Patents
Literature
188 results about "Computer data storage" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Computer data storage, often called storage or memory, is a technology consisting of computer components and recording media that are used to retain digital data. It is a core function and fundamental component of computers.
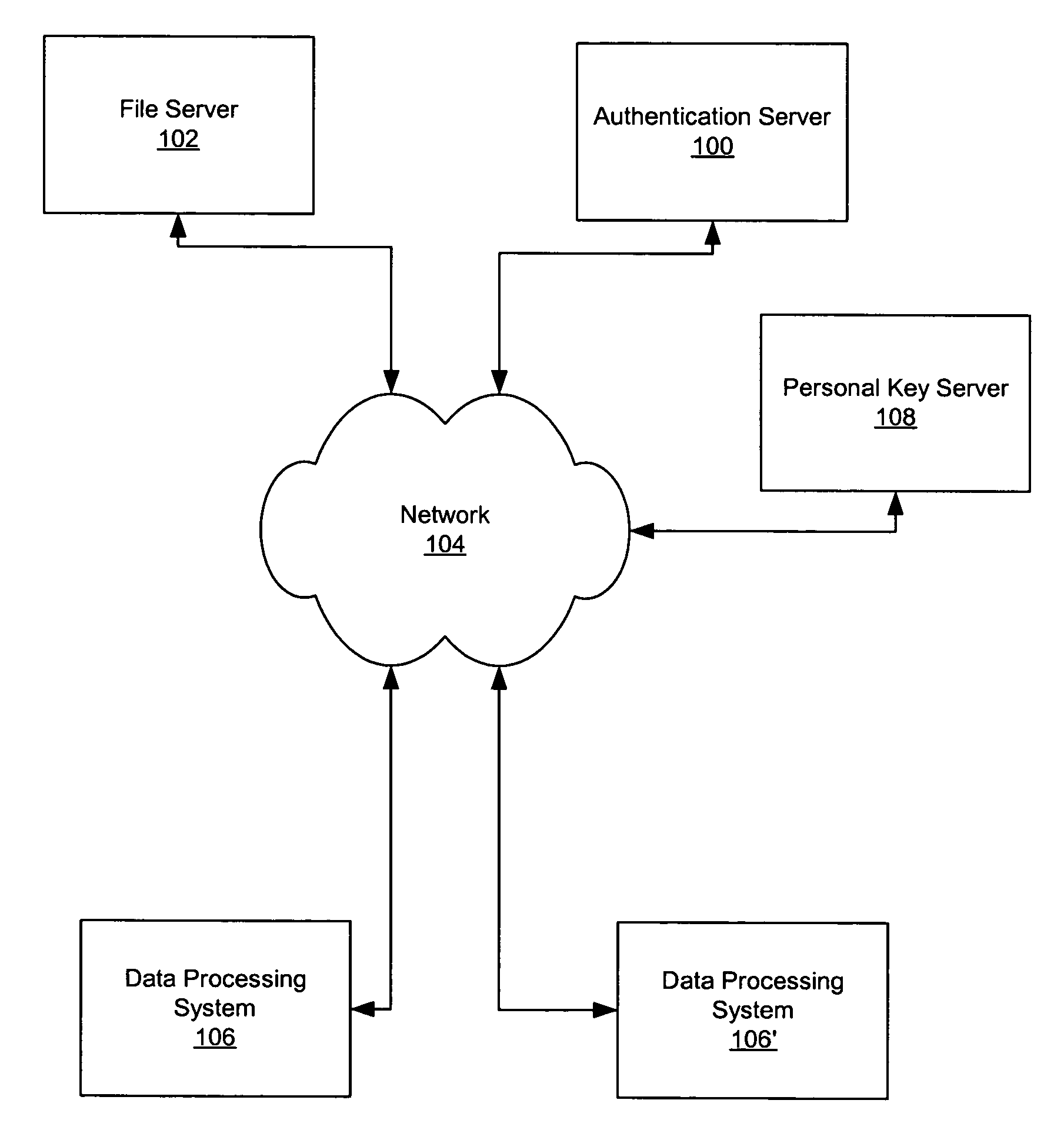
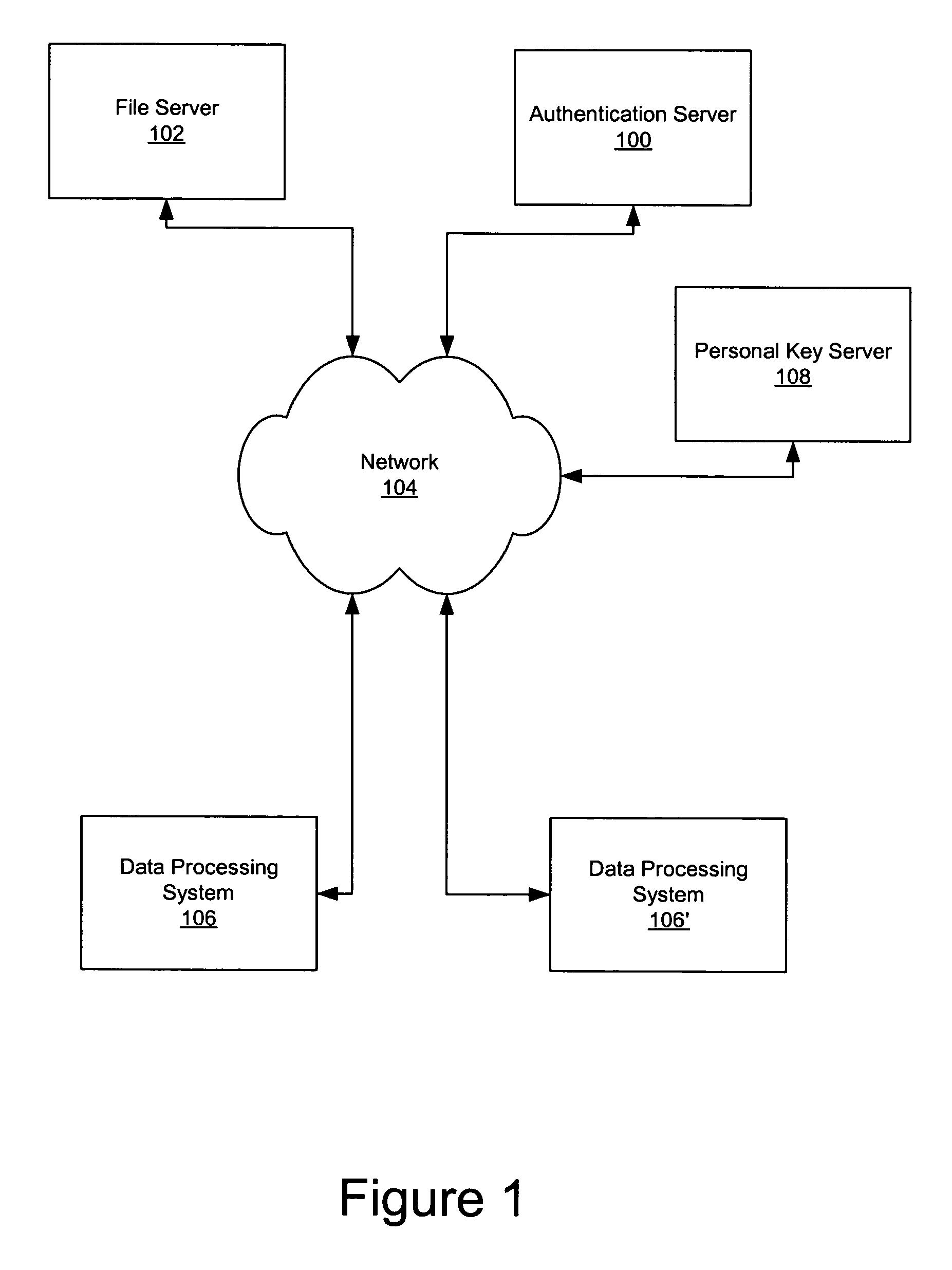
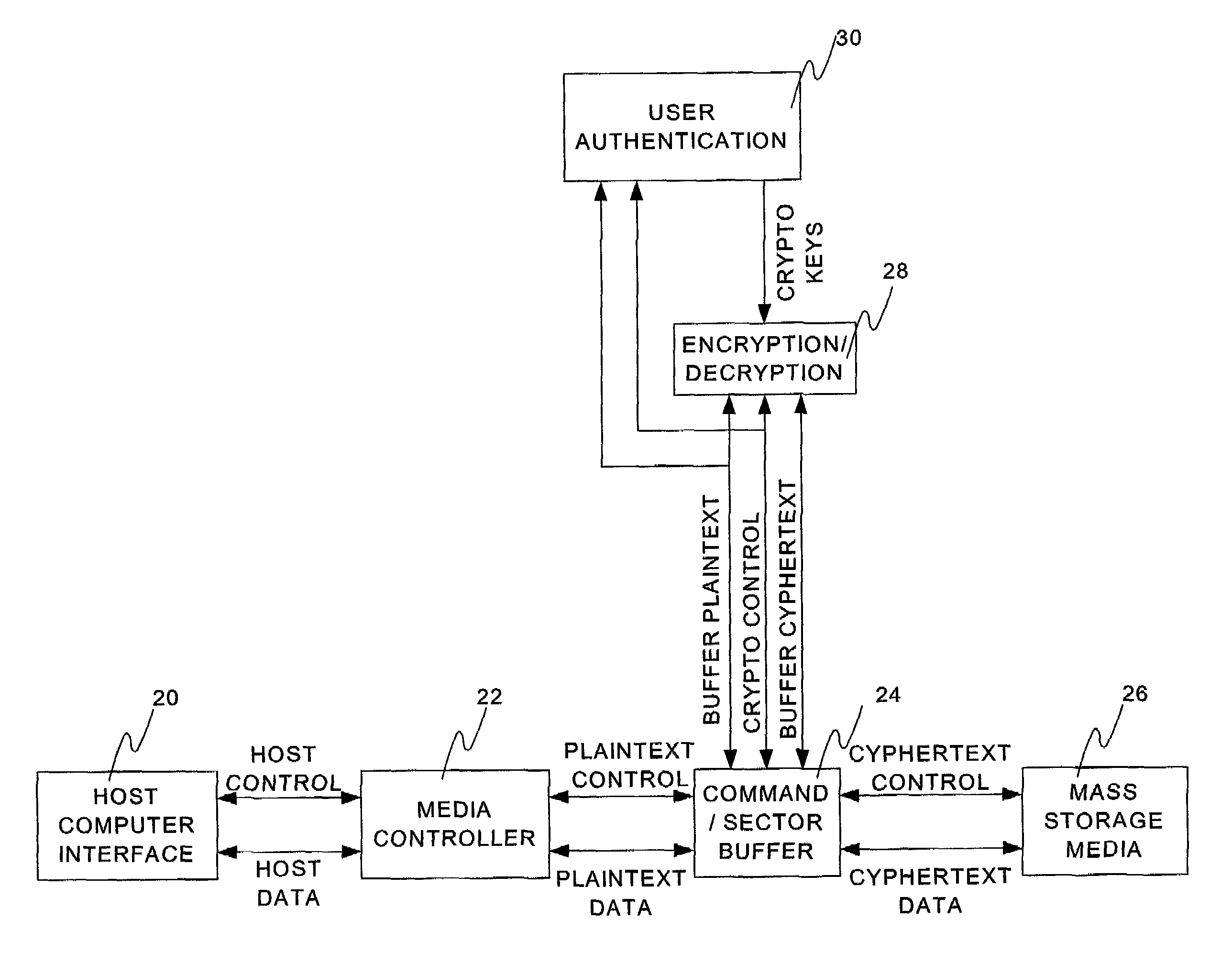
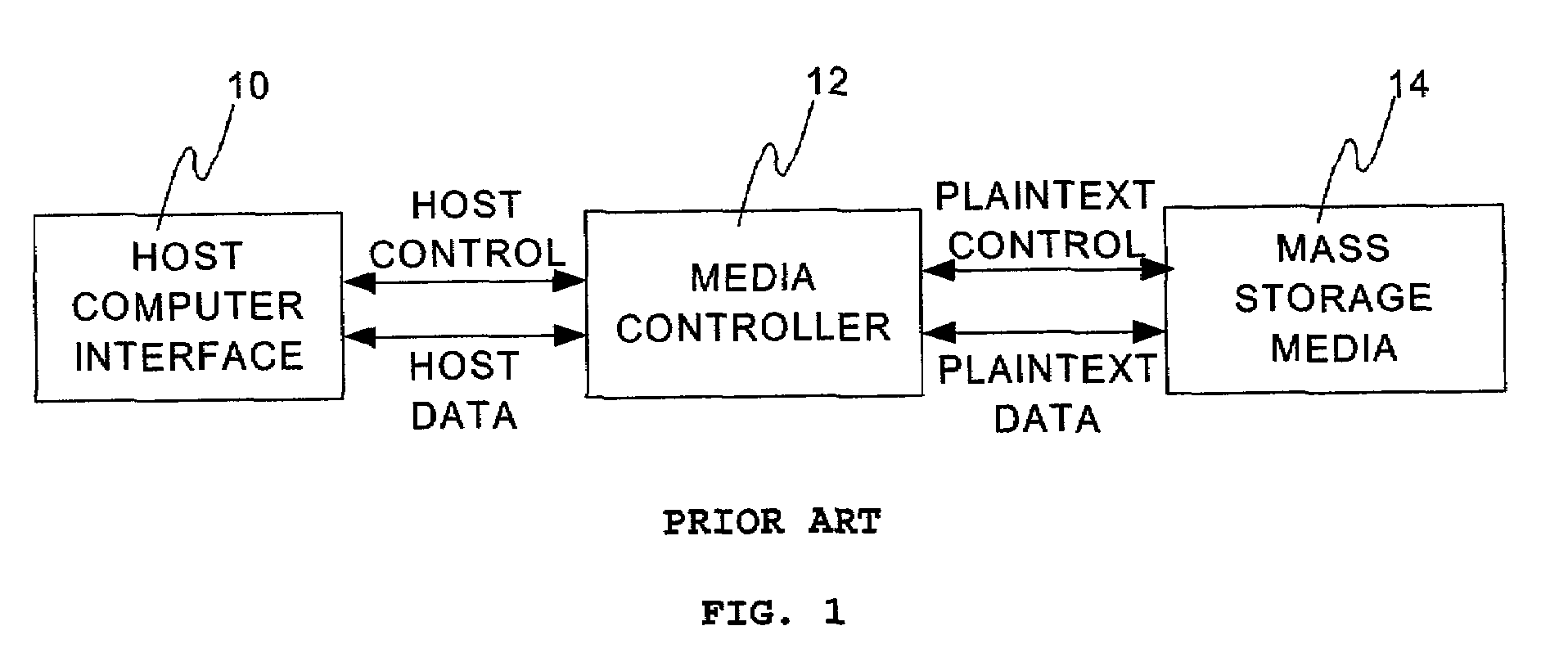
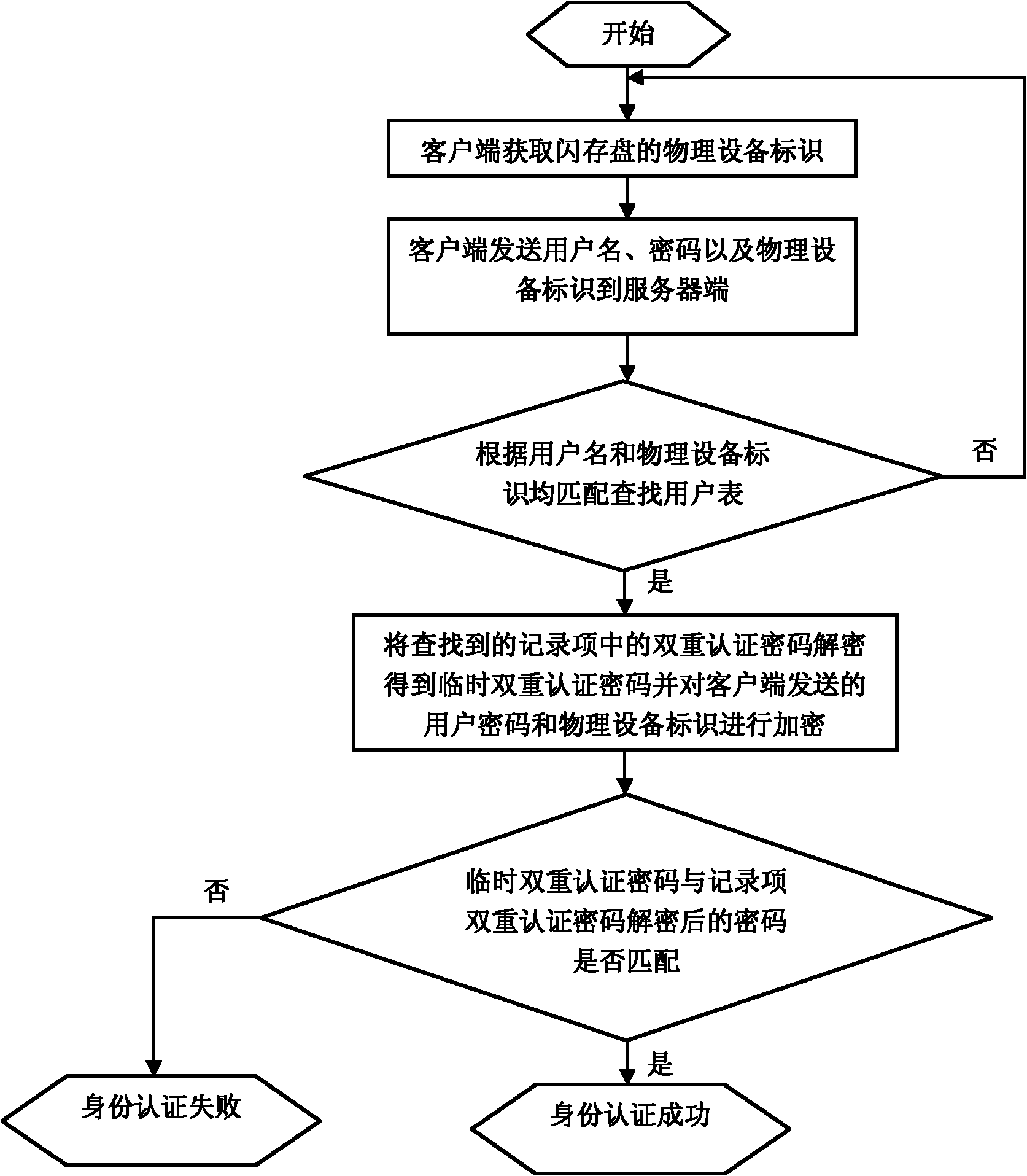
Secure data storage and retrieval with key management and user authentication
InactiveUS6947556B1Key distribution for secure communicationUser identity/authority verificationDigital dataPassphrase
Methods, systems and computer program products are provided which provide for controlling access to digital data in a file by encrypting the data with a first key, encrypting the first key with a second personal key generated from a password / passphrase associated with the file and further encrypting the encrypted first key with a control key which is managed by the system. In certain embodiments, user authentication may also be provided by issuing a ticket which is utilized to create, access and administer the files in the system.
Owner:IBM CORP
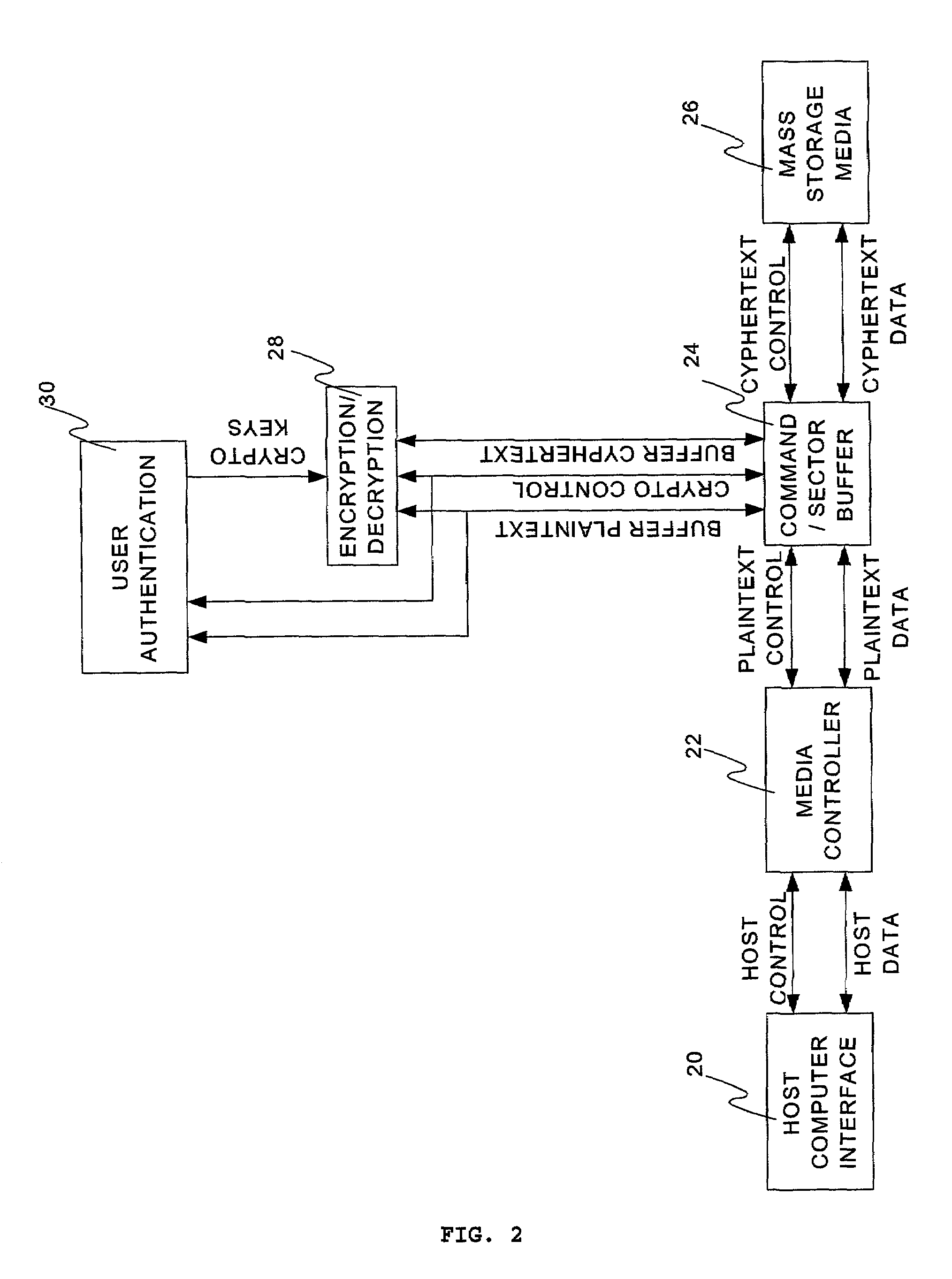
Apparatus and method for secure data storage
ActiveUS7069447B1Eliminate requirementsUser identity/authority verificationUnauthorized memory use protectionPasswordComputer data storage
A computer data storage device for storing confidential data incorporating data encryption and user authentication. The user authentication supports multiple distinct users each having their own PIN code or password and distinct access rights. Attempts to attack the data by multiple unsuccessful login attempts is detected during user authentication and users are locked out until the card is reactivated. A special supervisory Security Officer ID and PIN code or password is provided to allow for the customization and configuration of the device as well as administering the user ID's and their access rights.
Owner:SOTERIA ENCRYPTION II LLC
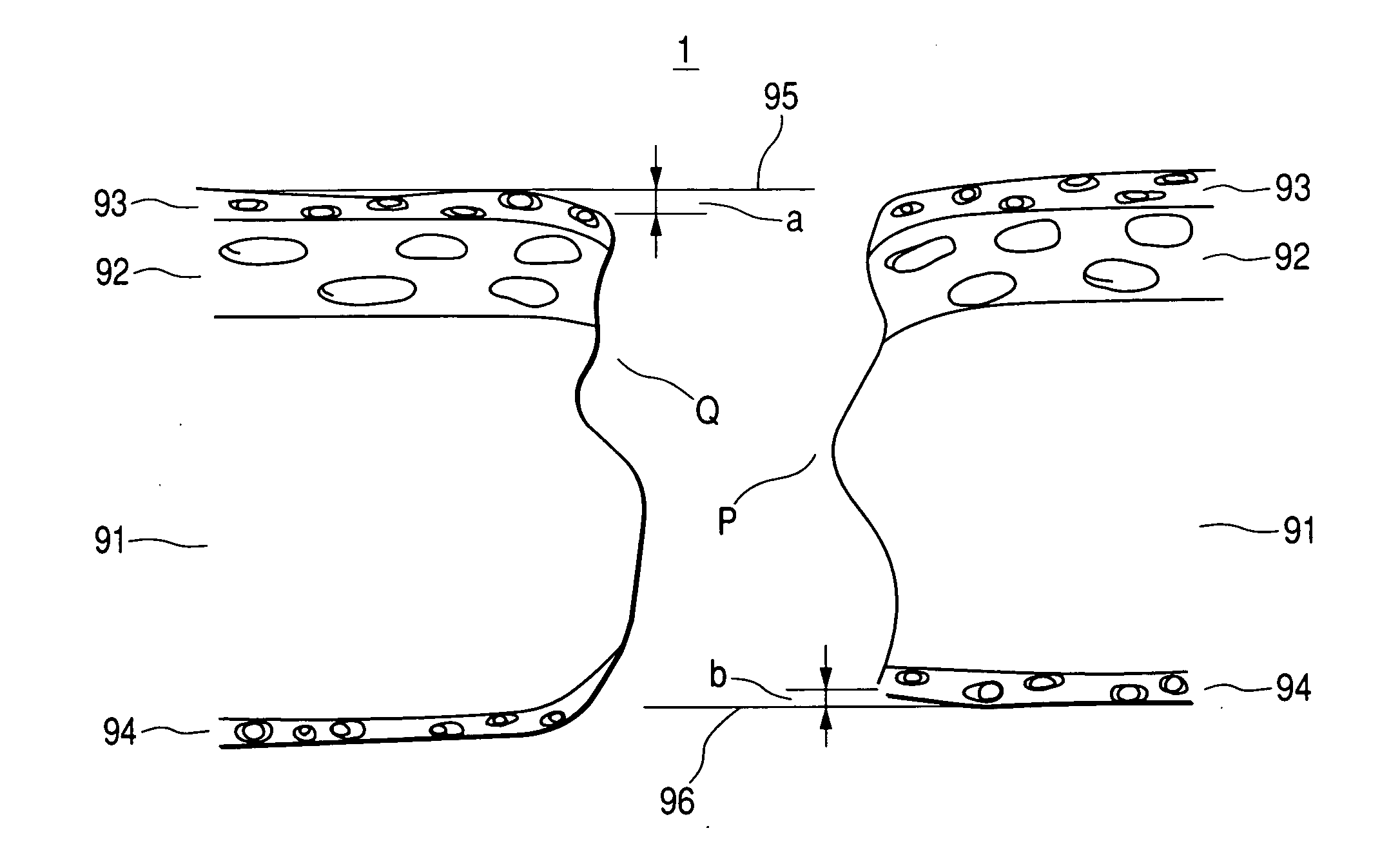
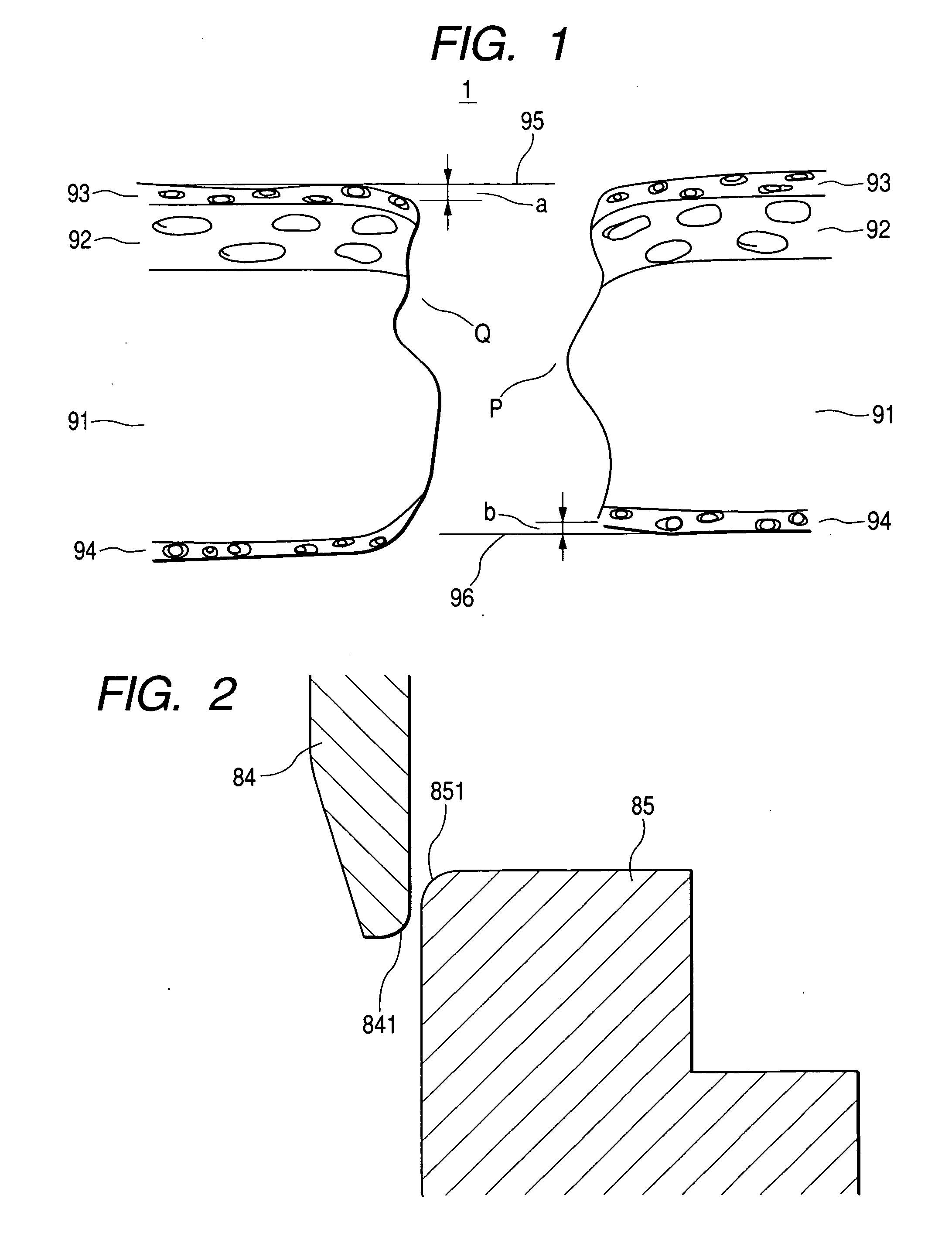
Magnetic recording medium
InactiveUS20070009769A1Large recording capacityGood running durabilityMagnetic materials for record carriersRecord information storageMagnetic tapeComputer data storage
A magnetic recording medium including a magnetic layer 93 containing ferromagnetic powder and a binder, a support 91, and a backcoat layer 94, provided in this order, and being obtained by slitting to width a magnetic material of broad width and continuous length. The magnetic recording medium has no ridge protruding above the surface plane of the magnetic layer along the slit edge thereof. The magnetic recording medium achieves large recording capacity, is free from the tape pack problems such as appearance of a radial pattern and the output reduction problem, produces no fine scrapings in high speed running, which would cause head clogging and dropouts, thereby exhibiting good running durability and electromagnetic characteristics, and is particularly useful for computer data storage applications.
Owner:FUJIFILM HLDG CORP +1
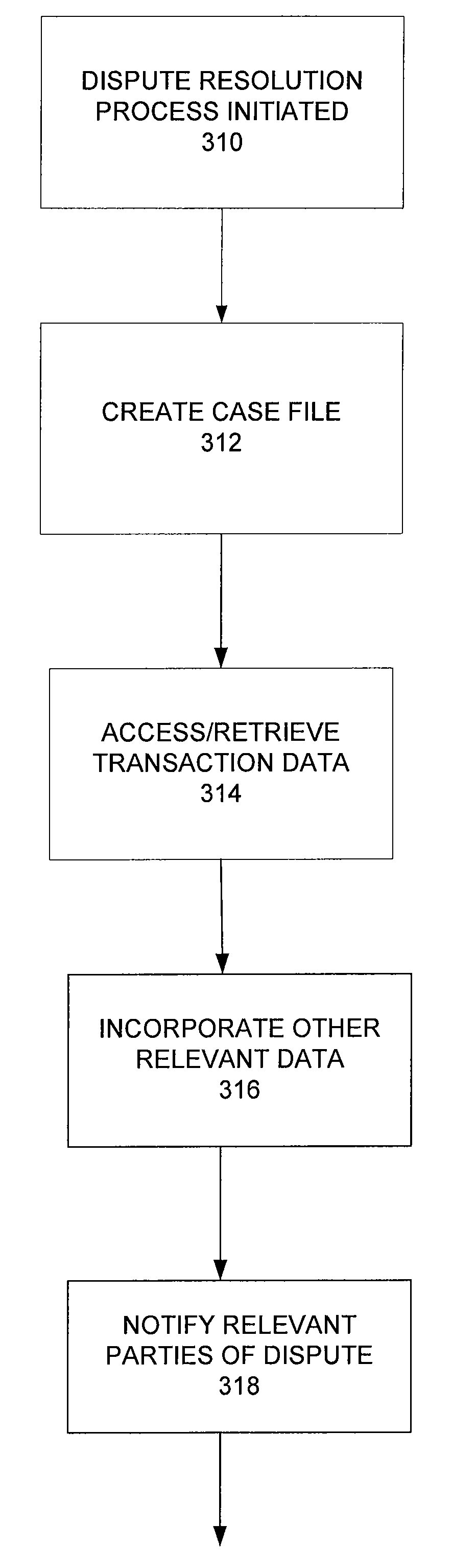
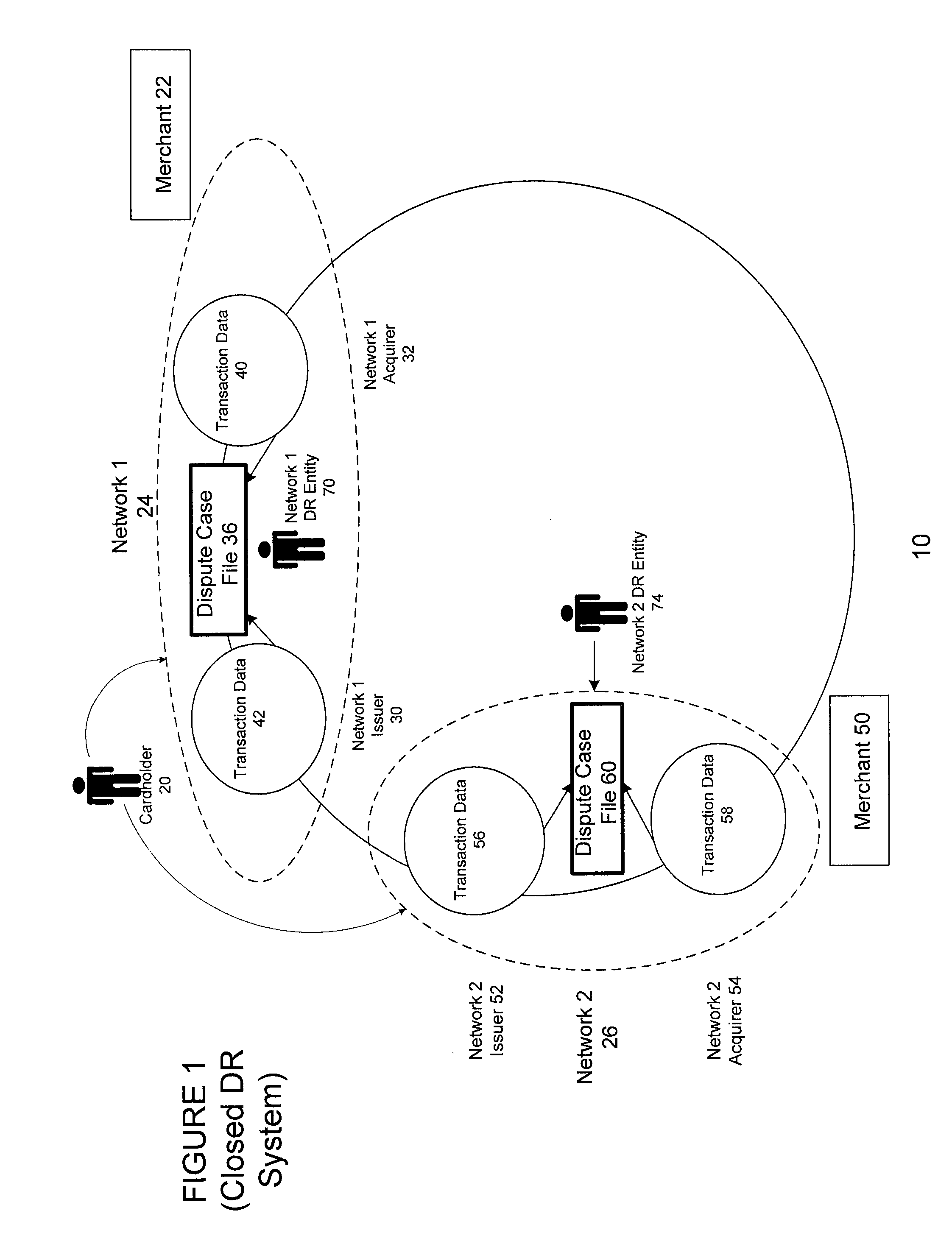
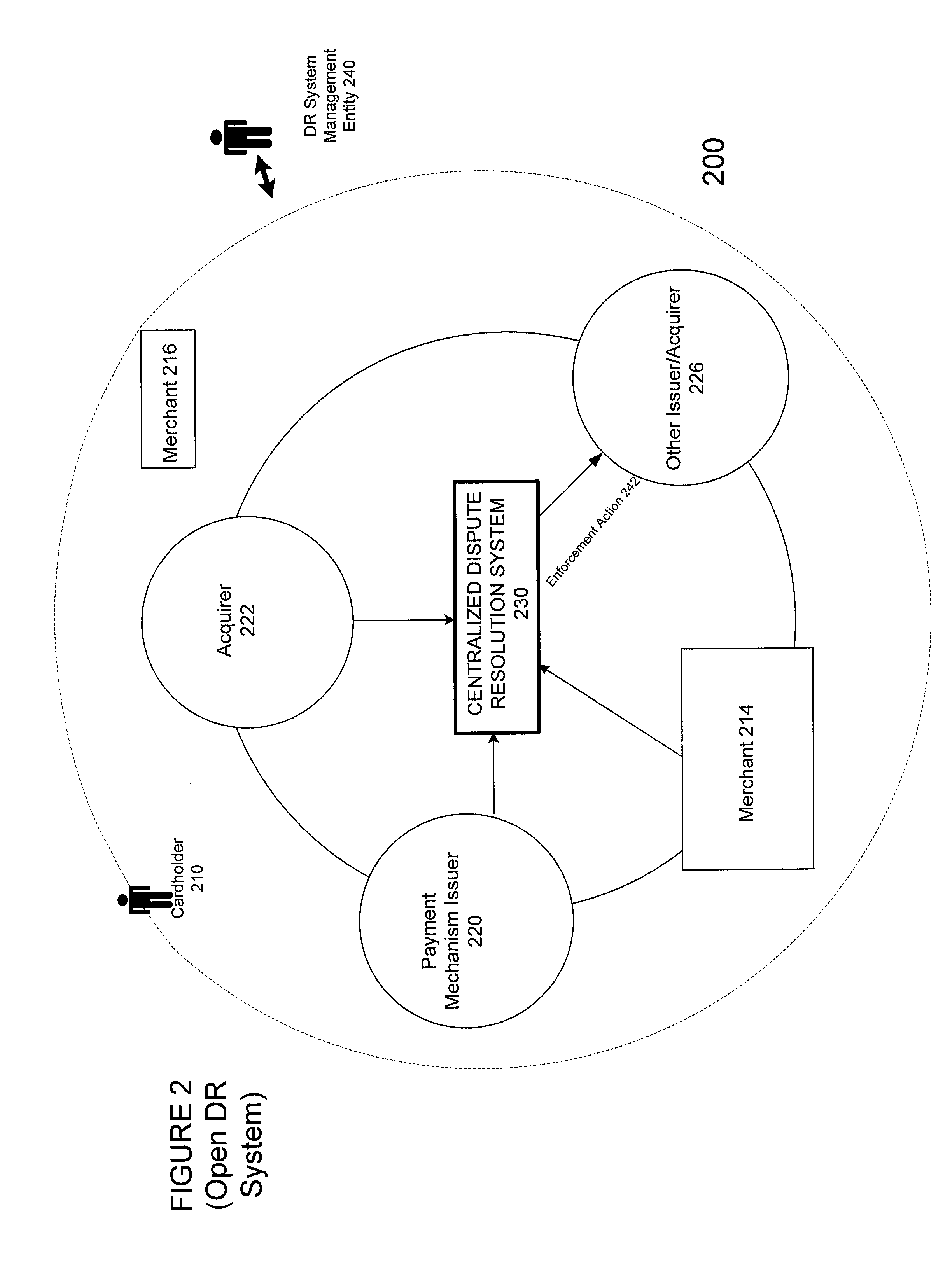
Centralized dispute resolution system for commercial transactions
InactiveUS20090030710A1Raise the possibilityReduce incentivesFinanceCredit schemesComputer data storageClient-side
A centralized dispute resolution system for use in commercial credit or debit card transactions. The inventive system utilizes a common data storage, interfaces, processes, procedures, rules, and other elements of a dispute resolution system that are made available to cardholders, merchants, card issuers, payment processors, and other parties that may be involved in a dispute or in a process intended to resolve a dispute. The system may be implemented using a client-server architecture with communication between clients and one or more server elements provided by a communications network.
Owner:VISA USA INC (US)
Inventory system
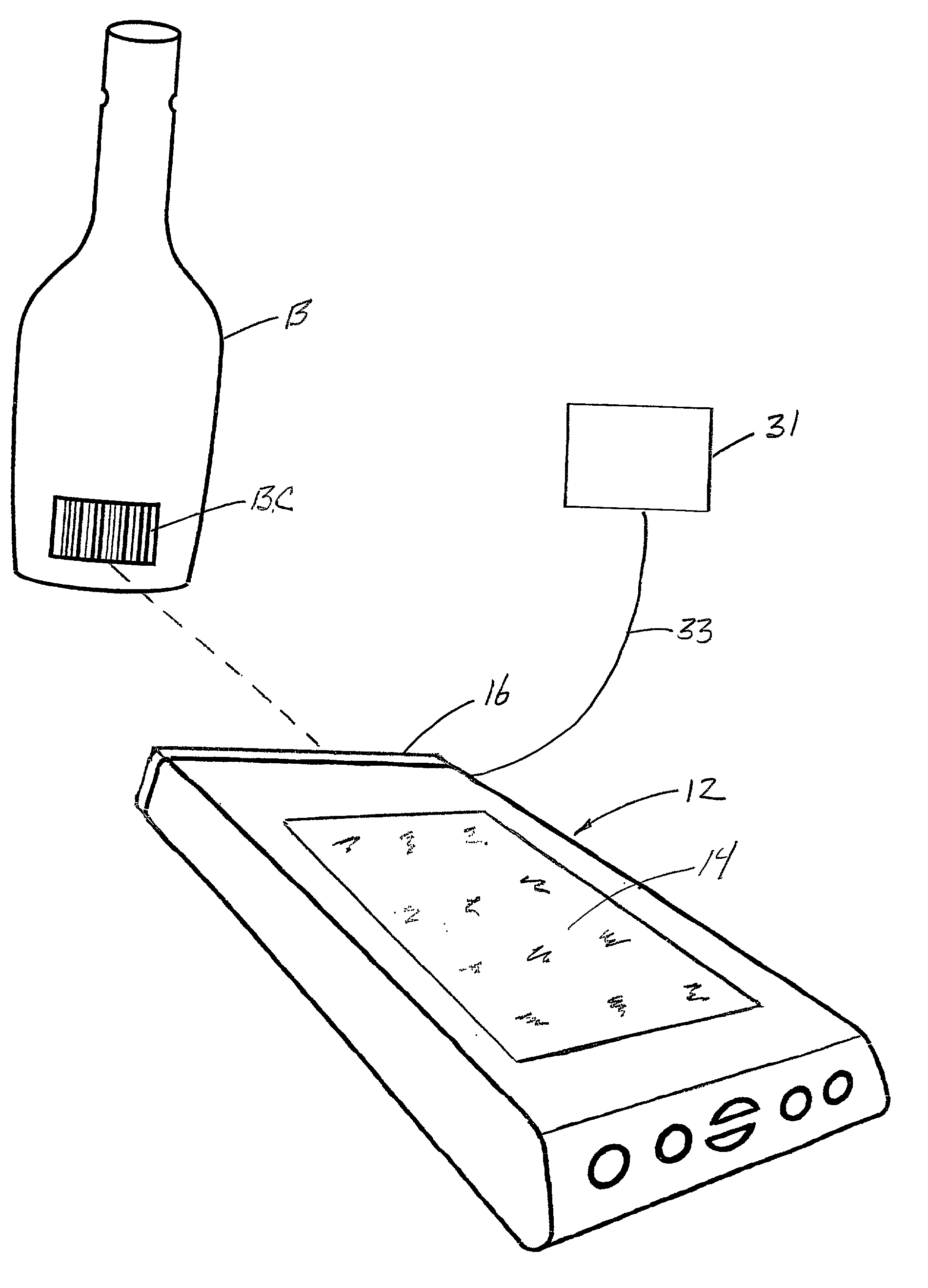
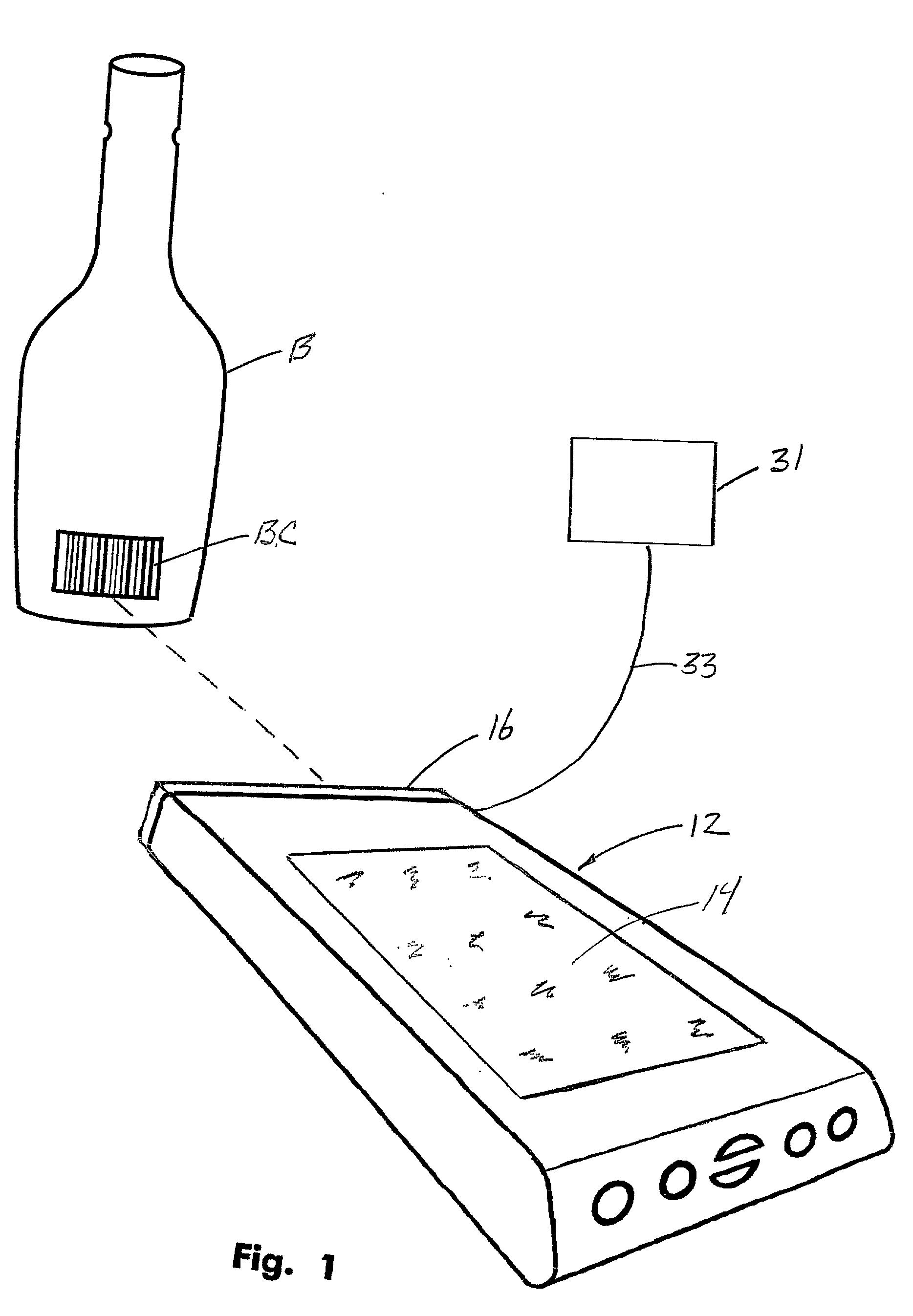
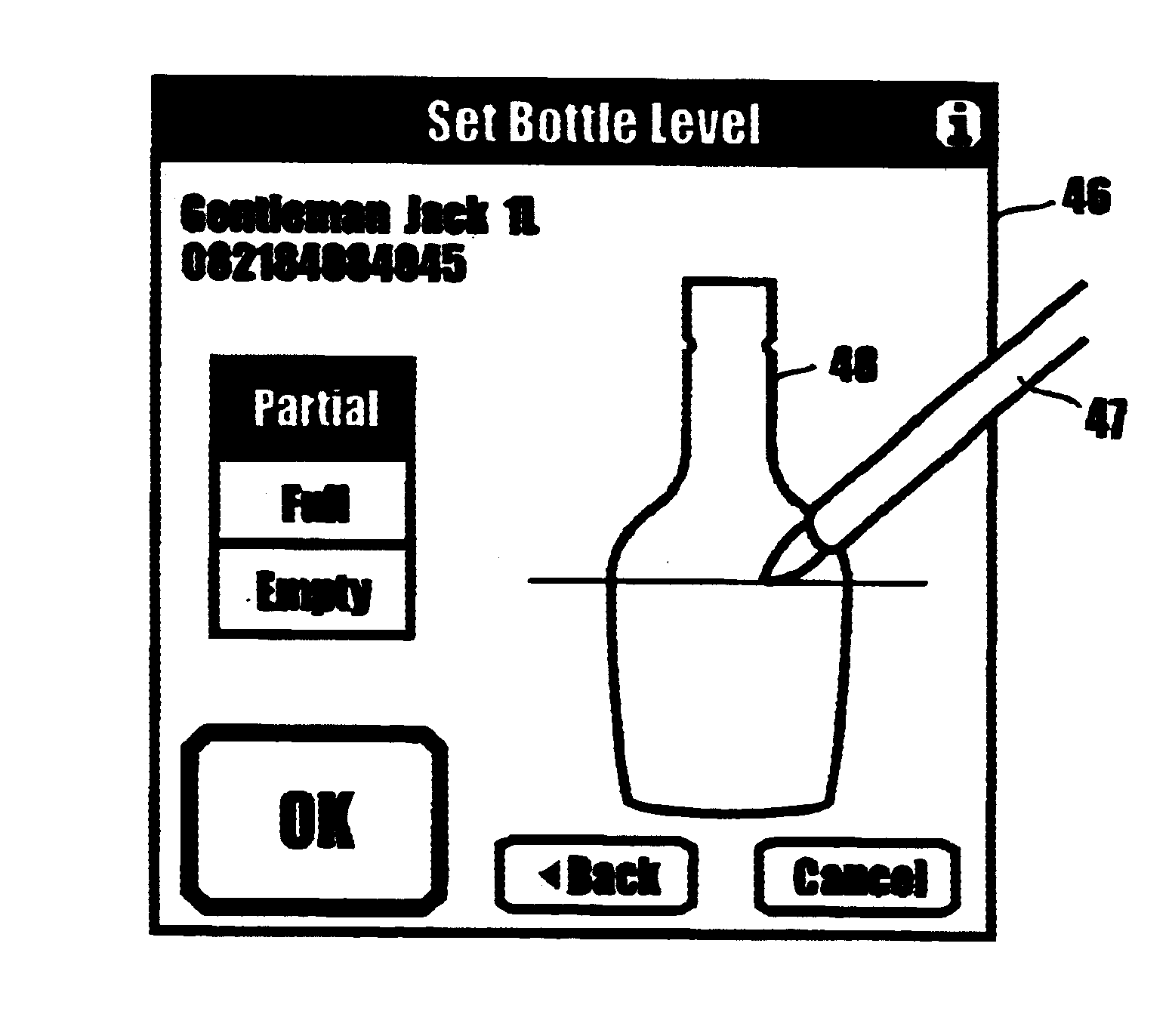
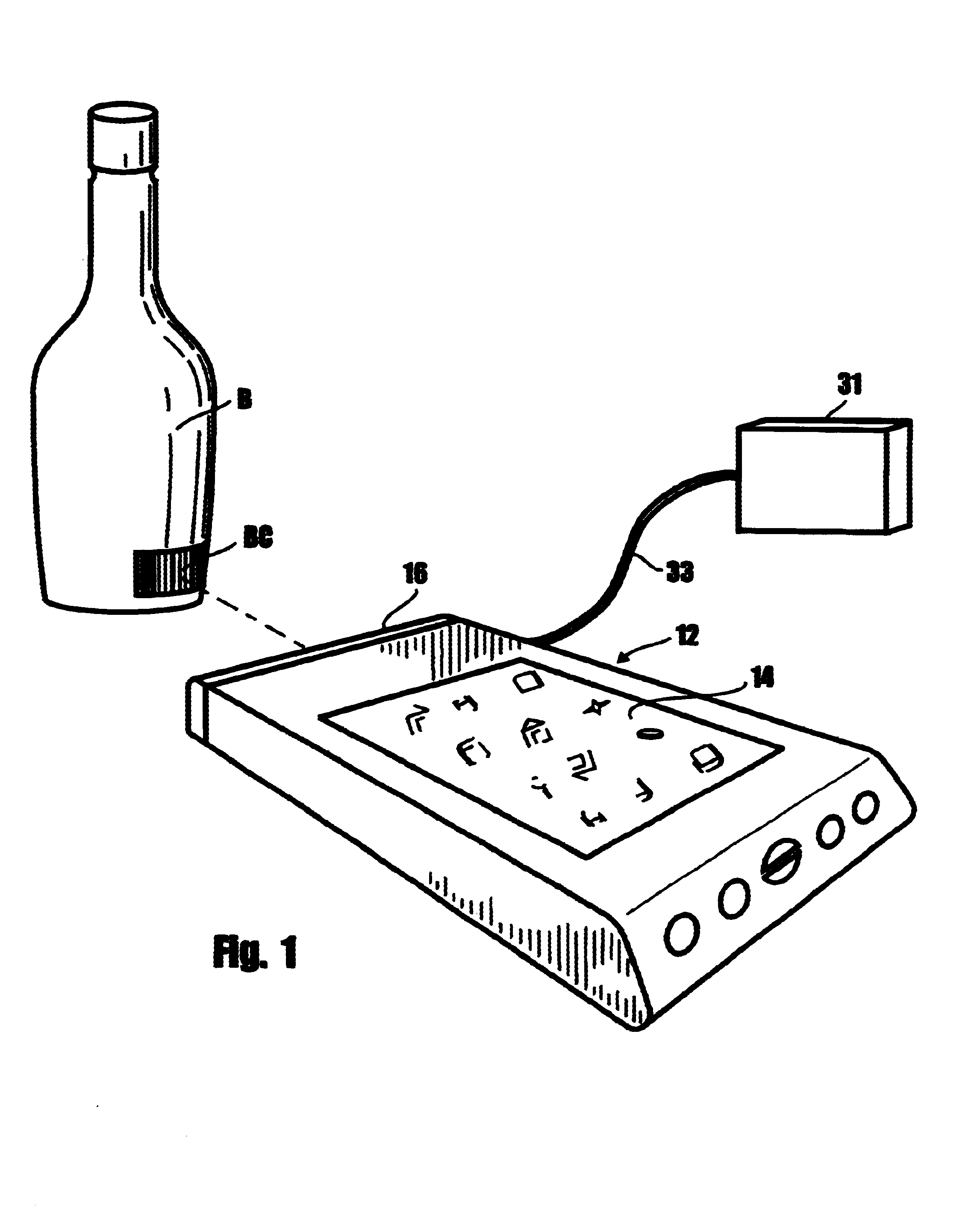
InactiveUS20030034392A1Accurately determinedDigital data processing detailsCo-operative working arrangementsData memoryTouchscreen
A computer-based system for taking the physical inventory of beverages dispensed in full and partially full containers so as to effectively control the theft and overpouring. The products to be inventoried, such as liquor bottles are identified by conventional barcodes that can be scanned by a scanner that is operably interconnected with a hand-held computer. The step of scanning the barcodes produces, on the touch-sensitive screen of the hand-held computer, product information concerning the product contained within the scanned bottle including a silhouette of the bottle. In accomplishing the inventory, the user indicates by touching on the silhouette of the bottle the fluid level within the bottle. This information is inputted in the computer data storage and is used to calculate the volume of beverage remaining in the bottle.
Owner:BIRCH STREET SYST LLC
Secure data storage with key update to prevent replay attacks
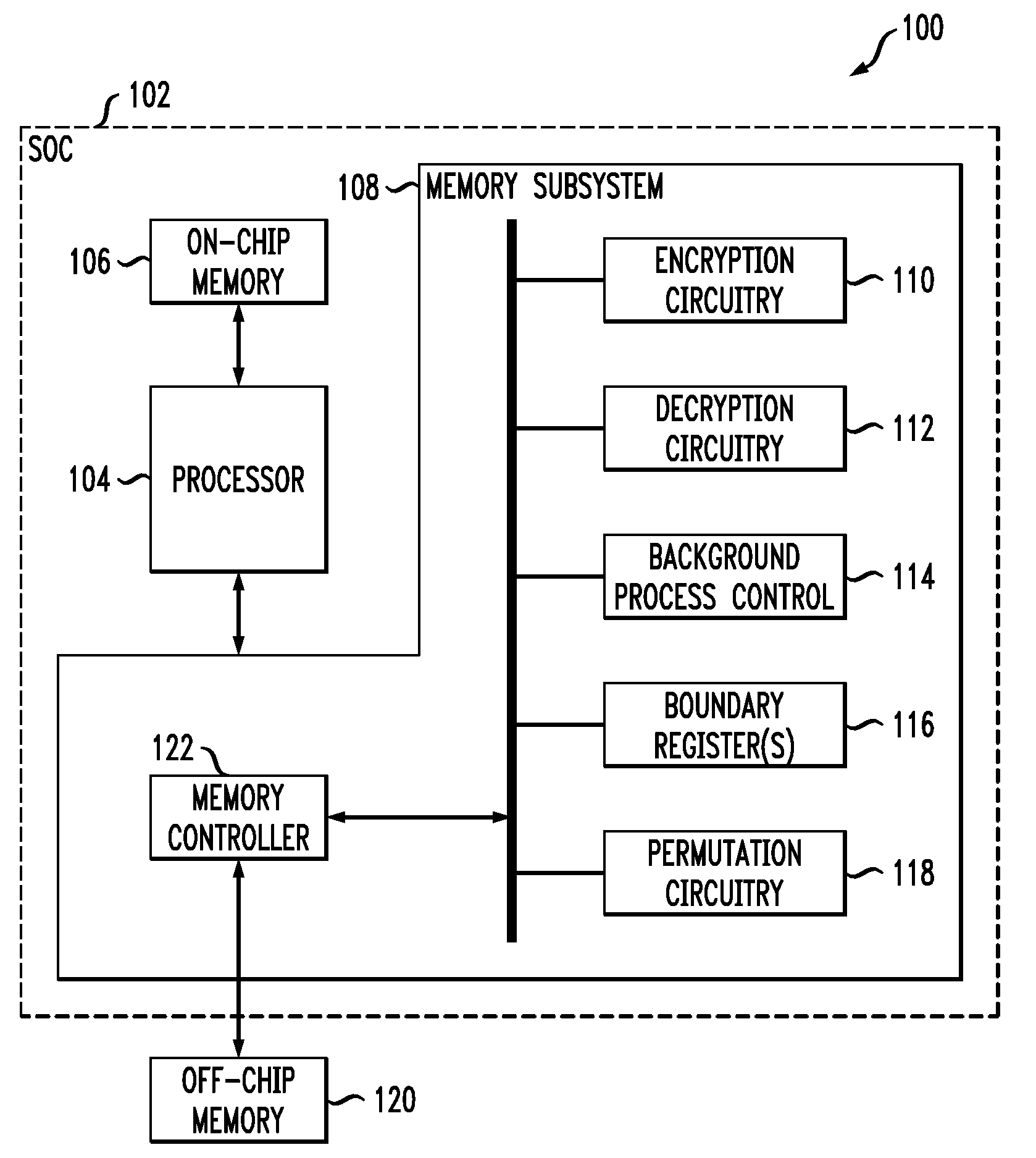
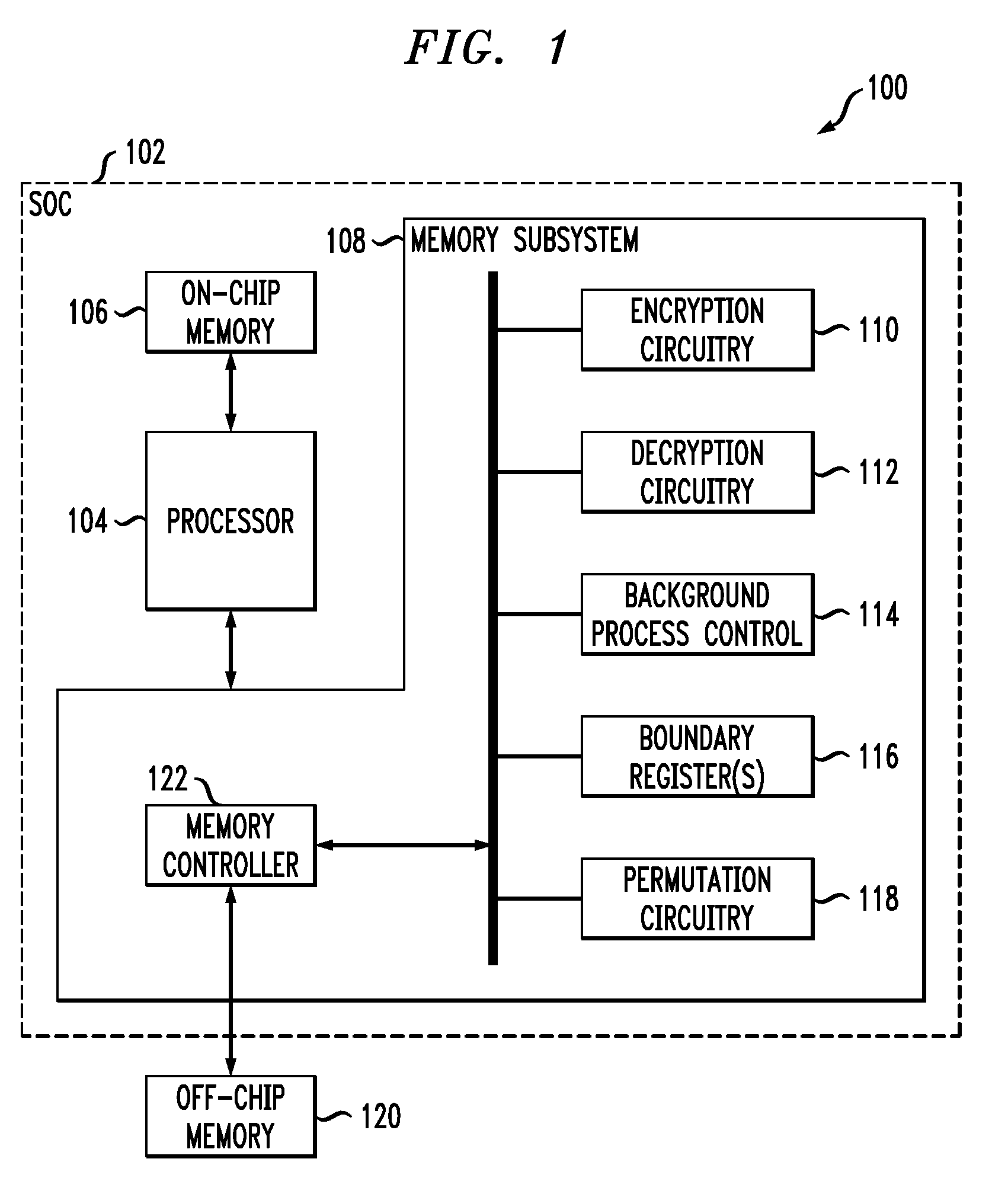
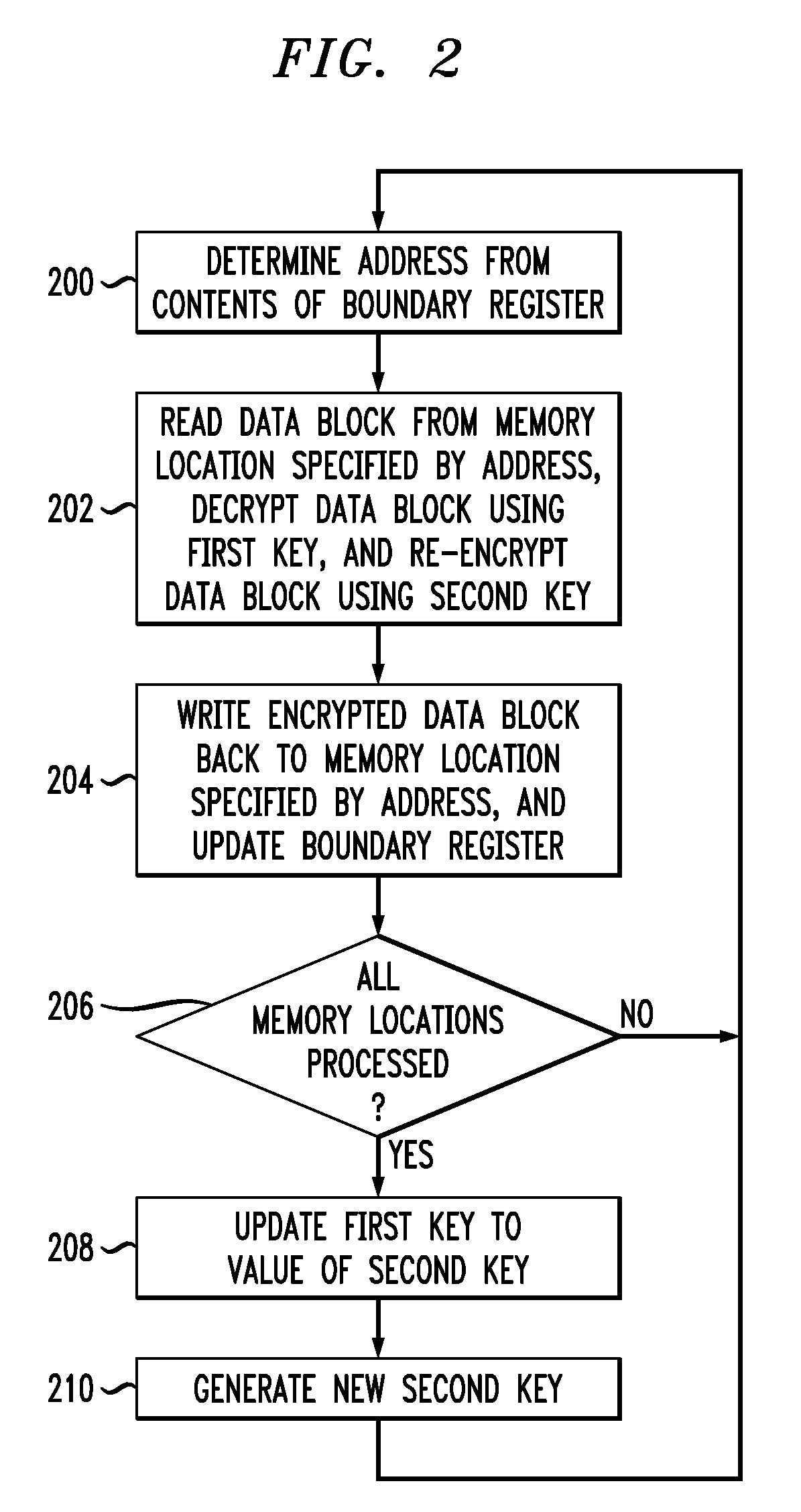
InactiveUS20090187771A1Undermines effectivenessAvoid problemsEncryption apparatus with shift registers/memoriesUnauthorized memory use protectionProcessor registerComputer data storage
A key update process applied to encrypted memory in a processing system determines an address from contents of a boundary register, reads an encrypted data block from a memory location specified by the address, decrypts the encrypted data block using a first key, re-encrypts the decrypted data block using a second key, writes the re-encrypted data block back to the memory location specified by the address, and updates the boundary register. These operations are repeated for one or more additional addresses. The boundary register contents are also used to determine appropriate keys for use in other read and write transactions to the memory. The key update process can be run as a background process, separate from the other read and write transactions to the memory, so as to incur minimal processing overhead.
Owner:LUCENT TECH INC
Method and system for name and address validation and correction
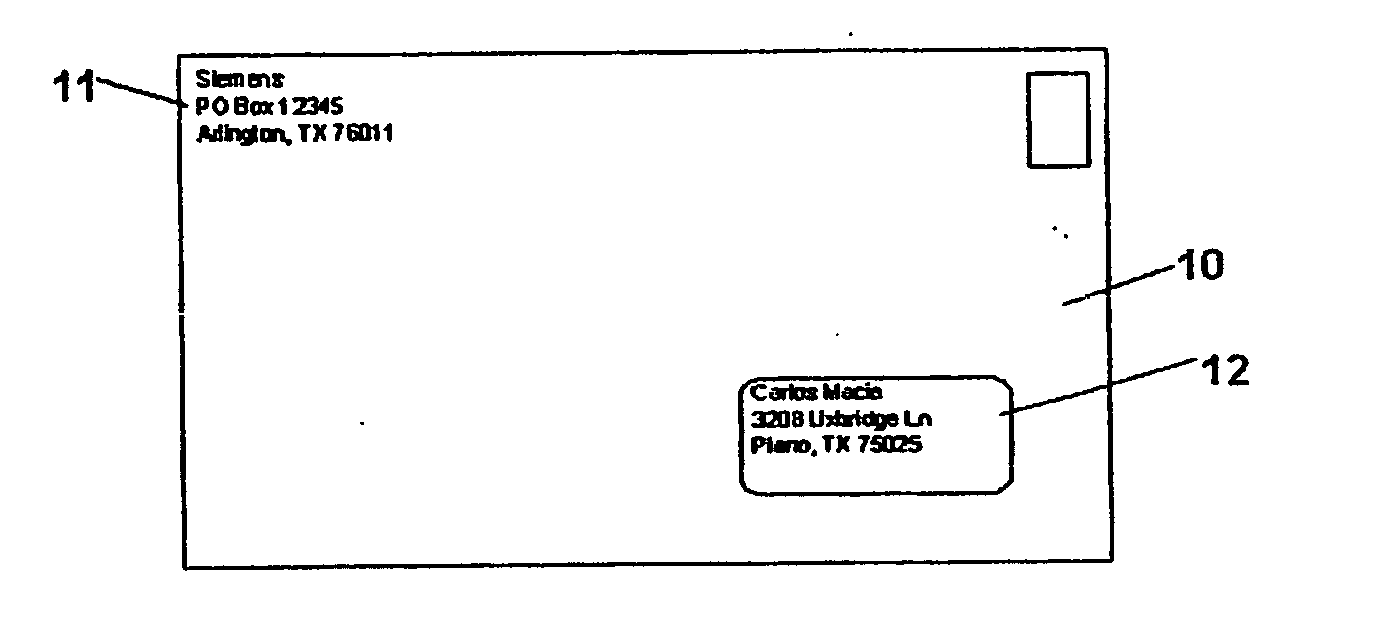
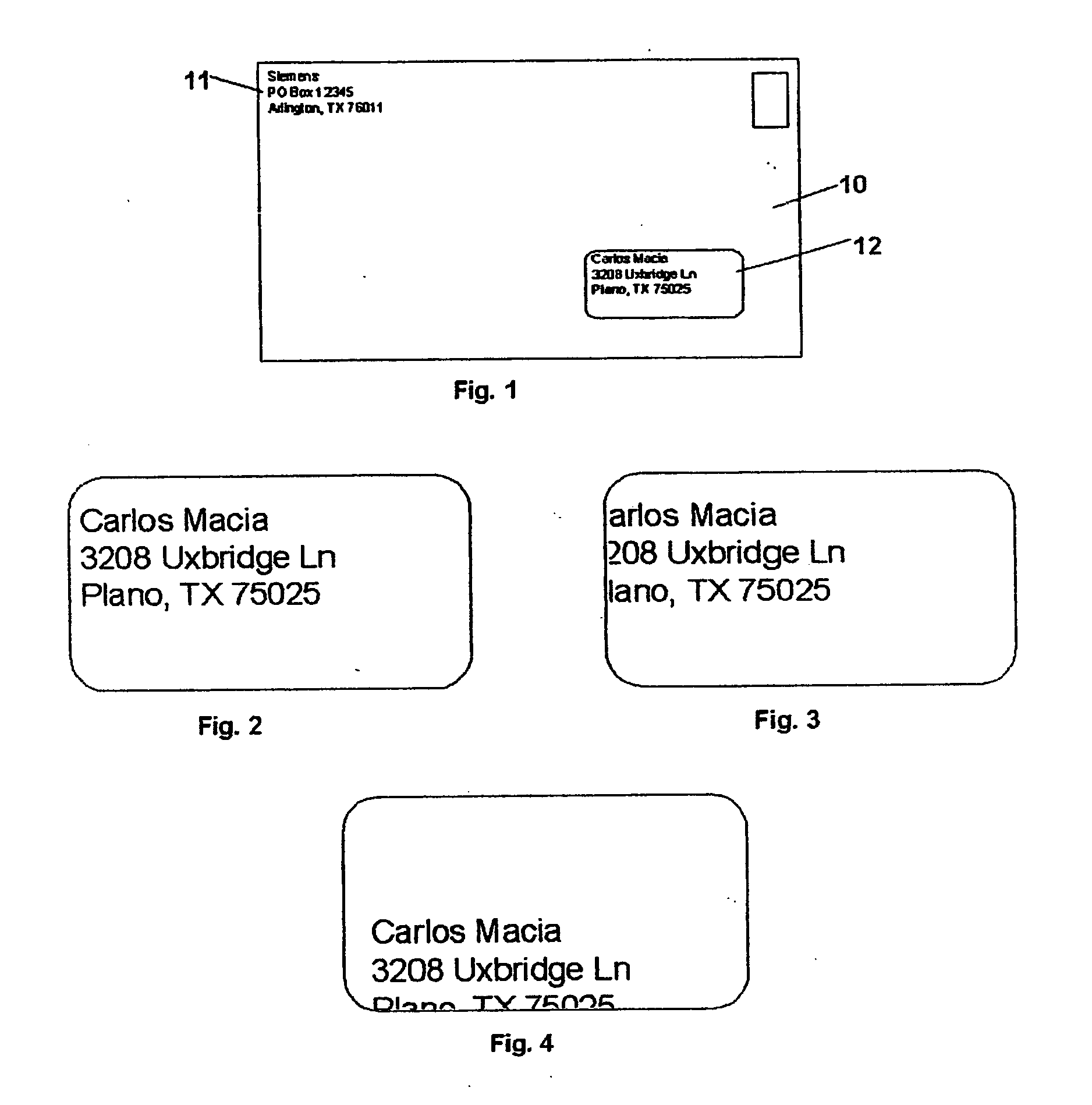
InactiveUS20050137991A1Improve efficiencyAccurate informationProgram controlSortingMostly TrueComputer data storage
A method of correcting postal name and address information according to the invention includes the step of comparing the name and address information to at least one database of known names and associated addresses to determine if the name and address information matches a known postal recipient. if no match is found, the name and address information is corrected by comparing fields of the name and address information with corresponding fields from the database of known names and addresses, and deducing an incorrect or missing field in the name and address information. An action is then taken using the corrected name and address information, depending on the setting in which the method is used. In most cases, the corrected name and address information will be saved to a computer data storage medium for future use. If a series of name and address records are being read from mail pieces being processed on a postal sorting machine, the final step may comprise sorting a mail piece using the corrected name and address information.
Owner:SIEMENS LOGISTICS & ASSEMBLY SYST
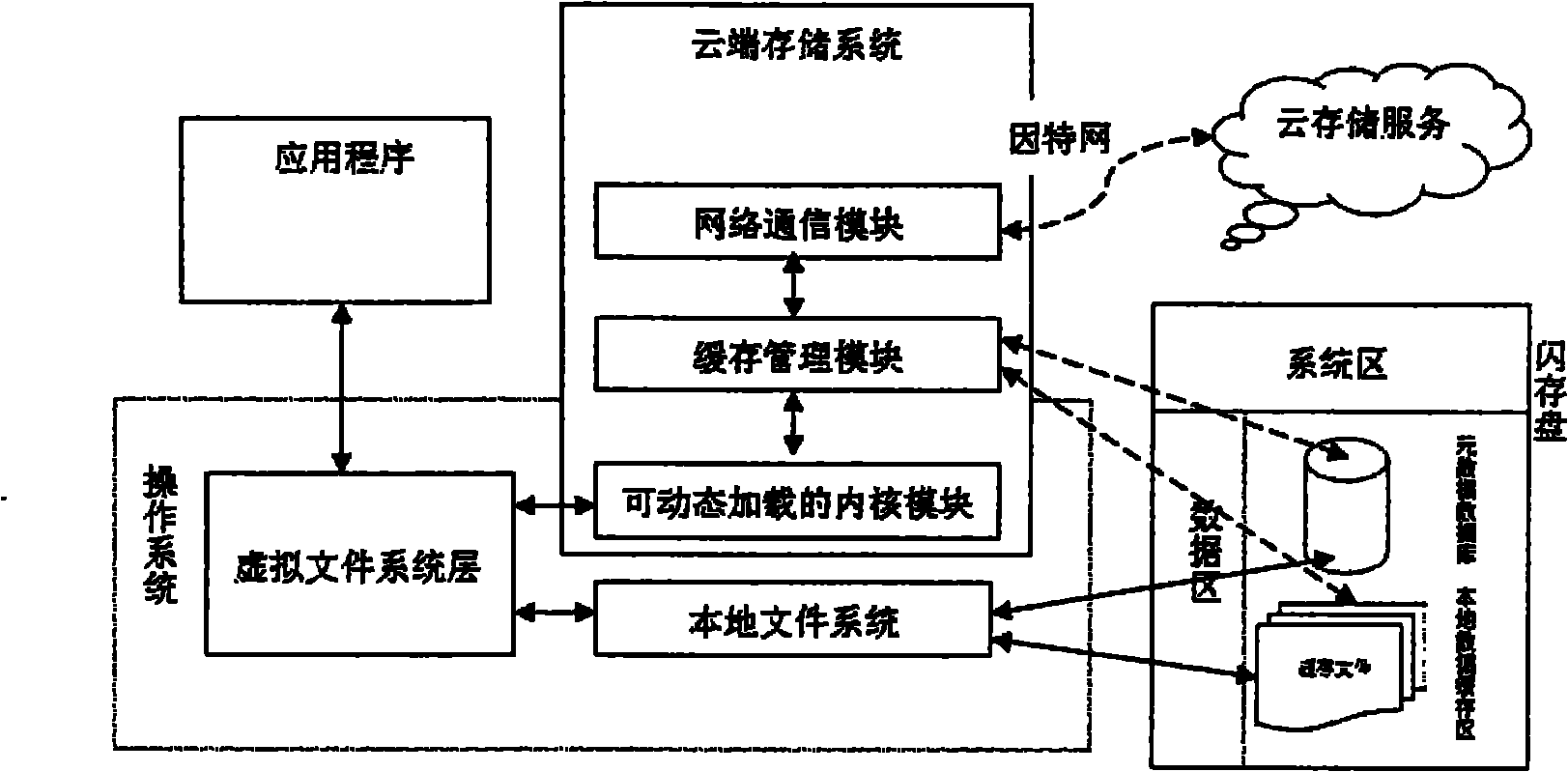
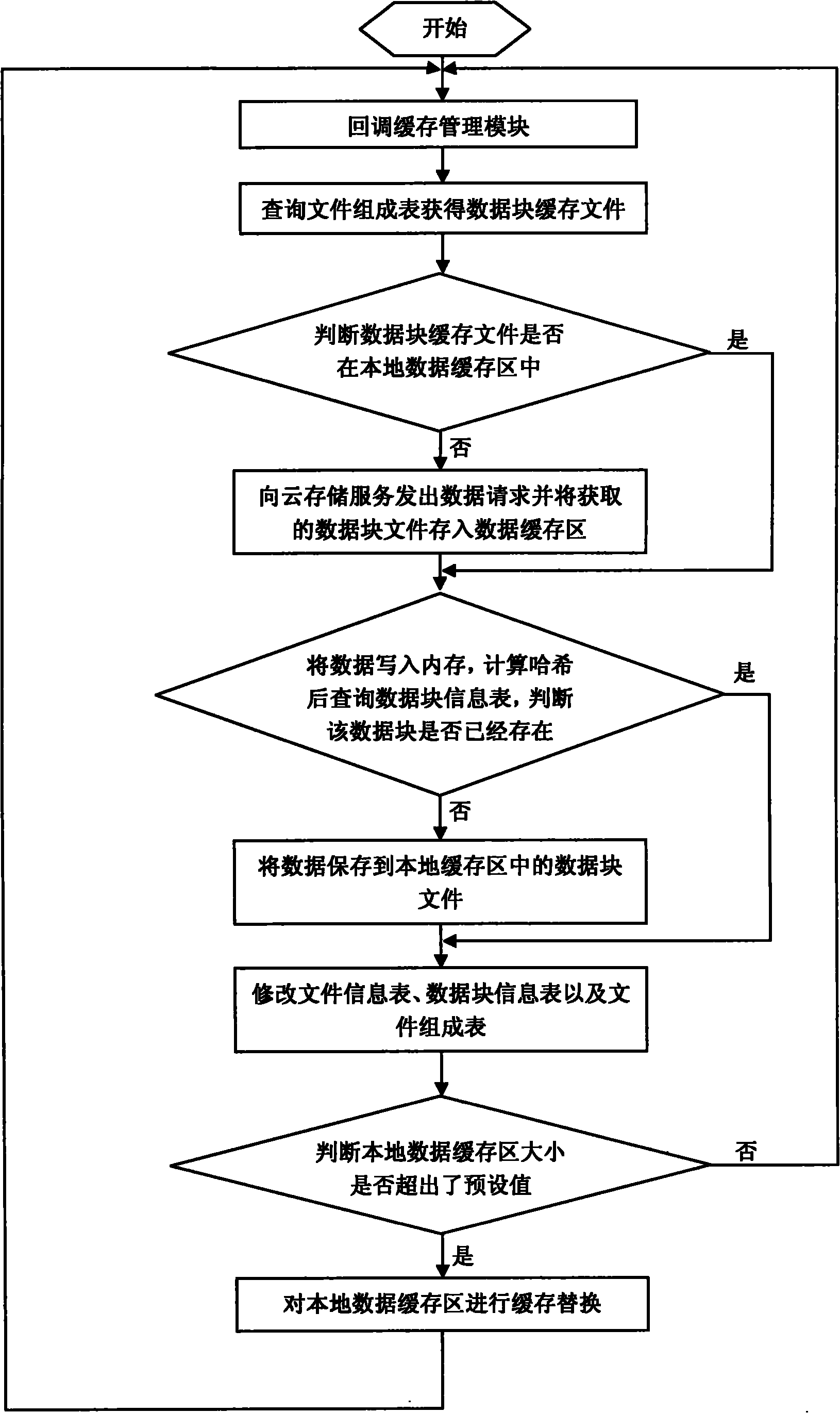
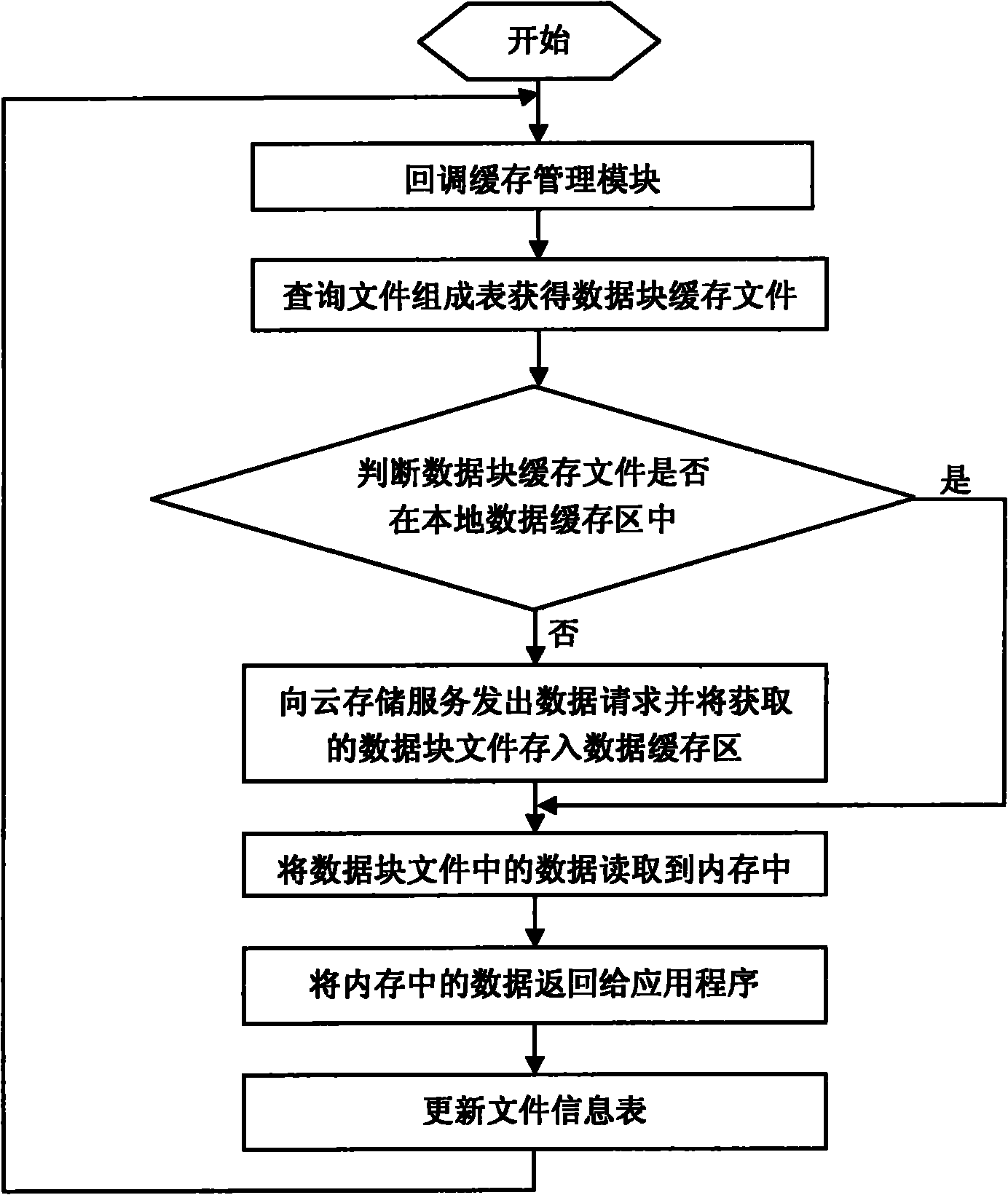
Data caching method of cloud storage system
The invention relates to a data caching method of a cloud storage system, belonging to the technical field of computer data storage. The method comprises the steps of: taking a flash disk as a carrier of the cloud storage system, starting a computer from the flash disk and loading an operation system in a system area of the flash disk into a memory of the computer; scanning data block caching files in a local data caching area by the cloud storage system and storing each obtained data block caching file in the memory; capturing the operation commands of an upper application program by the cloud storage system through a virtual file system layer, wherein the operation commands comprise the steps of creating the files, modifying the files, reading the files and deleting the files, and the new data blocks formed after the operation are cached in the local data caching area in file form; and storing the formed new data block caching files to a cloud storage server by a network communication module and obtaining data block caching files from the cloud storage server when the needed data block caching files do not exist in the local data caching area. The method improves the response speed and realizes the access of the cloud storage data under the situation of off-network.
Owner:广东赛特斯信息科技有限公司
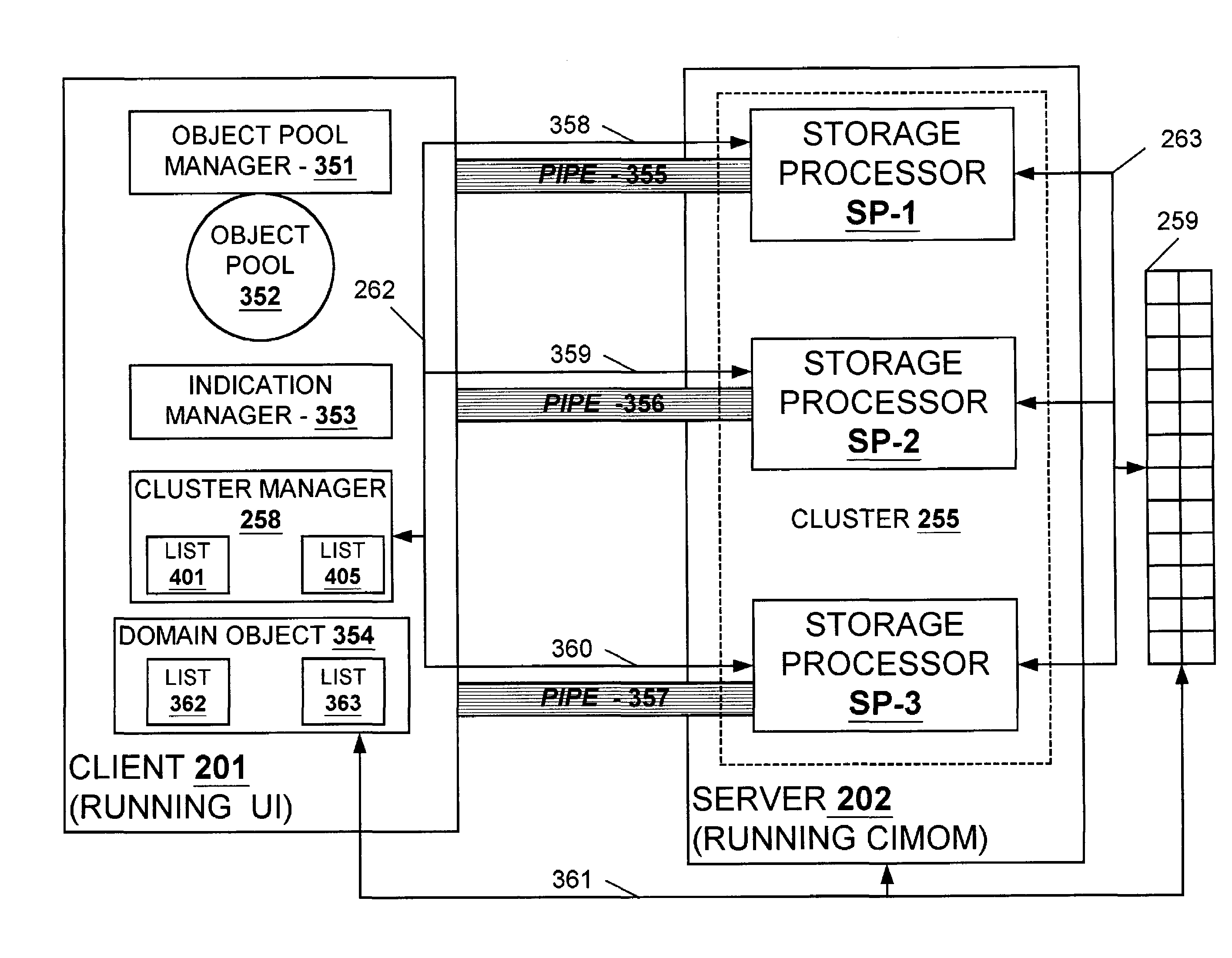
Robust indication processing failure mode handling
A technique for handling failure modes which may occur during the processing of indications. In a client-server environment such as a client-server network used in computer data storage running object-oriented software, the client may subscribe for certain indications on certain objects in the servers. When the state of any of those certain objects change, an indication is fired back to the client to indicate a state change. Failures in the client, server, or connection therebetween reduce the effectiveness of this state-change notification scheme. The present invention mitigates the impact of such failures, employing a technique by which a failed storage processor in a server can failover to another storage processor in the same server to enable the seamless transition of the processing of such indications to the other processor without stopping and by which the server can destroy any of its resources that were dedicated to the processing of indications for a specific client if and when such client fails.
Owner:EMC IP HLDG CO LLC
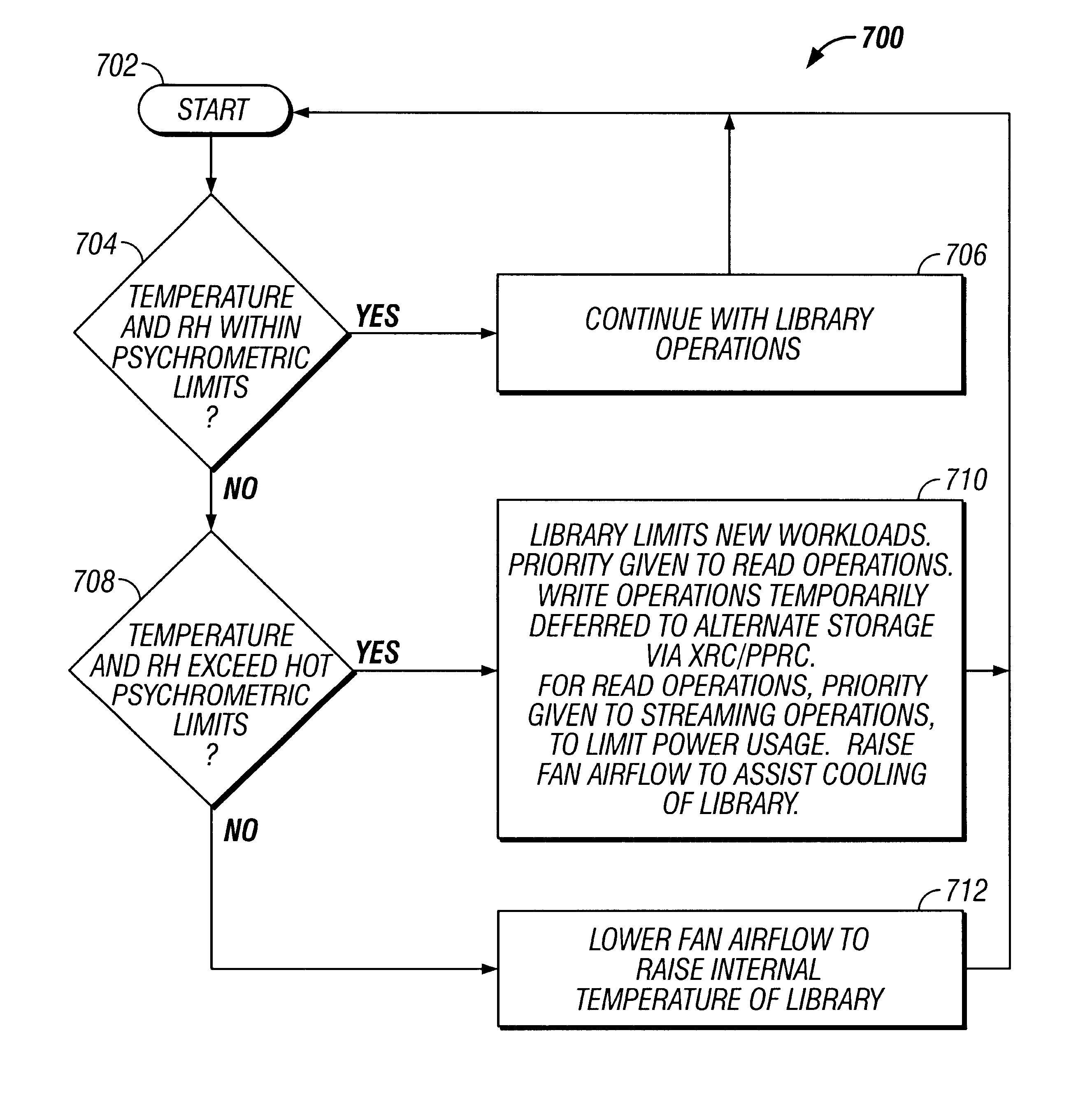
System and method for autonomic environmental monitoring, adjusting, and reporting capability in a remote data storage and retrieval device
InactiveUS6676026B1Reducing temperature influence on carrierAir-treating devicesComputer data storageEngineering
A data storage and retrieval system such as a robotic library has a large plurality of removable storage media, such as tape cartridges, for purposes of I / O. To enhance performance and reliability of the library, a thermodynamic model of the library is constructed and stored in the library, and environmental conditions such as the temperature, humidity, and flow rate of cooling air coming into, flowing through, and leaving the library are monitored. The thermodynamic model of the library includes an acceptable operating range for the library in a psychrometric chart; and the product of the effective thermodynamic mass and specific heat of the library.
Owner:IBM CORP
System and method for unified messaging in inter/intranet telephony
InactiveUS7257201B2Telephone data network interconnectionsSpecial service for subscribersThe InternetComputer data storage
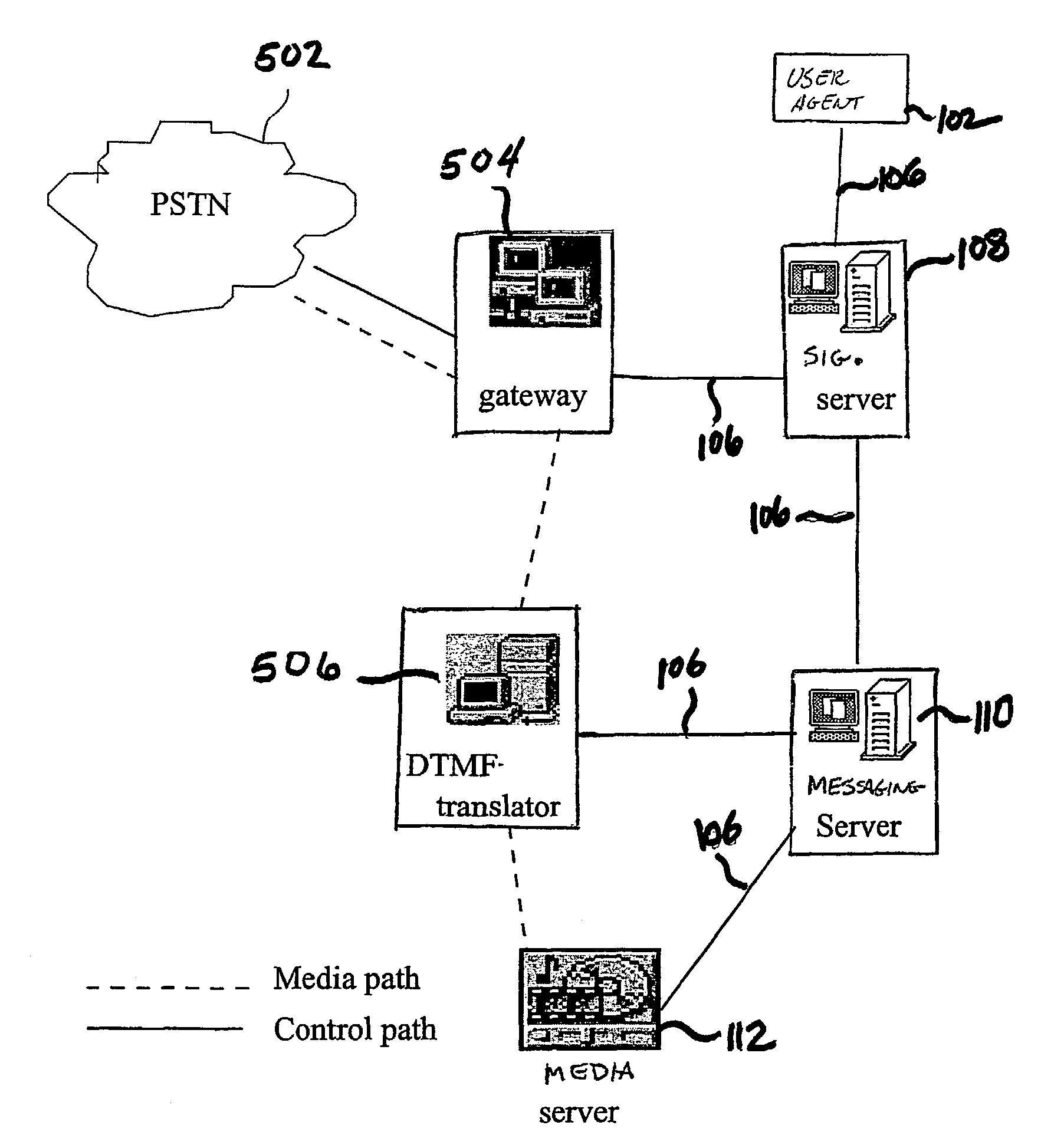
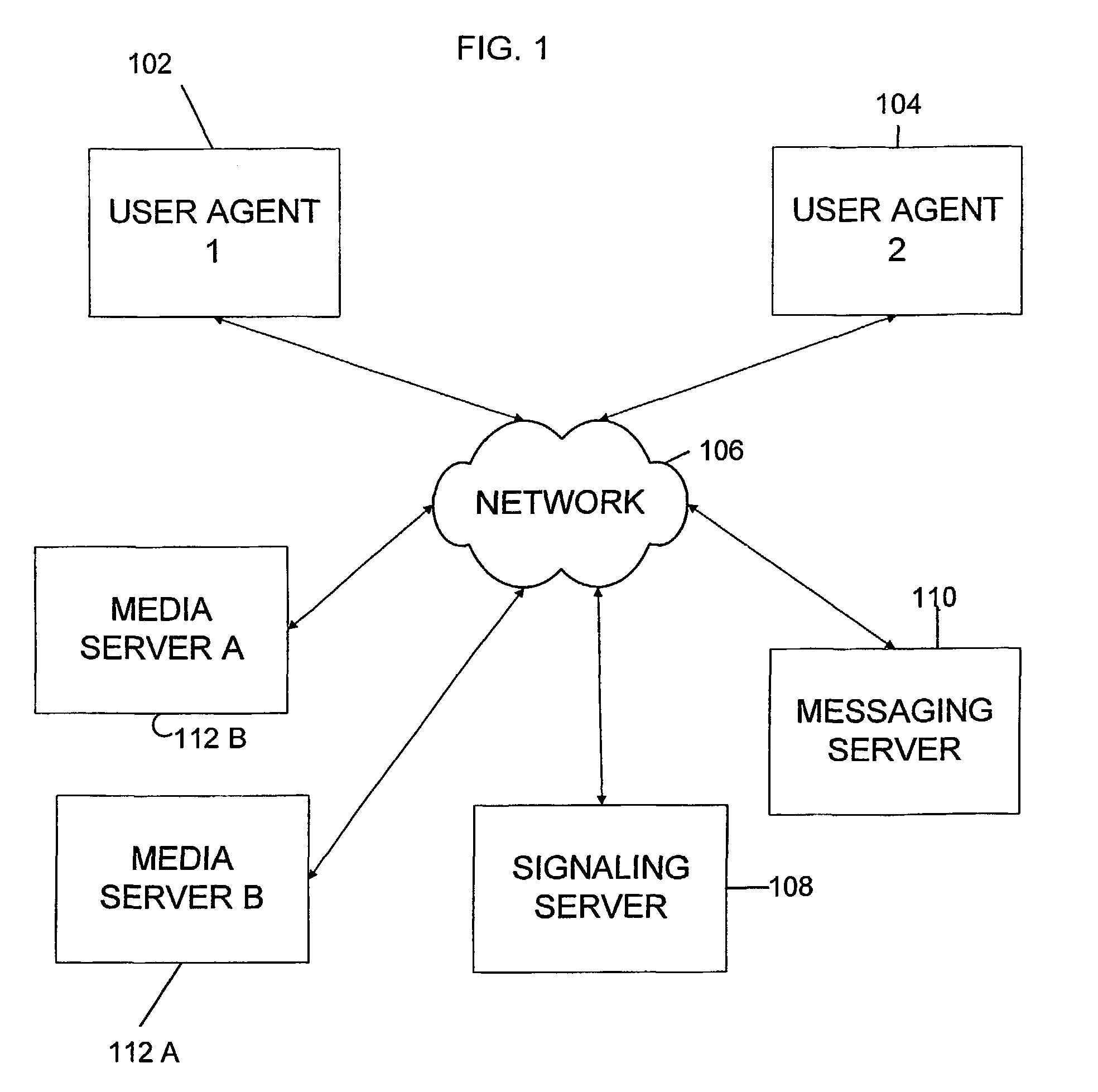
A network telephony system is provided which enables unified messaging services. The system generally includes at least one user agent (102,104) operatively coupled to a data network (106) and a signalling server operatively coupled to the data network (106). The user agents (102,104) are telephony endpoints, such as standalone Internet telephony appliances or personal computers with appropriate telephony software. A messaging server (110) is provided which is operatively coupled to the data network (106) and is responsive to the signaling server (108). The system also includes a media server (112A,112B) which is operatively coupled to the network and includes computer data storage media for storing message files. The media server is responsive to the messaging server (110) and, on occurrence of a message condition, is directly accessible to a calling party to store a message file for subsequent retrieval by a called party.
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK
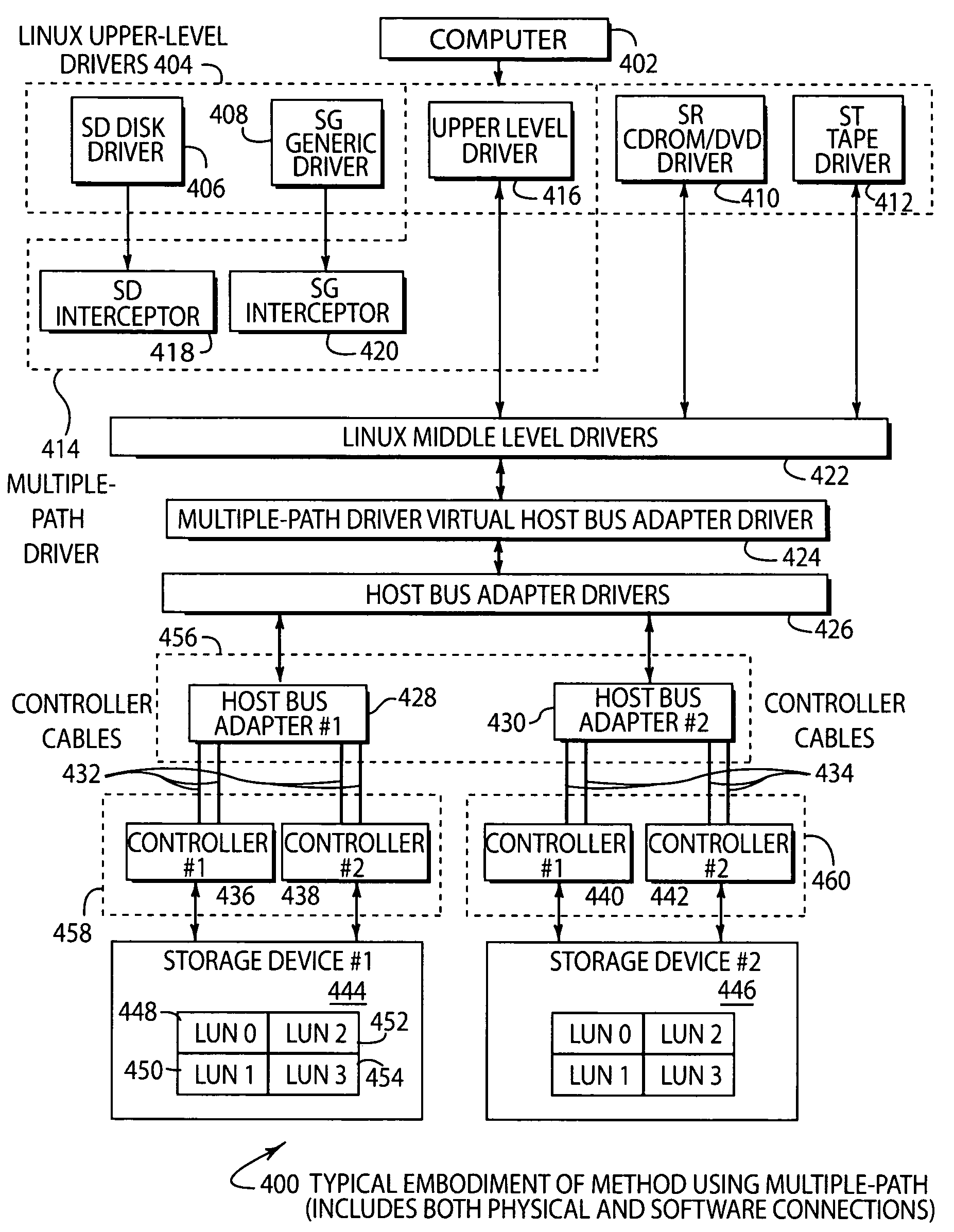
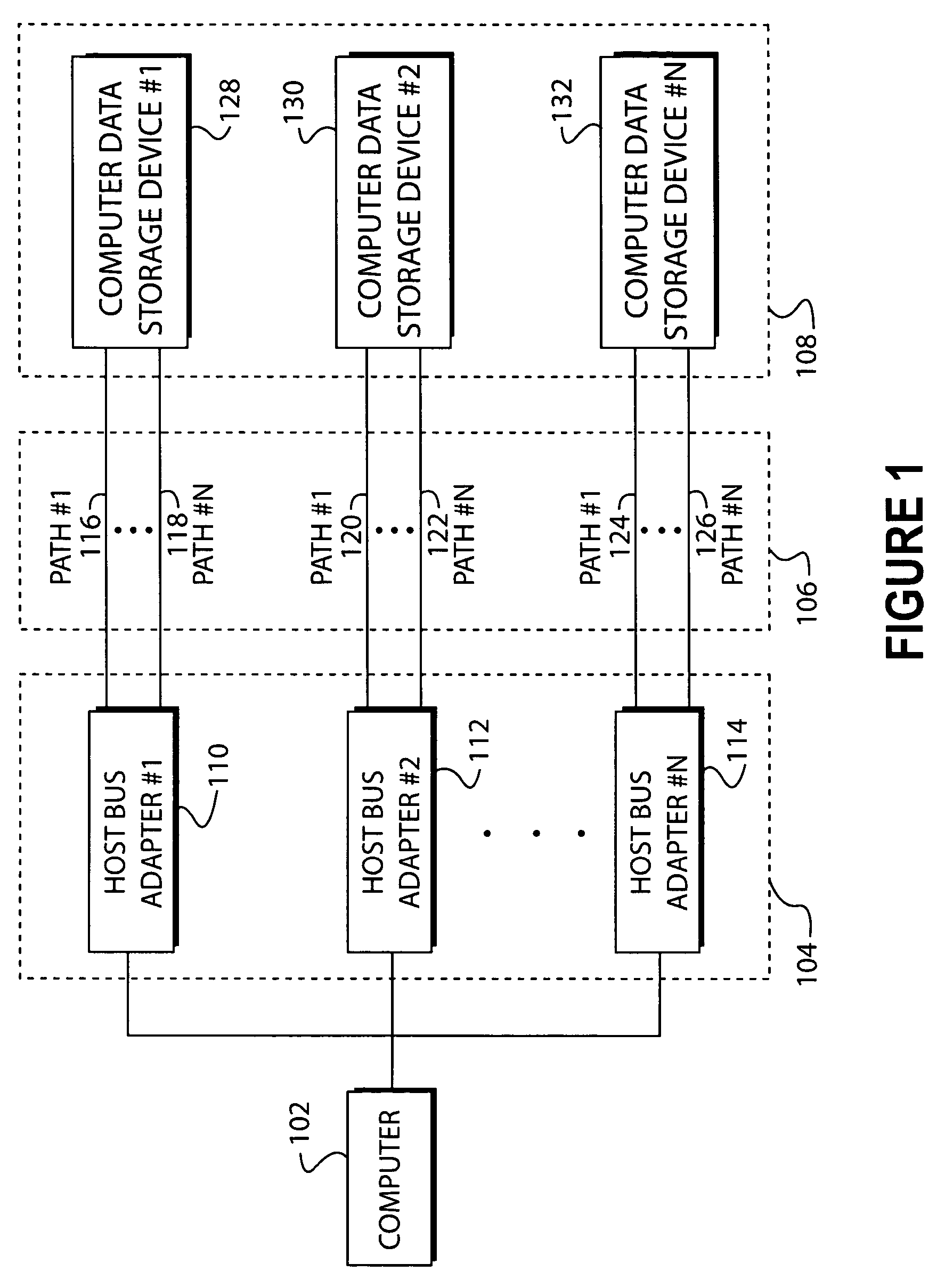
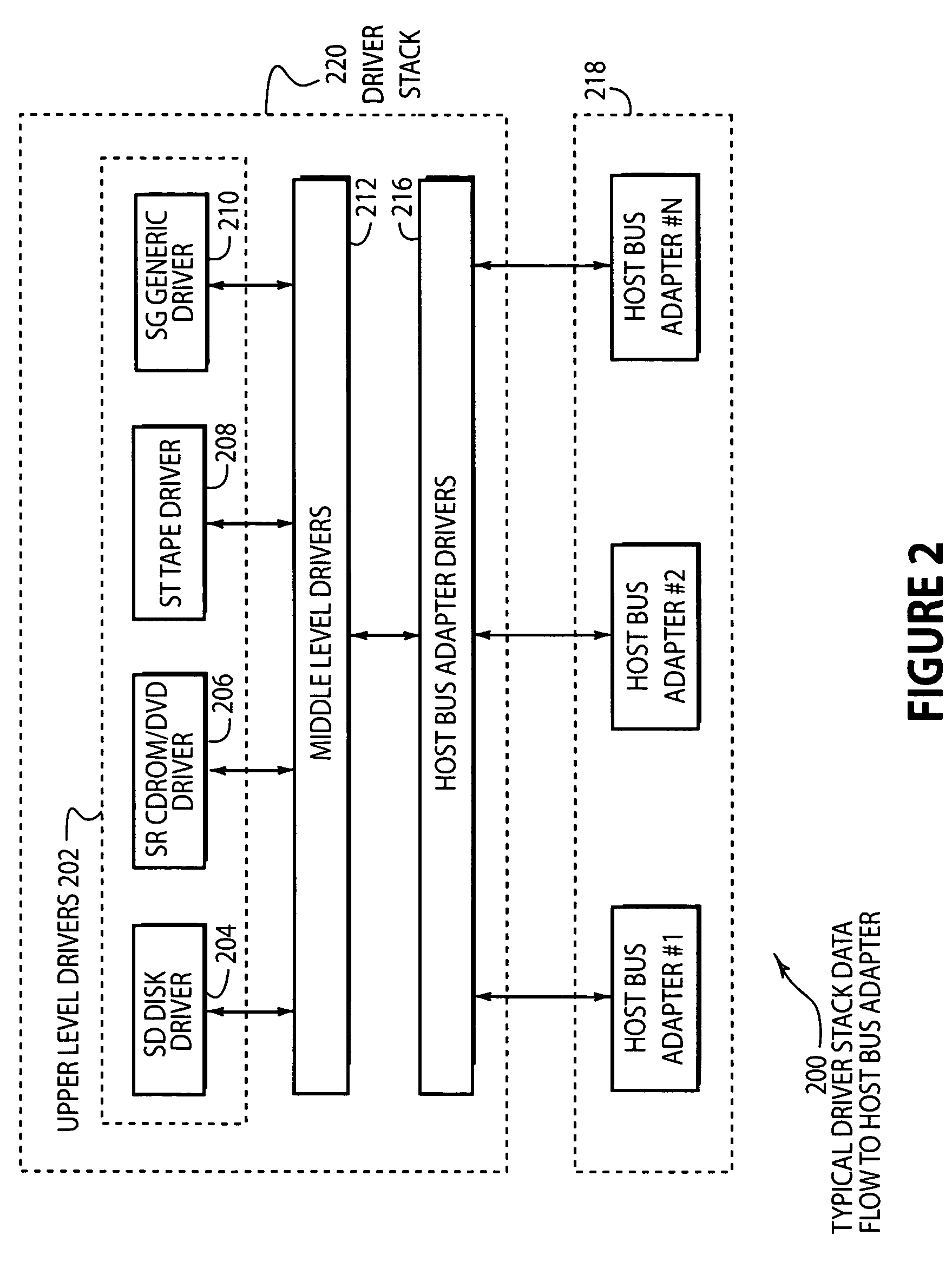
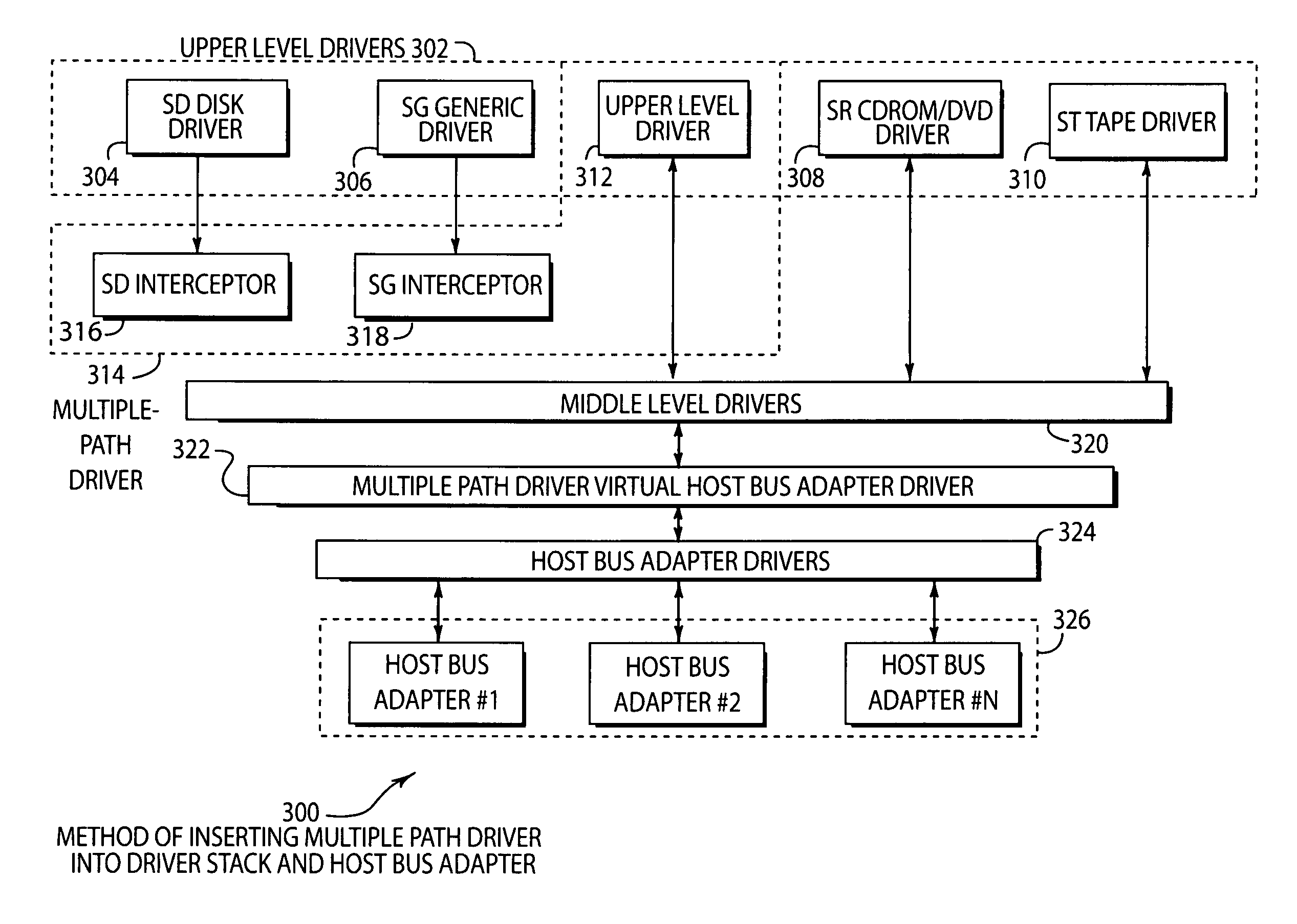
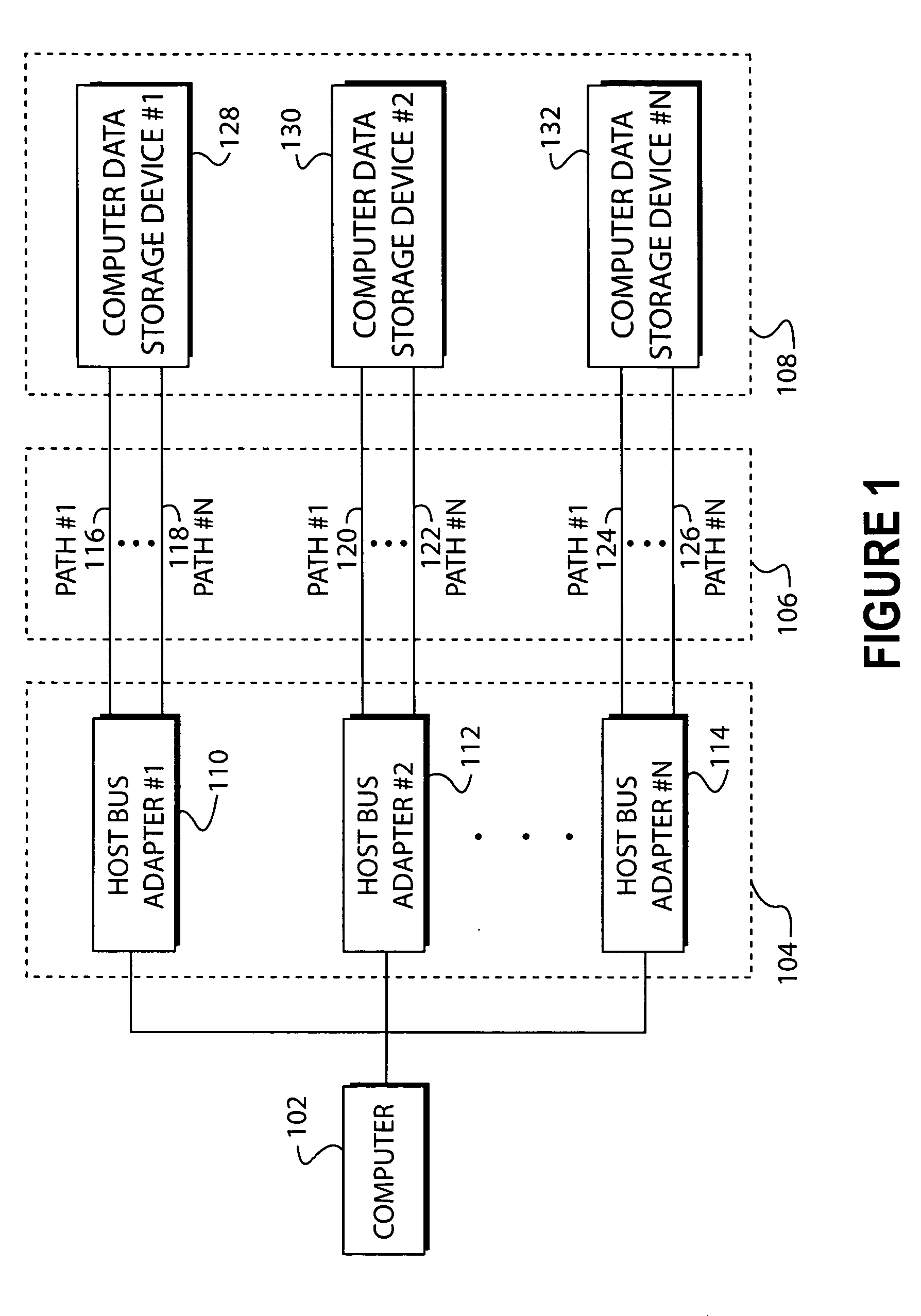
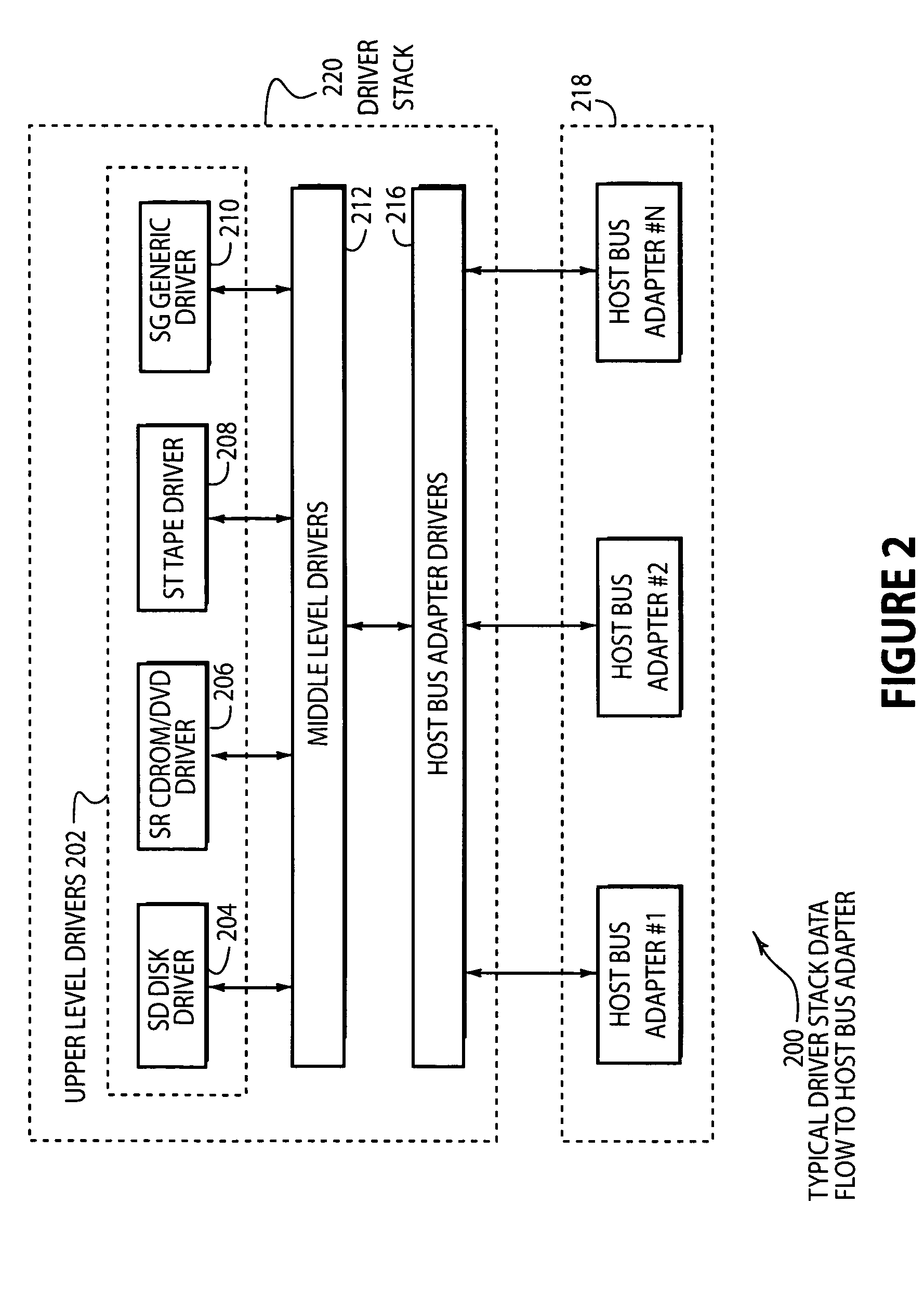
System and method of creating virtual data paths using a multiple-path driver
InactiveUS7421710B2Minimize impactImprove throughputMemory adressing/allocation/relocationInterprogram communicationOperational systemGNU/Linux
Owner:AVAGO TECH INT SALES PTE LTD
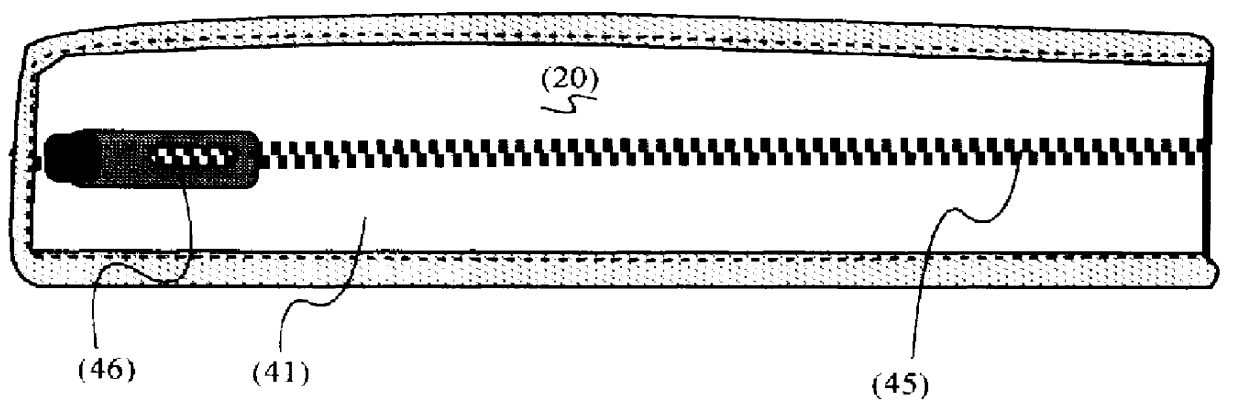
Computer cord storage and dispensing organizer and system
InactiveUS6026961AMinimal damageEquipment quickly and efficientlyDigital data processing detailsCoupling device detailsEngineeringComputer data storage
A computer cord storage and dispensing organizer pack and system for securing and organizing cords, connectors, lines, power supply, computer mouse, and other equipment is disclosed, the pack being small enough for insertion into a laptop computer carrying case, the pack having pockets for gathering computer equipment, the pockets of the pack having apertures or channels for cords to extend, the pockets and channels being optimized to create an efficient cord interface between pack and computer, and a compact holder during travel, thereby reducing tangle, setup time, loss of components, and damage to equipment.
Owner:COMPAQ COMP CORP +1
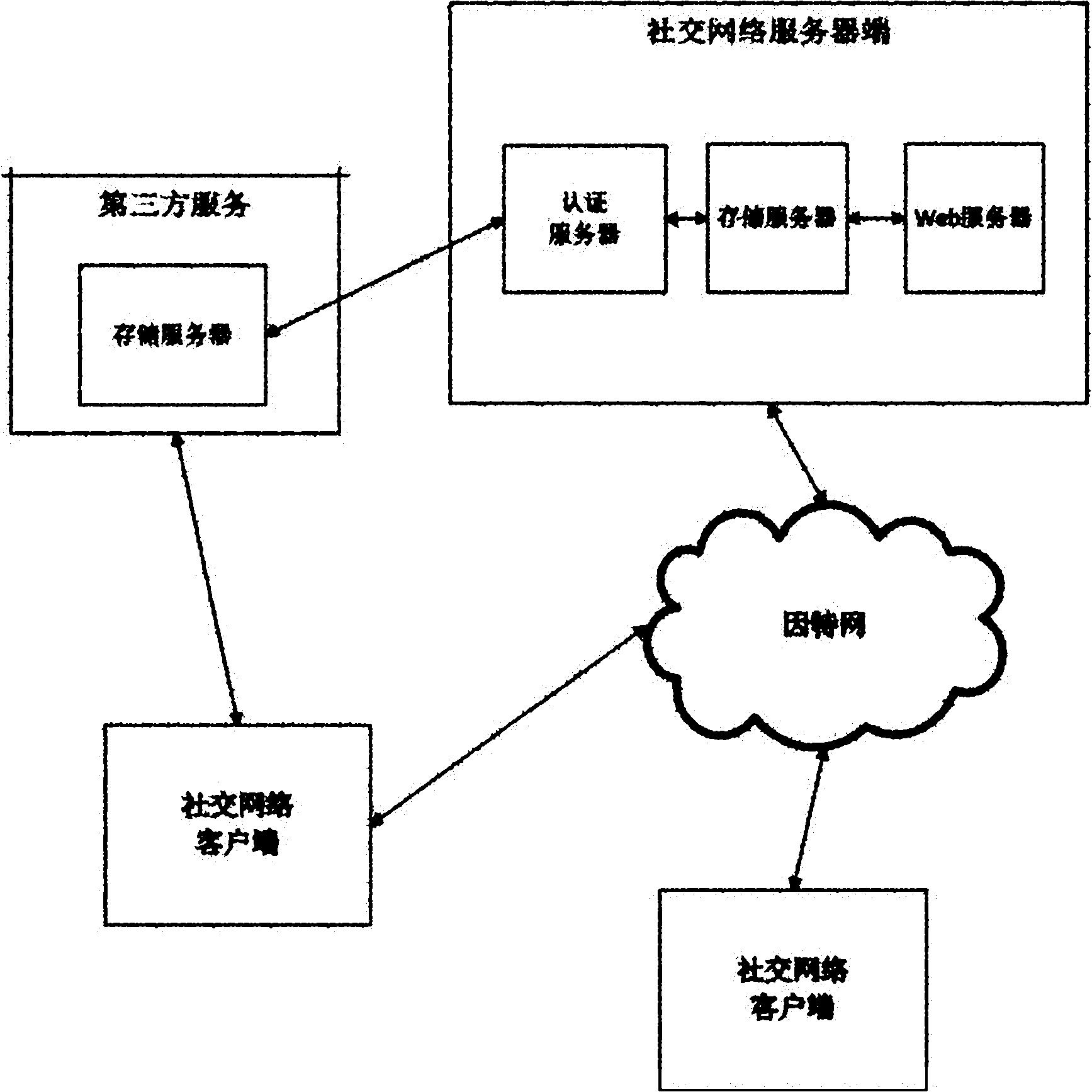
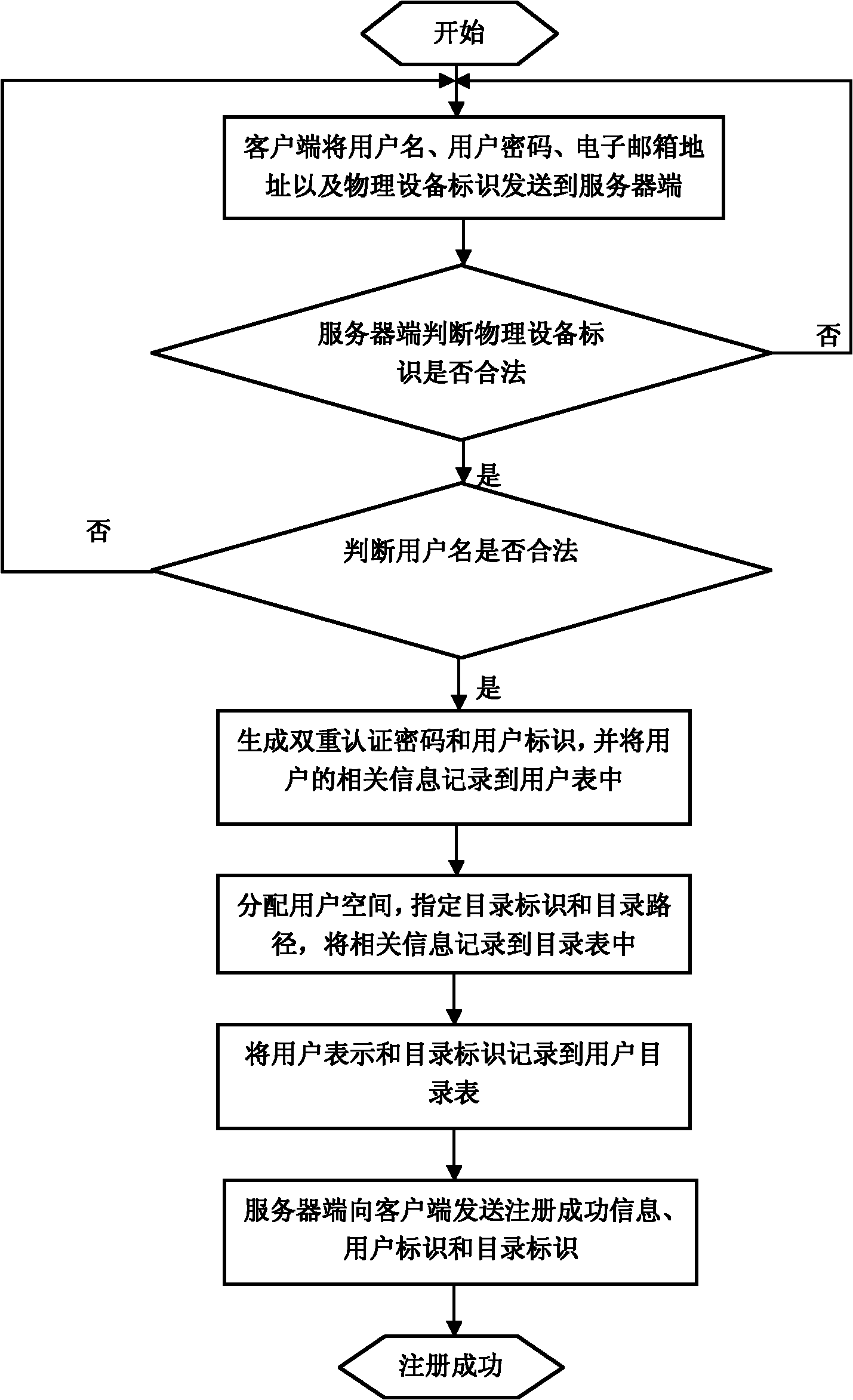
Method for sharing and acquiring data in social network service (SNS)
ActiveCN102158468ASafe storageReduce the possibility of malicious accessTransmissionOperational systemData store
The invention relates to a method for sharing and acquiring data in a social network service (SNS), belonging to the technical fields of computer network and computer data storage. A flash disk is used as an identity authentication device. The method comprises the steps as follows: the SNS uses a server-side to carry out user registration, perform the identity authentication and access data on a user, and carry out social circle registration as well as read files under Web; the user carries out interaction with the server-side by a client-side; a remote server-side is logged in by double authentication, namely the physical identification of the identity authentication device and user password; a user personal space and a shared space which is not in the social circle are respectively mounted to a local operating system in the form of an catalog; and different catalogs are established in the shared space in accordance with different social circles, and the user reads files which are shared in the different social circles by accessing the corresponding catalogs. By using the method, the user can share data selectively in the different social circles without extra management.
Owner:TSINGHUA UNIV
Inventory system
InactiveUS6616037B2Accurately determinedDigital data processing detailsCo-operative working arrangementsBarcodeHand held
A computer-based system for taking the physical inventory of beverages dispensed in full and partially full containers so as to effectively control the theft and overpouring. The products to be inventoried, such as liquor bottles are identified by conventional barcodes that can be scanned by a scanner that is operably interconnected with a hand-held computer. The step of scanning the barcodes produces, on the touch-sensitive screen of the hand-held computer, product information concerning the product contained within the scanned bottle including a silhouette of the bottle. In accomplishing the inventory, the user indicates by touching on the silhouette of the bottle the fluid level within the bottle. This information is inputted in the computer data storage and is used to calculate the volume of beverage remaining in the bottle.
Owner:BIRCH STREET SYST LLC
Method for deleting duplicated data in file system in real time
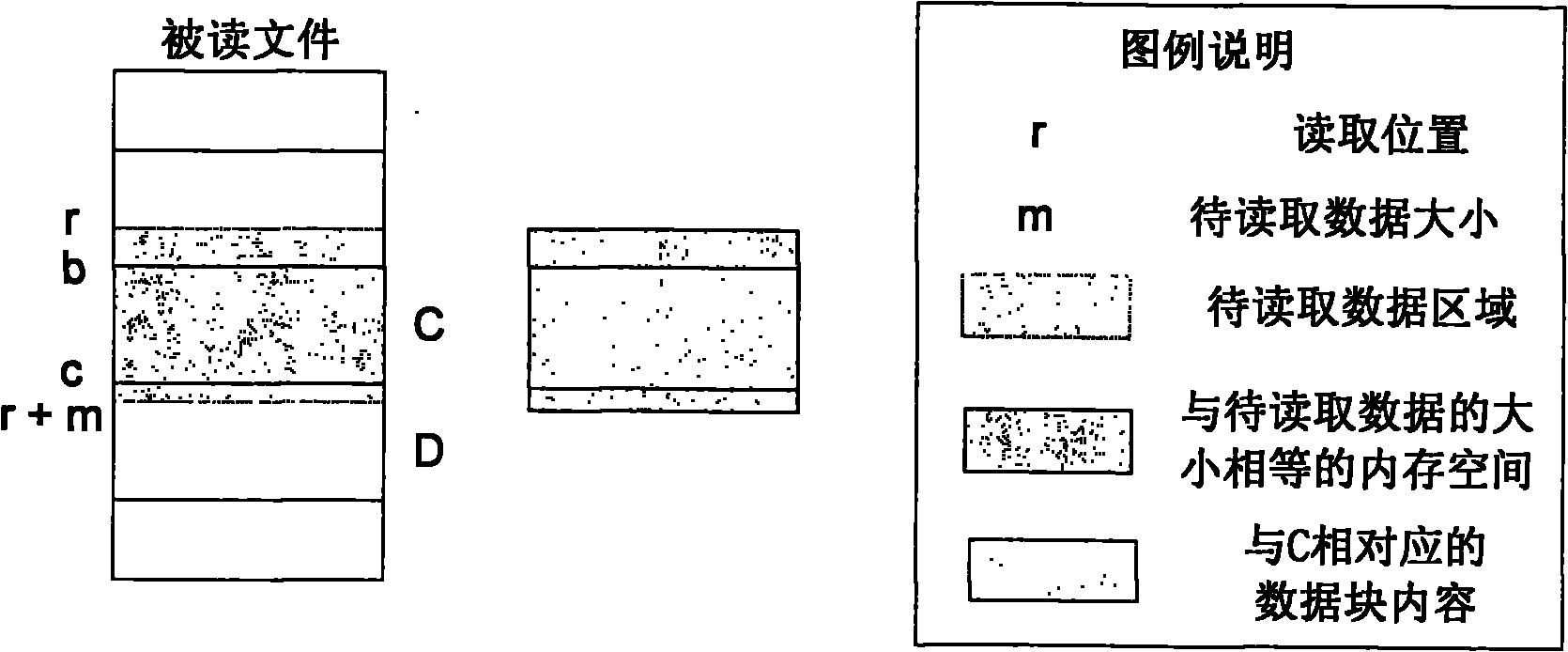
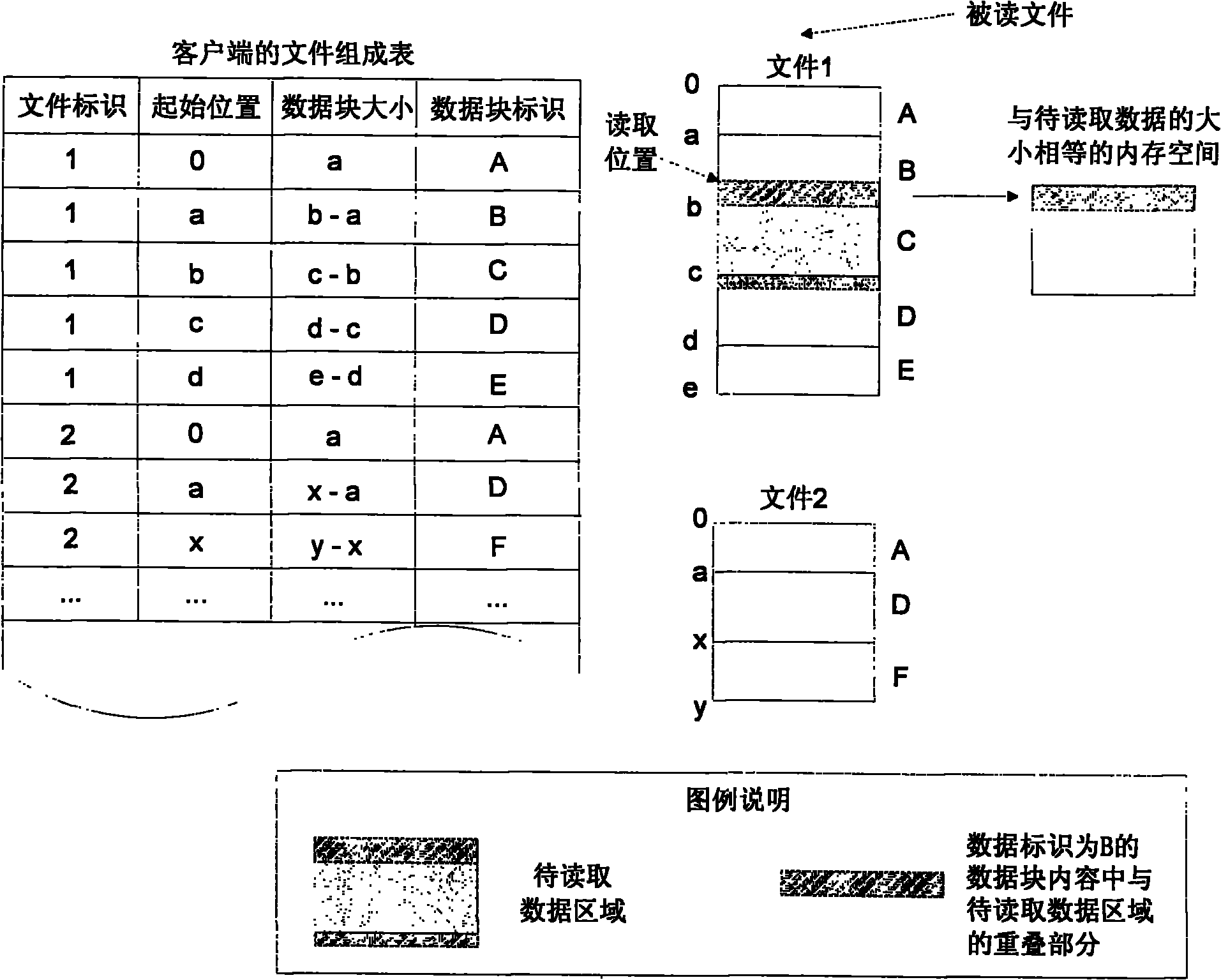
InactiveCN101908073ASave storage spaceImprove processing efficiencySpecial data processing applicationsDatasheetEmbedded database
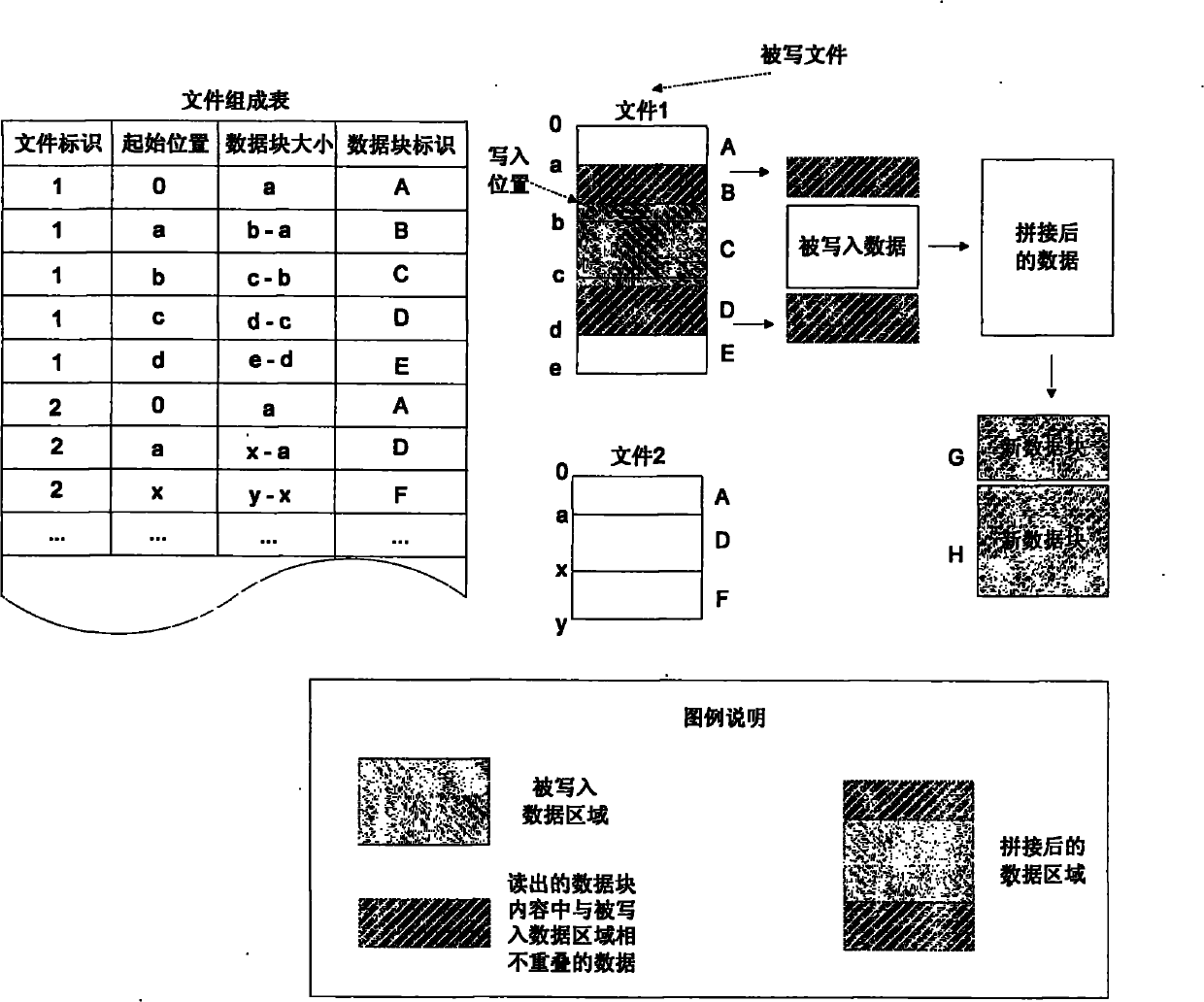
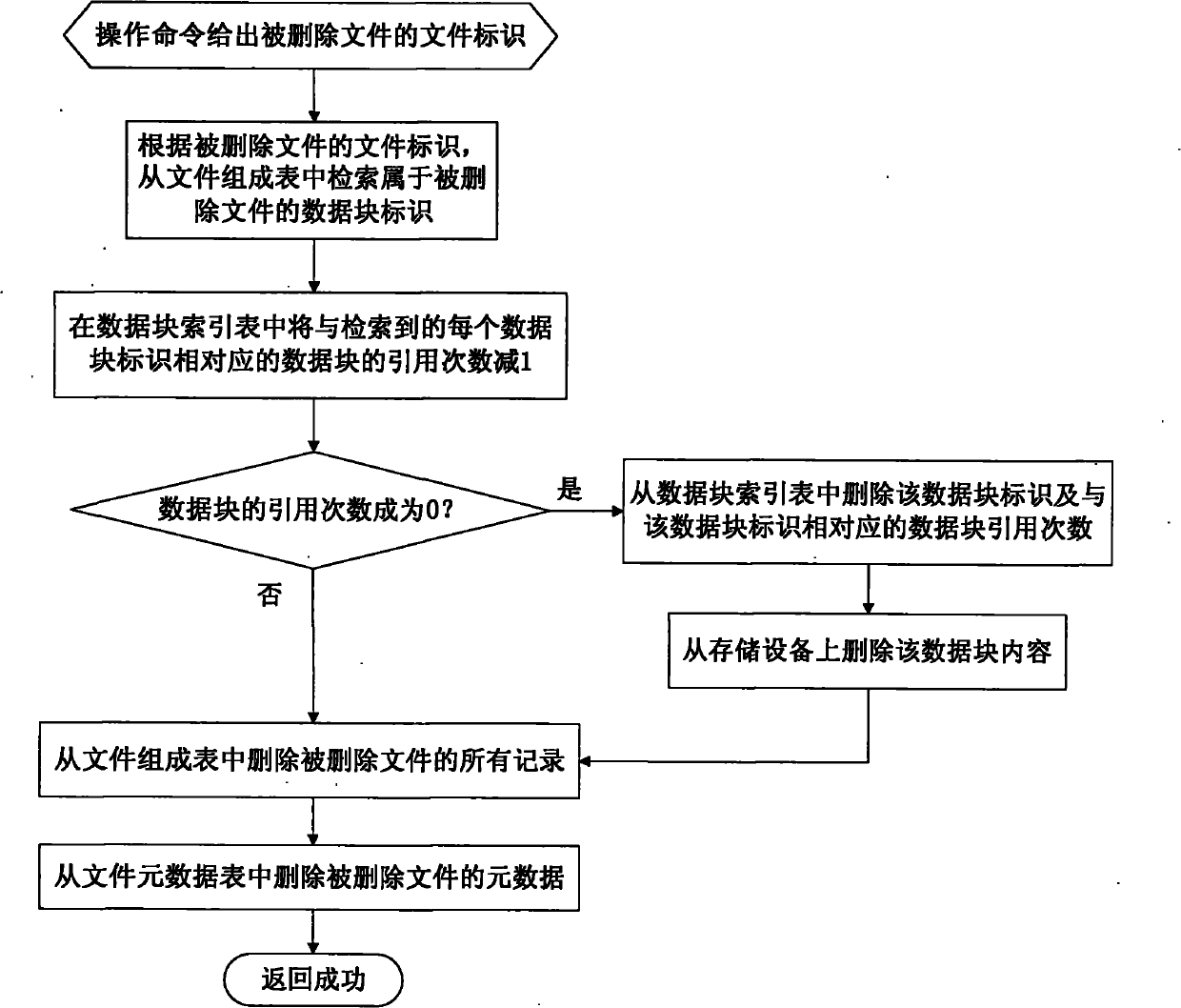
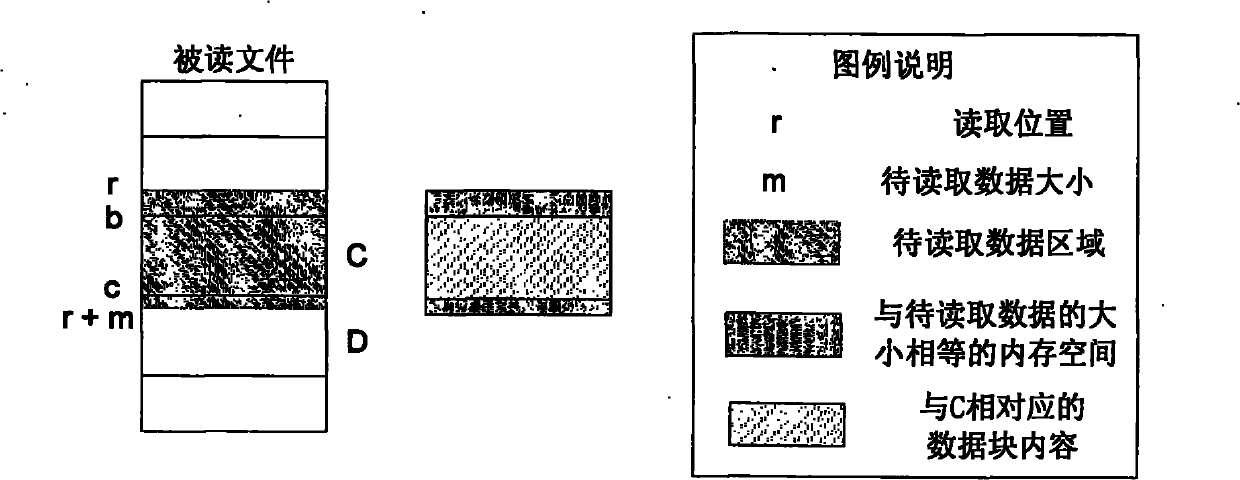
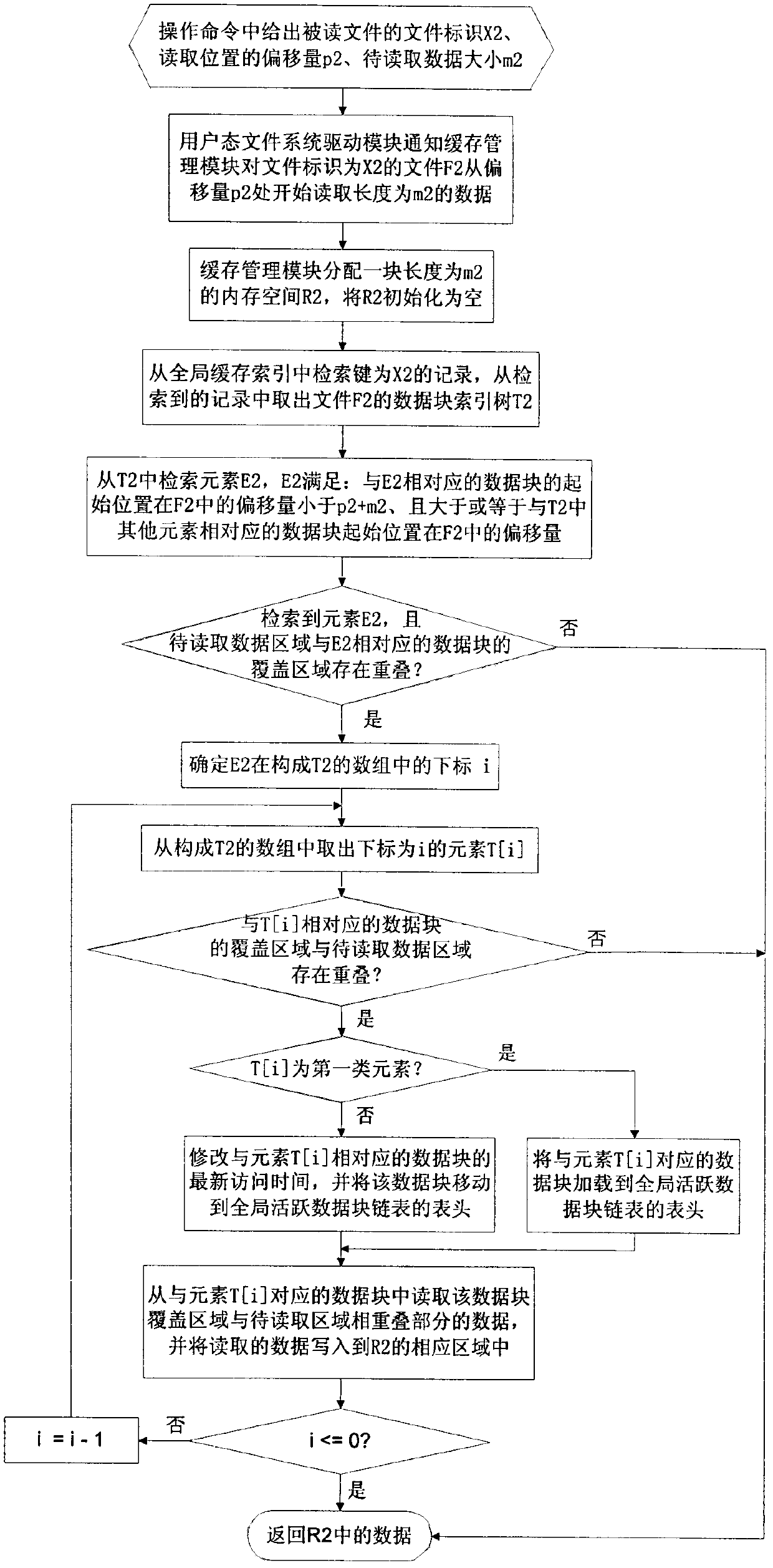
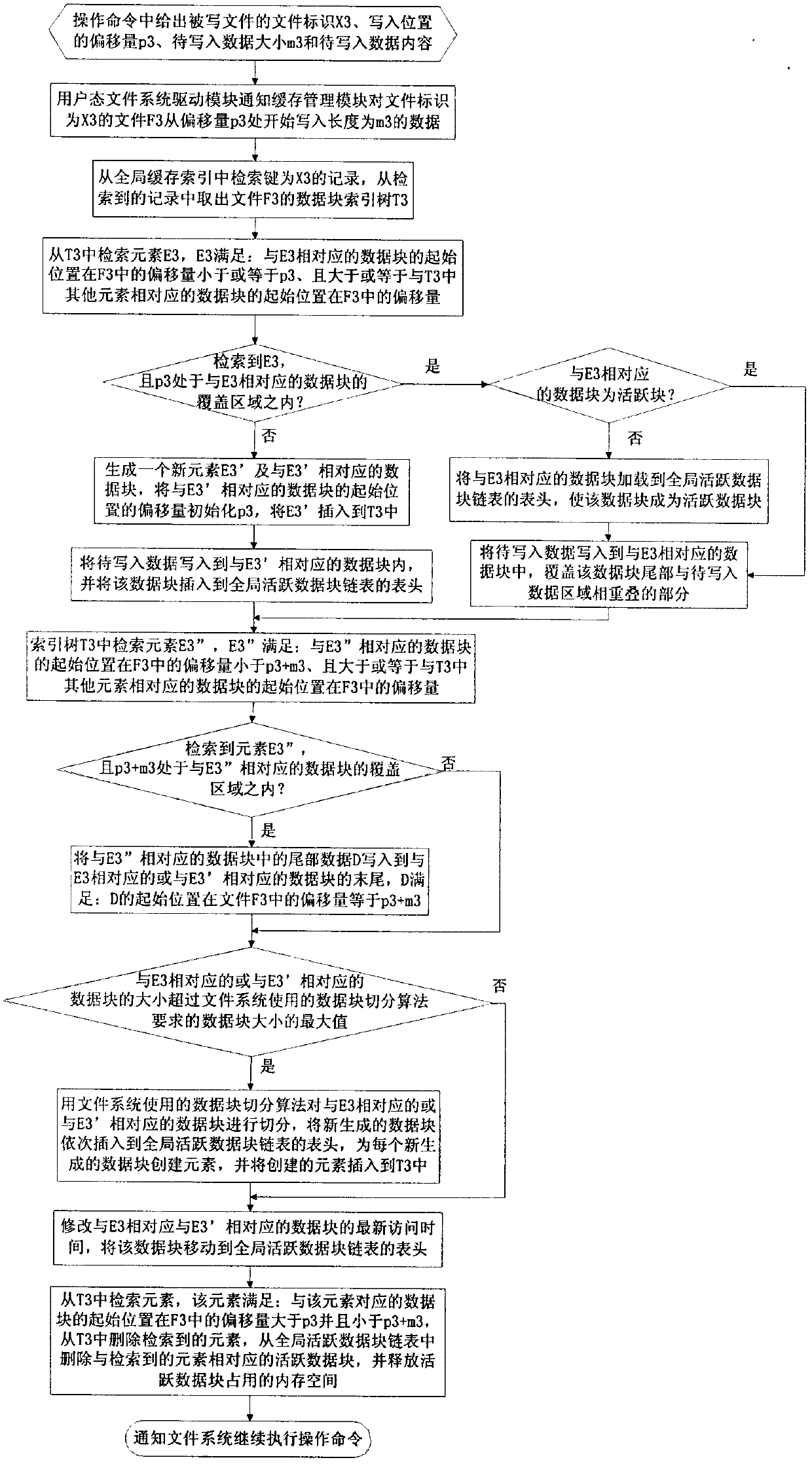
The invention relates to a method for deleting duplicated data in a file system in real time, and belongs to the technical field of computer data storage. In a file system establishment stage, a file metadata table, a data block index and a file constitution table are set in an embedded database; and in a file system operation stage, operating commands initiated to the file system by applications are received and responded through a file system driver, and include establishing a new file, writing data to an existing file, reading data from the existing file and deleting the existing data. The method simultaneously supports fixed-length and variable-length file blocking methods, and can delete the duplicated data in the file system in real time, save storage space and improve the utilization efficiency of storage equipment; and the process of deleting the duplicated data is completely transparent to the applications and a user, the file operation of various conventional applications is seamlessly compatible, and almost all negative effects on the user experience are avoided.
Owner:TSINGHUA UNIV
Real-time repetition removal and transmission method for data in network file system
InactiveCN101917396ASave storage spaceImprove reliabilityTransmissionSpecial data processing applicationsNetwork File SystemBlock method
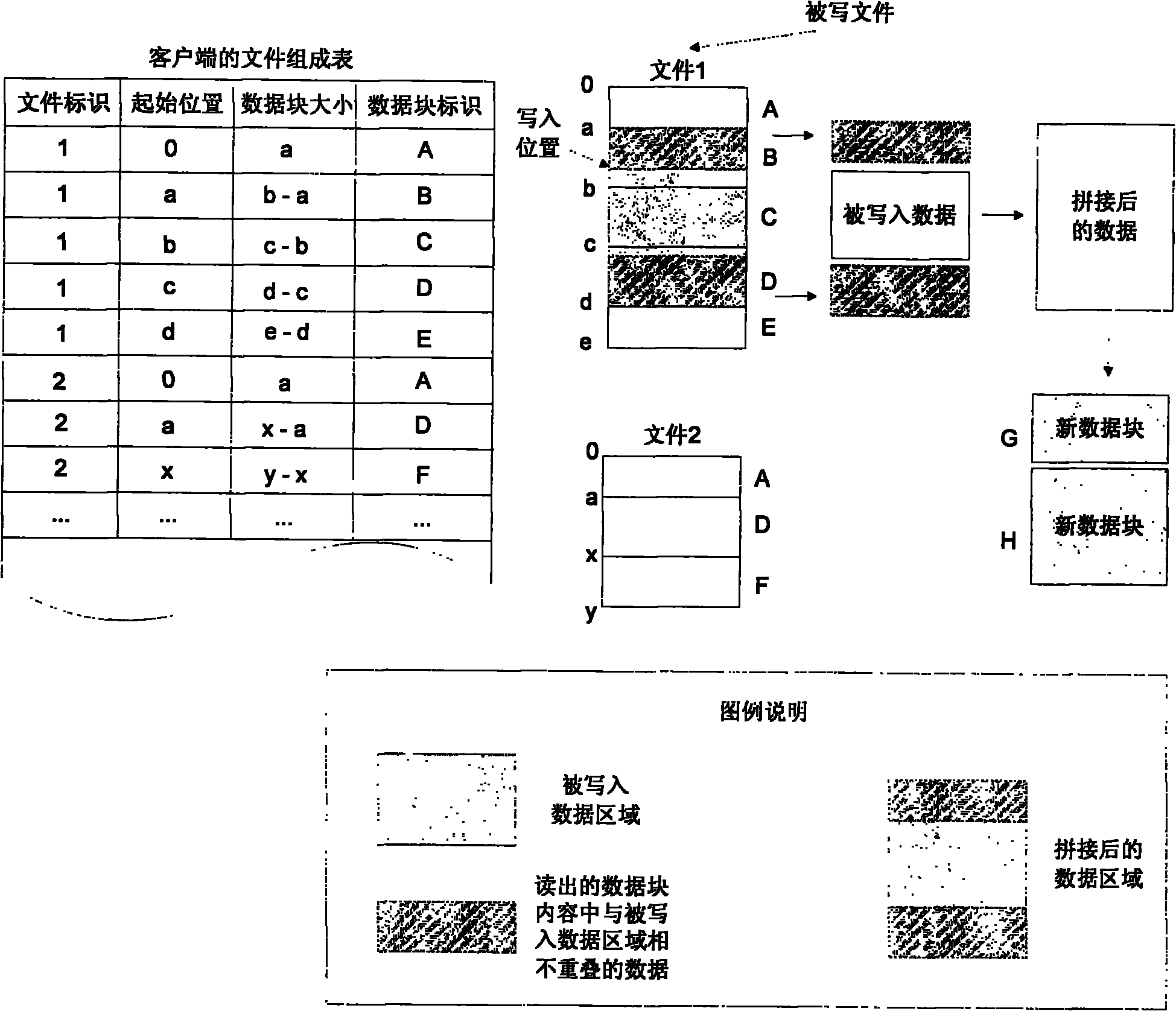
The invention relates to a real-time repetition removal and transmission method for data in a network file system, and belongs to the technical field of computer data storage. The method comprises the following steps of: setting a file metadata table, a data block index table and a file composition table in a client and a server respectively, and setting a to-be-transmitted message queue for storing data and updating message in the client; receiving and responding an operating command initiated to the network file system by a client application program through a file system drive by the client, wherein the operating command comprises the operation of creating a new file, writing data into an existing file, reading the data from the existing file and deleting the existing file; and settinga network service interface for uploading and downloading data block contents and receiving and answering client message in the server. The method can delete the repeated data so as to save the storage space, avoid transmitting the existing data of the opposite side between the client and the server and reduce the overhead of network bandwidth; meanwhile, the method supports a file blocking method of fixed length and unfixed length so as to improve the utilization rate of the storage space.
Owner:TSINGHUA UNIV
Data storage array method and system
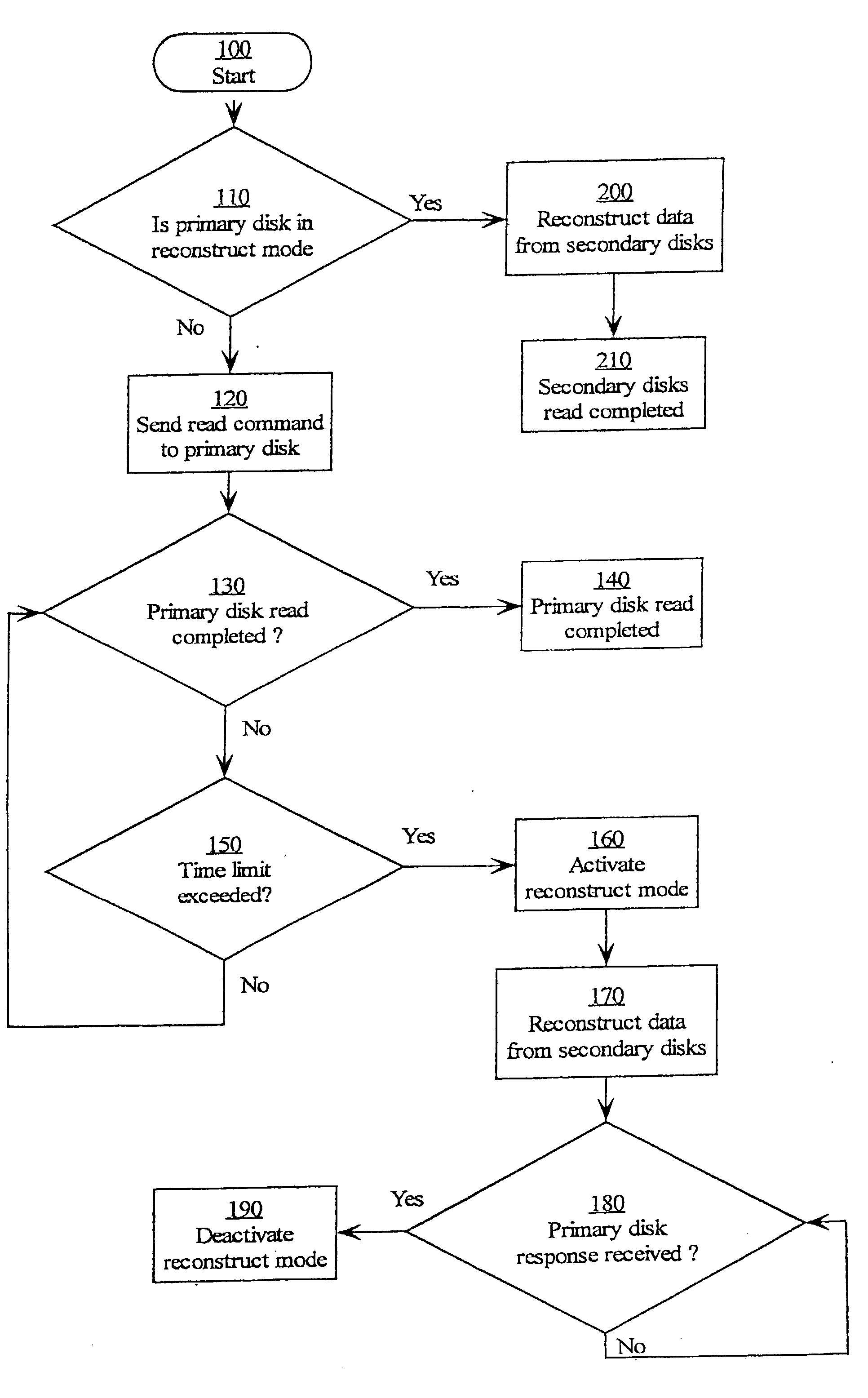
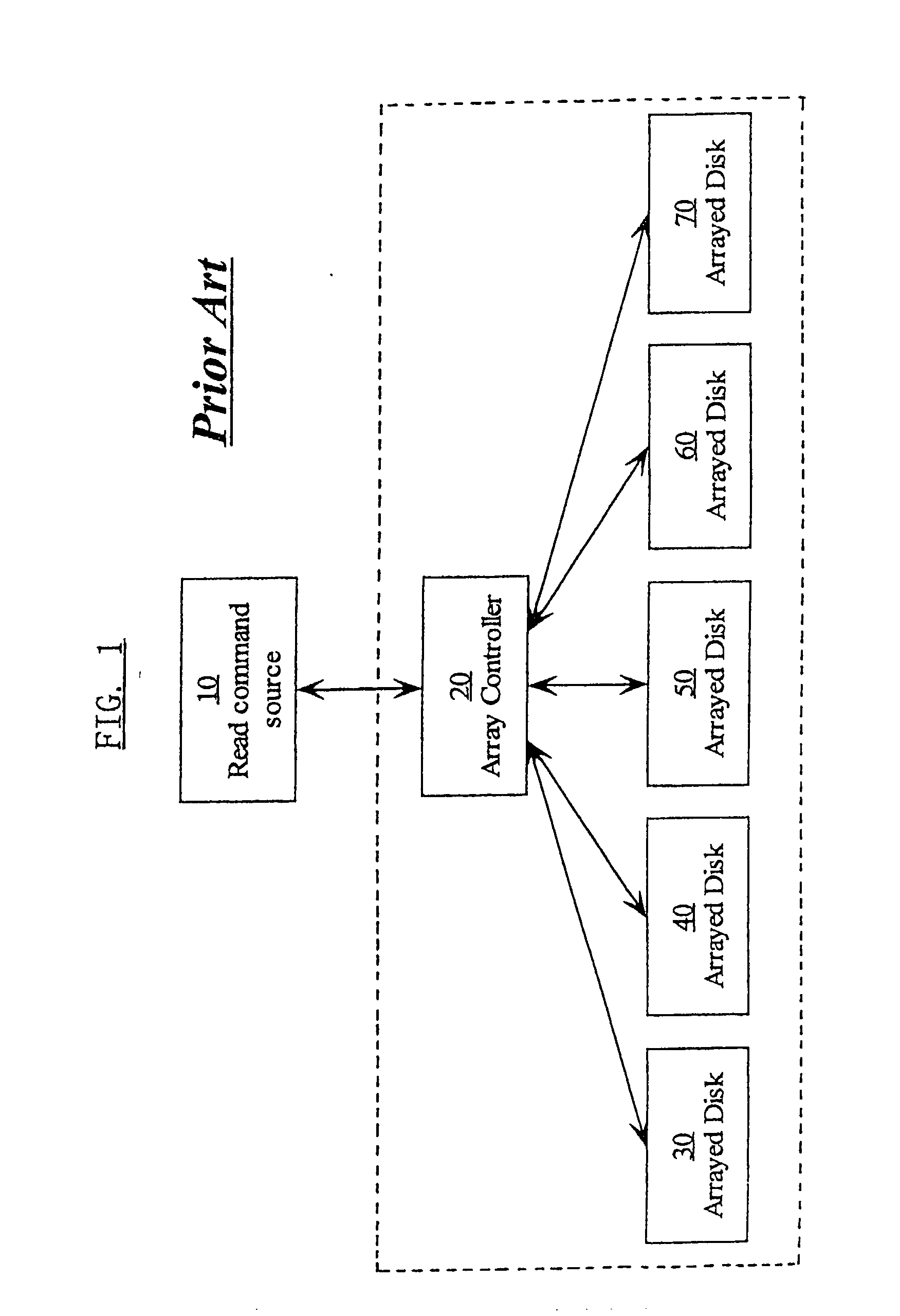
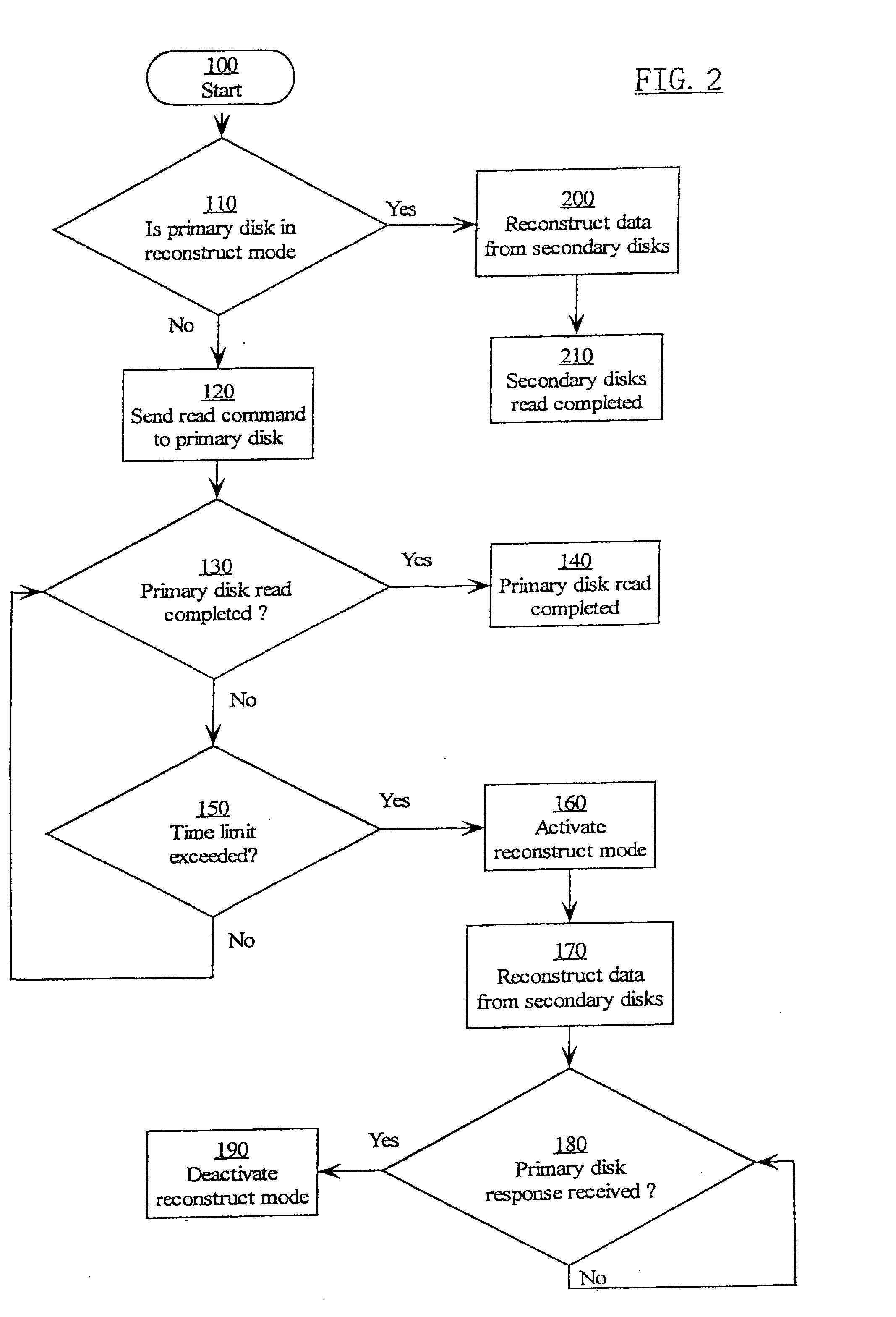
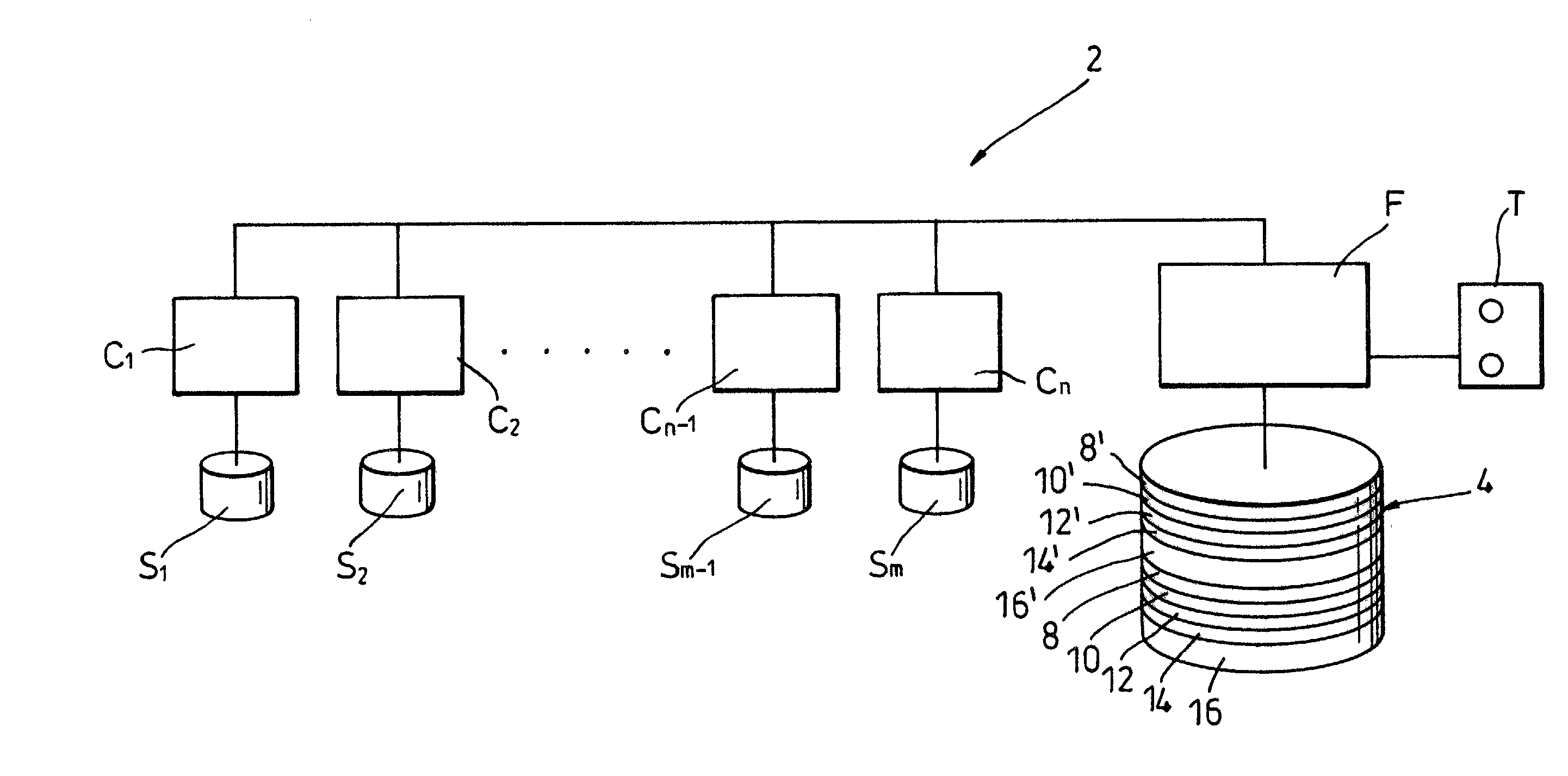
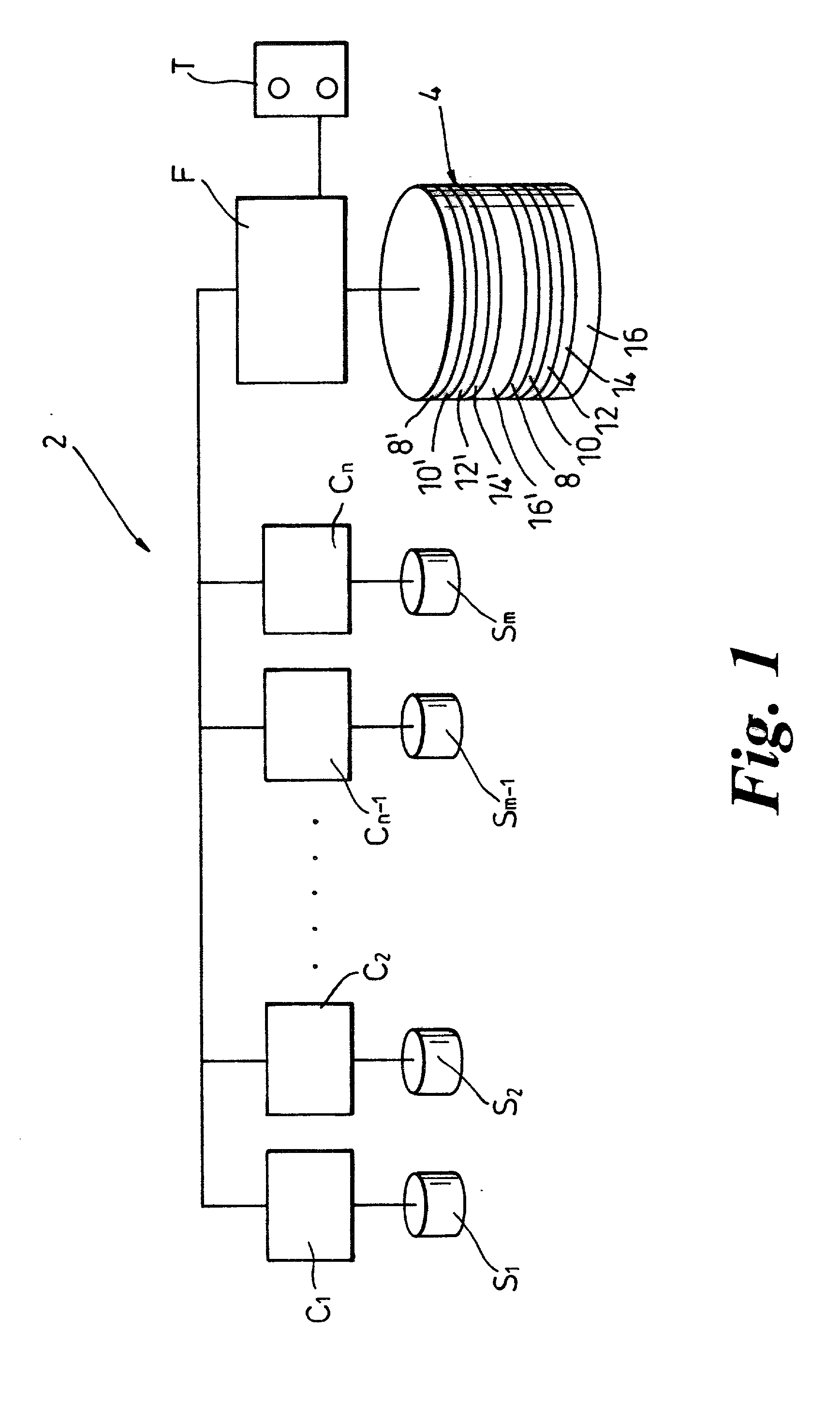
InactiveUS20030212858A1Memory loss protectionError detection/correctionOriginal dataComputer data storage
A method and system for reading data from a redundant array of computer data storage media elements without having to wait for a timeout in a drive in the redundant array. If the requested data is from a drive that is temporarily in a timeout, the requested data is reconstructed using other drives in the redundant array, and the reconstructed data is sent to the requester via an array controller. When the drive holding the originally requested data comes back from the timeout and responds to the original request by transmitting the original data, the array controller ignores the original data since the request has already been fulfilled by the reconstructed data.
Owner:IBM CORP
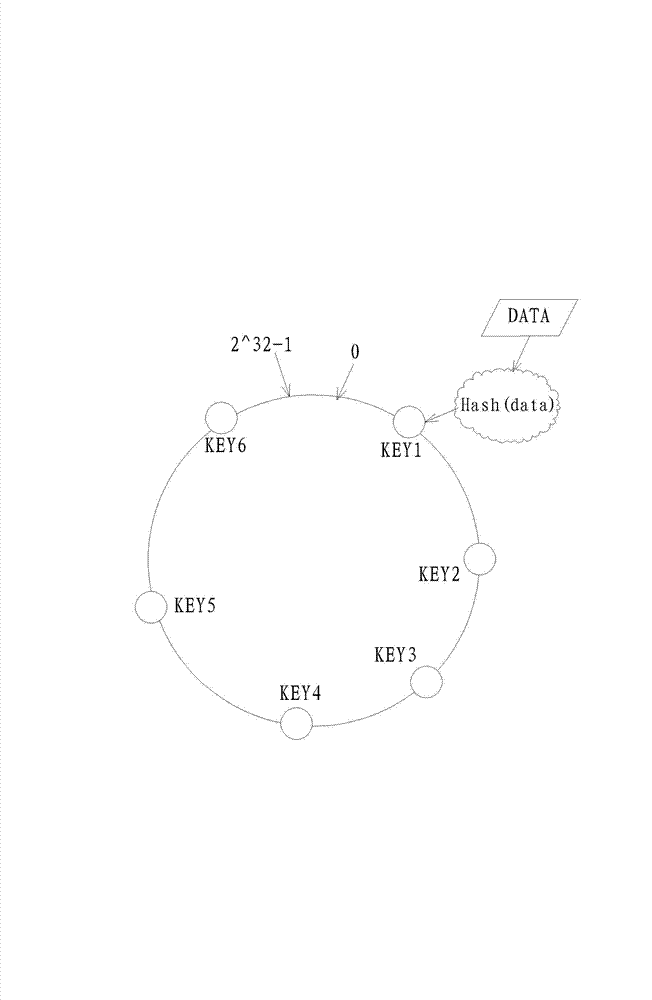
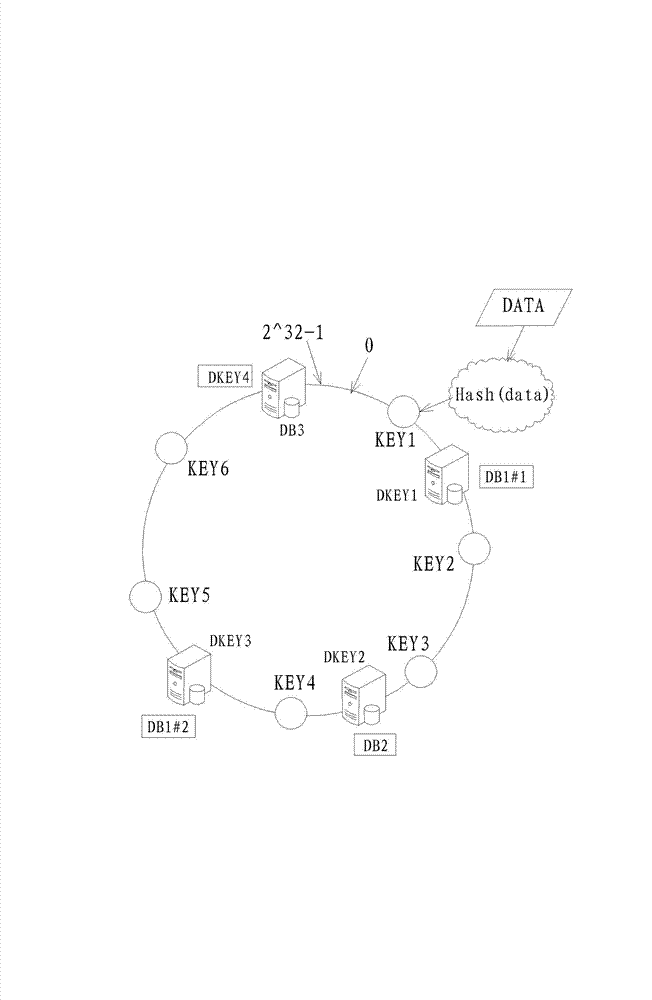
Massive data storage method
ActiveCN102737127AIndex orderedSolve immediacy issuesSpecial data processing applicationsArray data structureIp address
The invention relates to the technical field of computer data storage, and discloses a massive data storage method, which comprises the following steps of: 1, obtaining a currently active memory database server list; 2, organizing data to be stored into a format storable for a database, and mapping the data to be stored into an annular Hash space, wherein the data also comprises a host Internet protocol (IP) address of a data source and an IP address of a destination memory database server; 3, mapping the IP address of the memory database server to the annular Hash space; and 4, establishing a mapping array for the Hash positions of two databases, namely a Hash position storage array for each virtual server of a database server, to obtain mapping relationships between the data, a virtual database and an actual database, and storing the data to be stored by pieces. The method is applied to the instant storage of massive data.
Owner:XIAMEN UNIV
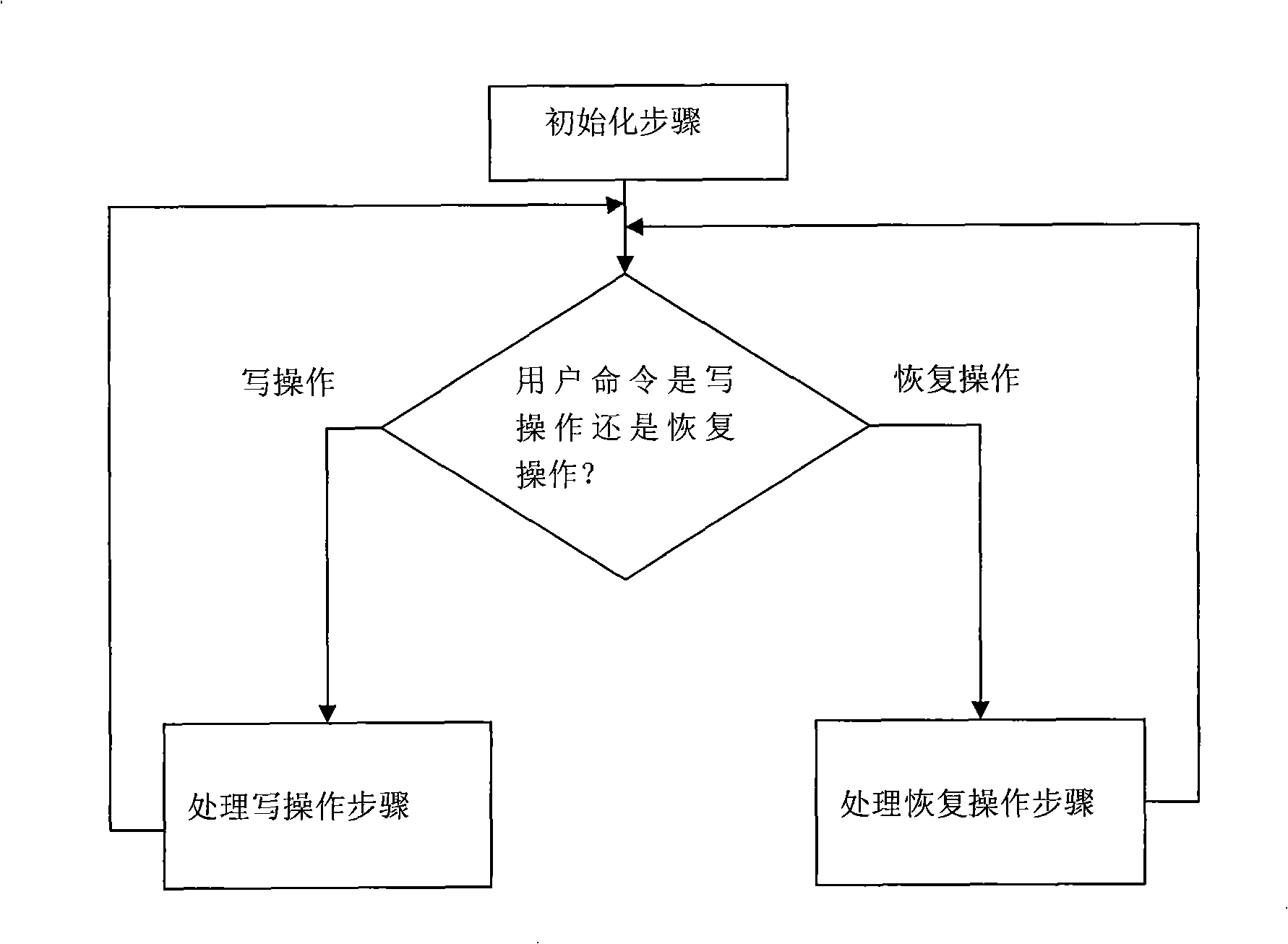
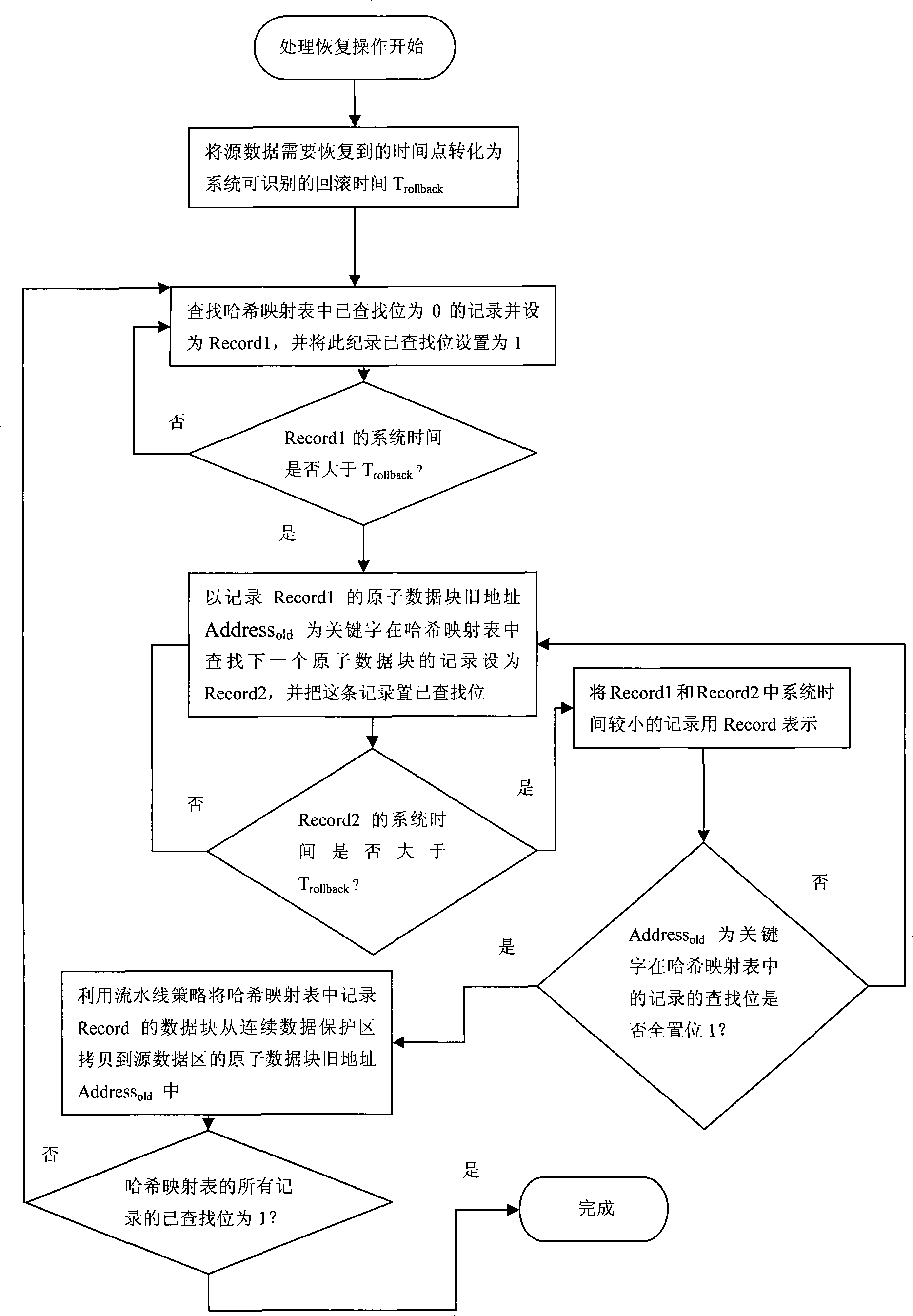
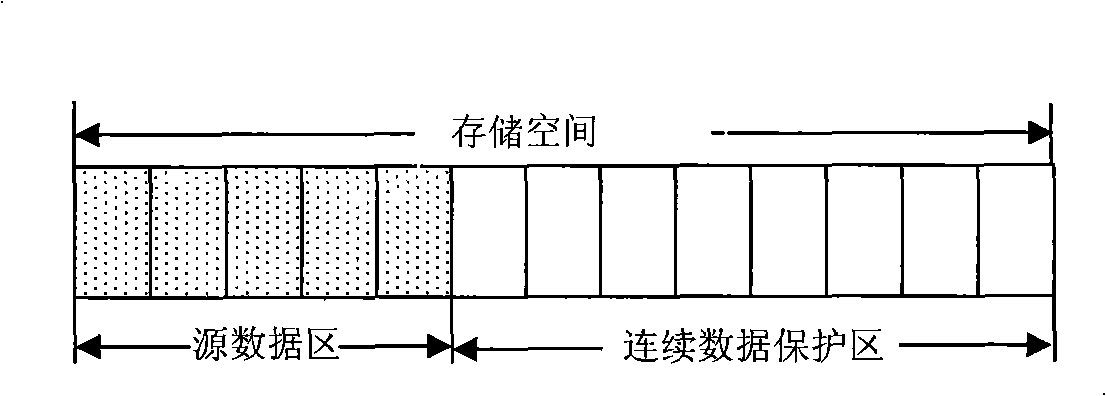
Method for protecting and recovering continuous data based on time stick diary memory
The invention relates to a method for the protection and recovery of continuous data stored in a time-stamp diary, which pertains to a computer data storage and backup method and aims at reducing the time of processing a write operation and a recovery operation and increasing processing parallelism. The method comprises the steps that: (1) a storage area is divided into a source data area and a continuous data protection area; a Hush mapping table is initialized; (2) a user command is judged, and the write operation is carried out sequentially; the recovery operation is carried out as the step (4); (3) the write operation is processed; by adopting a production line strategy, a copy operation and a new write operation are carried out in parallel; a source data record is inserted into the Hush mapping table; the step (2) is carried out; (4) the recovery operation is processed, and the source subdata block record needing copying is searched in the Hush mapping table; corresponding source subdata block record is written into the source data area by adopting the production line strategy; then the step (2) is carried out. The proposal of time-stamp diary storage is adopted in the invention; the production line strategy is adopted when the write operation and the recovery operation are processed; therefore, write operation processing time and target recovery time are shorter.
Owner:HUAZHONG UNIV OF SCI & TECH
System and method of creating virtual data paths using a multiple-path driver
InactiveUS20050091441A1Maximize data throughputMinimize impactMemory adressing/allocation/relocationInput/output processes for data processingOperational systemGNU/Linux
Disclosed is a system and method for transmitting computer data within a single computer system along more than one physical data path by providing a multiple-path driver that creates virtual (or non-physical) data paths without modifying the source code of the operating system. The system and method may be used with any computer hardware regardless of manufacturer. In one embodiment, a multiple-path driver may be used within a Linux operating system to create virtual data paths and transmit data between the upper-level drivers of the Linux system and at least one computer data storage device without modifying the Linux source code.
Owner:AVAGO TECH INT SALES PTE LTD
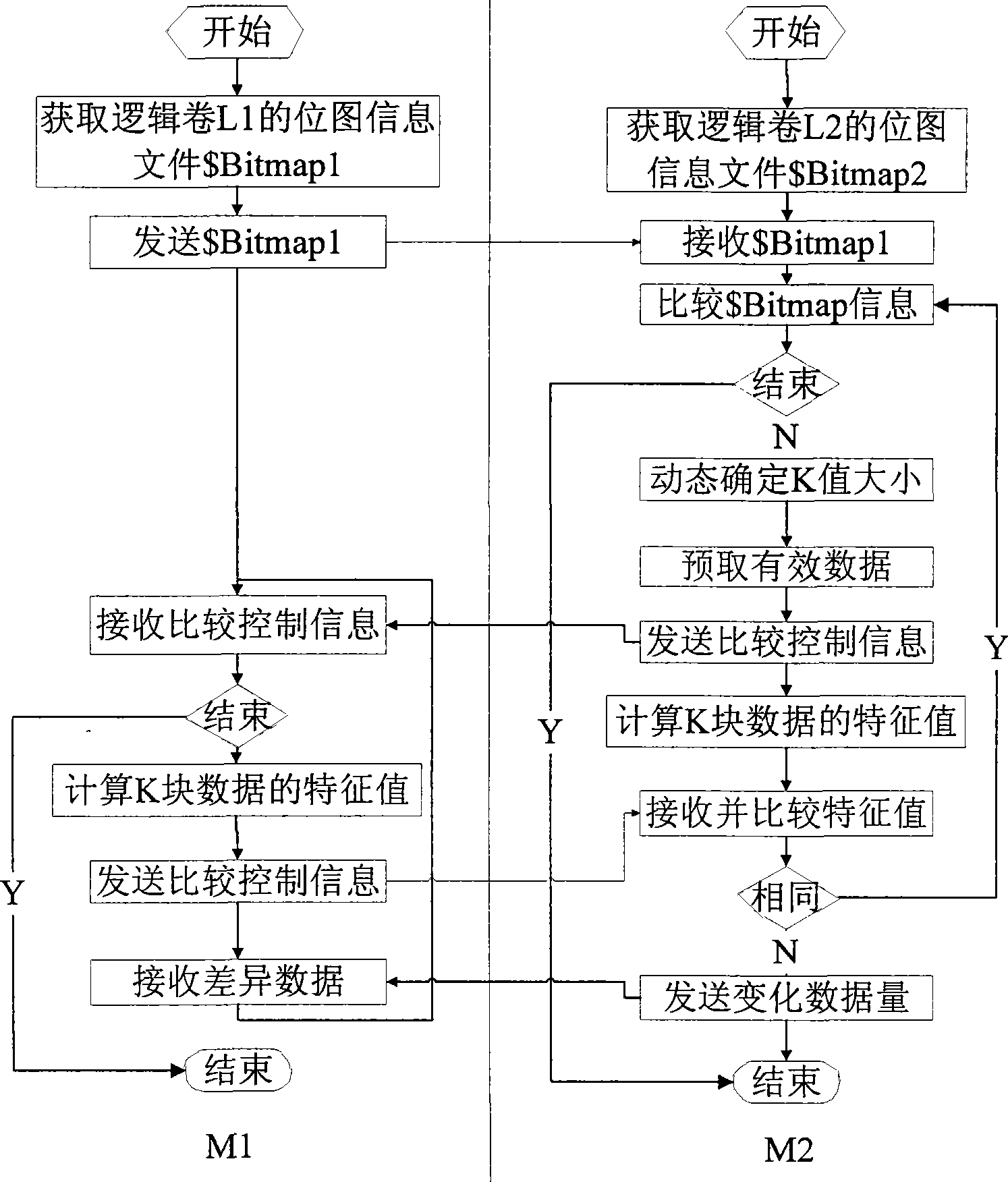
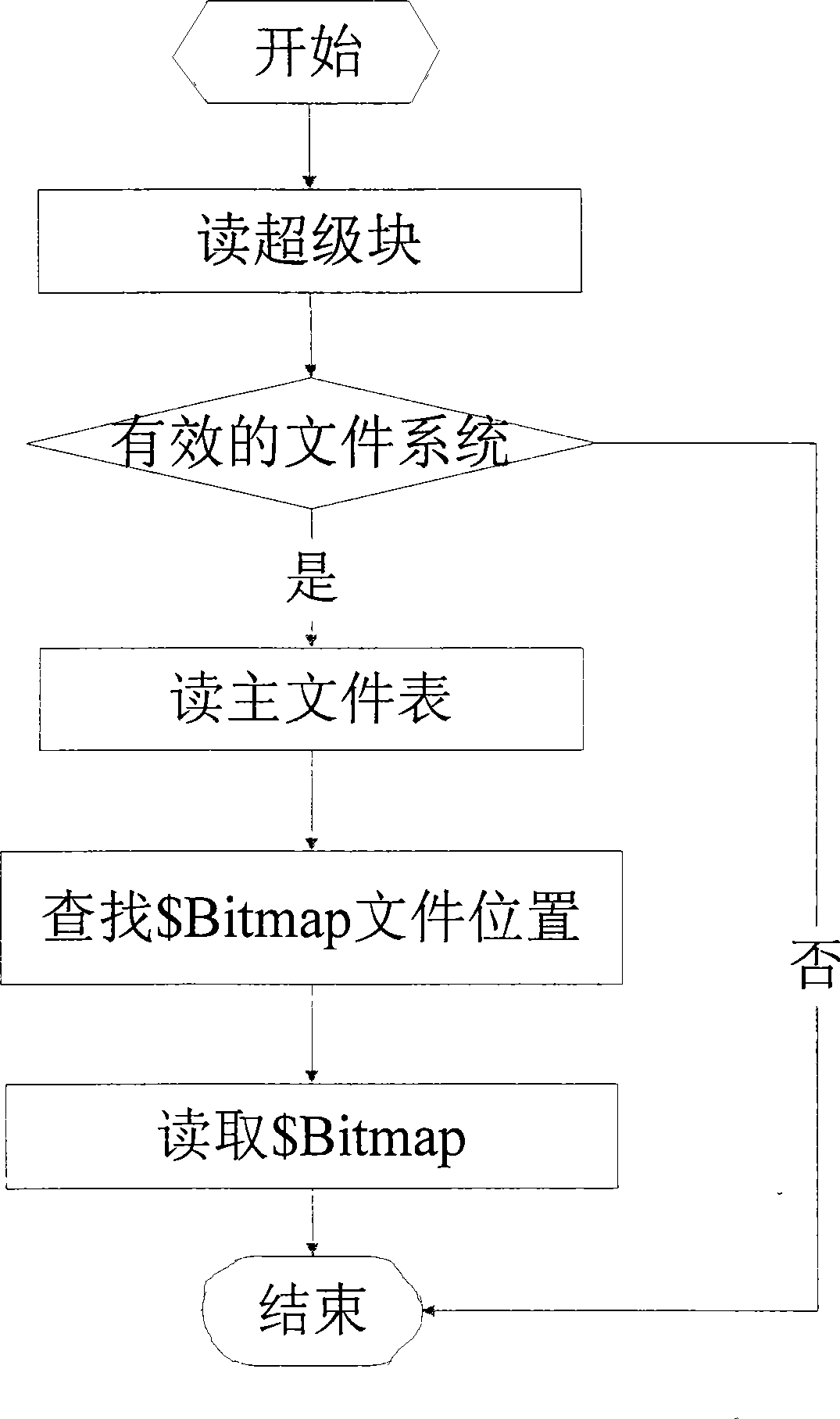
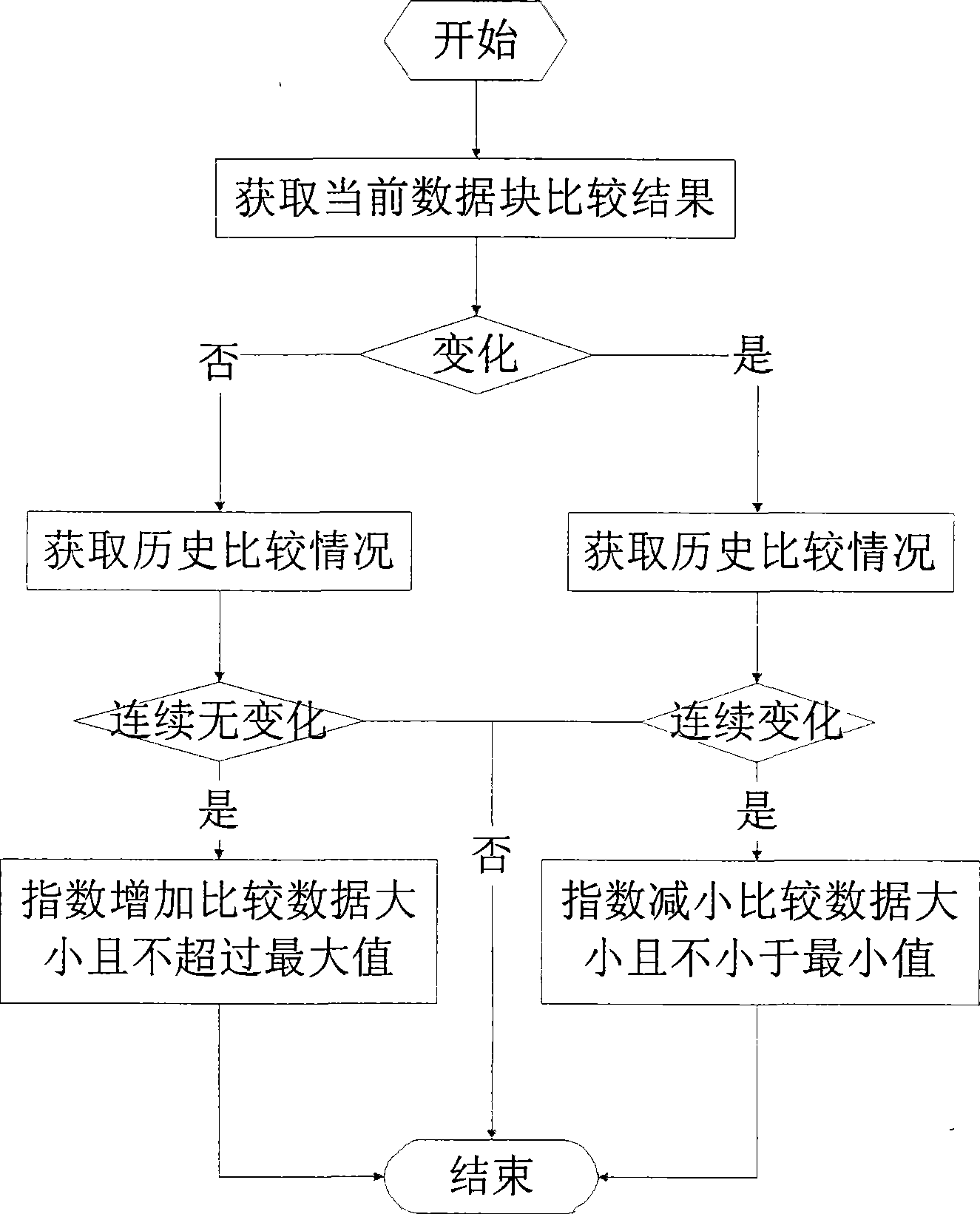
Logical volume rapid synchronization method based on data differentia
InactiveCN101387976AReduce the scope of the comparisonReduce data volumeRedundant operation error correctionSpecial data processing applicationsFile synchronizationData synchronization
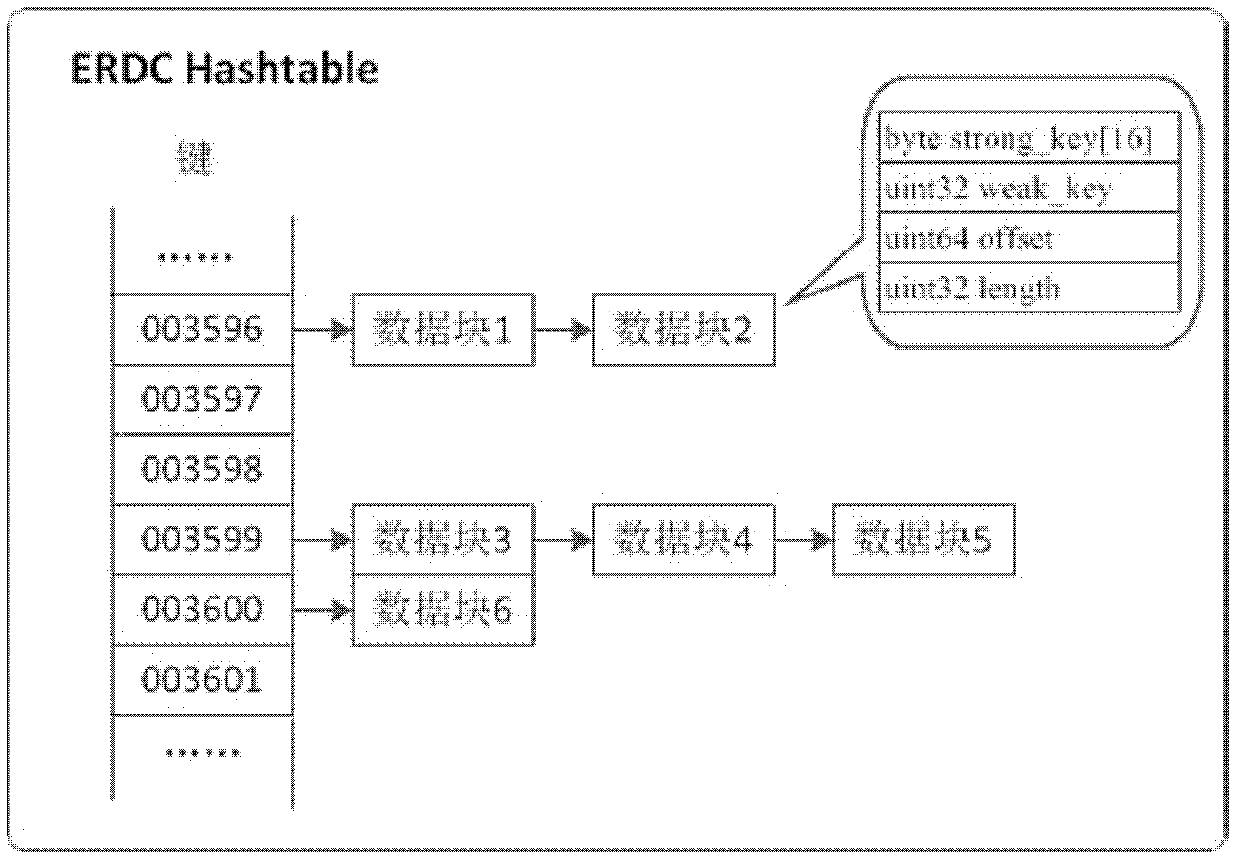
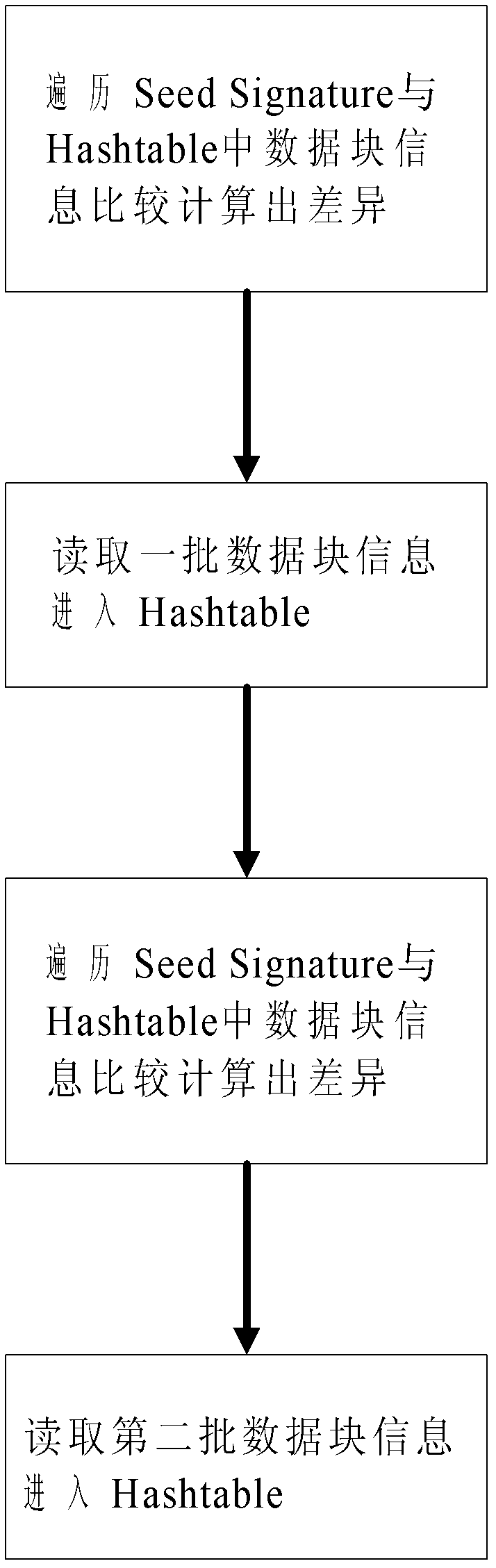
The invention relates to a rapid synchronization method of logical volumes based on data difference, which belongs to the technical field of computer data storage. The method comprises steps of finding out used data blocks on each logical volumes according to file system information of source volumes and destination volumes, comparing corresponding data block pairs on the source logical volumes and the destination logical volumes, then computing two eigenvalues of a data block pair, synchronizing the data block pair if the two eigenvalues are varied, or not synchronizing if not. The invention only compares the used data blocks in case of data synchronization, thereby obviously reducing the range of data comparison, and simultaneously only the changed data blocks are synchronized during synchronization, thereby effectively reducing the quantity of synchronized data.
Owner:TSINGHUA UNIV +1
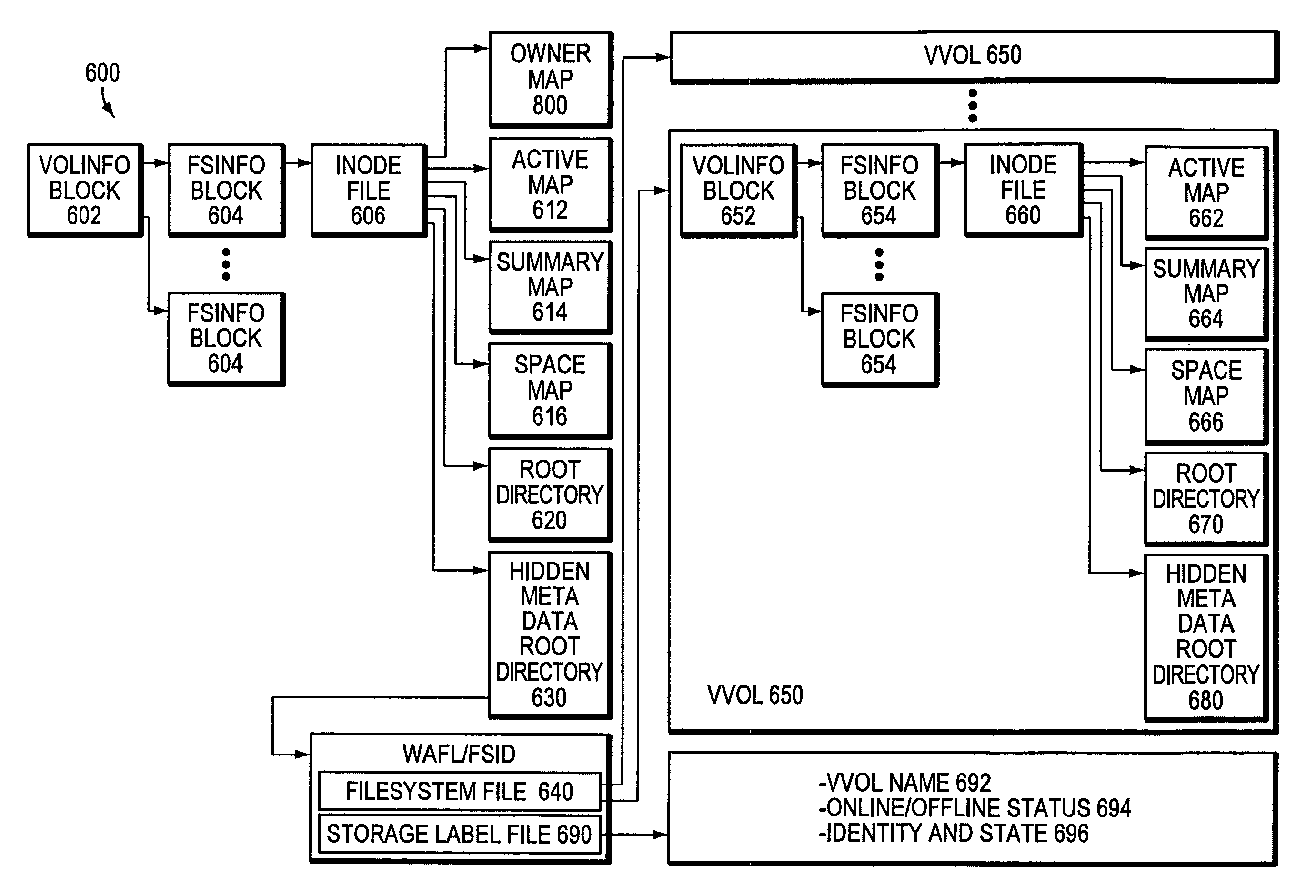
Technique for translating a hybrid virtual volume file system into a pure virtual file system data stream
ActiveUS7321962B1Improve efficiencySoftware simulation/interpretation/emulationMemory systemsVirtual file systemData stream
A method for transferring data of a hybrid virtual volume of a computer data storage system from a source to a destination is disclosed. The method first translates intermingled virtual and physical volume block numbers of the hybrid virtual volume into a data stream having only virtual volume block numbers. The method then sends the data stream to a destination computer.
Owner:NETWORK APPLIANCE INC
Method for rebuilding data of magnetic disk array
InactiveCN101329641AImprove performanceImprove usabilityRedundant operation error correctionVisit timeReconstruction method
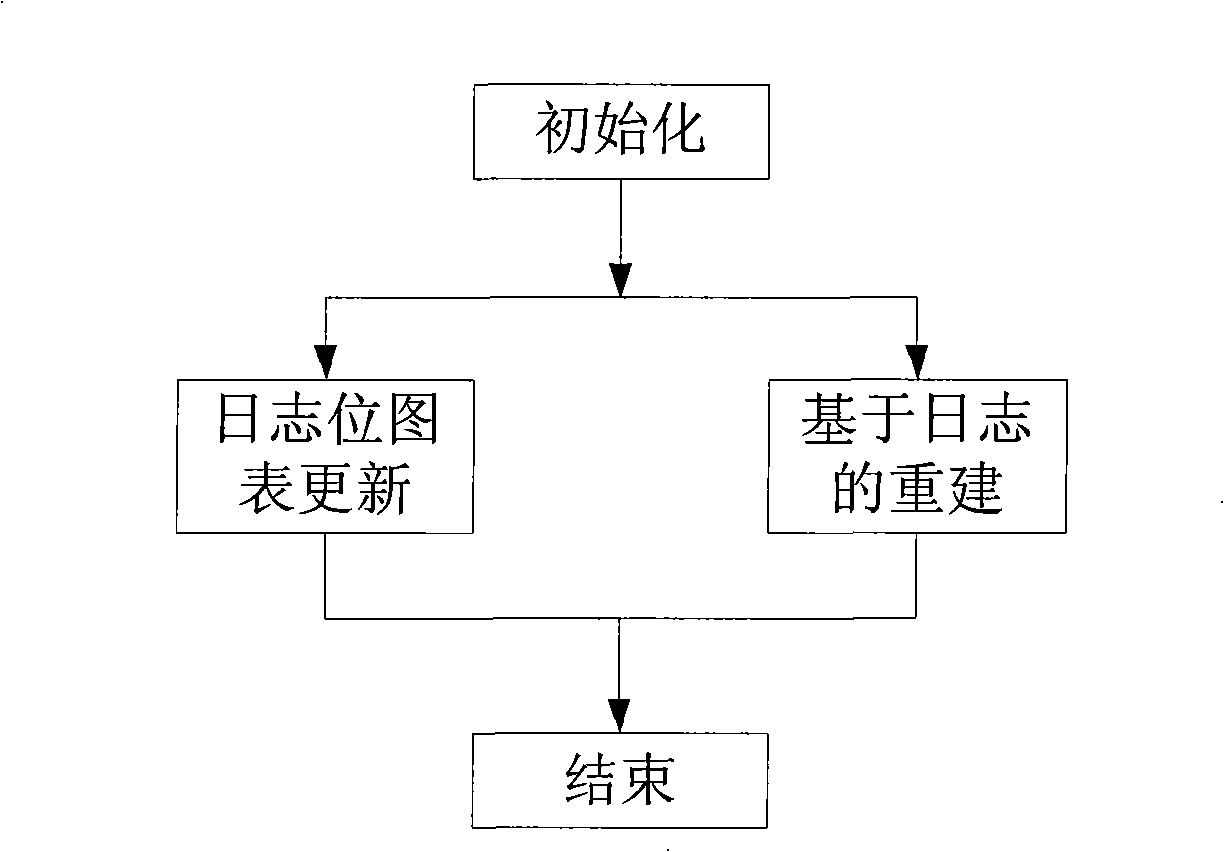
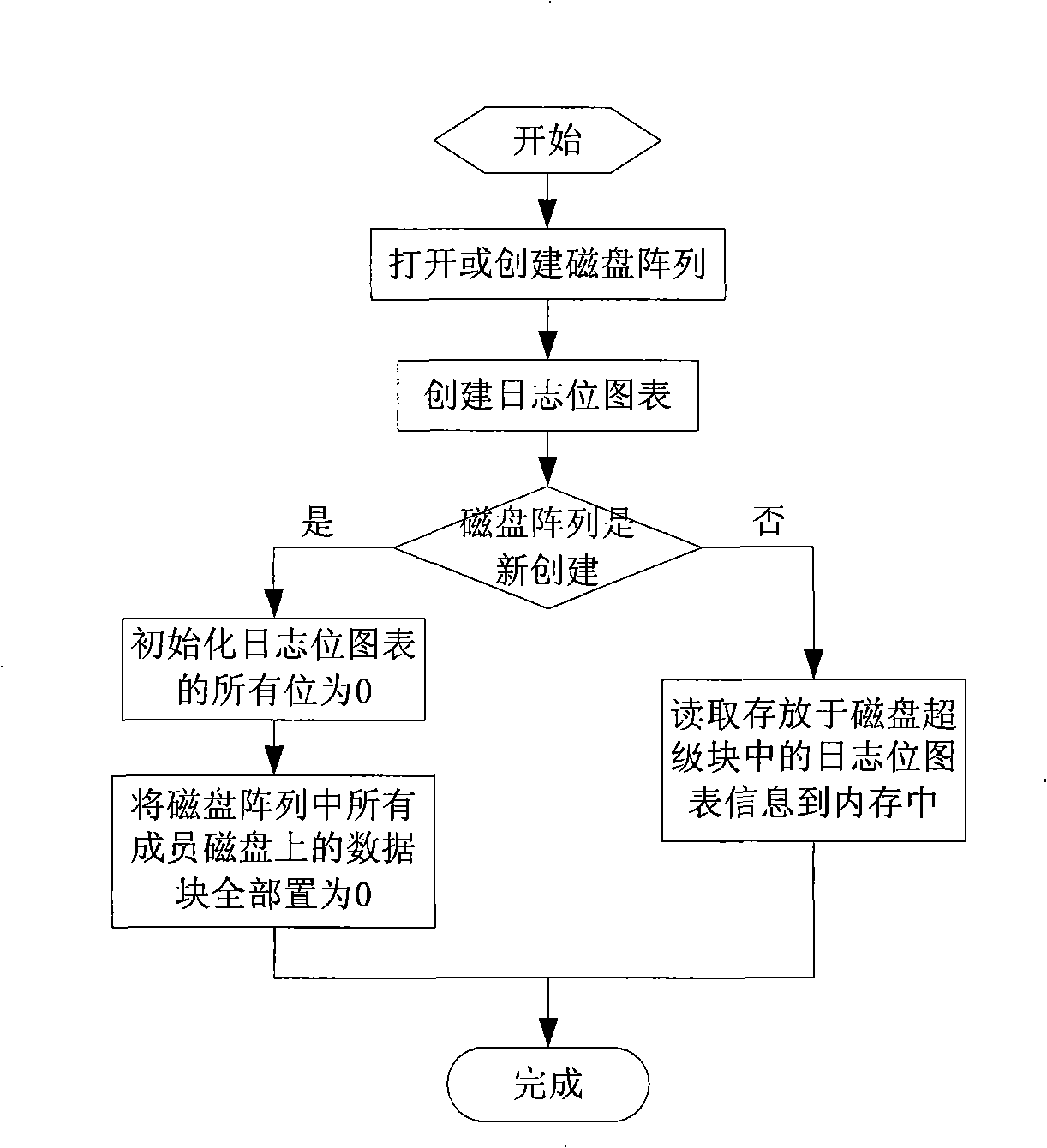
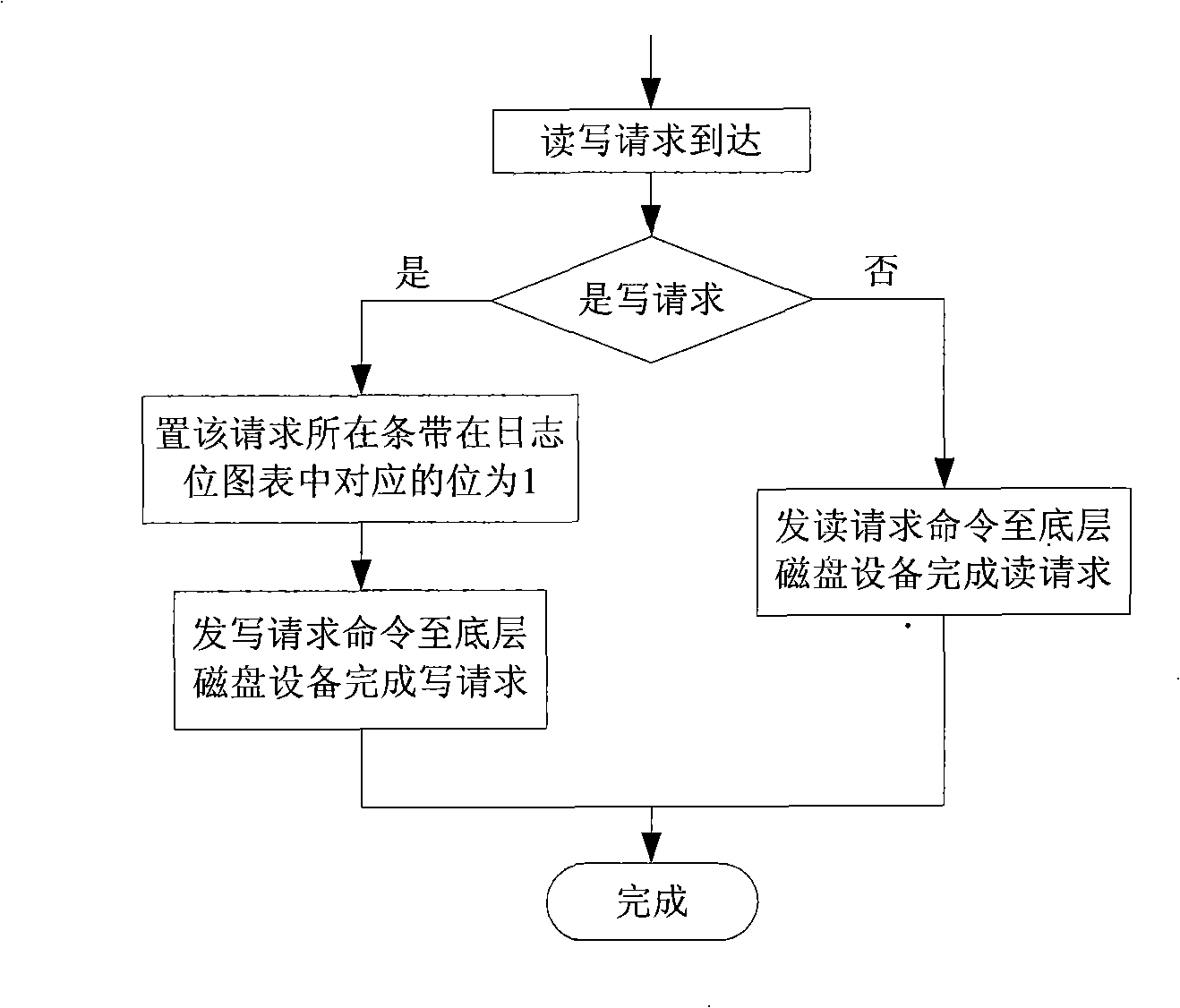
The invention relates to a disk array data reconstruction method which pertains to a computer data storage method and solves the problem that the existing disk array data reconstruction method takes too much time and affects the reading and writing performances and reliability of a storage system. A disk array of the invention is provided with a main control module, reading and writing processing modules and a reconstruction module and comprises the steps of initialization, diary pot diagram update, reconstruction based on diaries and finishing. The method instructs data reconstruction process by the real-time monitoring of disk space using status of the disk array; when space that is not accessed is reconstructed, the only requirement is to write 0 in all corresponding data blocks newly added into a disk, thus greatly reducing physical disk visiting time brought by reconstruction, increasing reconstruction speed and reducing the response time of user access; the reconstruction method does not change the reconstruction procedure or the distribution manner of disk array data, can conveniently optimize various traditional disk array data reconstruction methods and is applicable to the construction of storage systems with high performance, high usability and high reliability.
Owner:HUAZHONG UNIV OF SCI & TECH
Index-based computer continuous data protection method
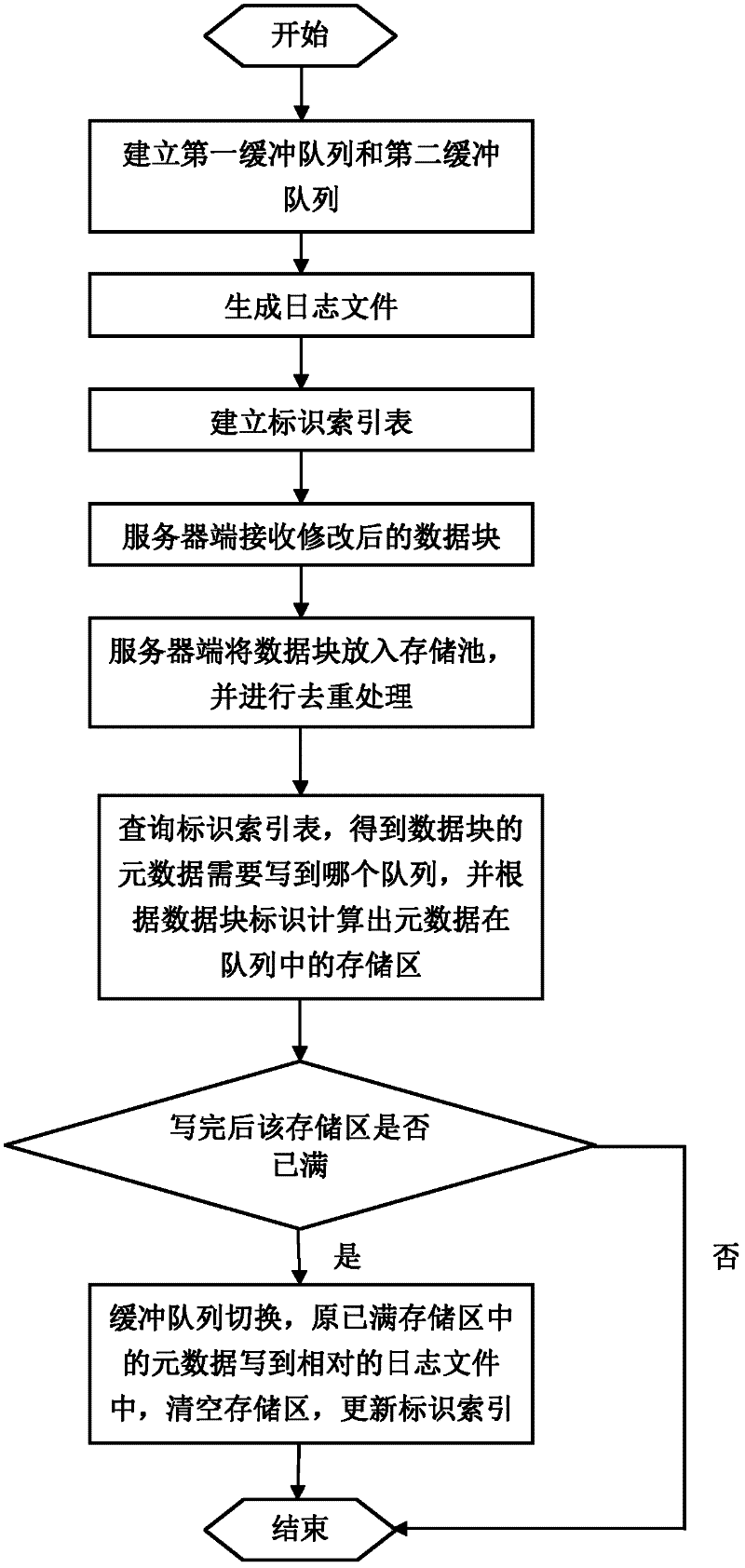
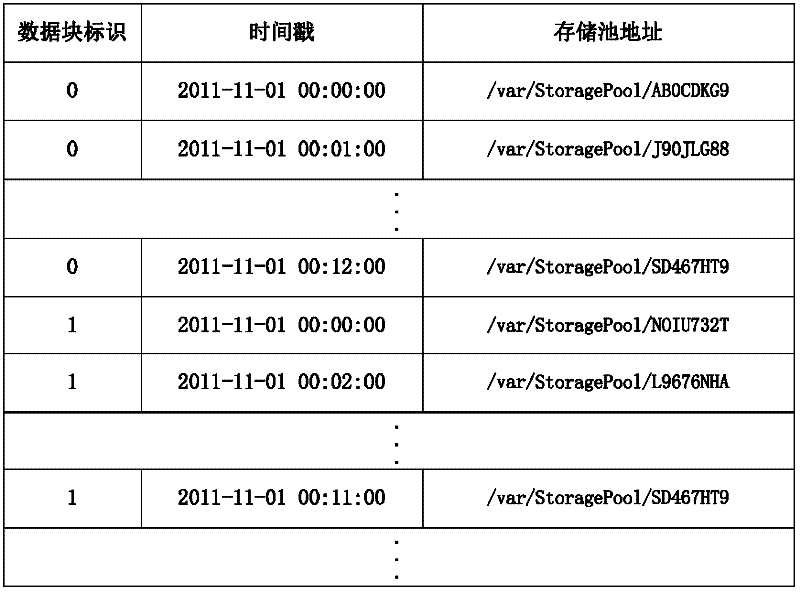
ActiveCN102521269AAvoid blockingImprove query speedMemory adressing/allocation/relocationSpecial data processing applicationsInternal memoryTimestamp
The invention relates to an index-based computer continuous data protection method and belongs to the technical field of computer data storage and protection. Metadata of a data block comprises a data block identification, a timestamp and a storage pool address; an internal memory at a server side is internally provided with two buffer queues and an identification index table; a journal file is set up on a hard disk; after the data block is received by a storage pool, duplicate removal treatment is carried out; the metadata is stored and written into the storage area of one buffer queue by the server side according to the identification index table and the data block identification; if the storage area is full after the metadata is written up, the metadata in the storage area can be written into the journal file, and the identification index table is updated; and the following metadata can be written into the storage area of the other buffer queue. The method provided by the inventioncan be used for caching the metadata by the virtue of two buffer queues, thus preventing a system from being blocked; the identification index table and the journal file are set up, so that the queryspeed of the metadata is accelerated; and furthermore, the storage pool of the server side can be used for carrying out duplicate removal treatment on the data block, so that the storage space can besaved.
Owner:TSINGHUA UNIV
Cache method for file system with changeable data block length
InactiveCN101968795AImprove efficiencyImprove performanceMemory adressing/allocation/relocationSpecial data processing applicationsData segmentApplication software
The invention relates to a cache method for a file system with changeable data block length, belonging to the technical field of computer data storage. The method of the invention comprises the following steps: intercepting operating commands from a computer application program by a driving module of a user state file system, wherein the operating commands comprises opening the existing files, reading data from the opened files, writing data into the opened files, modifying the file attributes and closing the opened files; operating a cache management module in a daemon process mode; and temporarily saving partial data which is read and written recently in each currently opened file into data blocks with random length in the internal storage of a computer, thereby reducing the frequency of access of the file system to external storage devices, and improving the efficiency and throughput of accessing data in the file system. The method of the invention can enable the data reconstruction and data segmenting processes to be transparent to the user and computer application programs, thereby enabling the file system to support a repeating data deleting function under the condition that the compatibility is not affected, and effectively improving the utilization efficiency of the physical storage space.
Owner:TSINGHUA UNIV
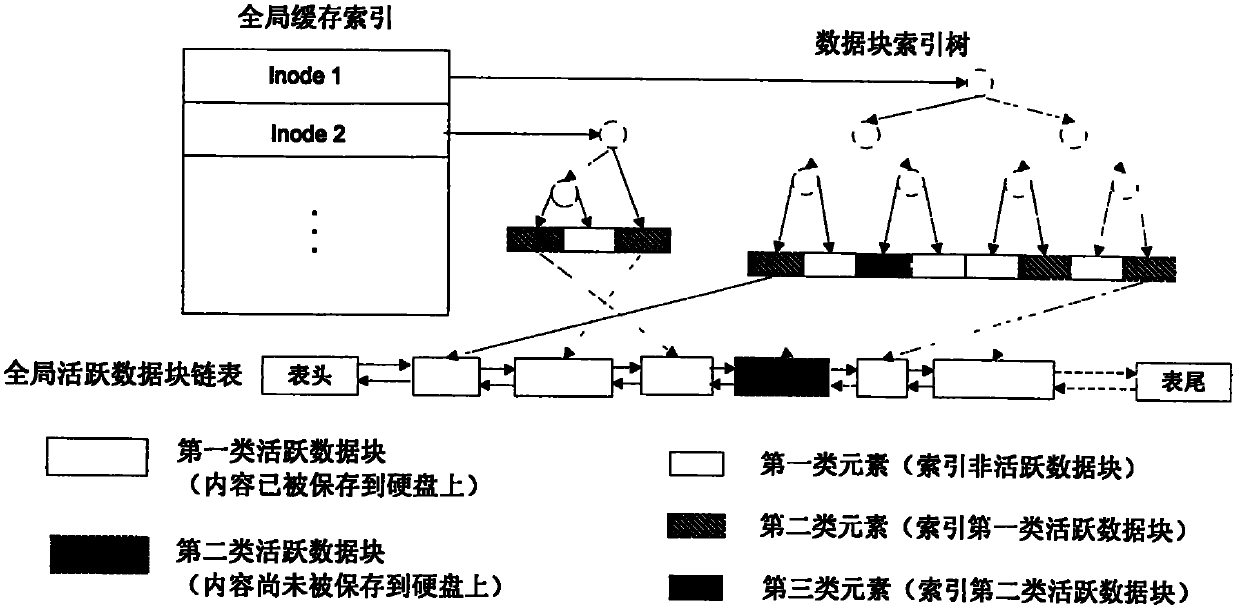
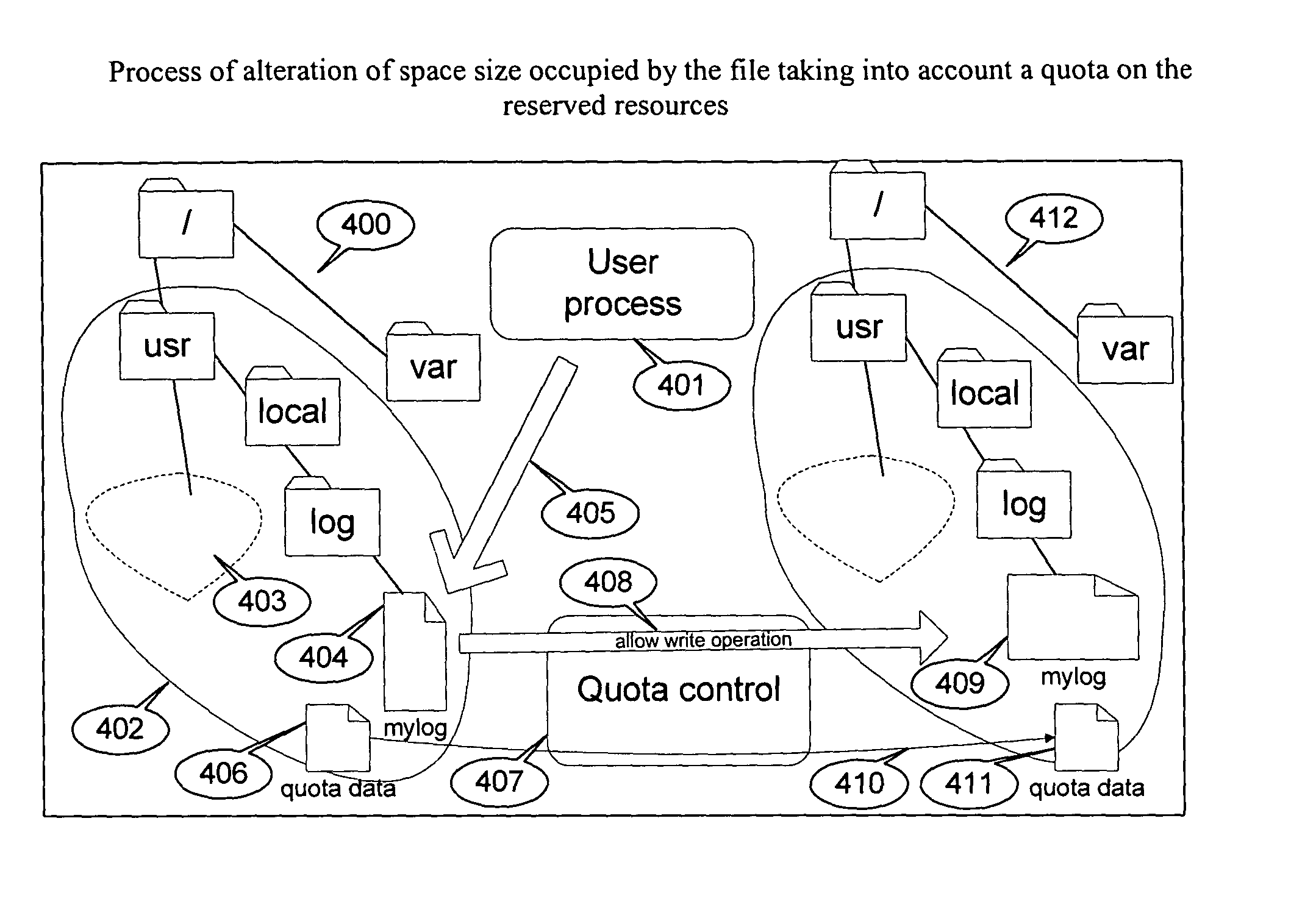
Method of implementation of data storage quota
ActiveUS20050066134A1Complete understandingData processing applicationsSpecial data processing applicationsFile systemData memory
The present invention provides a methodology of organization of control over the process of space or other quantitative parameter of resource allocation in computer data storages. More specifically, the present invention organizes areas of quoted space or time. A method and system of the present invention includes an establishment of quotas for an area of a file system that takes into account the belonging of a file to a certain subtree or subtrees of the file system. The quota management of the present invention is established within a usual computer system which includes a hierarchic file system, as well as a set of unique users, that could be united into groups.
Owner:VIRTUOZZO INT GMBH
Continuous data caching system and data caching method thereof
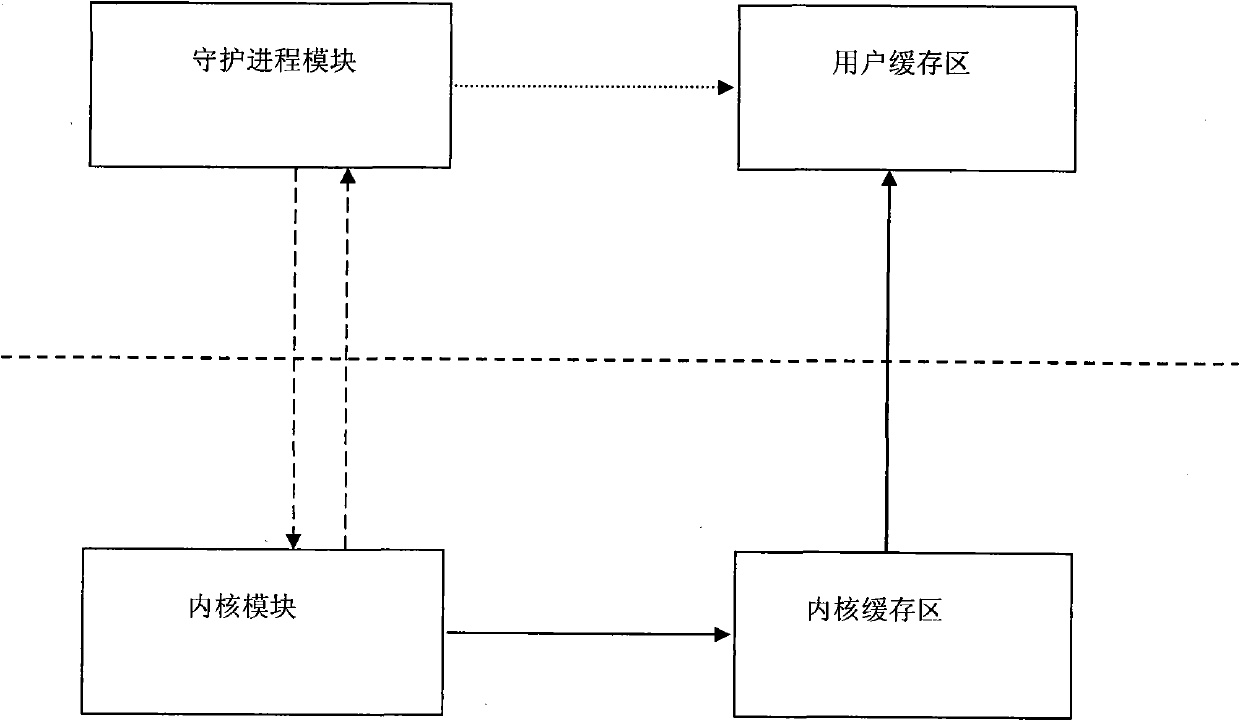
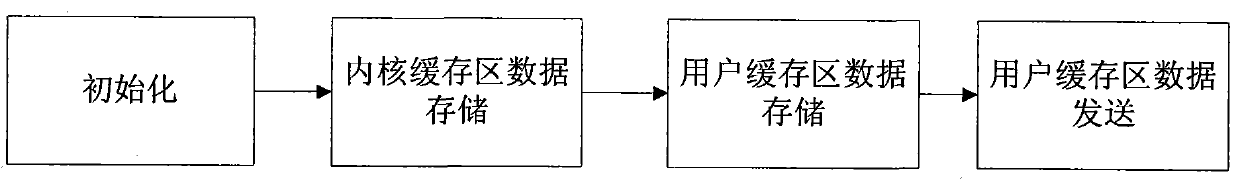
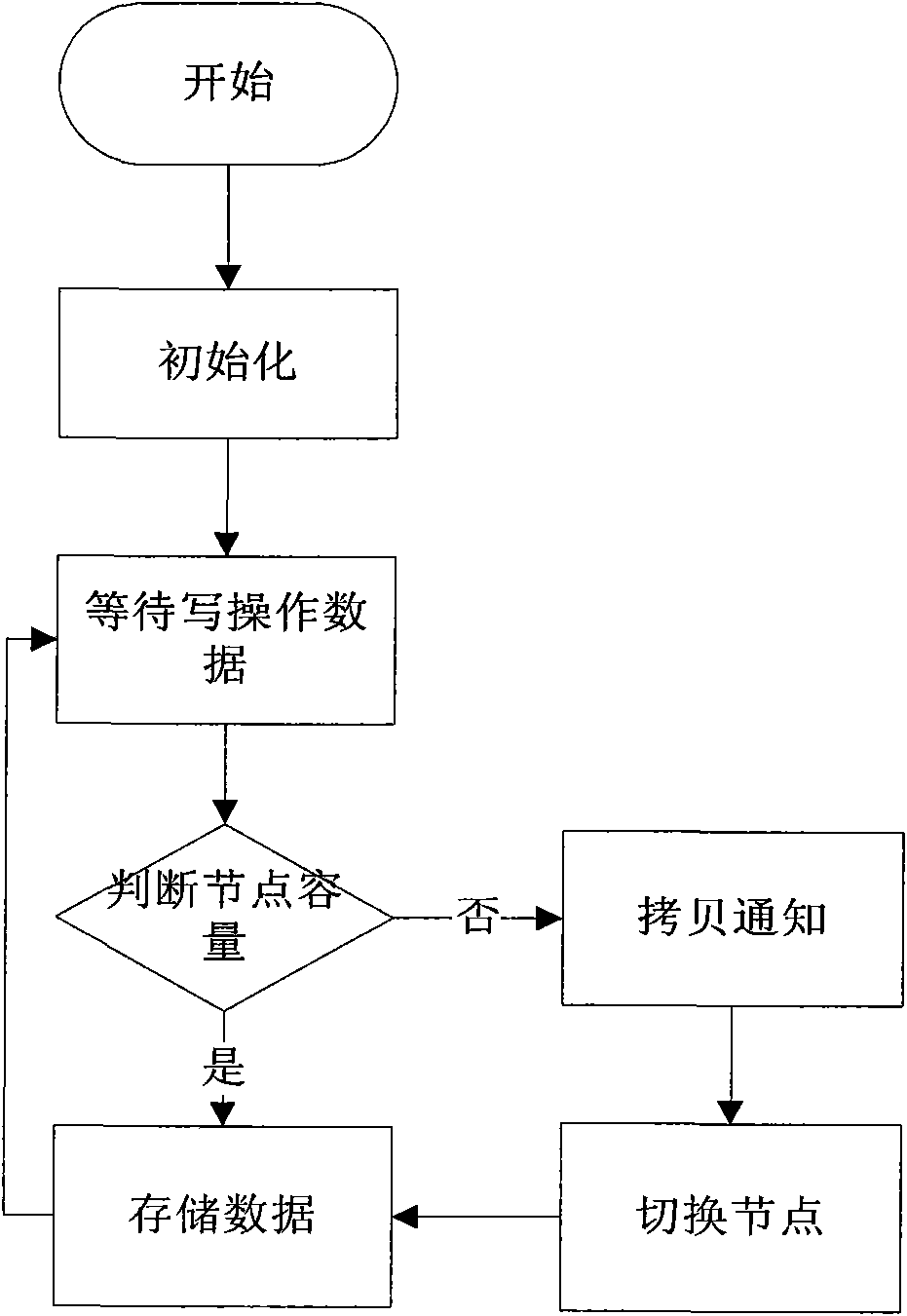
InactiveCN101770412AReduce complexityReduce performance overheadMemory adressing/allocation/relocationRedundant operation error correctionComputer data storageNetwork performance
The invention discloses a continuous data caching system and a data caching method thereof, belonging to computer data storage system and backup method and solving the problem that continuous data capturing capability and protective capability are unmatched brought by burst I / O and network performance fluctuation. The inventive system is composed of a core cache zone, a user cache zone, a core module and a daemon process module. The inventive method comprises initializing, storing core cache zone data, storing user cache zone data, and transmitting user cache zone data. The inventive system adopts two-level cache mechanism comprising core cache and user cache, is structured on TCP / IP protocol, has little performance expenditure and reduces user node complexity. The inventive method adopts smaller core cache zone and larger user cache zone, thus lowering core processing complexity, allocating or recycling user cache zone node timely by proposing cache anticipation algorithm, optimizing use ratio of user cache zone and saving system internal storage resource.
Owner:HUAZHONG UNIV OF SCI & TECH
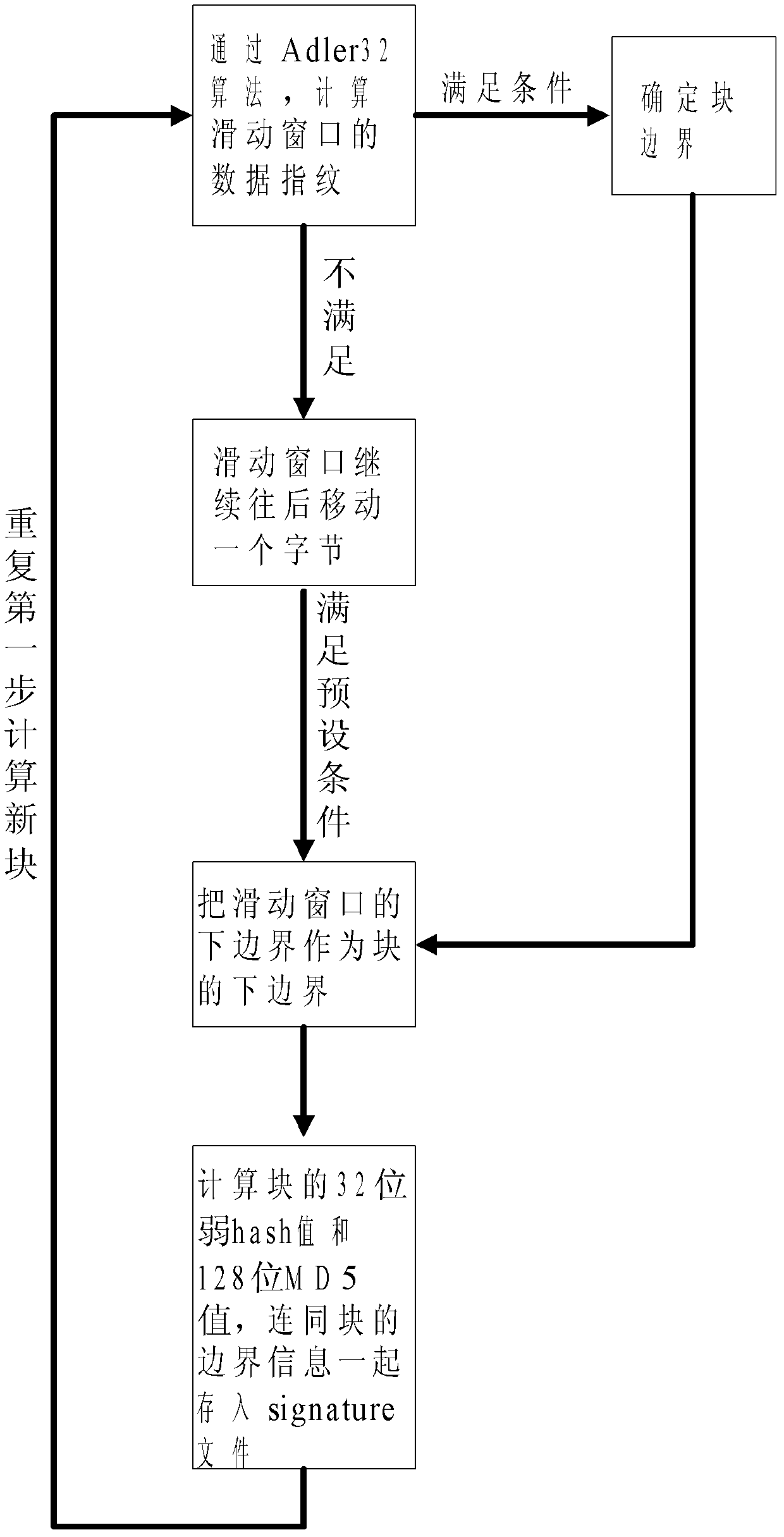
Difference synchronizing method for oversized file
The invention discloses a difference synchronizing method for an oversized file and belongs to the technical field of computer data storage. The method comprises the steps that a cloud computer calculates to obtain a difference file, and sends the difference file to a target computer, and the target computer only synchronizes different data blocks needing to be synchronized by comparing the data blocks of a target file and those of the difference file and eventually generates a new file which is identical with the cloud file. The difference synchronizing method for the oversized file has the advantages of being good in support for oversized files, excellent in Hash algorithm, good in support for multiple platforms and the like.
Owner:上海咏云信息技术有限公司 +1
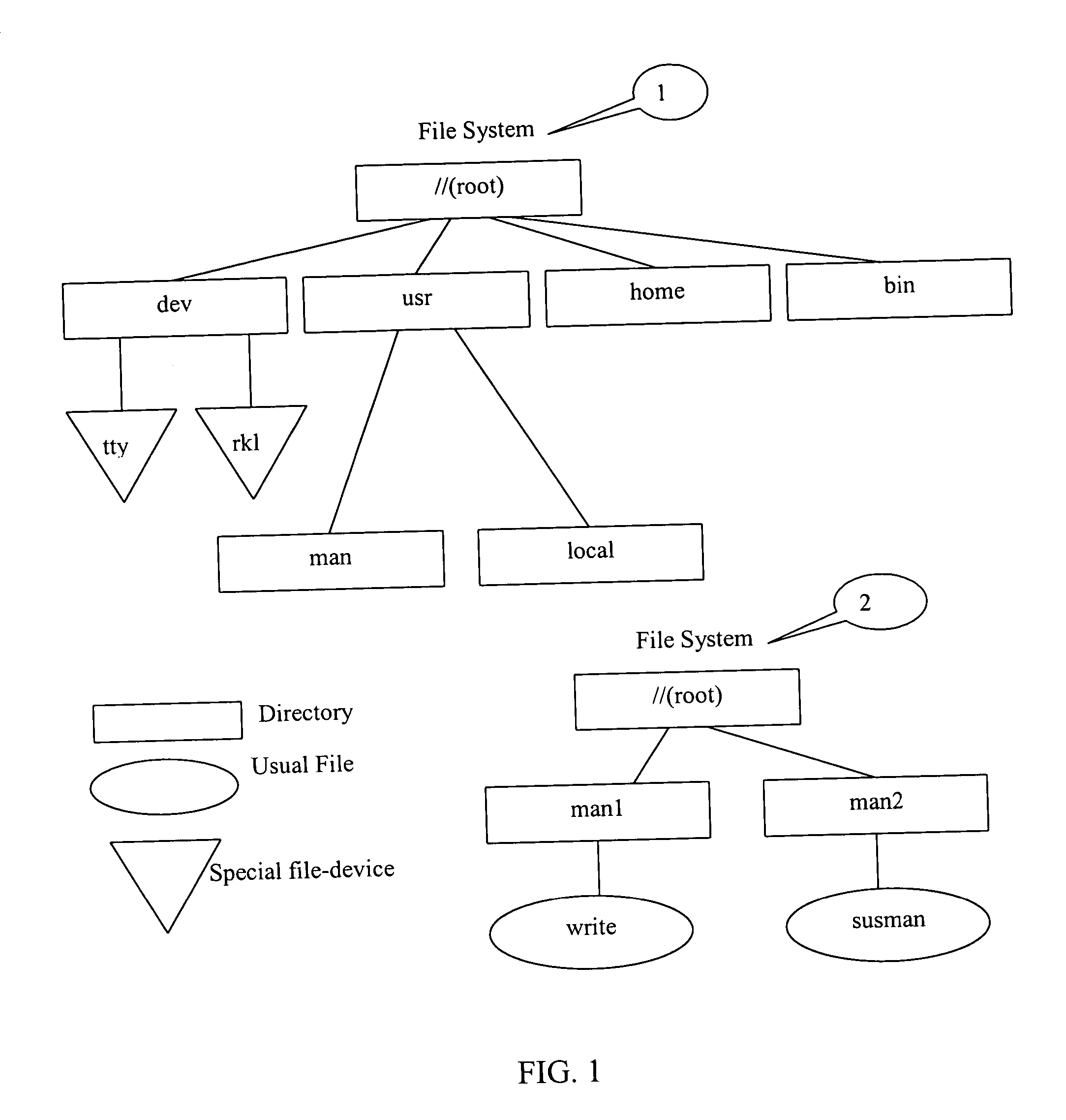
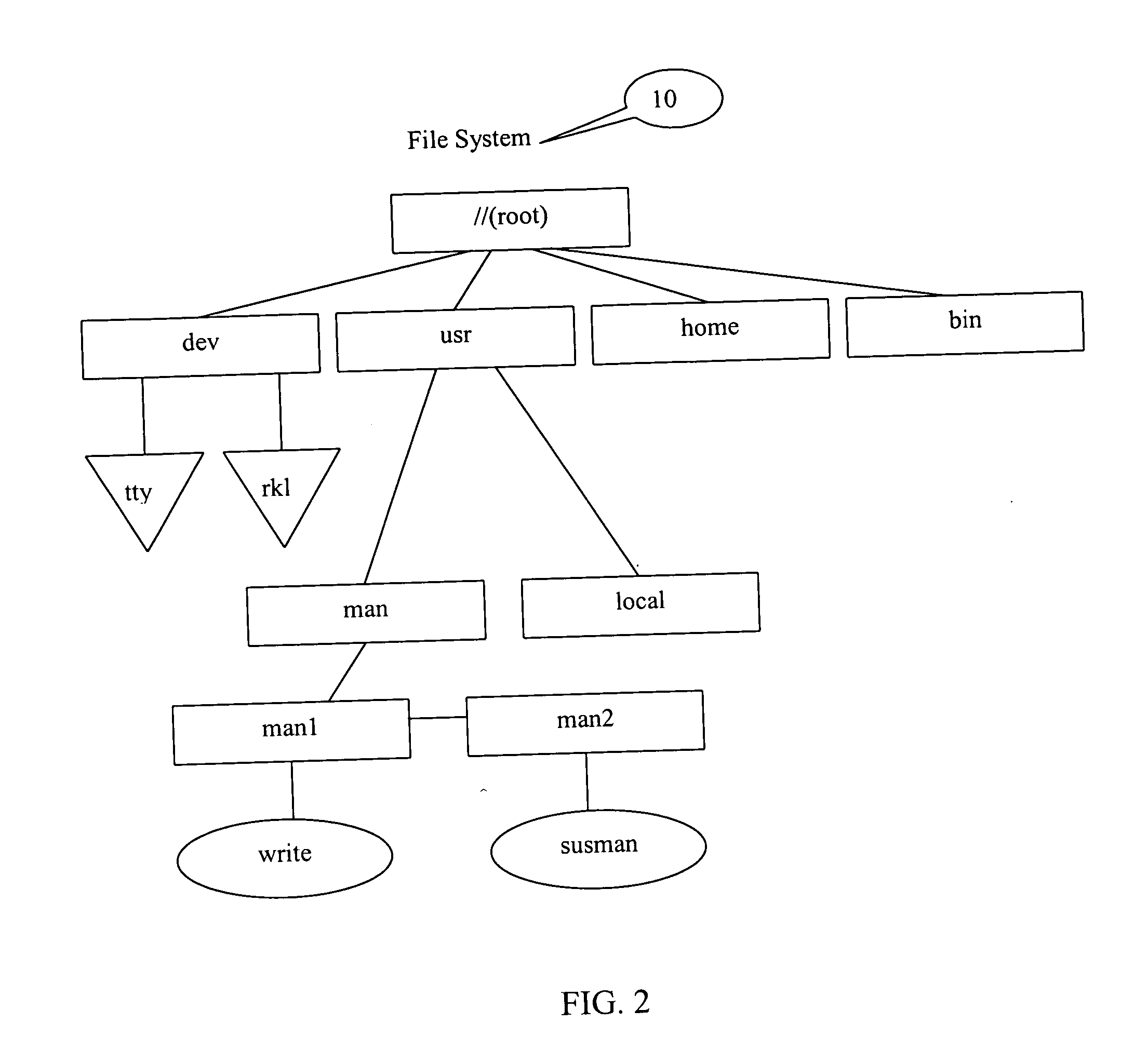
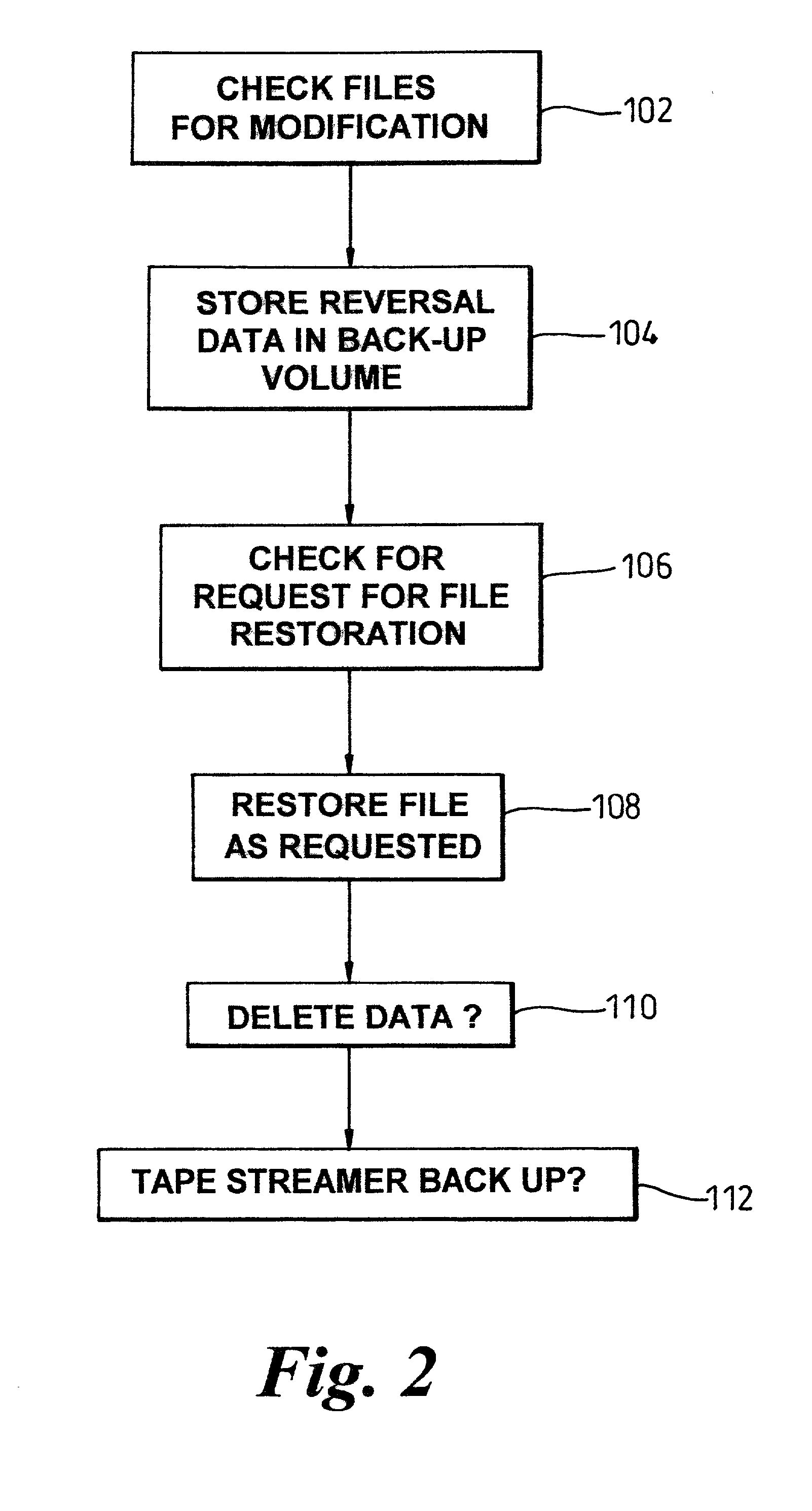
Computer file storage and recovery method
InactiveUS20020059328A1Multiple digital computer combinationsRedundant operation error correctionRecovery methodRestoration method
A fileserver connected to client computers by a network includes a data store partitioned into one or more client-accessible volumes. The data store is also partitioned into one or more back-up volumes of a client-accessible volume, store in a corresponding back-up volume data which will permit reversal of the modification of the contents of said file, detect if a client requests restoration of said file to a previous version and restore said file to the requested previous version on detecting said request. Such a configuration of fileserver allows clients to restore the fileserver files to various previous versions without recourse to the more time-consuming process of retrieving required reconstruction data from, for example, a tape streamer back-up system.
Owner:HEWLETT PACKARD CO
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com