A right authentication method for network user
An authentication method and user authority technology, which is applied in the field of network user authority authentication, can solve problems such as low scalability, complicated installation, and terminal system restrictions, and achieve the effect of convenient use and low cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
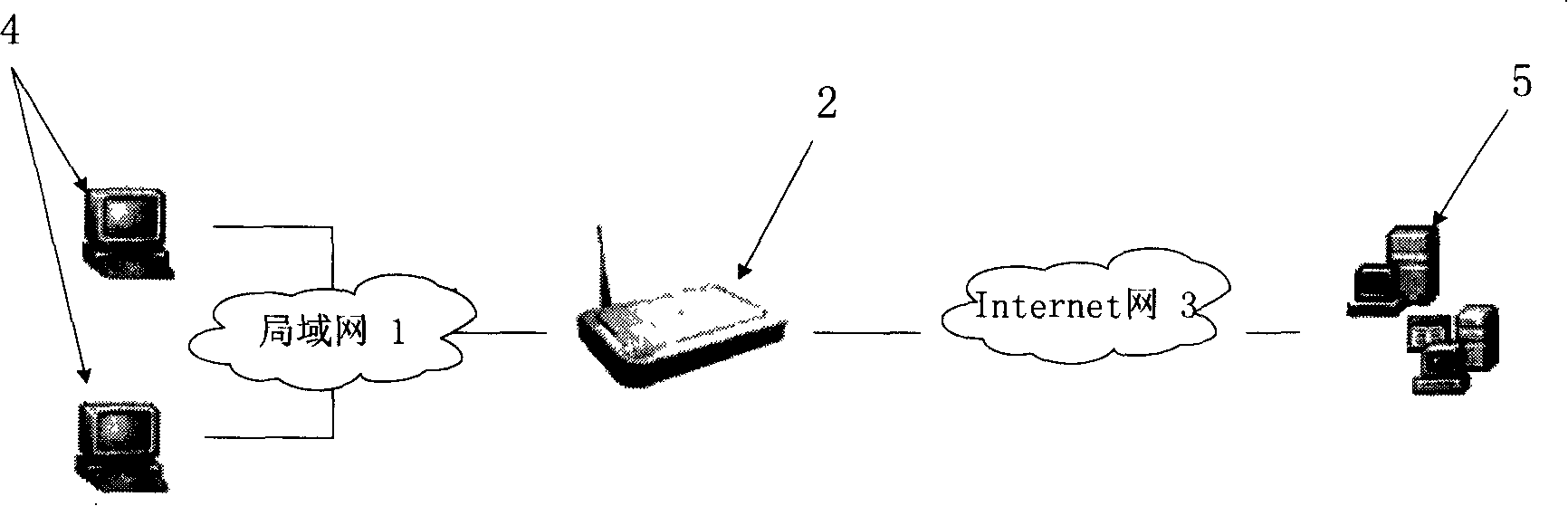
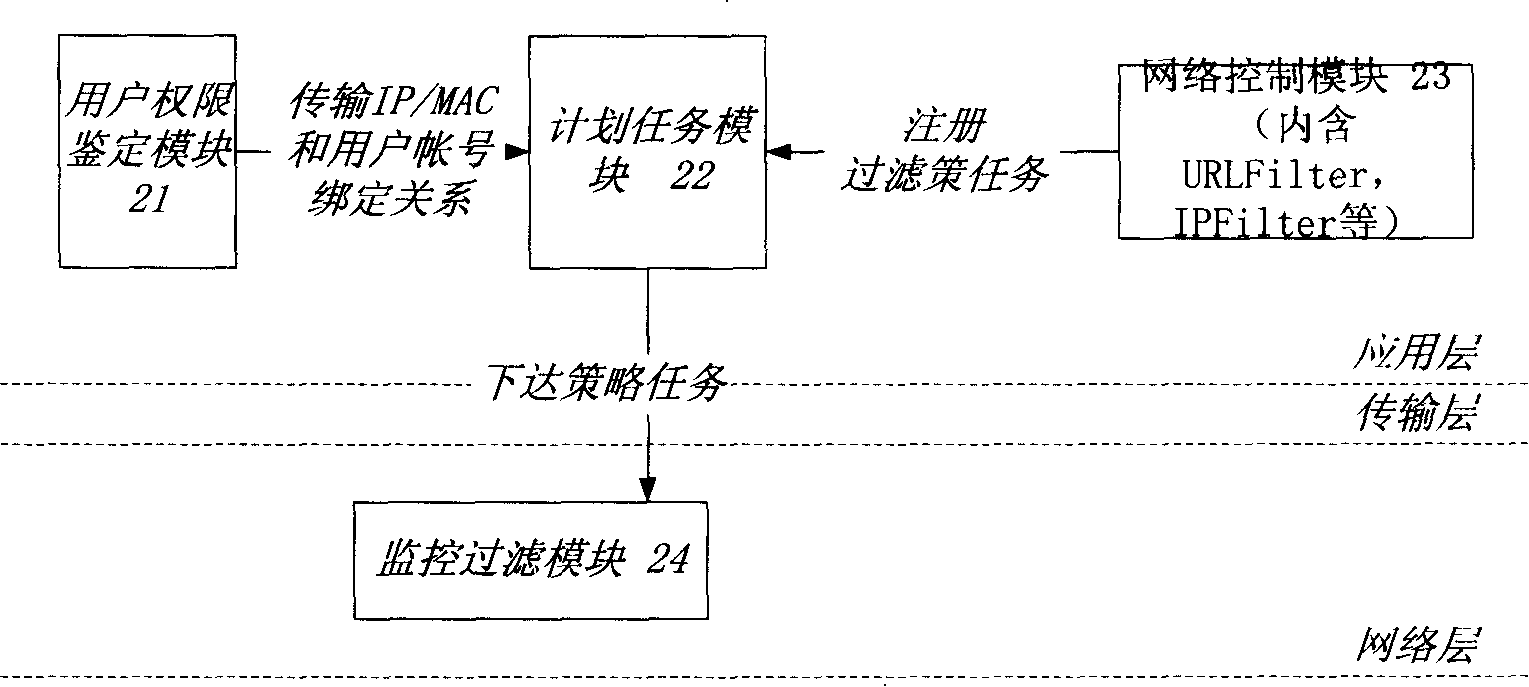
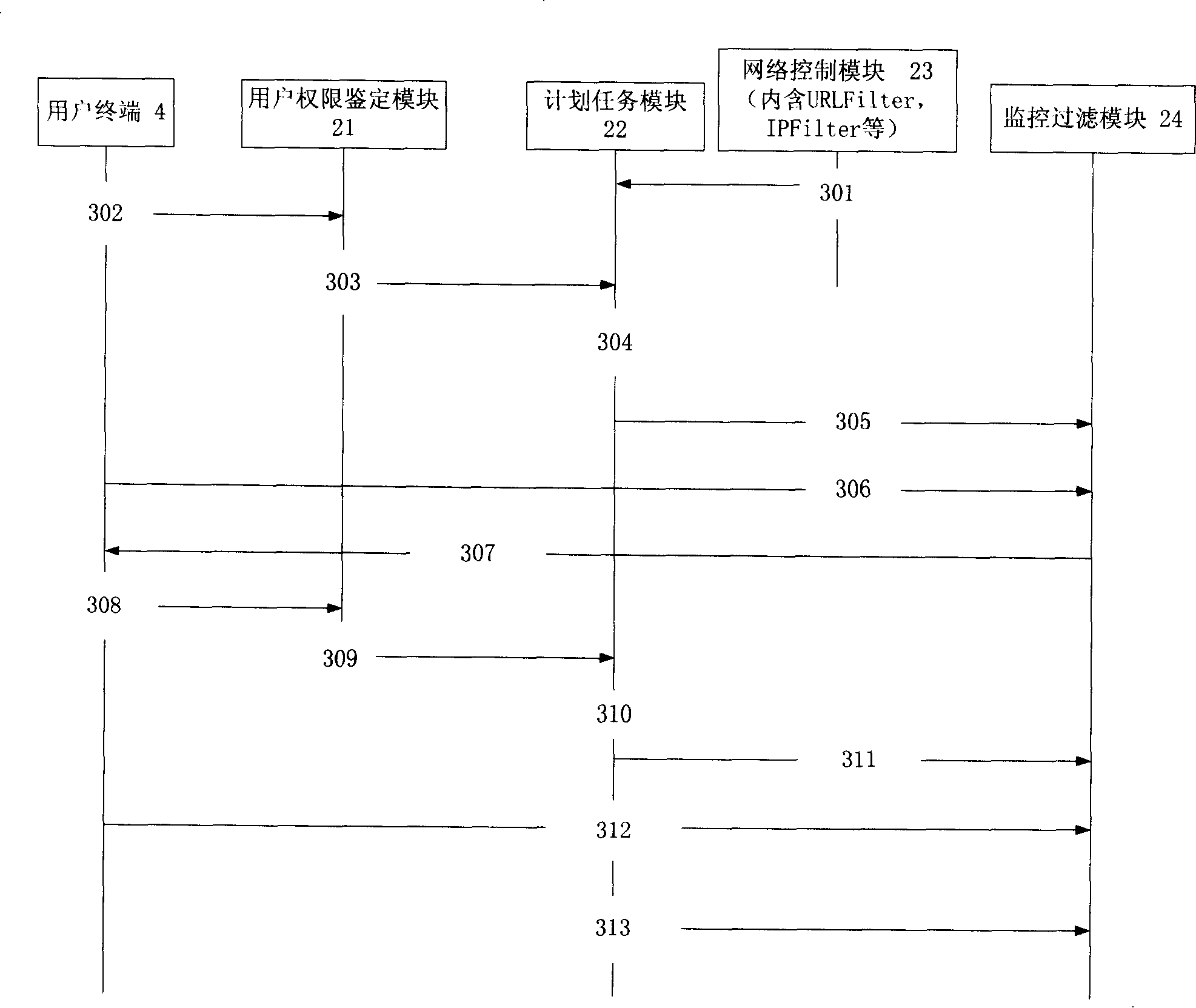
[0030] First of all, the network system to which the method of the present invention is applied is described, and the structure is as follows figure 1 As shown, the whole system is composed of user terminal 4 in LAN 1, gateway or routing device 2 between LAN 1 and INTERNER network 2 installed with user authority database and its management system. Among them, the user rights management system has an internal structure such as figure 2 As shown, the system includes a user authority authentication module 21, a network control module 23, a planned task module 22, and a monitoring and filtering module 24, wherein:
[0031] (1) User authority identification module 21: for accepting the authority identification of the user, the user can log in in multiple ways, such as Http, Ftp, Telnet, Upnp, etc., whether the user name and password registered by this module are correct on the one hand, and at the same time Analyze the IP address registered by the user;
[0032] (2) Network cont...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com