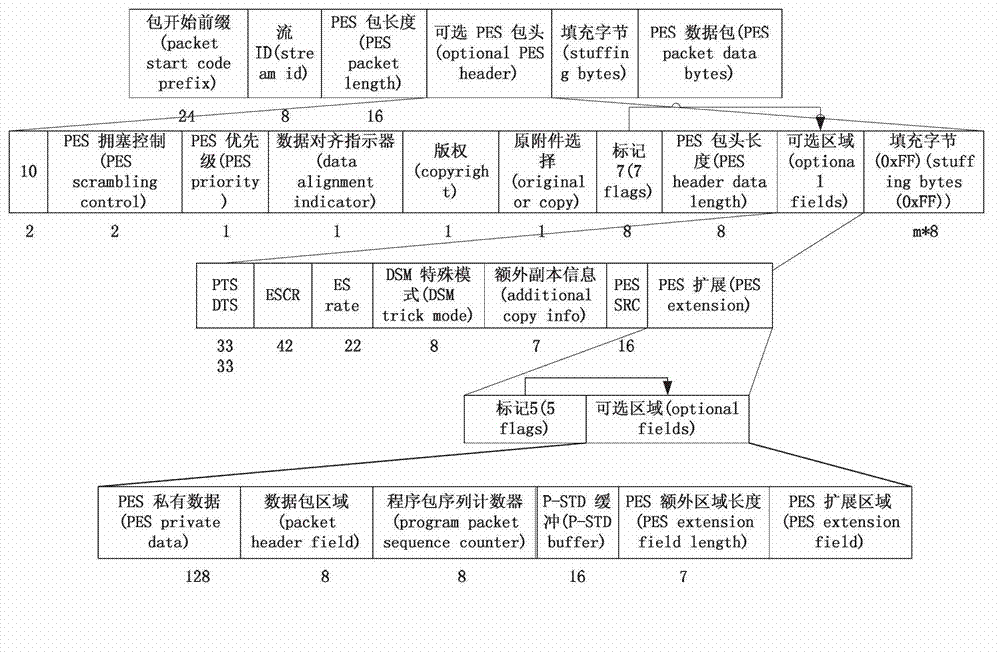
Patents
Literature
2330 results about "GNU/Linux" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Linux (/ˈlɪnəks/ LIN-əks) is a family of open source Unix-like operating systems based on the Linux kernel, an operating system kernel first released on September 17, 1991, by Linus Torvalds. Linux is typically packaged in a Linux distribution.
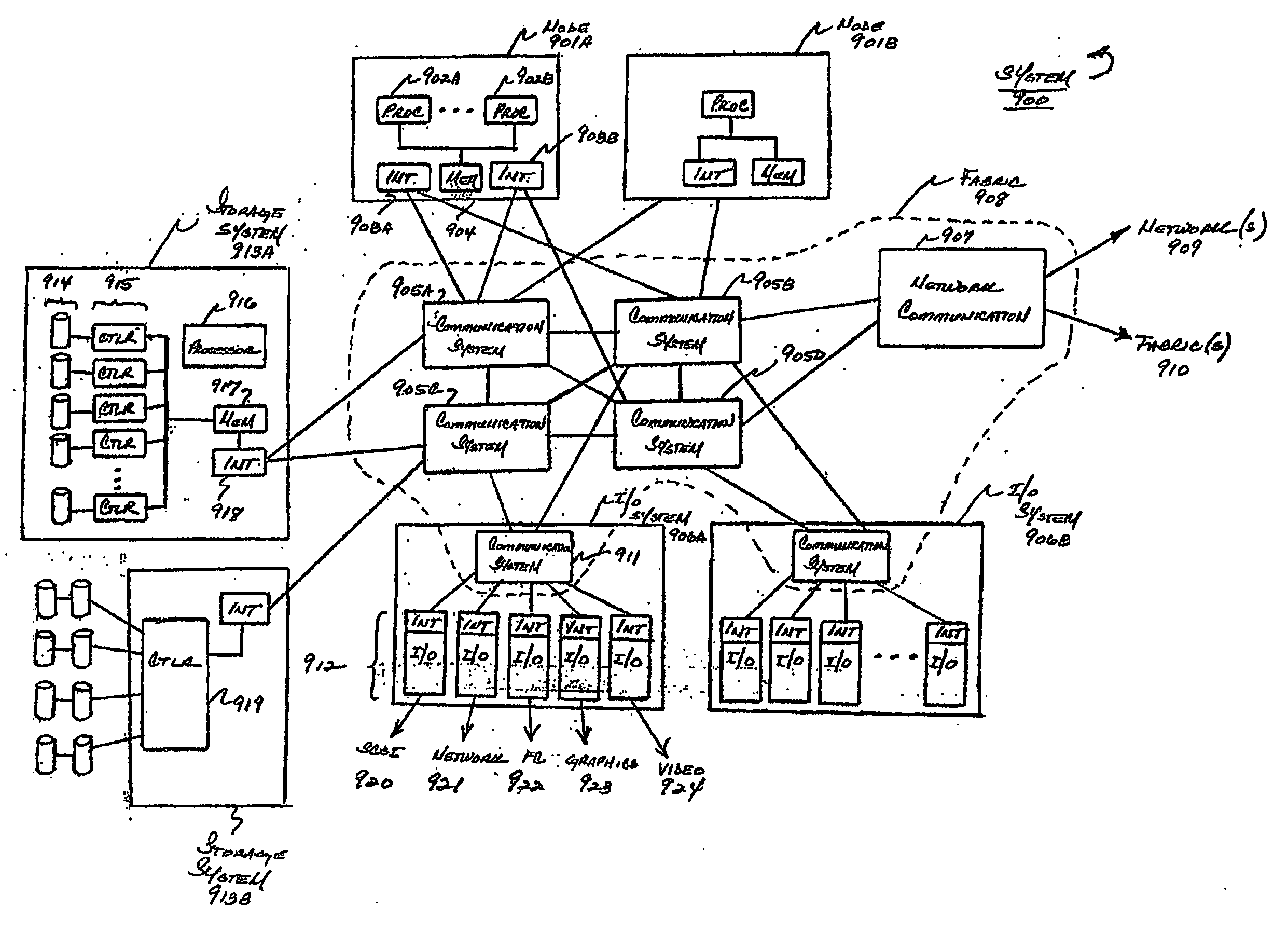
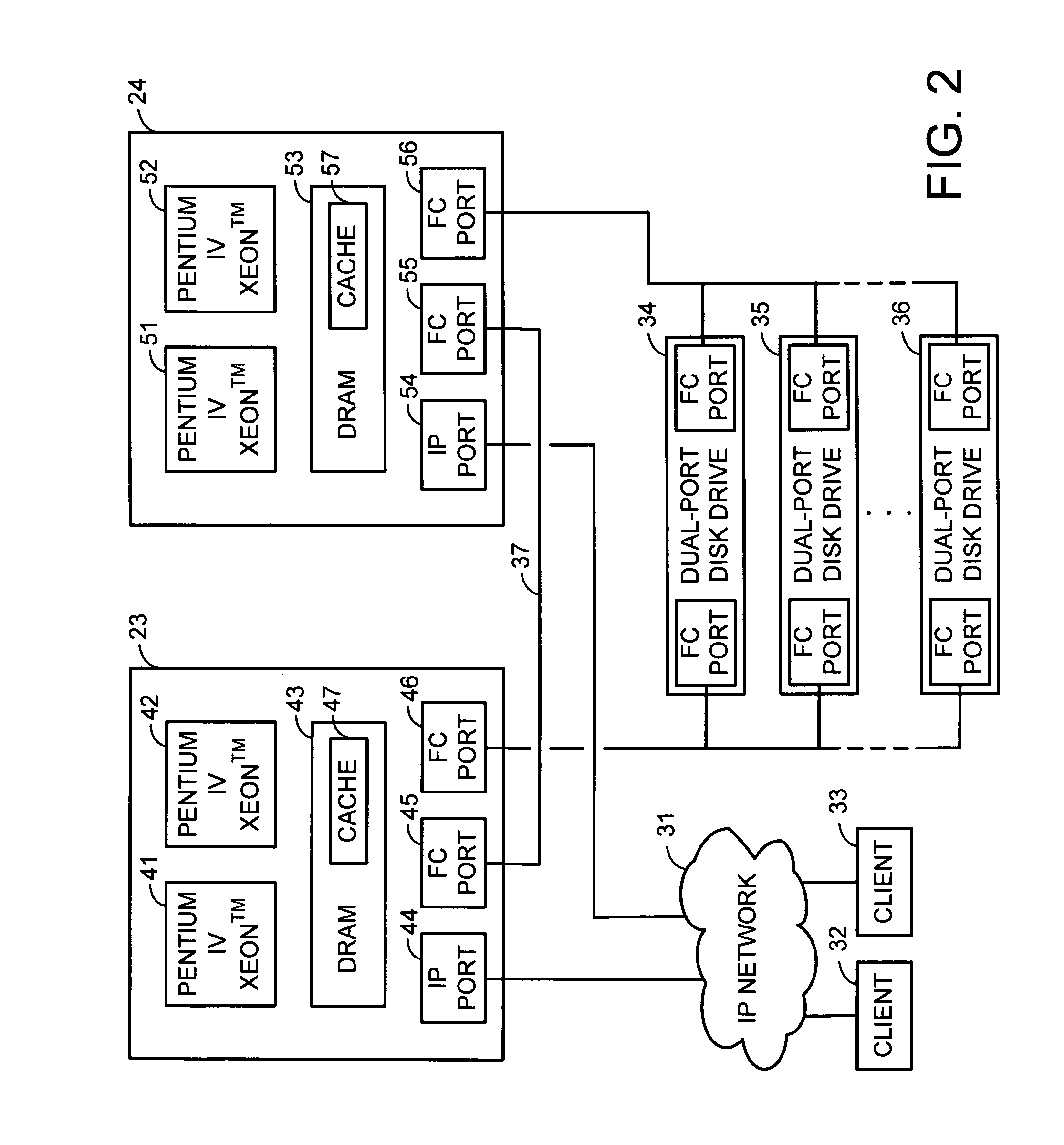
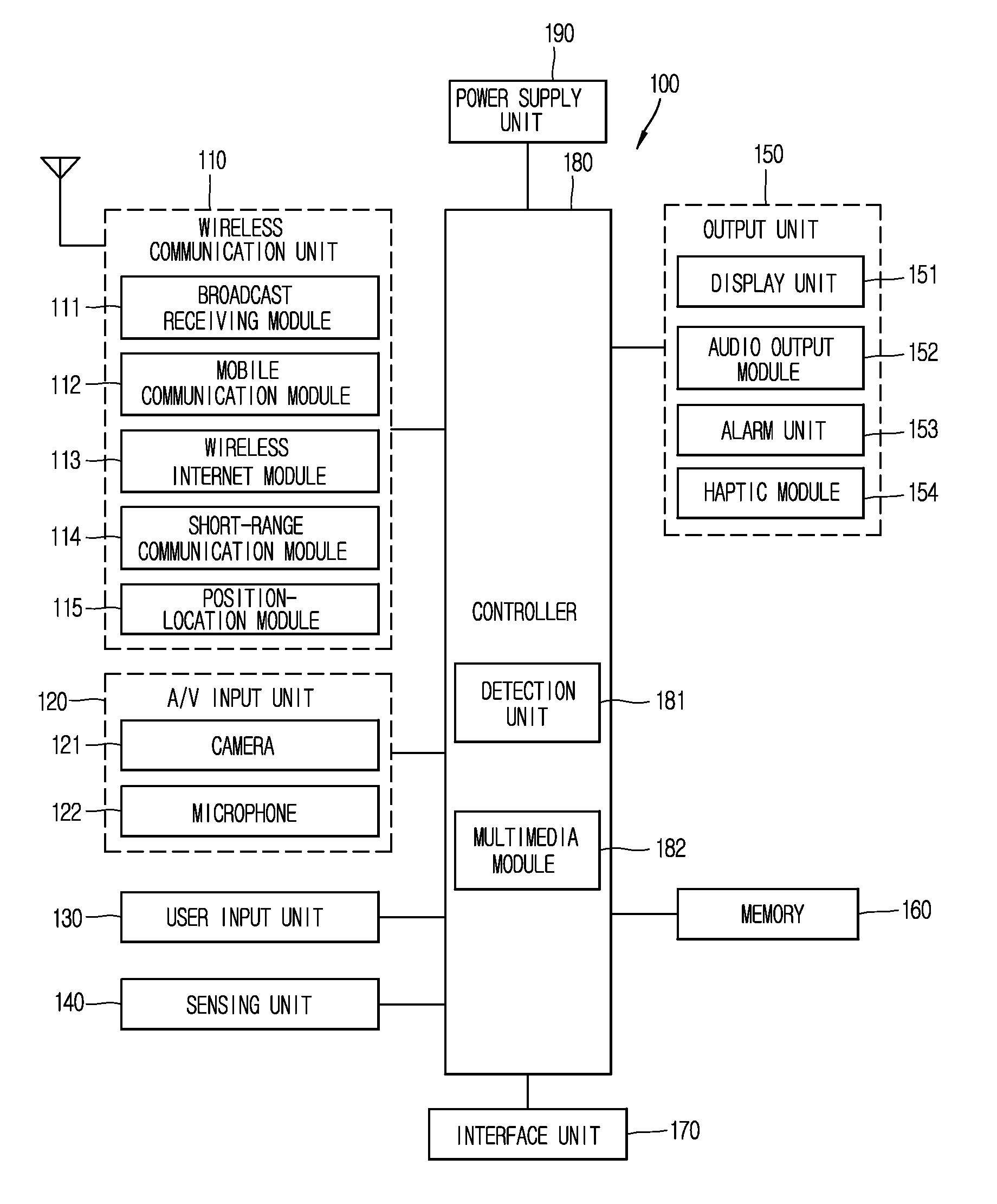
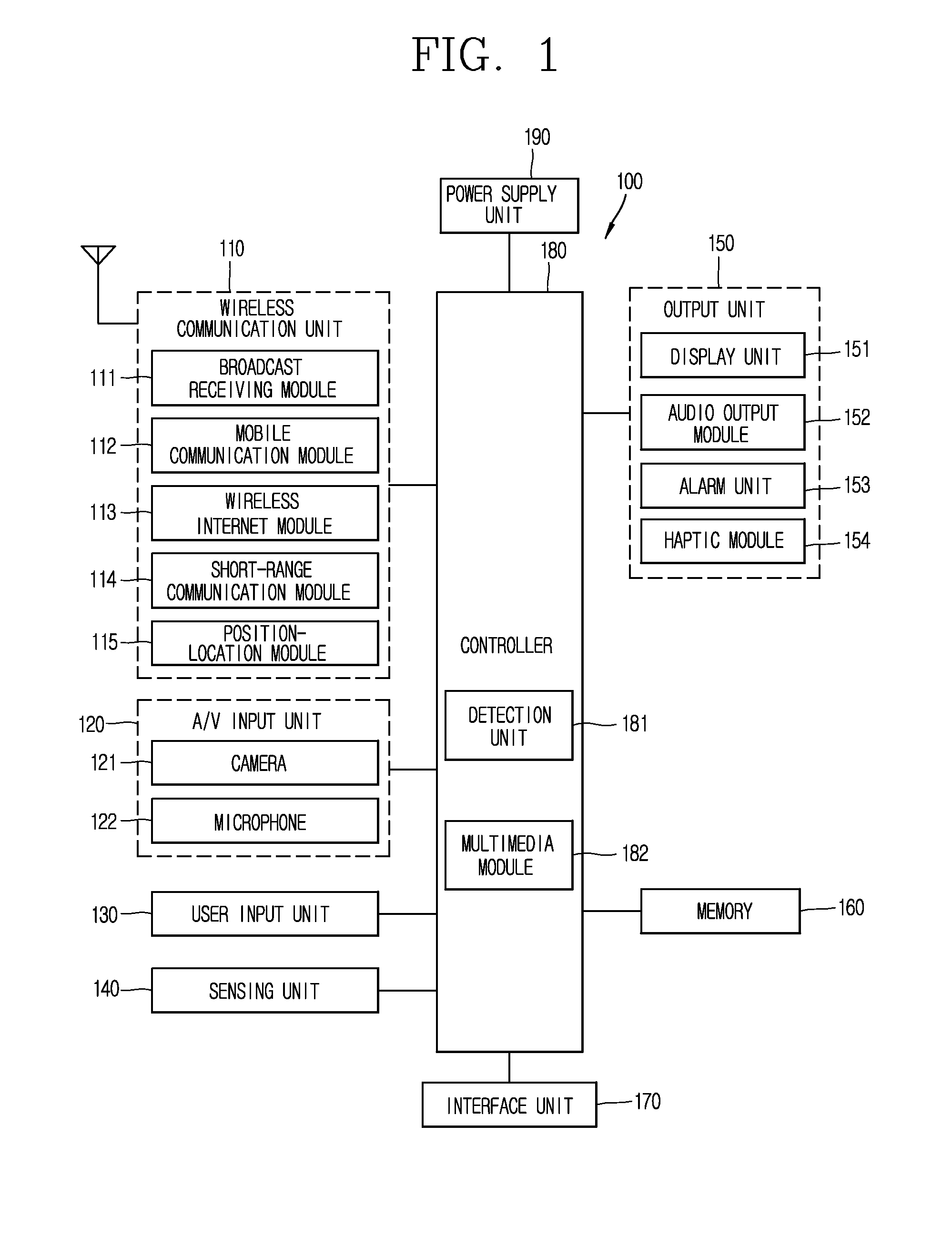
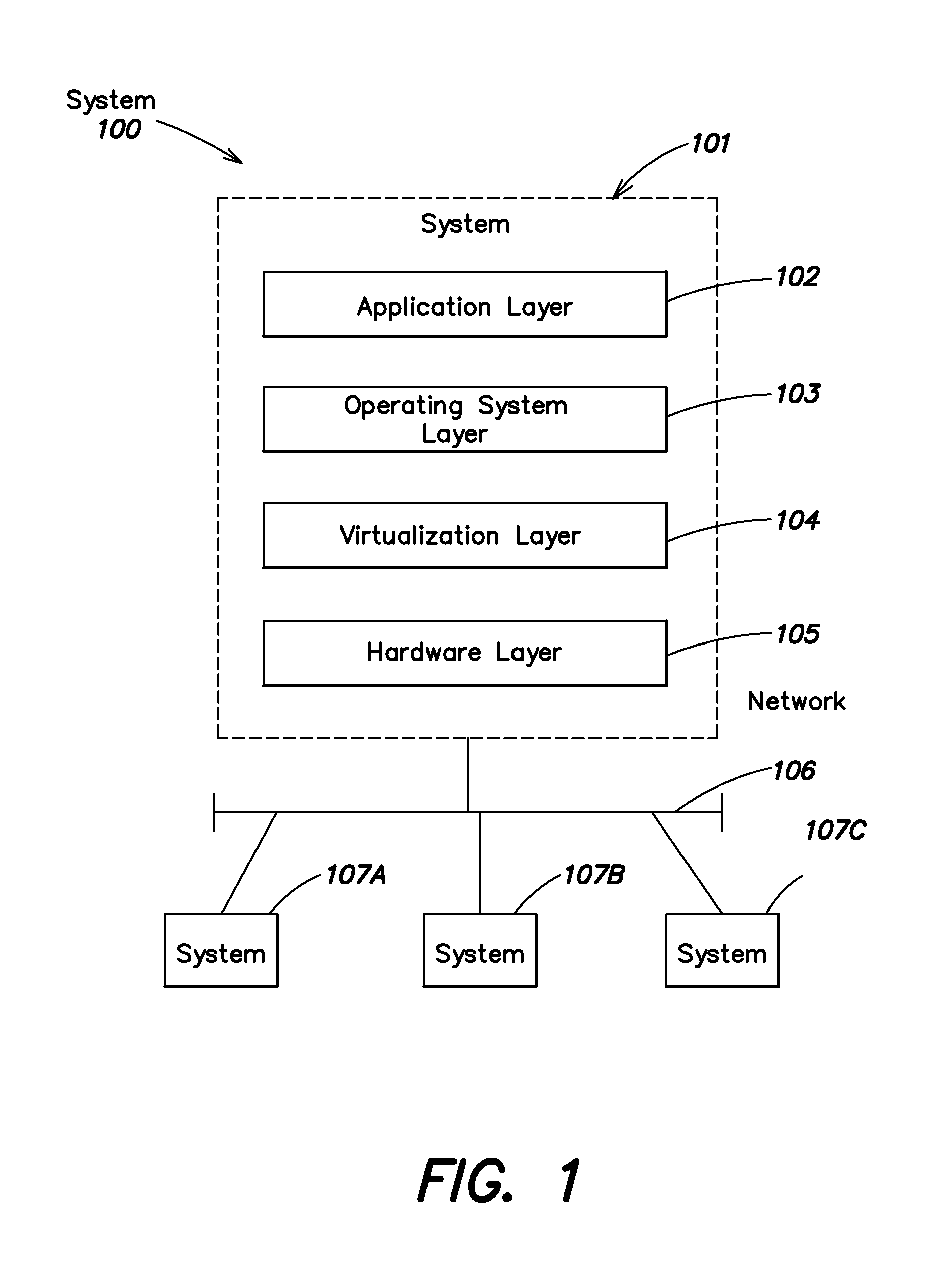
System and method for managing virtual servers
ActiveUS20050120160A1Grow and shrink capabilityMaximize useResource allocationMemory adressing/allocation/relocationOperational systemPrimitive state
A management capability is provided for a virtual computing platform. In one example, this platform allows interconnected physical resources such as processors, memory, network interfaces and storage interfaces to be abstracted and mapped to virtual resources (e.g., virtual mainframes, virtual partitions). Virtual resources contained in a virtual partition can be assembled into virtual servers that execute a guest operating system (e.g., Linux). In one example, the abstraction is unique in that any resource is available to any virtual server regardless of the physical boundaries that separate the resources. For example, any number of physical processors or any amount of physical memory can be used by a virtual server even if these resources span different nodes. A virtual computing platform is provided that allows for the creation, deletion, modification, control (e.g., start, stop, suspend, resume) and status (i.e., events) of the virtual servers which execute on the virtual computing platform and the management capability provides controls for these functions. In a particular example, such a platform allows the number and type of virtual resources consumed by a virtual server to be scaled up or down when the virtual server is running. For instance, an administrator may scale a virtual server manually or may define one or more policies that automatically scale a virtual server. Further, using the management API, a virtual server can monitor itself and can scale itself up or down depending on its need for processing, memory and I / O resources. For example, a virtual server may monitor its CPU utilization and invoke controls through the management API to allocate a new processor for itself when its utilization exceeds a specific threshold. Conversely, a virtual server may scale down its processor count when its utilization falls. Policies can be used to execute one or more management controls. More specifically, a management capability is provided that allows policies to be defined using management object's properties, events and / or method results. A management policy may also incorporate external data (e.g., an external event) in its definition. A policy may be triggered, causing the management server or other computing entity to execute an action. An action may utilize one or more management controls. In addition, an action may access external capabilities such as sending notification e-mail or sending a text message to a telephone paging system. Further, management capability controls may be executed using a discrete transaction referred to as a “job.” A series of management controls may be assembled into a job using one or management interfaces. Errors that occur when a job is executed may cause the job to be rolled back, allowing affected virtual servers to return to their original state.
Owner:ORACLE INT CORP
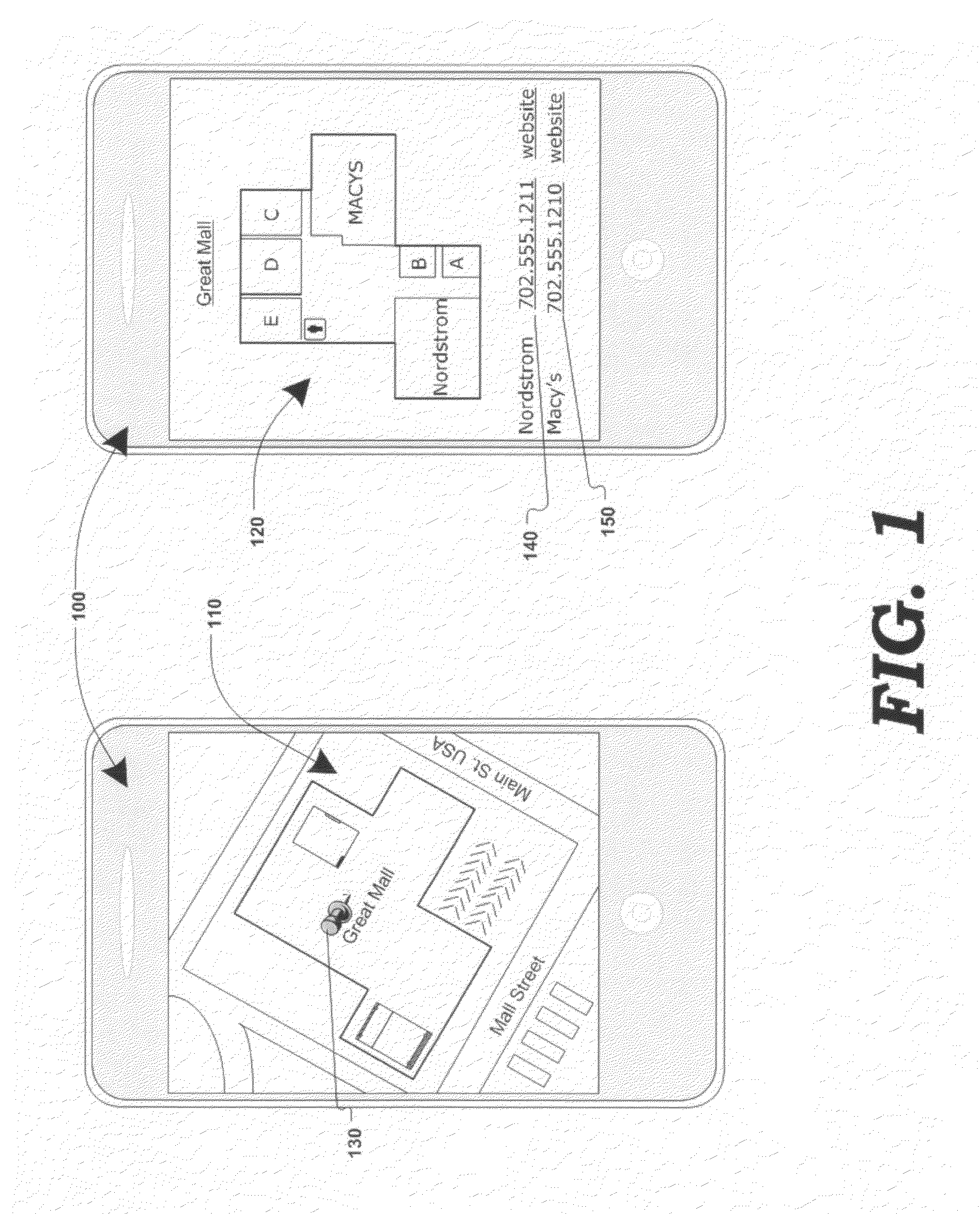
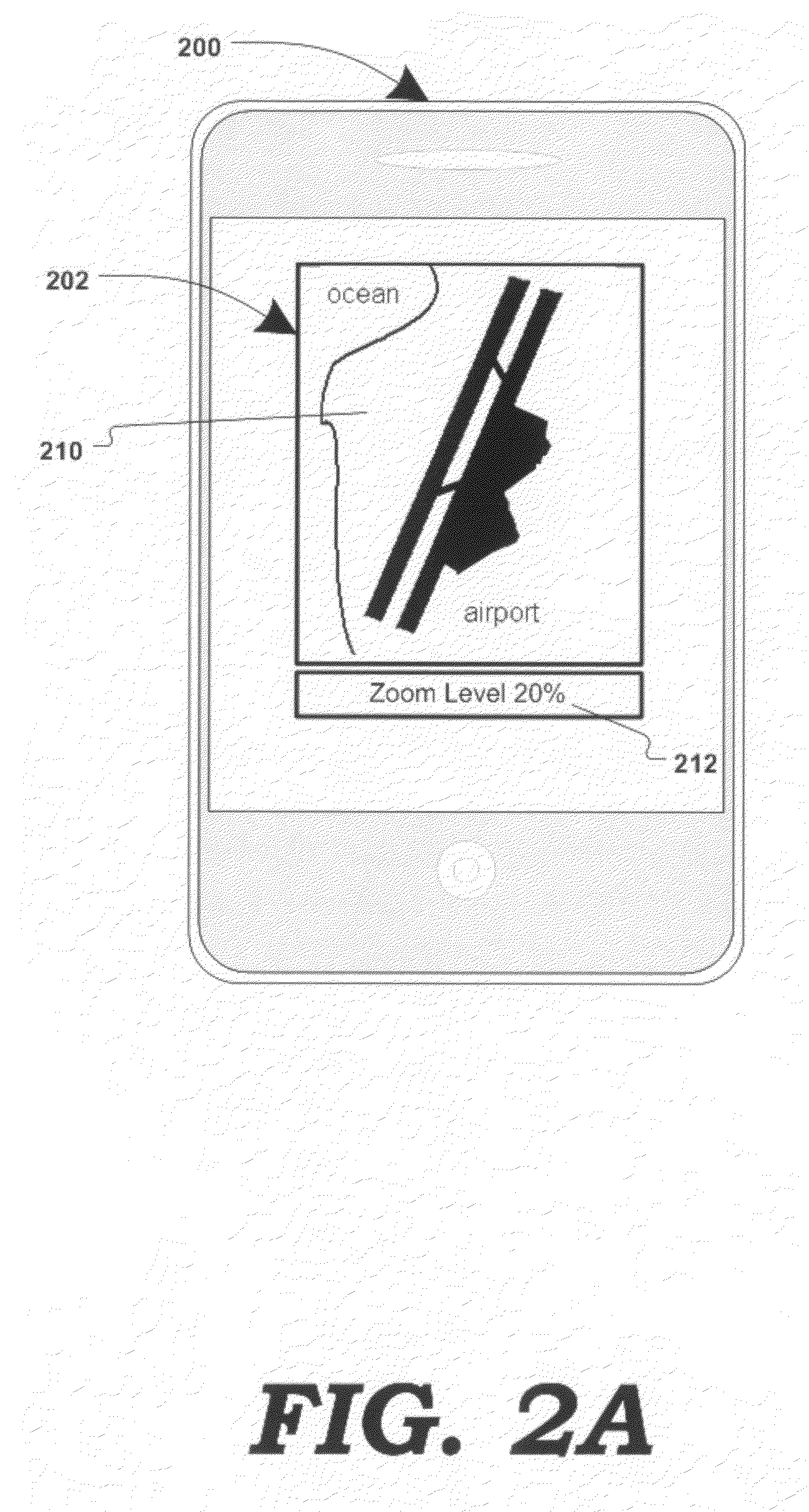
Displaying content associated with electronic mapping systems
Various methods, systems and apparatus for displaying alternate content in a digital mapping system, are disclosed. One such method may include detecting a change in a zoom level of an electronic map displaying geographic content (e.g. tile-based digital map, satellite image, etc.) on a computing device (e,g. desktop / laptop, smart phone, etc, running Windows®, Linux®, Mac OS®, iOS®. Android®, etc.); determining a predetermined (eg. maximum) zoom level has been reached; retrieving alternate content, and displaying the alternate content in addition to, or in place of, some-or-all of the geographic content. The method may further include detecting a zoom-out command while the alternate content is being displayed, and in response, restoring the display of the geographic content (e.g. at the maximum zoom level and / or last state of the geographic content display prior to displaying the alternate content.) Alternate content may be associated with any portion of geographic content displayed (e.g. the portion of the geographic content visible at the maximum zoom level) and may be selected via various algorithms and be manipulate-able via map display application controls.
Owner:JAKOBSON GABRIEL +1
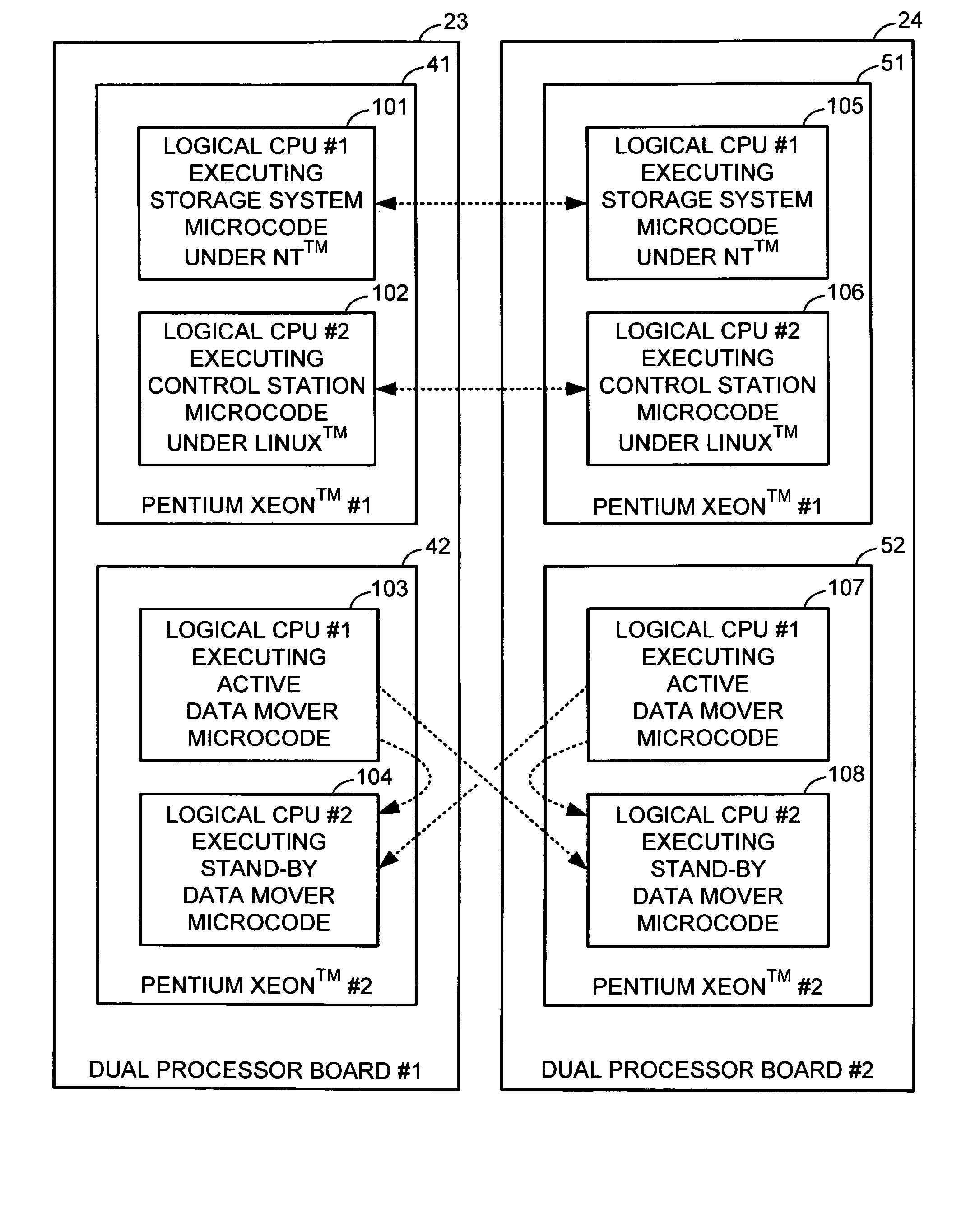
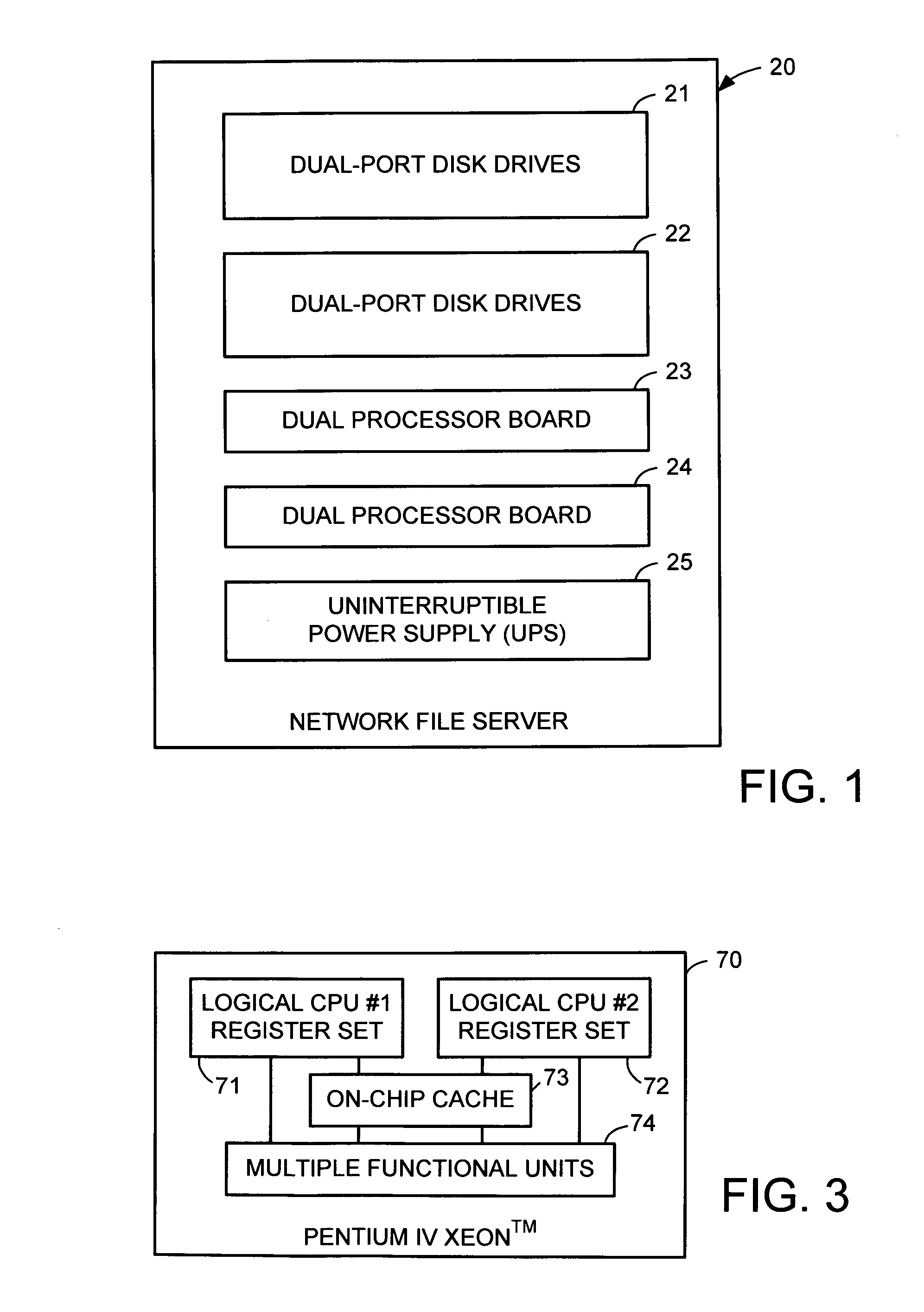
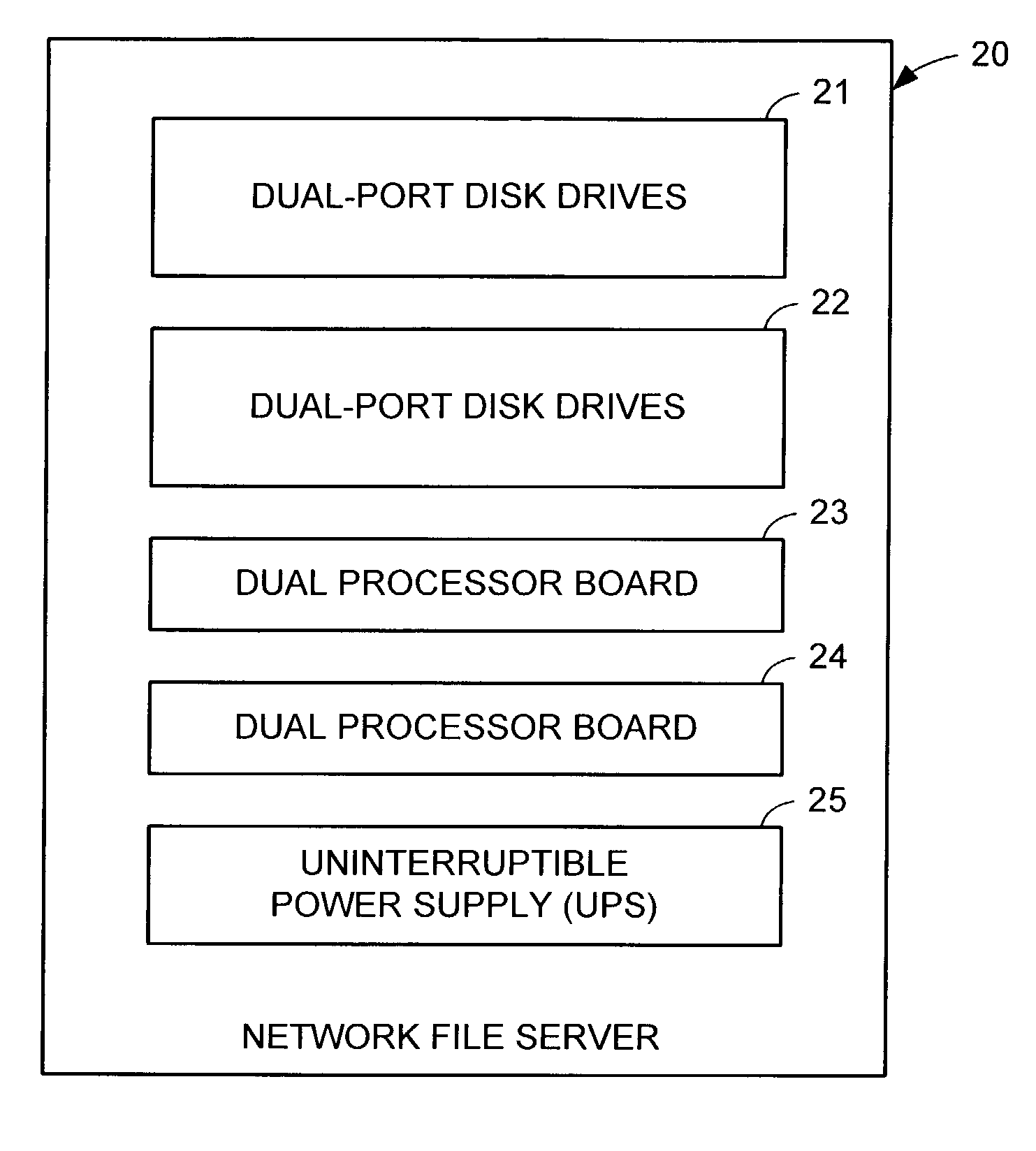
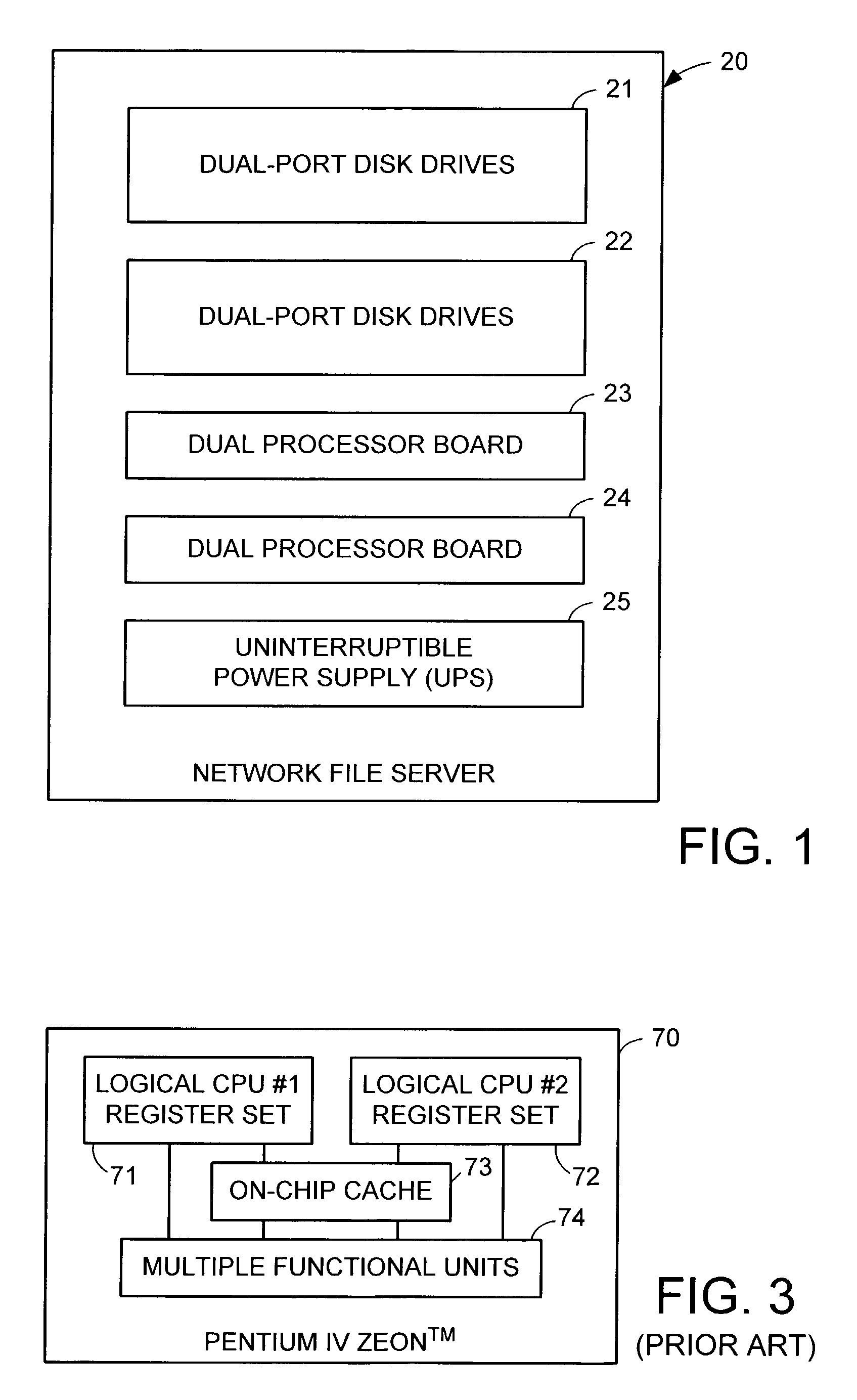
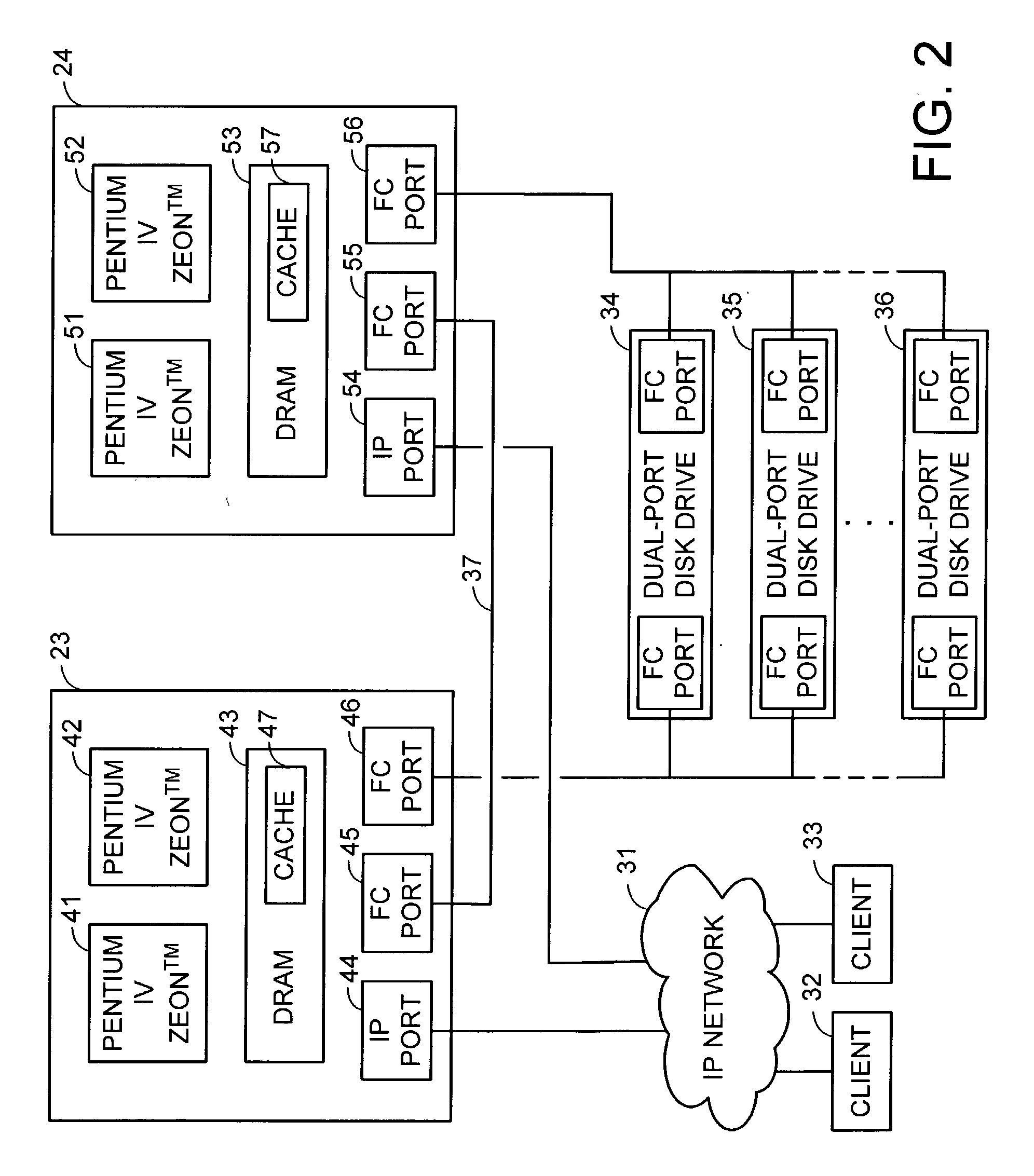
Redundant multi-processor and logical processor configuration for a file server
A redundant file server includes at least two dual processor boards. Each physical processor has two logical processors. The first logical processor of the first physical processor of each board executes storage system code under the Microsoft NT™ operating system. The second logical processor of the first physical processor of each board executes control station code under the Linux operating system. The first logical processor of the second physical processor of each board executes data mover code. The second logical processor of the second physical processor of each board is kept in a stand-by mode for assuming data mover functions upon failure of the first logical processor of the second physical processor on the first or second board.
Owner:EMC IP HLDG CO LLC
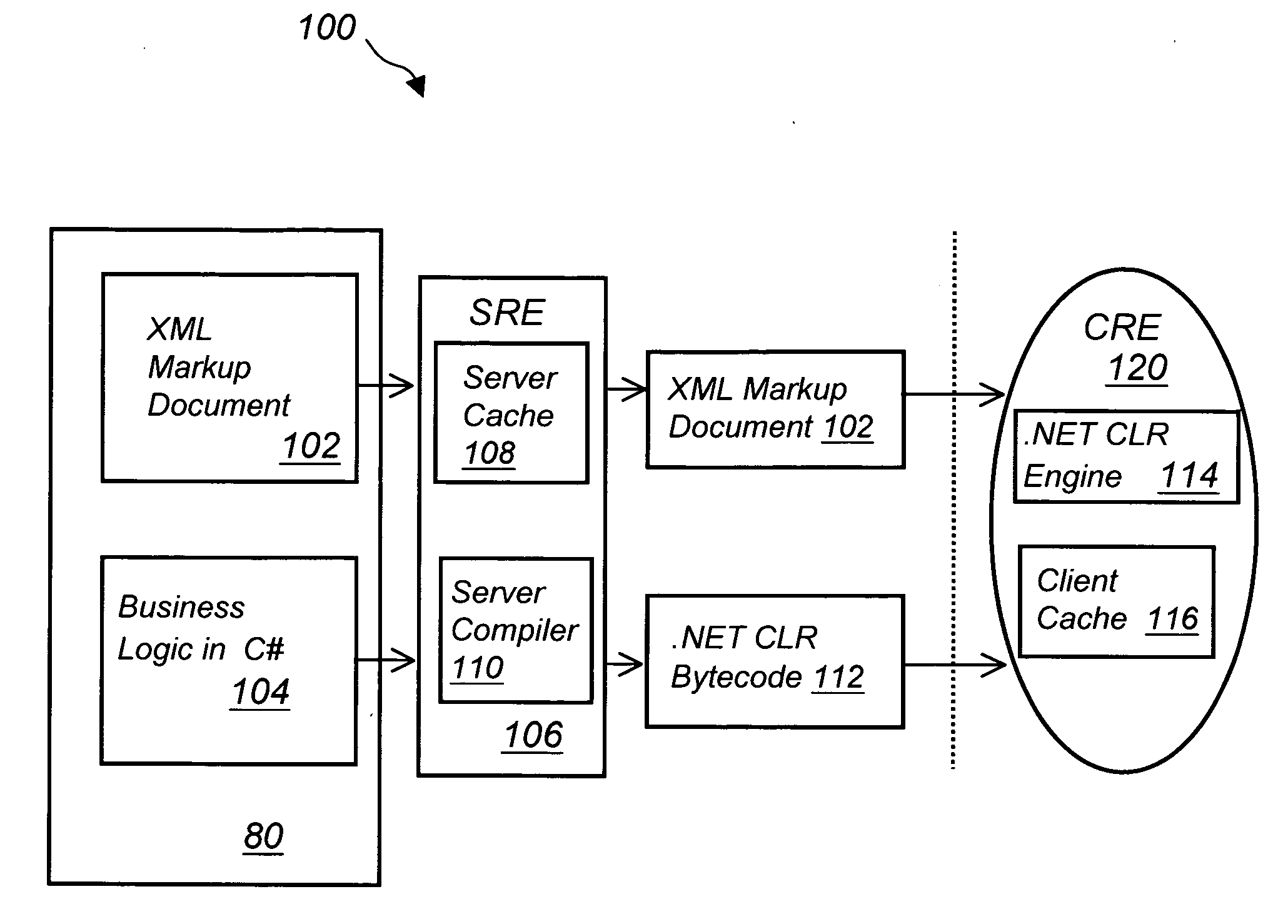
System and method for developing and deploying computer applications over a network
InactiveUS20050155027A1Reduce bandwidth costsReduce maintenance costsNatural language data processingProgram loading/initiatingVisual BasicOperational system
A method of developing a computer application by coding a markup document in an XML markup language, coding a business logic component using any programming language, compiling the business logic component into a specific executable code, converting the XML document into a specific markup language document and deploying the converted markup document and the executable code to a client machine running a specific operating system via a network connection. The XML markup document can be converted in any markup language including XUL, SVG, Xforms, XML related languages, HTML, HTML related languages, text, and combinations thereof. The business logic component can be written using any programming language including Java, JavaScript, J#, C#, C, C++, Visual Basic, ActionScript, XSL, XQuery, and XPath, among others. The computer application can run in any operating system including next generation Windows Longhorn, Windows 2000, Linux, Unix, Apple or Palm operating systems, among others.
Owner:NEXAWEB
Mobile terminal and method of performing NFC payment using the mobile terminal
Provided is a mobile terminal that has a function of changing a payment credit card at the time of near field communication (NFC) payment in a low battery state, and a method of performing the NFC payment using the mobile terminal. In the mobile terminal according to the present invention, unlike in a mobile terminal in the related art in which payment is simply performed with a default credit card, if the NFC payment is requested in the low battery state where the mobile terminal is powered off, a payment application based on a light operating system, which is executed on an embedded Linux, is displayed, and the NFC payment with a credit card selected from the payment application based on the corresponding light operating system is performed. Therefore, a credit card payment can be effectively performed in a low battery state as well.
Owner:LG ELECTRONICS INC
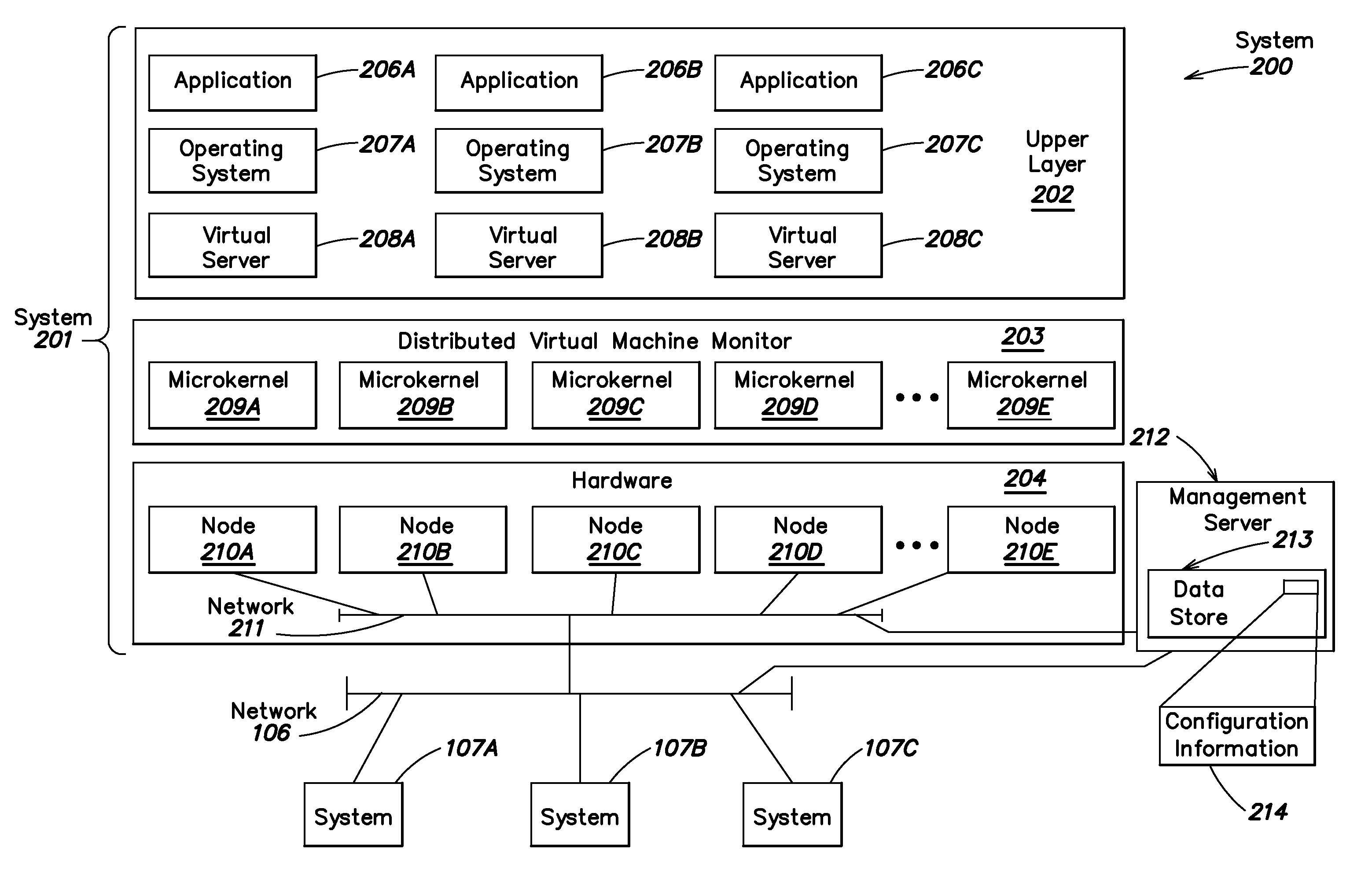
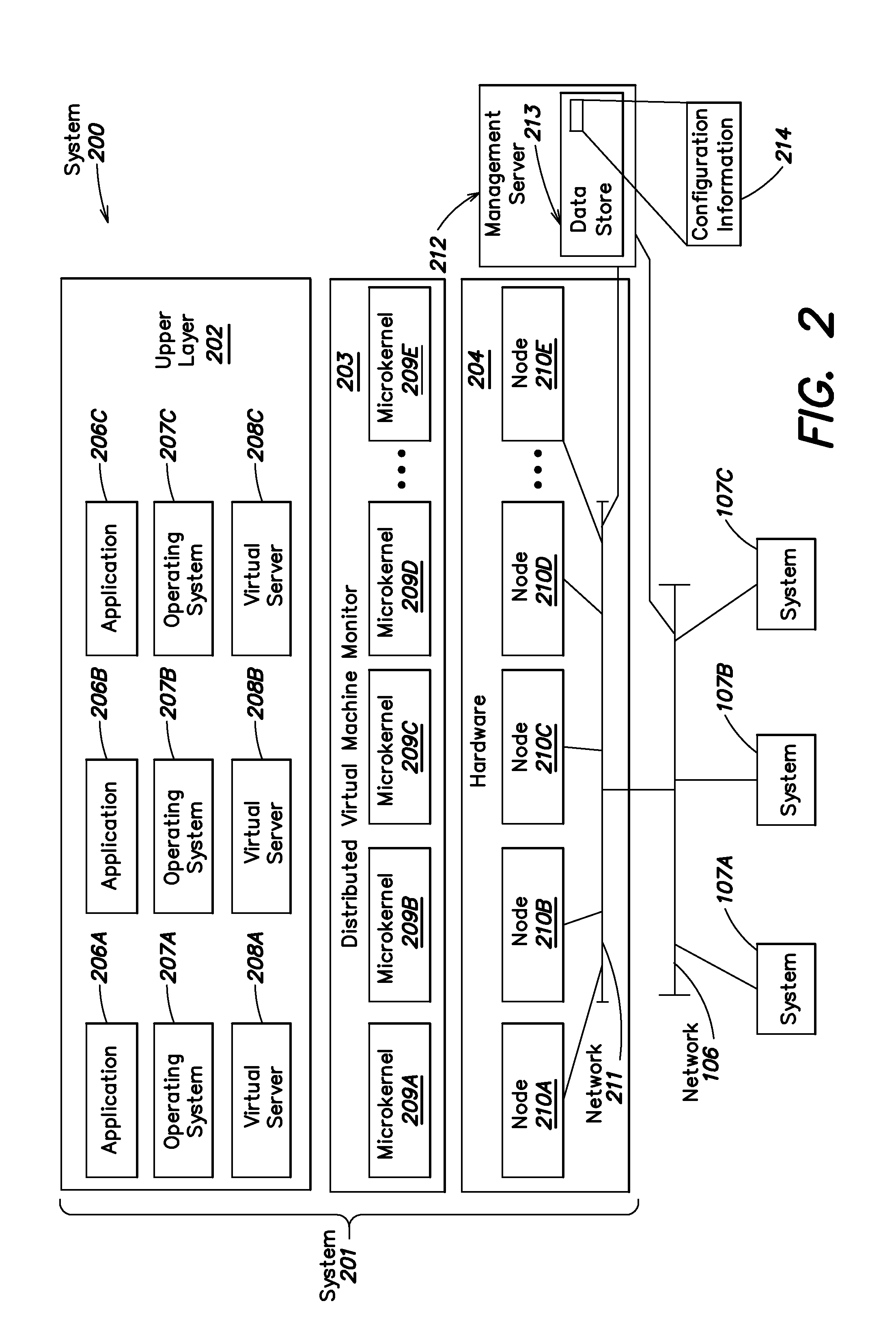
Distributed virtual machine monitor for managing multiple virtual resources across multiple physical nodes
ActiveUS8776050B2Grow and shrink capabilityMaximize useResource allocationMemory adressing/allocation/relocationOperational systemGNU/Linux
A management capability is provided for a virtual computing platform. In one example, this platform allows interconnected physical resources such as processors, memory, network interfaces and storage interfaces to be abstracted and mapped to virtual resources (e.g., virtual mainframes, virtual partitions). Virtual resources contained in a virtual partition can be assembled into virtual servers that execute a guest operating system (e.g., Linux). In one example, the abstraction is unique in that any resource is available to any virtual server regardless of the physical boundaries that separate the resources. For example, any number of physical processors or any amount of physical memory can be used by a virtual server even if these resources span different nodes.
Owner:ORACLE INT CORP
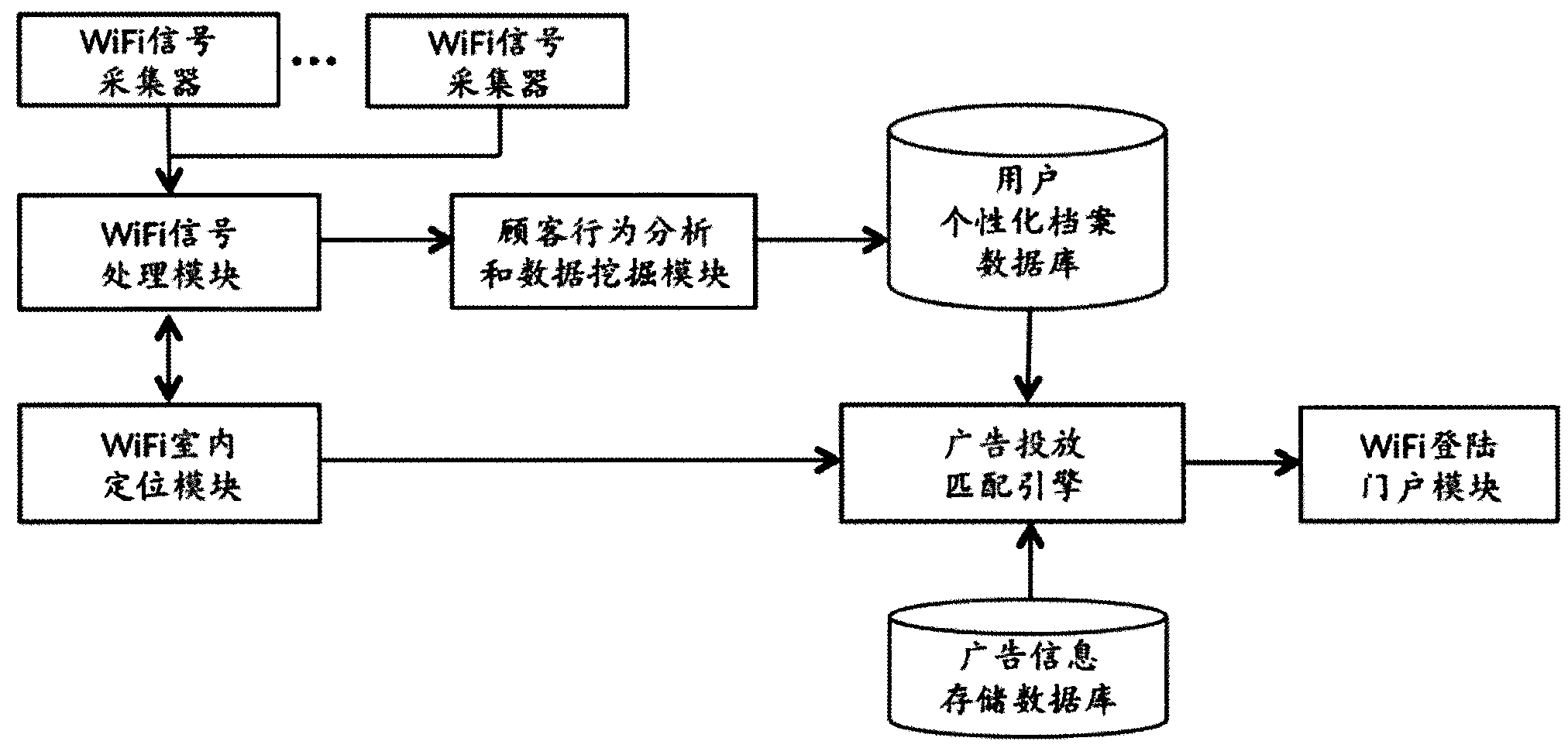
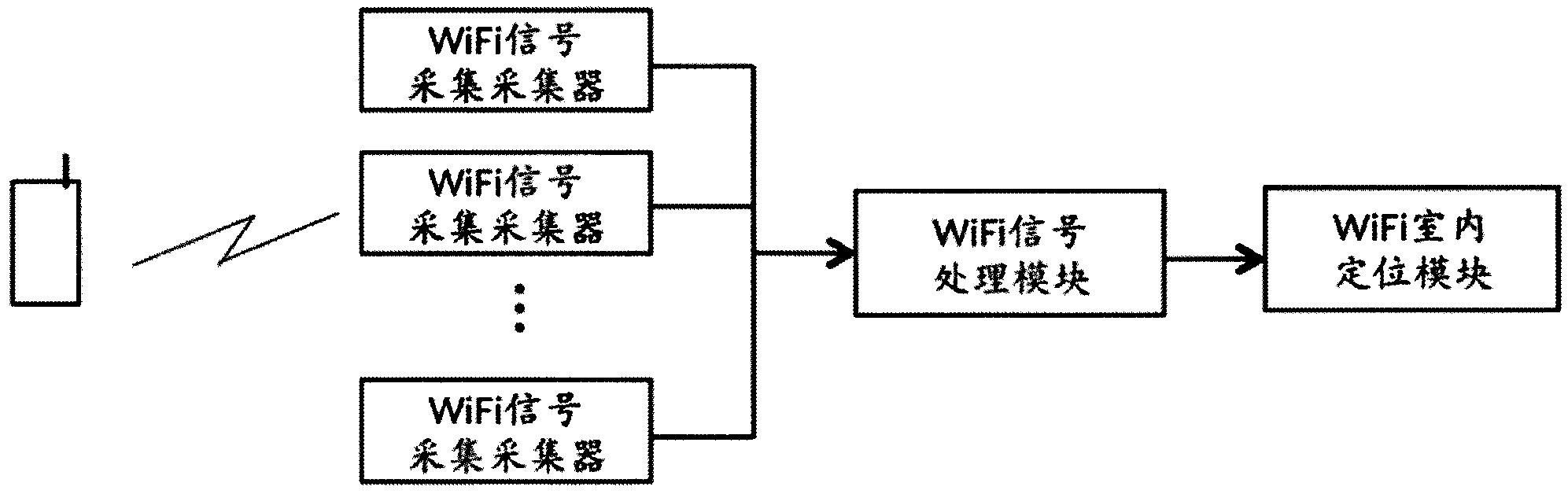
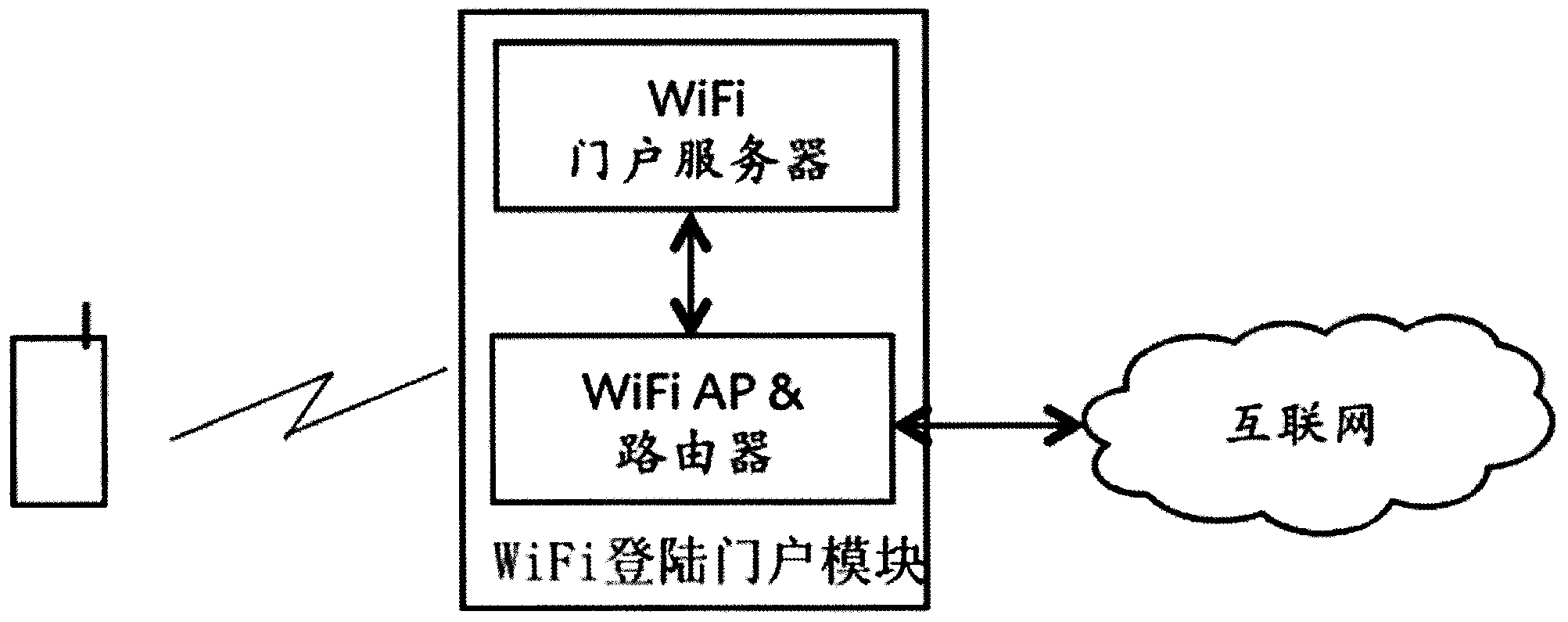
Information pushing system of WiFi (wireless fidelity) terminal and implementation method thereof
ActiveCN103402177AImprove experienceReal-time field precision marketingBroadcast service distributionMessaging/mailboxes/announcementsPersonalizationBehavioral analytics
The invention discloses an information pushing system of a WiFi (wireless fidelity) terminal and an implementation method thereof. The system comprises a WiFi signal collector, a WiFi signal processing module, a WiFi indoor positioning module, a customer activity analyzing and data mining module, a user personality file database, an advertisement information storage database, an advertisement putting and matching engine and a WiFi logging portal module. The system is suitable for all terminals with the WiFi function, such as mobile phones, PADs (personal access device) and PCs (personal computer), and different software platforms, such as Andriod, wP, iOS, Windows, MAC OS and Linux, the WiFi terminals do not need any software modification and updating, and the applicable range is wide. The possible hobby of a consumer is judged through data analysis and mining, and the real-time and on-site precise marketing is realized for target users, so on one hand, the experience of the user consuming in business places is improved, and on the other hand, the commercial value of sellers and factories is improved.
Owner:江苏数原信息技术有限公司
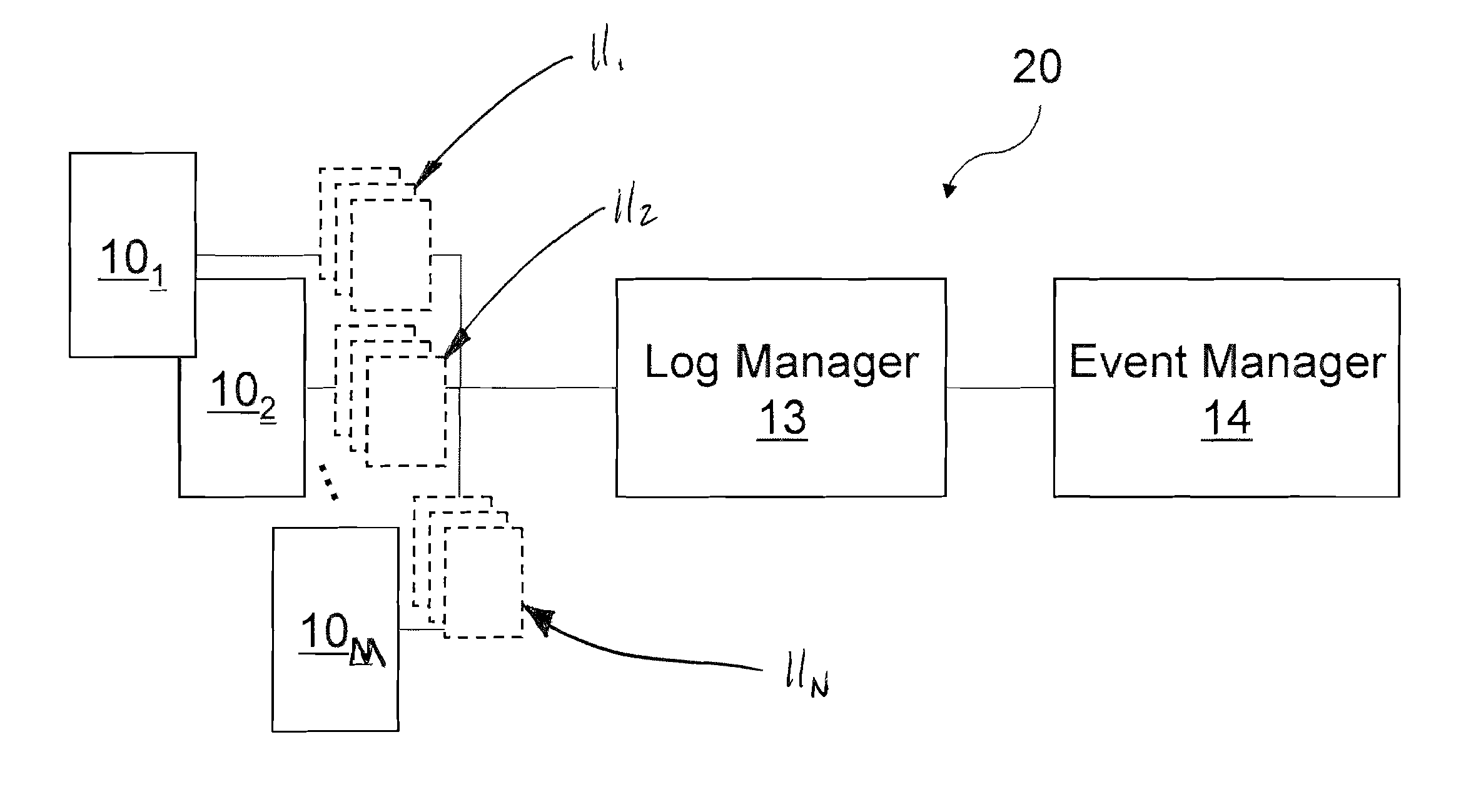
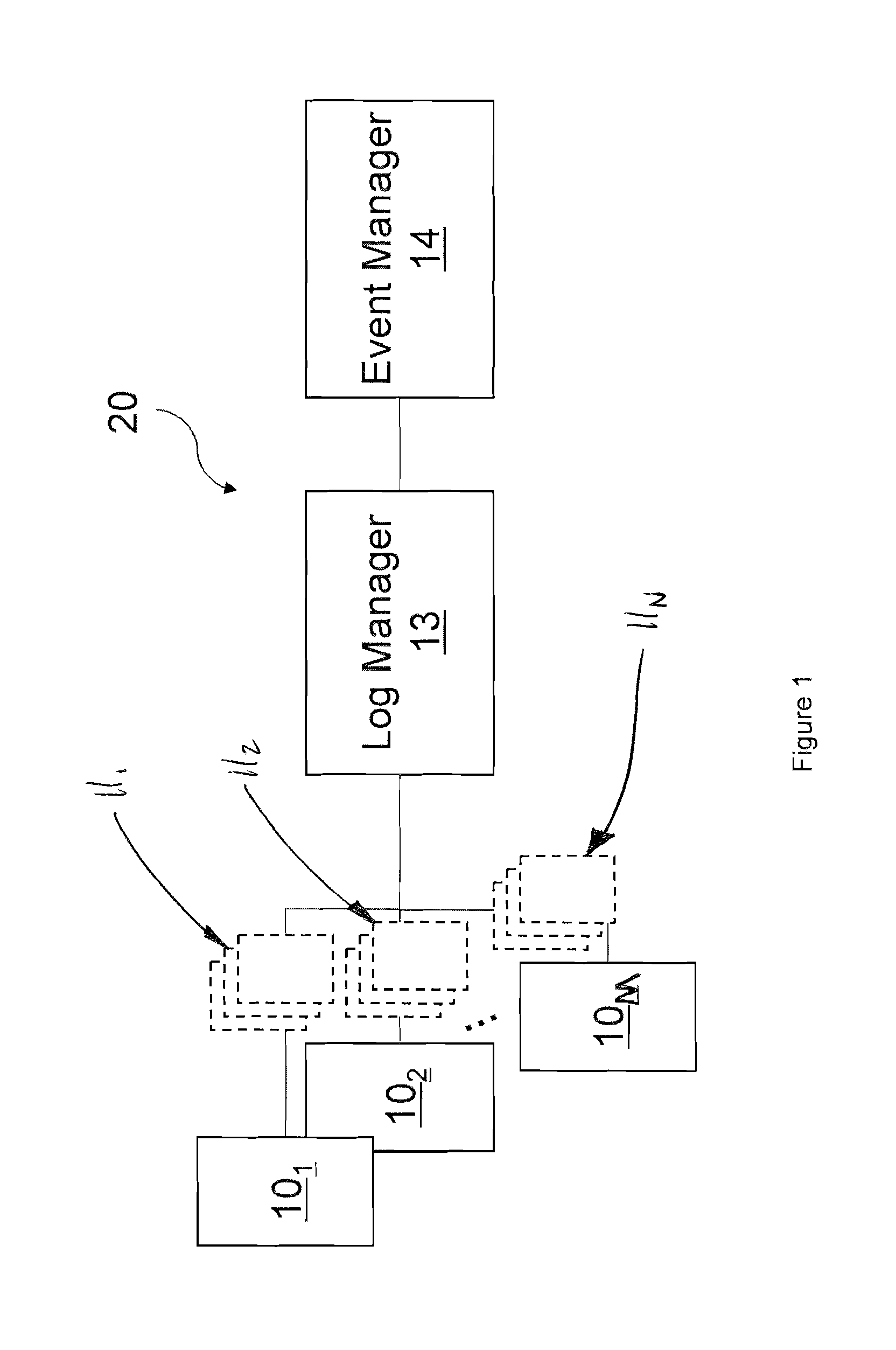
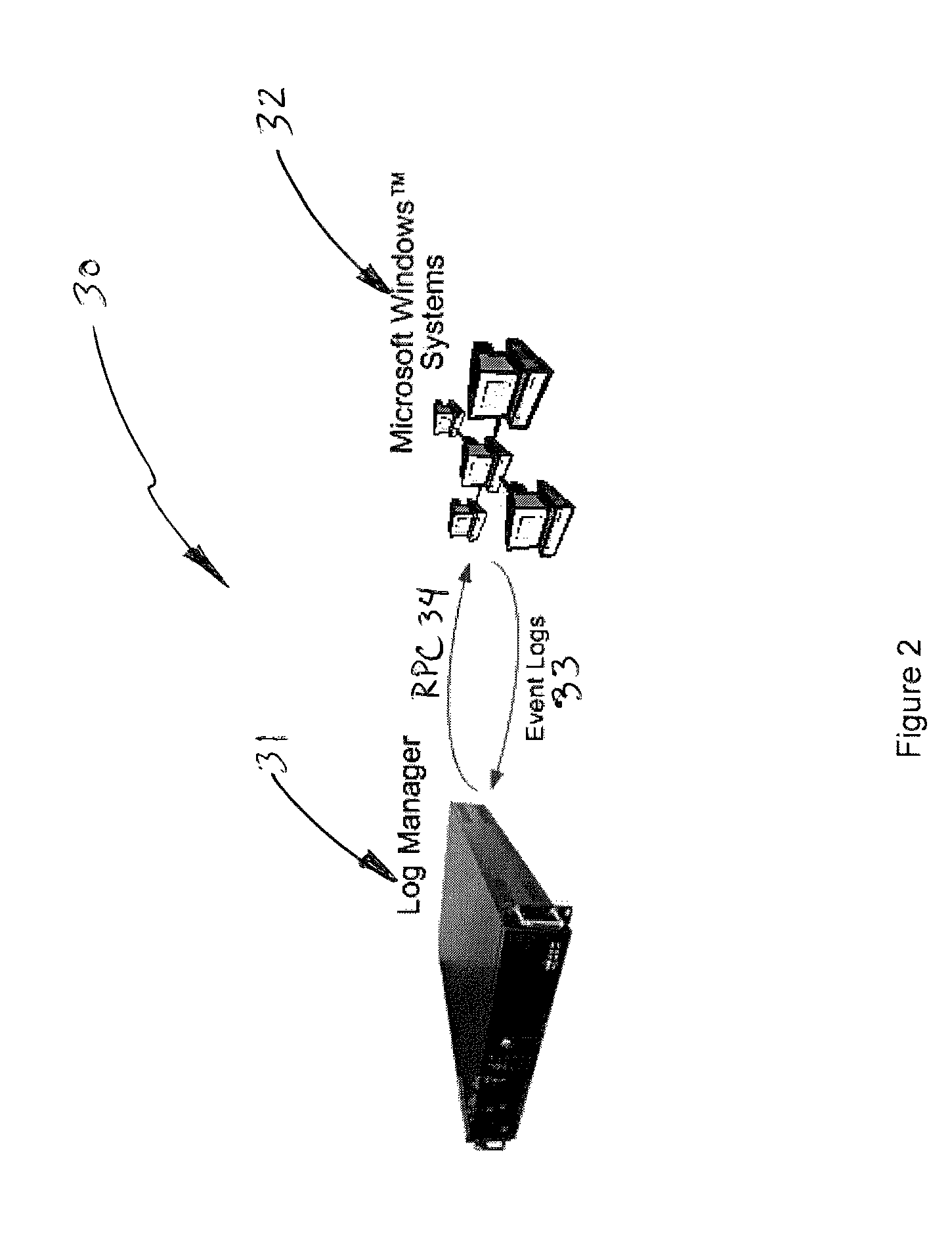
Log collection, structuring and processing
ActiveUS7653633B2Facilitates automated selective accessEasy to processMultiplex system selection arrangementsError detection/correctionUnixLog management
The present invention generally relates to log message processing such that events can be detected and alarms can be generated. For example, log messages are generated by a variety of network platforms (e.g., Windows servers, Linux servers, UNIX servers, databases, workstations, etc.). Often, relatively large numbers of logs are generated from these platforms in different formats. A log manager described herein collects such log data using various protocols (e.g., Syslog, SNMP, SMTP, etc.) to determine events. That is, the log manager may communicate with the network platforms using appropriate protocols to collect log messages therefrom. The log manager may then determine events (e.g., unauthorized access, logins, etc.) from the log data and transfer the events to an event manager. The event manager may analyze the events and determine whether alarms should be generated therefrom.
Owner:LOGRHYTHM INC
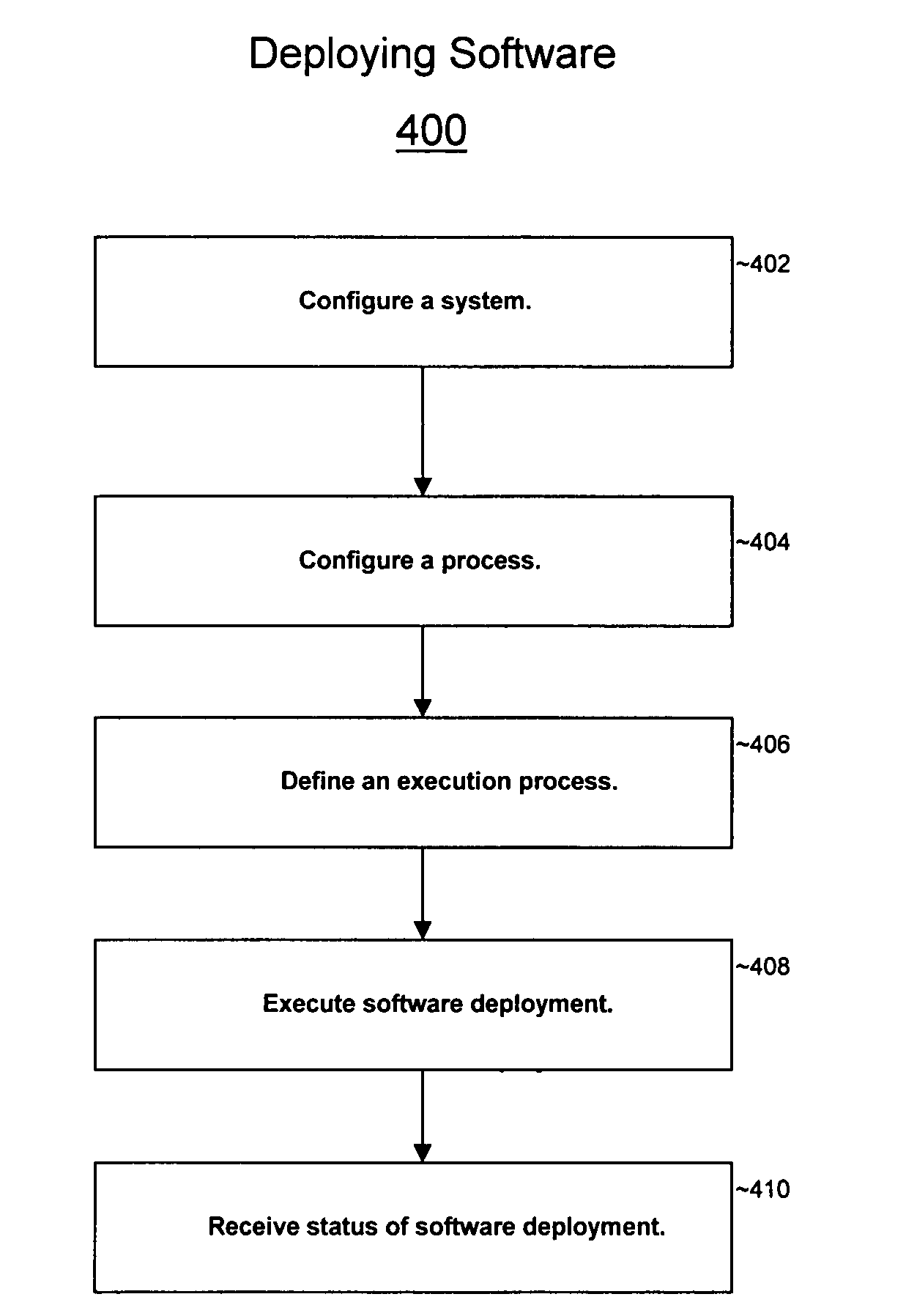
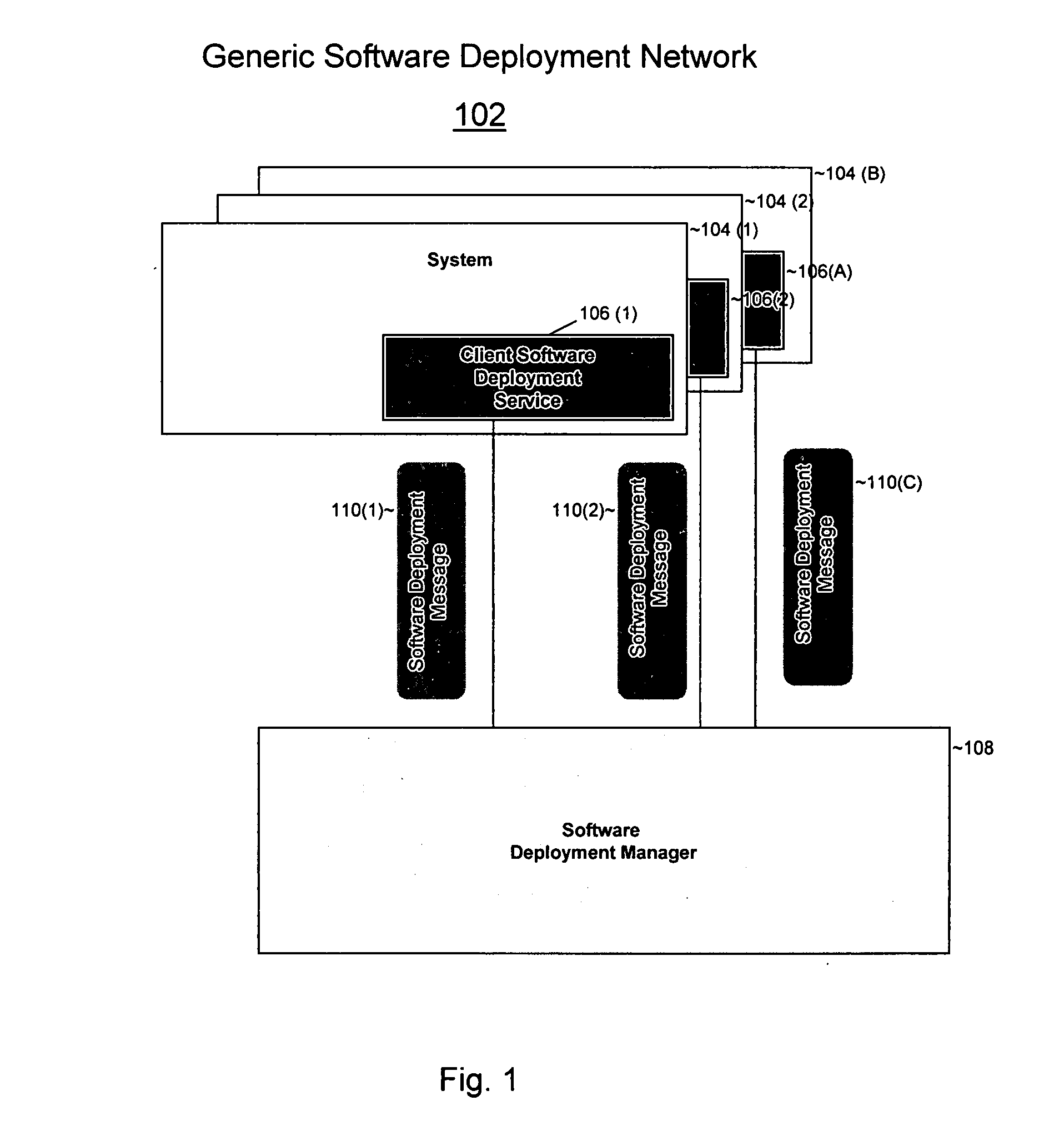
Software deployment system
The present invention provides a system and method for deploying software onto multiple heterogeneous systems at the same time. A generic software deployment manager may deploy software by communicating with client software deployment services residing on the systems that are receiving the software deployment. The software deployment manager can operate independent of the software and the operating system on which software is being deployed by communicating with the client software deployment service. To execute a software deployment, the software deployment manager may send software deployment messages containing generic commands that signify operations to be performed to deploy software. The client software deployment service provides an interface between the software deployment manager and the recipient system by translating these generic commands to commands that are compatible with the local operating system. The software deployment manager may transmit software deployment messages simultaneously to each of the systems within a system group or an environment so that software can be efficiently deployed without incompatibilities in the network. The software deployment manager may deploy software in Linux, Windows, Unix, Macatosh, Java, or any other operating system and may deploy any software.
Owner:SAP AG
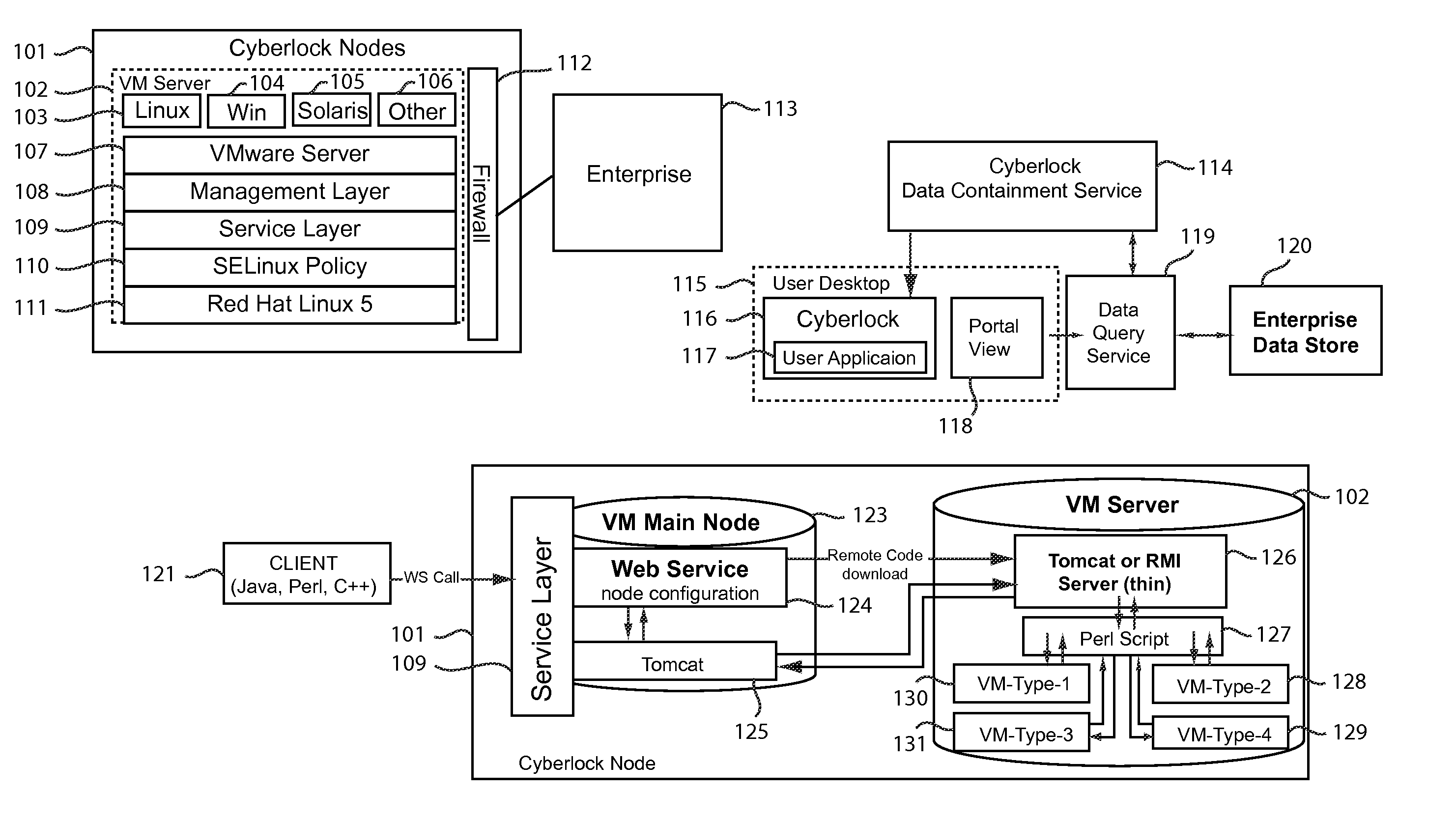
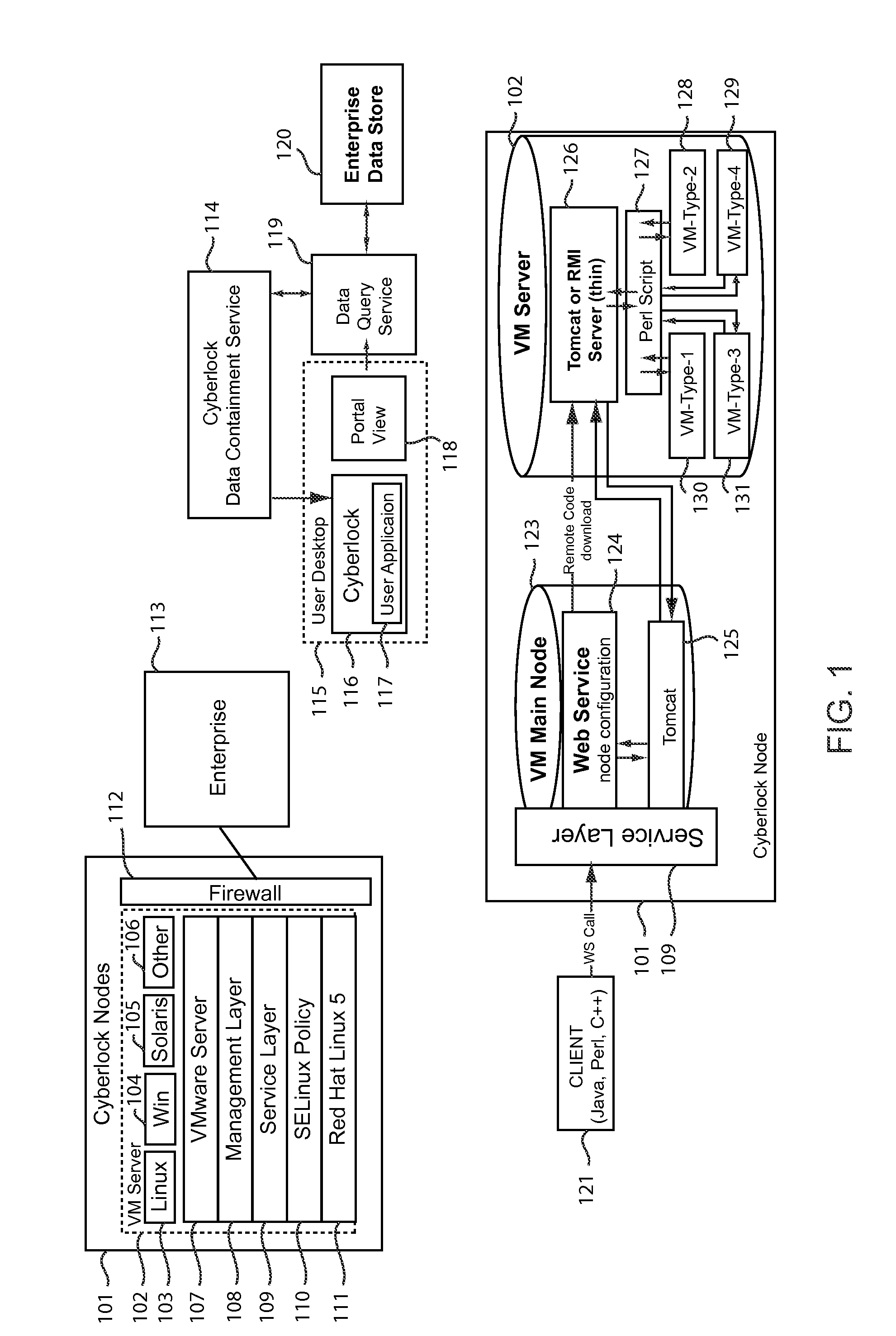
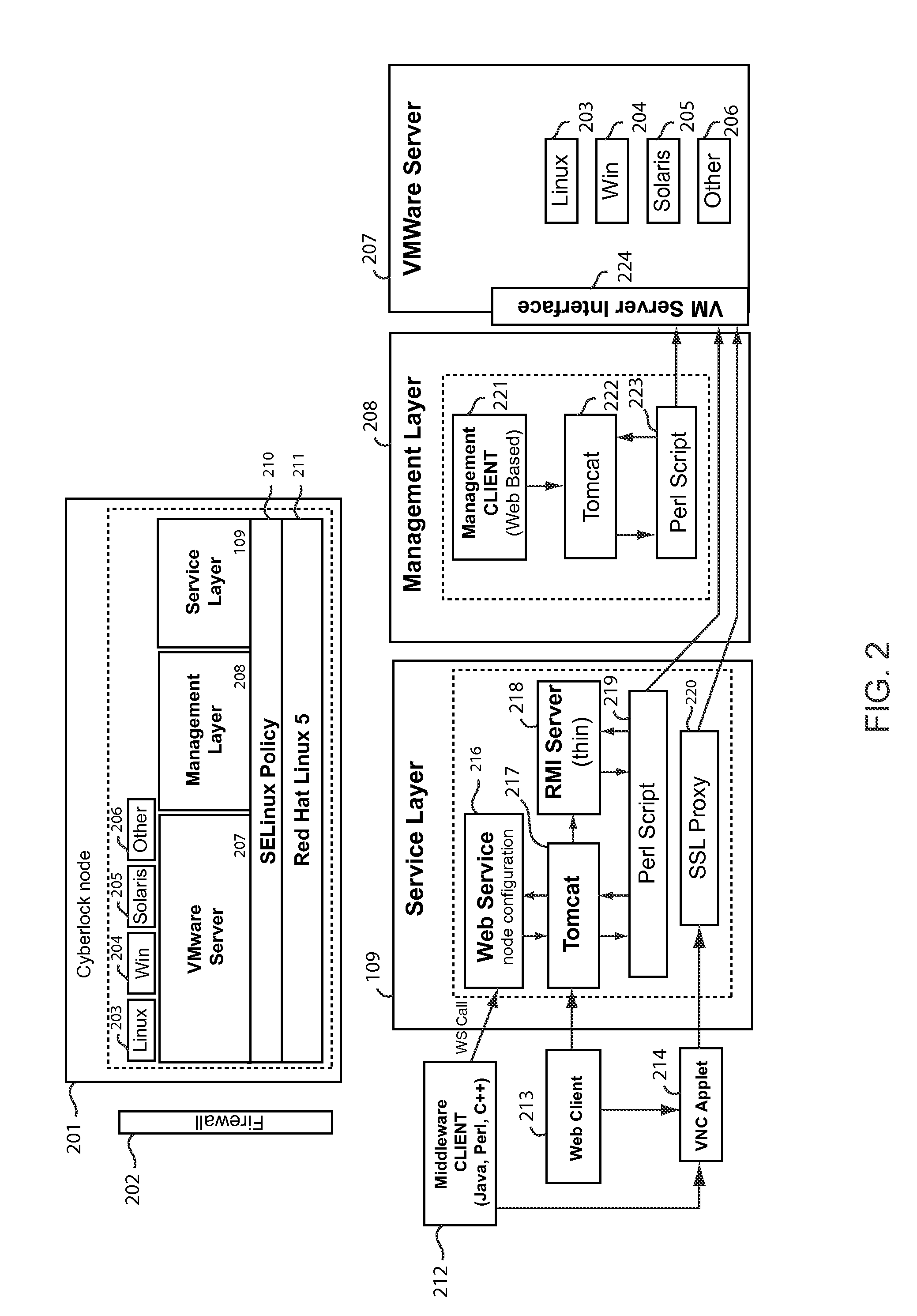
System and method for providing a virtualized secure data containment service with a networked environment
ActiveUS8756696B1NetworkingEffective strategyMemory loss protectionUnauthorized memory use protectionVirtualizationOperational system
The present invention relates to a technique for debugging and testing potential virus, trojans, and other malware programs. The present invention, named Cyberlock™ provides a technique to analyze malware programs on a network in a secure manner, which allows multiple users to access or monitor the analysis. In the present invention, a virtual machine (VM) may be run on a network, emulating the operation of a Windows, LINUX, or Apple operating system (or other O / S), and the malware or suspected malware may be executed on that virtual machine. The virtual machine is isolated on the network, but accessible to one or more users, in such a manner than the malware or suspected malware may be analyzed.
Owner:SRA INTERNATIONAL
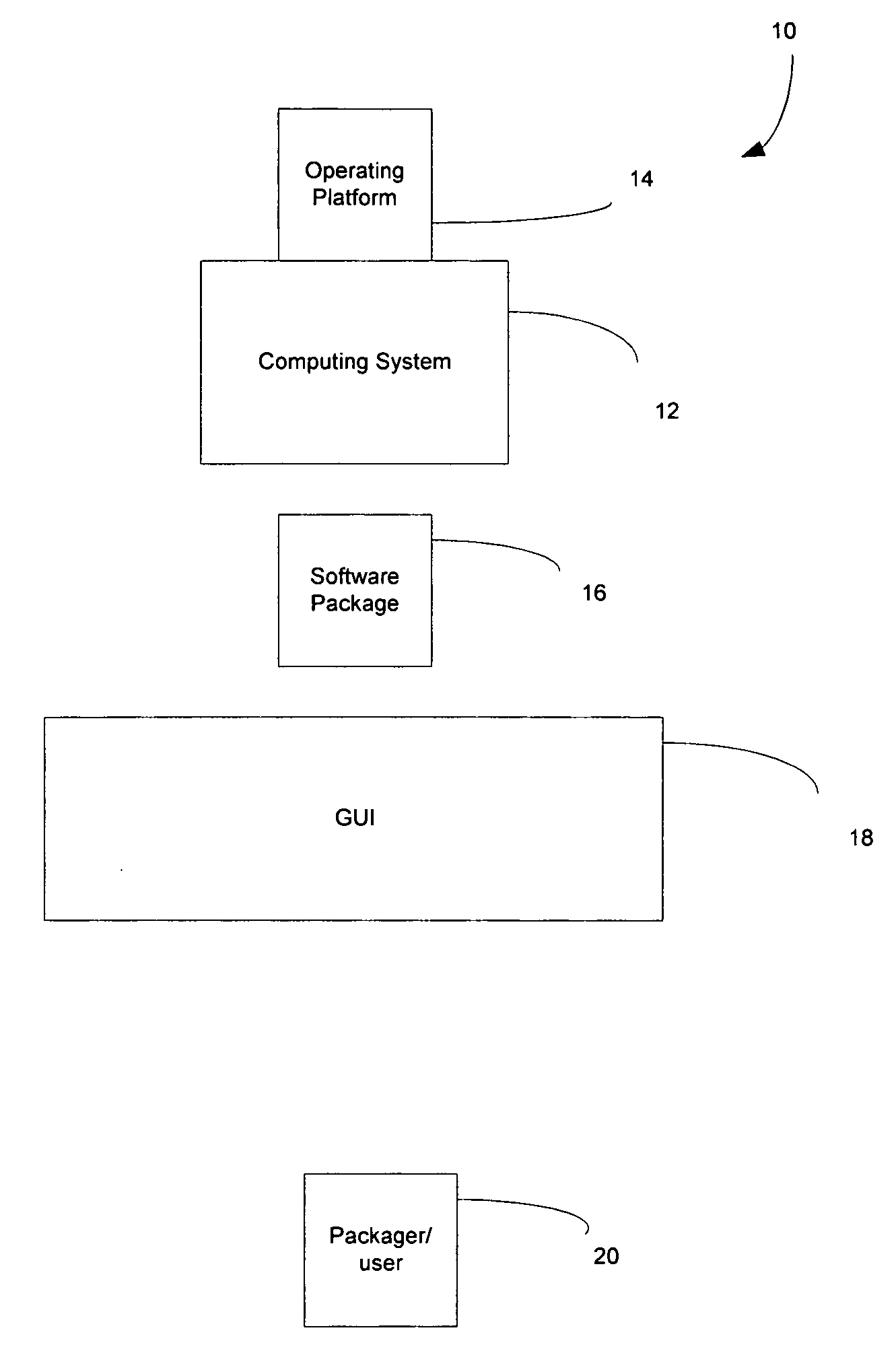
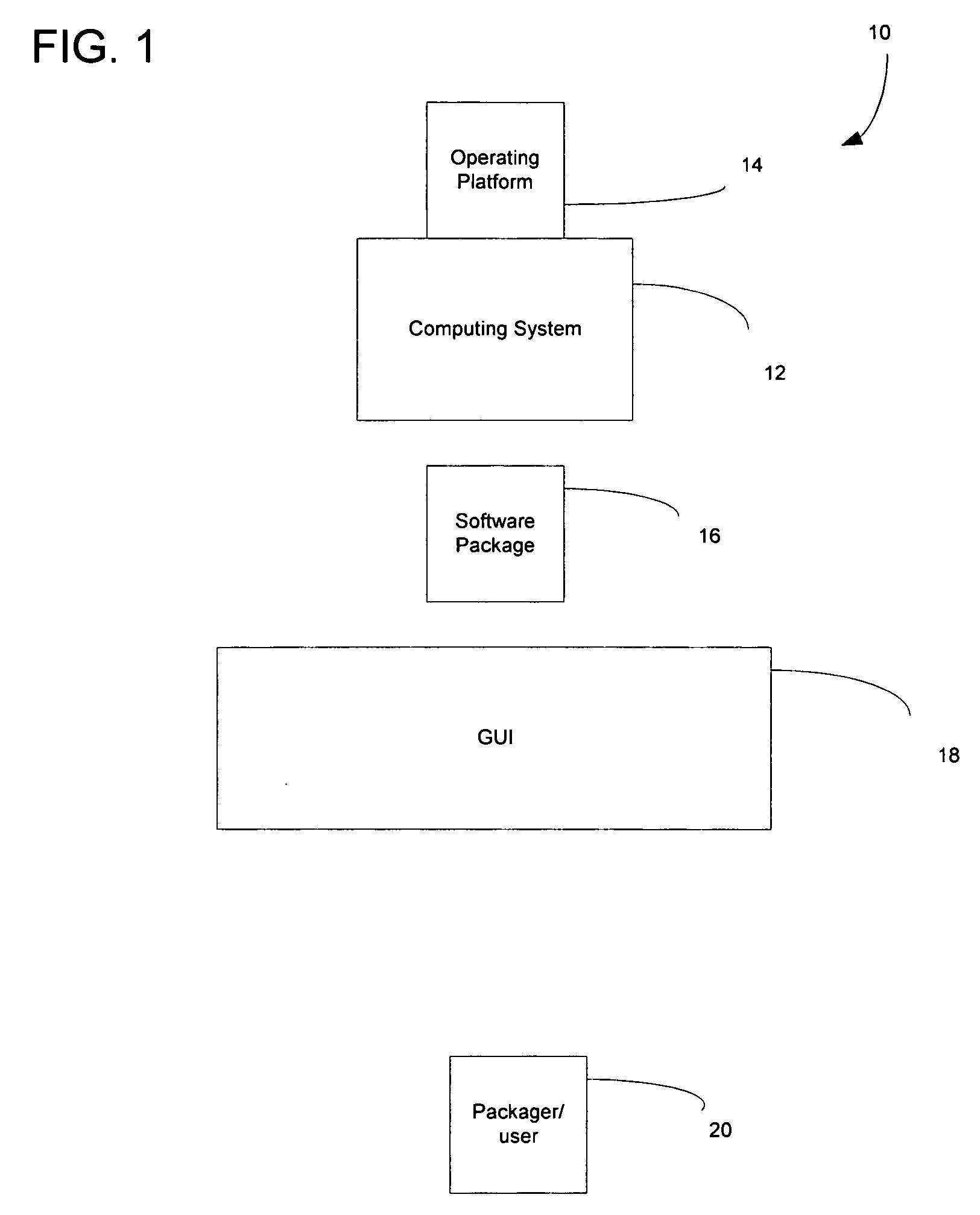
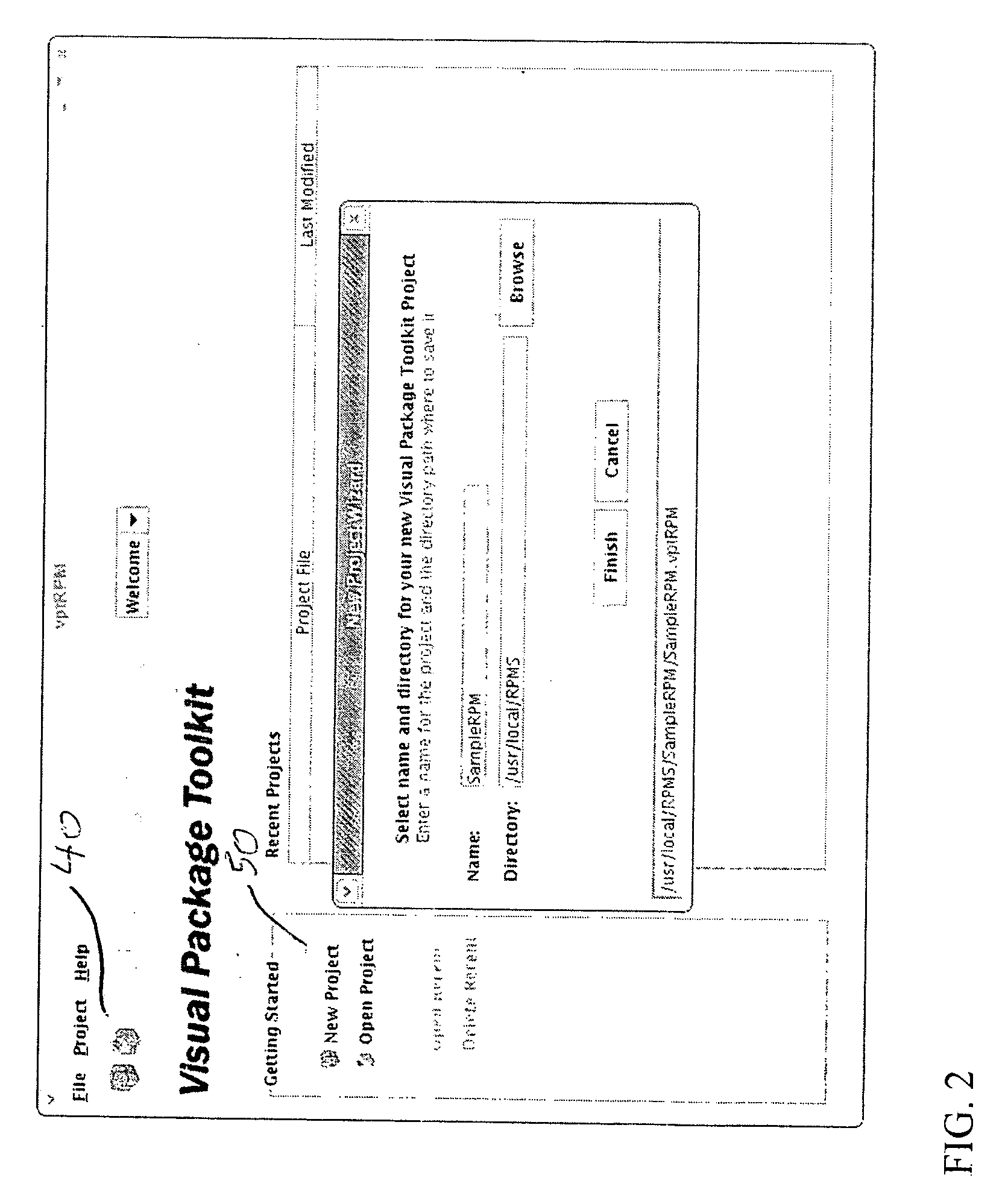
System and method for packaging software
A method and system for packaging software using a graphical user interface (GUI) to simplify the creation and modification of System V and Red Hat Package Manager (RPM) software packages. The software packaging system provides a fully interactive graphical interface portable across many platforms including Linux, Unix System V, Solaris, and AIX. RPM is a popular and powerful packaging system that installs and removes system software, enforces dependencies, and is freely available on a number of different platforms. The software packaging system of the present invention simplifies and speeds the creation of deployable RPM software packages, a complex and time consuming task if created using the RPM command line method. The GUI provides for the collection of information required for RPM software package creation, modification, and feature manipulation reducing the skill level and time that needed to perform these functions using the RPM command line.
Owner:NEXONE
Redundant multi-processor and logical processor configuration for a file server
A redundant file server includes at least two dual processor boards. Each physical processor has two logical processors. The first logical processor of the first physical processor of each board executes storage system code under the Microsoft NT(TM) operating system. The second logical processor of the first physical processor of each board executes control station code under the Linux operating system. The first logical processor of the second physical processor of each board executes data mover code. The second logical processor of the second physical processor of each board is kept in a stand-by mode for assuming data mover functions upon failure of the first logical processor of the second physical processor on the first or second board.
Owner:EMC IP HLDG CO LLC
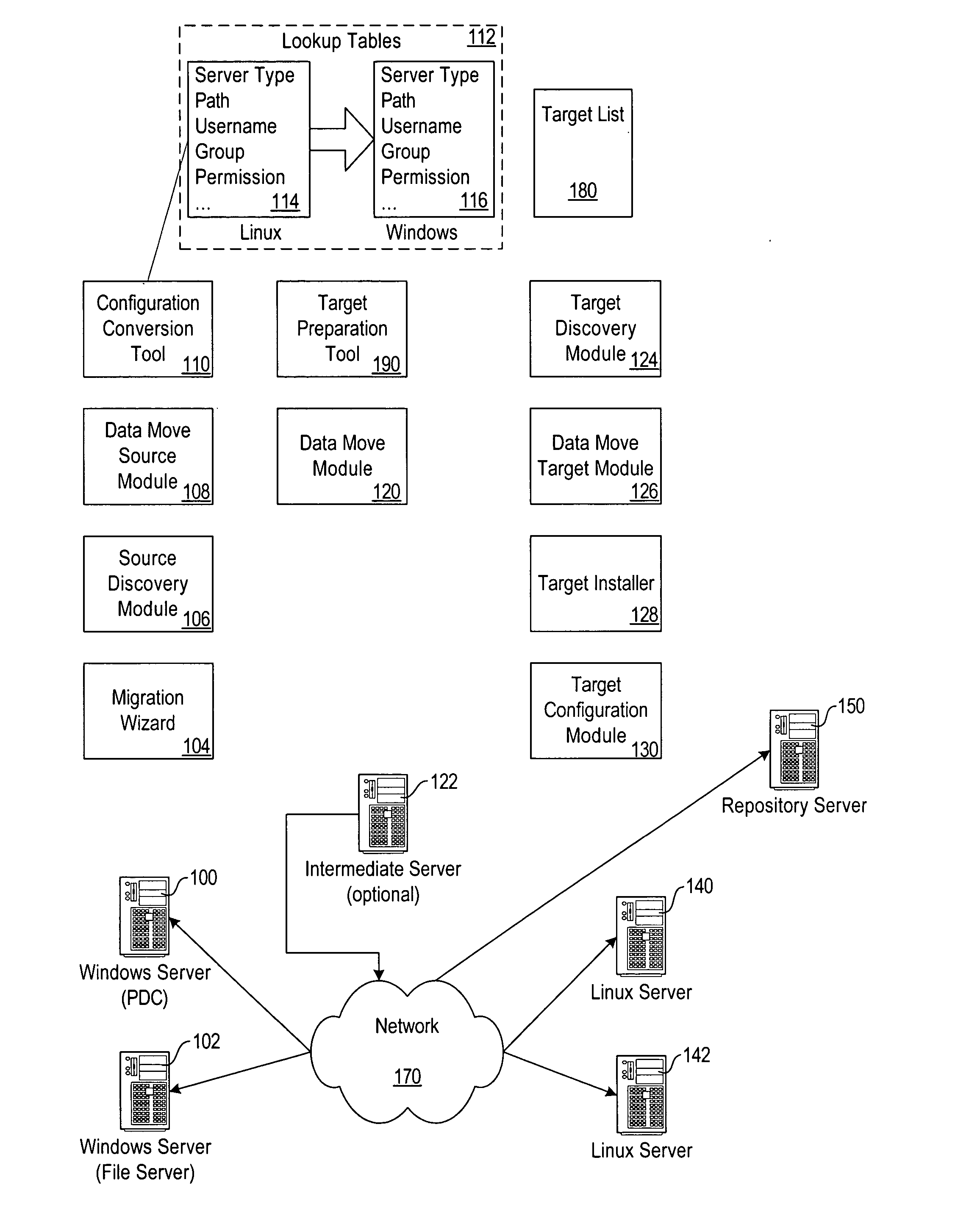
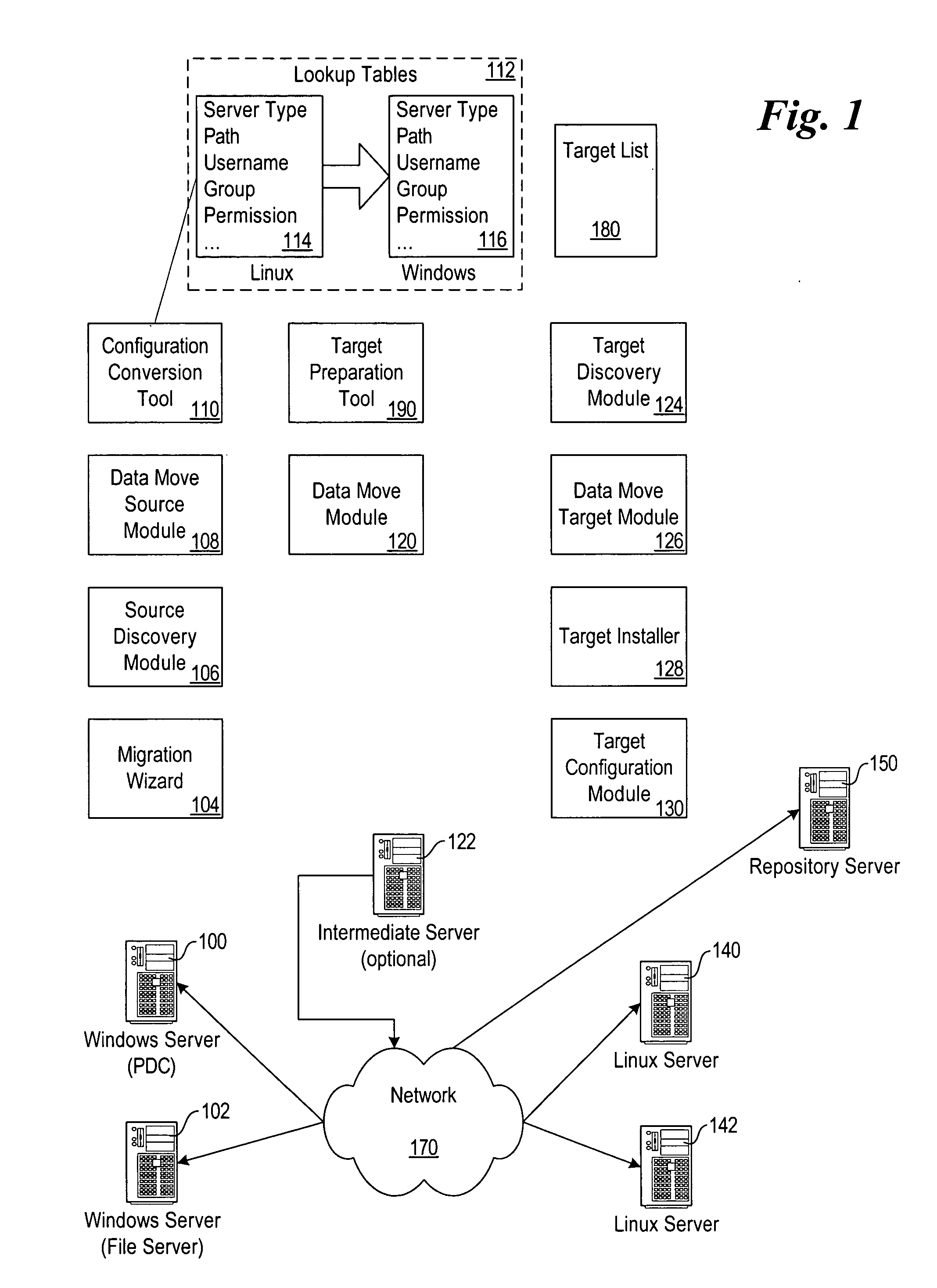
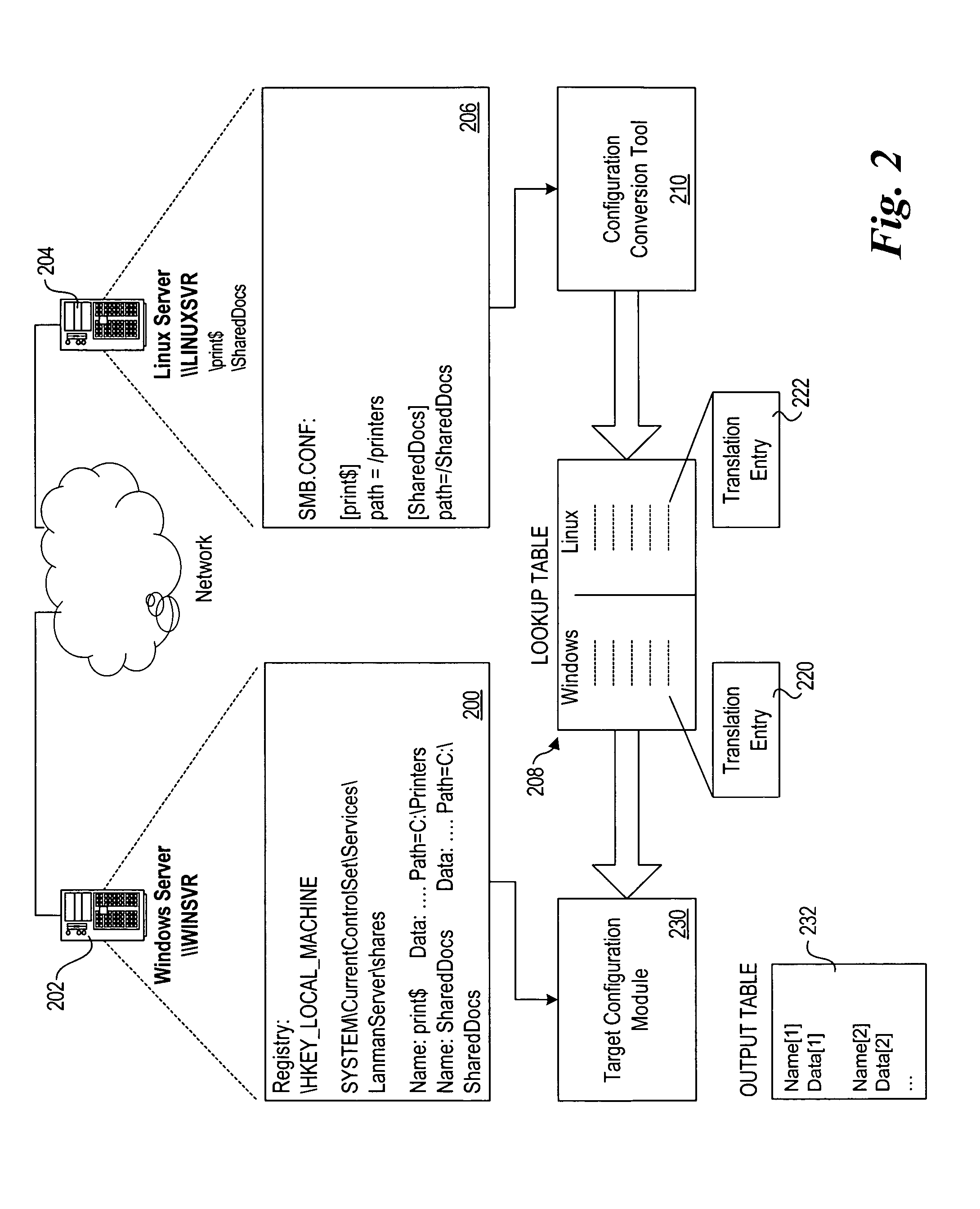
System and method for automated migration from Linux to Windows
A system and method for automating the migration of configuration settings and data from computer systems running the Linux operating system to computer systems running the Windows operating system. The invention utilizes data from one or more sources to create the configuration of the target system, and translates between settings related to the Linux systems and Windows systems involved. As a result, it simplifies the otherwise complex and time-consuming task of migrating from one server to another, specifically when migrating between two operating systems that provide similar functionality but are configured in distinctly different ways.
Owner:BEYONDTRUST
Content filtering gateway realizing method based on network filter
InactiveCN101068229AEasy maintenanceNot easy to attackNetwork connectionsInternal memoryCommunications security
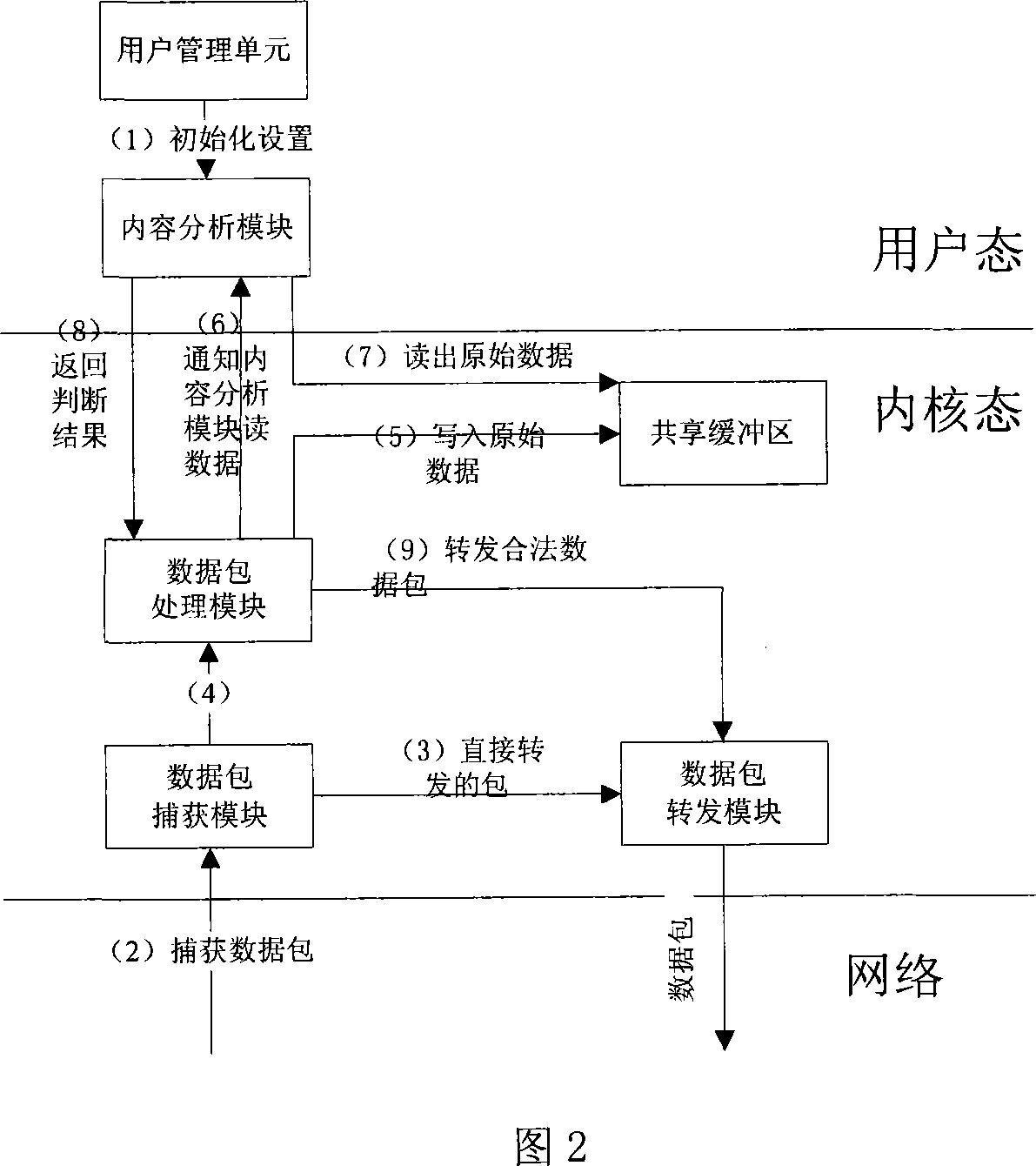
A method for realizing content filtering gateway based on network filter includes realizing network content analysis and real time monitor as well as realizing purpose of filtering application layer information at network layer based on Linux system platform, utilizing network filter Net-filter frame to carry out collection and filtering on data packet under kernel state for optimizing network path of data packet and for raising collection efficiency of data, furthermore using shared internal memory technique of user space and kernel space to submit session content from kernel state to content filtering module of user state.
Owner:BEIJING UNIV OF TECH
Method for dynamically monitoring performance of server cluster and alarming real-timely
InactiveCN101707632AMonitor running status in real timeAdd or remove nodesData switching networksOperational systemData information
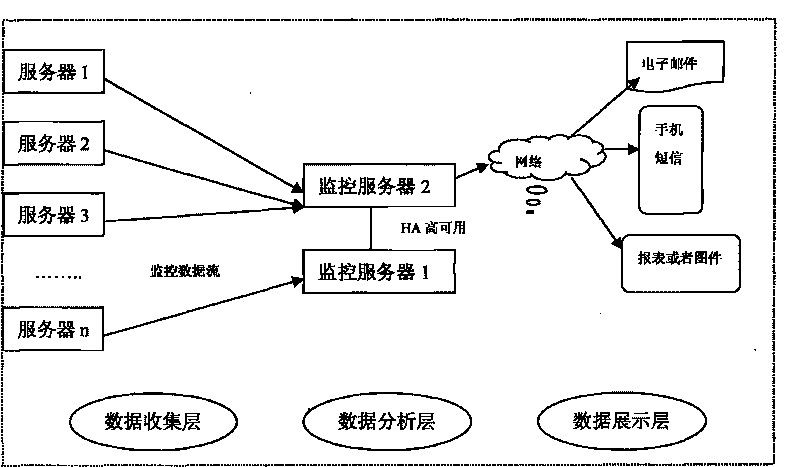
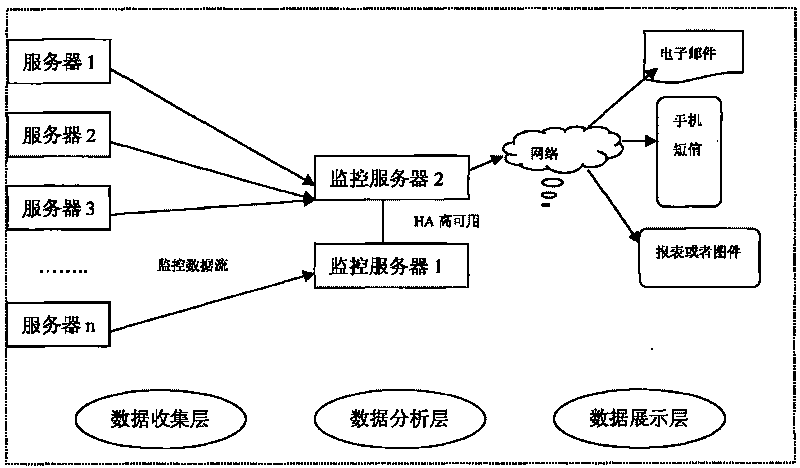
The invention discloses a method for dynamically monitoring the performance of a server cluster and alarming real-timely, which comprises a server cluster. All the servers adopt a Linux operating system, and the architecture comprises a data collection layer, a data analysis layer and a data presentation layer; the data collection layer comprise the server cluster, the data analysis layer comprise monitor servers, and the data presentation layer comprises emails, short messages, report forms or maps; and the monitor servers of the data analysis layer monitor the servers of the data collection layer through a network, and the data analysis layer transmits monitoring data to the data presentation layer through the network. Compared with the prior art, the method for dynamically monitoring the performance of the server cluster and alarming real-timely has the advantages that a Linux-based platform can collect, analyze and present the performance data of the server, and real-time alarming can be realized, the obtained data information is timely and accurate, the method is flexible and convenient, and occupancy rate for server resources is low.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Trusted computer system
InactiveUS7103914B2Improve robustnessHigh level of assuranceMemory loss protectionDigital data processing detailsOperational systemGNU/Linux
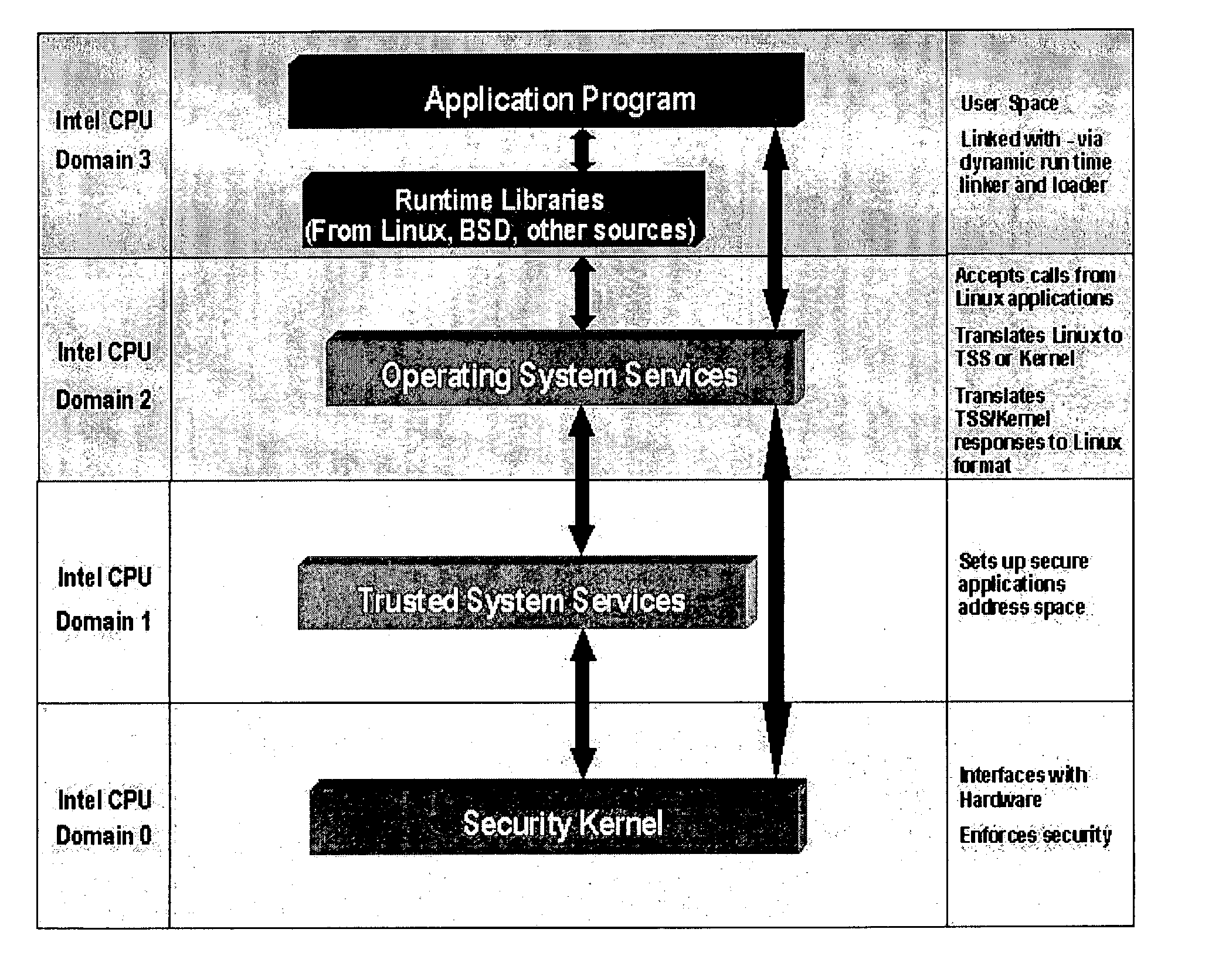
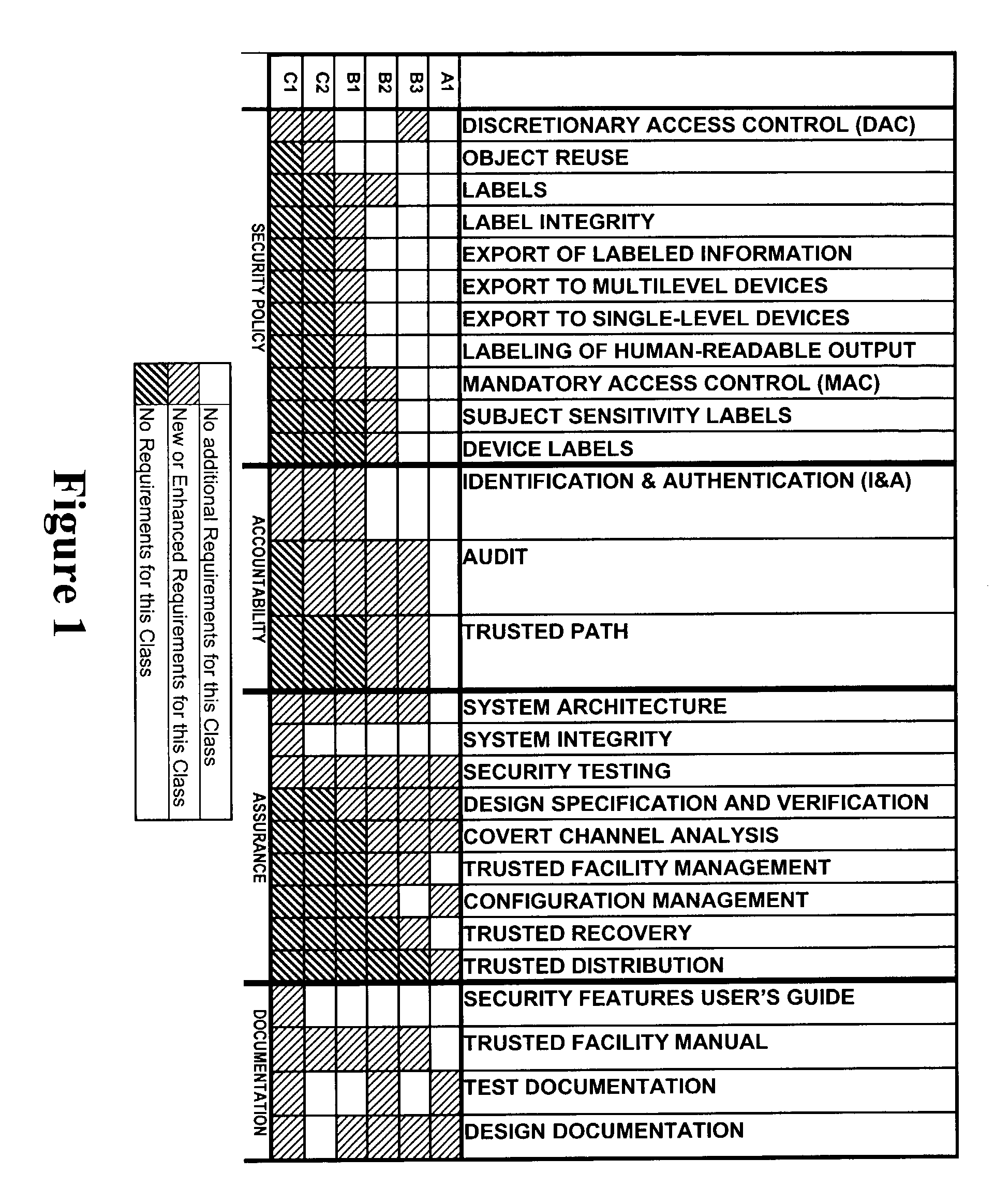
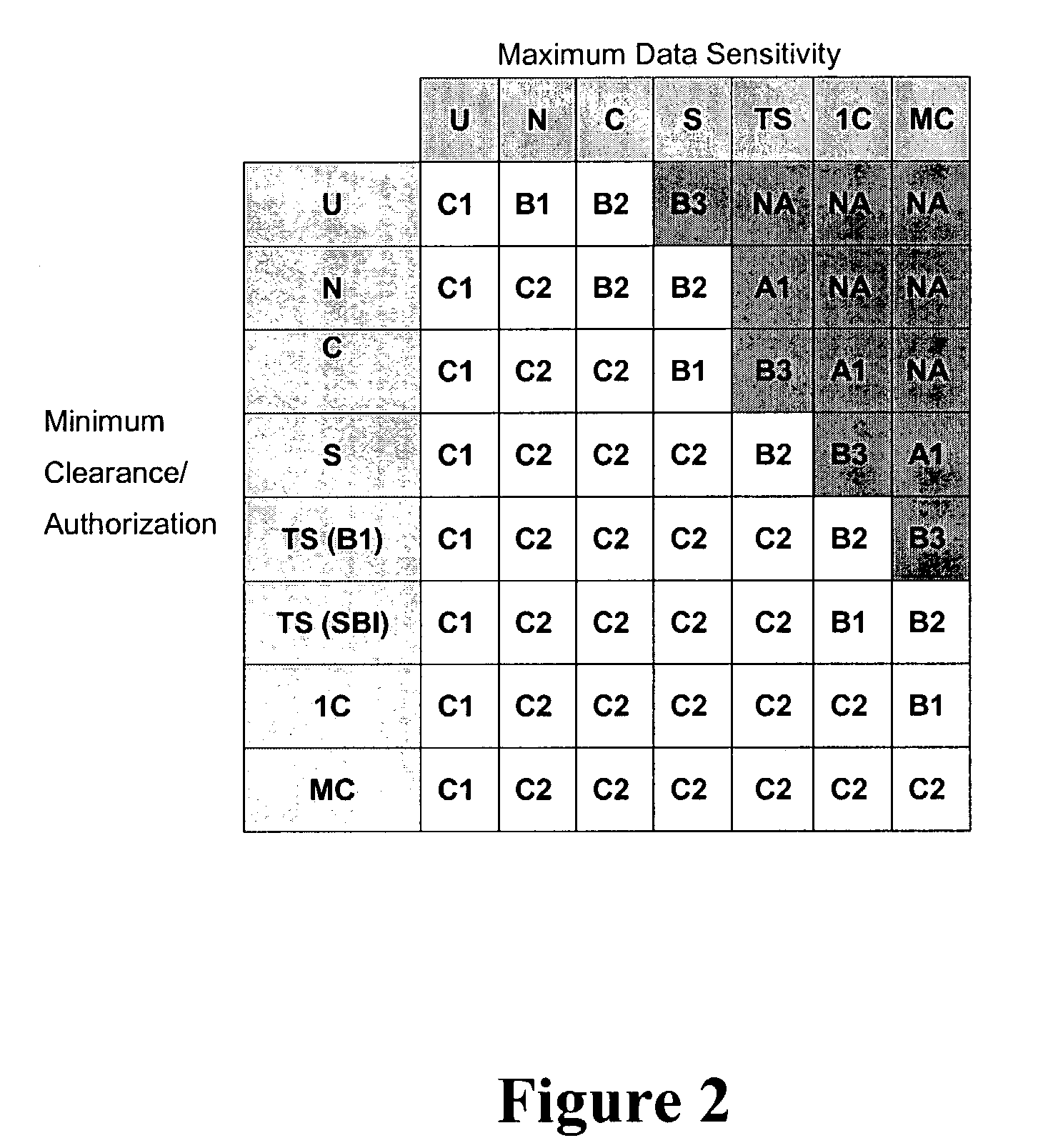
A trusted computer system that offers Linux® compatibility and supports contemporary hardware speeds. It is designed to require no porting of common applications which run on Linux, to be easy to develop for, and to allow the use of a wide variety of modern development tools. The system is further designed to meet or exceed the Common Criteria EAL-5 or higher rating through incorporation of required security features, as well as a very high level of assurance for handling data at a wide range of sensitivity (e.g., classification) levels in a wide range of operational environments. This is achieved through the implementation of a well-layered operating system which has been designed from the ground up to enforce security, but which also supports Linux operating system functions and methods.
Owner:BAE SYST INFORMATION & ELECTRONICS SYST INTERGRATION INC +1
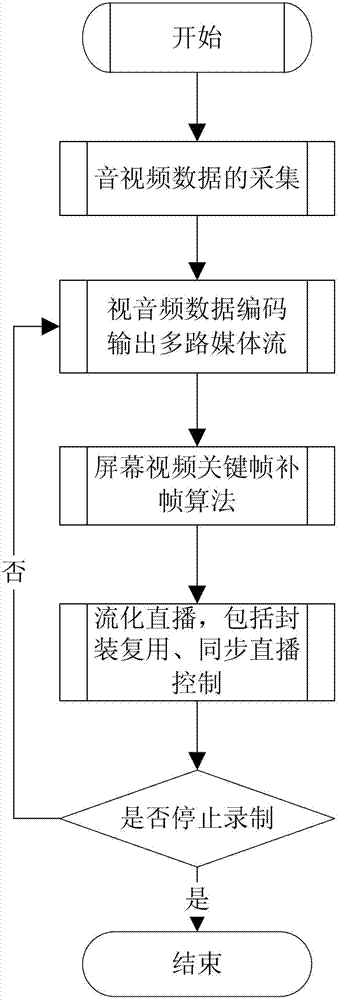
Multi-scene streaming media courseware recording and direct-broadcasting method
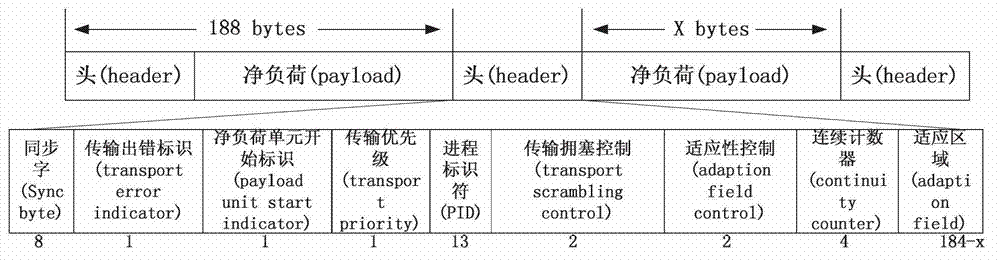
ActiveCN102821308ASupport synchronous controlRealize synchronous controlTelevision system detailsColor television detailsFile synchronizationComputer graphics (images)
The invention relates to a multi-scene streaming media courseware recording and direct-broadcasting method, which is characterized in that a recorded teacher camera video multimedia file is synchronized with a screen video multimedia file through a screen video key frame interpolation algorithm in recording; real-time video stream and real-time audio stream are coded to a transport stream (TS) file by synchronously encapsulating and multiplexing a video (PES) photoelectric scanning packet and an audio PES packet to be distributed to a web direct-broadcasting server, the teacher camera video and the screen video are synchronously broadcasted through the multi-video-source synchronous direct-broadcasting control. The method supports the windows / Linux cross-platform run and also supports the multi-source recording and stream direct-broadcasting technology of the teacher camera video, the teacher audio and the screen video, and the media courseware can be directly broadcasted while being recorded.
Owner:XI AN JIAOTONG UNIV
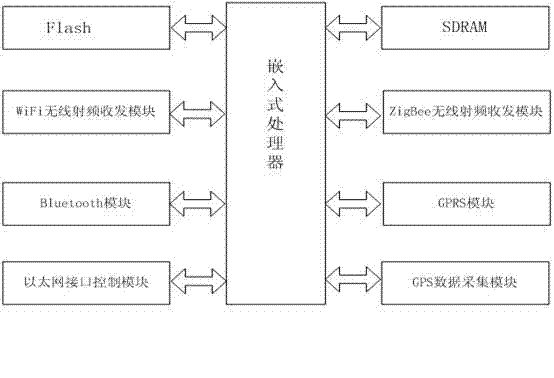
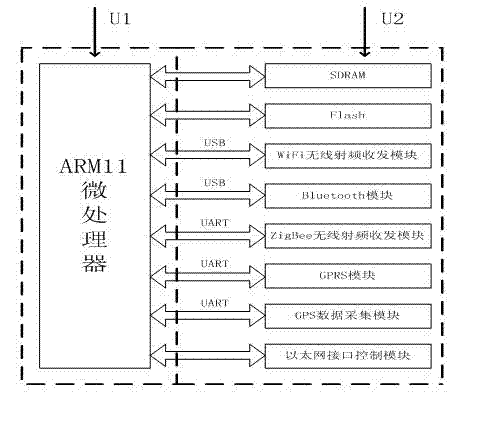
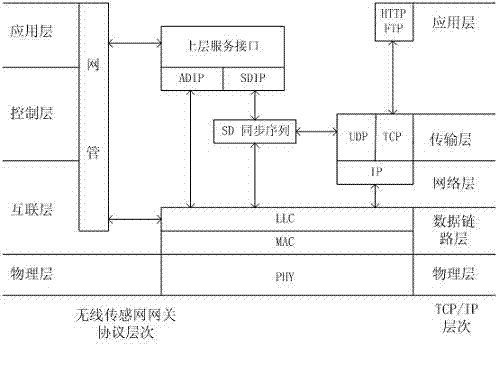
Multi-protocol multi-interface wireless sensor network gateway
InactiveCN102448202AImprove anti-interference abilityReduce power consumptionHigh level techniquesWireless communicationGeneral Packet Radio ServiceTransceiver
The invention discloses a multi-protocol multi-interface wireless sensor network gateway and relates to the technical field of a wireless sensor network. The gateway mainly consists of an embedded processor, an SDRAM (Synchronous Dynamic Random Access Memory), a Flash memory, a WiFi (Wireless Fidelity) wireless radio frequency transceiver module, a ZigBee wireless radio frequency transceiver module, a GPRS (General Packet Radio Service) module, a Bluetooth module, a GPS (Global Positioning System) data acquisition module and an Ethernet interface control module. A networked operating system Linux is used as an operating system of the multi-protocol multi-interface wireless sensor network gateway and can be compatible with a TCP / IP (Transmission Control Protocol / Internet Protocol) protocol IPv6 (Internet Protocol Version 6). The multi-protocol multi-interface wireless sensor network gateway has the advantages that conversion among various protocols is completed by treatment of a design protocol conversion program; the multi-protocol multi-interface wireless sensor network gateway can be used for setting up networks with various architectures, interconnecting the networks with various architectures and transmitting data; various network access schemes are provided for the wireless sensor network; the multi-protocol multi-interface wireless sensor network gateway has strong anti-interference capability, low power consumption and small volume; and portable equipment is provided for interconnection among the networks with various architectures and building of an integrated network.
Owner:CHINA UNIV OF MINING & TECH
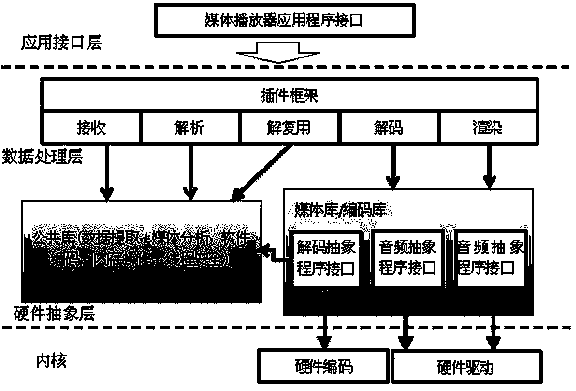
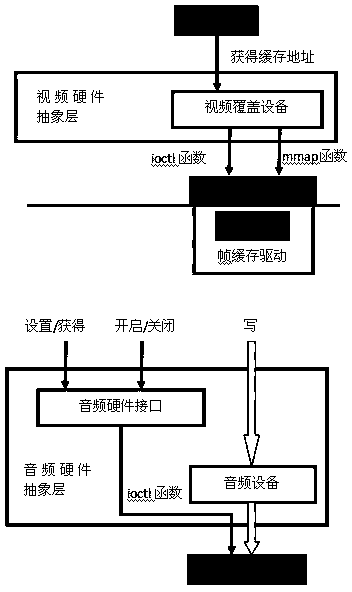
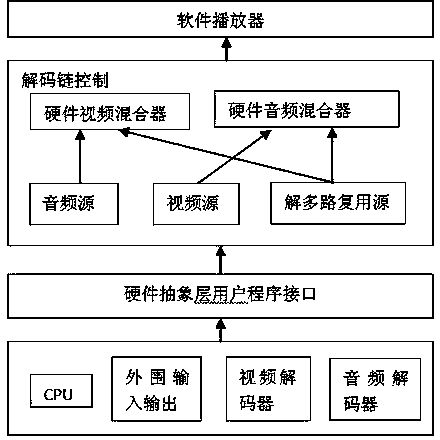
General player applied to Android and Linux smart televisiosn
InactiveCN104333808AFix compatibility issuesImprove service experienceSelective content distributionQuality of serviceGNU/Linux
The invention discloses a general player applied to Android and Linux smart televisions. The general player is divided into three layers, namely an application interface layer, a data processing layer and a hardware abstraction layer. The application interface layer provides a unified media calling method for a streaming media application, and comprises a playing control interface, a parameter feedback interface and a service quality interface. Functions of data processing layer are mainly achieved by a media plug-in system, and the data processing layer comprises a receiving sub module, a packet analysis sub module, a demultiplexing sub module, a decoding sub module, an output sub module, etc. The hardware abstraction layer mainly comprises a hardware decoding link, an audio output link and a video output link, and upwards exists on a platform hardware adaptation layer in streaming media middleware in a local interface base mode. The general player applied to the Android and Linux smart televisions solves the problem of player compatibility, and can provide a streaming media playing function and a better service streaming media business.
Owner:FUDAN UNIV
Apparatus and method for realizing zero copy based on Linux operating system
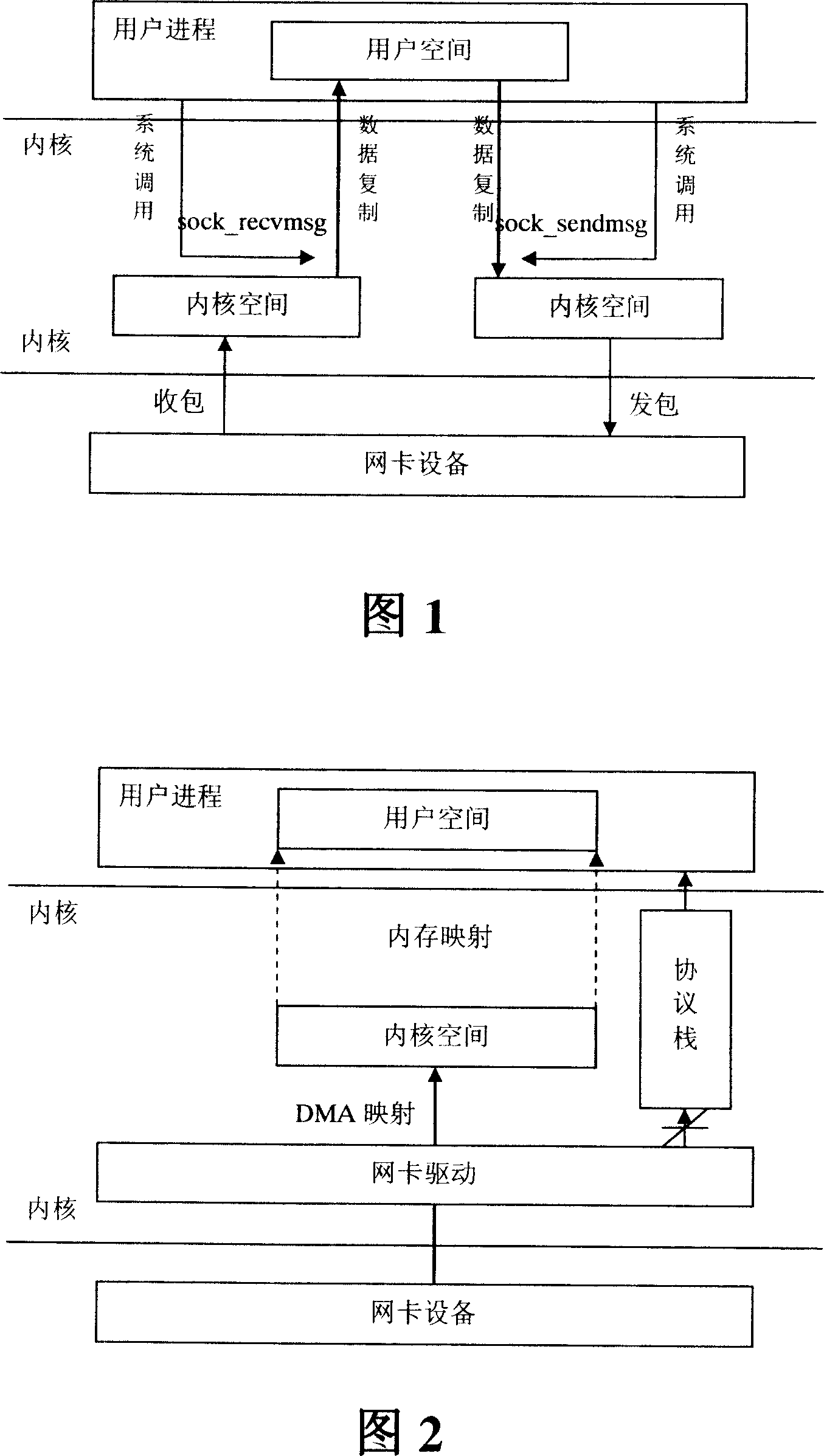
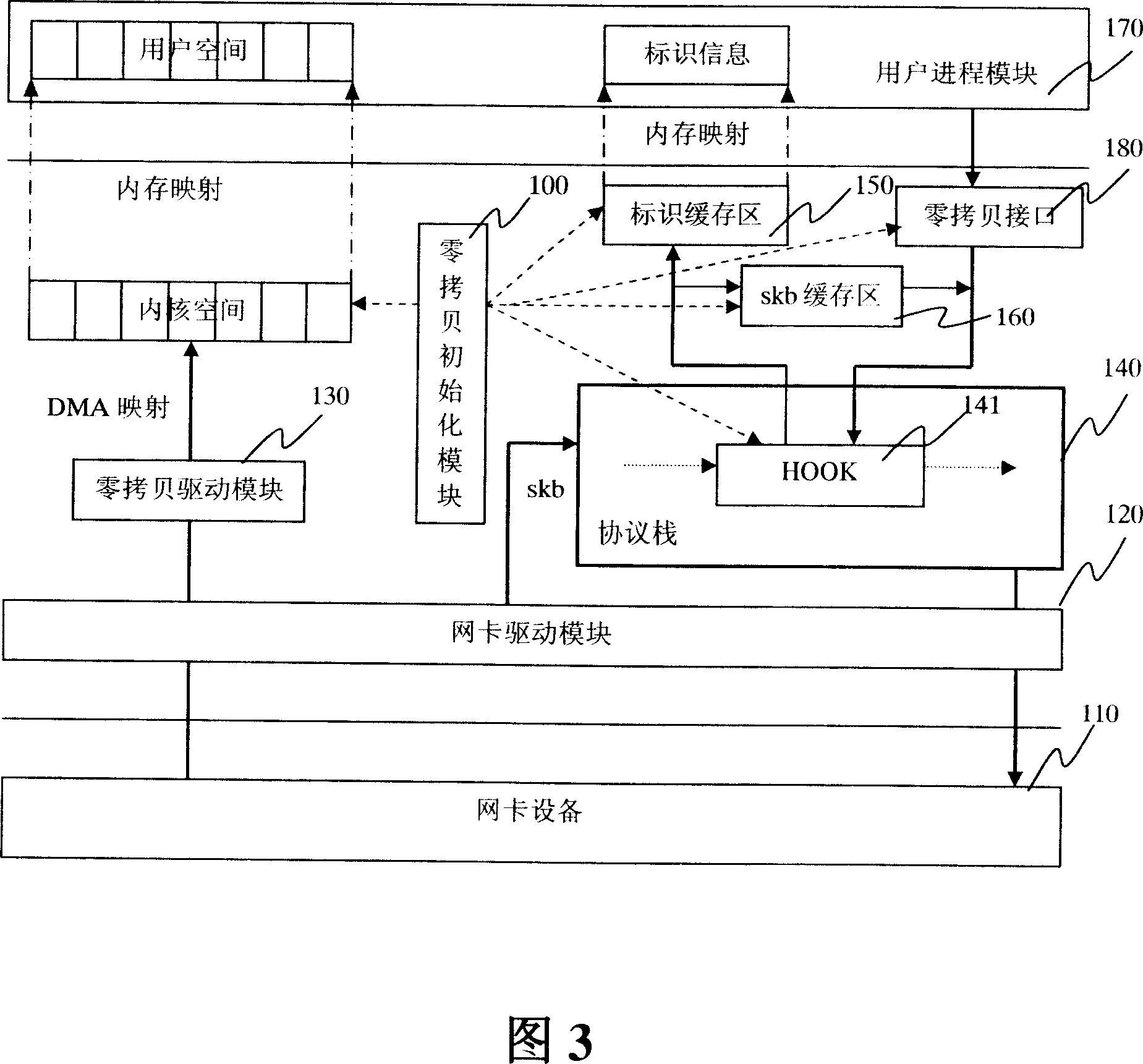
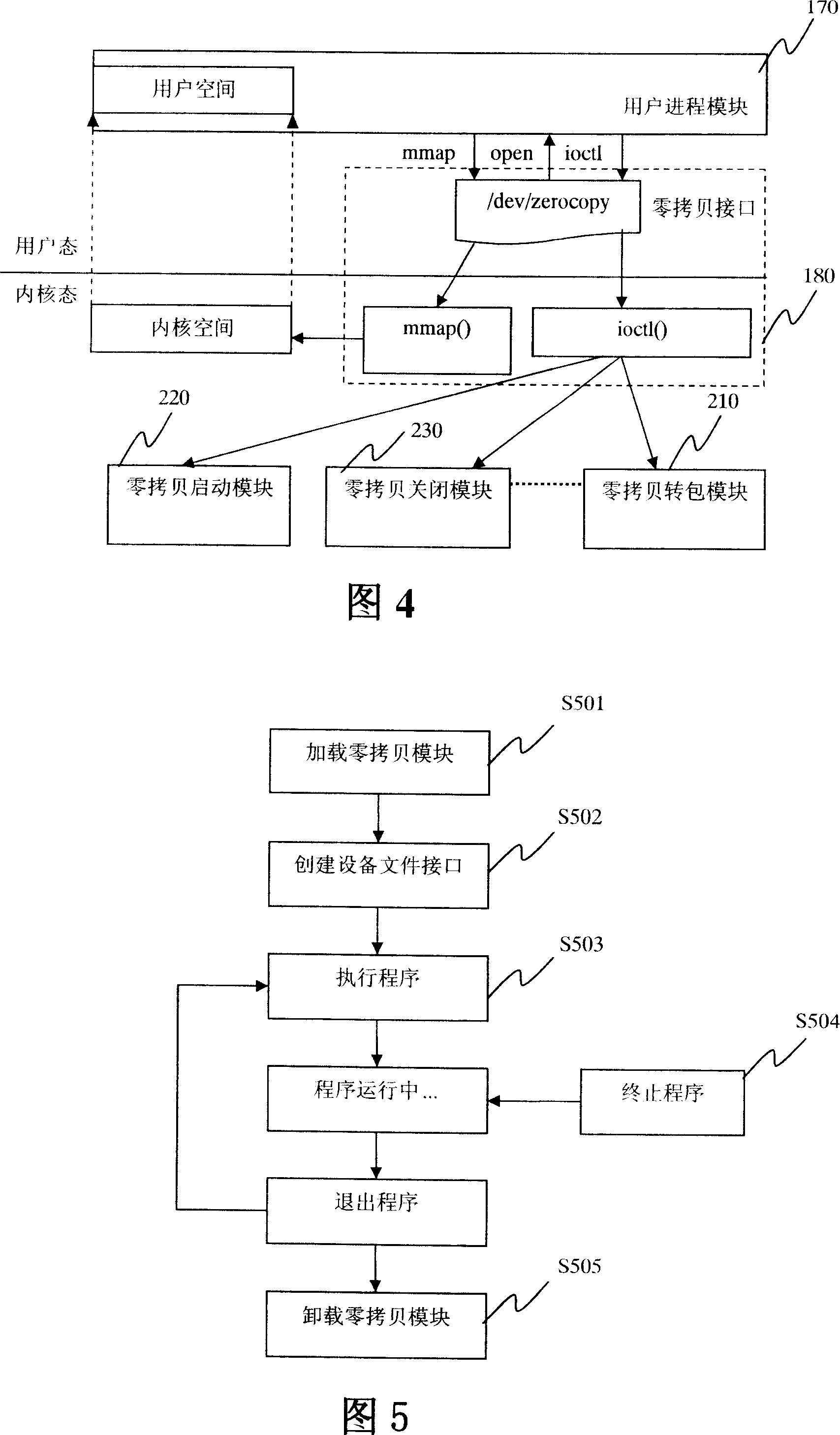
ActiveCN101135980ARealize zero copy of dataRegistration is flexibleMultiprogramming arrangementsTransmissionAnalysis dataZero-copy
The apparatus comprises: a zero-copy initializing module used for allocating a segment of inner core space in the inner core, and dividing the inner cored space into multi data blocks, and identifying each block; a network card driving module used for sending the received data packet to the data block in the inner core to save; recording the identifier of the data block in skb of the data packet, and sending the skb to the protocol stack; a protocol stack used for receiving and analyze the skb of the data packet, and getting the identifier of the data block; a identifier buffer connected to the protocol stack and is directly mapped to the user progress module, and is used for saving the identifier of data block obtained by the protocol stack; a user progress module used for getting the identifier from the identifier buffer, and getting the data packet from the data block in the inner core space.
Owner:FORTINET
Method and system for detecting and defending multichannel network intrusion
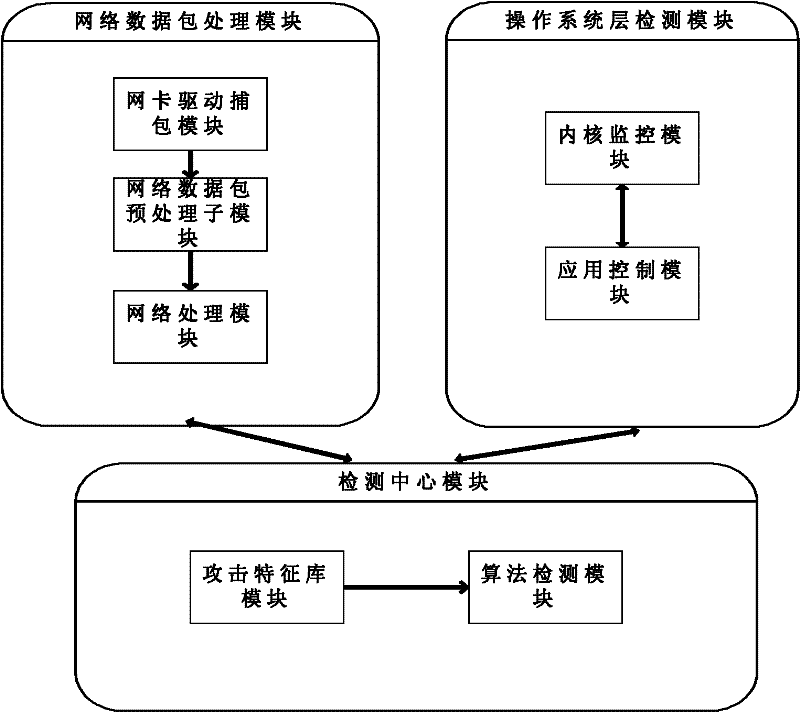
InactiveCN102546624AImprove real-time performanceImprove execution efficiencyData switching networksOperational systemPacket processing
The invention relates to a method and a system for detecting and defending multichannel network intrusion, wherein a half-polling manner is used in a network card driver at a network side to capture a data packet and from a rule for judging abnormal traffic. At an operating system side, secure access control is realized by additionally setting authority control in a Capability module of Linux, meanwhile, monitoring and control treatment is performed on a kernel layer of an operating system, and the monitoring of Trojan and other abnormal operations or virus destruction is realized by carrying out credential privilege arbitration on processes, operating an i-node and carrying out secure control on an application layer. Formed feature data are gathered and sent to a Bayes model for classification, an improved backward propagation neural network (BPNN) is guided in to carry out data training so as to make the produced rule capable of defending corresponding attacks. The system disclosed by the invention comprises three modules and five submodules, wherein the three modules include a network data packet processing module, an operating system layer detecting module ad a detection center module.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
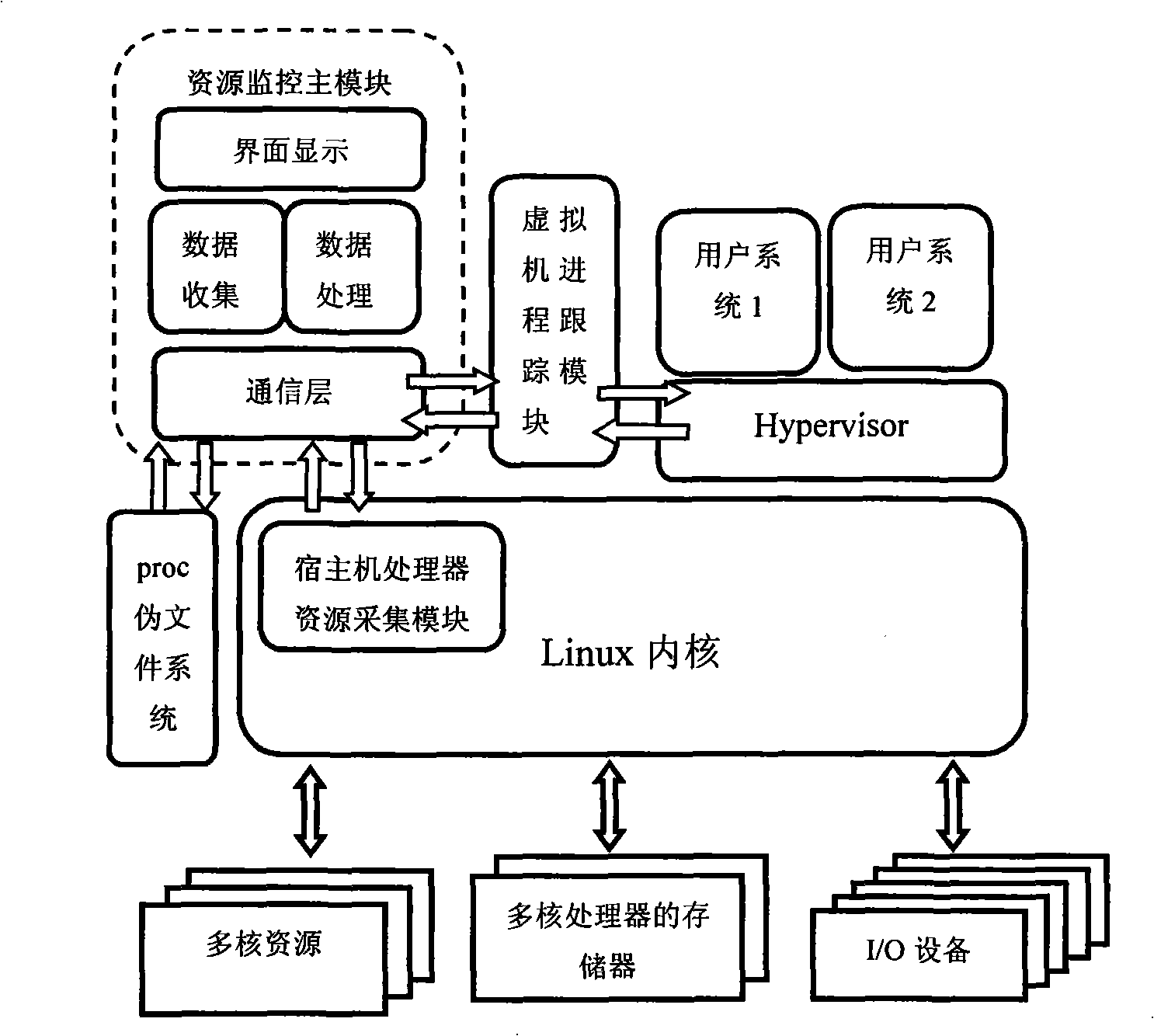
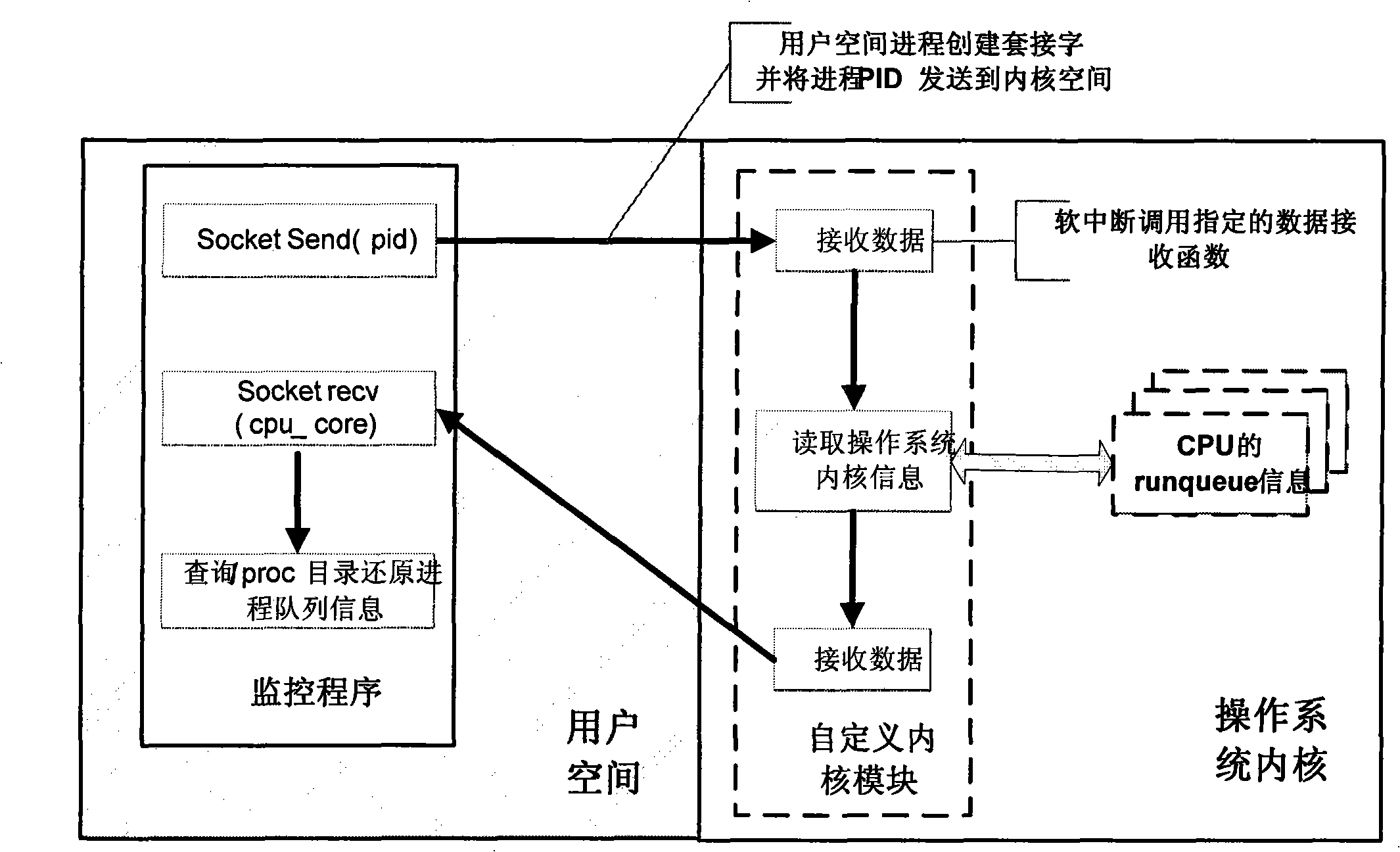
Resource monitoring method and system for multi-core processor based on virtual machine
InactiveCN101403983AComprehensive monitoringMonitor process informationResource allocationProgram loading/initiatingOperational systemGNU/Linux
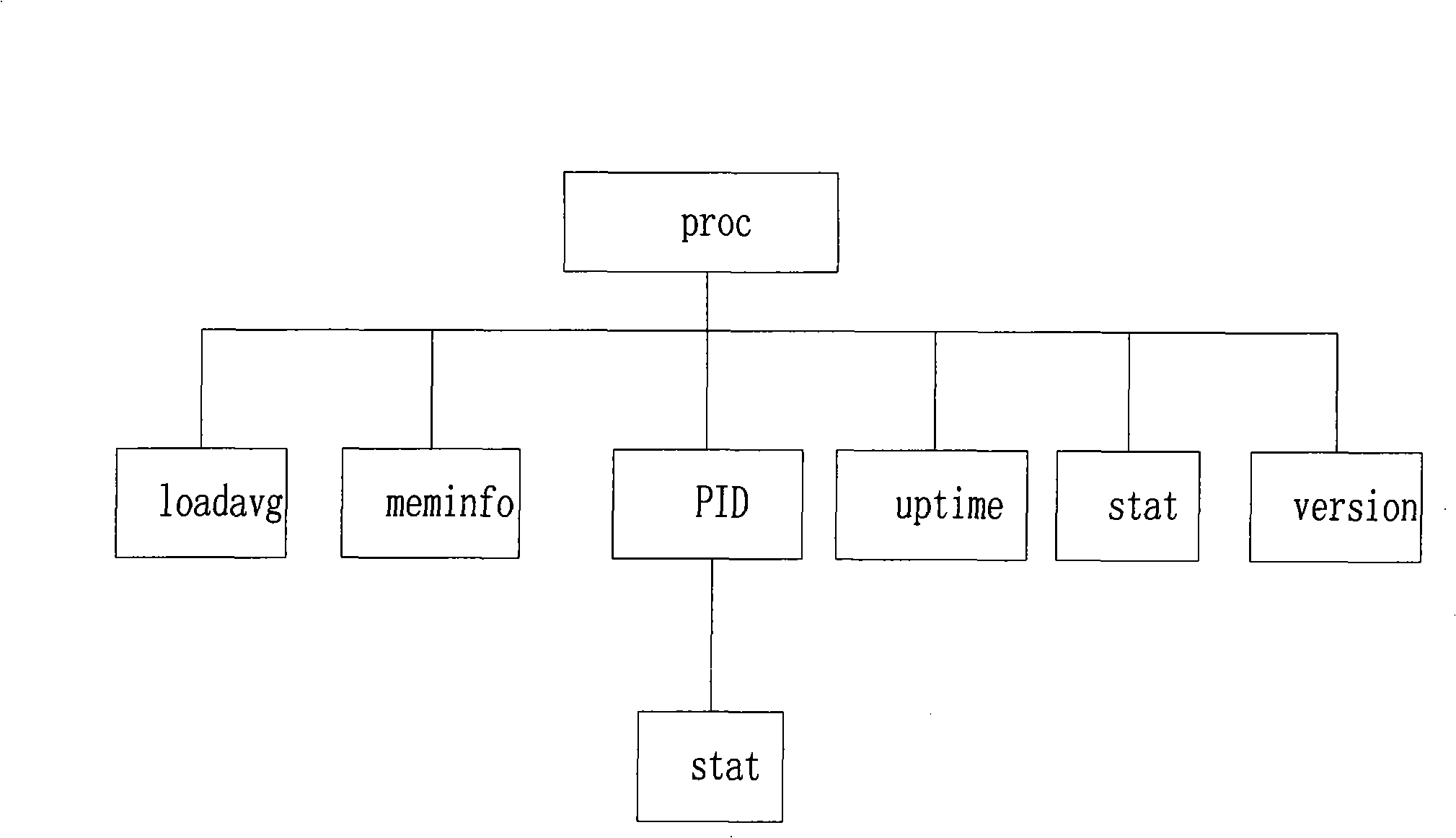
The invention relates to a resource monitoring system of a multi-core processor based on a virtual machine and a method thereof. The current host system resource usage information is obtained by taking / proc fake file system in Linux as a bridge, adopting a method that a host machine processor resource collection module is added in the inner core of Linux, and communicating with the inner core of Linux; the communication between the daemon process of a resource monitoring main module and Hypervisor is established by the process track module of the virtual machine, so as to obtain the resource information of a client operation system which runs on the virtual machine; the resource monitoring main module processes the information and displays the information graphically, therefore, the aim that the software and hardware resources of a host system and a client system which is arranged on the virtual machine are monitored is realized.
Owner:BEIHANG UNIV
System and method for updating dirty data of designated raw device
ActiveUS20090113130A1Shorten the timeMemory adressing/allocation/relocationMicro-instruction address formationGNU/LinuxDirty data
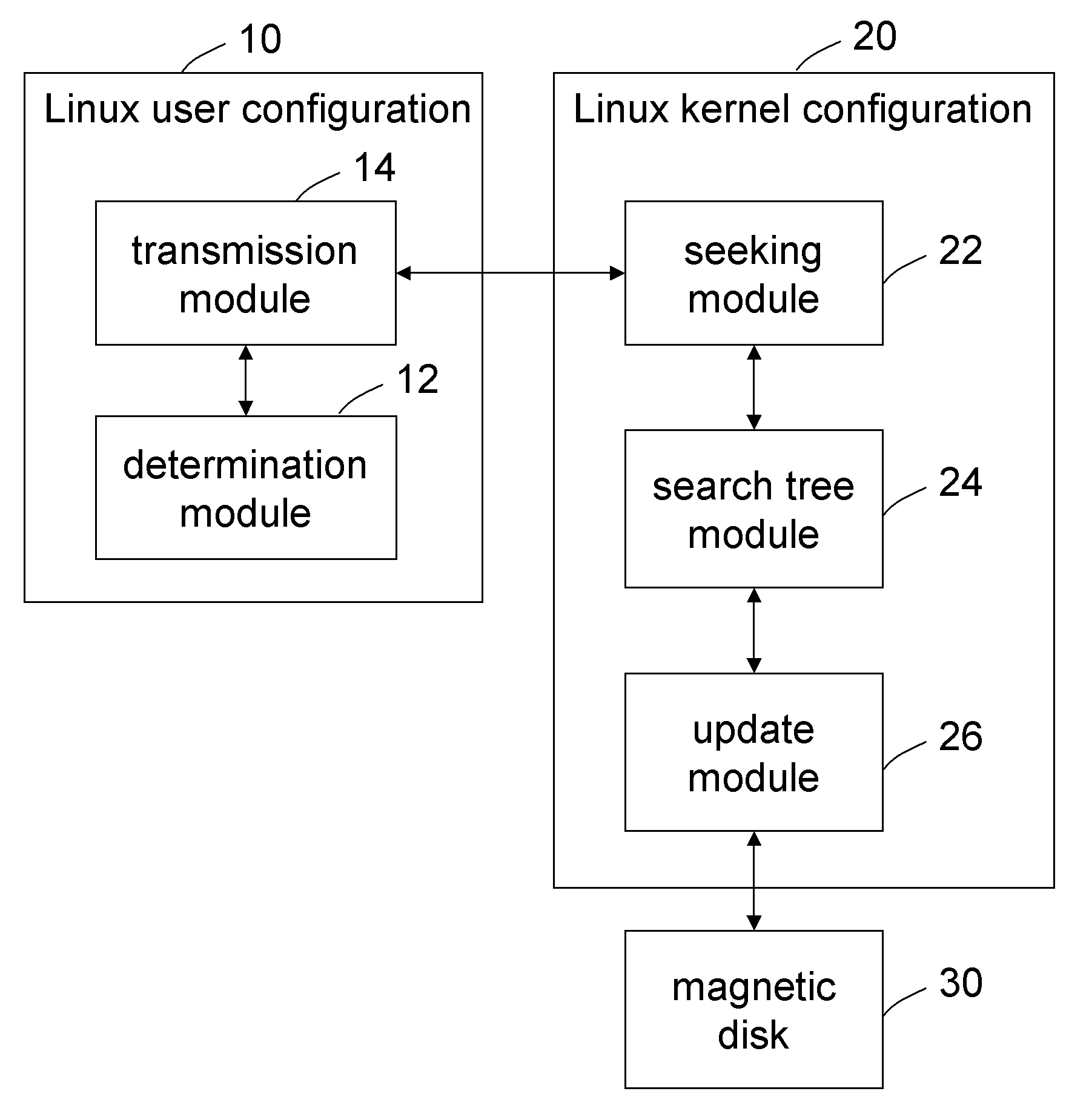
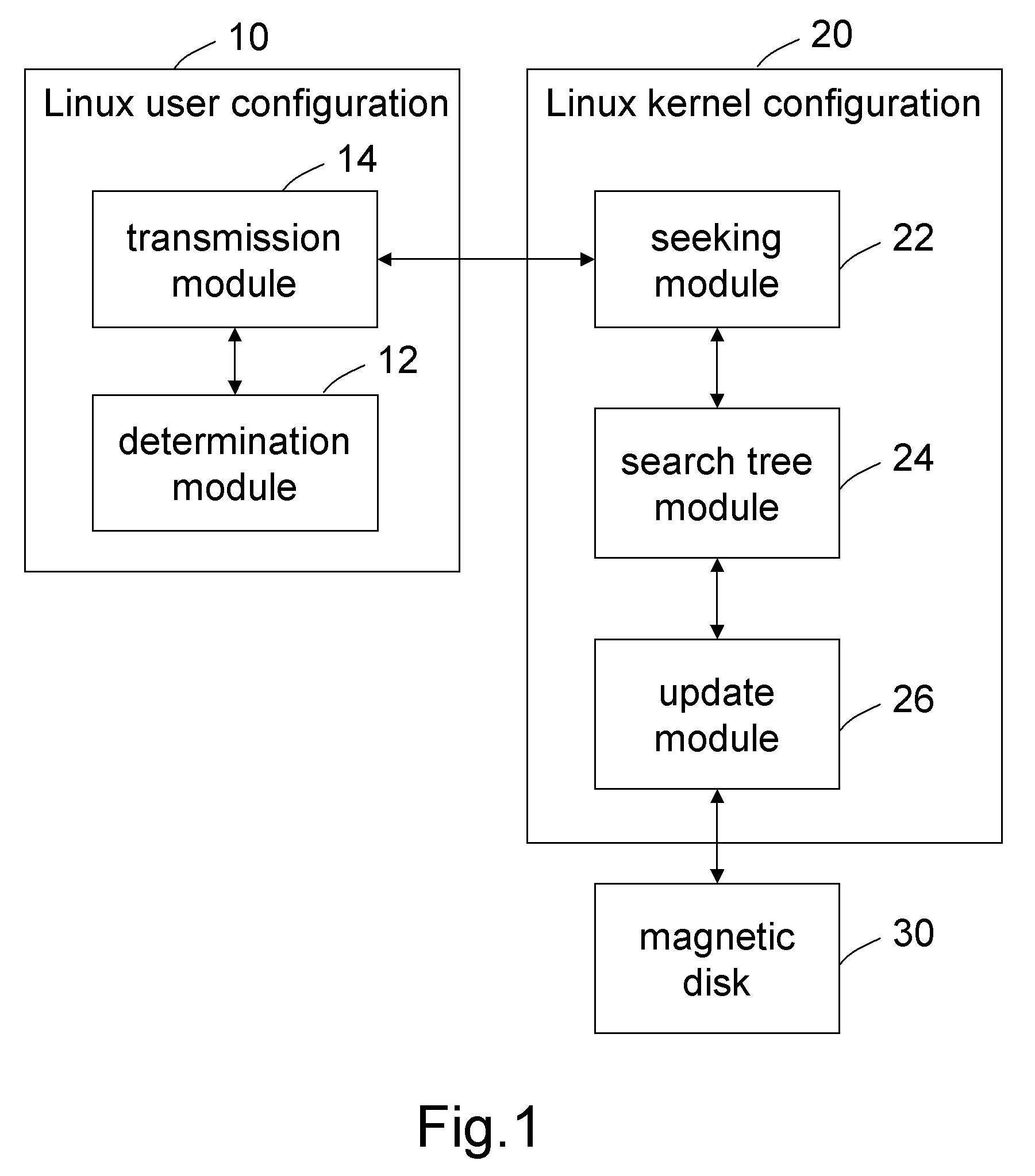
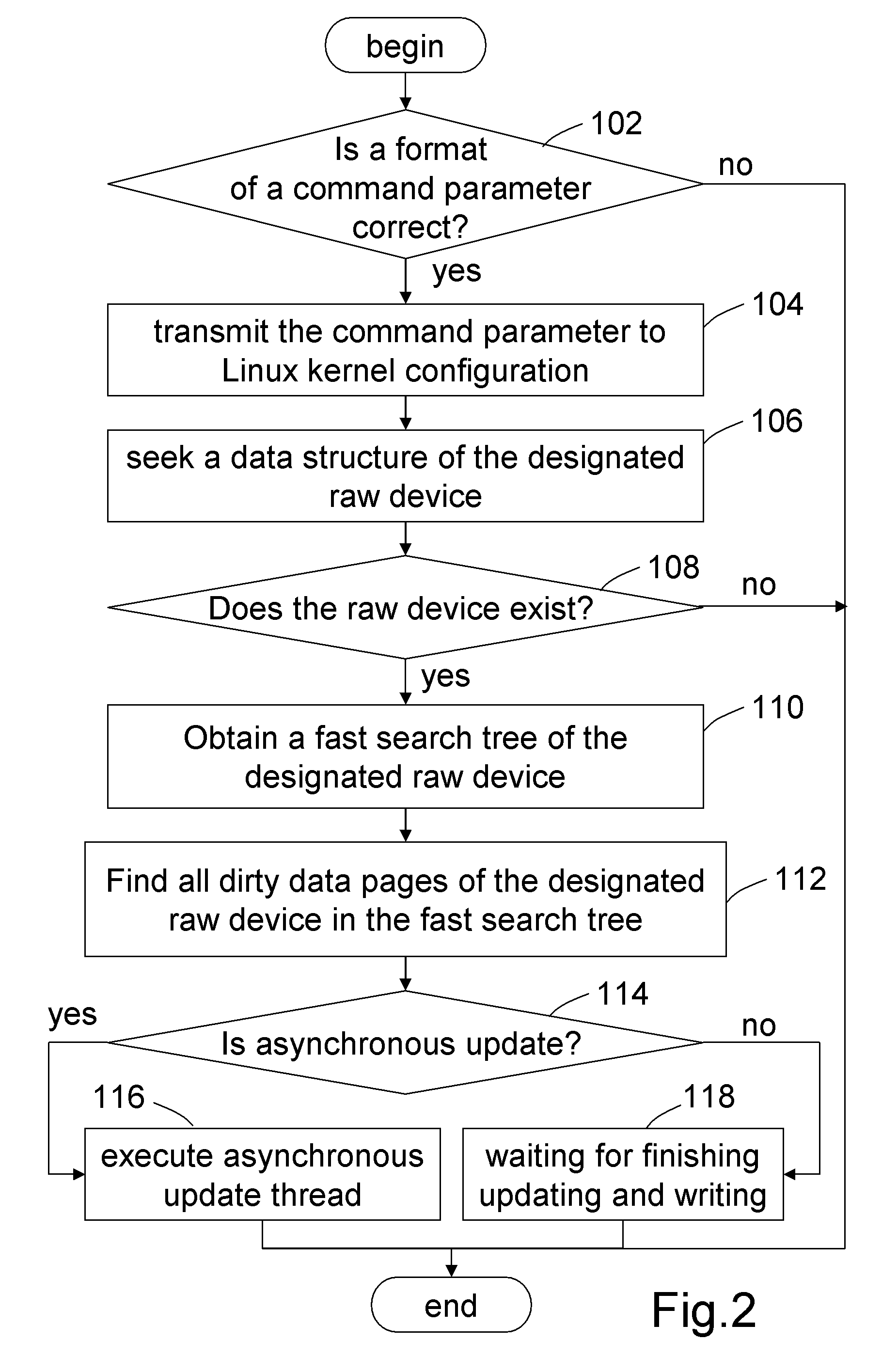
A system and method for updating dirty data of designated raw device is applied in Linux system. A format of a command parameter for updating the dirty data of the designated raw device is determined, to obtain the command parameter with the correct format and transmit it into the Kernel of the Linux system. Then, a data structure of the designated raw device is sought based on the command parameter, to obtain a fast search tree of the designated raw device. Finally, all dirty data pages of the designated raw device are found by the fast search tree, and then are updated into a magnetic disk in a synchronous or asynchronous manner. Therefore, the dirty data of an individual raw device can be updated and written into the magnetic disk without interrupting the normal operation of the system, hereby ensuring secure, convenient, and highly efficient update of the dirty data.
Owner:INVENTEC CORP
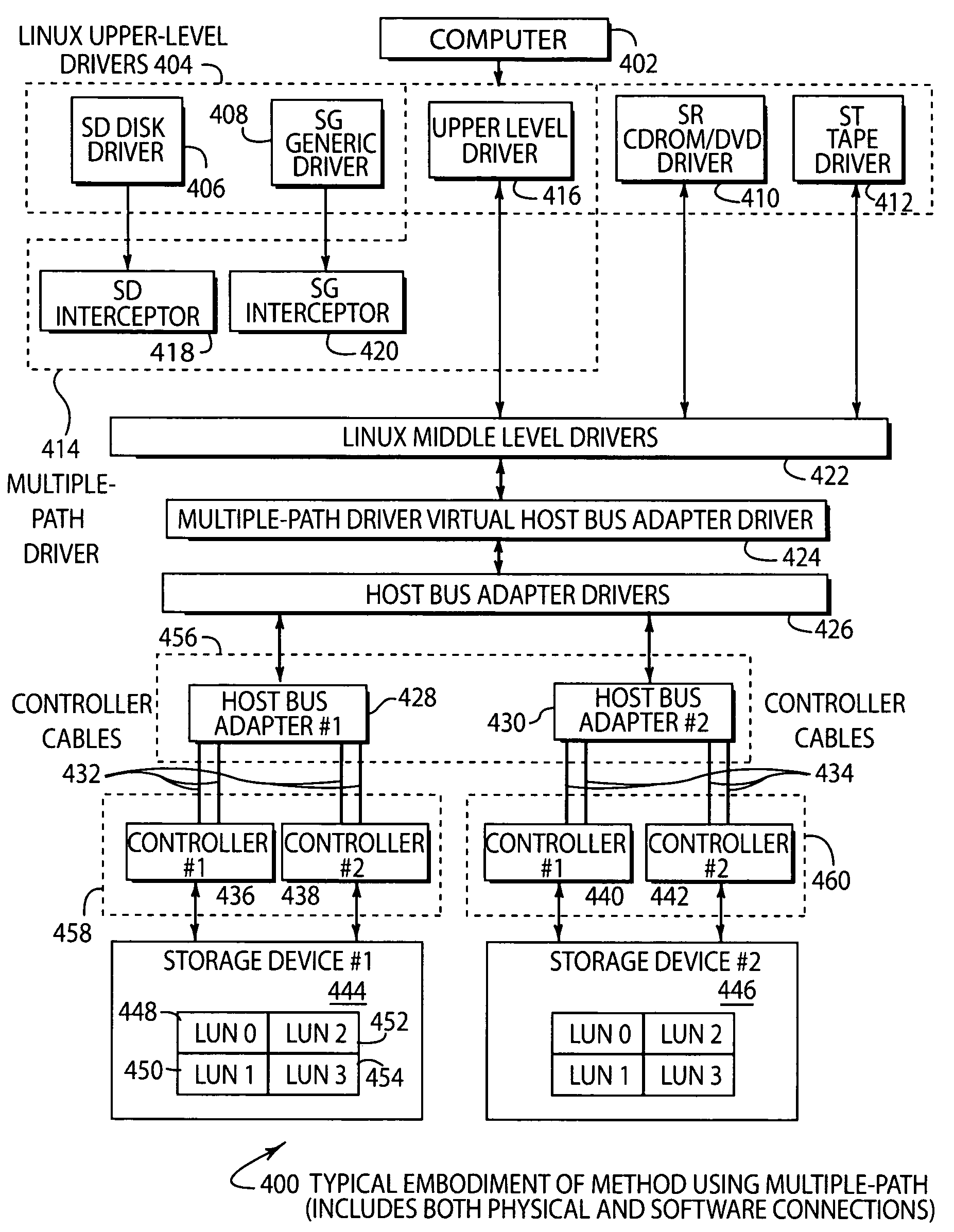
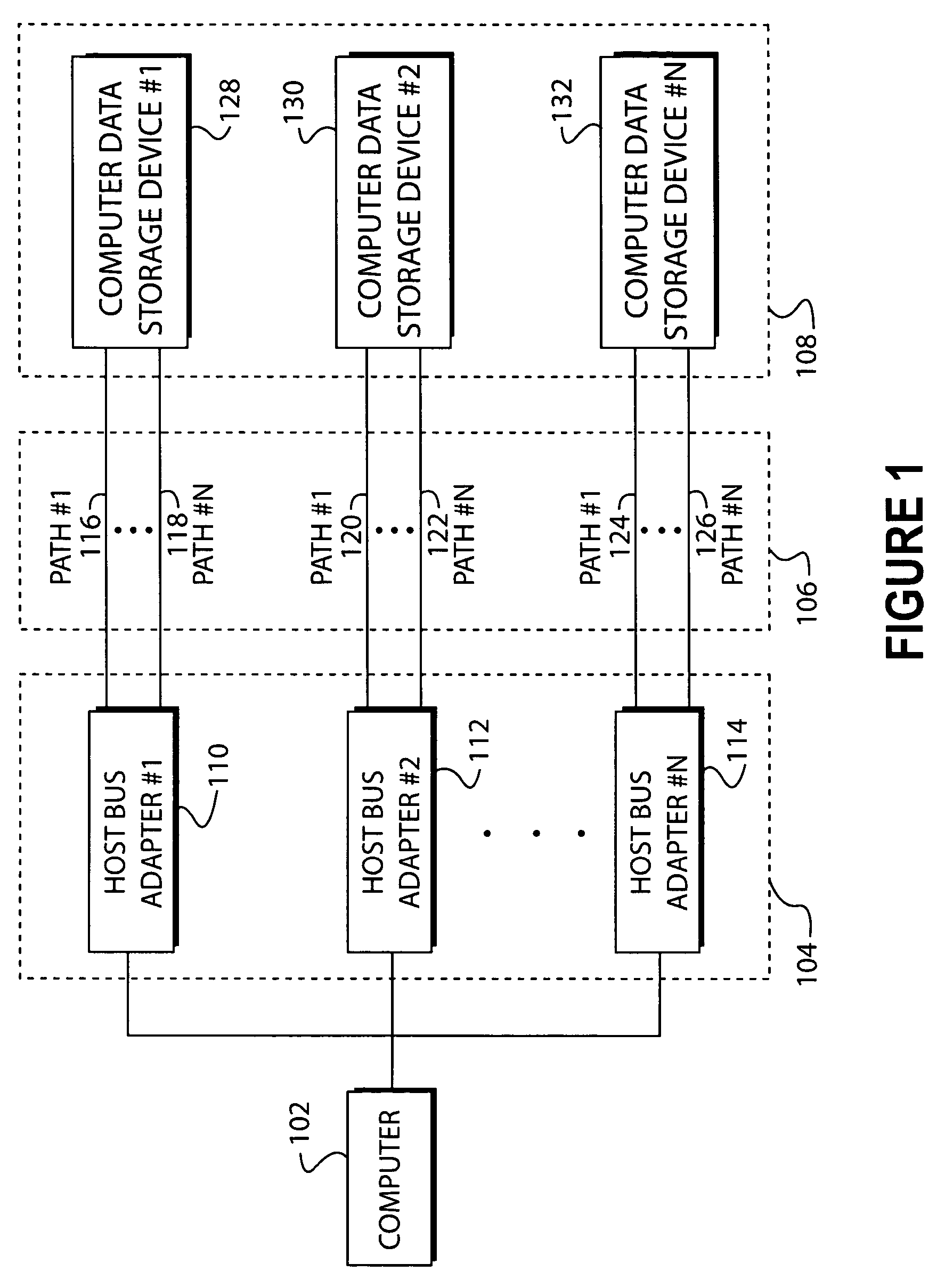
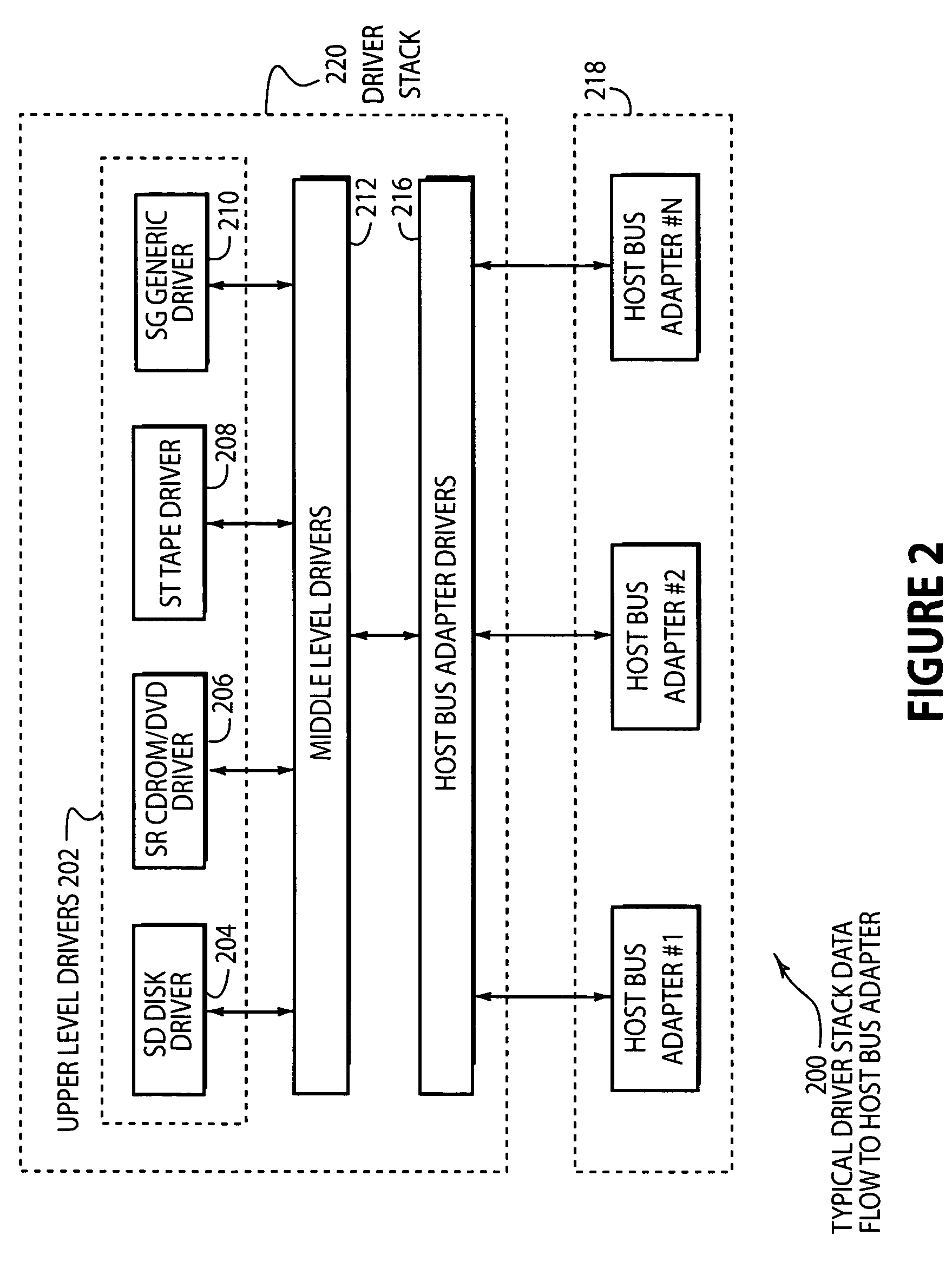
System and method of creating virtual data paths using a multiple-path driver
InactiveUS7421710B2Minimize impactImprove throughputMemory adressing/allocation/relocationInterprogram communicationOperational systemGNU/Linux
Owner:AVAGO TECH INT SALES PTE LTD
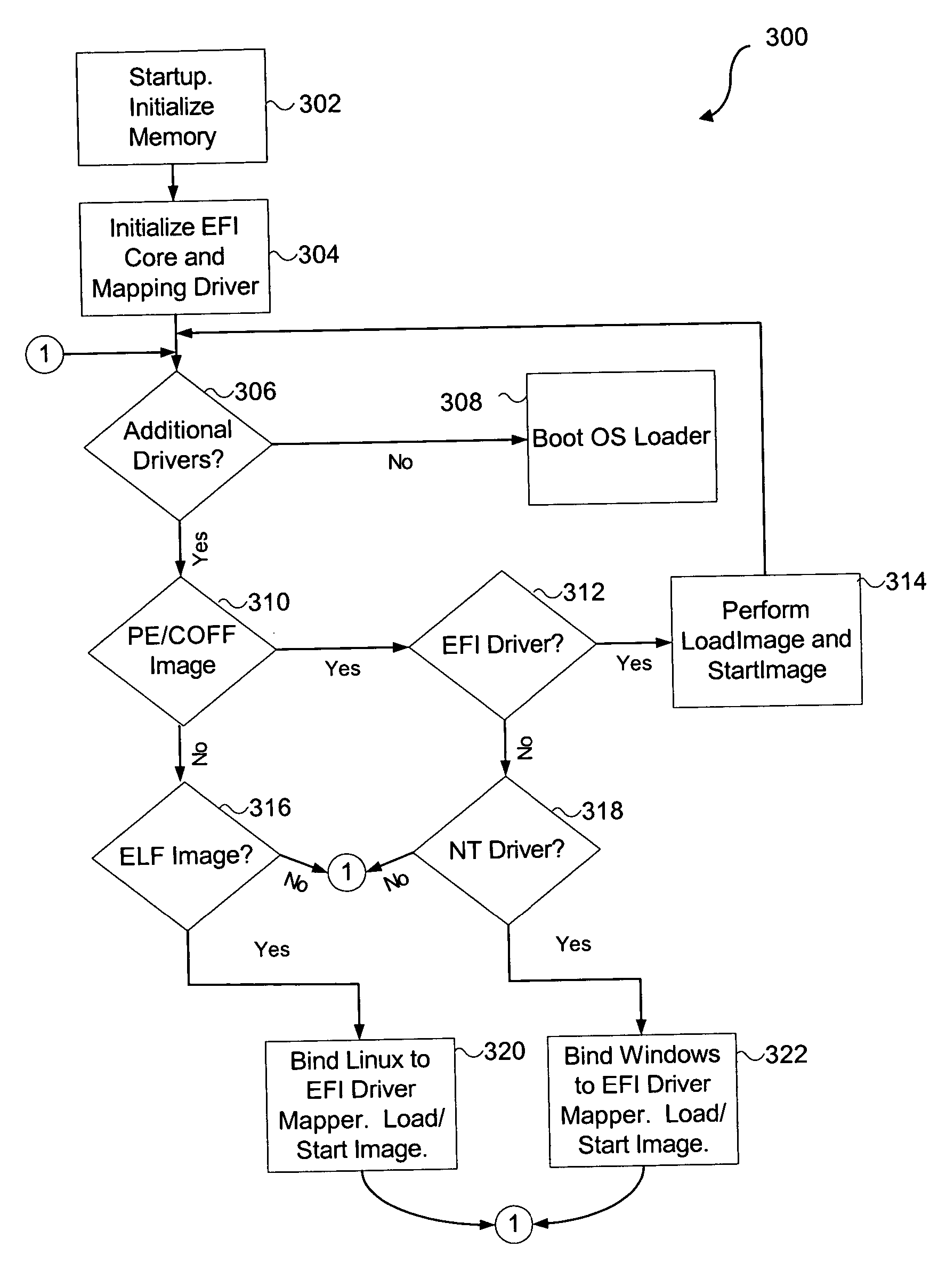
Method and system to encapsulate a driver written for an operating system (OS) runtime environment in an OS independent environment firmware extension
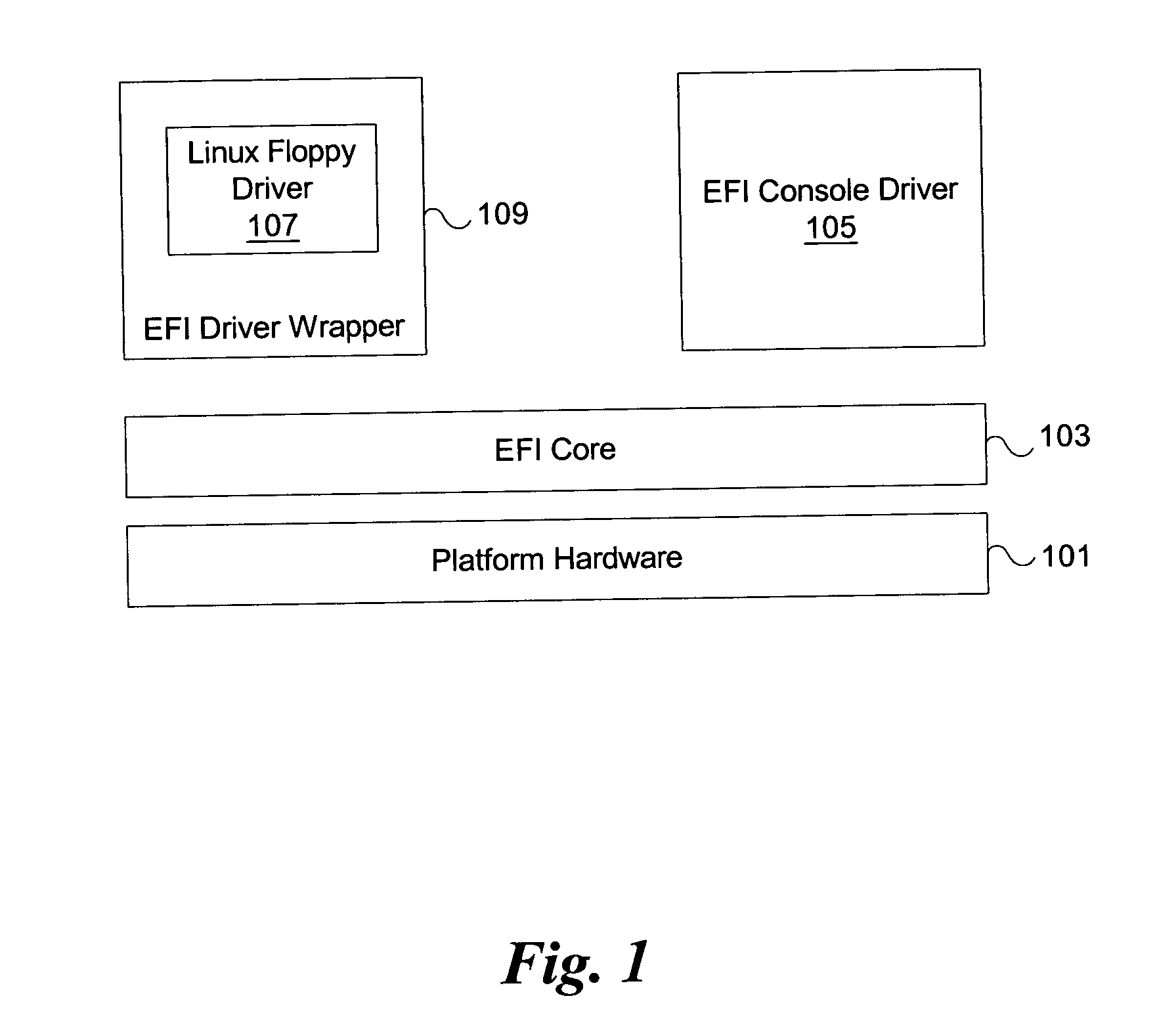
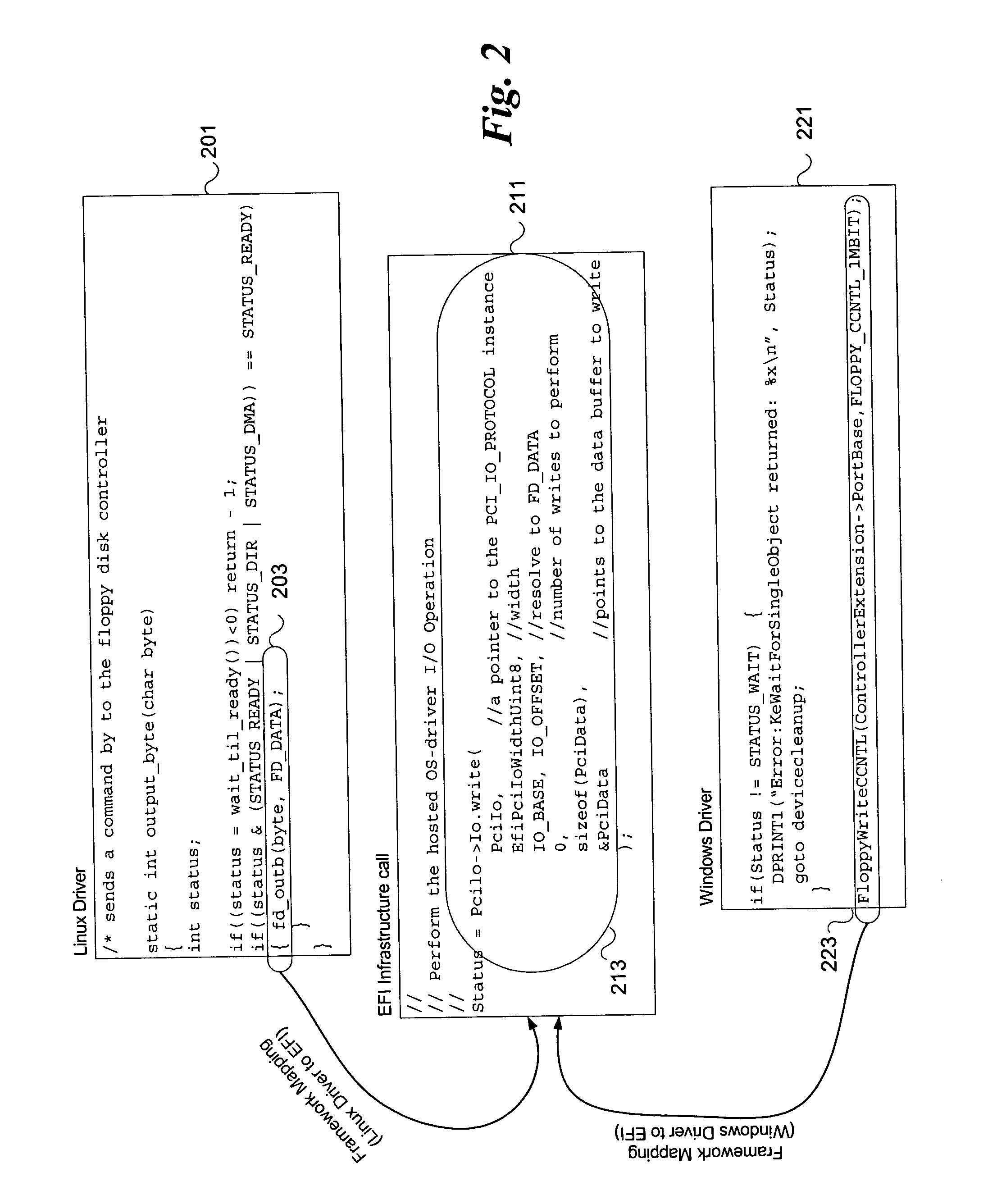
InactiveUS20050076196A1Digital computer detailsProgram loading/initiatingOperational systemGNU/Linux
A system and method is described that takes an existing operating system (OS) level driver and transforms it into a firmware extension, in one embodiment, for the extensible firmware interface (EFI). In one embodiment, an existing driver is stored in flash memory, without modification. When initializing the system, a mapping driver examines this image. Based on a determined image format and subtype, it is known whether the existing driver is compatible with Linux, Windows, fcode, or another type. Based on the type, the mapping driver either fills in the blanks and maps directly to the EFI services, or rewrites some of the flash with binary (in memory). The driver is typically compressed when in flash memory. Once the OS is booted, the OS uses its own driver.
Owner:INTEL CORP
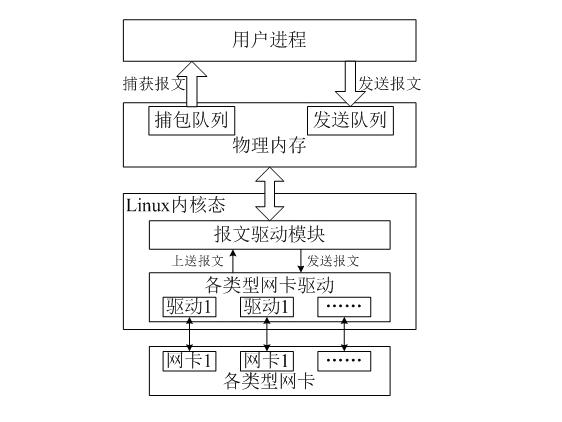
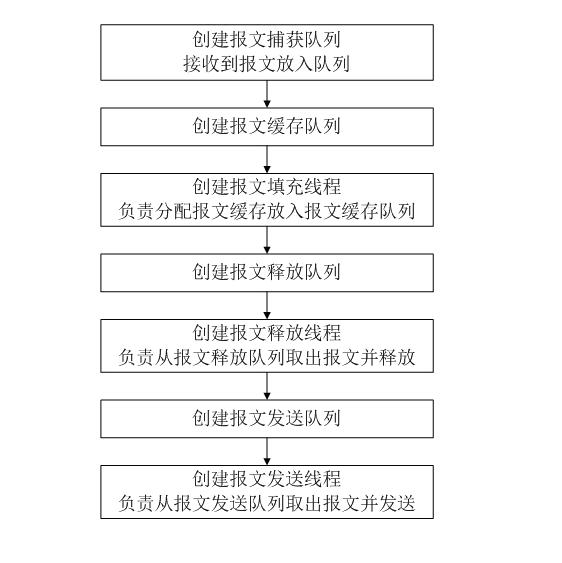
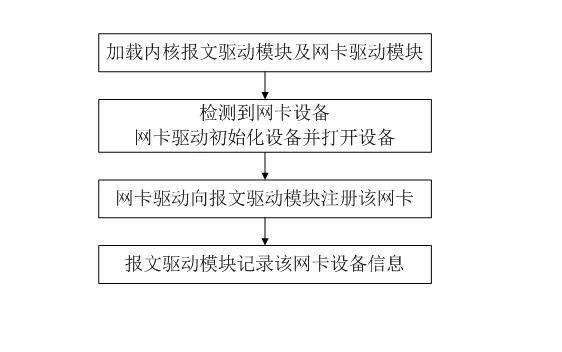
Network card drive-based zero copy Ethernet message capturing and transmitting implementation method under Linux
ActiveCN101917350AEasy to captureIncrease sending rateData switching networksTraffic capacityZero-copy
The invention discloses a network card drive-based zero copy Ethernet message capturing and transmitting implementation method under Linux. The method comprises the following steps of: 1, mapping the whole physical memory to a user process space by using a user process; 2, managing message received by a message driving module and message to be transmitted by the message driving module in a queue mode; 3, isolating the influence of discrimination of various network card drives on the user process by using the message driving module; and 4, after the various network card drives are loaded successfully, registering equipment and related operating methods to the message driving module. The method is implemented layer by layer so that the method can simultaneously support multiple types of network cards and is easy to add support for new network cards. The method can realize high-performance message capture and transmission without one-time copy in the message capture and transmission process, and is suitable for the situations with high requirement for transceiving of the message such as network traffic monitoring and analysis and the like.
Owner:南京中新赛克科技有限责任公司
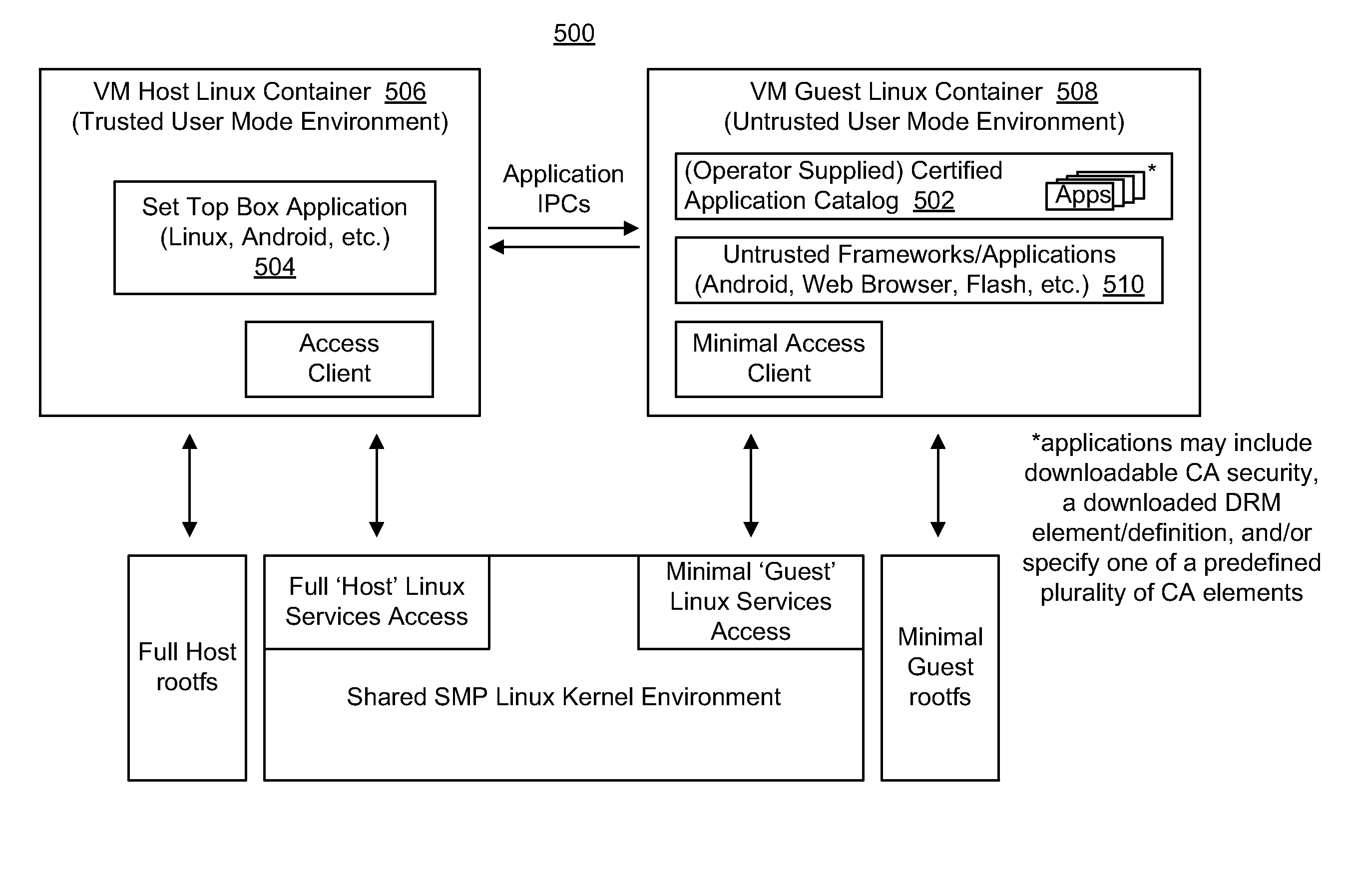
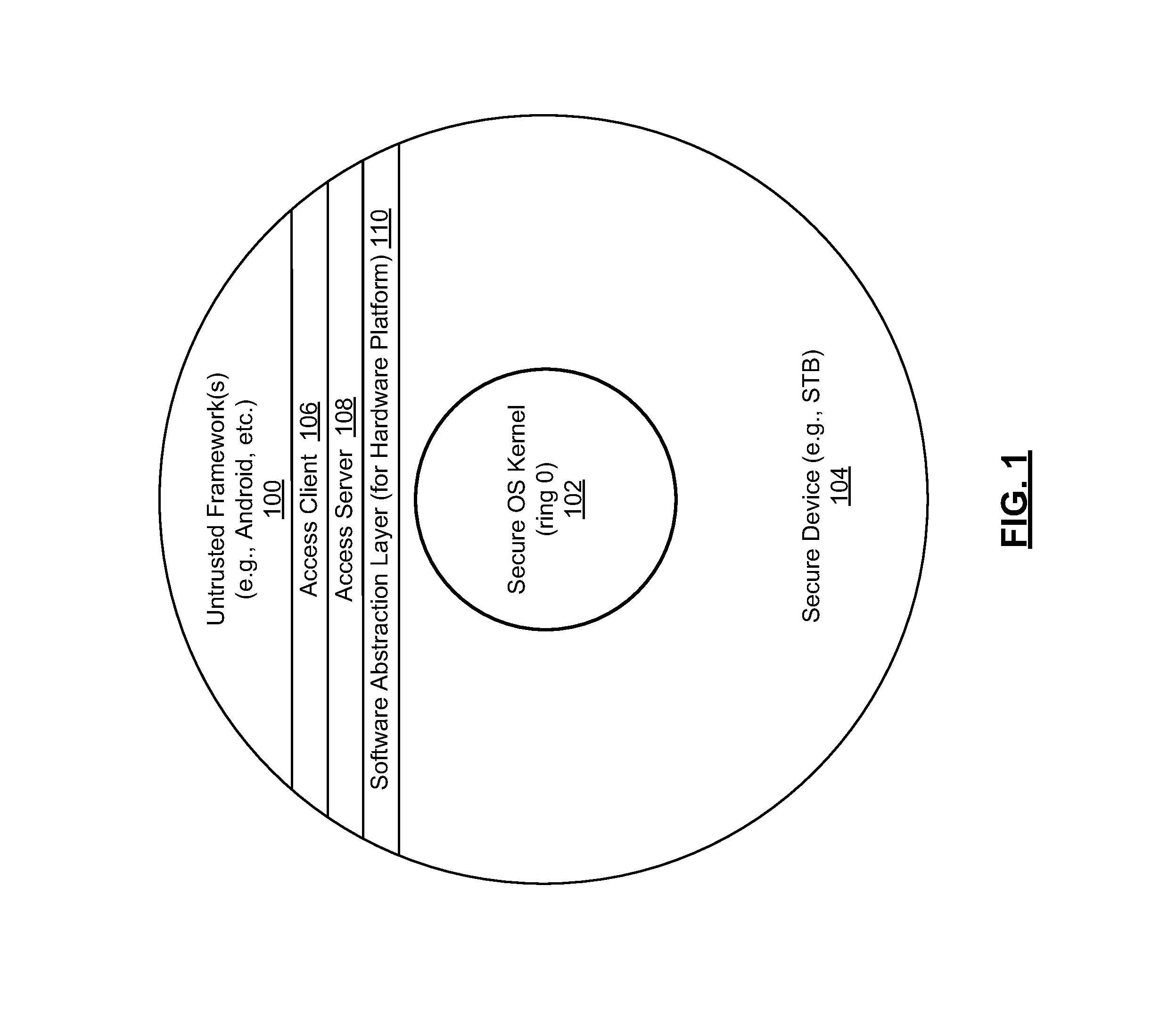
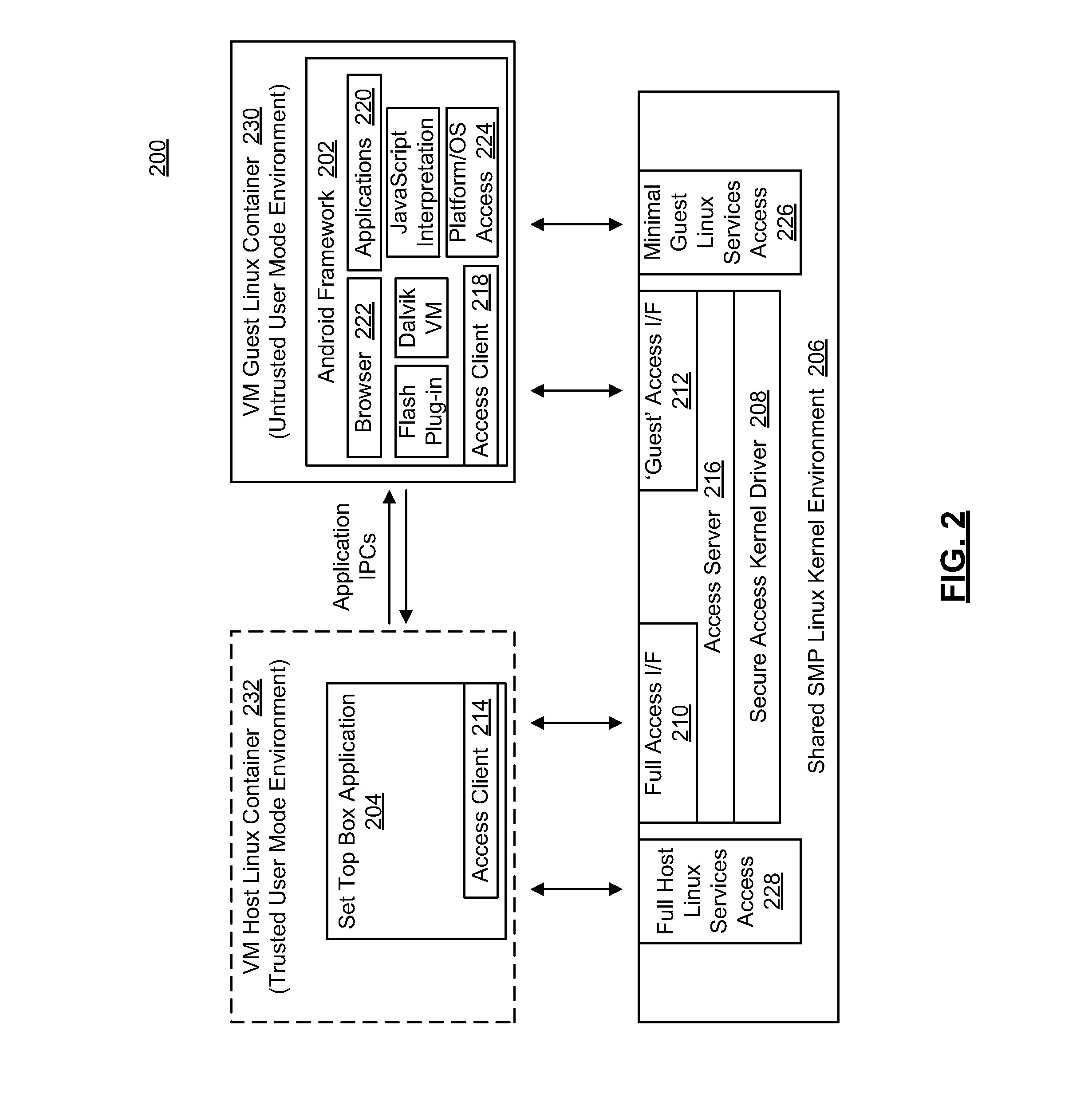
Set Top Box Application in a Concurrent Dual Environment
ActiveUS20140115580A1Selective content distributionSoftware simulation/interpretation/emulationVirtualizationOperational system
A set top box or like device utilizing virtualization techniques to isolate secure device resources from an untrusted software framework incorporated in the device. In one implementation, a first virtual machine container is provided for secure execution of a traditional set top box application, while a second virtual machine container is utilized to host a software framework or untrusted portions of a software framework. A secure access client / server interface is provided to support interactions between the first and second virtual machine containers. The software framework may comprise, for example, an Android framework supported by an underlying Linux operating system environment and isolated in a Linux resource container. Virtual container constructs in various embodiments may employ varying levels of hardware sandboxing, including use of dedicated processing resources in multi-processor environments. In further embodiments, the software framework may be partitioned into trusted and untrusted portions that are executed in separate virtual containers.
Owner:AVAGO TECH INT SALES PTE LTD
Tethered Digital Butler Consumer Electronic Device and Method
ActiveUS20070042767A1Low costEasy user identification/authorizationTransmission systemsDigital data processing detailsPersonalizationFeature set
The present invention relates to a tethered digital butler consumer electronics product and method. The tethered digital butler, of a price and form factor suitable for consumer electronics markets of developed and developing countries, includes a communications and multi-media console and a wireless remote. The remote may resemble a handheld personal computer (HPC), a palm-held personal computer (PPC or PDA) or a smart phone, but has a low cost and feature set supported by the console that is novel in the consumer electronics market. In particular, this disclosure relates to combining telephone service, device control and, optionally, a fingerprint reader for easy user identification / authorization and personalization. As another option, a camera can be incorporated into the remote, thereby enabling video conferencing and other visual features. Alternatively, the remote may be packaged separately from a console and sold to interact with capabilities of a communications and console, set-top box, multi-media PC or other consumer electronics device from a different source, such as one running on a Windows, OS X or Linux platform, with or without telephone capabilities. The remote may include a media reader and remote USB port.
Owner:NEXSTEP
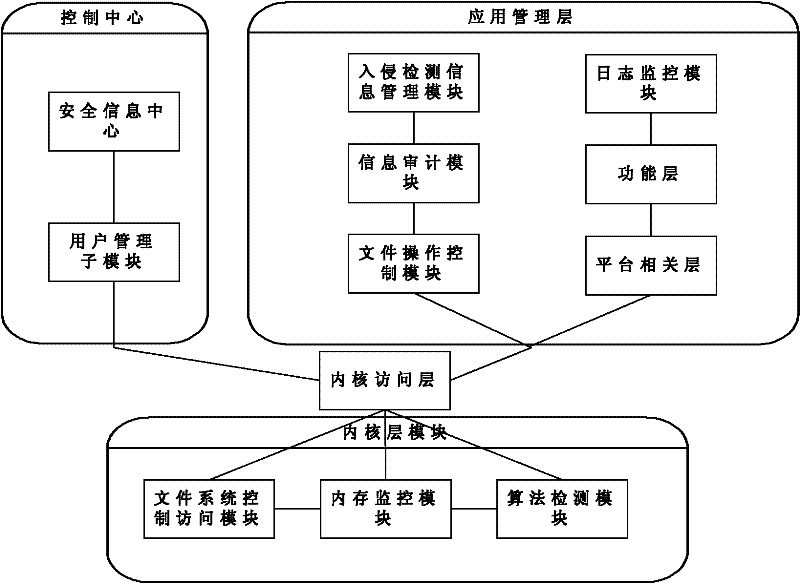
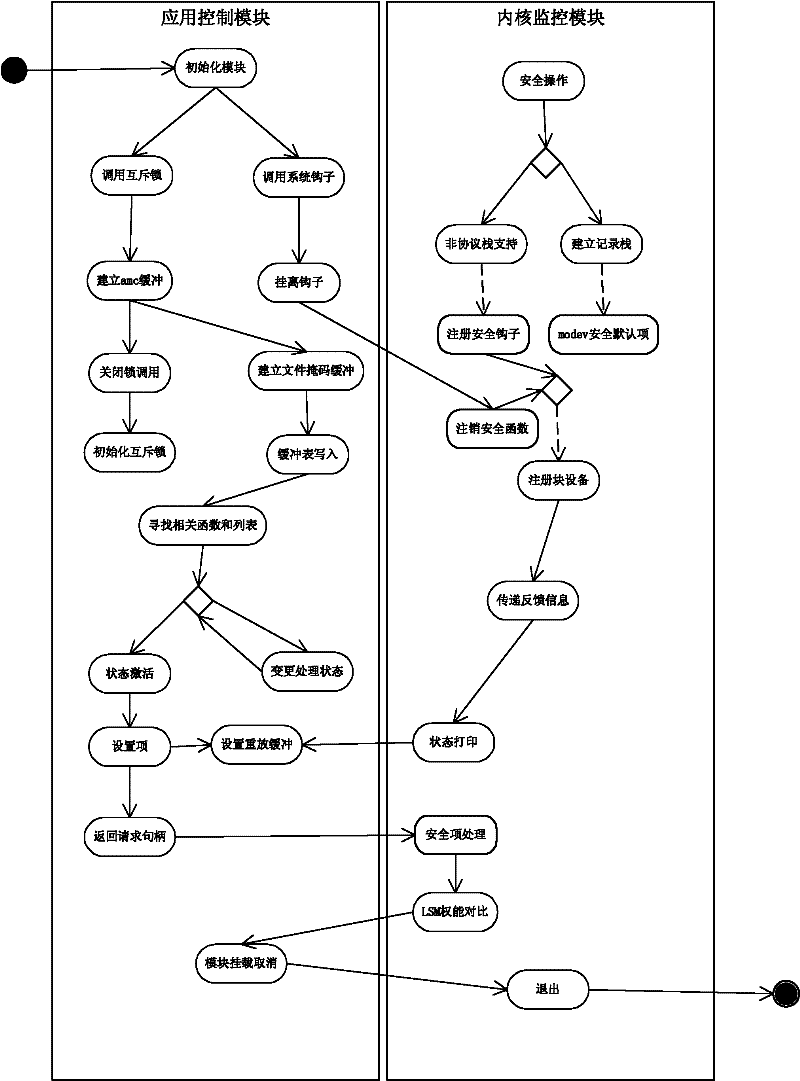
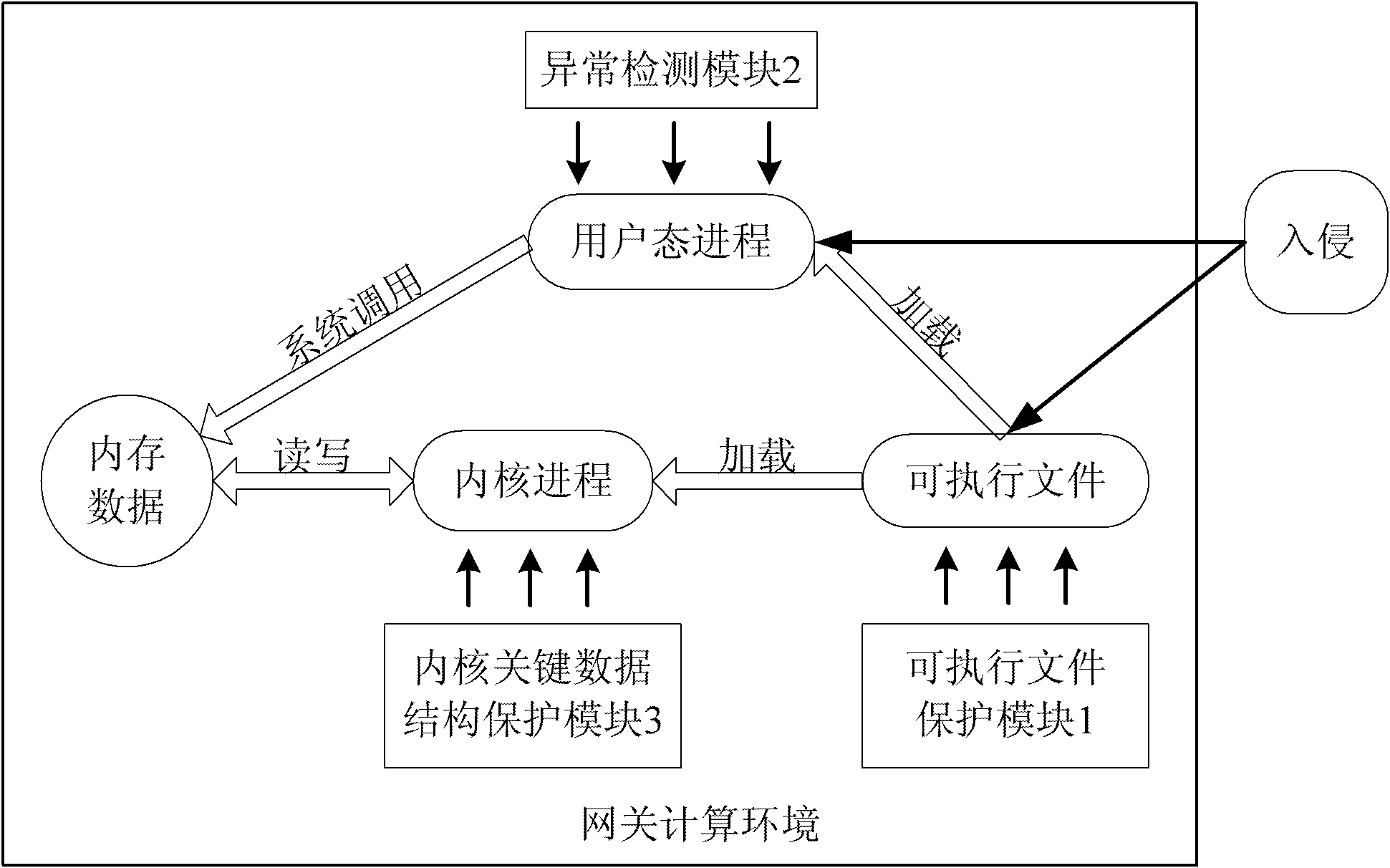
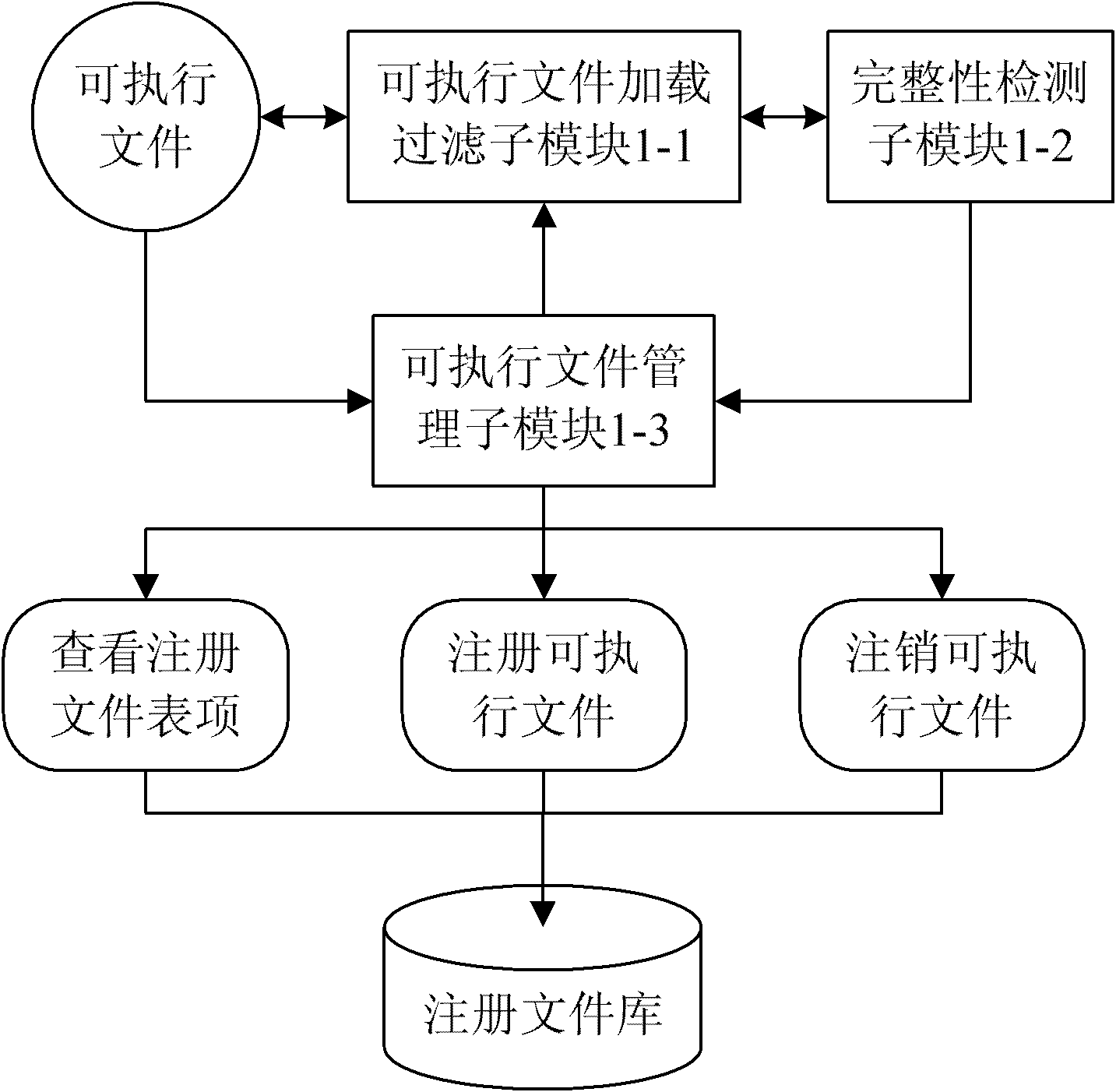
Module and method for LINUX host computing environment safety protection
The invention relates to a module and a method for LINUX host computing environment safety protection, which belong to the field of computer system safety, and solve the safety threats to an LINUX host. The module comprises an executable file protection module, an anomalous detection module and an inner core key data structure protection module, wherein the executable file protection module is used for registering, canceling, completeness protection functions of an executable program, and carrying out completeness detection before the operation of any program so as to ensure the process safety of a user state loaded in an internal memory; the anomalous detection module is used for setting up a process lawful action set, extracting process actions in a system during the operation process, and jugging whether the process action is anomalous or not through being matched with a normal action so as to prevent the process from being infected by a rogue program; and the inner core key data structure protection module is used for providing the backup, completeness detection and recovery functions of the inner core important data structure in the operating system, detecting whether the inner core important data structure is modified or not during the operation process, and recovering the important data structure according to the previous backup if the inner core important data structure is modified. The module and the method can completely and effectively protect the operation environment safety of the LINUX host.
Owner:HARBIN INST OF TECH
Universal method for submitting gaming machine source code software to a game certification laboratory
InactiveUS20060122937A1Data processing applicationsUser identity/authority verificationOperational systemGeneral purpose computer
A universal computer-implemented method for submitting source code to an authorized game certification laboratory. Initial source code and subsequent source code patches may be transferred from the manufacturer's software development environment into the laboratory's software development environment in a controlled fashion using packaging installation technology normally used for deploying software applications. The packaging technology contains automation actions for automating the synchronization and / or management of the source code and related files between the two software development environments. The entirety of the source code or any source code patch sequence may be removed by executing the corresponding uninstall function. The package containing the original source code or the source code patch sequences and related files may be code signed such as to provide persistent proof of origin which may be verified at any time. The method may be implemented under any operating system such as Microsoft Windows, Linux, UNIX and Apple Mac OS without the laboratory having to learn a complex source code configuration management software.
Owner:MUDALLA TECH INC THOITS LOVE HERSHBERGER & MCLEAN
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com