Patents
Literature
99 results about "Partial application" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer science, partial application (or partial function application) refers to the process of fixing a number of arguments to a function, producing another function of smaller arity. Given a function f:(X×Y×Z)→N, we might fix (or 'bind') the first argument, producing a function of type partial(f):(Y×Z)→N. Evaluation of this function might be represented as fₚₐᵣₜᵢₐₗ(2,3). Note that the result of partial function application in this case is a function that takes two arguments.
System and method for developing and administering web applications and services from a workflow, enterprise, and mail-enabled web application server and platform
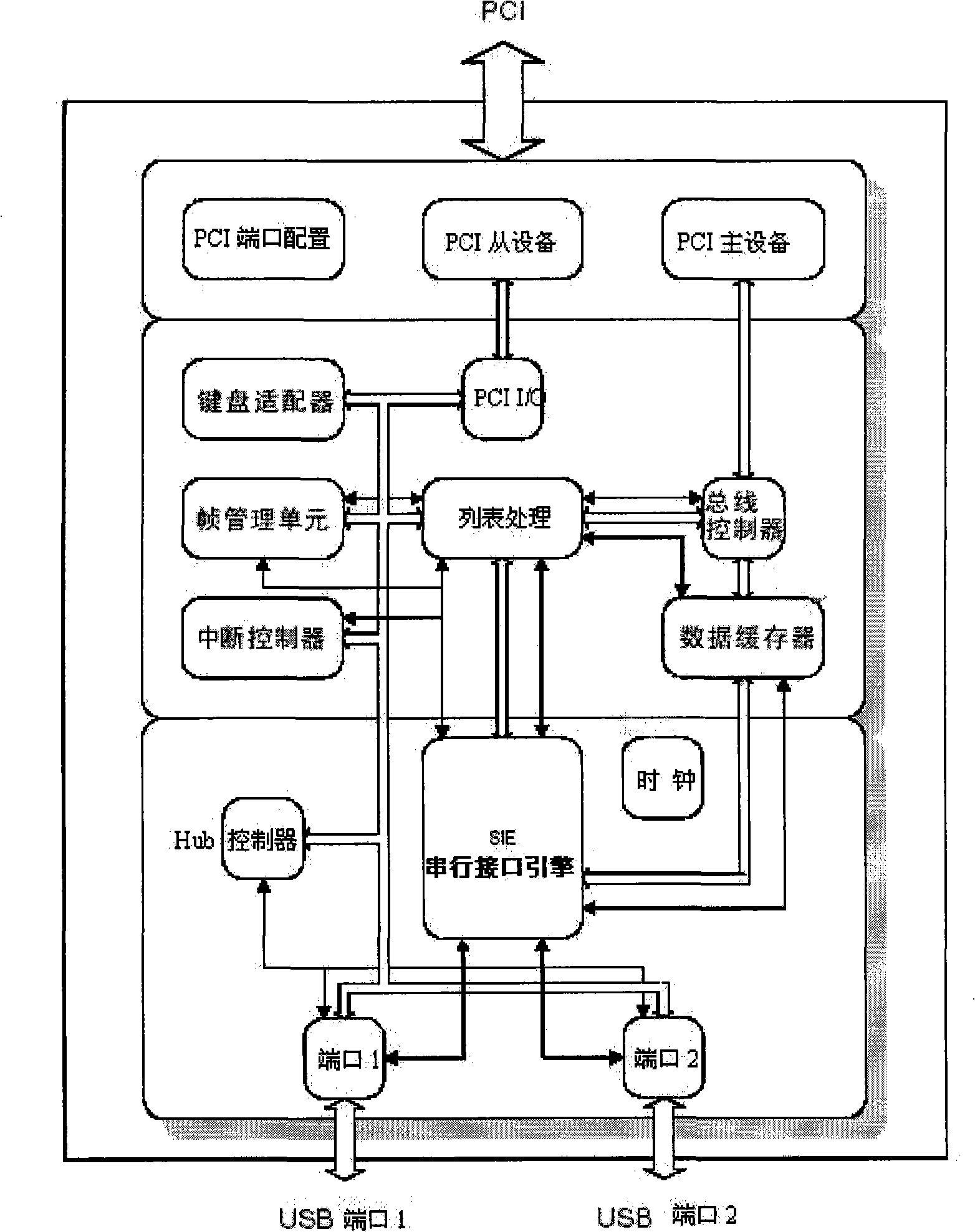
ActiveUS20040201604A1Digital computer detailsOffice automationDocumentation procedurePartial application
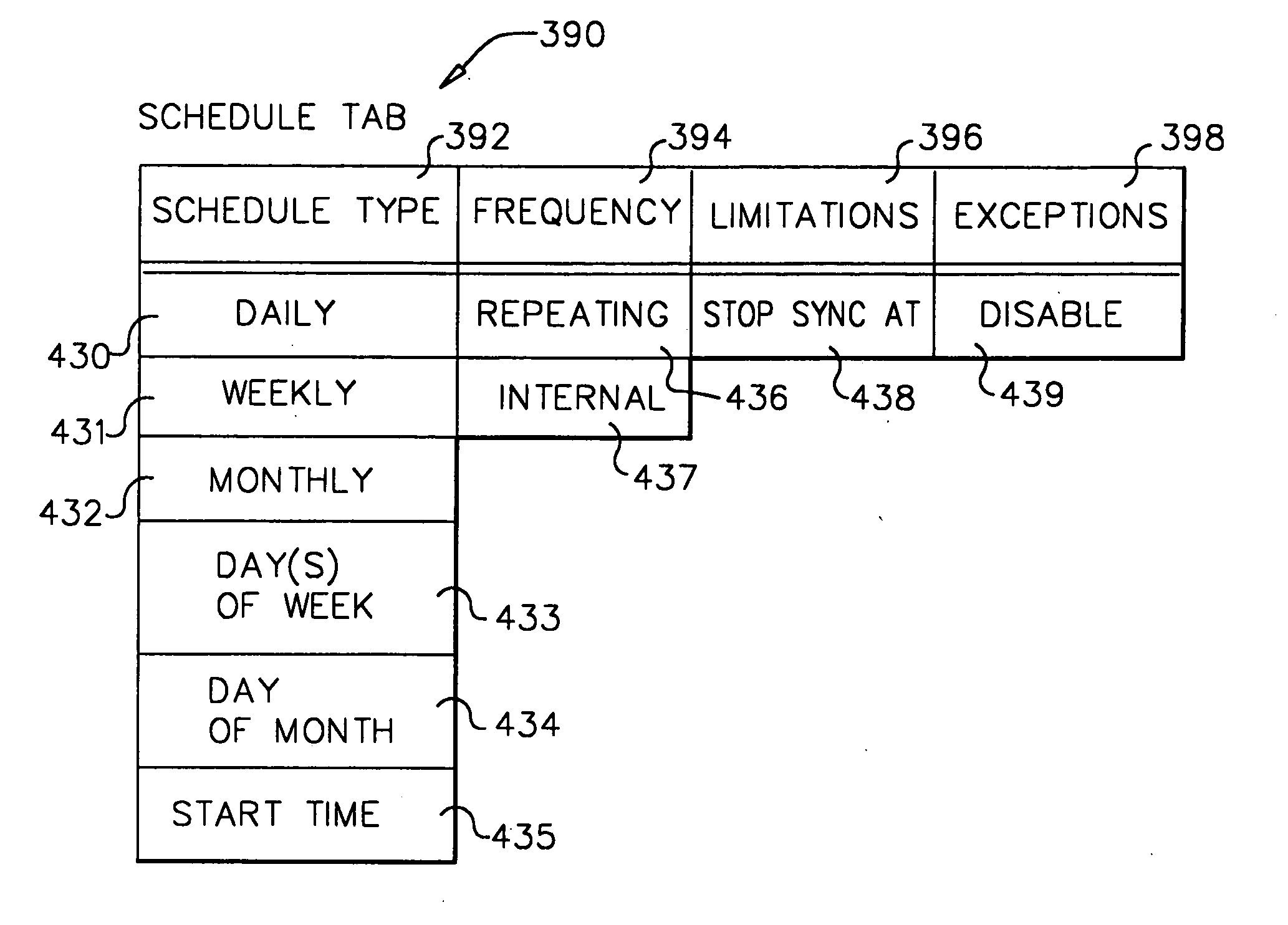
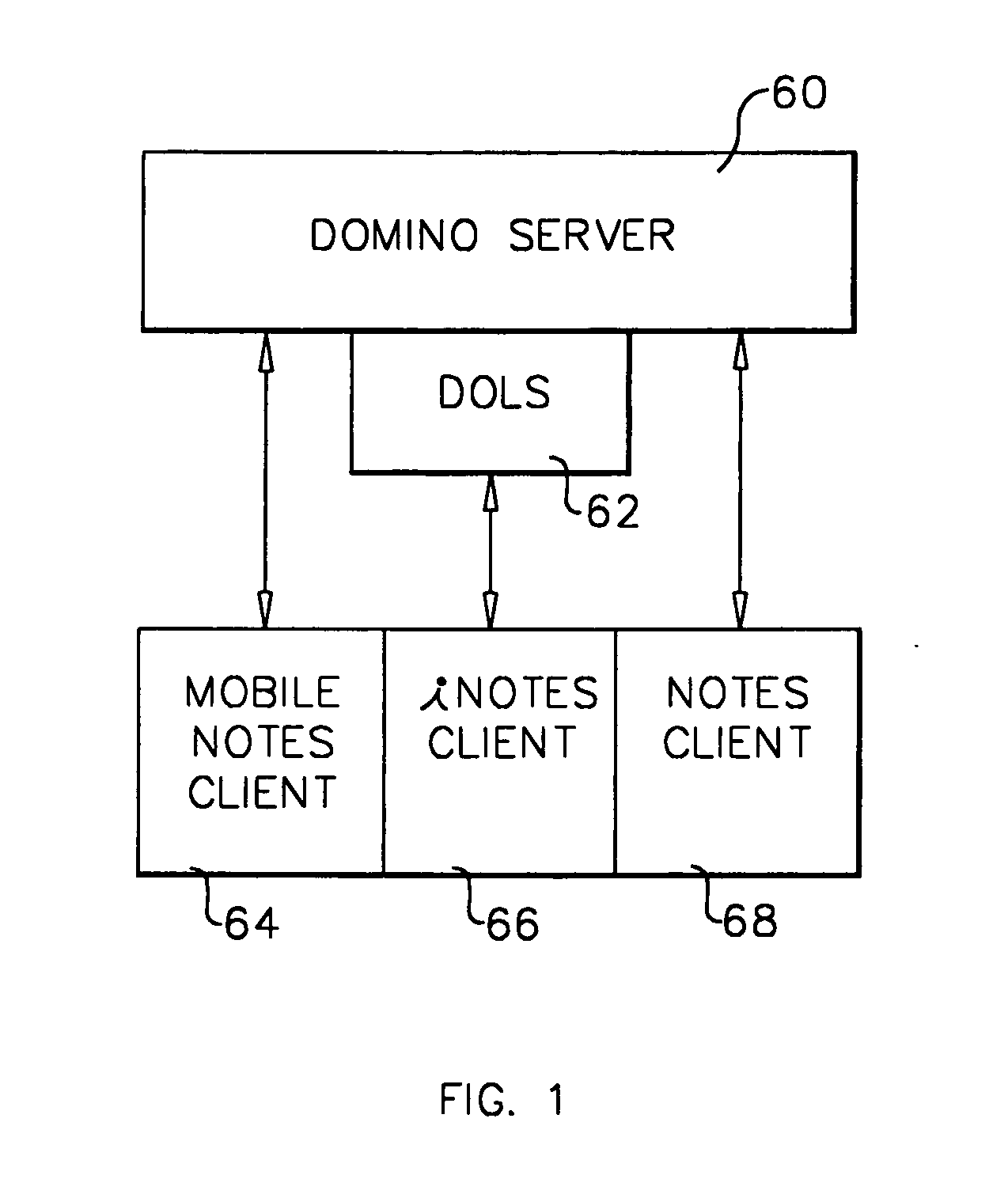
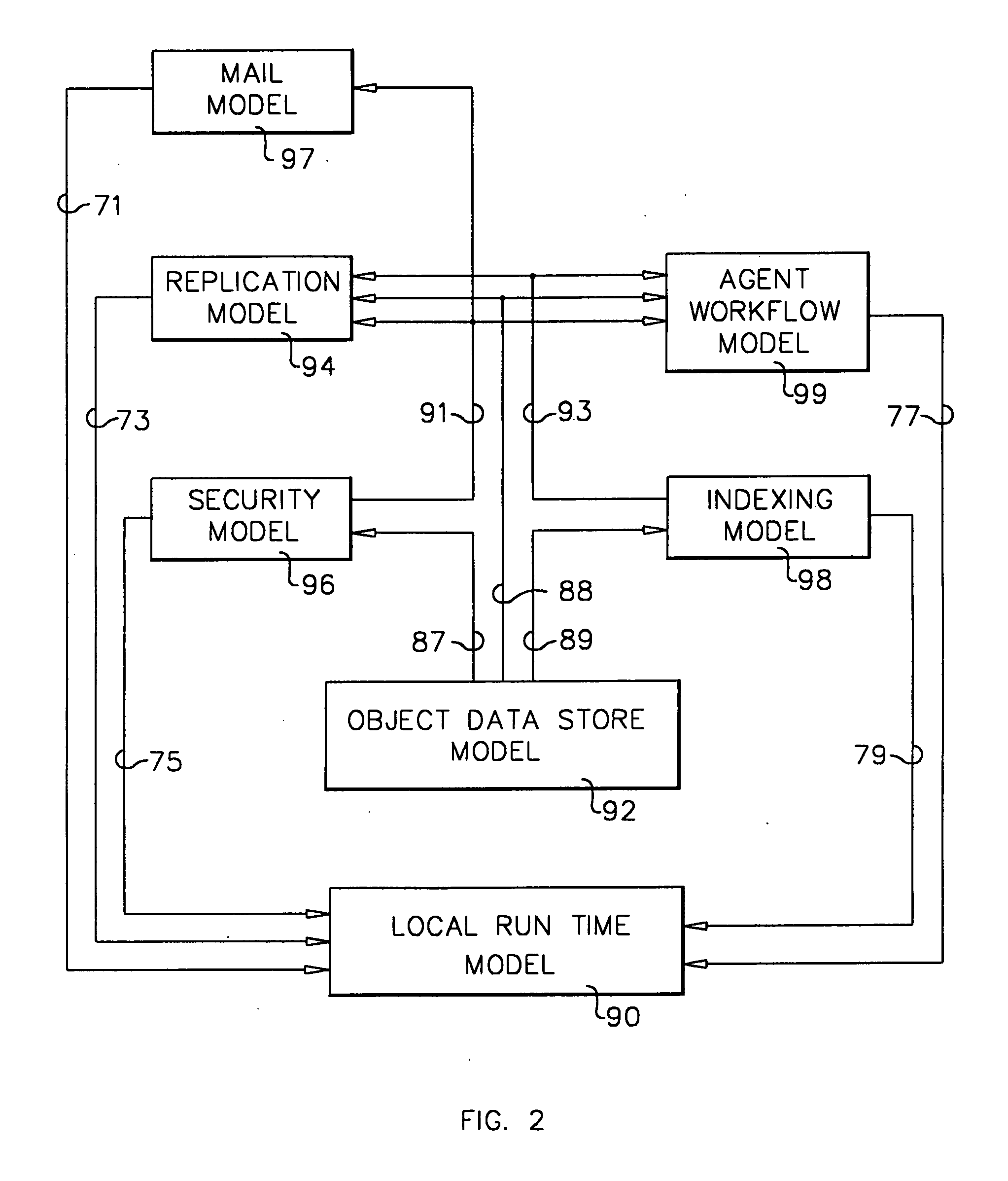
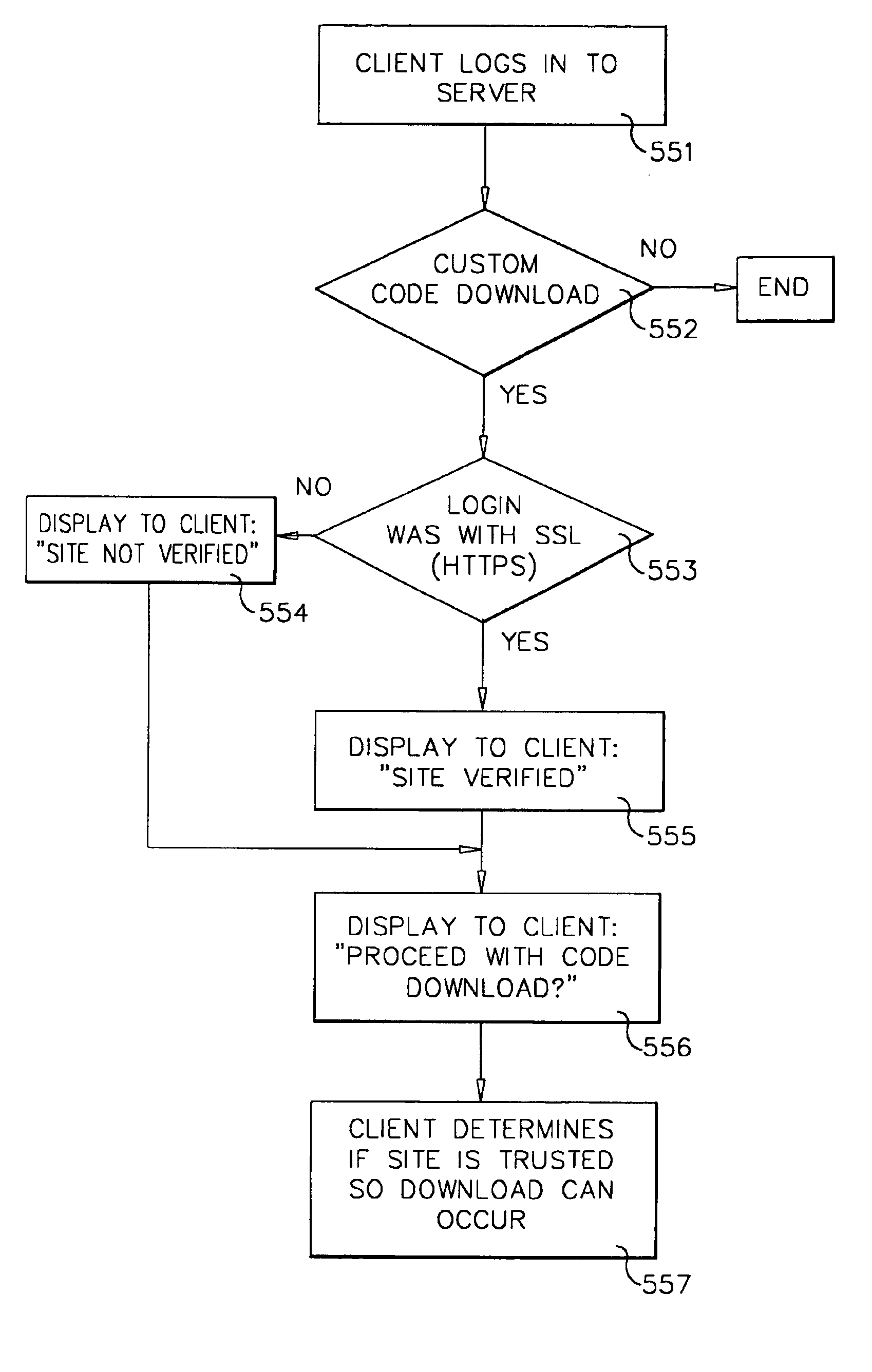
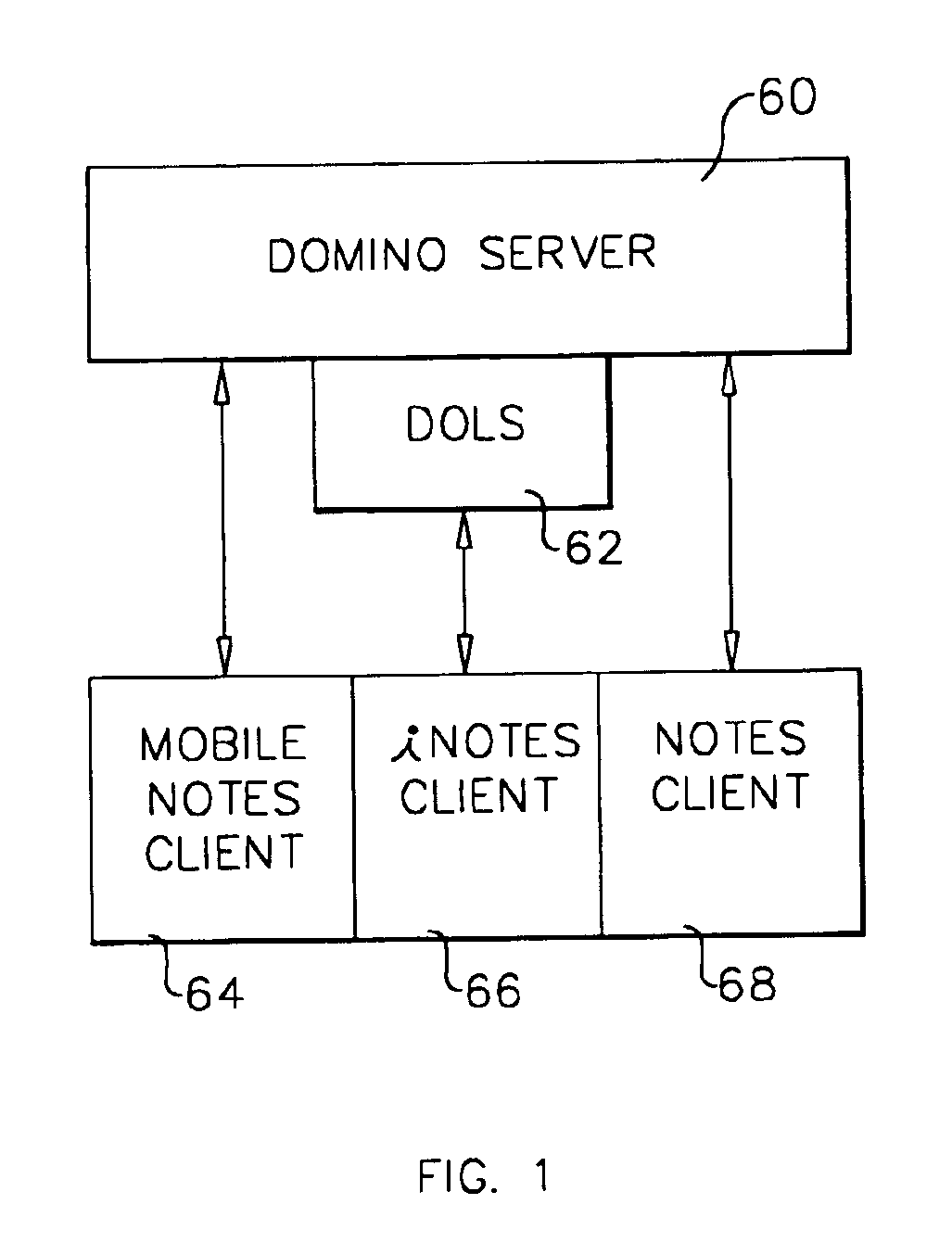
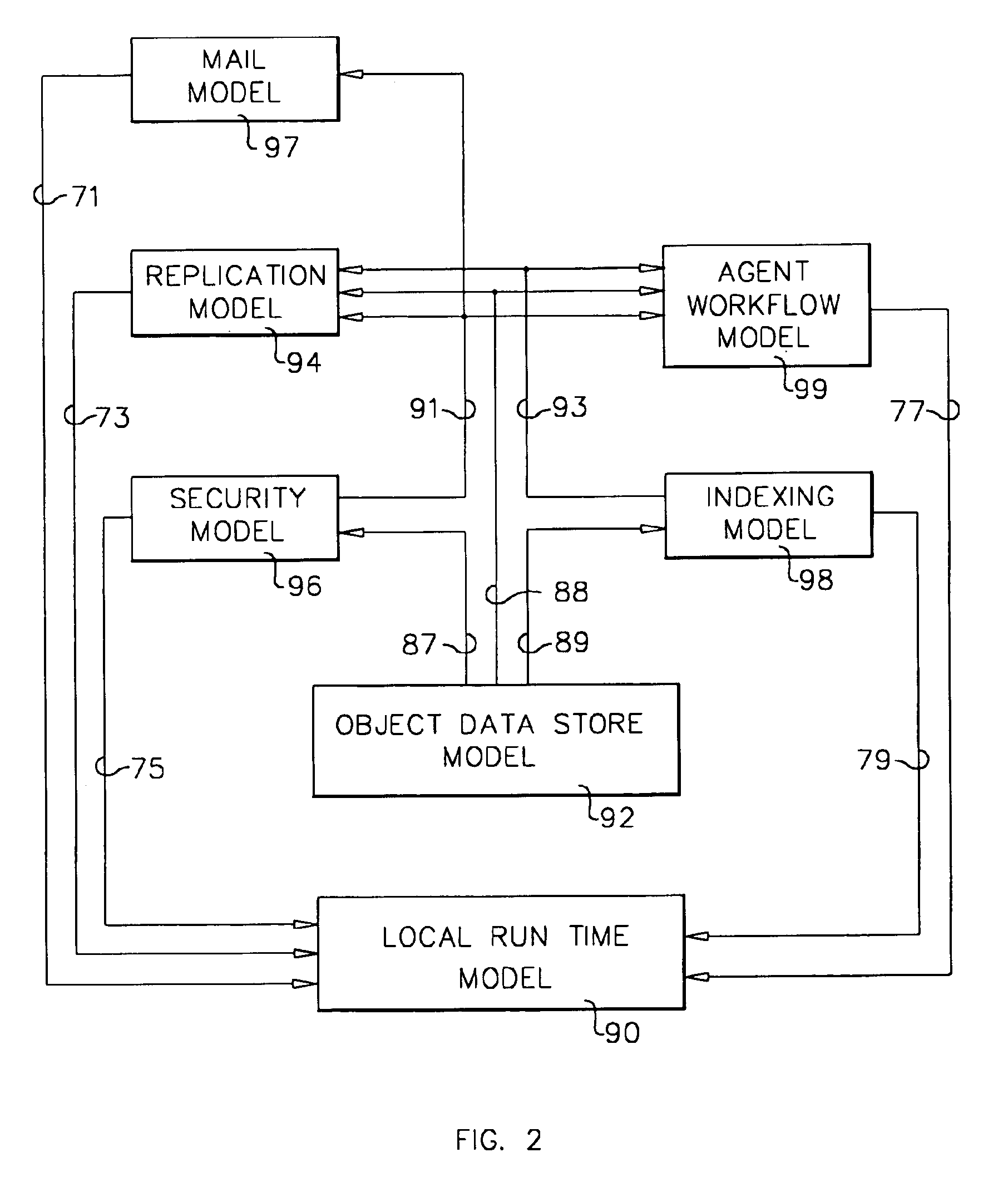
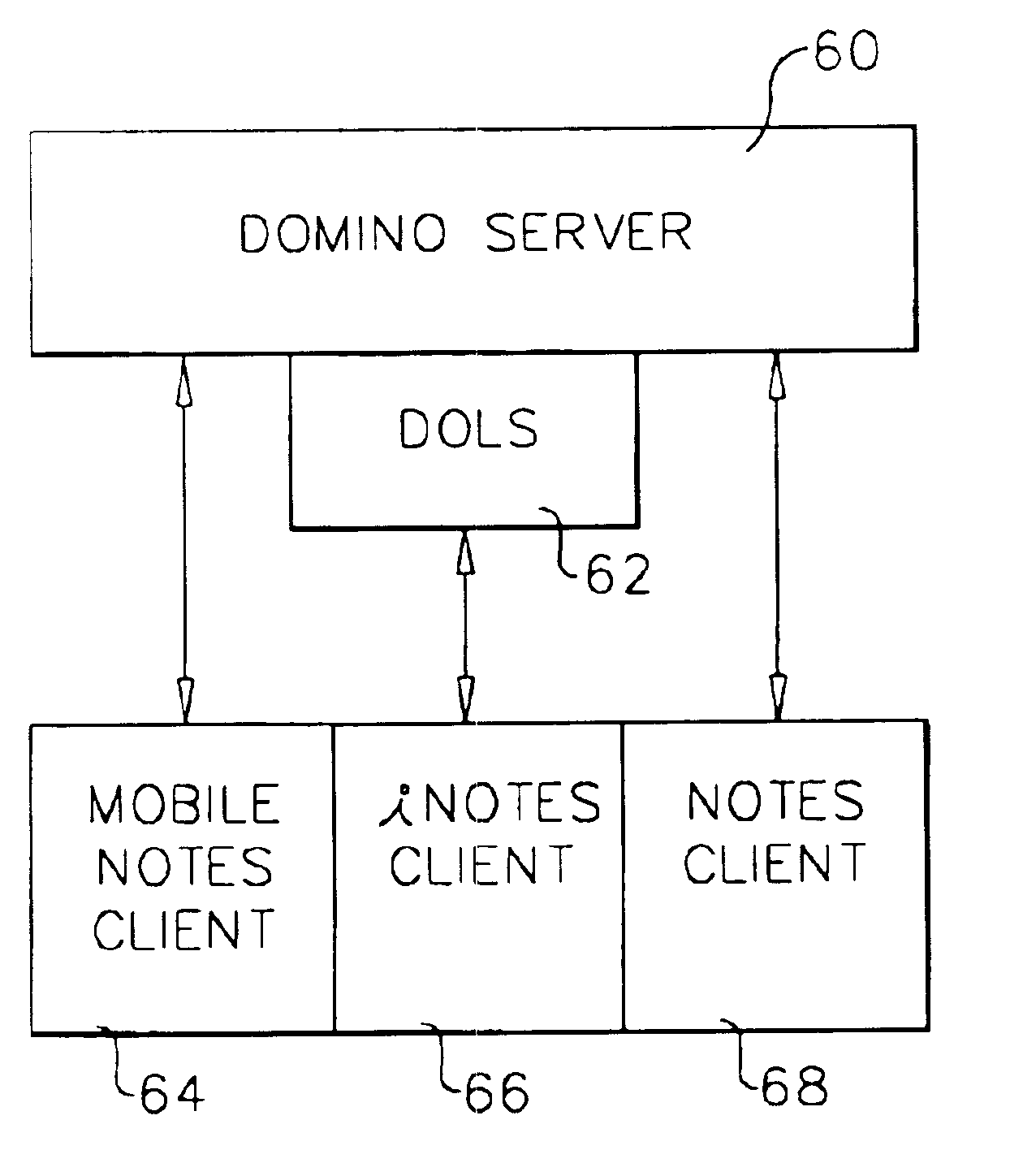
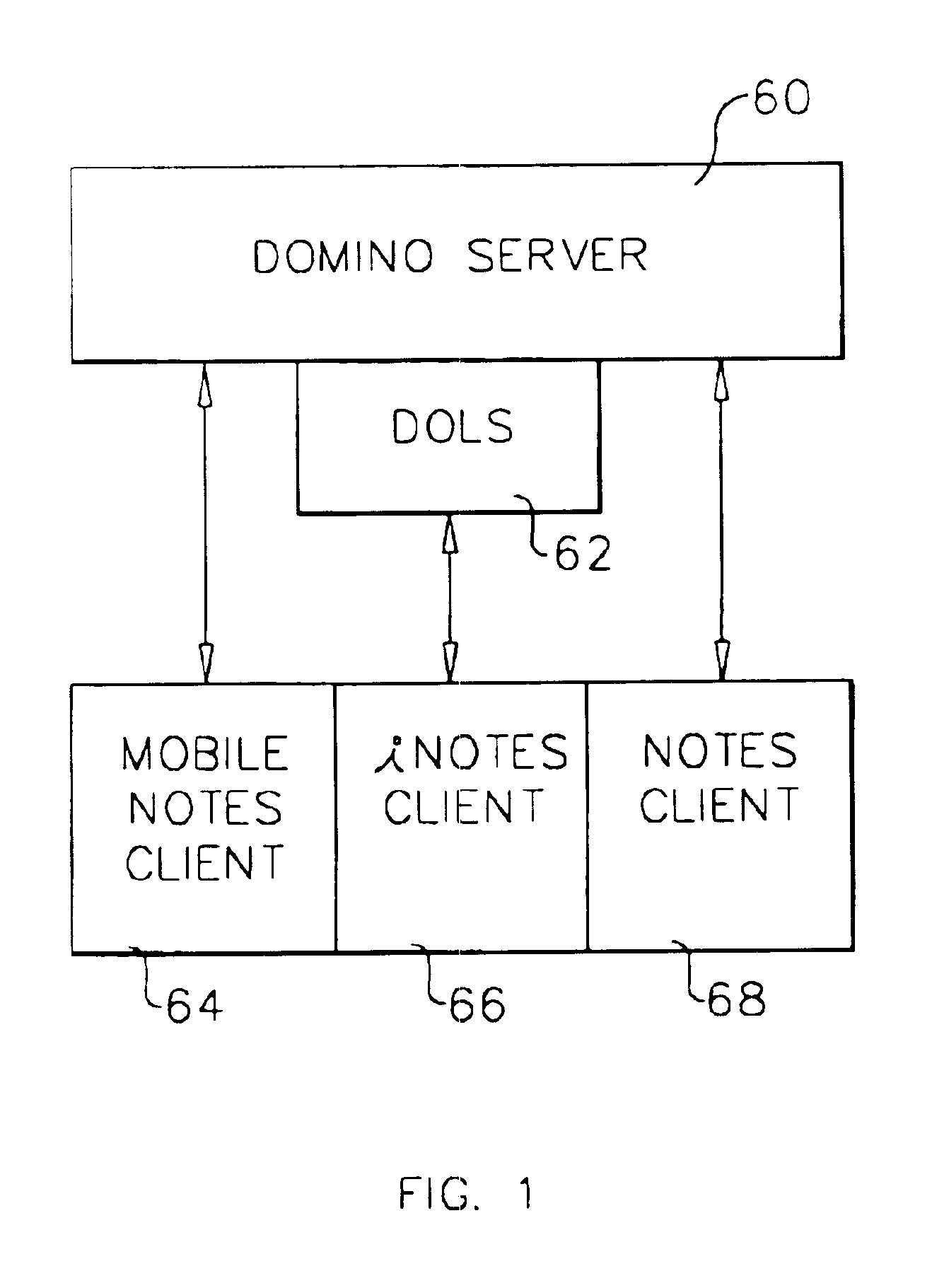
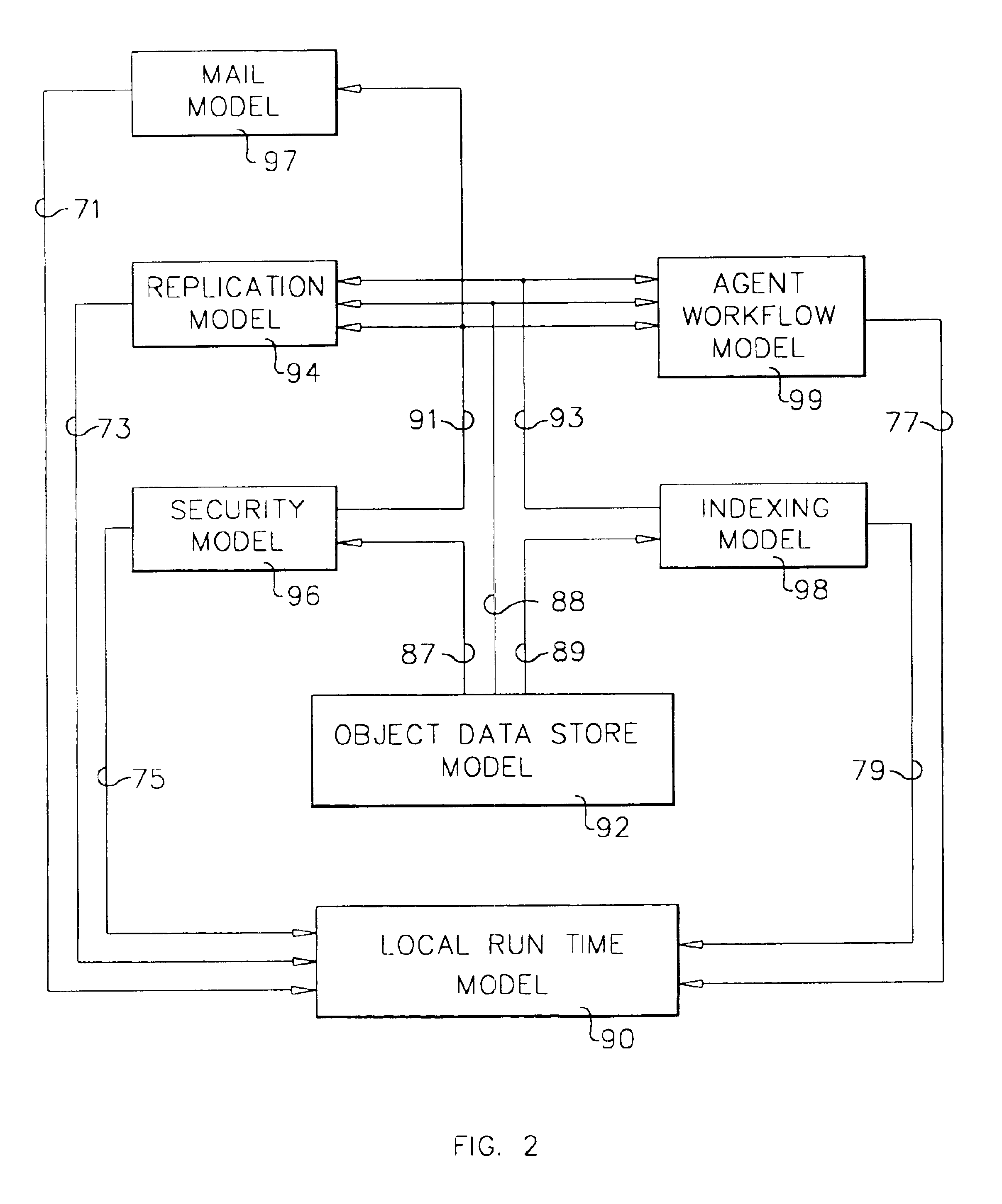
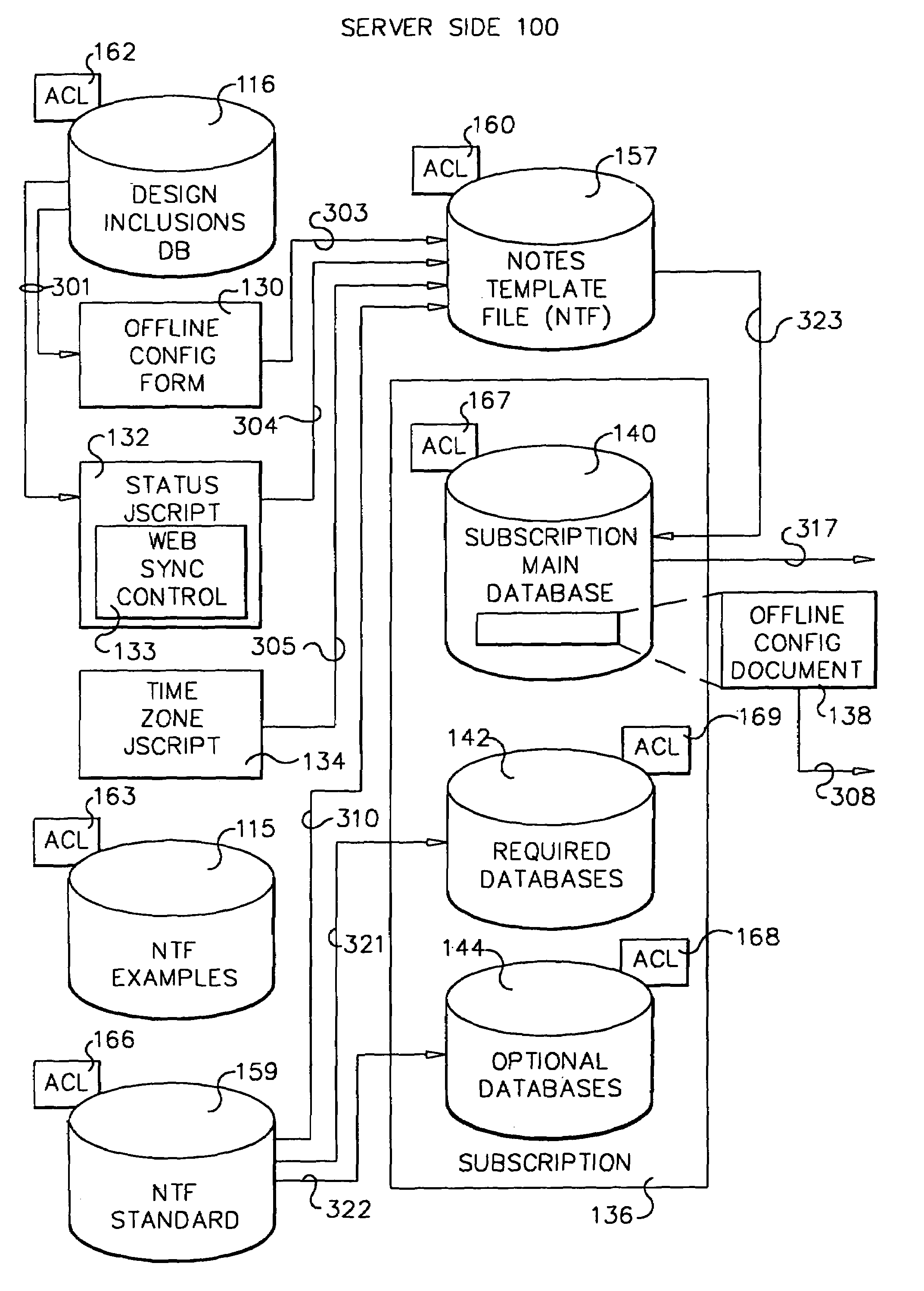
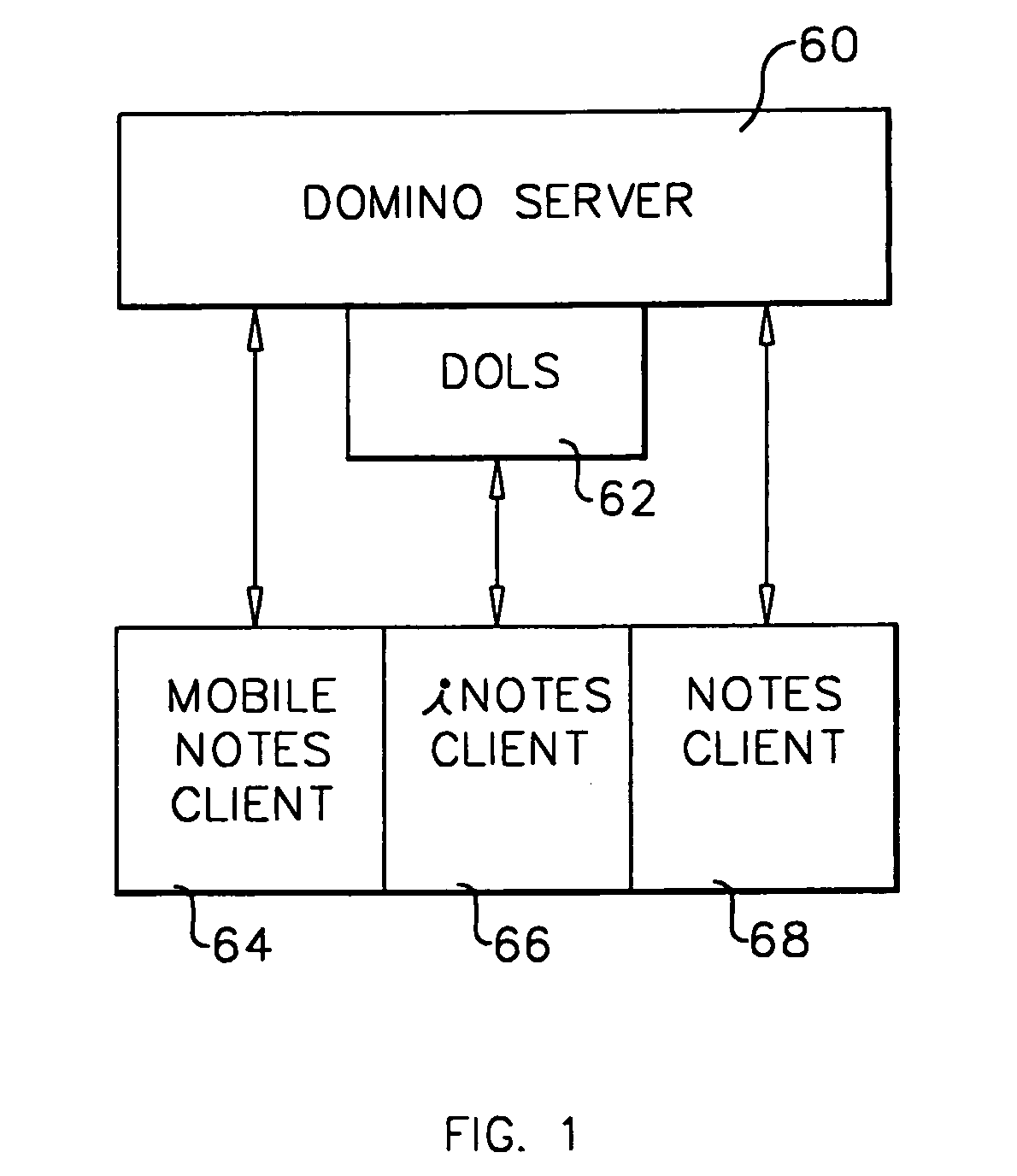
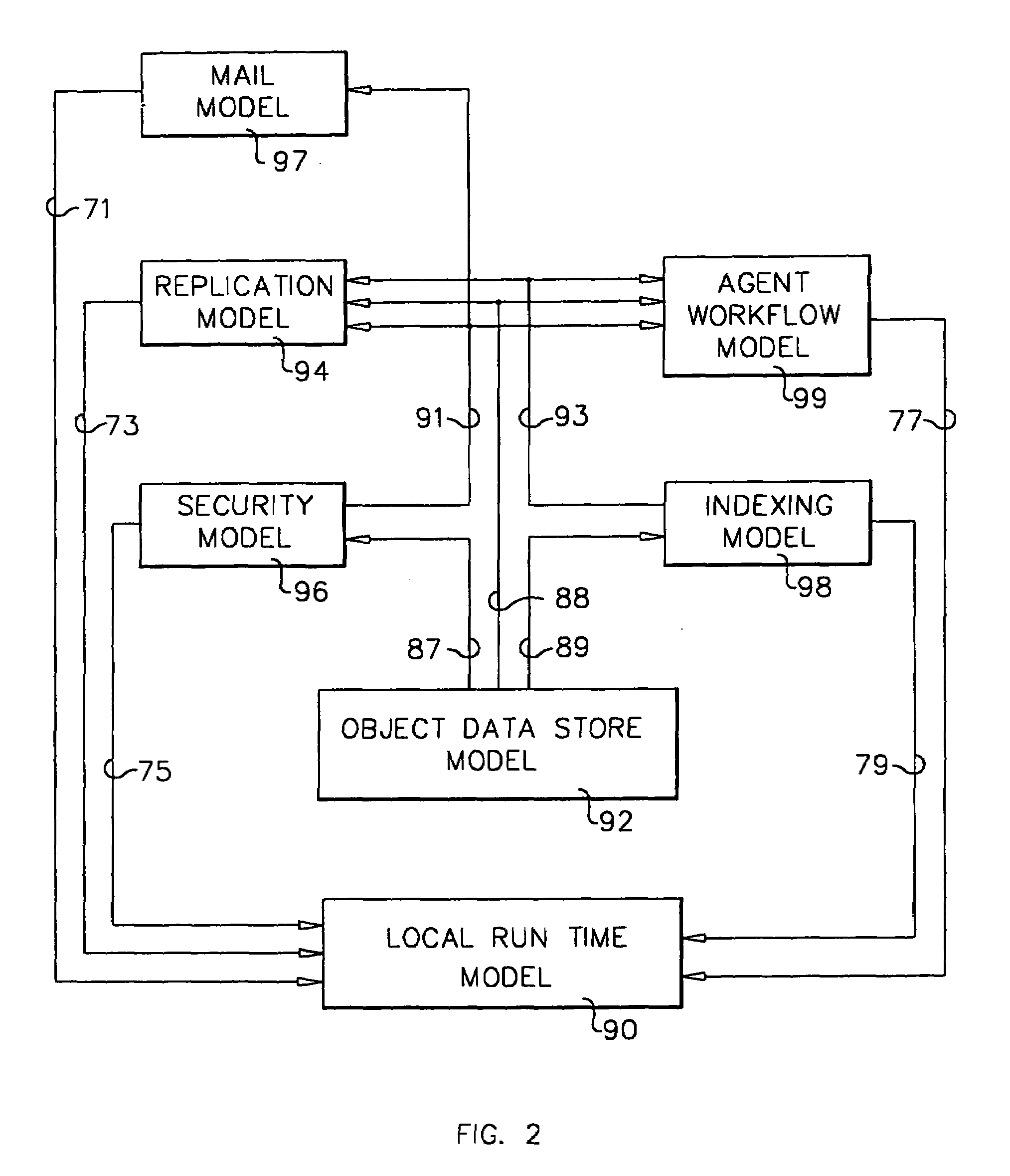
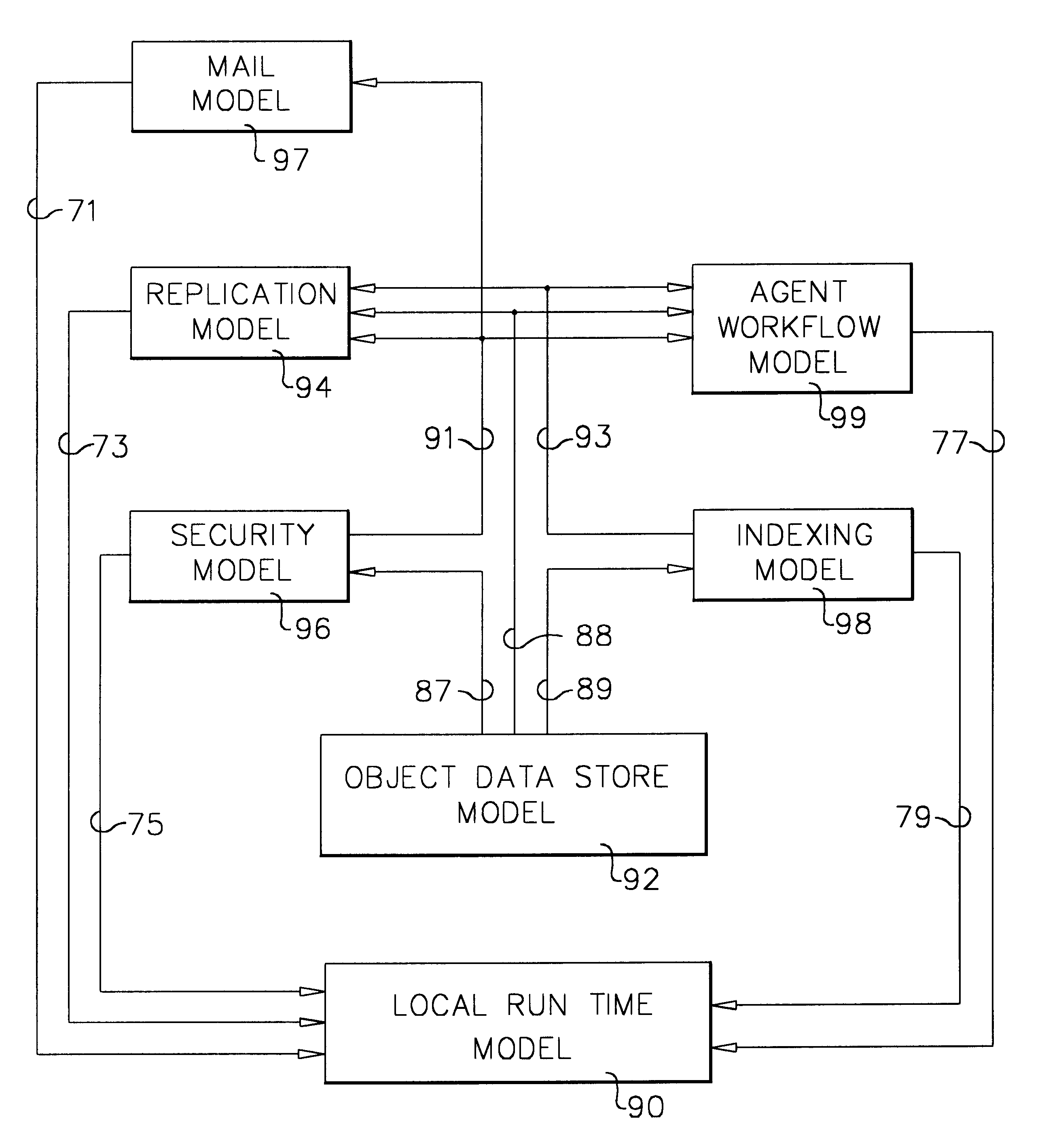
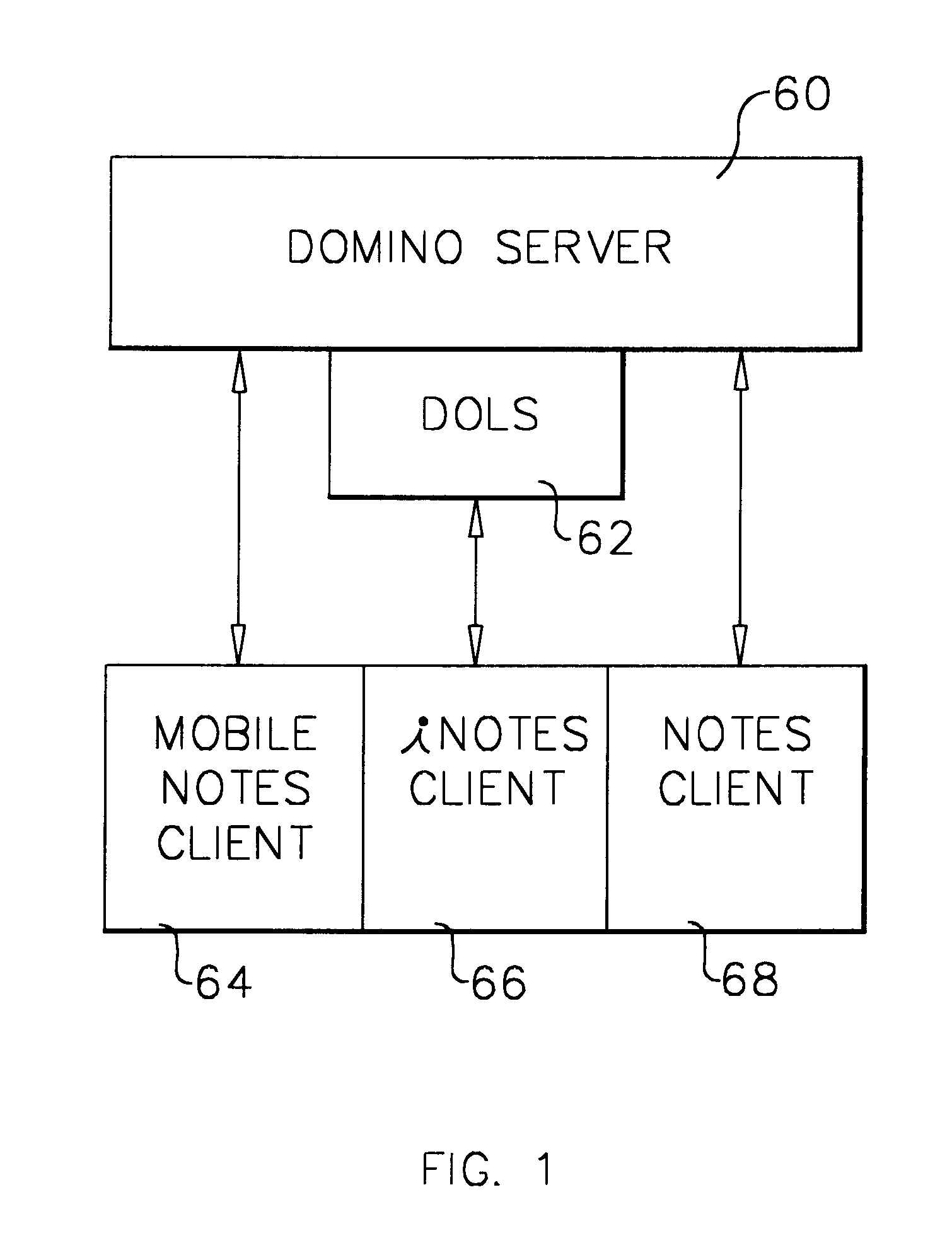
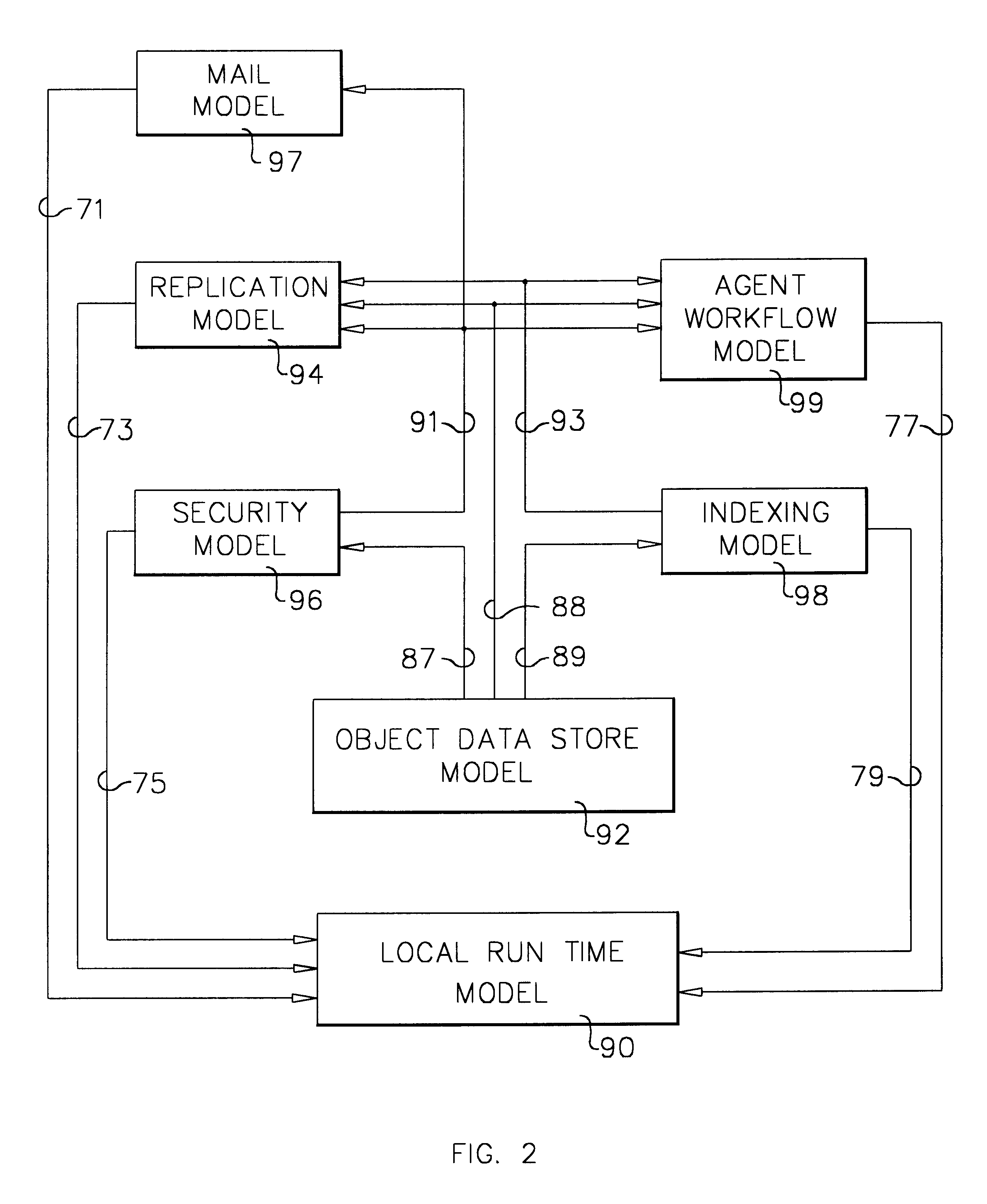
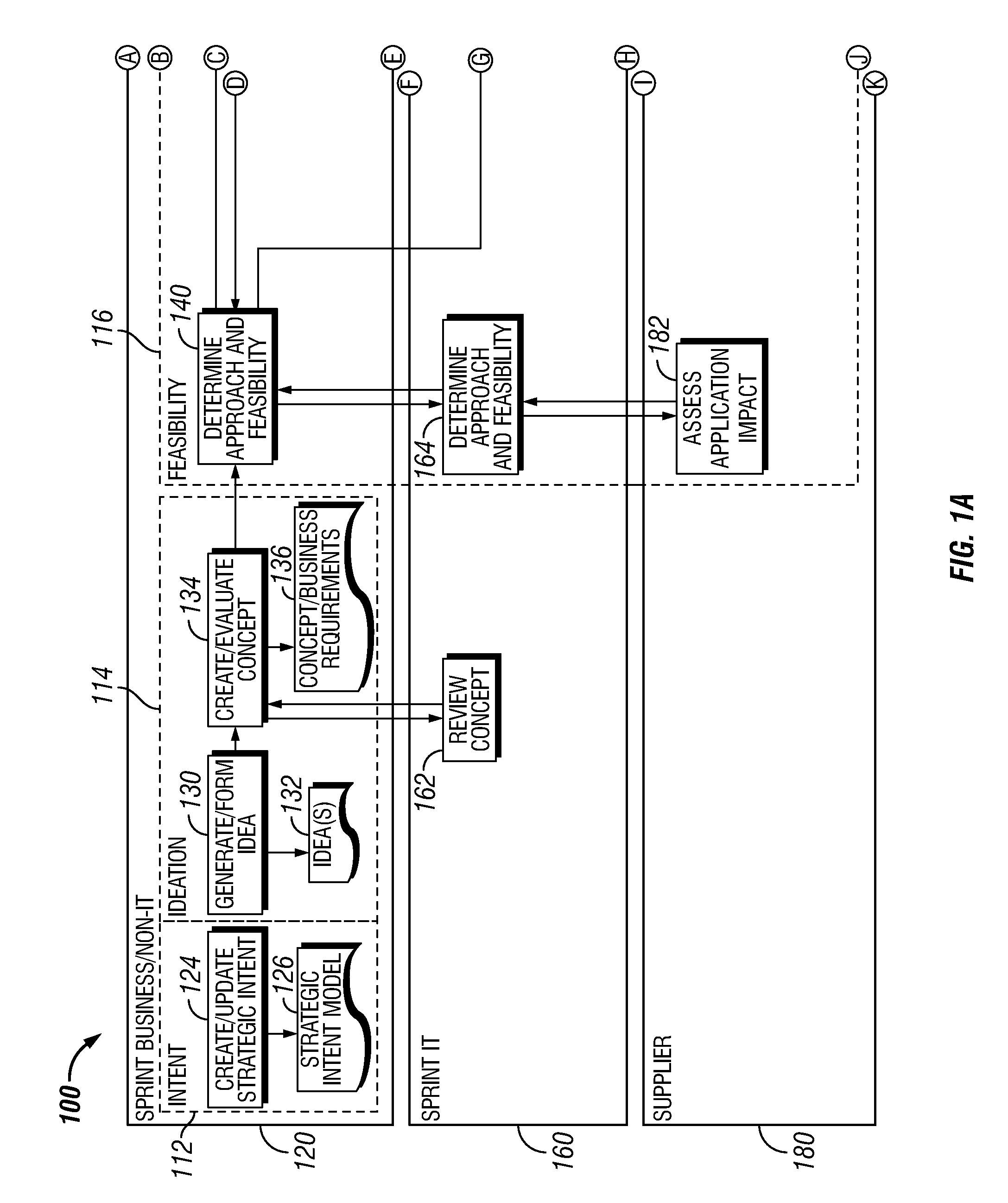
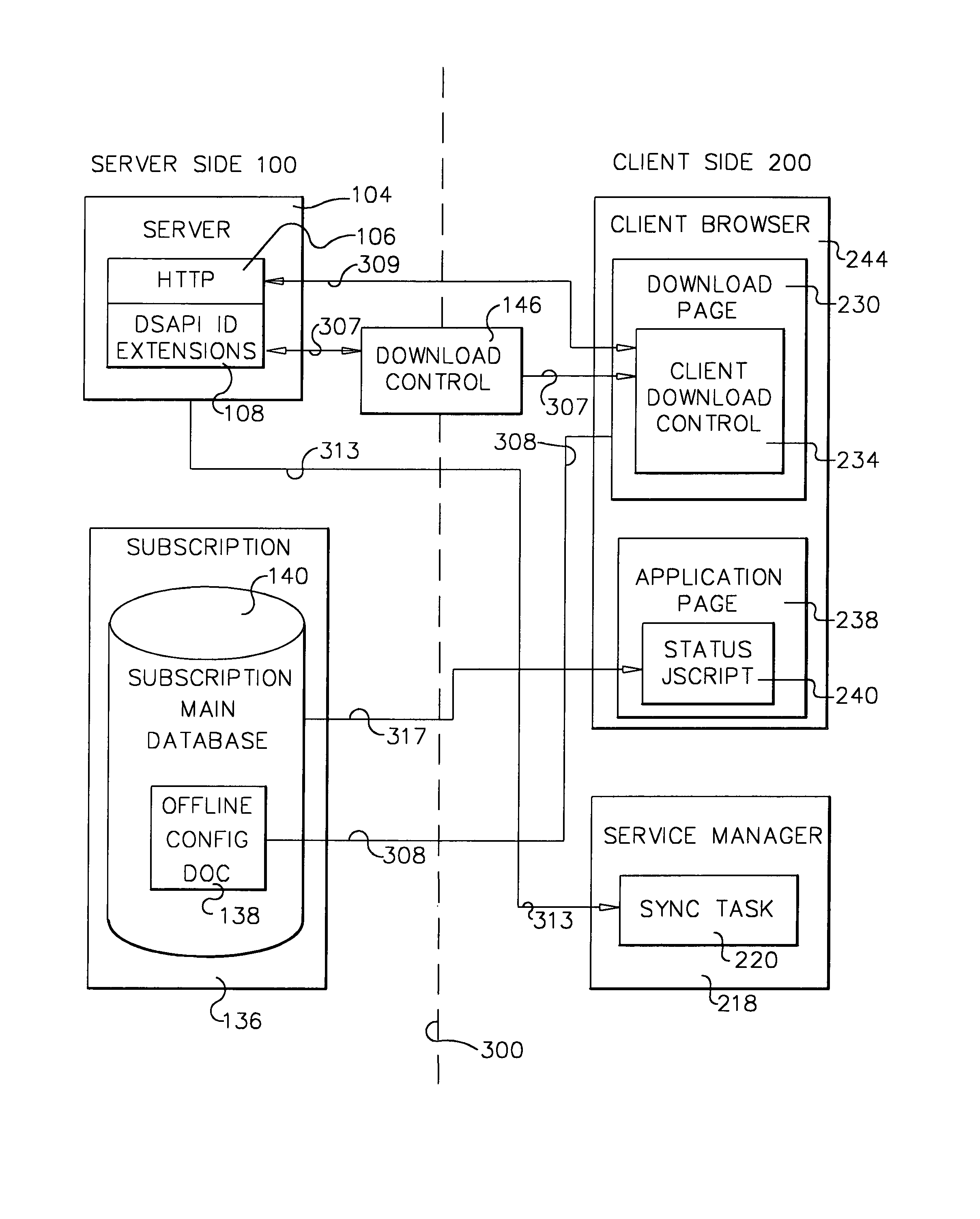
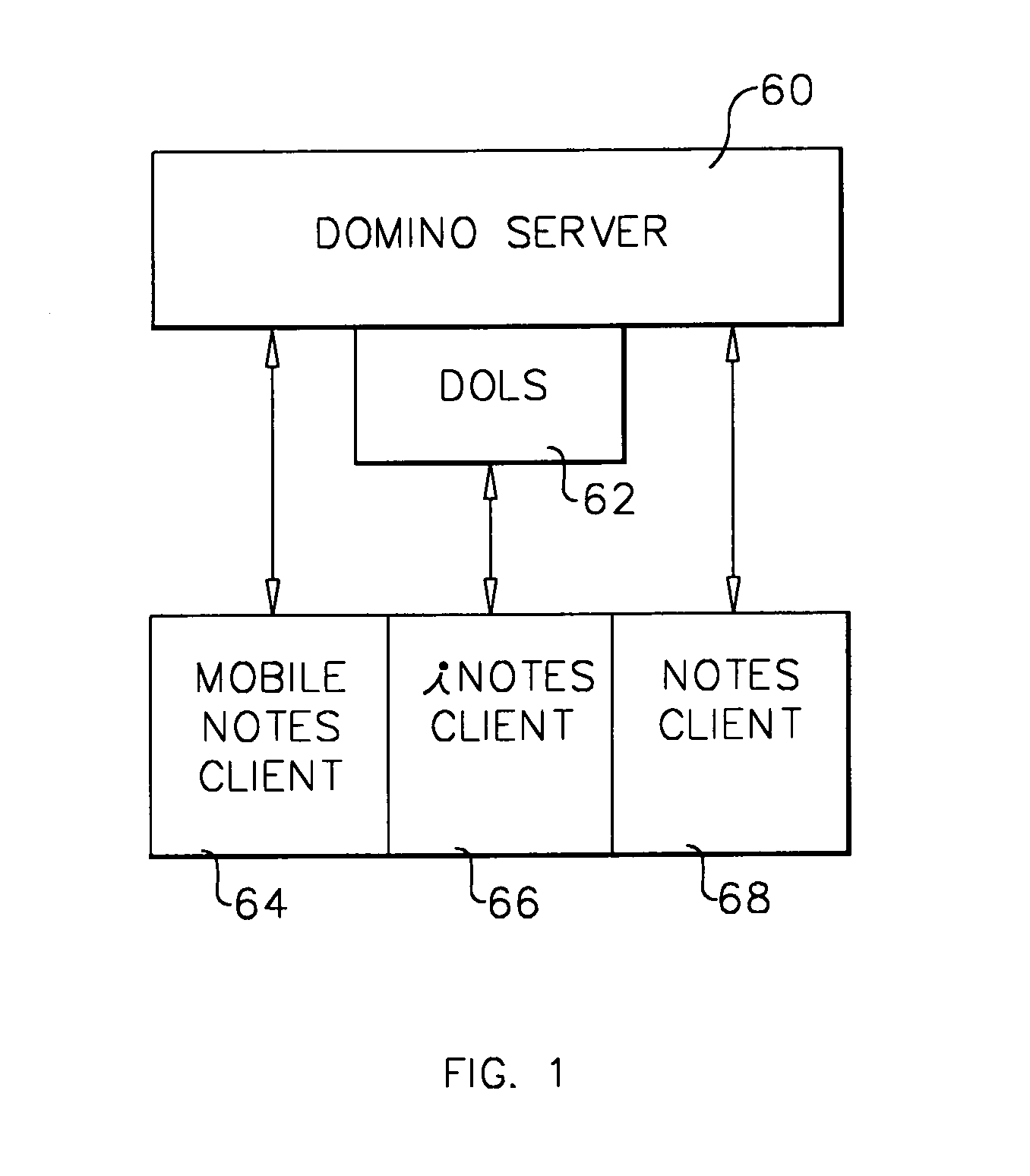
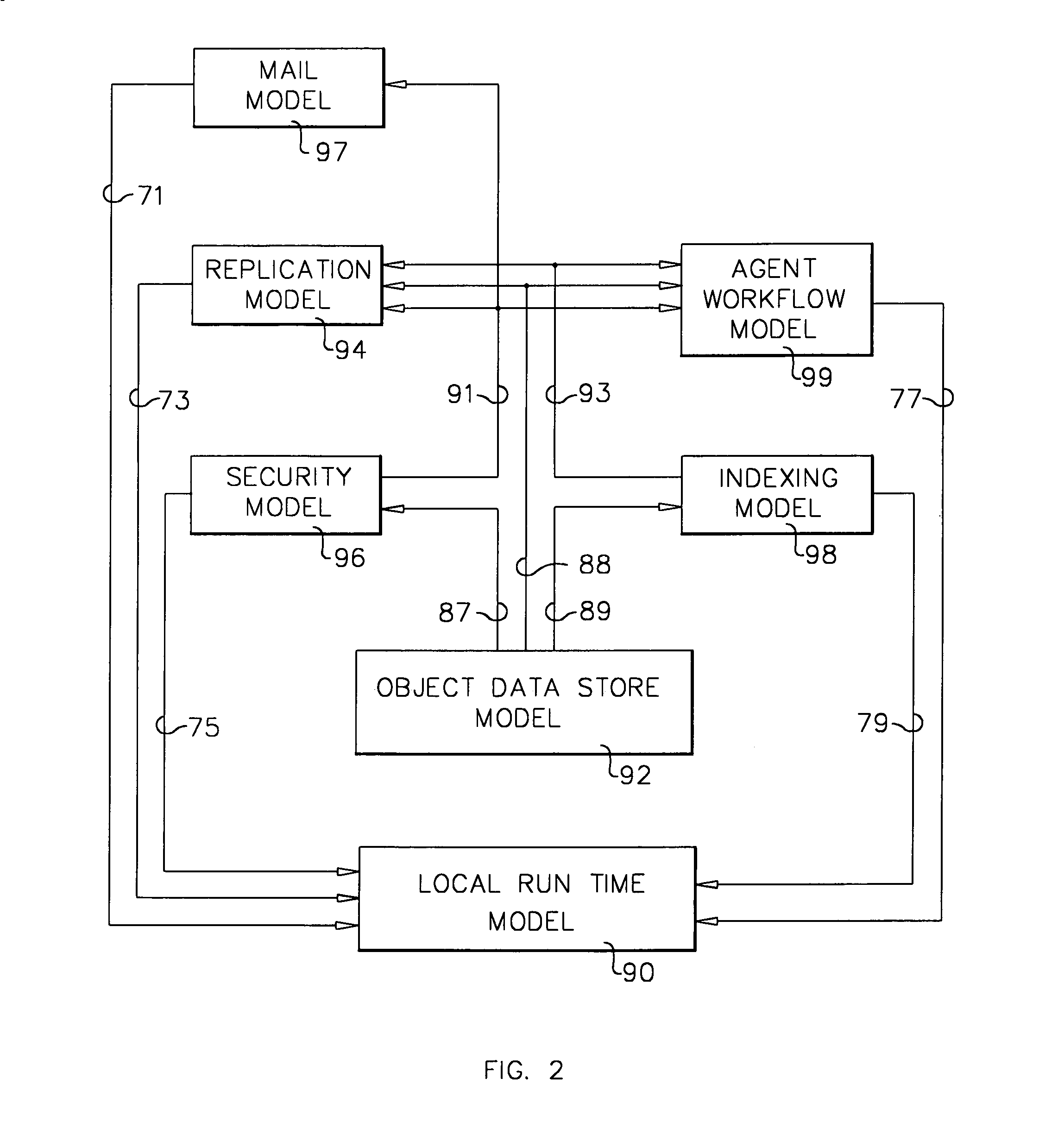
A workflow, enterprise, and mail-enabled application server and platform supports distributed computing and. remote execution of web applications. Lotus Domino online services (DOLS) is used by a web site administrator to configure Internet Notes (iNotes) clients to auto download from server, thus providing iNotes clients with web access using HTTP with various browsers, and with local processing and replication. A local run time model comprises a hierarchy of models including object data store model, security model, indexing model, replication model, agent workflow model and mail model. DOLS provides a layered security model that allows flexibility for controlling access to all or part of an application. The highest level of security is managed through a database access control list (ACL). Further refinements within the security model provide access to specific documents, and their views, forms or folders, and include read access lists, write access lists, form access lists and readers and authors fields.
Owner:HCL TECH LTD
System and method for a web based trust model governing delivery of services and programs
InactiveUS6854016B1Broaden applicationDigital data processing detailsMultiple digital computer combinationsPartial applicationApplication software
A workflow, enterprise, and mail-enabled application server and platform supports distributed computing and remote execution of web applications. Lotus Domino Offline Services (DOLS) is used by a web site administrator to configure Internet Notes (iNotes) clients to auto download from server, thus providing iNotes clients with web access using HTTP with various browsers, and with local processing and replication. A local run time model comprises a hierarchy of models including object data store model, security model, indexing model, replication model, agent workflow model and mail model. DOLS provides a layered security model that allows flexibility for controlling access to all or part of an application. The highest level of security is managed through a database access control list (ACL). Further refinements within the security model provide access to specific documents, and their views, forms or folders, and include read access lists, write access lists, form access lists and readers and authors fields.
Owner:TREND MICRO INC
System and method for managing concurrent scheduled or on-demand replication of subscriptions
InactiveUS6845383B1Broaden applicationDigital data authenticationOffice automationPartial applicationApplication software
A workflow, enterprise, and mail-enabled application server and platform supports distributed computing and remote execution of web applications. Lotus Domino online services (DOLS) is used by a web site administrator to configure Internet Notes (iNotes) clients to auto download from server, thus providing iNotes clients with web access using HTTP with various browsers, and with local processing and replication. A local run time model comprises a hierarchy of models including object data store model, security model, indexing model, replication model, agent workflow model and mail model. DOLS provides a layered security model that allows flexibility for controlling access to all or part of an application. The highest level of security is managed through a database access control list (ACL). Further refinements within the security model provide access to specific documents, and their views, forms or folders, and include read access lists, write access lists, form access lists and readers and authors fields.
Owner:IBM CORP
System and method for developing and administering web applications and services from a workflow, enterprise, and mail-enabled web application server and platform
InactiveUS7219304B1Digital data processing detailsAnalogue secracy/subscription systemsDocumentation procedurePartial application
A workflow, enterprise, and mail-enabled application server and platform supports distributed computing and remote execution of web applications. Lotus Domino online services (DOLS) is used by a web site administrator to configure Internet Notes (iNotes) clients to auto download from server, thus providing iNotes clients with web access using HTTP with various browsers, and with local processing and replication. A local run time model comprises a hierarchy of models including object data store model, security model, indexing model, replication model, agent workflow model and mail model. DOLS provides a layered security model that allows flexibility for controlling access to all or part of an application. The highest level of security is managed through a database access control list (ACL). Further refinements within the security model provide access to specific documents, and their views, forms or folders, and include read access lists, write access lists, form access lists and readers and authors fields.
Owner:HCL TECH LTD
System and method for providing a distributable runtime
InactiveUS6742026B1Multiple digital computer combinationsTransmissionPartial applicationApplication software
A workflow, enterprise, and mail-enabled application server and platform supports distributed computing and remote execution of web applications. Lotus Domino online services (DOLS) is used by a web site administrator to configure Internet Notes (iNotes) clients to auto download from server, thus providing iNotes clients with web access using HTTP with various browsers, and with local processing and replication. A local run time model comprises a hierarchy of models including object data store model, security model, indexing model, replication model, agent workflow model and mail model. DOLS provides a layered security model that allows flexibility for controlling access to all or part of an application. The highest level of security is managed through a database access control list (ACL). Further refinements within the security model provide access to specific documents, and their views, forms or folders, and include read access lists, write access lists, form access lists and readers and authors fields.
Owner:IBM CORP
Enterprise software development process for outsourced developers
InactiveUS7849438B1ResourcesSpecific program execution arrangementsSoftware development processParallel computing
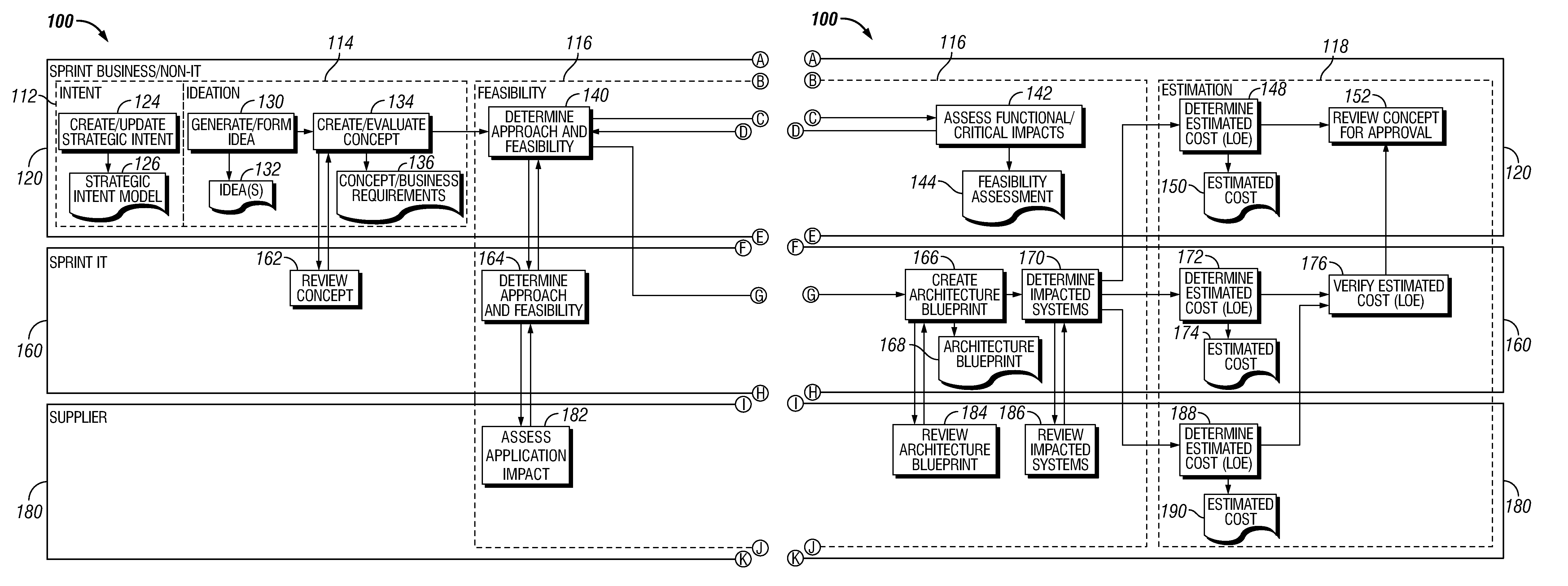
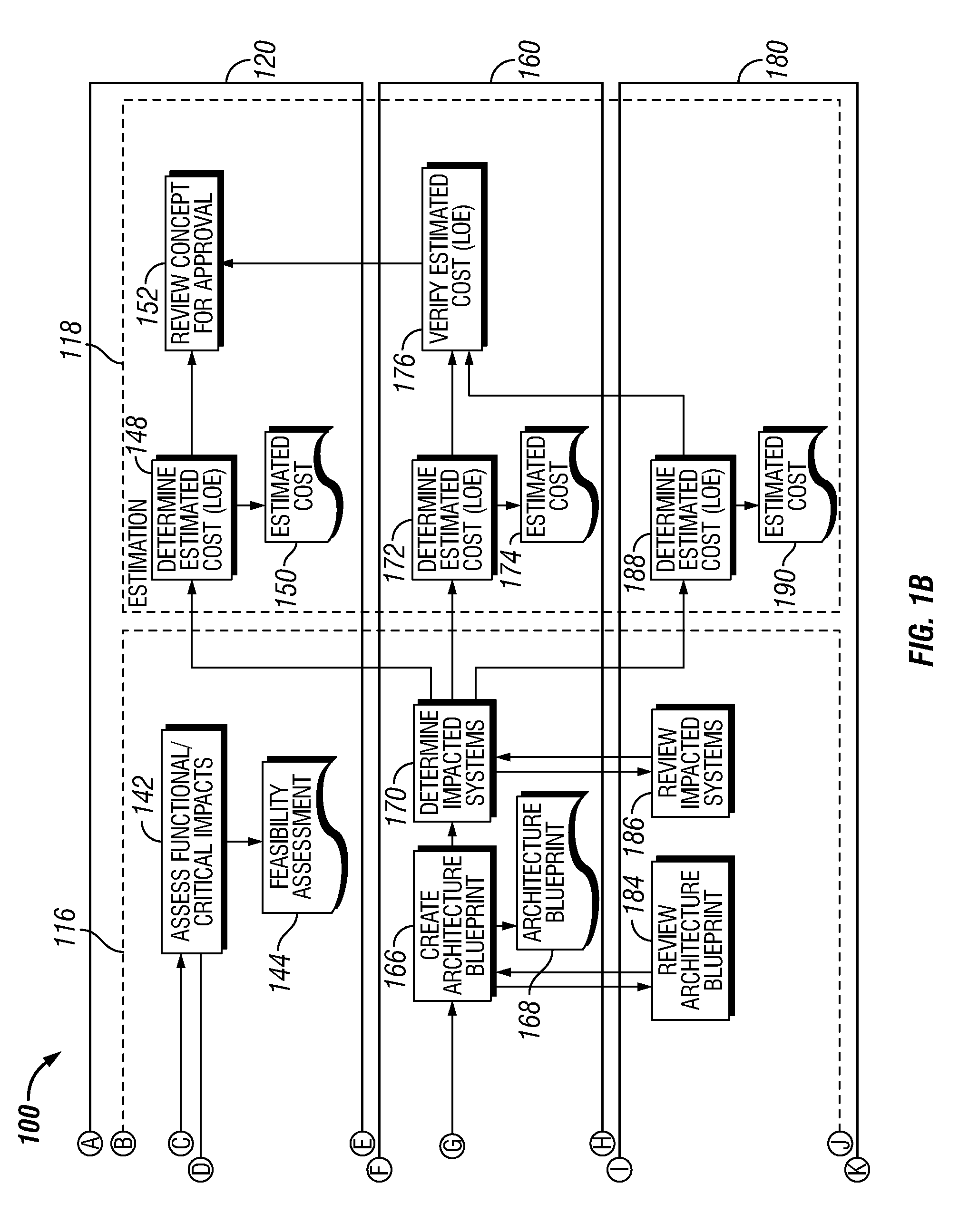
An enterprise development process for outsourced software development is provided. The process includes generating, by a business unit of an entity or organization, a concept requiring one or more computer applications, such as a project. An information technology unit of the entity may then create an integrated architecture blueprint including a design of at least a portion of the one or more computer applications. One or more outsourced suppliers of the entity, design at least a portion of the application according to the integrated architecture blueprint. The information technology unit integrates the application into a computing production environment of the entity.
Owner:SPRINT CORPORATION
System and method for downloading security context elements governing execution of downloadable and distributable agents
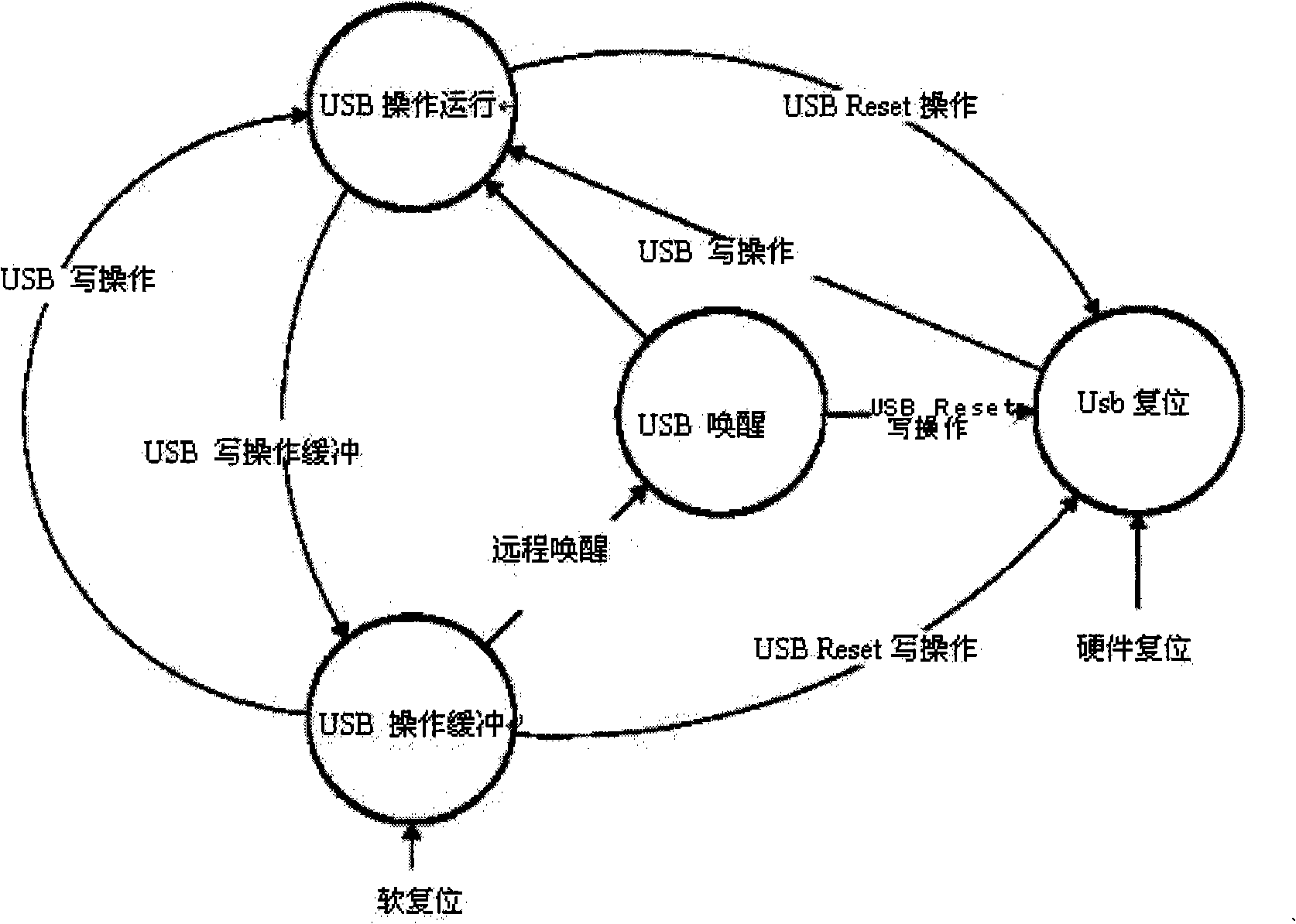
ActiveUS7360082B1Optimize workflowSynchronising transmission/receiving encryption devicesUser identity/authority verificationPartial applicationApplication software
A workflow, enterprise, and mail-enabled application server and platform supports distributed computing and remote execution of web applications. Lotus Domino online services (DOLS) is used by a web site administrator to configure Internet Notes (iNotes) clients to auto download from server, thus providing iNotes clients with web access using HTTP with various browsers, and with local processing and replication. A local run time model comprises a hierarchy of models including object data store model, security model, indexing model, replication model, agent workflow model and mail model. DOLS provides a layered security model that allows flexibility for controlling access to all or part of an application. The highest level of security is managed through a database access control list (ACL). Further refinements within the security model provide access to specific documents, and their views, forms or folders, and include read access lists, write access lists, form access lists and readers and authors fields.
Owner:GOOGLE LLC
Method and apparatus of managing items on clipboard of portable terminal
InactiveUS20120246594A1Function increaseNatural language data processingProgram controlPartial applicationApplication software
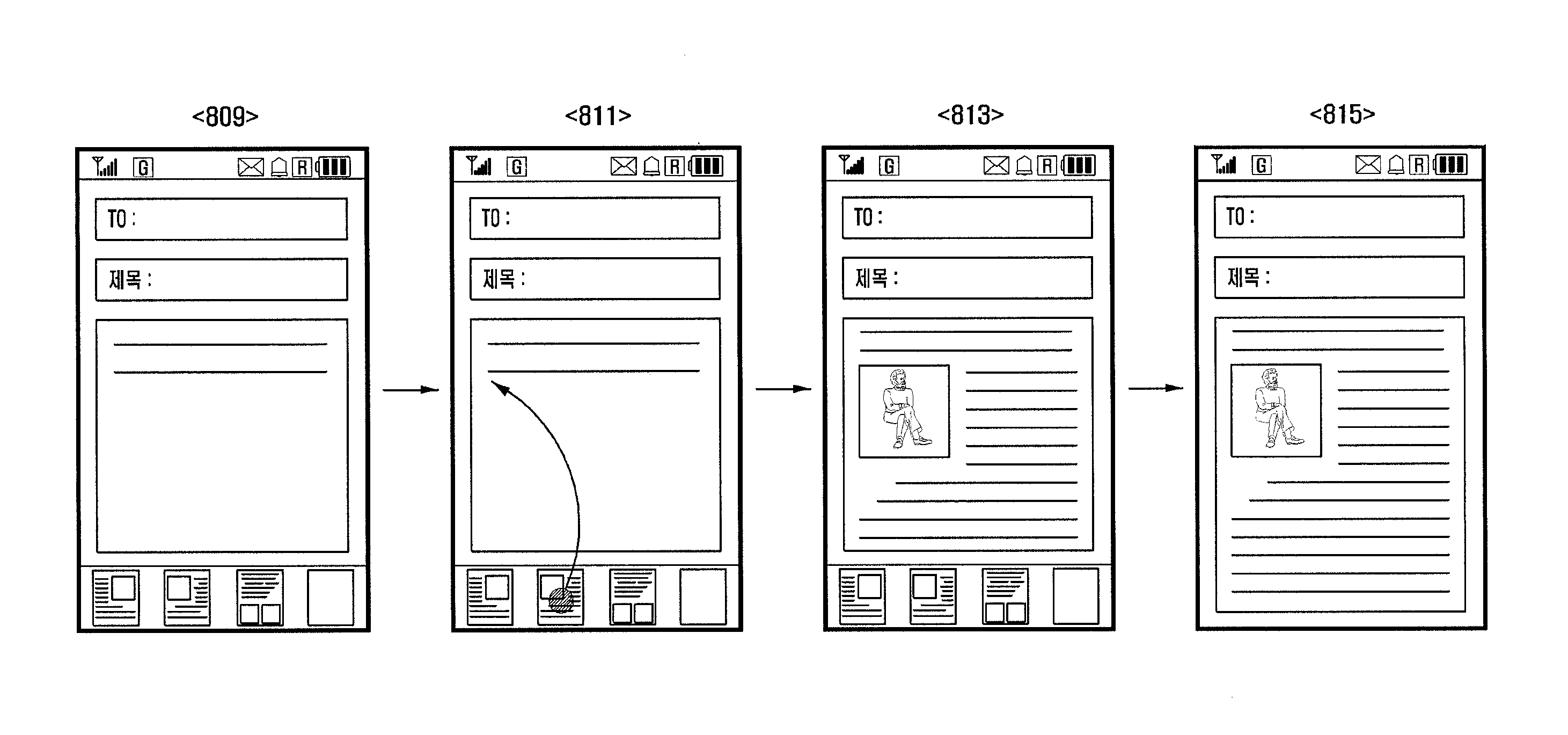
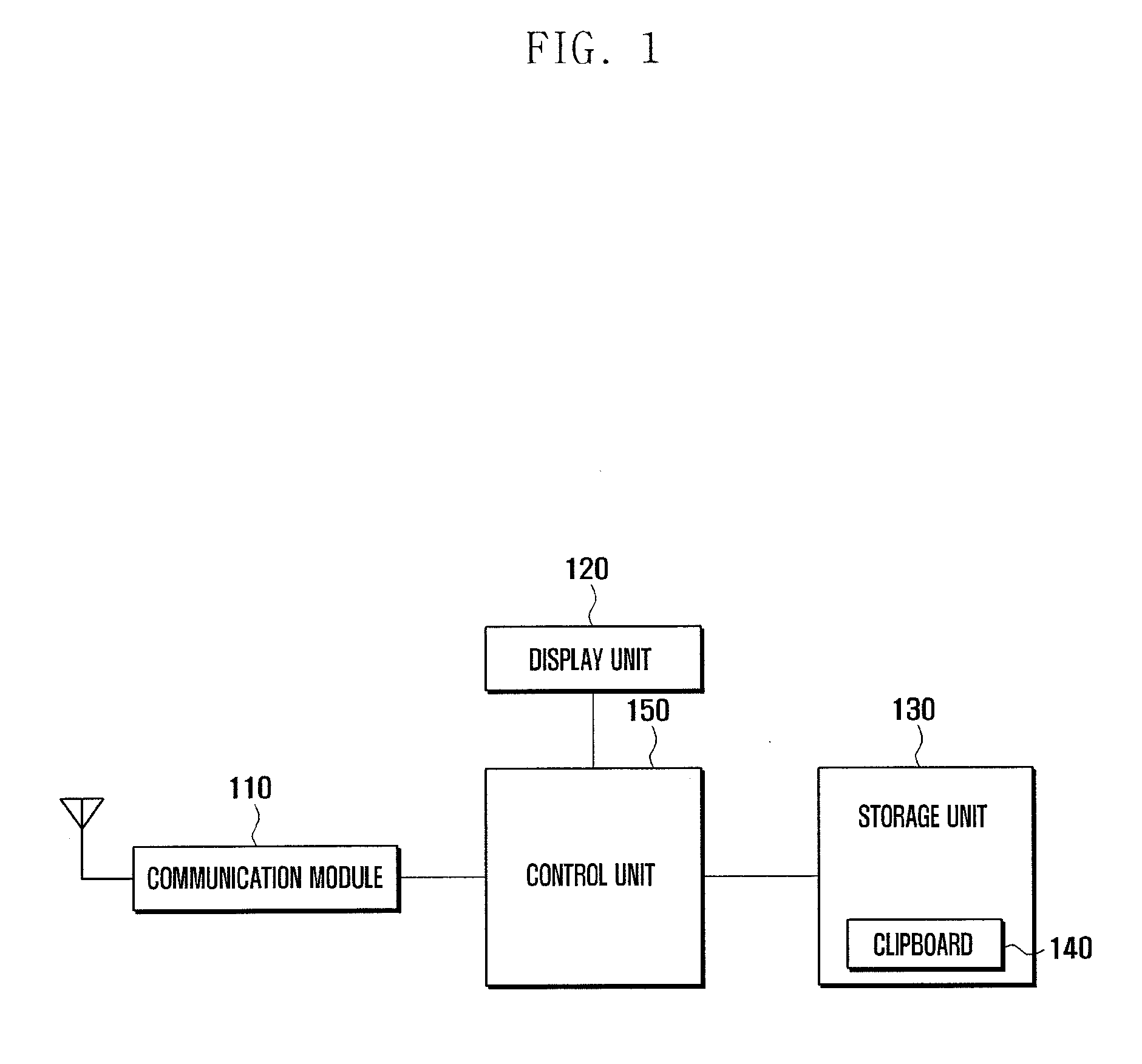
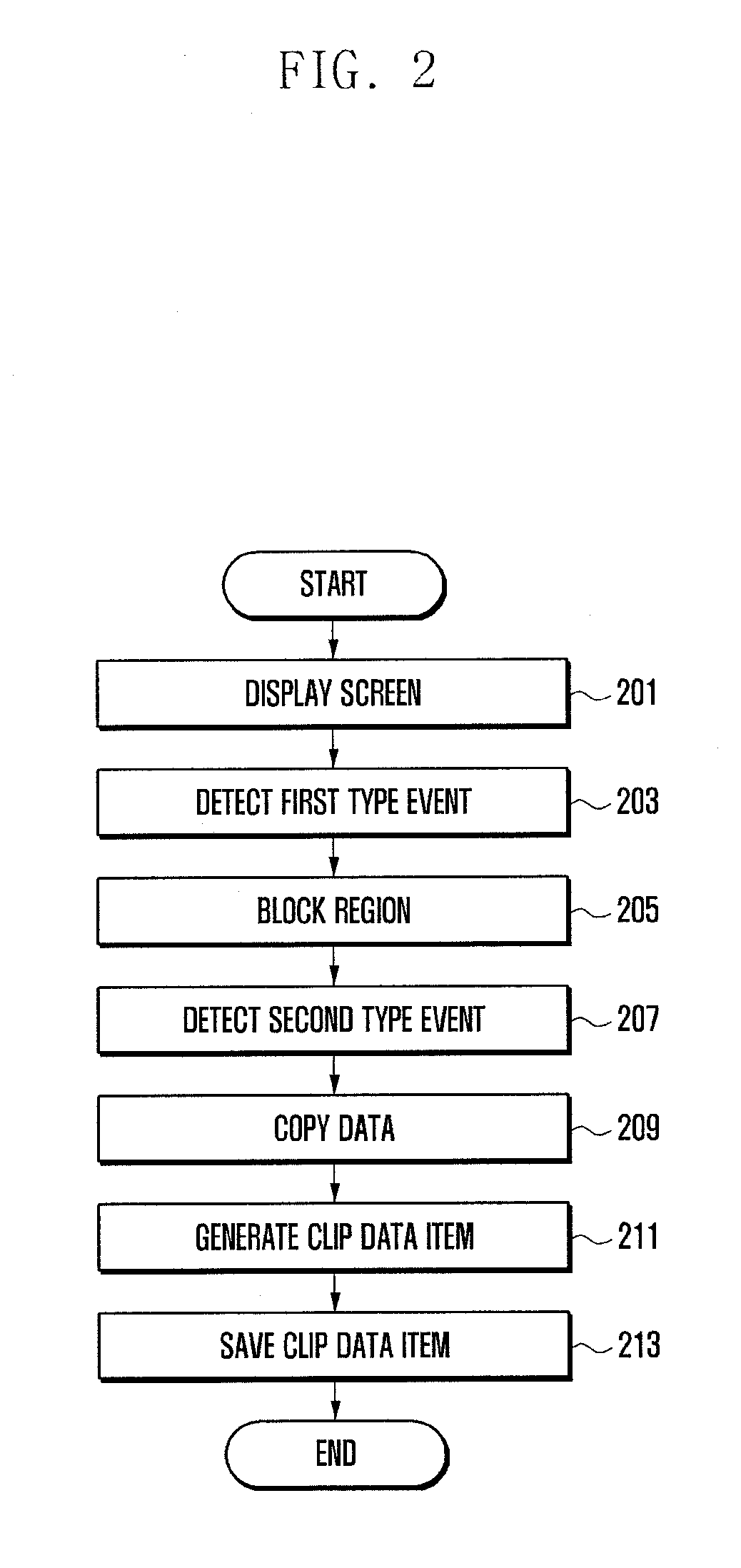
A portable terminal and a method for managing items on a clipboard of the portable terminal are provided for a user to copy text and data items simultaneously onto the clipboard and paste the copied items individually where the user desires. The portable terminal of the present invention includes a touchscreen and a control unit which controls presenting a display region showing a screen corresponding to user command on the touchscreen in response to an execution of at least one application, presenting a clipboard region at a part of the touchscreen in response to a user command, and displaying clip data selected by the user among at least one clip data appearing in the clipboard region on the display region.
Owner:SAMSUNG ELECTRONICS CO LTD
Battery management method and device
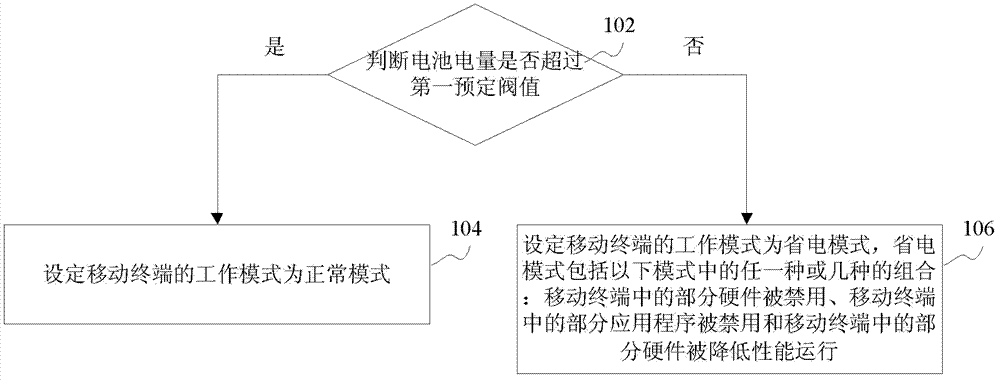
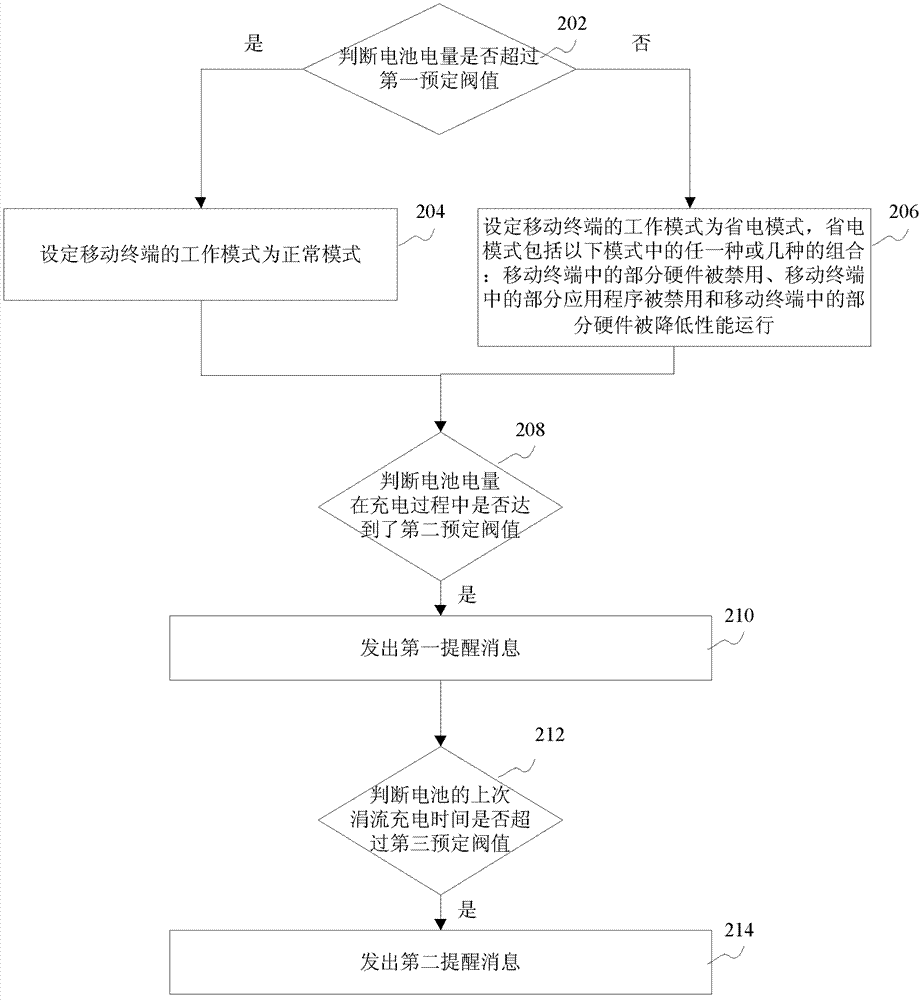
InactiveCN103369124AExtend battery lifeExtend your lifeSubstation equipmentSecondary cells servicing/maintenanceNormal modePartial application
The invention discloses a battery management method and device, which belong to the field of batteries. The battery management method includes: judging whether an electric quantity of the battery exceeds a first preset threshold value; if so, setting a work mode of a mobile terminal into a normal mode; and if not so, setting the work mode of the mobile terminal into a power-saving mode. The power saving mode includes any one or a combination of the following modes: forbidding use of some hardwares in the mobile terminal; forbidding use of some application programs in the mobile terminal and operation of some hardwares with degraded performance in the mobile terminal. Through automatic switch of the work mode of the mobile terminal according to whether the electric quantity of the battery exceeds the preset threshold value, the battery management method and device enable an endurance time of the mobile terminal to be prolonged and a charging and discharging rule of the lithium battery to be met so that an effect that a service life of the battery is prolonged is achieved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Application support for network devices
ActiveUS20130254675A1Well formedInput/output for user-computer interactionSoftware engineeringUser inputPartial application
A system may receive application data in a client-incompatible format and convert at least a portion of the application data into an alternate client-compatible format. In one example, the incompatible format may comprise Enhanced Binary Interchange Format (EBIF) while a client-compatible format may include a web format such as JavaScript, XML or HTML. Interactions (e.g., commands and user input) associated with the application may be received and converted. The interactions may then be processed using the application.
Owner:COMCAST CABLE COMM LLC
Smart television and method for receiving remote controller input by smart television
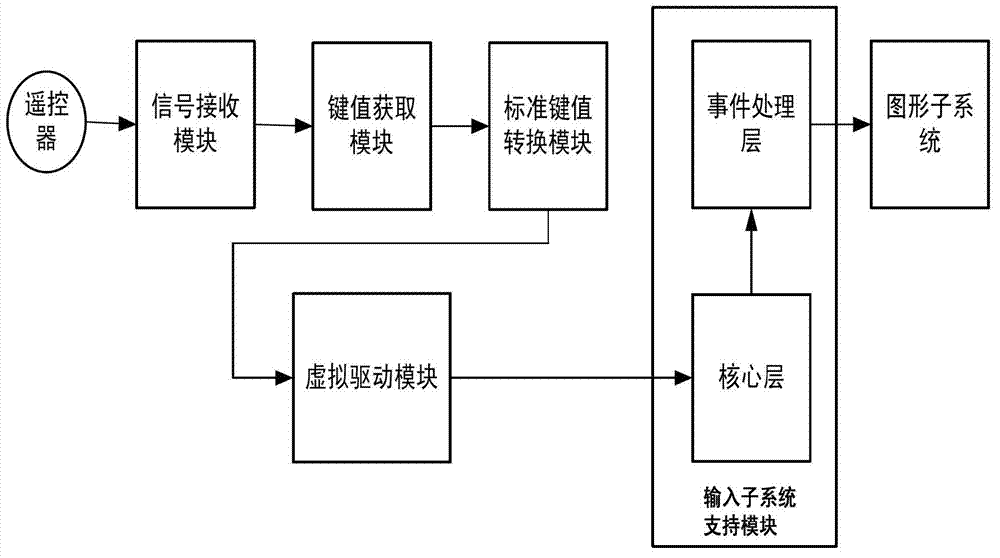
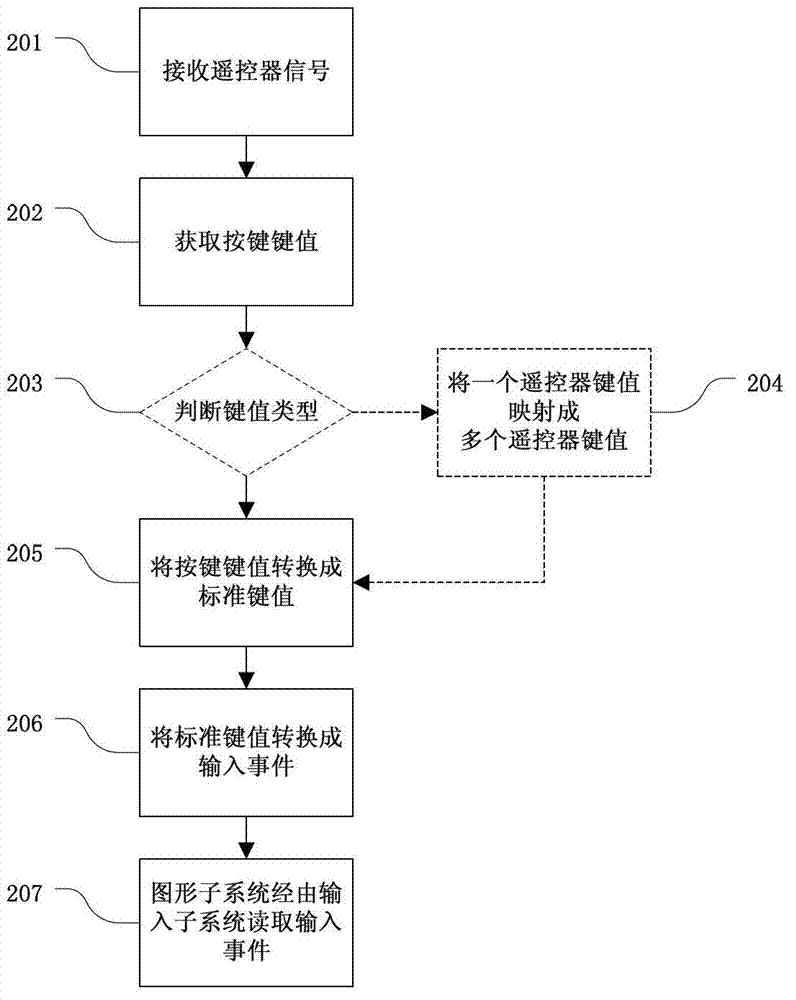
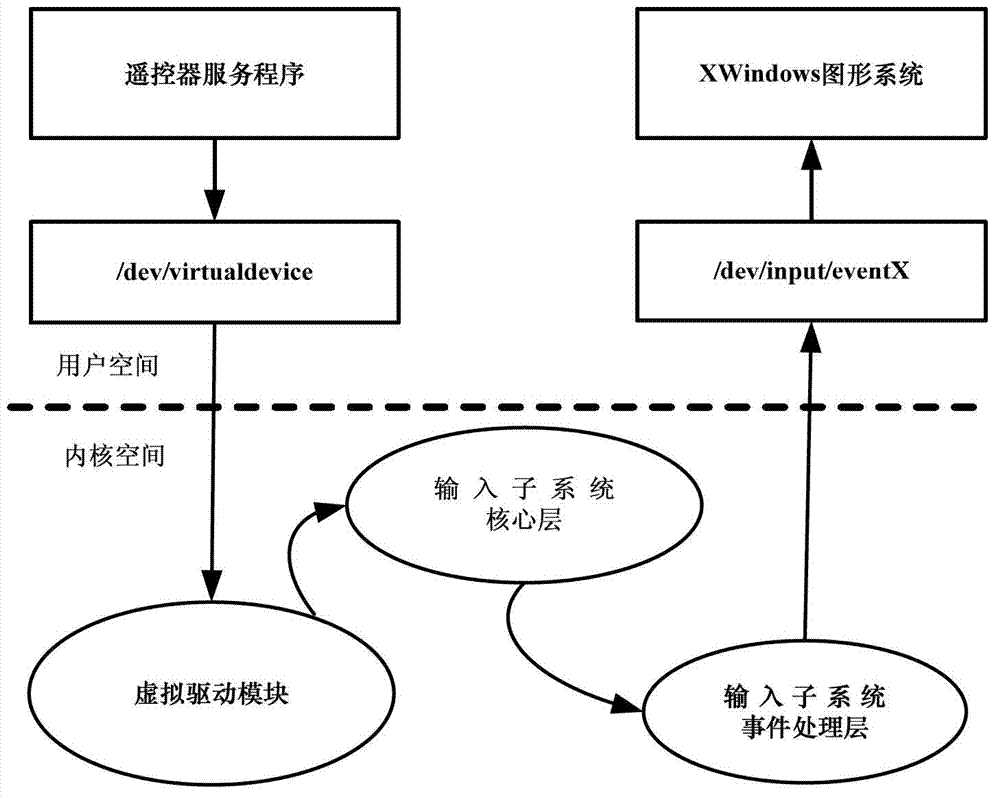
InactiveCN102790918AInput/output for user-computer interactionSelective content distributionComputer hardwareRemote control
The invention relates to a smart television and a method and system for receiving remote controller input by the smart television. The method comprises the following steps: receiving a remote control signal from a remote controller; acquiring the corresponding remote controller key value according to the remote control signal; converting the remote controller key value to be a standard key value of a smart television operating system; and converting the standard key value to be a corresponding input event by virtual drive, so that the relevant input treatment is carried out on the input event by the smart television operating system. According to the smart television and method for receiving remote controller input by smart television, the key value information acquired from the traditional remote controller is converted to be standard keyboard and mouse information, and then is submitted to the operating system of the smart television in the form of the operating system input event through the virtual drive, so that the keyboard and mouse operation of most of application procedures can be supported when the traditional remote controller code is reused.
Owner:INST OF ACOUSTICS CHINESE ACAD OF SCI
Invalidating processing method for application icons, and communication terminal
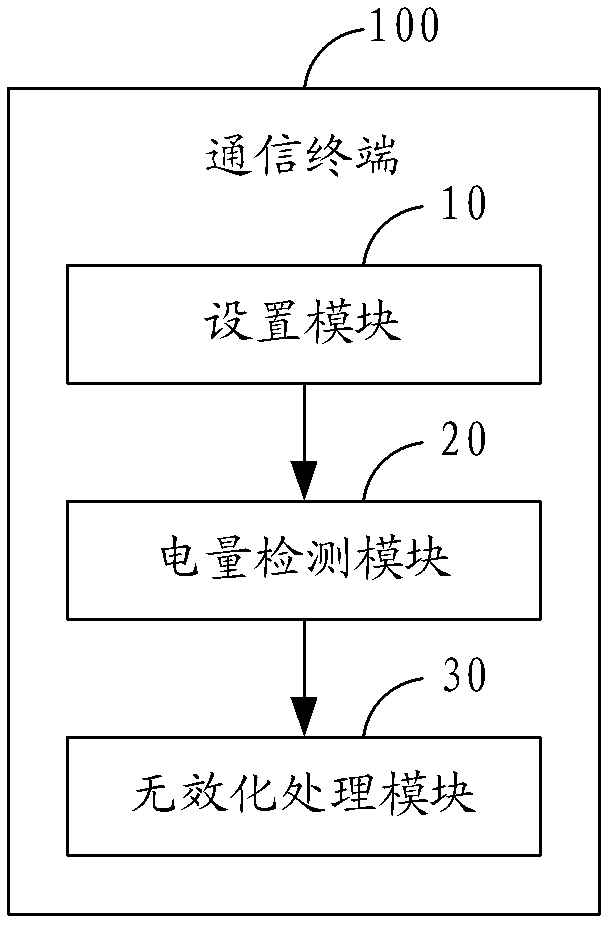
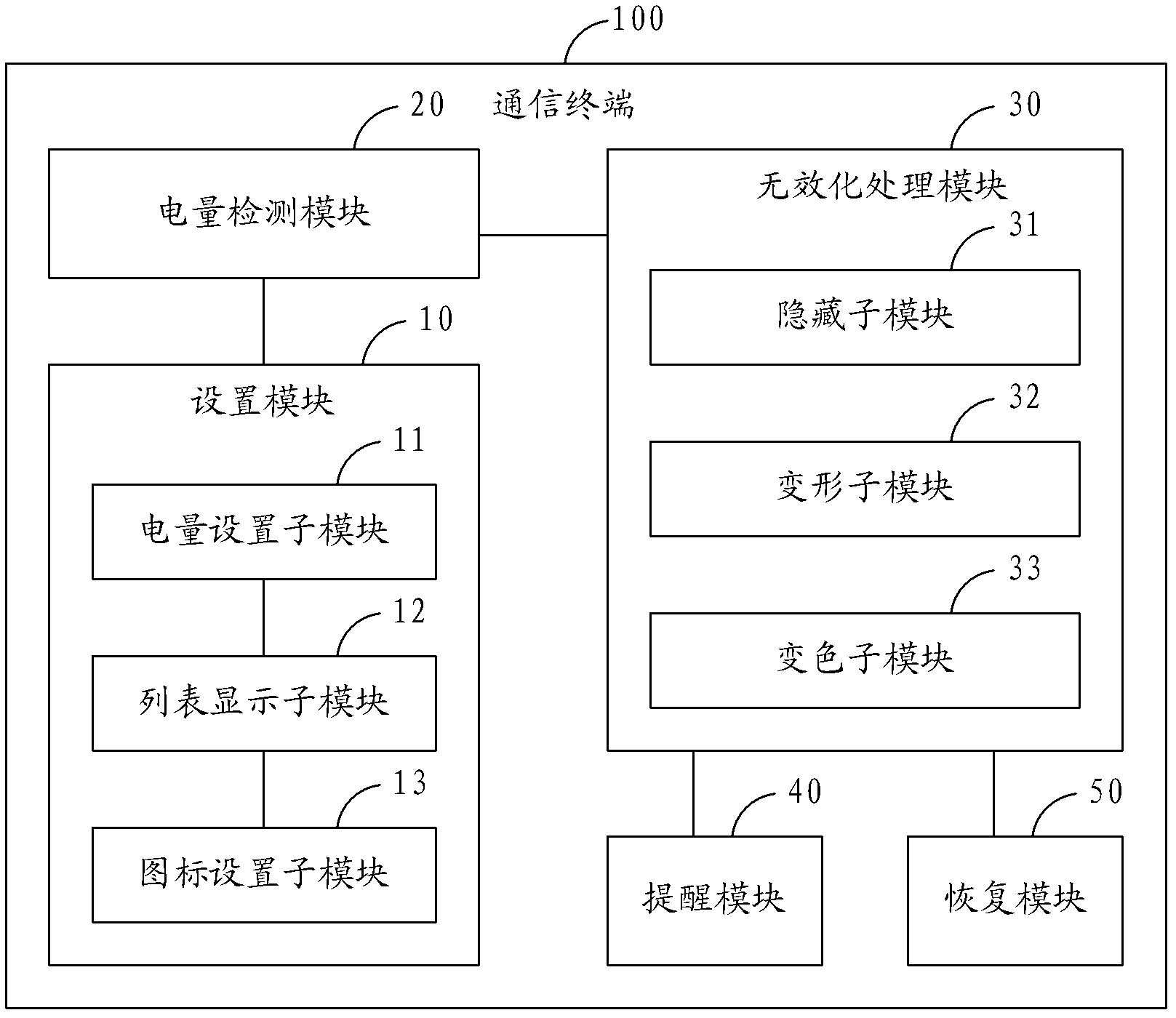
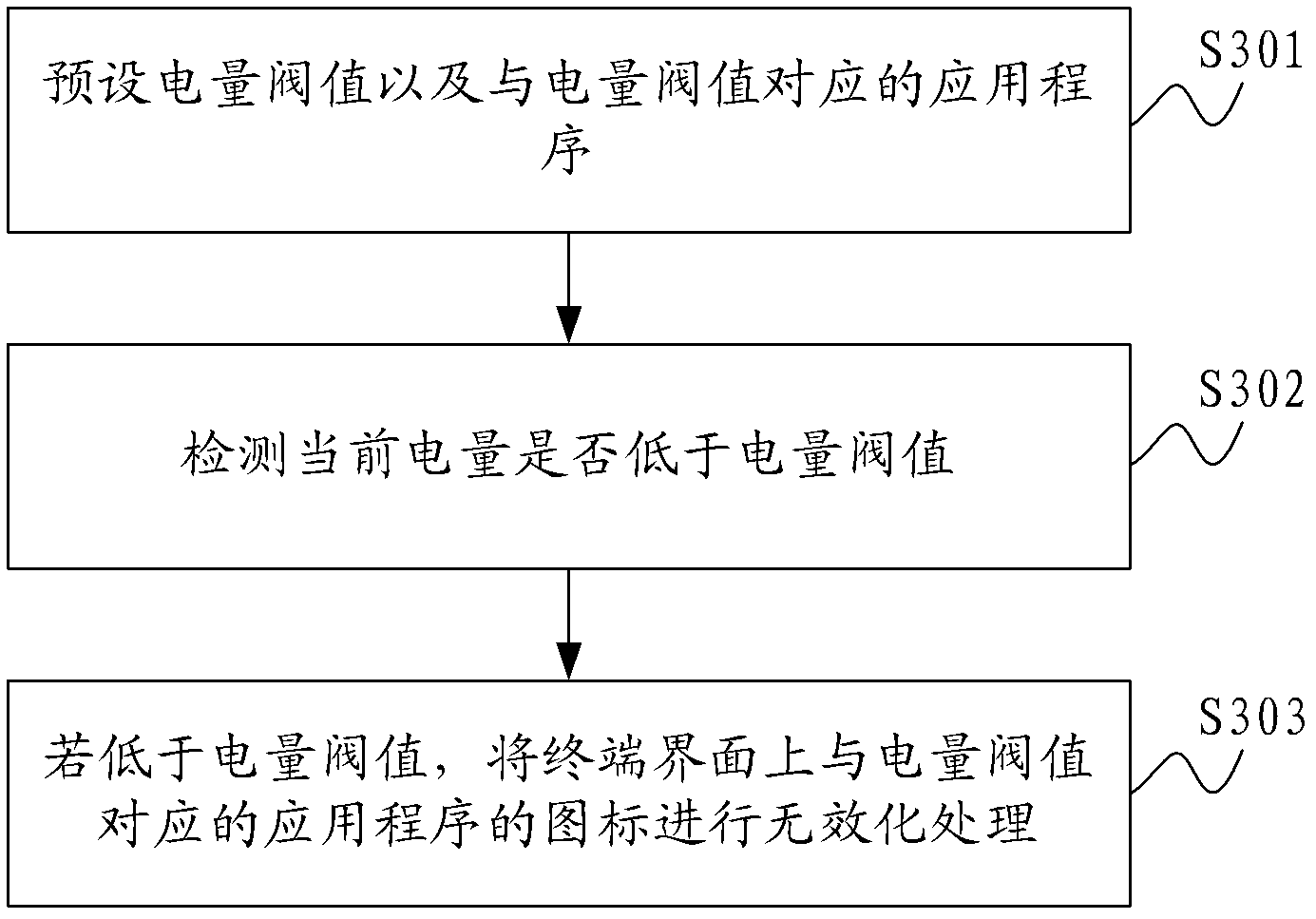
InactiveCN103207660AAchieve power saving effectPower supply for data processingElectricityCurrent electric
The invention is applicable to the technical field of communication, and provides an invalidating processing method for application icons. The method comprises the steps of: presetting an electric quantity threshold value and a application corresponding to the electric quantity threshold value; detecting whether the current electric quantity is less than the electric quantity threshold value or not; and if the current electric quantity is less than the electric quantity threshold value, carrying out invalidating processing on the application icon corresponding to the electric quantity threshold value. Correspondingly, the invention further provides a communication terminal. Consequently, by utilizing the method, validation processing can be carried out on partial application icons when the current electricity quantity is not enough, so that users are limited to start the applications corresponding to the icons, and furthermore, an electricity-saving effect is achieved.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Method and apparatus for application awareness in a network
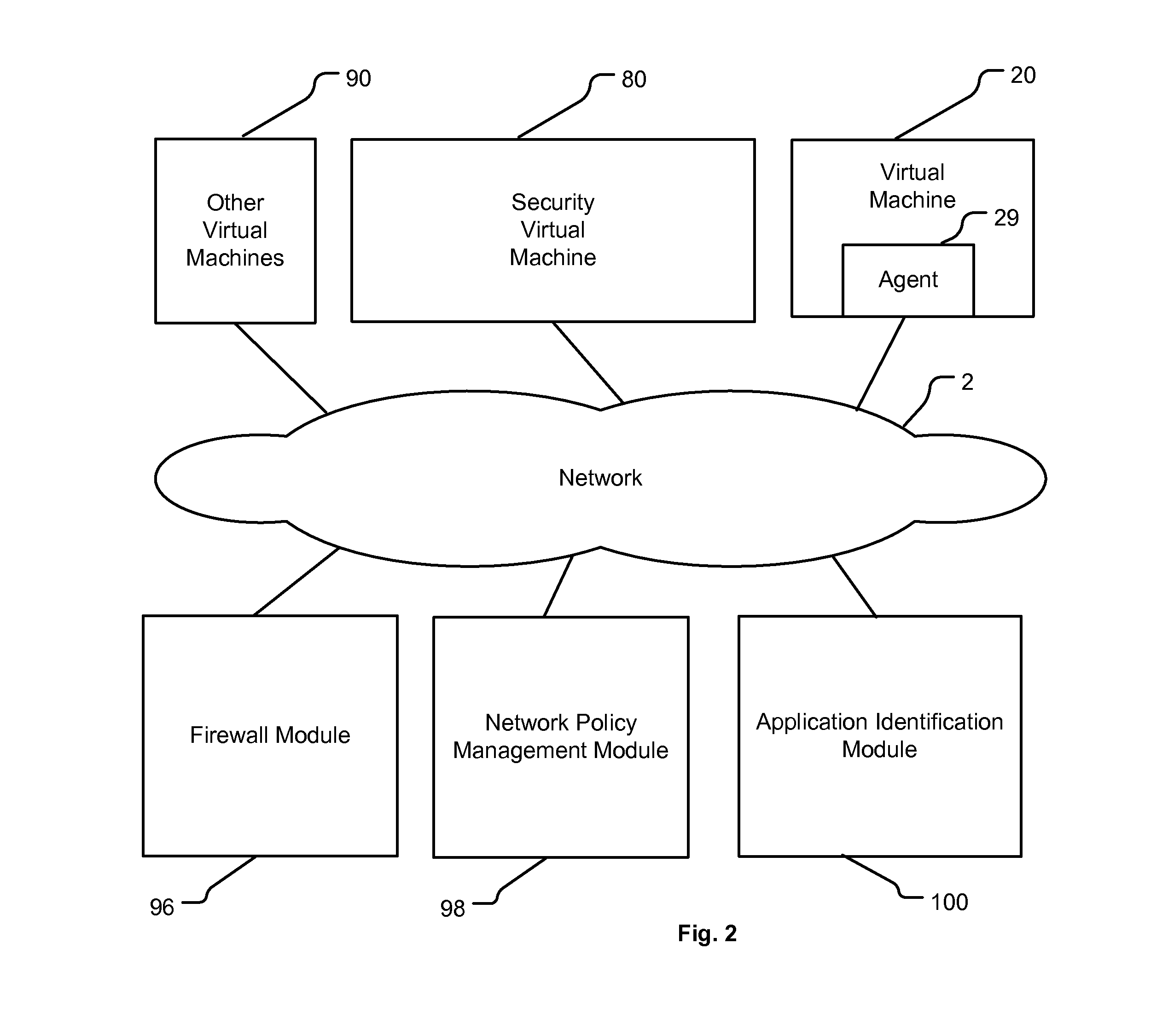
ActiveUS9444841B2Digital data authenticationPlatform integrity maintainanceVirtualizationTransport layer
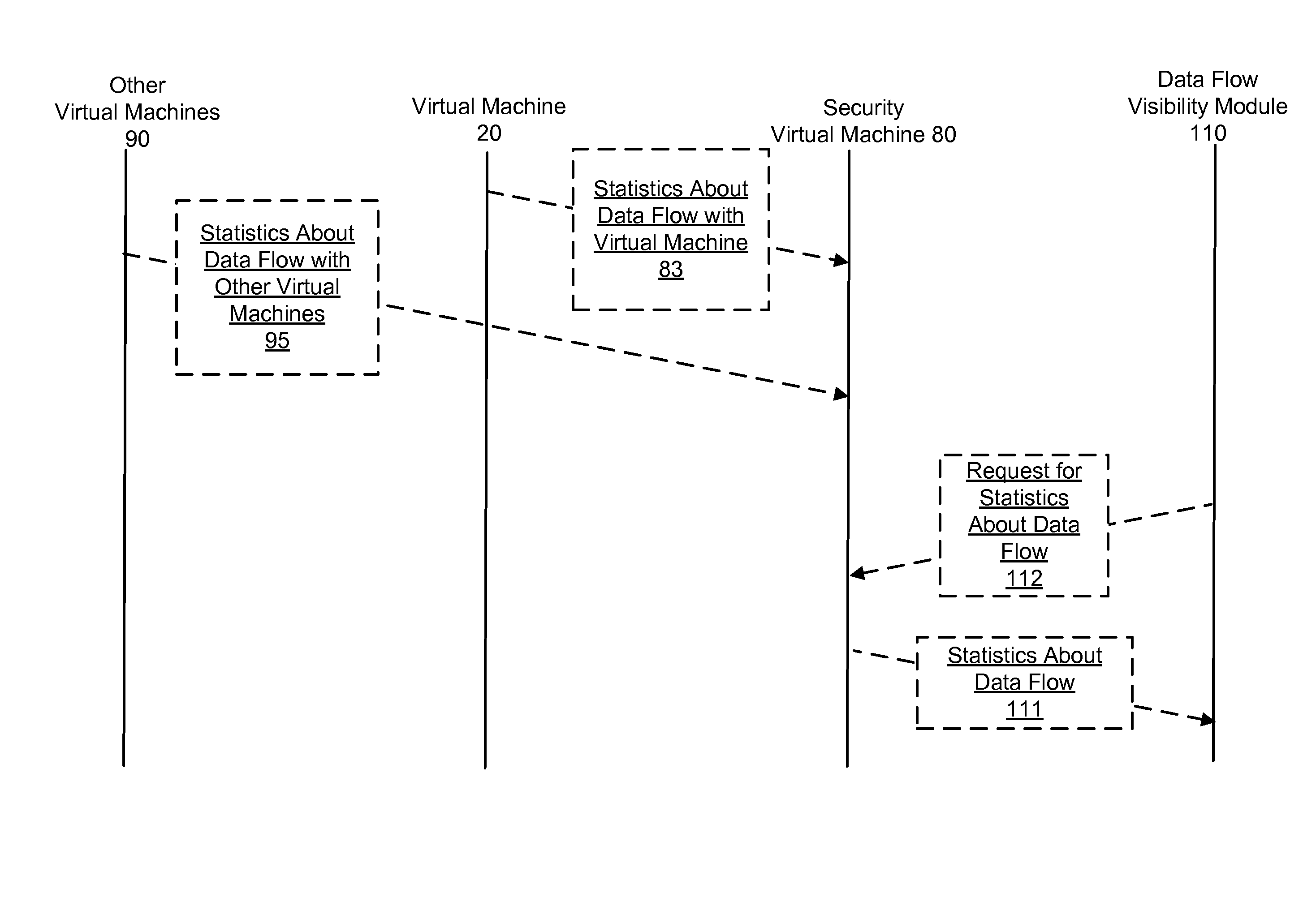
A method for enforcing a network policy is described herein. In the method, a network socket event request from an application executing in a first context is intercepted by an agent prior to the request reaching a transport layer in the first context. A context refers to virtualization software, a physical computer, or a combination of virtualization software and physical computer. In response to the interception of the request, the agent requests a decision on whether to allow or deny the network socket event request to be communicated to a security server executing in a second context that is distinct from the first context. The request for a decision includes an identification of the application. The agent then receives from the security server either an allowance or a denial of the network socket event request, the allowance or denial being based at least in part on the identification of the application and a security policy. The agent blocks the network socket event from reaching the transport layer when the denial is received from the security server. In one embodiment, the method is implemented using a machine readable medium embodying software instructions executable by a computer.
Owner:VMWARE INC
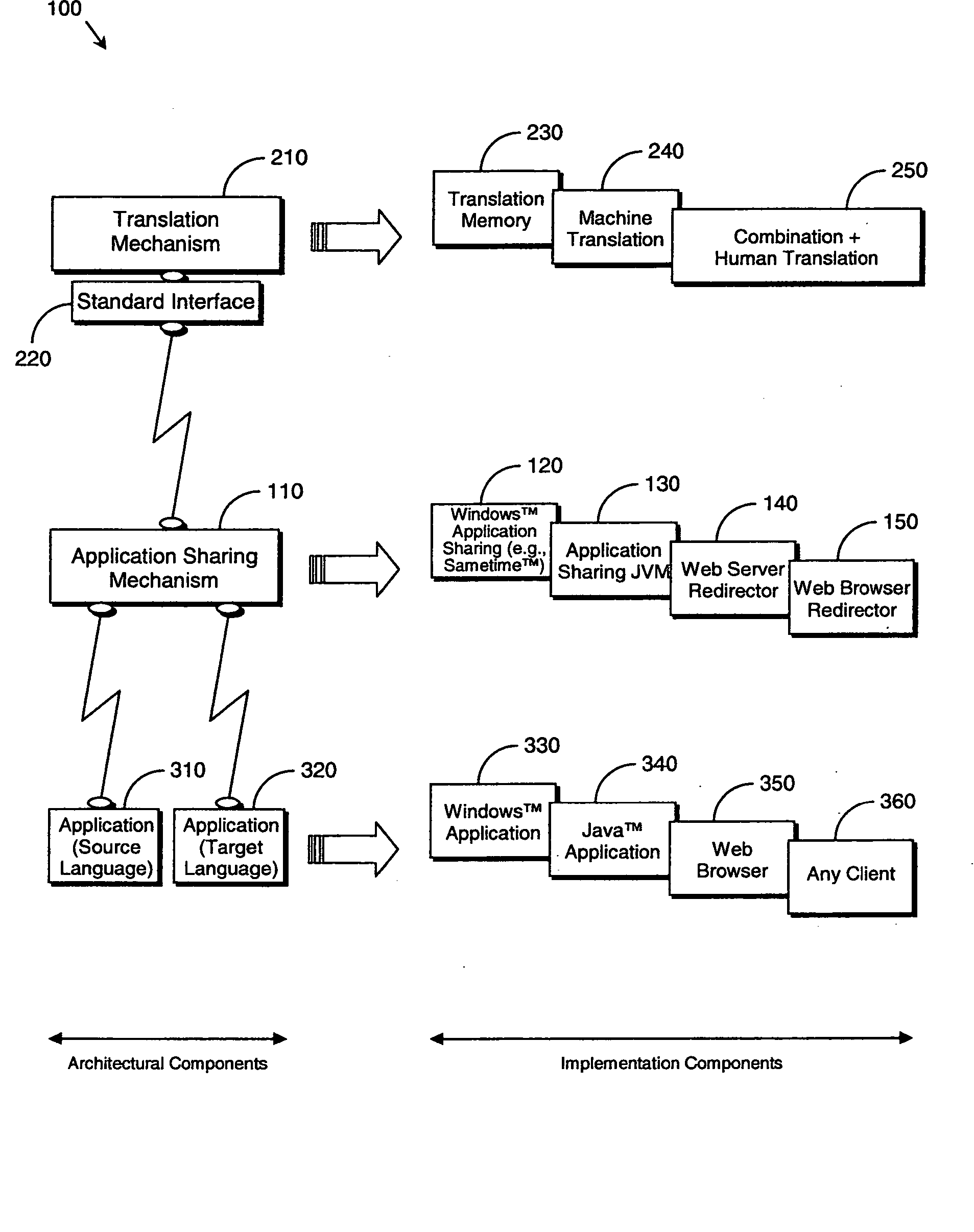
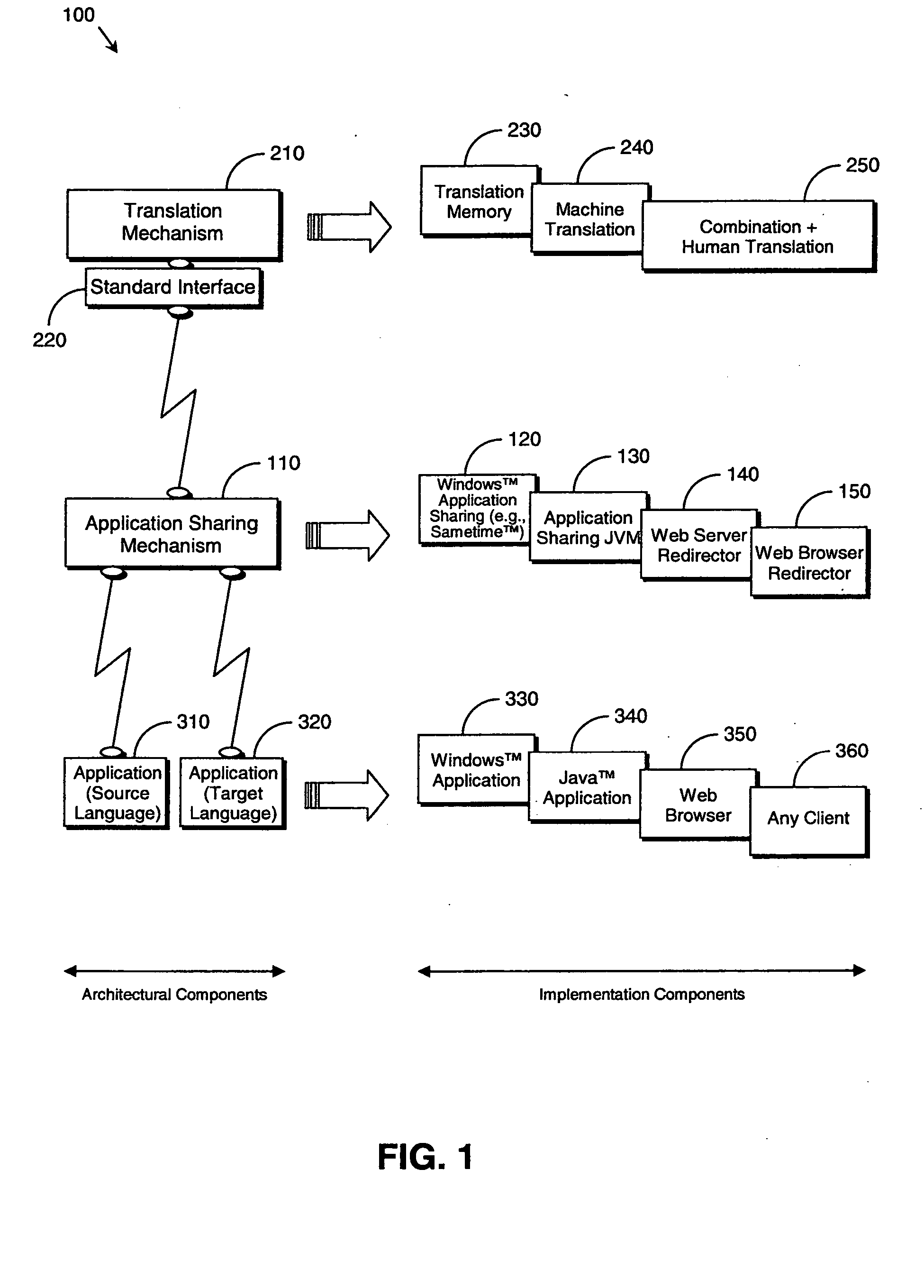
System and method for application sharing
A system (100) and method for application sharing based on automatic translation by: running an application in a source language (310), automatically translating (210) at least part of the application from the source language to a target language, and sharing (110) the application in the target language (320). Interception of the application occurs at as high as possible a level so that text methods can be intercepted. The translation may use translation memory (230), machine translation (240) or a combination of these with human translation (250). The sharing may be performed by Windows™ application sharing (120), Java™ application sharing (130), web server redirection (140) or web browser redirection (150). This provides the following advantage(s): An application sharing system can be used, with a link to an automated translated system (either translation memory or machine translation depending on the usage) such that the remote / copy version of the application appears translated. This remote / copy version can be either local to a single machine or displayed remotely with a system such as sametime. It can also apply to web sites, applied locally or from the server.
Owner:IBM CORP
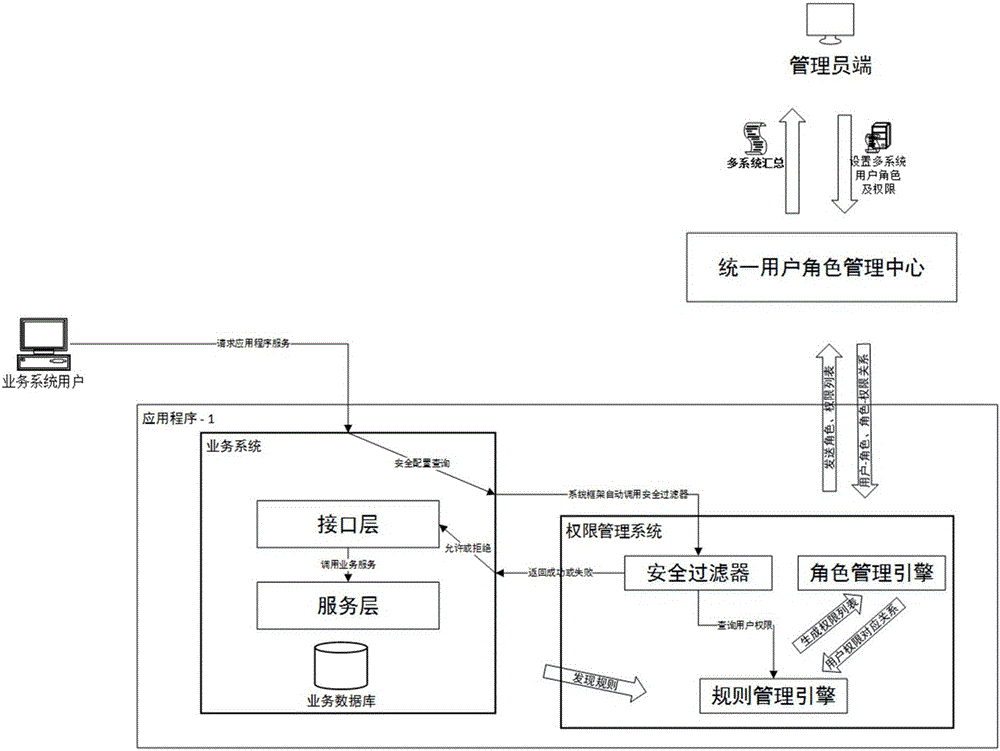
Multi-system role authority management method and system based on unified interface
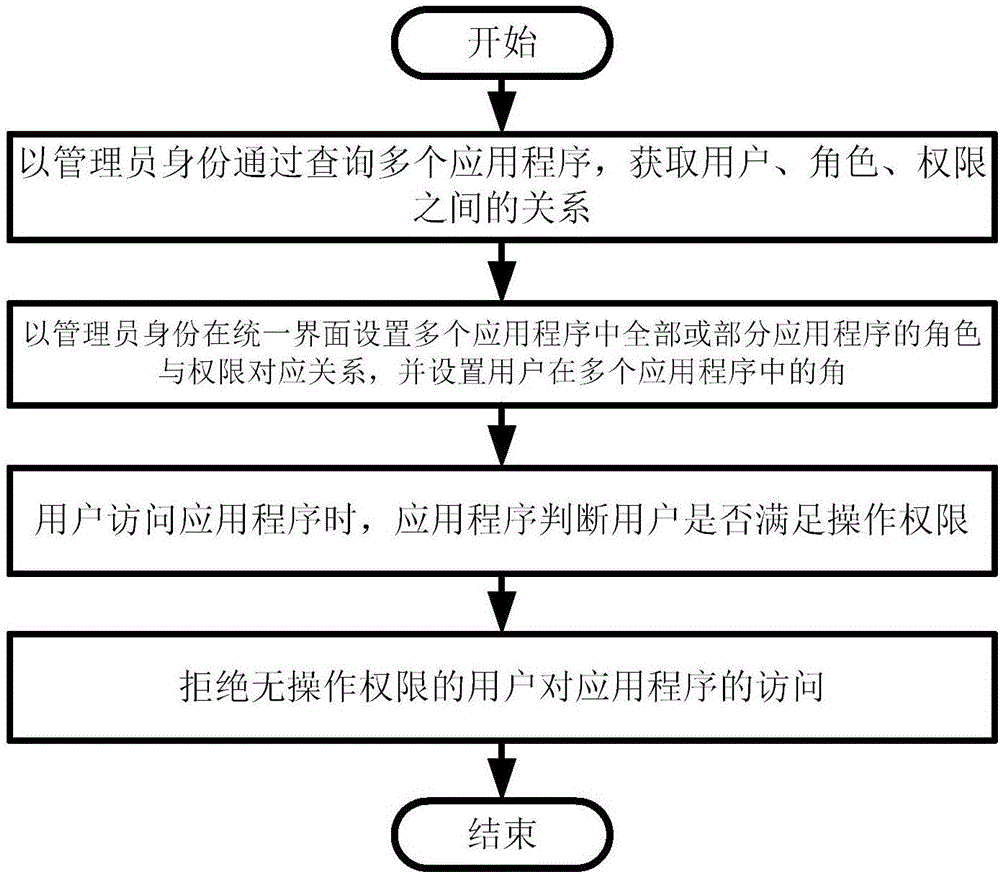
ActiveCN106790001AReduce complexityImprove reliabilityData switching networksPartial applicationApplication software
The invention provides a multi-system role authority management method and system based on a unified interface. The method comprises the following steps: step 1: inquiring multiple application programs as an administrator to obtain the relationship between a user, a role and authority; step 2: setting a corresponding relation of roles and authority of all or a part of application programs in the multiple application programs on the unified interface as the administrator, and setting the roles of the user in the multiple application programs; step 3: when the user accesses the application programs, judging whether the user has operation authority by the application programs; and step 4: refusing the user having no operation authority to access the application programs.
Owner:CETC CHINACLOUD INFORMATION TECH CO LTD
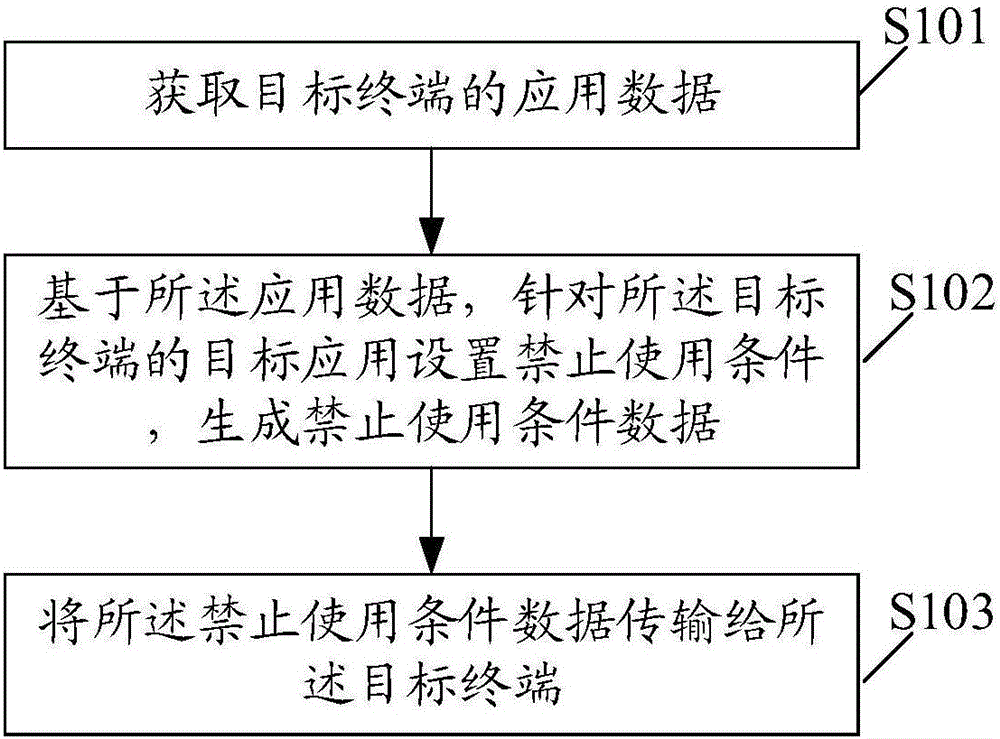
Remote control method and system, and terminal
InactiveCN106790417AServe as a supervisory reminderSubstation equipmentTransmissionRemote controlPartial application
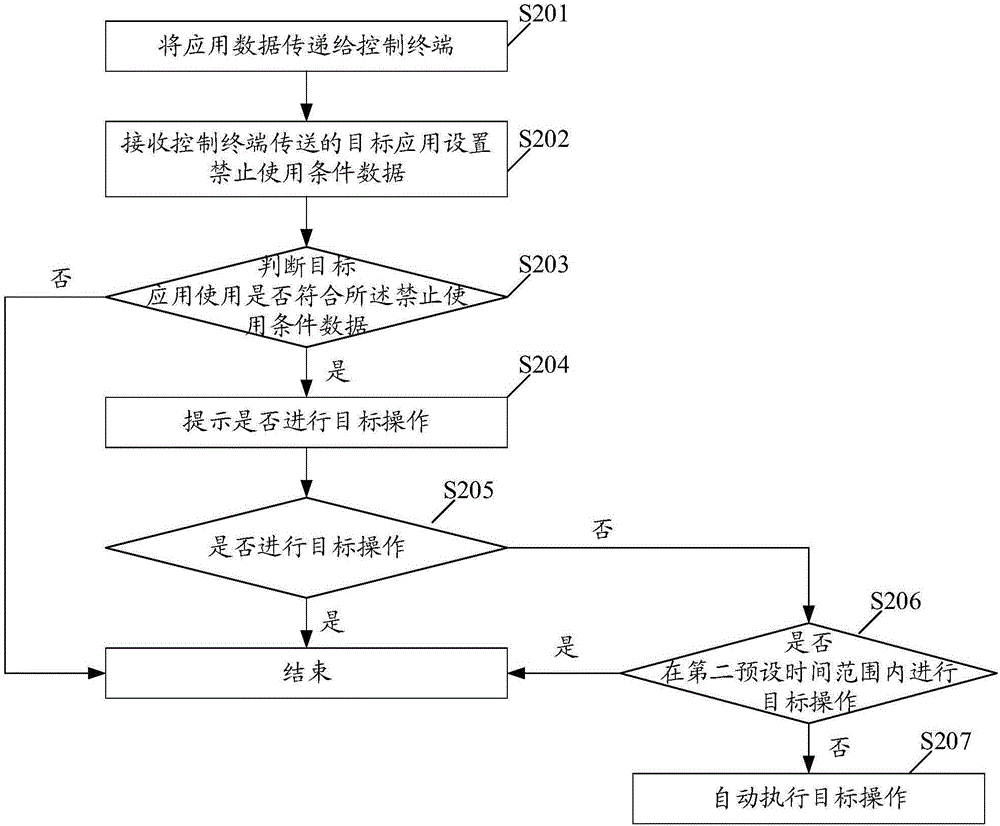
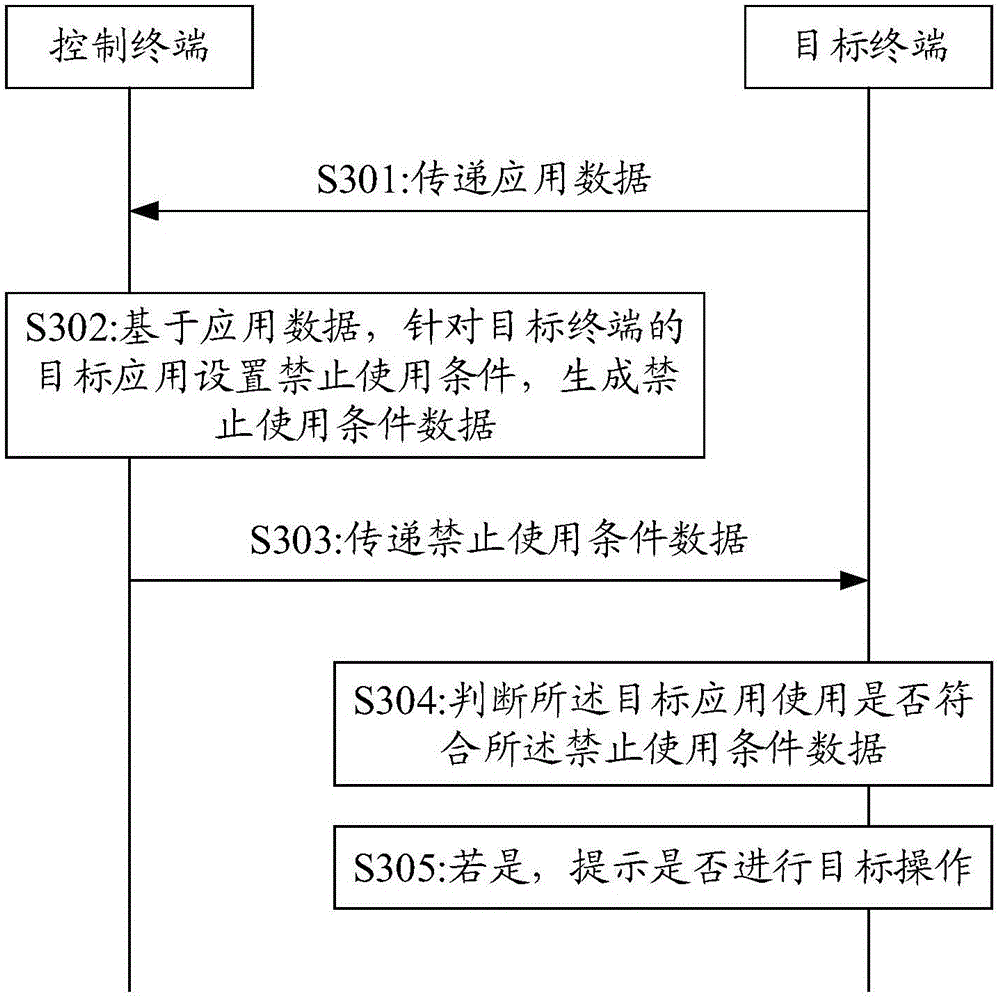
The embodiment of the invention discloses a remote control method and system, and a terminal. The remote control method comprises the steps of transferring application data to a control terminal; receiving use prohibition condition data which is sent by the control terminal and is set for target applications; judging whether use of the target applications satisfies the use prohibition condition data or not; and prompting whether to carry out target operation or not if the use of the target applications satisfies the use prohibition condition data. Through application of the embodiment of the invention, parents can manage a mobile phone of a child and sets use prohibition conditions for partial applications installed in the mobile phone of the child. When the use of the applications carried out by the child satisfies the use prohibition conditions, whether to carry out target operation, such as power-off or application logout, or not is prompted, thereby acting in monitoring and prompting.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Method for intelligent and automated transmission of local context in converged signaling
ActiveUS20080285738A1Help desk personnel more efficientTelevision system detailsDigital computer detailsPartial applicationApplication software
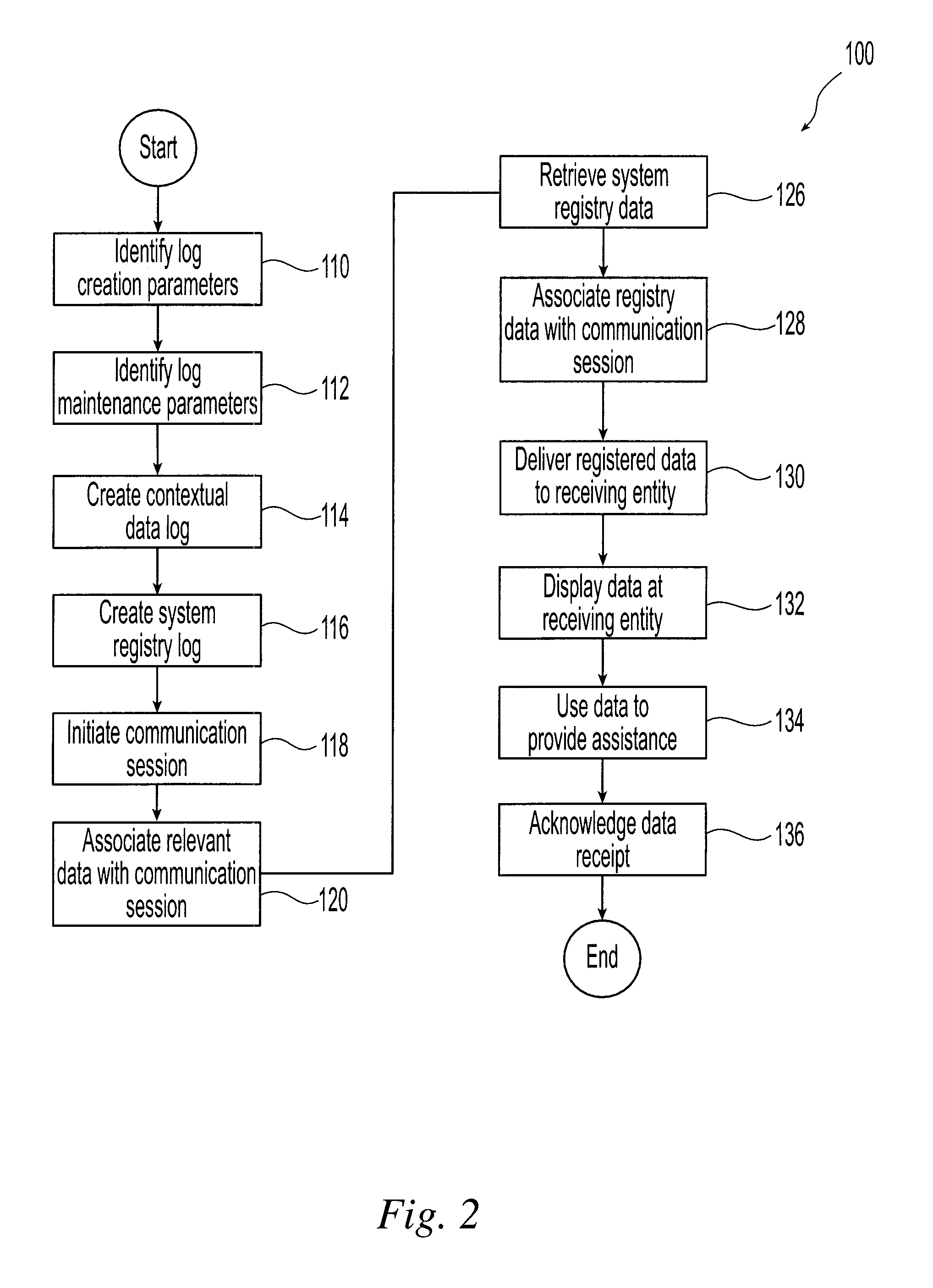
Methods and systems are provided for associating contextual data with communication sessions, in particular in technical help desk scenarios. A context logger service running on a central server or on an individual computing device is used to create a log of application specific, often ephemeral, contextual data for a plurality of applications running one or more systems that are in communication with the context logger service across one or more networks. When a communication session between an initiating entity and a receiving entity to request assistance regarding a subject application running on one of the systems is initiated, and if the communication session is deemed to be a candidate for the automatic association of such context data, at least a portion of the application specific contextual data contained in the log is associated with the communication session and delivered to the receiving entity. The receiving entity uses the associated application specific contextual data to provide the requested assistance, or otherwise improve the operations at the receiving entity.
Owner:MAPLEBEAR INC
Method for achieving control over Android smart television based on virtual input equipment
InactiveCN103796058AEasy to controlMeet diversified control needsInput/output for user-computer interactionSelective content distributionTechnology of televisionPartial application
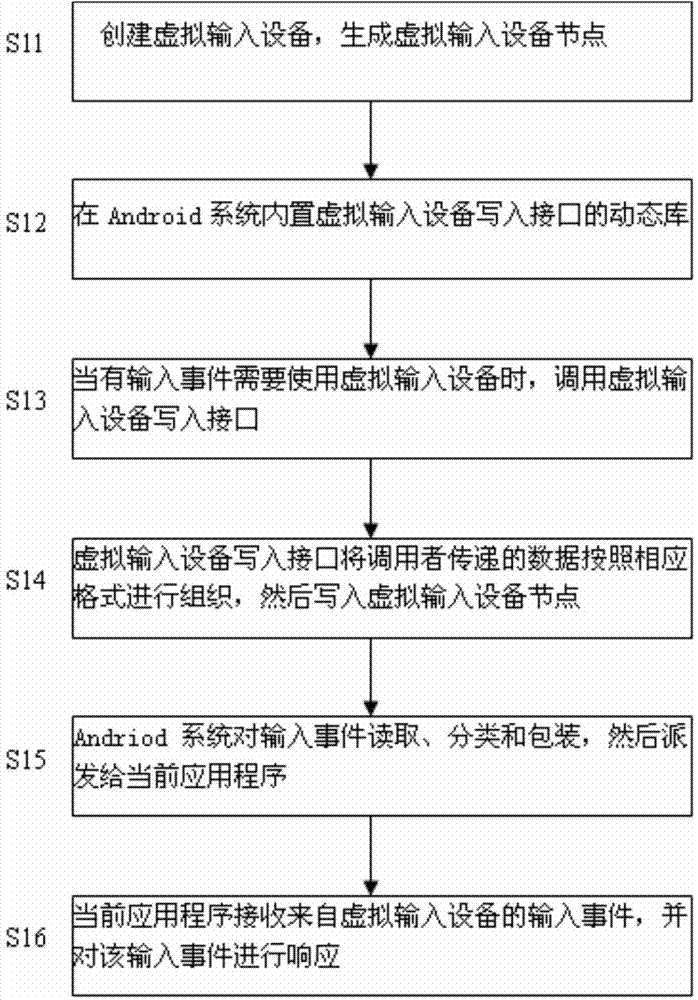
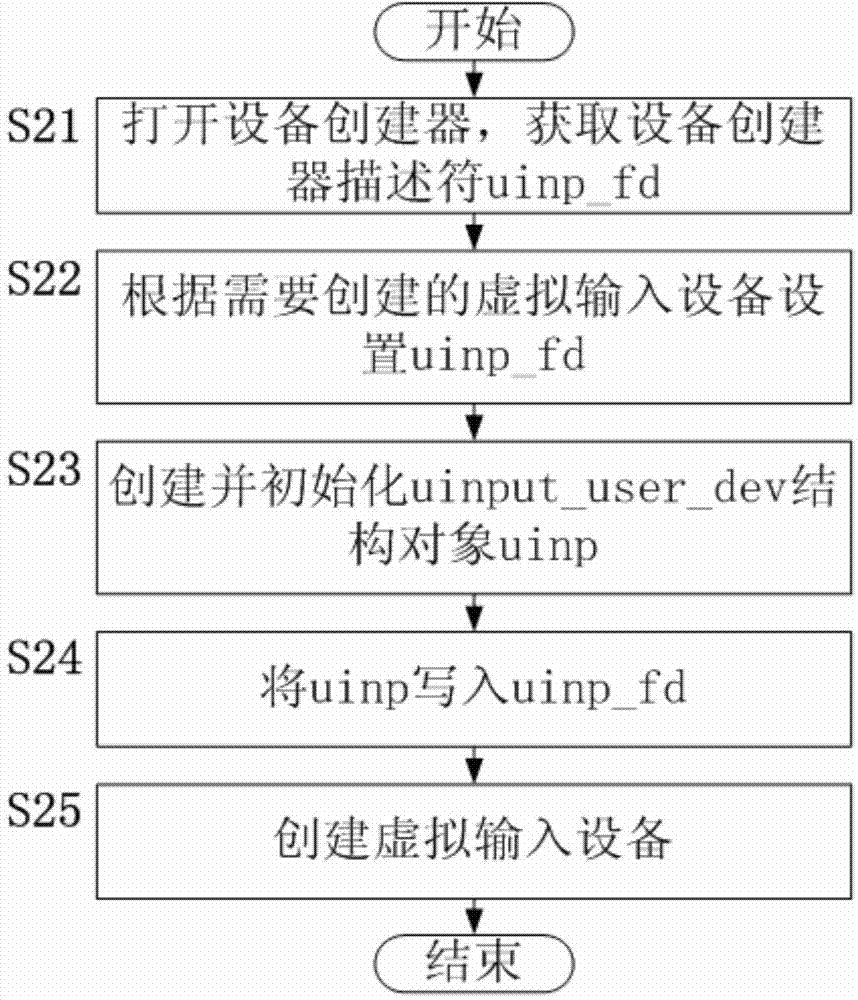
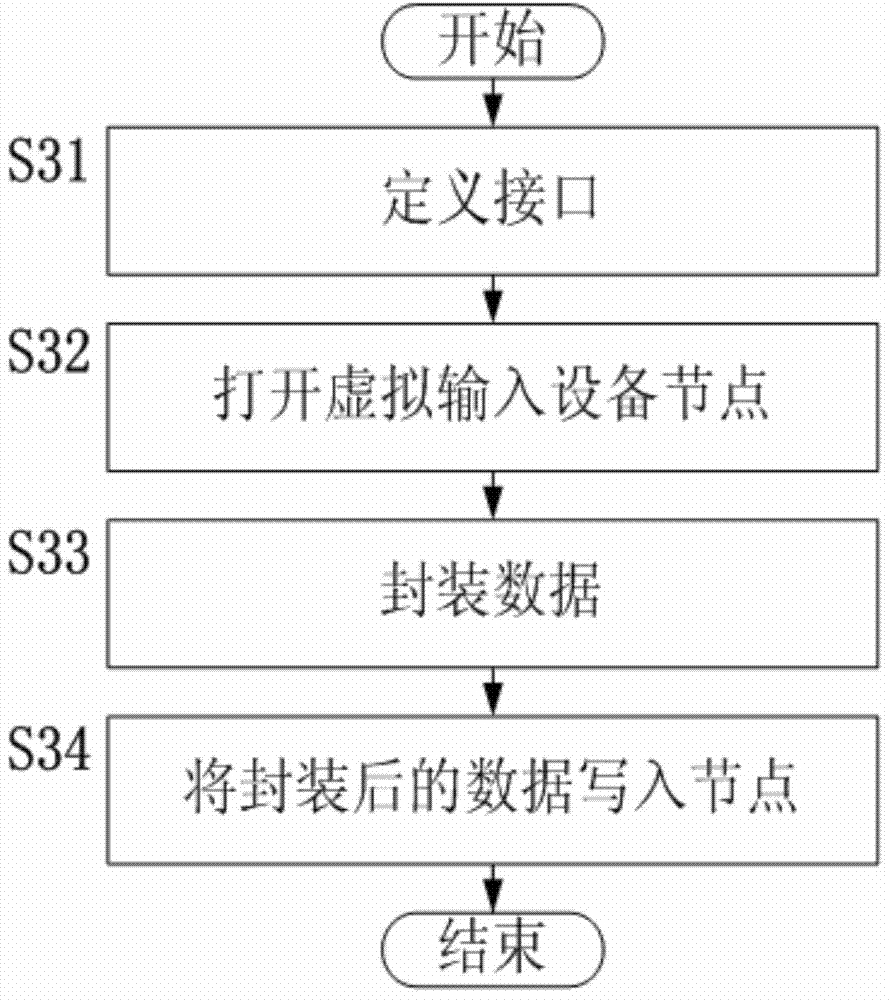
The invention relates to the technical field of smart televisions and discloses a method for achieving control over an Android smart television based on virtual input equipment. The method for achieving control over the Android smart television based on the virtual input equipment solves the problem, existing in the prior art, that due to the lack of the support of input equipment, part of application programs of the Android smart television can not be controlled. The method for achieving control over the Android smart television based on the virtual input equipment comprises the steps that (a) the virtual input equipment is established when an Android system is initialized, and a virtual input equipment node is generated; (b) a dynamic library of a virtual input equipment writing-in interface is set in the Android system; (c) when input events exist and the virtual input equipment needs to be used, the virtual input equipment writing-in interface is called; (d) the virtual input equipment writing-in interface organizes data transmitted by a caller according to a corresponding format, and then the virtual input equipment node is written in; (e) the Android system reads, classifies and packages the input events, and then sends the input events to a current application program; (f) the current application program receives the input events from the virtual input equipment and then responses to the input events. The method for achieving control over the Android smart television based on the virtual input equipment is suitable for control of the Android smart television.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
Method and interface for upgrading flash through USB interface for digital LCD TV
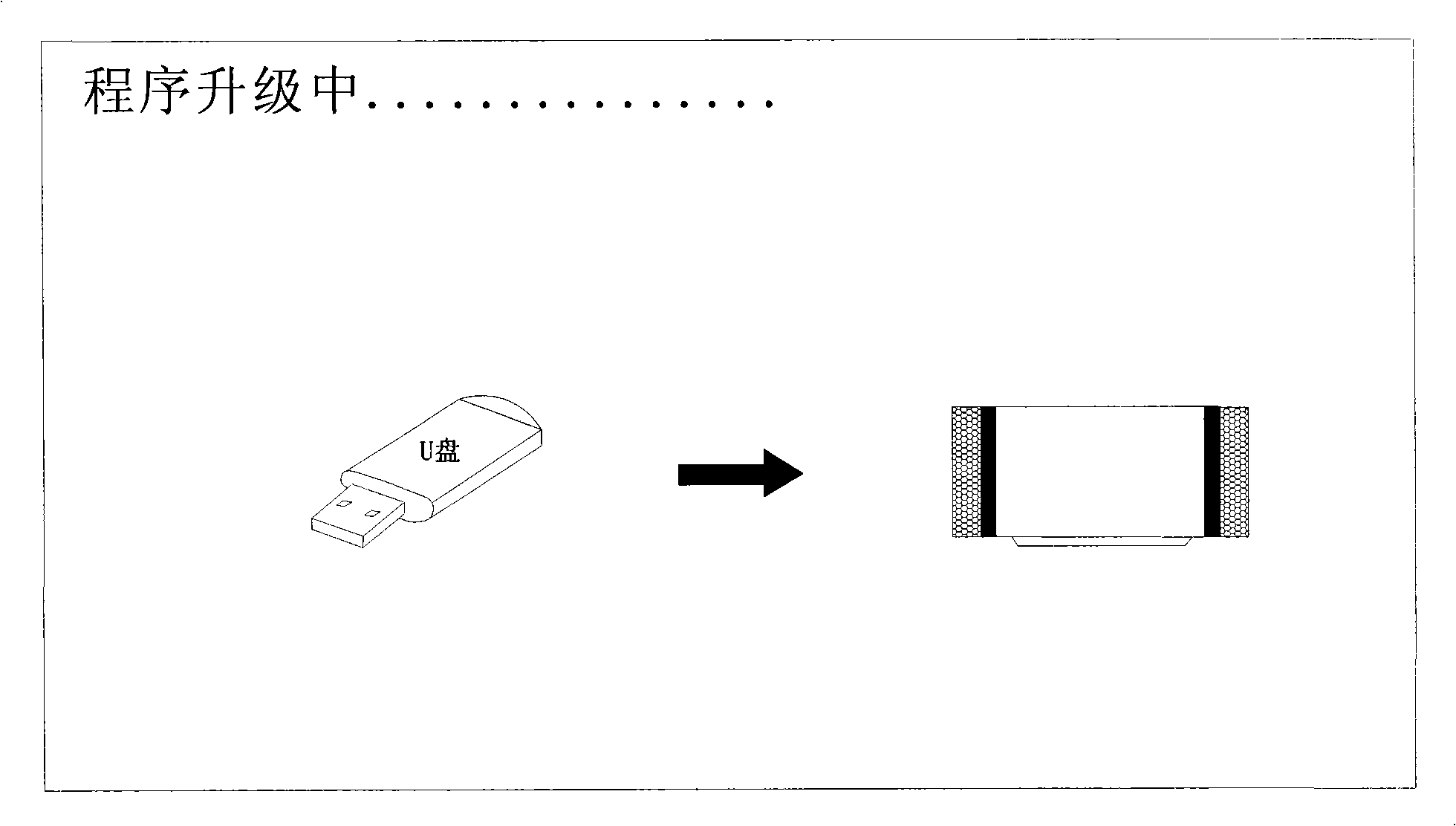
InactiveCN101316314AProgram upgrade is convenient and simpleEfficient upgrade speedTelevision system detailsColor television detailsOperational systemSoftware system
The invention discloses an upgrade method of a USB interface used for a digital liquid-crystal-display television and an interface thereof. The technical characteristics of the invention are that: a USB input interface which is connected with a TV board is designed; a software control program capable of reading the USB interface is added into Pmon (which is a program for TV boot); an operating system software stored on a USB disc, boot LOGO pictures, a PMON program, partial application software comprising APP, MiddleWare and Driver program, factory partial initialization data packet are copied into Nand flash again so as to realize the upgrade of a TV software system. The upgrade method and the interface disclosed by the invention can solve the failure caused by damage and loss of the data of the system software during production and repairing and have the advantages of being simple and quick.
Owner:HISENSE VISUAL TECH CO LTD
Systems And Methods For Regulating Execution Of Computer Software
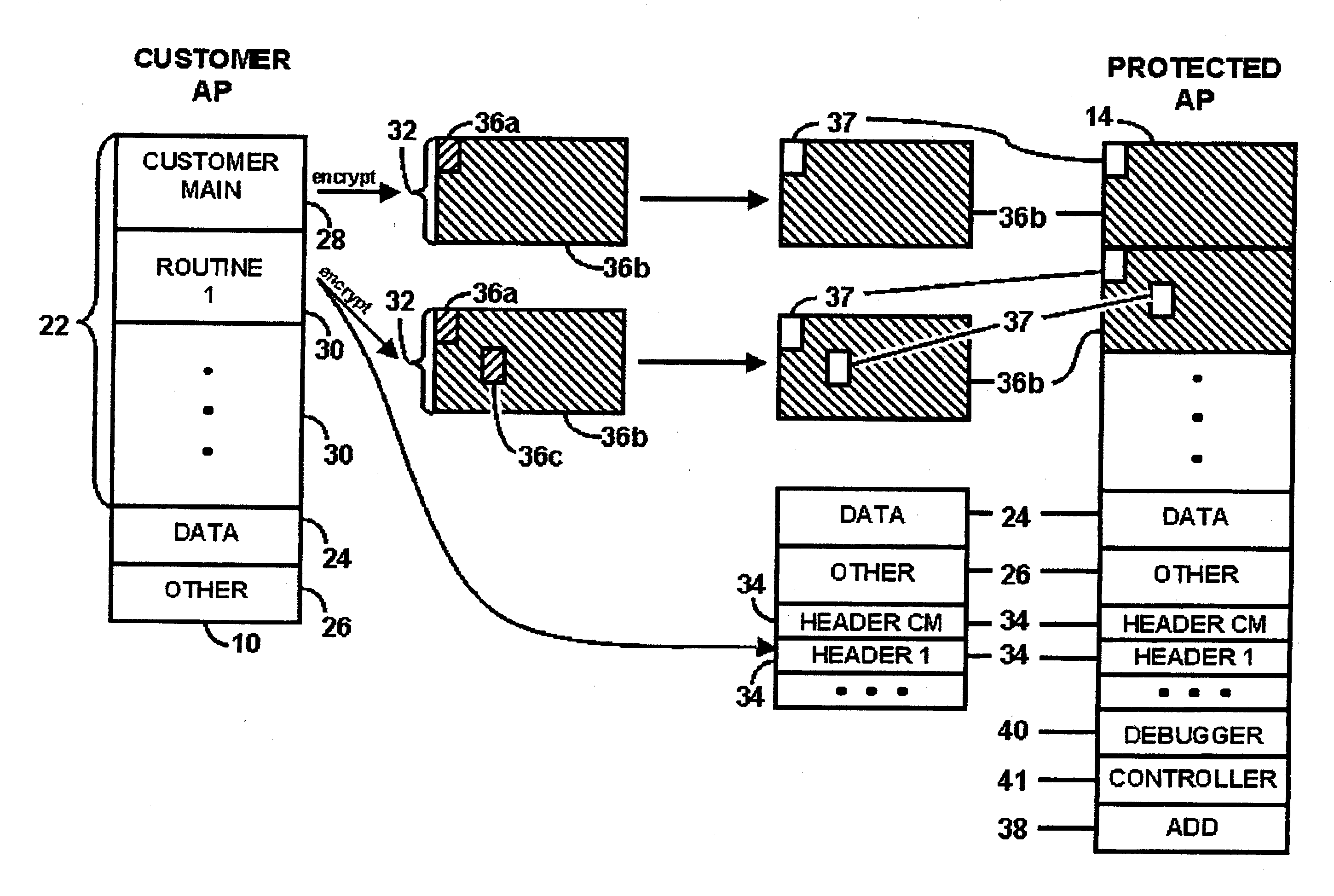
InactiveUS20090328003A1Access is deniedSacrificing protectionDigital computer detailsUnauthorized memory use protectionResponse processOperational system
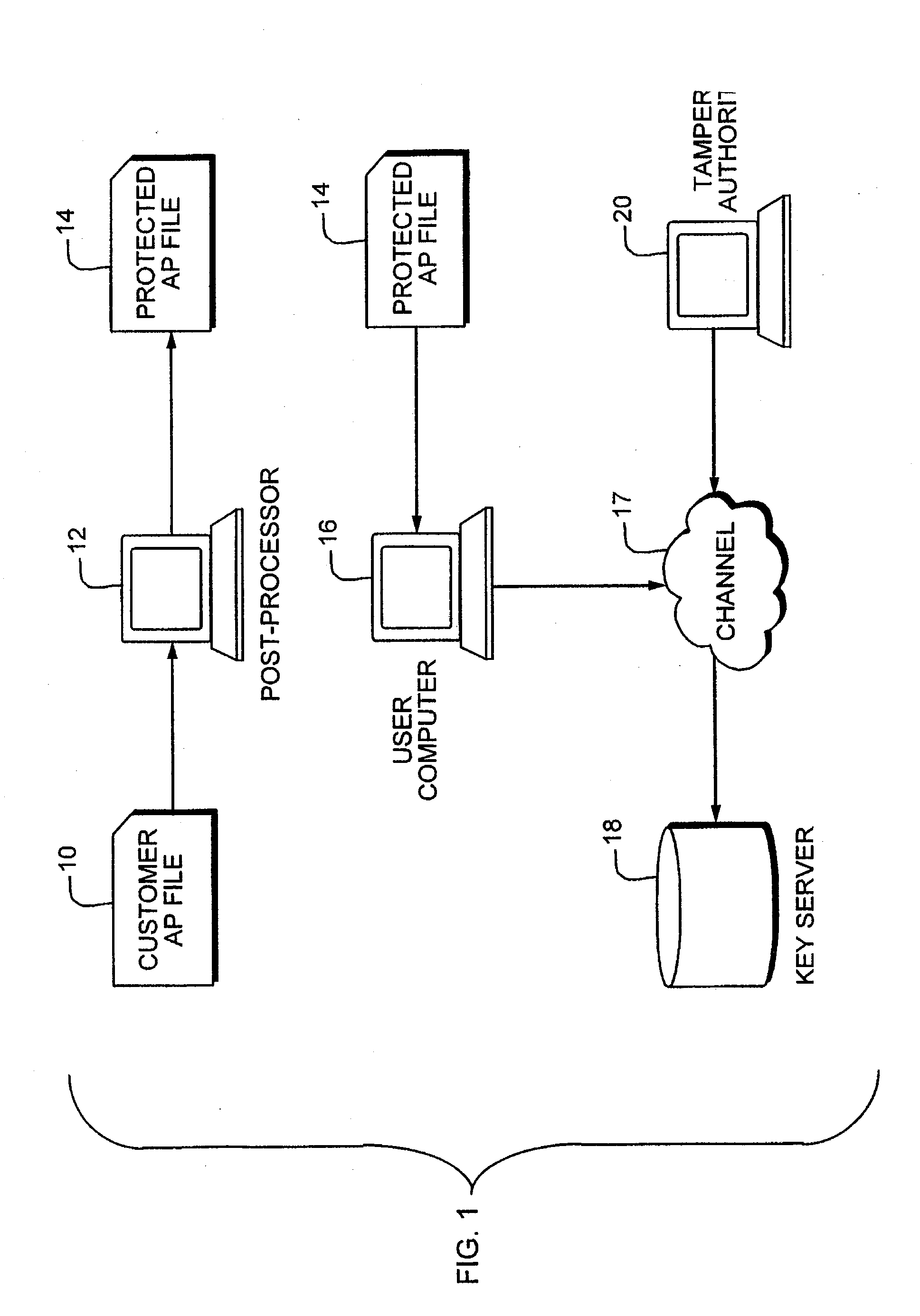
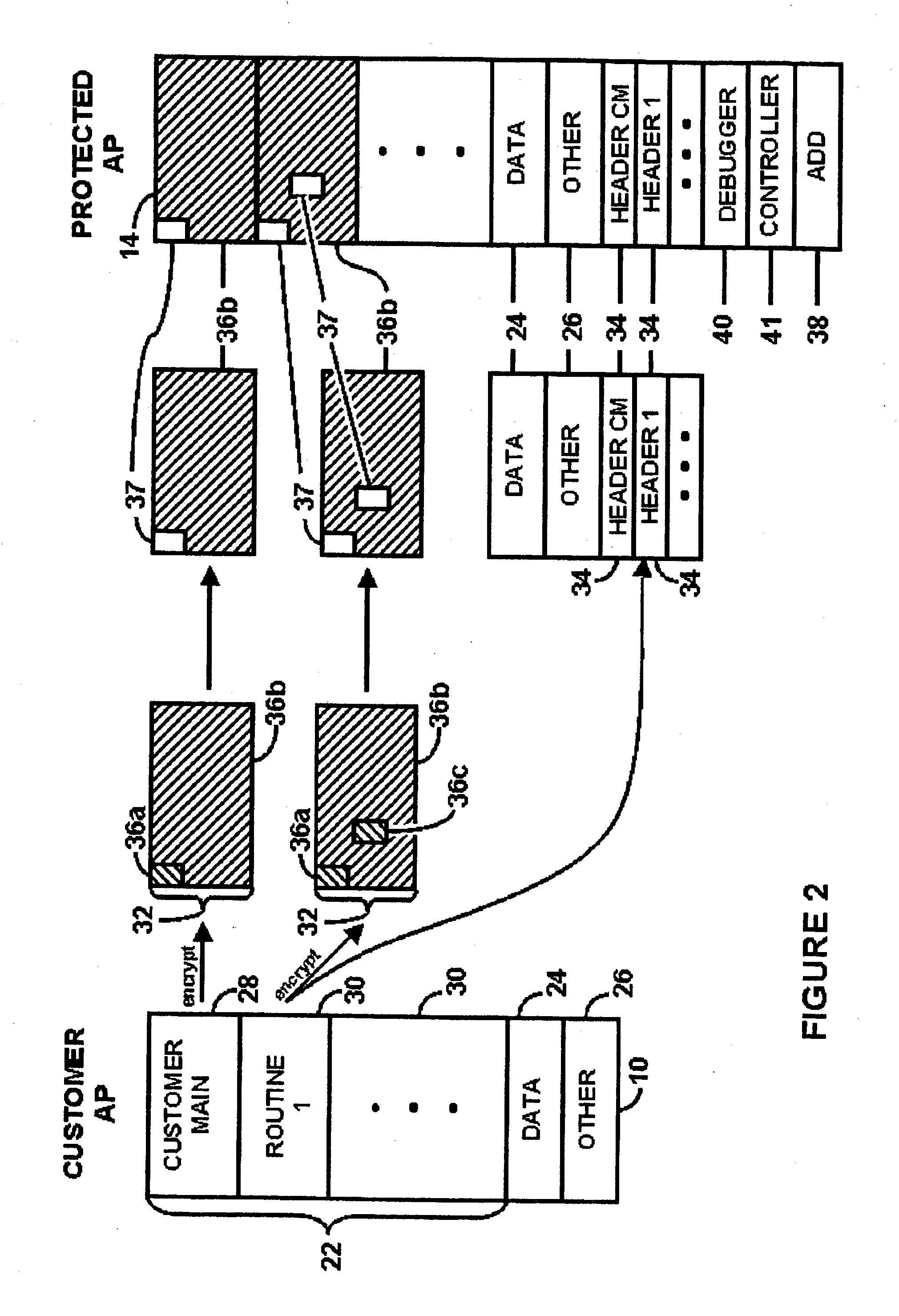
A method for regulating execution of an application program includes a process for preparing the application and a process for executing the application. The preparation process divides the application program into related segments and encrypts instructions of at least one segment. The preparation process positions encrypted instructions in at least two discontiguous regions within an executable file and associates header information with at least one discontiguous region. The header identifies a decryption key and the location of the other discontiguous region. The resulting execution file thus has portions that would not execute and would cause an operating system to call a responsive process. The execution process initiates execution of the protected application when at least a portion of the application instructions are available to the computer only in encrypted form. The user is authenticated, after which the encrypted portions can be decrypted and execution resumed. The processes may also include capability to detect and respond to tampering, or the ability to block execution snooping via a debugger. Also provided are systems and methods to allow debugging of code extensions to protected applications without sacrificing protection of the application. A Secure Debugger allows extension developers to examine memory and set breakpoints in their own extensions, without permitting them to view information in the rest of the protected application.
Owner:REVULYTICS INC
Management method and system of application programs
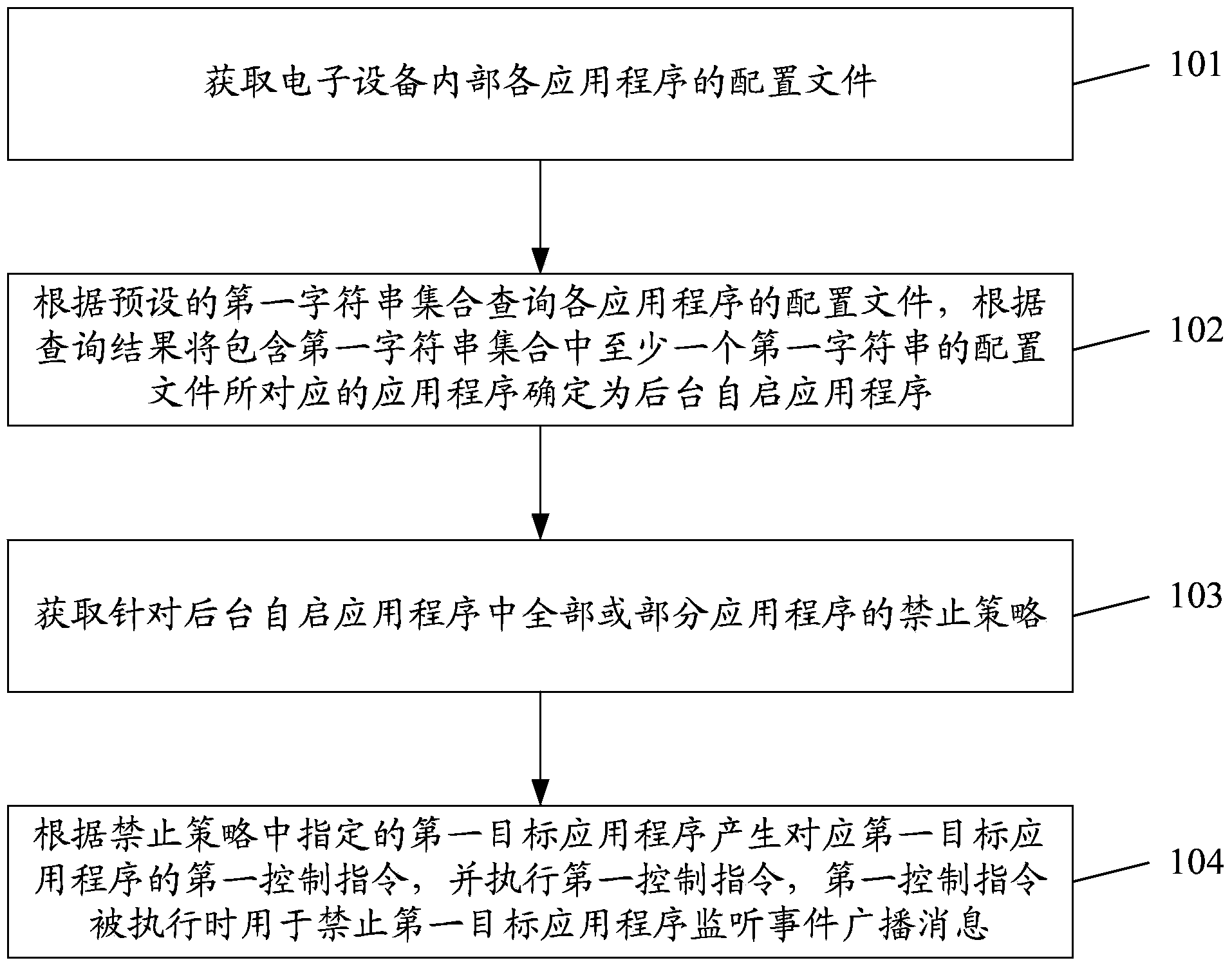
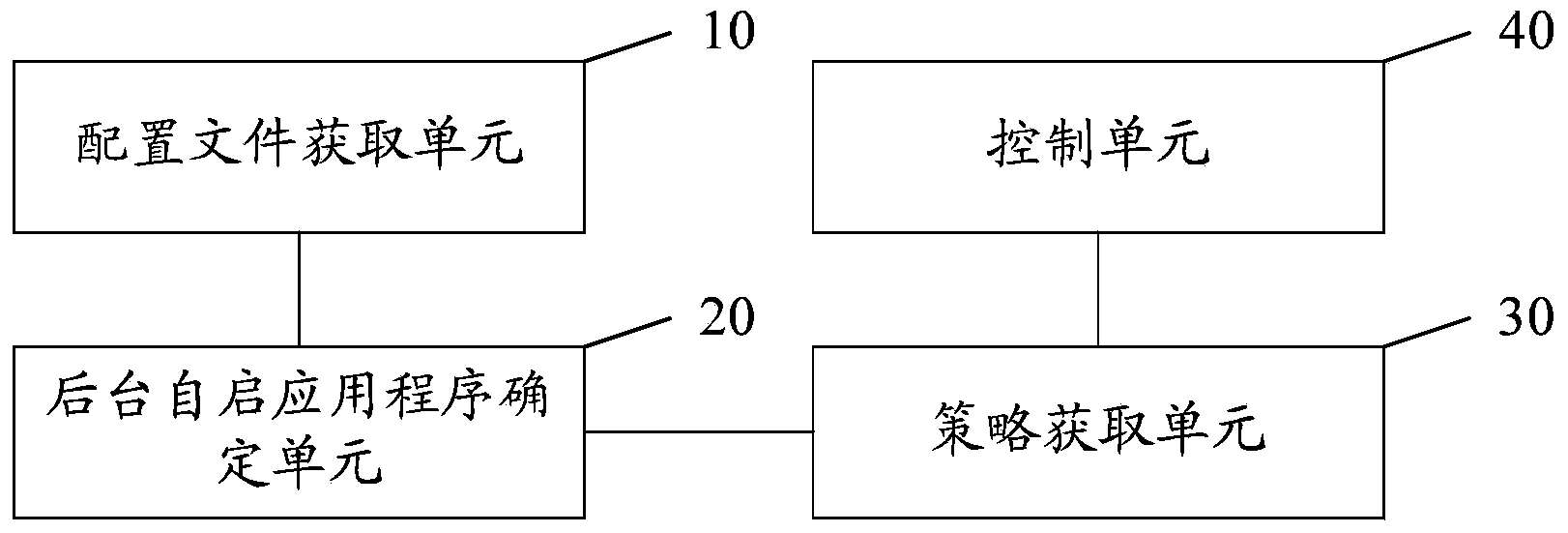
The invention discloses a management method of application programs. The method comprises the steps that configuration files of various application programs in electronic equipment are obtained, according to a preset first character string set, the configuration files of the application programs are checked, and according to the checking results, an application program corresponding to a configuration file which comprises at least a first character string in the first character string set is determined as a background self-starting application program; the first character string set is a set of character strings of event broadcast messages of the electronic equipment; and forbidding strategies for all or parts of the application programs in the background self-starting application program are obtained, according to an appointed target application program in the forbidding strategies, first control instructions corresponding to the target application program are generated, the first control instructions are carried out, and when the first control instructions are carried out, the target application program is forbidden to monitor the event broadcast messages. The invention further discloses a management system of the application programs.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Installing an application from one peer to another including configuration settings
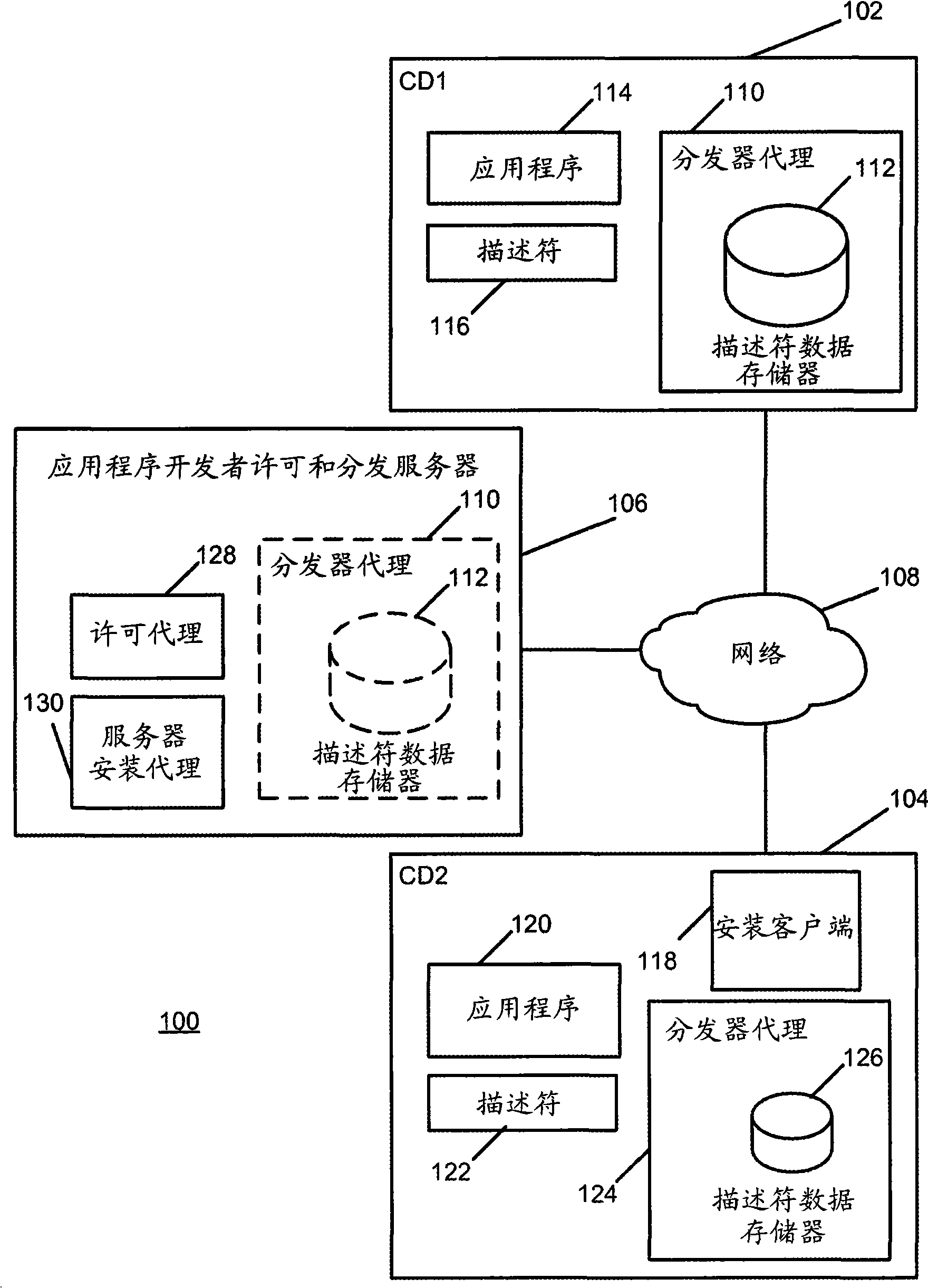
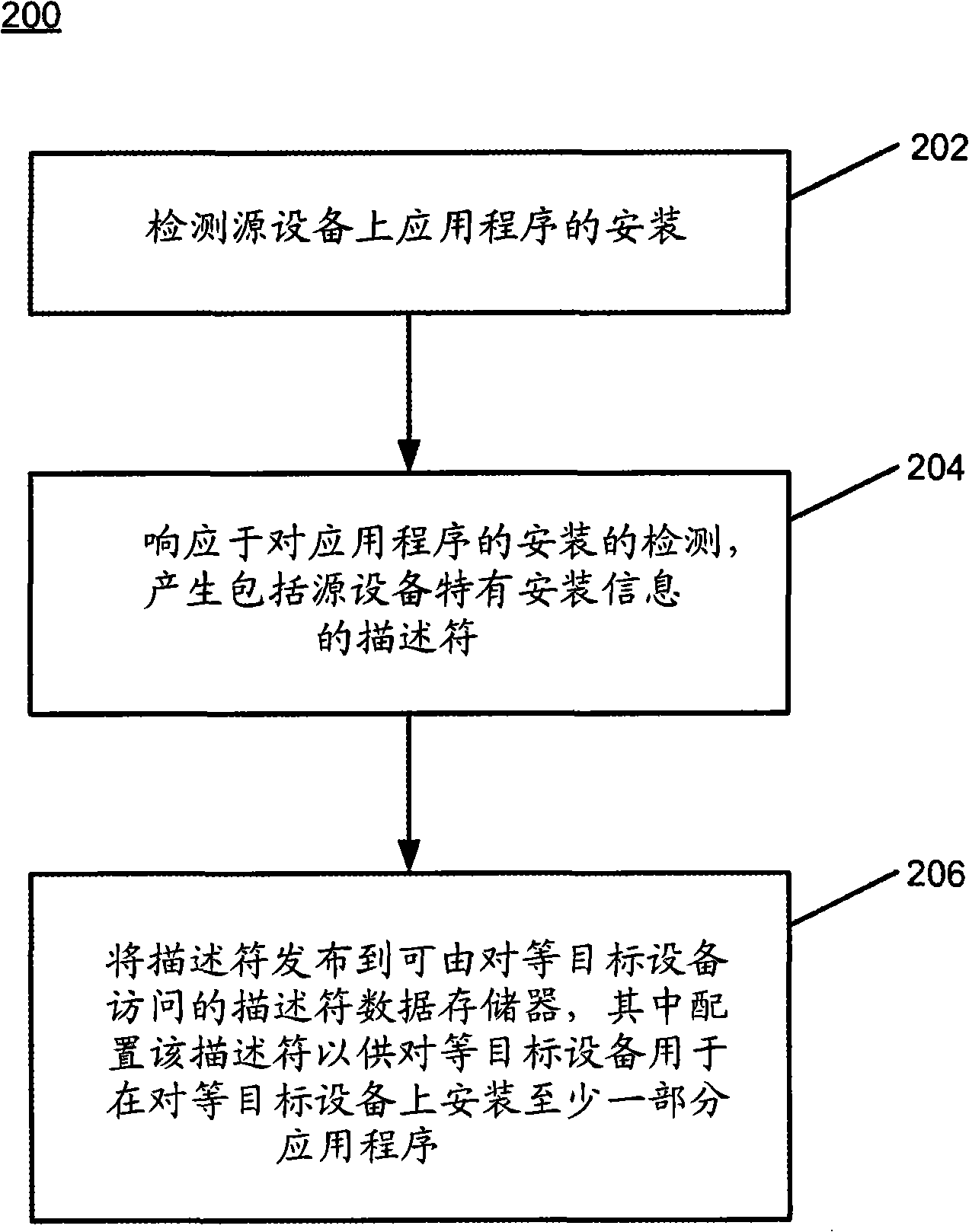
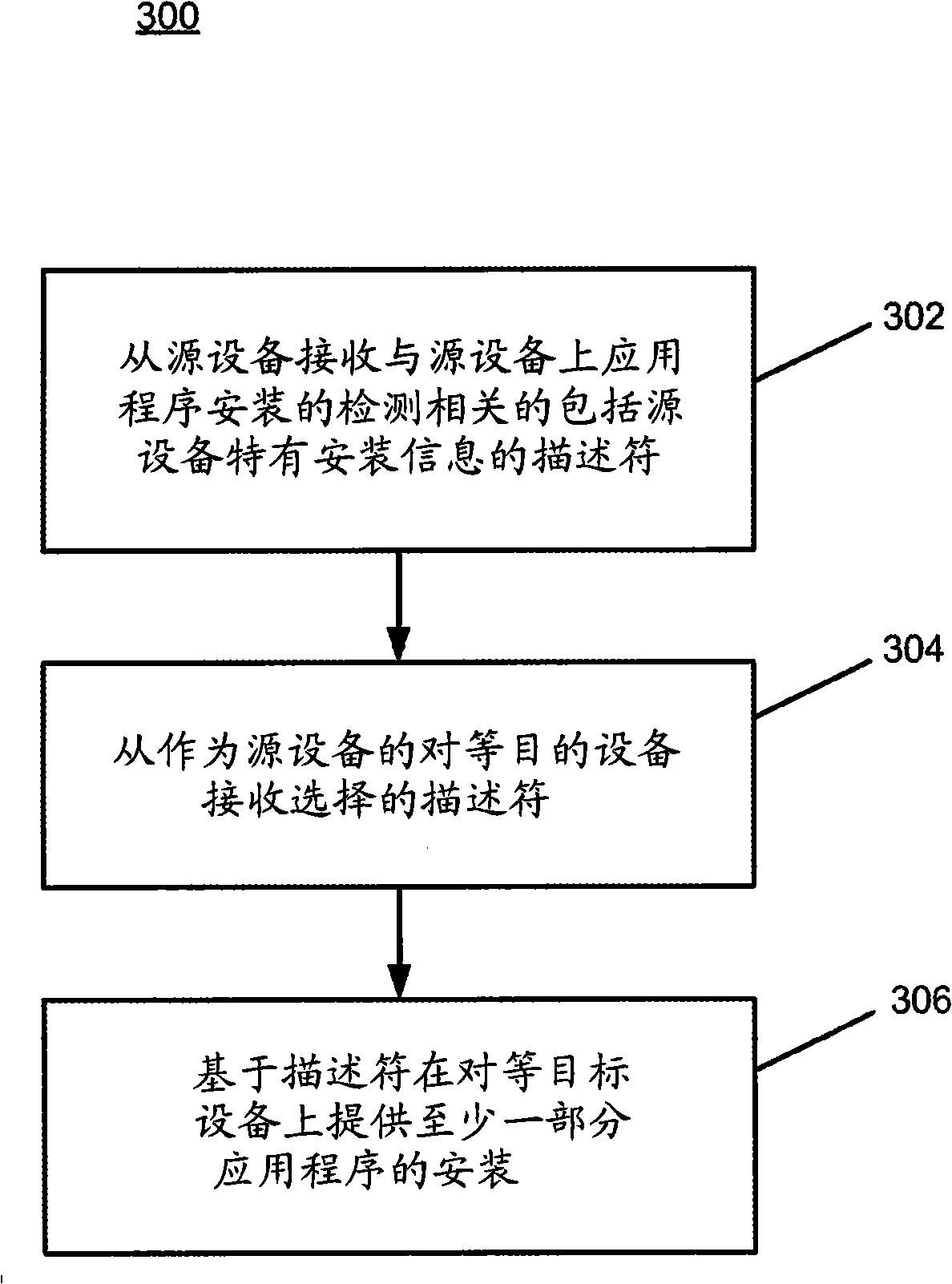
InactiveCN101336423AMultiple digital computer combinationsSoftware deploymentPartial applicationData memory
The invention discloses methods, systems, and computer program products for installing an application. According to one method, an installation of an application on a source device is detected. Responsive to detecting the application installation, a descriptor is produced including source-device-specific installation information. The descriptor is published to a descriptor data store accessible by a peer destination device. The descriptor is configured for use by the peer destination device for installing at least a portion of the application on the peer destination device.
Owner:森内拉科技有限责任公司
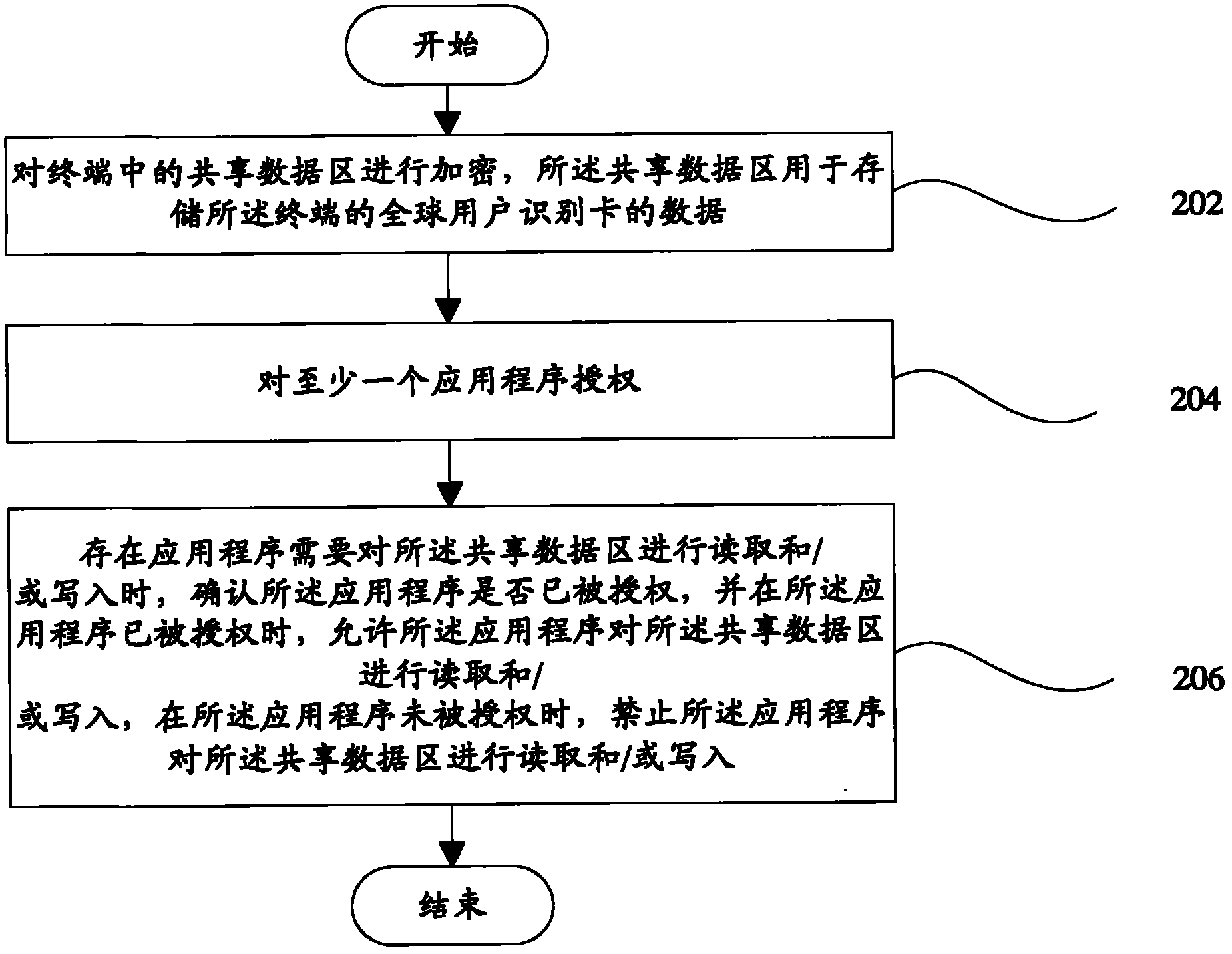
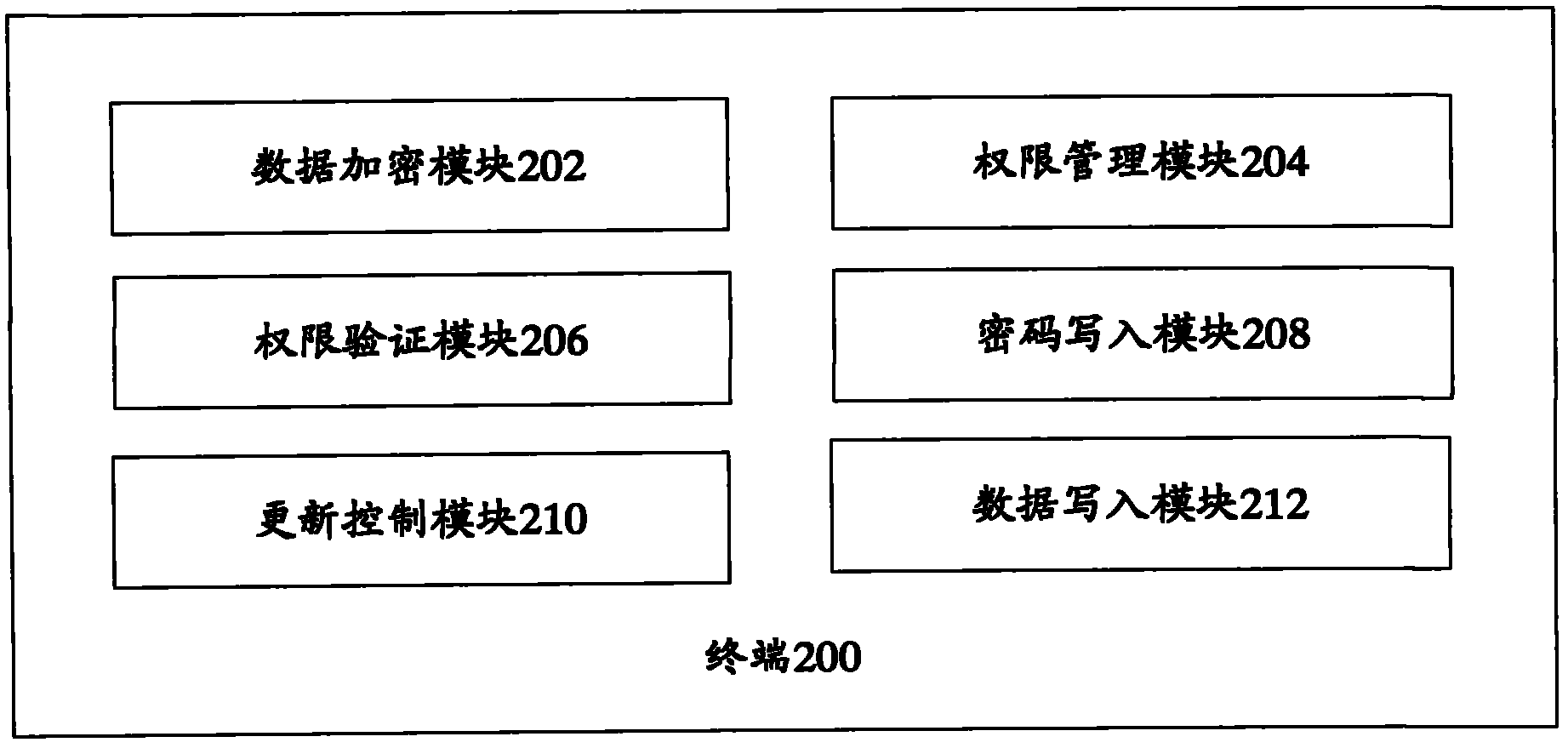
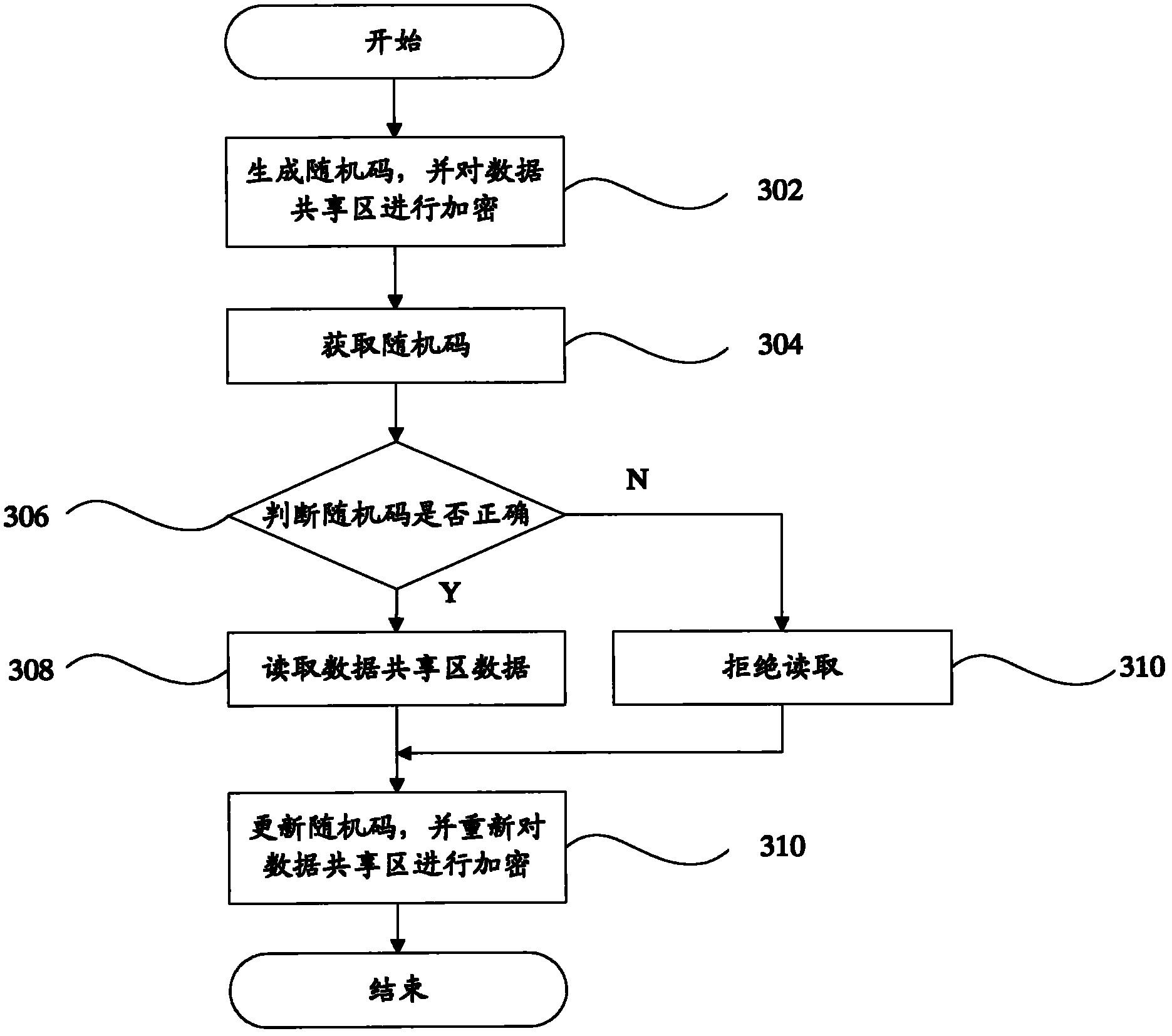
Data protection method and terminal
The invention provides a data protection method and a terminal. The data protection method comprises the following steps: step 102, encrypting a shared data area in the terminal; step 104, authorizing at least one application program; and step 106: when the application program needs to read and / or write the shared data area, determining whether the application program is authorized; if the application program is authorized, allowing the application program to read and / or write the shared data area; if the application program is not authorized, forbidding the application program to read and / or write the shared data area. According to the invention, as the shared area is encrypted so that only a part of application programs authorized by a user can access the shared area, malicious programs can be prevented from damaging the data security of the shared area.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Method, device and mobile device for reliable unloading of application program
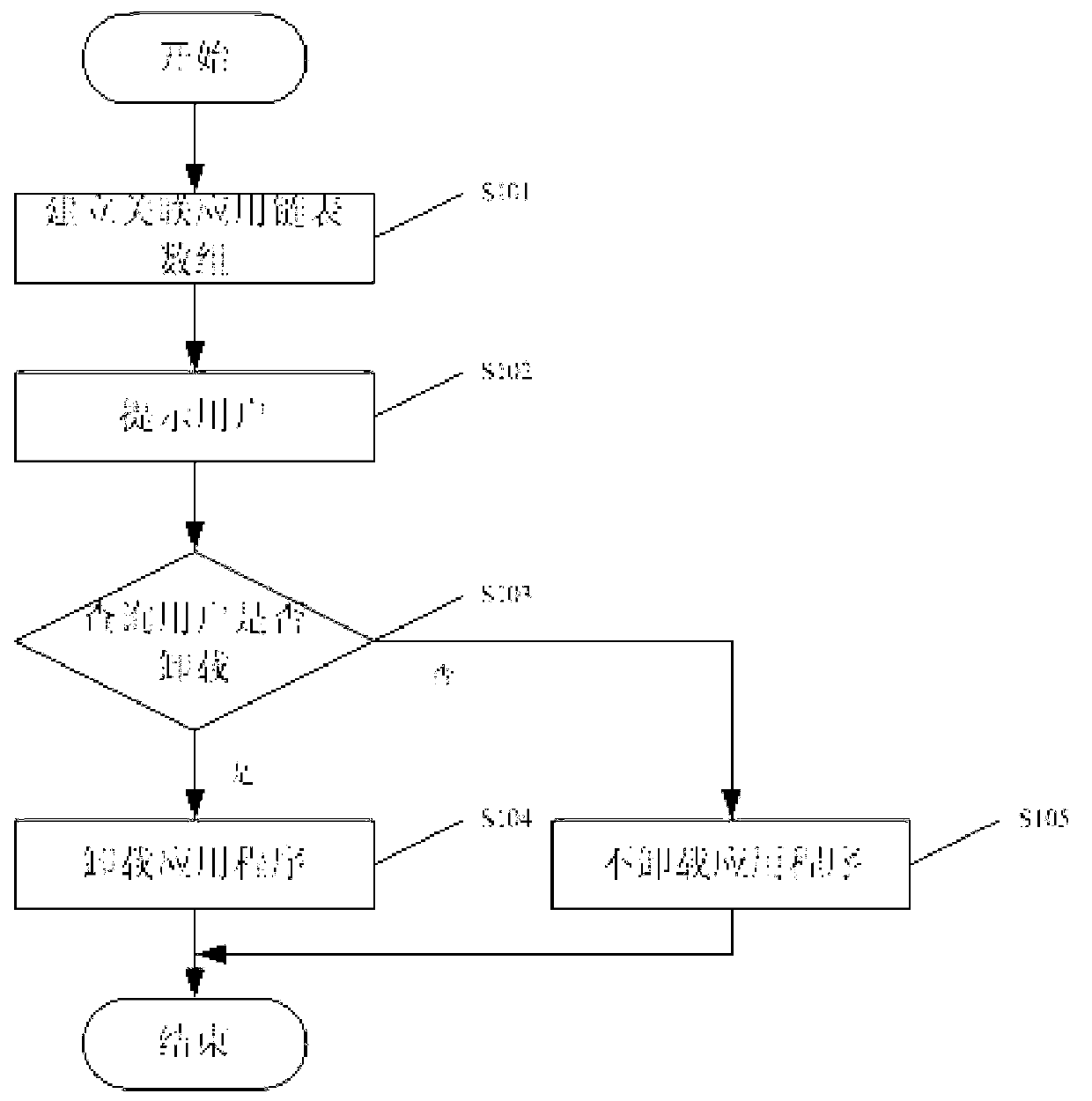
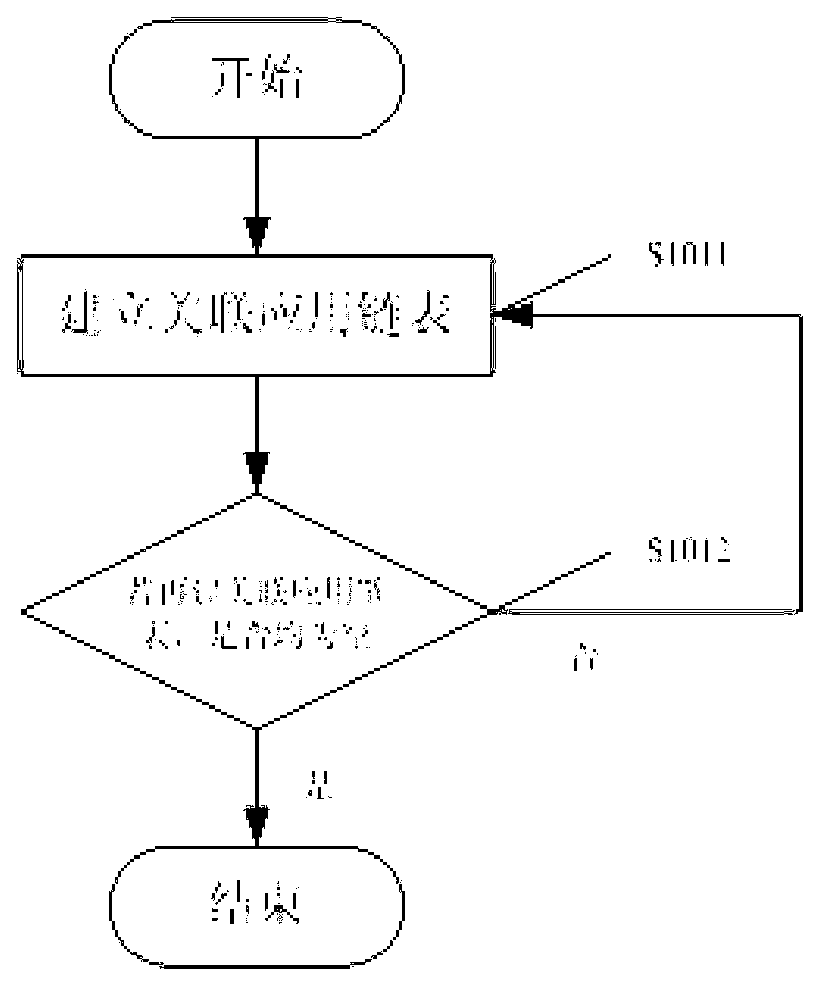
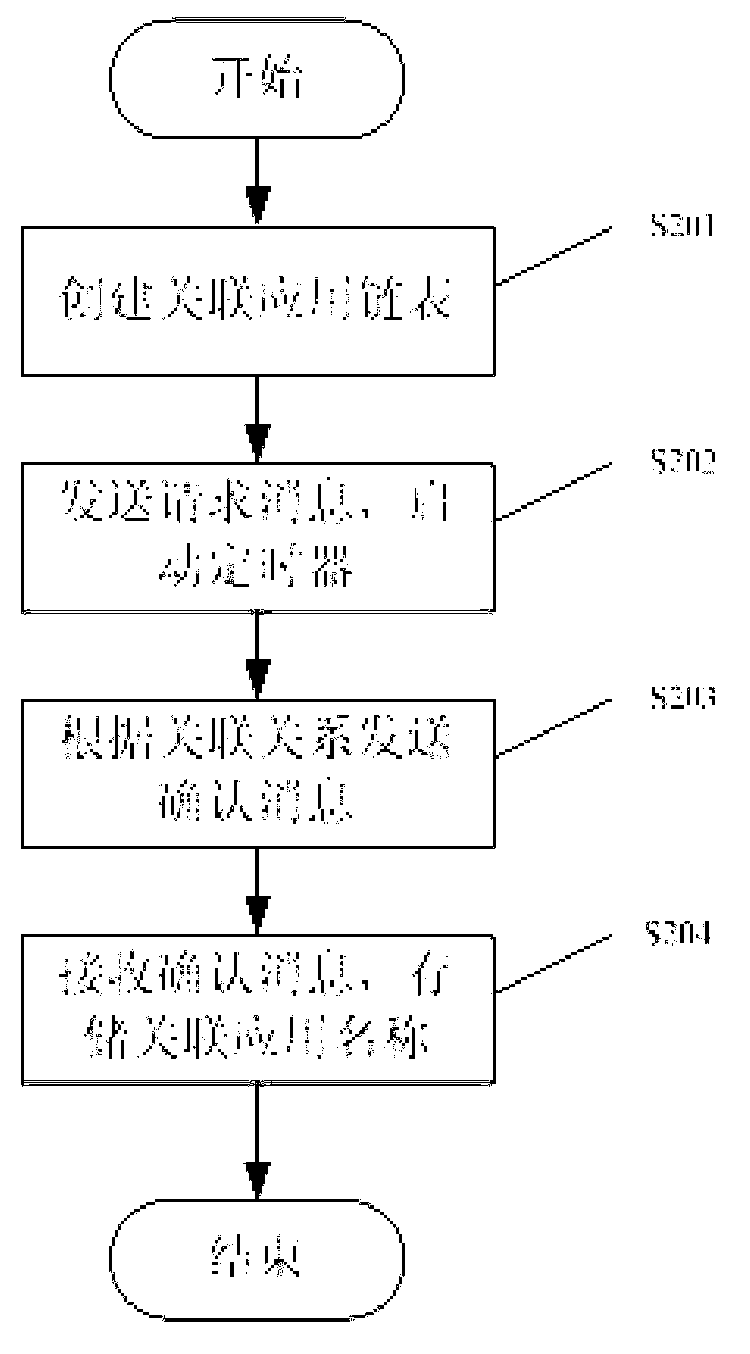
ActiveCN103136024AEfficient acquisitionReduce usageProgram loading/initiatingPartial applicationComputer engineering
The invention discloses a method, device and mobile device for reliable unloading of an application program. The method includes: the application program to be unloaded broadcasts request messages to other application programs in an operation system; the other application programs receive the request messages, if the application programs for receiving the request messages are relates to the application program for broadcasting the request messages, confirmed messages are returned back to the application program for sending the request messages; after the application program for broadcasting the request messages receives the confirmed messages, a name of the application program for returning the confirmed messages is stored in an associated application list; and finally all application programs related to the application program to be unloaded are unloaded according to the associated application list. By adopting the method, the correlative application programs in the system are unloaded simultaneously, and the problem that other application programs cannot be used due to the fact that one part of application programs are unloaded only is solved.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Configurable collection of computer related metric data
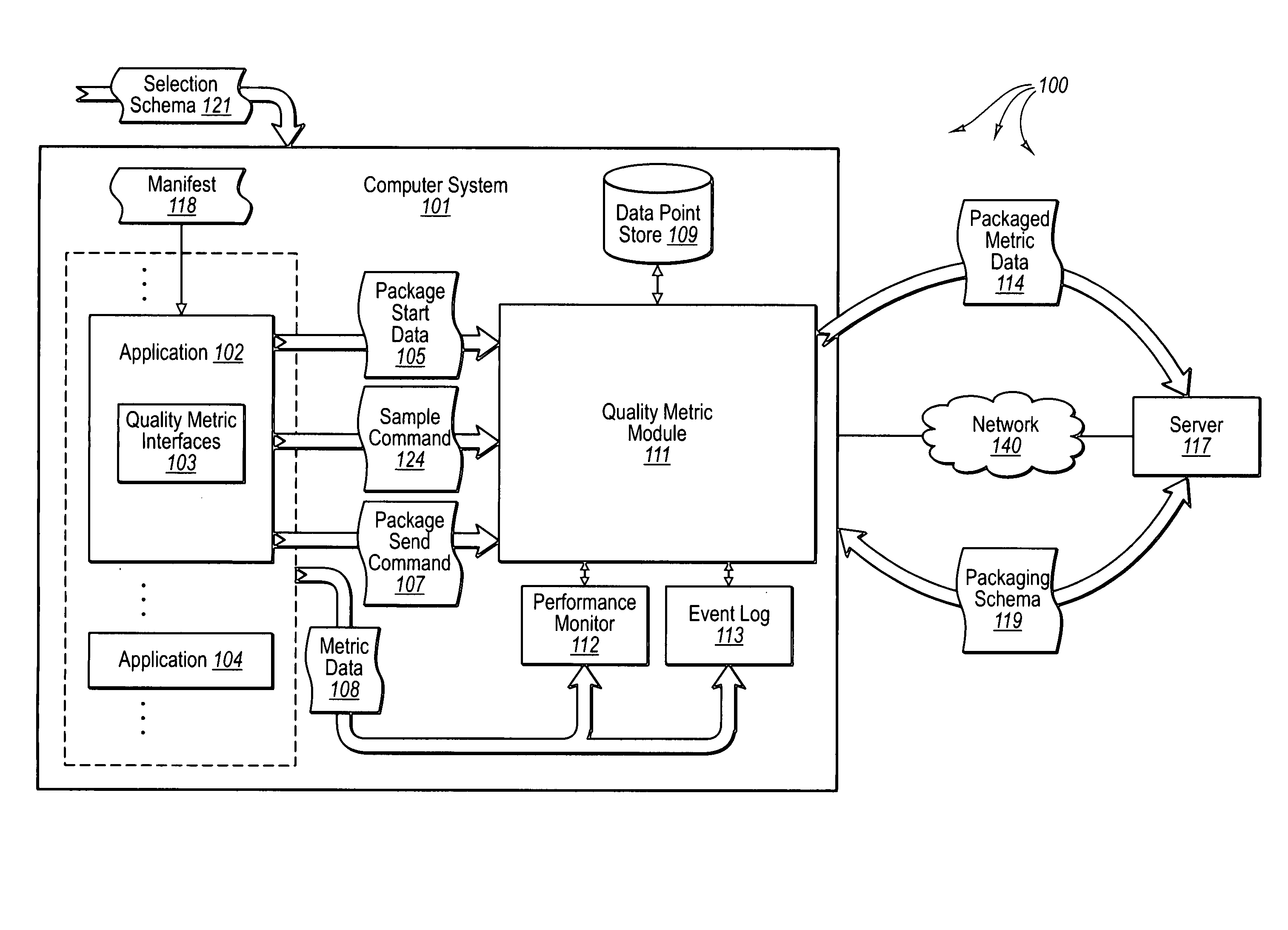
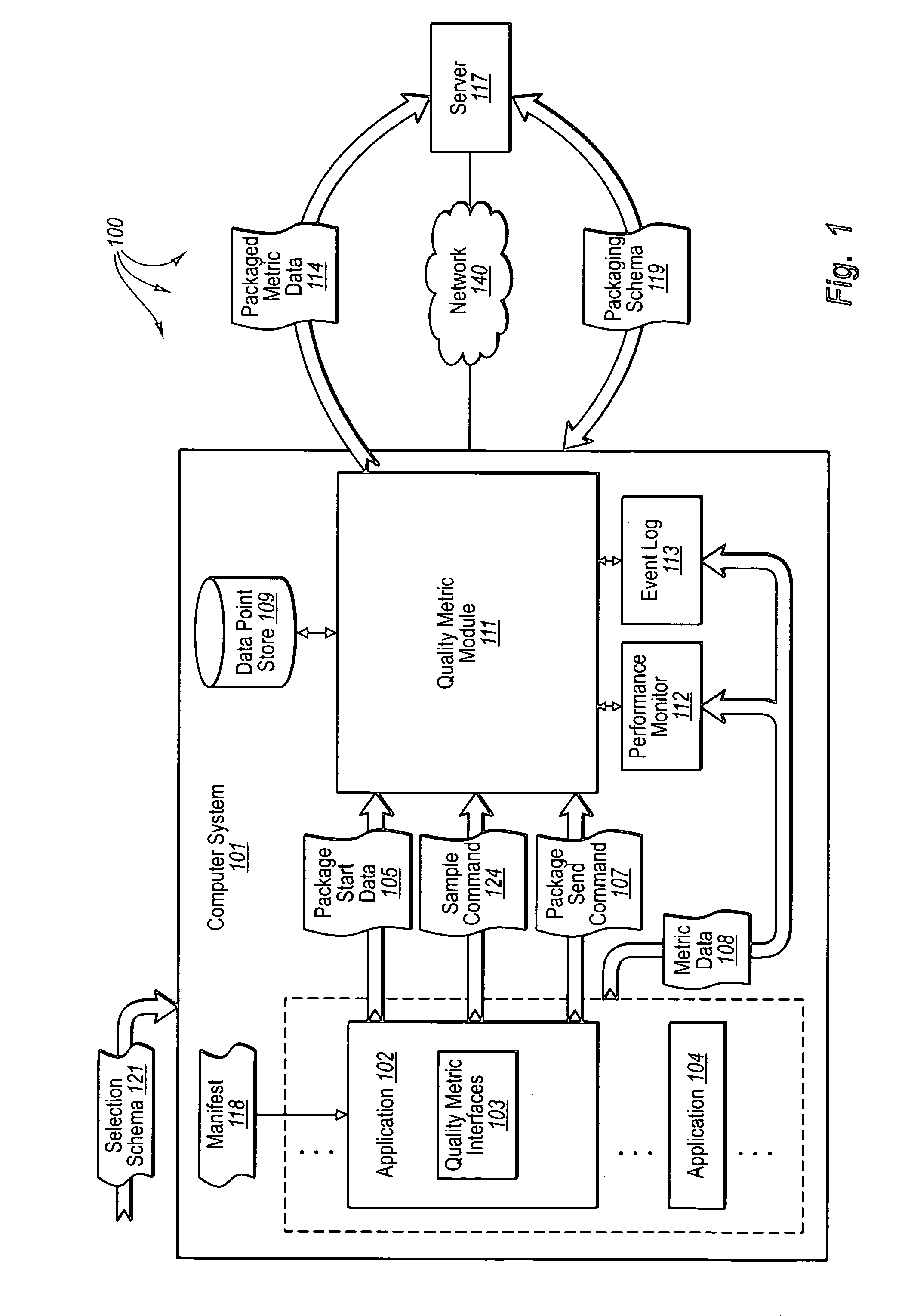
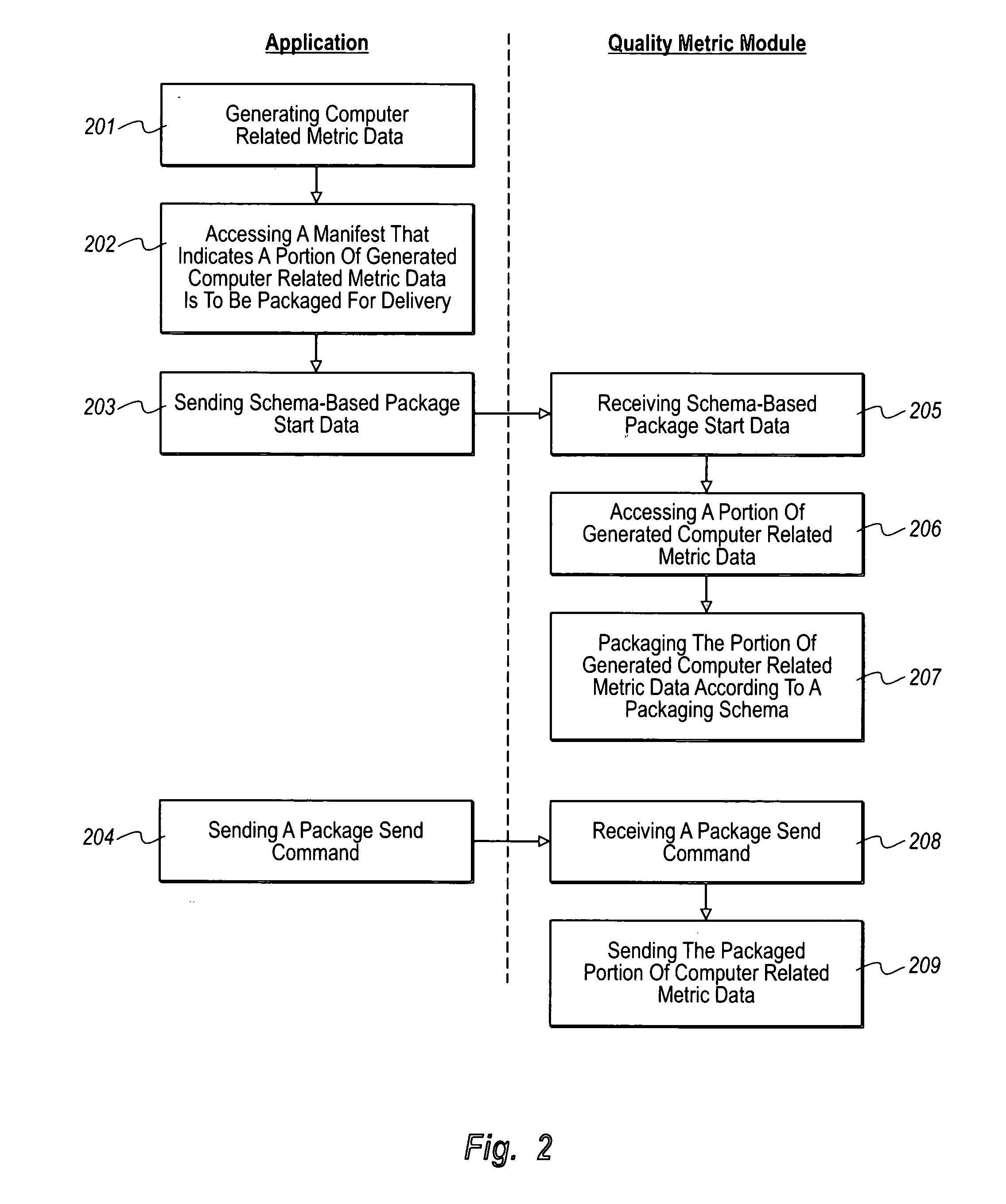
The present invention relates it directed to configurable collection of computer related metric data. A computer system generates computer related metric data related to an application. The application accesses a manifest that indicates a portion of the generated computer related metric data (e.g., a subset) is to be packaged for delivery. The application sends schema-based package start data to cause the portion of generated computer related metric data to be packaged. A quality metric module receives the schema-based package start data and accesses the indicated portion of computer related metric data. The quality metric module packages the portion of computer related metric data according to a packaging schema. The application sends a package send command to cause the packaged portion of computer related metric data to be delivered. The quality metric module receives the package send command and sends the packaged portion of computer related metric data in response to the package send command.
Owner:MICROSOFT TECH LICENSING LLC
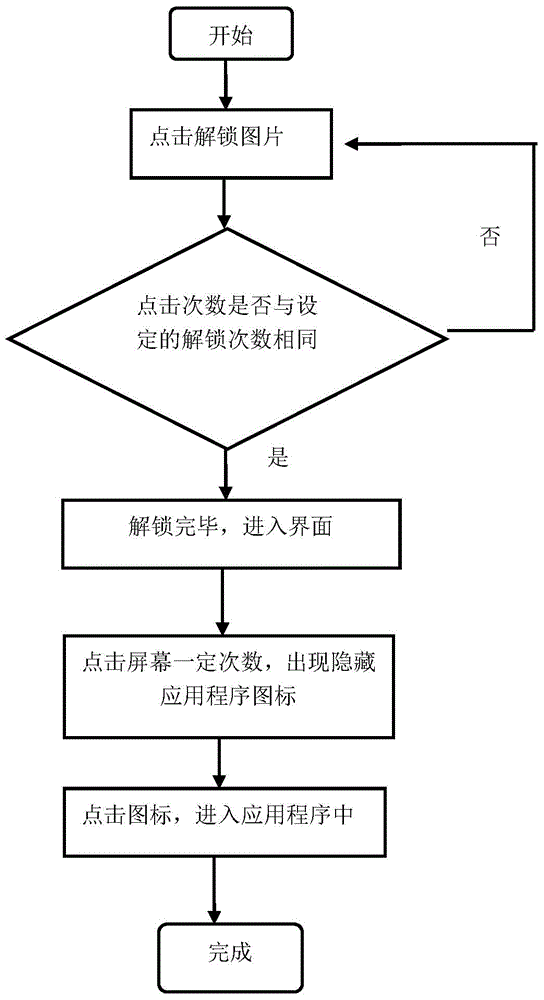
Touch screen terminal hidden unlocking method and system
ActiveCN104317517AEasy to operateImprove securityDigital data authenticationInput/output processes for data processingPartial applicationComputer terminal
The invention relates to a touch screen terminal hidden unlocking method. The method includes the following steps: step 1, touching a switch button, turning on a screen of a touch screen terminal, displaying an unlocking picture, and entering a to-be-unlocked state; step 2, clicking a fixed position on the unlocking picture, wherein number of clicking times is identical with number of unlocking times set during screen locking customization; step 3, completing unlocking, wherein after entering a touch screen terminal interface when unlocking is completed, the interface only displays icons of a part of application programs, and icons of another part of application programs are hidden. A method for entering the hidden application program icons includes the following steps: step 1, clicking any position of a touch screen for one or several times to enable the hidden application program icons to appear on the screen; step 2, clicking the icons appearing on the screen to enter the application programs for other operations. Unlocking of a main screen and the hidden icons is realized mainly on the basis of the number of clicking times, so that the mode is high in safety, and interestingness for a user to operate the touch screen terminal is high.
Owner:SUZHOU TIANPING ADVANCED DIGITAL TECH
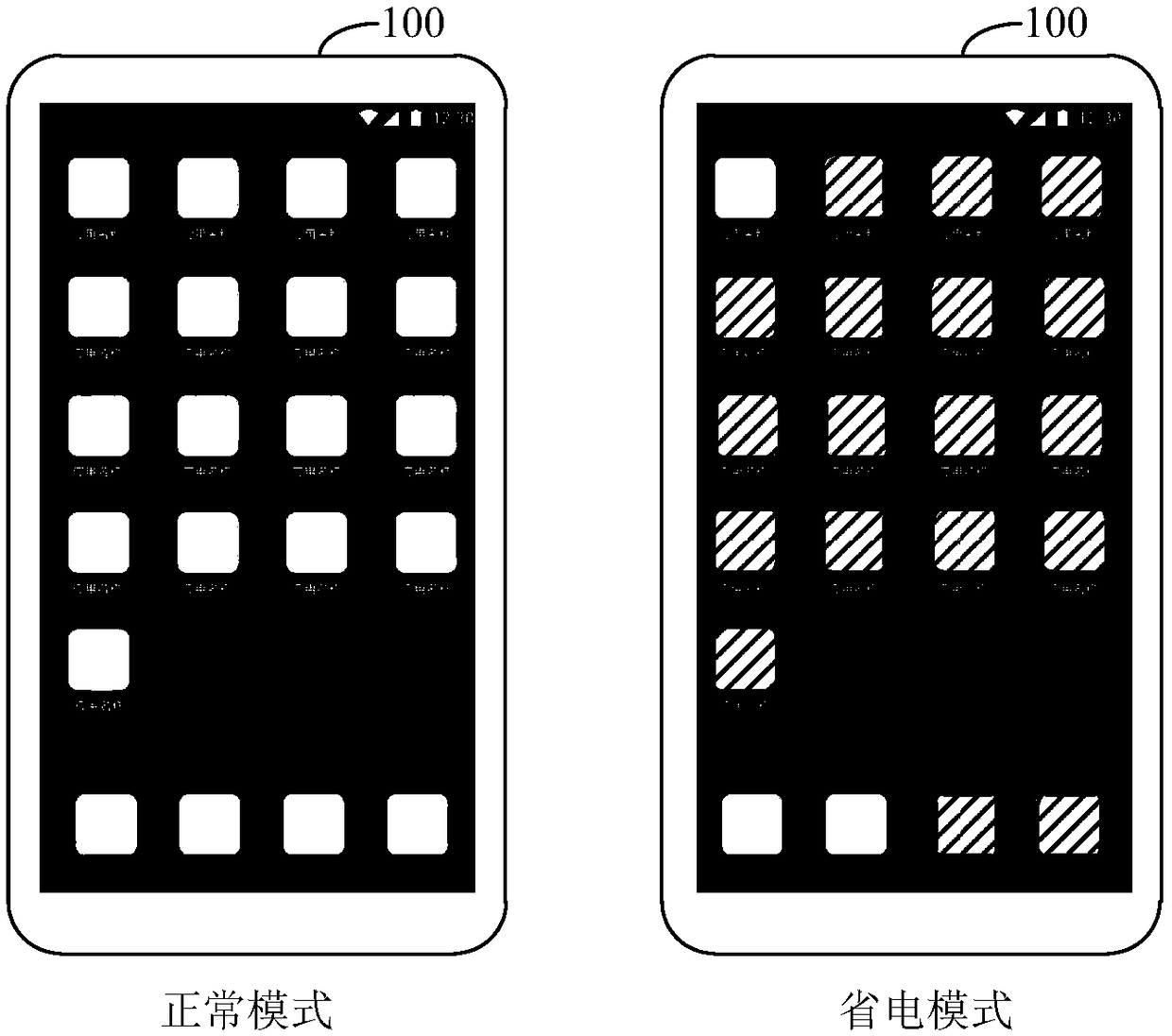
Mobile terminal and power-saving mode control method thereof
ActiveCN109164905AReduce memory loadDigital data processing detailsInput/output processes for data processingBattery chargeMode control
The invention relates to a mobile terminal and a power-saving mode control method thereof. The power-saving control method of the mobile terminal comprises the following steps: monitoring the batterypower of the mobile terminal; when the battery charge is less than or equal to a charge threshold value, the mobile terminal enters a power saving mode, wherein entering into the power saving mode includes switching a desktop program run by the mobile terminal from a first state to a second state, wherein the number and position of desktop icons in the second state are consistent with the number and position of desktop icons in the first state, and setting a partial application icon of the desktop in the second state to a disabled state. The mobile terminal and the power-saving mode control method thereof can reduce the memory burden of the user for mode switching, and are more convenient for the user to adapt to mode switching.
Owner:SHANGHAI TRANSSION CO LTD
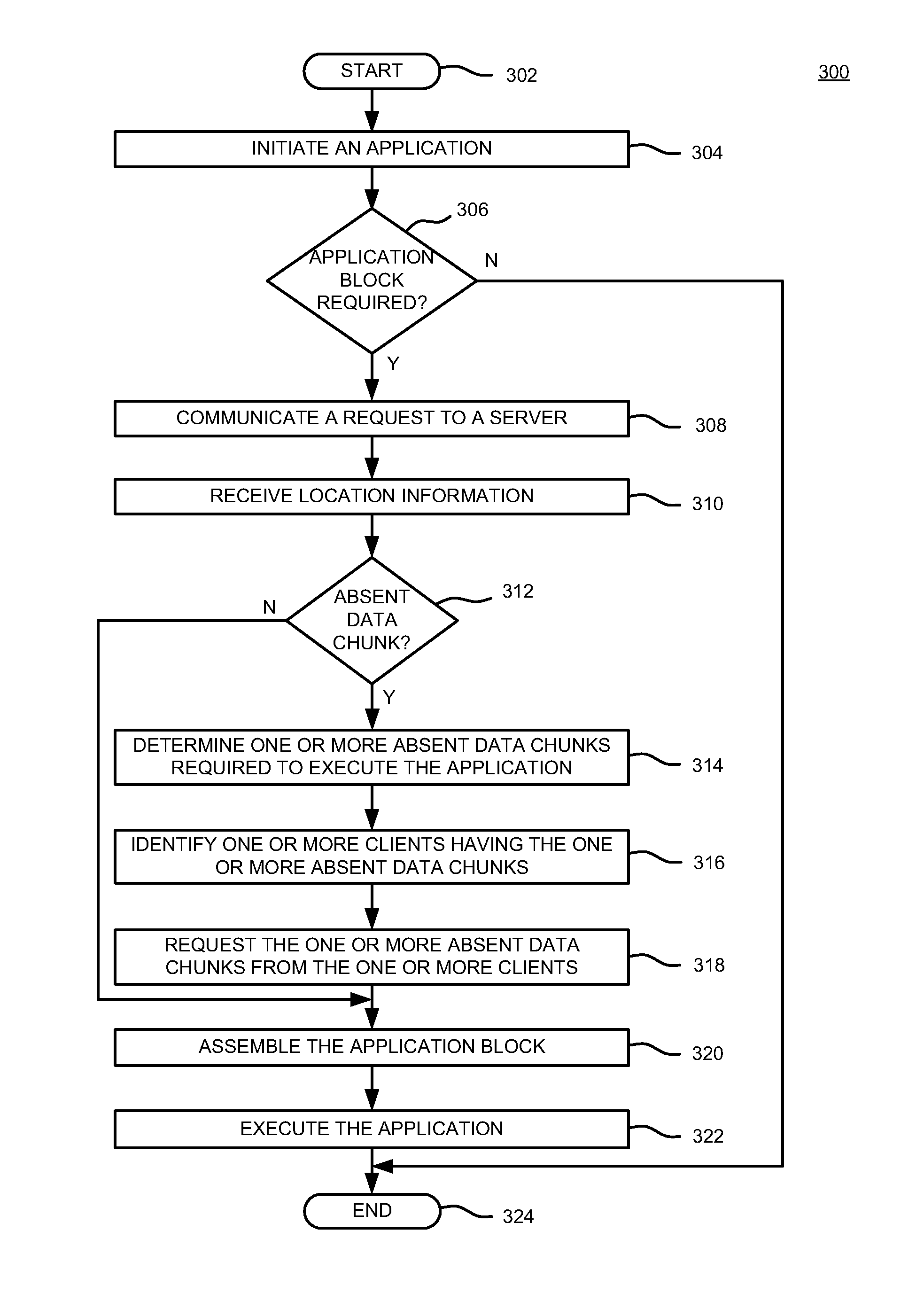
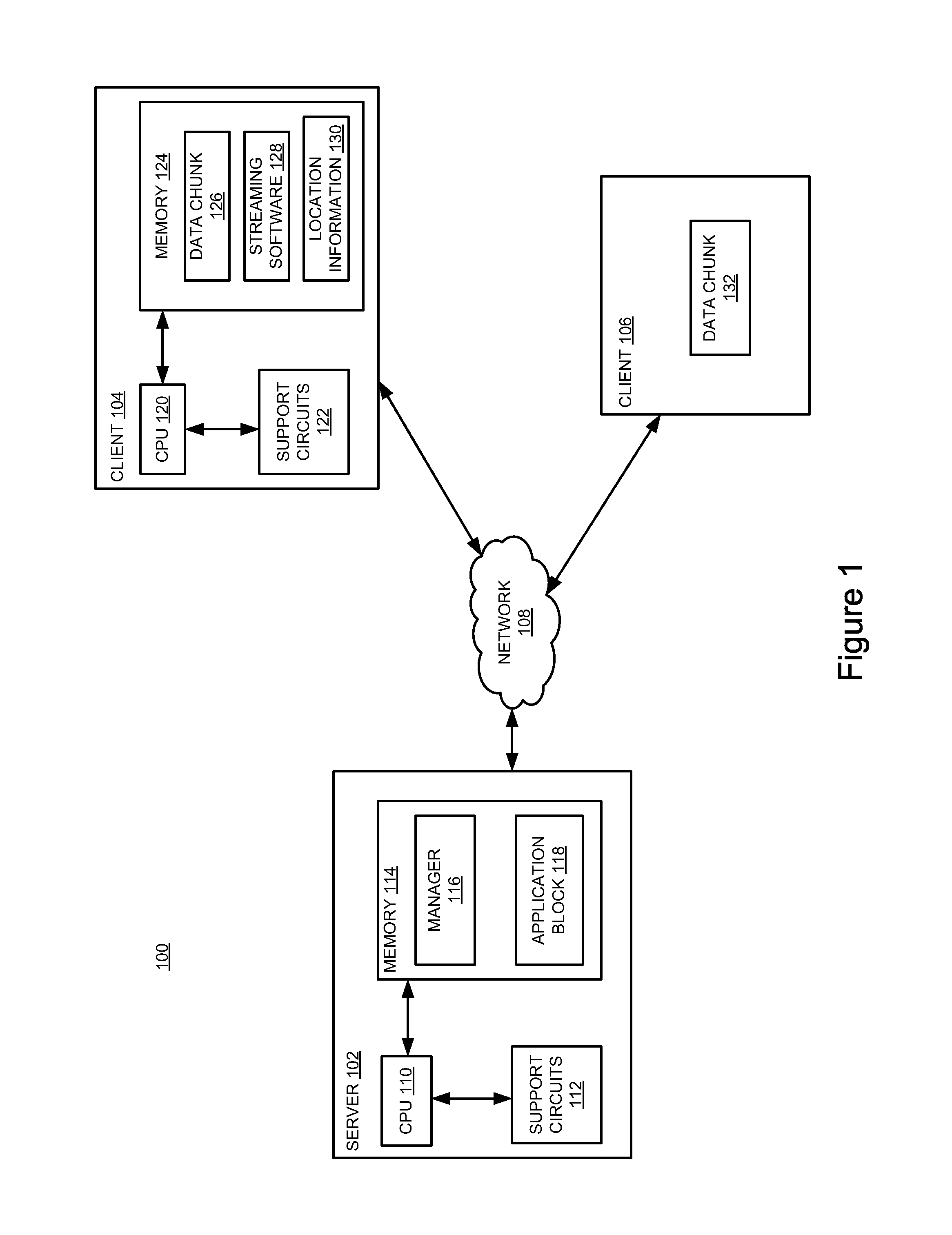
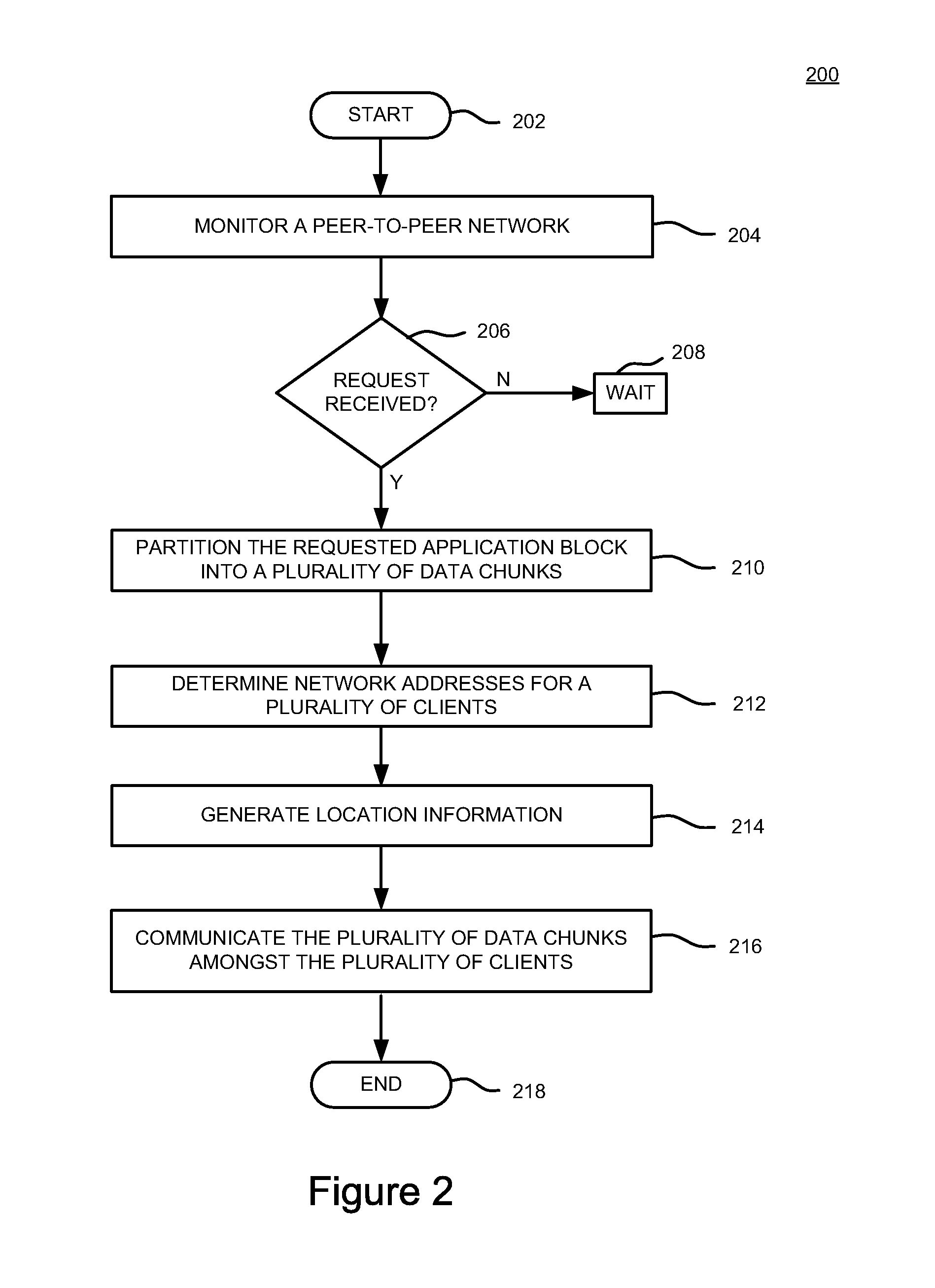
Method and apparatus for streaming applications to a plurality of clients within a peer to-peer network
A method and apparatus for streaming applications to a plurality of clients within a peer-to-peer network is provided. In one embodiment, a method for distributing application blocks to facilitate application streaming within a peer-to-peer network includes processing location information regarding a plurality of data chunks amongst a plurality of clients, wherein the plurality of data chunks form at least a portion of an application block and communicating the location information amongst the plurality of clients, wherein the location information is used to request at least one data chunk of the plurality of data chunks.
Owner:CA TECH INC
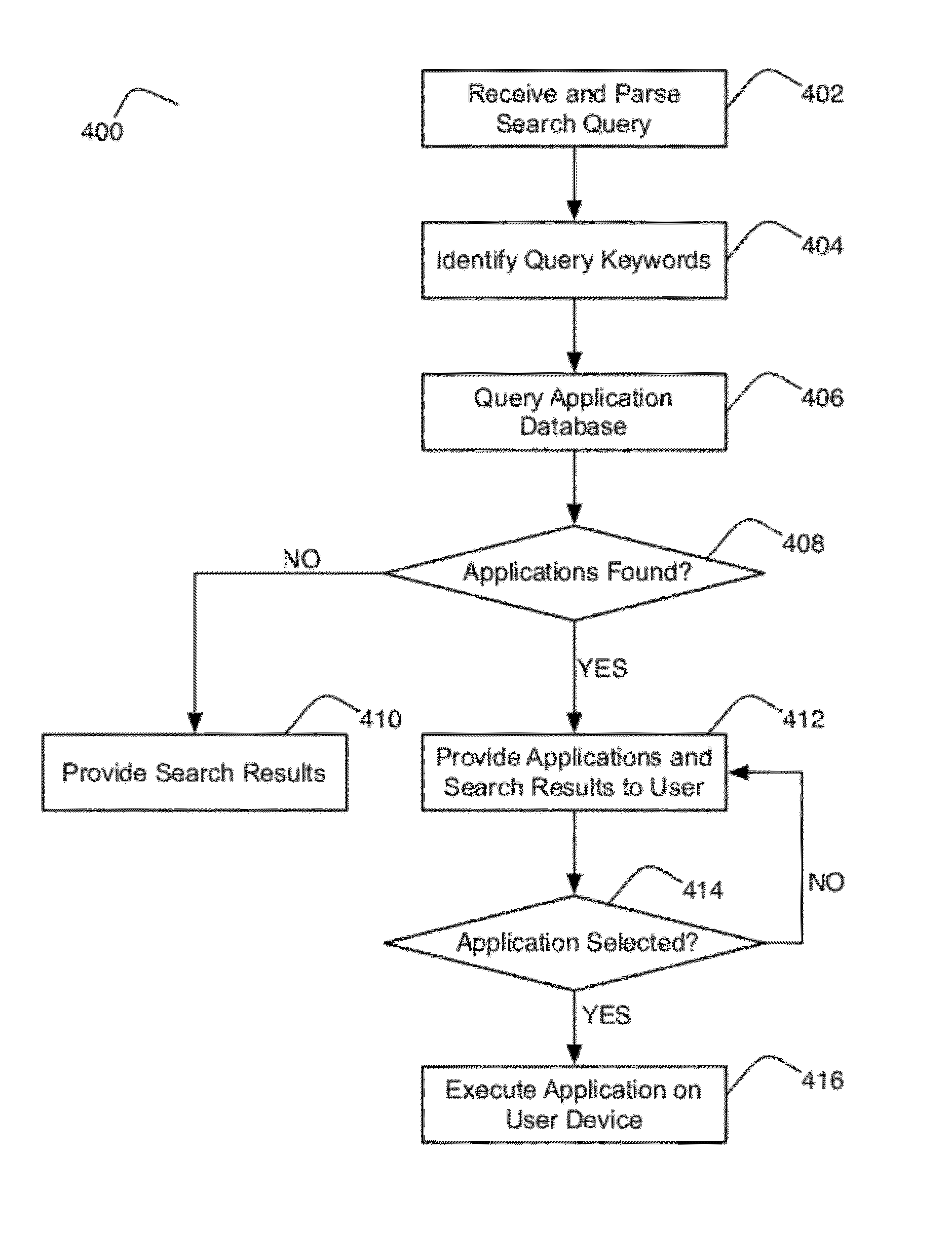
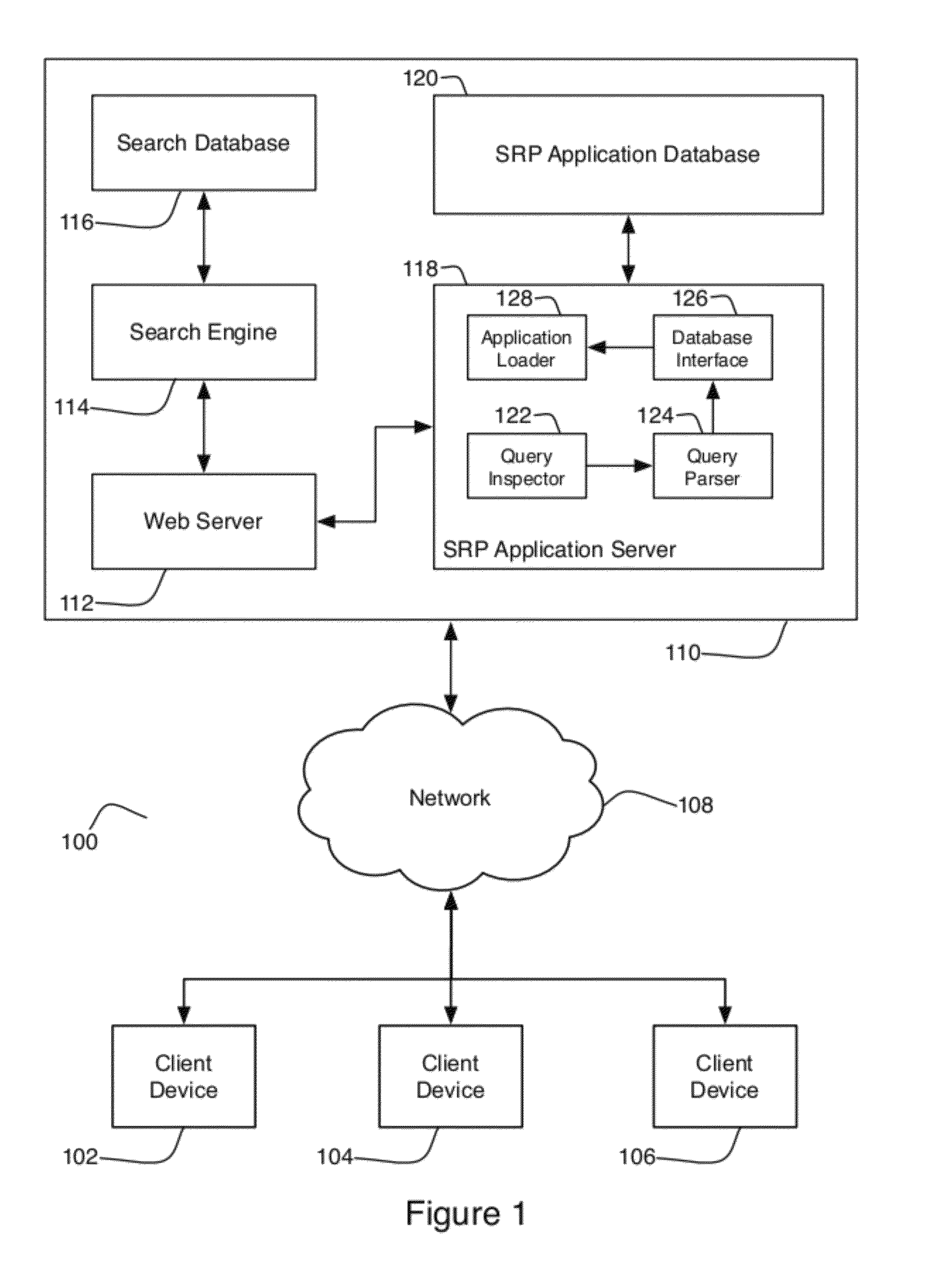
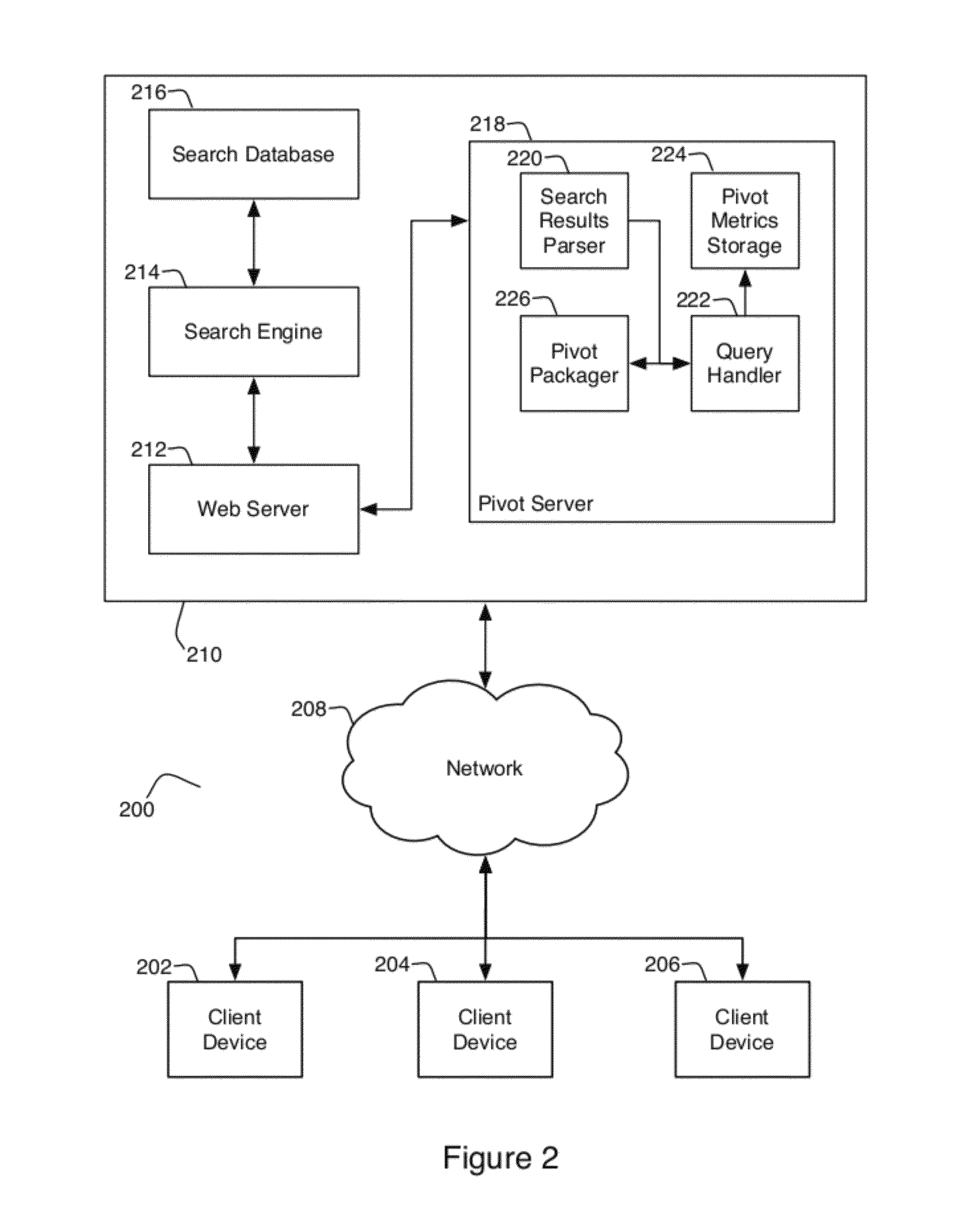
Systems and methods for providing advanced search result page content
ActiveUS8386455B2Handy search resultsDigital data processing detailsSpecial data processing applicationsPartial applicationApplication software
The present invention provides a method and system for generating search results including receiving a search request including at least one search term and accessing a corpus of data to determine relevant content for inclusion in a search result set on the basis of the search request. The method and system includes determining a plurality of applications associated with the search request and generating a search result output display for the presentation of at least a portion of the search result set and at least a portion of the applications.
Owner:R2 SOLUTIONS
Method for performing management and control of mobile phone through APP
InactiveCN105812575AKeep communication functionImprove experienceSubstation equipmentPartial applicationHome screen
The invention provides a method for performing management and control of a mobile phone through an APP. According to information of a management and control time in a management and control policy, a management and control APP directly covers a home screen of a to-be-managed and controlled mobile phone by utilizing a lock screen when the management and control time is up; when the to-be-managed and controlled mobile phone is subjected to screen locking at the management and control time, all functions of the to-be-managed and controlled mobile phone are not simply and directly forbidden, but a familiarity number communication function is kept, so that a to-be-managed and controlled person does not become an uncontrolled person; additionally, at the management and control time, even during a screen locking period, the to-be-managed and controlled mobile phone is allowed to use partial applications conditionally, so that the management and control policy is more human-friendly, and the user experience can be effectively improved.
Owner:GREEN NET WORLD FUJIAN NETWORK TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com