks or construction seams, the cutting is completed, pressure water is adopted for clean flushing, accumulated water in the grooves is naturally dried in the air or is dried through blowing, then, cementing materials are filled for seam sealing, and when the cutting seams need to be widened, a double-angle grinding machine can be adopted for grinding sheet parallel cutting. The structure and the method provided by the invention have the advantages that the construction is fast and convenient, economy and applicability are realized, the environment is protected, and good economic benefits and social benefits are realized.
Owner:CHINA GEZHOUBA GRP INT ENG
Adjustable gas block method, system and device for a gas operation firearm
Methods, systems and devices for an adjustable gas block with variable gas port dimensions to control the amount of gas in the gas block before the gas enters into the gas tube. The adjustable gas block includes a gas block barrel bore to slide over a barrel and a gas tube bore to mate with the firearm gas tube, a gas port between the barrel bore and the gas tube bore, a sliding regulator plate to slide one of the gas ports into alignment with the block gas port and the barrel gas port, and a spring and detent pin to hold the sliding regulator plate in alignment with the barrel gas port. An alignment hole in the gas tube bore can align the block gas port with the barrel gas port.
Owner:HEARING PROTECTION LLC
Fluoroboric acid blocking remover and acidification de-blocking method
The invention discloses a fluoroboric acid blocking remover and an acidification de-blocking method. The blocking remover is composed of prepad acid, subject acid and afterpad acid. The prepad acid and the afterpad acid are prepared from the same constituents which include, by mass, 10% of hydrochloric acid, 0.8-1.5% of clay stabilizer, 0.2-1.0% of ferrous stabilizer, 0.25-1.0% of corrosion inhibitor, 0.4-1.0% of water block removal agent, 0.2-1.0% of mutual solvent and the balance water. The subject acid is prepared from, by mass, 6% of acetic acid, 2% of fluoroboric acid, 0.8-1.5% of clay stabilizer, 0.2-1.0% of ferrous stabilizer, 0.25-1.0% of corrosion inhibitor, 0.4-1.0% of water block removal agent, 0.2-1.0% of mutual solvent and the balance water. By the adoption of the fluoroboric acid blocking remover, de-blocking of a low-yield unconventional tight sandstone oil and gas reservoir caused by water blocking reaction, inorganic scale and inflow fluid emulsification can be achieved effectively.
Owner:CHINA PETROLEUM & CHEM CORP +1
False-AP detecting and blocking method, wireless device and router
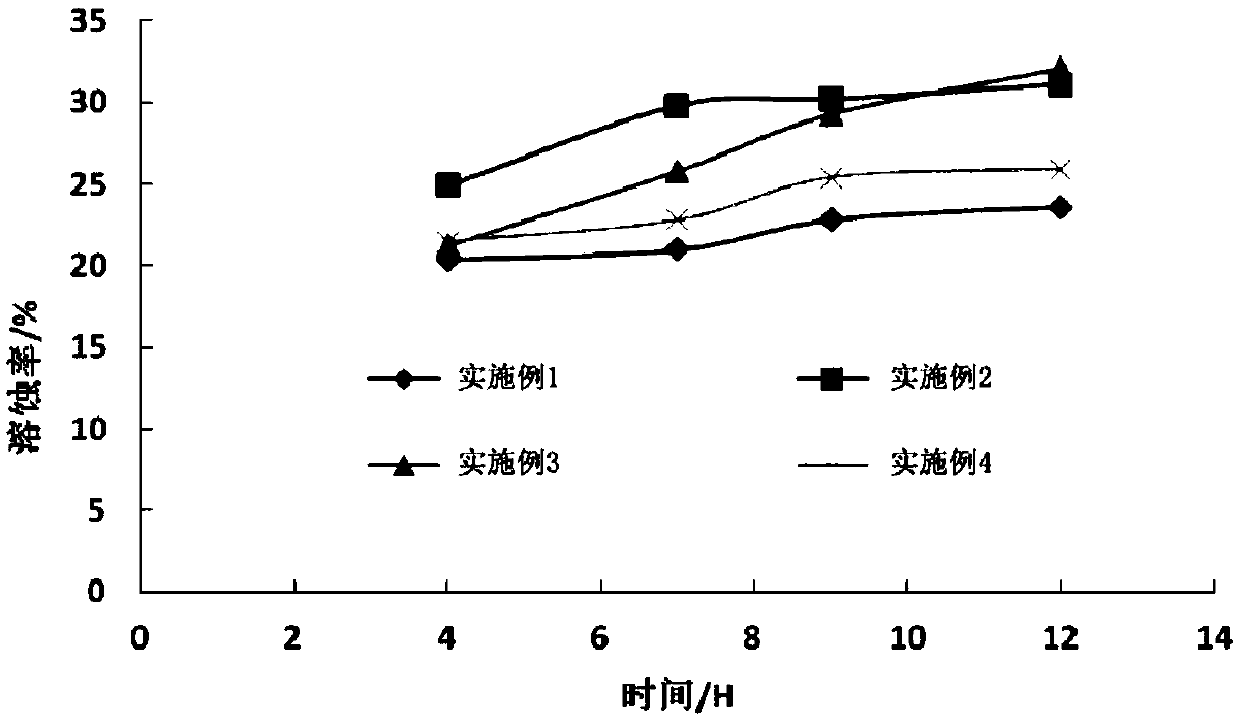
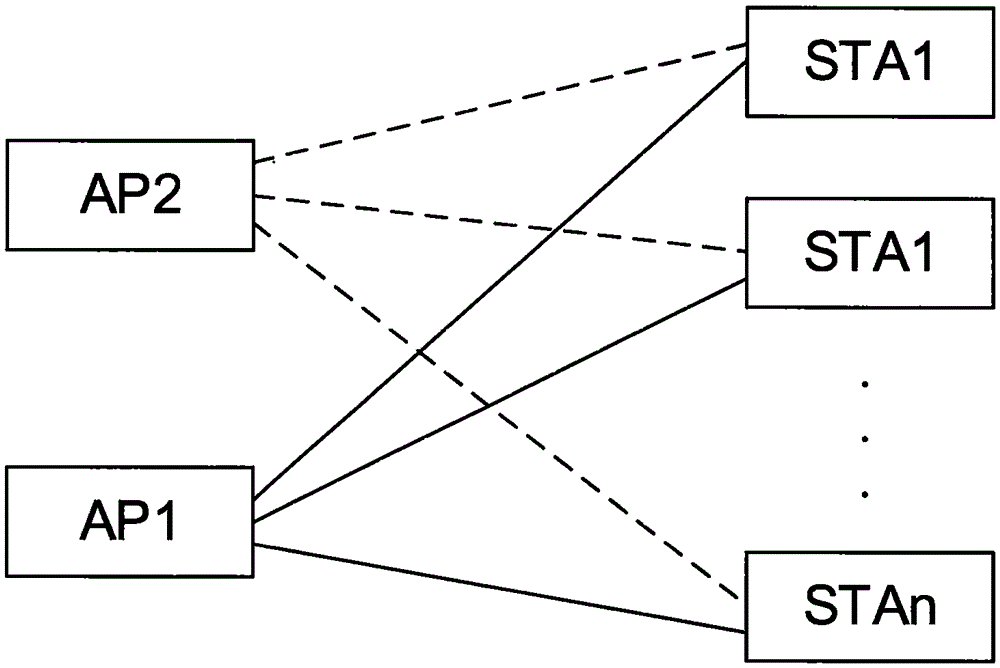
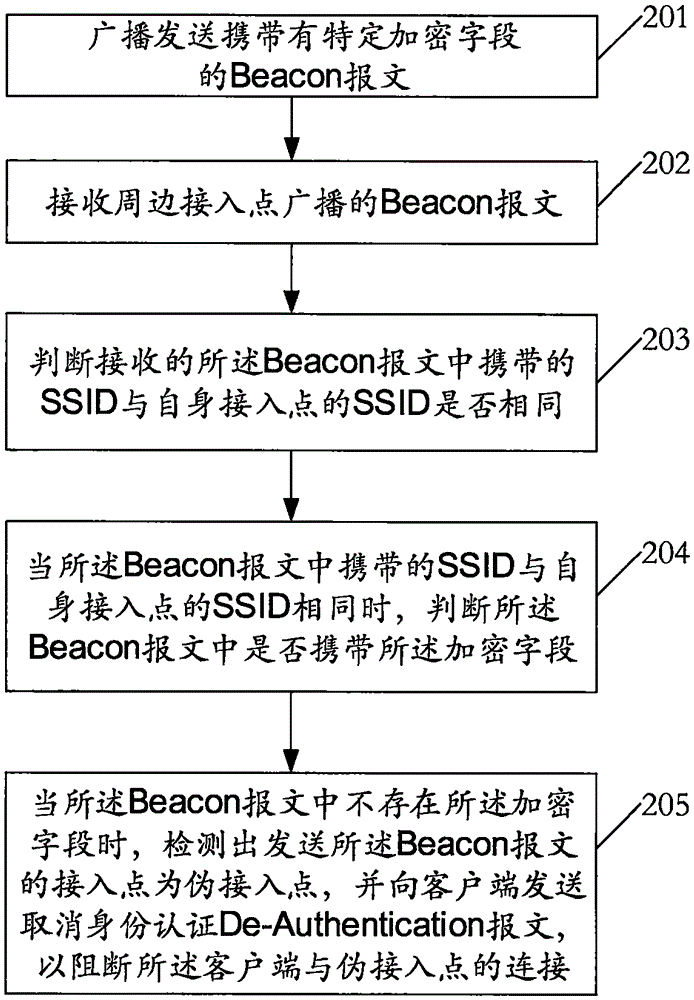
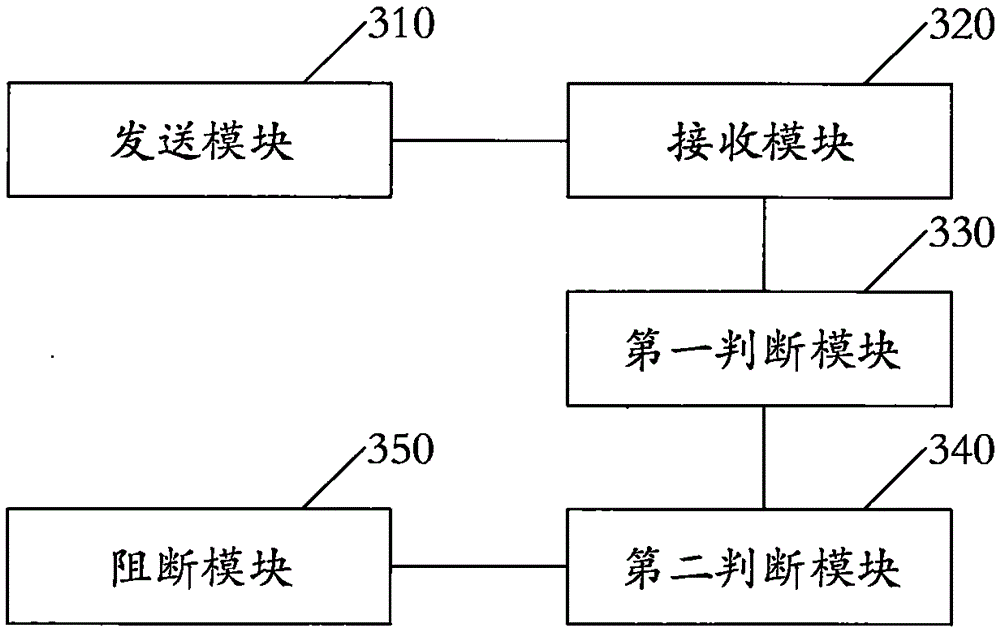
InactiveCN105657713ATo achieve effective identificationBlock connectionSecurity arrangementComputer hardwareBlocked Connection
The invention relates to the field of wireless network application and discloses a false-AP detecting and blocking method, a wireless device and a router. By broadcasting a Beacon message carrying a specific encrypted field and receiving Beacon messages broadcast by peripheral APs, whether SSIDs carried in the received Beacon messages are identical with an SSID of a self AP or not is judged; when the SSIDs carried in the received Beacon messages are identical with the SSID of the self AP, whether the encrypted field is carried in the Beacon messages or not is judged, it is detected that the AP sending the corresponding Beacon message is a false AP when the encrypted field does not exist in the corresponding Beacon message, and a De-Authentication message for canceling identity authentication is sent to a client side to block connection between the client side and the false AP. The false AP is effectively identified, and the client side is blocked and protected against the risk that personal information is stolen due to the fact that the client side is connected with the false AP.
Owner:ZHUHAI NETBOX INFORMATION TECH
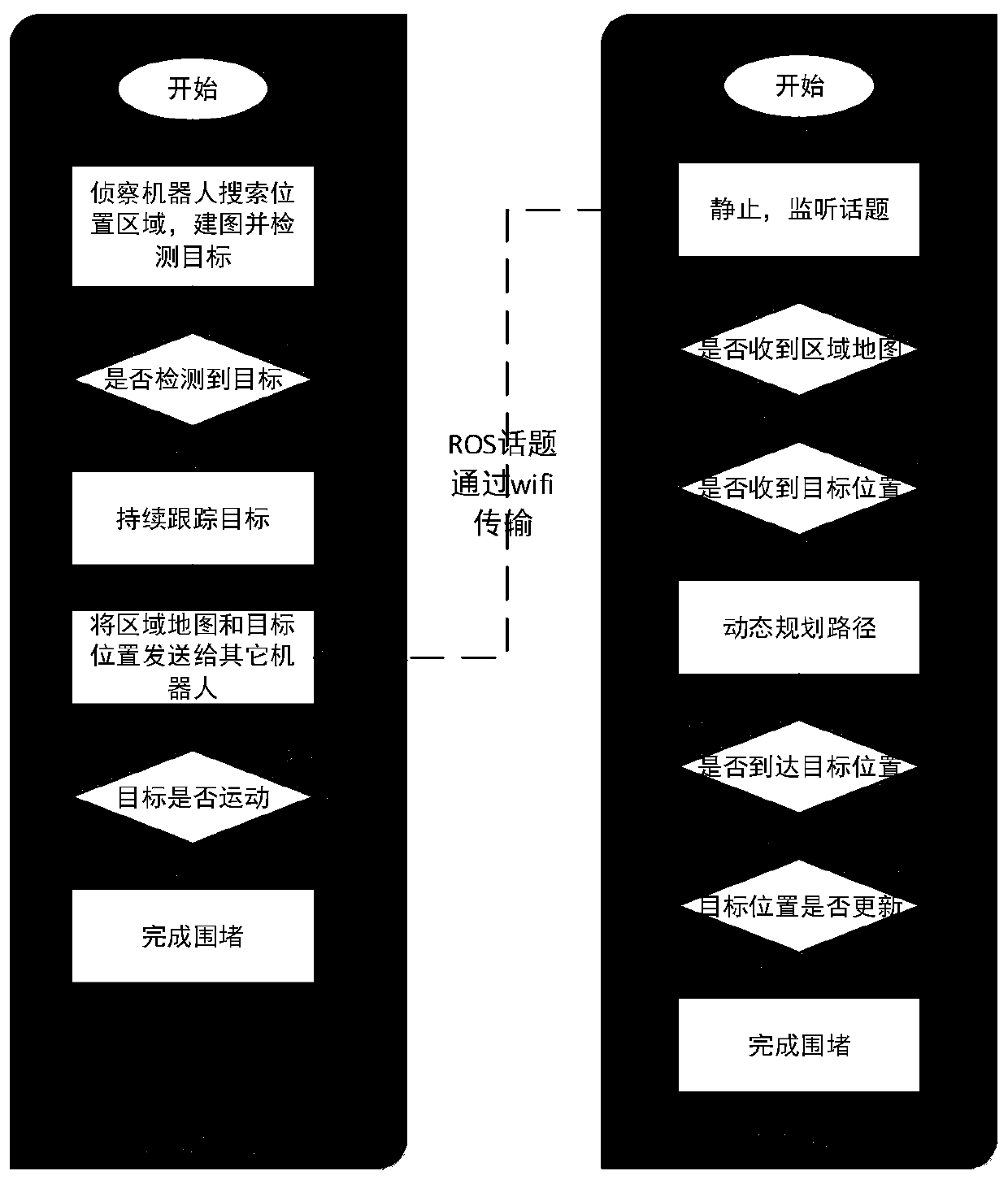
Collaborative search blocking method based on ground robot
ActiveCN109917818AImproved hardware levelImprove stabilityTarget-seeking controlPosition/course control in two dimensionsImaging processingRadar
The invention relates to the technologies of image processing, real-time mapping, path planning, robots and the like, and provides a collaborative search blocking platform of a ground robot. The collaborative searching and blocking method based on the ground robot uses a ground robot carrying a camera and a processor to carry out target searching; one robot additionally carries a laser radar; therobot carrying the laser radar establishes an environment map by using the laser radar, and the map is transmitted to other robots, all the robots acquire image information of the surrounding environment through cameras, the image information is processed, an appointed target object is identified in a plurality of objects by utilizing a pre-trained detection and tracking algorithm, the appointed target object is tracked for a long time, and data transmission among the robots is performed through a wireless network; when a certain robot detects a target, the robot can track the target and sendthe position information of the target to other ground robots in real time, and real-time path planning and encircling are carried out. The method is mainly applied to robot design occasions.
Owner:TIANJIN UNIV
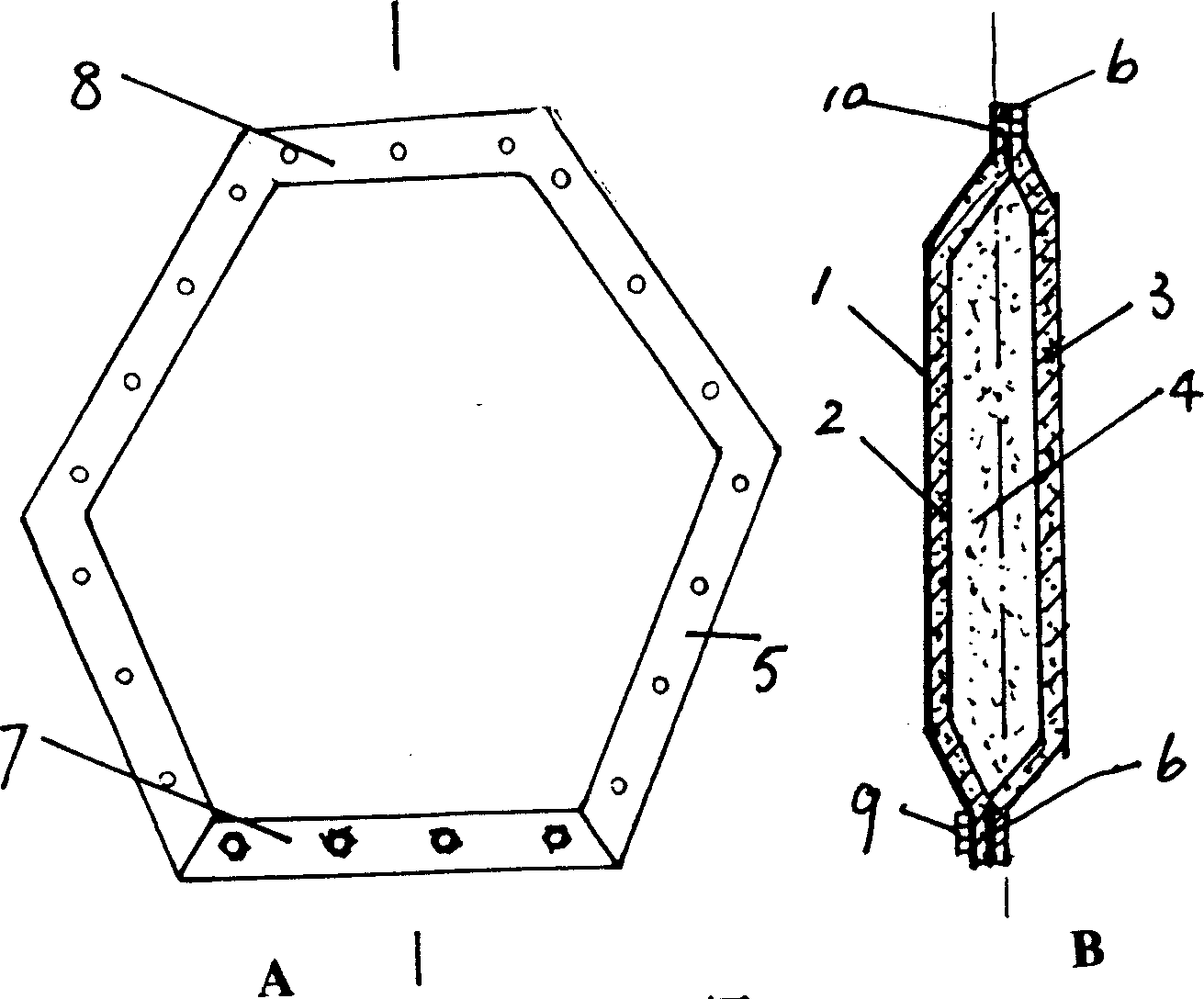
Radar dome unit piece and manufacturing process, connecting method and dividing method thereof
InactiveCN1464590AImprove electrical performanceHigh strengthRadiating element housingsRadarBlock method
The present invention provides a unicell for radar dome with waterproof resin glue covering and glass epoxy layer outer layer, glass epoxy layer as inner layer ,while froth core layer located between the inner layer and outer layer. Seam structure of peripheral of the unicell is plane overlapping edge with solid glass steel layer integrately formed with the unicell, in which stainless steel screw cap is preburied in the upper overlapping edge, and attachment hole is opened in the lower overlapping edge. The present invention further provides manufacturing technique, attaching method and partiting method for unicell. The present invention realizes blocking method without parallel for adjacent edge, improves electrical property of radom, and enhances overall strength of radom, also improves wind resistance ability and leak resistance ability.
Owner:上海之合玻璃钢有限公司
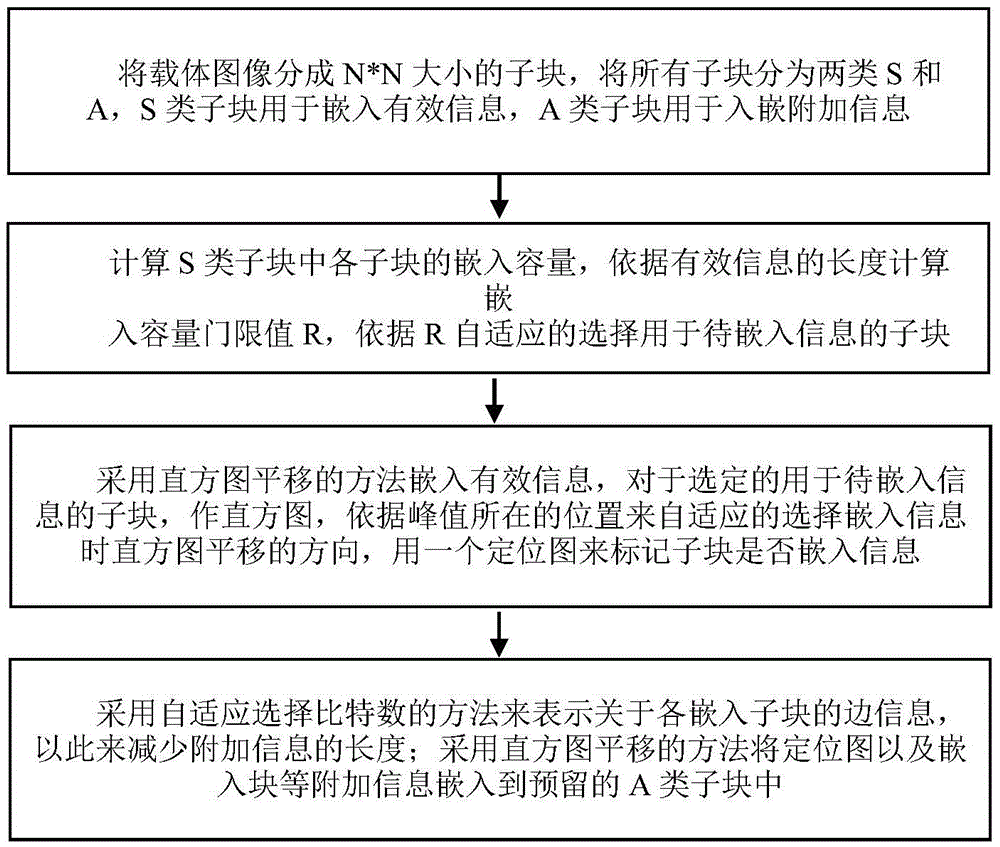
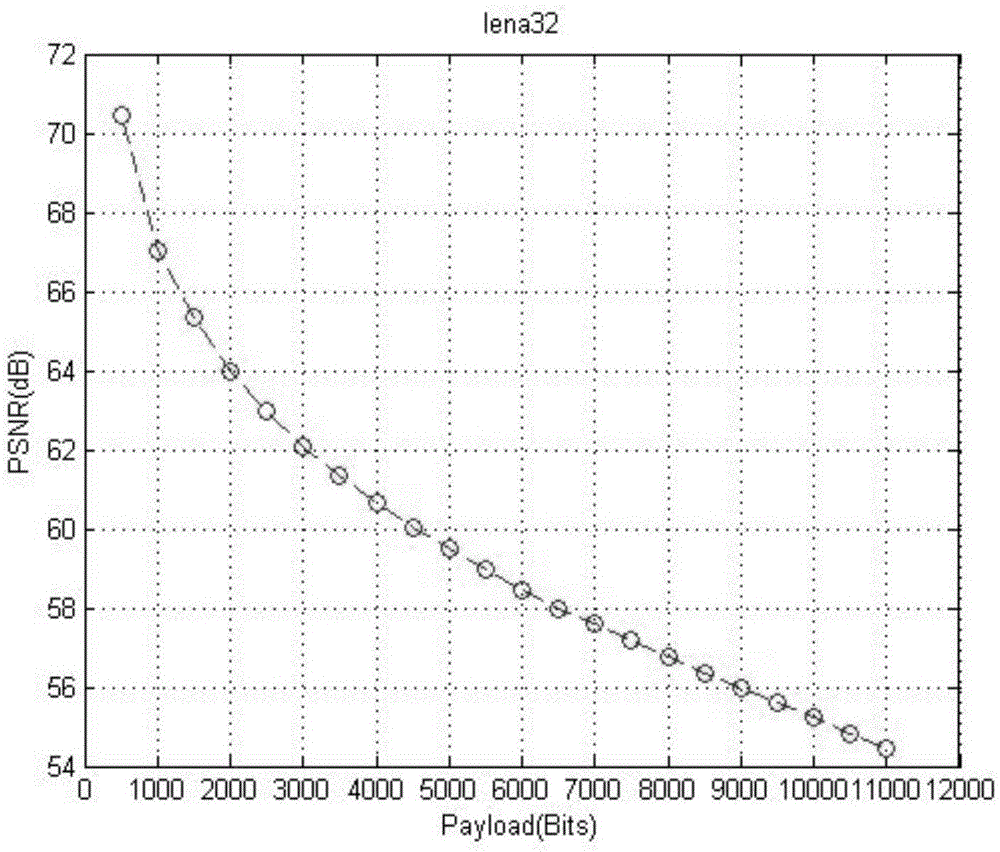
Reversible information hiding method based on blocked self-adaptive histogram translation
InactiveCN105488773ALossless extractionImprove peak signal-to-noise ratioImage enhancementImage analysisImaging qualityPeak value
The invention relates to the field of multimedia information security, in particular relates to a reversible information hiding method based on blocked self-adaptive histogram translation. The method comprises the following steps: (1) blocking a carrier image, and computing a peak value of each sub-block histogram; (2) self-adaptively selecting a sub-block for embedding information according to embedding capacity of each sub-block; (3) adopting a method for self-adaptively selecting histogram translation direction while embedding the information. The invention is a novel histogram translation method which is capable of effectively embedding the information and losslessly extracting the embedded information and recovering an original image; through the adoption of the blocked method, the embedded information is safer and the integral embedding rate is improved, the self-adaptive selected histogram translation direction can effectively improve the peak signal to noise ratio of the image to further improve the image quality, thereby providing help for the medical treatment, military and the like applications. Through the adoption of the method, the higher the precision of the image is, the better the reversible information hiding effect is.
Owner:SUN YAT SEN UNIV
Mechanical pipeline under-pressure blocker and blocking method thereof
ActiveCN101666413AShorten the construction periodReduce construction costsPipe elementsSlagEngineering
The invention provides a mechanical pipeline under-pressure blocker and a blocking method thereof. The blocker mainly comprises a process pipe, an under-pressure pipeline mouth gag and an under-pressure pipeline lower blocker, wherein a mechanical encasing-pipe sealing device consists of an upper body, a lower body, a flexible sealing rubber cushion, a sealing support rubber cushion, an upper antiskid anchor ear and a lower antiskid anchor ear; the upper body consists of an upper body pipe and an upper semicircular encasing-pipe plate; the periphery of the upper semicircular encasing-pipe plate is provided with a turned-over edge, and the middle of the upper semicircular encasing-pipe plate is provided with a hole; the lower end of the upper body pipe is welded with the hole, and the upper end of the upper body pipe is welded with a flange; the upper part of the flange is provided with a mouth rim, and a screw hole is horizontally arranged on the mouth rim; the lower body consists of a slag discharge pipe with an opening on the upper end, and a lower semicircular encasing-pipe plate; the periphery of the lower semicircular encasing-pipe plate is provided with a turned-over edge, the middle of the lower semicircular encasing-pipe plate is provided with a hole, and the upper opening of the slag discharge pipe is welded with the hole; and the turned-over edges on the peripheries of the upper semicircular encasing-pipe plate and the lower semicircular encasing-pipe plate are fixed on an under-pressure pipeline by screw bolts. Compared with the prior art, the blocker can block the cast iron pipeline under pressure during operation so as to shorten the construction period and reduce the construction cost.
Owner:济南市公明新技术开发有限公司
Computer system, virtual machine monitor and scheduling method for virtual machine monitor
ActiveUS8423999B2Reduce power consumptionReduce processing timeEnergy efficient ICTMultiprogramming arrangementsComputerized systemPhysics processing unit
In a computer system according to the background art, when a request to halt a virtual processor was detected, the virtual processor was blocked. In the blocking method, latency of virtual halt exit of the virtual processor was so long that a problem of performance was caused. A virtual machine monitor selects either of a busy wait method for making repeatedly examination until the virtual halt state exits while the virtual processor stays on the physical processor and a blocking method for stopping execution of the virtual processor and scheduling other virtual processors on the physical processor while yielding the operating physical processor and checking off scheduling of the virtual processor to the physical processor, based on a virtual processor halt duration predicted value of the virtual processor which is an average value of latest N virtual processor halt durations of the virtual processor.
Owner:HITACHI LTD
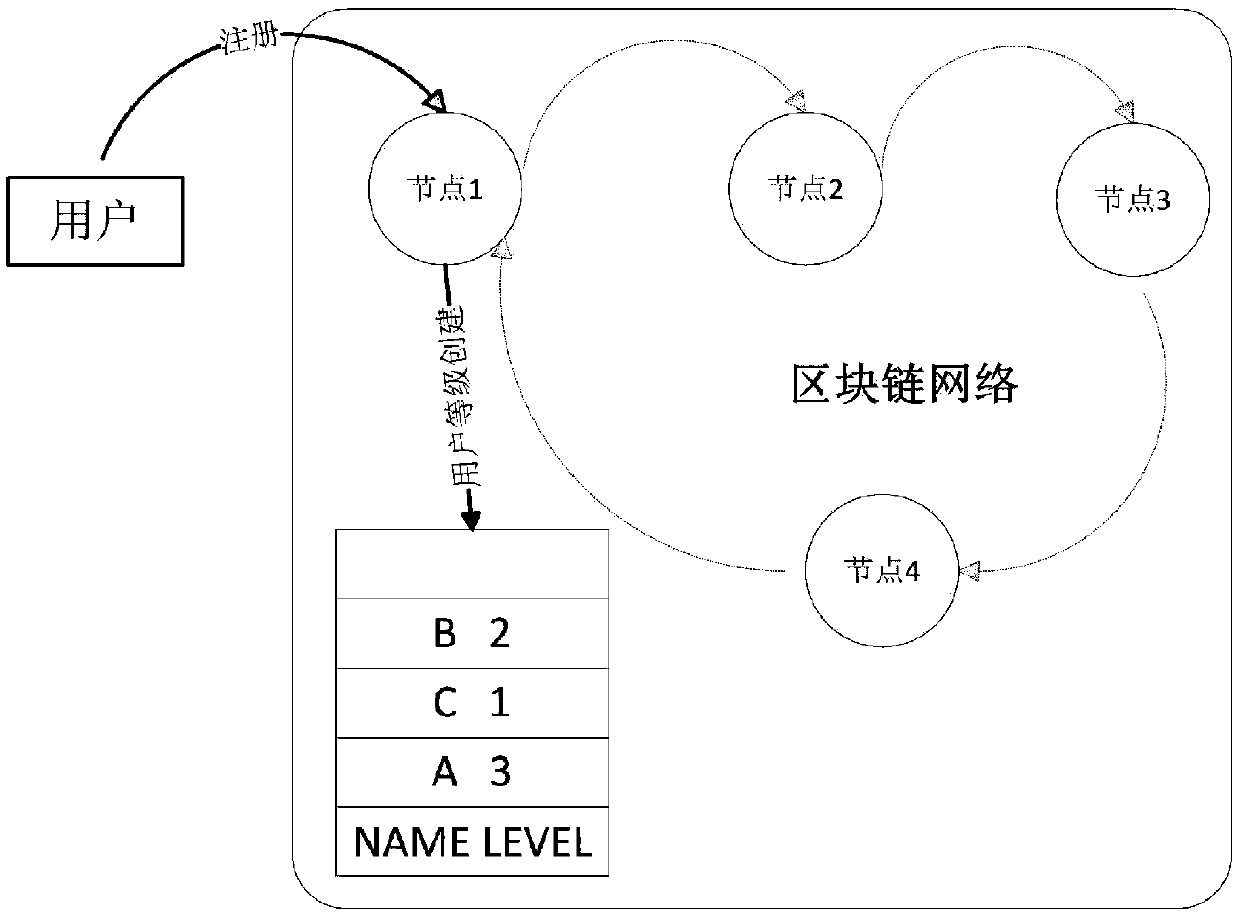
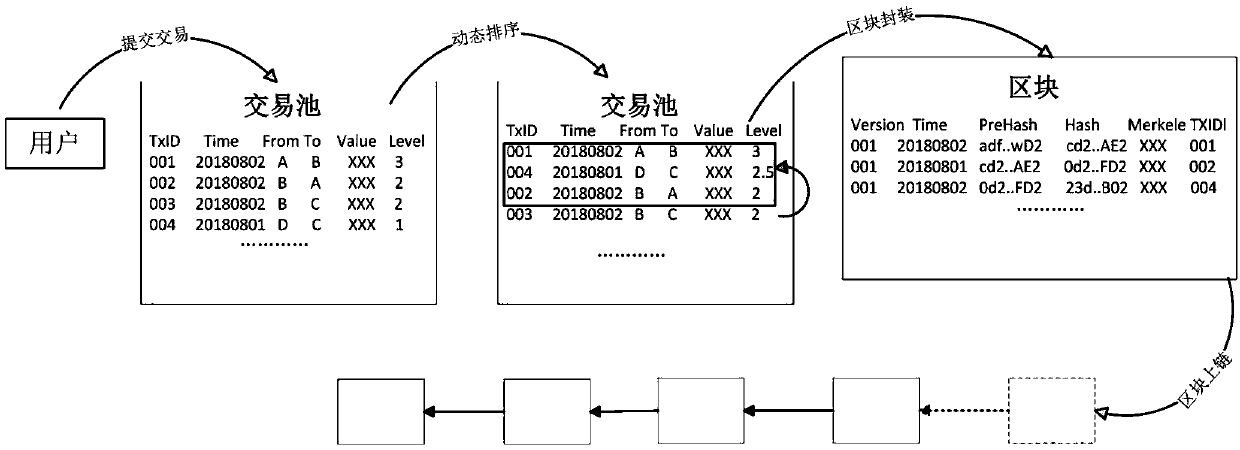
A block chain transaction out-block method based on user level
ActiveCN109544332AGuaranteed priorityFinanceManufacturing computing systemsThe InternetFinancial transaction
The invention discloses a block chain transaction out-block method based on a user level, and belongs to the field of Internet. The method comprises the following steps: S1, creating grade informationof user transaction; S2: constructing and submitting the transaction; S3: putting the transaction submitted in a period of time into the transaction pool and waiting for triggering the out-of-block condition; S4: After the block-out condition is triggered, the transaction grade is dynamically adjusted and sorted; S5: acquiring a high-level transaction encapsulation block in the transaction pool;S6: Transaction consensus is uplinked. The invention utilizes the transaction pool in each node of the block chain network and the transaction level submitted by the user to ensure the priority levelof the transaction of the user, and has the characteristic of writing the block first.
Owner:贵阳信息技术研究院 +1
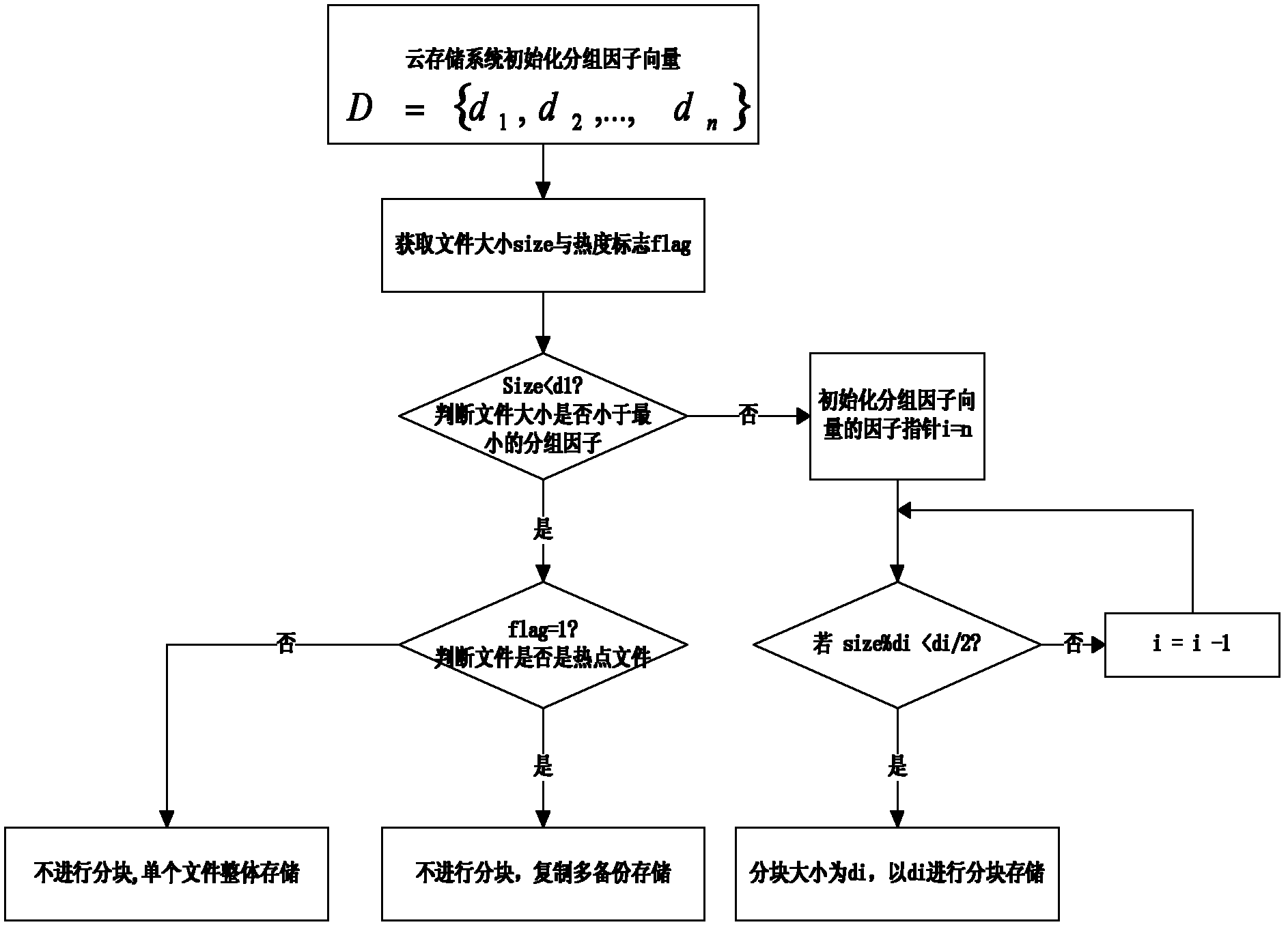
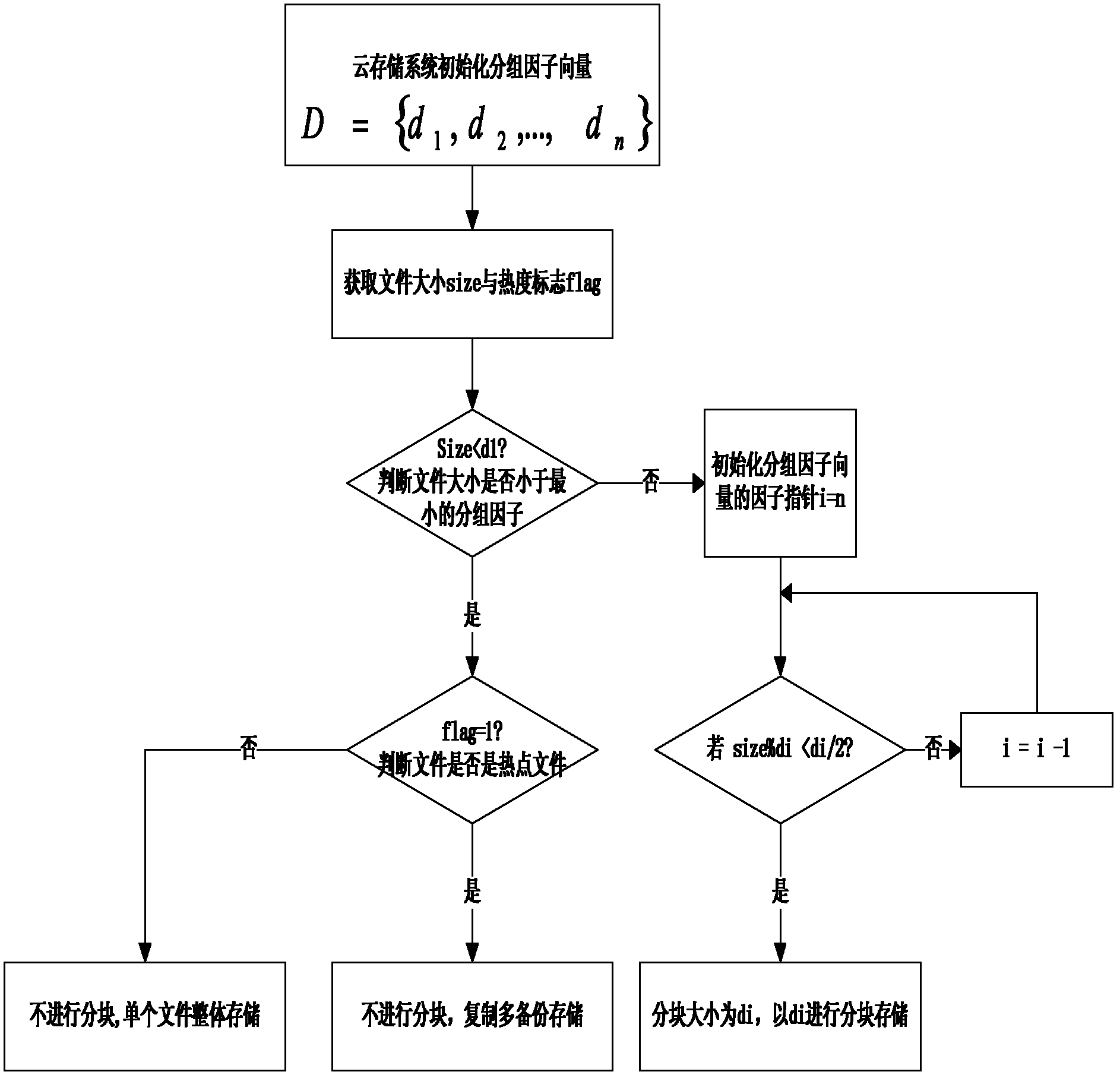
Block size variable data blocking method for cloud storage system
InactiveCN102508902AAvoid occupyingImprove space utilizationTransmissionSpecial data processing applicationsComputer hardwareBlock method
The invention discloses a method for blocking and storing a stored file in a cloud storage system by adopting a dynamic adaptation method, and mainly aims to solve the problems of low space utilization rate and disk fragments caused by the use of a fixed block size in the prior art. The implementation scheme comprises the following steps of: setting a grouping factor vector by using the cloud storage system, obtaining the size and heat mark of a file when the file is to be stored, and when the size of the file is smaller than a minimum grouping factor, using the final size of the file; if the heat mark is 1, copying and storing the file, and on the contrary, directly storing the file on a single node; and when the size of the file is larger than the minimum grouping factor, comparing the size of the file with a grouping factor to obtain an optimal block size. Compared with the method using the fixed block size, the invention has higher file uniformity, can better solve a load balancing problem caused by hot files, and is particularly suitable for the cloud storage system.
Owner:XIDIAN UNIV
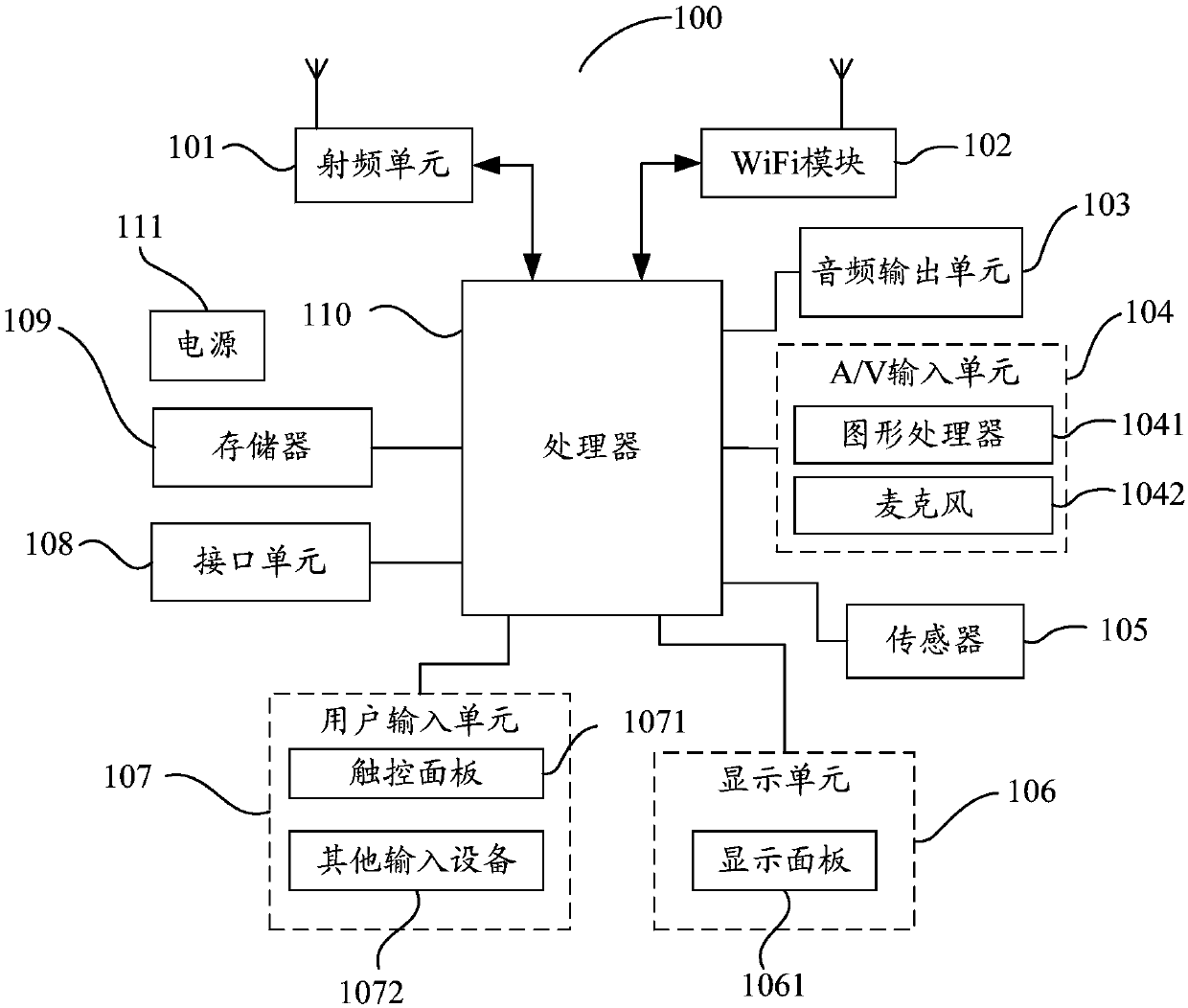
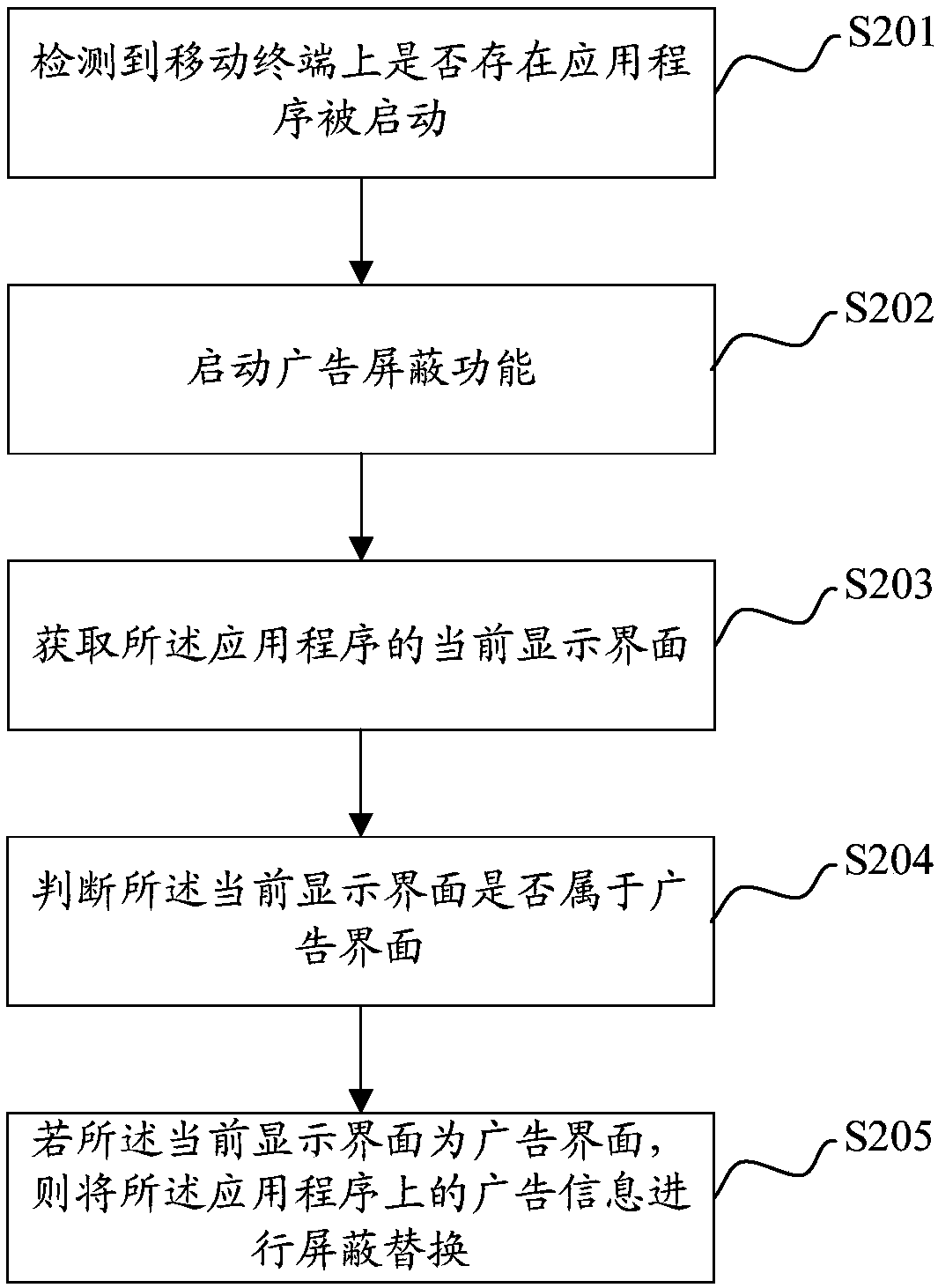
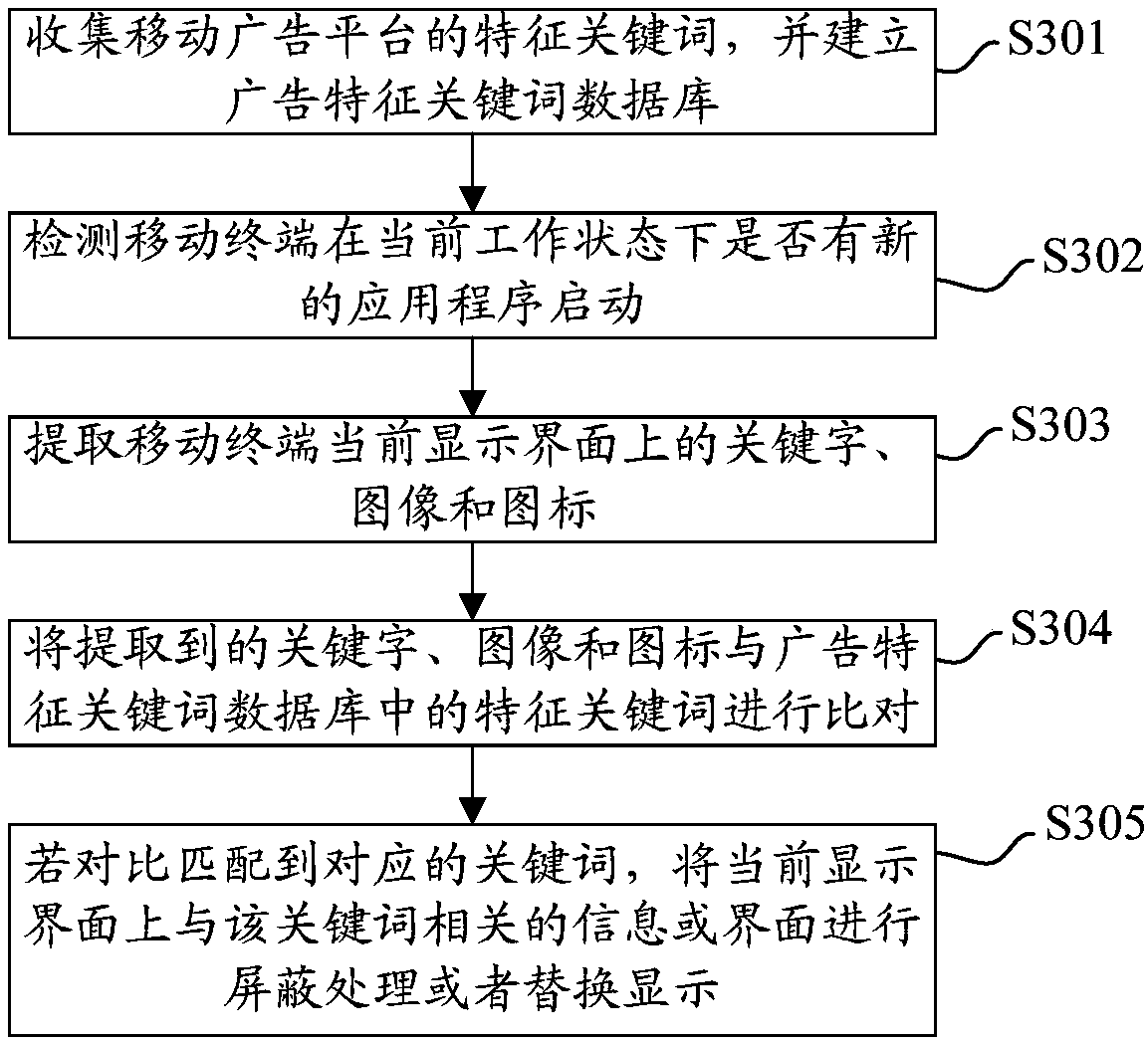
Advertisement blocking method, mobile terminal and computer-readable storage medium
InactiveCN107562864AImprove experienceNo need to worry about misuseSubstation equipmentSpecial data processing applicationsComputer terminalApplication software
Owner:NUBIA TECHNOLOGY CO LTD
Automatic identification and blocking method of spam cell
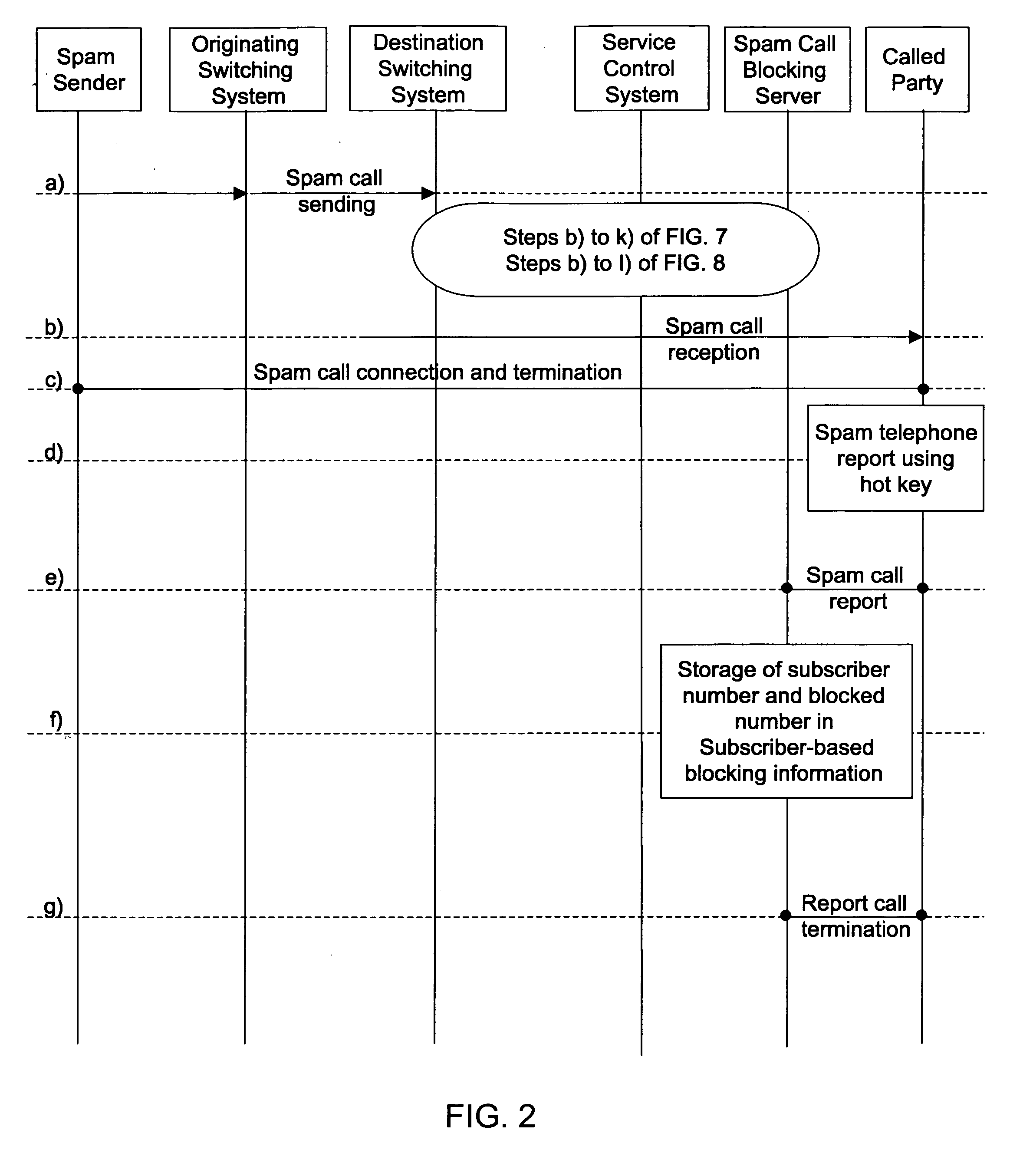
InactiveUS7613286B2Easy to reportEasy and rapid registrationInterconnection arrangementsSpecial service for subscribersInformation transmissionAuditory display
Disclosed herein is a method of visually or auditorily indicating spam status or a spam class for a calling number through a called terminal. The method includes the steps of the destination switching system requesting service from a spam call blocking server by delivering the calling number and a called number to the spam call blocking server; the spam call blocking server inquiring about spam status or a spam class for the calling number; if the spam status is ‘blocked’, or if the spam status is ‘blocked’ and the spam class is equal to or higher than a predetermined class, the spam call blocking server transmitting the spam status or spam class; the service control system activating caller identification service of a called party; the service control system including information about the spam status or spam class in caller identification information for the caller identification service; the service control system transmitting call connection information and the caller identification information to a destination switching system and, thus, the destination switching system making a call with a called terminal; and the destination switching system delivering the caller identification information to the destination terminal and, thus, providing visual or auditory display through the called terminal.
Owner:UANGEL CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com