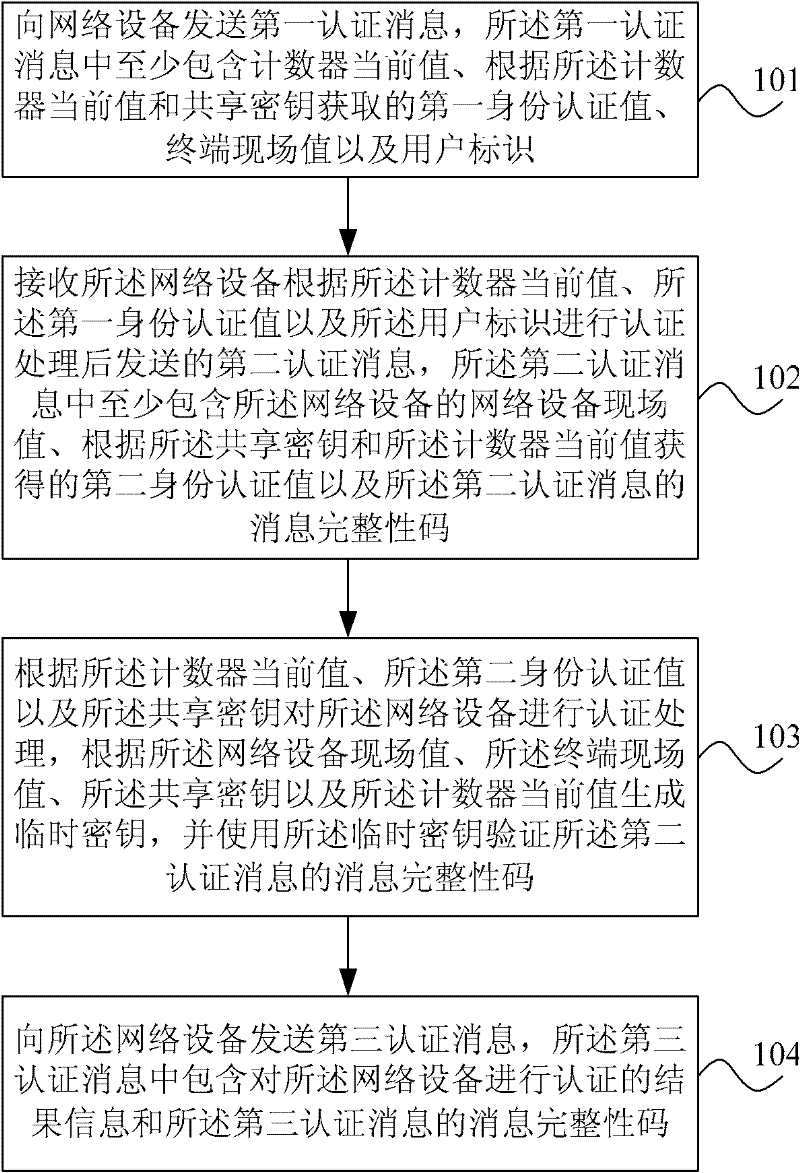
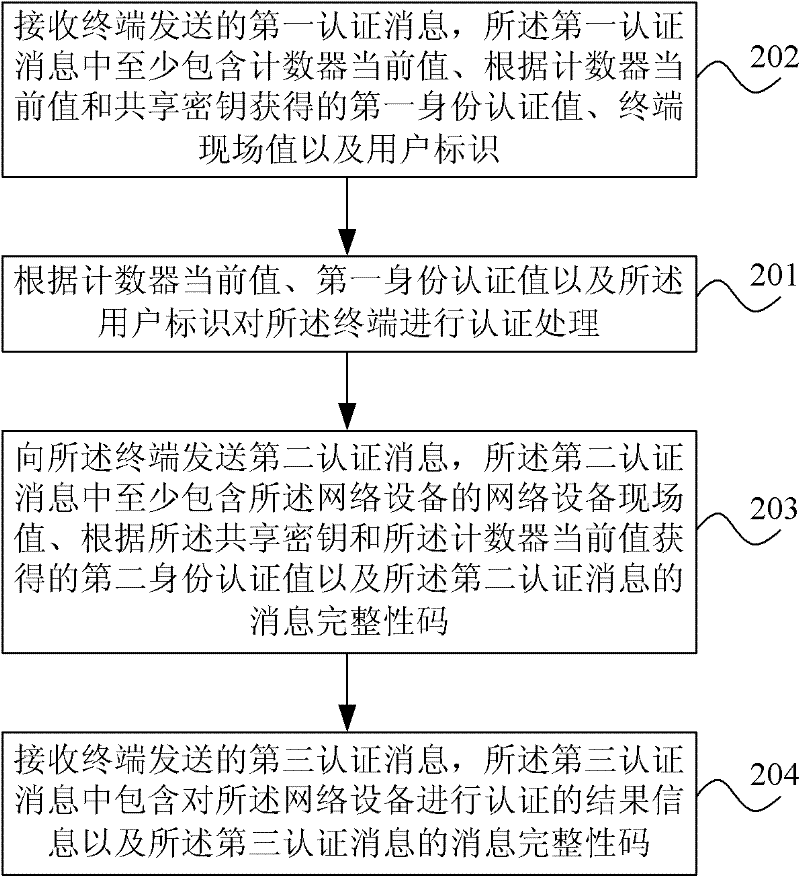
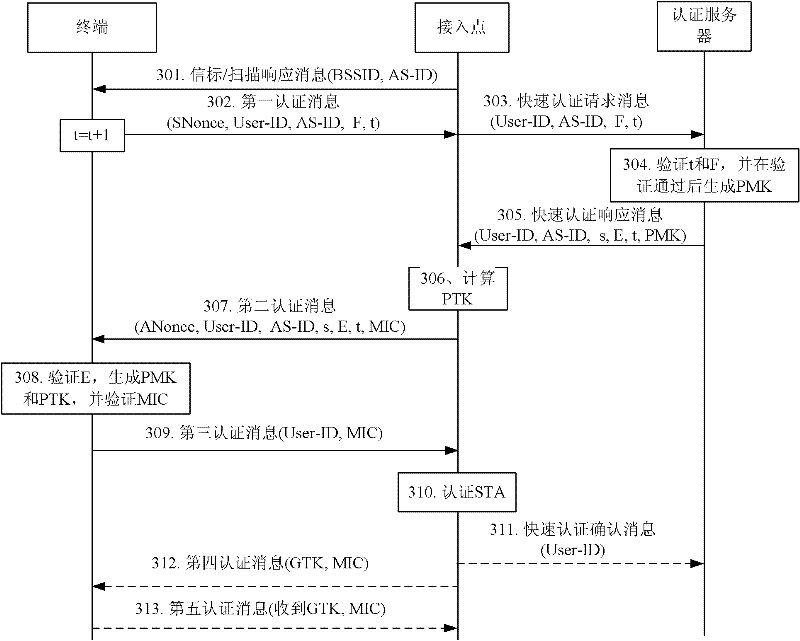
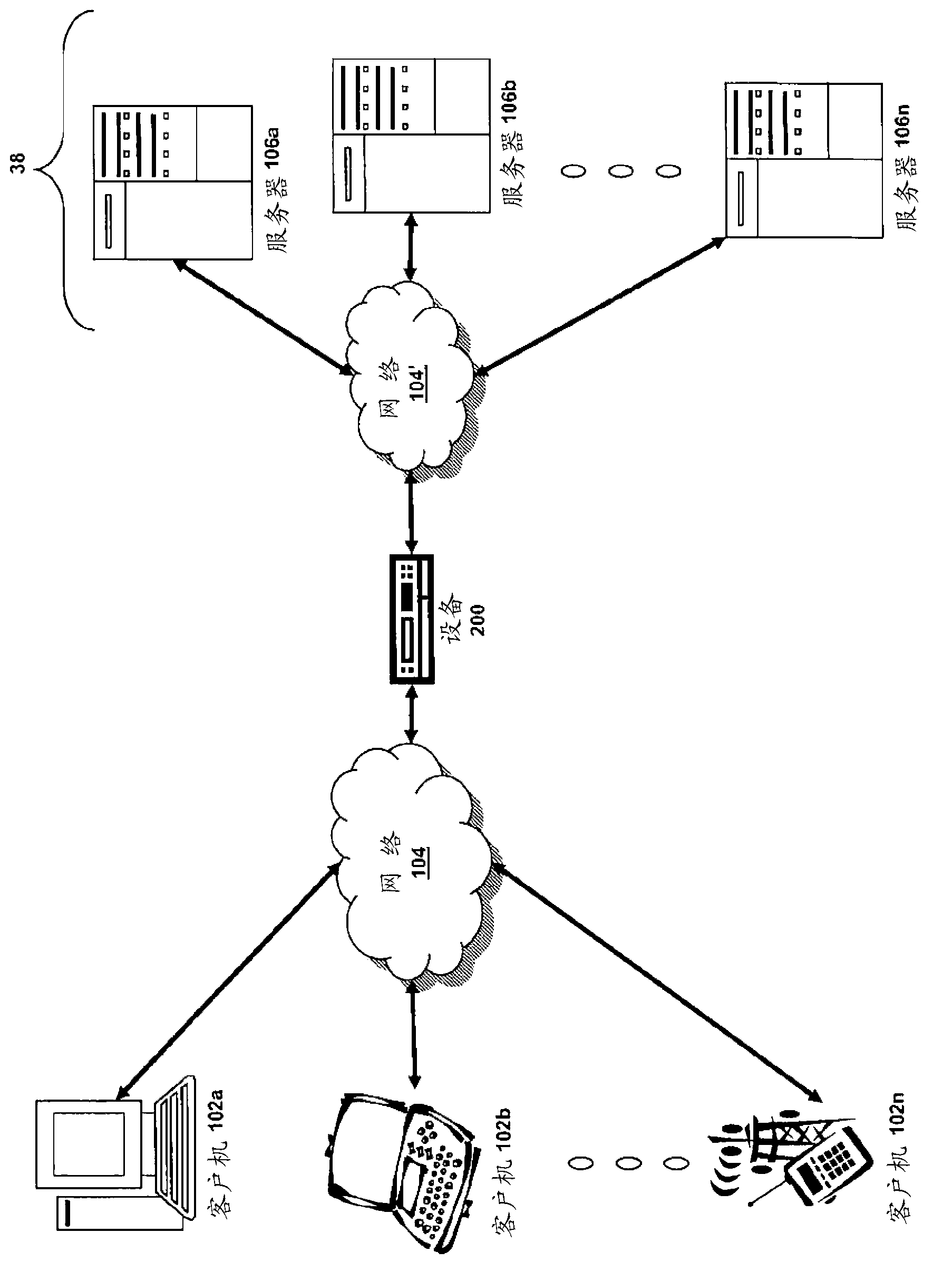
Patents
Literature
138 results about "Extensible Authentication Protocol" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
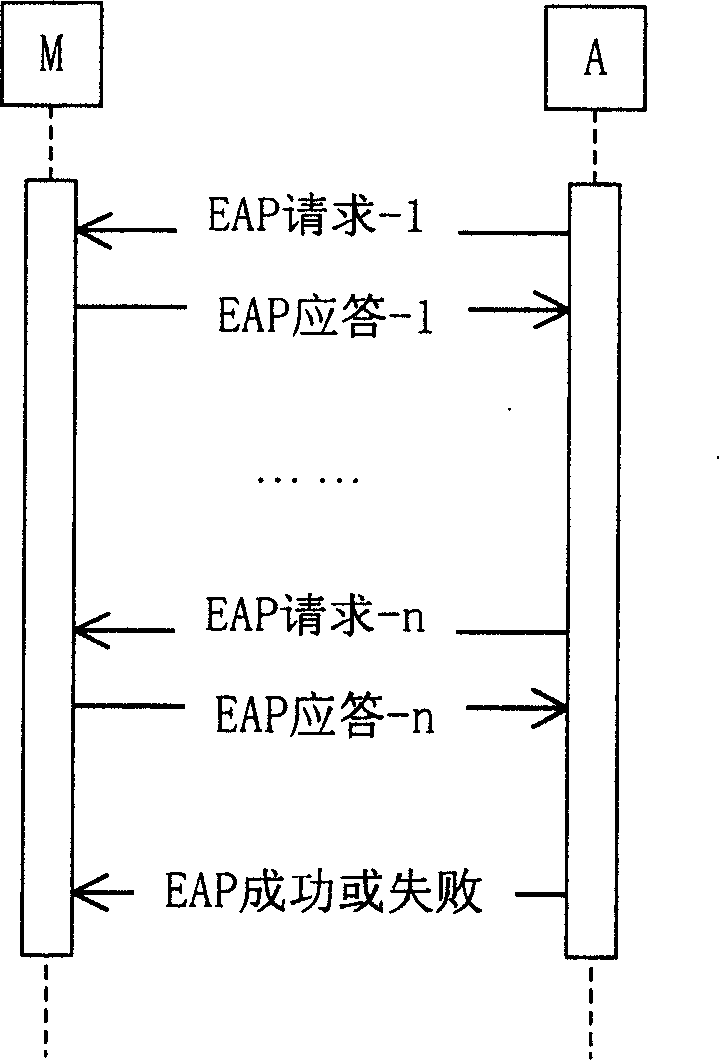
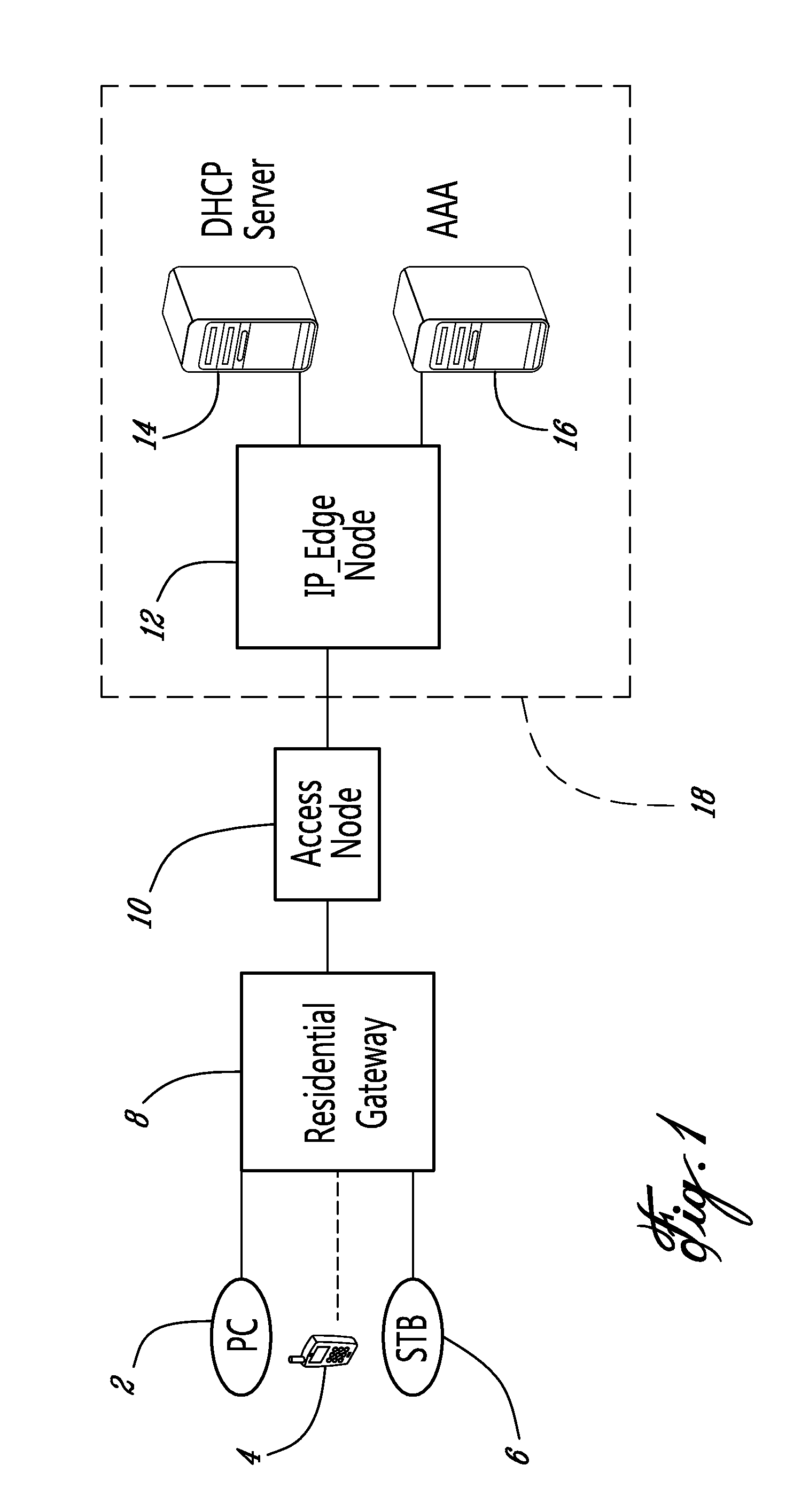
Extensible Authentication Protocol ('EAP') is an authentication framework frequently used in network and internet connections. It is defined in RFC 3748, which made RFC 2284 obsolete, and is updated by RFC 5247.
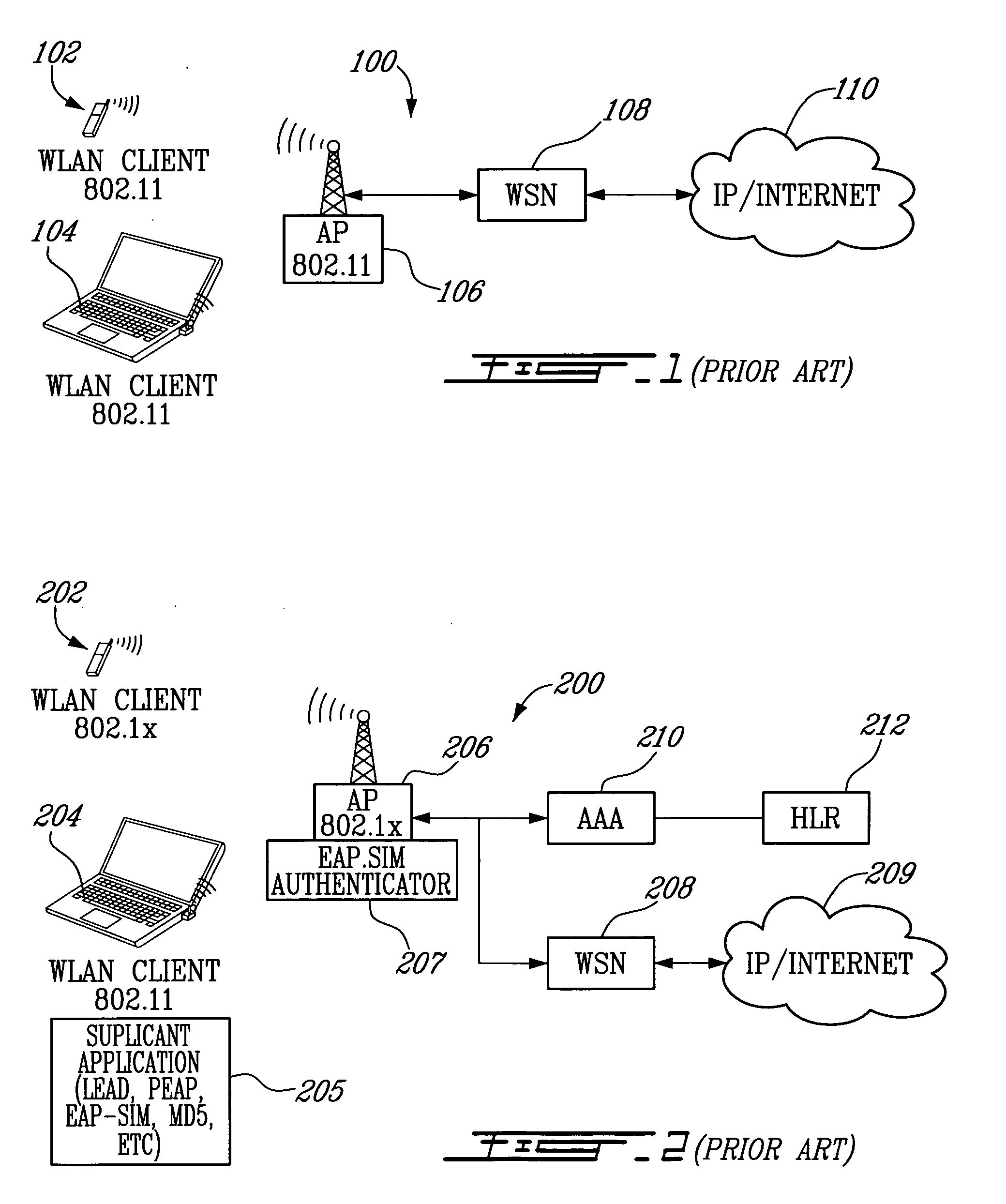
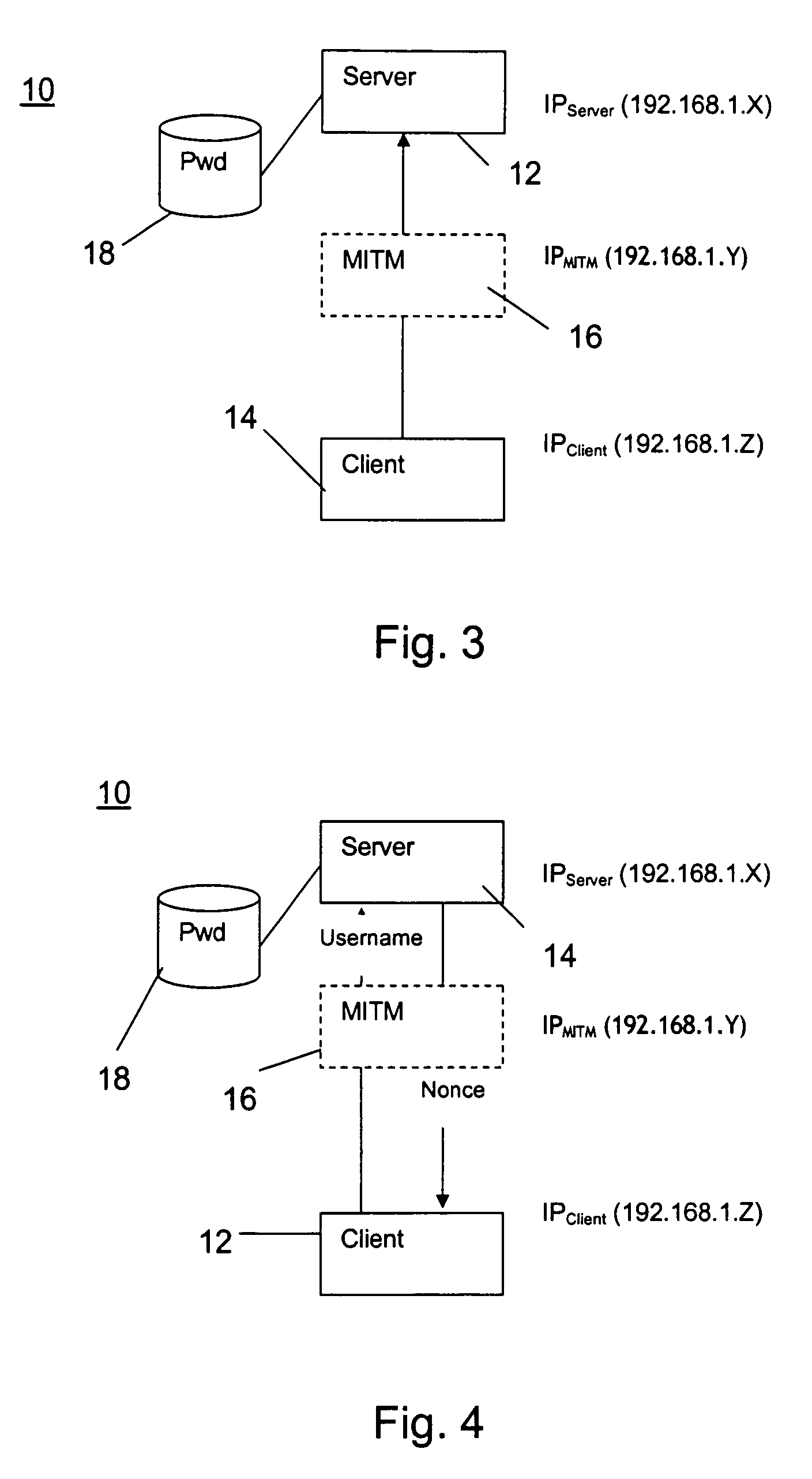
Wireless authentication protocol
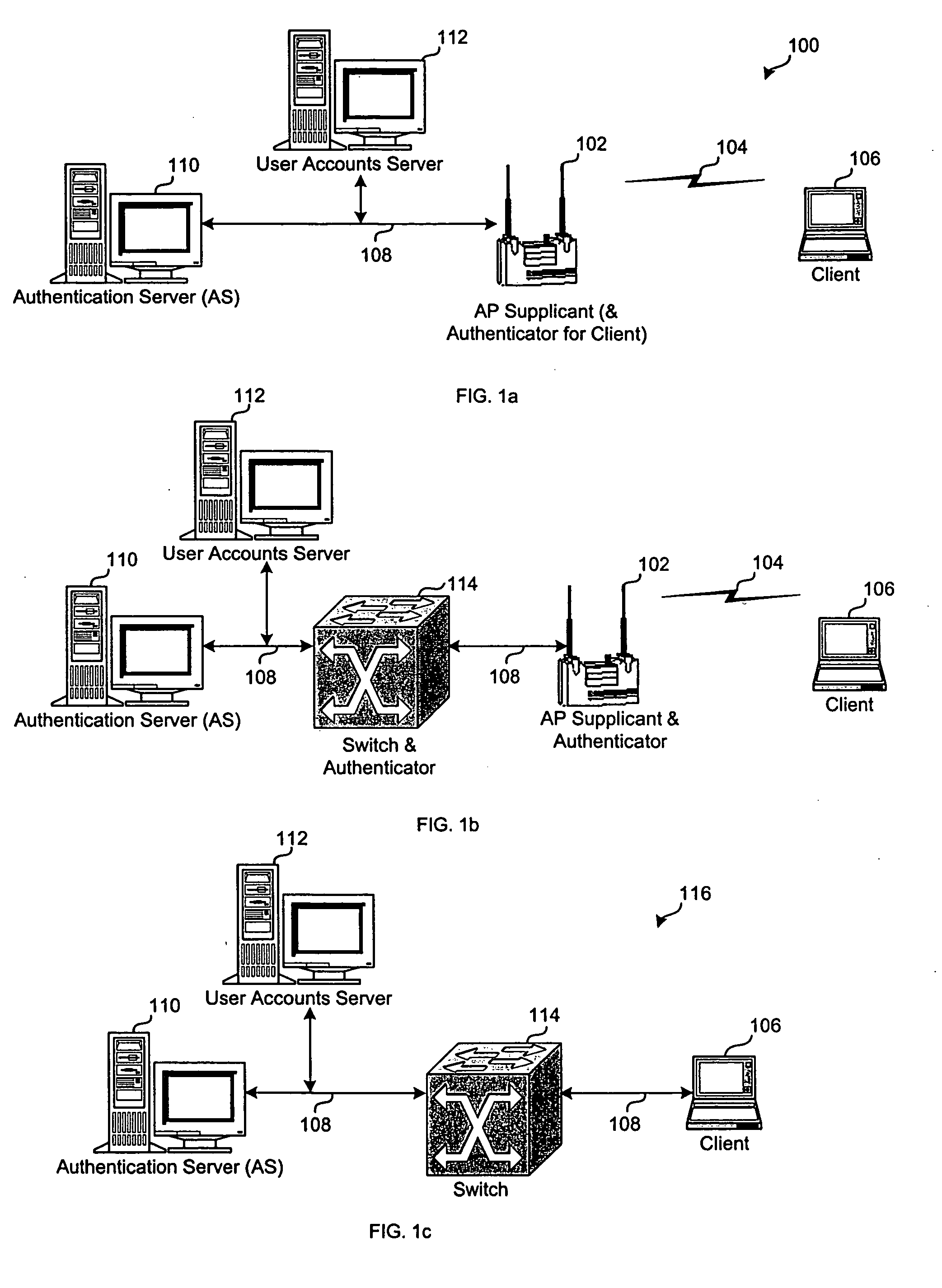
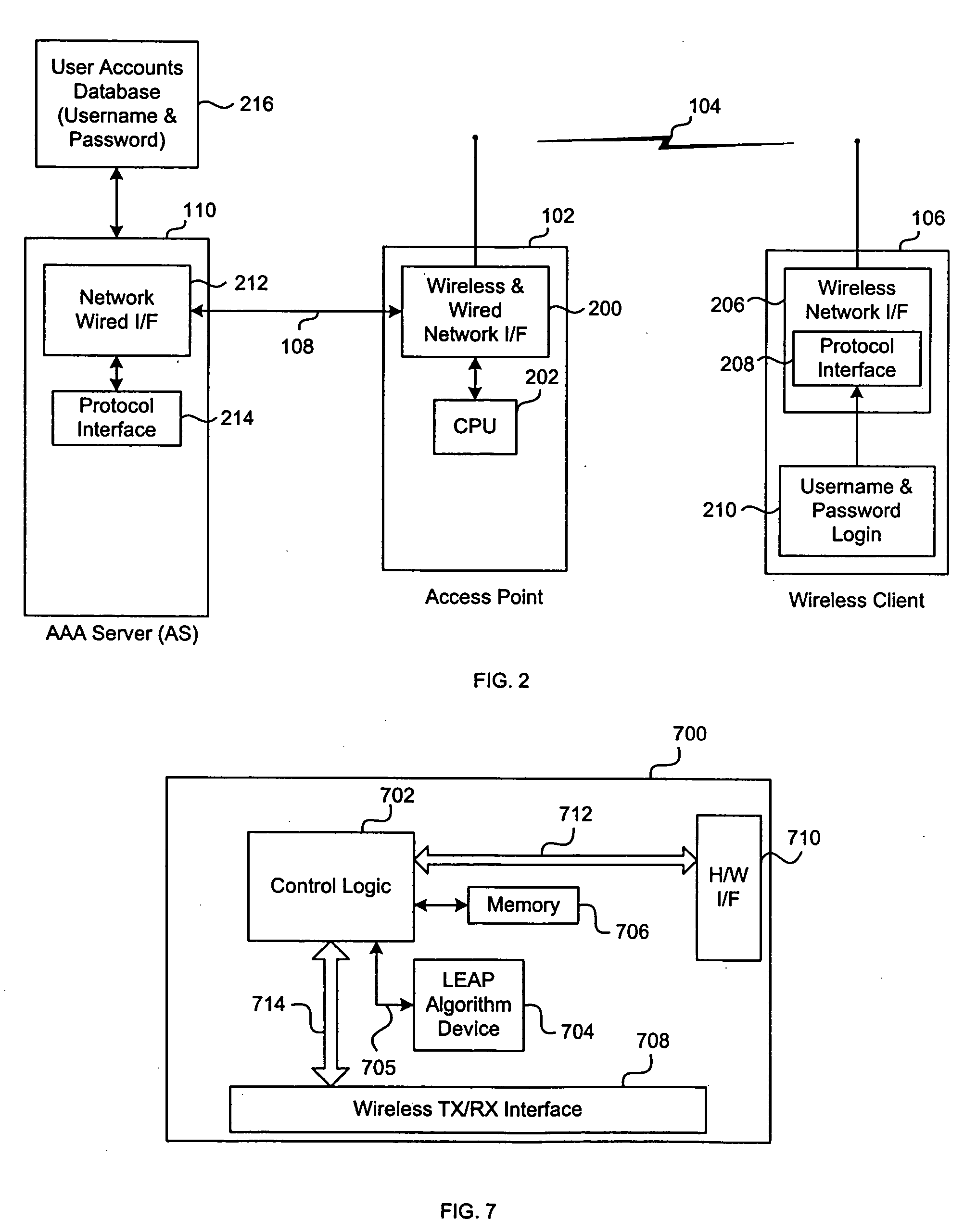
ActiveUS6996714B1User identity/authority verificationNetwork topologiesWireless Application ProtocolClient-side
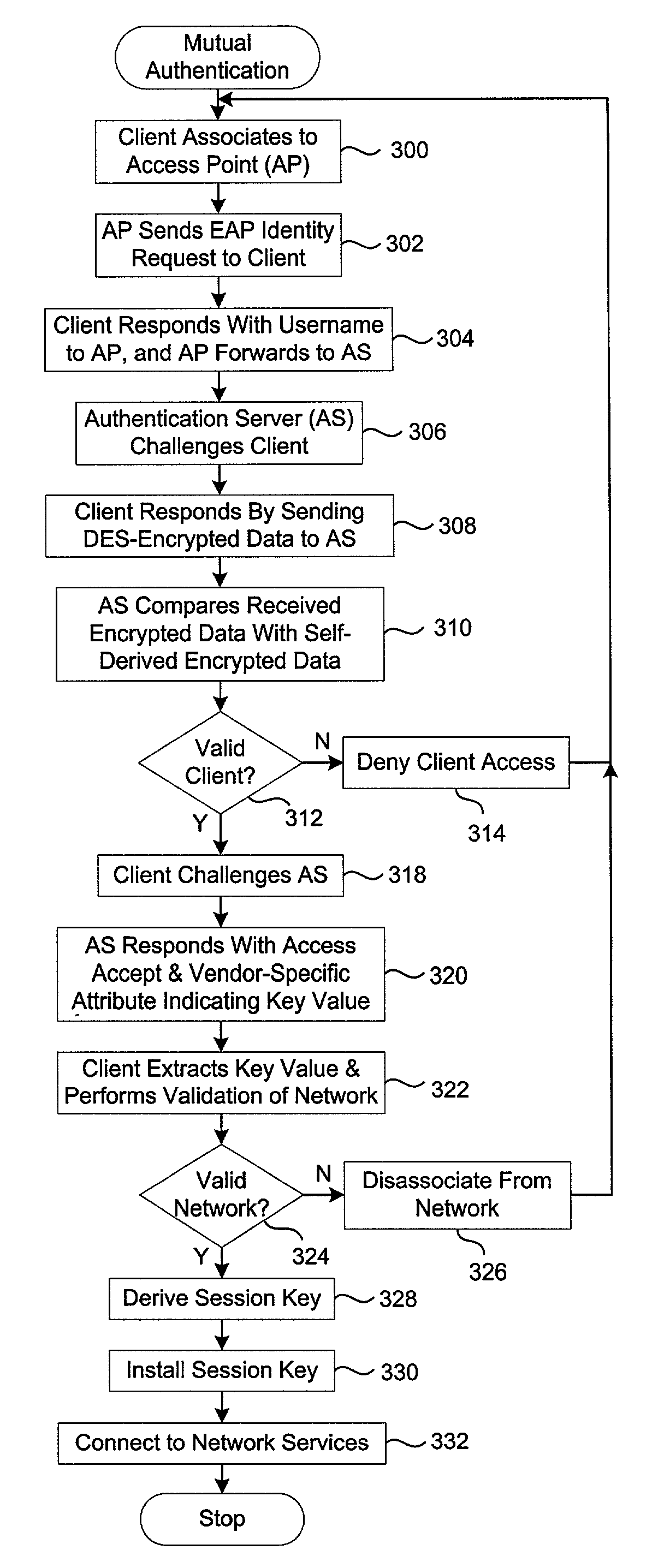
A wireless authentication protocol. Access to a network is managed by providing a challenge-handshake protocol within the Extensible Authentication Protocol for authentication between a client and the network.
Owner:CISCO TECH INC
Using a key lease in a secondary authentication protocol after a primary authentication protocol has been performed
InactiveUS6920559B1Key distribution for secure communicationUser identity/authority verificationThird partyElectronic systems
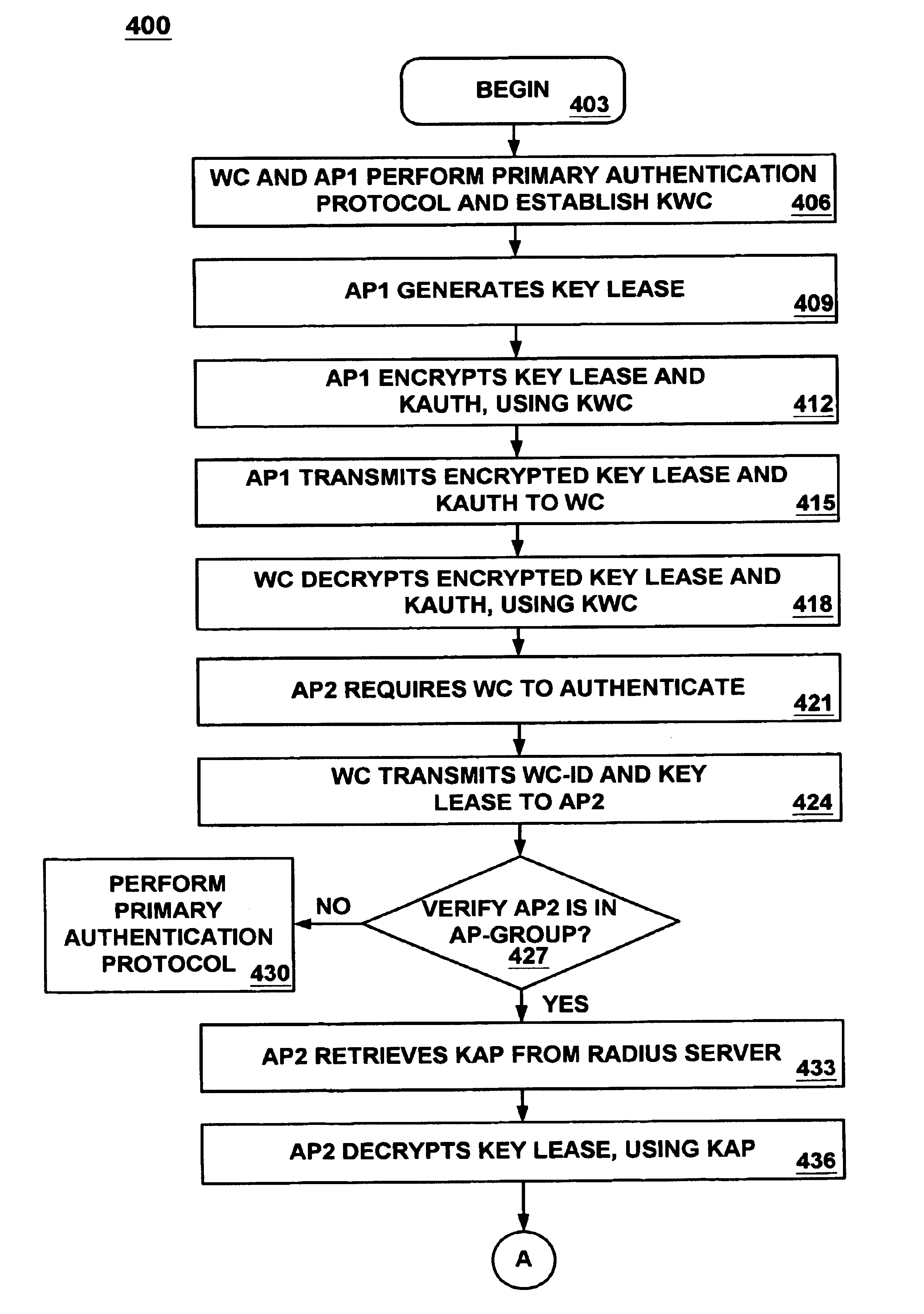
The present invention provides a method and system for using a key lease in a secondary authentication protocol after a primary authentication protocol has been performed. In one embodiment, the primary authentication protocol comprises a strong, secure, computationally complex authentication protocol. Moreover, the secondary authentication protocol comprises a less complex (compared to the primary authentication protocol) and less secure (compared to the primary authentication protocol) authentication protocol which can be performed in a length of time that is shorter than a length of time required to perform the primary authentication protocol. In one embodiment, a wireless client electronic system (WC) completes the primary authentication protocol with a wireless network access point electronic system of a wireless network (AP). When the WC is required to authenticate with another AP, the WC authenticates itself with another AP by using the secondary authentication protocol. However, the WC is required to periodically complete the primary authentication protocol, guarding against the possibility that the secondary authentication protocol may be exploited by an unauthorized intruder to attack the wireless network. In one embodiment, a third party technique is implemented to store a key necessary to perform the secondary authentication protocol.
Owner:VALTRUS INNOVATIONS LTD +1
Combining a browser cache and cookies to improve the security of token-based authentication protocols
InactiveUS7240192B1Improve securityDigital data processing detailsAnalogue secracy/subscription systemsClient-sideComputer science
Combining a browser cache and cookies to improve the security of token-based authentication protocols. A client stores a first portion of an authentication token as information (e.g., a cookie) in a first memory area. The client stores a second portion of the authentication token as server-inaccessible information (e.g., cached web content) in a second memory area. A server obtains the first and second portions from the client to recreate the authentication token to authenticate the client.
Owner:MICROSOFT TECH LICENSING LLC
Method and apparatus for re-authenticating computing devices
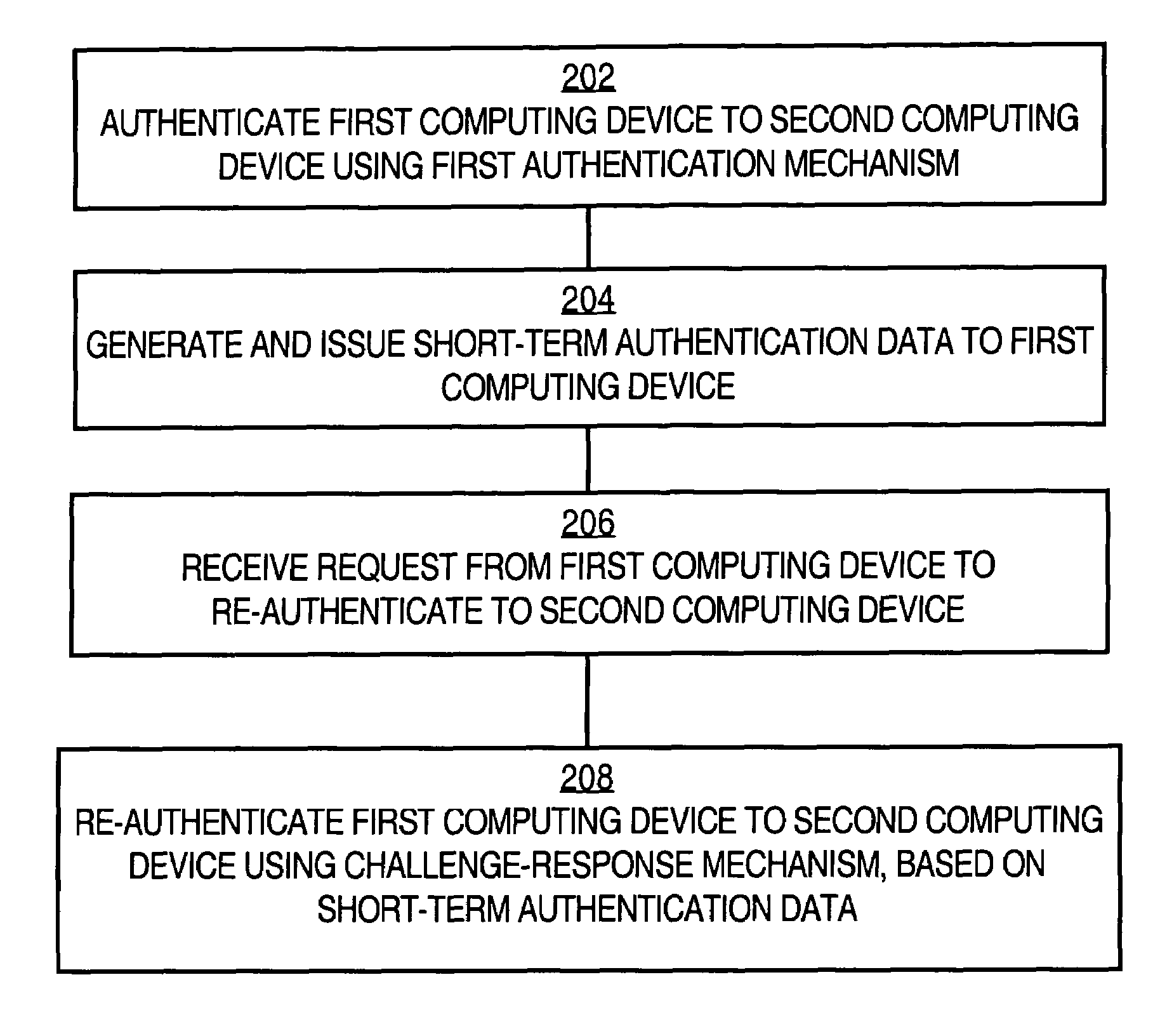
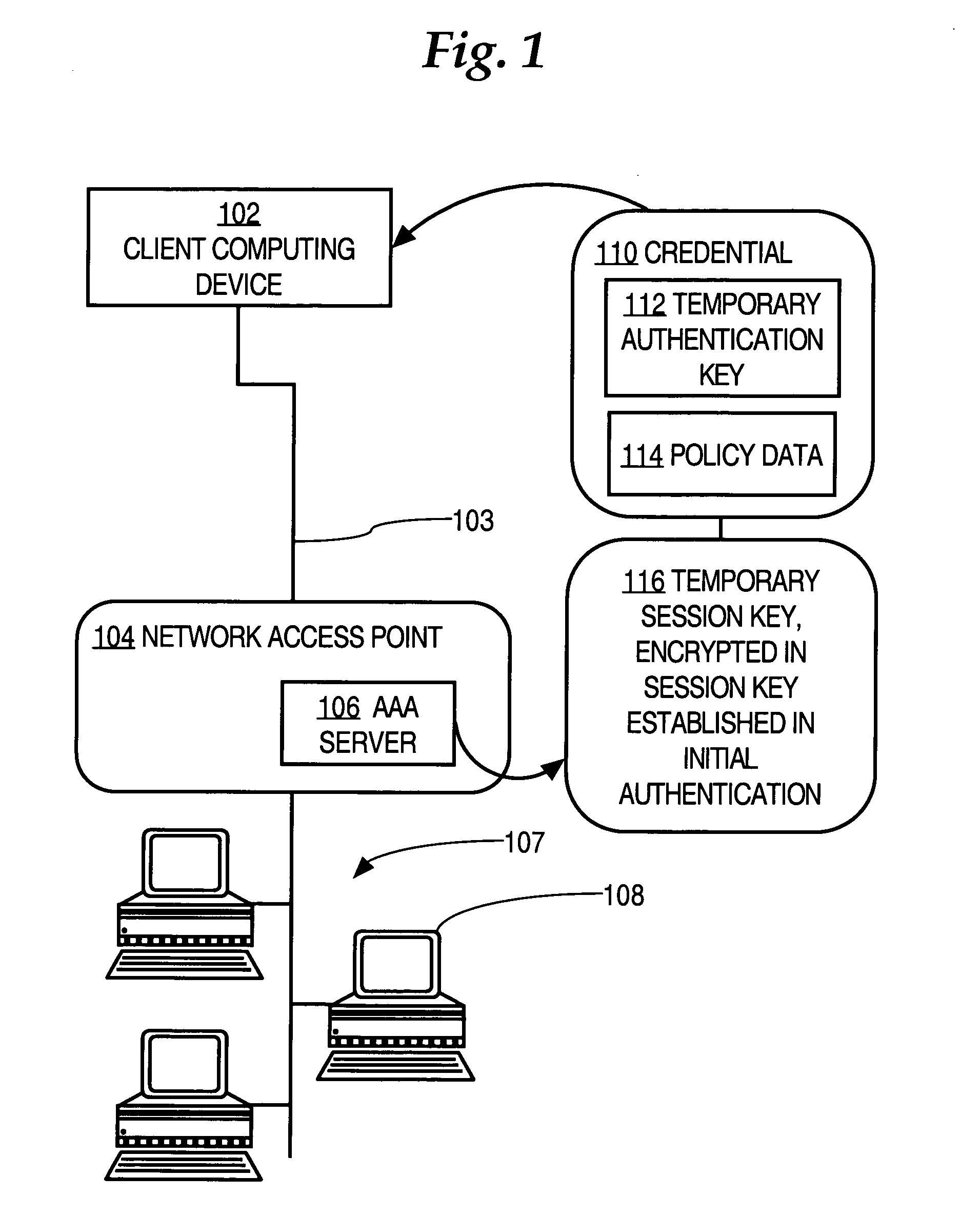
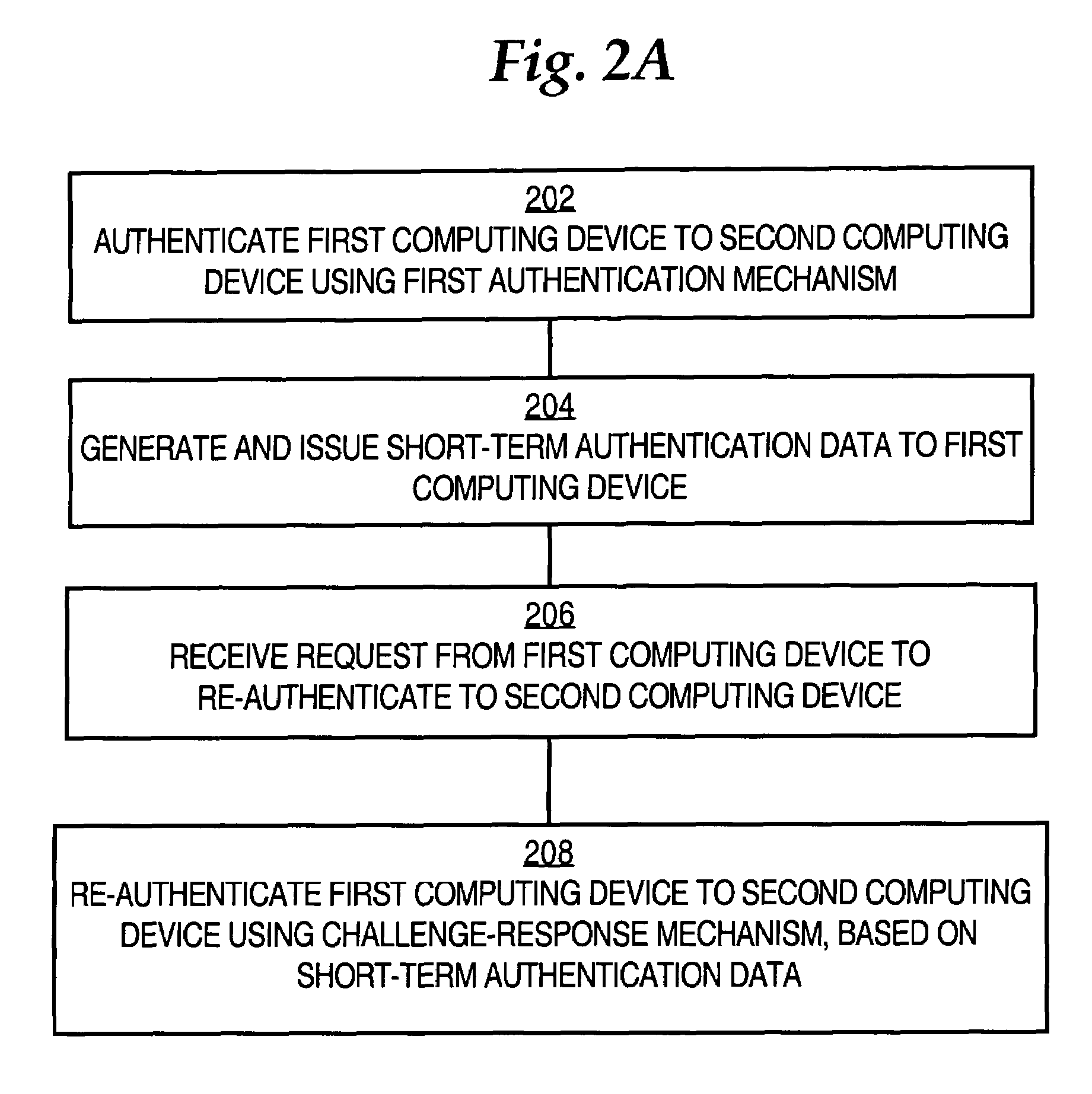
ActiveUS7370350B1Few message exchangeDigital data processing detailsUser identity/authority verificationShort termsChallenge response
A method of authenticating a first computing device in communication over a network to a second computing device is disclosed. The first computing device is authenticated to the second computing device using a first authentication mechanism. The first authentication mechanism is based on Extensible Authentication Protocol (EAP) or IEEE 802.1x authentication. Short-term re-authentication data is generated and issued to the first computing device. Later, a request from the first computing device to re-authenticate to the second computing device is received. The first computing device is re-authenticated to the second computing device using a challenge-response mechanism in which the first computing device authenticates itself by presenting the short-term authentication credential to the second computing device. Accordingly, re-authentication proceeds more quickly and with fewer message exchanges.
Owner:CISCO TECH INC
Method for distributing certificates in a communication system
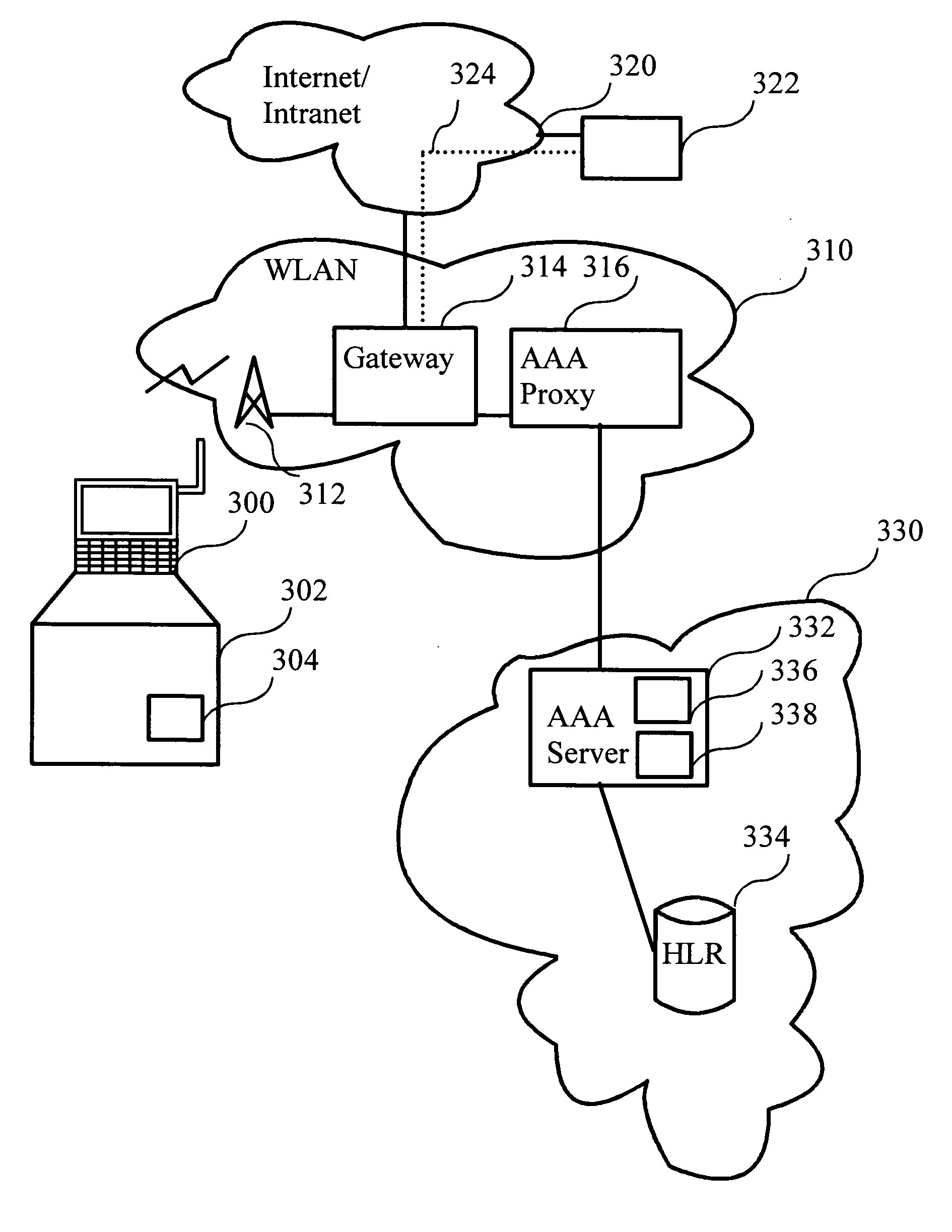
ActiveUS20060253703A1Improve reliabilityEasy to manageKey distribution for secure communicationWireless commuication servicesCommunications systemMaster key
The invention relates to a method a method for delivering certificates in a communication system using Extensible Authentication Protocol (EAP). The identity of a mobile node is sent to a gateway from which the identity is sent to a network entity. In the network entity is selected at least one first certificate based on information relating to the mobile node. In the network entity is signed the at least one first certificate using a master key. The at least one first certificate is provided from the network entity to the mobile node.
Owner:INTELLECTUAL VENTURES FUND 83 LLC
Wireless authentication protocol
A wireless authentication protocol. Access to a network is managed by providing a challenge-handshake protocol within the Extensible Authentication Protocol for authentication between a client and the network.
Owner:CISCO TECH INC
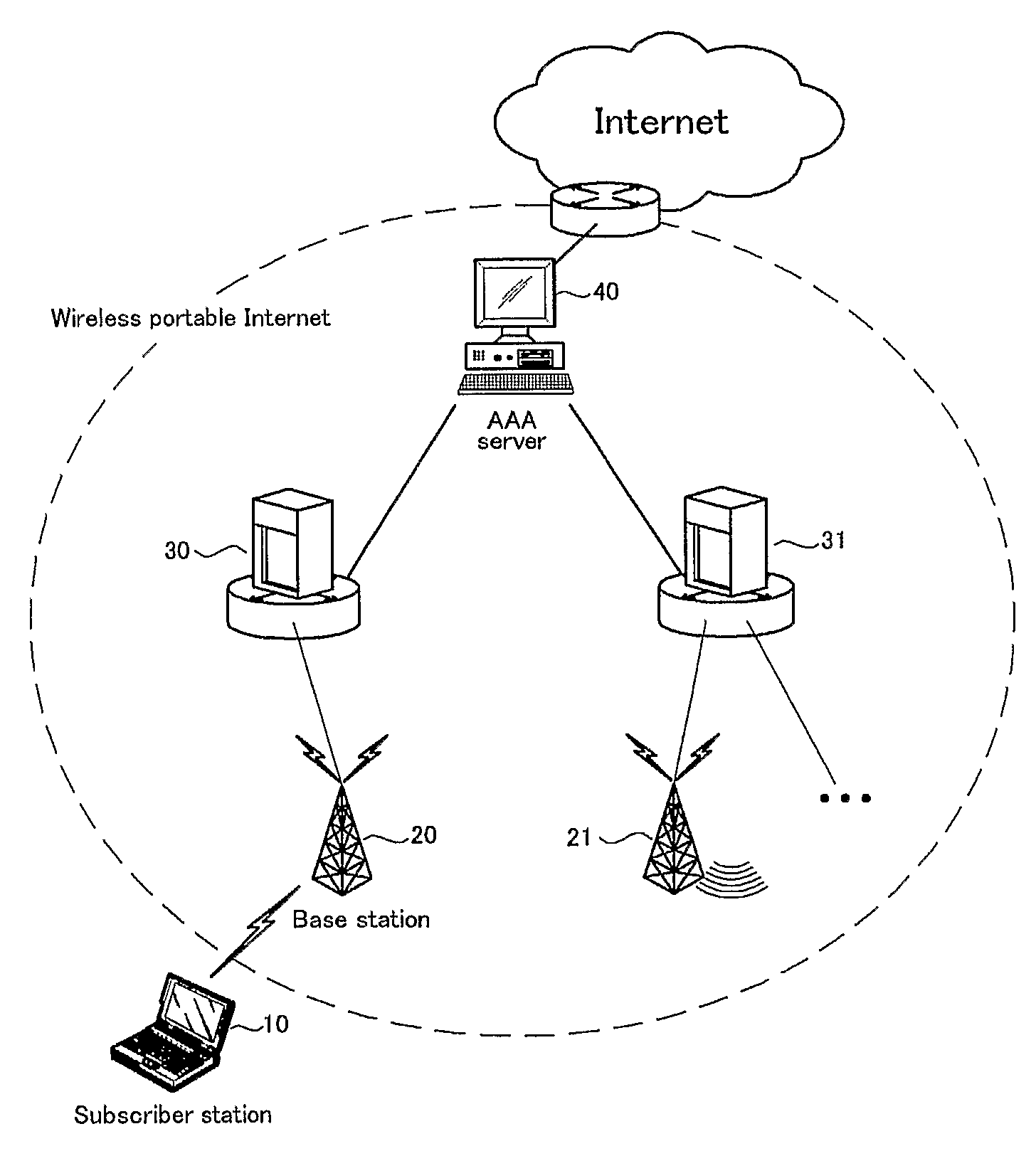
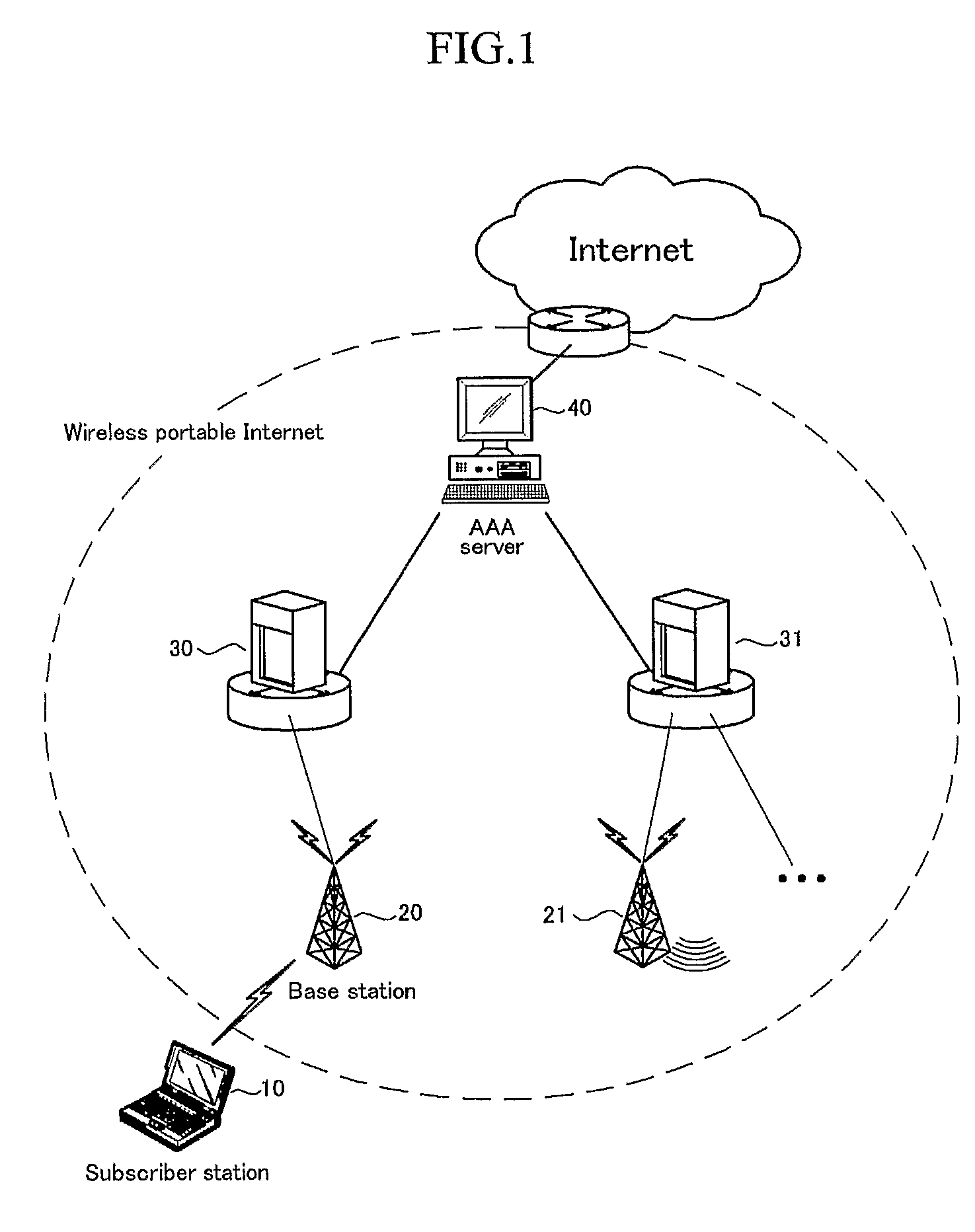
Method for Security Association Negotiation with Extensible Authentication Protocol in Wireless Portable Internet System
ActiveUS20070297611A1Digital data processing detailsUser identity/authority verificationSecurity associationThe Internet
The present invention relates to a security association negotiation method of extensible authentication protocol (EAP) for authenticating a subscriber station user in a wireless portable Internet system. An exemplary security association negotiation method using a user authentication in a wireless portable Internet system according to an embodiment of the present invention includes following steps. A base station generates an authentication key for authenticating a user of a subscriber station. The base station receives a security association capability request message including security association capability information of the subscriber station from the subscriber station after generating the authentication key. The base station determines whether the base station is able to accept a security association capability of the subscriber station included in the security association capability request message. The base station transmits a security association capability response message including the security association capability information which is selected for a security association with the subscriber station by the base station when the security association capability of the subscriber station can be accepted. According to the present invention, a subscriber authentication for EAP may be efficiently performed without an additional message after a handover.
Owner:SAMSUNG ELECTRONICS CO LTD +4
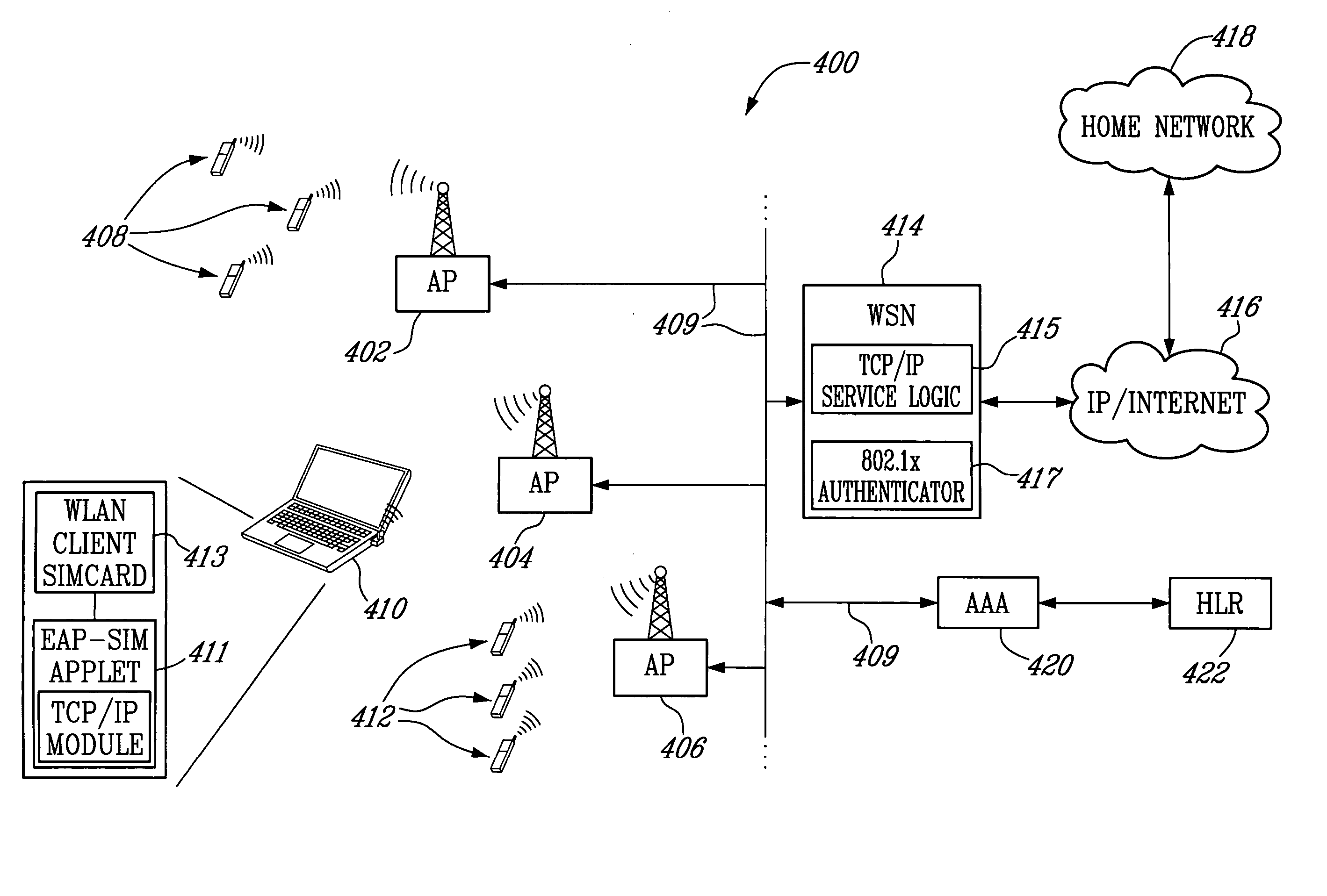
Wireless local area network (WLAN) authentication method, WLAN client and WLAN service node (WSN)
InactiveUS20060046693A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsThe InternetWireless lan
A method, Wireless Local Area Network (WLAN) client, and WLAN Service Node (WSN) that allows an Extensible Authentication Protocol—Subscriber Information module (EAP-SIM) module of the WLAN client, which module may be wither downloaded from the Internet or pre-installed in the WLAN client, to extract user credentials from a Subscriber Information Module (SIM) card, and to package the credentials into the EAP-SIM format and further into the TCP / IP format, before sending them to the WSN via a serving Access Point (AP). The WSN receives the credentials and unpacks them from the TCP / IP format and further from the EAP-SIM format, and authenticates / authorizes the WLAN client. WLAN access is authorized for the WLAN client upon successful authorization.
Owner:TELEFON AB LM ERICSSON (PUBL)
Method and apparatus for providing multiple authentication types using an authentication protocol that supports a single type
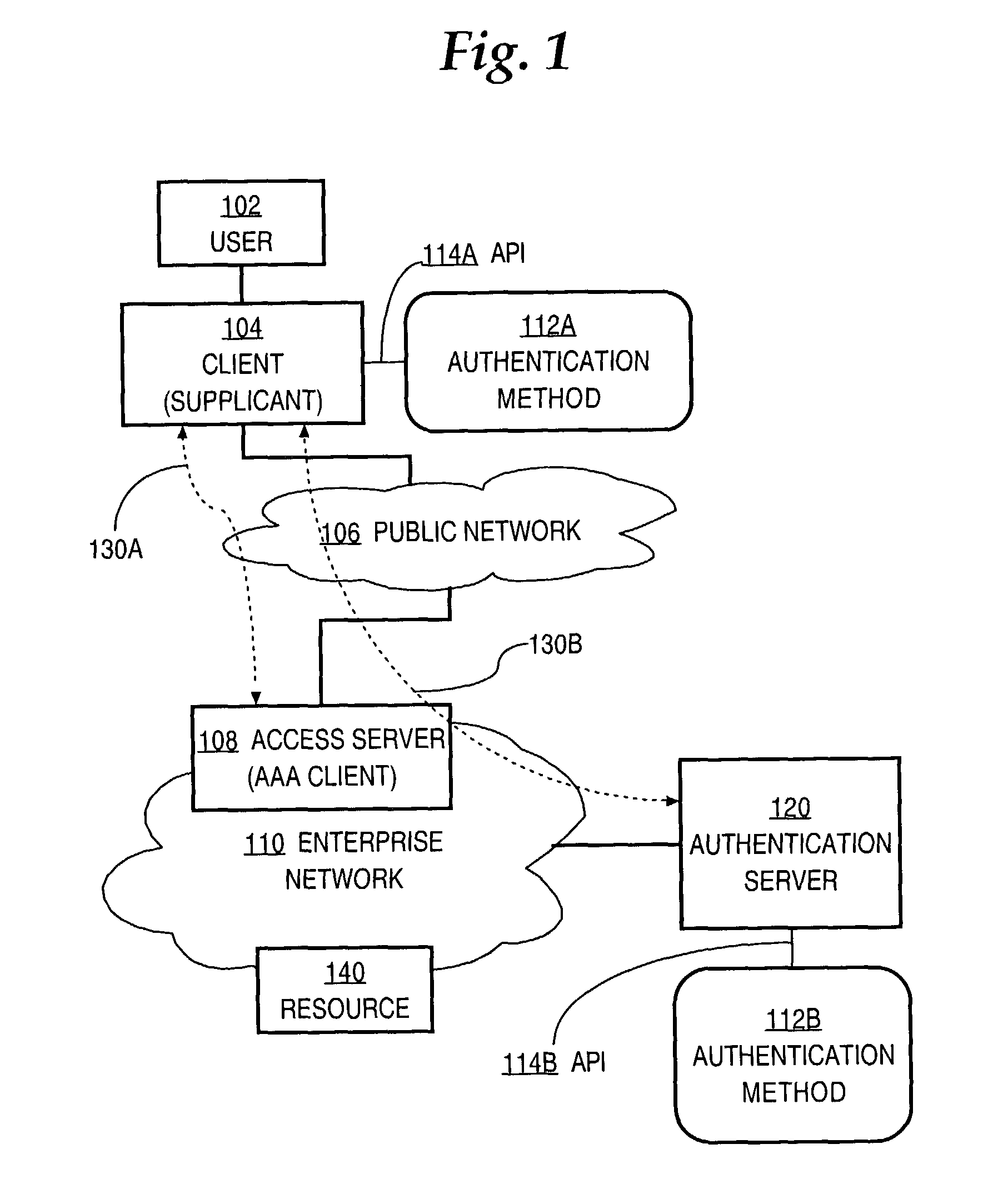
ActiveUS7421503B1Digital data processing detailsMultiple digital computer combinationsData fieldSingle type
A method is disclosed for providing multiple authentication types within an authentication protocol that supports a single type of authentication for a client in communication with an authorization server over a network. One or more authentication request packets compliant with an authentication protocol are sent to the client. Each of the packets comprises a type value that specifies multiple authentication, and a data field having a value that is structured in compliance with the authentication protocol. Each of the packets is associated with one of a plurality of different authentication conversations with the client. A plurality of responses is received from the client for each of the authentication conversations. The sending and receiving steps are repeated until results are determined for the authentication conversations. The client is authenticated based on results of each of the plurality of authentication conversations. Embodiments provide multiple Extensible Authentication Protocol (EAP) authentication methods.
Owner:CISCO TECH INC
Secure network access method
ActiveUS7286671B2SavingSecuring network accessDigital data processing detailsAnalogue secracy/subscription systemsAccess methodCarrier signal
The present invention provides network-layer authentication protocols for authenticating mobile client and access router to each other. The present invention uses Router Discovery as a carrier to implement the authentication protocols. In an embodiment of the present invention, a mobile client sends out a solicitation message to request connectivity service. The solicitation message contains a proof of identity of the mobile client. An access router that receives the solicitation message will not respond to it until the proof of the identity is verified. Only when the proof of identity of the mobile client is verified, will the access router respond and return an advertising message to the mobile client, thereby preventing unauthorized mobile clients from obtaining network access.
Owner:GK BRIDGE 1
Apparatus and Method for Processing Eap-Aka Authentication in the Non-Usim Terminal
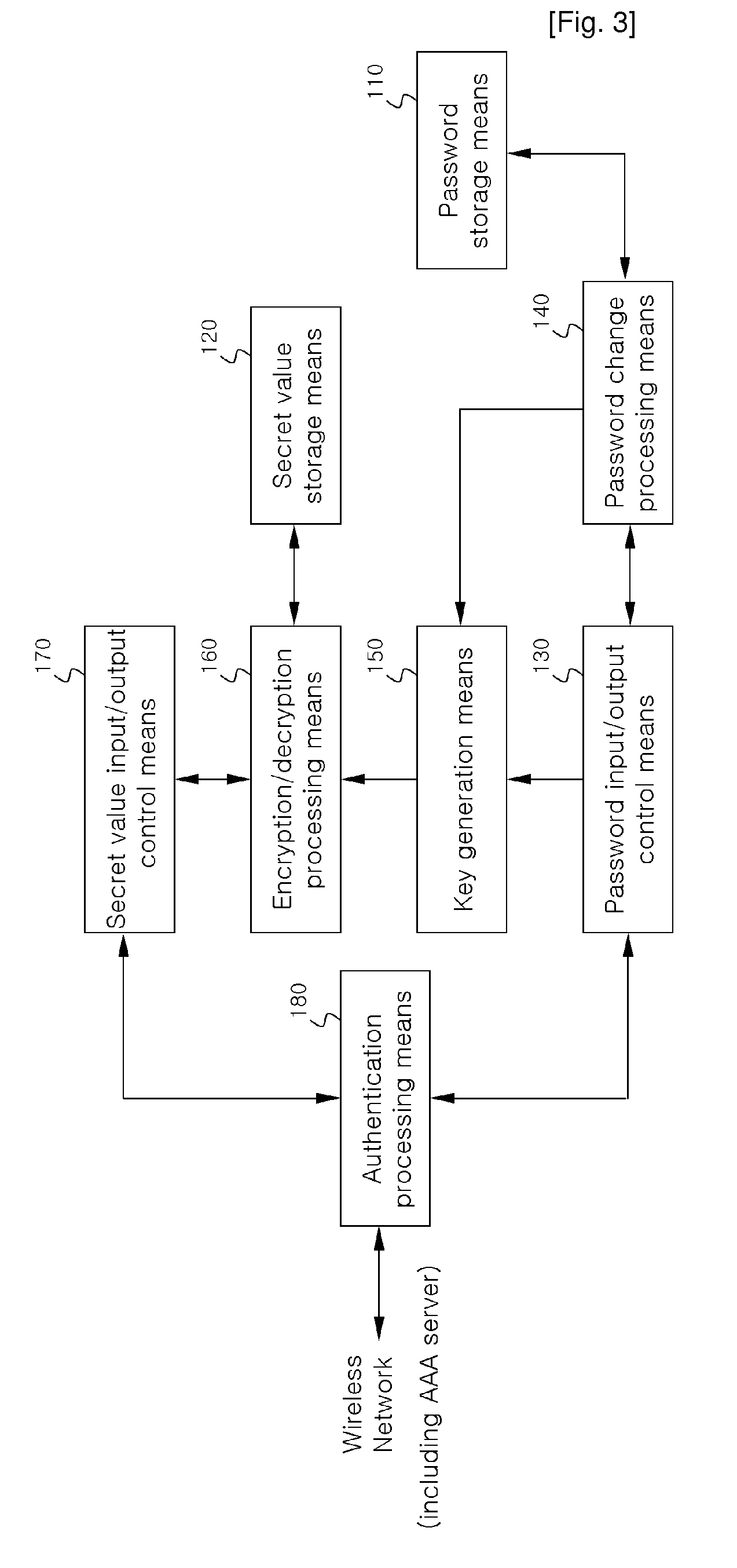
InactiveUS20080317247A1Key distribution for secure communicationUser identity/authority verificationComputer hardwarePassword
Disclosed are an apparatus and a method for processing authentication using Extensible Authentication Protocol-Authentication and Key Agreement (EAP-AKA) in a non-Universal Subscriber Identity Module (USIM) terminal without a USIM card.According to the present invention, although the USIM card used for user authentication function is absent, the secret value that used to be stored in the USIM card for user authentication is directly stored in the non-USIM terminal. Therefore, both a user password and a secret value are applied for EAP-AKA authentication of the terminal and the user and user authentication problems caused by lack of the USIM card can be overcome.
Owner:POS DATA CO LTD
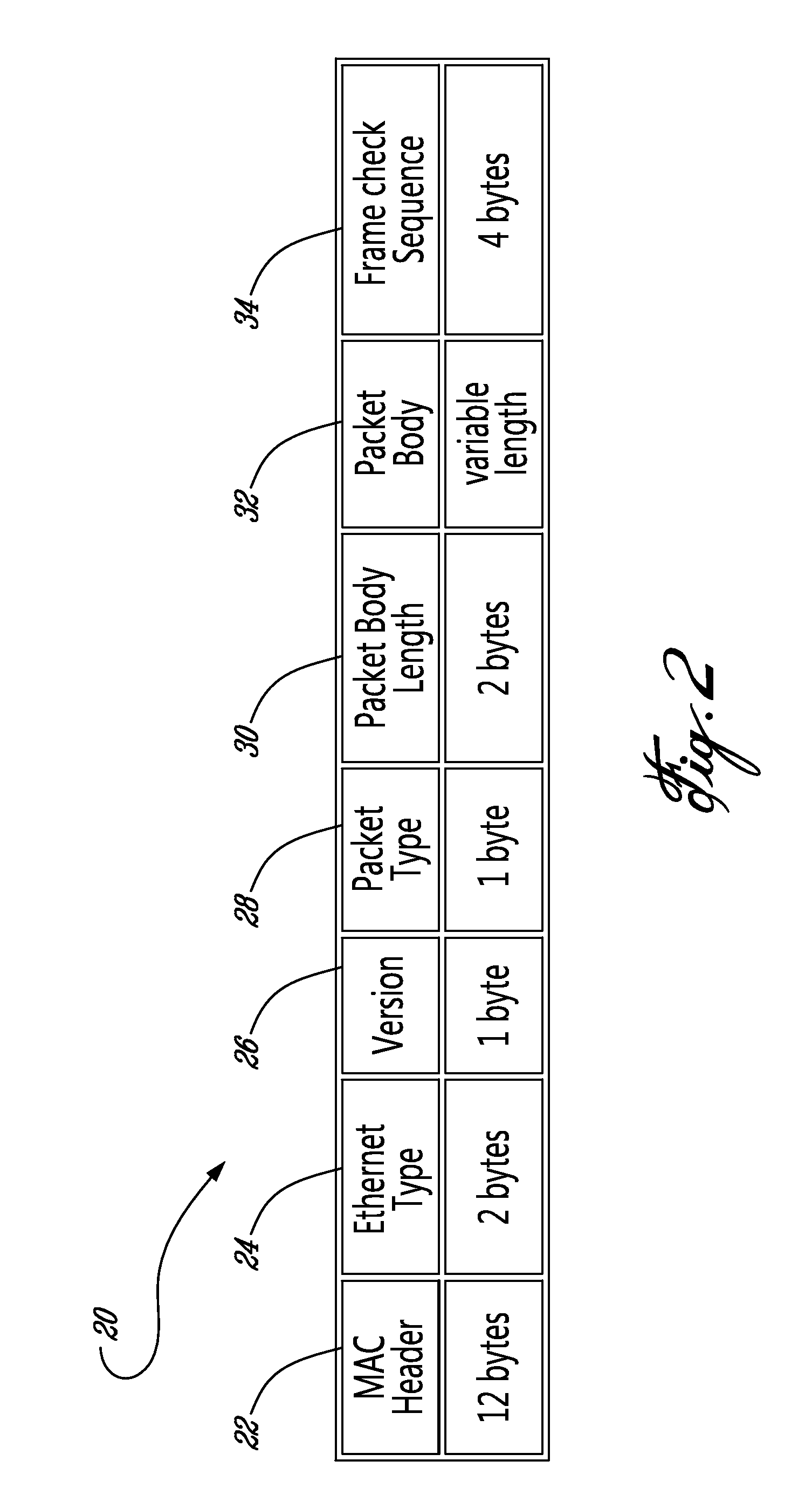
Communication protocol
ActiveUS7796589B2Time-division multiplexData switching by path configurationNetwork Communication ProtocolsData structure
One aspect relates to a communication protocol for communicating between one or more entities, such as devices, hosts or any other system capable of communicating over a network. A protocol is provided that allows communication between entities without a priori knowledge of the communication protocol. In such a protocol, for example, information describing a data structure of the communication protocol is transferred between communicating entities. Further, an authentication protocol is provided for providing bidirectional authentication between communicating entities. In one specific example, the entities include a master device and a slave device coupled by a serial link. In another specific example, the communication protocol may be used for performing unbalanced transmission between communicating entities.
Owner:AMERICA POWER CONVERSION CORP
Scheme for sub-realms within an authentication protocol
ActiveUS20060224891A1Reduce security risksUser identity/authority verificationMultiple digital computer combinationsVirtual fieldPassword
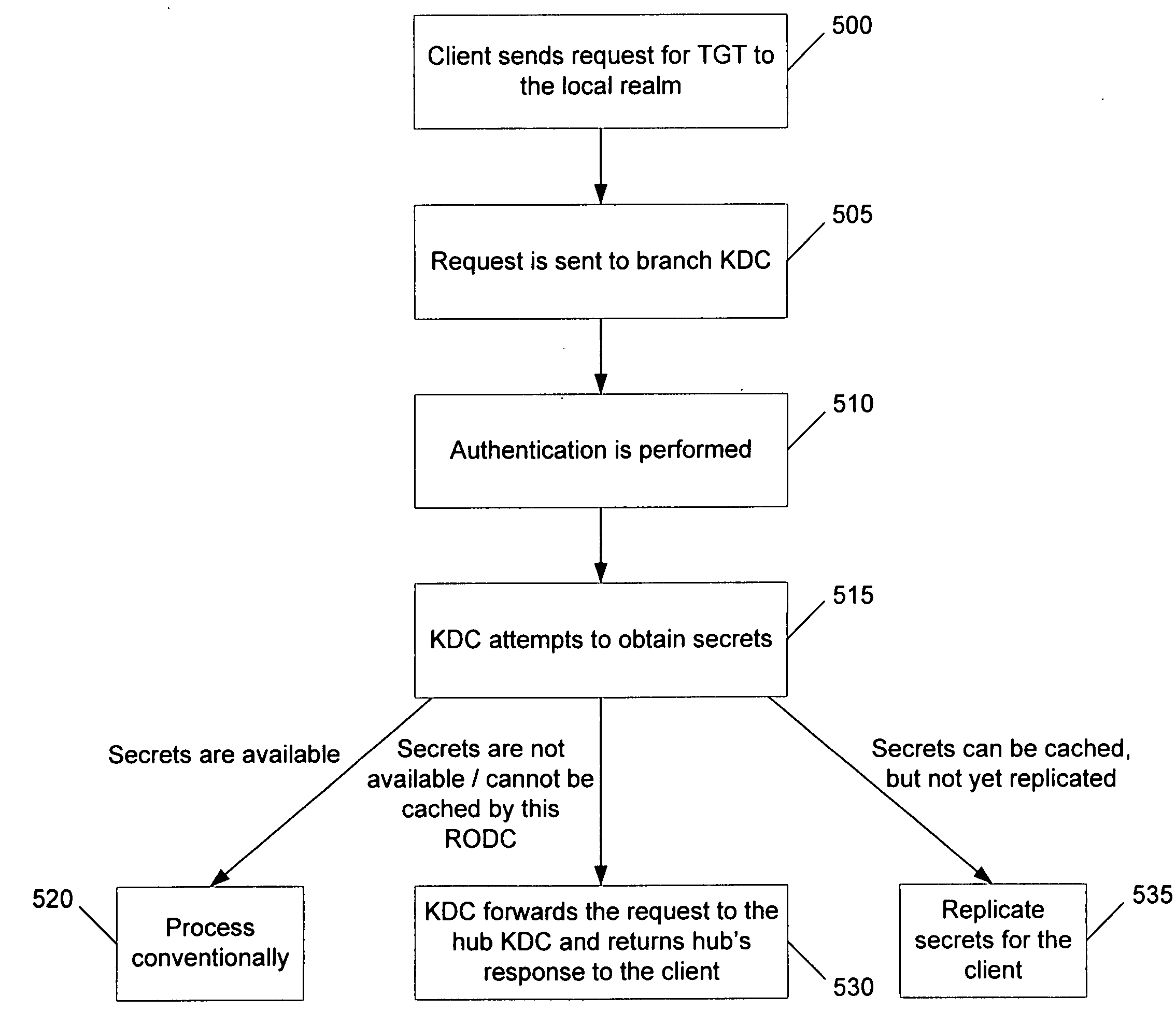
Branch domain controllers (DCs) contain read only replicas of the data in a normal domain DC. This includes information about the groups a user belongs to so it can be used to determine authorization information. Password information, however, is desirably replicated to the branch DCs only for users and services (including machines) designated for that particular branch. Moreover, all write operations are desirably handled by hub DCs, the primary domain controller (PDC), or other DCs trusted by the corporate office. Rapid authentication and authorization in branch offices is supported using Kerberos sub-realms in which each branch office operates as a virtual realm. The Kerberos protocol employs different key version numbers to distinguish between the virtual realms of the head and branch key distribution centers (KDCs). Accounts may be named krbtgt_<ID> where <ID> is carried in the kvno field of the ticket granting ticket (TGT) to indicate to the hub KDC which krbtgt′ key was used to encrypt the TGT.
Owner:MICROSOFT TECH LICENSING LLC
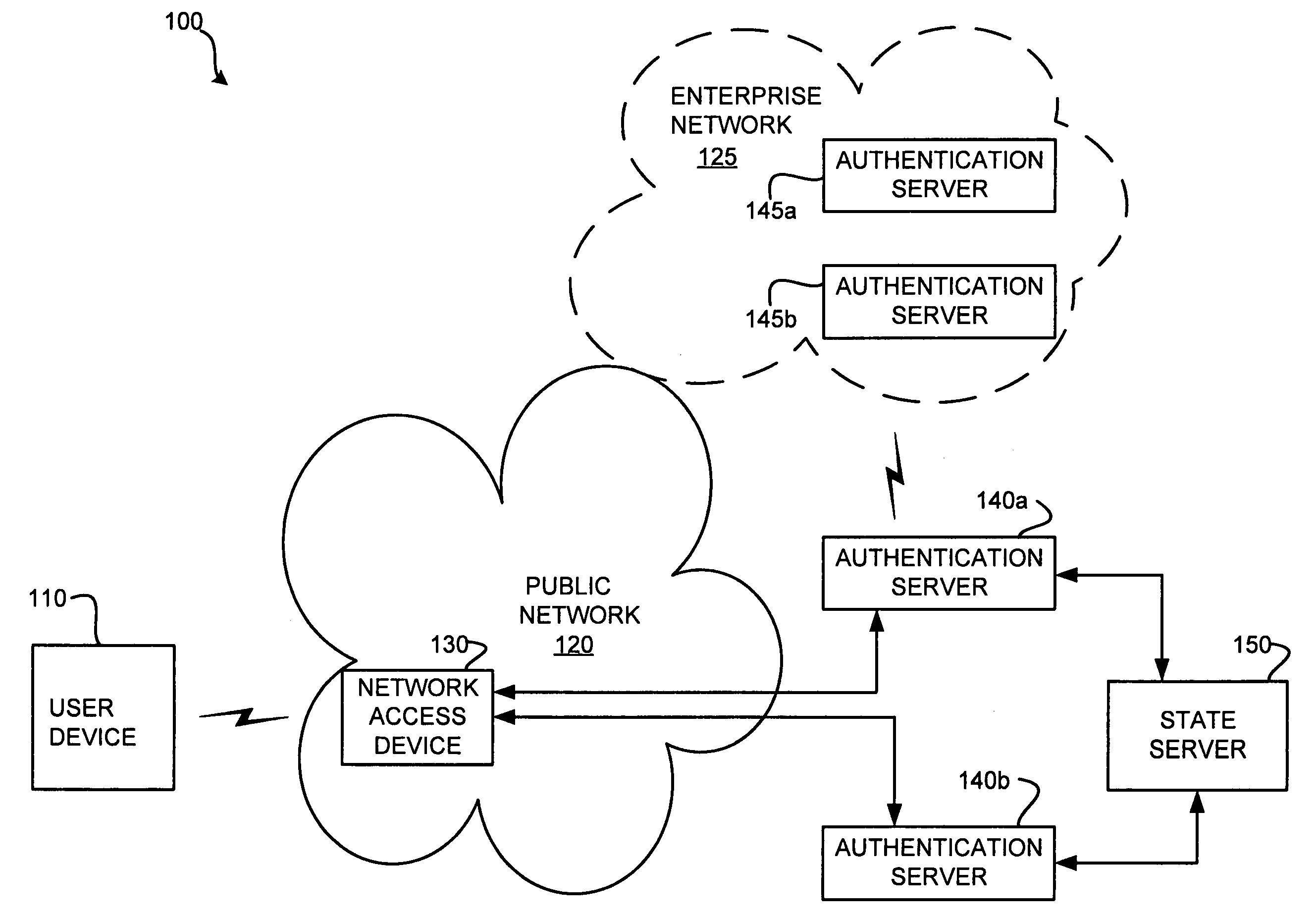
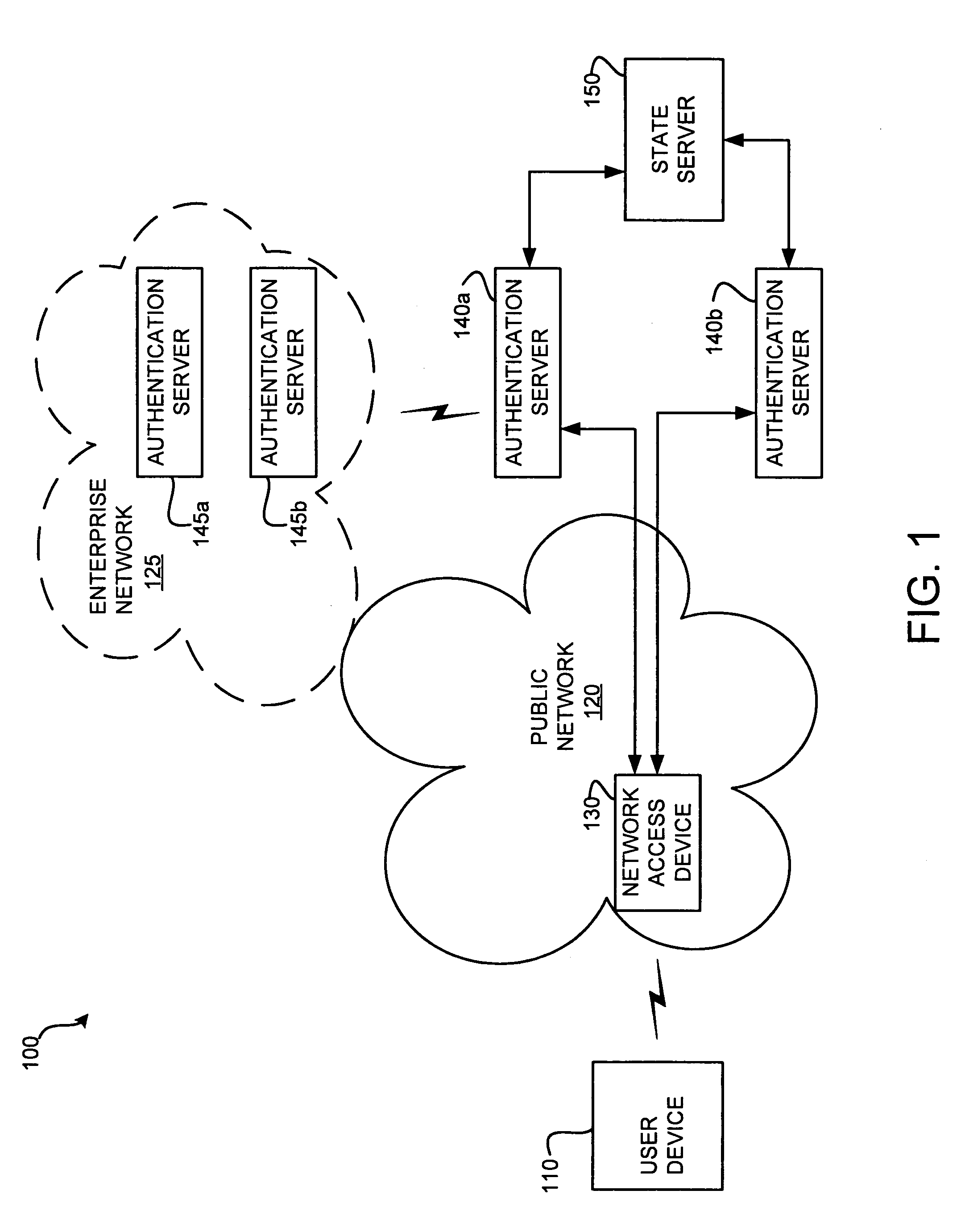
Extensible authentication protocol (EAP) state server
InactiveUS20060288406A1Digital data processing detailsMultiple digital computer combinationsComputer hardwareAuthentication
A method and system that may include two or more authentication devices configured to authenticate a user via an authentication session. The method and system may also include a device operably coupled to the two or more authentication devices and being configured to manage the authentication session.
Owner:VERIZON PATENT & LICENSING INC
Method for implementing EAP authentication in remote authentication based network
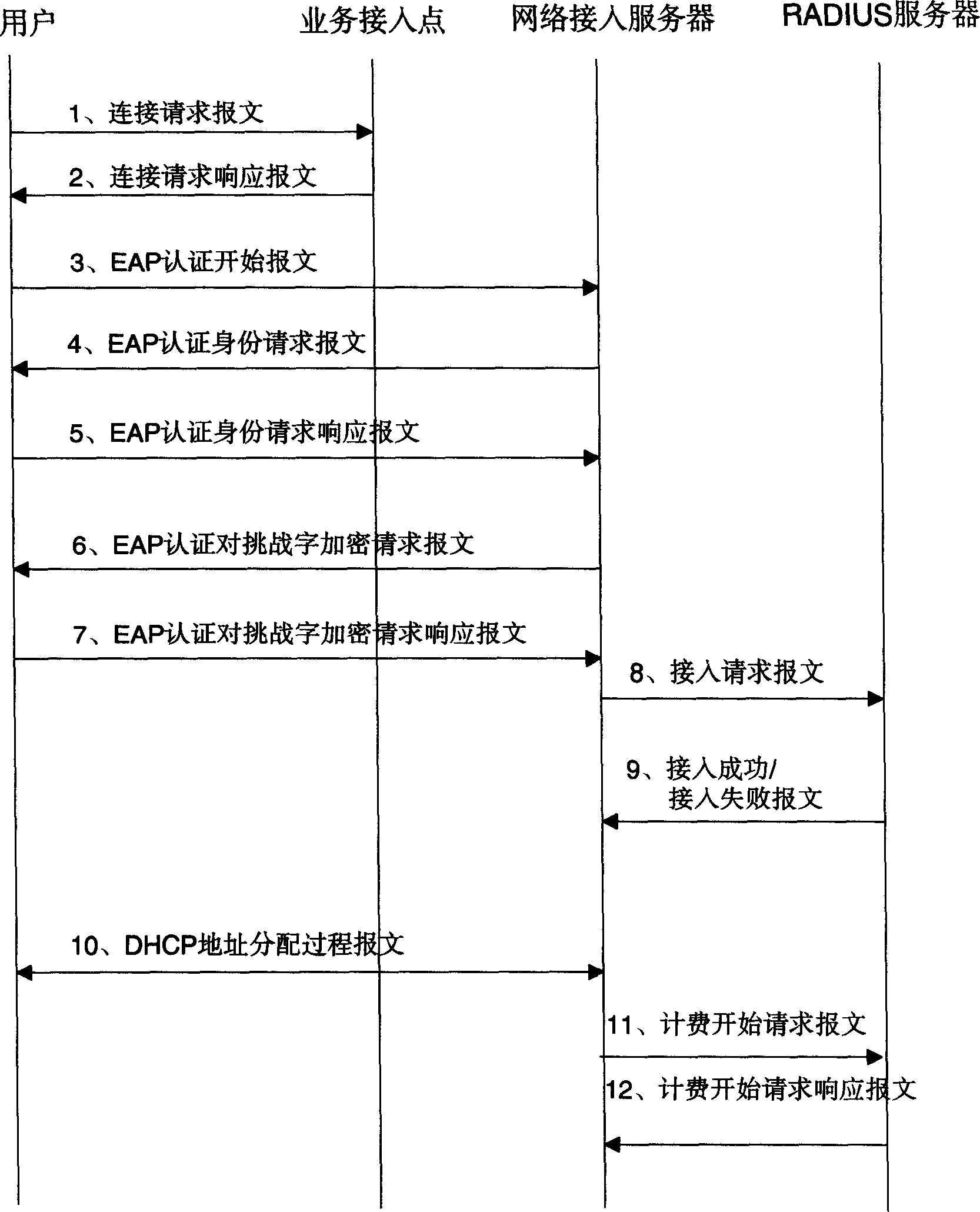
InactiveCN1486029AImprove securityAchieve protectionUser identity/authority verificationData switching by path configurationAuthentication serverNetwork Access Control
The invention refers to a method for realizing EAP authentication in network based on remote authentication. The method includes: the user sends out EAP authentication message; after the network access control appliance receives the authentication message, it packages the information into remote authentication messages, and transmits to remote authentication server to carry on authentication; theremote authentication server traces back the result to the net access control appliance, and sends out the EAP message to user through network access control appliance.
Owner:HUAWEI TECH CO LTD
Access authentication processing method and system, terminal as well as network equipment
ActiveCN102685741AFast and secure initial access authenticationPrevent replay attacksSecurity arrangementComputer terminalKey distribution
The embodiment of the invention provides an access authentication processing method and system, a terminal as well as a network equipment. According to the embodiment of the invention, the EAP (Extensible Authentication Protocol) authentication process and the four-step handshaking process in the prior art can be saved; and the authentication and key distribution process can be finished only by three authentication messages, so that the number of the messages is greatly reduced; however, message replay attack can be similarly prevented through the current counter value of a counter. Therefore, the embodiment of the invention can be suitable for two standard processes 802.11i and 802.11r; and by using the embodiment of the invention, rapid and safe initial access authentication of WLAN can be achieved, the time required by initial access authentication is reduced and the complexity of the implementation is reduced.
Owner:HUAWEI DEVICE CO LTD
Systems and methods for an extensible authentication framework
The present disclosure describes systems and methods of an authentication framework to implement varying authentication schemes in a configurable and extendable manner. This authentication framework provides a level of abstraction in which requirements for credential gathering and authentication workflow are independent from the agents or authentication implementation that does the credential gathering and authentication workflow. A higher level of abstraction and a more comprehensive authentication framework allows handling the associated authentication transactions of complex authentication schemes without requiring any specific understanding of their internals. For example, the requirements to gather certain credentials for a particular authentication scheme may be configured and maintained separately from the client-side authentication agent that gathers the credentials.; The flexible, configurable and extendable authentication framework supports a wide variety of authentication scheme and supports third party, proprietary and customized authentication schemes.
Owner:CITRIX SYST INC
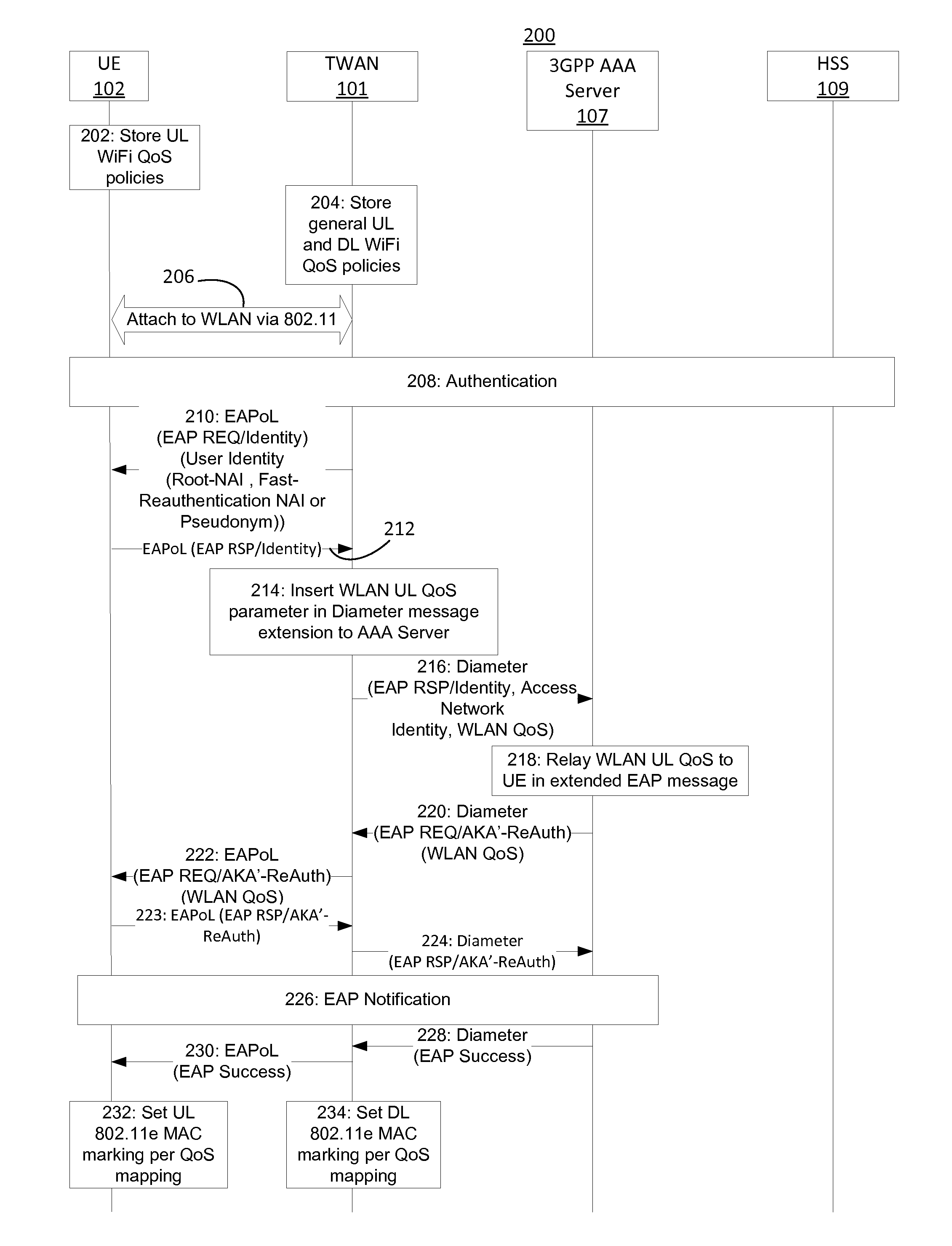
Mobile network operator (MNO) control of WIFI QOS via eap/diameter
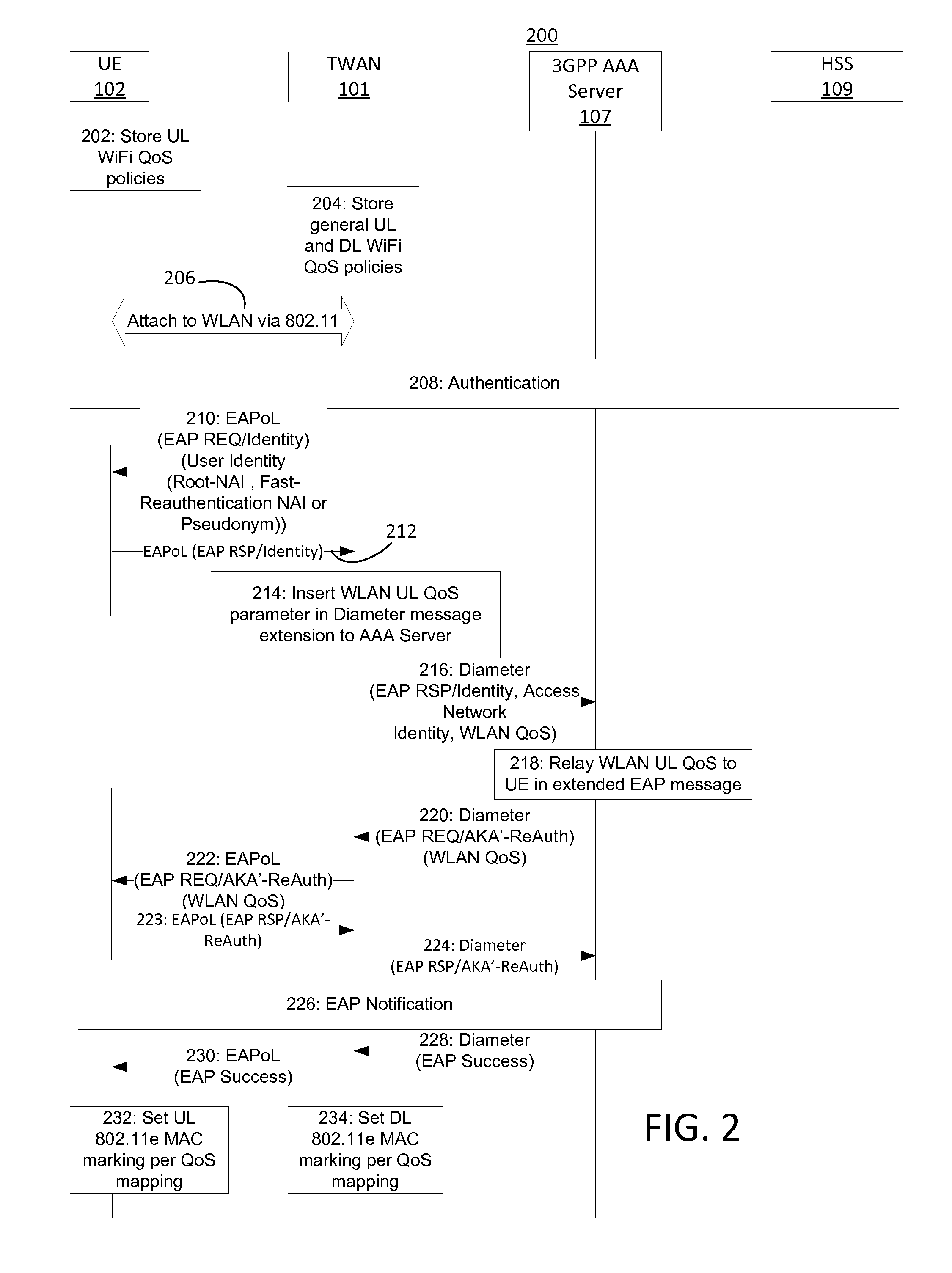
ActiveUS20160227443A1Well formedNetwork traffic/resource managementNetwork topologiesQuality of serviceUser equipment
A mobile network operator (MNO) may control WiFi QoS. 3GPP has specified control mechanisms for various levels of quality of service (QoS) over the cellular access and core network. Embodiments described herein provide differentiation of WiFi QoS based on MNO requirements. In particular, extensible authentication protocol (EAP) and diameter messages may be extended to include a wireless local area network QoS parameter. This may be used by user equipment to set the uplink 802.11e User Priority (UP) for offloaded or evolved packet core-routed WiFi traffic.
Owner:INTERDIGITAL PATENT HLDG INC
Authentication method for accessing mobile subscriber to core network through femtocell
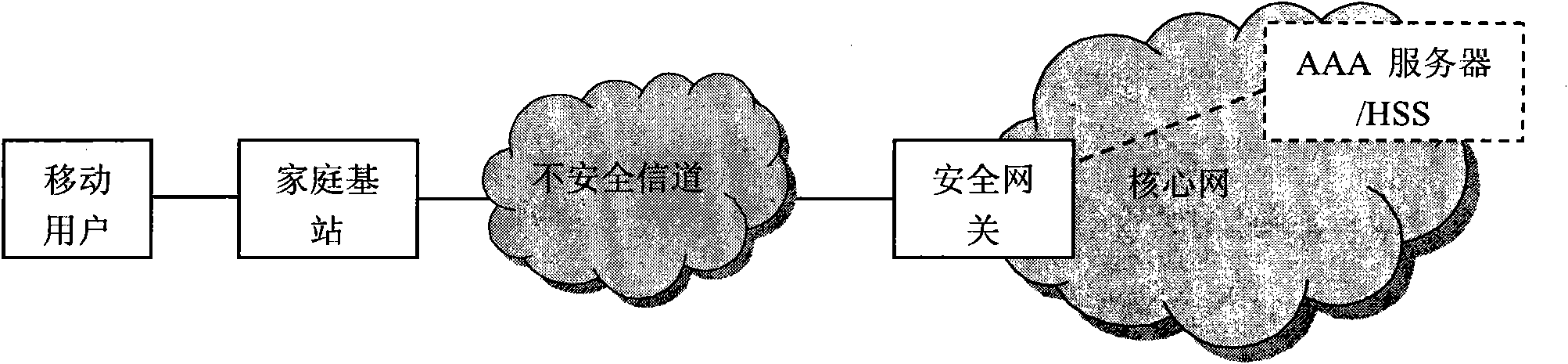
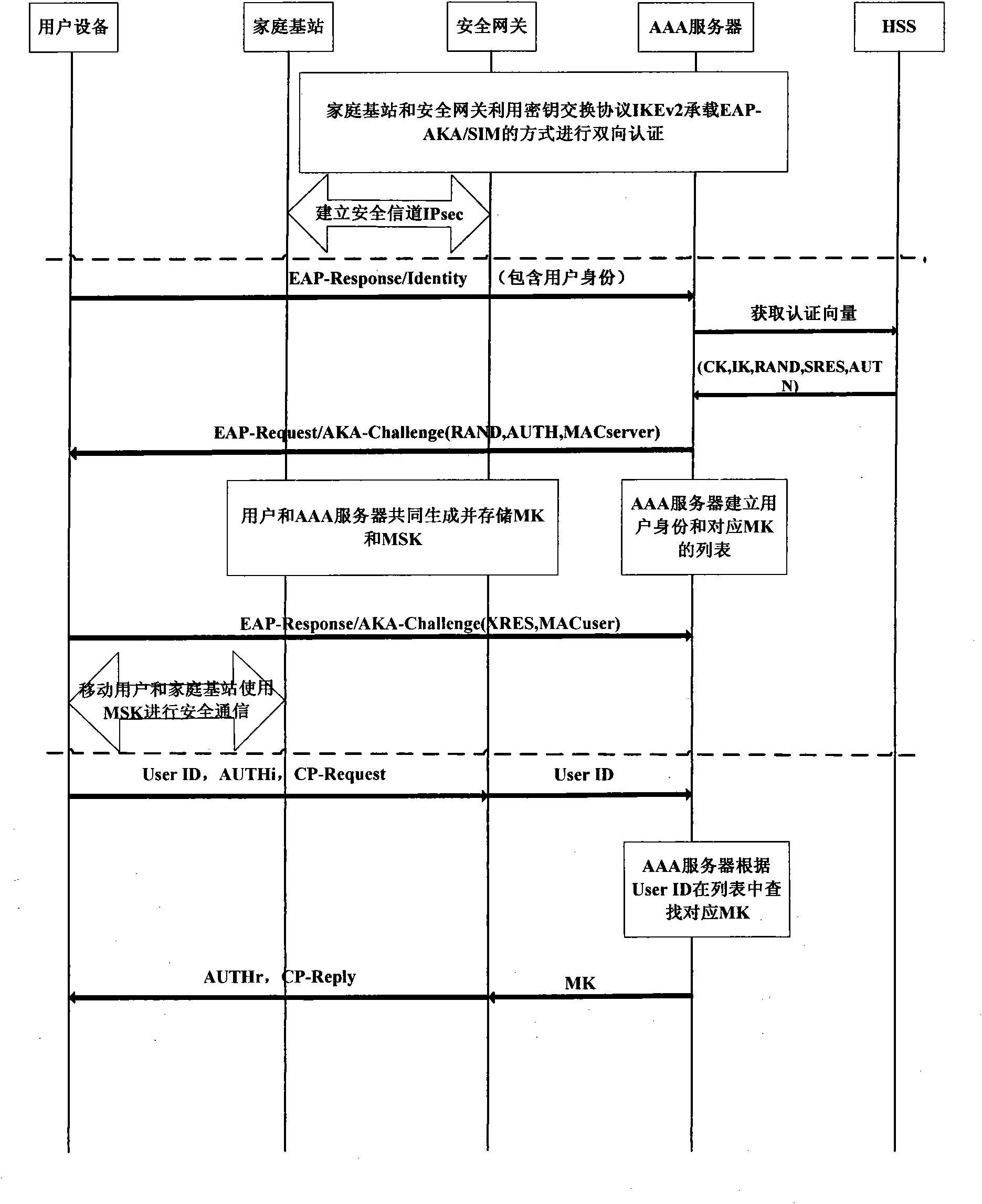
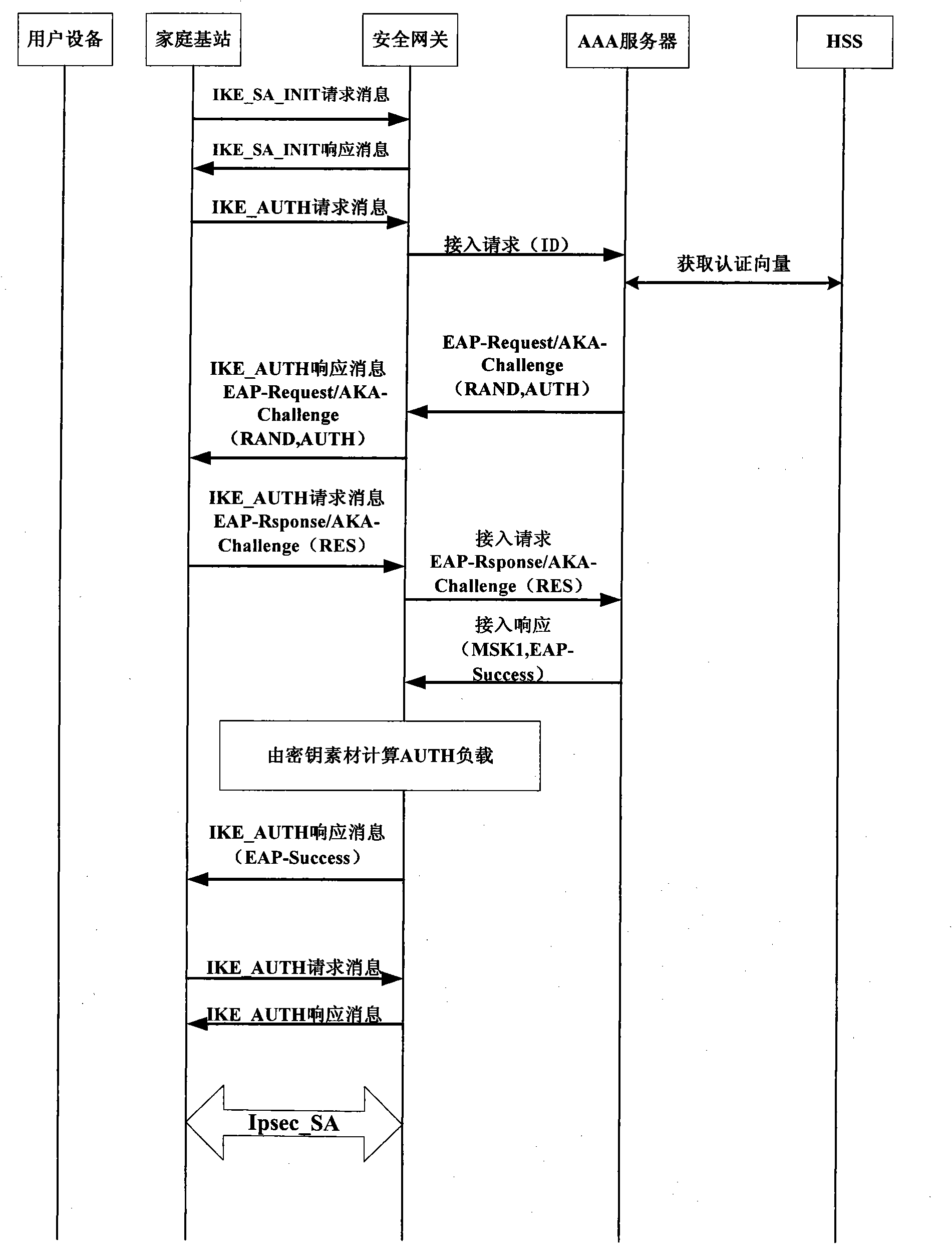
InactiveCN101867928AEnsure safetyReduce transmissionTransmissionSecurity arrangementKey exchangeInternet Key Exchange
The invention discloses an authentication method for accessing a mobile subscriber to a core network through a femtocell, which mainly makes up for the defect that a complete authentication method for accessing the mobile subscriber to the core network is not provided in the 3GPP standard. Under the condition of not changing network equipment in the 3GPP standard, the conventional extensible authentication protocol and key agreement EAP-AKA and internet key exchange IKEv2 are improved. The authentication method comprises that: (1) a secure channel IPsec is established between the femtocell and a secure gateway; (2) the mobile subscriber is subjected to access authentication and pre-generates an important authentication parameter MK for a step (3); and (3) the mobile subscriber and the core network perform bidirectional authentication by using the IPsec established by the step (1) and the MK pre-generated by the step (2). Compared with the traditional authentication method using the EAP-AKA and the IKEv2, the authentication method optimizes authentication steps under the condition of not reducing security, reducing authentication overhead, has the advantages of security and quickness, and is suitable for scenes that the mobile subscriber accesses the core network through the femtocell.
Owner:XIDIAN UNIV
Secure device authentication protocol
InactiveUS8990574B1User identity/authority verificationPublic key infrastructure trust modelsTrusted authorityDisplay device
Disclosed is a system and method by which a multimedia source device communicates with a display device, allowing the multimedia devices to securely confirm the identity of the devices and confirm their trustworthiness through a trust authority.
Owner:PRIMA CINEMA
Connection establishing method, terminal and access point
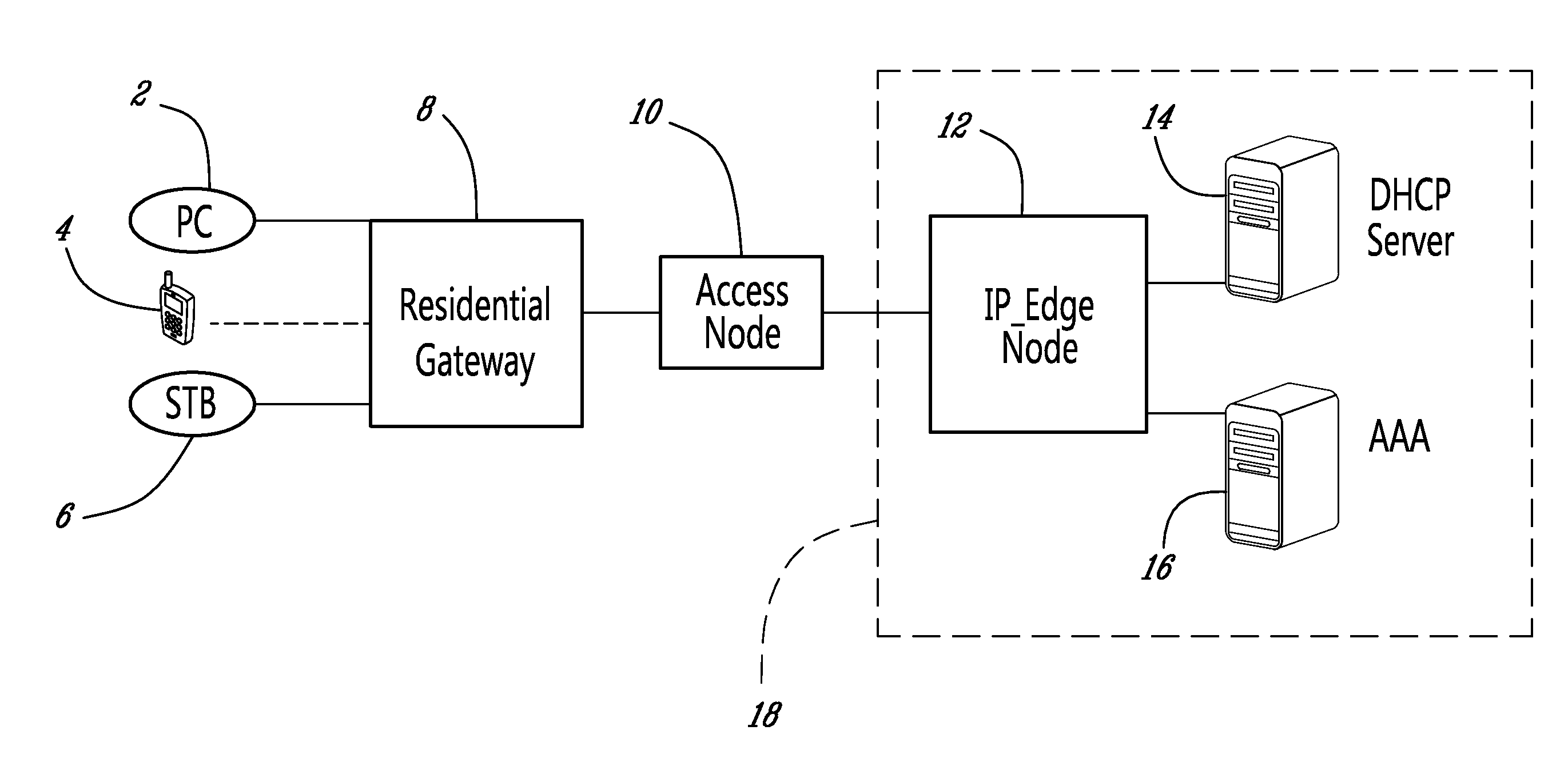
ActiveCN102883316AReduce battery consumptionReduce the number of interactionsEnergy efficient ICTUser identity/authority verificationComputer hardwareUser identifier
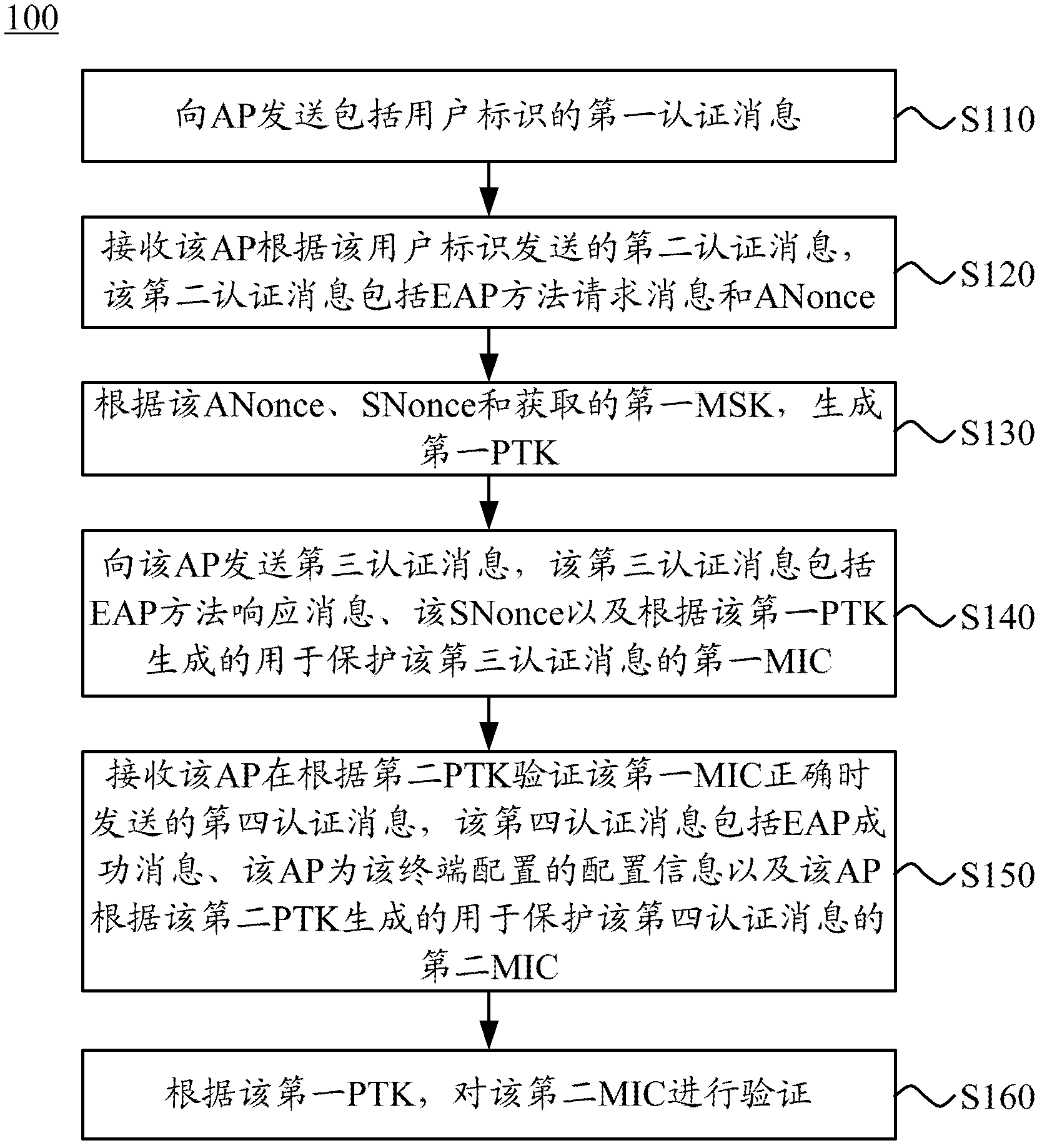
The invention discloses a connection establishing method, a terminal and an access point (AP). The method comprises the following steps of: sending a first authentication message comprising a user identifier to the AP; receiving a second authentication message which is sent by the AP according to the user identifier and comprises an extensible authentication protocol (EAP) method request message and a site value ANonce of the AP; generating a first pairwise transient key (PTK) according to the ANonce, an SNonce and acquired first minimum shift keying (MSK); sending a third authentication message to the AP, wherein the third authentication message comprises an EAP method response message, the SNonce and first minimal inhibitory concentration (MIC) generated according to the first PTK; receiving a fourth authentication message which is sent by the AP when the first MIC is checked to be correct according to a second PTK, wherein the fourth authentication message comprises an EAP success message, configuration information configured by the AP to the terminal, and second MIC; and checking the second MIC according to the first PTK. By the method, the terminal and the AP of the embodiment of the invention, the interaction number of empty messages can be reduced, and the connection establishment time is shortened, so that electric consumption of the terminal can be reduced, and the user experience is enhanced.
Owner:HUAWEI DEVICE CO LTD
Authentication protocol
InactiveUS7509495B2Improve securityDigital data processing detailsUser identity/authority verificationIp addressPassword
Owner:CINNOBER FINANCIAL TECH
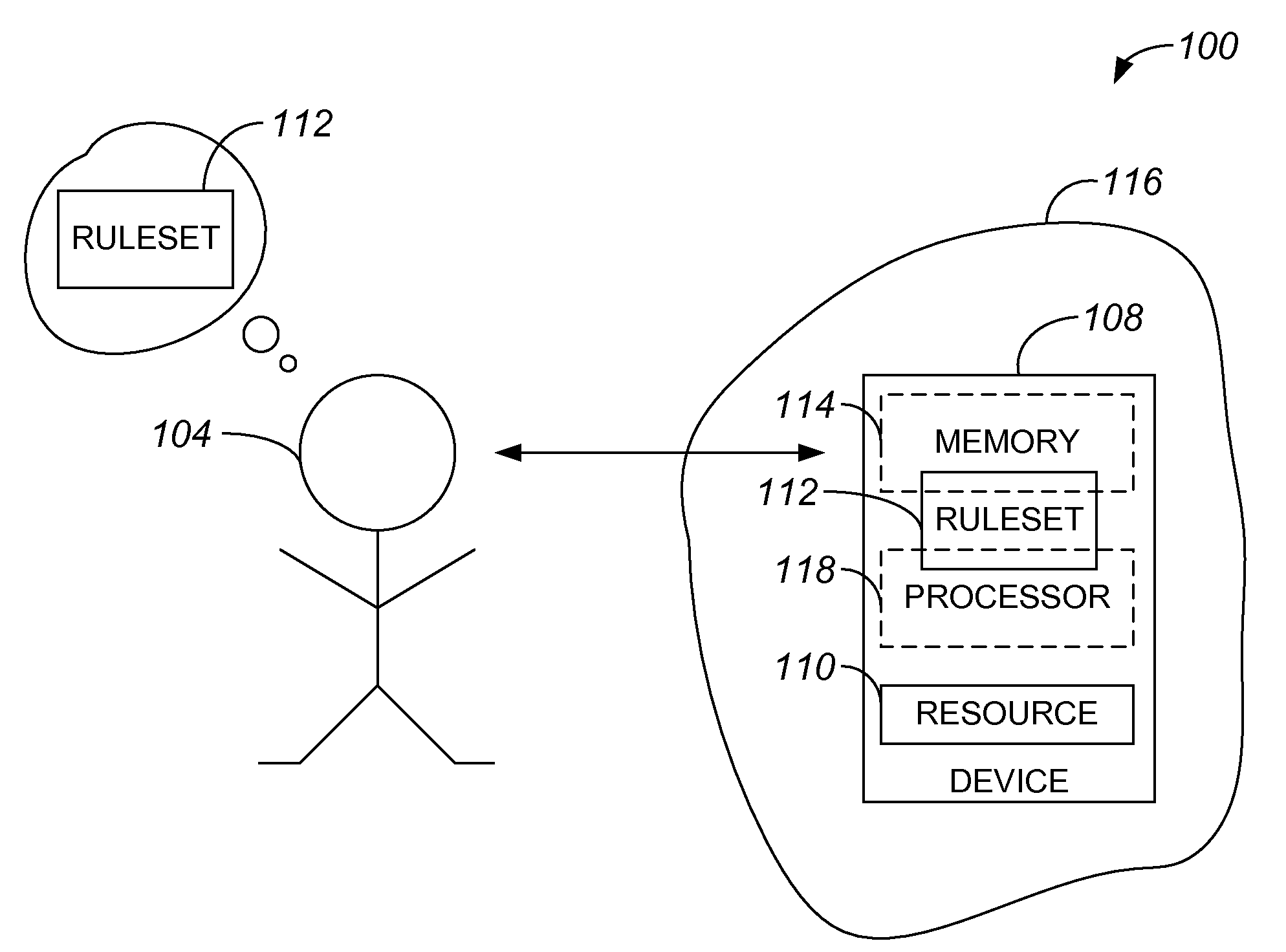
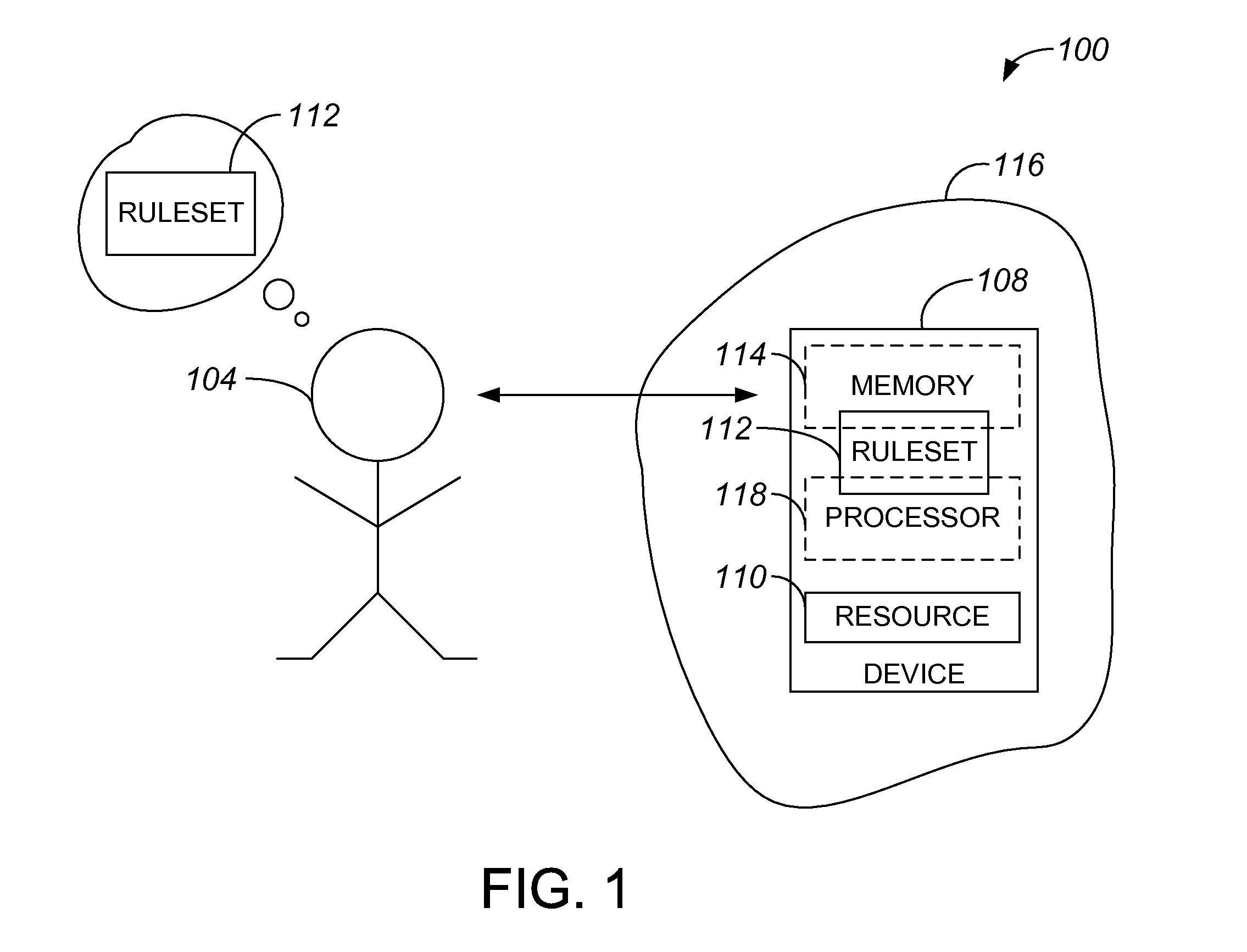
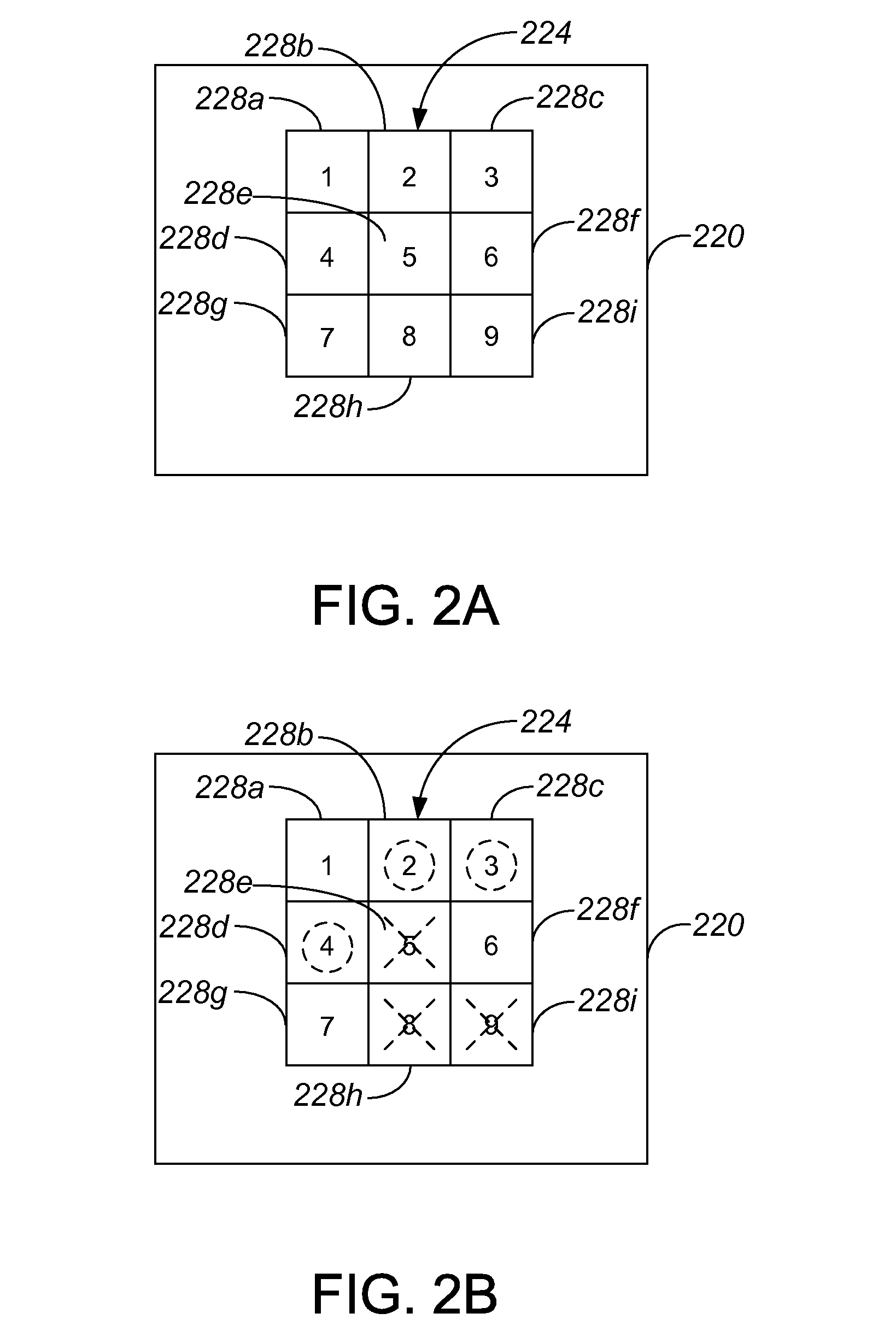
Challenge-based authentication protocol
ActiveUS20080072056A1Public key for secure communicationDigital data processing detailsSuccessful completionComputer security
Methods and apparatus for authenticating a user are disclosed. According to one aspect of the present invention, a method for authenticating a user includes displaying a first representation of a challenge. The challenge is based on a ruleset. The method also includes receiving a first input, determining if the first input furthers a successful completion of the first representation of the challenge, and determining if the first input completes the first representation of the challenge. If it is determined that the first input completes the first representation of the challenge and that the first input furthers the successful completion of the first representation of the challenge, the method further includes positively augmenting a security indicator.
Owner:CISCO TECH INC
Device for Realizing Security Function in Mac of Portable Internet System and Authentication Method Using the Device
InactiveUS20100161958A1Efficiently performing security functionMultiple keys/algorithms usageUser identity/authority verificationComputer hardwareSecurity association
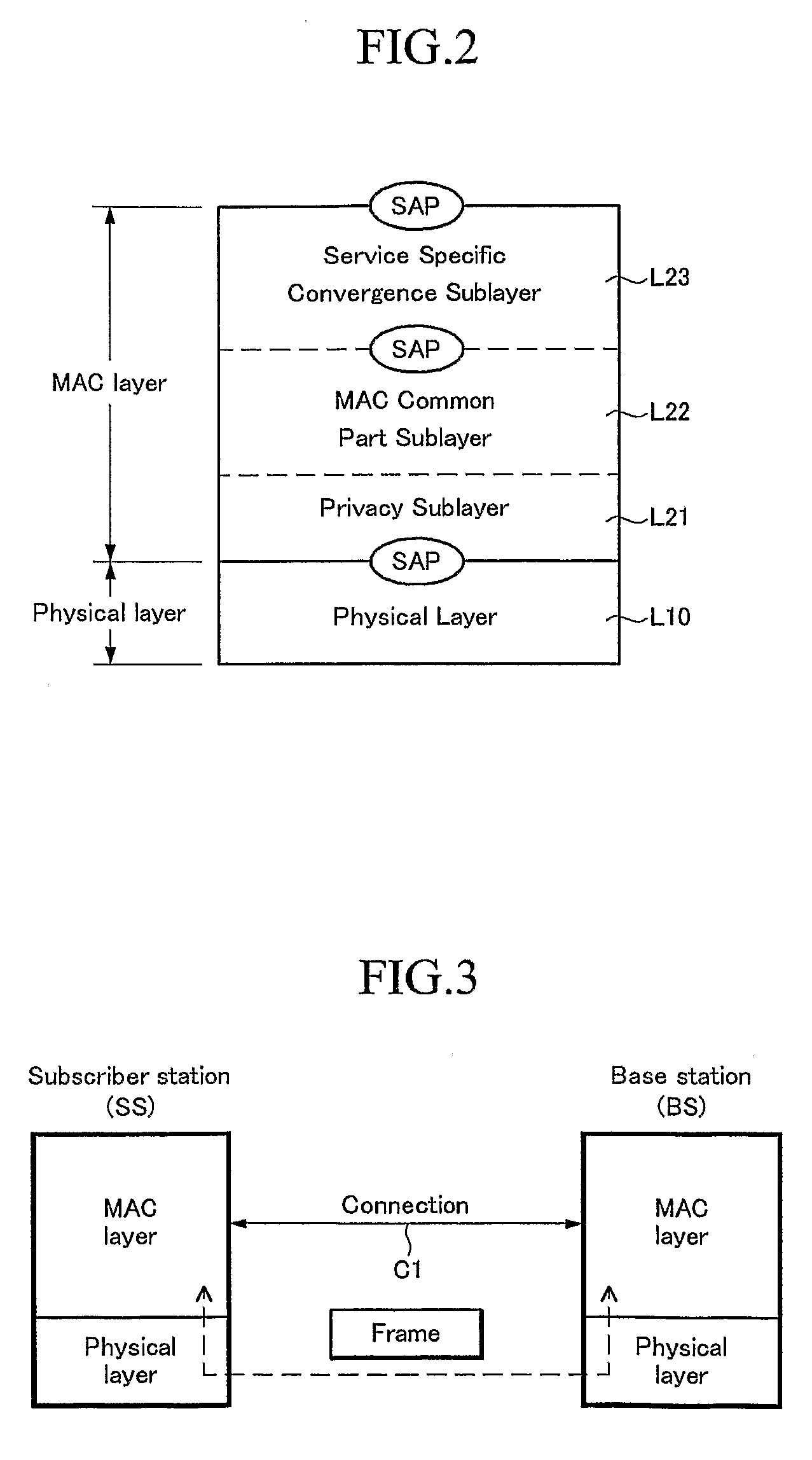
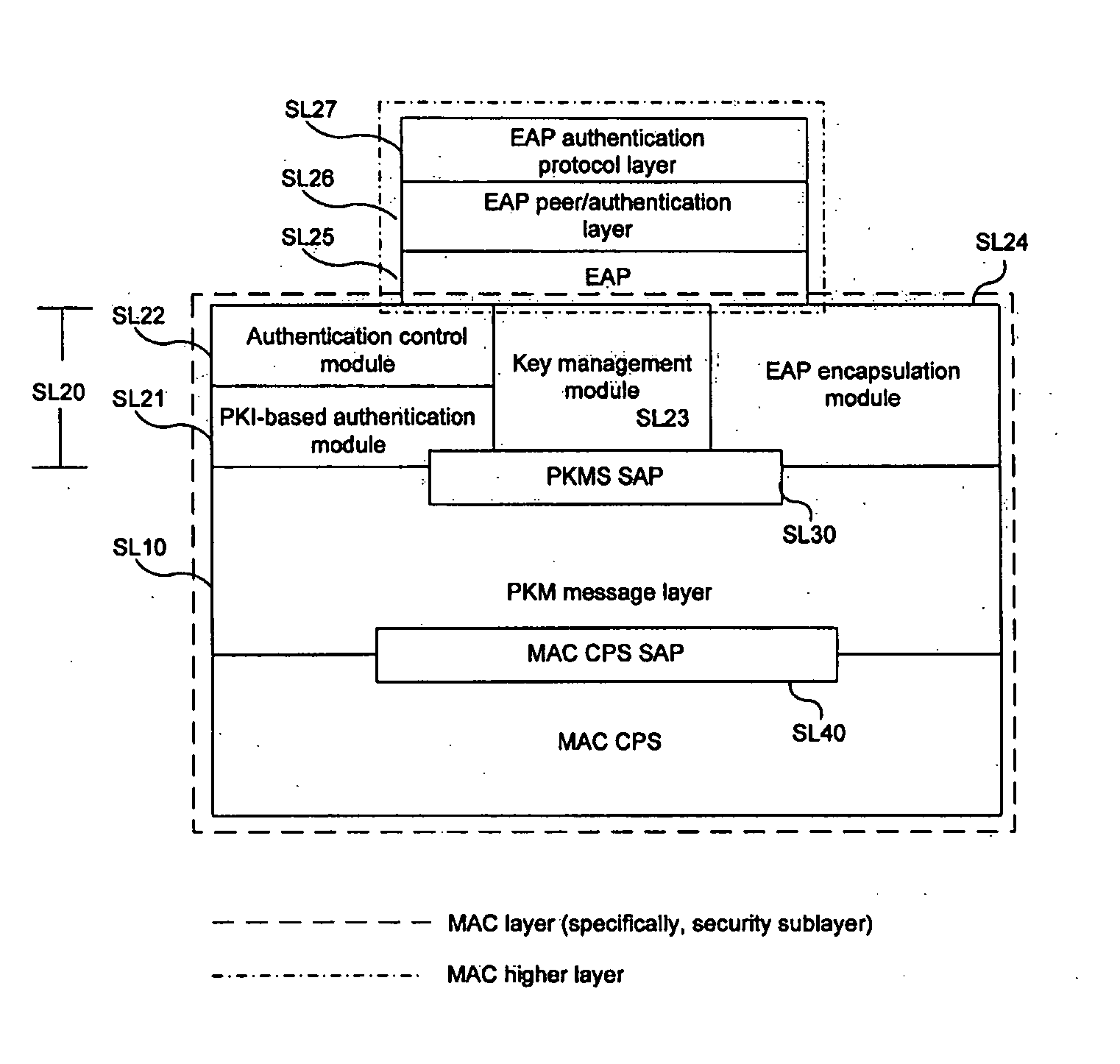
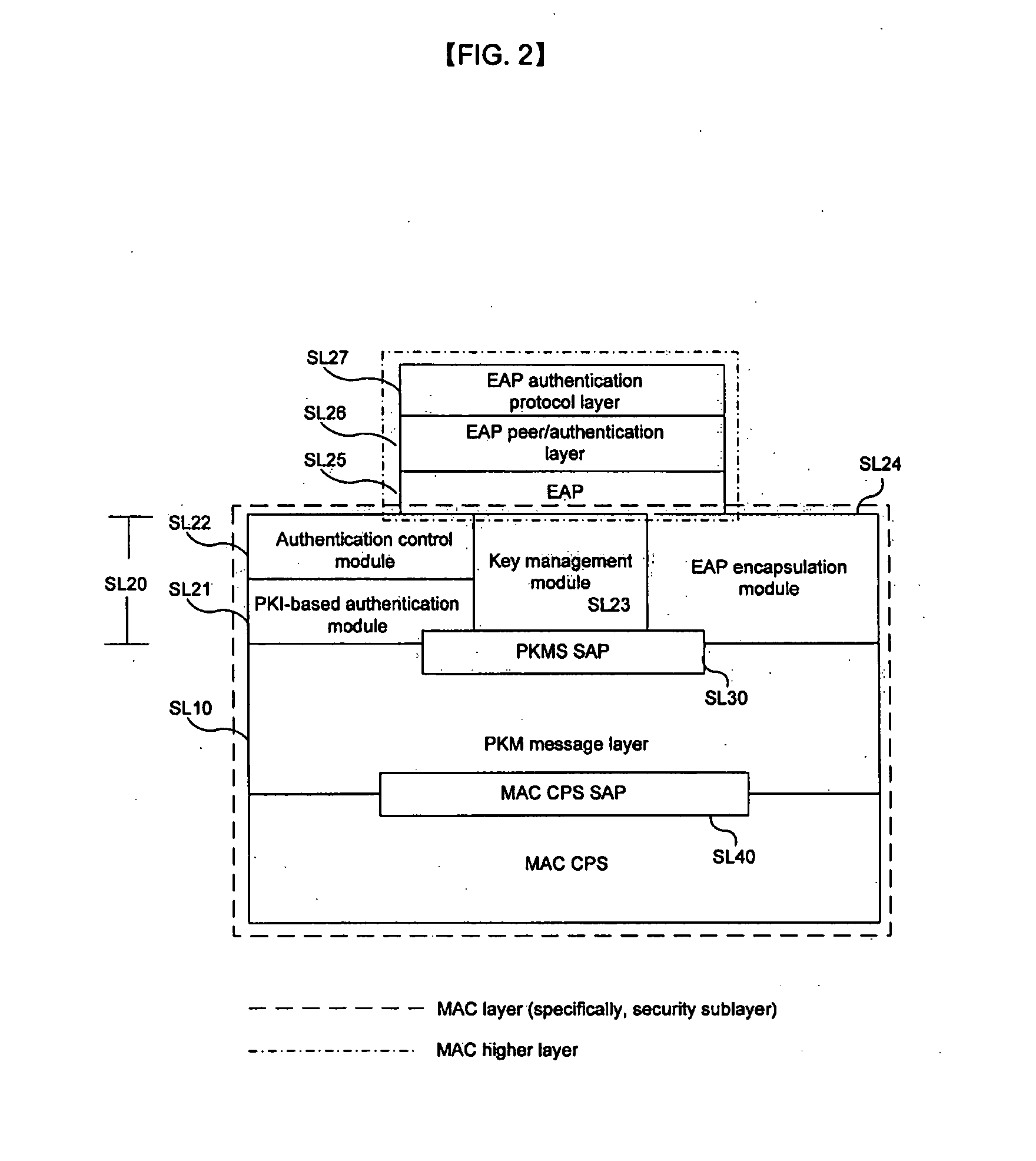
The present invention relates to a device for performing a security function in a medium access control (MAC) layer in a wireless portable Internet system and an authentication method thereof. In the wireless portable Internet system including a physical layer and the MAC layer, a security sublayer (i.e., the device for performing the security function in the MAC layer) is provided on an MAC common part sublayer. The security sublayer includes a privacy key management (PKM) control management module, a traffic data encryption / authentication module, a control message processing module, a message authentication module, a Rivest Shamir Adleman (RSA)-based authentication module, an authentication control / security association (SA) control module, and an extensible authentication protocol (EAP) encapsulation / decapsulation module.
Owner:SAMSUNG ELECTRONICS CO LTD +4
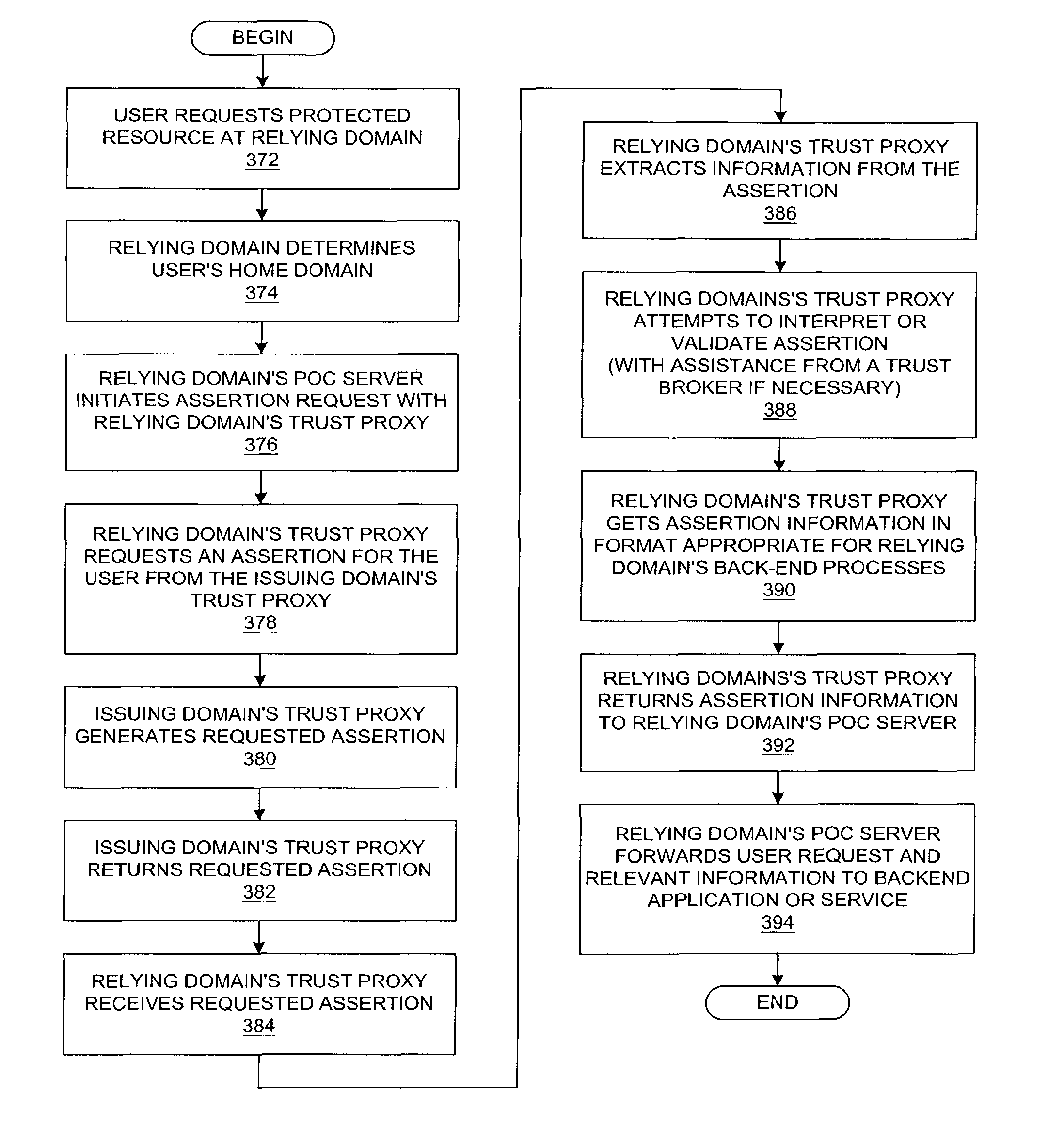
Method and system for native authentication protocols in a heterogeneous federated environment
InactiveUS8042162B2Digital data processing detailsUser identity/authority verificationInternet privacyTrust relationship
A method is presented in which federated domains interact within a federated environment. Domains within a federation can initiate federated single-sign-on operations for a user at other federated domains. A point-of-contact server within a domain relies upon a trust proxy within the domain to manage trust relationships between the domain and the federation. Trust proxies interpret assertions from other federated domains as necessary. Trust proxies may have a trust relationship with one or more trust brokers, and a trust proxy may rely upon a trust broker for assistance in interpreting assertions.
Owner:IBM CORP
A method for expanding WLAN authentication protocol
InactiveCN1671136ASecuring communicationWLAN Authentication and Privacy InfrastructureMutual authentication
A method for adding other authentication protocol in IEEE802.11 WAPI (WLAN Authentication and Privacy Infrastructure), especially adding the authentication protocol based on key shared by access point and mobile terminal, and based on EAP (Extensible Authentication Protocol), said method realizes adding new protocol in original WAPI and selecting between original WAPI and new added protocol, permitting the mutual authentication between the access point with / without new added protocol and mobile terminal, insuring compatible with original WAPI protocol, said invention can escalate access point with WAPI and mobile terminal, in authentication, both of original WAPI and new added protocol can be set forced use, and also can set use access point and terminal neachievediation protocol, in all supporting new added protocol using WAPI or new added protocol, in one part does not support new added protocol using original WAPI.
Owner:神州亿品科技(北京)有限公司
Method, system and equipment for transporting signaling
InactiveCN101599896AAchieve separationEasy to handleMessaging/mailboxes/announcementsData switching networksNetwork packetThird generation
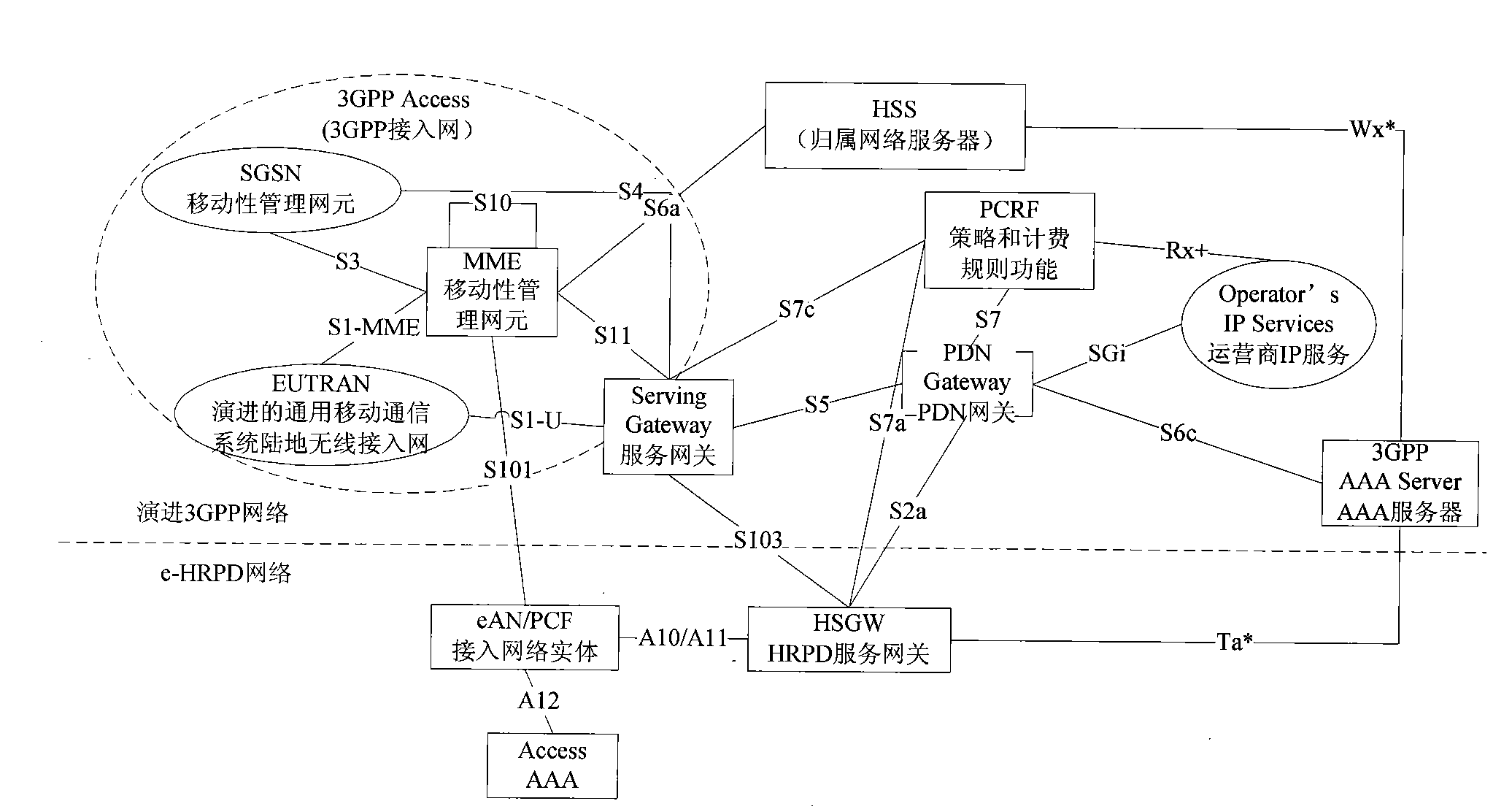
The invention discloses a method, a system and equipment for transporting signaling, belonging to the communication field. The method for transporting singling comprises the following steps: signaling information from a terminal is received by an extensible authentication protocol (eAN) / PCF through a first default route, and the signaling information is sent to an HRDP serving gateway (HSGW) through a second default route; or signaling information from the HSGW is received by the eAN / PCF through the second default route, and the signaling information is sent to the terminal through the first default route; and the bearing separation of the signaling information and data is achieved through the bearing signaling information of the first default route and the second default route. The system for transporting singling comprises user equipment (UE), the eAN / PCF and the HSGW. The sorting of a user plane data packet and signaling in a band can be avoided by using signaling outside the band, the performance of the system for transporting signaling is improved, the processing capacity of the HSGW and the capacity of a serviceable terminal are enhanced, the band width of the surface of the signaling is ensured, the signaling can not lose under the high load of the system for transporting signaling, and the stability and the reliability of the system for transporting signaling are improved. Because the surface of the signaling and the user plane are logically separated, the system for transporting signaling more structurally meets the requirement of the third generation partnership project (3GPP).
Owner:HUAWEI TECH CO LTD
Systems and methods for host authentication
ActiveUS20110283344A1Digital data processing detailsComputer security arrangementsComputer hardwareAuthentication system
Systems and methods provide for authenticating a device. A method for authenticating a device can include receiving, at communications node, a first message, wherein the first message includes a first Extensible Authentication Protocol (EAP) packet which includes an EAP (Identify) ID response and a first destination address; generating, by the communications node, a second message, wherein the second message includes the first EAP ID response and a second destination address which is different from the first destination address; and transmitting, by the communications node, the second message toward the second destination address.
Owner:TELEFON AB LM ERICSSON (PUBL)
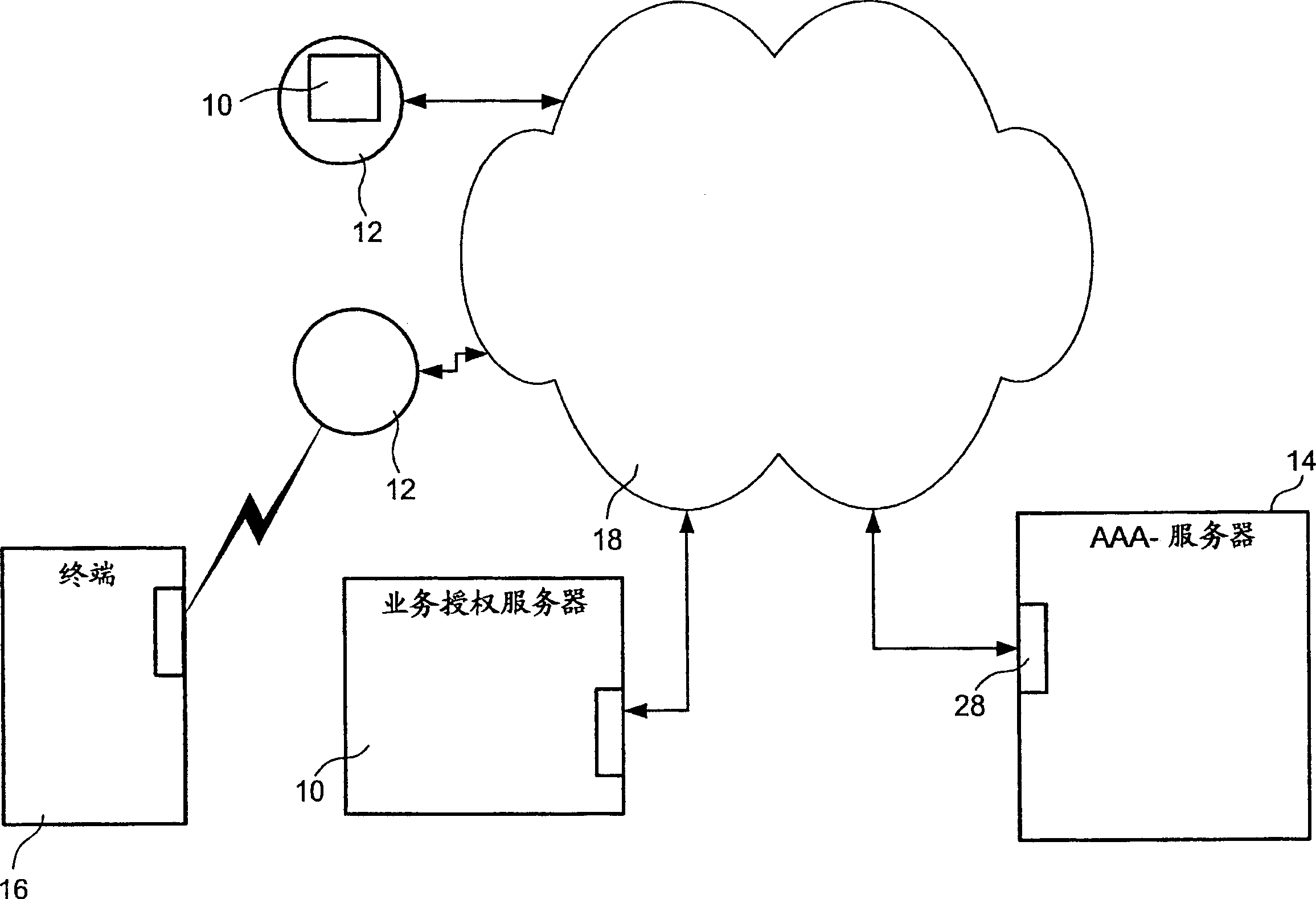
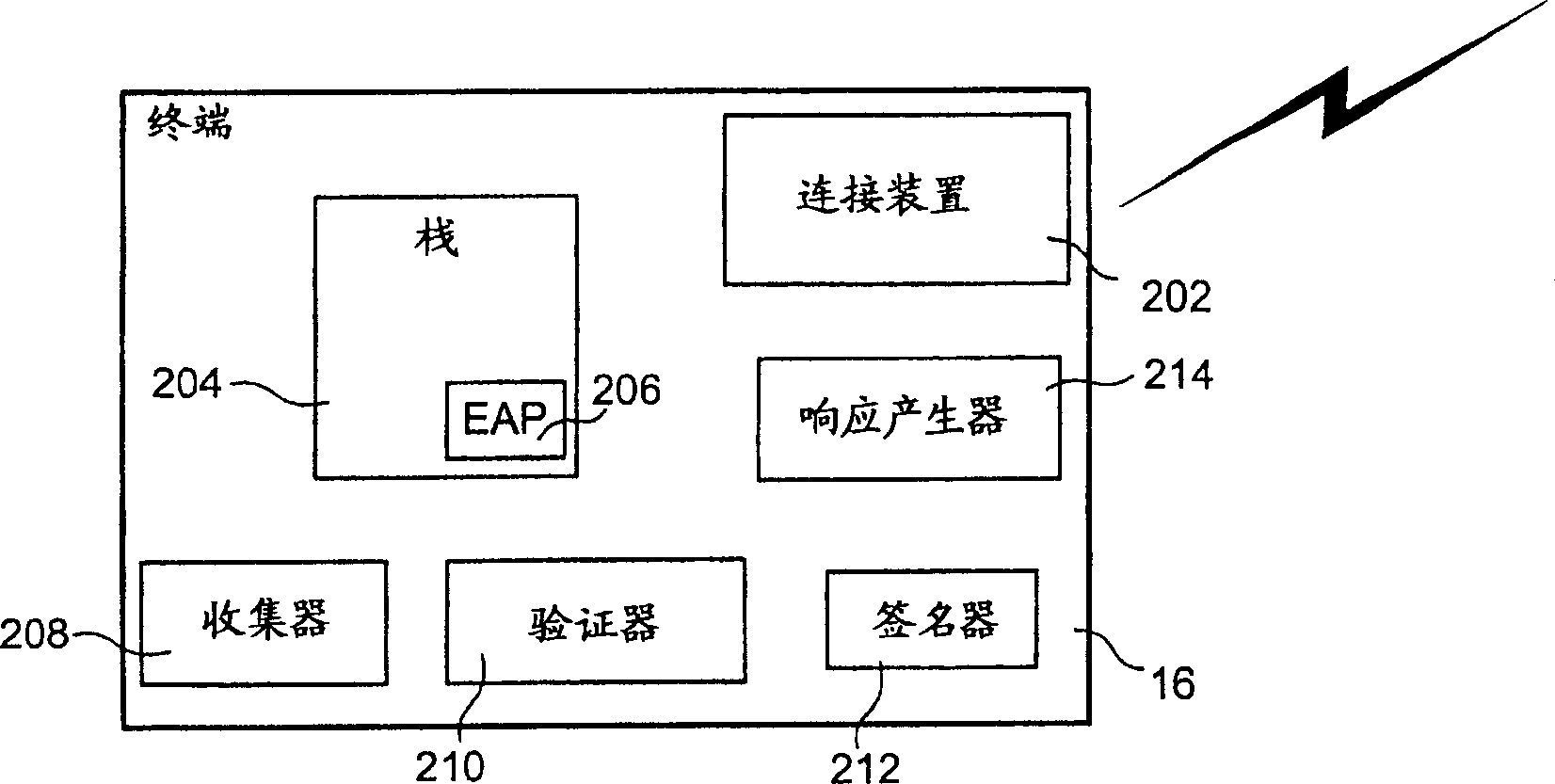
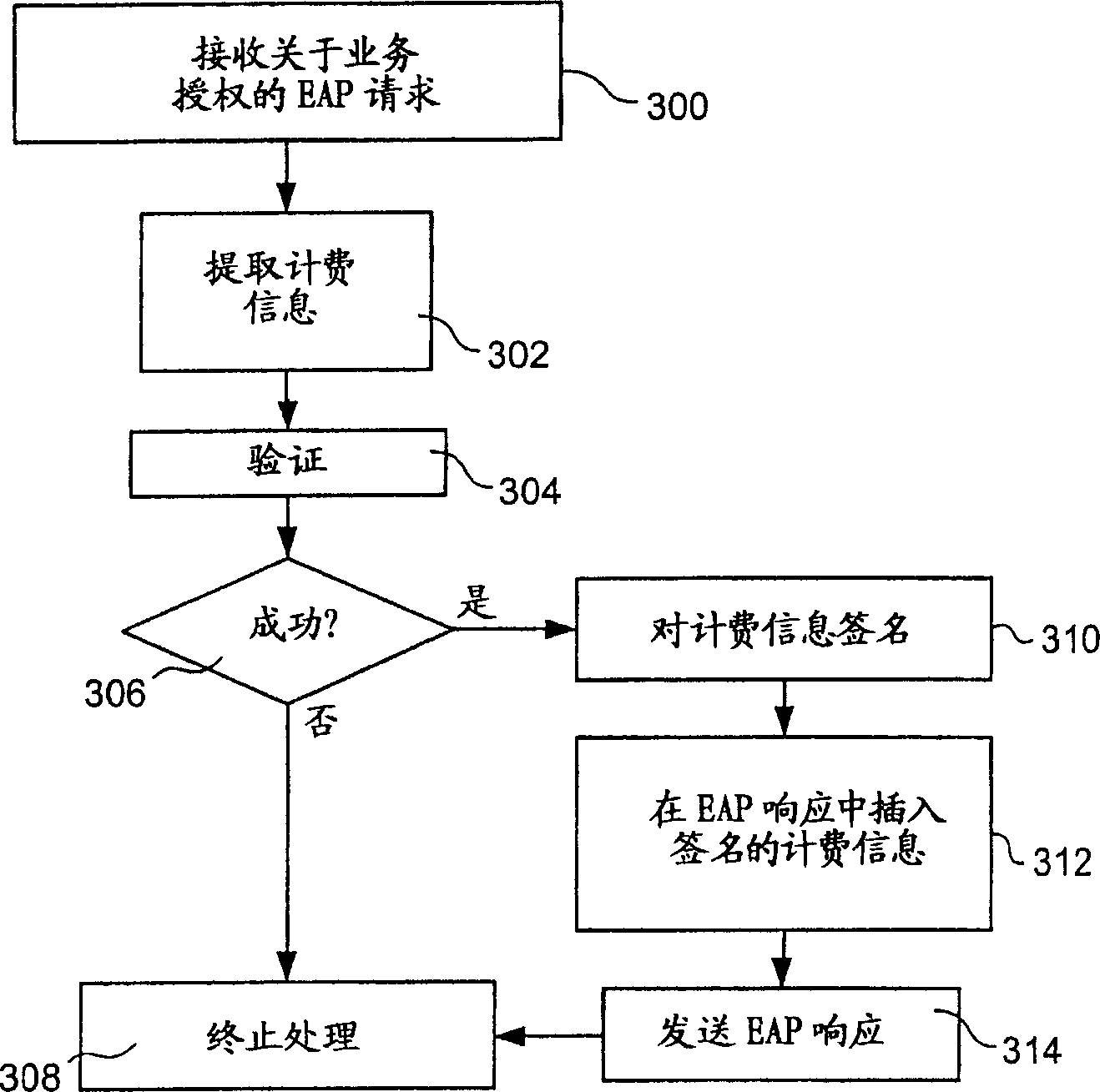
Method system and device for transferring accounting information
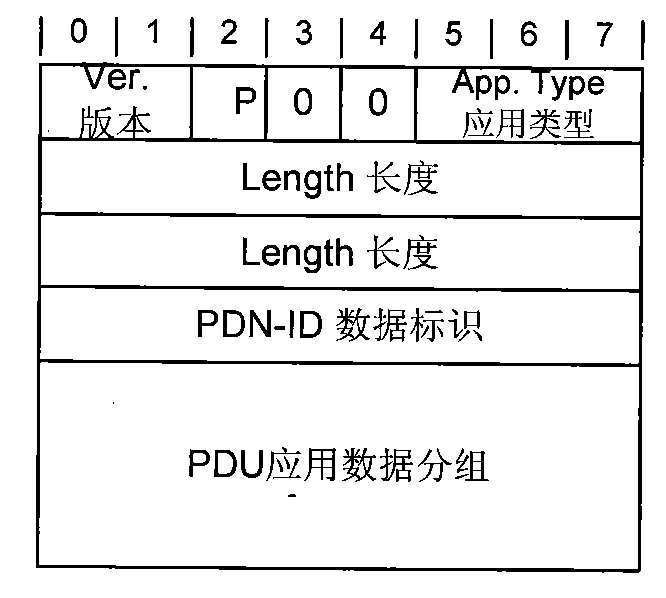
A method in a system for transferring accounting information, a system for transferring accounting information, a method in a terminal, a terminal, a method in an Extensible Authentication Protocol (EAP) service authorization server, an EAP service authorization server, a computer program, a computer program, an Extensible Authentication Protocol response (EAP-response) packet. The method in a system comprises: metering data related to service used by at least one terminal, providing the metered data as accounting information to at least one Extensible authentication Protocol (EAP) service authorization server, sending, by means of an Extensible Authentication Protocol request (EAP-request), a service authorization request from said at least one EAP service authorization server to said at least one terminal, digitally signing accounting information, in said at least one terminal, including, at said at least one terminal, the digitally signed accounting information in an Extensible Authentication Protocol response (EAP-response), and sending the digitally signal accounting information to an AAA-server.
Owner:CORE WIRELESS LICENSING R L
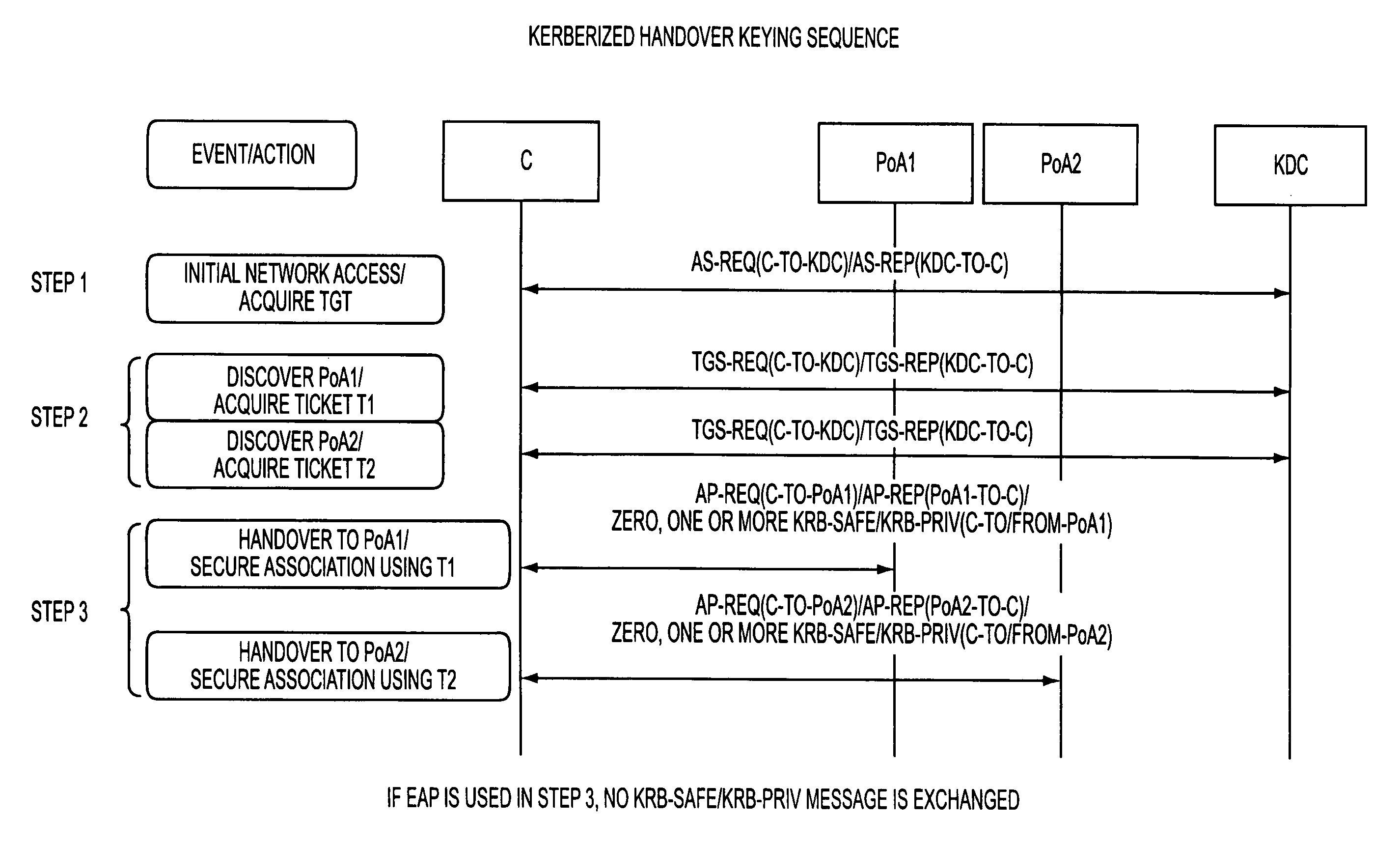
Kerberized handover keying
ActiveUS8332923B2Key distribution for secure communicationDigital data processing detailsSecurity associationOperation mode
A media-independent handover key management architecture is disclosed that uses Kerberos for secure key distribution among a server, an authenticator, and a mobile node. In the preferred embodiments, signaling for key distribution is based on re-keying and is decoupled from re-authentication that requires EAP (Extensible Authentication Protocol) and AAA (Authentication, Authorization and Accounting) signaling similar to initial network access authentication. In this framework, the mobile node is able to obtain master session keys required for dynamically establishing the security associations with a set of authenticators without communicating with them before handover. By separating re-key operation from re-authentication, the proposed architecture is more optimized for a proactive mode of operation. It can also be optimized for reactive mode of operation by reversing the key distribution roles between the mobile node and the target access node.
Owner:TELCORDIA TECHNOLOGIES INC +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com