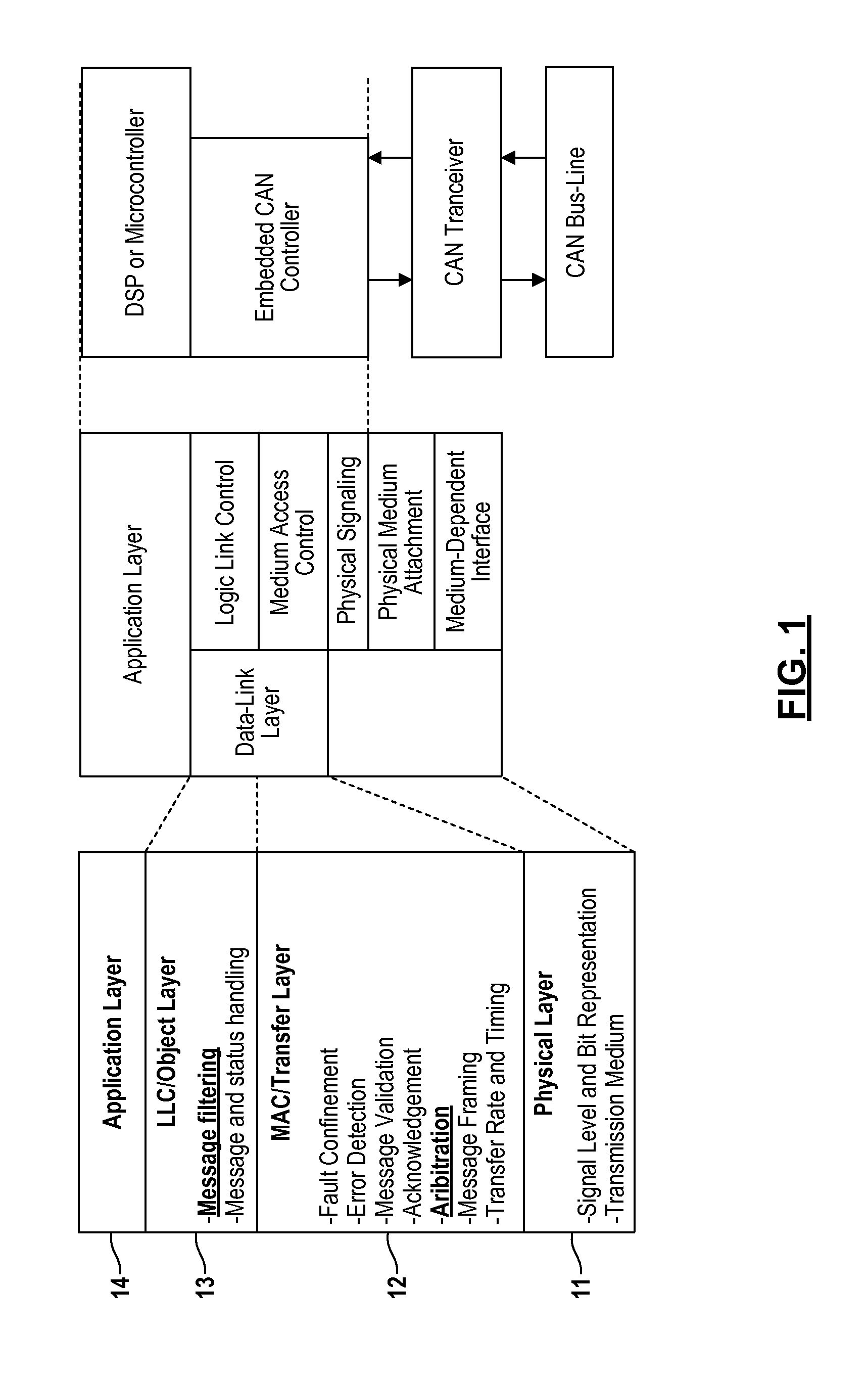
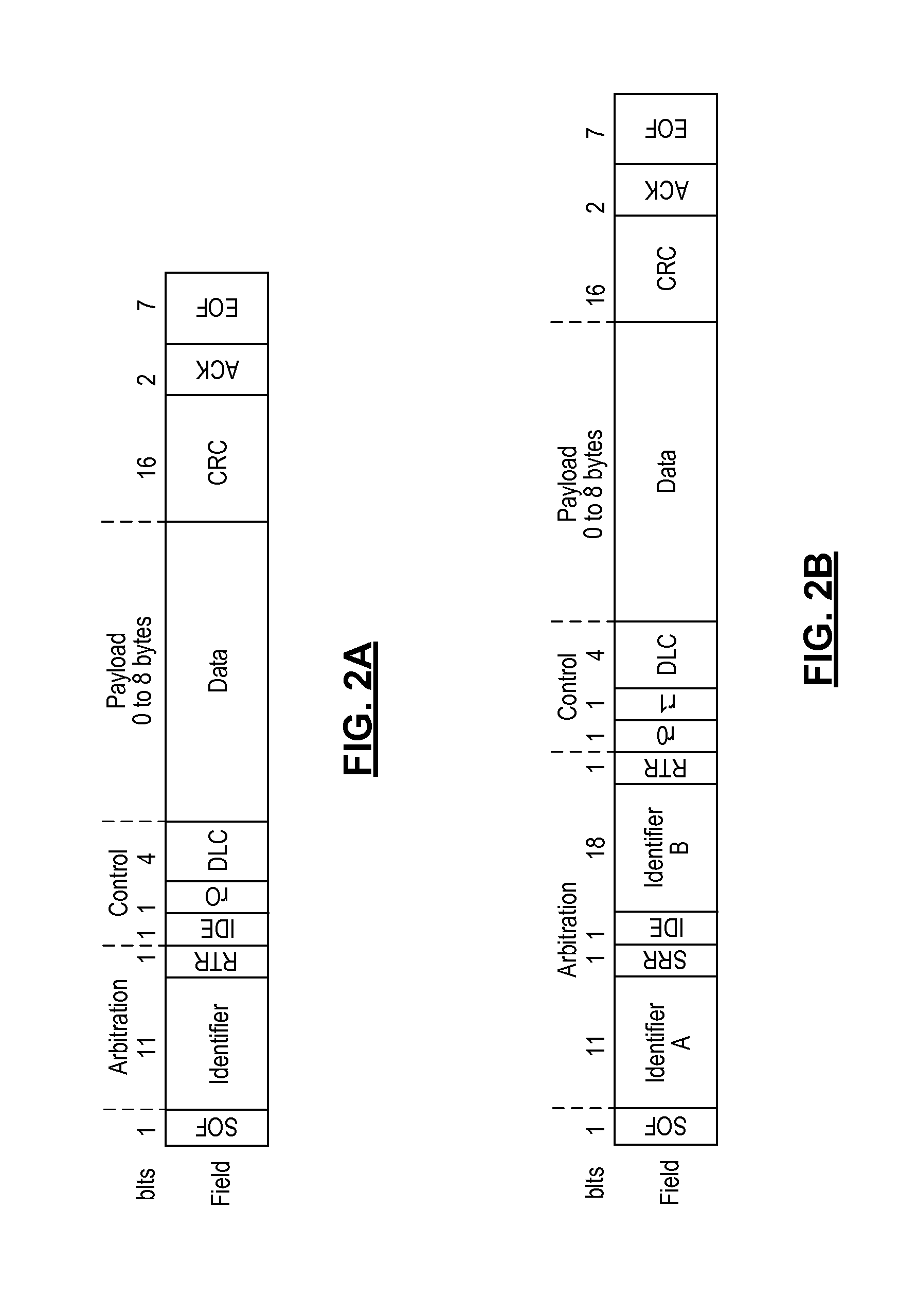
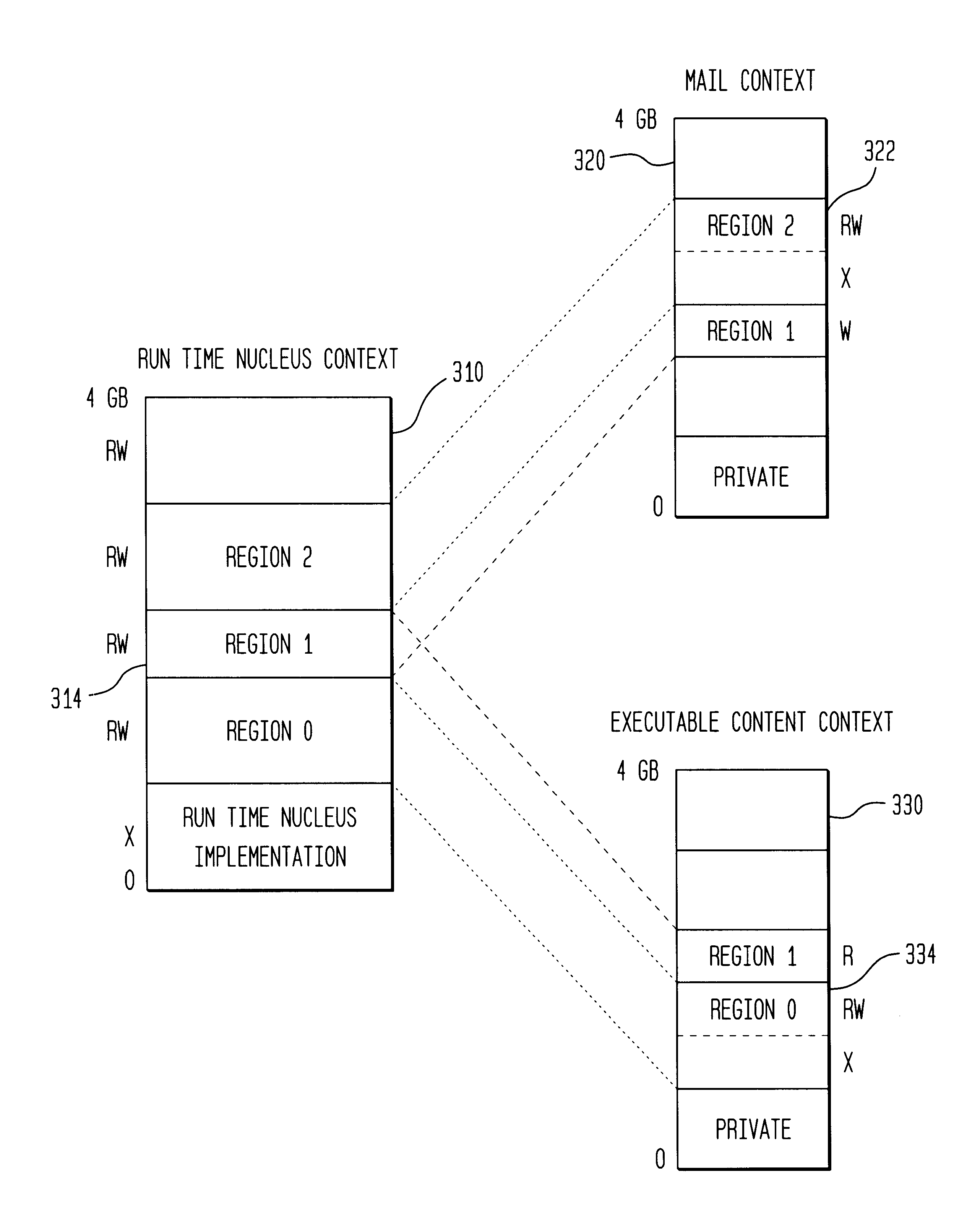
Patents
Literature
9153 results about "Running time" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
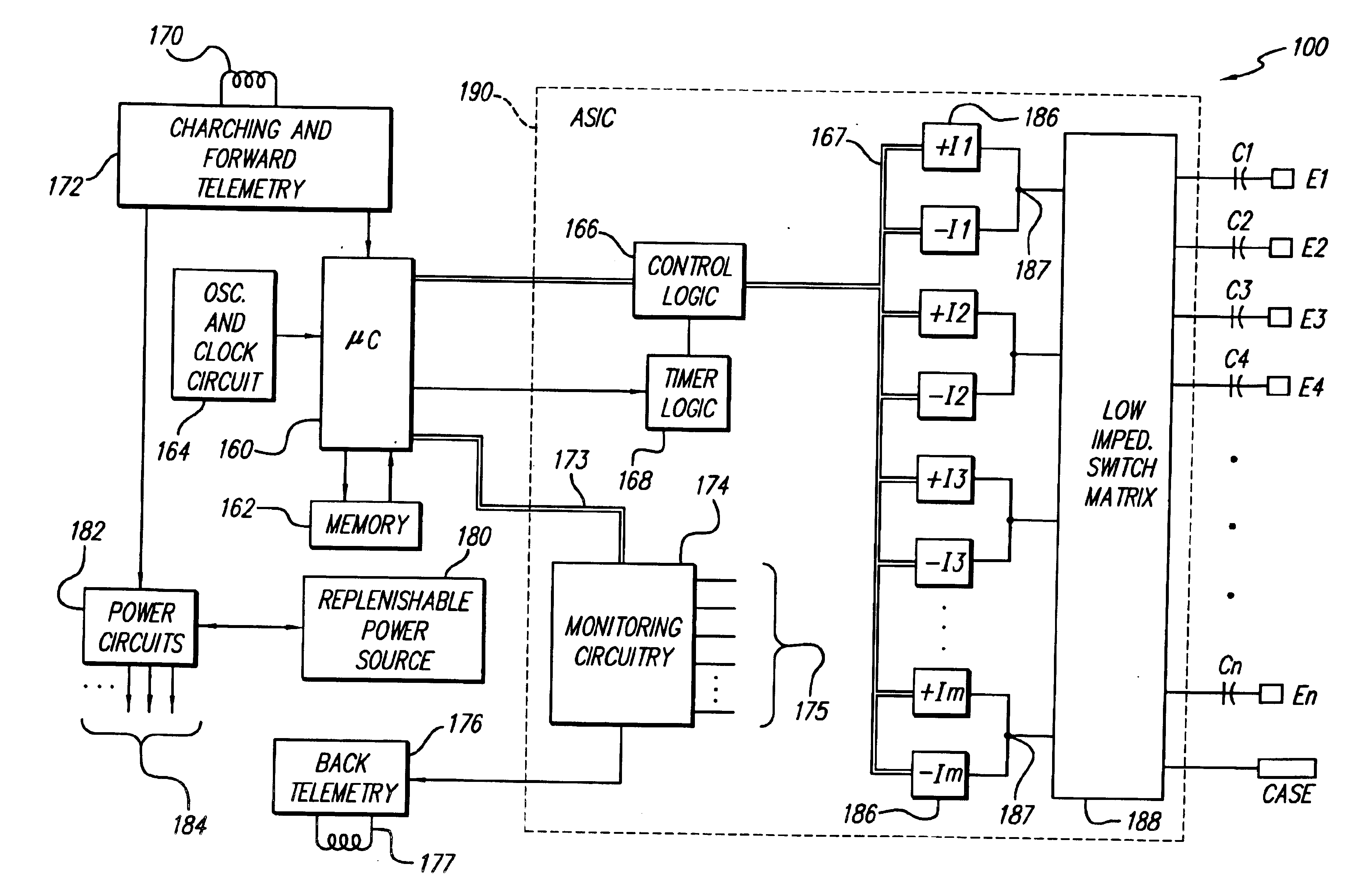
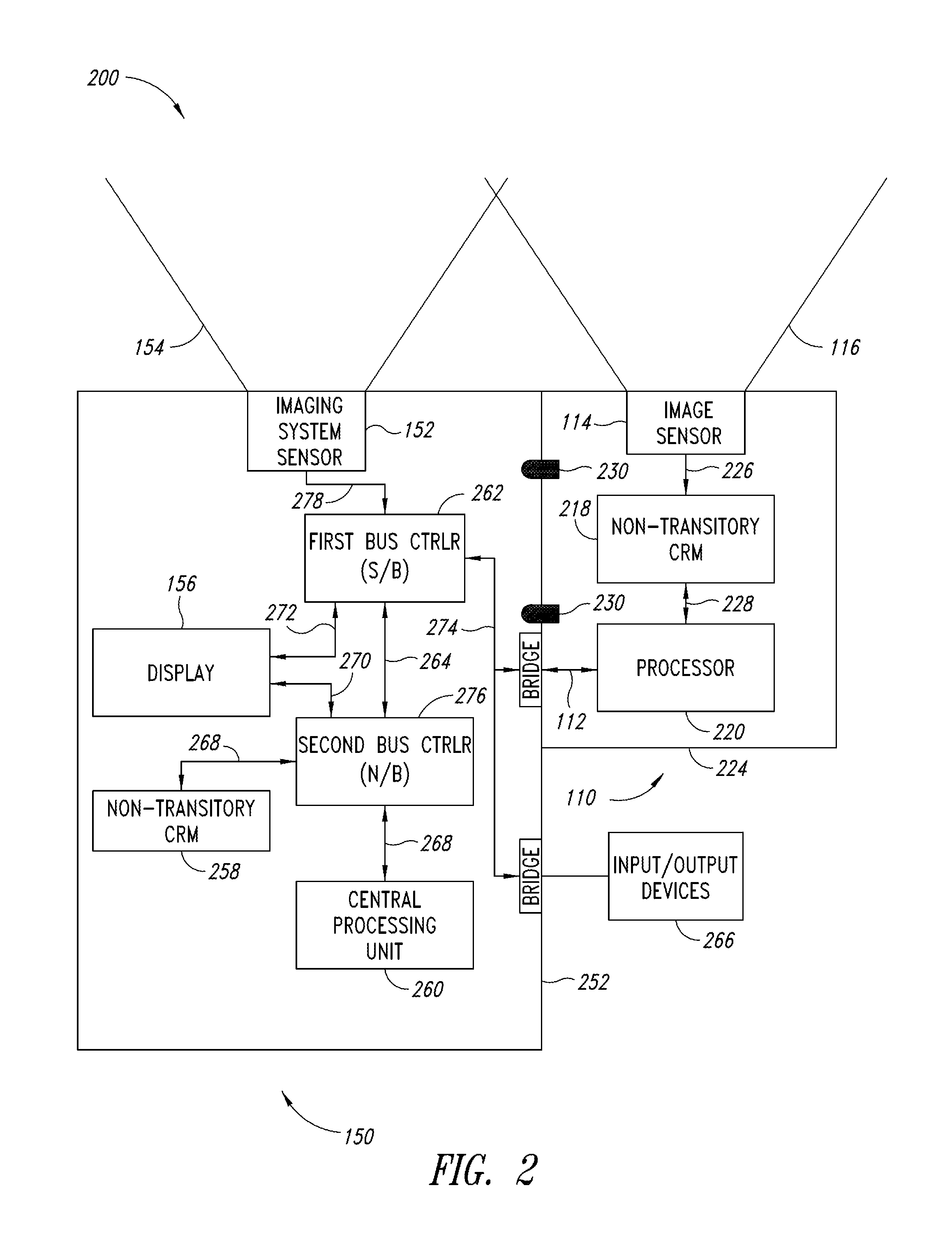
Rechargeable spinal cord stimulator system
InactiveUS6895280B2Provide comfortAvoid displacementSpinal electrodesCircuit arrangements on support structuresReal-time clockElectrical battery
A spinal cord stimulation (SCS) system includes multiple electrodes, multiple, independently programmable, stimulation channels within an implantable pulse generator (IPG) which channels can provide concurrent, but unique stimulation fields, permitting virtual electrodes to be realized. The SCS system includes a replenishable power source (e.g., rechargeable battery), that may be recharged using transcutaneous power transmissions between antenna coil pairs. An external charger unit, having its own rechargeable battery can be used to charge the IPG replenishable power source. A real-time clock can provide an auto-run schedule for daily stimulation. An included bi-directional telemetry link in the system informs the patient or clinician the status of the system, including the state of charge of the IPG battery. Other processing circuitry in the IPG allows electrode impedance measurements to be made. Further circuitry in the external battery charger can provide alignment detection for the coil pairs.
Owner:BOSTON SCI NEUROMODULATION CORP
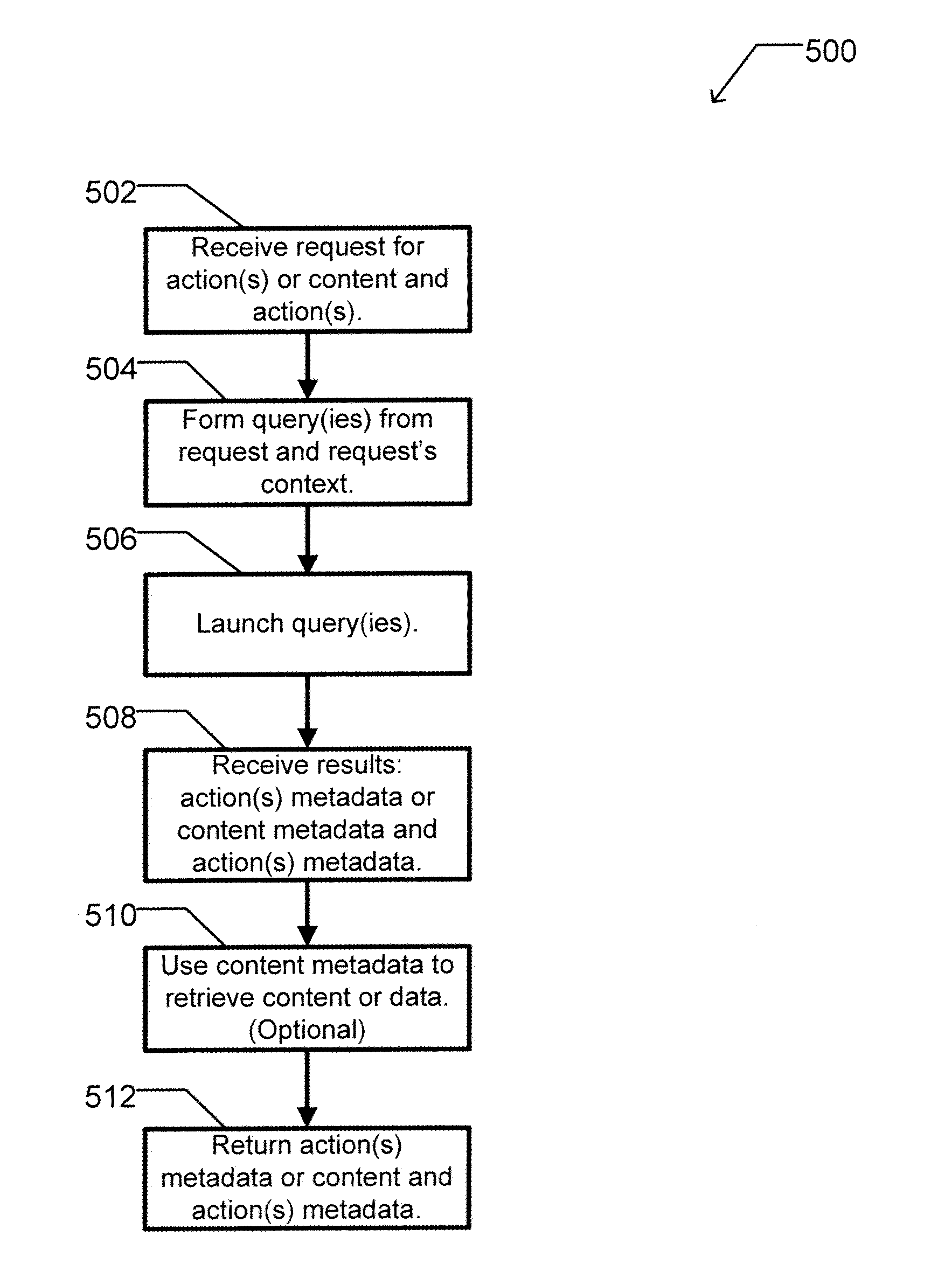
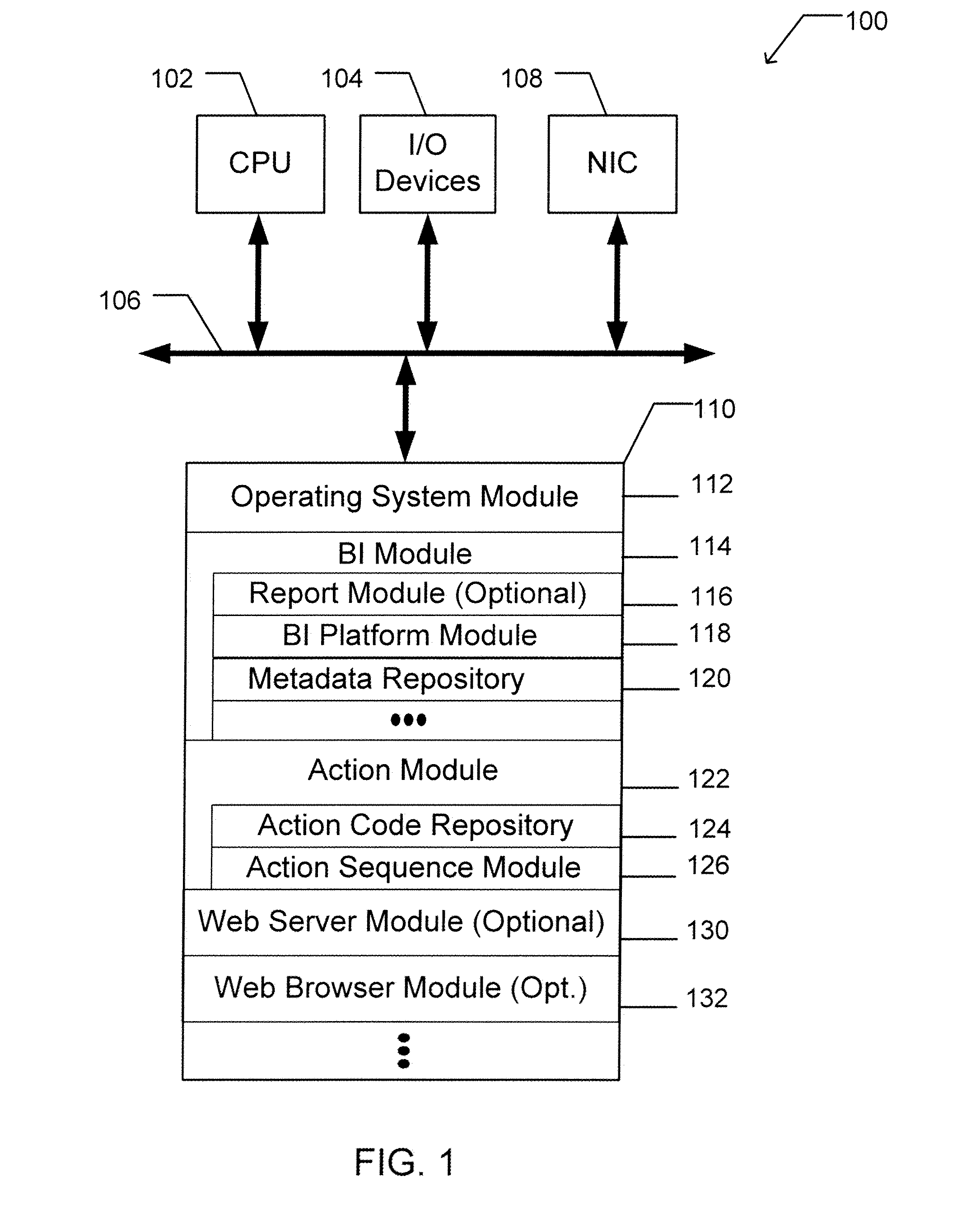
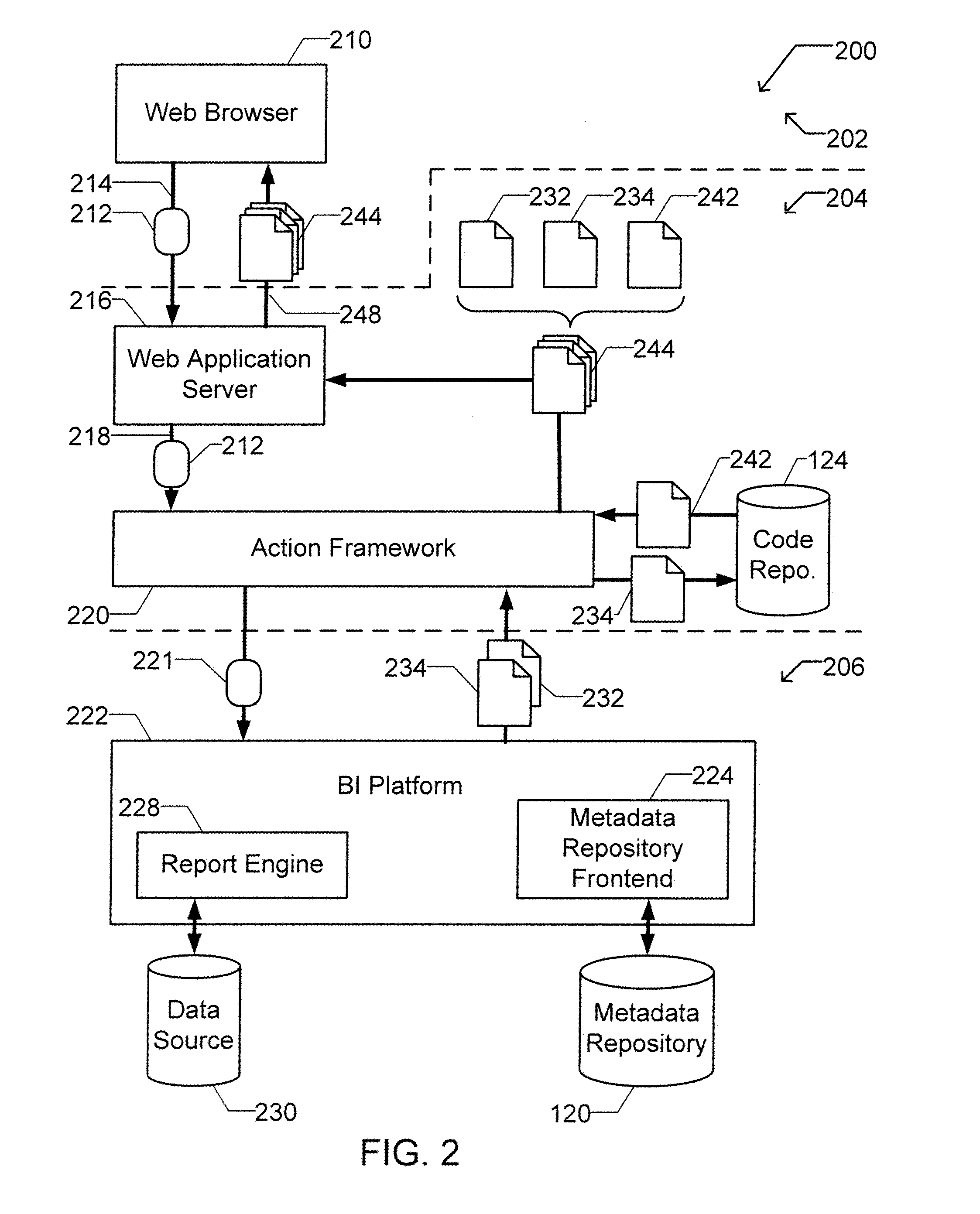
Apparatus and method for dynamically selecting componentized executable instructions at run time
A computer readable storage medium includes executable instructions to receive a request for an action. An action context is received where the action context includes an application requesting the action. A set of metadata is searched for metadata corresponding to the action, where the search is limited by the action context. Selected metadata for the action is inserted into a collection. The selected metadata is a result of searching the set of metadata. The selected metadata includes a reference to the set of executable instructions that implements the action and a description of the action. The collection is then returned.
Owner:BUSINESS OBJECTS SOFTWARE
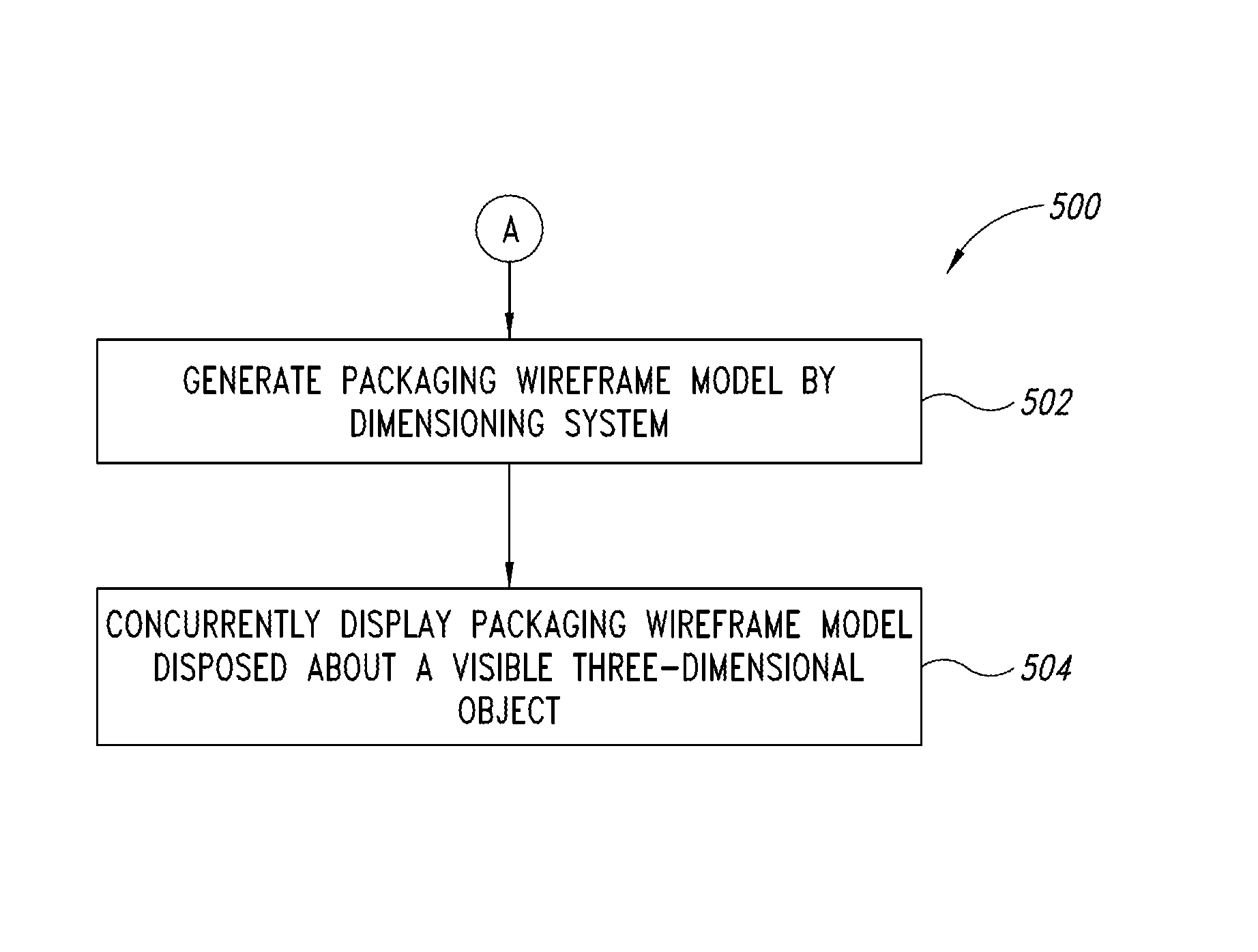
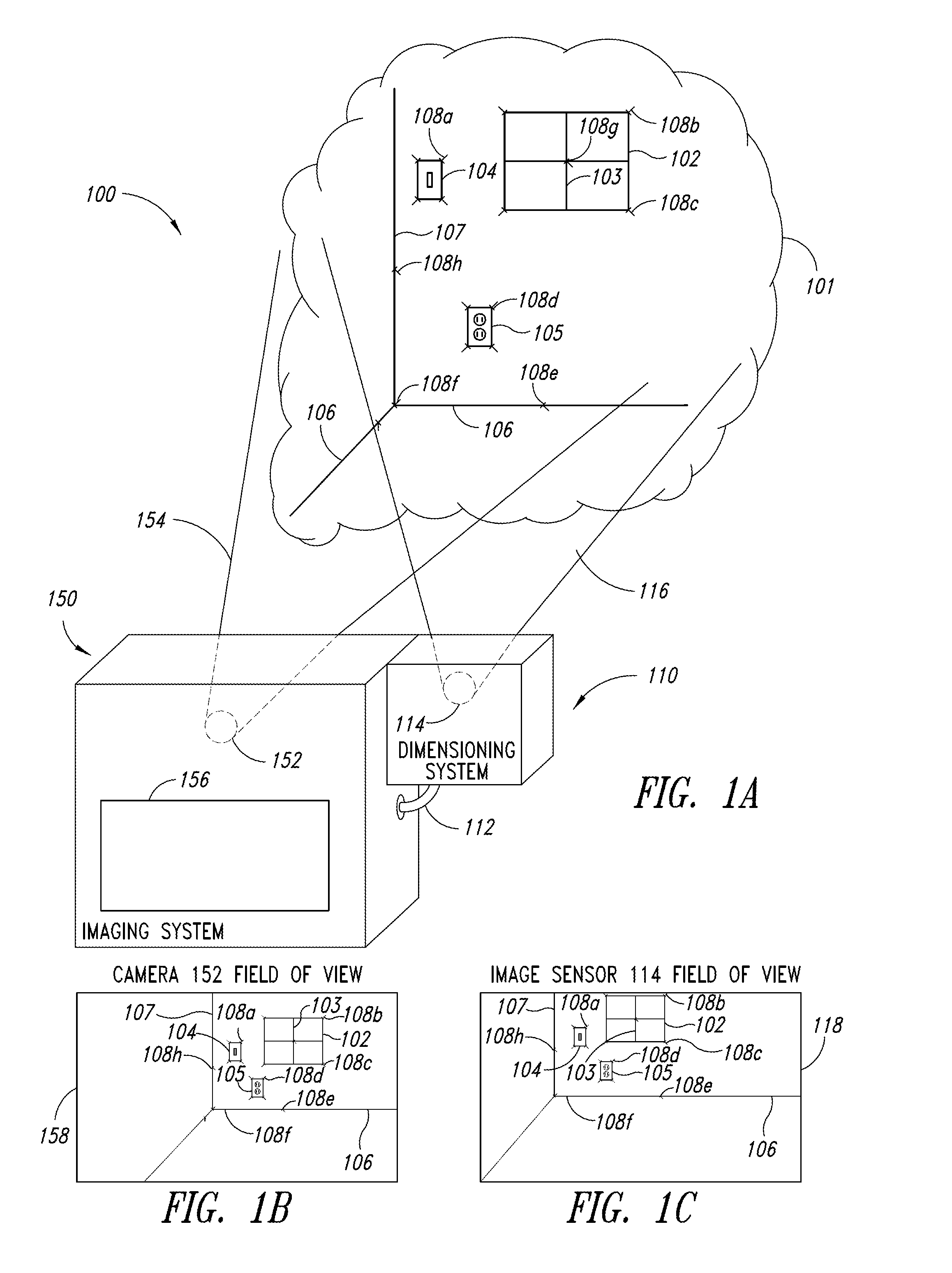
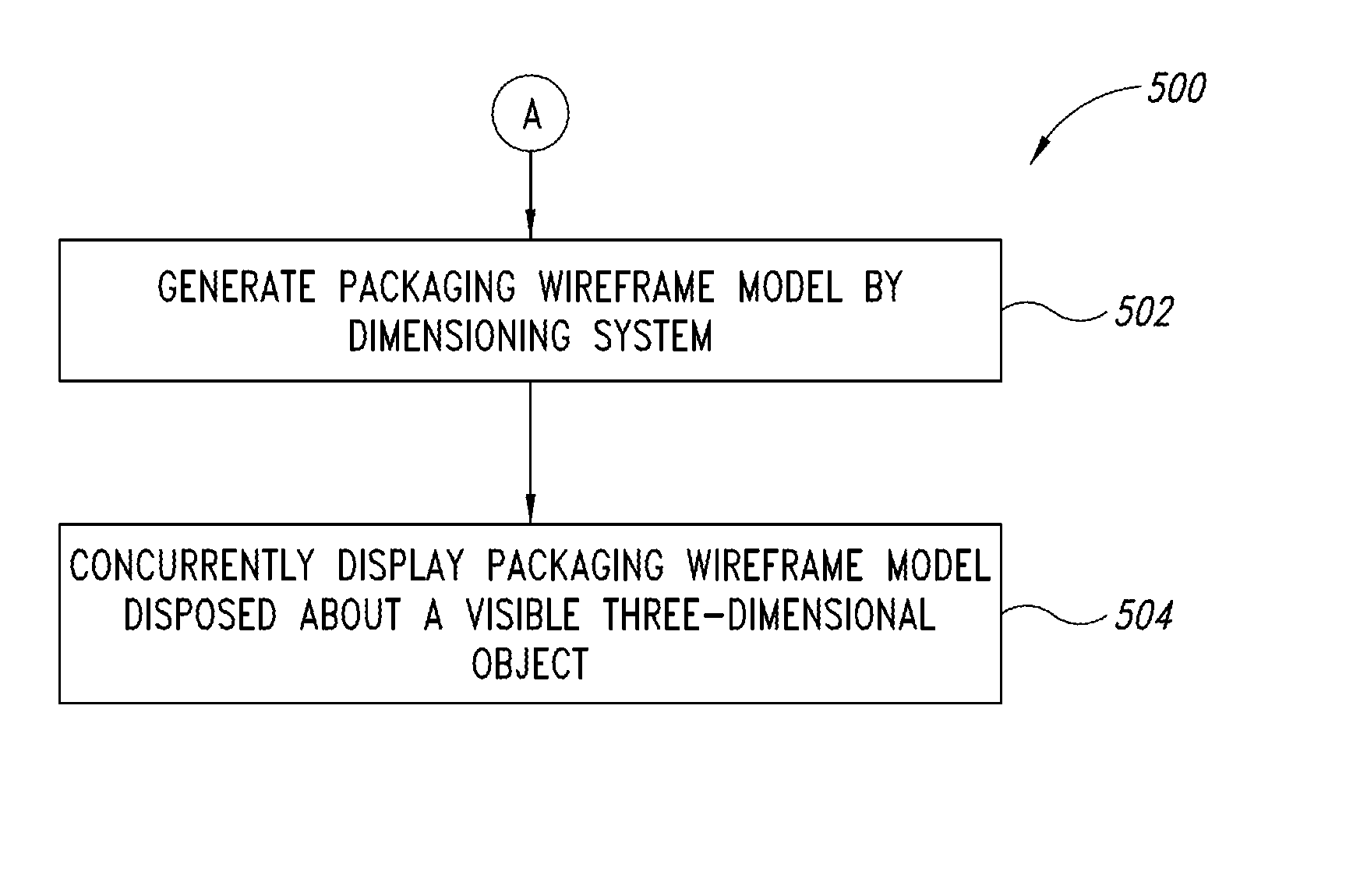
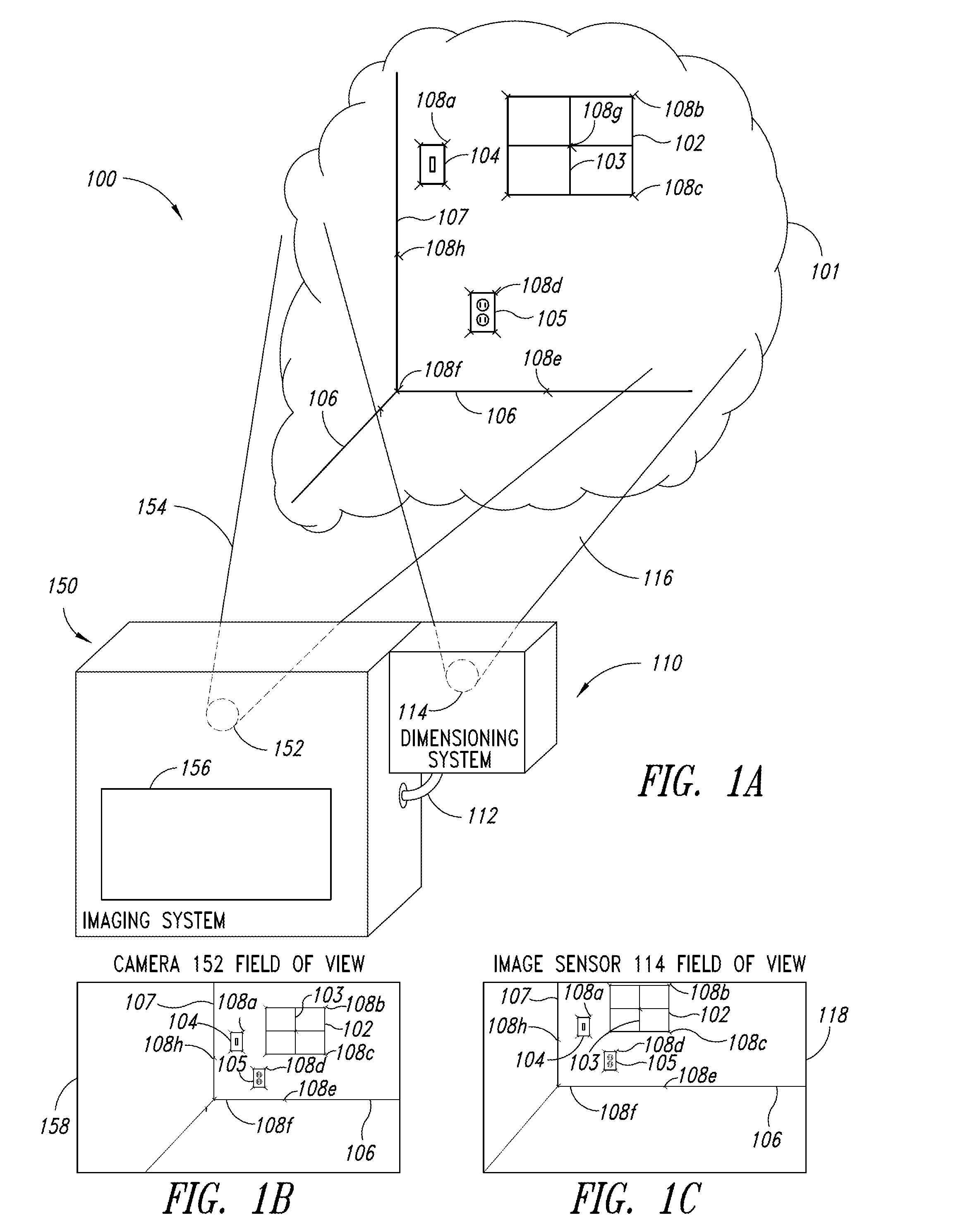
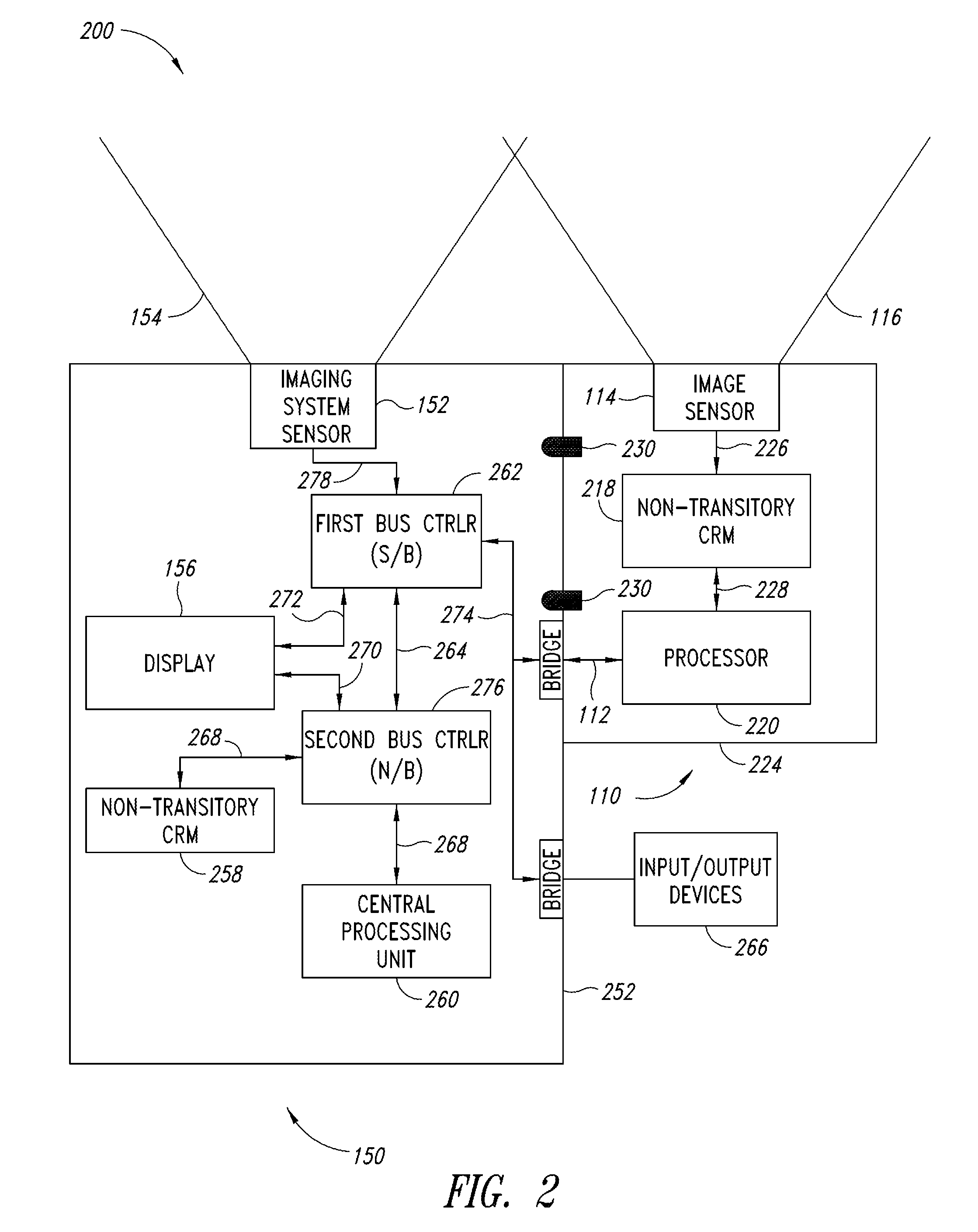
Dimensioning system calibration systems and methods
Systems and methods of determining the volume and dimensions of a three-dimensional object using a dimensioning system are provided. The dimensioning system can include an image sensor, a non-transitory, machine-readable, storage, and a processor. The dimensioning system can select and fit a three-dimensional packaging wireframe model about each three-dimensional object located within a first point of view of the image sensor. Calibration is performed to calibrate between image sensors of the dimensioning system and those of the imaging system. Calibration may occur pre-run time, in a calibration mode or period. Calibration may occur during a routine. Calibration may be automatically triggered on detection of a coupling between the dimensioning and the imaging systems.
Owner:INTERMEC IP
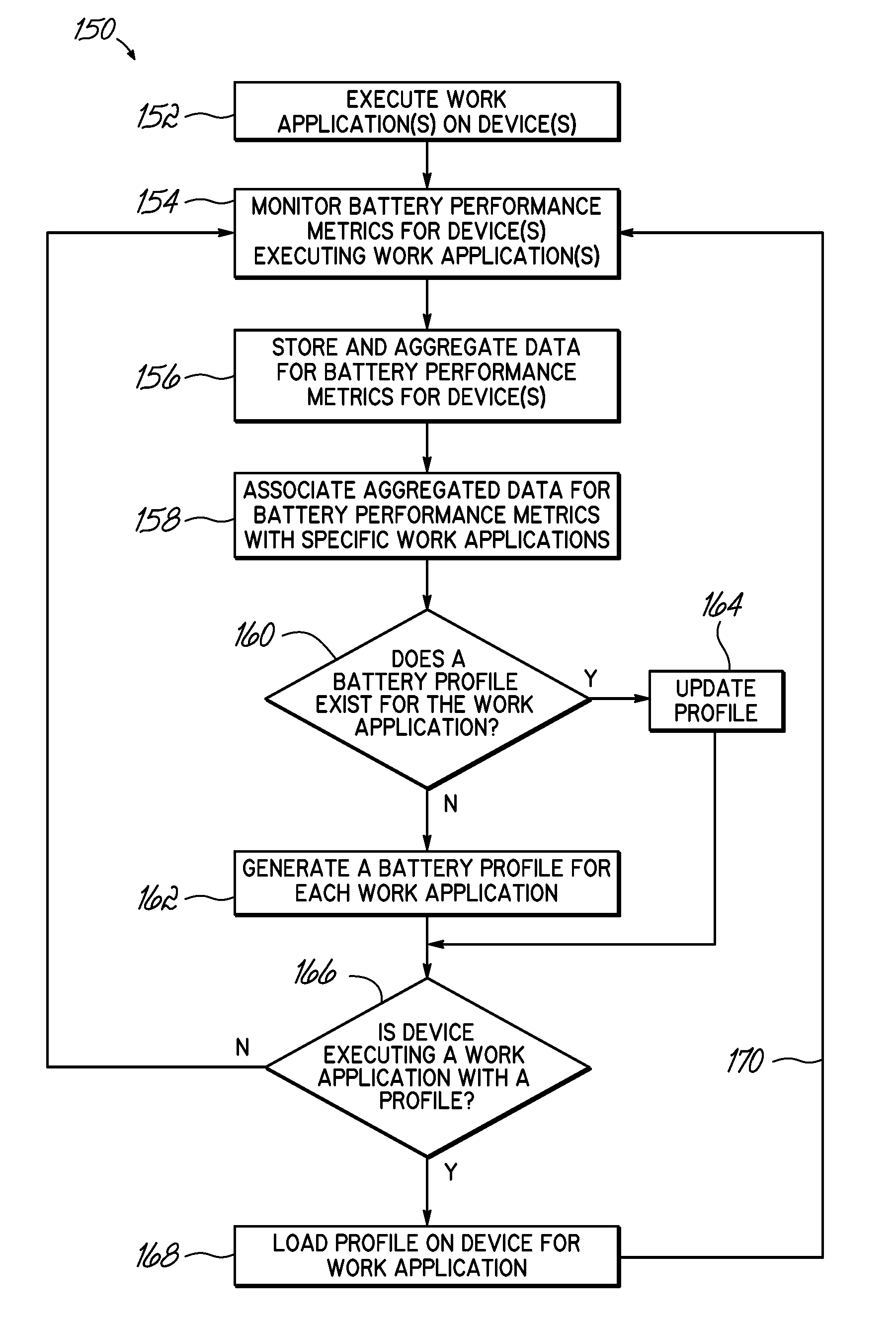
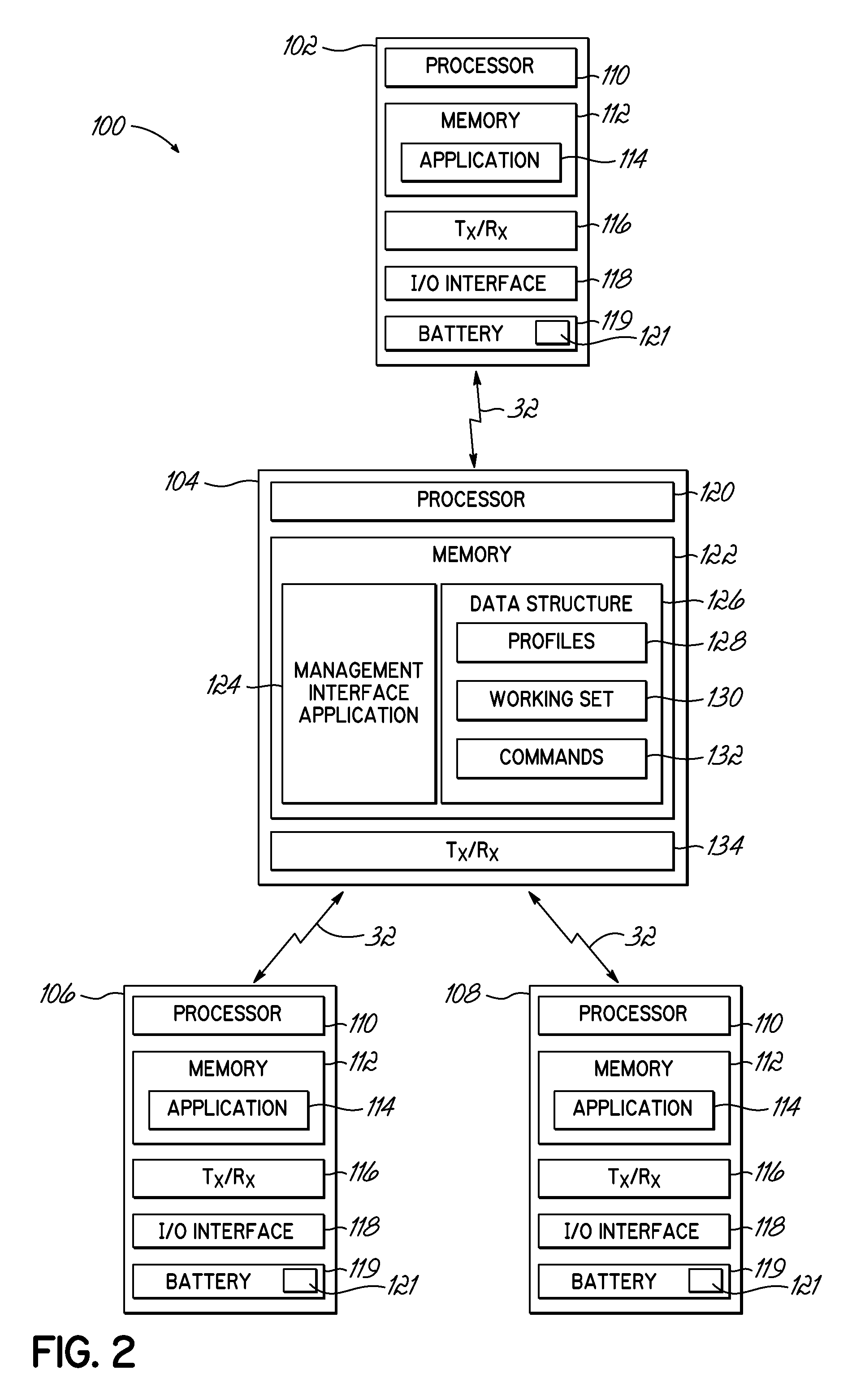
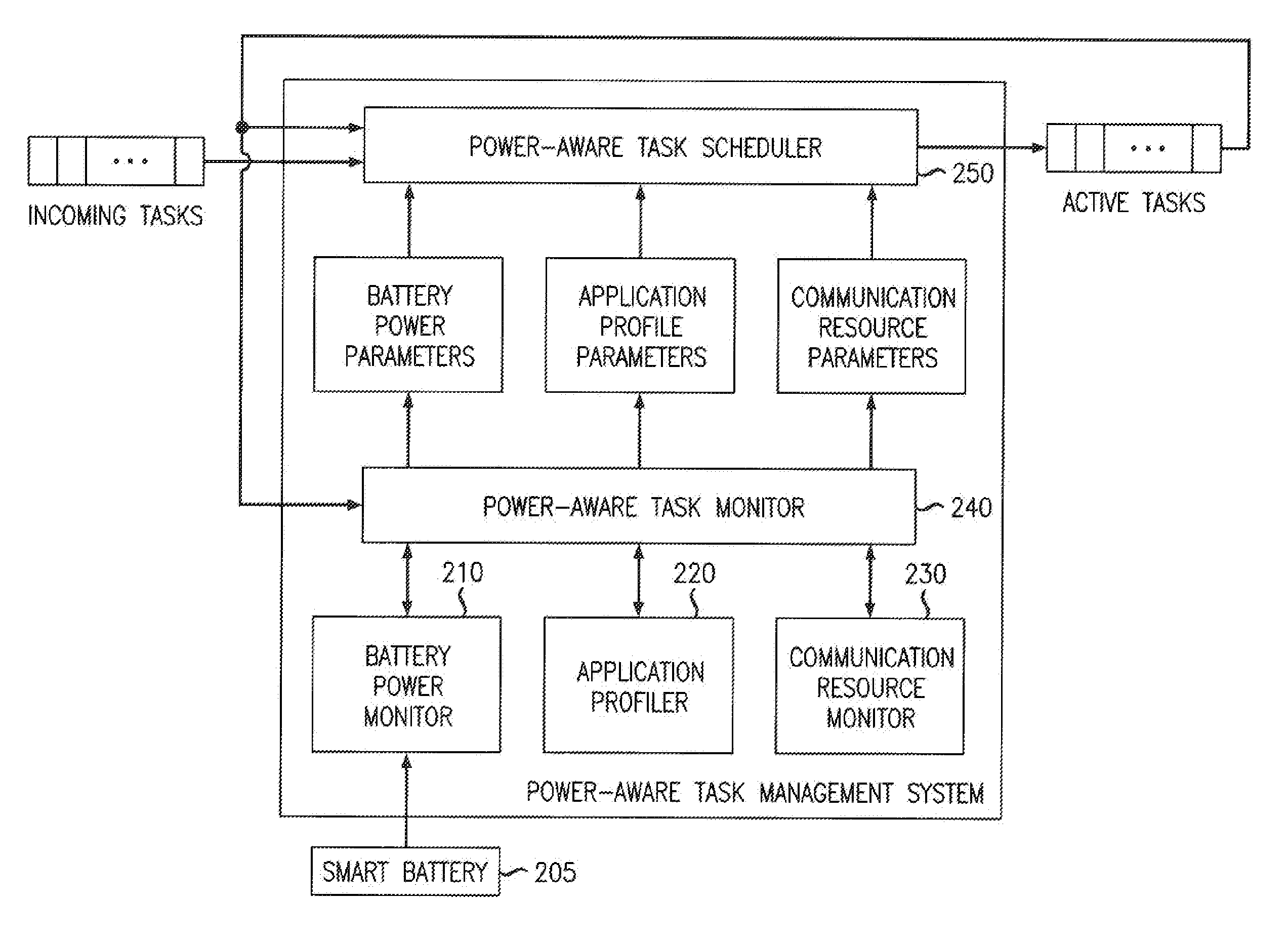
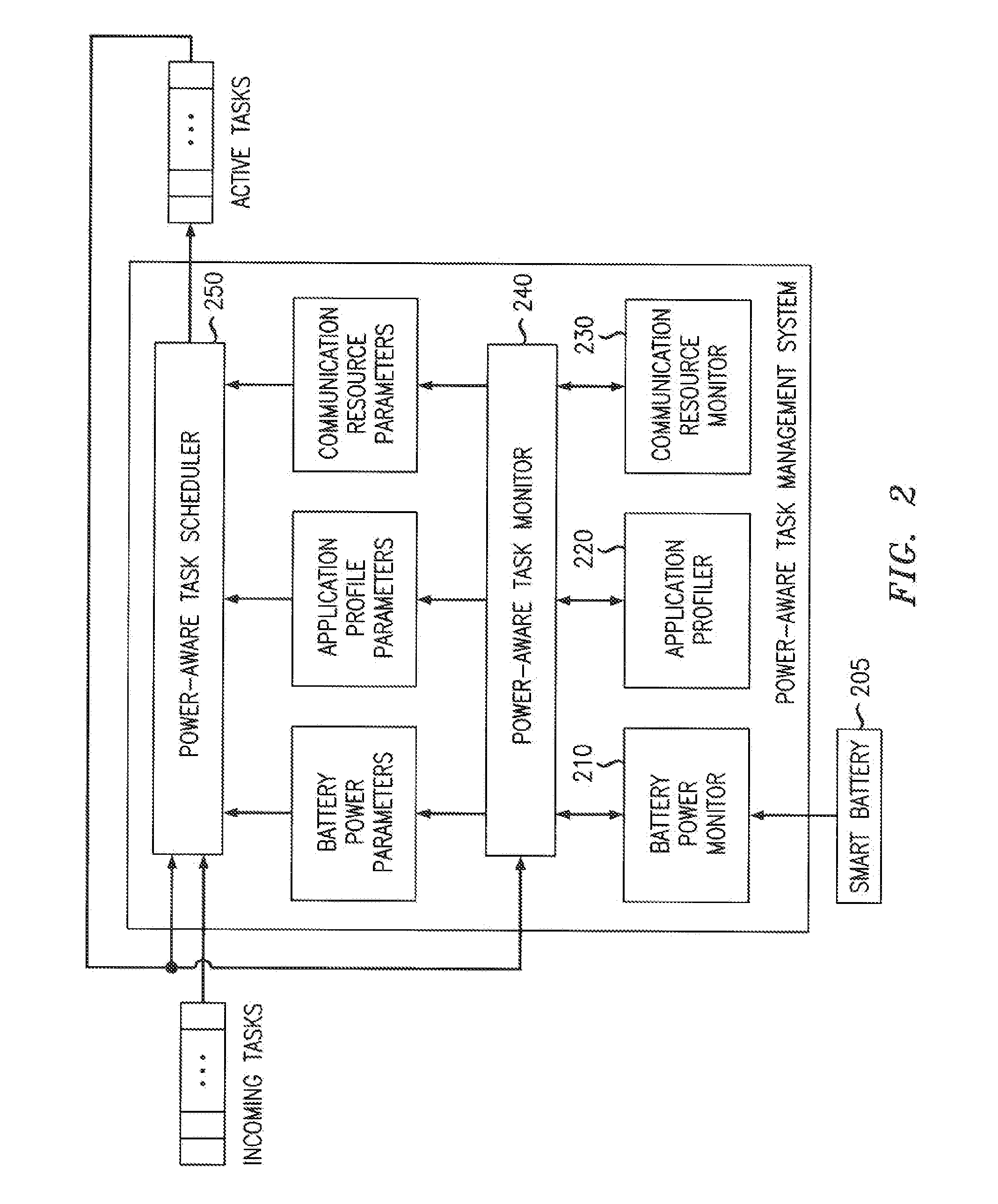
Receiving application specific individual battery adjusted battery use profile data upon loading of work application for managing remaining power of a mobile device
A method and system of managing power usage of devices including selectively executing a program application on a plurality of battery powered devices. Battery usage data is generated for a battery in one or more of the devices during execution of the work application. The battery usage data includes the run-time of the battery for the work application being executed. The data is aggregated and stored for the plurality of devices in memory. An application specific battery profile is generated using the stored battery usage data. The application specific battery profile is associated with the work application being run by the client devices.
Owner:VOCOLLECT
Dimensioning system calibration systems and methods
Systems and methods of determining the volume and dimensions of a three-dimensional object using a dimensioning system are provided. The dimensioning system can include an image sensor, a non-transitory, machine-readable, storage, and a processor. The dimensioning system can select and fit a three-dimensional packaging wireframe model about each three-dimensional object located within a first point of view of the image sensor. Calibration is performed to calibrate between image sensors of the dimensioning system and those of the imaging system. Calibration may occur pre-run time, in a calibration mode or period. Calibration may occur during a routine. Calibration may be automatically triggered on detection of a coupling between the dimensioning and the imaging systems.
Owner:INTERMEC IP
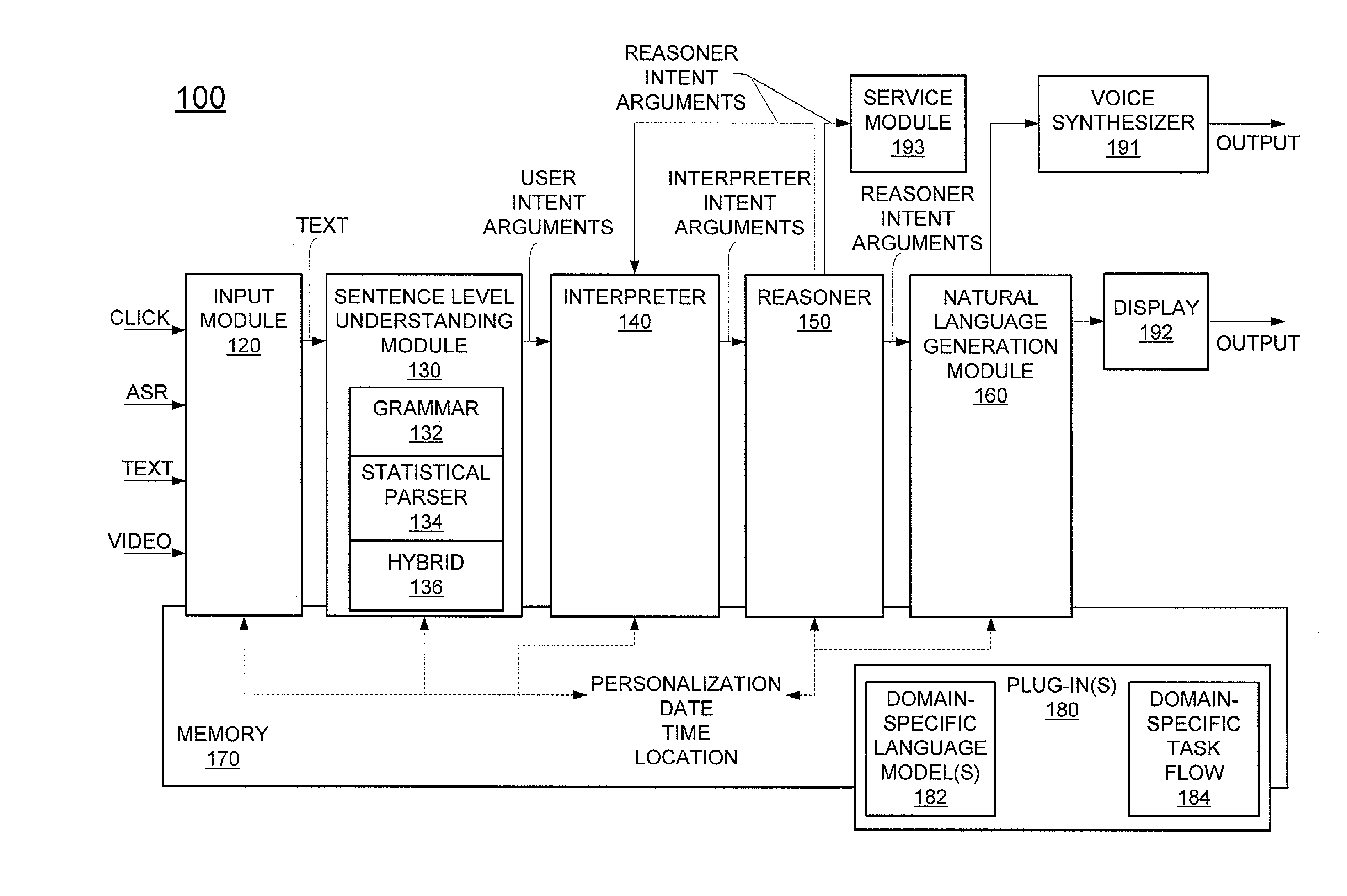
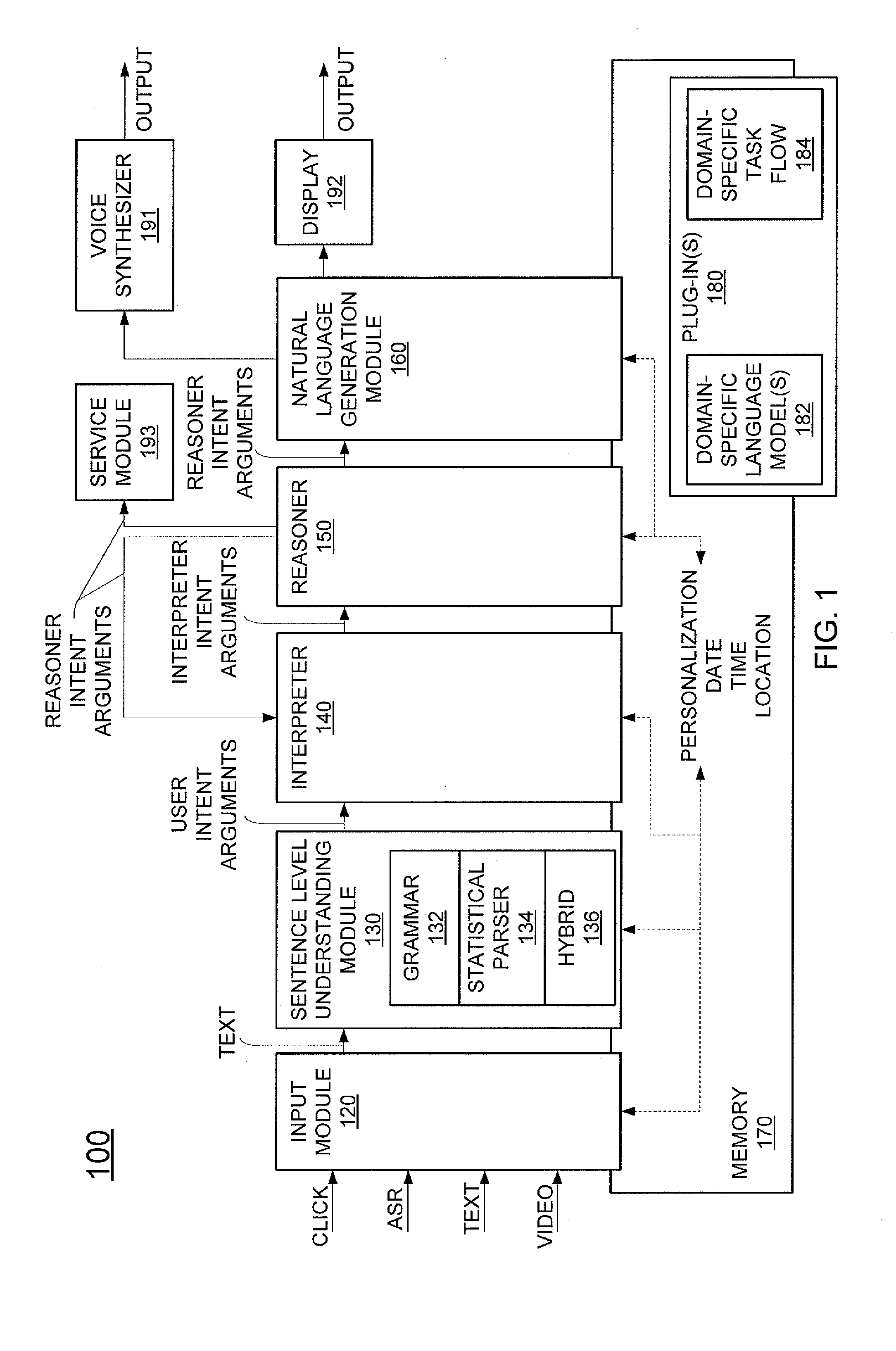
Generic virtual personal assistant platform
ActiveUS20130152092A1Natural language translationMultiprogramming arrangementsLanguage understandingA domain
A method for assisting a user with one or more desired tasks is disclosed. For example, an executable, generic language understanding module and an executable, generic task reasoning module are provided for execution in the computer processing system. A set of run-time specifications is provided to the generic language understanding module and the generic task reasoning module, comprising one or more models specific to a domain. A language input is then received from a user, an intention of the user is determined with respect to one or more desired tasks, and the user is assisted with the one or more desired tasks, in accordance with the intention of the user.
Owner:SRI INTERNATIONAL
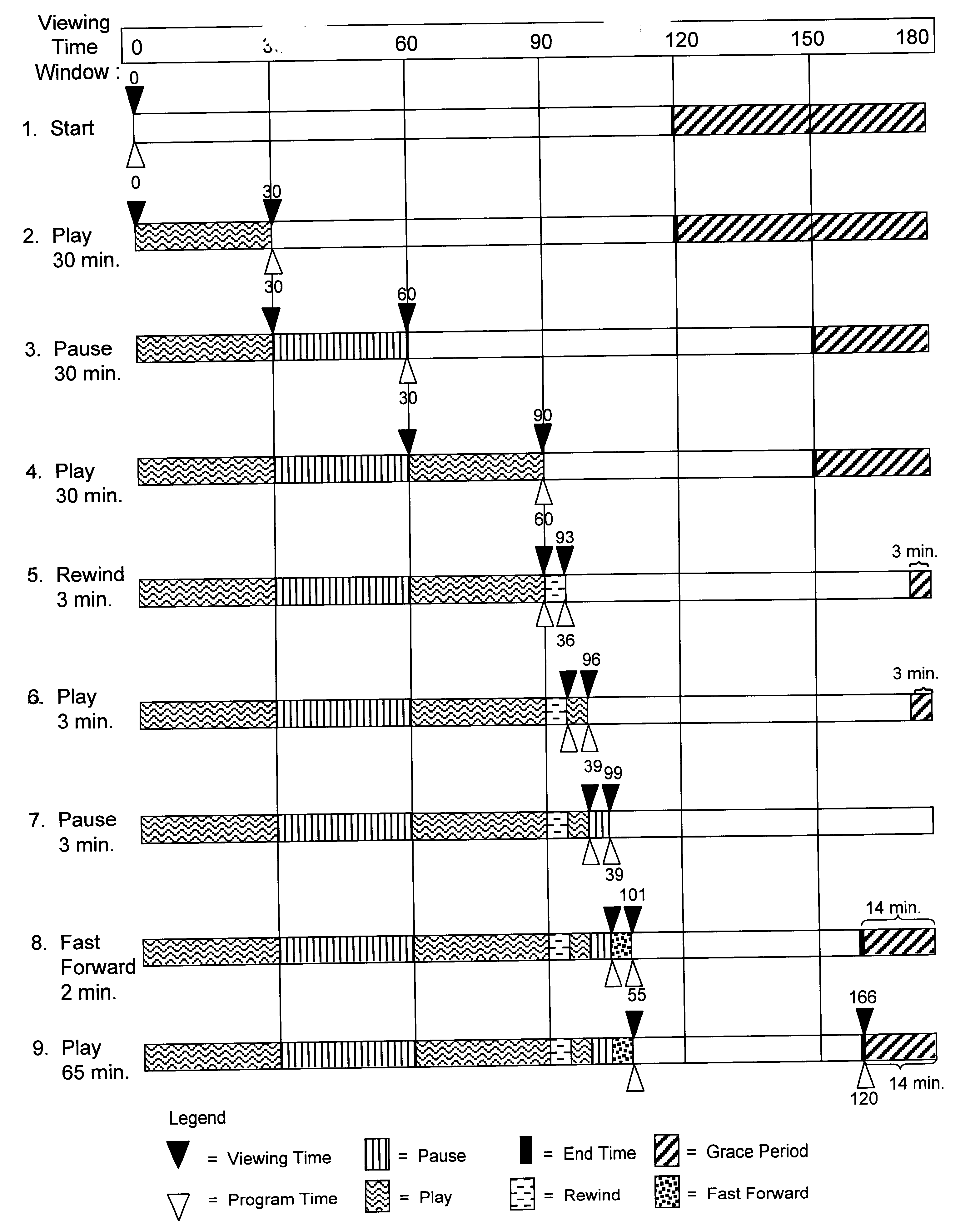
Method and system for providing interactive media VCR control
InactiveUS6609253B1Easy to modifyShorten the construction periodTelevision system detailsRecording carrier detailsTelevision systemInteractive television
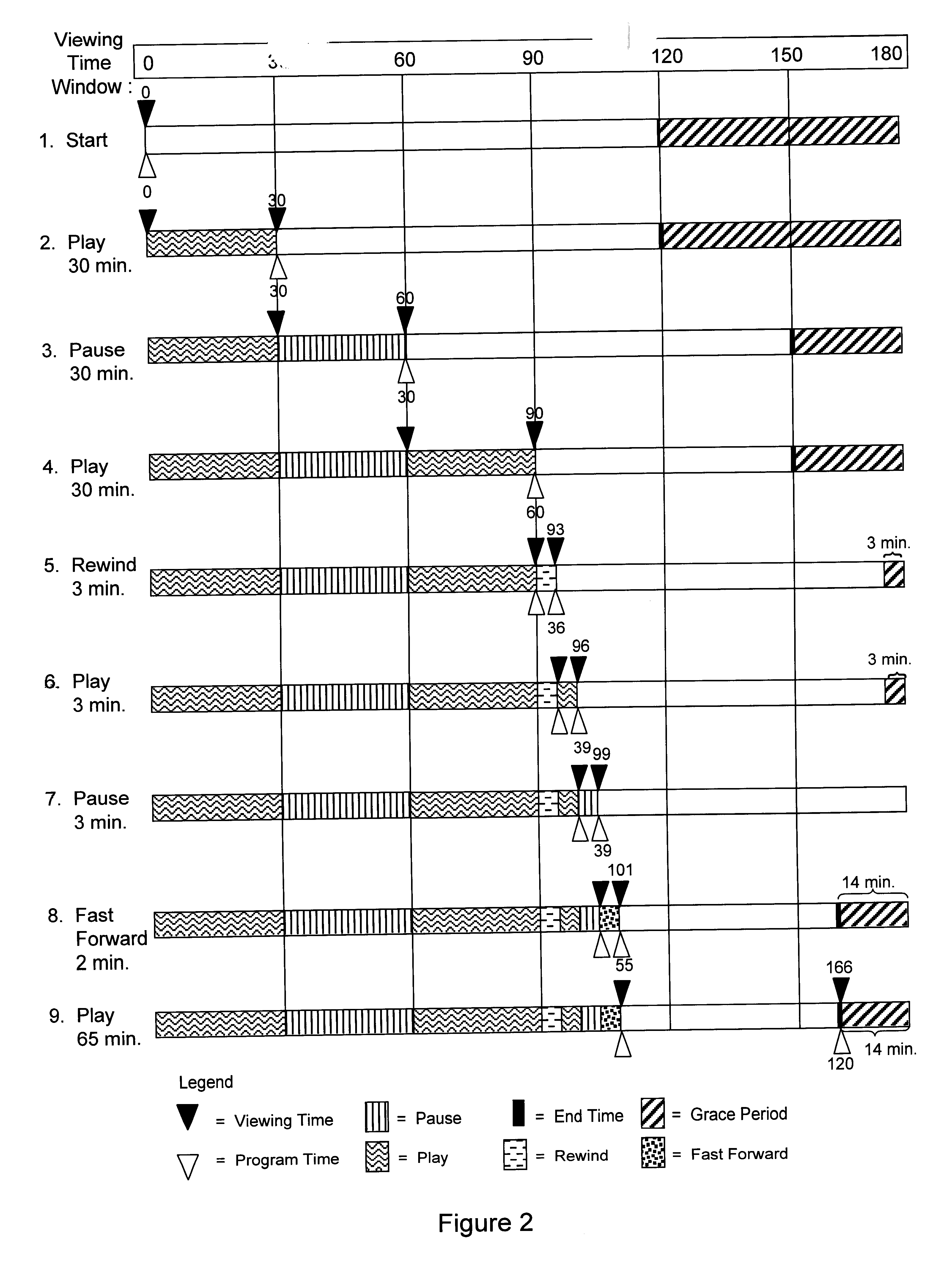
A method and system for providing flexible subscriber VCR control of an interactive media system that limits the consumption of bandwidth capacity, the method comprising establishing a viewing time window during which a subscriber can watch an ordered program, enabling the subscriber to freely pause, rewind, and fast-forward the program so long as the end of the program does not exceed the end of the window, automatically tracking the remaining program running time against the time remaining in the window, deactivating the pause and rewind features if the remaining program running time equals the time remaining in the window, and reactivating the pause and rewind features if the program is fast-forwarded such that the time remaining in the window exceeds the remaining program running time. The system of the present invention is any interactive media system that delivers video streams such as an interactive television system that supports services such as pay-per-view and video-on-demand, or an internet-based interactive media system that downloads video streams through the internet to be played on a subscriber's personal computer or other viewing device.
Owner:HANGER SOLUTIONS LLC
Distributed maximum power point tracking system, structure and process
ActiveUS20080238195A1Sure easyExtended operating timeBatteries circuit arrangementsConversion with intermediate conversion to dcNuclear engineeringControl system
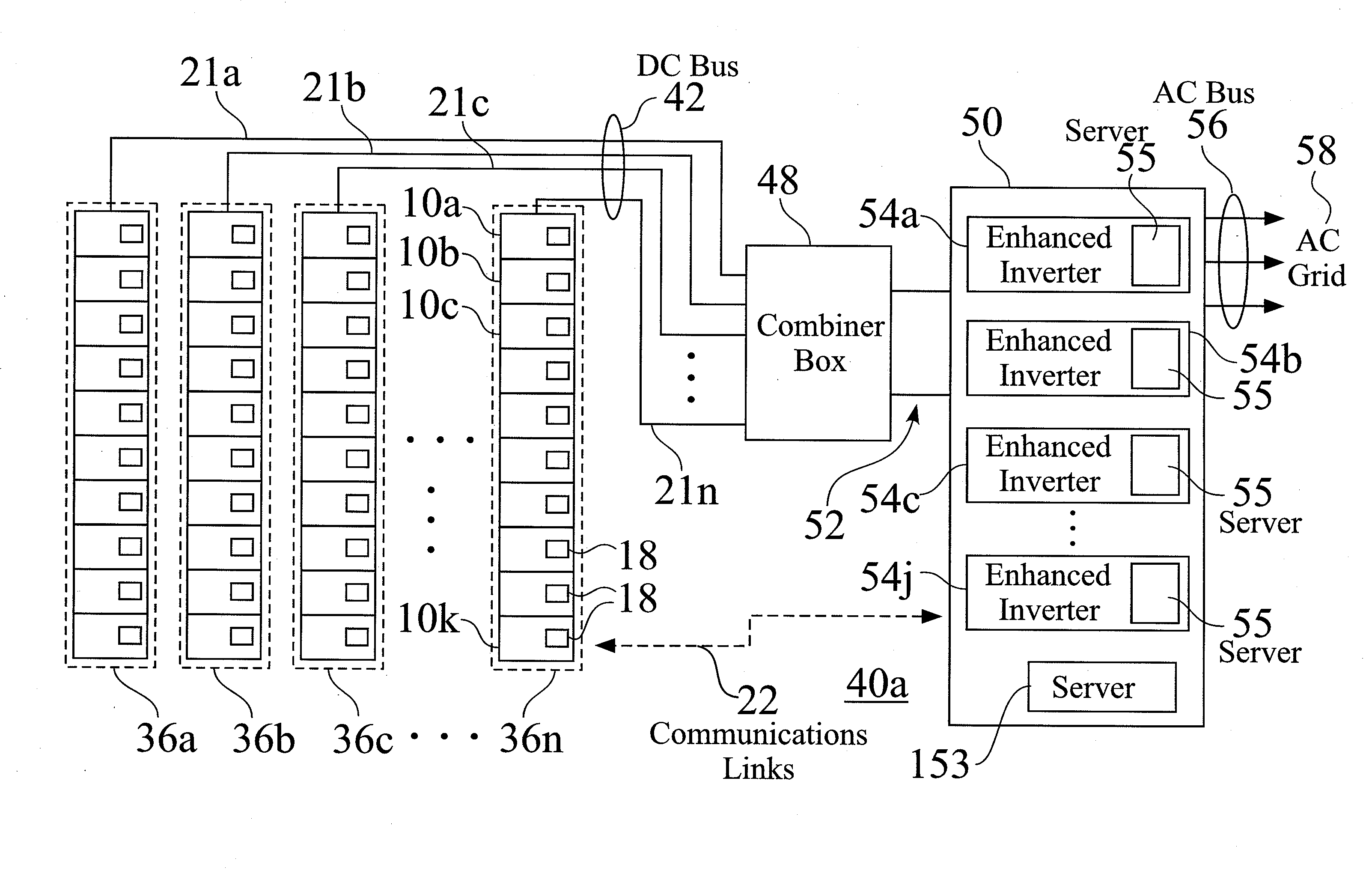
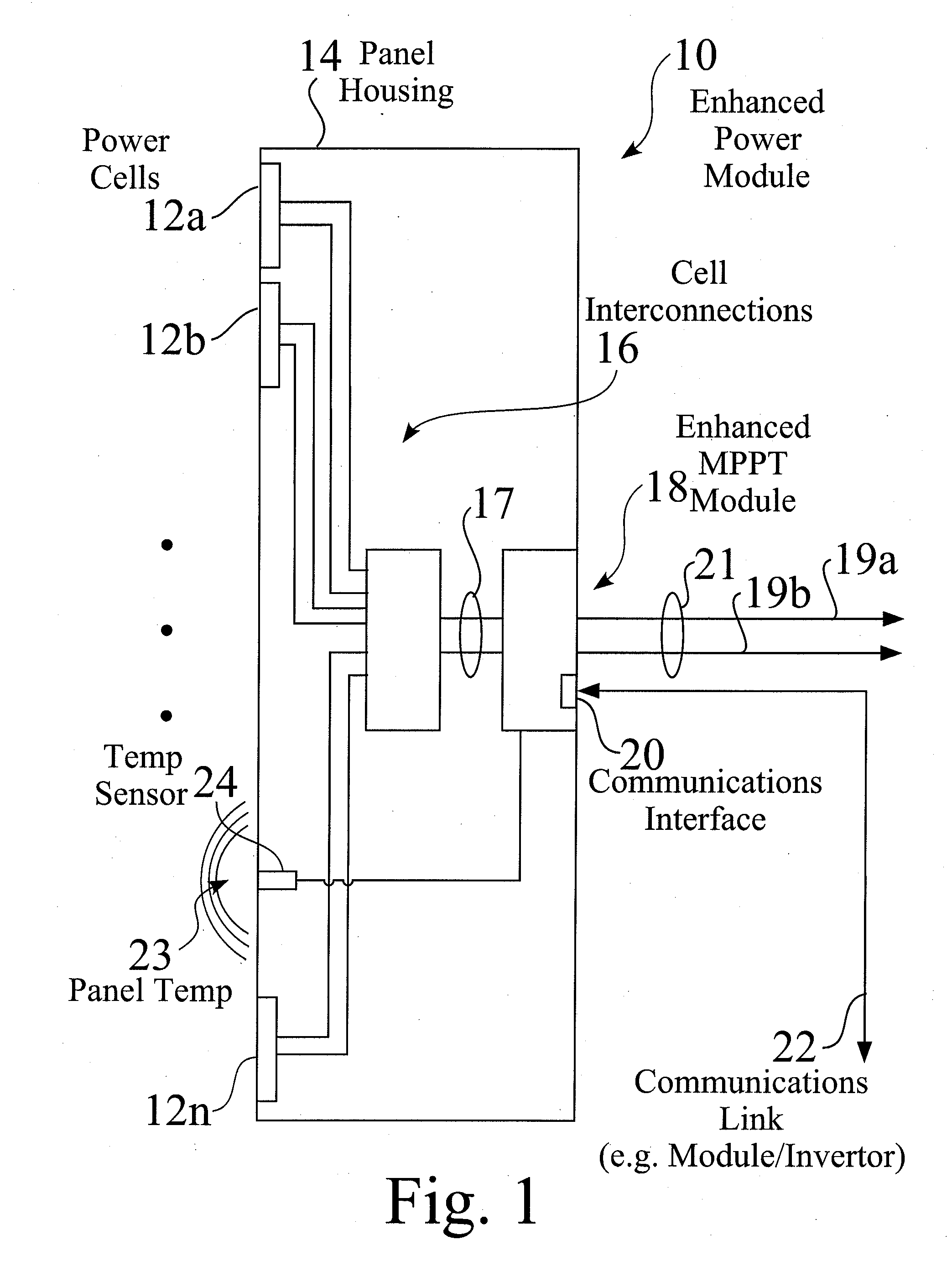
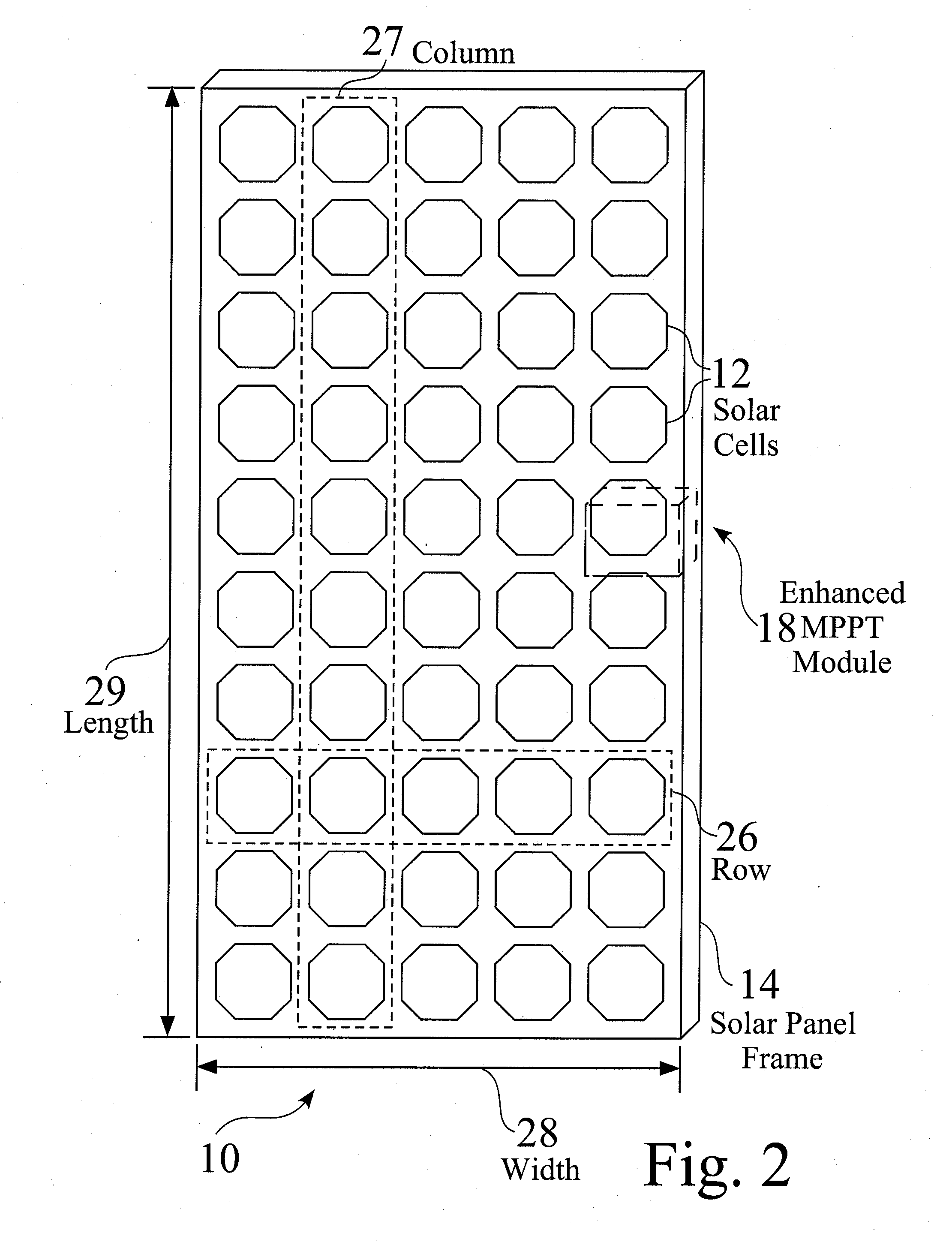
Distributed maximum power point tracking systems, structures, and processes are provided for power generation structures, such as for but not limited to a solar panel arrays. In an exemplary solar panel string structure, distributed maximum power point tracking (DMPPT) modules are provided, such as integrated into or retrofitted for each solar panel. The DMPPT modules provide panel level control for startup, operation, monitoring, and shutdown, and further provide flexible design and operation for strings of multiple panels. The strings are typically linked in parallel to a combiner box, and then toward and enhanced inverter module, which is typically connected to a power grid. Enhanced inverters are controllable either locally or remotely, wherein system status is readily determined, and operation of one or more sections of the system are readily controlled. The system provides increased operation time, and increased power production and efficiency, over a wide range of operating conditions.
Owner:SOLAREDGE TECH LTD
Building distributed software services as aggregations of other services
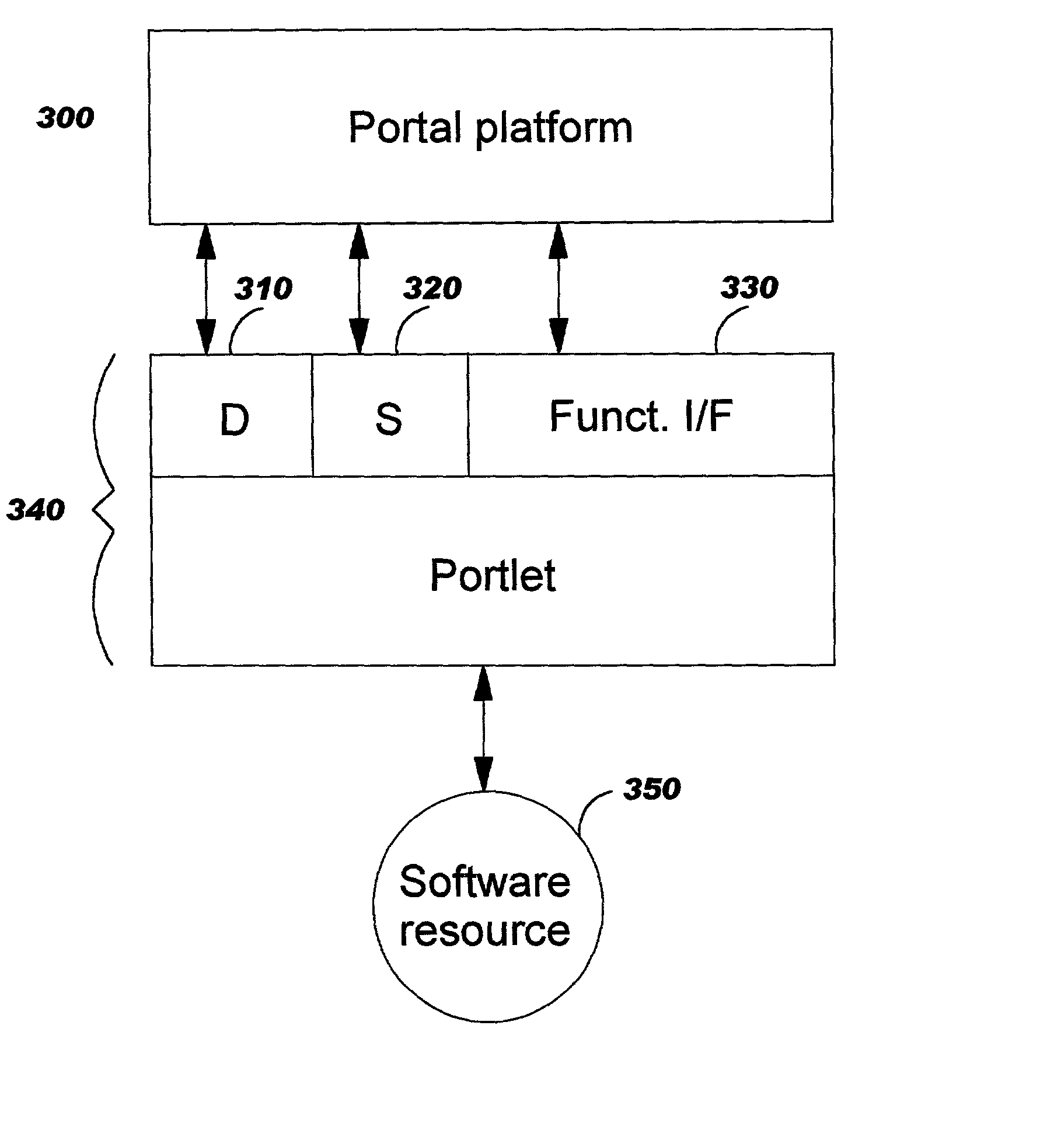
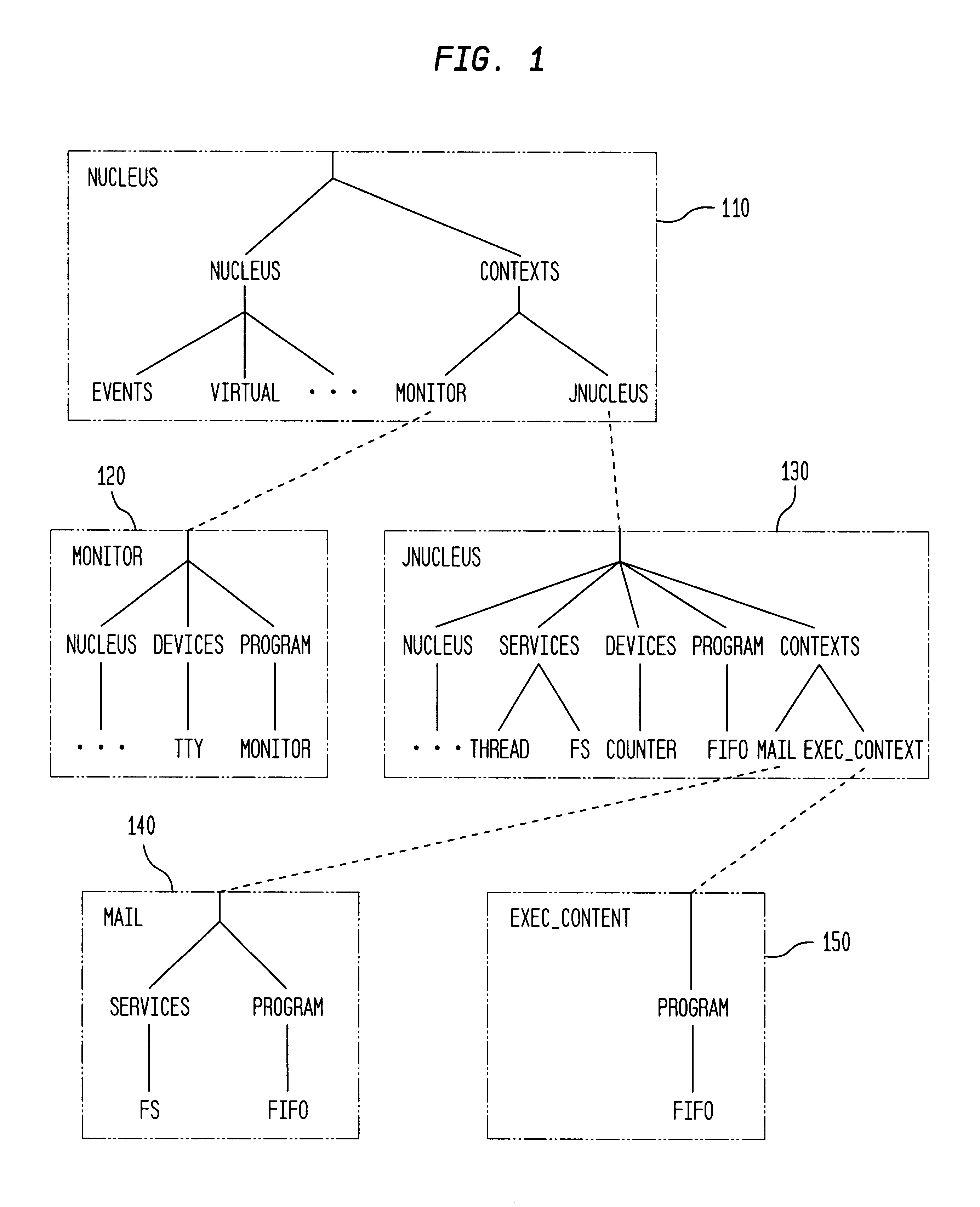
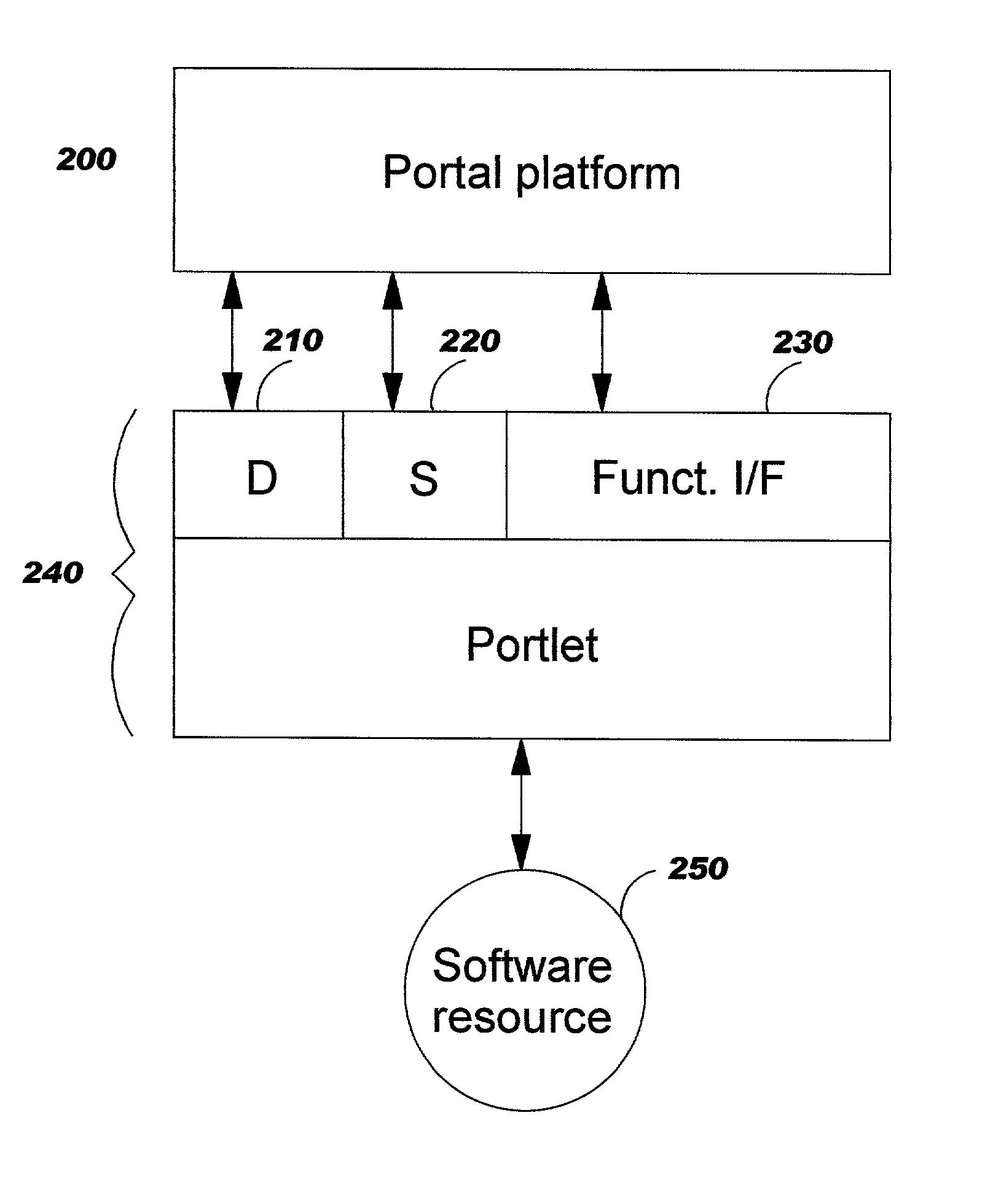
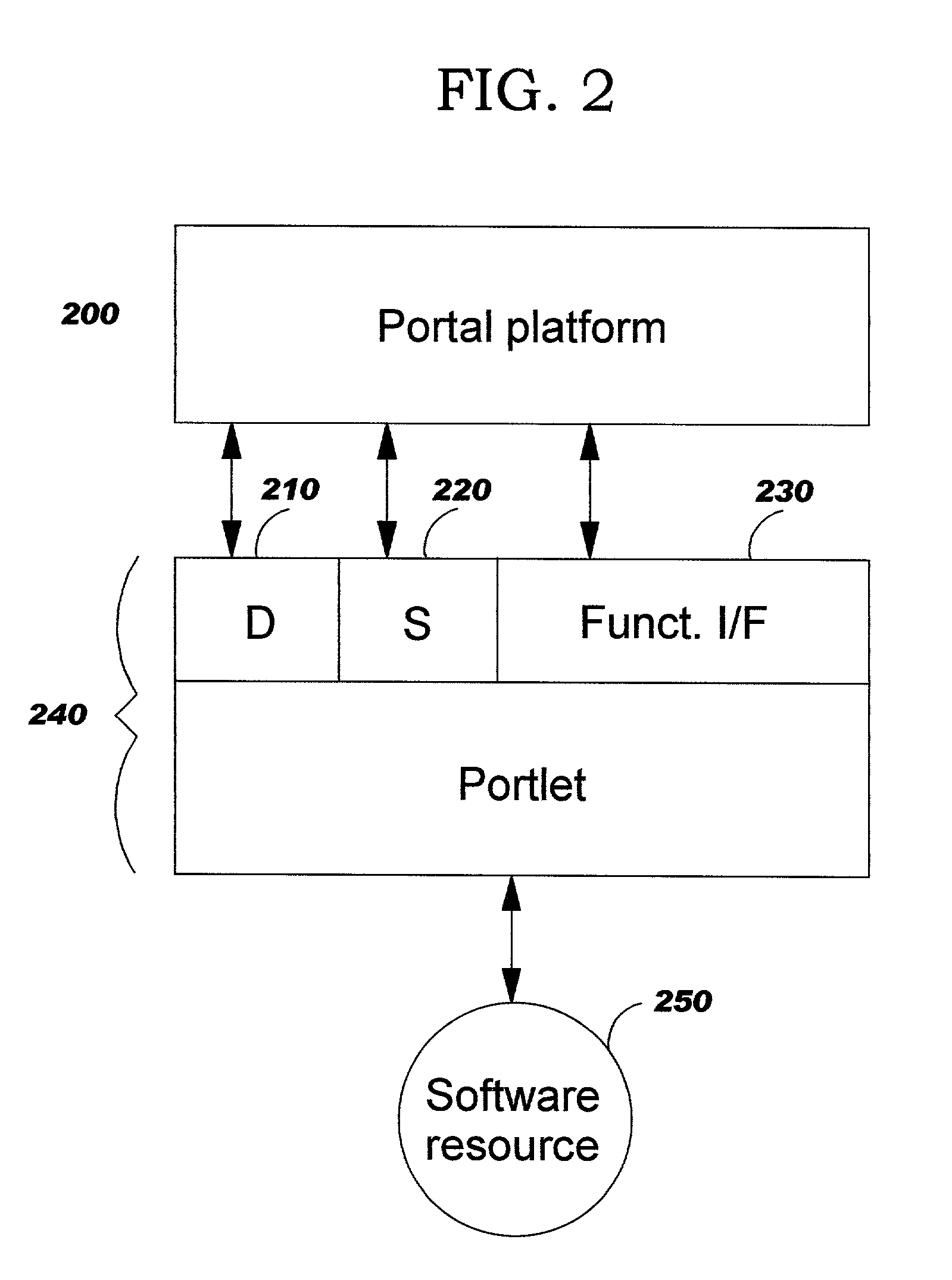
InactiveUS6985939B2Fast and efficient constructionData processing applicationsMultiple digital computer combinationsPortletWeb service
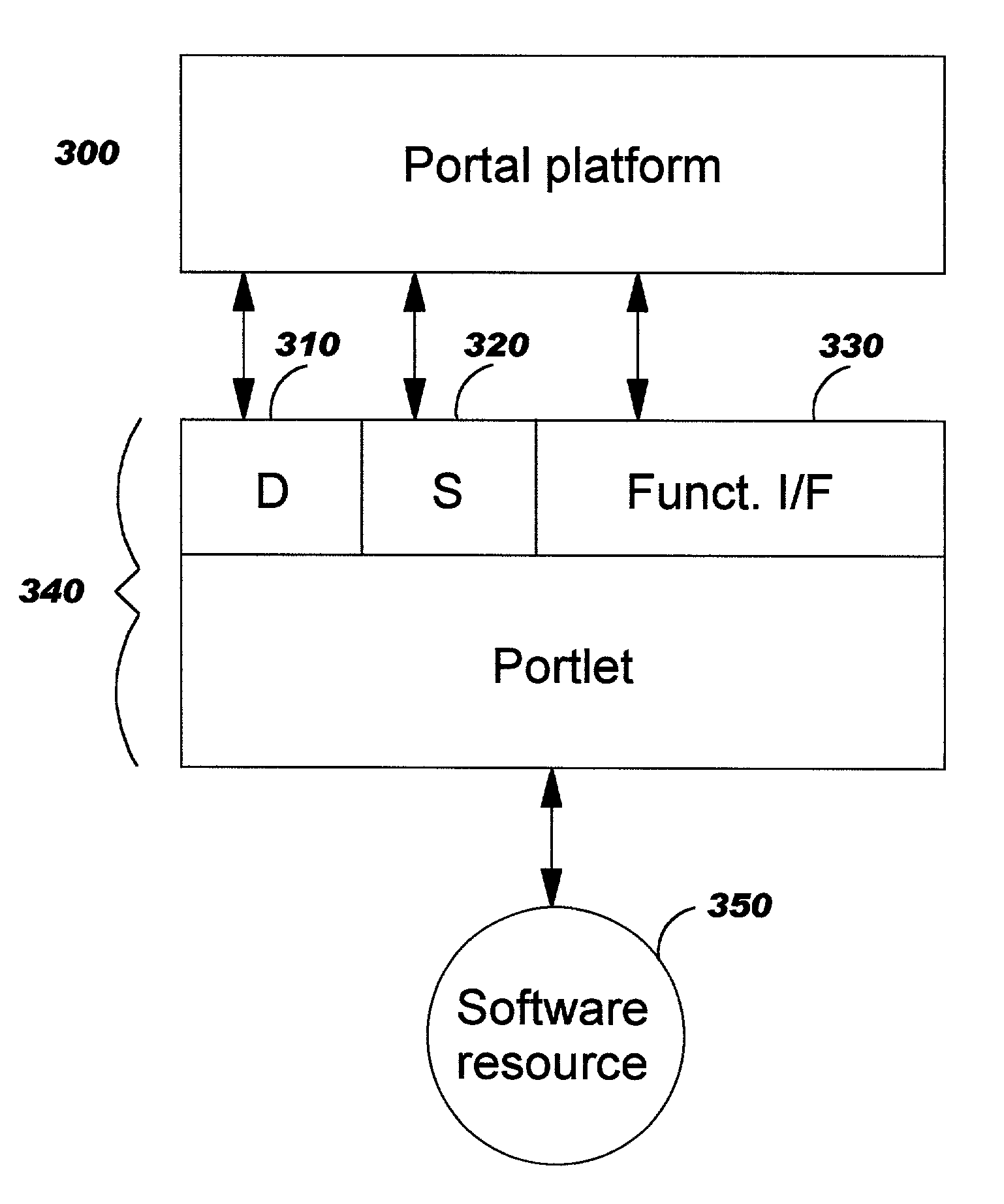
Methods, systems, and computer program products are disclosed for dynamically integrating software resources (such as web services and other back-end software resources) using the services of a content framework (such as a portal platform). A portlet model is leveraged to allow programmatic portlets to serve as proxies for web services, thereby extending portlets beyond their traditional visual role. A deployment interface and a system interface are described for these portlet proxies. The deployment interface is used for composing new web services, and a composition tool is described. The system interface allows for run-time management of the web services by the portal platform. The service provider for a particular function may be bound to the portlet proxy at development time or at run-time.
Owner:INT BUSINESS MASCH CORP
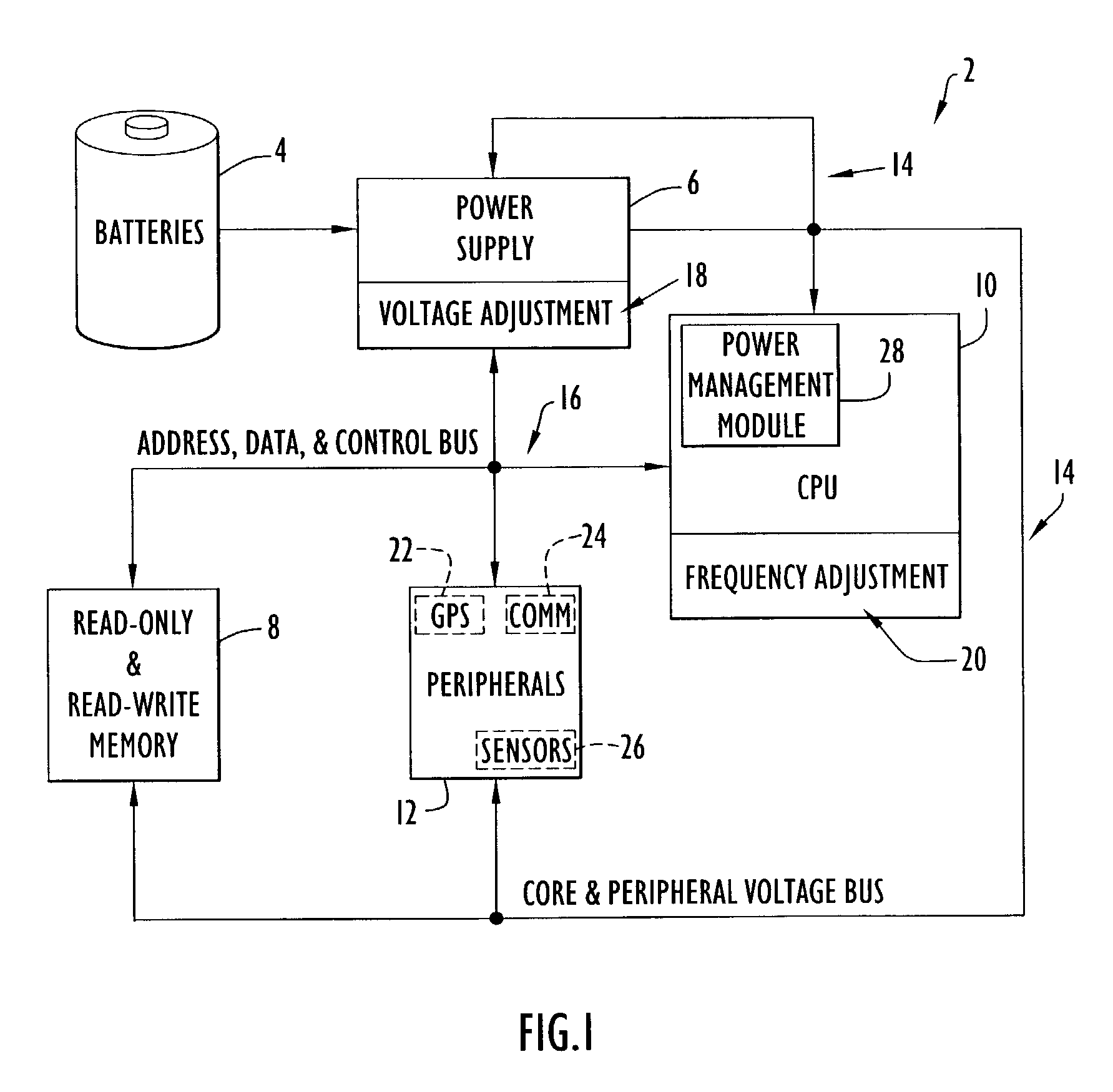
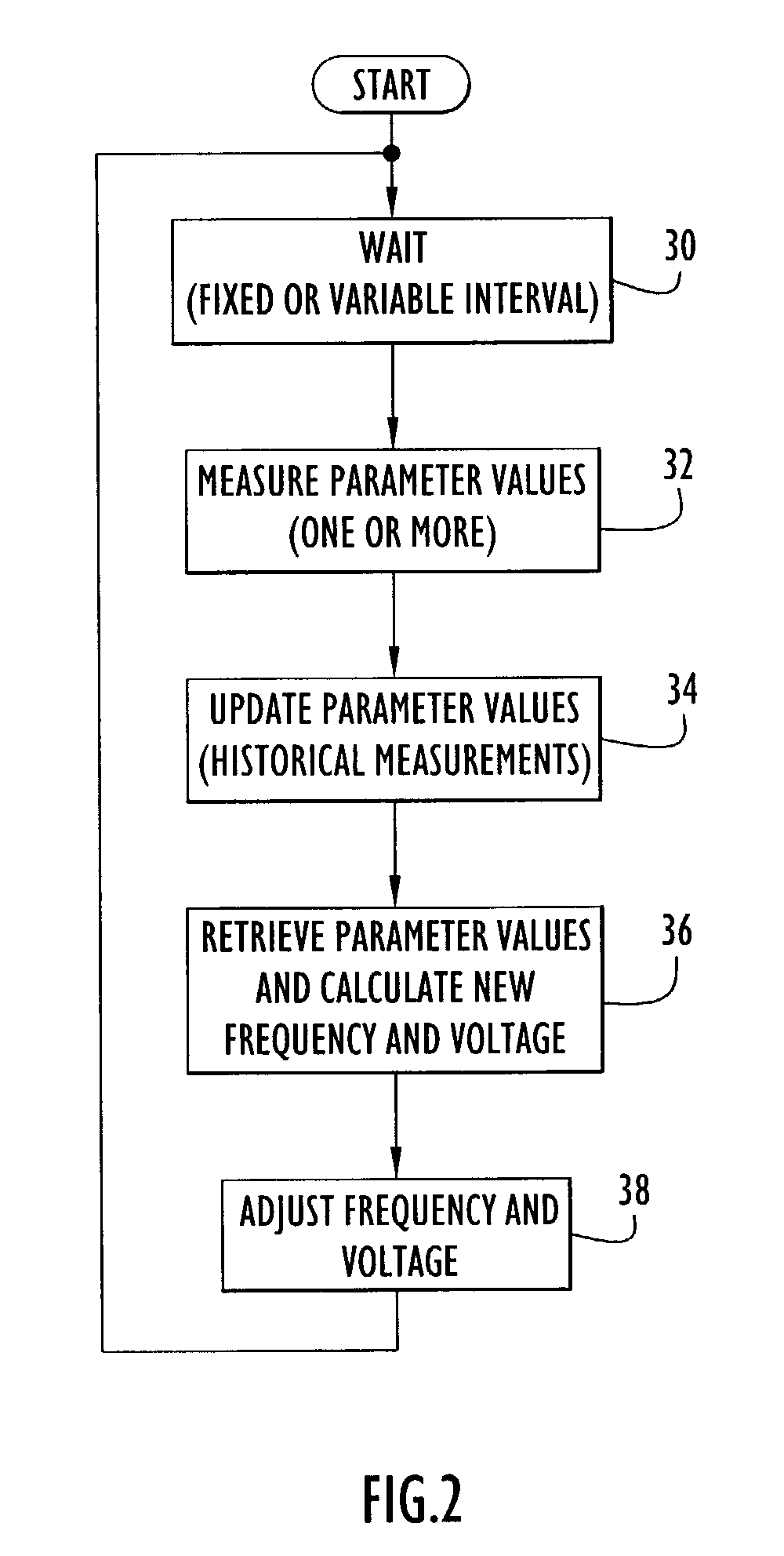
Method and apparatus for optimizing performance and battery life of electronic devices based on system and application parameters
InactiveUS7111179B1Reduce power consumptionExtending device operating lifeEnergy efficient ICTBatteries circuit arrangementsOperational systemElectrical battery
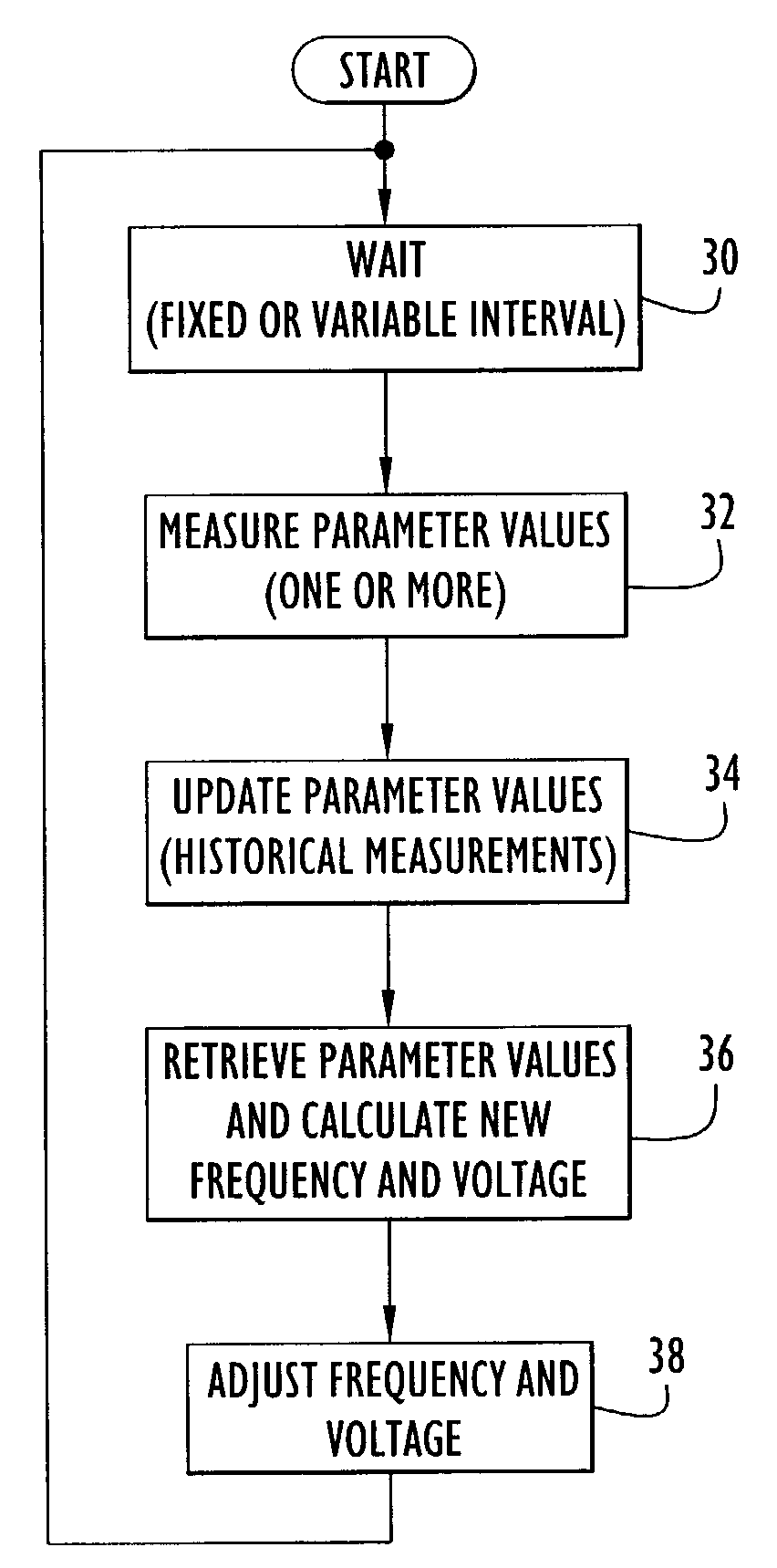
An electronic device (e.g., computer system, etc.) employing dynamic power management of the present invention adjusts power consumption in accordance with an analysis of parameters and events occurring over one or more time-periods. Preferably, the electronic device monitors microprocessor, operating system, peripheral and / or device-level events and adjusts run-time parameters, such as microprocessor clock frequency and voltage, to reduce power consumption with minimal perceived degradation in performance.
Owner:MOSAID TECH
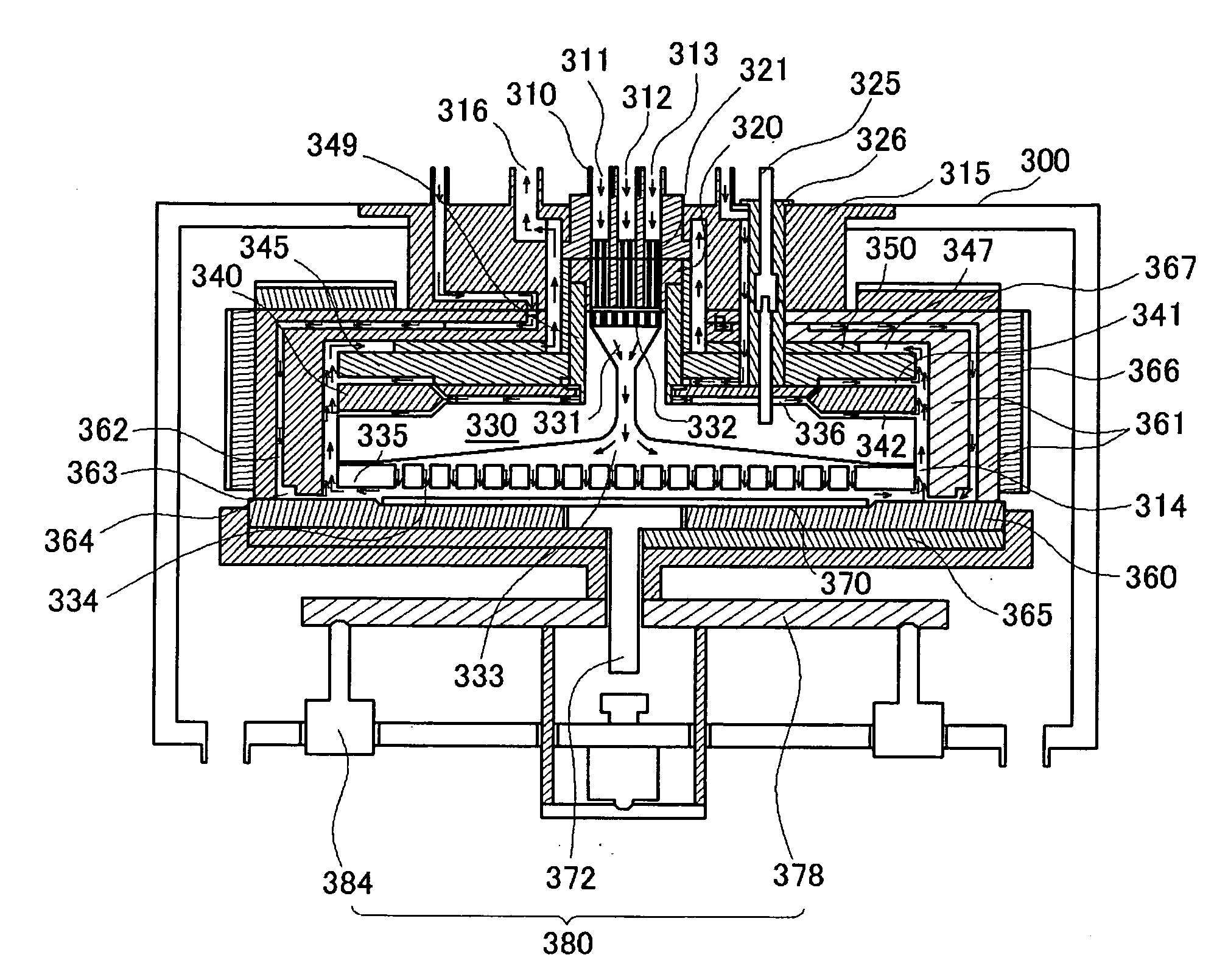
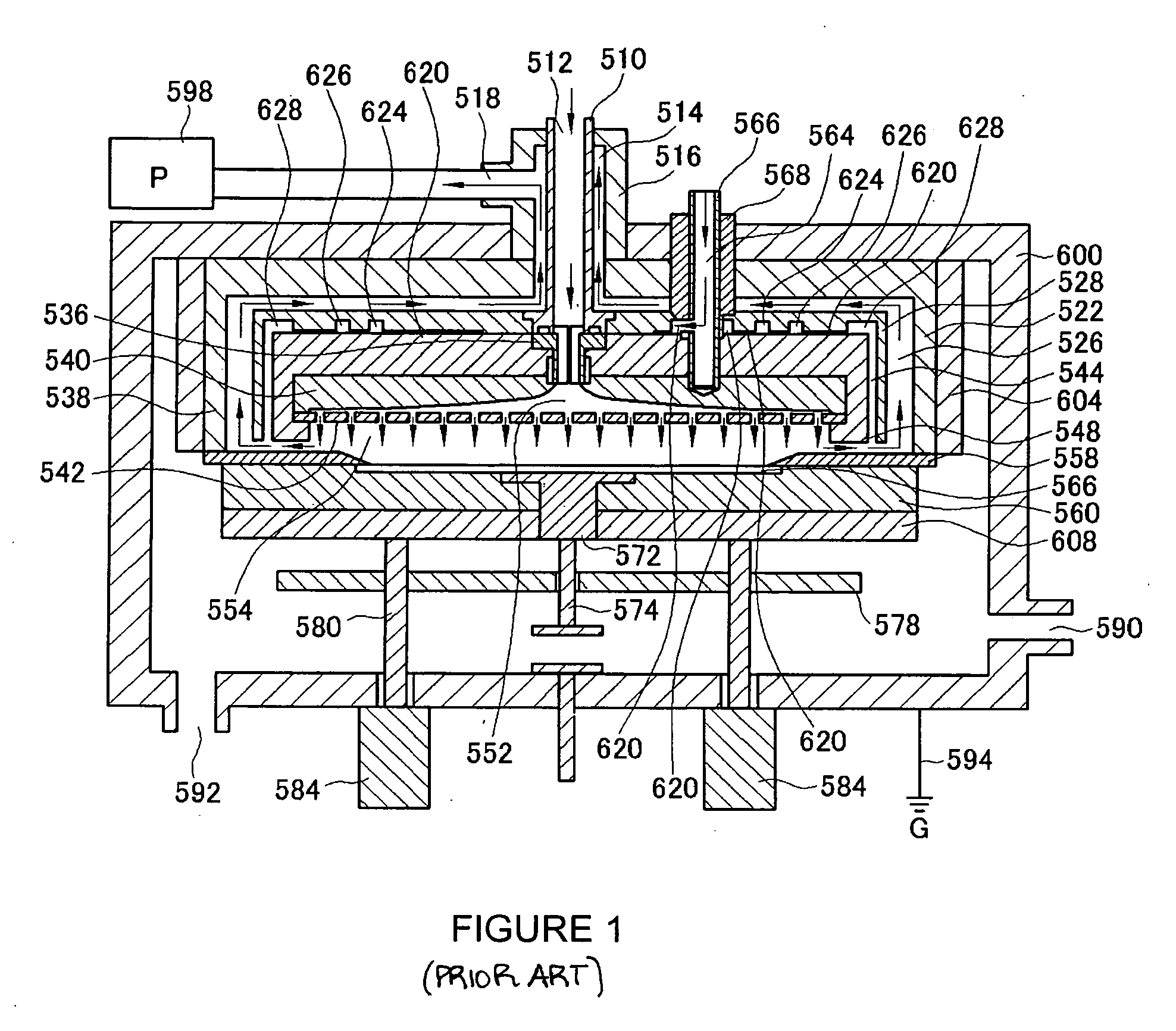
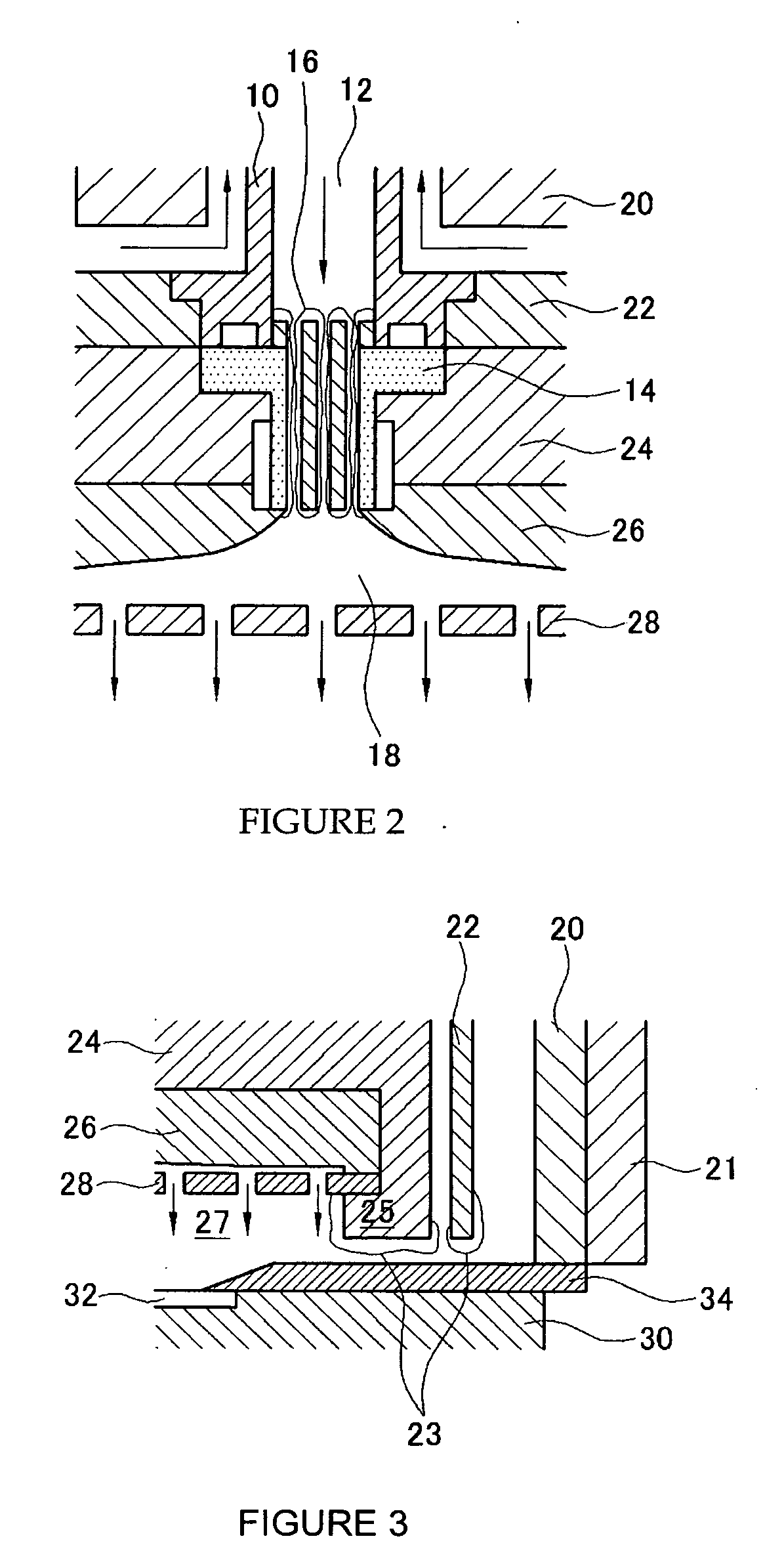
Atomic layer deposition apparatus
InactiveUS20060137608A1Uniform thicknessEasy to controlChemical vapor deposition coatingEngineeringAtomic layer deposition
An atomic layer deposition (ALD) apparatus is, suitable for thermal ALD and plasma-enhanced ALD of conductive and non-conductive films. The ALD apparatus can maintain electrical insulation of a gas dispersion structure, such as a showerhead assembly, which acts as an RF electrode to generate plasma inside a reaction chamber while depositing electrically conductive films in the reaction chamber. Fine tubules of micro-feeding tube assembly prevents plasma generation in them and reactive gases each have separate flow paths through the micro-feeding tube assembly. Process gases out of the micro-feeding tube assembly enter narrow grooves of a helical flow inducing plate and form helical flows which mix well each other. Symmetrically mounted pads on showerhead assembly and flow guiding plate maintain a symmetrical gap through which an inert gas flows continuously to keep reactive gases outside the gap and unwanted film deposition in the gap. Longer operating time before maintenance (cleaning) and thus higher productivity can be achieved.
Owner:ASM GENITECH KOREA
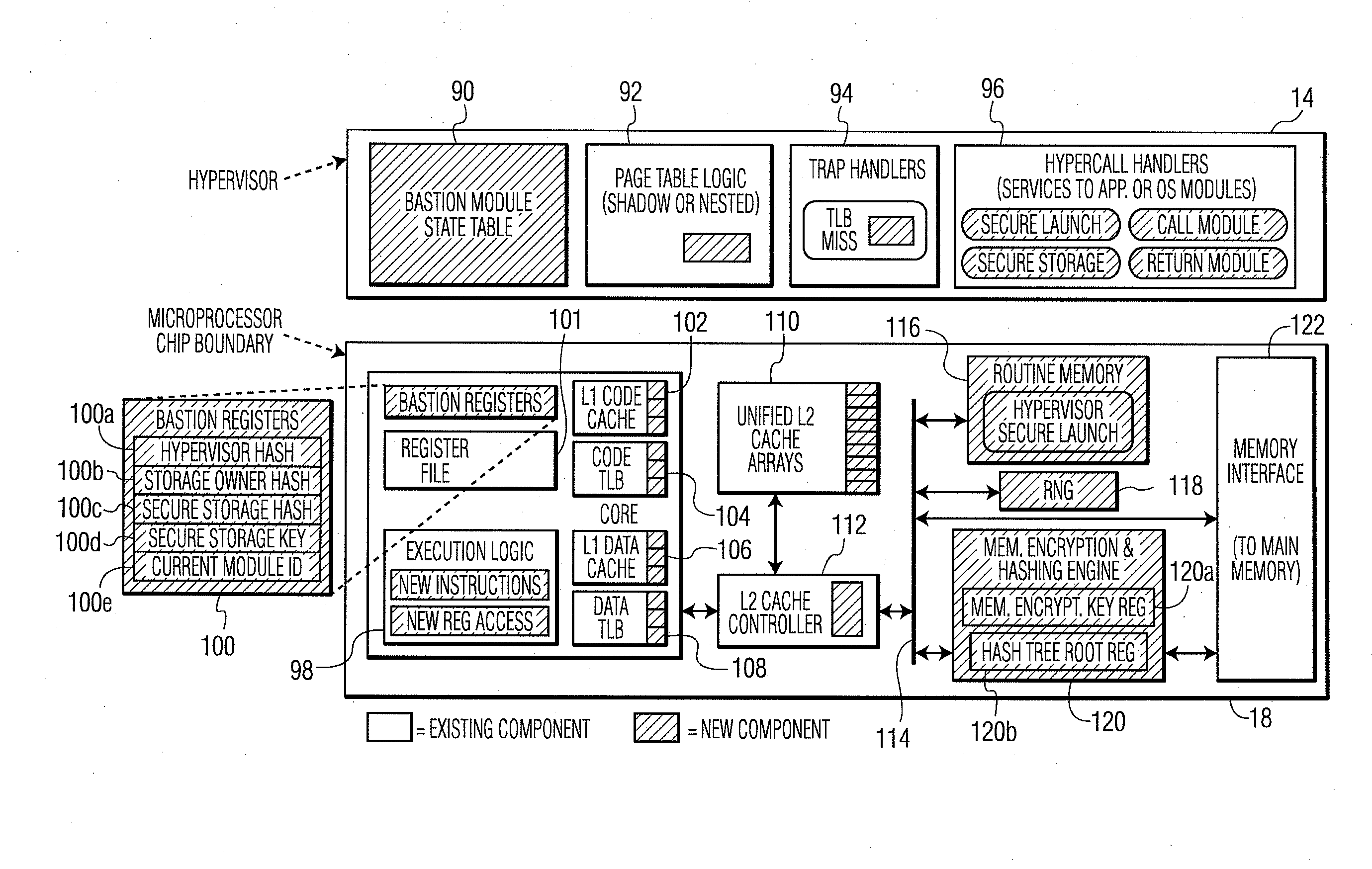
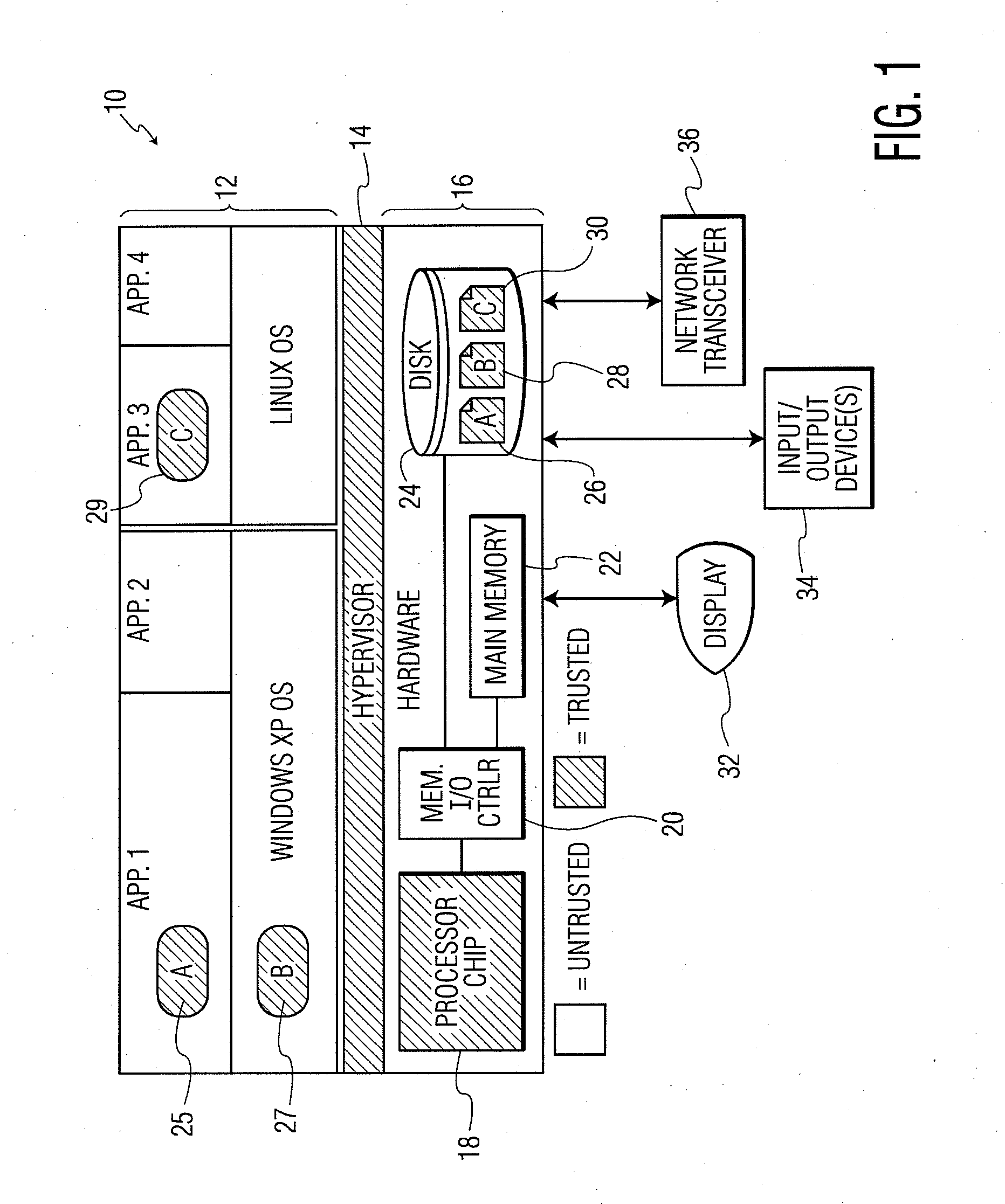
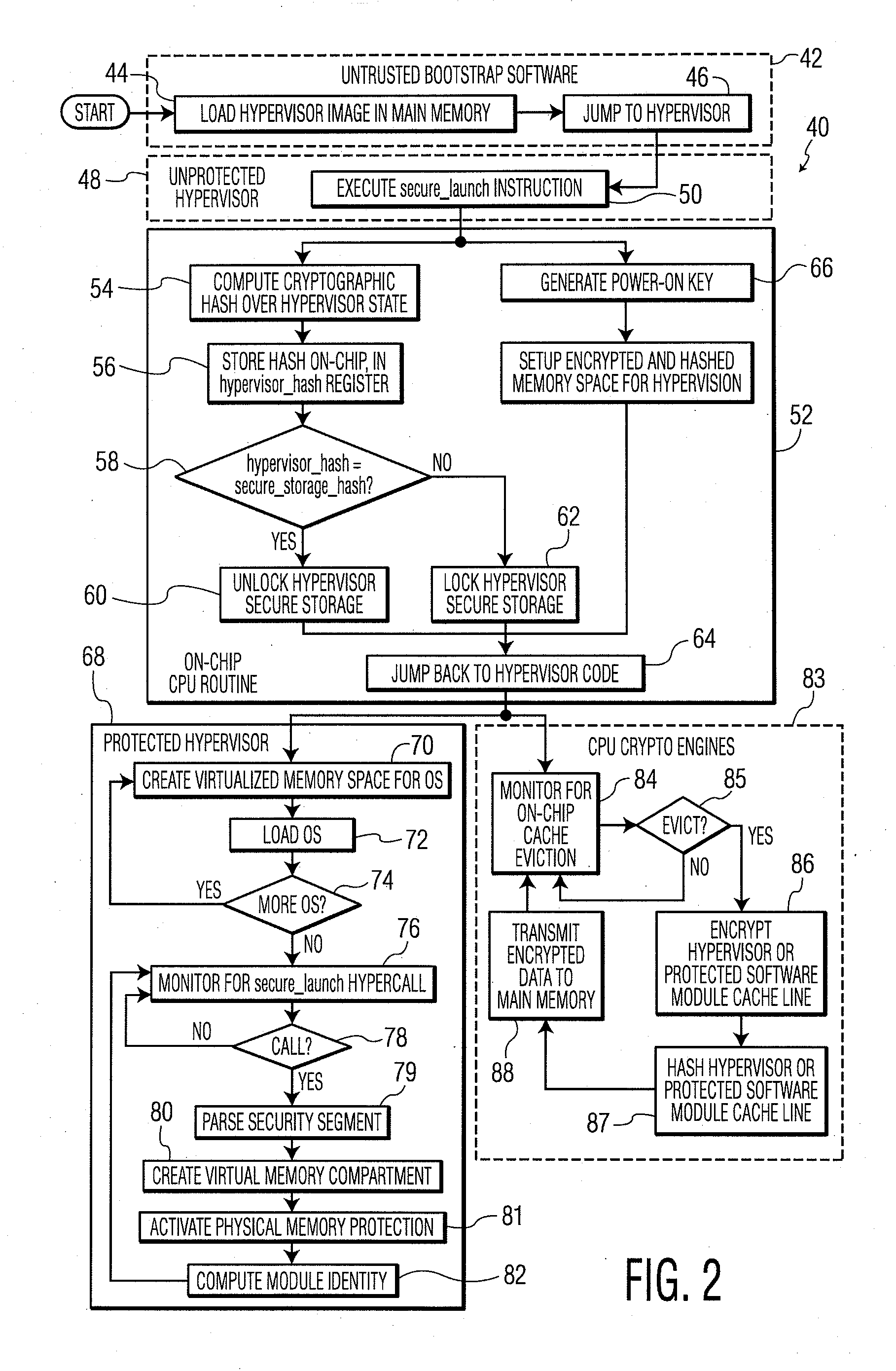
System and Method for Processor-Based Security
ActiveUS20100281273A1Avoid accessUnauthorized memory use protectionHardware monitoringExternal storageMemory interface
A system and method for processor-based security is provided, for on-chip security and trusted computing services for software applications. A processor is provided having a processor core, a cache memory, a plurality of registers for storing at least one hash value and at least one encryption key, a memory interface, and at least one on-chip instruction for creating a secure memory area in a memory external to the processor, and a hypervisor program executed by the processor. The hypervisor program instructs the processor to execute the at least one on-chip instruction to create a secure memory area for a software area for a software module, and the processor encrypts data written to, and decrypts data read from, the external memory using the at least one encryption key and the verifying data read from the external memory using the at least one hash value. Secure module interactions are provided, as well as the generation of a power-on key which can be used to protect memory in the event of a re-boot event. Lightweight, run-time attestation reports are generated which include selected information about software modules executed by the processors, for use in determining whether the processor is trusted to provide secure services.
Owner:CORESECURE TECH LLC
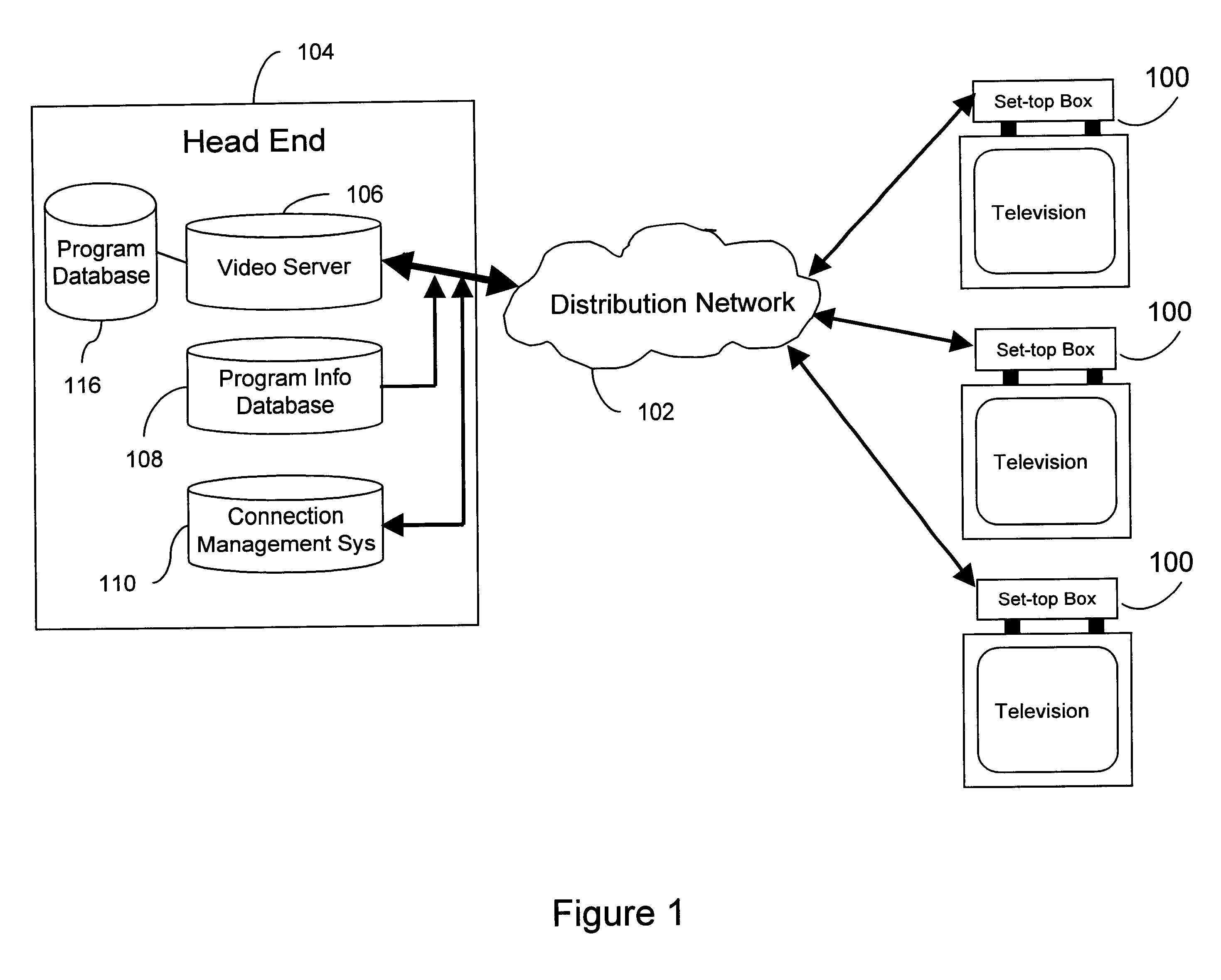
System and method for managing and presenting entity information
InactiveUS20060101005A1Easy to displayShorten the timeDigital data processing detailsMaps/plans/chartsTime rangeRunning time
Owner:YANG WENDY W +1
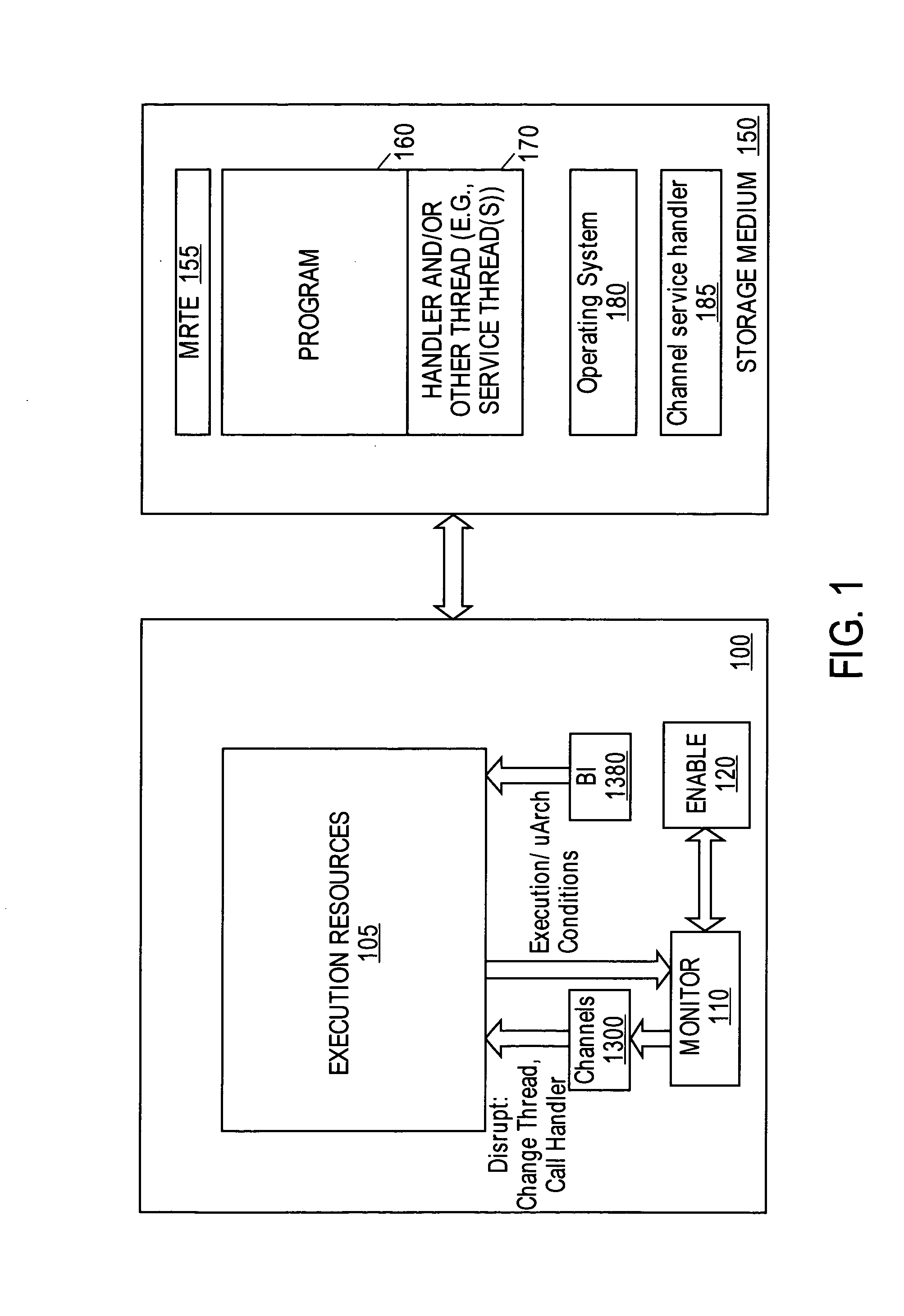
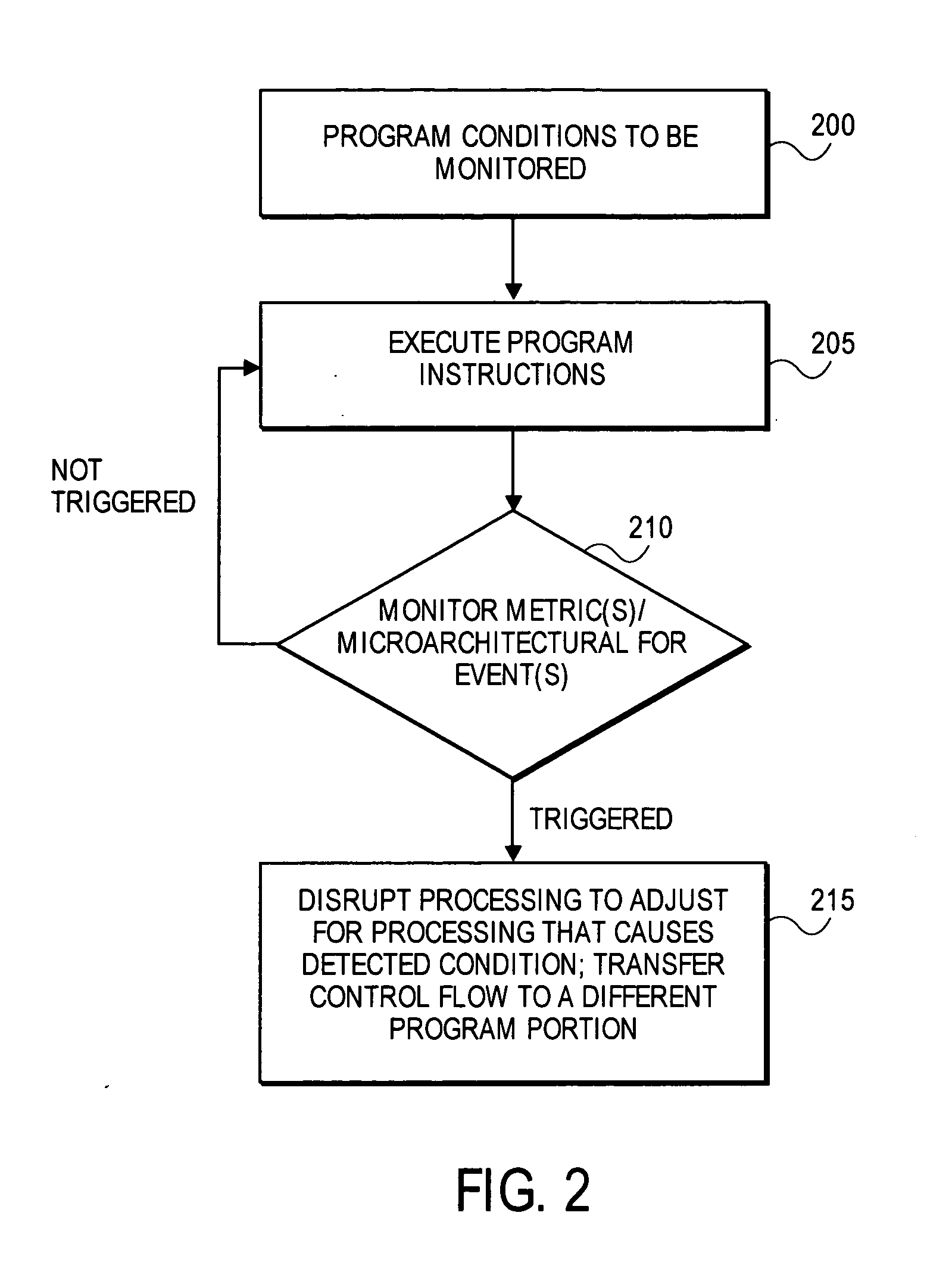
System to profile and optimize user software in a managed run-time environment
InactiveUS20070214342A1Error detection/correctionGeneral purpose stored program computerParallel computingRunning time
Method, apparatus, and system for monitoring performance within a processing resource, which may be used to modify user-level software. Some embodiments of the invention pertain to an architecture to allow a user to improve software running on a processing resources on a per-thread basis in real-time and without incurring significant processing overhead.
Owner:INTEL CORP
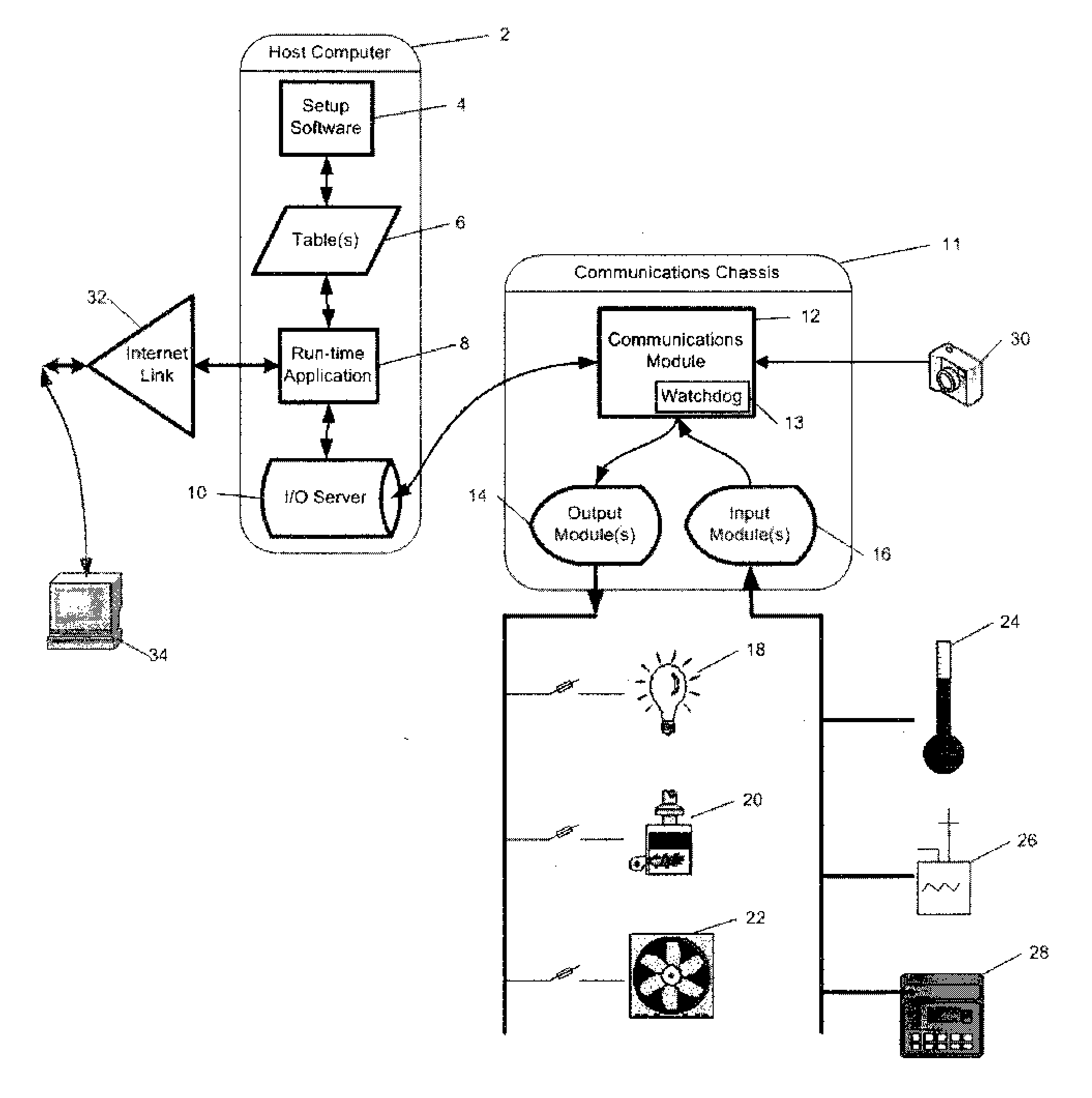
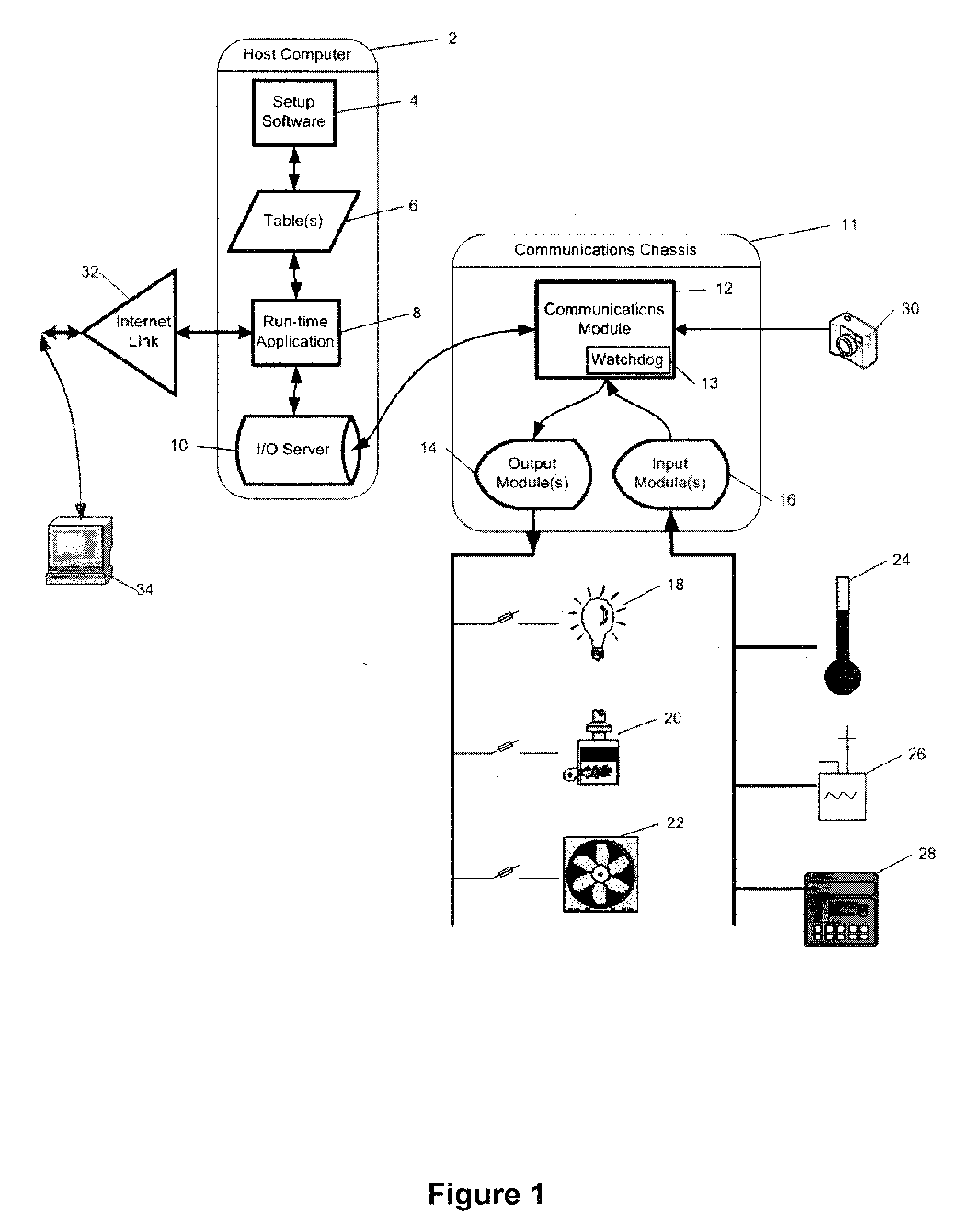
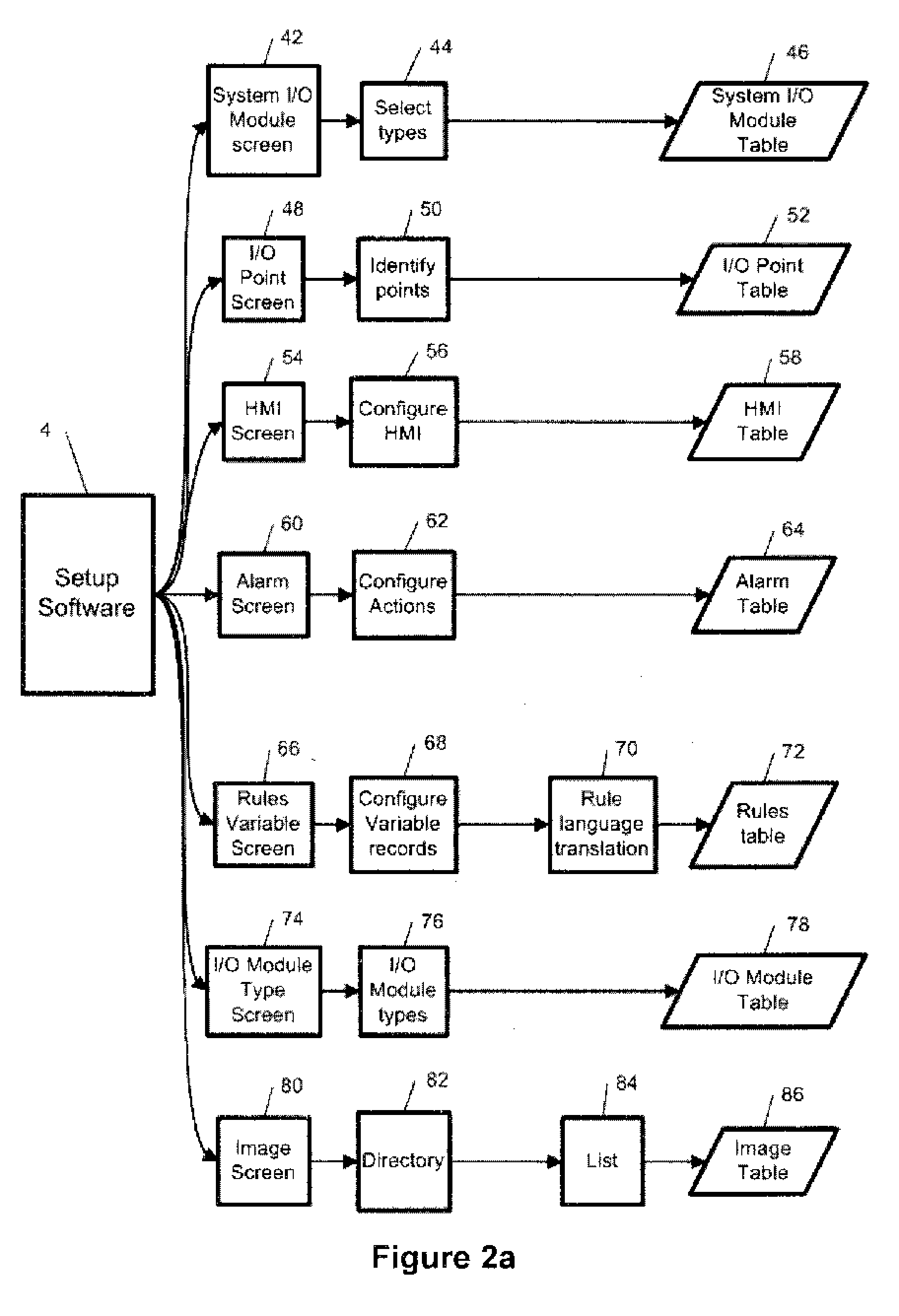
Method and apparatus for tabular process control
InactiveUS20060253205A1Eliminate input/output address configurationEnhances earlyNatural language translationComputer controlAutomatic controlData acquisition
The invention discloses methods and apparatus based on tabular concepts which greatly simplify the configuration, maintenance and run-time operations of a broad range of electronic equipment control systems, including, but not limited to: (a) industrial controls, (b) supervisory control and data acquisition, such as heating, ventilation and air conditioning, and (c) home automation, including systems or stand-alone equipment, such as video recording devices. The tabular concepts of the invention are applied in three primary stages, namely (i) data input or configuration, including automated data population, (ii) generic operating rule application to tables of rules data variables, and (iii) English (or other) language translations of the current rule sets, for ease of verification. By each of these methods alone and through combination of all of these methods, the current invention makes the configuration and operation of automated equipment easily accessible to persons who do not have technical skills in either process control, automation, or software programming. Development of software for automatic control of equipment is also greatly simplified by these inventions.
Owner:GARDINER MICHAEL
Generic, multi-instance method and GUI detection system for tracking and monitoring computer applications
ActiveUS20070083813A1Facilitates code reuse and modular packagingPromote publicationError detection/correctionDigital computer detailsObject structureClient-side
Presented is a system and method for monitoring events derived from a computer target application presentation layer including the steps of providing, independent of recompiling the target application's source code, a script running at a level within the target application. The script scans run-time instantiations of objects of the target application, and allocates structures in real-time to the object instantiations. These allocated structures are adapted to create a reflection of the target application structure, which is used along with detected object instantiations that match a predetermined object structure to capture a portion of an environmental spectrum of the detected object. Further, the system can process state machine events occurring on at least one of a server machine and a client / localized machine, correlate the state machine events with the environmental spectrum, and deduce a user experience based on the correlated state machine events.
Owner:KNOA SOFTWARE INC
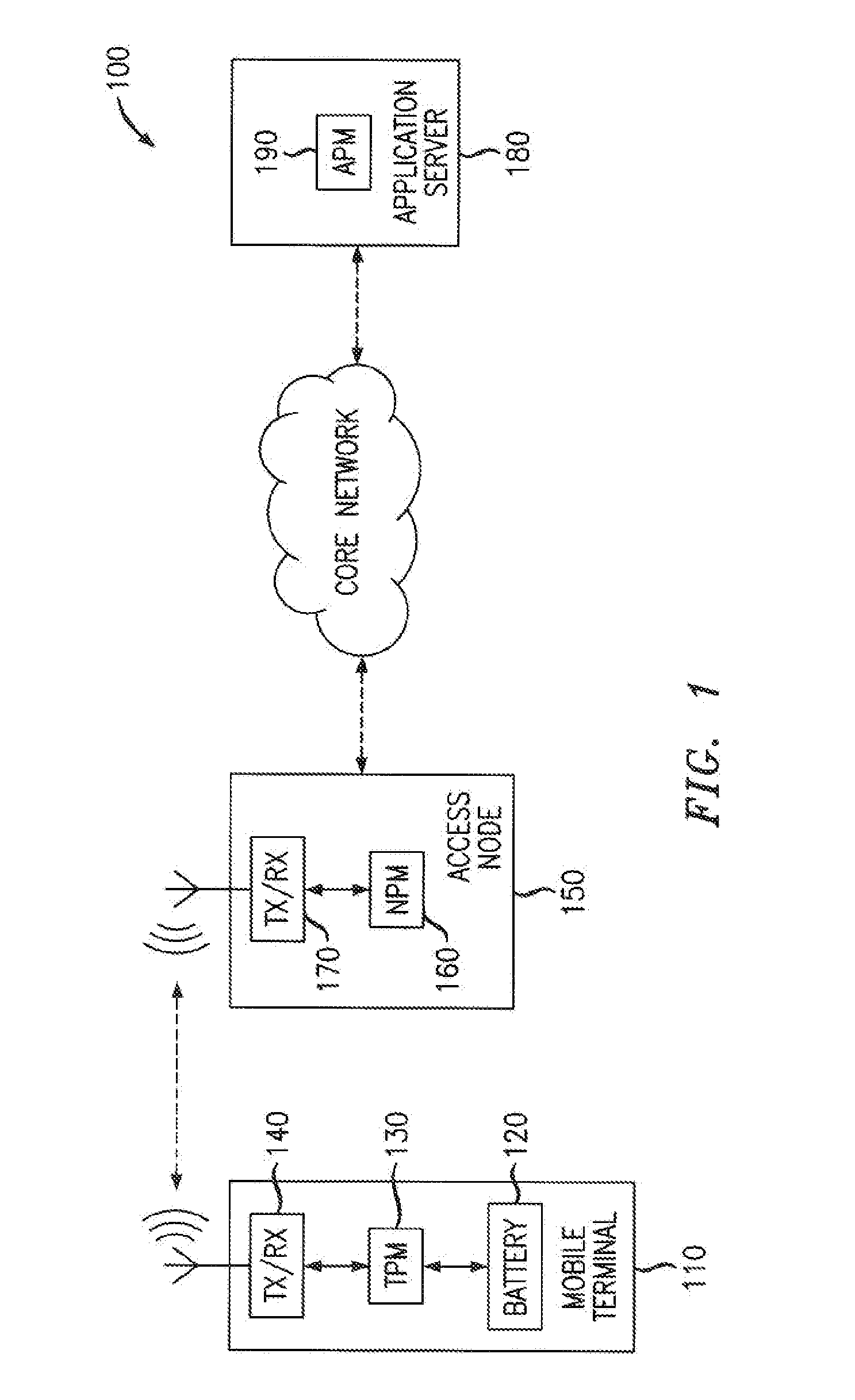
Method And Apparatus Of Smart Power Management For Mobile Communication Terminals Using Power Thresholds
ActiveUS20120210325A1Provide functionalityReduce energy consumptionPower managementEnergy efficient ICTRunning timeComputer science
A method is provided for use in a mobile communication terminal configured to support a plurality of applications, wherein each application is executed by performing one or more tasks. The method includes, in response to a scheduling request from an application, obtaining an indication of power supply condition at a requested run-time of at least one of the tasks. The method further includes obtaining a prediction of a rate of energy usage by the task at the requested run-time, estimating, from the predicted rate of energy usage, a total amount of energy needed to complete the task, and making a scheduling decision for the task. The scheduling decision comprises making a selection from a group of two or more alternative dispositions for the task. The selection is made according to a criterion that relates the run-time power-supply condition to the predicted rate of energy usage by the task and to the estimate of total energy needed to complete the task.
Owner:ALCATEL LUCENT SAS
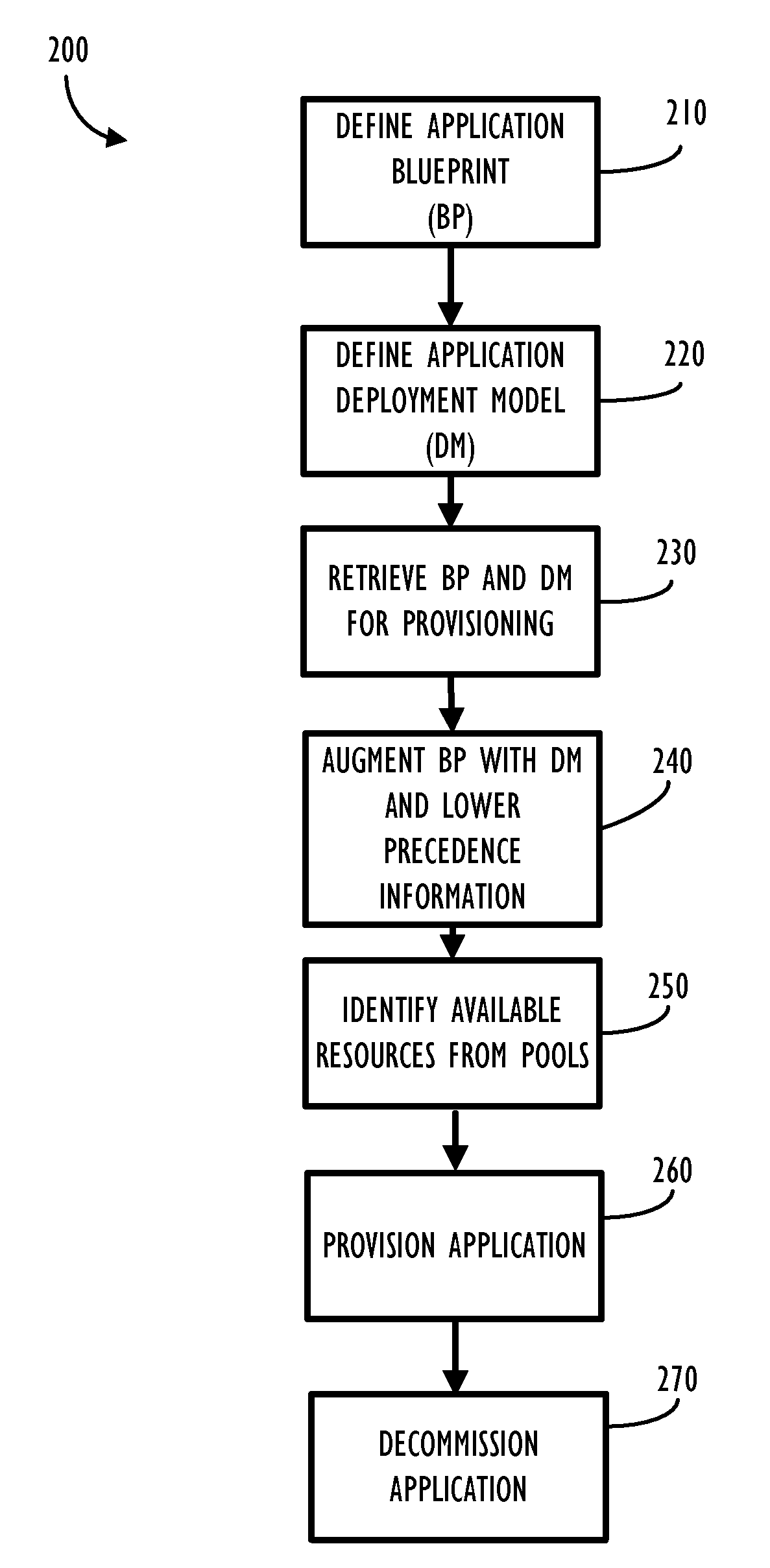
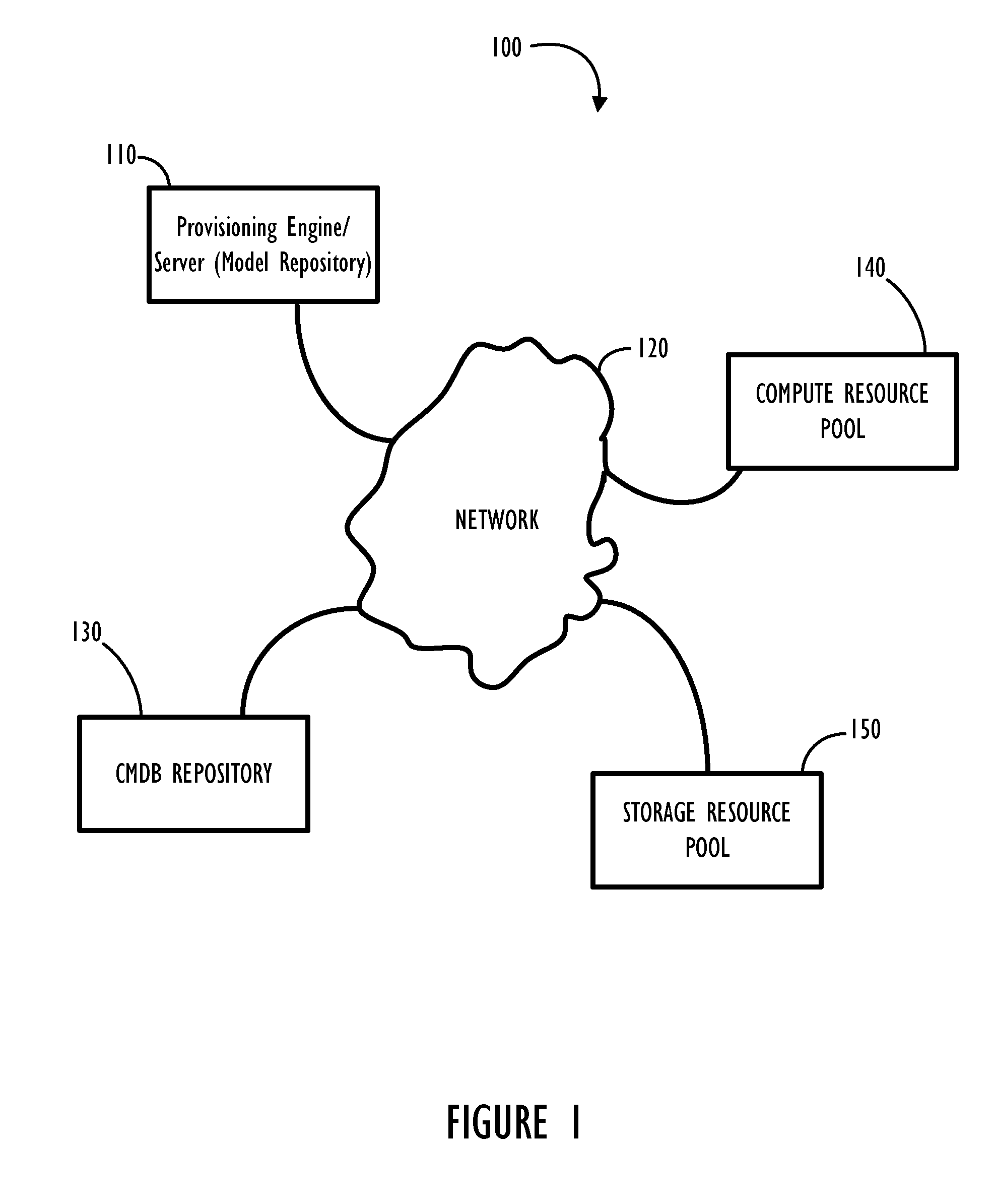
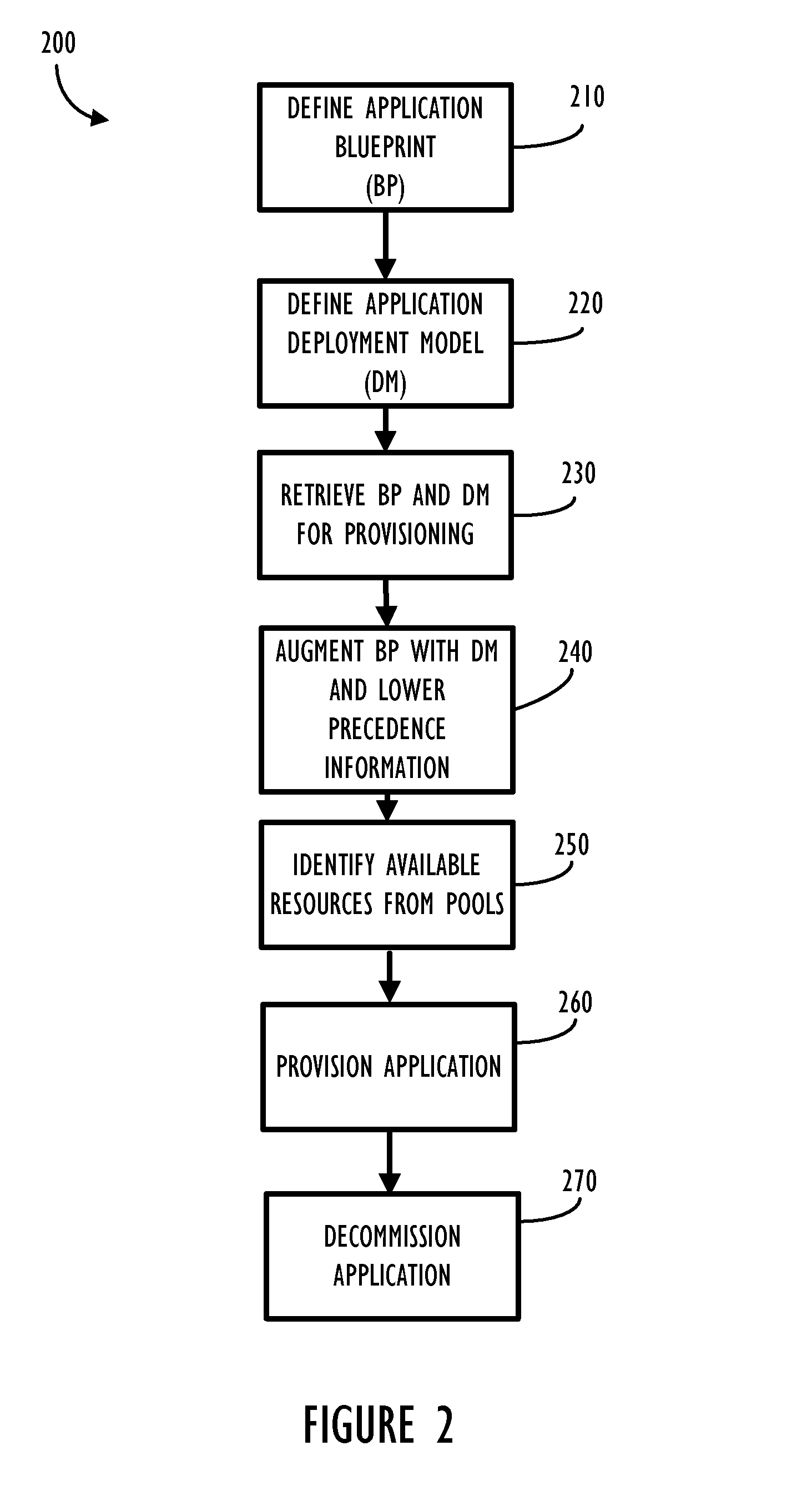
Application Blueprint and Deployment Model for Dynamic Business Service Management (BSM)
ActiveUS20110321033A1Error detection/correctionVersion controlProgram managementApplication software
Disclosed are systems and methods for model based provisioning of applications and servers (both physical and virtual) to execute provisioned applications in a reliable and repeatable manner. Several aspects of a complex application management including compliance, change tracking, monitoring, discovery, processing steps, CMDB integration are disclosed within a comprehensive hierarchy of definition templates forming a model. This model can then be used at provisioning time to instantiate a compliant instance of the provisioned application. This model can also be used at run-time for managing run-time aspects of the provisioned application. Additionally, the model based approach can help track applications even when or if applications drift from their intended design and policies for use.
Owner:BMC SOFTWARE
Programmatic management of software resources in a content framework environment
Methods, systems, and computer program products are disclosed for dynamically integrating software resources (such as web services and other back-end software resources) using the services of a content framework (such as a portal platform). A portlet model is leveraged to allow programmatic portlets to serve as proxies for web services, thereby extending portlets beyond their traditional visual role. A deployment interface and a system interface are described for these portlet proxies. The deployment interface is used for composing new web services, and a composition tool is described. The system interface allows for run-time management of the web services by the portal platform. The service provider for a particular finction may be bound to the portlet proxy at development time or at run-time.
Owner:IBM CORP
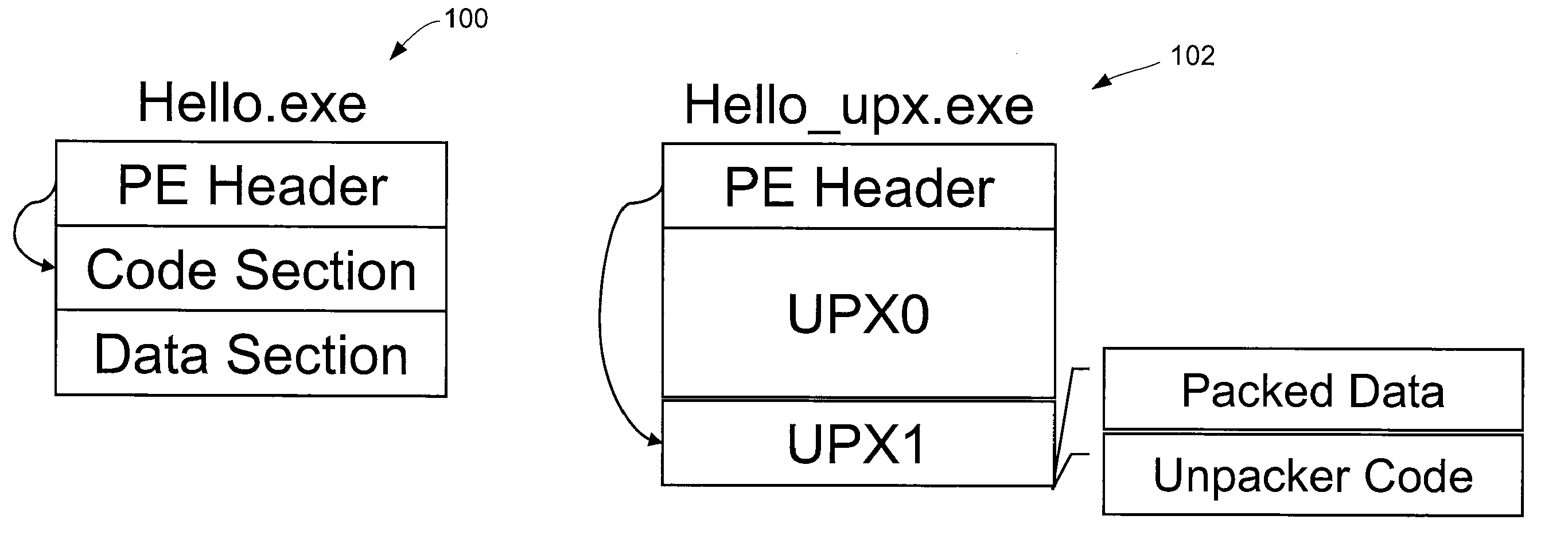
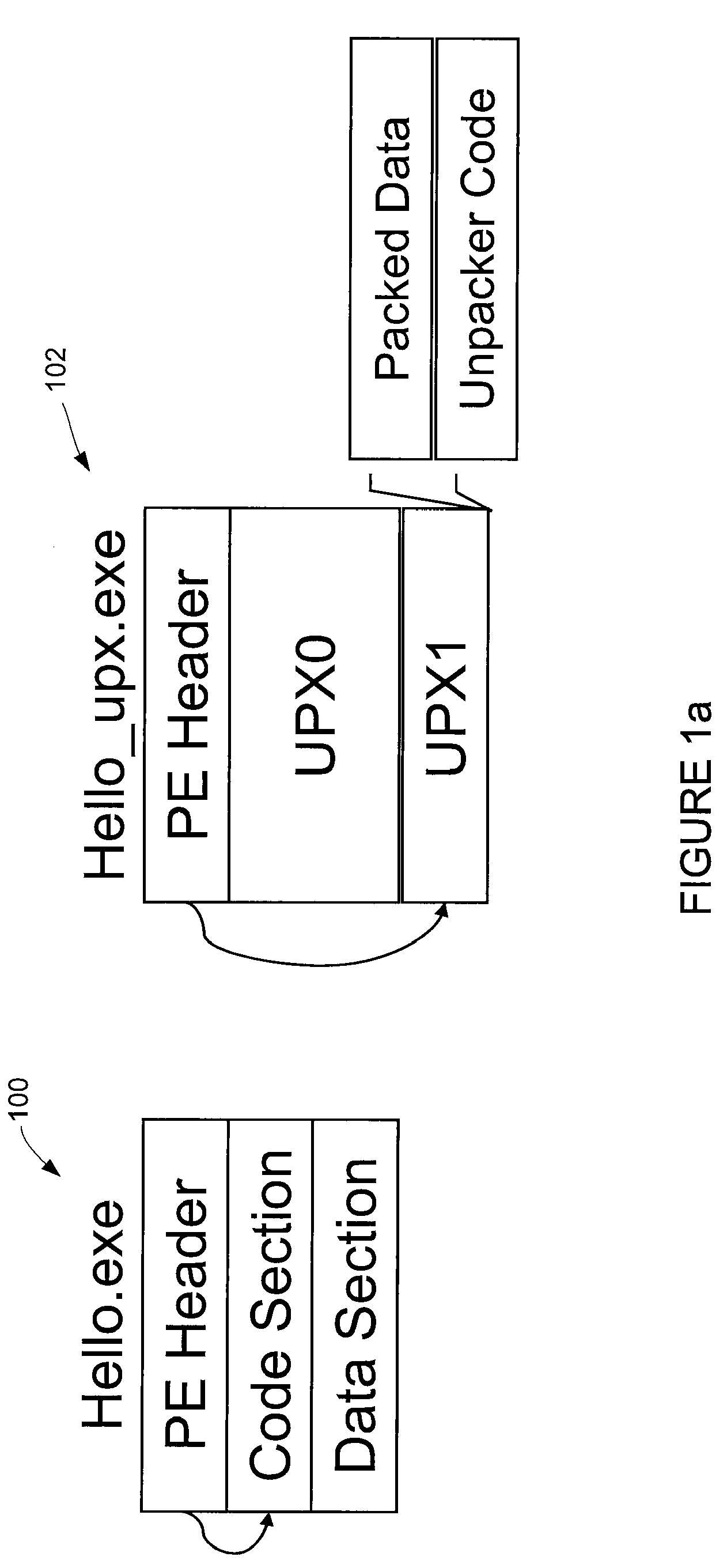
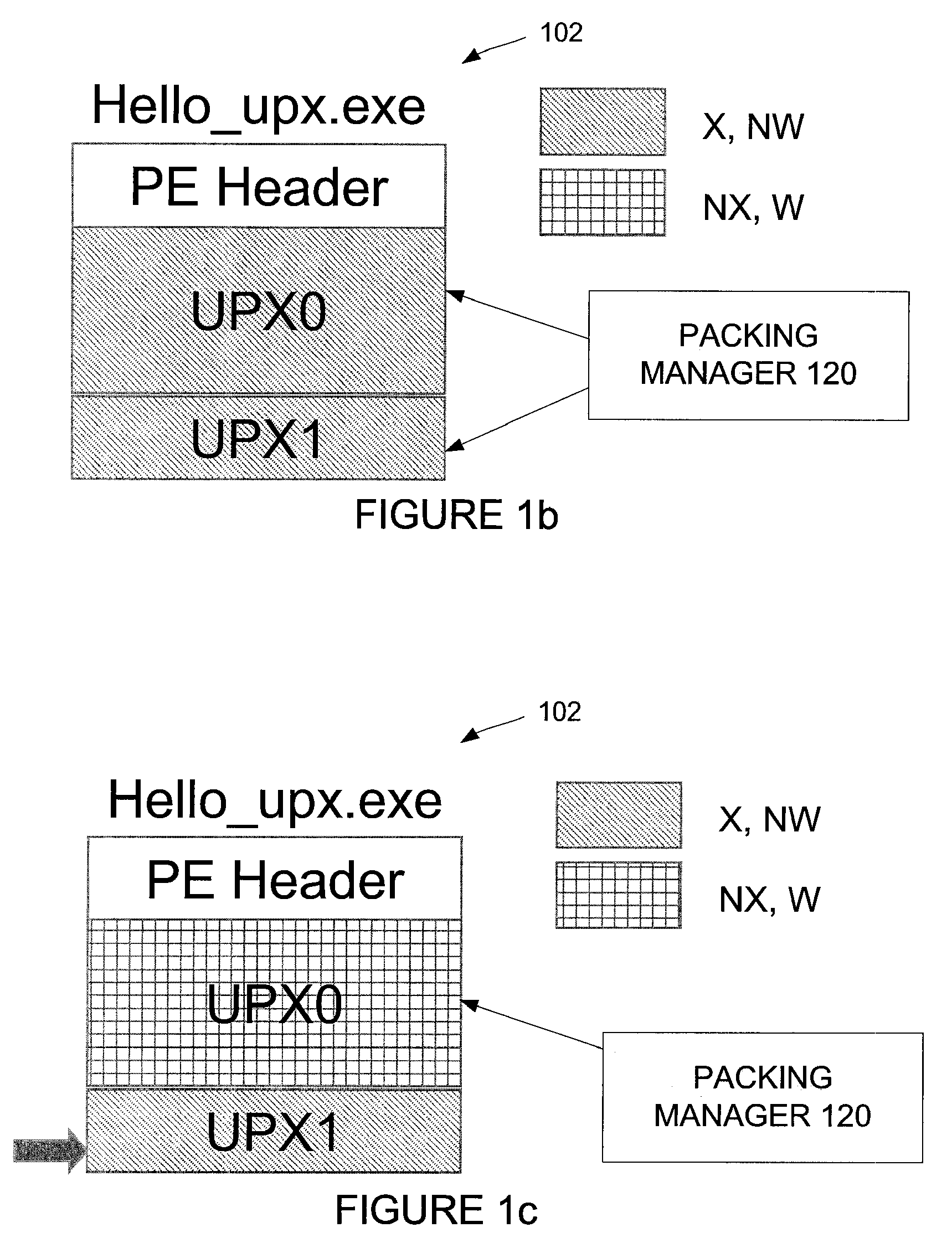
Automated unpacking of executables packed by multiple layers of arbitrary packers
The packing manager provides an automated method that allows existing AV scanning technology to be applied to detect known malware samples packed by one or more packers that are potentially proprietary. The packing manager tracks the memory areas to which an executable binary writes and executes, and so can unpack programs packed by multiple arbitrary packers without requiring reverse-engineering of the packers or any human intervention. By tracking page modification and execution of an executable binary at run time, the packing control module can detect the instant at which the program's control is first transferred to a page whose content is dynamically generated, so AV scanning can then be invoked. Thus, code cannot be executed under the packing control manager without being scanned by an AV scanner first.
Owner:NORTONLIFELOCK INC
System and method for securing tenant data on a local appliance prior to delivery to a SaaS data center hosted application service
InactiveUS20100198730A1Key distribution for secure communicationData processing applicationsData centerApplication software
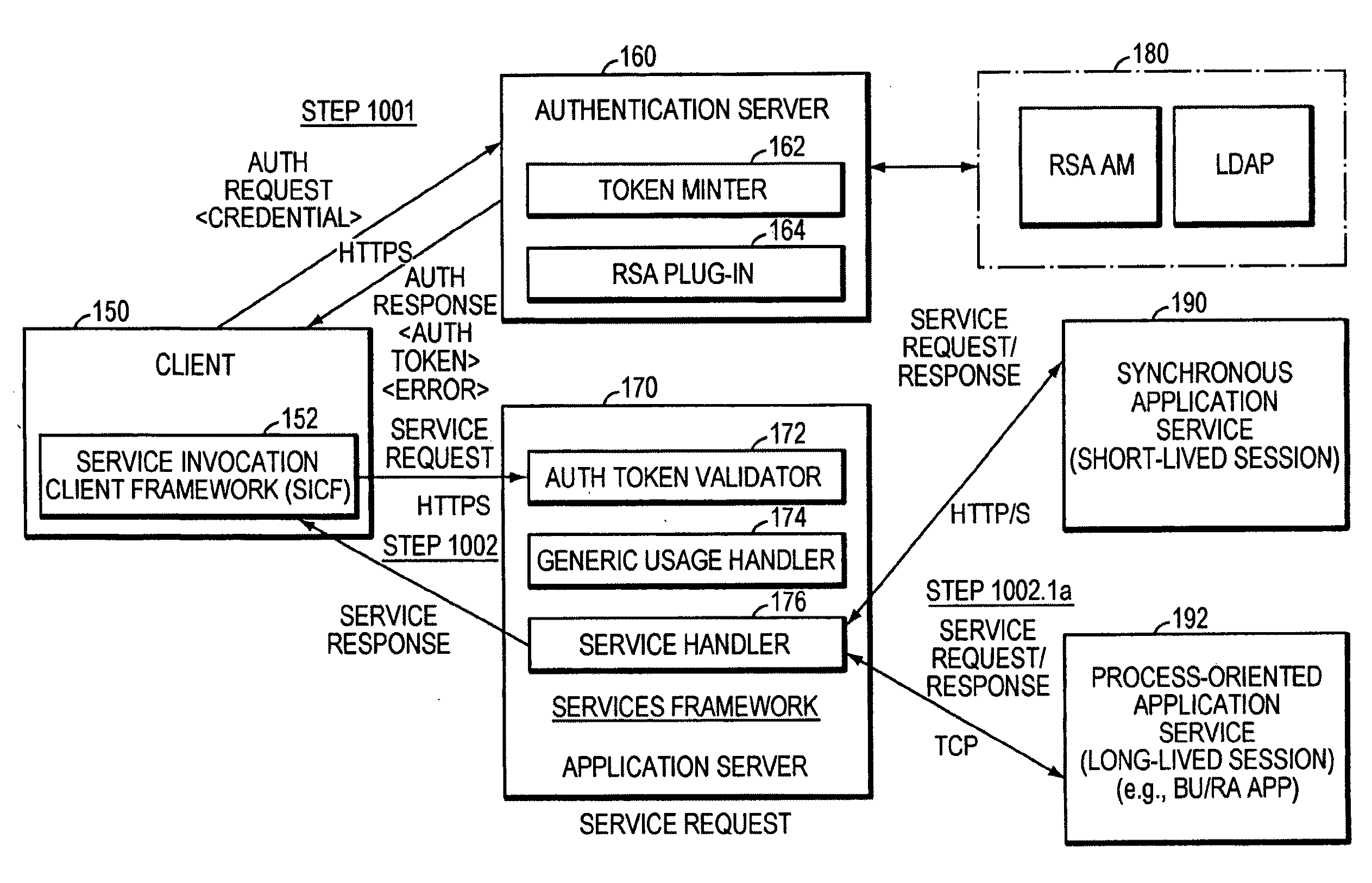
An extensible servicing hosting platform is provided that supports the design, build and concurrent deployment of multiple web accessible services on a services hosting platform. The services hosting platform comprises a services hosting framework capable of hosting multiple service applications, each of which may be shared by multiple tenants that each customize their use of a particular application service by extending the application service to exploit run time platform services within a service execution pipeline. The services hosting framework may easily be leveraged by applications to decrease the time associated with developing, deploying and maintaining high quality services in a cost effective manner.
Owner:EMC IP HLDG CO LLC
Reconfigurable service provision via a communication network
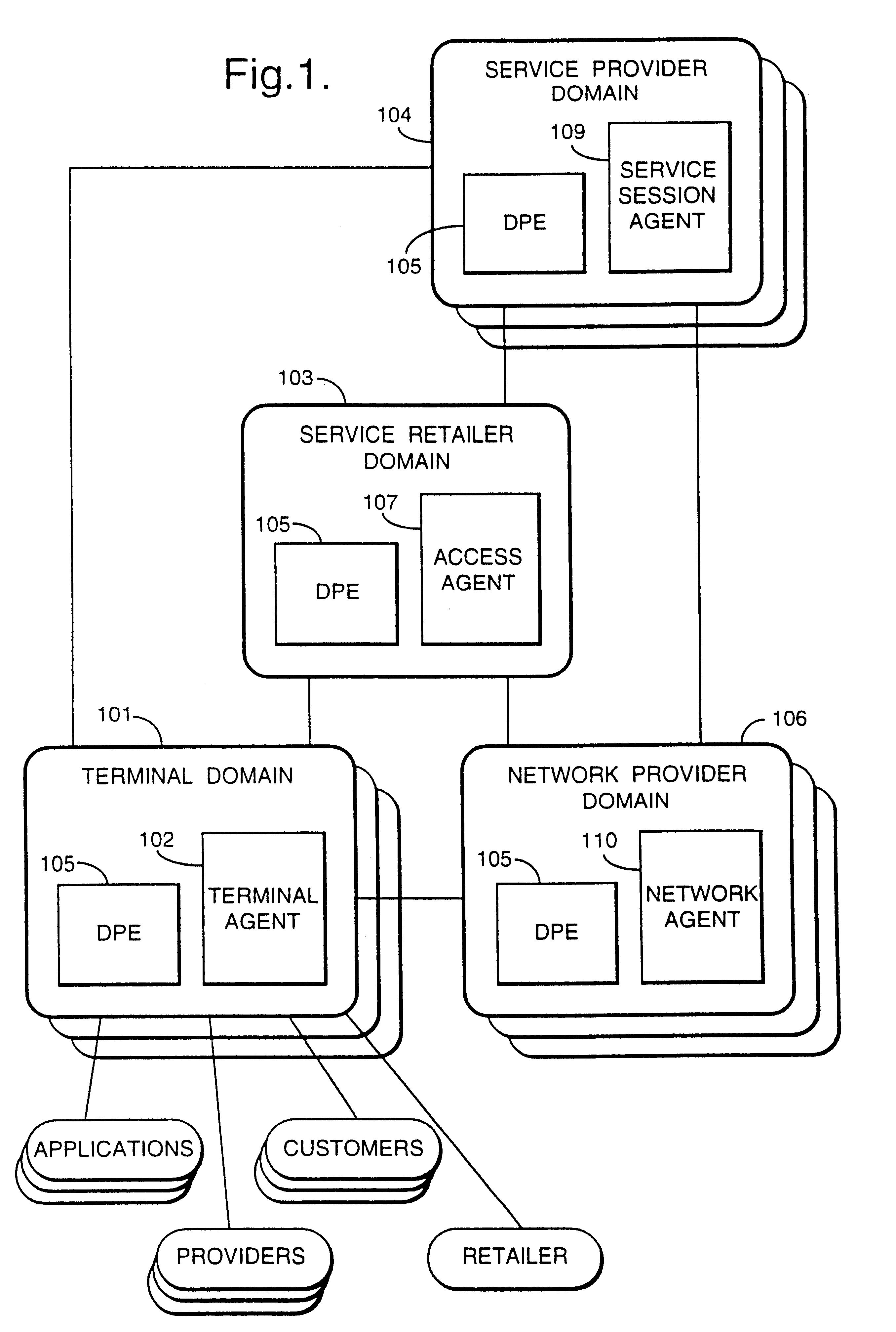
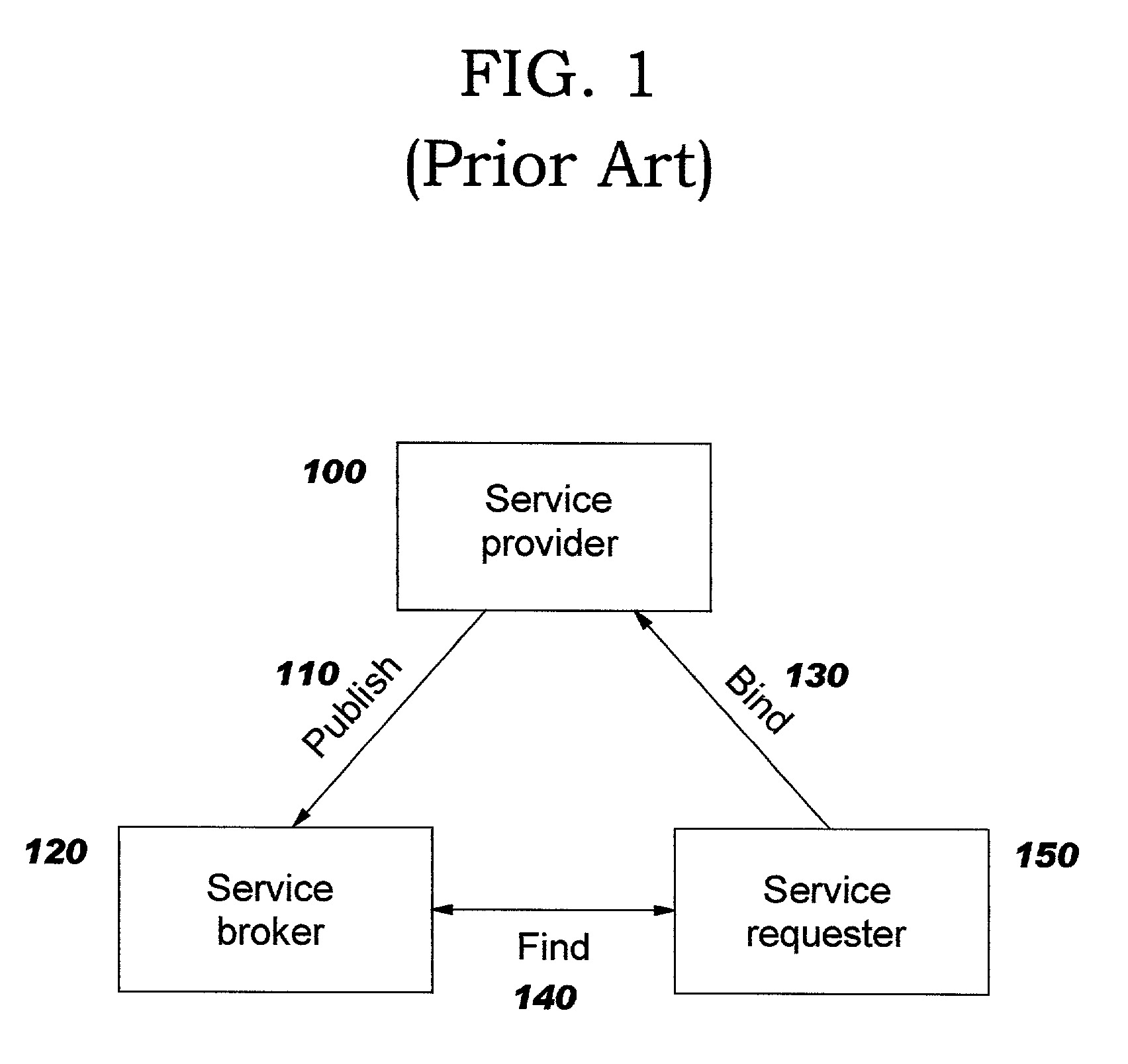
InactiveUS6330586B1Customer base for information services is particularly wideLarge capacityMultiplex system selection arrangementsData processing applicationsReconfigurabilityReusable software
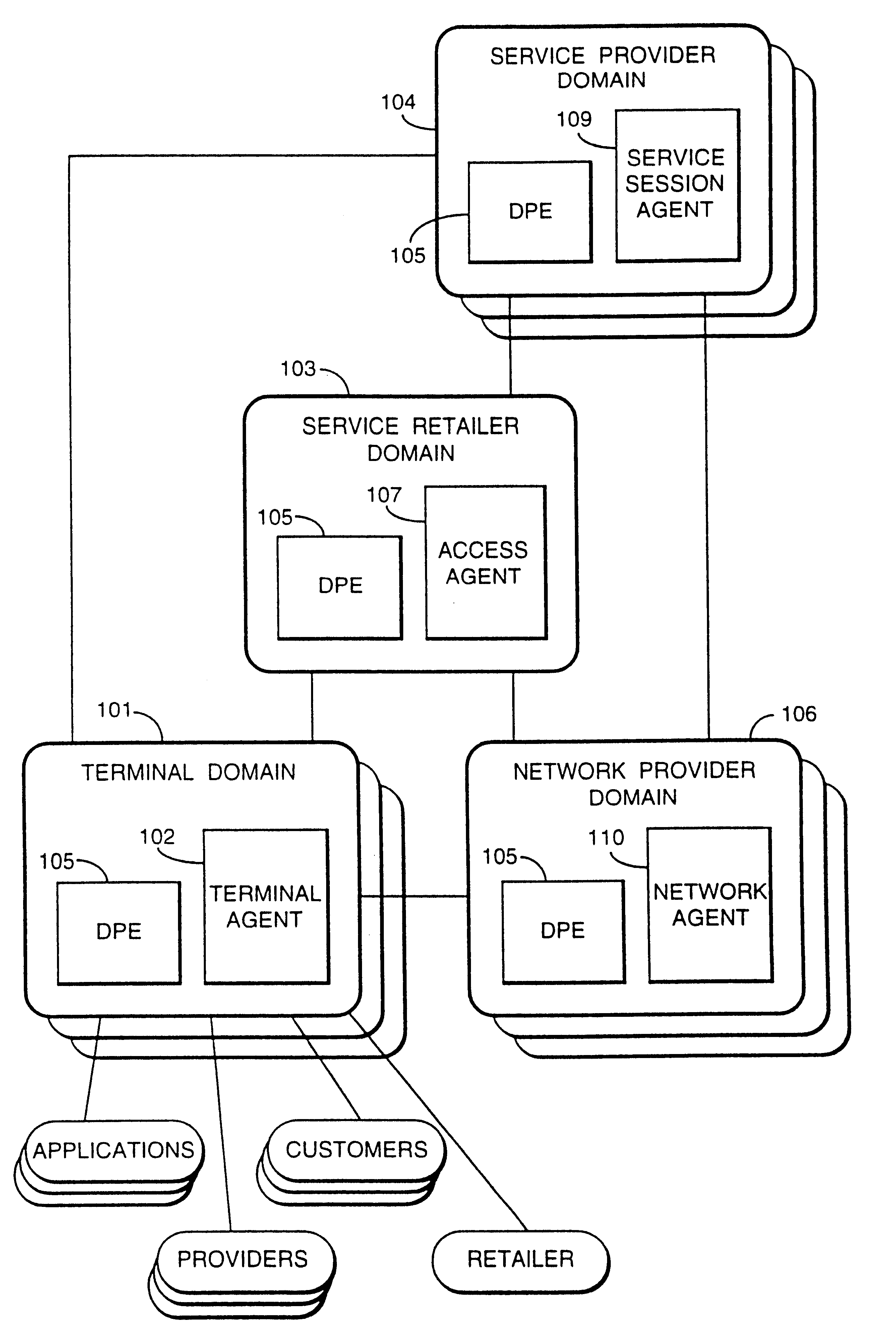
A services provision system provides information services over one or more communications networks and has a software infrastructure divided into domains. Each domain has an intelligent software agent and this community of agents sits in a computing environment represented in each domain by a DPE kernel. The community of agents co-operates to provide service and service management functionality to a user. At least one of the agents is reconfigurable to change the functionality the system makes available. Reconfigurability is based on the use of a plurality of reusable software modules, the agent reconfiguring by selecting a new combination of modules. The software modules themselves incorporate rules, or policies, which determine process steps offered by the modules at run-time. These policies are external to the modules and may be loaded at run-time, allowing dynamic modification to functionality of the system. The system as a whole offers functionality associated with using services, providing them and managing them and the reconfigurability allows it to offer the different types of functionality in an efficient way. It also allows access control to functionality at different levels with particularly good security against fraudulent use.
Owner:BRITISH TELECOMM PLC
Methods and apparatus for storage and execution of access control clients
ActiveUS20120108205A1Service provisioningUnauthorised/fraudulent call preventionPersonalizationThird party
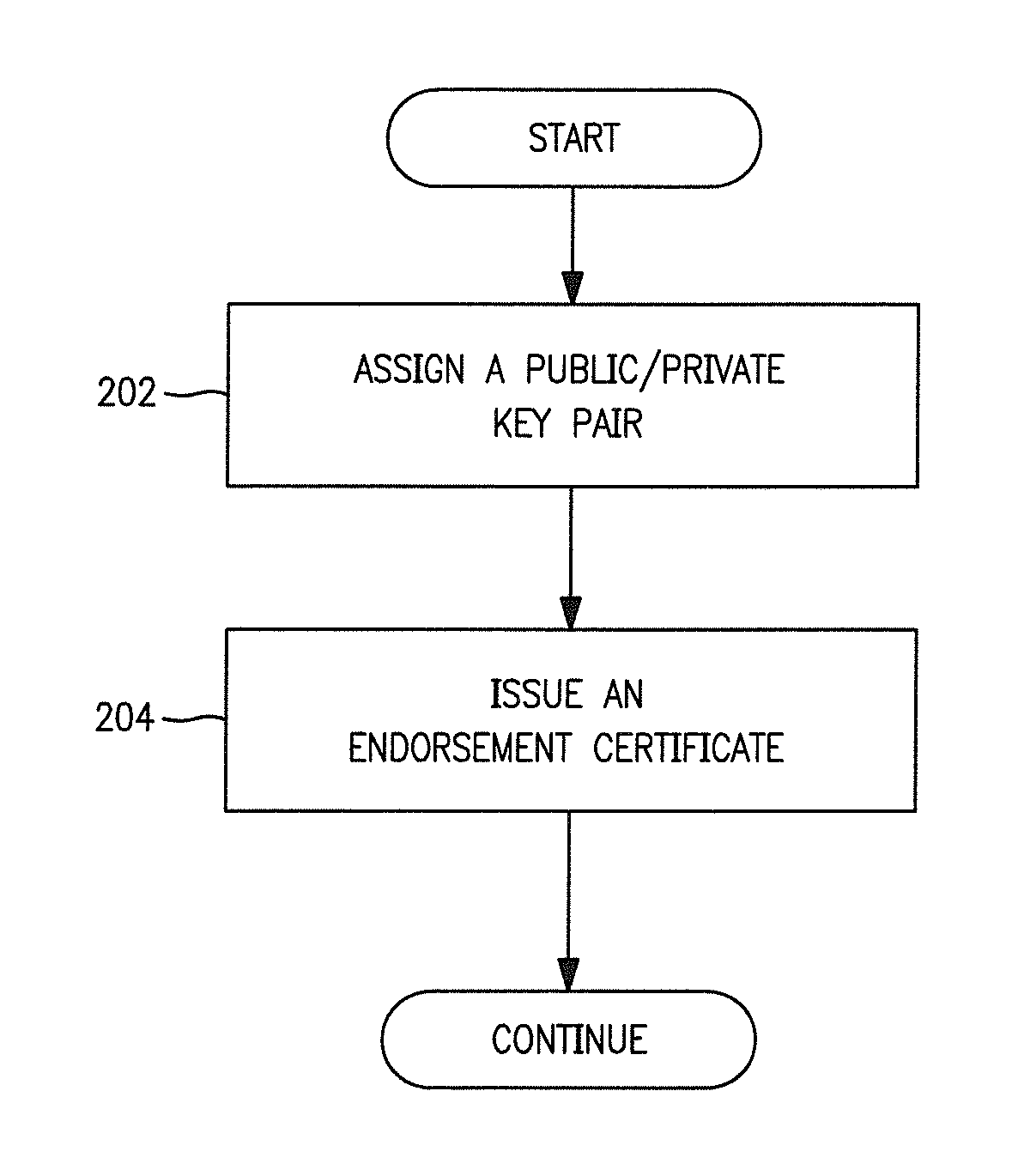
Methods and apparatus for secure provision of access control entities (such as electronic or virtual Subscriber Identity Module (eSIM) components) post-deployment of the host device on which the access control entity will be used. In one embodiment, wireless (e.g., cellular) user equipment is given a unique device key and endorsement certificate which can be used to provide updates or new eSIMs to the user equipment in the “field”. The user equipment can trust eSIM material delivered by an unknown third-party eSIM vendor, based on a secure certificate transmission with the device key. In another aspect, an operating system (OS) is partitioned into various portions or “sandboxes”. During operation, the user device can activate and execute the operating system in the sandbox corresponding to the current wireless network. Personalization packages received while connected to the network only apply to that sandbox. Similarly, when loading an eSIM, the OS need only load the list of software necessary for the current run-time environment. Unused software can be subsequently activated.
Owner:APPLE INC
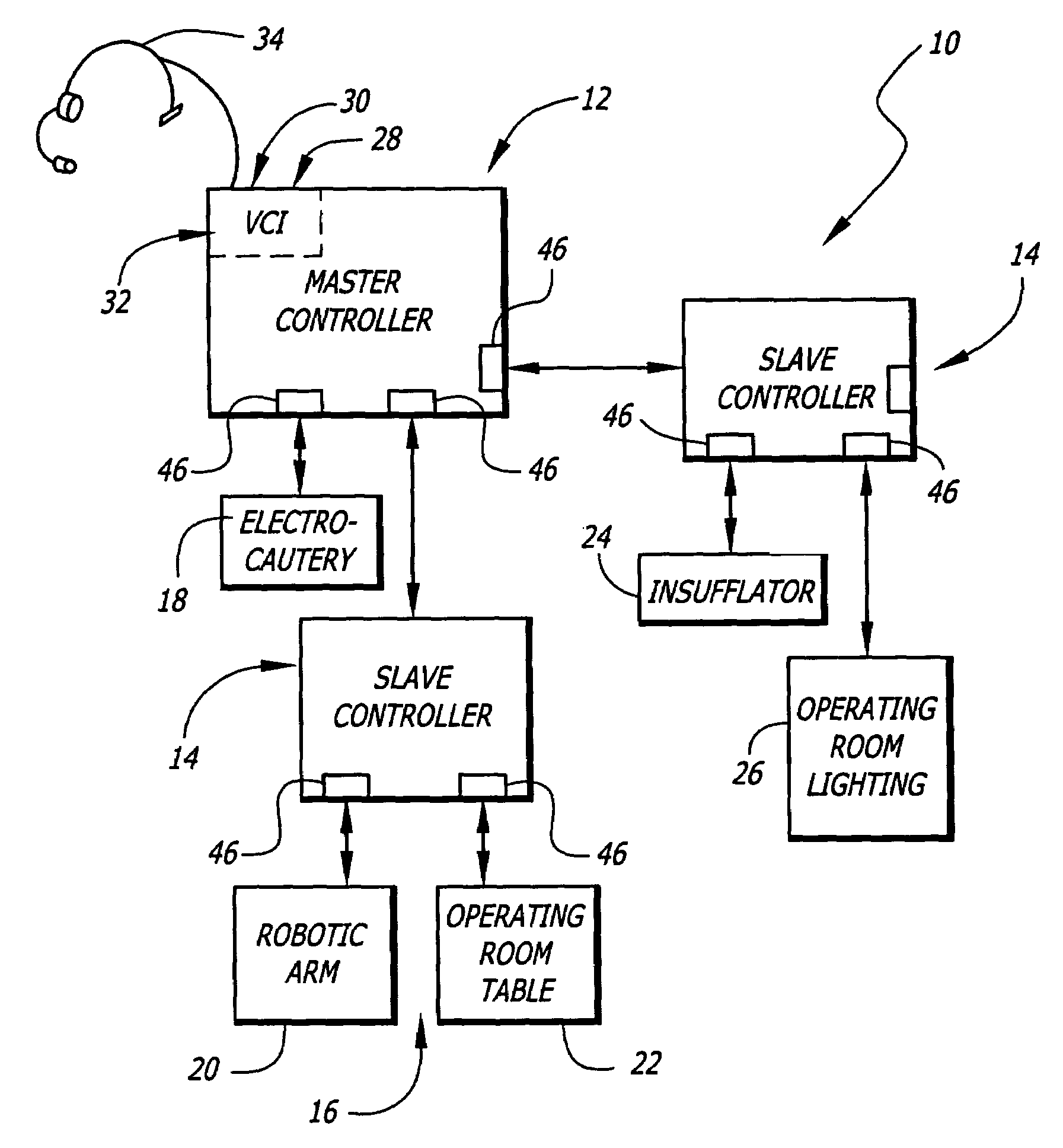
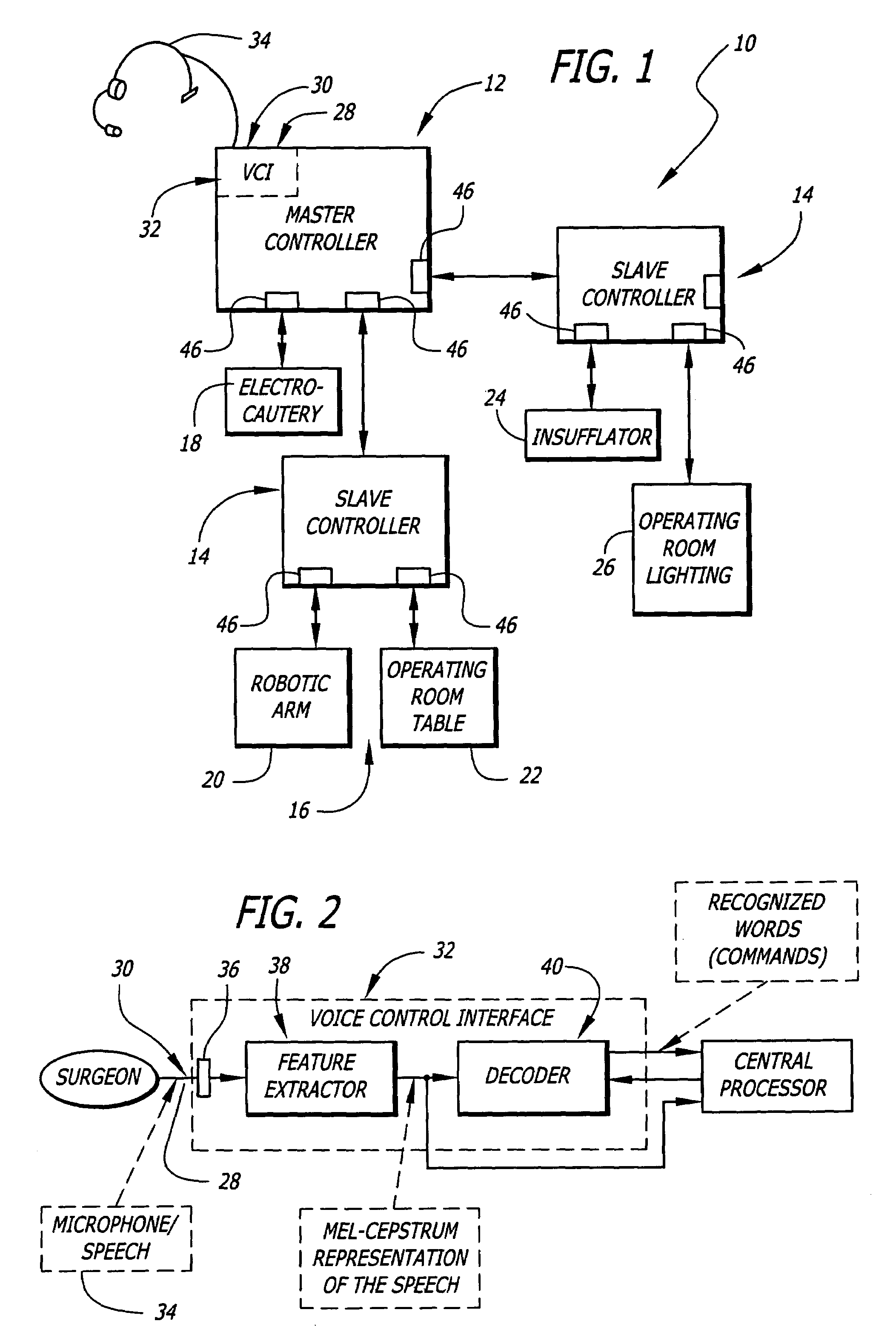
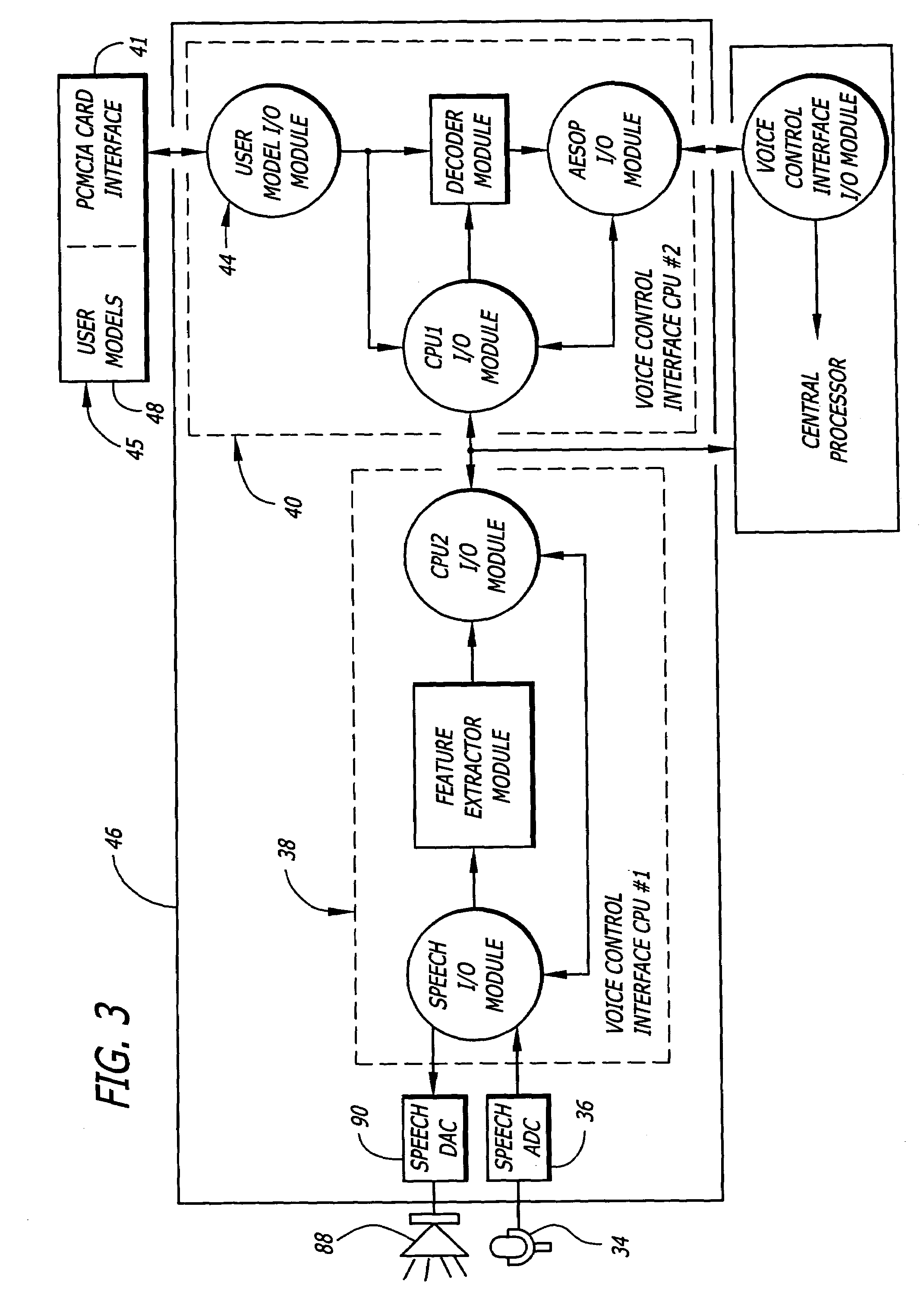
General purpose distributed operating room control system
The present invention pertains to control systems and provides a run time configurable control system for selecting and operating one of a plurality of operating room devices from a single input source, the system comprising a master controller having a voice control interface and means for routing control signals. The system additionally may include a plurality of slave controllers to provide expandability of the system. Also, the system includes output means for generating messages to the user relating to the status of the control system in general and to the status of devices connected thereto.
Owner:INTUITIVE SURGICAL OPERATIONS INC
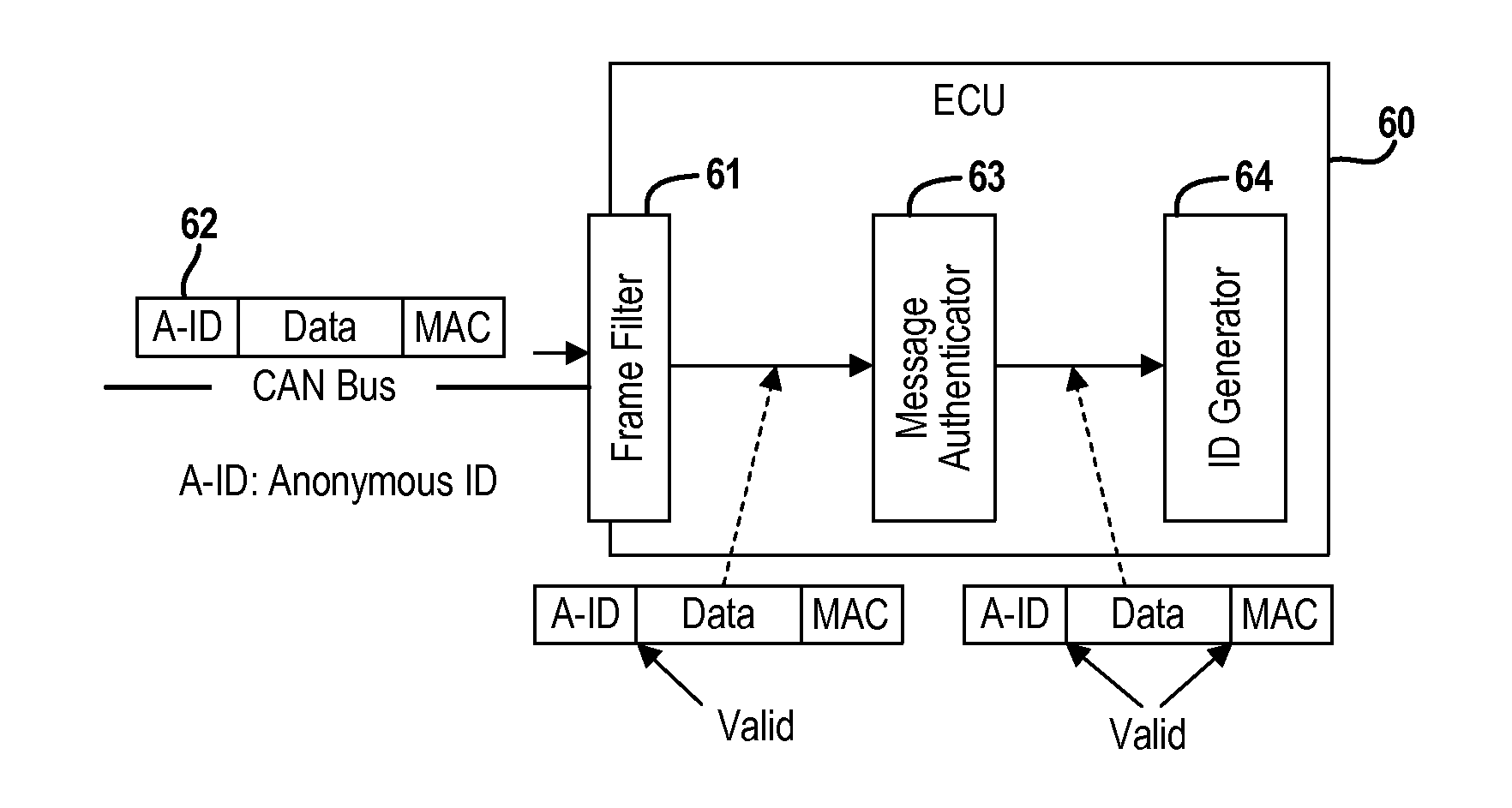
Real-Time Frame Authentication Using ID Anonymization In Automotive Networks
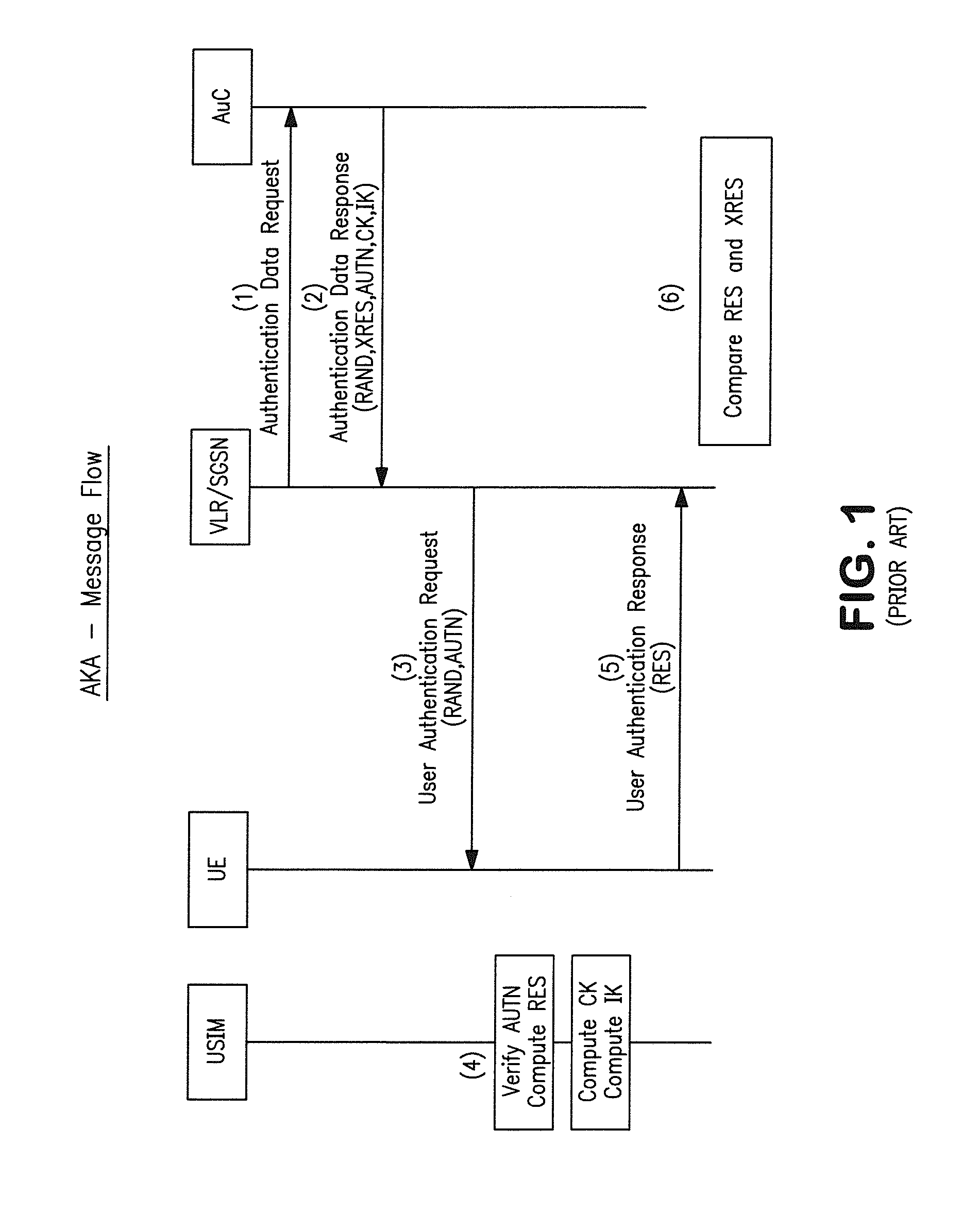
ActiveUS20150089236A1Reduce message authentication delay tmReduce delaysKey distribution for secure communicationSynchronising transmission/receiving encryption devicesComputer networkData integrity
A real-time frame authentication protocol is presented for in-vehicle networks. A frame identifier is made anonymous to unauthorized entities but identifiable by the authorized entities. Anonymous identifiers are generated on a per-frame basis and embedded into each data frame transmitted by a sending ECU. Receiving ECUs use the anonymous identifiers to filter incoming data frames before verifying data integrity. Invalid data frame are filtered without requiring any additional run-time computations.
Owner:RGT UNIV OF MICHIGAN
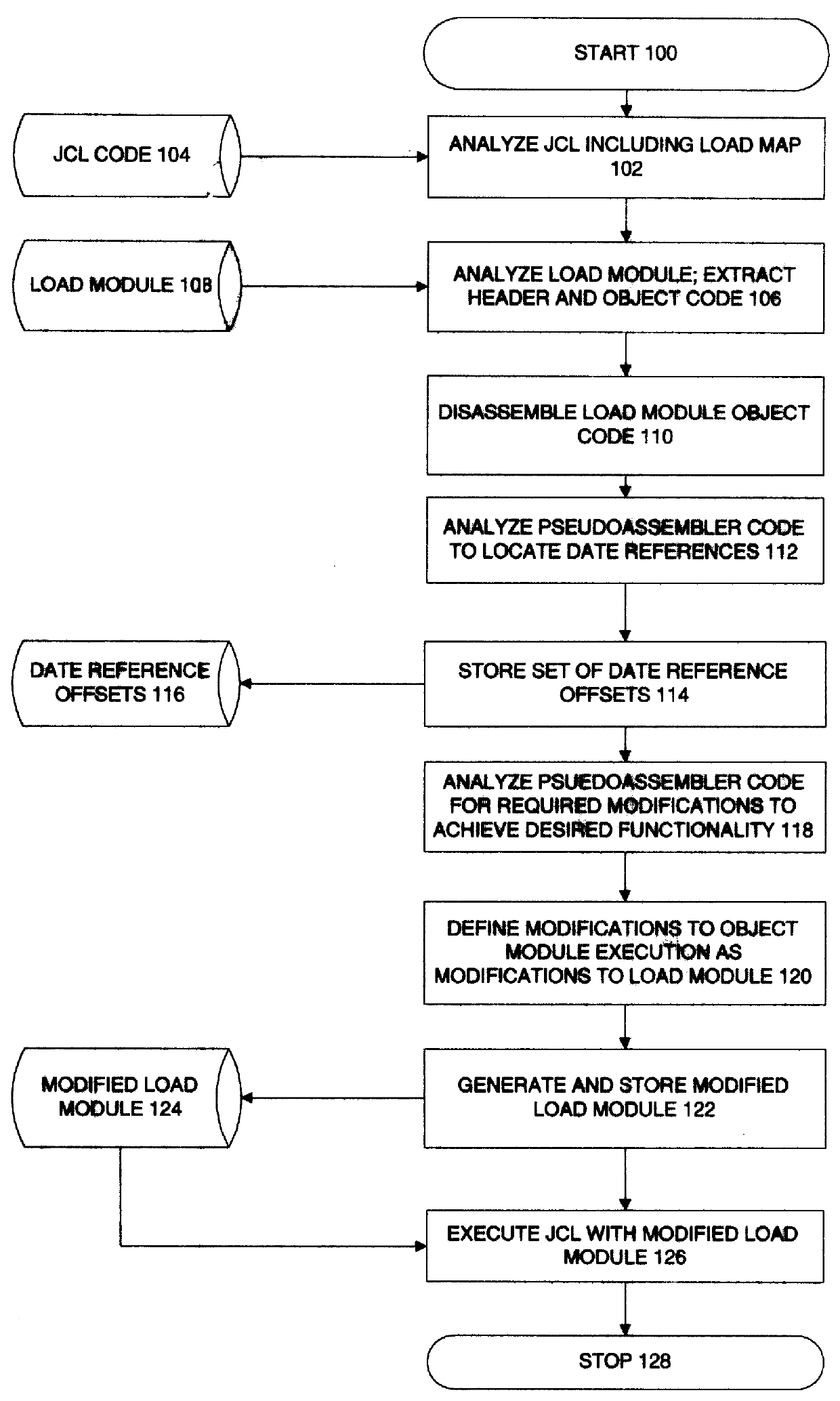
Object code logic analysis and automated modification system and method
InactiveUS6071317ALow costImprove automationSoftware maintainance/managementProgram loading/initiatingOperational systemObject code
A method and system for modifying computer program logic with respect to a predetermined aspect, comprising (a) before run time: analyzing compiled computer program logic of a module for processes involving the predetermined aspect before run time, substantially without decompilation or reference to computer program source code; and storing a set of modifications relating to computer program logic modifications of the module relating to the predetermined aspect; and (b) at run time: based on the stored set of modifications, selectively transferring program control from the module to a separate logical structure, executing modified logical operations with respect to the predetermined aspect, and subsequently returning program control to the module. The predetermined aspect may be, for example, a data type, algorithm type, or interface specification. In a preferred embodiment, the predetermined aspect is date related data, and more particularly, to logical operations relating to date related data which are flawed. The system preferably operates in a mainframe environment, wherein the compiled computer program constitutes one or more load modules, executing under an operating system, wherein the computer program logic modifications preferably comprise program flow control diversions in an original object module, which selectively transfer logical control to a separate object module to effect modifications to the computer program logic, followed by a return of control to the original object module.
Owner:HANGER SOLUTIONS LLC +1
Integrating operating systems and run-time systems
InactiveUS6546546B1Specific access rightsMemory adressing/allocation/relocationOperational systemApplication software
The Virtual Machine is viewed by many as inherently insecure despite all the efforts to improve its security. This invention provides methods, apparatus, and computer products to implement a system that provides operating system style protection for code. Although applicable to many language systems, the invention is described for a system employing the Java language. Hardware protection domains are used to separate Java classes, provide access control on cross domain method invocations, efficient data sharing between protection domains, and memory and CPU resource control. Apart from the performance impact, these security measures are all transparent to the Java programs, even when a subclass is in one domain and its superclass is in another, when they do not violate the policy. To reduce the performance impact, classes are grouped and shared between protection domains and map data lazily as it is being shared. The system has been implemented on top of the Paramecium operating system used as an example of an extensible operating system application.
Owner:IBM CORP
Provisioning aggregated services in a distributed computing environment
ActiveUS20030135628A1Multiple digital computer combinationsDigital data authenticationDistributed Computing EnvironmentDistributed services
Methods, systems, and computer program products are disclosed for provisioning software resources used with aggregated web services. The disclosed techniques enable heterogeneous identity systems to be joined in the dynamic, run-time web services integration environment. Authentication and authorization may now be performed for the aggregated service, as well as for its sub-services. SOAP ("Simple Object Access Protocol") messages, as an example, may be used to relay identity information among distributed services, whereby credentials may be specified in the SOAP message header to accompany a service request specified in the SOAP message body.
Owner:IBM CORP
High-performance extensible document transformation
InactiveUS6941511B1Reduce processing timeImproved performance characteristicsDigital data information retrievalDigital computer detailsBusiness-to-businessDocument transformation
The present invention provides a method, system, and computer program product for applying transformations to extensible documents, enabling reductions in the processing time required to transform arbitrarily-structured documents having particular well-defined elements. Signatures for structured document types are defined, along with one or more transformations to be performed upon documents of that type. The transformations are specified using syntax elements referred to as maps. A map specifies an operation code for the transformation to be performed, and describes the input and output of the associated transformation. A special map processing engine locates an appropriate transformation object to a particular input document at run-time, and applies the transformation operation according to the map definition. This technique is preferably used for a set of predetermined core transformations, with other transformations being processed using stylesheet engines of the prior art. The input documents may be encoded in the Extensible Markup Language (XML), or in other structured notations. The techniques of the present invention are particularly well suited to use in high-volume and throughput-sensitive environments such as that encountered by business-to-business transaction servers.
Owner:IBM CORP
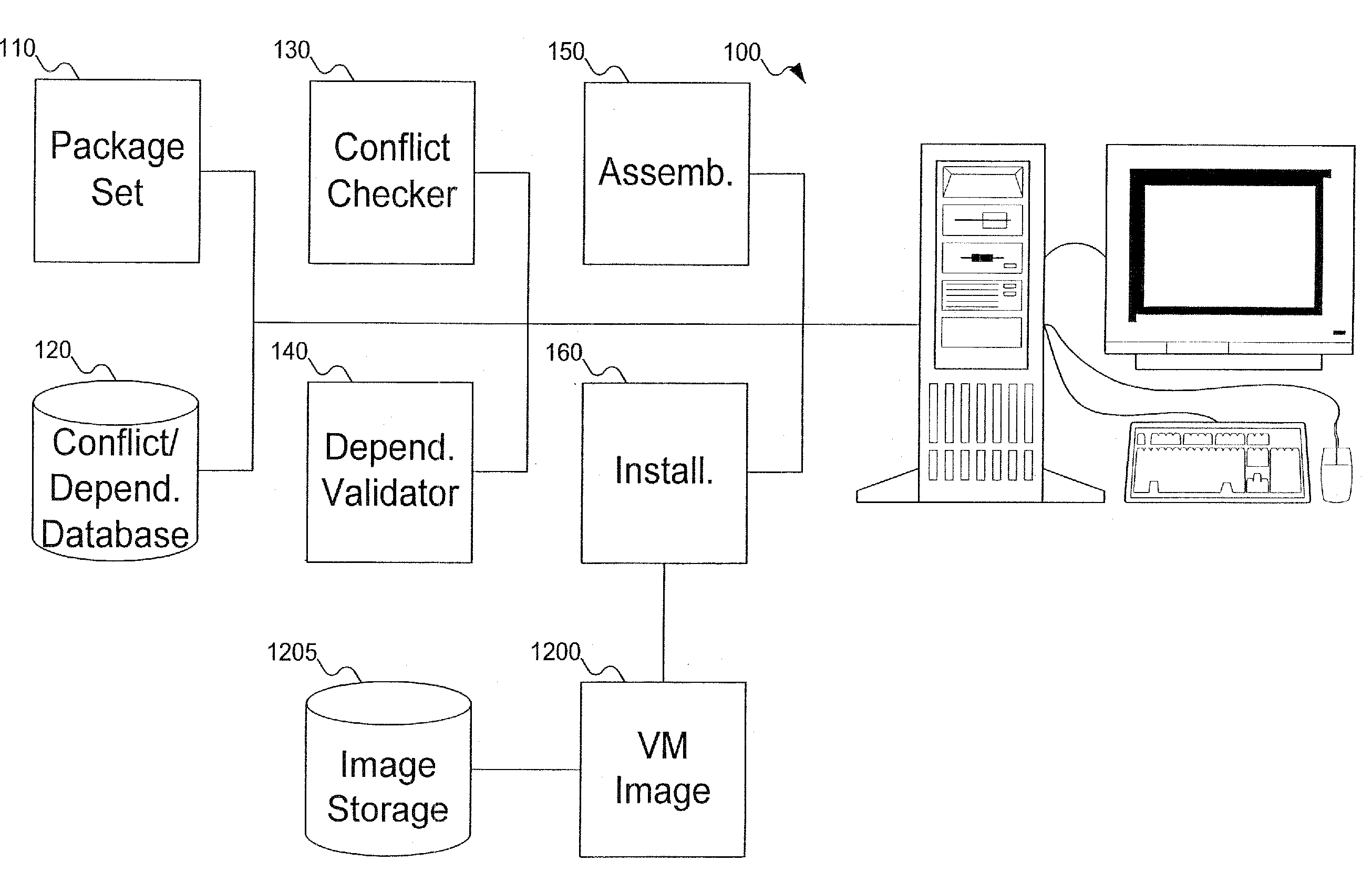
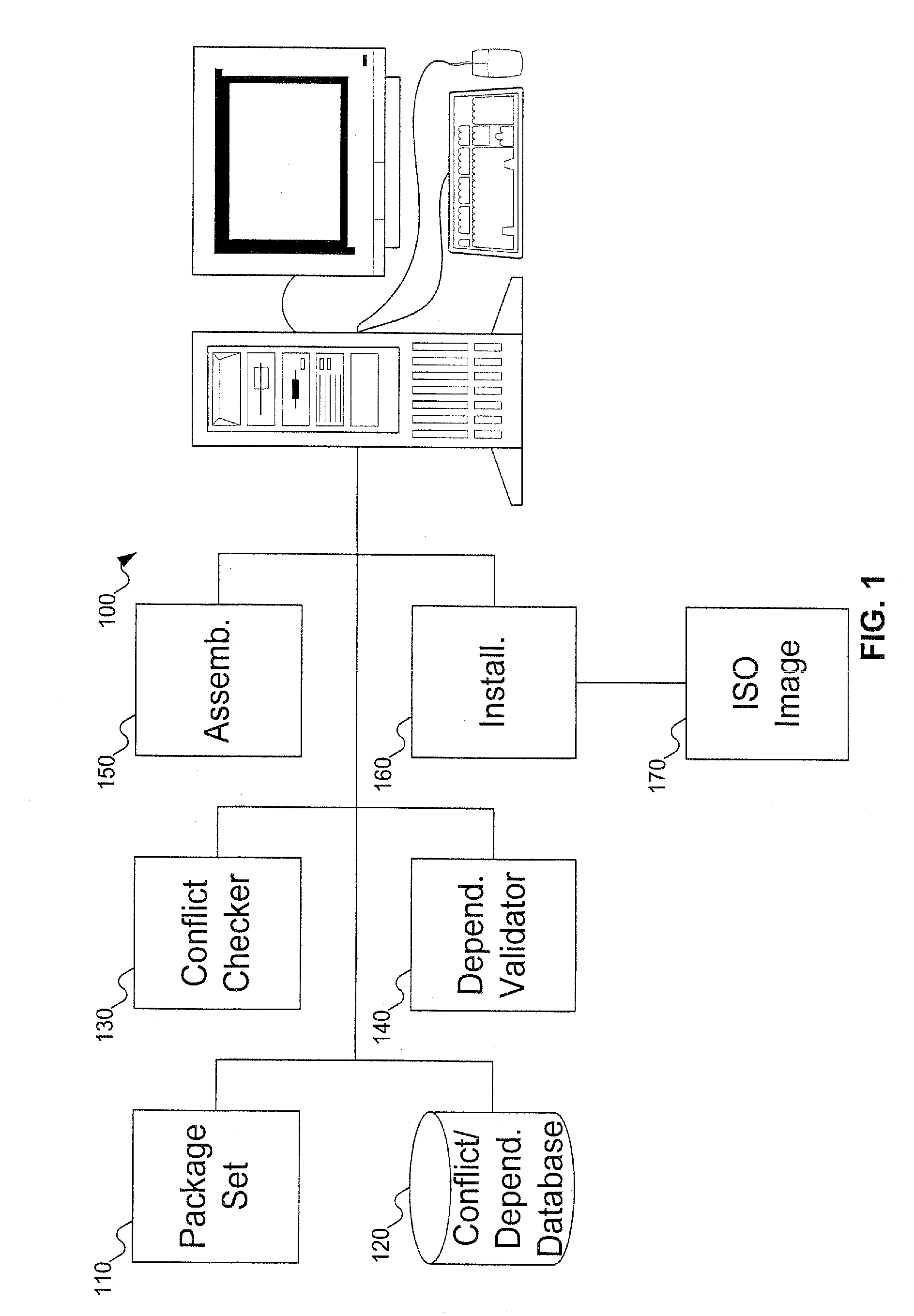
System and method for creating a customized installation on demand
A customized VM image, for example of Linux software, is created by allowing a user to select packages that the user is interested in installing. During the process, the user is informed if two of the packages that were selected will not be interoperable at run-time. The user is then given an opportunity to resolve the conflict. The user is also informed if selected packages depend on other packages that were not selected in order to run properly, and given the opportunity to include those needed packages in the VM image. Once the selected packages have been validated that they will interoperate and all dependencies are satisfied, the system can build and install the VM image. The VM image can also include applications, and not just packages used in assembling an operating system image.
Owner:ORACLE INT CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com