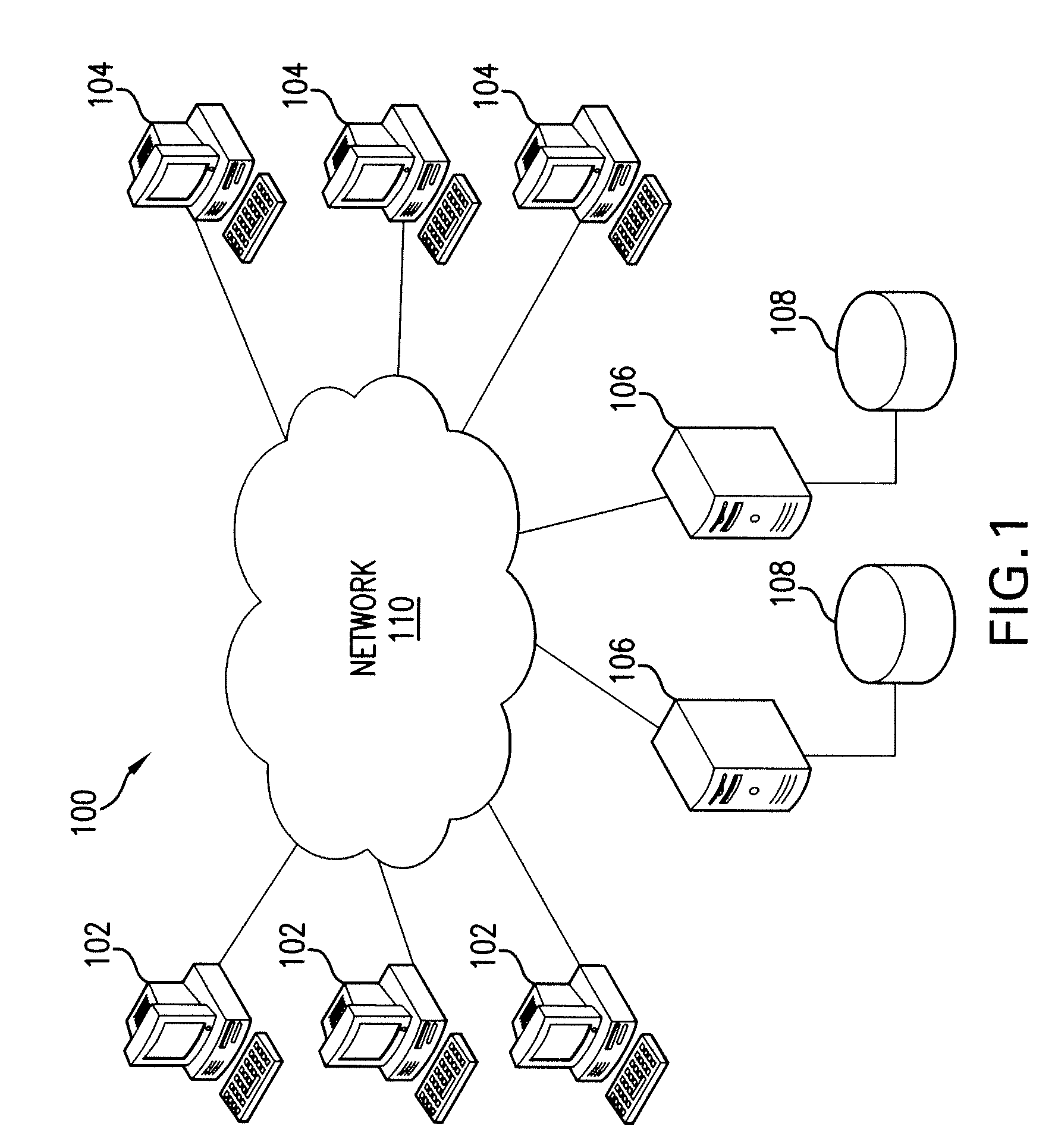
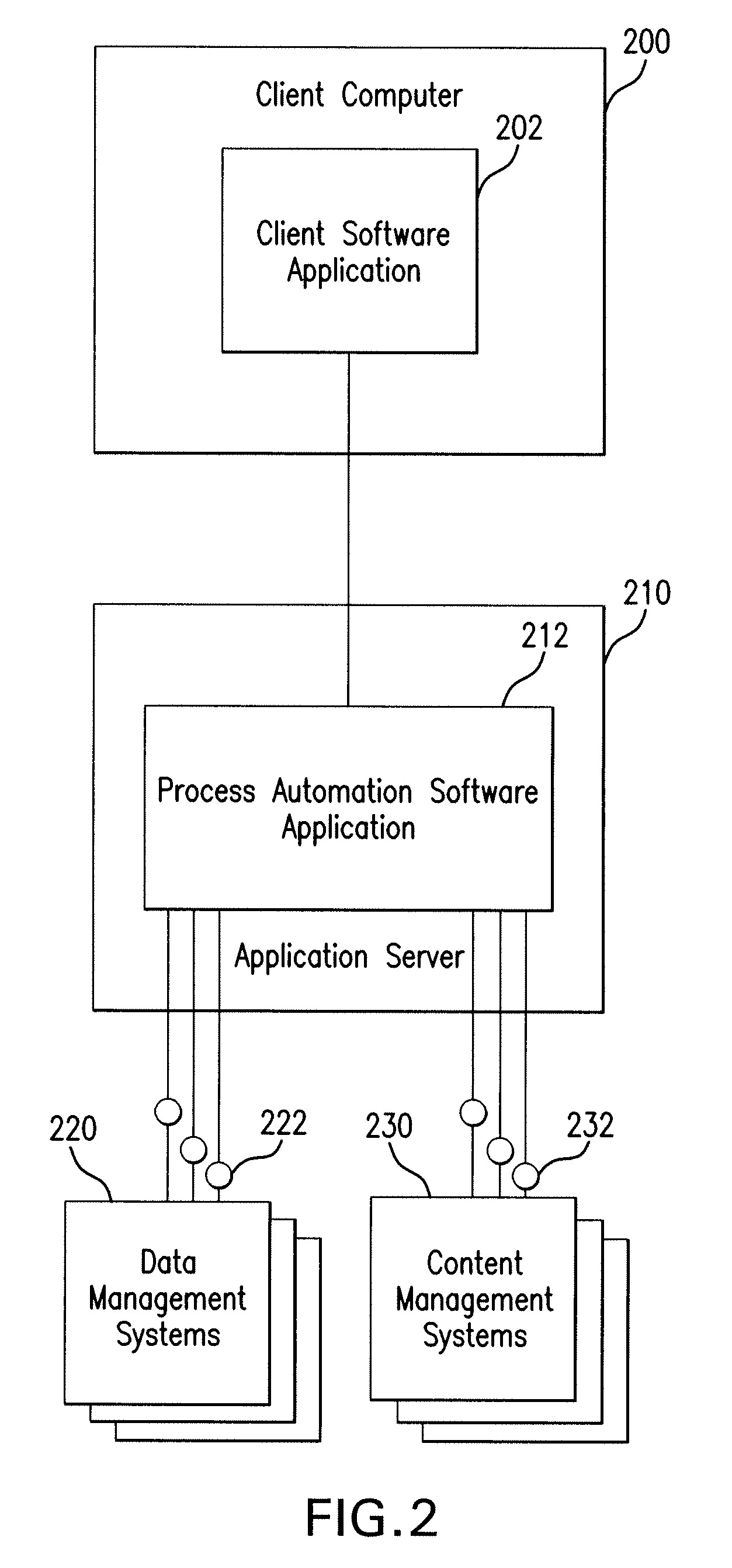
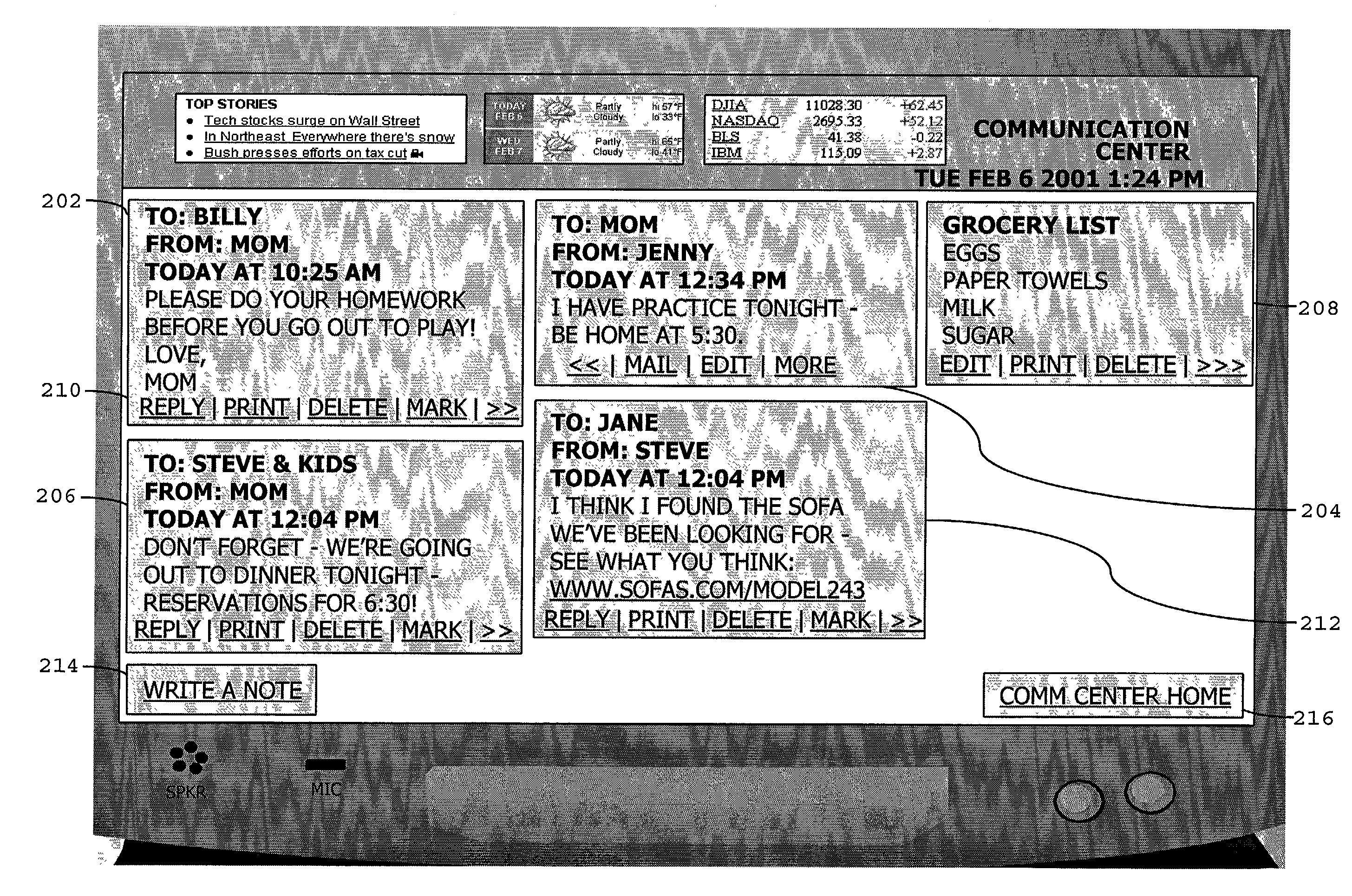
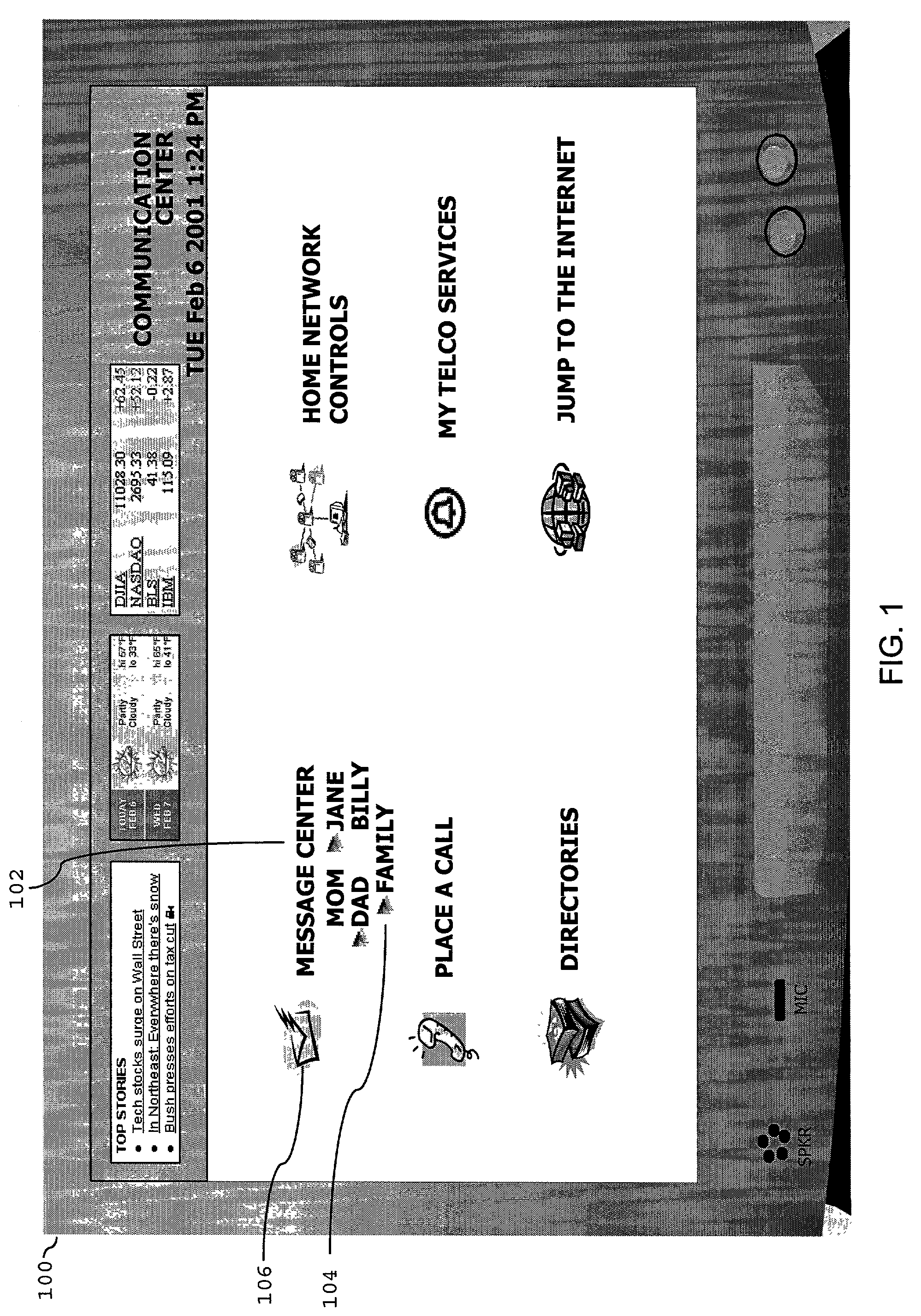
Patents
Literature
625 results about "Program logic" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Program logic is written using three classes of instructions: sequential processing, selection and iteration. These instructions do the actual data processing, such as input, output, add, subtract and copy (move).
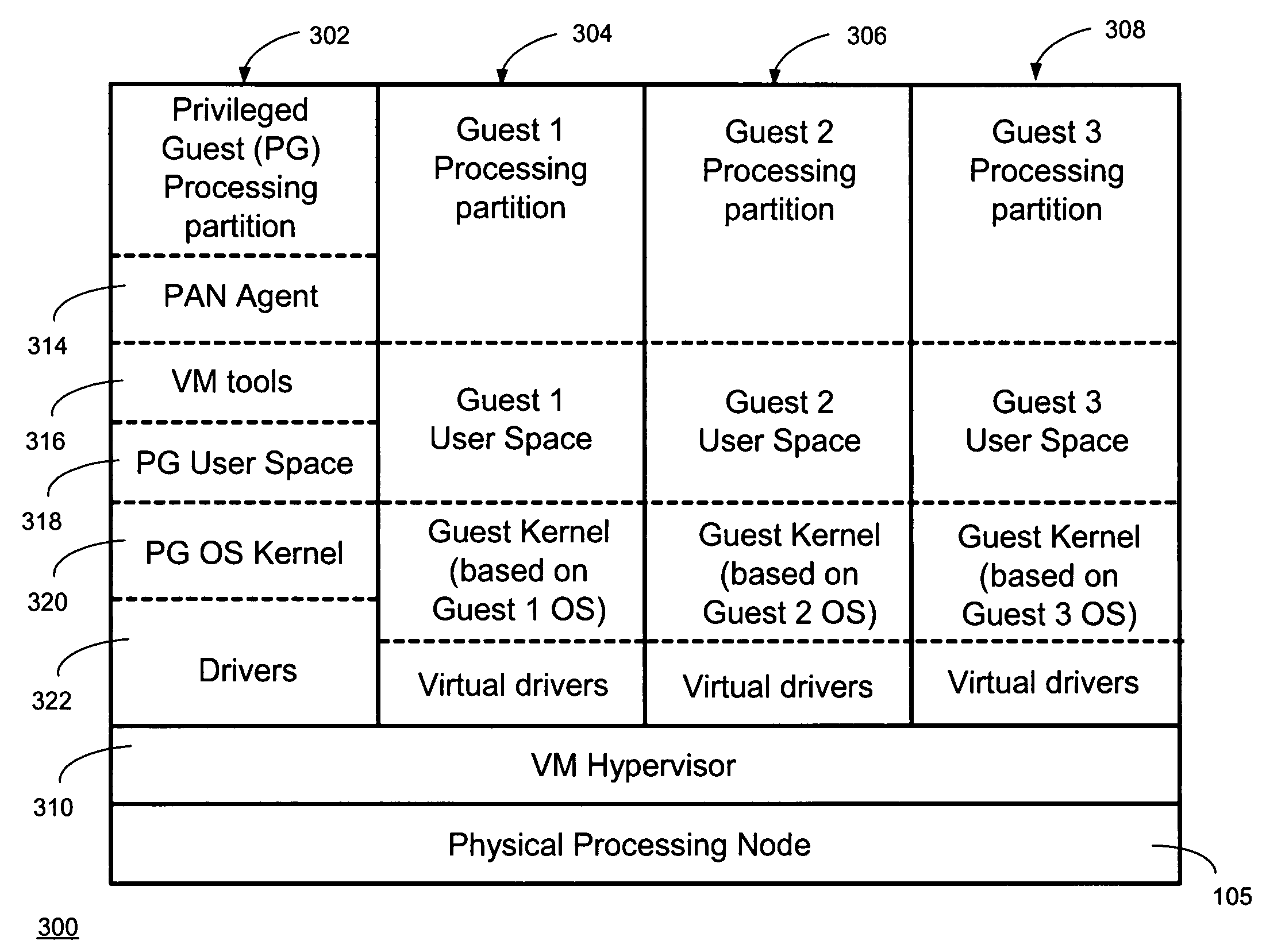
Providing virtual machine technology as an embedded layer within a processing platform
InactiveUS20080059556A1Satisfies specificationMultiple digital computer combinationsProgram controlAuto-configurationProcessor node
A platform, method, and computer program product, provides virtual machine technology within a processing platform. A computing platform automatically deploys one or more servers in response to receiving corresponding server specifications. Each server specification identifies a server application that a corresponding server should execute and defines communication network and storage network connectivity for the server. The platform includes a plurality of processor nodes and virtual machine hypervisor. The virtual machine hypervisor logic has logic for instantiating and controlling the execution of one or more guest virtual machines on a computer processor. In response to interpreting the server specification, control software deploys computer processors or guest virtual machines to execute the identified server application and automatically configures the defined communication network and storage network connectivity to the selected computer processors or guest virtual machines to thereby deploy the server defined in the server specification.
Owner:EGENERA
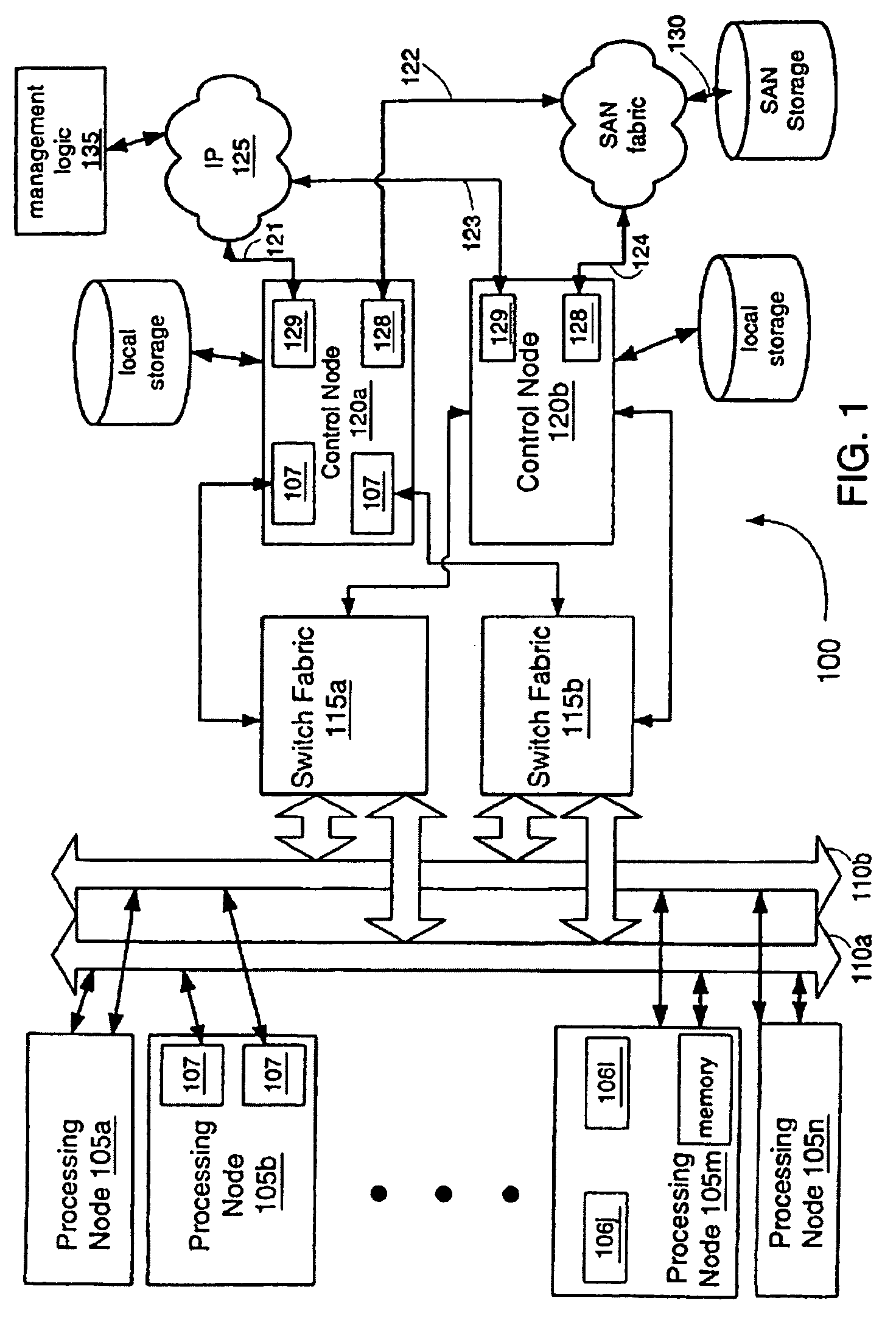
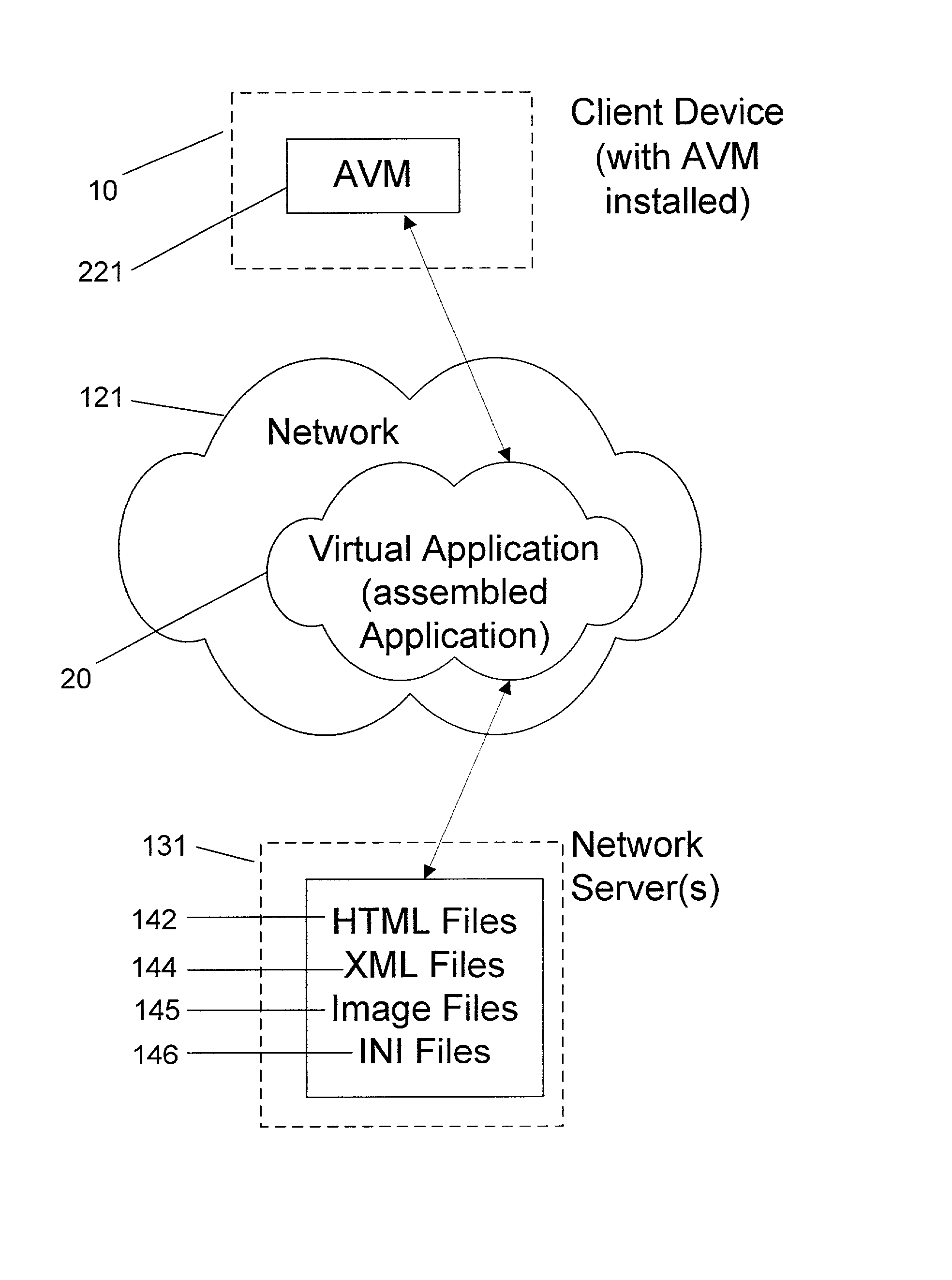
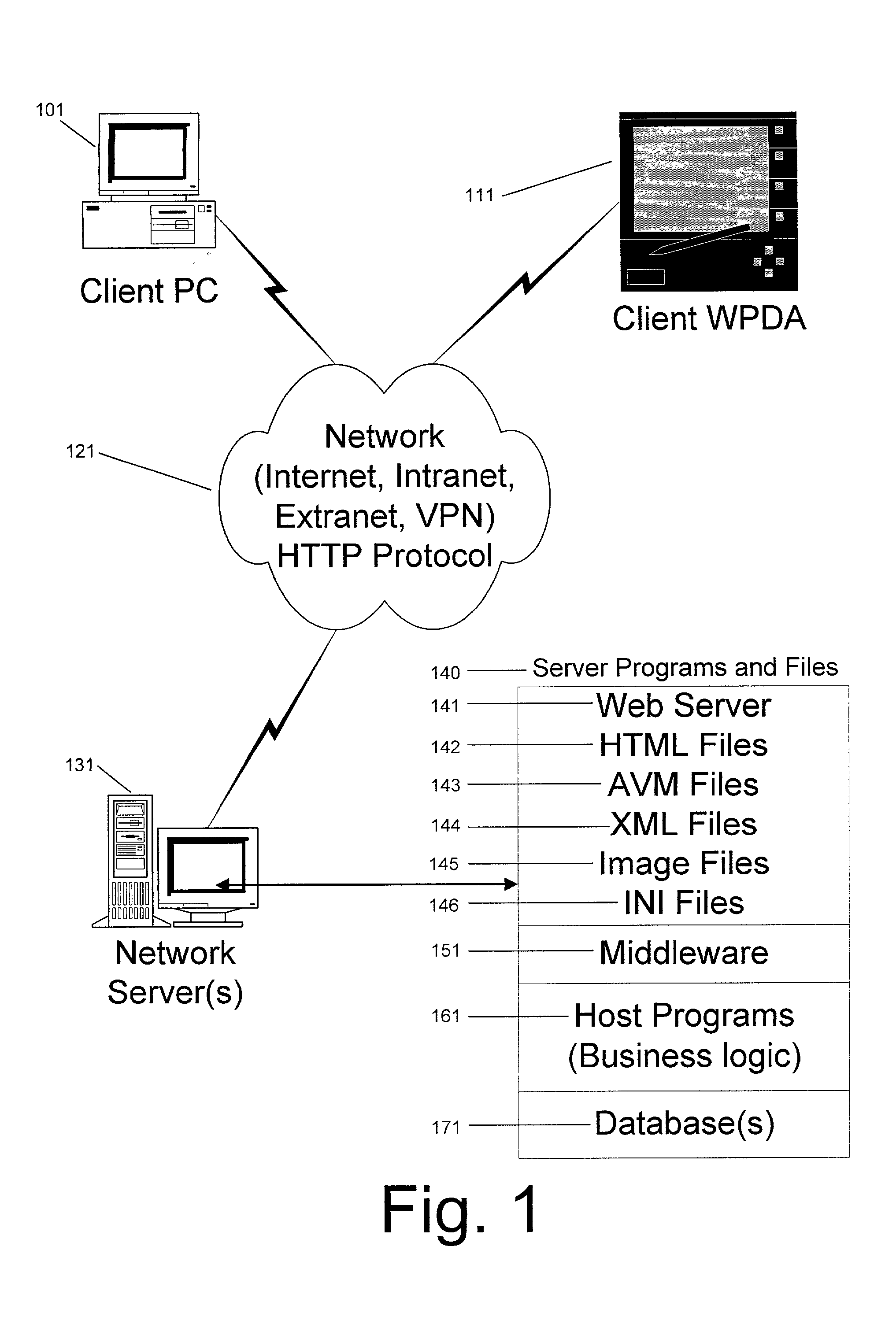
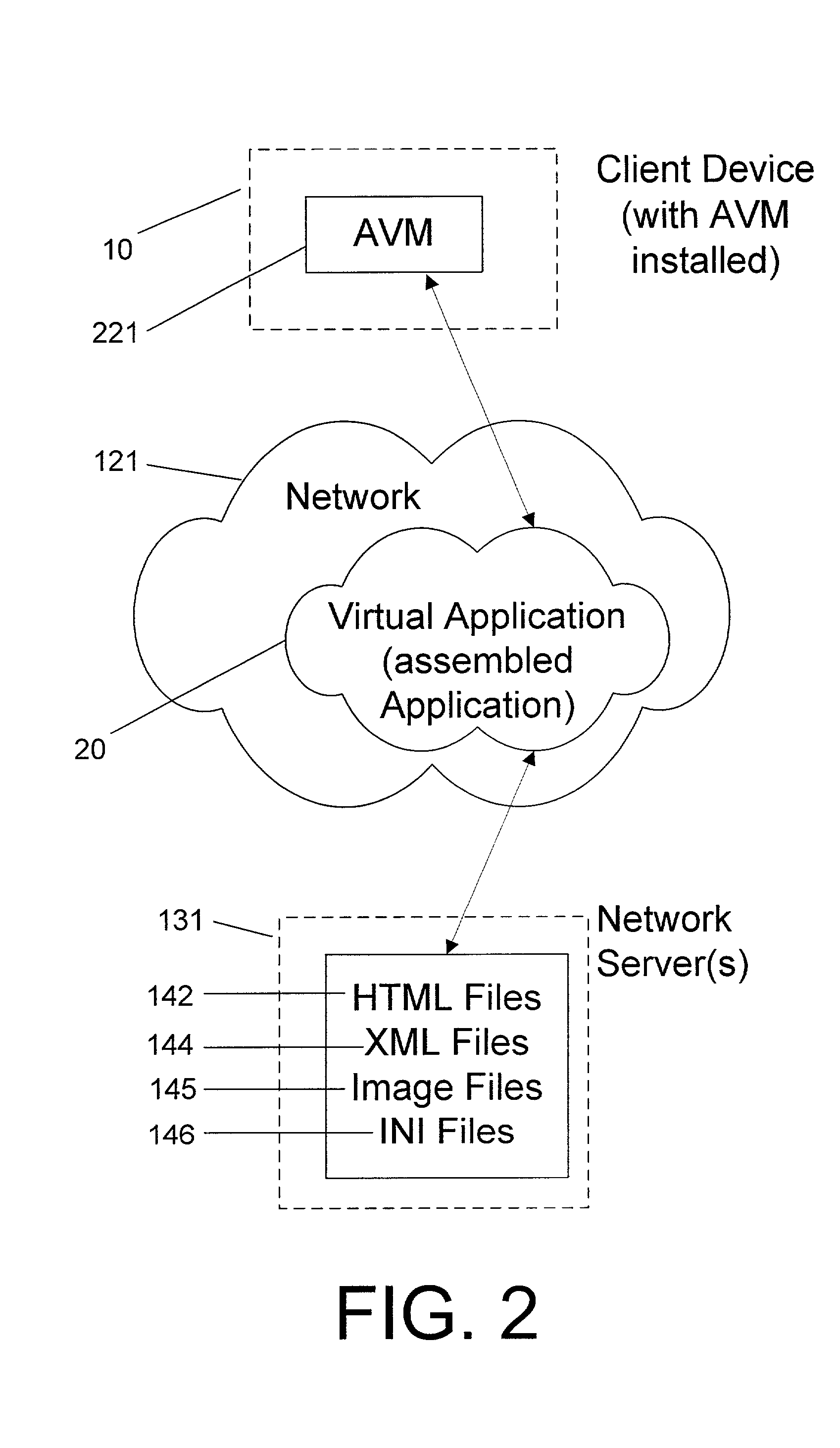
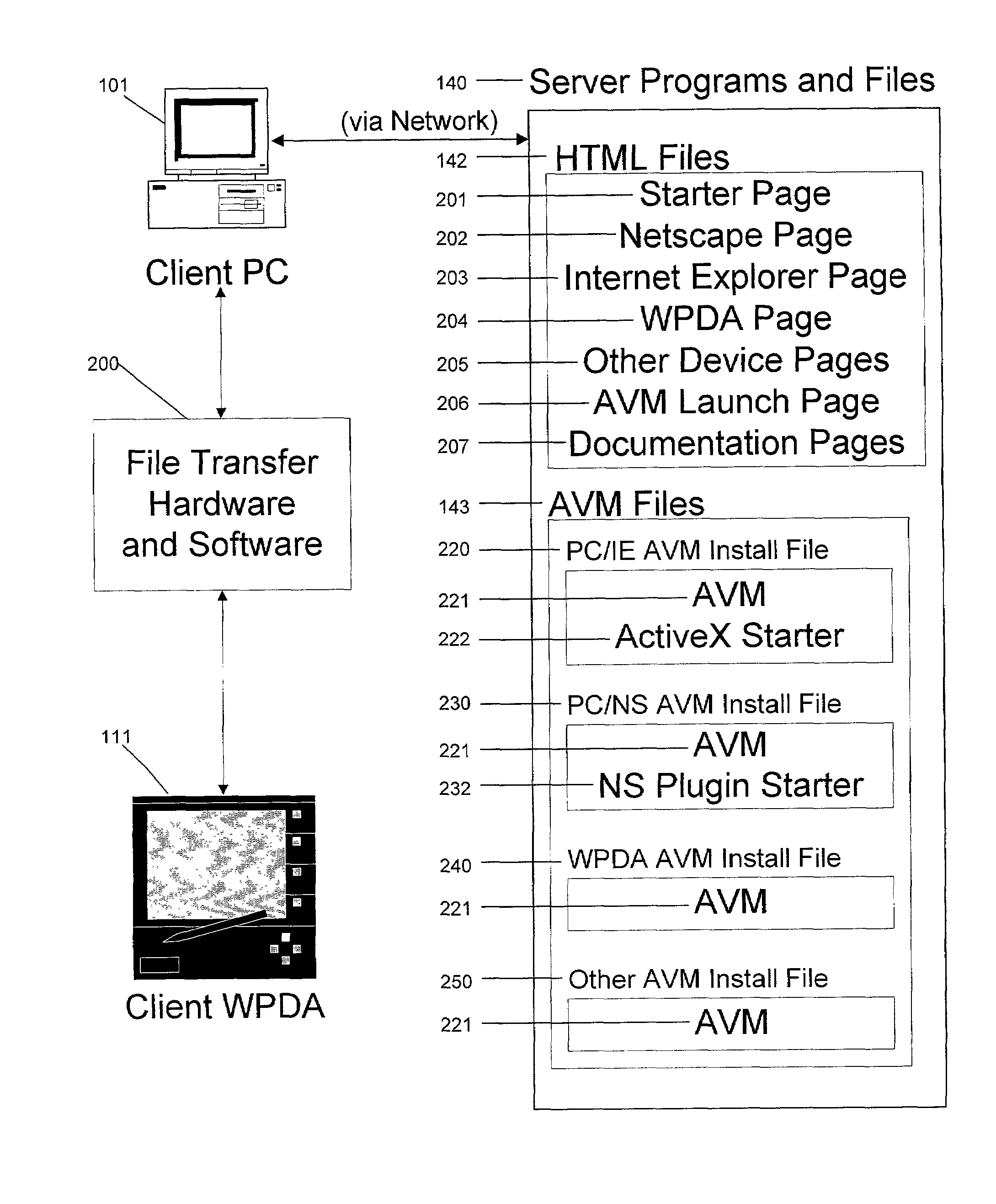
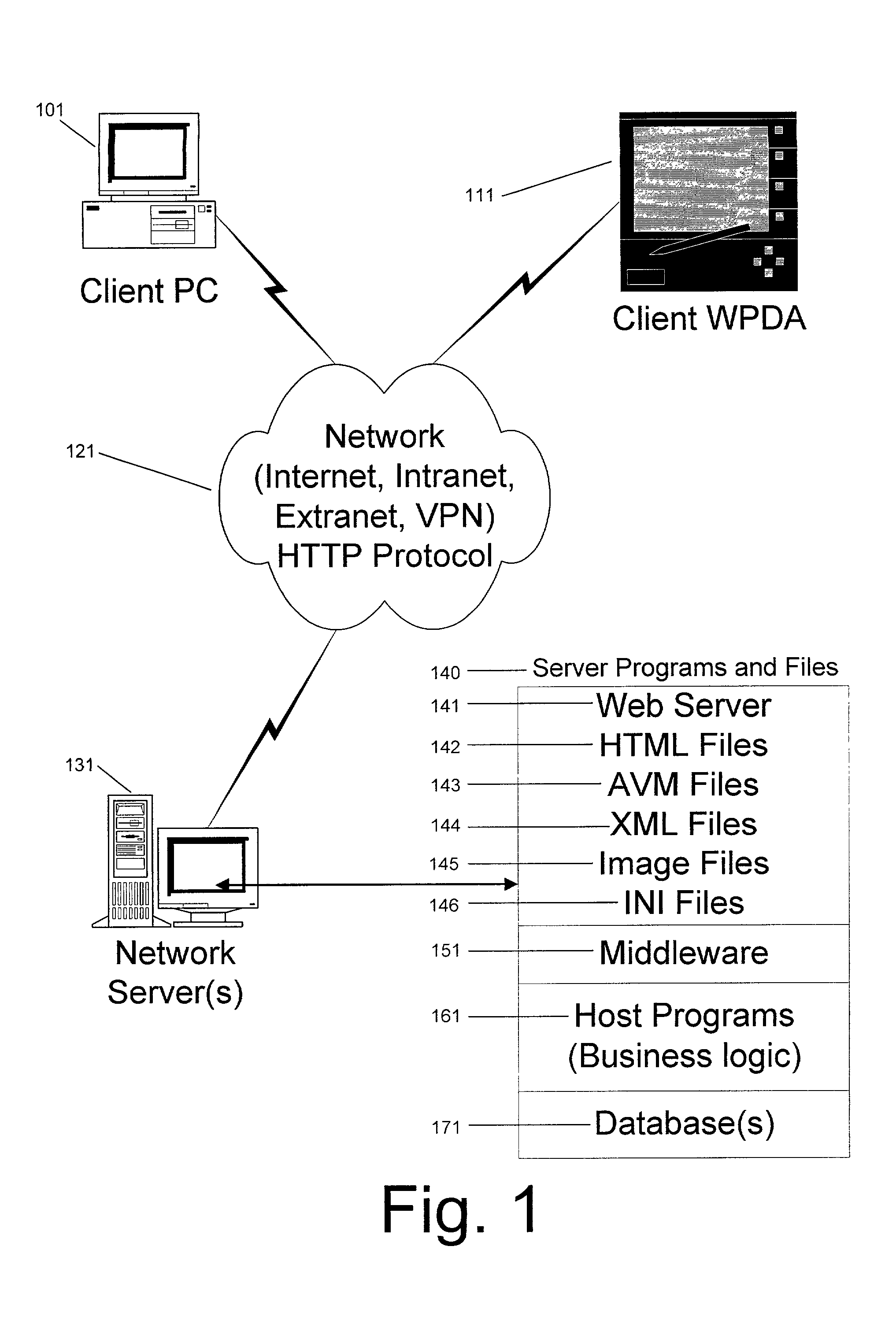
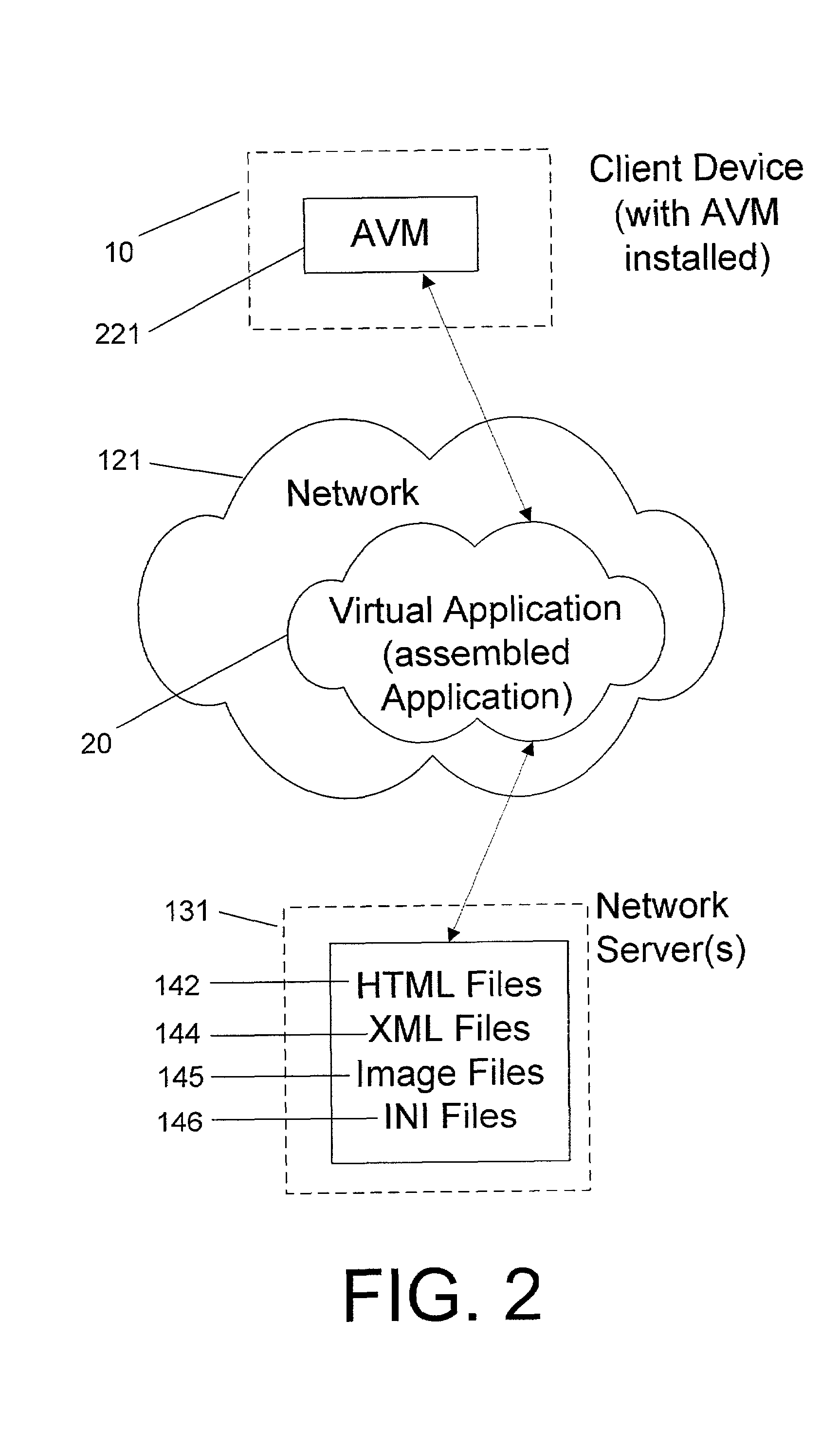
System and method for deploying and implementing software applications over a distributed network
ActiveUS20020129129A1Multiple digital computer combinationsProgram loading/initiatingApplication softwareProgram logic
A system for deploying applications over a distributed network to web-enabled devices uses a server, with stored text files containing application logic, and an application assembler. The application assembler downloads and installs on each web-enabled device. Then, the application assembler downloads one or more text files from the server, retrieves program logic from each of the downloaded text files, and assembles the retrieved program logic into a functioning application. In some instances, a plugin that is downloaded and installed on each web-enabled device is activated by web pages on the server to launch the application assembler.
Owner:DATACLOUD TECH LLC
Method and apparatus for managing location information in a network separate from the data to which the location information pertains
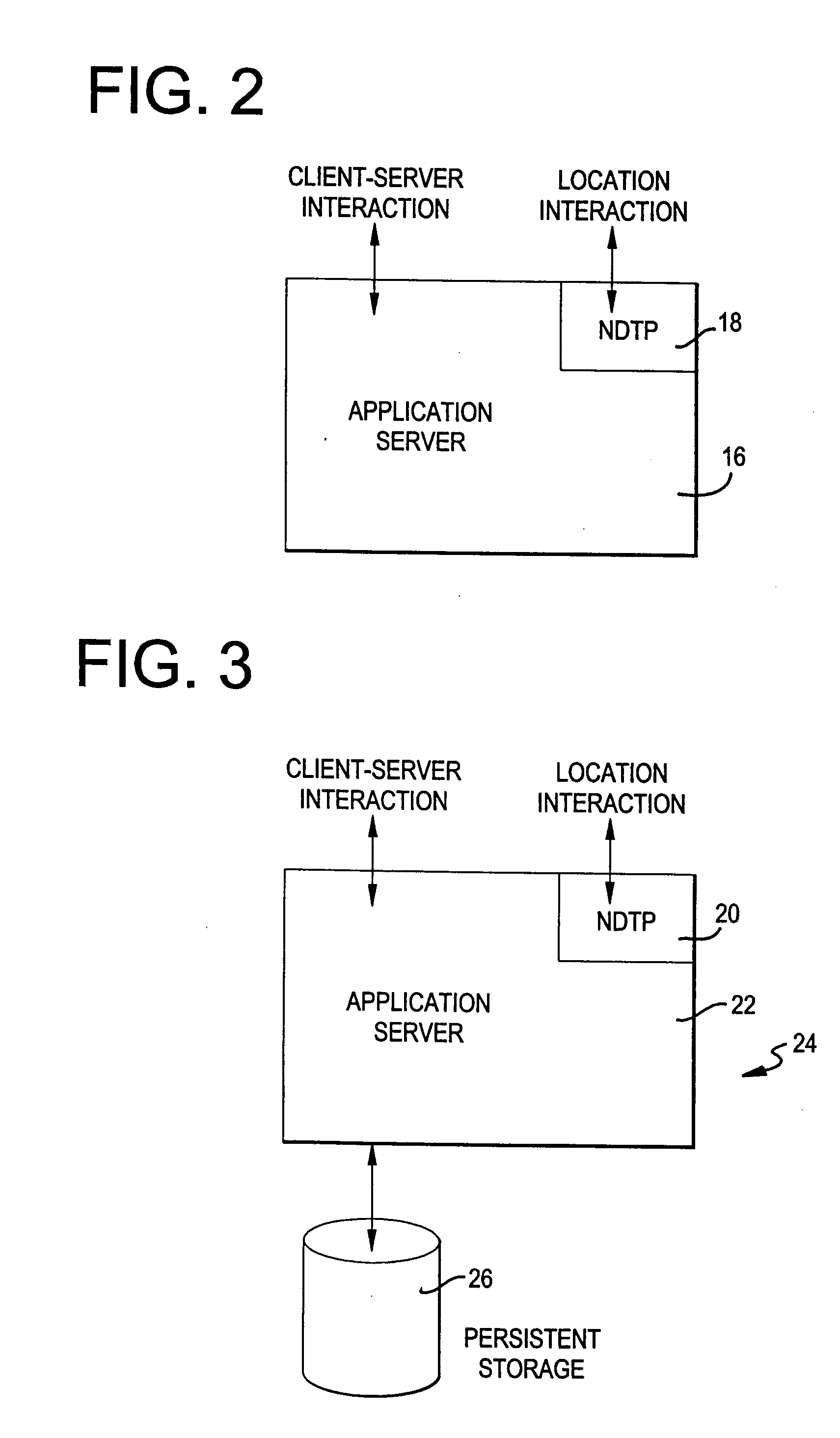
InactiveUS20080005275A1Multiple digital computer combinationsLocation information based serviceProgram logicComputer science
A system and method for storing and retrieving location information across a network is disclosed. The system and method utilize a transfer protocol configured to transport an identifier / location relationship to allow one or more locations to be associated with an identifier in the location store of a location server, where the identifier represents a unique entity and the location represents a location of data pertaining to the identifier. The location server contains programming logic operative to provide responses to location queries and capable of scaling a plurality of location servers according to system performance and logistical requirements.
Owner:ECONNECTIX
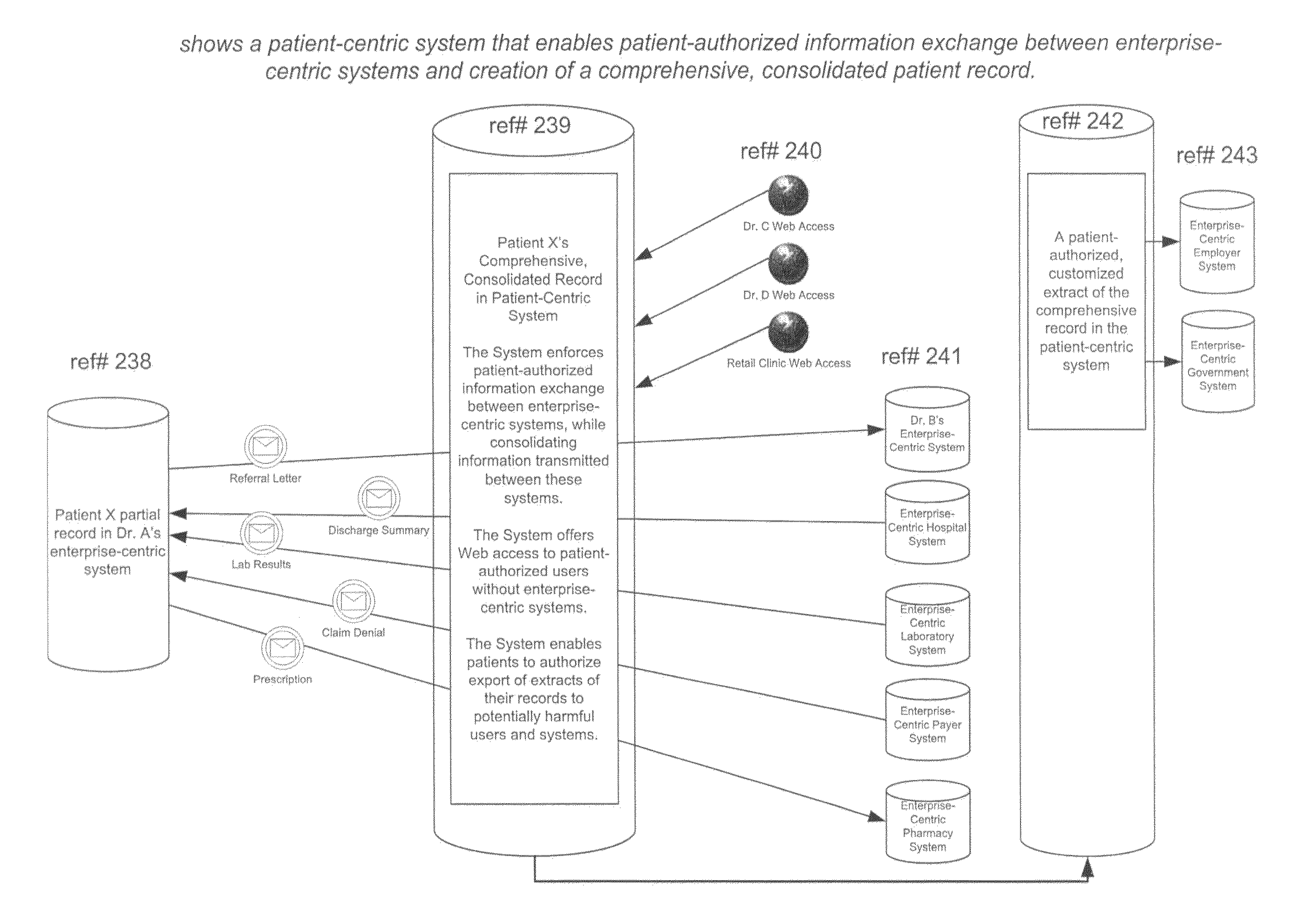
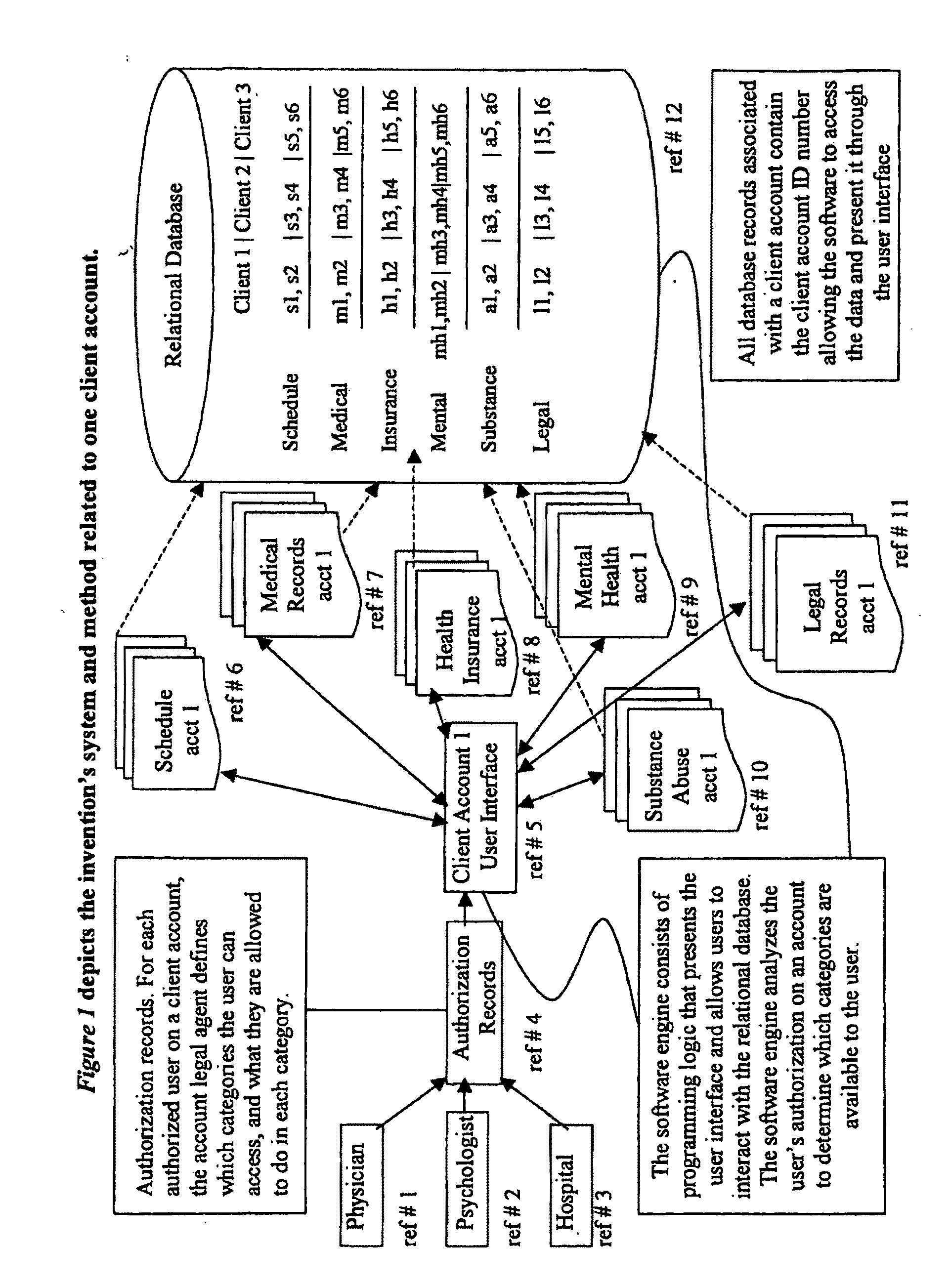
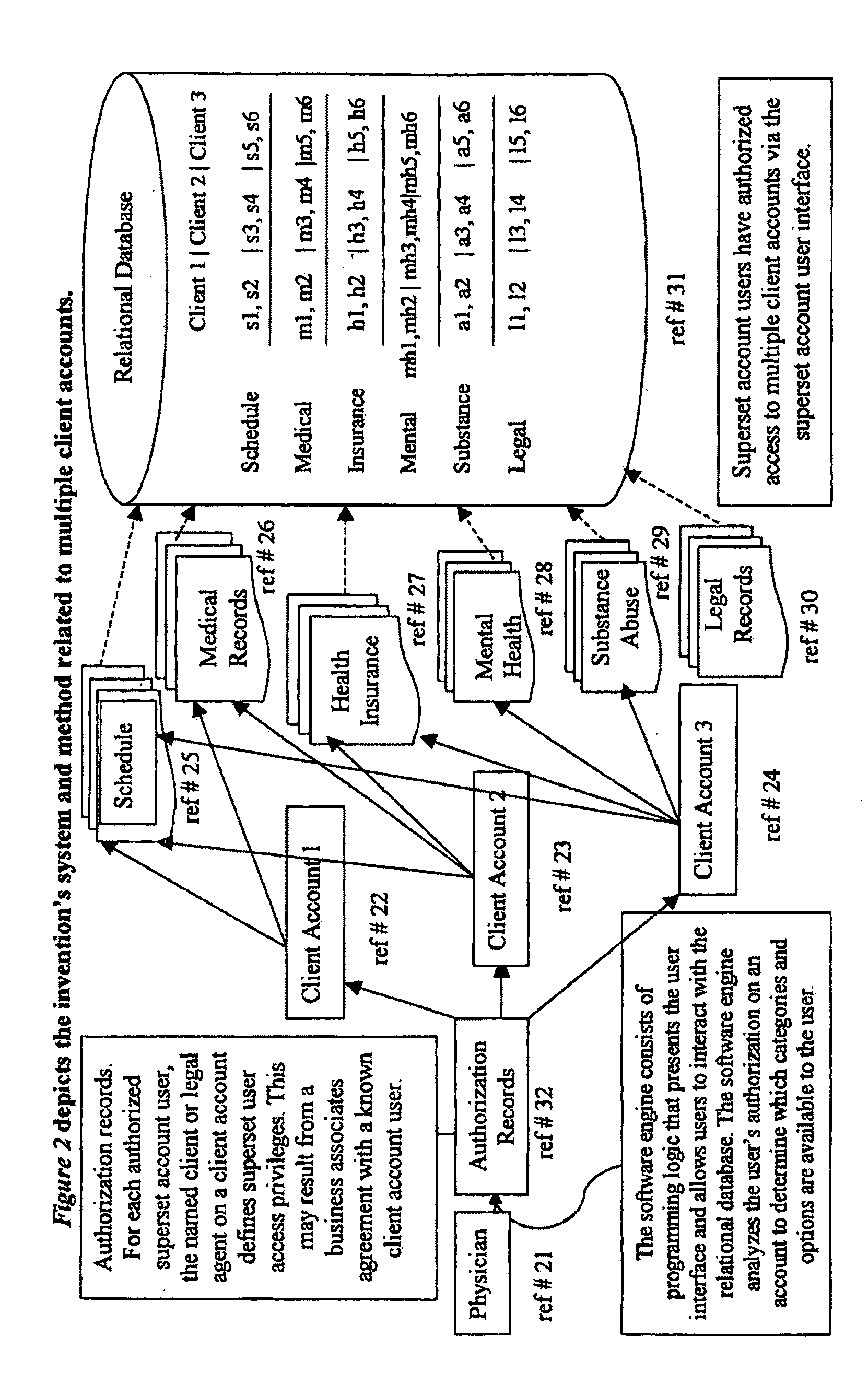
Client-centric e-health system and method with applications to long-term health and community care consumers, insurers, and regulators
InactiveUS20110082794A1Overcomes shortcomingFinanceUser identity/authority verificationRelational databaseWeb service
A patient-centric system and method for accessing personal health records of a patient, stored in relational databases and containing comprehensive records of multiple patients with each patient's records incorporating many different data categories and functions including manual or automated data exchange, consolidation, storage, routing and transmission, consistent with consent directives assigned to authorized users and computer systems of authorized users by the patient or designated representative thereof. The consent directives define privileges of access in each of said data categories and functions within the patients records. The patients records are stored in relational databases hosted by Web servers on a computer network through which the authorized users interact under the control of programming logic consistent with the consent directives assigned by the patient or designated representative thereof.
Owner:PROSOCIAL APPL
System and method for deploying and implementing software applications over a distributed network
ActiveUS7246351B2Multiple digital computer combinationsProgram loading/initiatingSystem usageProgram logic
Owner:DATACLOUD TECH LLC
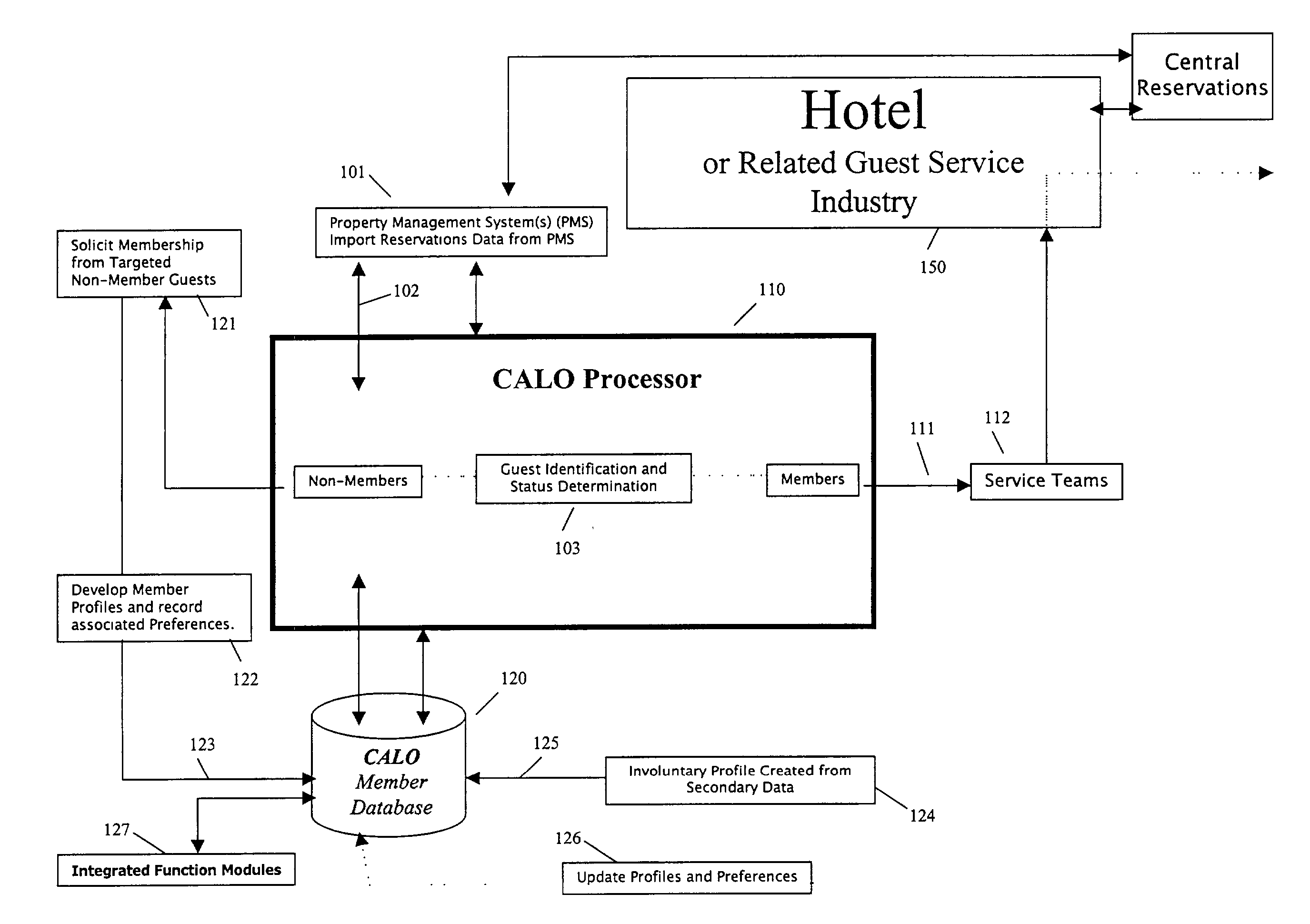
Guest relationship management system
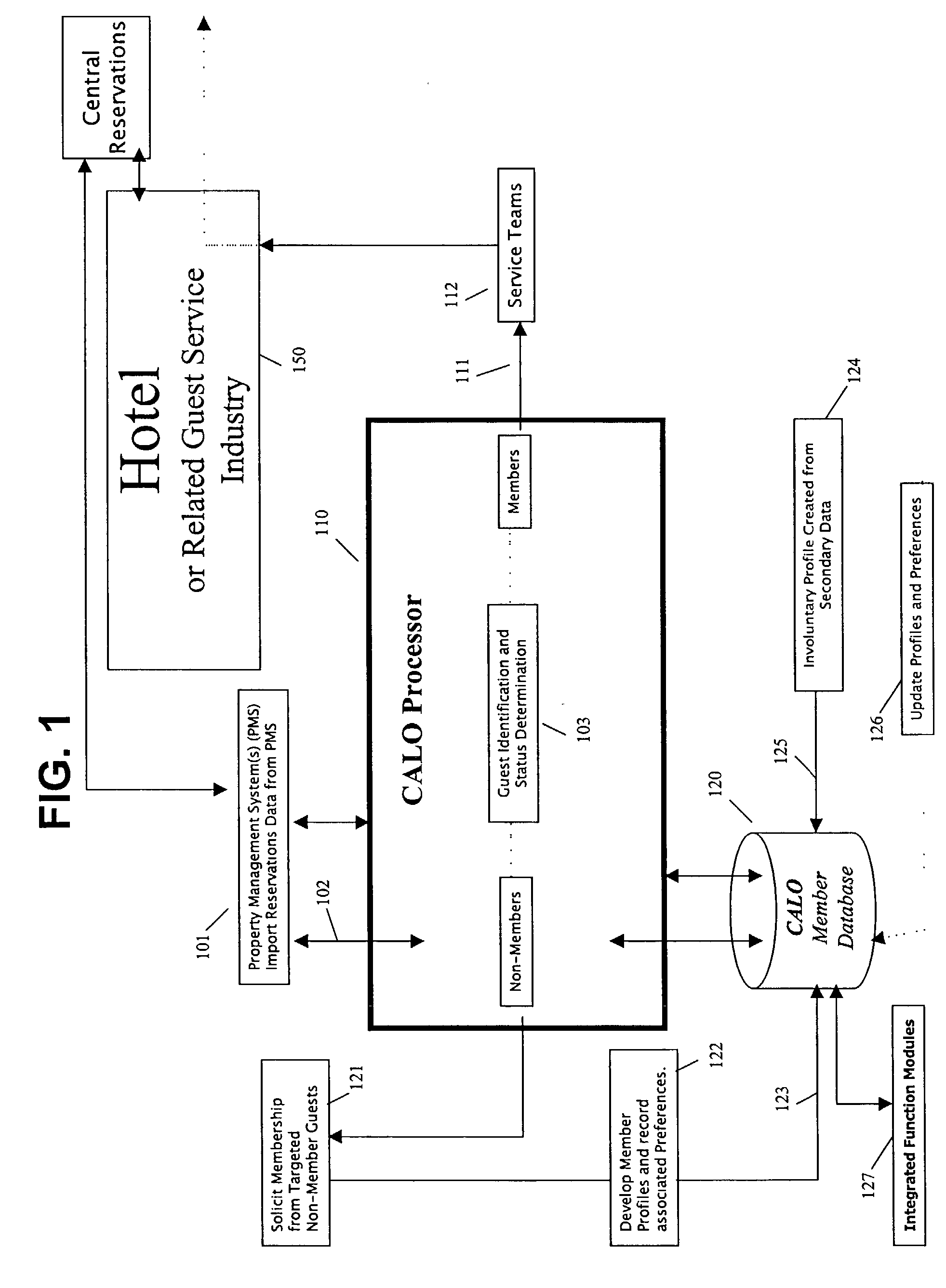
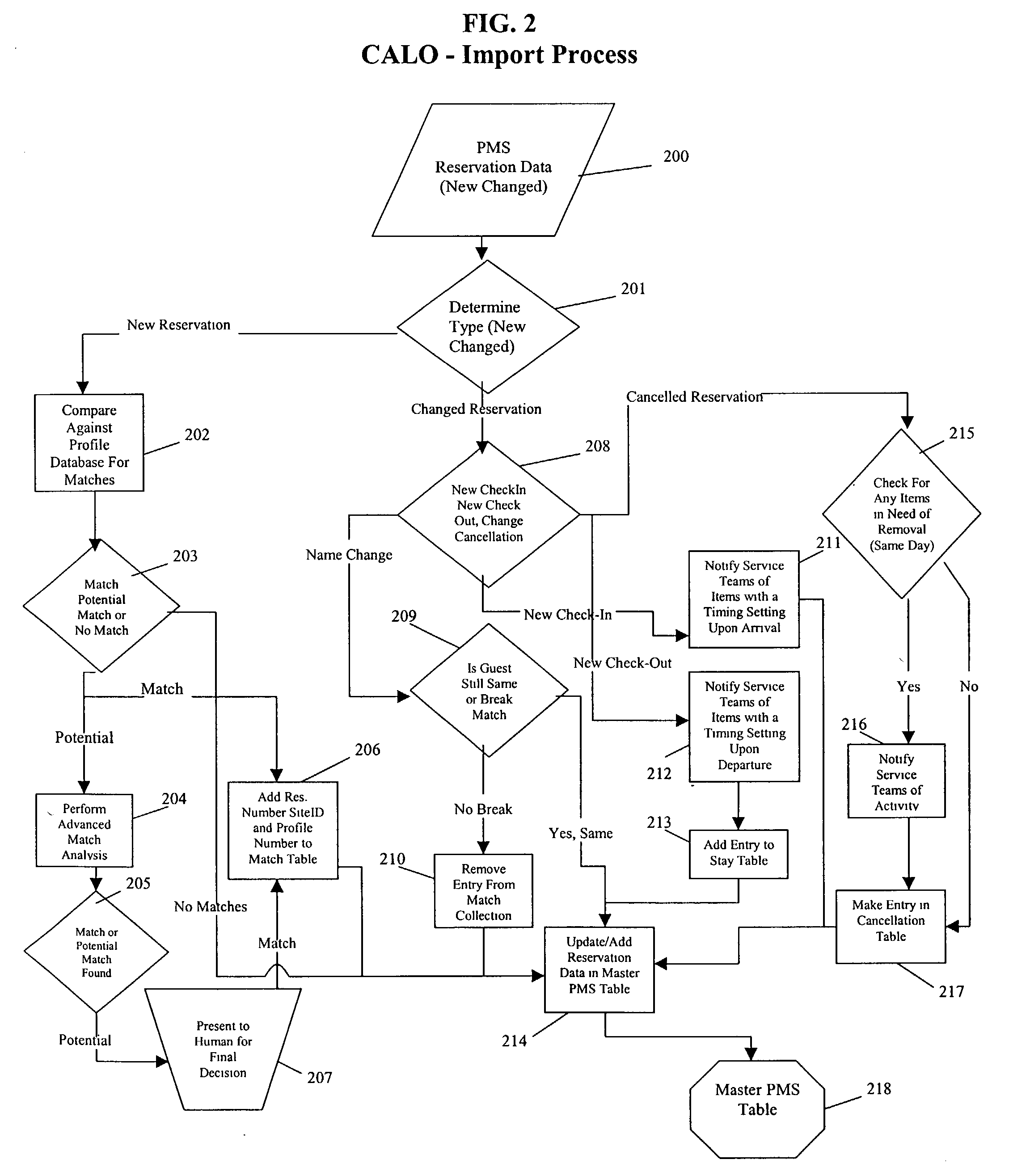
A method for implementing a guest profiling program that utilizes guest profiles, which. are developed and expanded by information gathered from various sources and managed in a central Guest Relationship Management System (GRMS). The GRMS is a web-architected internet application. The primary interface between the GRMS and hotel systems is a connection to each hotel's property management system (PMS). The GRMS extracts data from PMSs. PMS data is updated to the central GRMS for processing. The core application logic includes capabilities to identify reservations with attributes and to match guest reservations extracted from each hotel's PMS with profiled guests. Both automated and user-initiated data manipulation processes utilize the central GRMS profiles and PMS data to generate outputs designed to increase the quality and timeliness of services and to assist marketing efforts. The web-based architecture of GRMS enables consistent data sharing and processing capabilities with a plurality of hotels.
Owner:GENGARELLA JOHN S
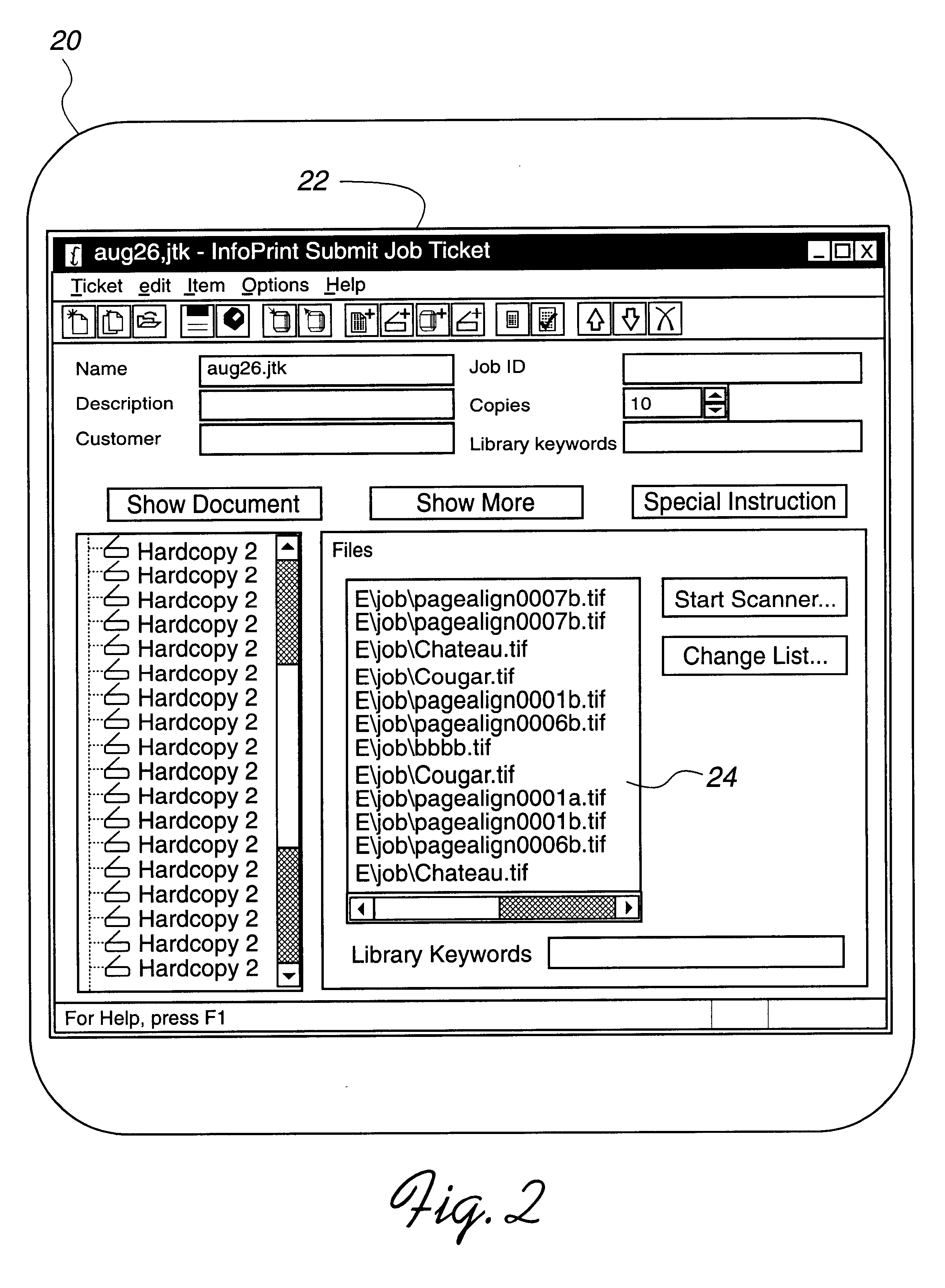
Progress indicator for multiple actions
InactiveUS6639687B1Digitally marking record carriersData processing applicationsGraphicsSoftware engineering
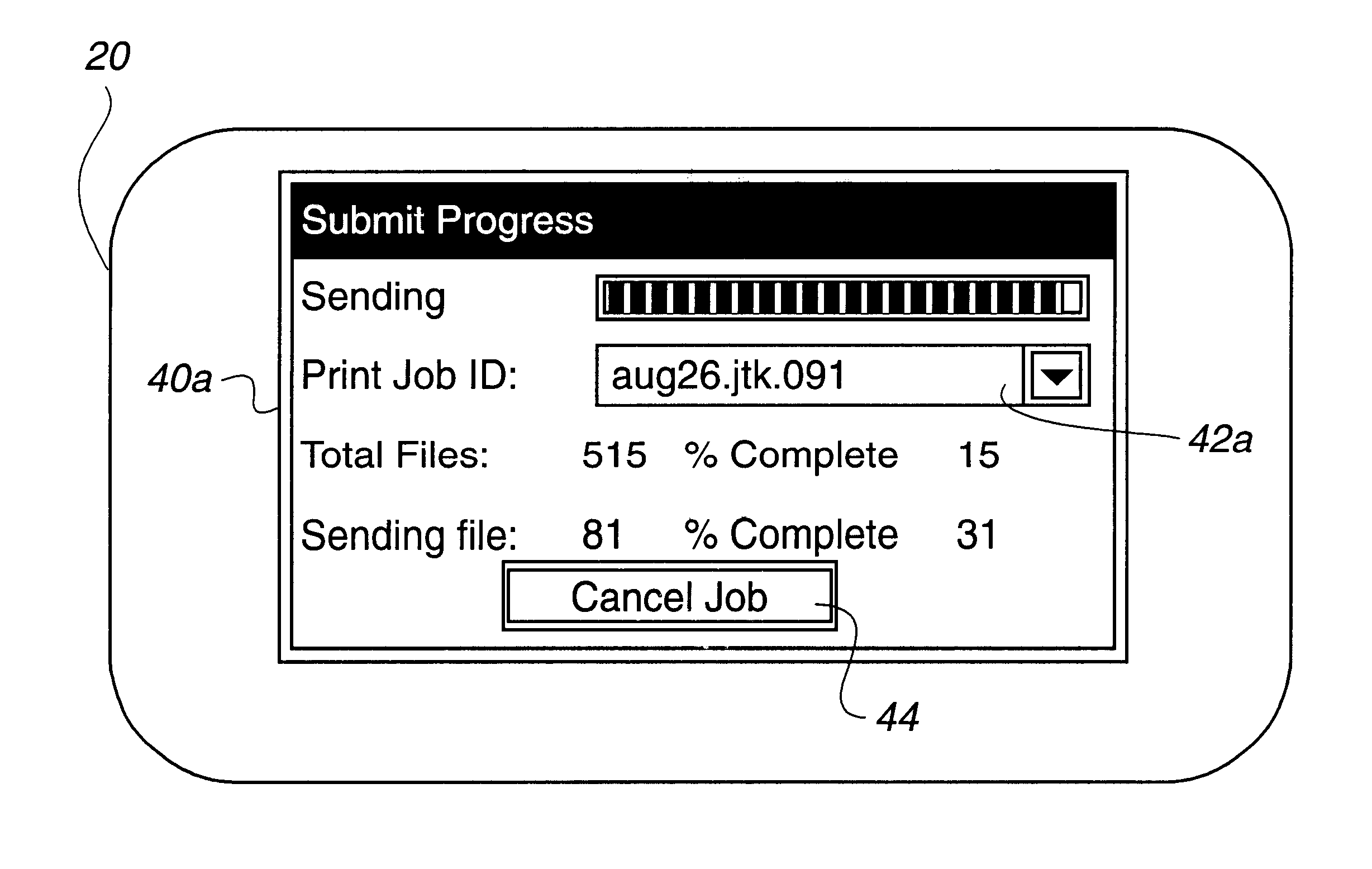
Disclosed is a progress indicator generated on a computer display. Program logic in a computer system monitors the execution of a plurality of tasks, such as the transmission of print jobs, and determines progress status information for each of the executing tasks. The program logic may be used to select one of the executing tasks and display on a computer display a graphical representation of the progress status information of the selected executing task.
Owner:IBM CORP
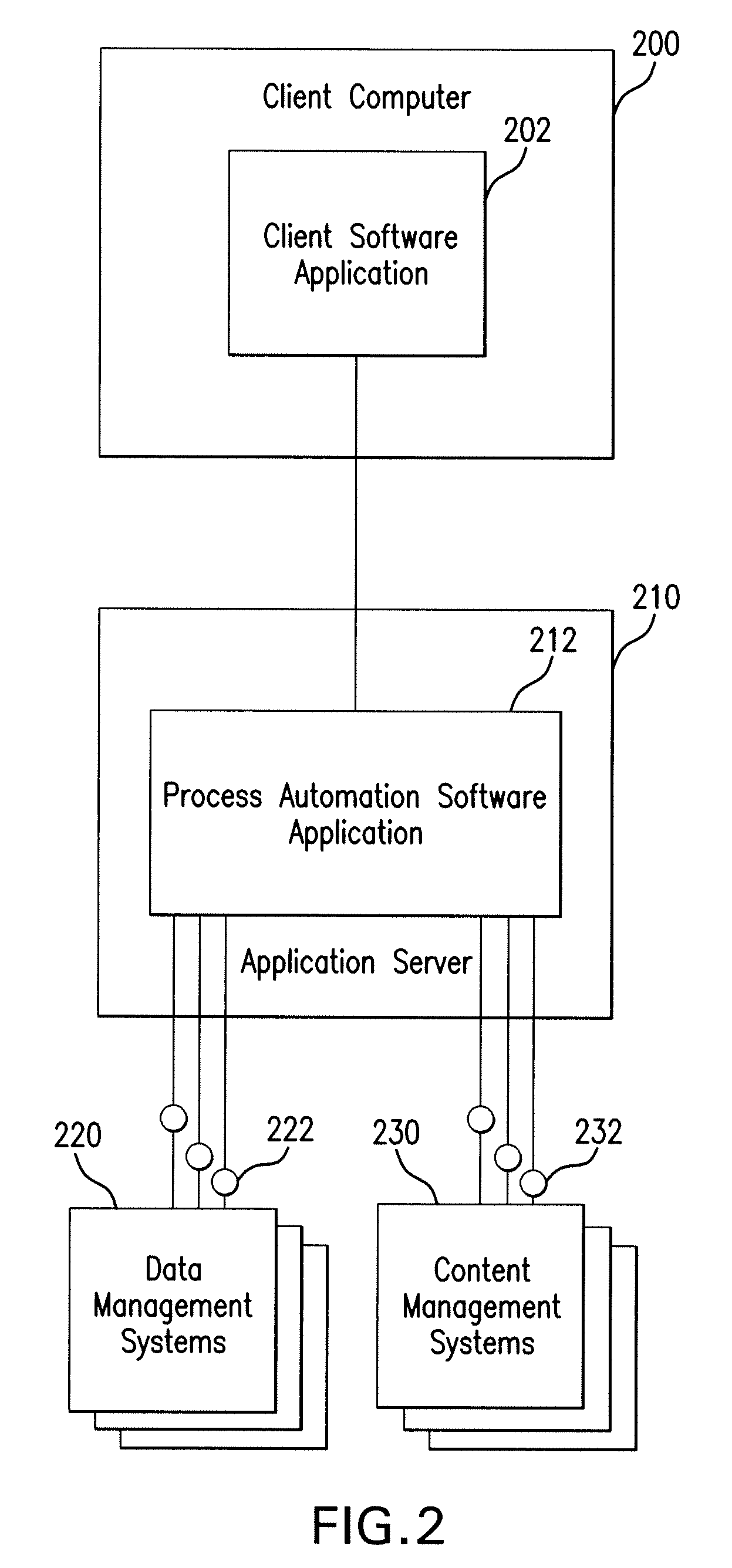
Method and system for managing enterprise content
InactiveUS20090249446A1Consistent flowDigital data processing detailsComputer security arrangementsUser inputData content
A method and system for providing a consistent flow documents and data content across different organizational units of a company or agency where the documents and data come from different enterprise systems and data stores but are related to linked processes that share models for organizing the content in the business context and in a format that enables a user to relate the content to the process step or steps they are performing. The system includes a network service that enables a configuration utility to automatically discover the objects and metadata and provides for a mapping of selected fields of the metadata to regions displayed in the user interface view with provision for filtering the data by mapping selected fields to a user input form. Thereby, a business analyst can create solutions without writing and maintaining complex program logic for each combination of presentation environment, enterprise system and data store.
Owner:OPEN TEXT CORPORATION
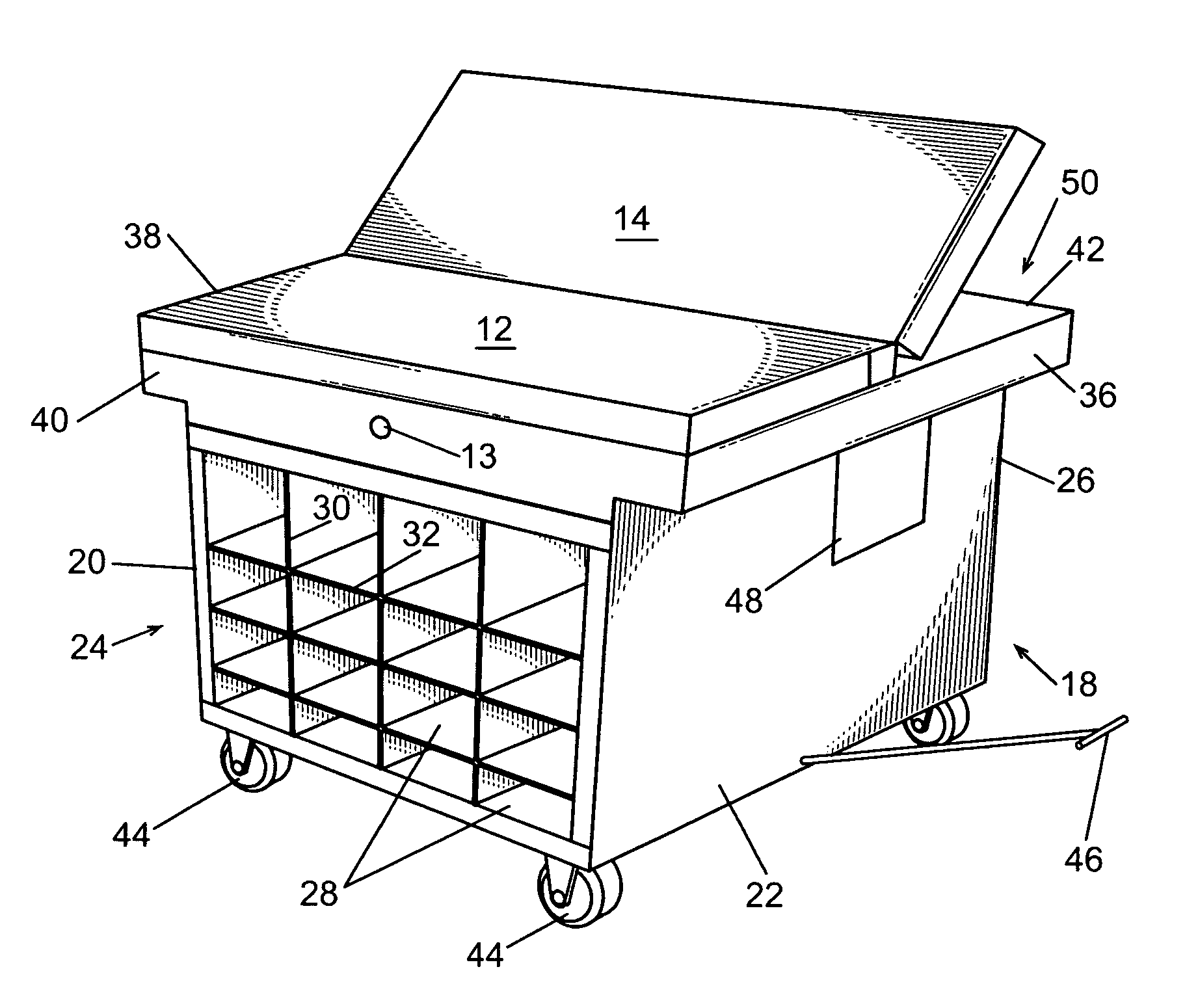
Audio/video programming and charging system and method
InactiveUS7210160B2Properly chargeOvercomes inadequacy and deficiencyBroadcast information characterisationPicture reproducers using cathode ray tubesDisplay deviceProgram logic
The preferred embodiment of the present invention provides a system and method for programming and / or charging one or more audio / video devices such that the audio / video devices will be programmed and charged to receive transmitted audio and video signals associated with an event, allowing a user to use the audio / video device to observe the sights and sounds of the event. A preferred embodiment of the present invention includes a cart with a docking port for each of a plurality of personal audio / video devices, a charger configured to charge the power source of each personal audio / video display device, and programming logic configured to program each of the personal audio / video devices.
Owner:IMMERSION ENTERTAINMENT L L C
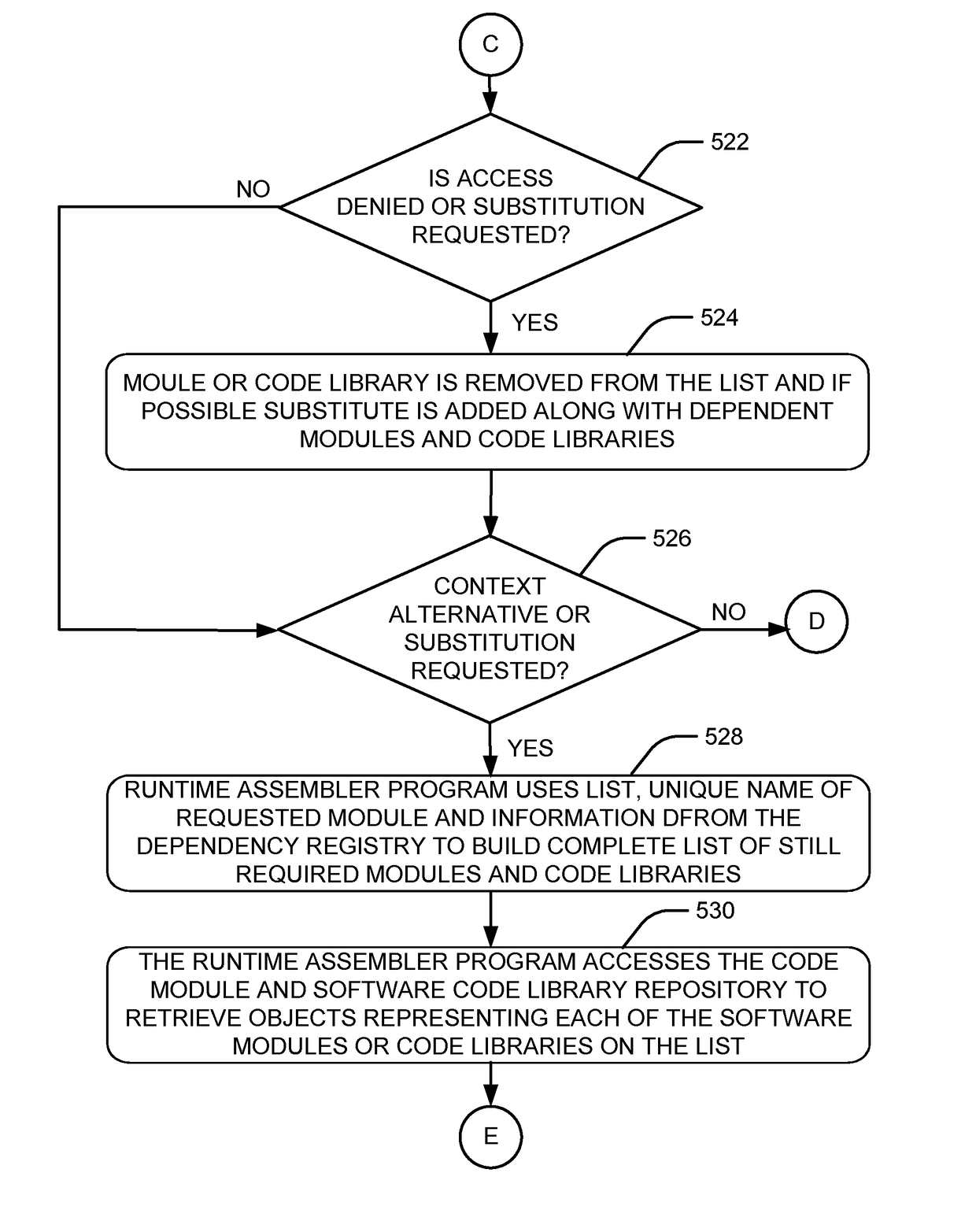
Incremental deployment of computer software program logic
ActiveUS20120278902A1Digital data processing detailsAnalogue secracy/subscription systemsSupplicantProgram logic
Systems and methods for requesting computer software program logic by a client computing device from a server are provided. The method at the server comprises receiving a request for the computer software program logic from the client device along with a first list comprising details about multiple modules running on the client device; determining a second list comprising details about multiple modules required to deploy the computer software program logic on the client device; checking whether the modules of the second list need to be substituted based on their availability or suitability; updating the second list; checking whether the client device has permission rights for accessing the modules of the updated second list; and sending an object comprising the modules of the updated second list to the client device, the updated second list comprising details about the modules required for deployment of logic on the client device.
Owner:CAMBRIDGE SEMANTICS
Object-oriented interface for portability to diverse operating systems or hardware platforms
InactiveUS6606742B1Program control using stored programsMultiprogramming arrangementsOperational systemComputerized system
An object-oriented interface is disclosed for conferring portability for object-oriented programming to diverse operating systems on diverse hardware platforms in a computer system. The object-oriented interface is executable on a plurality of different computer platforms and includes classes of object-oriented methods. The interface is responsive to the object-oriented programming which instantiates its objects from its own classes and invokes the object oriented methods of the interface. Operating system specific, procedural program logic is compiled for use on a given computer platform that includes given computer hardware and a given procedural operating system which is executable on the hardware. A determination is made if the object-oriented methods of the interface to be invoked during runtime execution are present in the program memory of the computer hardware. A runtime loader selectively loads into the program memory any required object-oriented methods of the interface during runtime before their invocation by the object-oriented programming. The object-oriented interface thereby provides native system services to the object-oriented programming from the given computer hardware and procedural operating system.
Owner:APPLE INC
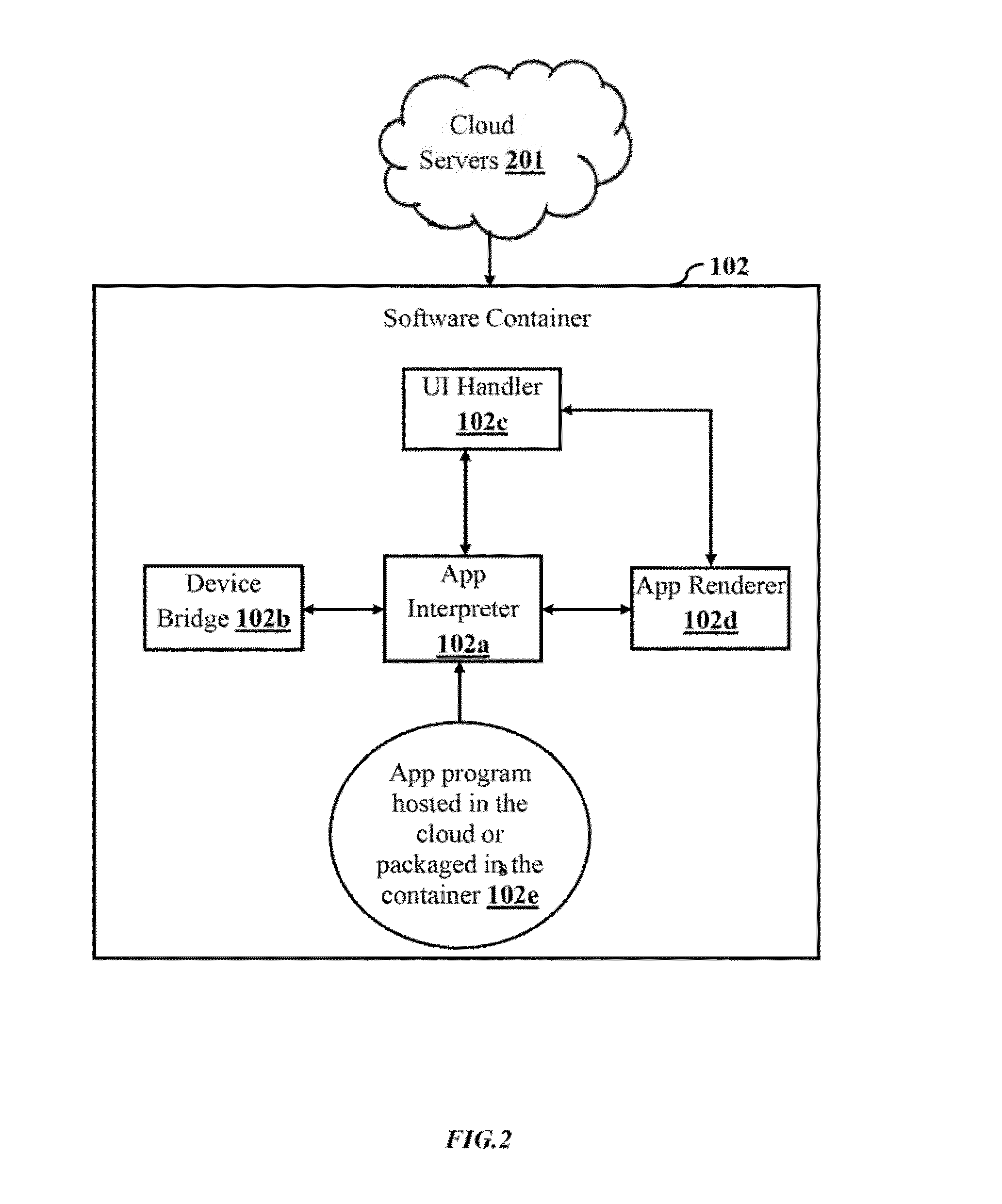
Method and system for hosting and running user configured dynamic applications through a software container on a computing device
The embodiments herein provide a method and system for hosting and running user configured dynamic applications through a software container on a computing device. The system comprises a first program component for embedding a program interpreter along with a program logic for running a dynamic application; a second program component for processing the user interactions with the dynamic applications; a third program component for interacting with several computing device capabilities to provide an interface between the dynamic applications and several computing device capabilities; and a rendering engine program for rendering the dynamic applications. The first program component is an application interpreter while the second program component is a user interactions handler and the third program component is a device-bridge. The software container automatically pools and displays a specific data from the added dynamic applications to the user based on the user request.
Owner:CHHAPARIA MAHESH KUMAR
Multimedia time warping system
InactiveUS20050132418A1Easy to operateLow costTelevision system detailsRecord information storageComputer hardwareMultiple forms
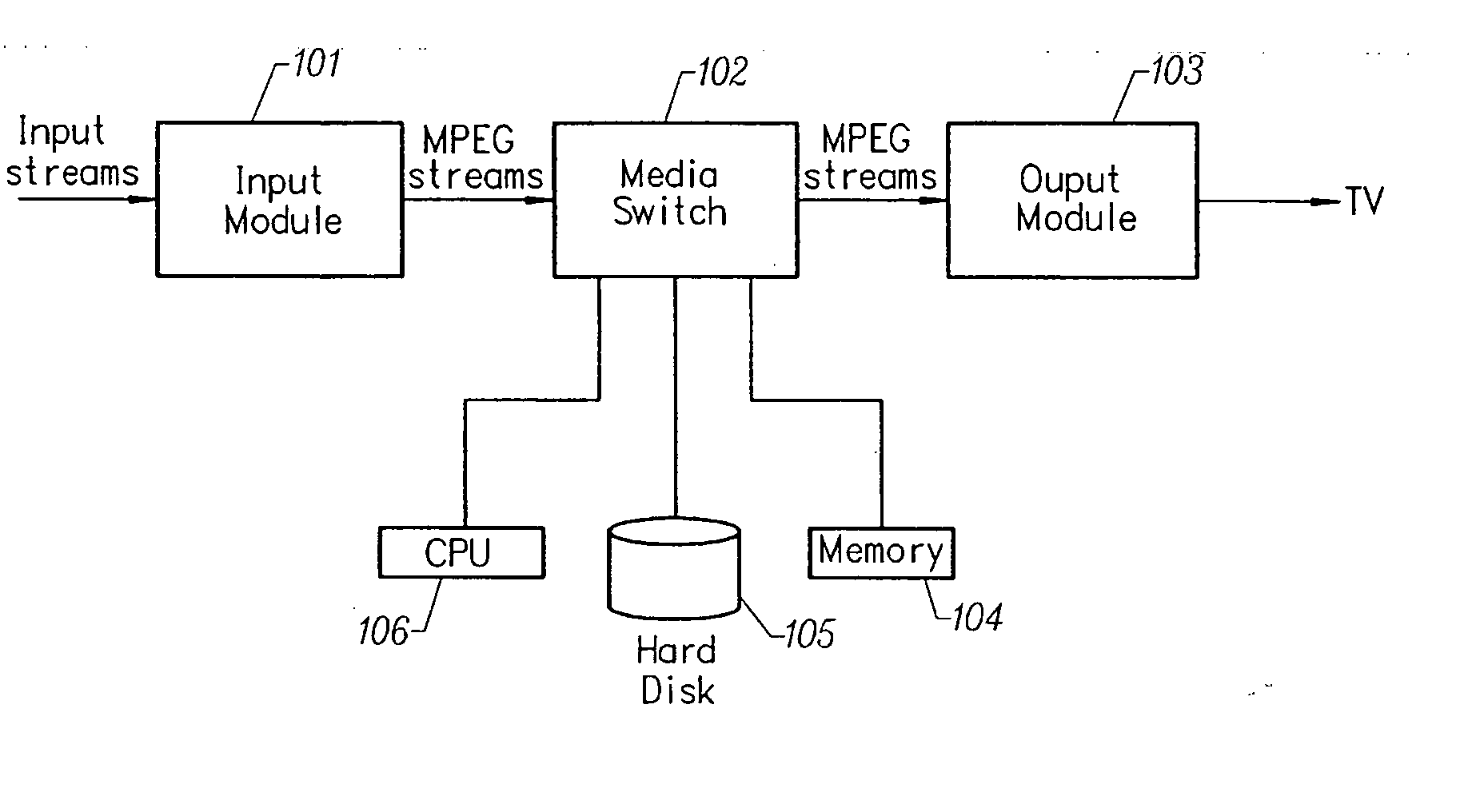
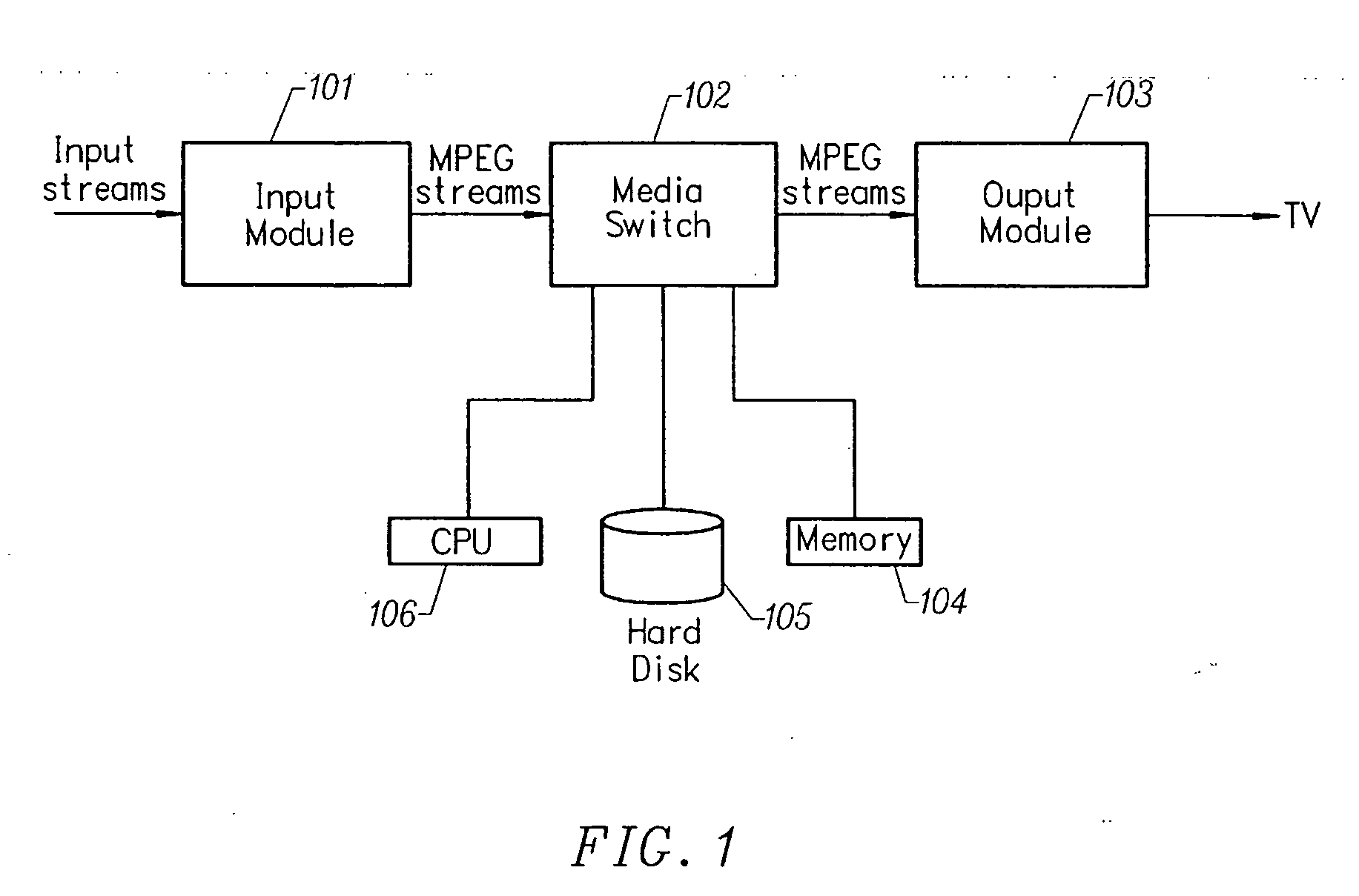
A multimedia time warping system allows the user to store selected television broadcast programs while the user is simultaneously watching or reviewing another program. The system accepts television (TV) input streams in a multitude of forms that are converted to an encoded formatted stream for internal transfer and manipulation and are parsed. Events are recorded that indicate the type of component that has been found, where it is located, and when it occurred. The program logic is notified that an event has occurred and the data is extracted from the buffers. The encoded streams are stored on a storage device and a decoder converts the encoded stream into TV output signals. User control commands affect the flow of the encoded stream.
Owner:TIVO SOLUTIONS INC
System and method for securely connecting network devices
ActiveUS20160182459A1Accounting/billing servicesUser identity/authority verificationInternet of ThingsProgram logic
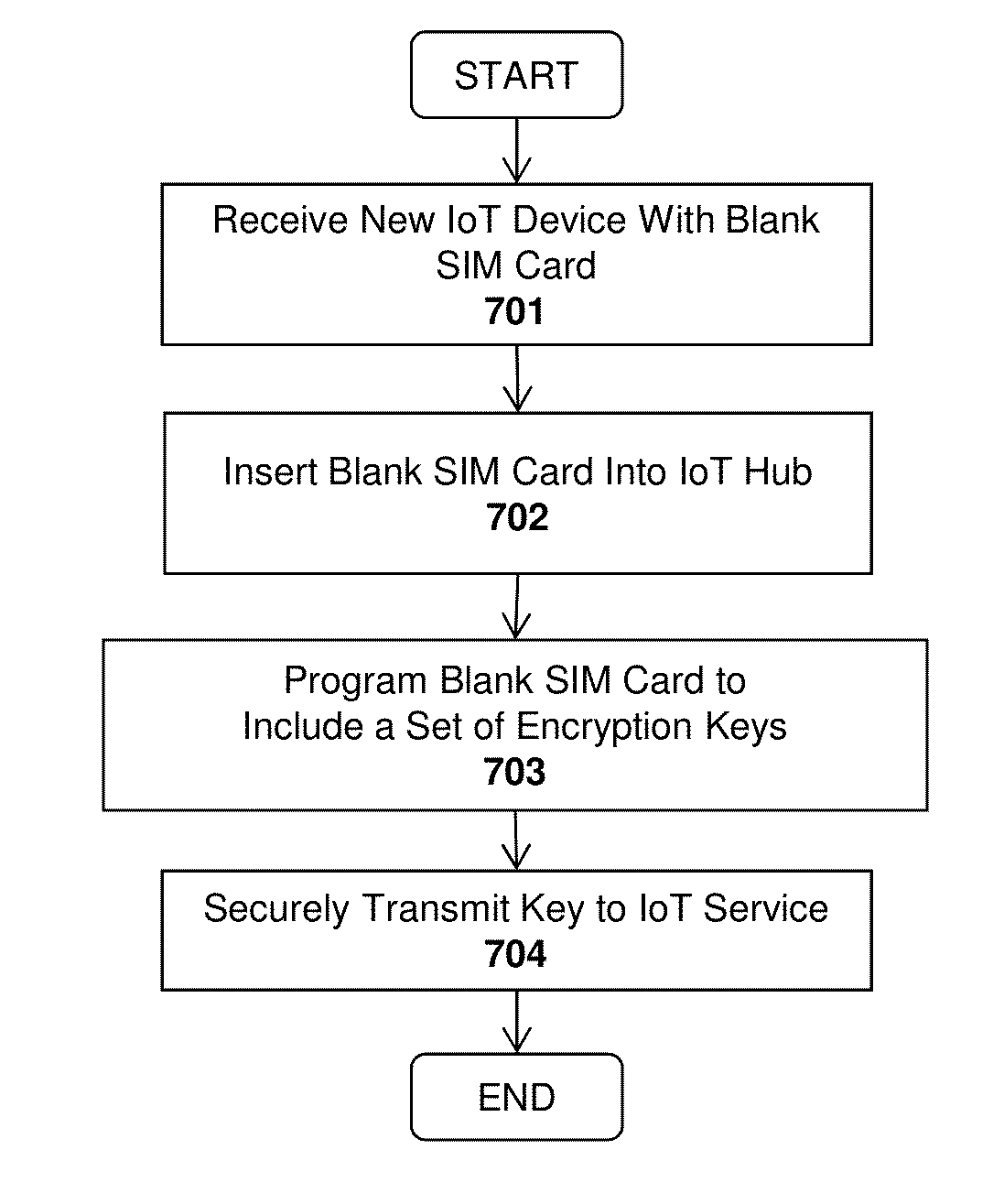
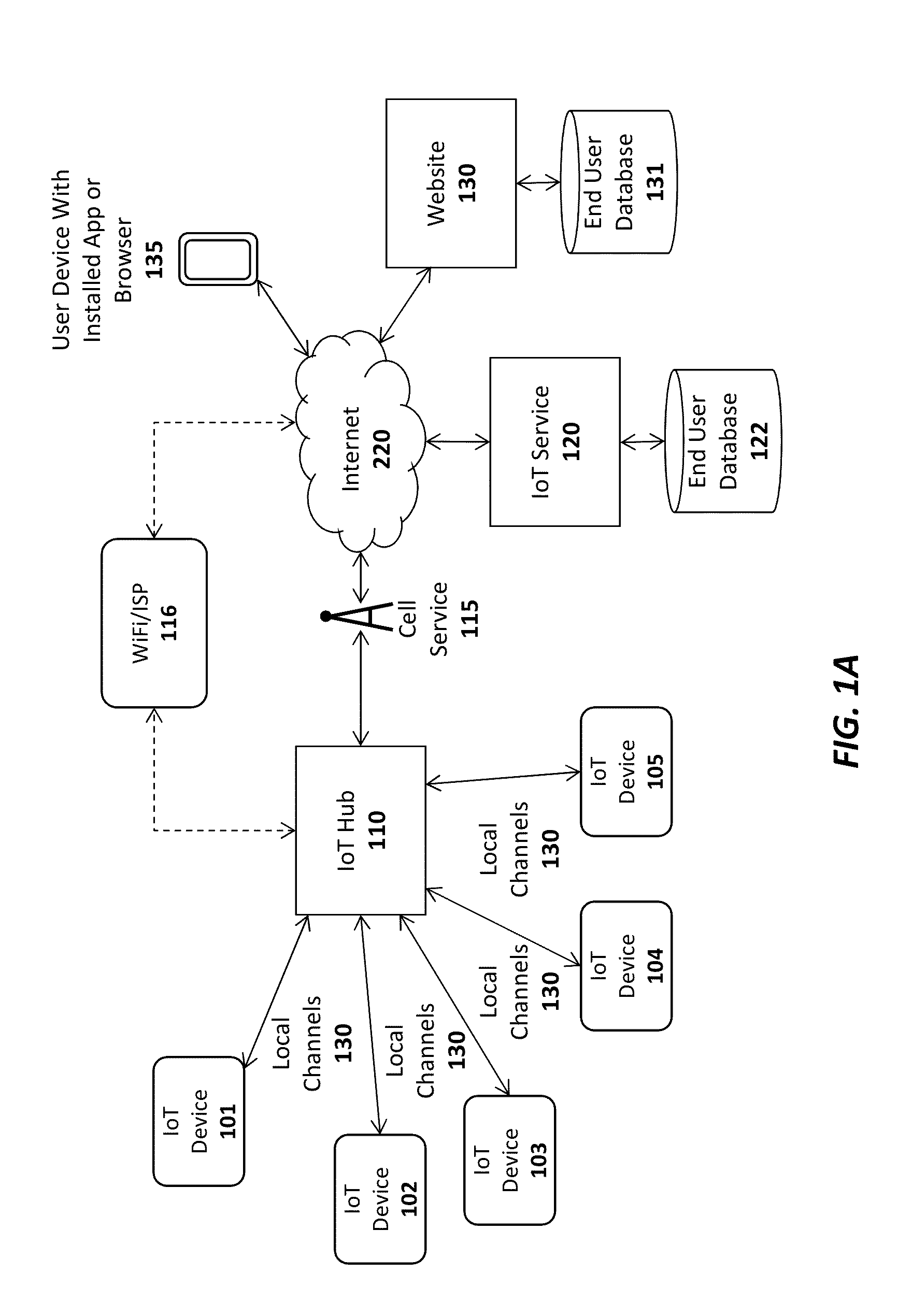
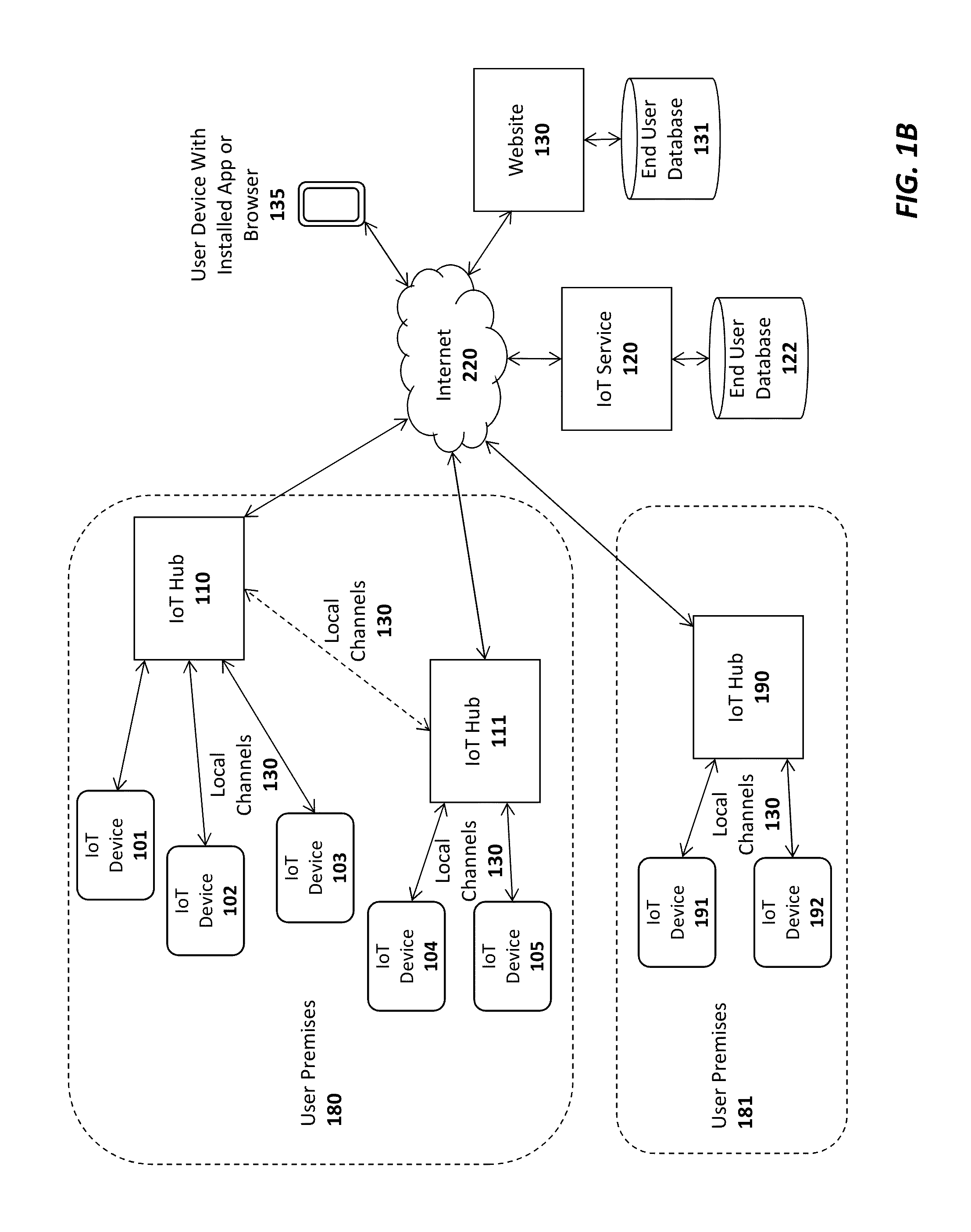
A platform, apparatus and method for Internet of Things Implementations. For example, one embodiment of a system comprises: an Internet of Things (IoT) hub comprising a network interface to couple the IoT hub to an IoT service over a wide area network (WAN), and programming logic to program an identification device with one or more encryption keys usable to establish encrypted communication with an IoT device; and at least one IoT device interfacing with the identification device following programming of the identification device by the IoT hub; wherein once the identification device is programmed and interfaced with the IoT device, the IoT device uses the one or more keys to establish a secure communication channel with the IoT hub and / or the IoT service.
Owner:AFERO
Fatigue driving detection method and anti-fatigue driving auxiliary device
InactiveCN102717765AReal-time monitoring of driving statusNot bound by driving habitsSignalling/lighting devicesTractorsThrottle controlSteering wheel
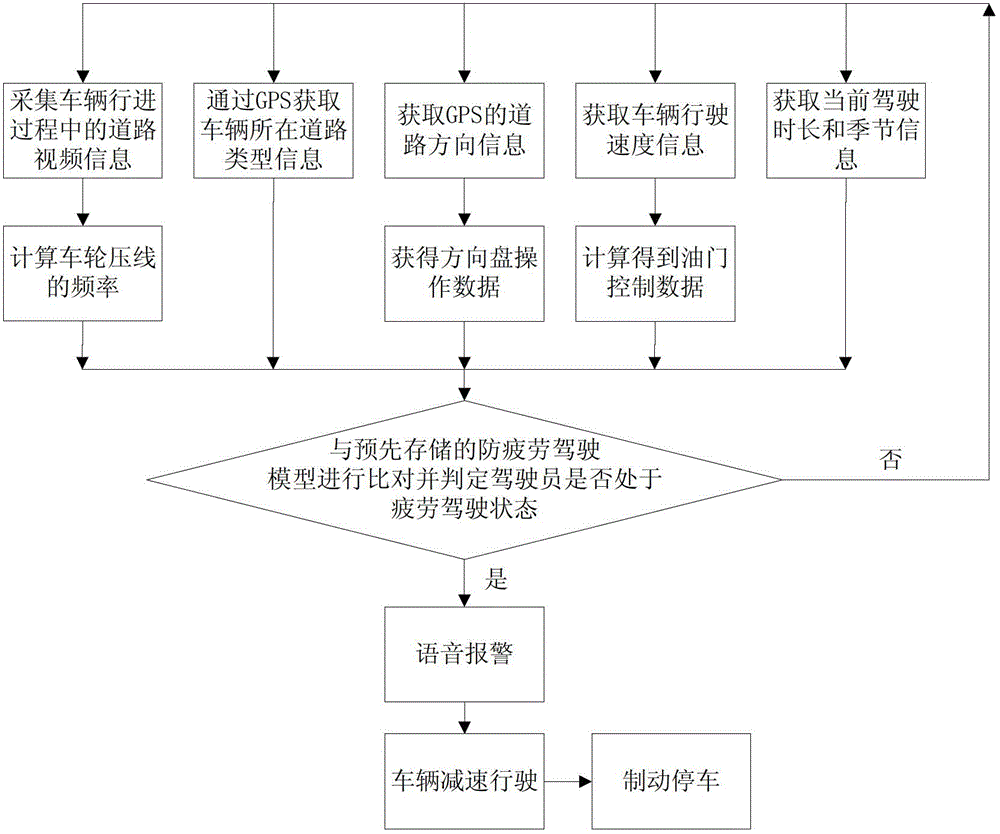
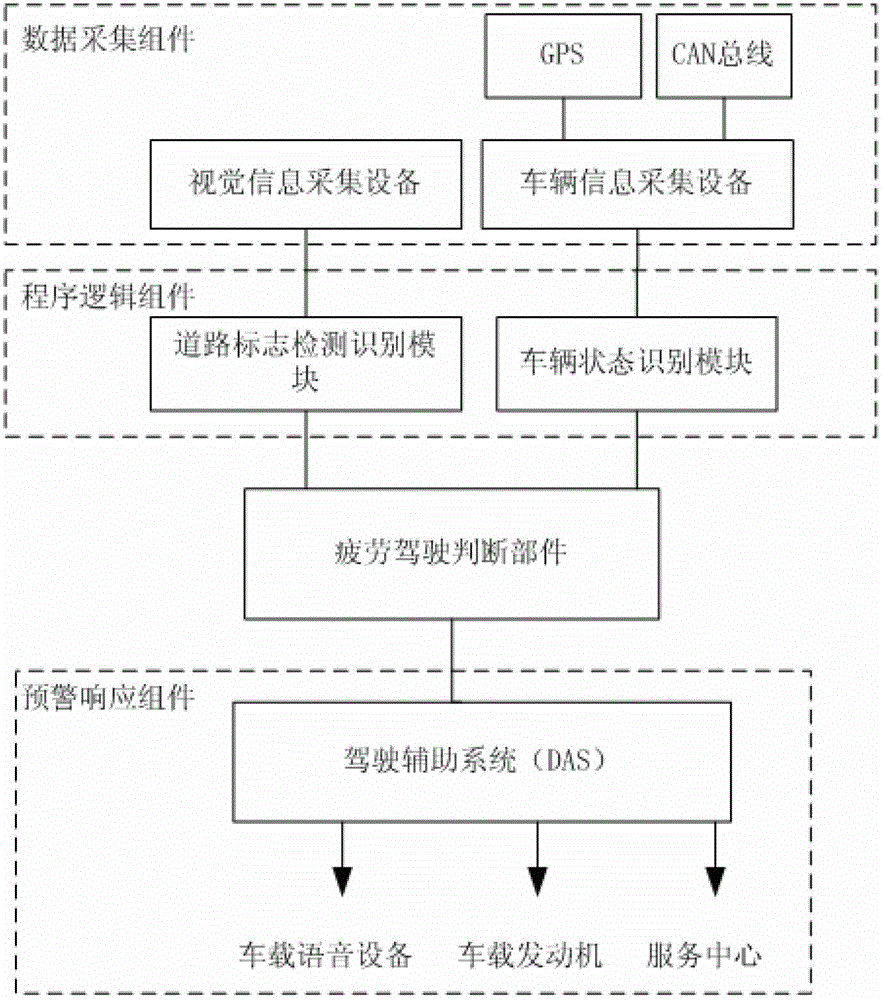
The invention provides a fatigue driving detection method and an anti-fatigue driving auxiliary device. The method comprises the following steps: collecting road video information during the driving of a vehicle to calculate line pressing frequency information of wheels; and comparing the line pressing frequency information, road type information, steering wheel operating data, throttle control data, current driving duration and season information with a pre-stored anti-fatigue driving model to judge whether a driver is in a fatigue driving state or not. The device comprises a data collecting component for collecting road video information and vehicle state, a program logic component for processing data collected by the data collecting component, and a fatigue driving judging component for comparing and judging; and a pre-warning respond component is used for voice alarming and deceleration and brake stop operation when the driver is in the fatigue driving state. The invention has the advantages of instantaneity, accuracy and wide adaptability.
Owner:湖南小泰赛格导航科技股份有限公司
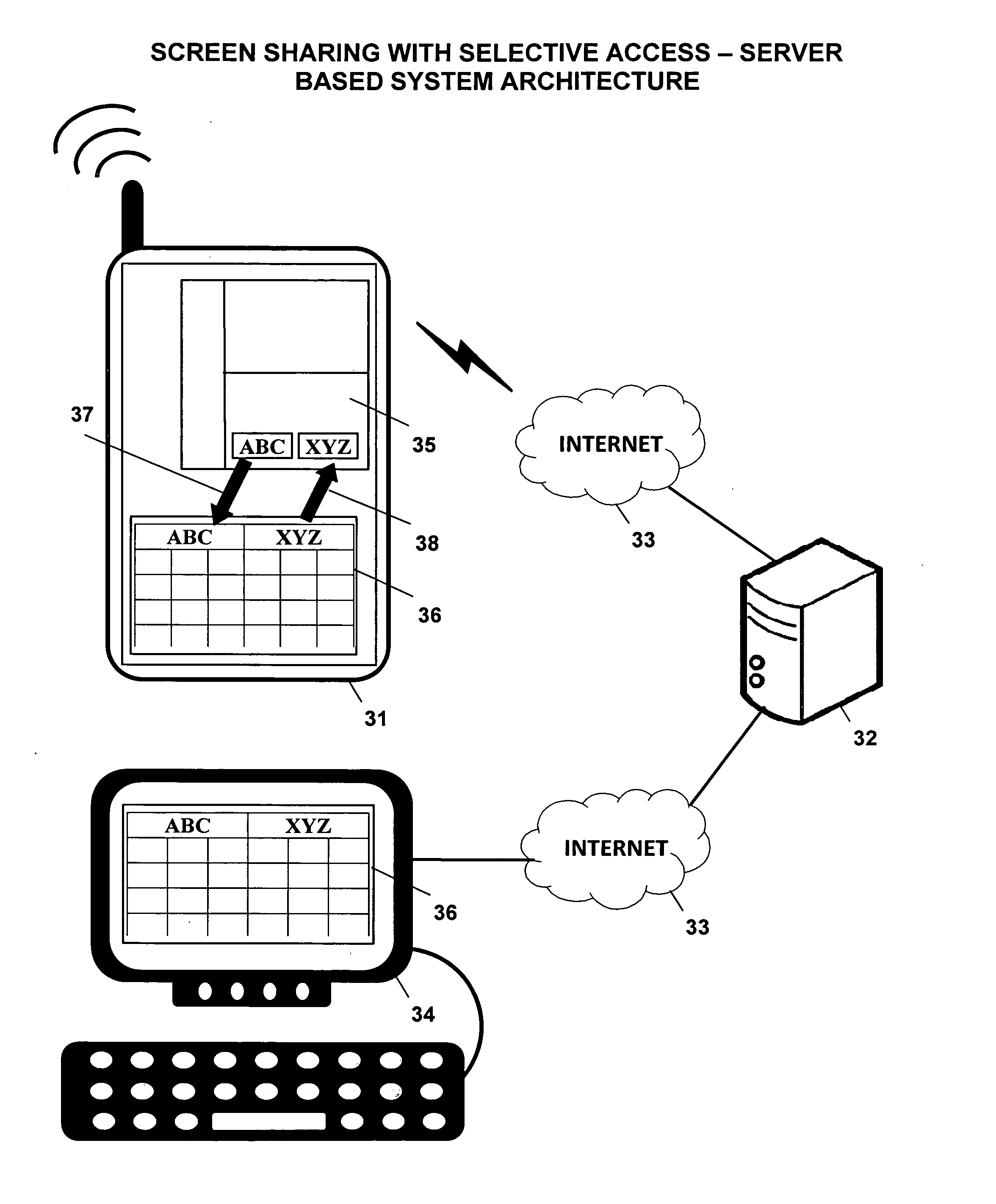
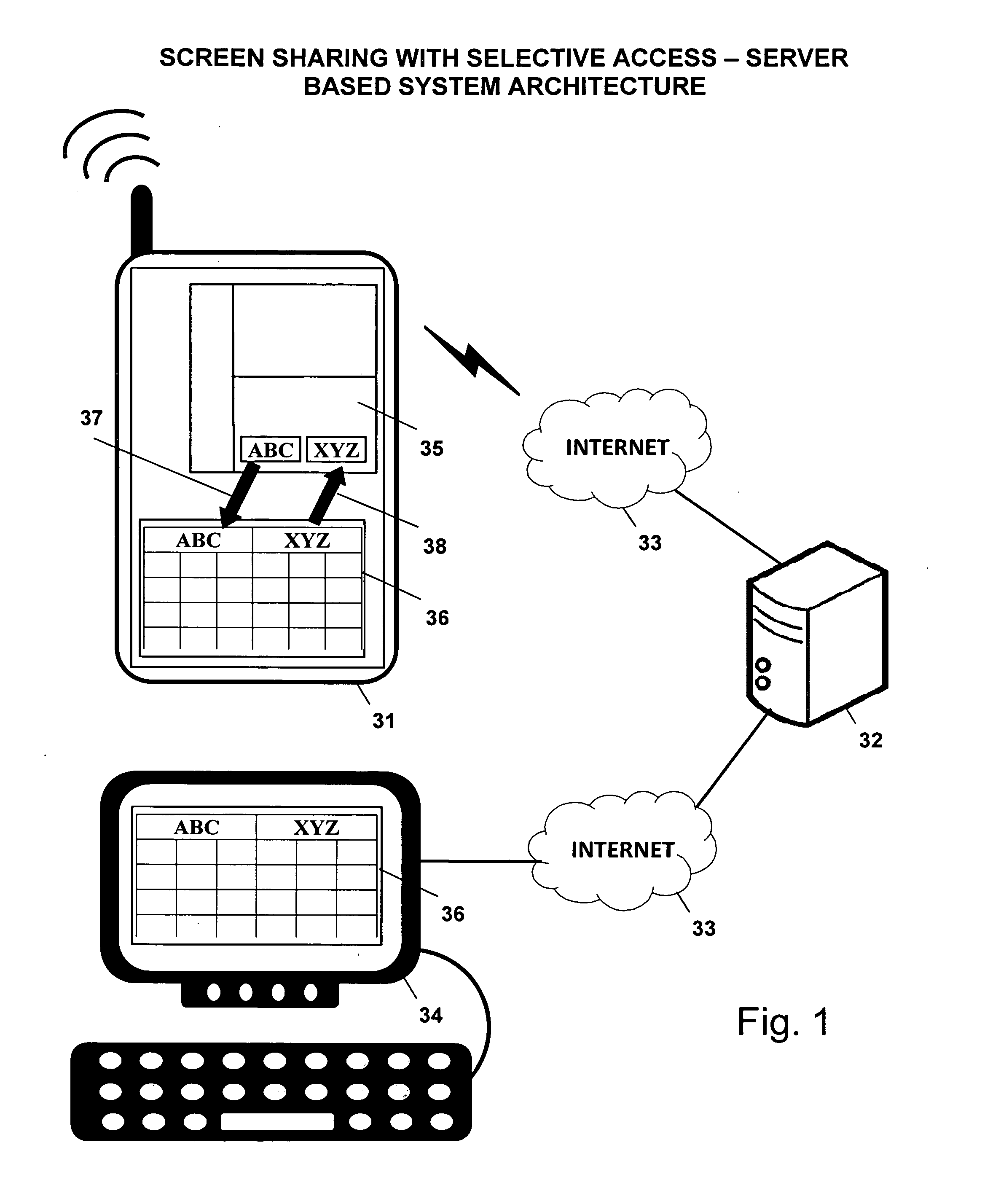
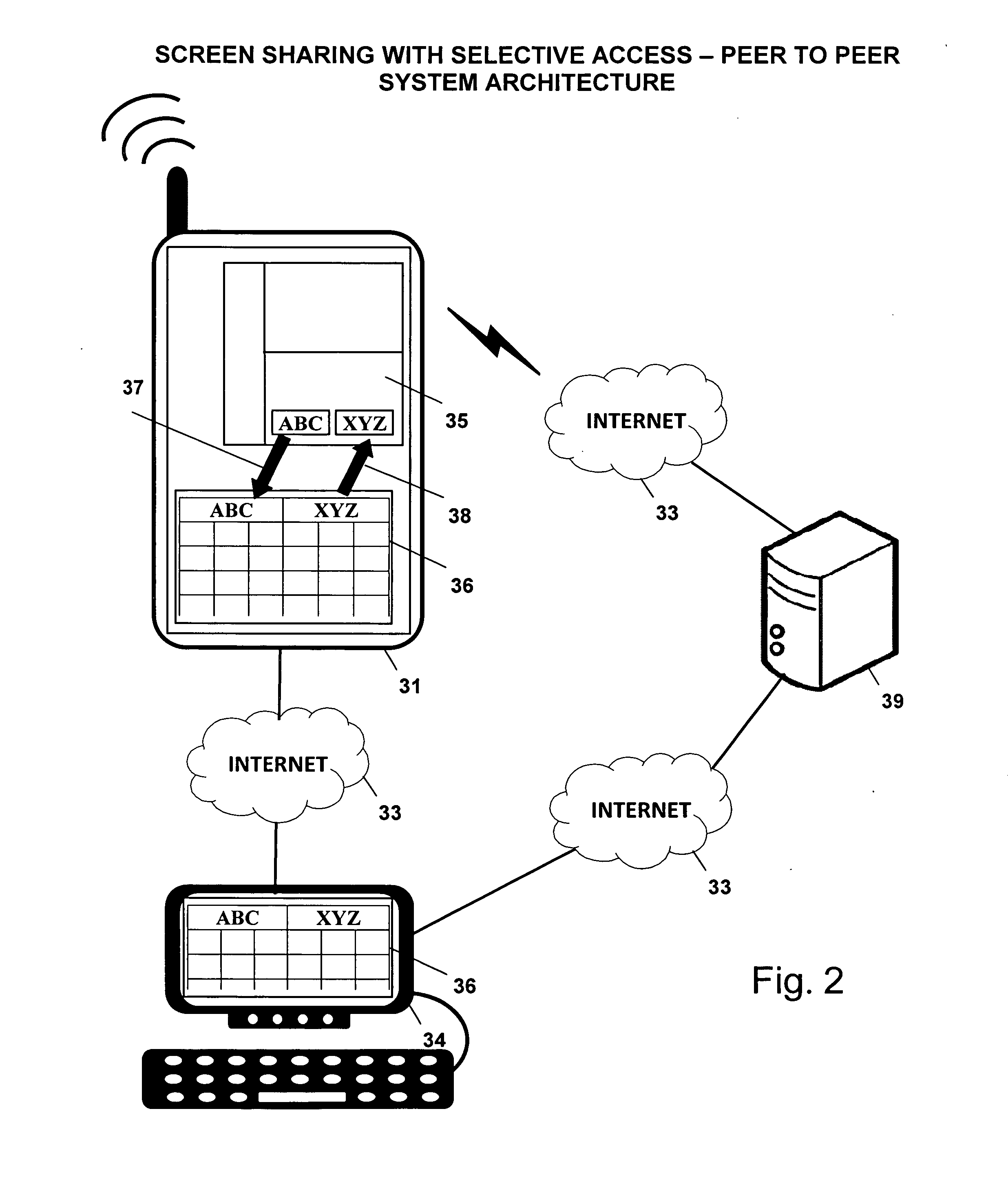
Screen sharing method with selective access to both data and logic of a shared application using a helper application
InactiveUS20110004888A1Guaranteed normal executionSelectively accessedInterprogram communicationExecution for user interfacesGraphicsGraphical user interface
A screen sharing system that enables selective access to application data and application logic is described. This screen sharing system is implemented by coupling a helper application (36) to an application that provides content referred to as content application (35).The helper application is an application that has the ability to programmatically access the content application (35) using window system graphical user interface application programming interface. Helper application (36) is used to get and set content application data and interact with the content application using window system input events that simulate user input.This method enables selective access to both application data and application logic that is necessary for use in a screen sharing system used by participants that may be trusted or may not be fully trusted.
Owner:SRINIVASAN SUDHARSHAN +2
Incremental deployment of computer software program logic
ActiveUS9696981B2Digital data processing detailsAnalogue secracy/subscription systemsSupplicantComputer software
Systems and methods for requesting computer software program logic by a client computing device from a server are provided. The method at the server comprises receiving a request for the computer software program logic from the client device along with a first list comprising details about multiple modules running on the client device; determining a second list comprising details about multiple modules required to deploy the computer software program logic on the client device; checking whether the modules of the second list need to be substituted based on their availability or suitability; updating the second list; checking whether the client device has permission rights for accessing the modules of the updated second list; and sending an object comprising the modules of the updated second list to the client device, the updated second list comprising details about the modules required for deployment of logic on the client device.
Owner:CAMBRIDGE SEMANTICS
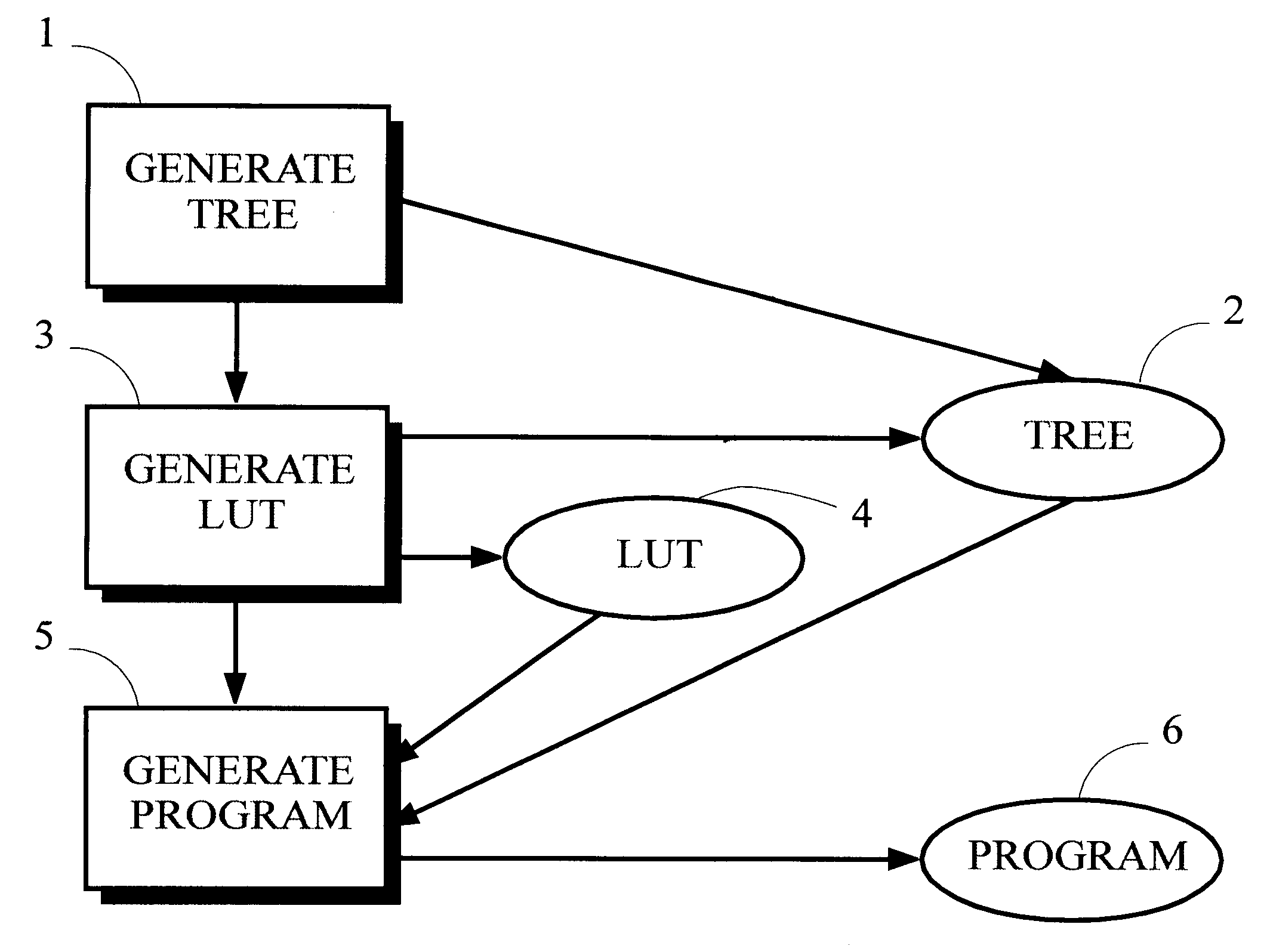
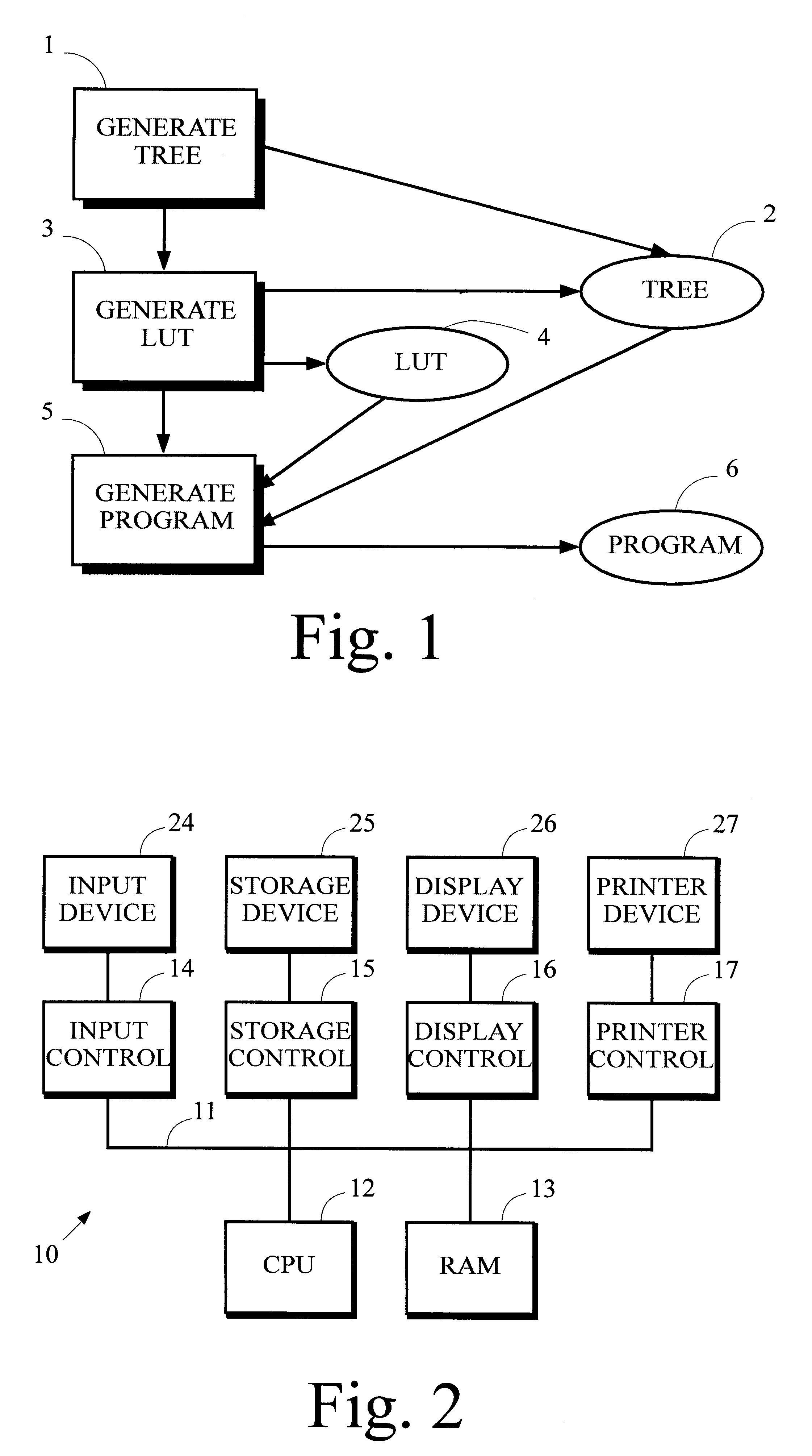
Automatic generation of program logic to decode variable-length codes
A program for decoding variable-length codes like Huffman codes is generated by receiving information describing a particular coding scheme that defines an association between source symbols and the variable-length codes, generating a binary tree that represents the coding scheme, generating a lookup table from the binary tree that can be used to decode variable-length codes having a length less than or equal to a threshold length, and processing the binary tree and the lookup table to generate the decode program.
Owner:SEIKO EPSON CORP
Testing method and testing device for starting up systems which are controlled by means of a program logic
InactiveUS7117395B2Possible to selectImprove clarityProgramme controlComputer controlPerformed ObservationProgram logic
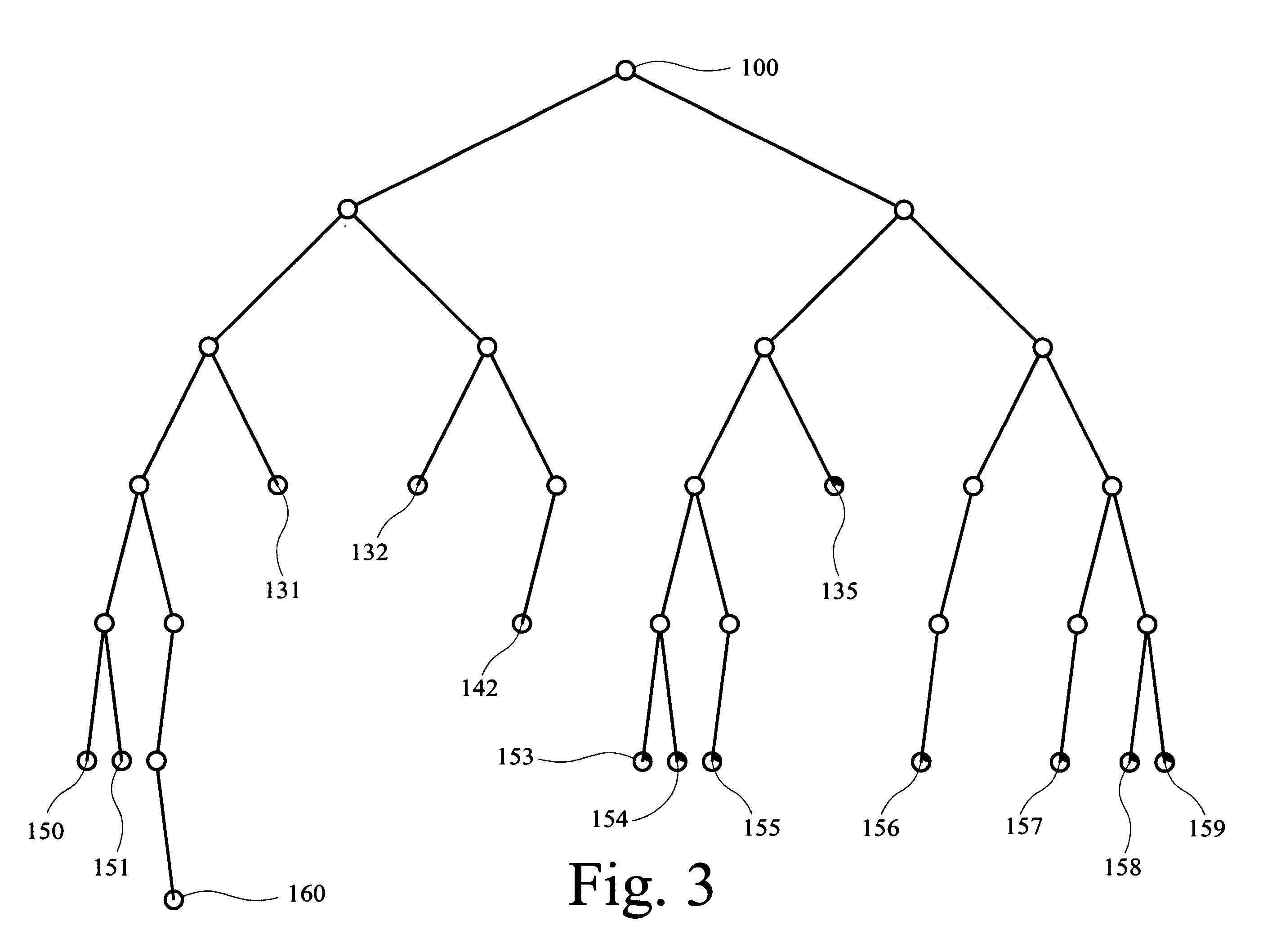
When systems controlled using a program logic, such as automation systems, are started up, it is necessary to observe individual program areas specifically. Program areas of this type are usually described by one or more modules of a program. This presents the problem that, in order to obtain an accurate analysis, the requests for these modules have to be identified in connection with the modules themselves, since they are ordinarily used multiple times. The present testing method and testing device are used to calculate and display a hierarchical request tree that shows the requests corresponding to a selected module. One or more requests for the selected module can be selected for observation by selecting individual lines of this request tree.
Owner:SIEMENS AG
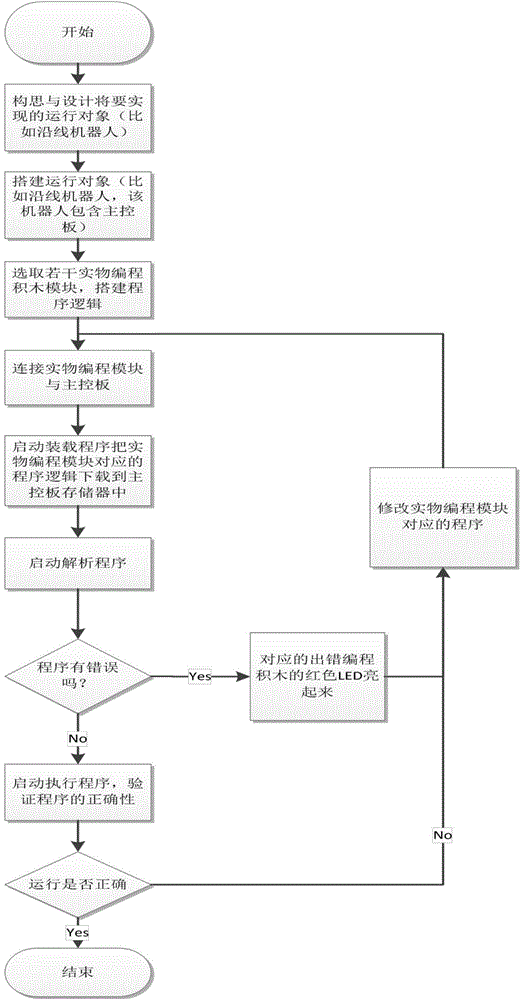
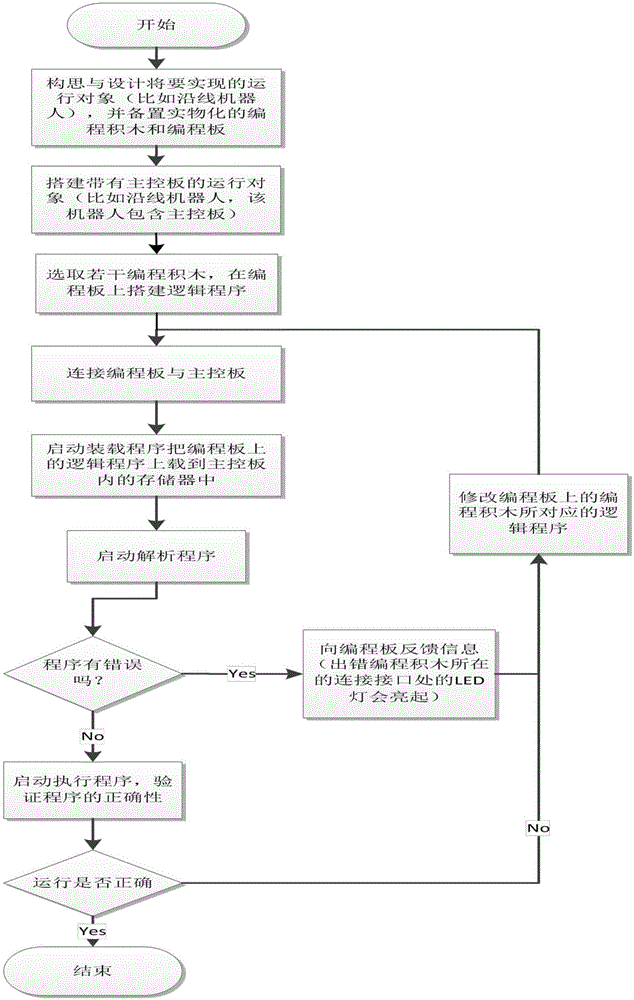
Physical programming method and applications of method in robot field
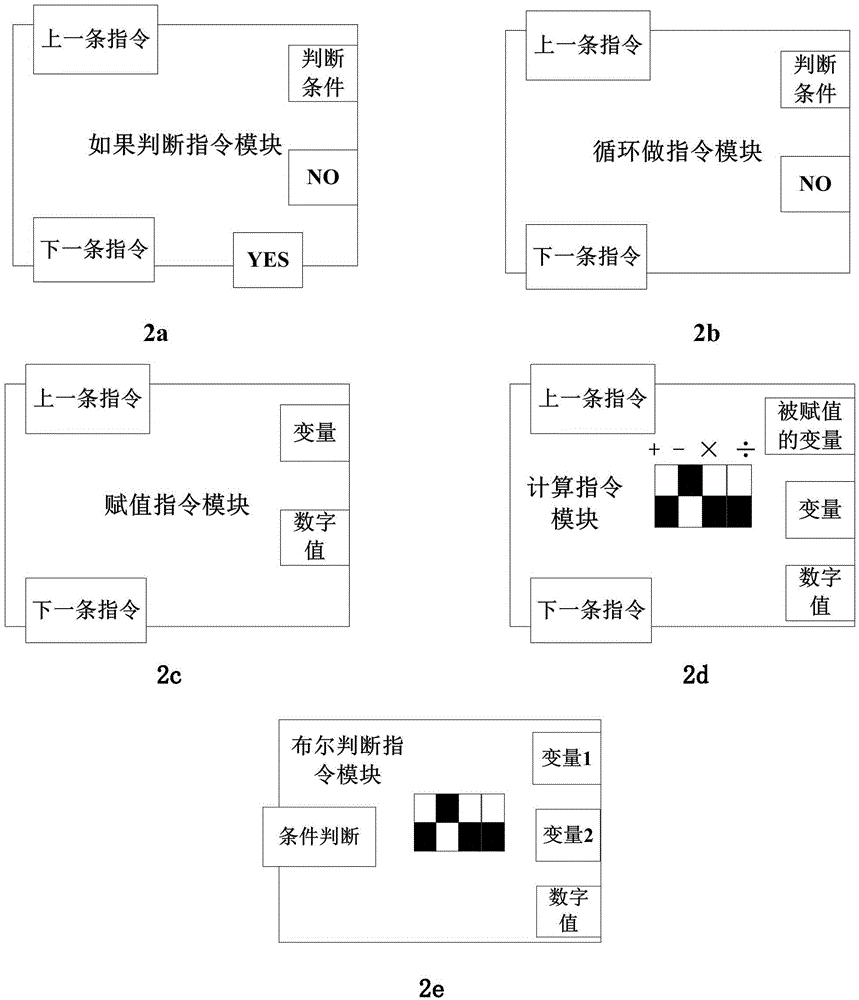
The invention discloses a physical programming method and applications of the method in a robot field. The method comprises steps: (1) a running object with a main control board is built; (2) physical programming building blocks are used for building program logic; (3) a physical programming module is connected with the main control board; (4) a program is loaded to a memory of the main control board; (5) the program is analyzed and whether the program logic is correct is detected; (6) if the program logic is correct, the program is executed, and whether the program is correctly executed is verified, and if the program logic is incorrect, error block information is fed back, the corresponding program is corrected, the third step is returned for continuing until the program logic is correct; and (7) if the running object runs correctly, termination is carried out, or otherwise, the program is corrected, and the third step is continued until correct running. Through visually reflecting the program spliced by the physical instruction model to running of the running object, kids and green hands can understand the program more specifically, and the program can be designed and corrected.
Owner:SUZHOU LEPAITE ROBOT CO LTD
Electronic mail system with authentication/encryption methodology for allowing connections to/from a message transfer agent
InactiveUS6986037B1User identity/authority verificationSecret communicationComputer hardwareClient-side
An electronic mail (“e-mail”) system is described that enforces authentication or encryption to / from Mail Transfer Agents and from Mail User Agents. In one embodiment, for example, an electronic mail (e-mail) system is described that comprises: a message transfer agent (MTA) available for a client to connect to; program logic for authenticating the client, through use of a certificate, in order to identify the client as approved for establishing a secured connection with the MTA; program logic for establishing a secured connection between the client and the MTA in instances where the client can be authenticated; program logic for testing encryption strength of the secured connection; and program logic for terminating the secured connection in instances where the secured connection has inadequate encryption strength.
Owner:PROOFPOINT INC
Materialized programming method based on programming plate and application thereof in robot field
ActiveCN105137887AUnderstand intuitiveClearly understandProgramme controlComputer controlMicrocomputerProgramming language
The invention relates to a materialized programming method based on programming plates and the application thereof in robot field. The programming method comprises steps of 1) preparing materialized programming building blocks and programming plates; 2) constructing an operation object, selecting programming blocks and constructing logic programs on the programming plates; 3) connecting the programming plates and a main control plate; 4) loading programs in a memory in the main control plate; 5) decoding and analyzing the programs; 6) testing whether the logic of the programs is right or not, if right, continuing the step and if not, returning to the step 3) to correct the programs until the logic is right; and 7) executing the programs and verifying whether program execution is right or not. According to the invention, the programs spliced through the materialized instruction building blocks are visually reflected on operation of the operation object like a robot; children and green hands can understand, design and modify the programs more specifically; the programing method has a profound application prospect; and based on the materialized programming plates, programs are constructed by use of the materialized building blocks, each of the building blocks does not need a chip or a single-chip microcomputer, so manufacturing cost is saved.
Owner:SUZHOU LEPAITE ROBOT CO LTD +1
System and/or methods for interpreting and/or re-presenting content in a gaming environment
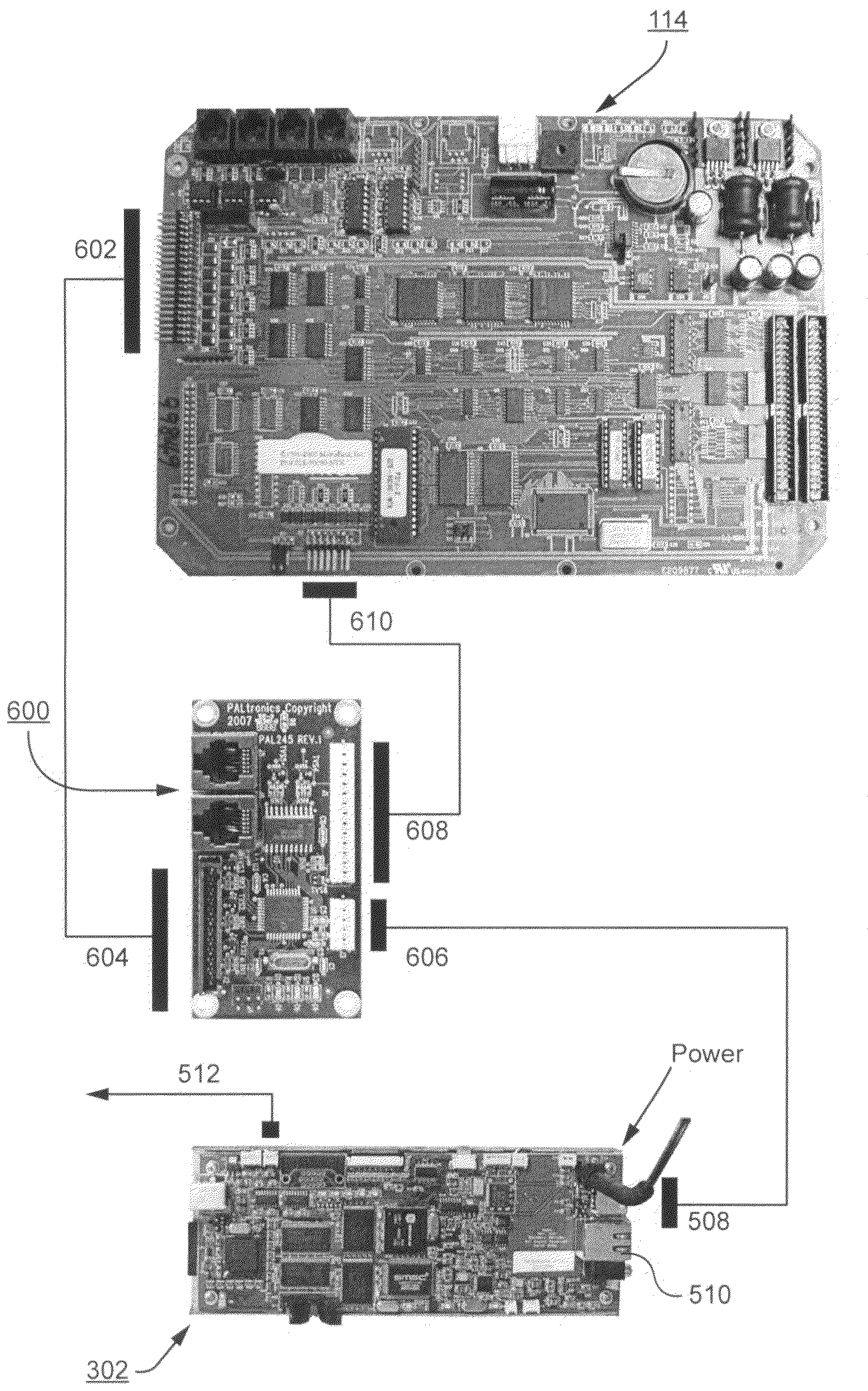
InactiveUS20090124329A1Reduce needAdd featureMultiple digital computer combinationsApparatus for meter-controlled dispensingHuman–computer interactionProgram logic
Certain exemplary embodiments described herein relate to gaming machines and / or table games having programmed logic circuitry for interpreting existing content in the gaming environment and re-presenting it to a player via a new, though familiar, user interface, while also allowing further content to be displayed to the player. This advantageously enables the patron experience to be changed through a richer interface to the gaming environment, while also reducing the need to perform major replacement services by re-presenting existing, and integrating new, components and features.
Owner:PALTRONICS INC
Method and system for managing enterprise content
A method and system for providing a consistent flow documents and data content across different organizational units of a company or agency where the documents and data come from different enterprise systems and data stores but are related to linked processes that share models for organizing the content in the business context and in a format that enables a user to relate the content to the process step or steps they are performing. The system includes a network service that enables a configuration utility to automatically discover the objects and metadata and provides for a mapping of selected fields of the metadata to regions displayed in the user interface view with provision for filtering the data by mapping selected fields to a user input form. Thereby, a business analyst can create solutions without writing and maintaining complex program logic for each combination of presentation environment, enterprise system and data store.
Owner:OPEN TEXT CORPORATION
Systems and methods for remote access to a display-based bulletin board in a shared user environment
ActiveUS6968362B2Multiple digital computer combinationsOffice automationTTEthernetApplication server
An electronic bulletin board for use in a shared always-on environment wherein a user may manipulate messages from a remote location. The electronic bulletin board may be implemented via database and programming logic on an application server accessible from any network node, including wireless devices. The always-on environment may be set up on a computer or broadband internet appliance or other communications device. Remote users may perform operations such as updating an existing message, posting a new message, download messages, and the like. The bulletin board also supports shared messages designed for special purposes, for example, an electronic grocery list that is accessible from remote locations.
Owner:BELLSOUTH INTPROP COR
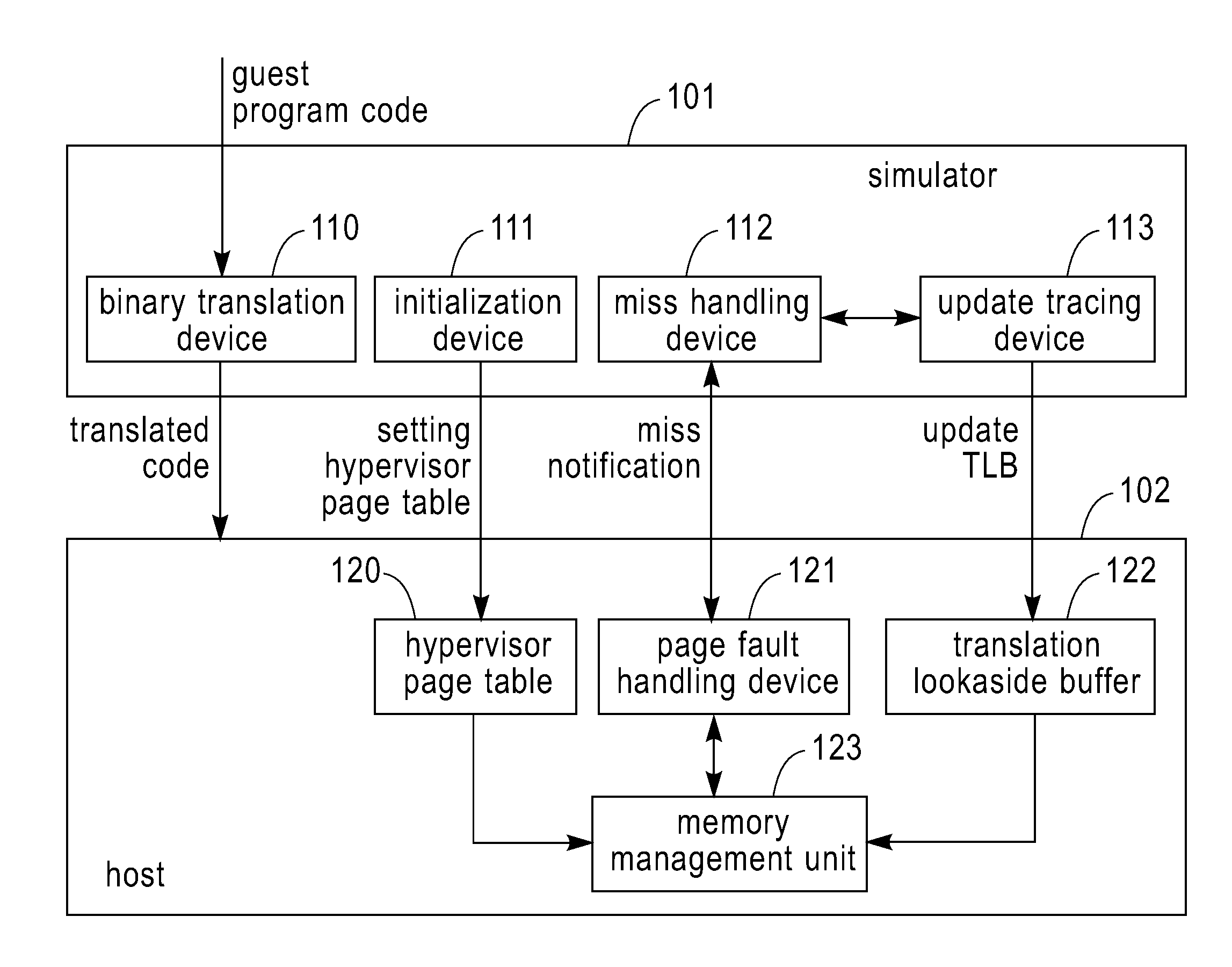
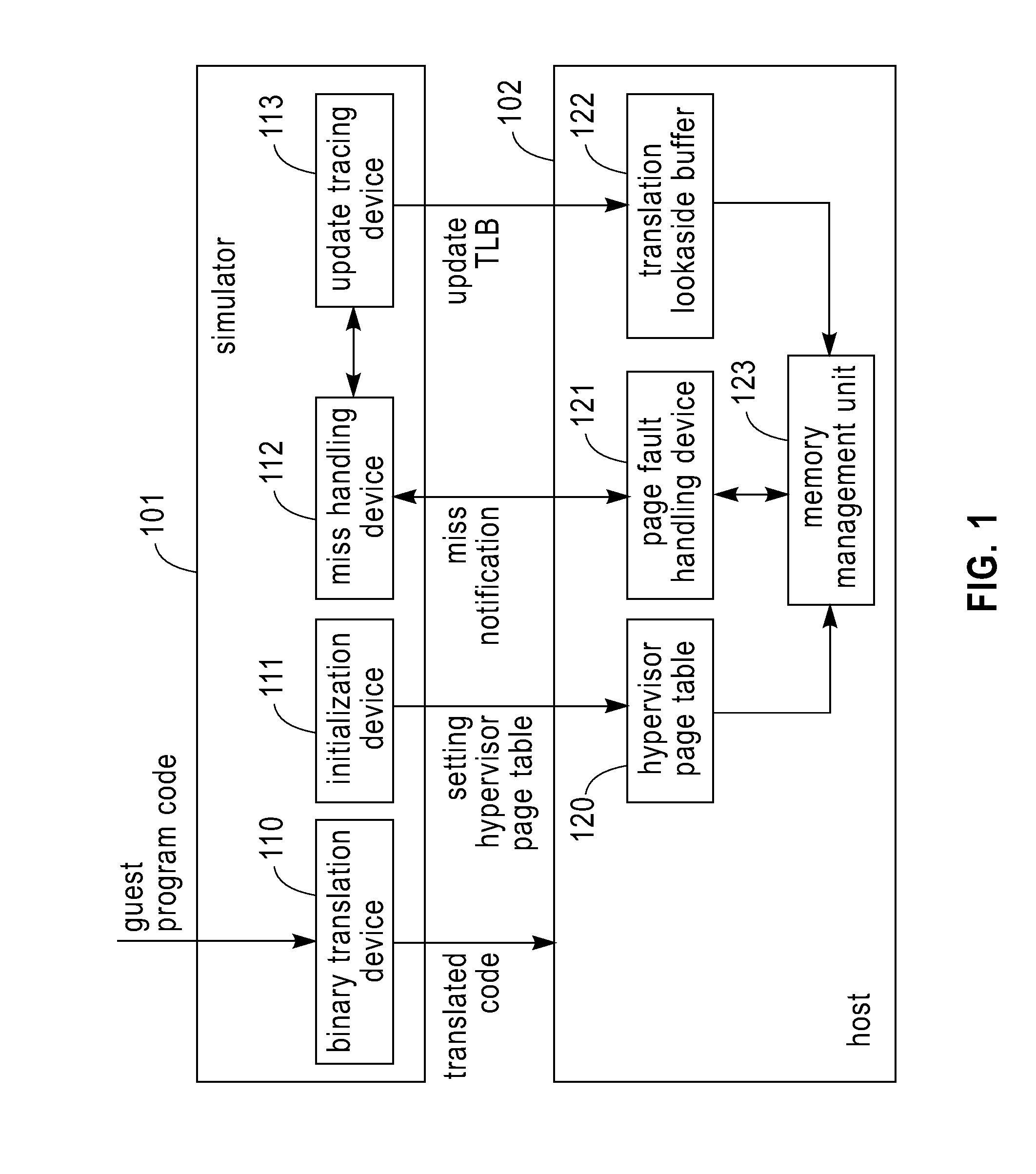
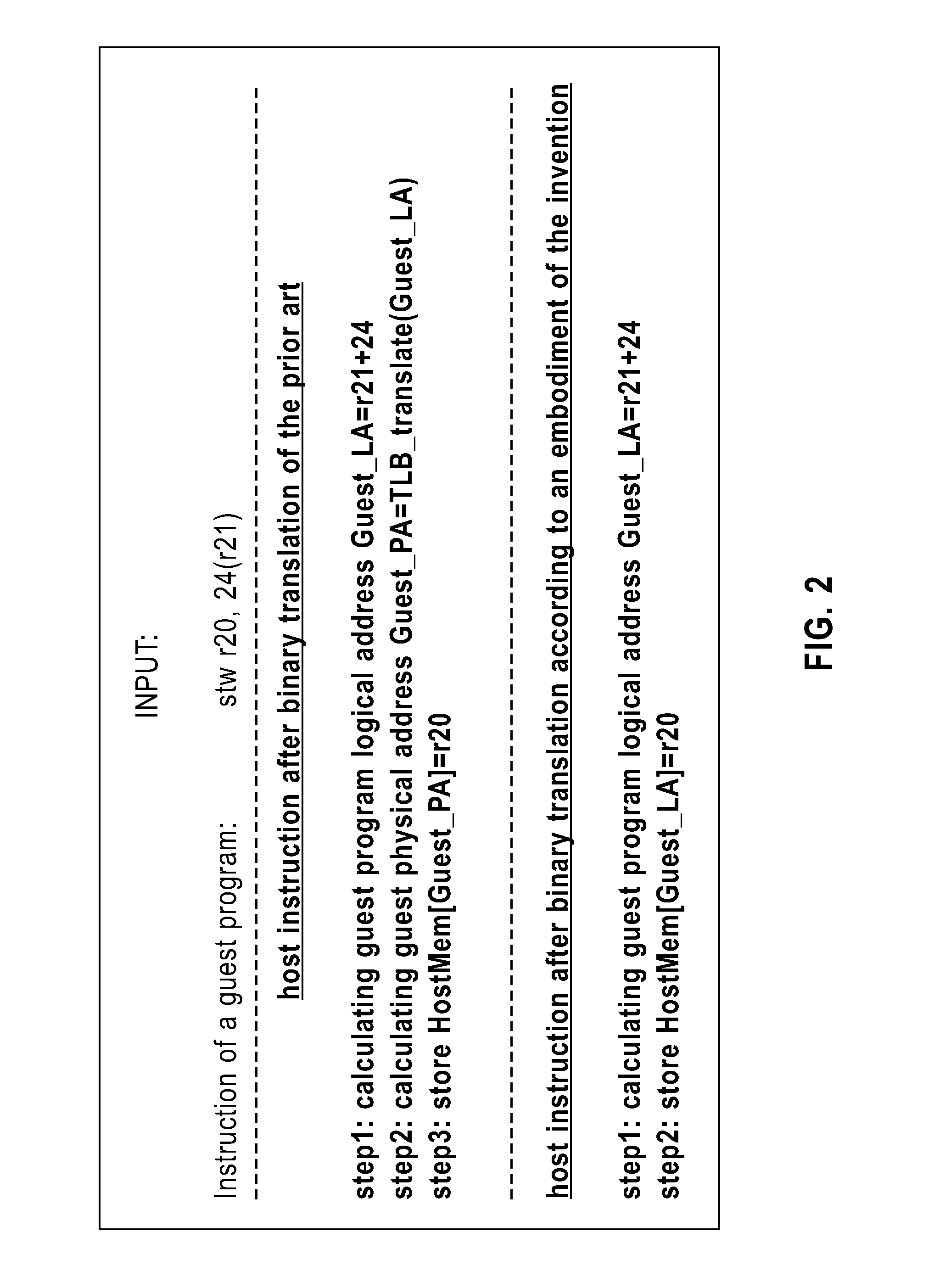
Simulator and simulating method for running guest program in host
ActiveUS20100161875A1Improve executionEfficient executionMemory adressing/allocation/relocationComputer security arrangementsCode TranslationPage table
A Simulator and a simulating method for running a guest program in a host are disclosed. The simulator includes: an initialization device configured for setting content of a hypervisor page table in the host, the hypervisor page table mapping a guest physical address space to a host physical address space. The simulator further includes a binary translation device configured for employing a program logical address to perform a memory access in code translation. The simulator also includes a miss handling device configured for updating a guest translation look-aside buffer by treating a miss in a host translation look-aside buffer caused by the execution of the translated code as a miss in the guest translation look-aside buffer, wherein the host translation look-aside buffer is configured to buffer entries for mapping addresses in a guest program logical address space to addresses in the guest physical address space. The simulator further includes an update tracing device configured for, in response to the update to the guest translation look-aside buffer, perform the update to the host translation look-aside buffer. Also disclosed is a method for running a guest program in a host.
Owner:IBM CORP
Systems and methods for visualizing pressures and pressure responses to sleep-related triggering events
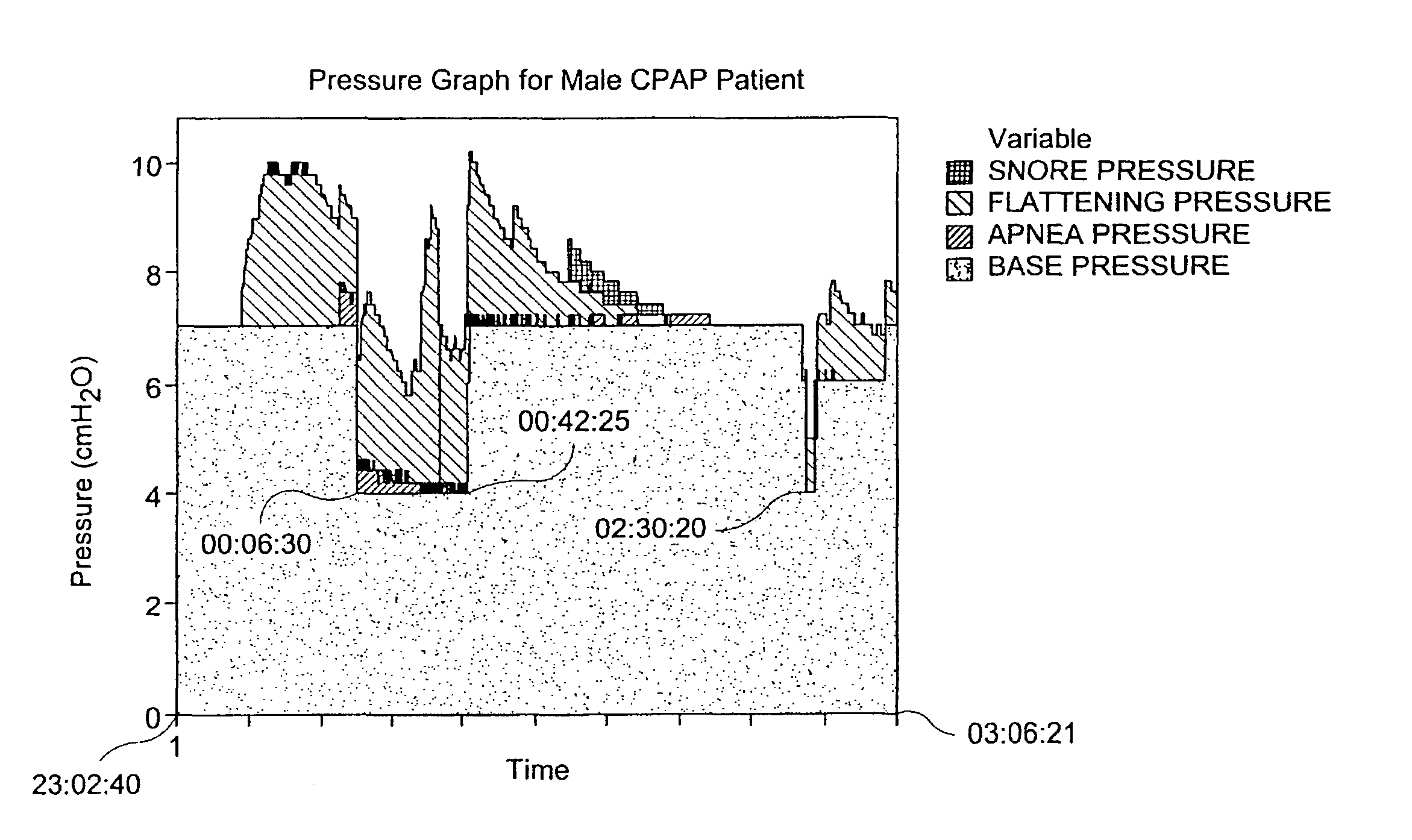
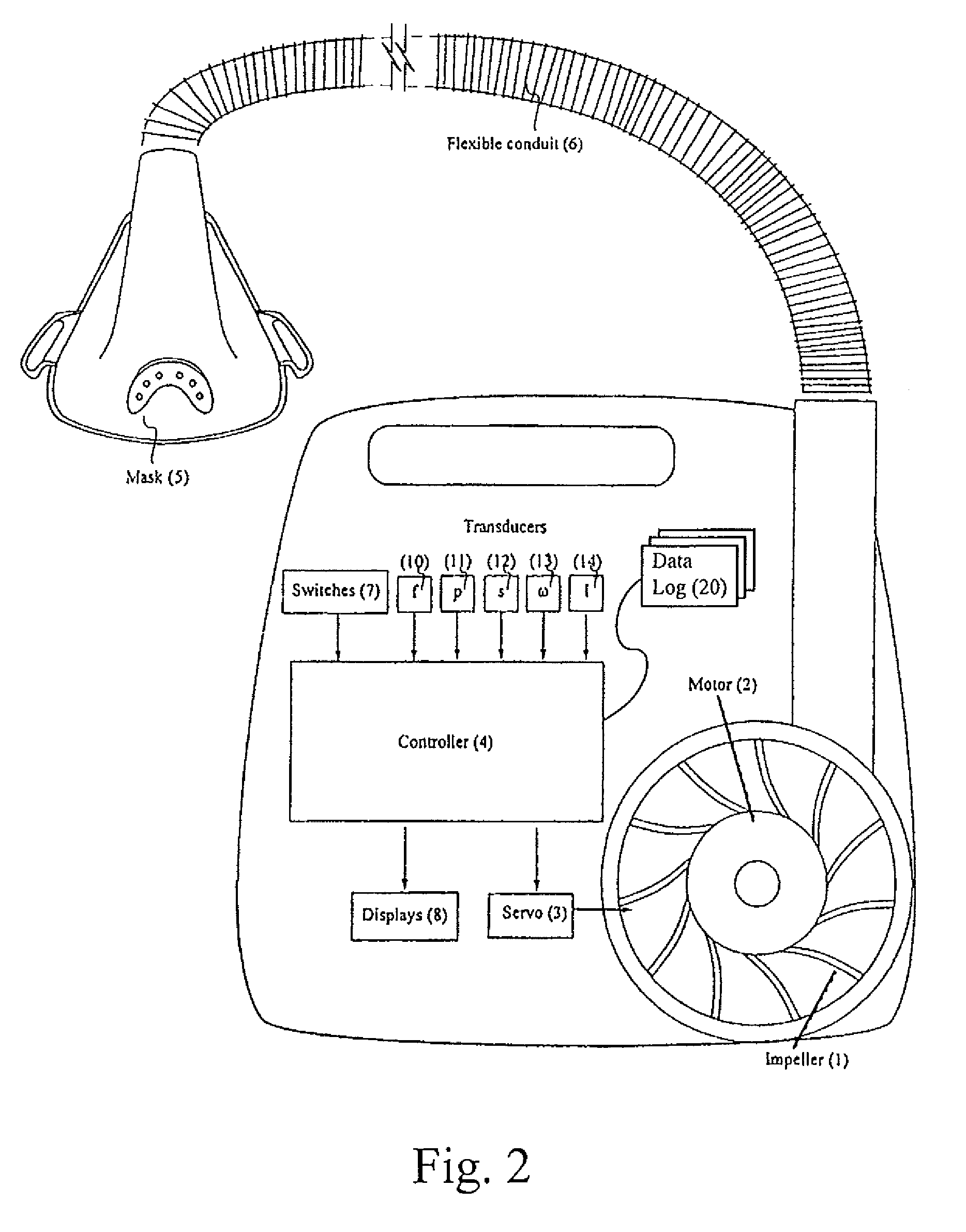
ActiveUS8276585B2RespiratorsOperating means/releasing devices for valvesHypopneaSleep disordered breathing
Systems and methods for visualizing patient treatment data collected while a patient suffering from sleep-disordered breathing is treated are provided. For example, according to certain example embodiments, a PAP device for treating a patient suffering from sleep-disordered breathing is provided. A processor may be set or programmed to generate a signal indicative of a triggering event. A flow generator may be configured to provide a supply of pressurized breathable gas to the patient based at least in part on the signal. Recording programmed logic circuitry may be provided to record in a data log pressures provided during patient treatment and triggering events occurring during patient treatment. Visualizing programmed logic circuitry in communication with the PAP device may be configured to read the data log and generate a visual depiction of provided pressures over time. Triggering events may include, for example, one or more of apnea, hypopnea, flattening, snore, etc.
Owner:RESMED LTD
Device for calling computer program to run by utilizing Chinese text
InactiveCN103279190ARealize intelligent controlEasy to callInput/output for user-computer interactionGraph readingInformation processingAutomatic control
The technical scheme relates to a device for calling a computer program to run by utilizing a Chinese text and belongs to the field of computer man-machine conversation automatic control technologies. The device for calling the computer program to run by utilizing the Chinese text comprises a Chinese text input module (1), a computer system (2), a Chinese text word segmentation module (3), a Chinese character and Chinese speech code conversion module (7), a computer program module (4) which is pre-stored in a computer and bound with input Chinese speech codes or keywords in Chinese characters, a program logic arranging and connecting module (5) which arranges bound programs according to a logic sequence of execution, and a program execution module (6) stored in the computer, and the above modules are sequentially connected in series according to an information processing sequence of the computer. By means of the device for calling the computer program to run by utilizing the Chinese text, a non-computer programmer can call the computer program to run by utilizing Chinese natural language.
Owner:QINGHAI HANLA INFORMATION SCI & TECH CO LTD
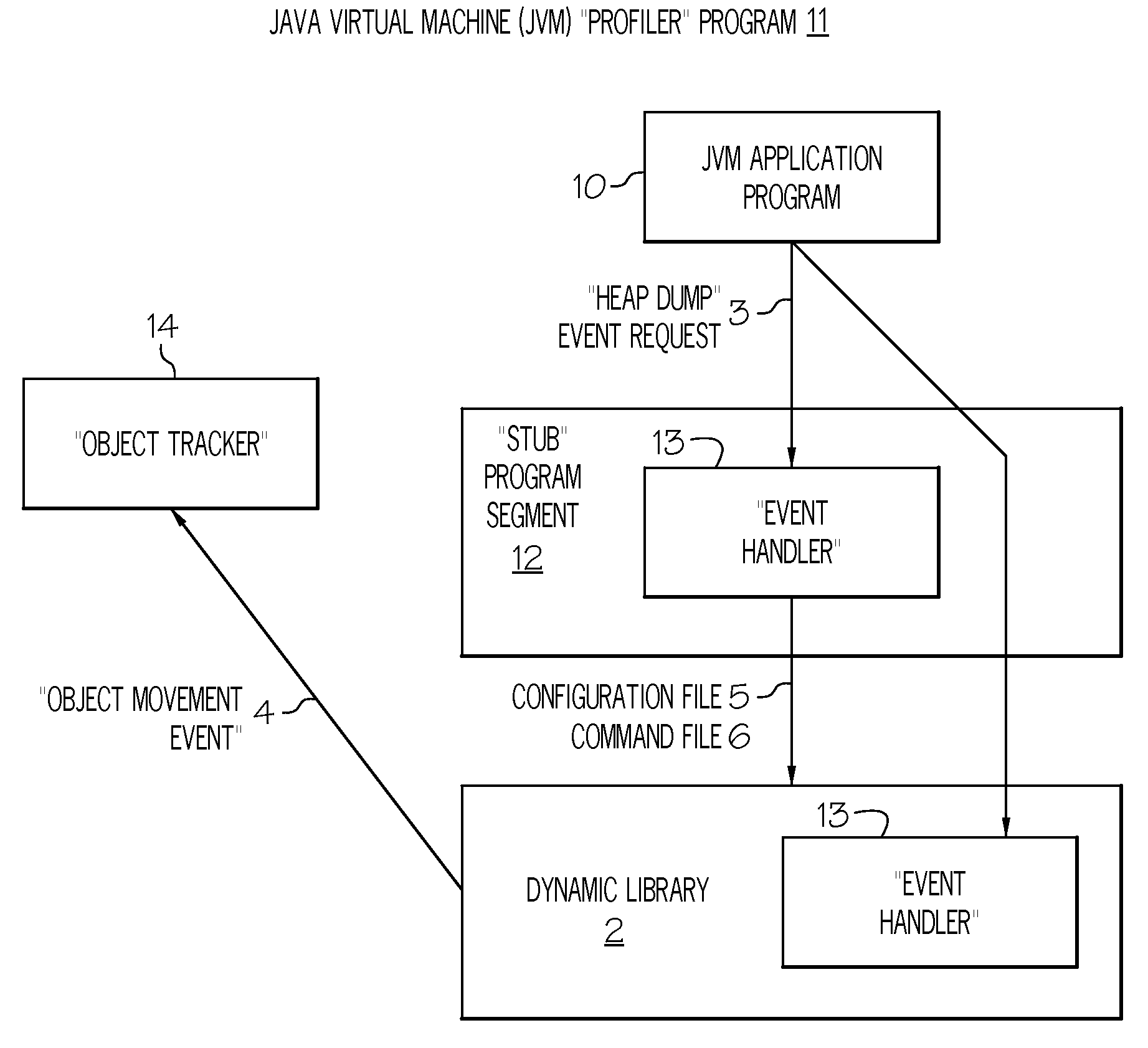
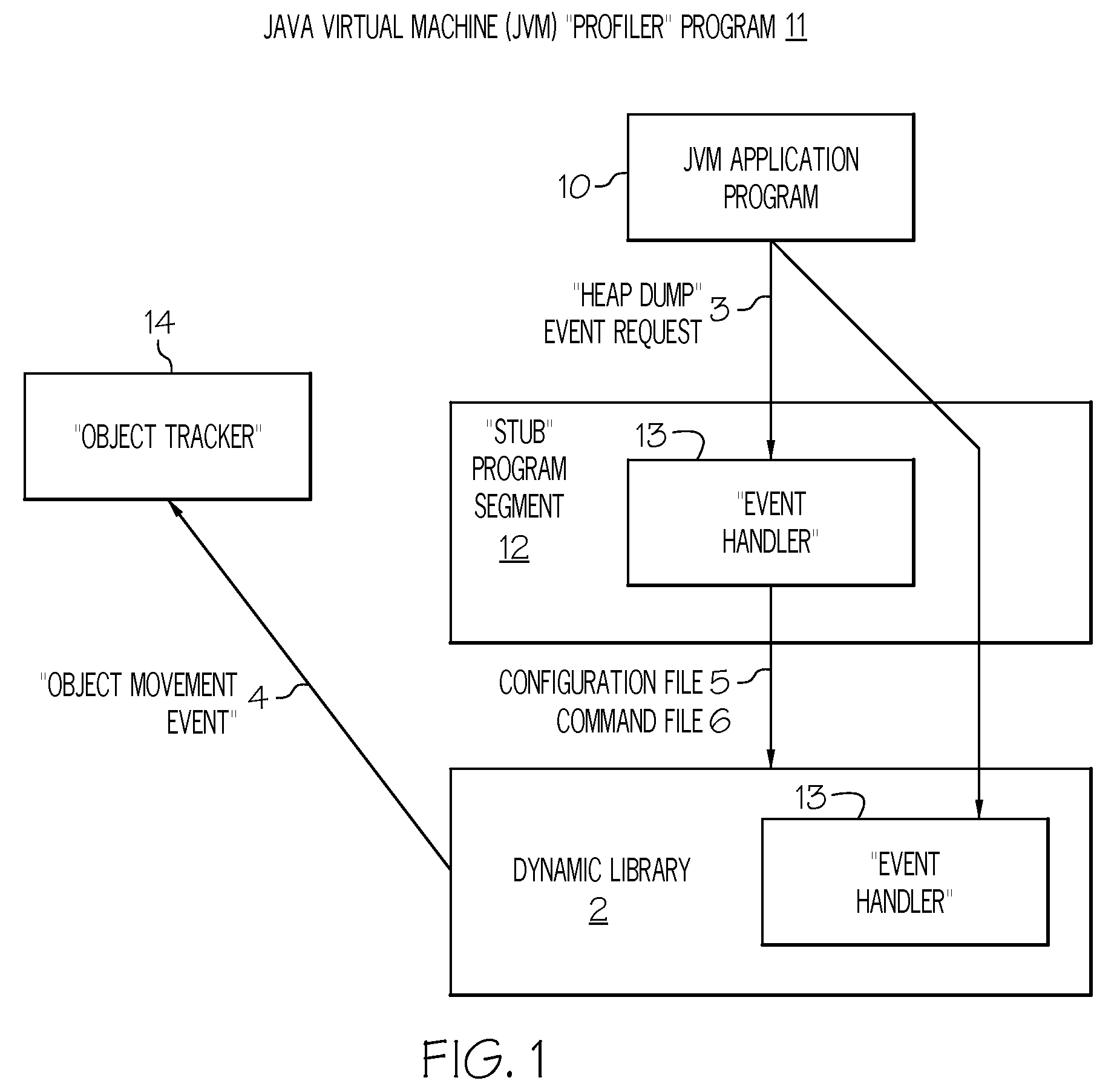
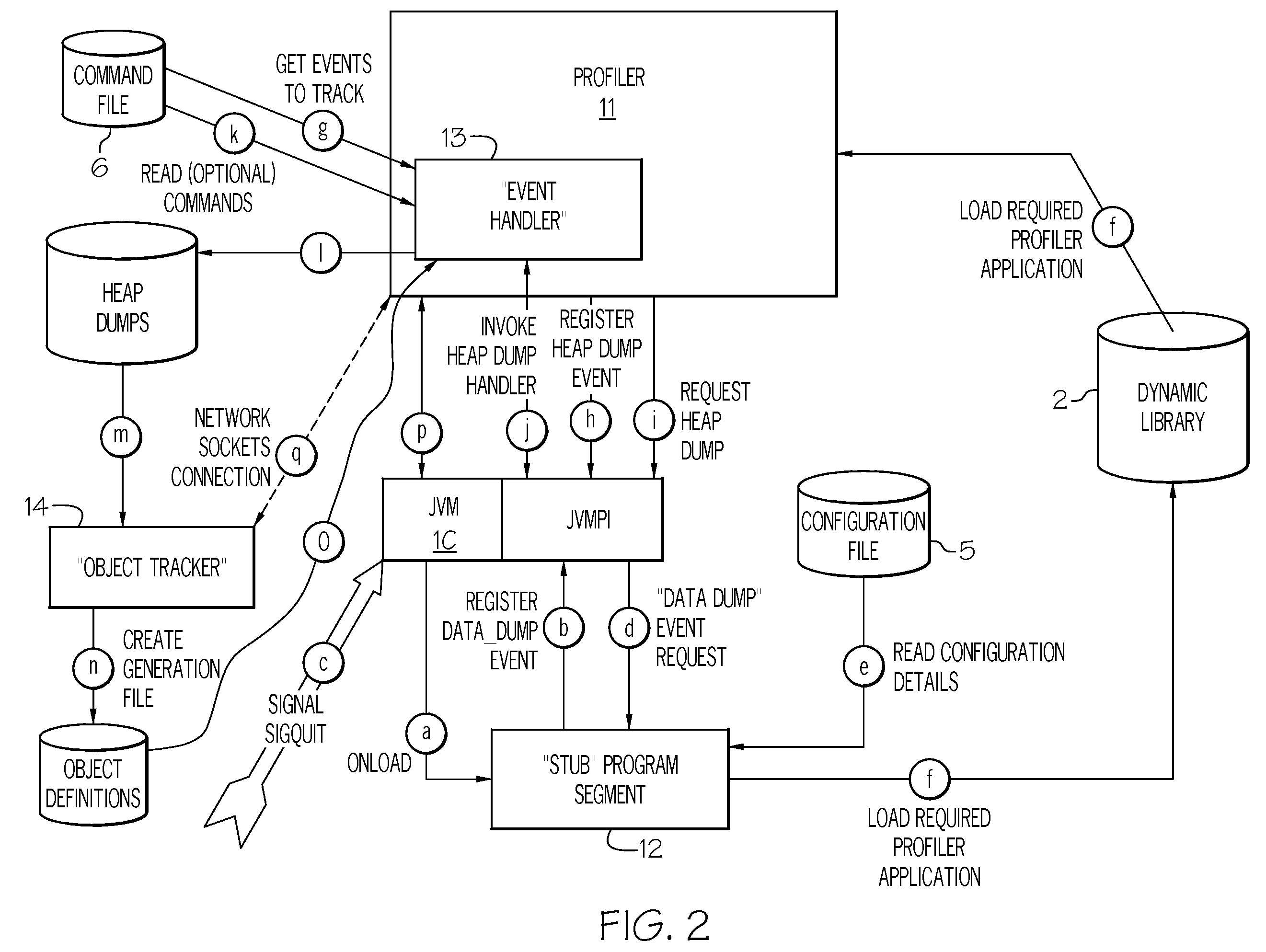
Method and system for analyzing memory leaks occurring in JAVA virtual machine data storage heaps
InactiveUS20080209404A1Error detection/correctionSpecific program execution arrangementsProgram segmentParallel computing
An invention is disclosed for analyzing memory leaks occurring in Java Virtual Machine (JVM) data storage, consisting of a dynamically modifiable JVM “profiler” and an “object tracker” tool for analyzing the output from the profiler. Specifically, a method and system is disclosed for programming a JVM profiler used to analyze and correct memory leaks in stored data heaps, consisting of a program segment (or “stub”) initialized by the JVM application program interface to determine the parameters to be passed to the main profiler memory leak analysis program logic, which is then initialized by the stub to examine a minimal number of “heap dumps” in order to identify data elements or objects for the existence and / or correction of memory leaks. Updated information on data elements or objects can be requested from the profiler as needed by use of the object movement tracking option to record the details of subsequent changes in data memory storage status once a heap dump has been obtained.
Owner:IBM CORP
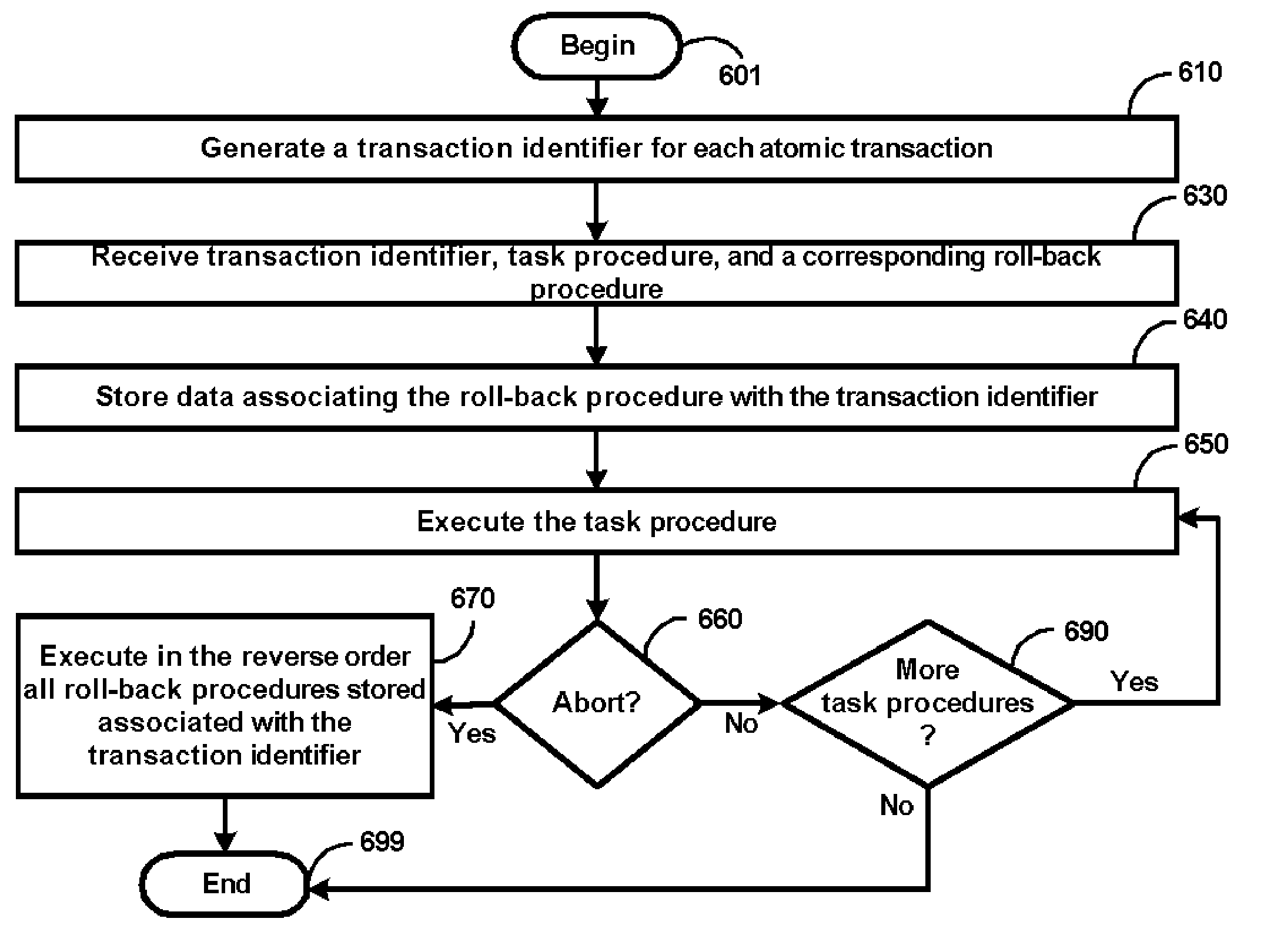
Custom Atomic Transactions in Programming Environments
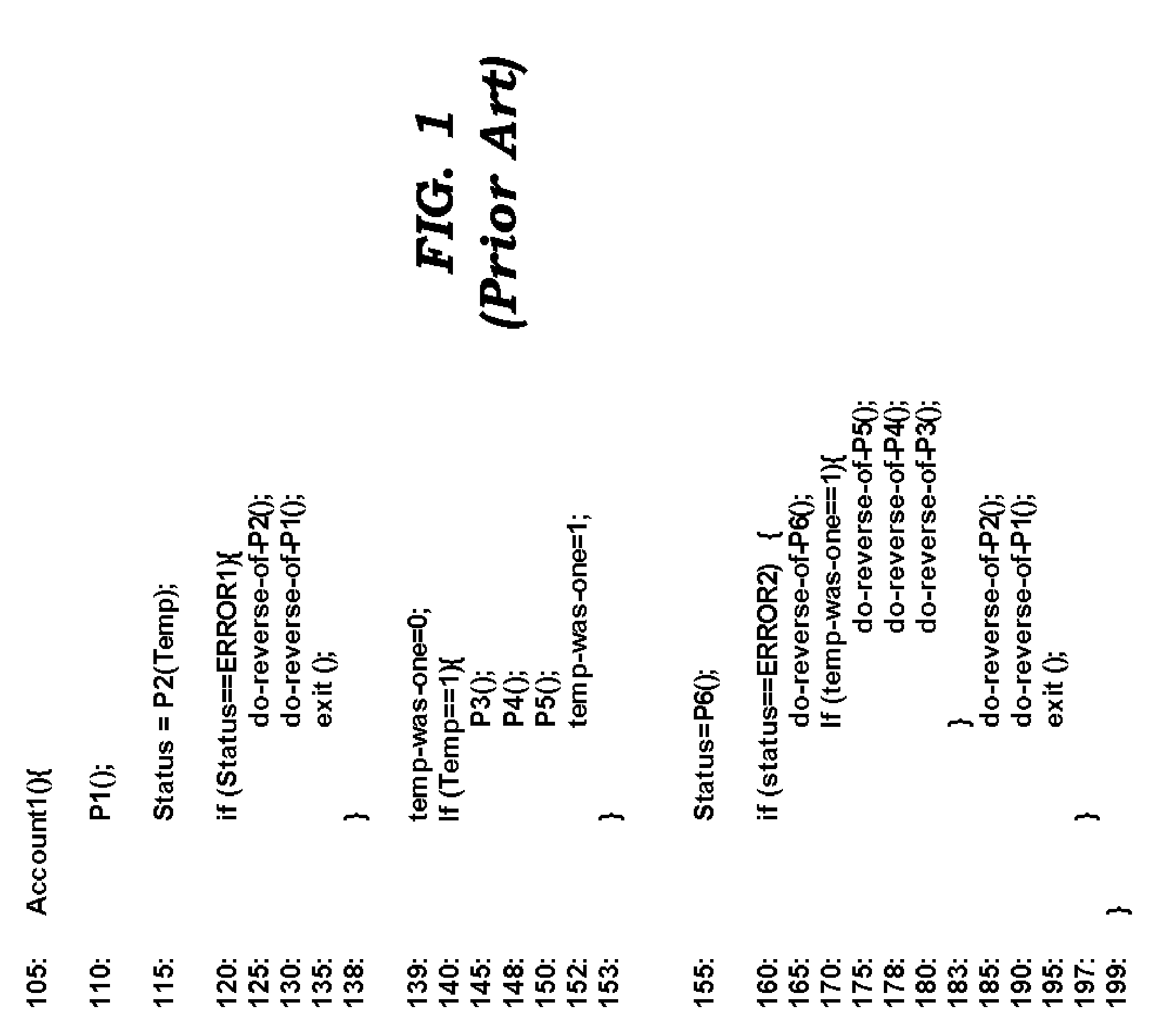
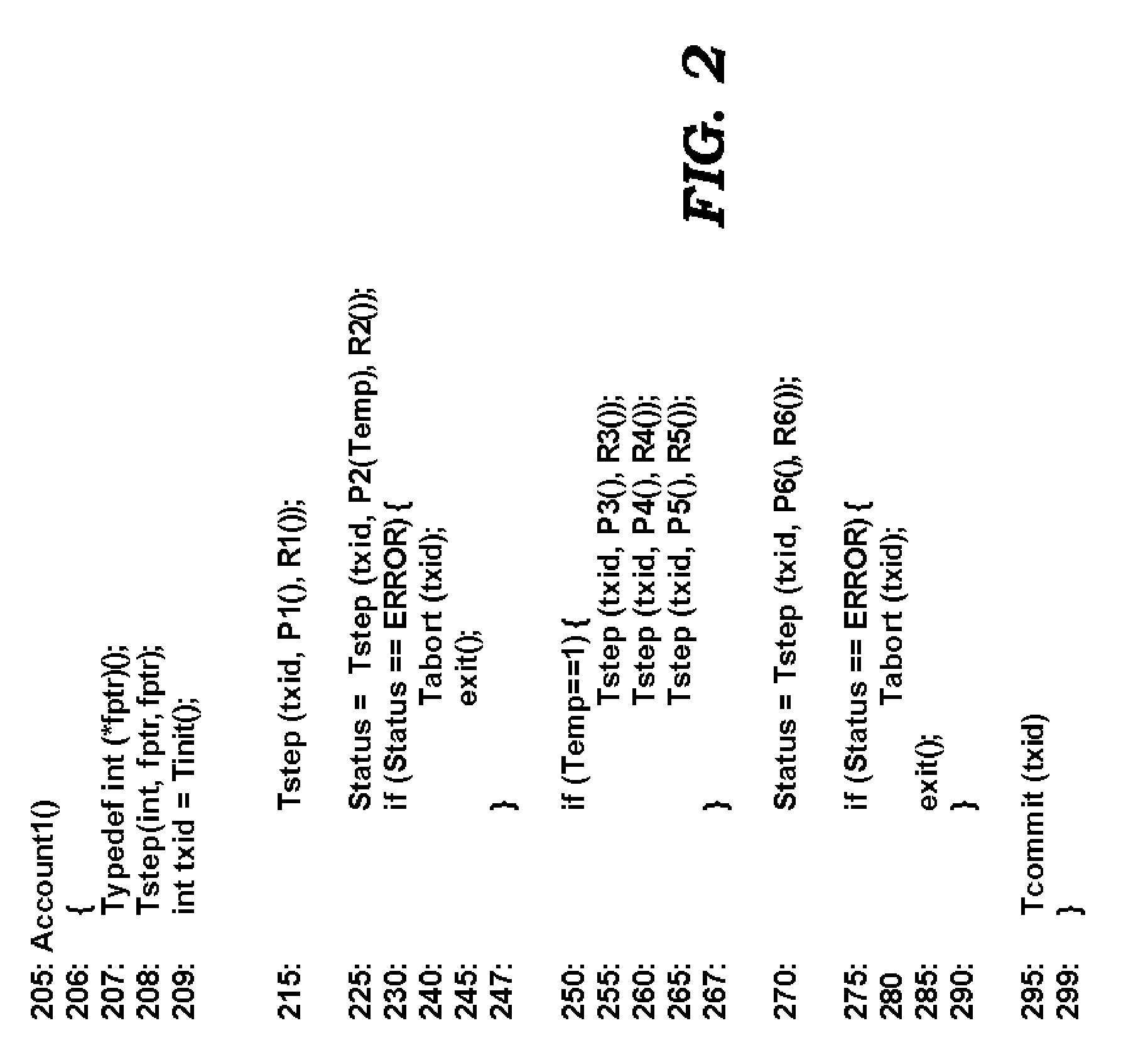
ActiveUS20060004882A1Error identificationSpecial data processing applicationsProgram logicBack procedures
An aspect of the present invention simplifies the implementation of custom atomic transactions. A program logic (implementing a custom atomic transaction) may request a unique transaction identifier from a programming environment. The program logic may then specify a task procedure, corresponding roll-back procedures, and the transaction identifier using an interface provided by the programming environment. The programming environment keeps track of the specified roll-back procedures. The information maintained by the programming environment may be used to execute the roll-back procedures if the atomic transaction is to be aborted. As the programming environment keeps track of the roll-back procedures to be executed, the implementation of atomic transactions may be simplified.
Owner:ORACLE INT CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com