Touch screen terminal hidden unlocking method and system
A touch-screen terminal and unlocking technology, which is applied in the directions of instruments, digital data authentication, and electronic digital data processing, etc., can solve problems such as hazards and information loss, and achieve the effects of high fun, high safety performance, and simple operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
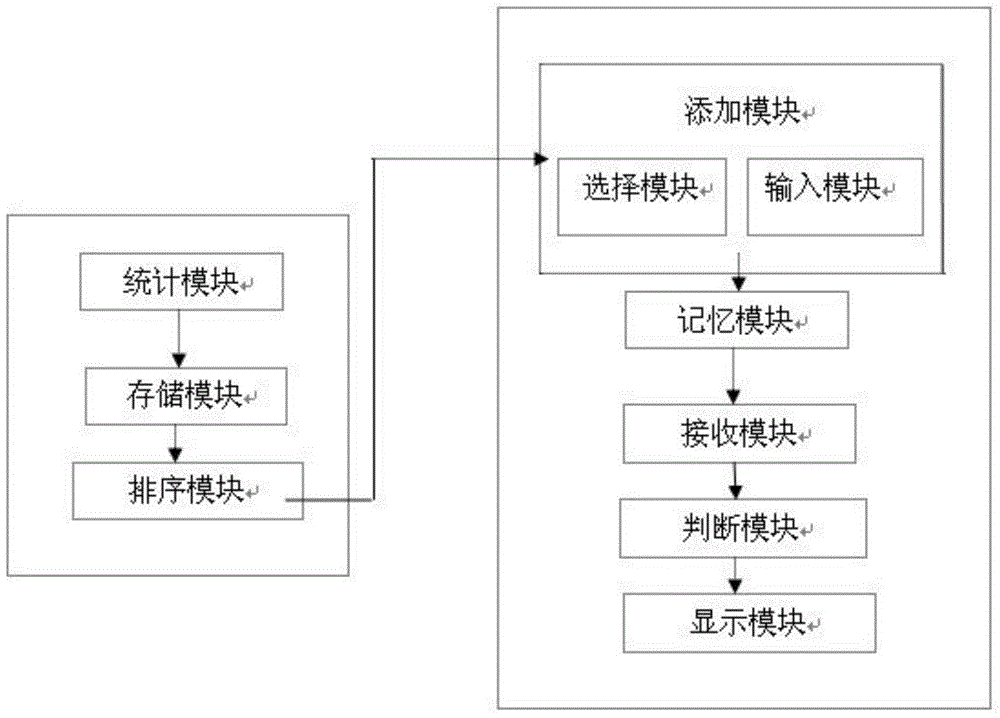
Image
Examples
Embodiment 1
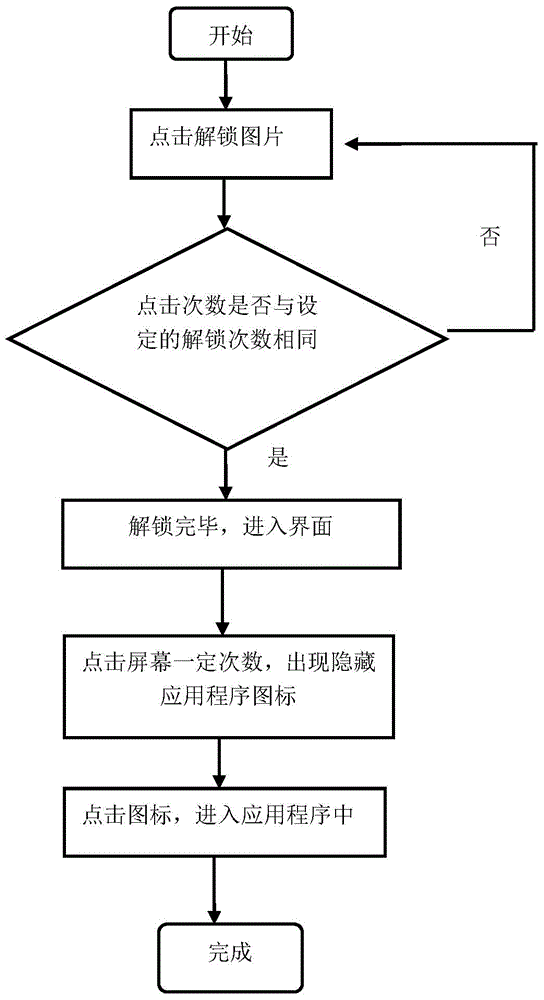
[0031] Such as figure 1 As shown, the present invention provides a hidden unlocking method for touch-screen terminals. In this embodiment, the above-mentioned hiding includes two meanings. Unlocking icons with crossed lines, other unlocking icons, etc.; secondly, after successful unlocking, some application icons that need to be kept secret are hidden to provide double confidentiality of information.
[0032] The hidden unlocking method of the touch screen terminal includes the following steps:
[0033] Step 1. Touch the switch key, the touch screen terminal lights up, displays the unlocking picture, and enters the waiting state for unlocking.
[0034] Step 2: The user clicks the set position on the unlock picture, and the number of clicks is the same as the number of unlocks set when customizing the lock screen, then enters the next step, and if the number of clicks is different from the number of unlocks set when customizing the lock screen, return To be unlocked.
[0035...
Embodiment 2
[0060] The difference between Embodiment 2 and Embodiment 1 is that for the method of hiding and unlocking the above-mentioned touch-screen terminal, the click position is arbitrary when clicking to unlock, as long as the number of clicks corresponds to the set number of times.
[0061] For example, the lock screen background pattern of the touch screen terminal is set as the background pattern of the whack-a-mole game, and the position where the hamster comes out is used as the click position, as long as the number of clicks corresponds to the set number of unlocking clicks, it can be unlocked. Because the position where the hamster comes out is random, so the click position for unlocking is also arbitrary, and the background pattern is in the form of animation. The hamster will re-drill into the hole as it hits, indicating that the click is successful, and it also greatly improves the unlocking process. of interest.
[0062] It is also possible to set any static pattern for ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com