Authentication method for accessing mobile subscriber to core network through femtocell
A technology for mobile users and home base stations, applied in the field of communication security, can solve problems such as malicious user attacks, no authentication methods, and threats to core network user terminals, and achieve the effects of ensuring security, reducing authentication overhead, and improving security and speed.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
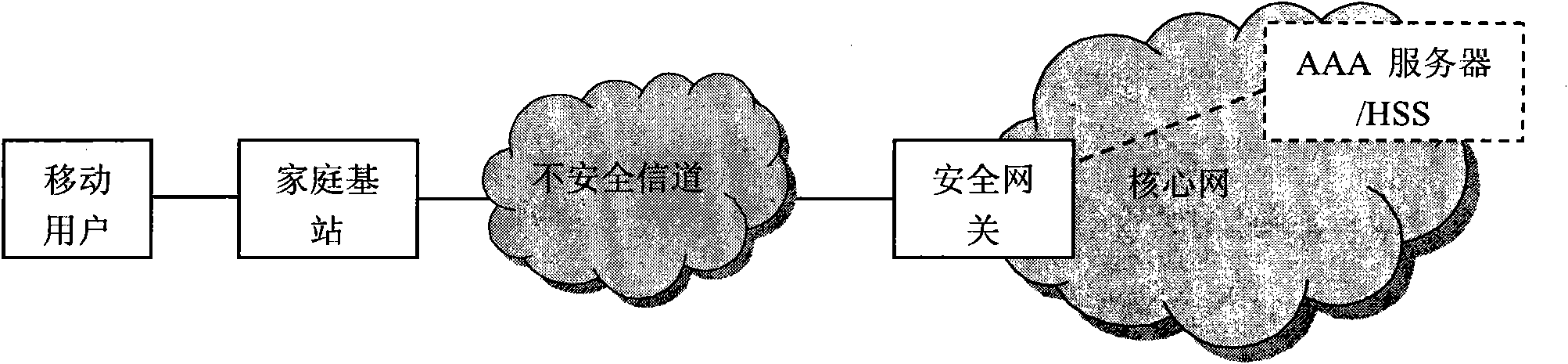
[0037] The implementation scheme of the home base station adopted in this method is to solidify the base station user identity card into the home base station equipment, without considering the authentication between the base station user and the equipment. The network structure diagram of the home base station is as follows figure 1 As shown, it mainly includes a mobile user terminal, a femtocell, a security gateway, an AAA server and an HSS server.
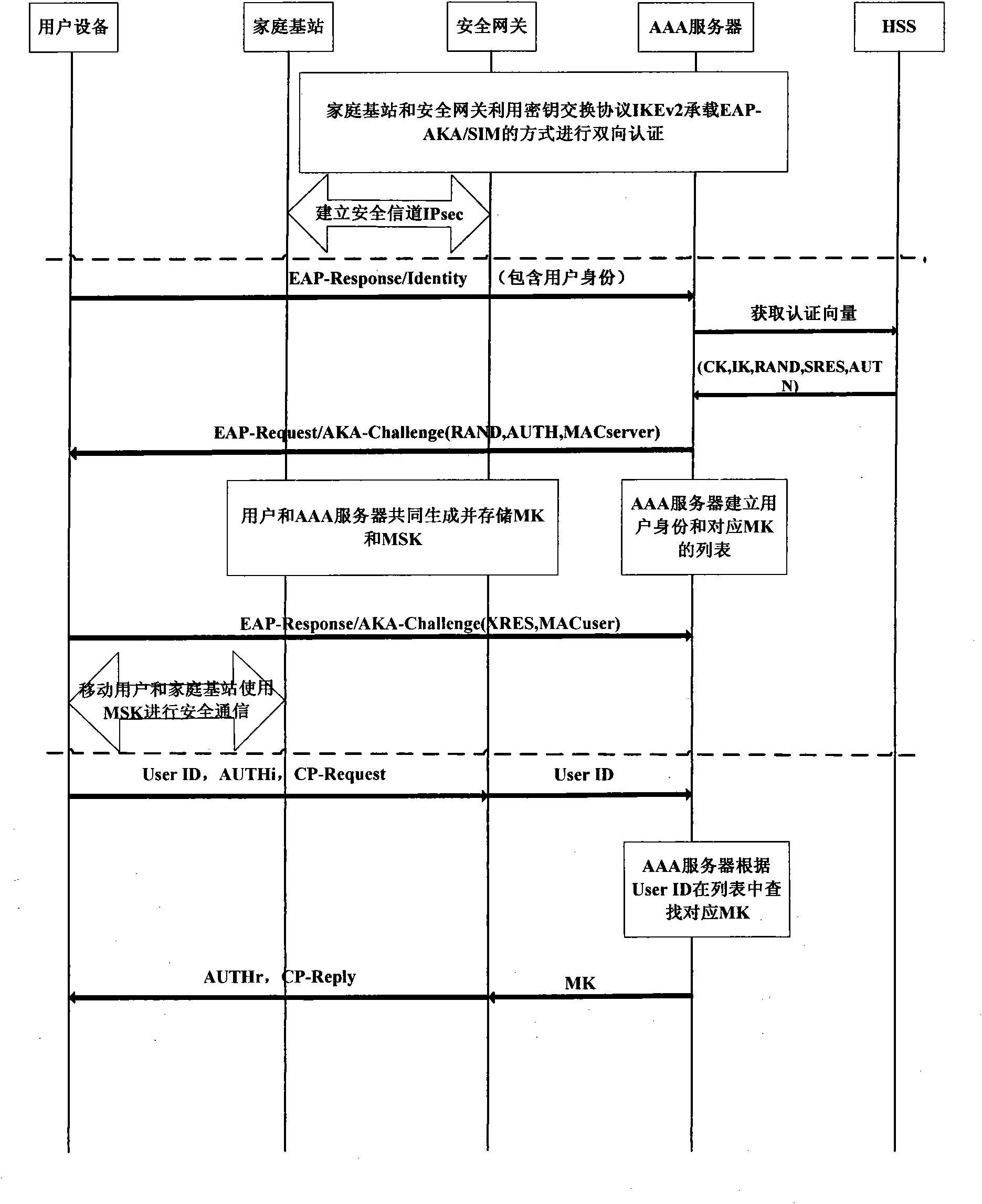
[0038] refer to figure 2 , the overall authentication process of the mobile user accessing the core network through the home base station in the present invention includes the following three steps:
[0039] In step 1, the home base station and the core network perform authentication and establish a secure channel IPsec.
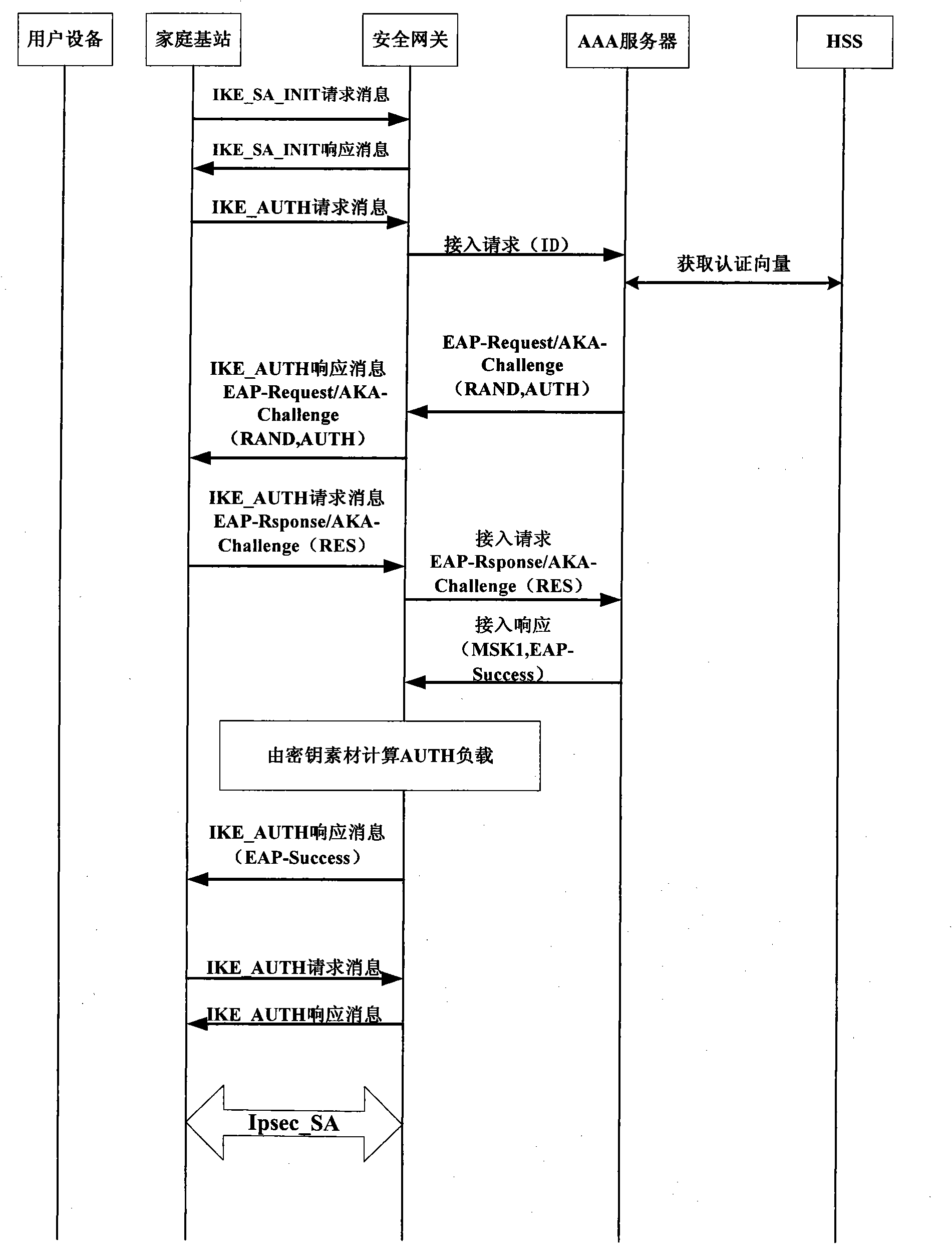
[0040] Such as image 3 As shown, the specific implementation of this step is to use the key exchange protocol IKEv2 provided in the 3GPP standard to carry EAP-AKA / SIM, and perform the following two-way aut...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com