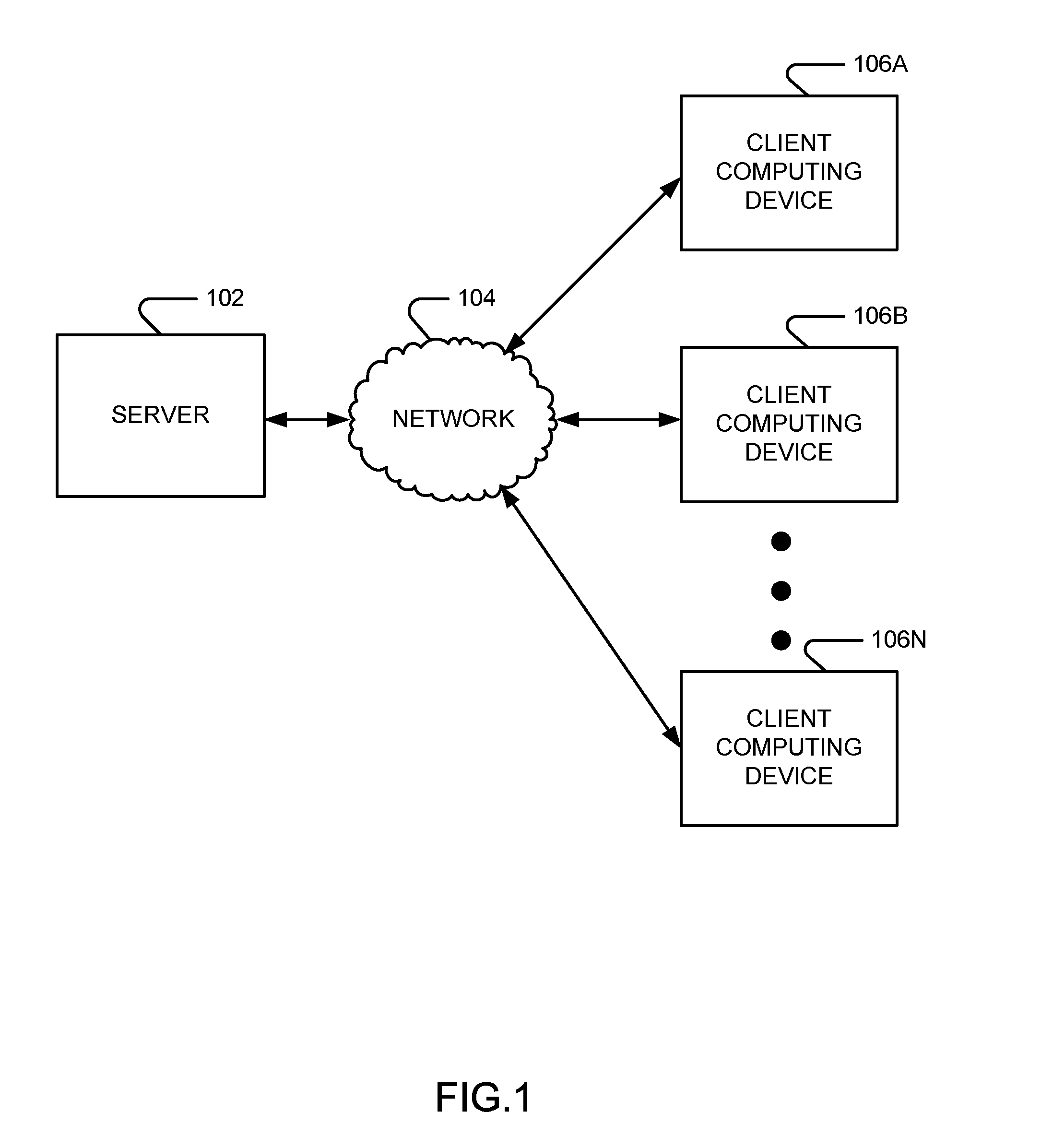
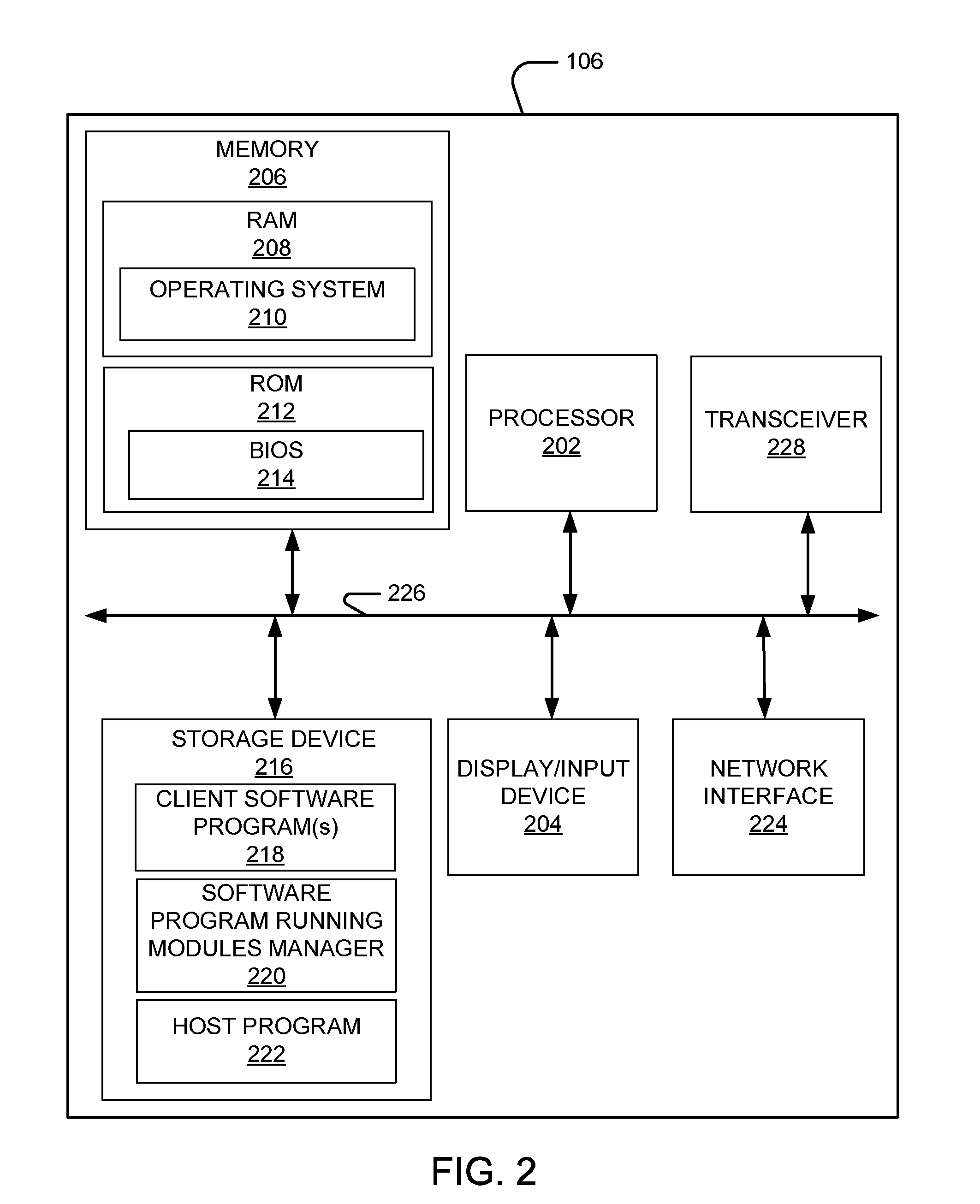
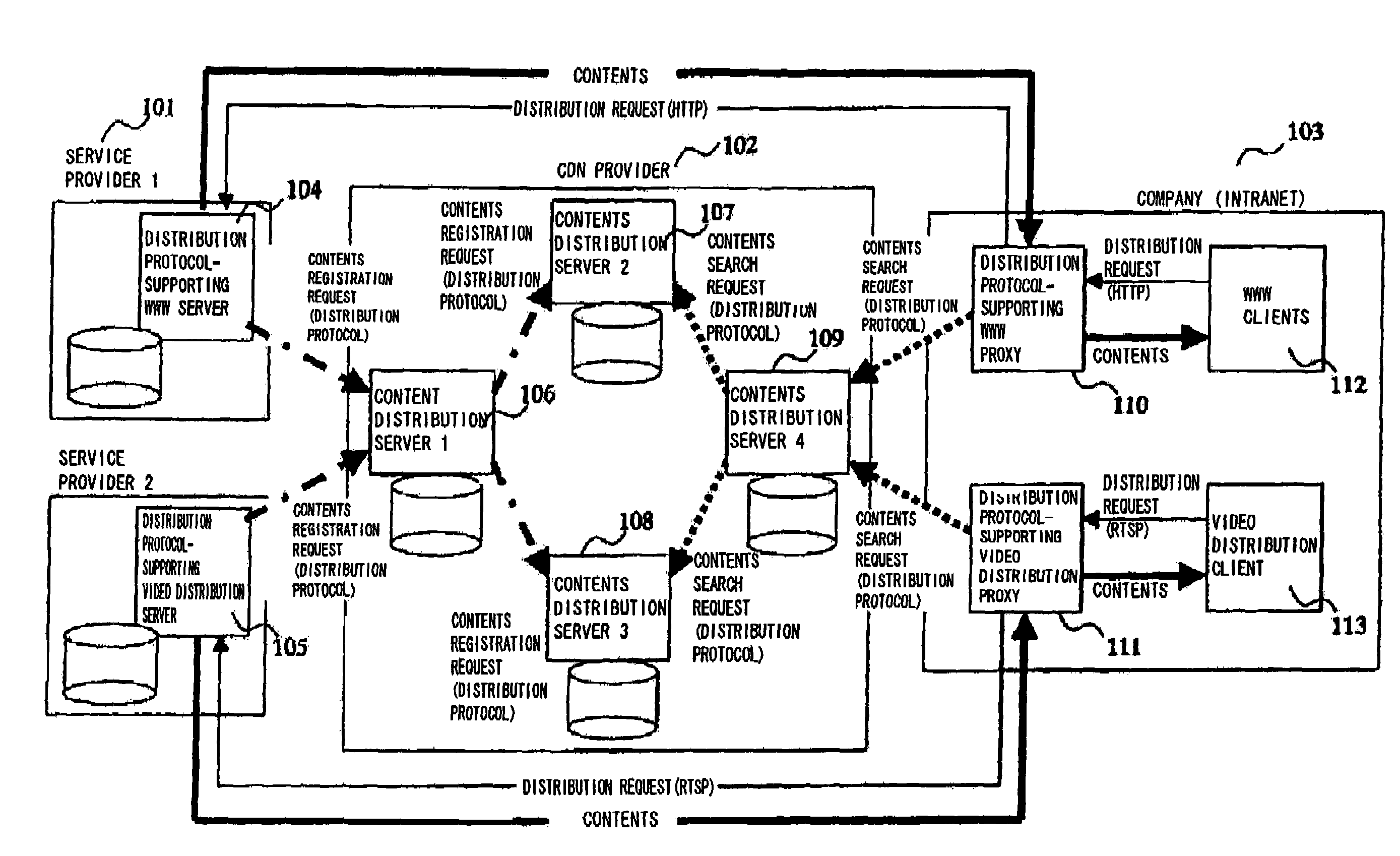
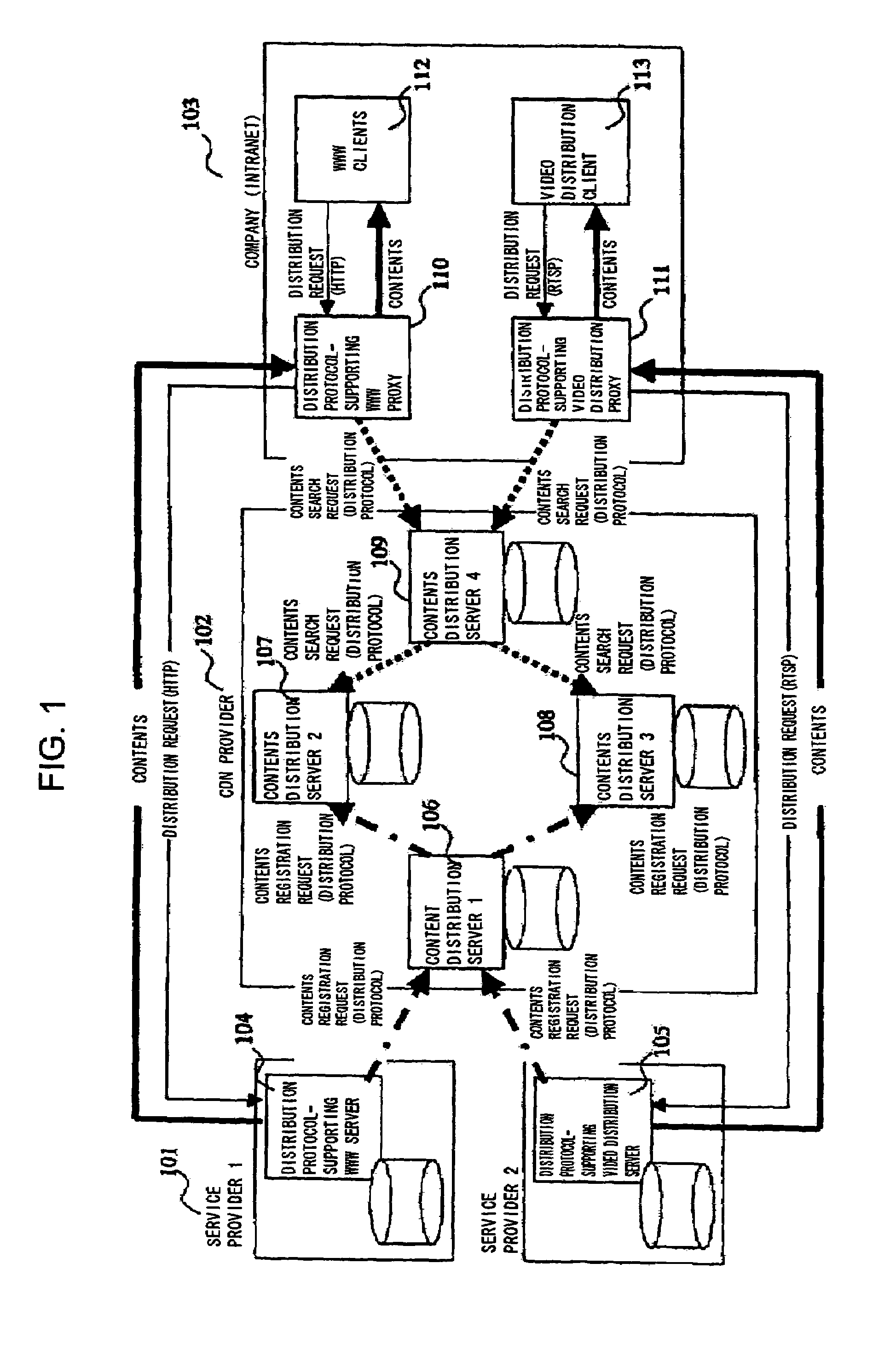
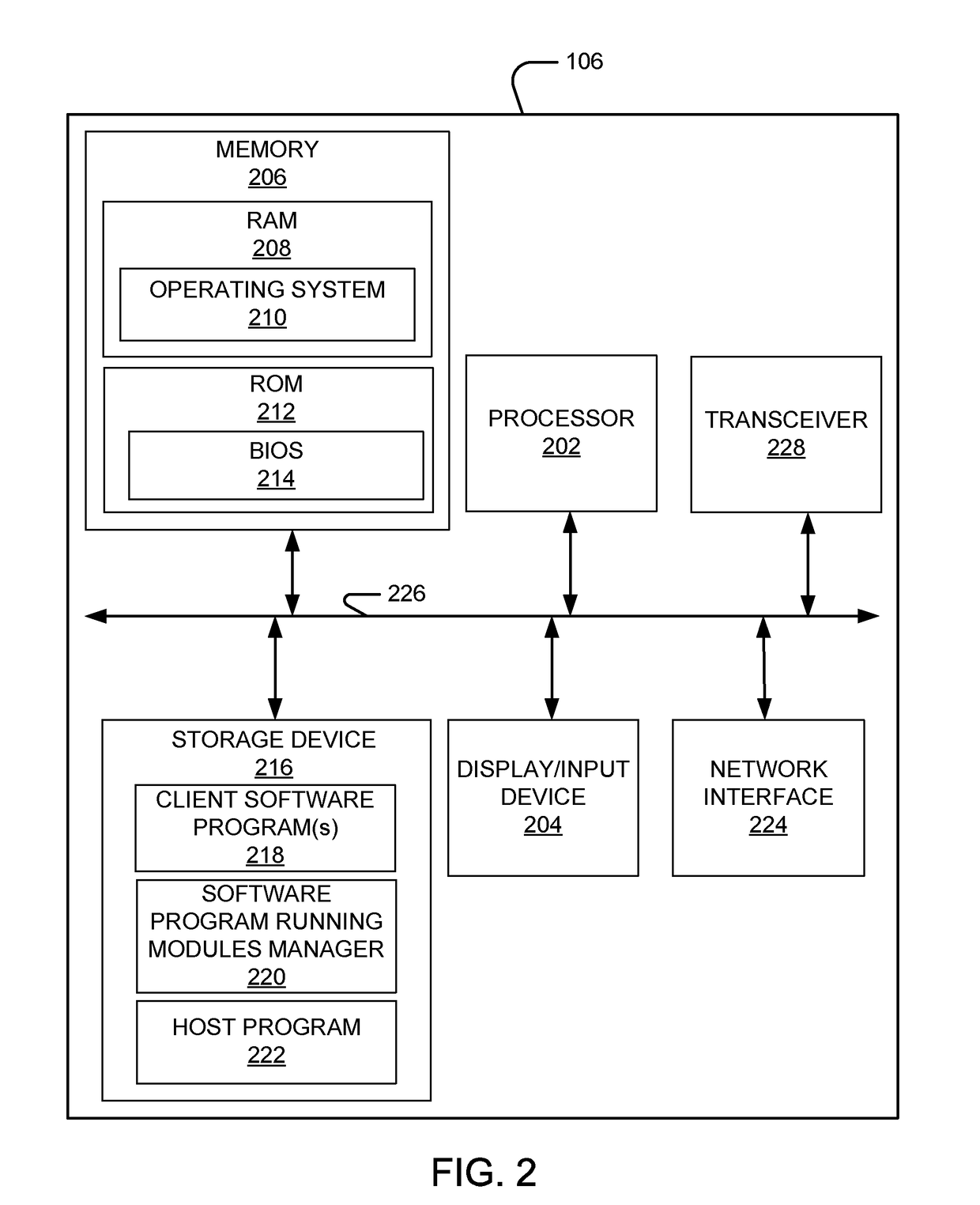
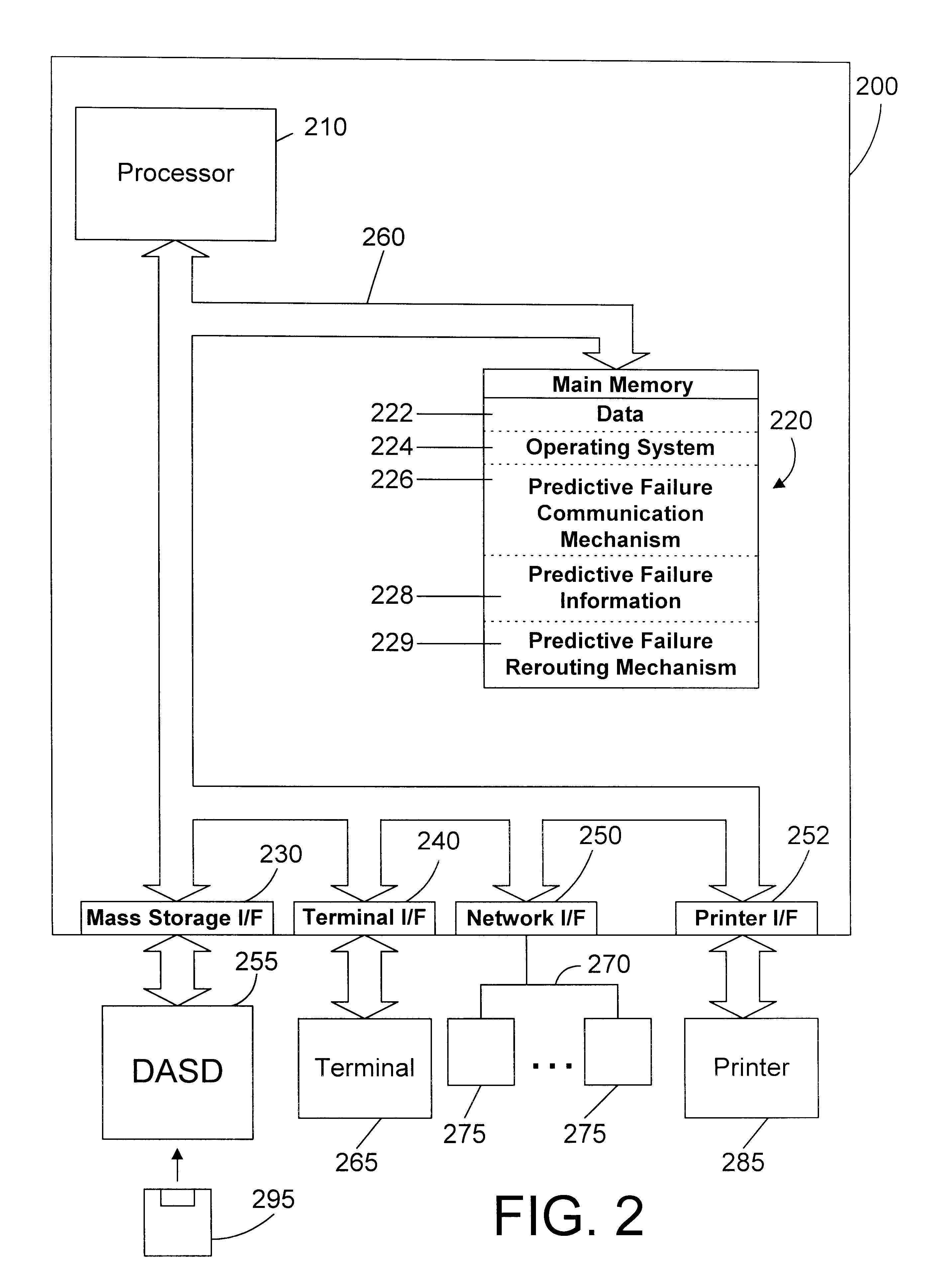
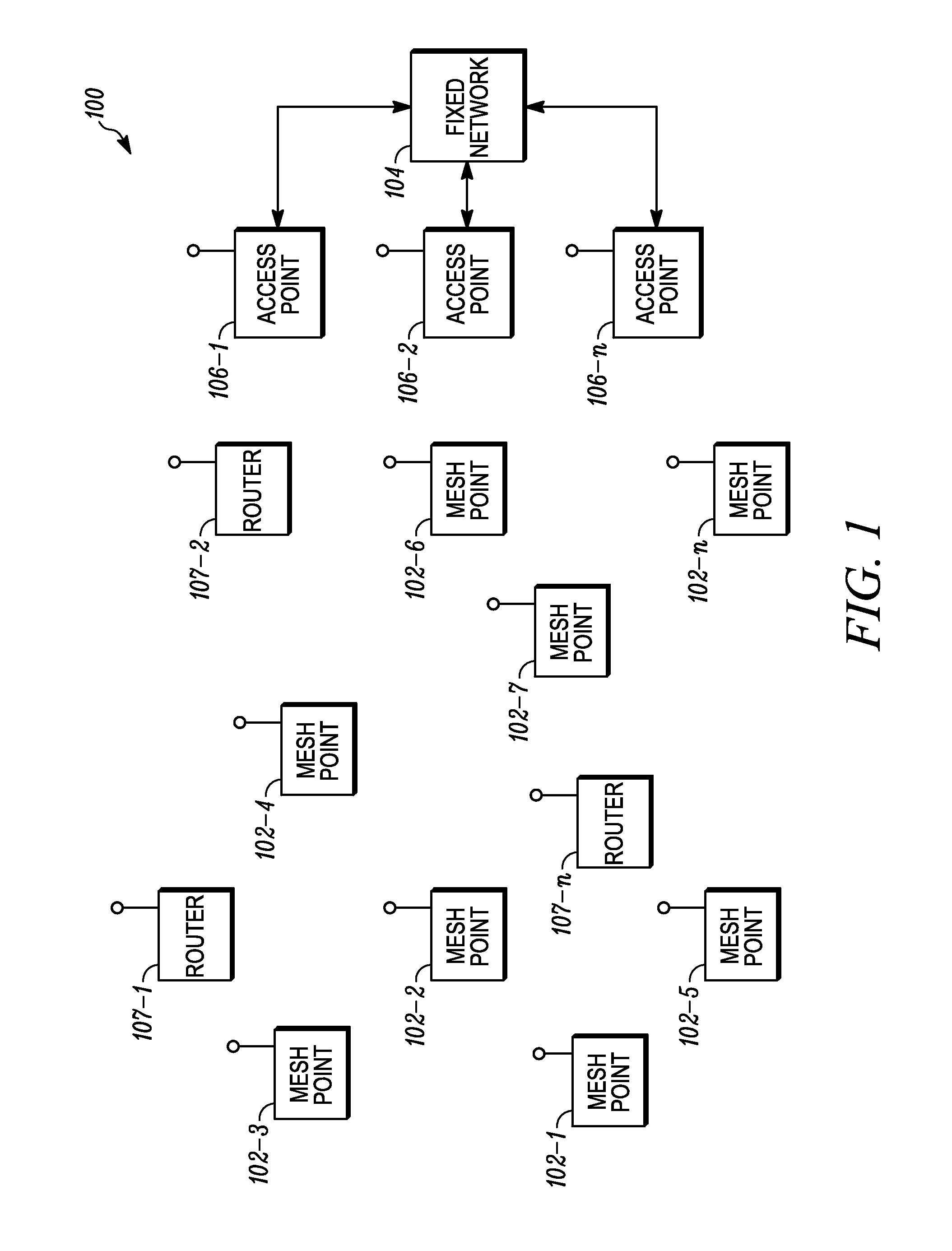
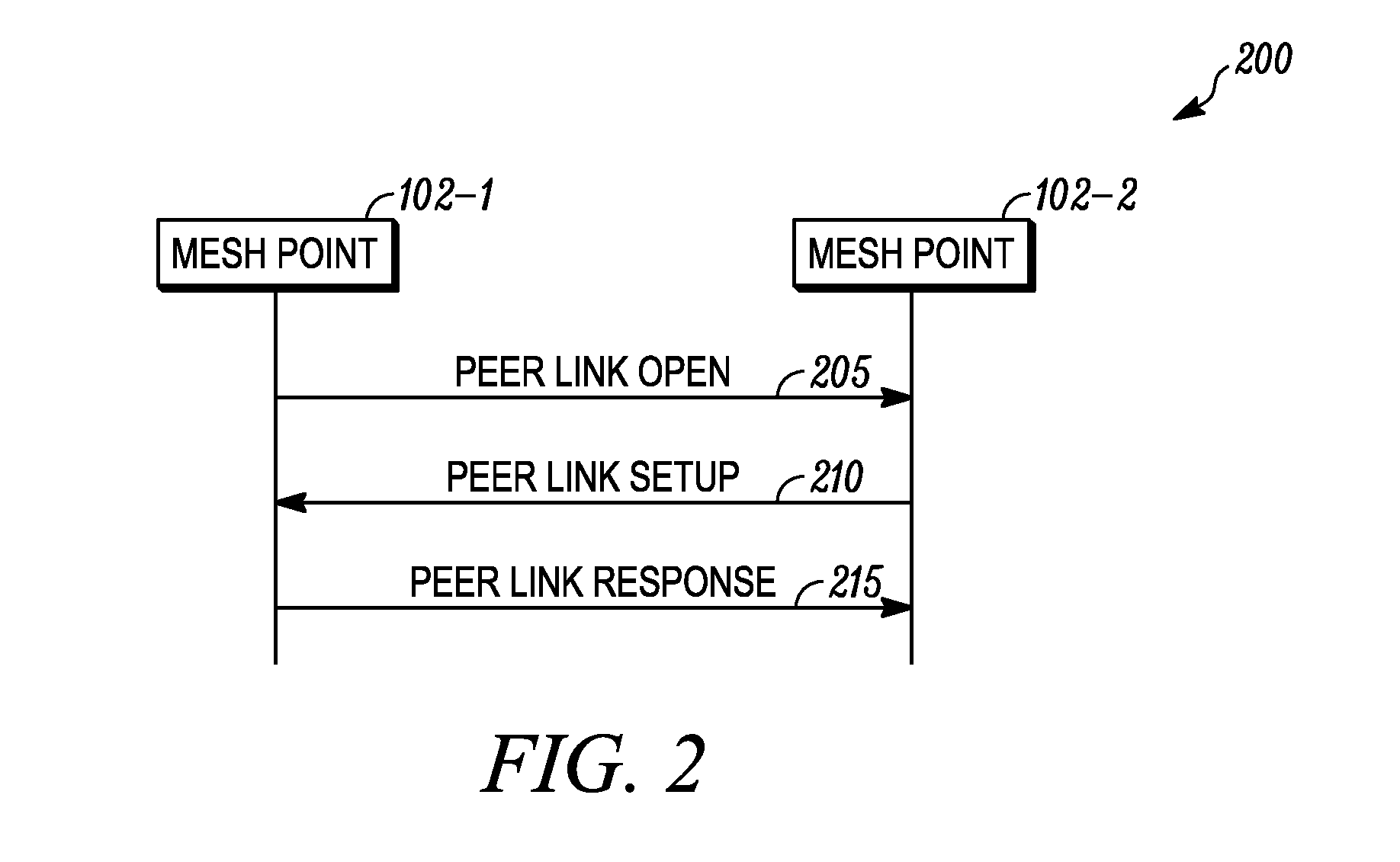
Patents
Literature
102 results about "Supplicant" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
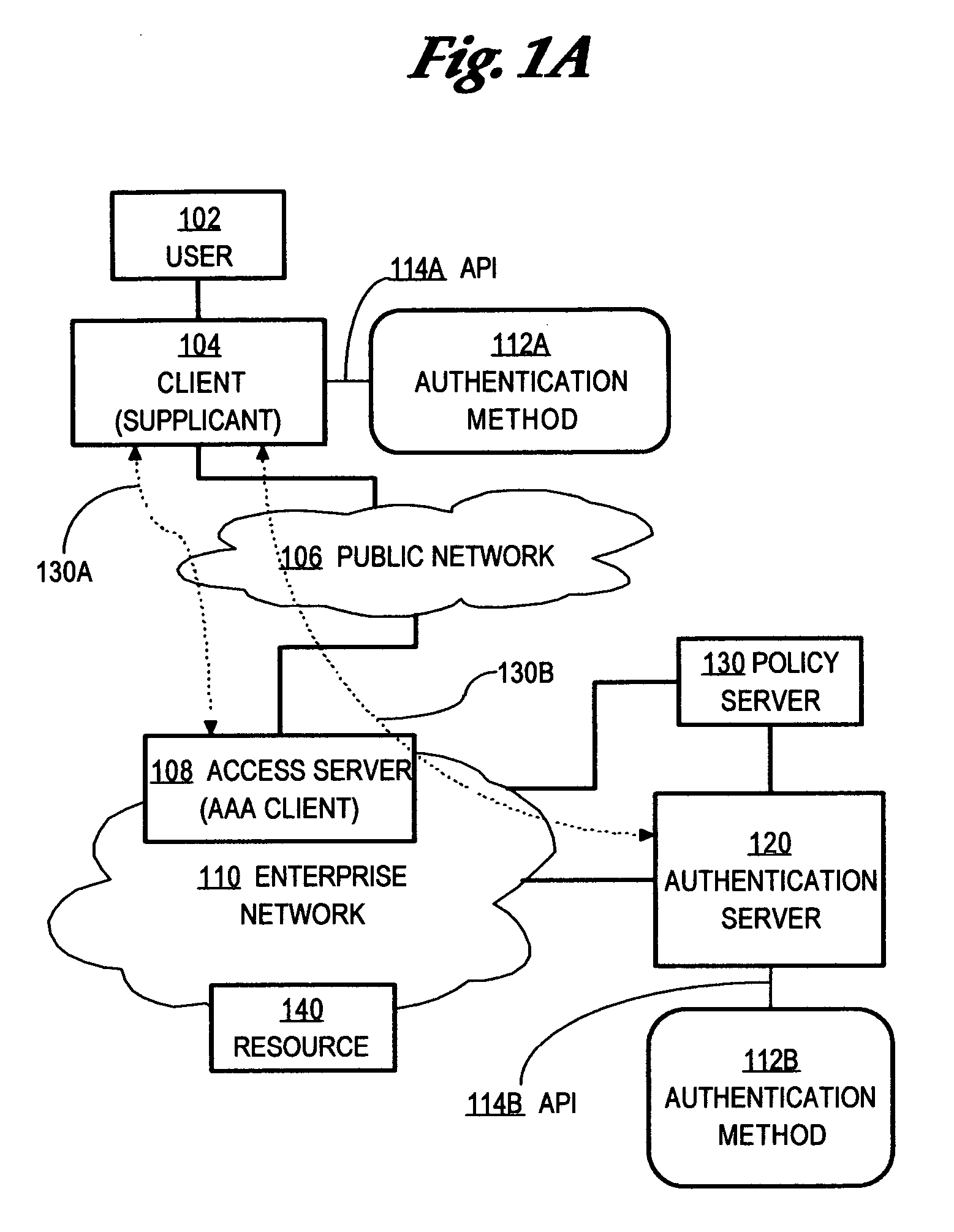
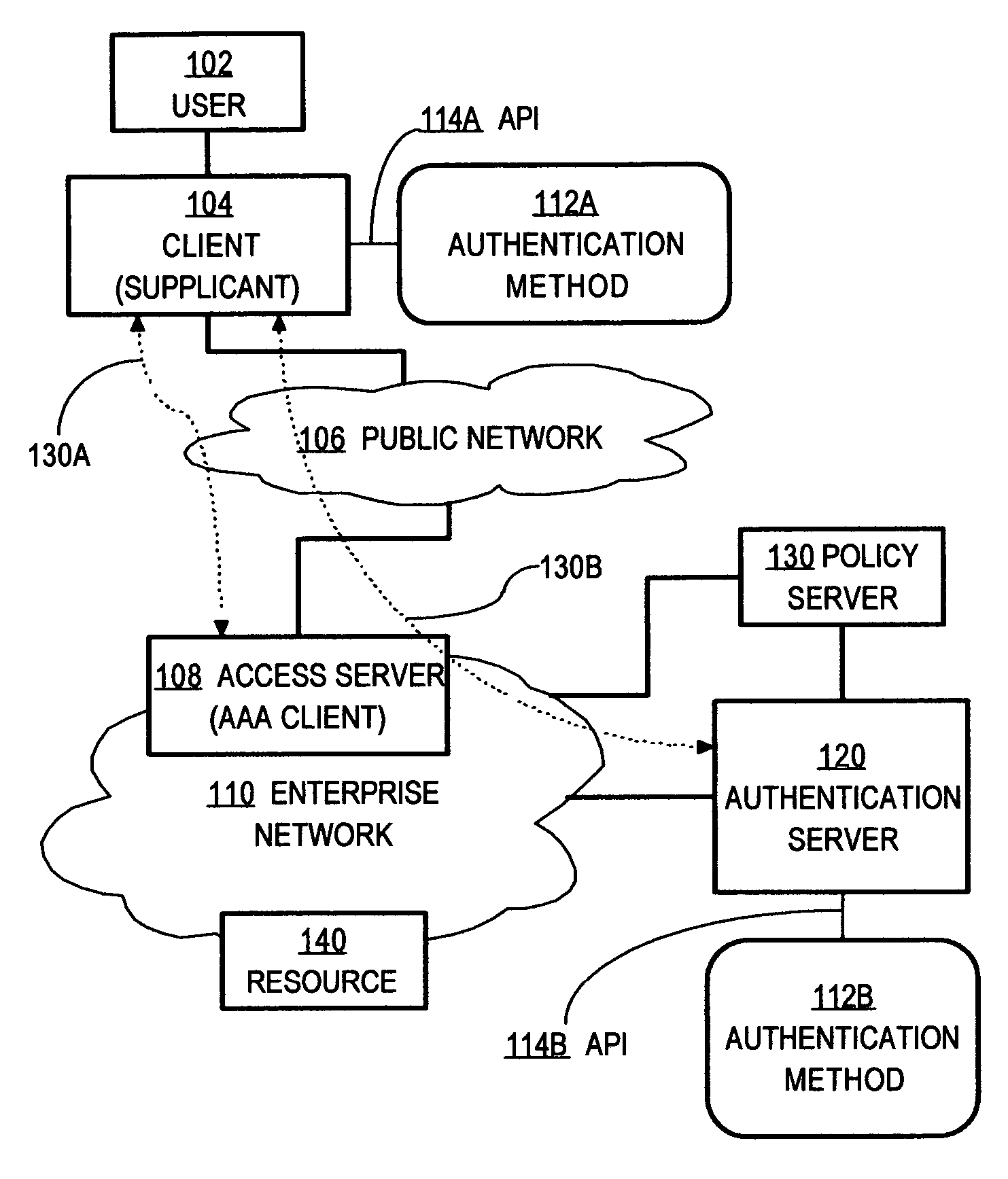
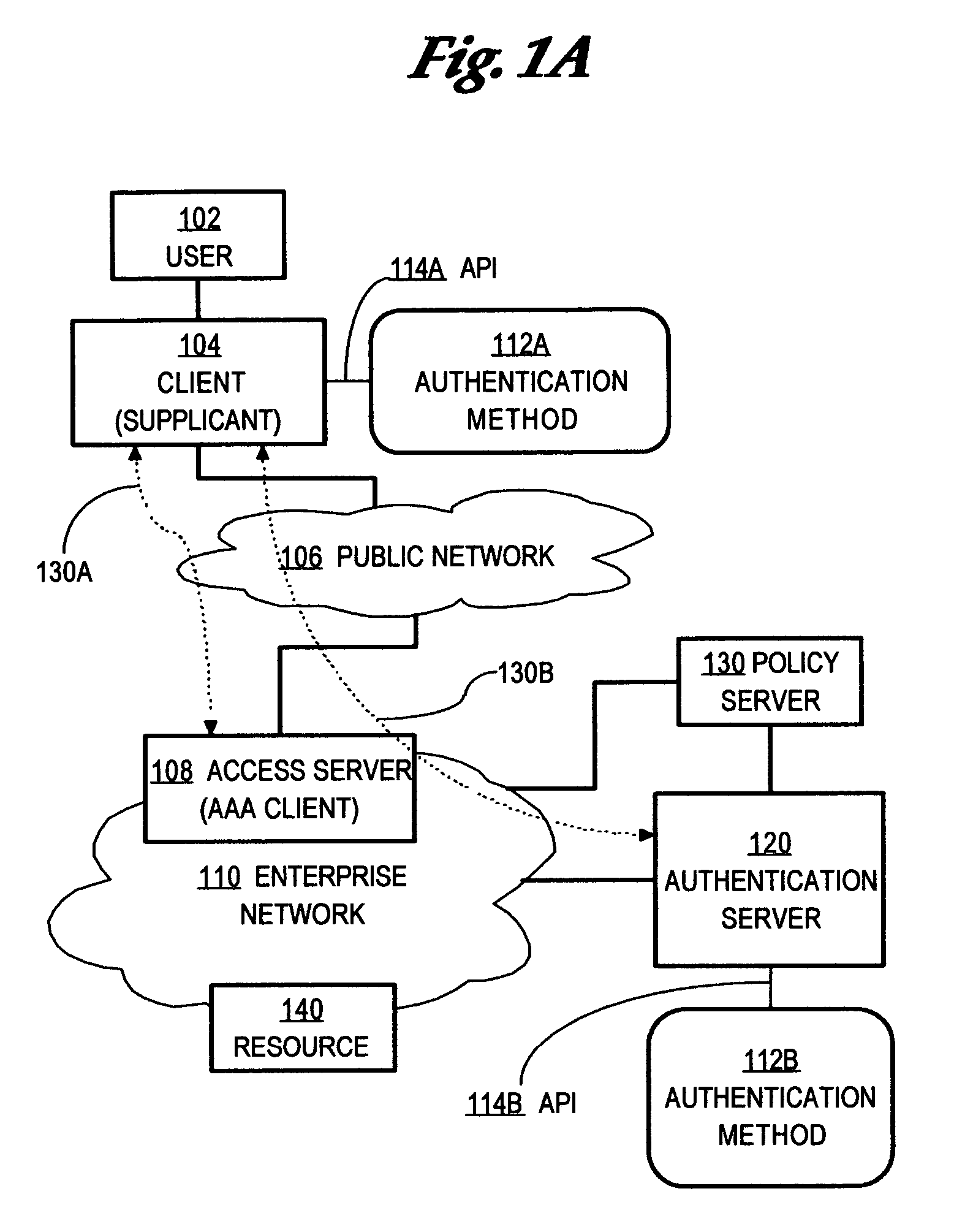
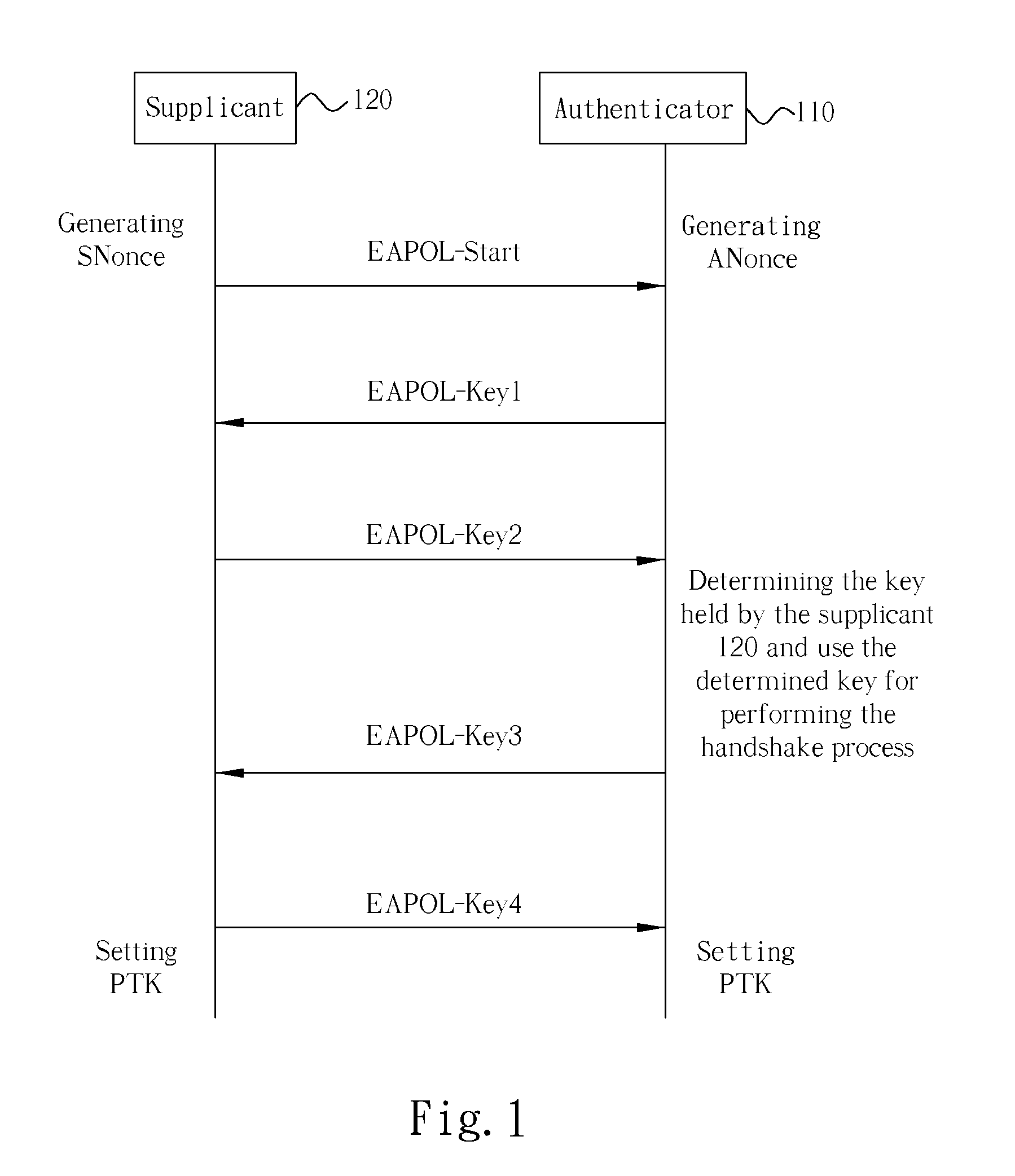
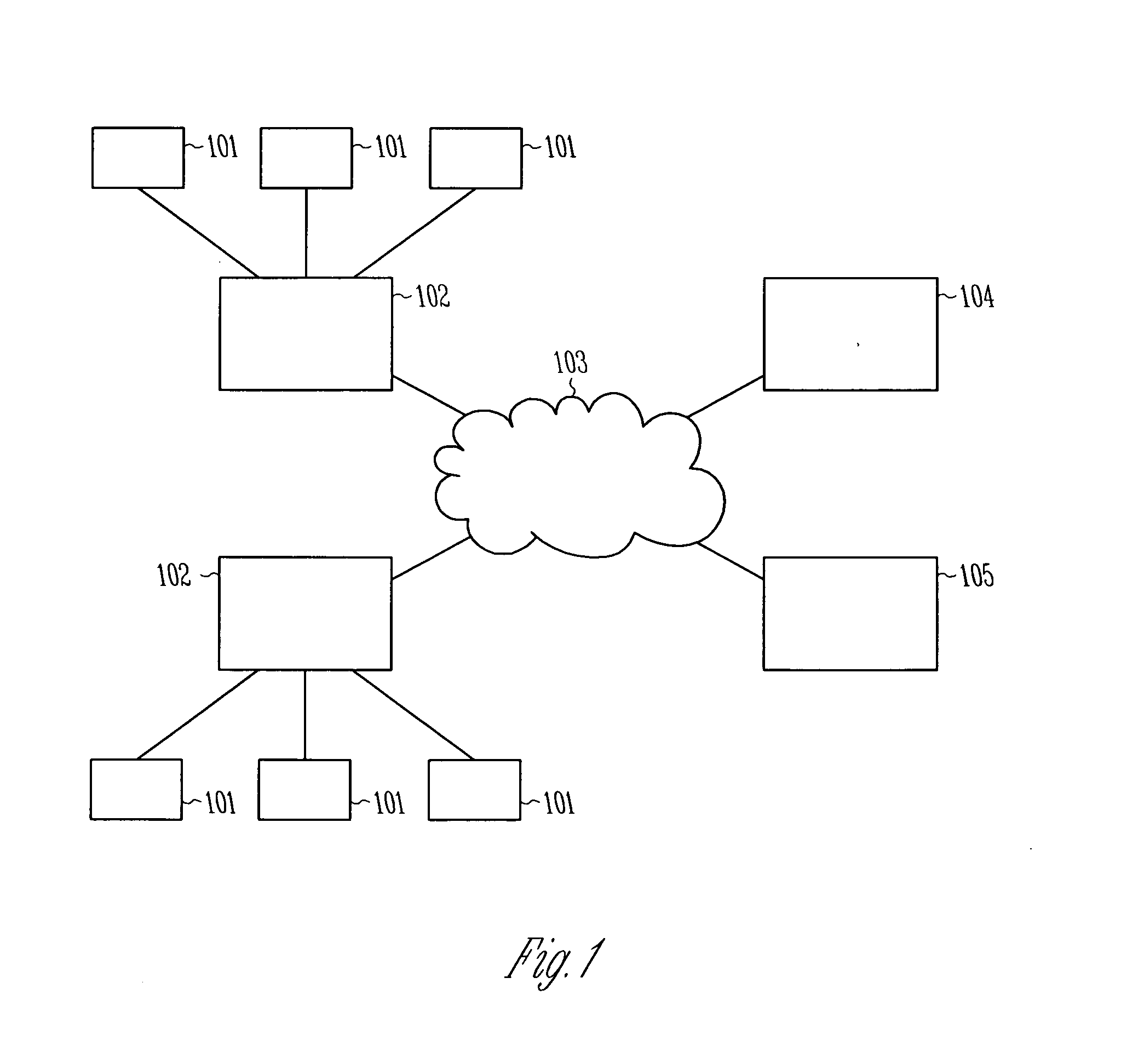
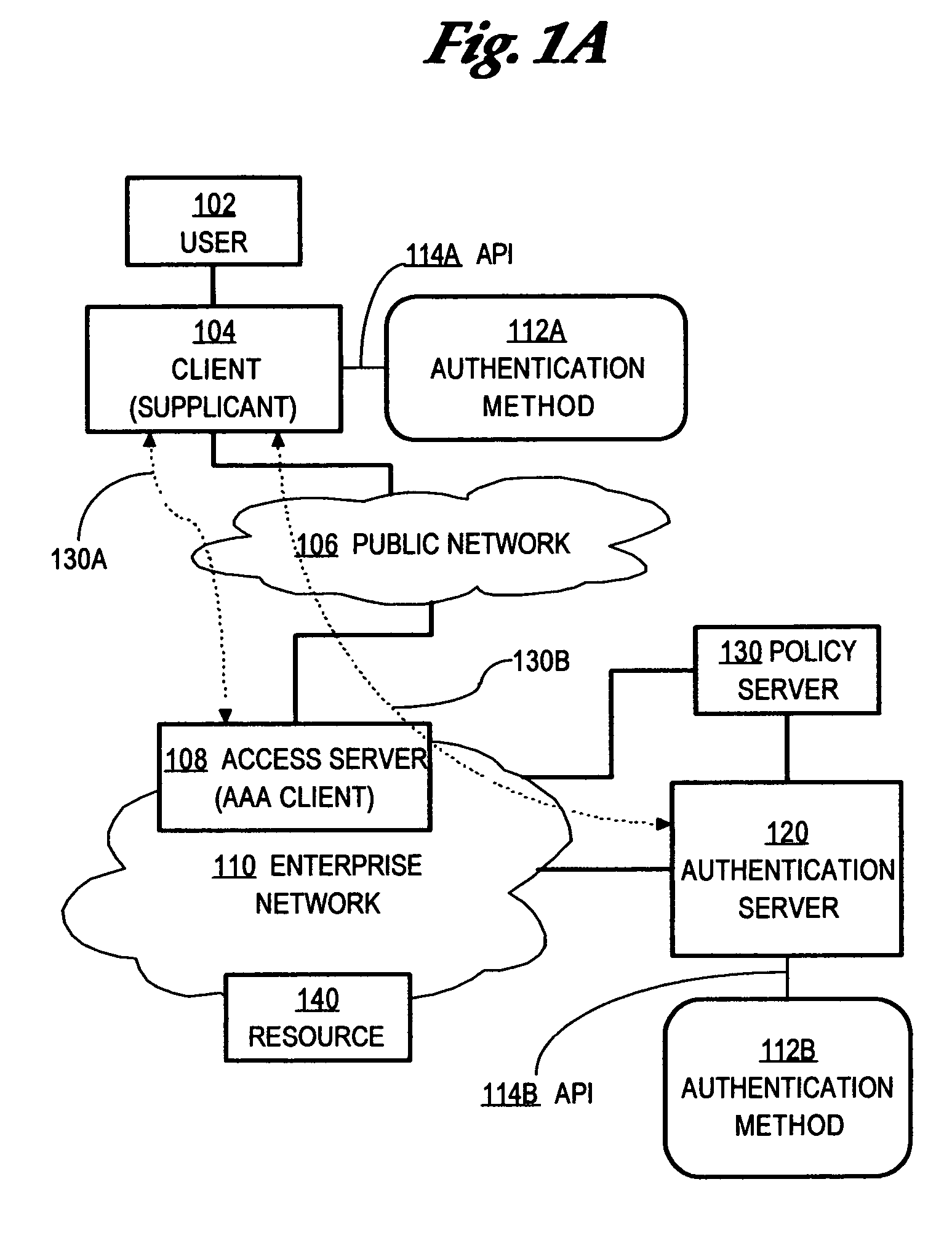
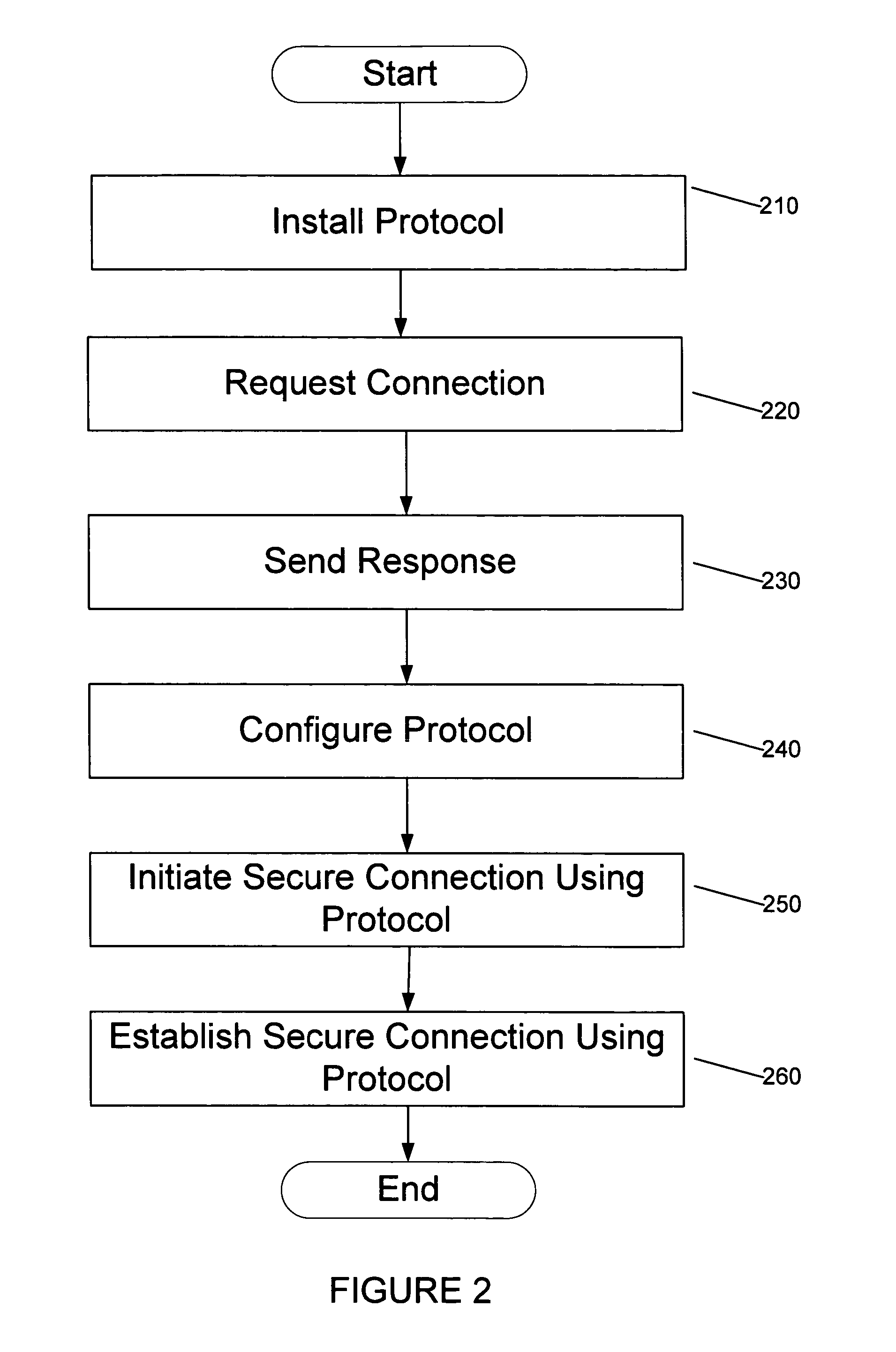
In computer networking, a supplicant is an entity at one end of a point-to-point LAN segment that seeks to be authenticated by an authenticator attached to the other end of that link. The IEEE 802.1X standard uses the term "supplicant" to refer either to hardware or to software. In practice, a supplicant is a software application installed on an end-user's computer. The user invokes the supplicant and submits credentials to connect the computer to a secure network. If the authentication succeeds, the authenticator typically allows the computer to connect to the network.
Privacy firewall
ActiveUS20140047551A1Impact efficiencyImpact performanceDigital data processing detailsRelational databasesSupplicantInternet privacy
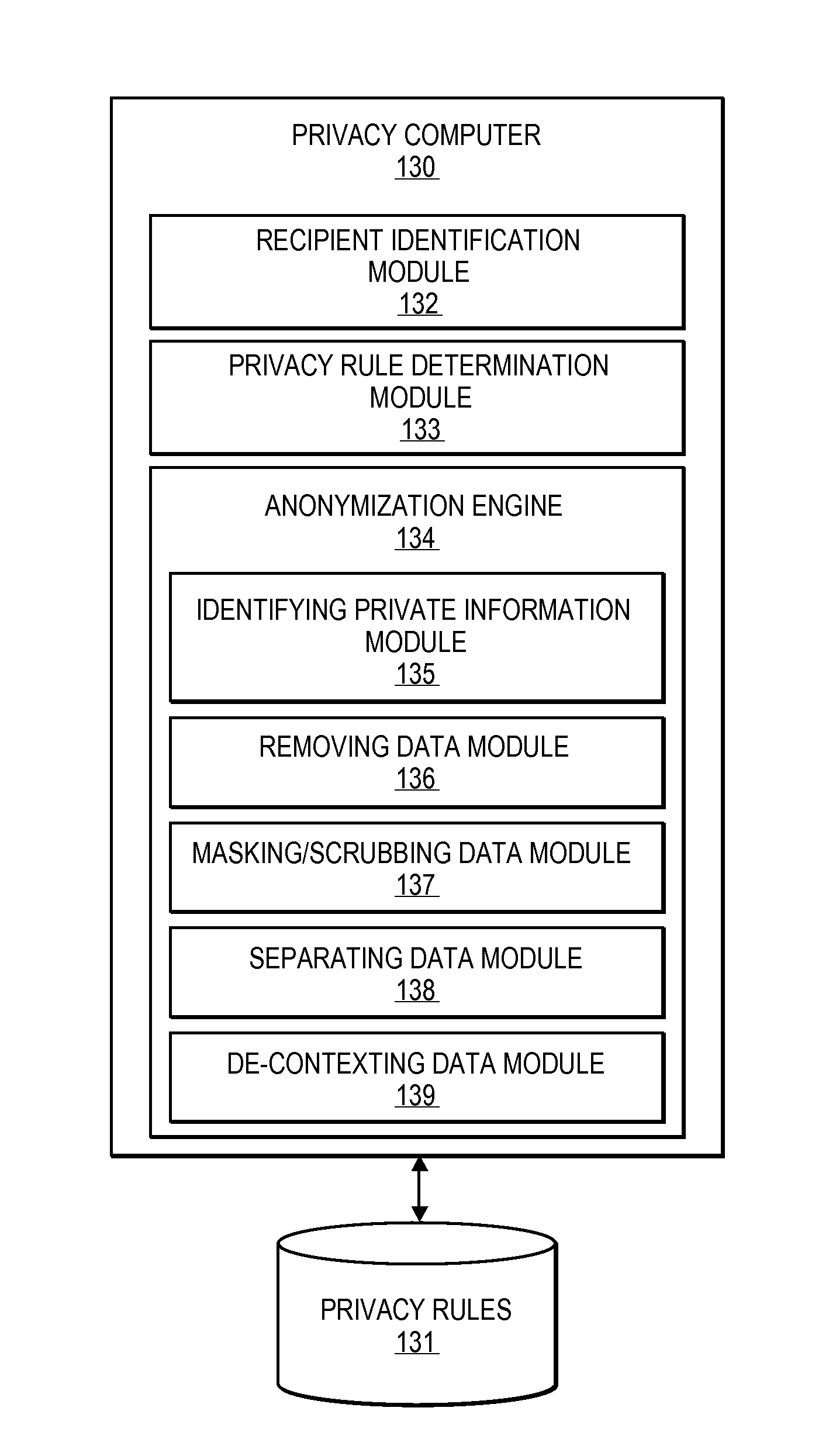
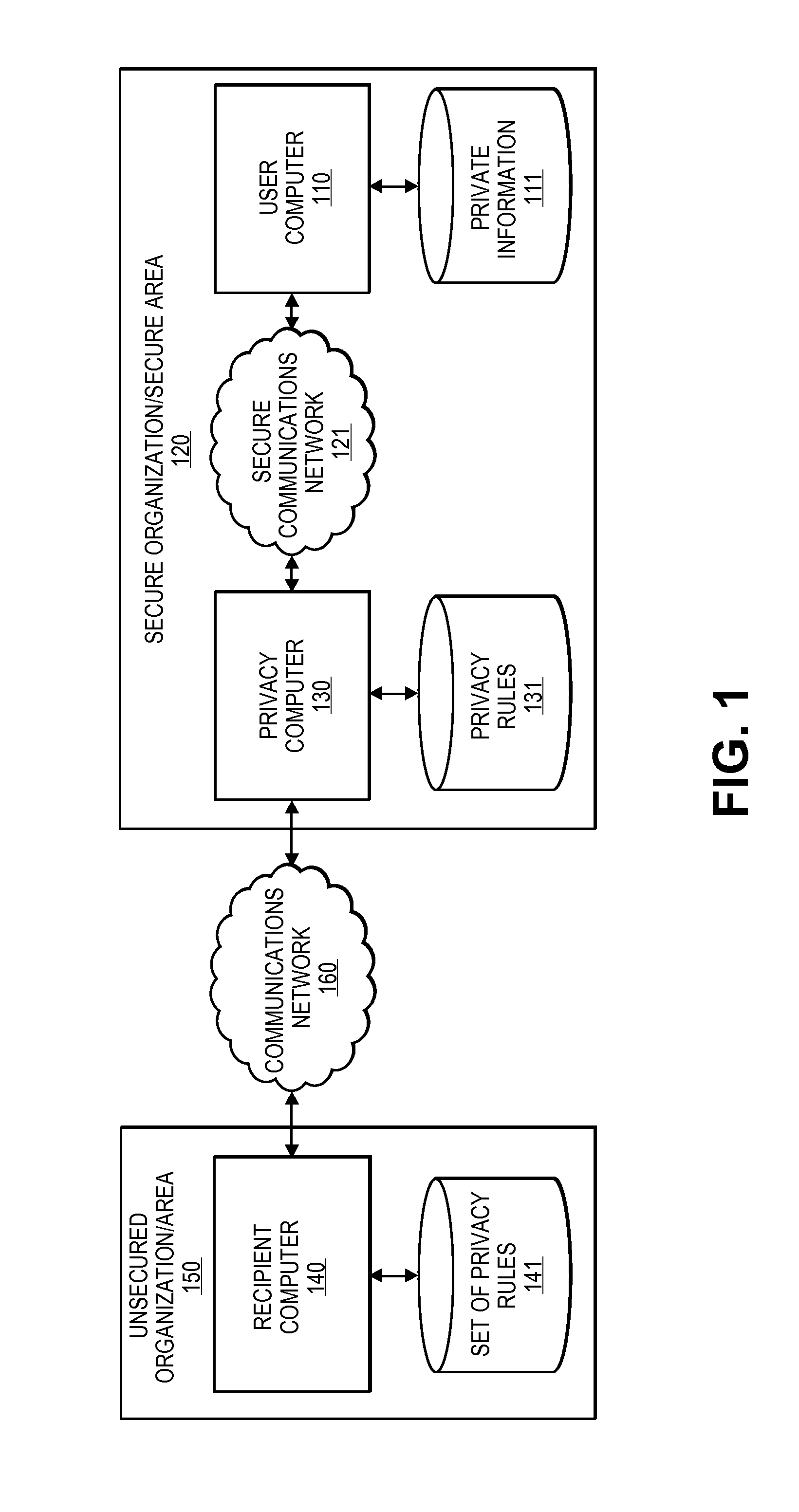
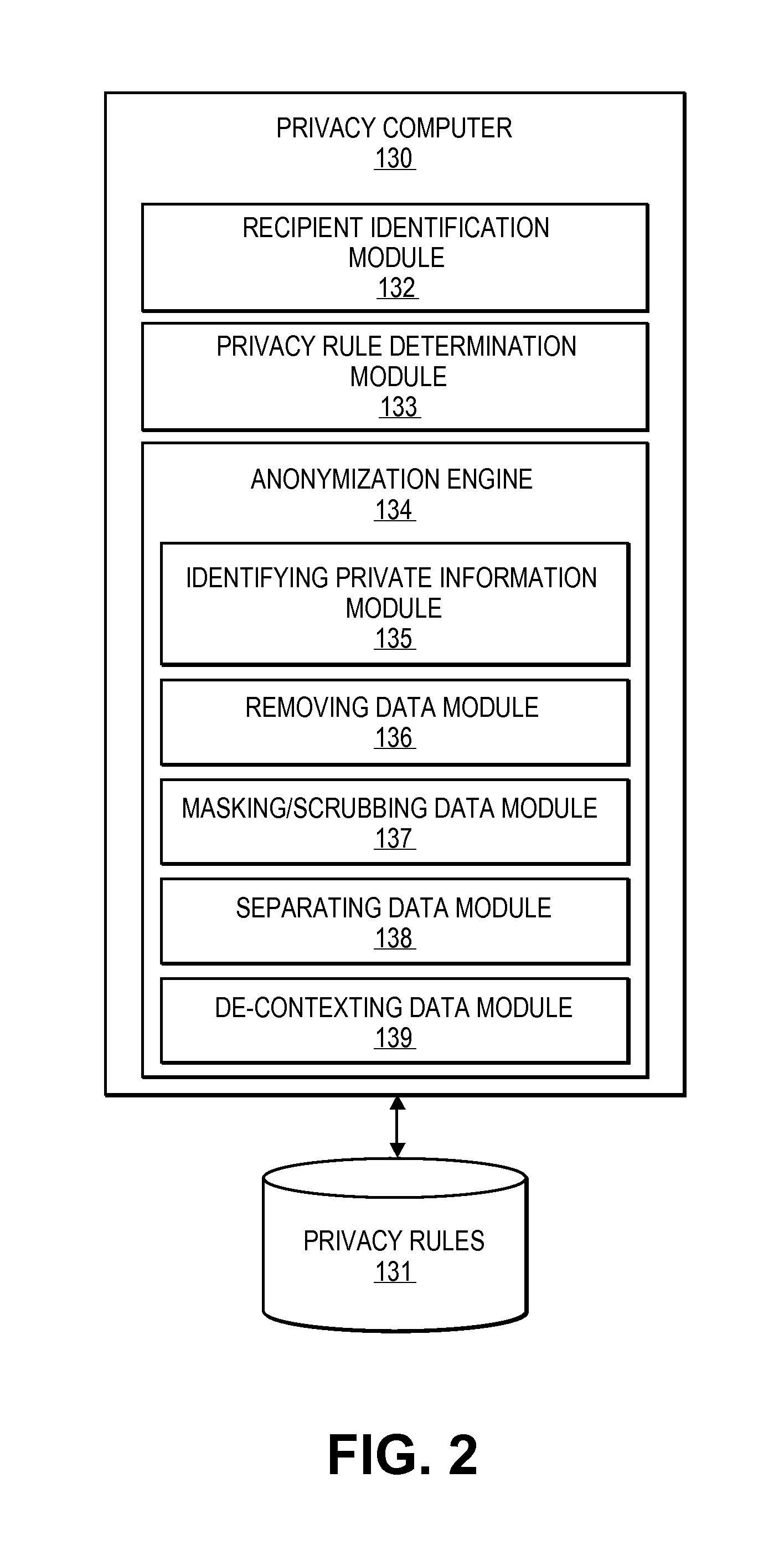
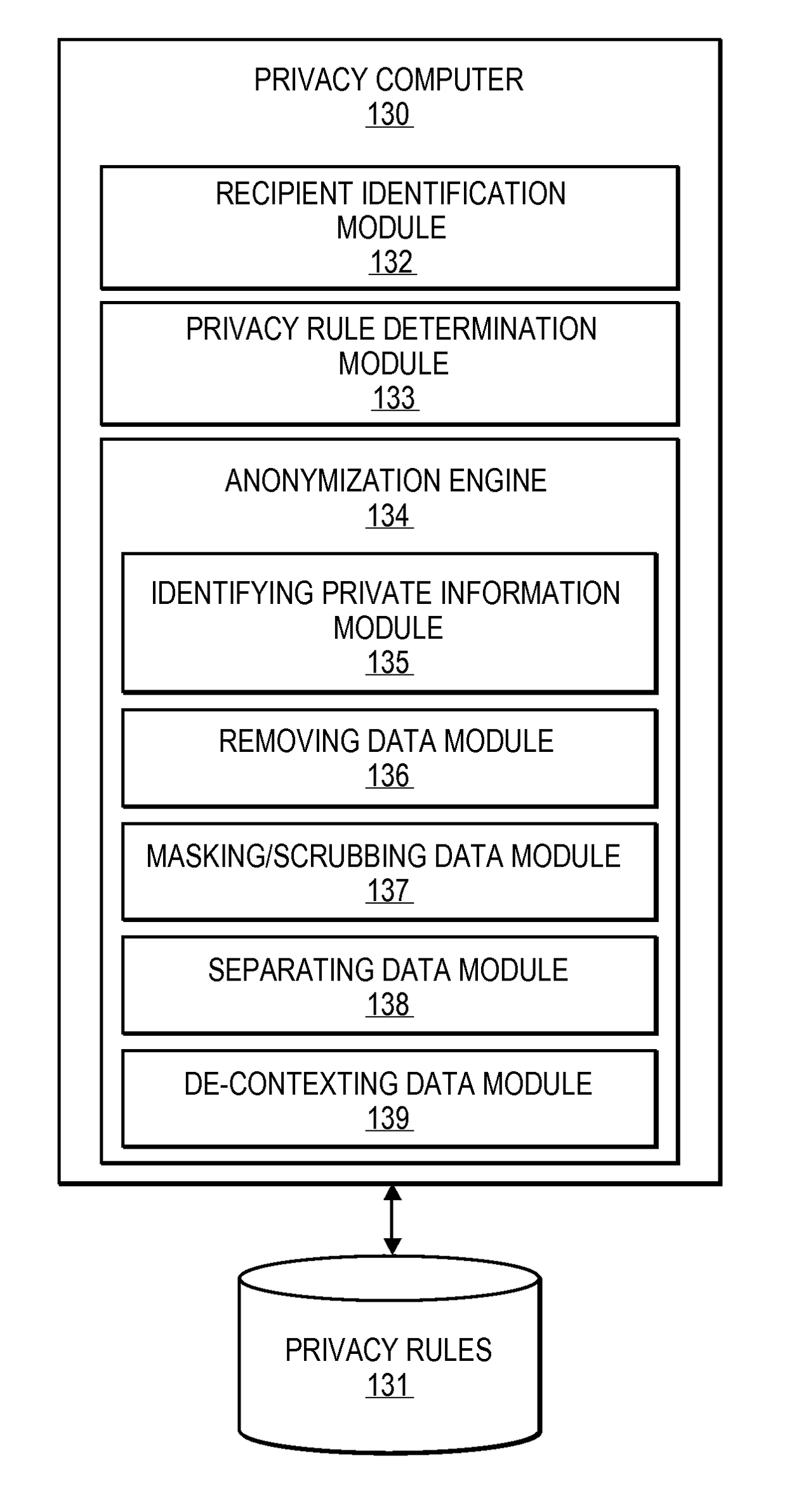
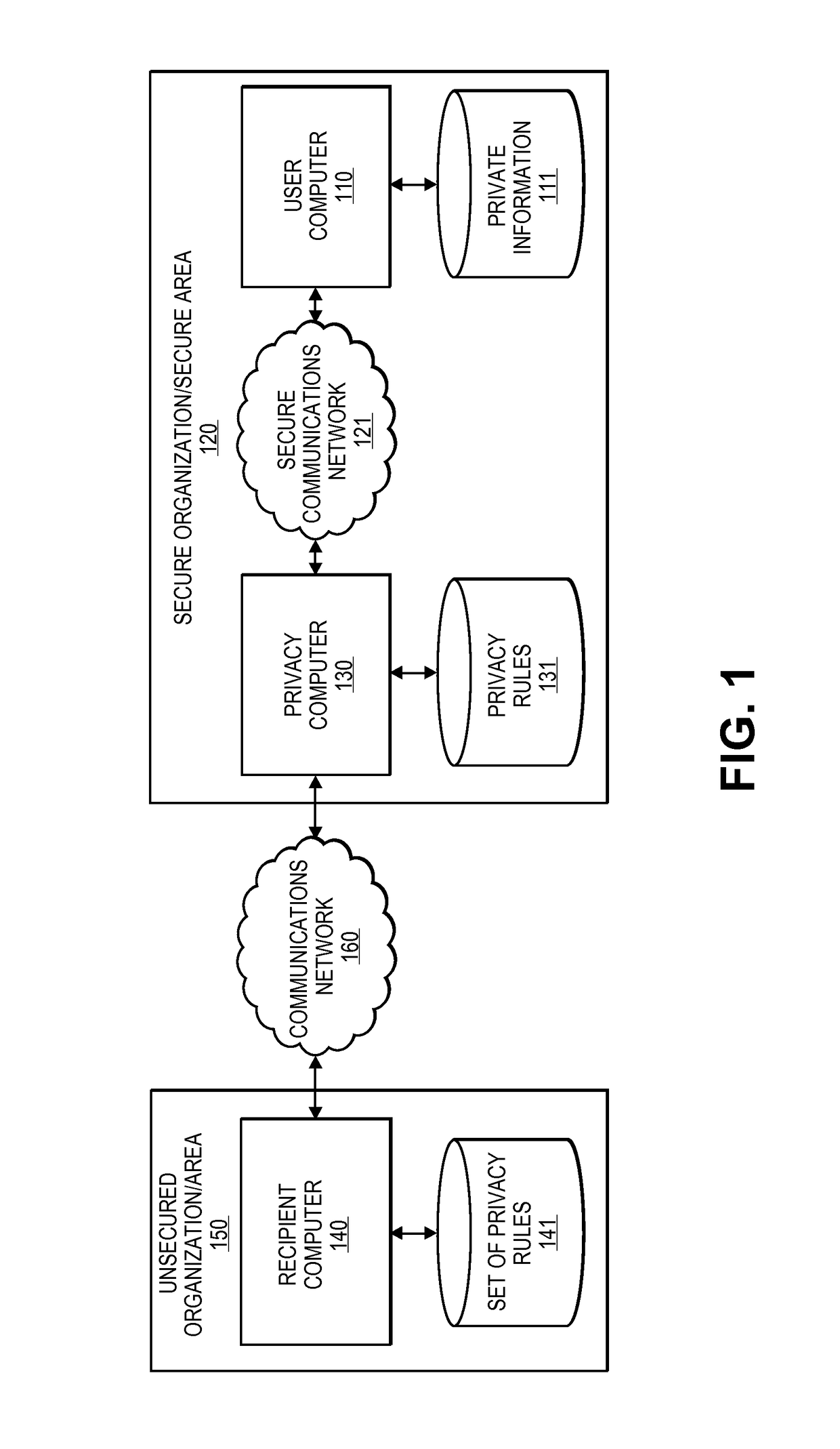
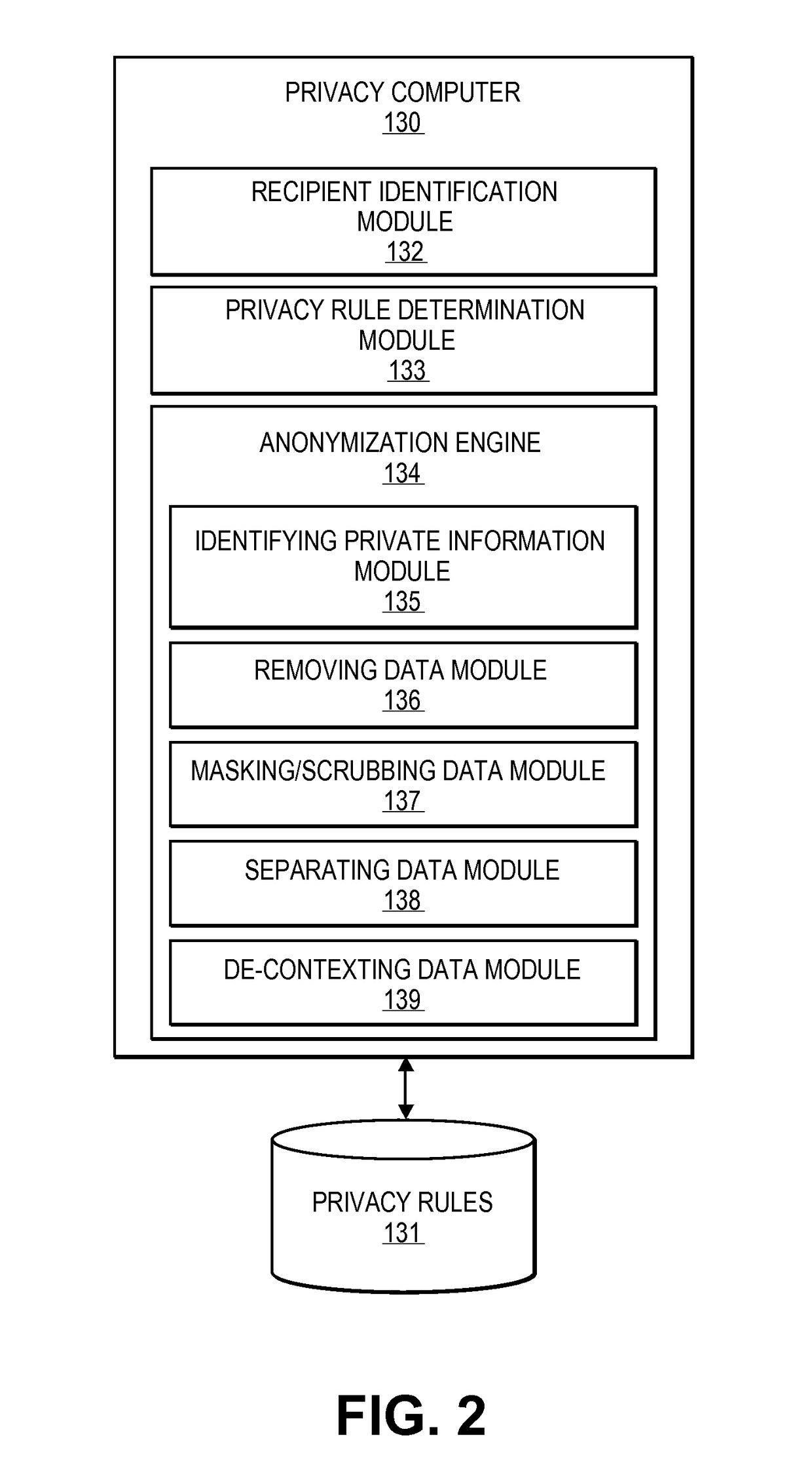
Embodiments of the invention relate to systems and methods for providing an anonymization engine. One embodiment of the present invention relates to a method comprising receiving a message directed at a recipient computer located outside a secure area by a privacy computer located within a secure area. The privacy computer may identify private information using a plurality of privacy rules and anonymize the message according to the plurality of privacy rules. Another embodiment may be directed to a method comprising receiving a request for sensitive data from a requesting computer. An anonymization computer may determine a sensitive data record associated with the request and may anonymize the sensitive data record by performing at least two of: removing unnecessary sensitive data entries from the sensitive data record, masking the sensitive data entries to maintain format, separating the sensitive data entries into associated data groupings, and de-contexting the data.
Owner:VISA INT SERVICE ASSOC
Privacy firewall
ActiveUS9665722B2Protect normal useAvoid identificationRelational databasesDigital data protectionSupplicantInternet privacy
Embodiments of the invention relate to systems and methods for providing an anonymization engine. One embodiment of the present invention relates to a method comprising receiving a message directed at a recipient computer located outside a secure area by a privacy computer located within a secure area. The privacy computer may identify private information using a plurality of privacy rules and anonymize the message according to the plurality of privacy rules. Another embodiment may be directed to a method comprising receiving a request for sensitive data from a requesting computer. An anonymization computer may determine a sensitive data record associated with the request and may anonymize the sensitive data record by performing at least two of: removing unnecessary sensitive data entries from the sensitive data record, masking the sensitive data entries to maintain format, separating the sensitive data entries into associated data groupings, and de-contexting the data.
Owner:VISA INT SERVICE ASSOC
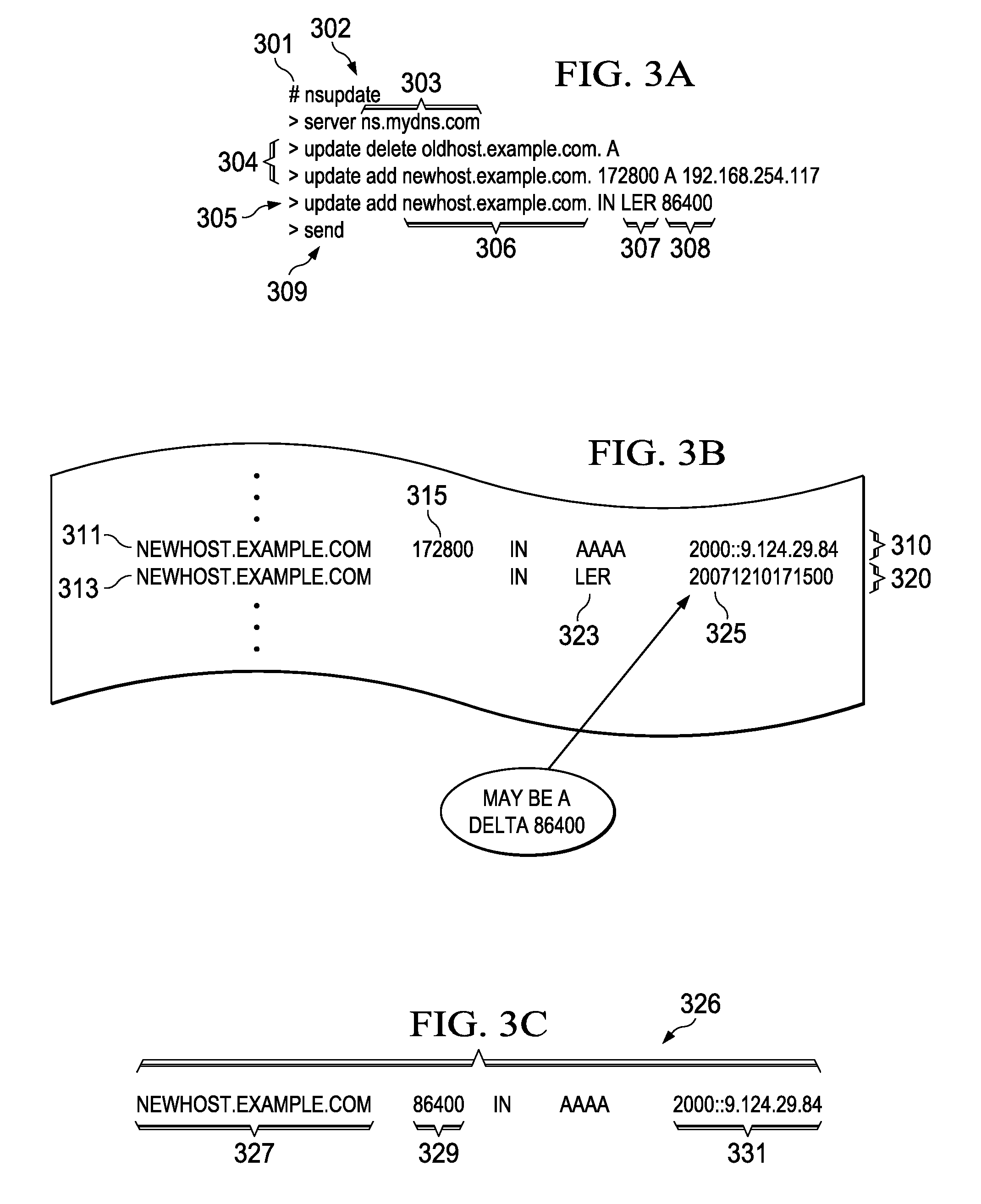
Dynamic expiration of domain name service entries
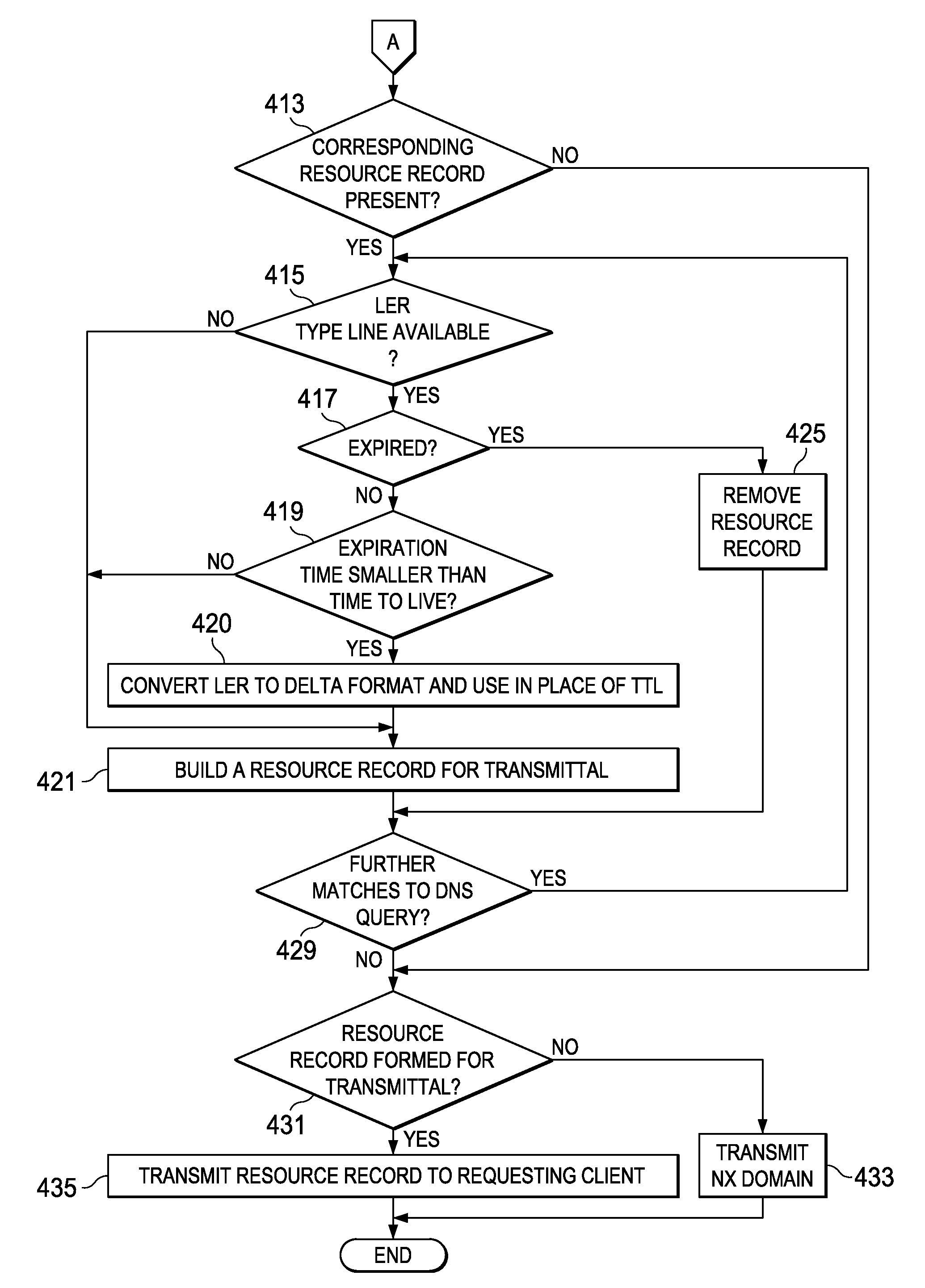
Disclosed is a computer implemented method and computer program product for transmitting a resource record to a requesting computer. An authoritative domain name server receives a DNS query from a requesting computer at a name server. The authoritative domain name server looks up the resource record based on the DNS query, wherein the resource record is associated with an epochal time and a time to live. The authoritative domain name server transmits the resource record response based on the epochal time.
Owner:INT BUSINESS MASCH CORP
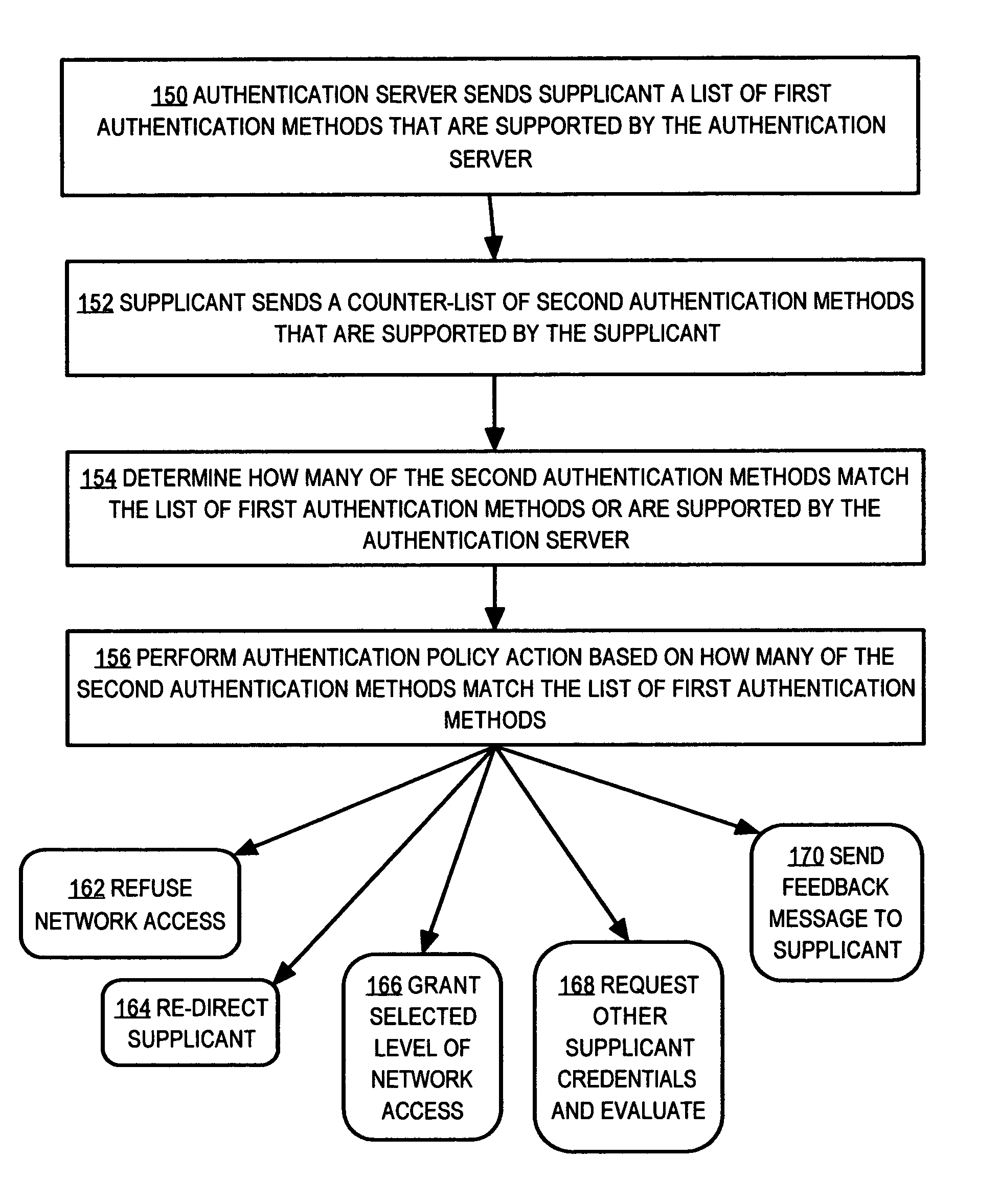
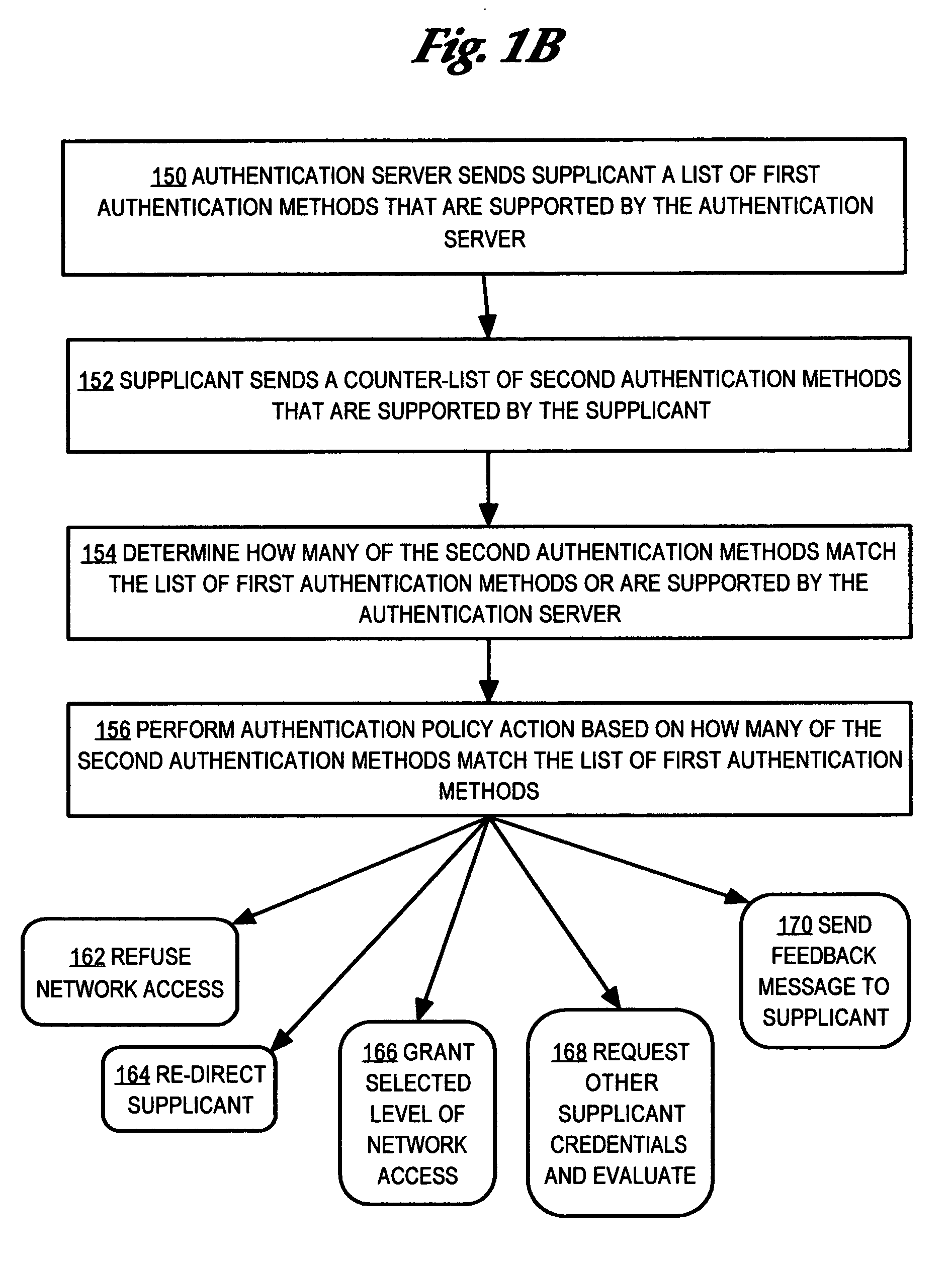
Method and apparatus for determining authentication capabilities
ActiveUS20060026671A1Public key for secure communicationDigital data processing detailsAuthentication serverClient-side
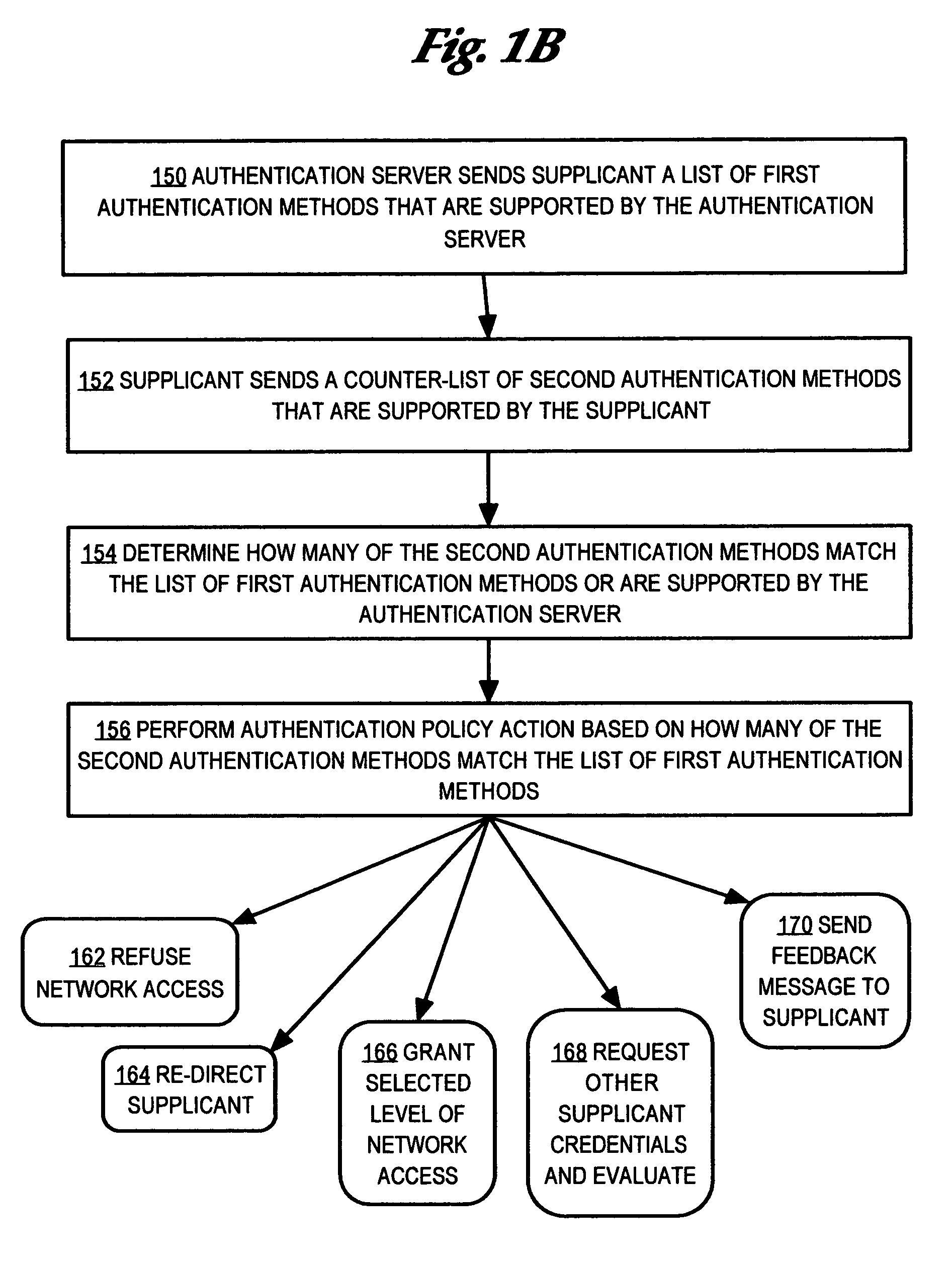
A method is disclosed for determining the authentication capabilities of a supplicant before initiating an authentication conversation with a client, for example, using Extensible Authentication Protocol (EAP). In one aspect, the method provides for sending, to a supplicant that is requesting access to a computer network subject to authentication of a user of the supplicant, a list of first authentication methods that are supported by an authentication server; receiving, from the supplicant, a counter-list of second authentication methods that are supported by the supplicant; determining how many second authentication methods in the counter-list match the first authentication methods; and performing an authentication policy action based on how many of the second authentication methods match the first authentication methods. Policy actions can include blocking access, re-directing to sources of acceptable authentication methods, granting one of several levels of network access, etc.
Owner:CISCO TECH INC
Resolving host name data
InactiveUS7284056B2Multiple digital computer combinationsTransmissionTransmission protocolSupplicant
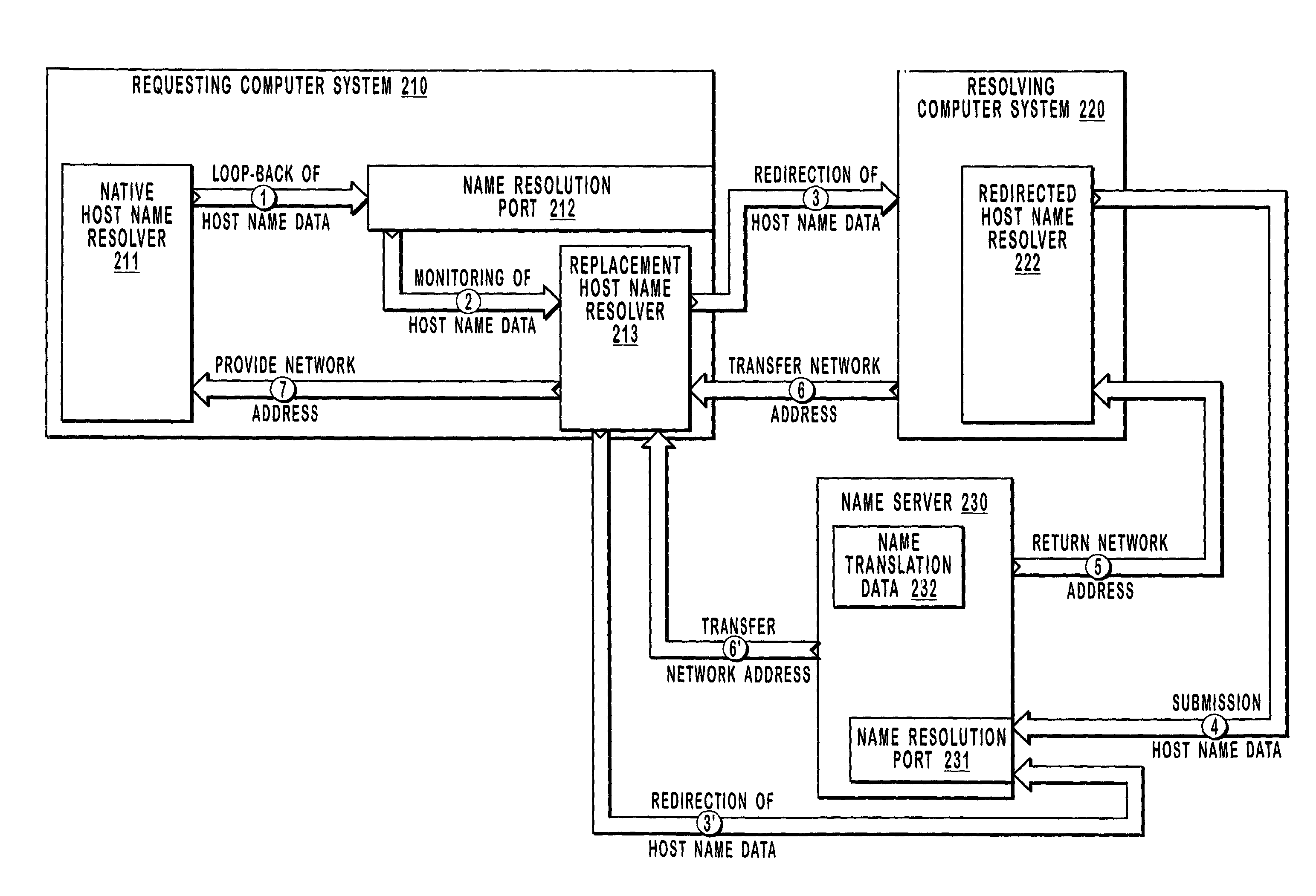
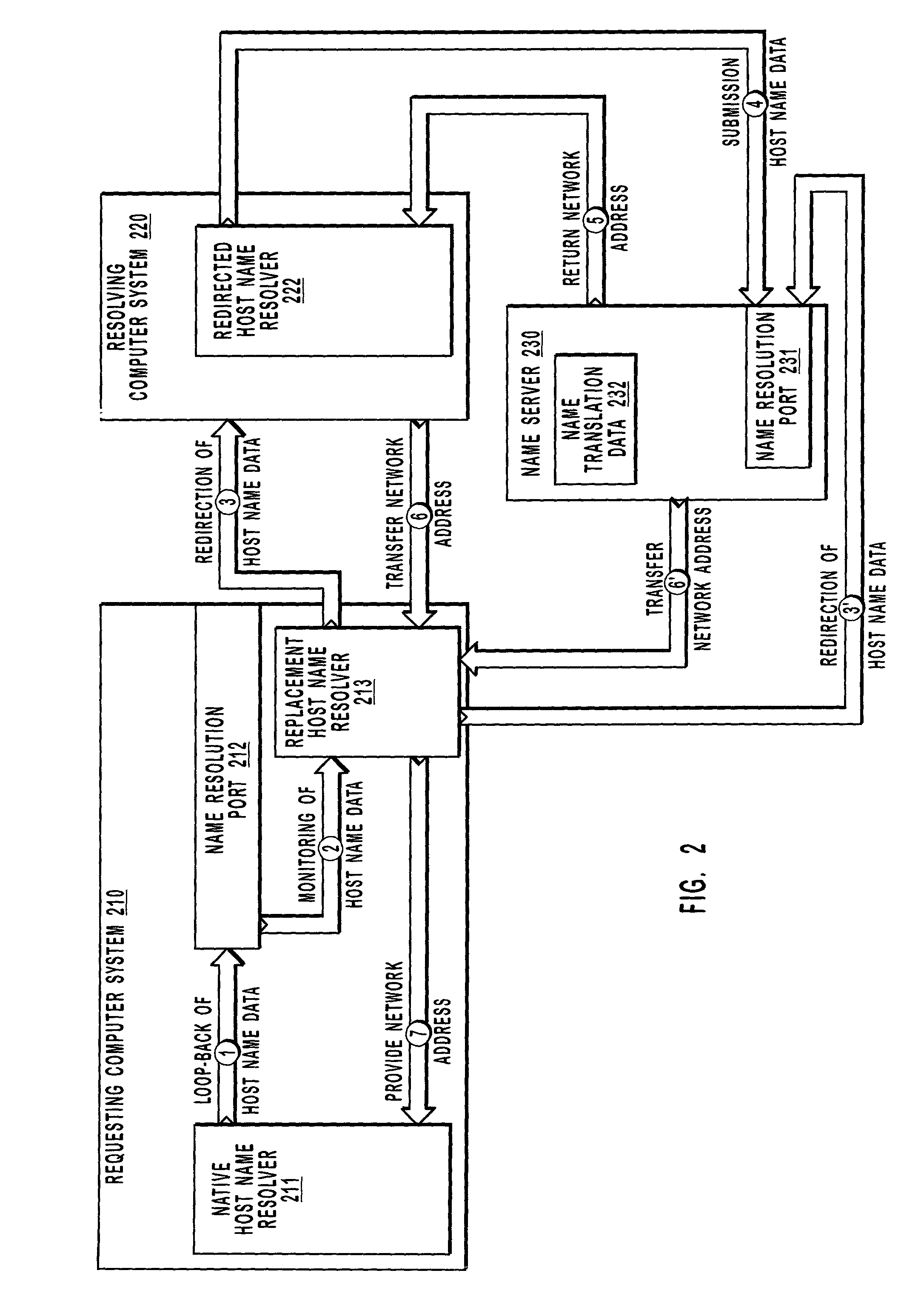
Host name data is “looped-back” from a native host name resolver included in a requesting computer system to a name resolution port that is also included in the requesting computer system. A replacement host name resolver monitors the name resolution port for host name data that is incompatible with name resolution techniques utilized by a network. The replacement host name resolver modifies the otherwise incompatible host name data for compatibility with name resolution techniques utilized by the network. Modifying host name data may include changing a transmission protocol associated with the host name data or formatting non-secure host name data for resolution with secure host name resolution techniques. The replacement host name resolver redirects compatible host name data to a module that may cause the host name data to be resolved into a network address. The network address may be provided to the native host name resolver.
Owner:MICROSOFT TECH LICENSING LLC
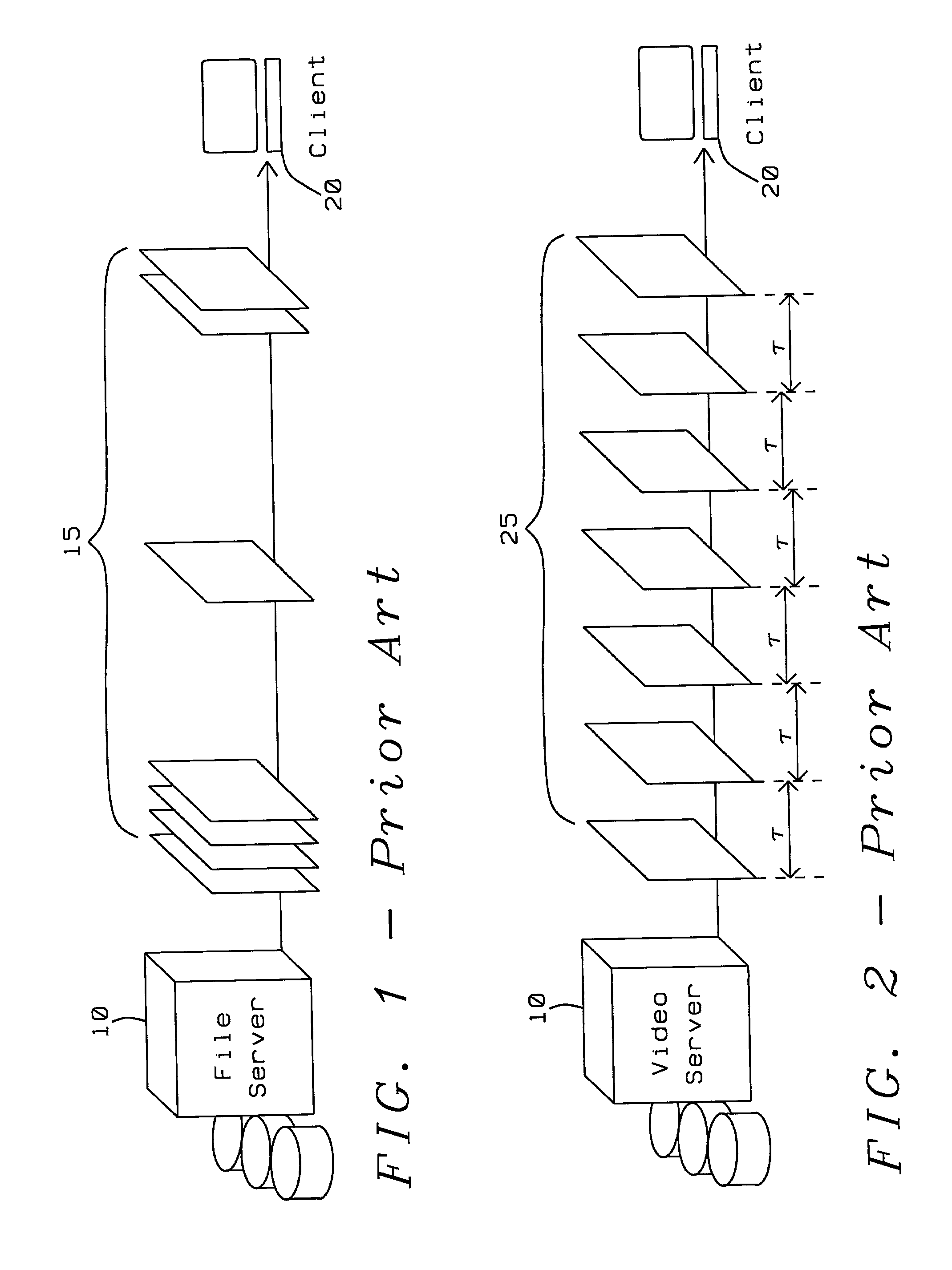
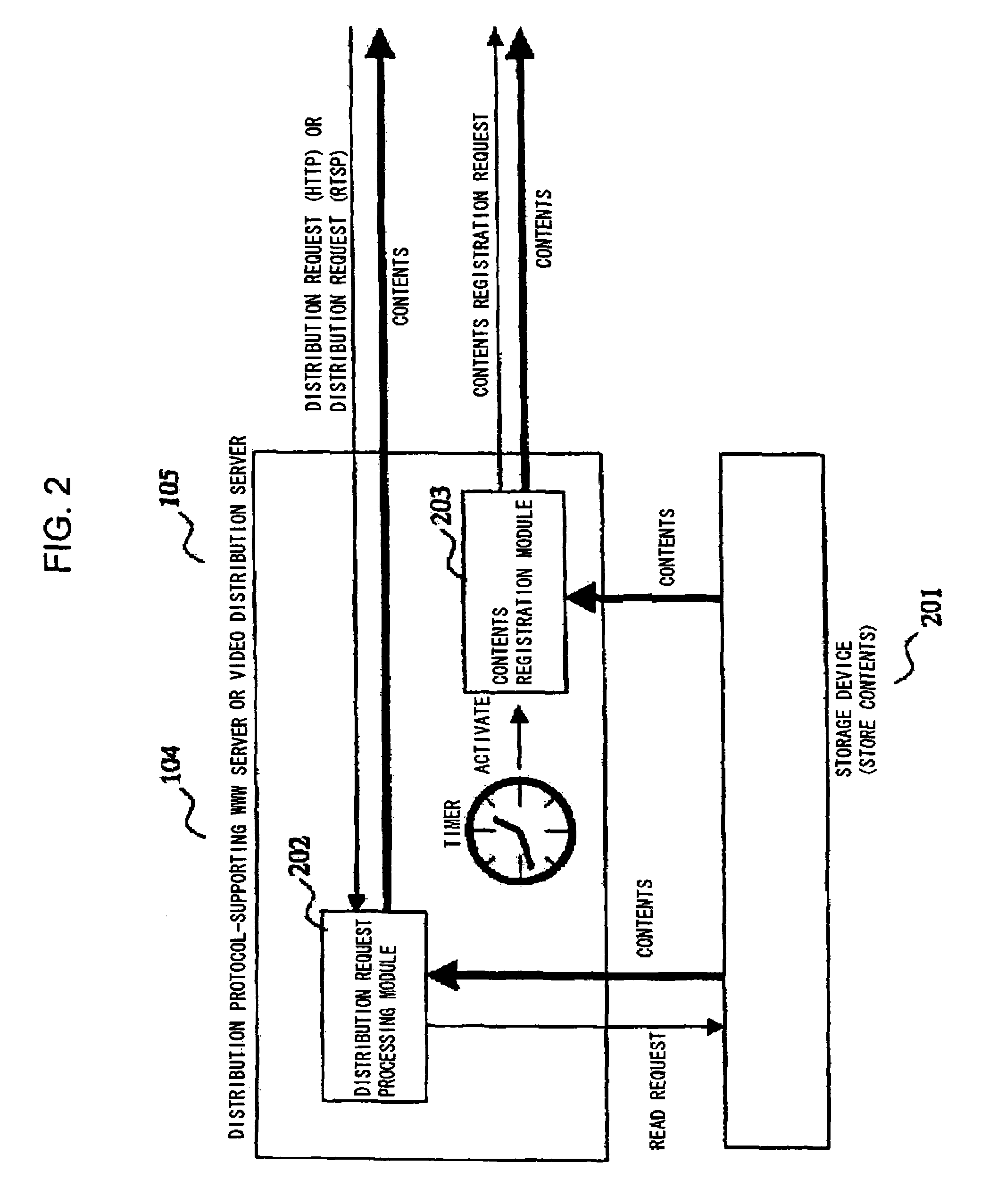
Video distribution system using dynamic disk load balancing with variable sub-segmenting
ActiveUS7039784B1Avoid interferenceDynamic loadingData processing applicationsMultiprogramming arrangementsComputer hardwareSupplicant
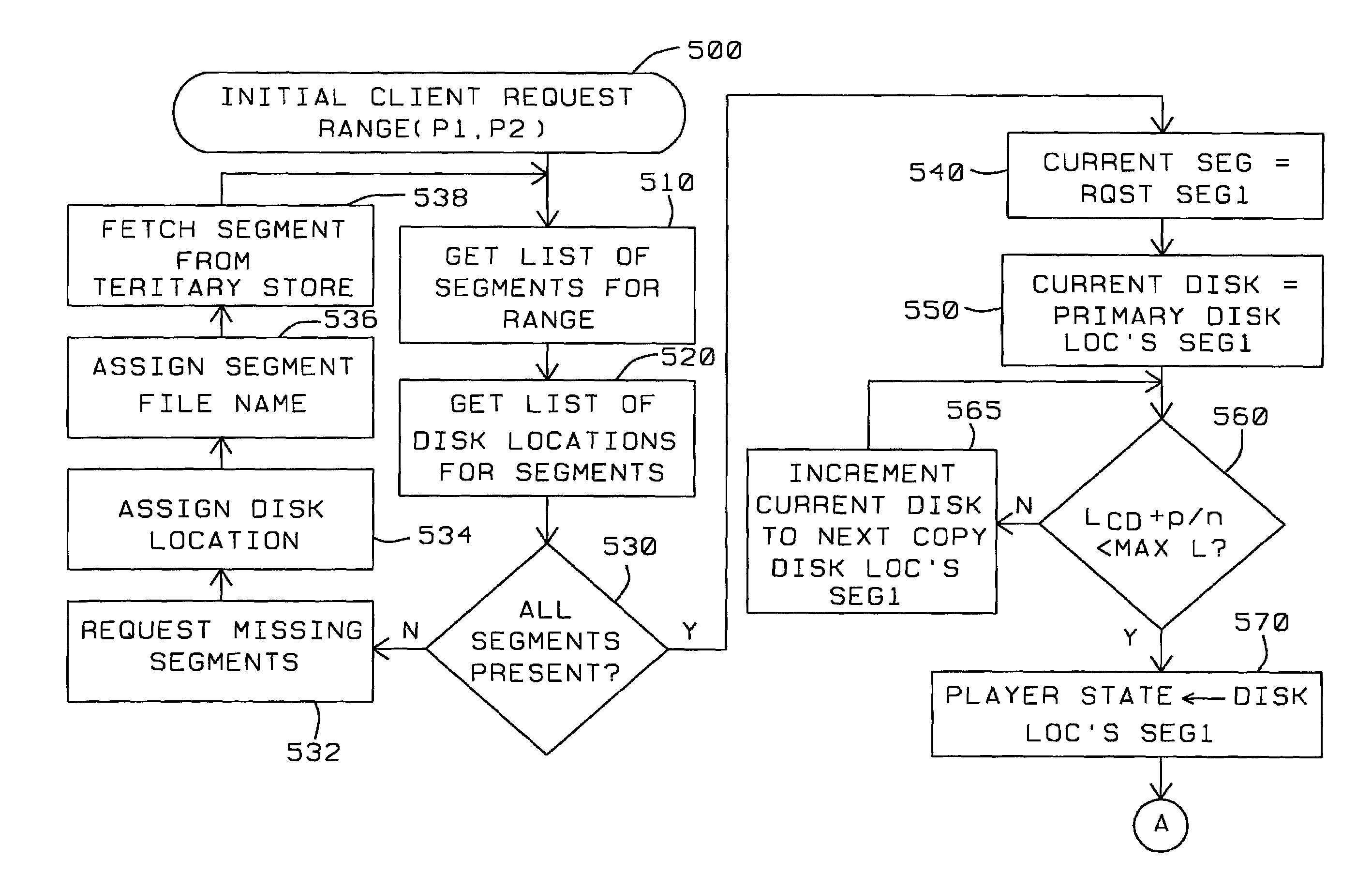
A method and apparatus for dynamically balancing the loading of video data storage devices facilitates the transfer of video data by acquiring a listing of locations and loading of all segments of a requested video data. Those storage devices containing copies of each segment of the video data having a least loading are selected. If the loading of the storage devices exceed their maximum capacity, the segment is divided into sub-segments and stored to storage devices with minimum loading. The presence of all segments of the requested video data is determined. If there are missing segments of the requested video data, each of those missing segments is assigned a file identification and file location, such that those missing segments are retrieved from a back-up storage device and assigned to data storage devices having the least loading for transfer to a requesting computer system.
Owner:INFOVALUE COMPUTING
Method and apparatus for determining authentication capabilities
ActiveUS7194763B2Public key for secure communicationDigital data processing detailsAuthentication serverClient-side
A method is disclosed for determining the authentication capabilities of a supplicant before initiating an authentication conversation with a client, for example, using Extensible Authentication Protocol (EAP). In one aspect, the method provides for sending, to a supplicant that is requesting access to a computer network subject to authentication of a user of the supplicant, a list of first authentication methods that are supported by an authentication server; receiving, from the supplicant, a counter-list of second authentication methods that are supported by the supplicant; determining how many second authentication methods in the counter-list match the first authentication methods; and performing an authentication policy action based on how many of the second authentication methods match the first authentication methods. Policy actions can include blocking access, re-directing to sources of acceptable authentication methods, granting one of several levels of network access, etc.
Owner:CISCO TECH INC
Cloud Broker and Procurement System and Method
InactiveUS20110213712A1Disadvantages and and and reduced eliminatedMethods reduced eliminatedComplete banking machinesTelephonic communicationService-level agreementGrade of service
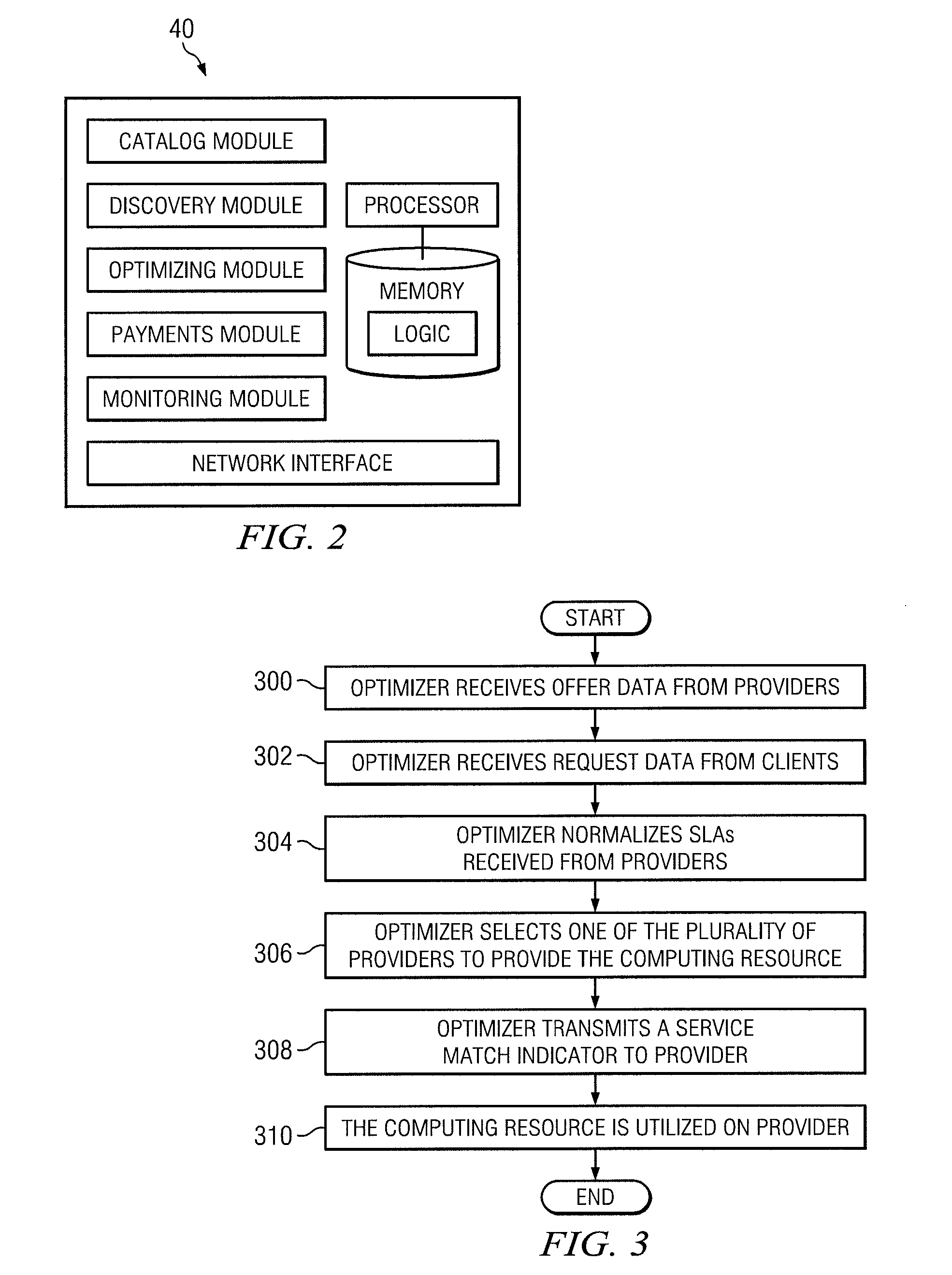
A cloud broker and procurement system and method is closed. In particular embodiments, the method includes receiving an offer of a computing resource from each of a plurality of providers. The method further includes receiving, from each of the plurality of providers, a service level agreement associated with each respective offered computing resource. Additionally, the method includes normalizing each of the service level agreements associated with the offered computing resources. The method further includes receiving a request from a requesting computer for a computing resource and selecting, based at least in part on the normalized service level agreements, one of the providers to provide the requested computing resource. The method also includes transmitting a service match indicator to the client, wherein the service match indicator indicates a time at which the offered computing resource will be utilized, and utilizing the computing resource on the selected provider.
Owner:COMP ASSOC THINK INC
Network content access control
InactiveUS6928545B1Digital data processing detailsAnalogue secracy/subscription systemsSupplicantWeb content
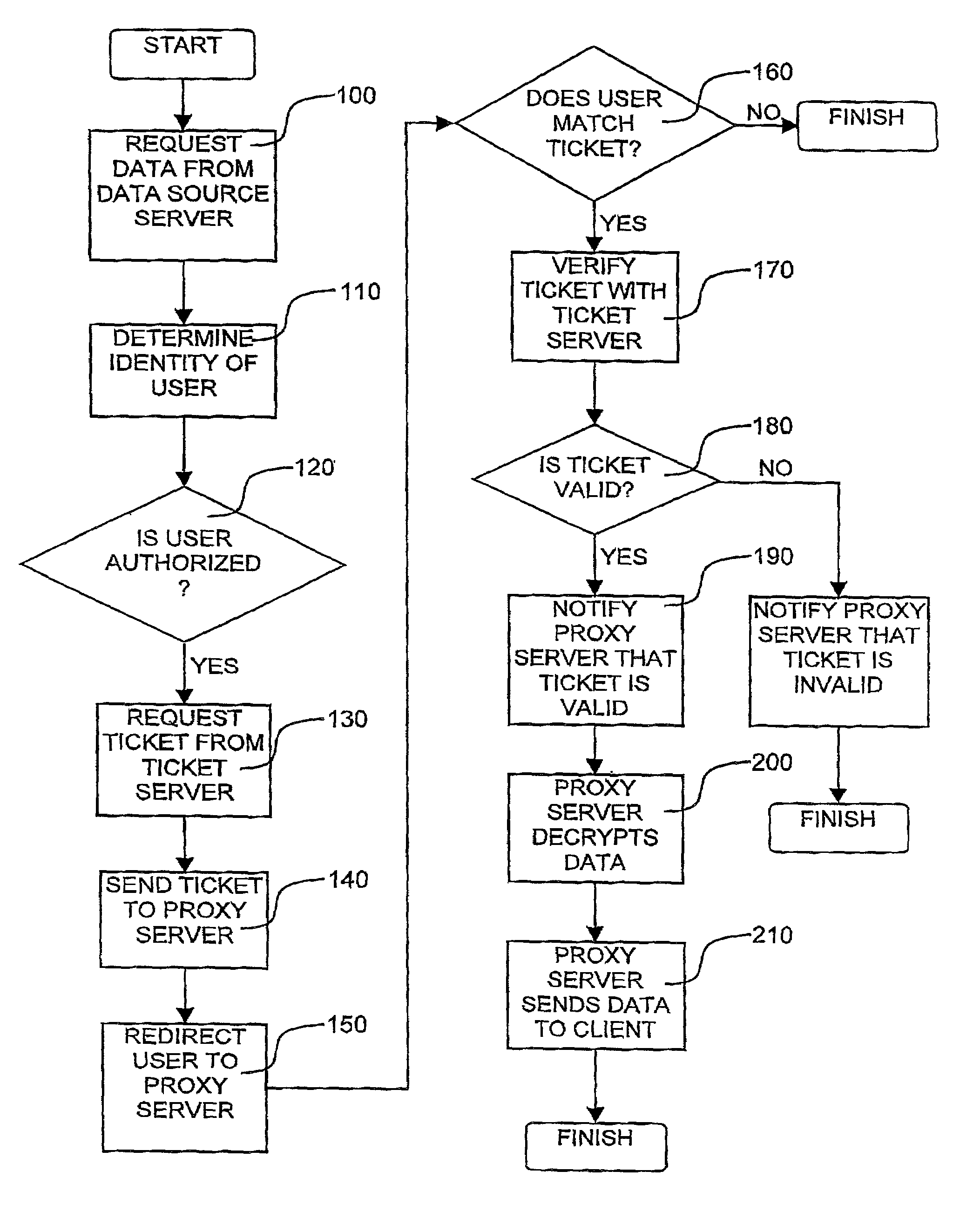
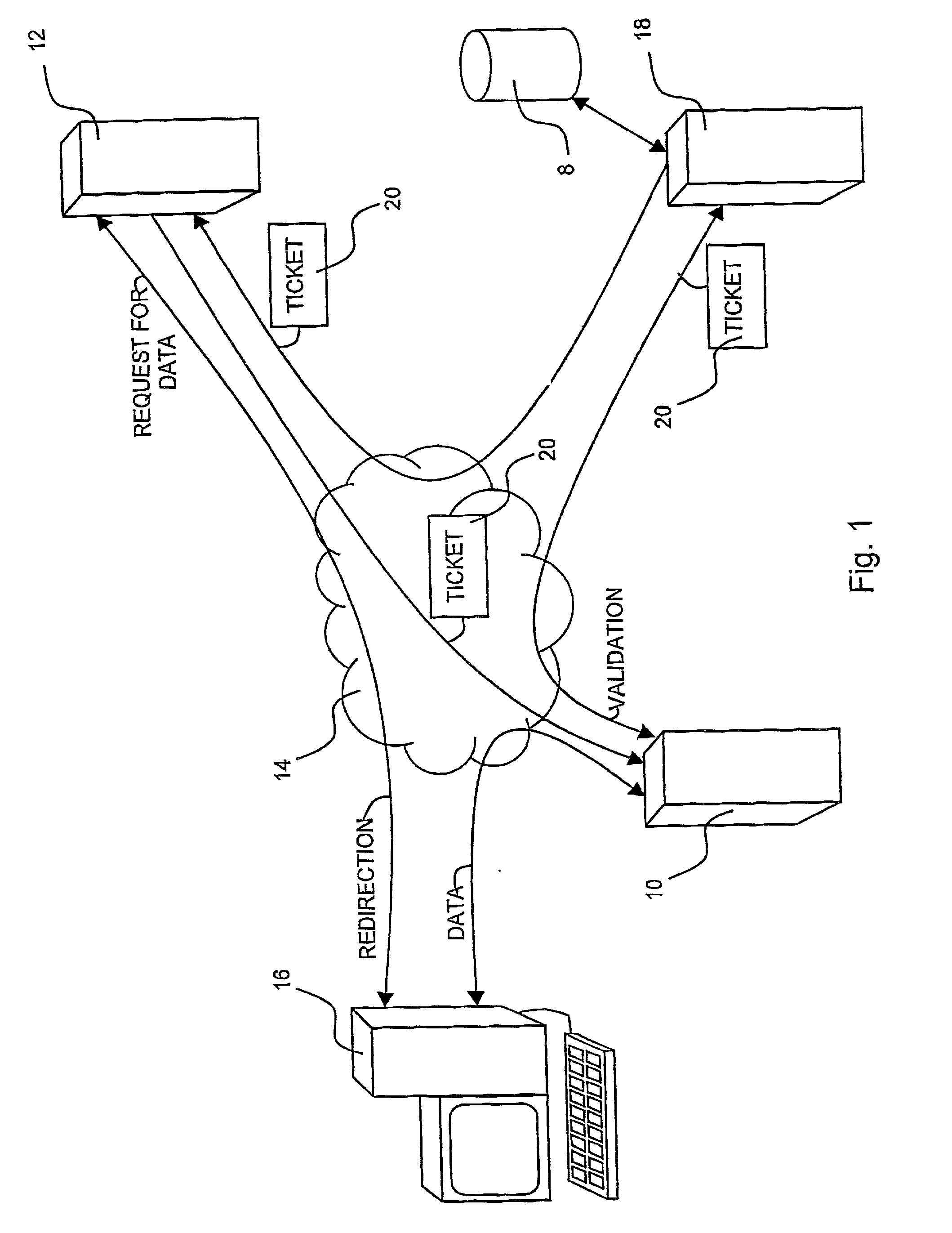
A method for preventing unauthorized access by a requestor to data sent via computer networks, including a) requesting, from a requesting computer, access to data from a first server, at the first server b) determining if the request is a valid request, c) receiving a ticket from a ticket server, if the request is a valid request d) providing the ticket identifying the requestor to a second server the data is stored, e) directing the requesting computer to request access to the data from the second server, at the second server f) receiving the request from the requesting computer, g) verifying the ticket as identifying the requestor, and h) sending the data to the requesting computer in response to the request.
Owner:FORCEPOINT LLC
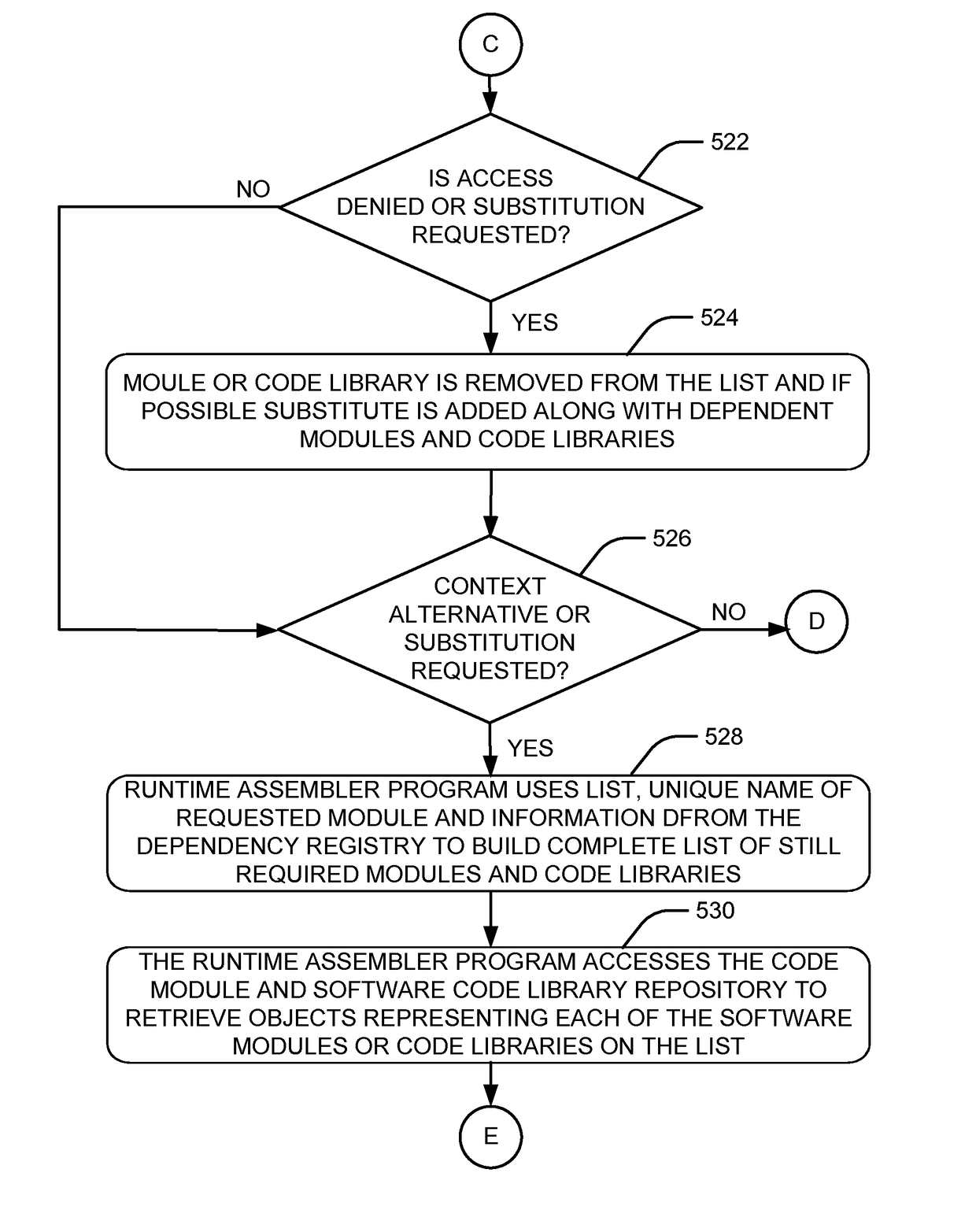
Incremental deployment of computer software program logic
ActiveUS20120278902A1Digital data processing detailsAnalogue secracy/subscription systemsSupplicantProgram logic
Systems and methods for requesting computer software program logic by a client computing device from a server are provided. The method at the server comprises receiving a request for the computer software program logic from the client device along with a first list comprising details about multiple modules running on the client device; determining a second list comprising details about multiple modules required to deploy the computer software program logic on the client device; checking whether the modules of the second list need to be substituted based on their availability or suitability; updating the second list; checking whether the client device has permission rights for accessing the modules of the updated second list; and sending an object comprising the modules of the updated second list to the client device, the updated second list comprising details about the modules required for deployment of logic on the client device.
Owner:CAMBRIDGE SEMANTICS
Data distribution server
InactiveUS7404201B2Reduce necessityEliminate overheadAnalogue secracy/subscription systemsMultiple digital computer combinationsSupplicantData Distribution Service
Owner:HITACHI LTD
Method used by an access point of a wireless LAN and related apparatus
InactiveUS20060107050A1Increasing internet securityKey distribution for secure communicationMultiple keys/algorithms usageComputer networkWireless lan
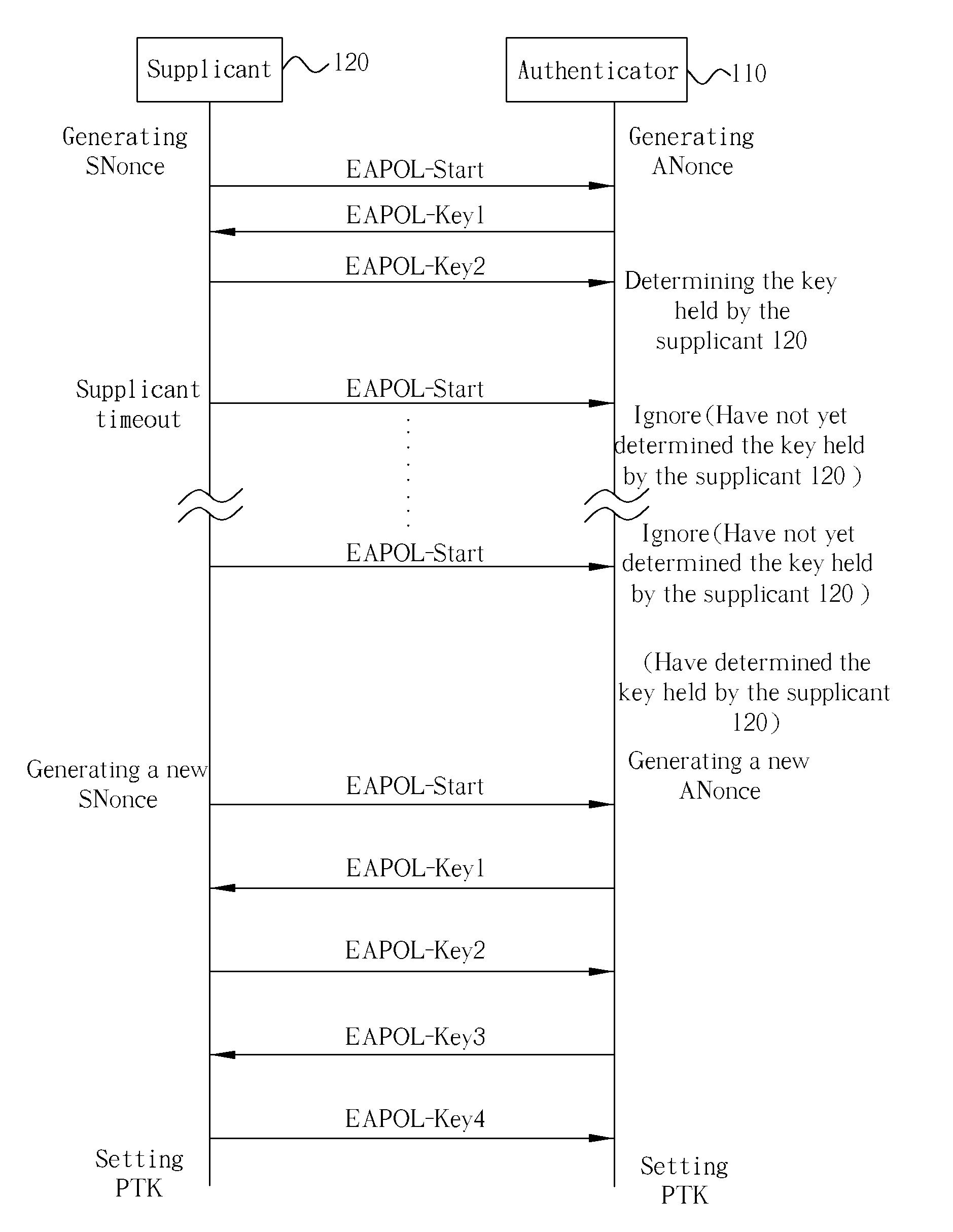
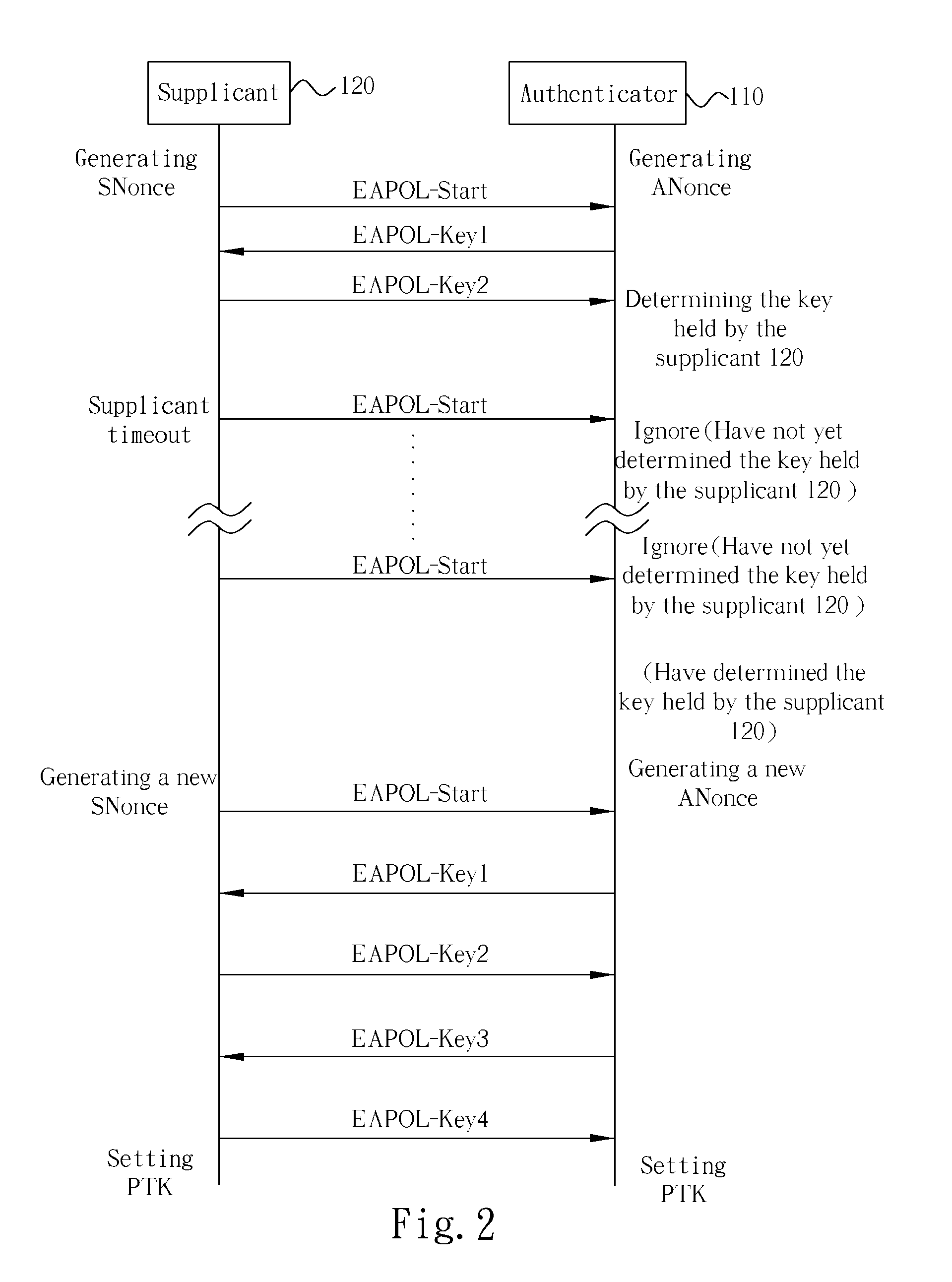
The present invention discloses a method used by an Authenticator of a wireless LAN. The Authenticator is capable of communicating wirelessly with a Supplicant of the wireless LAN. The Authenticator holds a plurality of candidate keys whereas the Supplicant holds one key. The key held by the Supplicant is included in the plurality of candidate keys held by the Authenticator. The method includes determining which one of the plurality of candidate keys is the key held by the Supplicant and communicating with the Supplicant wirelessly according to the determined key held by the Supplicant.
Owner:DRAYTEK
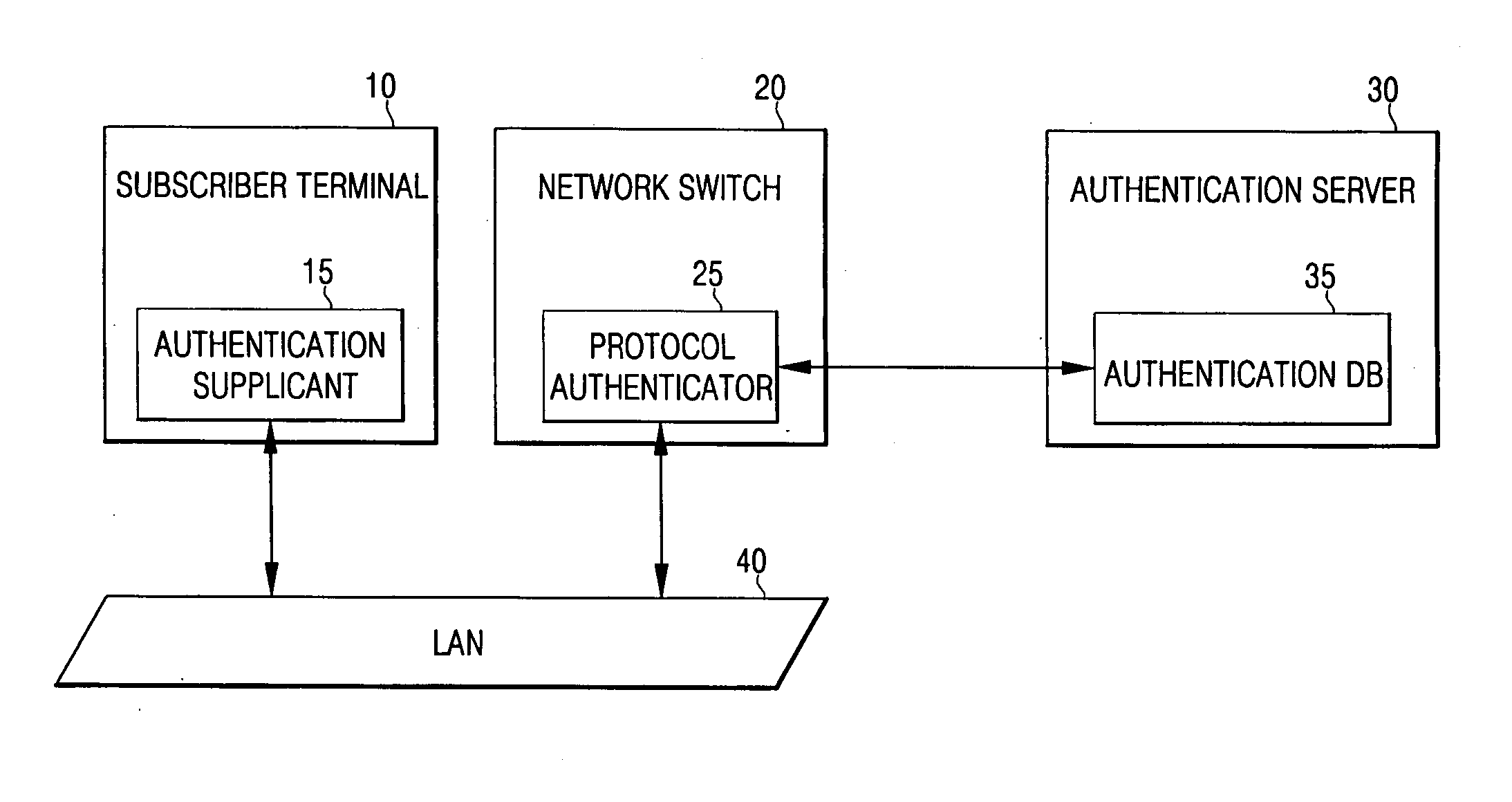
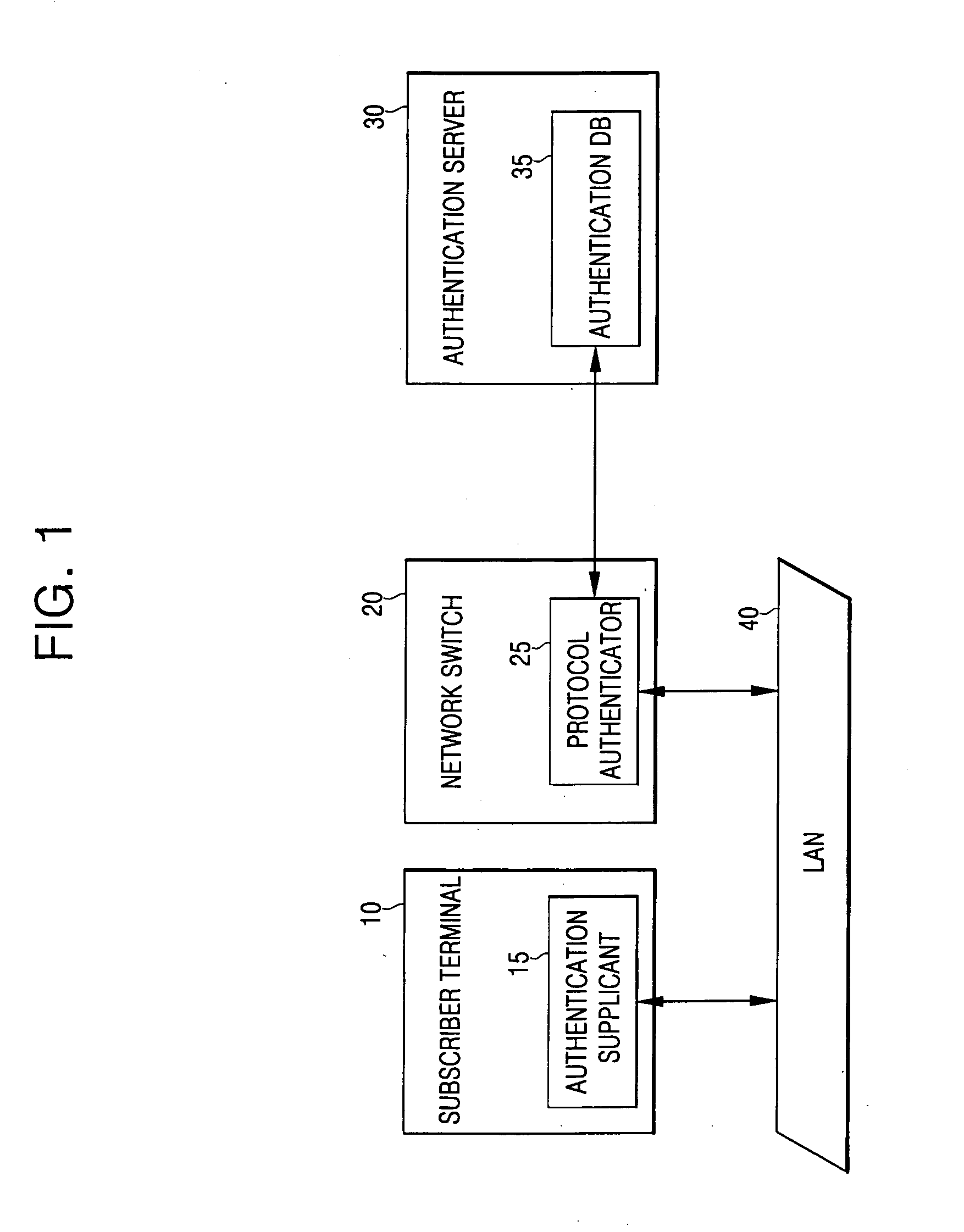
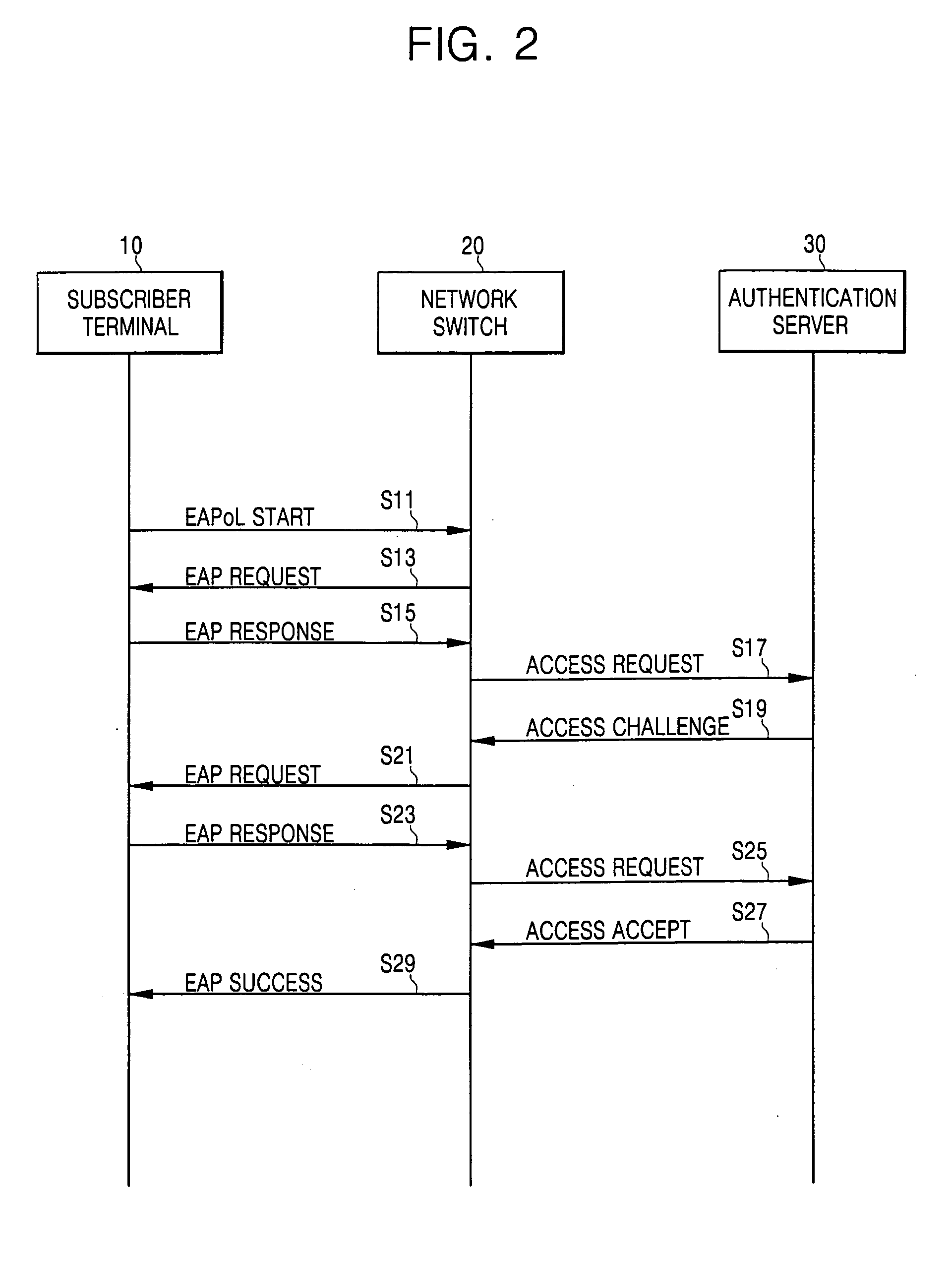
Apparatus and method for authenticating user for network access in communication system
InactiveUS20060070116A1Initial investment costReduce initial investment costDigital data processing detailsUser identity/authority verificationInternet service providerProtocol processing
An apparatus for authenticating a user for network access in a communication system comprises: an input module contained in a subscriber terminal for receiving and transferring identification information and a password for network access from a user; an authentication supplicant contained in network equipment for requesting network access authentication for the identification information and password transferred from the input module; an authentication server for storing information related to the network access authentication, and for performing authentication to determine whether to permit the subscriber terminal to access a network in response to the authentication request; and a protocol authenticator for performing protocol processing between the authentication supplicant and the authentication server. A corresponding method is disclosed. Thus, it is possible to authenticate subscriber terminals for network access without the installation, by an Internet service provider, of specific software (e.g., a supplicant program) in all of the subscriber terminals.
Owner:SAMSUNG ELECTRONICS CO LTD
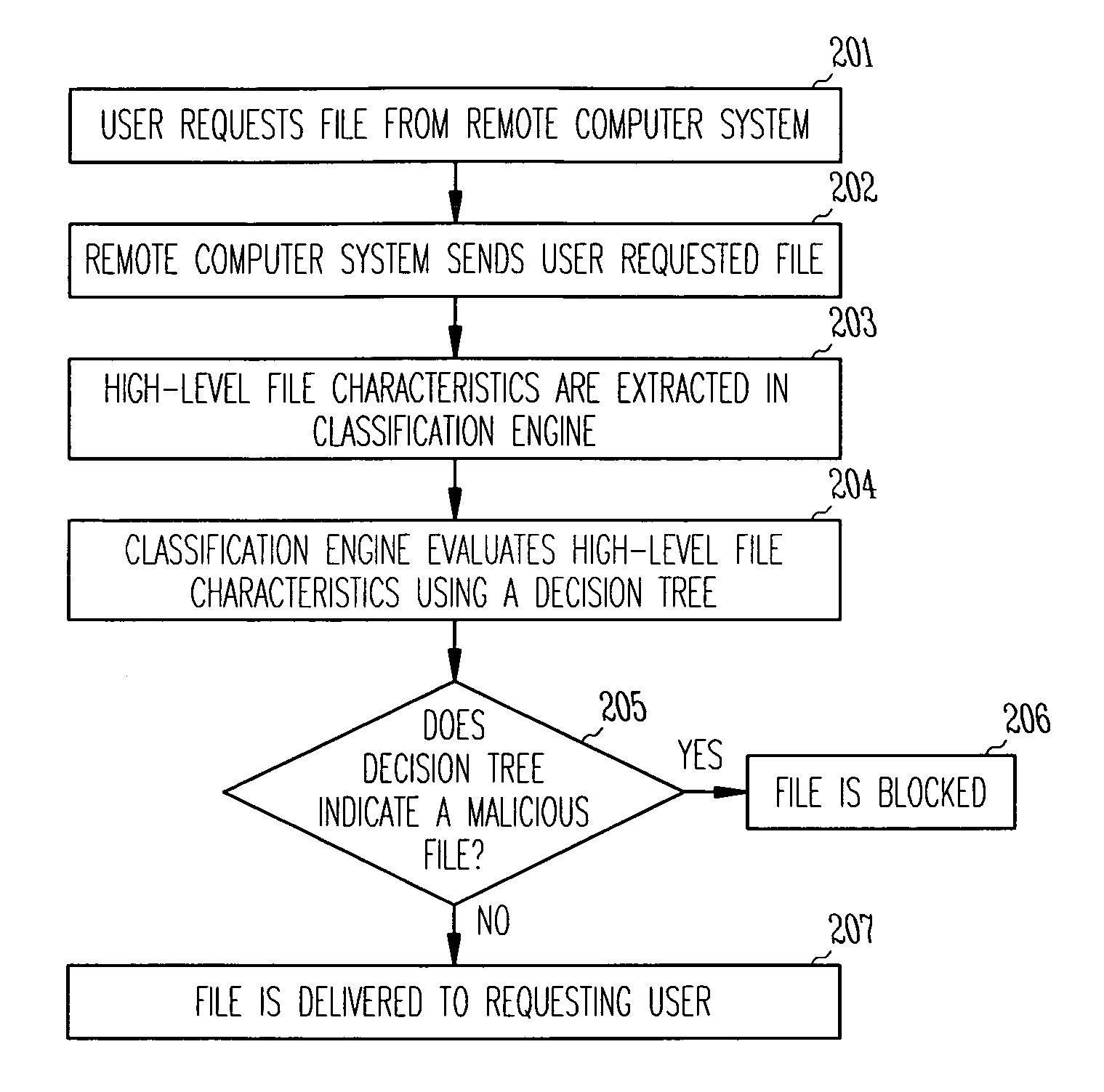
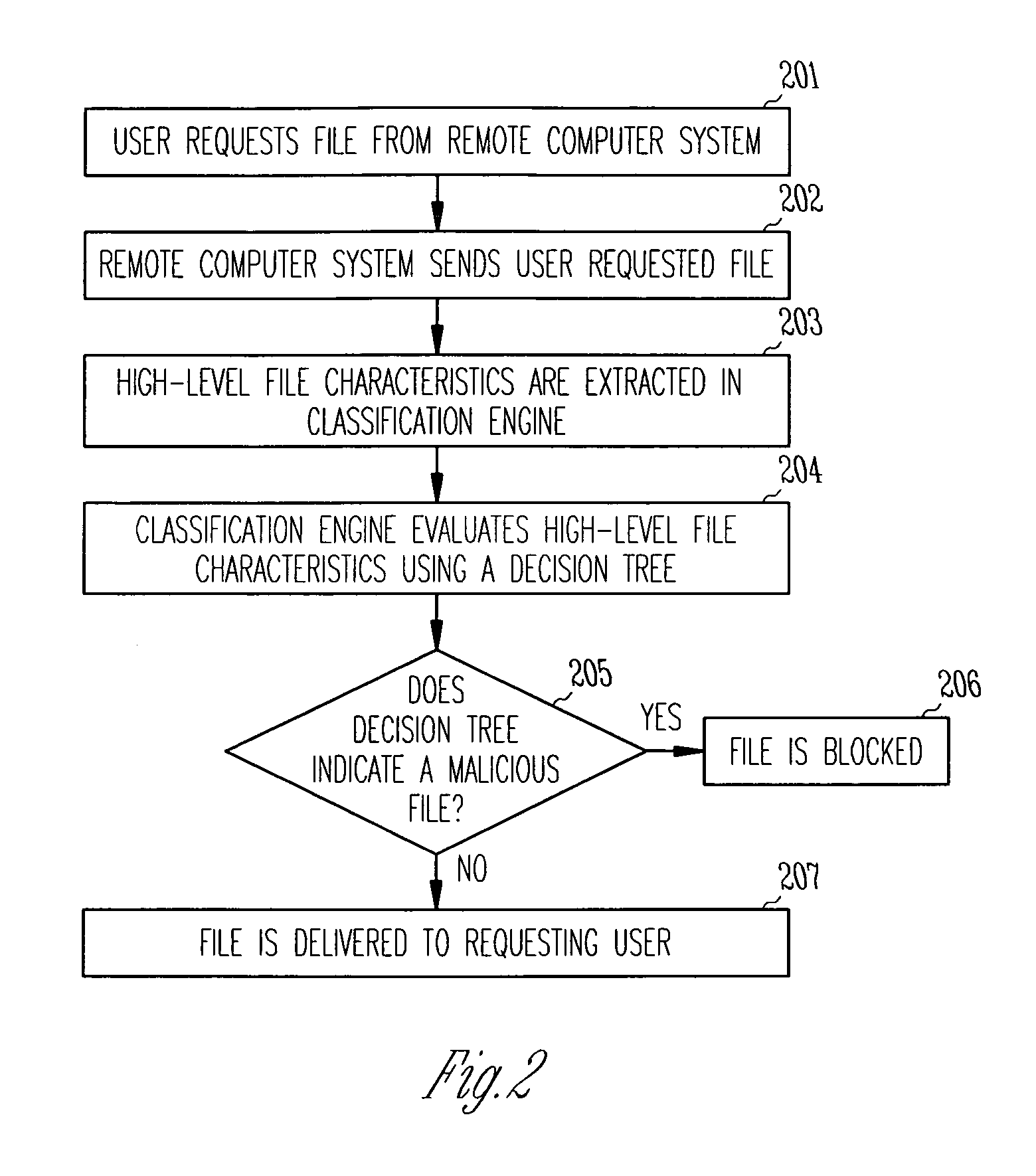
Malware detection via reputation system
A computer network device receives a digital file and extracts a plurality of high level features from the file. The plurality of high level features are evaluated using a classifier to determine whether the file is benign or malicious. The file is forwarded to a requesting computer if the file is determined to be benign, and blocked if the file is determined to be malicious.
Owner:MCAFEE LLC
Incremental deployment of computer software program logic
ActiveUS9696981B2Digital data processing detailsAnalogue secracy/subscription systemsSupplicantComputer software
Systems and methods for requesting computer software program logic by a client computing device from a server are provided. The method at the server comprises receiving a request for the computer software program logic from the client device along with a first list comprising details about multiple modules running on the client device; determining a second list comprising details about multiple modules required to deploy the computer software program logic on the client device; checking whether the modules of the second list need to be substituted based on their availability or suitability; updating the second list; checking whether the client device has permission rights for accessing the modules of the updated second list; and sending an object comprising the modules of the updated second list to the client device, the updated second list comprising details about the modules required for deployment of logic on the client device.
Owner:CAMBRIDGE SEMANTICS
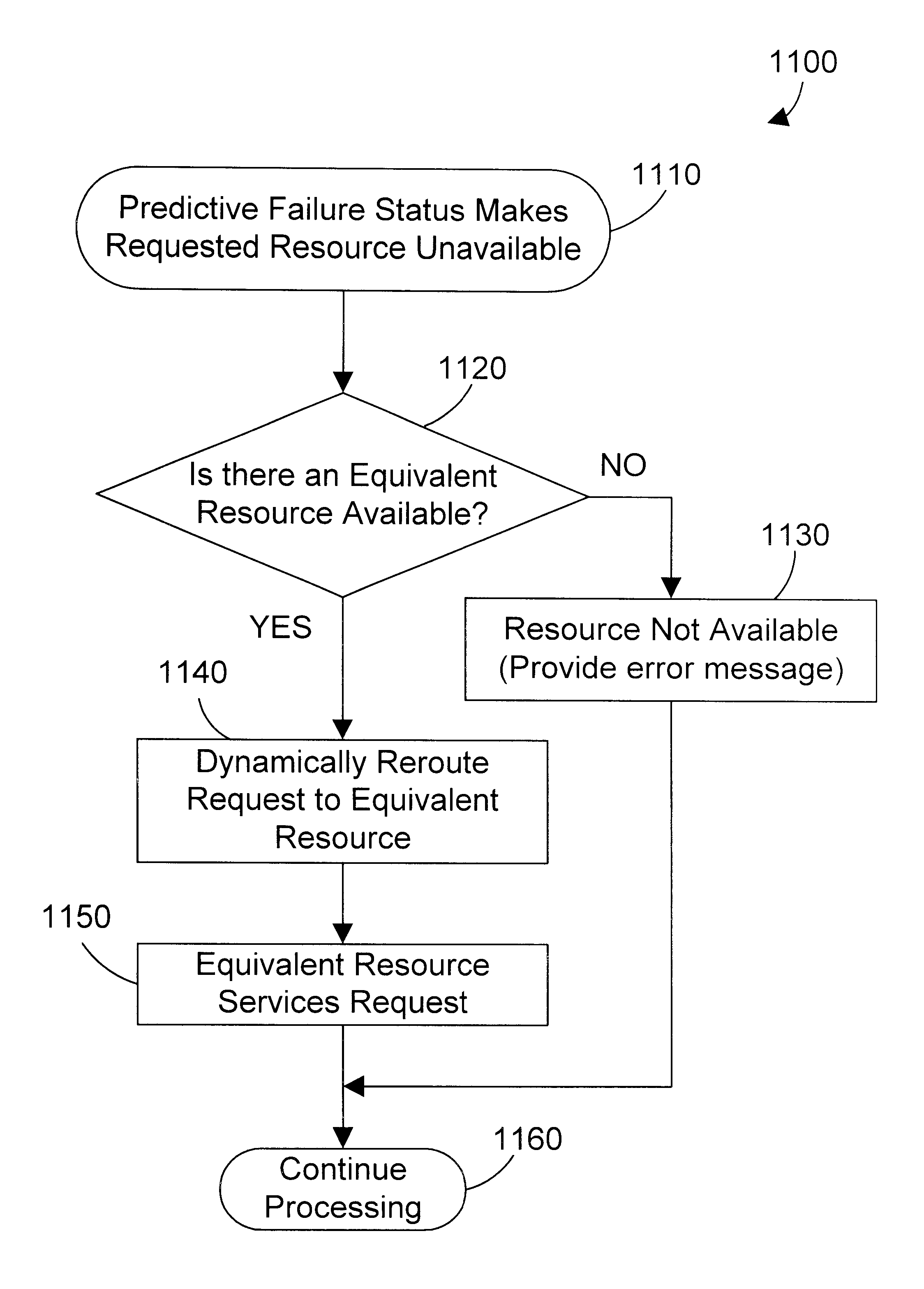
Apparatus and method for dynamically rerouting a network request based on shared predictive failure information
InactiveUS6802020B1Minimize impactAvoid failureLogical operation testingEmergency protective arrangements for automatic disconnectionTraffic capacitySupplicant
An apparatus and method shares predictive failure information between computer system in a computer network. The shared predictive failure information allows dynamically rerouting a network request to avoid a computer system that may fail according to its predictive failure information. According to a first embodiment, if the requested resource on the network has predictive failure information that indicates the resource may soon fail, a message is returned to the requesting computer with information that includes possible alternative sites from which the information may be obtained. If there is an alternative site, the requesting computer system may access the alternative site, thereby avoiding the computer system that may soon fail. If there is no alternative site, the requesting computer system may return an error message, or may simply access the original resource on the chance that is has not yet failed. According to a second embodiment, a router in the network may indicate one or more alternative paths to a resource if the predictive failure information for the router indicates it may soon fail. The requesting computer system may then access the requested resource via the alternative path. In this manner, predictive failure information can be used in rerouting network traffic between computer systems on a network to minimize the effect of a failing, computer system.
Owner:INT BUSINESS MASCH CORP
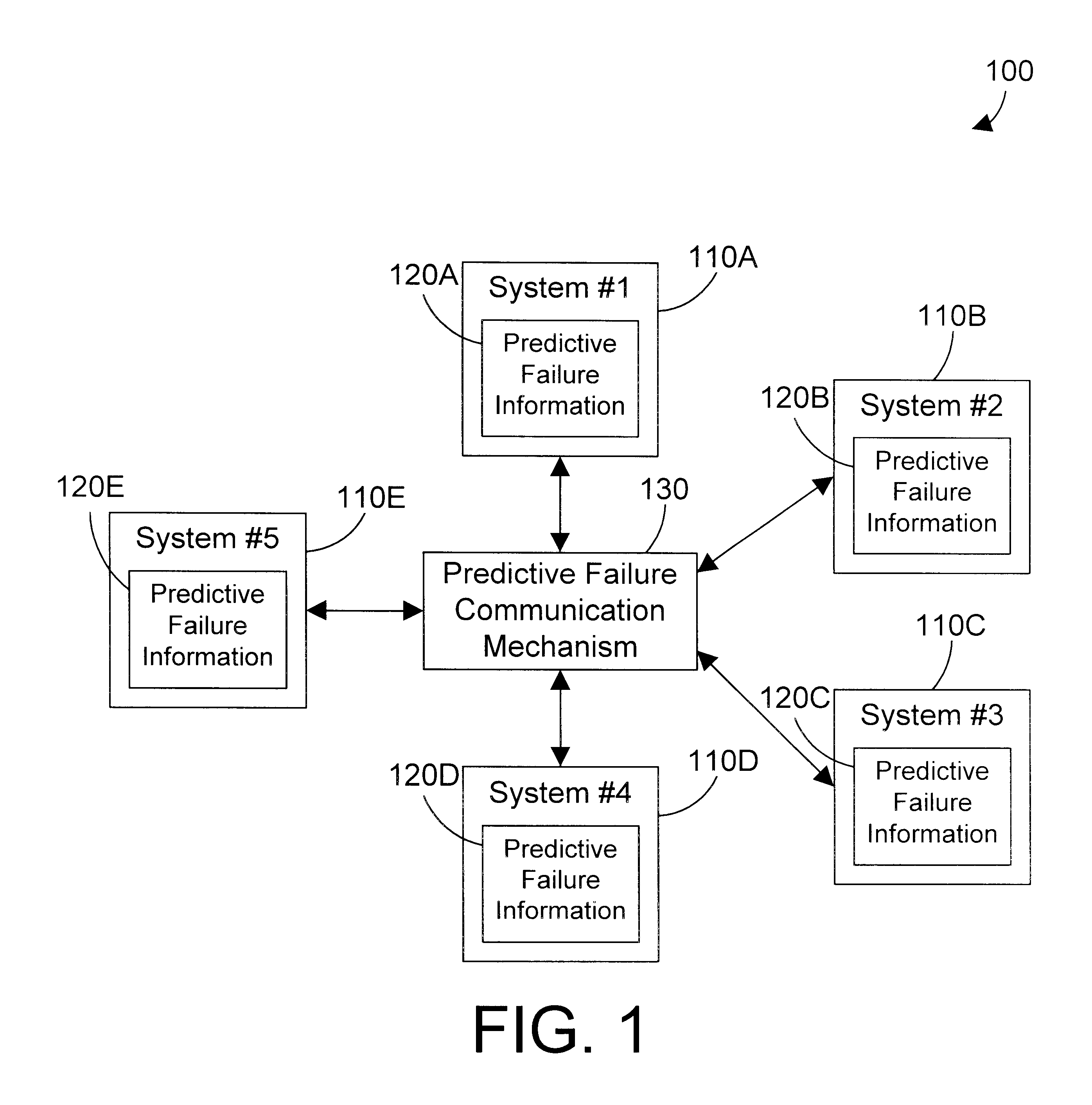
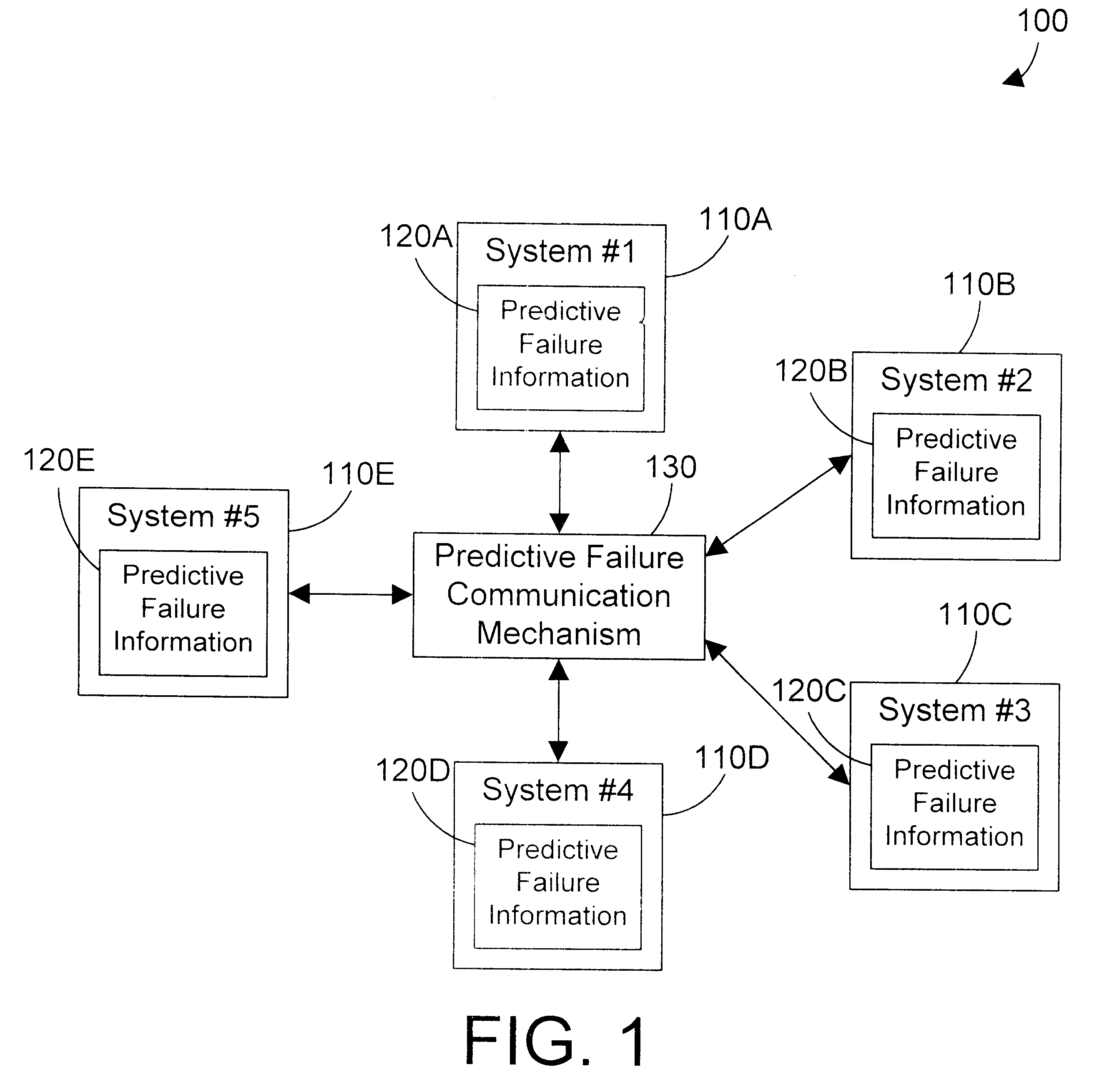
Apparatus and method for sharing predictive failure information on a computer network
InactiveUS6609212B1Avoid accessLogical operation testingEmergency protective arrangements for automatic disconnectionNetworking protocolSupplicant
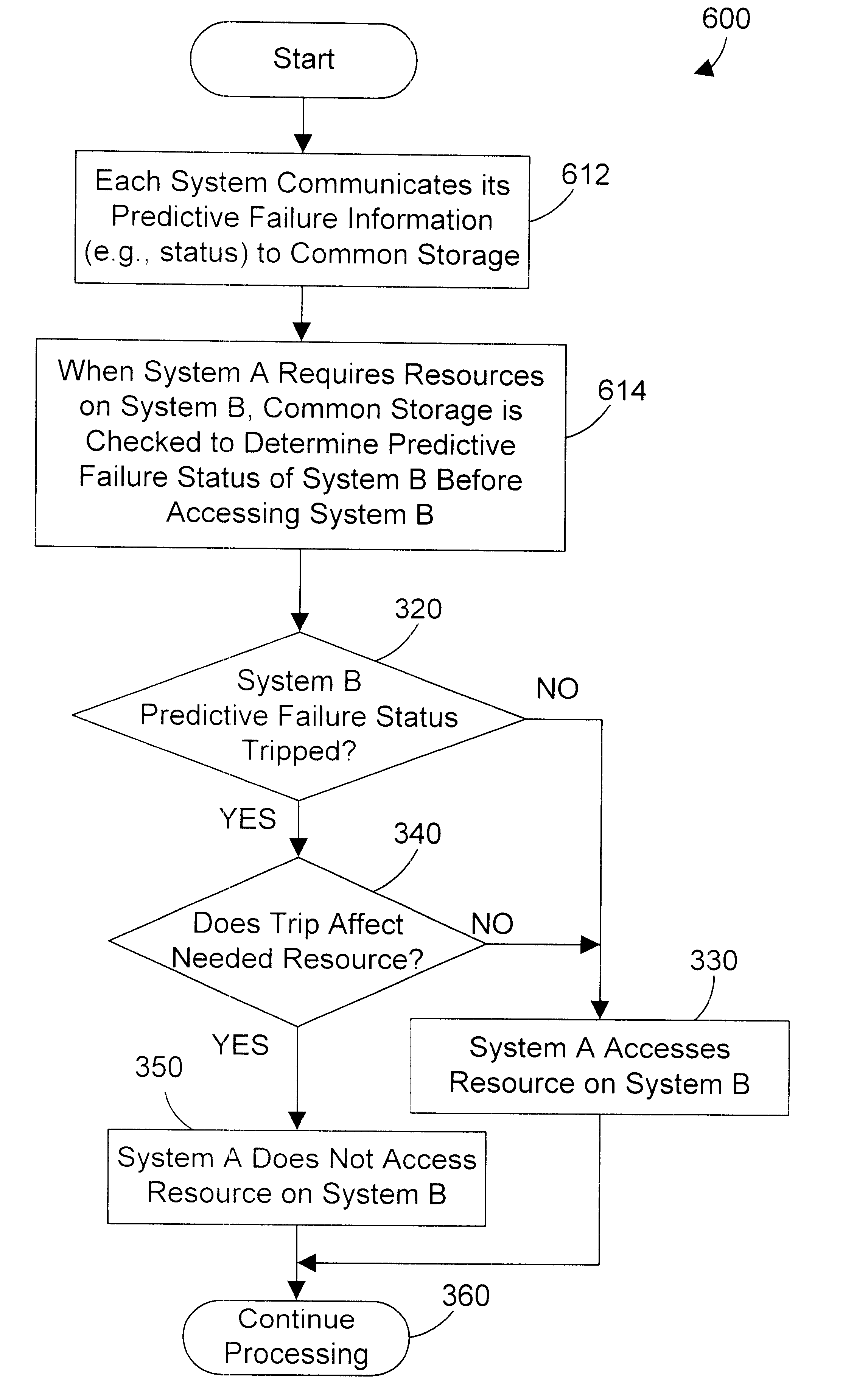
An apparatus and method shares predictive failure information between computer systems in a computer network. The shared predictive failure information allows a requester of a network resource to determine whether the resource will be available to perform the request based on its predictive failure information. According to a first embodiment, predictive failure information is written by each computer system on the network to a common storage that is accessible by one or more other computer systems on the network. When a computer system on the network needs a resource on another system, the requesting computer system can check the predictive failure status of the system that contains the needed resource by reading the predictive failure information in the common storage. If the predictive failure information indicates that the resource may perform the requested function, the requesting computer system issues the request to the resource. In a second embodiment, one or more network protocols for communicating between computer systems on the network are modified so that messages given in response to resource requests include the predictive failure status of the requested system. Thus, if a requester needs data from another computer system, a message returned from that system in response to the request preferably includes predictive failure status or information indicating whether or not the request can be granted. If the predictive failure status or information indicates that the request can be granted, the requester performs the operation on the requested computer system. In this manner, predictive failure information can be used in granting access to resources between computer systems on a network, which allows accesses to be prevented if the predictive failure information indicates that the resource is likely to fail before completing the request.
Owner:IBM CORP
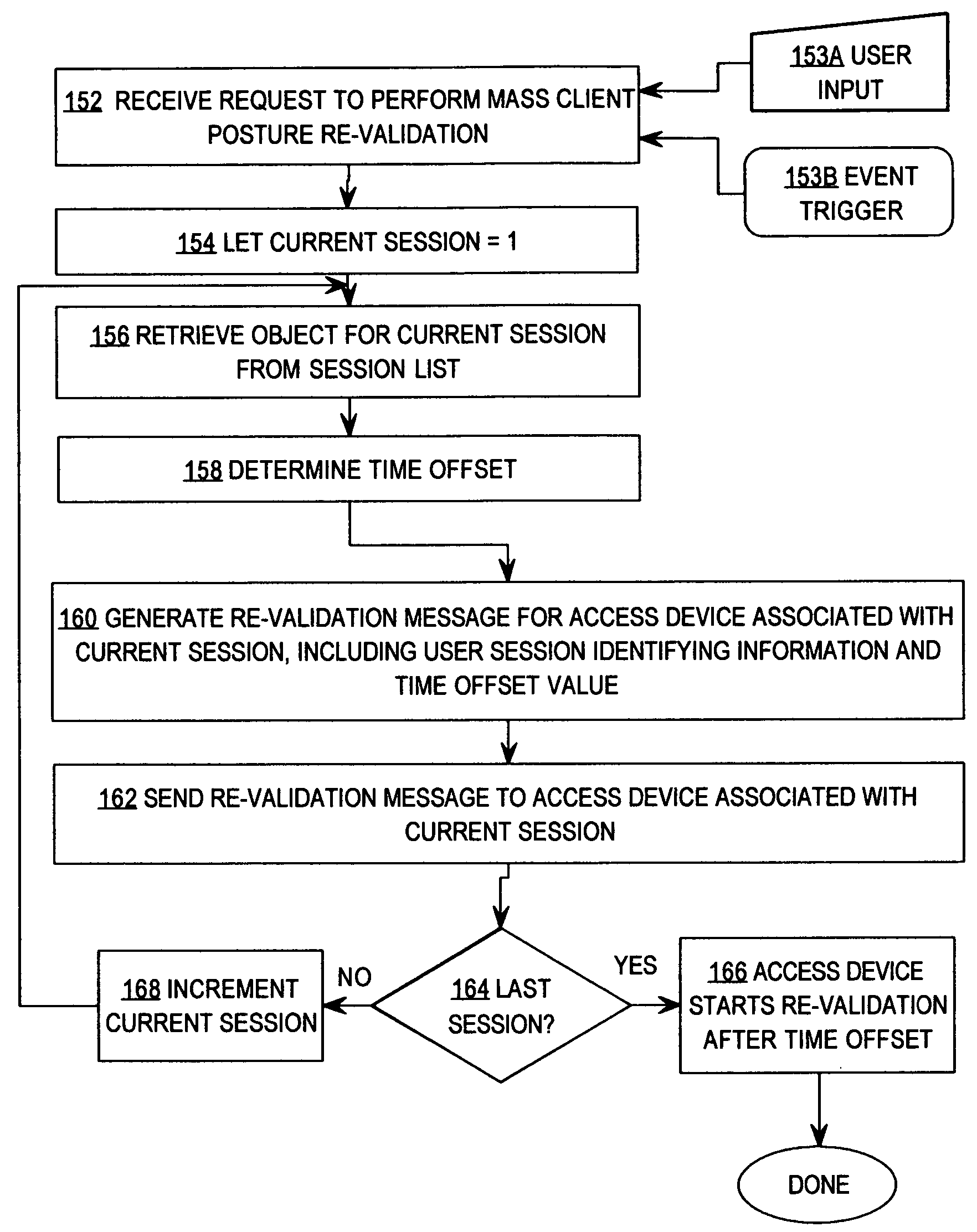
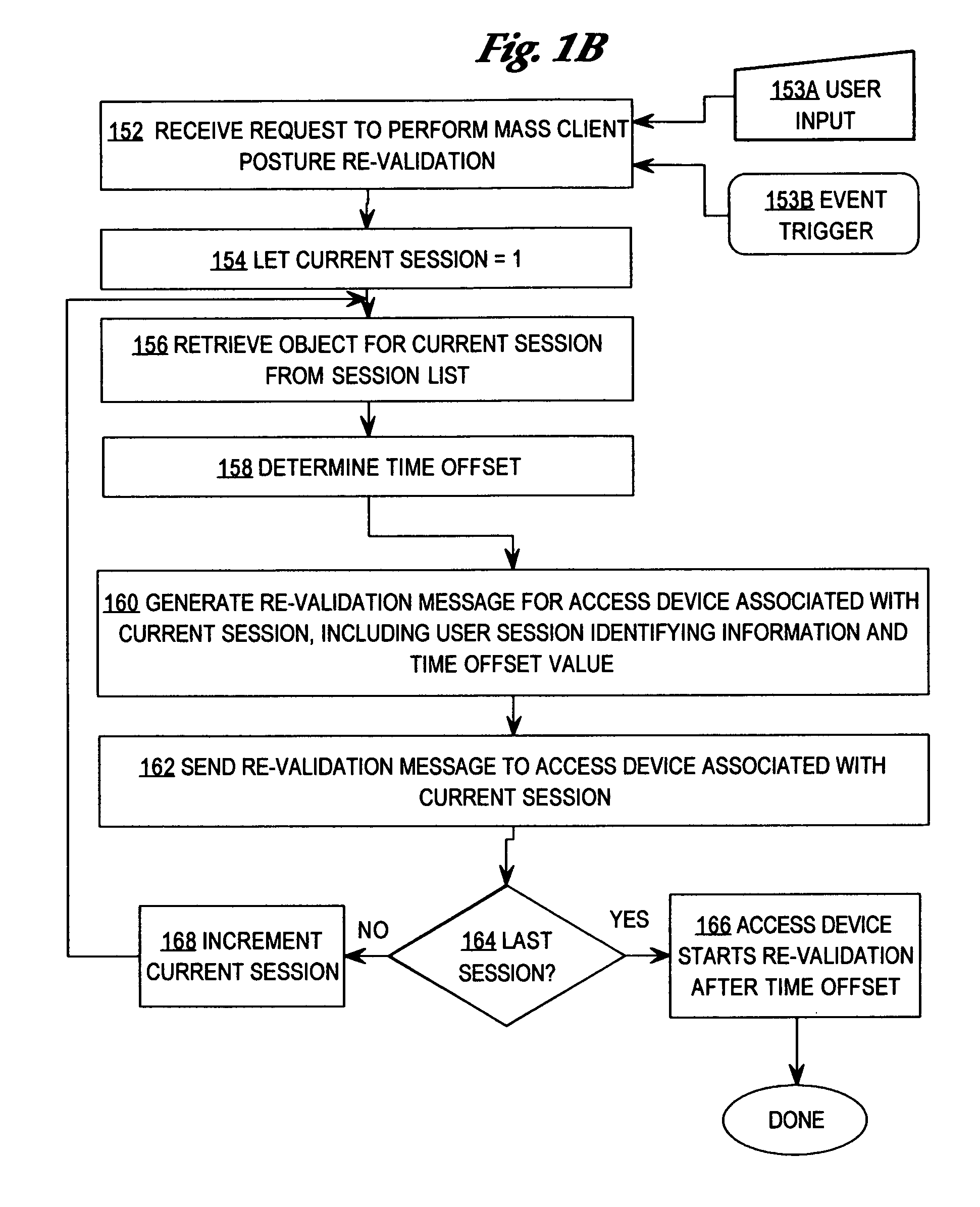
Method and apparatus for automatically re-validating multiple clients of an authentication system
ActiveUS20060026670A1Digital data processing detailsUser identity/authority verificationClient-sideAuthentication system
A method is disclosed for performing on-demand posture validation for all of multiple clients or supplicants of an authentication system, comprising creating and storing a session list identifying communication sessions relating to supplicants that access a computer network through an access device; receiving input requesting performing posture validation for all the supplicants; determining a time value for starting the posture validation for a particular supplicant identified in the session list; generating and sending to the access device, a request to perform posture validation, wherein the request comprises supplicant identifying information and the time value and instructs the access device to initiate the posture validation for that supplicant only after the time value has expired; and repeating the steps of determining, generating and sending for all supplicants in the session list.
Owner:CISCO TECH INC
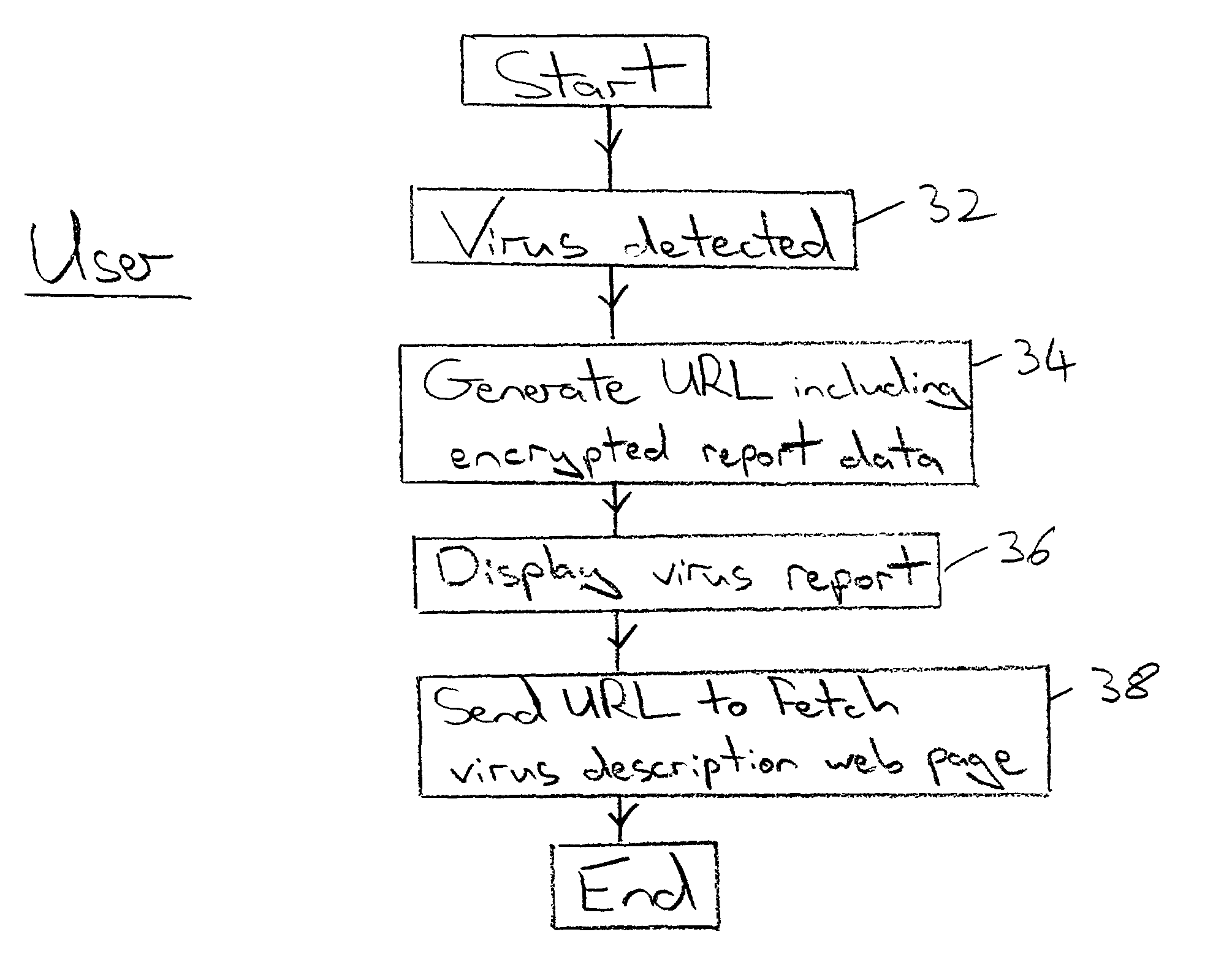
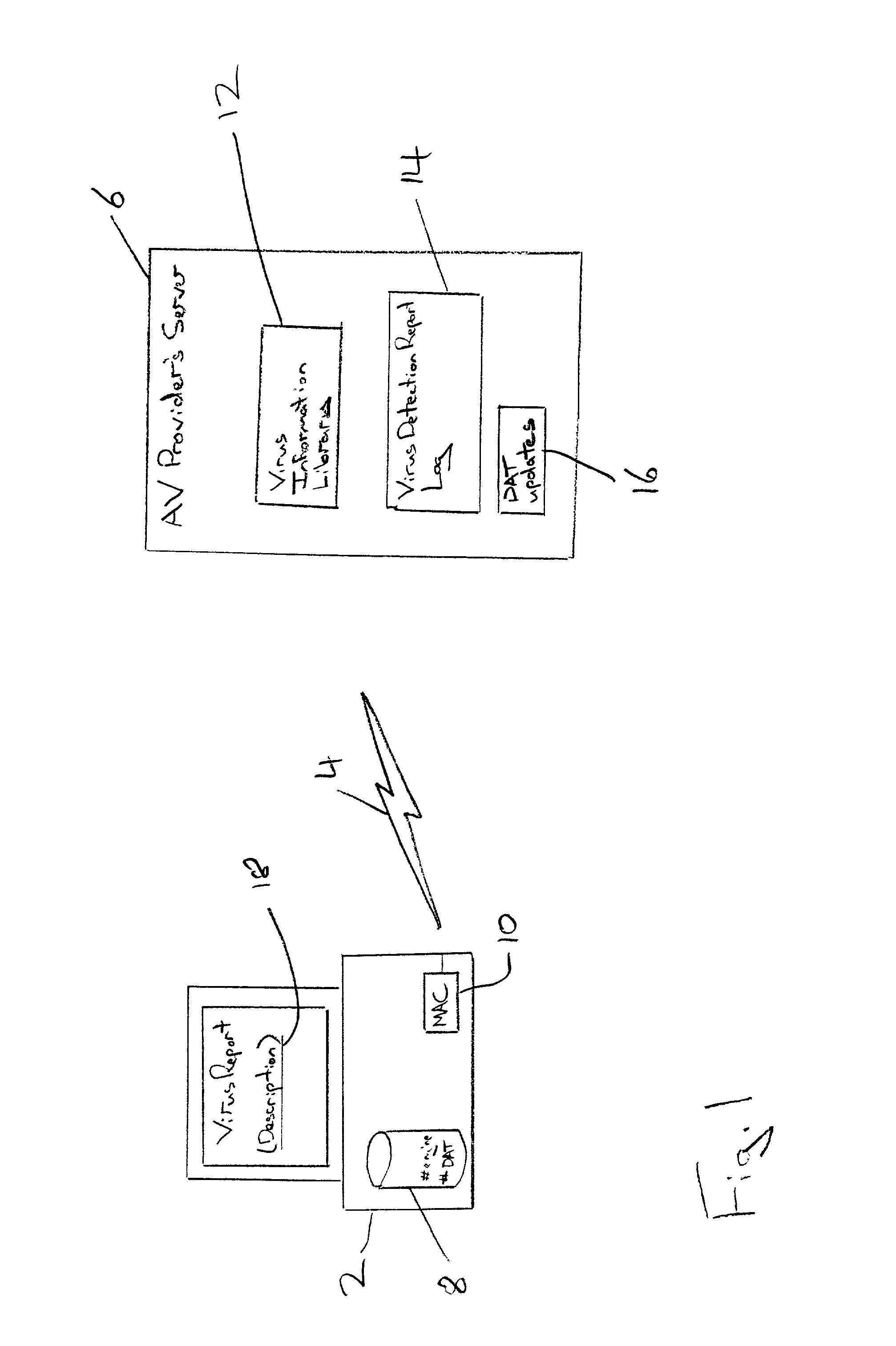
Event reporting between a reporting computer and a receiving computer
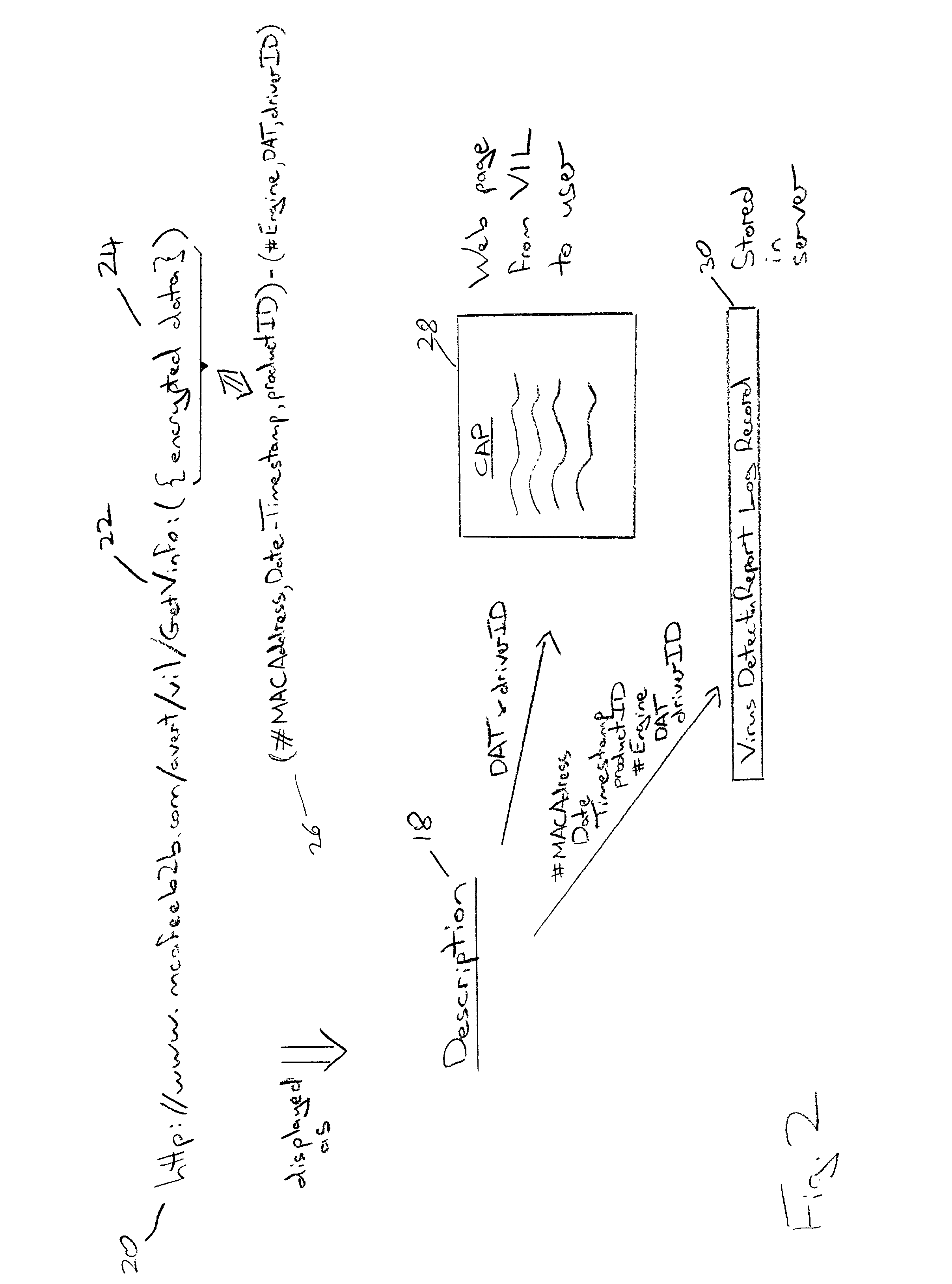
An event report, such as a virus detection event, is sent from a reporting computer 2 to a receiving computer 6 via an internet link 4. The report data may take the form of a URL requesting a web page 28 to be provided by the receiving computer 6, the URL bearing an encrypted form 24 of the report data that is used to identify the requested web page as well as pass further information to the receiving computer 6. Alternatively, the report data may be collated in the reporting computer 2 and passed to the receiving computer 6 when a computer virus definition data update is requested. The report data seeks to uniquely identify the event by incorporating the MAC address of the reporting computer 2, the date, time, computer product identifier, version identifier, update identifier and driver triggered. Additionally, a checksum derived from the infected file together with an indication of the corrective action, if any, taken by the reporting computer 2 may be included. The report data sent to the receiving computer 6 may be used to obtain real life information concerning the prevalence of particular viruses together with information characterising the anti-virus programs and their update status being employed by the user community.
Owner:MCAFEE LLC
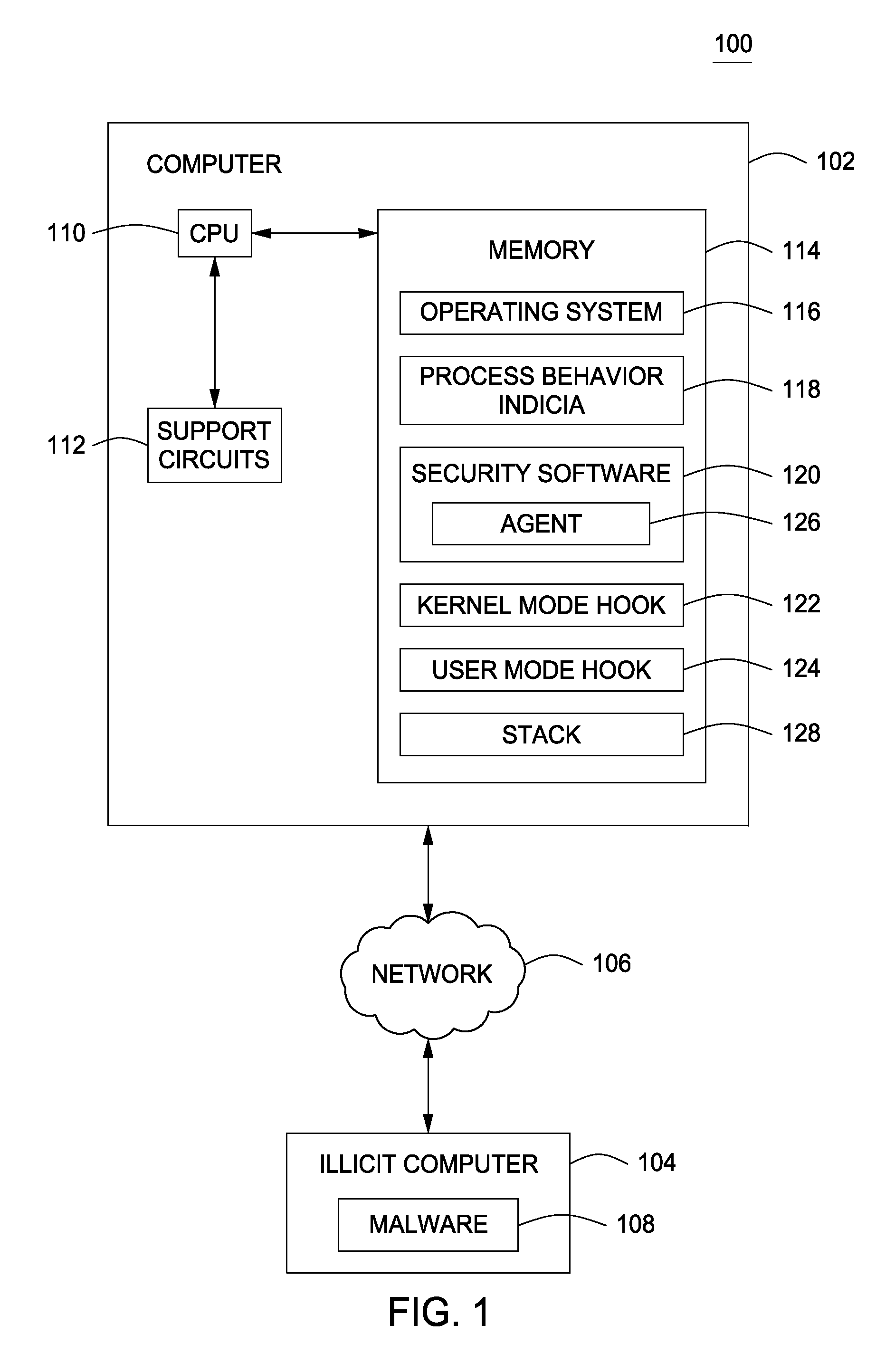
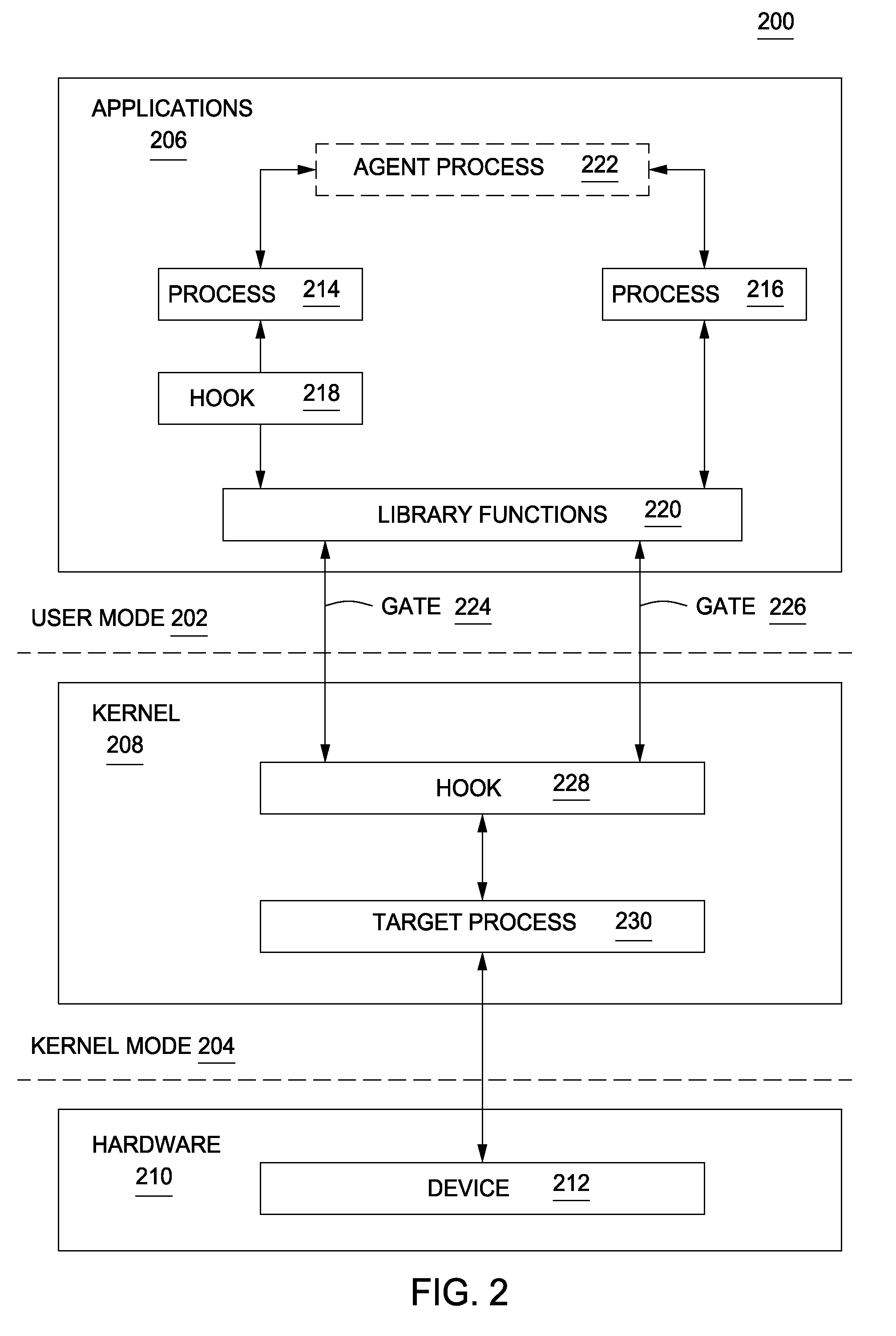
Method and apparatus for monitoring a computer to detect operating system process manipulation
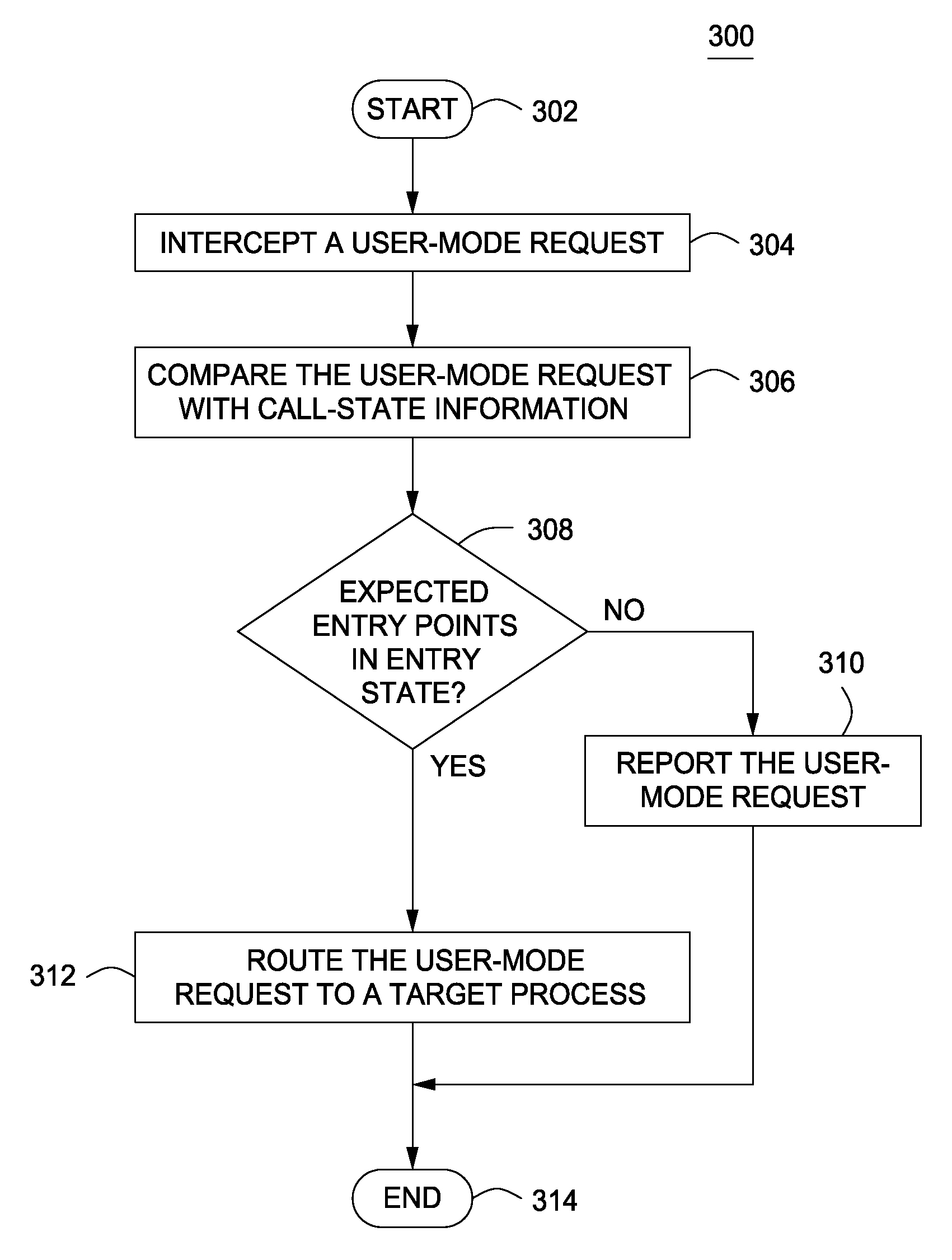
A method and apparatus for monitoring a computer to detect operating system process manipulation by malicious software programs is disclosed. In one embodiment, a method for detecting operating system process manipulation through unexpected process behavior includes accessing process behavior indicia regarding memory addresses used by at least one user mode process to request computer resources and comparing the process behavior indicia with a user mode request to identify operating system process manipulation.
Owner:CA TECH INC
Serving content from an off-line peer server in a photosharing peer-to-peer network in response to a guest request
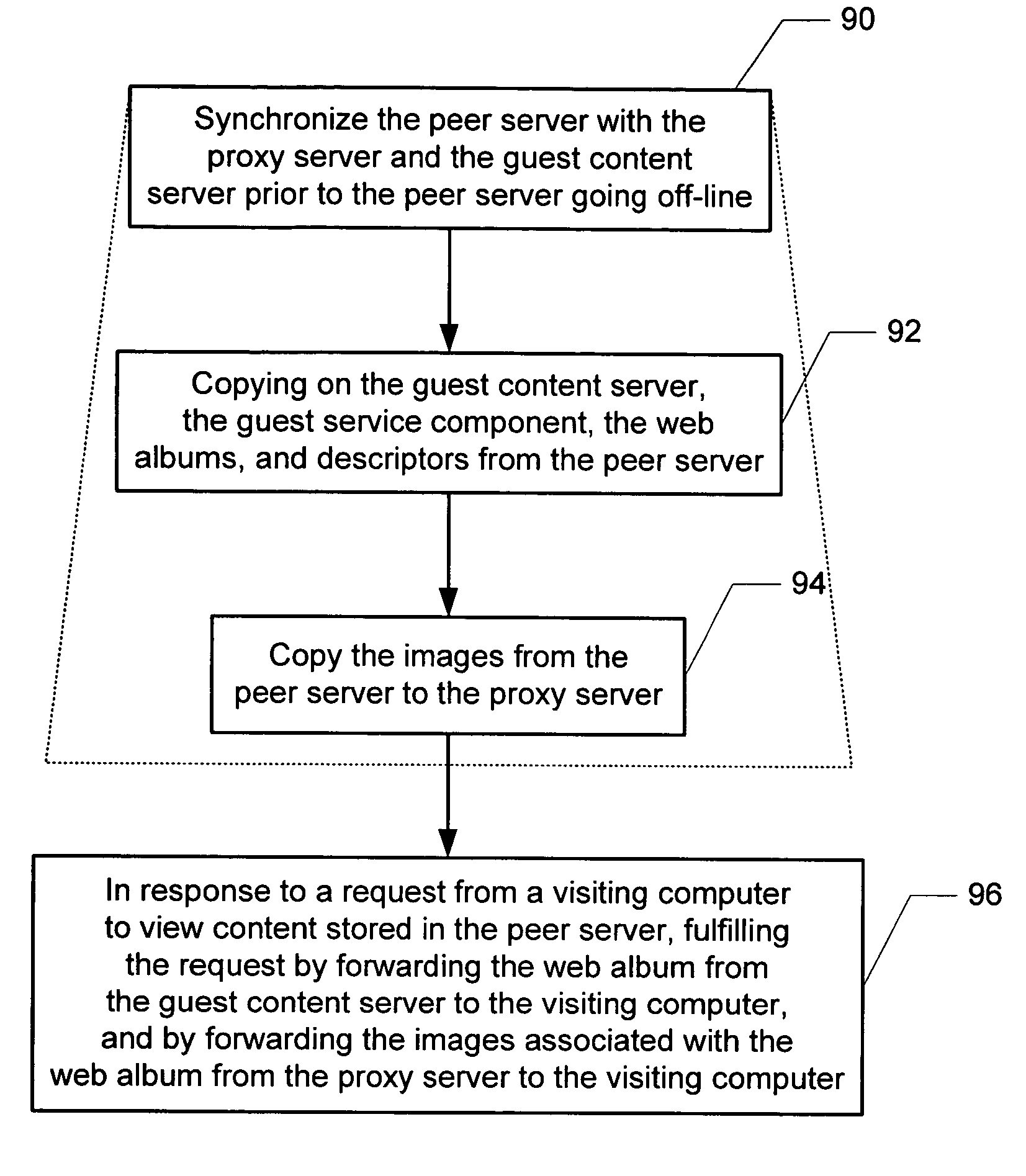
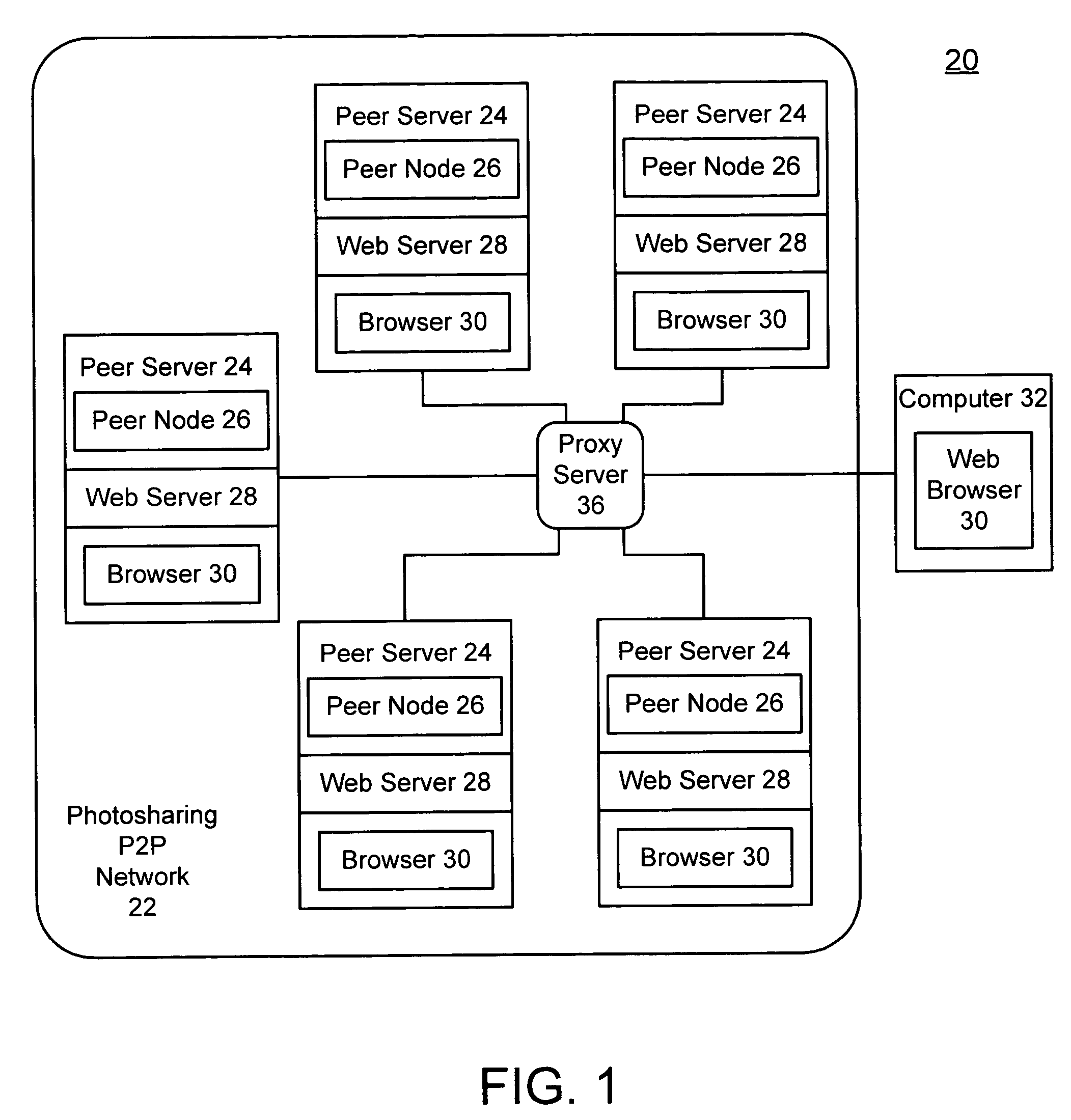
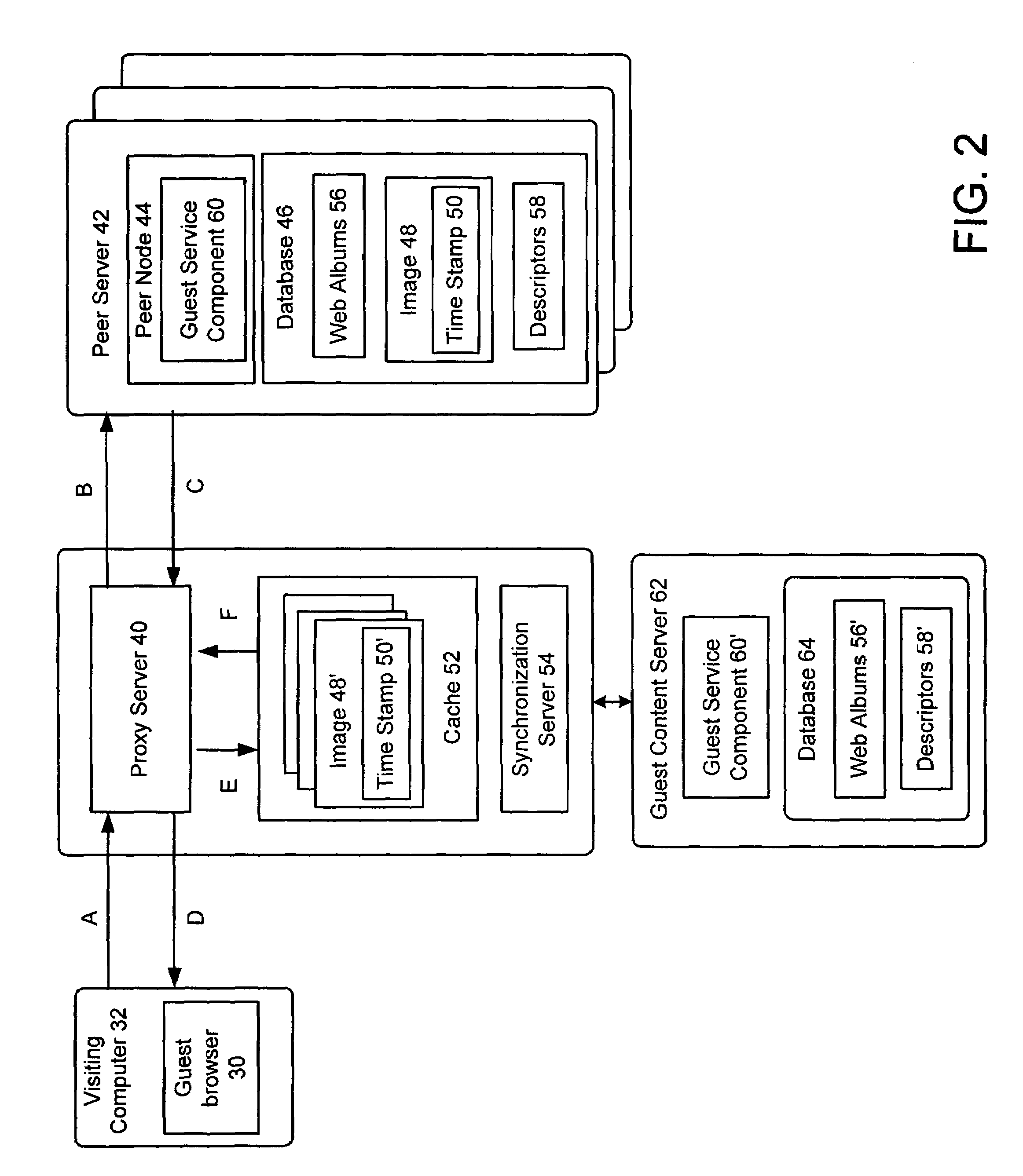
A method and system for serving content from a peer server in a photosharing peer-to-peer network is disclosed, wherein the peer server stores a web album and at least one associated digital image. Aspects of the invention include prior to the peer server going off-line, the peer server initiates a synchronization with a proxy server and a guest content server in which the web page a web page descriptor defining the web album is copied from the peer server to the guest content server, and the image associated with the web album is copied from the peer server to the proxy server. In response to a request from a requesting computer to view content stored in the peer computer when the peer server is off-line, the request is fulfilled by forwarding the web page from the guest content server to the requesting computer, and forwarding the image associated with a web page from the proxy server to the requesting computer, thereby successfully serving content from the peer server even when the peer server is off-line.
Owner:QURIO HLDG
Method and system for logging event data and persistently downloading the same
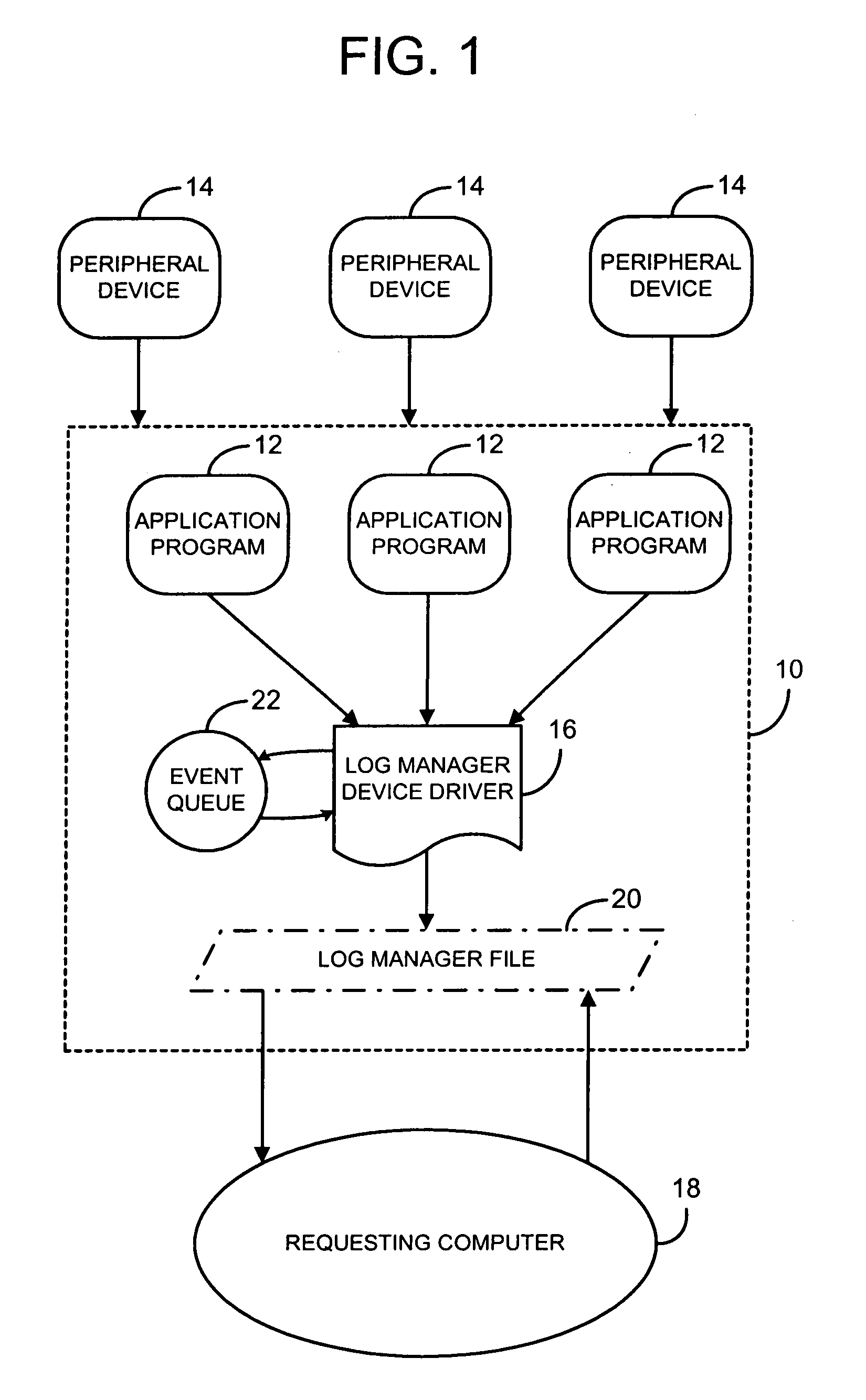
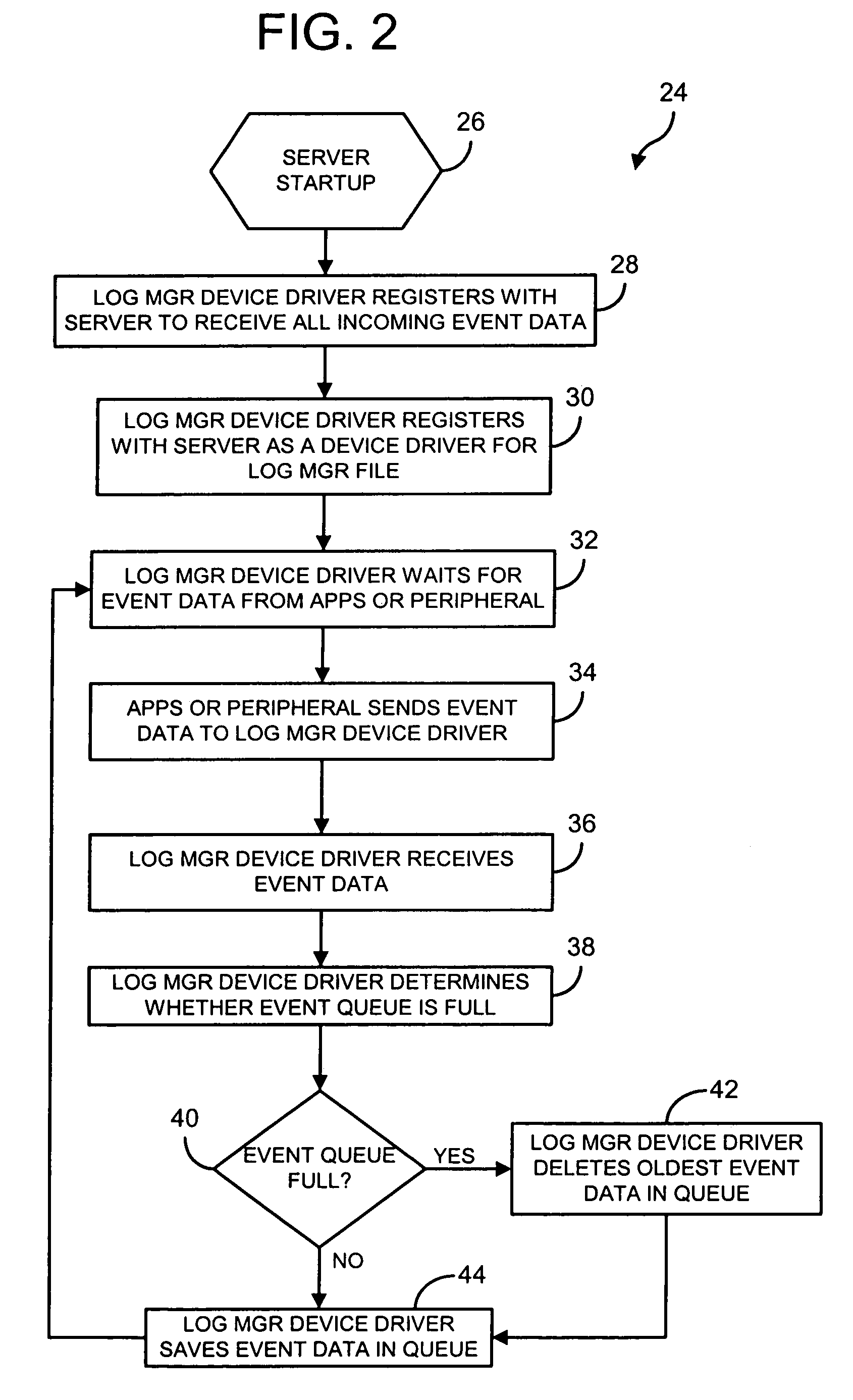
InactiveUS7065556B1Hardware monitoringMultiple digital computer combinationsSupplicantLog management
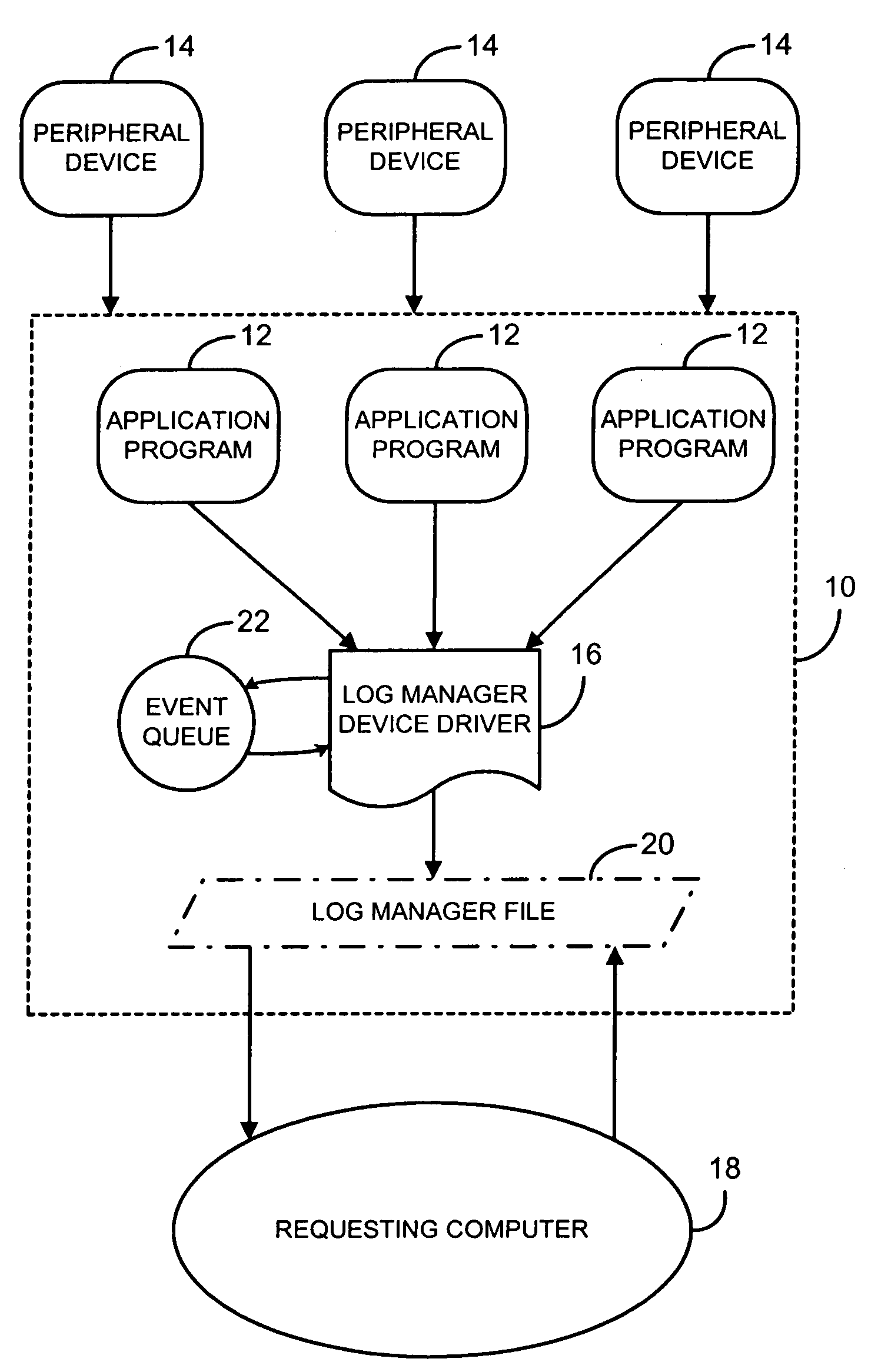
A method and system for logging event data from at least one operable application program or at least one peripheral device operably connected to a server using a log manager device driver. The method includes the steps of registering the log manager device driver with the server to receive all the event data from the server, registering the log manager device driver with the server as a log manager file, the log manager device driver receiving the event data, and the log manager device driver responding to a download request for said log manager file from a requesting computer.
Owner:HEWLETT PACKARD DEV CO LP
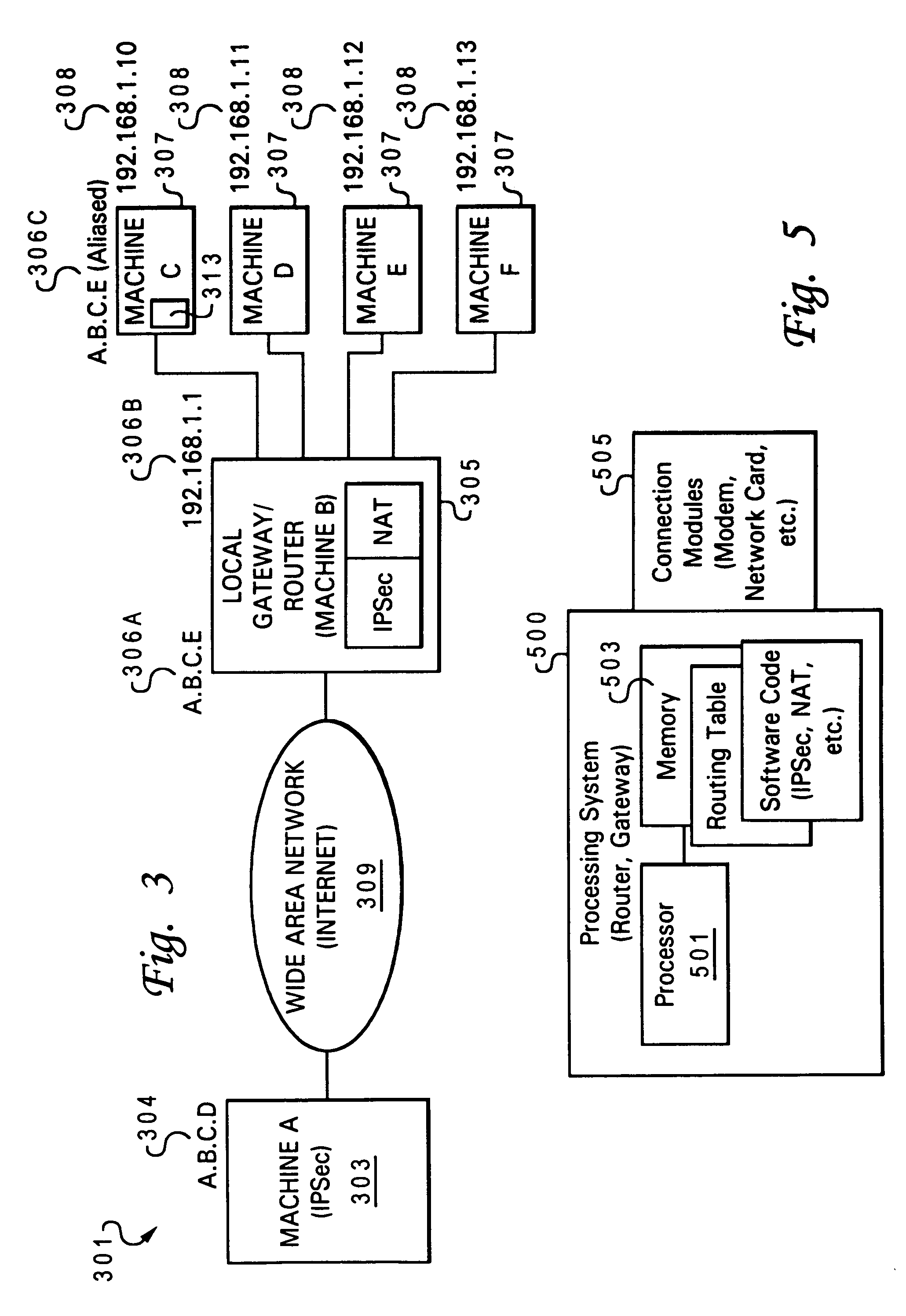
Secure IPsec tunnels with a background system accessible via a gateway implementing NAT
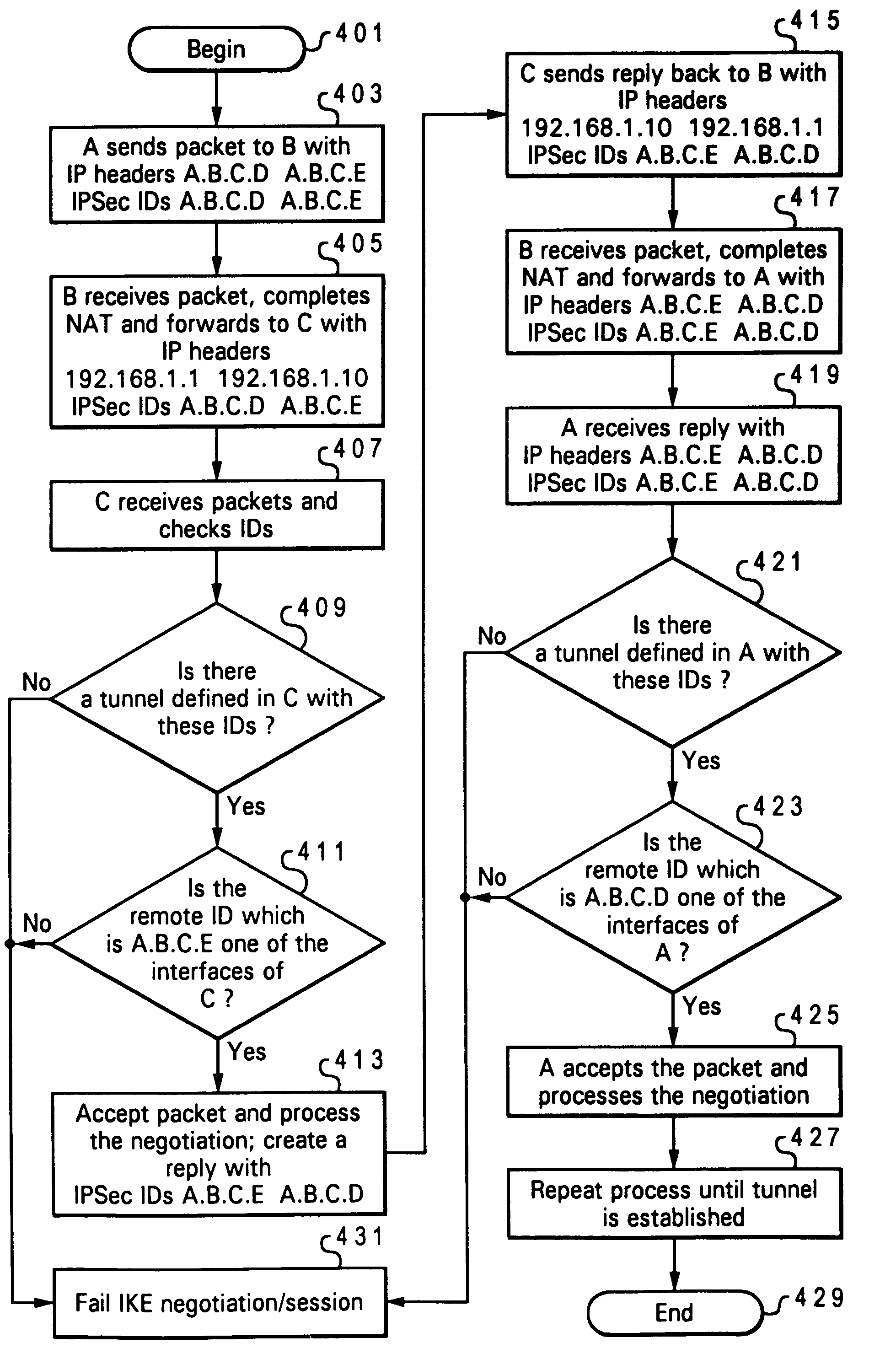
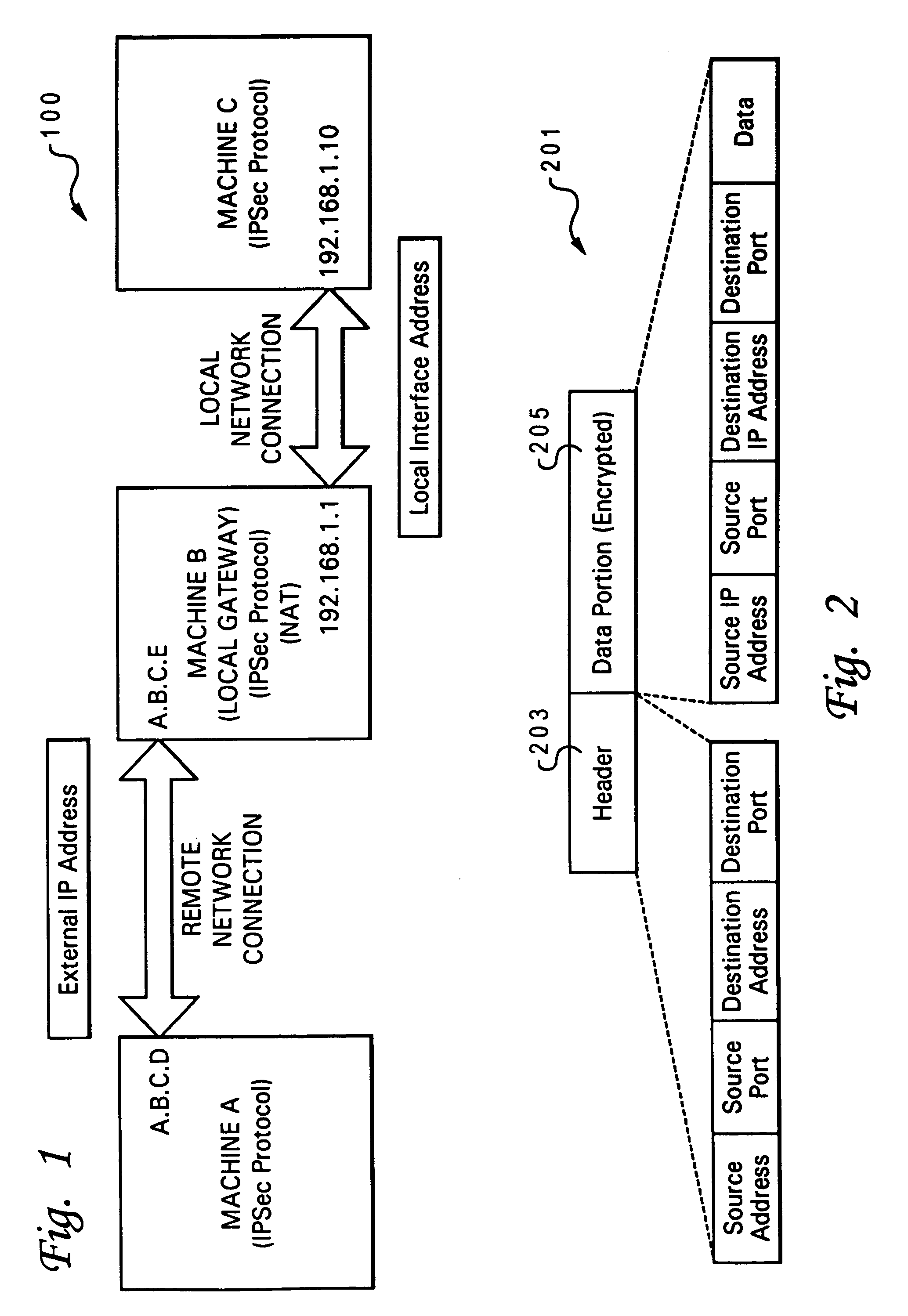
ActiveUS7159242B2Digital data processing detailsUser identity/authority verificationSecure communicationSupplicant
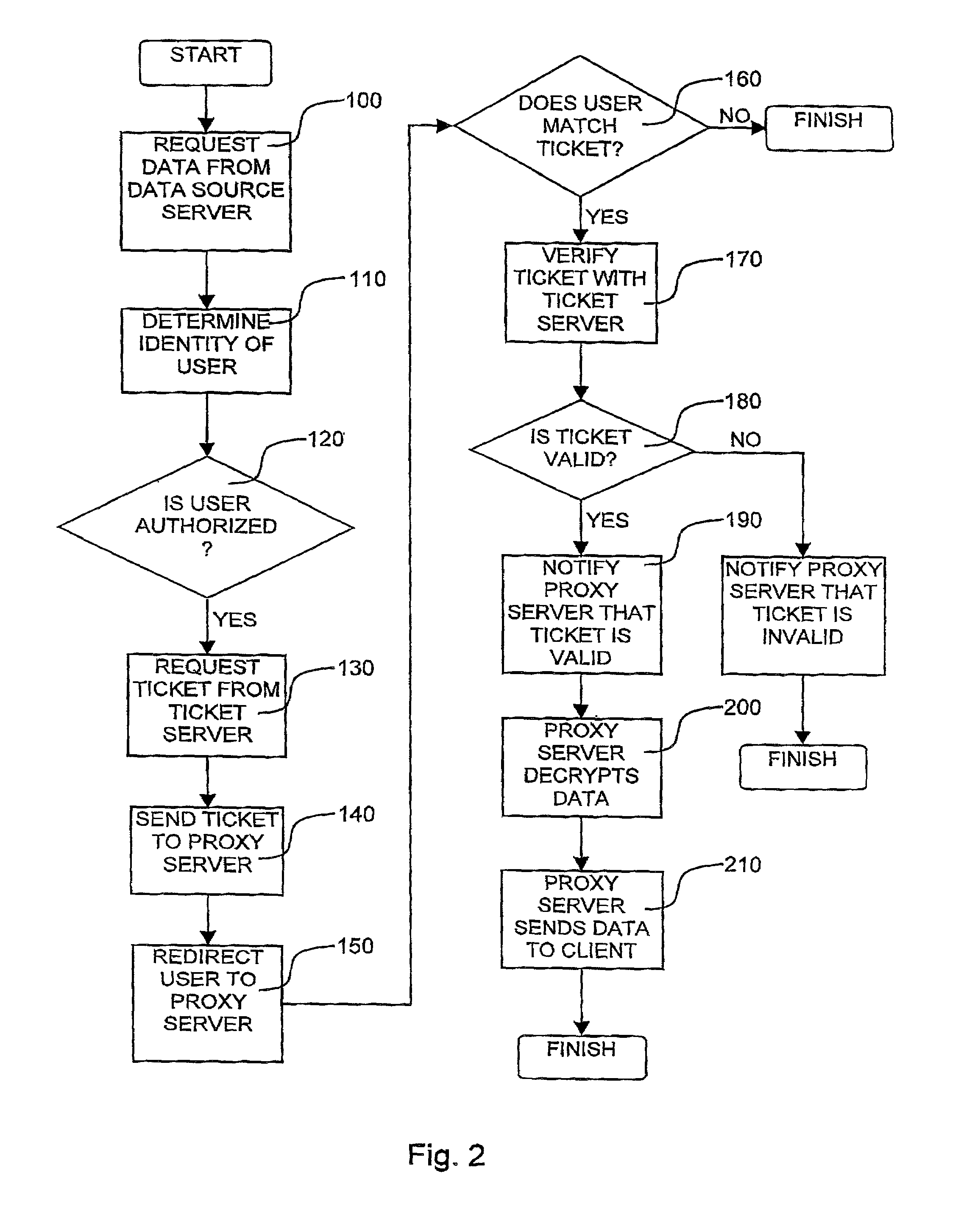
A method and system for enabling secure IPsec tunnels within NAT without compromising security. A local network is configured with a gateway machine connected to the Internet and having an IPsec ID for interfacing with the Internet and a local IP / interface address for interfacing with the local network. Client machines are connected to the gateway machine and communicate with the Internet via the gateway and network address translation (NAT) techniques. Each client machine is configured with a local IP / interface address. The client machines are also provided with an alias of the IPsec ID for the gateway machine. When an IPsec request is received by the gateway machine to establish a tunnel (secure communication) with one of the clients, the gateway machine forwards the packet to the particular client using NAT. The client machine receives the request and since it has an alias of the gateway's IPsec ID, the client machine will confirm that it has one of the IPsec IDs in the packet. The client machine sends the reply packet back to the gateway machine, which then forwards it to the requesting machine over the Internet. The requesting machine receives the packet and a confirmation that it has reached its intended recipient and opens the secure IKE tunnel with the particular client via the gateway machine. In this manner authentication of the IKE tunnel and establishment of a secure IPsec session is completed with a client machine that is accessible only via a gateway implementing NAT.
Owner:TREND MICRO INC
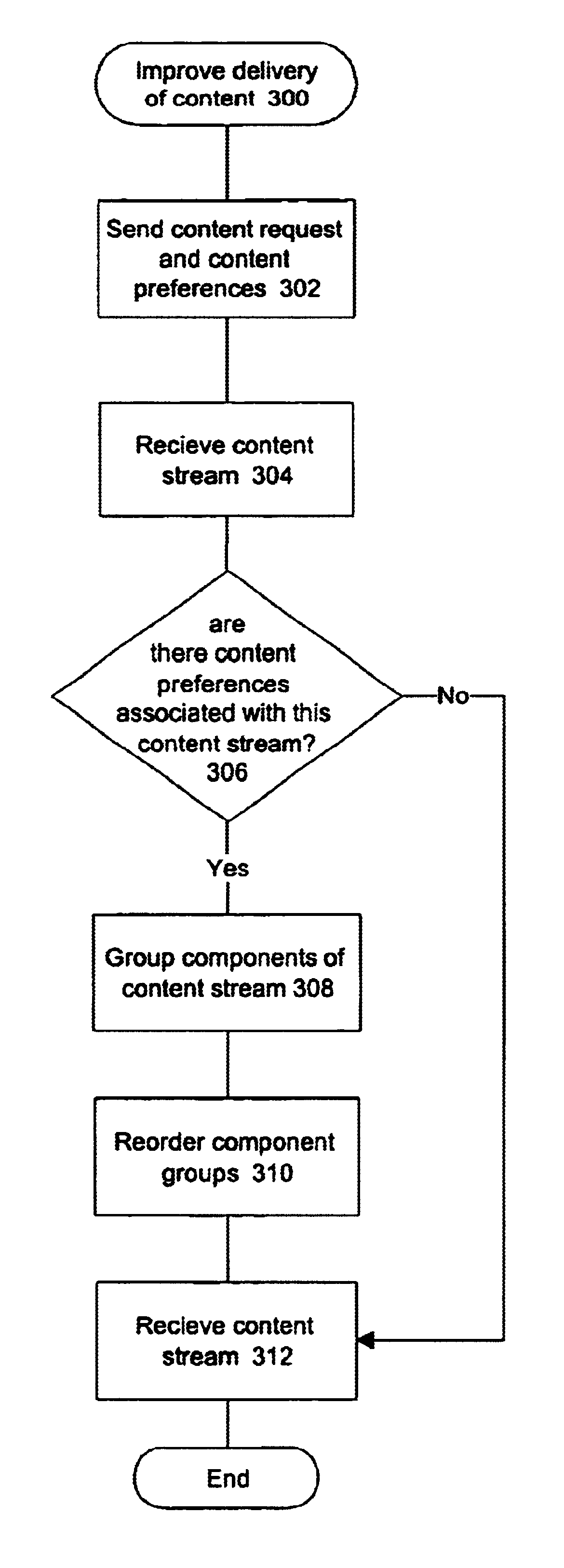
System for improving delivery of content by reordering after grouping components homogeneously within content stream based upon categories defined by content preferences
A method, apparatus and article of manufacture for improved delivery of content to a requesting computer connected to a communications network by a communications device by sending, from the requesting computer, a request for content and a plurality of content preferences. A content stream representing the content is then received on a communications device. Components within the content stream are grouped and reordered based upon at least one of the plurality of content preferences. The reordered content stream is then received on the requesting computer. The content stream may contain data formatted using languages such as HTML or XML. Grouping and reordering of the components can be used to compress the content stream and / or filter components from the content stream. Compression and filtering are especially useful in low bandwidth situations, for example analog or wireless modem connections.
Owner:CISCO TECH INC
Method for establishing secure associations within a communication network
ActiveUS20080226071A1Key distribution for secure communicationUser identity/authority verificationSecurity associationSecure authentication
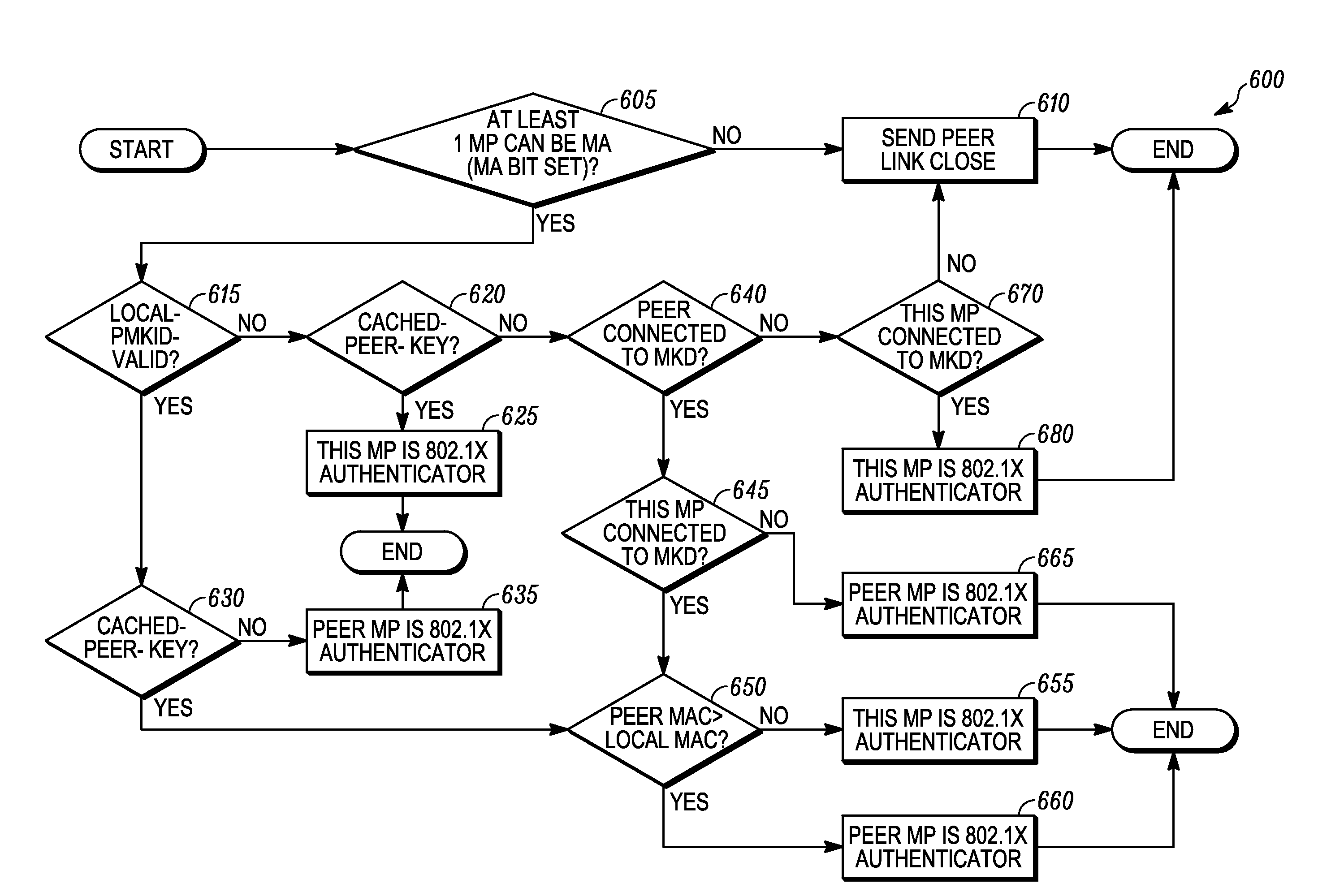
A method for security authentication within a wireless network is disclosed. A method within an adhoc mesh network for two devices to quickly determine roles (i.e. which is the authenticator and which is the supplicant) while establishing a security association is provided for. The invention further provides for the inclusion of cached key information in the role negotiation process and the application of role negotiation to a shortened three-way handshake.
Owner:ARRIS ENTERPRISES LLC
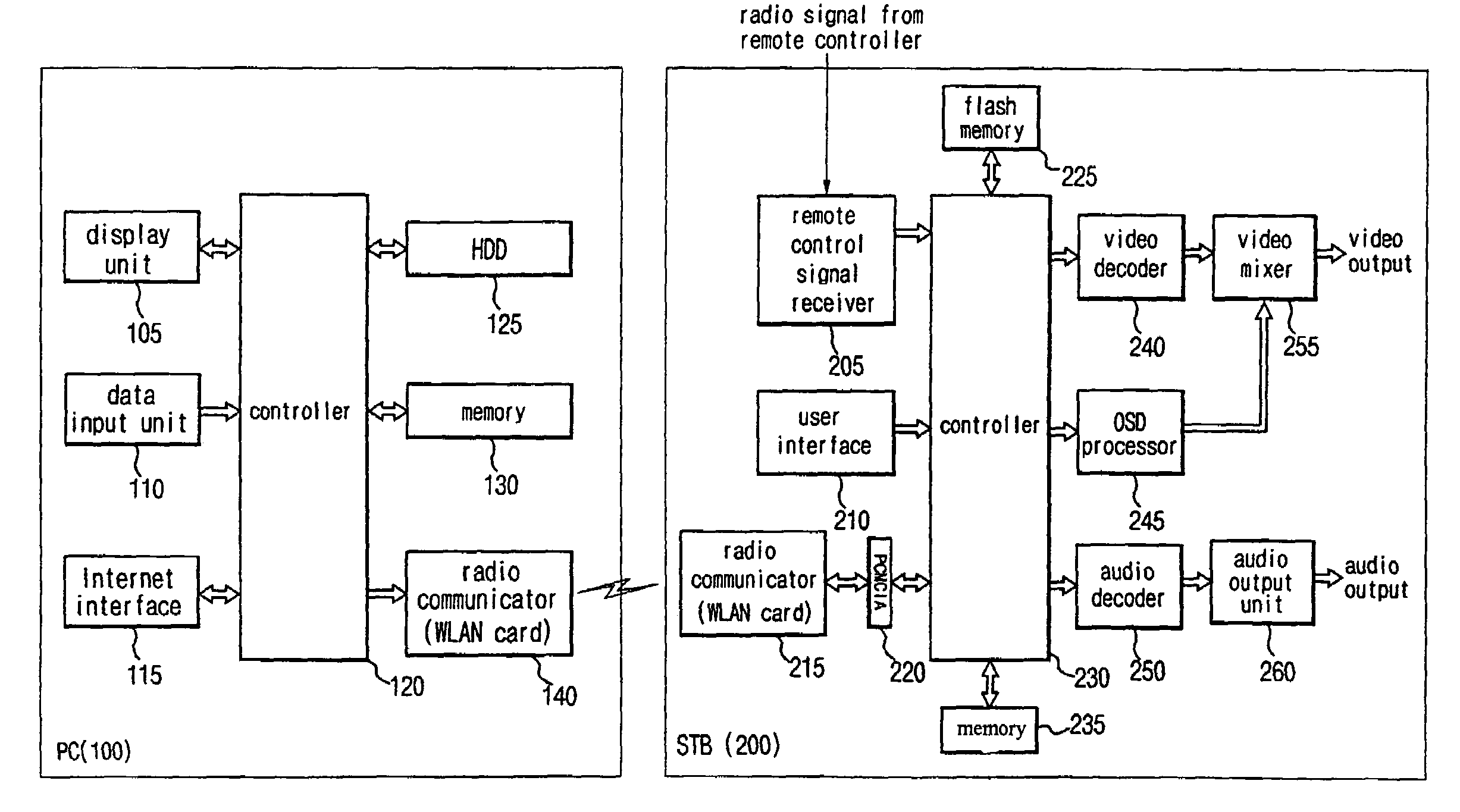
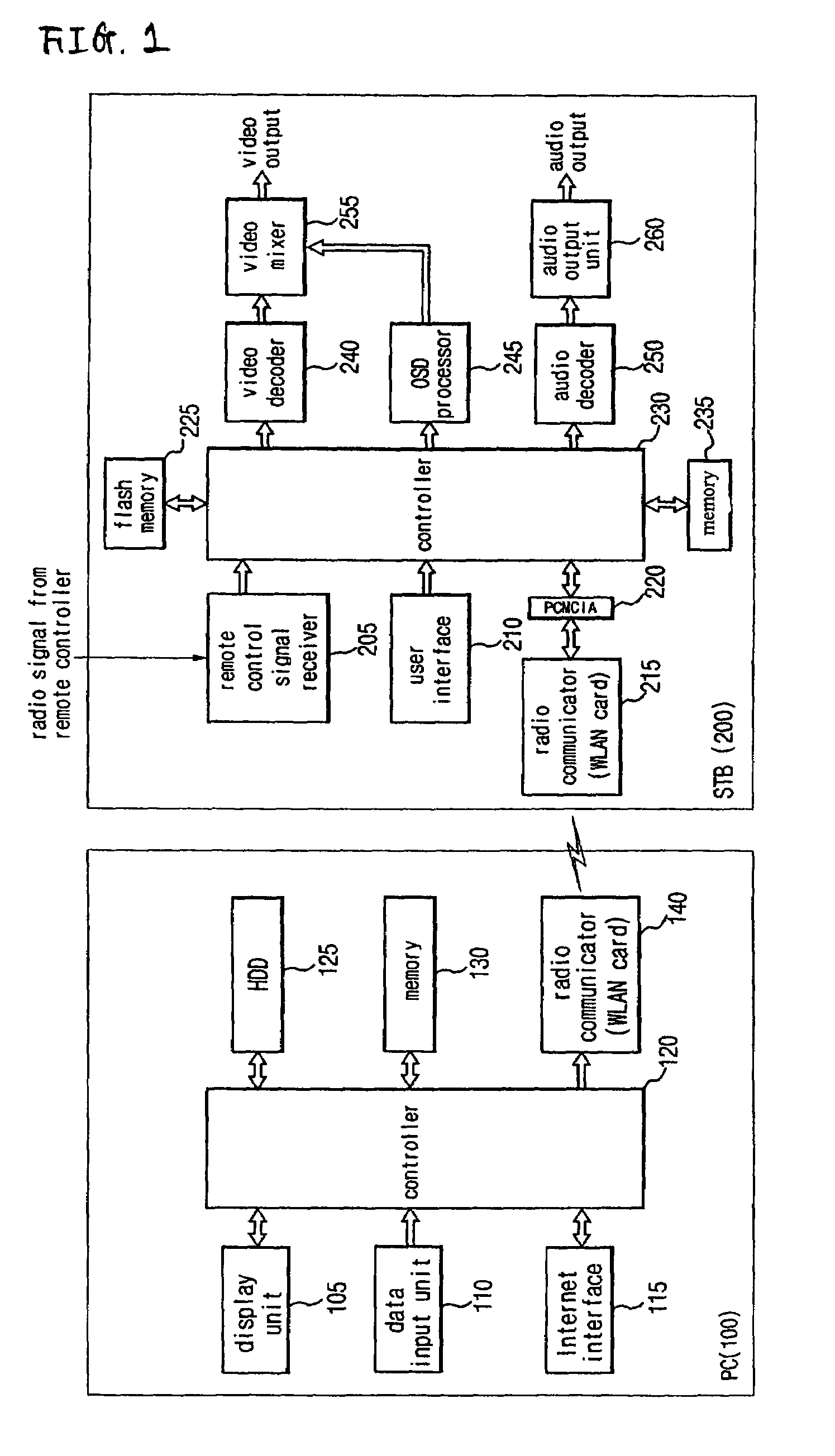
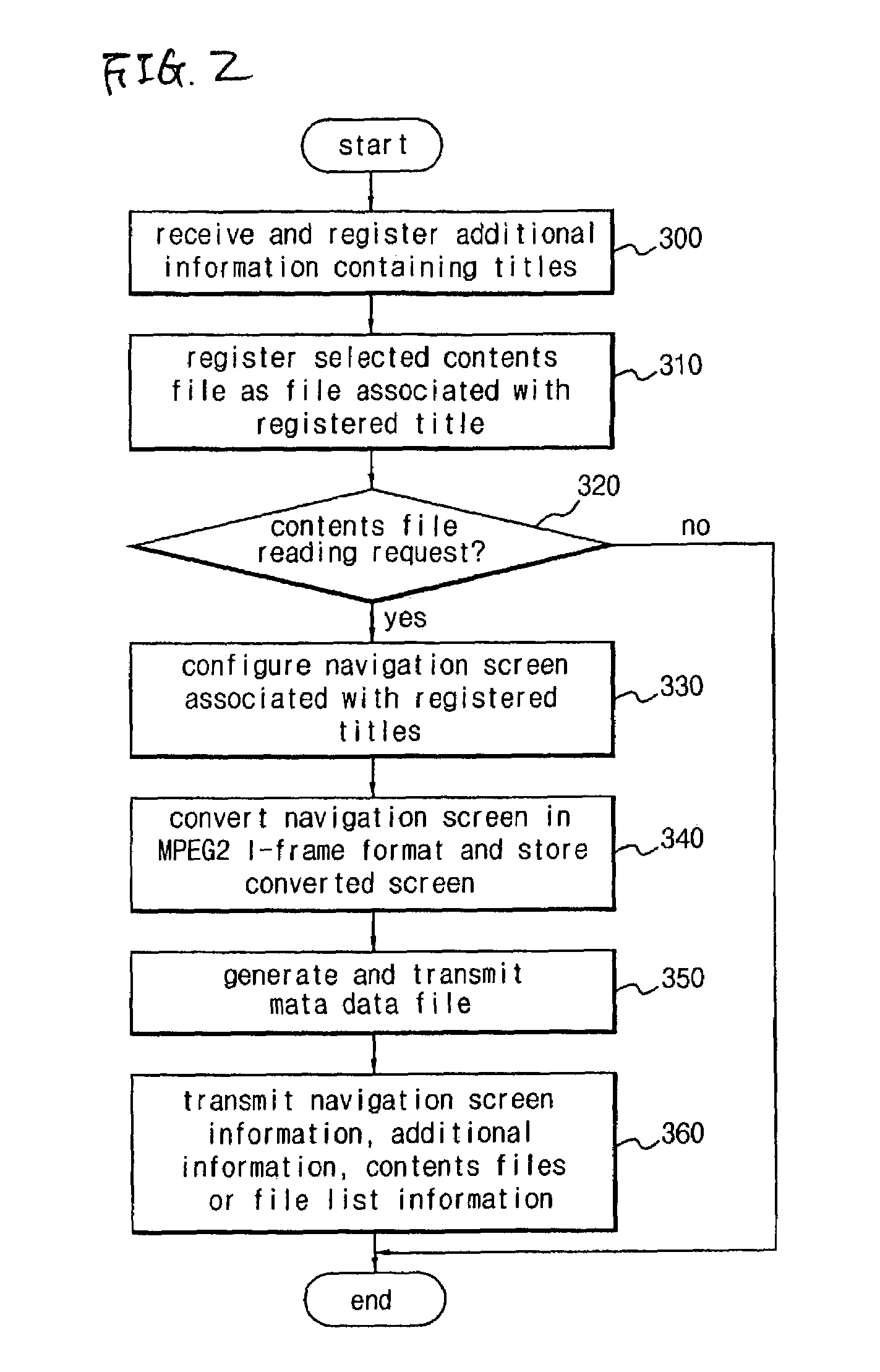
Wireless receiver for receiving multi-contents file and method for outputting data using the same
A wireless receiver for receiving a multi-contents file and a method for outputting data using the same, which can receive, navigation information for providing intuitively recognizable search interfaces to a user by radio in real time, receive various types of contents files by radio in real time, and output the received information and files through an AV device. A video decoder decodes a video stream on the basis of an MPEG standard. An audio decoder decodes an audio contents file. An OSD processor processes a text file and additional information. A video output unit selectively configures decoded video data and text data on one screen and performs encoding and outputting operations based on the format of a display unit. An audio output unit outputs decoded audio data. A user interface receives a user's command. A WLAN card communicates WLAN data with a computer system. A controller requests the computer system to transmit navigation screen information, at least one contents file or additional information of the contents file edited and processed by the computer system, analyzes a data stream received by radio from the computer system responsive to the request, and performs a control operation so that a result of the analysis is inputted into the decoder or OSD processor. A memory stores the stream and control program data.
Owner:EDITO CO LTD
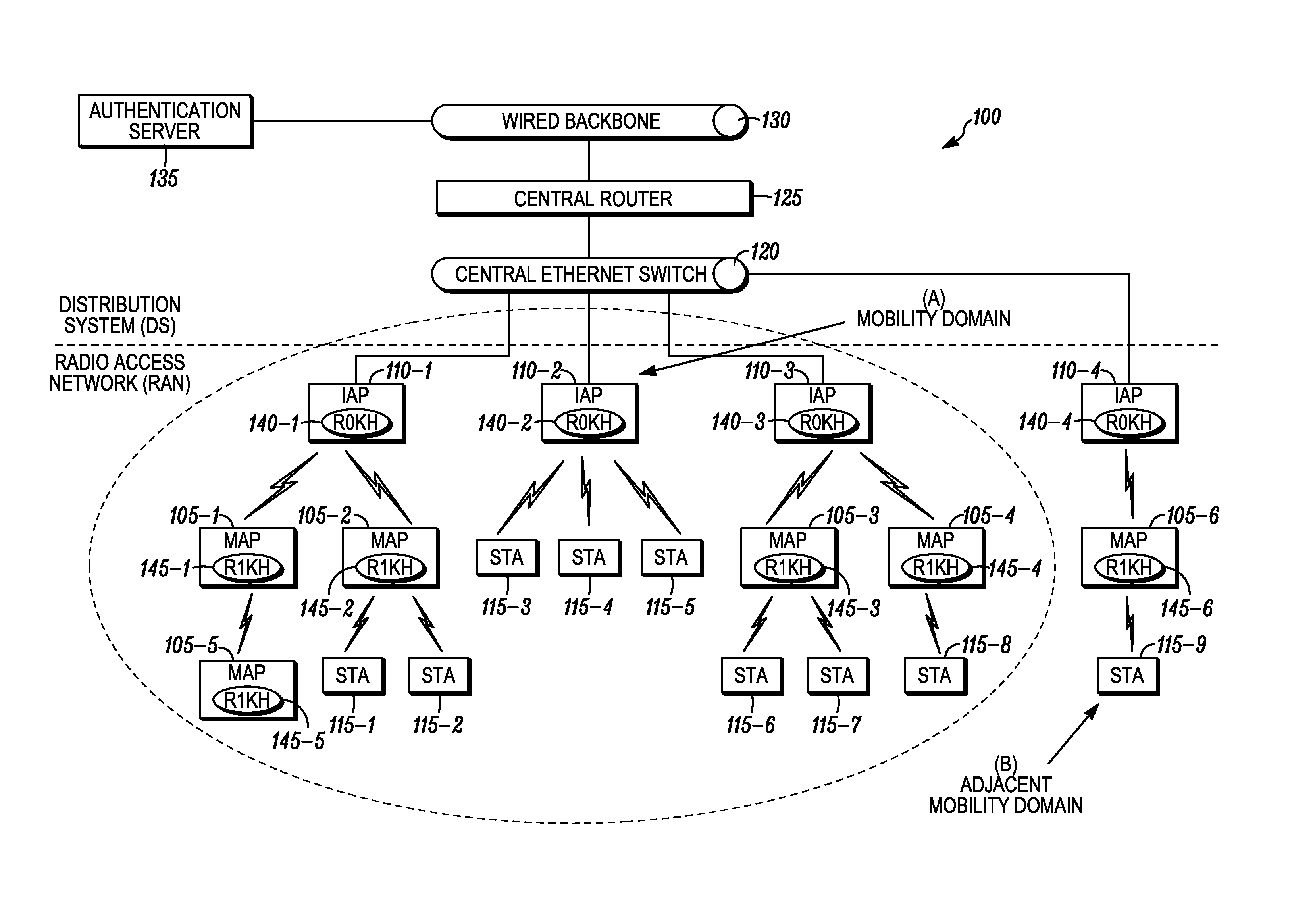
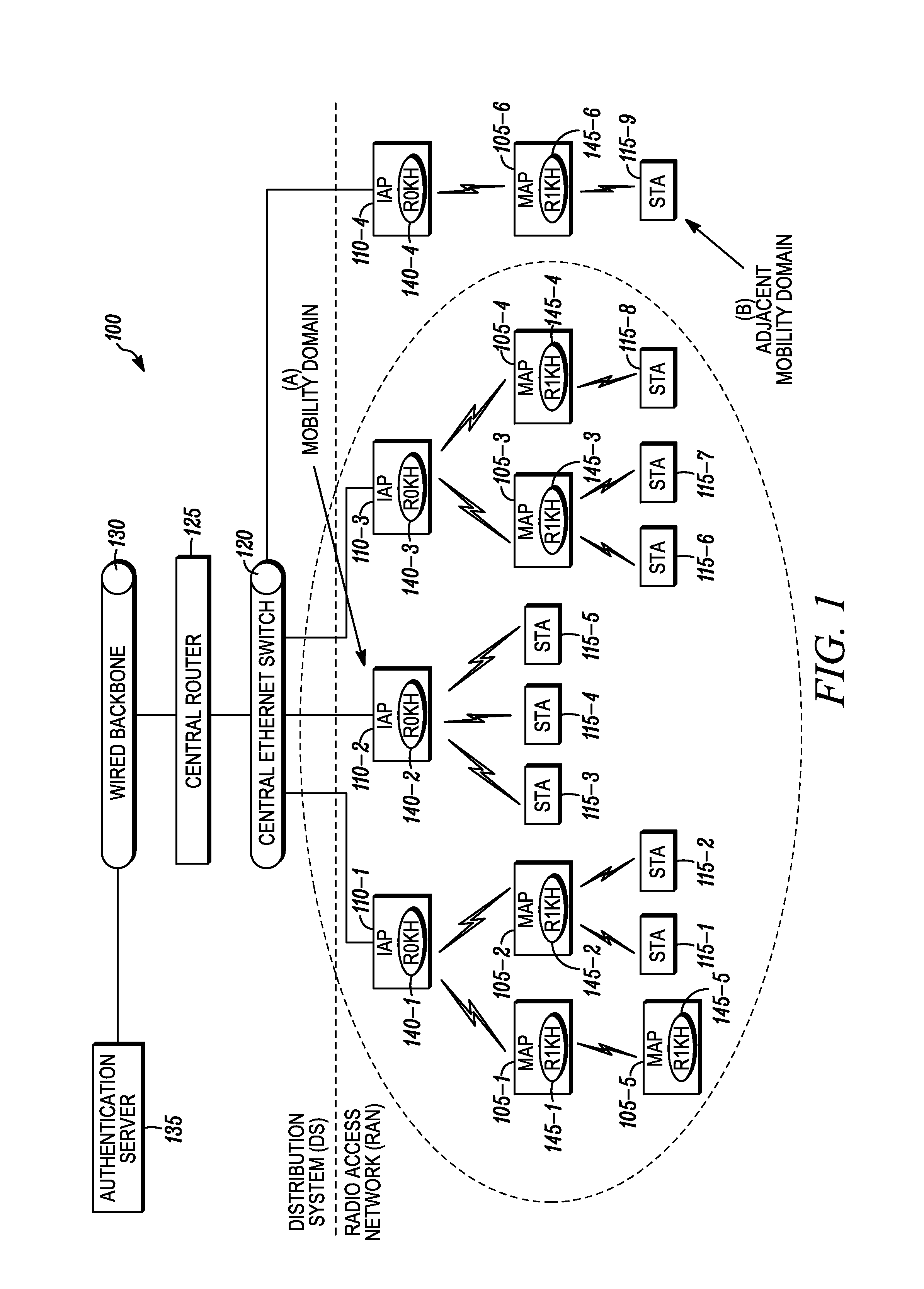
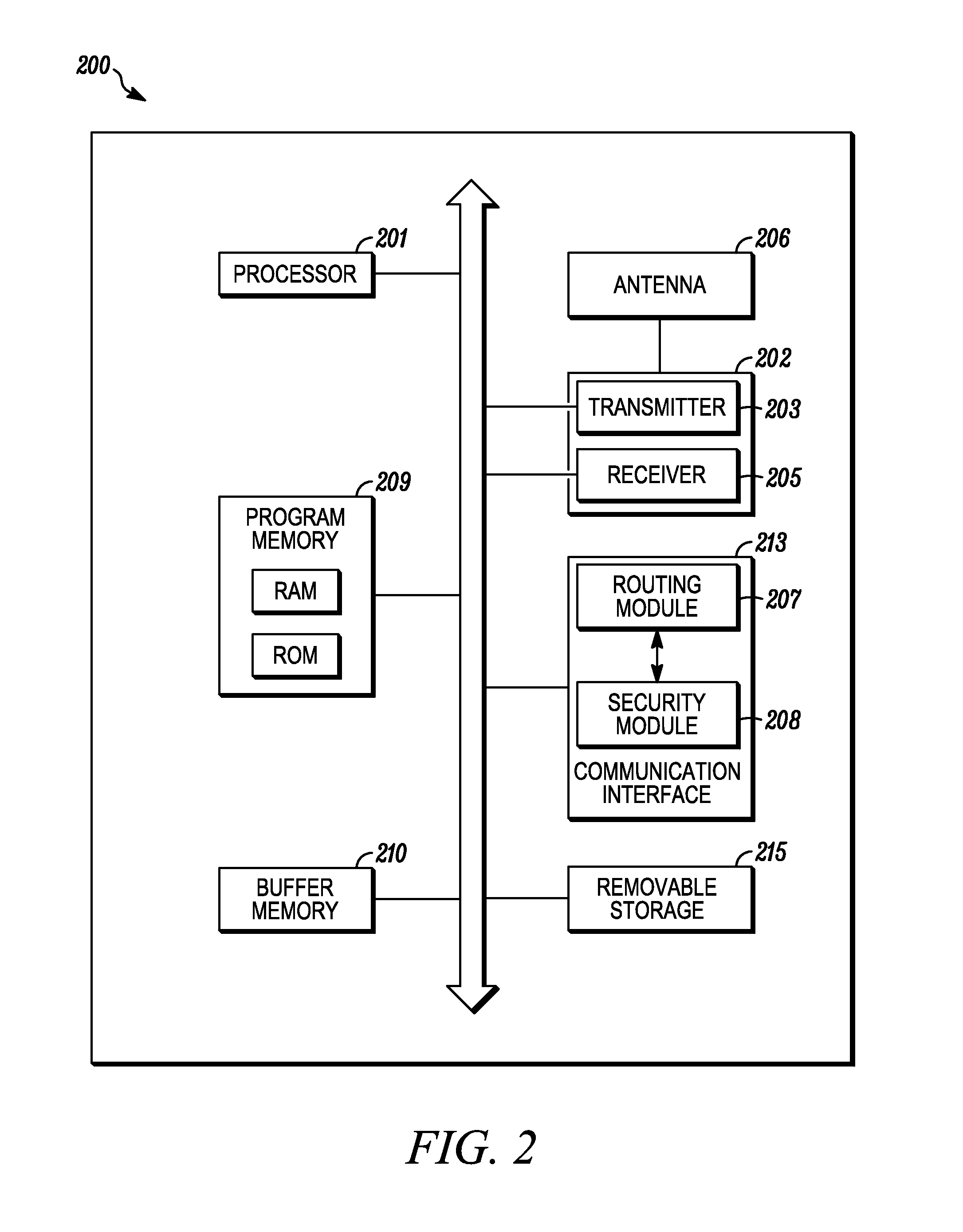
Method for providing fast secure handoff in a wireless mesh network
ActiveUS20090116647A1User identity/authority verificationNetwork topologiesWireless mesh networkSecurity association
Disclosed is a method for providing fast secure handoff in a wireless mesh network. The method comprises configuring multiple first level key holders (R0KHs) within a radio access network to which supplicants within the multi-hop wireless mesh network are capable of establishing a security association, configuring a common mobility domain identifier within the first level key holders of a mobility domain, and propagating identity of a first level key holder and the mobility domain identifier through the wireless mesh network to enable the supplicants within the mobility domain to perform fast secure handoff.
Owner:ARRIS ENTERPRISES LLC
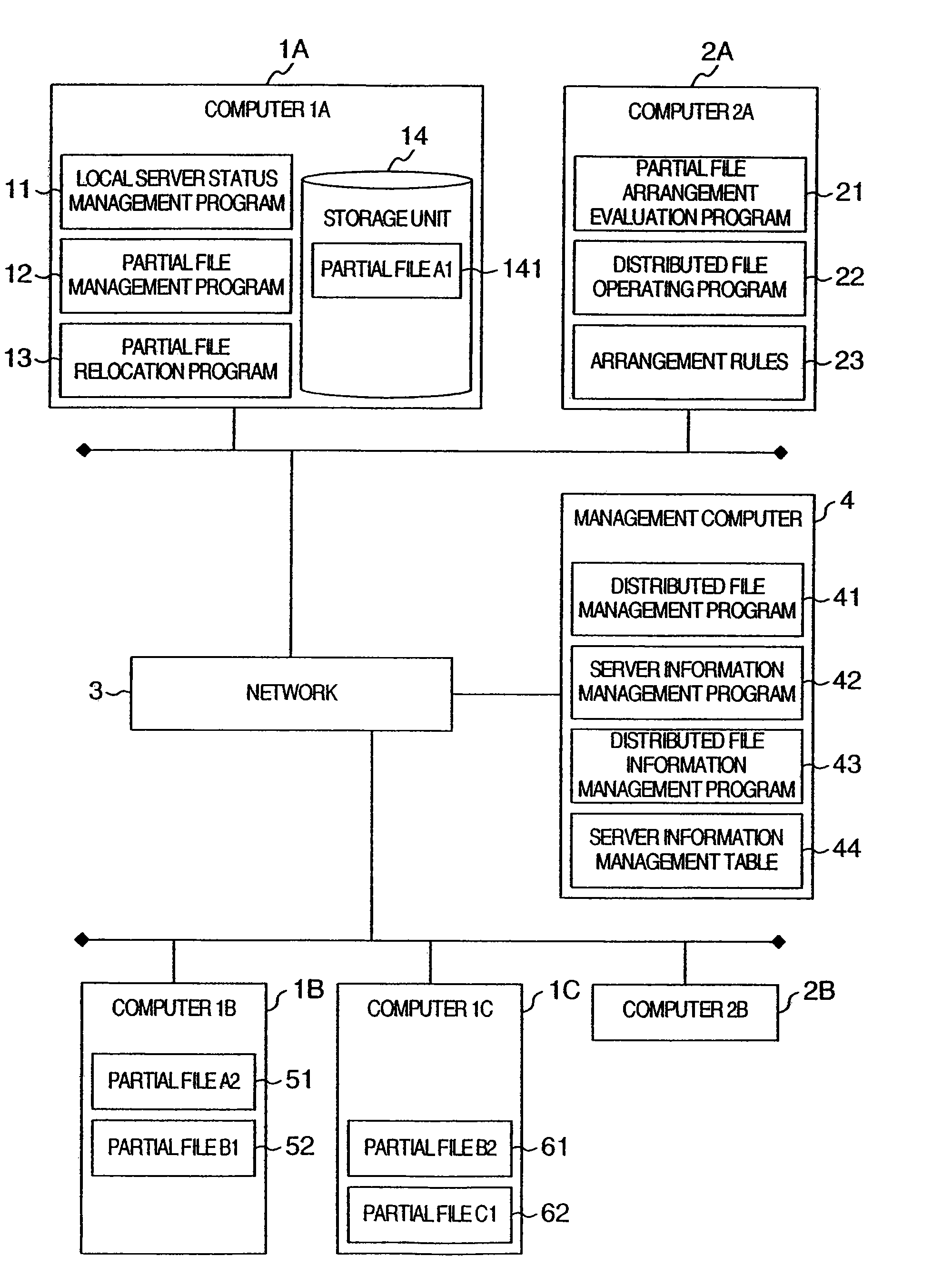
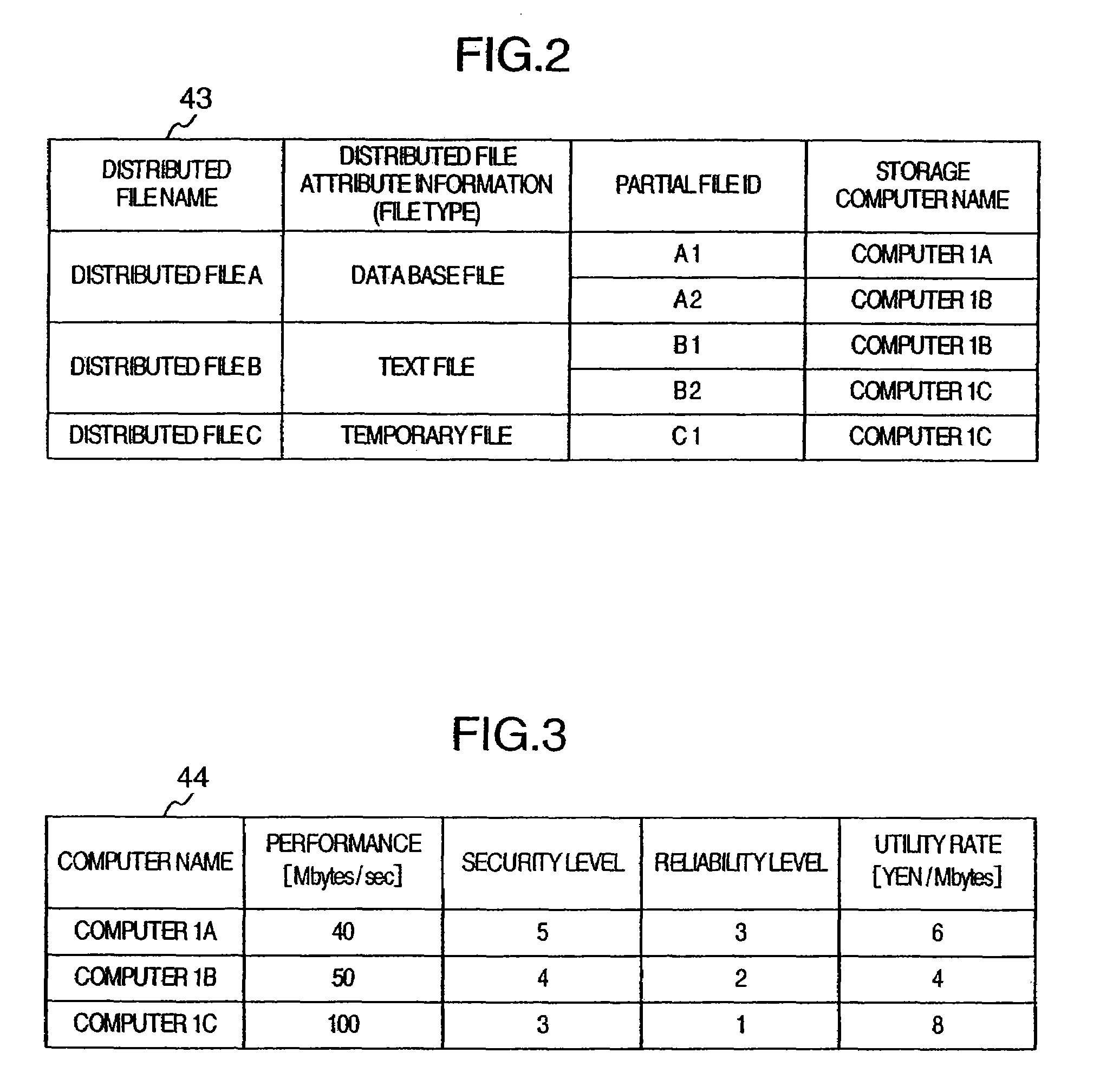
File distribution system in which partial files are arranged according to various allocation rules associated with a plurality of file types
InactiveUS7620698B2Digital data information retrievalMultiple digital computer combinationsSupplicantDistributed File System
In a distributed file system, when a user requests a computer to create a distributed file, a management computer acquires a list of computers complying with an allocation rule selected by the user from allocation rules taking the performance, security level, reliability level and utility rate into consideration. When the user requests the computer to access the distributed file, on the other hand, the partial files and the server information are collected from each computer. Each computer evaluates the allocation of the partial files based on the selected allocation rule and the server information from each computer, and if required, selects a destination computer and instructs the partial files to be moved to the destination computer.
Owner:GOOGLE LLC
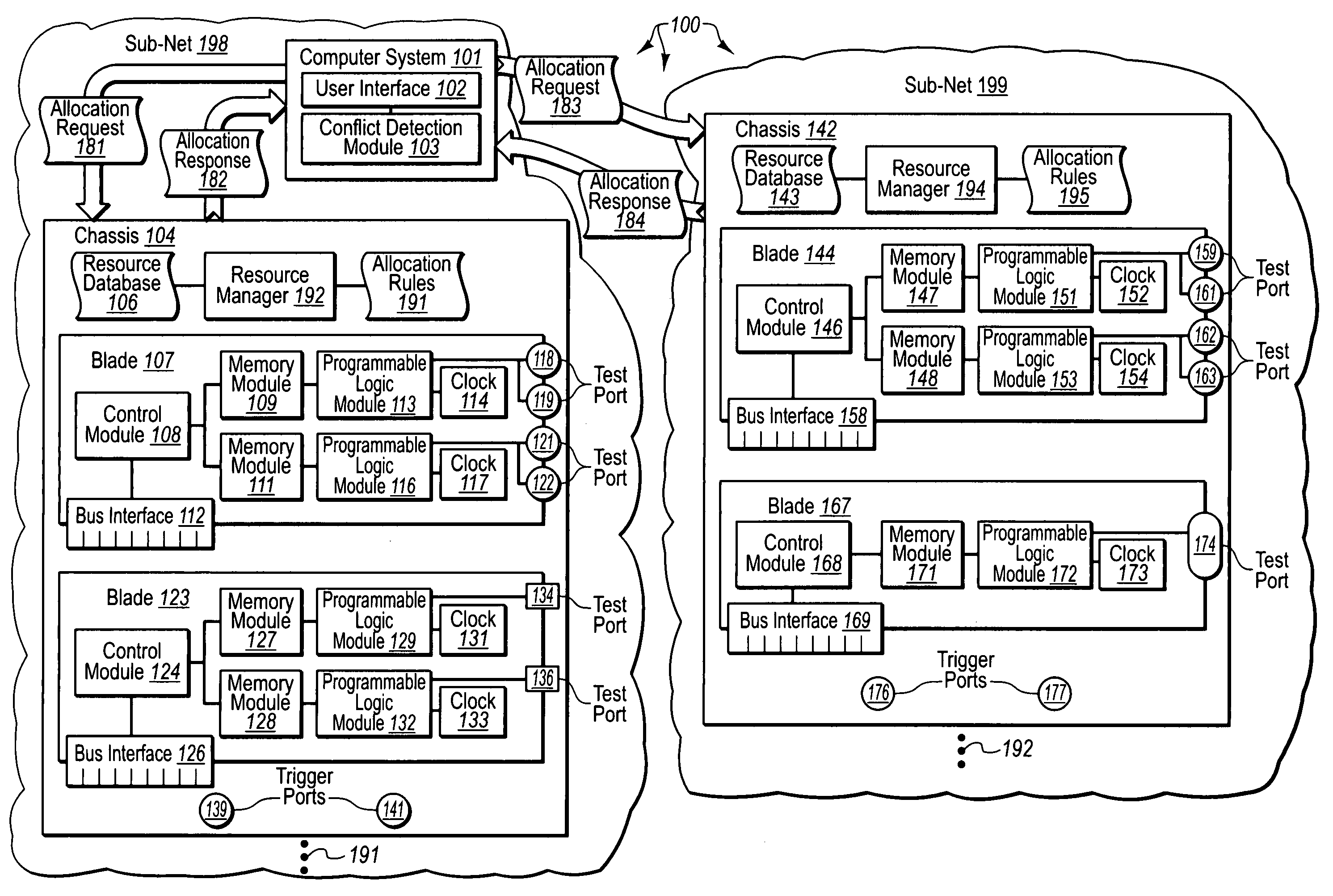
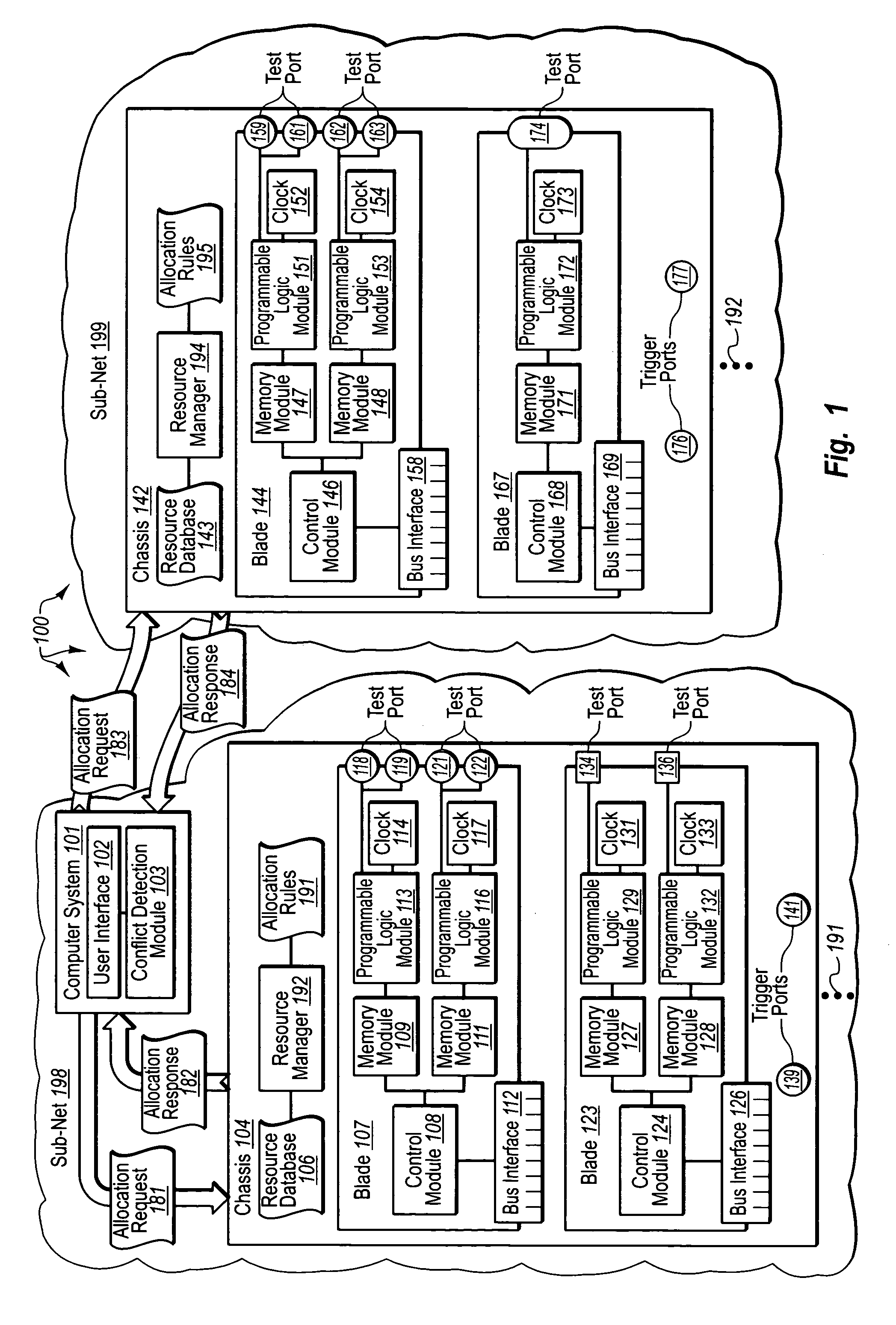
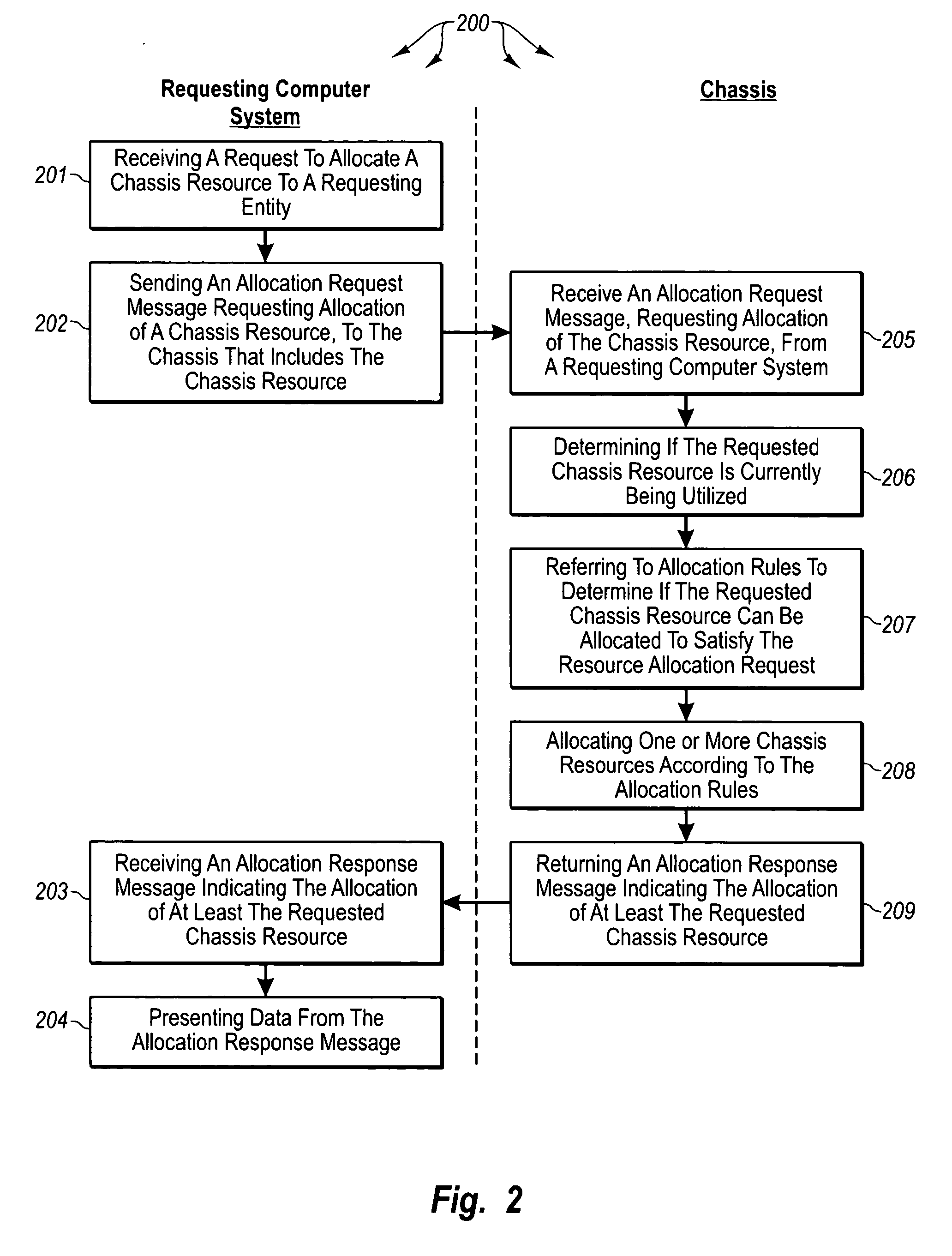
Managing resources of chassis that include configurable network diagnostic modules
The present invention provides for managing resources of chassis that include configurable network diagnostic modules. A computer system receives a request to allocate a chassis resource to a requesting entity. The computer system sends an allocation request message to a chassis that includes the chassis resource. The chassis receives an allocation request message from the requesting computer system. The chassis determines if the requested chassis resource is currently being utilized. The chassis refers to allocation rules to determine if the requested chassis resource can be allocated to satisfy the resource allocation request. The chassis allocates one or more resources according to the allocation rules and returns an allocation response to the requesting computer system. The computer system receives the allocation response and presents the allocation response at the requesting computer system.
Owner:FINISTAR CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com