Patents
Literature
406 results about "Telnet" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
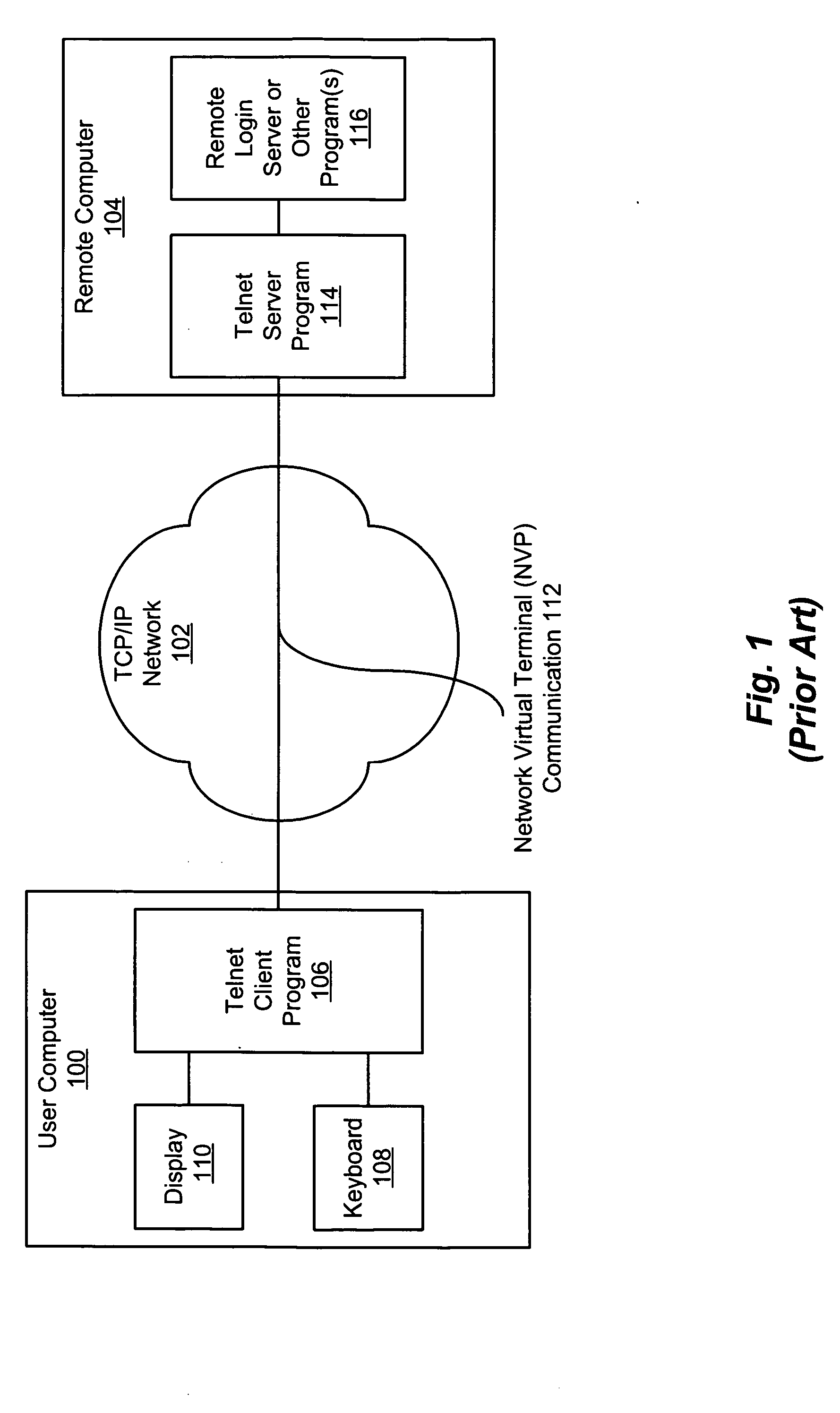
Telnet is an application protocol used on the Internet or local area network to provide a bidirectional interactive text-oriented communication facility using a virtual terminal connection. User data is interspersed in-band with Telnet control information in an 8-bit byte oriented data connection over the Transmission Control Protocol (TCP).
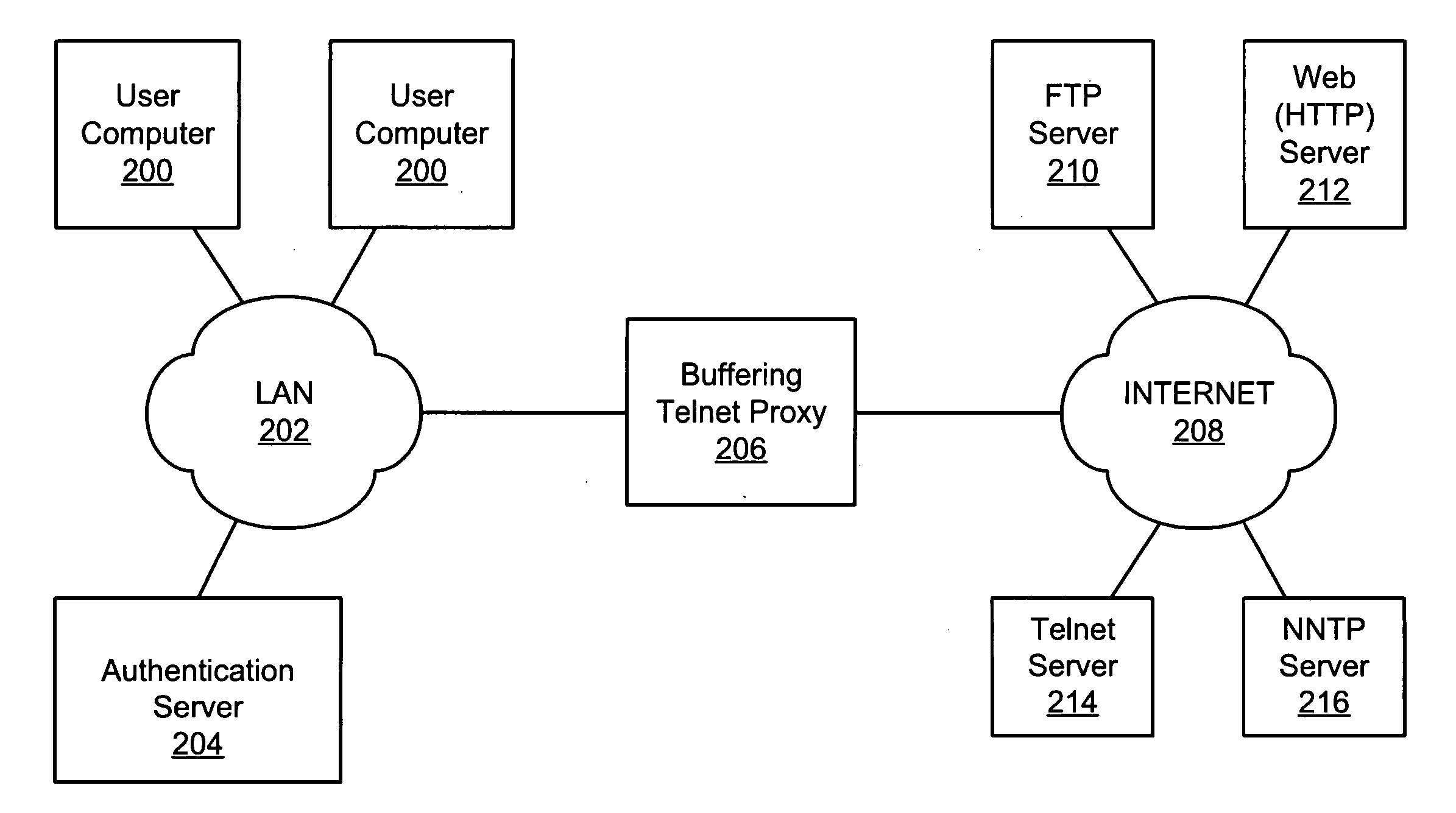
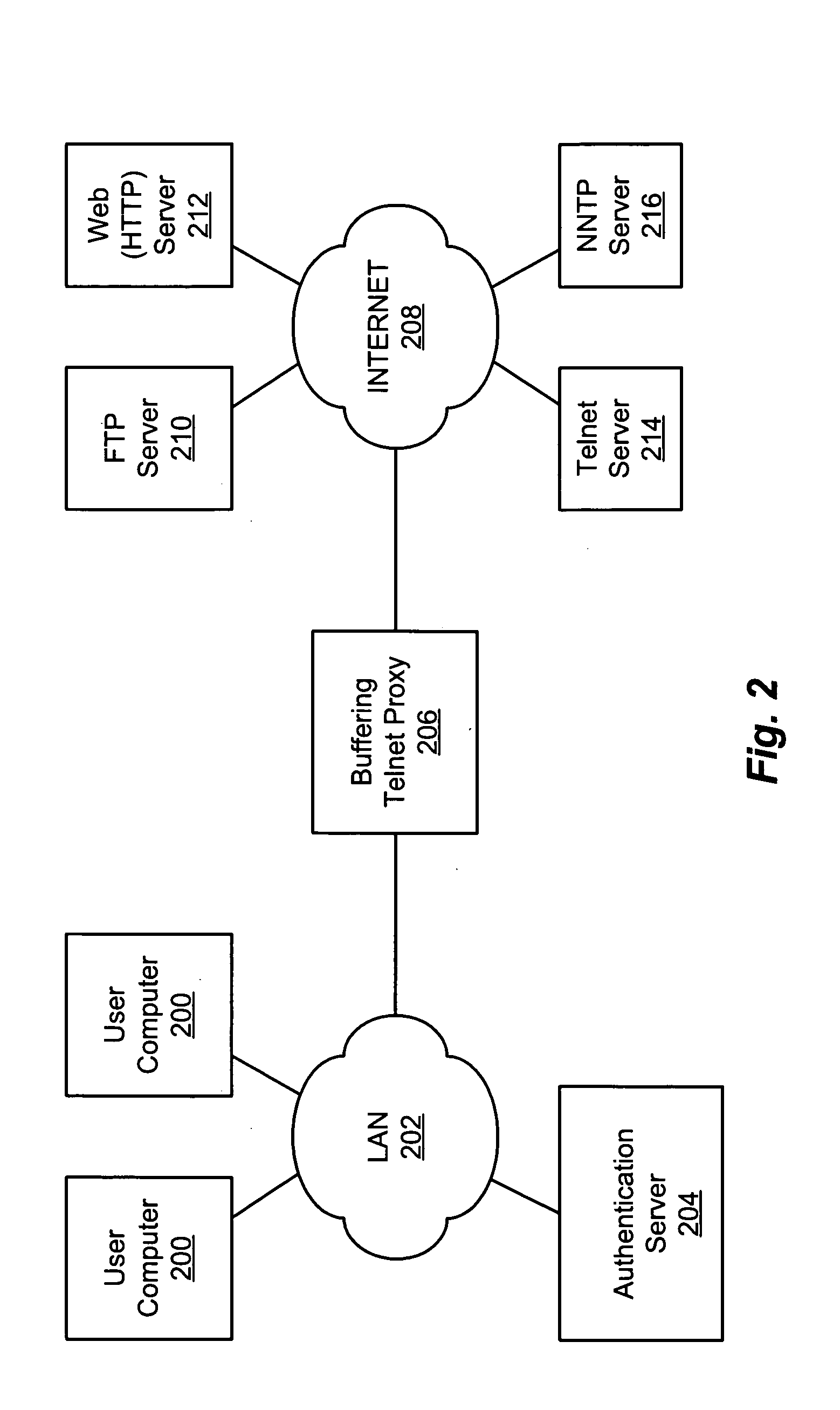
Buffering proxy for telnet access
A single- or multi-protocol buffering proxy accepts communication option negotiation commands from a client before establishing a connection between the client and a host. The proxy negotiates a limited set of options with the client before the connection is established and buffers (accepts and temporarily stores without responding to) other option negotiation commands from the client. The proxy accepts credentials from a user and establishes, or denies the connection based on the credentials. If the connection is established, the proxy buffers option negotiation commands sent by the host. After the proxy logs in to the host on behalf of the user or the user logs in directly, the proxy sends each party's buffered option negotiation commands to the other party, ceases buffering option negotiation commands and enters a “pass-through” mode, in which the proxy passes characters and commands between the parties until the session ends. The proxy uses the credentials to allow or deny subsequent connection requests, without re-prompting for credentials.
Owner:CA TECH INC
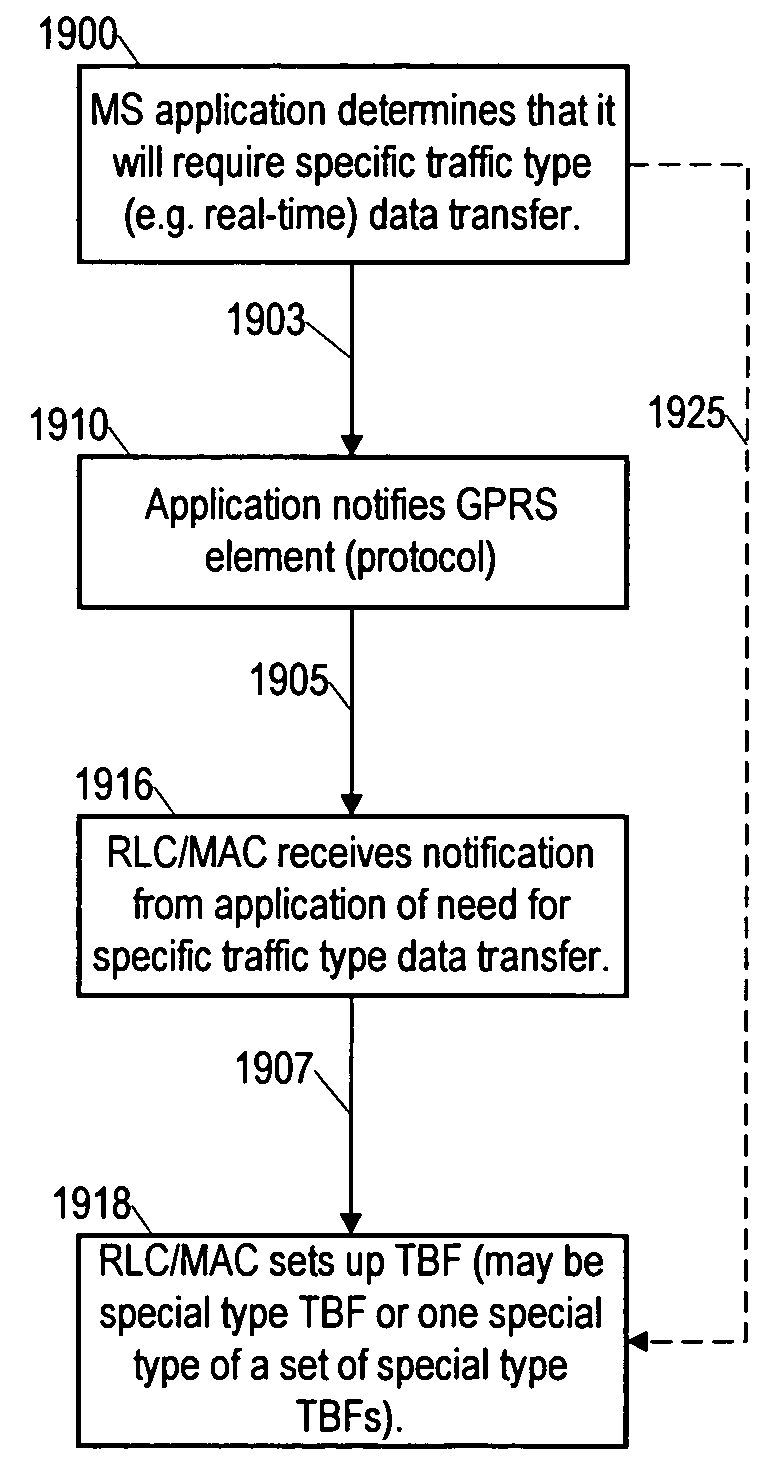
Method and arrangement for transferring information in a packet radio service with application-based choice of release mode
InactiveUS7054268B1Comfortable to useLower latencyError preventionFrequency-division multiplex detailsGeneral Packet Radio ServiceTraffic capacity
A method as described by which an application executing in an application layer of a multi-layer communication protocol forming part of a general packet radio service (GPRS) session can signal for the setup and release of Temporary Block Flow (TBF) which will not be released during application execution in silent (inactive) periods. When applications such as voice, telnet or web browsing have specific traffic type data that have inactive periods between active periods are to be carried over GPRS, the session consists of multiple active periods. Current TBF release procedures lead to multiple TBF setups during such sessions. With the method described, a special type of TBF can be set up with special procedures for release of this TBF which greatly minimizes the need for multiple TBF setups during a session containing data transfers with inactive periods between active data transmissions.
Owner:NOKIA MOBILE PHONES LTD
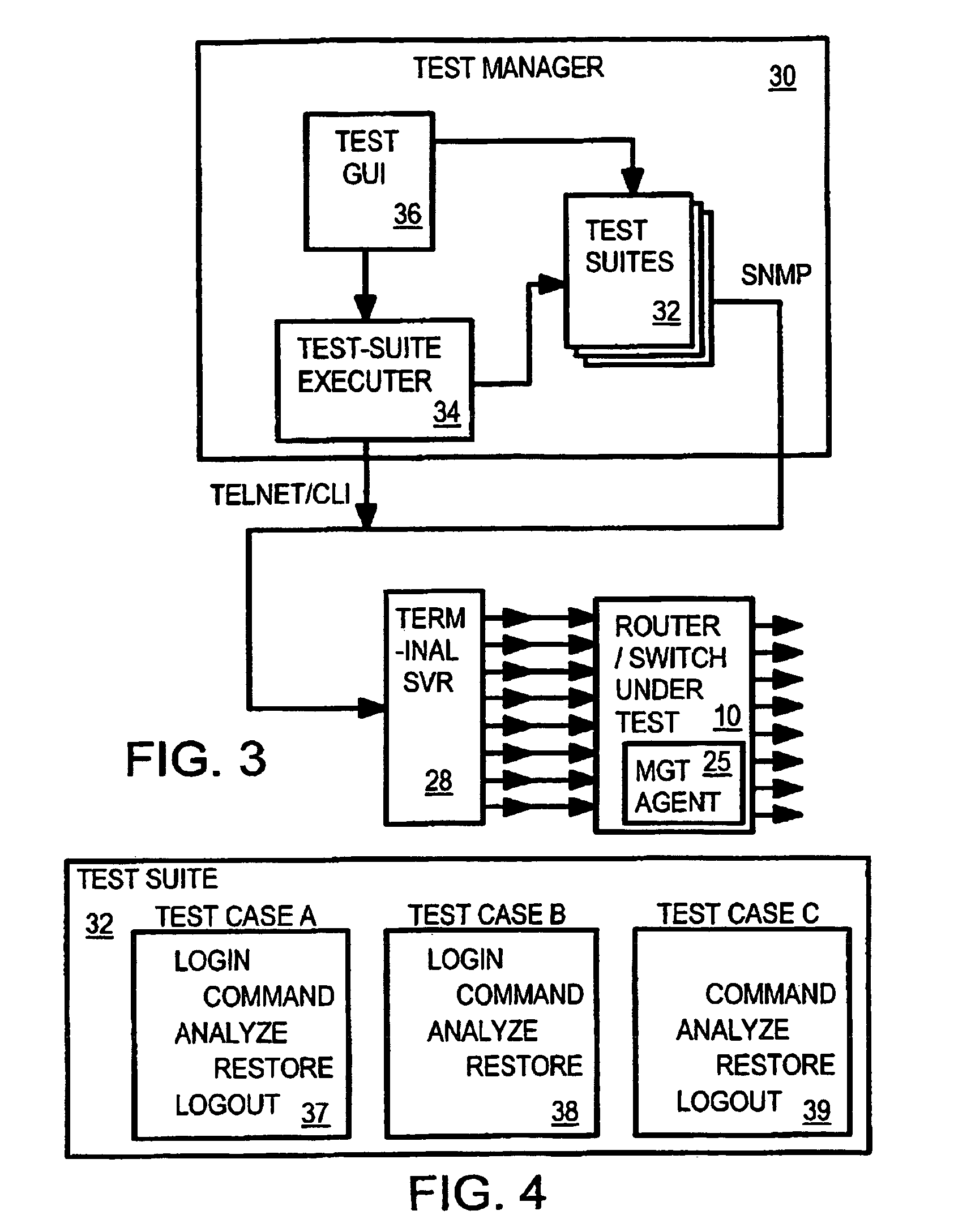
Interactive automatic-test GUI for testing devices and equipment using shell-level, CLI, and SNMP commands
ActiveUS7010782B2Digital variable displayResistance/reactance/impedenceComputer hardwareCommand-line interface
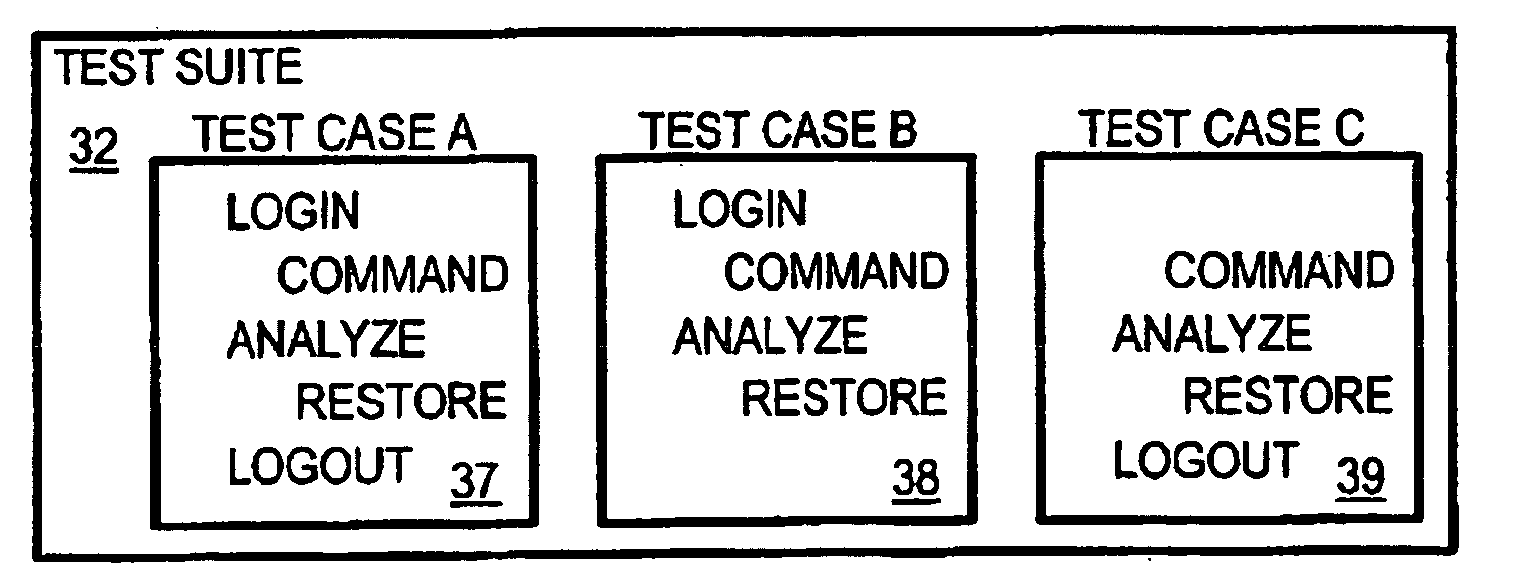
A test manager software program includes an interactive test graphical-user-interface (GUI) for testing network devices using high-level networking commands. The test GUI allows the test engineer user to enter high-level commands such as Simple Networking Management Protocol (SNMP) commands that read values in a management information database in a network device under test. The high-level commands can be sent from the test manager using a command-line interface (CLI) in a telnet session opened to the network device during testing. The user specifies high-level test, analyze, and restore commands in test cases that are collected into test suites. Rules for logging on to the network device under test are stored that include expected prompts from the network device and user responses such as passwords. Addresses of the network device under test can be re-mapped for testing other devices so the test suites can be reused.
Owner:SAPPHIRE INFOTECH
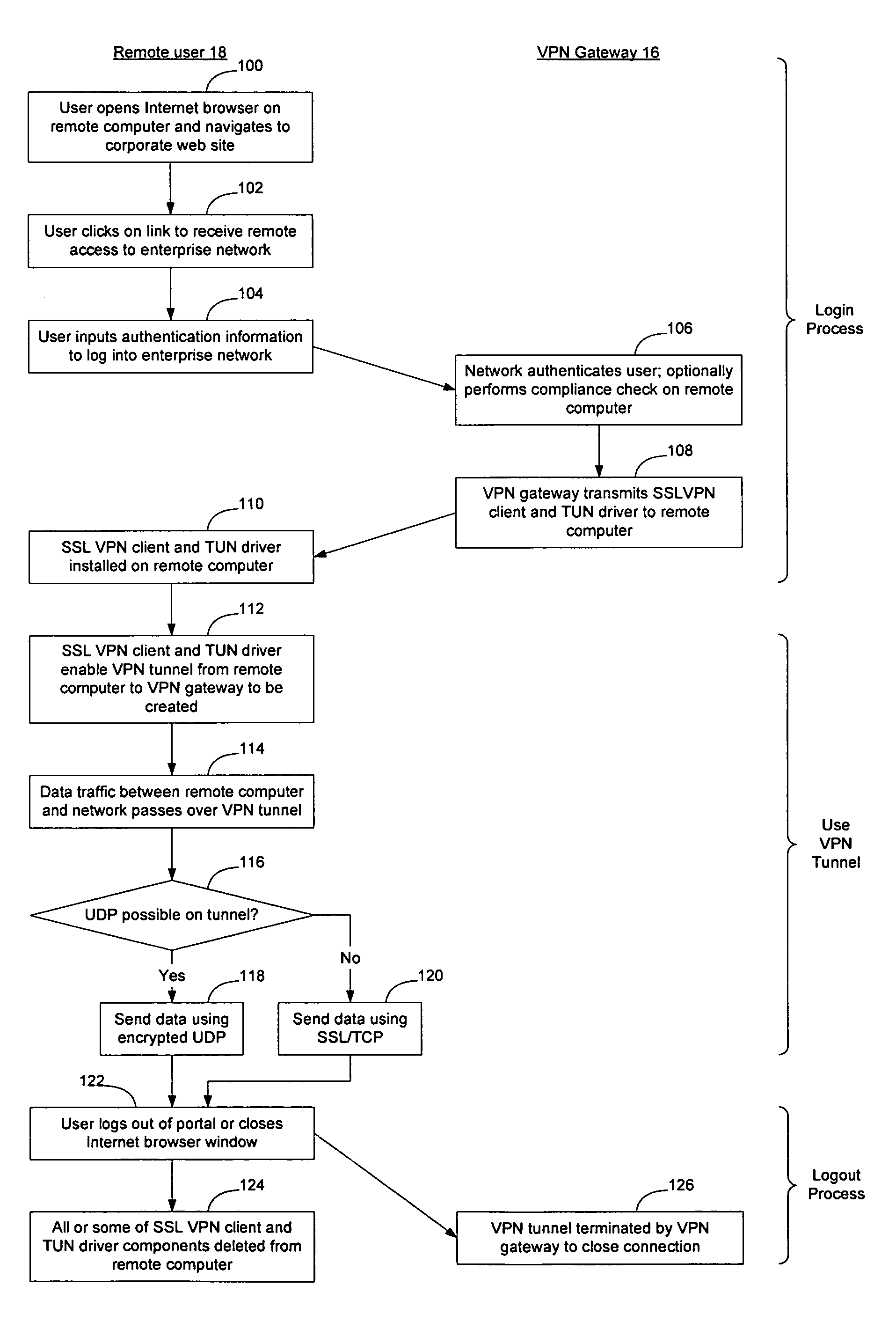
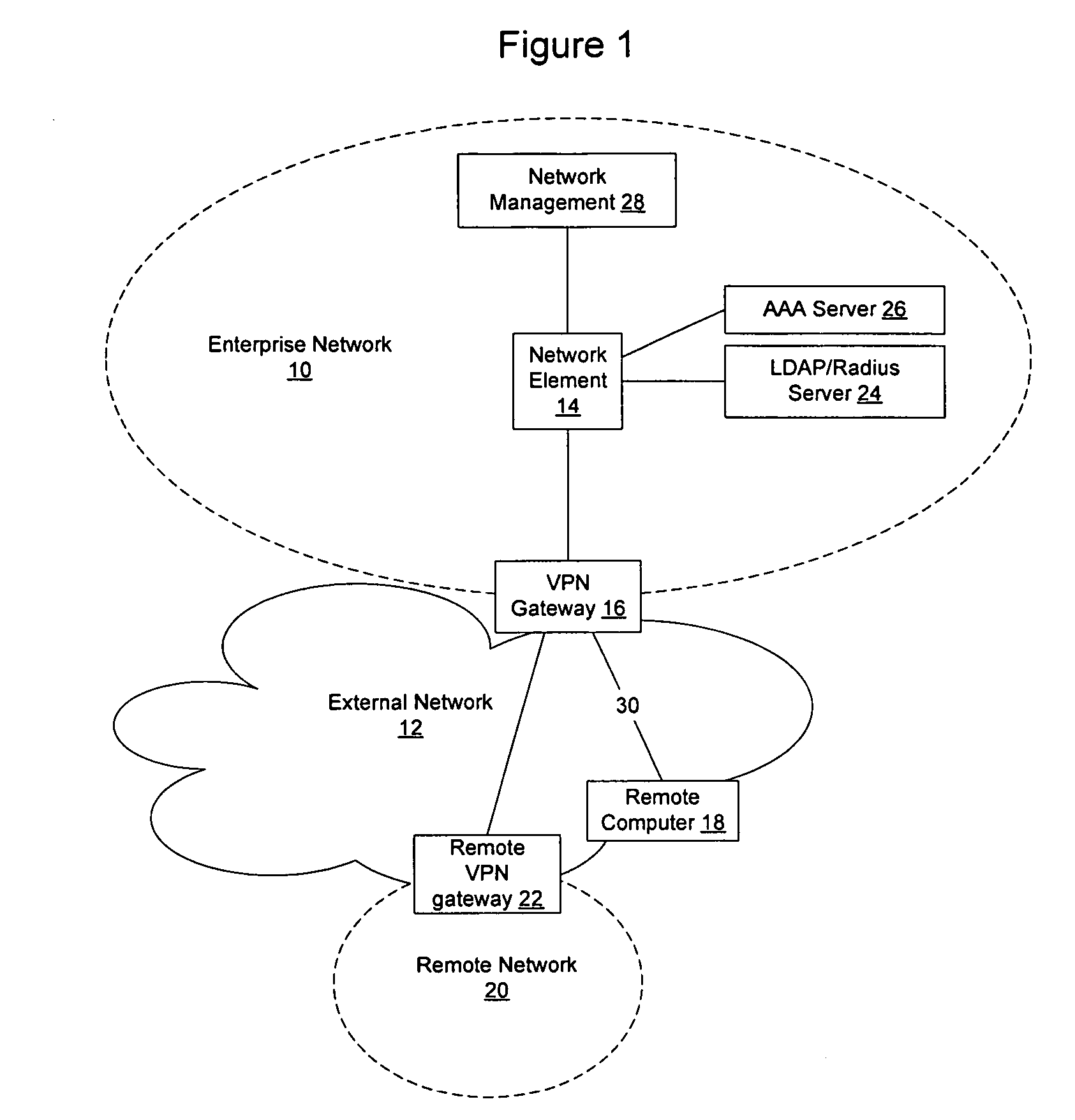
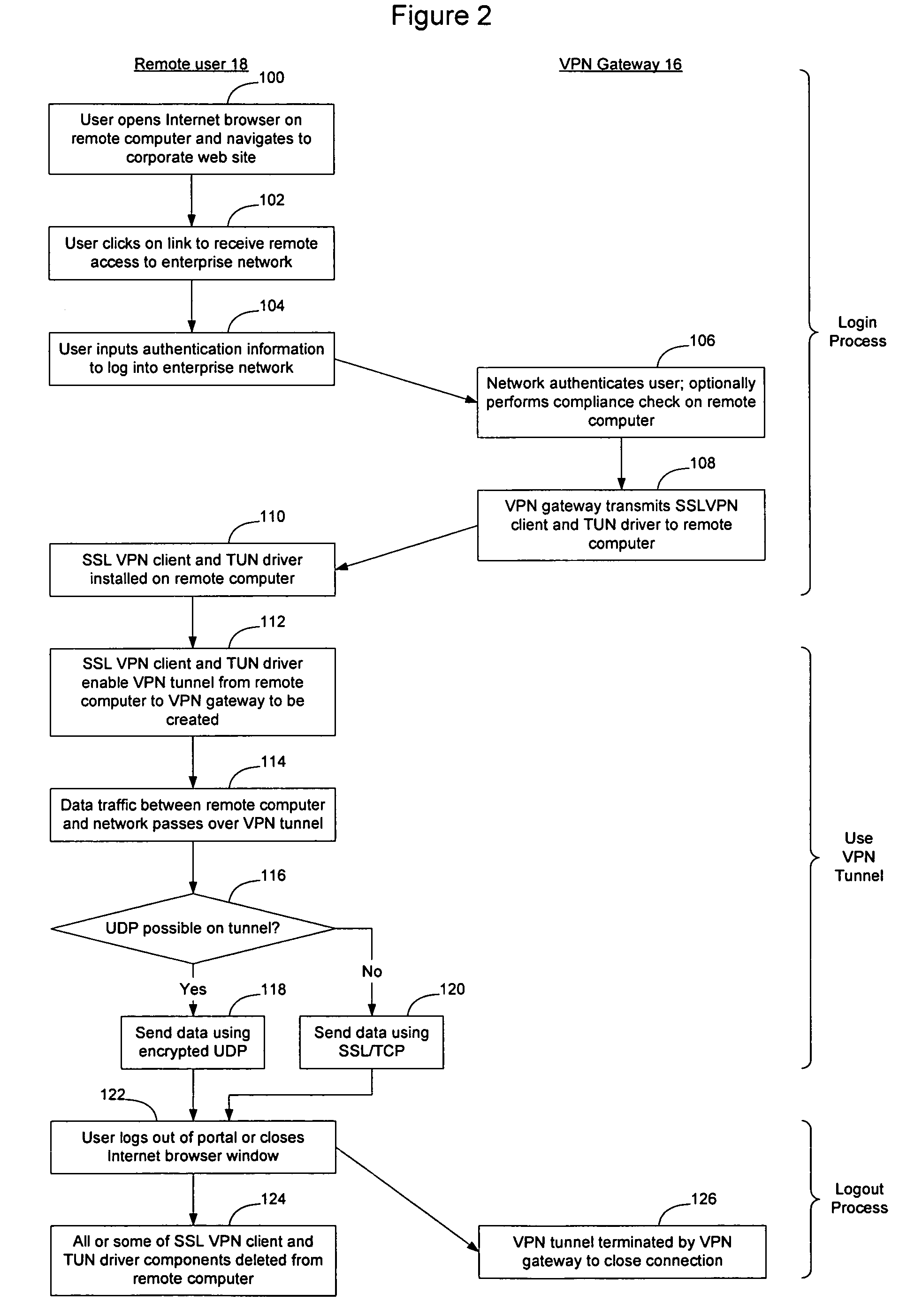
Method and apparatus for providing remote access to an enterprise network
InactiveUS20070150946A1Overcomes drawbackMultiple digital computer combinationsProgram controlData packThe Internet
VPN tunnels may be established using an Internet browser and dynamically downloadable VPN client software that may be installed as part of a remote login process. By causing the VPN client software to be dynamically downloaded during the session, the remote user does not need to pre-load any software onto the computer that will be used as the remote computer. Thus, any computer with an Internet browser may be used to log into the enterprise network without first requiring the user of that computer to acquire rights to install a VPN client on the computer. By causing some or all of the dynamically downloaded software components to be deleted upon termination of the session, the components of the software may be made to be not available once the session has ended. Encrypted UDP may be used to transmit data on the VPN tunnel where exchange of an initial UDP packet indicates the availability of UDP connectivity.
Owner:AVAYA INC
Network physical topology discovering method and network management server based on SNMP
ActiveCN101764709AOvercoming incomplete buildsPromote resultsData switching networksIp addressNetwork management
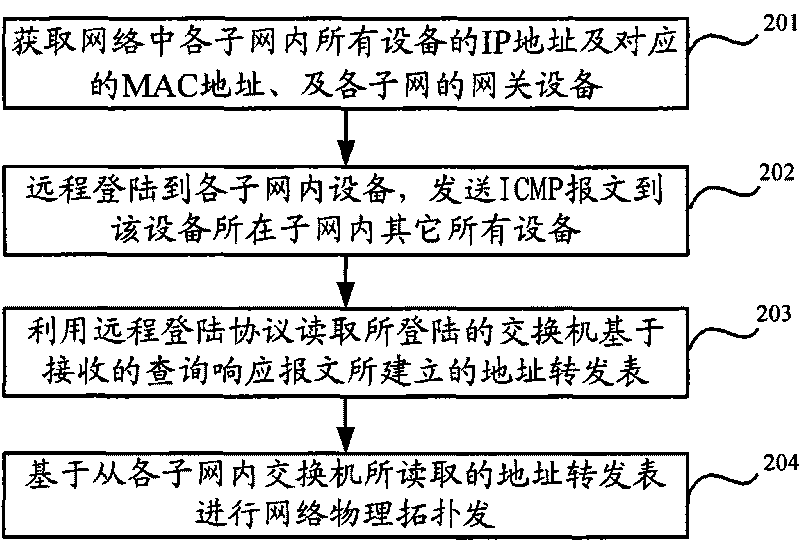
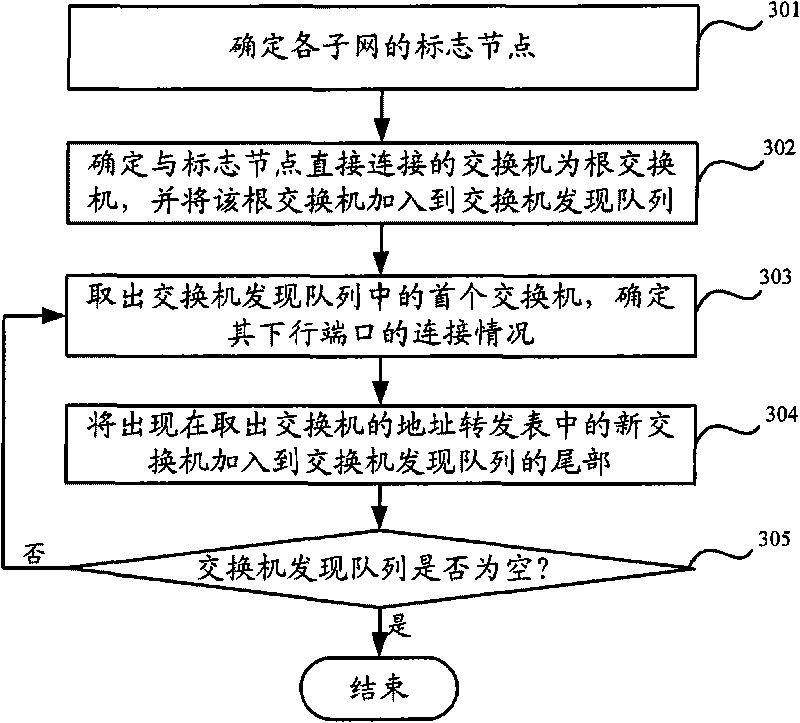
The invention relates to the field of network topology discovery, in particular to a network physical topology discovering method and a network management server based on SNMP. The method comprises the following steps: obtaining IP addresses and corresponding MAC addresses of all devices in subnets in the network and gateway devices of the subnets; utilizing a telnet protocol to perform remote login to all the devices in the subnets, controlling each logged-in device to send an inquiry request message to all other devices in the subnet at which the device is located; utilizing the telnet protocol to read address forwarding tables which are established by logged-in exchangers based on the received inquiry response messages; and carrying out network physical topology discovery based on the address forwarding tables which are read from the exchangers in the subnets. The network management server utilizes the telnet protocol to complete the network physical topology discovery. The method and the network management server enable the exchangers in the network to establish relatively complete address forwarding tables, and compared with the results of a traditional network physical topology discovery, the results of the physical topology discovery have a great improvement.
Owner:RUIJIE NETWORKS CO LTD
Real-time flow media communication transmission system and method
InactiveCN1764184AImprove performanceReduce jitterData switching networksExchange networkNetwork conditions
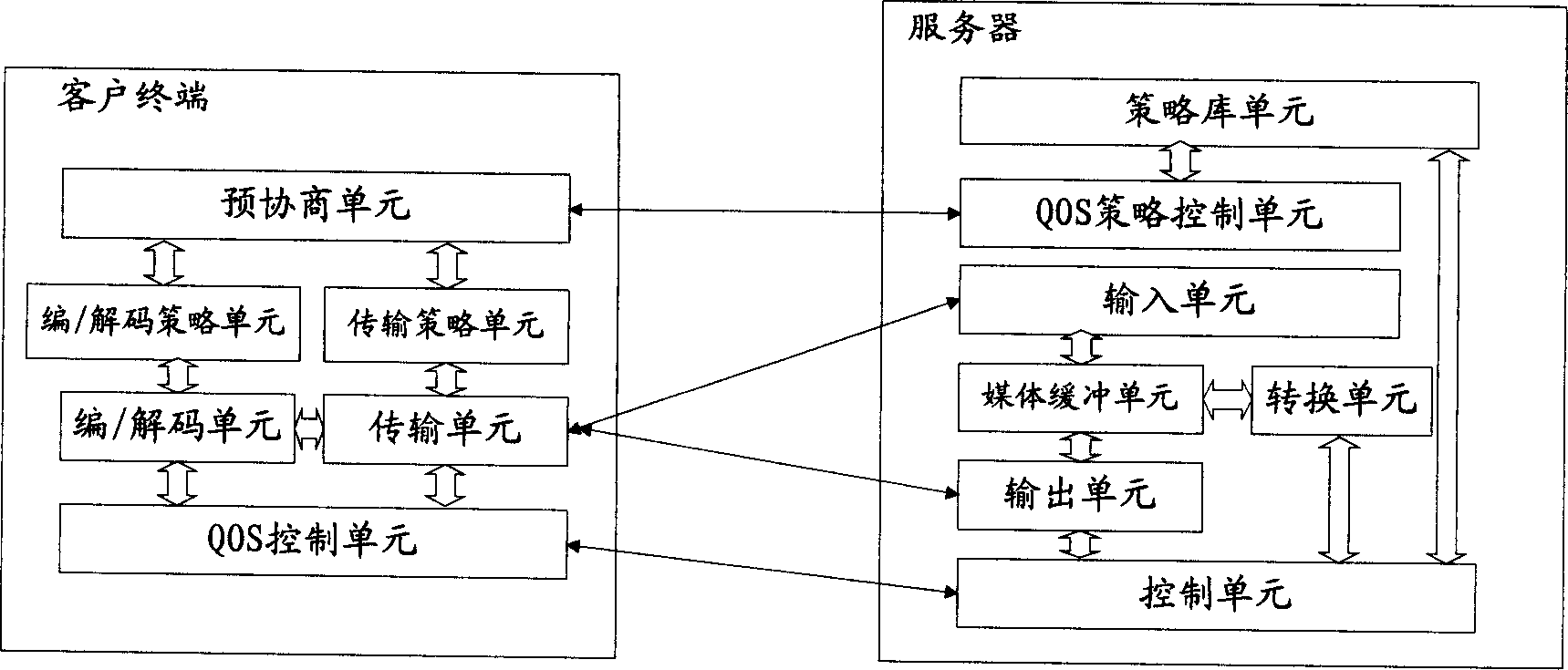
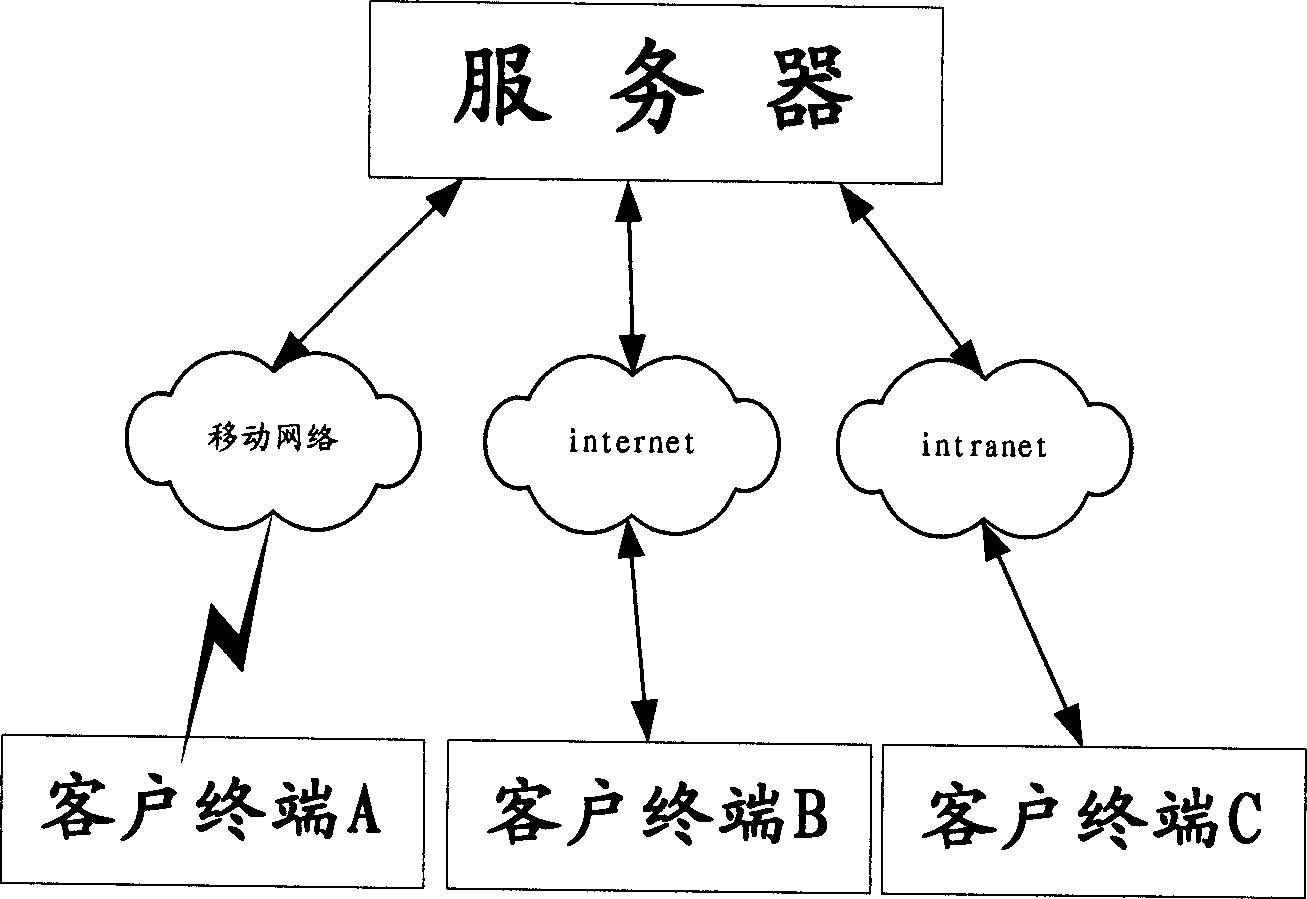
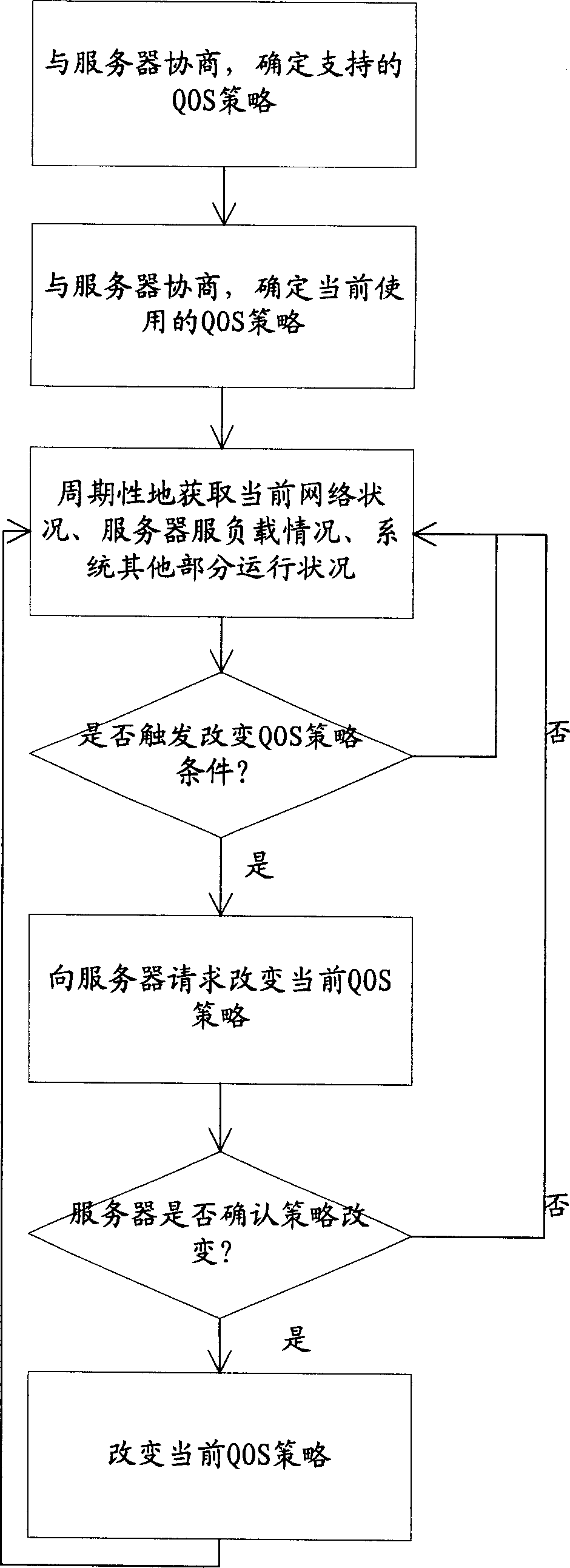
The invention provides a real-time flow media communication transmission method ,which comprises: 1. prestoring strategy to support different QOS both in server and client terminal respectively; 2. client terminal and server negotiate and determine current QOS strategy and form local strategy gradient table when client telnets; 3. server sets the conversion and transmission or client terminal according to negotiated result; 4. the client terminal and server exchange network running condition periodically to adjust QOS strategy real time. This invention comprehensive evaluates the prestored parameters, current network condition, current server load condition and objective running state to adaptive control encode and transmission means, and makes the whole system on optimal state.
Owner:ZTE CORP
System monitoring method based on cloud platform
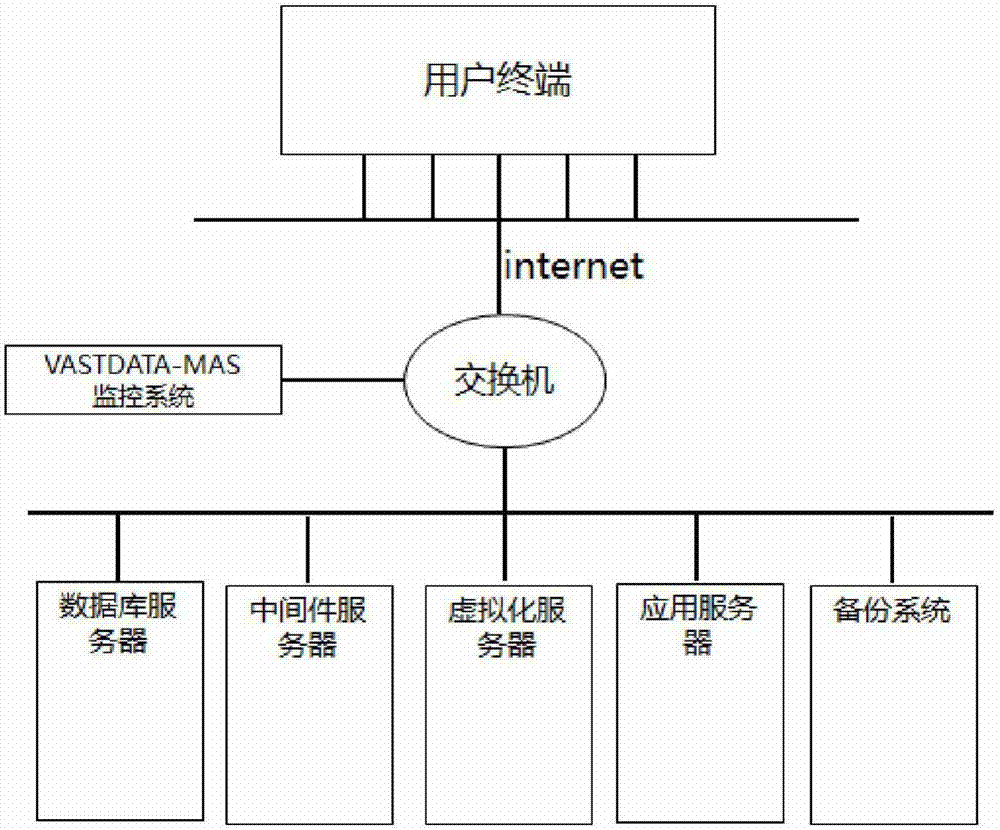
The invention discloses a system monitoring method based on a cloud platform and belongs to the computer technology field. Two ways such as 'Automatic discovery' and by-hand input are used for configuring configuration parameters of monitored objects in data acquisition of managed resources, and performance data is acquired by multiple acquisition ways such as SNMP Agent, Telnet, Vast data-MAS Agent, Http (Hyper Text Transport Protocol), ICMP (Internet Control Messages Protocol), TCP (Transmission Control Protocol) and IDBC (Internet Data Base Connection) via an active turning mechanism; warning messages and data from a third-party managing tool and a private user system are integrated and received by multiple ways; data is collected by a VASTDATE-MAS collecting and scheduling module and compared with a preset system threshold, and perfect event triggering, inquiring, informing, processing, and statistic analysis functions can be provided by the VASTDATE-MAS event and an informing module; the system monitoring method is easy to deploy, can realize plug and play and one-touch application.
Owner:BEIJING VASTDATA TECH
Wireless communication module
InactiveUS7309260B2Electronics SimplifiedEliminate needCoupling device detailsNetwork connectorsWireless communication protocolWireless Application Protocol
Owner:LANTRONIX
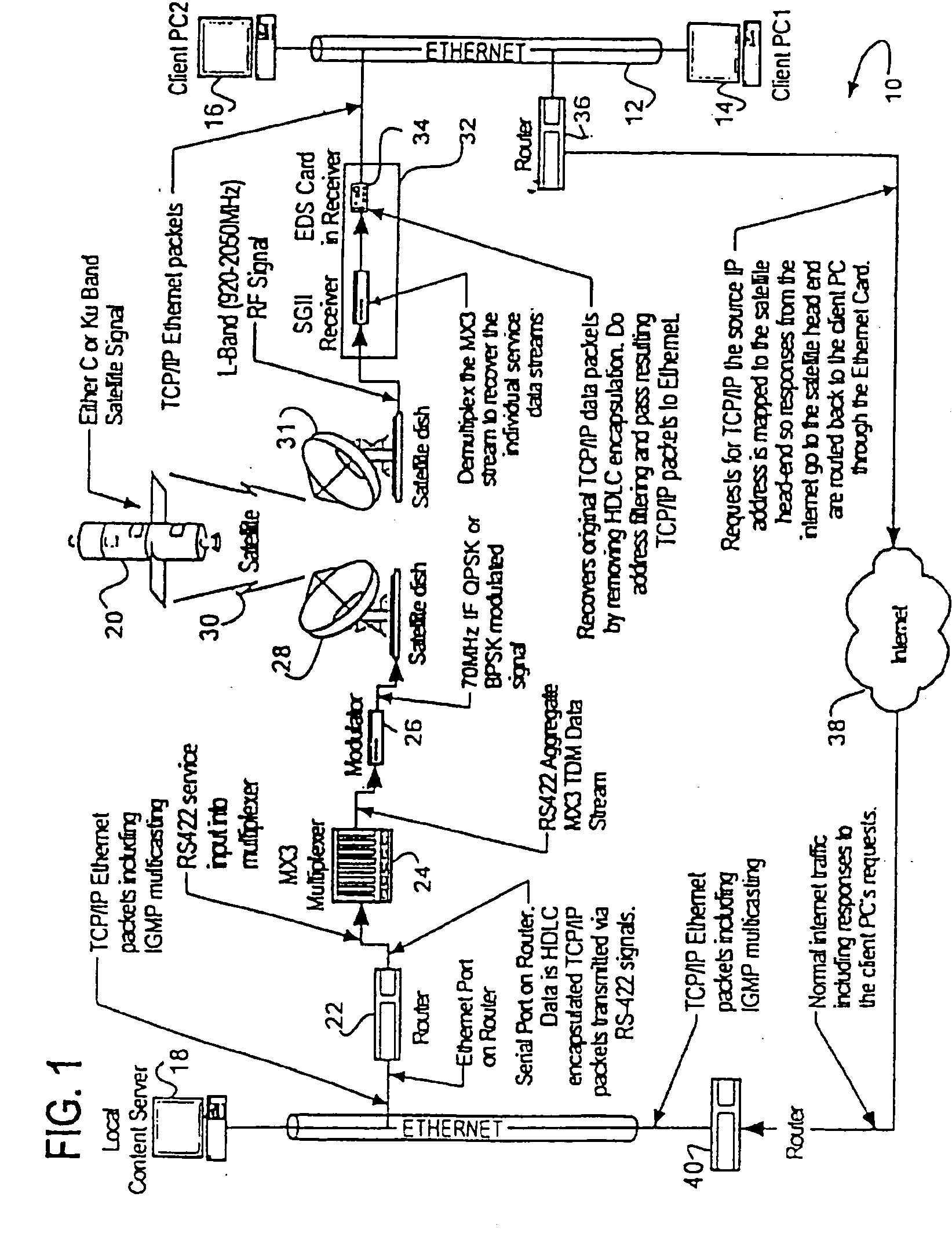
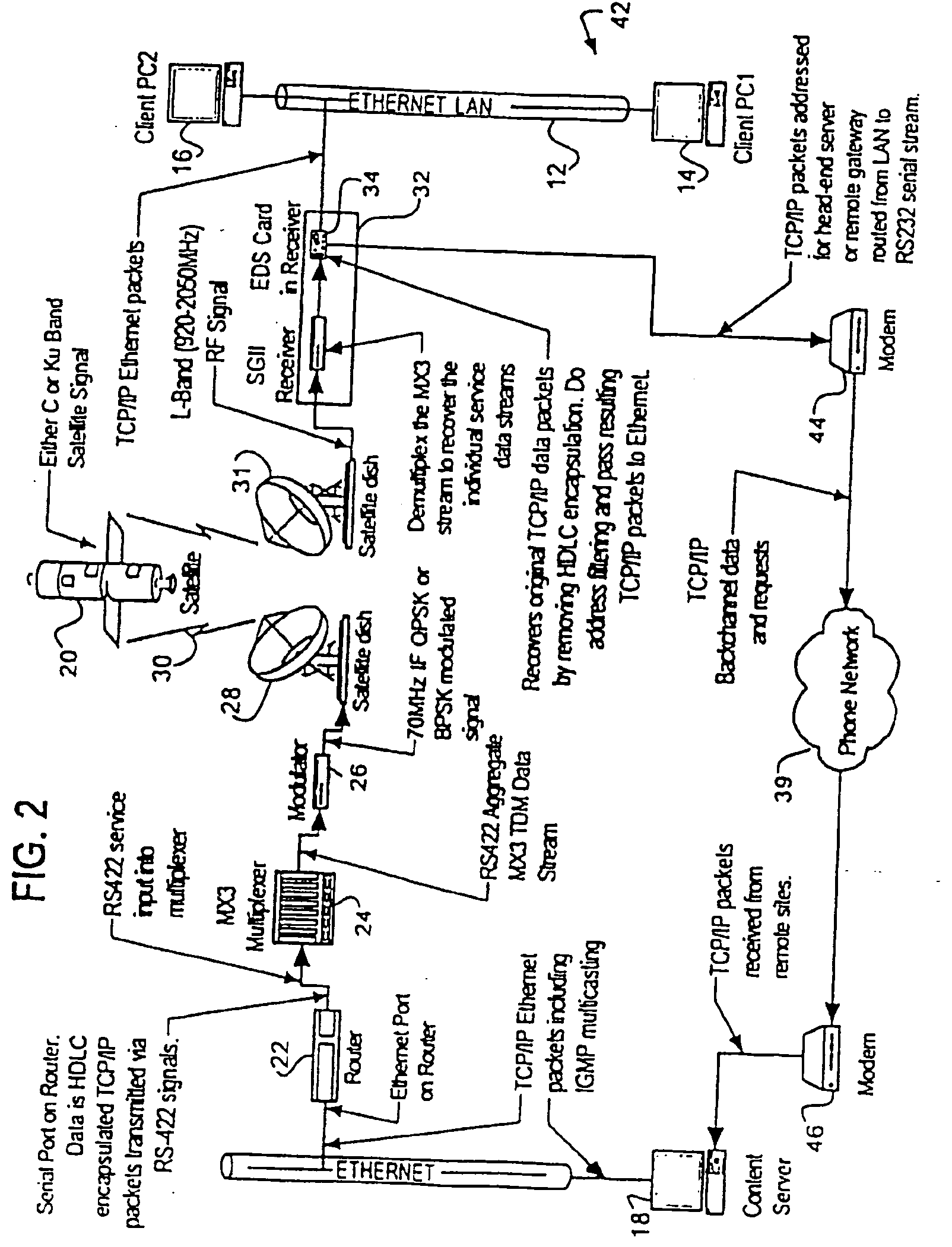
Satellite receiver/router, system, and method of use
ActiveUS20050099969A1The process is convenient and fastSpecial service provision for substationRadio transmissionTransfer systemThe Internet
This specification discloses a satellite transmission system for transmission of TCP / IP compatible packets from a head end computer through a satellite uplink, an extraterrestrial satellite, a satellite downlink, and an integrated satellite receiver / router for outputting of the TCP / IP compatible packets through a port on the receiver / router onto a computer LAN or WAN. The system may include an Internet or telecommunications backchannel. The receiver becomes router enabled by means of a removable insertion Ethernet / Router insertion card inserted into a slot in the receiver, although the transmission system may be used to simultaneously transmit a variety of other services through the receiver by use of other service slots in the receiver. The Ethernet / Receiver supports the IGMPv2 Multicasting (querier and non querier modes), standard TCP / IP (including UDP and Telnet), and SNMP protocols.
Owner:RATEZE REMOTE MGMT LLC
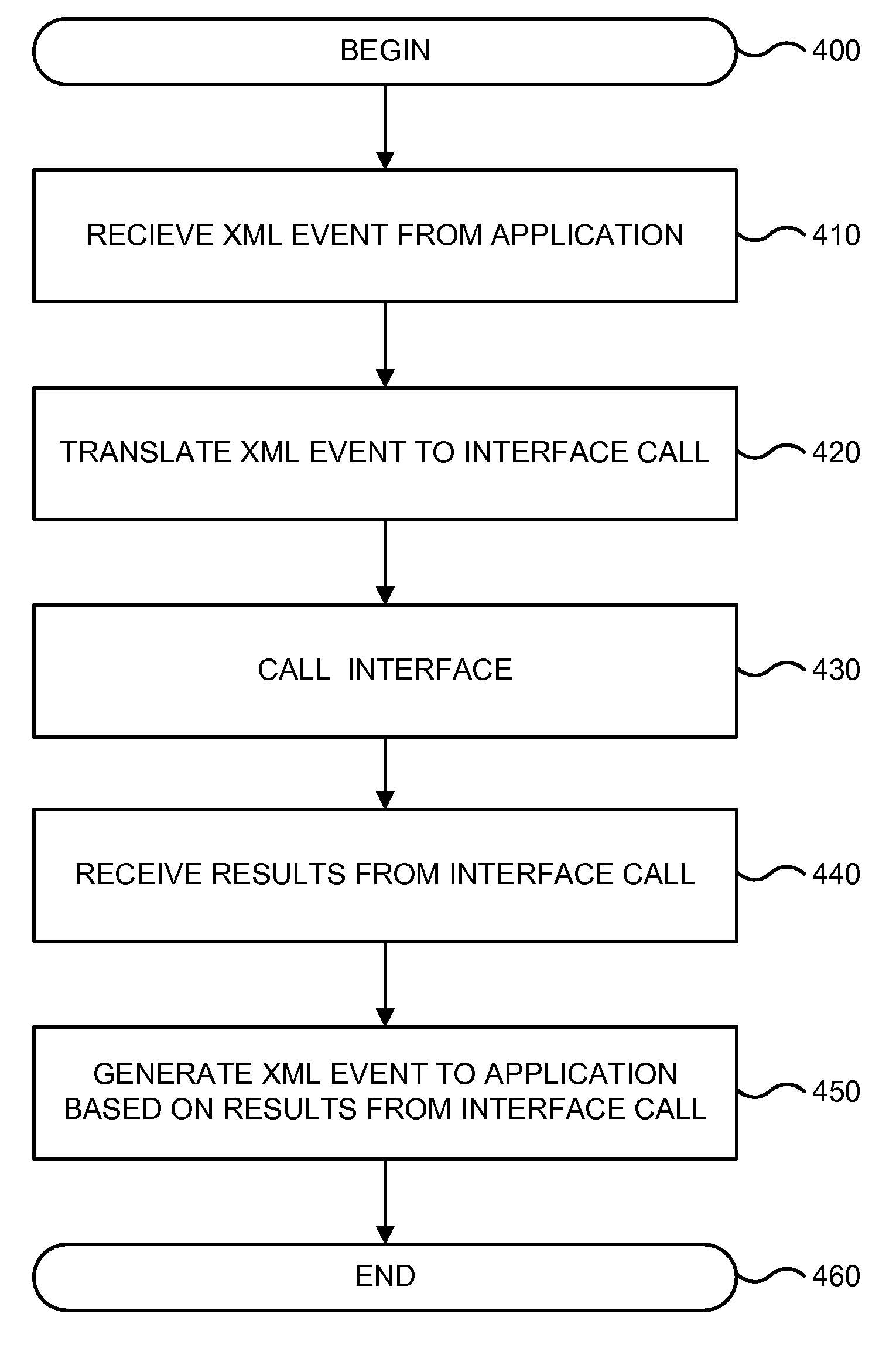
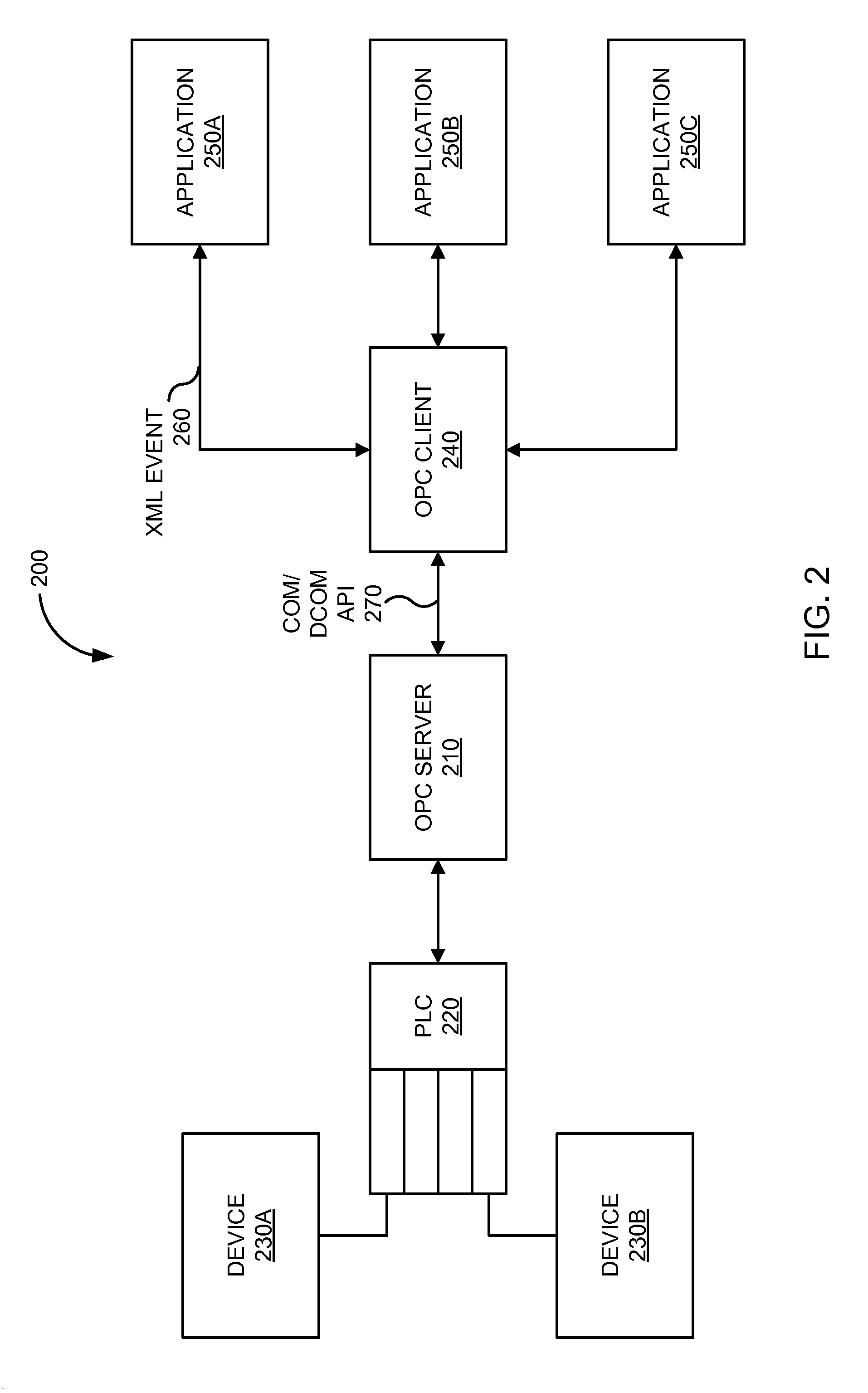
Xml-based event driven interface for opc data access
ActiveUS20100114994A1Digital data processing detailsNatural language data processingWeb serviceData access
Communication from applications may be carried in XML-based events through sockets, Web services, JMS, HTTP, telnet channels, and the like to an OPC client. The OPC client may include an event engine configured to process the XML-based events, and convert them to appropriate COM / DCOM API invocations. In some embodiments, the OPC client buffers collected data from the COM / DCOM API, and transmits the buffered data in an XML event to an application based on a subscription time schedule and / or value condition. The OPC client allows service oriented event-driven applications to interact with industry devices remotely via the open architecture provided by the OPC specification using a business level language syntax.
Owner:ORACLE INT CORP
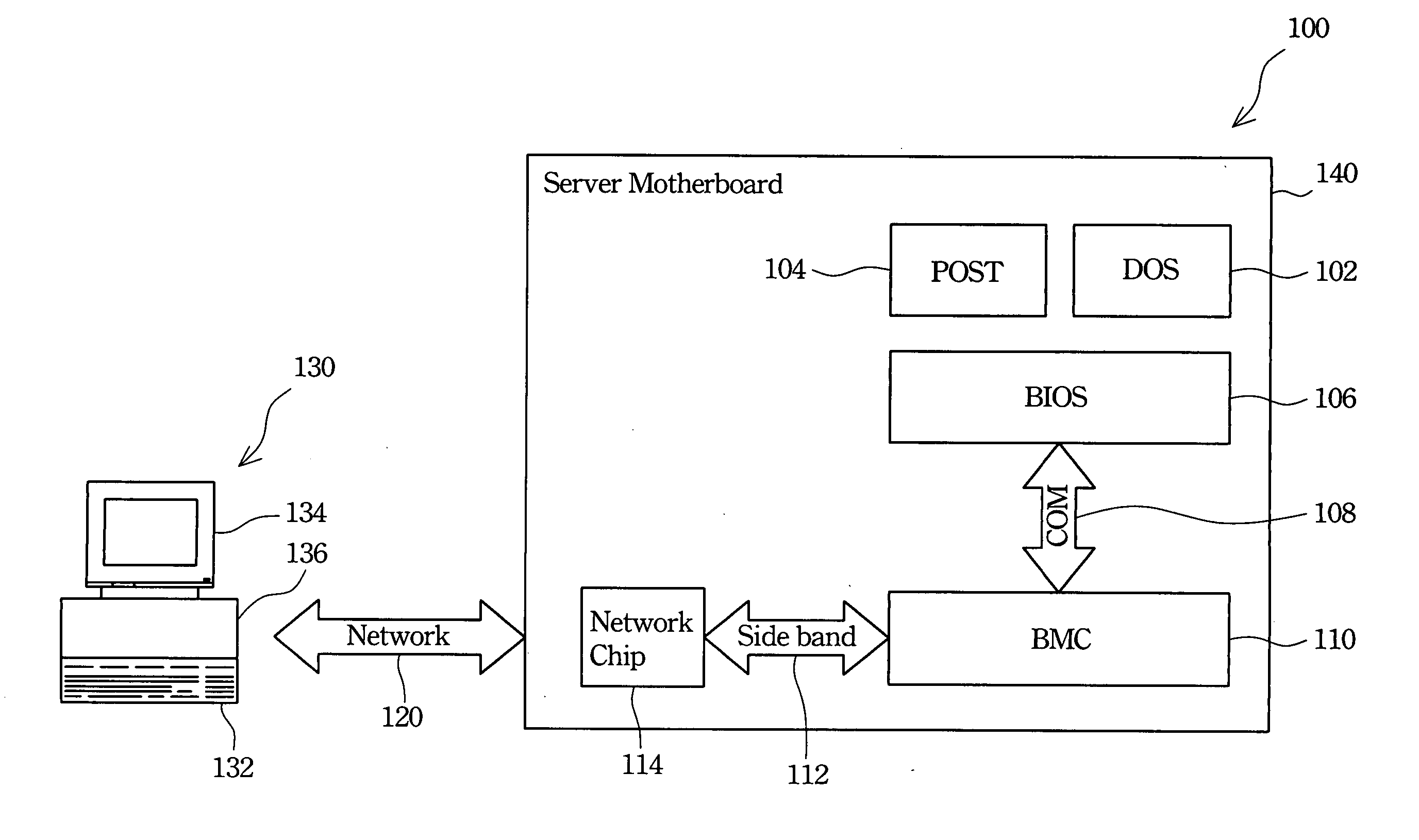
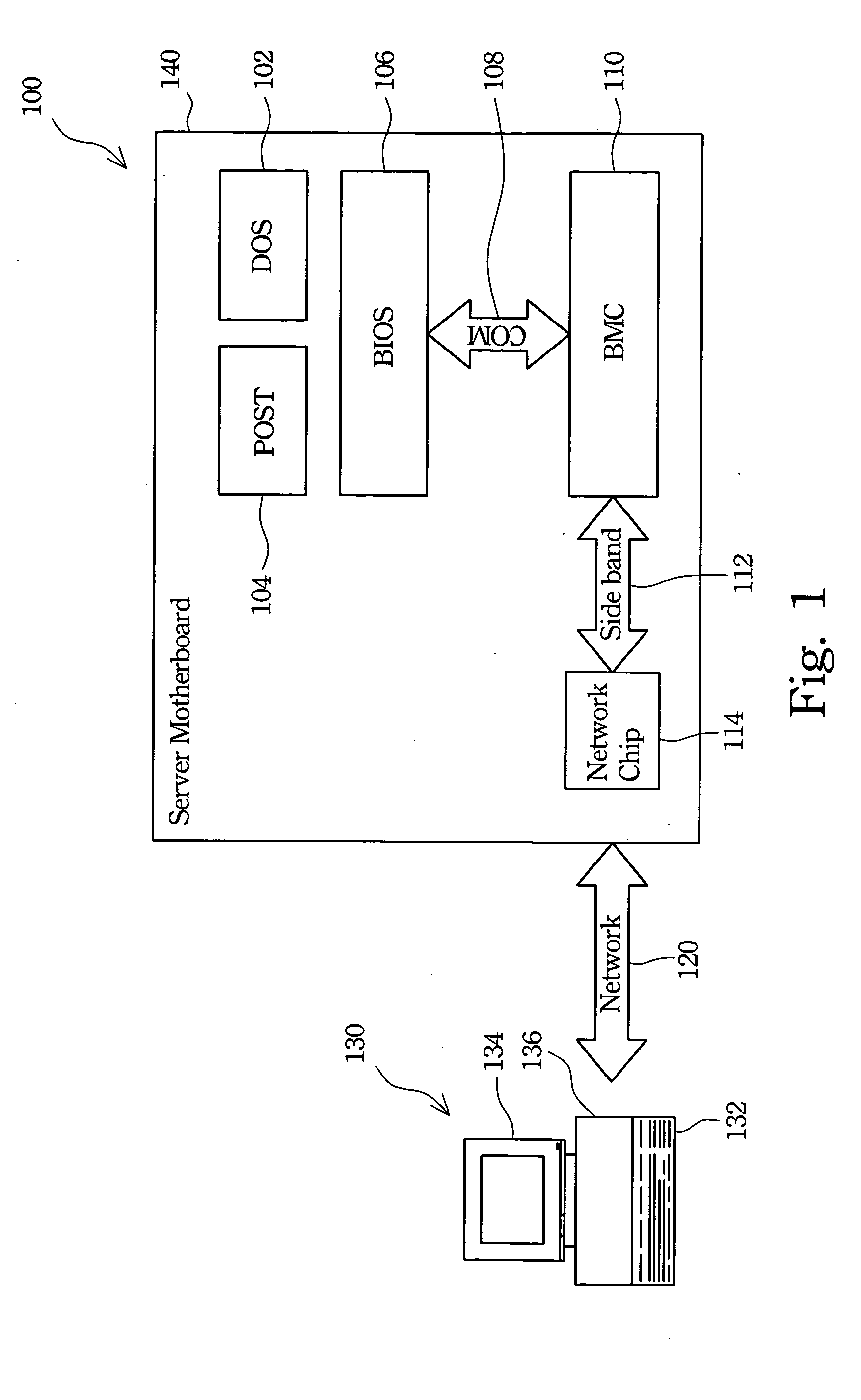
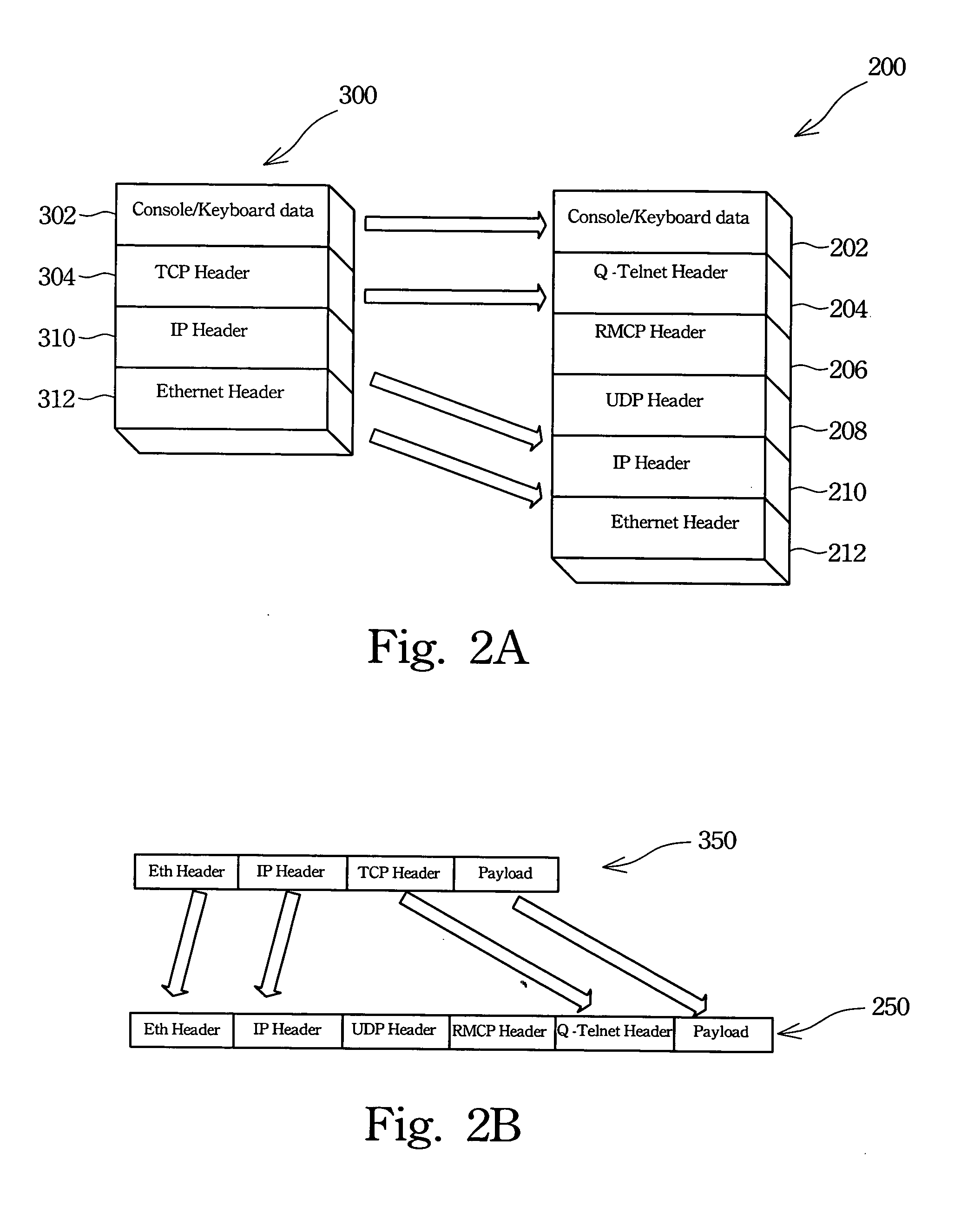
Remote control device
InactiveUS20050091360A1Low costImprove complicationsDigital computer detailsSubstation remote connection/disconnectionNetwork packetRemote control
A remote control device is described. The remote control device uses a network chip directly mounted on a motherboard of a server computer to remote control the server computer without any additional network card requirement. The remote control device includes a basic input output system (BIOS), a COM port, a baseboard management controller (BMC), and a network chip. The BIOS redirects video data to the COM port and then the same to the BMC. The BMC transforms the video data into network packets according to a Q-Telnet protocol. The BMC recognizes the Q-Telnet protocol and a standard Telnet protocol effectively. Therefore, the network chip uses a UDP 623 port to control the BMC and a TCP 23 port to transmit data and commands using the standard Telnet protocol.
Owner:QUANTA COMPUTER INC
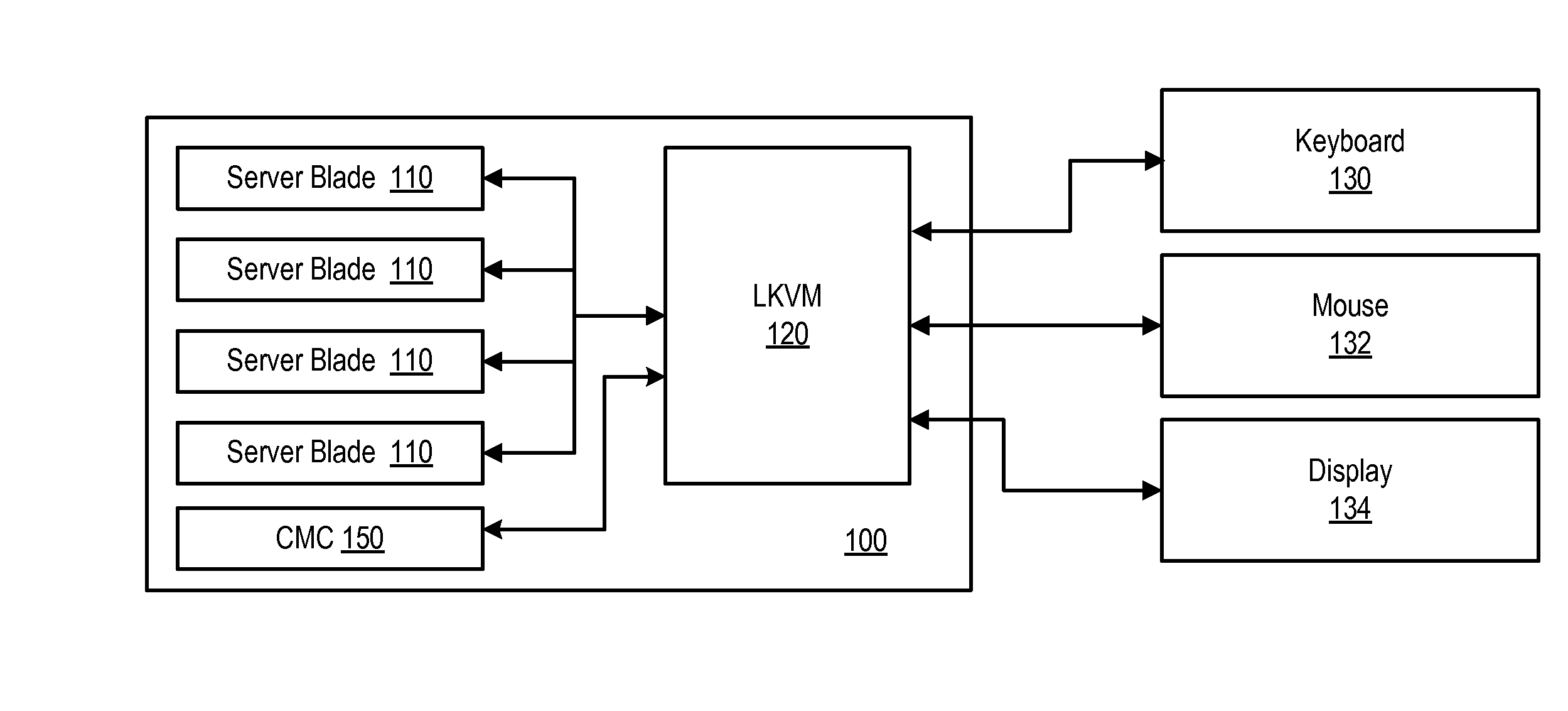
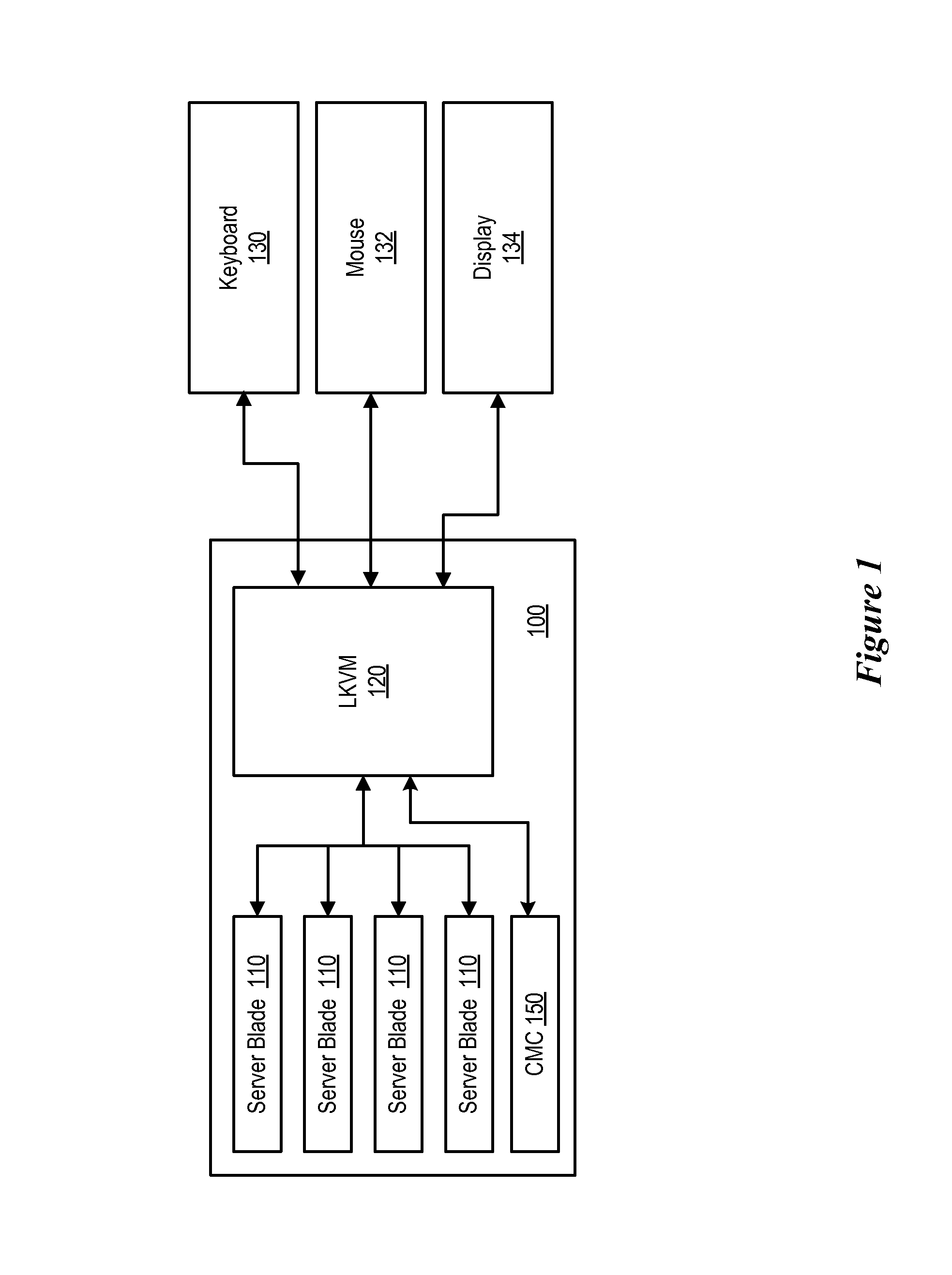
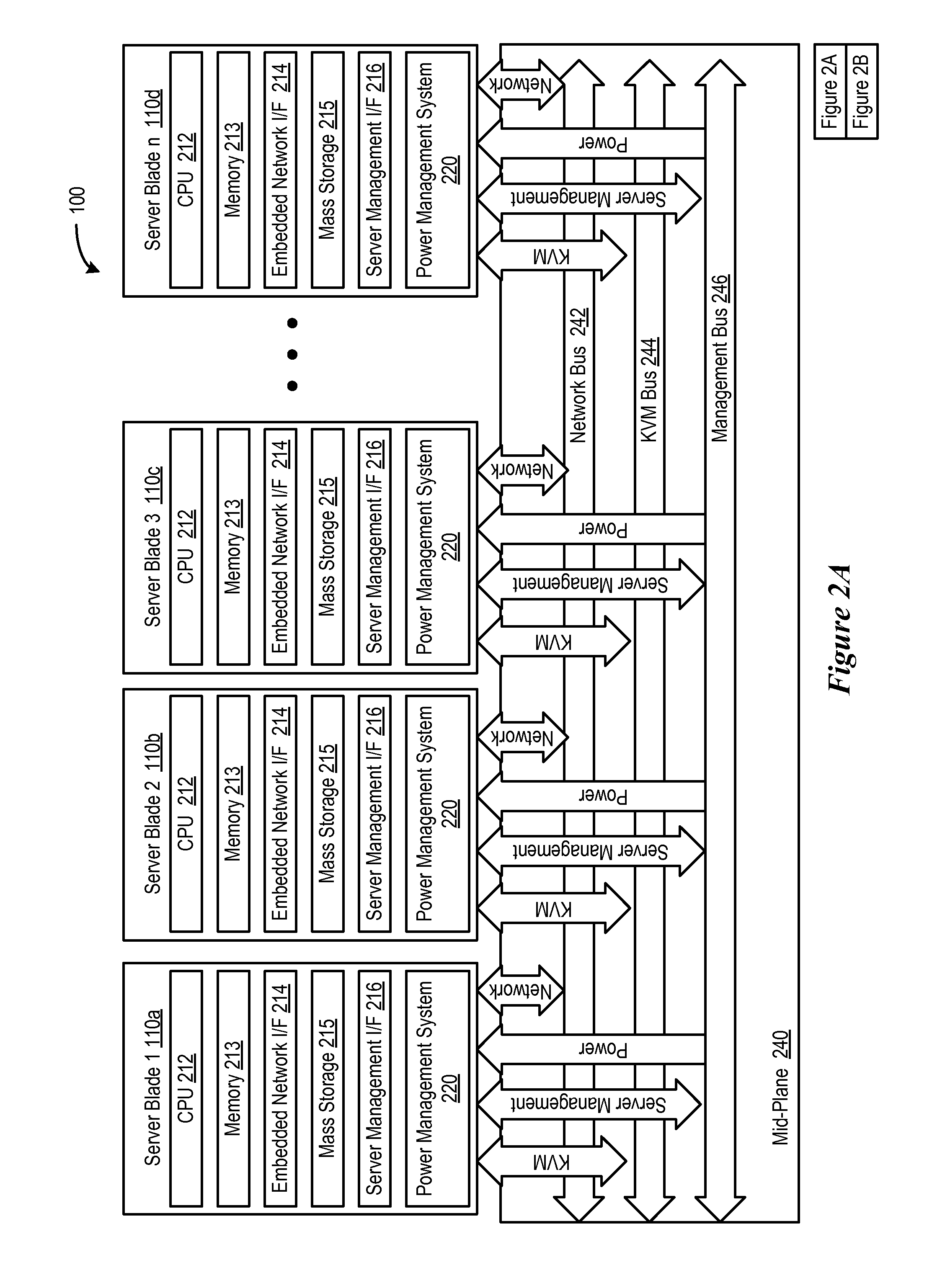
Chassis Management Access Console VIA a Local KVM Display
ActiveUS20080126627A1Digital computer detailsInput/output processes for data processingNetwork connectionPrivate network
A local KVM module with an on-screen display interface in which a chassis management controller is included within a list of servers which may be accessed by the local KVM module. The local KVM module includes keyboard, mouse and video connectors as well as a tiering network connector. When accessing the local KVM module, the CMC is presented as any other blade server, but with the name Chassis Management Controller (CMC). When a user selects the CMC module from the onscreen display, the user is presented with a text console, where the user can login to a text terminal interface of the CMC module. The text interface can be implemented as for example, a serial connection via a local area network (LAN) or through a tiny telnet client via a chassis private network.
Owner:DELL PROD LP
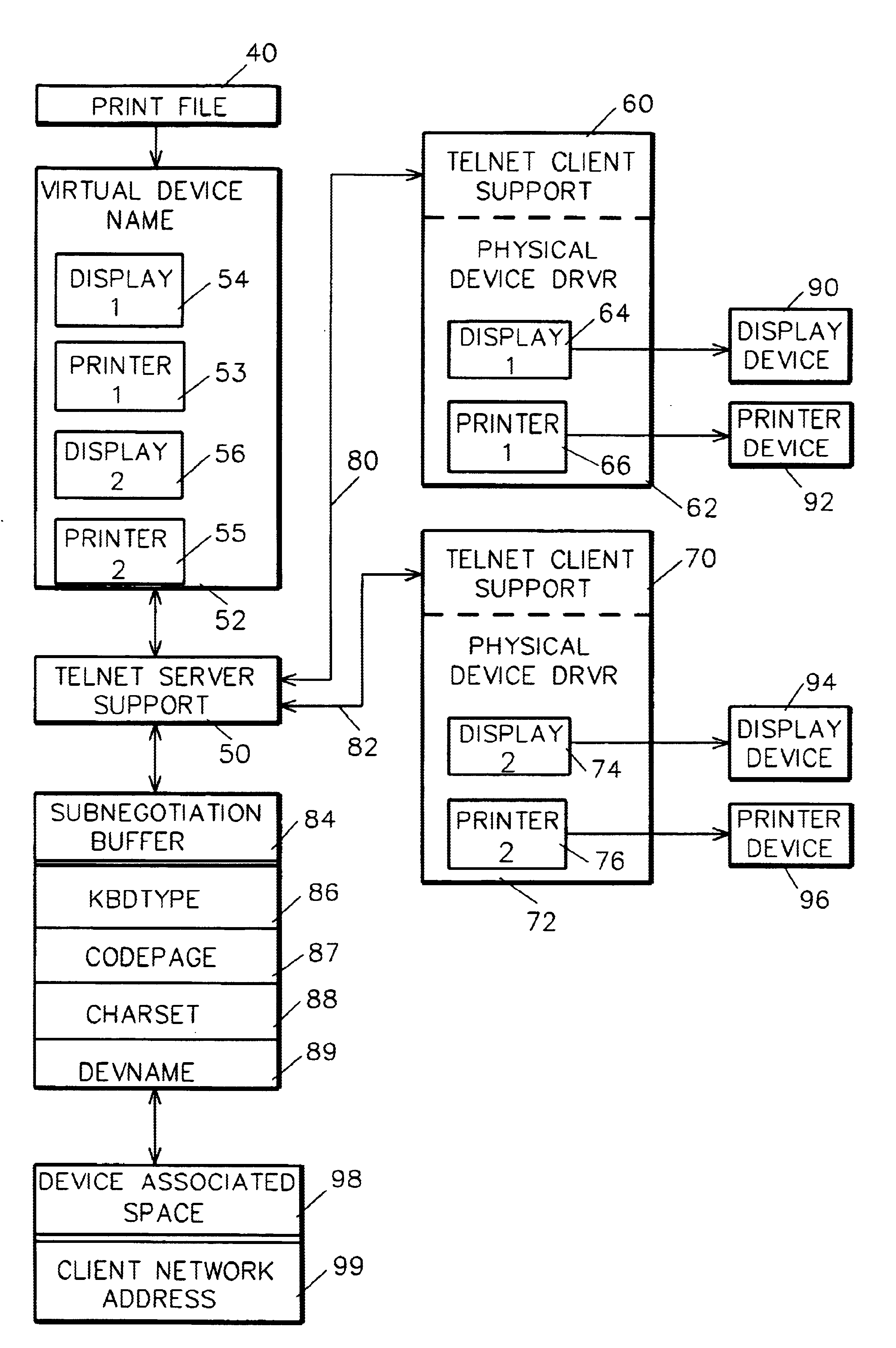
System and method for server virtual printer device name negotiation for mobile print support
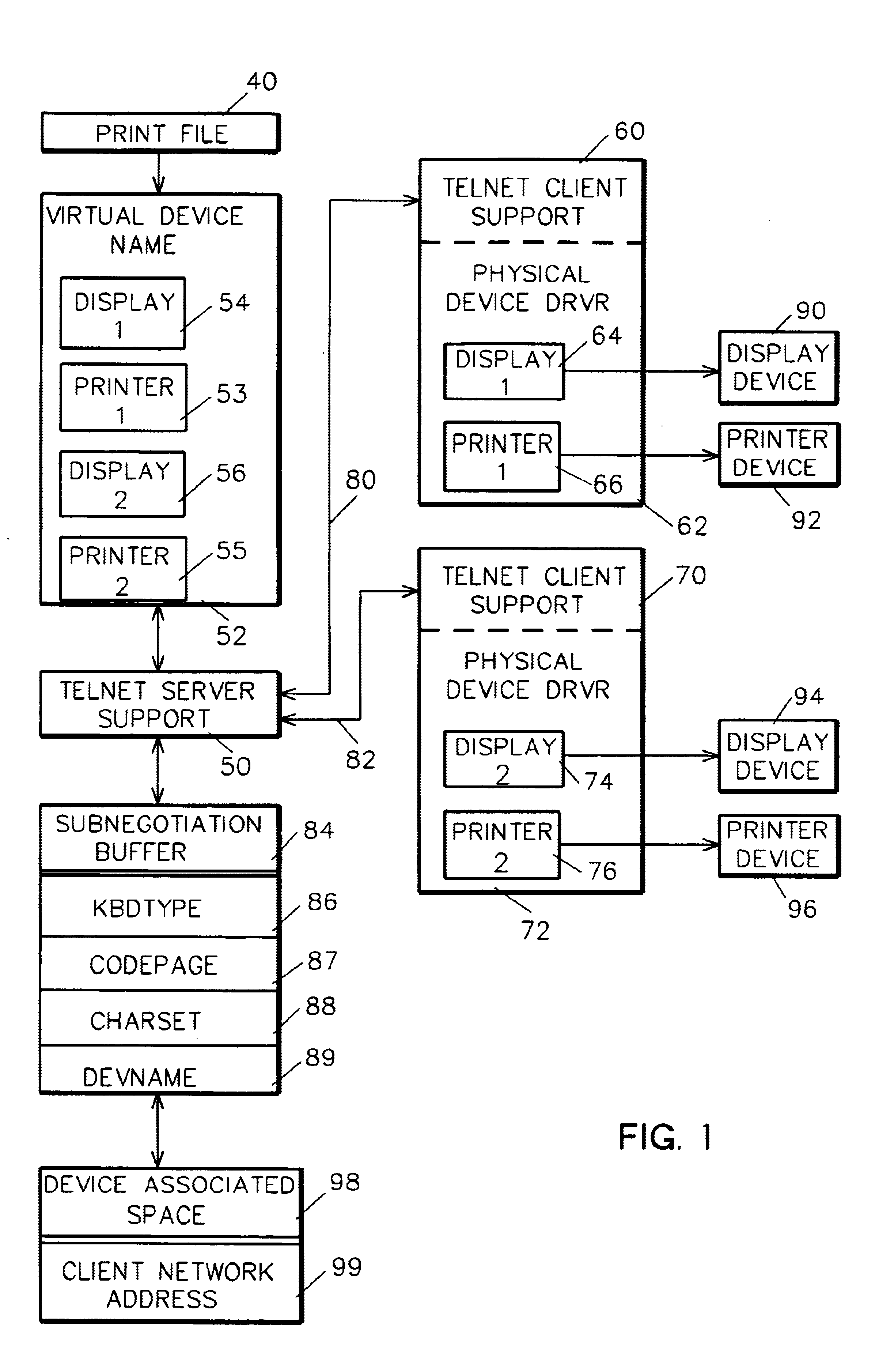
InactiveUS6704117B1Without loss of work management functionalityMultiple digital computer combinationsVisual presentationClient-sideVirtual device
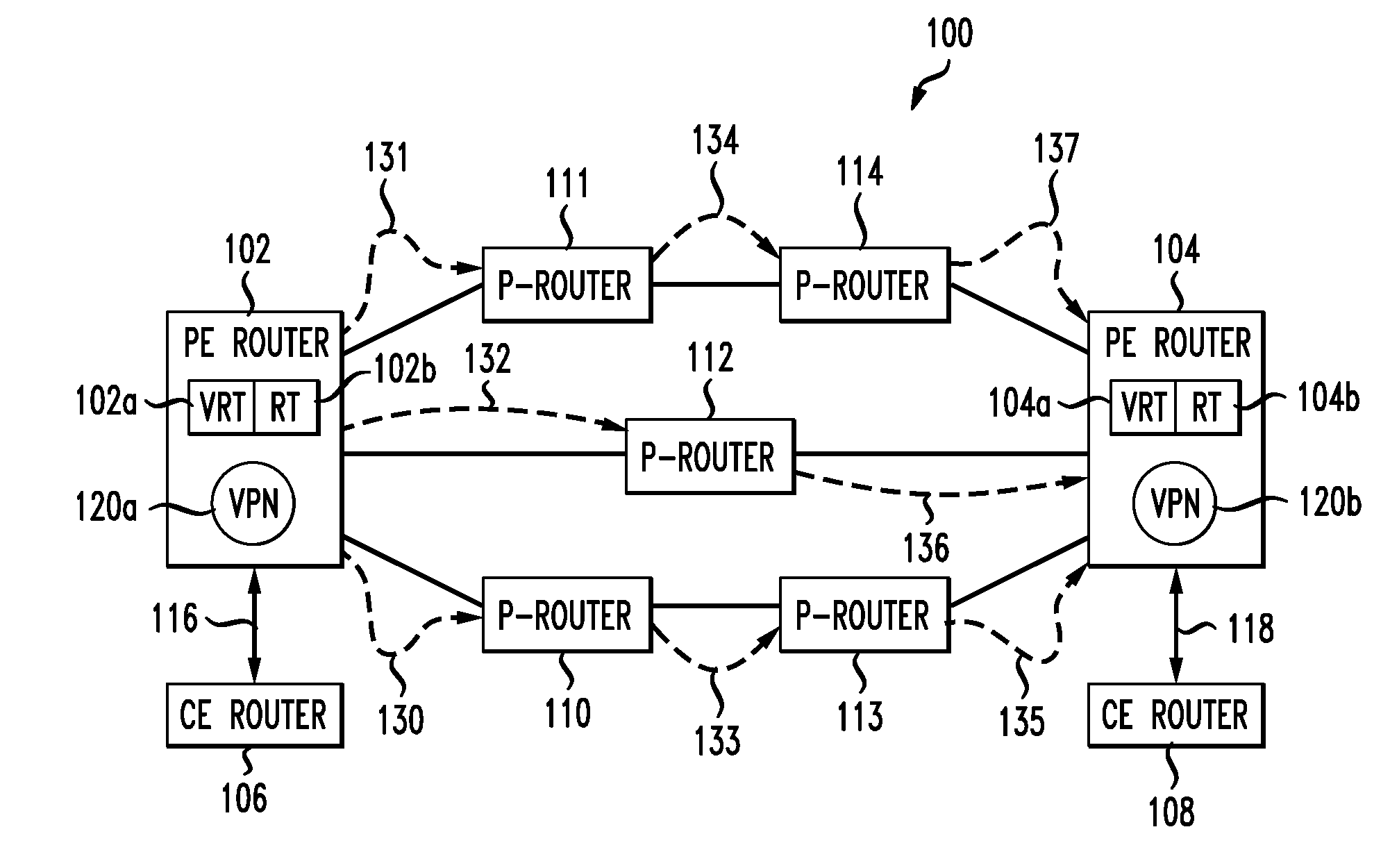
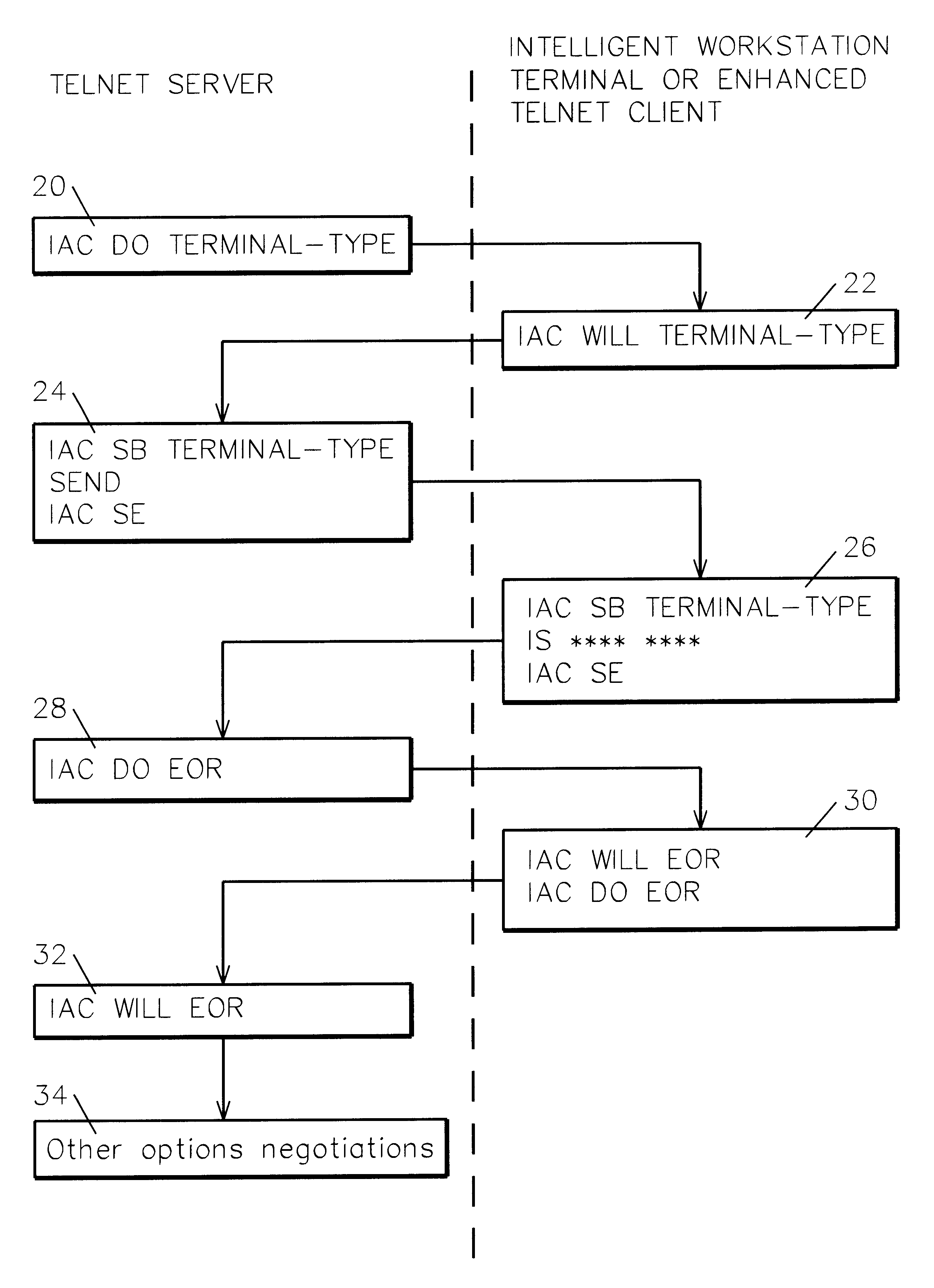
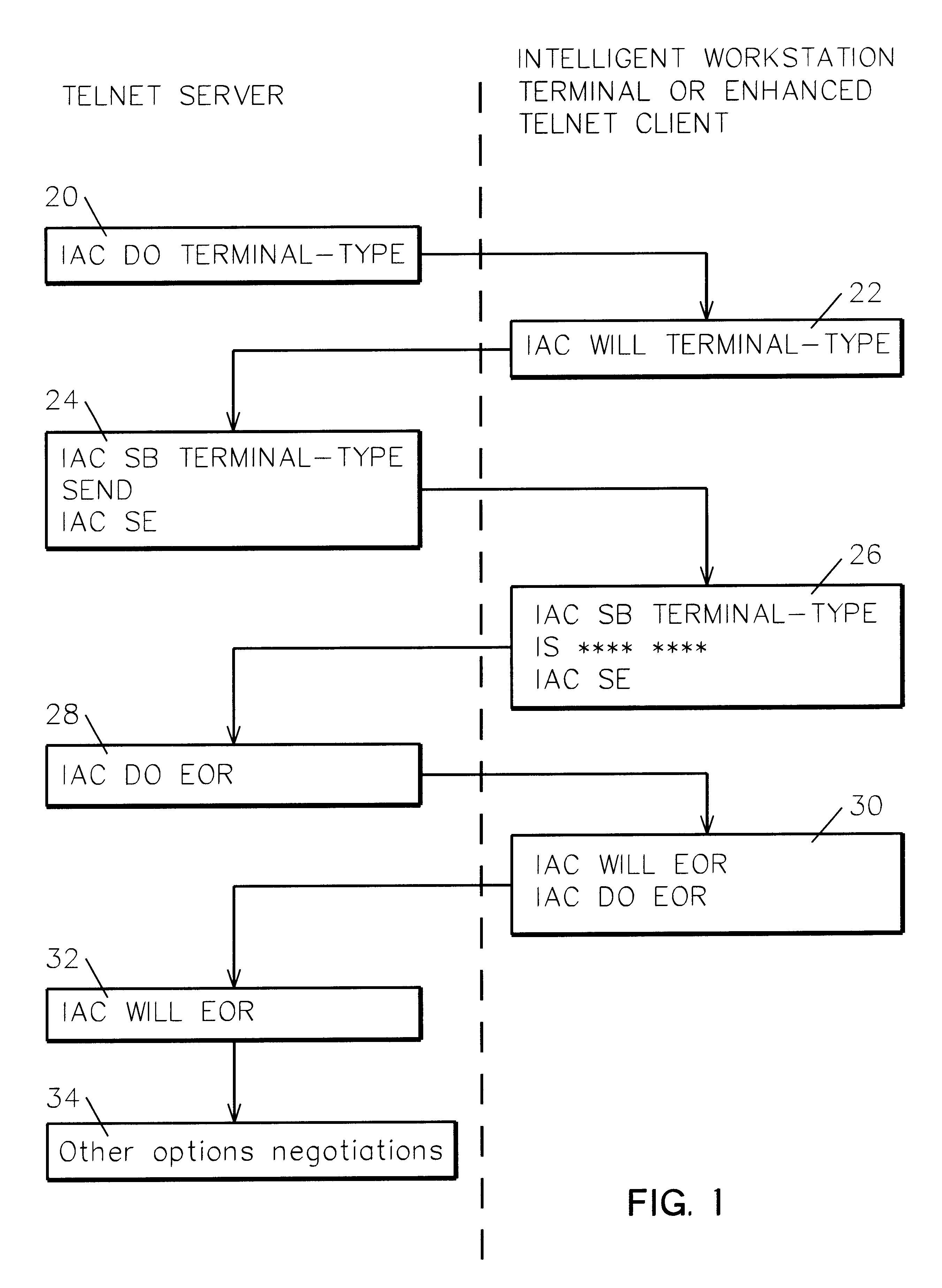
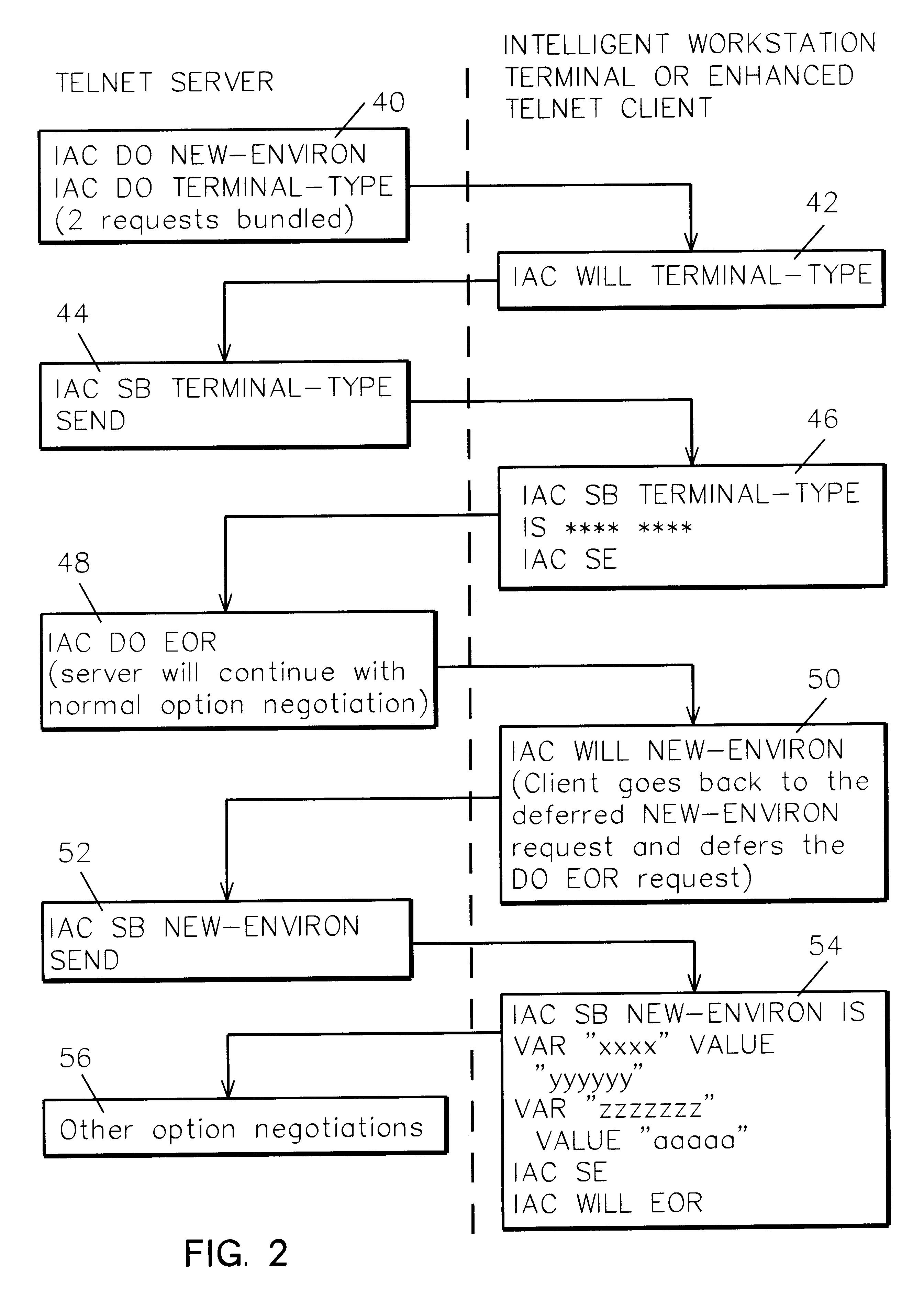
Client / server negotiation of virtual display and / or printer device selection to control session attributes, job routing to customized subsystems, user access control, and so forth. Within the Telnet Protocol, sanctioned and used with the "DO, DONT, WILL, WONT" structure, during subnegotiation a client requests and a server agrees to a specific virtual device name for the session display and / or printer.
Owner:SERVICENOW INC
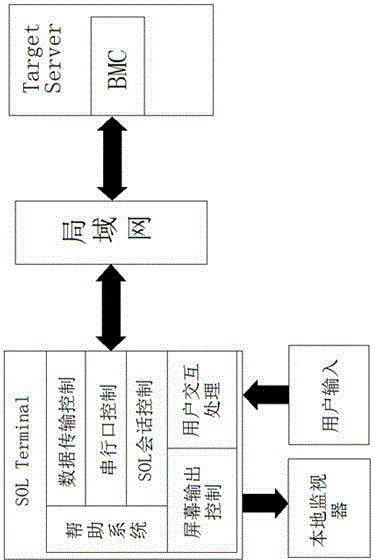
IPMI (intelligent platform management interface) based method for serial port redirection
InactiveCN104363117ASolve the problem of management chaosEasy to monitor remotelyData switching networksOperational systemIntelligent Platform Management Interface
The invention discloses an IPMI (intelligent platform management interface) based method for serial port redirection. The IPMI based method includes that an IPMI-based SOLTerminal (serial over local area network terminal) serves as an application program for user interaction to receive user input; a serial port of a target machine is redirected to an LAN (local area network) through interaction between the LAN and the target machine; the LAN feeds back serial port information to a user local monitor through the SOLTerminal to provide a monitoring, managing and configuring platform for a manager. Particularly, when management software, such as SSH and Telnet, dependent on a server operating system is not available on the conditions of server operating system nucleus crash or server shutdown and the like, the method plays a crucial role in system trouble locating and troubleshooting.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
A system for filtering spam in Internet and its implementation method
InactiveCN101087259AImprove intelligenceEfficient Learning EvolutionOffice automationData switching networksHuman useOperational system
The invention relates to a system and method to filter the wasted mails on internet. At present there is a lot of wasted mails, human use keywords to filter it, build black name list, and set regulation to prevent, but the result is unobvious, hard to maintain, high requirement for professional skill. The invention consists of hardware, software which is installed on hardware and supported network, the software includes Linux operating system, analyzing engine for wasted mails, extended black name list, internet library and management interface. The periphery supporting network includes complain device for wasted mails, analyzing system for wasted mails, which can work as transparent gateway before LAN or mail sever, take over MX interface to work before mail sever. The method includes the hardware connection, telnet management, management of wasted mails and anti-waste setting, and the operation is convenient, easy to maintain, high identifying rate, high stability, low misjudgment rate, and plug and play.
Owner:SHENZHEN DUHU NETWORK TECH
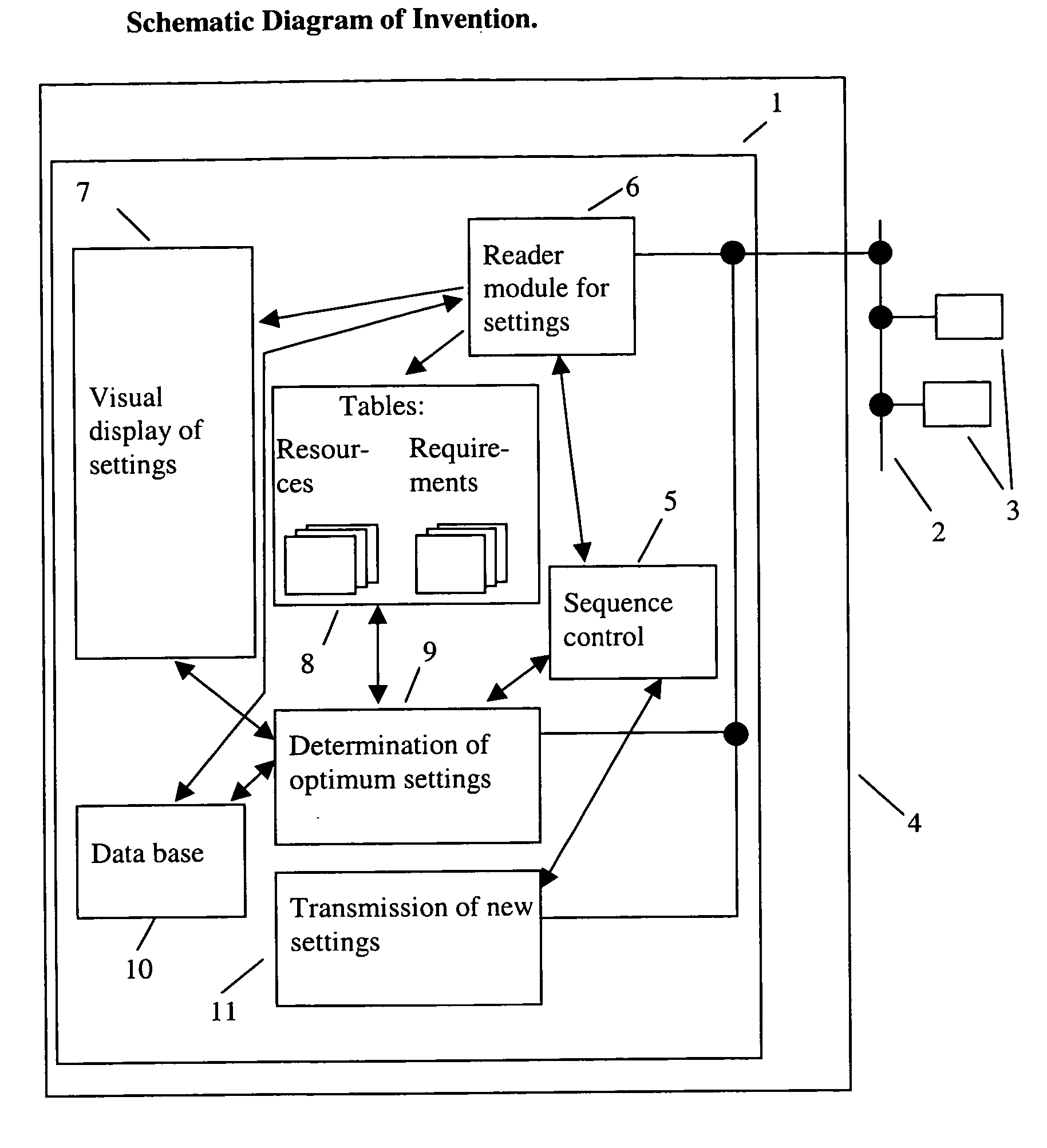
Method for configuration of devices in a computer network by a computer program
InactiveUS20060173979A1Impossible to detectDigital data processing detailsUnauthorized memory use protectionAuto-configurationOriginal equipment manufacturer
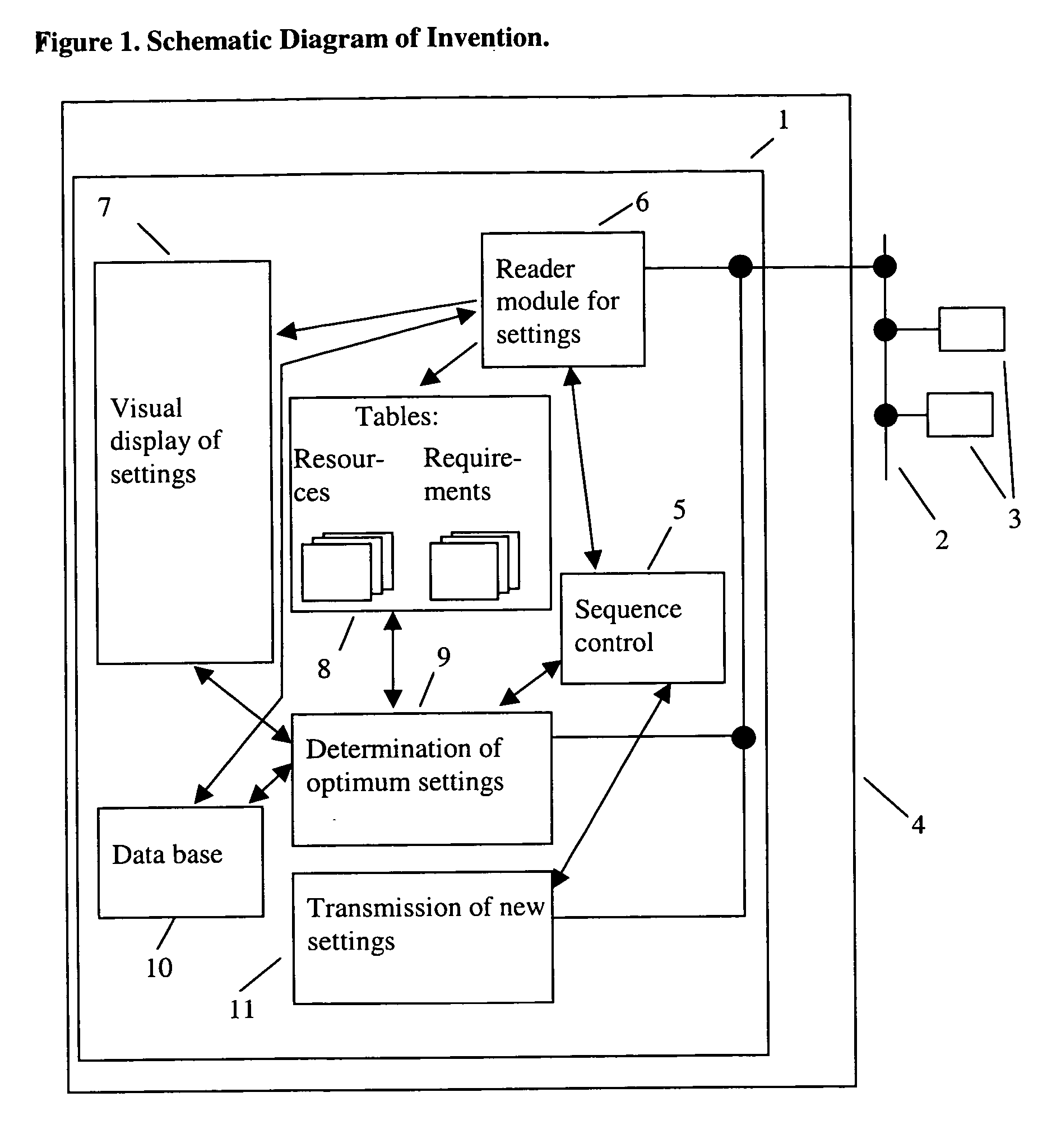
The Method provided is for the configuration of devices in a computer network by a computer program. The method renders fully automatic management of all devices in a LAN possible. Internet Service Providers and Original Equipment Manufacturers will be able to deliver products that configure themselves automatically. The invention regards a method to configure devices in a computer network which is executed by a computer program that makes the following steps: Query current settings of one or more devices in the network by using HTTP, FTP, Telnet or a comparable standard protocol. Determine optimum settings with the aid of a data base. Transfer of the previously determined optimum settings to configurable devices in the network. The new settings are being stored on the configurable devices in the network.
Owner:ROELLGEN BERND
Performance of ECMP Path Tracing in an MPLS Enabled Network
ActiveUS20090168664A1Data switching by path configurationElectrical componentsWeb trackingPath tracing
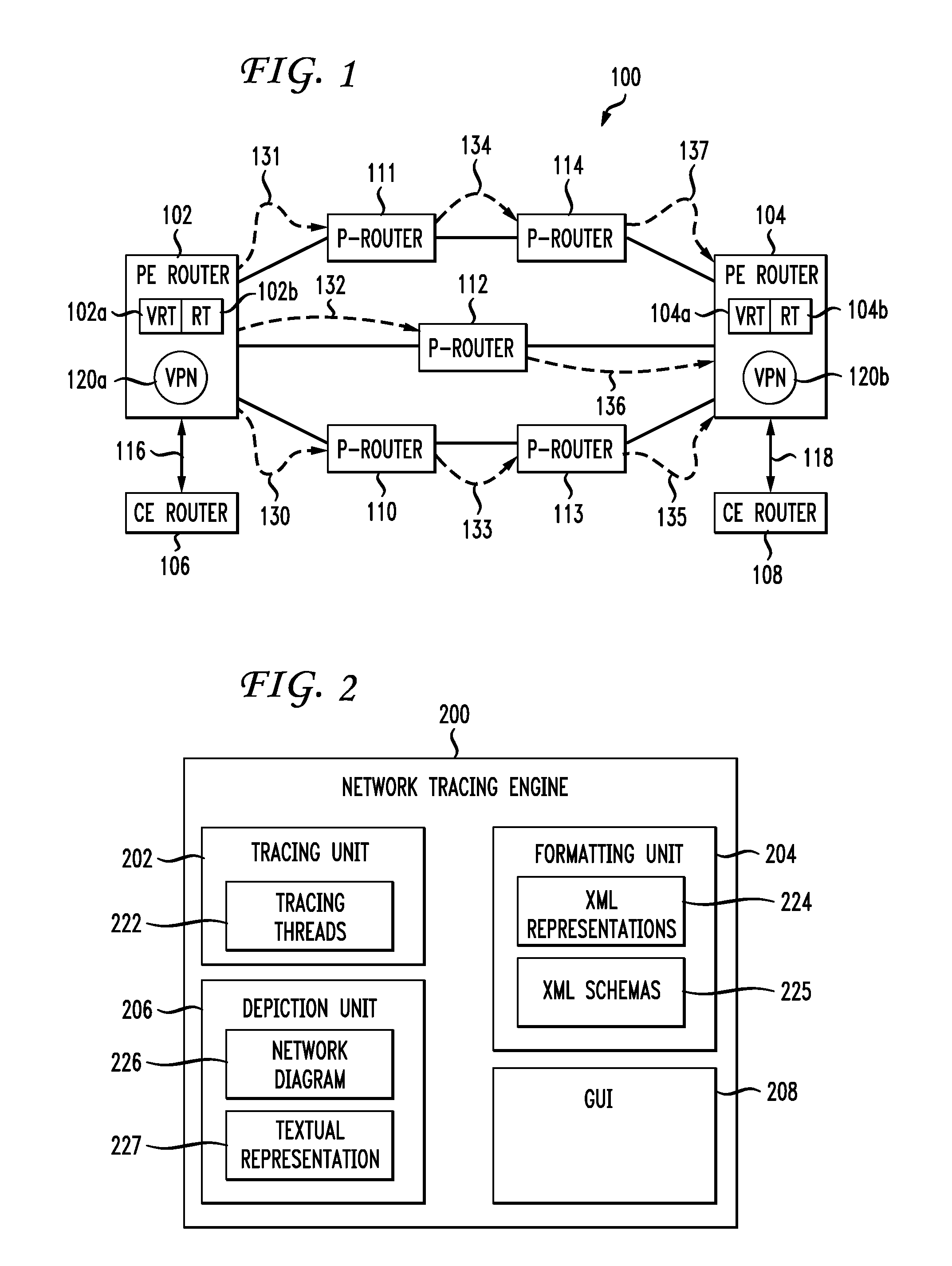
The preferred embodiments of the present invention are directed to a network tracing engine for tracing and depicting a topology (i.e. a network configuration) of a network using, for example, a network diagram. The network tracing engine preferably queries / telnets to interfaces of routers associated with one or more source-to-destination paths in a network concurrently and independently to ensure proper configuration of the routers and / or to generate a true depiction of a routing configuration without redundantly querying routers.
Owner:AT&T INTPROP I L P
Network device monitoring method and system
InactiveCN103516555AEase of useFlexibleData switching networksRelevant informationSimple Network Management Protocol
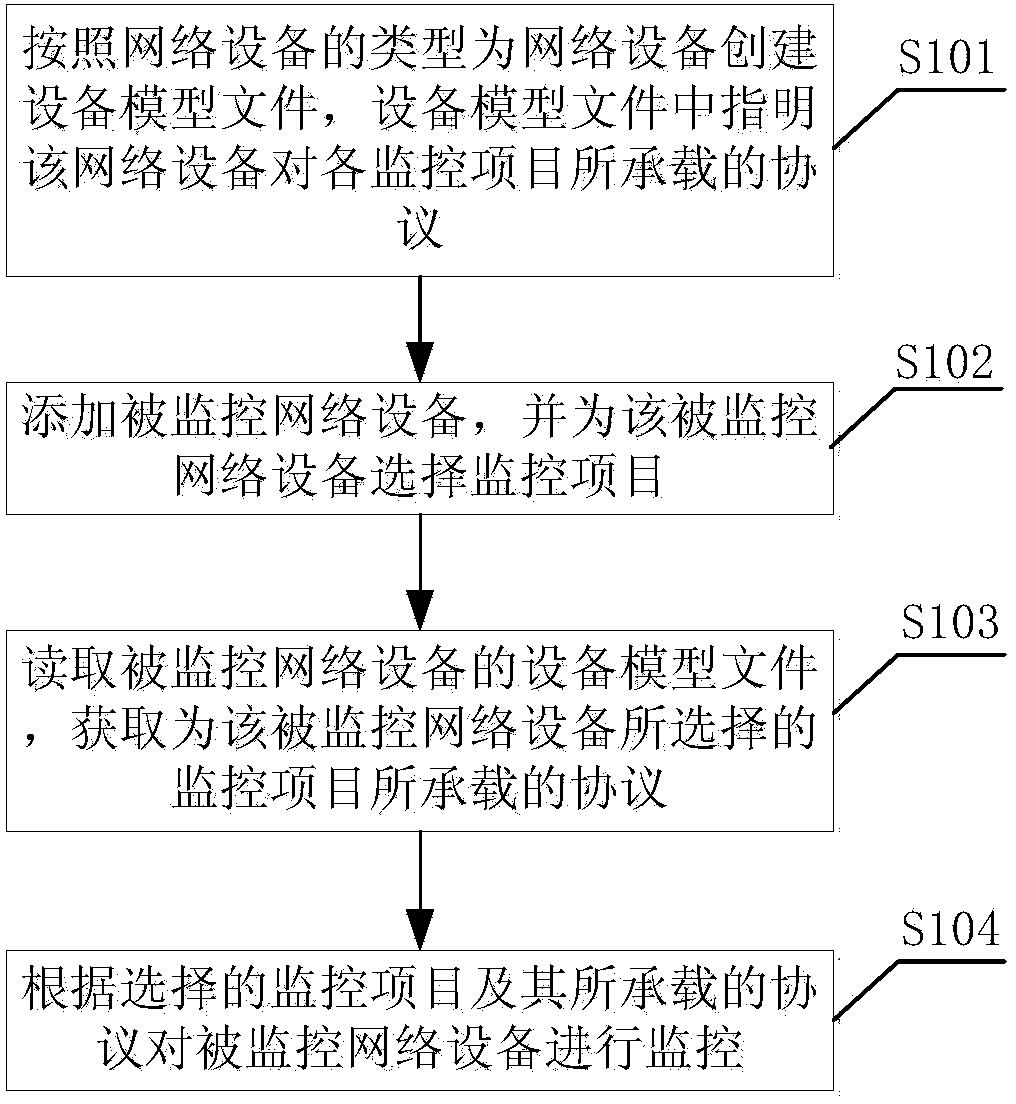
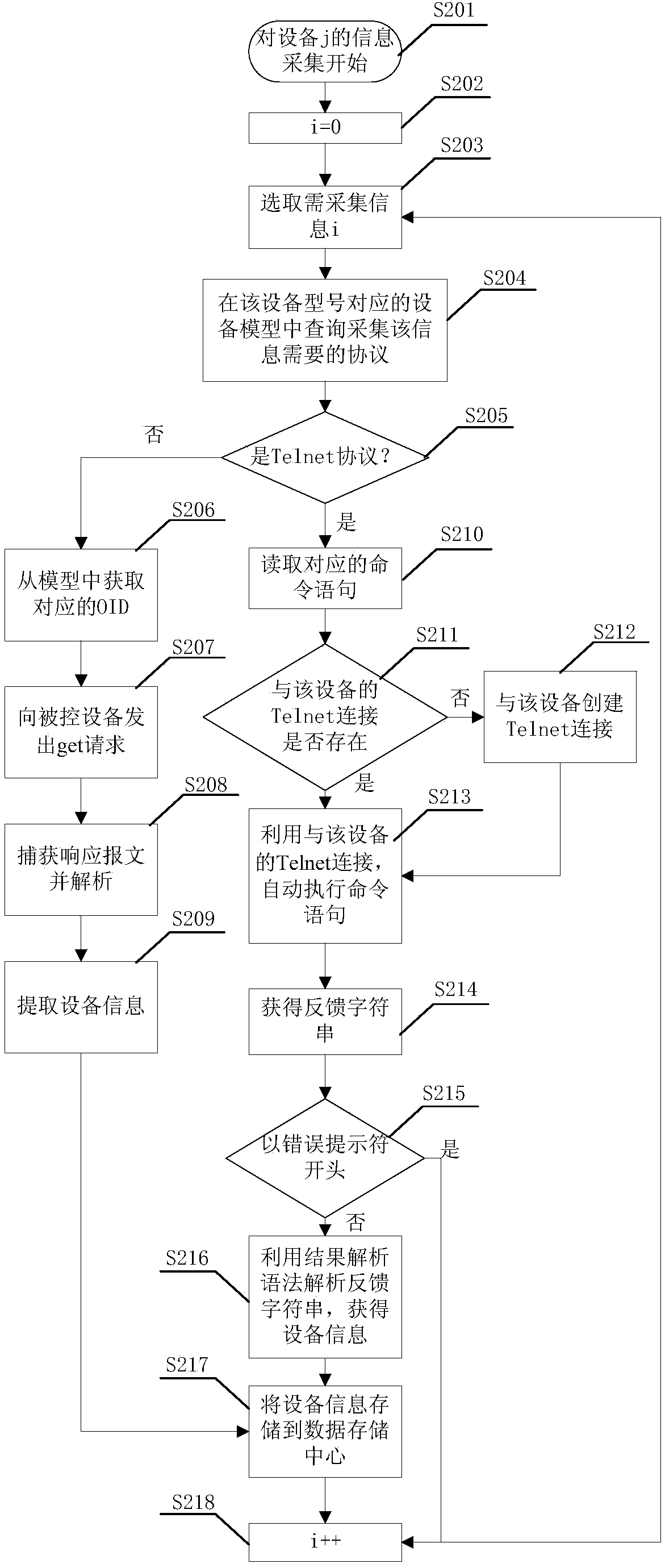
The invention relates to a network device monitoring method and system. The network device monitoring method comprises the following steps: (1) according to the types of network devices, creating device model files for the network devices, wherein monitoring project protocols borne by the network devices are indicated in the device model files; the monitoring project protocols can be SNMPs (Simple Network Management Protocols) and / or Telnet protocols; if the monitoring project protocols are the SNMPs, OIDs (Object Identifiers) corresponding to monitoring projects are indicated in the device model files; if the monitoring project protocols are Telnet protocols, command statements and result analysis grammar corresponding to the monitoring projects are indicated in the device model files; (2) adding network devices to be monitored, and selecting monitoring projects for the network devices to be monitored; (3) reading the device model files of the network devices to be monitored, and acquiring protocols borne by the monitoring projects and selected for the network devices to be monitored, and related information corresponding to the protocols; (4) according to the selected monitoring projects and the protocols borne by the monitoring projects, monitoring the network devices to be monitored. The network device monitoring method and system have high expansibility and compatibility.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Service authentication system, server, network equipment, and method for service authentication
InactiveUS20070050634A1Data processing applicationsRandom number generatorsUser authenticationAuthentication system
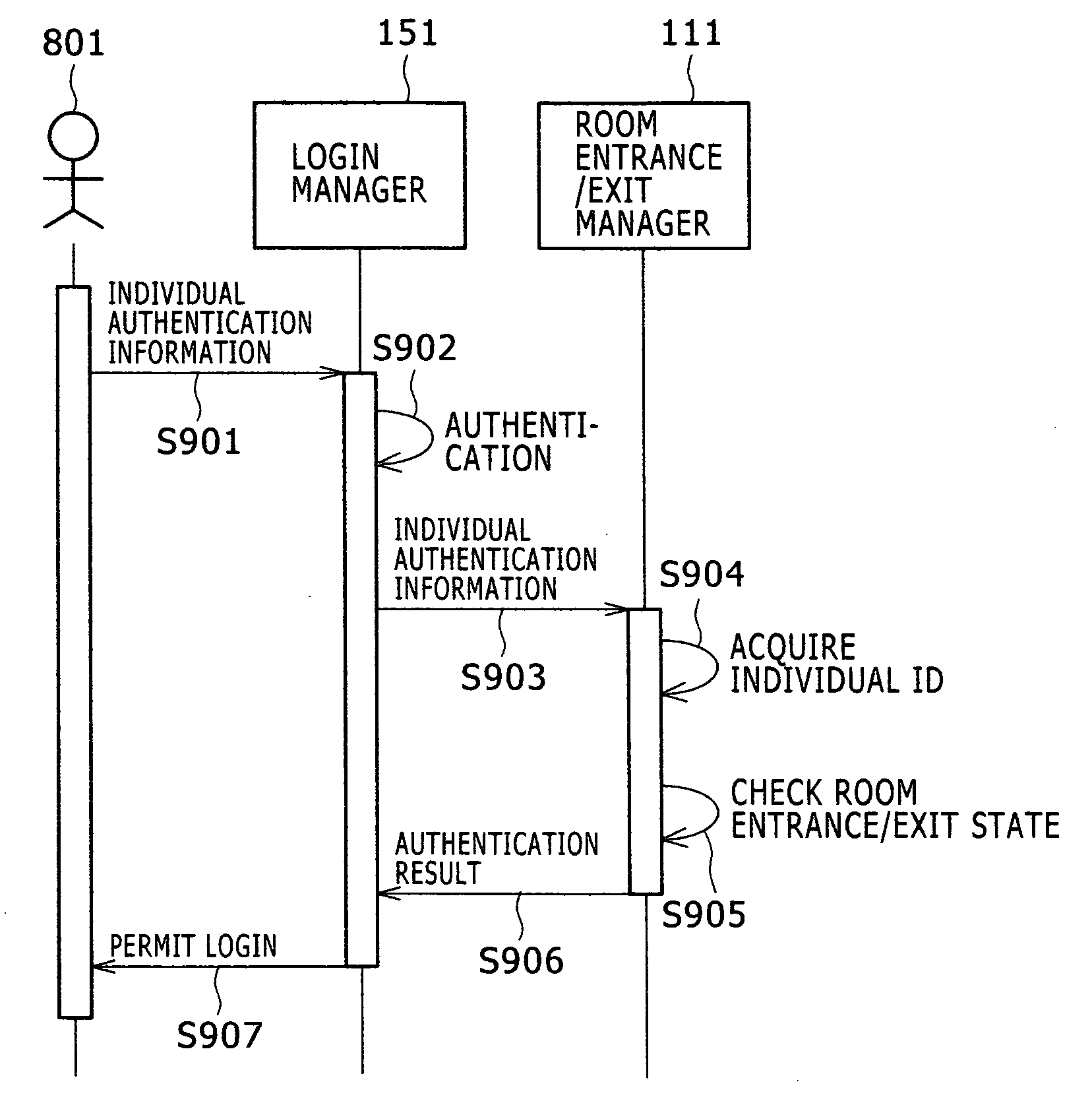
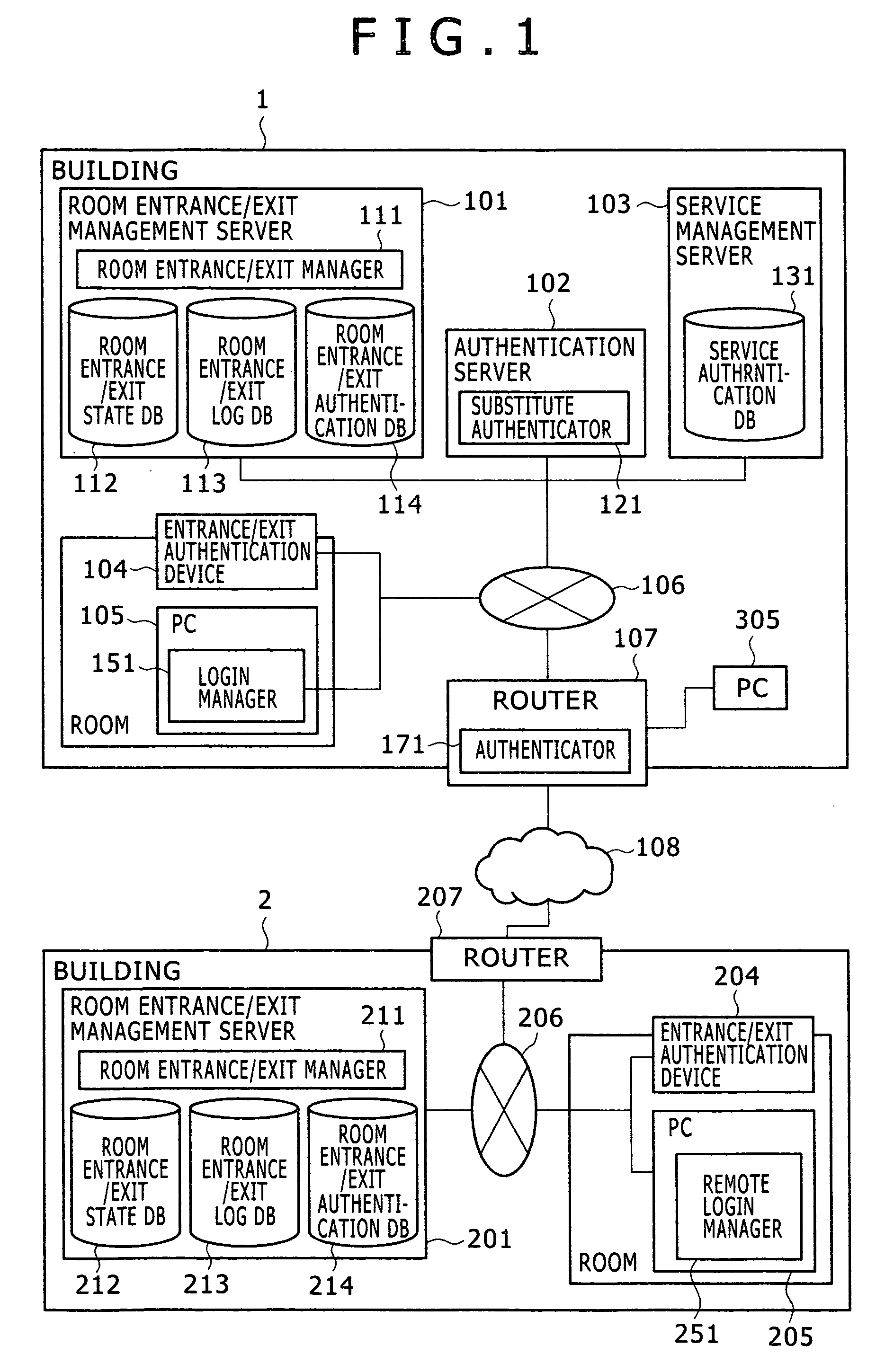
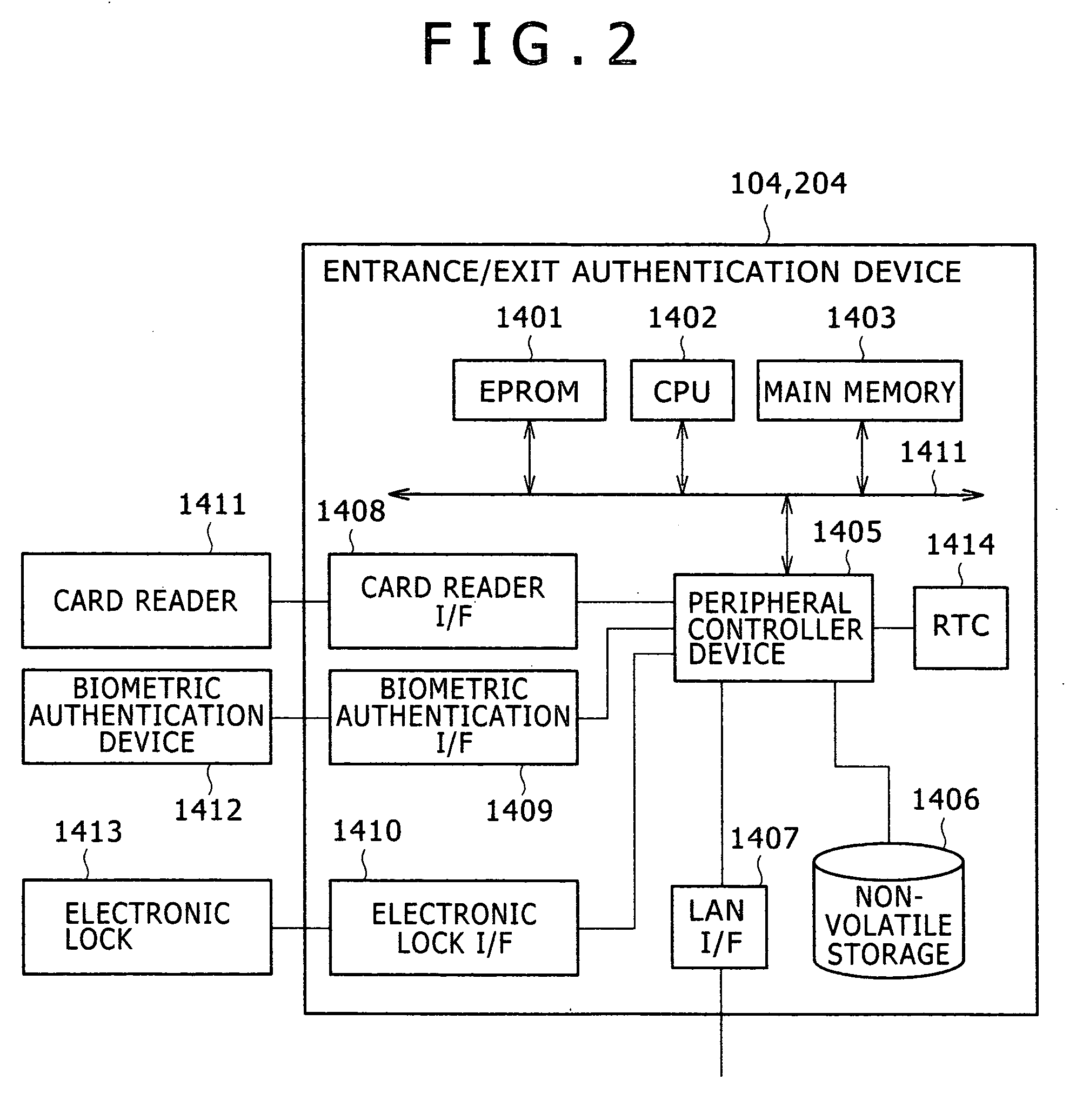
A service authentication system includes a room entrance / exit manager that manages locations of users, a login manager or remote login manager that manages PC login, an authenticator that performs user authentication, a substitute authenticator that performs various authentications in an integrated manner, and a service management server that stores user authentication information. When the user has requested authentication from the authenticator, the authenticator requests authentication from the substitute authenticator, which then obtains room entrance / exit information from the entrance / exit manager and authentication information from the service management server and authenticates them based on the obtained information.
Owner:HITACHI LTD
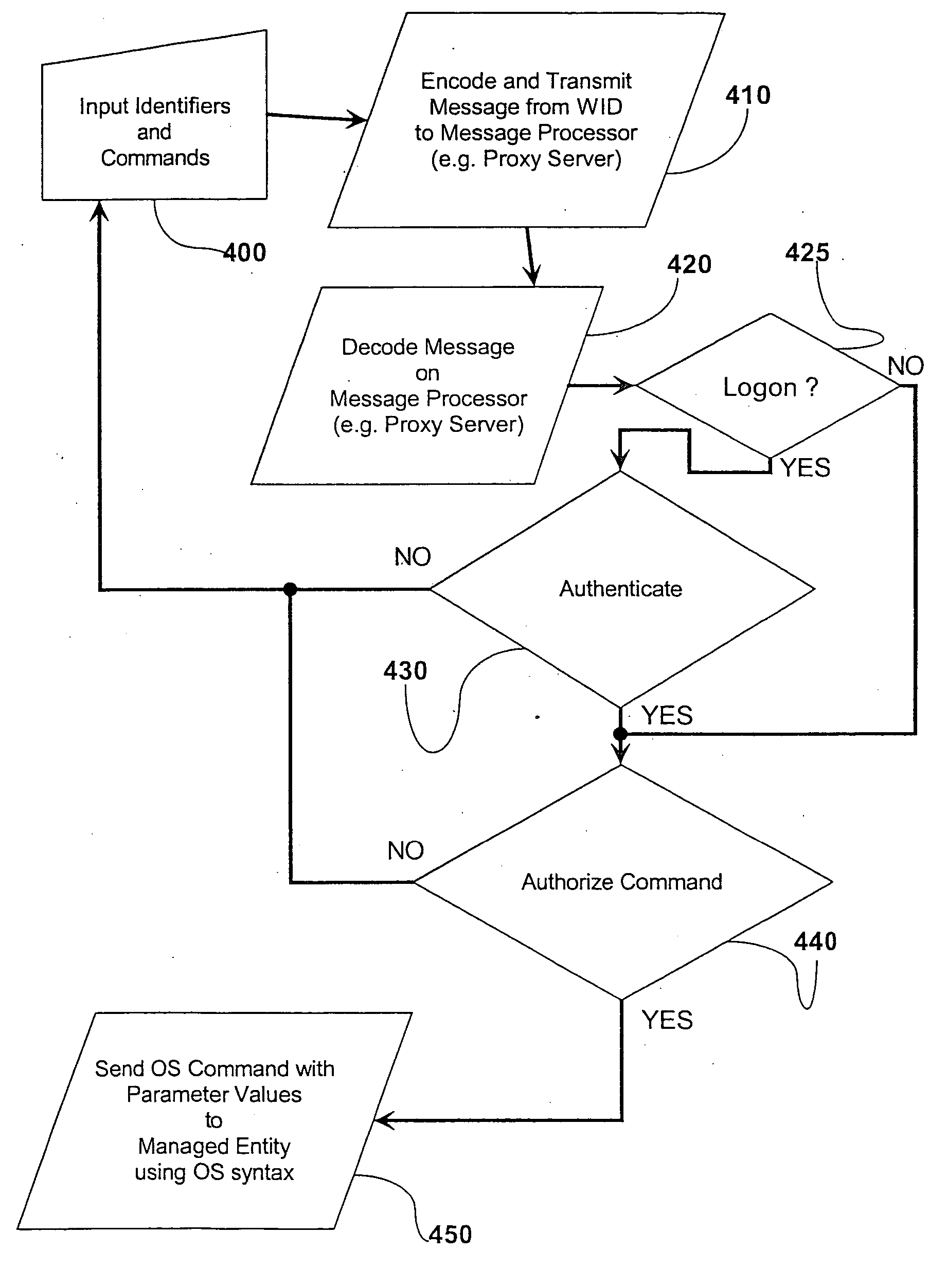
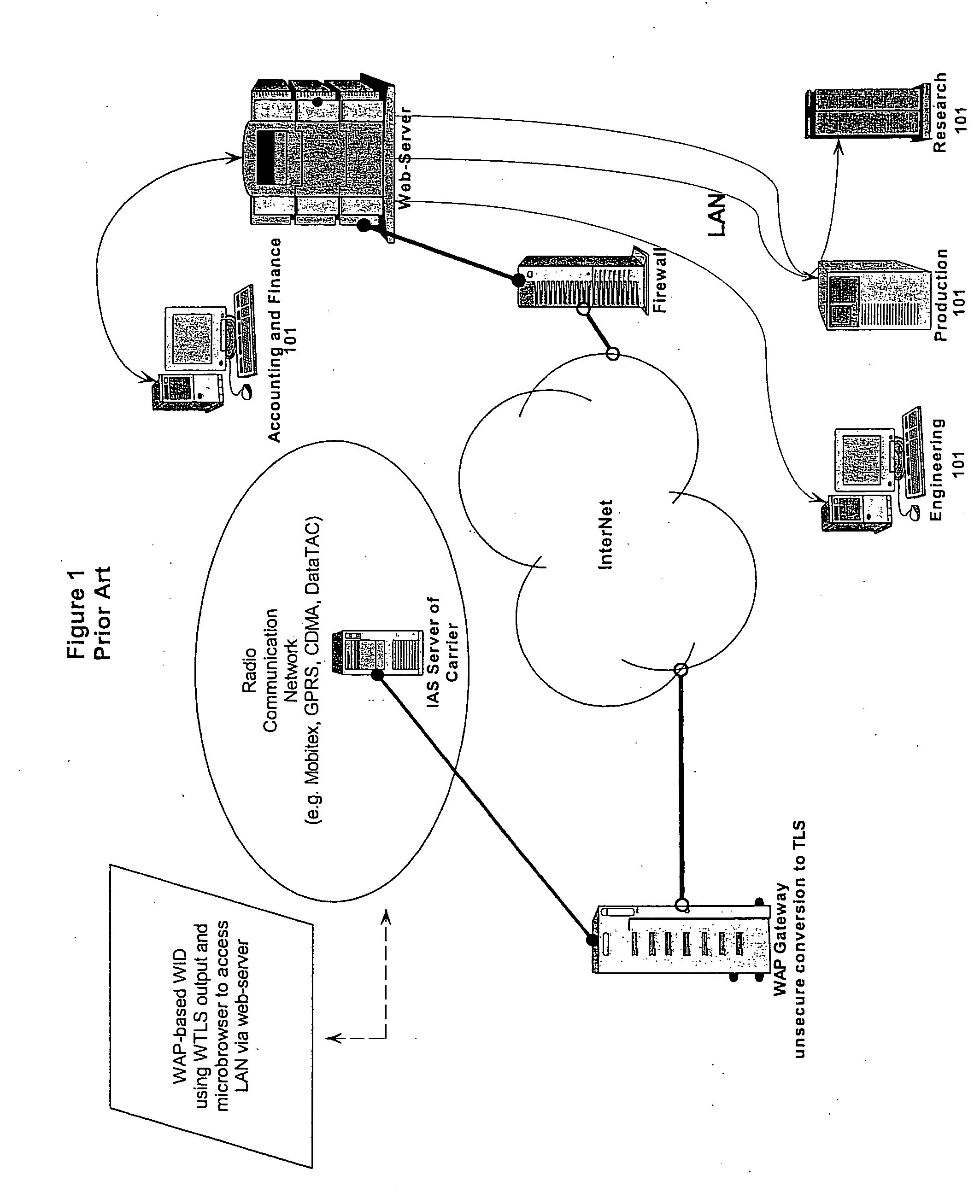
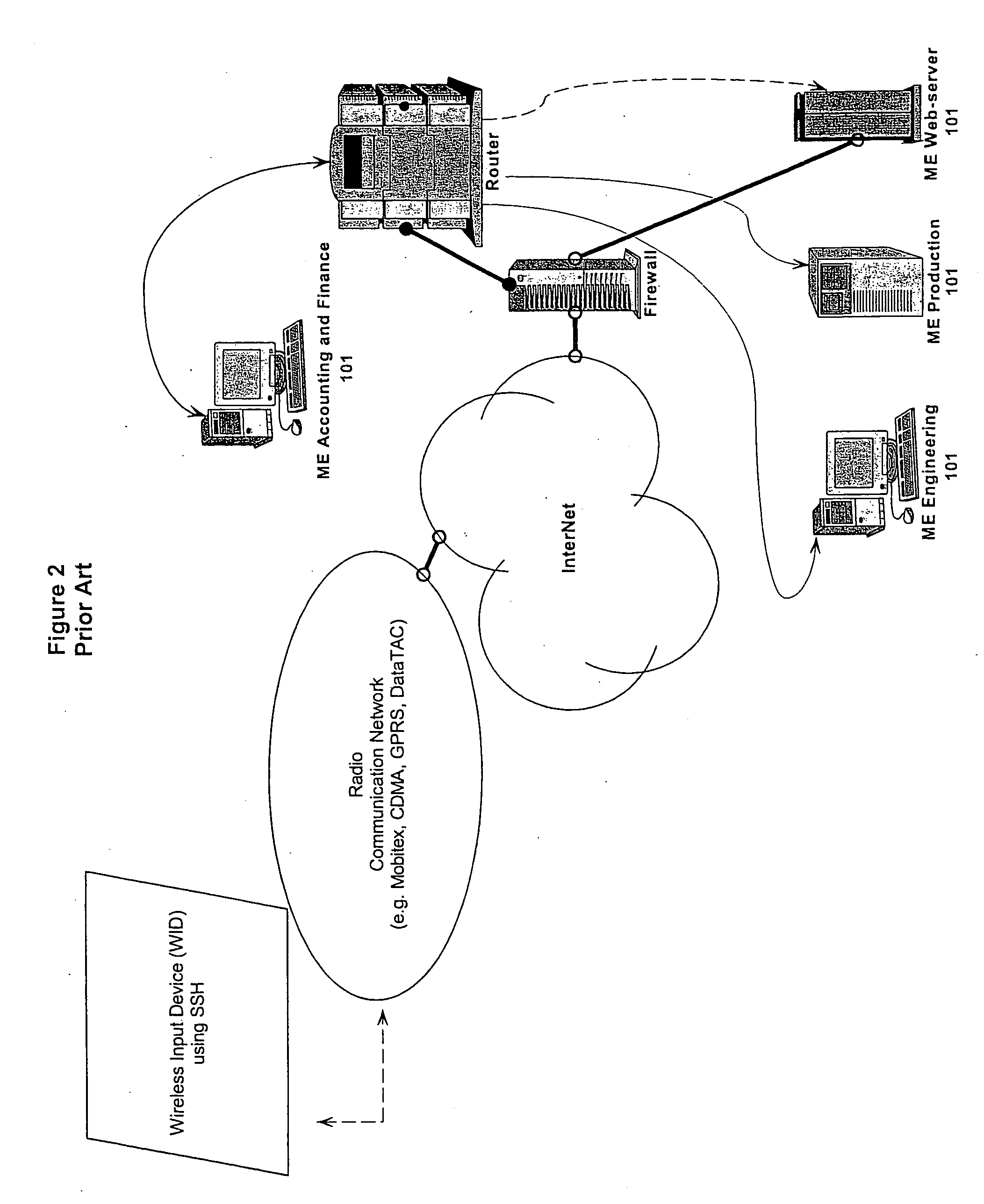
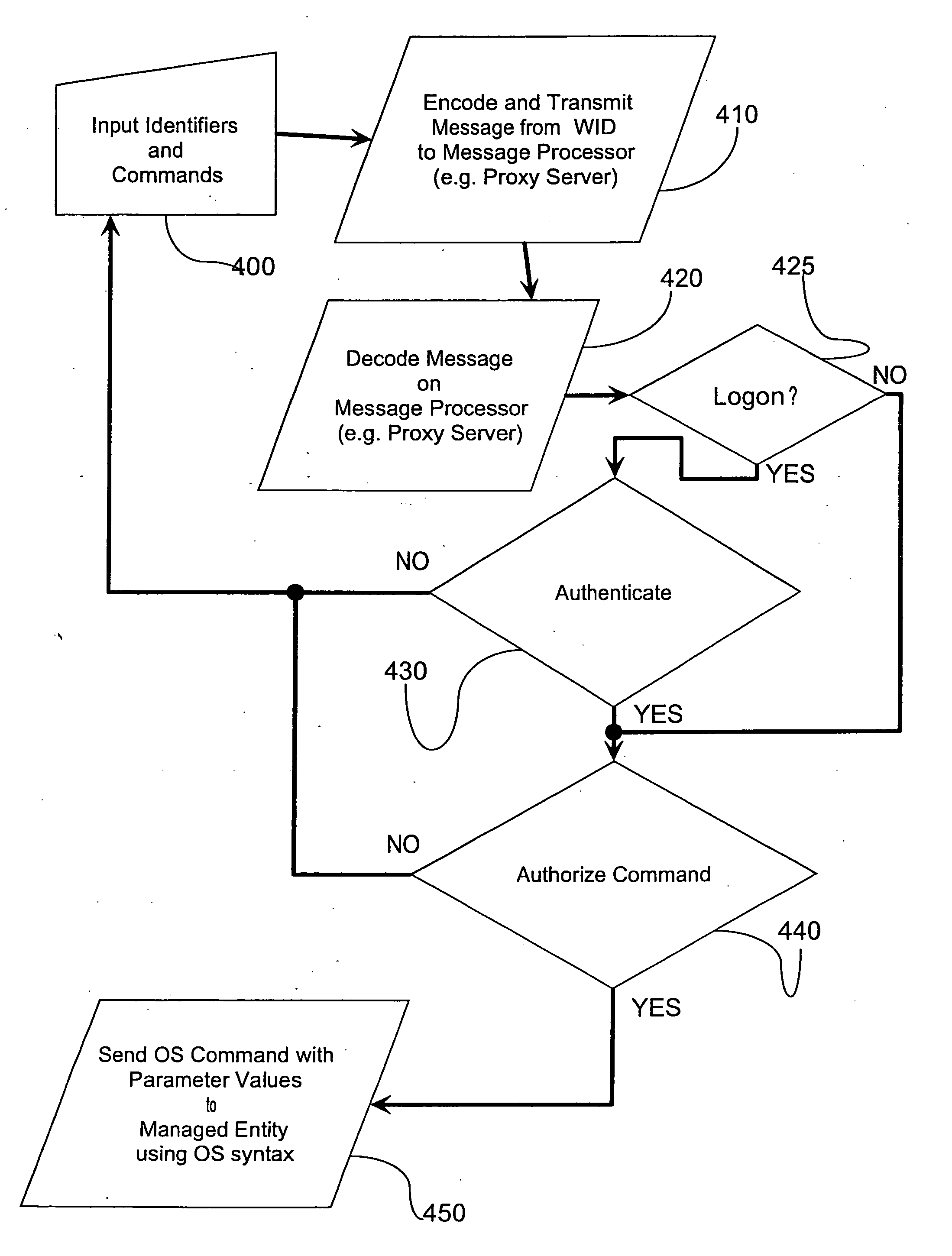
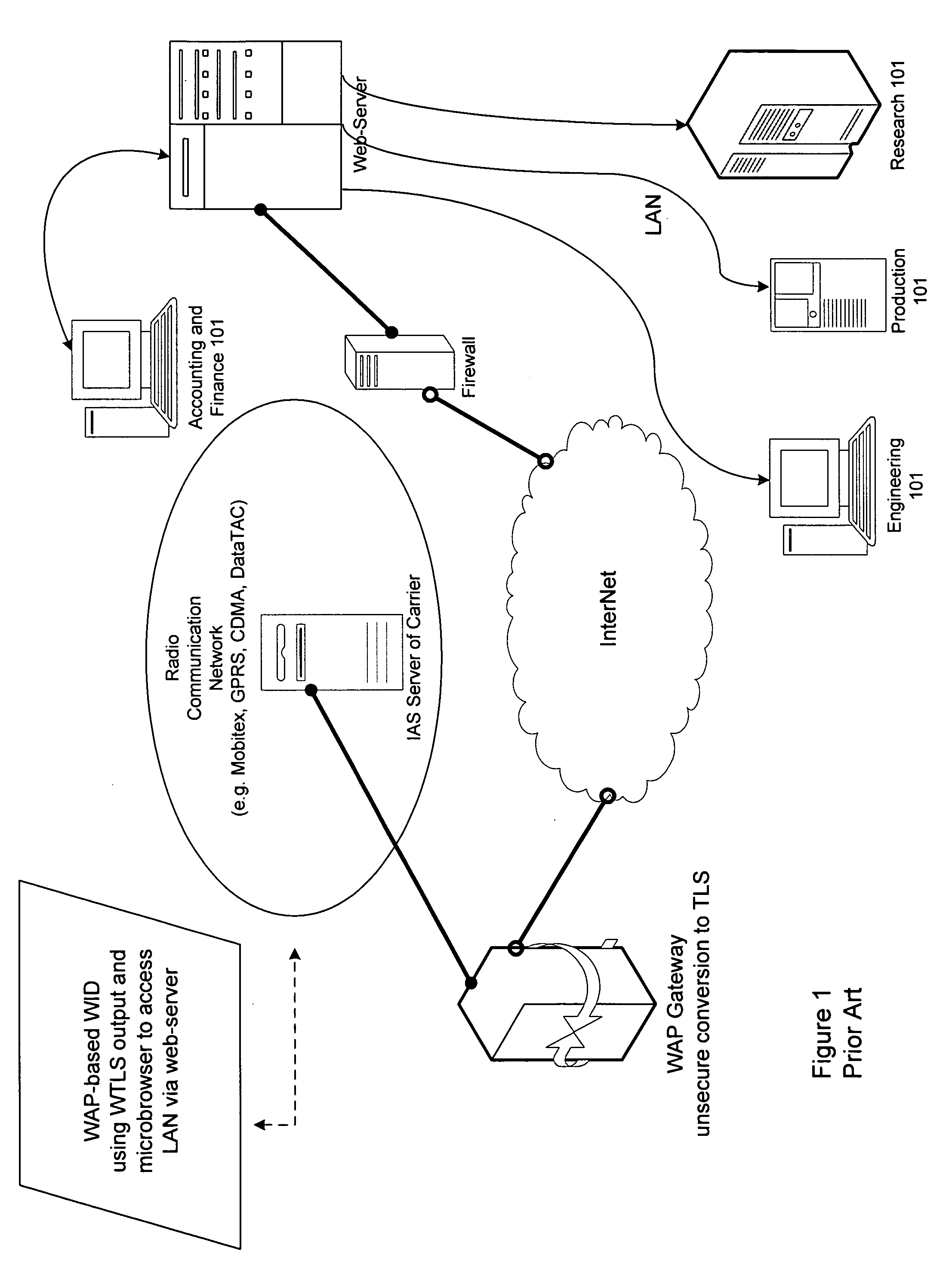
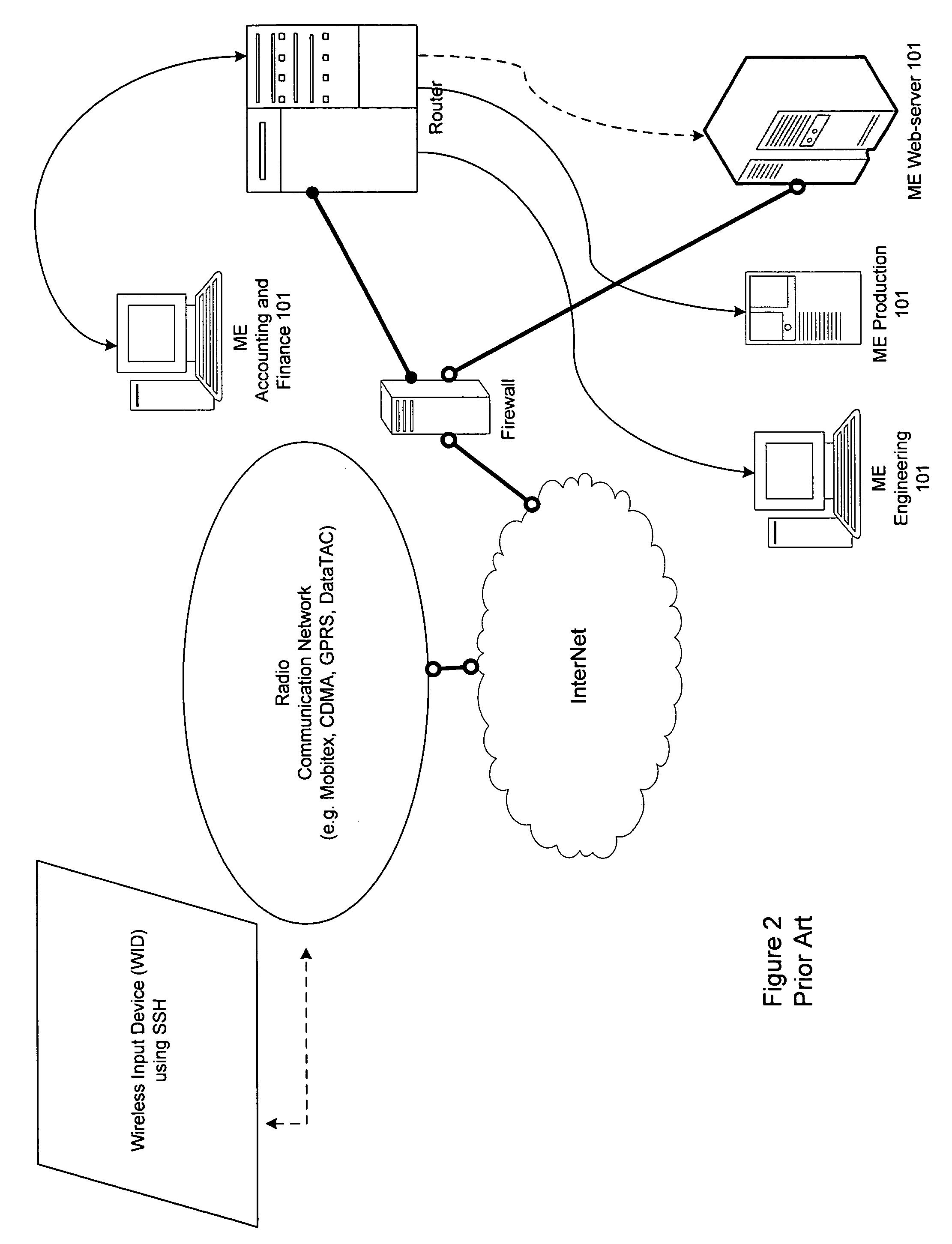
Proxy method and system for secure wireless administration of managed entities
InactiveUS20060218402A1Reduce usageIncrease varietyKey distribution for secure communicationUser identity/authority verificationTraffic capacityWeb service
A method, system and apparatus are described for avoiding the use of a web-server or generic security when providing network administration services remotely to managed entities using wireless technology. Instead a true Proxy device, not operating as a web-server, is used to pre-process all command traffic from wireless input devices (WID). The intervention between the WID and the managed entities of the Proxy isolating the managed entities from the WID, enhanced by encoding using a novel messaging protocol, further enhanced by a novel security model based on multiple pre-shared keys and algorithms together with identifiers and passwords that are not transmitted, achieves several bandwidth and security advantages including the ability to deliver TELNET services across the Internet and behind a firewall.
Owner:VERTIV IT SYST INC
Network terminal management method
InactiveCN102123050AComplete managementAutomate managementData switching networksIp addressTerminal equipment
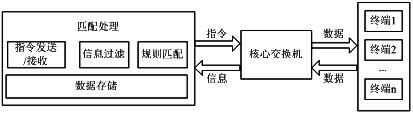
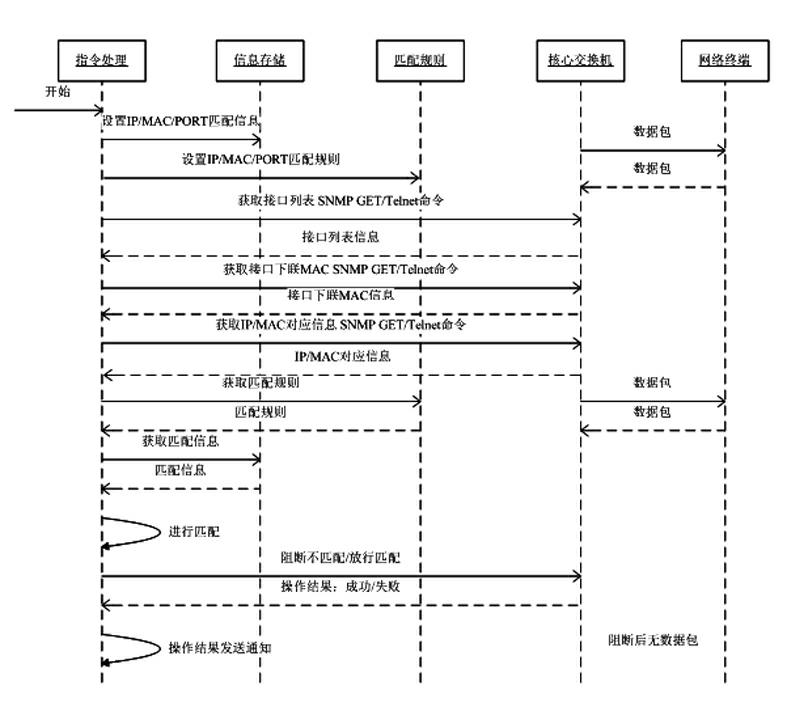
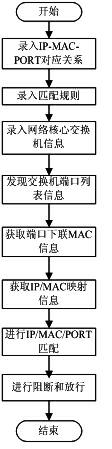
The invention discloses a network terminal management method, which comprises the following steps of: 1) inputting a correspondence relationship between a port of a switch and an Internet protocol (IP) address and a media access control (MAC) address of a terminal; 2) setting a terminal matching rule; 3) inputting simple network management protocol (SNMP) network related information required to be managed, or inputting the Telnet / secure shell (SSH) related information of each core switch manually; 4) acquiring the port list information of the core switch; 5) acquiring the downlink information of the MAC address of each port of the core switch; 6) acquiring a correspondence relationship list of the IP address and the MAC address in a network; 7) matching the port of the core switch, the IP address and the MAC address according to the configured terminal matching rule; and 8) blocking the terminal which does not accord with the matching rule, releasing the terminal which accords with the matching rule, and giving an alarm for an operation result.
Owner:勤智数码科技股份有限公司
Full-automatic firing method for wideband individual line subscriber based on flowpath optimization
InactiveCN101510831AImprove accuracyImprove human resourcesData switching networksAsynchronous communicationSystem configuration
The invention relates to a fully-automatic subscribing method for broadband special line users based on process optimization, which comprises the steps: a special line automatic subscribing system receives a work order from BSS, resolves the work order, obtains information of such as equipment to be configured, and searches upper and lower correlative equipment information, login manner and login password according to the existing equipment information, and then logins in the equipment according to the equipment information to configure related data order; the special line automatic subscribing system is configured with thread counts for processing the work order, starts a work order receiving module, and selects a system operation mode through reading configuration files, namely a parent-child process or an automatic reset mode; socket communication is utilized to simulate telnet to login in the equipment and issue orders, the port information of the equipment is validated and judged during the process of issuing orders and the execution result of the orders issued currently is validated and judged; if other socket demands are connected at the same time, other thread counts are assigned to do the work so as to fulfill the long connection asynchronous communication between the automatic subscribing system and the socket of BSS.
Owner:LINKAGE SYST INTEGRATION
Network file automatic dump method and system
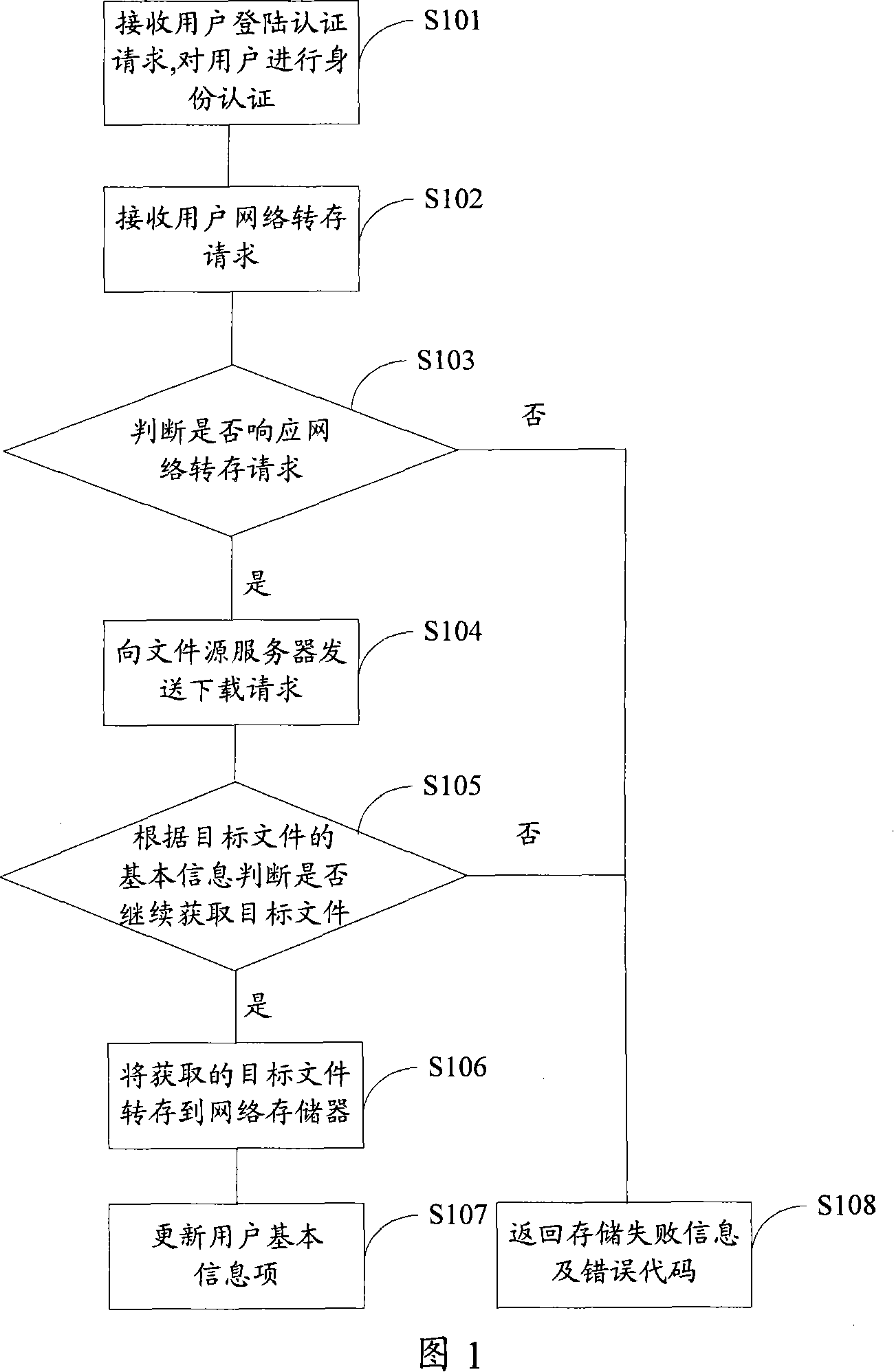
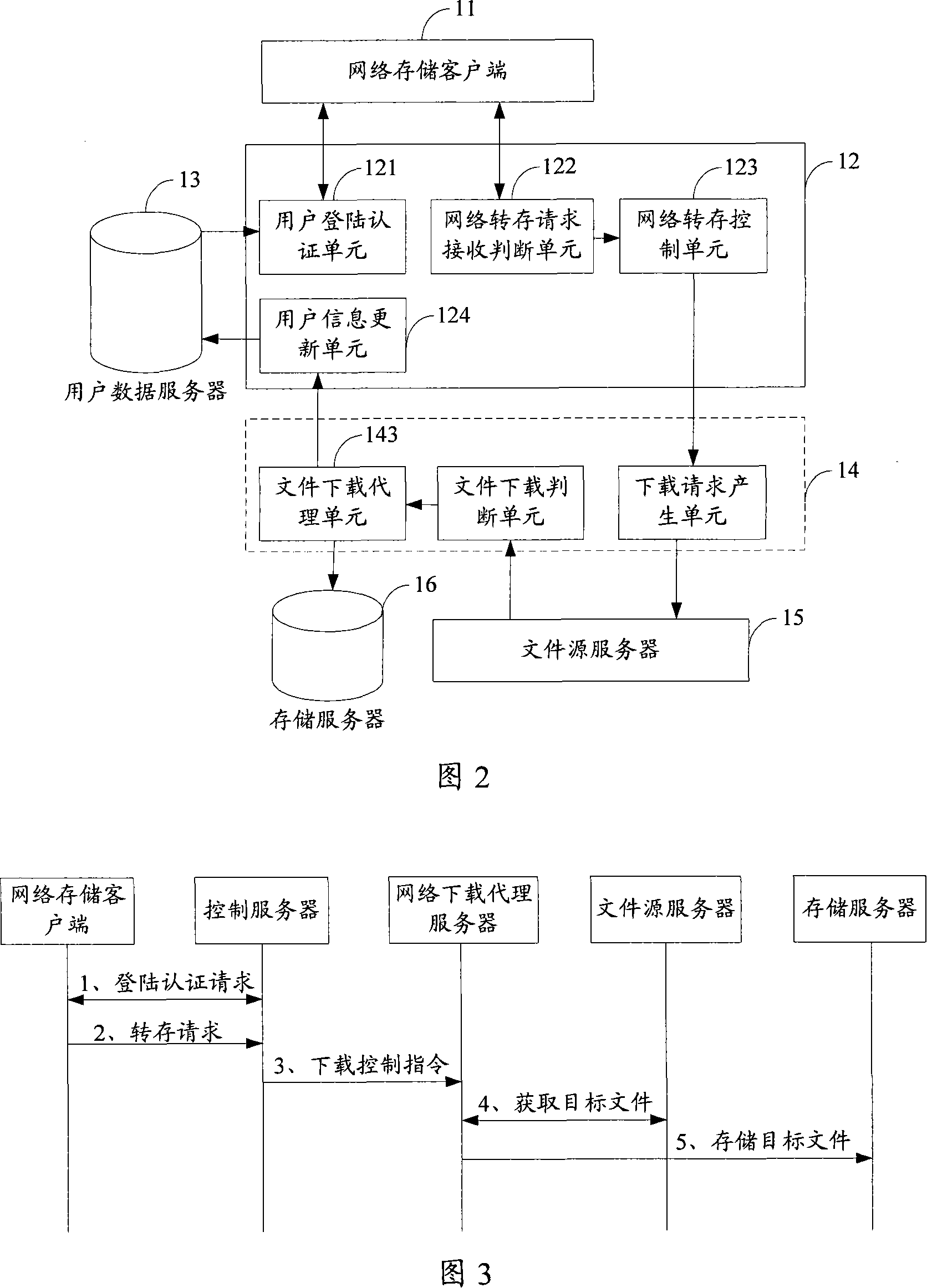
InactiveCN101072163AReduce waiting timeSpecial service provision for substationUser identity/authority verificationNetwork addressingNetwork address
The method includes following steps: (1) the method receives network transfer storing request (NTSR) from client end the user locates at, and NTSR carries network address of object file, and relative path for storing the object file of the object file; (2) obtaining the object file from server corresponding to network address of the object file; (3) storing the obtained object file to the server according to relative path for the object file. The system includes network storage client end, file source server, and storage server. The system also includes control server and proxy server for network down loading. Features are: reducing time for waiting operation of transfer storing network files, no need of complex TELNET protocol, and simplified operation of transfer storing network files.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Secure access logic control method based on terminal access behavior and platform server
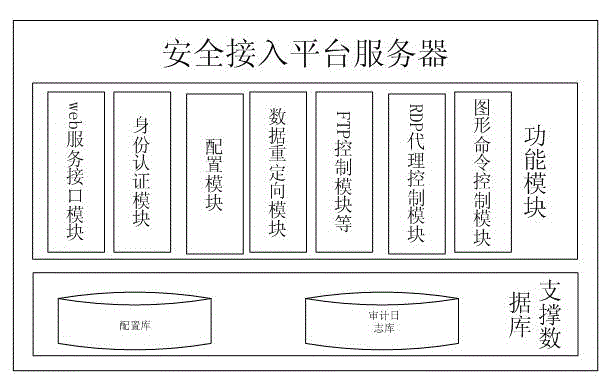
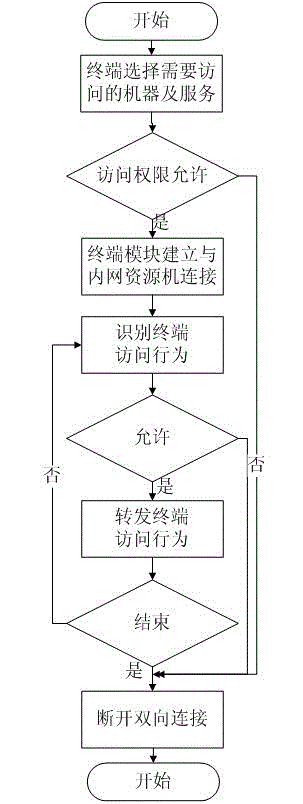
ActiveCN102984159ASimplify the difficulty of resource managementAvoid log audit complexityUser identity/authority verificationDot matrixFree interface
The invention discloses a secure access logic control method based on a terminal access behavior and a secure access platform server. A logic control module of the terminal access behavior is arranged at a secure access platform server terminal; information, such as terminal access authority, scene judging parameters, a dot matrix area command comparison table and the like is configured; each data package of terminal access intranet resource is redirected into an agent program which corresponds to the logic control module; and the logic control module identifies the terminal access behavior in various modes to control forwarding or discard. The method of the invention executes classification and identification of character commands, such as FTP (File Transfer Protocol), TELNET, SSH (Secure Shell) and the like, RDF (Resource Description Framework) graphical interface operation and user free interface system operation for the terminal access behavior on the secure access platform server terminal, and judges whether the execution is permitted or not according to identified commands and user authority logic control, so that the difficulty of resource management is simplified, the repeated authentication of each system is avoided; and the identification and the logic control of the character commands, the graphical interface operation and the like are solved.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER +3
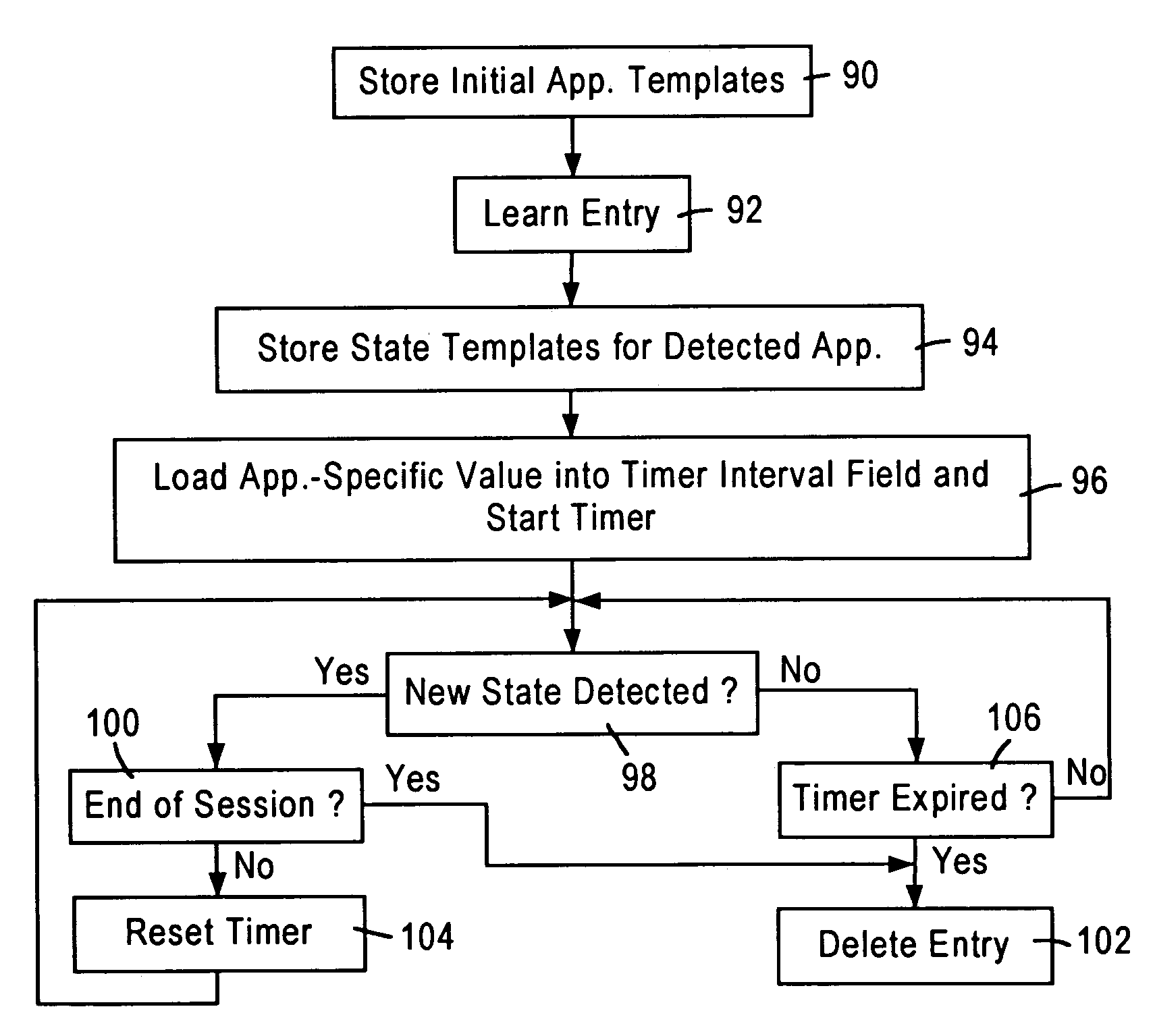
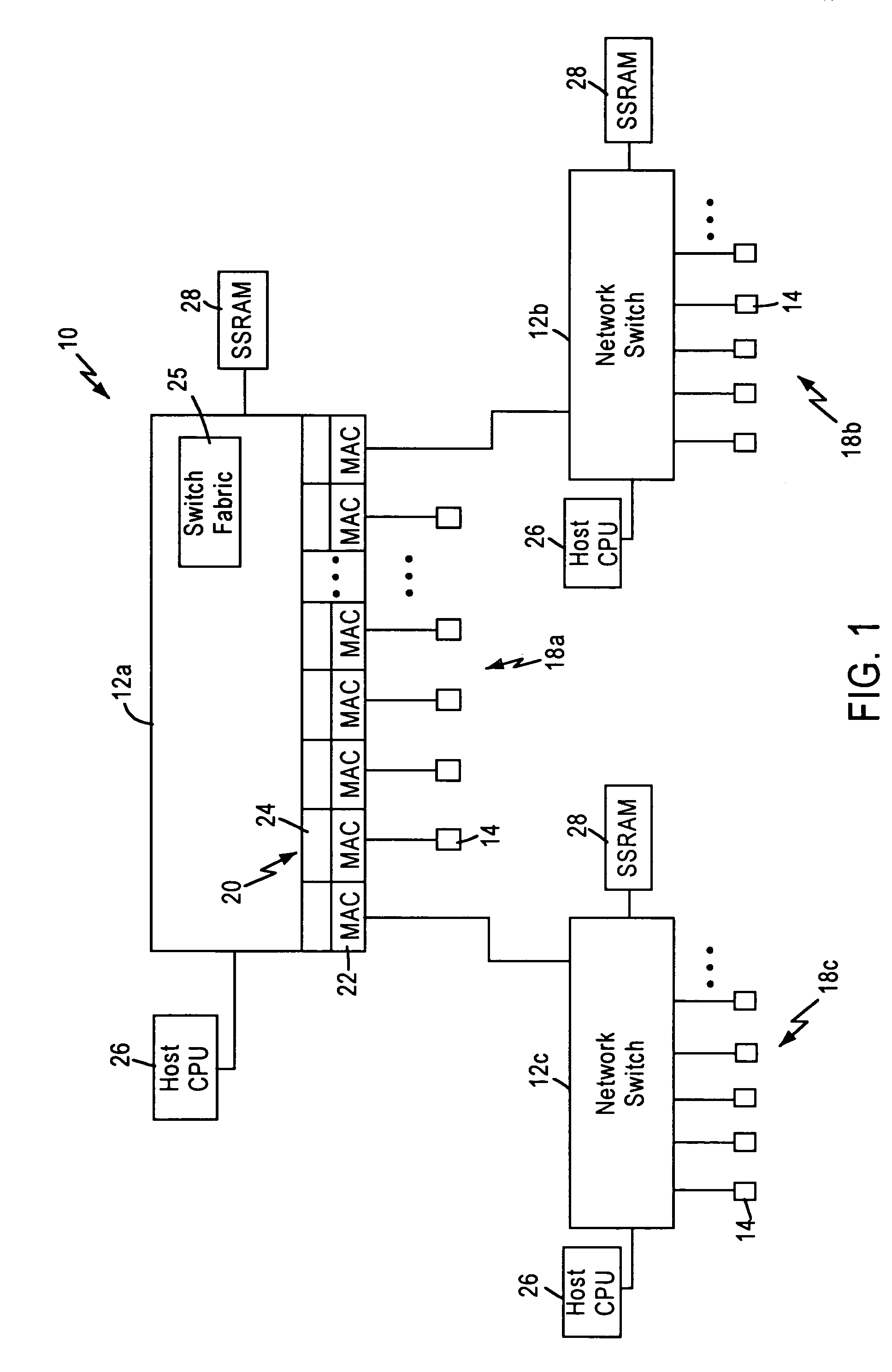
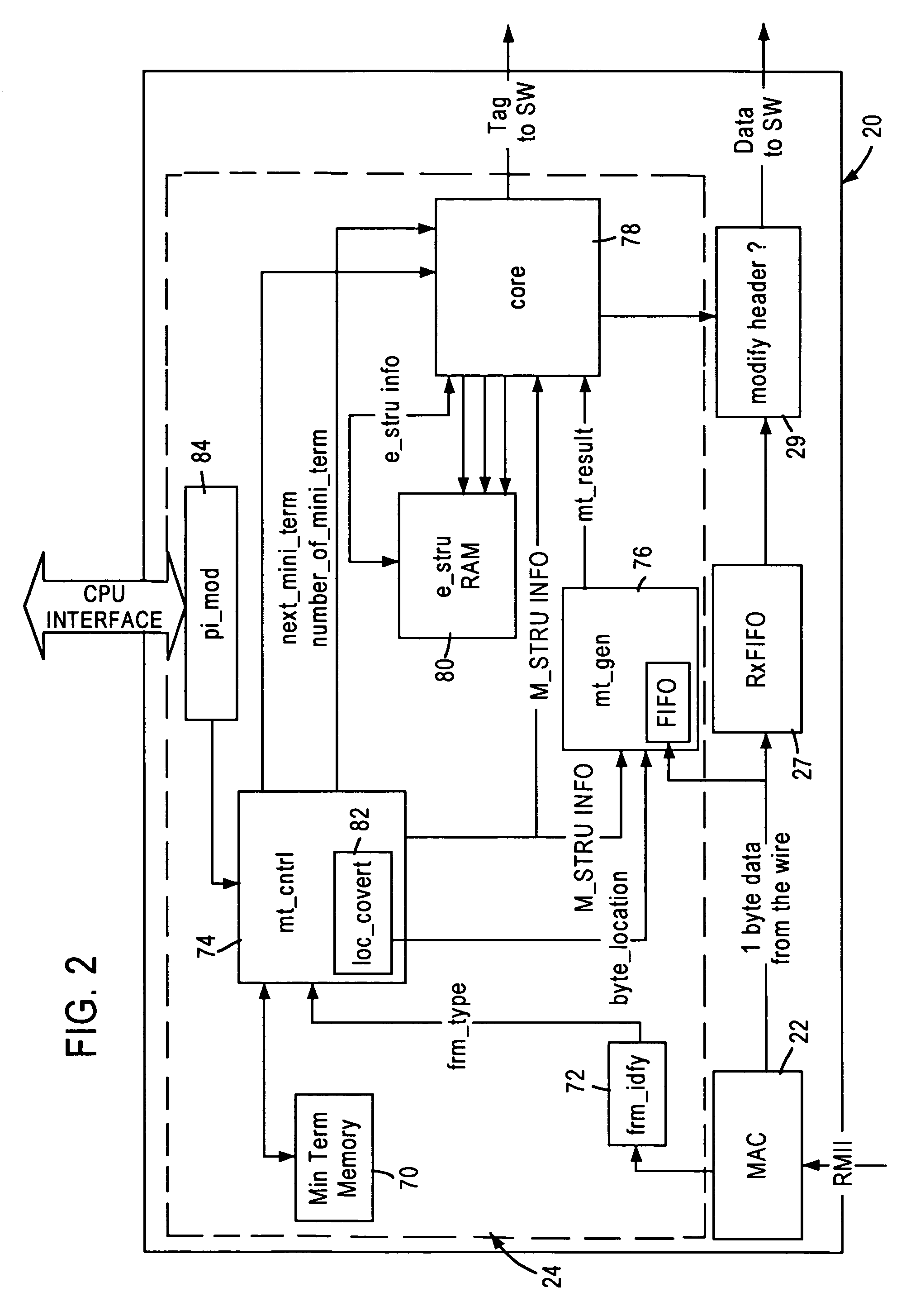
Selective address table aging in a network switch based on application state determined from a received data packet
InactiveUS7002955B1Minimizing relearningMore precise aging intervalsNetworks interconnectionBus networksData streamNetwork packet
A network switch, configured for performing layer 2 and layer 3 switching in an Ethernet (IEEE 802.3) network without blocking of incoming data packets, includes a network switch port having a packet classifier module configured for evaluating an incoming data packet on an instantaneous basis. The packet classifier module performs simultaneous comparisons between the incoming data stream of the data packet and multiple templates configured for identifying respective data protocols. Each template is composed of a plurality of min terms, wherein each min term specifies a prescribed comparison operation within a selected data byte of the incoming data packet. Hence, the packet classifier module is able to monitor data flows between two network nodes interacting according to a prescribed network application. The packet classifier module determines the application state for a prescribed network application from a received layer 2 data packet, enabling switching logic within the network switch to utilize application-specific aging intervals for respective network applications such as HTTP, SNMP, ftp, Telnet, etc. in order to delete aged address entries from a network switch address table based on the supported network application. Determination of the application state from the received layer 2 data packet also enables the network switch to detect the end of a data flow for deletion of the corresponding address entry from the network switch address table.
Owner:ADVANCED MICRO DEVICES INC
Proxy method and system for secure wireless administration of managed entities
InactiveUS20060285692A1Reduce usageIncrease varietyKey distribution for secure communicationDigital data processing detailsWeb servicePassword
A method, system and apparatus are described for avoiding the use of a web-server or generic security when providing network administration services remotely to managed entities using wireless technology. Instead a true Proxy device, not operating as a web-server, is used to preprocess all command traffic from wireless input devices (WID). The intervention between the WID and the managed entities of the Proxy isolating the managed entities from the WID, enhanced by encoding using a novel messaging protocol, further enhanced by a novel security model based on multiple pre-shared keys and algorithms together with identifiers and passwords that are not transmitted, achieves several bandwidth and security advantages including the ability to deliver TELNET services across the Internet and behind a firewall.
Owner:AVOCENT HUNTSVILLE CORPORATION
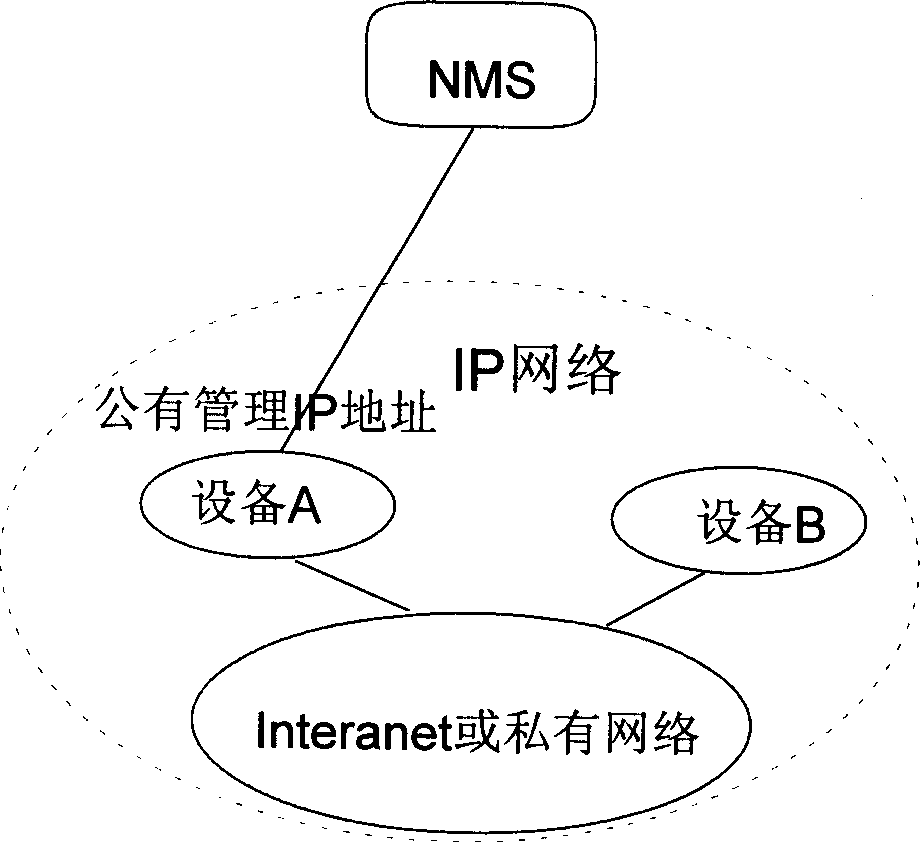
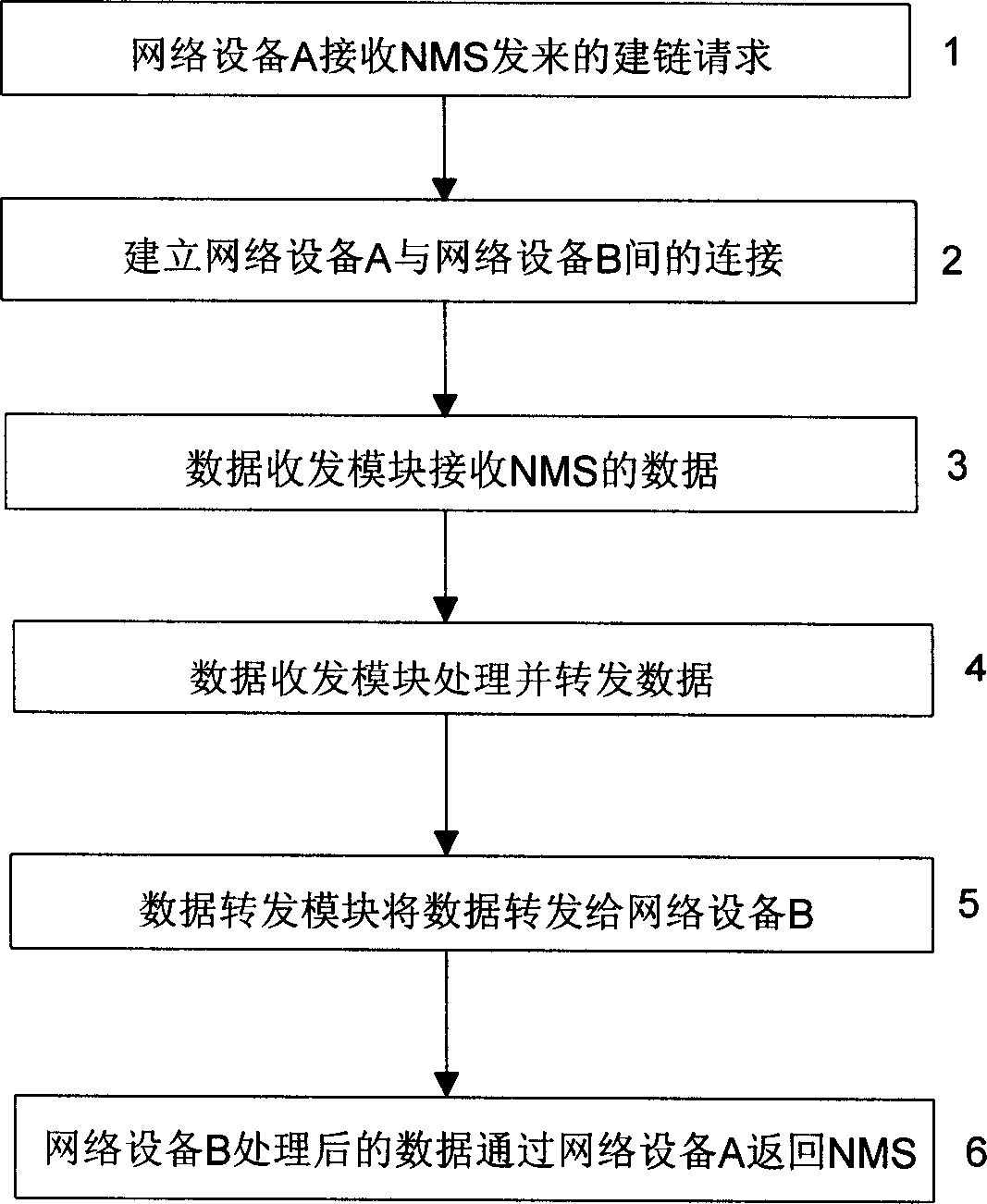
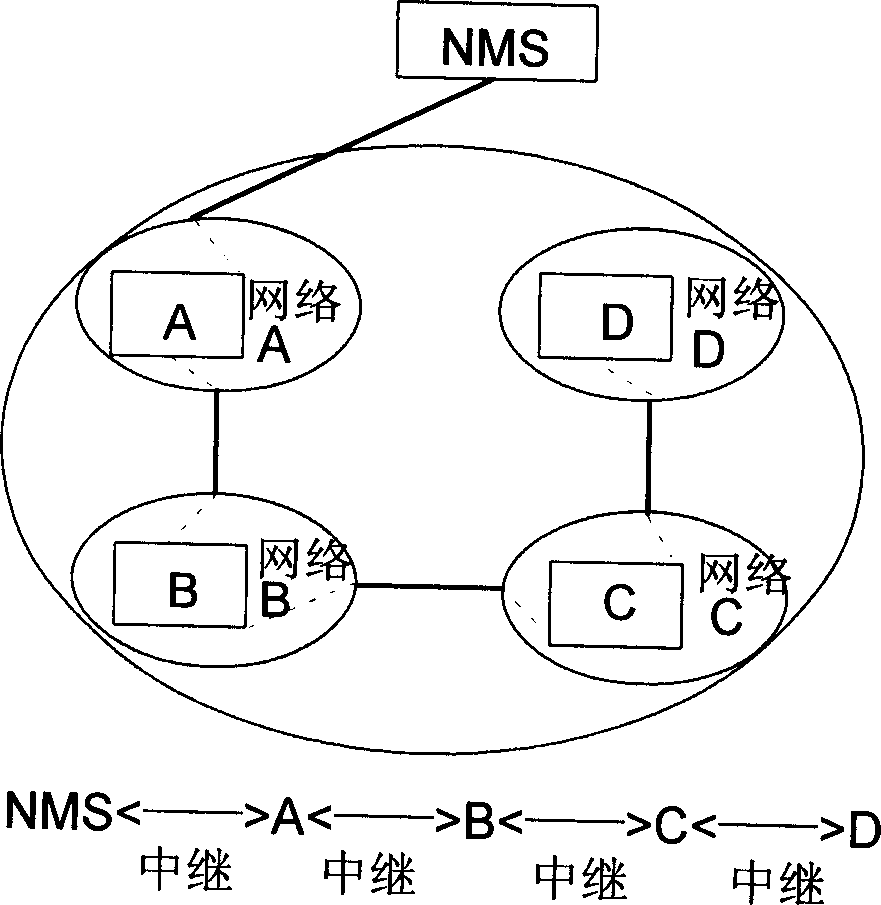
Relay management method of network equipment based on Telnet protocol
InactiveCN1437358AEasy to manageOvercome the shortcomings of the relay management functionData switching by path configurationTTEthernetWorkstation
A realization method of junction management for network equipment based on remote login Internet protocol includes the following steps: first the network equipment will receive connection request transmitted from network managing station (NMS) for setting up transmission control protocol based on remote login and connection between network equipments to be managed based on Telnet TCP; then, the network equipment will receive management data in format of remote login Internet protocol (Telnet IP) from NMS and the data will be sent to data forwarding module in network equipment after it has been processed accordingly; at last, the data forwarding module will forward the abovesaid management data to the network equipment to be managed and to receive the feedback management data which has been processed by the network equipment, also to send it to NMS.
Owner:HUAWEI TECH CO LTD
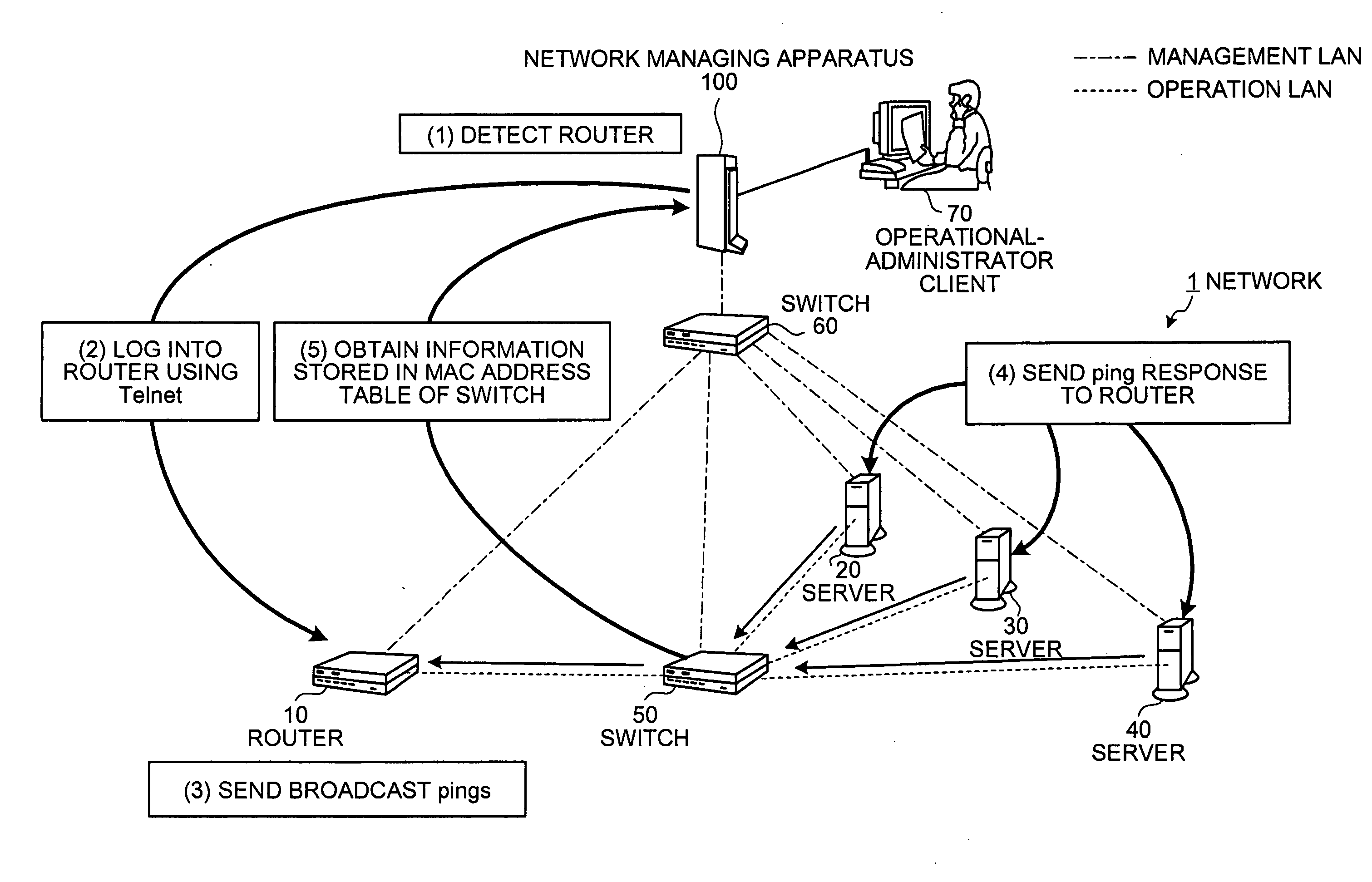
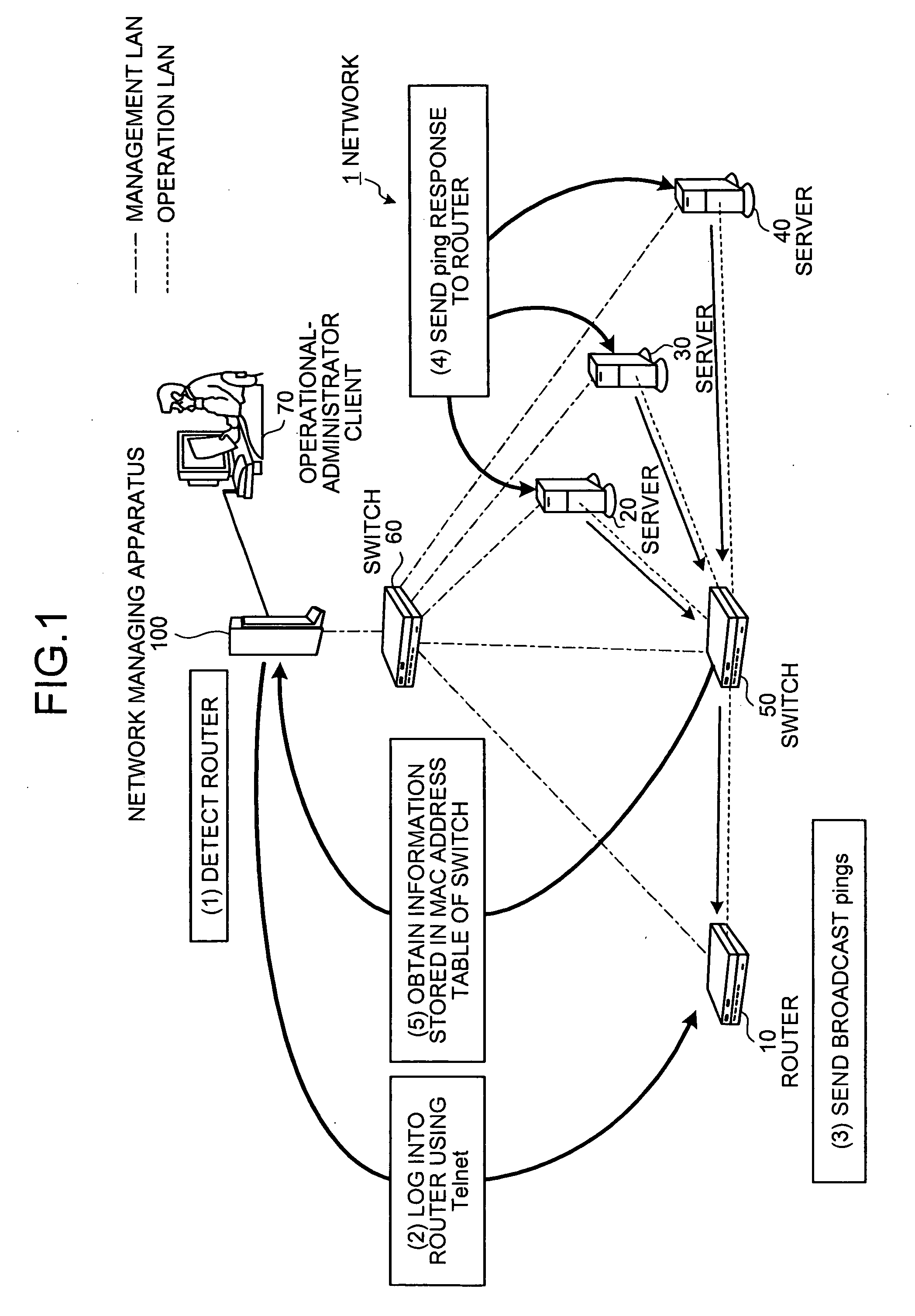
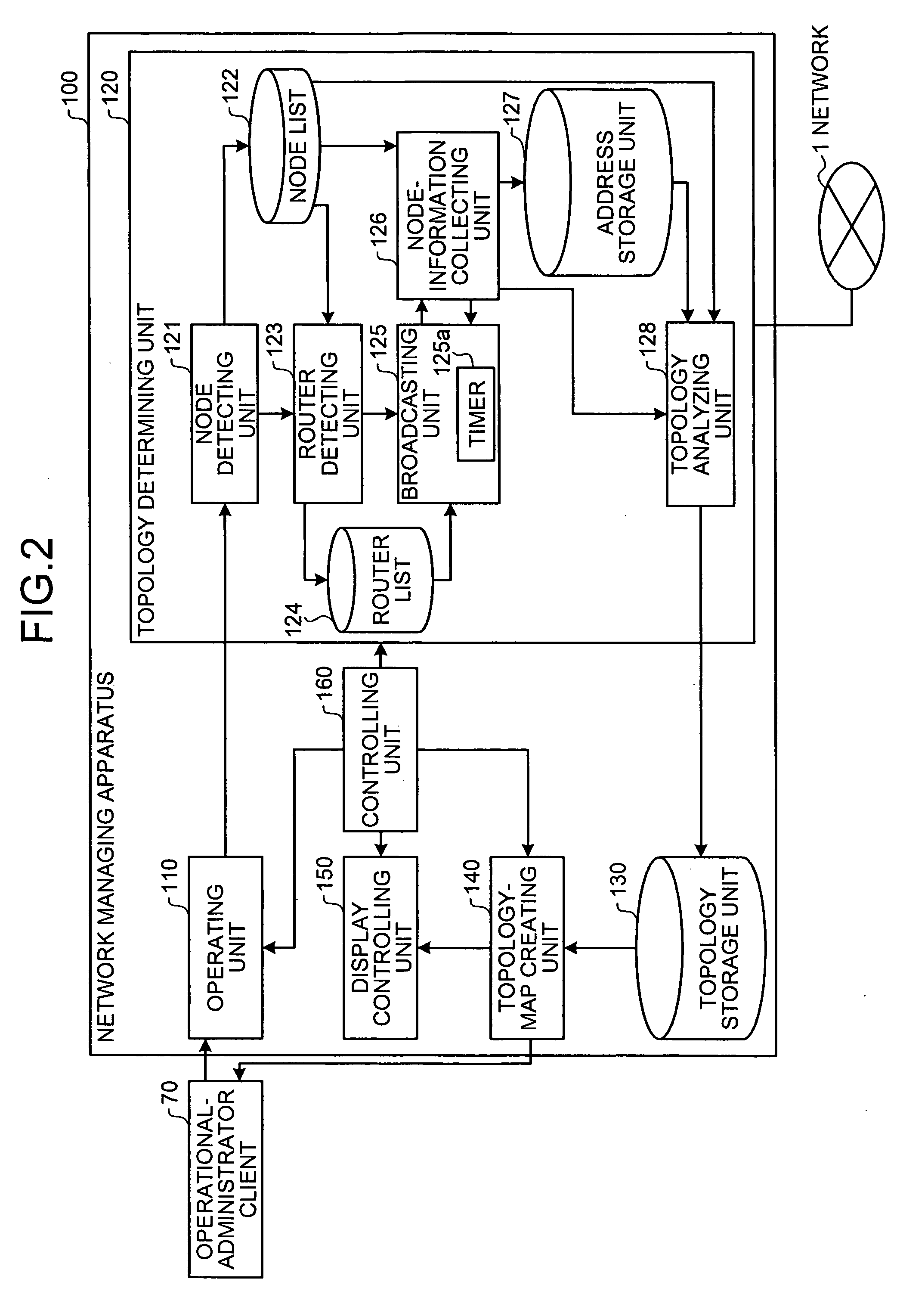
Apparatus, method, and computer product for topology-information collection
A network managing apparatus detects a router capable of using Telnet from among nodes in a network and causes that router to send a broadcast ping to other nodes. Each node in the network returns a ping reply to the router. The ping and the ping reply pass through a switch before arriving at their destinations. When the ping and the ping reply pass thorough the switch, the switch extracts MAC addresses of sender nodes and store them in its MAC address table. Thus, accurate topology of the network can be obtained from the MAC address table of the switch.
Owner:FUJITSU LTD
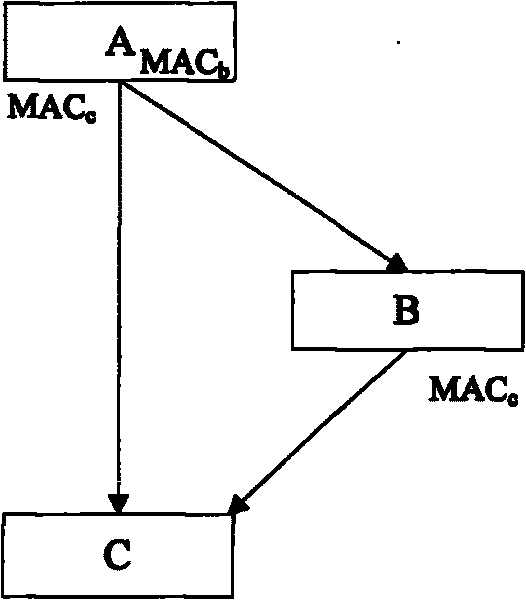
A right authentication method for network user
The invention relates to a method of a network user purview certification, which utilizes a built-in user purview database and the gateway or the router (2) of the management system thereof. The method comprises the steps that user information is obtained though a user landing; whether the user information is correct or not is judged, the IP address or the MAC address of the terminal (4) is bond with corresponding purview; the gateway or the router refuses or forwards the message outside according to the binding address, and the source IP address or the source MAC address reaching to other data messages. The method utilizes, binds and combines a user authentication code and the IP / MAC address of the terminal message, can manage the use purview though the gateway or the router, and can not be required to limit the network user terminal environment and install any software and equipment on the terminal equipment, and only if the terminal is connected with the external network through the gateway or the router of the invention, and the identification, the authentication and the management to the network users can be realized by using protocols of an Http protocol, a Telnet protocol or a UPNP protocol, etc.; therefore the cost is lower, and the operation is convenient.
Owner:ZTE CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com