Vulnerability simulation overload honeypot method
A vulnerability honeypot and vulnerability simulation technology, which is applied in the field of network information security, can solve problems such as excessive resource requirements, low interaction capabilities, and attackers' detection, and achieve the effects of reducing costs, large simulation scale, and reducing the number
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
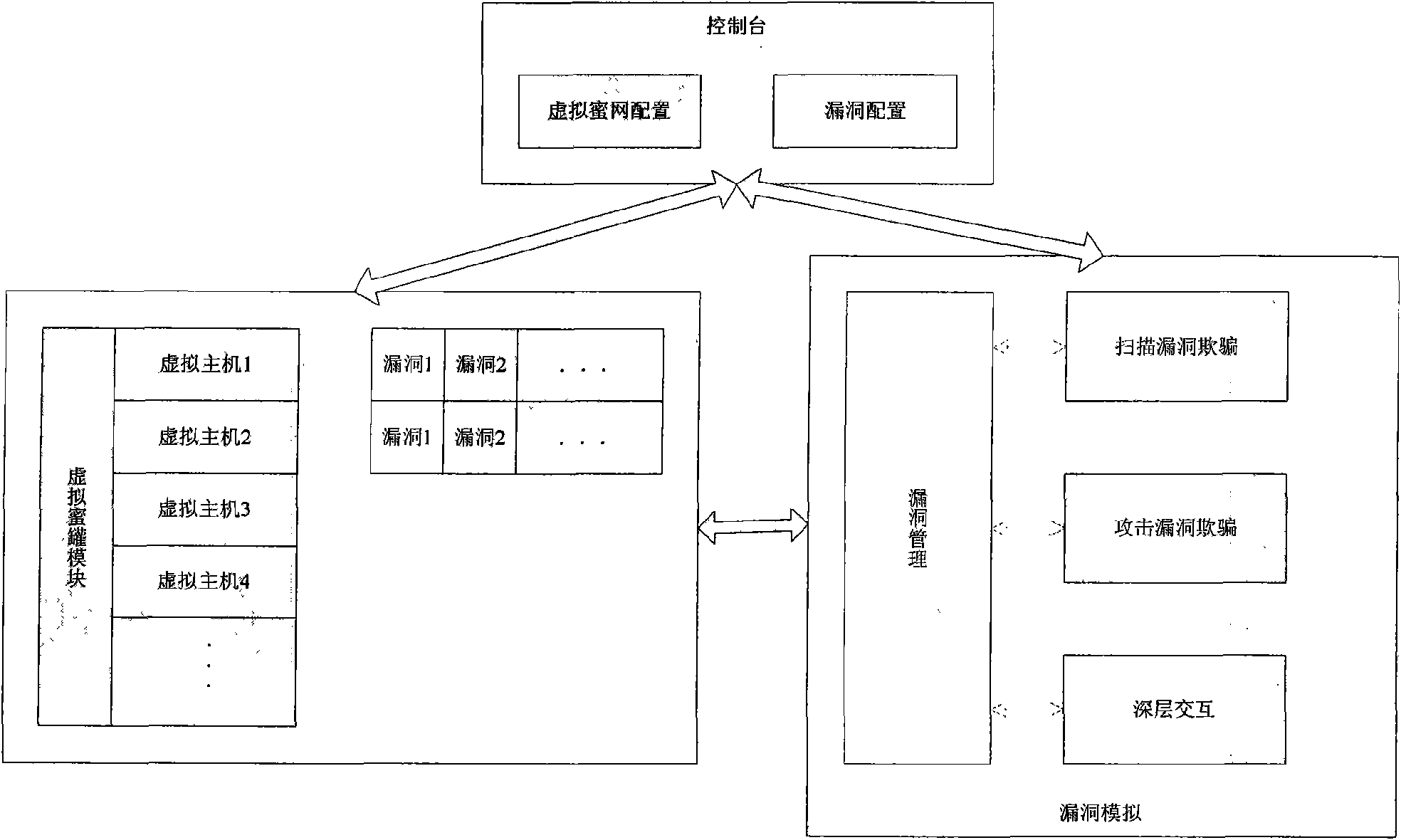
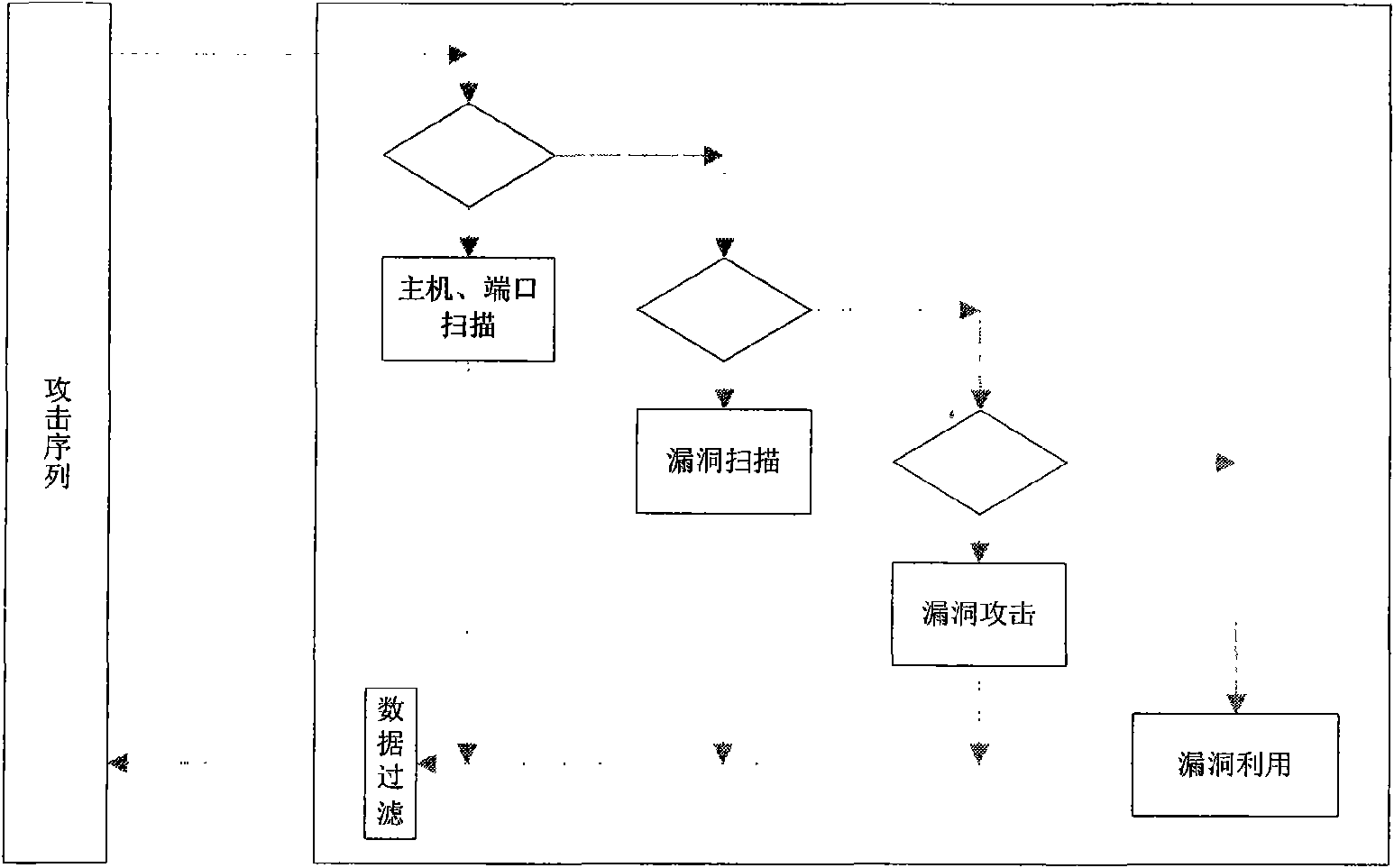
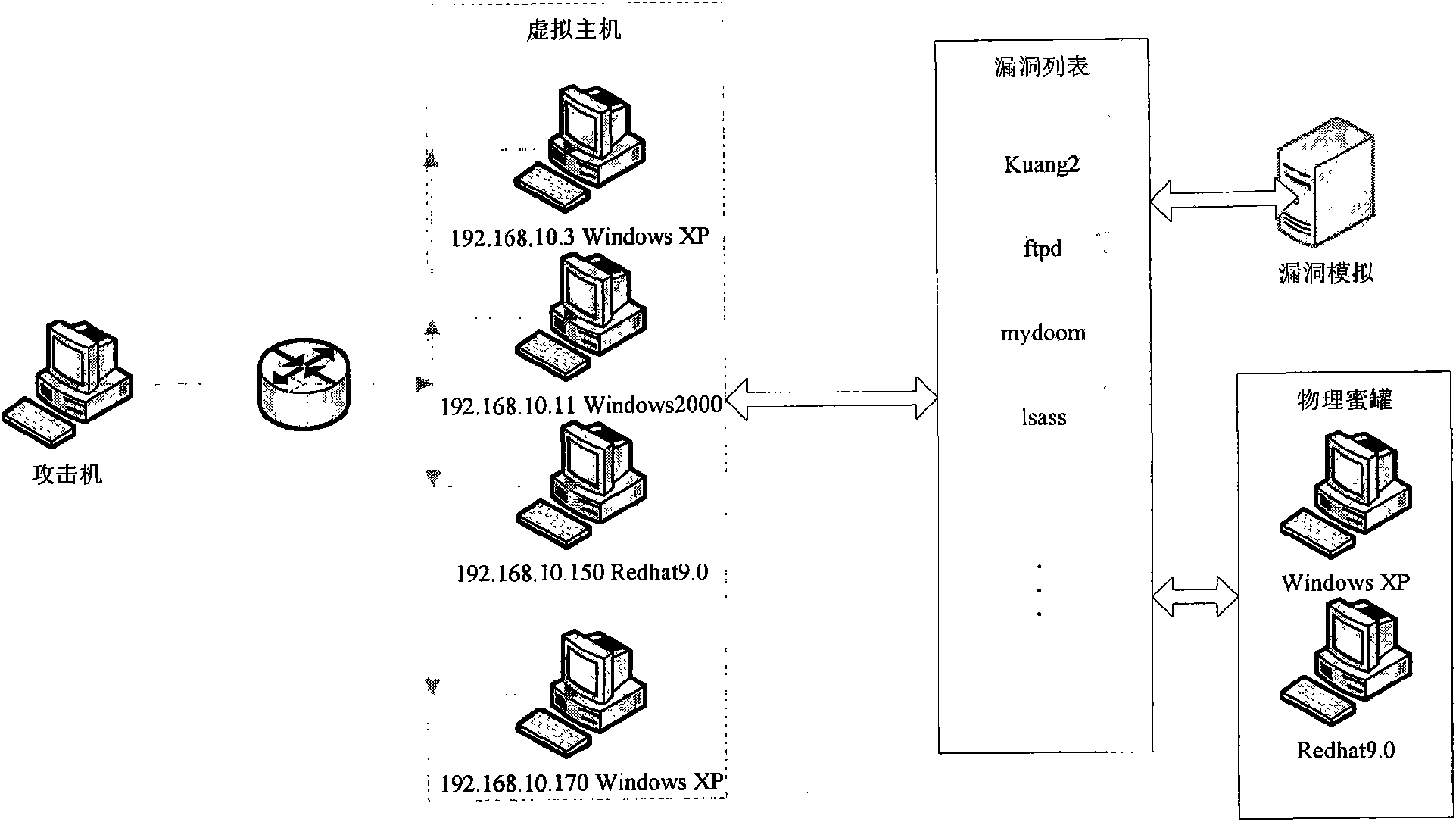
[0043] The implementation of the present invention will be illustrated by an application example below. In this application example, the network topology of this system is composed of virtual honeypot, vulnerability simulation, and physical honeypot. There is a host connected to the network, on which multiple virtual hosts are virtualized as needed, and the system and service conditions of each virtual host are configured, and vulnerability information is configured for the virtual host. The vulnerability simulation module provides the function of vulnerability simulation for the virtual host, and realizes the interaction function with the attacker. The blue dotted line in the figure indicates the virtual network connection status. From the perspective of an attacker, multiple virtual hosts are connected to the network and have corresponding vulnerabilities, which are no different from real hosts. However, when communicating with the virtual host, it is actually interacting w...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com