Module and method for LINUX host computing environment safety protection
A computing environment and security protection technology, applied in computer security devices, computing, platform integrity maintenance, etc., can solve the problem of affecting network performance, unable to detect attack types, and cannot well meet the needs of LINUX host computing environment security, etc. question
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
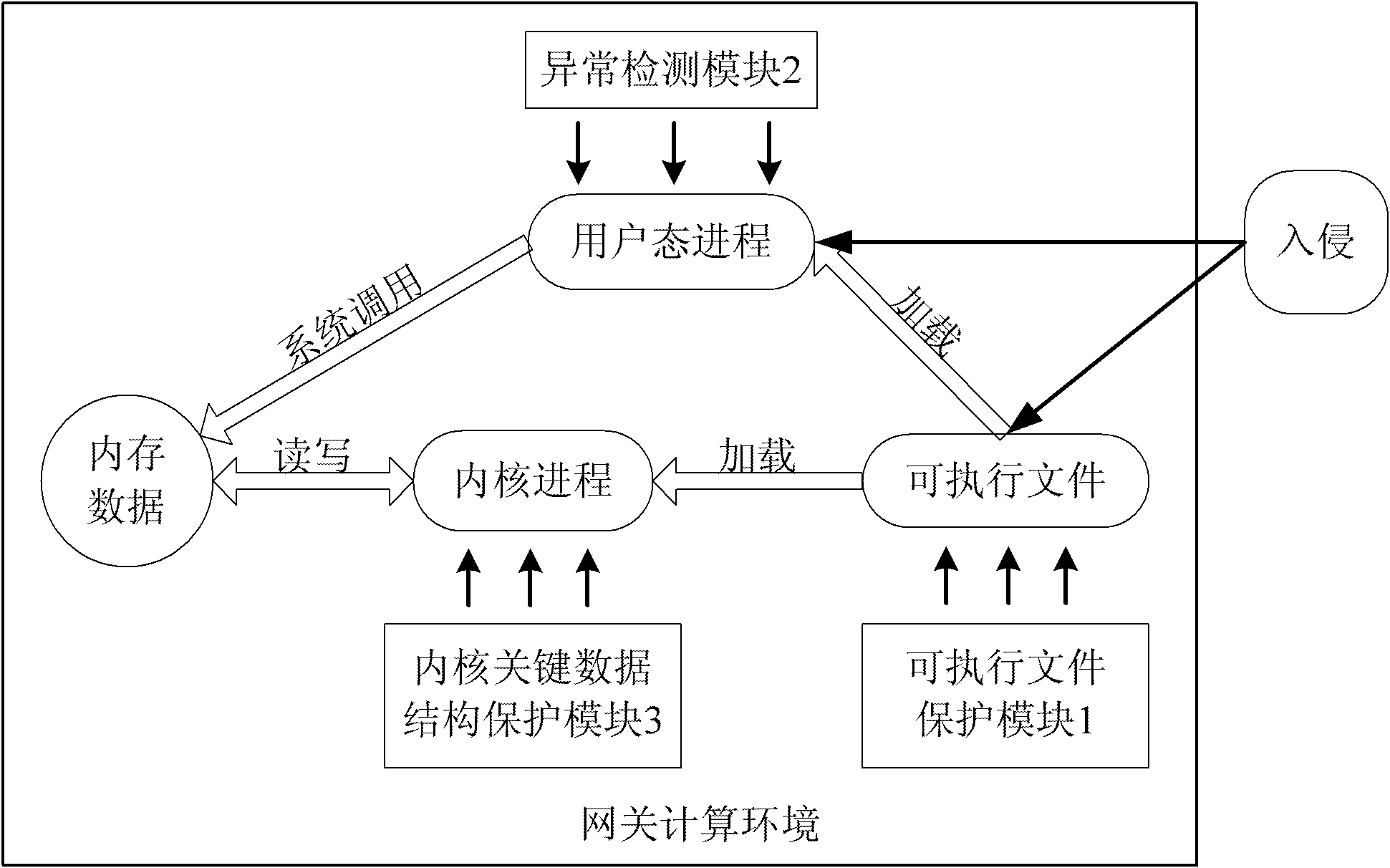
[0037] Specific implementation mode one: combine figure 1 Describe this embodiment, this embodiment comprises executable file protection module 1, anomaly detection module 2 and core key data structure protection module 3;
[0038] Executable file protection module 1 is used for the registration and logout of executable programs and the integrity protection function, and performs integrity detection on any program before running. Executable files are tampered with and malicious code is injected to ensure the security of user-mode processes loaded into memory and to protect static executable files in the operating system;
[0039] Anomaly detection module 2 is used to establish a set of legitimate process behaviors. This module extracts the process behaviors in the system during operation, and judges whether the process behaviors in the system are abnormal by matching with normal behaviors, prevents processes from being injected by malicious programs, and realizes computing of ...
specific Embodiment approach 2
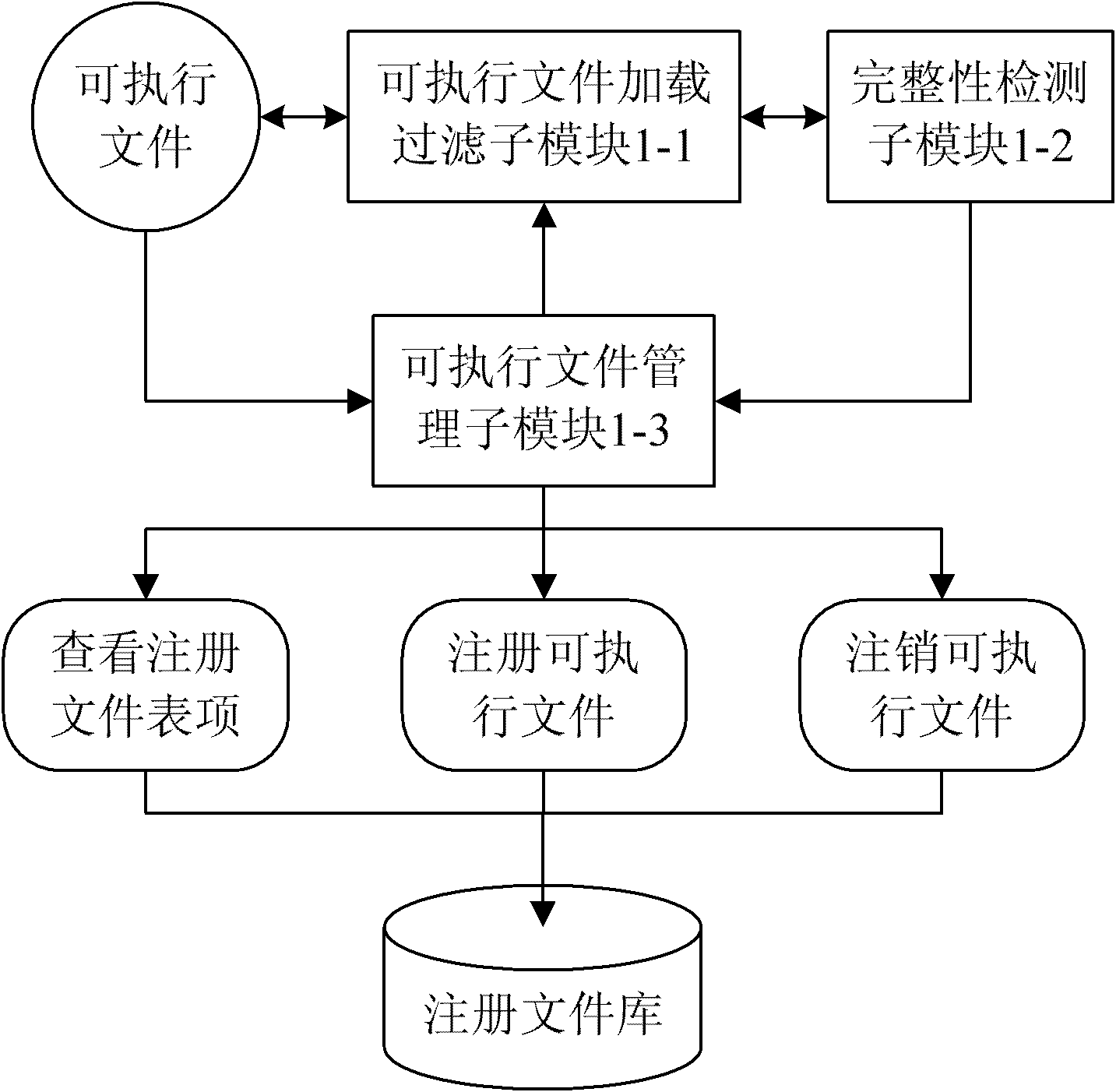
[0041] Specific implementation mode two: combination figure 2 Describe this embodiment, the difference between this embodiment and specific embodiment 1 is that the executable file protection module 1 includes an executable file loading filtering submodule 1-1, an integrity detection submodule 1-2 and an executable file management submodule 1 -3;
[0042]The executable file loading and filtering sub-module 1-1 is used to intercept the loading request of the executable file, and initiate an integrity detection request to the integrity detection sub-module 1-2, and make a decision based on the result obtained from the integrity detection sub-module 1-2 Whether to allow the program to load and run; the method for intercepting the executable file loading request is: by adding a hook program, intercepting the system call for loading the executable file in the kernel, and parsing out the file system information such as the file path in the parameter, so as to return ;
[0043] Th...
specific Embodiment approach 3
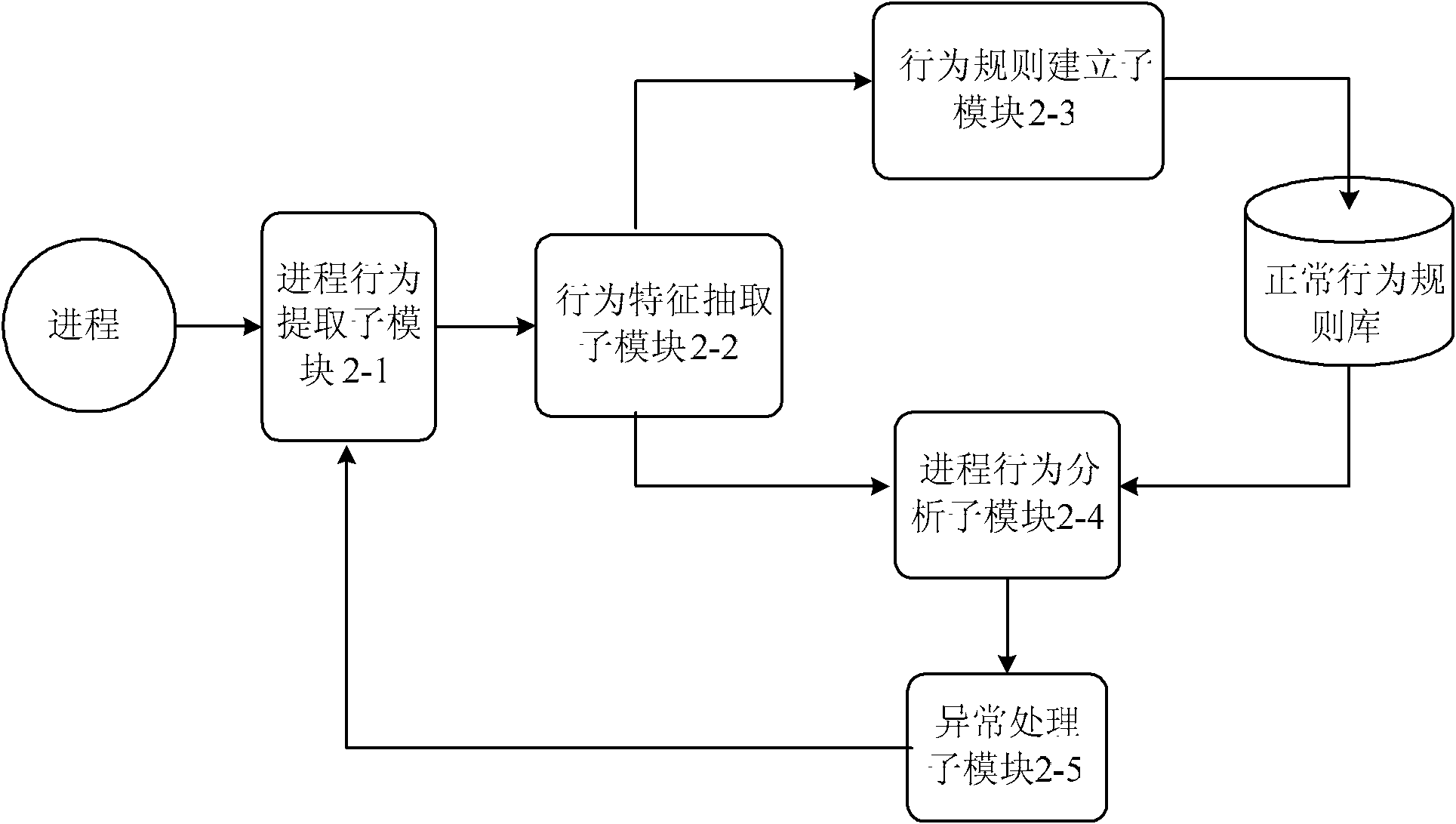
[0055] Specific embodiment three: This embodiment is described in conjunction with the figure. The difference between this embodiment and specific embodiment one is that the anomaly detection module 2 includes a process behavior extraction sub-module 2-1, a behavior feature extraction sub-module 2-2, and a behavior rule establishment sub-module. Module 2-3, process behavior analysis sub-module 2-4 and exception handling sub-module 2-5;
[0056] The process behavior extraction sub-module 2-1 is used to collect the process behavior. The process behavior is the system call sequence of the process. This module is mainly composed of processing system call interrupt hijacking, obtaining system call and sorting system call, and transferring process behavior information 4 parts.
[0057] The behavior feature extraction sub-module 2-2 is used for preprocessing and formatting the process behavior collected by the process behavior extraction sub-module 2-1;
[0058] The behavior rule es...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com