Patents
Literature
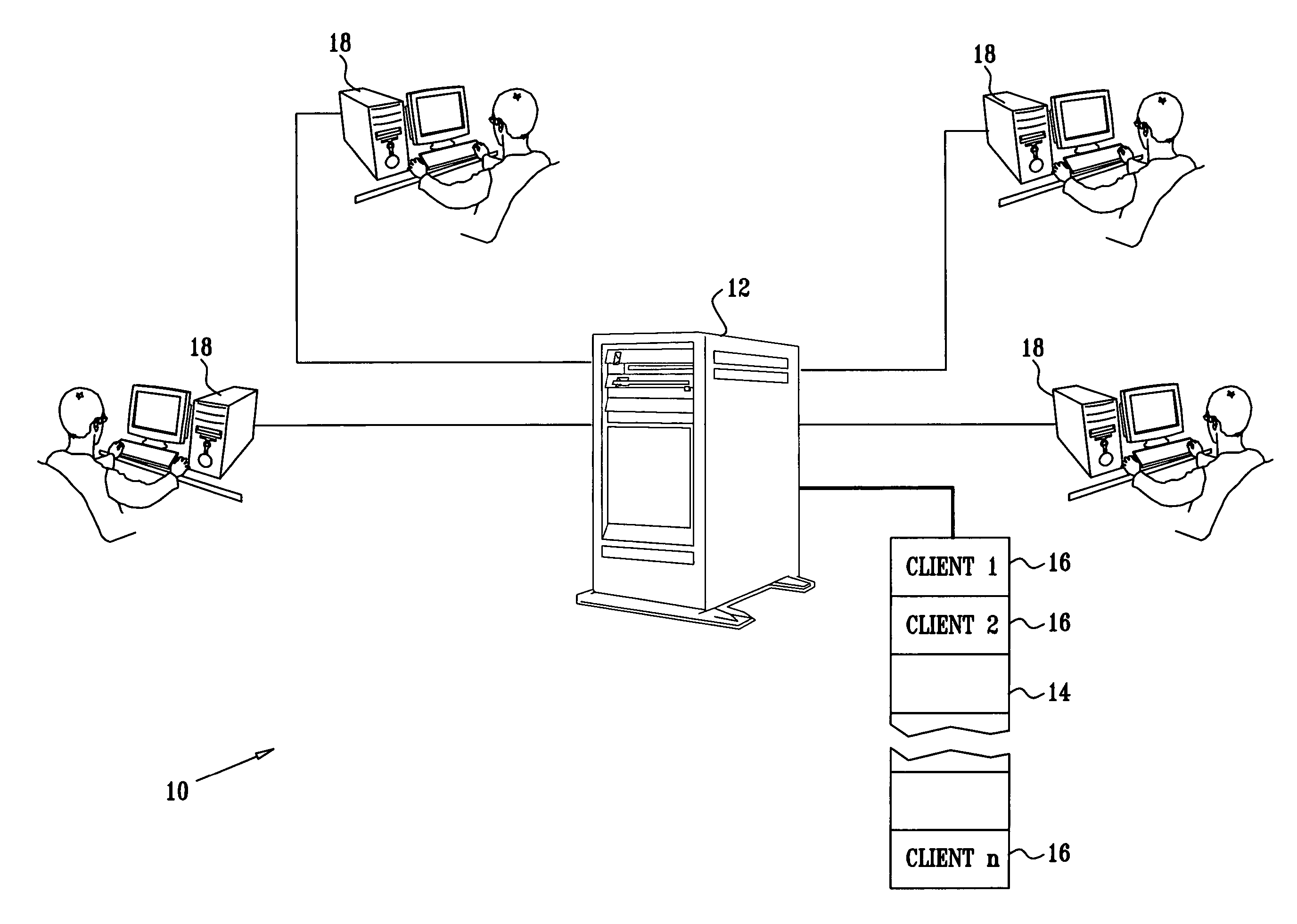
305 results about "Child process" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
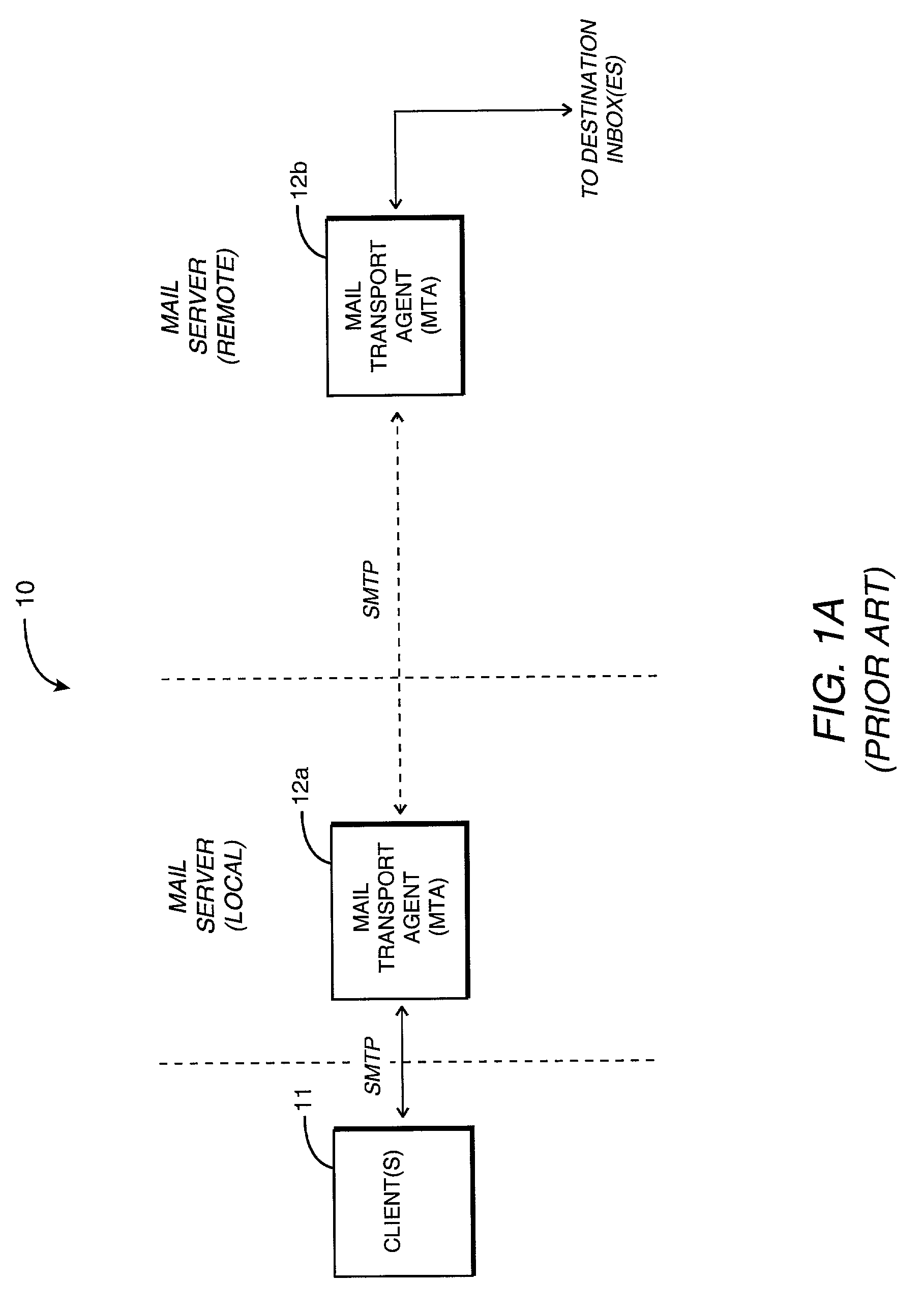
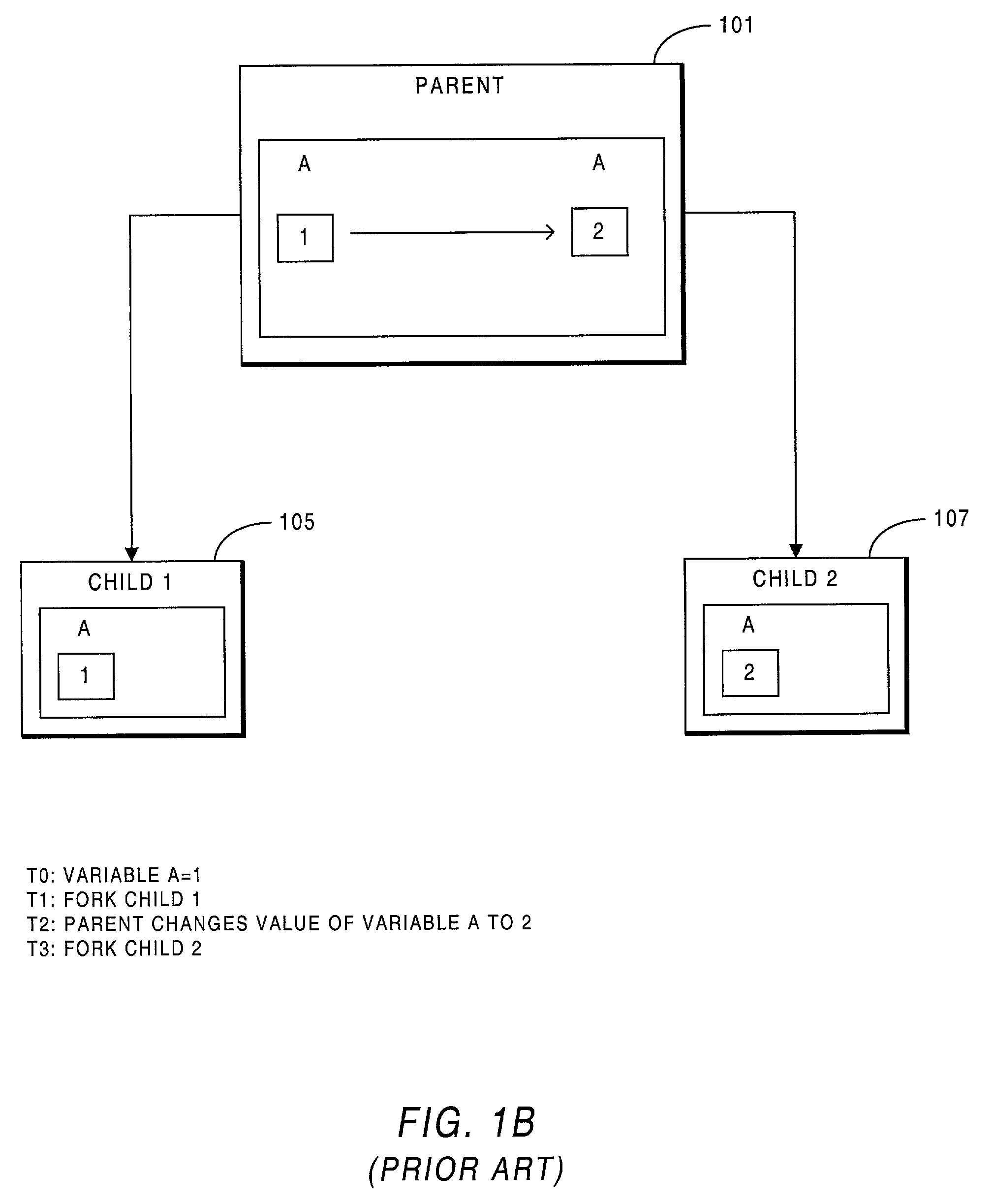
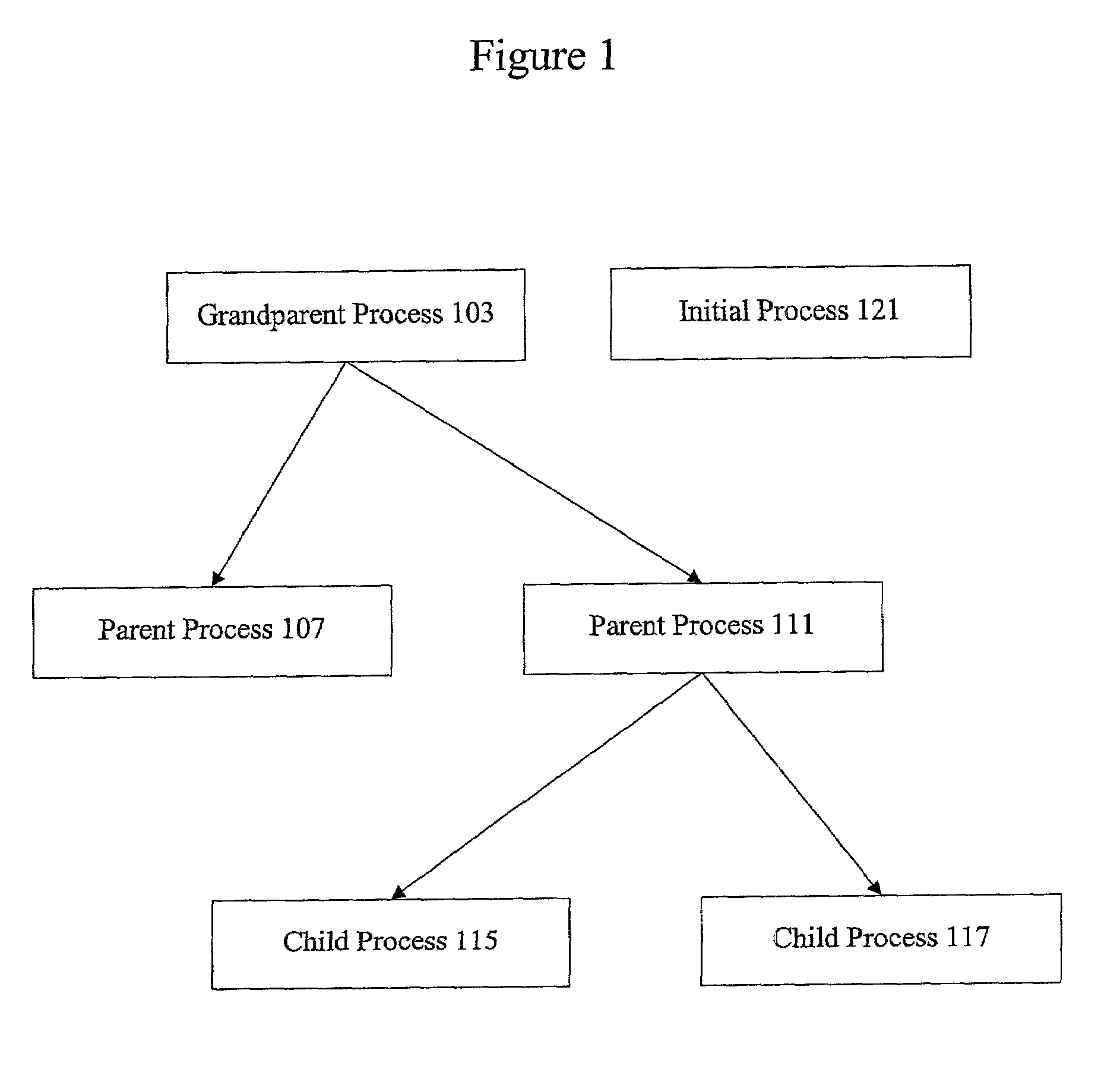
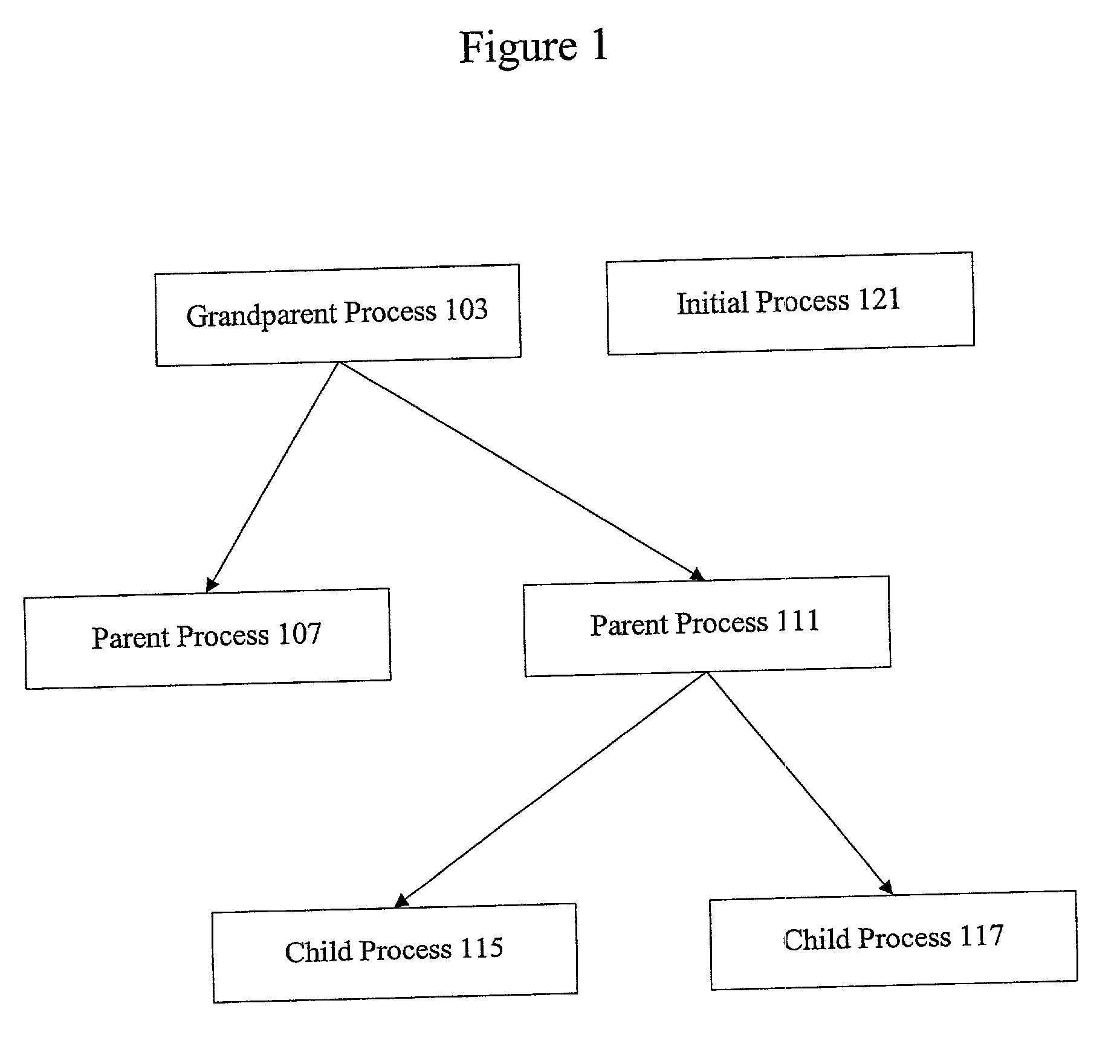
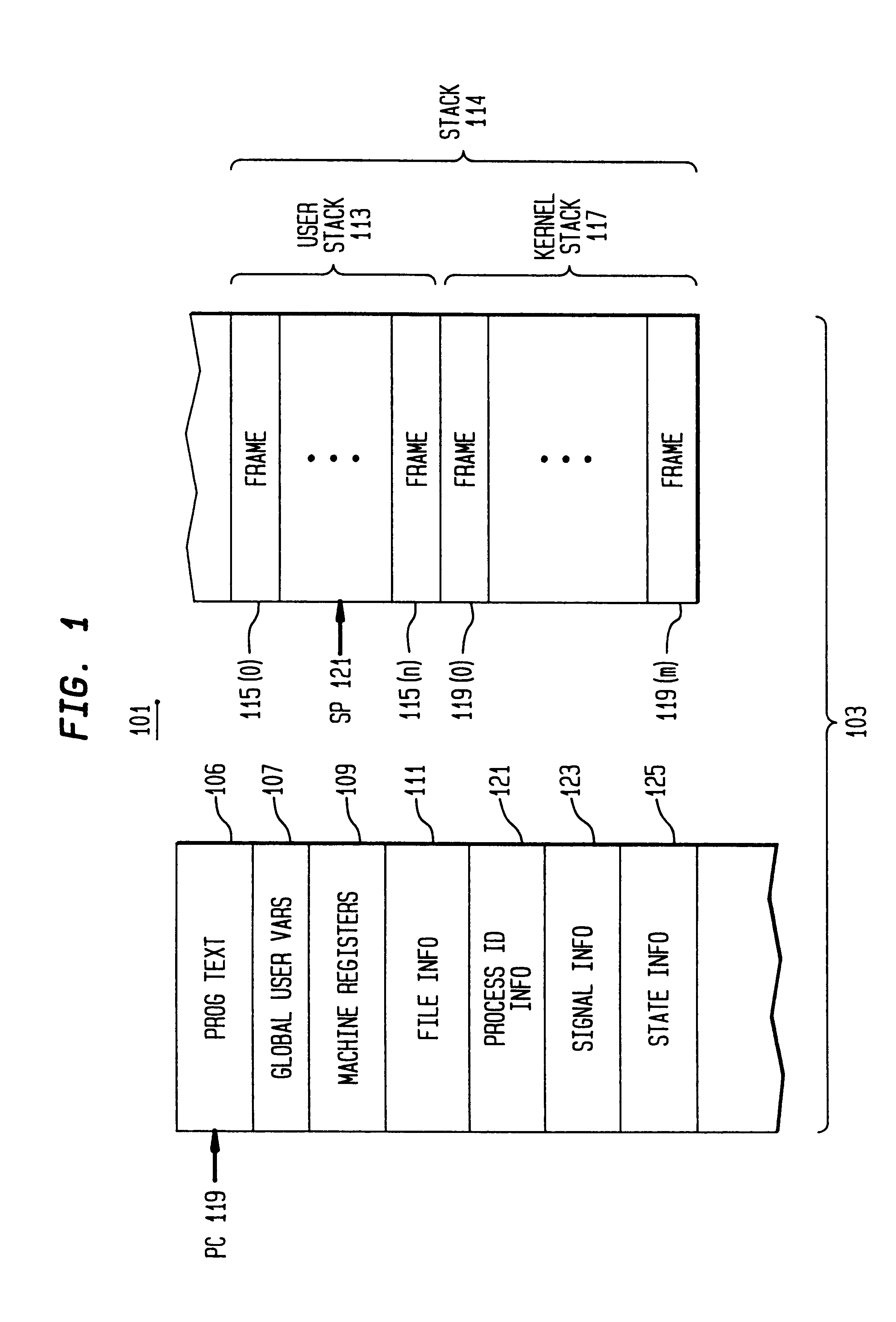
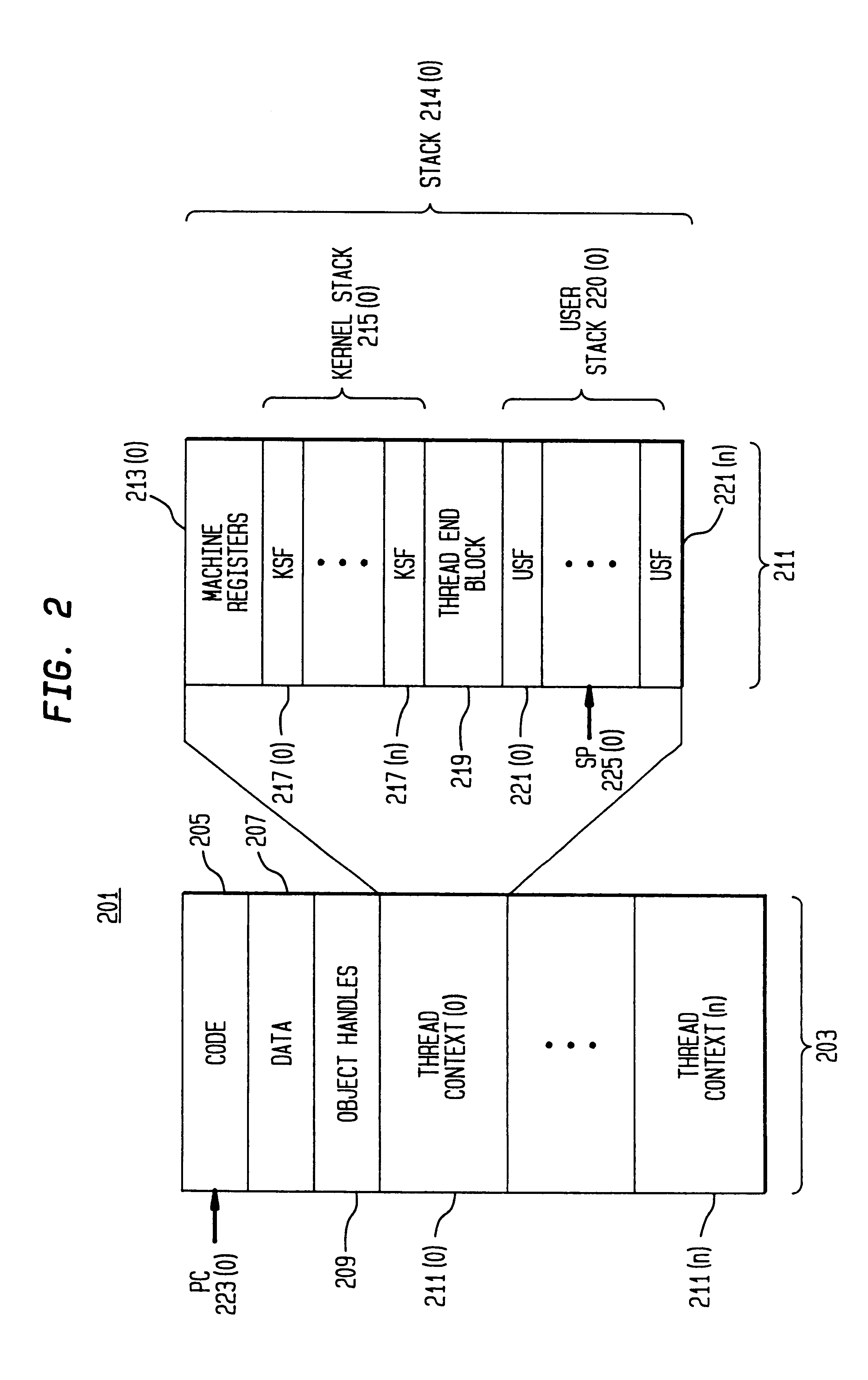
A child process in computing is a process created by another process (the parent process). This technique pertains to multitasking operating systems, and is sometimes called a subprocess or traditionally a subtask.
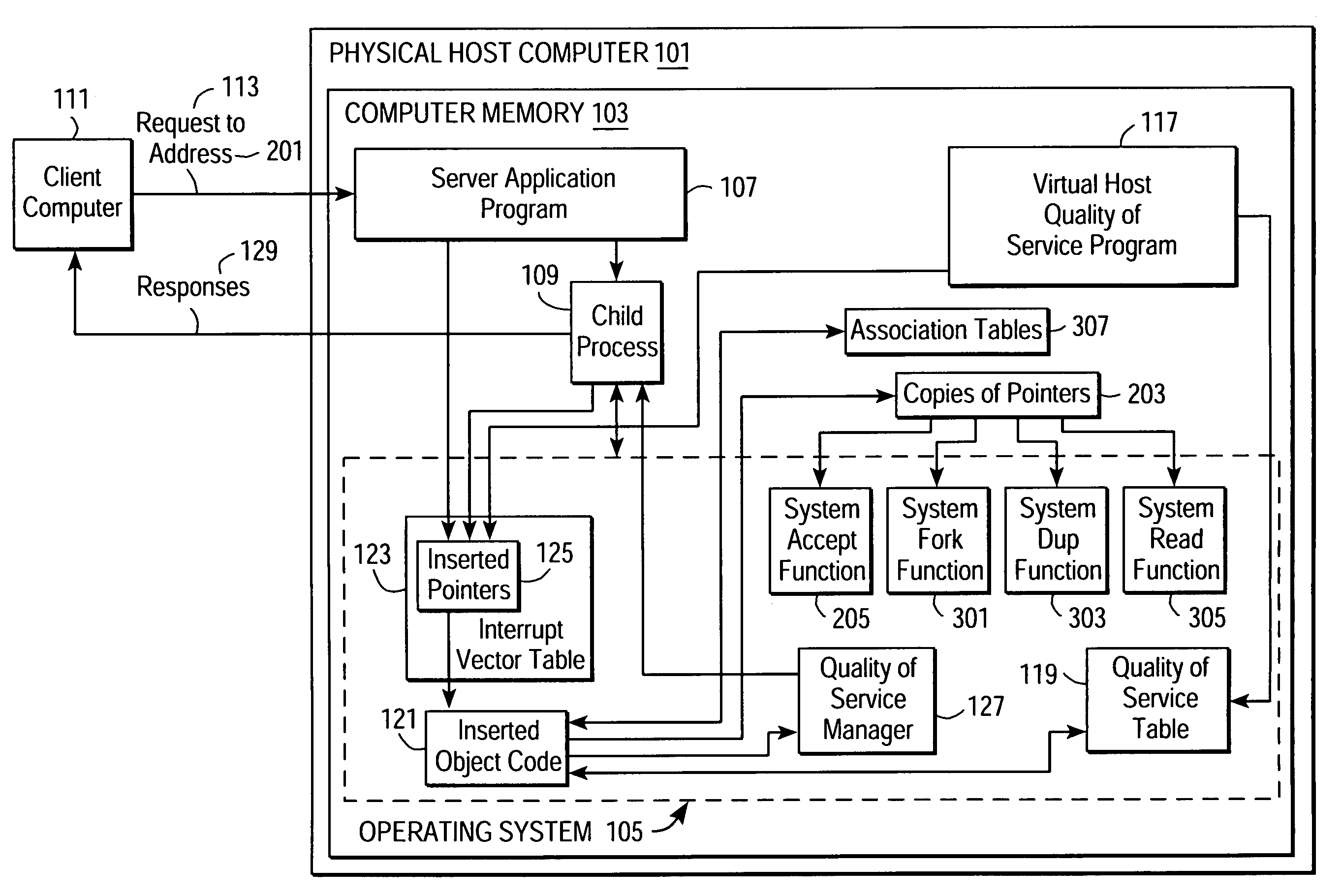
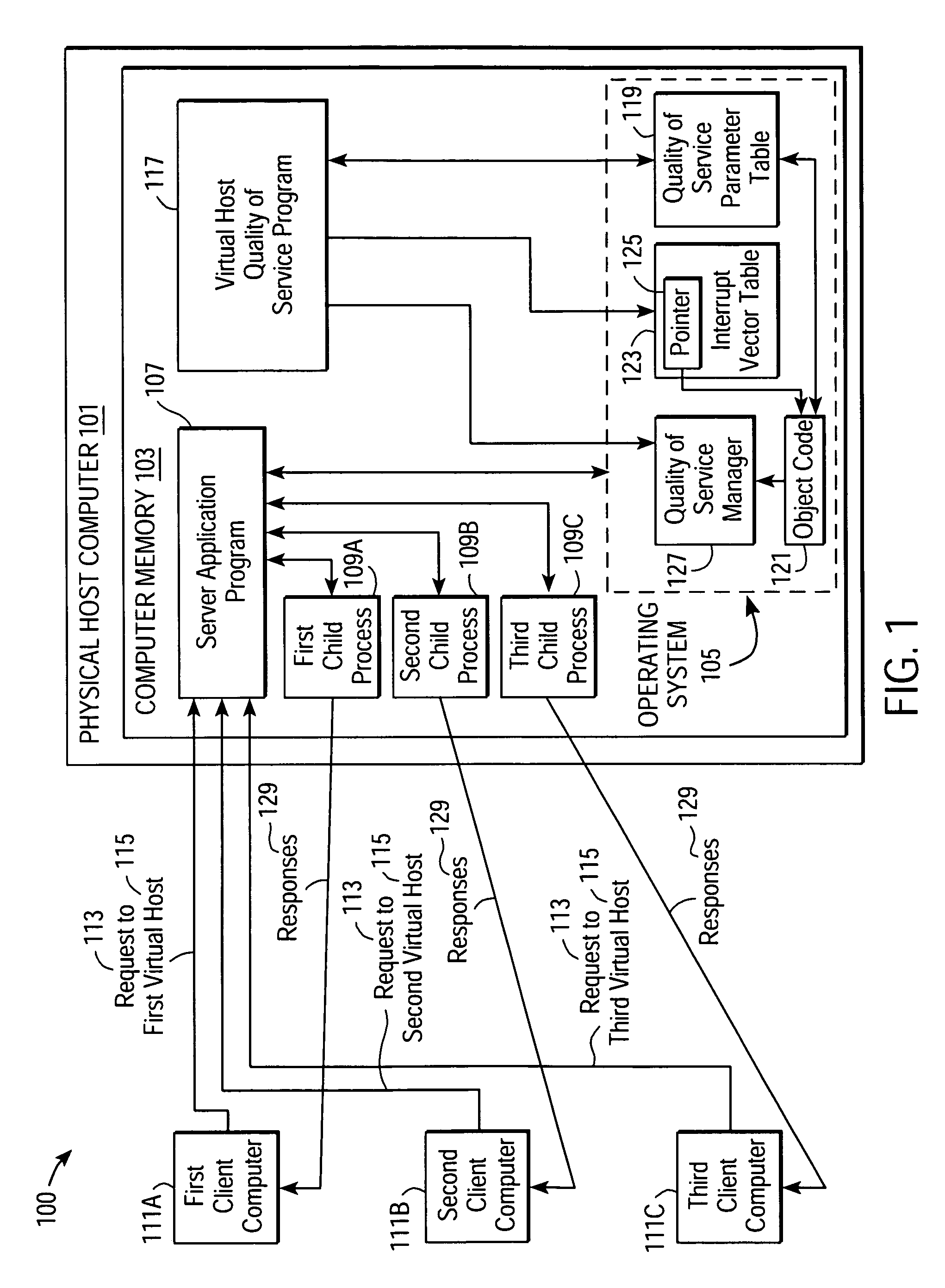
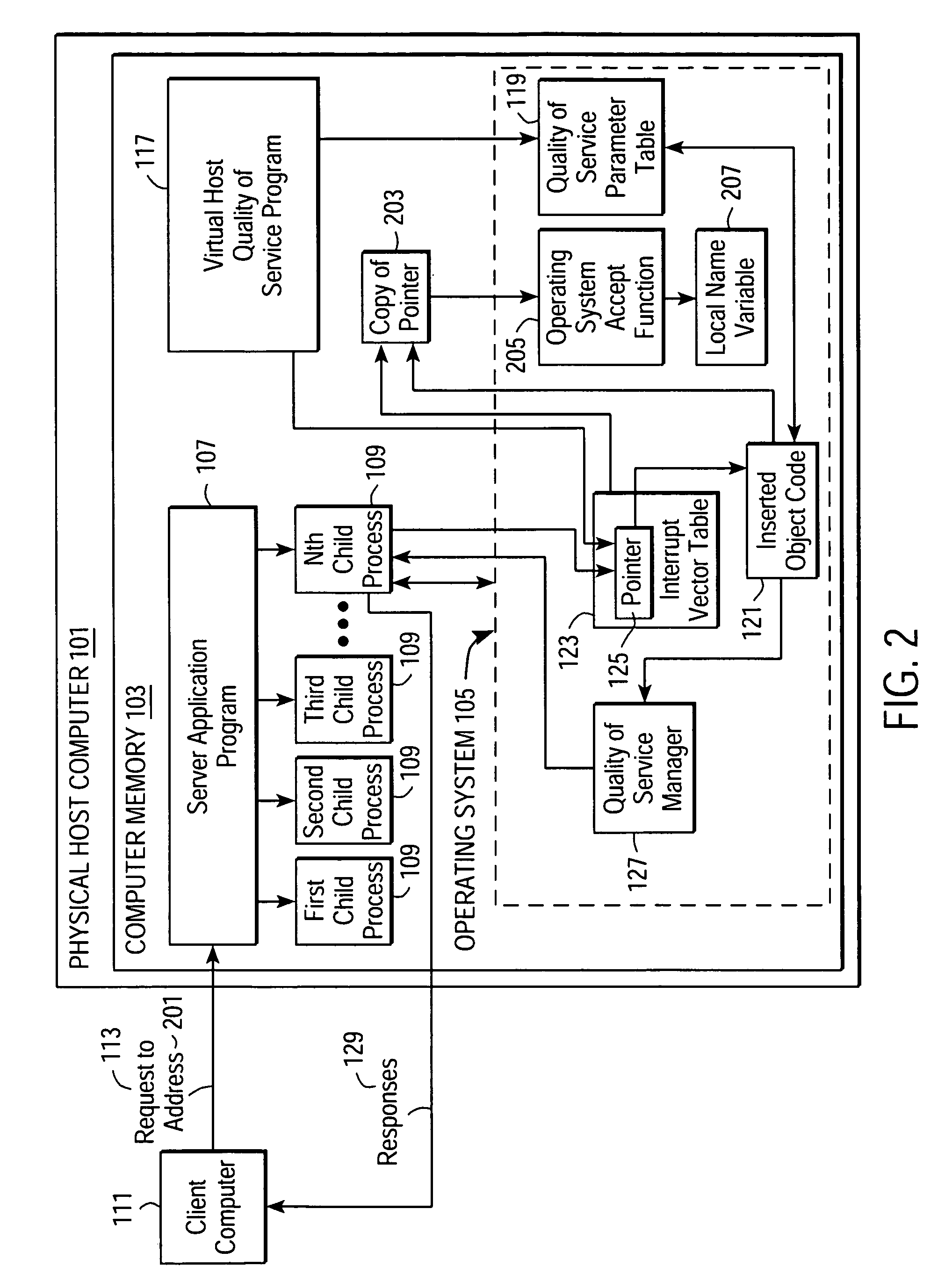
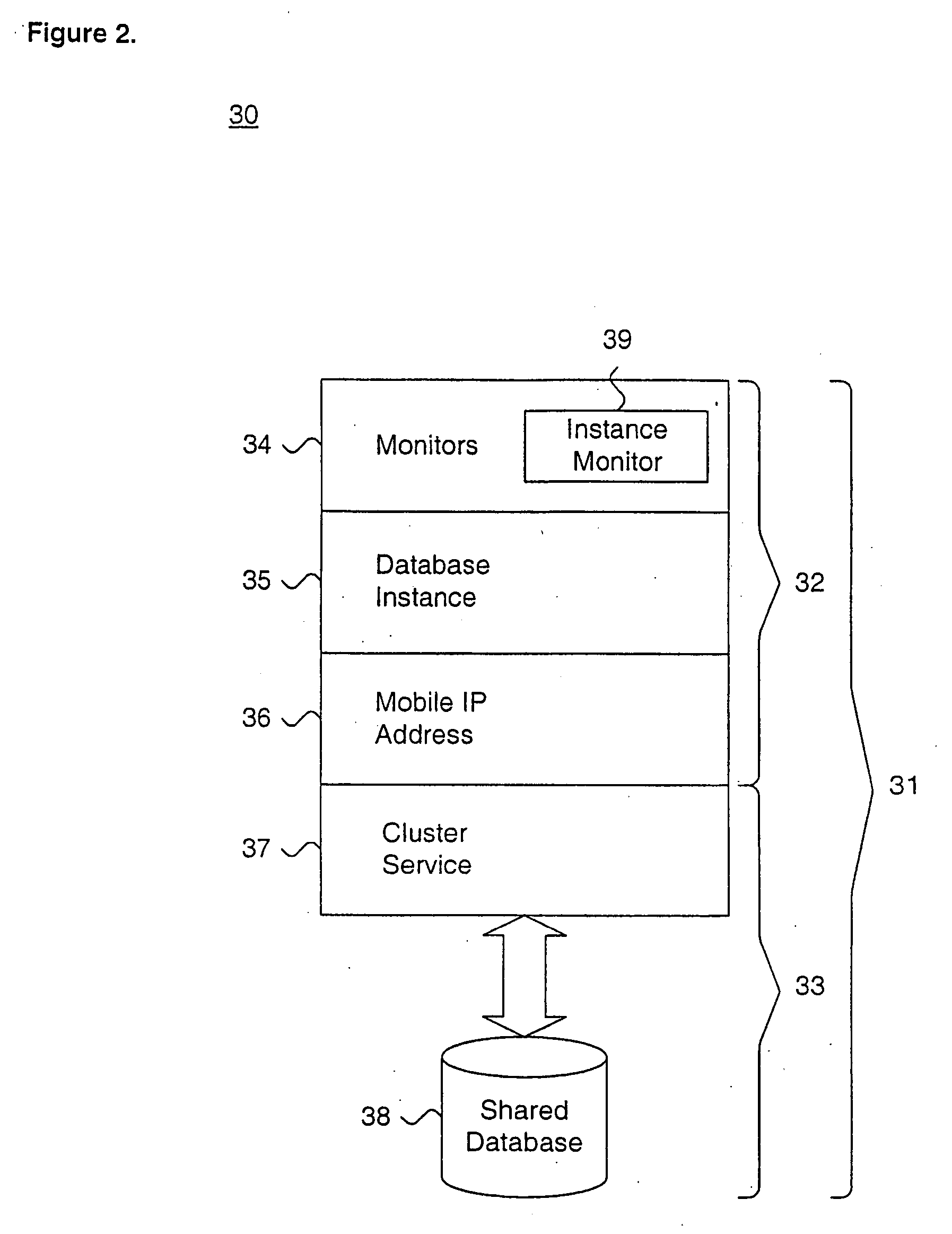
Providing quality of service guarantees to virtual hosts
InactiveUS6976258B1Appropriate quality of serviceGuaranteed service qualityEnergy efficient ICTInterprogram communicationOperational systemApplication software
A method facilitates providing appropriate quality of service guarantees to a plurality of virtual hosts on a single physical host computer. A server application program and its child processes service communication requests made to the plurality of virtual hosts. Quality of service parameters associated with the virtual hosts are stored. Communication requests made to a specific one of the virtual hosts are detected. The quality of service parameters associated with the specific virtual host are obtained. Operating system resources are utilized to guarantee, to a child process of the server application program, a quality of service according to the obtained quality of service parameters associated with the virtual host. Communication between the virtual host and the client is allowed to proceed, the communication being managed by the child process.
Owner:HANGER SOLUTIONS LLC
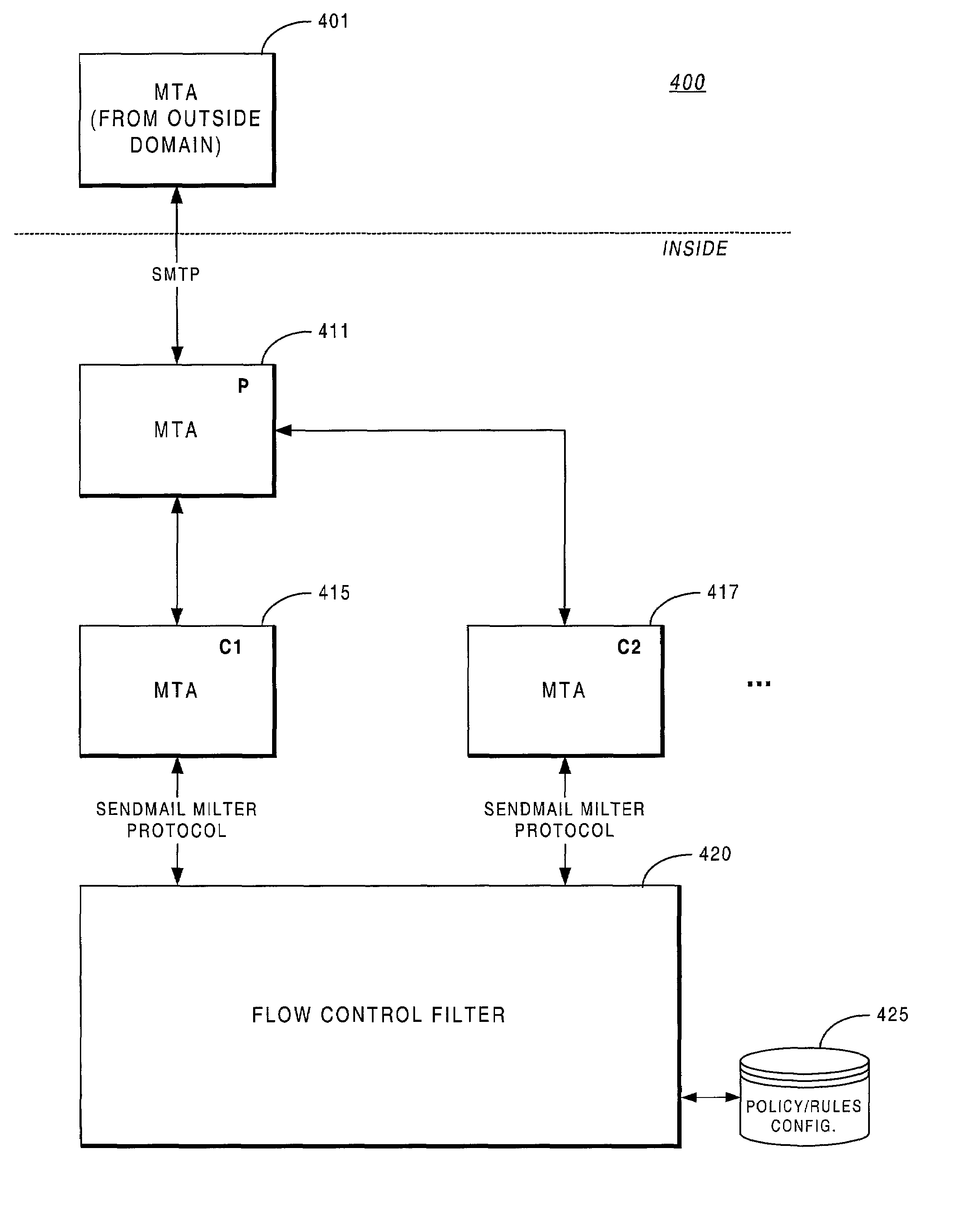
E-mail system providing filtering methodology on a per-domain basis
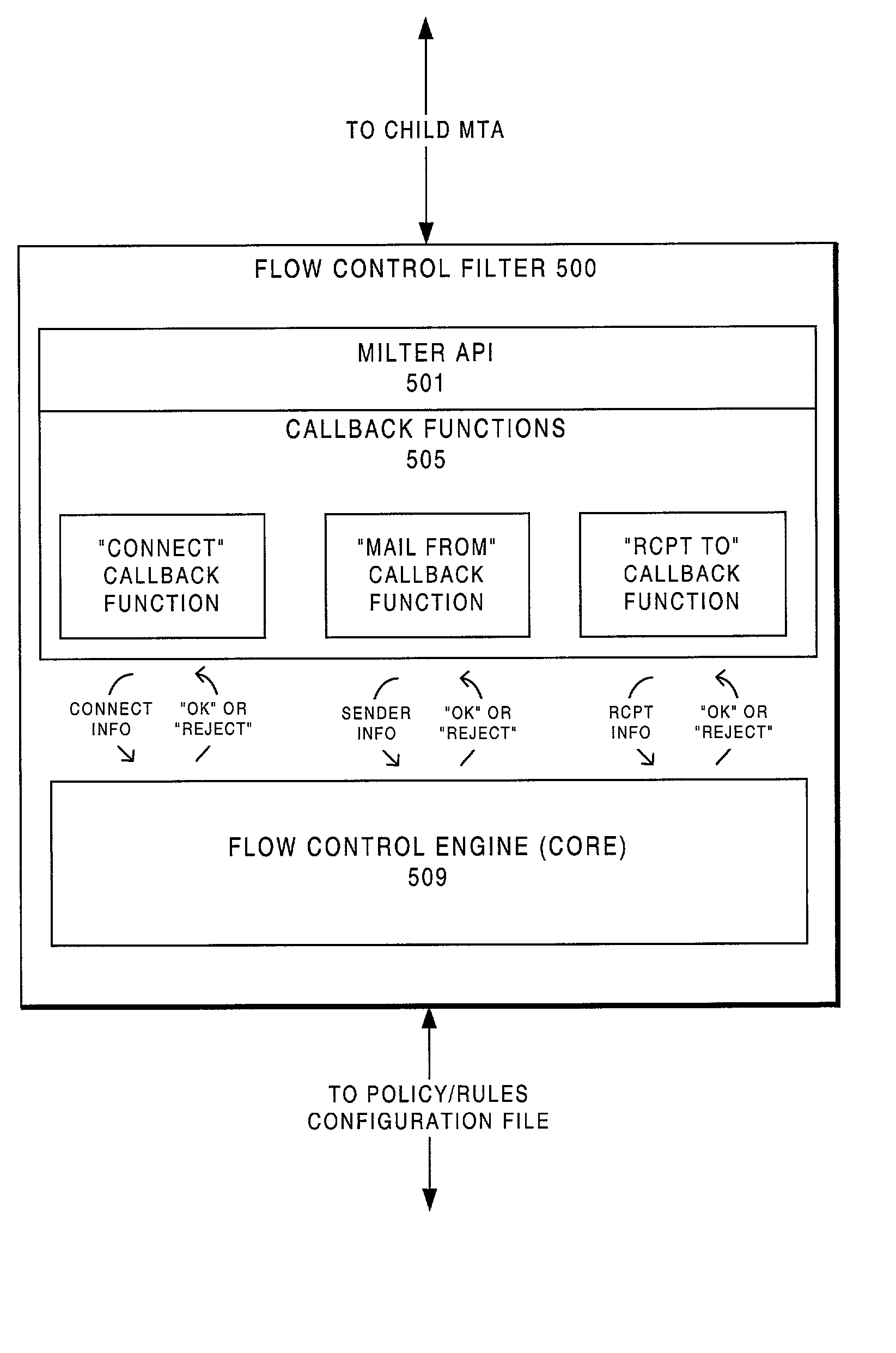
ActiveUS7146402B2Easy to scaleMultiple digital computer combinationsData switching networksTraffic capacityIp address
An e-mail system is described that includes a flow control filter, which is particularly suited for filtering on a per-domain (host) basis. During processing of incoming e-mail, each child MTA process created to handle a particular new connection connects to a flow control filter service, so that it can interact with the service during arrival of a message. This interaction provides a complete description of the incoming client, including IP address and host name, as well as the complete SMTP interaction. Since the flow control filter service monitors all children processes, it attains a global view of traffic flowing through the system. By virtue of its global view, the flow control filter service can track information on a per domain basis, including total volume of e-mail received from a particular domain over a given period of time. Since the knowledge lost by the forking process is captured by the flow control filter service, the service is in a position to enforce policy-based rules, including placing restrictions on child processes, based on the per-domain tallies encountered.
Owner:PROOFPOINT INC
Application level speculative processing
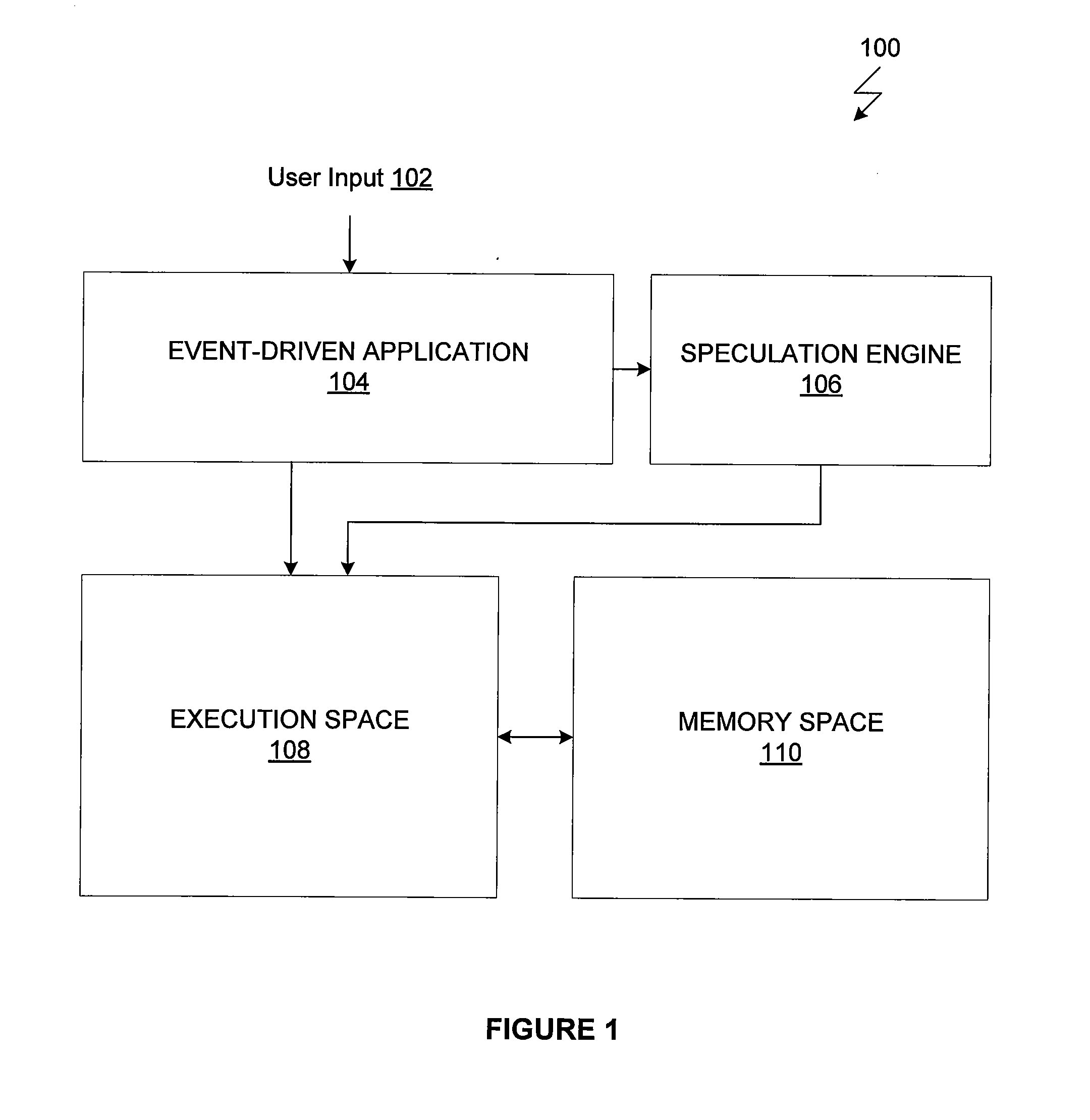
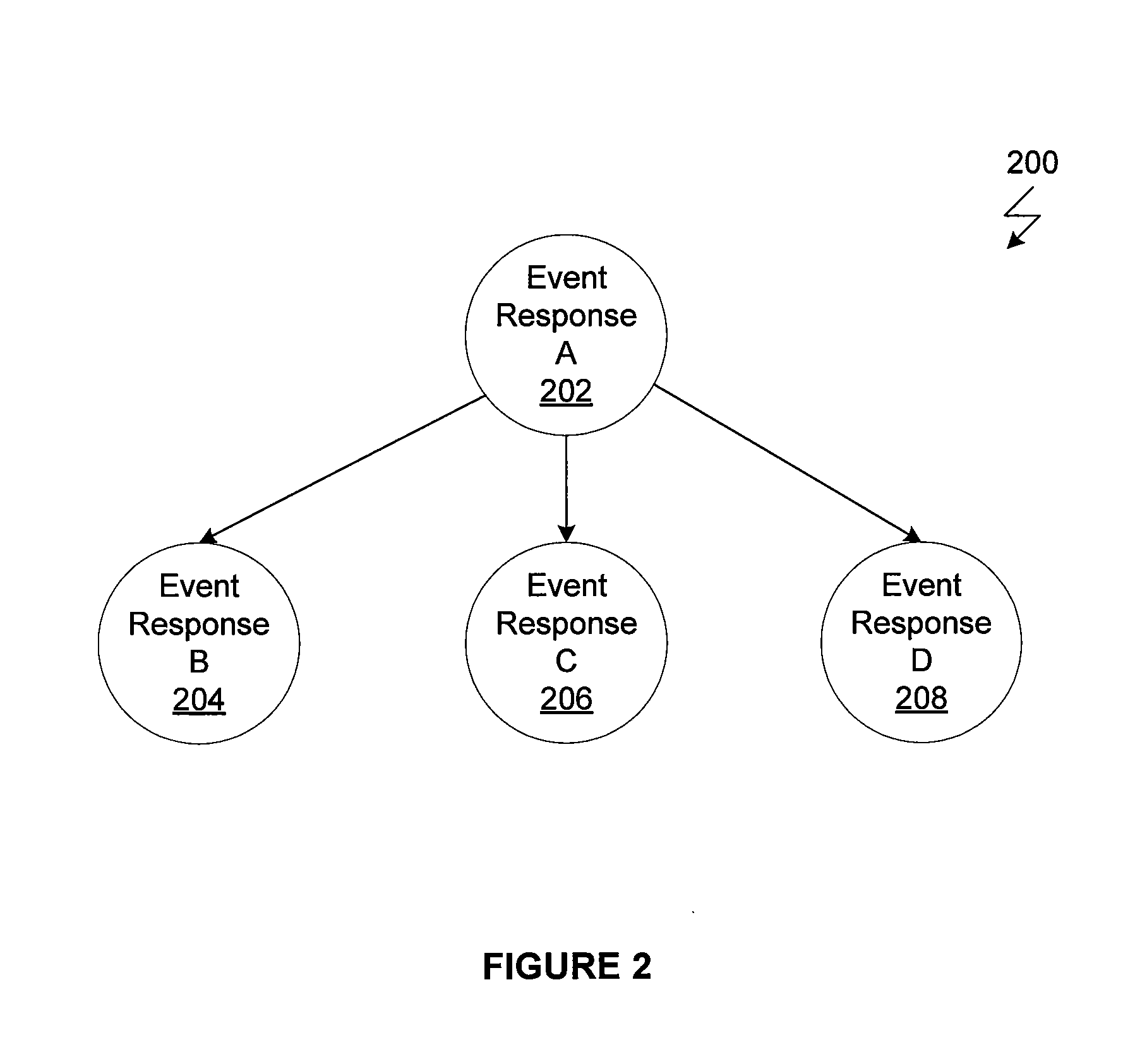
ActiveUS20130239125A1Avoiding time-consuming requirementReduce waiting timeSpecific program execution arrangementsTransaction processingReal-time computingChild process
One or more embodiments of the invention is a computer-implemented method for speculatively executing application event responses. The method includes the steps of identifying one or more event responses that could be issued for execution by an application being executed by a master process, for each event response, generating a child process to execute the event response, determining that a first event response included in the one or more event responses has been issued for execution by the application, committing the child process associated with the first event response as a new master process, and aborting the master process and all child processes other than the child process associated with the first event response.
Owner:AUTODESK INC
E-mail system providing filtering methodology on a per-domain basis
ActiveUS20030050988A1Multiple digital computer combinationsData switching networksTraffic capacityTime segment
An e-mail system is described that includes a flow control filter, which is particularly suited for filtering on a per-domain (host) basis. During processing of incoming e-mail, each child MTA process created to handle a particular new connection connects to a flow control filter service, so that it can interact with the service during arrival of a message. This interaction provides a complete description of the incoming client, including IP address and host name, as well as the complete SMTP interaction. Since the flow control filter service monitors all children processes, it attains a global view of traffic flowing through the system. By virtue of its global view, the flow control filter service can track information on a per domain basis, including total volume of e-mail received from a particular domain over a given period of time. Since the knowledge lost by the forking process is captured by the flow control filter service, the service is in a position to enforce policy-based rules, including placing restrictions on child processes, based on the per-domain tallies encountered.
Owner:PROOFPOINT INC
System and Method for Process Hollowing Detection
ActiveUS20170272462A1Platform integrity maintainanceTransmissionUser deviceApplication programming interface
A method and system for remediating a process hollowing intrusion on a user device comprising detecting a process starting on the user device, preparing the process to monitor Application Programming Interface (API) calls between the process and an operating system of the user device, determining whether the process is associated with a process hollowing intrusion based on information associated with the process and / or the API calls, and executing security policies against the process associated with the process hollowing intrusion. In examples, it is determined whether the child process is associated with a process hollowing intrusion in response to determining whether one or more API calls associated with known process hollowing intrusions modify executable memory of and / or modify an entry point address of the child process.
Owner:CARBON BLACK
Methods and systems for creating and communicating with computer processes
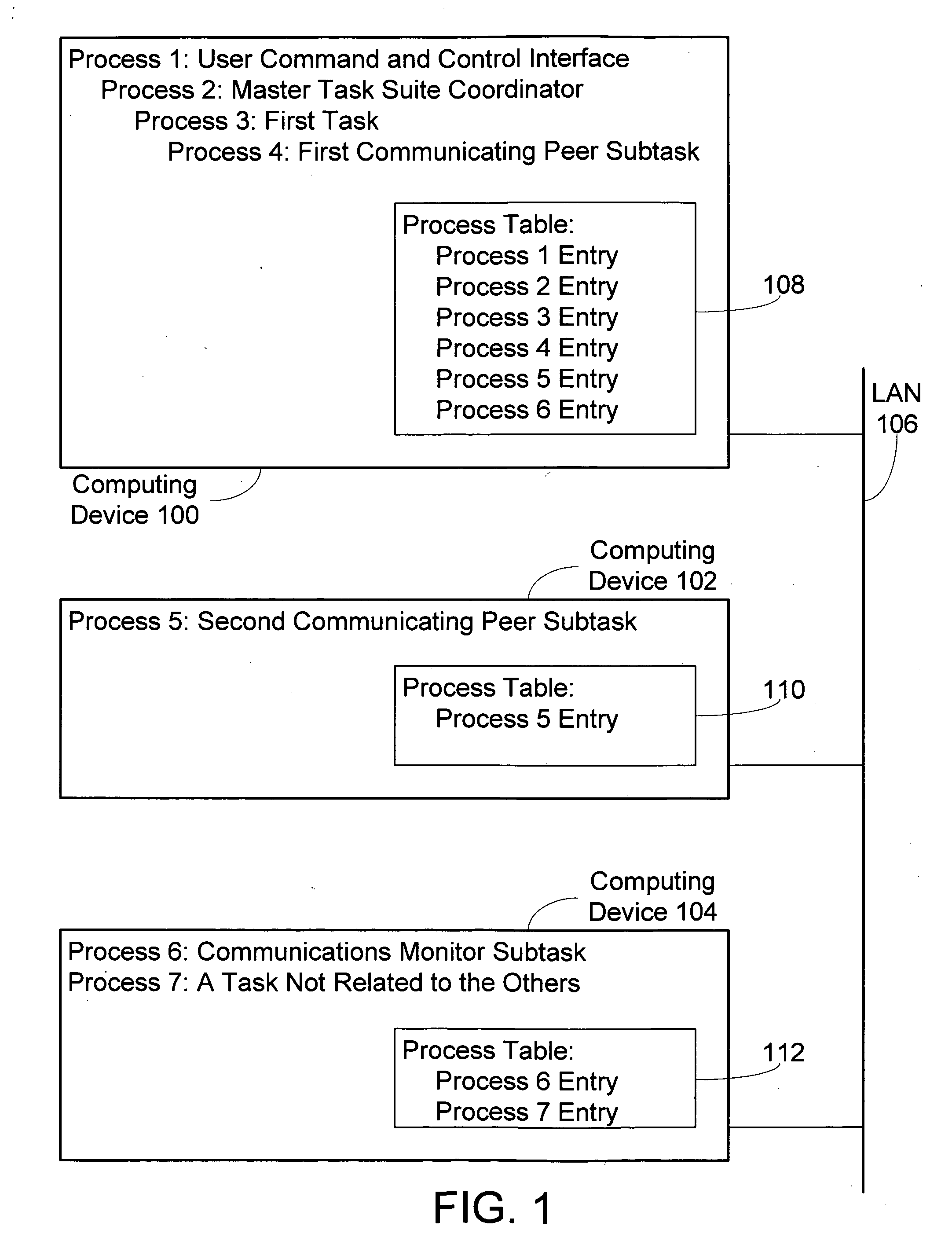
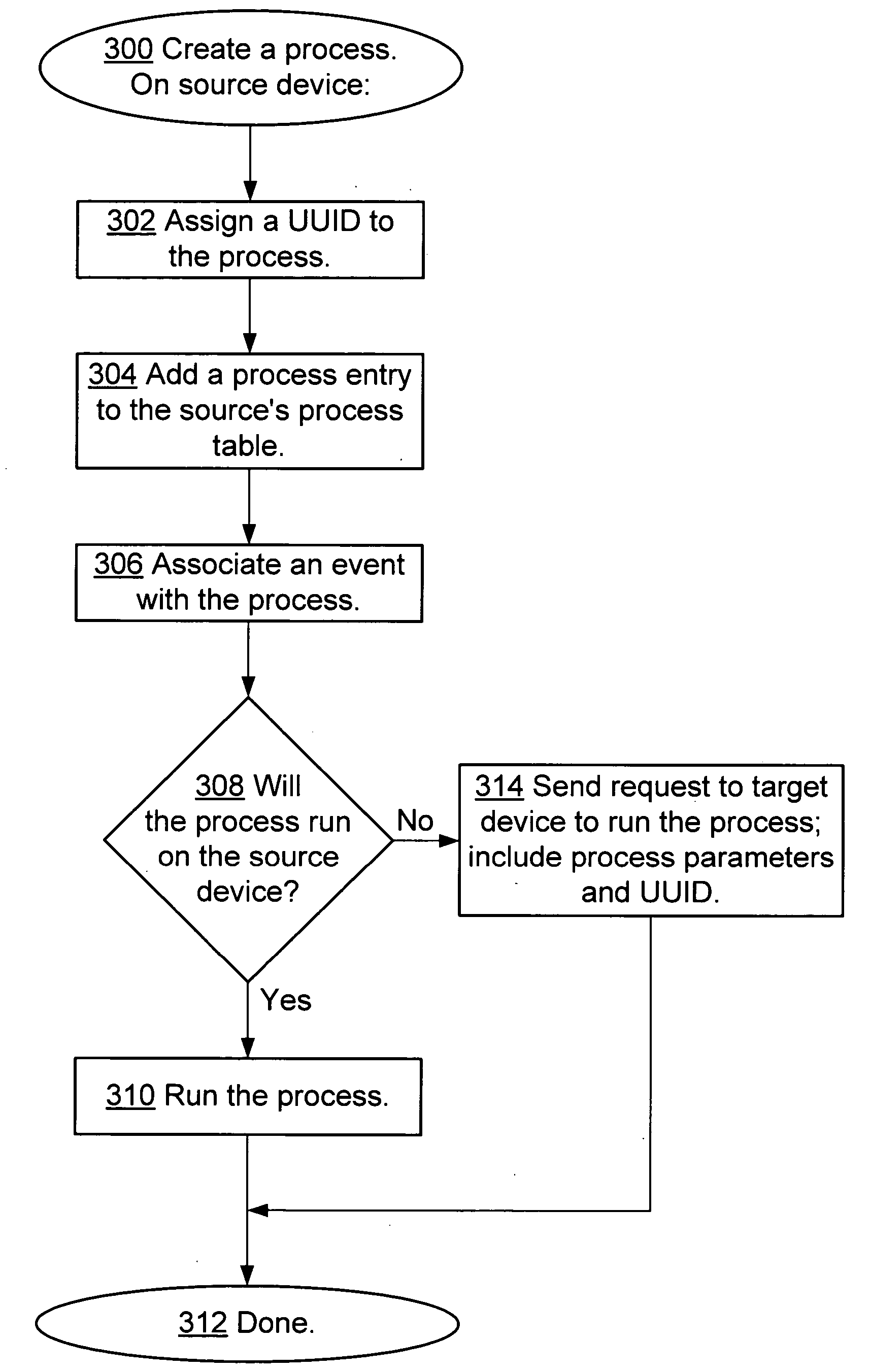
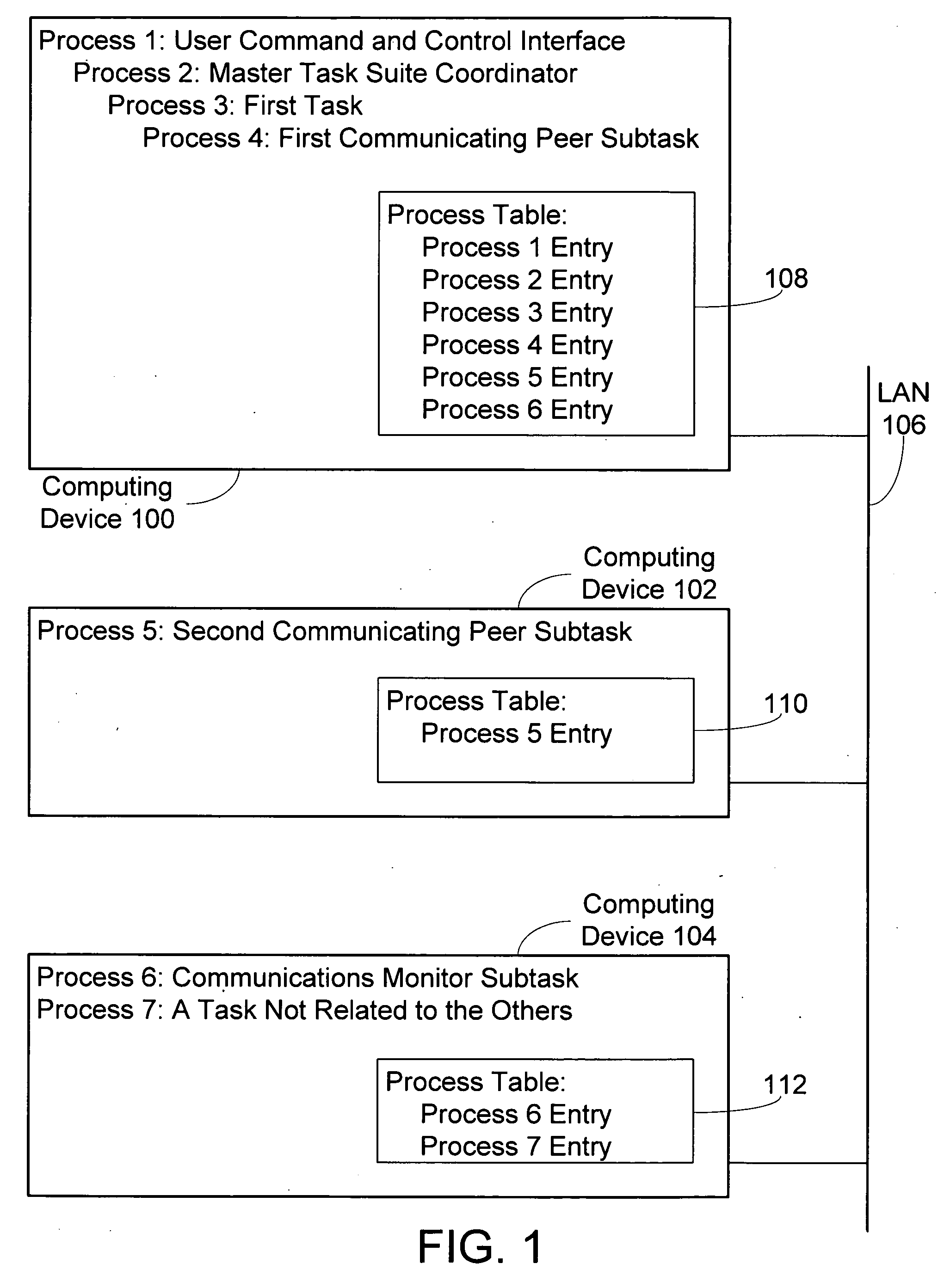
InactiveUS20050138624A1Interprogram communicationMemory systemsUniversally unique identifierApplication programming interface
Disclosed are mechanisms for creating and communicating with computer processes. An application programming interface (API) presents services of the system to applications. The API is usable with all processes, local and remote, and is transparent with respect to the location of processes. A process table stores information about processes created using the system. The process table supports centralized process control and peer-to-peer process communication and synchronization. Each process is assigned a Universally Unique Identifier (UUID) that uniquely identifies the process no matter the computing device on which it runs. A parent UUID and a group UUID may be attached to the process and used for enforcing dependencies (e.g., for halting the process and all of its child processes) and for managing arbitrary, user-defined groups, respectively. A global event is associated with each process. When a process receives this event, it performs a controlled shutdown, cleans up, and reports status.
Owner:MICROSOFT TECH LICENSING LLC
Methods and systems for creating and communicating with computer processes
InactiveUS20050132384A1Mechanism usedInterprogram communicationSecuring communicationUniversally unique identifierApplication programming interface
Disclosed are mechanisms for creating and communicating with computer processes. An application programming interface (API) presents services of the system to applications. The API is usable with all processes, local and remote, and is transparent with respect to the location of processes. A process table stores information about processes created using the system. The process table supports centralized process control and peer-to-peer process communication and synchronization. Each process is assigned a Universally Unique Identifier (UUID) that uniquely identifies the process no matter the computing device on which it runs. A parent UUID and a group UUID may be attached to the process and used for enforcing dependencies (e.g., for halting the process and all of its child processes) and for managing arbitrary, user-defined groups, respectively. A global event is associated with each process. When a process receives this event, it performs a controlled shutdown, cleans up, and reports status.
Owner:MICROSOFT TECH LICENSING LLC
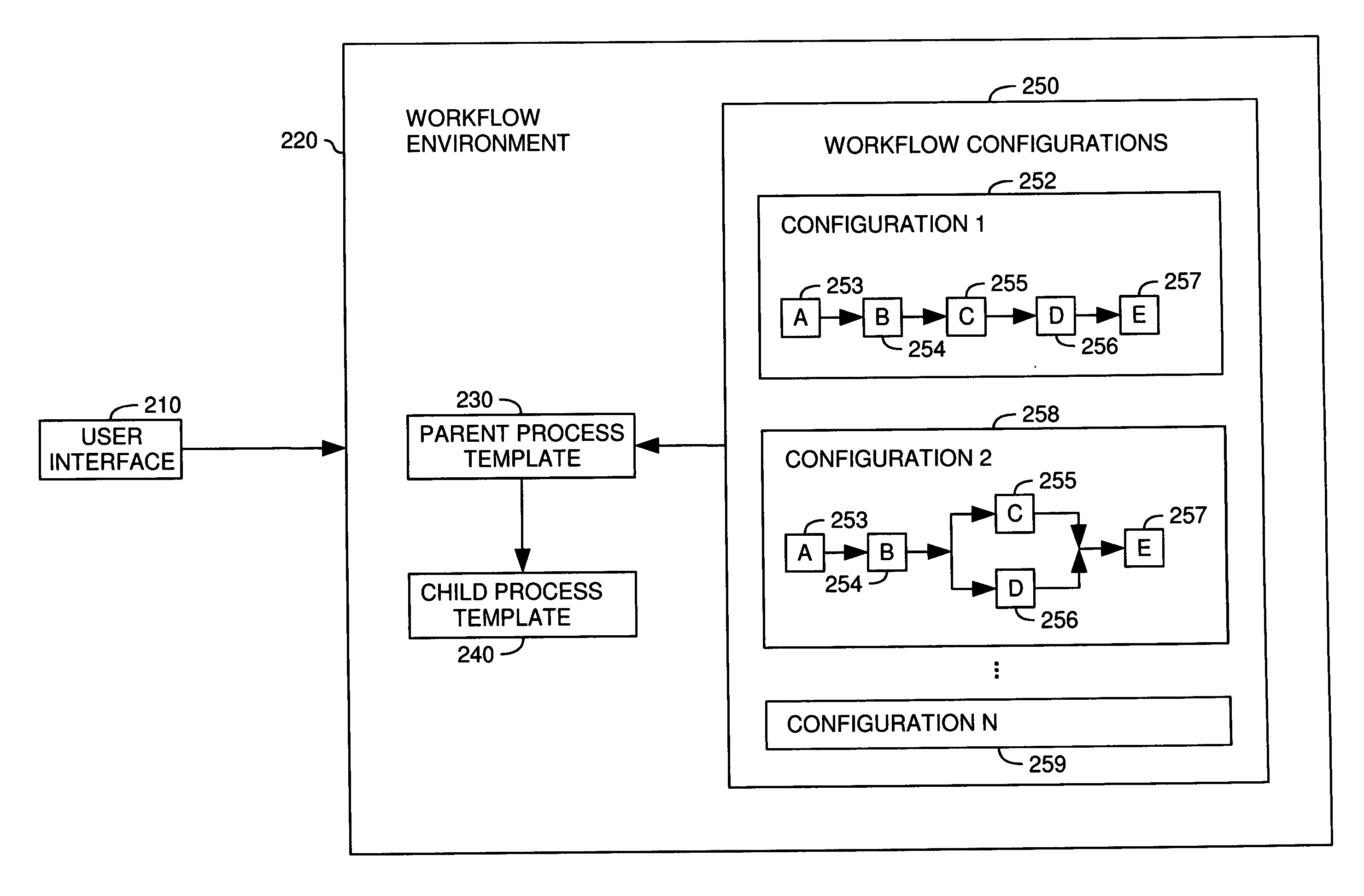
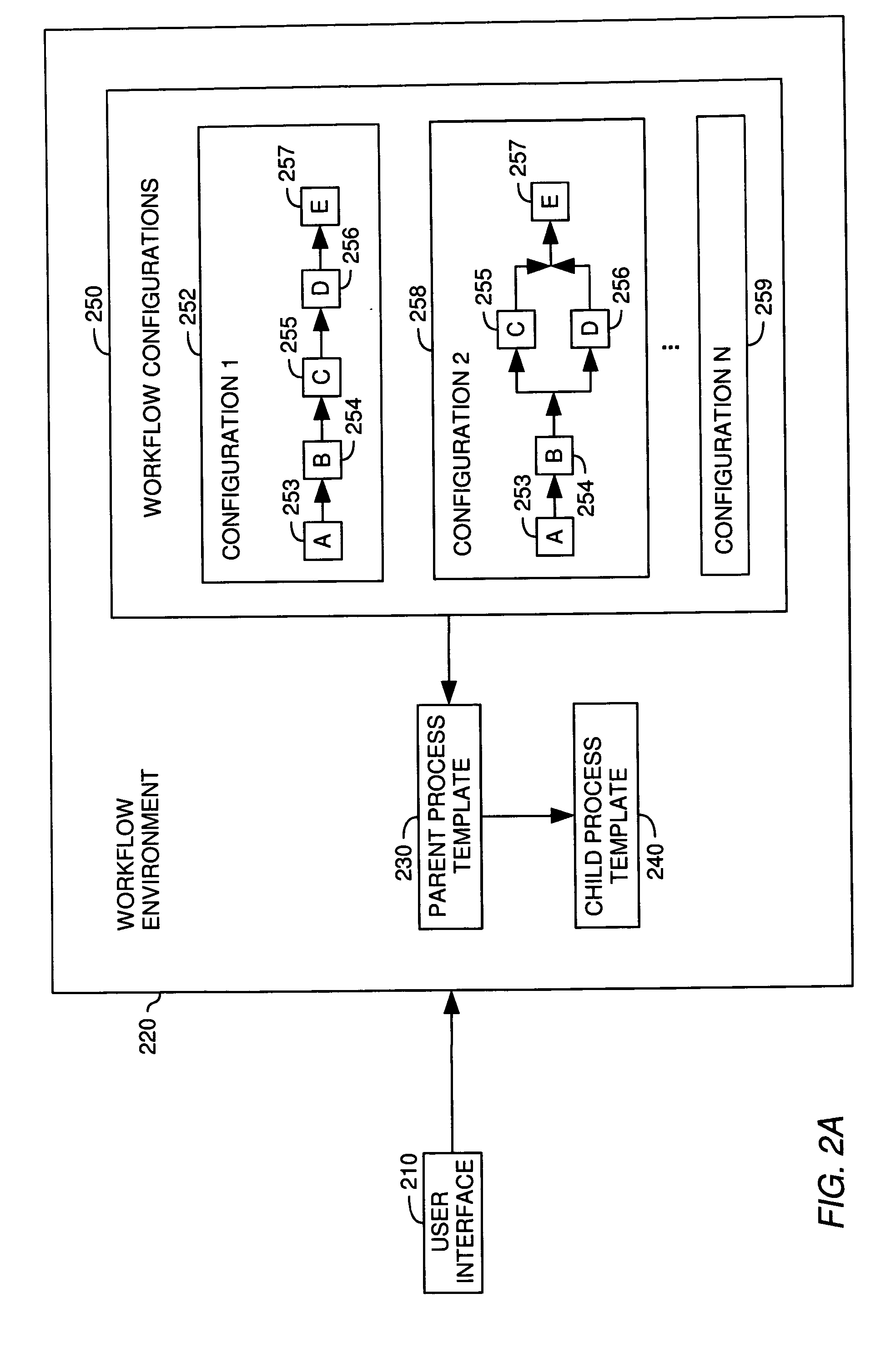
Data driven dynamic workflow
A method, system and article of manufacture for workflow processing and, more particularly, for managing creation and execution of data driven dynamic workflows. One embodiment provides a computer-implemented method for managing execution of workflow instances. The method comprises providing a parent process template and providing a child process template. The child process template is configured to implement an arbitrary number of workflow operations for a given workflow instance, and the parent process template is configured to instantiate child processes on the basis of the child process template to implement a desired workflow. The method further comprises receiving a workflow configuration and instantiating an instance of the workflow on the basis of the workflow configuration. The instantiating comprises instantiating a parent process on the basis of the parent process template and instantiating, by the parent process template, one or more child processes on the basis of the child process template.
Owner:IBM CORP
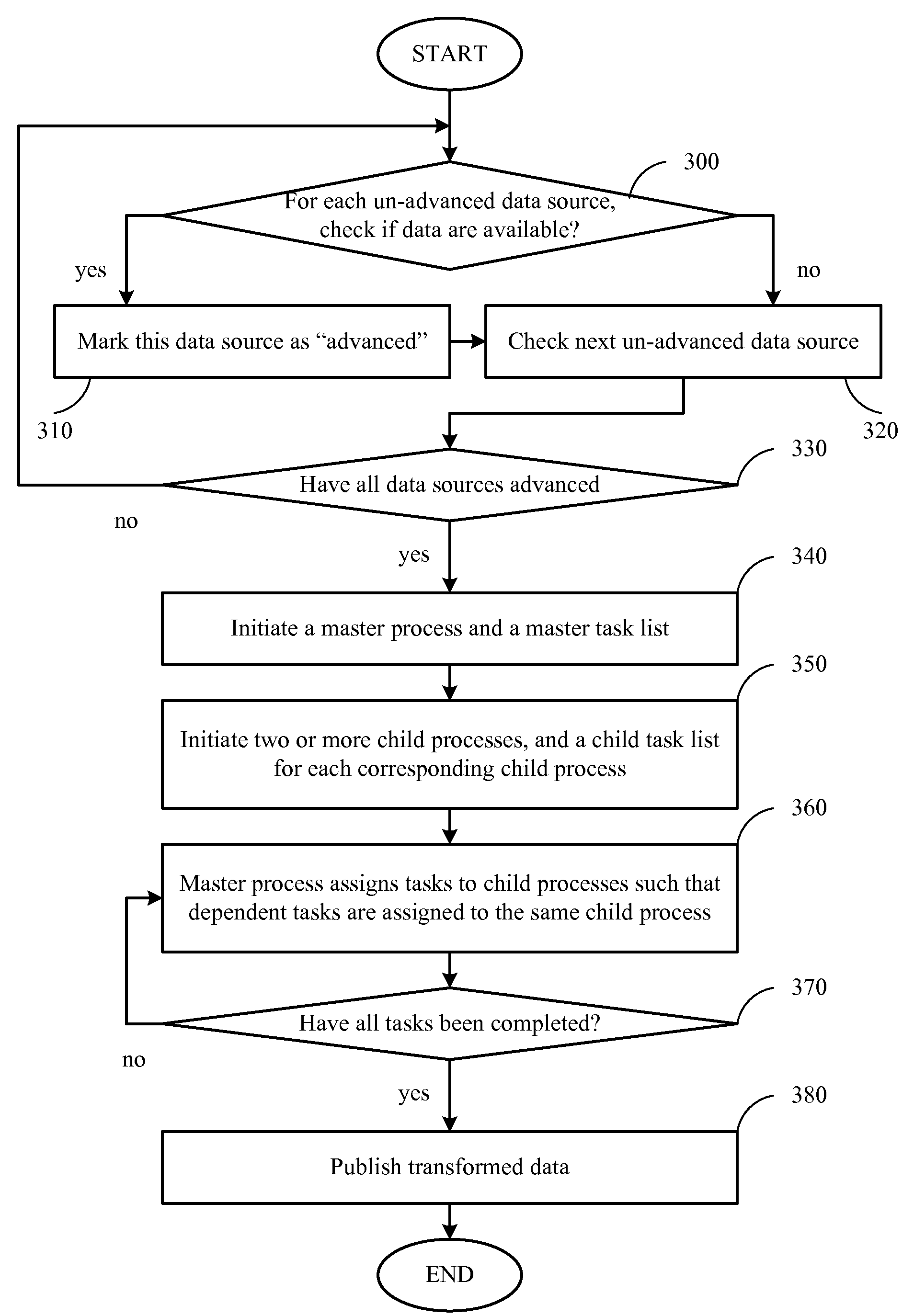
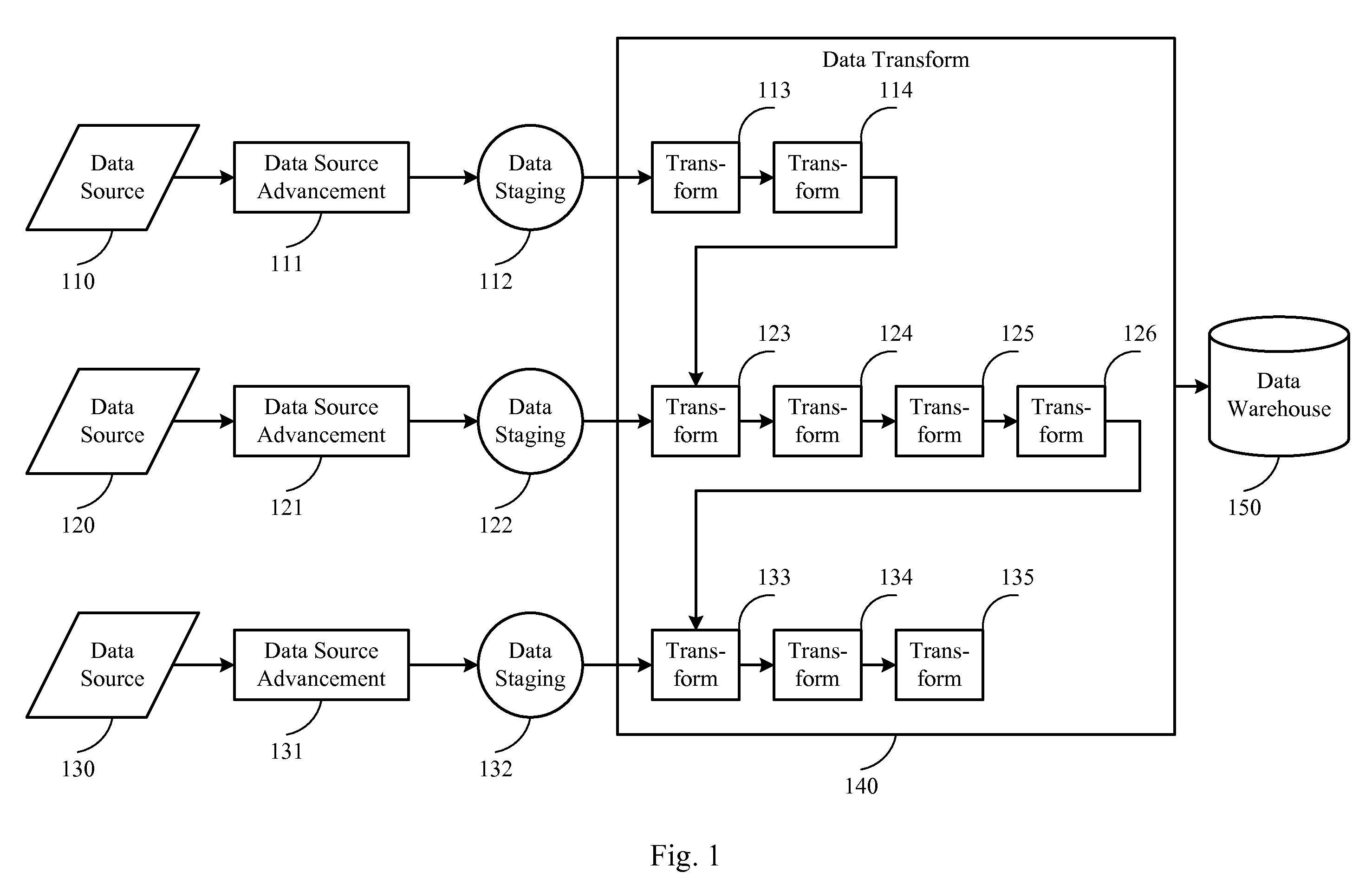
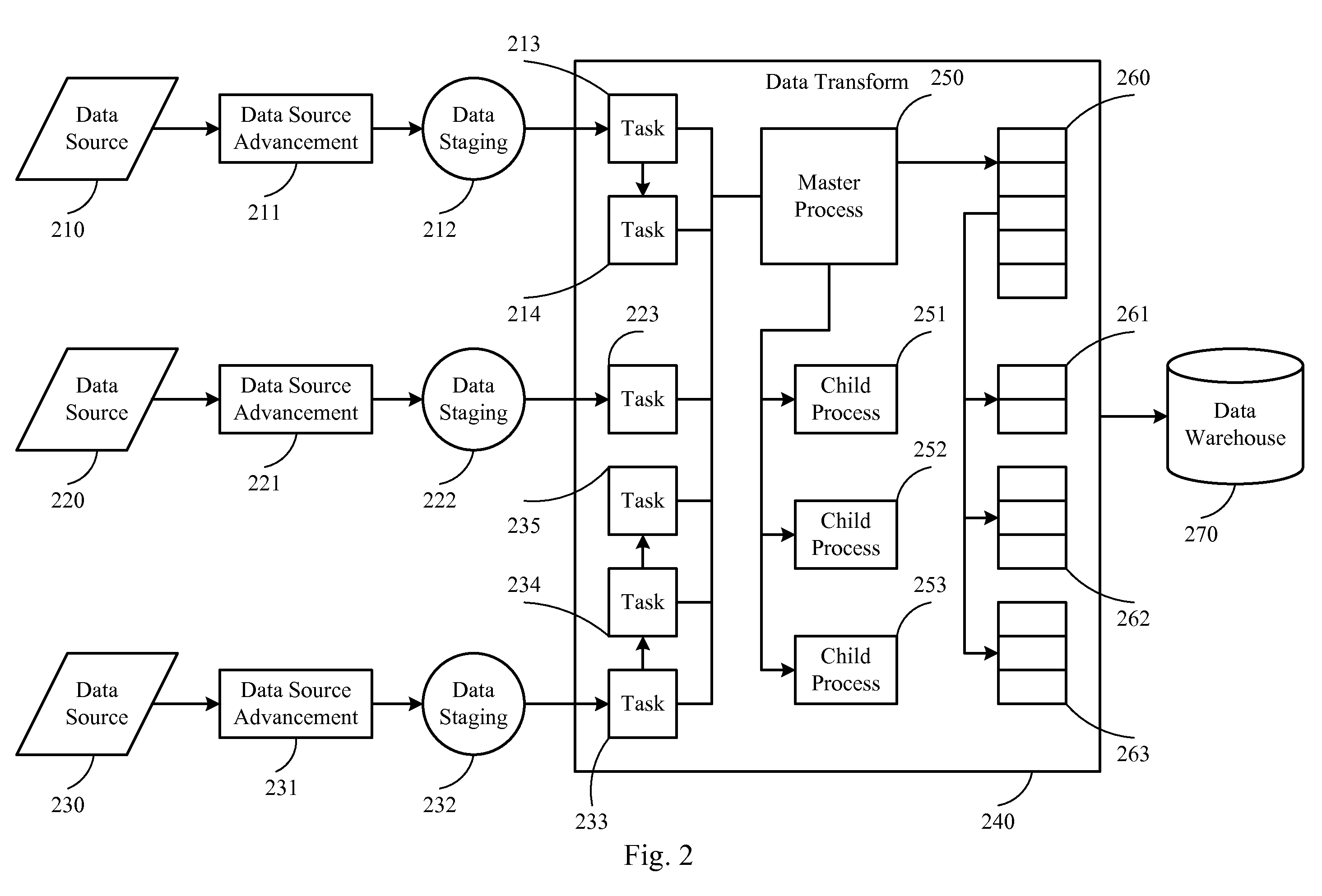
Parallel processing for etl processes
A technique for parallel processing of data from a plurality of data sources in conjunction with an Extract-Transform-Load (ETL) process, the data being part of a related data set, which comprises the following: staging a unit of extracted data from each of the plurality of data sources, thereby generating a plurality of units of staged data; identifying a plurality of tasks relating to transforming the staged data; assigning a subset of the tasks to each of a plurality of child processes being managed by a master process, such that dependent tasks are assigned to a same child process; concurrently executing the subsets of tasks assigned to the child processes, thereby generating a plurality of units of transformed data from the plurality of units of staged data; and publishing the transformed data after all tasks are completely executed, thereby ensuring that the published data represent the related data set.
Owner:OATH INC
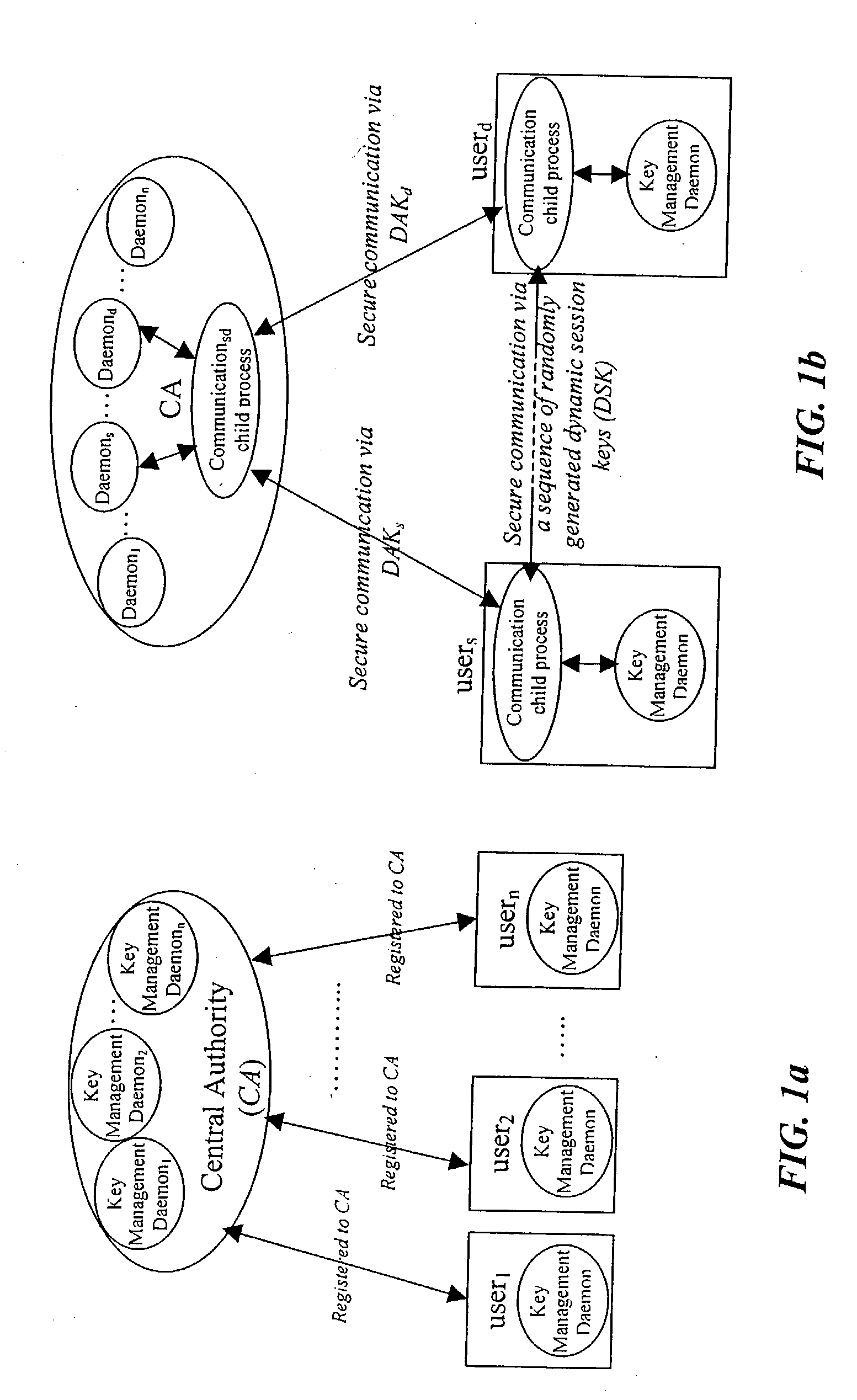
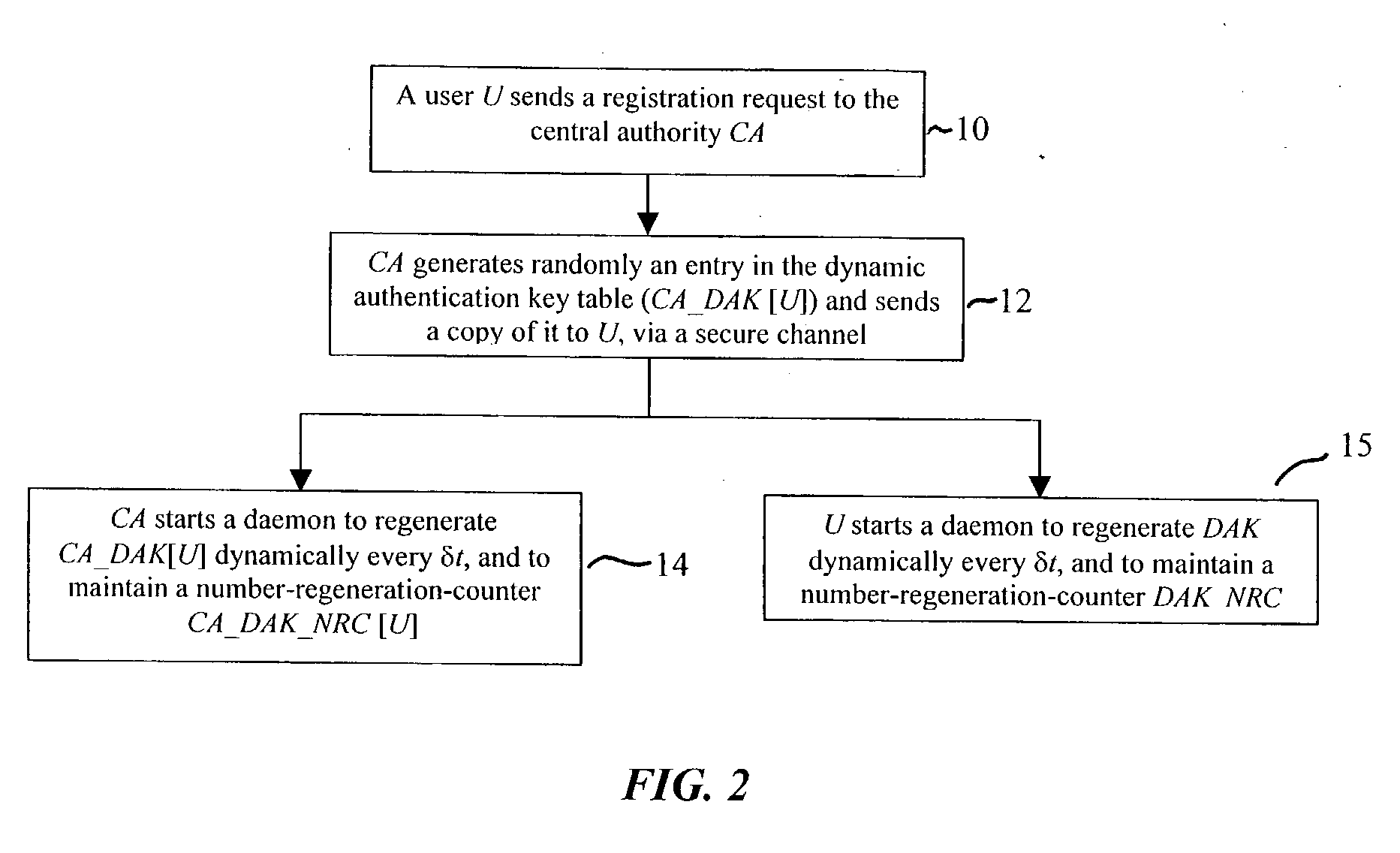
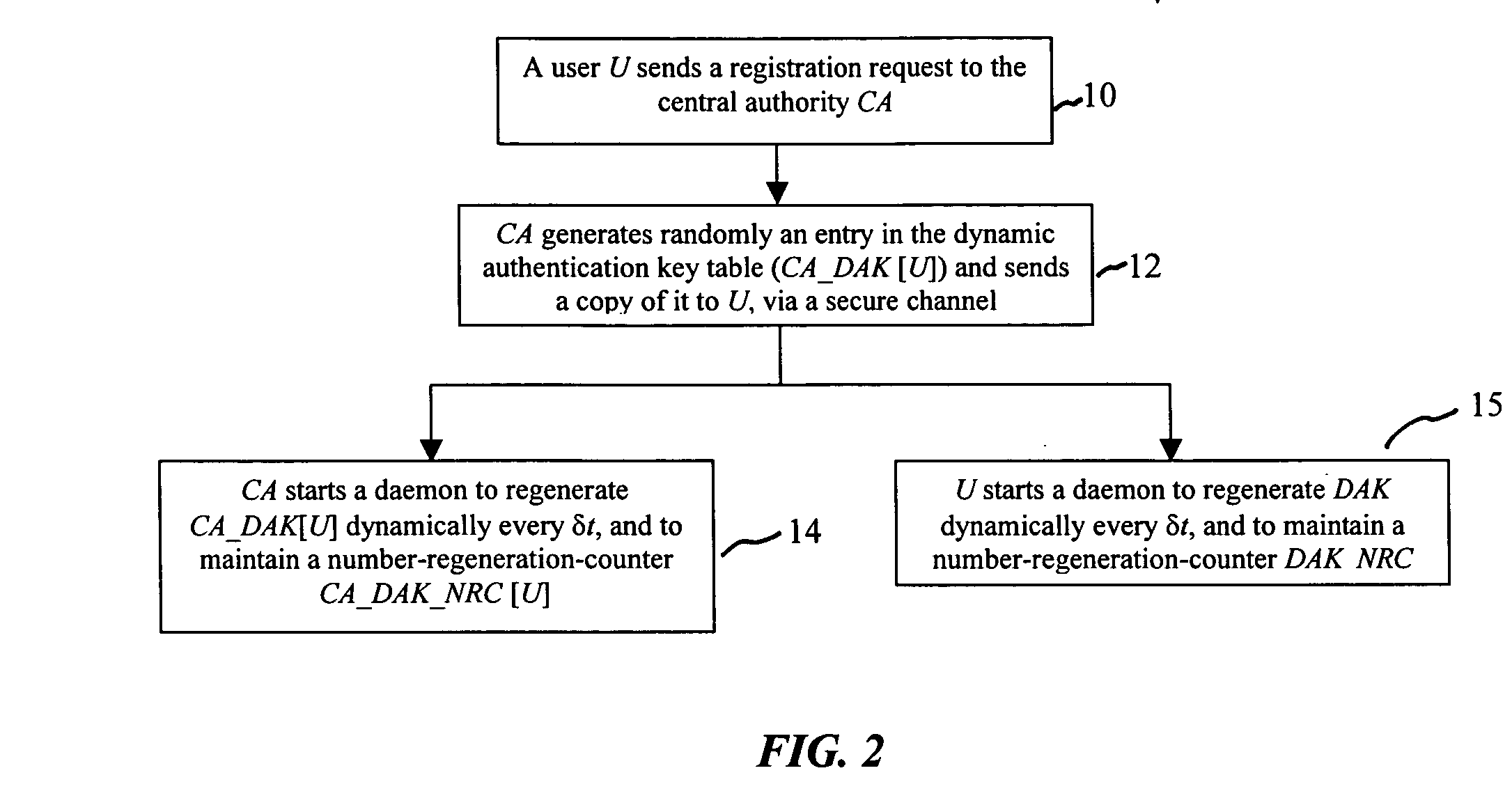
Computer system security via dynamic encryption
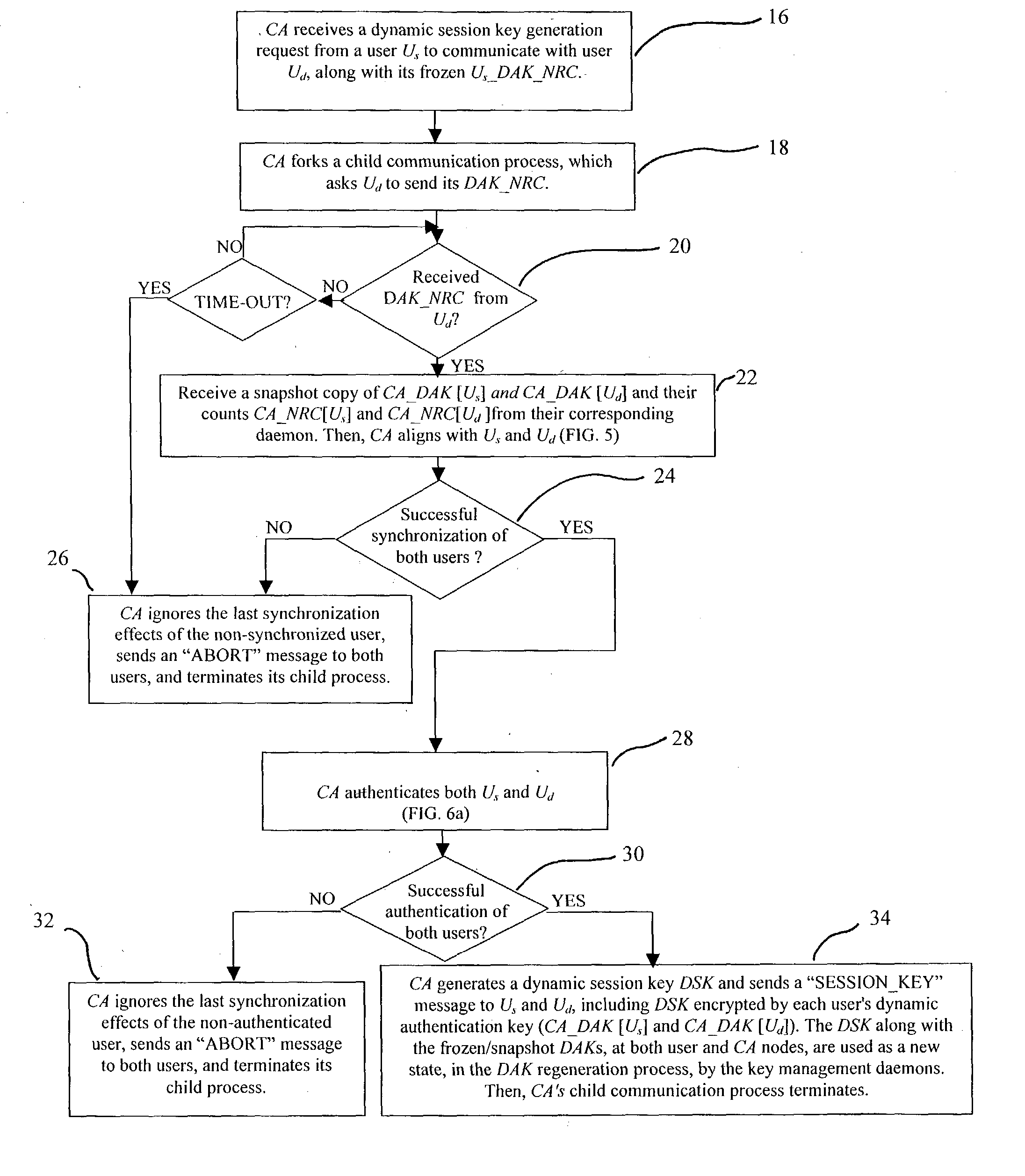
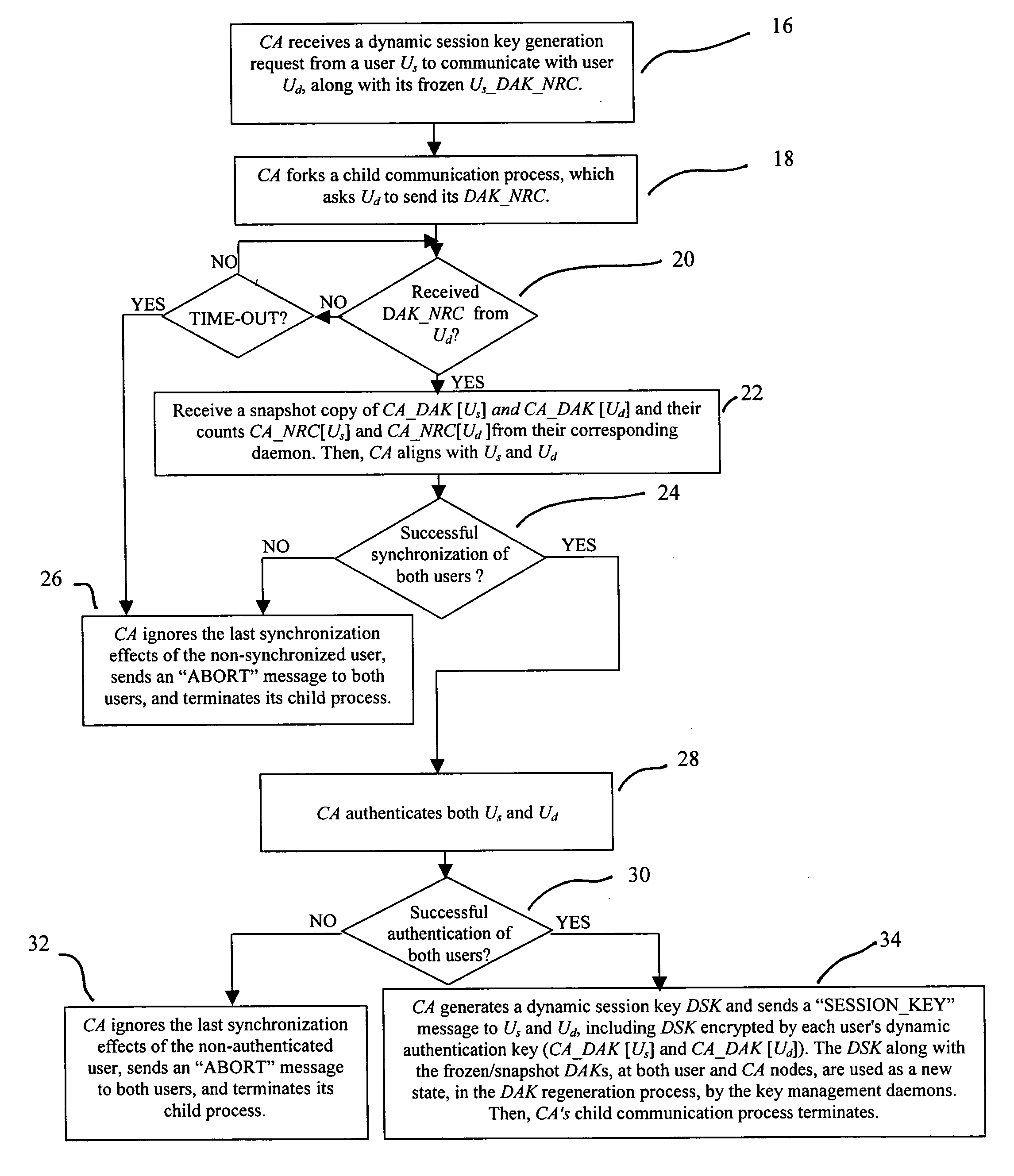
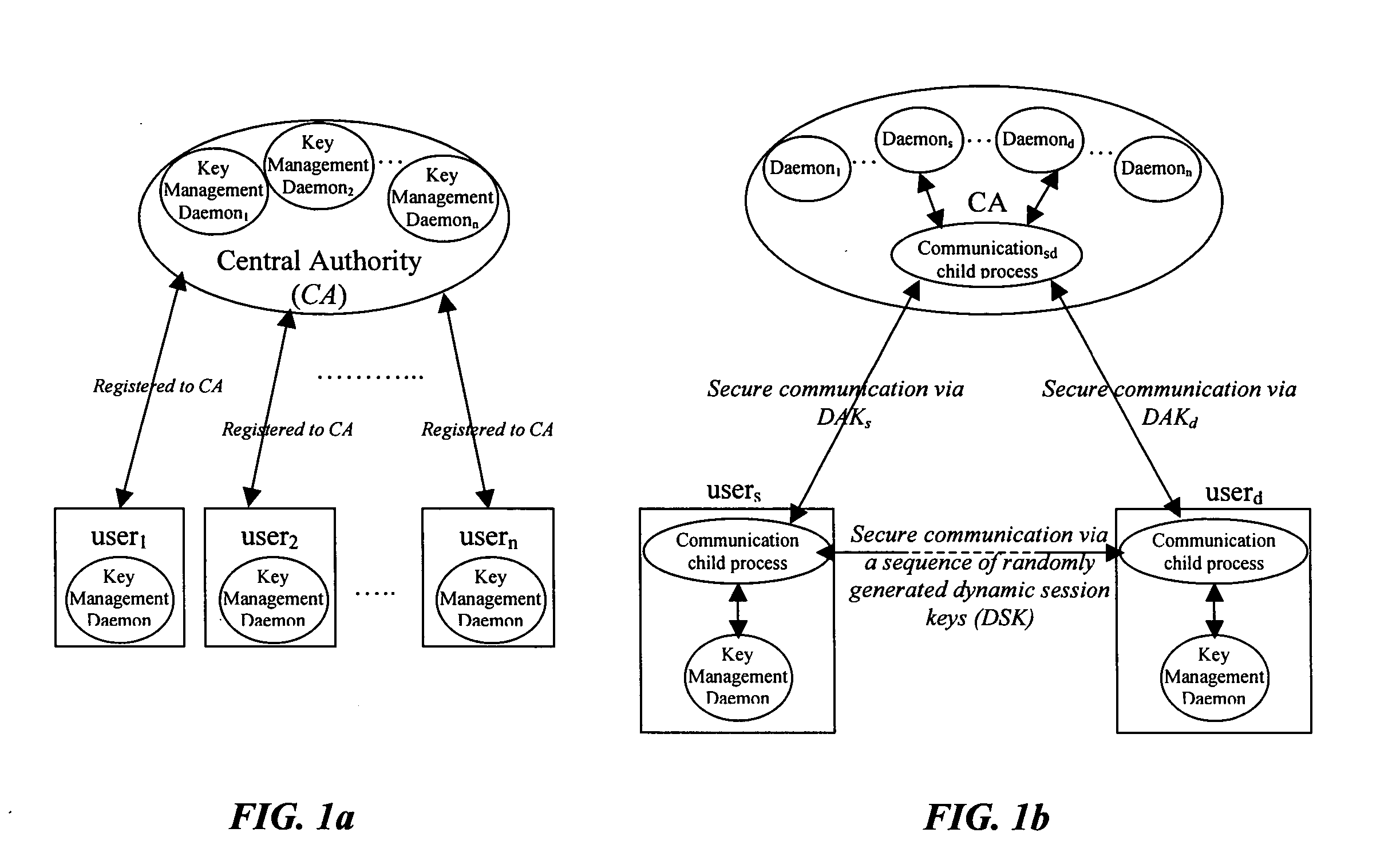
InactiveUS20040179682A1Minimize exchangeThe process is simple and fastKey distribution for secure communicationSynchronising transmission/receiving encryption devicesSecure communicationSystemic approach
A dynamic computer system security method and system using dynamic encryption and full synchronization between system nodes. A data record from a data stream created by a source user is encrypted with an initial dynamic session key. A new dynamic session key is generated based upon a data record and a previous dynamic session key. The new dynamic session key is then used to encrypt the next data record. A central authority is used to synchronize and authenticate both source and destination users with dynamic authentication keys. The central authority and users constantly regenerate new dynamic authentication keys. A child process is forked to ensure synchronization and authentication of dynamic authentication keys of each node upon a request for a secure communication establishment from a user. The central authority generates the initial dynamic session key with the current dynamic authentication key to begin a secure communication session.
Owner:MOXCHANGE LLC
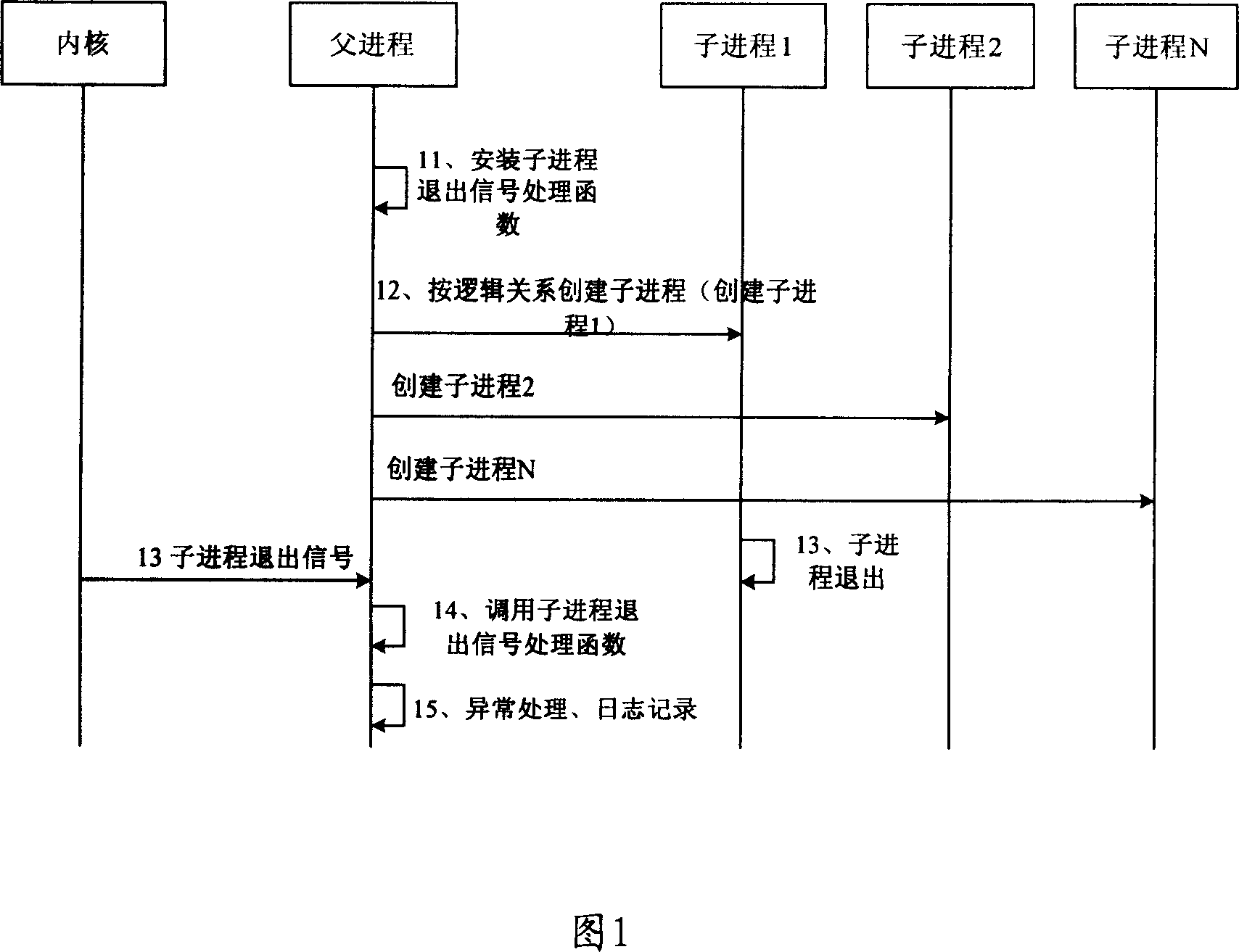
Method and system for monitoring process
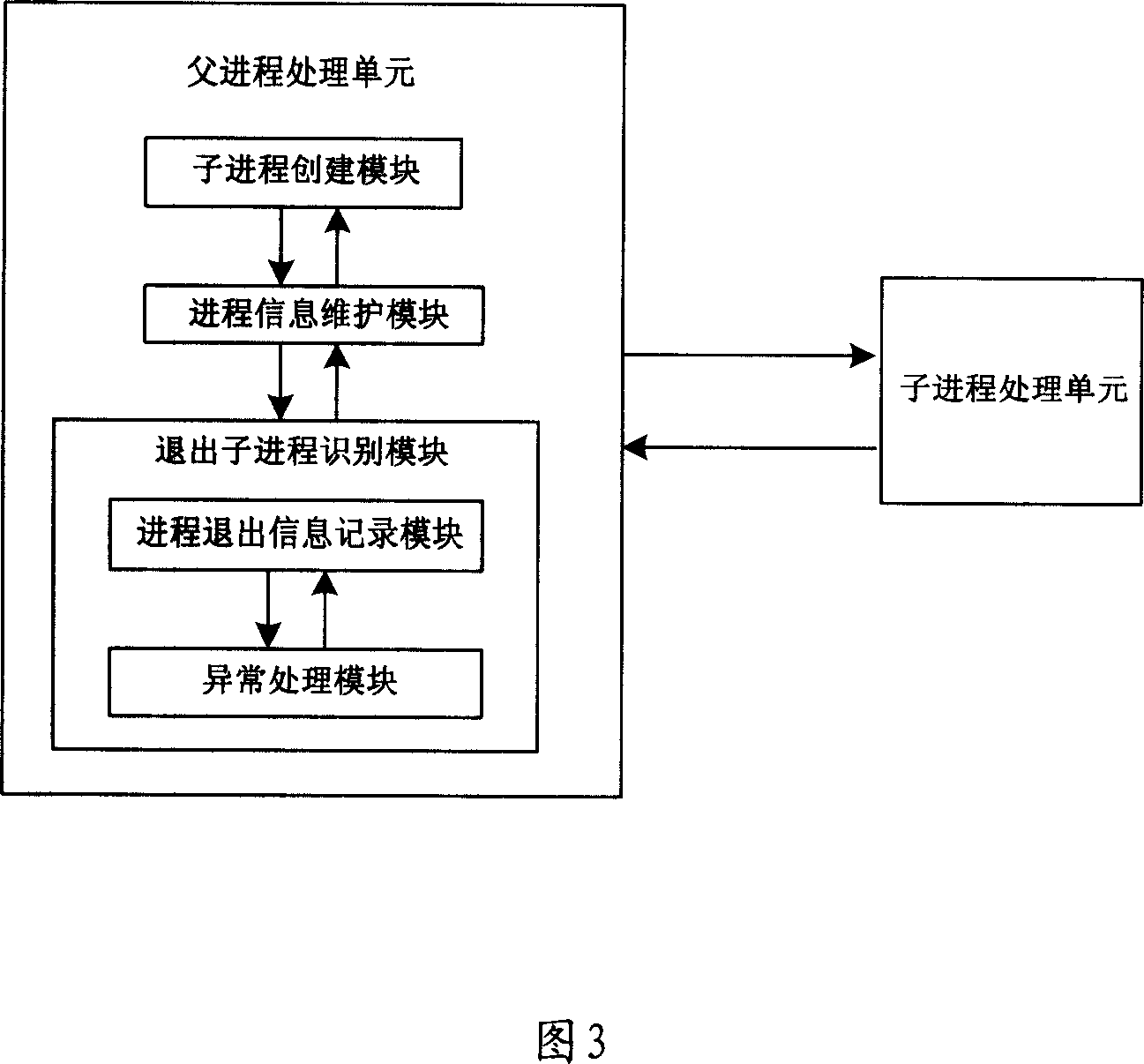
ActiveCN1996257AAvoid exception creepPrevent crashMultiprogramming arrangementsRelationship - FatherEngineering
A monitoring method and system for process comprises sending designated signal to the father process of the said son process when the son process retracts, with the designated signal composed of process marker that corresponds to a son process, with the said father process identifying the retracted son process based on the received signal. The system comprises son process handling unit and father process handling unit. Using this said method and system, it can make timely monitoring to the process abnormal retracting, with all kinds of son process retracting circumstances and corresponding abnormal retracting reasons.
Owner:HUAWEI TECH CO LTD
Realization progress start-up and control process
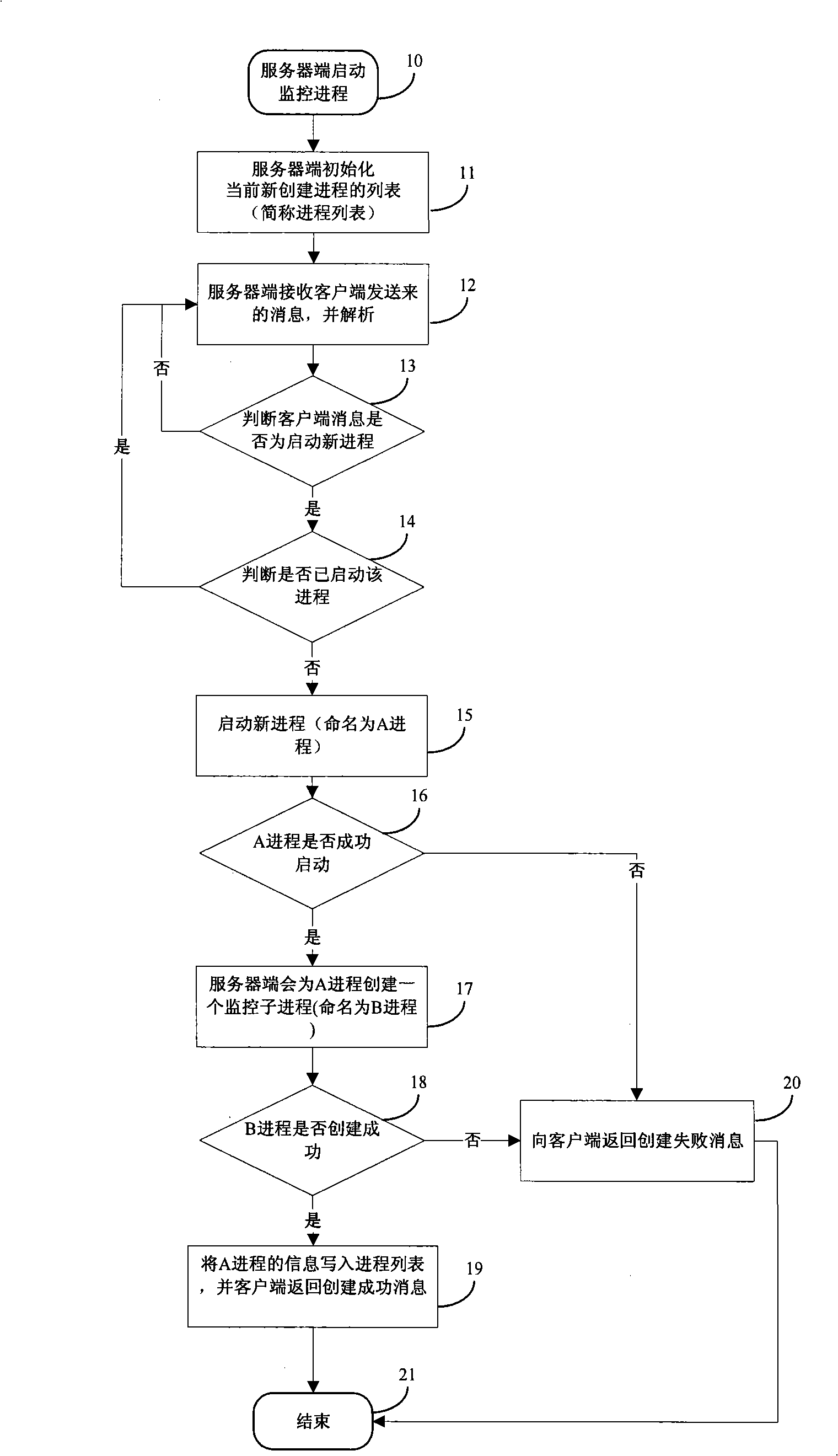
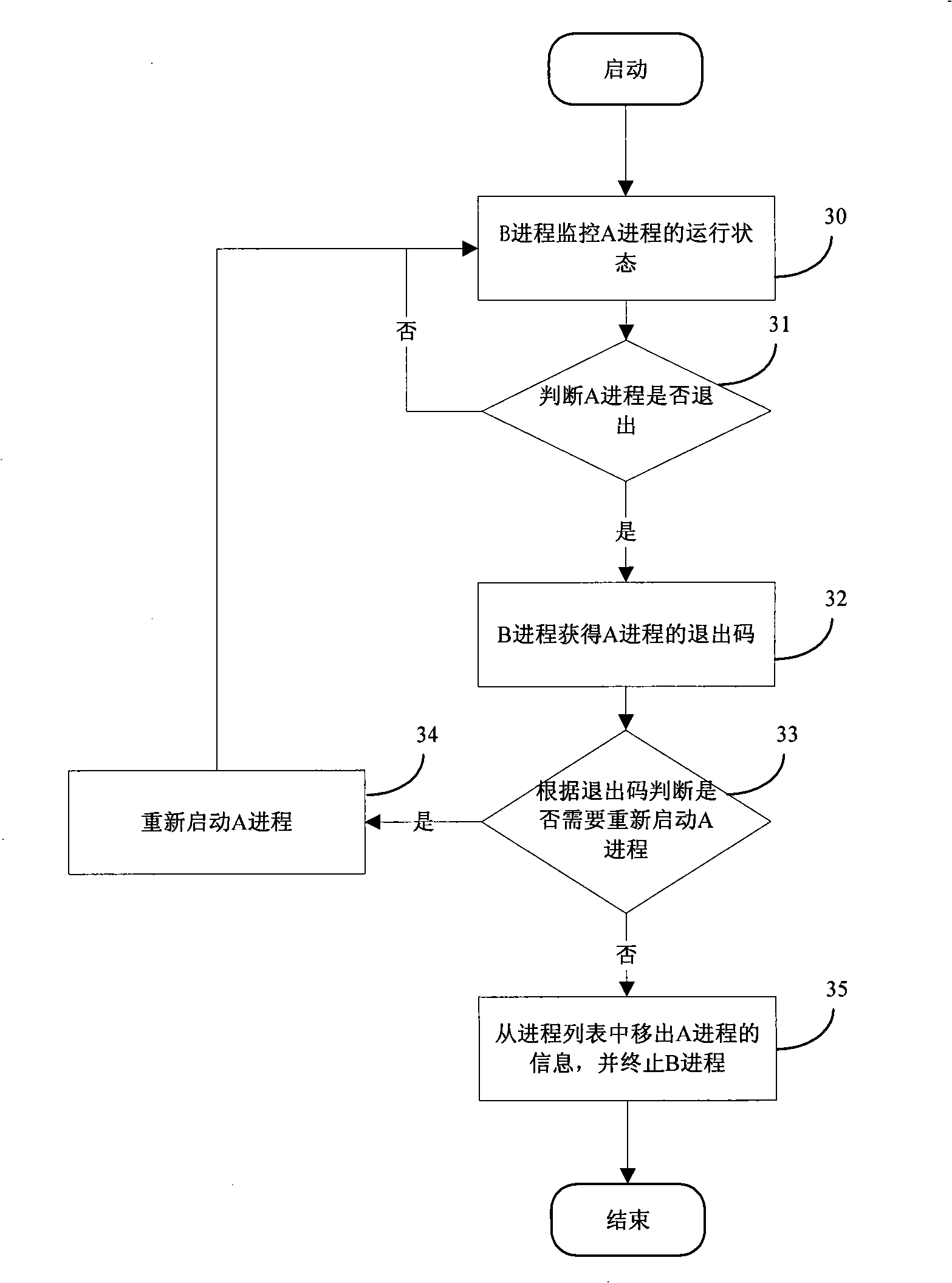
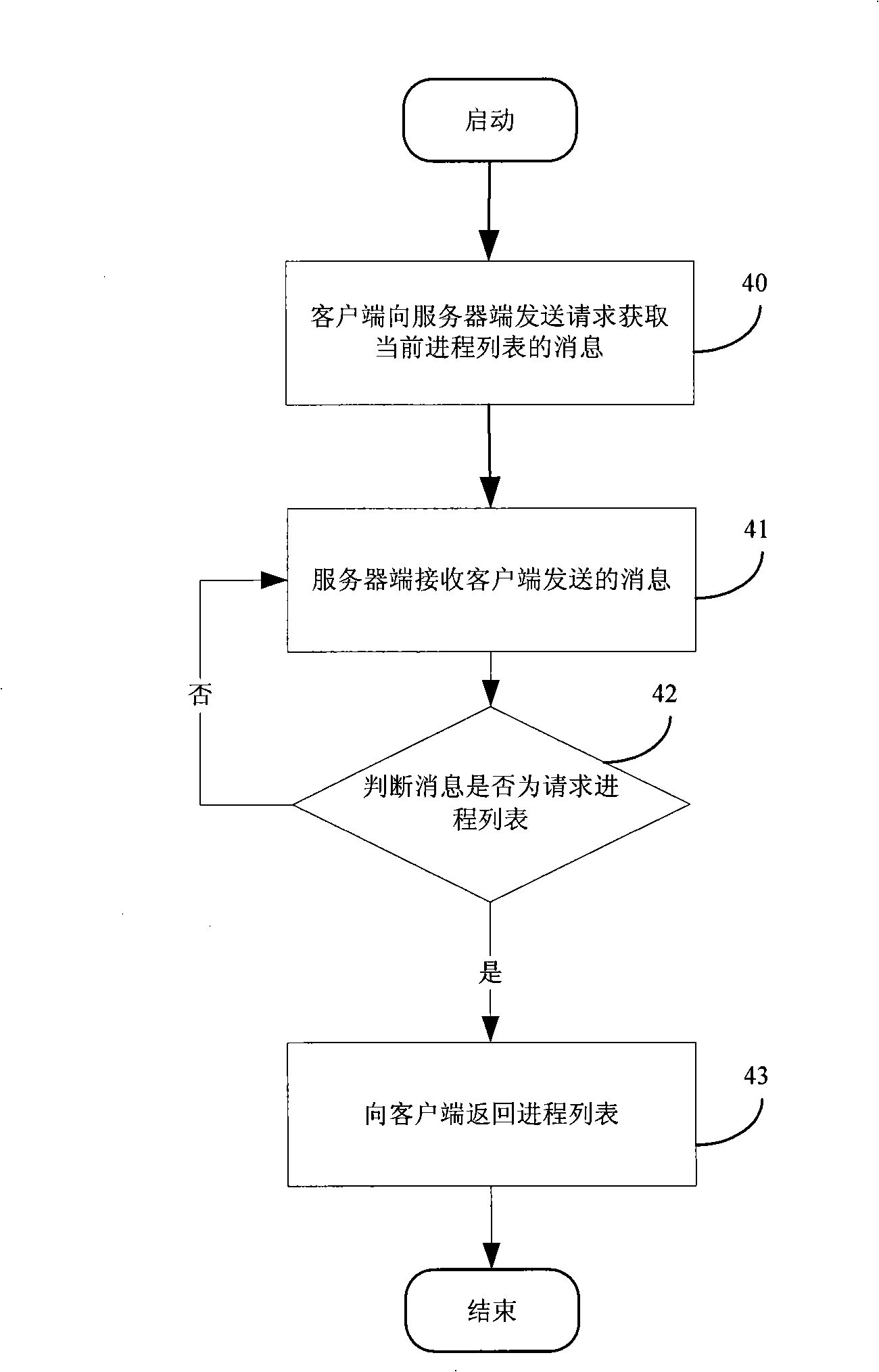
InactiveCN101290587ARealize remote monitoringFlexible Configuration Boot SequenceMultiprogramming arrangementsTransmissionStaringSoftware engineering
The invention discloses a method for staring and monitoring processes. The method comprises the following steps that: a server opens a monitoring process after startup and initializes a current process list; after receiving a startup process message sent by a client, the server inquires whether the process exists in the process list and starts the process if no; a monitoring child process corresponding to the newly started process is created so as to monitor the running state of the newly started process; the server writes the information of the currently started process into the process list and returns a message of successful process creation to the client. The method realizes that: the server starts the new process by receiving the startup process message sent by the client, and can carry out remote monitoring to the newly started process.
Owner:ZTE CORP
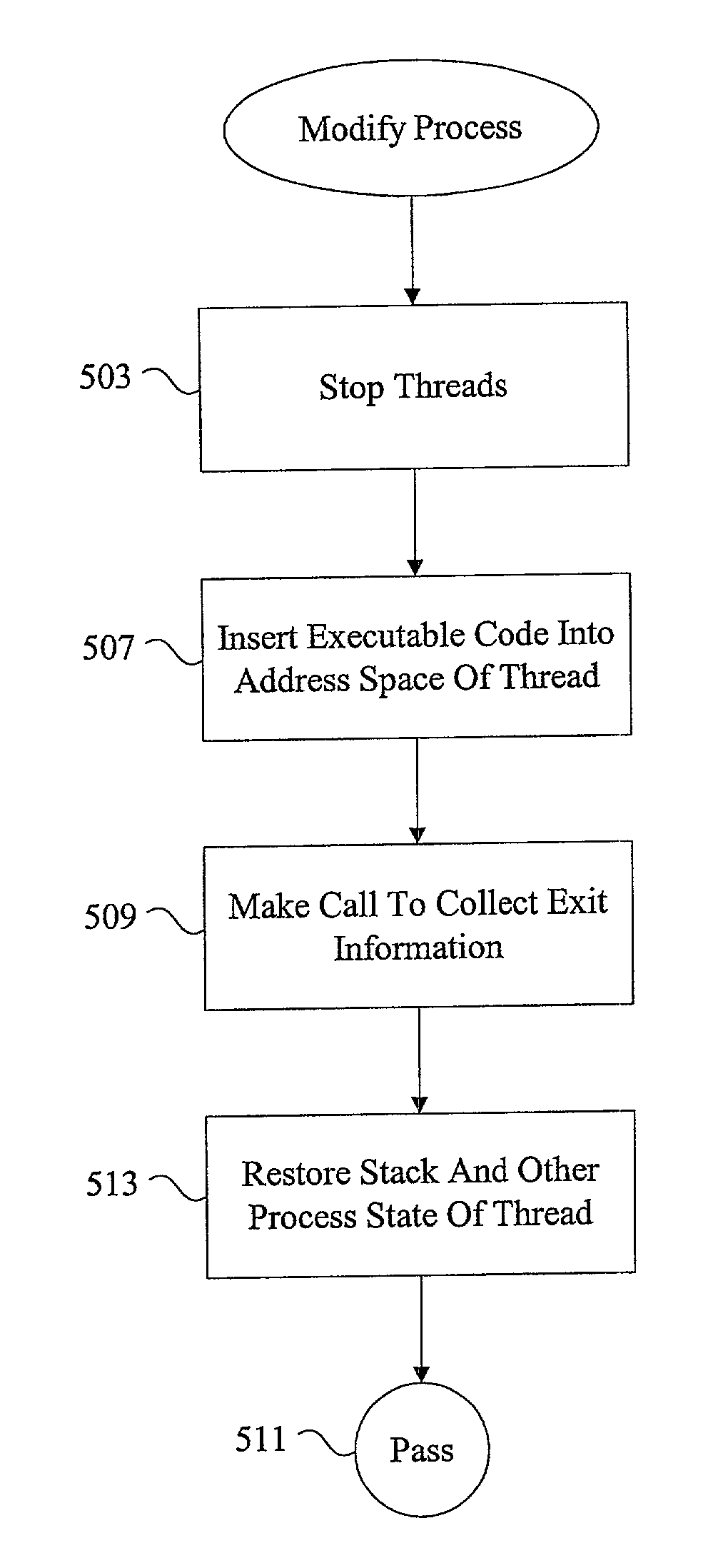
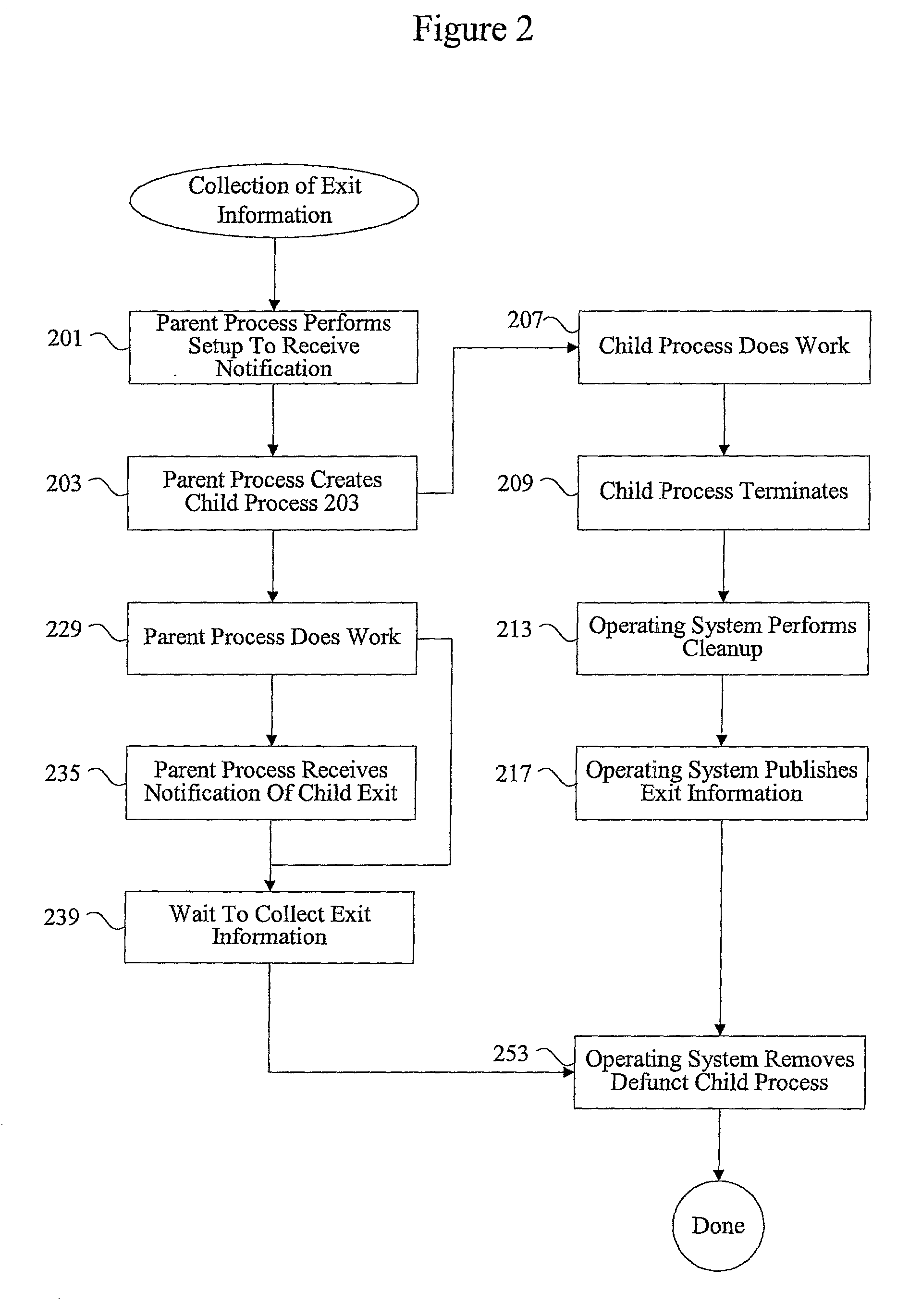
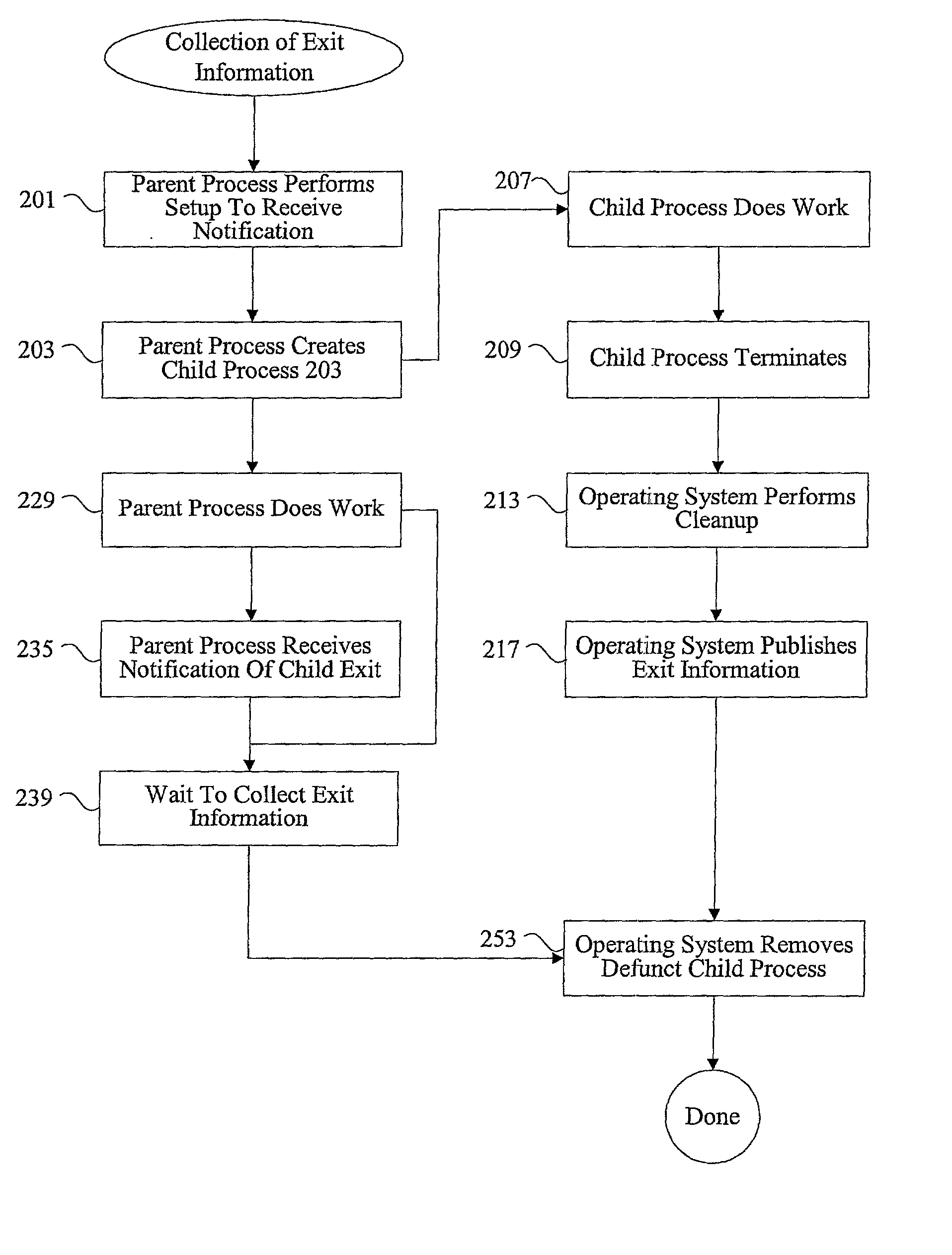
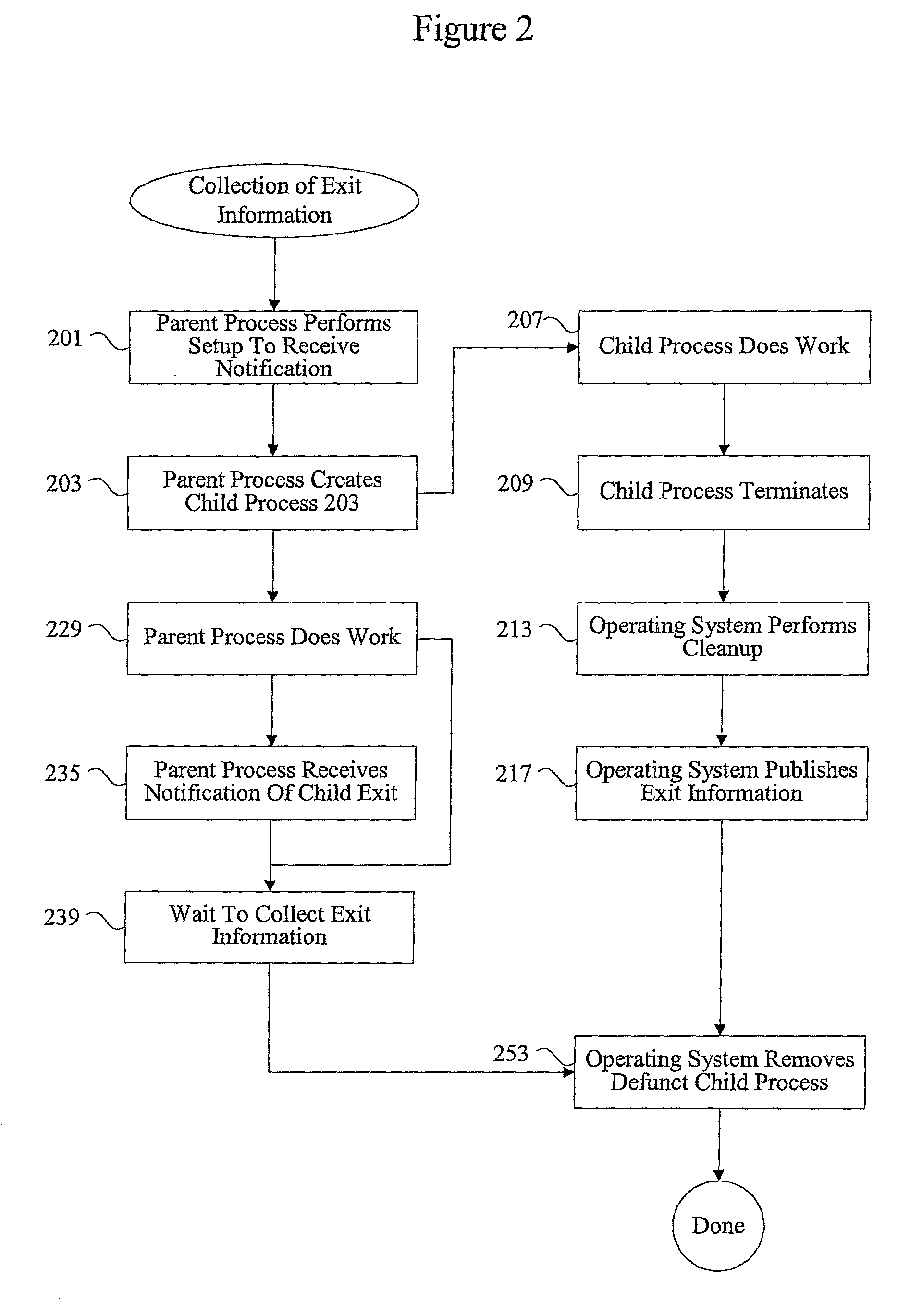
Methods and apparatus for managing defunct processes
InactiveUS7124403B2Program initiation/switchingSpecific program execution arrangementsSoftware engineeringParent process
The present invention relates to managing defunct processes. A parent process that does not collect exit information associated with a child process may leave a defunct child process. A defunct child process is identified. The parent process of the defunct child process is modified. The parent process can be modified by changing an existing thread or instantiating a new thread to collect exit information associated with the child process. Collecting exit information causes the removal of the defunct child process.
Owner:ORACLE INT CORP
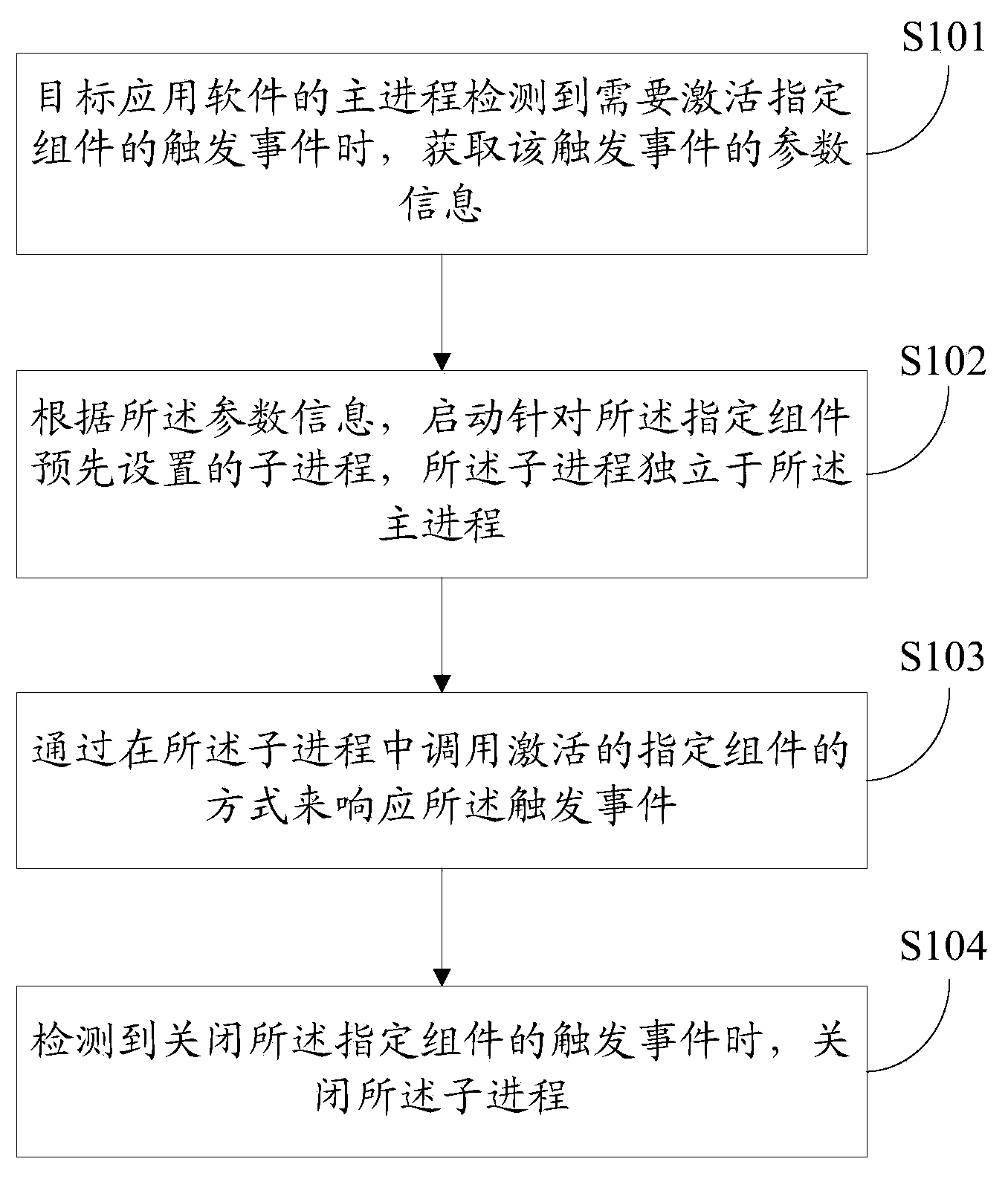
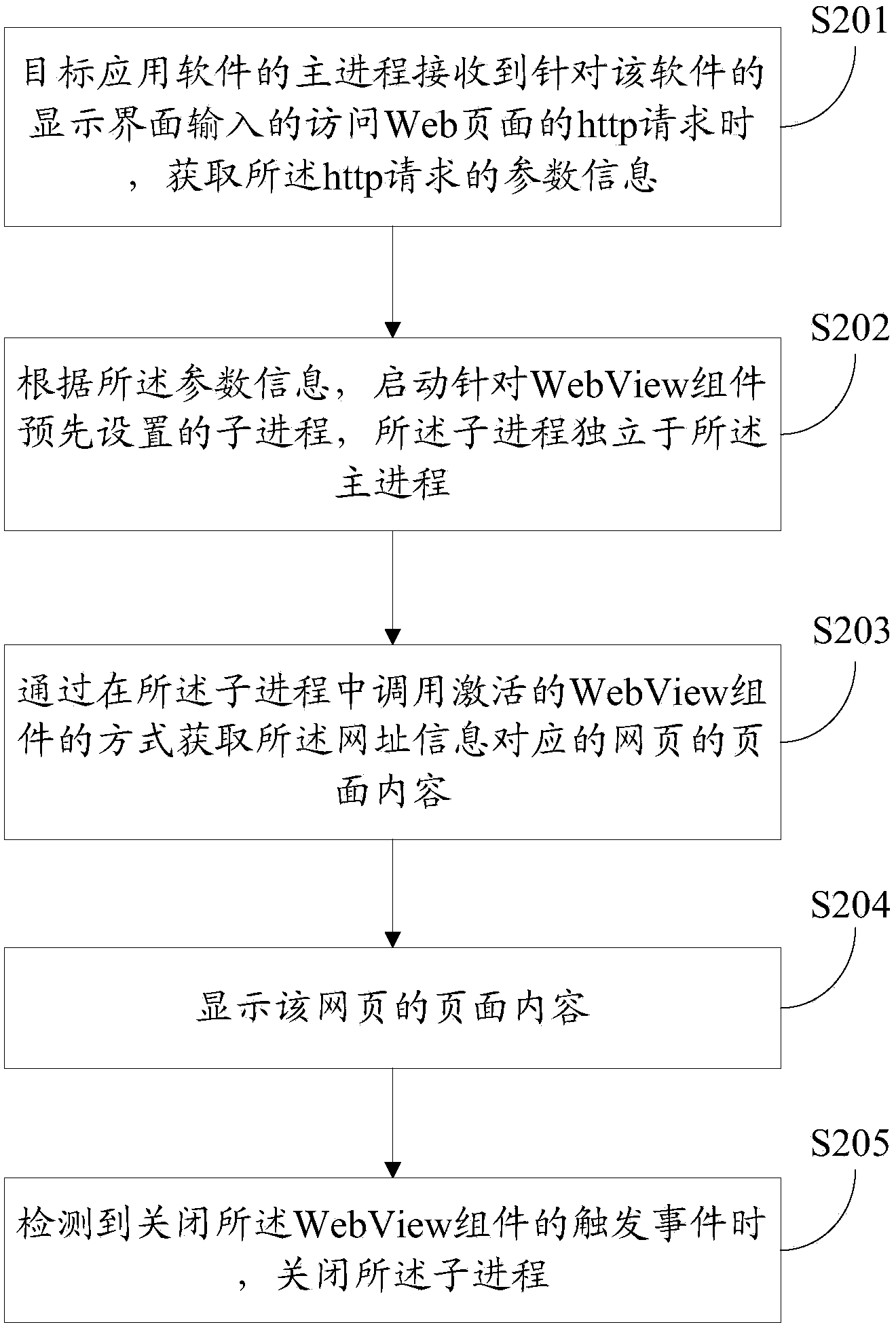
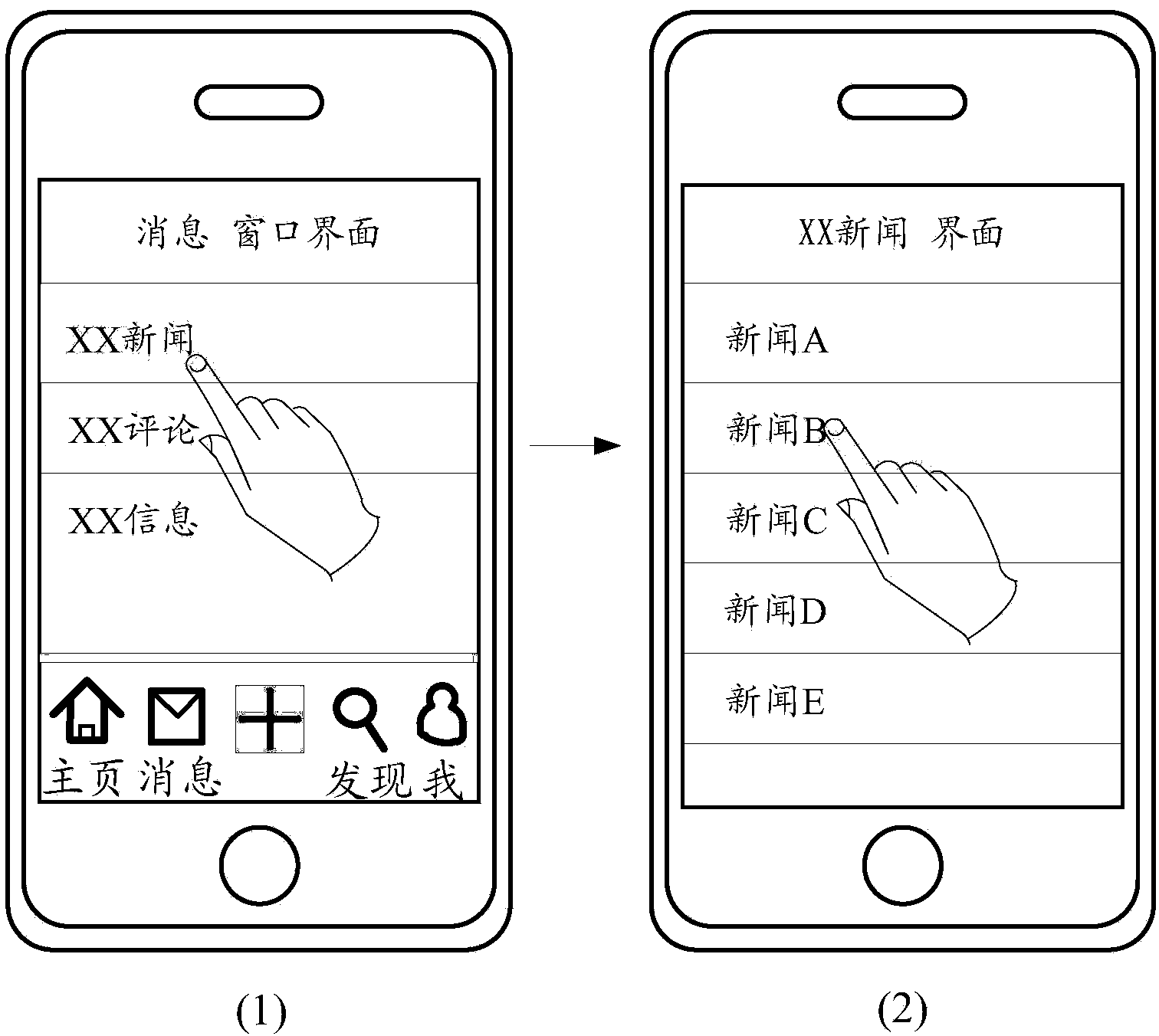
Software operating method and device and terminal
ActiveCN104268019AImprove operational efficiencyEfficient use of memory resourcesProgram initiation/switchingResource allocationSoftware engineeringComputer terminal
The invention discloses a software operating method. The software operating method includes that when a host process of a target application software detects a trigger event which is required to activate an assignment component, parameter information of the trigger event is obtained; according to the parameter information, a subprocess which is preset in allusion to the assignment component is started, and the subprocess is independent of the host process; the trigger event is responded in a mode of calling the activated assignment component in the subprocess; when a trigger event which closes the assignment component is detected, the subprocess is closed. The invention further discloses a software operating device and a terminal. By means of the software operating method and device and the terminal, internal storage resources of a system can be effectively utilized, and the operating efficiency of the application software can be increased.
Owner:GUANGZHOU KINGSOFT NETWORK TECH
Customizing Policies for Process Privilege Inheritance
InactiveUS20090328129A1Digital data processing detailsUnauthorized memory use protectionSoftware engineeringParent process
An approach is provided that uses policies to determine which parental privileges are inherited by the parent's child processes. A parent software process initializes a child software process, such as by executing the child process. The parent process is associated with a first set of privileges. The inheritance policies are retrieved that correspond to the parent process. A second set of privileges is identified based on the retrieved inheritance policies, and this second set of privileges is applied to the child software process.
Owner:IBM CORP
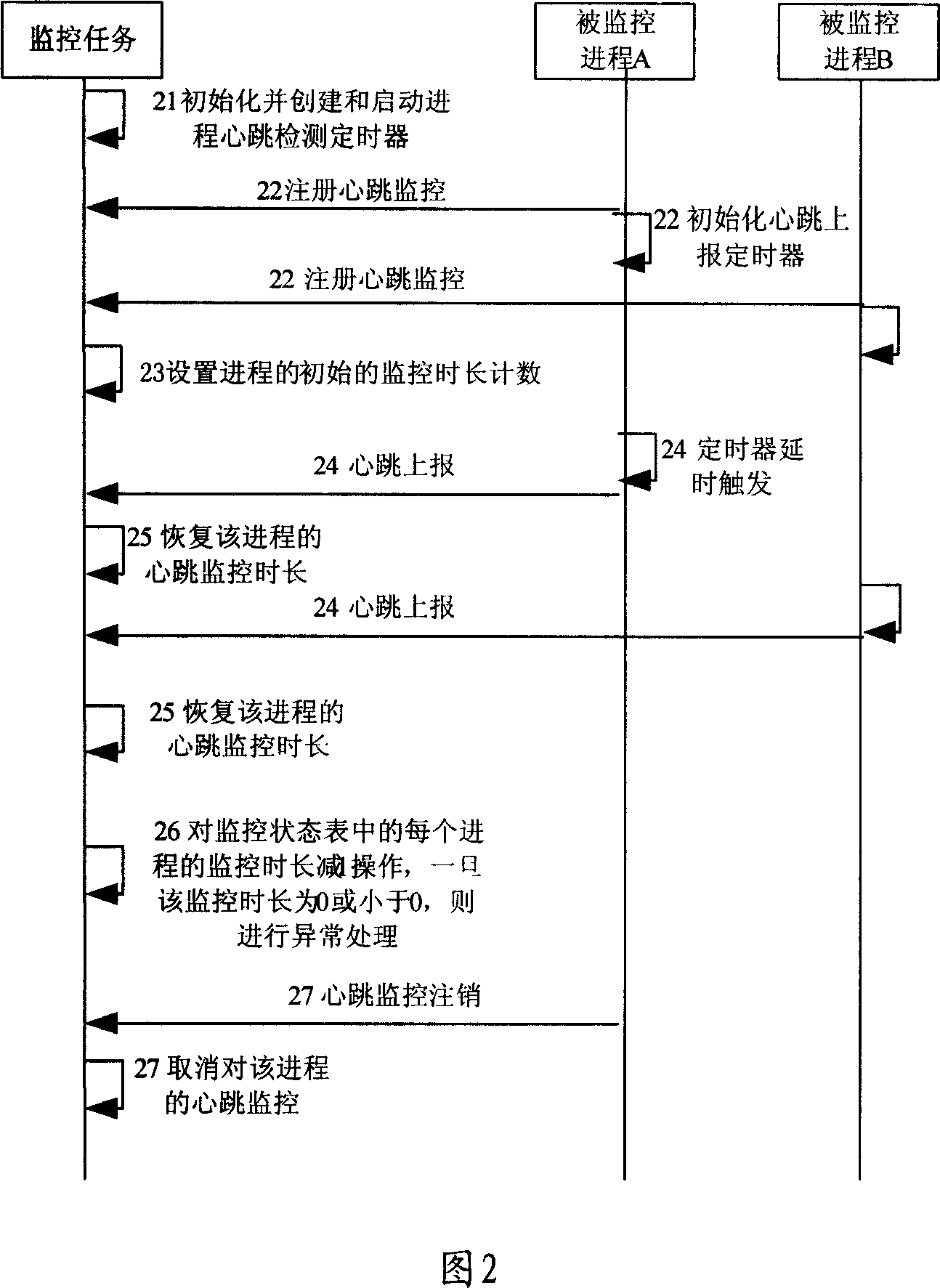
Process monitoring method and device and intelligent terminal
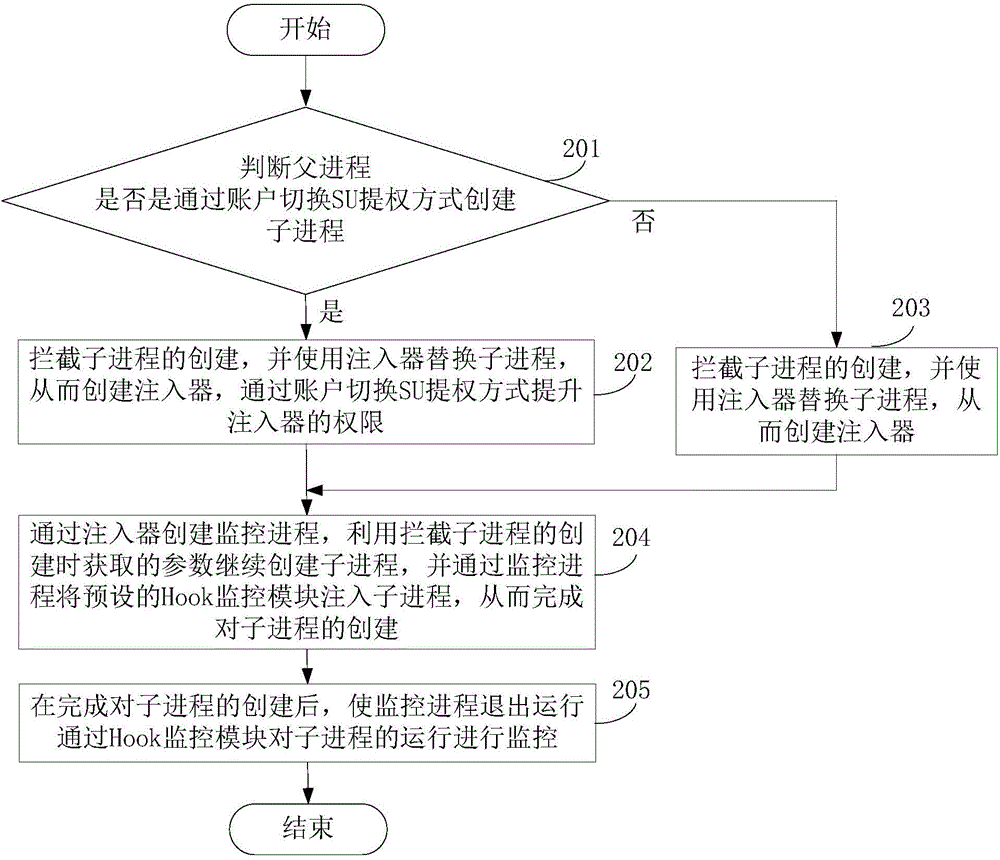
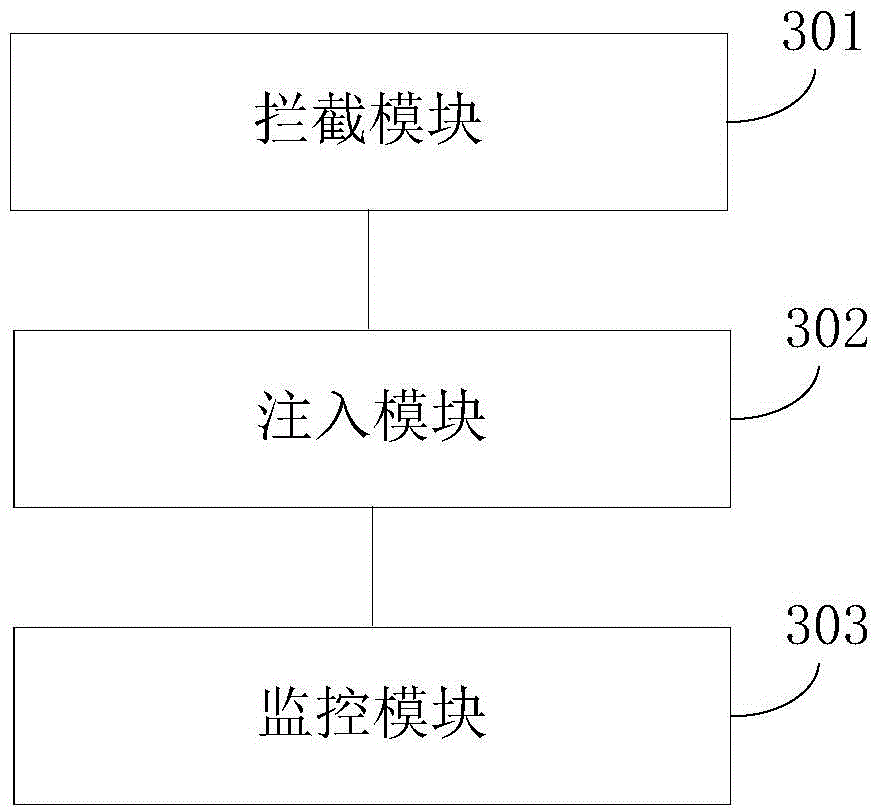
ActiveCN104156662AMalicious Behavior BlockingAvoid threatsPlatform integrity maintainanceEngineeringParent process
The invention discloses a process monitoring method and device and an intelligent terminal and belongs to the technical field of communication. The method comprises the steps that when a parent process establishes a child process, the establishment of the child process is intercepted, an injector is used for replacing the child process, and thus the injector is established; a monitoring process is established through the injector, the child process is established continually by using parameters obtained when the establishment of the child process is intercepted, a preset Hook monitoring module is injected into the child process through the monitoring process, and thus the establishment of the child process is completed; after the establishment of the child process is completed, the monitoring process stops operating, and the operation of the child process is monitored through the Hook monitoring module. The device comprises an intersecting module, an injecting module and a monitoring module. The intelligent terminal comprises a distributing platform and a Hook platform. The process monitoring method and device and the intelligent terminal can monitor any child process.
Owner:BEIJING QIHOO TECH CO LTD
Methods and apparatus for managing defunct processes
InactiveUS20030037290A1Program initiation/switchingEmergency protective arrangements for automatic disconnectionSoftware engineeringParent process
The present invention relates to managing defunct processes. A parent process that does not collect exit information associated with a child process may leave a defunct child process. A defunct child process is identified. The parent process of the defunct child process is modified. The parent process can be modified by changing an existing thread or instantiating a new thread to collect exit information associated with the child process. Collecting exit information causes the removal of the defunct child process.
Owner:ORACLE INT CORP
Full-automatic firing method for wideband individual line subscriber based on flowpath optimization
InactiveCN101510831AImprove accuracyImprove human resourcesData switching networksAsynchronous communicationSystem configuration
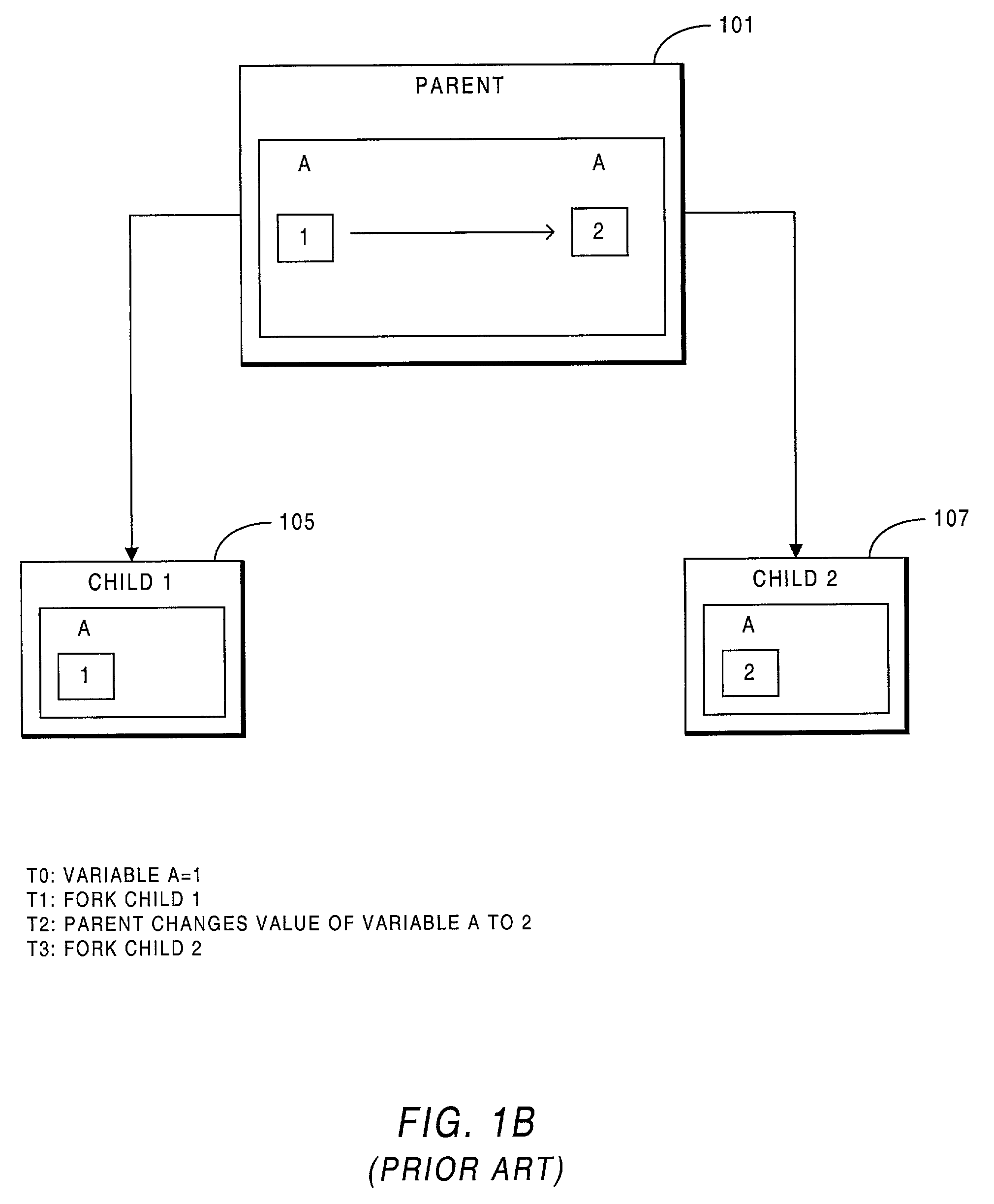
The invention relates to a fully-automatic subscribing method for broadband special line users based on process optimization, which comprises the steps: a special line automatic subscribing system receives a work order from BSS, resolves the work order, obtains information of such as equipment to be configured, and searches upper and lower correlative equipment information, login manner and login password according to the existing equipment information, and then logins in the equipment according to the equipment information to configure related data order; the special line automatic subscribing system is configured with thread counts for processing the work order, starts a work order receiving module, and selects a system operation mode through reading configuration files, namely a parent-child process or an automatic reset mode; socket communication is utilized to simulate telnet to login in the equipment and issue orders, the port information of the equipment is validated and judged during the process of issuing orders and the execution result of the orders issued currently is validated and judged; if other socket demands are connected at the same time, other thread counts are assigned to do the work so as to fulfill the long connection asynchronous communication between the automatic subscribing system and the socket of BSS.
Owner:LINKAGE SYST INTEGRATION
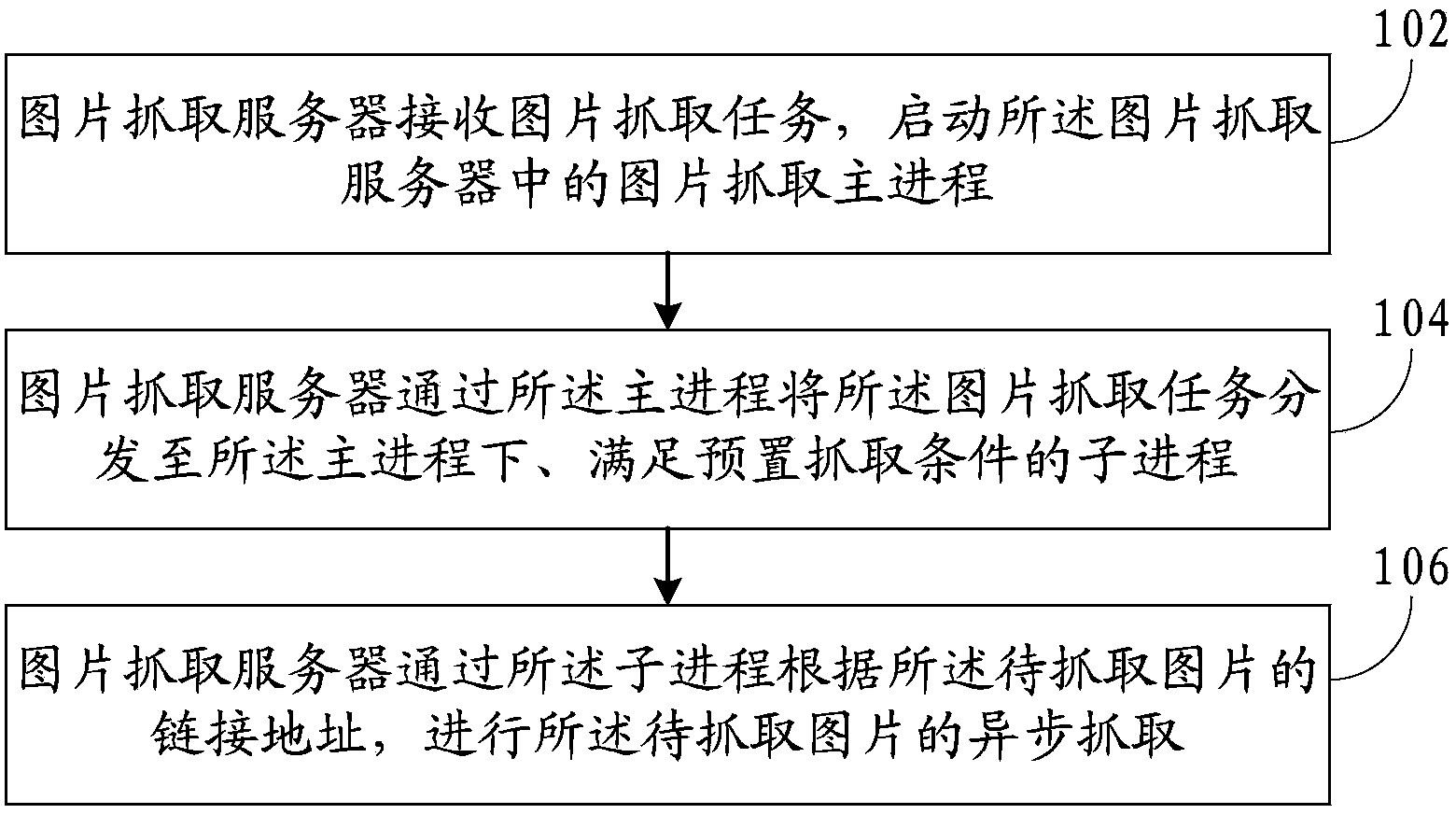
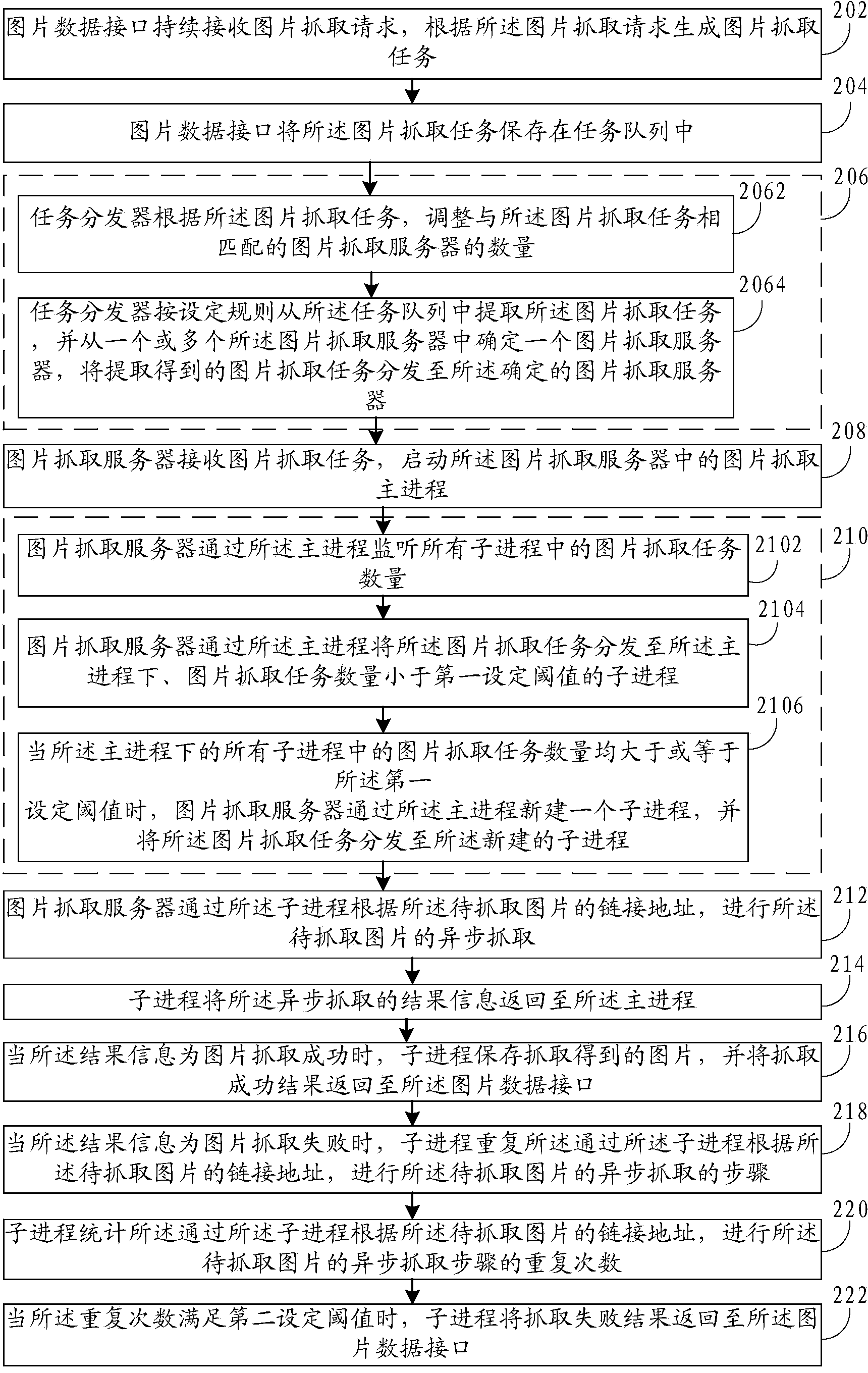
Method and system for capturing images
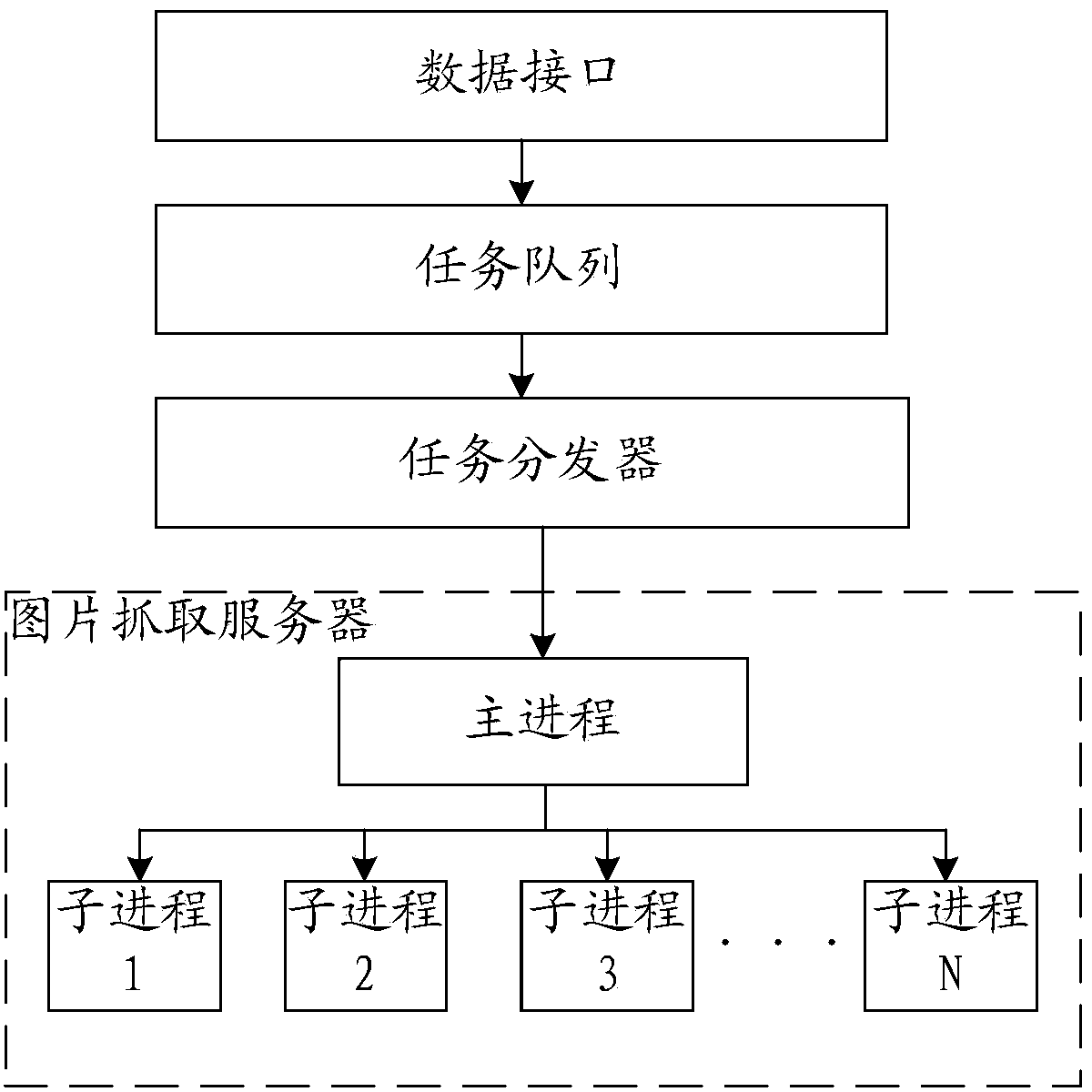
InactiveCN103645939AImprove crawling efficiencyReduce waiting timeMultiprogramming arrangementsImage captureChild process
The invention discloses a method and system for capturing images. The method comprises the following steps: an image capturing server receives an image capturing task and starts an image capturing host process in the image capturing server, wherein the image capturing task includes chained addresses of images to be captured; the image capturing task is distributed by the host process to child processes which are subordinate to the host process and meet preset capturing conditions; the images to be captured are captured asynchronously through the child processes according to the chained addresses of the images to be captured. The method and system for capturing the images solve the problems that image capturing efficiency is low, the capturing process consumes much time, and the task requirement for capturing billions of images can not be met.
Owner:BEIJING QIHOO TECH CO LTD +1
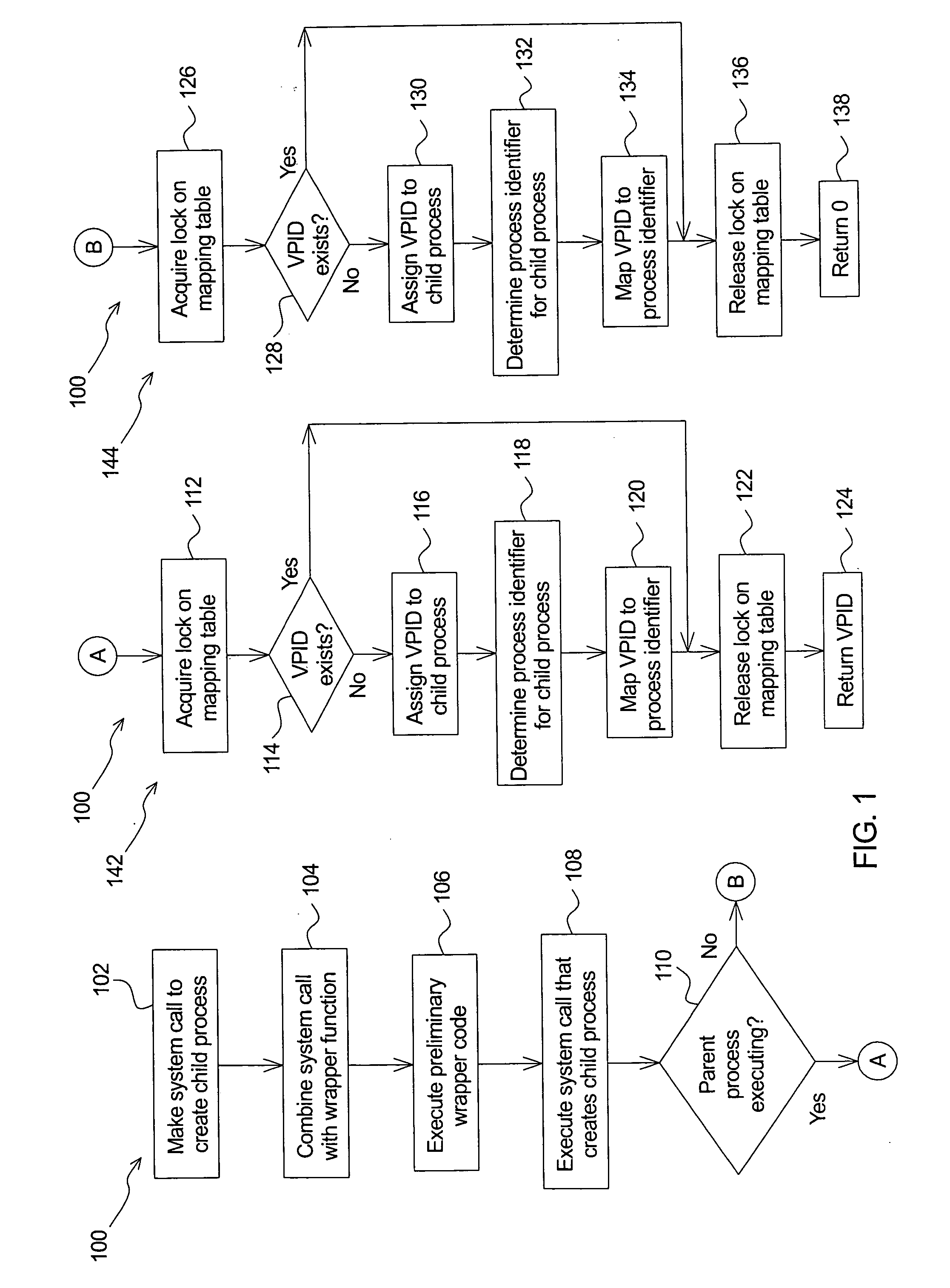
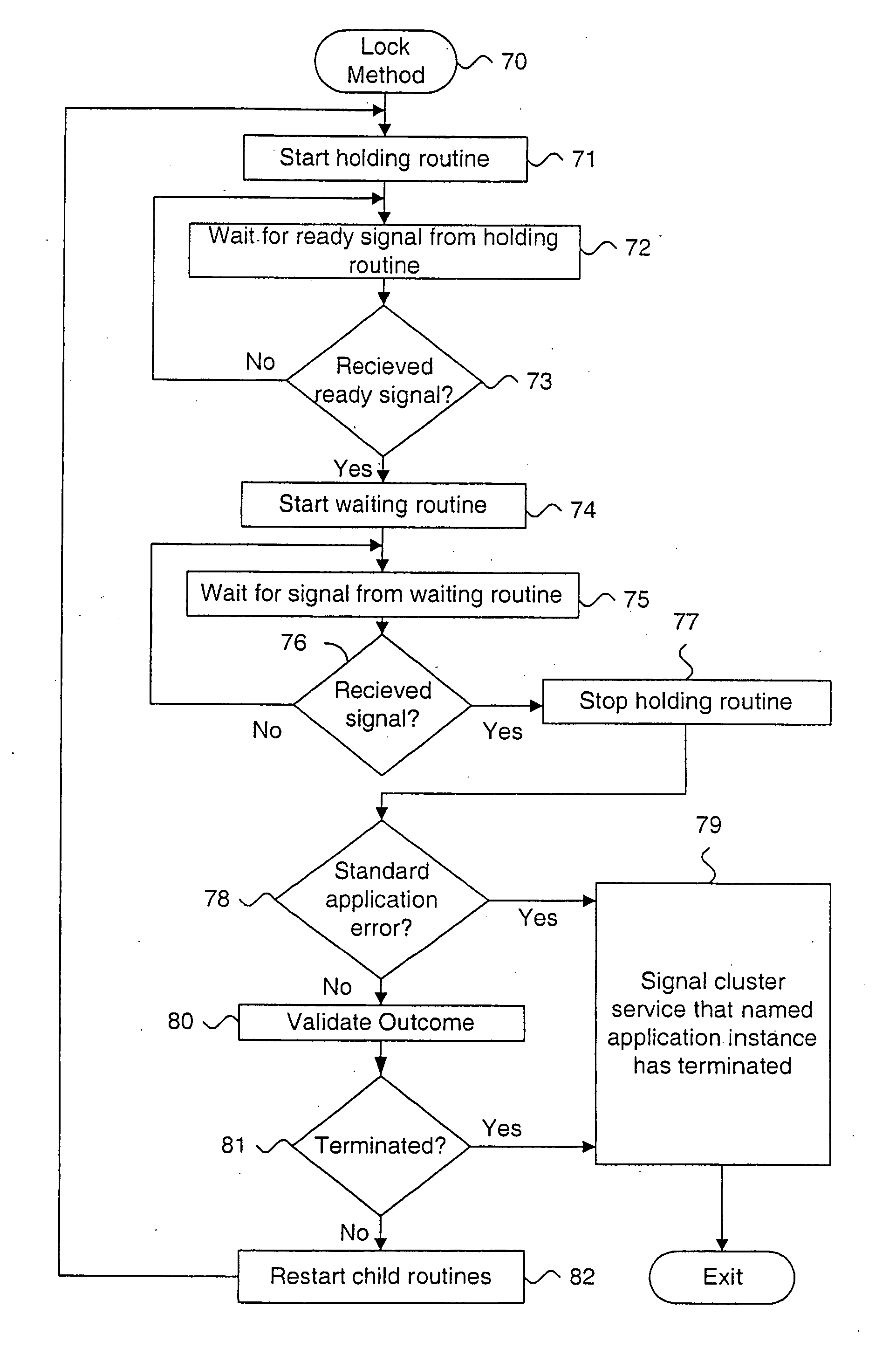
System and method for detecting termination of an application instance using locks
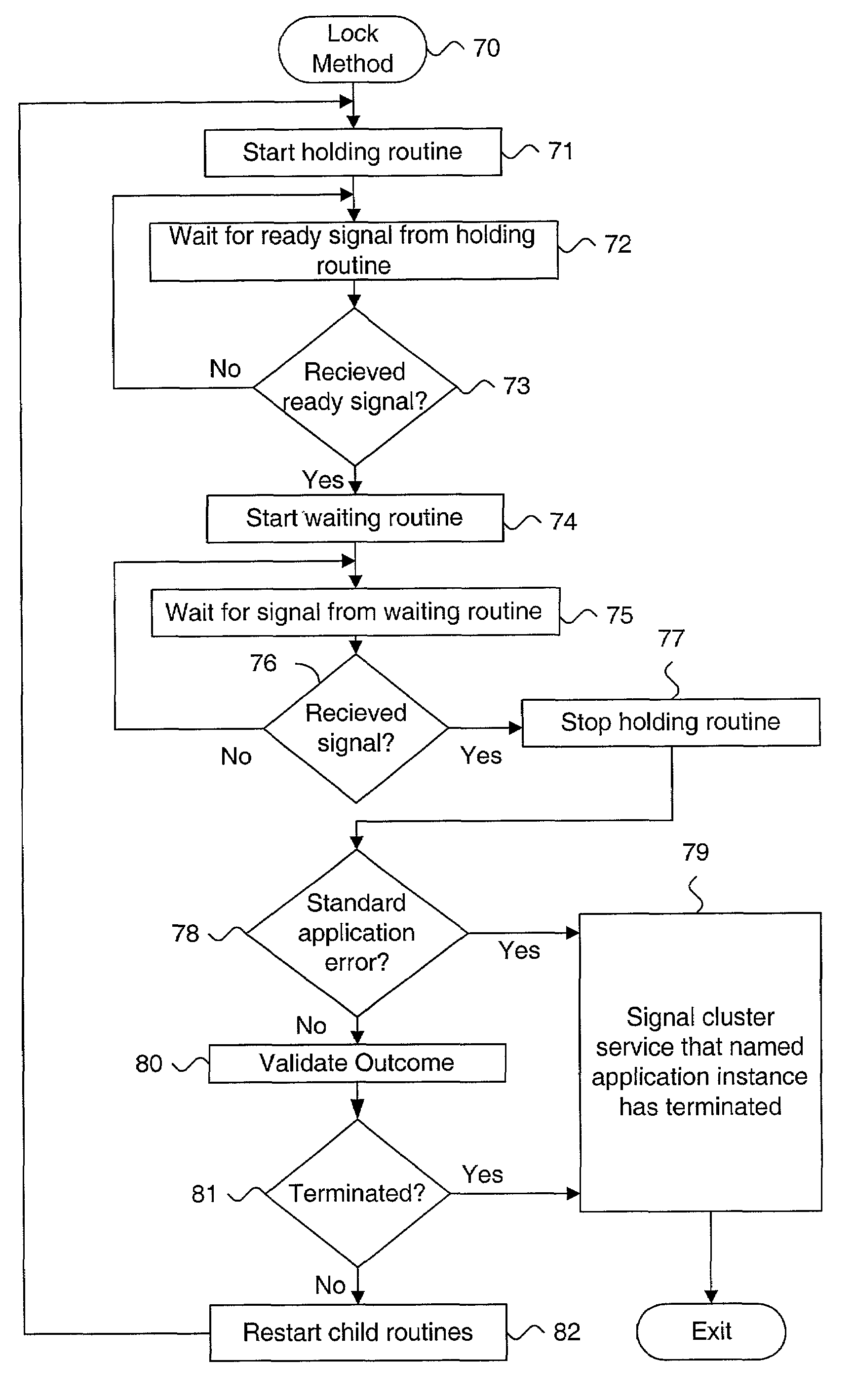
InactiveUS7058629B1Digital data information retrievalData processing applicationsApplication procedureData bank
A system and method for detecting termination of an application, such as a database instance, that uses locks is described. A holding child process is started from a parent process. The holding child process connects to a monitored application instance, acquires an exclusive lock on the monitored application instance and returns a ready signal upon successfully acquiring the exclusive lock. A waiting child process is started from the parent process subsequent to the holding child process. The holding child process connects to the monitored application instance, blocks on the exclusive lock on the monitored application instance and returns a result signal upon at least one of acquiring the exclusive lock and clearing the block on the exclusive lock. The return signal is processed at the parent process. Using locks provides immediate detection that the application has terminated. Methods for blocking against the application are also described.
Owner:ORACLE INT CORP
Secure multi-user web hosting
InactiveUS20060089967A1Efficiently hostReduce overheadMultiple digital computer combinationsTransmissionWeb siteClient-side
A web server is able to efficiently host multiple web sites. Since overhead is significantly reduced, the server can accommodate a large number of concurrent users without service delays or disruptions, even under heavy load conditions. A persistent controller process executes on the server, and responsively to a user request for access to a resource of one of the clients, a child process is spawned. The user request is then served using the child process.
Owner:ZEND TECHNOLOGIES
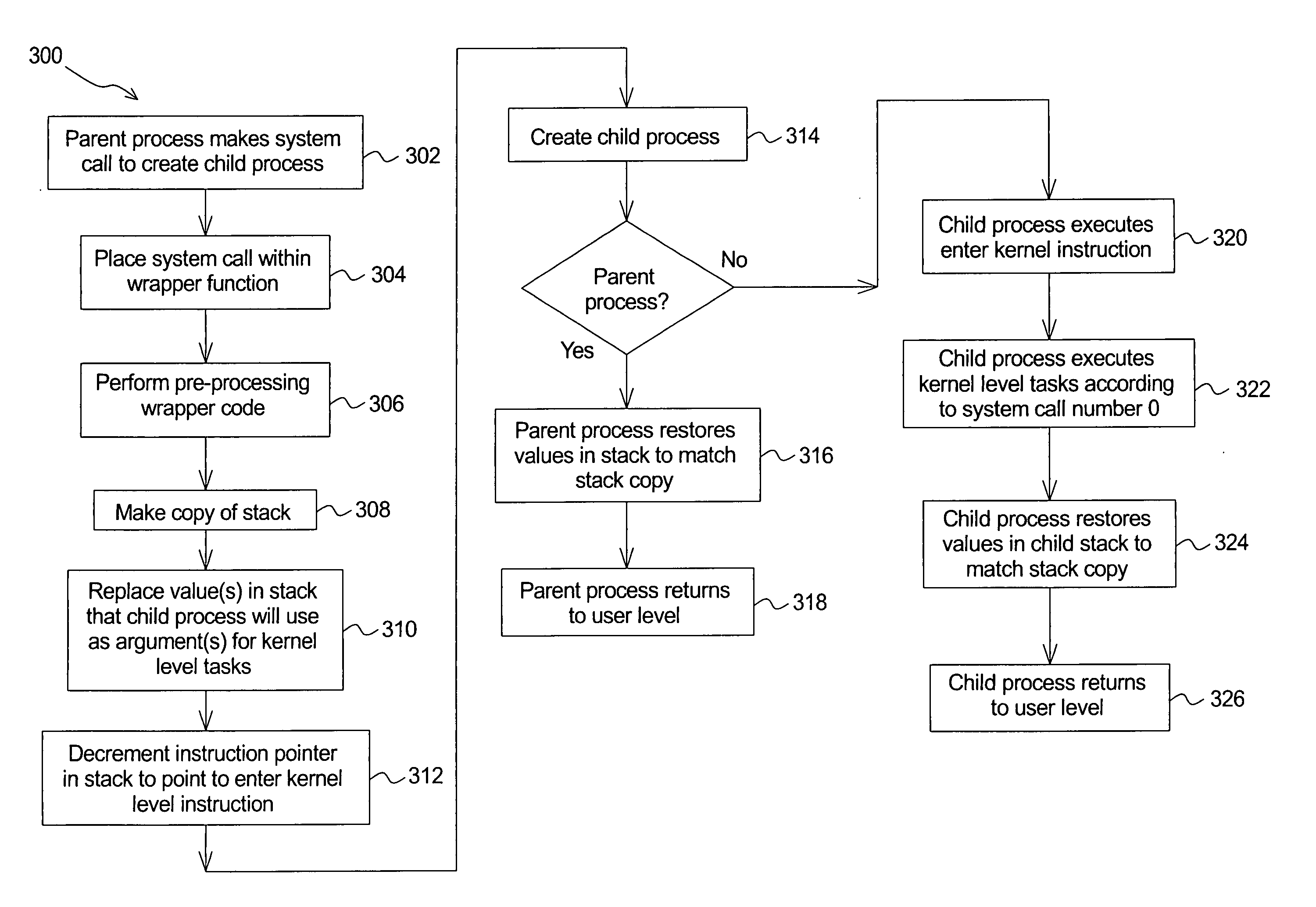
Method of performing kernel task upon initial execution of process at user level
ActiveUS20050251803A1Program initiation/switchingDigital data processing detailsKernel levelSystem call
An embodiment of a method of performing a kernel level task upon initial execution of a child process at a user level begins with setting an instruction pointer for an initial child process instruction to an instruction to enter a kernel level. The method continues with beginning the child process which places a return value in a register for the child process and which causes the child process to enter the kernel level. The method concludes with executing a system call having a system call number of the return value. The system call comprises the kernel level task.
Owner:VALTRUS INNOVATIONS LTD +1
System and method for detecting termination of an application instance using locks
InactiveUS20060190453A1Data processing applicationsDigital data information retrievalApplication procedureData bank
A system and method for detecting termination of an application, such as a database instance, that uses locks is described. A holding child process is started from a parent process. The holding child process connects to a monitored application instance, acquires an exclusive lock on the monitored application instance and returns a ready signal upon successfully acquiring the exclusive lock. A waiting child process is started from the parent process subsequent to the holding child process. The holding child process connects to the monitored application instance, blocks on the exclusive lock on the monitored application instance and returns a result signal upon at least one of acquiring the exclusive lock and clearing the block on the exclusive lock. The return signal is processed at the parent process. Using locks provides immediate detection that the application has terminated. Methods for blocking against the application are also described.
Owner:ORACLE INT CORP
Instructions and logic to fork processes of secure enclaves and establish child enclaves in a secure enclave page cache
ActiveUS20160246720A1Memory architecture accessing/allocationMemory adressing/allocation/relocationApplication softwarePage cache
Instructions and logic fork processes and establish child enclaves in a secure enclave page cache (EPC). Instructions specify addresses for secure storage allocated to enclaves of a parent and a child process to store secure enclave control structure (SECS) data, application data, code, etc. The processor includes an EPC to store enclave data of the parent and child processes. Embodiments of the parent may execute, or a system may execute an instruction to copy parent SECS to secure storage for the child, initialize a unique child ID and link to the parent's SECS / ID. Embodiments of the child may execute, or the system may execute an instruction to copy pages from the parent enclave to the enclave of the child where both have the same key, set an entry for EPC mapping to partial completion, and record a page state in the child enclave, if interrupted. Thus copying can be resumed.
Owner:INTEL CORP
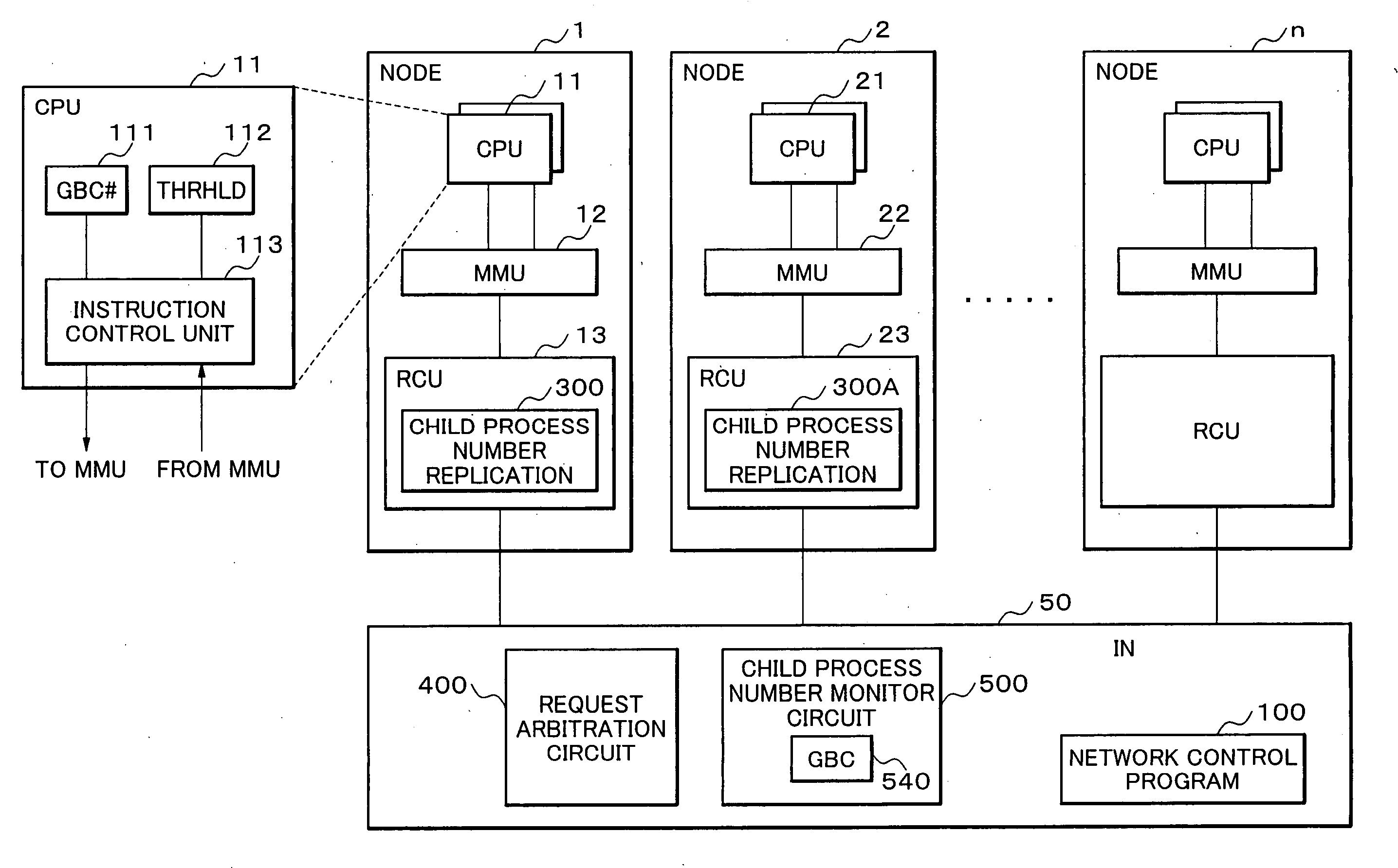
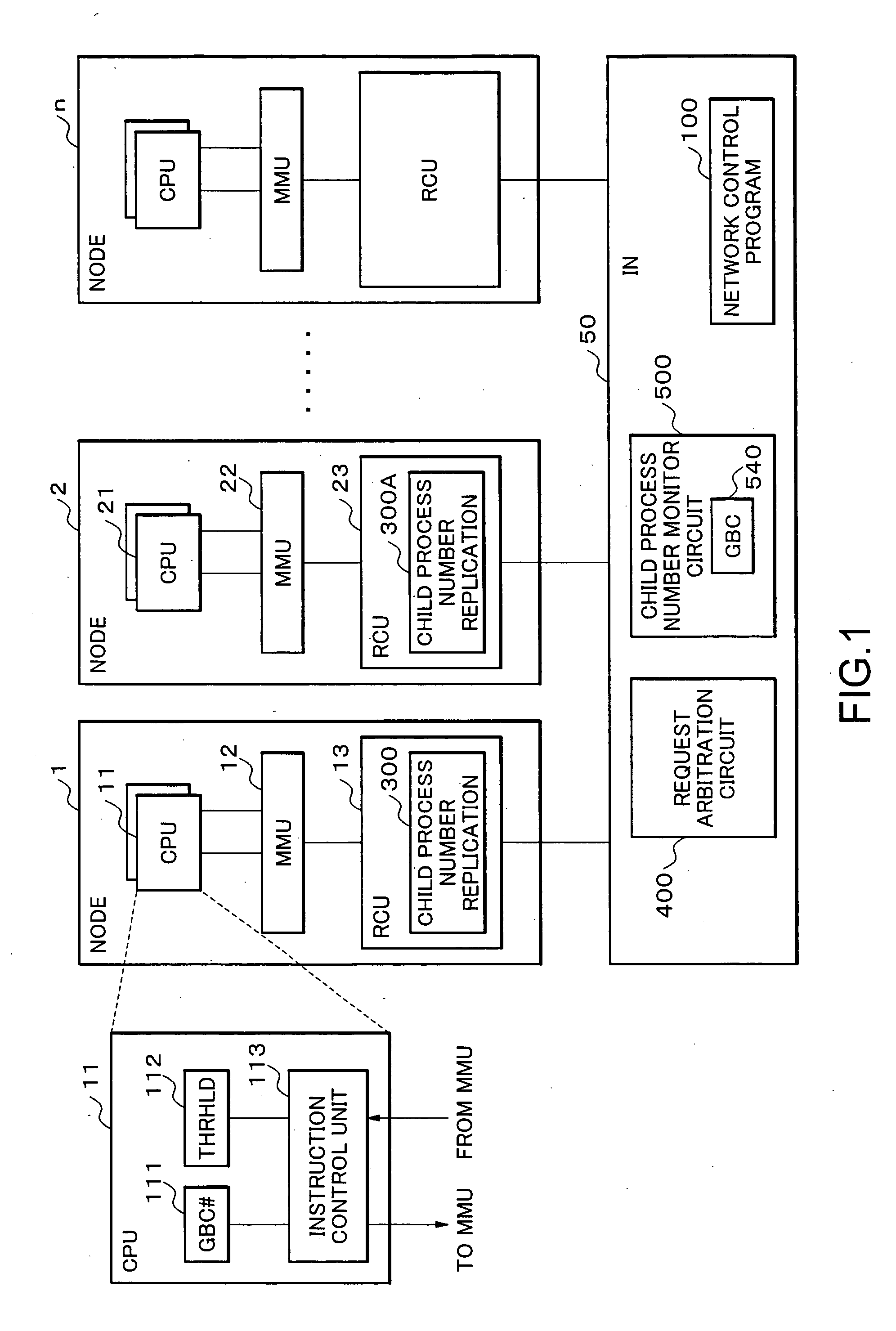
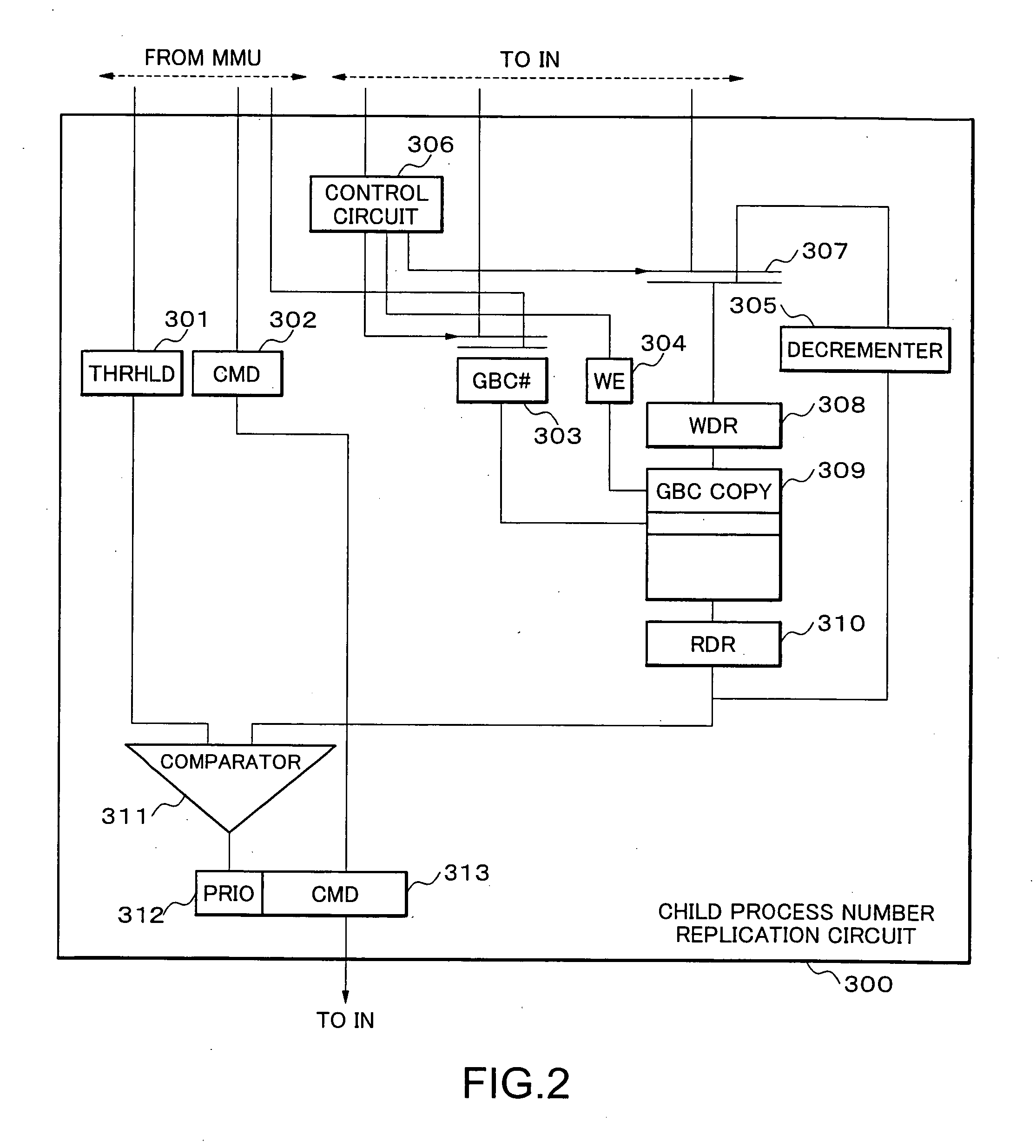
Parallel processing system, interconnection network, node and network control method, and program therefor
InactiveUS20060059489A1Shortened TATImprove system efficiencyProgram synchronisationMemory systemsNetwork controlInterconnection
The parallel processing system includes a plurality of nodes which are interconnected over an interconnection network; wherein the parallel processing system divides a computer job into parallel jobs by a parent process performed by a computer arranged in the nodes, and the parallel jobs are processed by the plurality of child processes using the plurality of computers arranged in the plurality of nodes; and a transfer process through the interconnection network from a slow child process in the child processes is performed on a basis of priority over other transfer processes.
Owner:NEC CORP
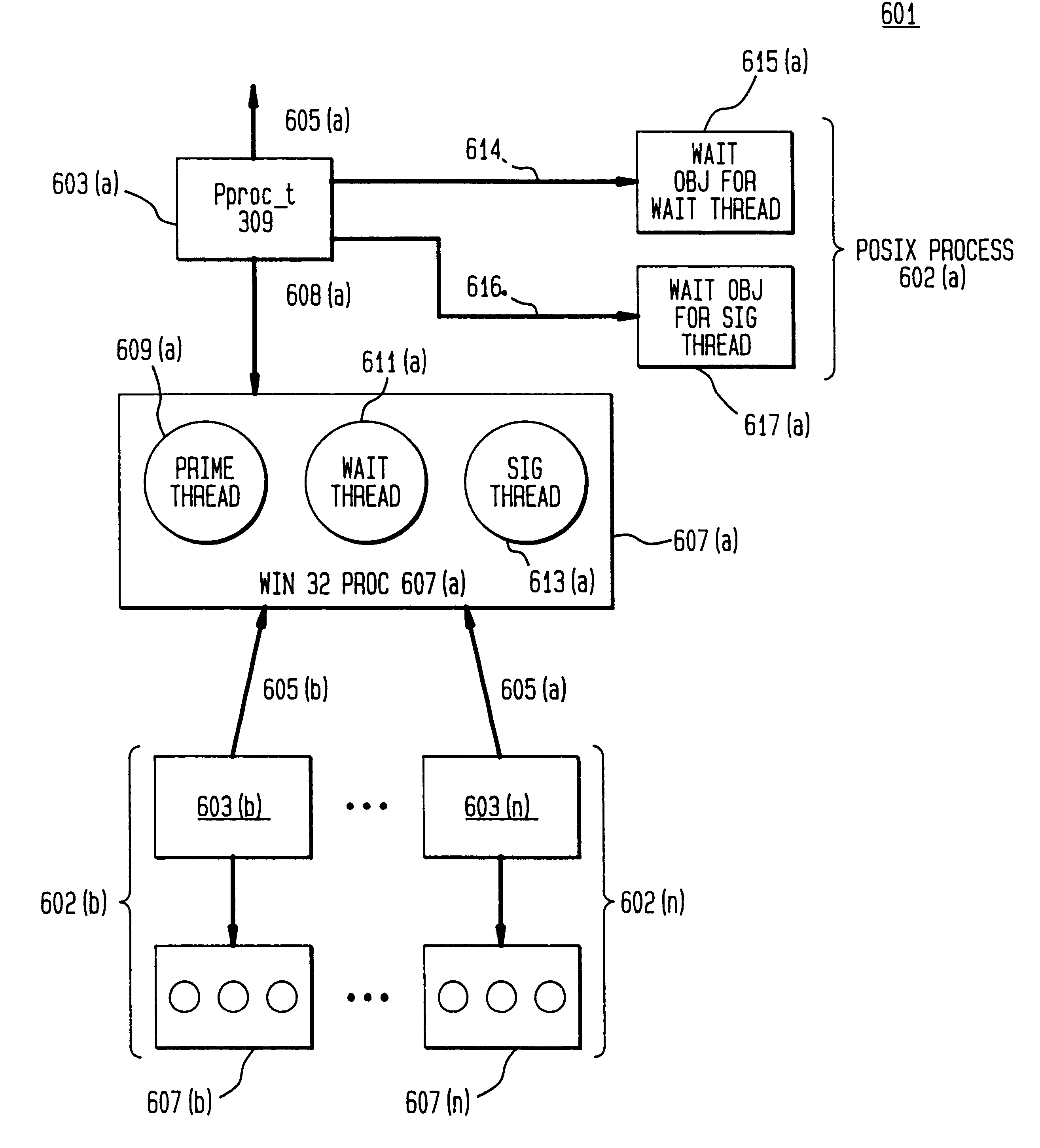
Porting POSIX-conforming operating systems to Win32 API-conforming operating systems
InactiveUS6292820B1Multiprogramming arrangementsProgram code adaptionOperational systemSignal processing
Techniques for porting operating systems of a first class whose representatives include operating systems implementing the POSIX standard to operating systems of a second class whose representatives include operating systems implementing the Win32 API. Processes belonging to operating systems of the first class are characterized by a single thread, parent-child relationships, and signal handlers that execute on the top of the stack; processes belonging to operating systems belonging to the second class have multiple threads, do not have parent-child relationships, and do not necessarily execute their signal handlers at the top of the stack. Techniques are disclosed for implementing signal handling as required for operating systems of the first class and providing a signal to a parent process of the first class when one of its child processes terminates. Processes of the second class adapted for implementing processes of the first class are disclosed, as well as implementations of the POSIX fork and exec functions using those processes.
Owner:RAKUTEN INC
Computer system security via dynamic encryption
ActiveUS20040179685A1Minimize exchangeThe process is simple and fastKey distribution for secure communicationSynchronising transmission/receiving encryption devicesSecure communicationSystemic approach
A dynamic computer system security method and system using dynamic encryption and full synchronization between system nodes. A data record from a data stream created by a source user is encrypted with an initial dynamic session key. A new dynamic session key is generated based upon a previous dynamic session key and a selected previously encrypted data record. The new dynamic session key is then used to encrypt the next data record. A central authority is used to synchronize and authenticate both source and destination users with dynamic authentication keys. The central authority and users constantly regenerate new dynamic authentication keys. A child process is forked to ensure synchronization and authentication of dynamic authentication keys of each node upon a request for a secure communication establishment from a user. The central authority generates the initial dynamic session key with the current dynamic authentication key to begin a secure communication session.
Owner:MOXCHANGE LLC
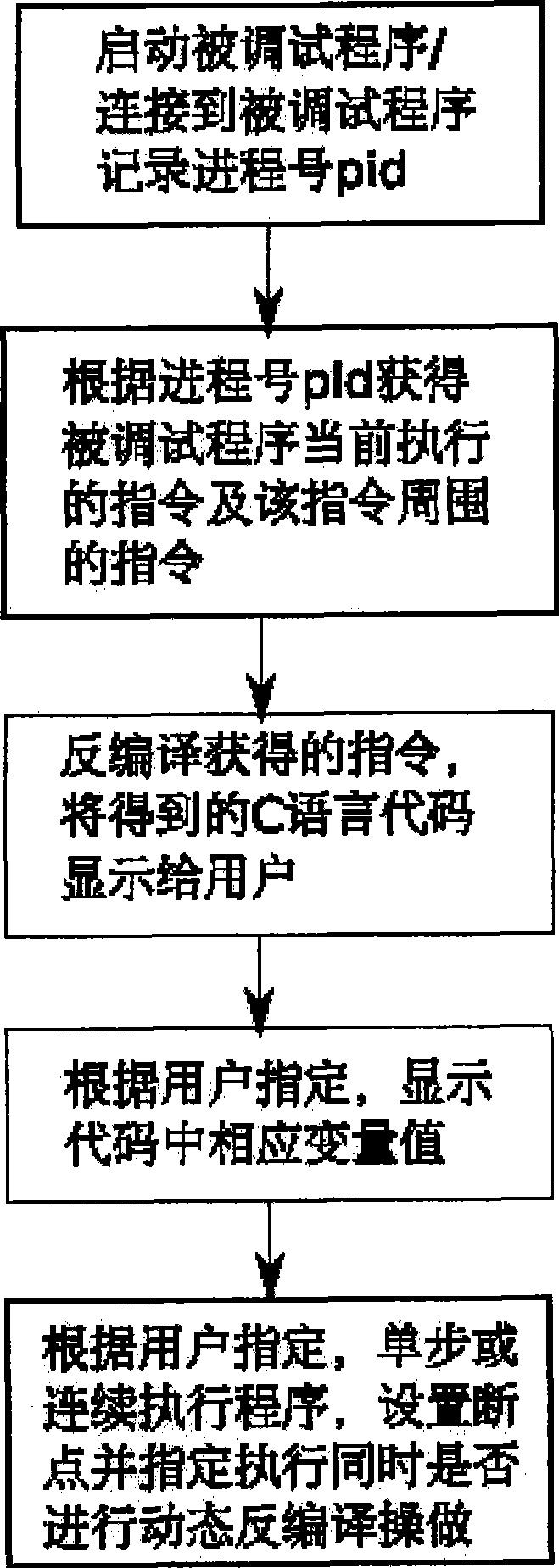
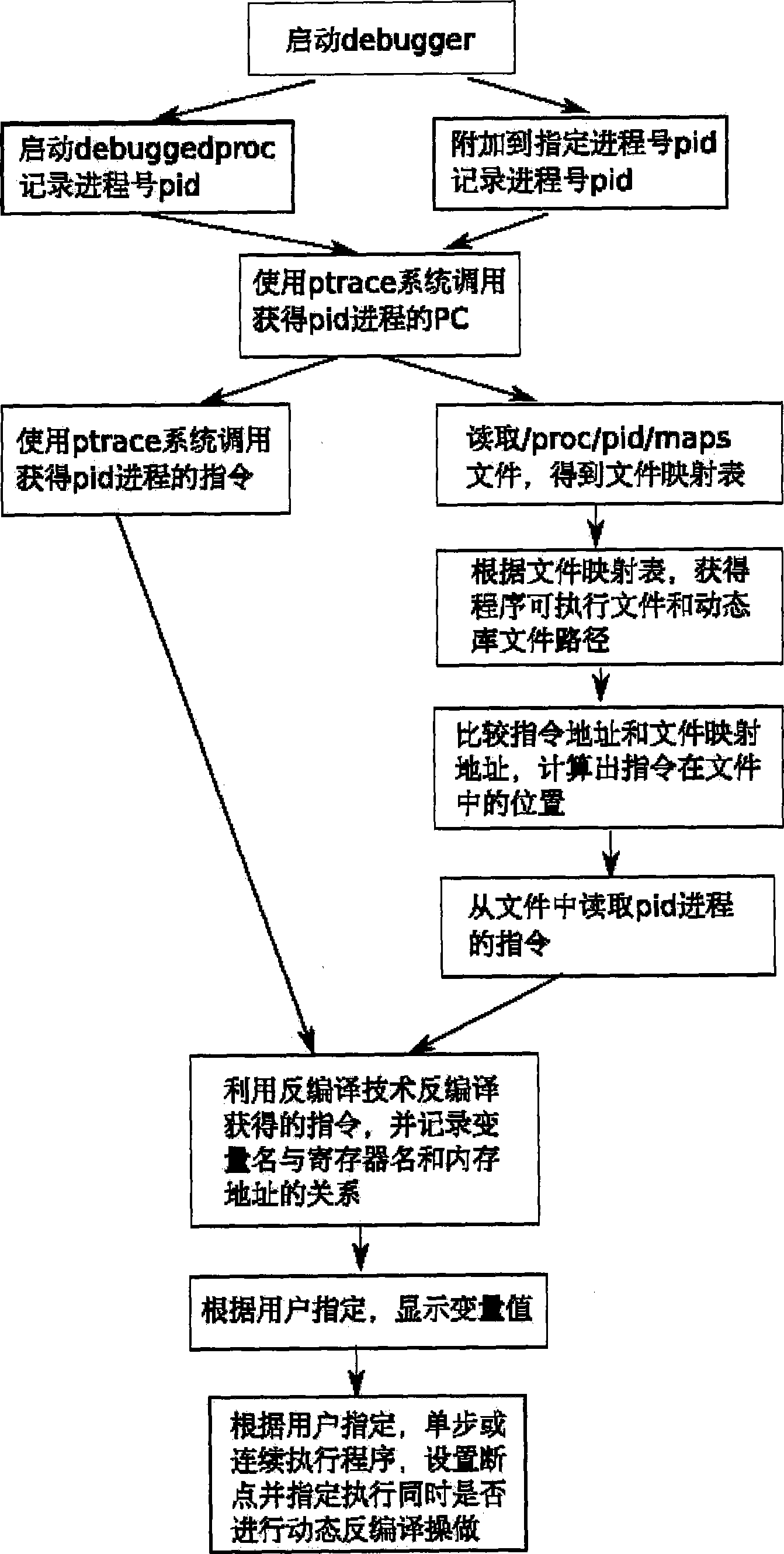
Method for debugging binary application program based on dynamic inverse compiling technique
ActiveCN101414278AImprove efficiencyEasy to callSoftware testing/debuggingProgram controlApplication softwareDebugger
The invention relates to a debug method of a binary application program based on a dynamic decompiling technology. Debug staff starts the application program by a debugger or assigns a process number of a process to be debugged, if the debugged program is started by the debugger, the debugger records a process number of a sub-process; when the program is executed to a breakpoint, an operating system suspends the debugged program, and the debugger obtains a command; an instruction of the debugged program is obtained by a system call or application programming interface (API) which is provided by the operating system, the instruction is decompiled by the dynamic decompiling technology, and the obtained C language code is displayed to the debug staff. The debug method has the advantages of being capable of facilitating the debug staff to debug the binary application program without reading complicated assembly codes, and effectively enhancing efficiency of debugging programs.
Owner:INSIGMA TECHNOLOGY CO LTD
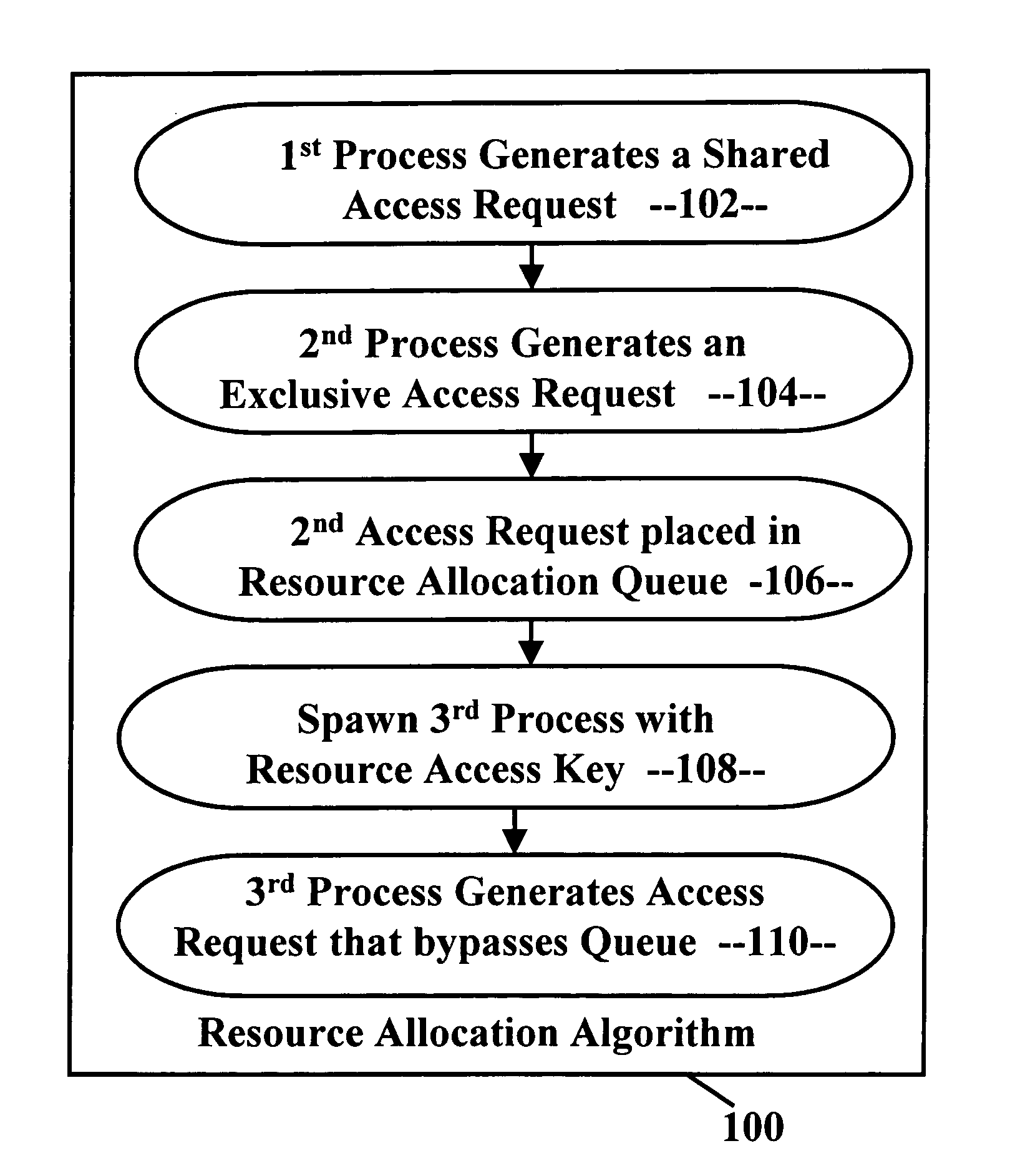
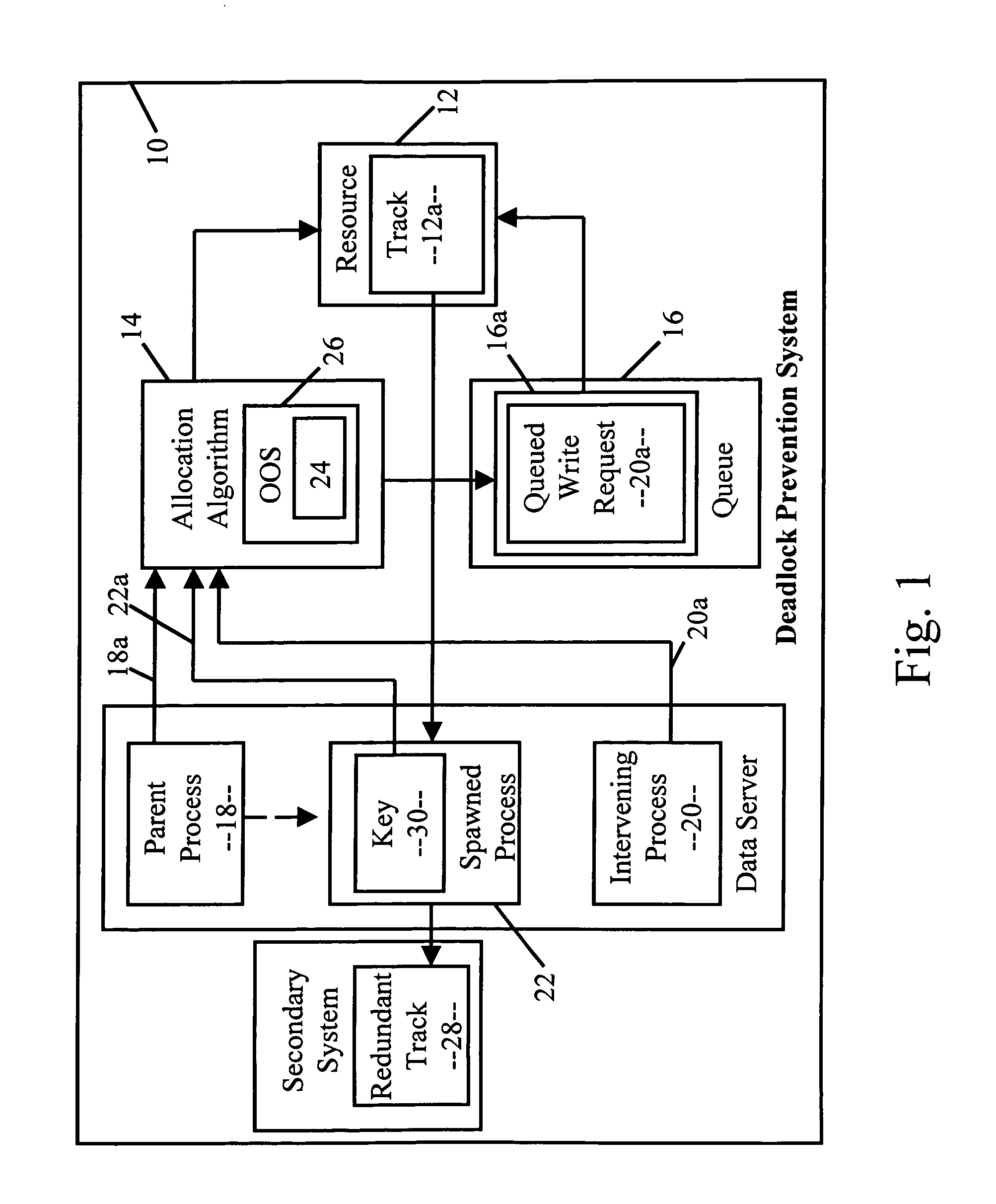
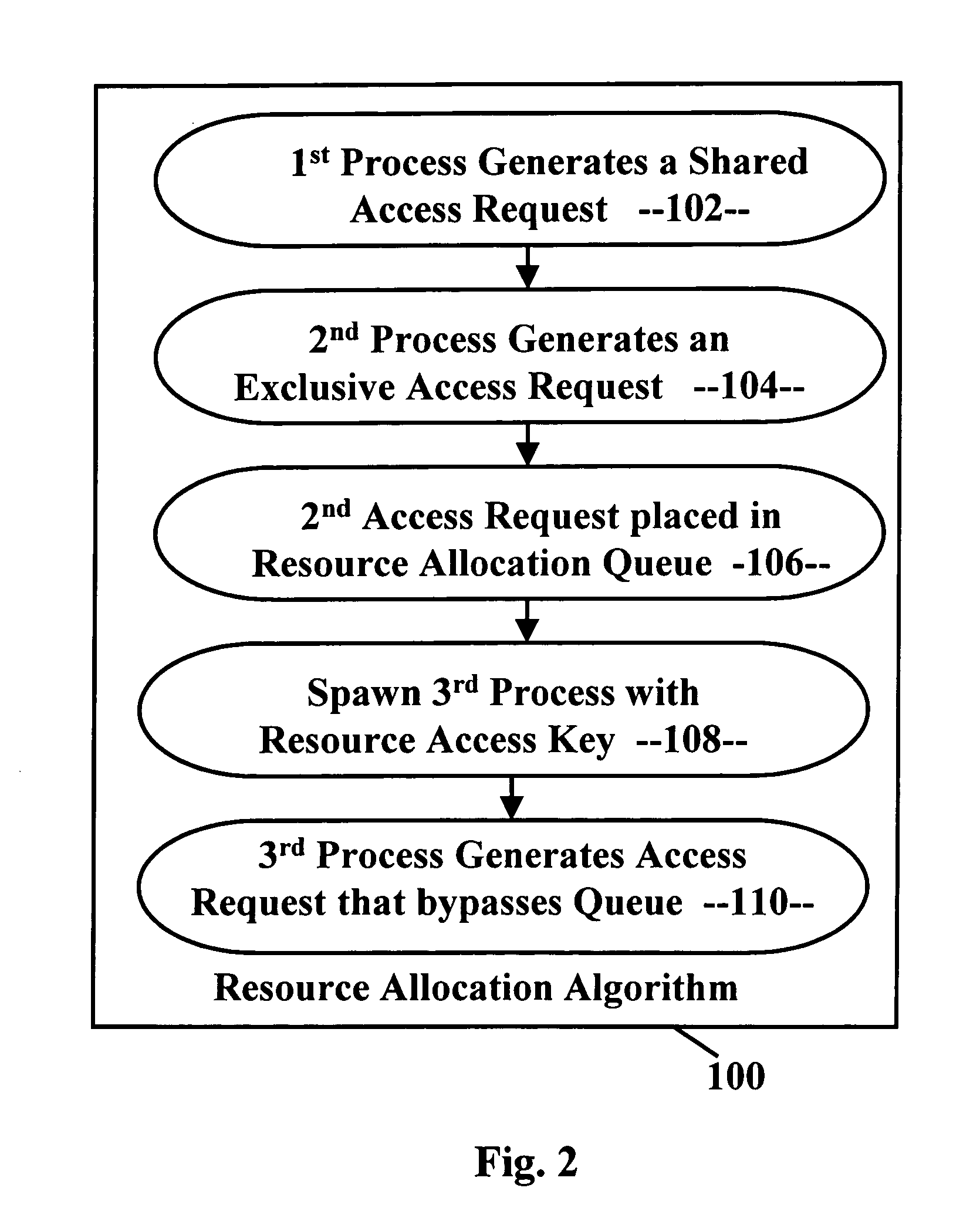
Deadlock-prevention system
A deadlock-prevention system includes a resource-access key passed from a parent process to a spawned process that includes the parent processes' level of access to a system resource. Optionally, the resource-access key includes a shared-access request based on the expectation by the parent process that the child process will need shared-access to a system resource. The resource-access key is presented by the child process to a resource-allocation algorithm. The resource-allocation algorithm identifies the resource-access key, allows the child process to bypass a resource-allocation queue, and grants shared access to the resource to the child process, preventing deadlock.
Owner:JARVIS THOMAS C +1
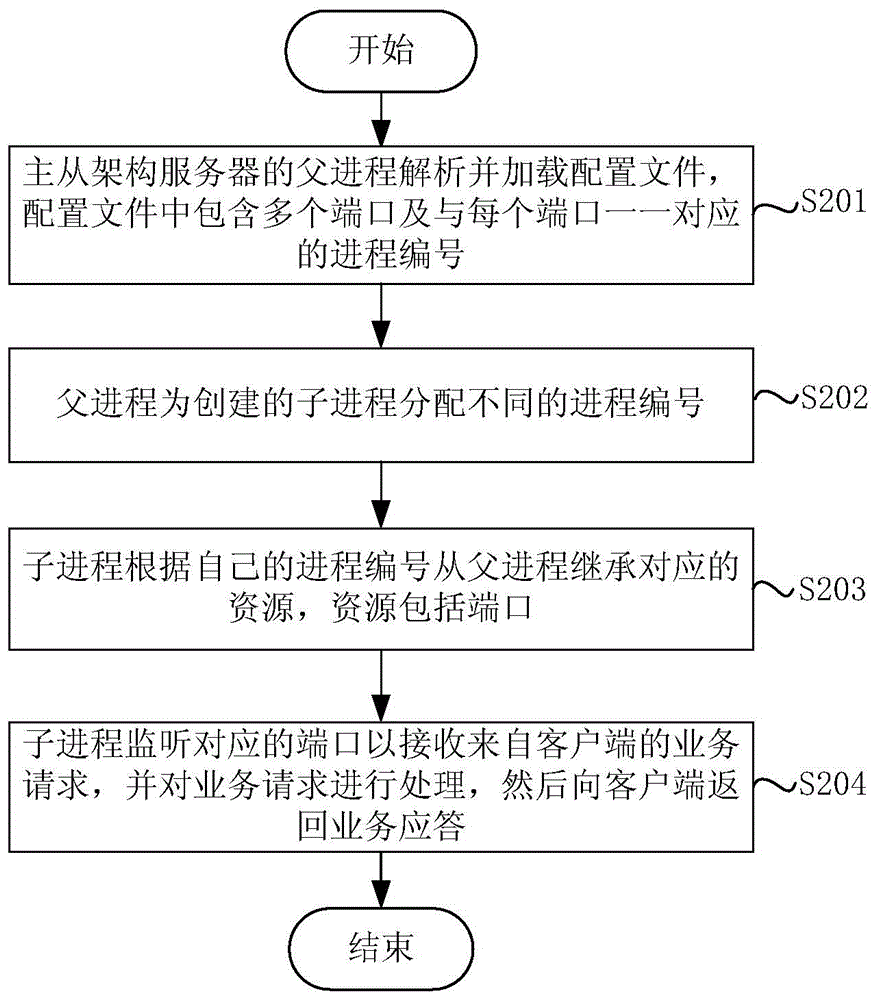
Master-slave architecture server, service processing method thereof and service processing system thereof
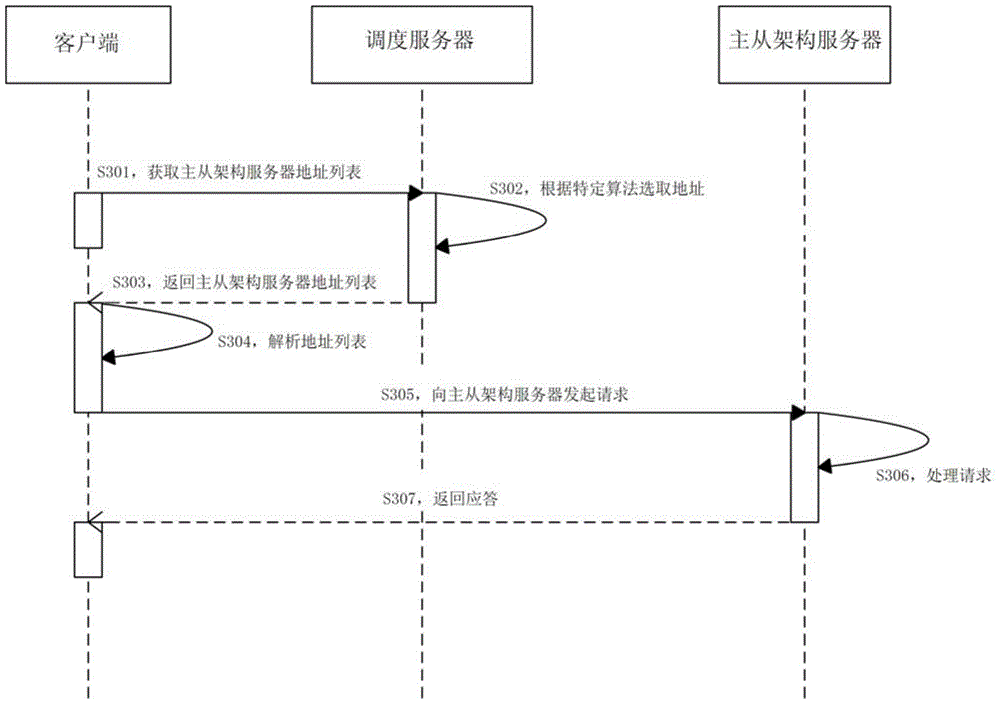
ActiveCN105337755AAvoid panic herdImprove processing efficiencyData switching networksSerial codeParent process
The invention discloses a master-slave architecture server, a service processing method thereof and a service processing system thereof. The service processing method of the master-slave architecture server comprises the steps of analyzing and uploading a configuration file by a parent process of the master-slave architecture server, wherein the configuration file includes multiple ports and a process serial number which is in one-to-one correspondence with each port; distributing different process serial numbers for established sub-processes by the parent process; inheriting corresponding resources from the parent process based on the process serial number by each sub-process, wherein the resources include ports; and, by the sub-processes, monitoring corresponding ports to receive a service request from a client, processing the service request and then returning a service response to the client. According to the embodiment of the invention, as different sub-processes respectively monitor reading-writing events of different ports, the service request of one port can be completely processed by one sub-process, the sub-processes are completely independent and no longer compete with each other for the service request, and a thundering-herd phenomenon is accordingly avoided.
Owner:TAOBAO CHINA SOFTWARE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com