Alarm and blocking method for illegal external connections
An external and legal technology, applied in the field of information security, can solve the problems of weak security protection, single function, complex mechanism, etc., to achieve the effect of improving security and transmission efficiency, avoiding leakage risks, and improving security performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0058] The present invention will be described in detail below through specific embodiments and accompanying drawings.
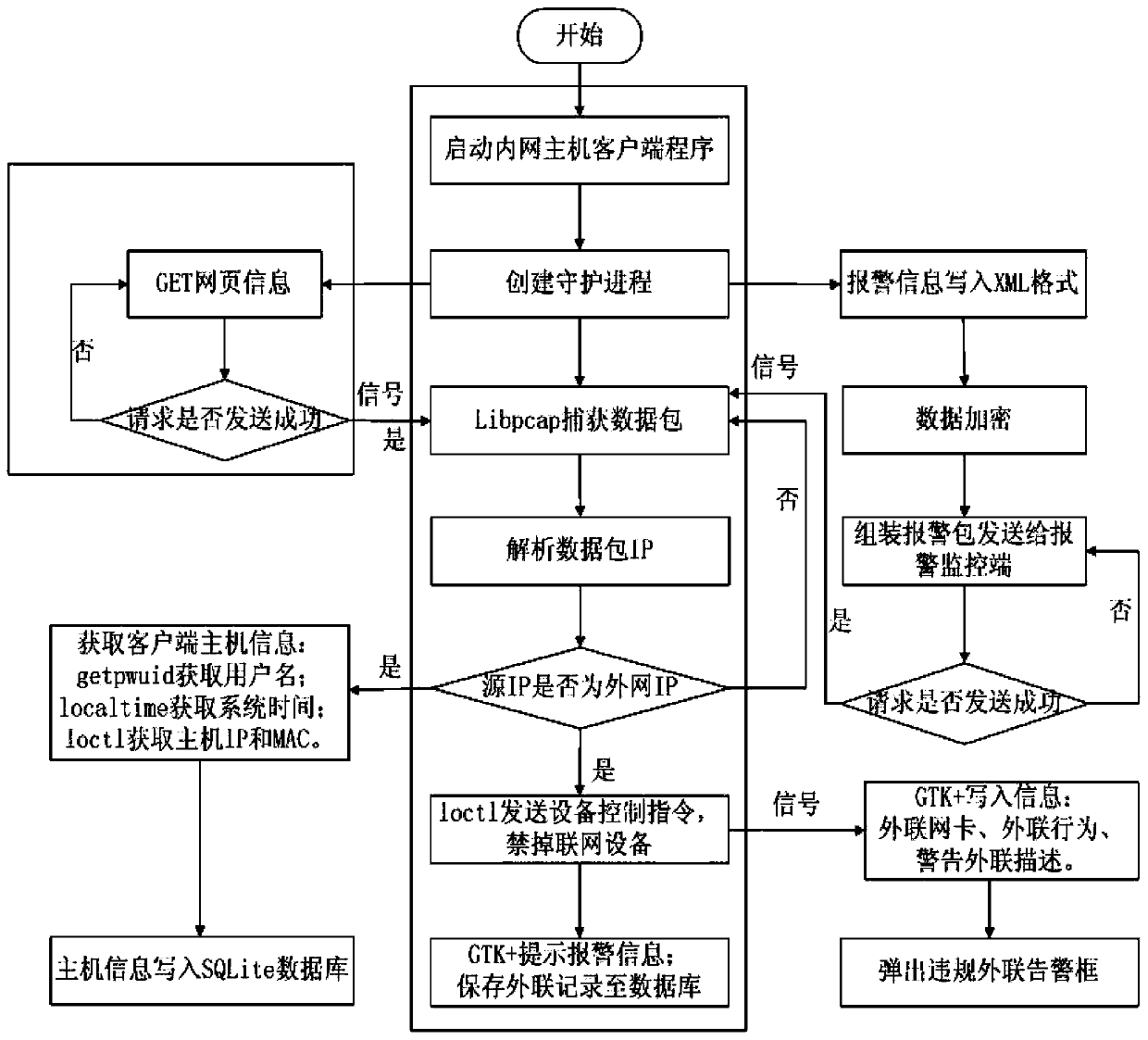
[0059] In an embodiment of the present invention, a method for violating outreach real-time alarm and blocking, the steps are:
[0060] The intranet host client monitors the intranet computer networking in real time;
[0061] Intranet host client monitors in real time the networking behaviors of intranet computers dial-up Internet access through ordinary telephone lines, ISDN Integrated Services Digital Network (Integrated Services Digital Network), ADSL, etc., and through wireless Internet access;
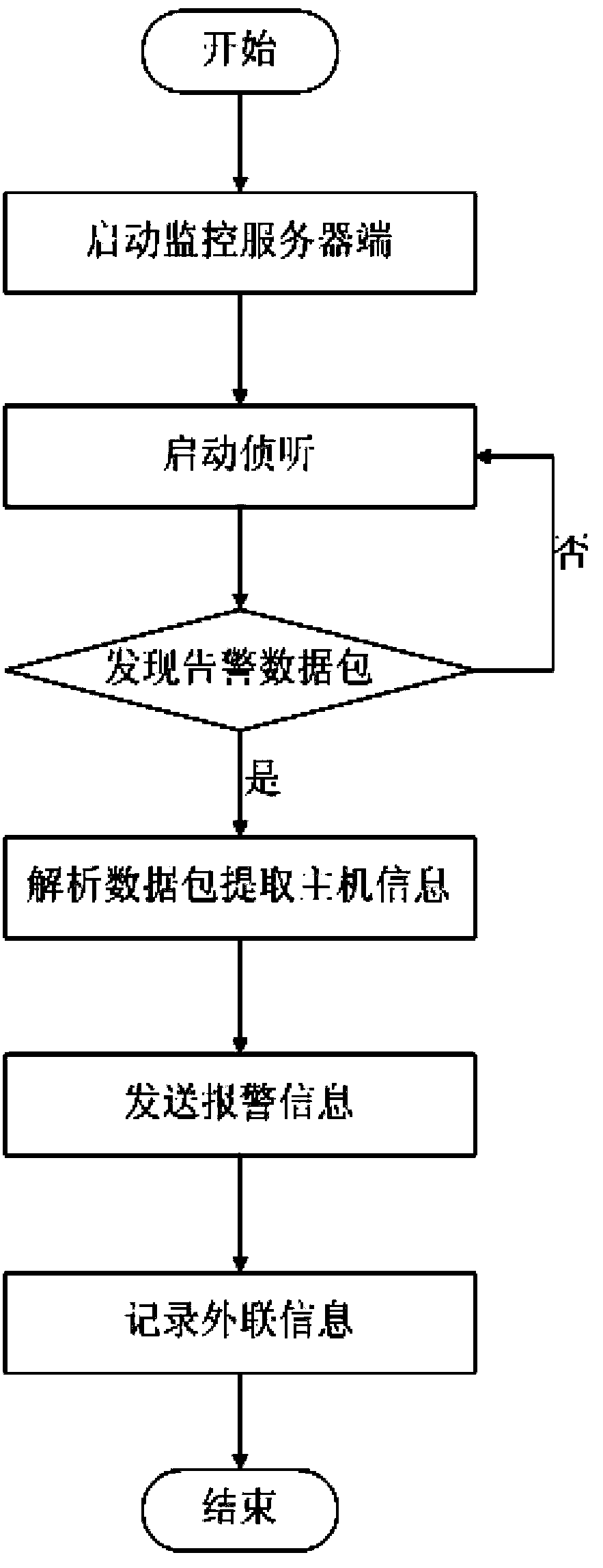
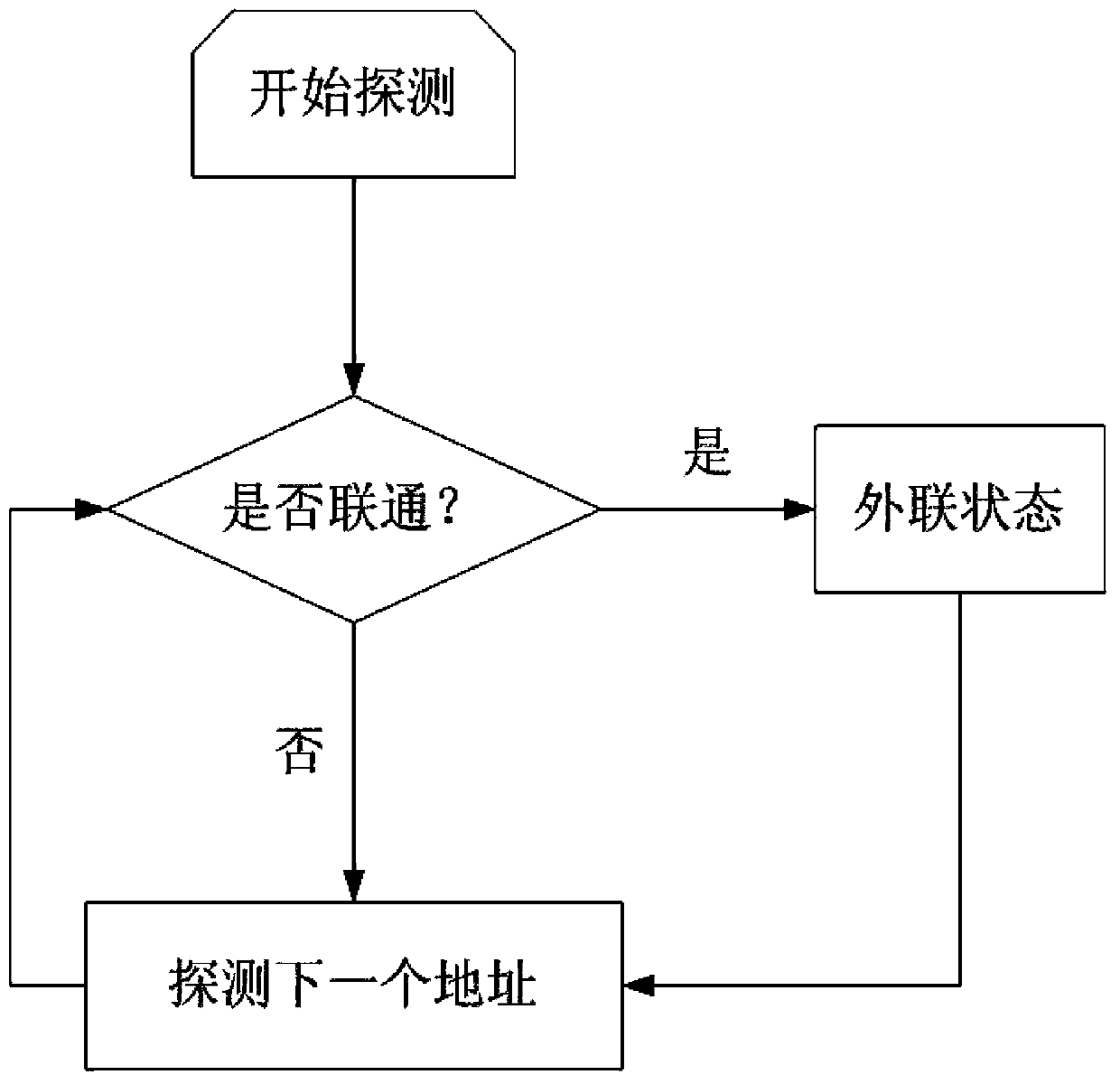
[0062] In an embodiment of the present invention, the intranet host client uses the libnet function library to actively send an alarm data packet to the external network alarm monitoring terminal to detect whether an external connection behavior has occurred. If the external network alarm monitoring terminal receives the external network data packet, it means t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com