Patents
Literature
817results about "Public key infrastructure trust models" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
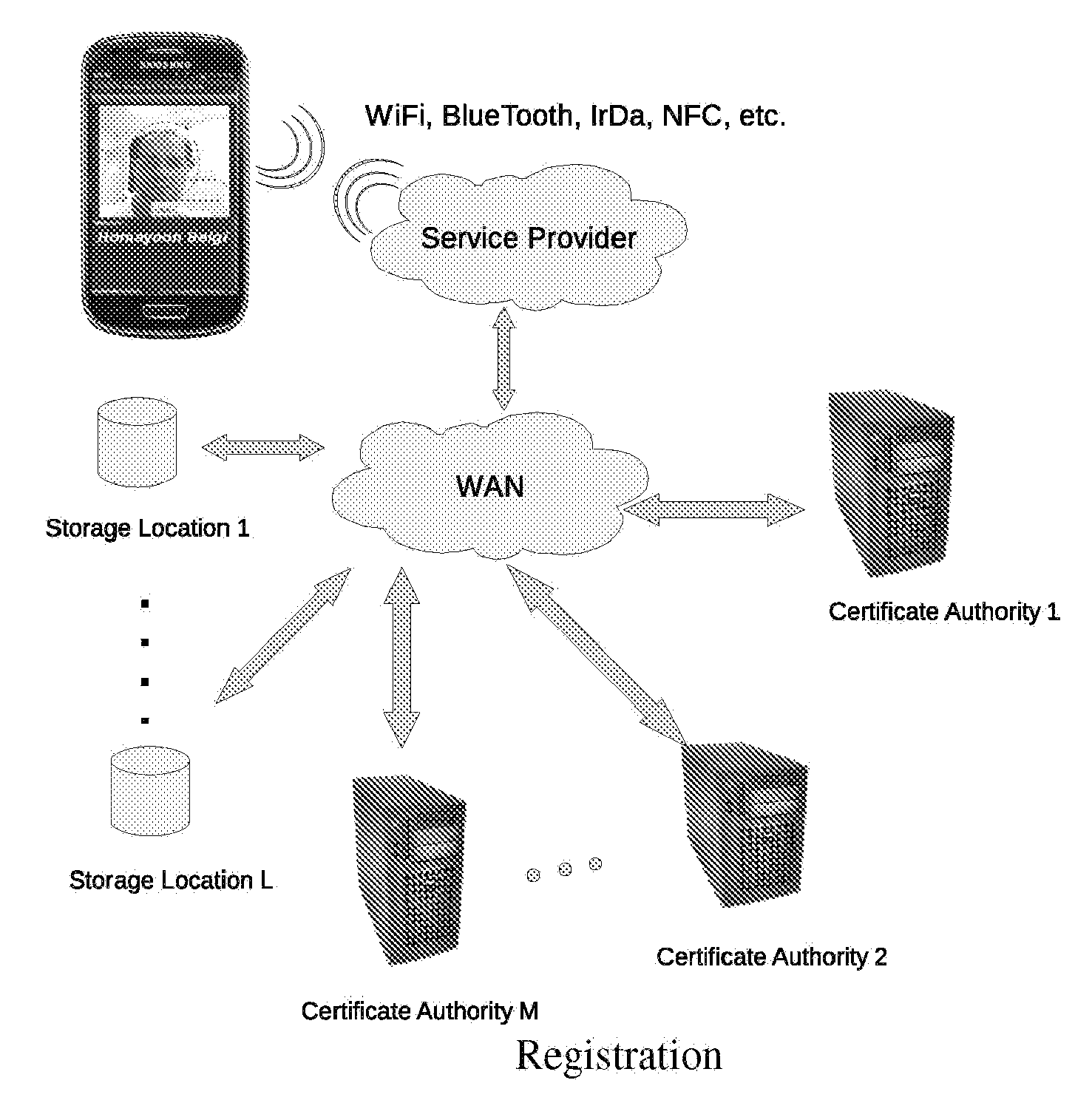
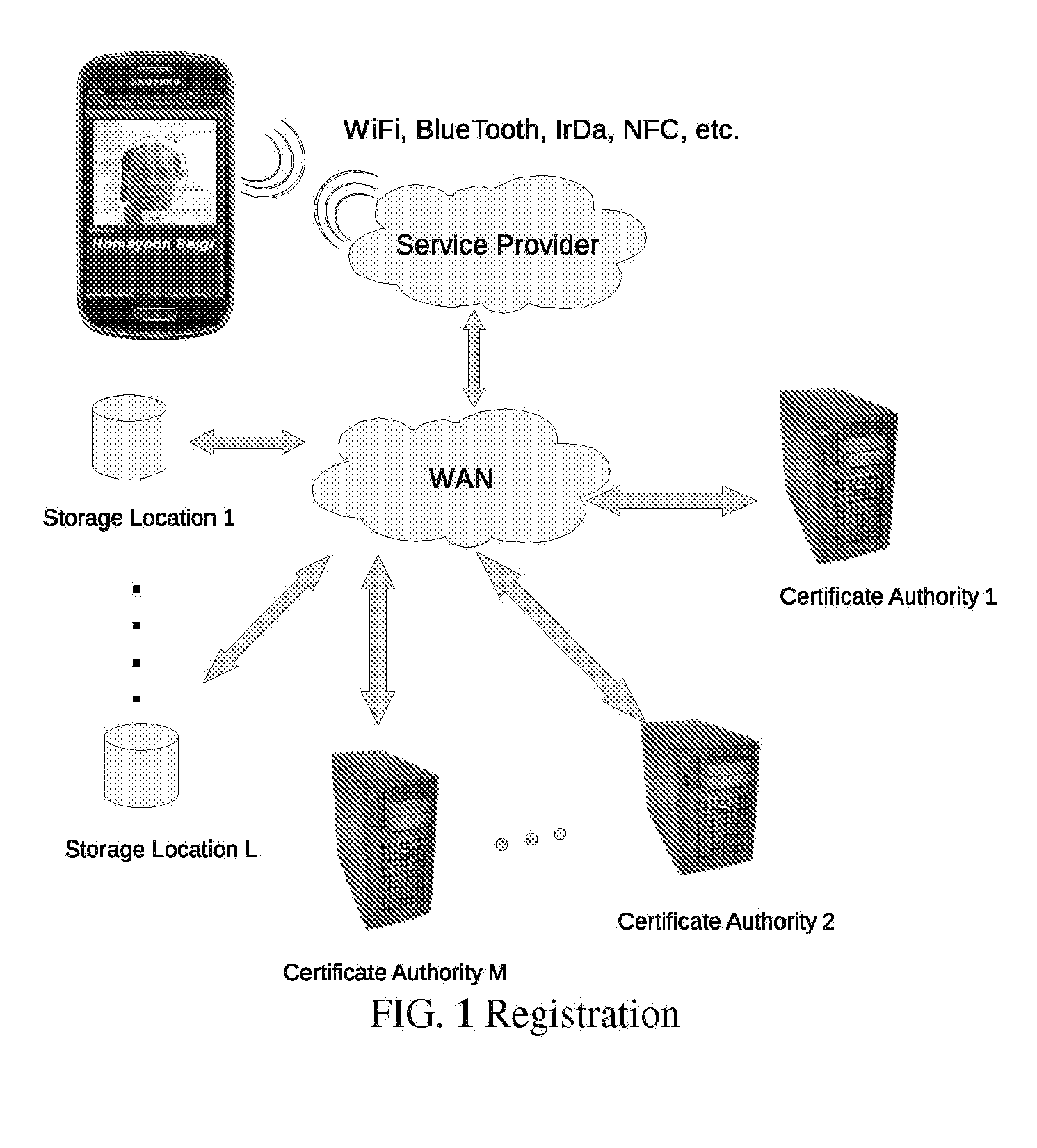
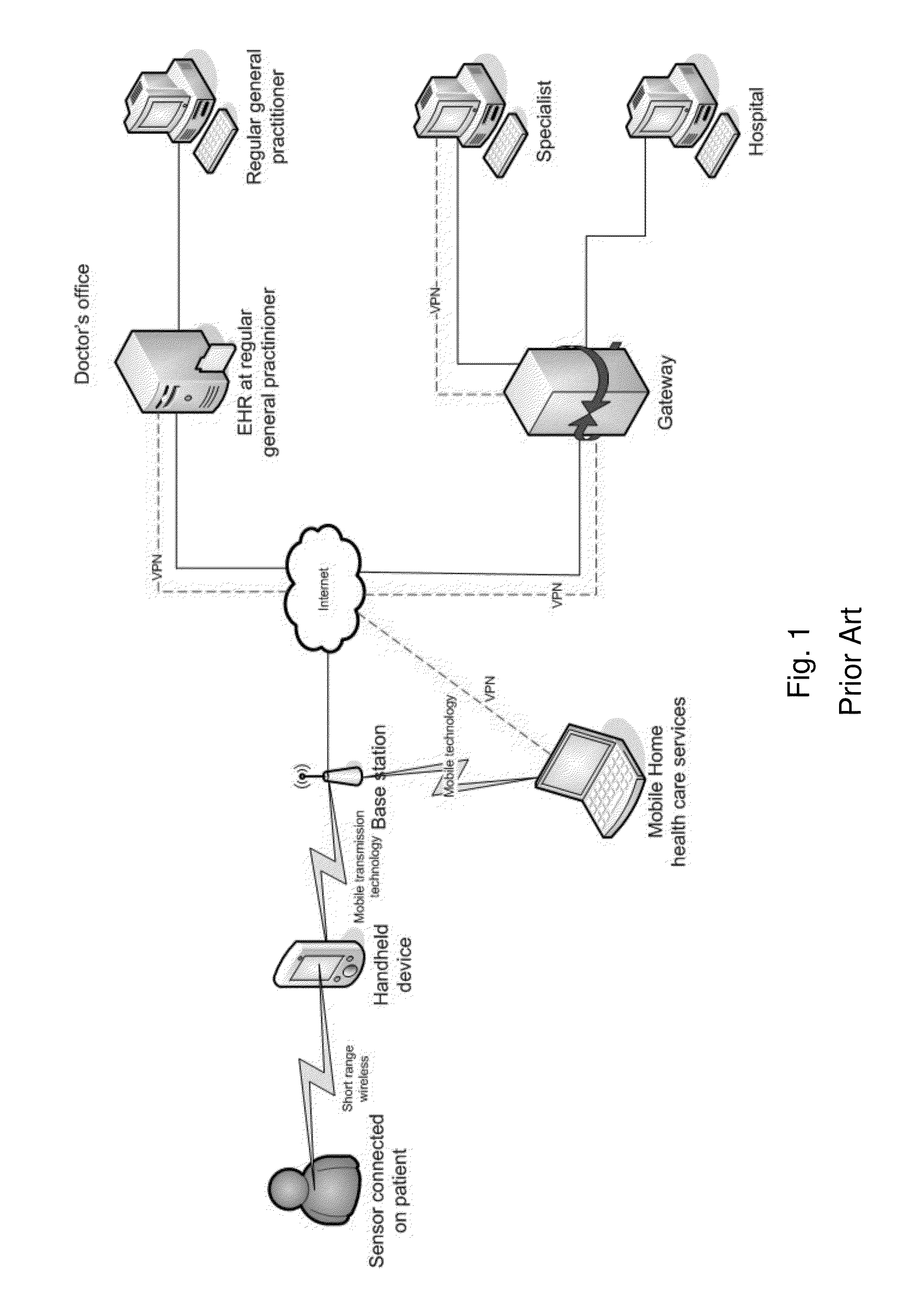
Trusted and secure techniques, systems and methods for item delivery and execution
InactiveUS6185683B2Avoid deletionEasy to identifyTelevision system detailsPulse modulation television signal transmissionDocumentation procedureDocument preparation
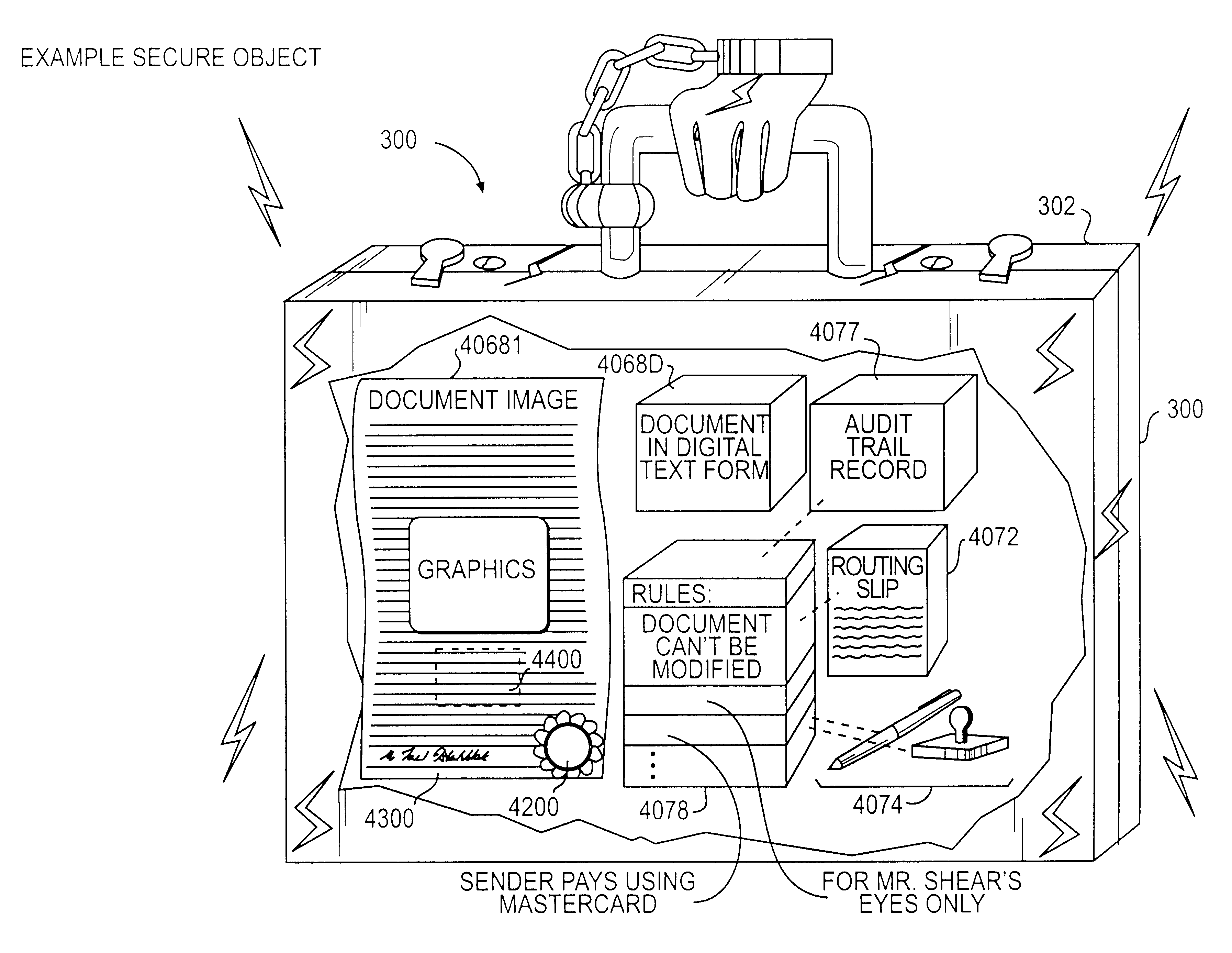
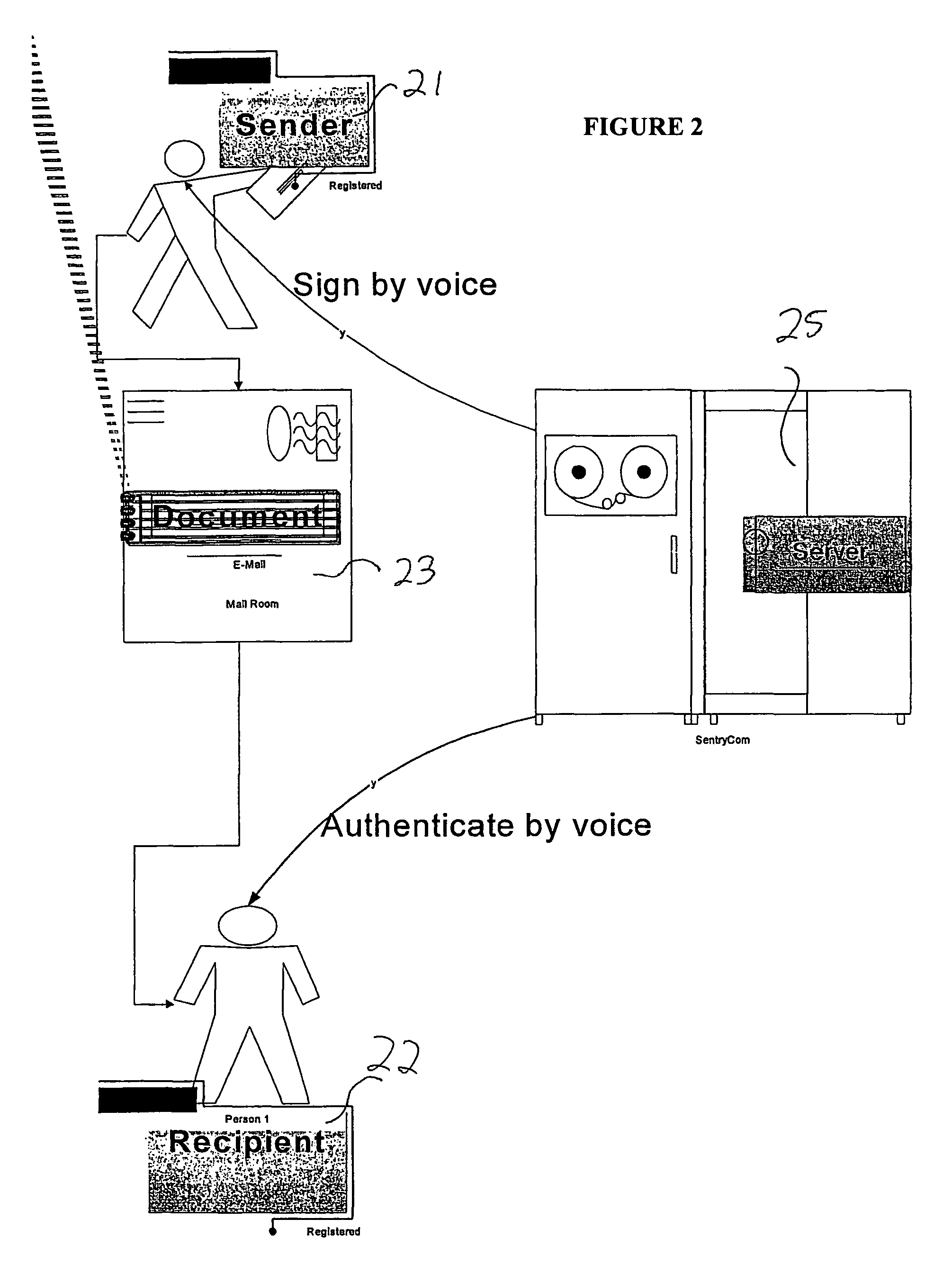
Documents and other items can be delivered electronically from sender to recipient with a level of trustedness approaching or exceeding that provided by a personal document courier. A trusted electronic go-between can validate, witness and / or archive transactions while, in some cases, actively participating in or directing the transaction. Printed or imaged documents can be marked using handwritten signature images, seal images, electronic fingerprinting, watermarking, and / or steganography. Electronic commercial transactions and transmissions take place in a reliable, "trusted" virtual distribution environment that provides significant efficiency and cost savings benefits to users in addition to providing an extremely high degree of confidence and trustedness. The systems and techniques have many uses including but not limited to secure document delivery, execution of legal documents, and electronic data interchange (EDI).
Owner:INTERTRUST TECH CORP
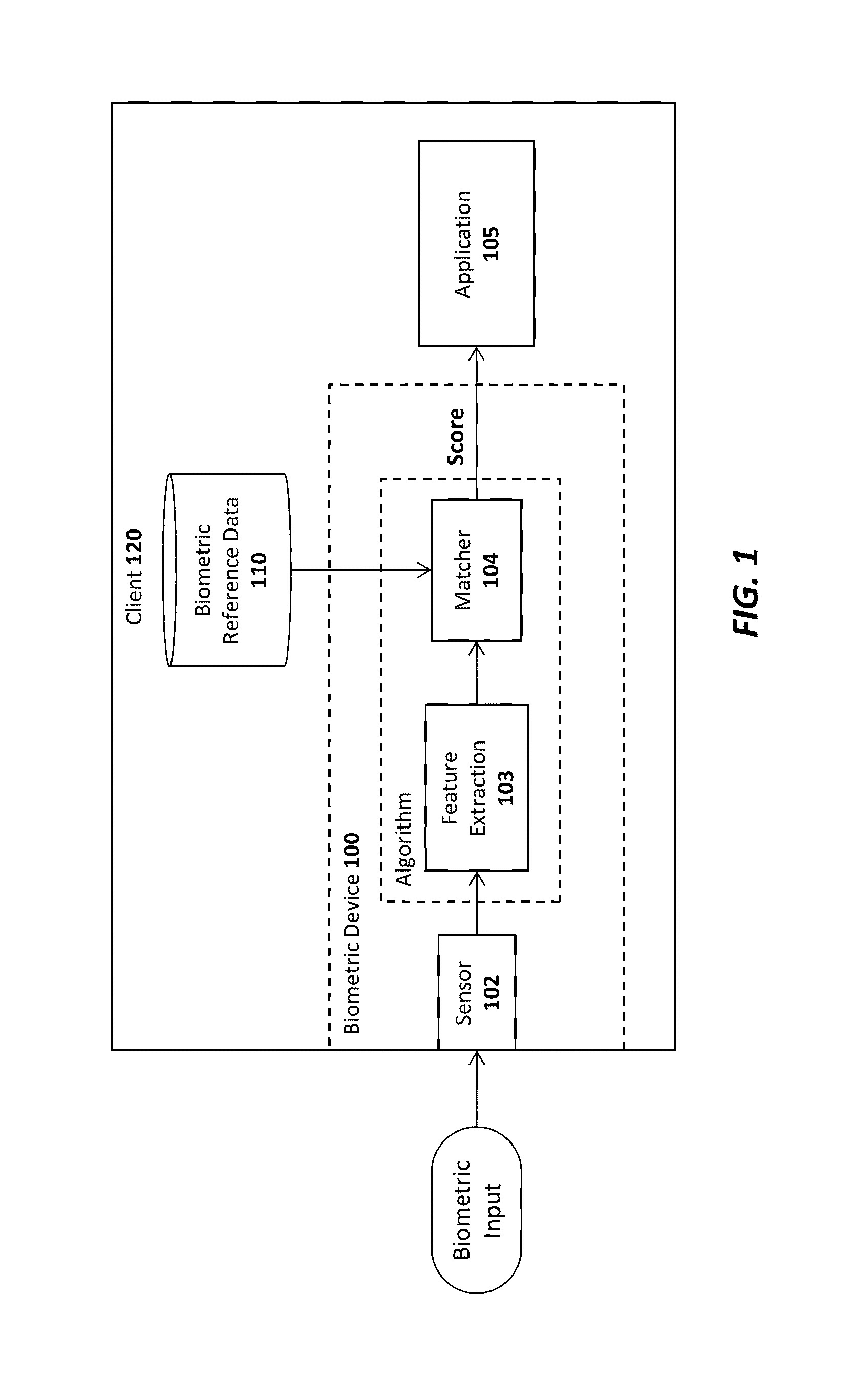
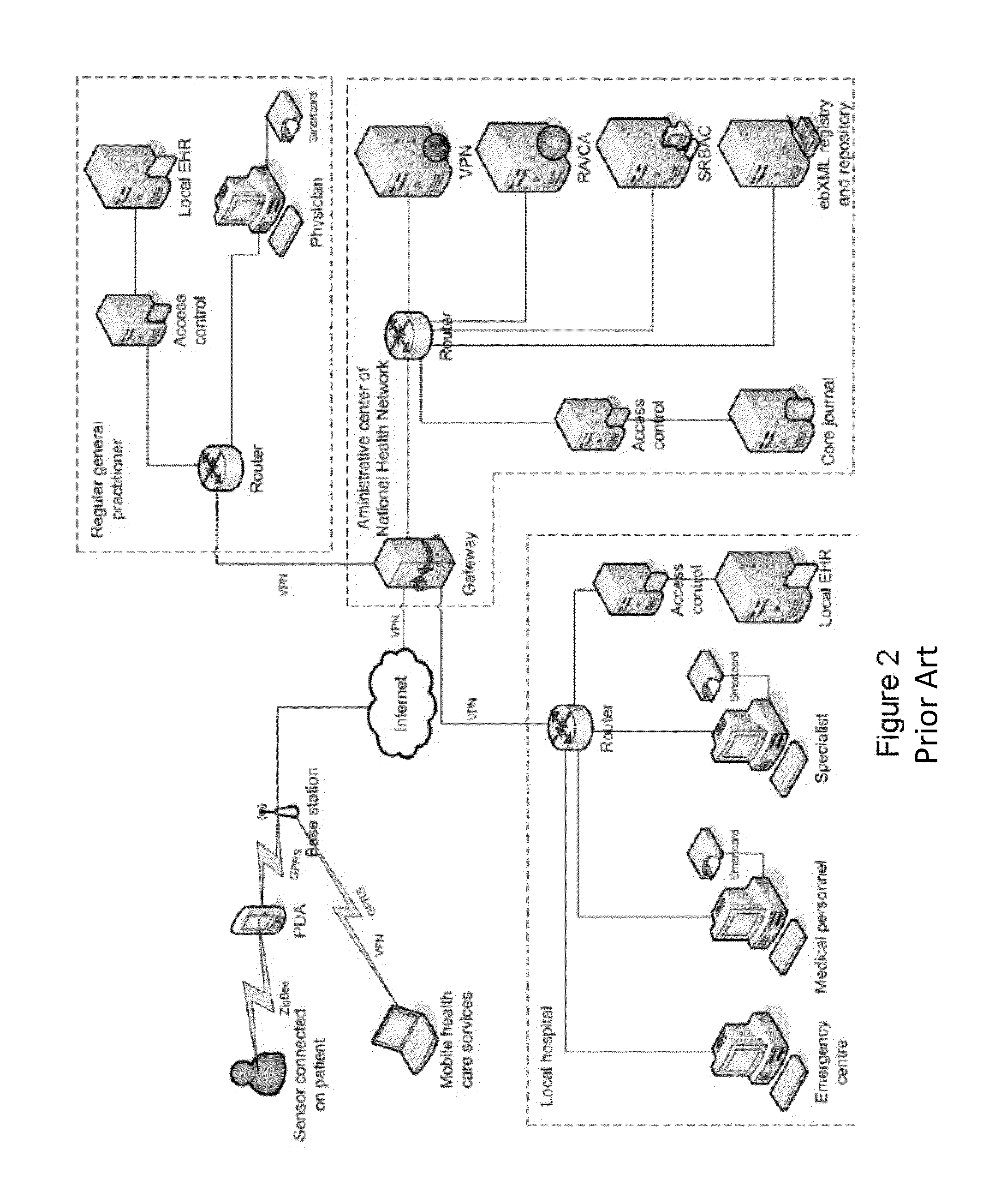
Advanced authentication techniques and applications
ActiveUS20140289833A1Digital data processing detailsMultiple digital computer combinationsEngineeringDatabase
A system, apparatus, method, and machine readable medium are described for performing advanced authentication techniques and associated applications. For example, one embodiment of a method comprises: receiving a policy identifying a set of acceptable authentication capabilities; determining a set of client authentication capabilities; and filtering the set of acceptable authentication capabilities based on the determined set of client authentication capabilities to arrive at a filtered set of one or more authentication capabilities for authenticating a user of the client.
Owner:NOK NOK LABS
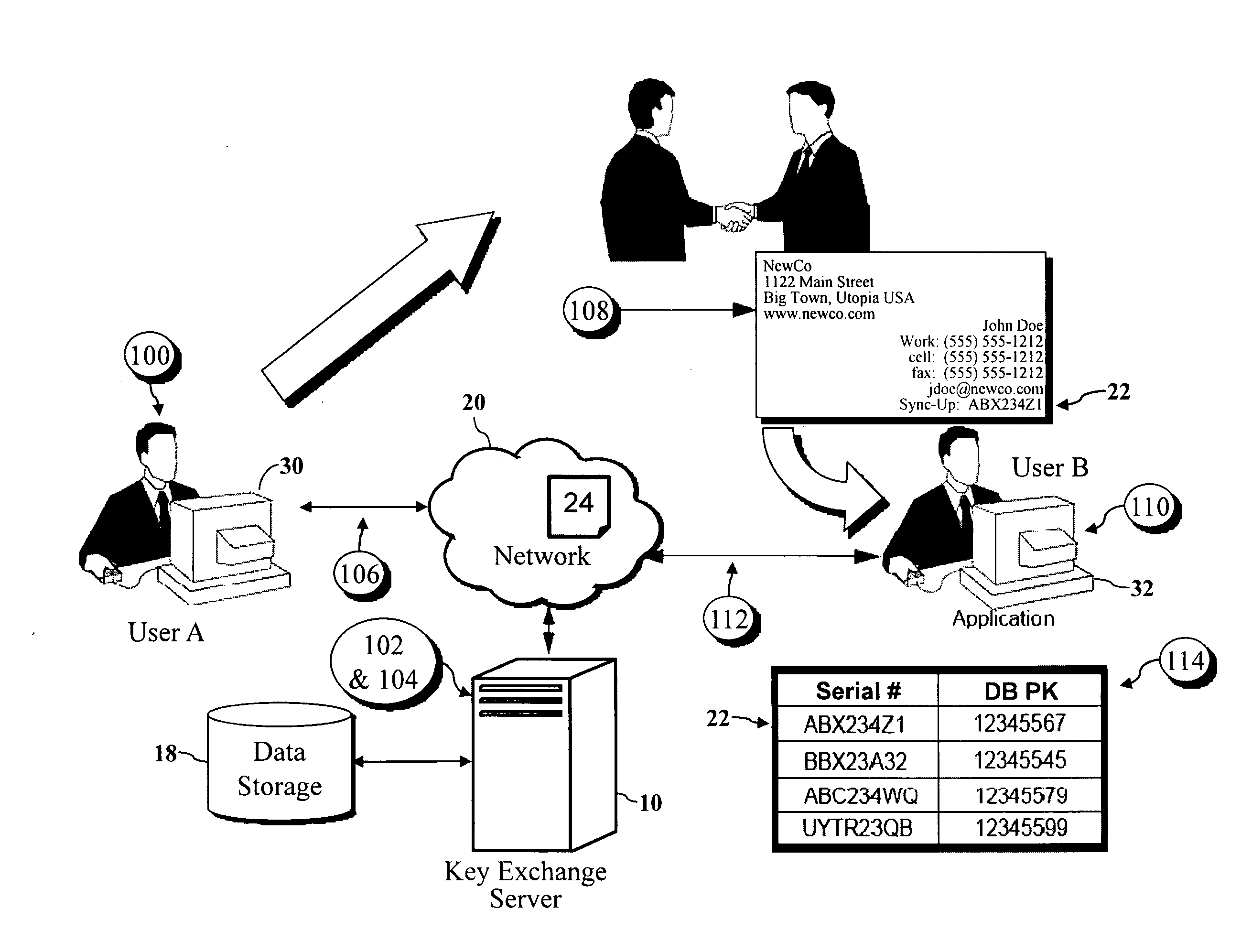
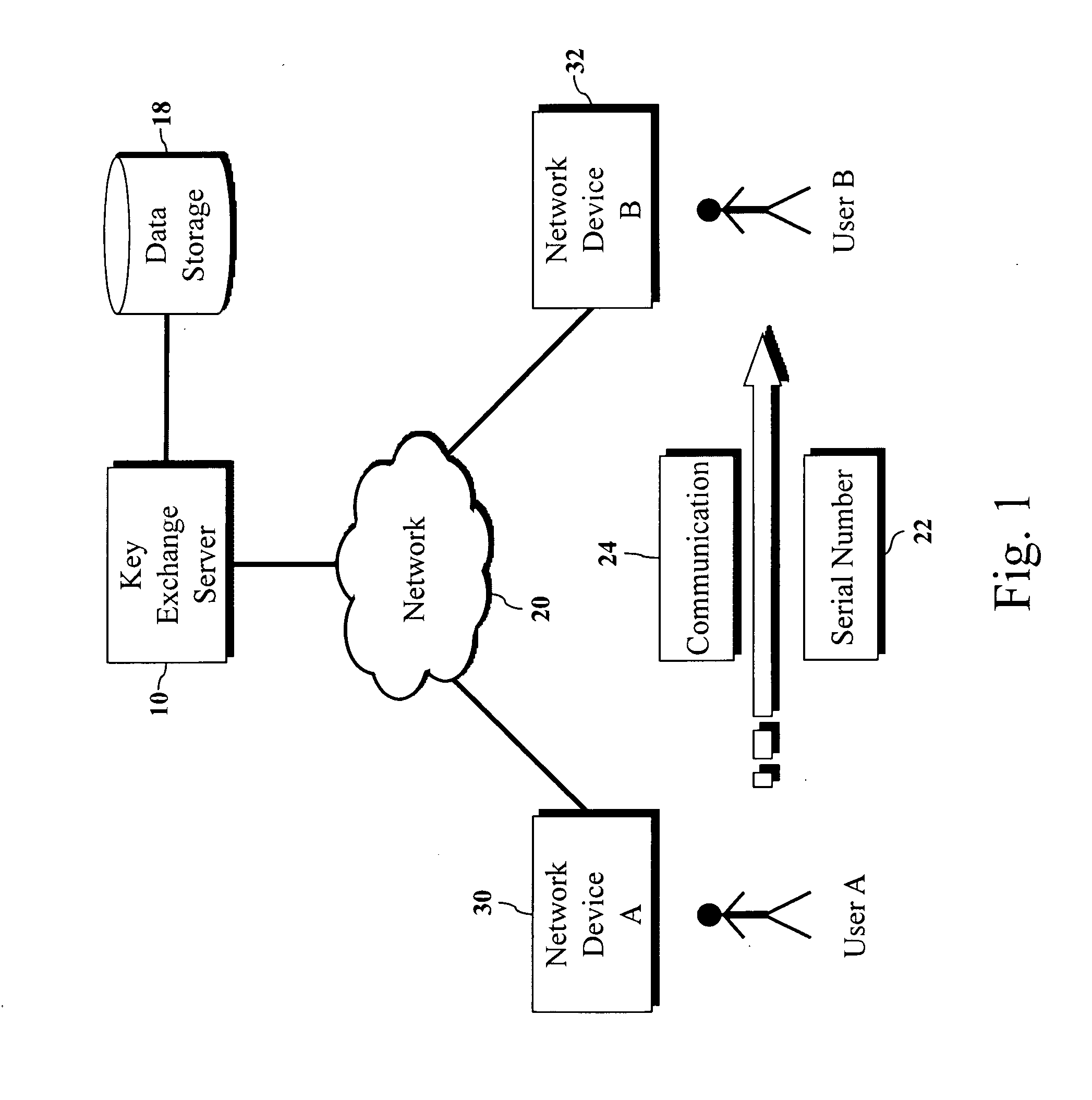
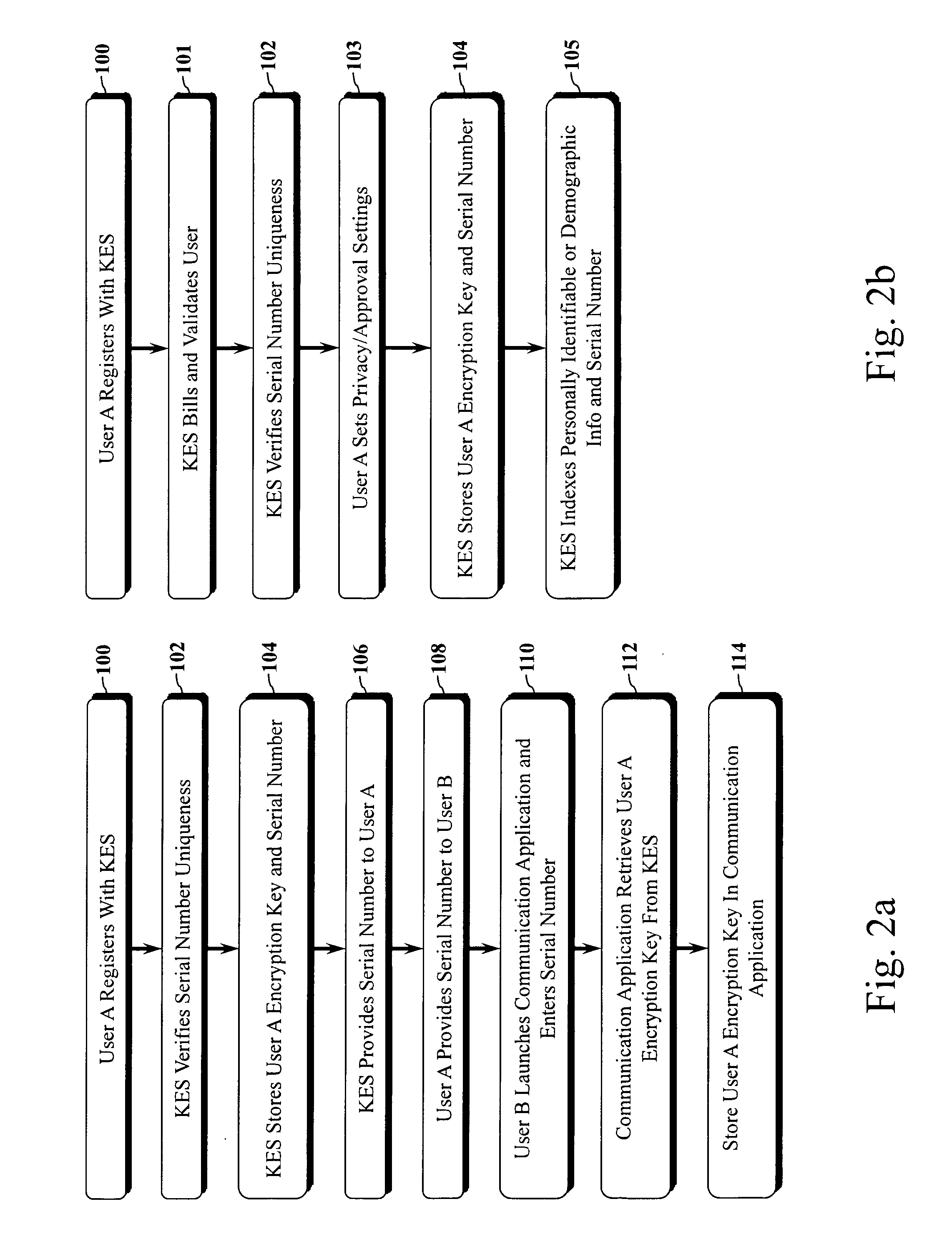
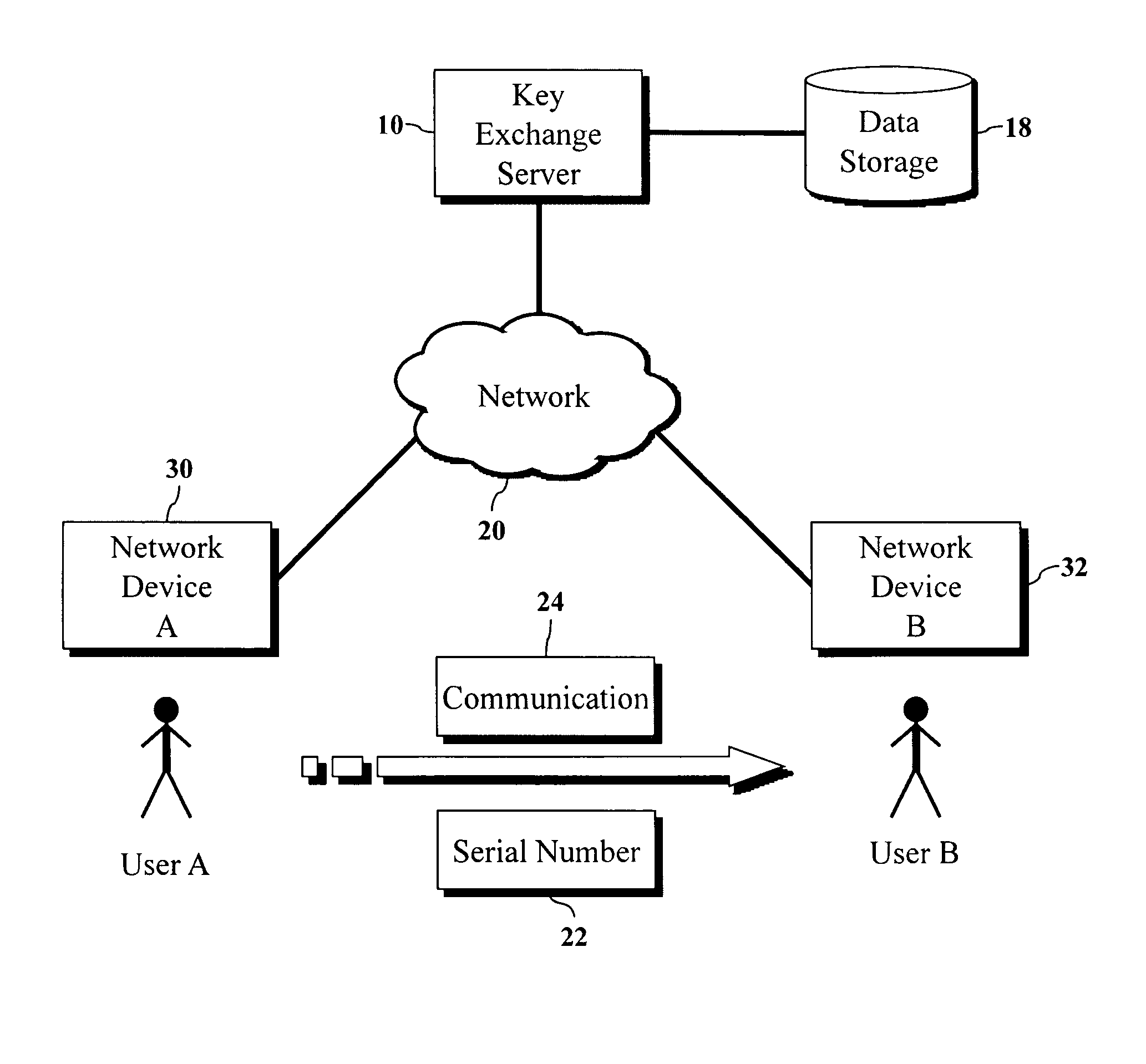
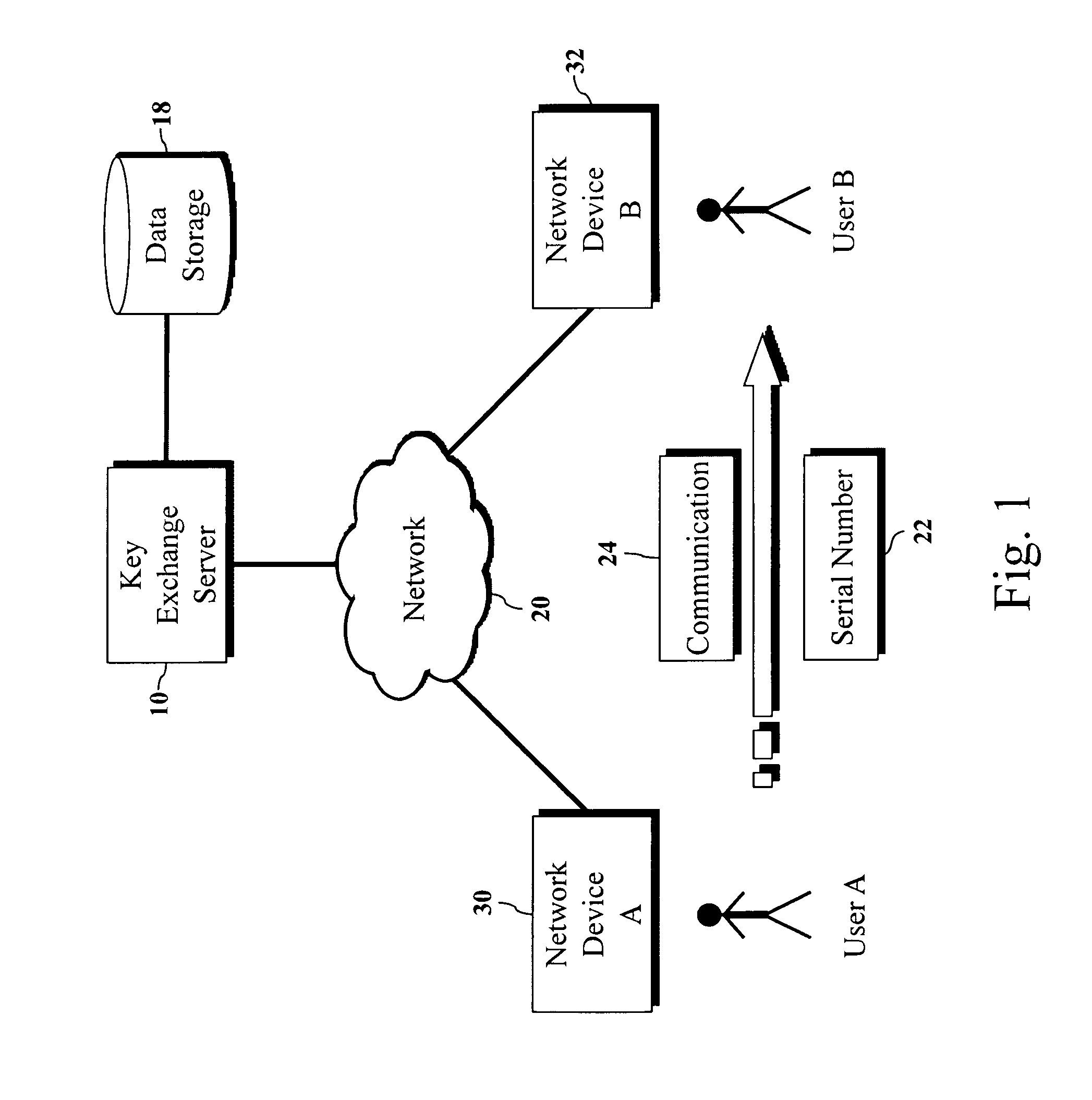
Encryption key exchange system and method
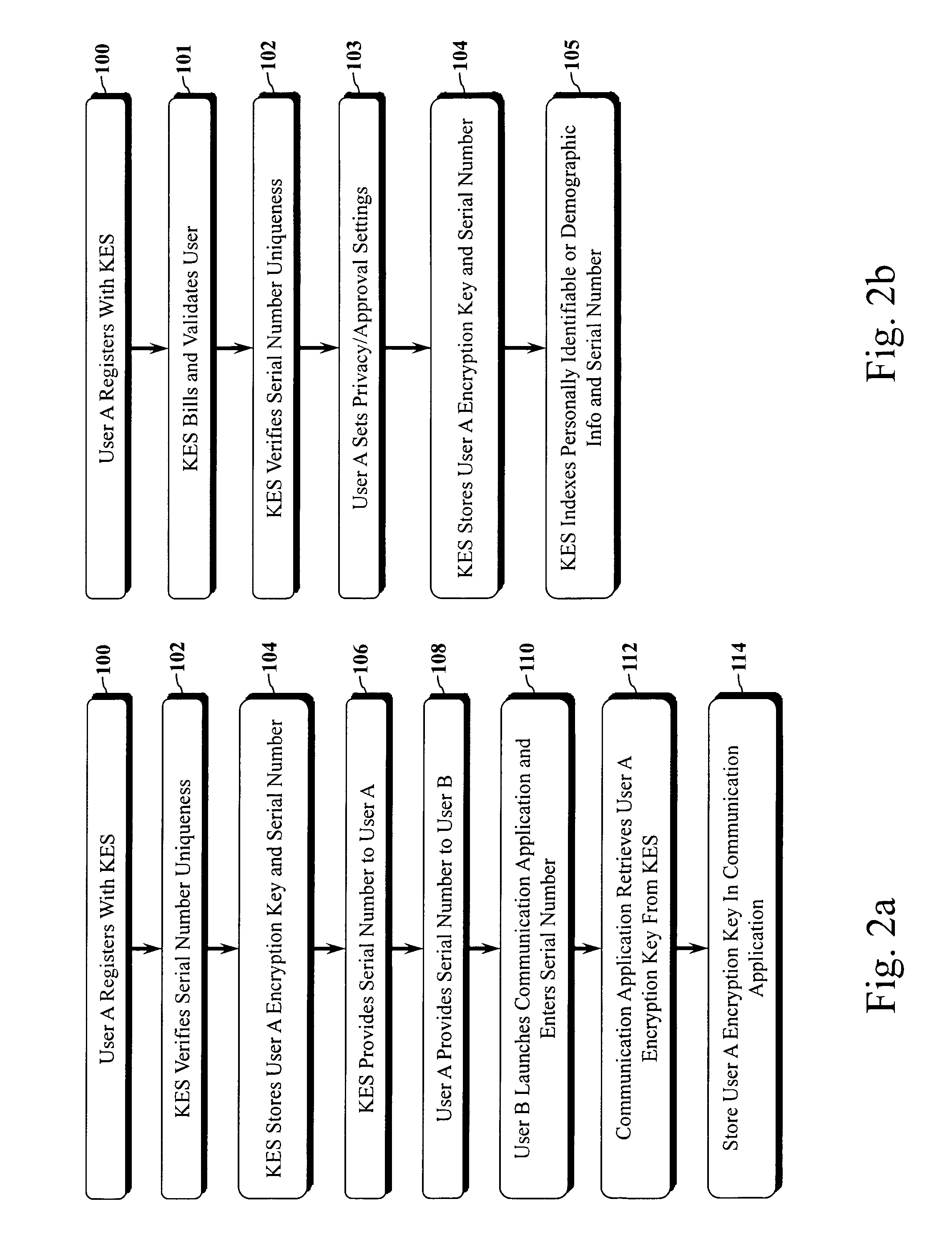
InactiveUS20120204032A1Improve usabilityUser identity/authority verificationPublic key infrastructure trust modelsUsabilityEncryption
The present invention is a computer-implemented key exchange system and methods for improving the usability of encryption technologies such as Public Key Infrastructure (PKI). One aspect of the present invention includes registering users, verifying user identity, and classifying users such that the users may send a communications such that communication recipients can verify the user identity and classification of the communication sender. Another aspect of the present invention includes users initiating relationships with other users, approving the establishment of relationships, and exchanging encryption keys between users after the establishment of a relationship.
Owner:SYNC UP TECH
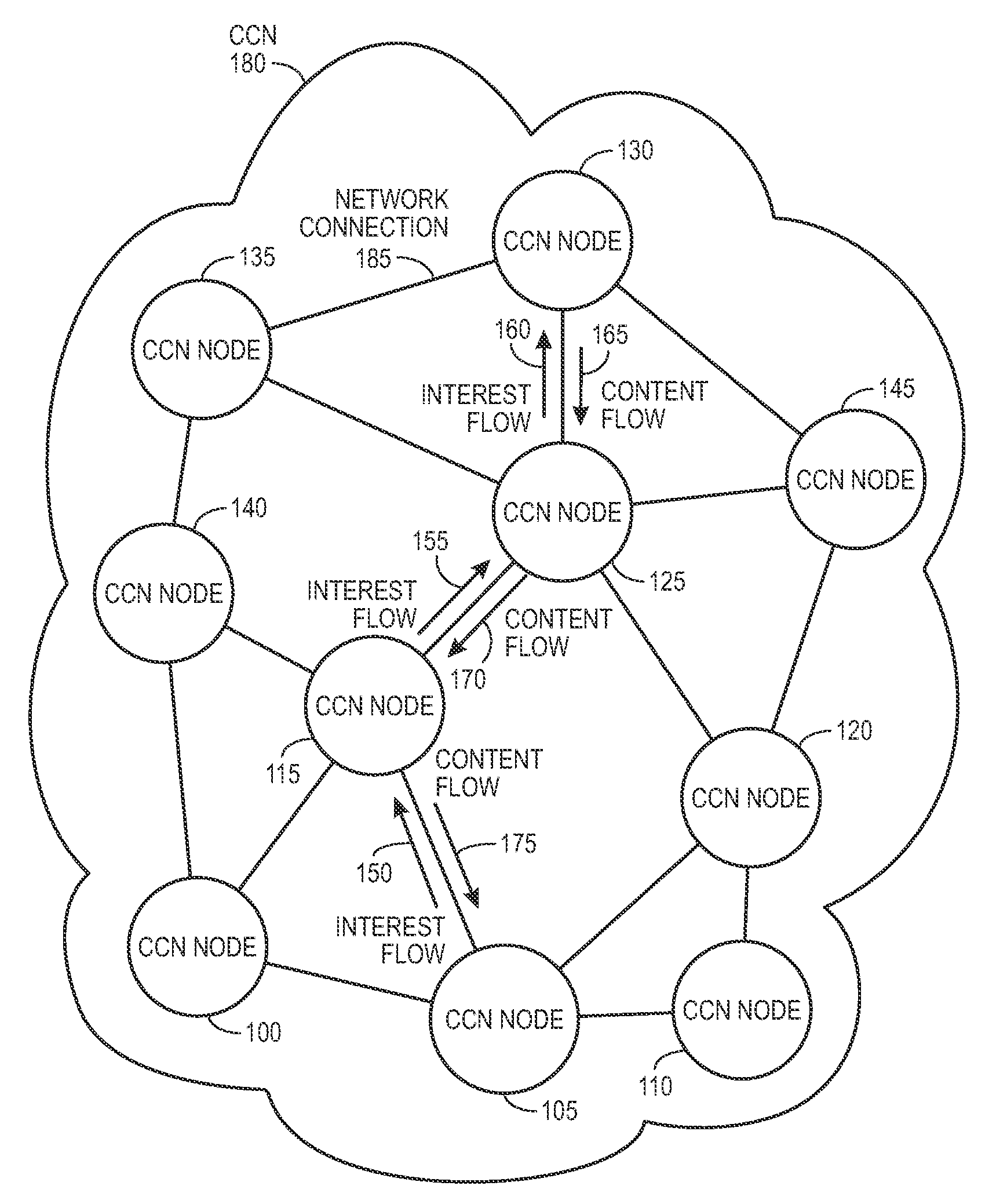
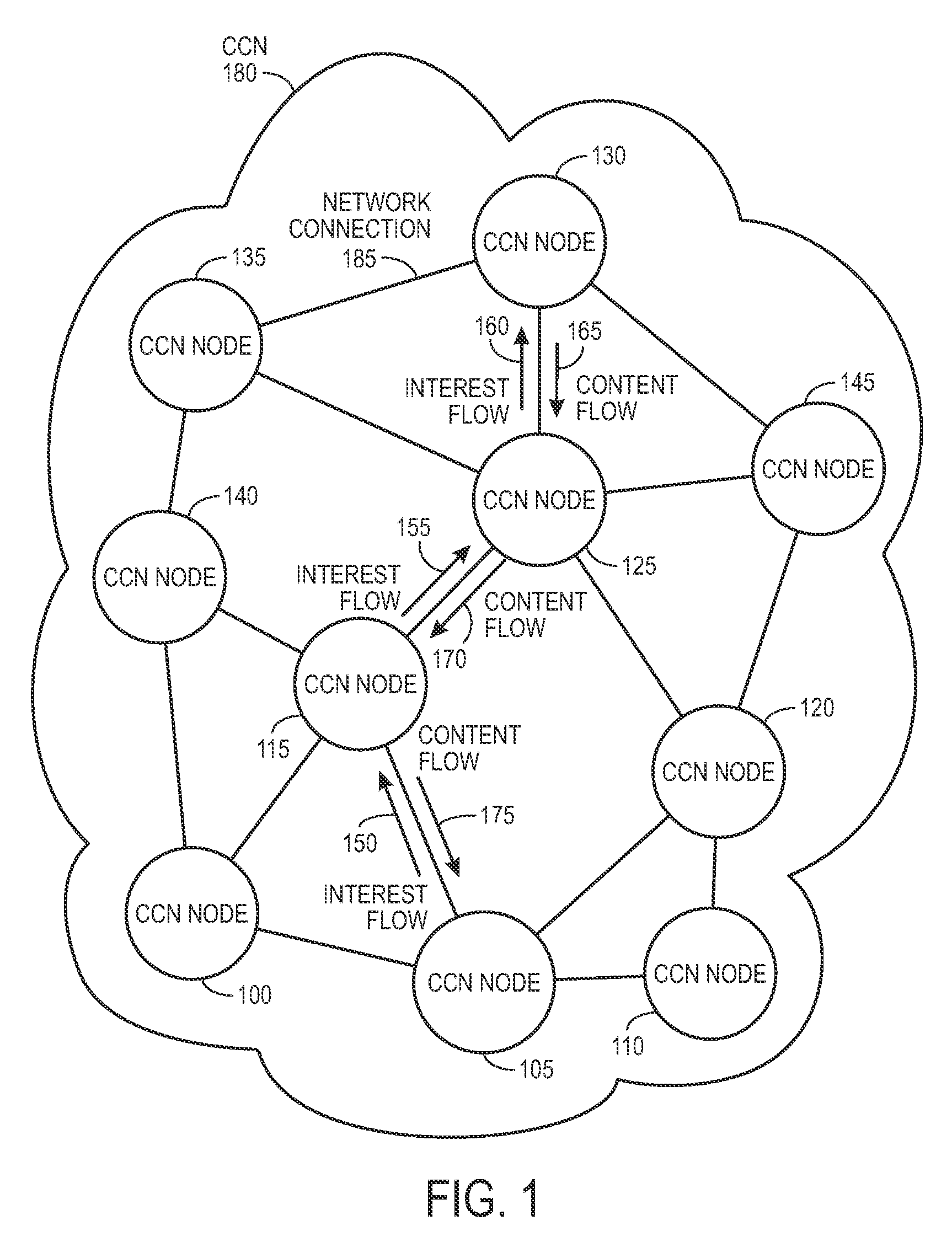
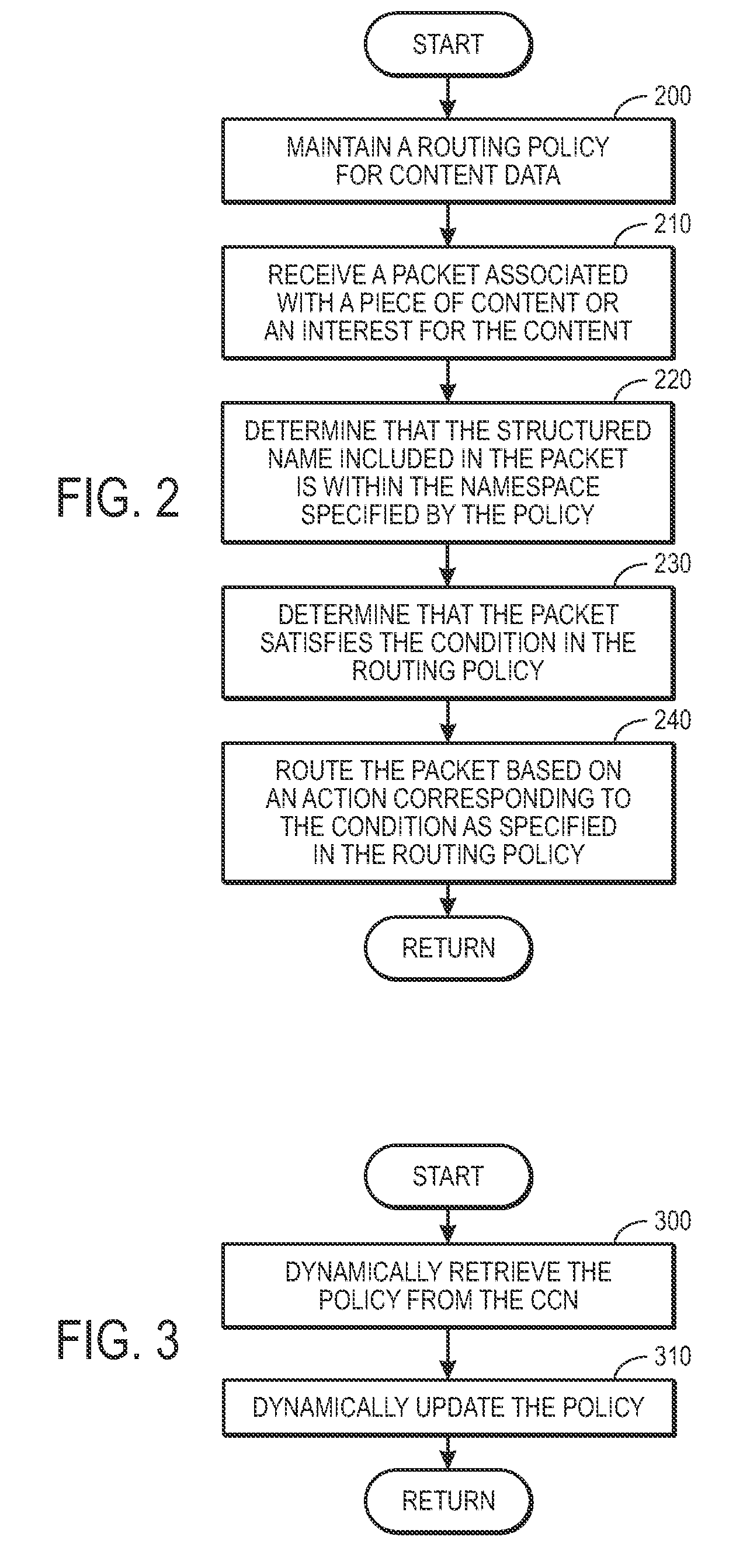
Controlling the spread of interests and content in a content centric network
ActiveUS20090288163A1Easy flow controlExpected levelMemory loss protectionMultiple keys/algorithms usageContent centricSystem maintenance
One embodiment of the present invention provides a system for controlling the spread of interests and content in a content centric network (CCN). During operation, the system maintains a routing policy for content data. The system also receives a packet associated with a piece of content or an interest for the content. Next, the system determines that the structured name included in the packet is within the namespace specified in the routing policy. The system further determines that the packet satisfies the condition in the routing policy. Subsequently, the system routes the packet based on in part the action corresponding to the condition as specified in the routing policy.
Owner:CISCO TECH INC
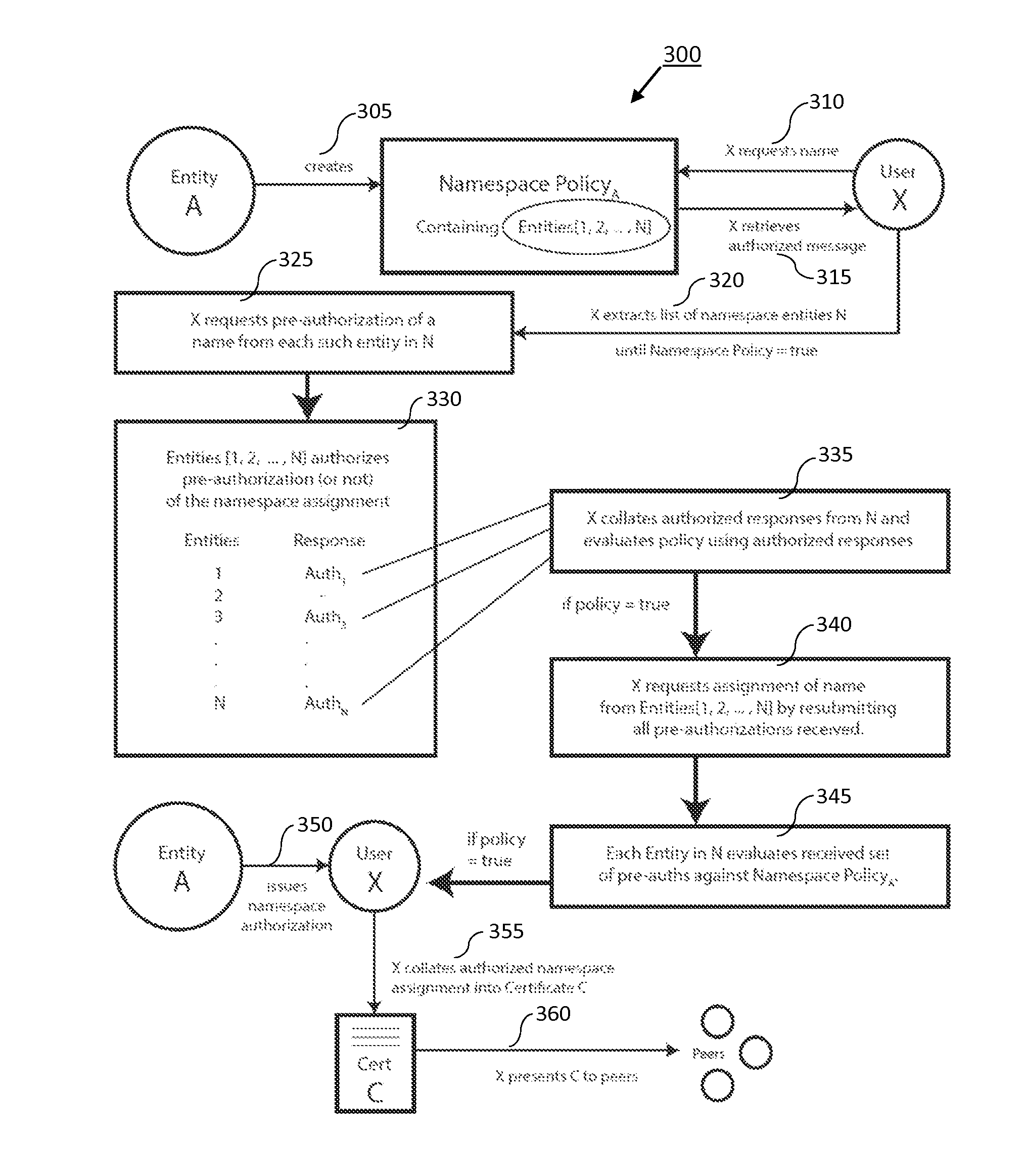
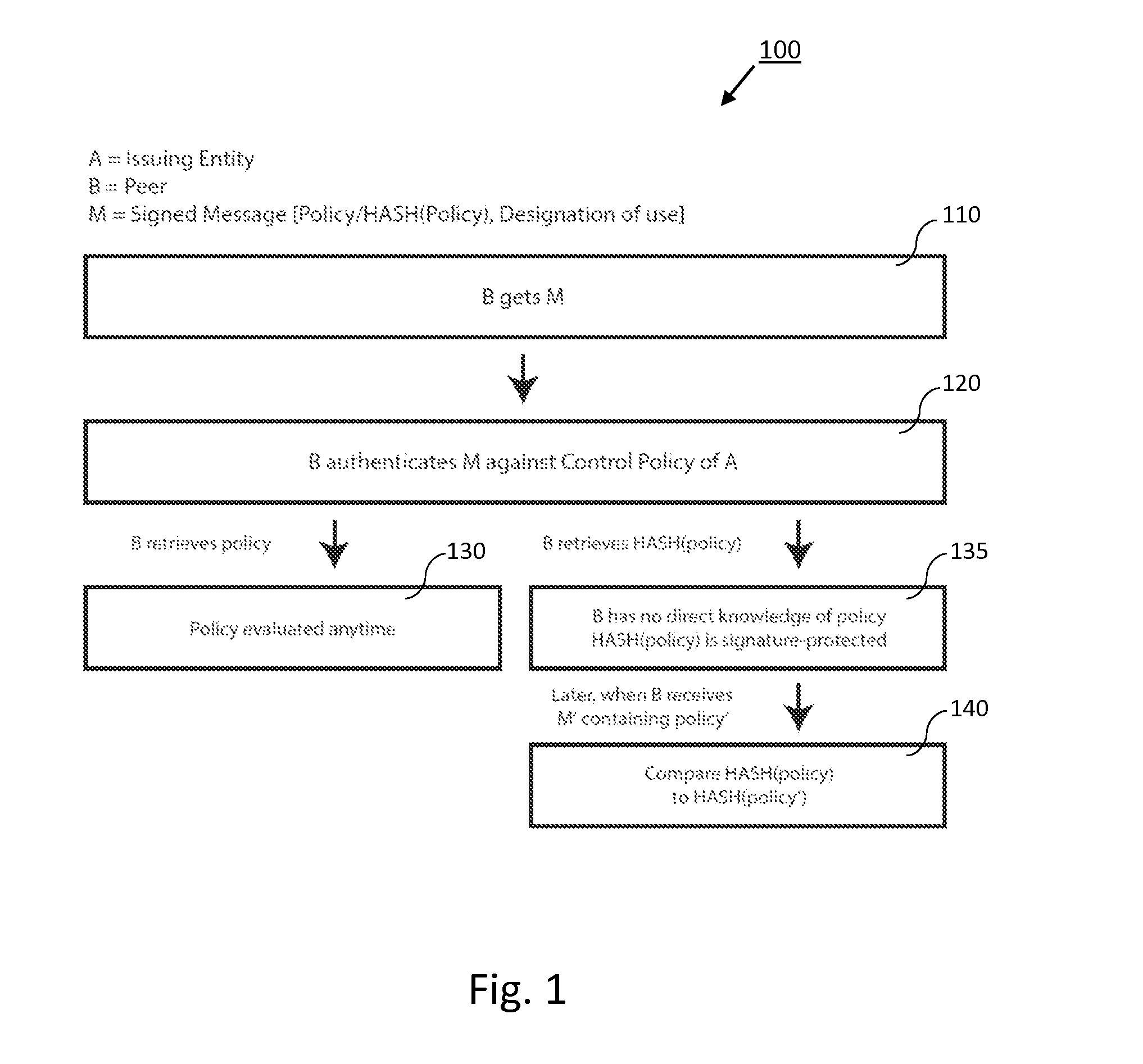
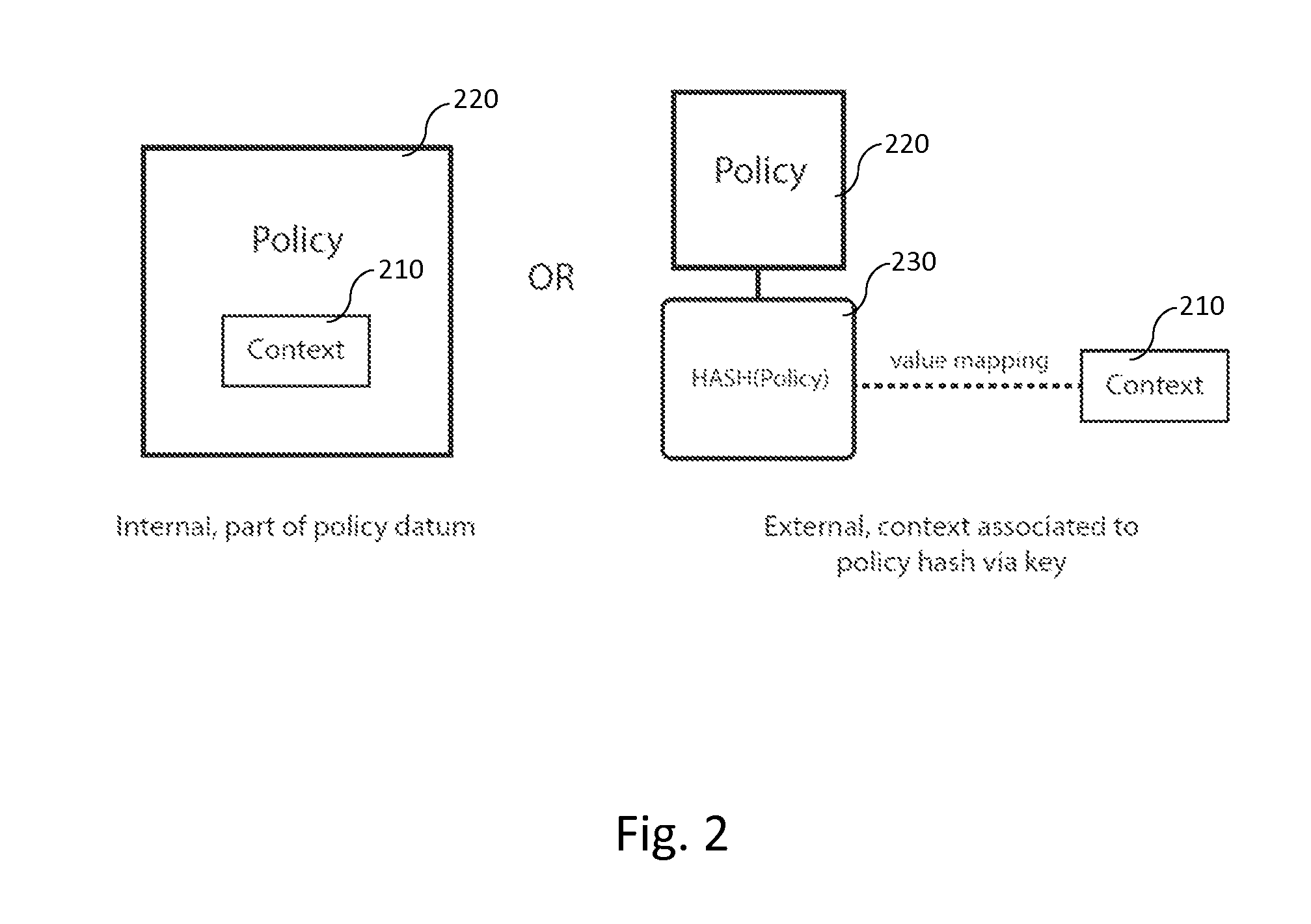
Generalized entity network translation (GENT)
ActiveUS20150244690A1Many choicesGood conditionUser identity/authority verificationPublic key infrastructure trust modelsSystem integrationRoot certificate
Generalized Entity Network Translation provides new state of the art methodology for extending RKI techniques into a truly generalized framework capable of operating at exceptional levels of authenticity without the need for roots, certificate authorities, or other static points in an infrastructure. More astounding is its ability to create trusted authentic entity relationships that require no externally stored state outside of the shared context between discrete peers. The present invention provides, among other things, novel improvements to blockchain-derived systems and provides strong proof of ownership, renewal, roll-backs, and localized state and many blockchain systems more palatable choices for system integration.
Owner:ENT TECH
Network message generation for automated authentication
ActiveUS8819253B2Avoids presentationImprove user experienceDigital data processing detailsUser identity/authority verificationUser deviceNetwork generation
A message generation mechanism for a network interface is provided. The message generation mechanism is operable to generate a message which includes data for signing and authentication procedure instructions. The message is for conveying information to a user device for presentation to a user via a user interface of the user device. The data is arranged in the message in a manner which permits the user device to utilize the data in an automated signing procedure. The automated signing procedure may be a digital signing procedure. The data for signing may be random data, pseudo-random data or secure random data and may be arranged in the message in a manner which avoids presentation to the user.
Owner:ORACLE INT CORP
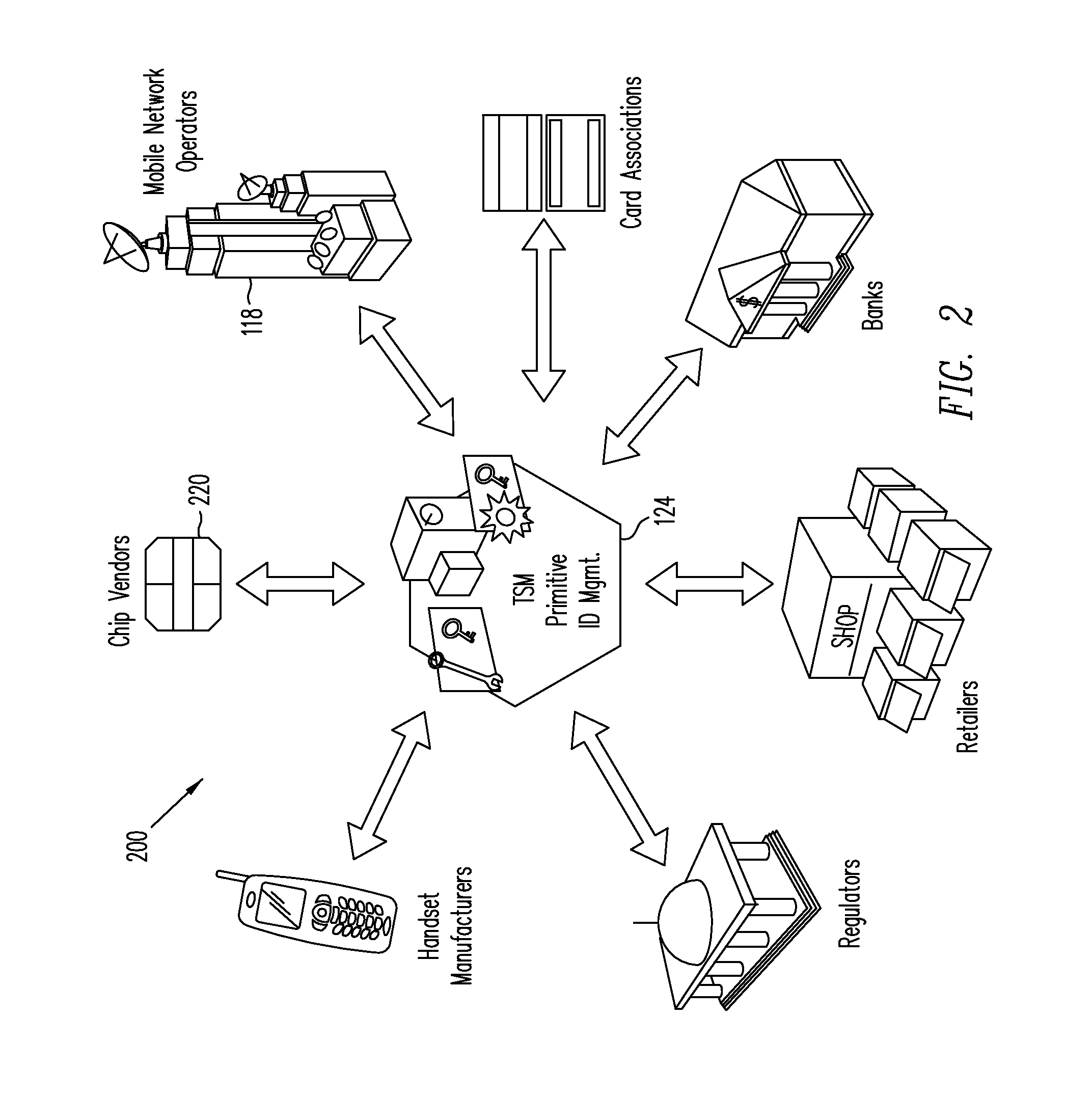
Trusted Integrity Manager (TIM)
A system for use with a trusted service manager (TSM) and a mobile device having a subscriber unique identifying data, according to one embodiment, includes: a server in which the server validates an application against the unique and identifying data of the mobile device and provides the validated application for the mobile device; and a secure element (SE) acting as a client in which the SE is present in the mobile device as client; the validated application from the server is installed in the SE; and the SE is adapted to execute the validated application to perform a service process. The service process includes enablement of payment functions on the mobile device, in which enablement of payment functions includes: providing secure communication between the mobile device and the server; secure provisioning of a payment instrument on the mobile device, wherein authentication and verification for the payment instrument on the mobile device is provided by the server; and binding the payment instruments and the validated application to the mobile device to provide a strong ID management for enhanced user protection and system security and integrity.
Owner:PAYPAL INC
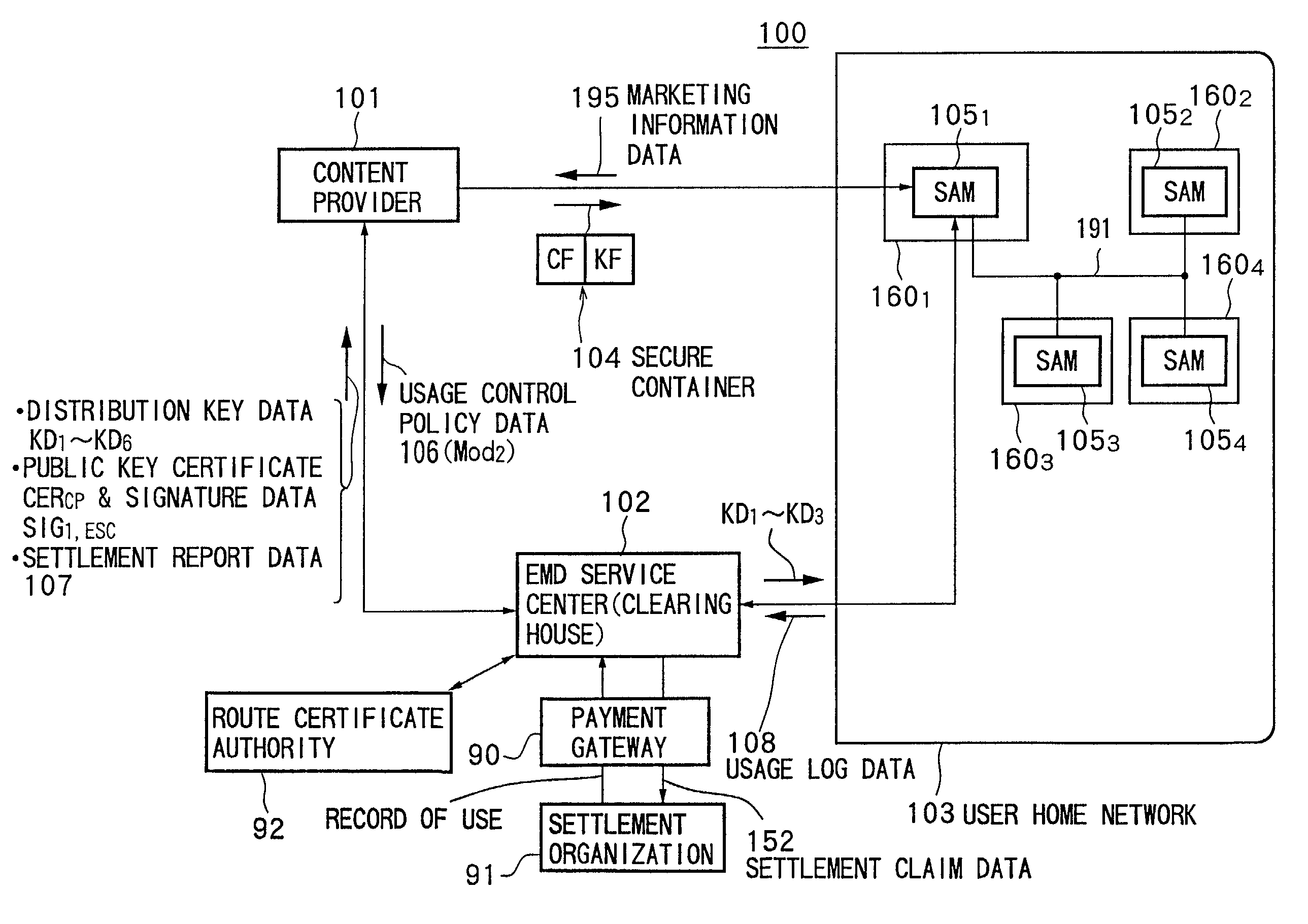
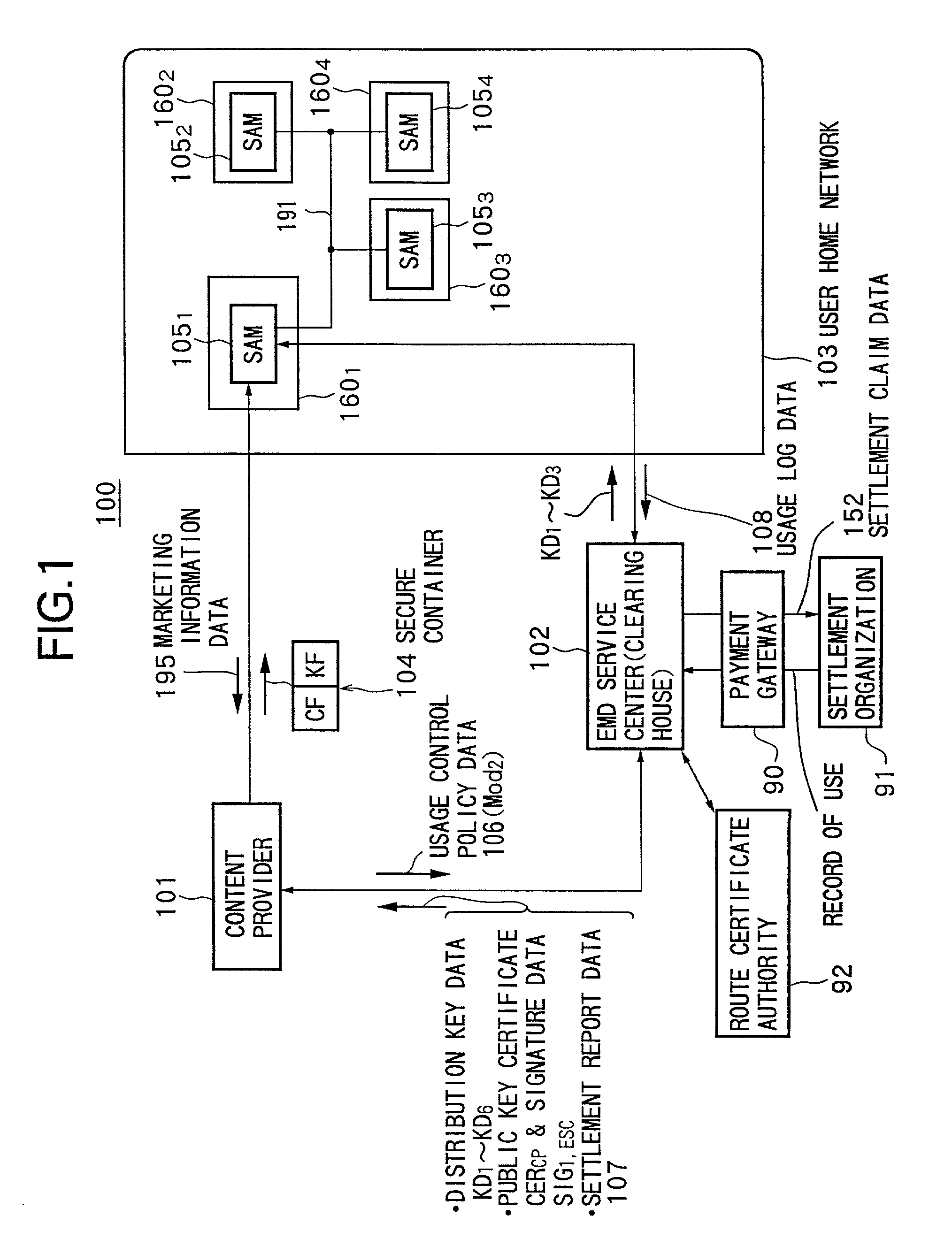
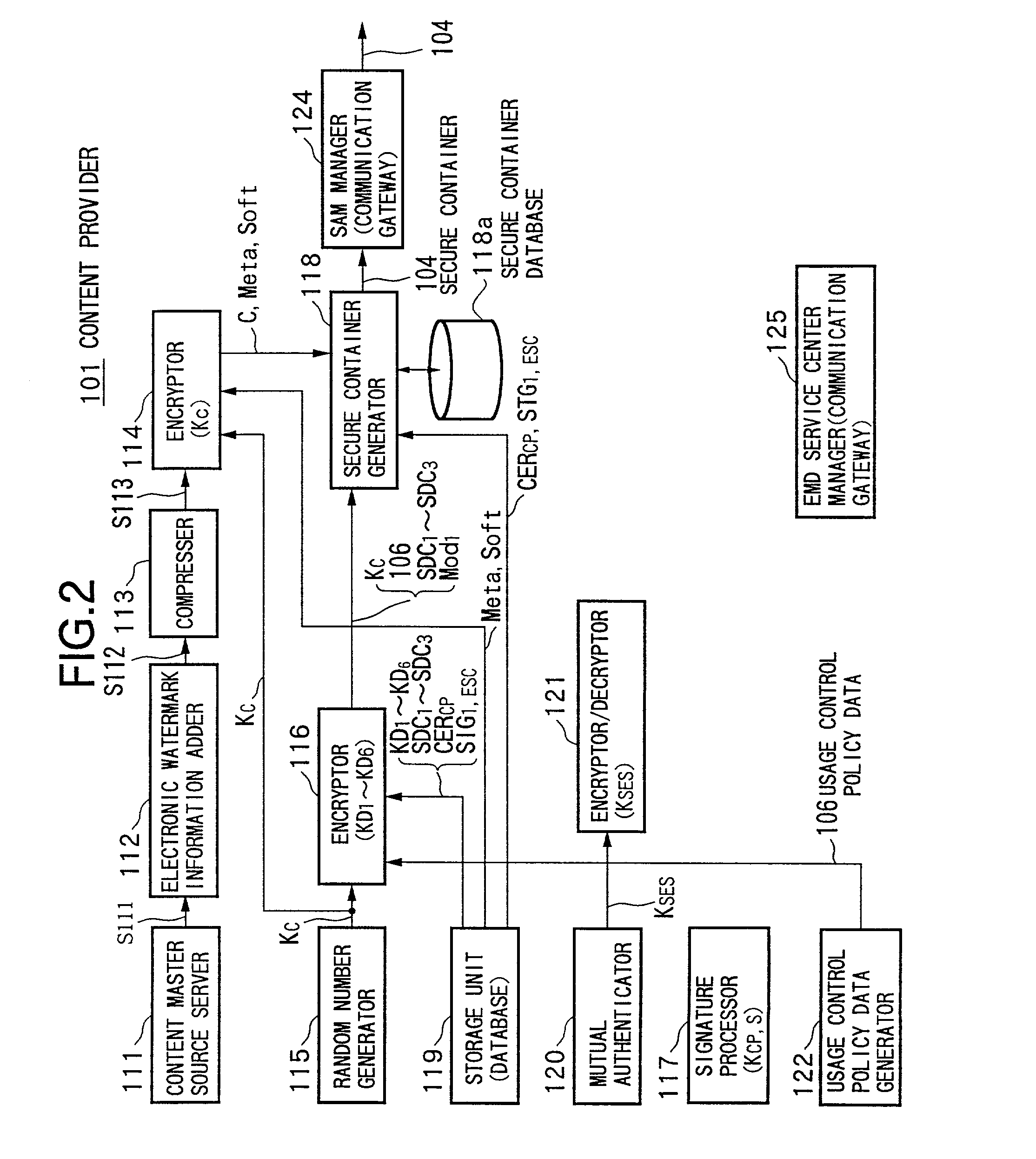
Data providing system, device, and method
InactiveUS7073073B1Reduce loadKey distribution for secure communicationDigital data processing detailsData storingData store
Owner:SONY CORP
Authentication card system
InactiveUS6990588B1Recognizable more easily and securelyUser identity/authority verificationCo-operative working arrangementsComputer terminalUser authentication
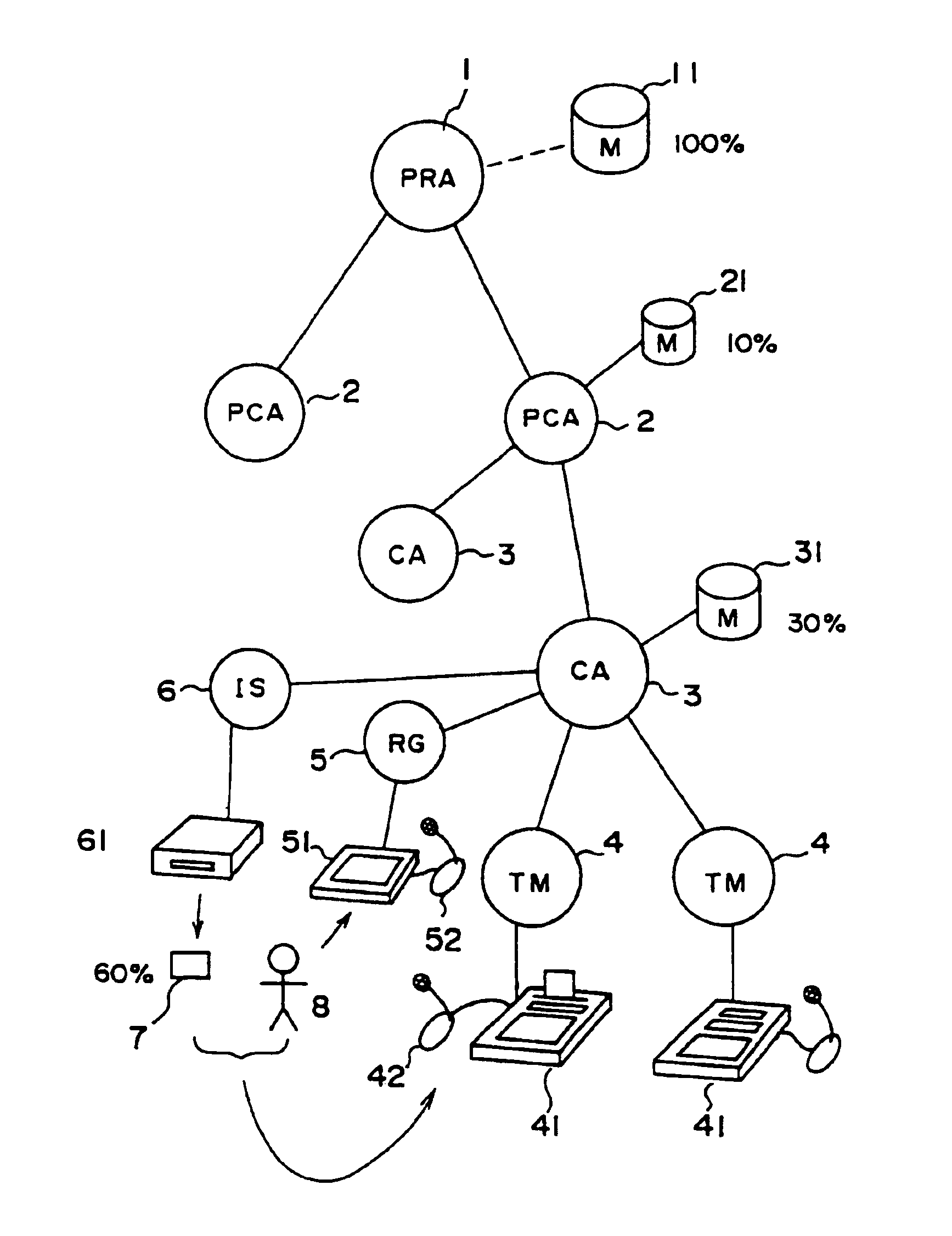
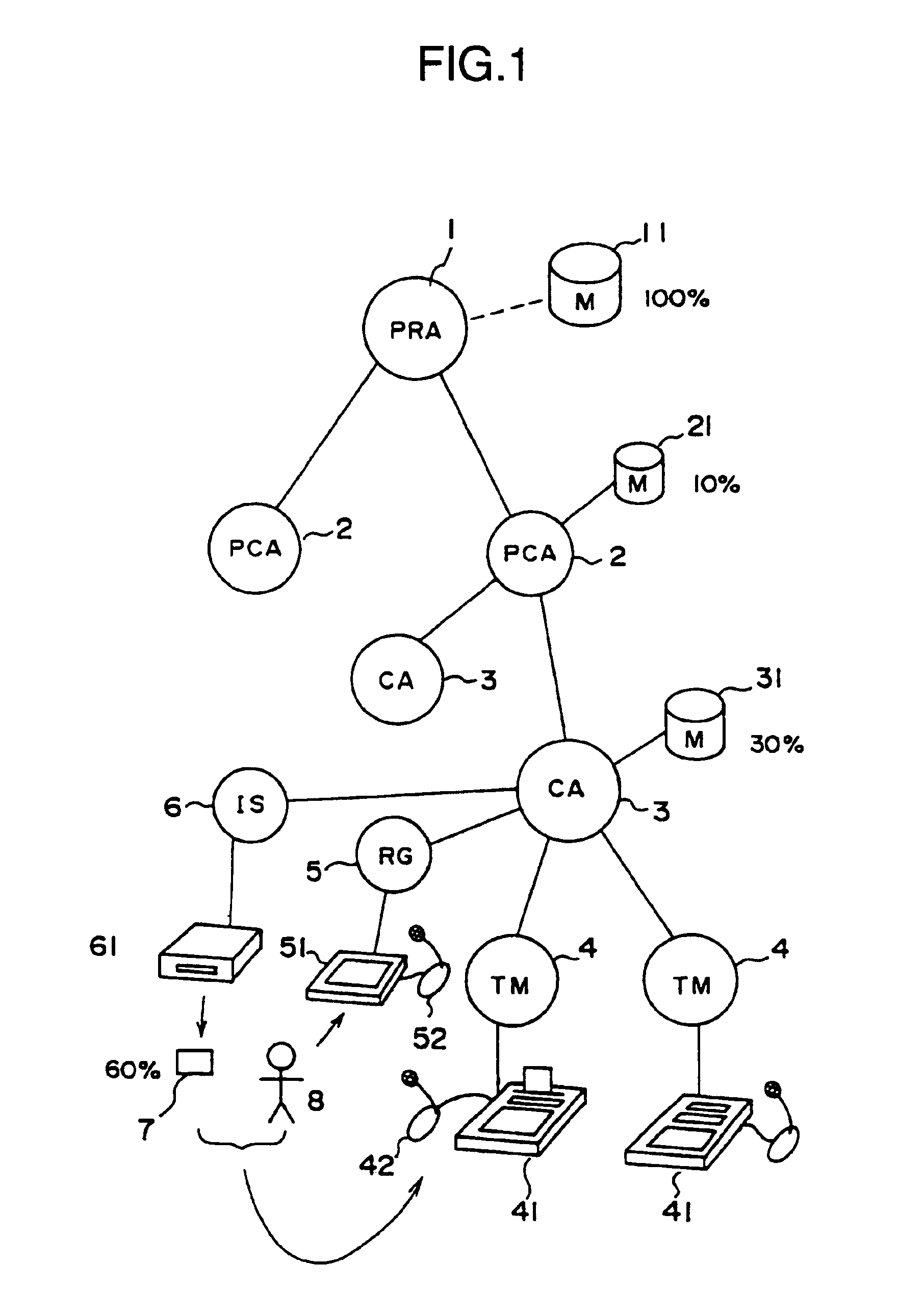
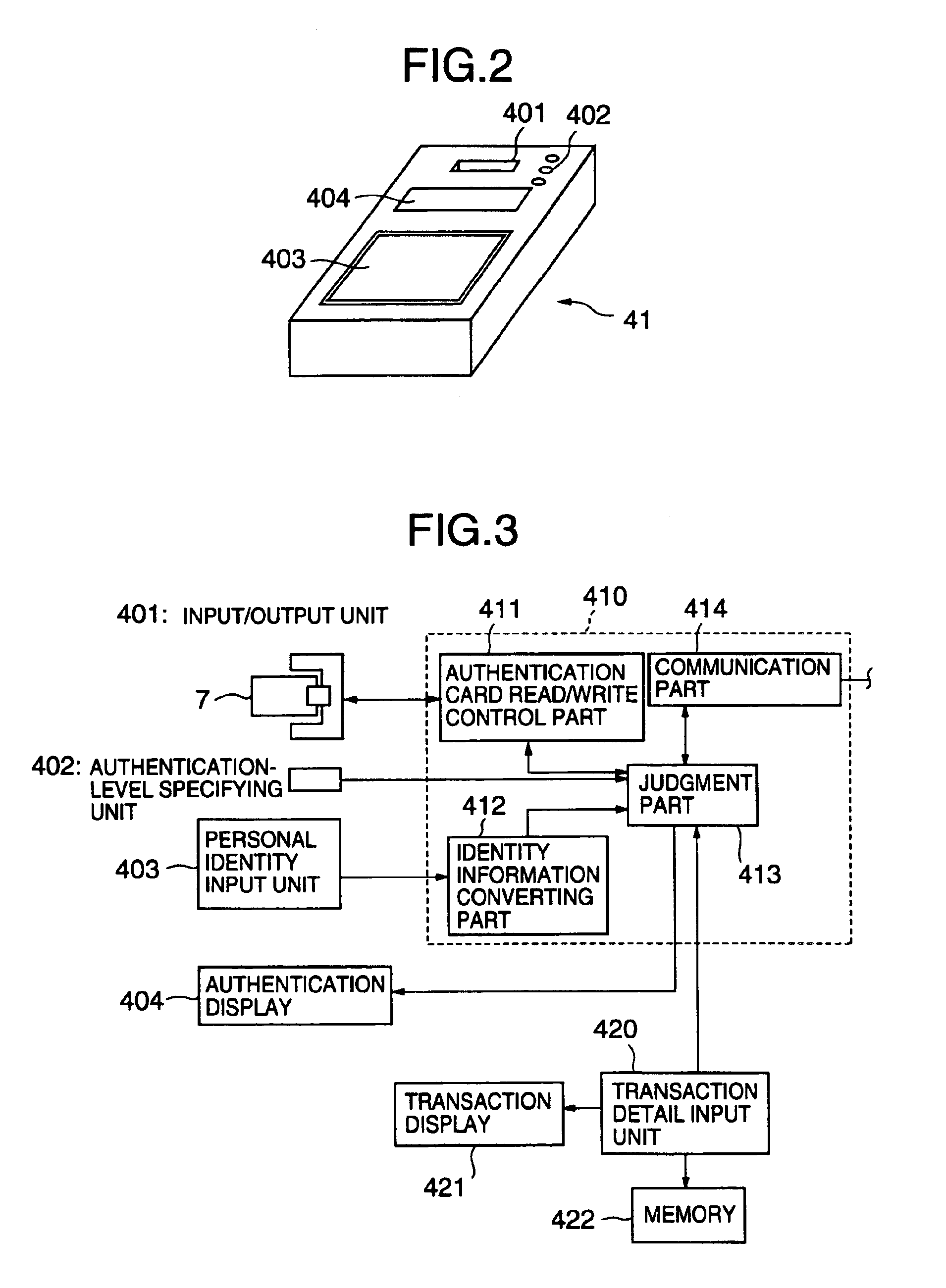
Biological individuality data for use in distinguishing the individuality of a user (8) are picked up, and a user authentication card (7) with at least part of the biological individuality data recorded thereon is issued. The contents of the record in the user authentication card (7) are read out by an authentication-card reader (41), and compared with biological individuality data input by the user through an identity acquisition device. Such personal authentication is directly executed at an authentication access terminal (4). The system also includes certification authorities (2), (3), each of which records part of the biological individuality data so that the certification authorities can additionally authenticate personal identification in response to inquiry from the authentication access terminal (4), thus improving the reliability. The authentication IC card used in the system is provided with a CPU, an authentication file storing identity information, and an application file classified into files according to the depth of authentication.
Owner:YASUKURA YUTAKA
Security system for handheld wireless devices using-time variable encryption keys
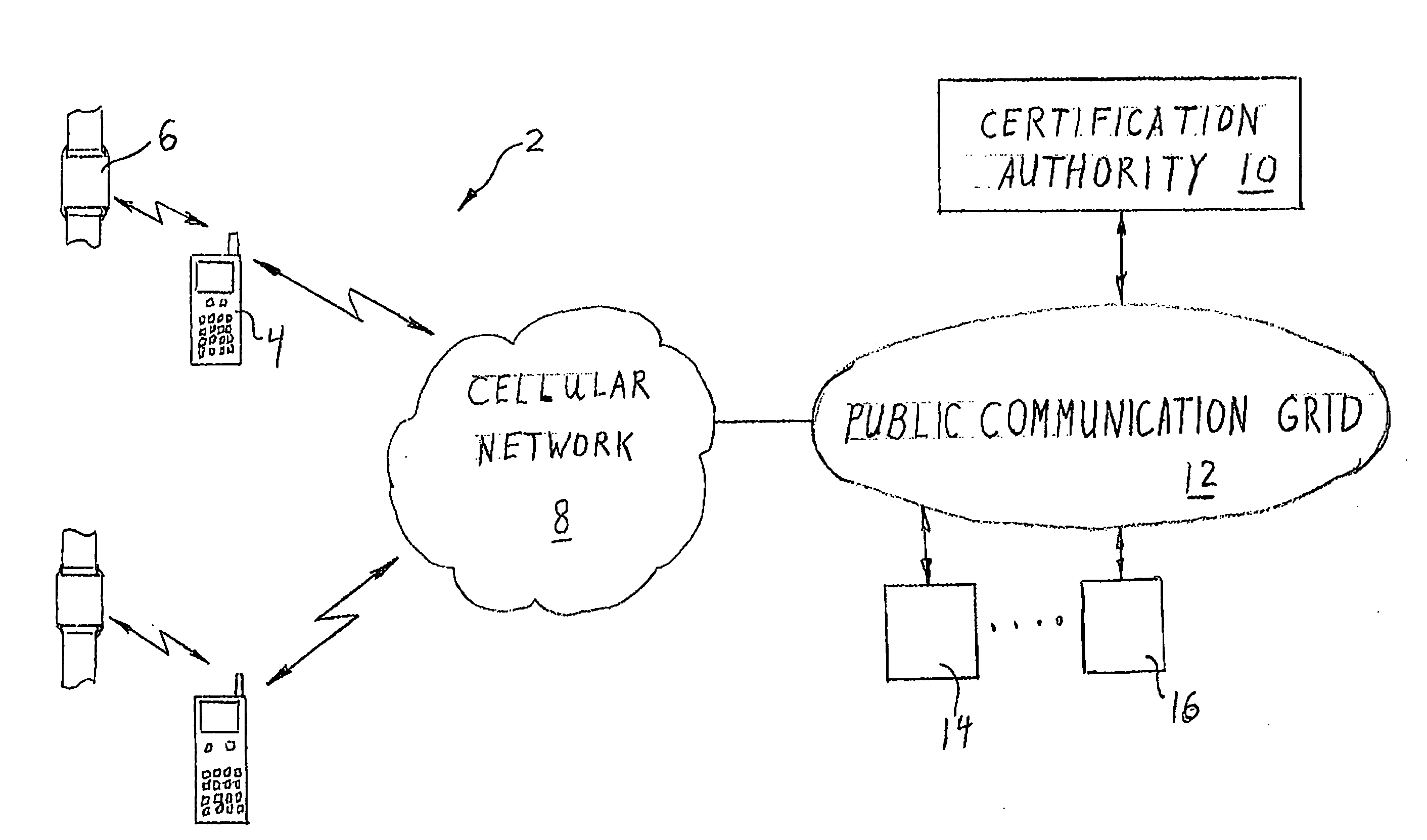
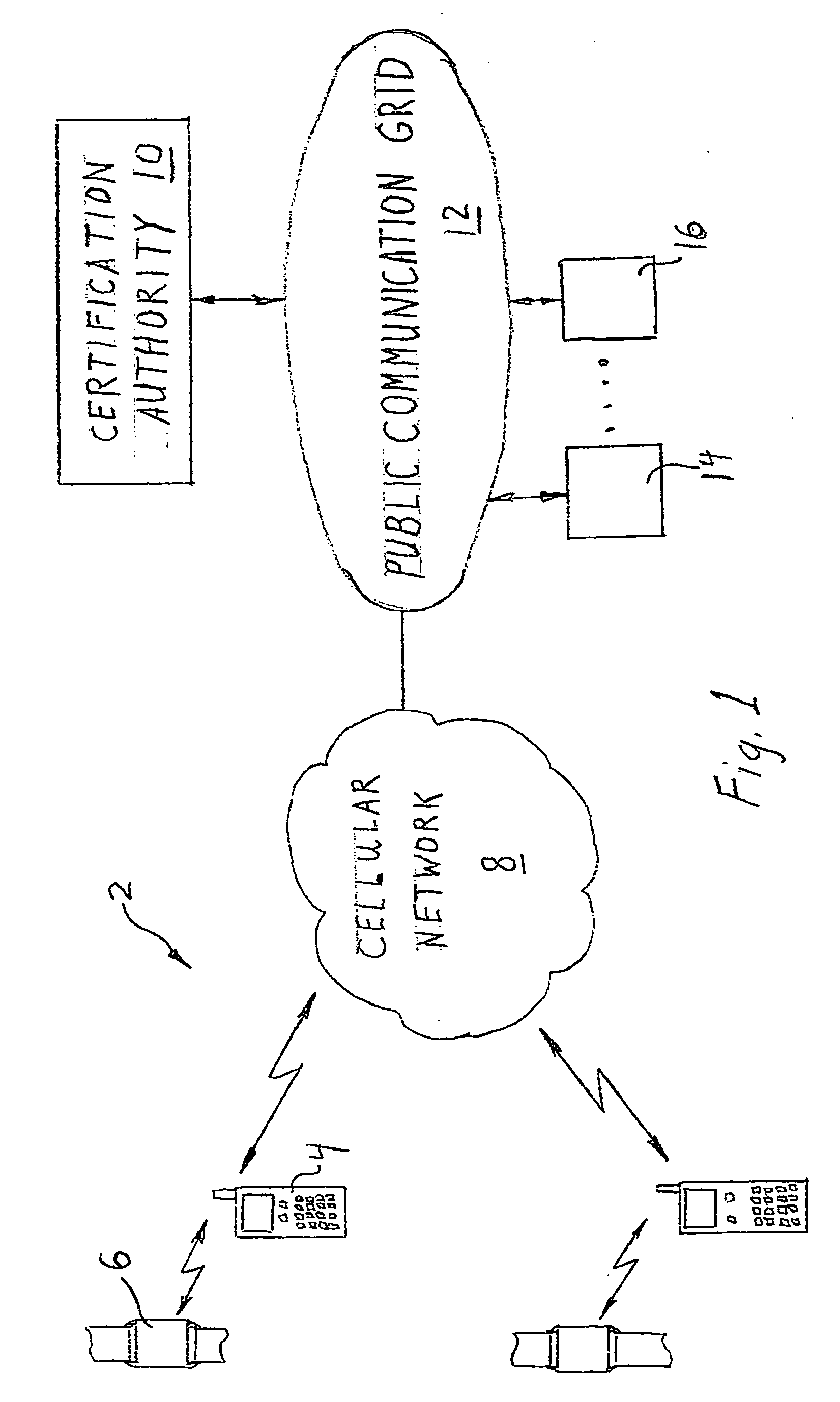
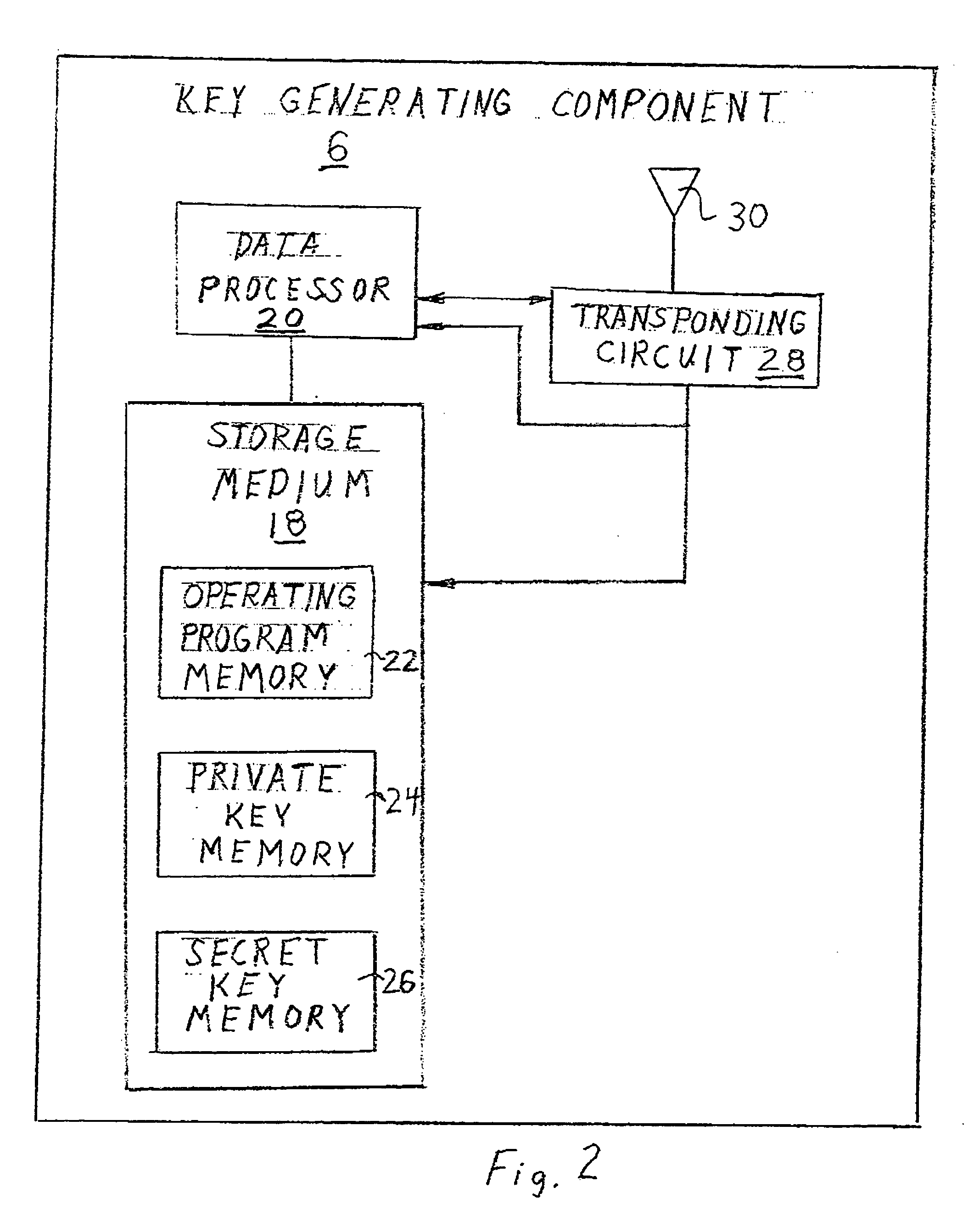
ActiveUS20080022089A1Least costOperational securityNetwork topologiesPublic key infrastructure trust modelsCommunications systemWireless broadcasting
In one embodiment, the invention provides a portable wireless personal communication system for cooperating with a remote certification authority to employ time variable secure key information pursuant to a predetermined encryption algorithm to facilitate convenient, secure encrypted communication. The disclosed system includes a wireless handset, such as PDA, smartphone, cellular telephone or the like, characterized by a relatively robust data processing capability and a body mounted key generating component which is adapted to be mounted on an individual's body, in a permanent or semi-permanent manner, for wirelessly broadcasting, within the immediate proximity of the individual, a secret or private key identifying signal corresponding to a time variable secure key information under the control of the certification authority. The key identifying signal is generated in a format that facilitates secure wireless communication with the individual in accordance with a predetermined encryption algorithm including a PKI encryption algorithm. The disclosed system may be used with a console for coordinating access to a variety of different communication system and networks.
Owner:MLR
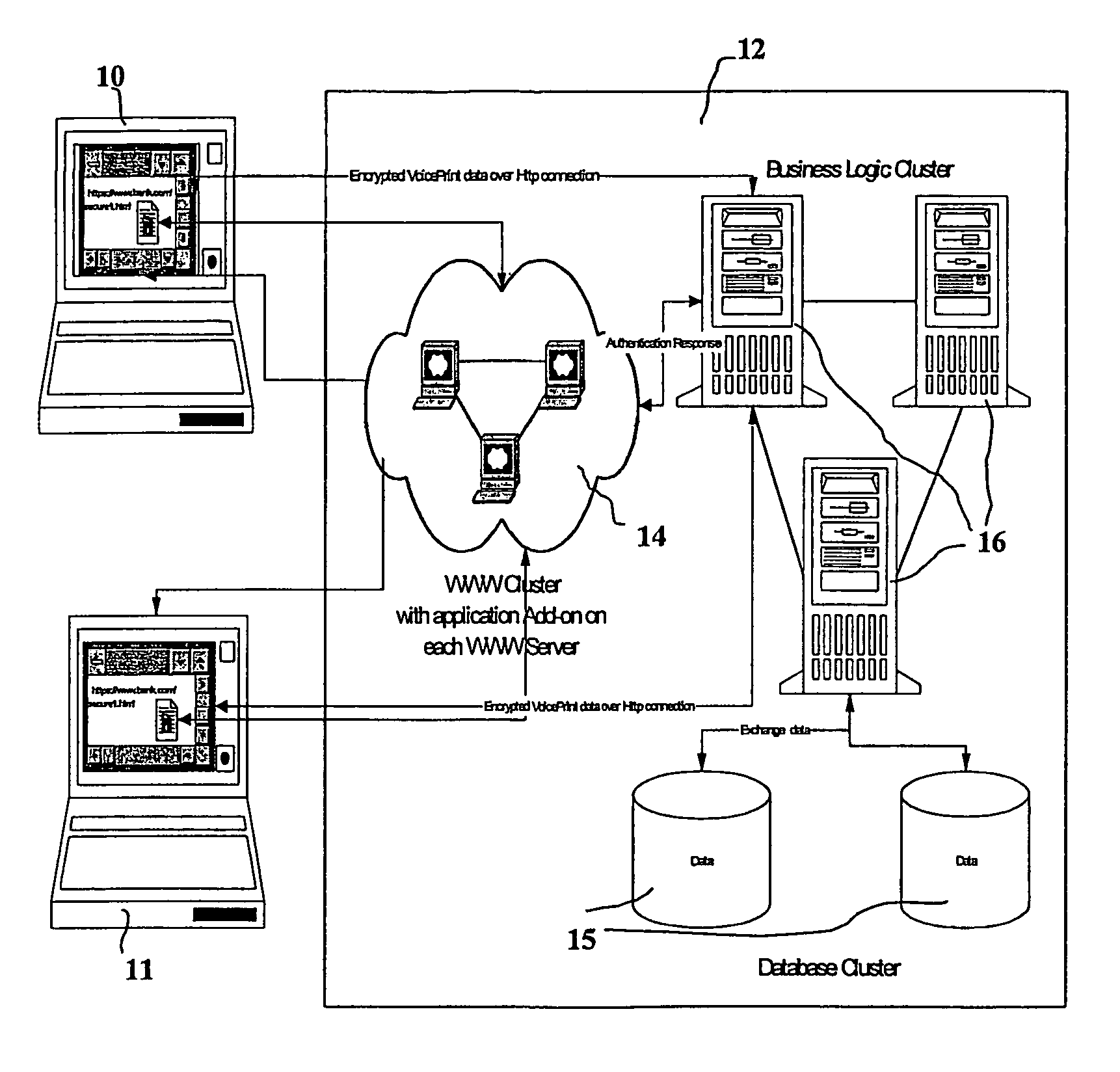
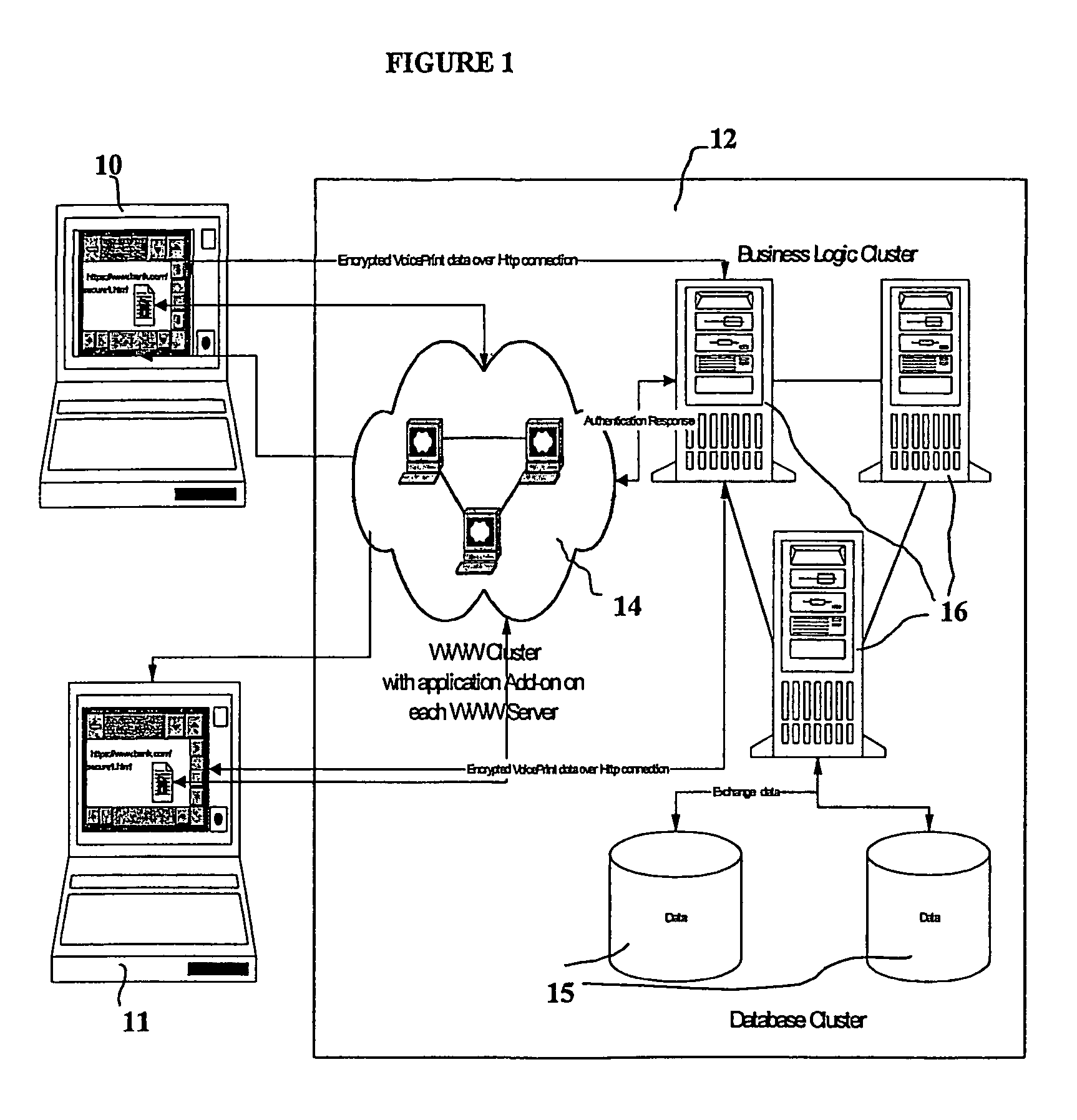
Biometric-based system and method for enabling authentication of electronic messages sent over a network
InactiveUS7689832B2Digital data processing detailsUser identity/authority verificationReal time validationData authenticity
A network based mechanism for real time verification and authentication of data and user identities. The present invention enables a method whereby biometric elements, such as voice prints, are utilized to enhance the Public Key Infrastructure as a means to decrypt data and verify data authenticity, such that the user's private key is authenticated remotely on a one-time basis. The present invention comprises an authentication server (25) with various software modules that enable authentication of user identity, secure user access to data, digital signatures, secure messaging and secure online transactions.
Owner:SENTRYCOM
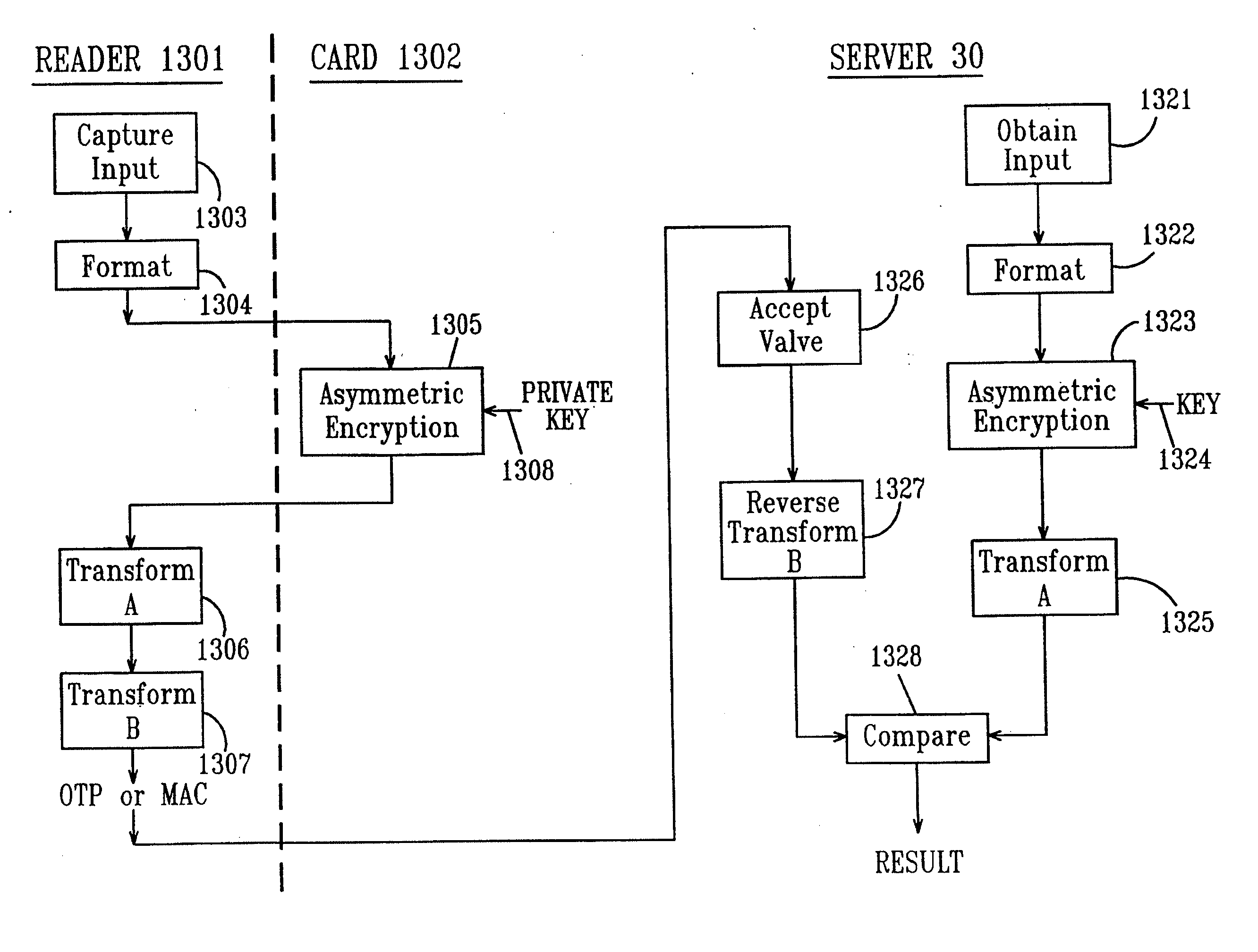
Remote authentication and transaction signatures
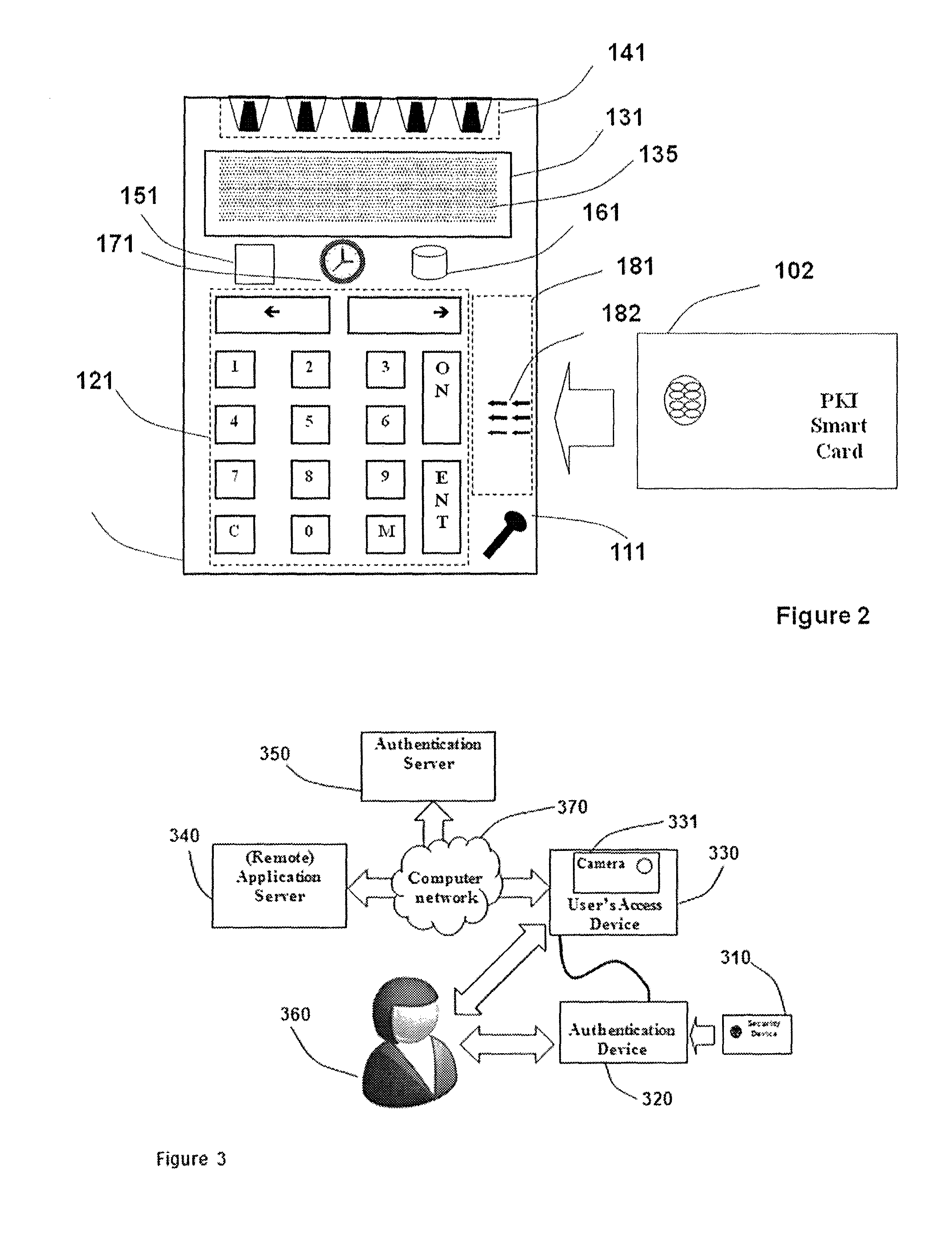
InactiveUS20110258452A1Simple ideaUser identity/authority verificationPayment architecturePersonalizationSmart card
The invention provides a method, apparatus, computer readable medium and signal which allows the usage of devices containing PKI private keys such as PKI-enabled smart cards or USB sticks to authenticate users and to sign transactions. The authenticity of the user and / or the message is verified. Furthermore the operation (authentication and / or signing) occurs without the need for an application to have some kind of a direct or indirect digital connection with the device containing the private key. In addition the operation occurs without the need for the PKI-enabled device containing the private key (e.g. a PKI smart card or USB stick) to either support symmetric cryptographic operations or to have been personalized with some secret or confidential data element that can be read by a suitable reader.
Owner:ONESPAN NORTH AMERICA INC
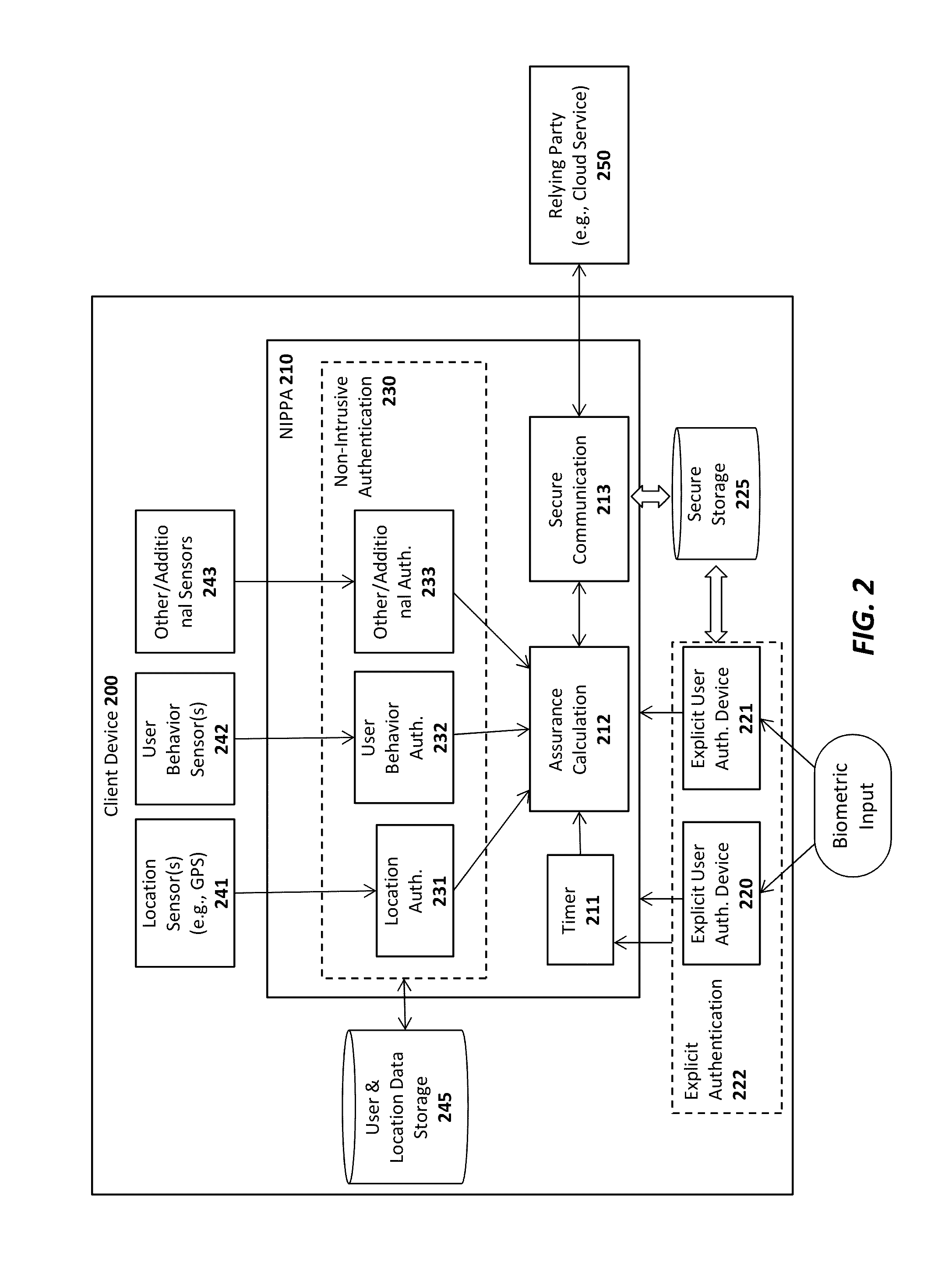
Access Control Through Multifactor Authentication with Multimodal Biometrics
ActiveUS20150347734A1Safe storageImprove securityDigital data processing detailsUser identity/authority verificationThe InternetFinancial transaction
A system is provided in which a person may use a Cellular (Mobile) Telephone, a PDA or any other handheld computer to make a purchase. This is an example only. The process may entail any type of transaction which requires authentication, such as any financial transaction, any access control (to account information, etc.), and any physical access scenario such as doubling for a passport or an access key to a restricted area (office, vault, etc.). It may also be used to conduct remote transactions such as those conducted on the Internet (E-Commerce, account access, etc.). In the process, a multifactor authentication is used.
Owner:BEIGI HOMAYOON
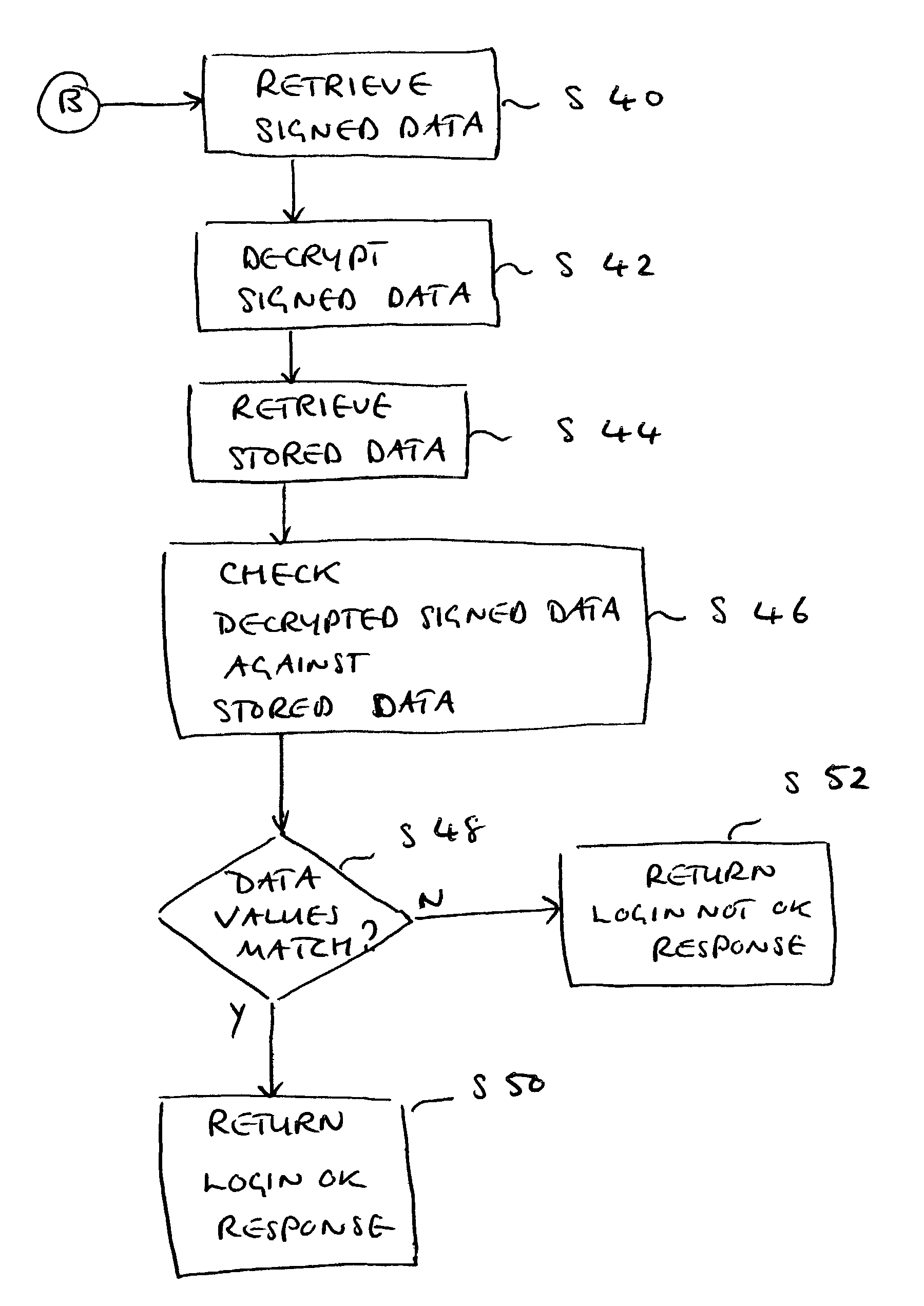
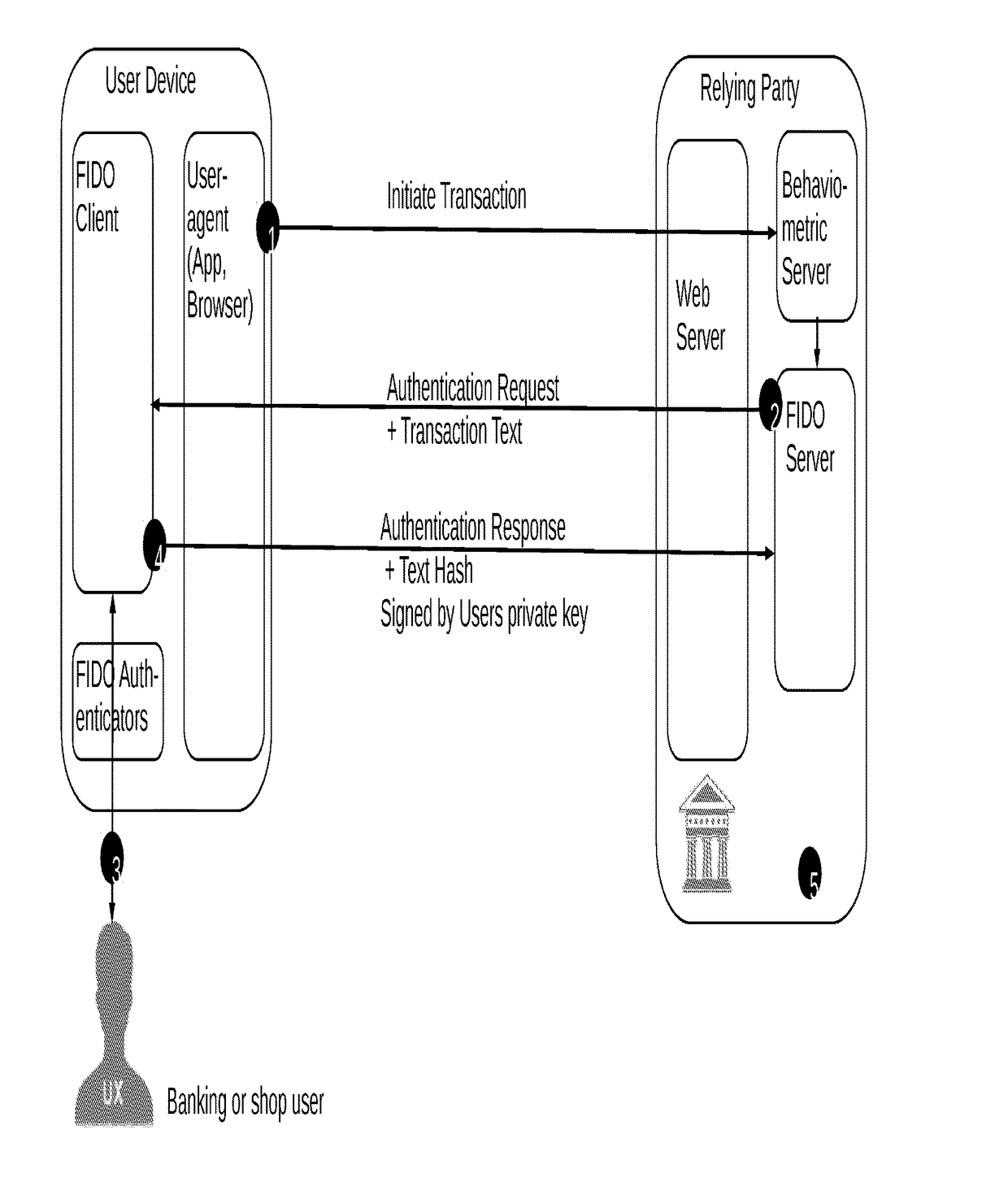
Secure authentication of a user of a device during a session with a connected server
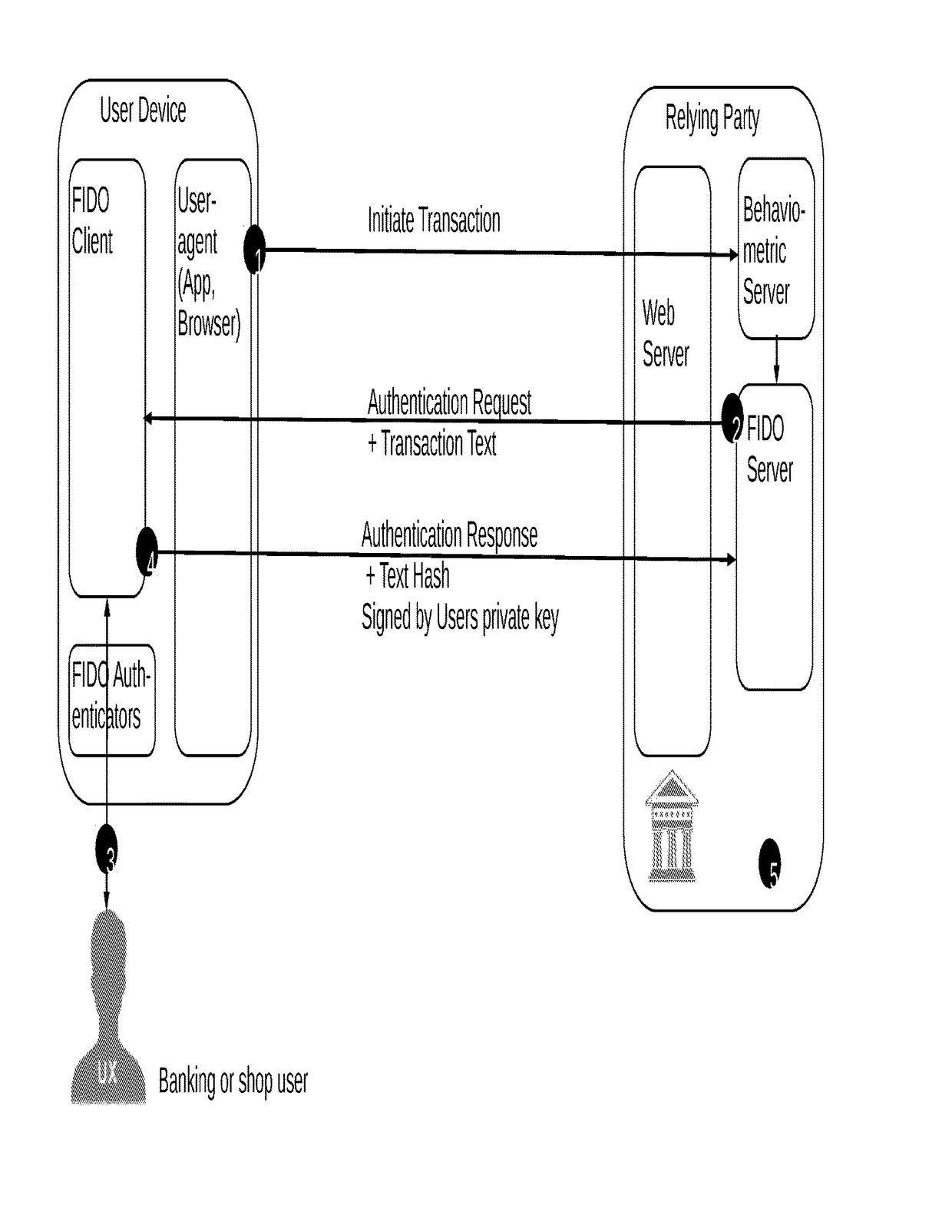
ActiveUS10075437B1Reduce decreaseLow costMultiple keys/algorithms usagePublic key for secure communicationData matchingUser device
A computer-implemented method for secure authentication of a user to a service for executing a transaction, the method being implemented in a system including a user device including a FIDO-client, a FIDO-server of a relying party providing the service, a behaviometric server and a web server associated with the relying party, the method including a preparation stage and an authentication stage. In the preparation stage a TLS-connection is established between the user device and the web-server, behavioral input data is collected from user device, and a transaction initiation message is transmitted to the behaviometric server. In the authentication stage, behaviometric data received in the transaction initiation message is compared to a second set of behaviometric data to determine whether the data matches, and if the data matches, the transaction is authenticated by the FIDO server.
Owner:BEHAVIOSEC
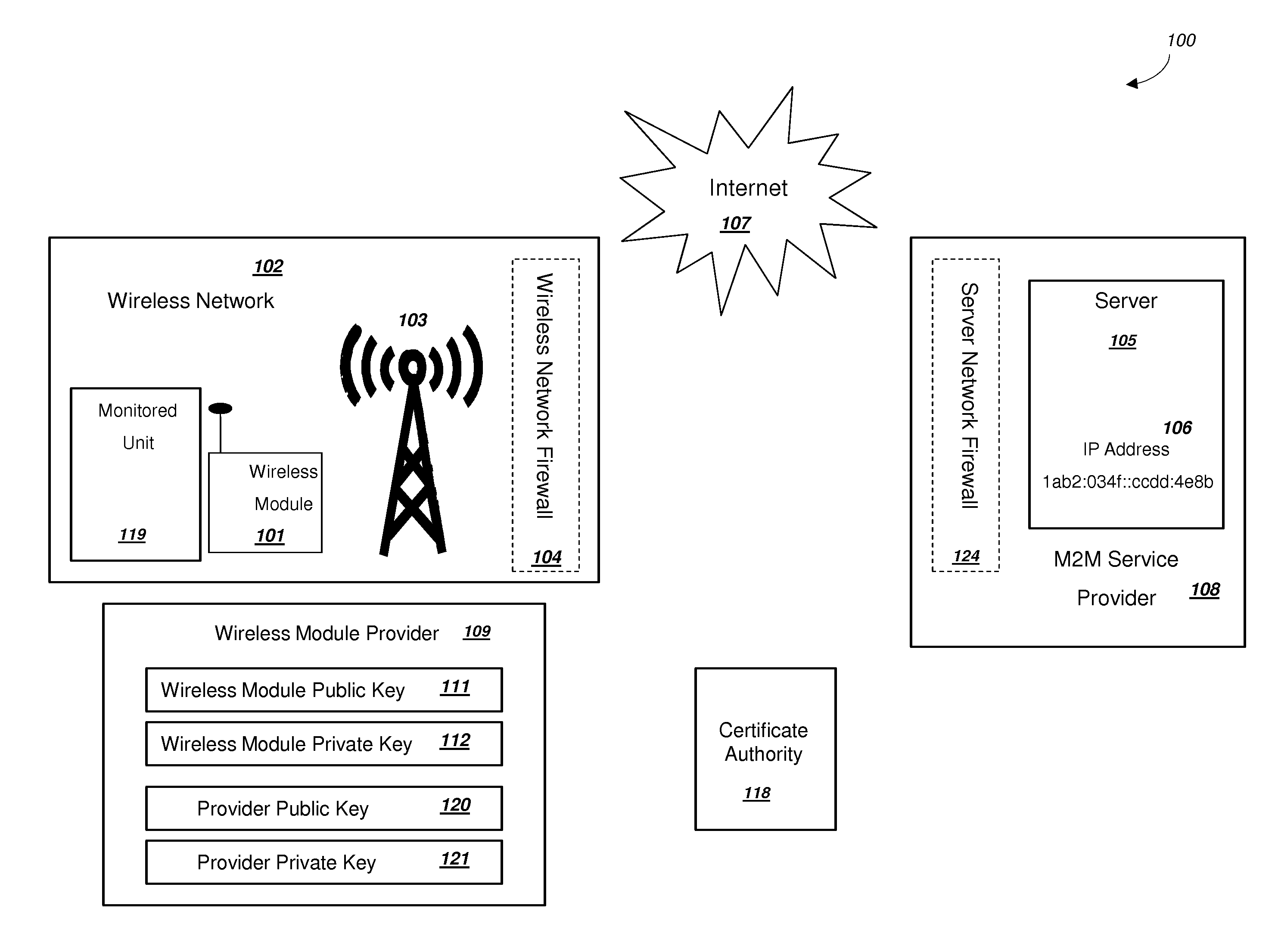
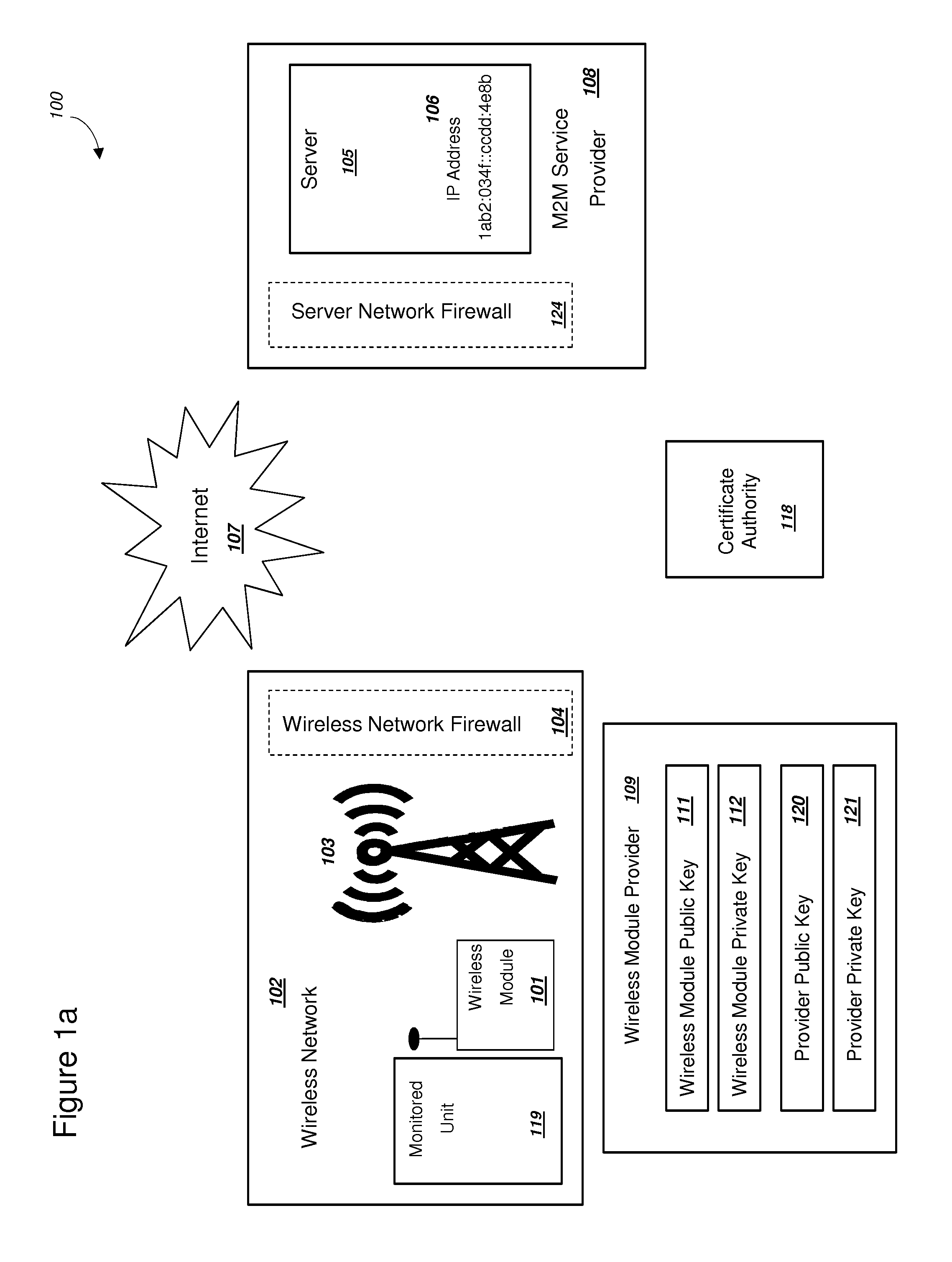
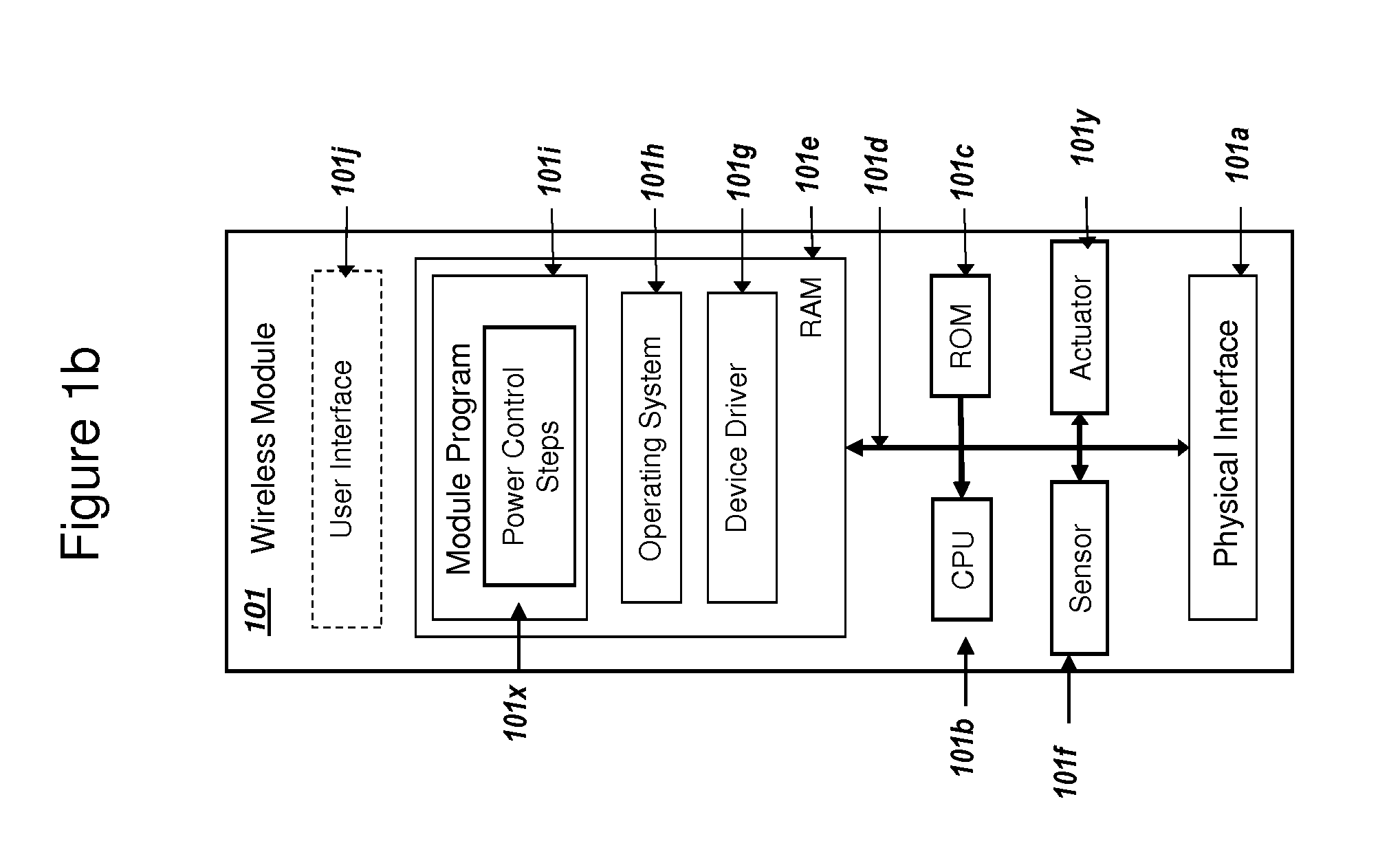
Secure PKI Communications for "Machine-to-Machine" Modules, including Key Derivation by Modules and Authenticating Public Keys
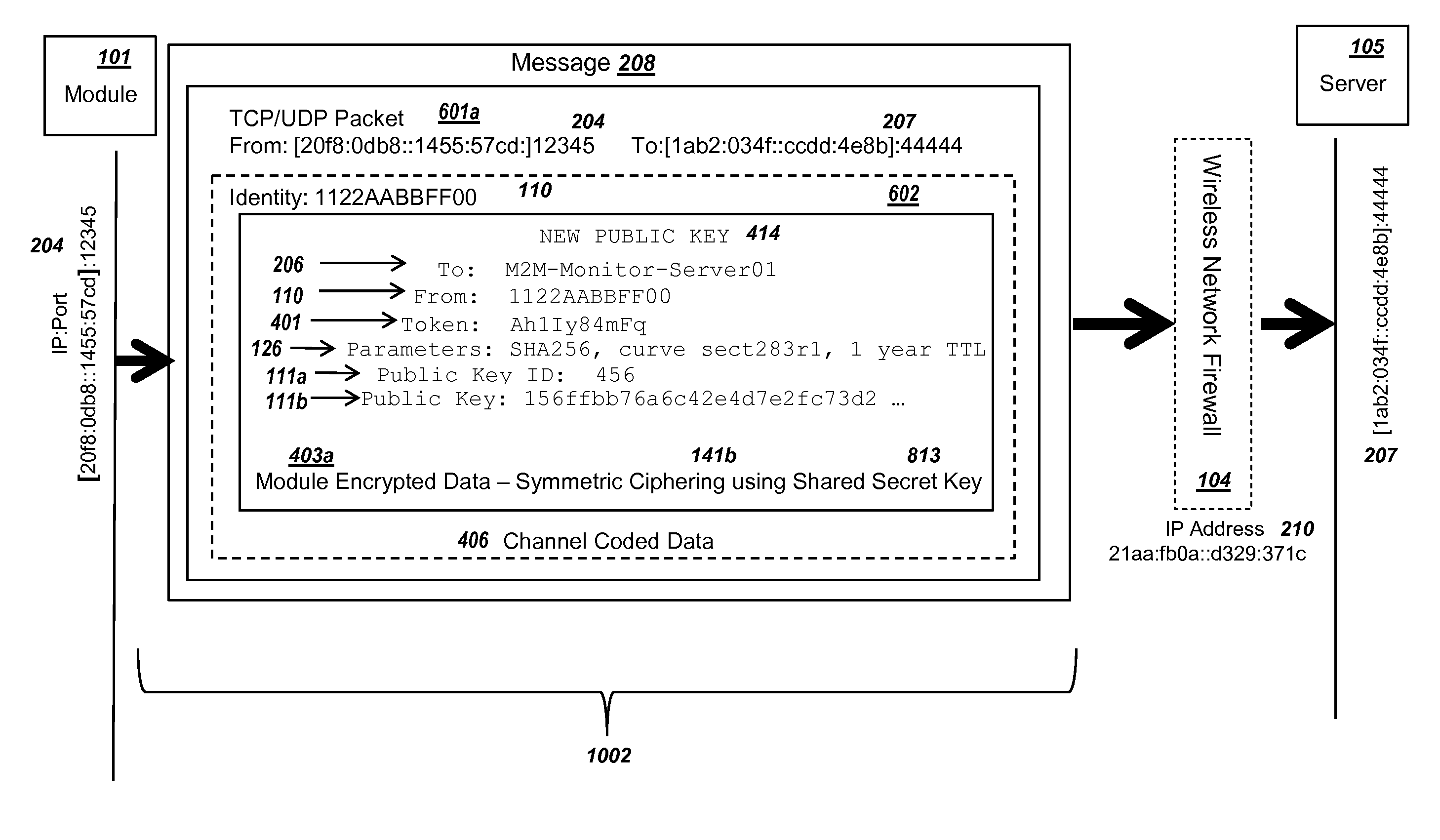
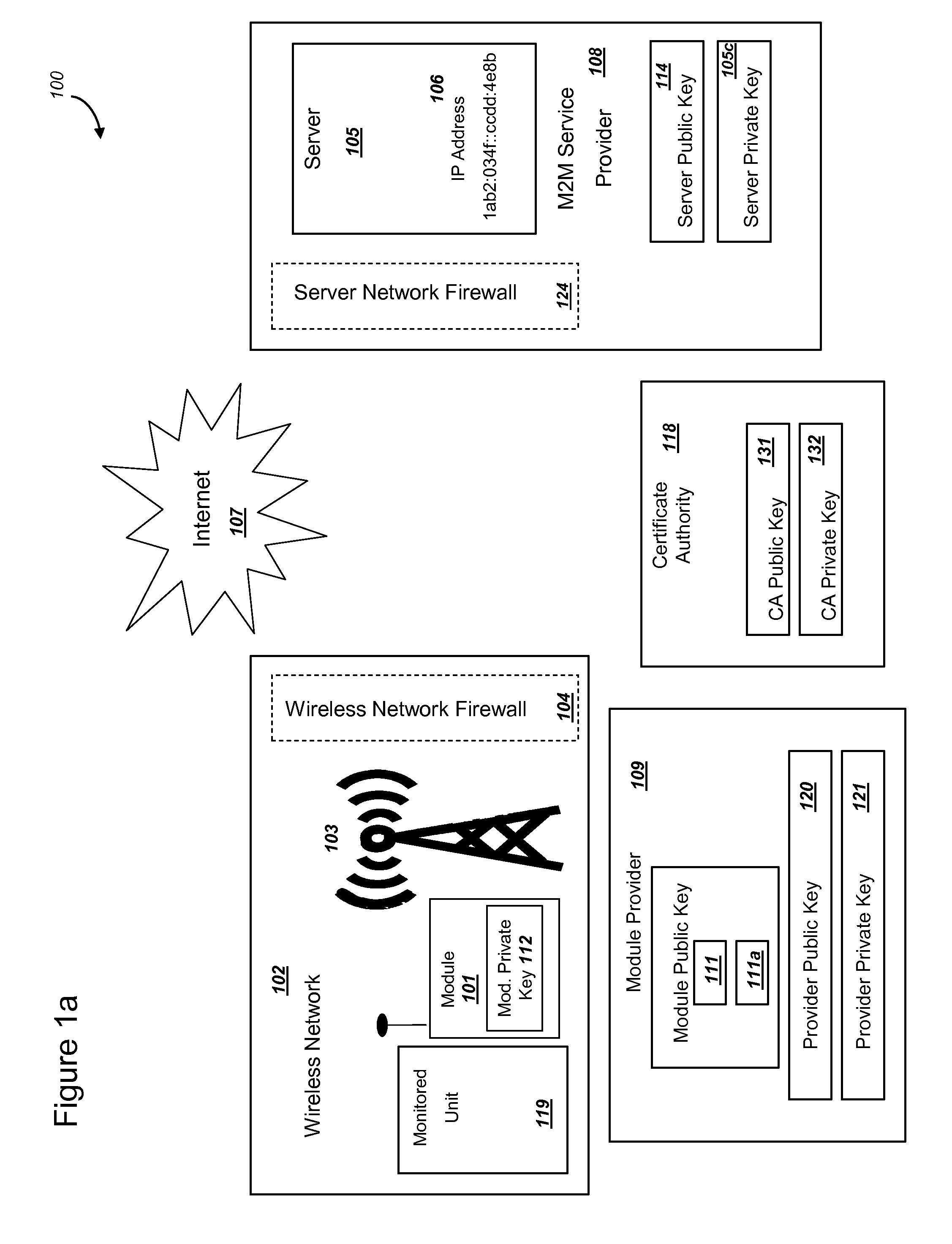
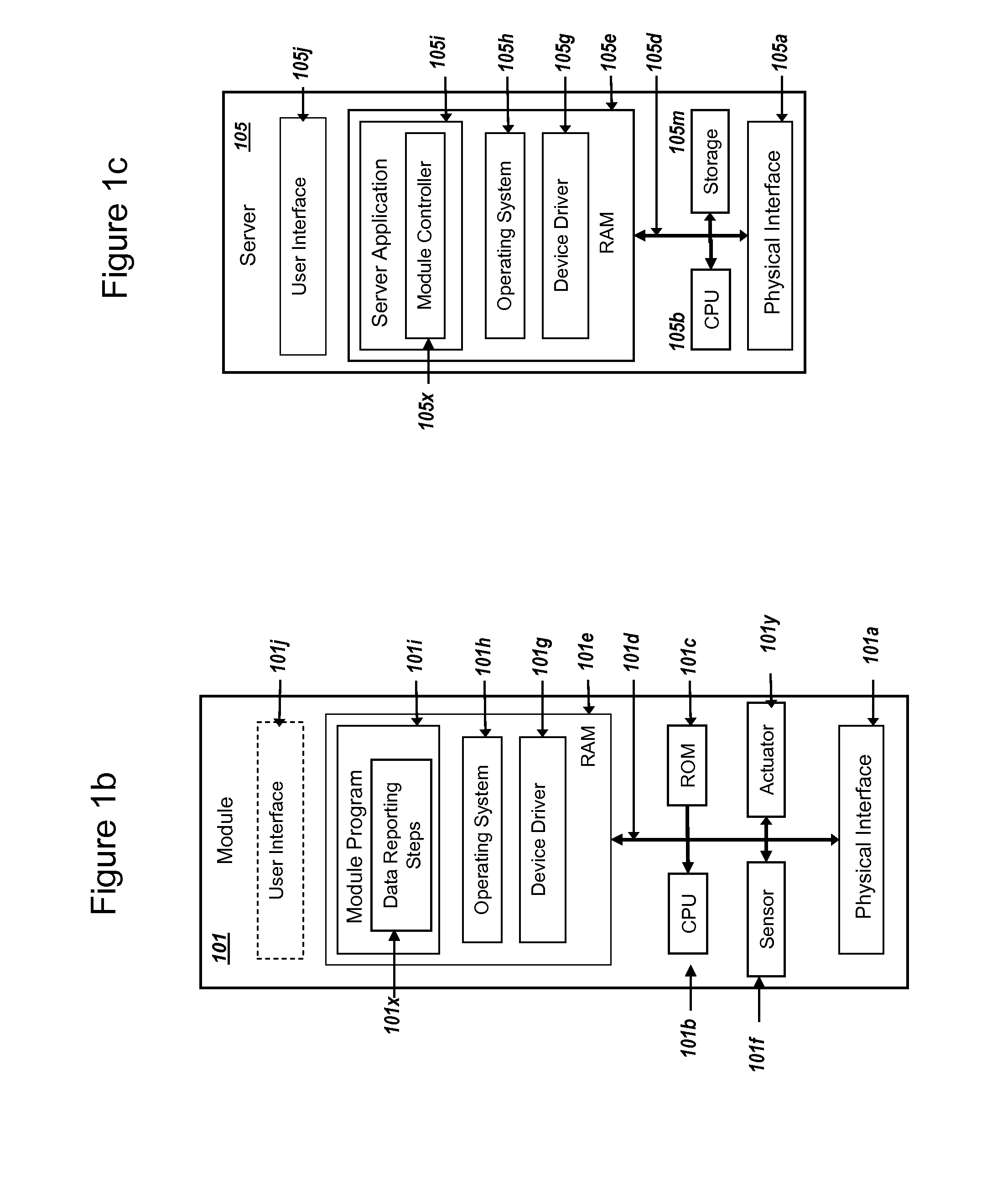
ActiveUS20150095648A1Extend battery lifeImprove efficiencyKey distribution for secure communicationMultiple keys/algorithms usageComputer hardwareDigital signature
Methods and systems are provided for efficient and secure “Machine-to-Machine” (M2M) between modules and servers. A module can communicate with a server by accessing the Internet, and the module can include a sensor and / or actuator. The module and server can utilize public key infrastructure (PKI) such as public keys to encrypt messages. The module and server can use private keys to generate digital signatures for datagrams sent and decrypt messages received. The module can internally derive pairs of private / public keys using cryptographic algorithms and a set of parameters. A server can use a shared secret key to authenticate the submission of derived public keys with an associated module identity. For the very first submission of a public key derived the module, the shared secret key can comprise a pre-shared secret key which can be loaded into the module using a pre-shared secret key code.
Owner:NETWORK 1 TECH +1
Method and system for establishing cryptographic communications between a remote device and a medical device
ActiveUS8472630B2Less processing powerKey distribution for secure communicationPublic key for secure communicationComputer hardwareMaster key
A method and system establishing cryptographic communications between a remote device and a medical device, with the medical device having less processing power than the remote device are disclosed. The method may comprise establishing unencrypted communication between the remote device and the medical device, generating an asymmetric key pair by the remote device comprising a public key and a private key, generating a key request message and sending of the key request message together with the public key to the medical device, generating a pre-master key and encryption of the pre-master key with the received public key by the medical device, generating a key response message and sending of the key response message together with the encrypted pre-master key from the medical device to the remote device, decrypting the encrypted pre-master key with the private key by the remote device, and deriving a master key as a symmetric key from the pre-master key.
Owner:ROCHE DIABETES CARE INC
System and method for secure relayed communications from an implantable medical device
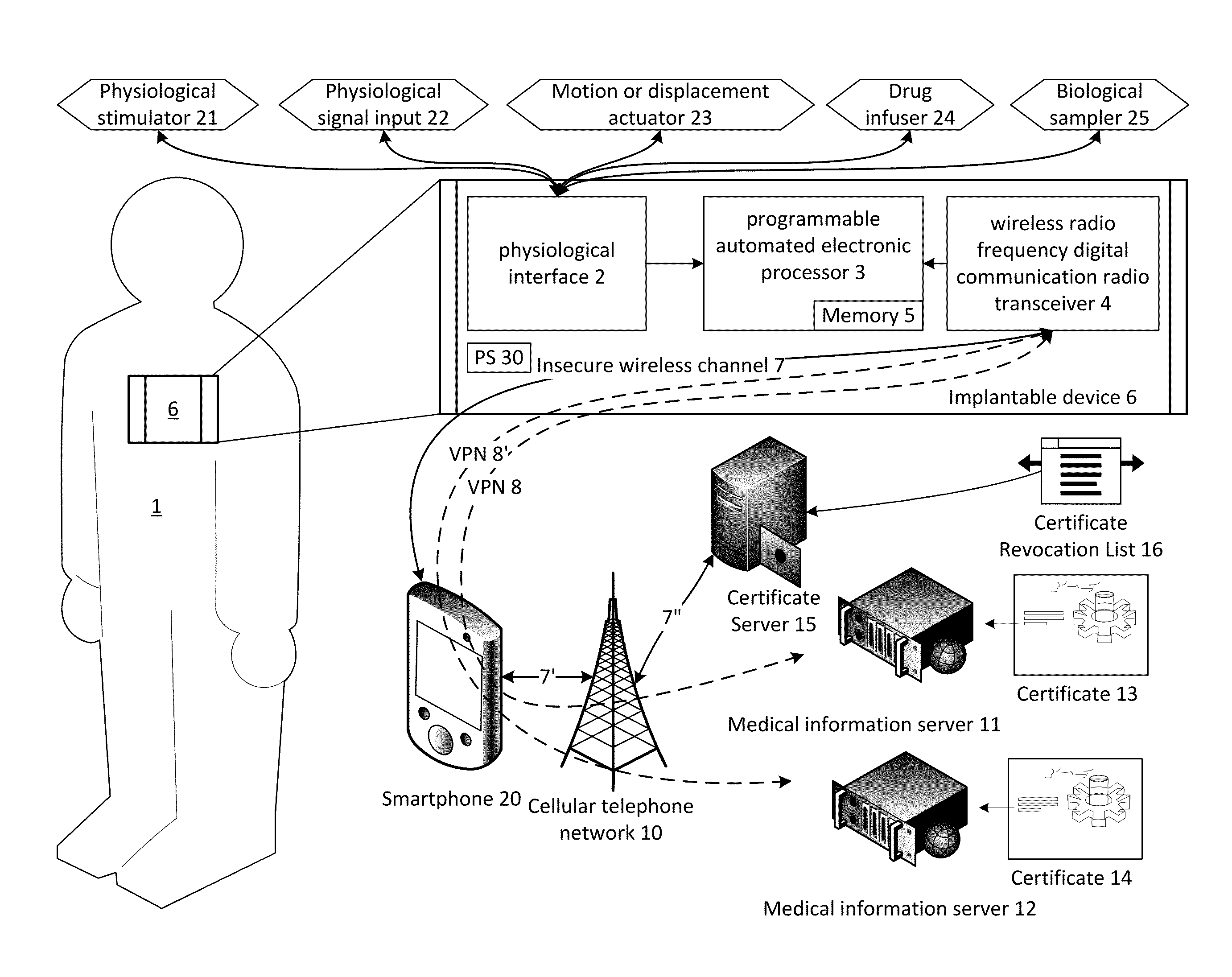
ActiveUS9215075B1Good security mechanismLarge block sizePhysical therapies and activitiesDrug and medicationsSecure communicationMedical equipment
The present invention provides systems and methods for supporting encrypted communications with a medical device, such as an implantable device, through a relay device to a remote server, and may employ cloud computing technologies. An implantable medical device is generally constrained to employ a low power transceiver, which supports short distance digital communications. A relay device, such as a smartphone or WiFi access point, acts as a conduit for the communications to the internet or other network, which need not be private or secure. The medical device supports encrypted secure communications, such as a virtual private network technology. The medical device negotiates a secure channel through a smartphone or router, for example, which provides application support for the communication, but may be isolated from the content.
Owner:POLTORAK TECH
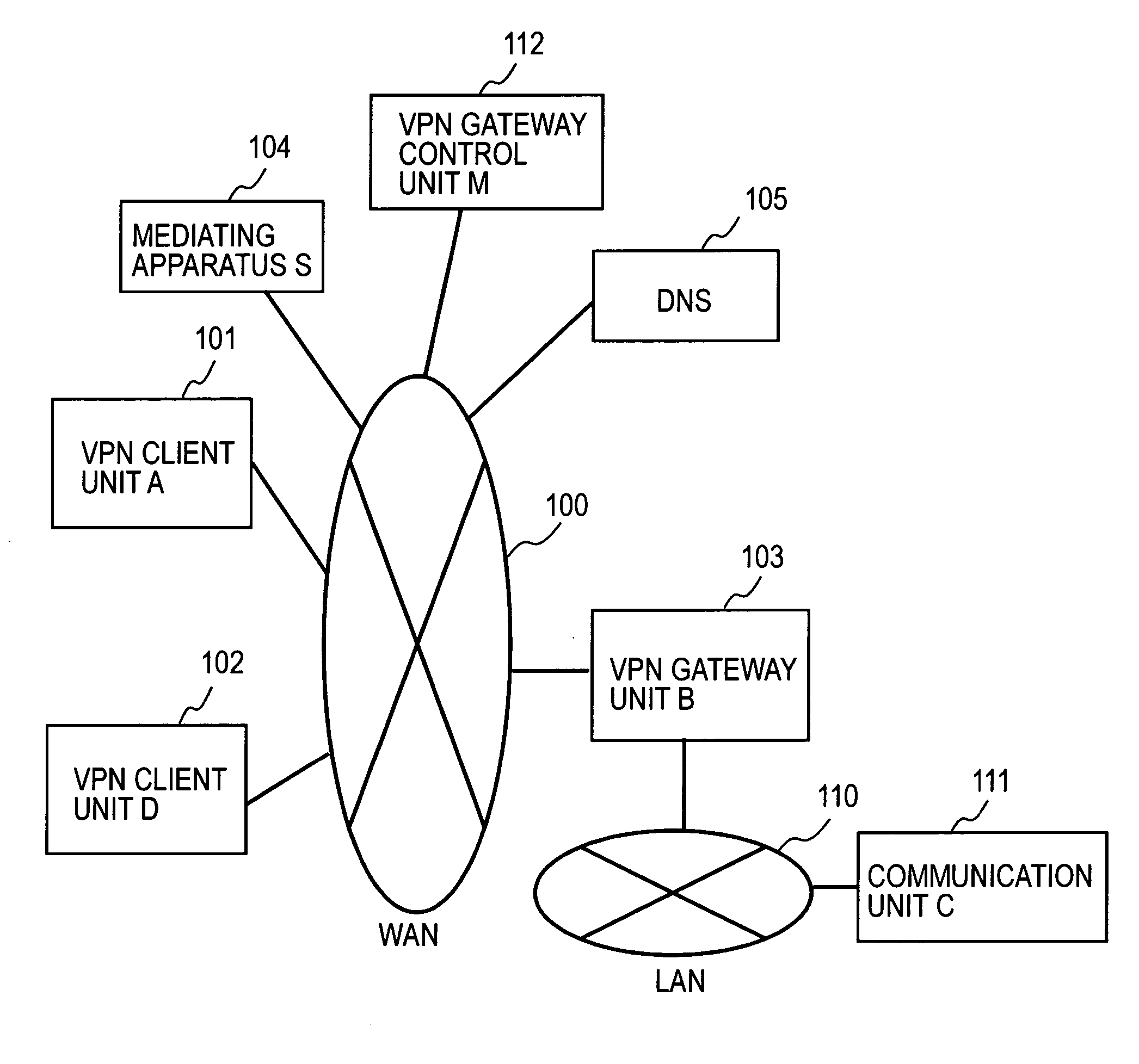
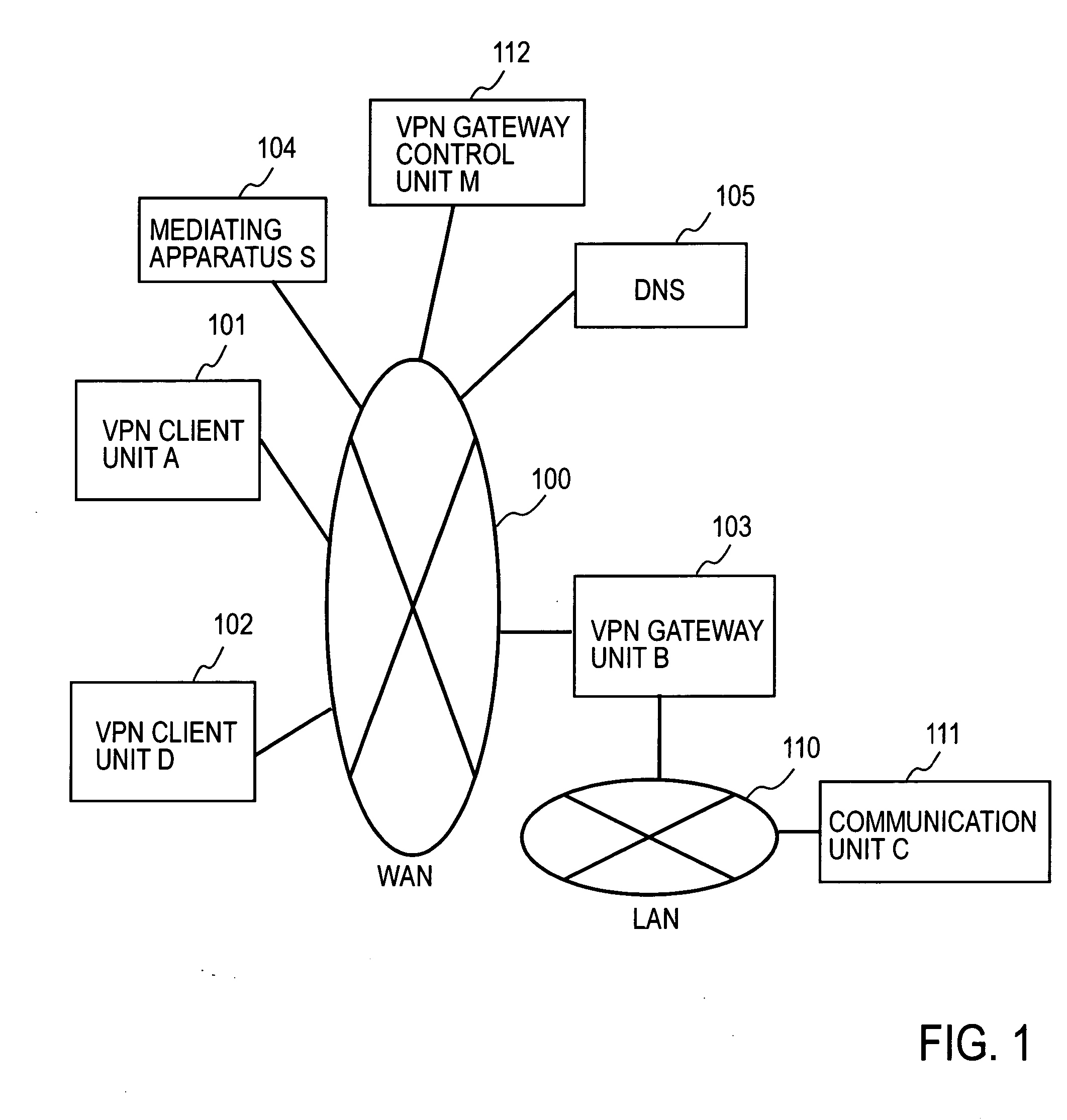
Remote access vpn mediation method and mediation device
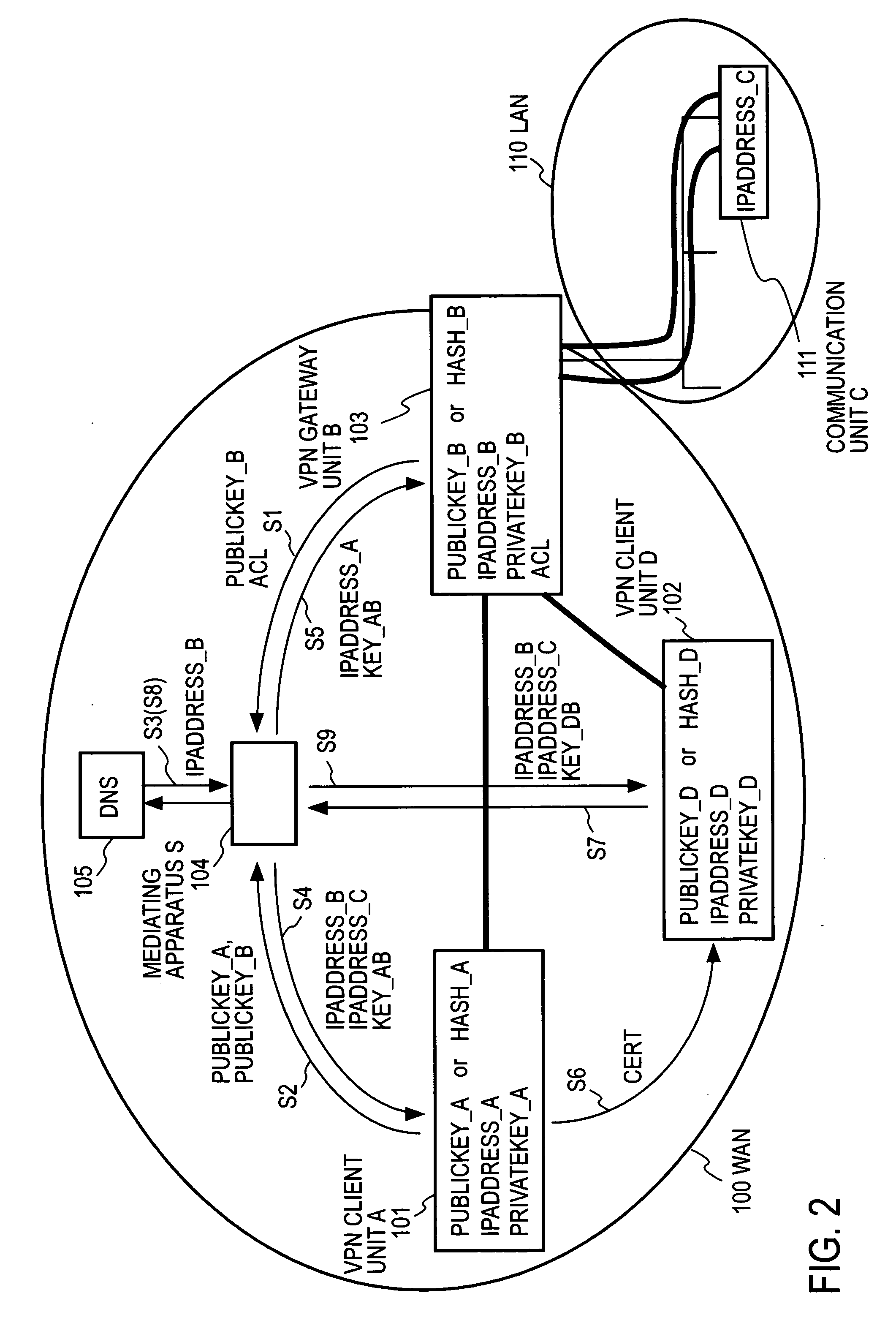
InactiveUS20060143702A1Secure distributionKey distribution for secure communicationDigital data processing detailsPrivate IPCommunication unit
A mediating apparatus is provided on an IP network, and stores an access control list (ACL) retained in a VPN gateway unit. The mediating apparatus: receives a retrieval request from a VPN client unit; acquires a private IP address of a communication unit by reference to ACL; searches DNS to acquire therefrom an IP address of the VPN gateway unit; generates a common key that is used for authentication between the VPN client unit and the VPN gateway unit and for encrypted communication therebetween; sends the IP address of the VPN gateway unit, the private IP address of the communication unit, and the common key to the VPN client unit; and sends the IP address of the VPN client unit and the common key to the VPN gateway unit.
Owner:NIPPON TELEGRAPH & TELEPHONE CORP
Remote authentication and transaction signatures
InactiveUS8667285B2Simple ideaDigital data processing detailsUser identity/authority verificationPersonalizationSmart card
The invention provides a method, apparatus, computer readable medium and signal which allows the usage of devices containing PKI private keys such as PKI-enabled smart cards or USB sticks to authenticate users and to sign transactions. The authenticity of the user and / or the message is verified. Furthermore the operation (authentication and / or signing) occurs without the need for an application to have some kind of a direct or indirect digital connection with the device containing the private key. In addition the operation occurs without the need for the PKI-enabled device containing the private key (e.g. a PKI smart card or USB stick) to either support symmetric cryptographic operations or to have been personalized with some secret or confidential data element that can be read by a suitable reader.
Owner:ONESPAN NORTH AMERICA INC
Power Management and Security for Wireless Modules in "Machine-to-Machine" Communications
ActiveUS20150071139A1Efficient power controlExtend battery lifeMultiple keys/algorithms usagePublic key for secure communicationPublic land mobile networkThe Internet
Methods and systems are provided for power management and security for wireless modules in “Machine-to-Machine” communications. A wireless module operating in a wireless network and with access to the Internet can efficiently and securely communicate with a server. The wireless network can be a public land mobile network (PLMN) or a wireless local area network (LAN). The wireless module may include a sensor and may be installed next to a monitored unit. The wireless module may utilize active states for collecting and sending data, and sleep states at other times to conserve a battery and / or energy usage. The wireless module minimize the time spent in a radio resource control (RRC) connected state. Messages between the wireless module and server can be transmitted according to a user datagram protocol (UDP). The wireless module and server can utilize public key infrastructure (PKI) for encryption and digital signatures.
Owner:NIX JOHN A +1
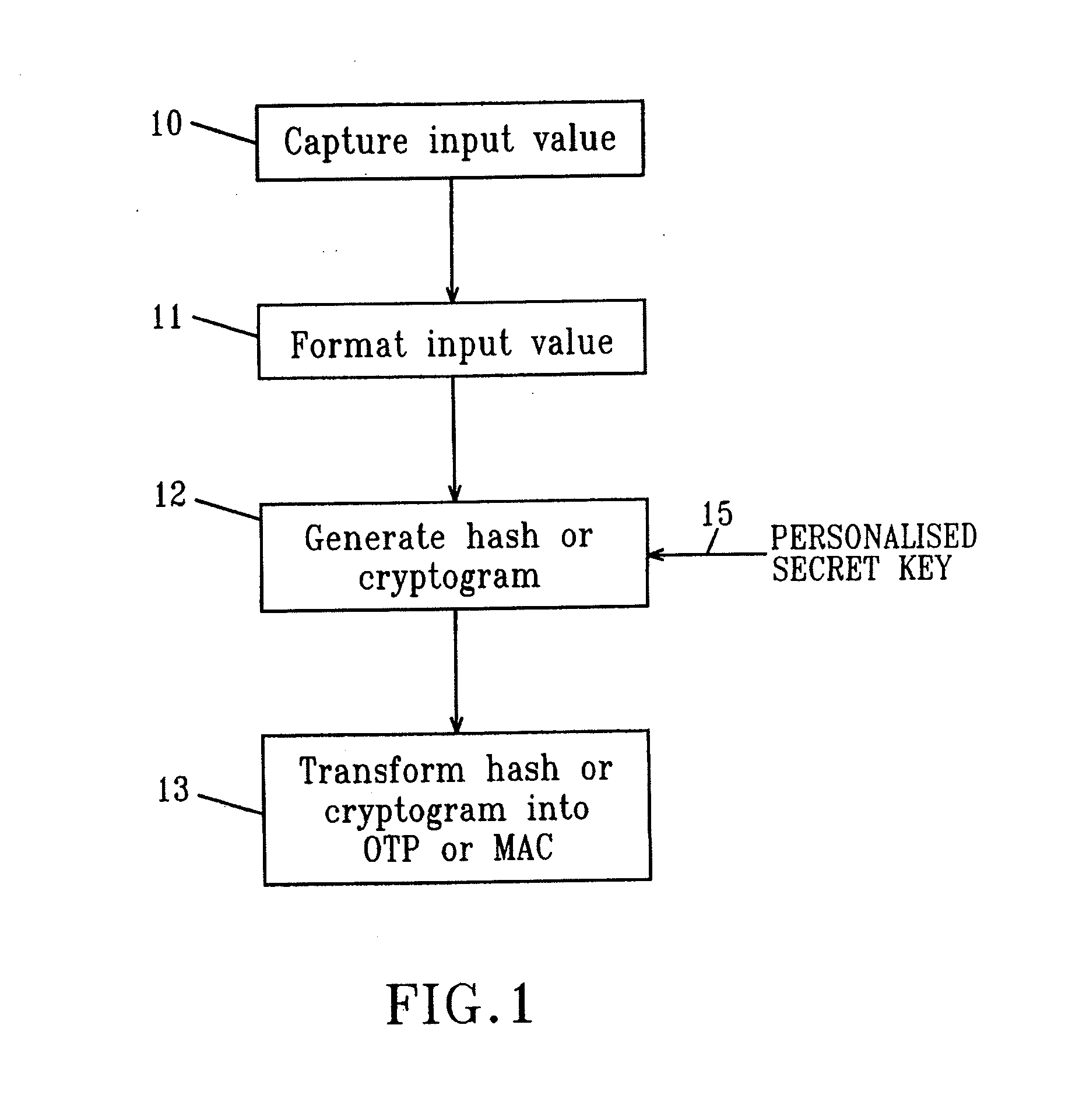
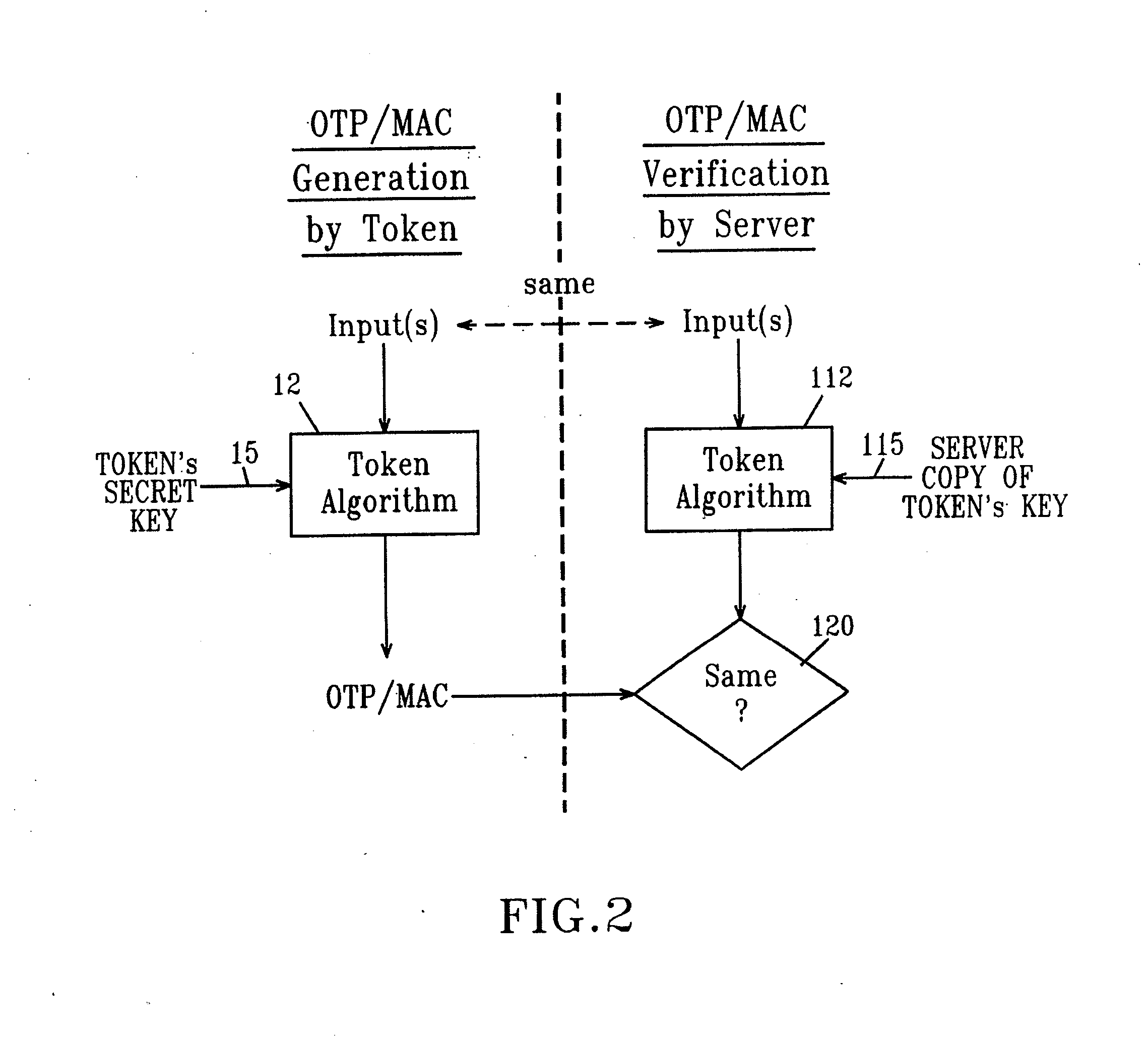
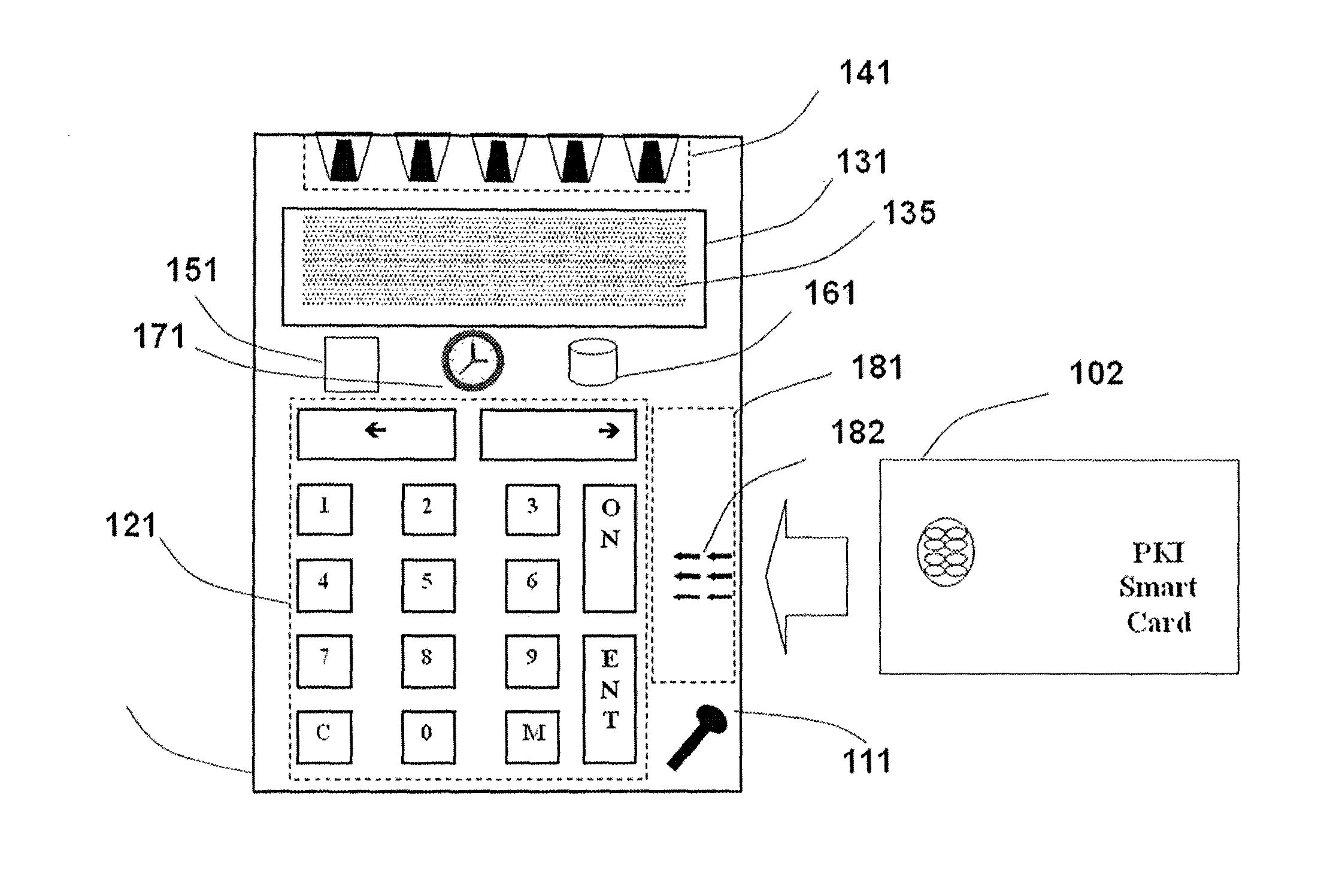
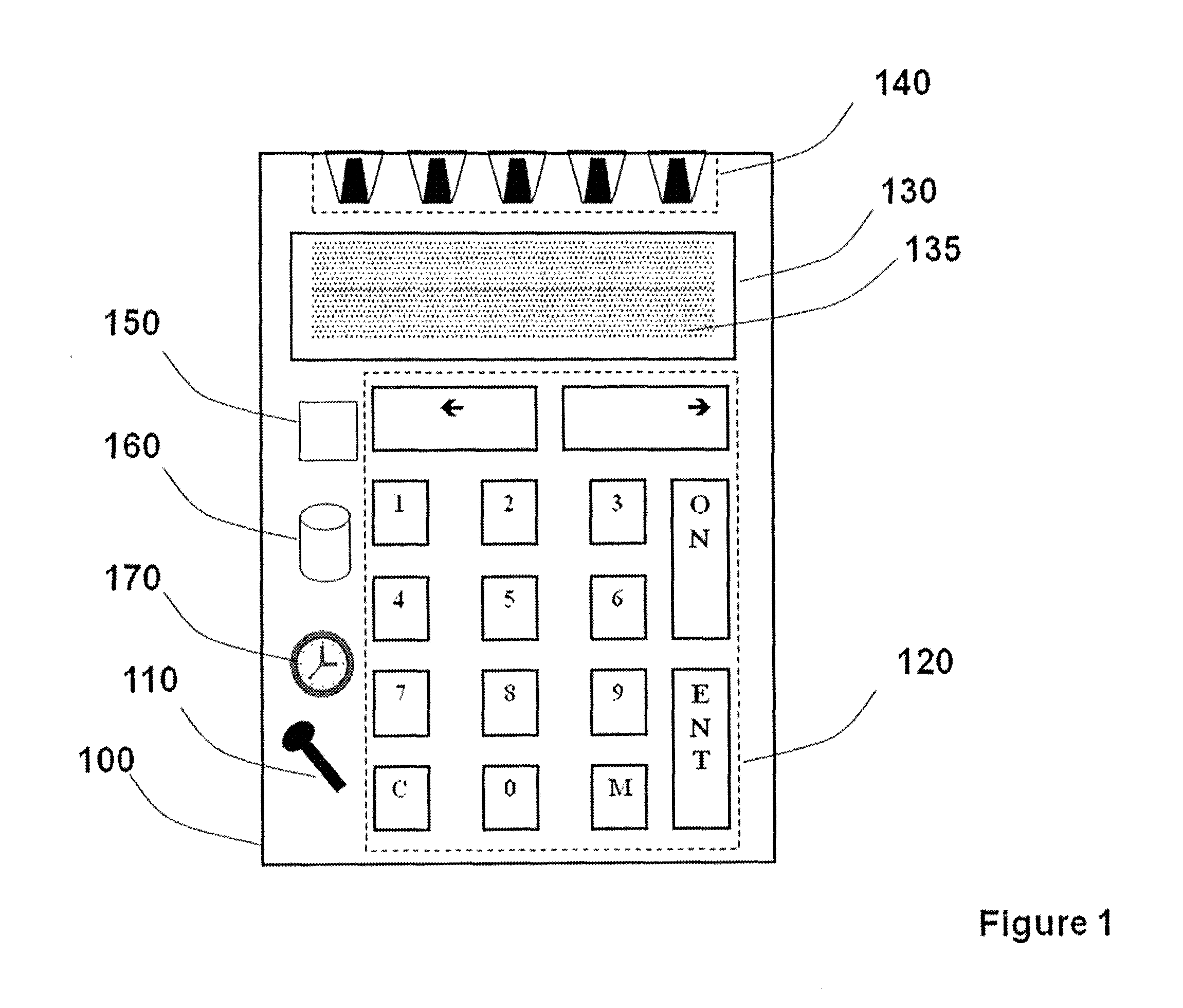
Strong authentication token with visual output of pki signatures
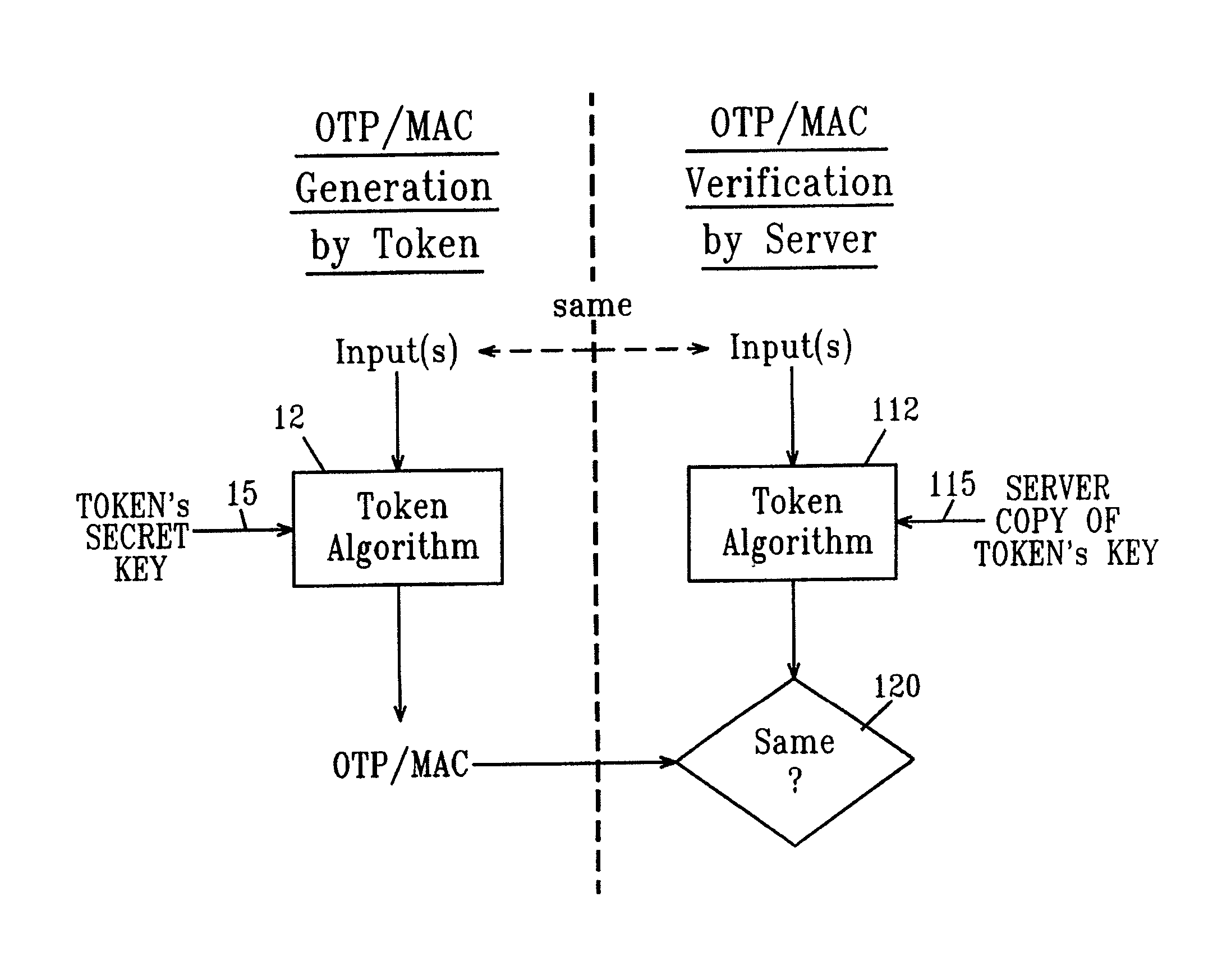
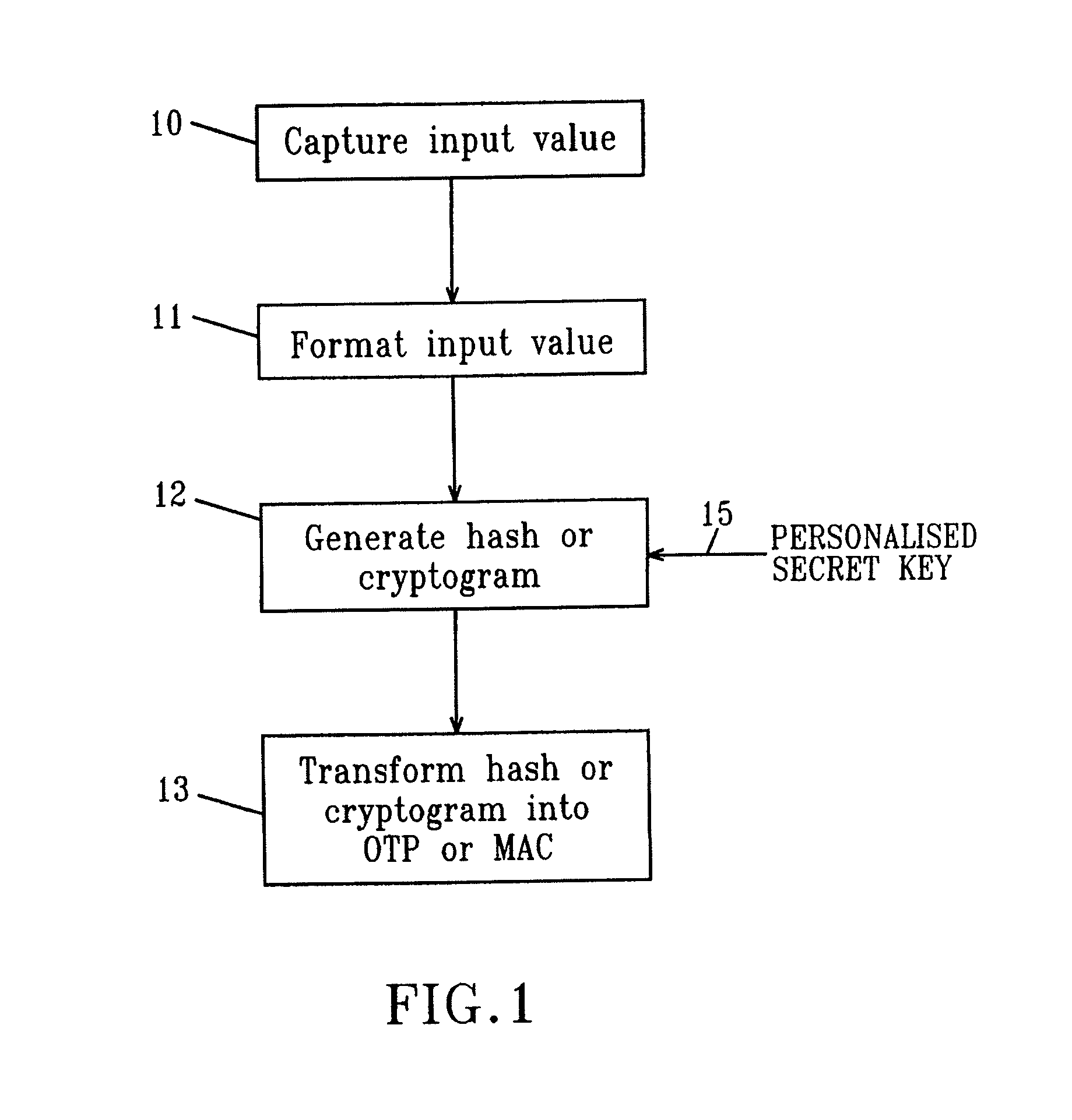
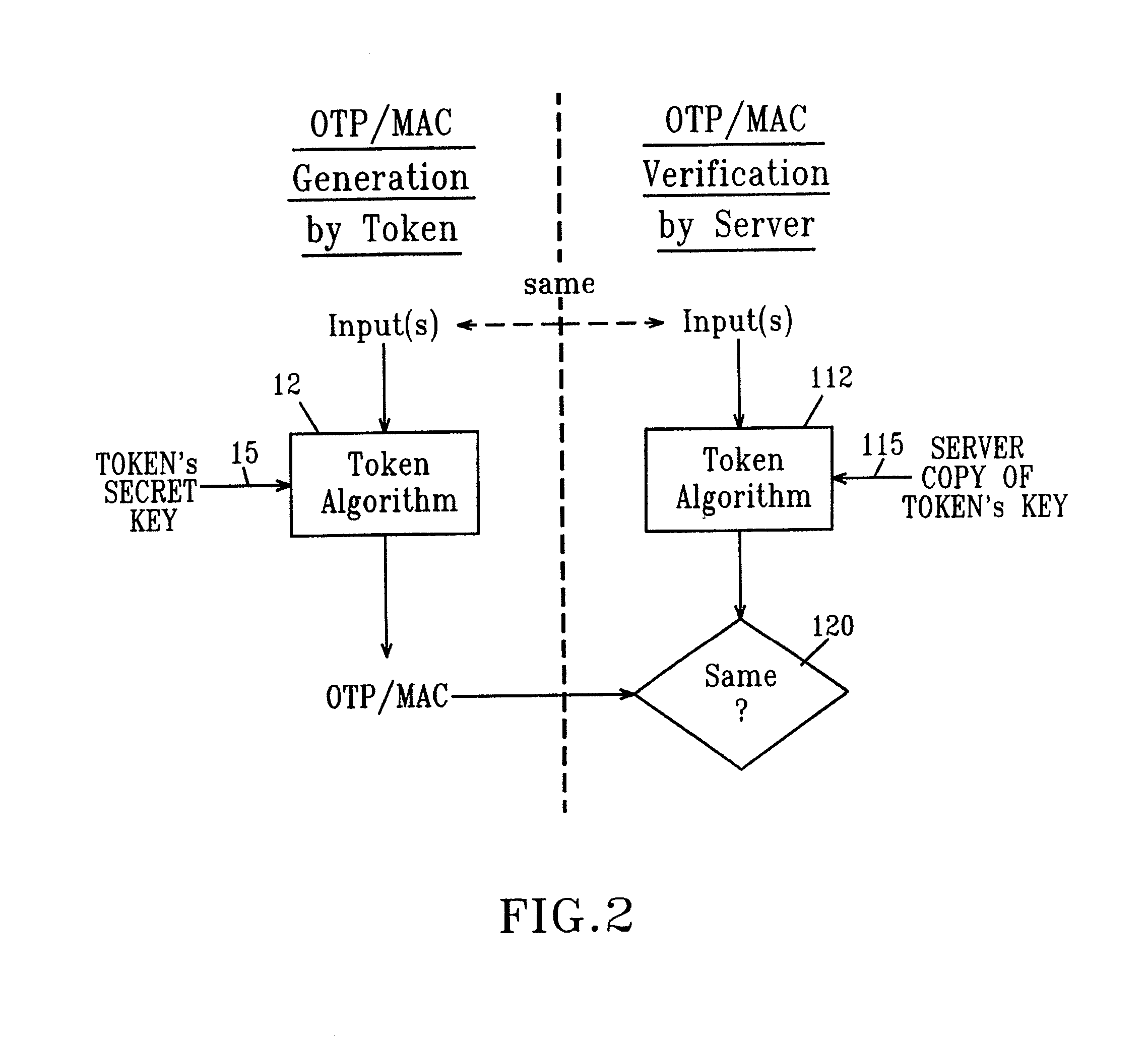
InactiveUS20130198519A1Improve securityUser identity/authority verificationDigital data authenticationDisplay deviceSecret code
A handheld authentication device comprising a data processor and a display is adapted to: generate an input value; submit the input value to an asymmetric cryptographic operation; obtain the result of said asymmetric cryptographic operation; generate an authentication message substantially comprising the result of the asymmetric cryptographic operation; encode the authentication message into one or more images; and display these images on the display. A method for securing computer-based applications remotely accessed by a user comprises capturing images displayed on the display of an authentication device of the user whereby these images have been encoded with an authentication message generated by the authentication device and whereby the authentication message comprises the result of an asymmetric cryptographic operation on an input value; decoding the images to retrieve the authentication message; retrieving the result of the asymmetric cryptographic operation from the authentication message; verifying the authentication message.
Owner:ONESPAN NORTH AMERICA INC
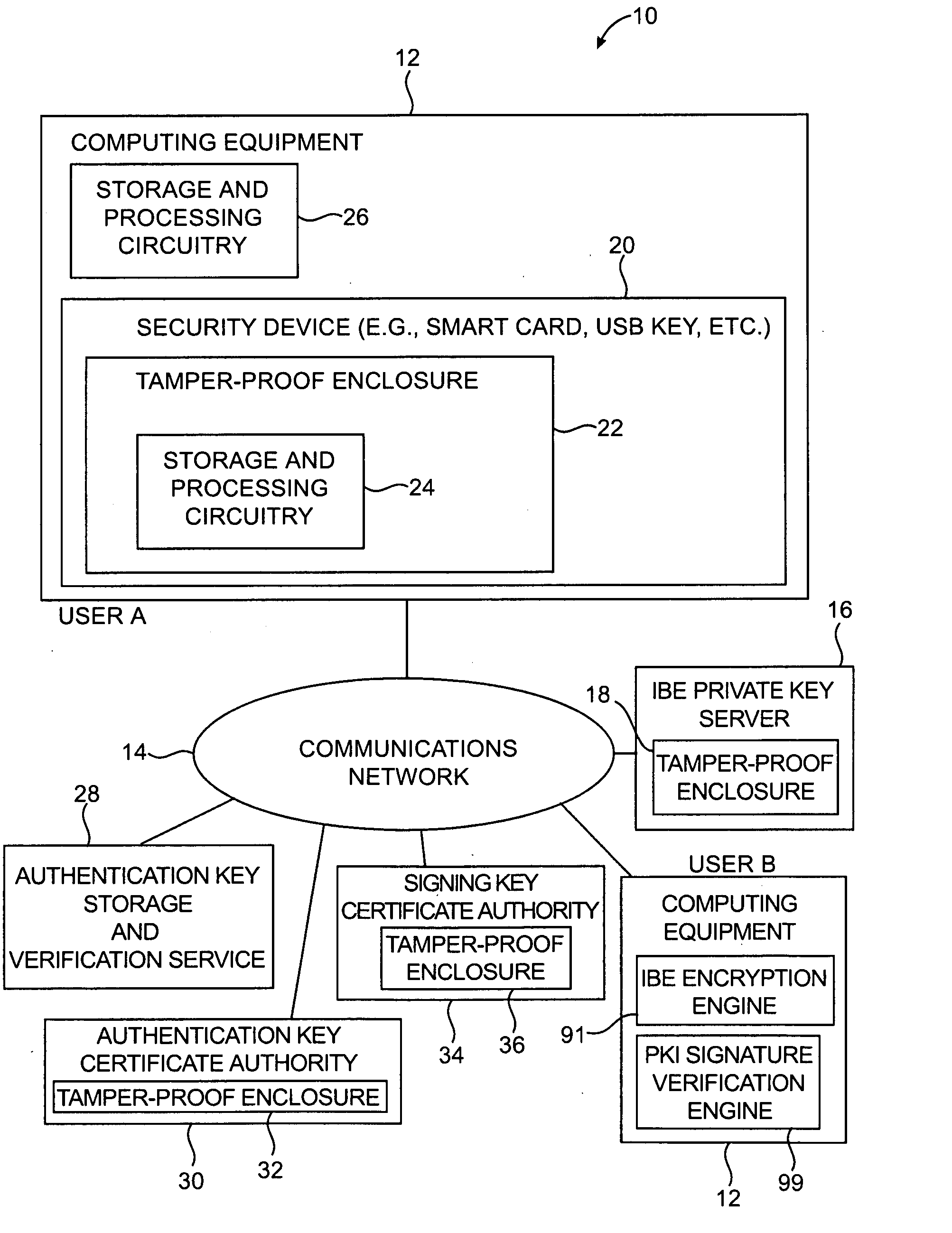
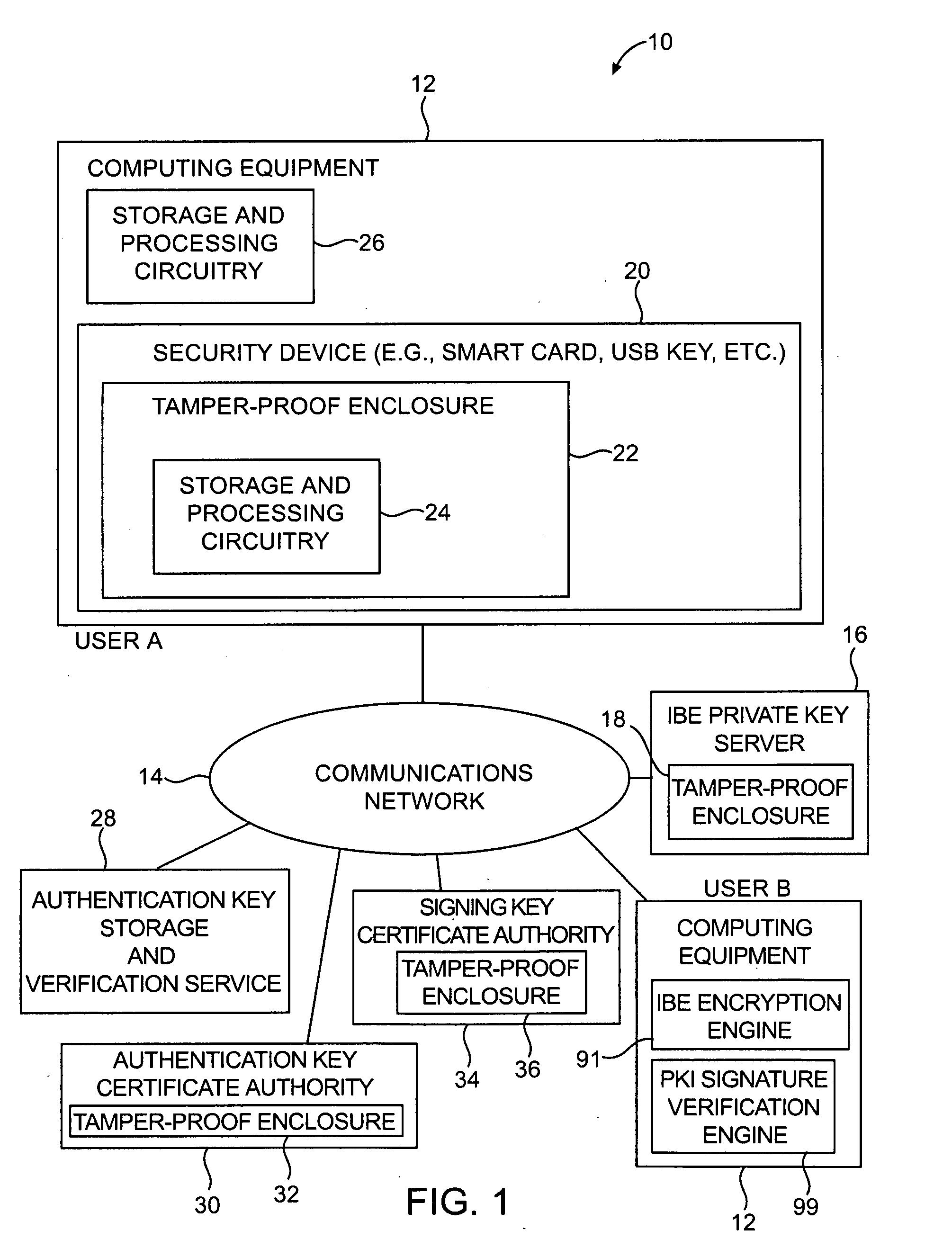
Security device for cryptographic communications
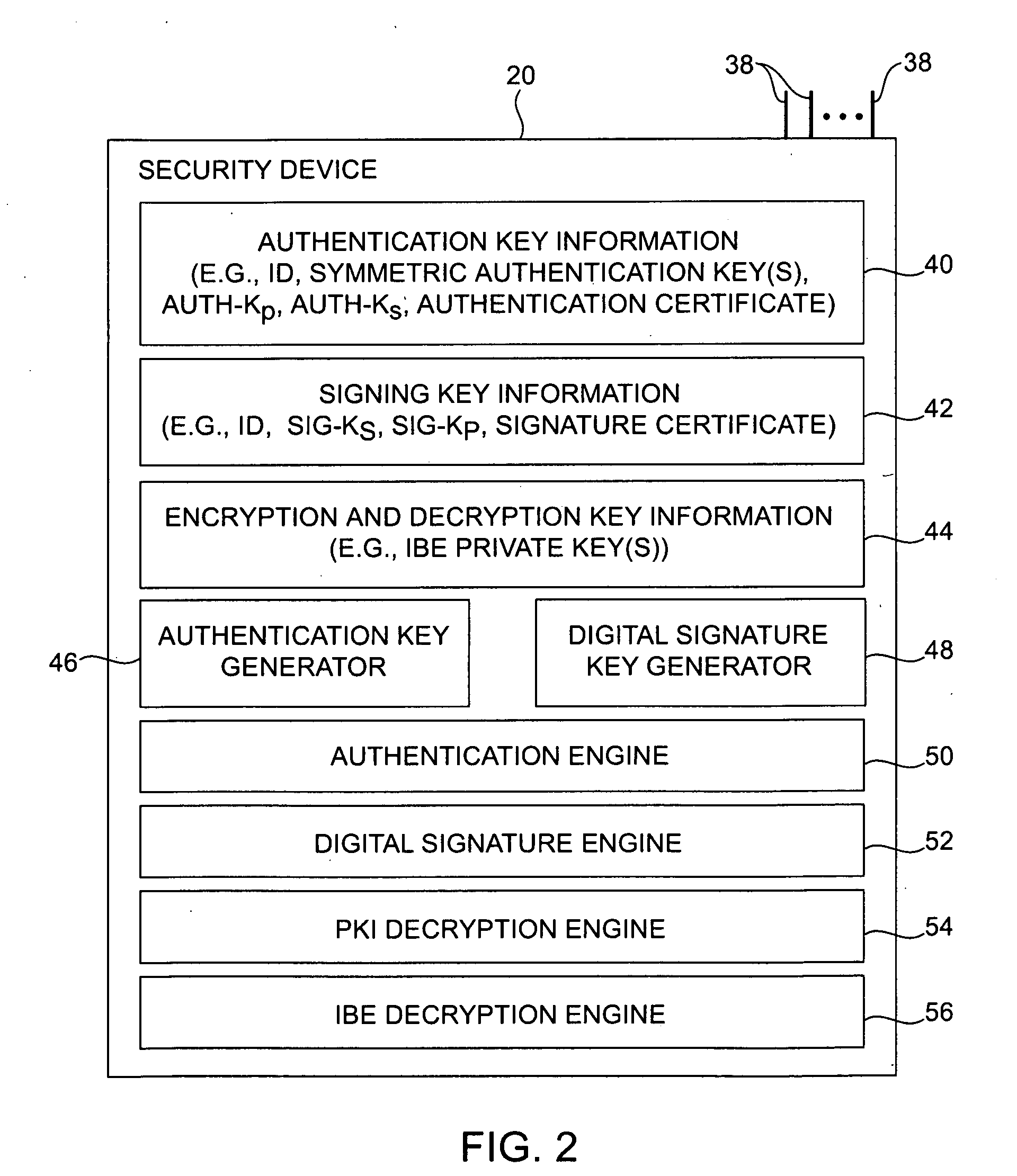
InactiveUS20060095771A1Preventing possible interception of this information by an attackerDigital data processing detailsUser identity/authority verificationDigital signatureSmart card
Cryptographic systems and methods are provided in which authentication operations, digital signature operations, and encryption operations may be performed. Authentication operations may be performed using authentication information. The authentication information may be constructed using a symmetric authentication key or a public / private pair of authentication keys. Users may digitally sign data using private signing keys. Corresponding public signing keys may be used to verify user signatures. Identity-based-encryption (IBE) arrangements may be used for encrypting messages using the identity of a recipient. IBE-encrypted messages may be decrypted using appropriate IBE private keys. A smart card, universal serial bus key, or other security device having a tamper-proof enclosure may use the authentication information to obtain secret key information. Information such as IBE private key information, private signature key information, and authentication information may be stored in the tamper-proof enclosure.
Owner:MICRO FOCUS LLC
Virtual Identity Credential Issuance and Verification Using Physical and Virtual Means
InactiveUS20180254909A1Promote disseminationUser identity/authority verificationPublic key infrastructure trust modelsMachine-readable mediumElectronic equipment
Systems, methods, and non-transitory machine readable medium for authenticating an identity of a user and facilitating a transaction between the user and a relying party include establishing a communication path with a first electronic device of the user, receiving, an identity credential data points of the user from an identity credential issuer, receiving an identity credential issued by the identity credential issuer from the user, authenticating the identity credential received from the user with the identity credential data points of the user from the identity credential issuer, storing the authenticated identity credential of the user as a virtual identity credential in the memory, establishing a communication path with a second electronic device of the relying party, and facilitating transmission of identity credential information or identity credential verification commands between the user and the relying party.
Owner:LAMARK SOLUTIONS INC
Communication system and method in public key infrastructure
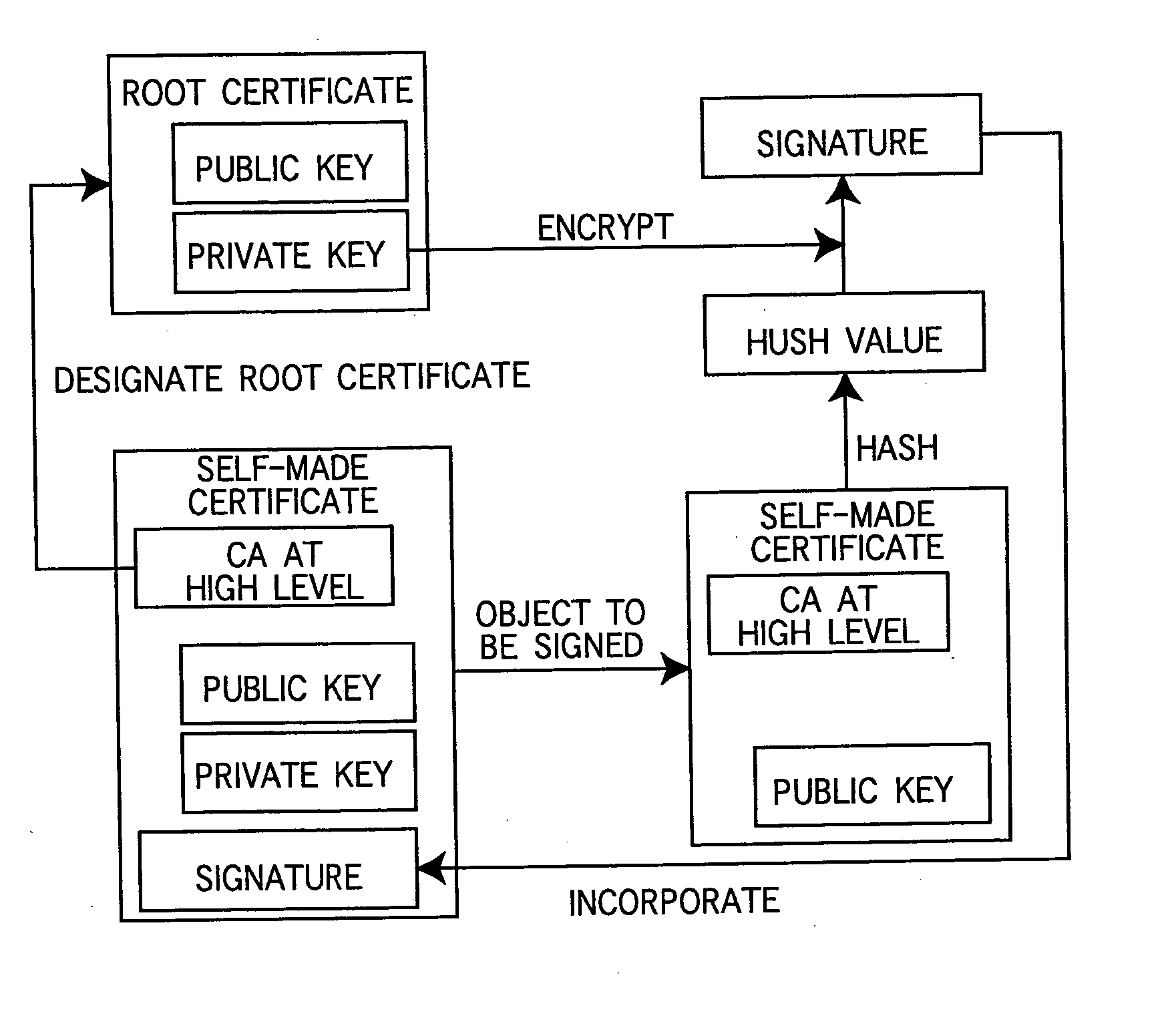
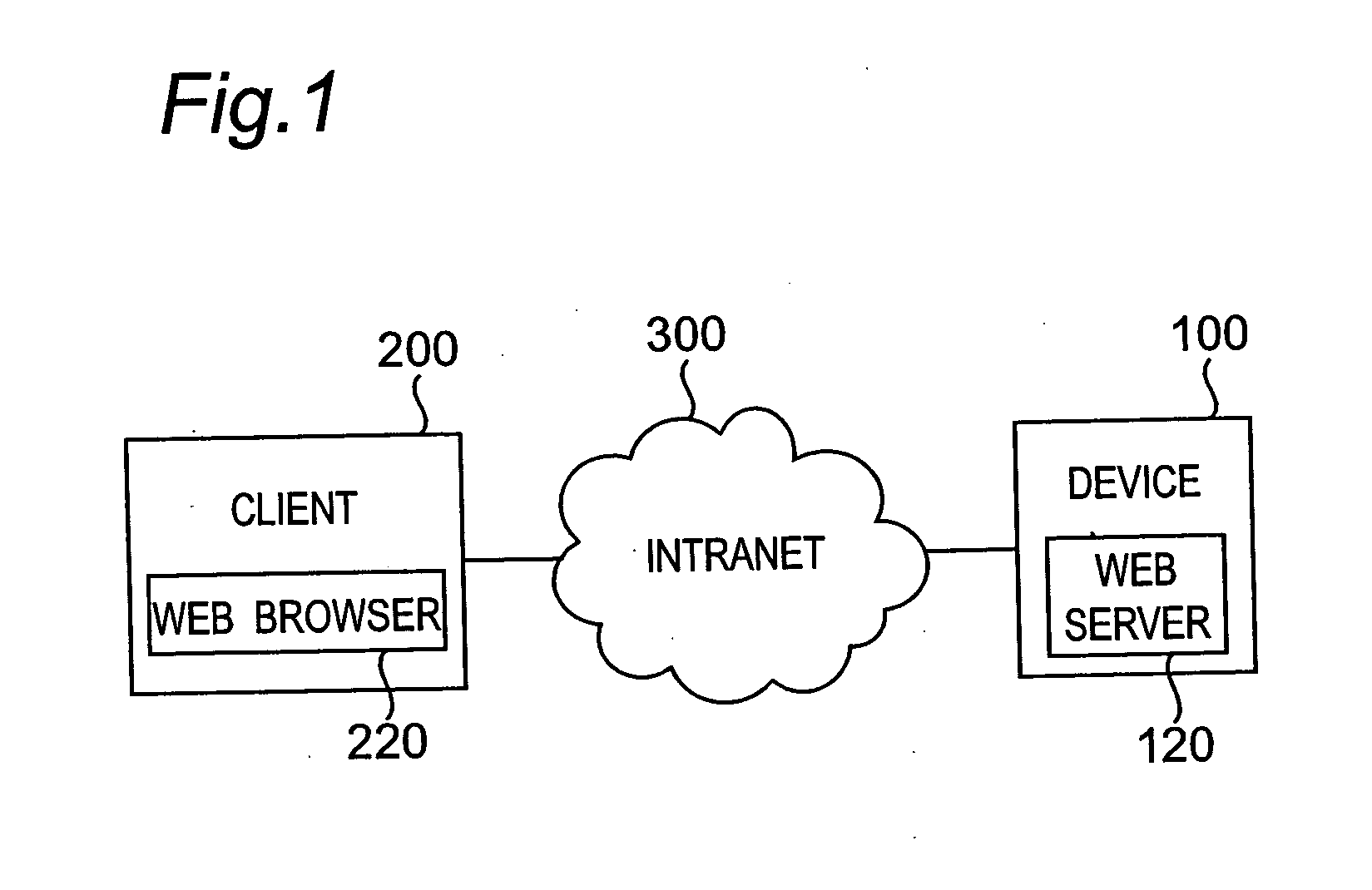
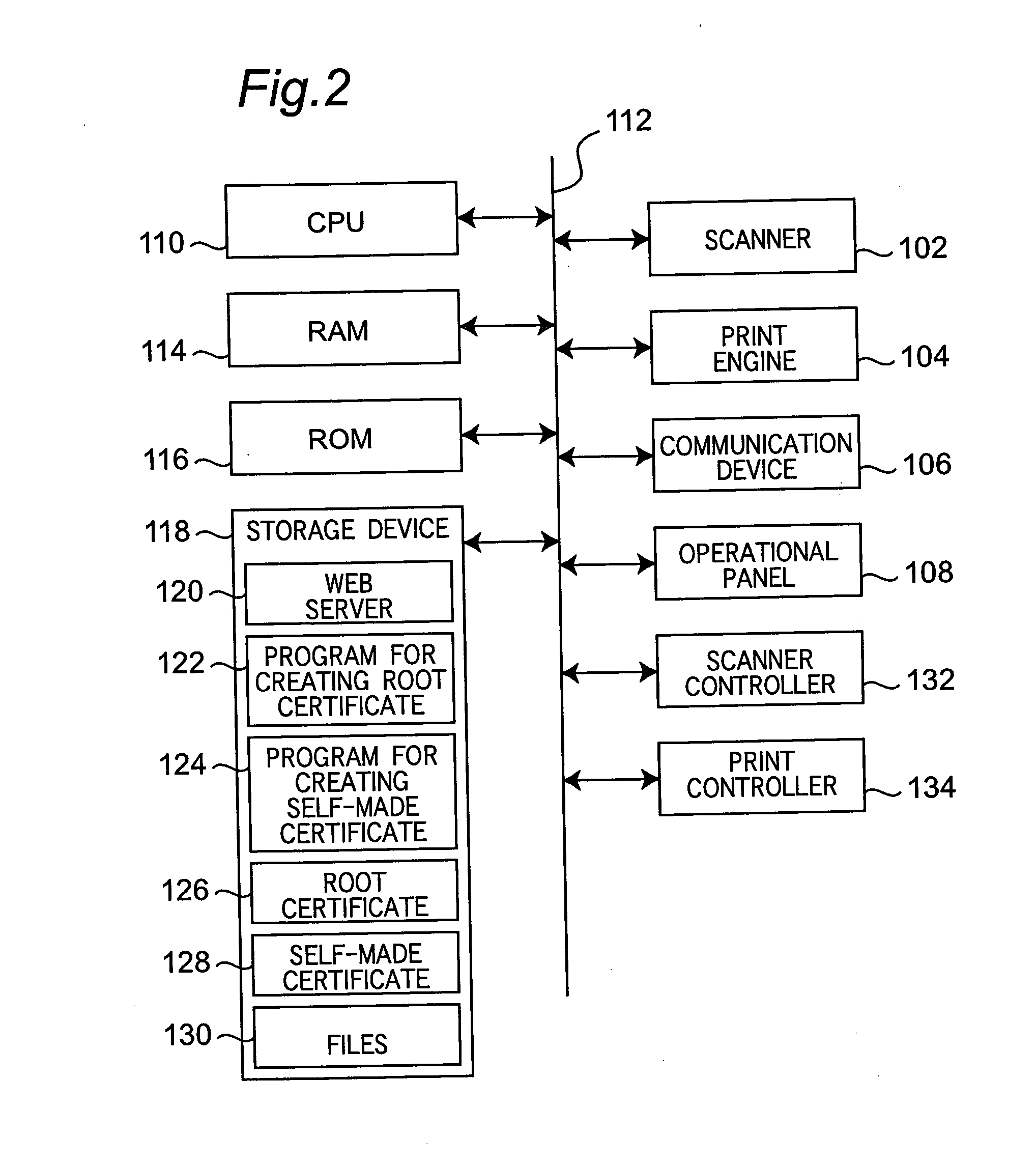
InactiveUS20050005097A1User identity/authority verificationCoding/ciphering apparatusRoot certificateCommunications system
In a communication system wherein a device and a client communicate data with each other through a network, the device holds a root certificate including a public key in a pair of the public key and a private key and signed with the public key. When data is sent, a certificate creator creates a second certificate including the root certificate designated as a certificate authority at a higher level and signed with the root certificate, and the second certificate is sent to the client. In the client, the root certificate has been stored beforehand, and a verifier verifies the signature of the second certificate with the root certificate.
Owner:MINOLTA CO LTD
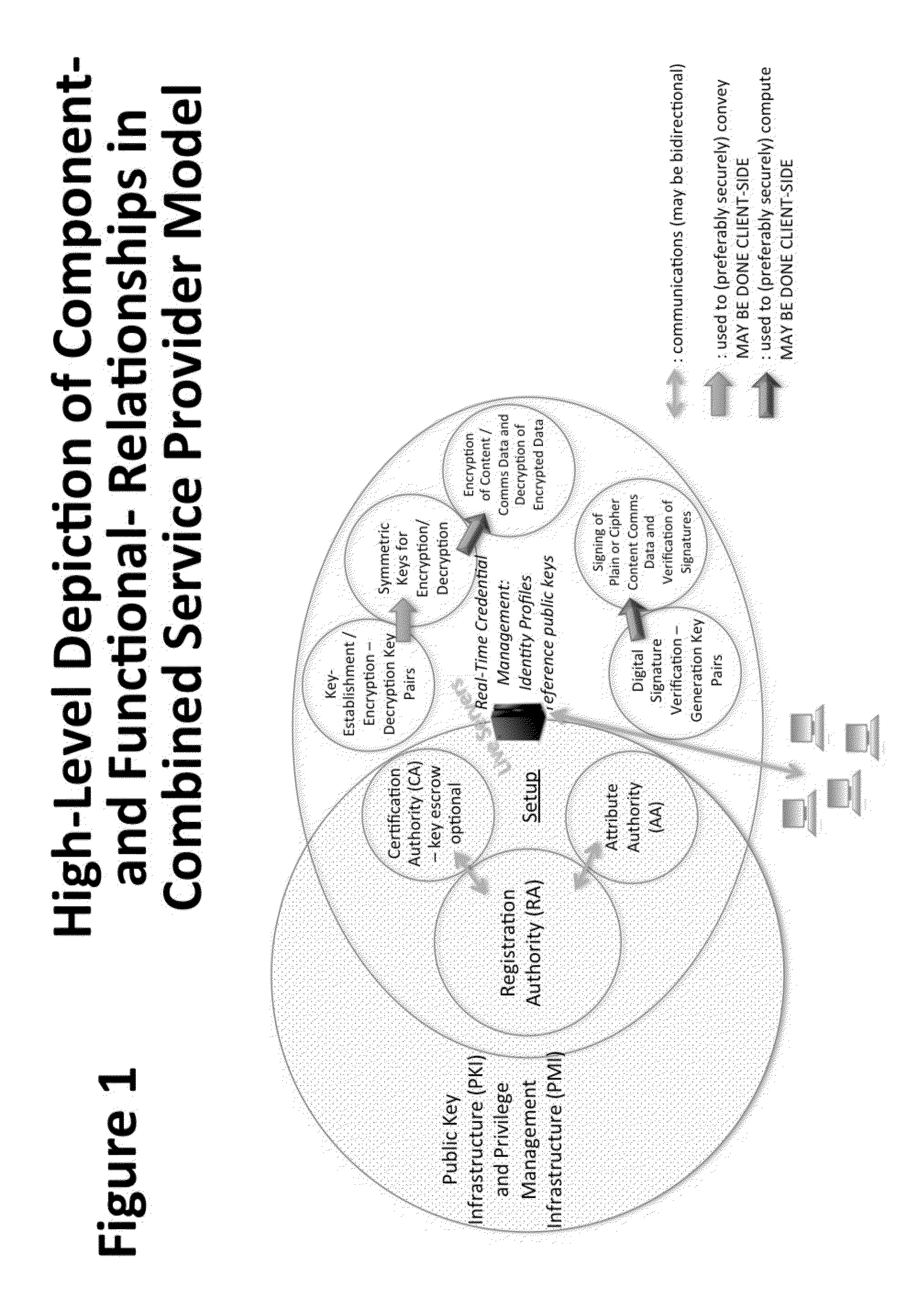
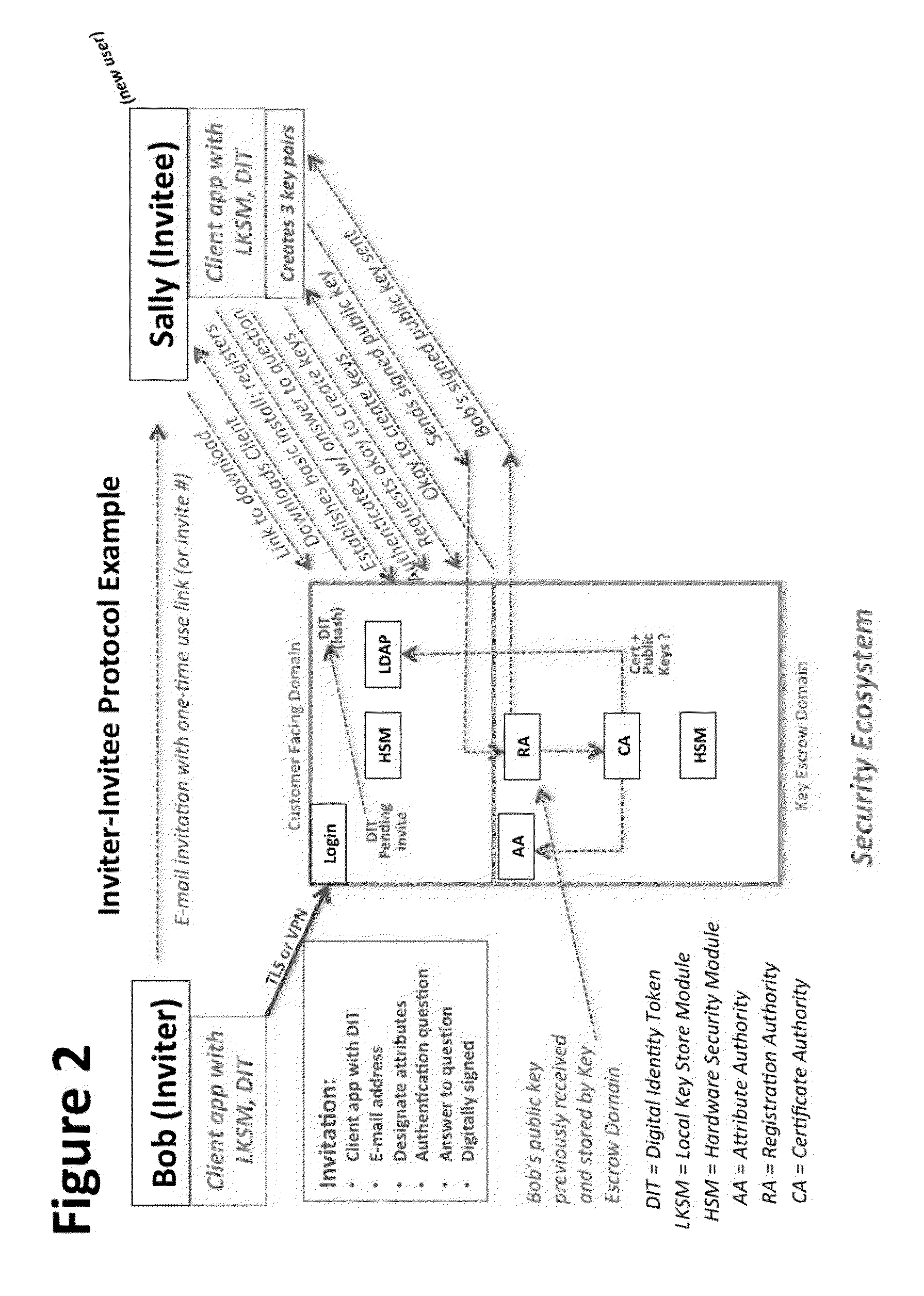
System and Method to Enable PKI- and PMI- Based Distributed Locking of Content and Distributed Unlocking of Protected Content and/or Scoring of Users and/or Scoring of End-Entity Access Means - Added
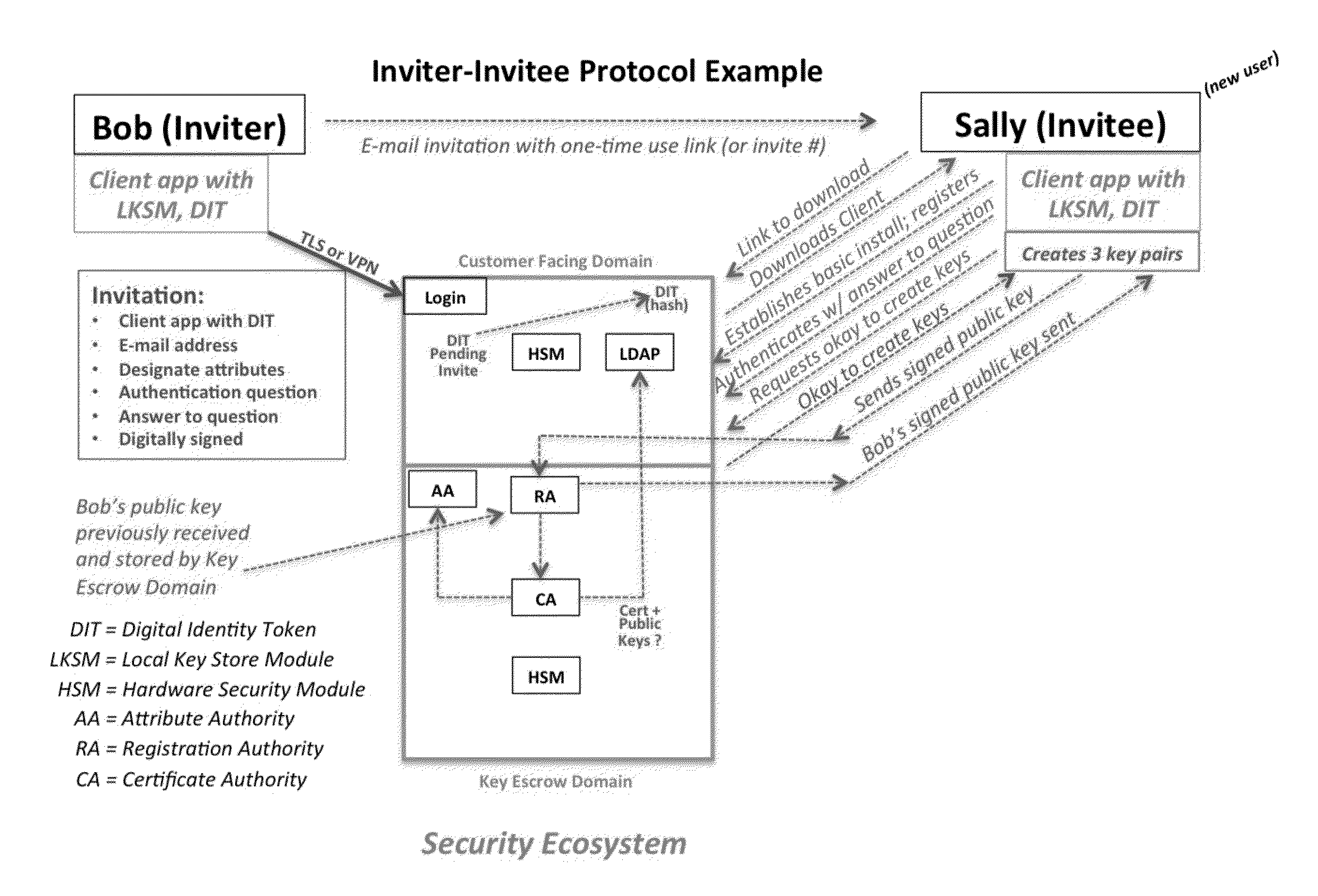
ActiveUS20150312233A1Key distribution for secure communicationUser identity/authority verificationTrust relationshipThin client
A central server configured with an Attribute Authority (“AA”) acting as a Trusted Third Party mediating service provider and using X.509-compatible PKI and PMI, VPN technology, device-side thin client applications, security hardware (HSM, Network), cloud hosting, authentication, Active Directory and other solutions. This ecosystem results in real time management of credentials, identity profiles, communication lines, and keys. It is not centrally managed, rather distributes rights to users. Using its Inviter-Invitee protocol suite, Inviters vouch for the identity of Invitees who successfully complete the protocol establishing communication lines. Users establish and respond to authorization requests and other real-time verifications pertaining to accessing each communication line (not end point) and sharing encrypted digital files. These are auditable, brokered, trusted-relationships where such relationships / digital agreements can each stand-alone (for privacy) or can leverage build-up of identity confidence levels across relationships. The service is agnostic to how encrypted user content is transported or stored.
Owner:T CENT
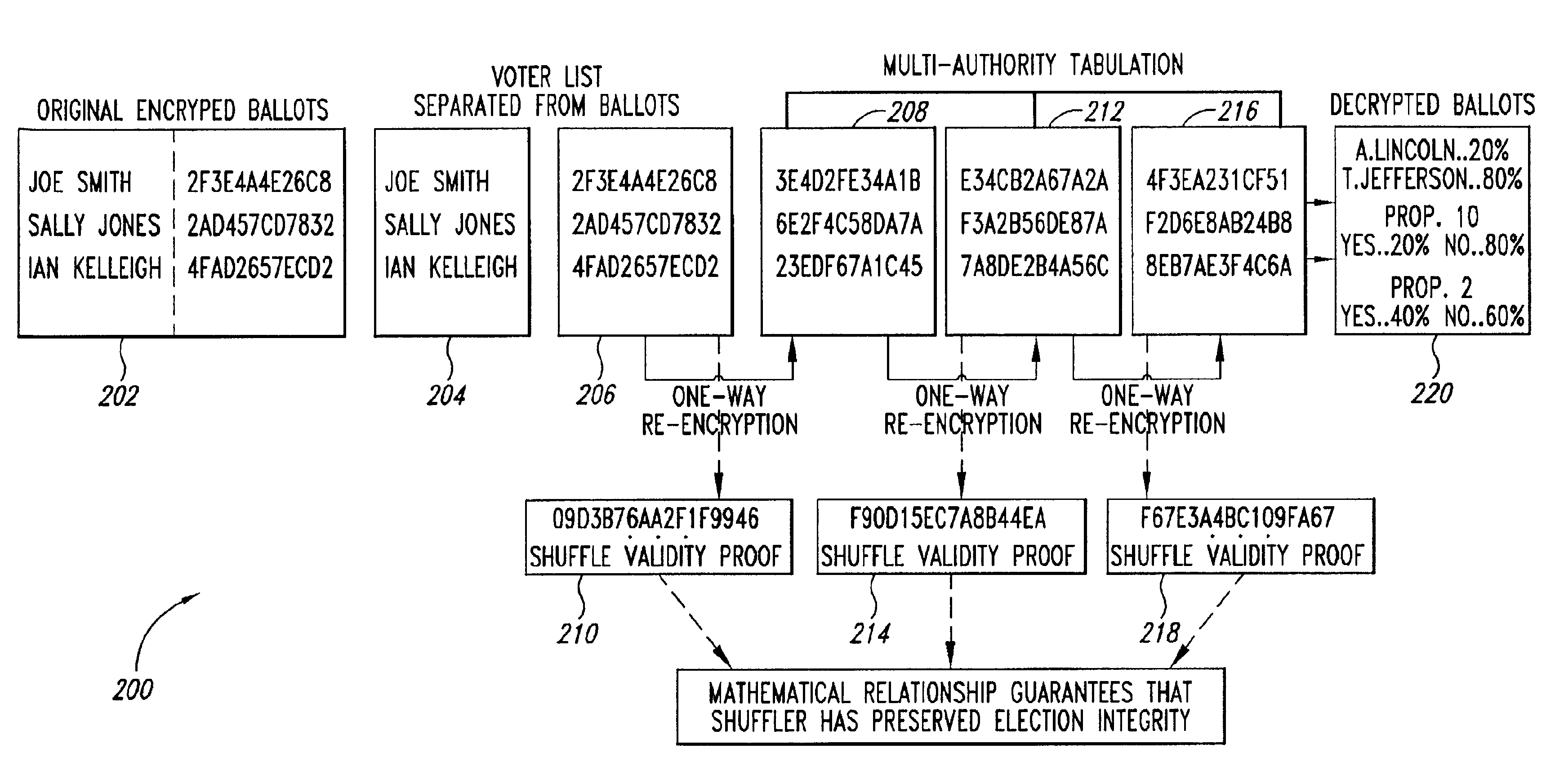
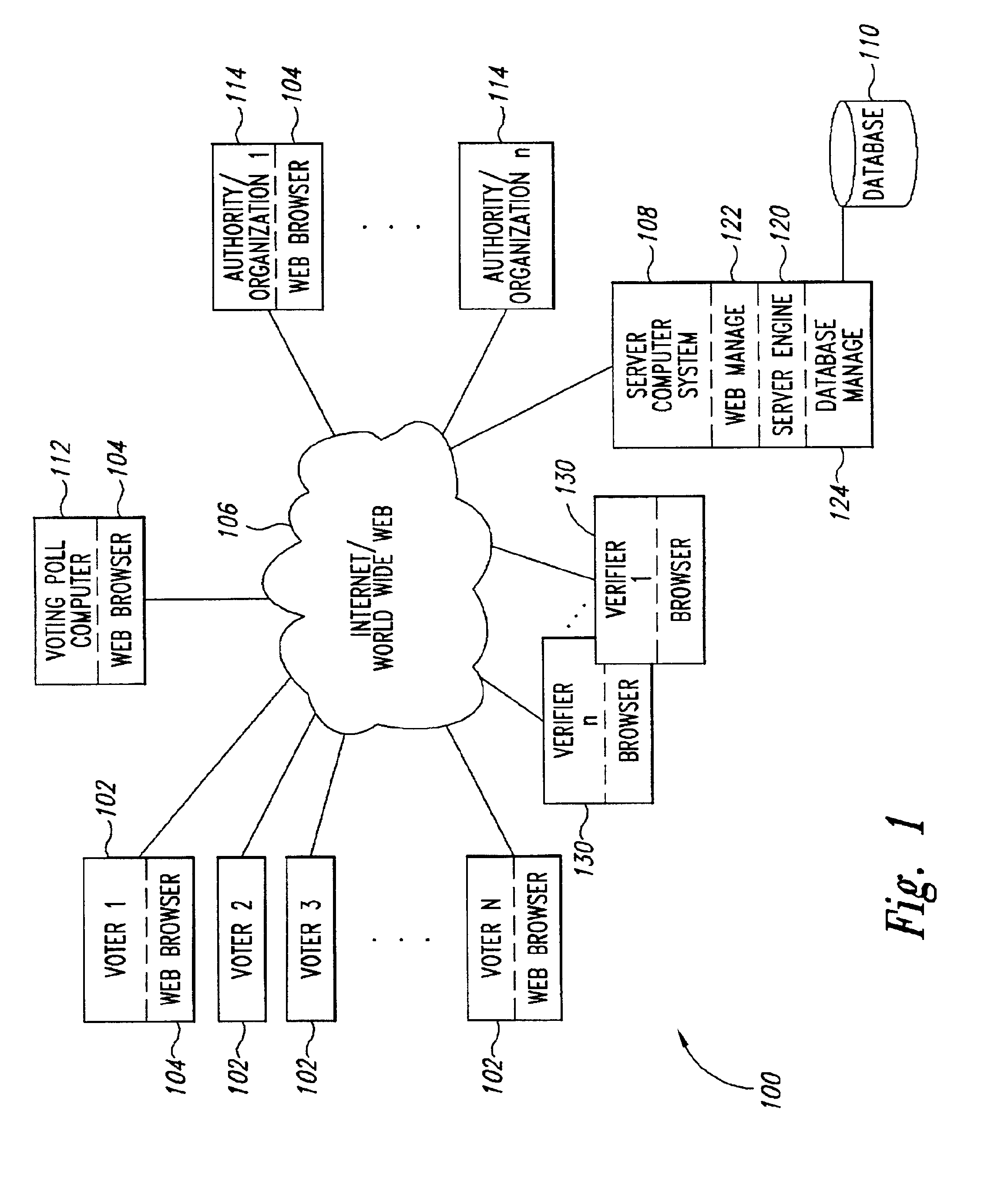
Verifiable, secret shuffles of encrypted data, such as elgamal encrypted data for secure multi-authority elections
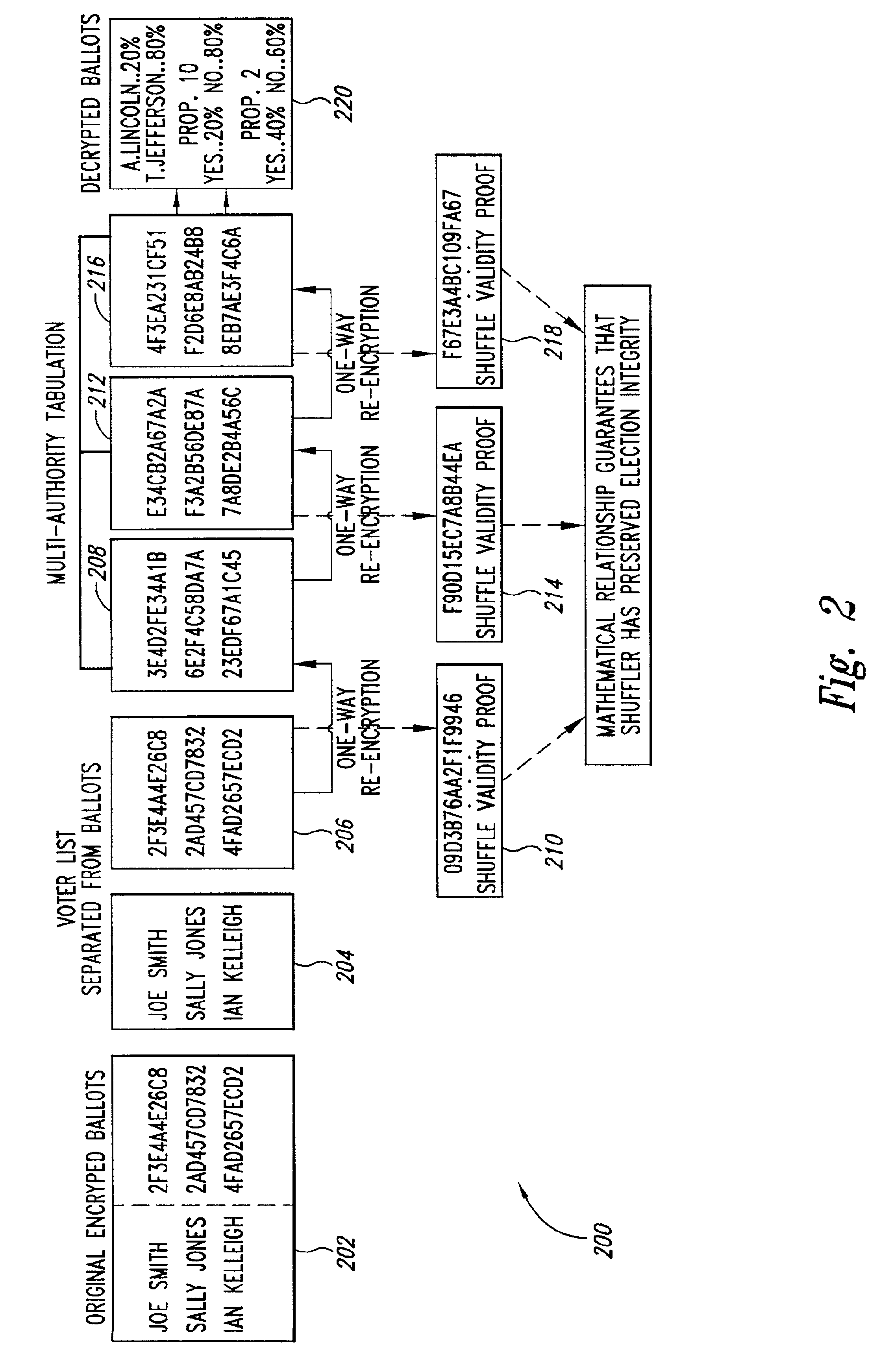
InactiveUS6950948B2Easy to identifyVoting apparatusKey distribution for secure communicationOriginal dataComputer security
A cryptographic process permits one to verifiably shuffle a series of input data elements. One or more authorities or individuals “shuffle,” or “anonymize” the input data (e.g. public keys in discrete log form or ElGamal encrypted ballot data). The process includes a validity construction that prevents any one or more of the authorities or individuals from making any changes to the original data without being discovered by anyone auditing a resulting proof transcript. The shuffling may be performed at various times. In the election example, the shuffling may be performed, e.g., after ballots are collected or during the registration, or ballot request phase of the election, thereby anonymizing the identities of the voters.
Owner:DEMOXI INC
System and method for graphical indicia for the certification of records
InactiveUS7017046B2User identity/authority verificationPublic key infrastructure trust modelsGraphicsDocument preparation
A system and method for authenticating records. Certification information may be encoded in graphical form. This graphical form, or design, may be referred to as an “Indicia.” The record at issue may be printed out by a computer or stored electronically and bear on it an indicia that relates to the authenticity of the document. The indicia (and record) may then be scanned and interpreted by the computer to authenticate the record.
Owner:DEV SPECIALIST
Method for a public-key infrastructure for vehicular networks with limited number of infrastructure servers
InactiveUS20110083011A1Provide securityCommunication securityDigital data processing detailsNetwork topologiesCommunications securitySecure communication
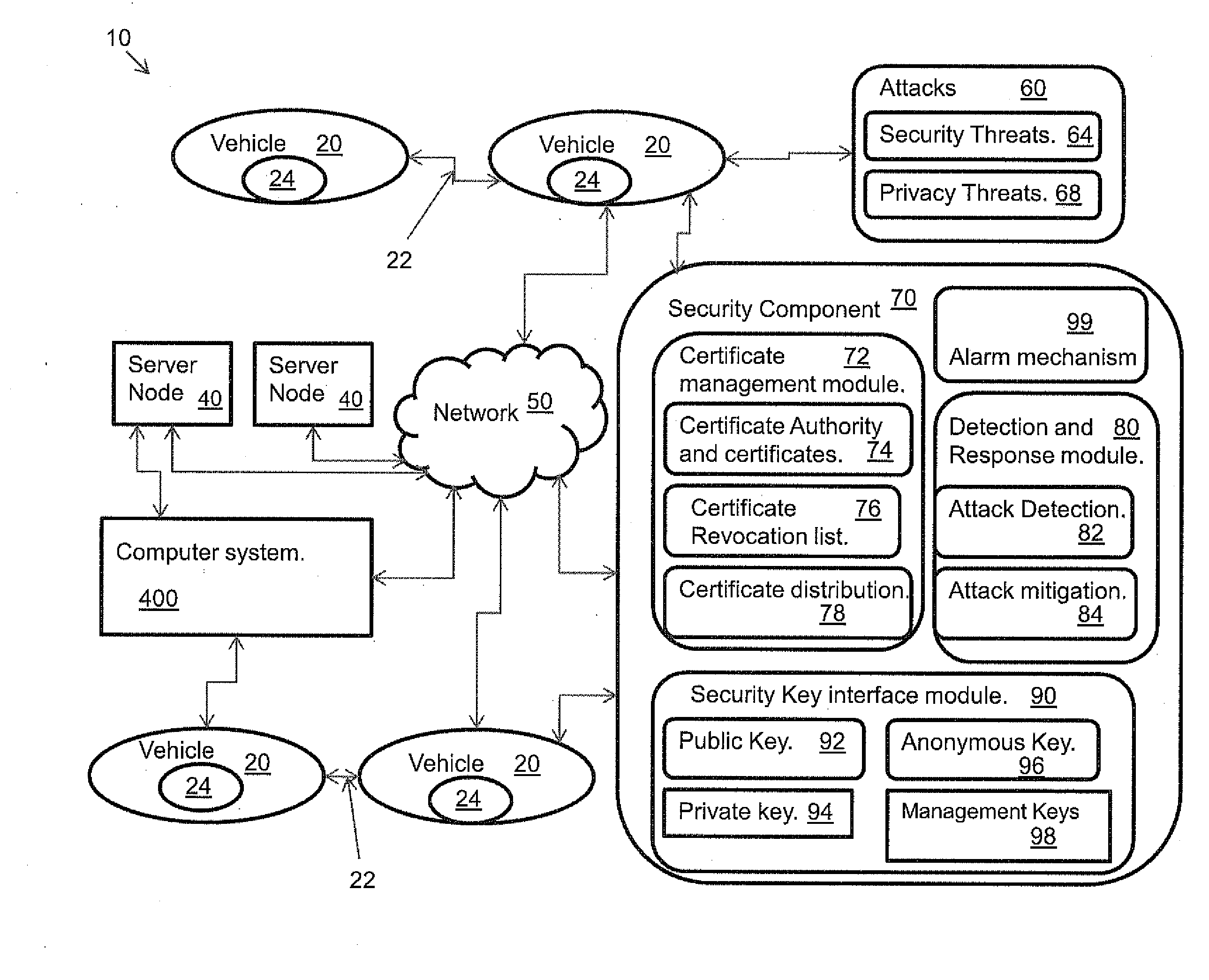
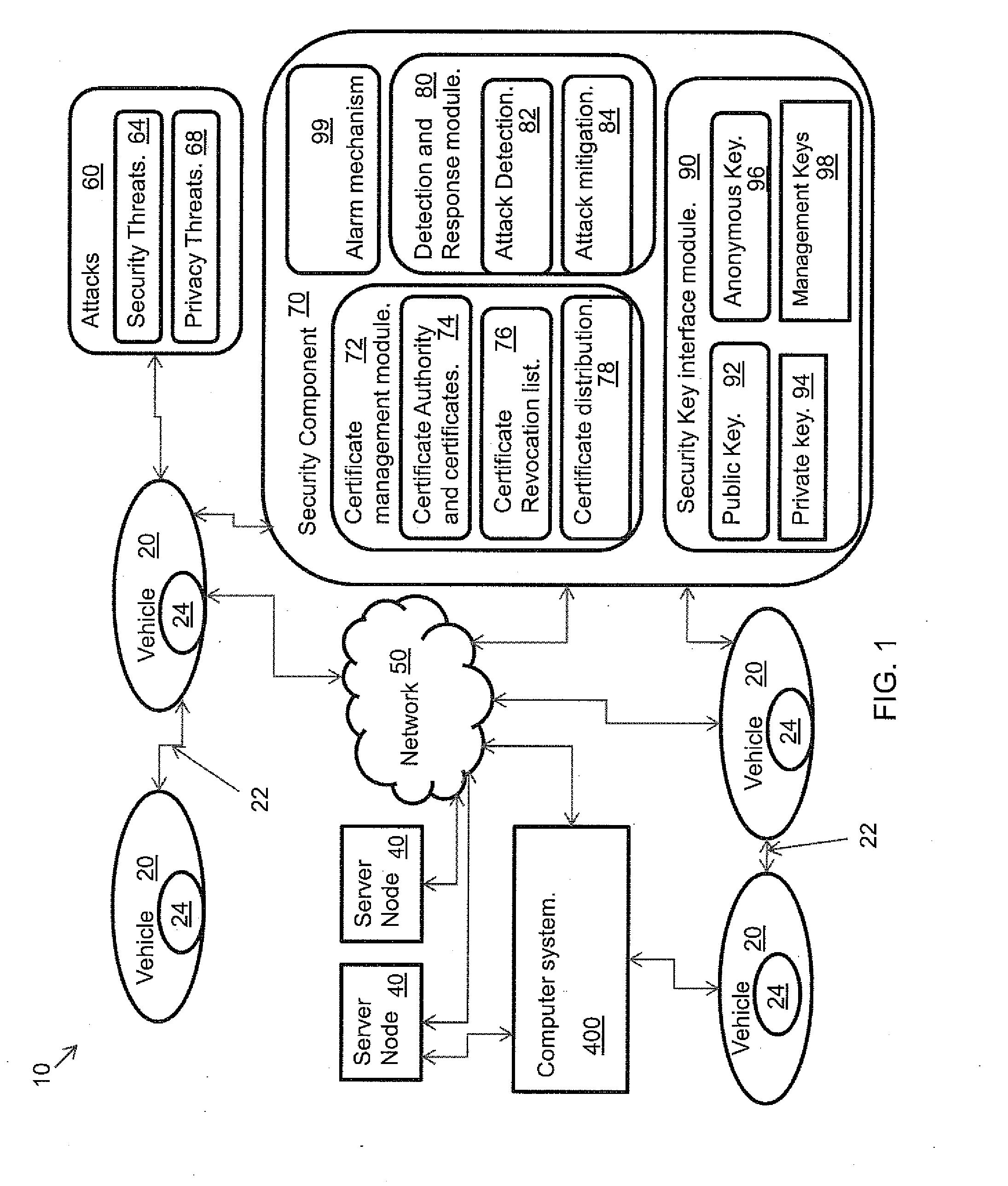
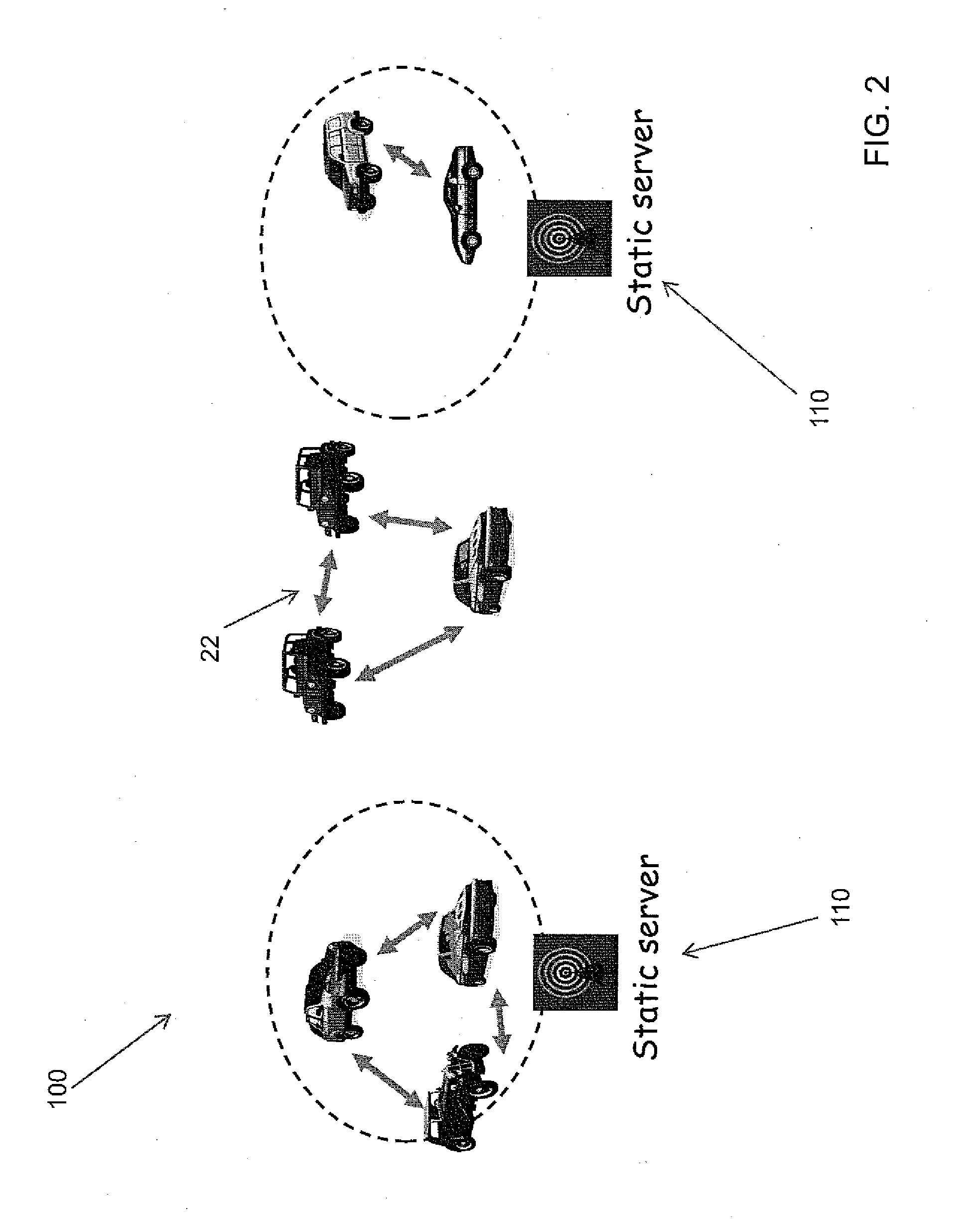
A system, and method related thereto, for providing a vehicular communications network public-key infrastructure. The system comprises a plurality of communications infrastructure nodes and a plurality of vehicles each having a communications component. The communications component provides vehicle to vehicle (V2V) communications, and communications via infrastructure nodes. A communications security component in each of the plurality of vehicles provides security for the communications between the plurality of vehicles using a plurality of security modules. The security modules include a certificate management module. A public key interface module may include a public key, a private key, an anonymous key and a management key. The system further includes a detection and response module for attack detection and attack mitigation. The communications security component assigns and installs at least one security key, a certificate of operation, and a current certificate revocation list. The communications component provides secure communications between the plurality of vehicles.
Owner:TELCORDIA TECHNOLOGIES INC
Identity verification method using a central biometric authority
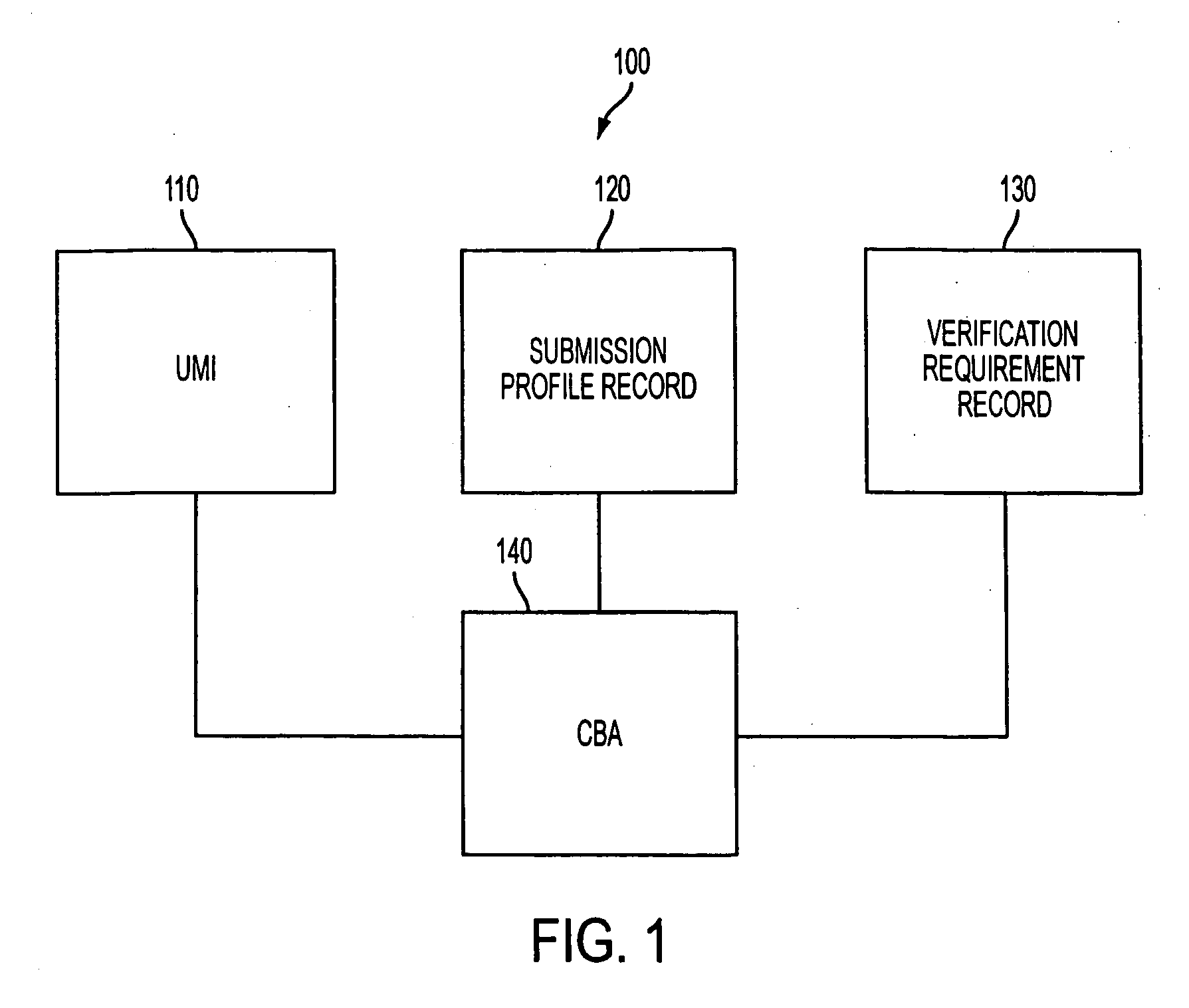
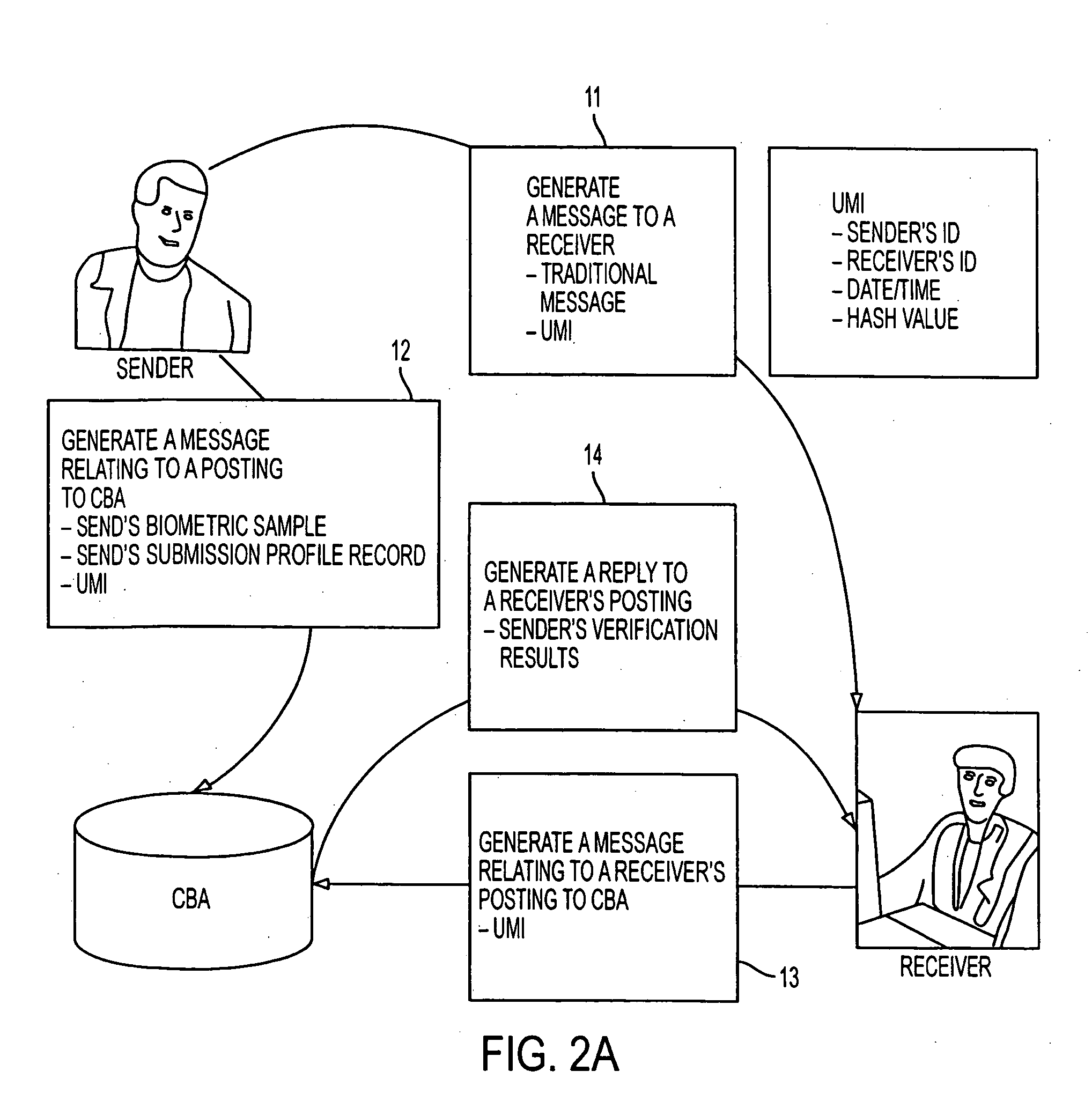
InactiveUS20050251688A1Improve performanceUser identity/authority verificationDigital data authenticationAuthenticationElectronic transaction
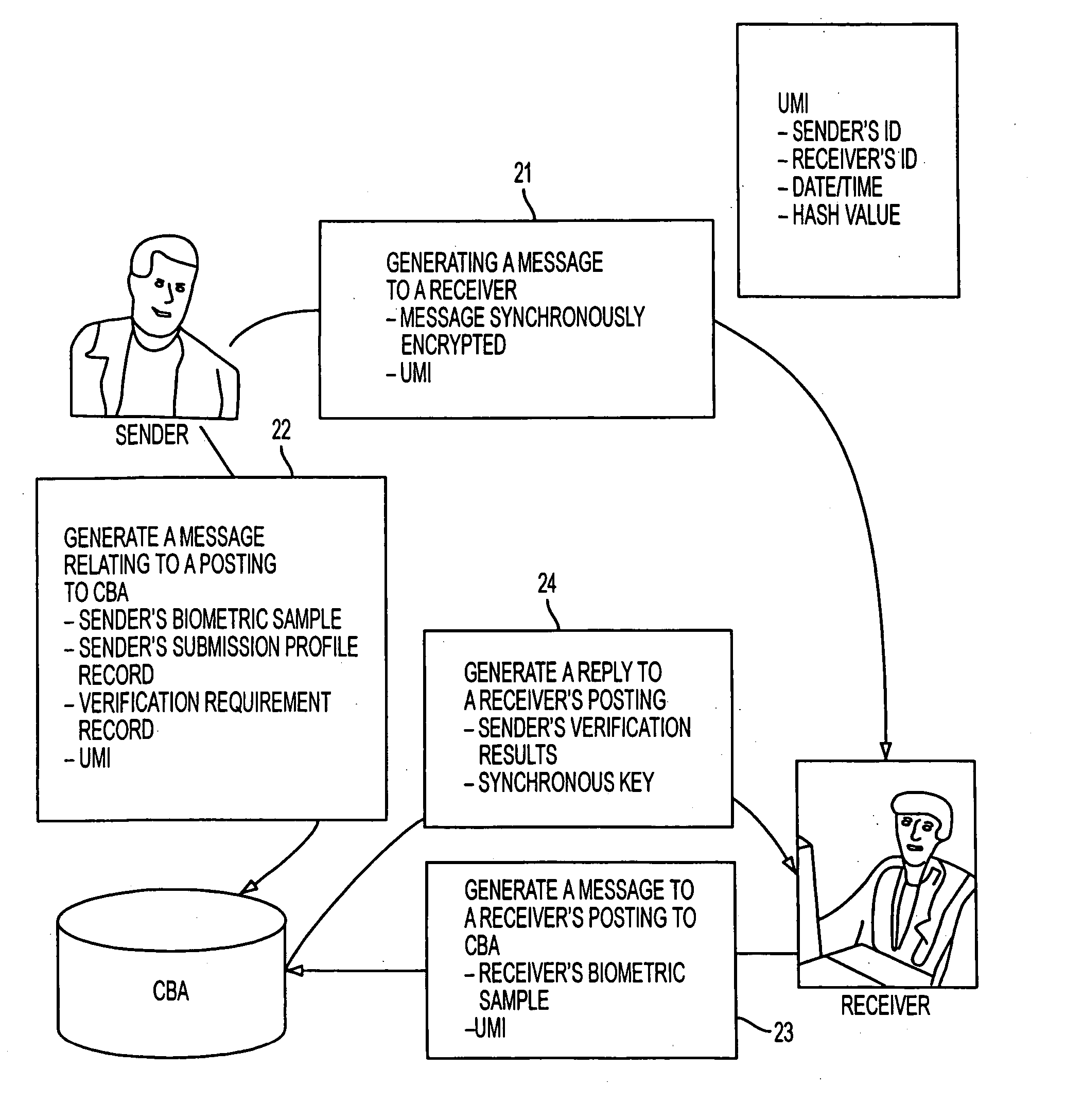
A method performs biometric verifications to authenticate the identification of users using a central biometric authority (CBA). This allows parties to an electronic transaction to be assured of each other's identity. Specifically, at the sender side, a first message to a receiver is generated, wherein the first message includes a message text and a unique message identifier (UMI). At the sender side, a second message concerning a posting to the CBA is also generated, wherein the second message includes the sender's biometric sample, the UMI, and the sender's submission profile record. At a receiver side, it is decided that if a receiver wishes to verify the sender's identity and if so, the first message is automatically verified. At the receiver side, a third message concerning a receiver's posting to the CBA is issued, the third message including only the UMI, as received from the sender side. Finally, at the CBA, a reply to the third message is provided, the reply including the sender's verification result.
Owner:FUSIONARC
Encryption key exchange system and method
InactiveUS9002018B2Improve usabilityKey distribution for secure communicationUser identity/authority verificationUsabilityEncryption
Owner:SYNC UP TECH
Popular searches
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com