Patents
Literature
400 results about "Virtual hosting" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
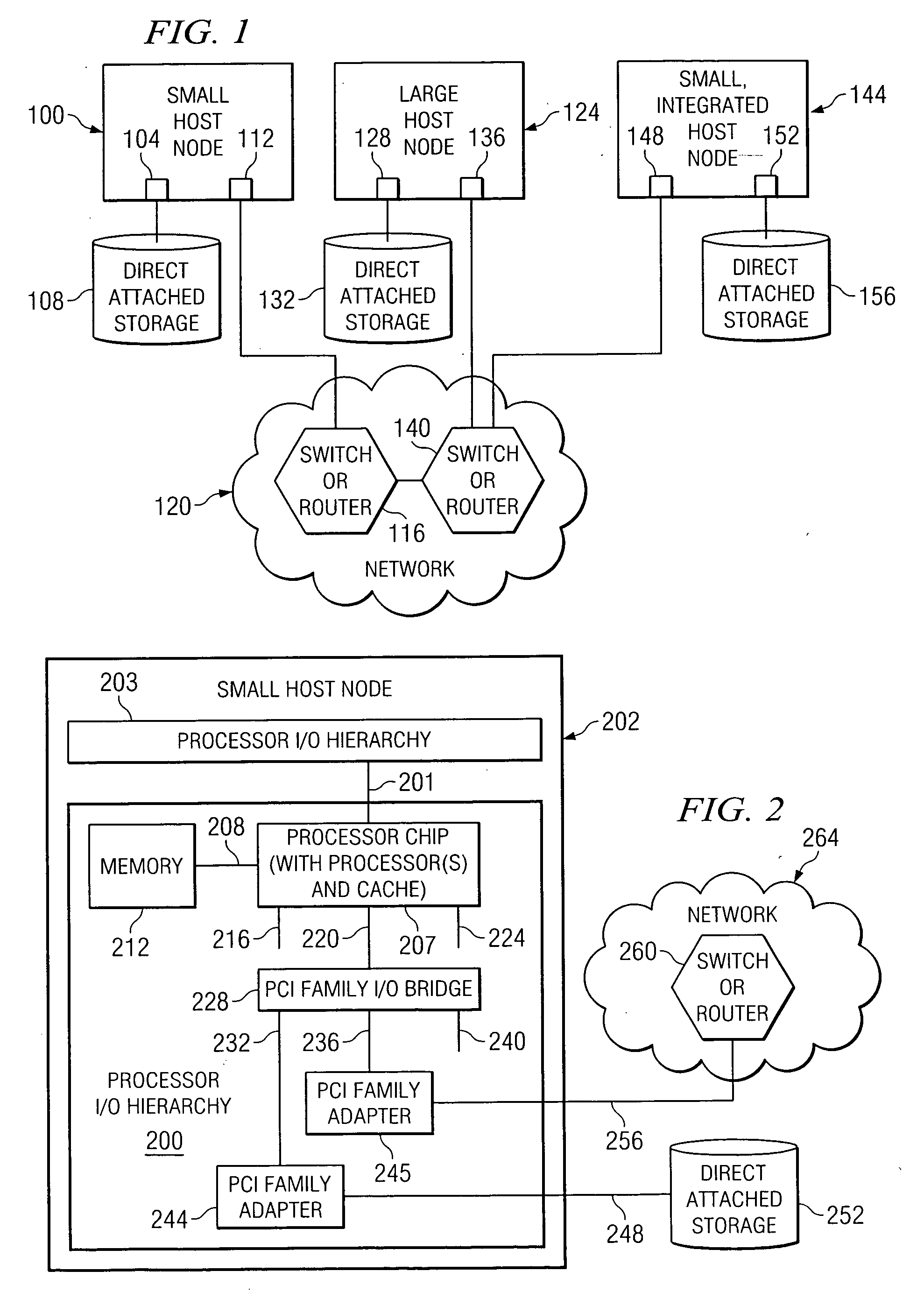
Virtual hosting is a method for hosting multiple domain names (with separate handling of each name) on a single server (or pool of servers). This allows one server to share its resources, such as memory and processor cycles, without requiring all services provided to use the same host name. The term virtual hosting is usually used in reference to web servers but the principles do carry over to other internet services.
System and method for managing virtual servers
ActiveUS20050120160A1Grow and shrink capabilityMaximize useResource allocationMemory adressing/allocation/relocationOperational systemPrimitive state
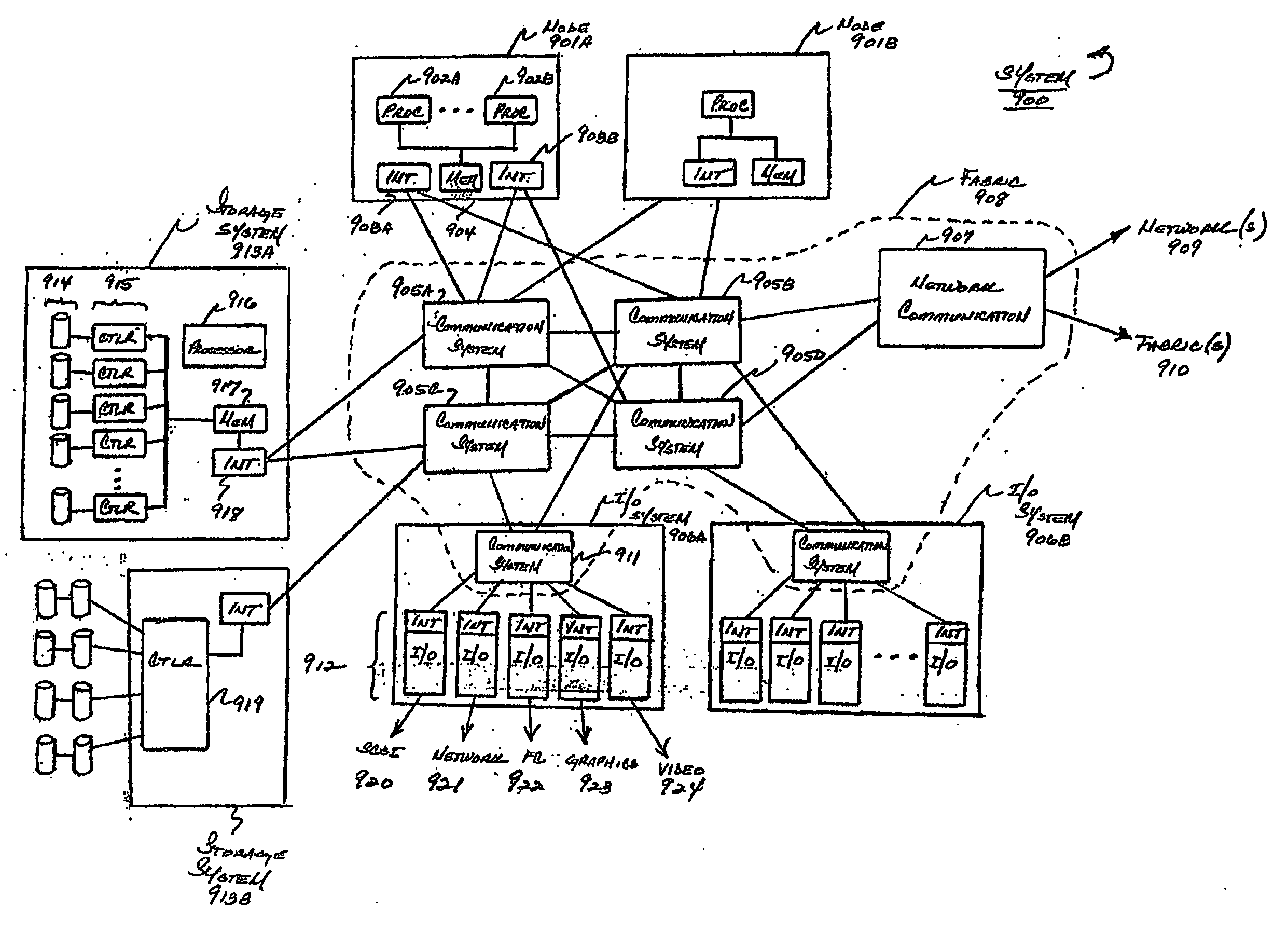
A management capability is provided for a virtual computing platform. In one example, this platform allows interconnected physical resources such as processors, memory, network interfaces and storage interfaces to be abstracted and mapped to virtual resources (e.g., virtual mainframes, virtual partitions). Virtual resources contained in a virtual partition can be assembled into virtual servers that execute a guest operating system (e.g., Linux). In one example, the abstraction is unique in that any resource is available to any virtual server regardless of the physical boundaries that separate the resources. For example, any number of physical processors or any amount of physical memory can be used by a virtual server even if these resources span different nodes. A virtual computing platform is provided that allows for the creation, deletion, modification, control (e.g., start, stop, suspend, resume) and status (i.e., events) of the virtual servers which execute on the virtual computing platform and the management capability provides controls for these functions. In a particular example, such a platform allows the number and type of virtual resources consumed by a virtual server to be scaled up or down when the virtual server is running. For instance, an administrator may scale a virtual server manually or may define one or more policies that automatically scale a virtual server. Further, using the management API, a virtual server can monitor itself and can scale itself up or down depending on its need for processing, memory and I / O resources. For example, a virtual server may monitor its CPU utilization and invoke controls through the management API to allocate a new processor for itself when its utilization exceeds a specific threshold. Conversely, a virtual server may scale down its processor count when its utilization falls. Policies can be used to execute one or more management controls. More specifically, a management capability is provided that allows policies to be defined using management object's properties, events and / or method results. A management policy may also incorporate external data (e.g., an external event) in its definition. A policy may be triggered, causing the management server or other computing entity to execute an action. An action may utilize one or more management controls. In addition, an action may access external capabilities such as sending notification e-mail or sending a text message to a telephone paging system. Further, management capability controls may be executed using a discrete transaction referred to as a “job.” A series of management controls may be assembled into a job using one or management interfaces. Errors that occur when a job is executed may cause the job to be rolled back, allowing affected virtual servers to return to their original state.
Owner:ORACLE INT CORP
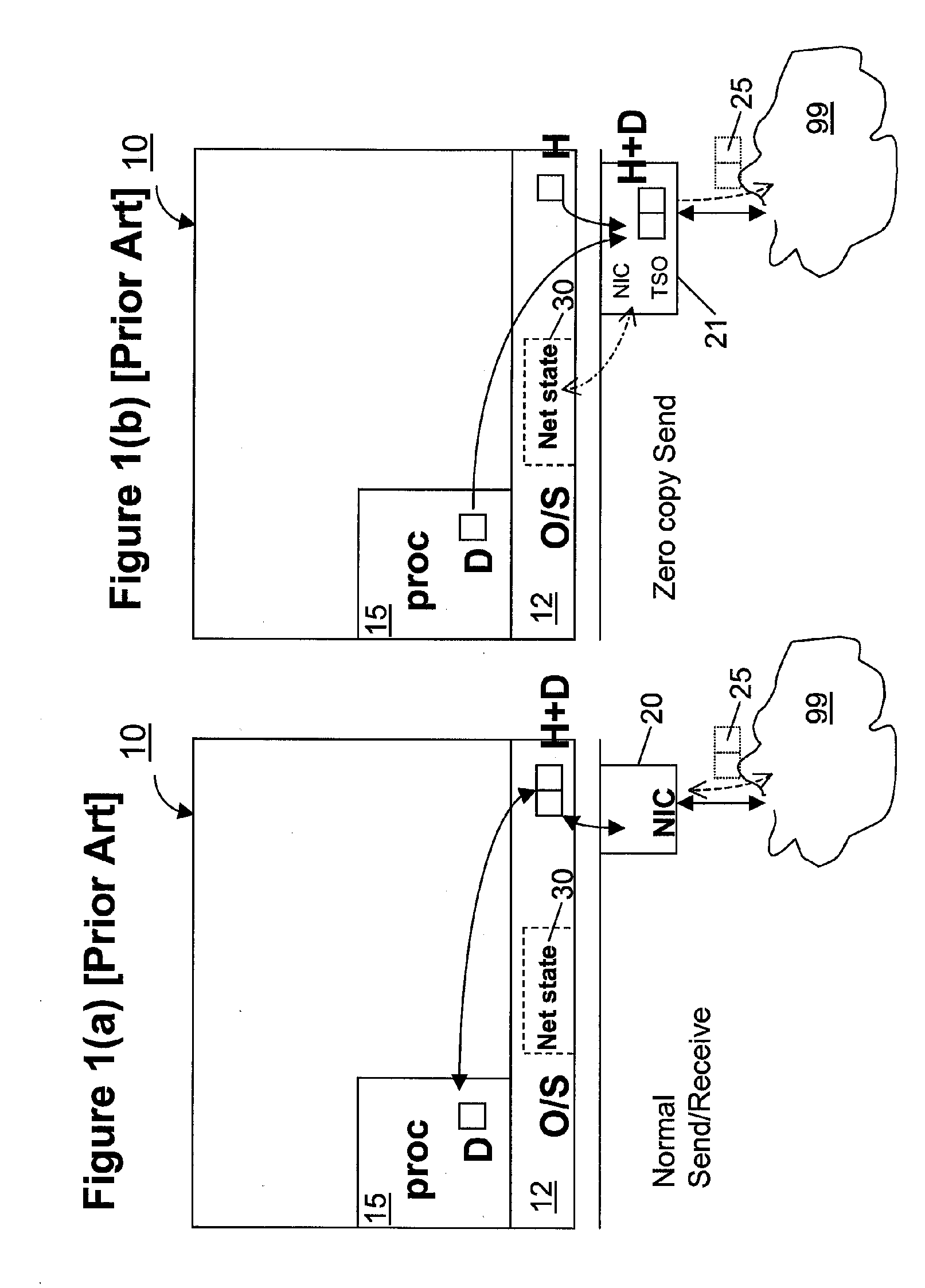
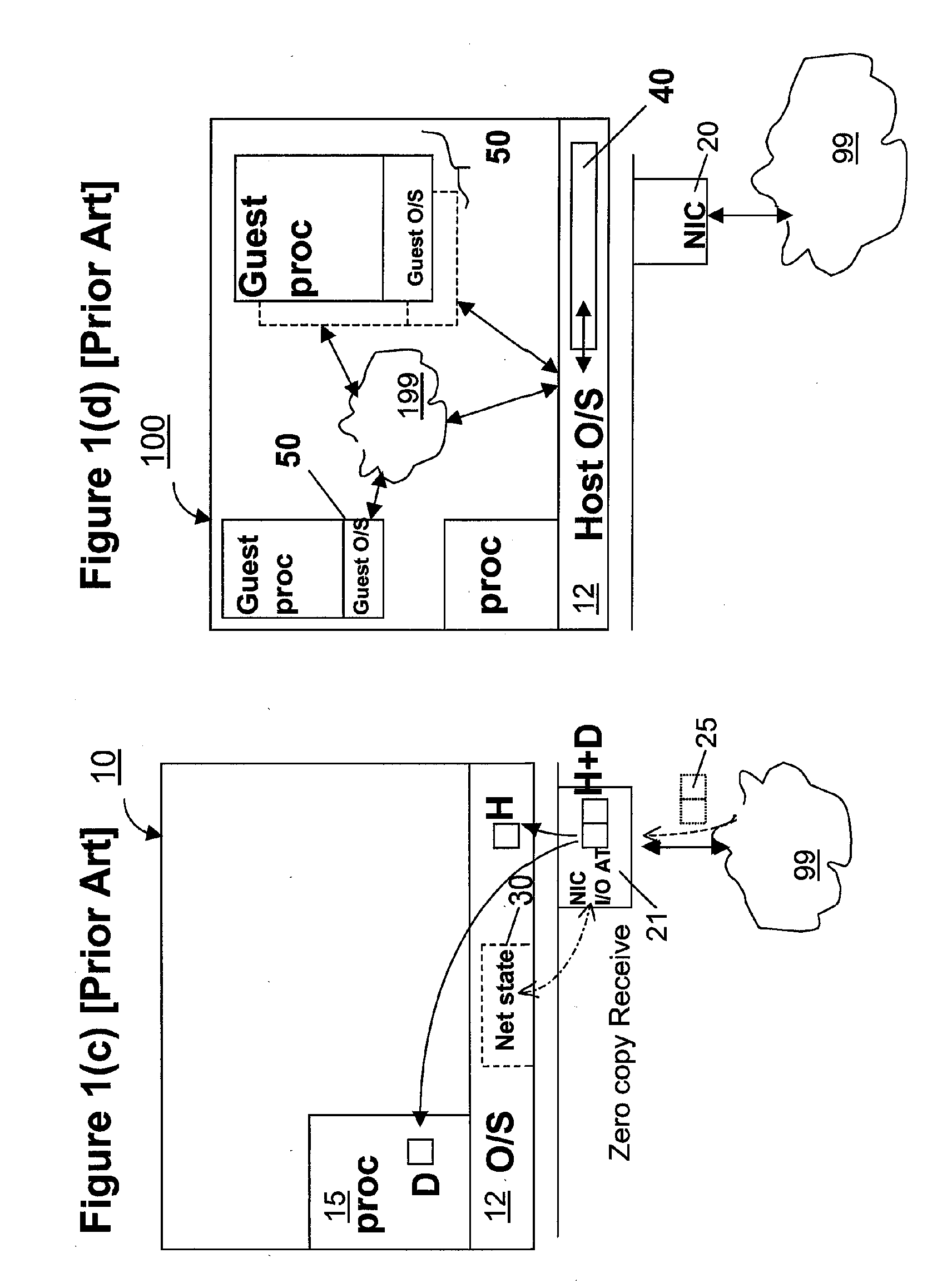
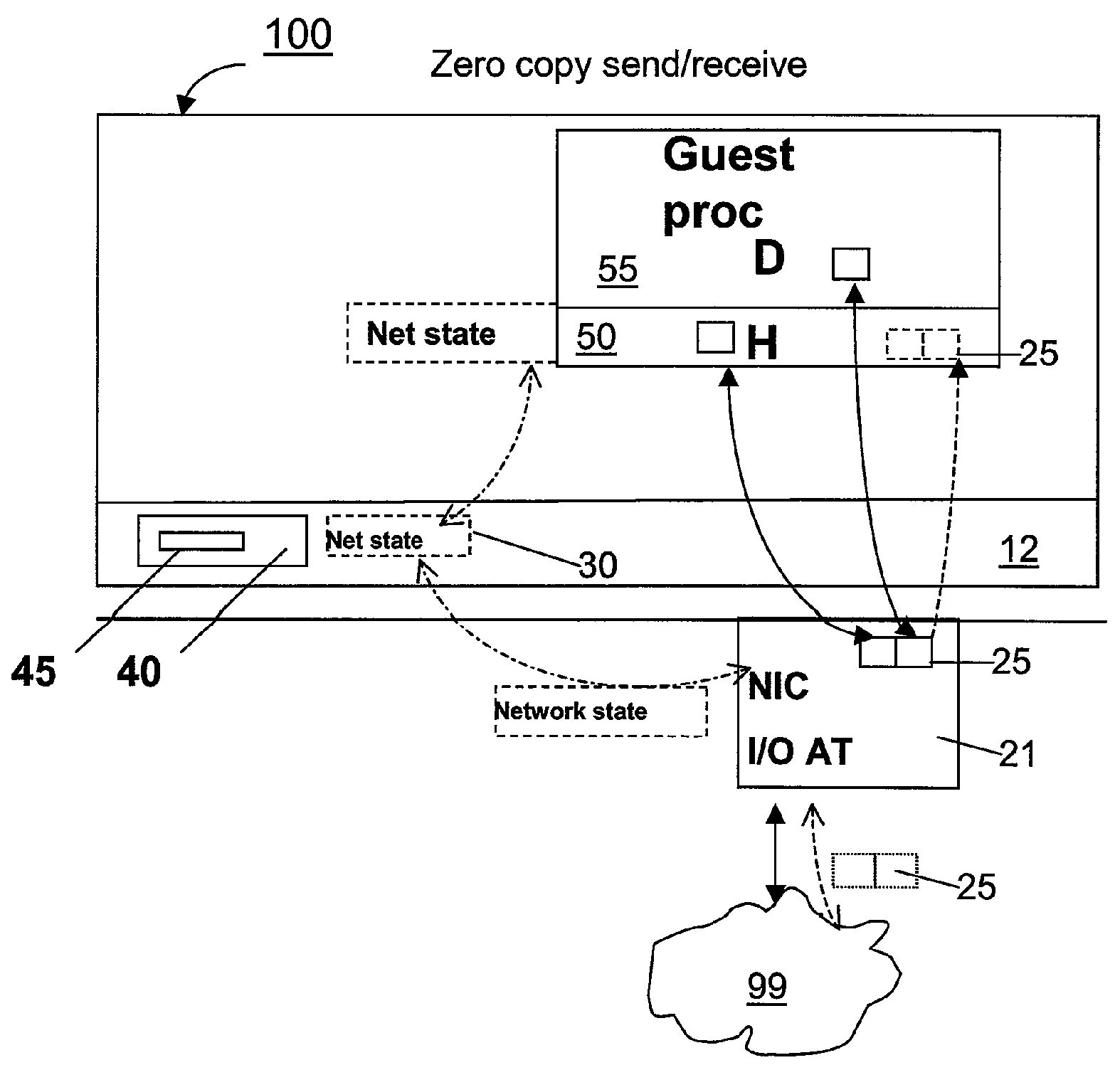
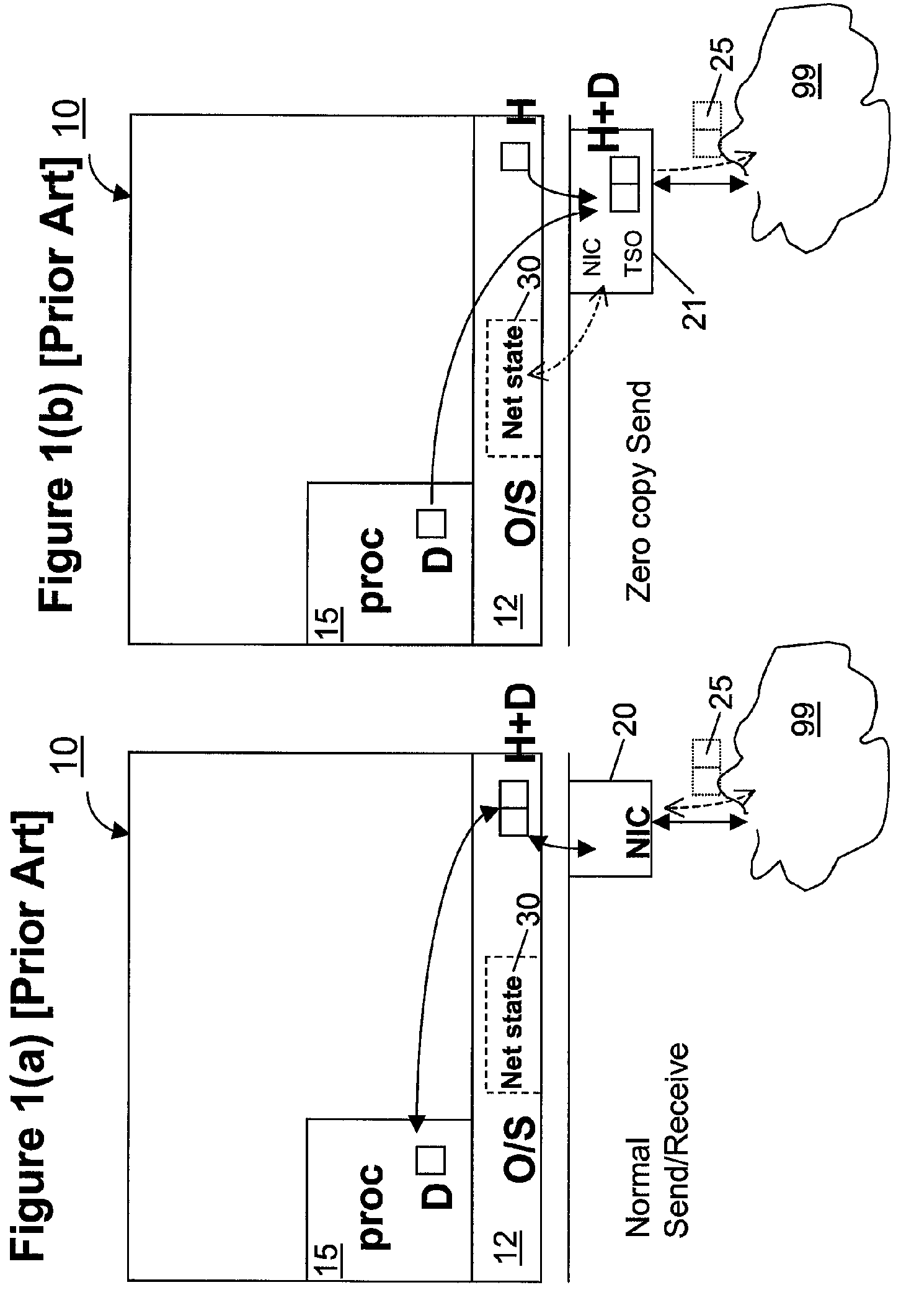
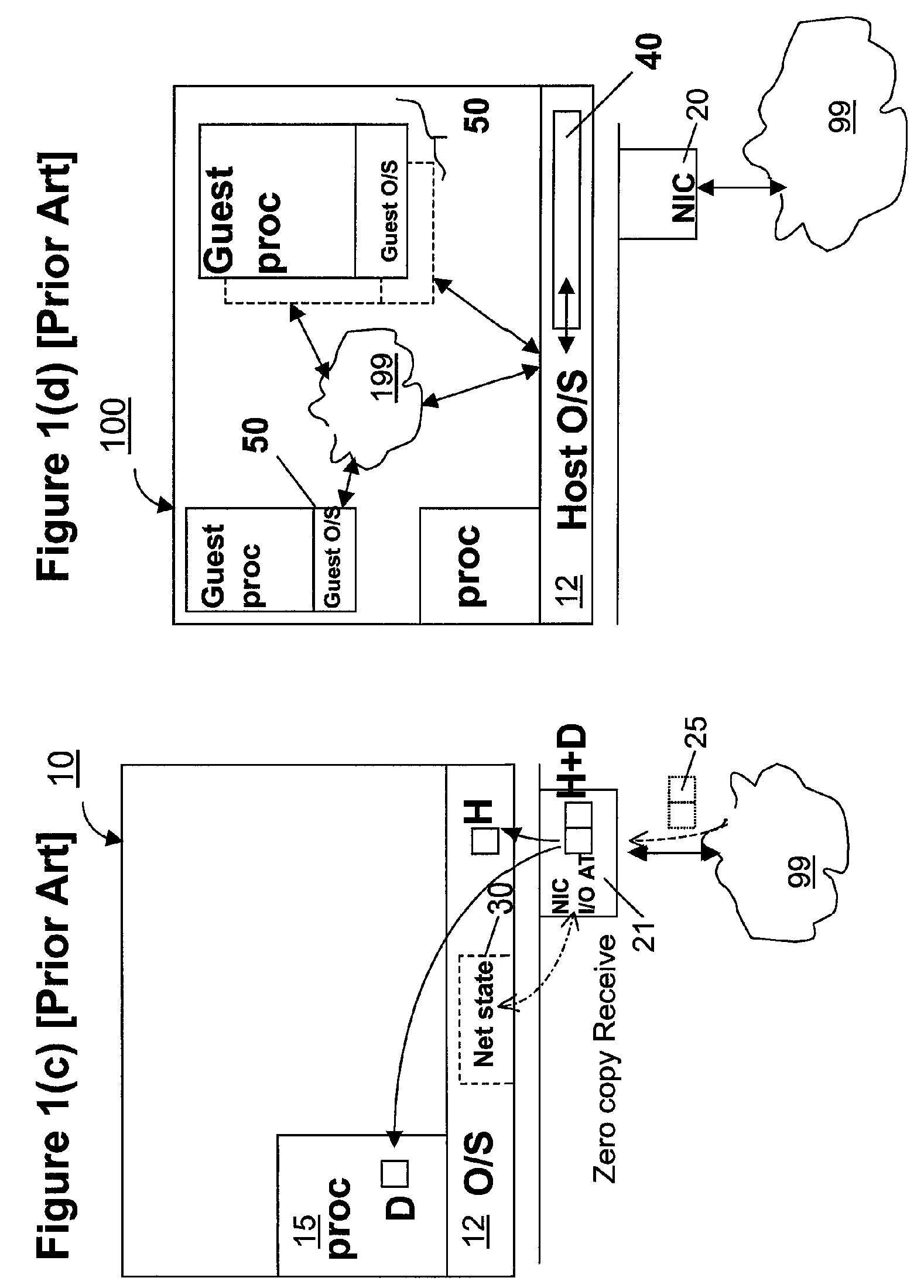
Zero-copy network I/O for virtual hosts
ActiveUS20070061492A1Eliminate the problemSolve excessive overheadDigital computer detailsTransmissionData packVirtualization
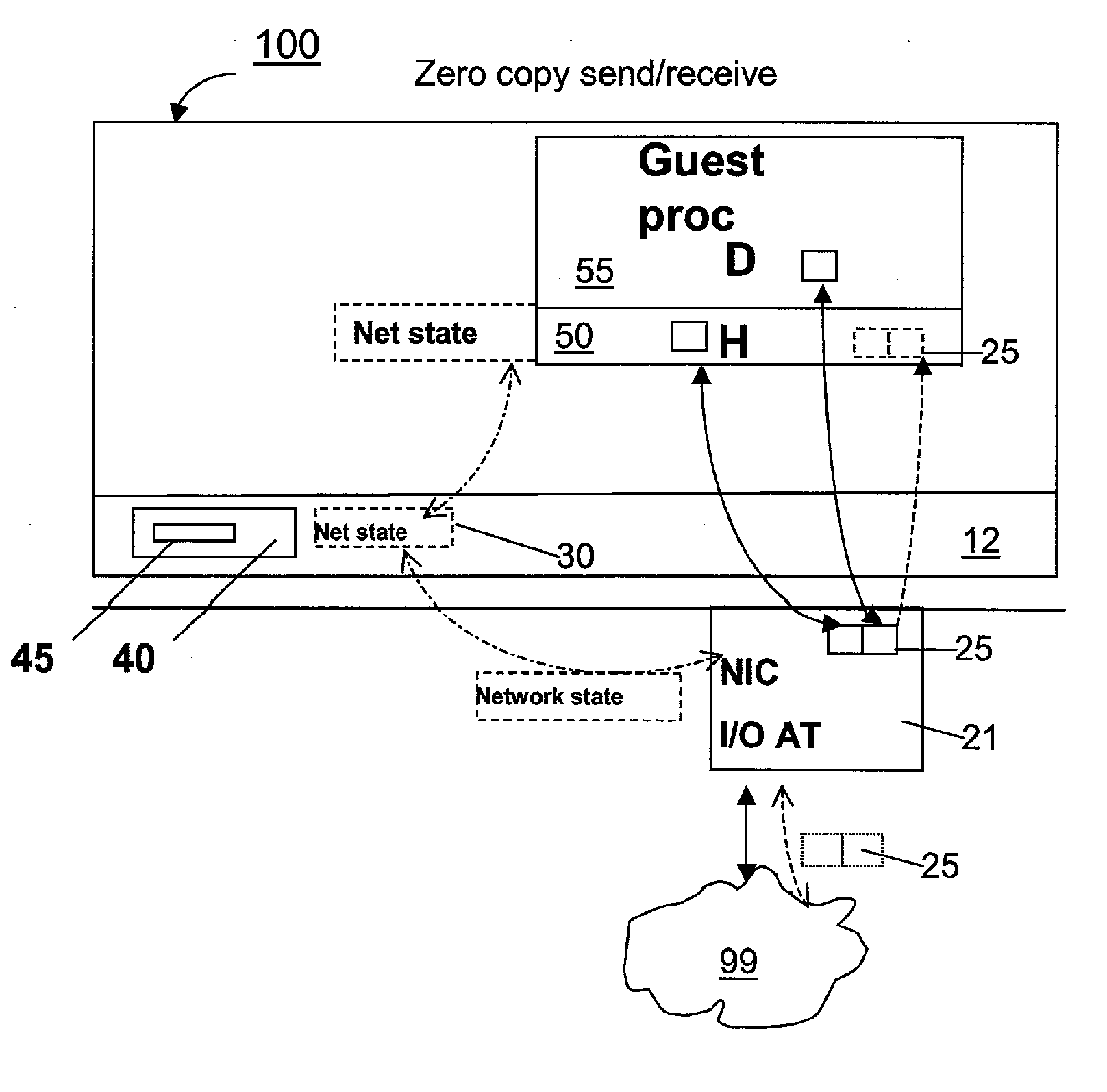
Techniques for virtualized computer system environments running one or more virtual machines that obviate the extra host operating system (O / S) copying steps required for sending and receiving packets of data over a network connection, thus eliminating major performance problems in virtualized environment. Such techniques include methods for emulating network I / O hardware device acceleration-assist technology providing zero-copy I / O sending and receiving optimizations. Implementation of these techniques require a host O / S to perform actions including, but not limited to: checking of the address translations (ensuring availability and data residency in physical memory), checking whether the destination of a network packet is local (to another virtual machine within the computing system), or across an external network; and, if local, checking whether either the sending destination VM, receiving VM process, or both, supports emulated hardware accelerated-assist on the same physical system. This optimization, in particular, provides a further optimization in that the packet data checksumming operations may be omitted when sending packets between virtual machines in the same physical system.
Owner:RED HAT
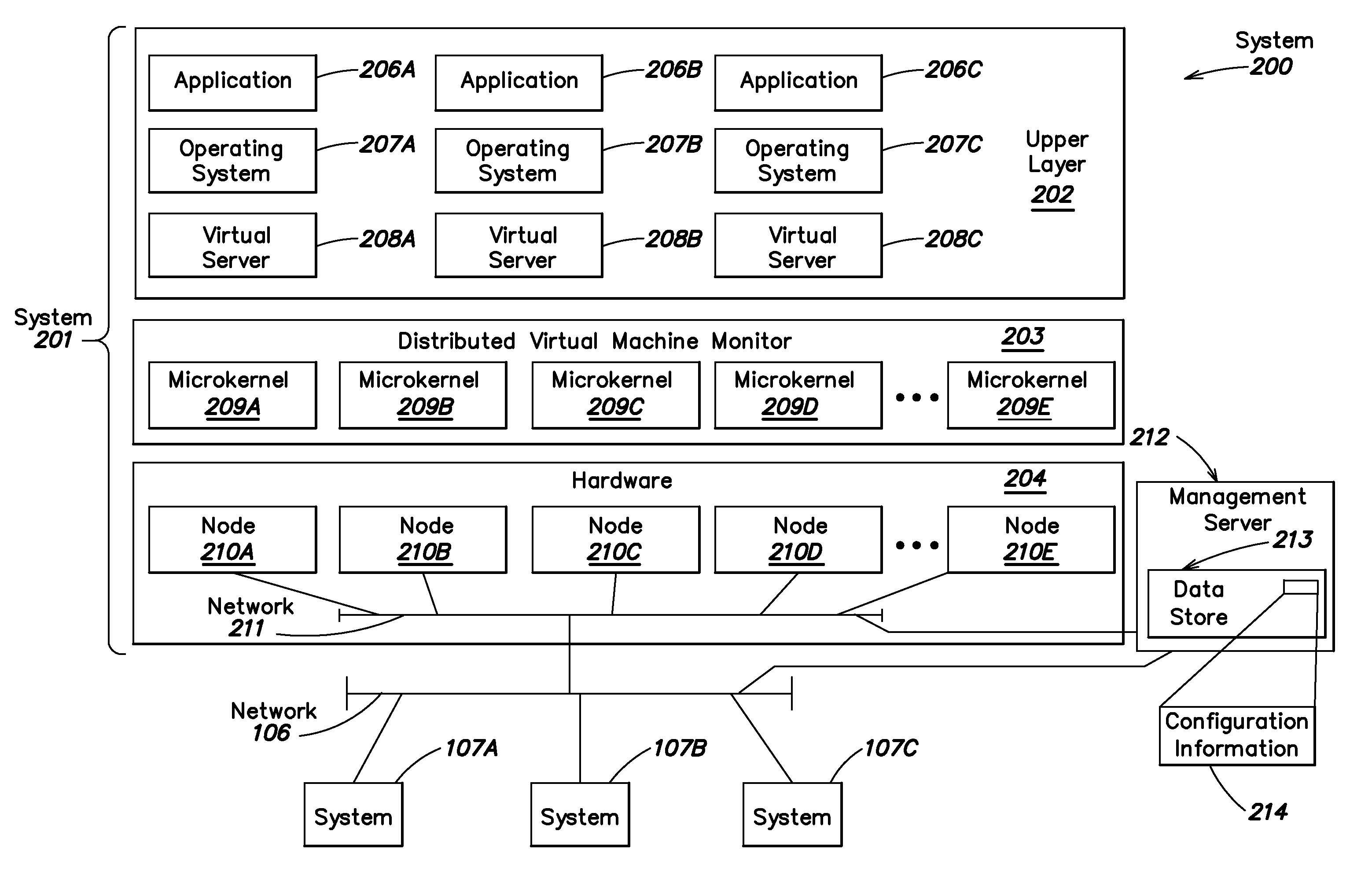
Distributed virtual machine monitor for managing multiple virtual resources across multiple physical nodes
ActiveUS8776050B2Grow and shrink capabilityMaximize useResource allocationMemory adressing/allocation/relocationOperational systemGNU/Linux
A management capability is provided for a virtual computing platform. In one example, this platform allows interconnected physical resources such as processors, memory, network interfaces and storage interfaces to be abstracted and mapped to virtual resources (e.g., virtual mainframes, virtual partitions). Virtual resources contained in a virtual partition can be assembled into virtual servers that execute a guest operating system (e.g., Linux). In one example, the abstraction is unique in that any resource is available to any virtual server regardless of the physical boundaries that separate the resources. For example, any number of physical processors or any amount of physical memory can be used by a virtual server even if these resources span different nodes.
Owner:ORACLE INT CORP
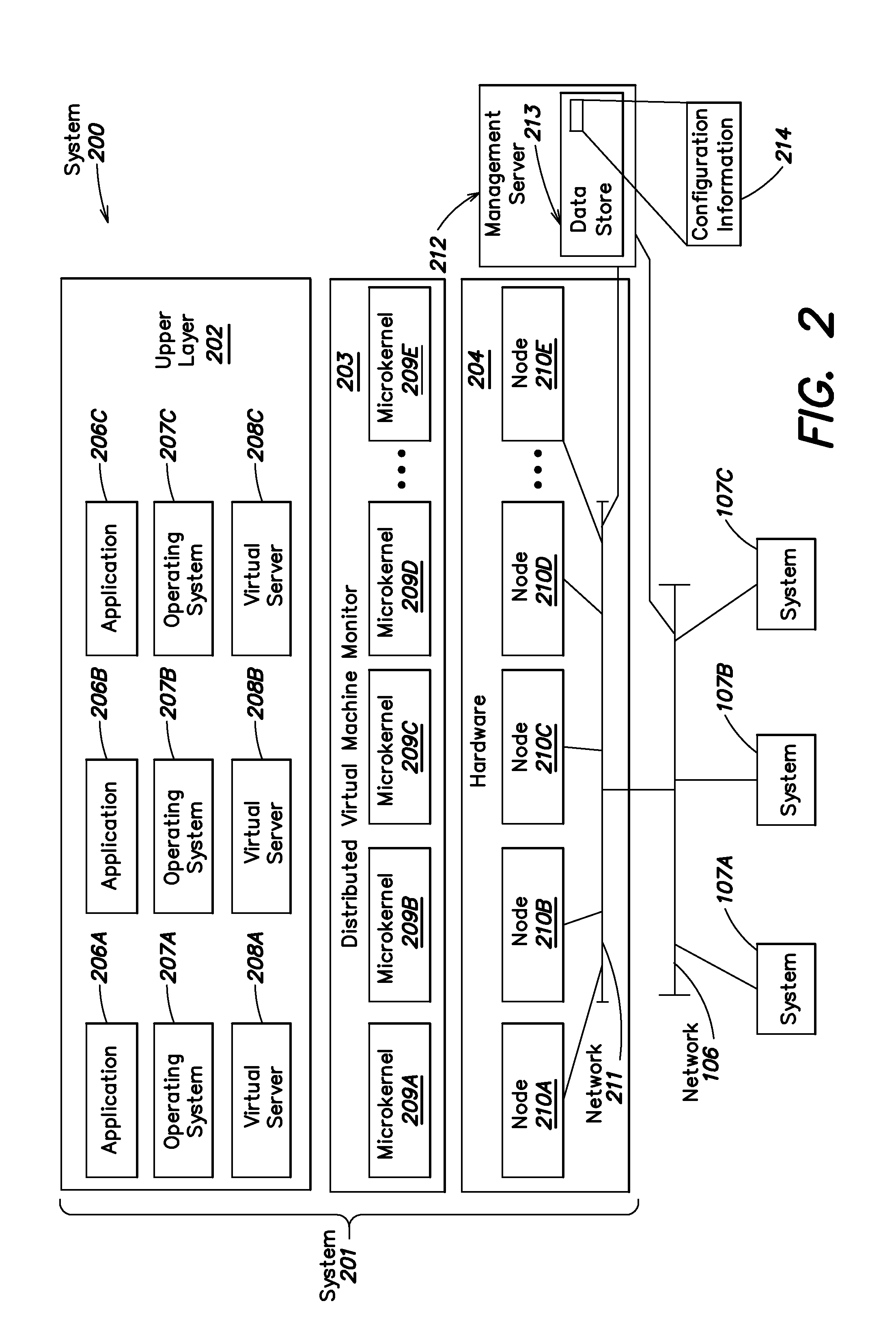
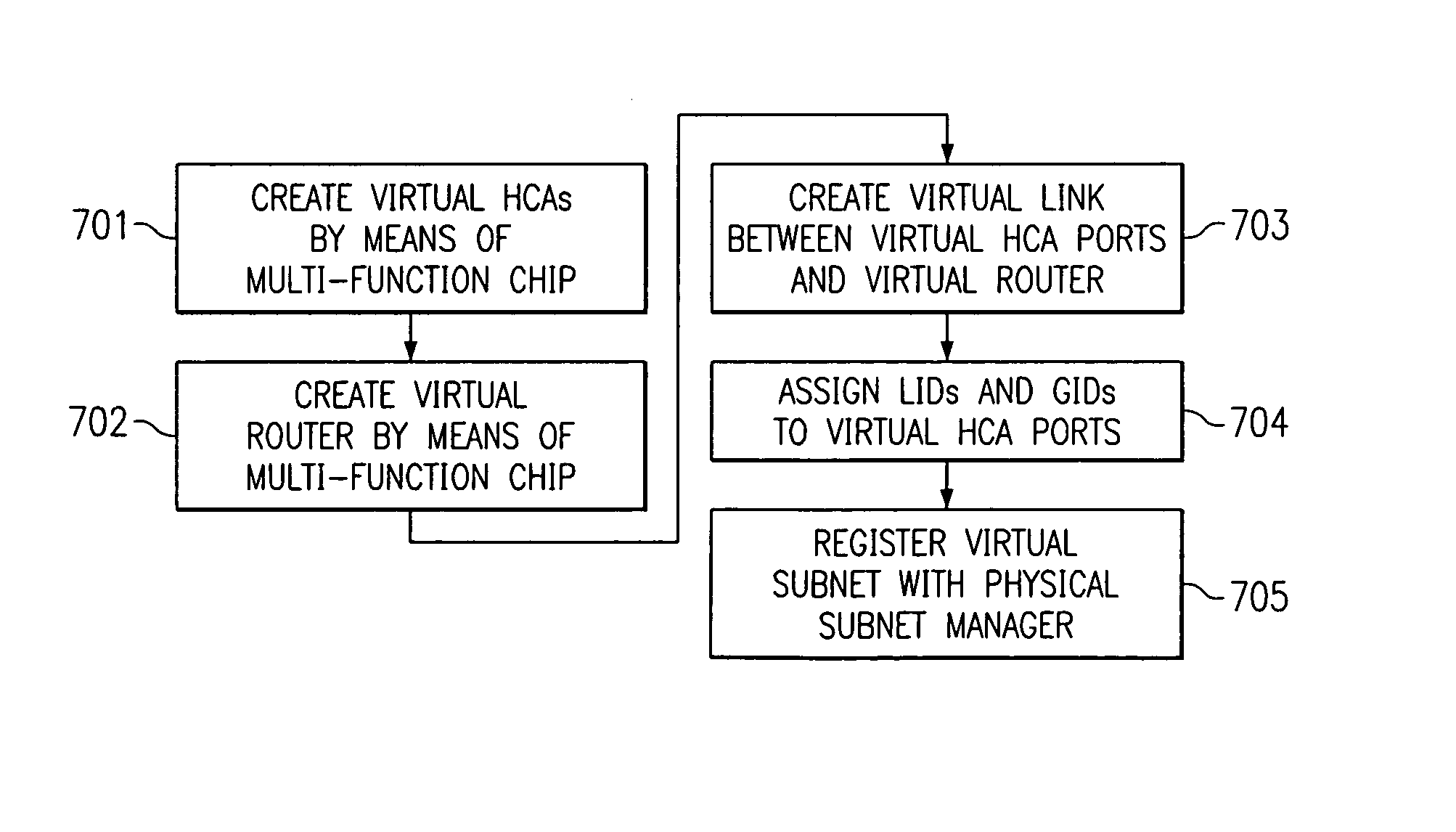
End node partitioning using virtualization
ActiveUS7093024B2Increases horizontal scaling capabilityMultiple digital computer combinationsWireless commuication servicesVirtualizationVirtual hosting
A mechanism for allowing a single physical IB node to virtualize a plurality of host channel adapters is provided. This includes providing the appearance of both a router and multiple virtual HCA's residing behind that router, to the external REAL subnet components. Each virtual host channel adapter will have unique access control levels. One or more InfiniBand subnets are virtualized in such a way that nodes residing both within the virtual subnets and in separate physical subnets are completely unaware of the virtualization. This virtualization of InfiniBand subnets significantly increases the horizontal scaling capabilities of a single InfiniBand physical component, while at the same time provides “native” network throughput for all the virtual hosts.
Owner:IBM CORP
Virtual host acceleration system
ActiveUS20030182423A1Improve performanceSufficient level of securityMemory adressing/allocation/relocationMultiple digital computer combinationsWeb siteContent distribution
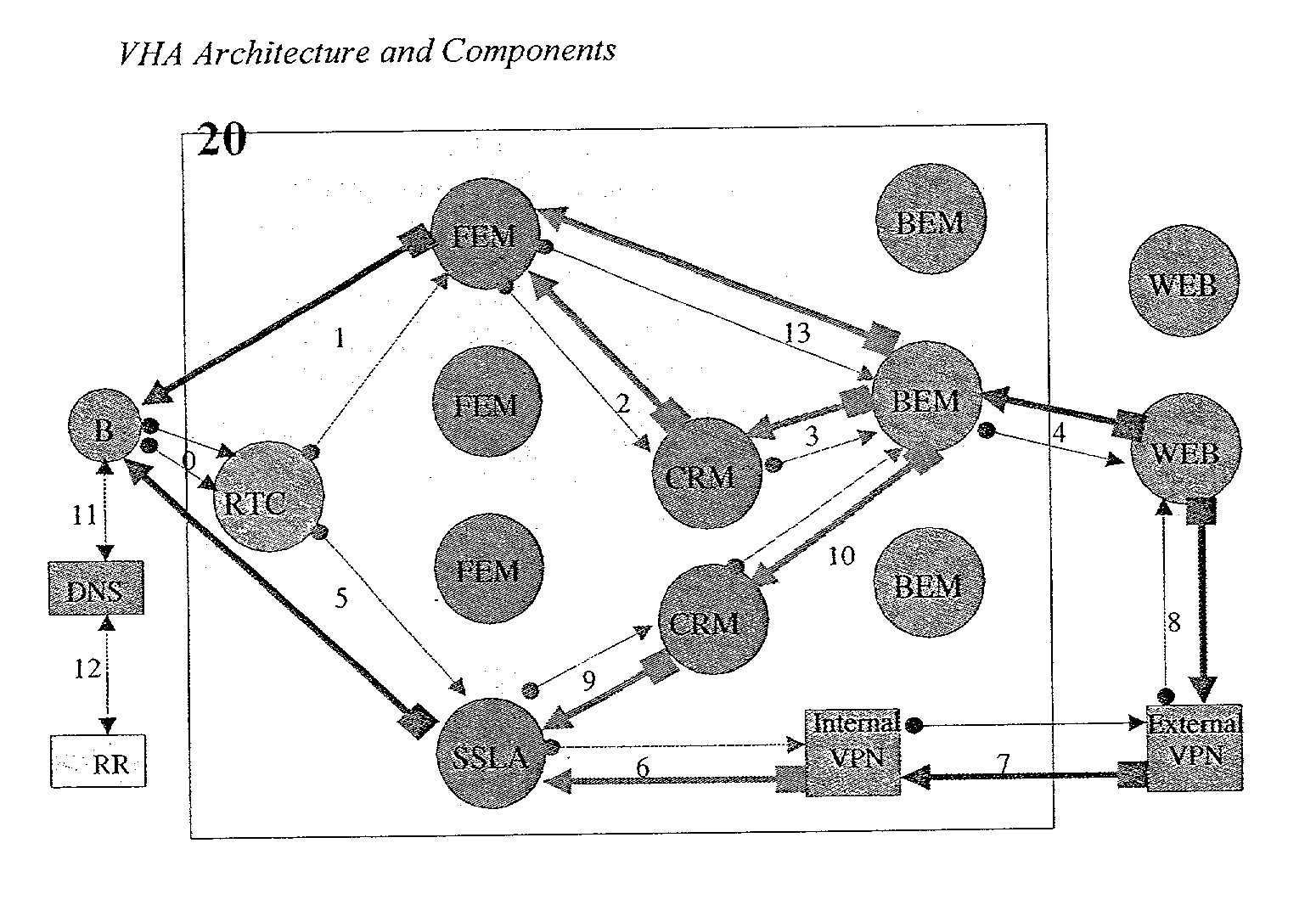
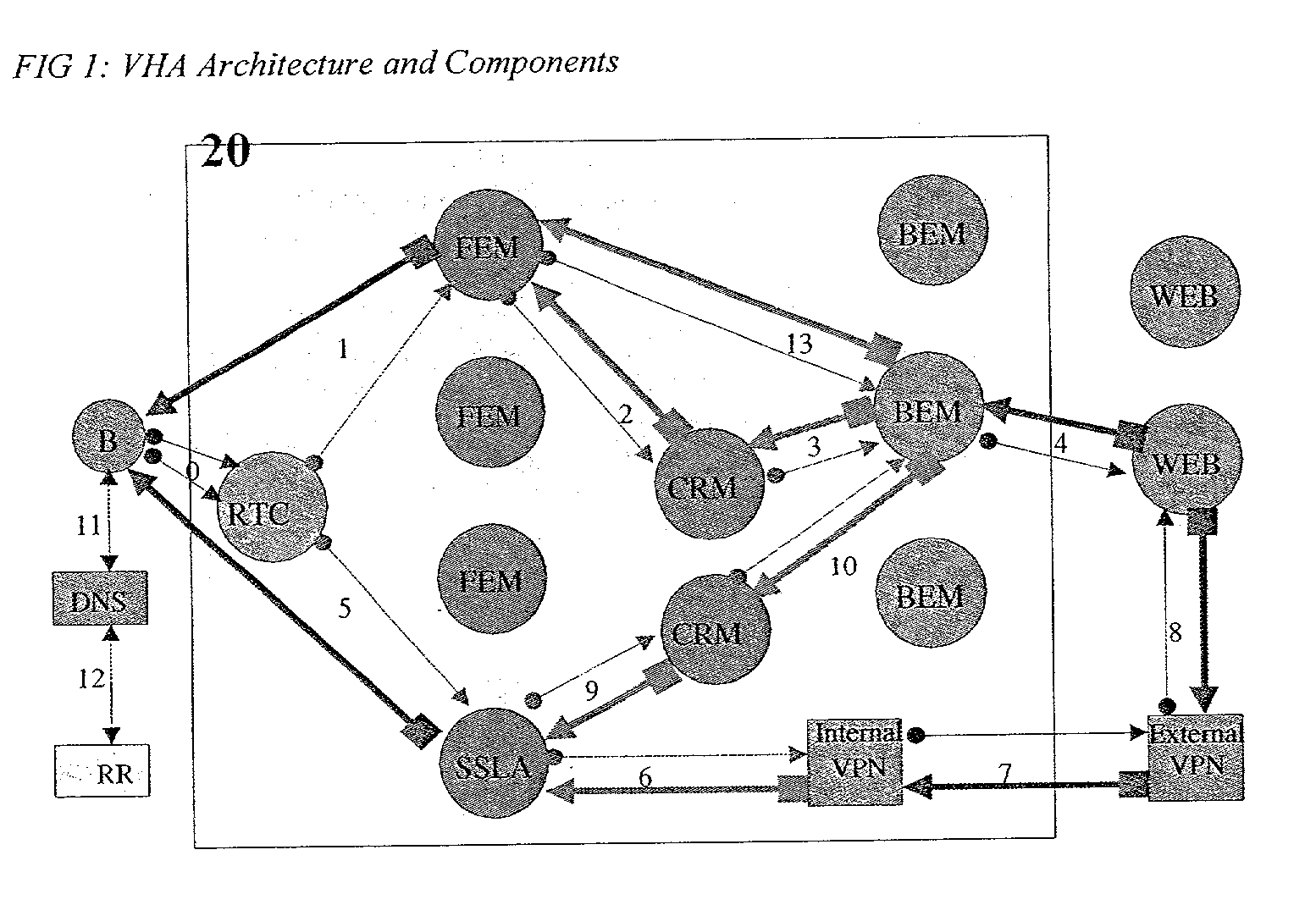
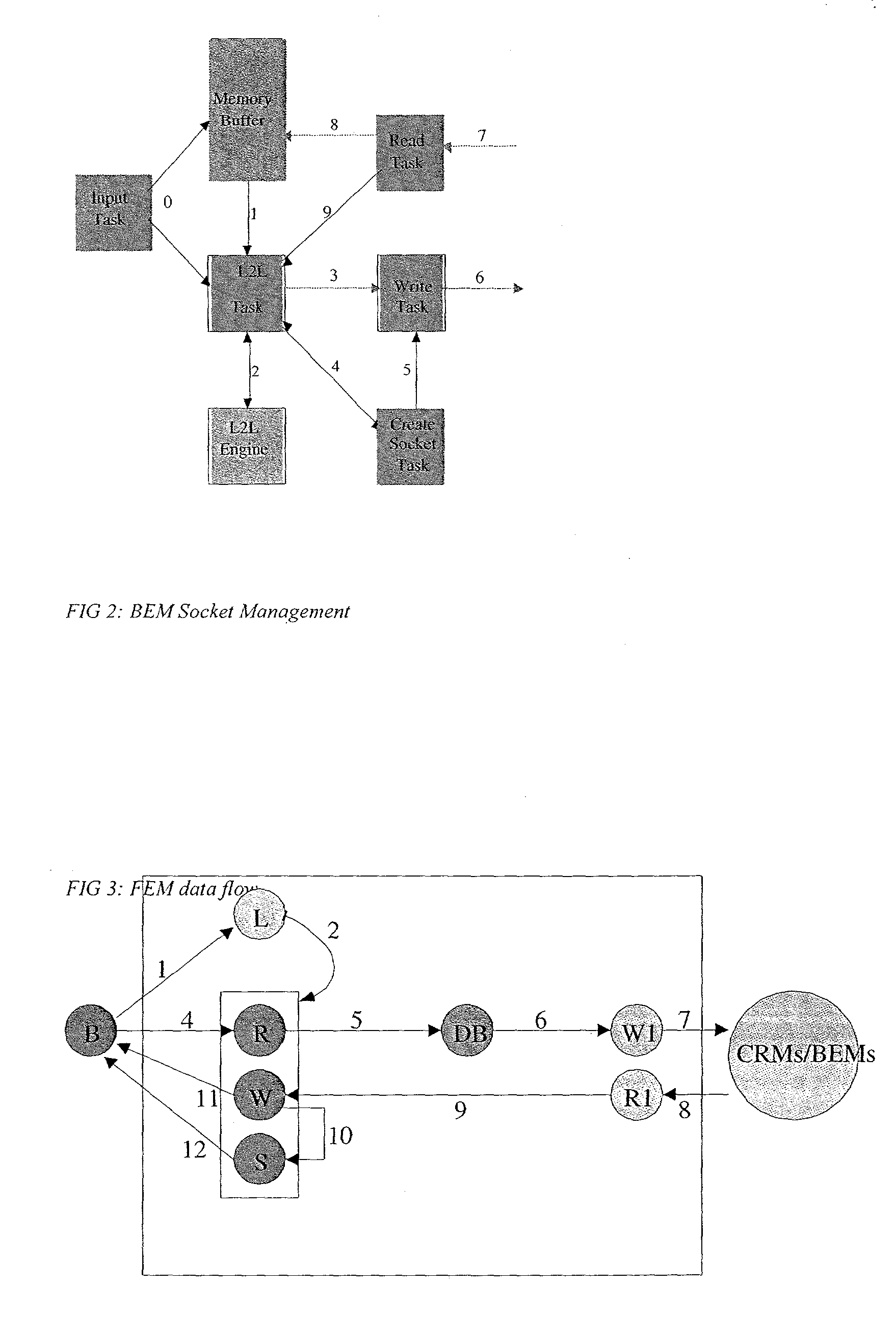
A method and a system for improving Web hosting performance, enhancing content distribution and security on the Internet and stabilizing WEB Site connectivity, by means of creating a TCP terminating buffer around subscriber WEB Sites. A DNS agent diverts client requests to WEB Sites to a Virtual Host Accelerating (VHA) Site in closest proximity. The VHA Site comprises a set of physically identical computer units and processing is enhanced on those units by means of a hardware devise to accelerate database searches. The VHA determines if the client request is of a permitted type and if the request can be processed from recycled data. Both static and dynamic requests can be serviced from recycled material and only in certain circumstances are requests forwarded to the WEB Sites by means of permanent open connections. In some cases SSL requests are also served from recycled material. The client receives a response via the VHA Site thereby severing all direct connectivity between the client and the target WEB Sites.
Owner:F5 NETWORKS INC +1
System and method to support subscription based Infrastructure and software as a service
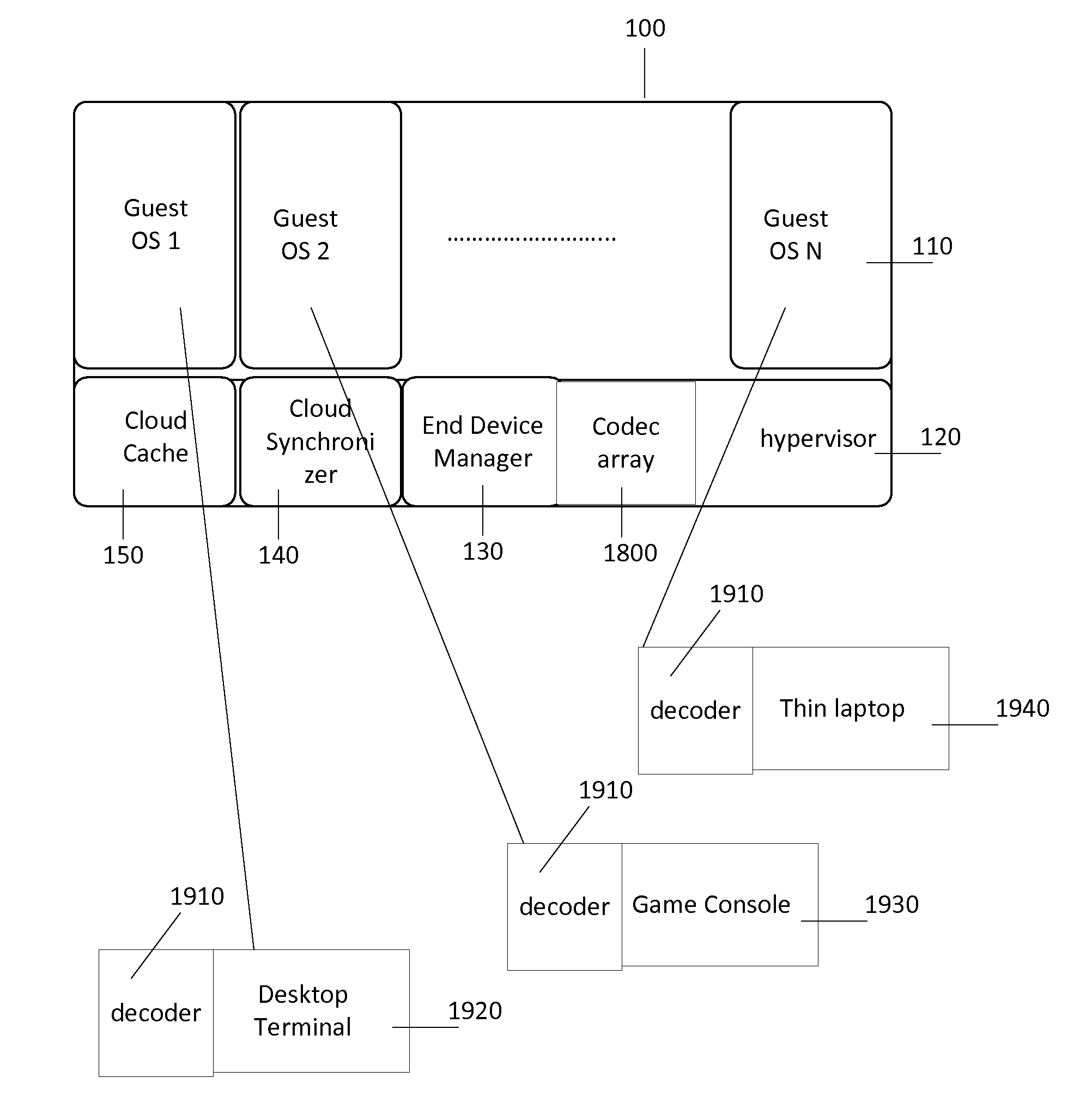
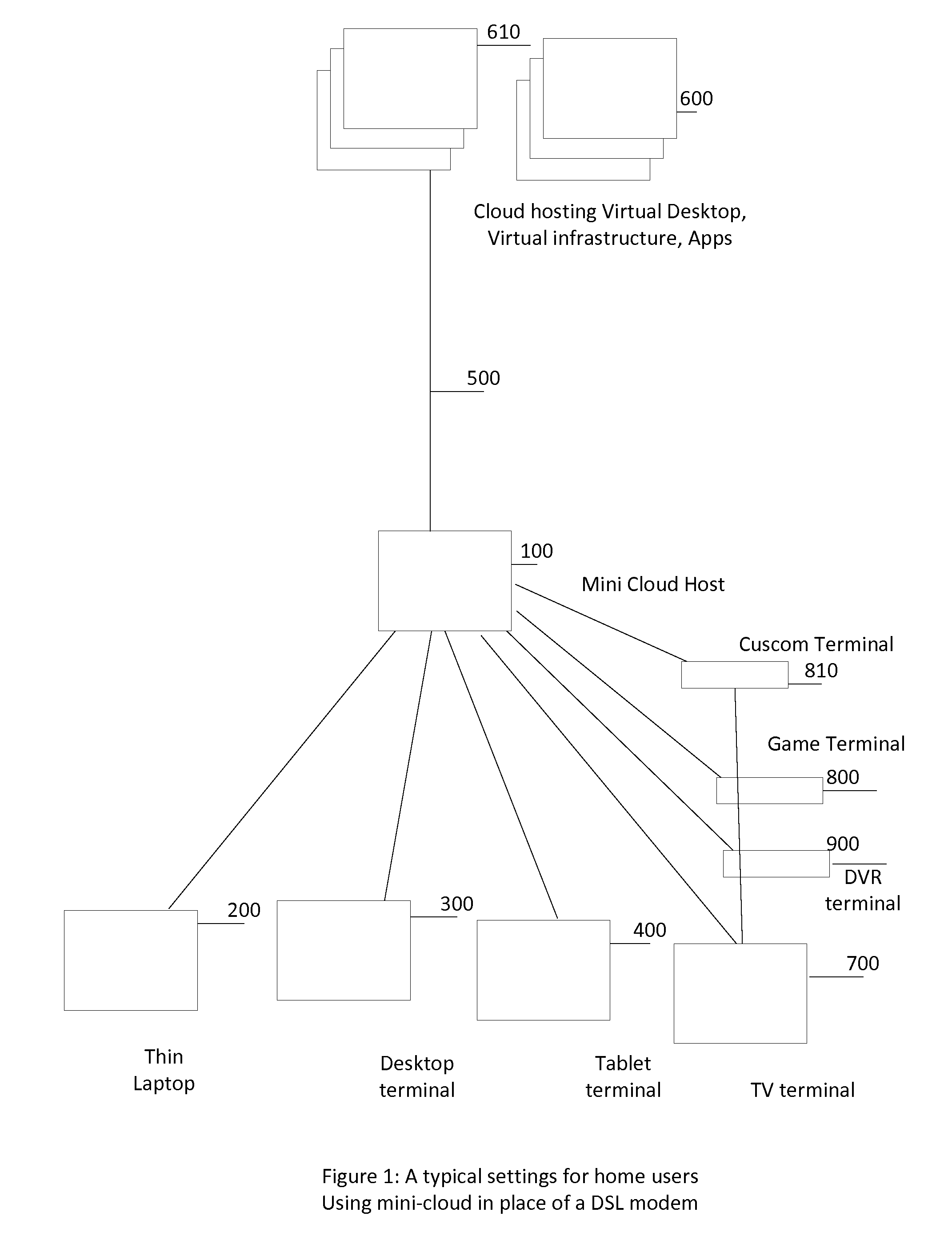
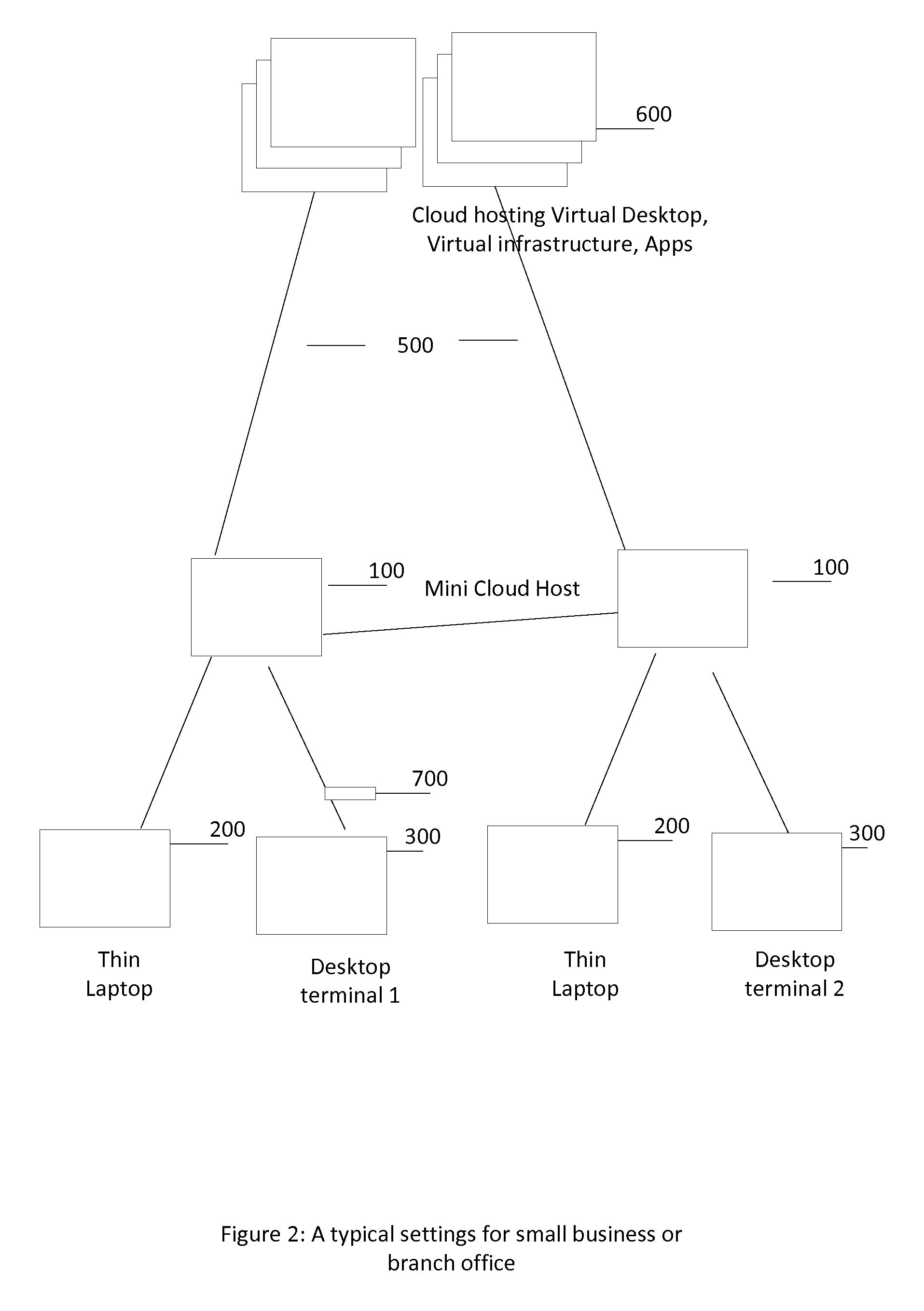
A mini-cloud system has been described to enable subscription or service model for computing infrastructure, software and Digital content. The mini-cloud system work as a pipe line for information delivery connecting end user, infrastructure provider, content provider, and retailer offering automatic provisioning of infrastructure, content lifecycle management, automatic upgrade, servicing, license managements based on subscription model. Mini-cloud system uses a subscription management component, virtualization host to back computing environment, then add routing component to connect to backend cloud infrastructure along with a digital content delivery framework. The system allow a user to subscribe a computing environment, preferred software applications, and digital content like move and pay a monthly utility bill.
Owner:XENCARE SOFTWARE
Octave pulse data method & apparatus
InactiveUS20050147057A1Network traffic/resource managementTariff metering apparatusHuman–machine interfaceAir interface
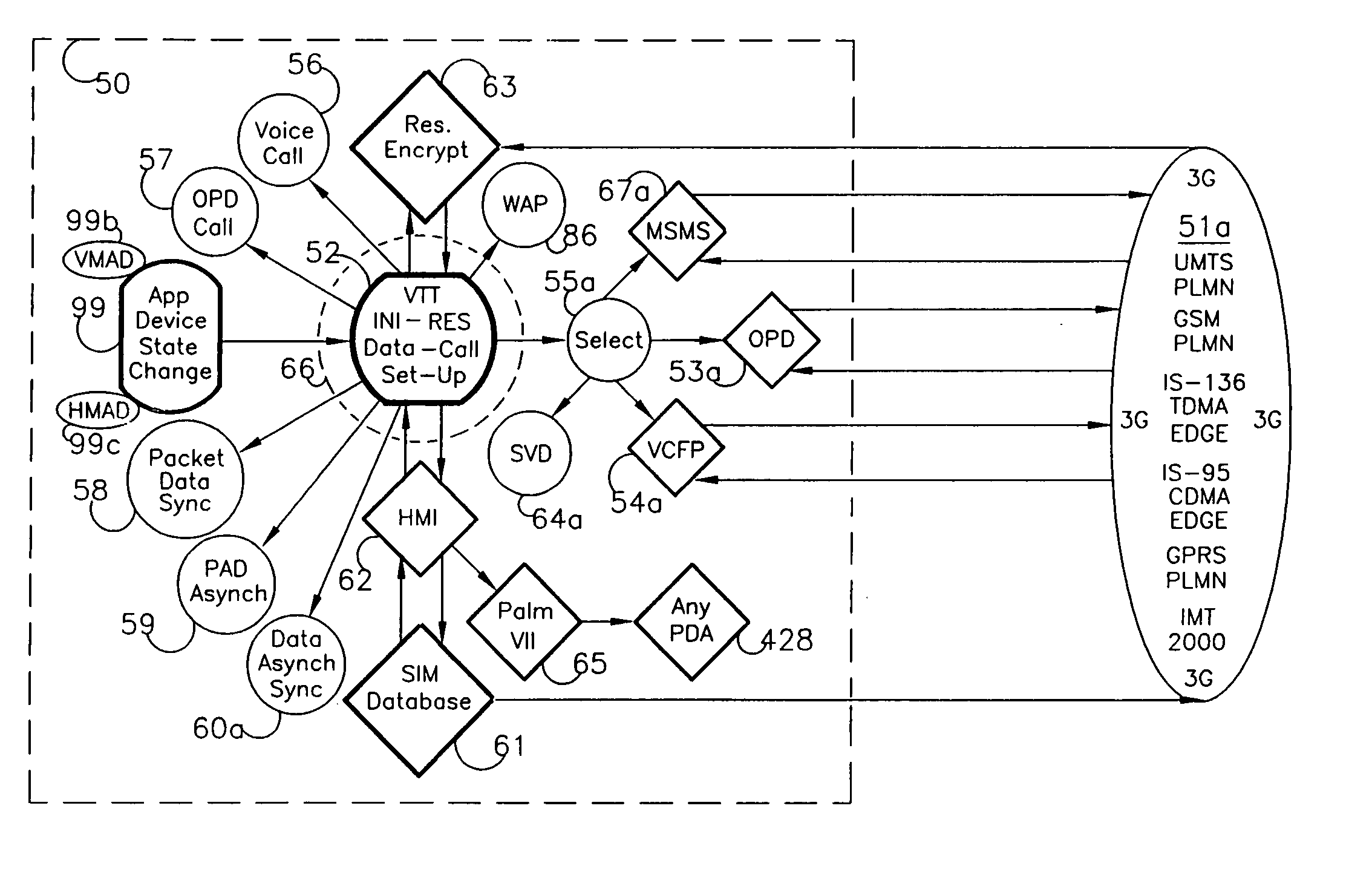
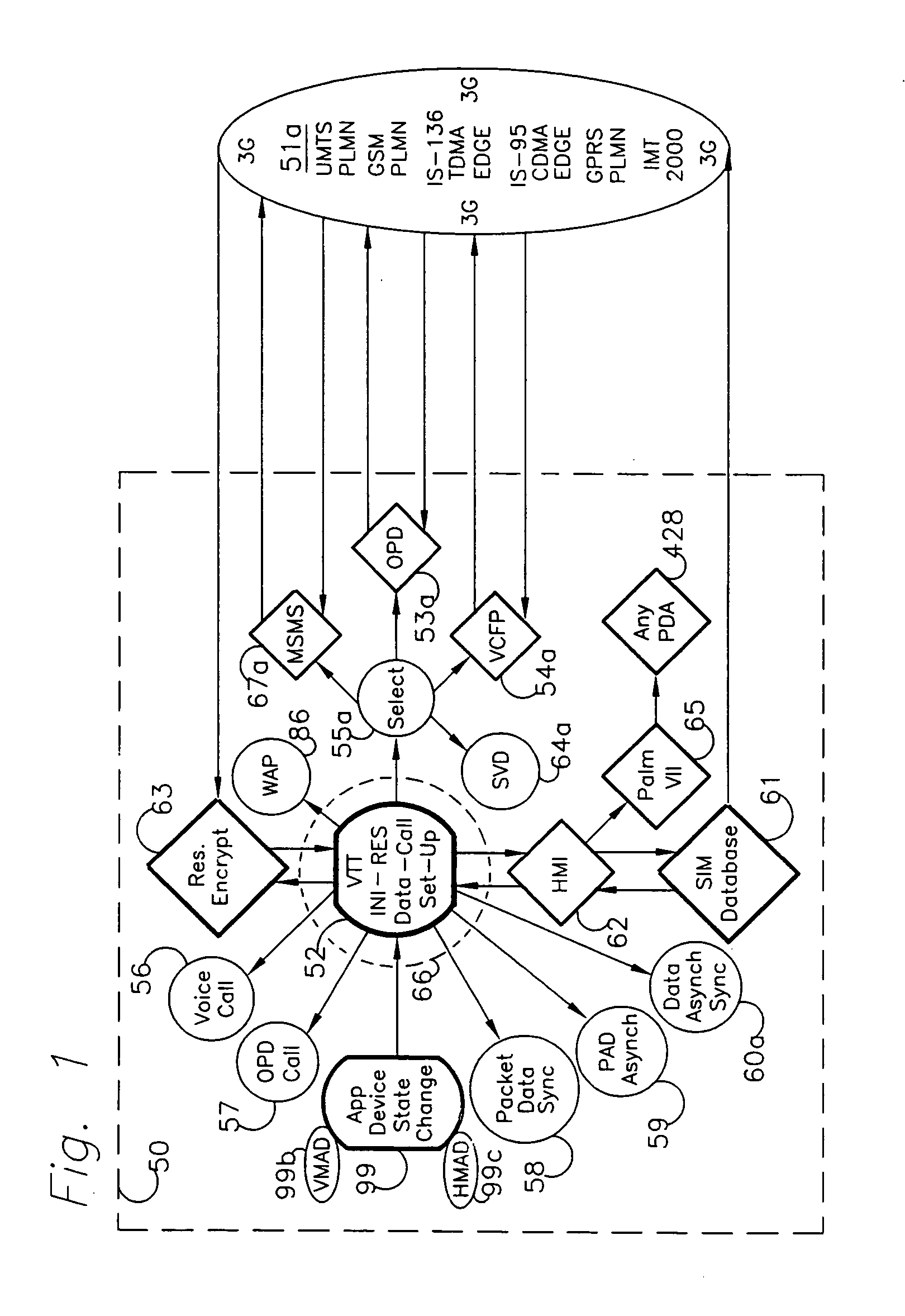
A method for communicating octave pulse signature messages between a wireless virtual transaction terminal and a virtual host system over a wireless telecommunications network that includes a digital traffic channel that transports speech frames and subframes over selected air interface channels, a pulse code modulated circuits that conveys speech frames and subframes through public land mobile networks and publicly switched telecommunications networks. The method comprises compling a communicative message derived from stored conventional alpha numeric characters using conventional human machine interface apparatus, the apparatus may be comprised of personal digital assistant tablet tap screen; generating an octave pulse message at the wireless virtual transaction terminal, the message comprising a plurality of octave pulse resonant signature encoding constructs; and encoding each octave pulse resonant signature with complex harmonic waveforms associated with musical constructs interpreted as musical notation. The method comprises manipulating speech frames and subframes over air interface traffic channels and using pulse code modulated circuits to convey maniupulated speech frames and subframes. Then, a communicative message derived from stored alpha numeric characters is compiled for wireless voice and data communication.
Owner:SYMSTREAM TECH HLDG NO 2 PTY LTD
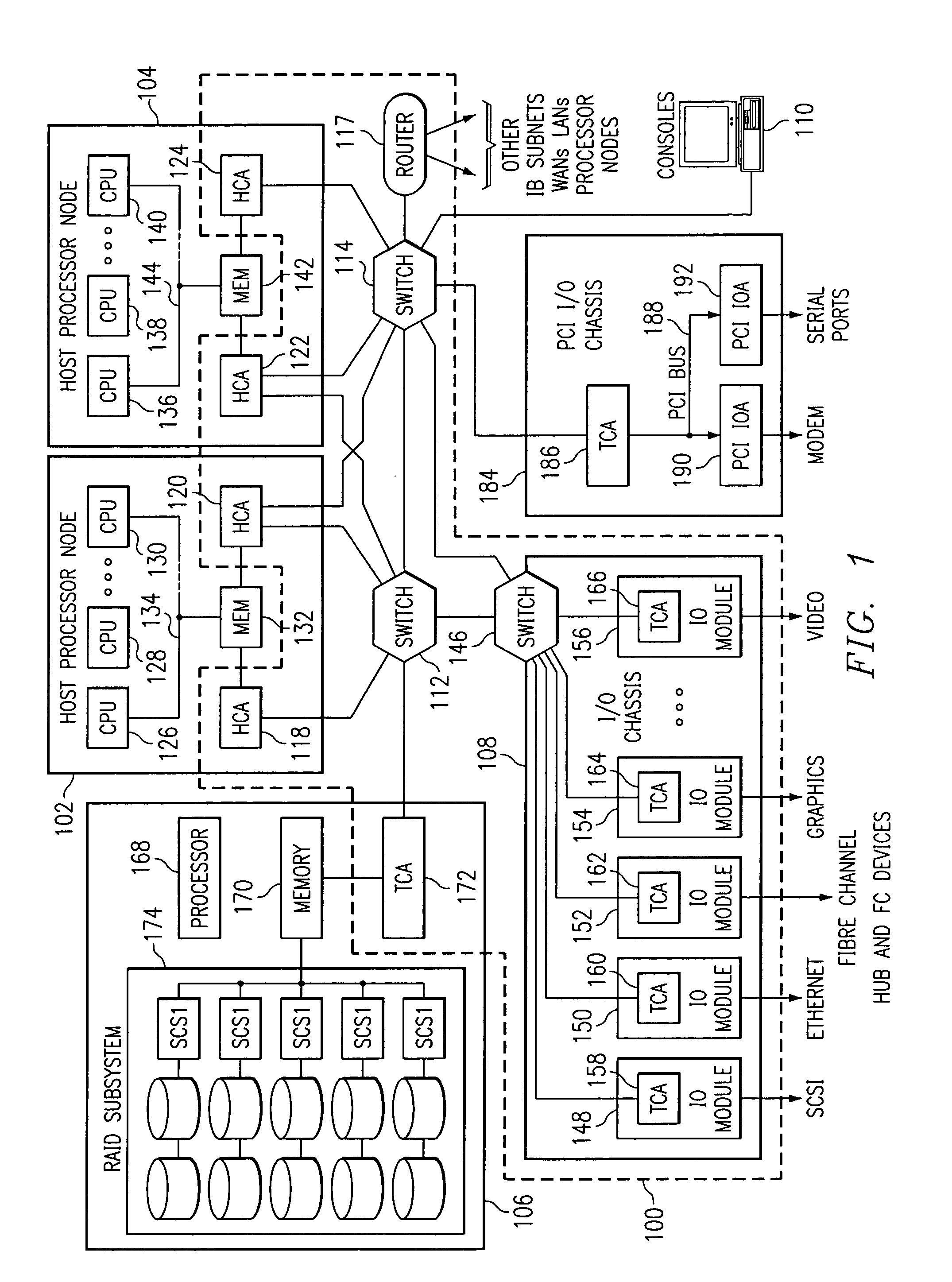
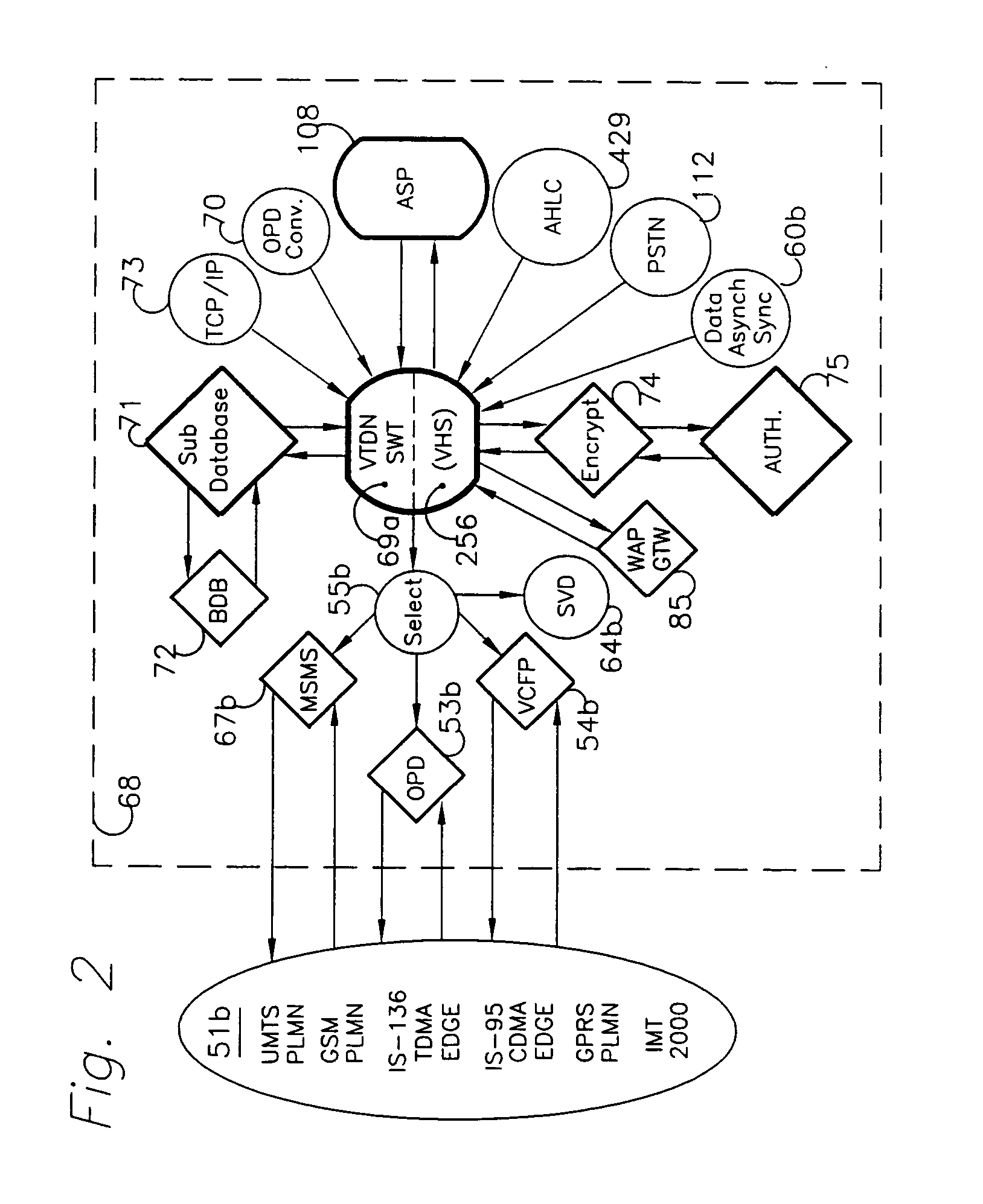
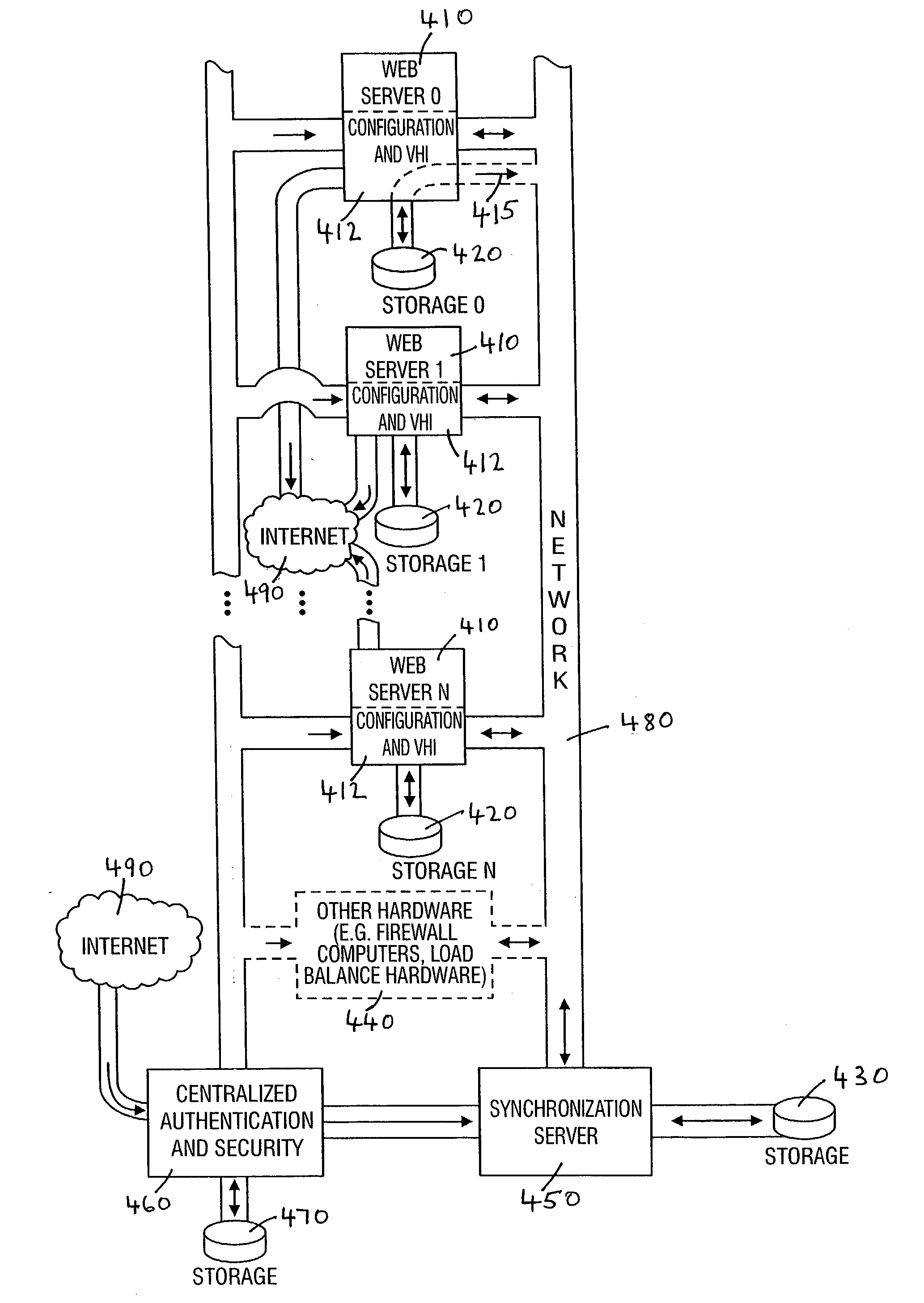
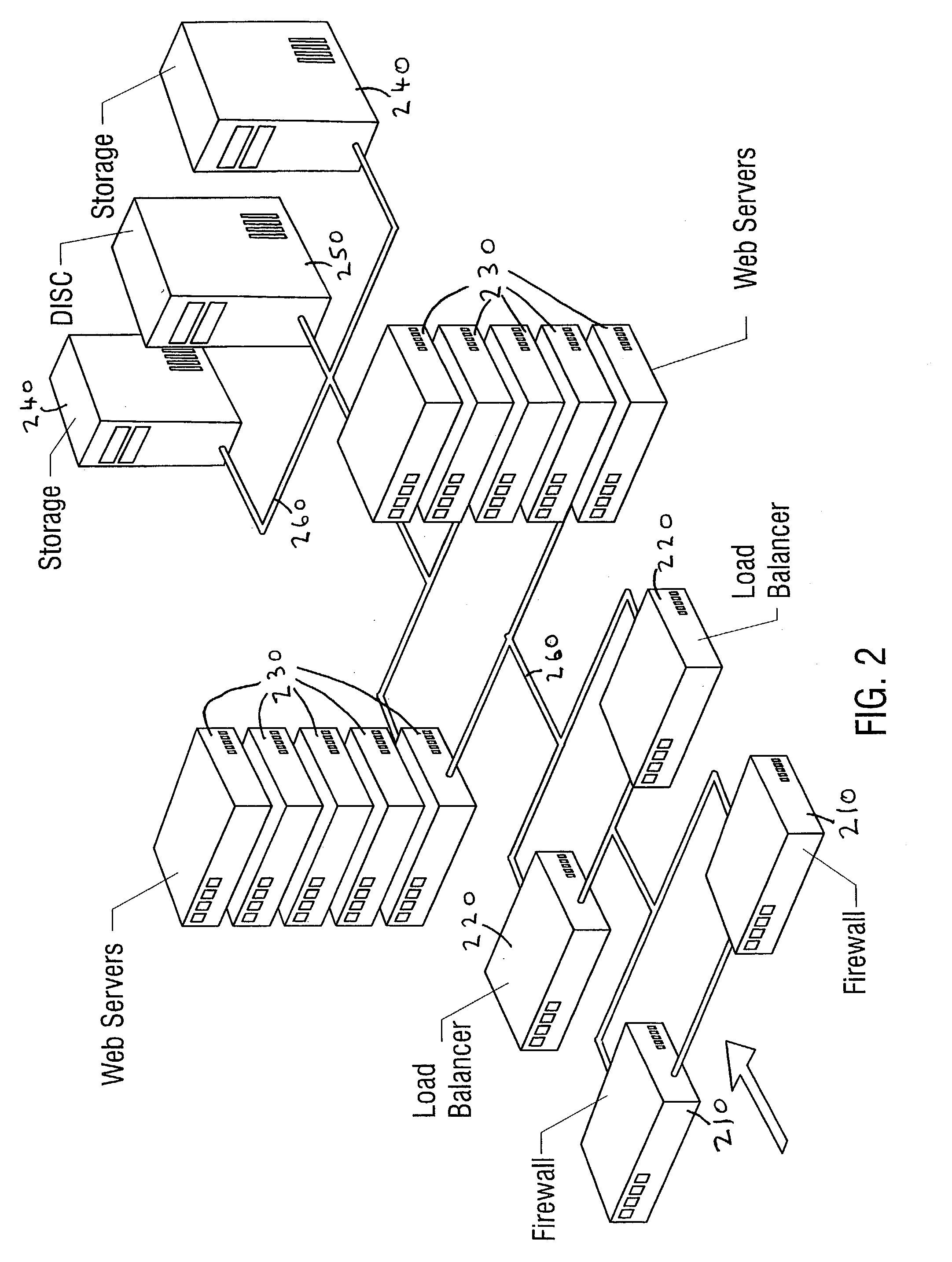
System and method for high performance shared web hosting
A system for shared web hosting includes a plurality of web servers coupled to a shared table data structure, wherein the web servers serve web pages to client computer systems. The web servers all couple to a security server that transmits web page requests to the shared table data structure. A website configuration server and virtual host information server couple to the shared table. The virtual host information server couples to a storage device that includes dynamic mapping information. Dynamic mapping information identifies the web server or web servers hosting a web site at any given time. The website configuration server includes static non-changing configuration information for each owner's web site. The non-changing information describes web sites hosted on the web server. The shared table also stores copies of recently accessed non-changing information and dynamic mapping information for web pages.
Owner:WEB COM HLDG
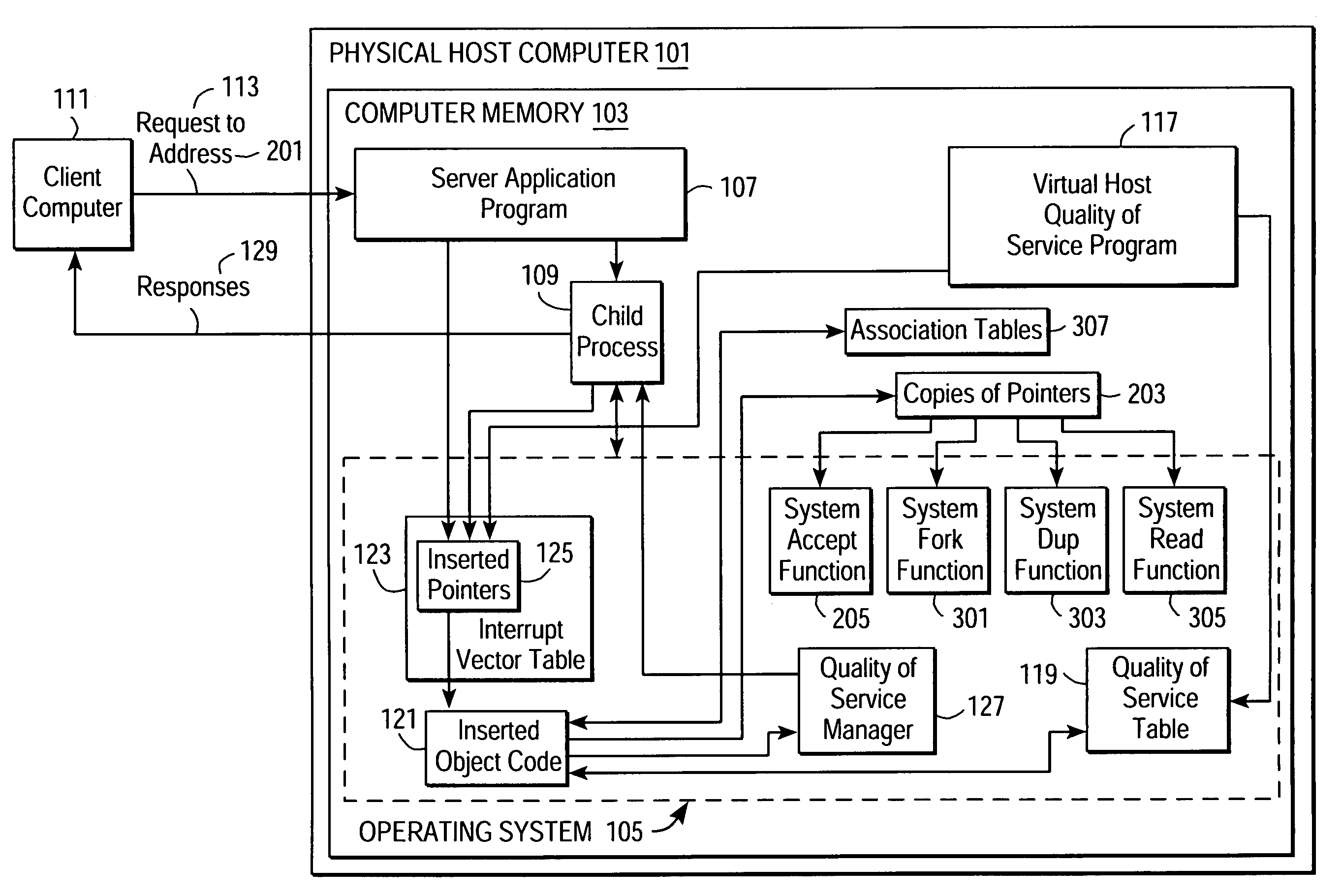
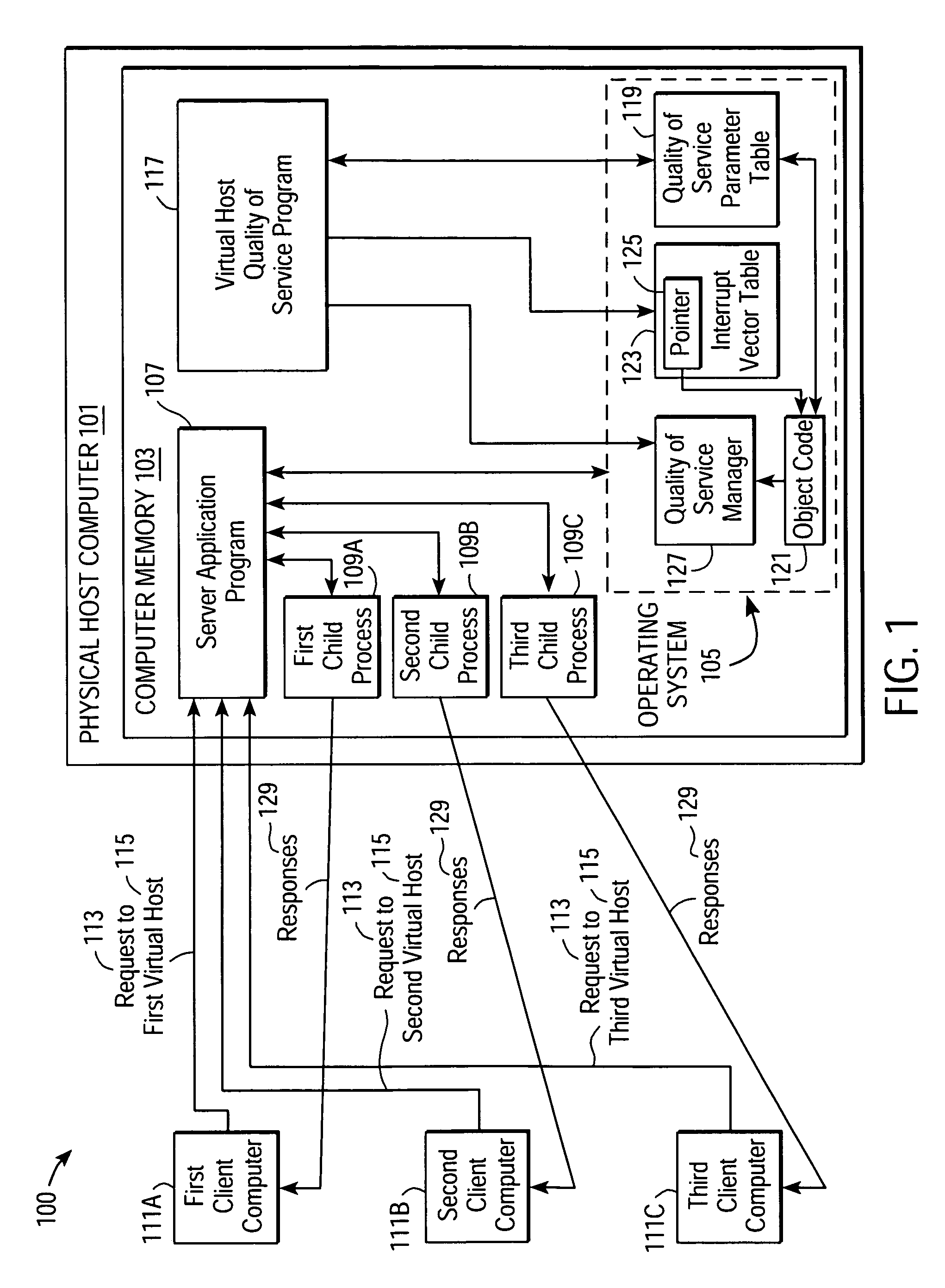
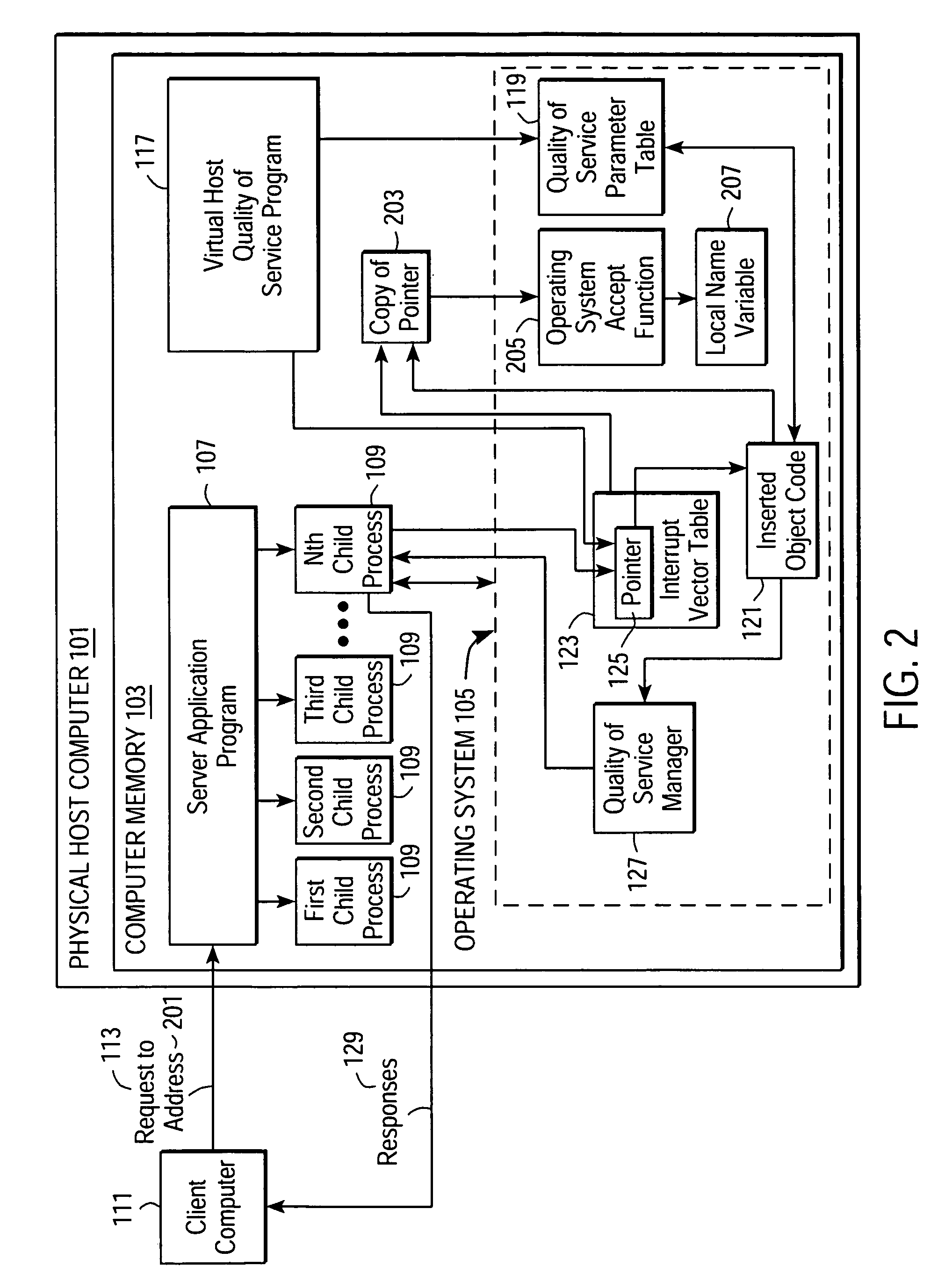
Providing quality of service guarantees to virtual hosts
InactiveUS6976258B1Appropriate quality of serviceGuaranteed service qualityEnergy efficient ICTInterprogram communicationOperational systemApplication software
A method facilitates providing appropriate quality of service guarantees to a plurality of virtual hosts on a single physical host computer. A server application program and its child processes service communication requests made to the plurality of virtual hosts. Quality of service parameters associated with the virtual hosts are stored. Communication requests made to a specific one of the virtual hosts are detected. The quality of service parameters associated with the specific virtual host are obtained. Operating system resources are utilized to guarantee, to a child process of the server application program, a quality of service according to the obtained quality of service parameters associated with the virtual host. Communication between the virtual host and the client is allowed to proceed, the communication being managed by the child process.
Owner:HANGER SOLUTIONS LLC
Virtual tunnel network router
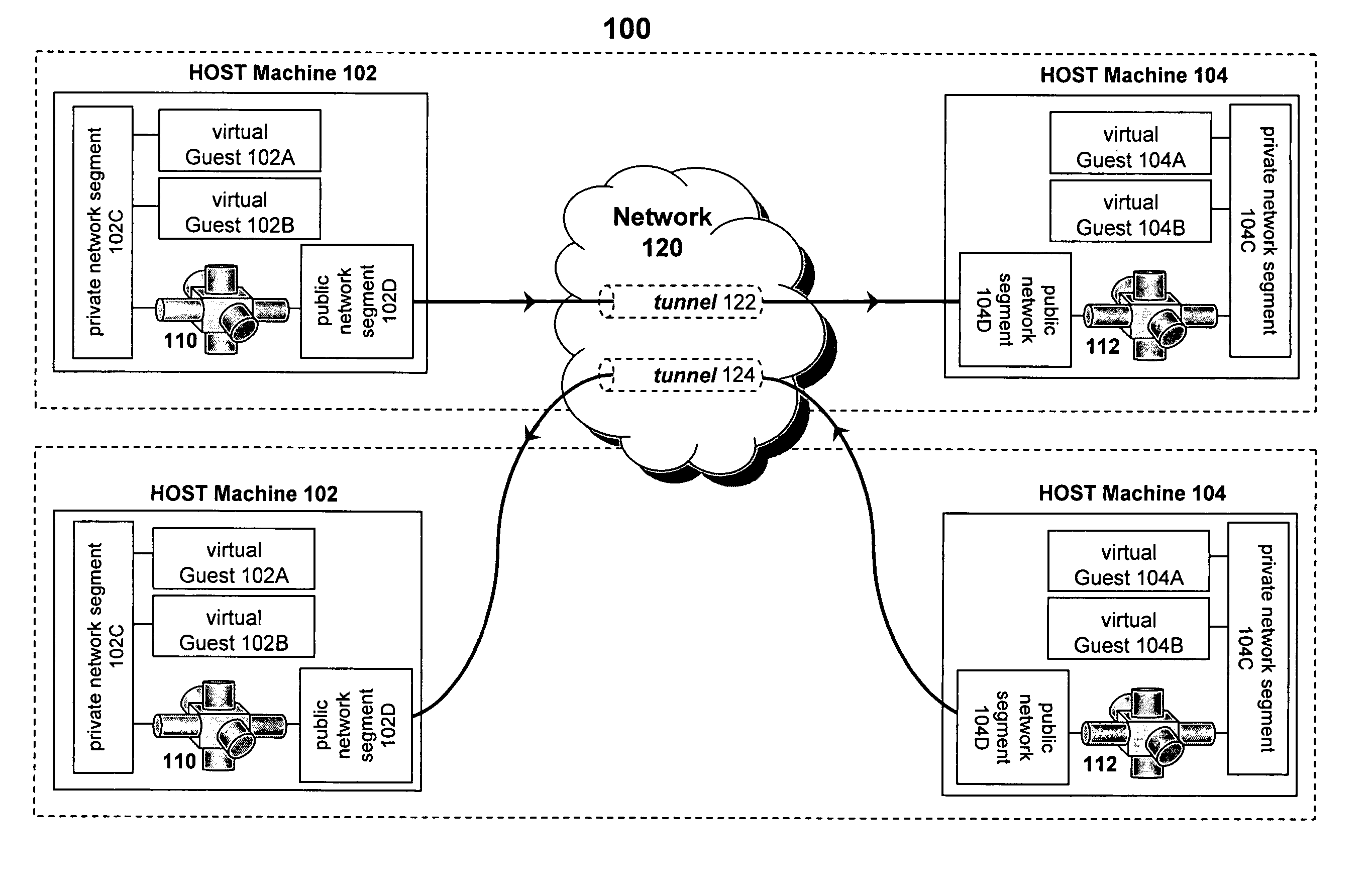
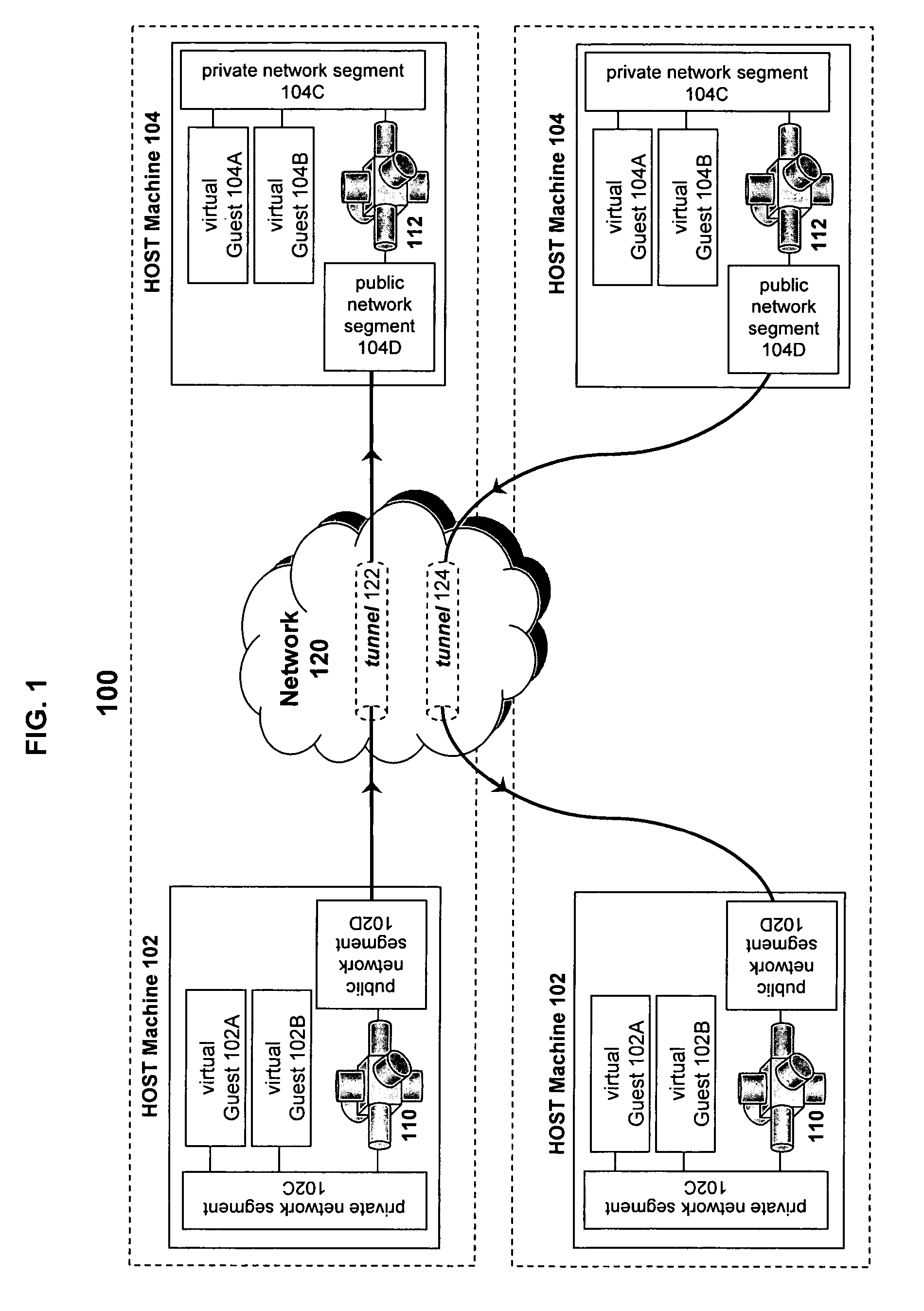
ActiveUS20070130366A1Facilitate communicationDigital computer detailsData switching networksVirtualizationPrivate network
A virtual host computer is presented that includes a virtualization software platform, at least one virtual machine executed by the virtualization software platform, a private network segment configured to prevent communications with at least one external computer, a public network segment configured to facilitate communications with the at least one external computer, and a virtual routing module that is executed as a virtual image by the virtualization software platform. The virtual routing module is configured to communicate with the at least one virtual machine via the private network segment, communicate with the public network segment, and execute a tunneling layer to form a private virtual network segment between the at least one virtual machine and the at least one external computer.
Owner:CA TECH INC
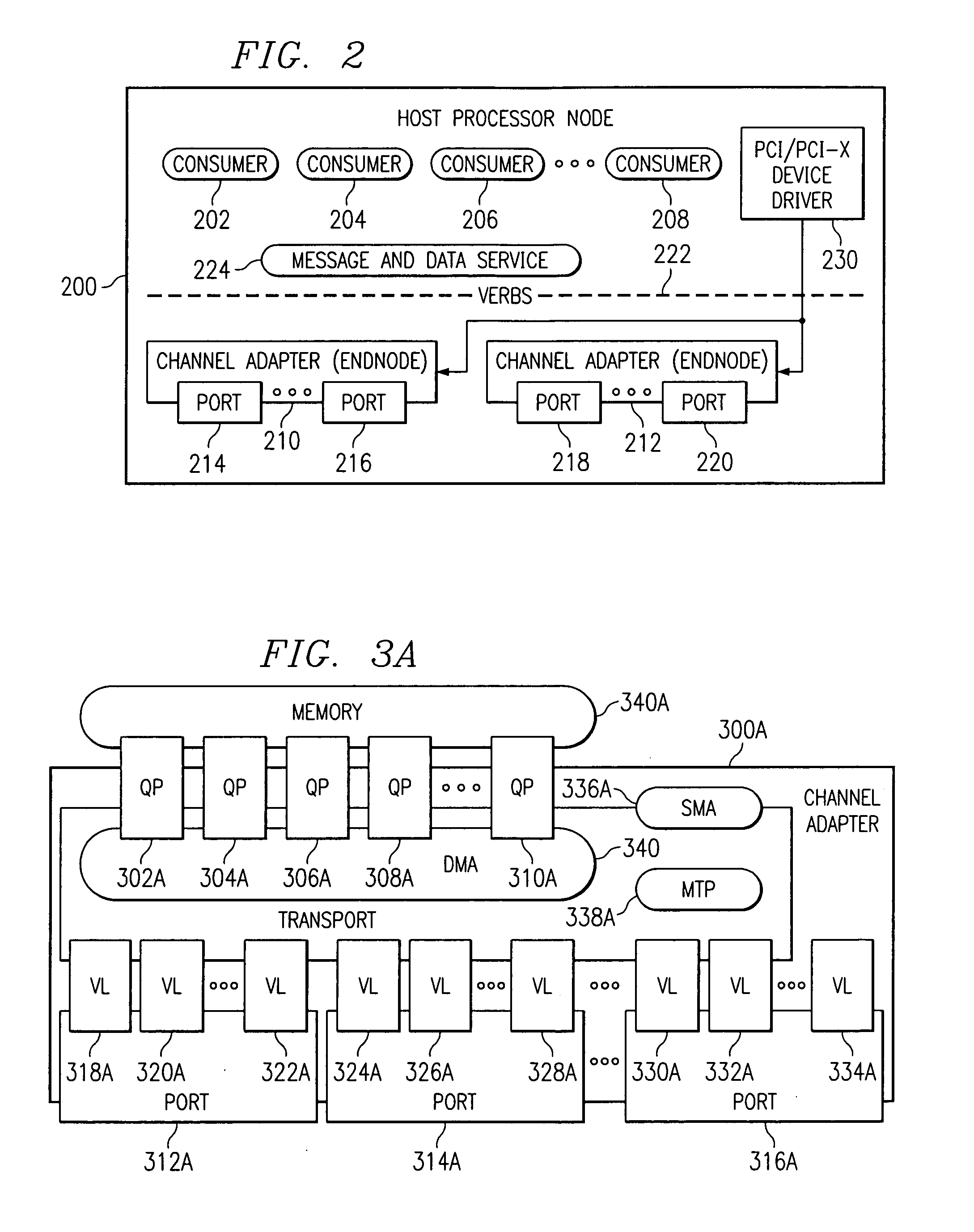
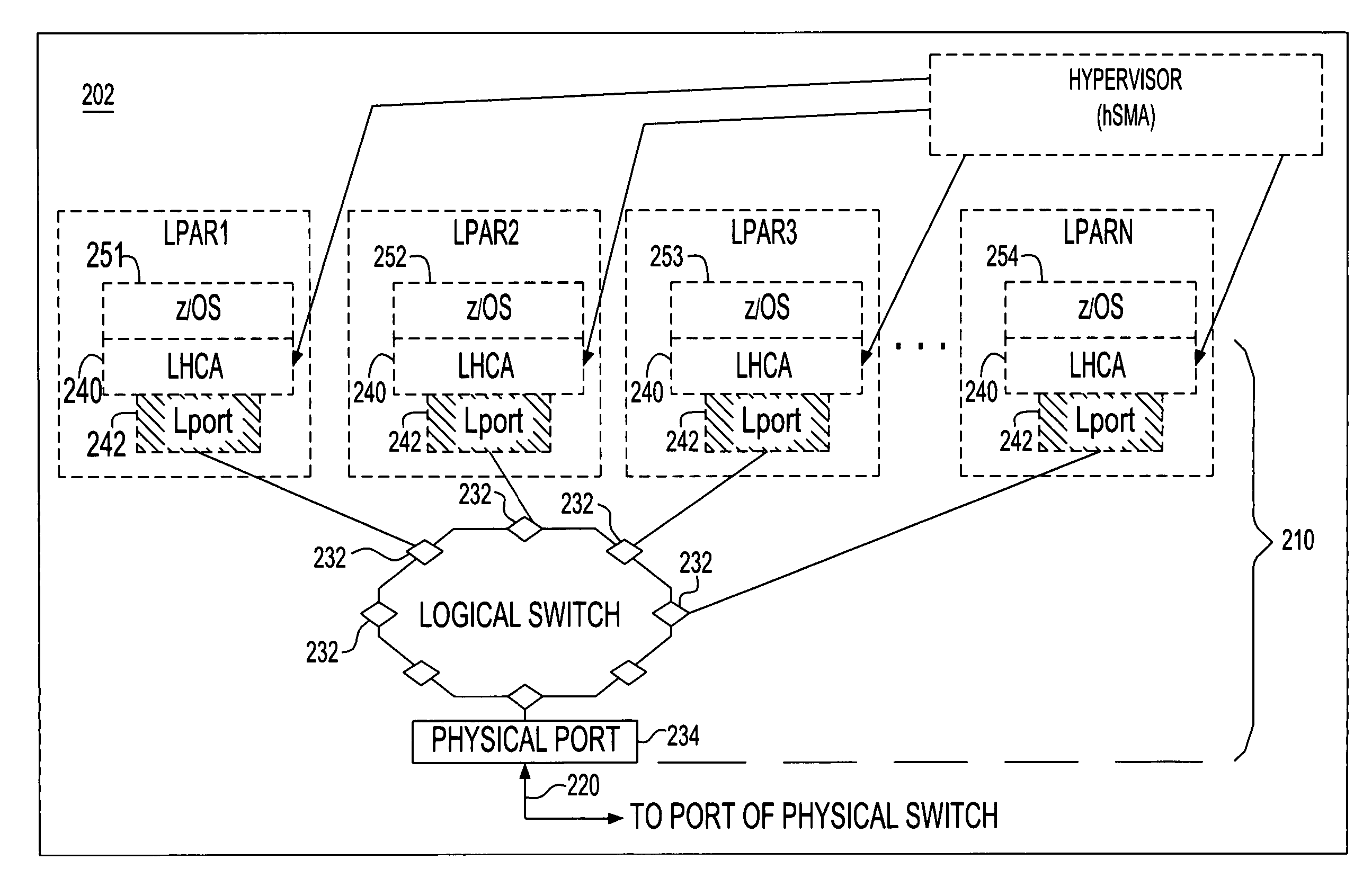
System and method for providing multiple virtual host channel adapters using virtual switches
InactiveUS20060230185A1Multiple digital computer combinationsTransmissionVirtualizationProcessor node
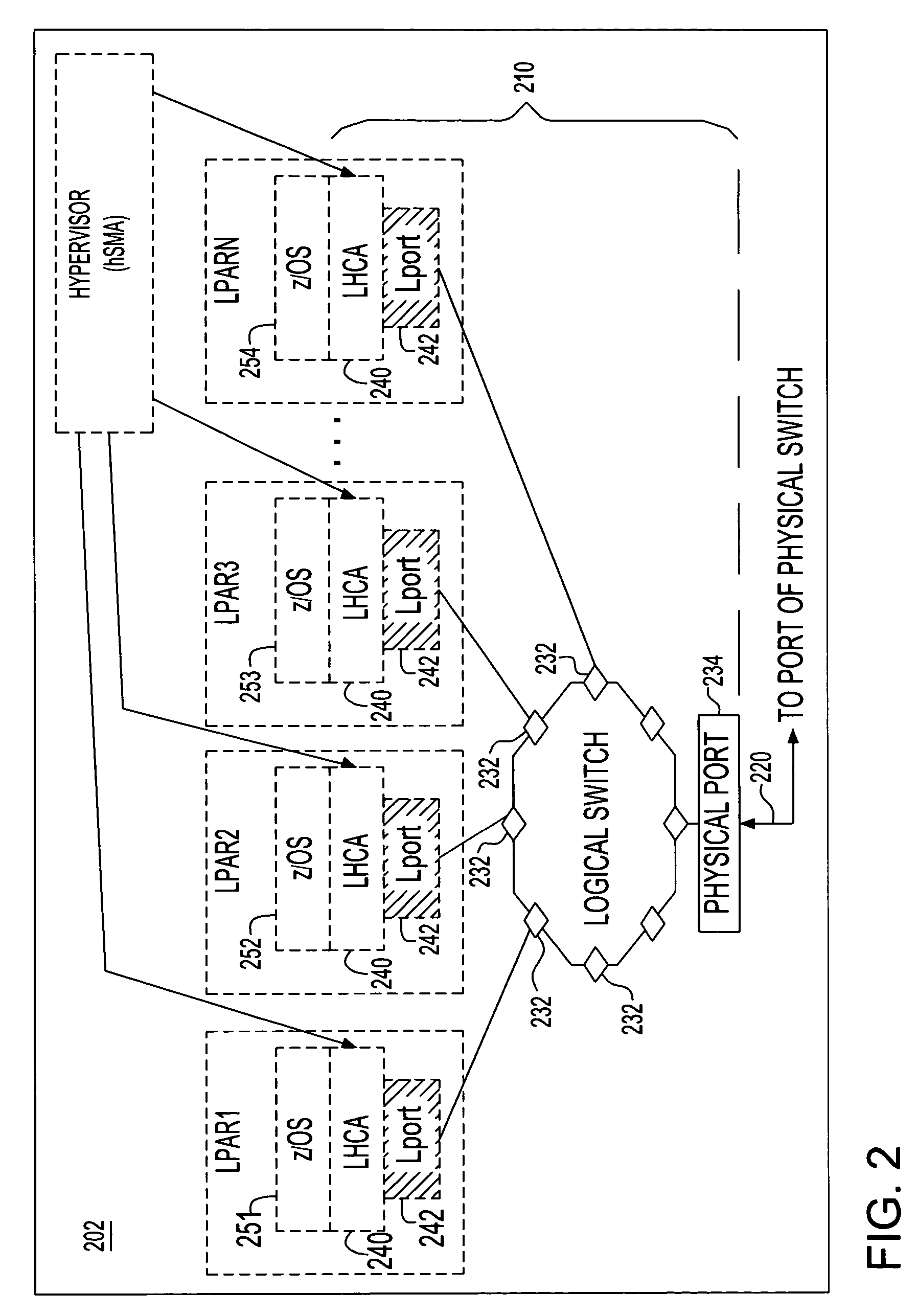
A processor node of a network is provided which includes one or more processors and a virtualized channel adapter. The virtualized channel adapter is operable to reference a table to determine whether a destination of the communication is supported by the virtualized channel adapter. When the destination is supported for routing via hardware, the virtualized channel adapter is operable to route the communication via hardware to at least one of a physical port and a logical port of the virtualized channel adapter. Otherwise, when the destination is not supported for routing via hardware, the virtualized channel adapter is operable to route the communication via firmware to a virtual port of the virtualized channel adapter. A corresponding method and a recording medium having information recorded thereon for performing such method are also provided herein.
Owner:IBM CORP
Wireless communication network for smart appliances
InactiveUS20110314163A1Multiprogramming arrangementsMultiple digital computer combinationsWireless transceiverTransceiver
A communications module, and a consumer device comprising the communications model, is provided for use in a communication network with one or more consumer devices or “smart” appliances. The communications module includes a wireless transceiver for communication with the network, for example in accordance with the ZigBee protocol, and an interface for communicating with a host processor of the consumer device. The module receives scheduled event data over a wireless link on behalf of the host processor, and schedules events for execution by the host processor upon receipt of commands transmitted by the module. The communications module may include a virtual host module, which translates commands between a protocol used by the host processor and a protocol used by the communications module. The communications module is also configured to automatically seek and join a network, and to discover and bind to services provided over the network.
Owner:MMB RES
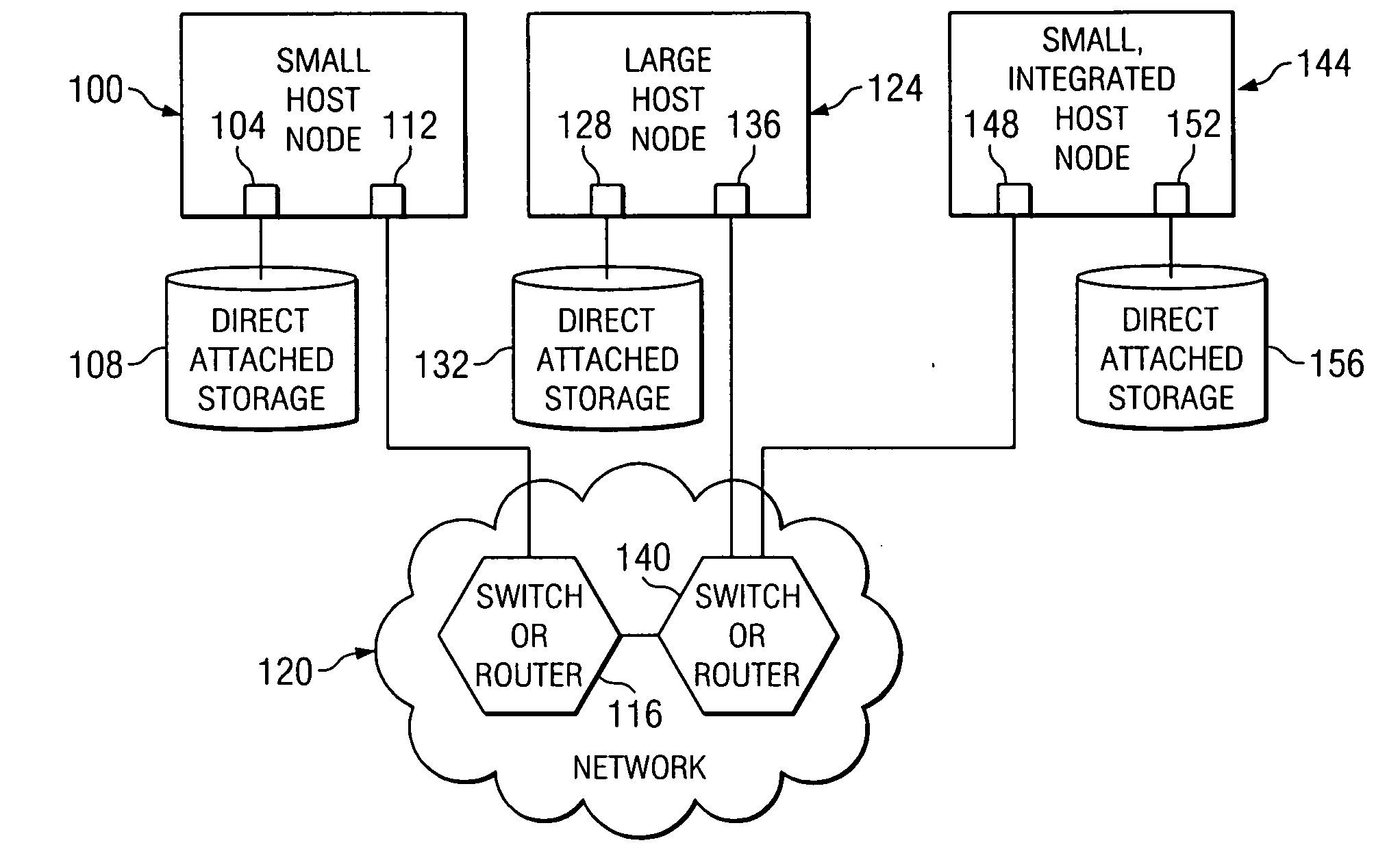
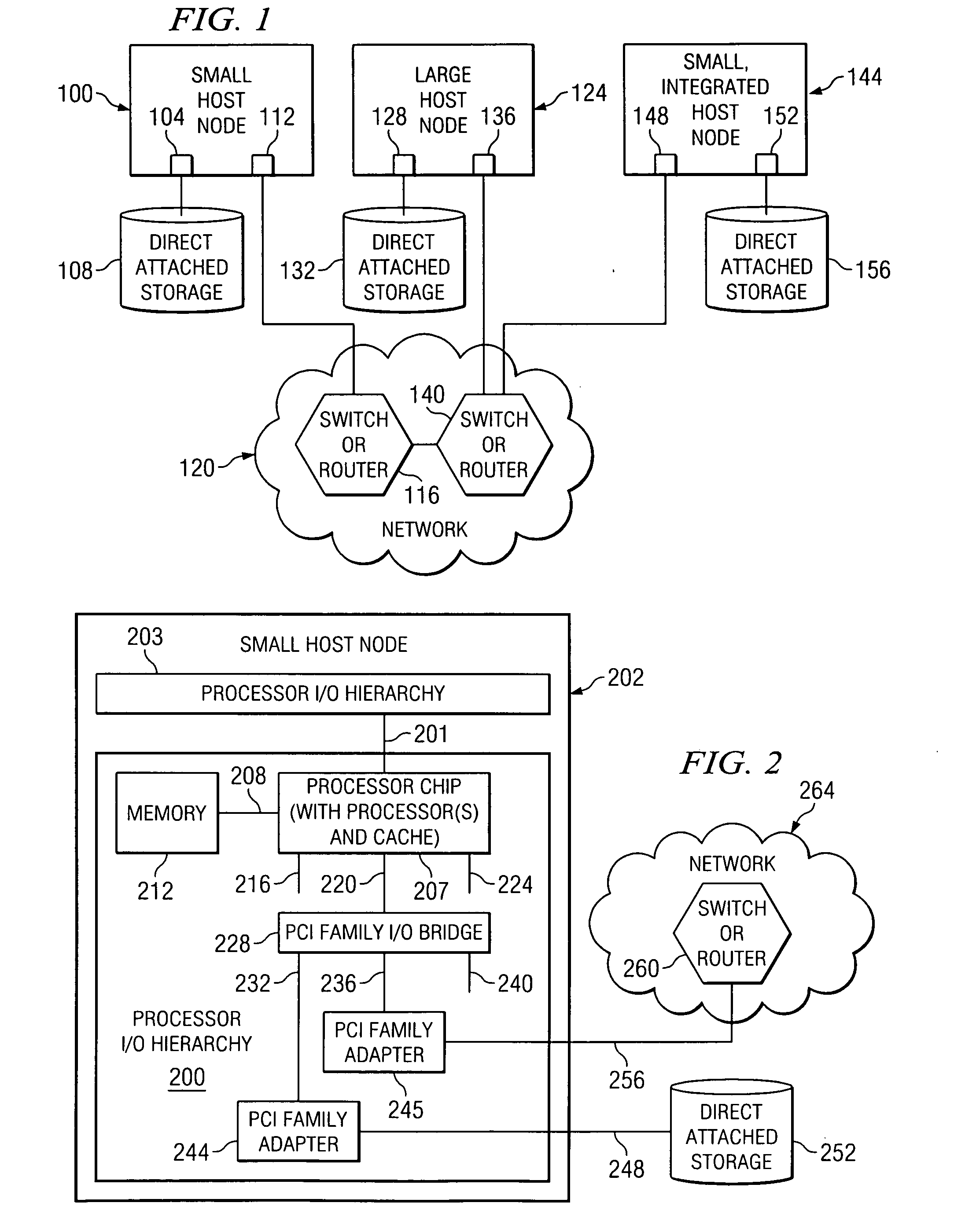
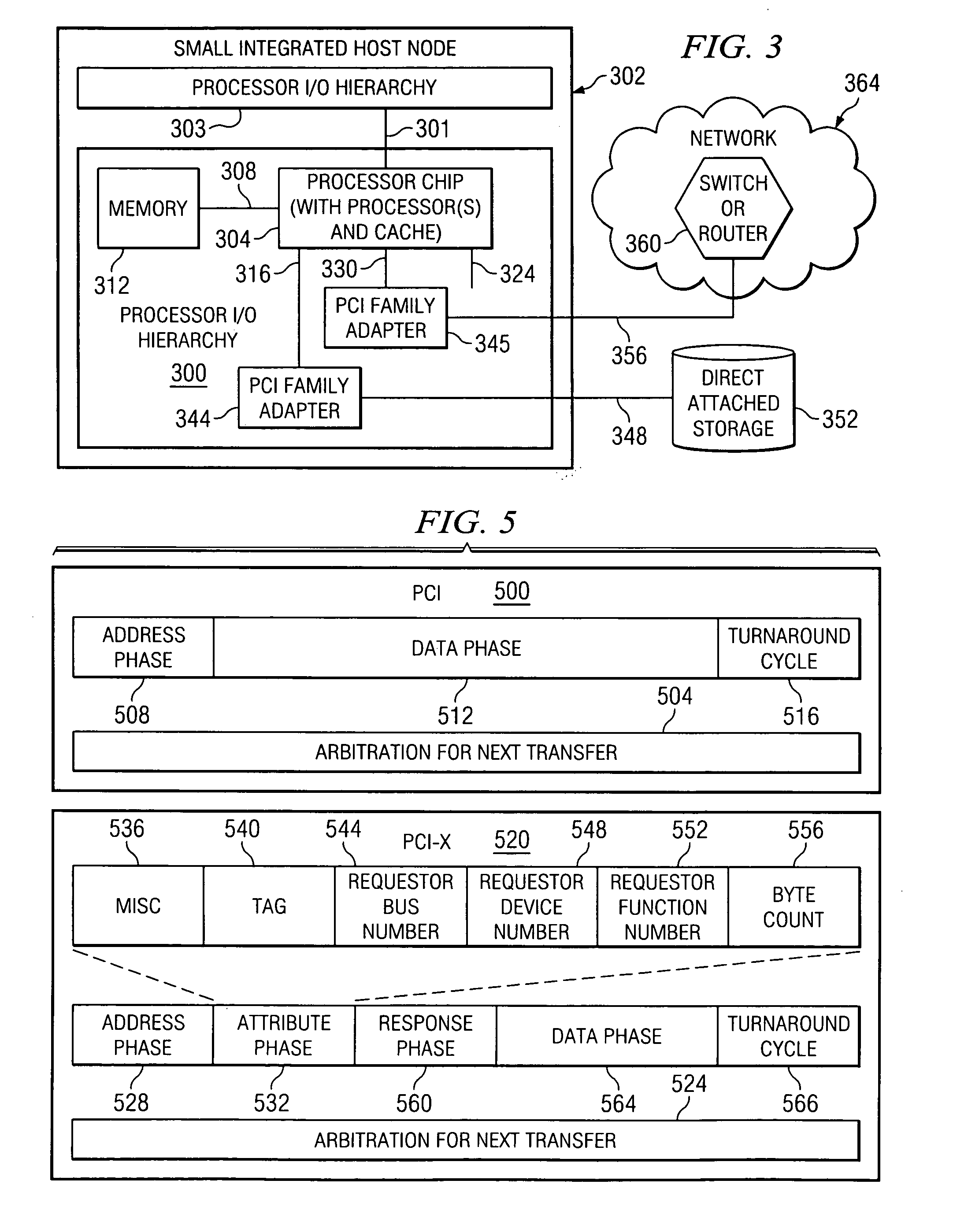
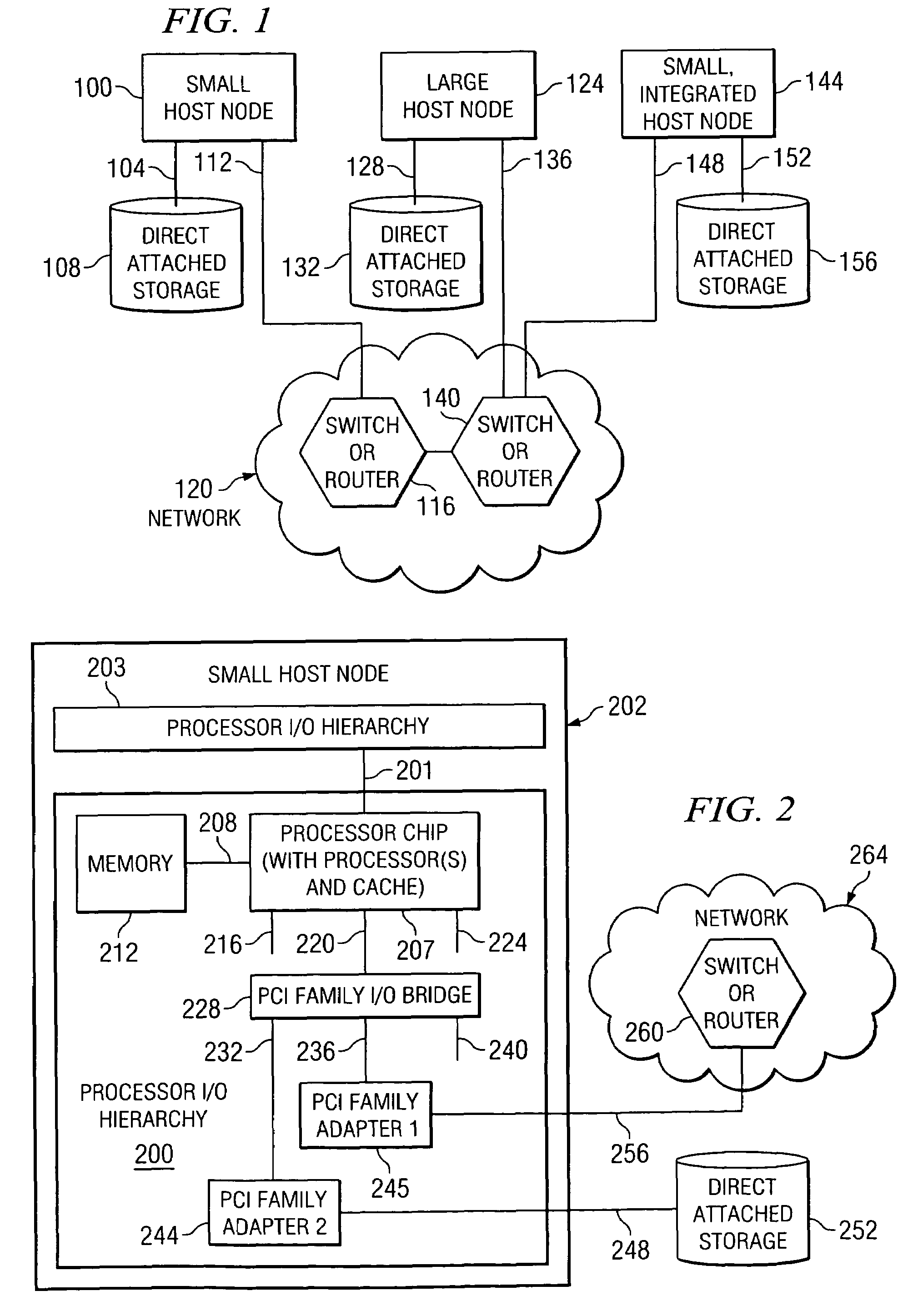
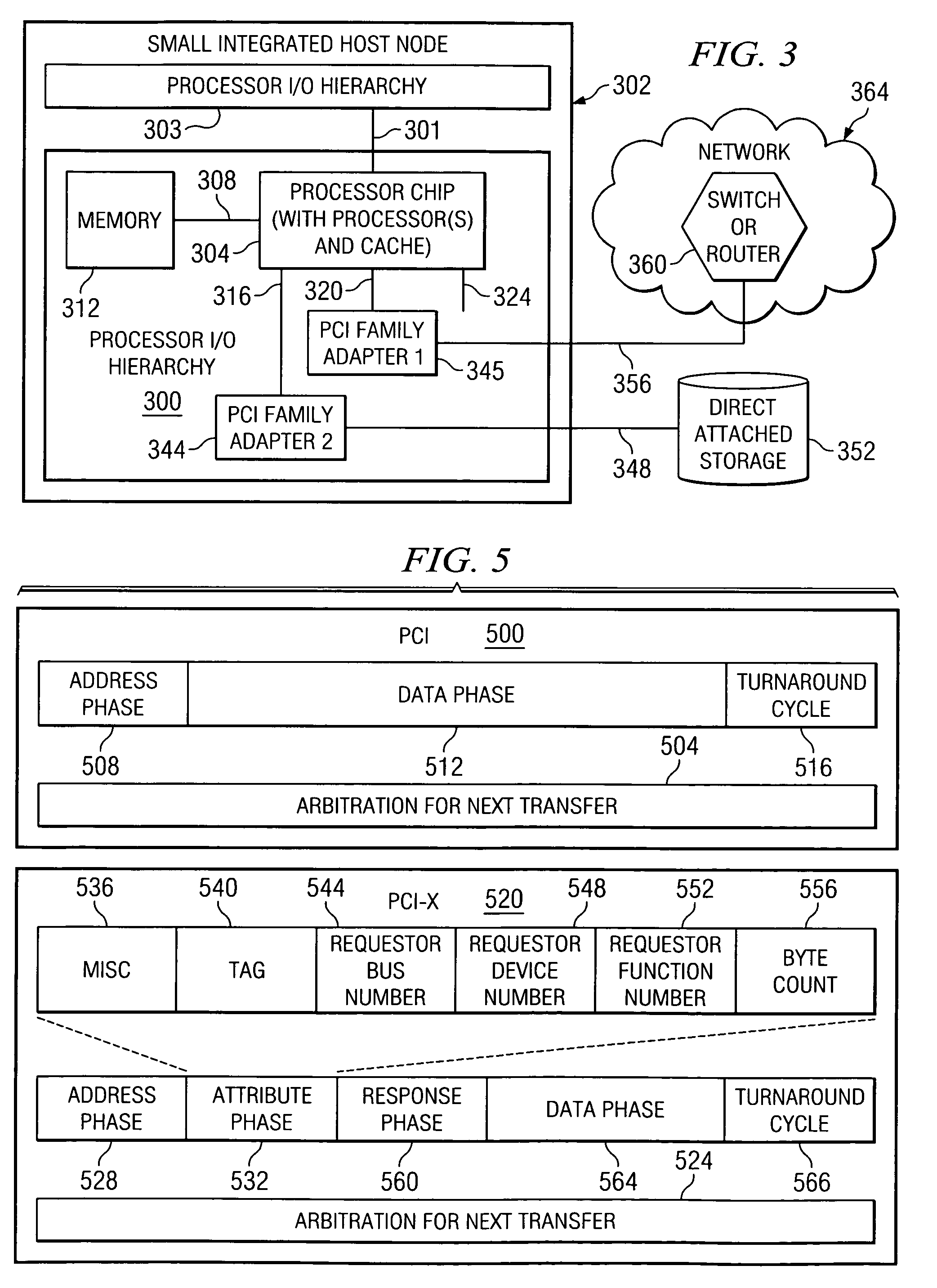
System, method, and computer program product for a fully trusted adapter validation of incoming memory mapped I/O operations on a physical adapter that supports virtual adapters or virtual resources
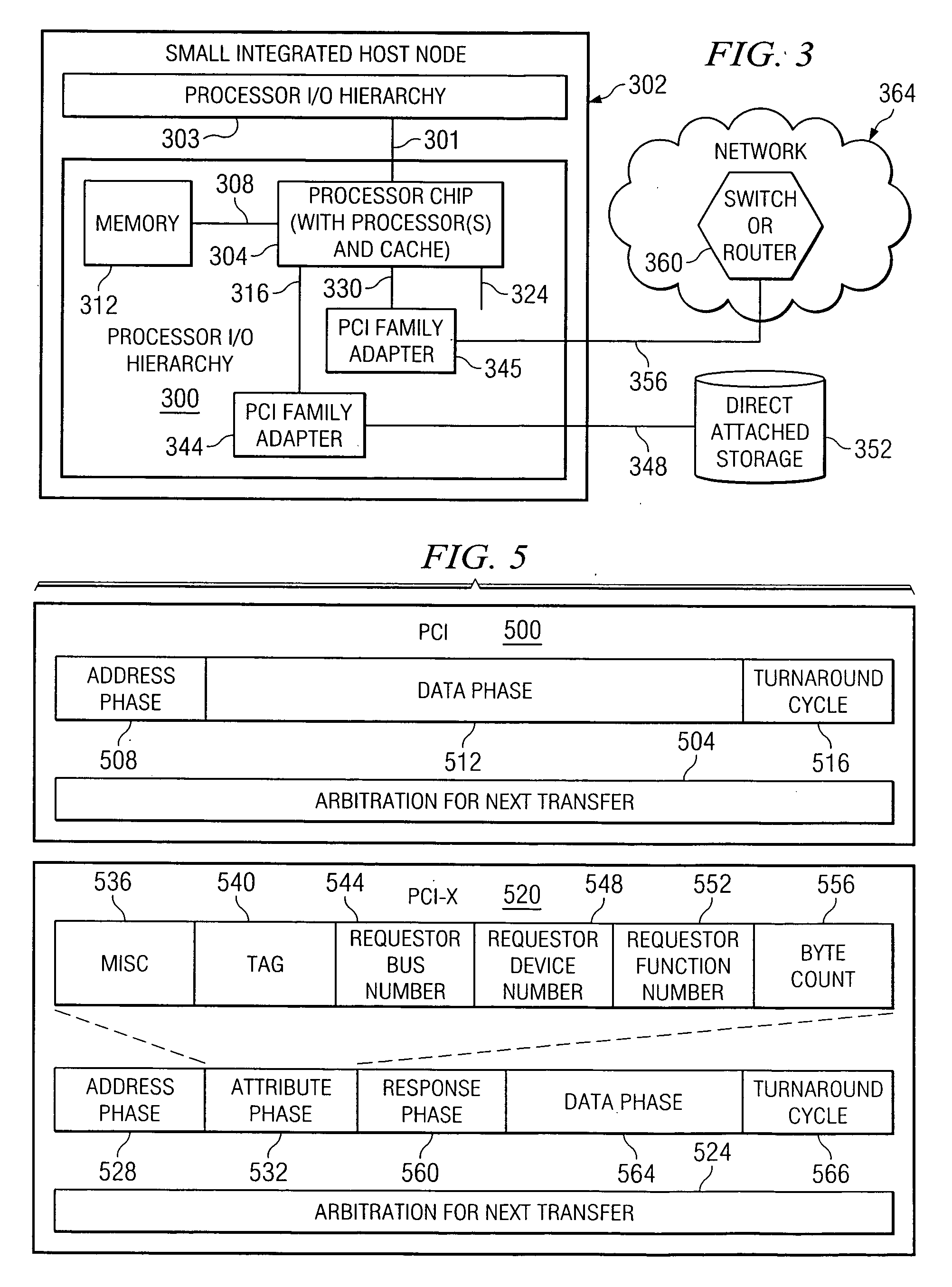
InactiveUS20060212608A1Memory adressing/allocation/relocationInput/output processes for data processingData processing systemTerm memory
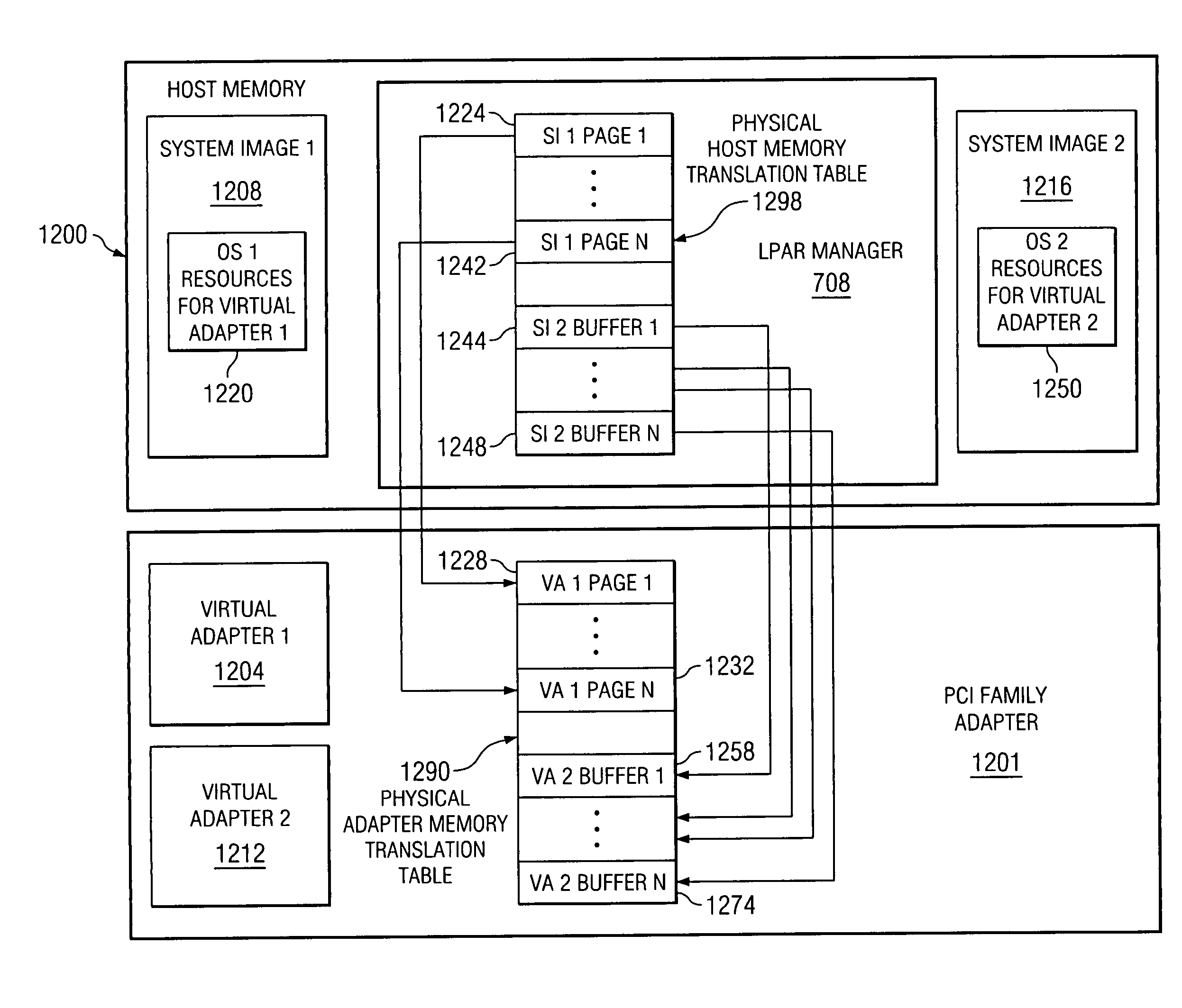
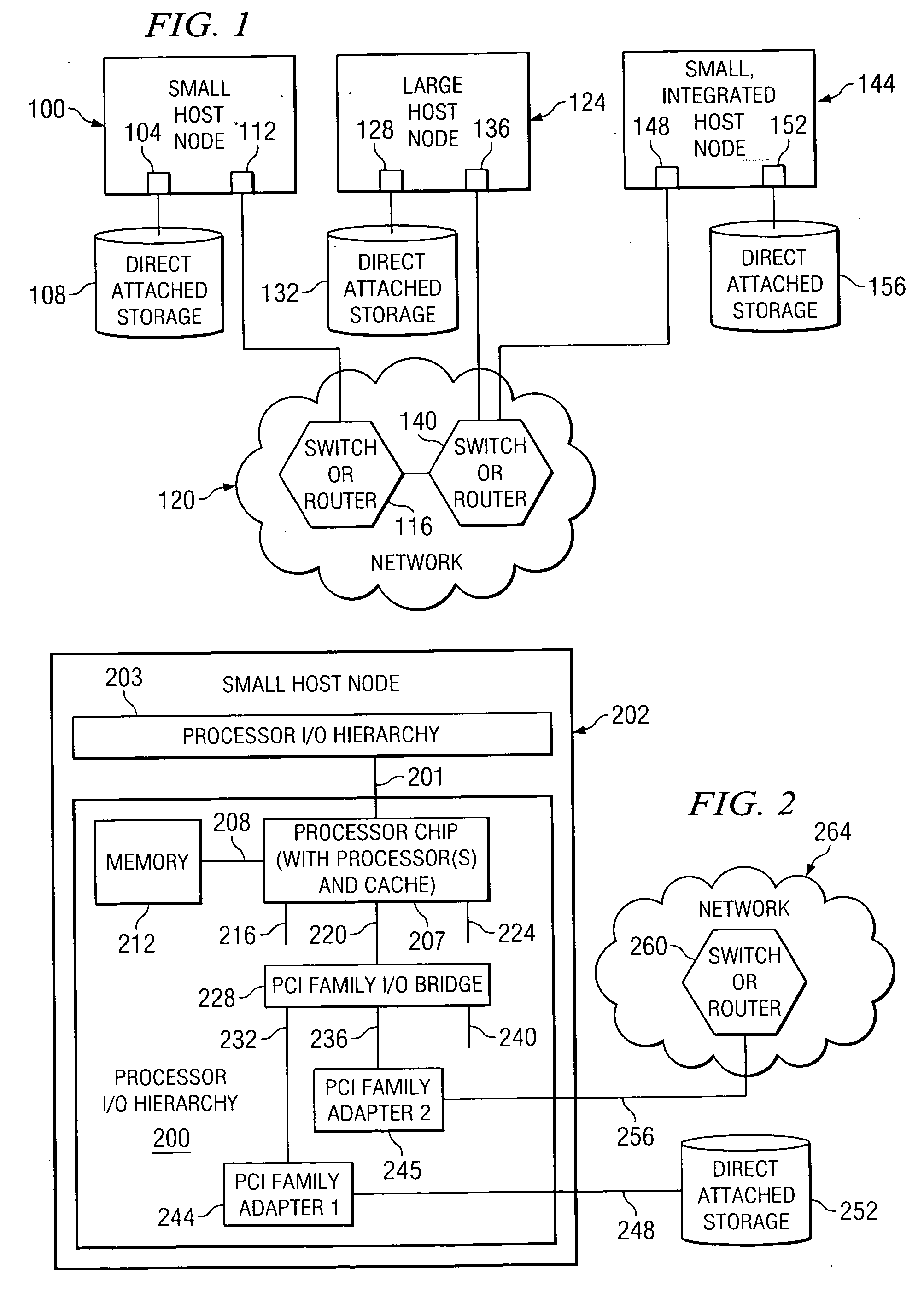
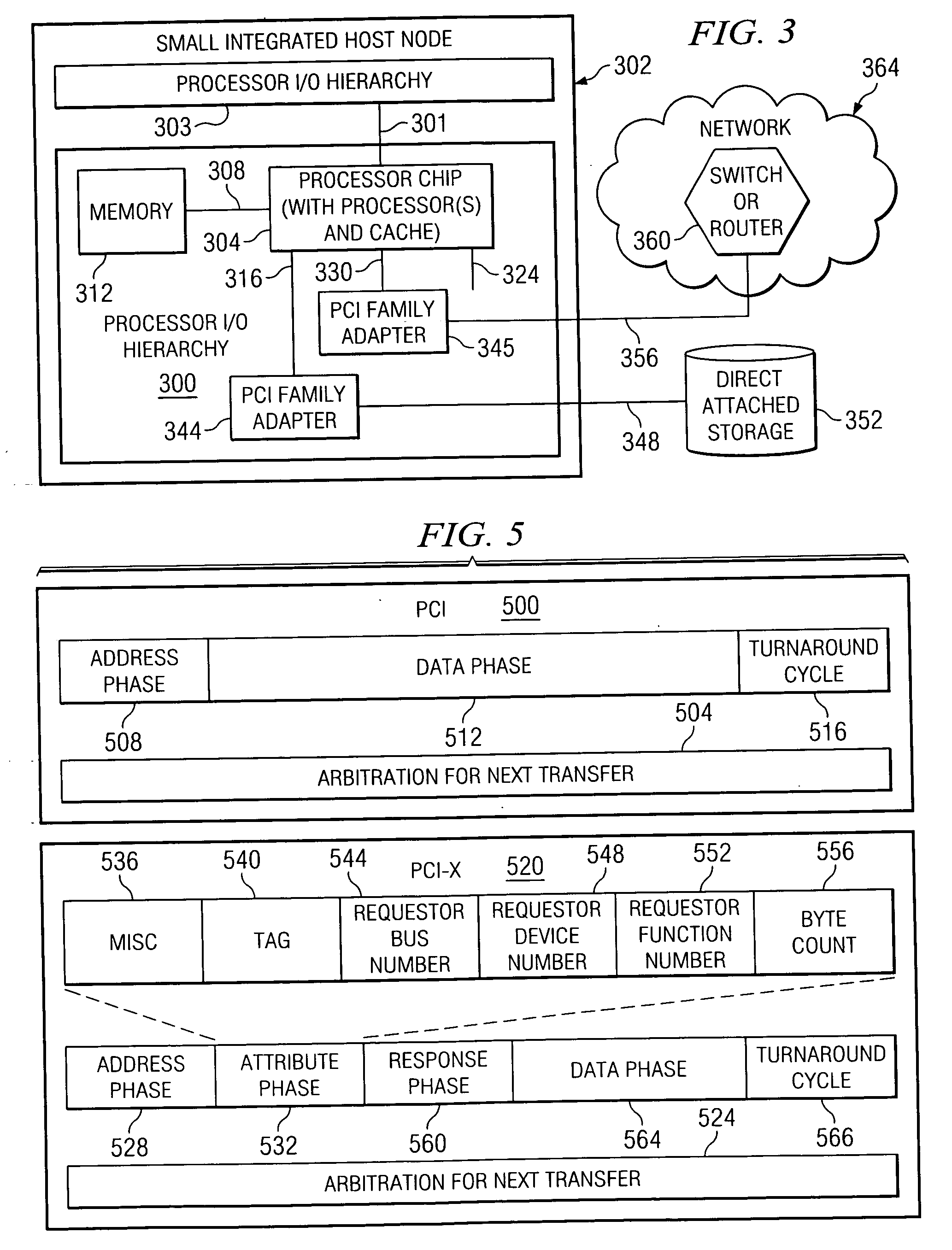
A method, computer program product, and distributed data processing system that allows a single physical I / O adapter to validate that a memory mapped I / O address referenced by an incoming I / O operation is associated with a virtual host that initiated the incoming memory mapped I / O operation is provided. Specifically, the present invention is directed to a mechanism for sharing a PCI family I / O adapter and, in general, any I / O adapter that uses a memory mapped I / O interface for communications. A mechanism is provided that allows a single physical I / O adapter to validate that a memory mapped I / O address referenced by an incoming memory mapped I / O operation used to initiate an I / O transaction is associated with a virtual host that initiated the incoming memory mapped I / O operation.
Owner:IBM CORP
System and method of virtual resource modification on a physical adapter that supports virtual resources
A method, computer program product, and distributed data processing system for modifying one or more virtual resources that reside within a physical adapter, such as a peripheral component interconnect (PCI), PCI-X, or PCI-E adapter, and that are associated with a virtual host is provided. Specifically, the present invention is directed to a mechanism for sharing conventional PCI I / O adapters, PCI-X I / O Adapters, PCI-Express I / O adapters, and, in general, any I / O adapter that uses a memory mapped I / O interface for host to adapter communications. A mechanism is provided for directly modifying one or more virtual resources that reside within a physical adapter, such as a PCI, PCI-X, or PCI-E adapter, and that are associated with a virtual host.
Owner:IBM CORP
Routing mechanism in PCI multi-host topologies using destination ID field
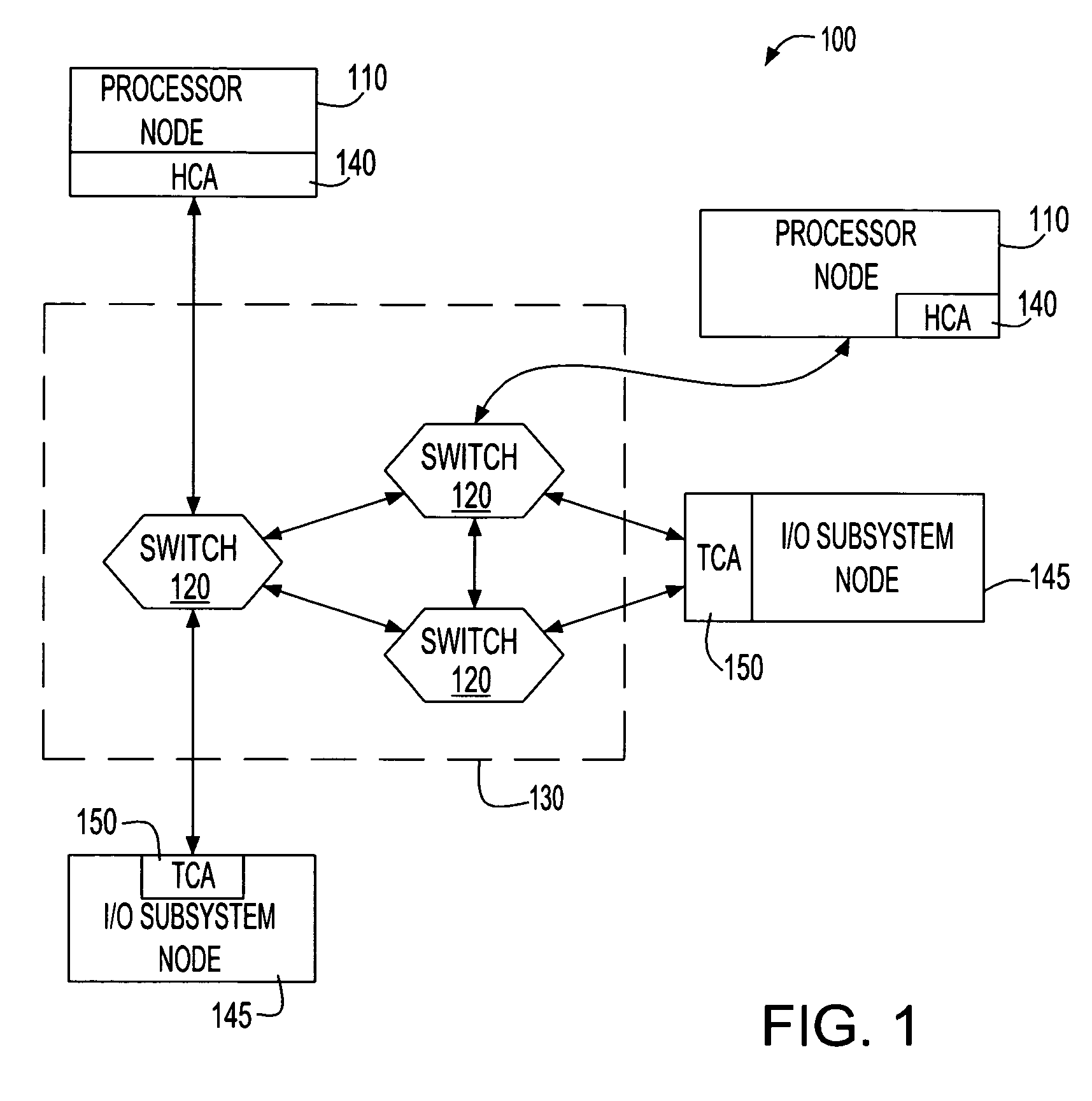
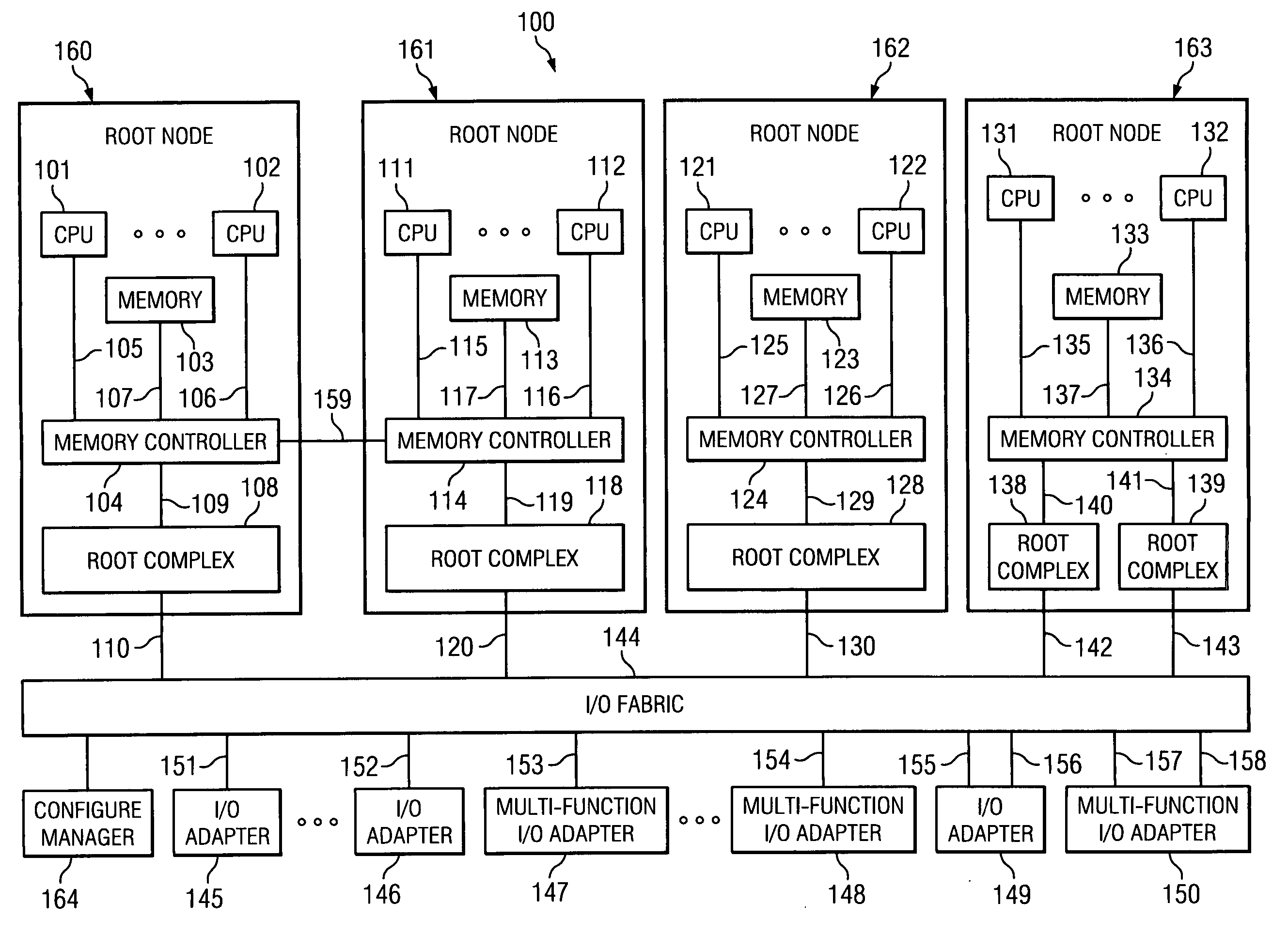
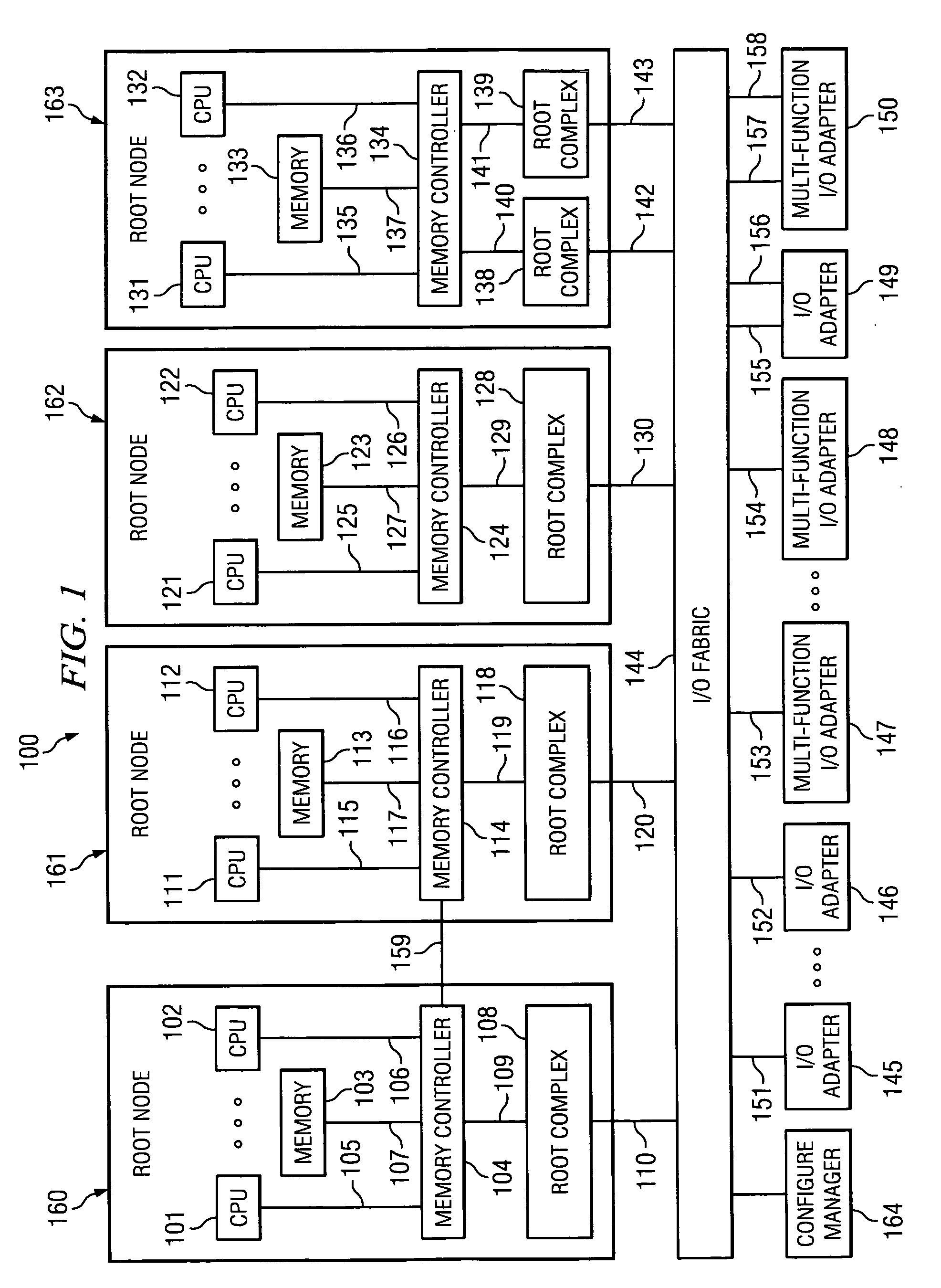
InactiveUS20070097950A1Data switching by path configurationElectric digital data processingField methodsPCI Express
Method and system for address routing in a distributed computing system, such as a distributed computing system that uses PCI Express protocol to communicate over an I / O fabric. A destination identifier is provided to identify a physical or virtual host or end point. When a physical or virtual host or end point receives a PCI data packet it compares a list of source identifiers with destination identifiers to determine if a source identifier included in the transaction packet is associated with a destination identifier included in the transaction packet to determine if the transaction packet has a valid association. If the transaction packet has a valid association, it is routed to the target device. The present invention enables each host that attaches to PCI bridges or switches and shares a set of common PCI devices to have its own PCI 64-bit address space and enables the routing of PCI transaction packets between multiple hosts and adapters, through a PCI switched-fabric bus using a destination identifier.
Owner:IBM CORP
System and method for providing quality of service in a virtual adapter
InactiveUS20060193327A1High quality of service level weightLower quality of serviceData switching by path configurationProgram controlQuality of serviceData processing system
A method, computer program product, and distributed data processing system for associating a quality of service level to one or more virtual I / O adapters or virtual resources that reside within a physical adapter and are associated with a virtual host is provided. Specifically, a mechanism by which a single physical I / O adapter associates one or more virtual I / O adapters or virtual resources to a quality of service level is provided.
Owner:IBM CORP
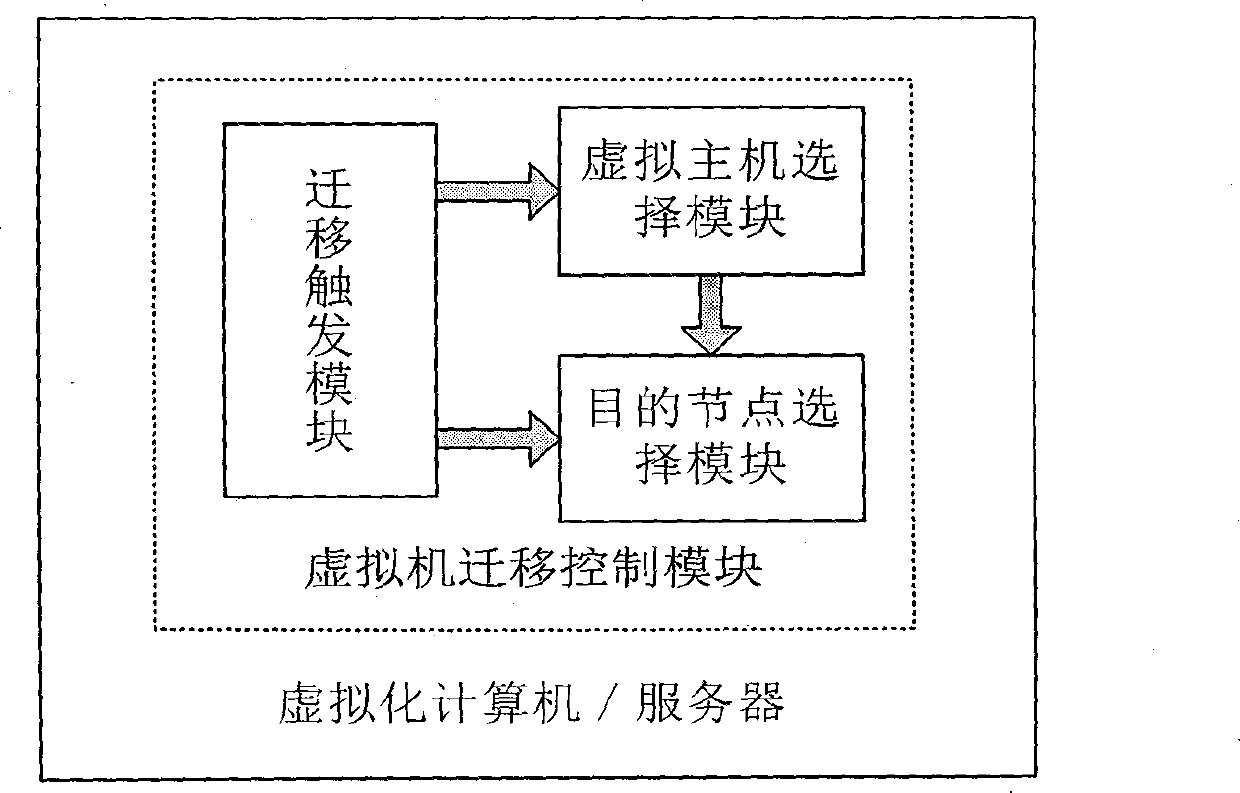
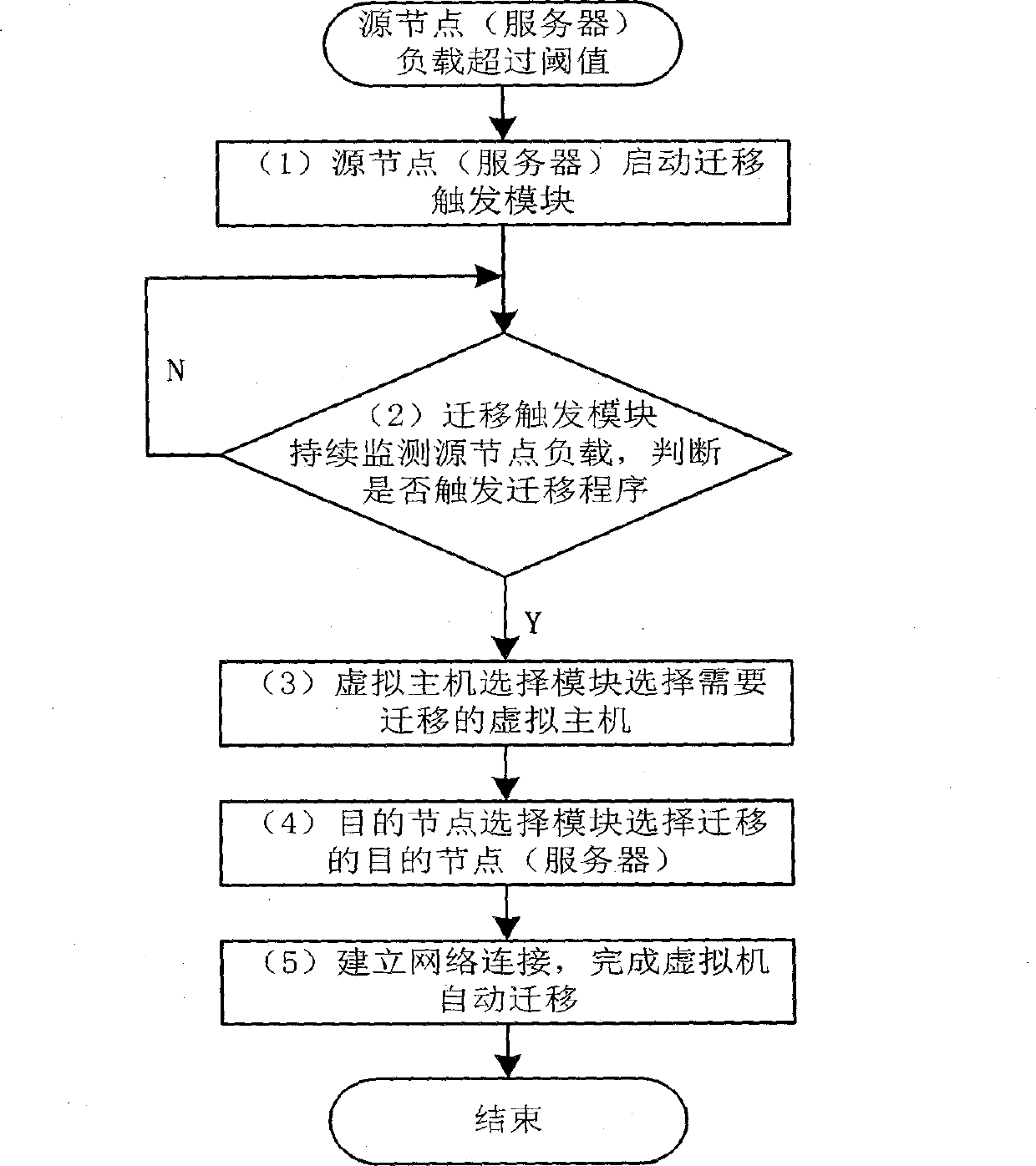
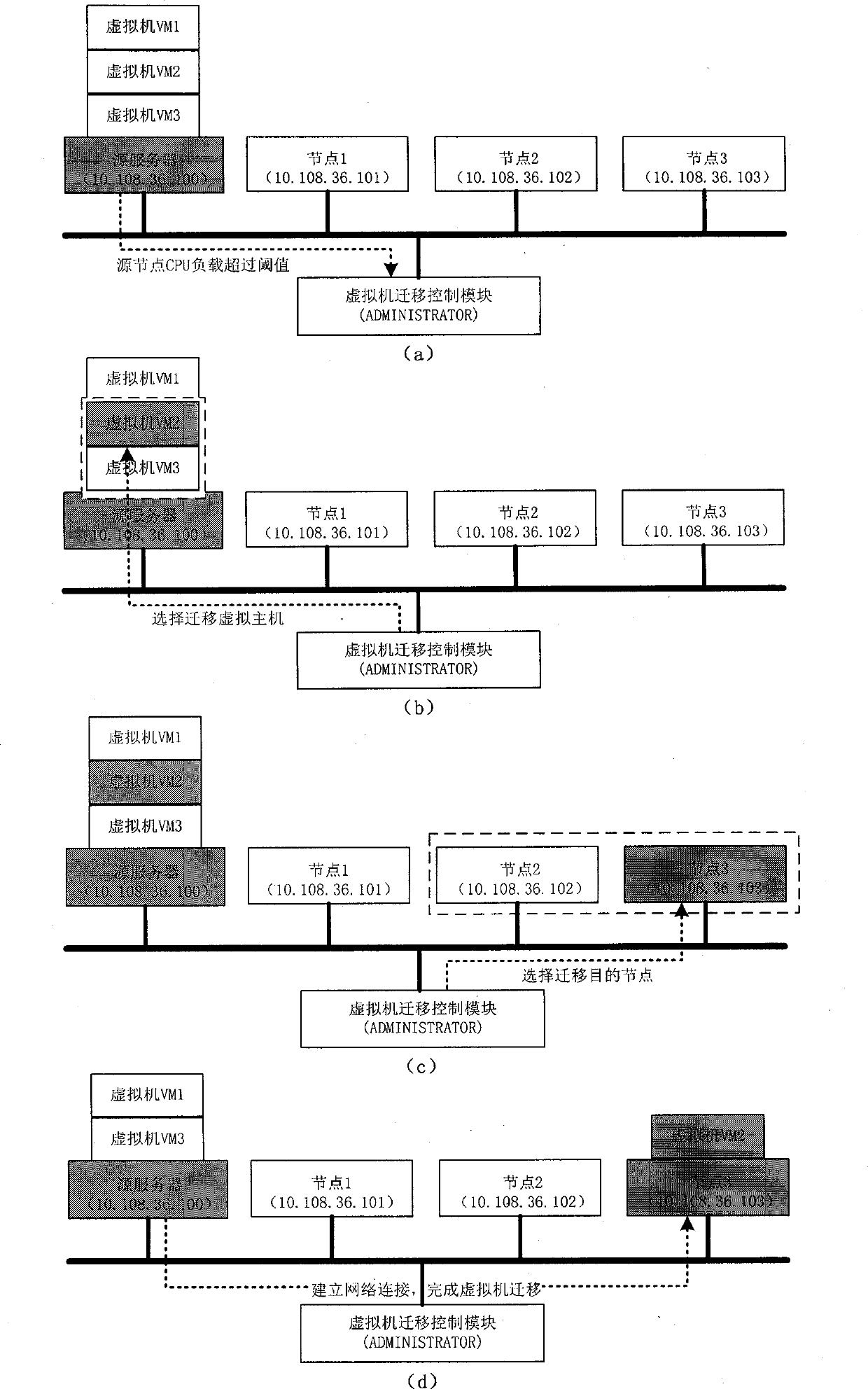
Decision method and control module facing to cloud computing virtual machine migration
The invention provides a decision method and a control module facing to cloud computing virtual machine migration. The control module is composed of a migration trigger module, a virtual machine choosing module and a destination node choosing module. The method includes: firstly setting load threshold value of the system through the migration trigger module, and enabling the system to effectively prevent instant load peak value from triggering unnecessary virtual machine migration by utilizing the load forecast technology; enabling the virtual machine choosing module to choose the virtual machine needing migration according to the migration cost minimum strategy, and reducing the migration cost of the virtual machine to the minimum value to save system resources; and finally, enabling the destination node choosing module to provide the destination node choosing strategy based on weighting probability choosing algorithm. Therefore, the problem of aggregation collision caused by migration of a large number of virtual machines is effectively solved. At last, the decision method can well achieve load balancing and enables resources to be used fair and reasonably.
Owner:BEIJING UNIV OF POSTS & TELECOMM
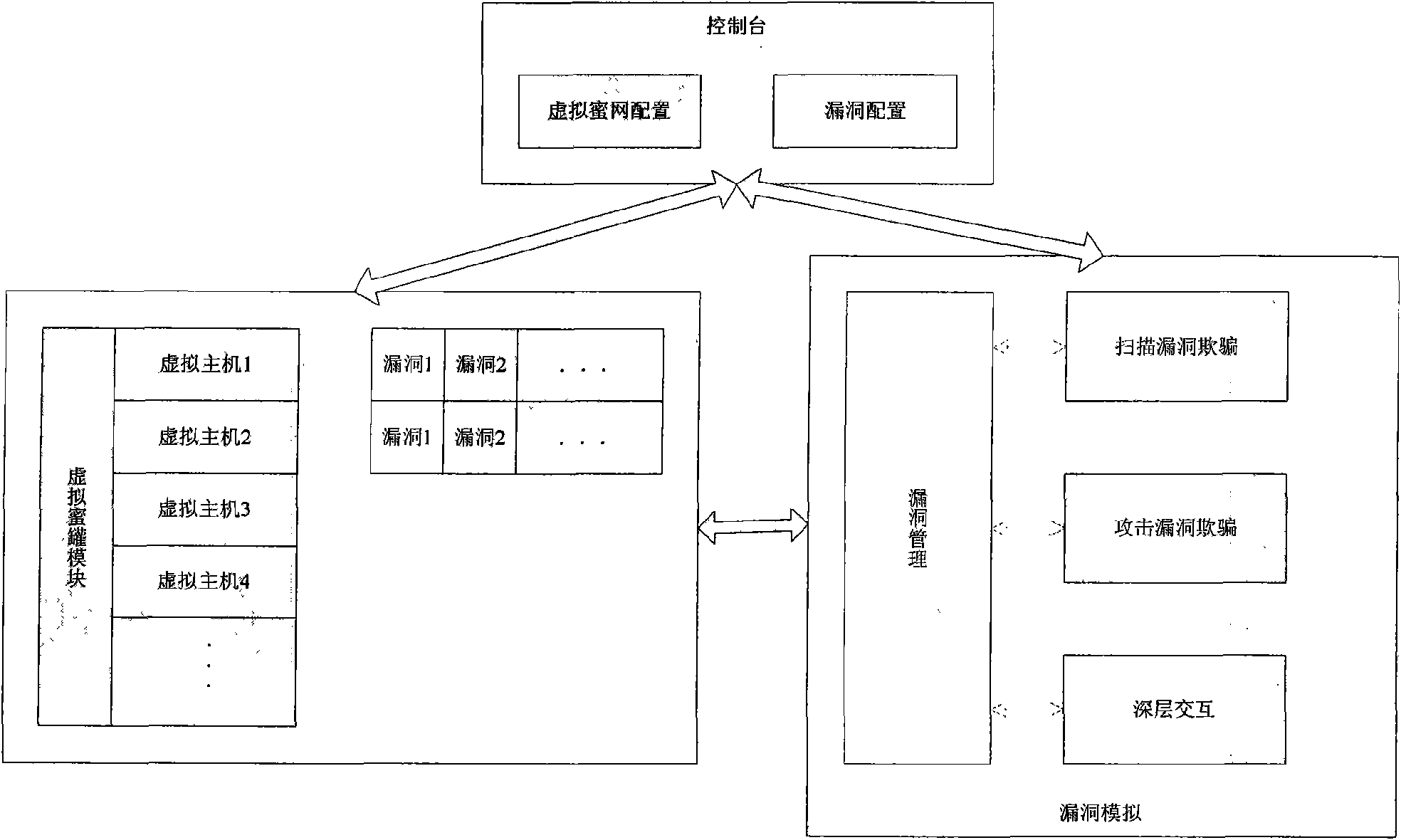
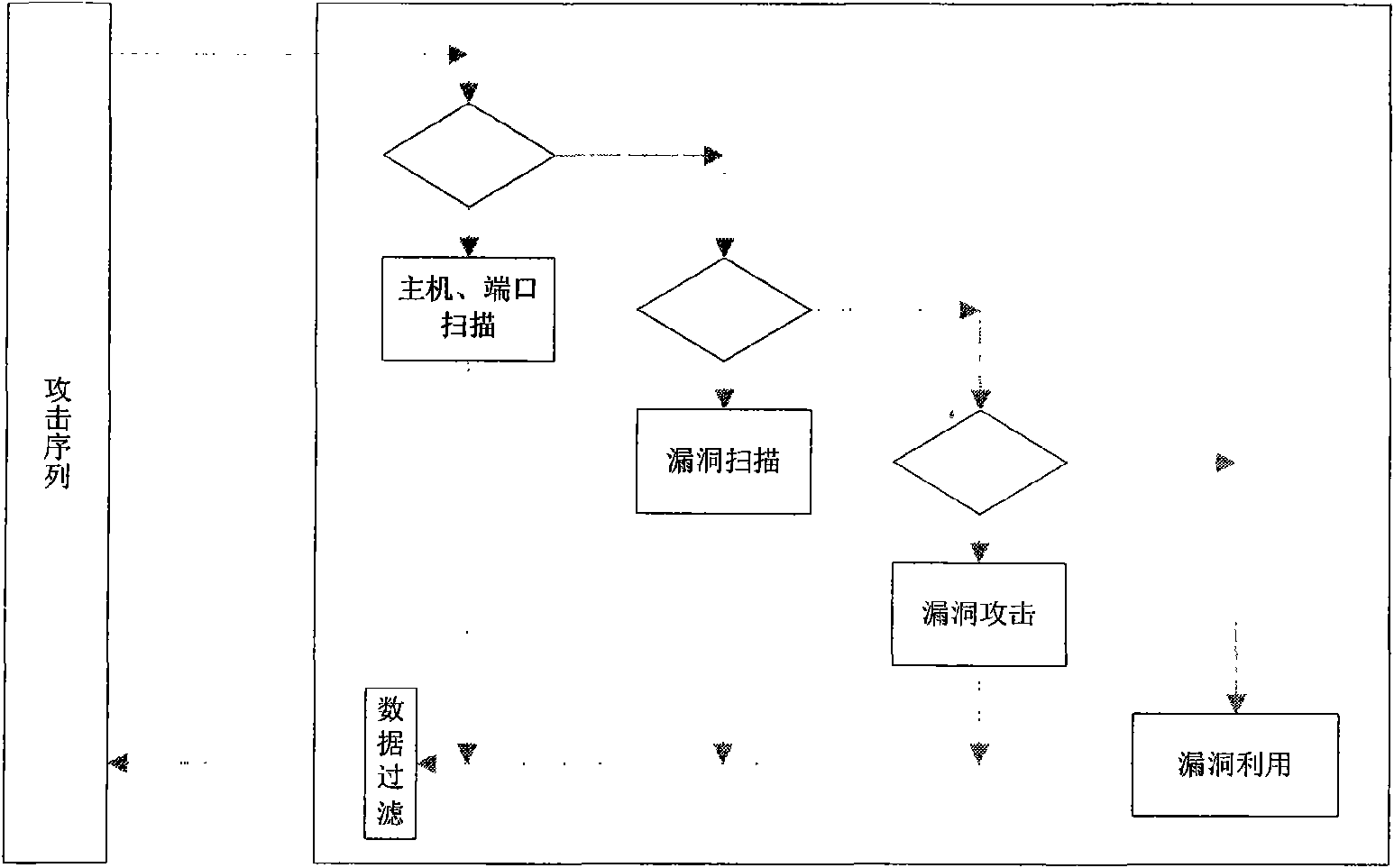
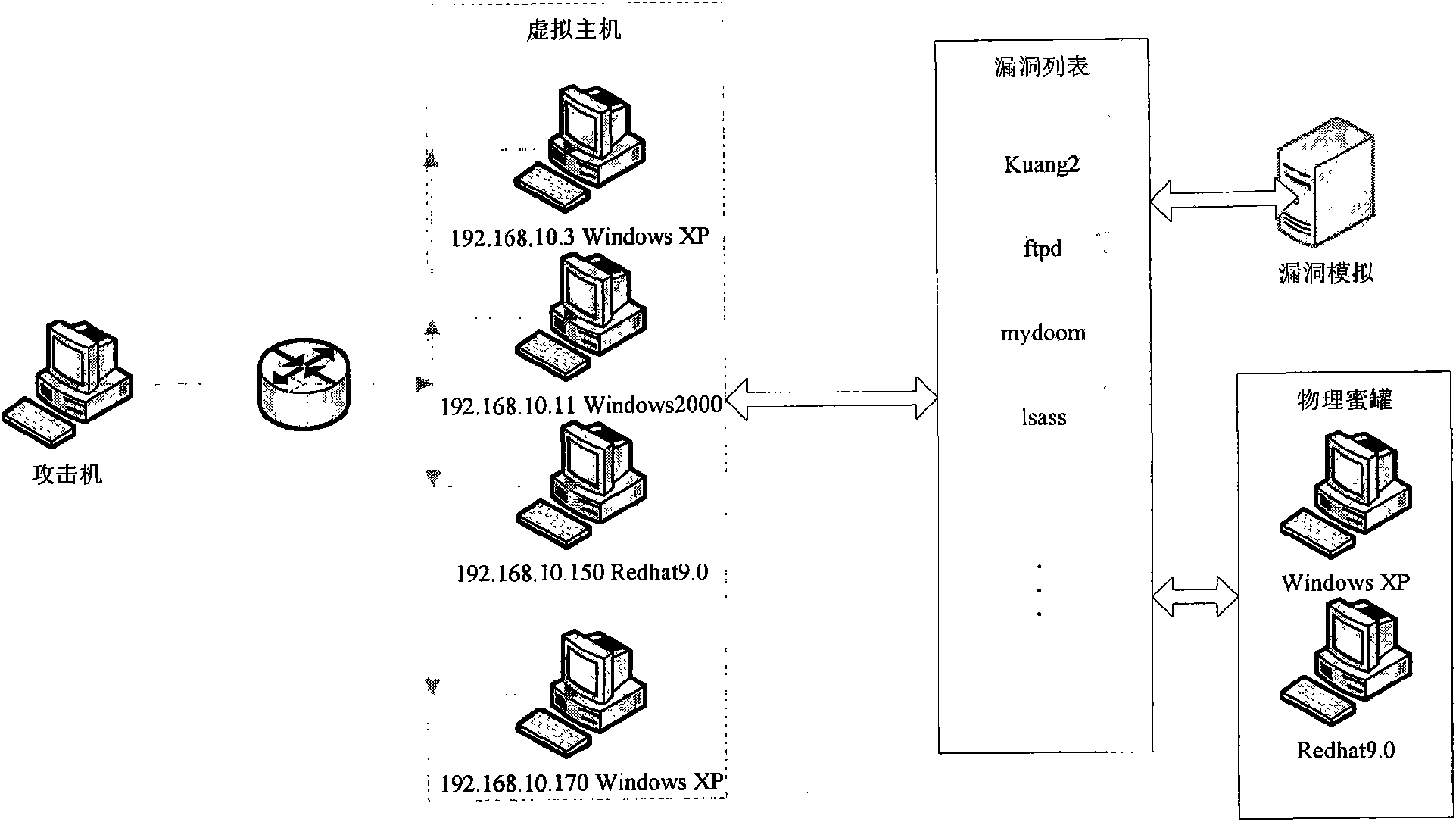
Vulnerability simulation overload honeypot method
InactiveCN101567887AAdd interactive functionComplete Attack DataData switching networksControl powerOperating system
The present invention discloses a vulnerability simulation overload honeypot method which comprises a host computer, a port scanning deception simulating module, a vulnerability scanning deception simulating module, a vulnerability scanning deception simulating module, a vulnerability attach deception simulating module, a data auditing module and a vulnerability utilizing module. When the attach sequence arrives at the simulated honeypot, a simulated honeypot system is used for processing according to the situation. When an attacker executes vulnerability scanning to the virtual host computer, the simulated honeypot responds and processes according to the vulnerability configuration information. Afterwards, these vulnerabilities are used for further attacking. Hereon, the simulated honeypot system transmits the vulnerability attack data flow to a vulnerability honeypot system. The vulnerability utilization attach of the attacker is processed and responded by a vulnerability attack simulating module. Finally, when the attacker successfully obtains the control power through the vulnerability attack, the attack data hereon is transmitted to a physical honeypot module. All attack processes and related data are recorded by a data auditing module for analyzing comprehensively. The method reduces the number of hardware devices in the honeynet and reduces the cost.
Owner:中国人民解放军总参谋部第五十四研究所 +2
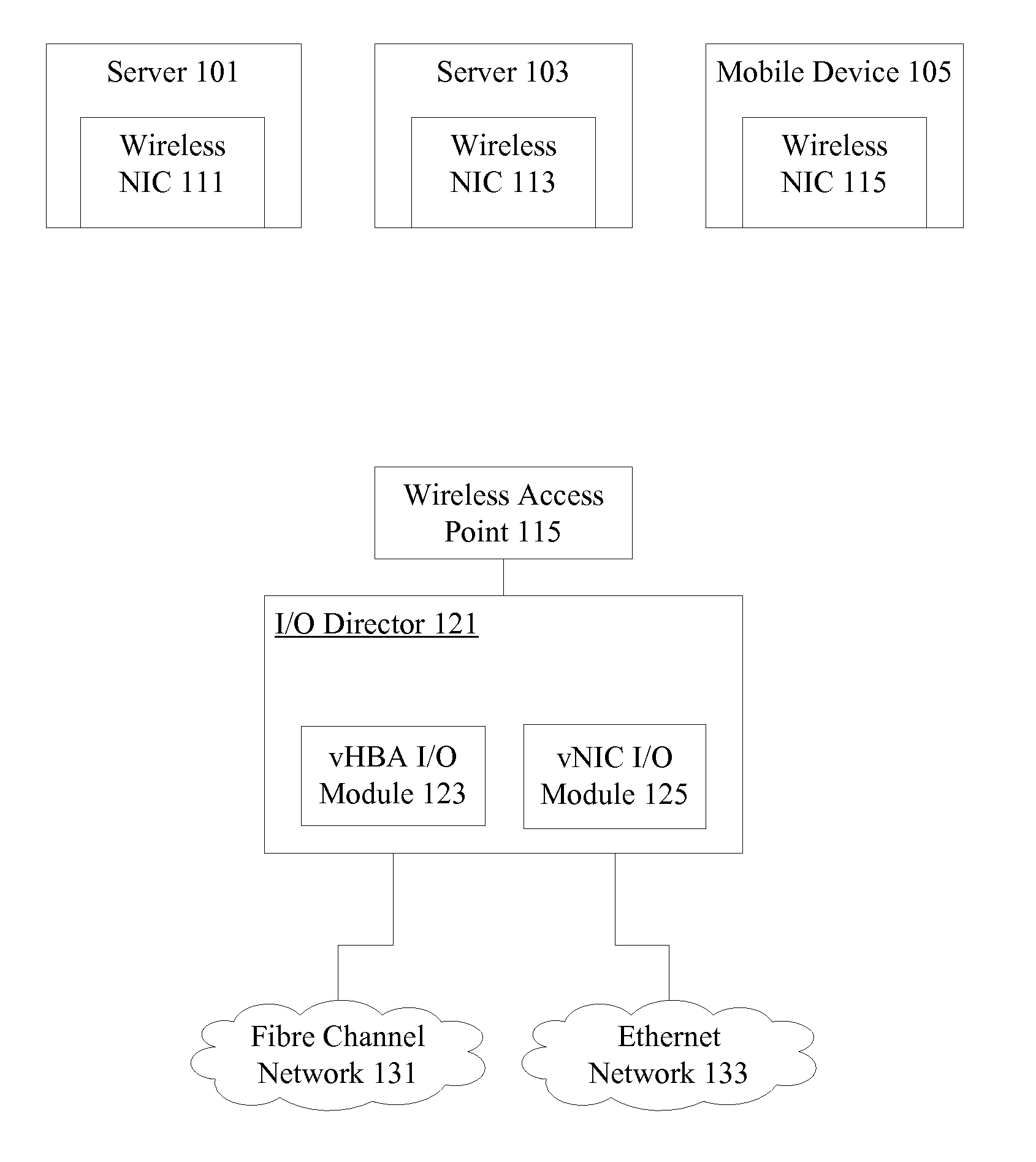
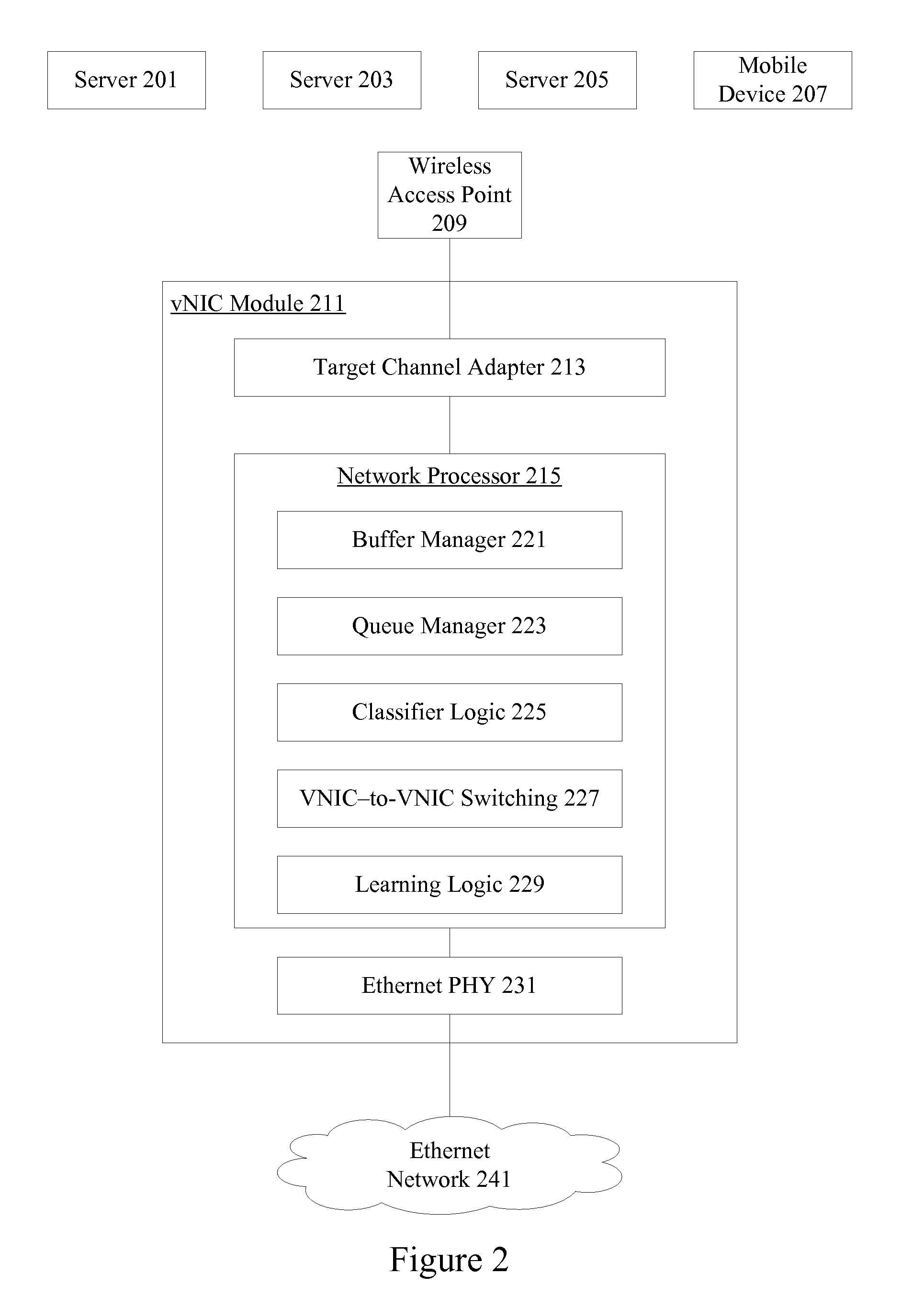
Wireless host I/O using virtualized I/O controllers
Mechanisms provide hosts such as servers and mobile devices with access to virtualized I / O resources including virtual Host Bus Adapters (vHBAs) and virtual Network Interface Cards (vNICs) over a wireless I / O interconnect. Host applications access virtualized I / O resources using virtual device drivers that communicate with virtualized I / O resources on an I / O director using a reliable communication protocol running over a wireless network. I / O data is throttled if necessary based on wireless network considerations.
Owner:ORACLE INT CORP
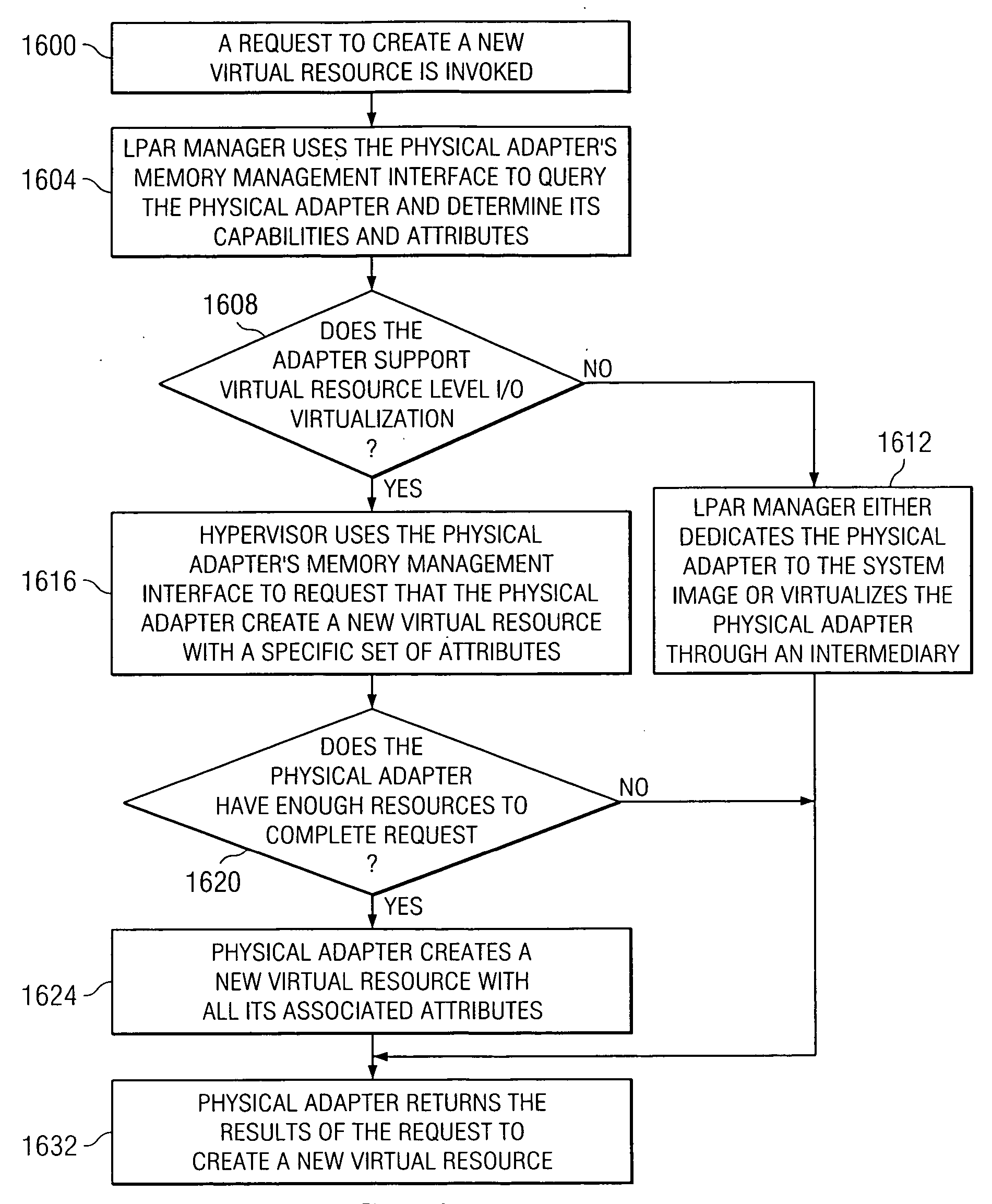
System and method for virtual resource initialization on a physical adapter that supports virtual resources
ActiveUS20060195620A1Memory adressing/allocation/relocationComputer security arrangementsResource virtualizationTerm memory
A method, computer program product, and distributed data processing system for directly sharing a network stack offload I / O adapter that directly supports resource virtualization and does not require a LPAR manager or other intermediary to be invoked on every I / O transaction is provided. The present invention also provides a method, computer program product, and distributed data processing system for directly creating and initializing one or more virtual resources that reside within a physical adapter, such as a PCI, PCI-X, or PCI-E adapter, and that are associated with a virtual host. Specifically, the present invention is directed to a mechanism for sharing conventional PCI (Peripheral Component Interconnect) I / O adapters, PCI-X I / O adapters, PCI-Express I / O adapters, and, in general, any I / O adapter that uses a memory mapped I / O interface for host to adapter communications. A mechanism is provided for directly creating and initializing one or more virtual resources that reside within a physical adapter, such as a PCI, PCI-X, or PCI-E adapter, and that are associated with a virtual host.
Owner:IBM CORP
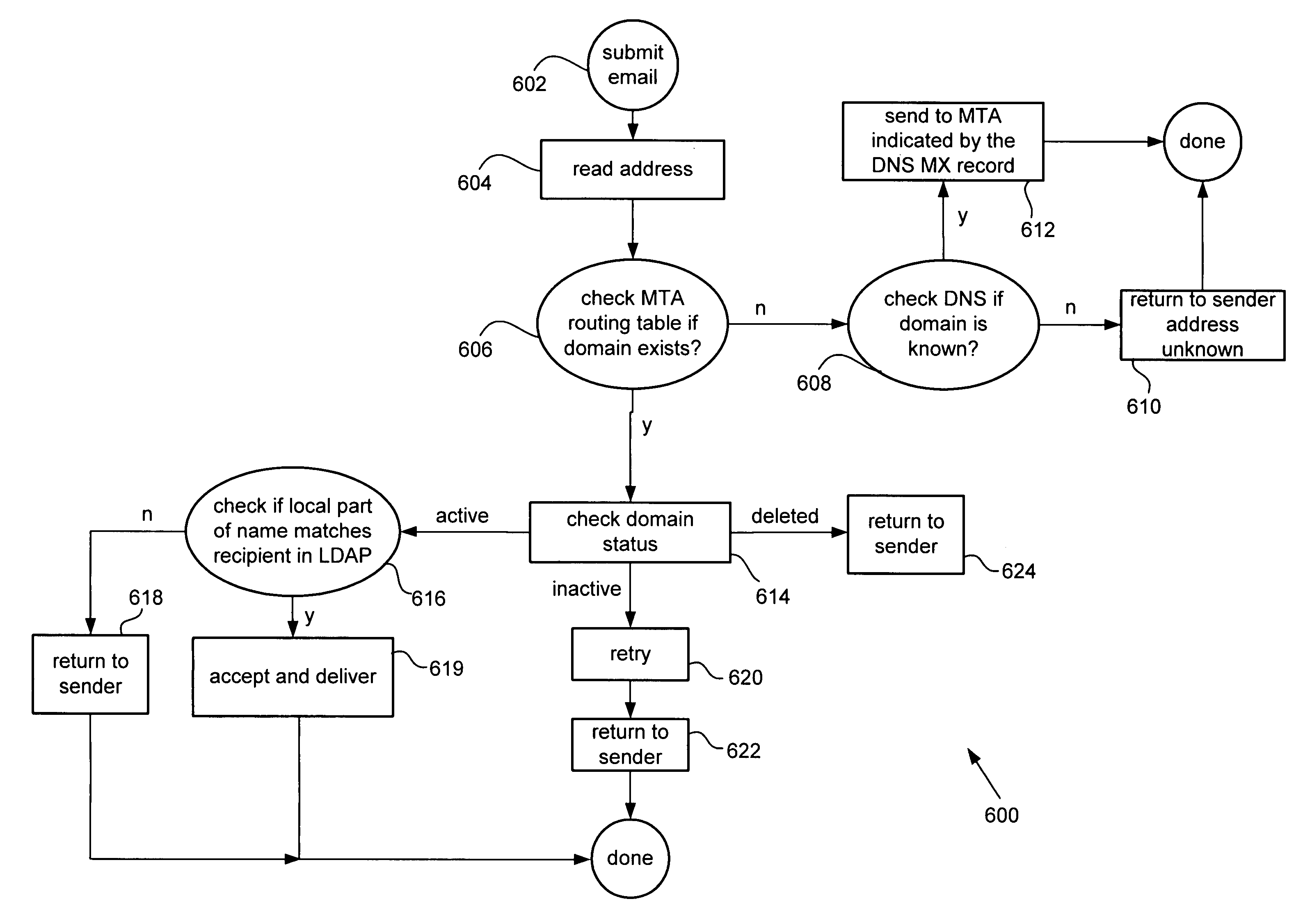
Methods and apparatus for providing a virtual host in electronic messaging servers
InactiveUS7058683B1Multiple digital computer combinationsTransmissionVirtual hostingDistributed computing
According to the present invention, methods, apparatus, and computer readable medium are disclosed for defining a virtual domain in an electronic messaging system are disclosed. A virtual domain node is defined that corresponds to a real (non-virtual) domain. The virtual domain node resided in a hierarchically organized directory. A plurality of virtual domain attributes are then assigned to the virtual domain node. The directory is a tree based hierarchical directory arranged in such a way even in a multiple domain environment, a name search operation is executed as if in a flat name space.
Owner:ORACLE INT CORP
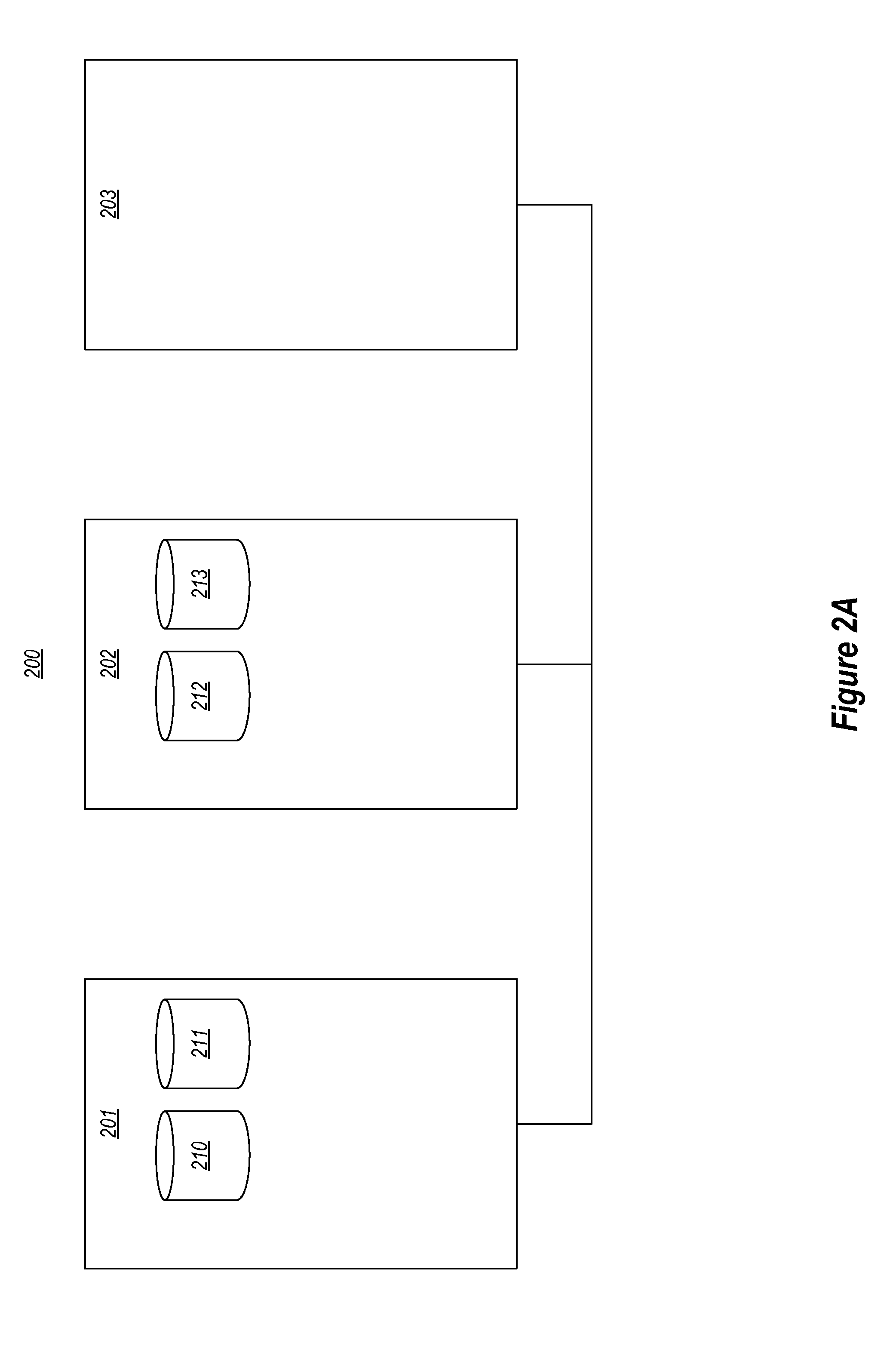
System and method for destroying virtual resources in a logically partitioned data processing system
InactiveUS20060195619A1Memory adressing/allocation/relocationMultiprogramming arrangementsTerm memoryPCI Express
A method, computer program product, and distributed data processing system for directly destroying one or more virtual resources that reside within a physical adapter and that are associated with a virtual host. Specifically, the present invention is directed to a mechanism for sharing conventional Peripheral Component Interconnect (PCI) I / O adapters, PCI-X I / O adapters, PCI-Express I / O adapters, and, in general, any I / O adapter that uses a memory mapped I / O interface for host to adapter communications.
Owner:IBM CORP
Virtual shared storage in a cluster
InactiveUS20130346532A1Low costIncrease typeError detection/correctionDigital computer detailsOperational systemVirtual hosting
The present invention minimizes the cost of establishing a cluster that utilizes shared storage by creating a storage namespace within the cluster that makes each storage device, which is physically connected to any of the nodes in the cluster, appear to be physically connected to all nodes in the cluster. A virtual host bus adapter (VHBA) is executed on each node, and is used to create the storage namespace. Each VHBA determines which storage devices are physically connected to the node on which the VHBA executes, as well as each storage device that is physically connected to each of the other nodes. All storage devices determined in this manner are aggregated into the storage namespace which is then presented to the operating system on each node so as to provide the illusion that all storage devices in the storage namespace are physically connected to each node.
Owner:MICROSOFT TECH LICENSING LLC
Method, system and program product for differentiating between virtual hosts on bus transactions and associating allowable memory access for an input/output adapter that supports virtualization
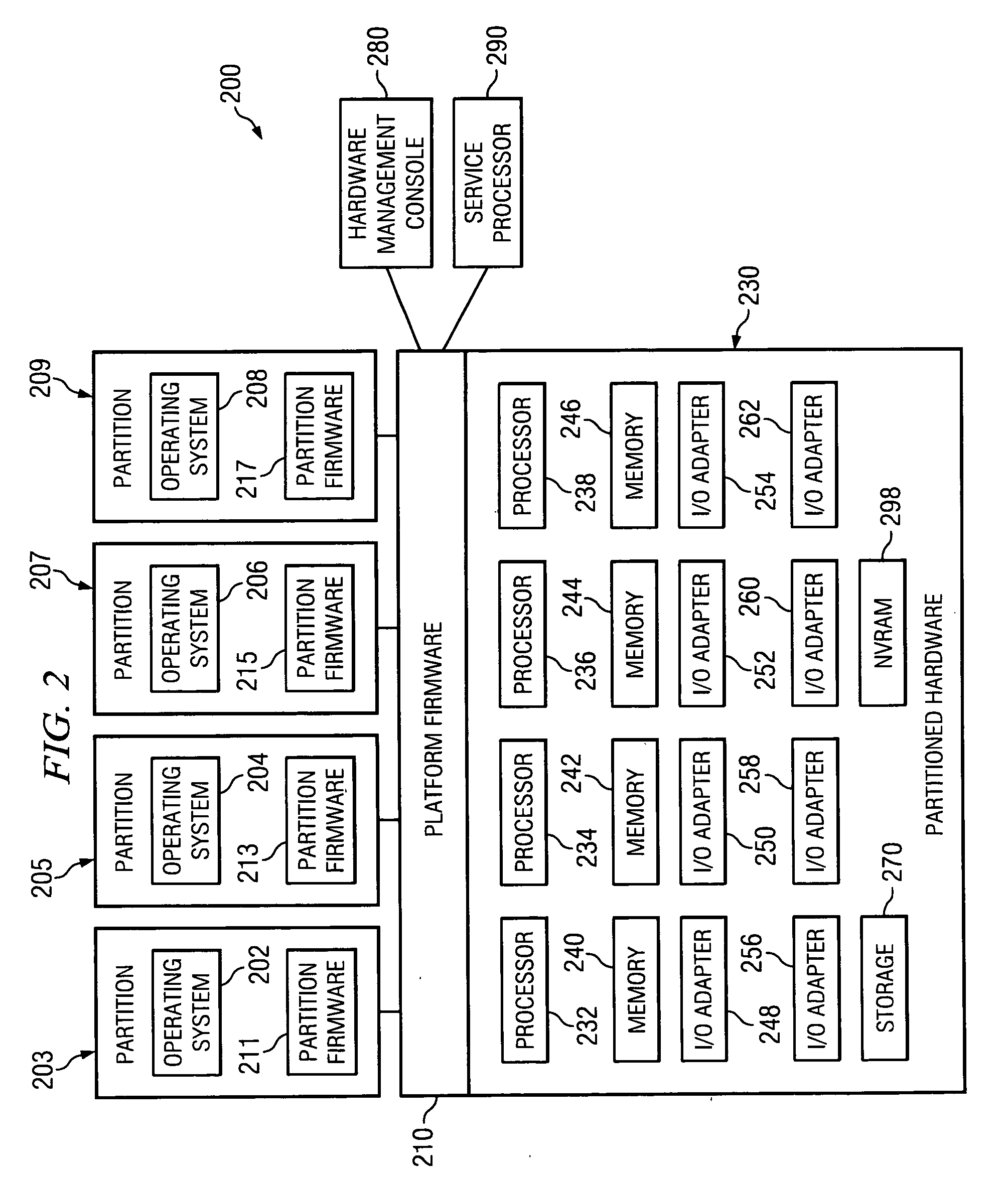
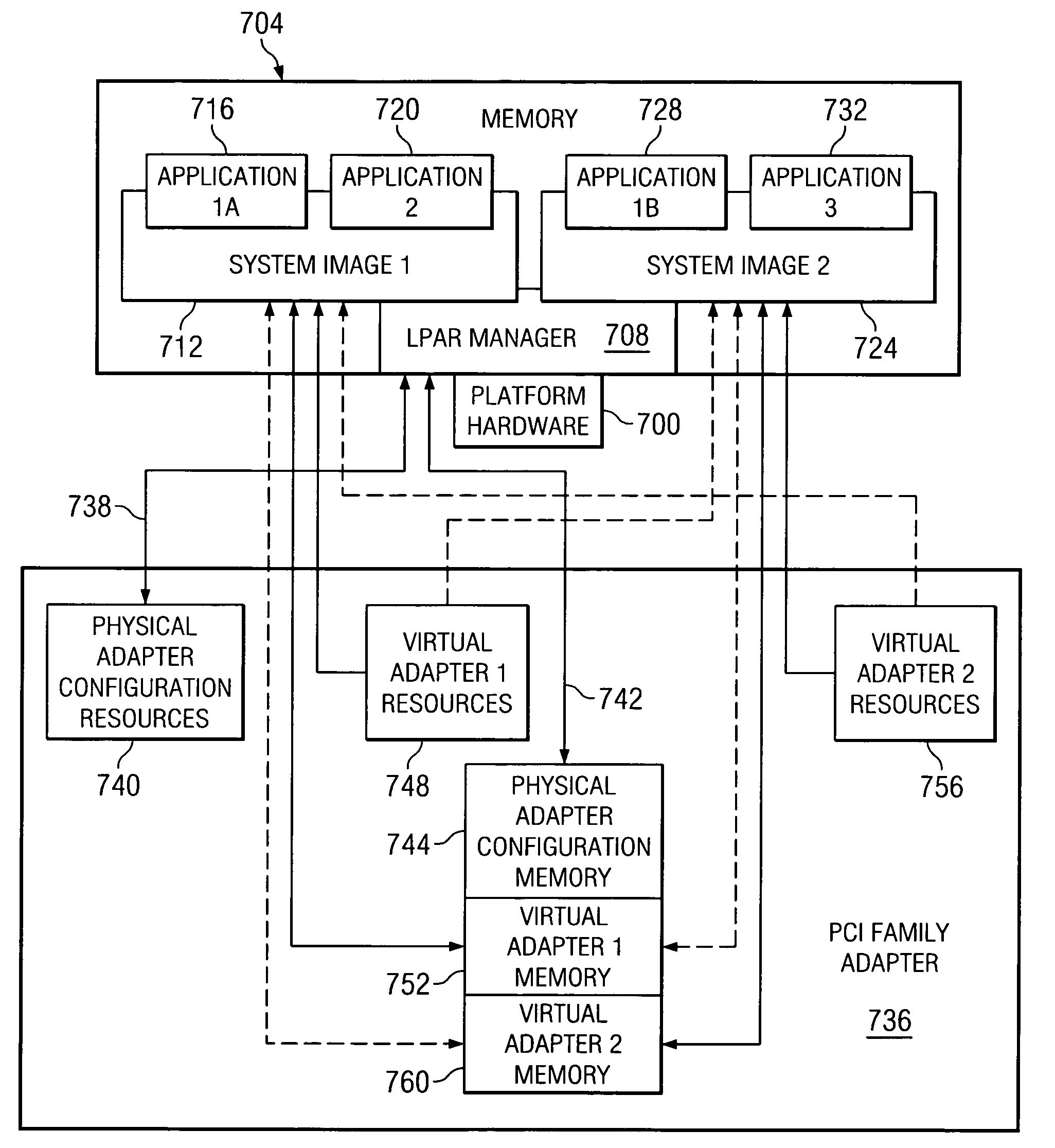
ActiveUS7493425B2Maintaining isolation of the exposed system memorySoftware simulation/interpretation/emulationMemory systemsVirtualizationVirtual hosting
A method, system and computer program product that allows a System Image within a multiple System Image Virtual Server to maintain isolation from the other system images while directly exposing a portion, or all, of its associated System Memory to a shared PCI Adapter without the need for each I / O operation to be analyzed and verified by a component trusted by the LPAR manager.
Owner:IBM CORP
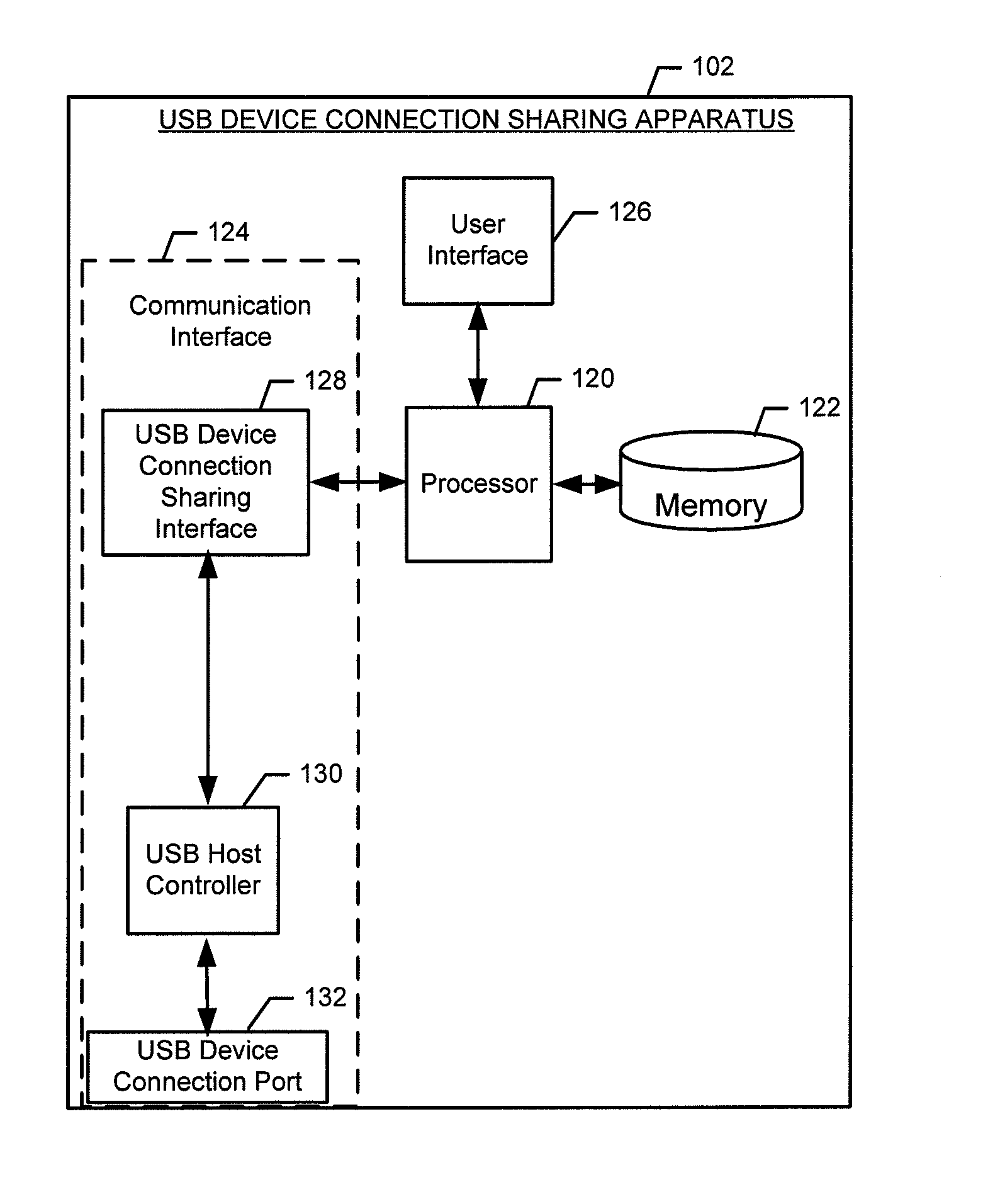
Methods and apparatuses for facilitating sharing device connections
Methods and apparatuses are provided for facilitating sharing device connections across multiple physical and / or virtual (logical) computers. A method may include receiving a USB device request from a virtual host controller driver of a client when a host is not in a power save mode and passing a USB device request to a host controller driver of the client when the host is in a power save mode. A method may also include activating a sharing switch of a host controller to connect a device connection port to the host when the host is not in a power save mode and to connect the device connection port to the client when the host is in a power save mode. Corresponding apparatuses and computer program products are also provided.
Owner:WSOU INVESTMENTS LLC
Network address translation for multicast virtual sourcing
InactiveUS20050089050A1Special service provision for substationData switching by path configurationNetwork address translationVirtual hosting
A method for using network address translation in switches and routers to define a virtual host as the source of a multicast channel within a single-source multicast model and to translate packet addresses from different multicast sources so that the packets appear to be originating from the virtual host. Address-translated packets are thus forwarded through a single-source multicast channel and received by the subscribing host(s) / clients as though the packets came from a single “virtual” source. This methodology can be used to map two or more sources simultaneously onto the same multicast channel. Such a mapping is useful, for example, to present multiple views of a sporting event video broadcast, provide advertisement insertion capability, or to support transparent fail-over to a backup video source in a critical multicast application. Subscribing client hosts in the multicast reception group simply subscribe to the single virtual host as the source of a multicast channel.
Owner:CISCO TECH INC
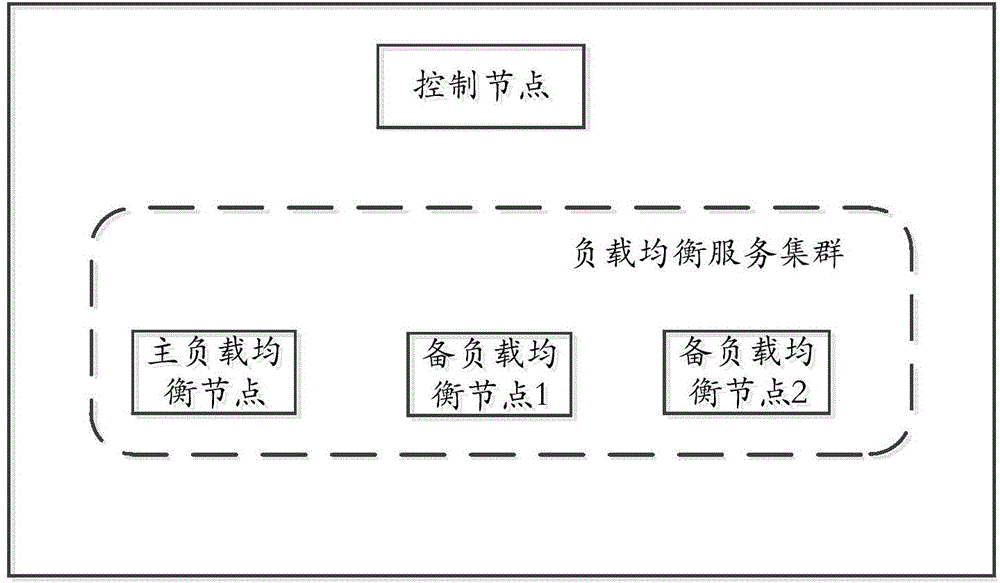
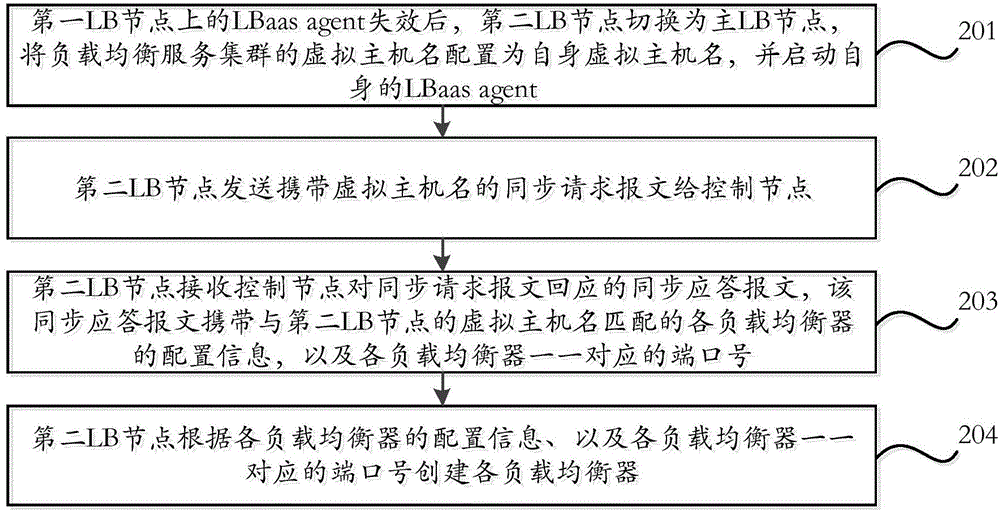
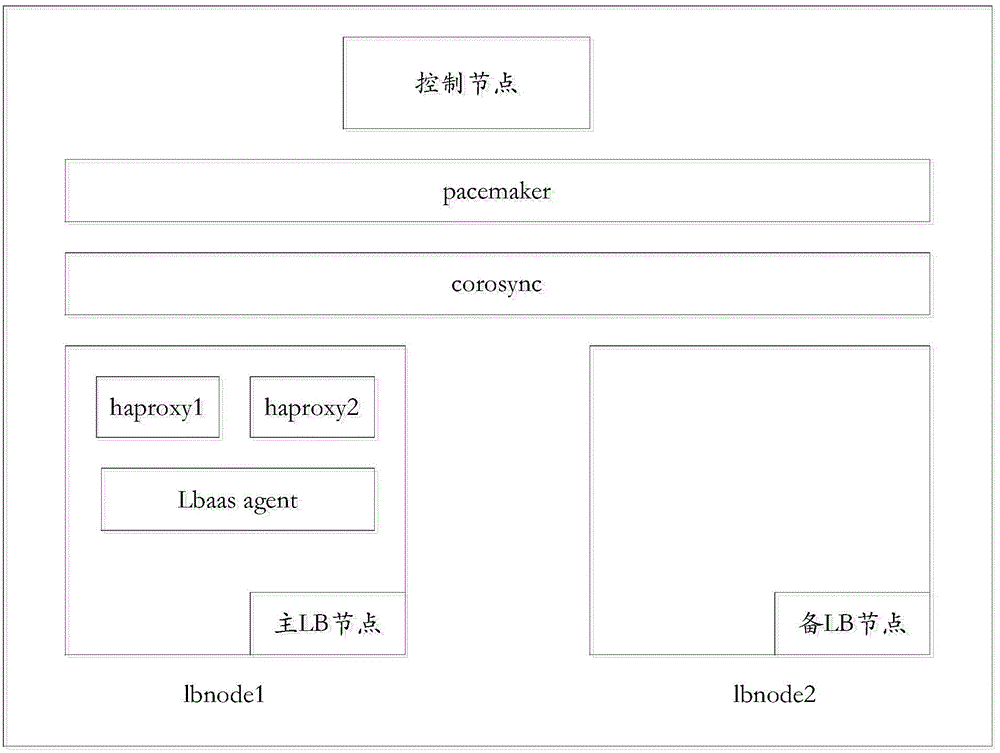
High available realizing method and equipment of load balancing service
ActiveCN104935672AHigh load balancing serviceTransmissionNetwork Load Balancing ServicesVirtual hosting
The invention discloses a high available realizing method of a load balancing service. The method is applied to load balancing nodes in a load balancing service cluster of Openstack. The method comprises the steps as follows: switching a second LB node used as any backup LB node of the load balancing service cluster as a main LB node after LBaas agent on the first LB node used as the main LB node of the load balancing service cluster is failed, configuring a virtual host name of the load balancing service cluster as a self virtual host name, and starting the LBaas agent; transmitting a synchronous request message carried with the virtual host name to a control node; receiving a synchronous response message returned by the control node, and creating each load balancer according to configuration information of each load balancer carried by the synchronous response message and port numbers which correspond to each load balancer one by one.
Owner:NEW H3C TECH CO LTD
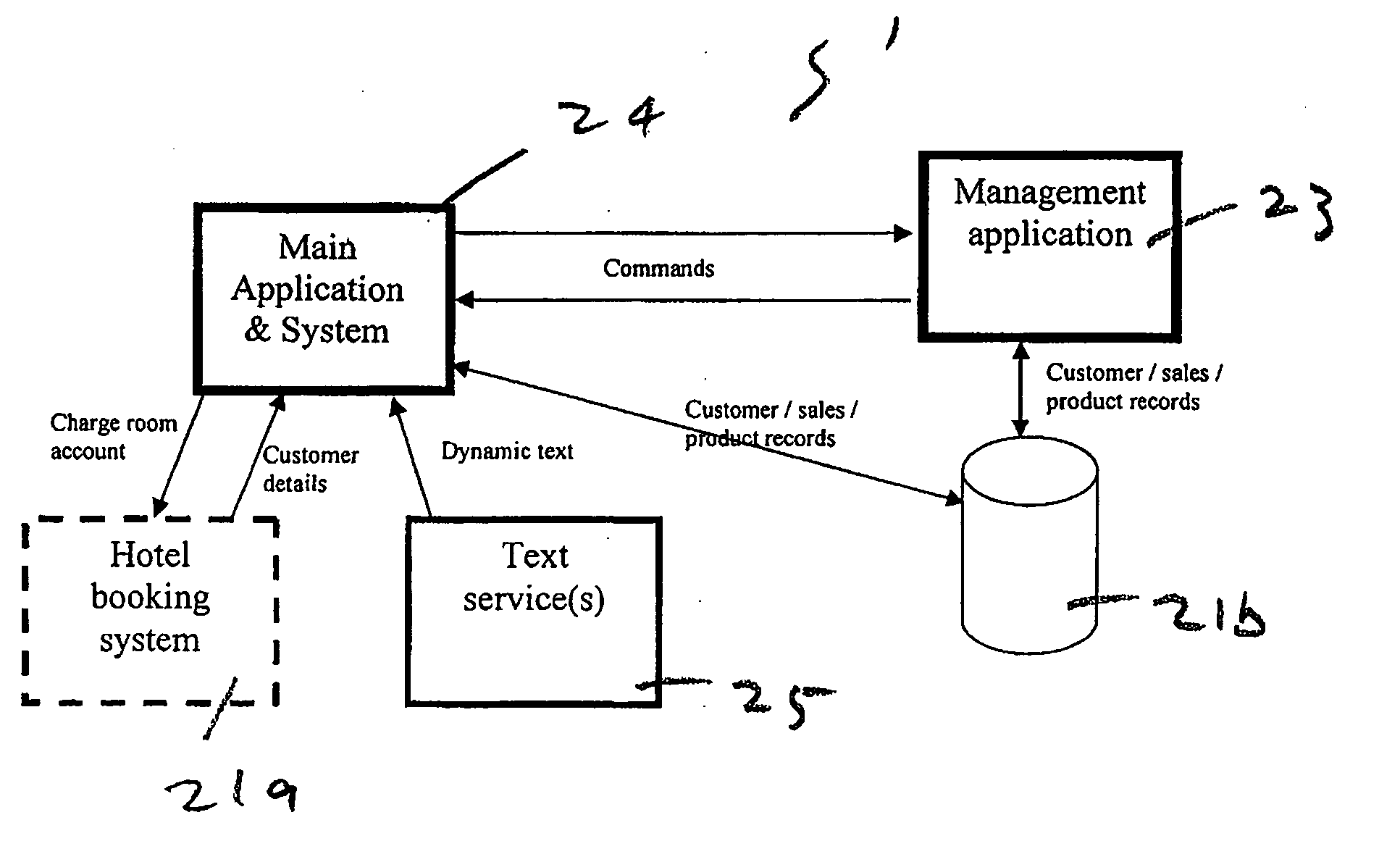
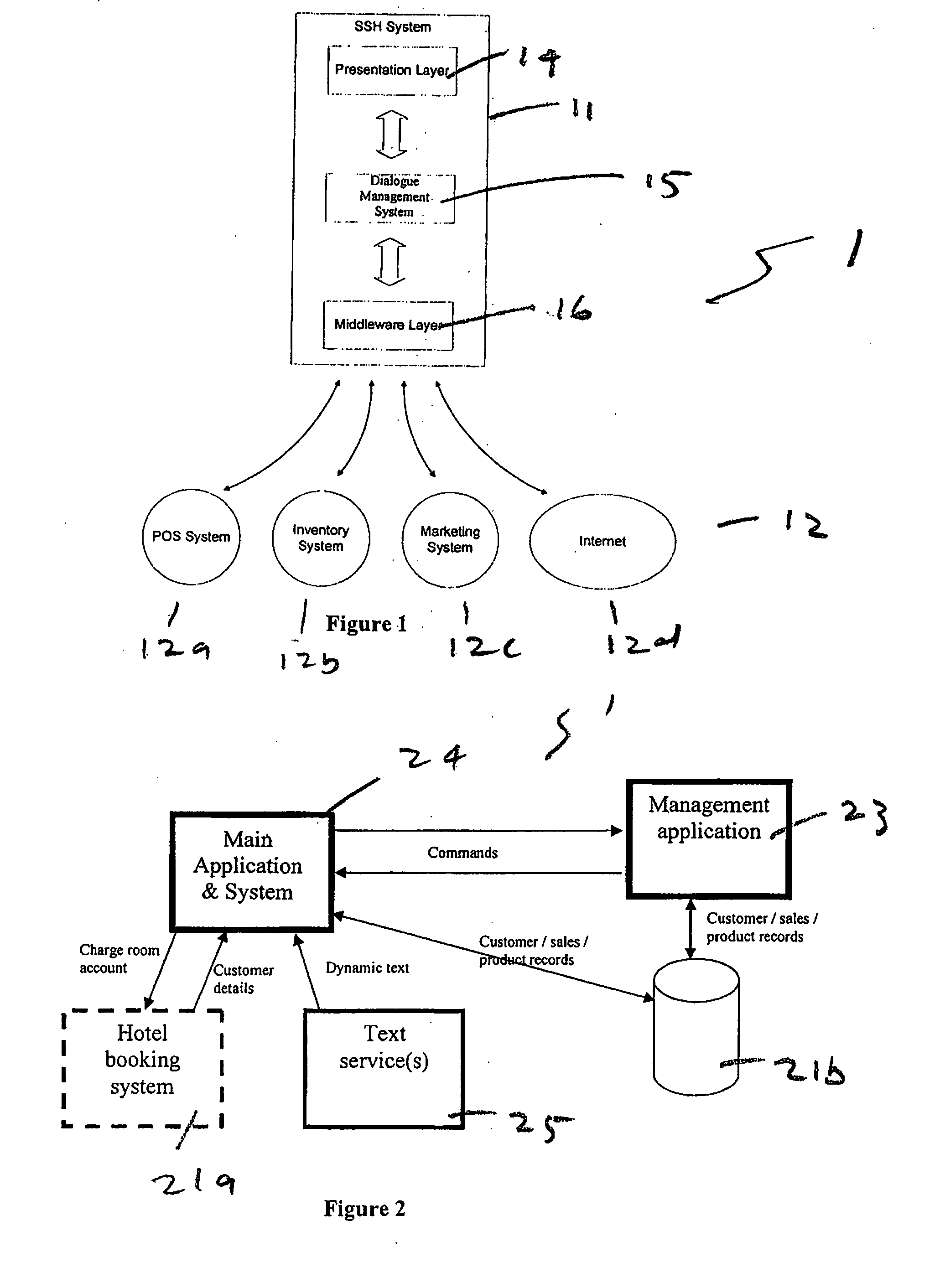
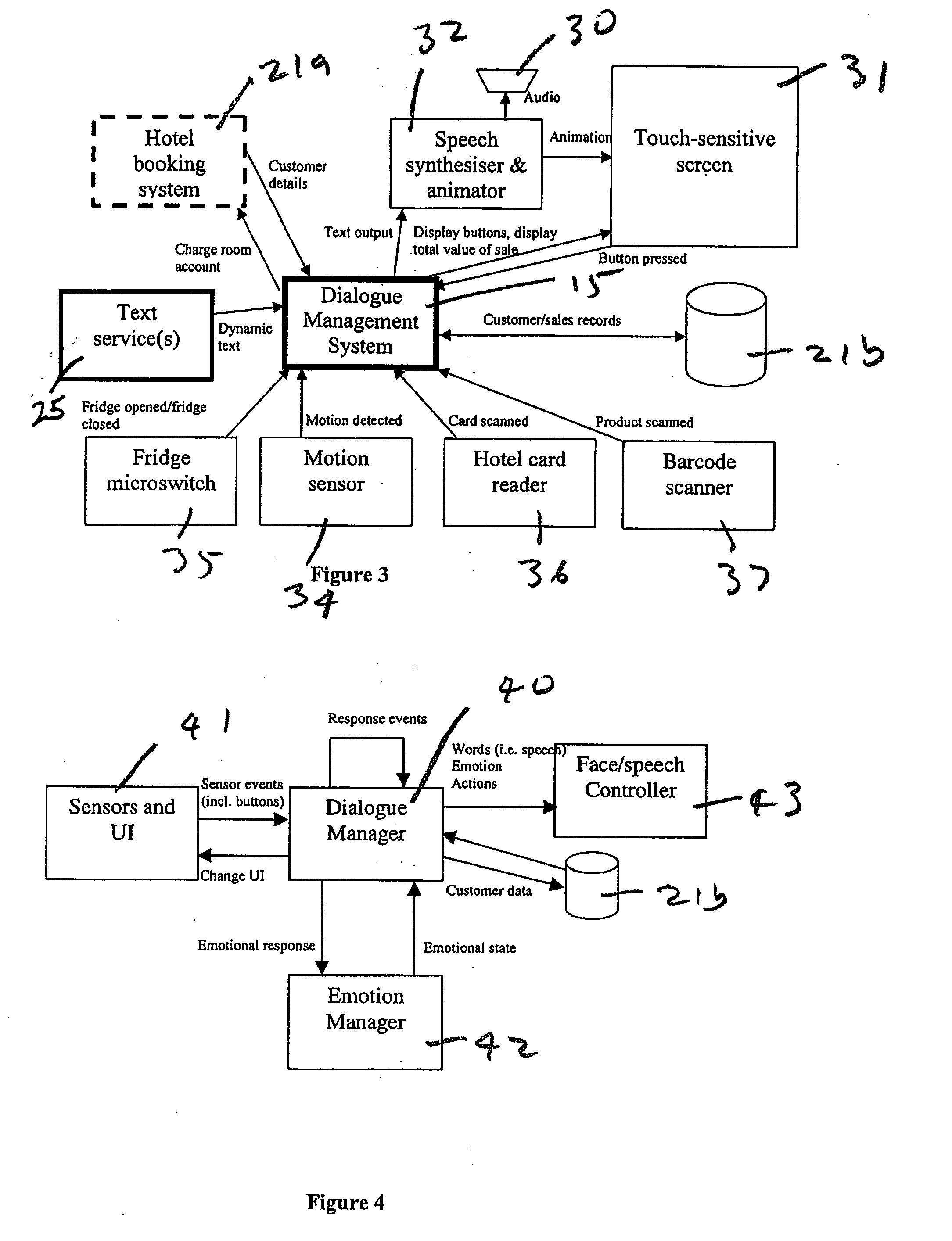
Virtual host
InactiveUS20070143127A1Facilitates communication and transactionReservationsCustomer communicationsAnimationBusiness management
The present invention relates to a self-service engine for implementation in a business management system for rendering a virtual host. The virtual host replaces a customer service representative usually employed in an enterprise, such as a retail outlet, hotel or the like, who assists a customer. The self-service engine determines responses to events based on a set of rules, and renders the response on output devices. The response might, for example, be rendered as an animated human with a voice output.
Owner:SHE TECH
Zero-copy network I/O for virtual hosts
ActiveUS7721299B2Eliminate the problemSolve excessive overheadDigital computer detailsTransmissionComputer hardwareVirtualization
Techniques for virtualized computer system environments running one or more virtual machines that obviate the extra host operating system (O / S) copying steps required for sending and receiving packets of data over a network connection, thus eliminating major performance problems in virtualized environment. Such techniques include methods for emulating network I / O hardware device acceleration-assist technology providing zero-copy I / O sending and receiving optimizations. Implementation of these techniques require a host O / S to perform actions including, but not limited to: checking of the address translations (ensuring availability and data residency in physical memory), checking whether the destination of a network packet is local (to another virtual machine within the computing system), or across an external network; and, if local, checking whether either the sending destination VM, receiving VM process, or both, supports emulated hardware accelerated-assist on the same physical system. This optimization, in particular, provides a further optimization in that the packet data checksumming operations may be omitted when sending packets between virtual machines in the same physical system.
Owner:RED HAT
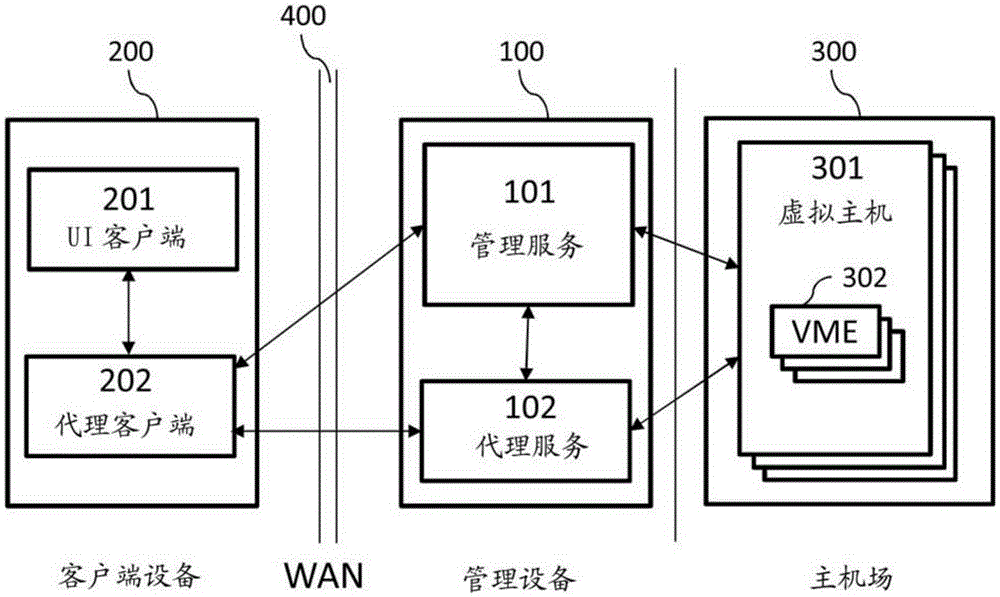
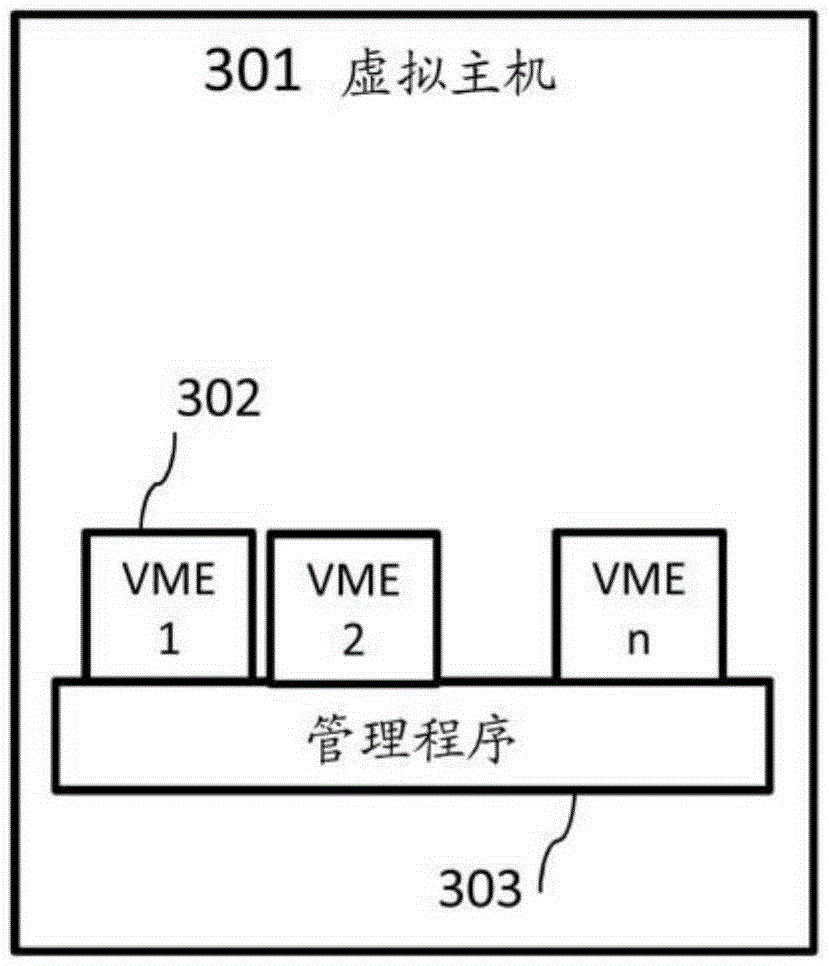
Method and system for enabling access of client device to remote desktop
A computer implemented method, computer program product, and systems for enabling access of a client device to a remote desktop. The remote desktop is implemented within a remote virtual machine engine (302) selected from one or more virtual machines running on a virtual host (301). A connection management component receiving from the client device 200 a connection request wherein the connection request is directed to establishing a connection between the client device (200) and the remote virtual machine engine (302). If authorization data associated with the connection request complies with a predefined access data structure and corresponding access rules, the connection management component requests destination data of the remote virtual machine engine (302), the destination data allowing to interact with the virtual machine engine (302) and, in response, receiving the destination data. Then it sends to a proxy service (102) a session request based on the destination data for establishing a session (1010) with the remote virtual machine engine (302) through the proxy service (102) in accordance with the authorization data. It receives from the proxy service (102) proxy connection data configured to allow the client device to establish a proxy connection (1009) via a wide area network (400). The proxy connection data is then sent to the client device (200) to enable the client device (200) for establishing the proxy connection between the client device (200) and the proxy service (102) over the wide area network (400) to access the remote virtual machine engine (302) through the session with the remote virtual machine engine (302).
Owner:TOCARIO
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com