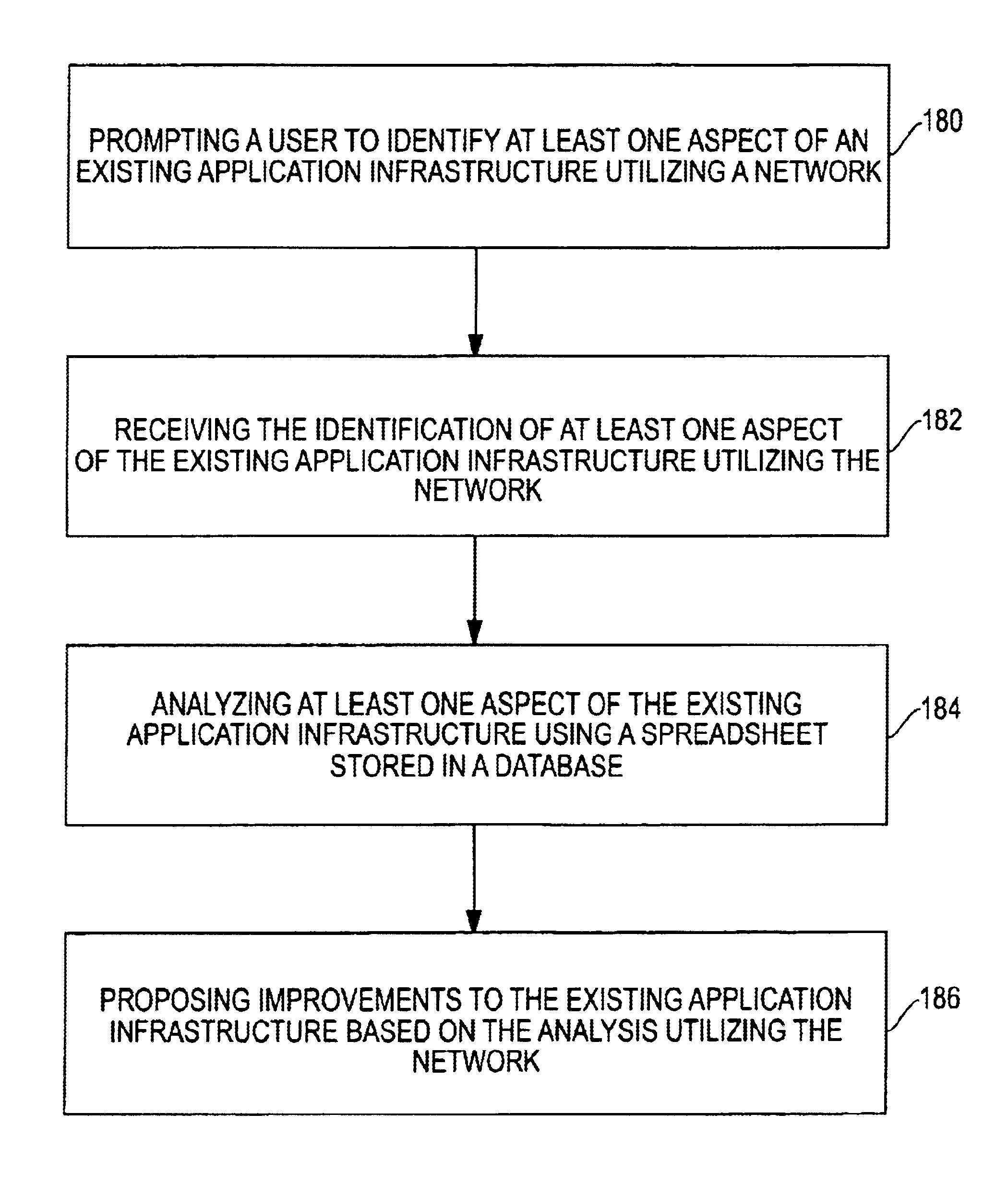
Patents
Literature
11327 results about "Application procedure" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
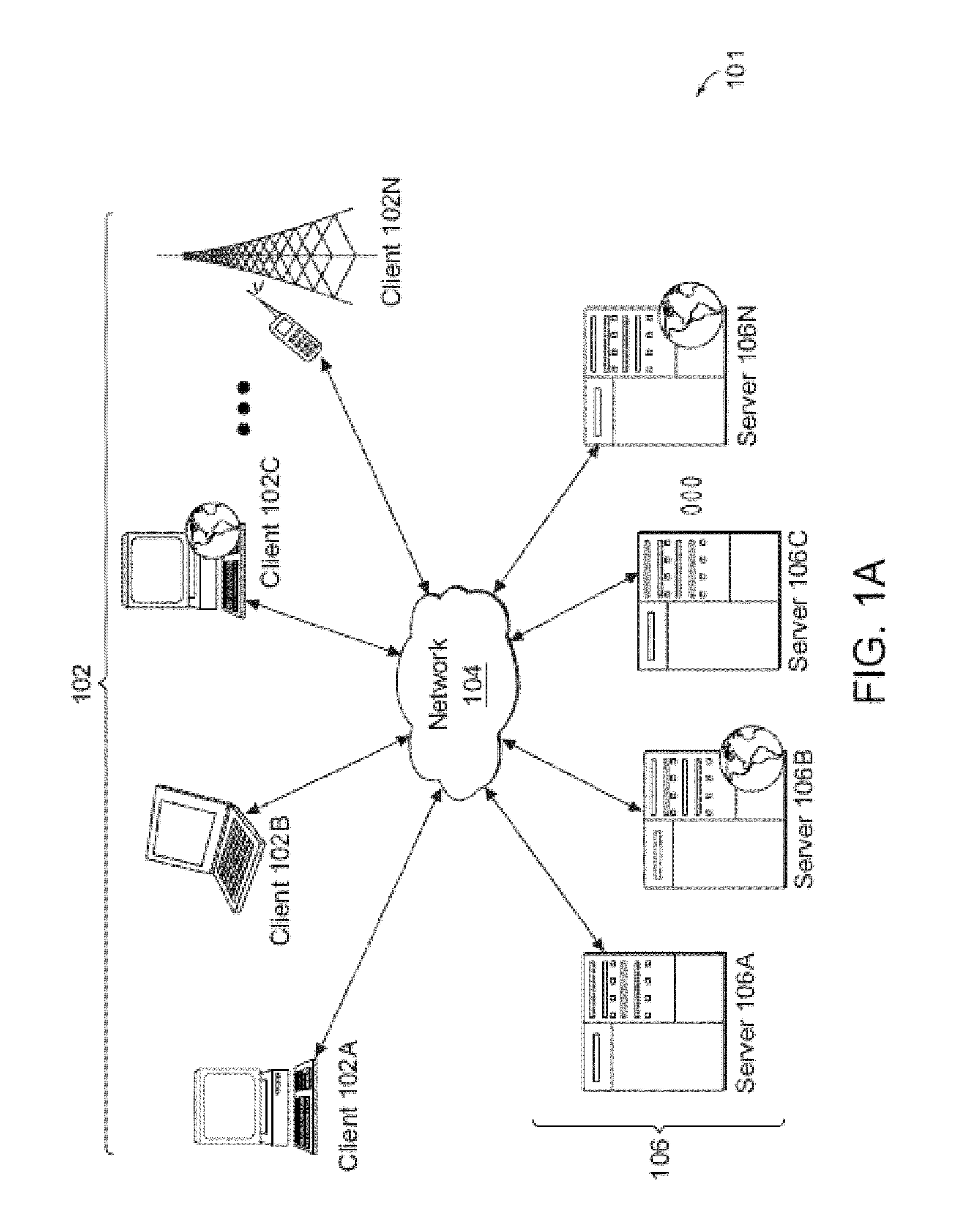
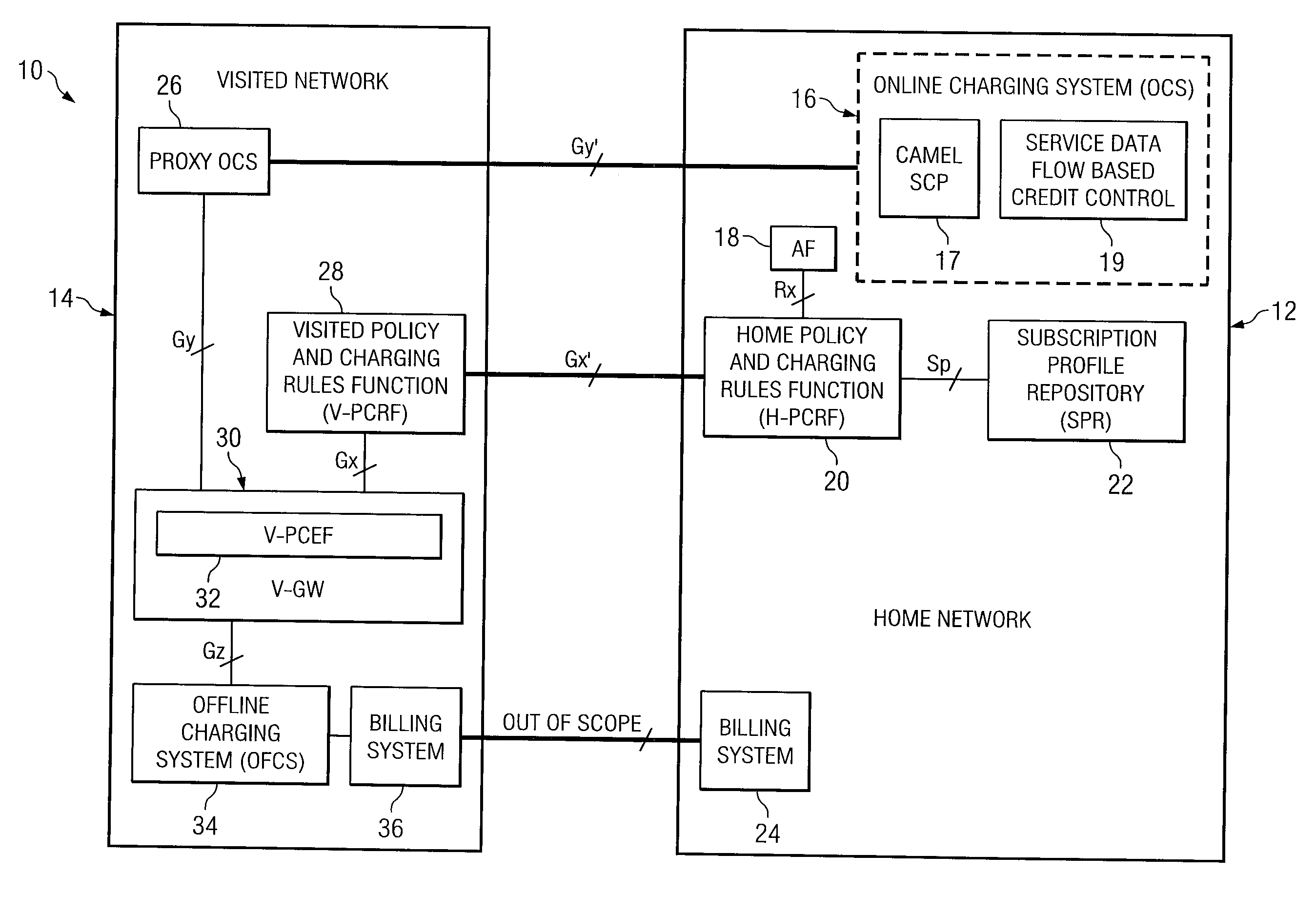
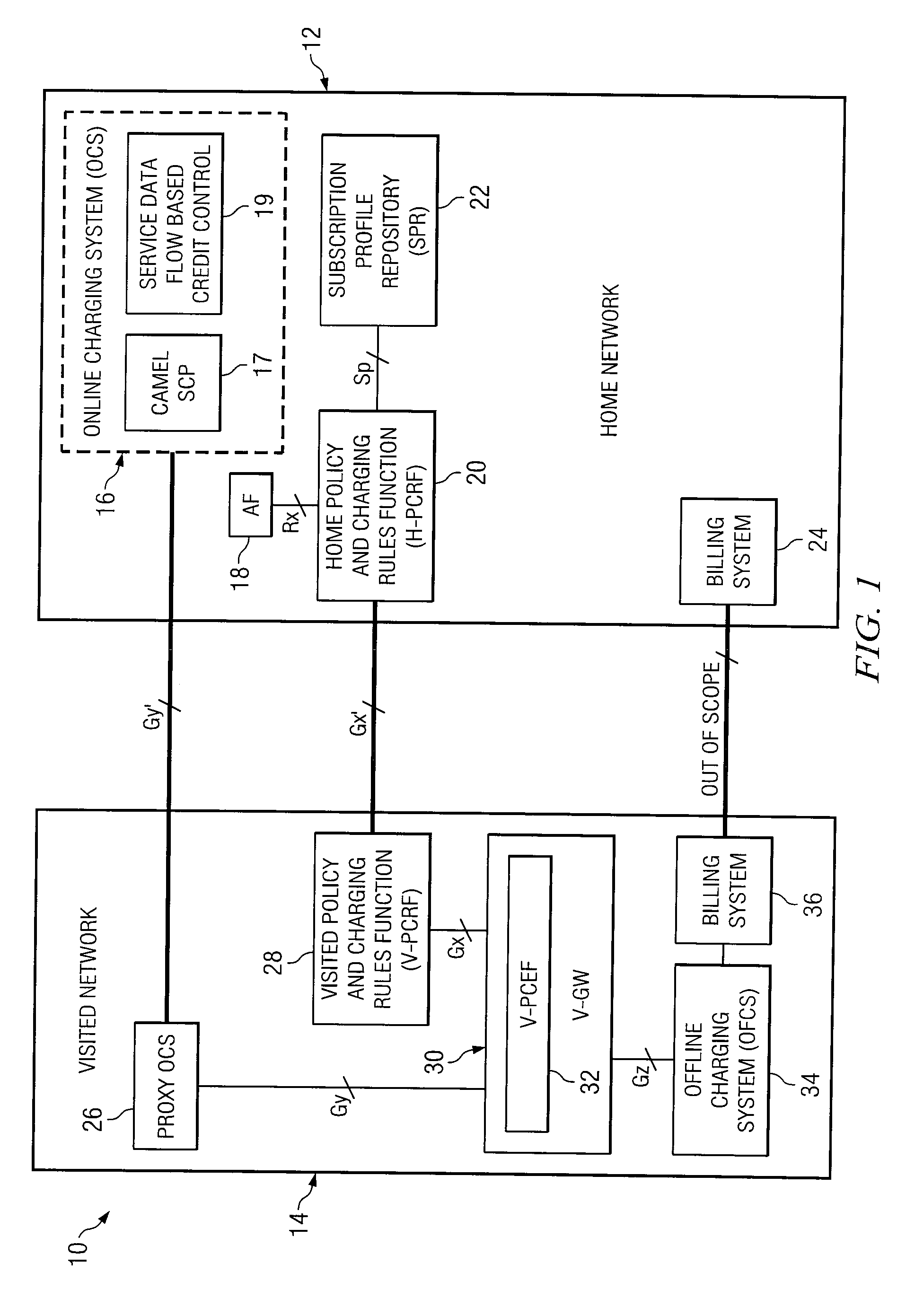
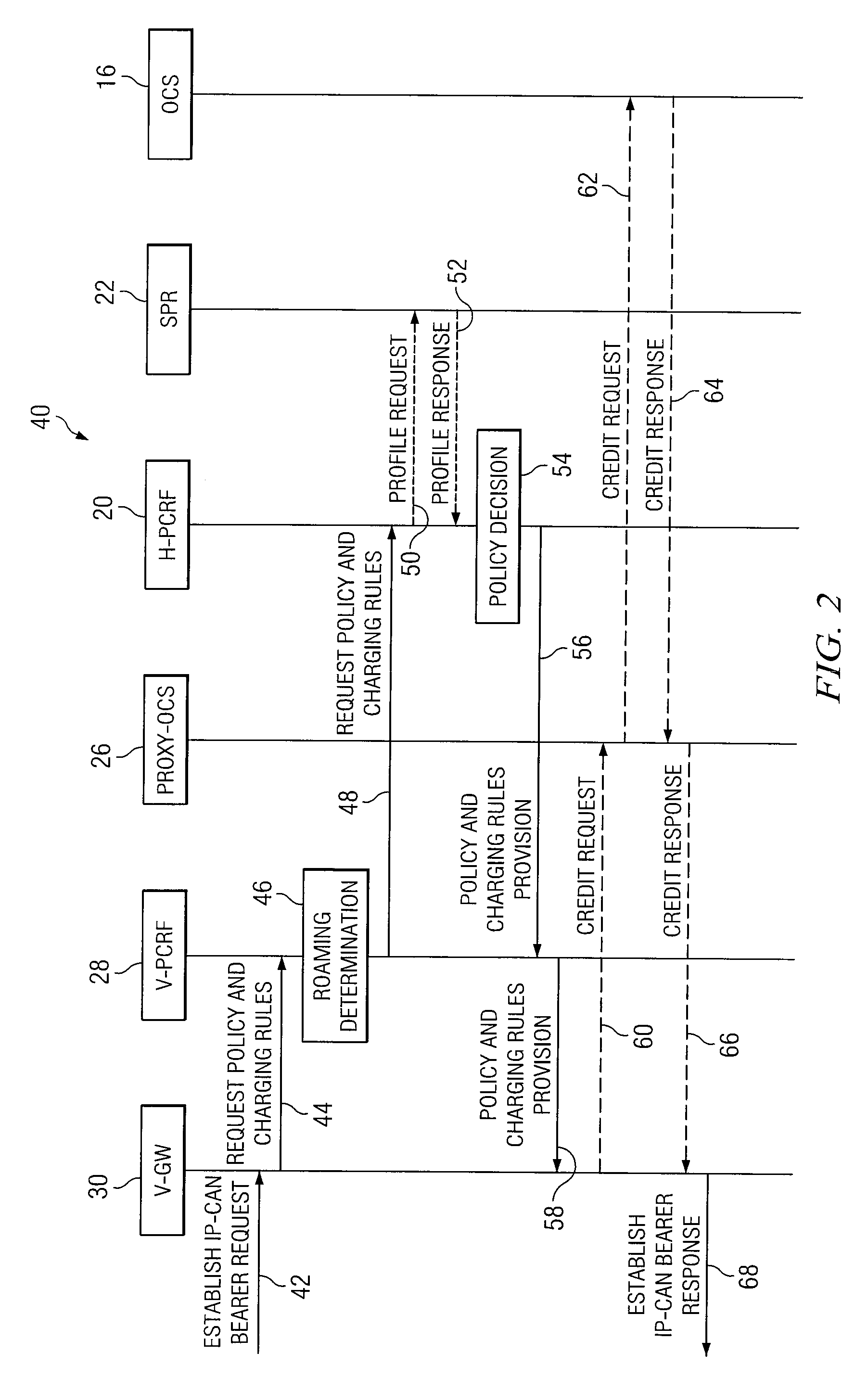
System and method for an application provider framework
InactiveUS6904449B1Broaden applicationMultiple digital computer combinationsOffice automationService provisionElectronic form
Owner:ACCENTURE GLOBAL SERVICES LTD
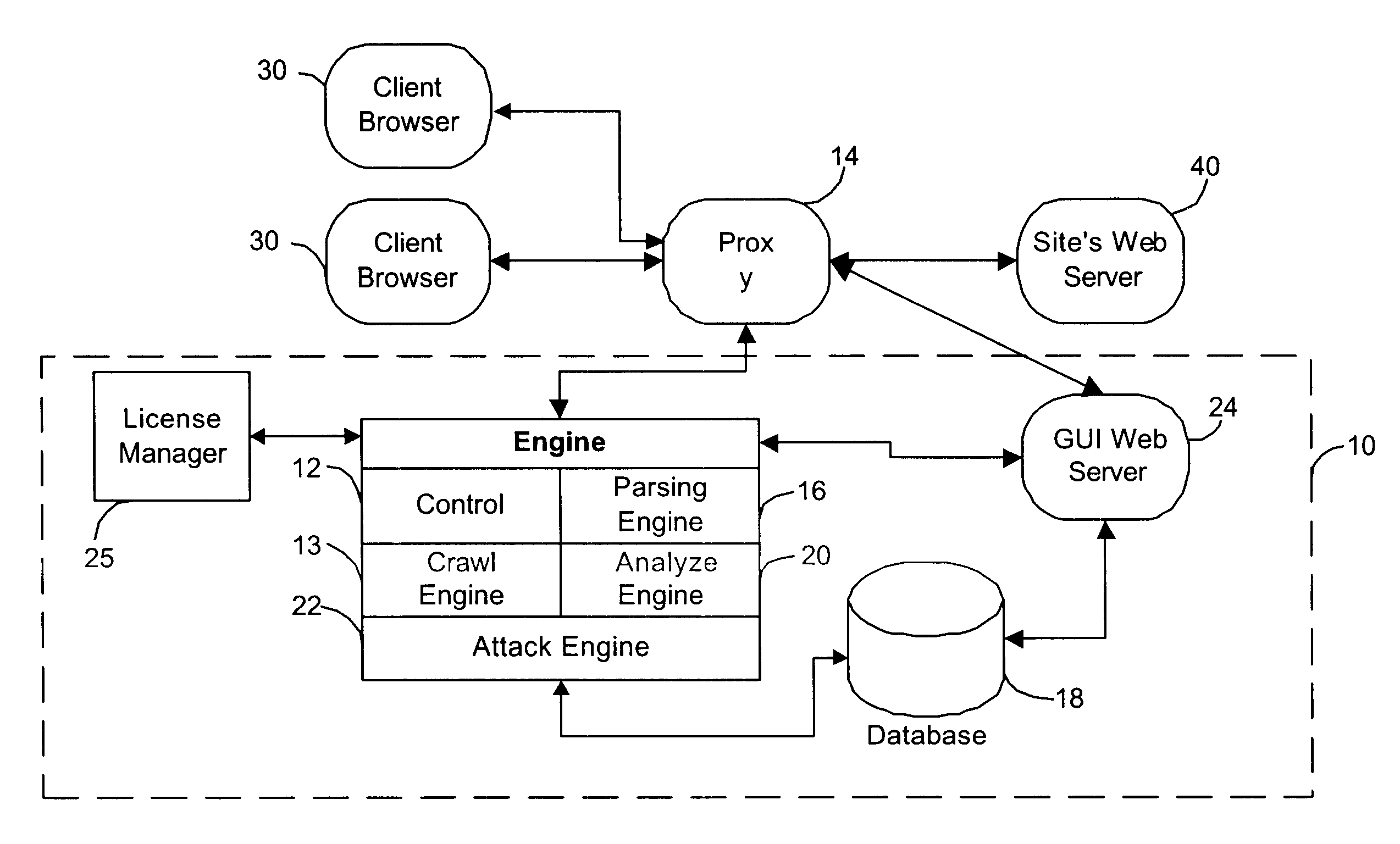
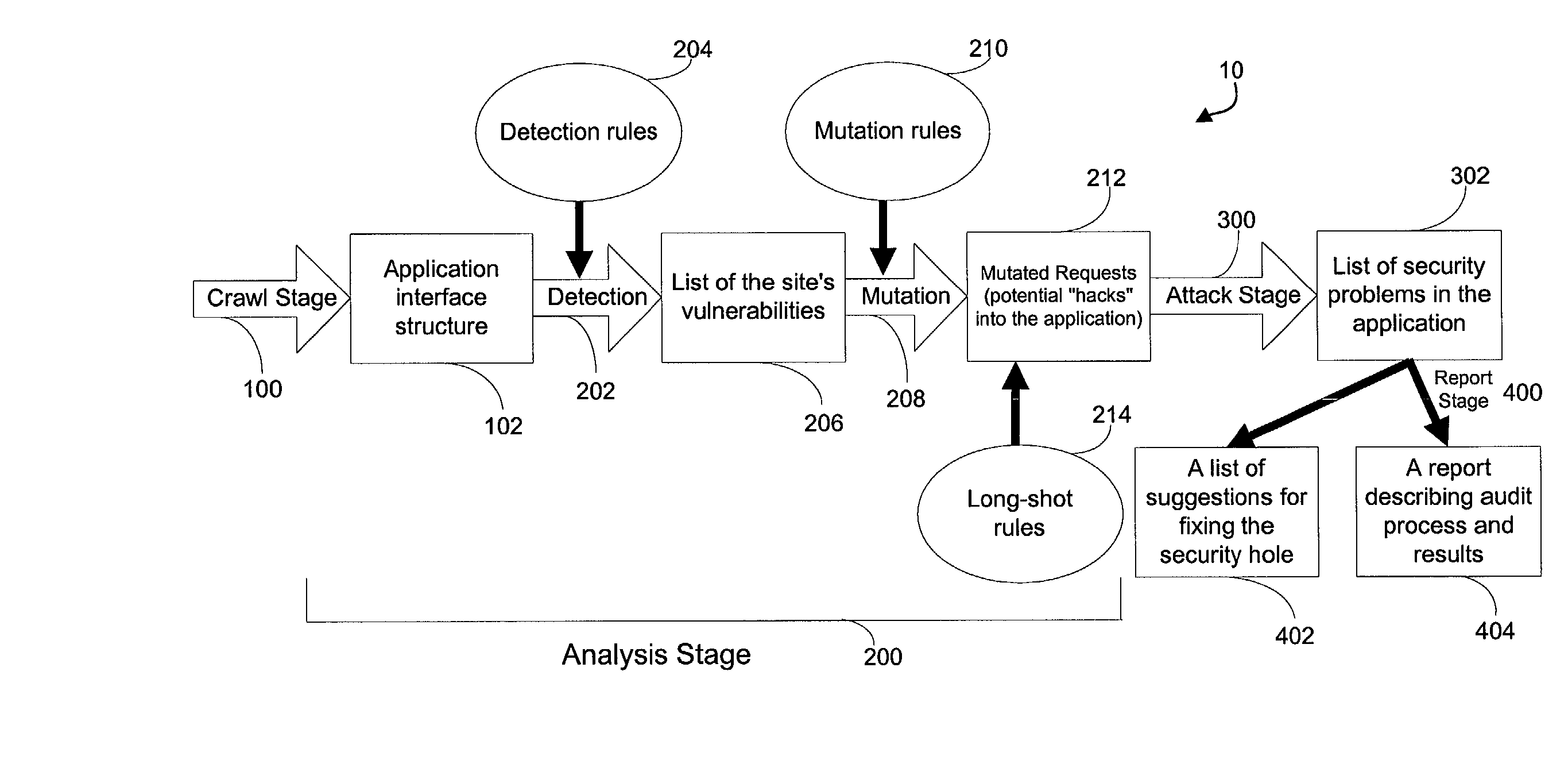
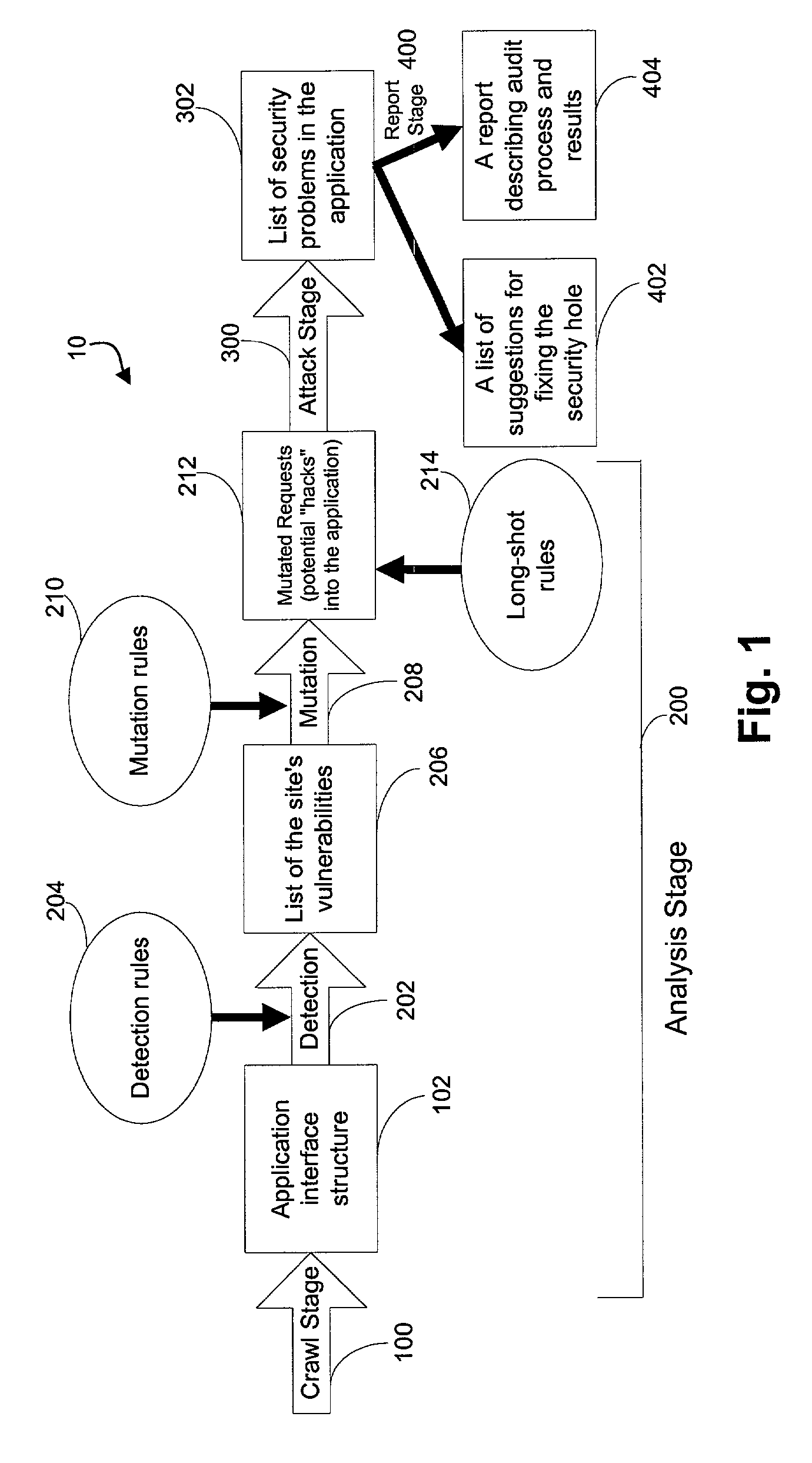
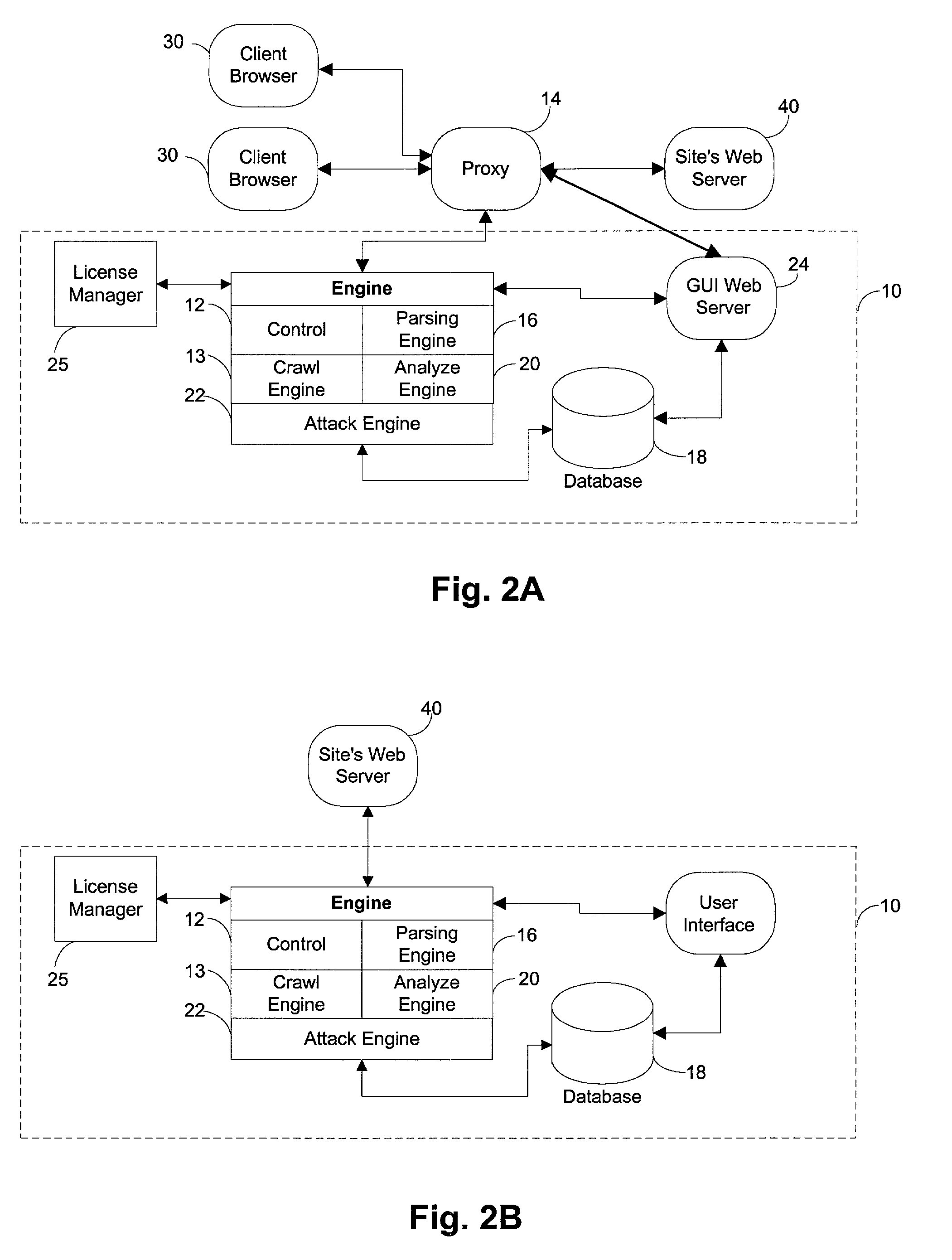
System for determining web application vulnerabilities
InactiveUS6584569B2Memory loss protectionUnauthorized memory use protectionWeb applicationApplication procedure
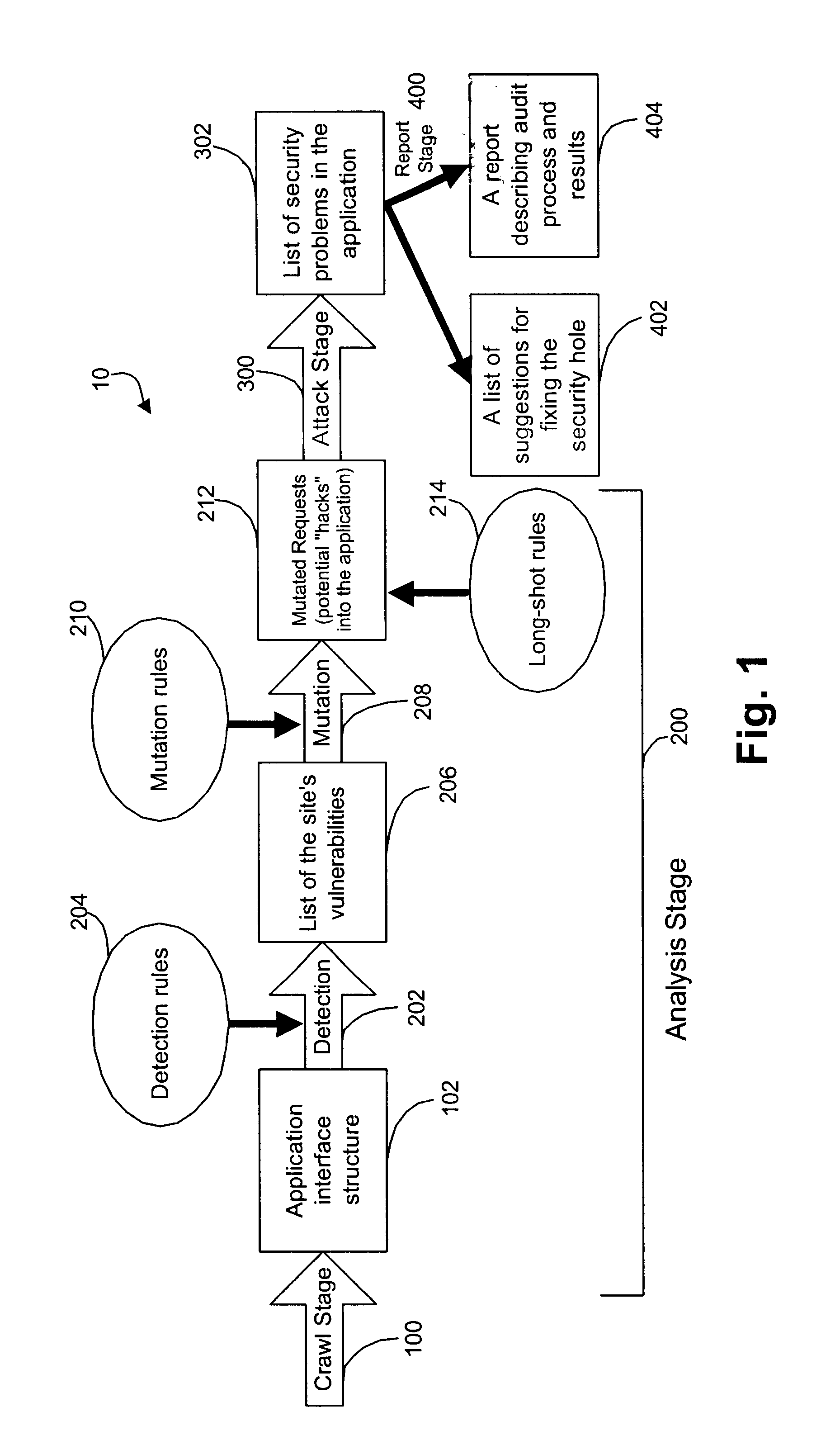
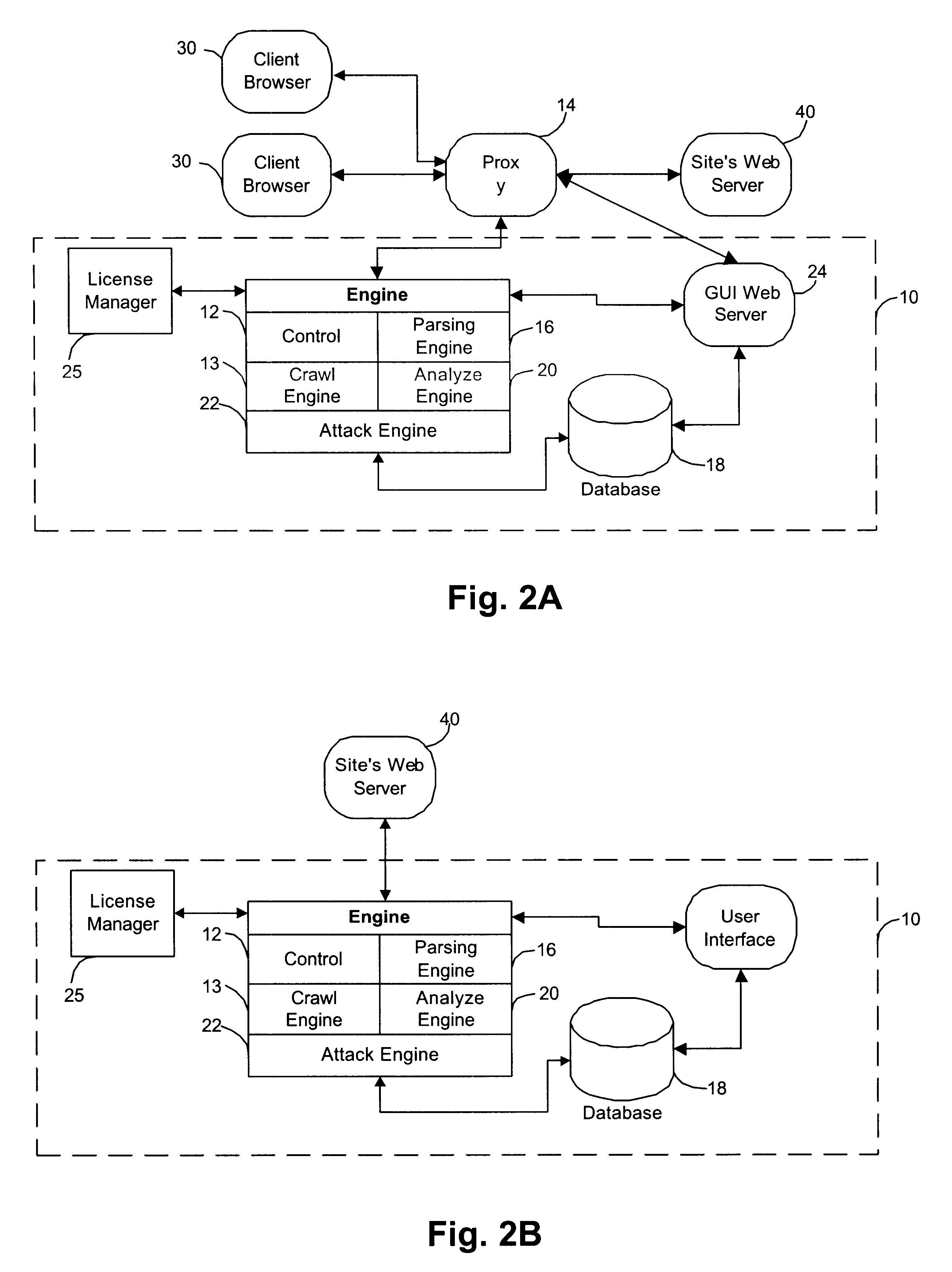
A method for detecting security vulnerabilities in a web application includes analyzing the client requests and server responses resulting therefrom in order to discover pre-defined elements of the application's interface with external clients and the attributes of these elements. The client requests are then mutated based on a pre-defined set of mutation rules to thereby generate exploits unique to the application. The web application is attacked using the exploits and the results of the attack are evaluated for anomalous application activity.
Owner:FINJAN BLUE INC
Method and apparatus for data communication
InactiveUS6094684AInterprogram communicationMultiple digital computer combinationsGraphicsGraphical user interface
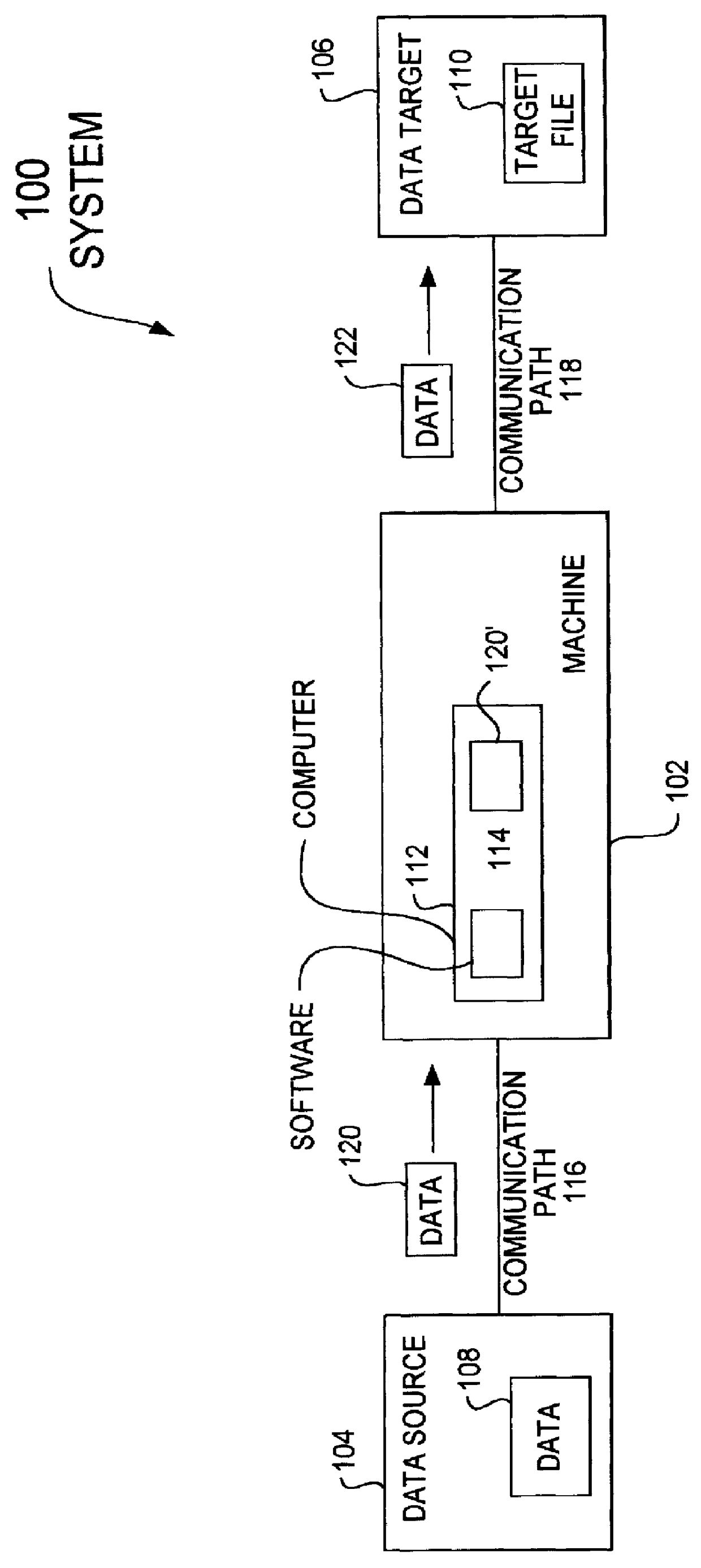
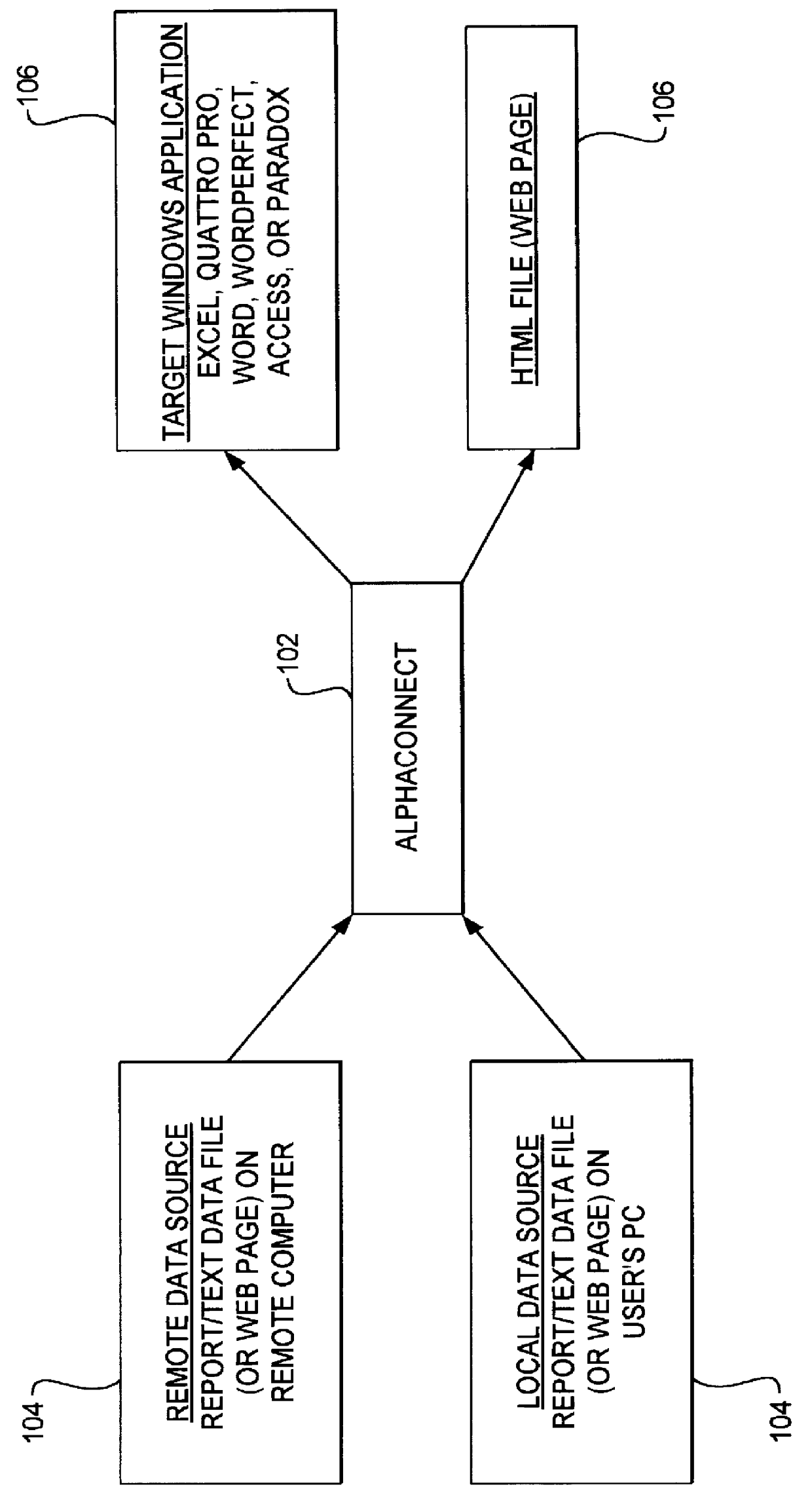
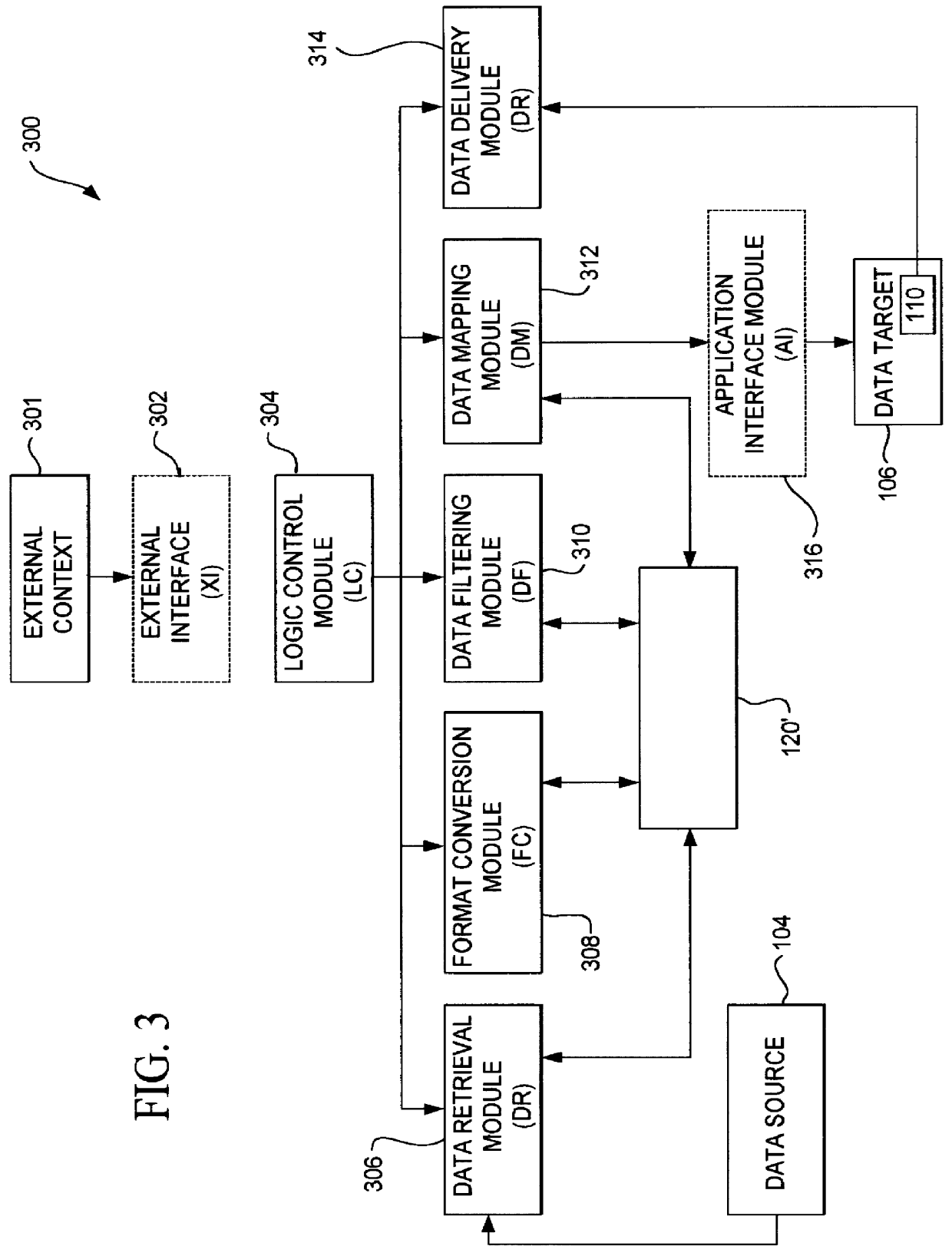
A data acquisition and delivery system for performing data delivery tasks is disclosed. This system uses a computer running software to acquire source data from a selected data source, to process (e.g. filter, format convert) the data, if desired, and to deliver the resulting delivered data to a data target. The system is designed to access remote and / or local data sources and to deliver data to remote and / or local data targets. The data target might be an application program that delivers the data to a file or the data target may simply be a file, for example. To obtain the delivered data, the software performs processing of the source data as appropriate for the particular type of data being retrieved, for the particular data target and as specified by a user, for example. The system can communicate directly with a target application program, telling the target application to place the delivered data in a particular location in a particular file. The system provides an external interface to an external context. If the external context is a human, the external interface may be a graphical user interface, for example. If the external context is another software application, the external interface may be an OLE interface, for example. Using the external interface, the external context is able to vary a variety of parameters to define data delivery tasks as desired. The system uses a unique notation that includes a plurality of predefined parameters to define the data delivery tasks and to communicate them to the software.
Owner:E BOTZ COM INC A DELAWARE +2
System and method for automated placement or configuration of equipment for obtaining desired network performance objectives
ActiveUS20040143428A1Significant valueEasy to explainGeometric CADProgram controlHard disc driveThe Internet
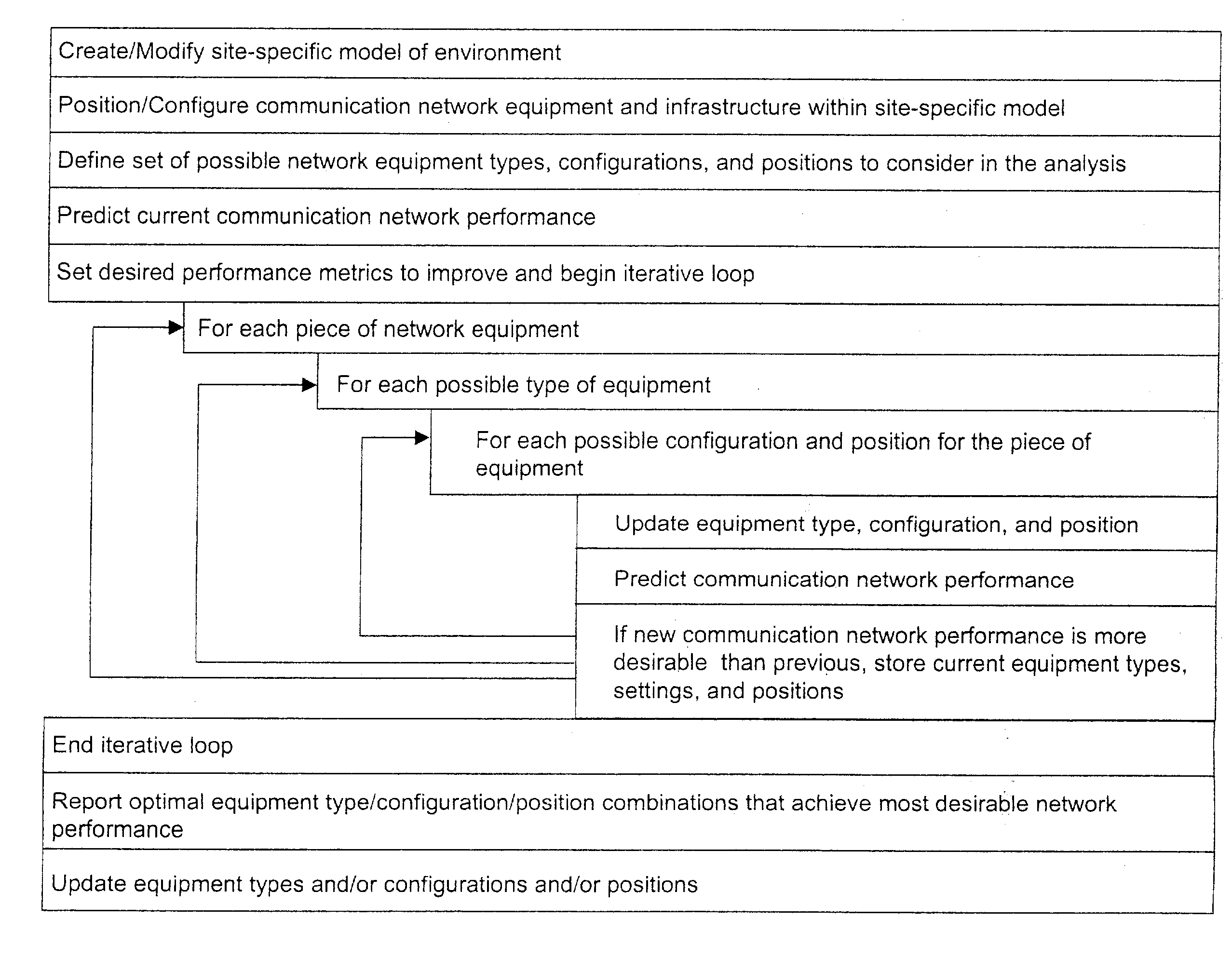
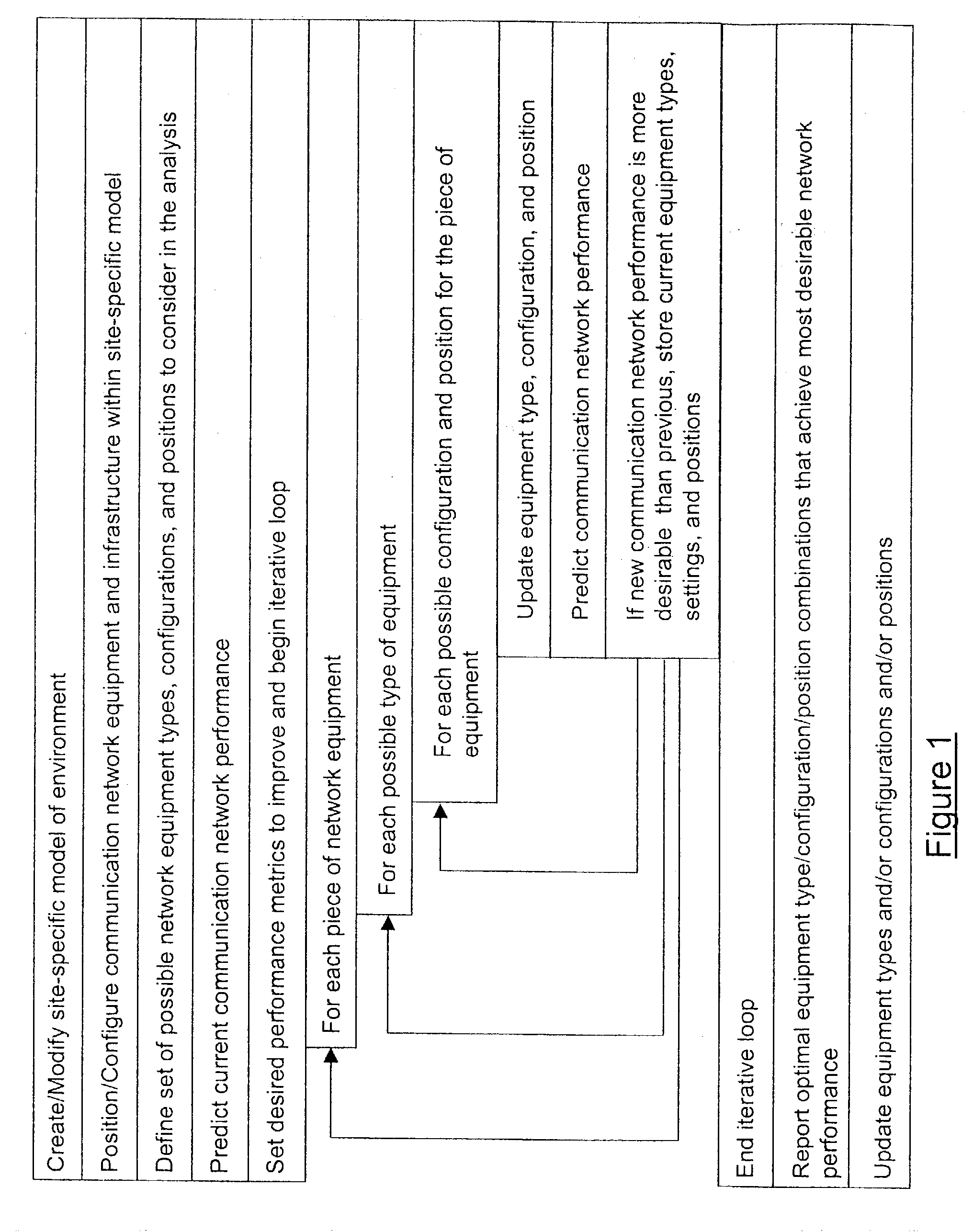
A method is presented for determining optimal or preferred configuration settings for wireless or wired network equipment in order to obtain a desirable level of network performance. A site-specific network model is used with adaptive processing to perform efficient design and on-going management of network performance. The invention iteratively determines overall network performance and cost, and further iterates equipment settings, locations and orientations. Real time control is between a site-specific Computer Aided Design (CAD) software application and the physical components of the network allows the invention to display, store, and iteratively adapt any network to constantly varying traffic and interference conditions. Alarms provide rapid adaptation of network parameters, and alerts and preprogrammed network shutdown actions may be taken autonomously. A wireless post-it note device and network allows massive data such as book contents or hard drive memory to be accessed within a room by a wide bandwidth reader device, and this can further be interconnected to the internet or Ethernet backbone in order to provide worldwide access and remote retrieval to wireless post-it devices.
Owner:EXTREME NETWORKS INC
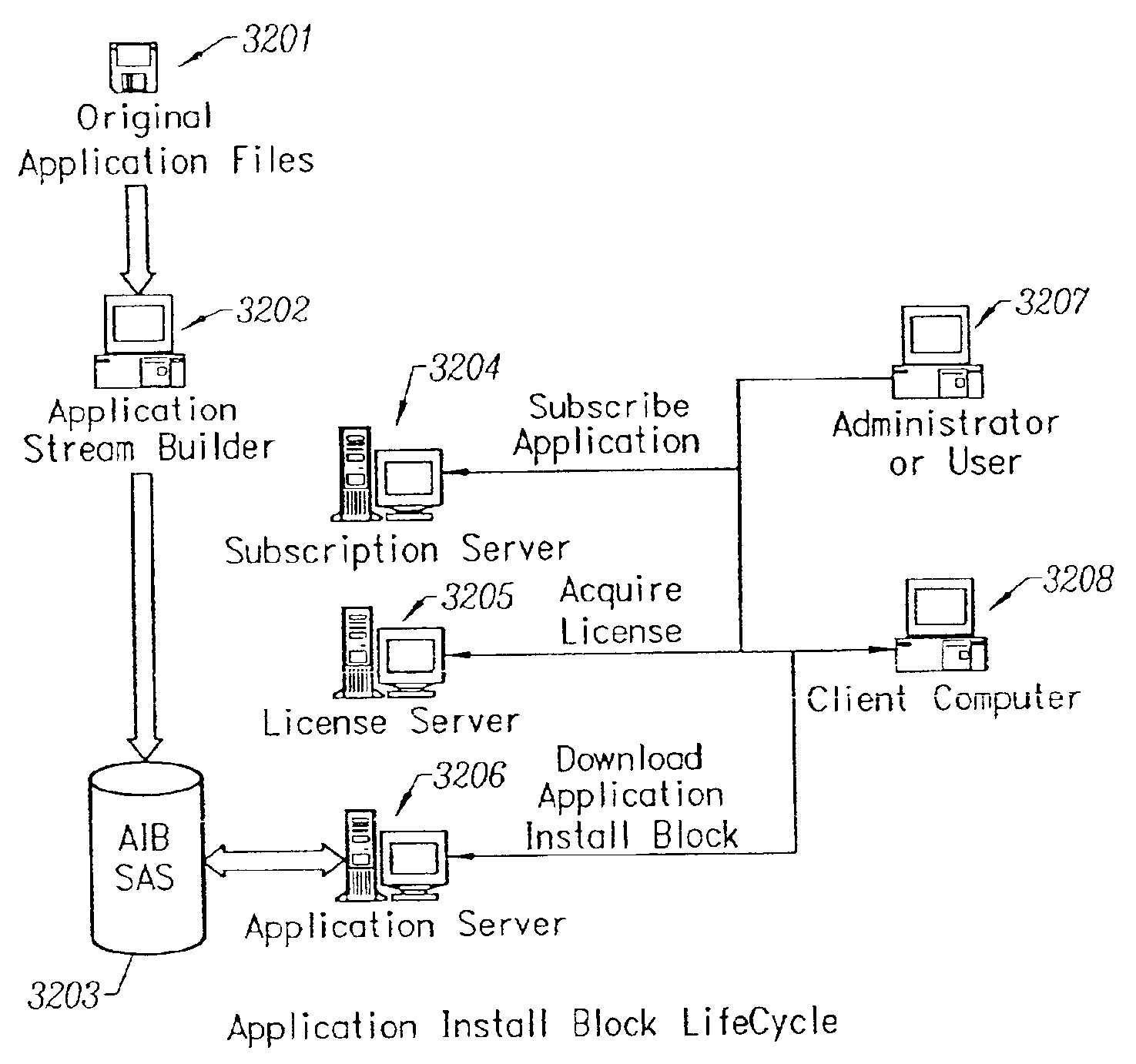
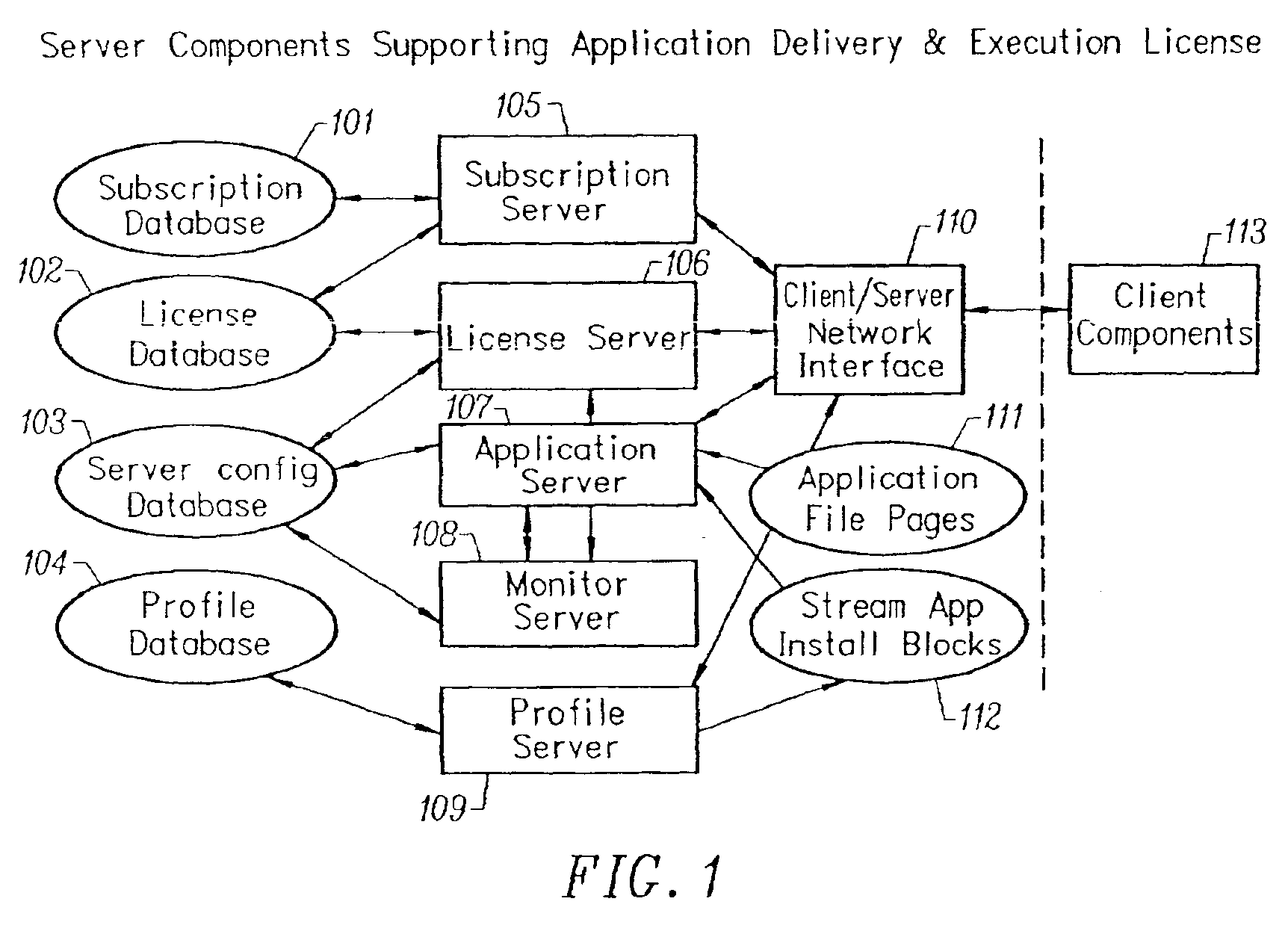
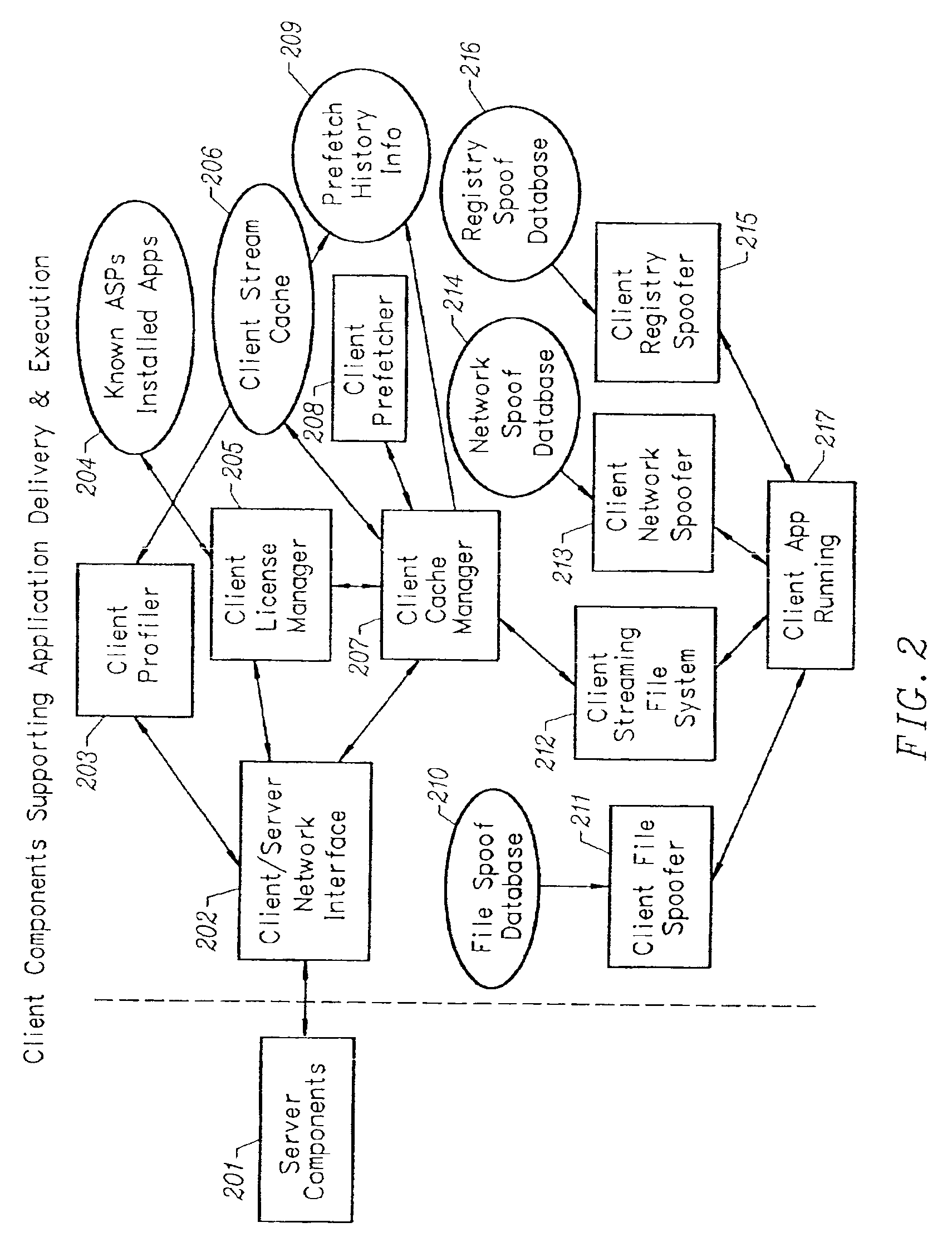
Client-side performance optimization system for streamed applications
InactiveUS6959320B2Efficiently stream and executeEasily integrates into client system 's operating systemMultiple digital computer combinationsProgram loading/initiatingApplication serverData file
An client-side performance optimization system for streamed applications provides several approaches for fulfilling client-side application code and data file requests for streamed applications. A streaming file system or file driver is installed on the client system that receives and fulfills application code and data requests from a persistent cache or the streaming application server. The client or the server can initiate the prefetching of application code and data to improve interactive application performance. A client-to-client communication mechanism allows local application customization to travel from one client machine to another without involving server communication. Applications are patched or upgraded via a change in the root directory for that application. The client can be notified of application upgrades by the server which can be marked as mandatory, in which case the client will force the application to be upgraded. The server broadcasts an application program's code and data and any client that is interested in that particular application program stores the broadcasted code and data for later use.
Owner:NUMECENT HLDG
Methods and systems for launching applications into existing isolation environments
ActiveUS20100281102A1Reduce the amount requiredReduce the amount of resourcesMultiple digital computer combinationsPlatform integrity maintainanceApplication softwareClient-side
Methods and systems that can launch applications into existing isolation environments do so by executing a run module on a computing machine to intercept requests to execute an application. A client communicating with the computing machine generates requests to execute an application on the computing machine. A run module identifies a profile associated with the requested application and queries an application delivery service to identify at least one isolation environment that corresponds to the profile. The run module receives from the application delivery service a response that identifies a first isolation environment associated with the application, and issues a command to a launch module to launch the application into the first isolation environment.
Owner:CITRIX SYST INC
Methods and systems for selecting a method for execution, by a virtual machine, of an application program
ActiveUS20070180450A1Low costReduce difficultyDigital data information retrievalDigital data processing detailsClient-sideClient machine
A method for selecting a method of execution for an application includes the step of receiving credentials. A plurality of applications available to a client machine is enumerated responsive to the received credentials. A request to execute an enumerated application is received. One of a predetermined number of methods for executing the requested application is selected responsive to a policy, the predetermined number of methods including a method for executing the requested application in a computing environment provided by a virtual machine.
Owner:CITRIX SYST INC
Automatic authentication method and system in print process
ActiveUS7313699B2Improve securityEliminate needDigital data processing detailsUser identity/authority verificationUser authenticationUser identifier
This invention provides an automatic authentication method and system in a print process, which can obviate the need for user's input operations of the user ID and password and can improve security since authentication is automatically done based on print information embedded in a file or information from an application program without any user's input.In a print process that requires user authentication, a printer driver extracts information related to an application and / or a document for the print process as attribute information, and user authentication is made by comparing the attribute information with information stored in a user registration information database of a server. If user authentication has succeeded, the printer driver controls a printer to print, and the server manages and stores accounting information and the like for respective departments in a department management information database.
Owner:CANON KK
System and method for implementing policy server based application interaction manager
ActiveUS20080046963A1Network connectionsSpecial data processing applicationsApplication IdentifierOperating system
In one example embodiment, an apparatus includes a policy repository for storing a policy for application interaction. The policy defines, for a subscriber, a priority associated with a set of specific application identifiers. The priority further defines establishment priority and retention priority for an application identified by a selected application identifier. Another example embodiment includes an apparatus including a processor operable to evaluate a policy for application interaction. The policy defines, for a subscriber, a priority associated with a set of specific application identifiers. The priority further defines establishment priority and retention priority for an application identified by a selected application identifier. The processor is further operable to execute a decision for the subscriber based on the evaluation of the policy.
Owner:CISCO TECH INC
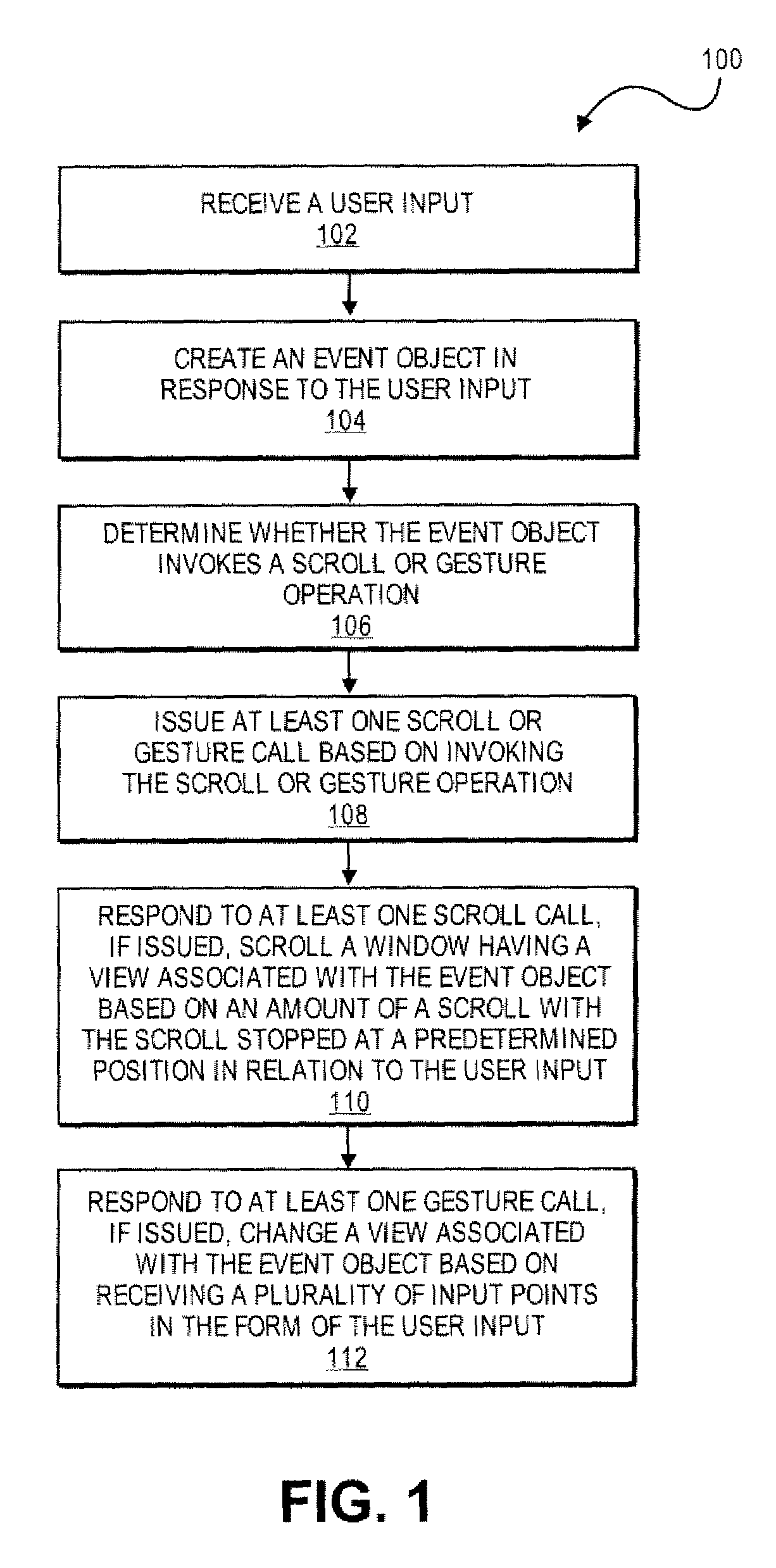
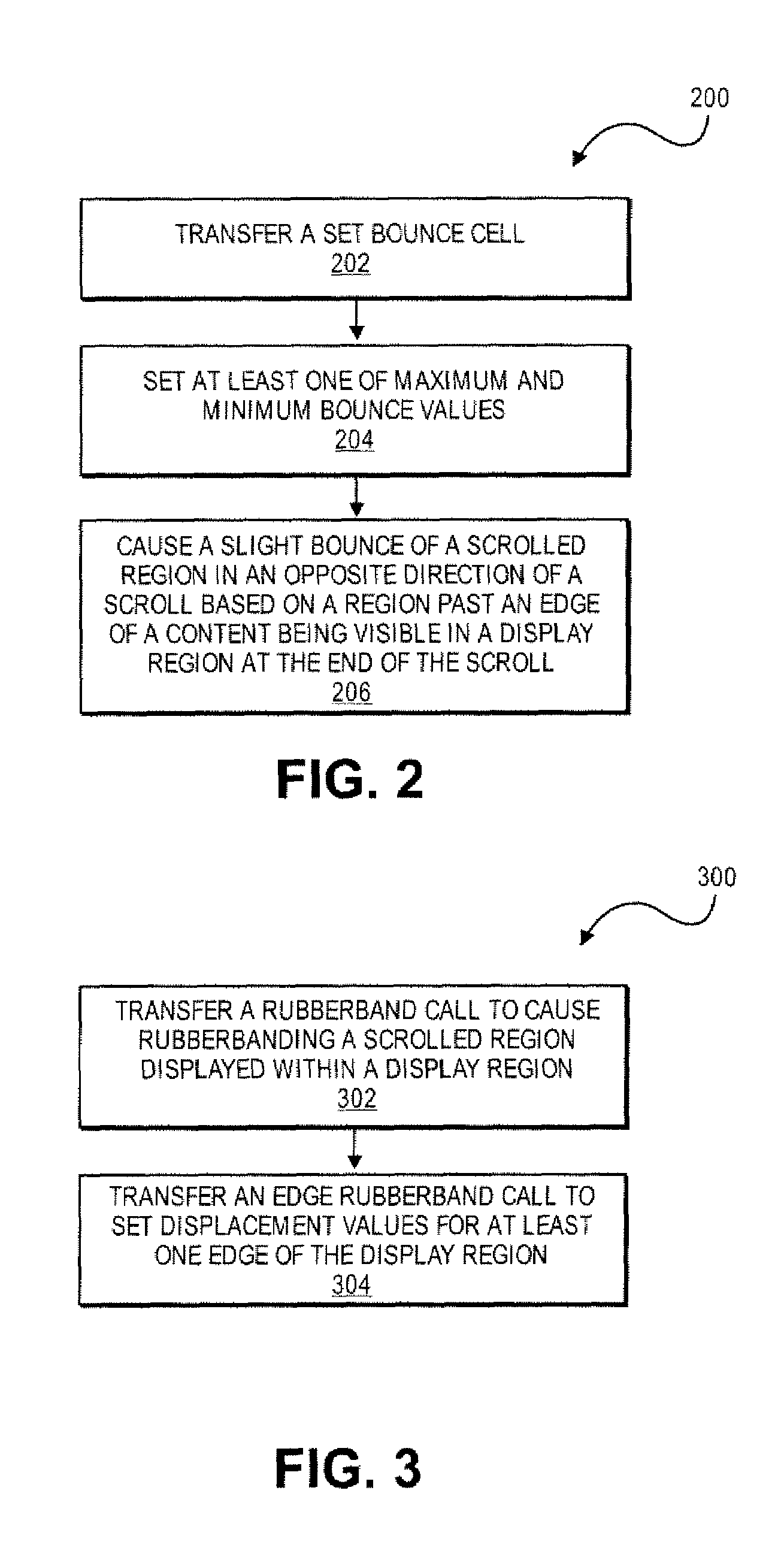
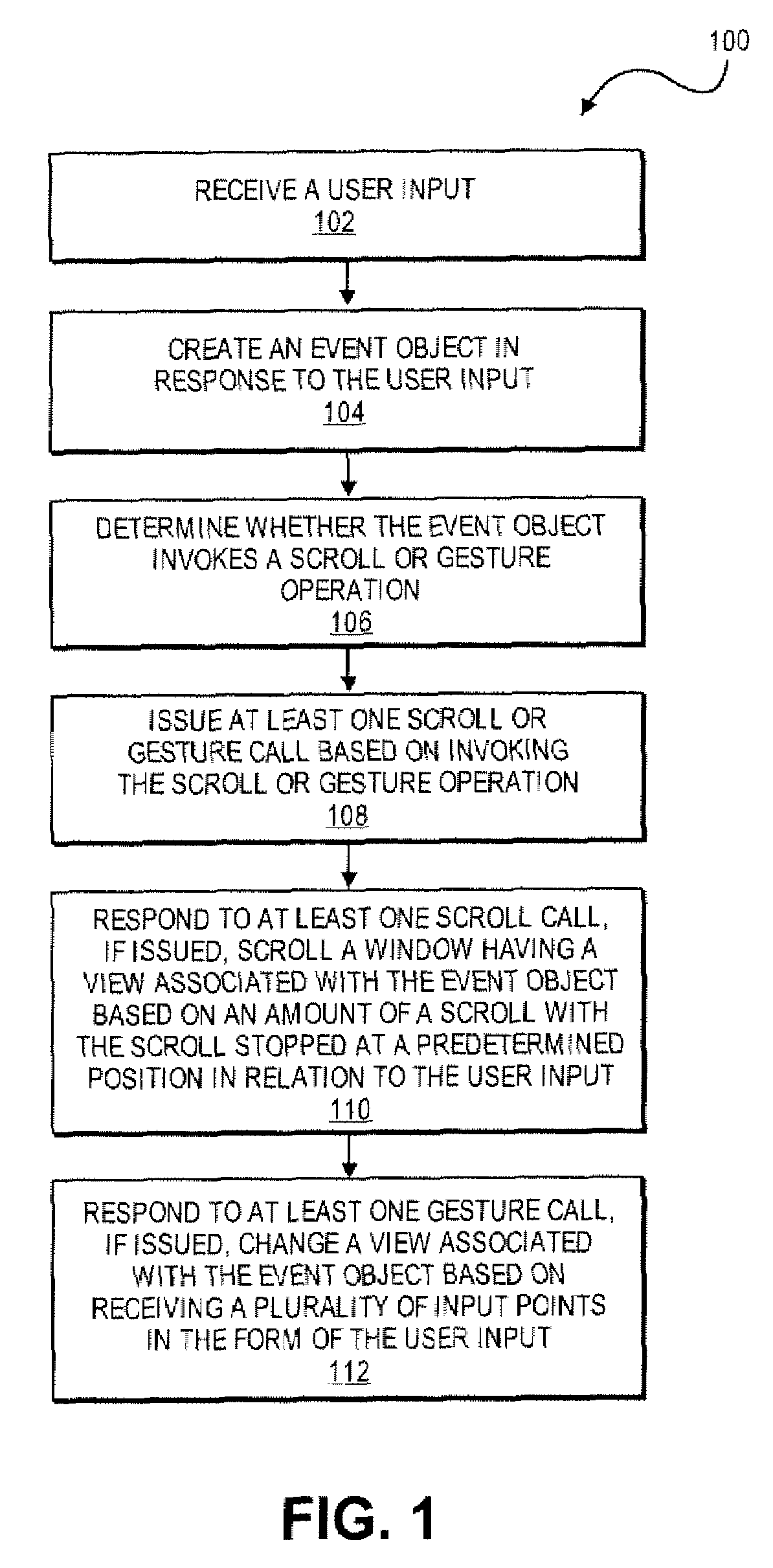
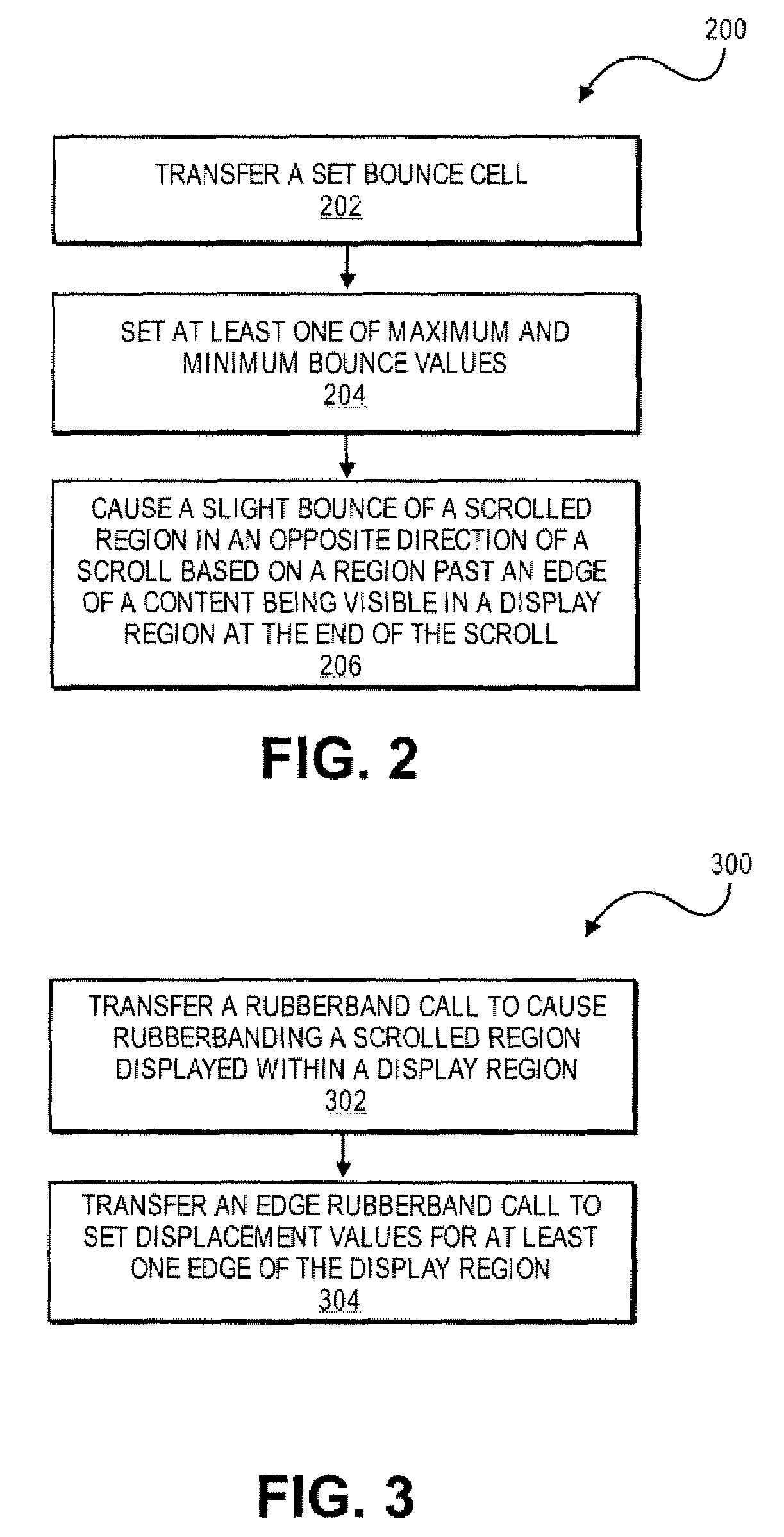
Application Programming Interfaces for Scrolling Operations
ActiveUS20080168384A1Interprogram communicationInput/output processes for data processingApplication softwareApplication programming interface
At least certain embodiments of the present disclosure include an environment with user interface software interacting with a software application. A method for operating through an application programming interface (API) in this environment includes transferring a set bounce call. The method further includes setting at least one of maximum and minimum bounce values. The set bounce call causes a bounce of a scrolled region in an opposite direction of a scroll based on a region past an edge of the scrolled region being visible in a display region at the end of the scroll.
Owner:APPLE INC
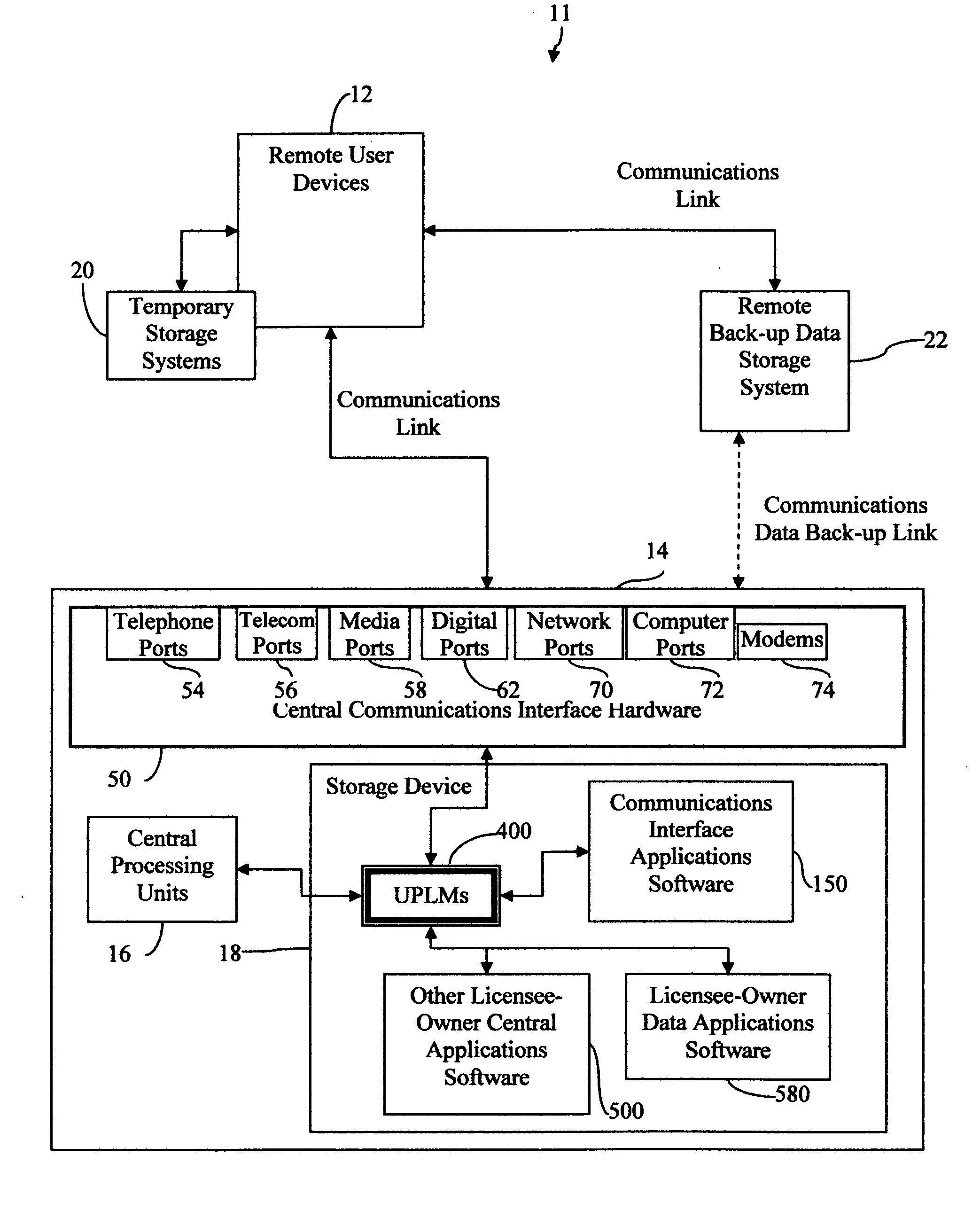
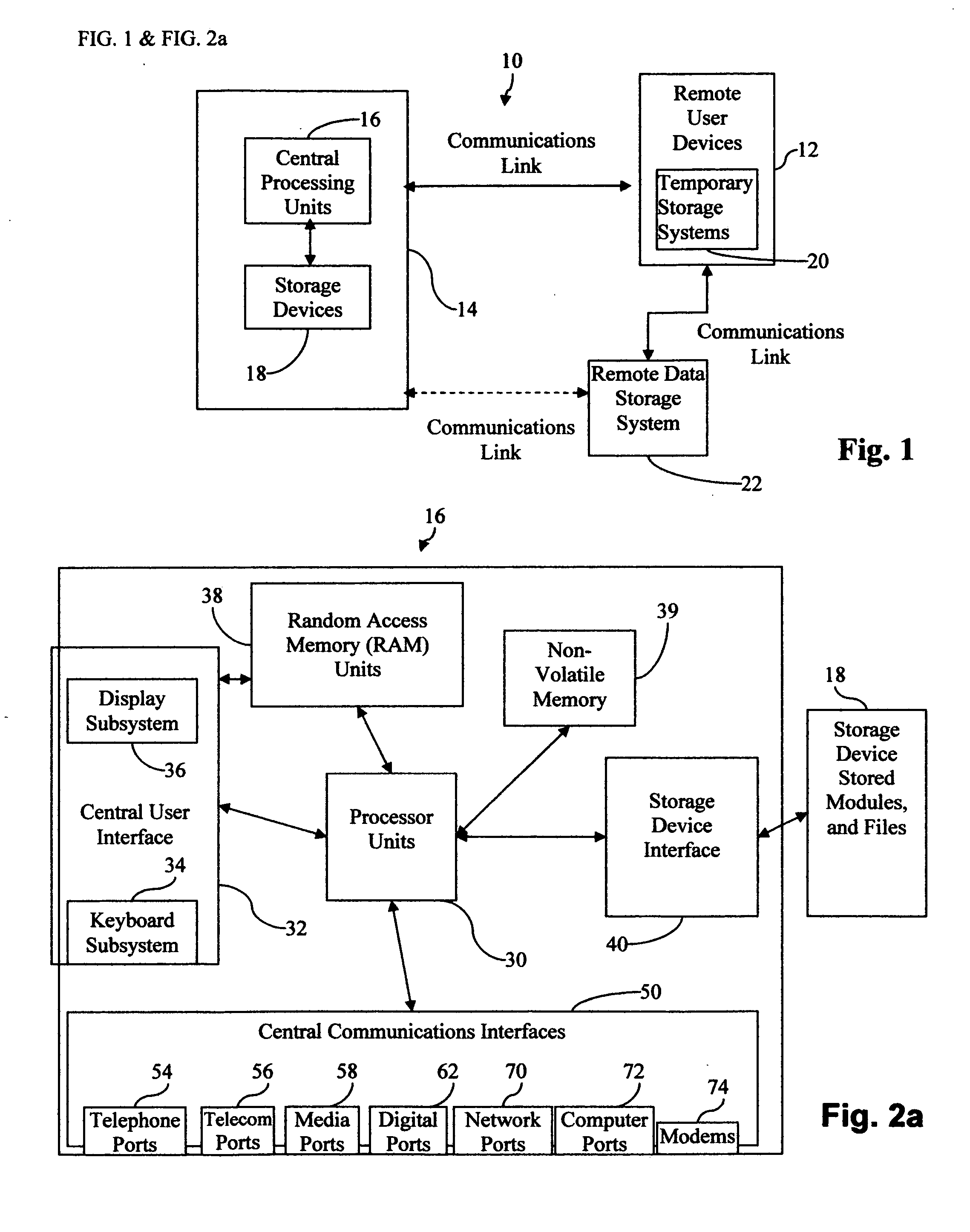
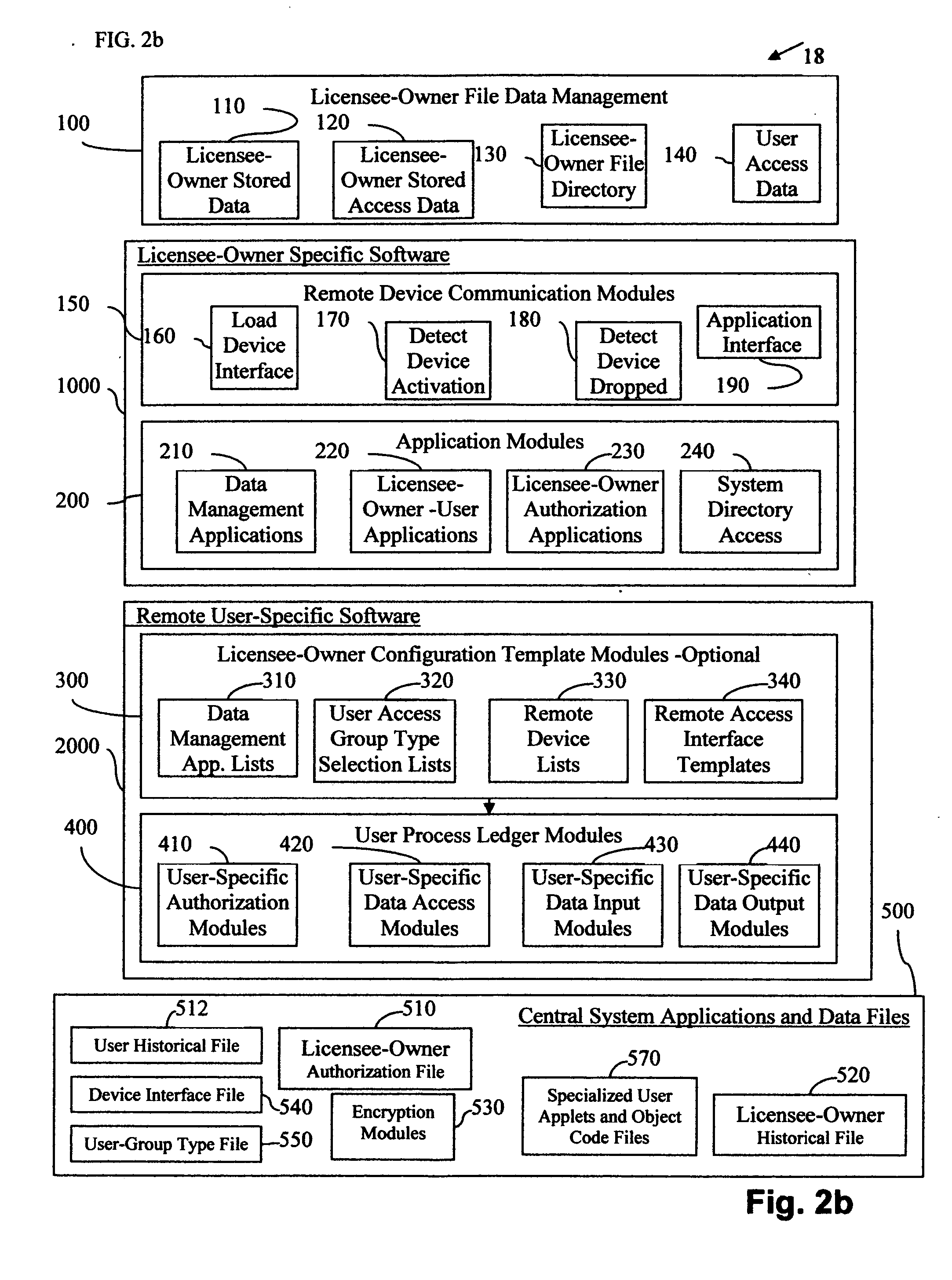
Central work-product management system for coordinated collaboration with remote users
InactiveUS20070143398A1Easy accessFinanceMultiple digital computer combinationsUser deviceWork product
A multi-component system for linking remote uses to a central work-product management system includes central processing device, central storage device, and a selection of different remote access devices and associated central system interface means for remote user to collaborate with central system licensee-owner work-product computer applications. The central storage device stores licensee-owner specific central application software associated with, licensee-owner specific data, and file and data management programs and the associated interface means allowing access to licensee-owner account by custom remote user specific applications The multi-component system for linking a remote user to a licensee-owner central work-product management system and devices are connected by the implementation of custom remote user specific interface applications which communicates with remote user devices, referred to herein as user process ledger modules, or UPLMs. After user recognition and access security is implemented, the UPLMs guide the remote user to limited segments of licensee-owner specific central system data locations implementing specific application procedures in the access to and development of the licensee-owner's and user's work-product. The central processing device implements the communications interface applications which upon remote user connection, recognition, and by access permission, executes associated specific UPLMs to exchange information with the remote user device, and implement any associated applications required for the processing of the remote user specific information, requested data input, data manipulation, or data output. Overall, the system provides an efficient, simple, highly direct, secure limited access mechanism for transferring specific user information from remote locations into an active central licensee-owner specific processing system accurately with minimal knowledge in the area of expertise of licensee-owner file and data management systems and associated application programs required for the development of a licensee-owner work-product.
Owner:GRAHAM JEAN A
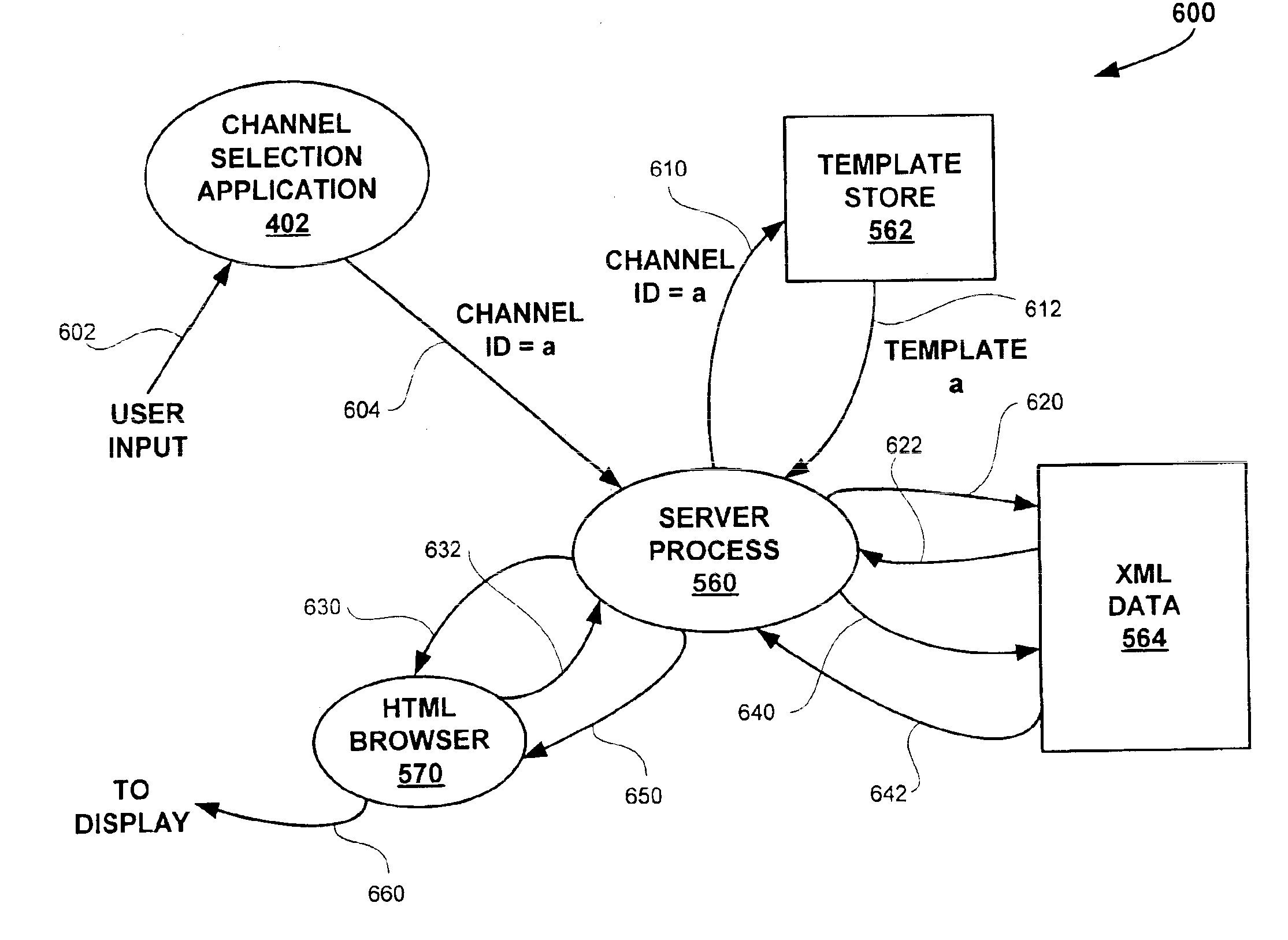
Method and apparatus for sharing common data objects among multiple applications in a client device
InactiveUS6934740B1Readily apparentData processing applicationsMultiple digital computer combinationsObject basedSoftware architecture
Disclosed is software architecture and method for sharing data objects among multiple applications in a client device. The architecture includes a server process in the client device for processing a template, such as a SHTML template for the Extended Markup Language (XML), based on a template identifier value received from a user application. Each of multiple applications has a template. Each template identifies a series of objects identified by tag values, such as XML entities, that are to be incorporated into a display page. A database of objects, such as a database of XML entities identified by tag values, is maintained that contains data objects for the applications. An update process periodically establishes a communication link with a remote server and requests download of a data document containing content data corresponding to at least a portion of several of the templates. The data document is parsed into the database of objects based on the structure of the data document, which generally conforms to a data type definition. When the server process processes different templates that reference the same data object, it will retrieve the data object from the database. Each template may then be rendered into a page of output data for display to a user. The architecture and method according to the present invention thus permit data objects to be shared by multiple applications and to be automatically updated. Each time a data object is updated, the data will be current for each user application that references the data object.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP +1
Application Programming Interfaces for Gesture Operations
InactiveUS20080168402A1AnimationExecution for user interfacesUser inputApplication programming interface
At least certain embodiments of the present disclosure include an environment with user interface software interacting wit a software application to provide gesture operations for a display of a device. A method for operating through an application programming interface (API) in this environment includes transferring a scaling transform call The gesture operations include performing a scaling transform such as a zoom in or zoom out in response to a user input having two or more input points. The gesture operations also include performing a rotation transform to rotate an image or view in response to a user input having two or more input points.
Owner:APPLE INC
System for determining web application vulnerabilities
InactiveUS20020010855A1Memory loss protectionError detection/correctionWeb applicationApplication procedure
A method for detecting security vulnerabilities in a web application includes analyzing the client requests and server responses resulting therefrom in order to discover pre-defined elements of the application's interface with external clients and the attributes of these elements. The client requests are then mutated based on a pre-defined set of mutation rules to thereby generate exploits unique to the application. The web application is attacked using the exploits and the results of the attack are evaluated for anomalous application activity.
Owner:FINJAN BLUE INC
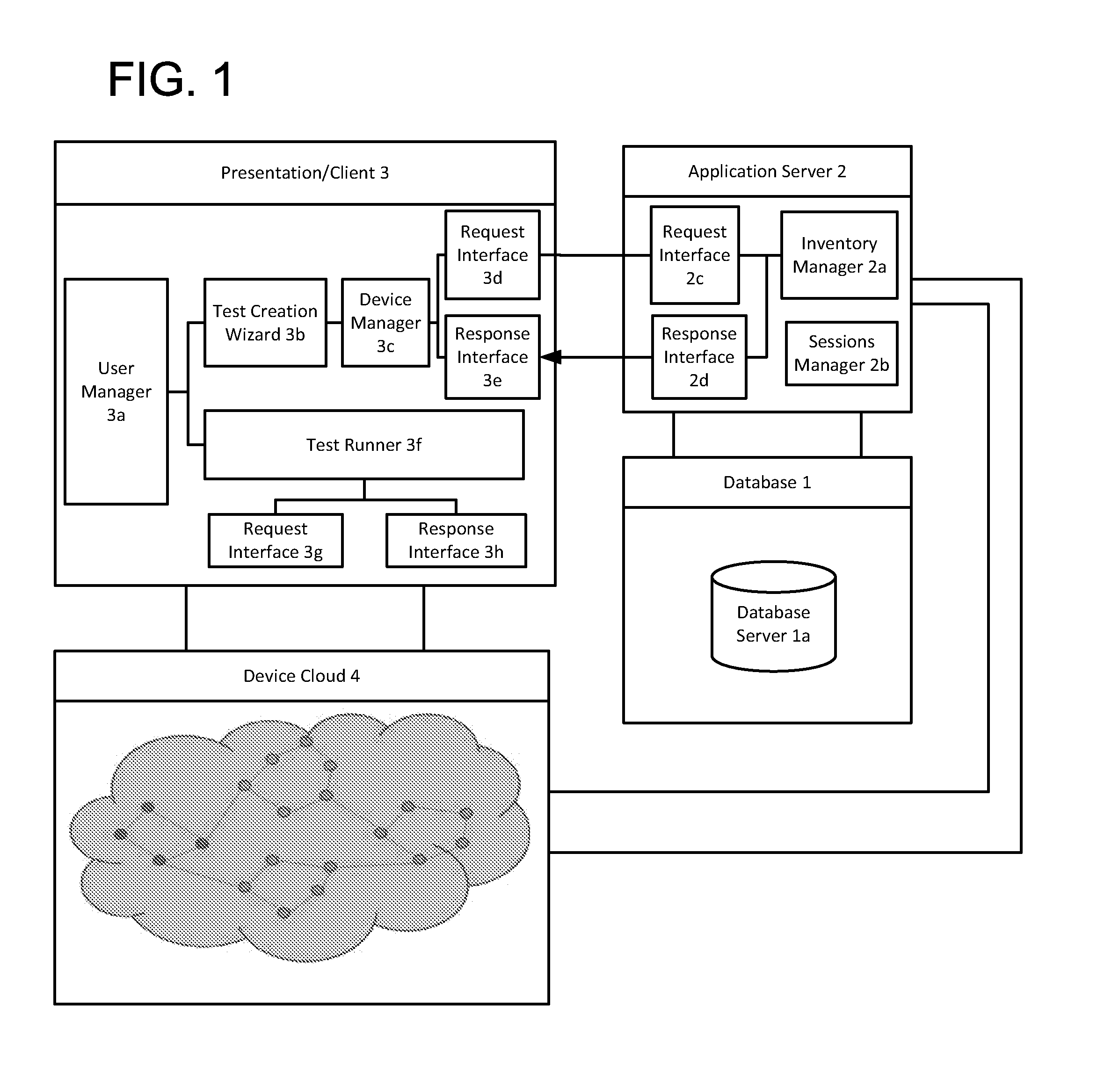
Automated application test system
An automated application test system comprises a plurality of clients (3) providing test interfaces to corresponding users, and a network of test nodes (4a) connected to the clients (3); wherein each said test node (4a) comprises one or more test devices locally connected to the test node (4a); and an agent (6) arranged to execute one or more test applications on the locally connected test devices (4b) in accordance with requests from the clients (3).
Owner:BARCLAYS EXECUTION SERVICES LTD
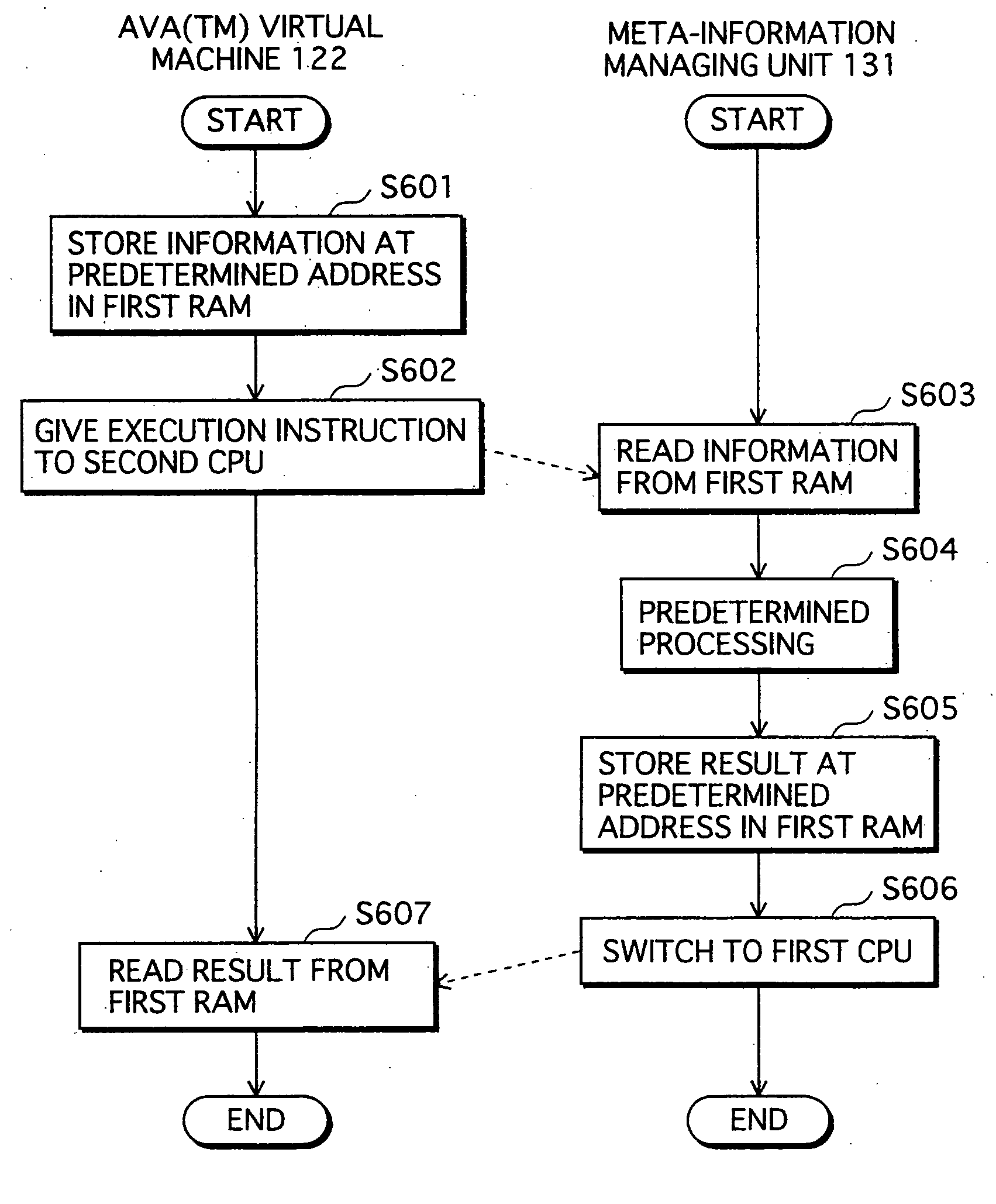
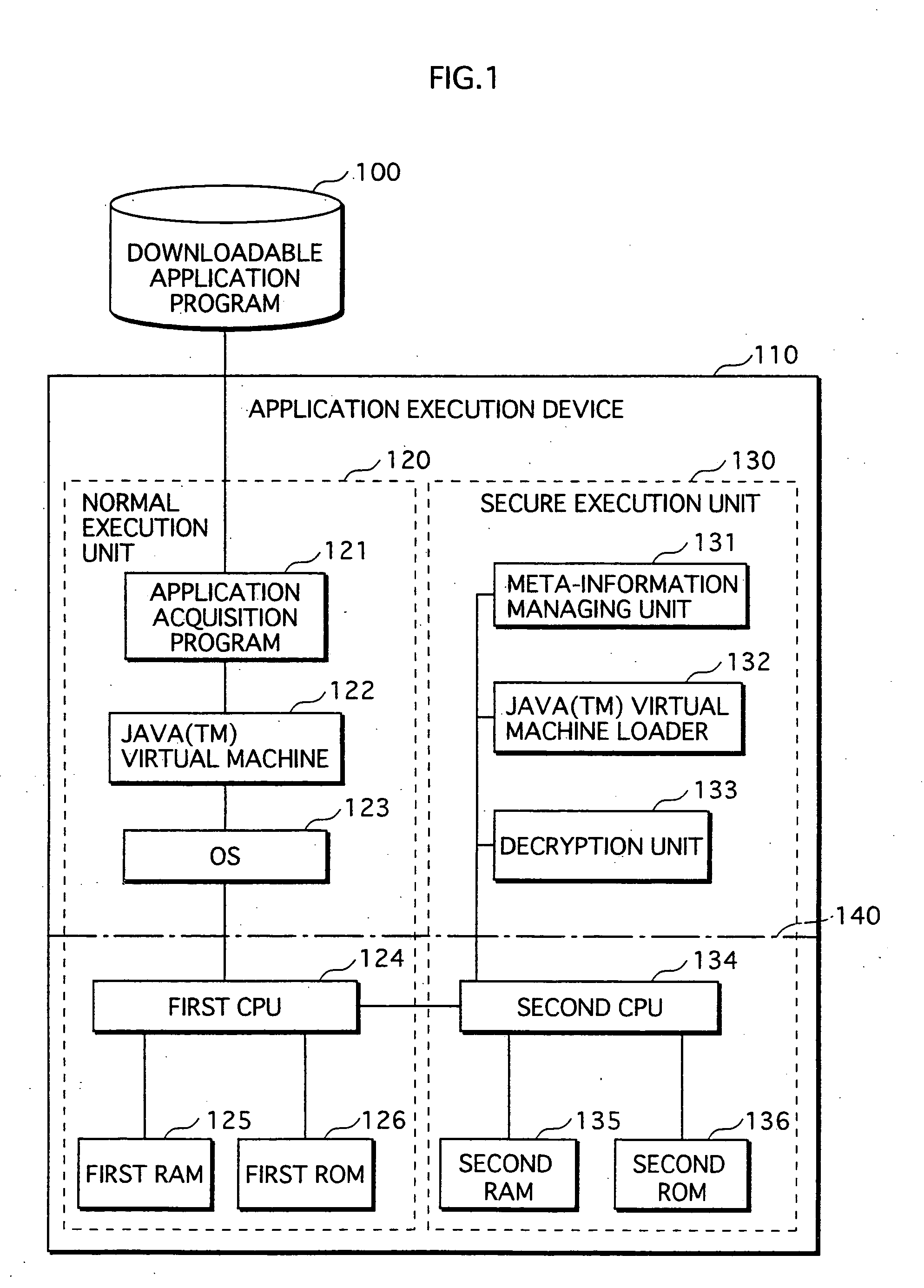
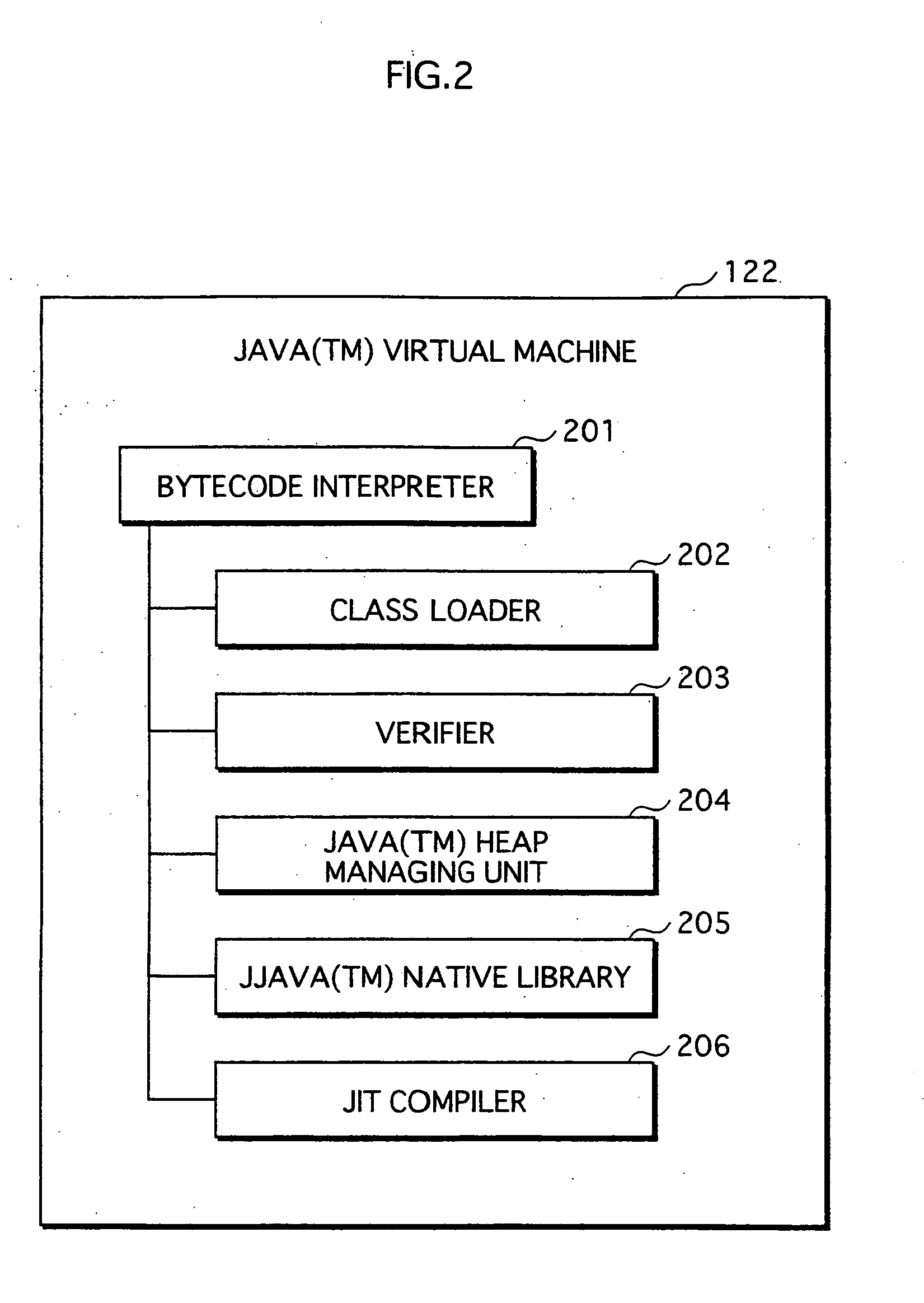
Application Execution Device and Application Execution Device Application Execution Method
InactiveUS20070271446A1High protection levelDigital computer detailsPlatform integrity maintainanceExecution unitOperating system
The conventional application protection technique complicates an application to make it difficult to analyze the application. However, with such a complication method, the complicate program can be analyzed sooner or later by taking a lot of time no matter how the degree of the complication is high. Also, it is impossible to protect the application from unauthorized copying. The meta-information managing unit that is to be executed in the secure execution unit stores the meta-information of the application in an area that can not be accessed by a debugger. When the meta-information is required by the normal execution unit to execute the application, a result of predetermined calculation using the meta-information is notified to the normal execution unit. In this way, the meta-information of the application can be kept secret.
Owner:PANASONIC CORP
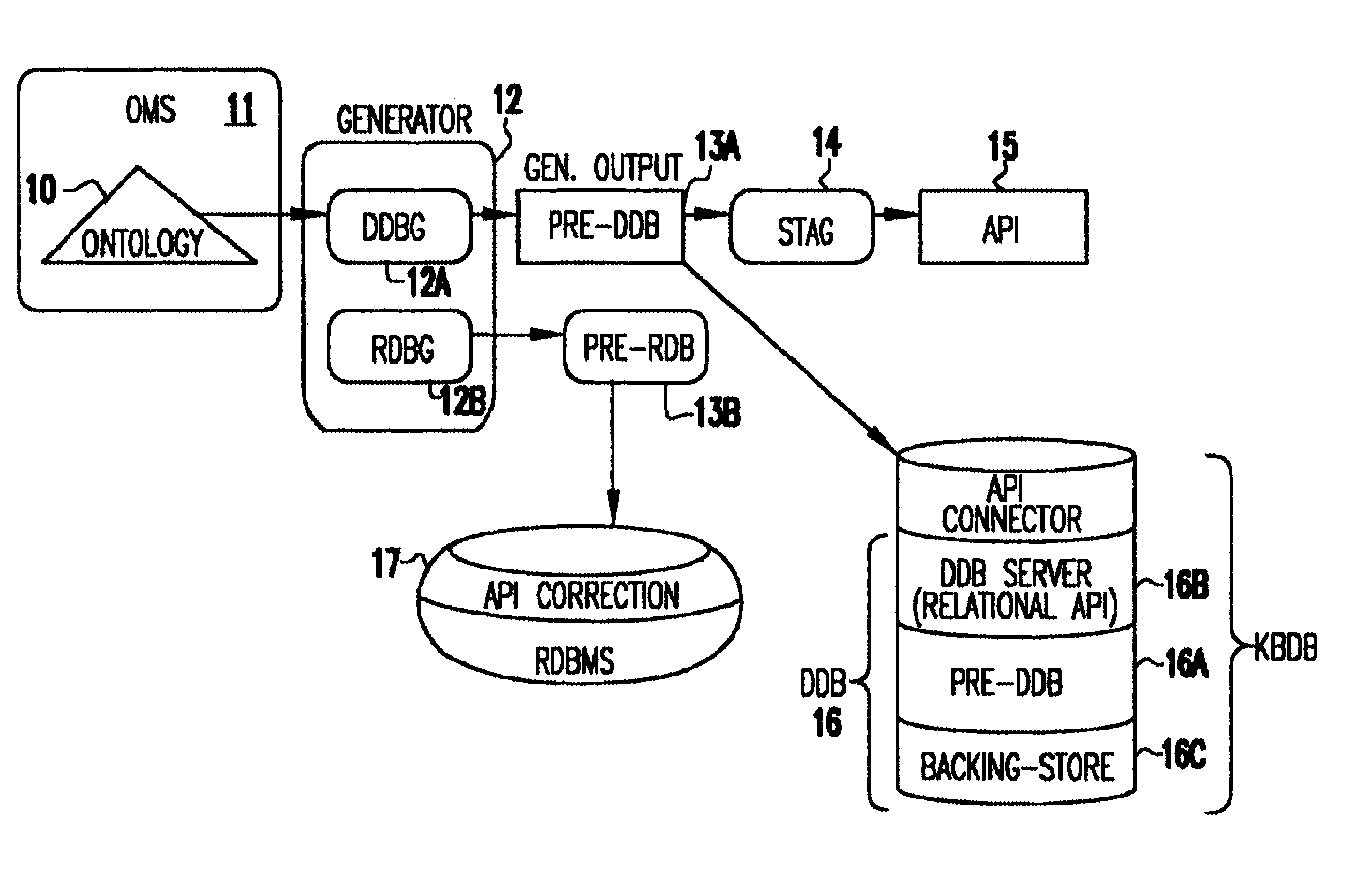
Ontology for database design and application development
InactiveUS6640231B1Improve fidelityImprove efficiencyData processing applicationsDigital data processing detailsEntity typeMaintainability
A system and method lets a user create or import ontologies and create databases and related application software. These databases can be specially tuned to suit a particular need, and each comes with the same error-detection rules to keep the data clean. Such databases may be searched based on meaning, rather than on words-that-begin-with-something. And multiple databases, if generated from the same basic ontology can communicate with each other without any additional effort. Ontology management and generation tools enable enterprises to create databases that use ontologies to improve data integration, maintainability, quality, and flexibility. Only the relevant aspects of the ontology are targeted, extracting out a sub-model that has the power of the full ontology restricted to objects of interest for the application domain. To increase performance and add desired database characteristics, this sub-model is translated into a database system. Java-based object-oriented and relational application program interfaces (APIs) are then generated from this translation, providing application developers with an API that exactly reflects the entity types and relations (classes and methods) that are represented by the database. This generation approach essentially turns the ontology into a set of integrated and efficient databases.
Owner:KYNDI
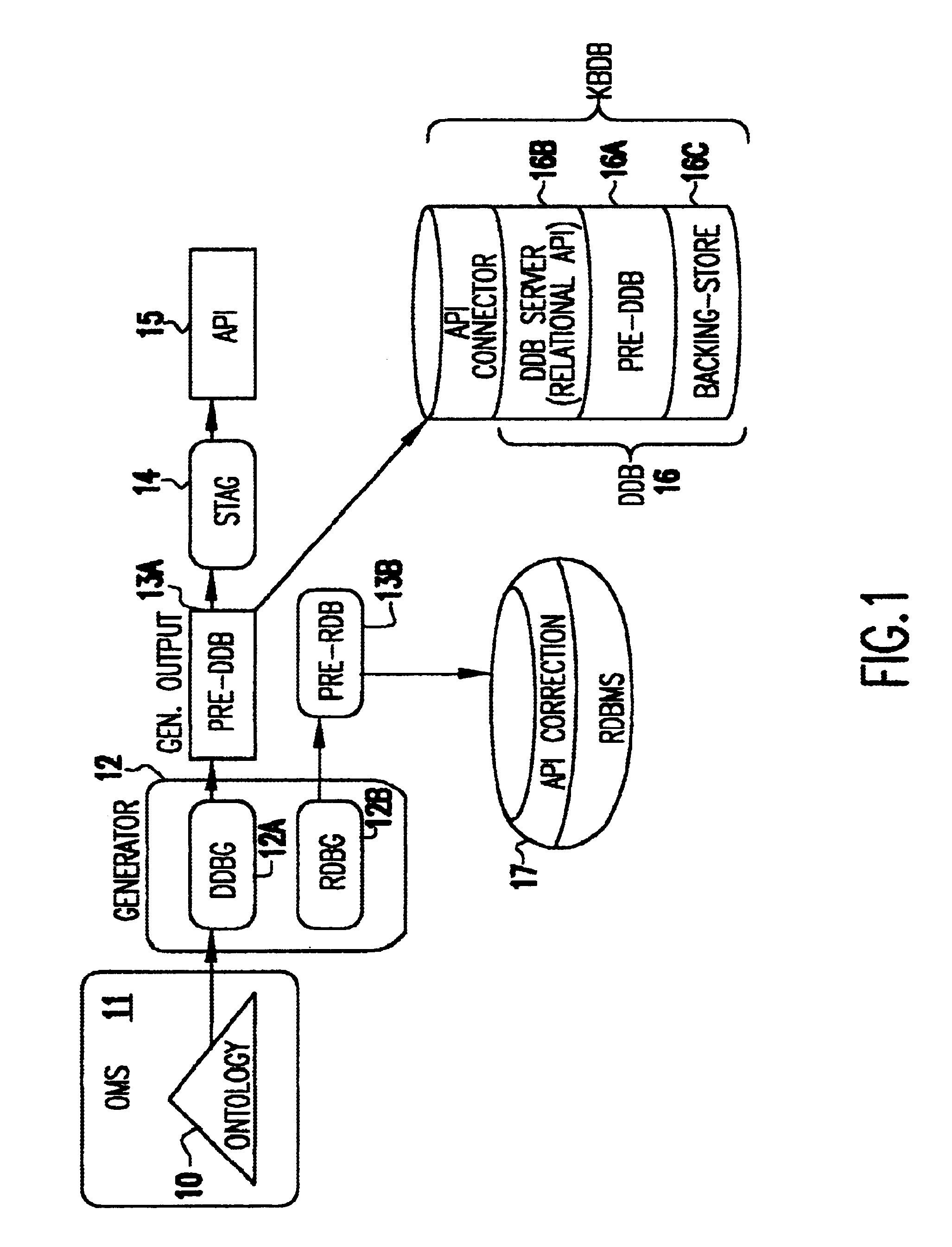
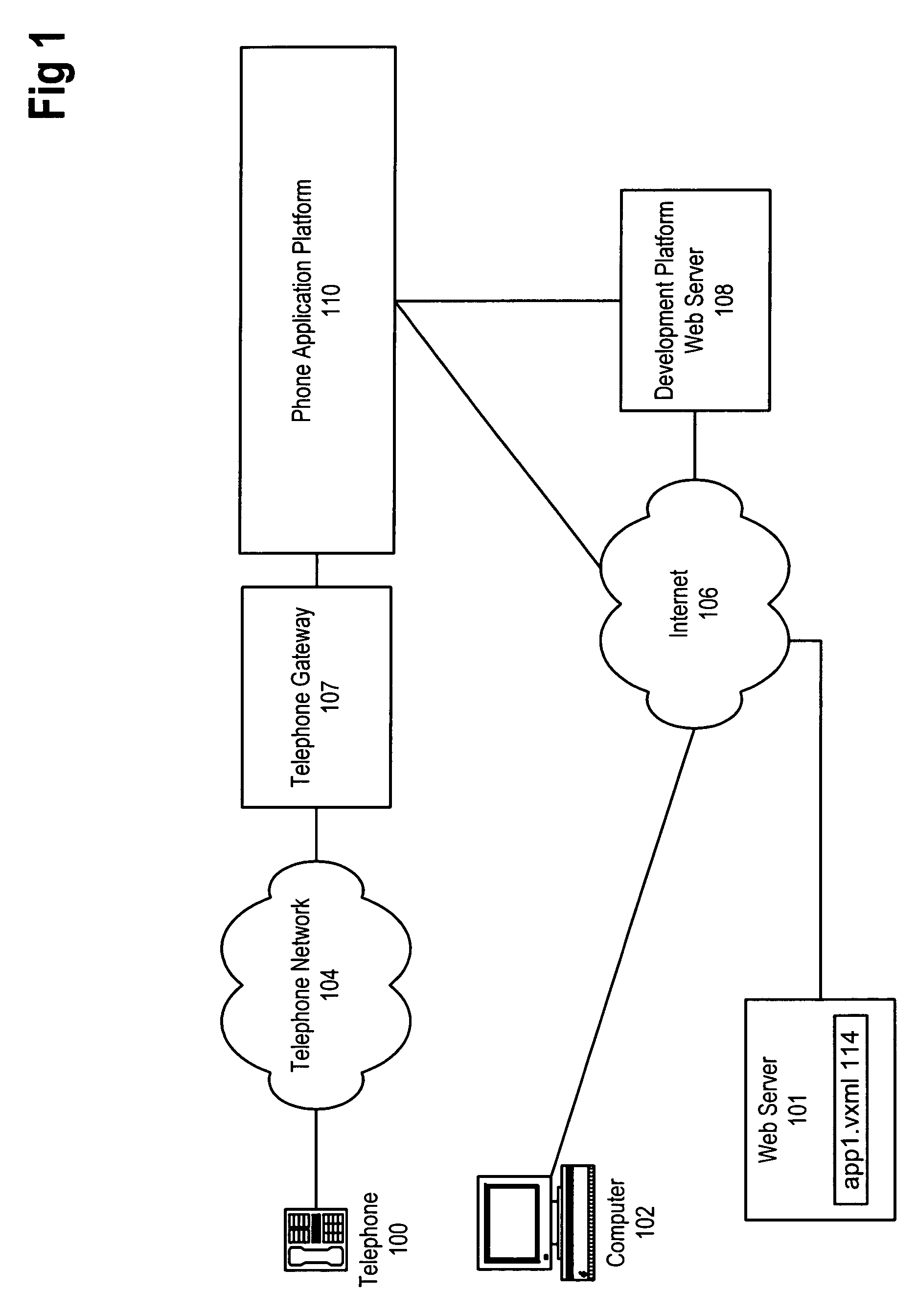
Method and apparatus for zero-footprint phone application development
InactiveUS7140004B1Avoid any surpriseTelephone data network interconnectionsError detection/correctionWeb browserApplication procedure
A zero-footprint remotely hosted phone application development environment is described. The environment allows a developer to use a standard computer without any specialized software (in some embodiments all that is necessary is a web browser and network access) together with a telephone to develop sophisticated phone applications that use speech recognition and / or touch tone inputs to perform tasks, access web-based information, and / or perform commercial transactions. Some embodiments support concurrent call flow tracking that allows a developer to observe, using a web browser, the execution of her / his application. A variety of reusable libraries are provided to enable the developer to leverage well-developed libraries for common playback, input, and computational tasks. Embodiments support rapid application deployment from the development environment to hosted application deployment to the intended audience.
Owner:MICROSOFT TECH LICENSING LLC
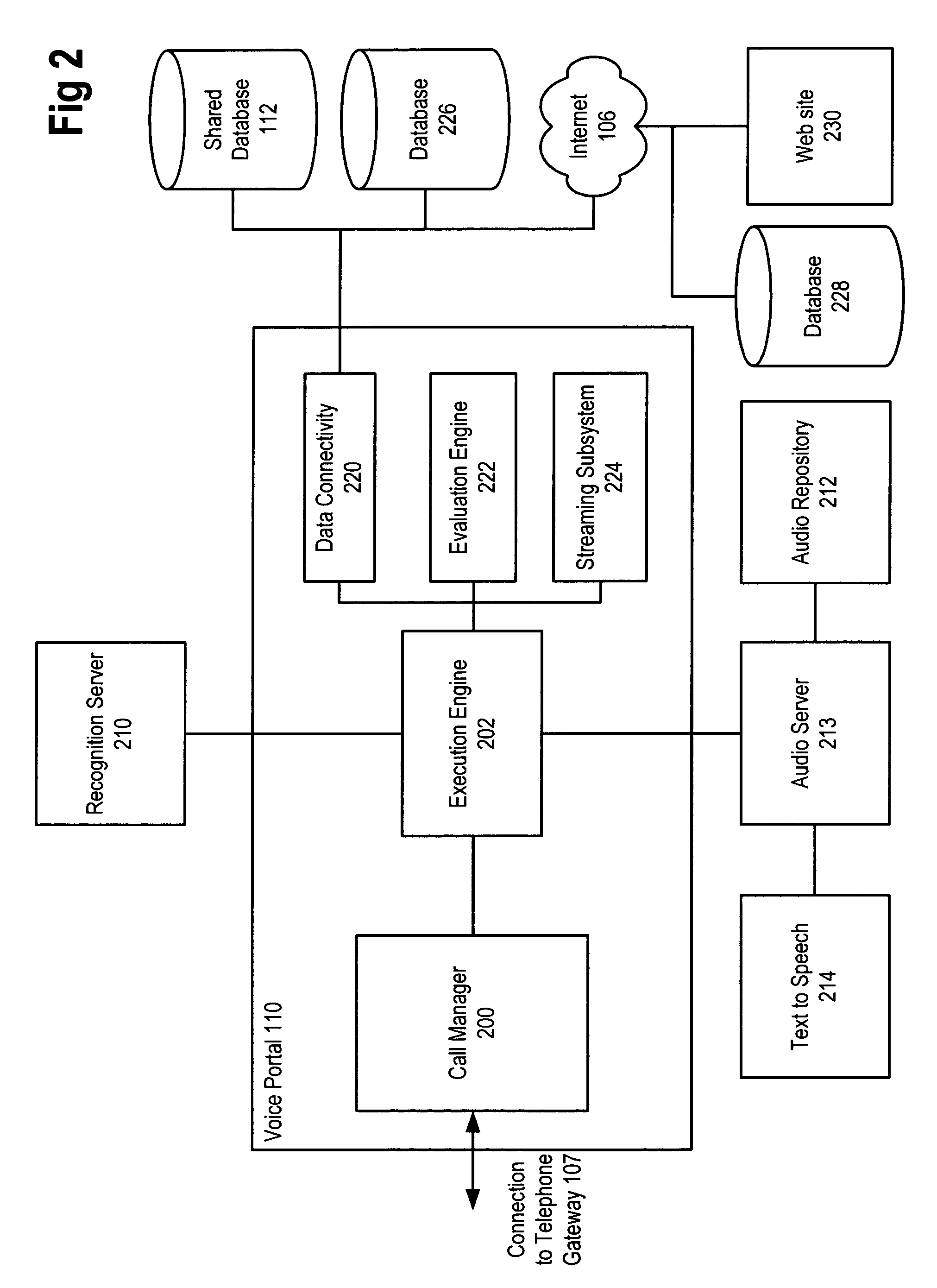
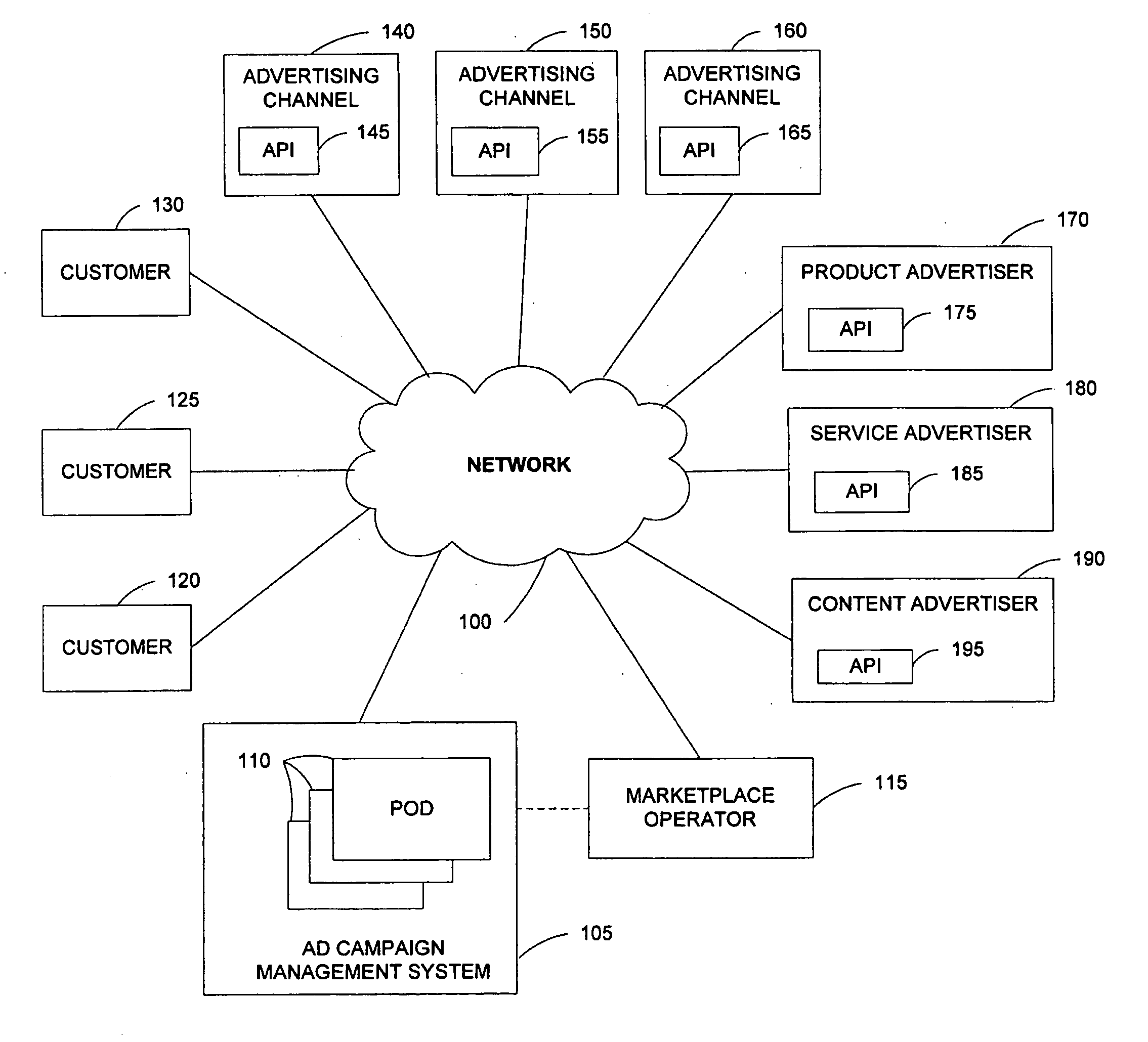
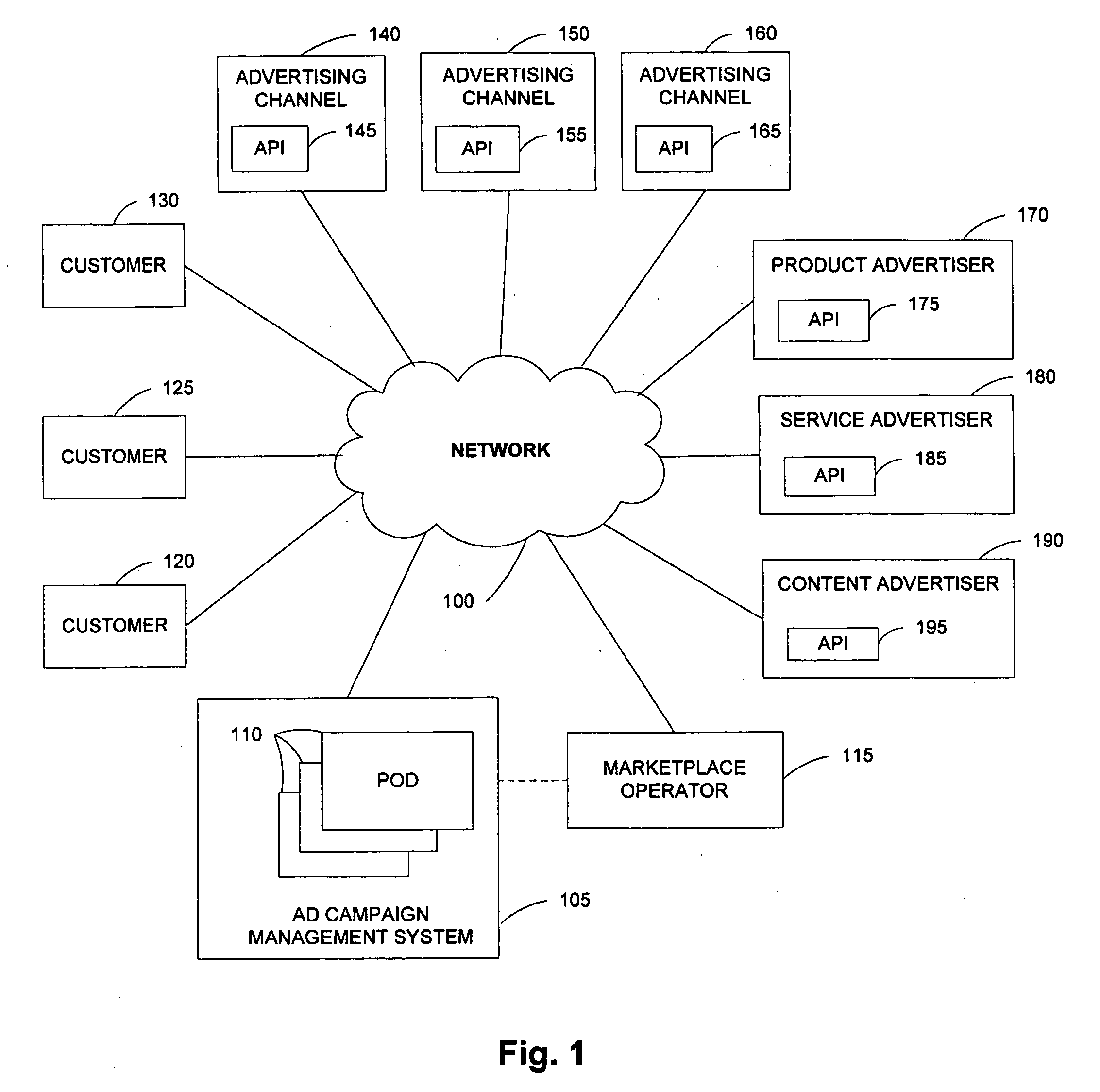
API for maintenance and delivery of advertising content
A system comprises multiple pods coupled to a network, each pod including a data store for storing advertisement campaigns for users, each advertisement campaign containing user information, advertisement information and bid information for requesting presentation of an advertisement upon the occurrence of a predetermined event; and an application program interface capable of accessing the data store; at least one pod including a forecasting component for enabling user selection of the predetermined event; and an optimization component for assisting with selection of the bid information.
Owner:OATH INC
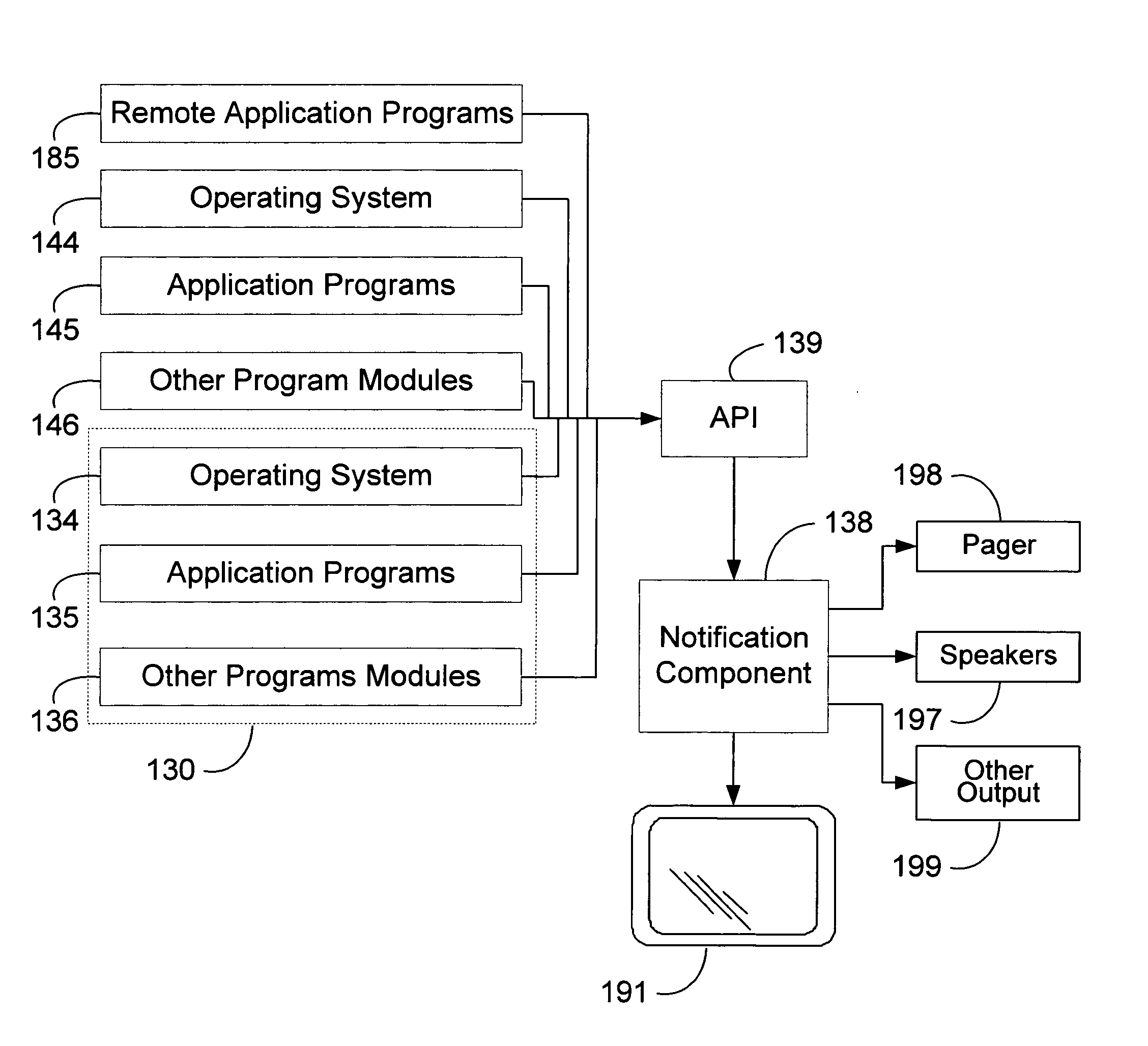
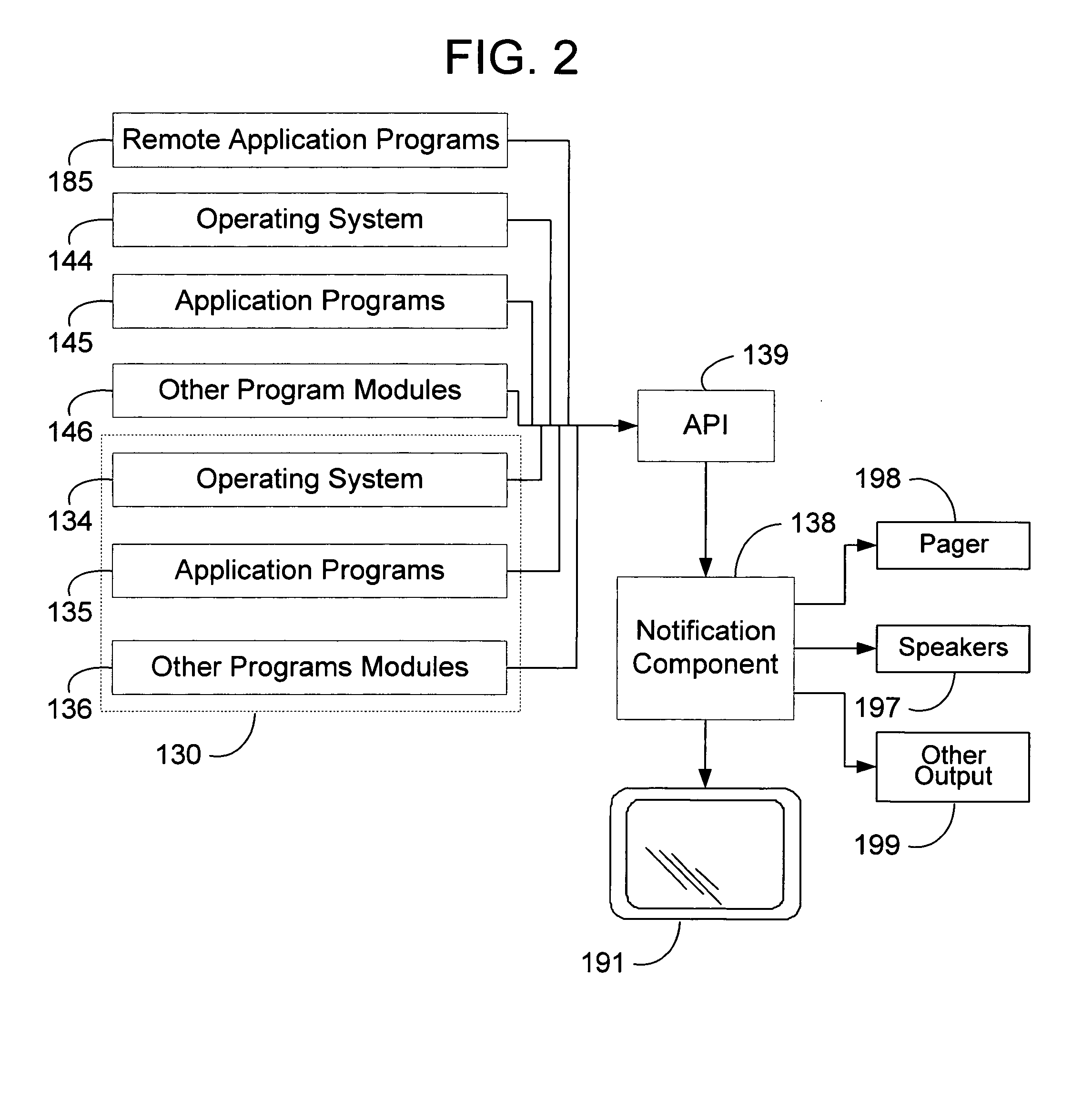
Method and system for displaying transient notifications
InactiveUS7155729B1Reducing development cycle timeLow costMultiprogramming arrangementsExecution for user interfacesPagerApplication programming interface
A notification component that is shared between all applications that provides notifications to users without interrupting the task that the user is working and allows users to manage the notifications from one location. The user can globally set preferences as to how the notifications should be rendered. These preferences include enabling or disabling notification classifications, which rendering type they want to use for each notification classification, and priority of notifications within each notification classification. The notification component allows the user to indicate what notifications the user want to sees and how the notifications are rendered. Rendering types include audio, visual, and pager styles. An application uses an application programming interface to send notification using schema based or text based notifications. The system parses the notification and provides the user the notification through notification classifications in accordance with the user preferences.
Owner:MICROSOFT TECH LICENSING LLC
Phone application state management mechanism
InactiveUS7376740B1Lowered byMore flexiblyData switching by path configurationMultiple digital computer combinationsApplication procedureState management
Owner:MICROSOFT TECH LICENSING LLC
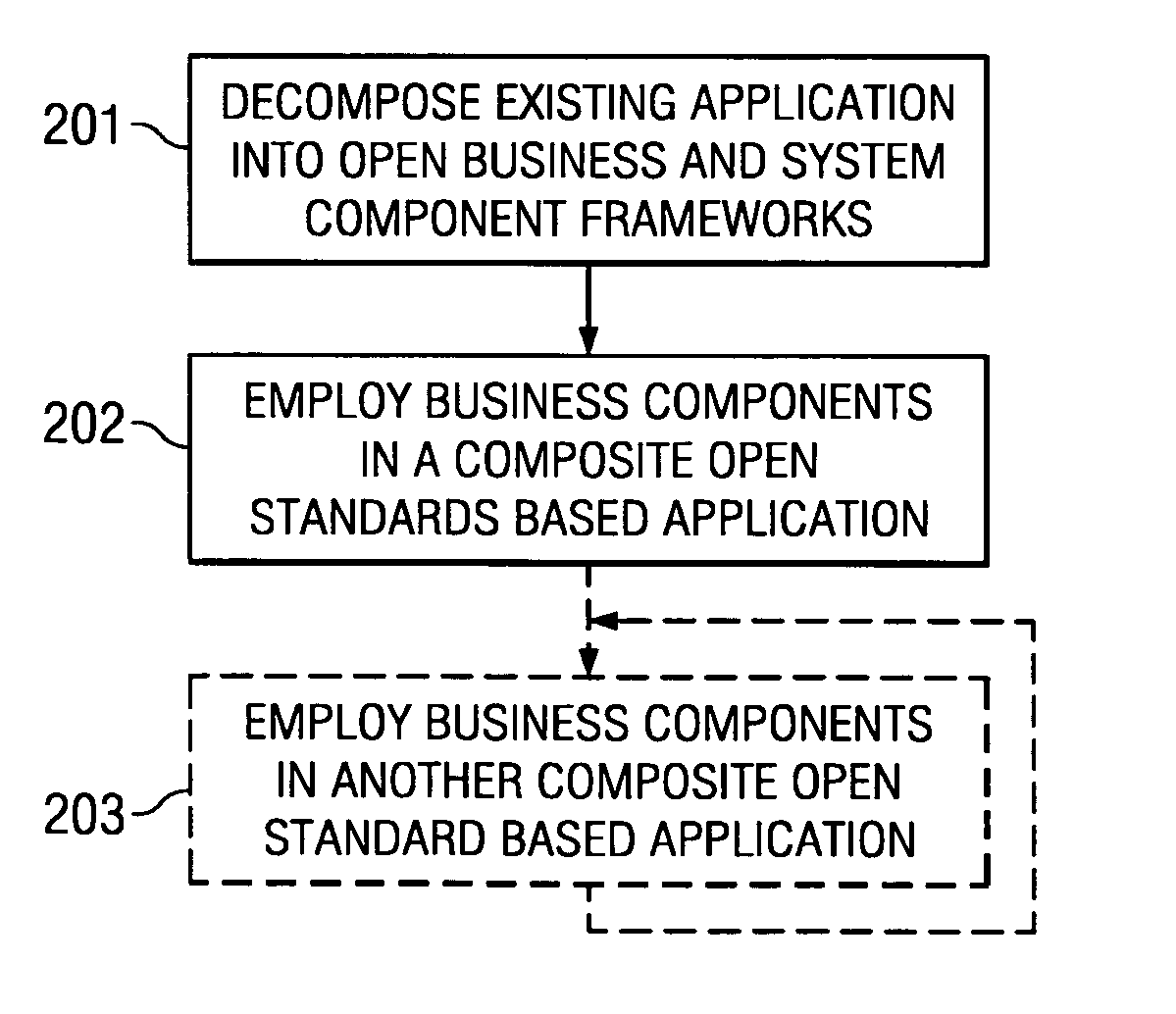
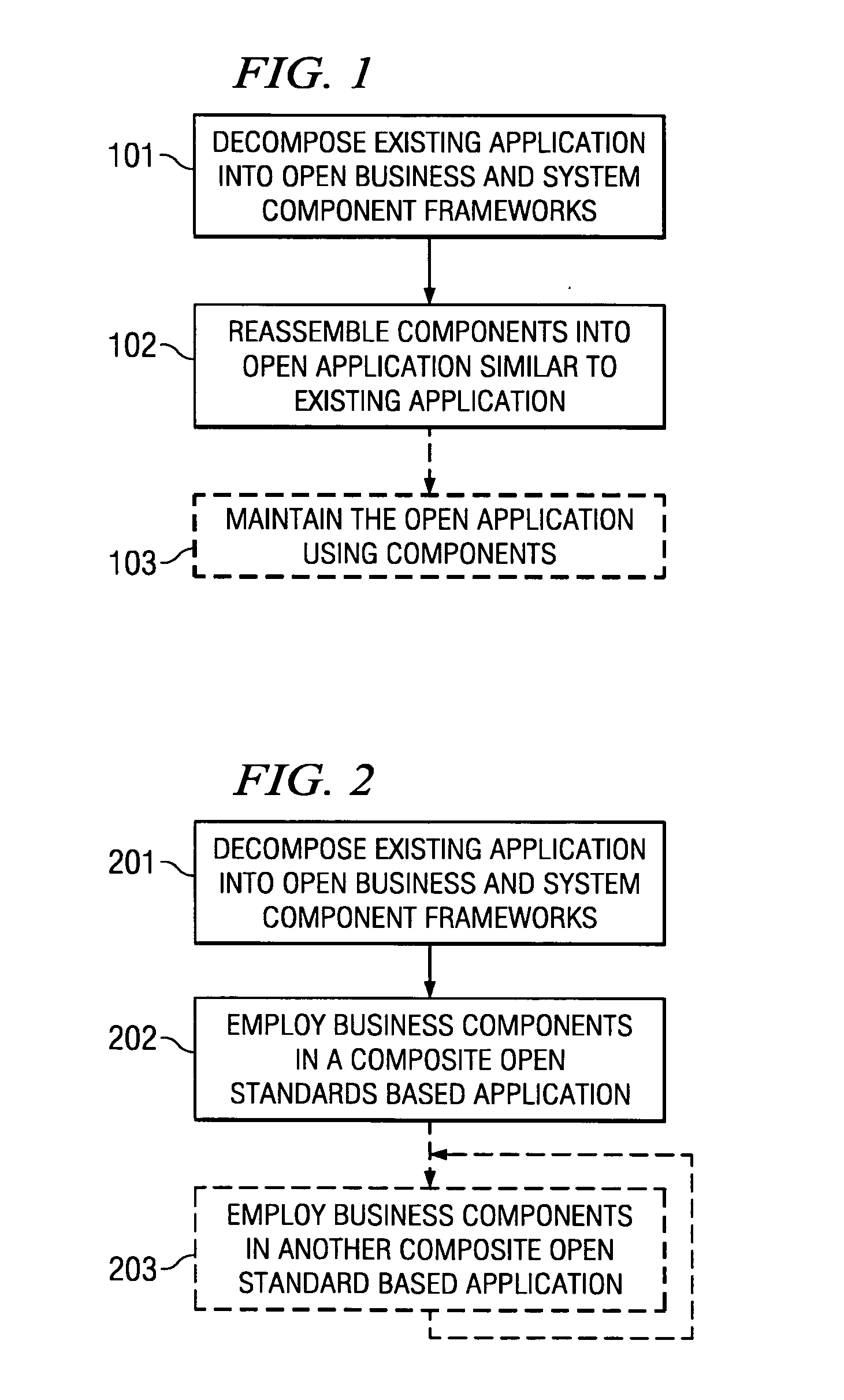
Systems and methods for modeling and generating reusable application component frameworks, and automated assembly of service-oriented applications from existing applications
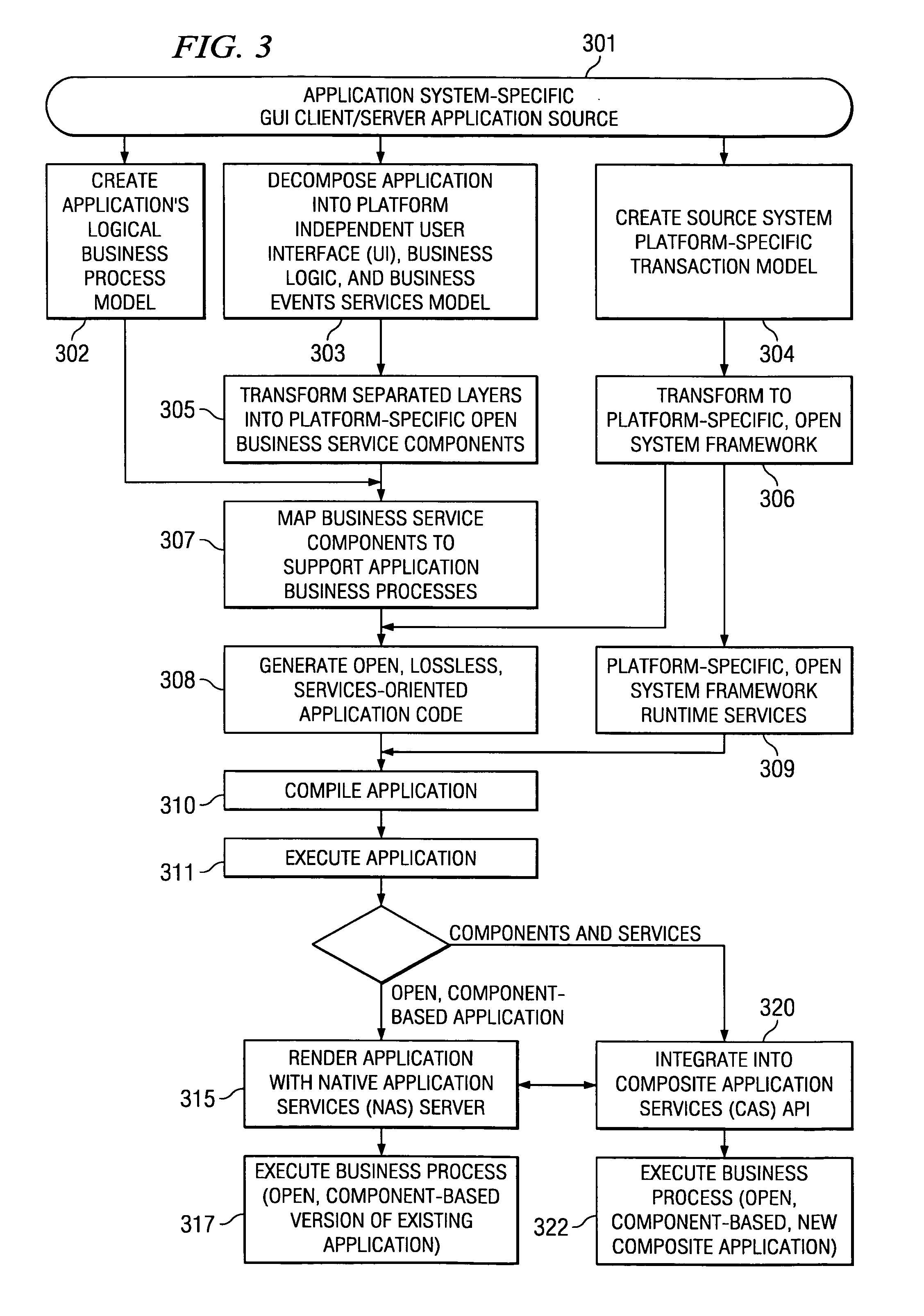
InactiveUS20050144226A1Effective and meaningful supportLower barrierSoftware maintainance/managementMultiple digital computer combinationsService oriented applicationsBusiness process
Embodiments of systems and methods model and generate open reusable, business components for Service Oriented Architectures (SOAs) from existing client / server applications. Applications are decomposed into business component frameworks with separate user interface, business logic, and event management layers to enable service-oriented development of new enterprise applications. Such layers are re-assembled through an open standards-based, Native Application Services (NAS) to render similar or near identical transactional functionality within a new application on an open platform, without breaking former production code, and without requiring a change in an end-user's business processes and / or user experience. In addition, the same separated layers may form re-usable business components at any desired level of granularity for re-use in external composite applications through industry-standard interfaces, regardless of usage, context, or complexity in the former Client / Server application.
Owner:SAP AG
Systems and methods for a mobile application development and development platform
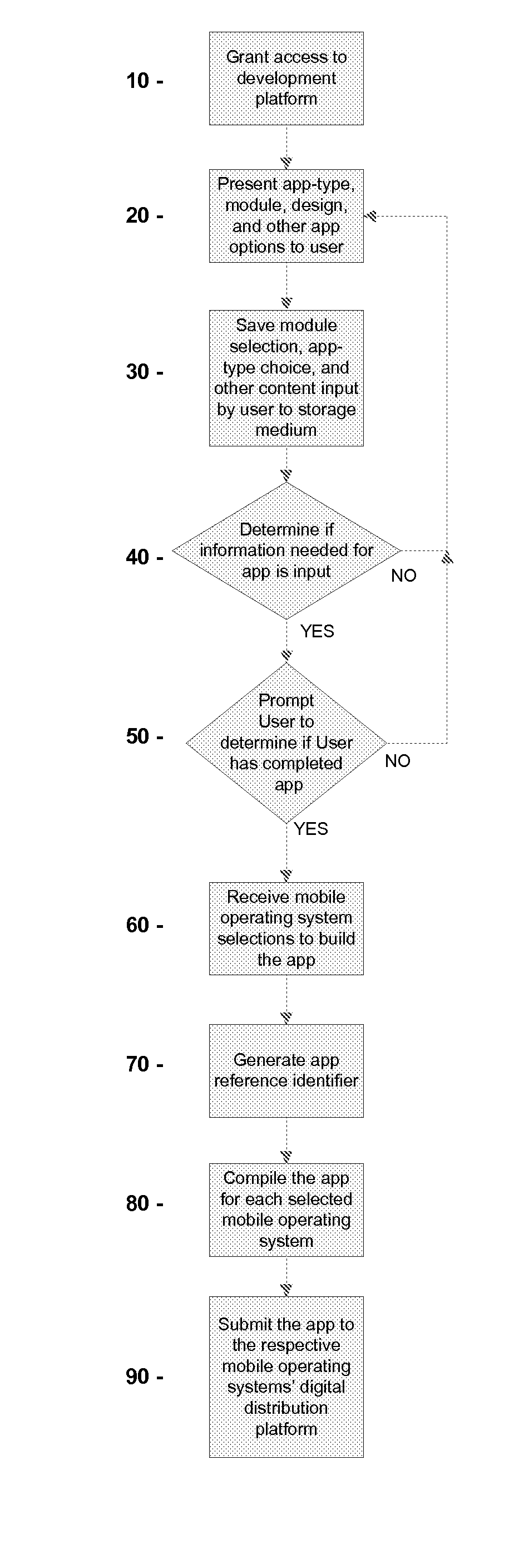
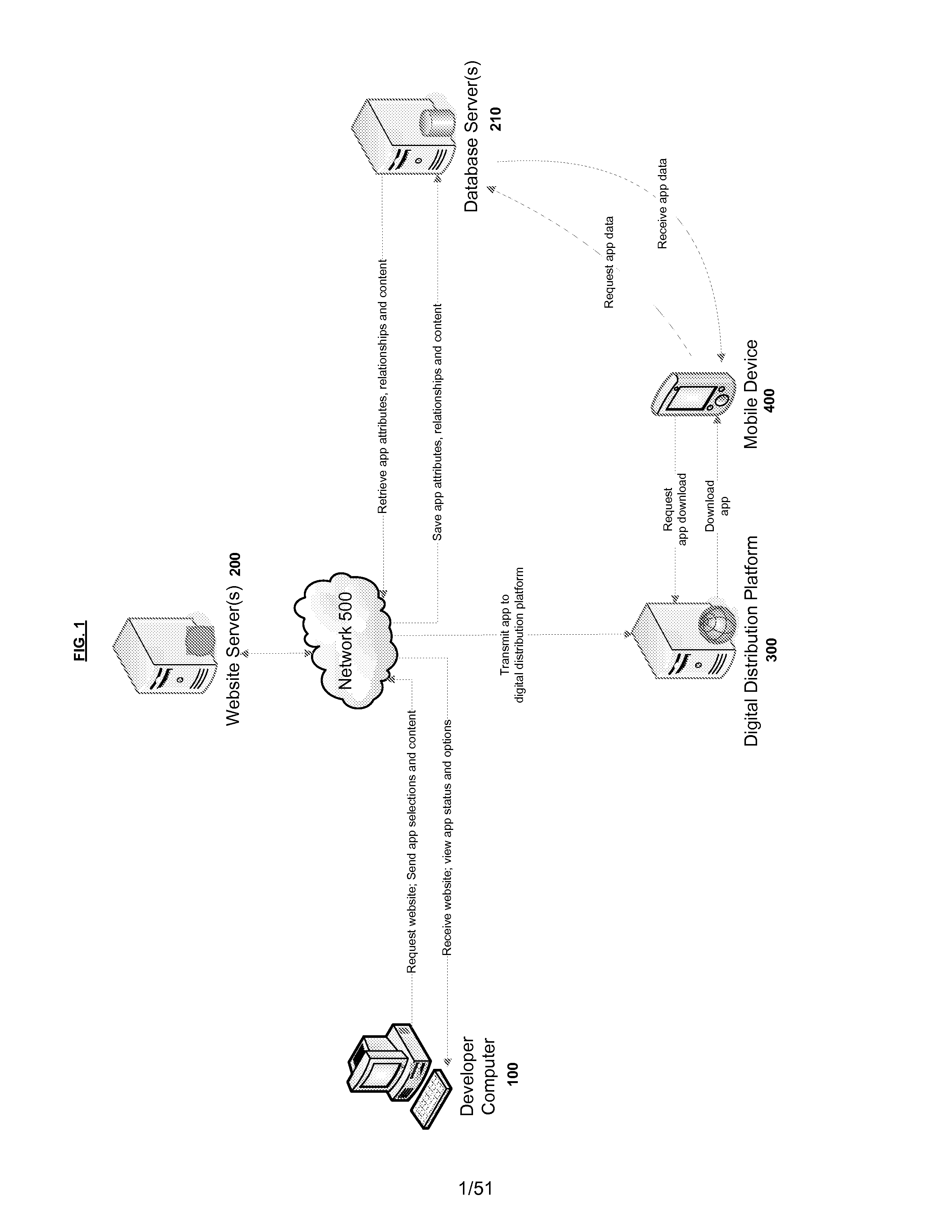
ActiveUS8261231B1High degreeVersion controlMultiple digital computer combinationsApplication softwareInternet based
Systems and methods for developing, customizing, and deploying mobile device applications are provided through a mobile application development and deployment platform. Preferably, these systems and methods are implemented in an Internet based environment that allows non-technical users to build sophisticated, highly-customizable cross-platform mobile applications. The platform allows users to select, input, create, customize, and combine various content, design characteristics, and application components, such as modules, some of which utilize features and functionality associated with various mobile devices and mobile operating systems. In certain embodiments, the platform allows users to compile, and generate a configuration file for, the mobile application that can be distributed to end users for execution on various mobile devices and mobile operating systems. When the mobile application is installed on, or executed by the mobile device, the configuration file may enable the retrieval of various data associated with the mobile application.
Owner:MEDIA DIRECT
System and method for mapping a design model to a common repository with context preservation
InactiveUS6343265B1Improved GUIEasy to understandData processing applicationsSoftware designModeling languageData structure
Disclosed is a system for mapping objects defined in a design model, such as an object oriented design model defined using a design language such as the Universal Modeling Language (UML), to a data model accessible to an application development tool. A design model is provided that includes at least two models. A first model includes a first class and a second model includes a second class. The first class and second class have the same name, and the first class and second class have at least one different attribute and method. The first model, the first class, and attributes and methods therein are mapped to a first data structure that indicates that the first class is included with the first model. The second model, the second class, and attributes and methods therein are mapped to a second data structure that indicates that the second class is included with the second model. In this way, the first class and the second class are distinguished according to their model in the data structures.
Owner:IBM CORP
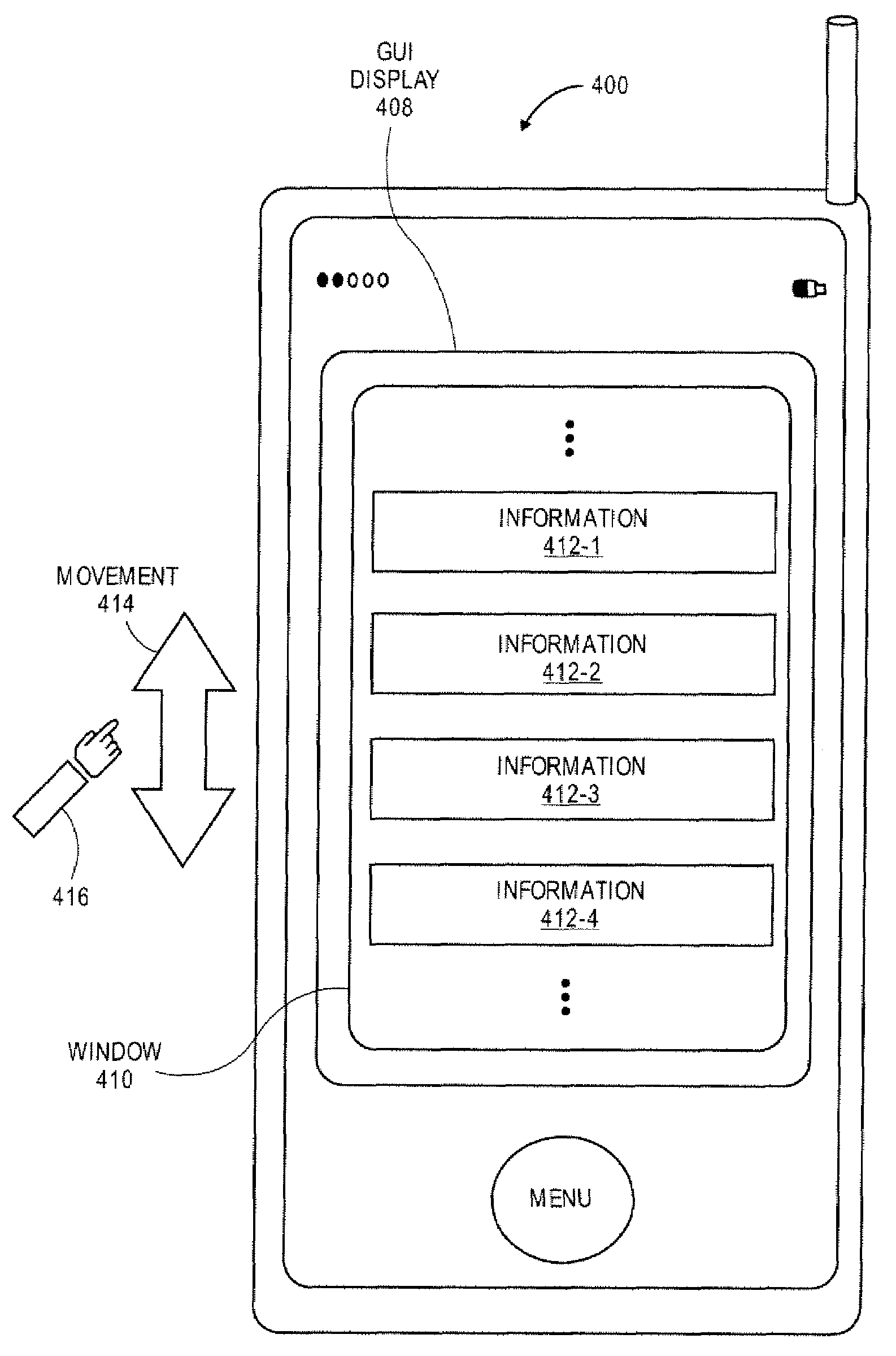
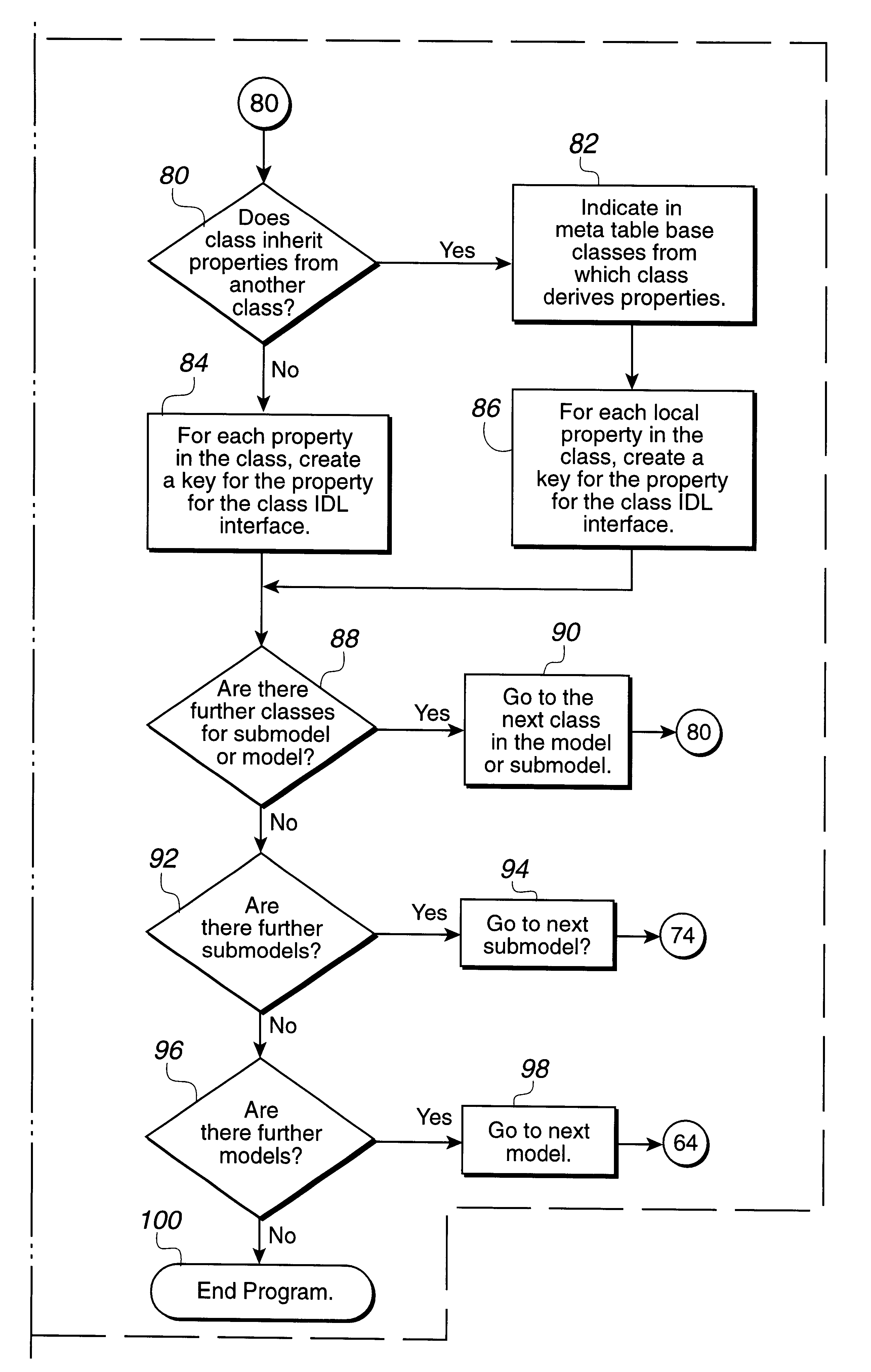
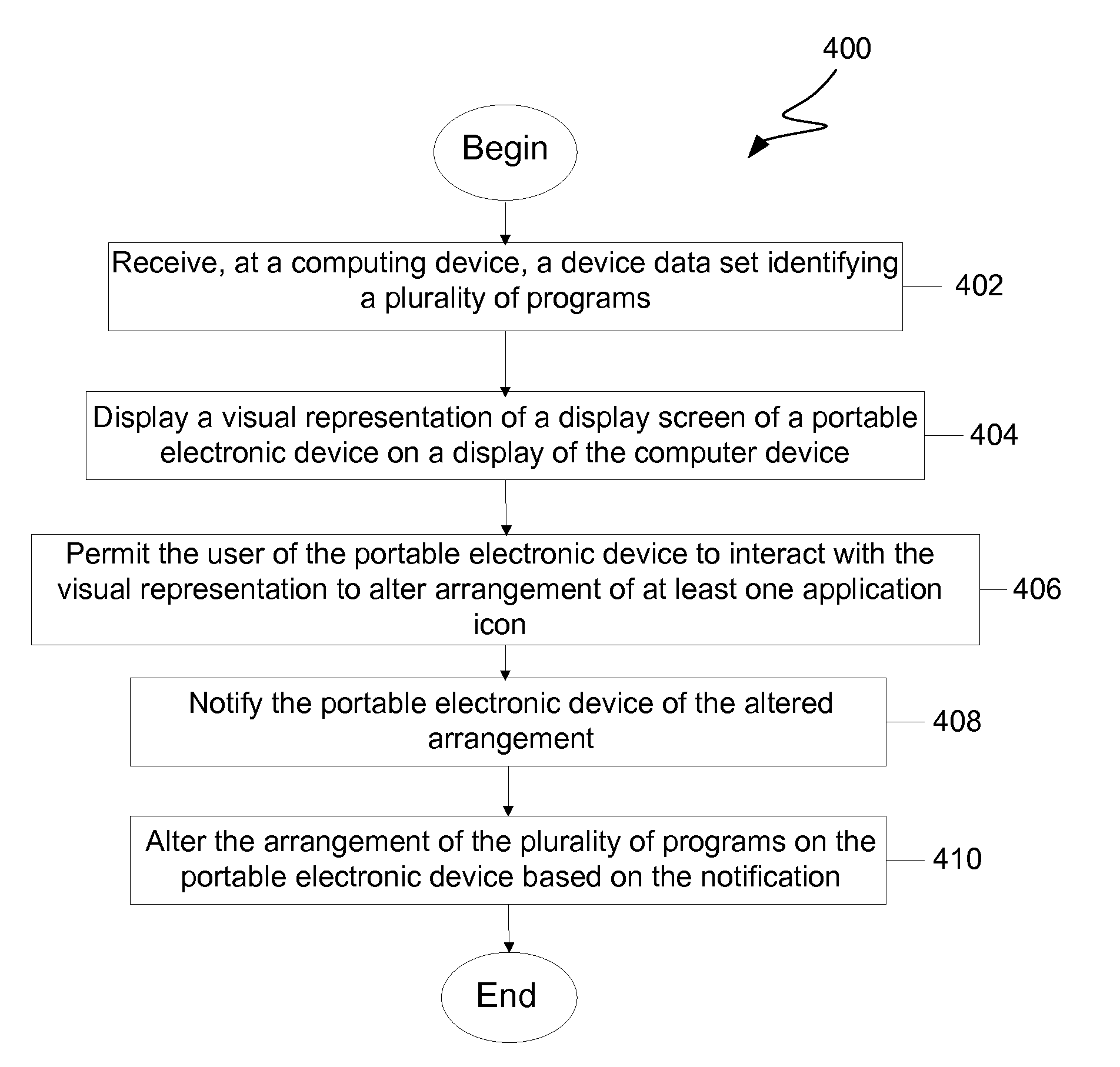
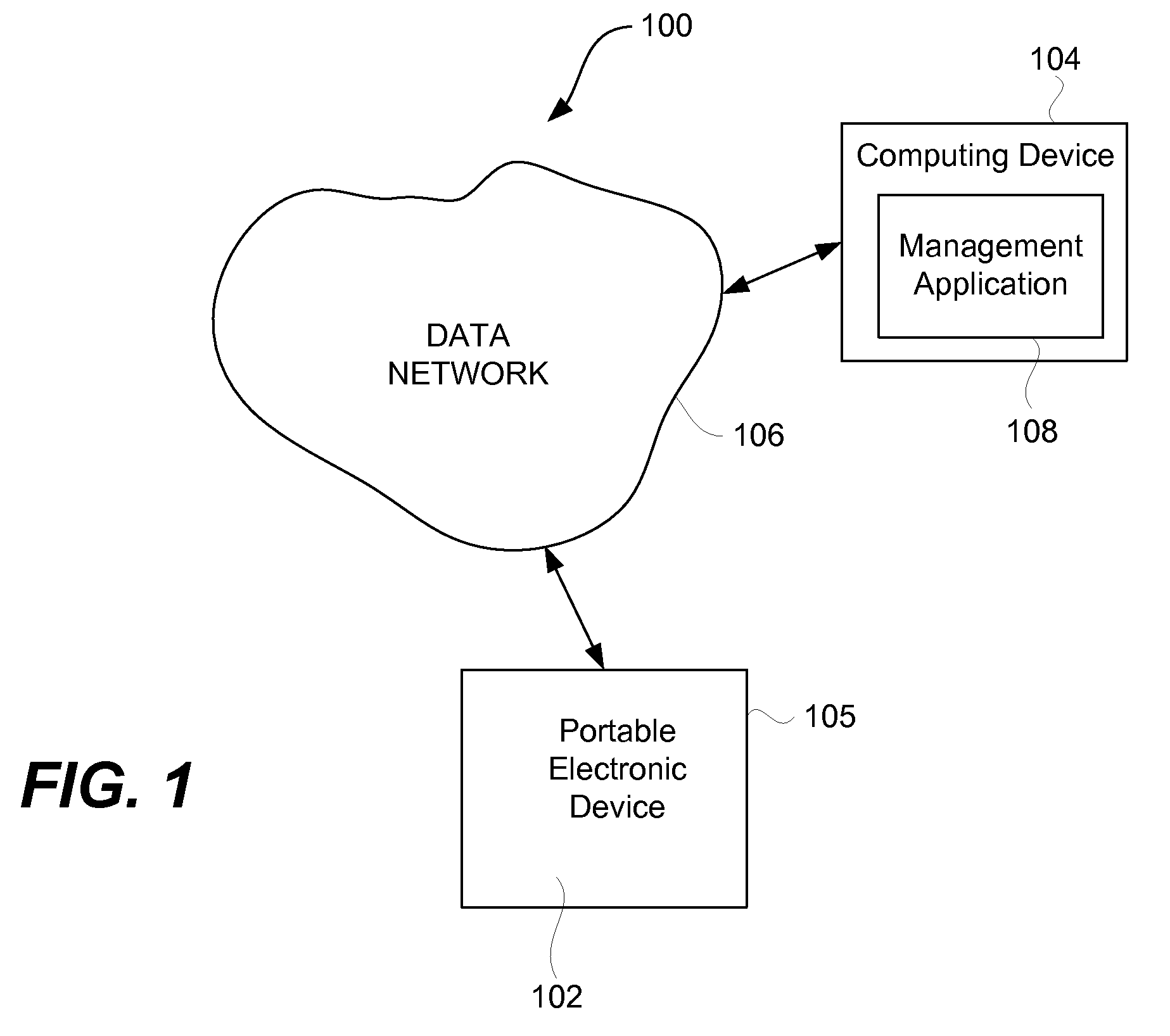
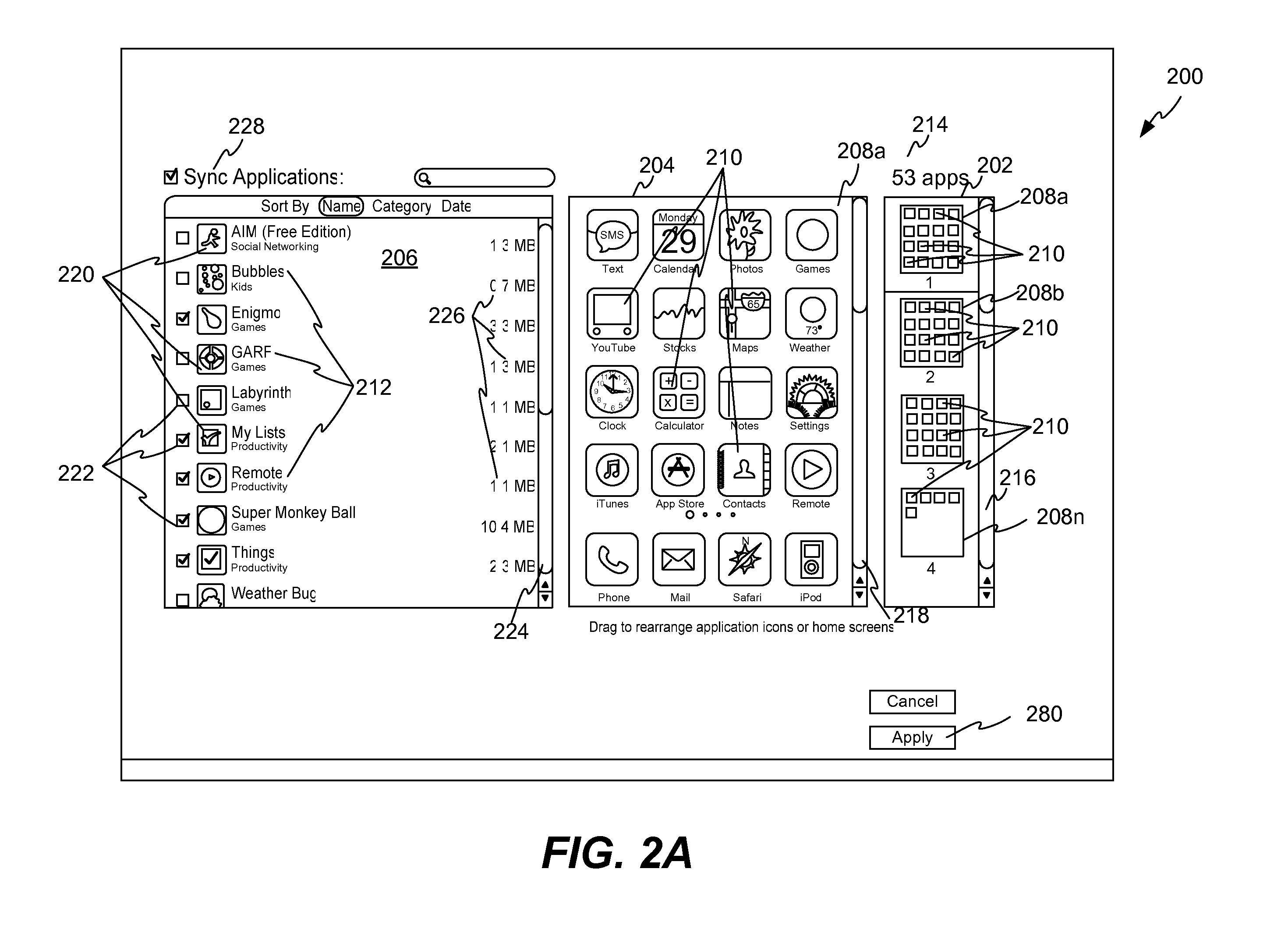
Management of Application Programs on a Portable Electronic Device
ActiveUS20110061010A1Execution for user interfacesInput/output processes for data processingGraphical user interfaceApplication procedure
A method, system, and graphical user interface (GUI) for management of application programs on a portable electronic device (PED) is discussed. A management application program operating on a computing device can provide management of the application programs on the PED by presenting a GUI. The user can interact with the GUI to (i) manage (e.g., position applications, arrange applications, add applications, and the like) the application programs, and (ii) arrange application icons on the PED.
Owner:APPLE INC
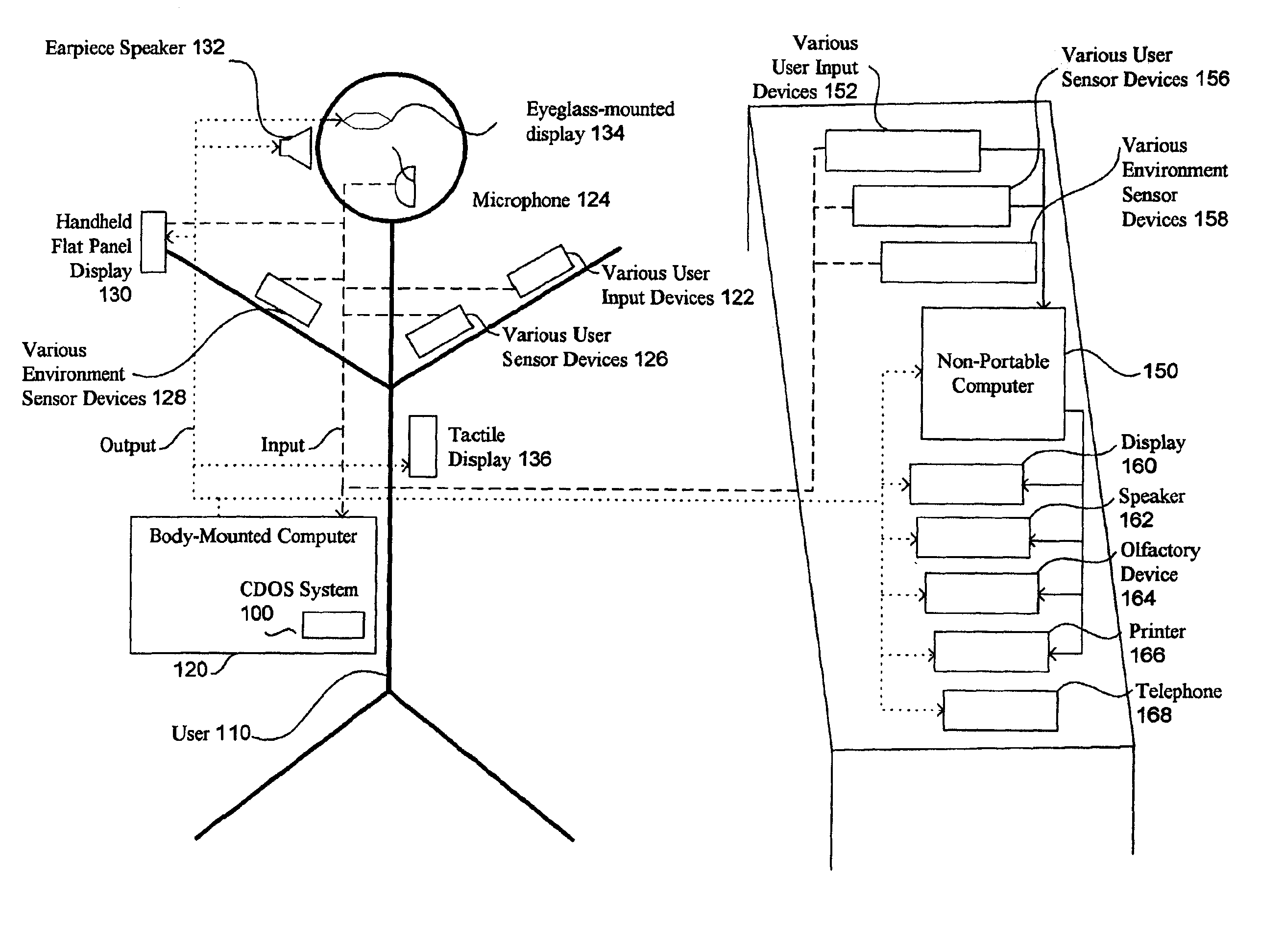
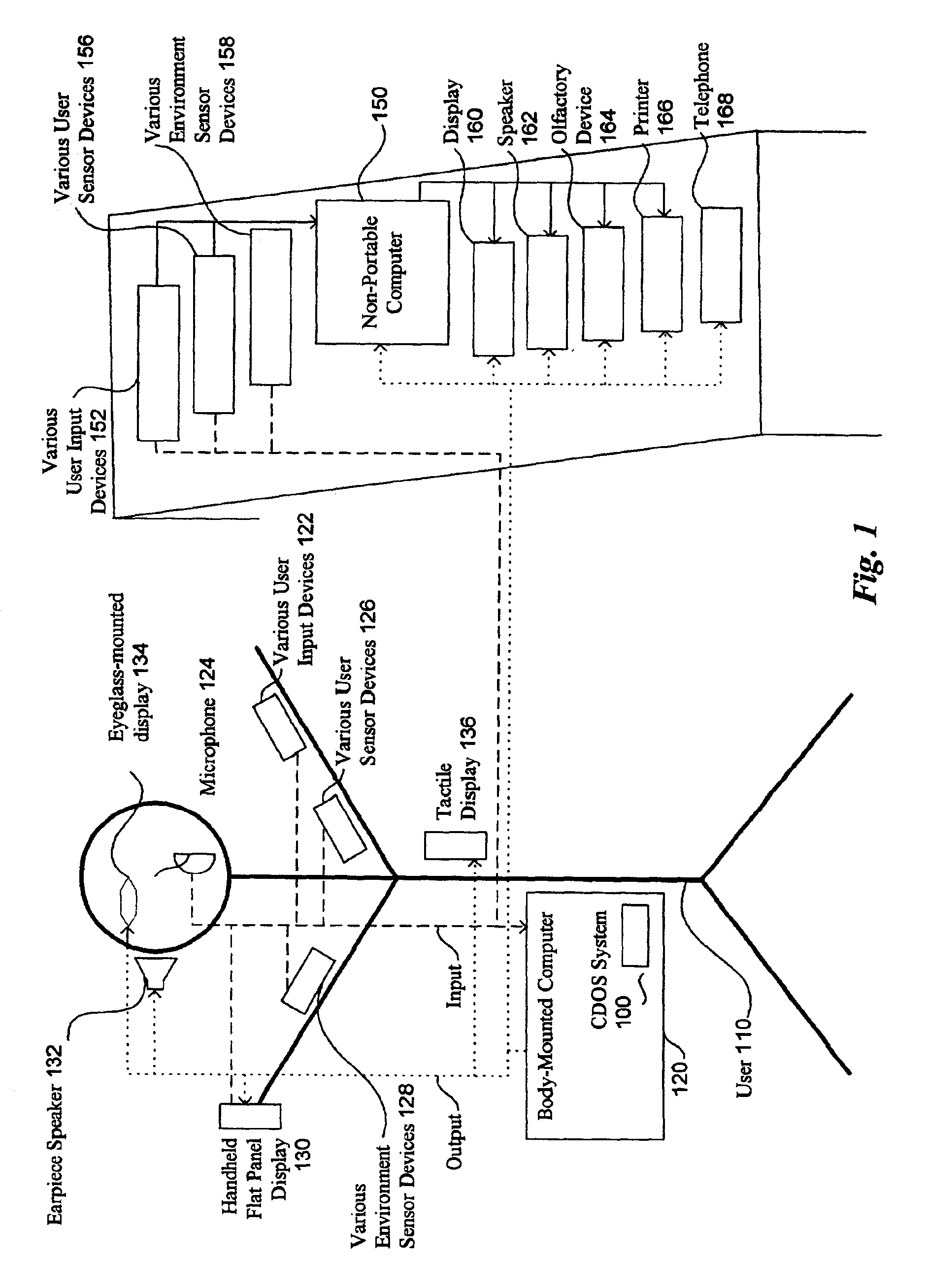
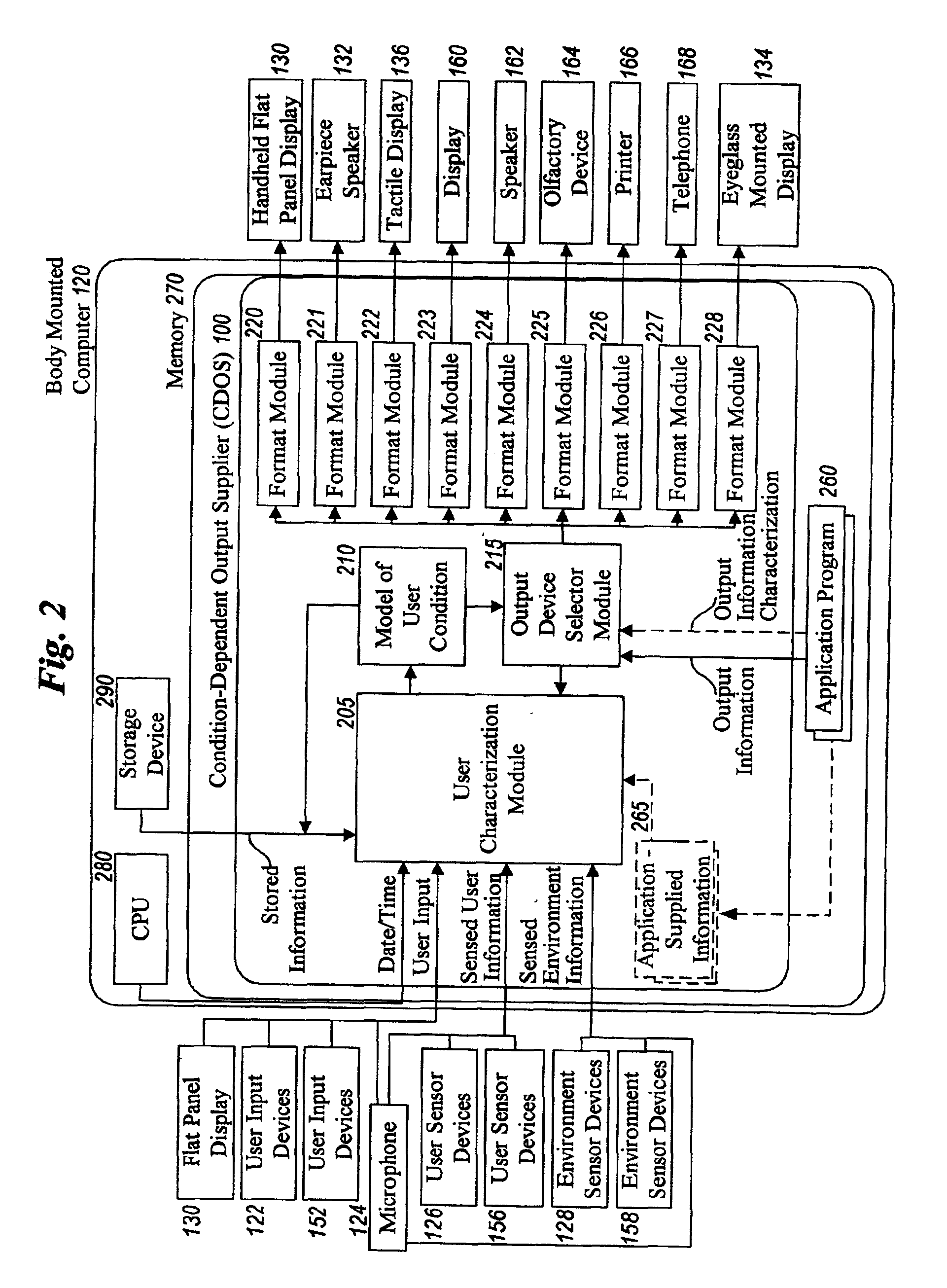
Method and system for controlling presentation of information to a user based on the user's condition
InactiveUS6874127B2Input/output for user-computer interactionDigital computer detailsAbstract conceptDisplay device
A system for controlling presentation of information to a user based on the user's current condition. In particular, the system monitors the user and the user's environment, and creates and maintains an updated model of the current condition of the user. The user condition can include a variety of condition variables, including abstract concepts such as the user's current cognitive load, desired level of privacy for output information, and desired scope of audience for output information. Upon receiving output information to be presented to the user (e.g., from an application program), the system determines an appropriate output device and an appropriate format with which to present the information to the user, and then presents the output information. The system can also receive description information about the output information that describes relevant factors for determining when and how to present the output information (e.g., the importance and urgency of the output information, the consequences of the user not receiving or ignoring the output information, etc.). Some versions of the system execute on a wearable computer having a variety of available output display devices.
Owner:MICROSOFT TECH LICENSING LLC
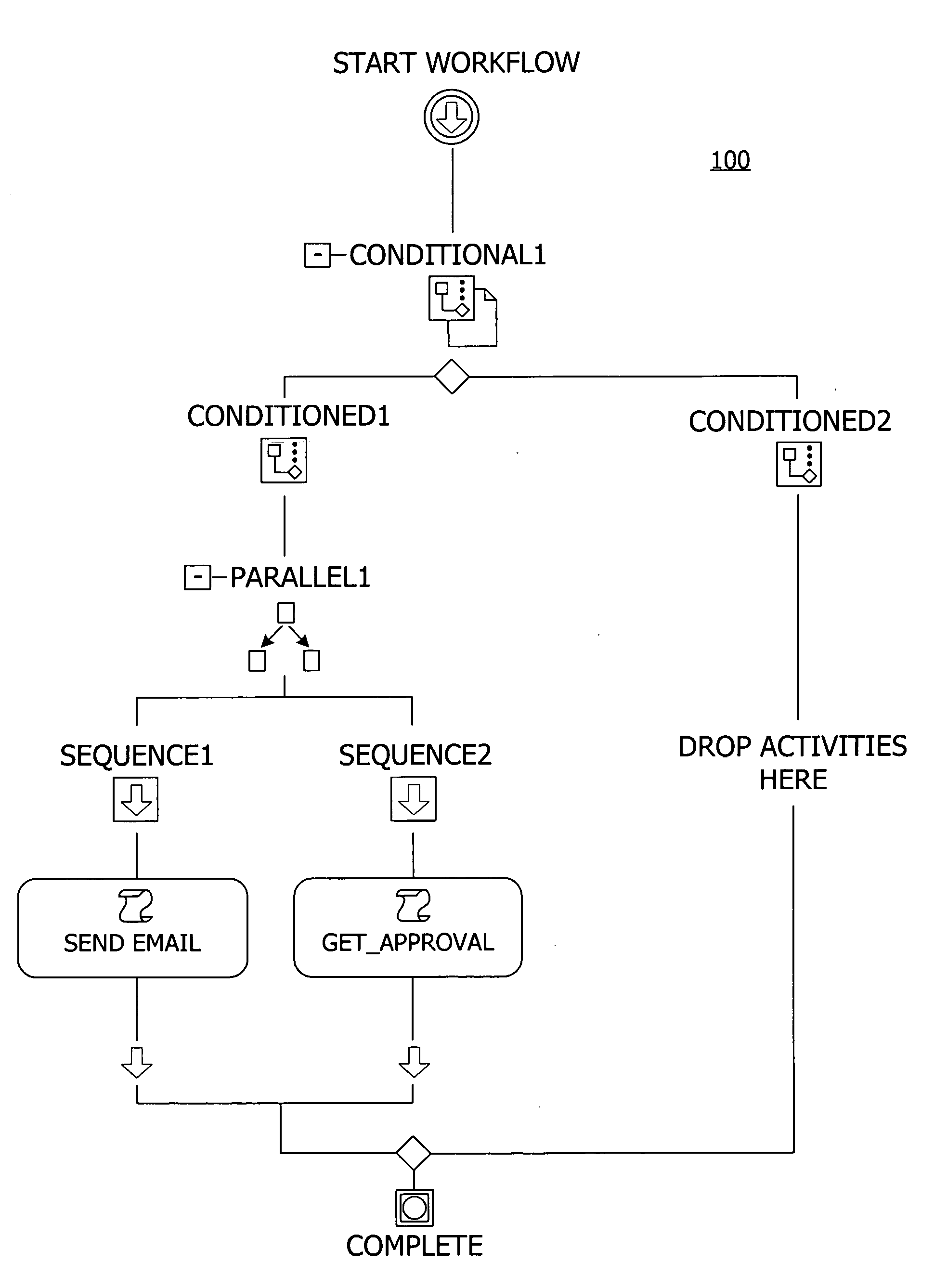
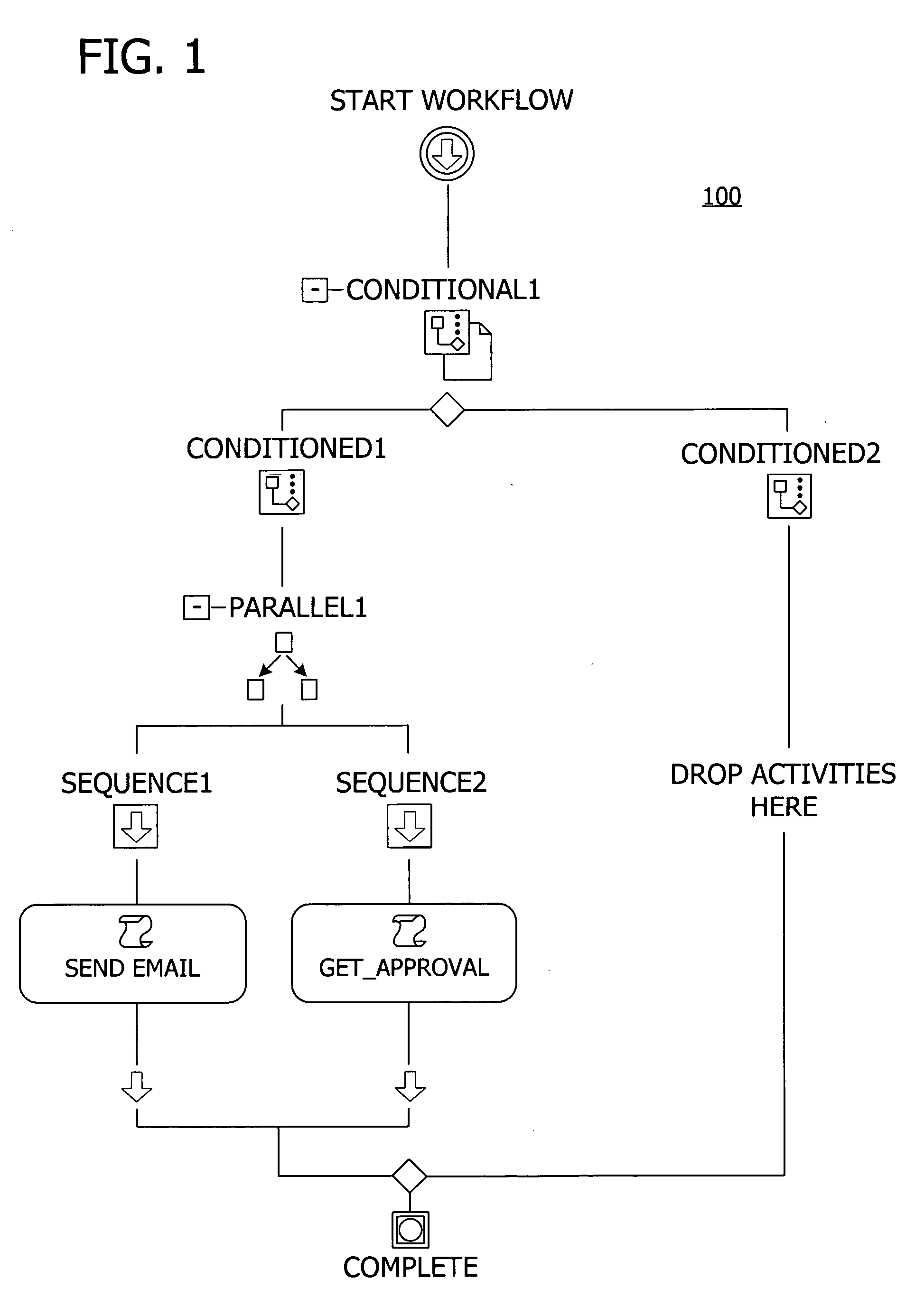
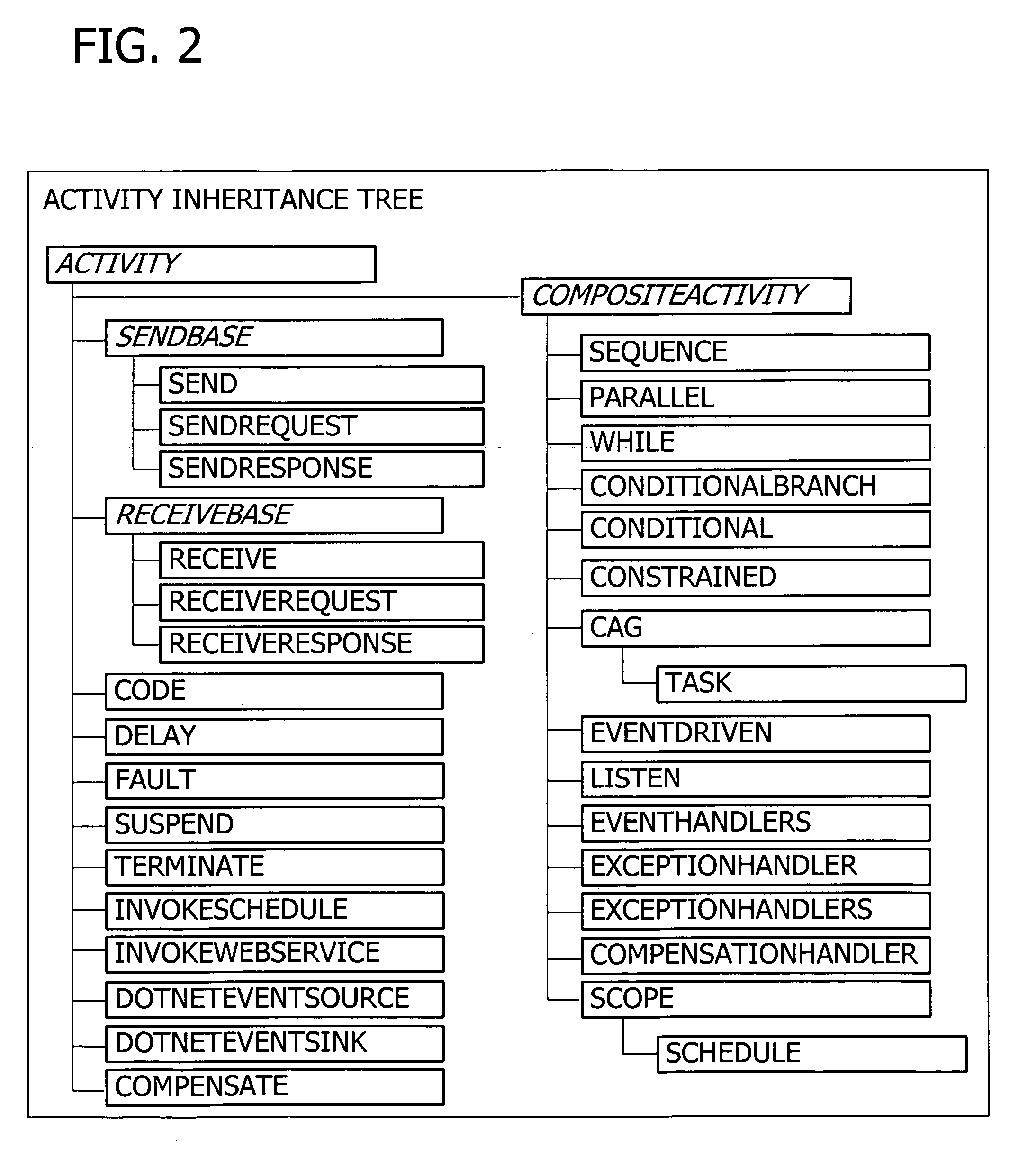
Programming interface for a componentized and extensible workflow model
InactiveUS20060074736A1Increase heightExtend the workflow modelResourcesExecution for user interfacesApplication programming interfaceTime aspect
Building a componentized workflow model via an application programming interface. Each step of the workflow is modeled as an activity that has metadata to describe design time aspects, compile time aspects, and runtime aspects of the workflow step. A user selects and arranges the activities to create the workflow via the application programming interfaces. The metadata associated with each of the activities in the workflow is collected to create a persistent representation of the workflow. Users extend the workflow model by authoring custom activities. Users also compile the workflow via the application programming interface.
Owner:MICROSOFT TECH LICENSING LLC
Packet switch and method thereof dependent on application content
InactiveUS20060031374A1Easy to controlControl moreMultiple digital computer combinationsData switching networksData packQuality of service
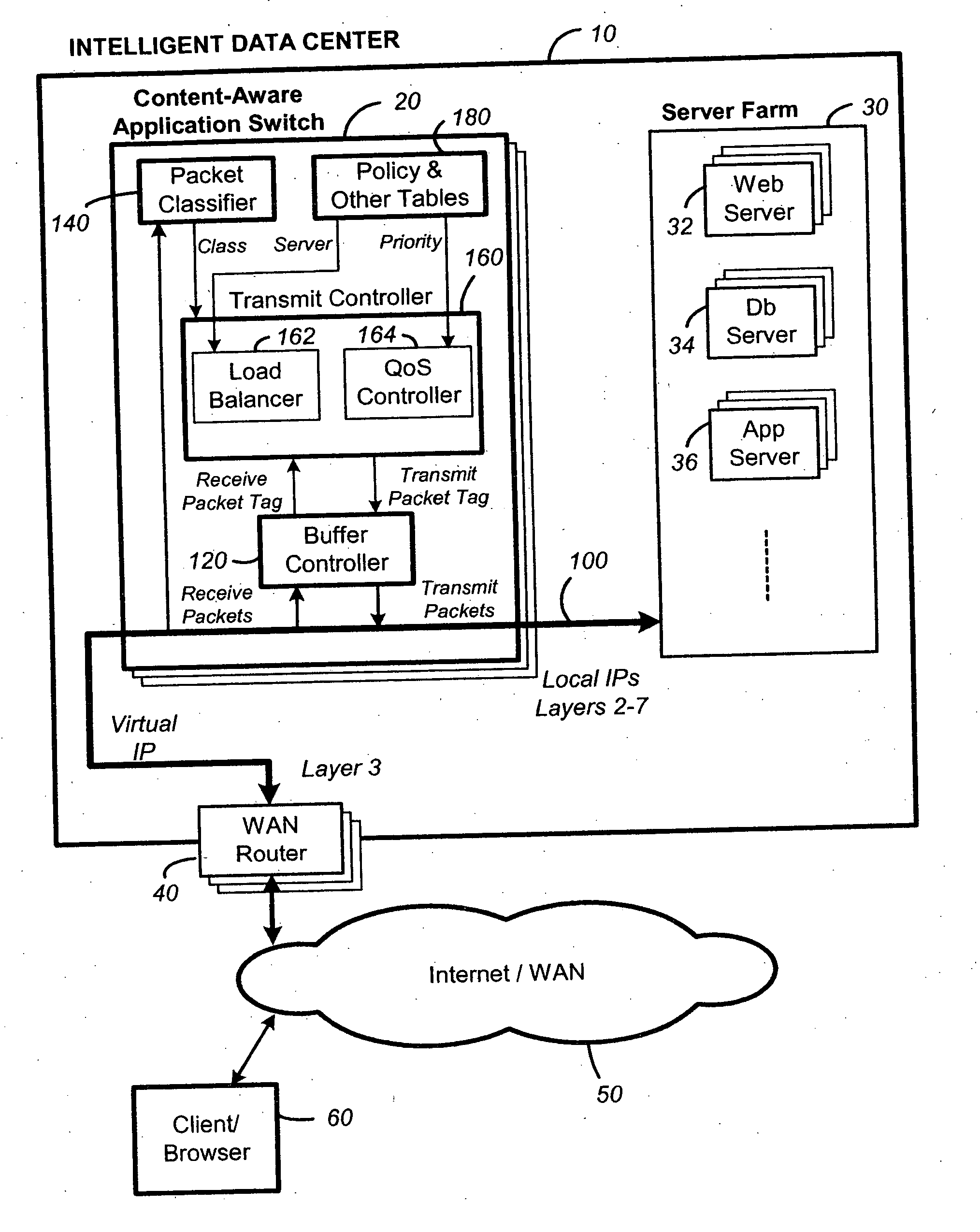
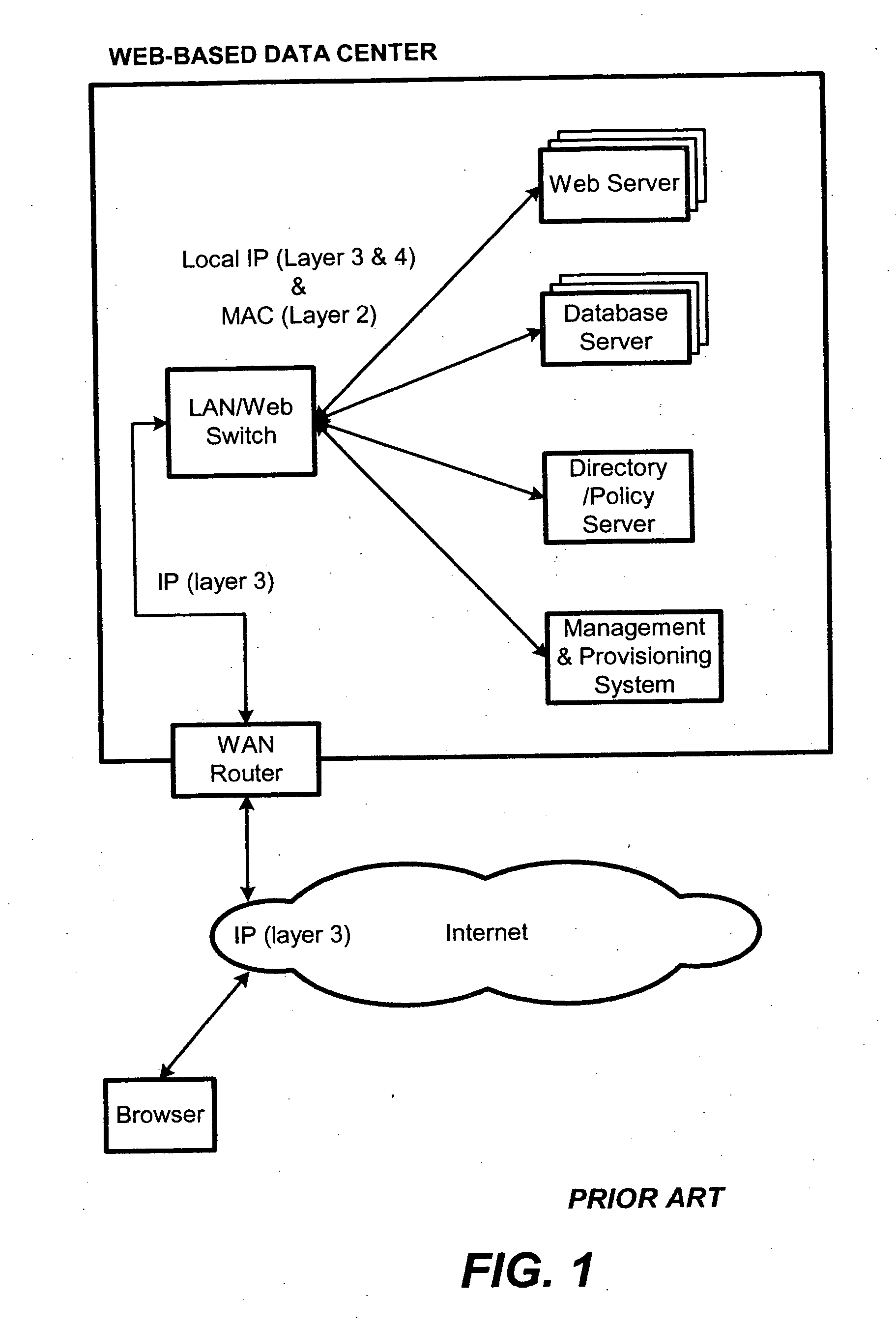
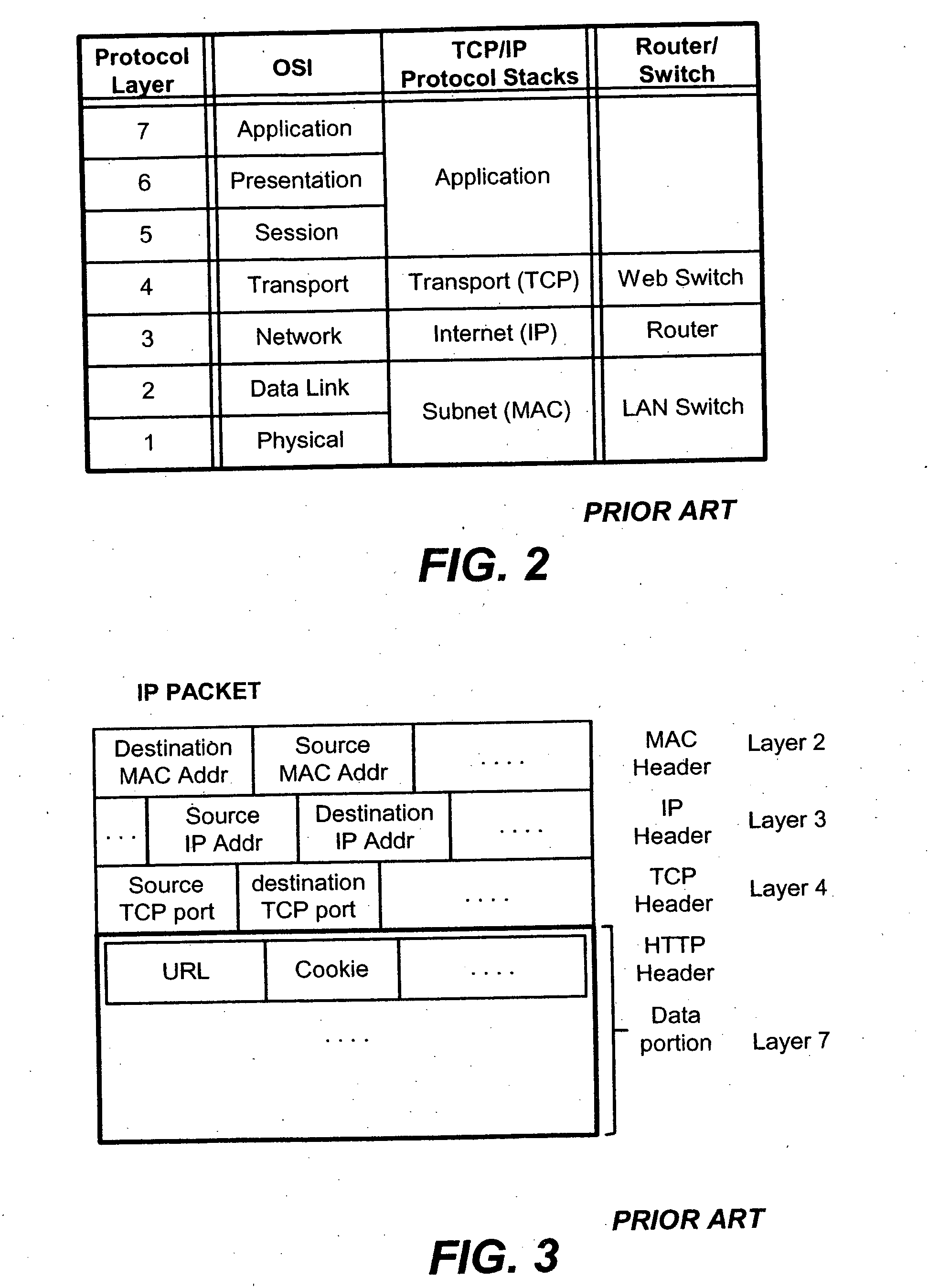
A content-aware application switch and methods thereof intelligently switch client packets to one server among a group of servers in a server farm. The switch uses Layer 7 or application content parsed from a packet to help select the server and to schedule the transmitting of the packet to the server. This enables refined load-balancing and Quality-of-Service control tailored to the application being switched. In another aspect of the invention, a slow-start server selection method assigned an initially boosted server load metric to a server newly added to the group of servers under load balancing. This alleviates the problem of the new server being swamped initially due to a very low load metric compared to that of others. In yet another aspect of the invention, a switching method dependent on Layer 7 content avoids delayed binding in a new TCP session. Layer 7 content is not available during the initial handshaking phase of a new TCP session. The method uses the Layer 7 content from a previous session as an estimate to help select the server and uses a default priority to scheduling the transmitting of the handshaking packets. Updated Layer 7 content available after the handshaking phase is then used to reset the priority for the transmit schedule and becomes available for use in load balancing of the next TCP session.
Owner:INT BUSINESS MASCH CORP
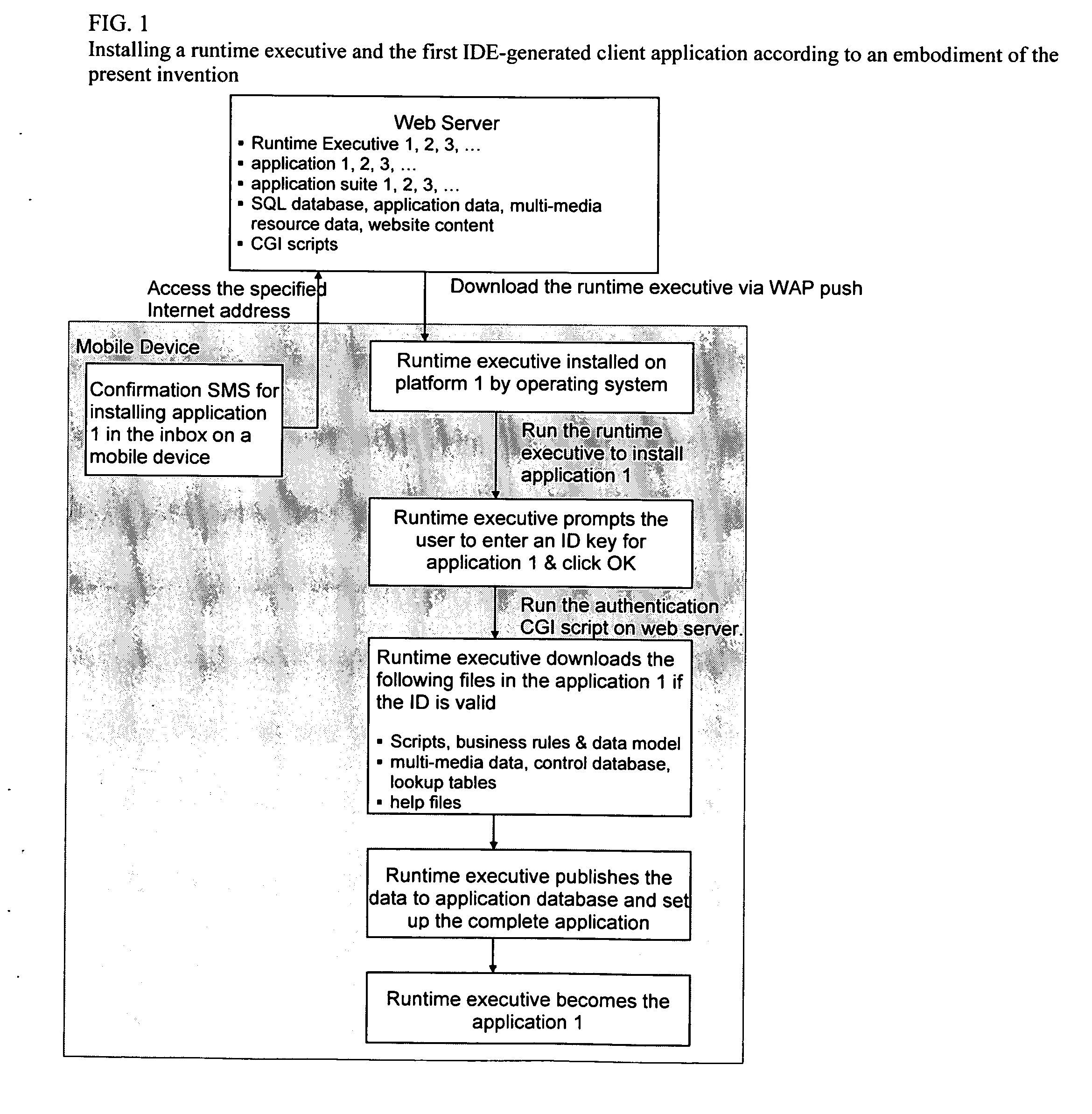
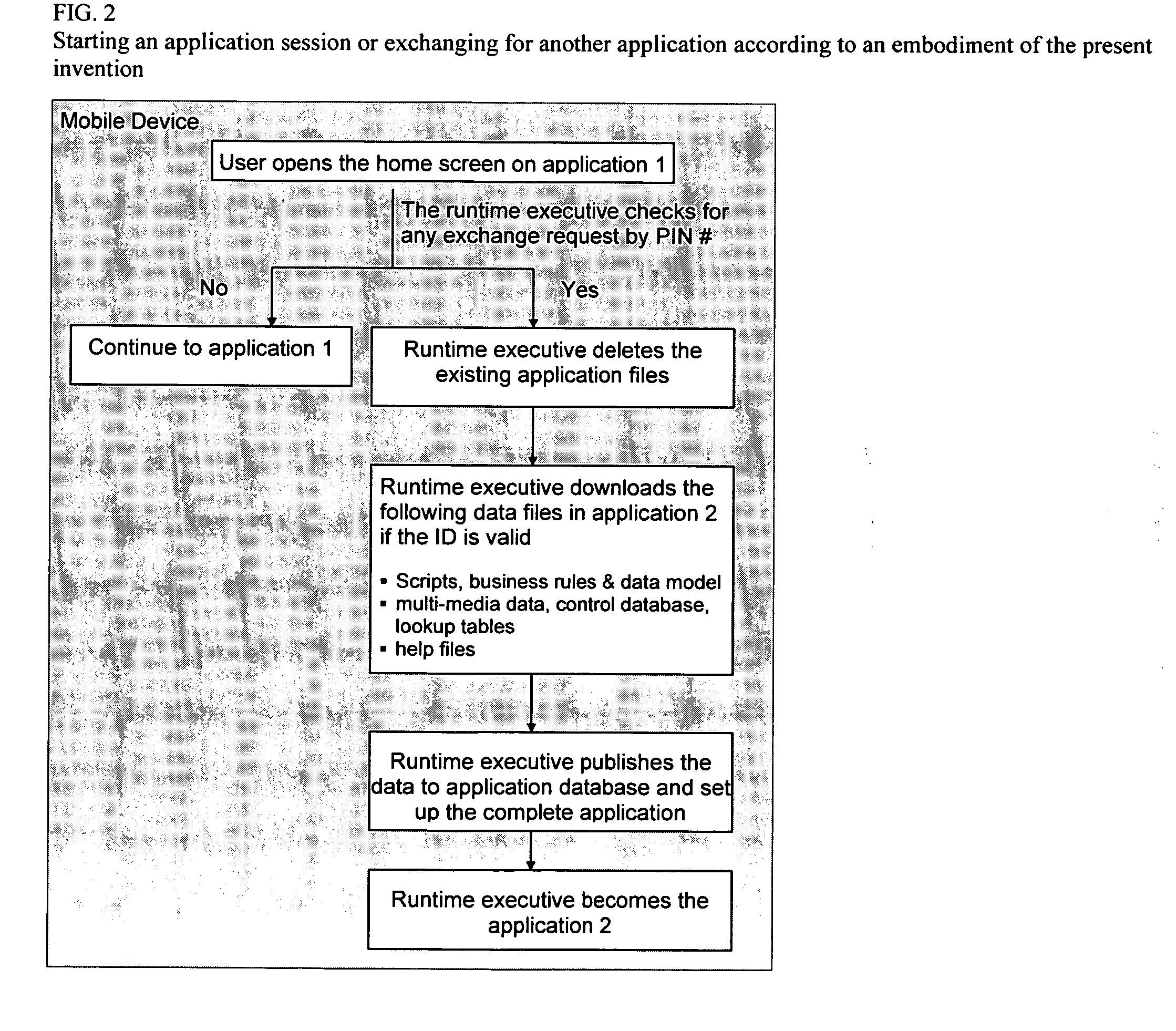
Method and system for designing, implementing, and managing client applications on mobile devices
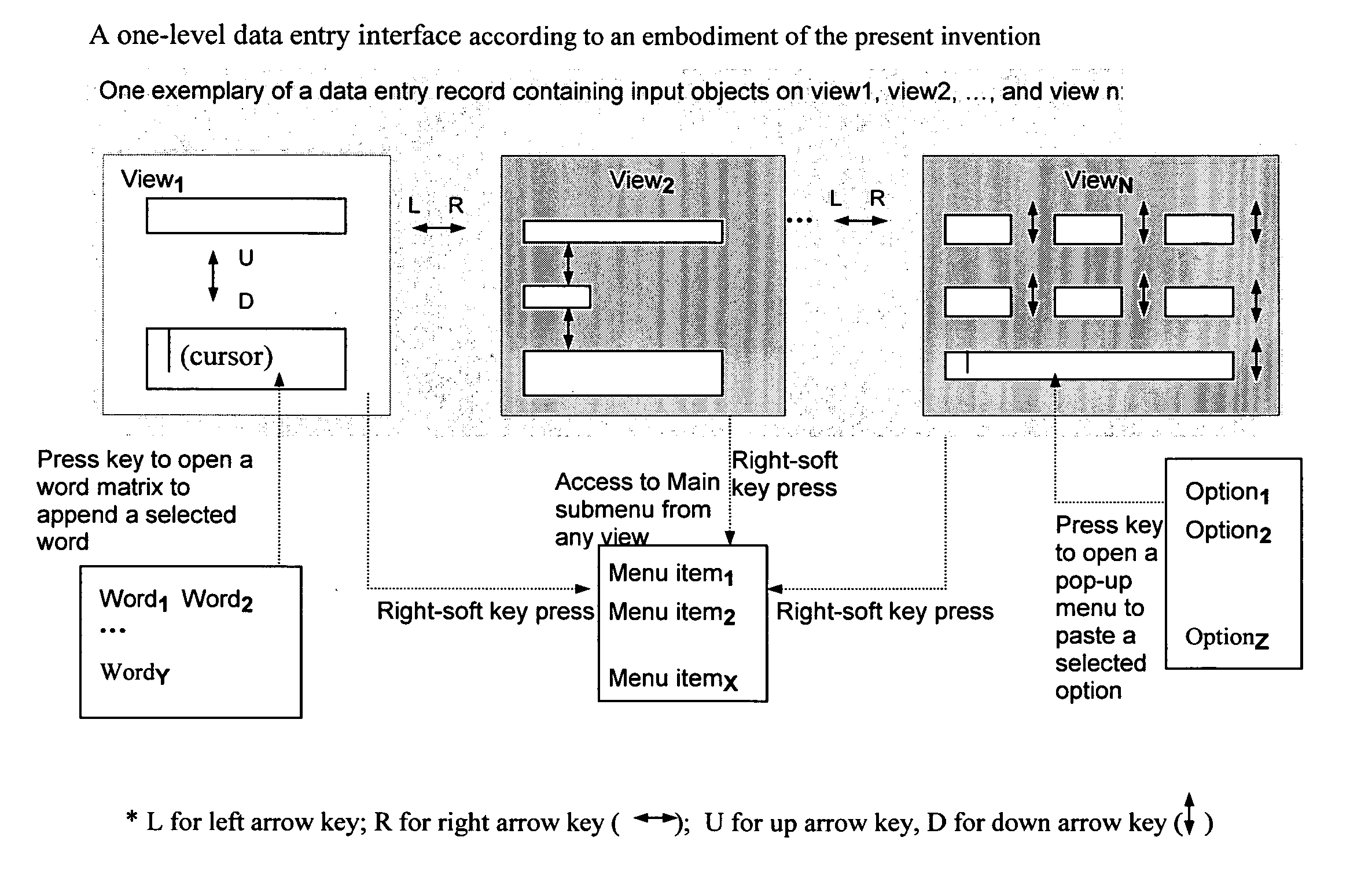
InactiveUS20080046557A1Easy accessEasy to navigateSoftware engineeringMultiple digital computer combinationsTypingData file
A system that designs, implements, and manages client applications on mobile devices using runtime executives and an IDE. In one aspect, the runtime executive delivers consistent GUI and application behavior within and across mobile development platforms. In another aspect, the runtime executive can set up data files of an IDE-generated client application on mobile devices and then become that application itself while supporting a pay-per-download subscription service. The runtime executive delivers multimedia content in presentation format via a one-level browsing interface, enables data entries across tabbed views with minimal typing and drilidowns via a one-level data entry interface, and precisely processes scripts and commands, including calls to COM libraries. The IDE allows non-programmers to design the GUI and the scripts for mobile device applications and compile them into application data files for multiple development platforms, which are then loaded and executed by runtime executives.
Owner:CHENG JOSEPH C
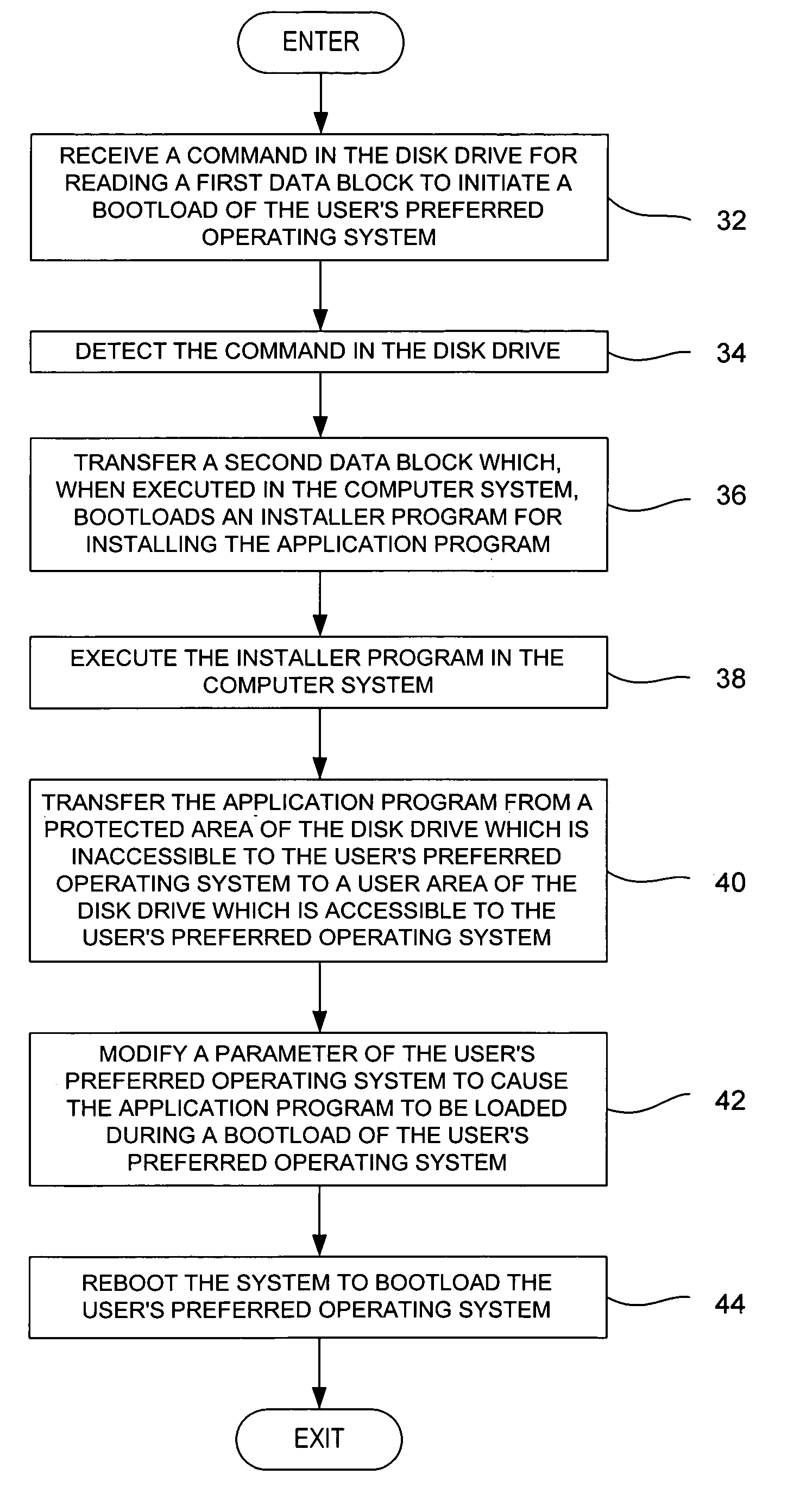
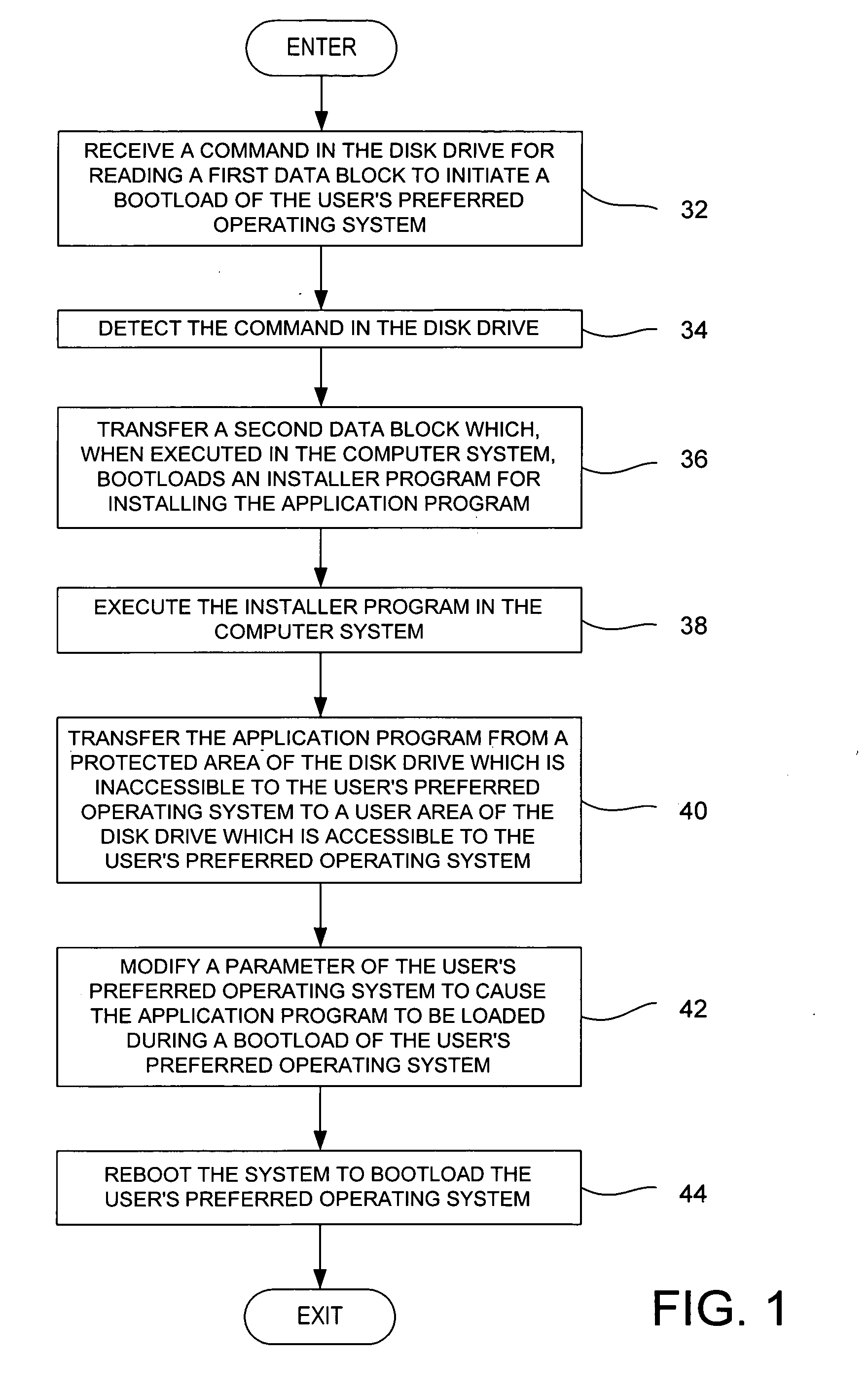
Method for installing an application program, to be executed during each bootload of a computer system for presenting a user with content options prior to conventional system startup presentation, without requiring a user's participation to install the program
The present invention may be embodied in a method, performed in a computer system having a disk drive, for installing an application program for execution under a user's preferred operating system without requiring user intervention. A command is received by the disk drive for reading a first data block to initiate a bootload of the user's preferred operating system. The disk drive detects the command and transfers a second data block which bootloads an installer program for installing the application program. The installer program is executed in the computer system to transfer the application program from a protected area of the disk drive to a user area of the disk drive, to modify a parameter of the user's preferred operating system to cause the application program to be loaded during a bootload of the user's preferred operating system, and to reboot the system to bootload the user's preferred operating system.
Owner:WESTERN DIGITAL TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com