Method and system for detecting and defending multichannel network intrusion
An intrusion detection and network technology, applied in the field of network communication, can solve problems such as slow calculation convergence speed, inability to adapt to DDOS attack classification and calculation, etc., to achieve the effect of improving system resource occupancy rate, increasing real-time performance, and efficient positioning and searching
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
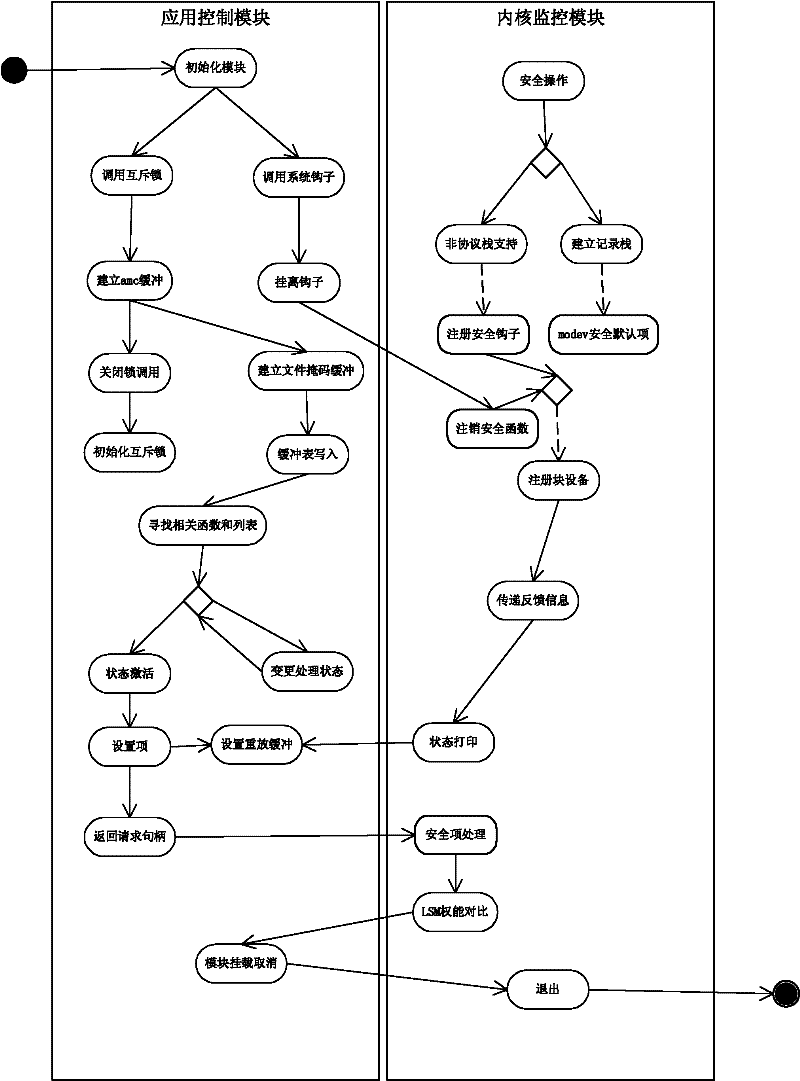
[0062] Now in conjunction with embodiment, accompanying drawing, the present invention will be further described:
[0063] The first part of the kernel access monitoring program
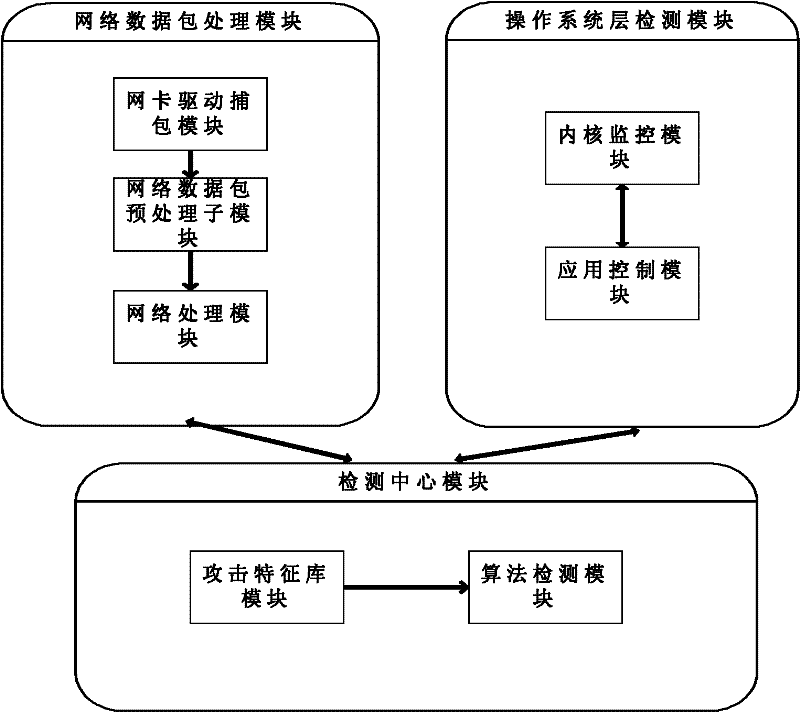
[0064] For DDOS distributed denial-of-service attacks in the network, as well as for the control of some hosts, we can use the monitoring in the kernel to resist some external attacks.
[0065] 1.1 Structure and interface model
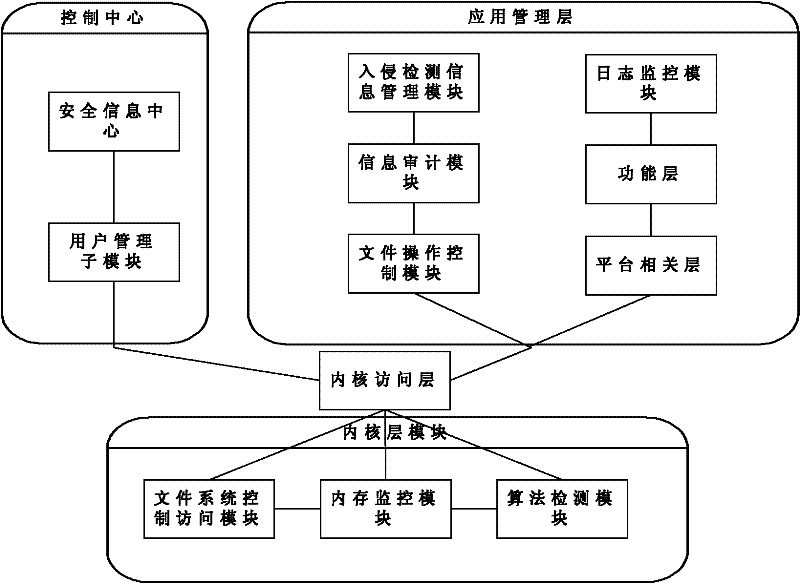
[0066] Existing projects are loaded in the driver mode, and the core module mainly deals with file access control. You can understand the position of the kernel driver access monitoring system in the existing security module through a complete security module:
[0067] From figure 2 We can see that several modules in the user application layer obtain the support of various modules in the kernel through the kernel interface, such as the file monitoring module, which controls file IO access through the kernel monitoring module in the kernel space, and then feeds back to the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com