Patents
Literature
197 results about "Workflow model" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Workflow model describes all the important information for the workflow. Namely processes, documents, process participants, their permissions, and so on. Related terms and methods:
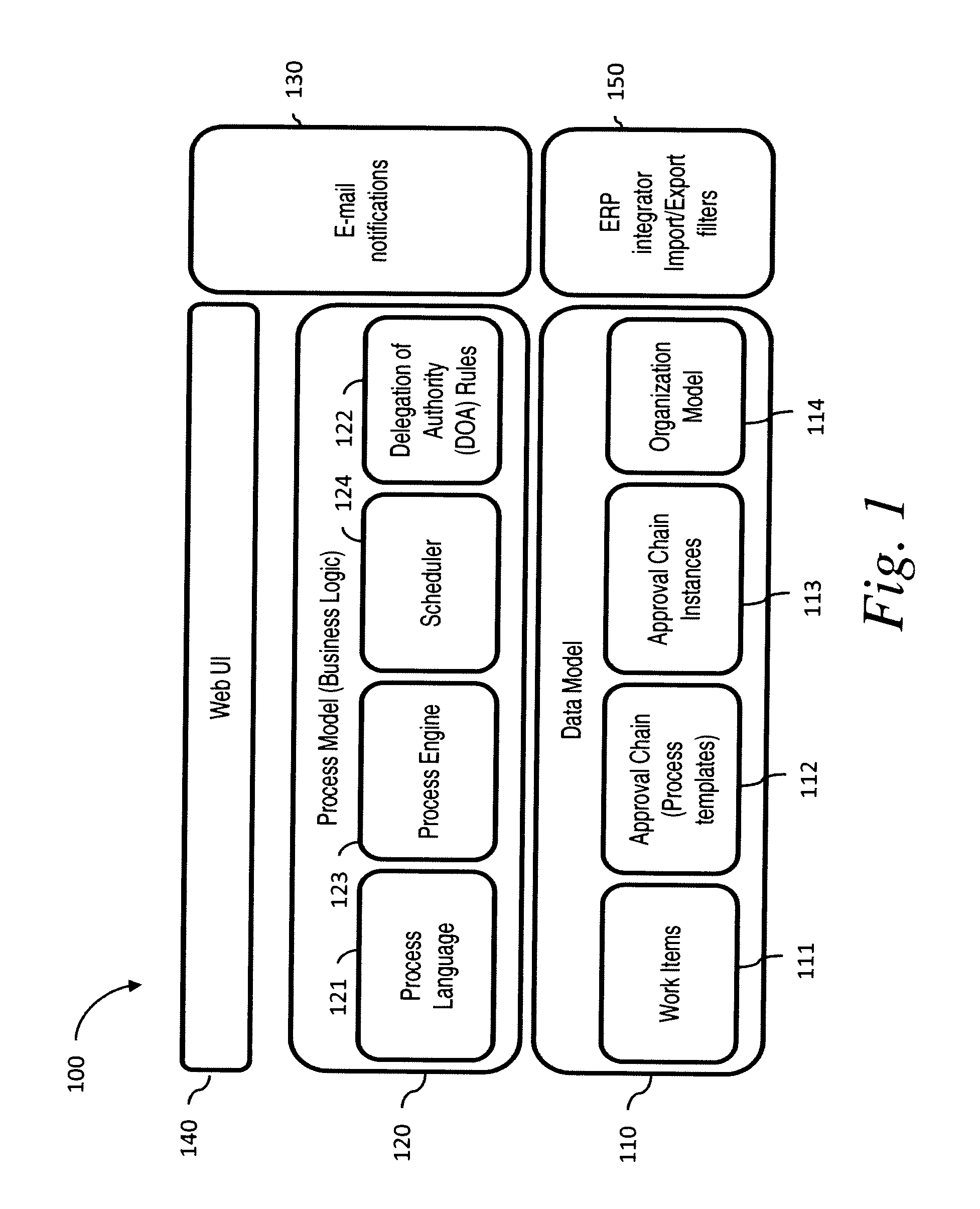
System and method for developing and administering web applications and services from a workflow, enterprise, and mail-enabled web application server and platform
ActiveUS20040201604A1Digital computer detailsOffice automationDocumentation procedurePartial application
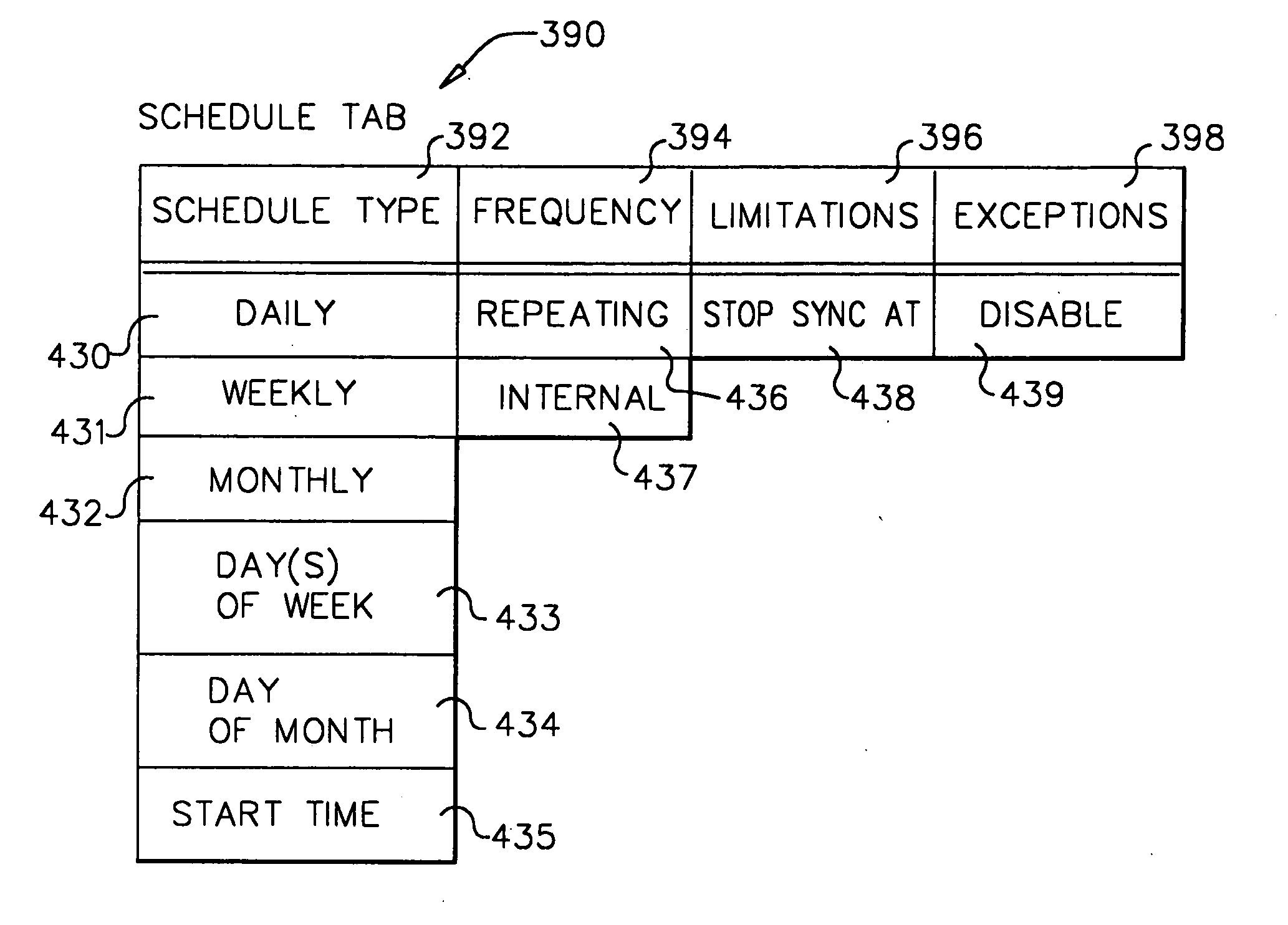
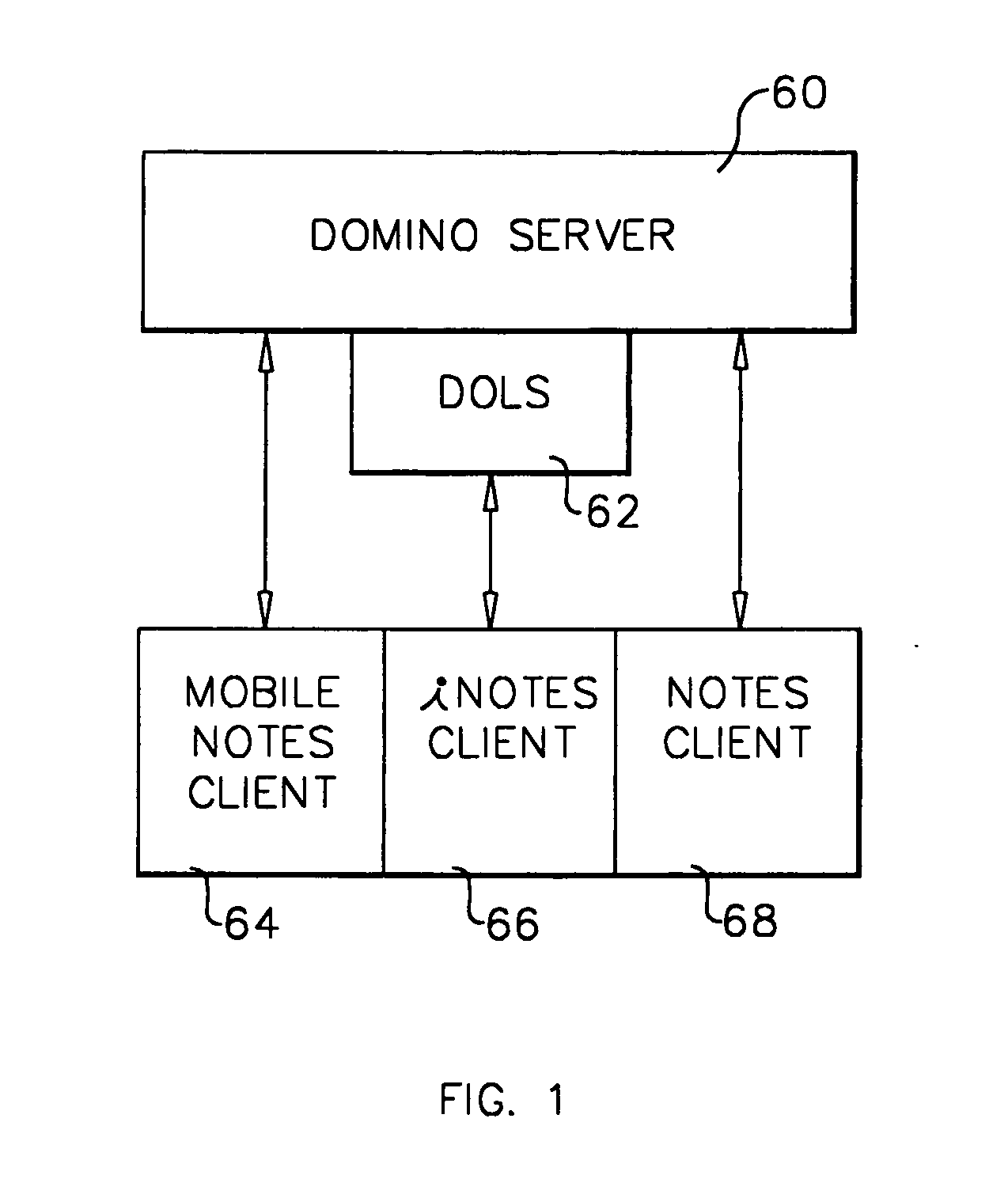
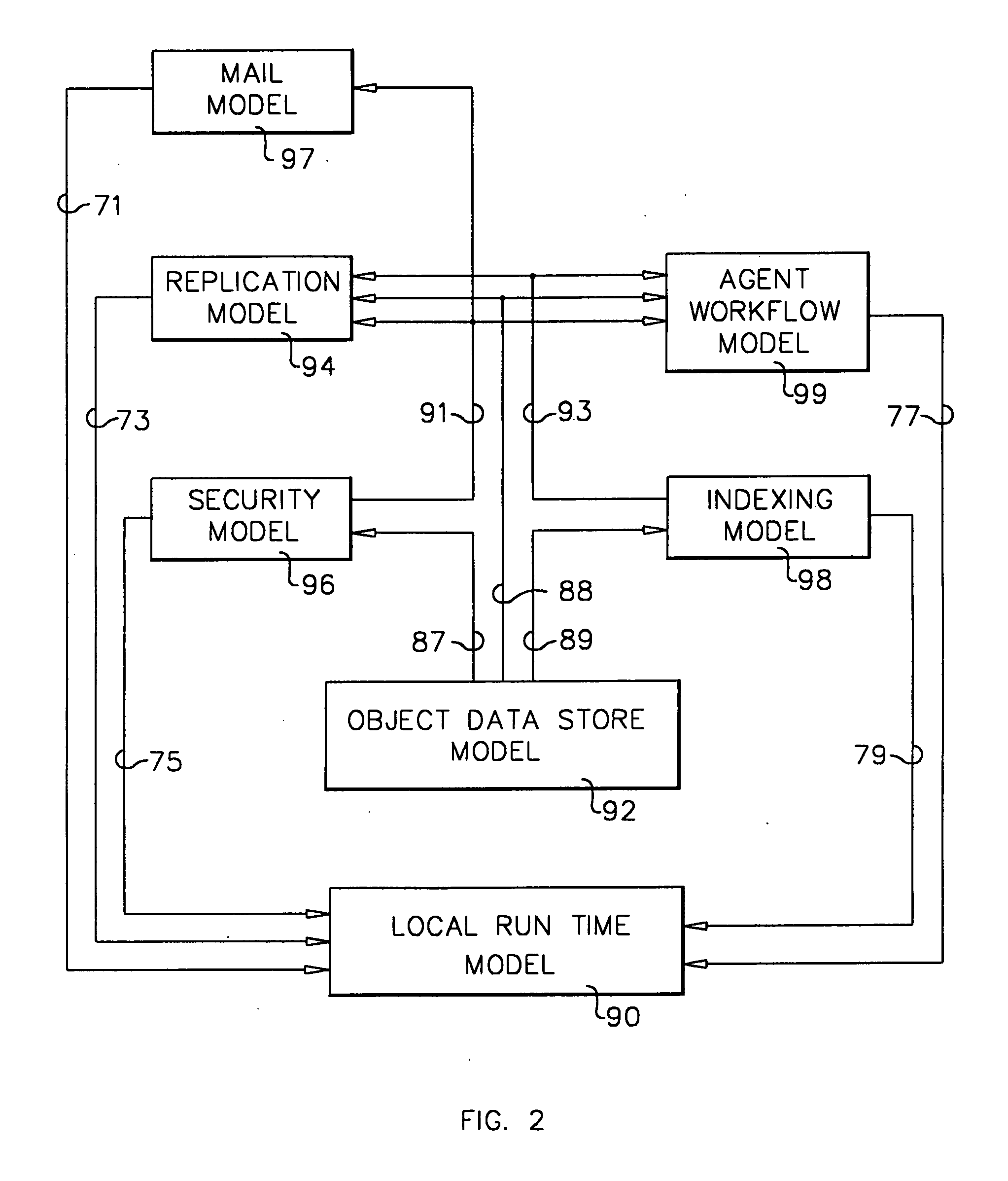
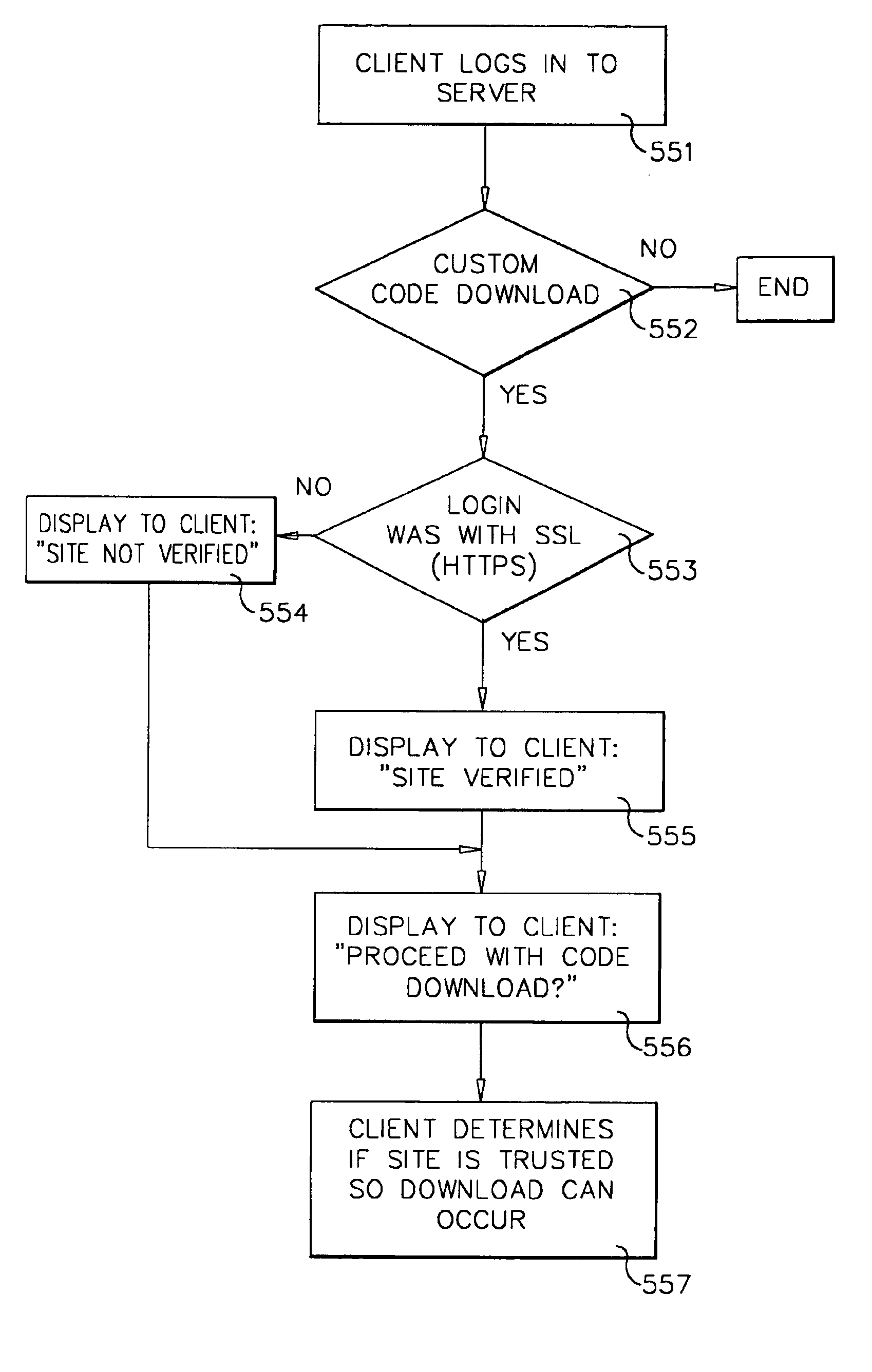
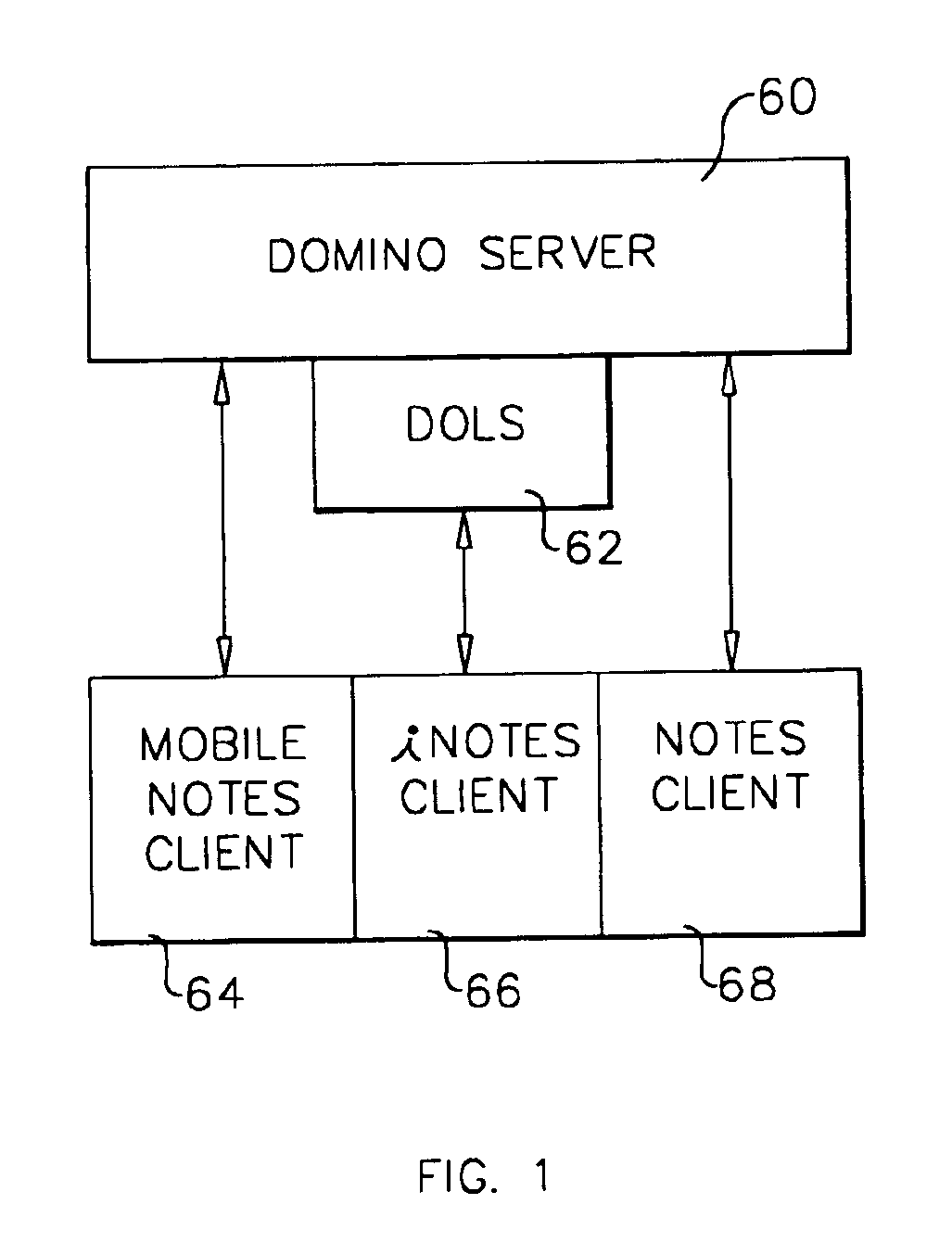
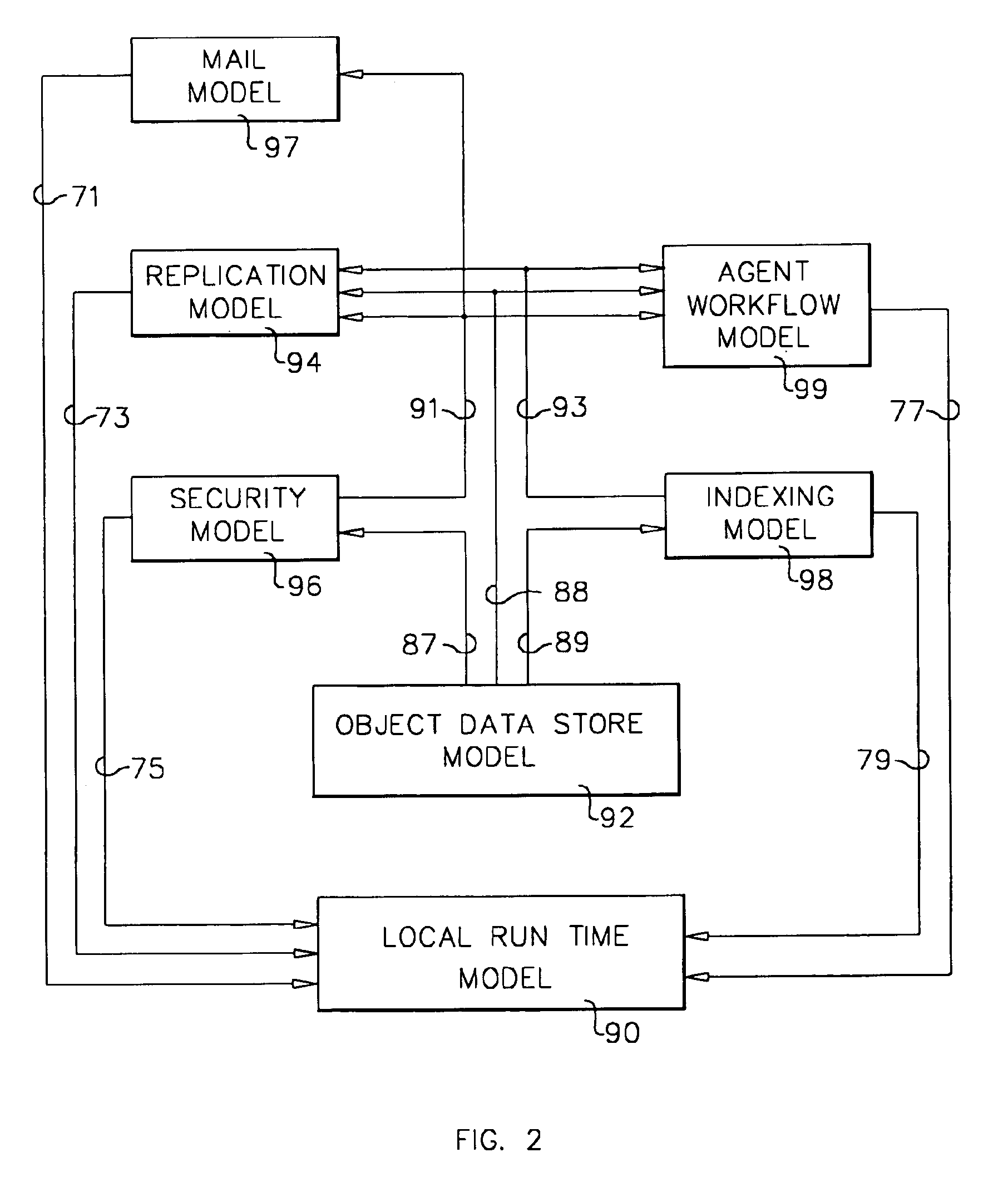
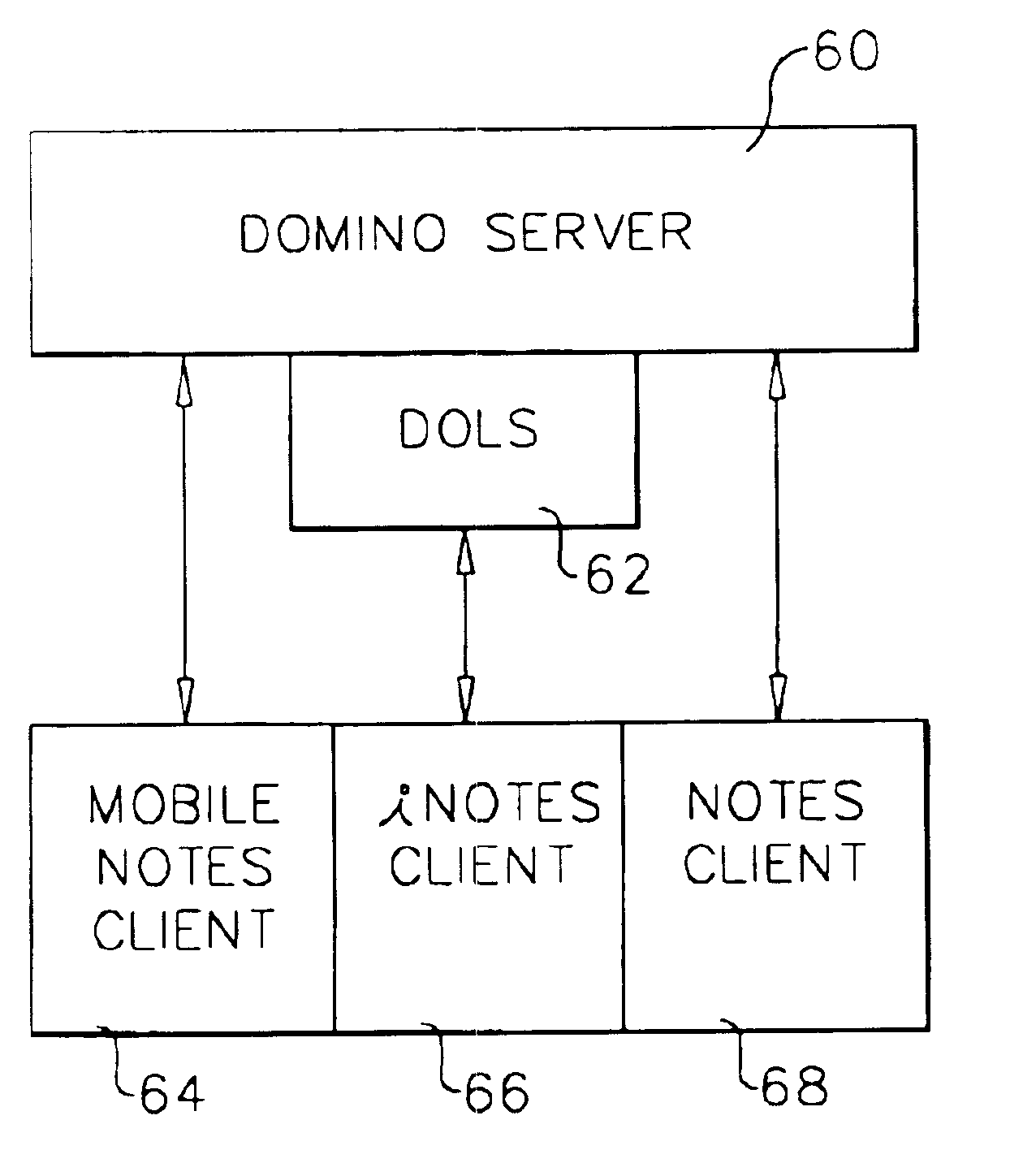
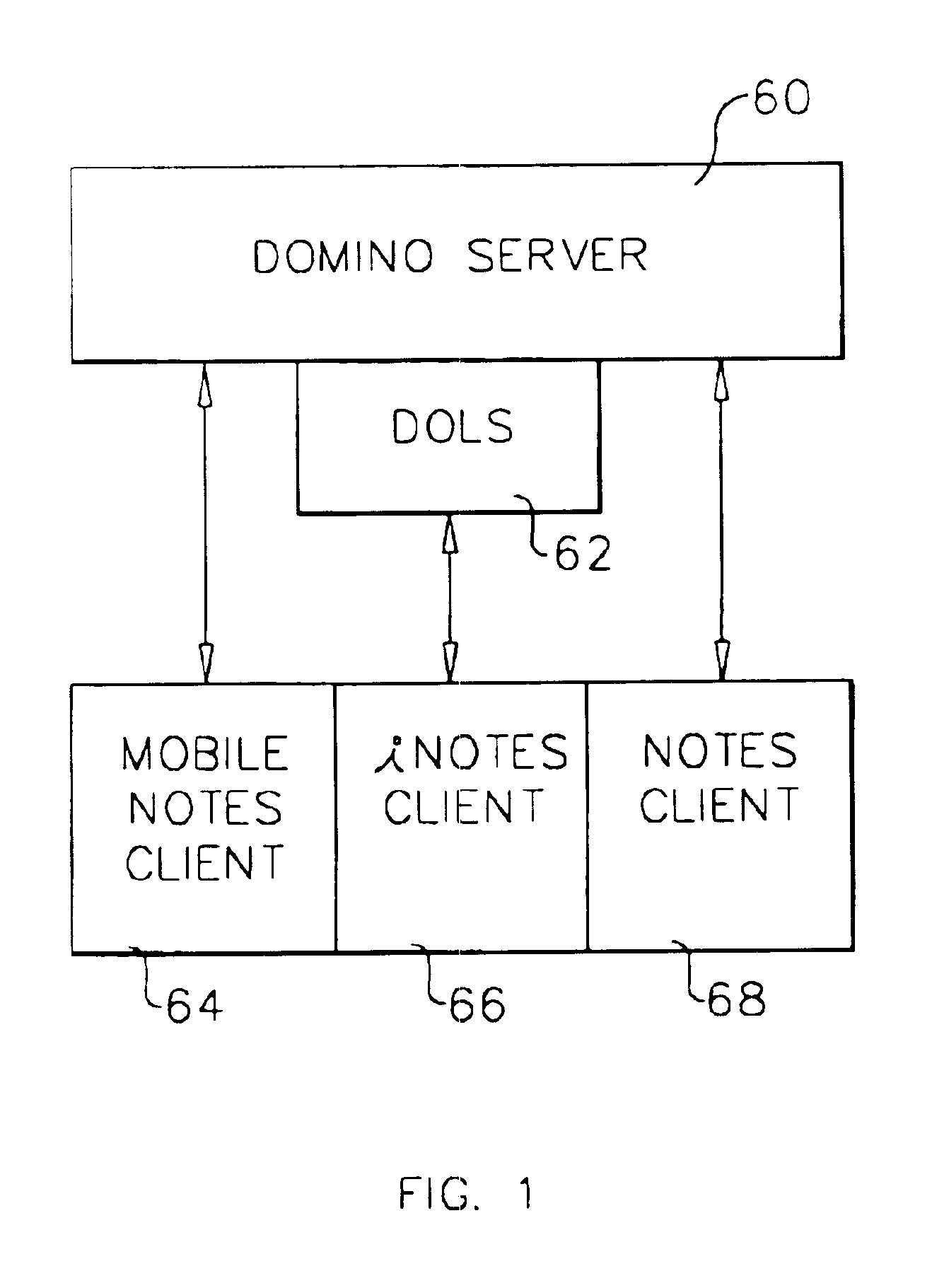
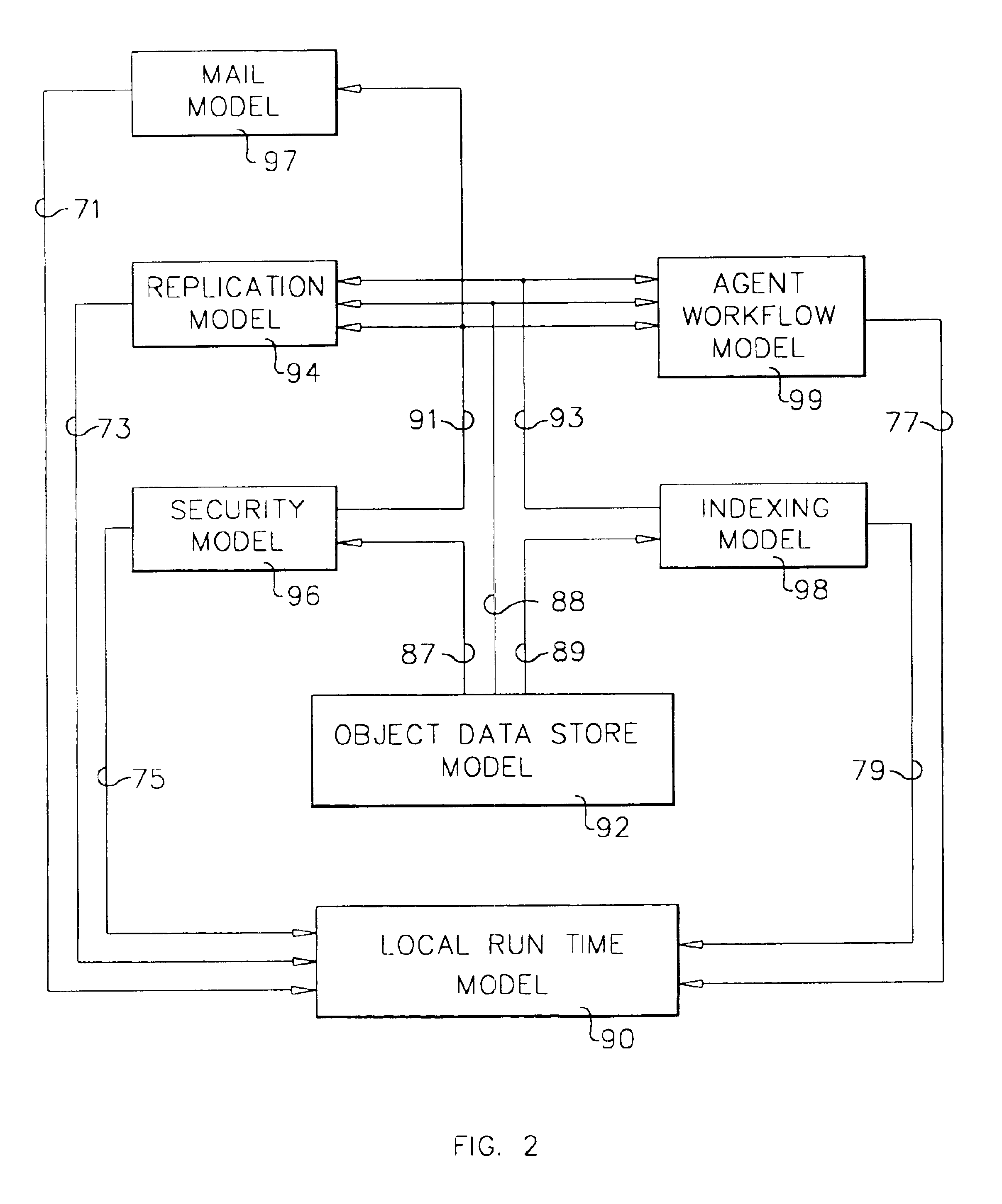
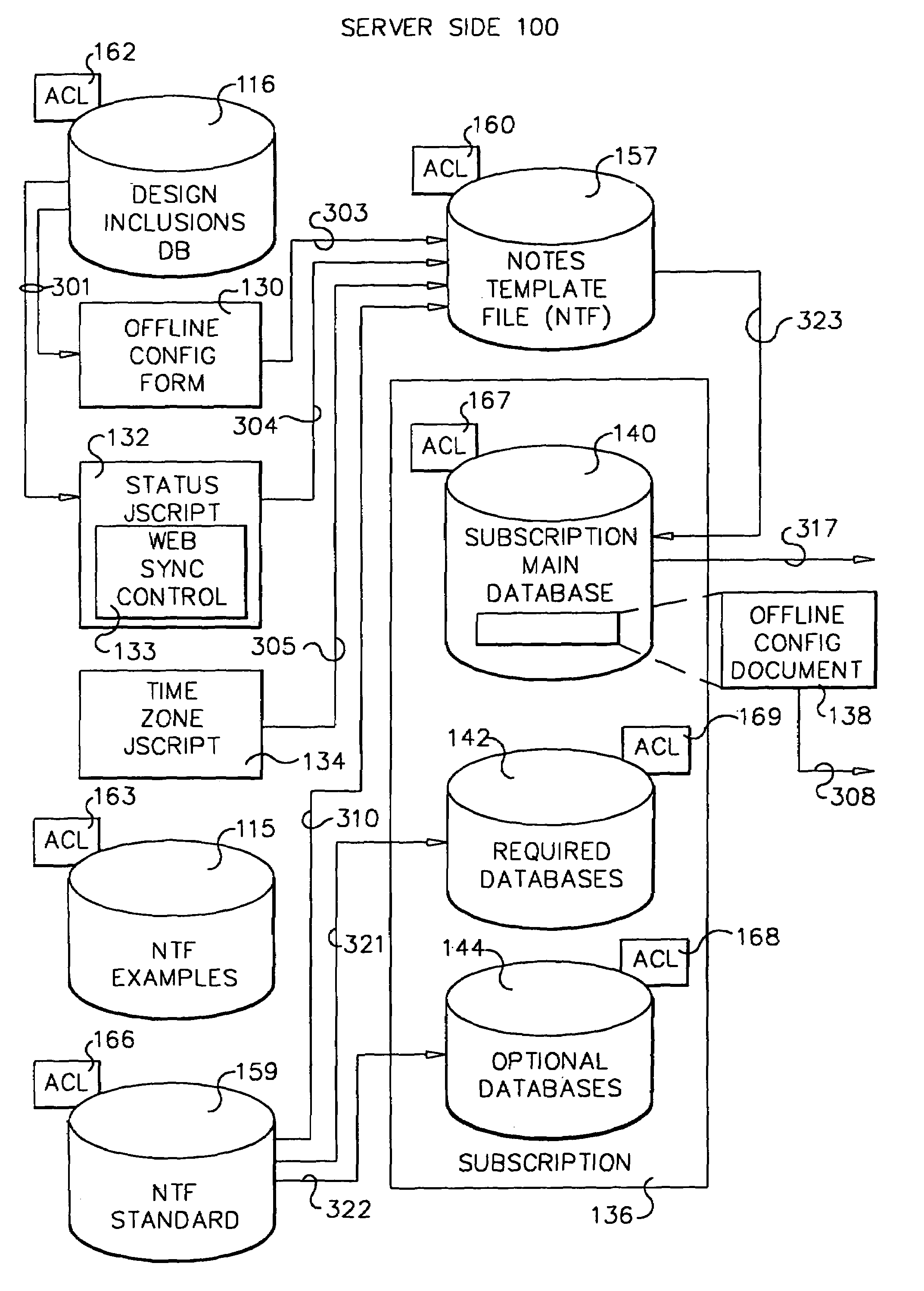
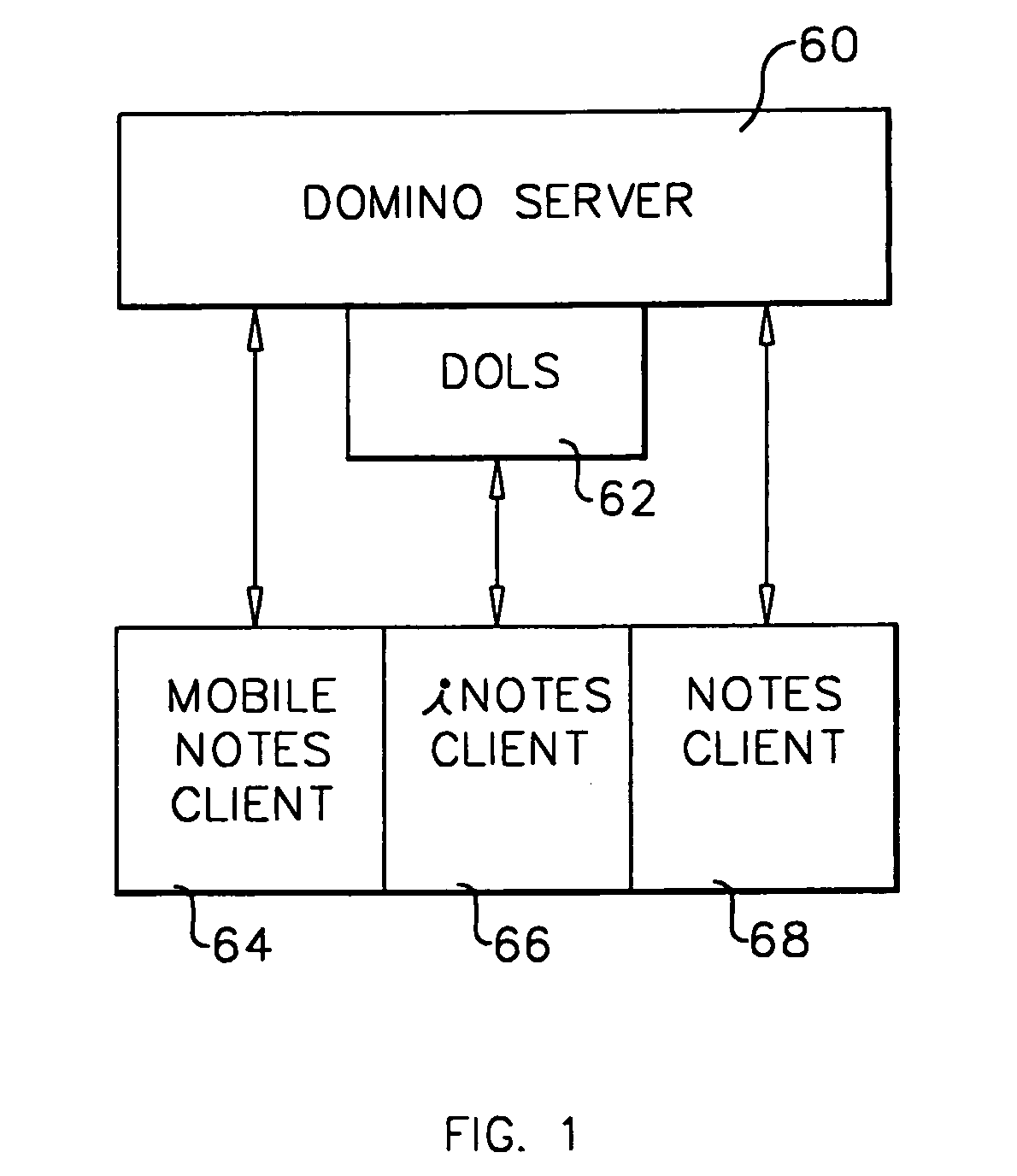
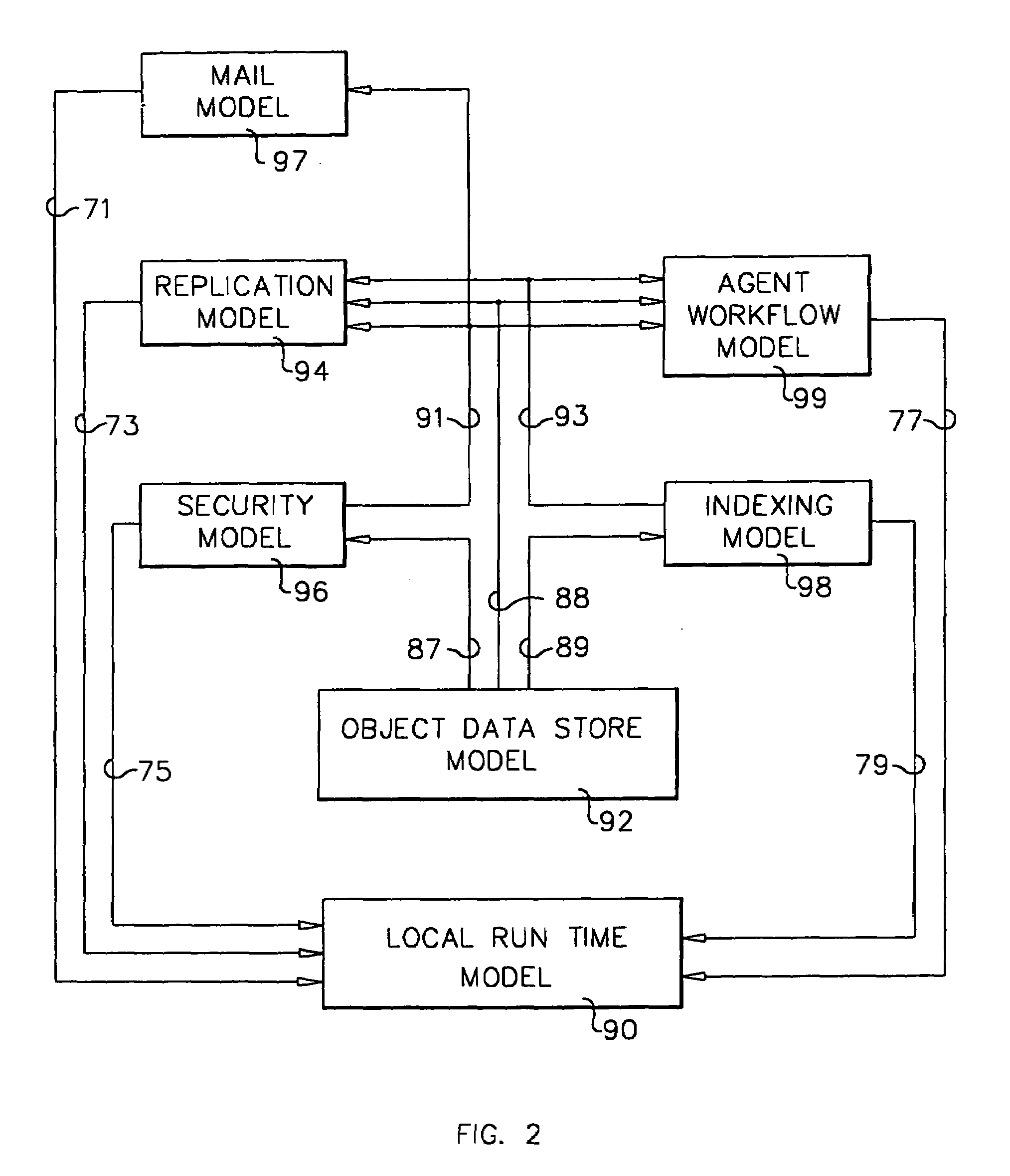
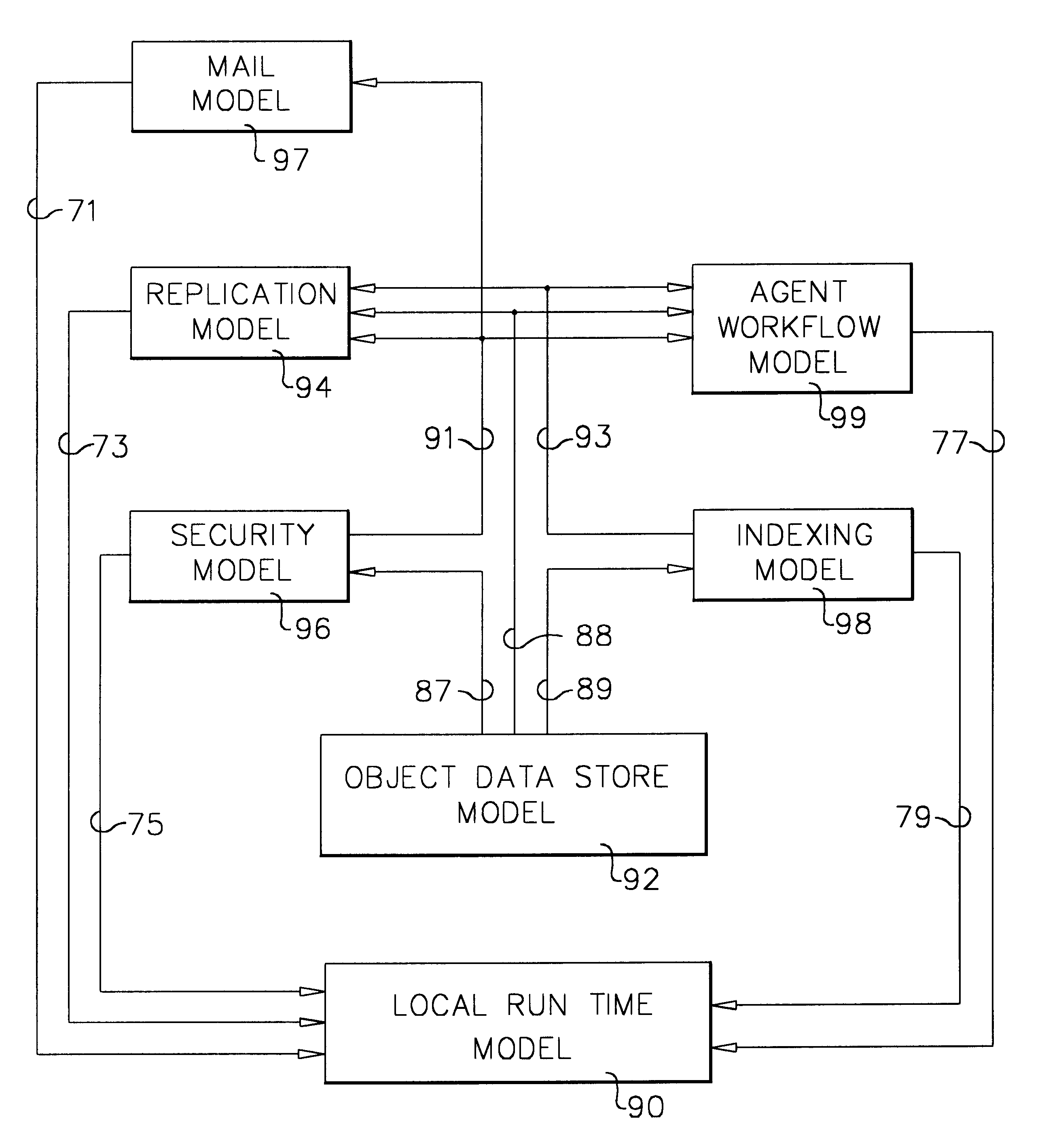
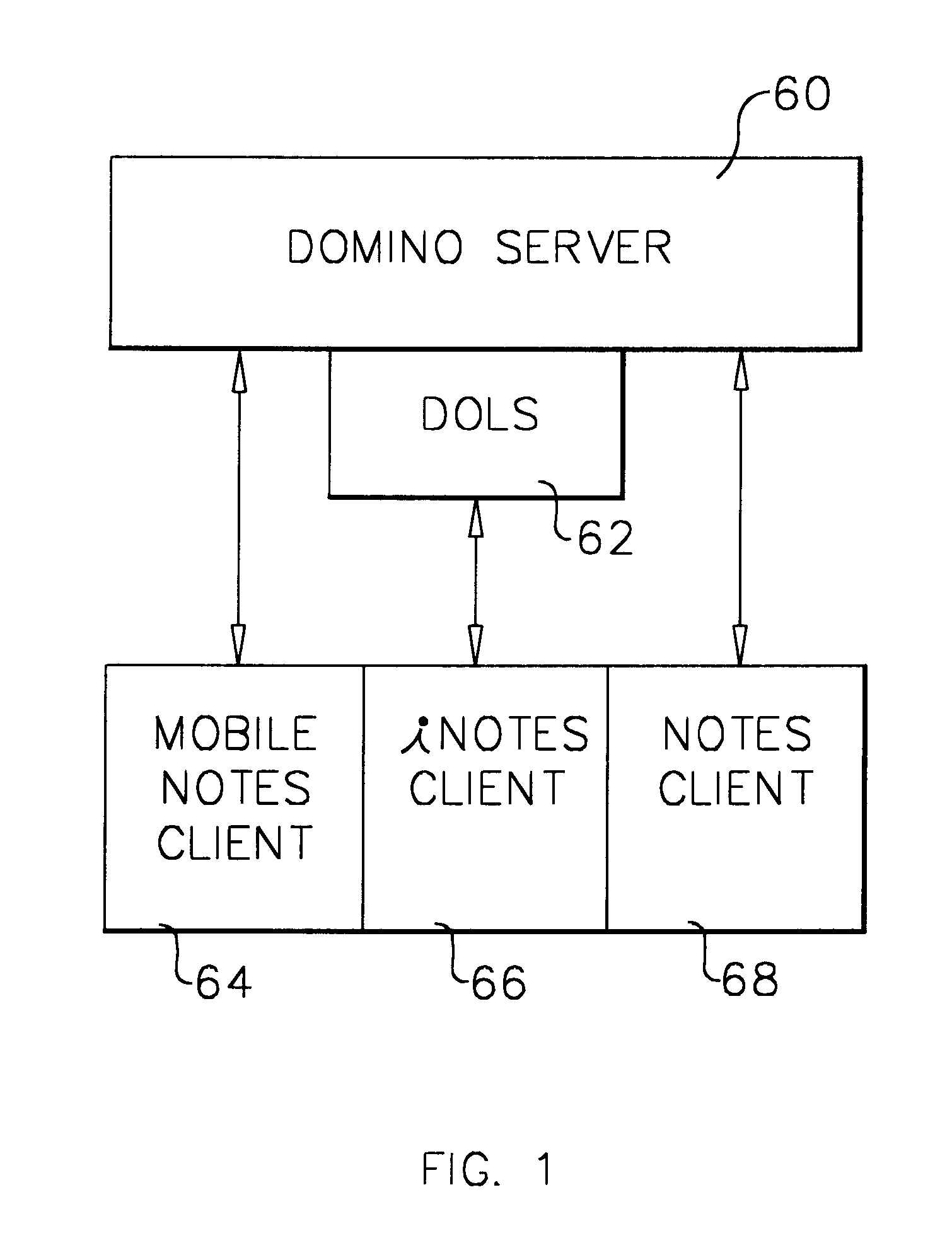
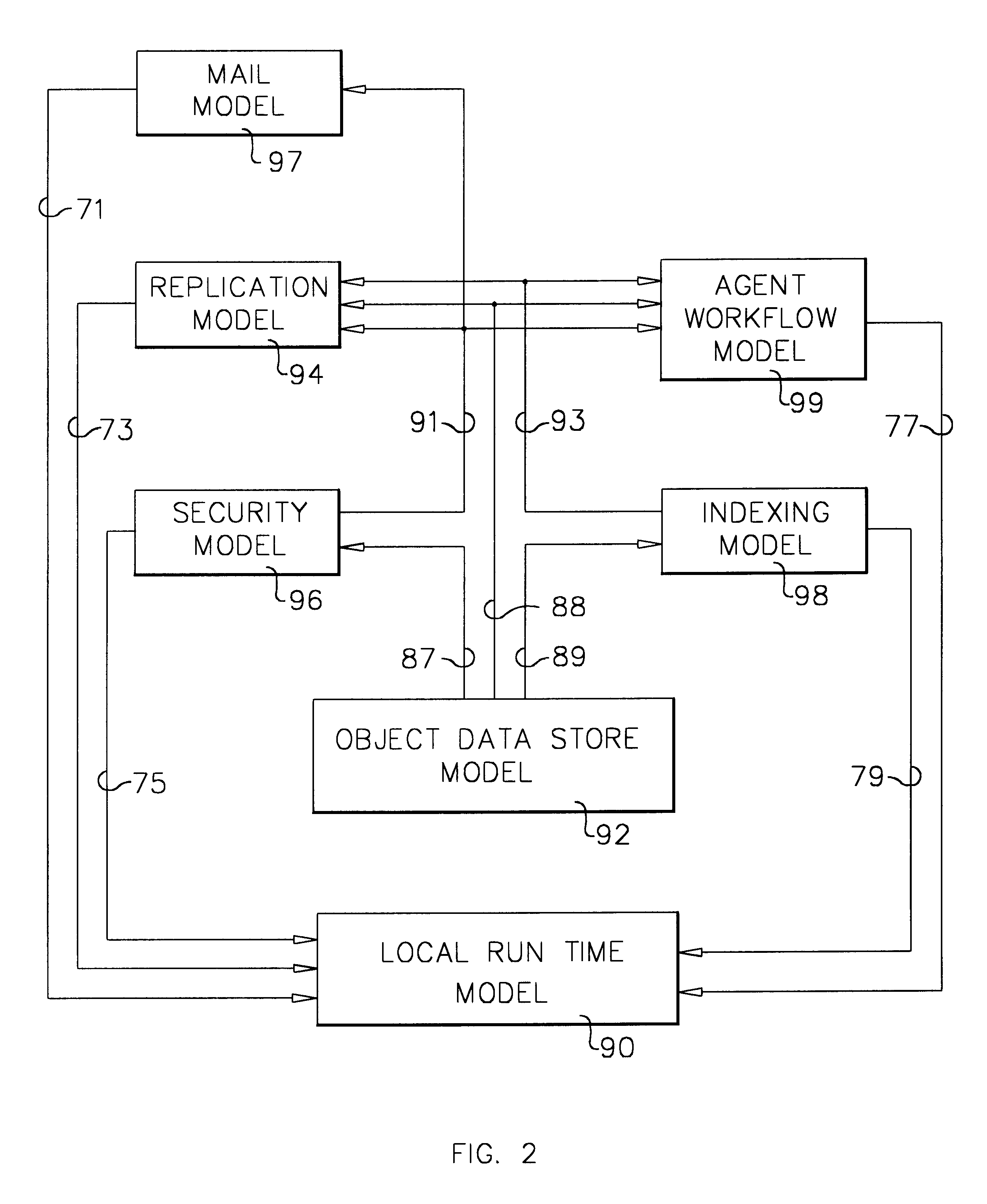
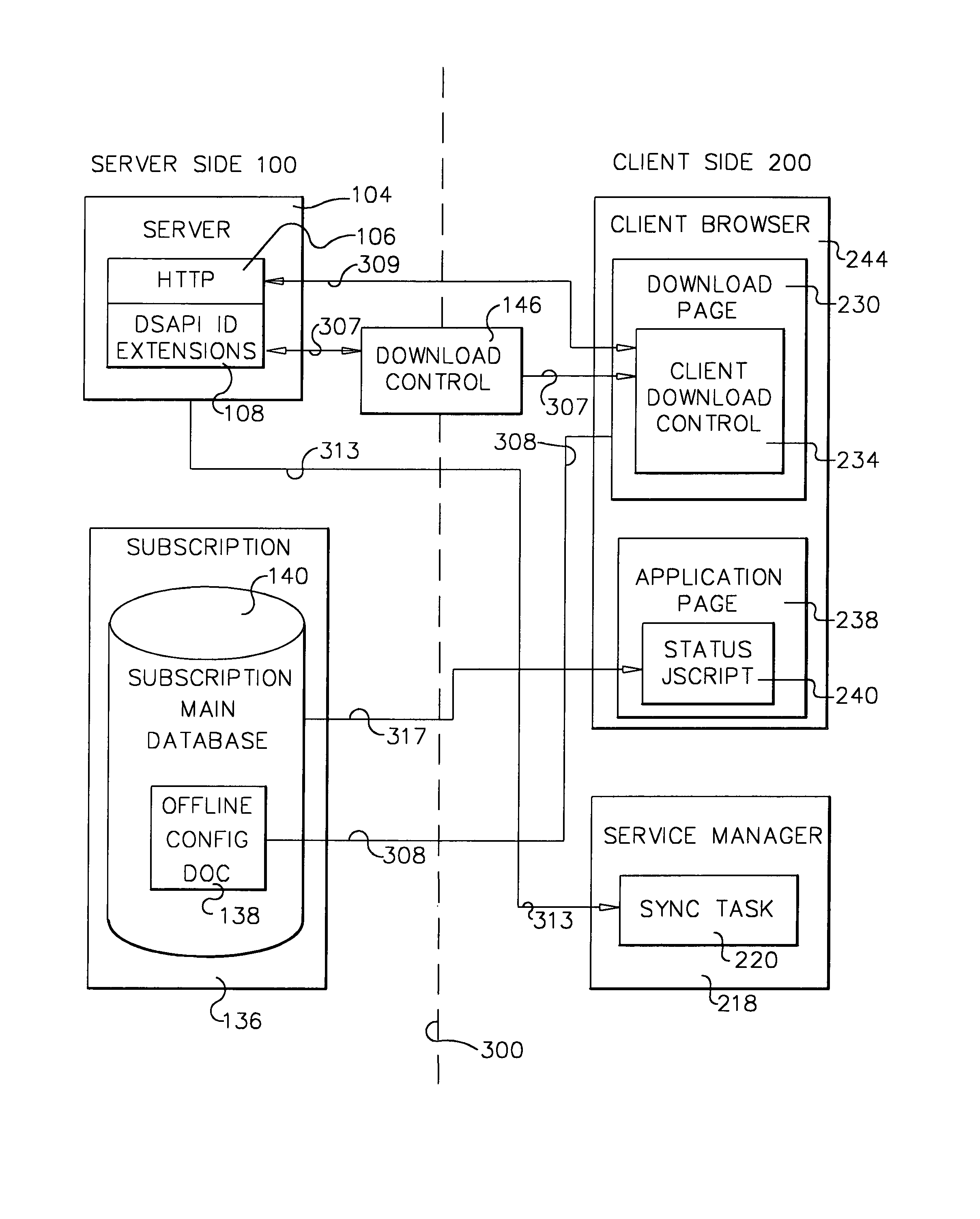
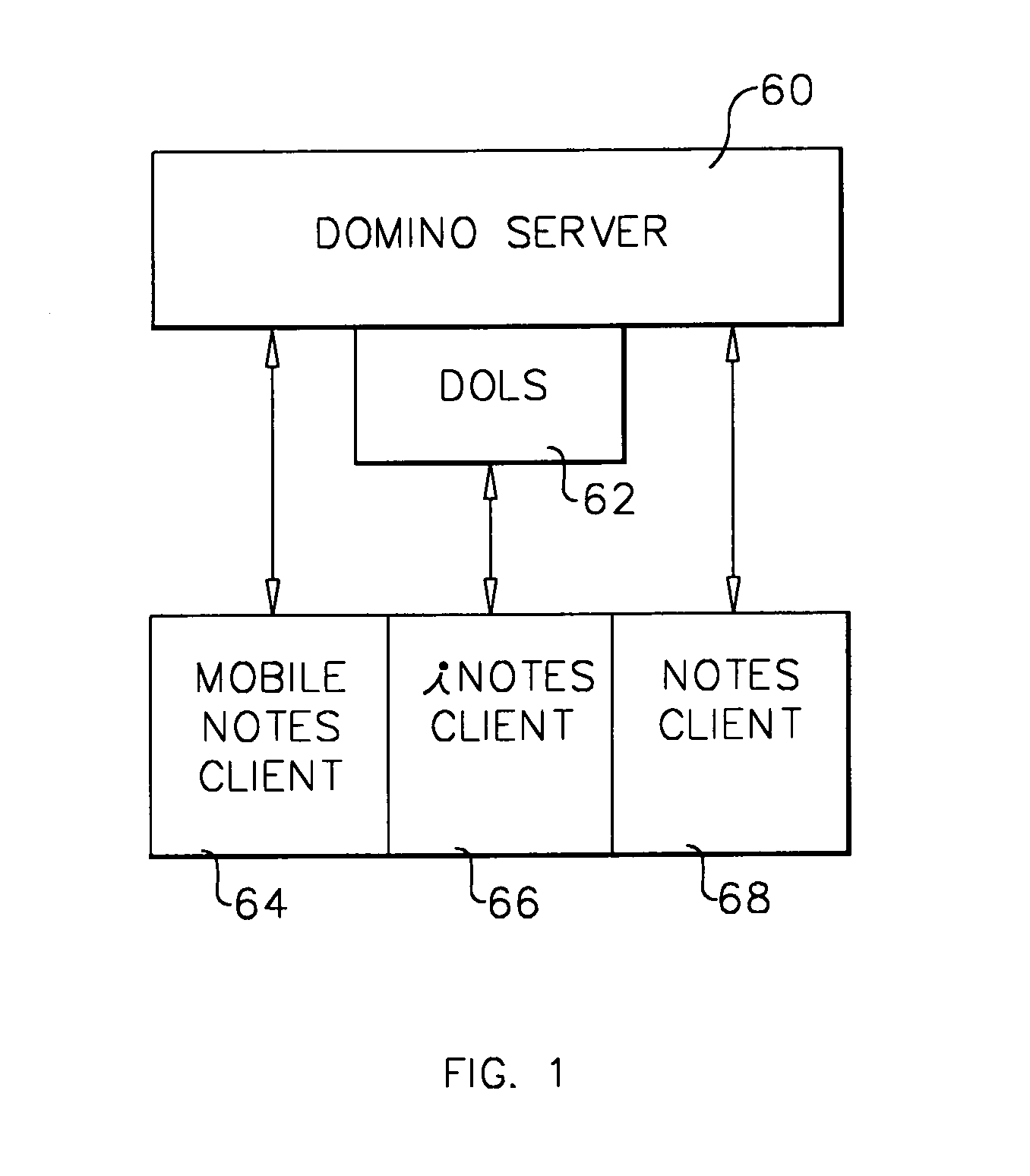
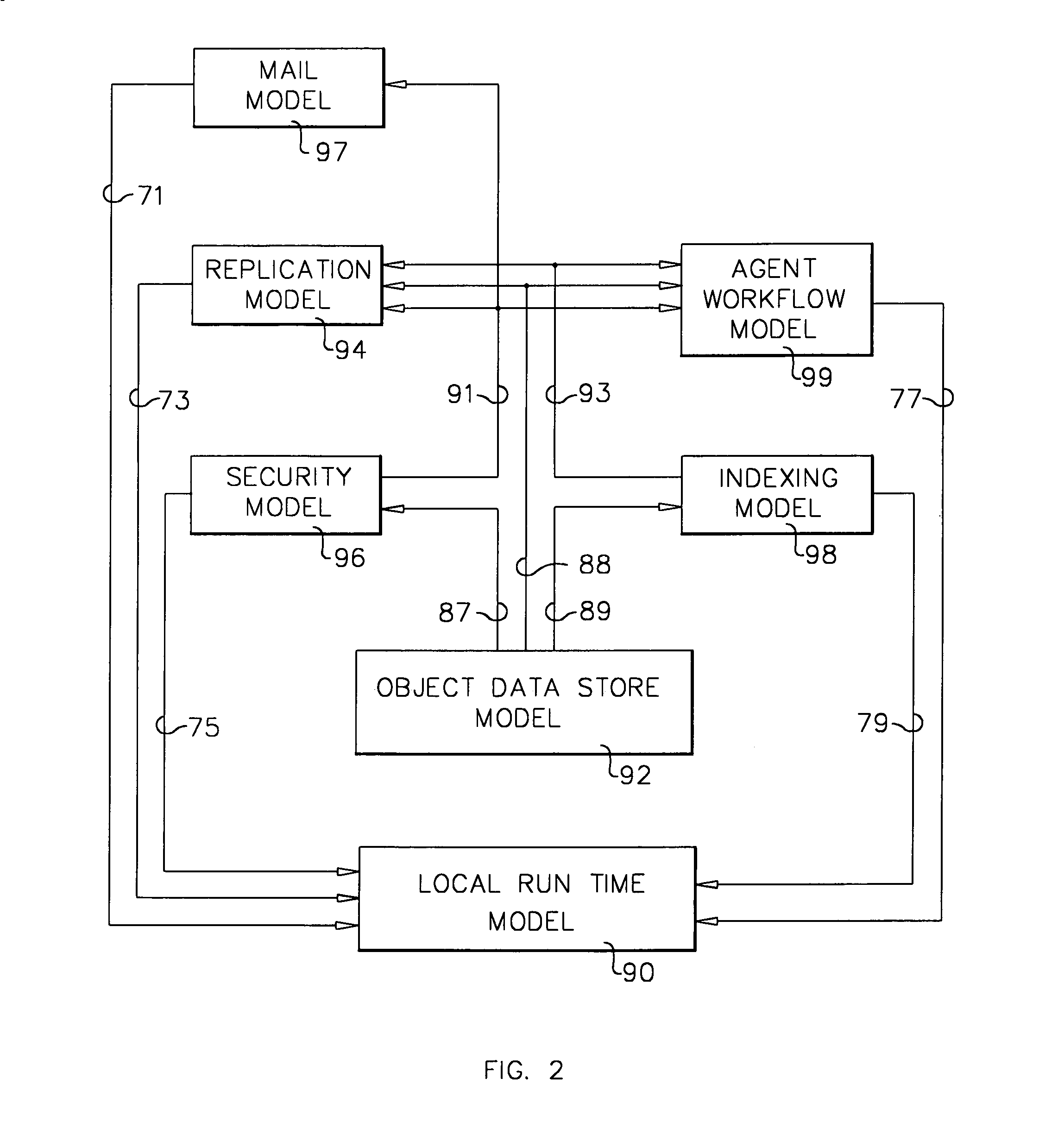
A workflow, enterprise, and mail-enabled application server and platform supports distributed computing and. remote execution of web applications. Lotus Domino online services (DOLS) is used by a web site administrator to configure Internet Notes (iNotes) clients to auto download from server, thus providing iNotes clients with web access using HTTP with various browsers, and with local processing and replication. A local run time model comprises a hierarchy of models including object data store model, security model, indexing model, replication model, agent workflow model and mail model. DOLS provides a layered security model that allows flexibility for controlling access to all or part of an application. The highest level of security is managed through a database access control list (ACL). Further refinements within the security model provide access to specific documents, and their views, forms or folders, and include read access lists, write access lists, form access lists and readers and authors fields.
Owner:HCL TECH LTD
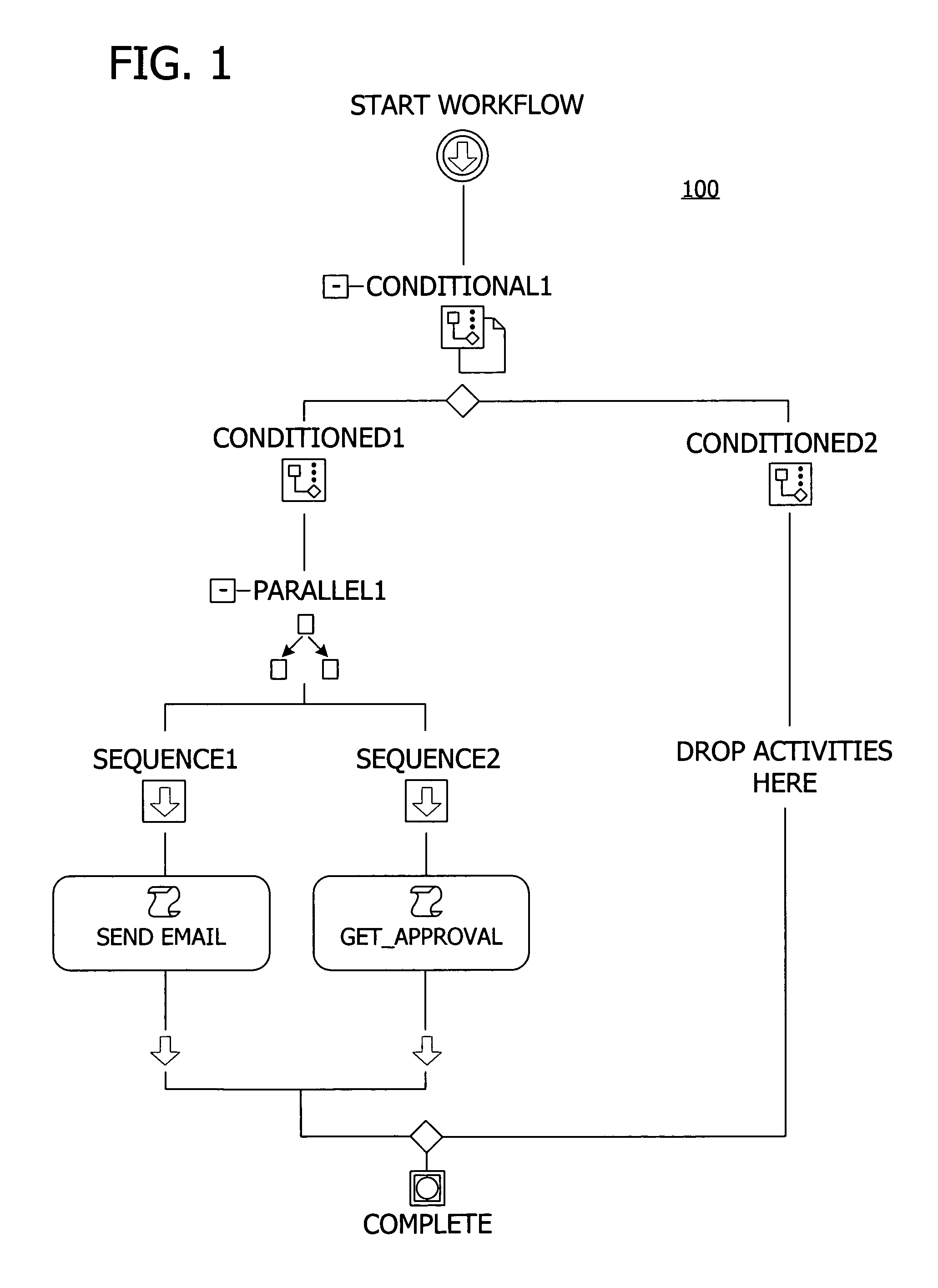
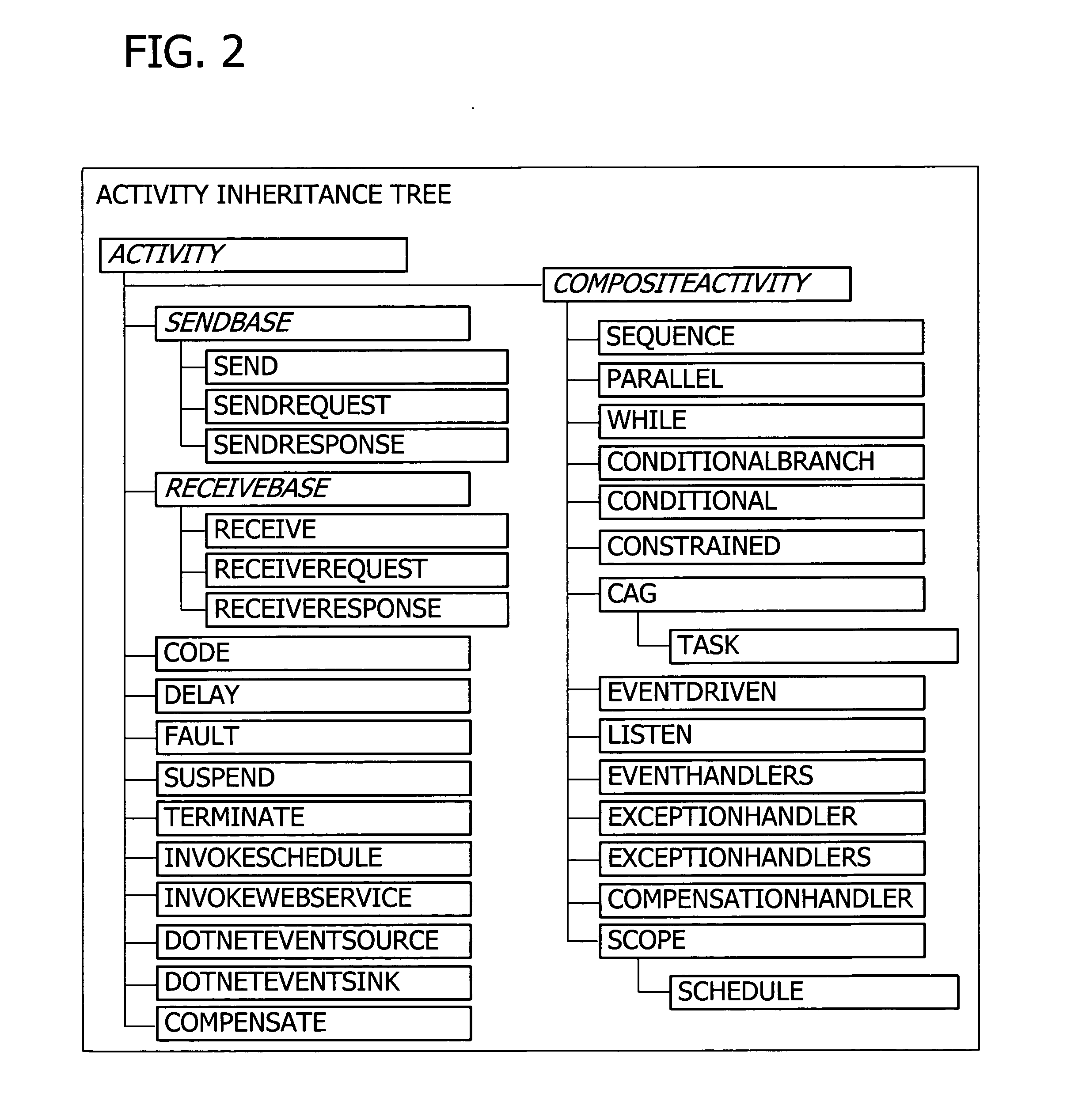
Extensible framework for designing workflows
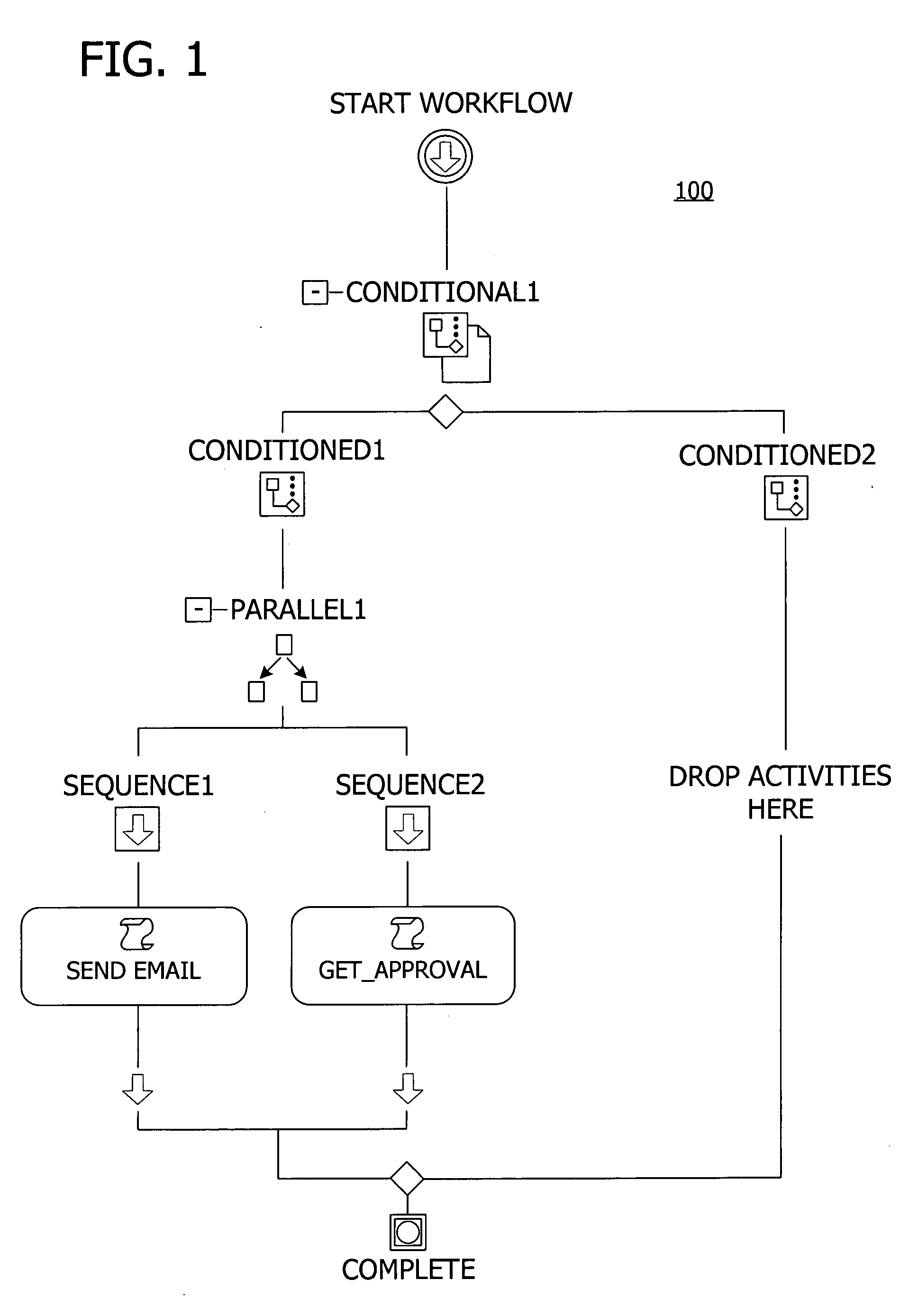
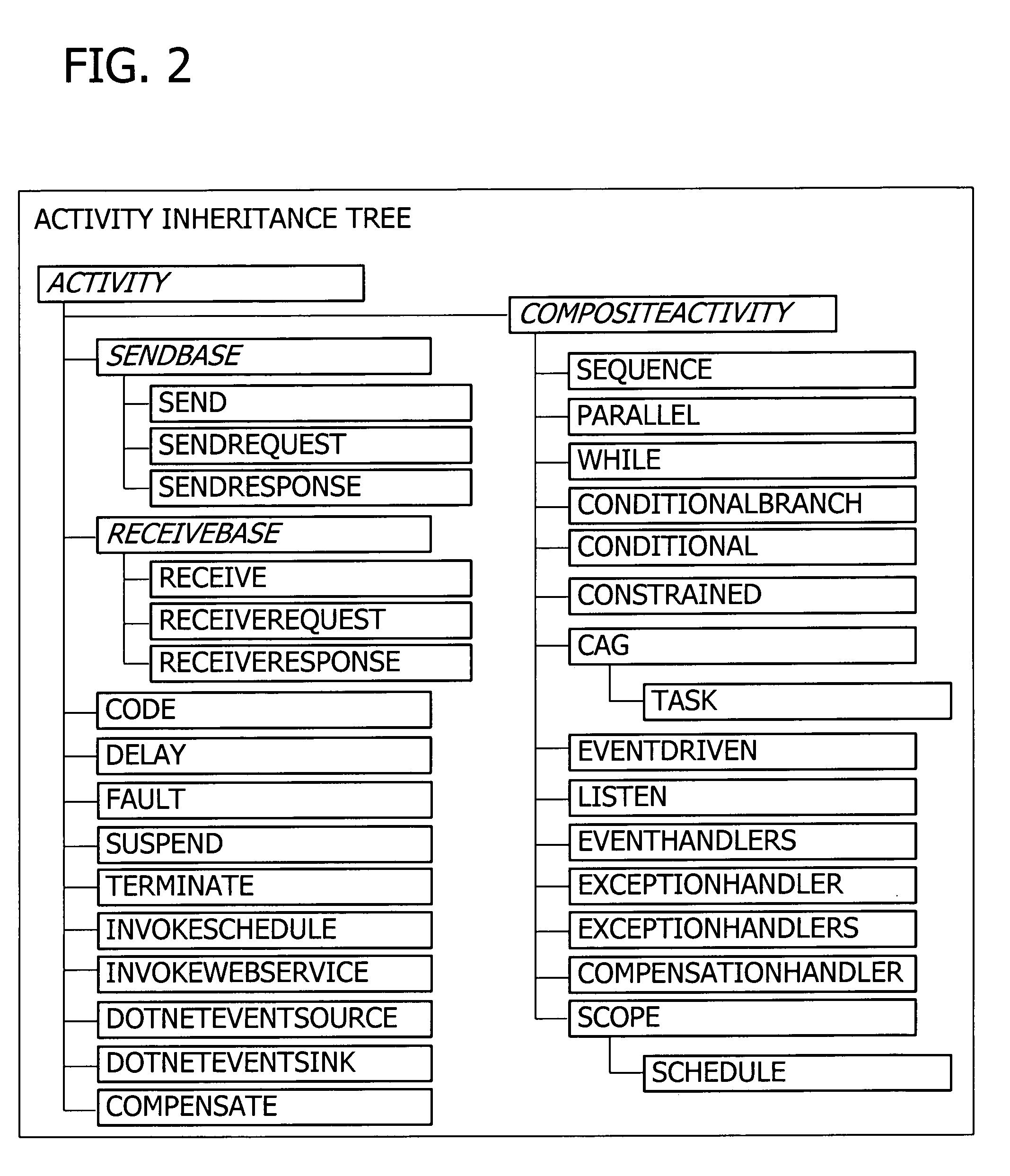
InactiveUS20060074730A1Increase heightExtend the workflow modelMultiprogramming arrangementsResourcesTime aspectWorkflow model
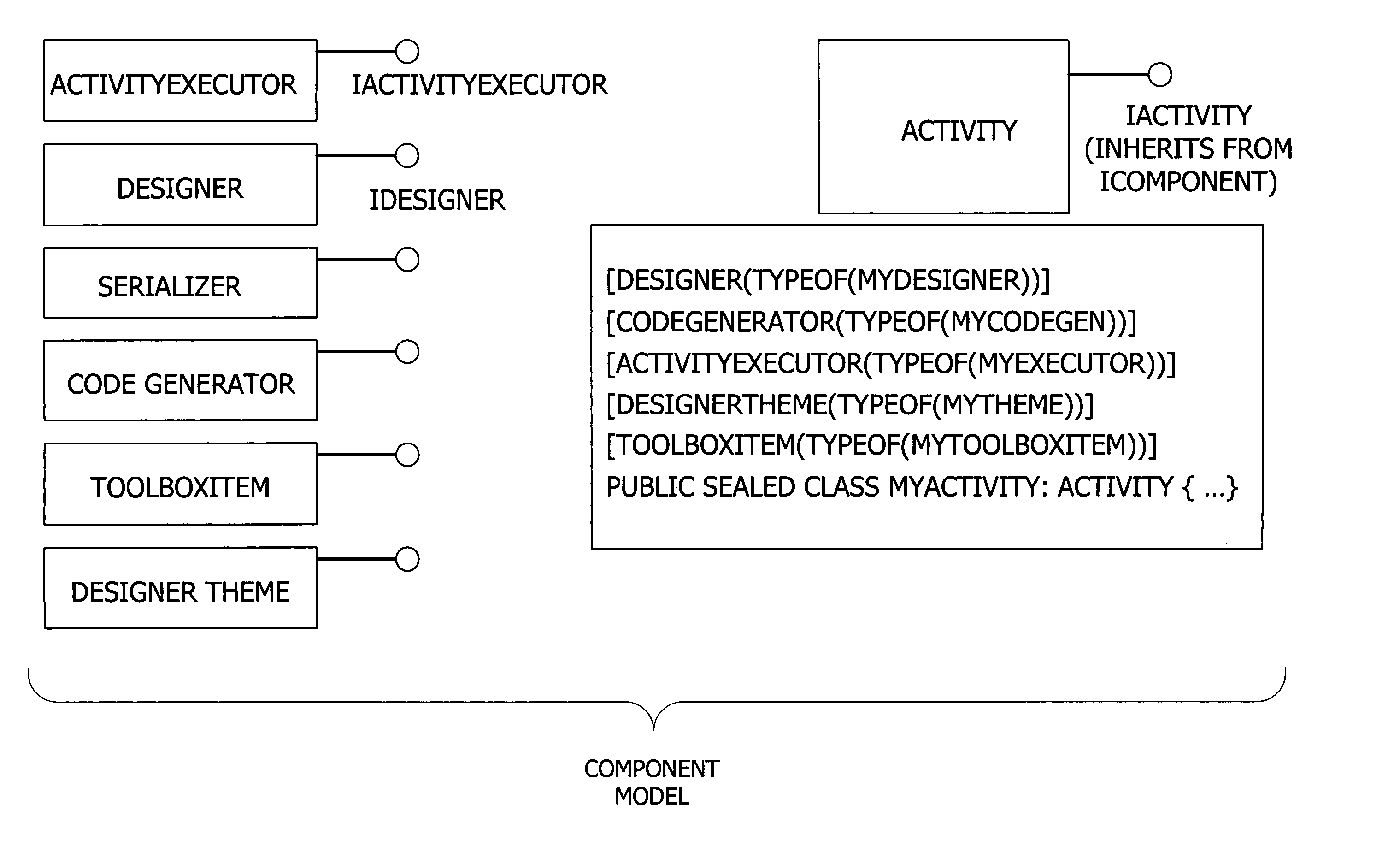
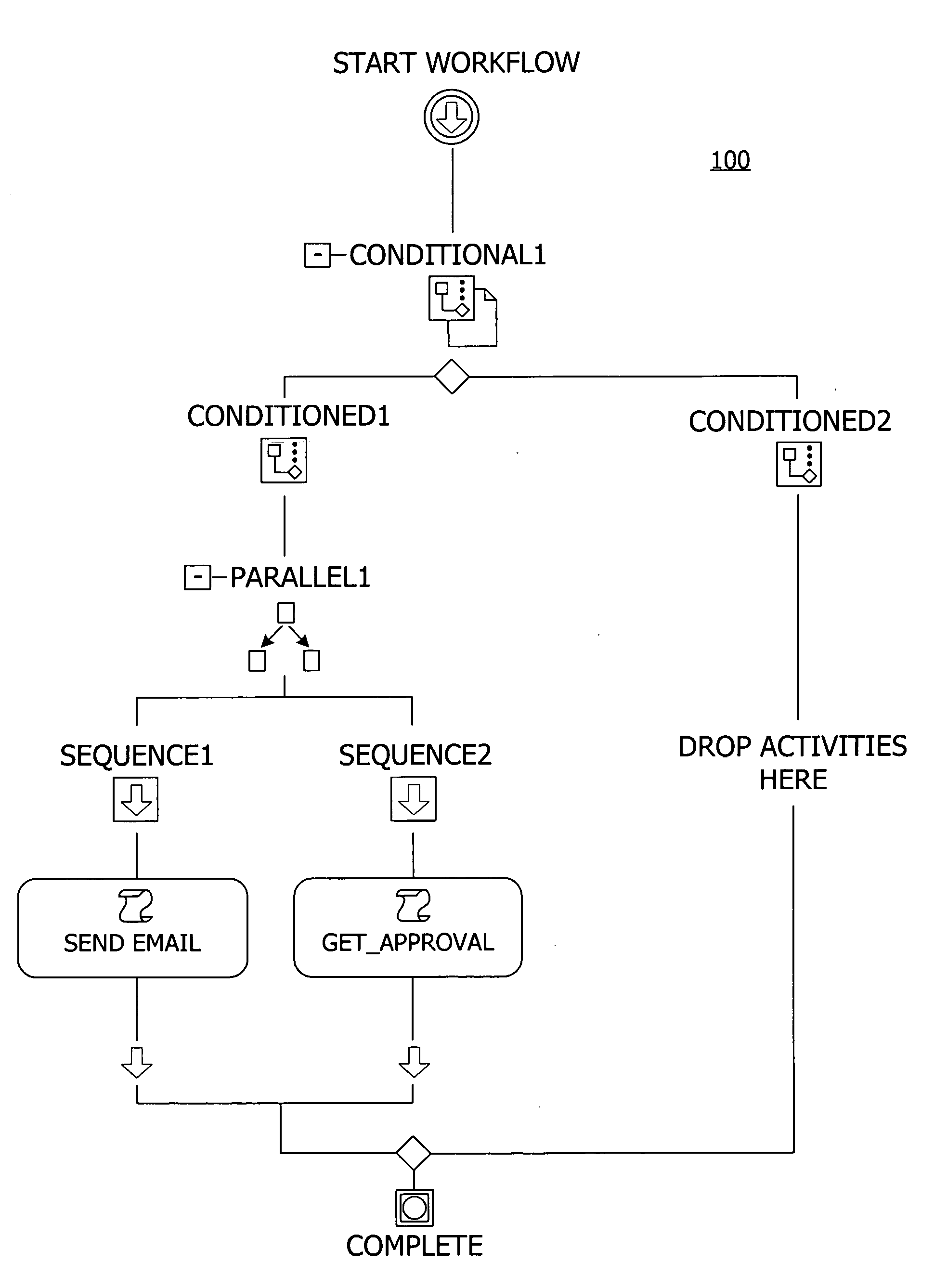
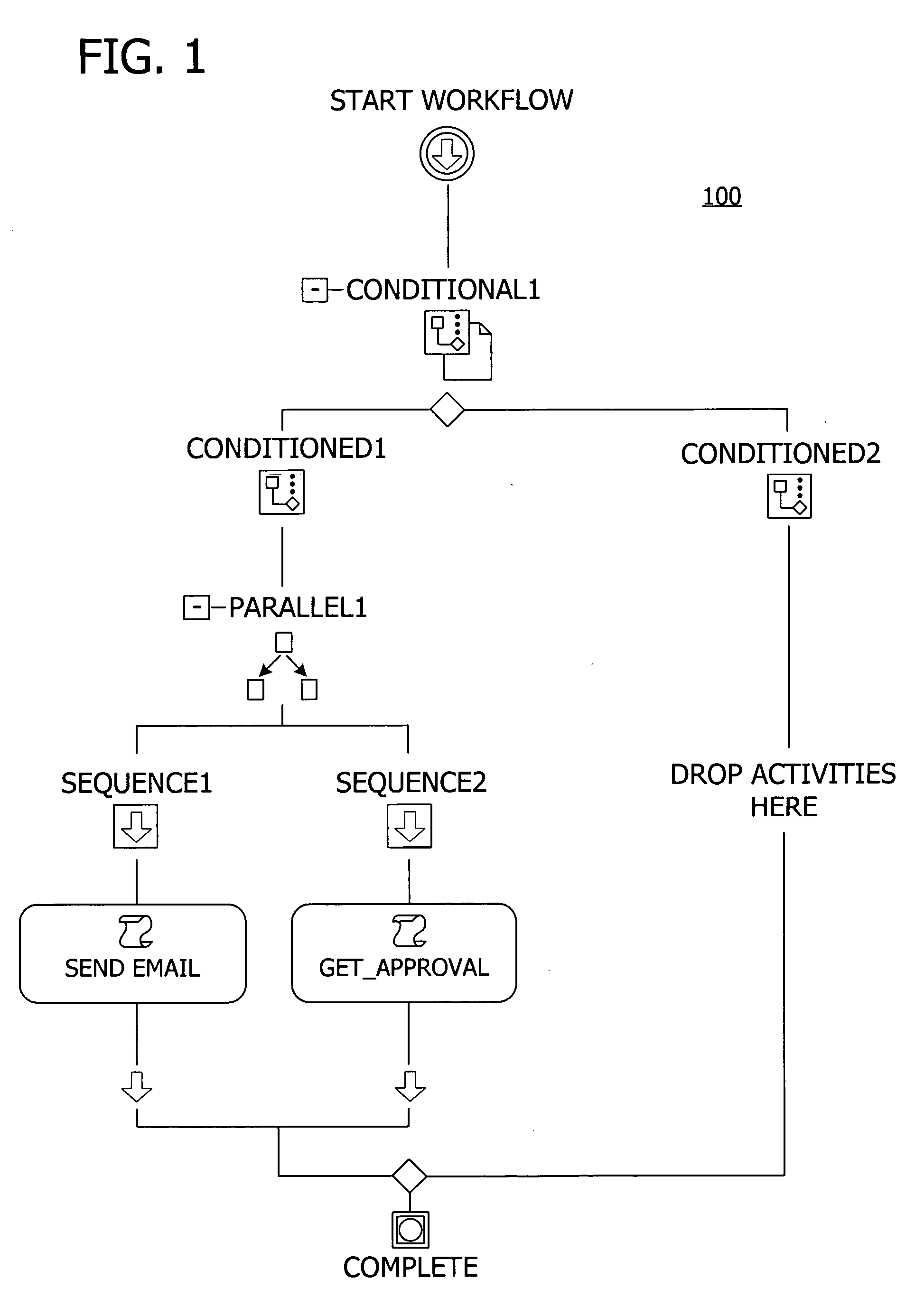
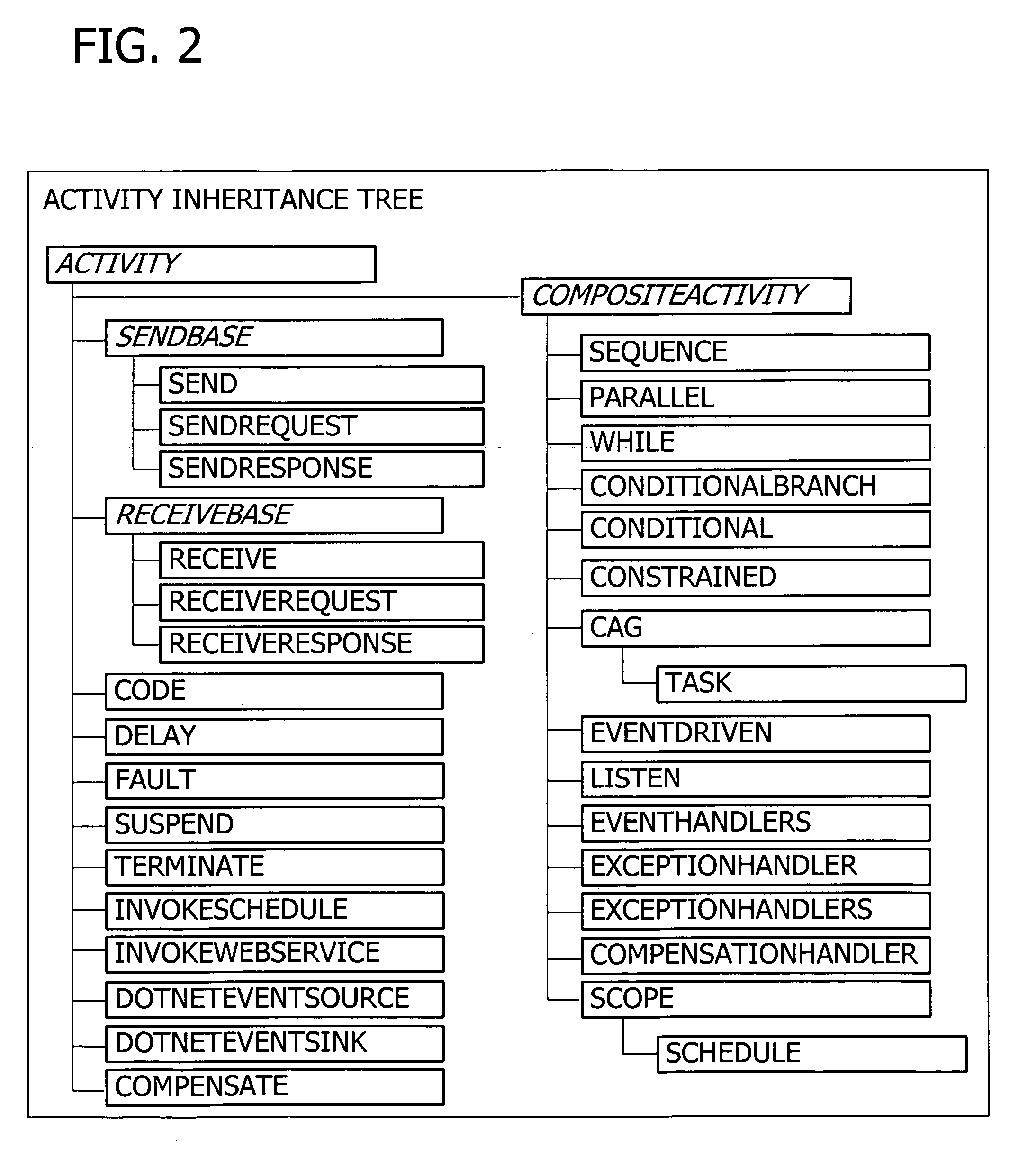
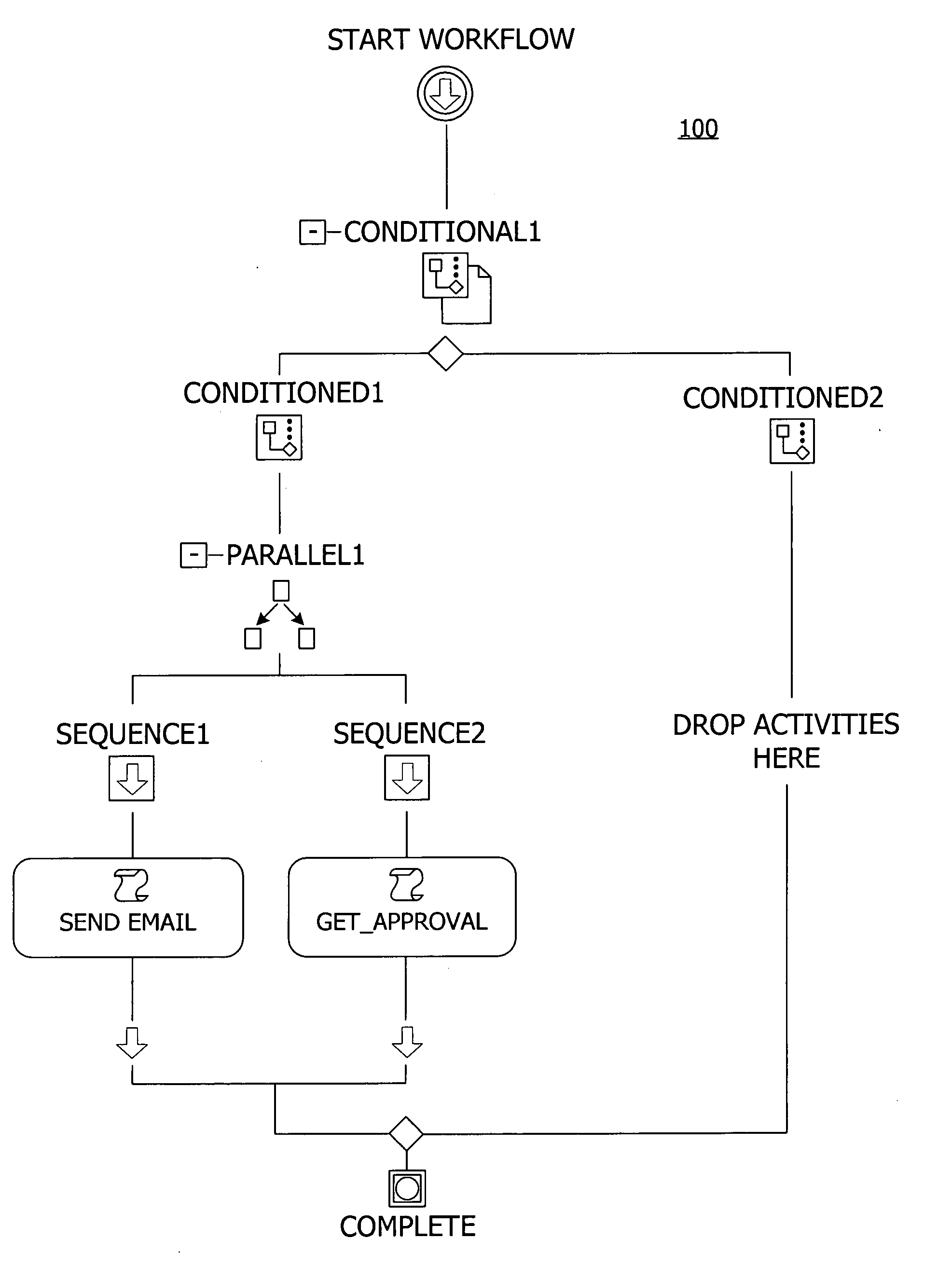
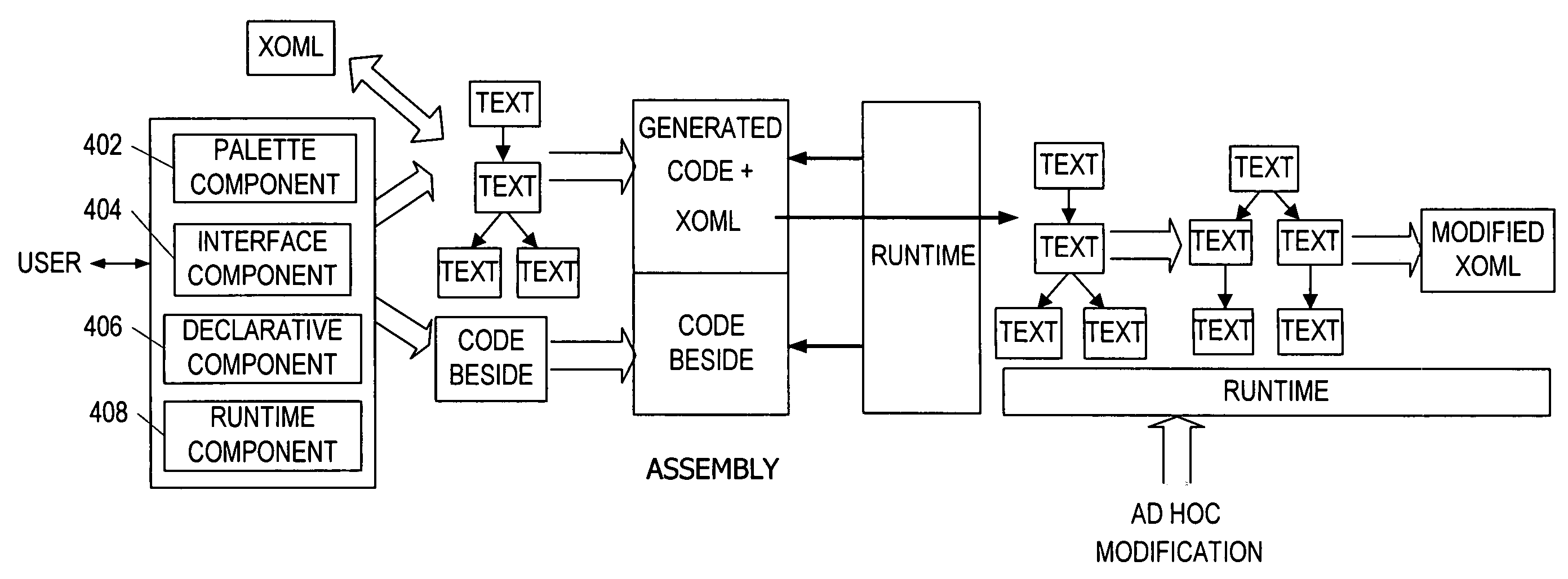
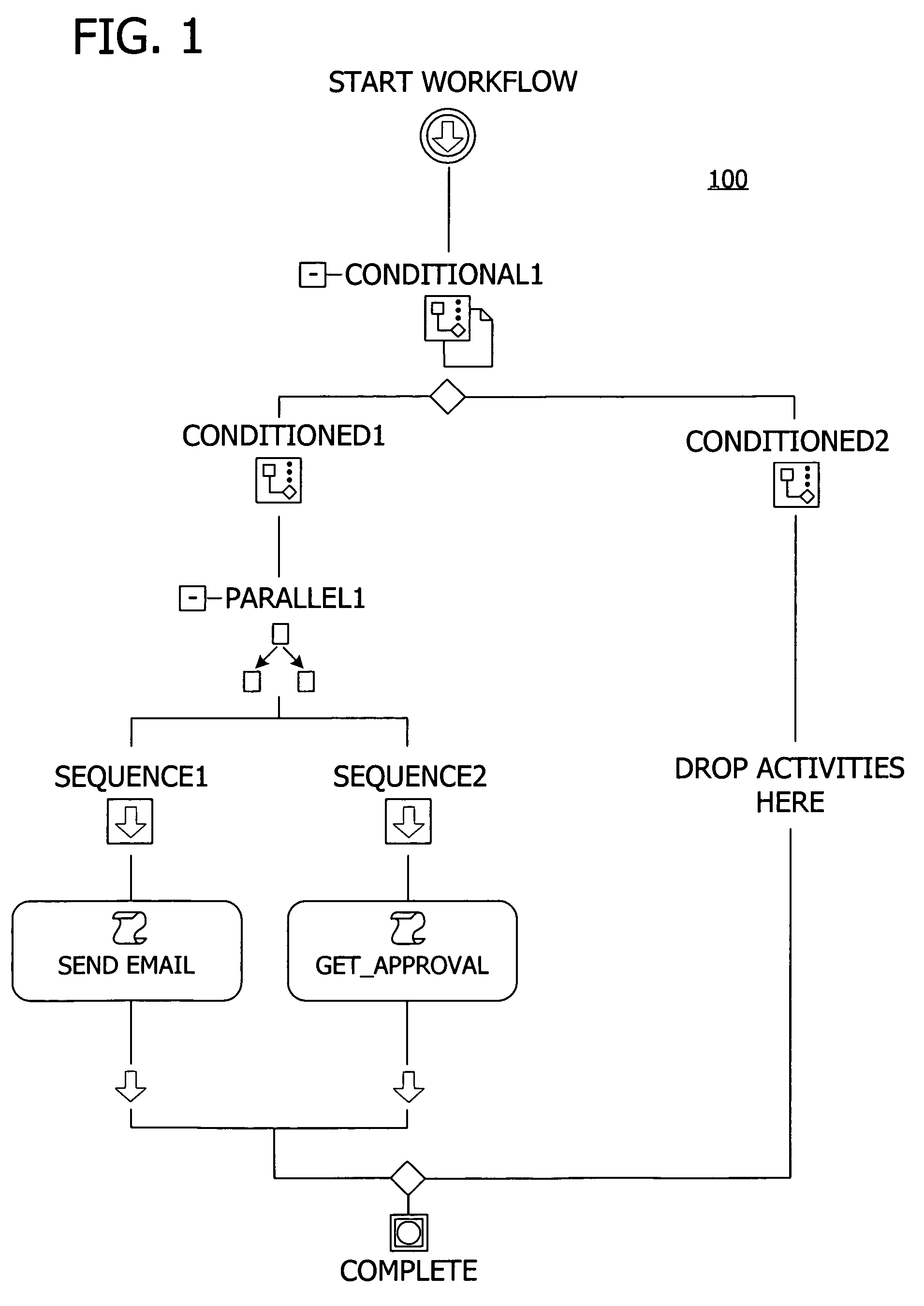
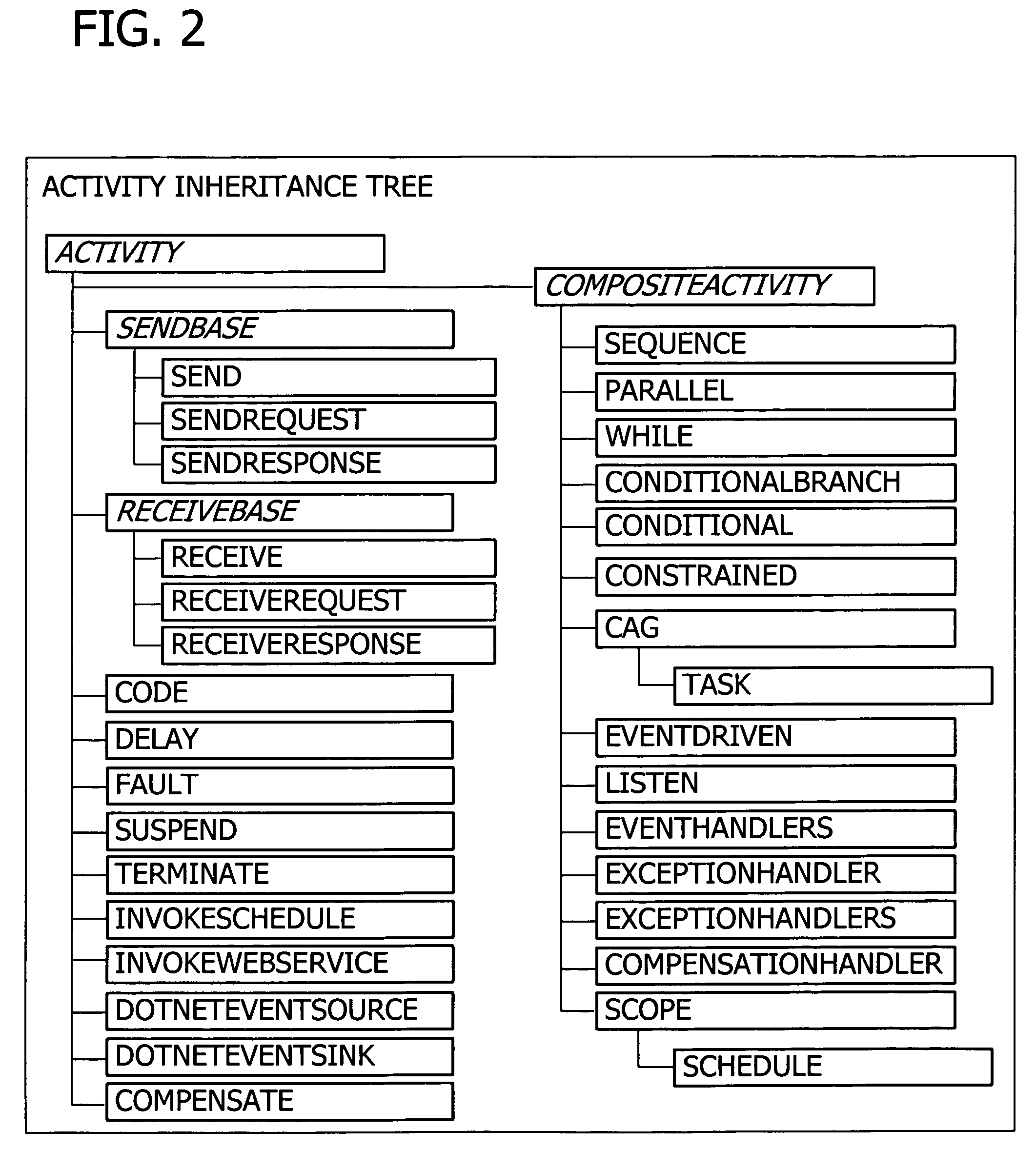
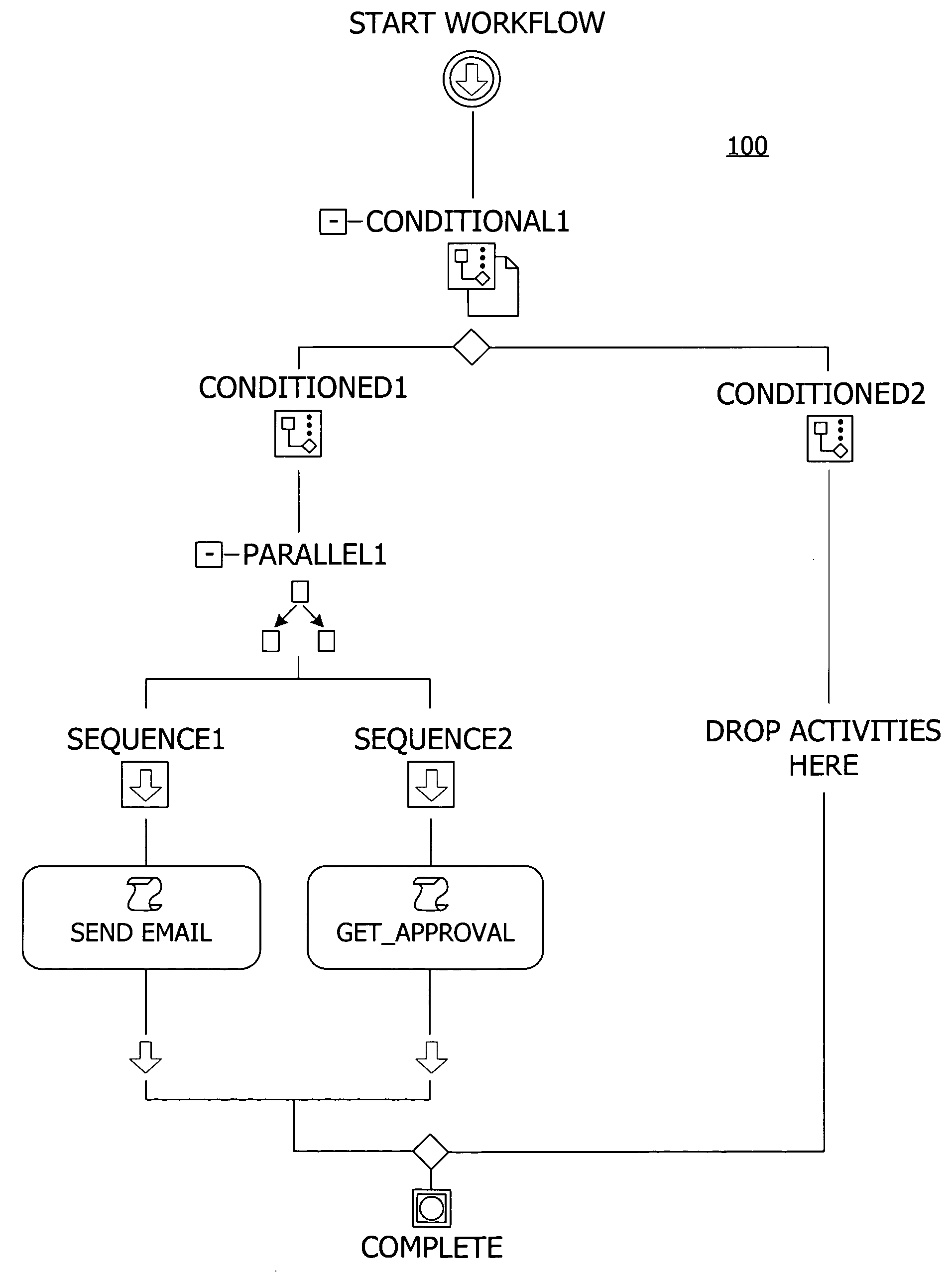
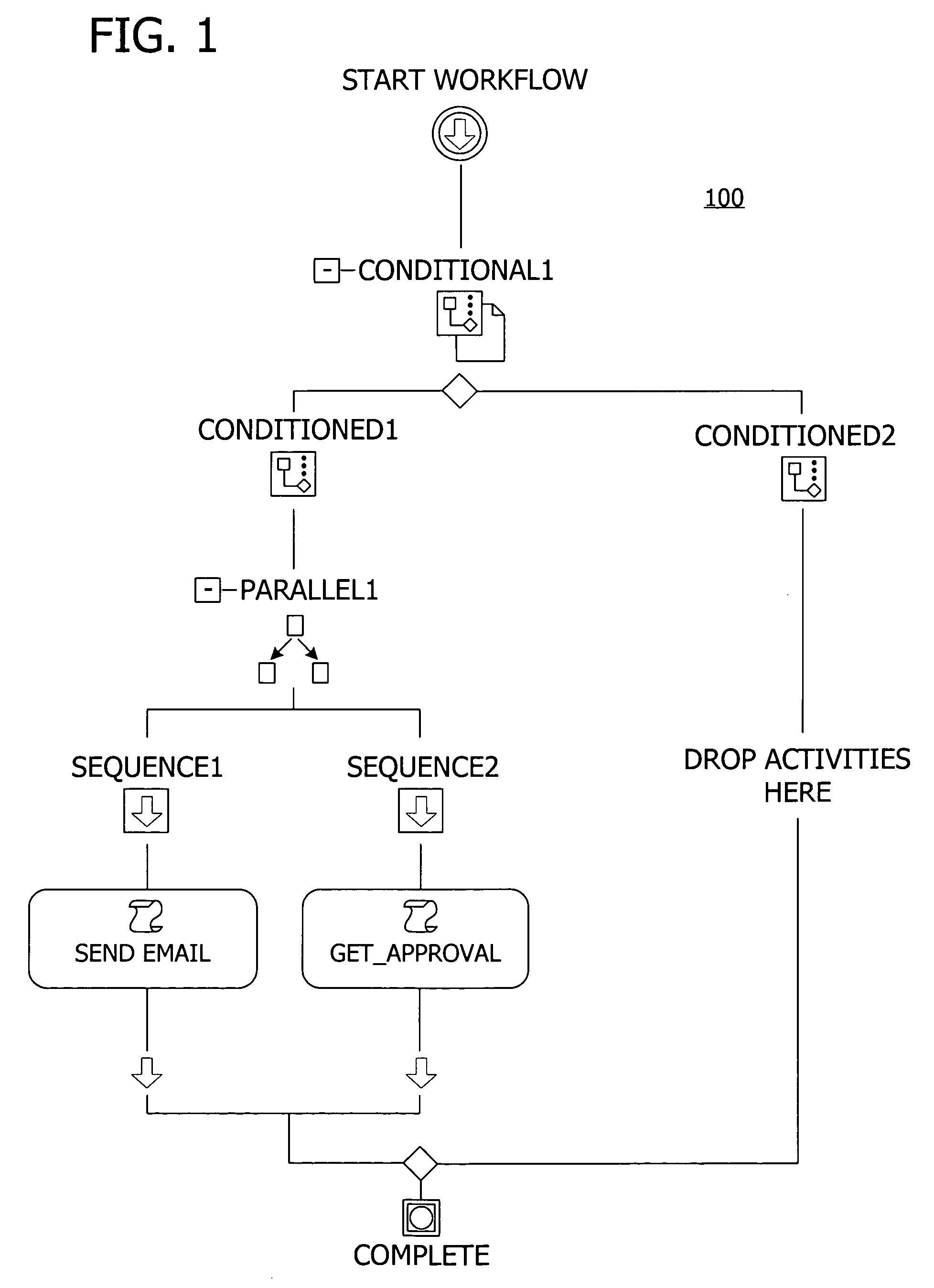
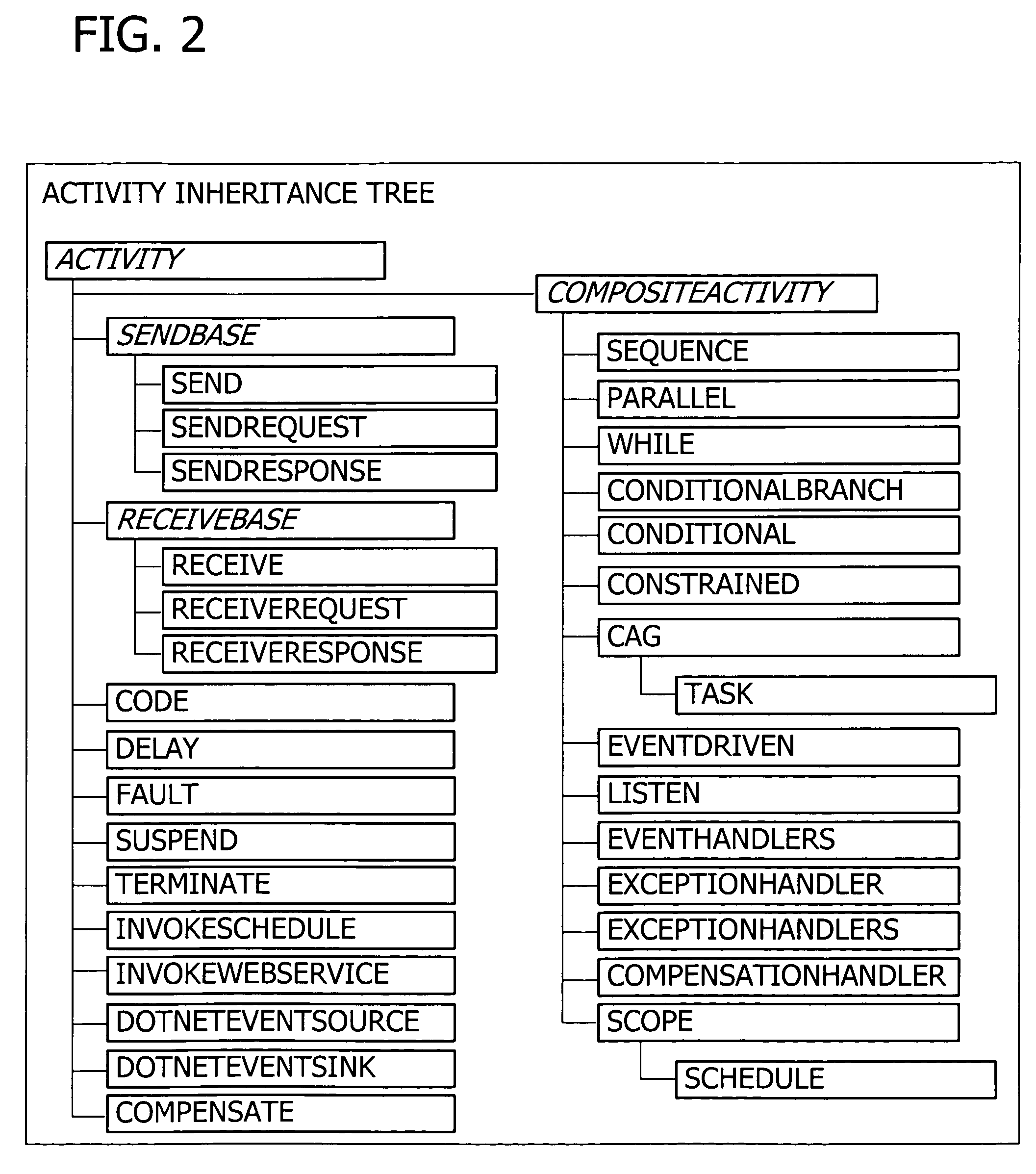
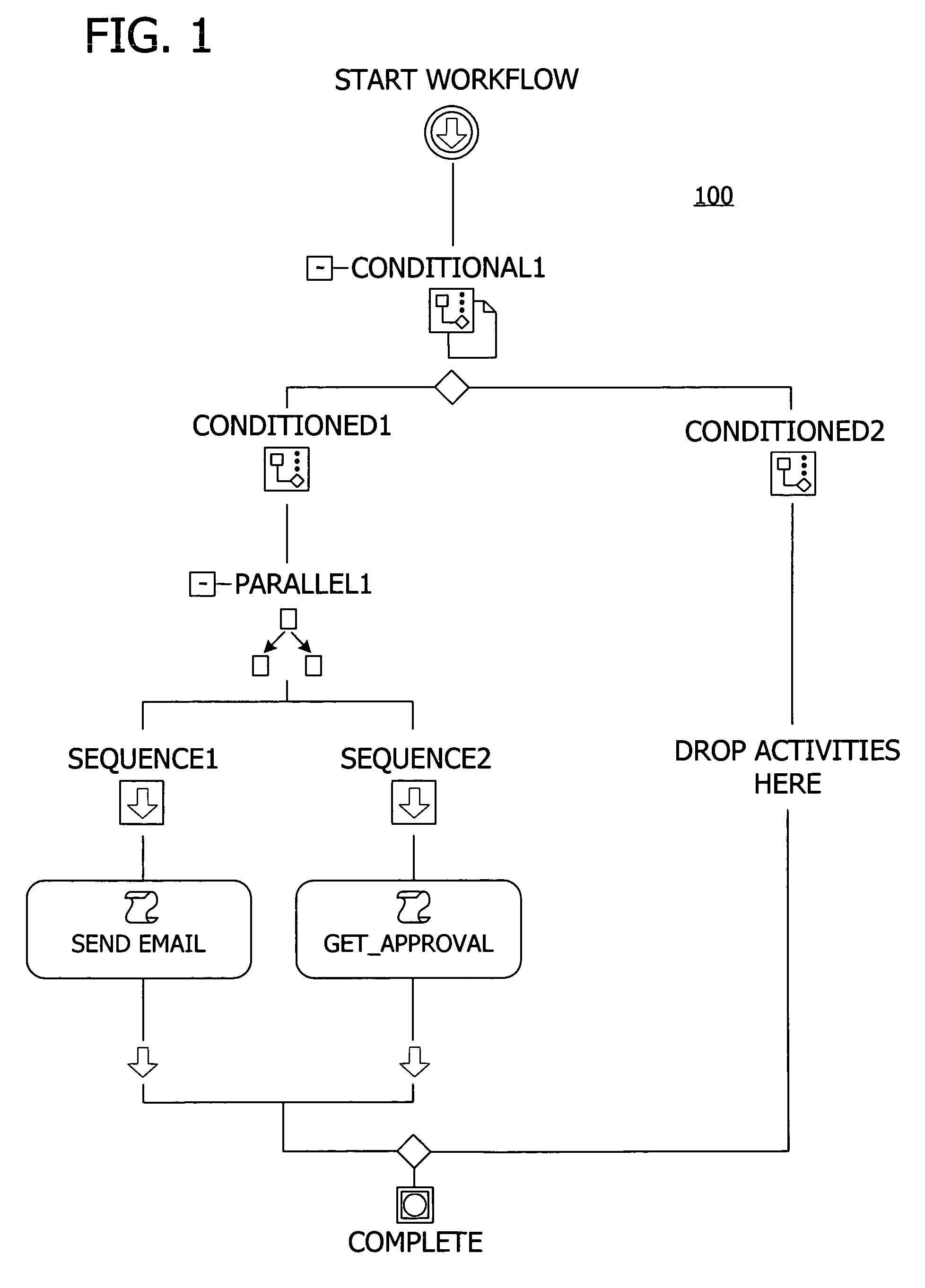
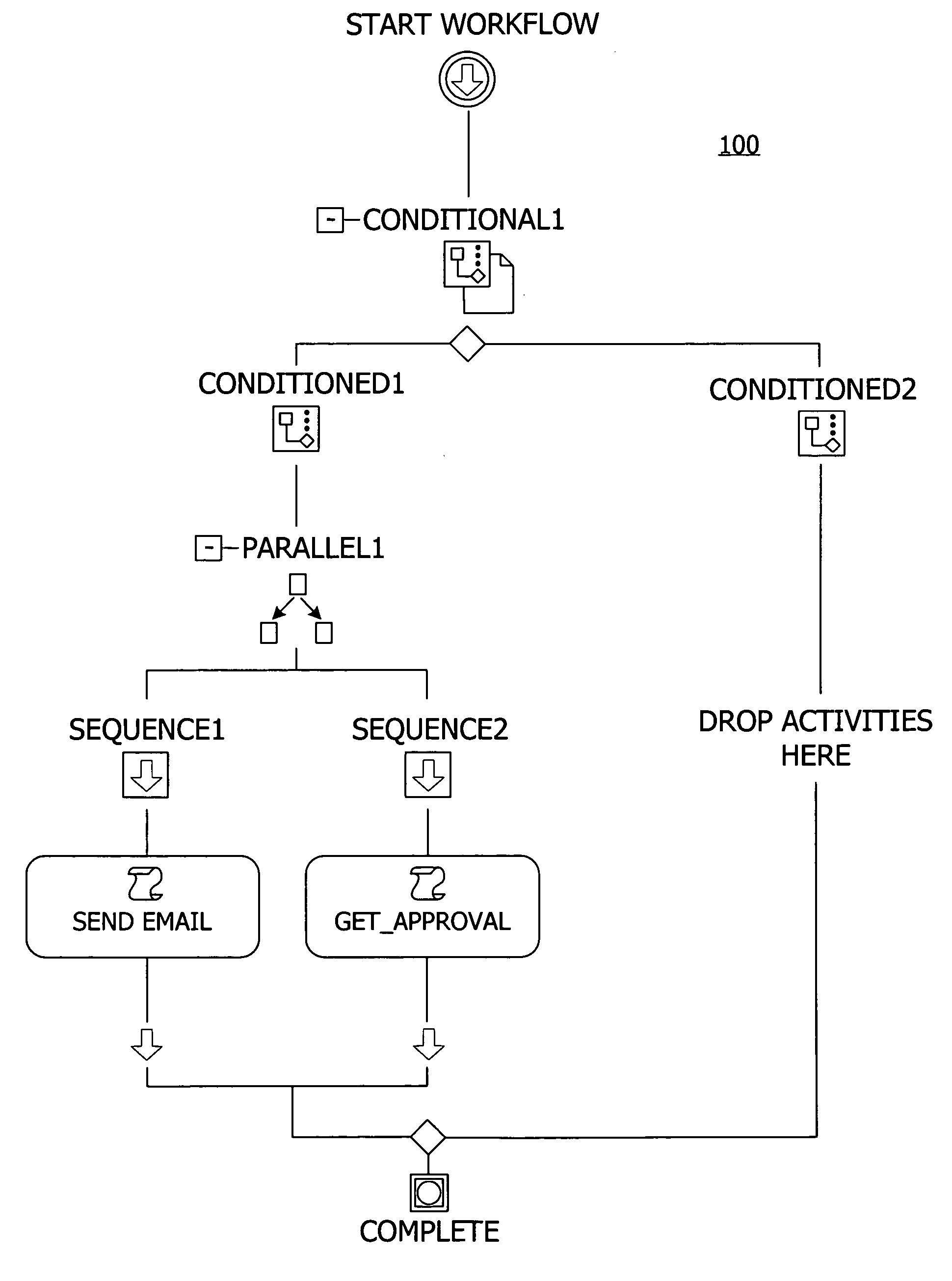
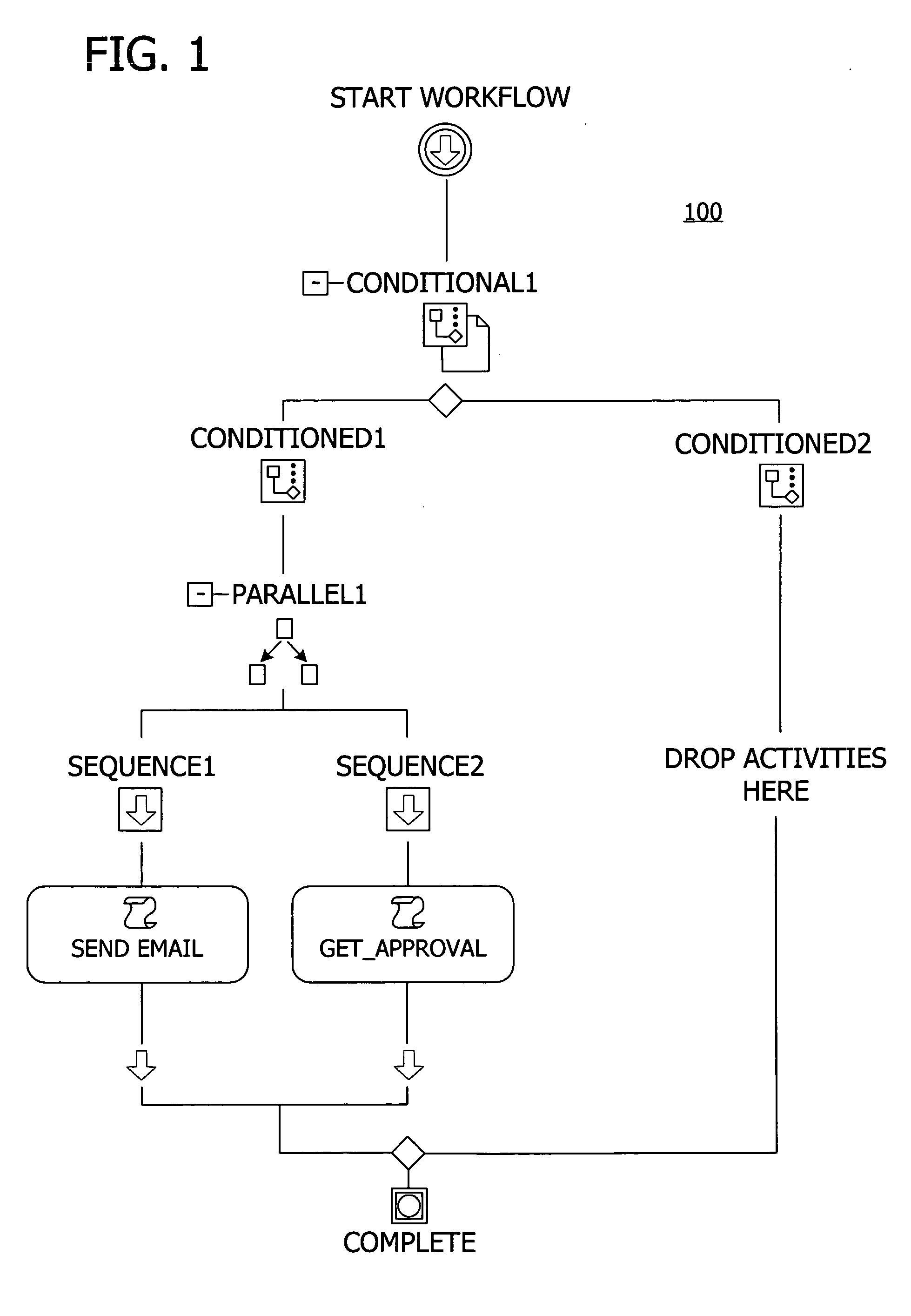
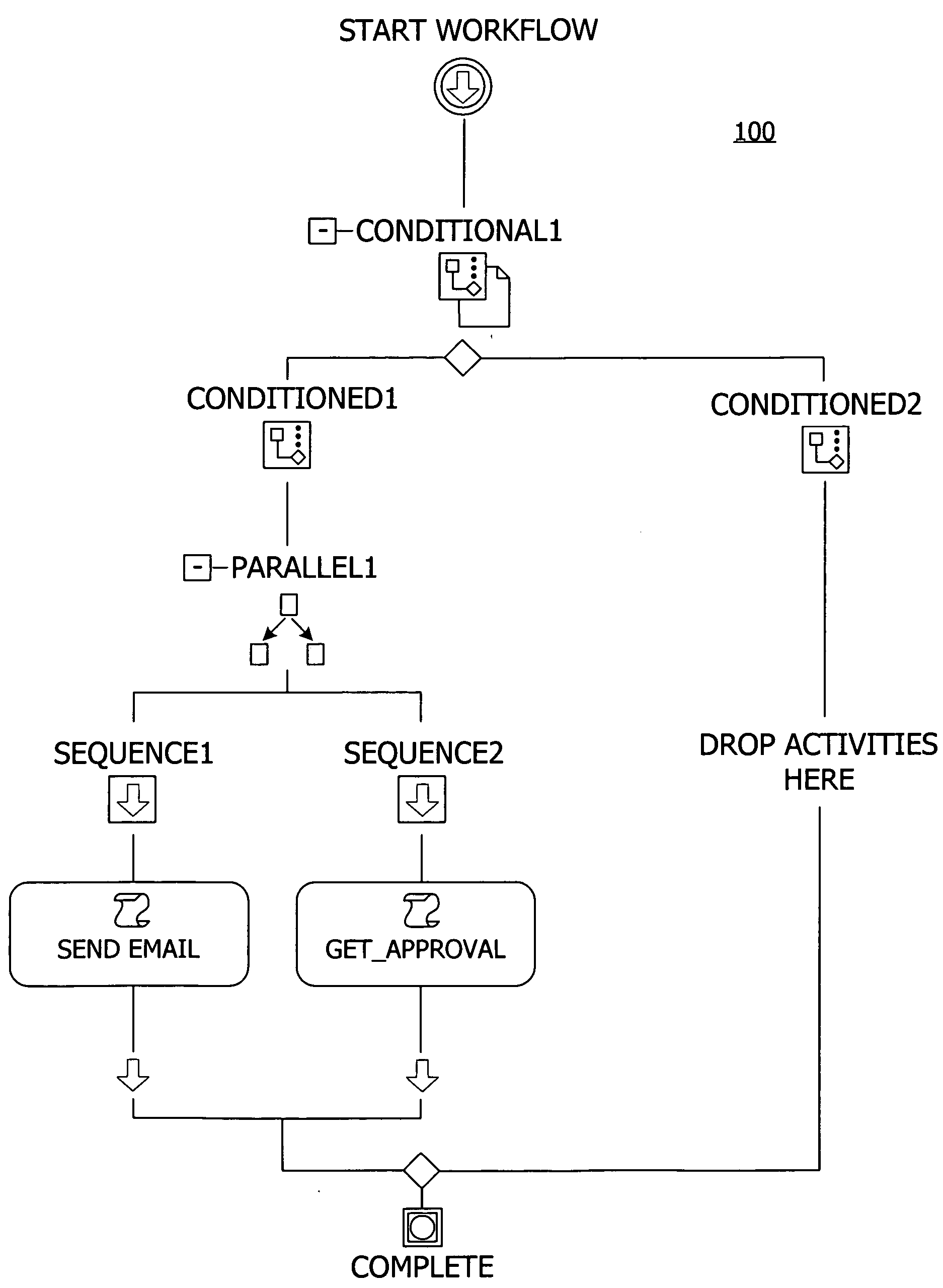
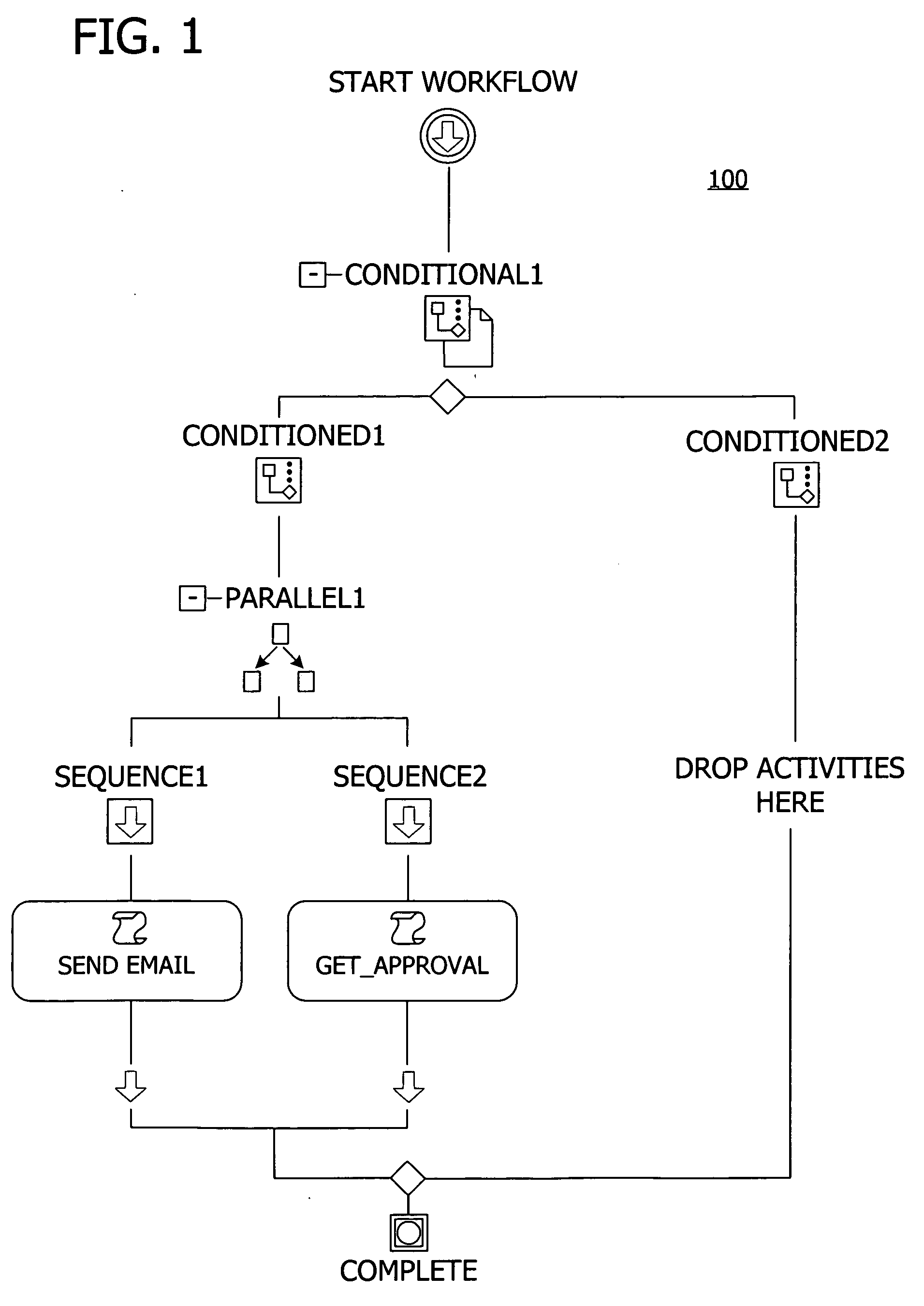
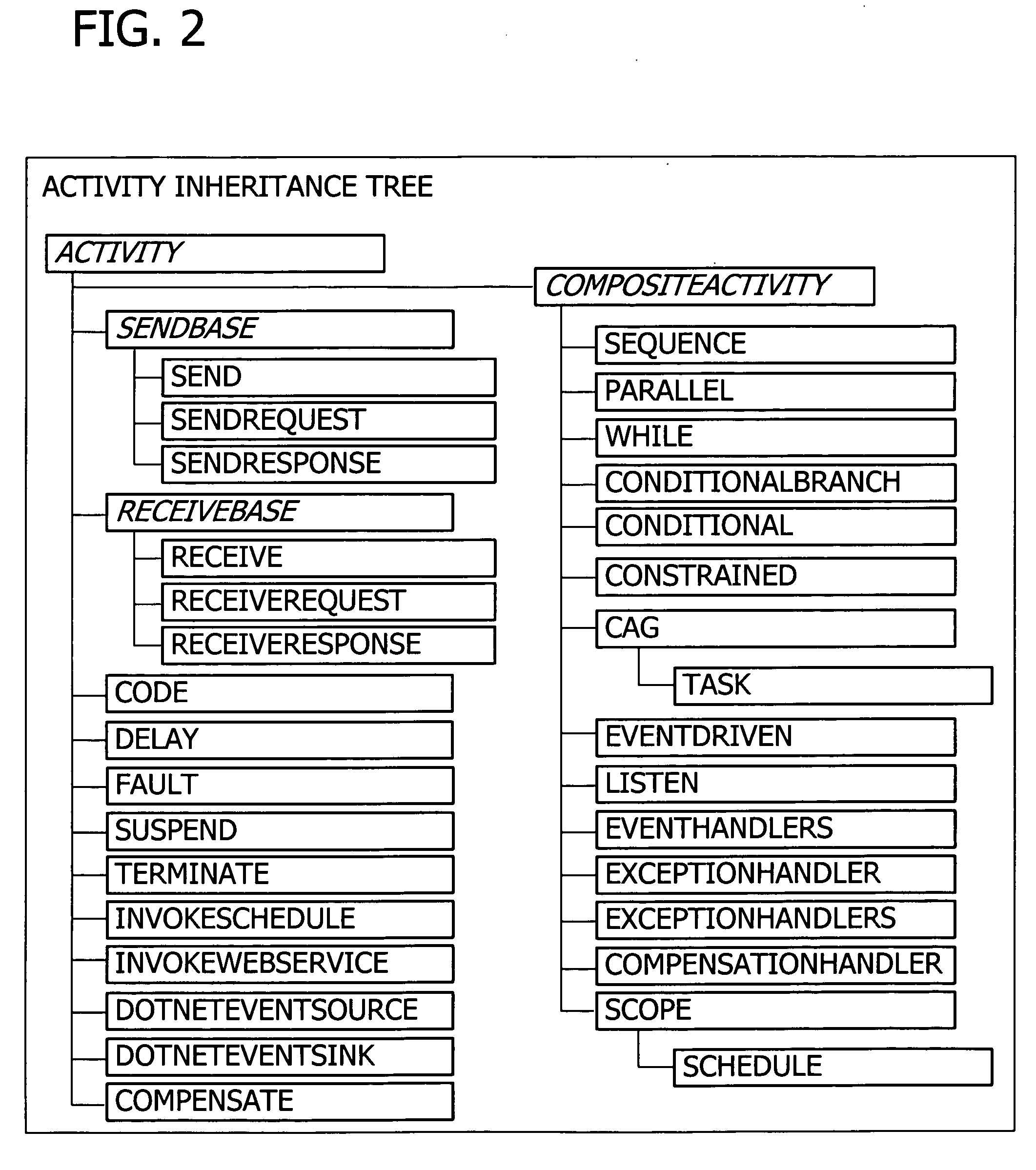
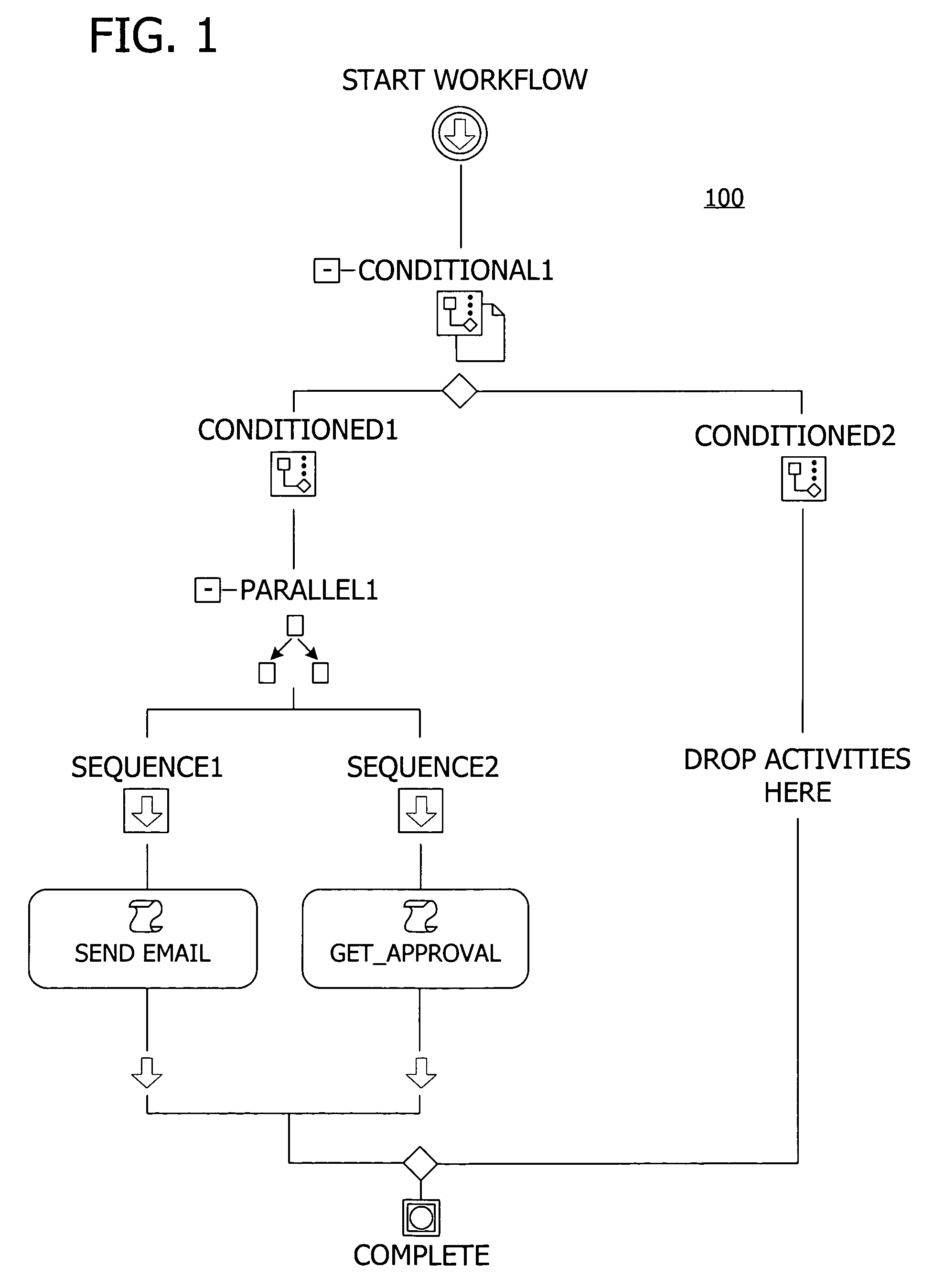
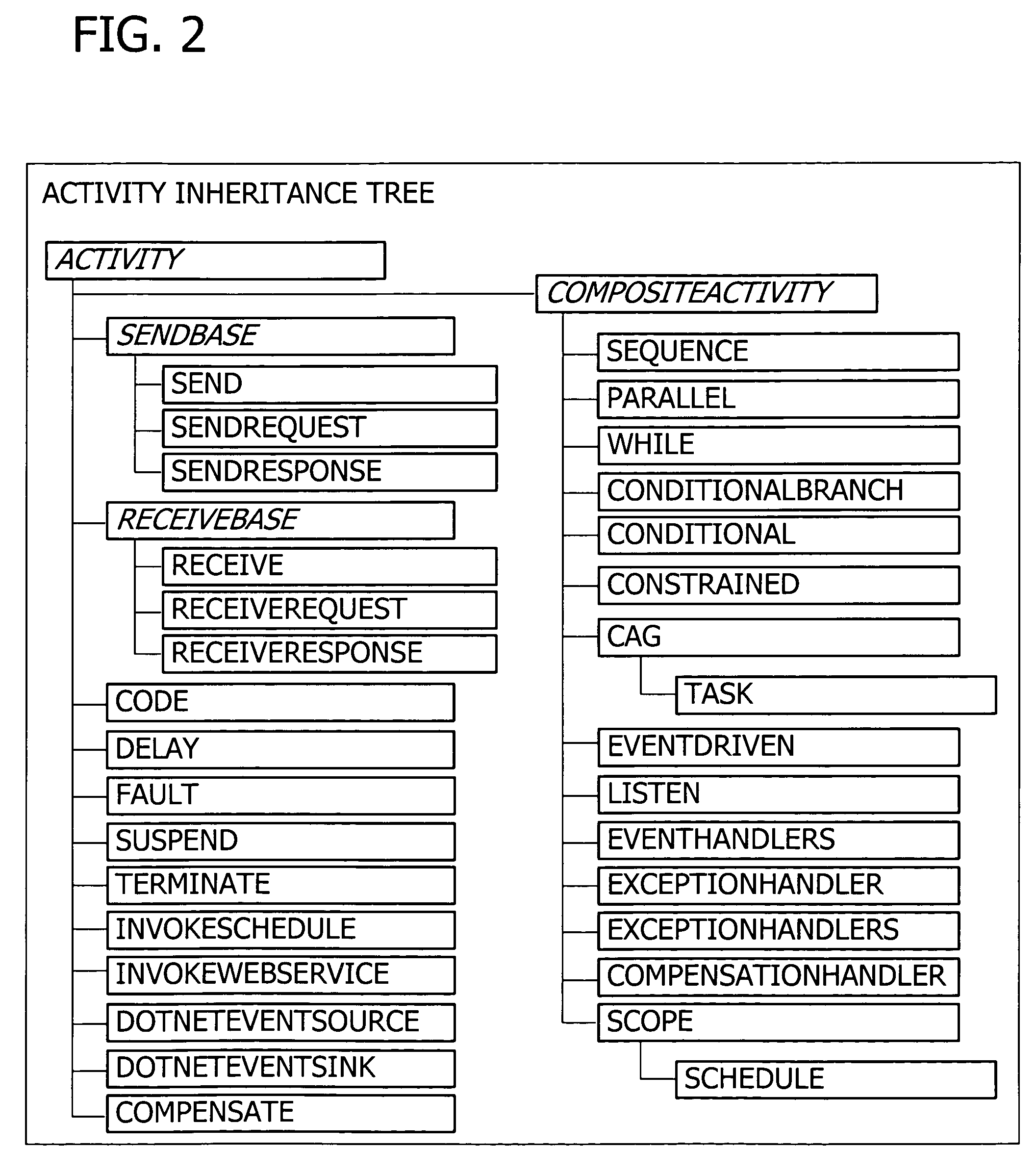
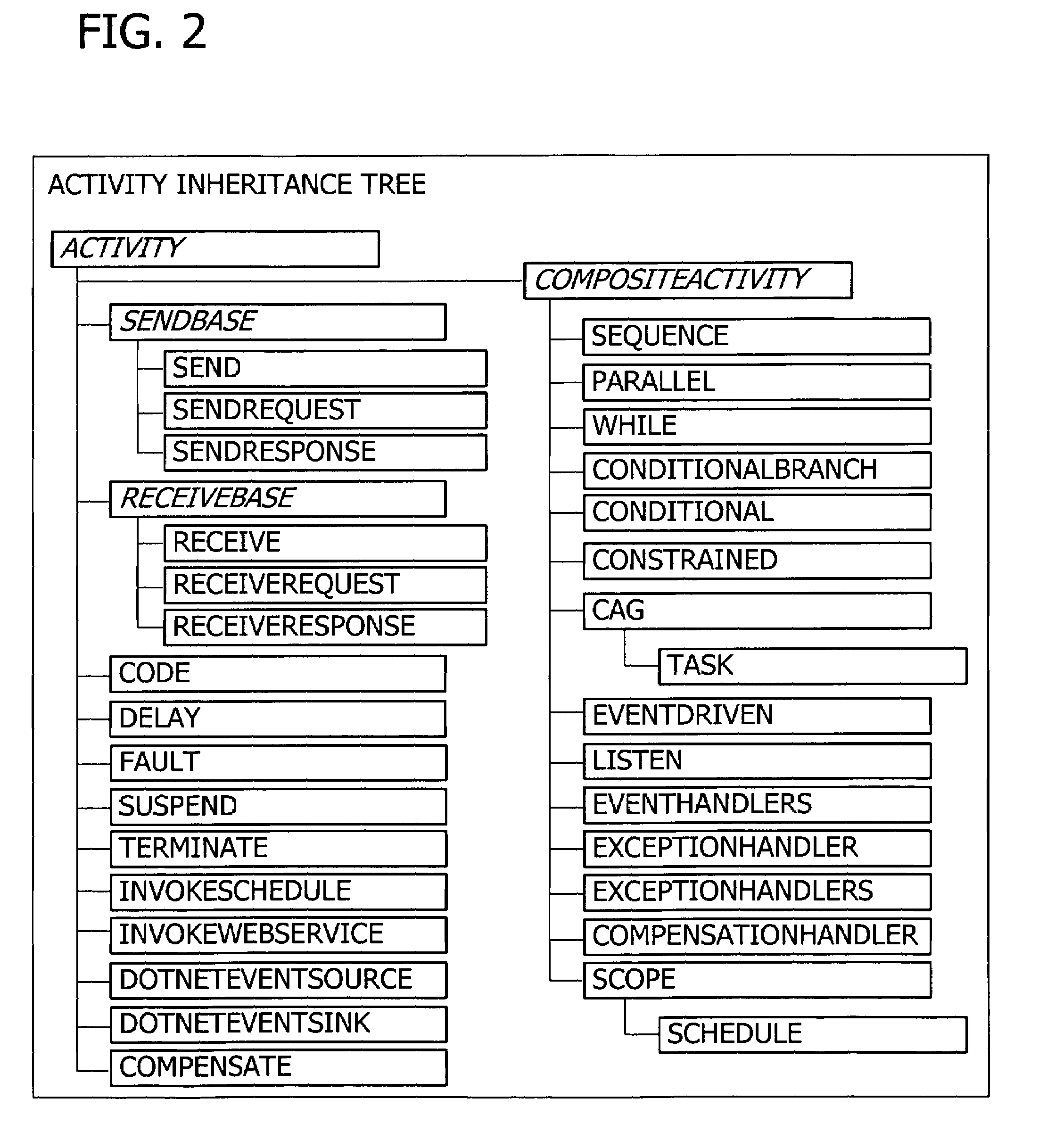
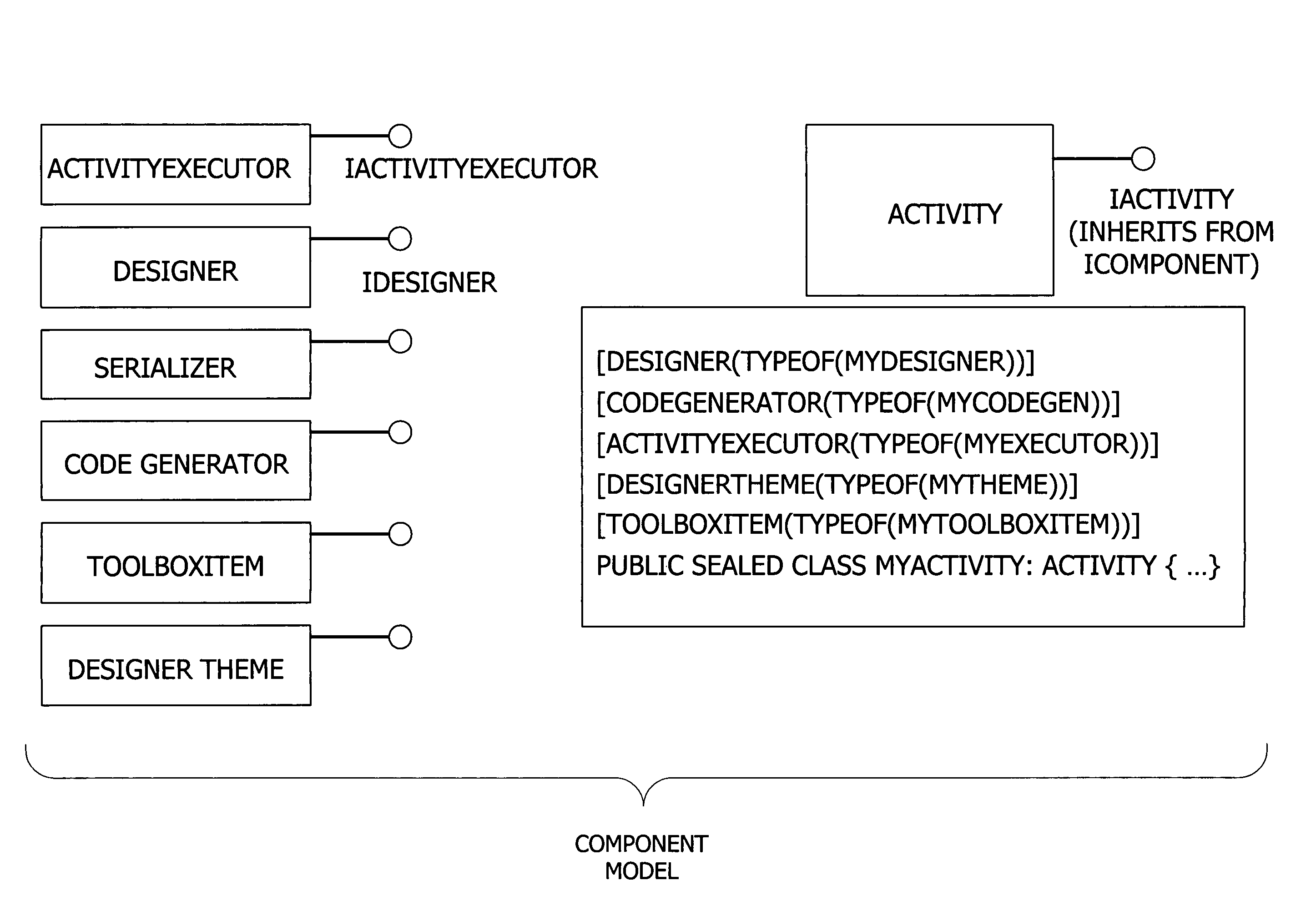
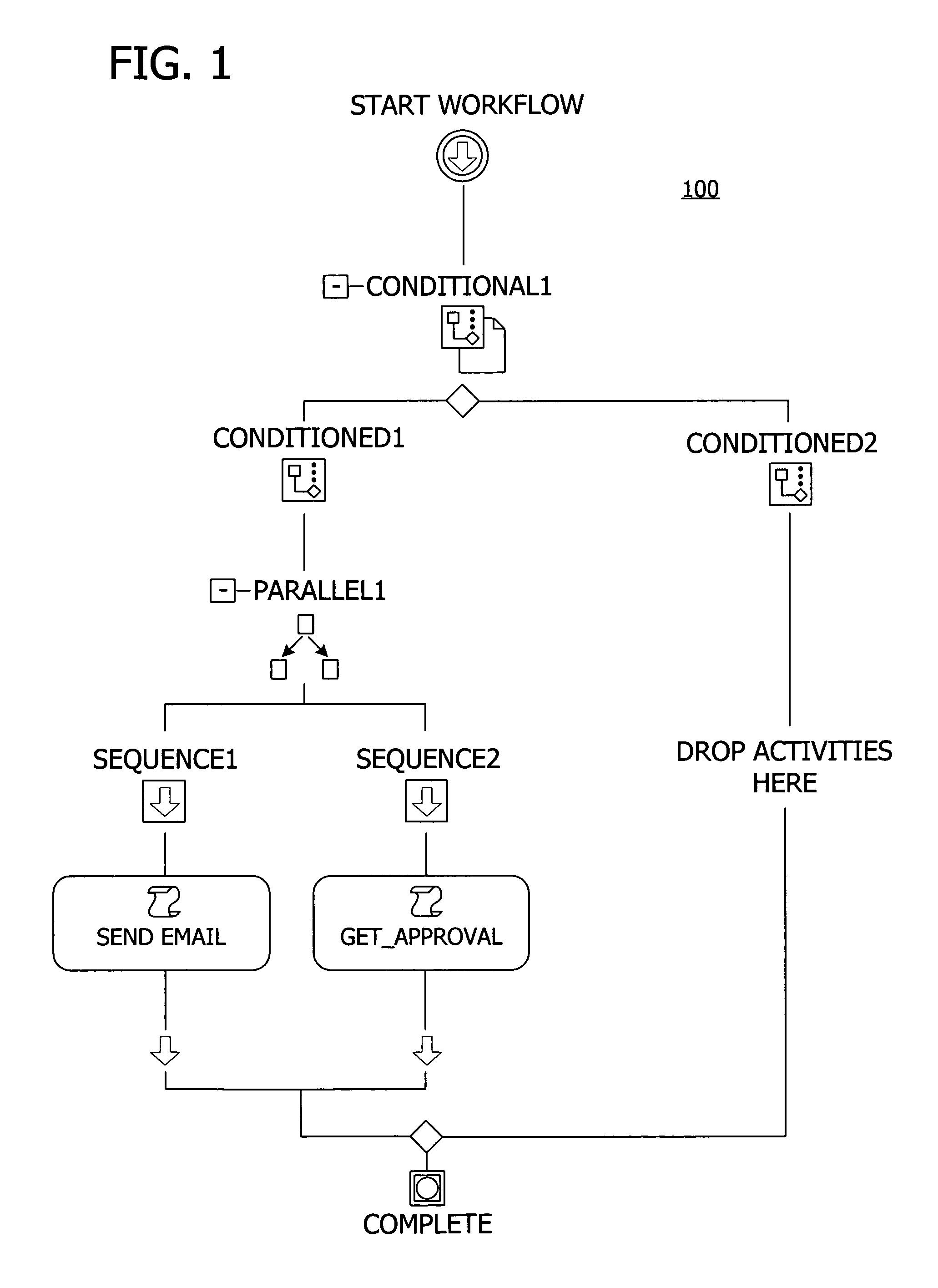
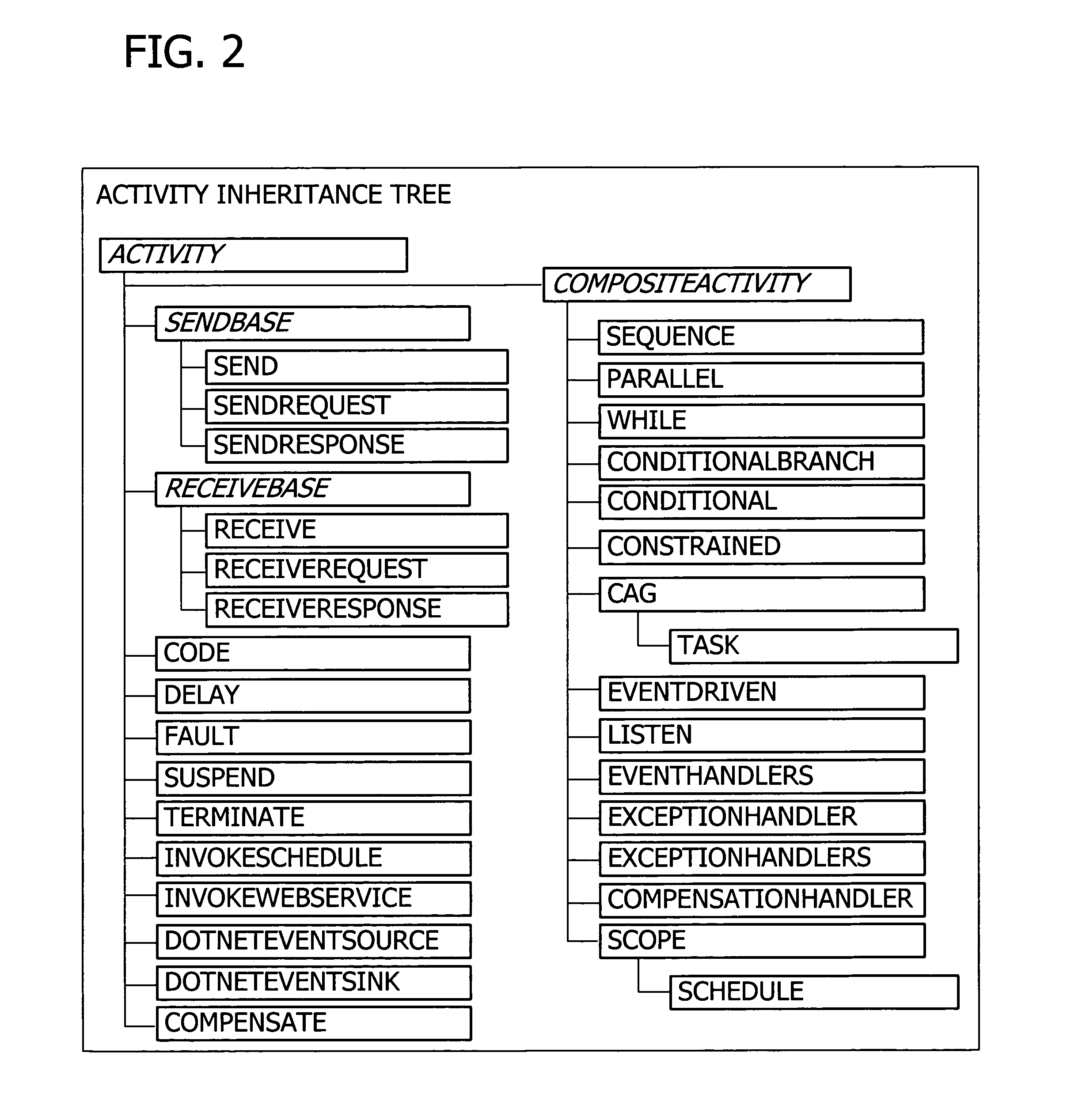
A user interface for building a componentized workflow model. Each step of the workflow is modeled as an activity that has metadata to describe design time aspects, compile time aspects, and runtime aspects of the workflow step. A user selects and arranges the activities to create the workflow via the user interface. The metadata associated with each of the activities in the workflow is collected to create a persistent representation of the workflow. Users extend the workflow model by authoring custom activities.
Owner:MICROSOFT TECH LICENSING LLC
Method and a System Relating to Network Management
InactiveUS20080294418A1OptimizationReduce the amount requiredData switching by path configurationMultiple digital computer combinationsNetwork managementManaged object
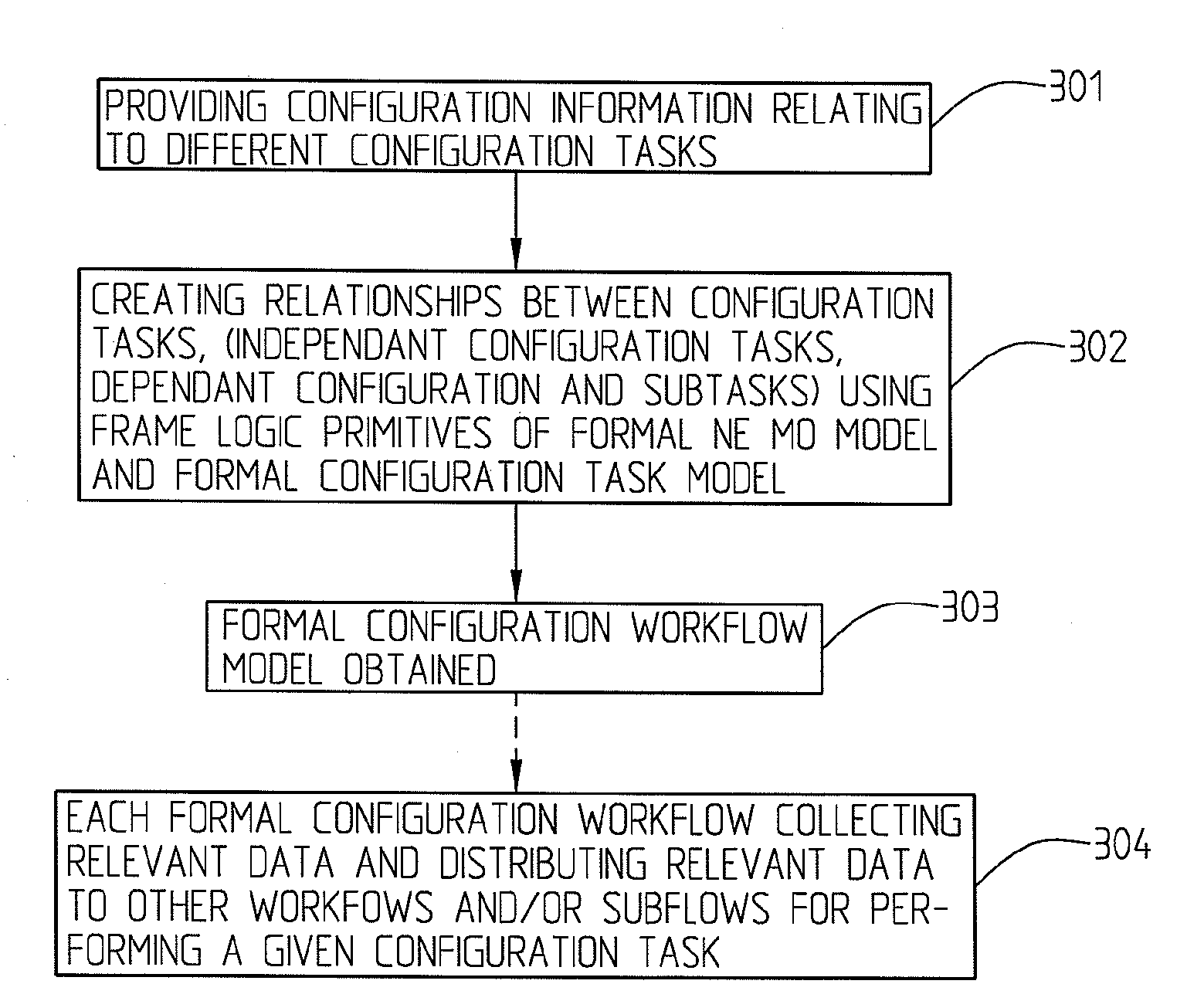
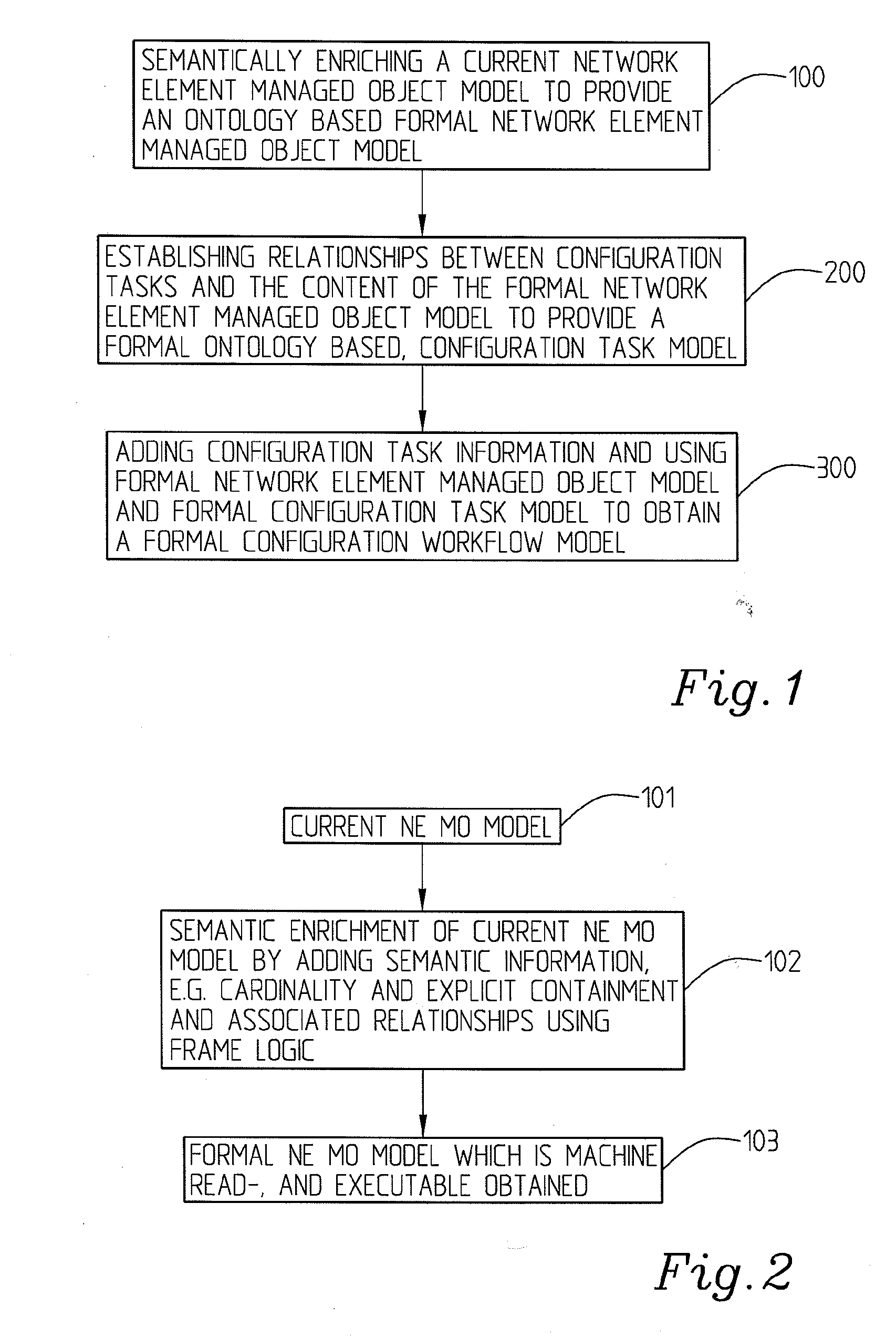
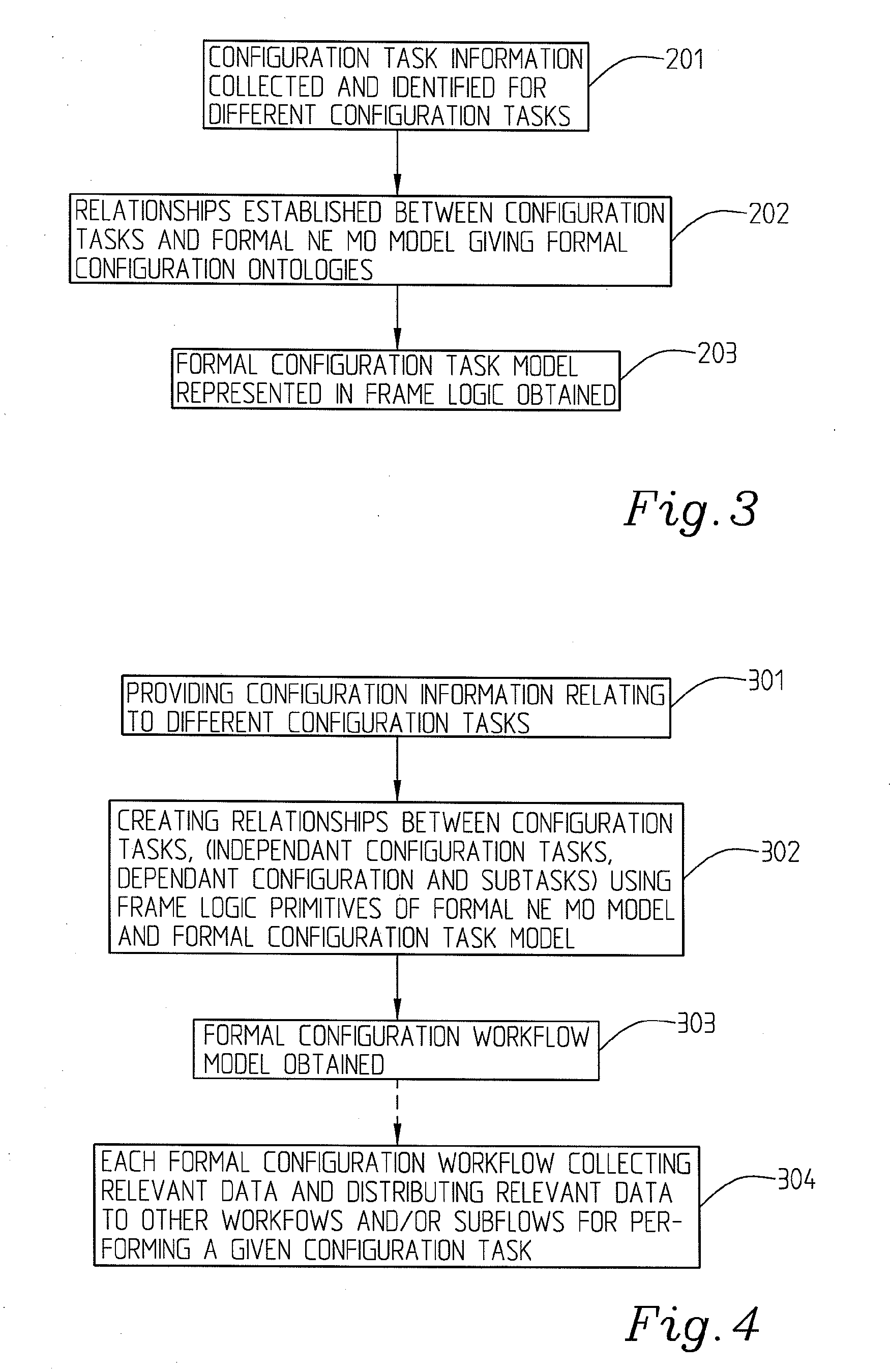
The present invention relates to a method for network management comprising configuration of control protocols between network elements in a network represented through a current, static, network element object model comprising a number of managed objects with attributes and instances and representing resources. It comprises the steps of: transforming the current network element object model to a machine readable and executable formal network element object model; identifying configuration tasks needed for the configuration of the relevant control protocols; modelling a formal configuration task model using information about the configuration tasks and the formal network element object model; building a formal configuration workflow model using the formal network element object model and the formal configuration task model, said formal configuration workflow model defining the relationships between different configuration tasks required for performing or completing a number of given actions or to achieve a number of given goals.
Owner:TELEFON AB LM ERICSSON (PUBL)
System and method for a web based trust model governing delivery of services and programs
InactiveUS6854016B1Broaden applicationDigital data processing detailsMultiple digital computer combinationsPartial applicationApplication software
A workflow, enterprise, and mail-enabled application server and platform supports distributed computing and remote execution of web applications. Lotus Domino Offline Services (DOLS) is used by a web site administrator to configure Internet Notes (iNotes) clients to auto download from server, thus providing iNotes clients with web access using HTTP with various browsers, and with local processing and replication. A local run time model comprises a hierarchy of models including object data store model, security model, indexing model, replication model, agent workflow model and mail model. DOLS provides a layered security model that allows flexibility for controlling access to all or part of an application. The highest level of security is managed through a database access control list (ACL). Further refinements within the security model provide access to specific documents, and their views, forms or folders, and include read access lists, write access lists, form access lists and readers and authors fields.
Owner:TREND MICRO INC
Programming interface for a componentized and extensible workflow model
InactiveUS20060074736A1Increase heightExtend the workflow modelResourcesExecution for user interfacesApplication programming interfaceTime aspect
Building a componentized workflow model via an application programming interface. Each step of the workflow is modeled as an activity that has metadata to describe design time aspects, compile time aspects, and runtime aspects of the workflow step. A user selects and arranges the activities to create the workflow via the application programming interfaces. The metadata associated with each of the activities in the workflow is collected to create a persistent representation of the workflow. Users extend the workflow model by authoring custom activities. Users also compile the workflow via the application programming interface.
Owner:MICROSOFT TECH LICENSING LLC
Ink-enabled workflow authoring
InactiveUS20060074735A1Increase heightExtend the workflow modelMultiprogramming arrangementsPayment architectureApplication programming interfaceDisplay device
An ink-enabled user interface for building a componentized workflow model. A touch screen display device allows each step of the workflow to be modeled as an activity that has metadata to describe design time aspects, compile time aspects, and runtime aspects of the workflow step. A user selects and arranges the activities via the touch screen device to create the workflow via user interfaces or application programming interfaces. The metadata associated with each of the activities in the workflow is collected to create a persistent representation of the workflow. Users extend the workflow model by authoring custom activities.
Owner:MICROSOFT TECH LICENSING LLC
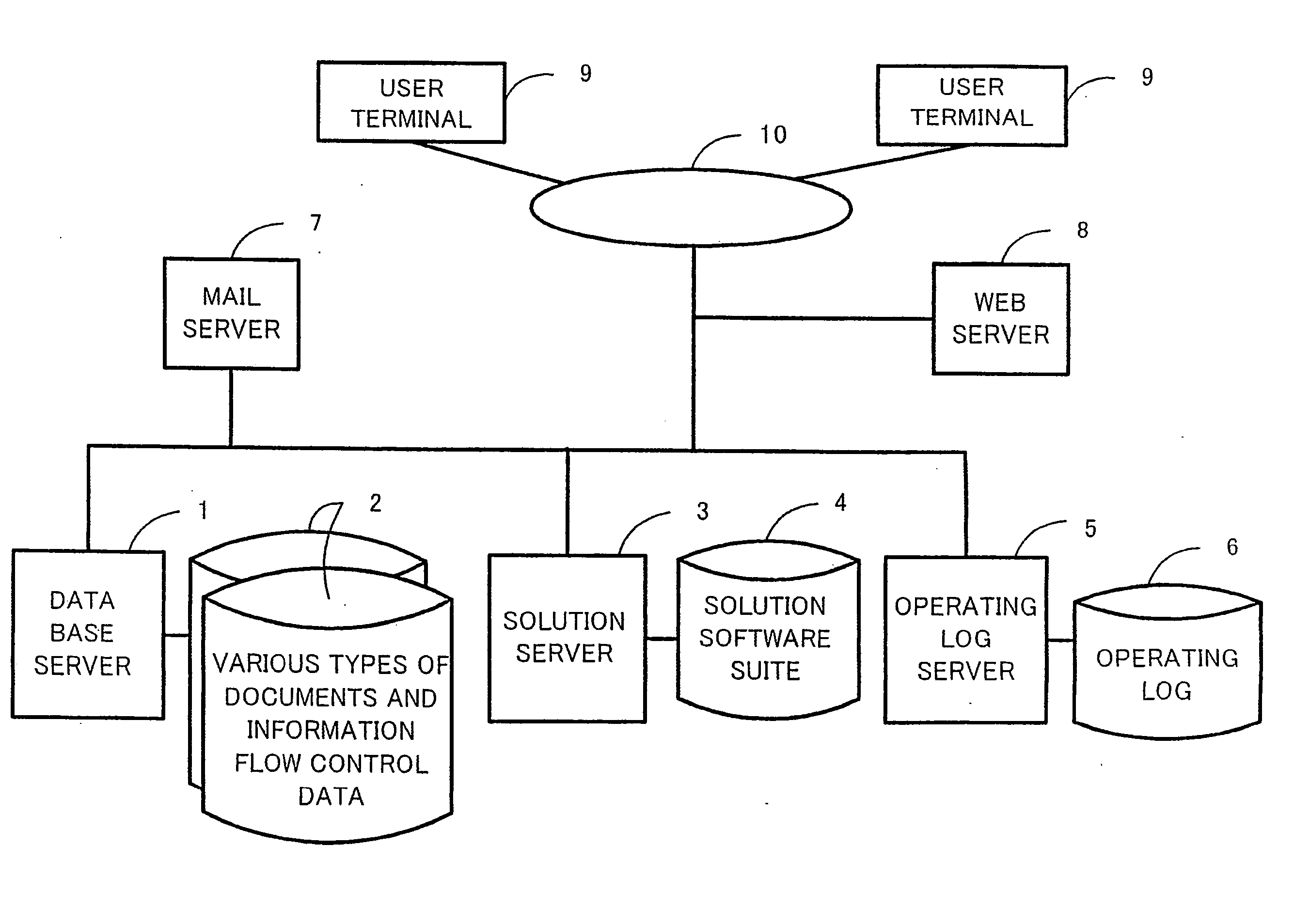
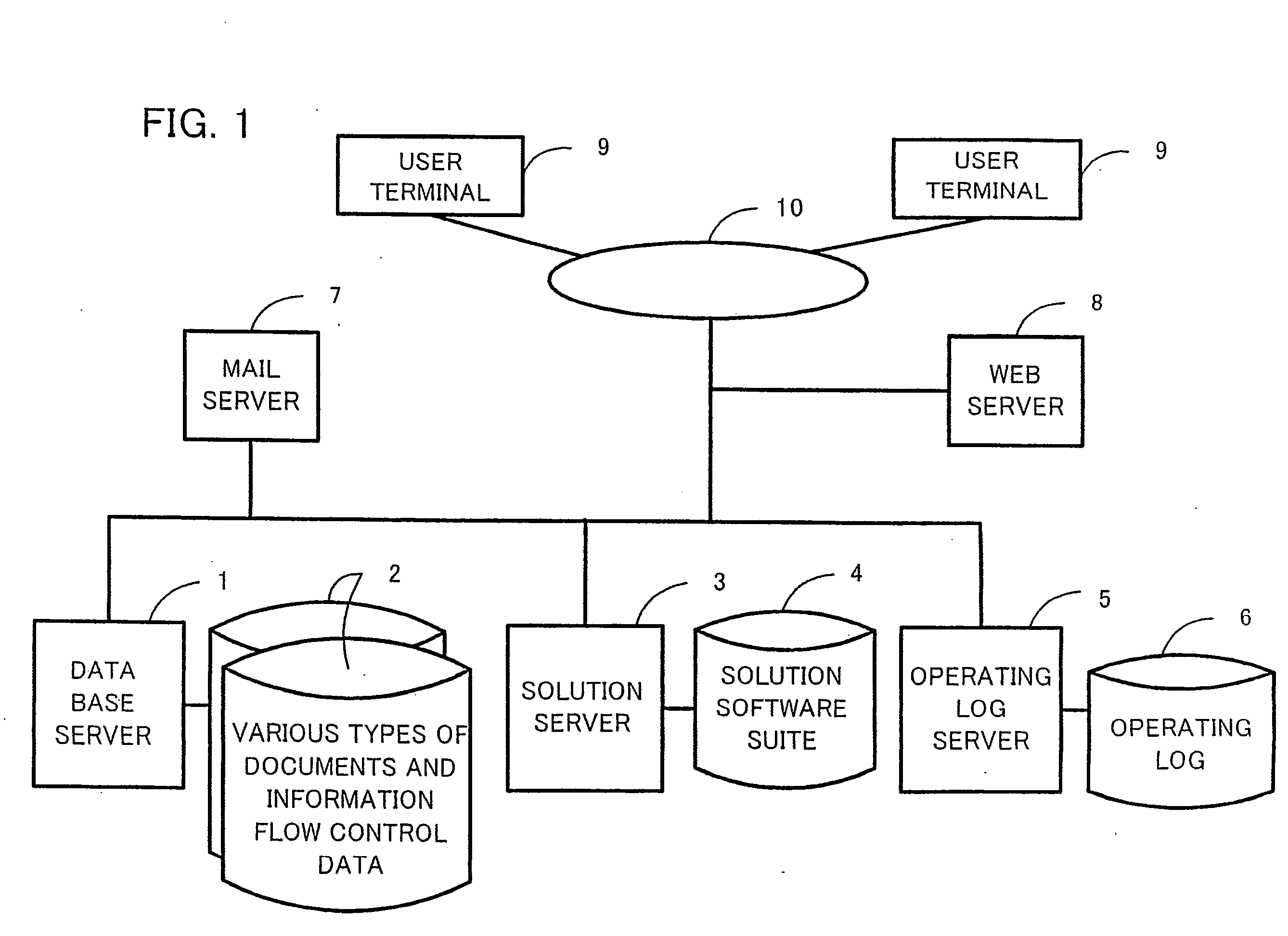
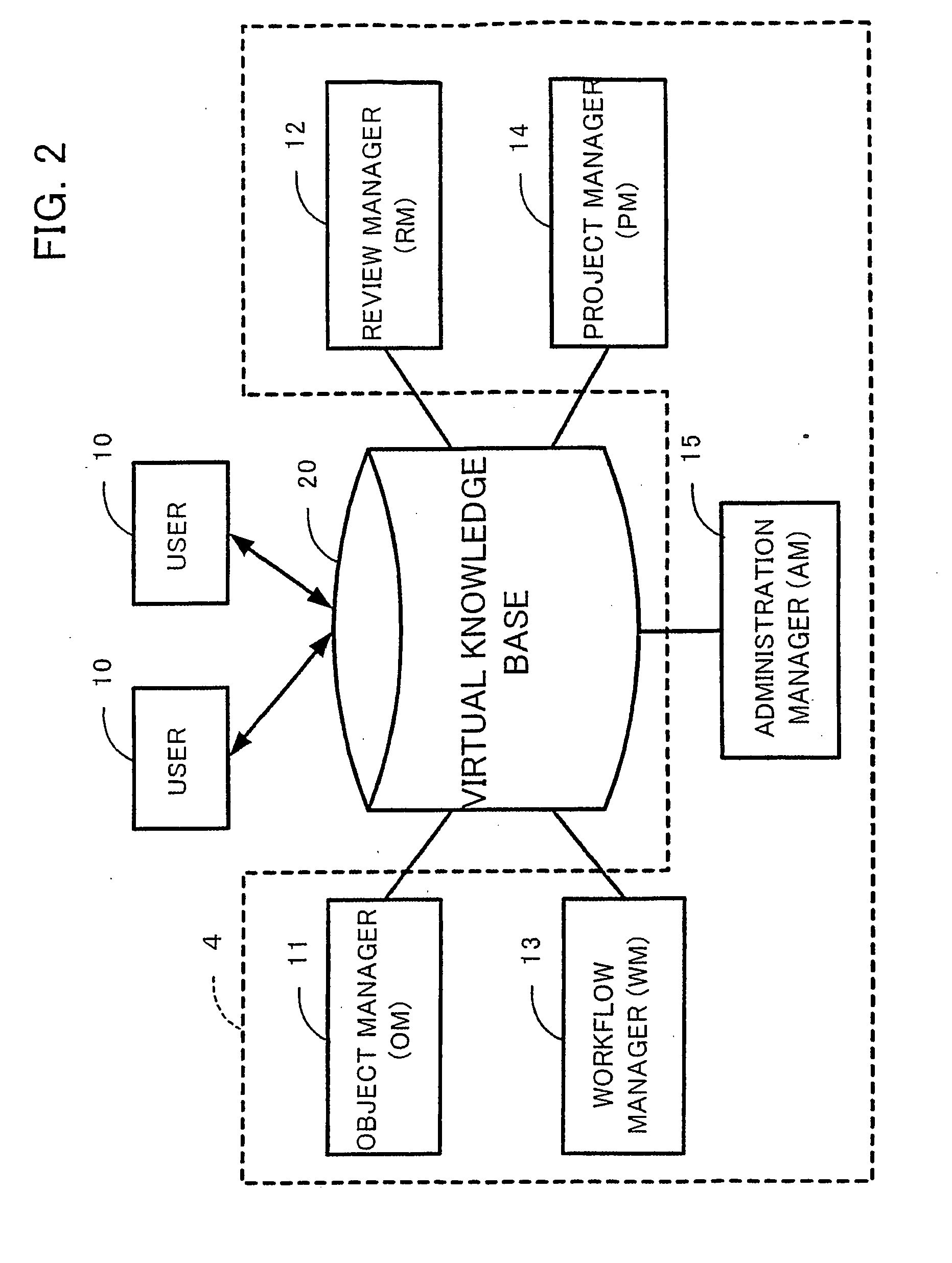
Virtual knowledge management system
InactiveUS20060111953A1Multiprogramming arrangementsOffice automationAutomatic controlDocument preparation
It is an object of the present invention to provide a virtual knowledge management system which controls the flow of information relating to the performance of business in an enterprise. The flow of information that is intensively administered by a virtual knowledge base 20 is automatically controlled on the basis of information flow control data 40 including document utilization authorization data, mail communications control data, workflow model data, project data and the like. The utilization of document objects by users is controlled in accordance with the document utilization authorization data. The forwarding of and reply to email messages among users is controlled in accordance with the mail communications control data. The order of work among a plurality of users involved in a certain business process is controlled in accordance with the workflow model data. The flow of information among a plurality of users involved in a certain project is controlled in accordance with the project data. The information flow control data 40 is configurable.
Owner:KNOWLEDGE IT CORP
Transformation of componentized and extensible workflow to a declarative format
InactiveUS7451432B2Extend the workflow modelMultiprogramming arrangementsOffice automationApplication programming interfaceApplication software
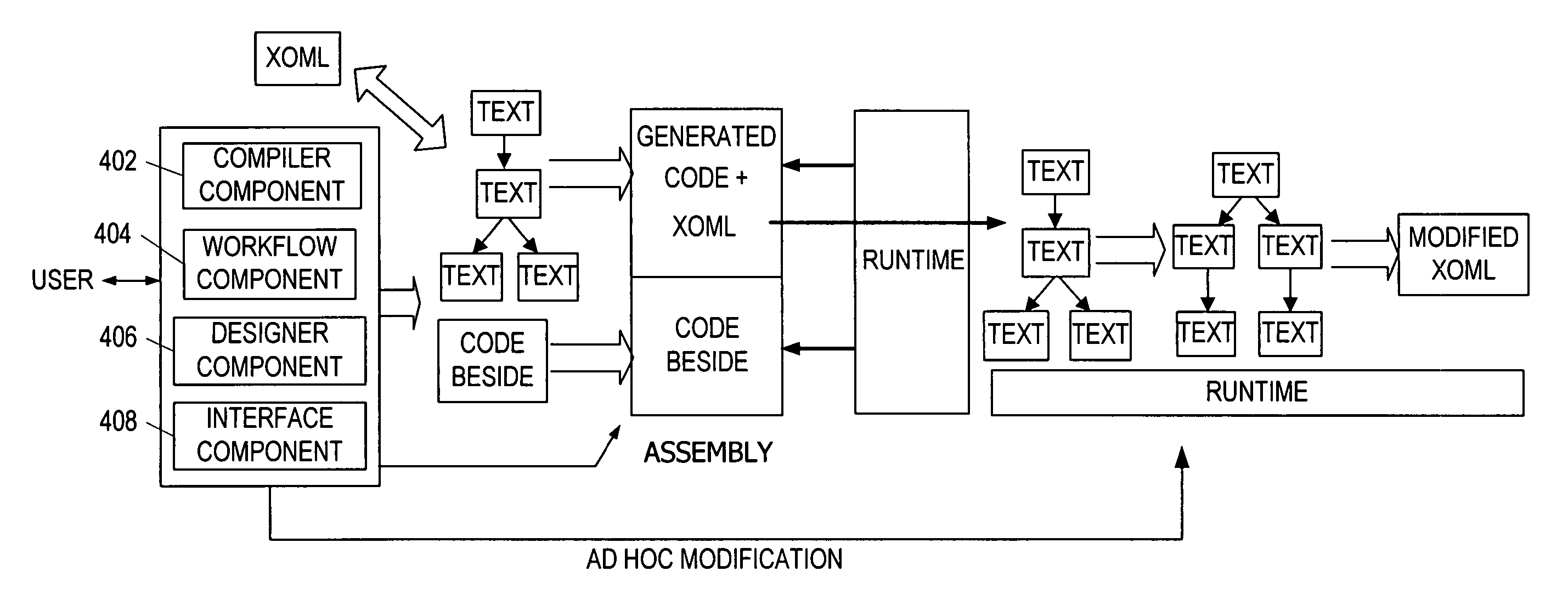
Building a componentized workflow model. Each step of the workflow is modeled as an activity that has metadata to describe design time aspects, compile time aspects, and runtime aspects of the workflow step. A user selects and arranges the activities to create the workflow via user interfaces or application programming interfaces. The metadata associated with each of the activities in the workflow is collected to create a persistent representation of the workflow. Users extend the workflow model by authoring custom activities. The workflow may be compiled and executed.
Owner:MICROSOFT TECH LICENSING LLC
Declarative representation for an extensible workflow model
InactiveUS20060074734A1Increase heightExtend the workflow modelProgram control using stored programsSoftware designApplication programming interfaceTime aspect
Representing a componentized workflow model via a declarative markup language. Each step of the workflow is modeled as an activity that has metadata to describe design time aspects, compile time aspects, and runtime aspects of the workflow step. A user selects and arranges the activities to create the workflow via user interfaces or application programming interfaces. The metadata associated with each of the activities in the workflow is collected to create a persistent representation of the workflow. Users extend the workflow model by authoring custom activities.
Owner:MICROSOFT TECH LICENSING LLC
Framework for seamlessly authoring and editing workflows at design and runtime
InactiveUS7565640B2Extend the workflow modelSoftware designResourcesApplication programming interfaceTime aspect
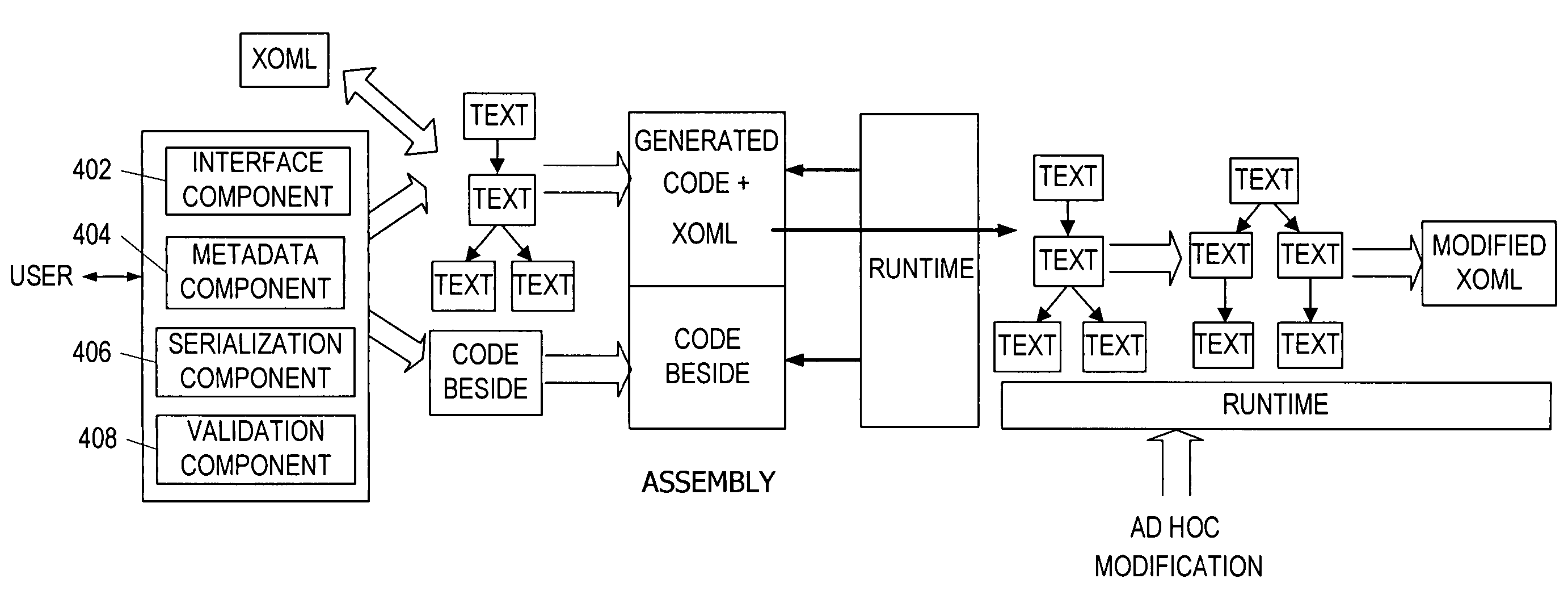
Modifying a componentized workflow model during execution of the workflow. Each step of the workflow is modeled as an activity that has metadata to describe design time aspects, compile time aspects, and runtime aspects of the workflow step. A user selects and arranges the activities to create the workflow via user interfaces or application programming interfaces. Metadata is associated with each of the activities in the workflow. During execution of the workflow, the user modifies the metadata to affect execution of the workflow without recompiling the workflow.
Owner:MICROSOFT TECH LICENSING LLC
Framework for seamlessly authoring and editing workflows at design and runtime
InactiveUS20060074733A1Increase heightExtend the workflow modelSoftware designResourcesApplication programming interfaceSoftware engineering
Modifying a componentized workflow model during execution of the workflow. Each step of the workflow is modeled as an activity that has metadata to describe design time aspects, compile time aspects, and runtime aspects of the workflow step. A user selects and arranges the activities to create the workflow via user interfaces or application programming interfaces. Metadata is associated with each of the activities in the workflow. During execution of the workflow, the user modifies the metadata to affect execution of the workflow without recompiling the workflow.
Owner:MICROSOFT TECH LICENSING LLC
Componentized and extensible workflow model
InactiveUS20060074732A1Extend the workflow modelMultiprogramming arrangementsOffice automationApplication programming interfaceTime aspect
Building a componentized workflow model. Each step of the workflow is modeled as an activity that has metadata to describe design time aspects, compile time aspects, and runtime aspects of the workflow step. A user selects and arranges the activities to create the workflow via user interfaces or application programming interfaces. The metadata associated with each of the activities in the workflow is collected to create a persistent representation of the workflow. Users extend the workflow model by authoring custom activities. The workflow may be compiled and executed.
Owner:MICROSOFT TECH LICENSING LLC
Declarative representation for an extensible workflow model
InactiveUS7631291B2Extend the workflow modelProgram control using stored programsSoftware designApplication programming interfaceSoftware engineering
Representing a componentized workflow model via a declarative markup language. Each step of the workflow is modeled as an activity that has metadata to describe design time aspects, compile time aspects, and runtime aspects of the workflow step. A user selects and arranges the activities to create the workflow via user interfaces or application programming interfaces. The metadata associated with each of the activities in the workflow is collected to create a persistent representation of the workflow. Users extend the workflow model by authoring custom activities.
Owner:MICROSOFT TECH LICENSING LLC
Programming interface for a componentized and extensible workflow model
InactiveUS7464366B2Extend the workflow modelResourcesExecution for user interfacesApplication programming interfaceTime aspect
Building a componentized workflow model via an application programming interface. Each step of the workflow is modeled as an activity that has metadata to describe design time aspects, compile time aspects, and runtime aspects of the workflow step. A user selects and arranges the activities to create the workflow via the application programming interfaces. The metadata associated with each of the activities in the workflow is collected to create a persistent representation of the workflow. Users extend the workflow model by authoring custom activities. Users also compile the workflow via the application programming interface.
Owner:MICROSOFT TECH LICENSING LLC
System and method for managing concurrent scheduled or on-demand replication of subscriptions
InactiveUS6845383B1Broaden applicationDigital data authenticationOffice automationPartial applicationApplication software
A workflow, enterprise, and mail-enabled application server and platform supports distributed computing and remote execution of web applications. Lotus Domino online services (DOLS) is used by a web site administrator to configure Internet Notes (iNotes) clients to auto download from server, thus providing iNotes clients with web access using HTTP with various browsers, and with local processing and replication. A local run time model comprises a hierarchy of models including object data store model, security model, indexing model, replication model, agent workflow model and mail model. DOLS provides a layered security model that allows flexibility for controlling access to all or part of an application. The highest level of security is managed through a database access control list (ACL). Further refinements within the security model provide access to specific documents, and their views, forms or folders, and include read access lists, write access lists, form access lists and readers and authors fields.
Owner:IBM CORP
System and method for developing and administering web applications and services from a workflow, enterprise, and mail-enabled web application server and platform
InactiveUS7219304B1Digital data processing detailsAnalogue secracy/subscription systemsDocumentation procedurePartial application
A workflow, enterprise, and mail-enabled application server and platform supports distributed computing and remote execution of web applications. Lotus Domino online services (DOLS) is used by a web site administrator to configure Internet Notes (iNotes) clients to auto download from server, thus providing iNotes clients with web access using HTTP with various browsers, and with local processing and replication. A local run time model comprises a hierarchy of models including object data store model, security model, indexing model, replication model, agent workflow model and mail model. DOLS provides a layered security model that allows flexibility for controlling access to all or part of an application. The highest level of security is managed through a database access control list (ACL). Further refinements within the security model provide access to specific documents, and their views, forms or folders, and include read access lists, write access lists, form access lists and readers and authors fields.
Owner:HCL TECH LTD
System and method for providing a distributable runtime
InactiveUS6742026B1Multiple digital computer combinationsTransmissionPartial applicationApplication software
A workflow, enterprise, and mail-enabled application server and platform supports distributed computing and remote execution of web applications. Lotus Domino online services (DOLS) is used by a web site administrator to configure Internet Notes (iNotes) clients to auto download from server, thus providing iNotes clients with web access using HTTP with various browsers, and with local processing and replication. A local run time model comprises a hierarchy of models including object data store model, security model, indexing model, replication model, agent workflow model and mail model. DOLS provides a layered security model that allows flexibility for controlling access to all or part of an application. The highest level of security is managed through a database access control list (ACL). Further refinements within the security model provide access to specific documents, and their views, forms or folders, and include read access lists, write access lists, form access lists and readers and authors fields.
Owner:IBM CORP
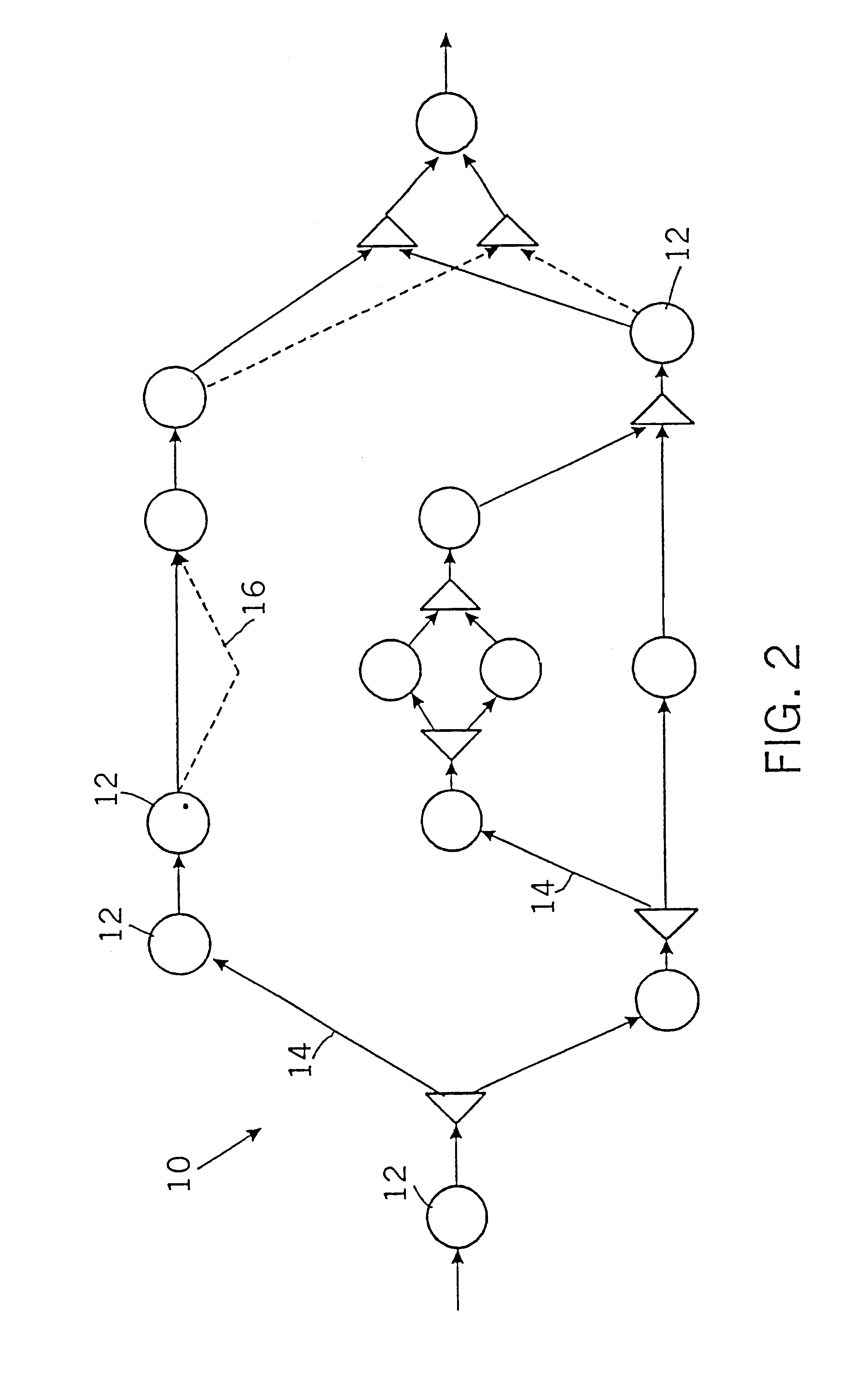
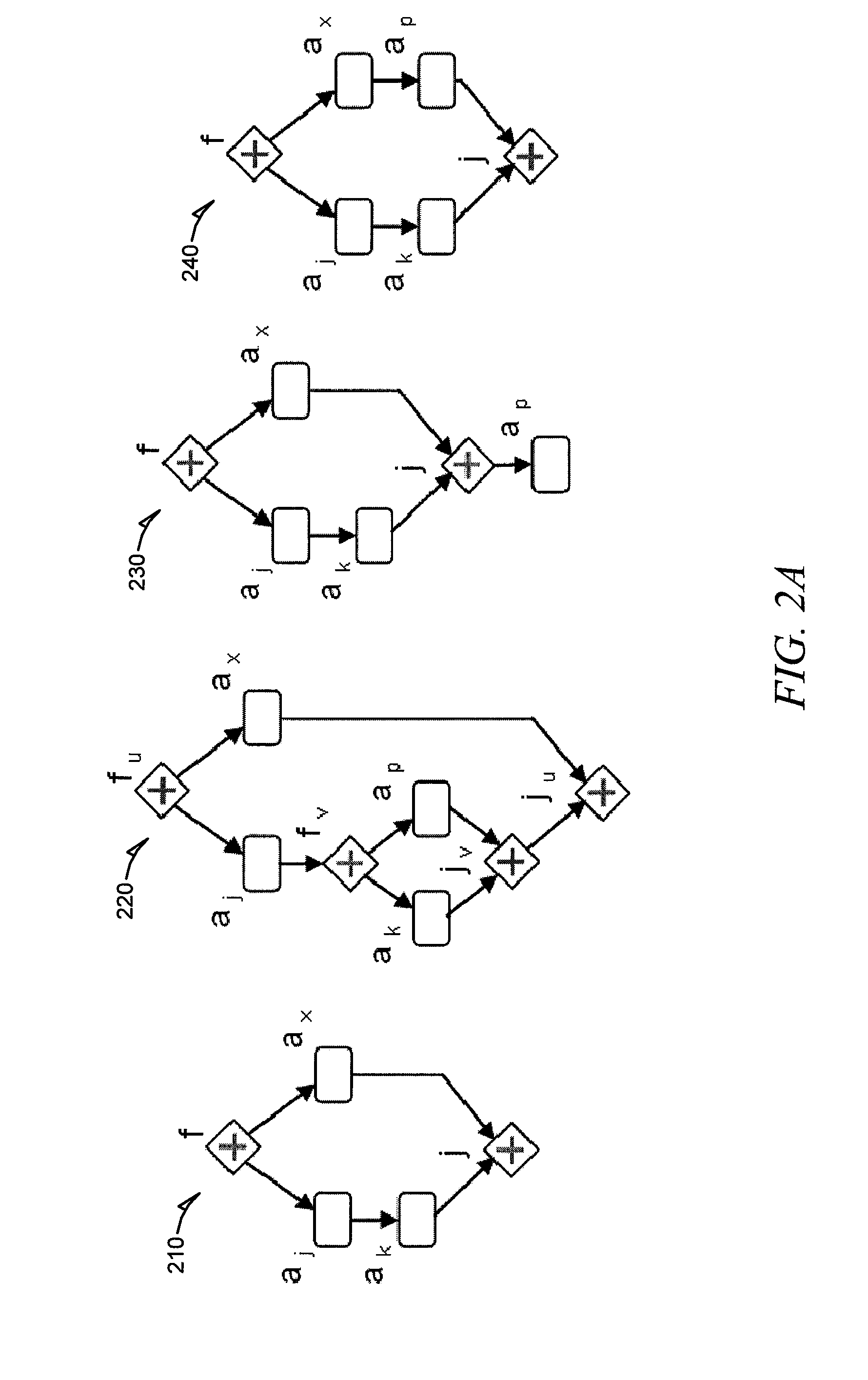
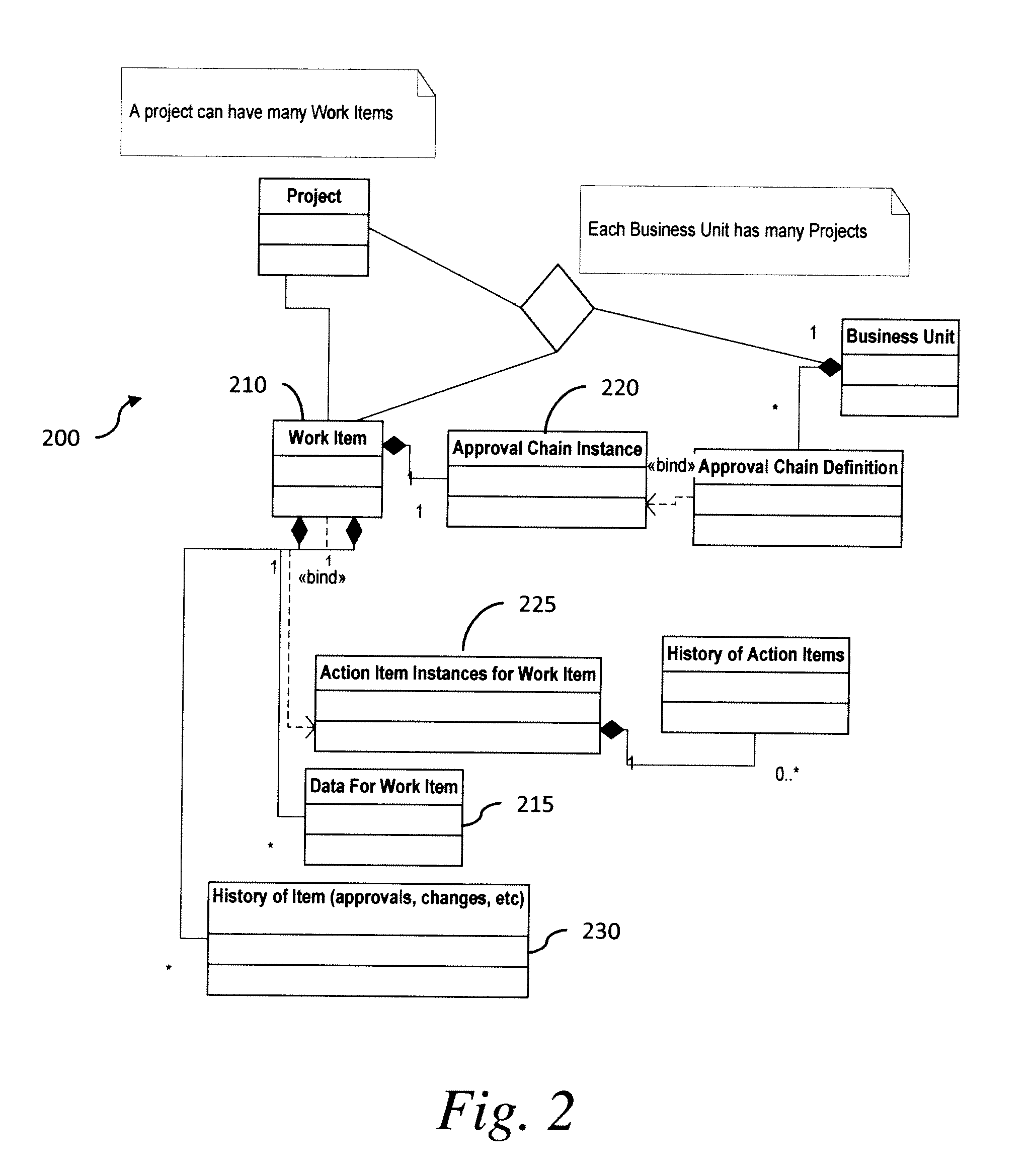
Workflow auto generation from user constraints and hierarchical dependence graphs for workflows
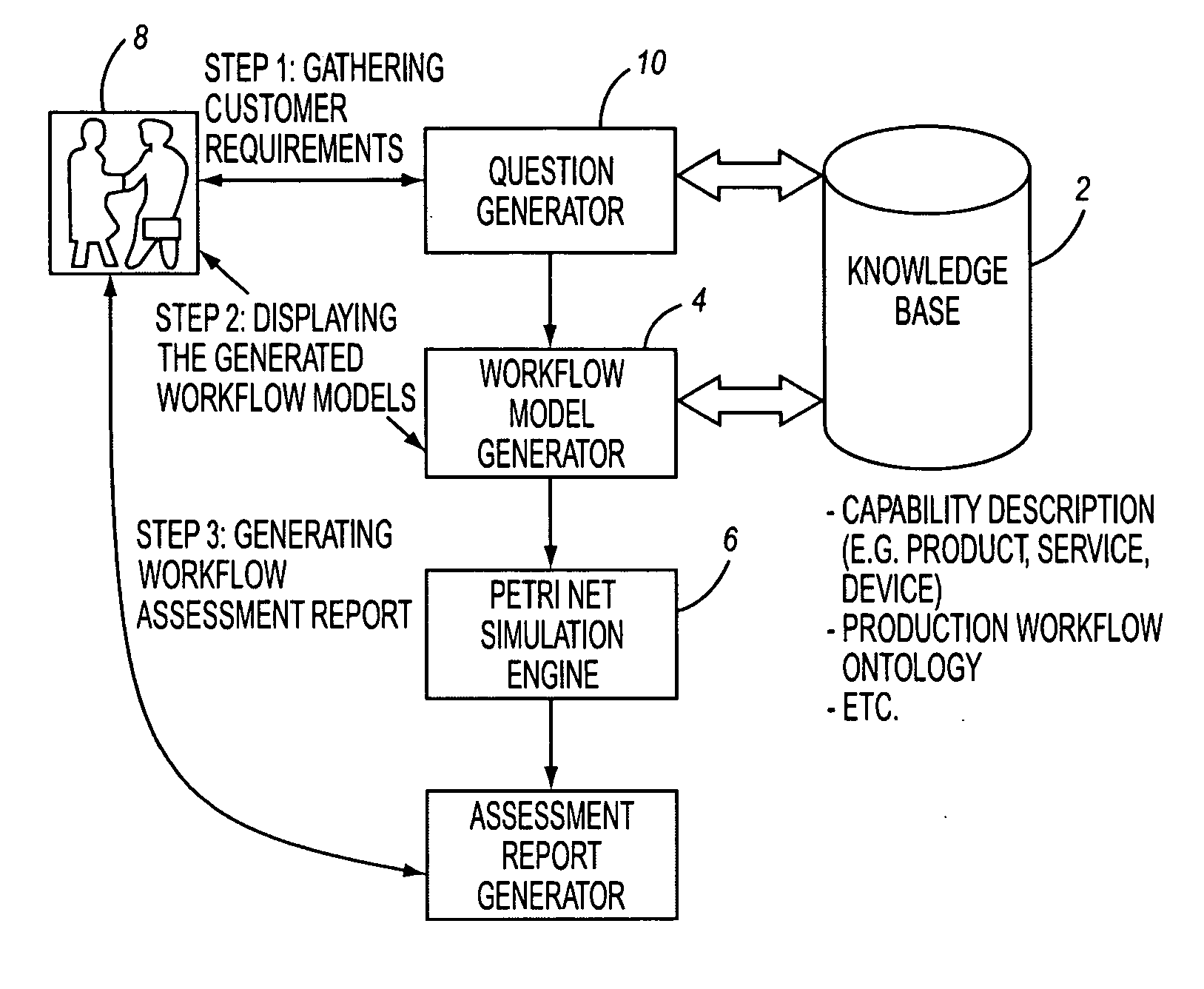
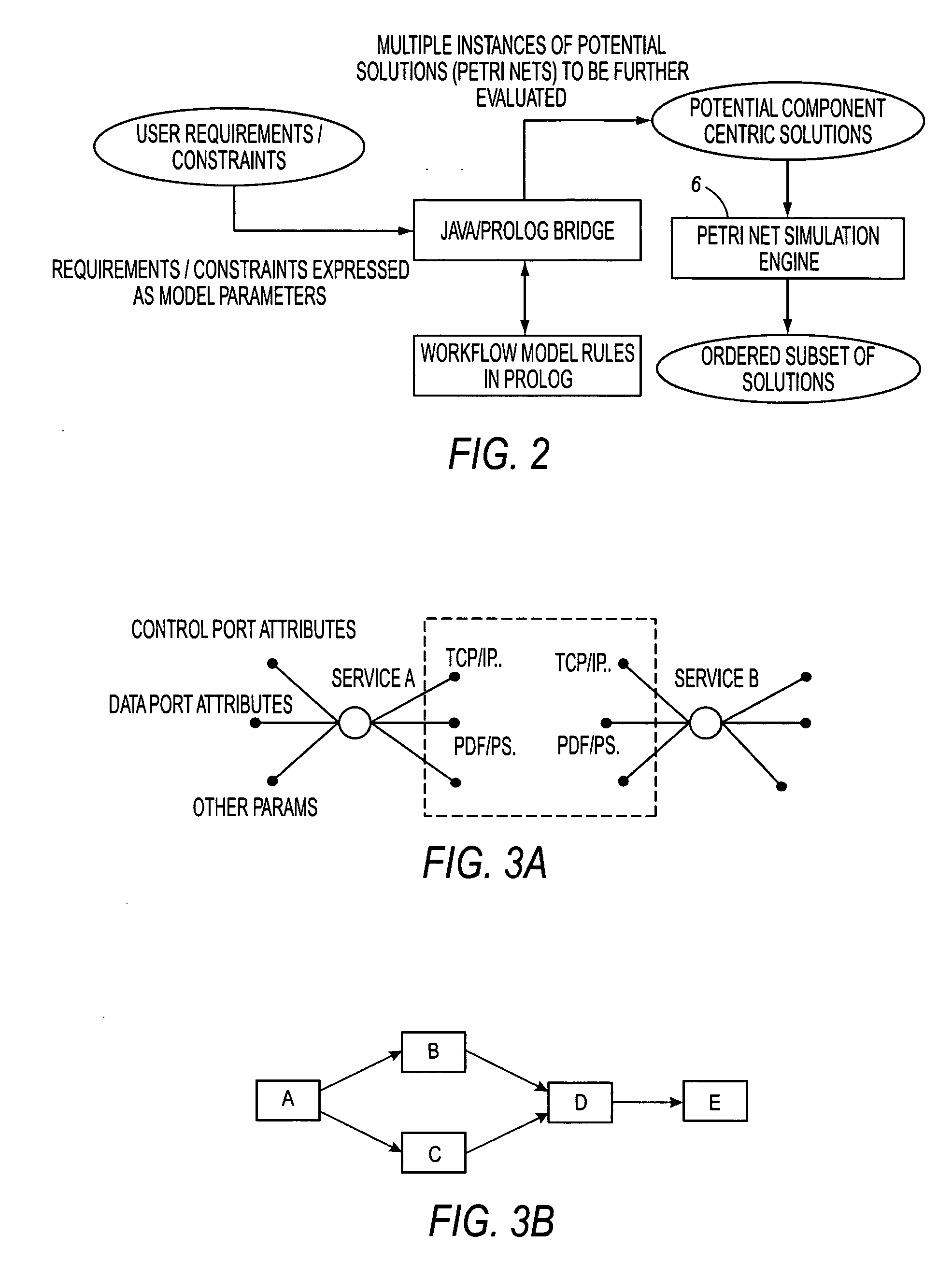
A system and method of automatically generating workflows. Generating the workflows is accomplished by obtaining customer requirements, providing a knowledge base including at least one service description and selecting at least one combination of service descriptions from the at least one service description based on satisfaction of the customer requirements and satisfaction of determination of connectivity between service descriptions for each combination of the at least one combination. At least one valid workflow model is generated by inference, each workflow model including a combination of the at least one combination.
Owner:XEROX CORP
Configurable workflow realization method and system
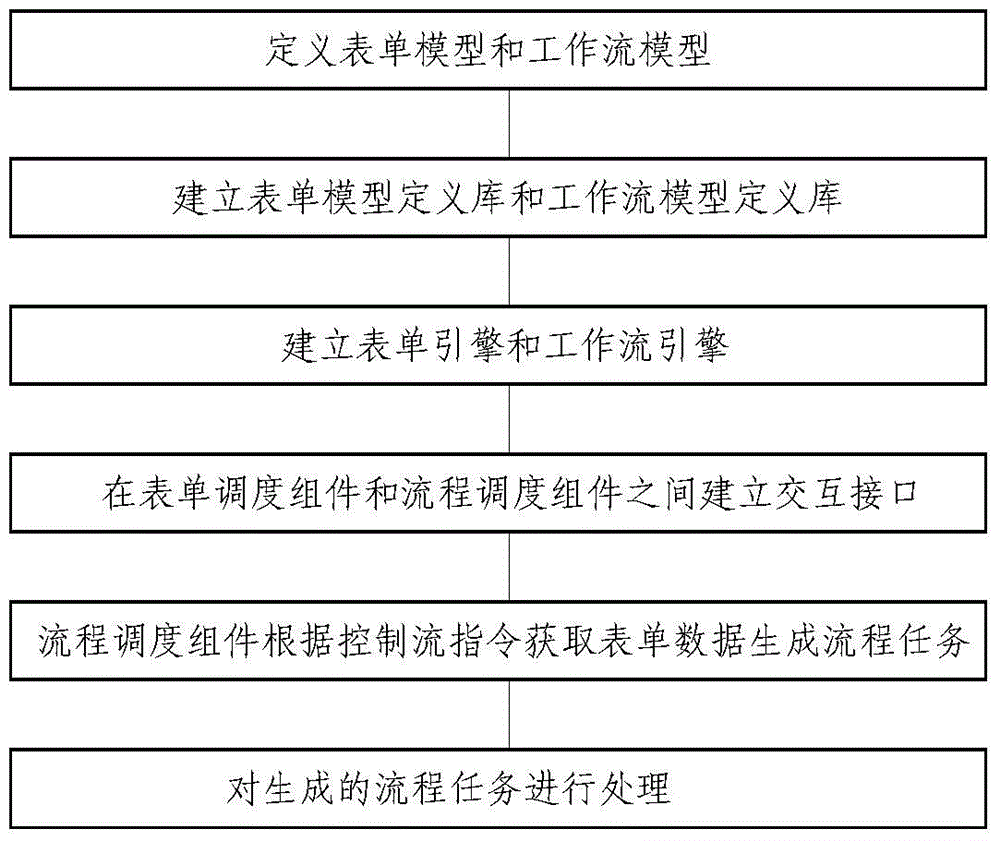
InactiveCN105046408AImplement customizationEfficient use ofResourcesControl flowSoftware engineering
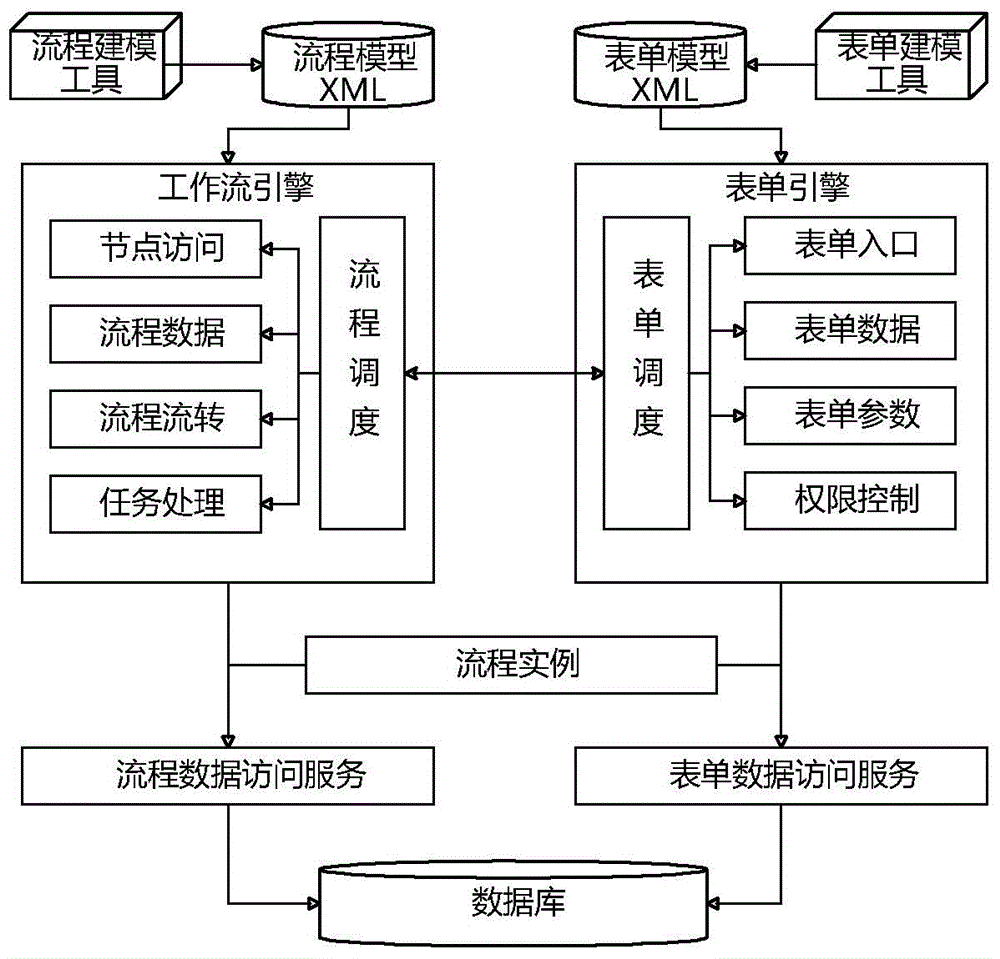
The invention discloses a configurable workflow realization method and system. The method comprises the following process that a table sheet model and a workflow model are defined; a table sheet model definition library and a workflow model definition library are established, and the defined table sheet model and the workflow model are respectively stored in the table sheet model definition library and the workflow model definition library; a table sheet engine and a workflow engine are established; an interactive interface is established between a table sheet scheduling component and a flow scheduling component so as to perform data interaction; the flow scheduling component acquires table sheet data via the interactive interface according to control flow instructions so as to generate a flow task; and the generated flow task is processed. The system comprises a table sheet modeling tool, a workflow modeling tool, the table sheet model definition library, the workflow model definition library, the table sheet engine component, the workflow engine component and a database. Table sheet and workflow customized definition is realized so that a conventional workflow framework is effectively utilized, and flexibility of flow circulation is also guaranteed simultaneously.
Owner:STATE GRID SHANDONG ELECTRIC POWER
Visualization rapid developing platform based on jbpm workflow engine
ActiveCN105700888AConvenient and fast process customization functionReduce development costsSoftware designSpecific program execution arrangementsGraphicsApplication server
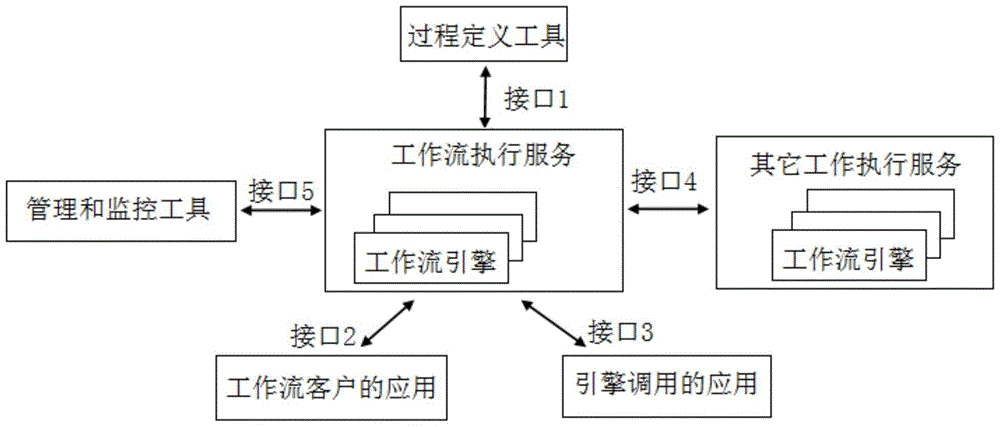
The invention discloses a visualization rapid developing platform based on a jbpm workflow engine; the visualization rapid developing platform comprises the following elements: an information configuration module used for checking configuration data source and application server information and configuration statistics monitor information, and the module is connected with a workflow configuration module and a management monitor module; the workflow configuration module used for customizing workflow business, using dragging to build a workflow model, and displaying the workflow in a figure mode; the management monitor module used for monitoring and checking running workflow embodiments, modifying running state of present workflow embodiment, and connecting a client server through an interface module; a process definition module used for providing means for a user to analyze and model the business process, and generating a process definition capable of being recognized and processed by a computer. The visualization rapid developing platform provides services for the business system as an independent product, and provides the convenient and fast visualization workflow customization function for the user, thus reducing developing and maintaining cost.
Owner:STATE GRID SHANDONG ELECTRIC POWER
Method and system for improving workflow performance in workflow application systems
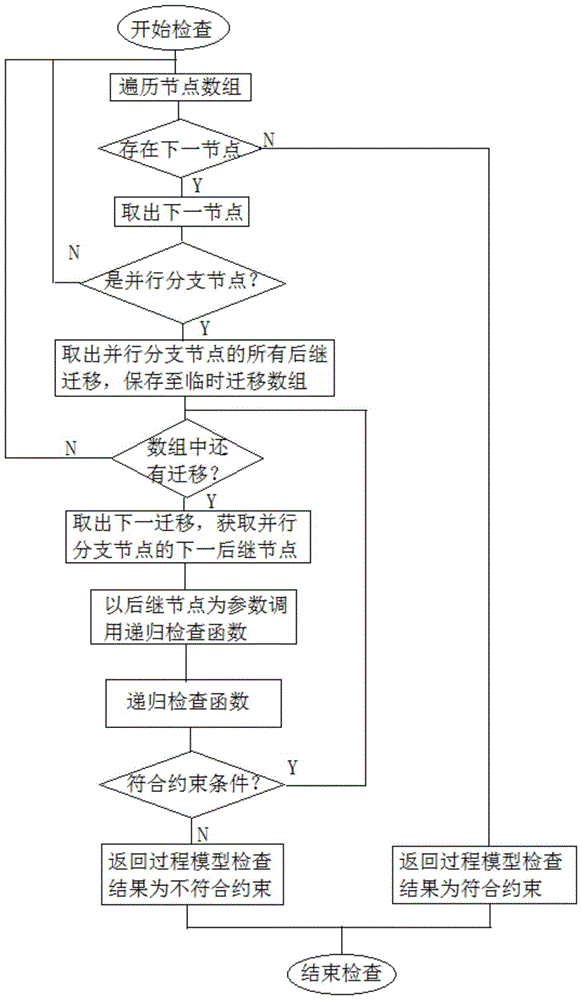
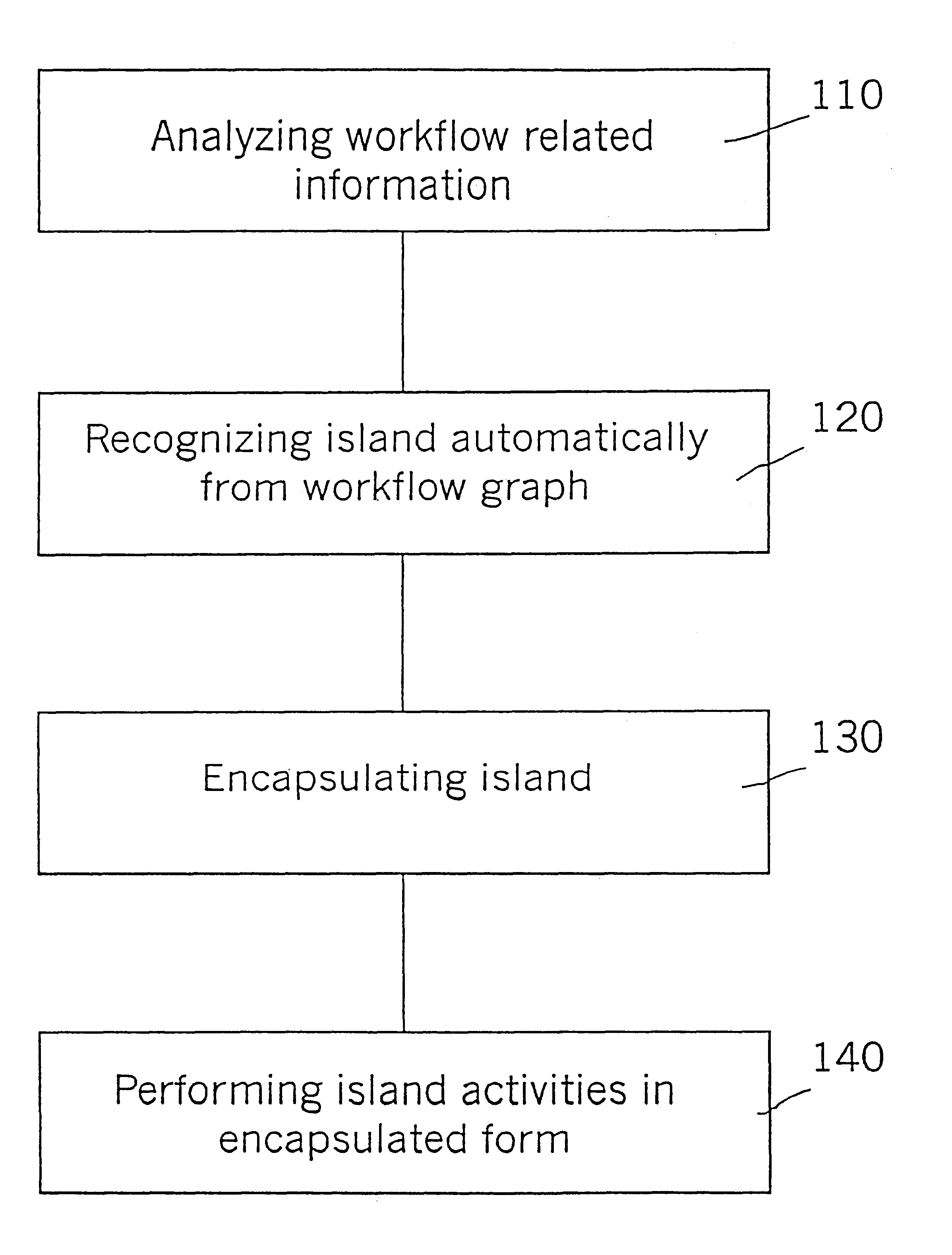
InactiveUS6816902B1Optimize workflowImprove performanceDigital computer detailsMultiprogramming arrangementsSoftware engineeringWorkstation
The invention identifies areas in a workflow graph that operate on one workstation-islands that can execute also remote from a central workflow server. Such a remote workstation can even operate physically disconnected from a central server during the interpretation / execution of the island. The workflow model is analyzed and those parts that are defined for execution on one specific workstation are encapsulated. Those parts, called "islands" can be interpreted or executed on the central workflow server, or can be downloaded from the server to a specific remote client workstation. Additionally, the islands in the workflow graph can optionally be transformed, either at the server or after downloading at the destination workstations, towards much more efficiently executable versions of the islands.
Owner:IBM CORP
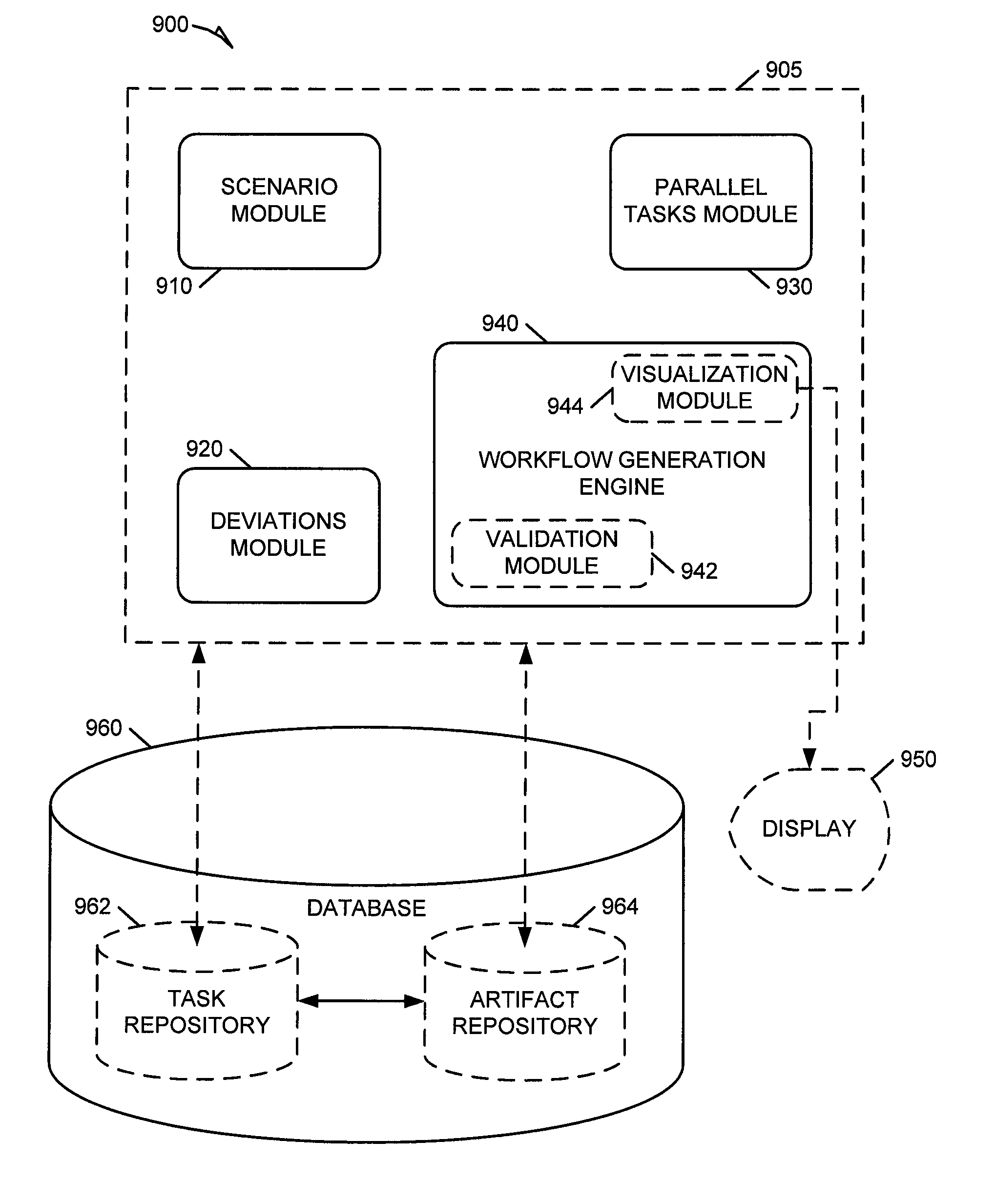
Systems and methods for scenario-based process modeling
Methods and systems for scenario-based process modeling are described. In one example embodiment, a system for scenario-based process modeling can include a scenario module, a deviations module, a parallel tasks module, and a workflow generation engine. The scenario module is to receive a series of tasks to define a standard process flow. The deviations module is to receive a deviation from the standard process flow. The parallel tasks module is to enable identification of one or more parallel tasks. The workflow generation engine is to generate a workflow model based on the standard process flow, deviation, and one or more parallel tasks.
Owner:SAP AG
System and method for downloading security context elements governing execution of downloadable and distributable agents
ActiveUS7360082B1Optimize workflowSynchronising transmission/receiving encryption devicesUser identity/authority verificationPartial applicationApplication software
A workflow, enterprise, and mail-enabled application server and platform supports distributed computing and remote execution of web applications. Lotus Domino online services (DOLS) is used by a web site administrator to configure Internet Notes (iNotes) clients to auto download from server, thus providing iNotes clients with web access using HTTP with various browsers, and with local processing and replication. A local run time model comprises a hierarchy of models including object data store model, security model, indexing model, replication model, agent workflow model and mail model. DOLS provides a layered security model that allows flexibility for controlling access to all or part of an application. The highest level of security is managed through a database access control list (ACL). Further refinements within the security model provide access to specific documents, and their views, forms or folders, and include read access lists, write access lists, form access lists and readers and authors fields.
Owner:GOOGLE LLC
Approach and tool blending ad-hoc and formal workflow models in support of different stakeholder needs
Owner:SIEMENS AG
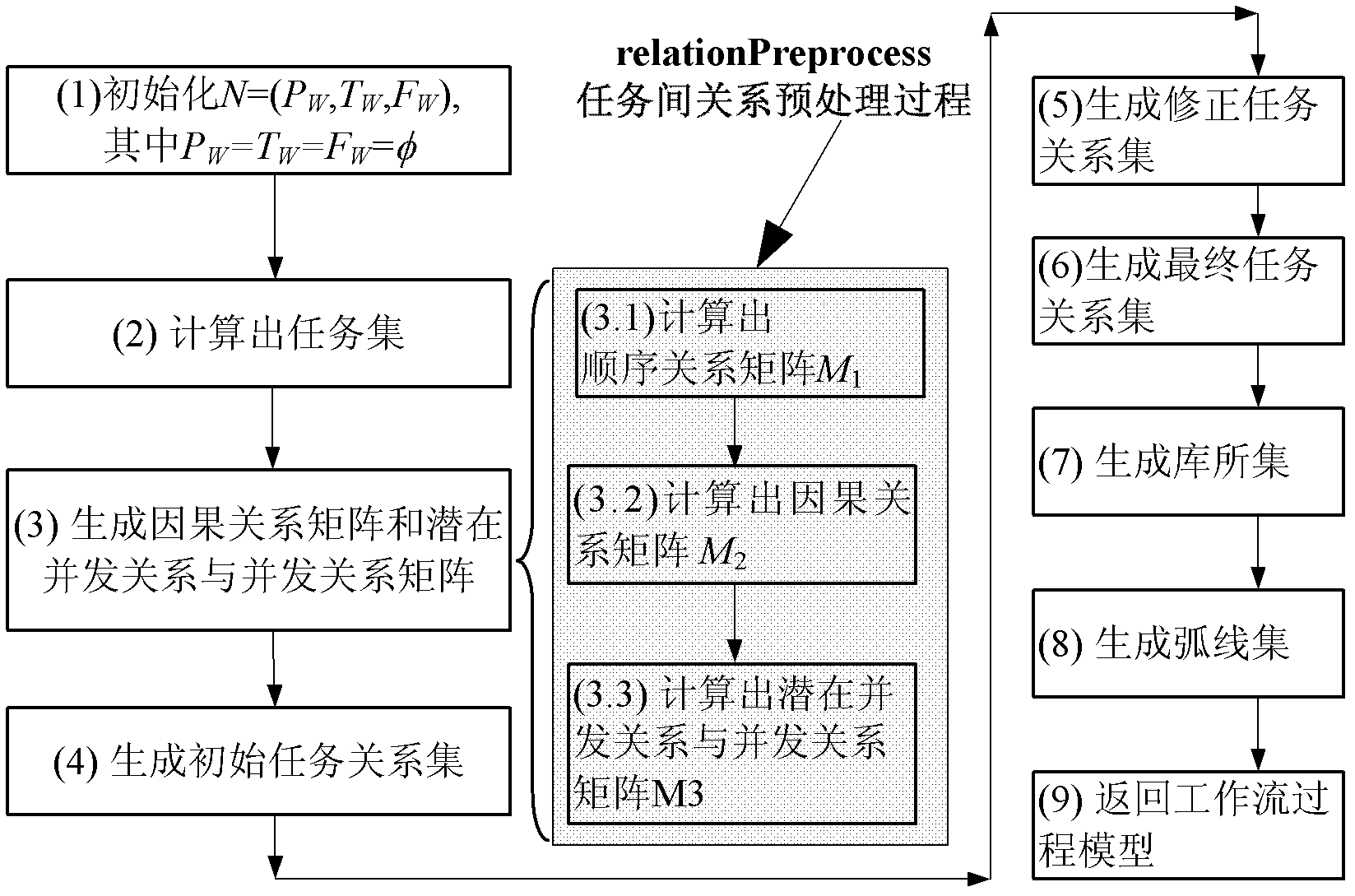
Workflow mining method based on subsequent tasks
InactiveCN102332125AImprove digging abilitySimplify dependenciesInstrumentsEvent typeCausal relations
The invention discloses a workflow mining method based on subsequent tasks. The workflow mining based on an event log takes the event log as an input and takes a workflow model described by a Petri network as an output result; by the method, event types are introduced to ensure that the workflow log comprises a subsequent task of the current task, and the subsequent task refers to an aggregate of the tasks to which an execute permission is transferred after the current task is finished; and the method comprises the following steps of: (1) setting an initial value for a workflow process model to be mined; (2) analyzing the event log W, and calculating a task set TW, an initial task and an end task TO; (3) calling a relation Preprocess process to obtain a causal relation matrix M2 and a potential concurrency relation and concurrency relation matrix M3; and (4) calculating an initial task relation set XW according to the matrixes M2 and M3. By the invention, an integrated workflow mining method based on the subsequent tasks is formed.
Owner:NANJING UNIV
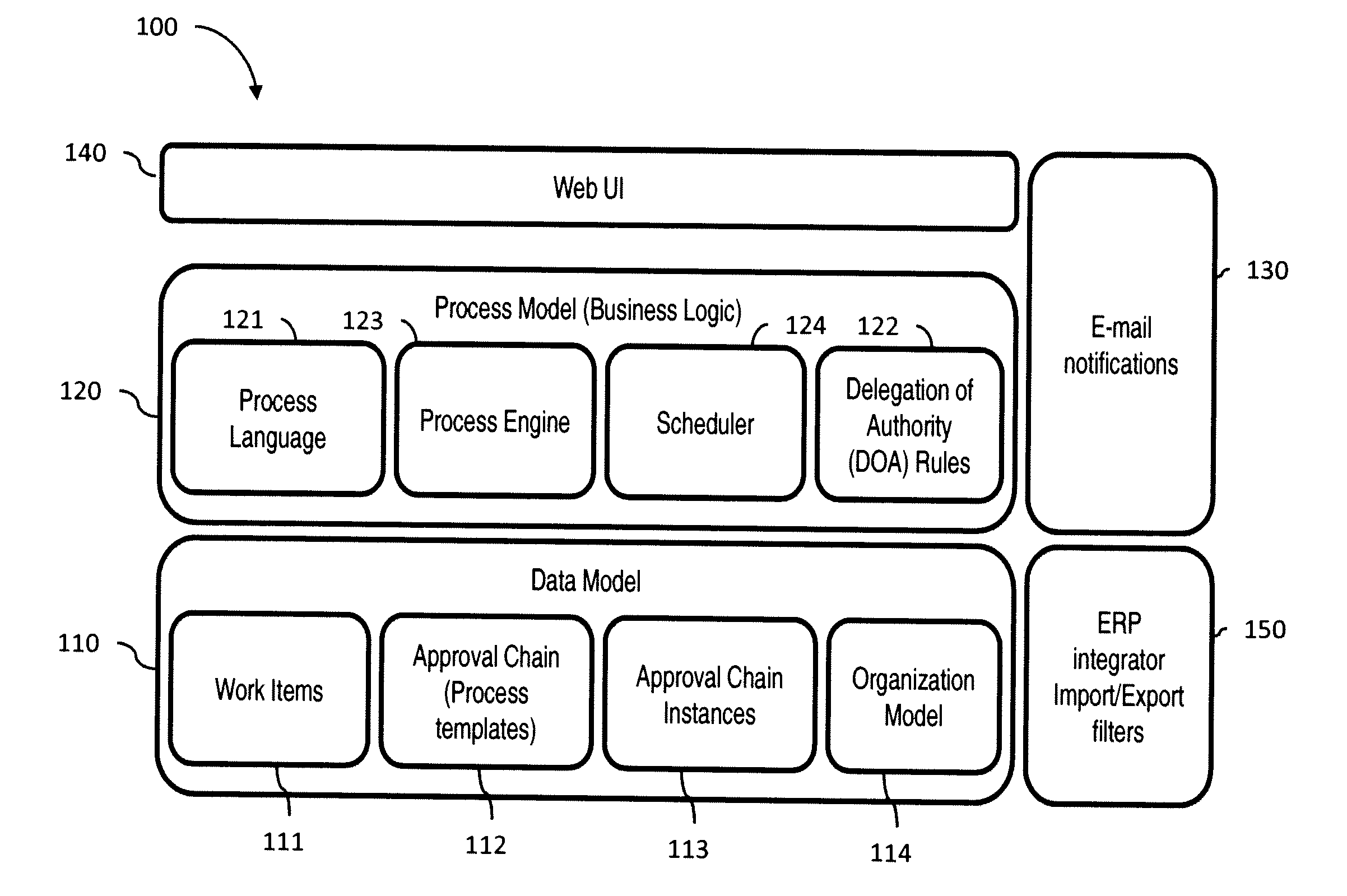
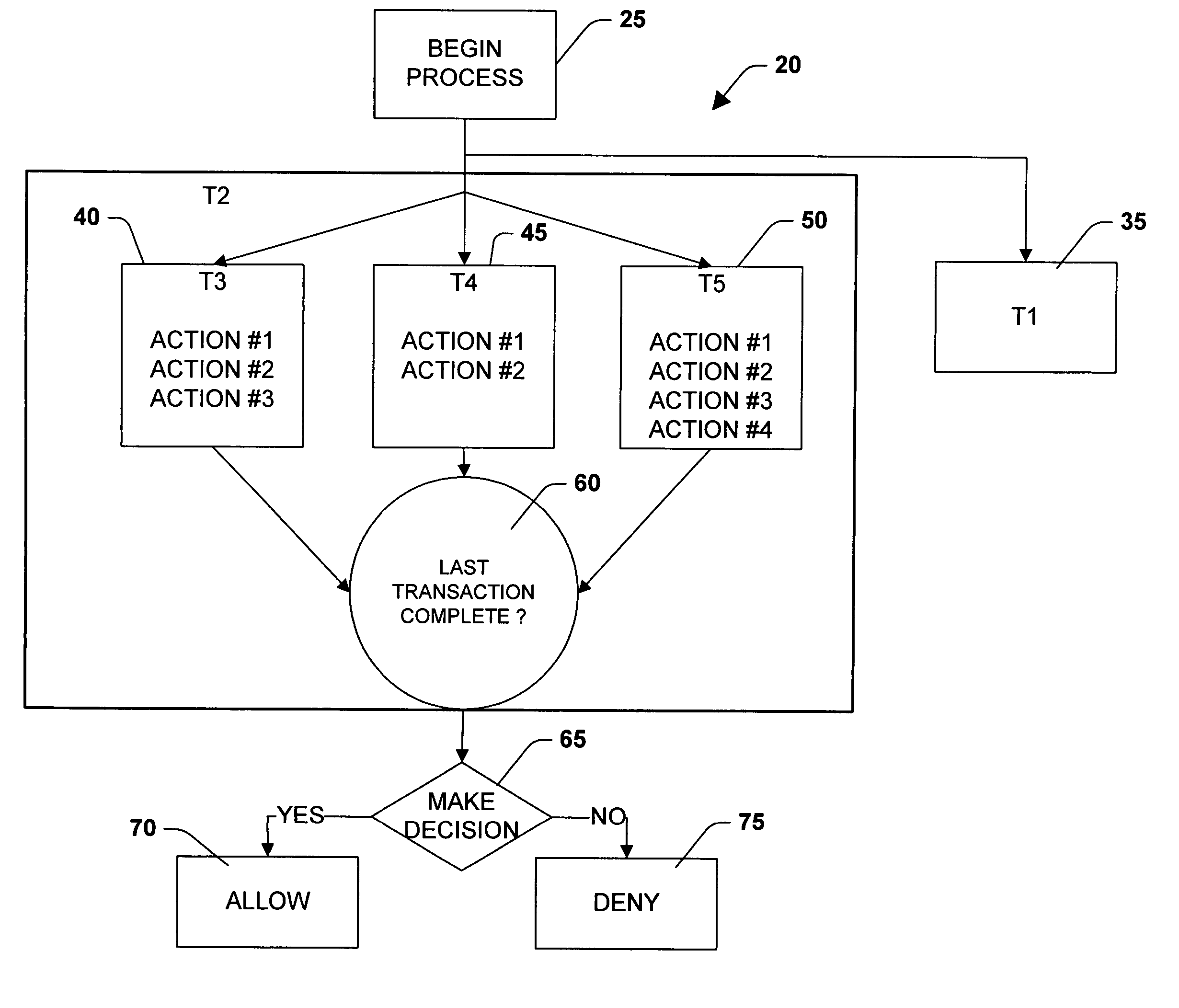
Model for business workflow processes
InactiveUS20050234902A1Easy to optimizeEasy to processDigital data processing detailsNatural language data processingSoftware engineeringBusiness process
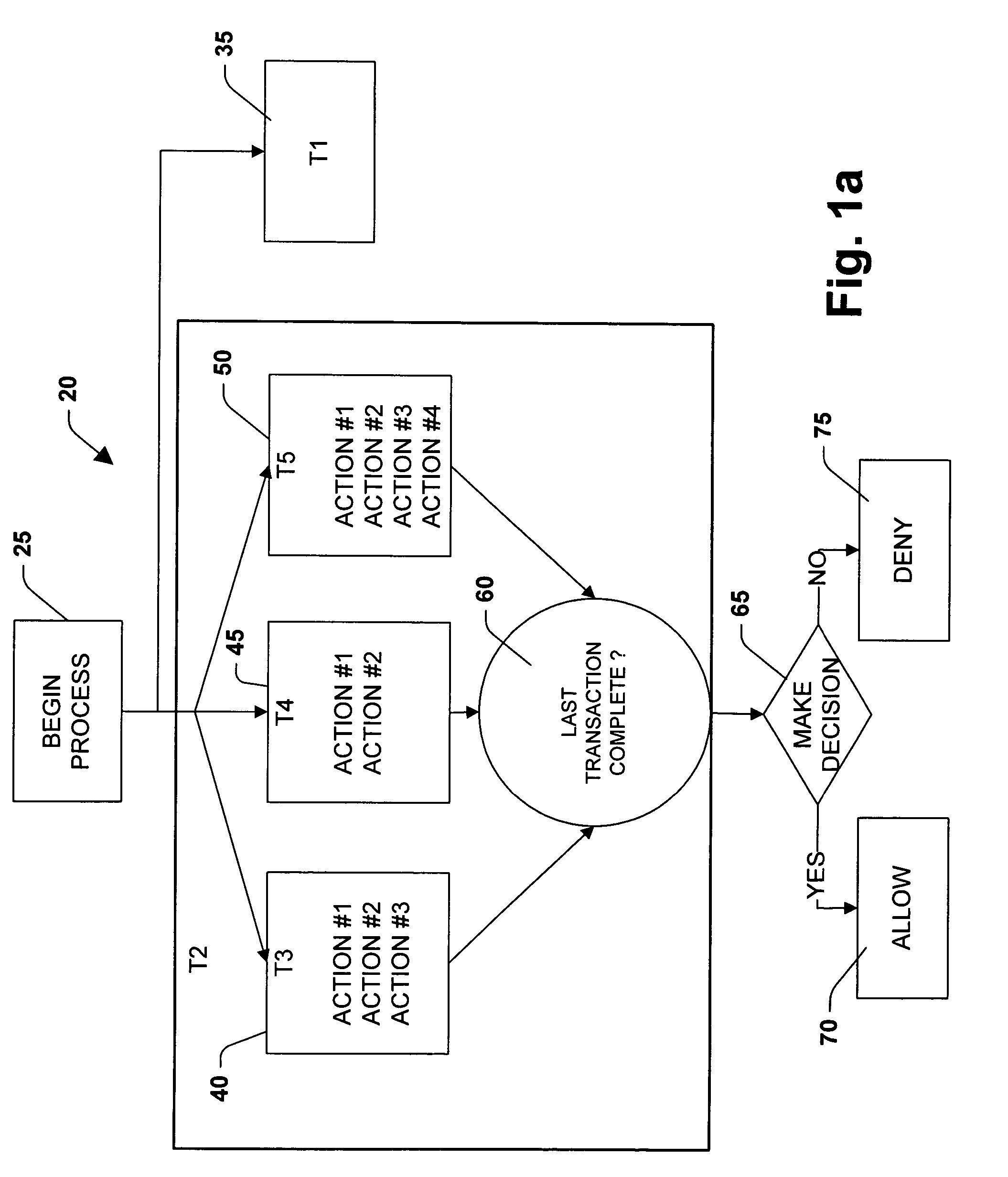
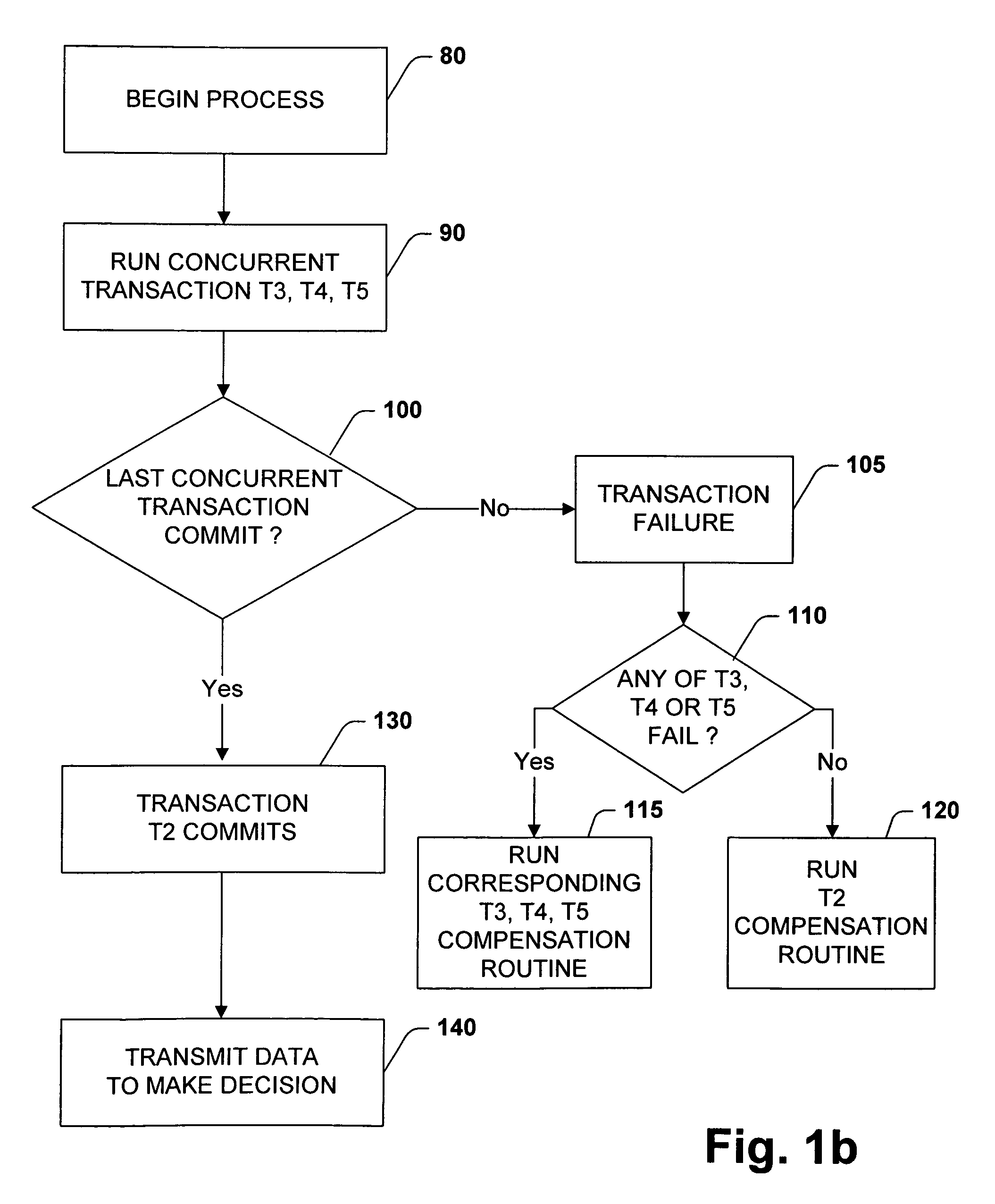
A methodology of reducing process algebra to a language that facilitates modeling a business workflow process is provided. A process algebra is reduced to a model for business workflow processes. The model is then reduced to a scheduling programming language to allow users to create models of business process by selecting between features of the model and conventional modeling features. The scheduling programming language can be represented as a graphical user interface program that is convertible to a schedule language written in a programmable language. The present invention provides for explicitly representing parallelism within the business workflow process by separating interdependent transactions from independent transactions. The isolation of certain transactions are relaxed, such that users can define transactional boundaries in order to increase granularity of the transaction at an action level and provide visibility of transactions at intermediate steps.
Owner:MICROSOFT TECH LICENSING LLC
System and Method for Generating a Service Oriented Data Composition Architecture for Integrated Asset Management
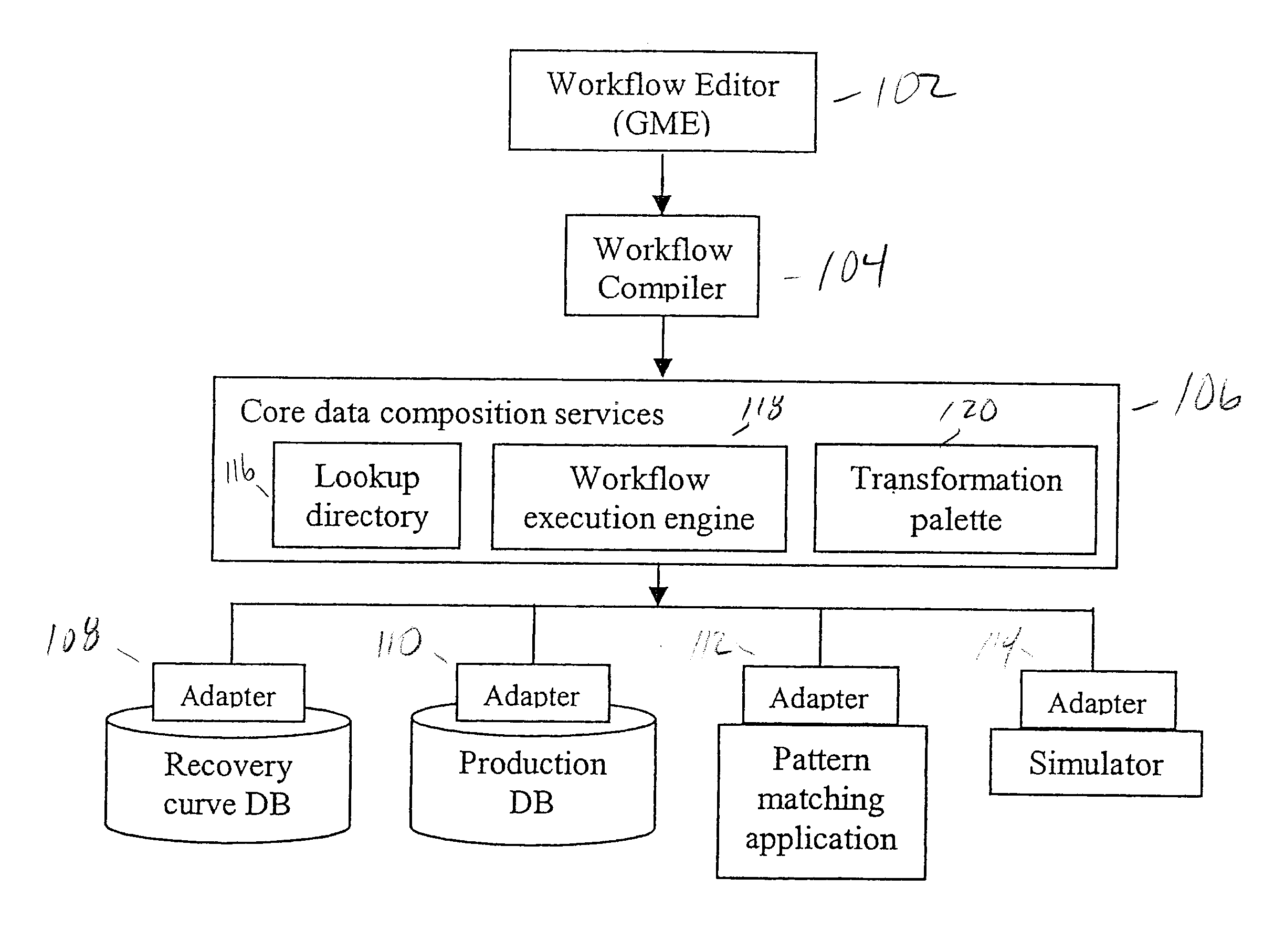
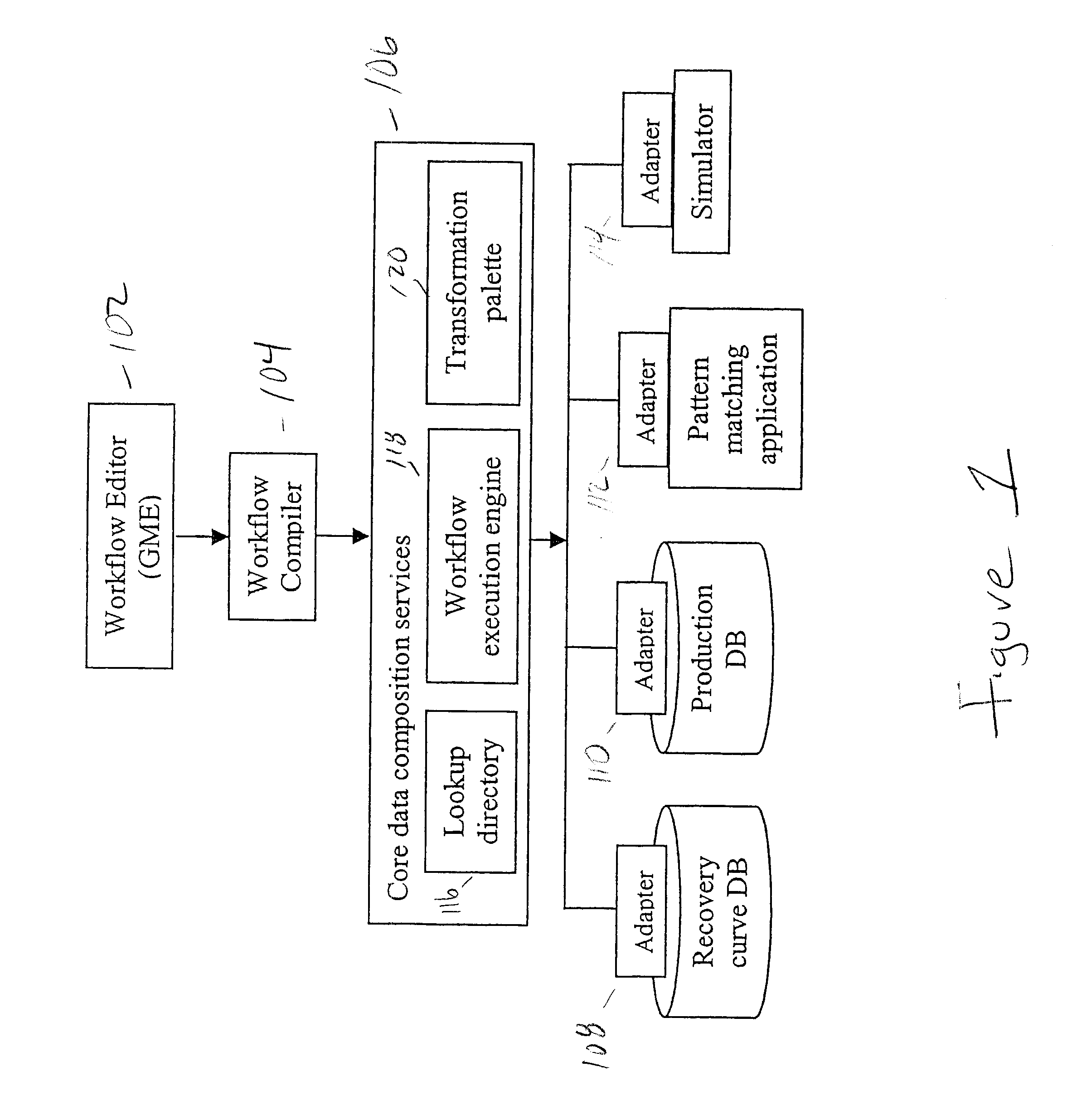
Systems and methods are directed to modeling an asset in an integrated asset management framework. To model the asset an interface generates a workflow through a plurality of domain objects associated with the asset. A directory manages a mapping of services to the plurality of domain objects, and a compiler generates a schedule of service calls based on the mapping of services to the domain objects in the directory. A workflow engine executes the schedule of service calls to produce a workflow model of the asset.
Owner:UNIV OF SOUTHERN CALIFORNIA +1
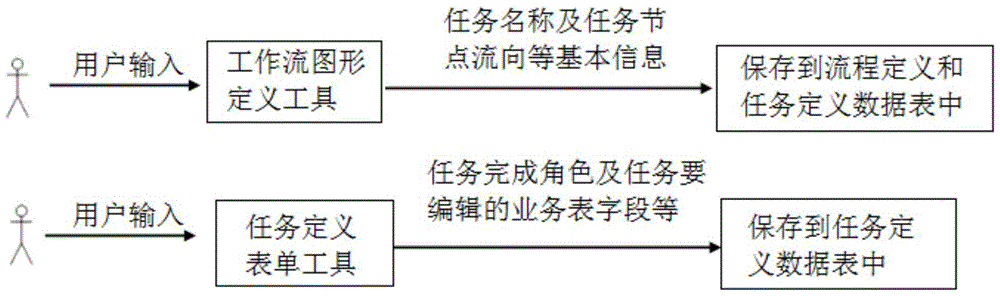
Method for automatically generating form for workflow model
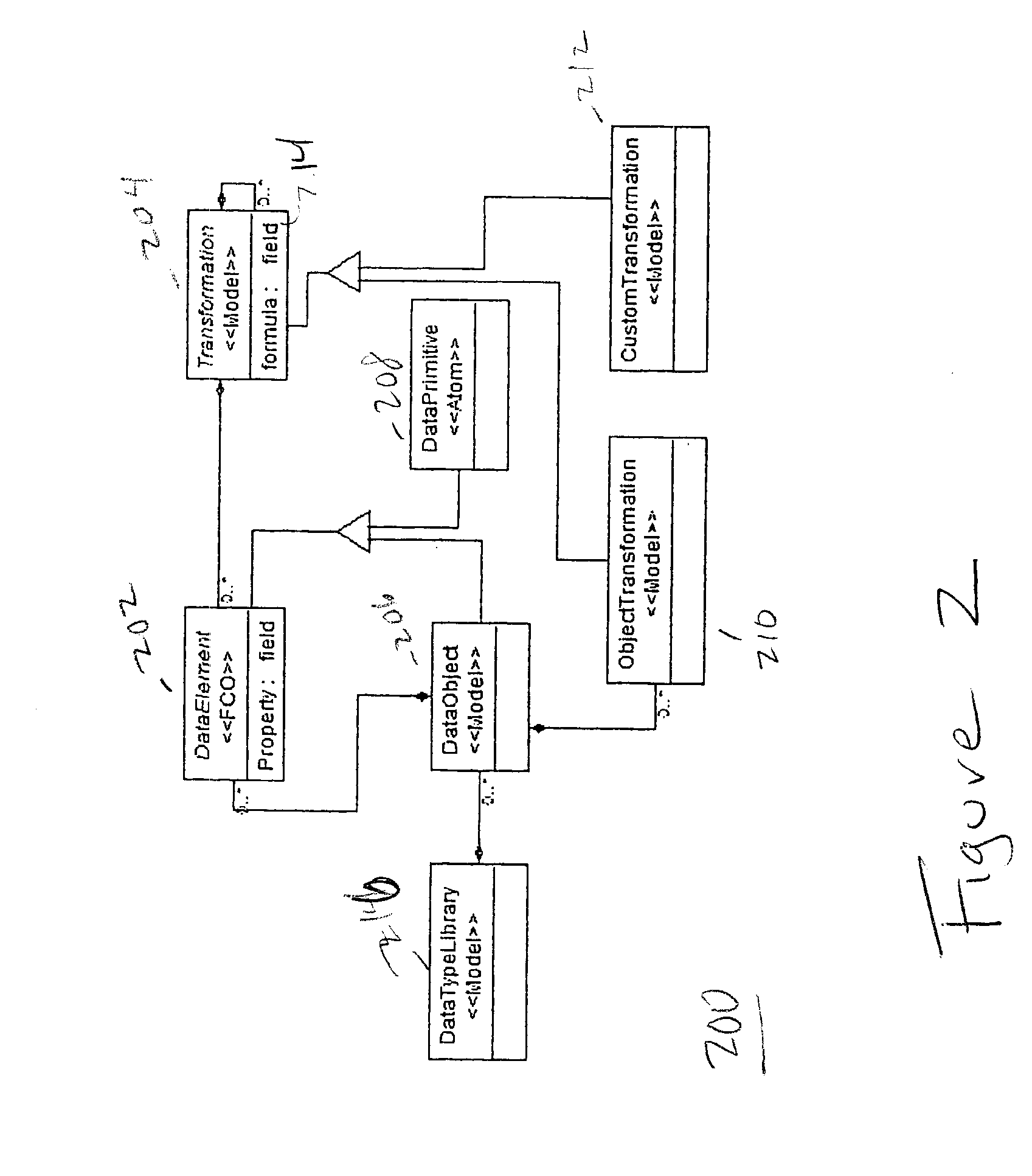
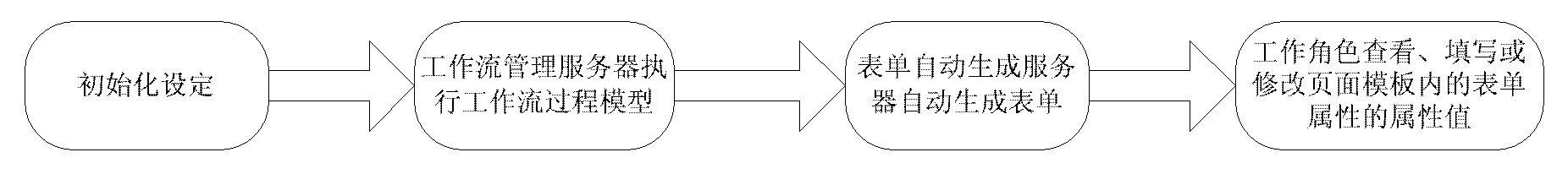
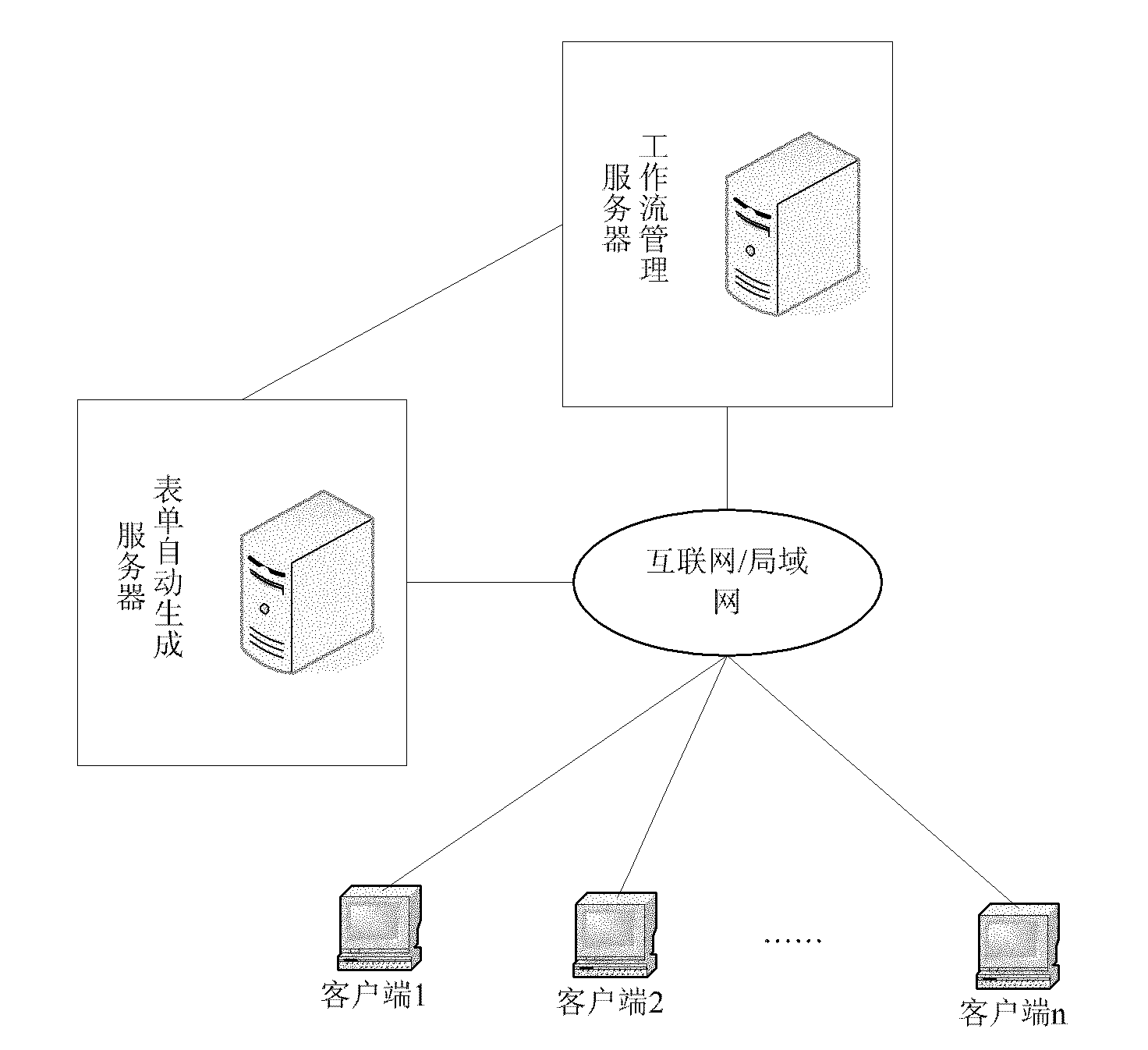
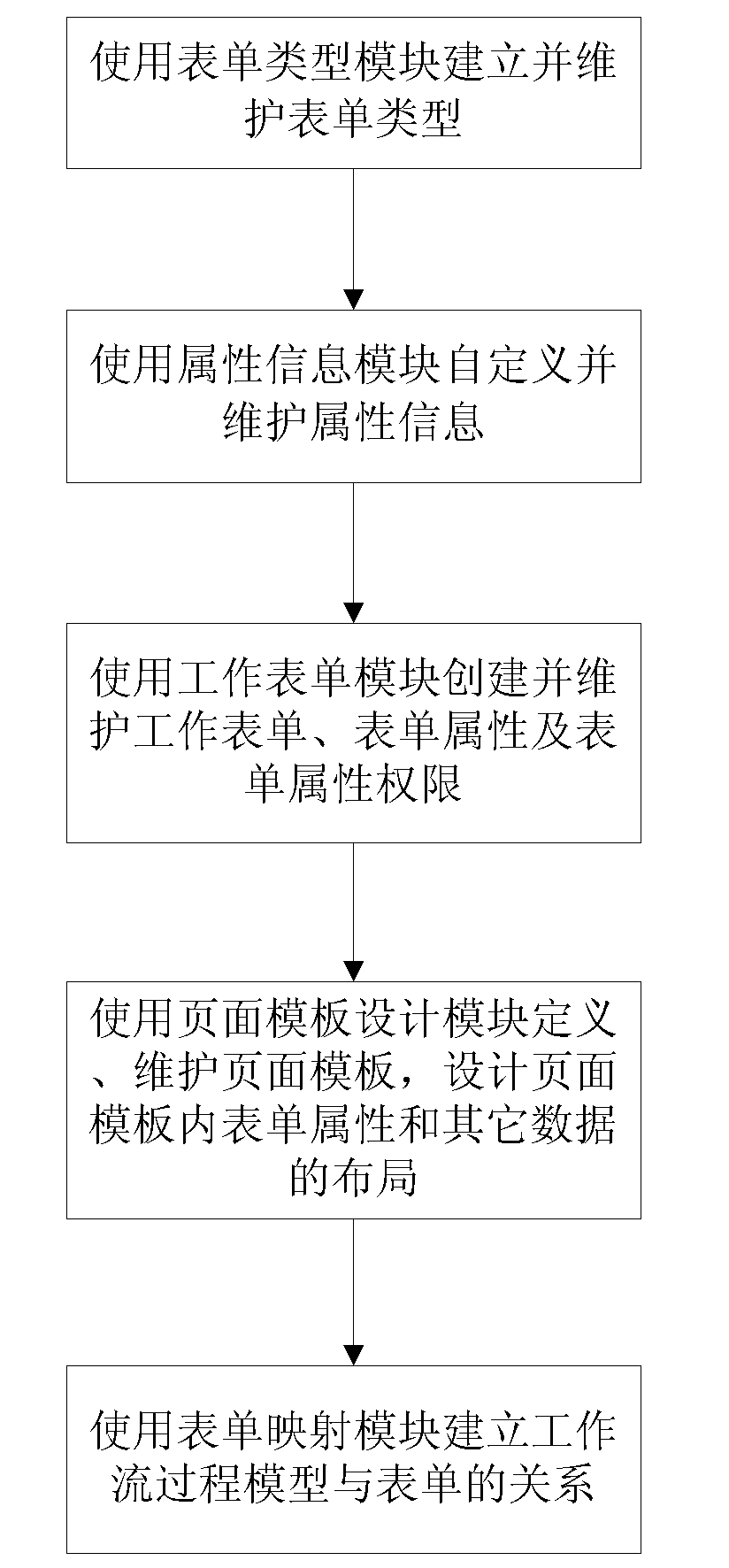
InactiveCN101937463AEnsure consistencyRealize automatic generationSpecial data processing applicationsWork taskWorkflow model
The invention discloses a method for automatically generating a form for a workflow model. In the method, related service data in the workflow model is used for flexibly defining the form as required according to division of work tasks and permission of corresponding work roles. The form is generated automatically, can be under read / write control according to the permission, the generating process of service data-related documents is simplified, the efficiency is improved and the normalization and standardization of documents and consistency of the service data are guaranteed.
Owner:XI AN JIAOTONG UNIV
Relational logic management system
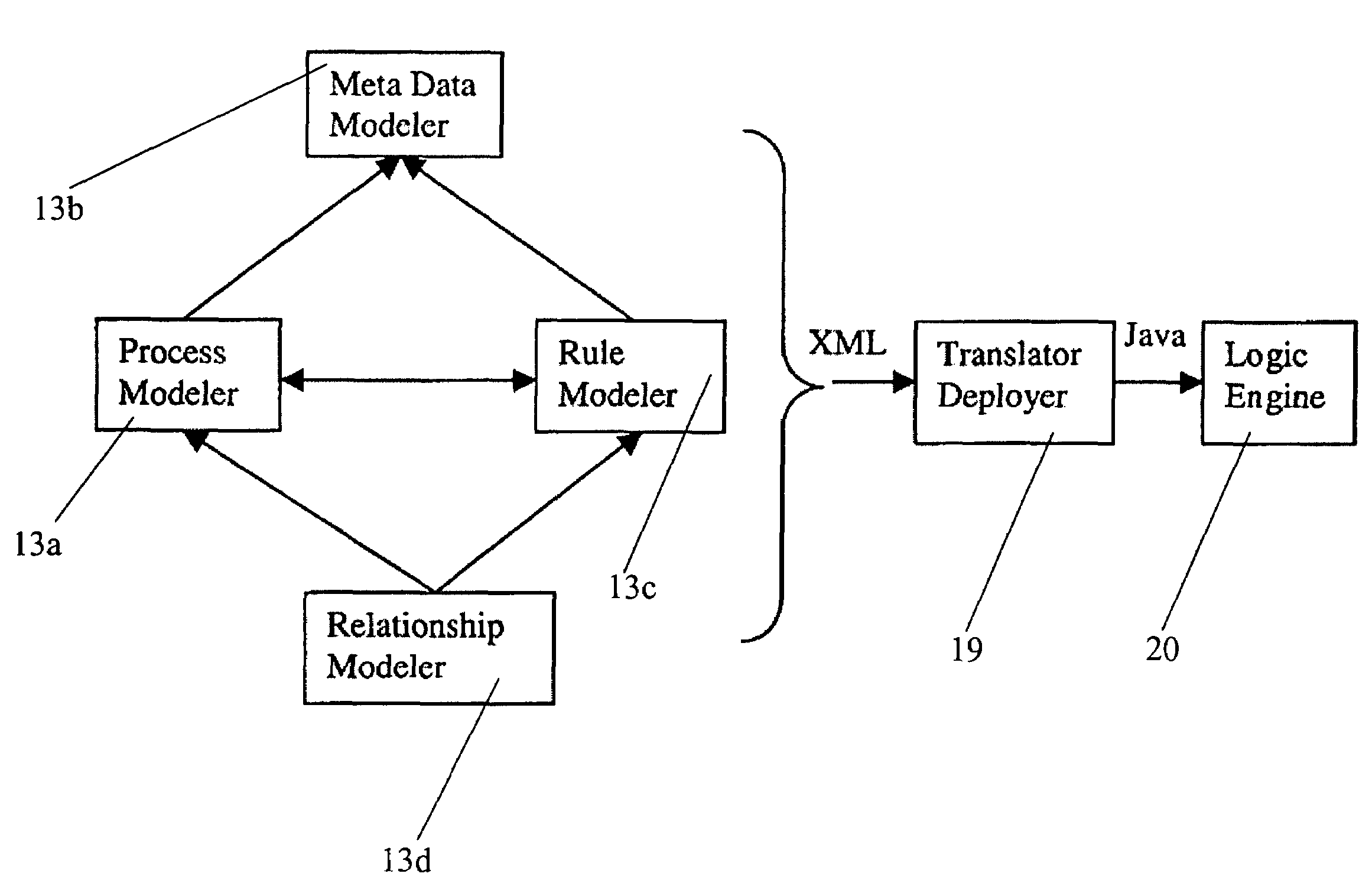
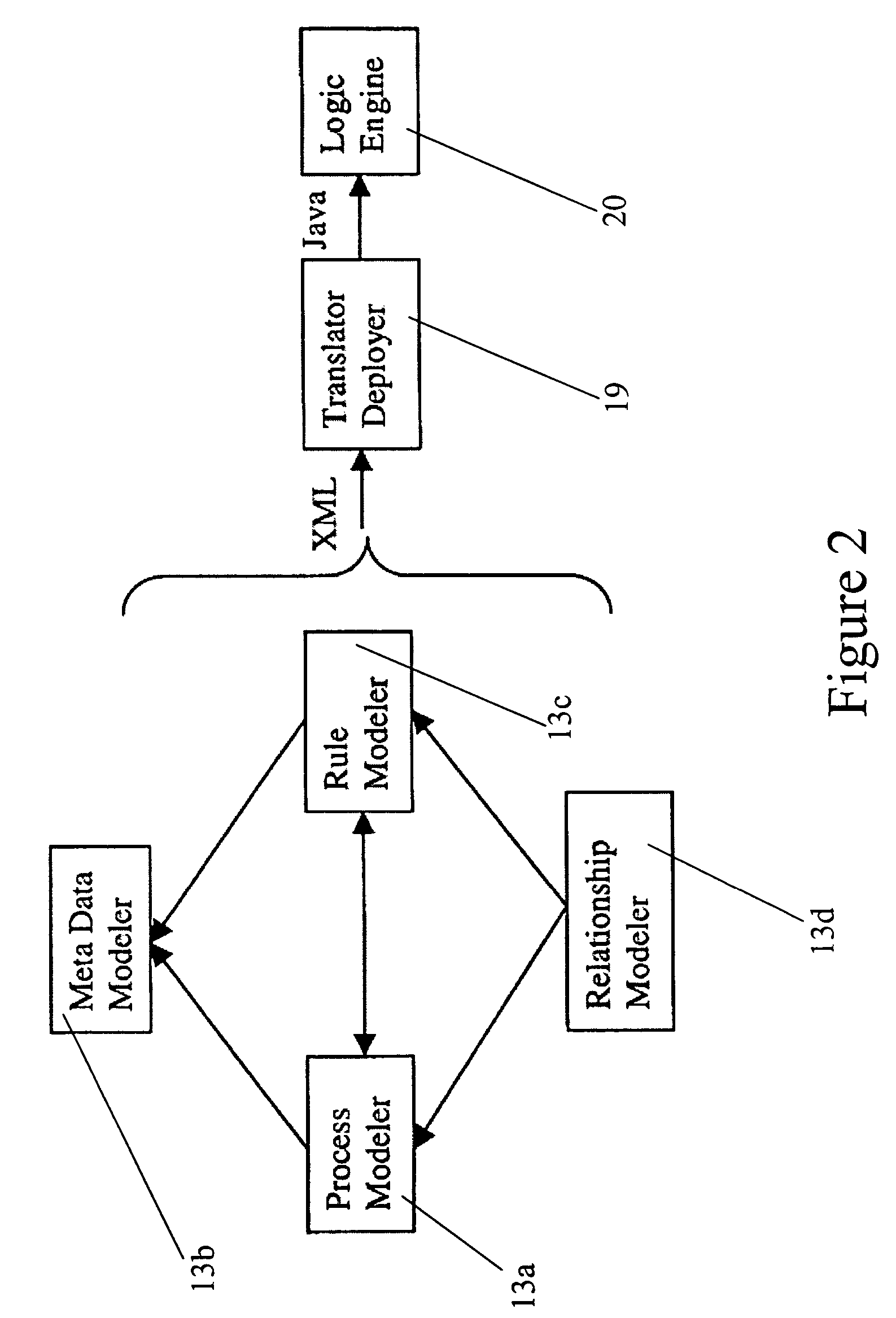
ActiveUS7428519B2Easy to trackEasy to reuseKnowledge representationResourcesControl flowWorkflow model
In one aspect, the invention relates to a method to propagate relations between a first rule set and a second rule set wherein the first and second rule sets are invoked by a common workflow model. The method includes tracing paths forward through the workflow model from the first rule set to the second rule set. Enumerating relations that extend forward from the first rule set to the second rule set is another step in the method. Additionally, using multi-valued logic, calculating the effects on the relations of control flow through the workflow model from the first rule set to the second rule set, tracing paths backward through the workflow model from the second rule set to the first rule set, enumerating relations that extend backward from the second rule set to the first rule set, and using multi-valued logic, calculating the effects on the relations of control flow backwards through the workflow model from the second rule set to the first rule set are also steps in the method.
Owner:FAIR ISAAC & CO INC
Extensible framework for designing workflows
A user interface for building a componentized workflow model. Each step of the workflow is modeled as an activity that has metadata to describe design time aspects, compile time aspects, and runtime aspects of the workflow step. A user selects and arranges the activities to create the workflow via the user interface. The metadata associated with each of the activities in the workflow is collected to create a persistent representation of the workflow. Users extend the workflow model by authoring custom activities.
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com