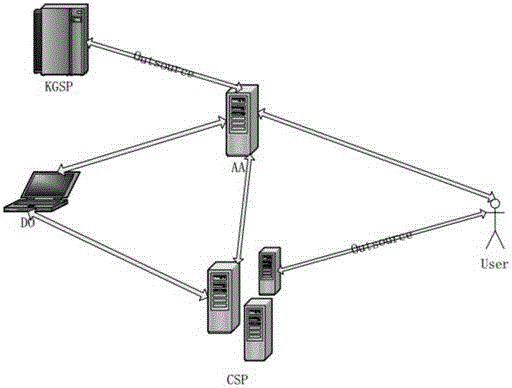
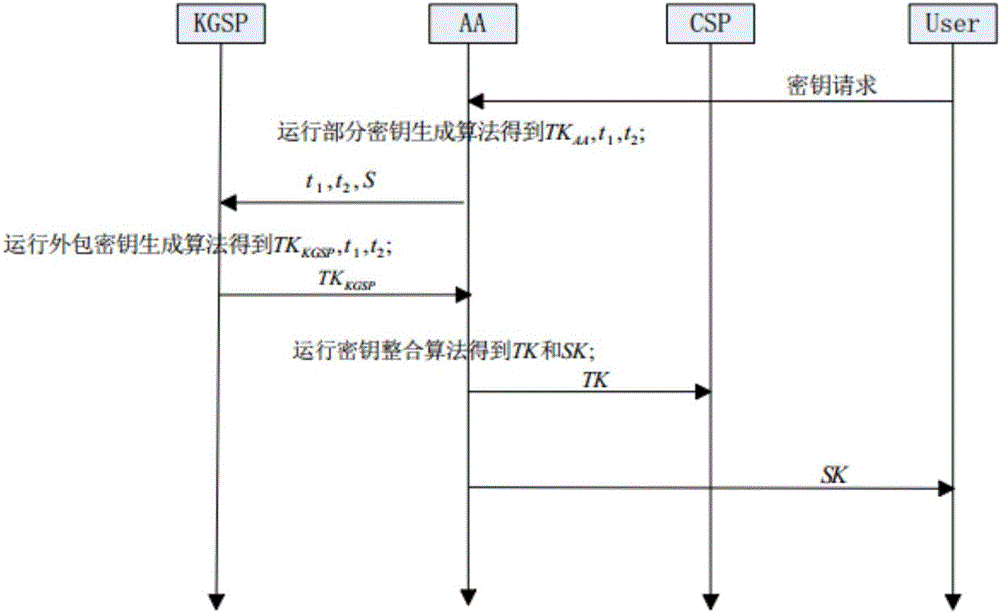
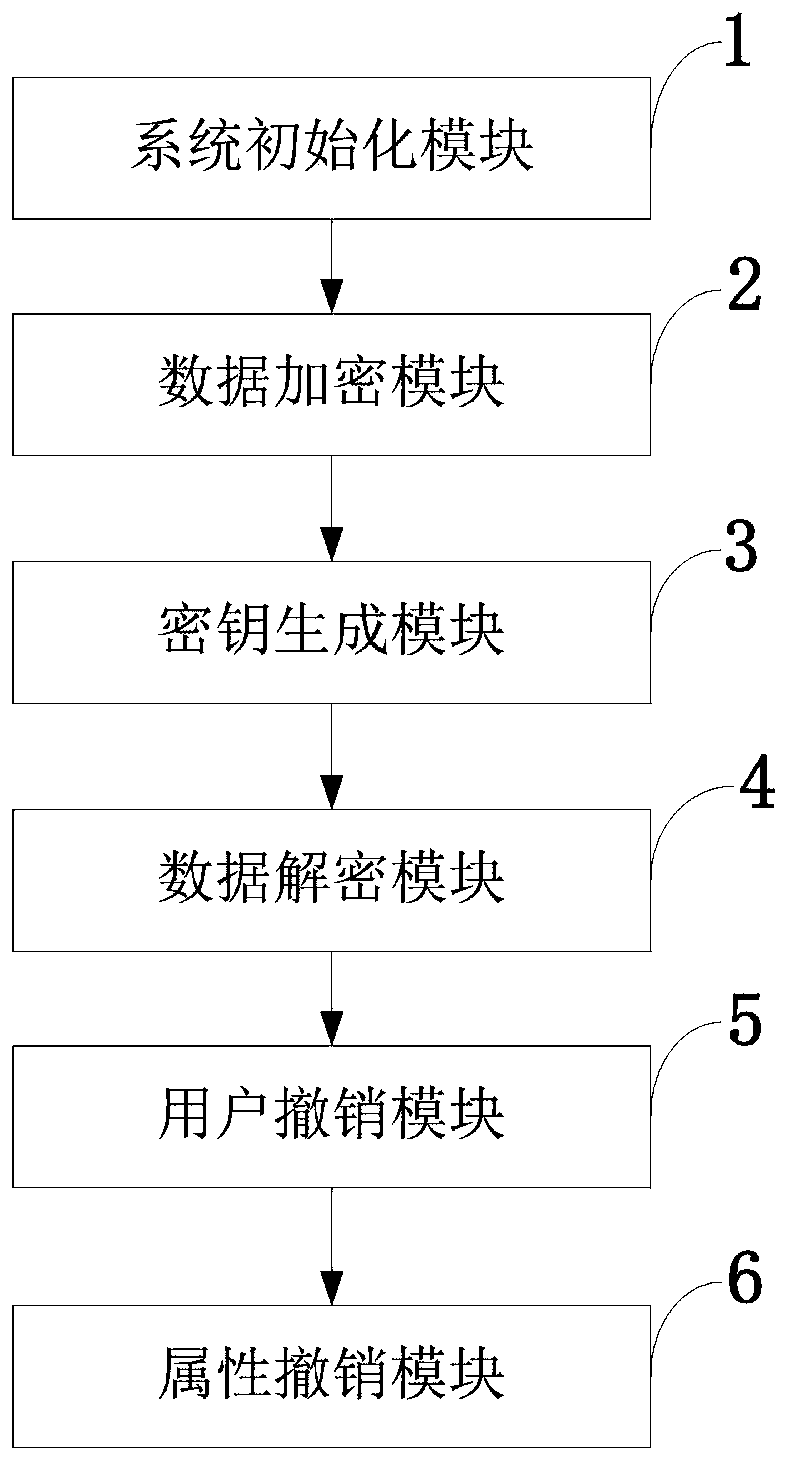
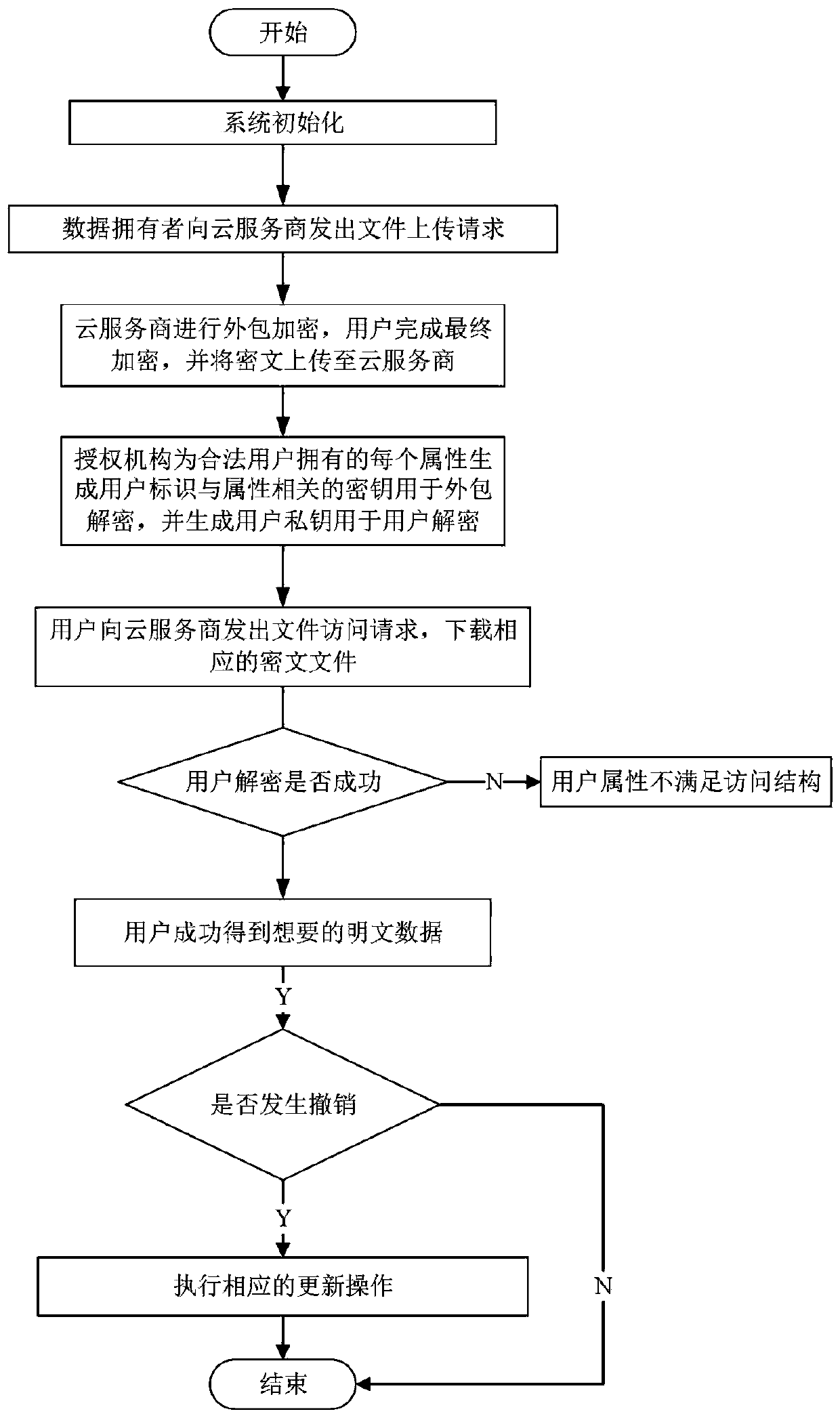
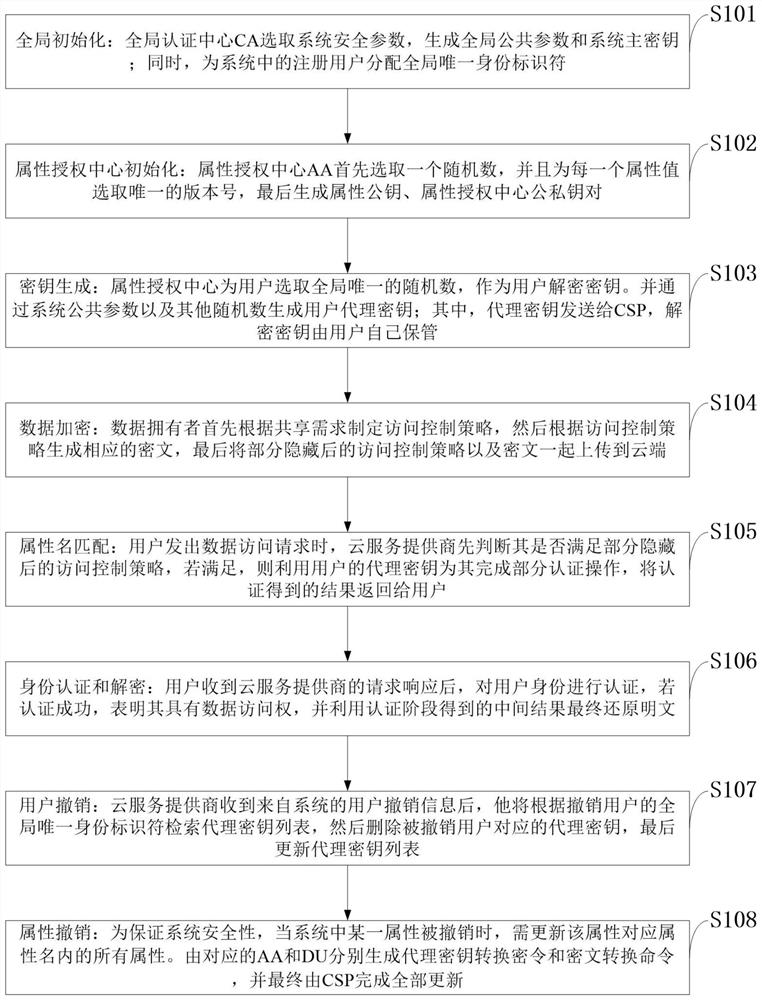
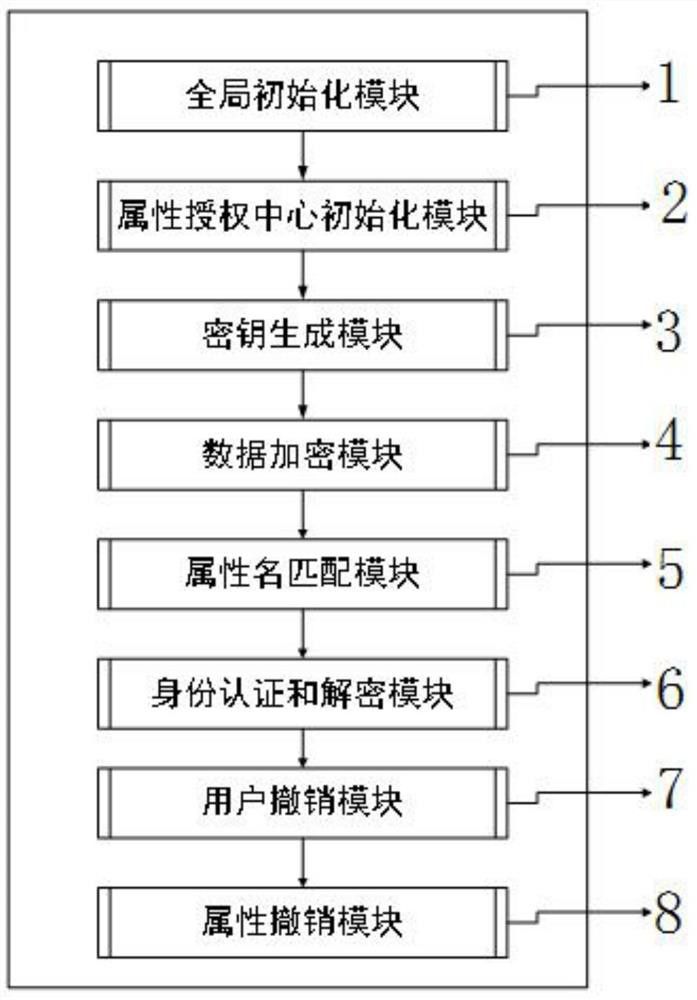
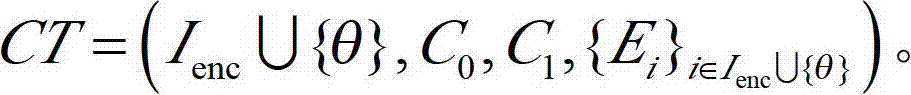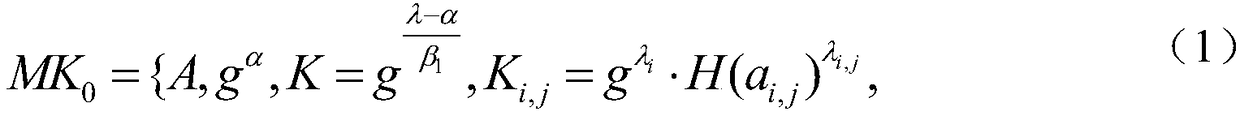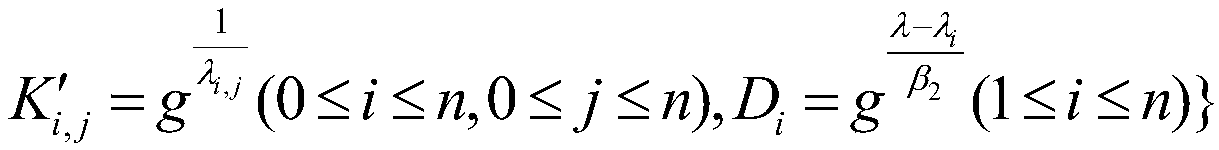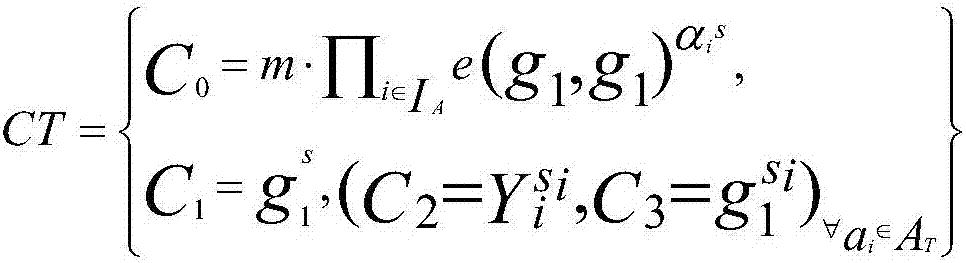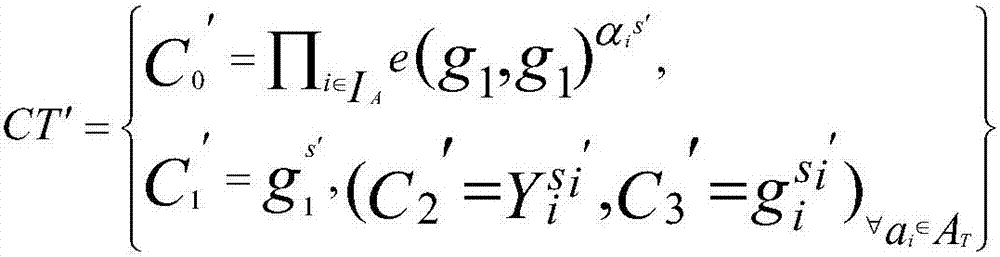Patents
Literature
139 results about "Attribute authority" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
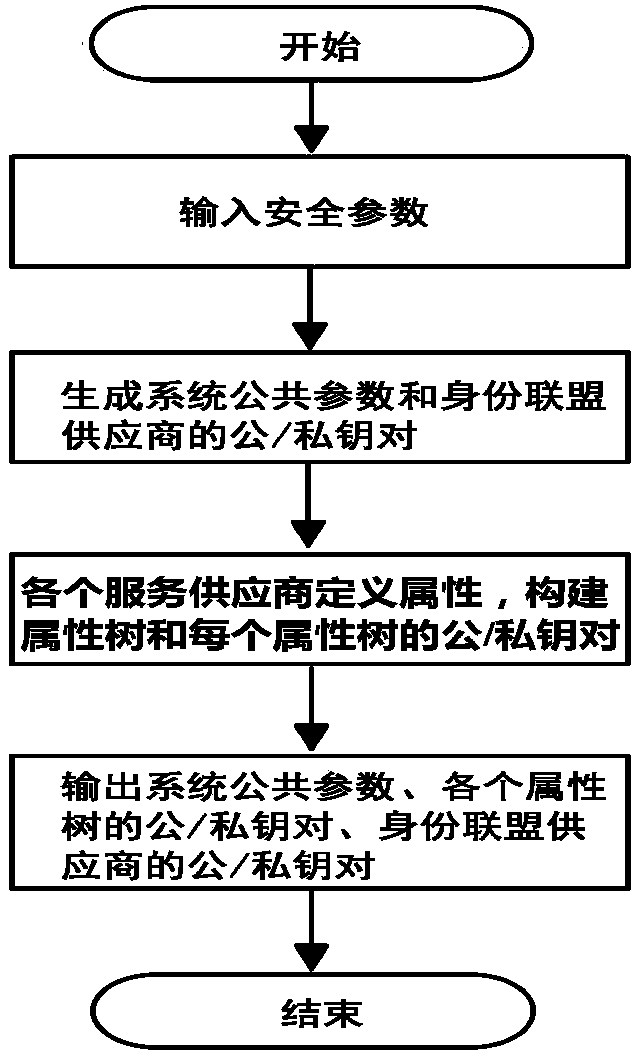
An attribute authority (also known as an attribute store) is a directory or database in which systems can securely add, modify, and save attributes. An attribute authority is a trusted source of data for ABAC decisions. Data sources such as MySQL databases, LDAP directories, Active Directories, and Web services can be configured as...
System and Method to Enable PKI- and PMI- Based Distributed Locking of Content and Distributed Unlocking of Protected Content and/or Scoring of Users and/or Scoring of End-Entity Access Means - Added
ActiveUS20150312233A1Key distribution for secure communicationUser identity/authority verificationTrust relationshipThin client
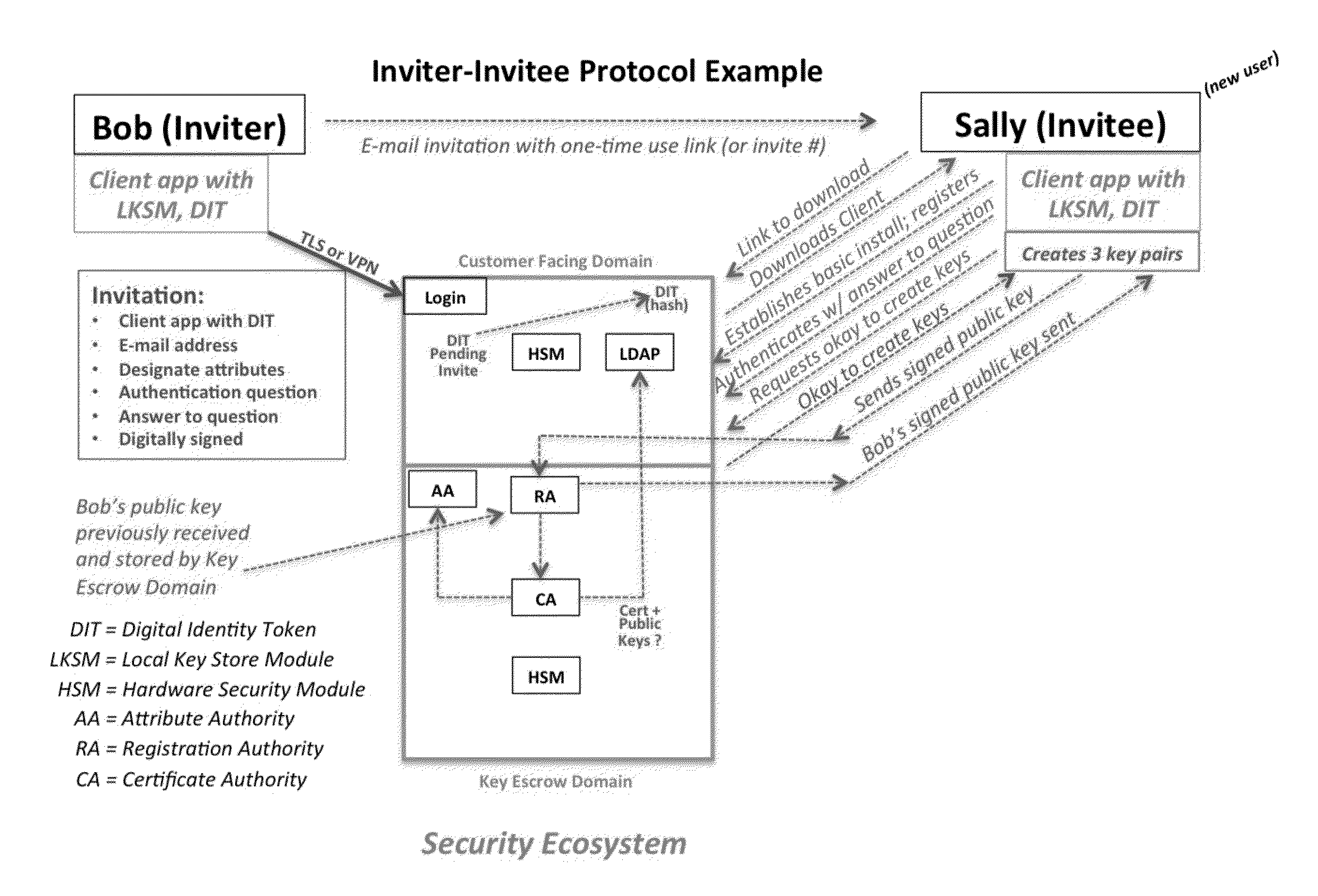
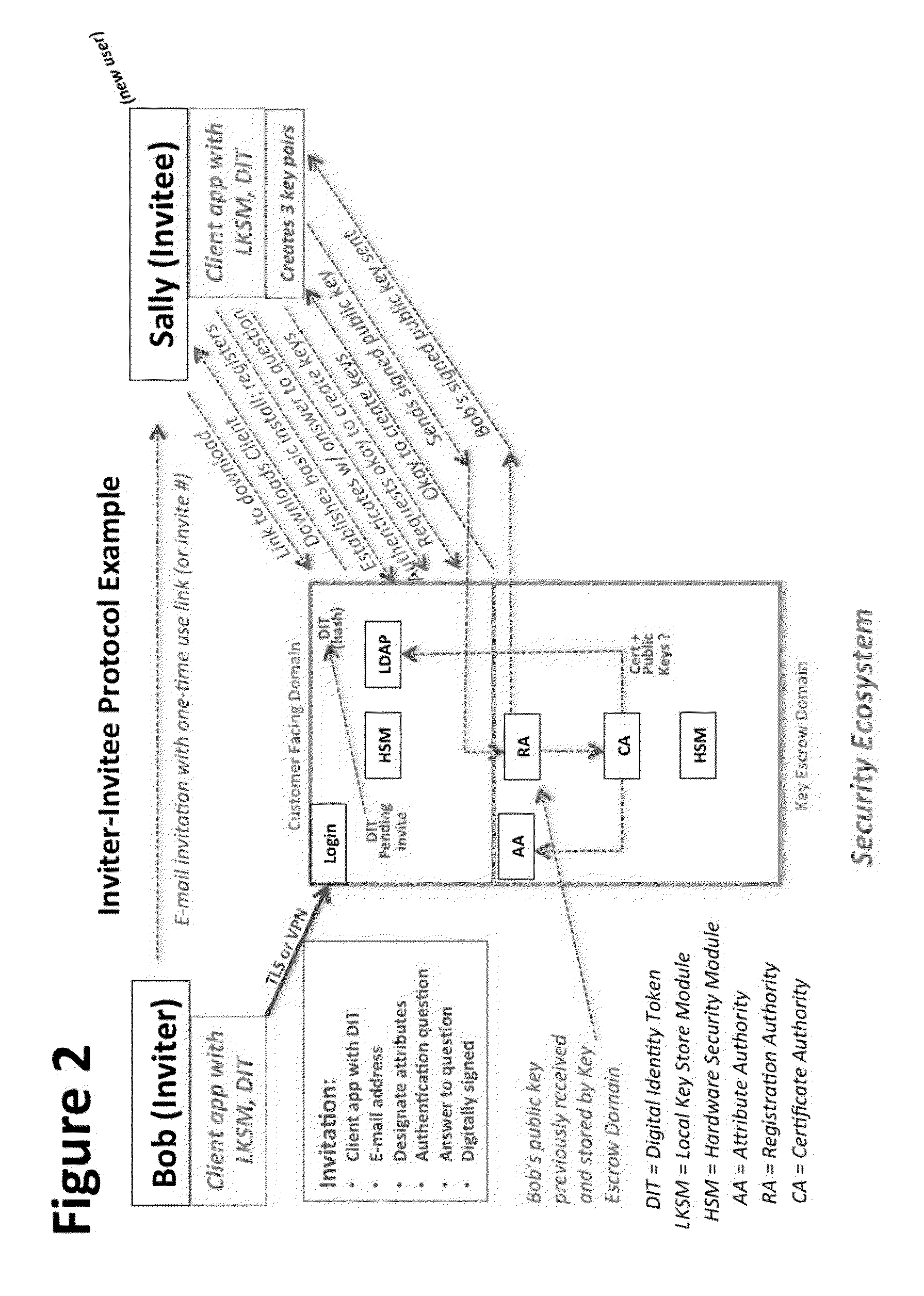
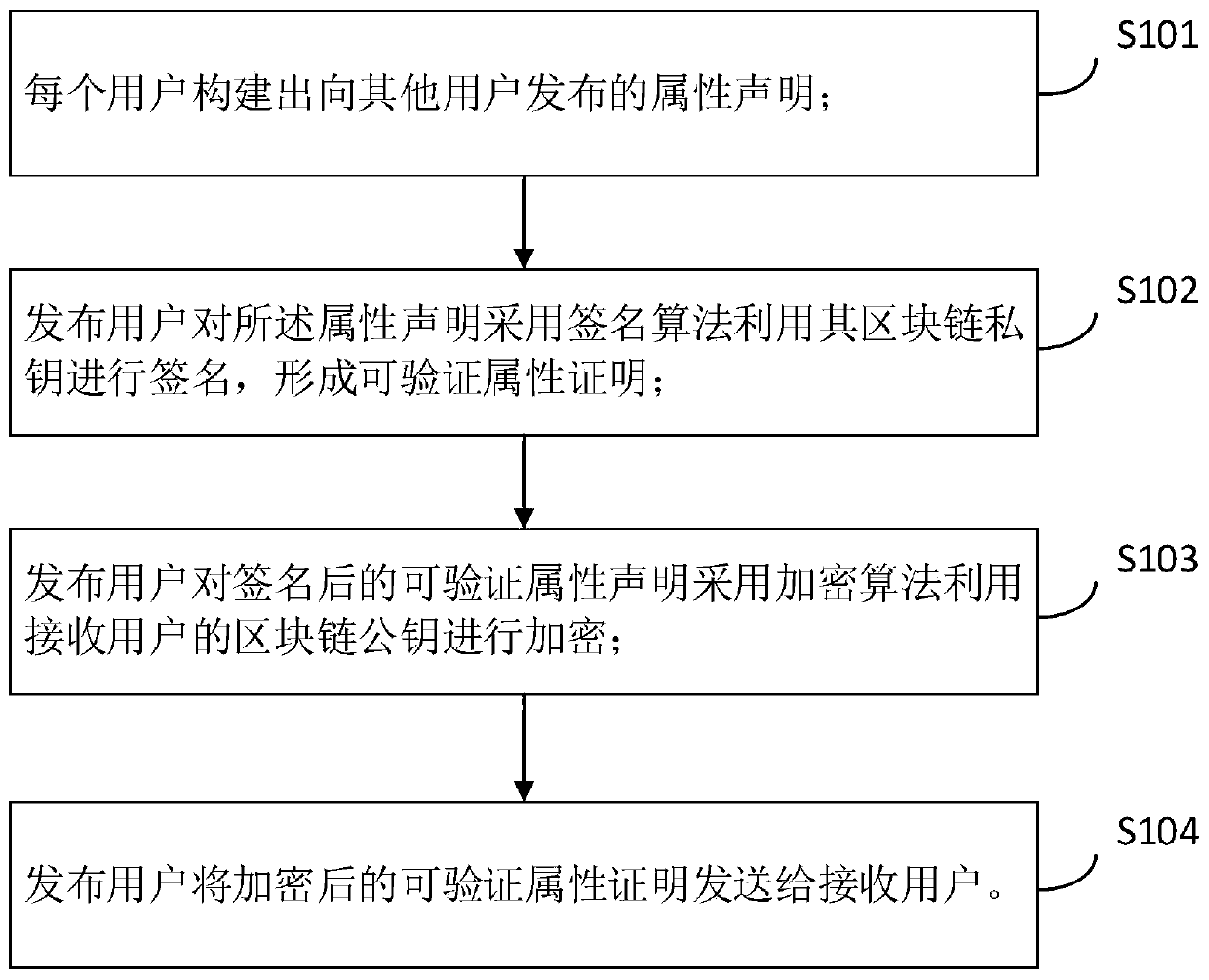
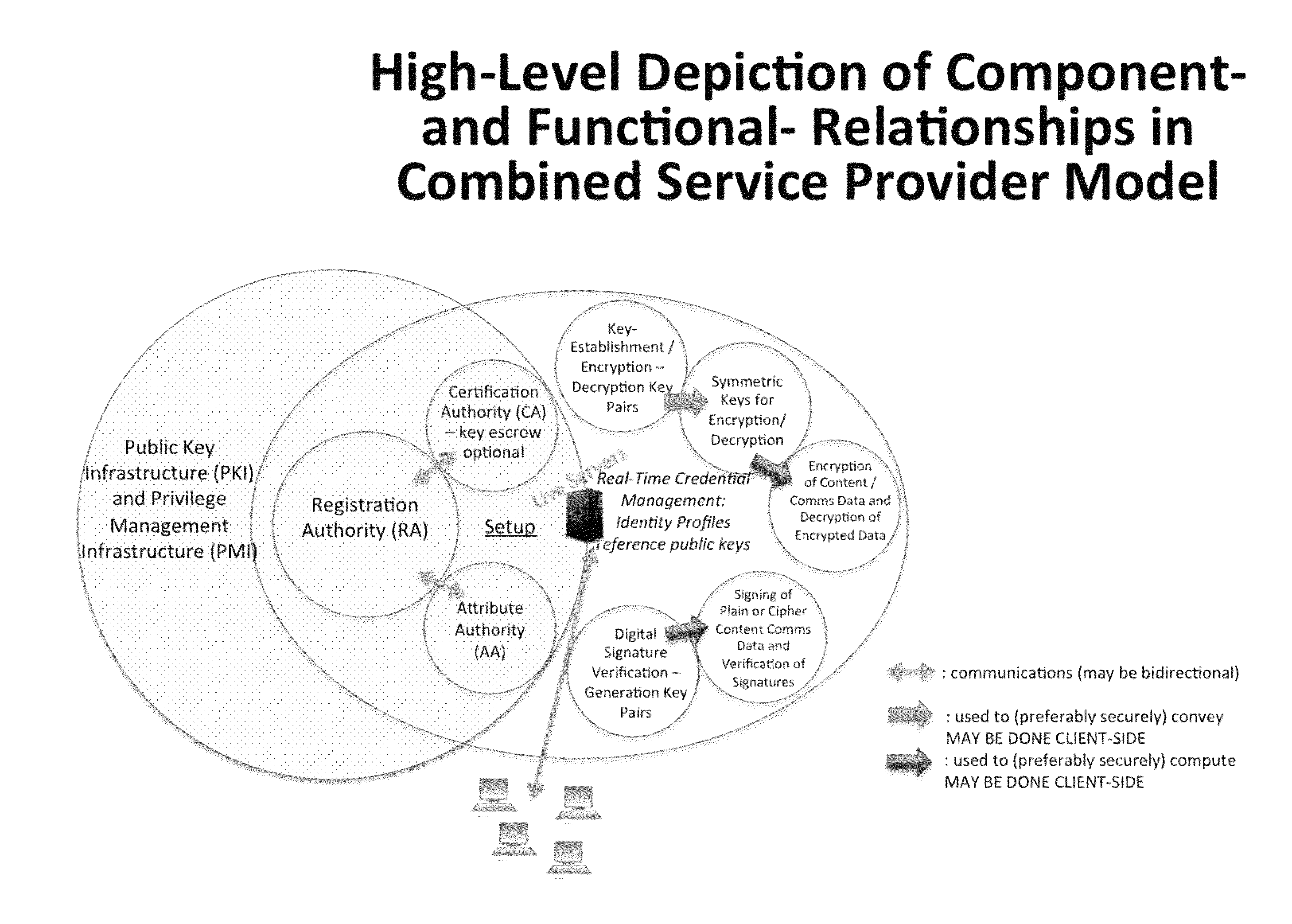
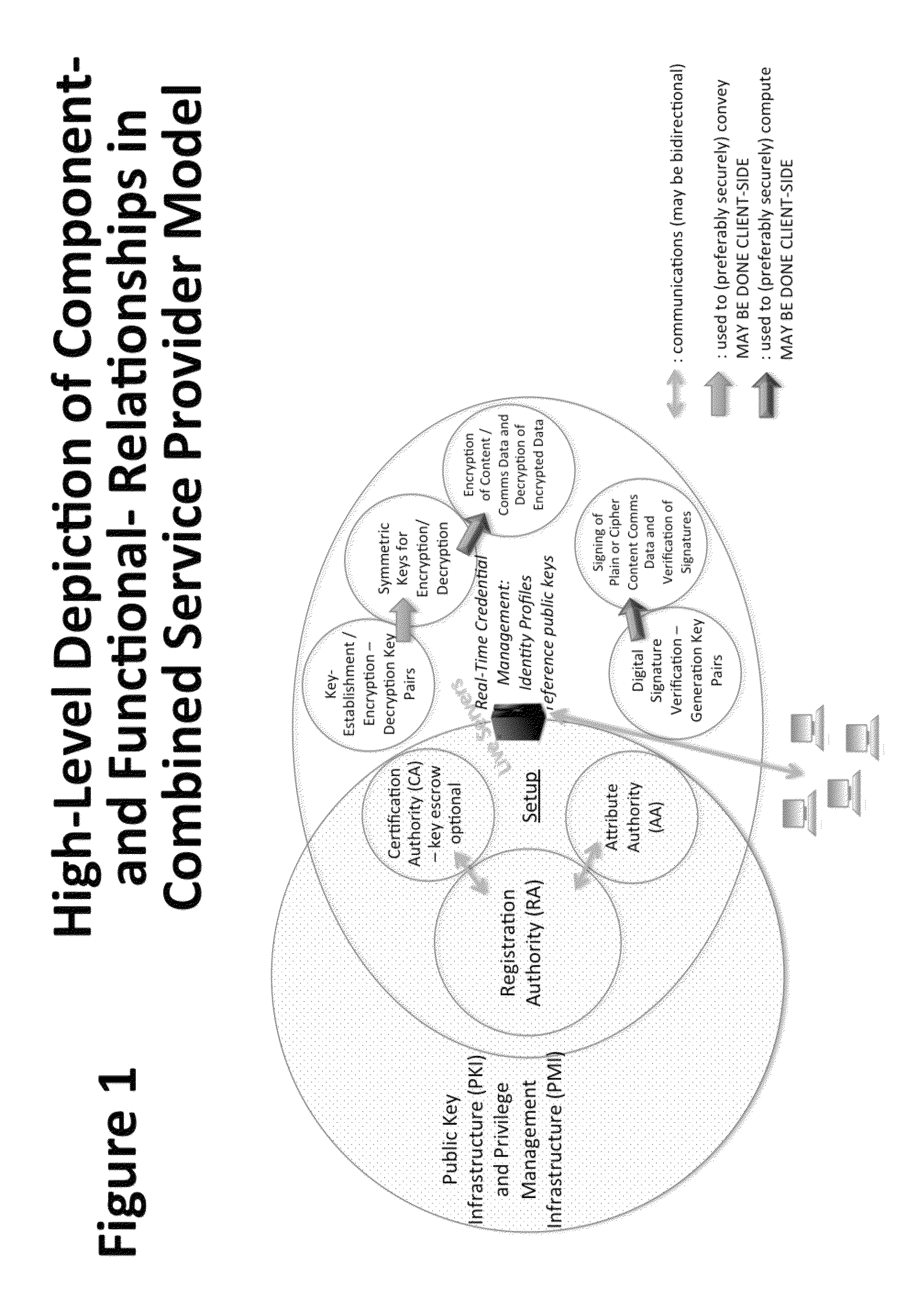
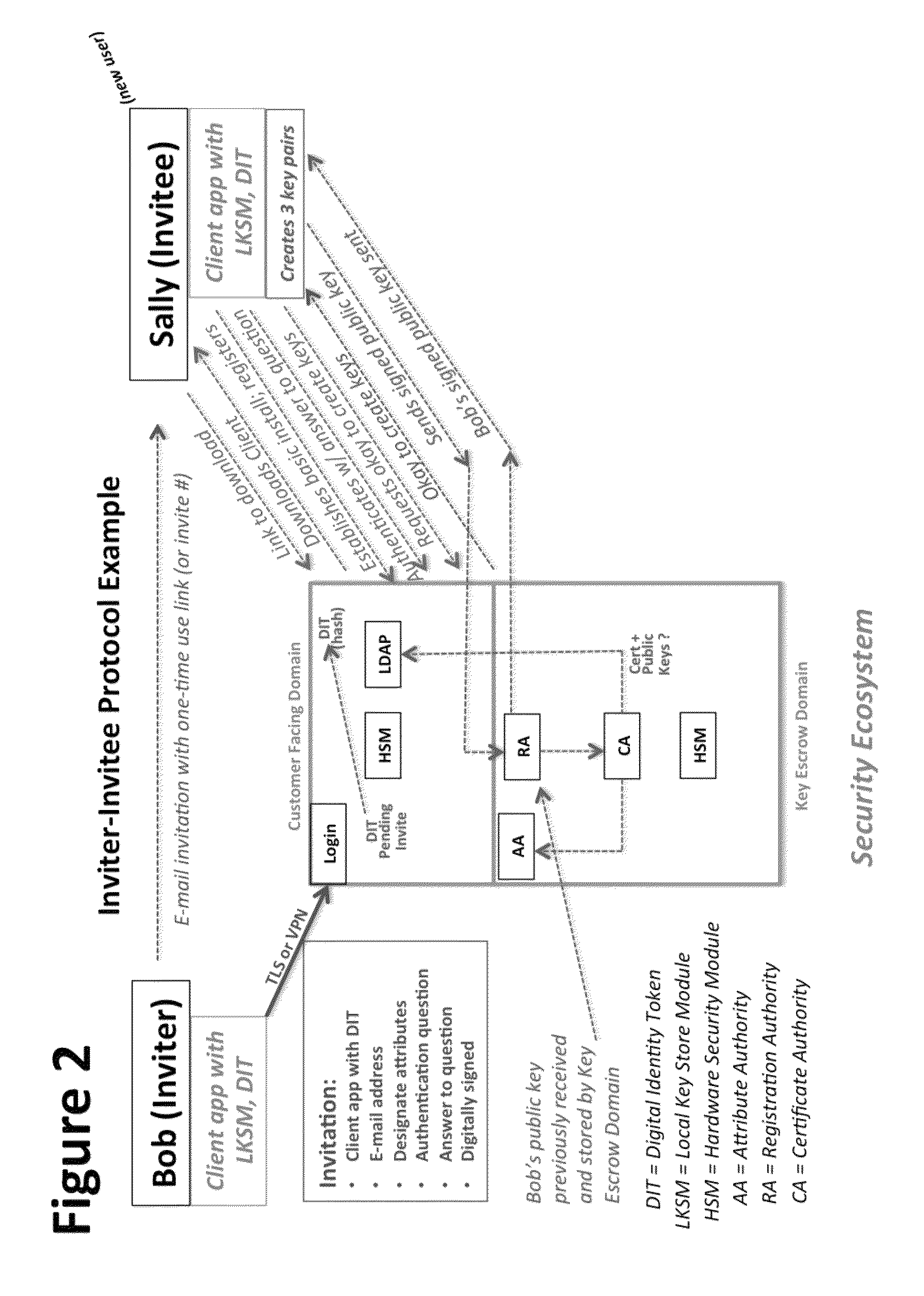
A central server configured with an Attribute Authority (“AA”) acting as a Trusted Third Party mediating service provider and using X.509-compatible PKI and PMI, VPN technology, device-side thin client applications, security hardware (HSM, Network), cloud hosting, authentication, Active Directory and other solutions. This ecosystem results in real time management of credentials, identity profiles, communication lines, and keys. It is not centrally managed, rather distributes rights to users. Using its Inviter-Invitee protocol suite, Inviters vouch for the identity of Invitees who successfully complete the protocol establishing communication lines. Users establish and respond to authorization requests and other real-time verifications pertaining to accessing each communication line (not end point) and sharing encrypted digital files. These are auditable, brokered, trusted-relationships where such relationships / digital agreements can each stand-alone (for privacy) or can leverage build-up of identity confidence levels across relationships. The service is agnostic to how encrypted user content is transported or stored.
Owner:T CENT
Attribute Certificate Verification Method and System
InactiveUS20080016335A1Data processing applicationsUser identity/authority verificationService provisionOperating system
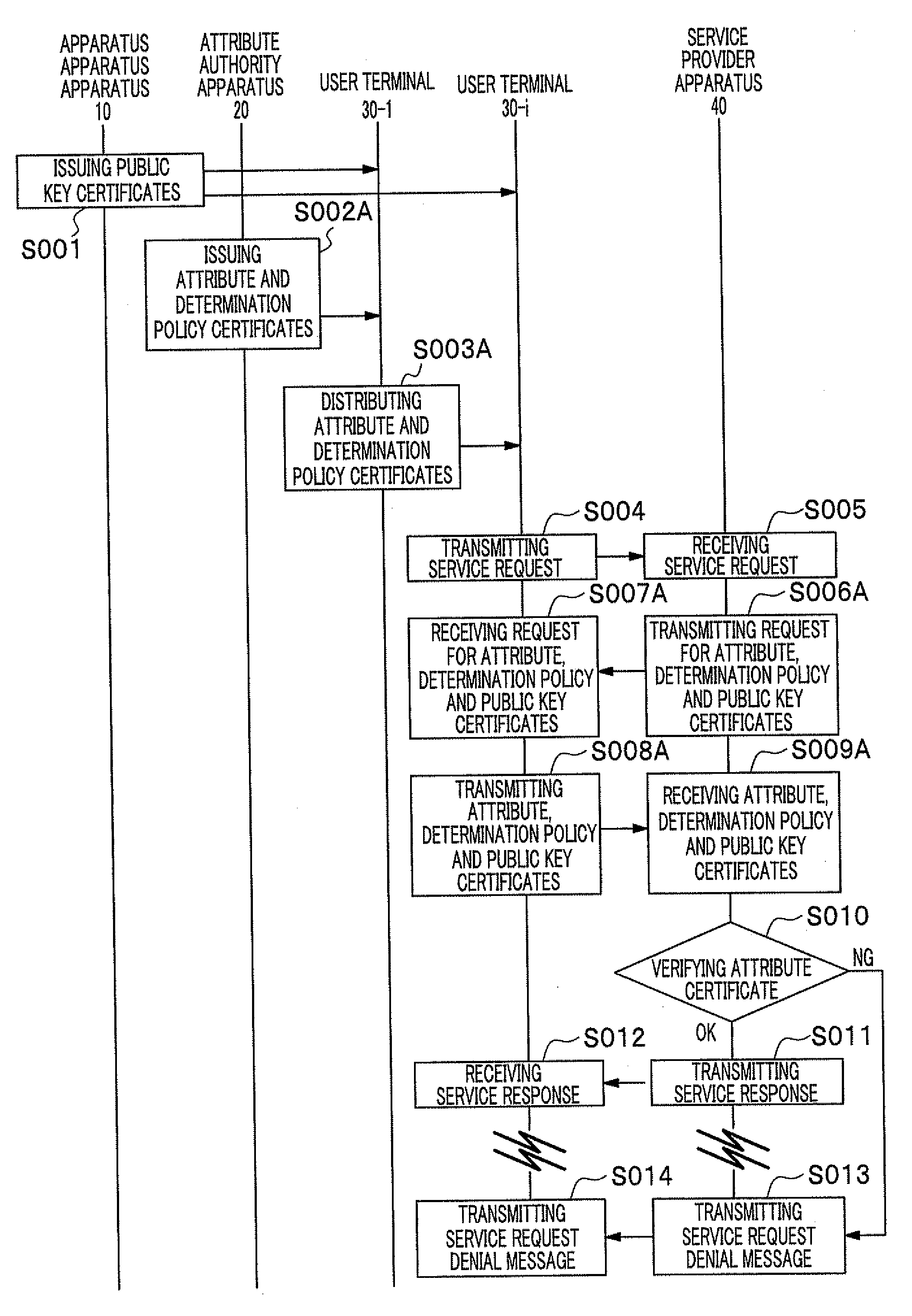
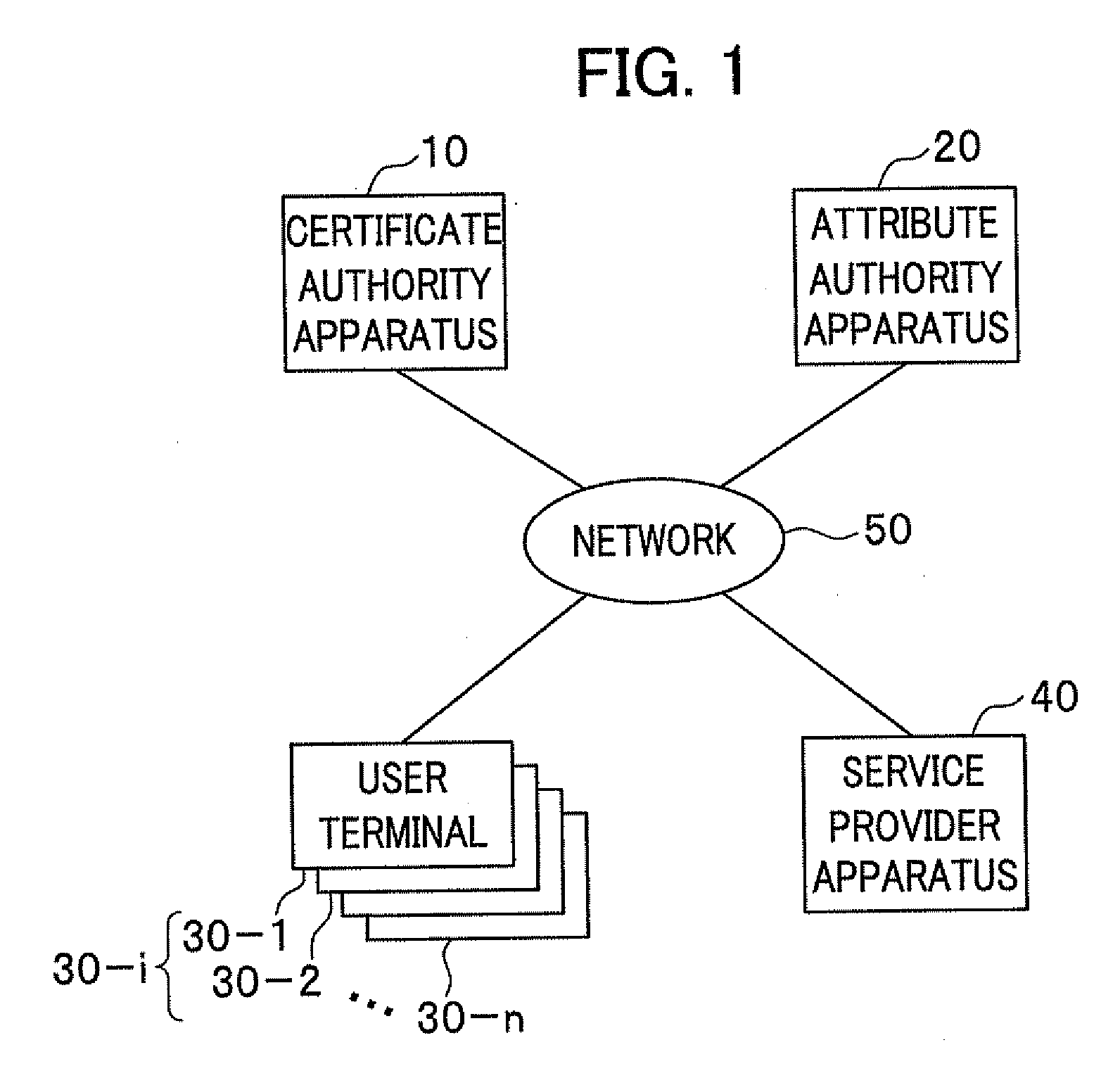
Upon issuance of an attribute certificate, an attribute authority apparatus makes a determination policy available. The determination policy includes information designating at least one item to be checked by a service provider apparatus for determination to be made to verify the attribute certificate, and a criterion for the determination. The determination policy may be recorded in the attribute certificate, or released to public, or made available by issuing a determination policy certificate released to public. Information for obtaining the determination policy certificate may be recorded in or outside the attribute certificate and furnished to the service provider apparatus. In order to verify an attribute certificate transmitted from a user terminal, a service provider apparatus obtains the determination policy, and determines whether data in the at least one item designated in the determination policy fulfill the criterion recorded in the determination policy.
Owner:HITACHI LTD
Method for realizing timely user attribute cancel based on ciphertext-policy attribute-based encryption
ActiveCN104113408AReduce workloadTroubleshoot update issuesKey distribution for secure communicationPlaintextBinary tree
Owner:XIDIAN UNIV
Government services cloud access control method based on attribute encryption
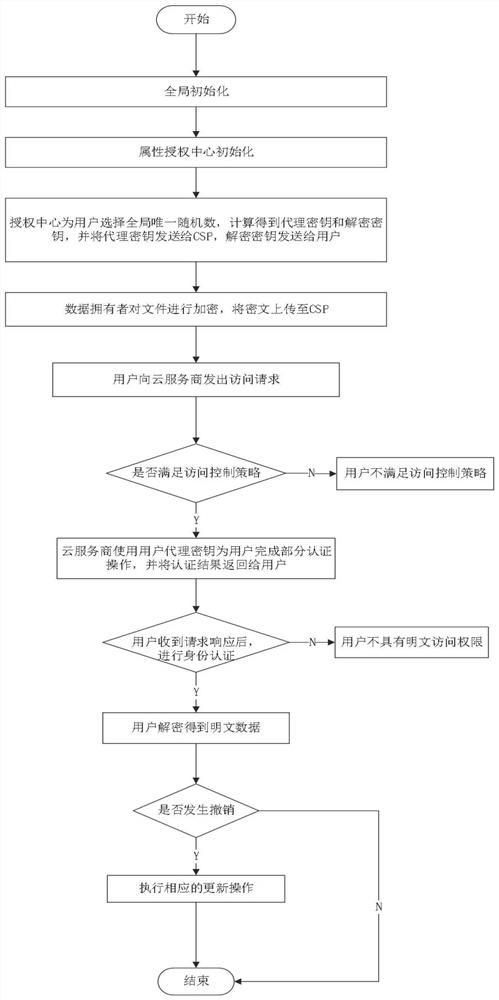
The invention discloses a government services cloud access control method based on attribute encryption. A central authority determines all attributes of a system, permits or revokes attribute authority management authority, and authenticates administrative staff; an attribute authority receives the login of administrative staff in the jurisdiction thereof and is simultaneously responsible for attribute revocation of the administrative staff; a cloud server stores data and carries out semi-decryption on an encrypted file when a user sends out a data request; a data uploader makes an access control strategy according to the security level of the file, and encrypts and uploads the file after name signing; and an access user sends out a data access request and finally decrypts the encrypted file. By adopting the attribute encryption scheme, the loads caused by user attribute revocation and encrypted file updating are reduced, the trap door information capturing of the user is controlled, and attribute revocation is carried out on the user under the condition that the encrypted file is not changed; in addition, by utilizing the name signing and attribute encryption scheme based on the identity, the safety authority of the user and fine-grained access control are realized.
Owner:XIDIAN UNIV
Distributed access control method for attribute-based encryption
ActiveCN104901942AAvoid collusionAbility to decrypt all system ciphertextsKey distribution for secure communicationUser identity/authority verificationPrivacy protectionEngineering
The invention provides a distributed access control method for attribute-based encryption, and mainly aims to solve the problems of security and privacy protection of massive data in a cloud environment. A multi-authority ciphertext-policy attribute-based encryption (CP-ABE) mechanism is provided on the basis of CP-ABE. According to the mechanism, the workload of a single authority is shared with a plurality of authorities, and efficient outsourcing decryption, user revocation and dynamic join and exit supporting attribute authority (AA) can be realized. Through adoption of an access control mechanism provided by the invention, efficient, distributed, extensible and fine-granularity access control can be realized while the security and privacy of the massive data are protected.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
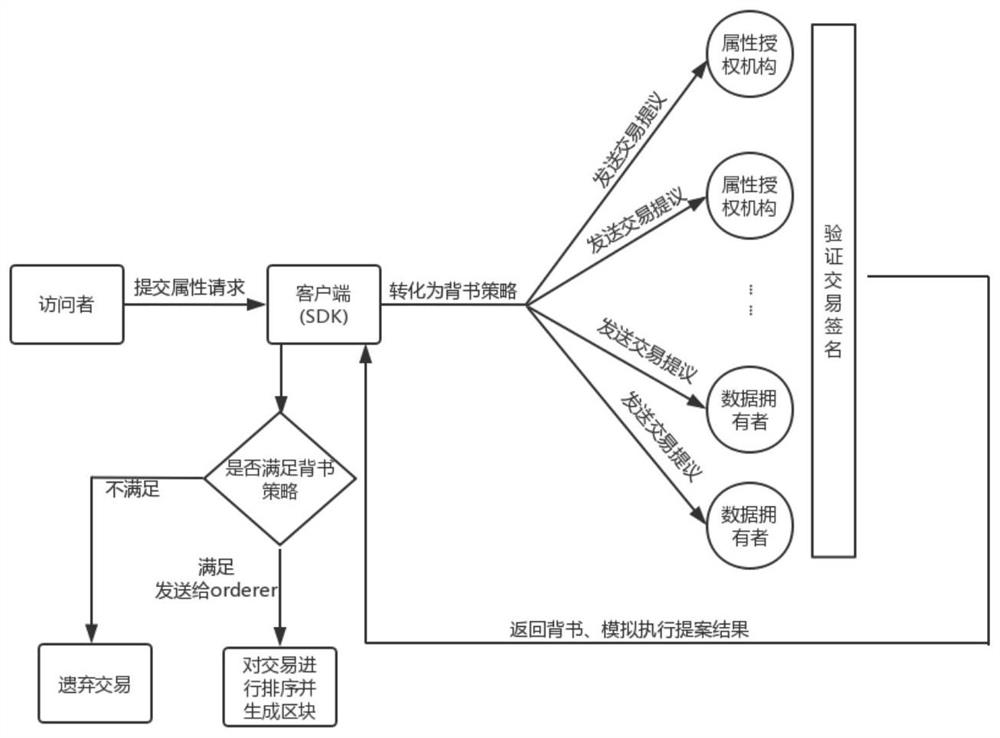
Ciphertext access control method based on CP-ABE (Ciphertext-Policy Attribute-Based Encryption)
ActiveCN105991278AEnsure safetyKey distribution for secure communicationAccess structureControl system
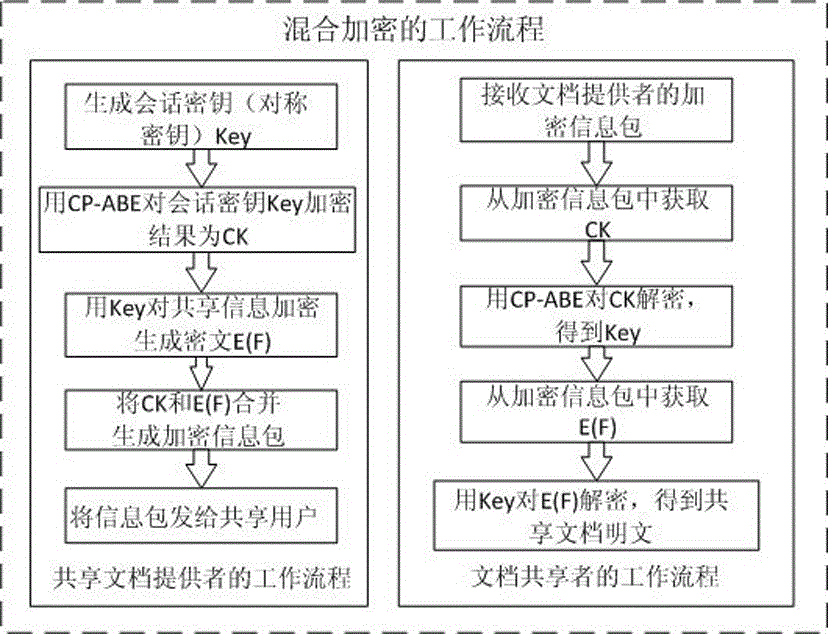
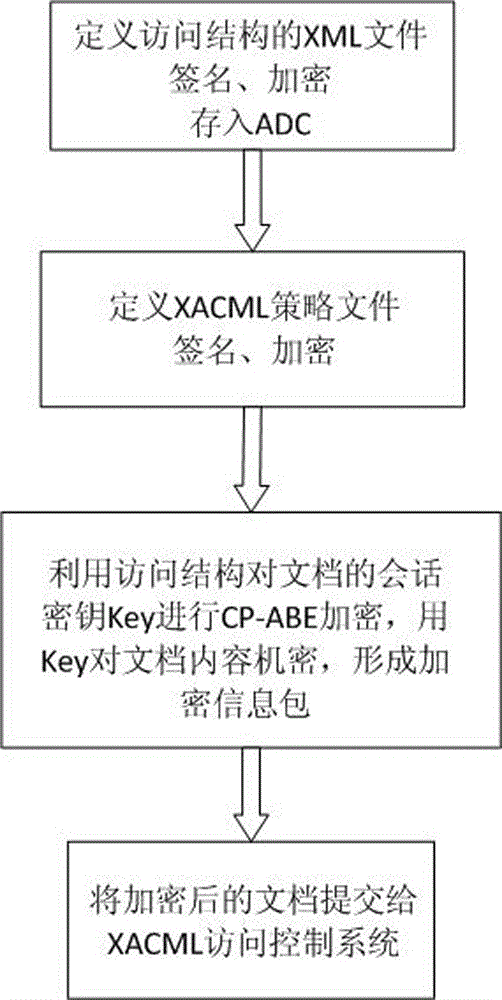
The invention discloses a ciphertext access control method based on CP-ABE (Ciphertext-Policy Attribute-Based Encryption), which belongs to the field of information security. The method comprises the following steps: preparation and maintenance work which comprises initialization of CP-ABE (Ciphertext-Policy Attribute-Based Encryption), user registration and auditing, generation of an asymmetric key pair for signature and encryption by the system and the user, generation of a CP-ABE attribute key SK for the user and key and attribute certificate management is carried out; 2, and file sharing requires a file provider, an extensible access control markup language (XACML) access control system and a sharing user to work cooperatively. The attribute certificate in a PMI system is used as an expression document for a CP-ABE attribute set and the access structure, the XACML expresses the CP-ABE policy, and security of the attribute set and the access control structure description is ensured. A hierarchical structure with an inheritance relationship is introduced, features such as distribution, authorization and calculability are supported, the attribute authorization ability needs to comply with constraints, and the method is applicable to a distributed and open network application environment.
Owner:INST OF APPLIED MATHEMATICS HEBEI ACADEMY OF SCI
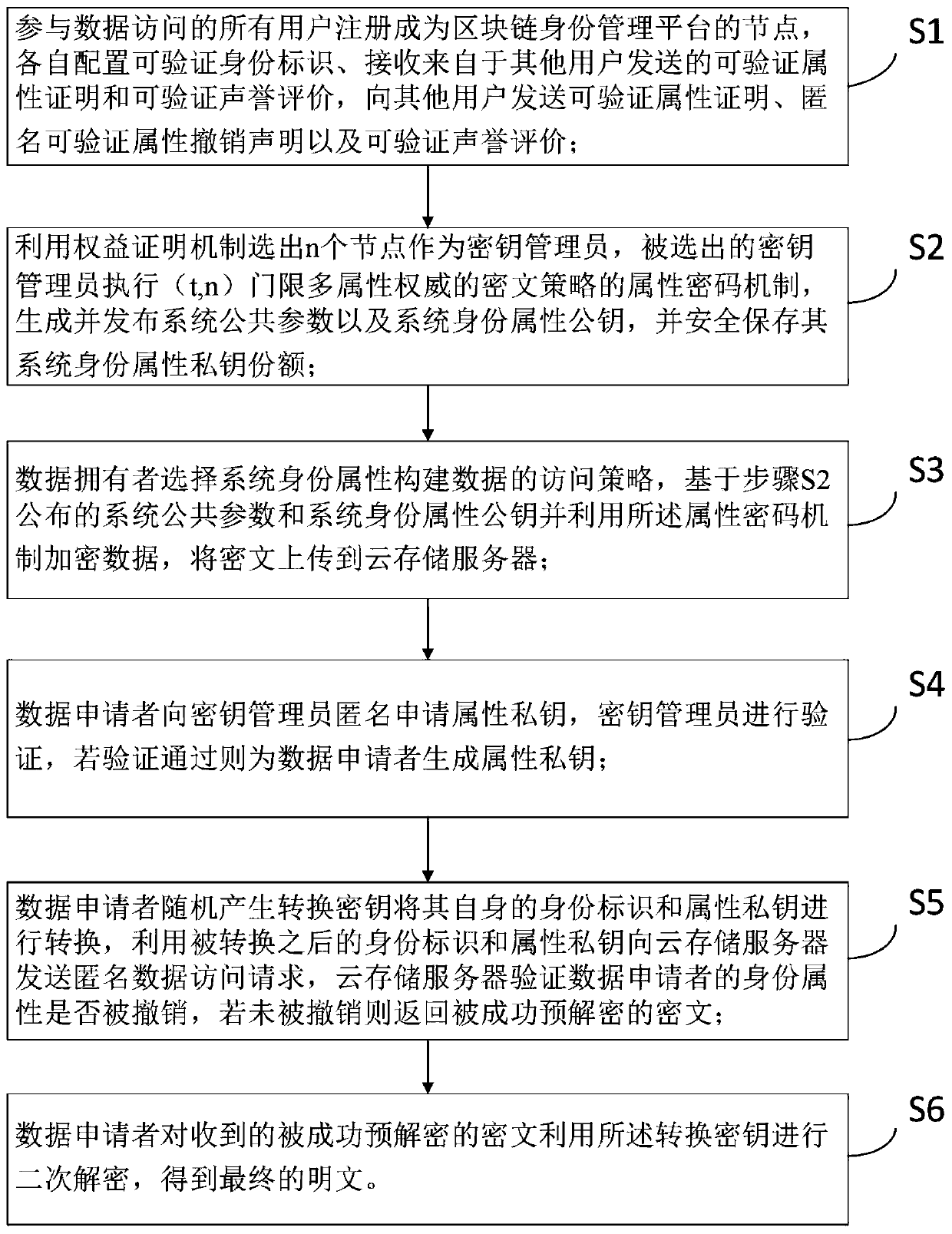
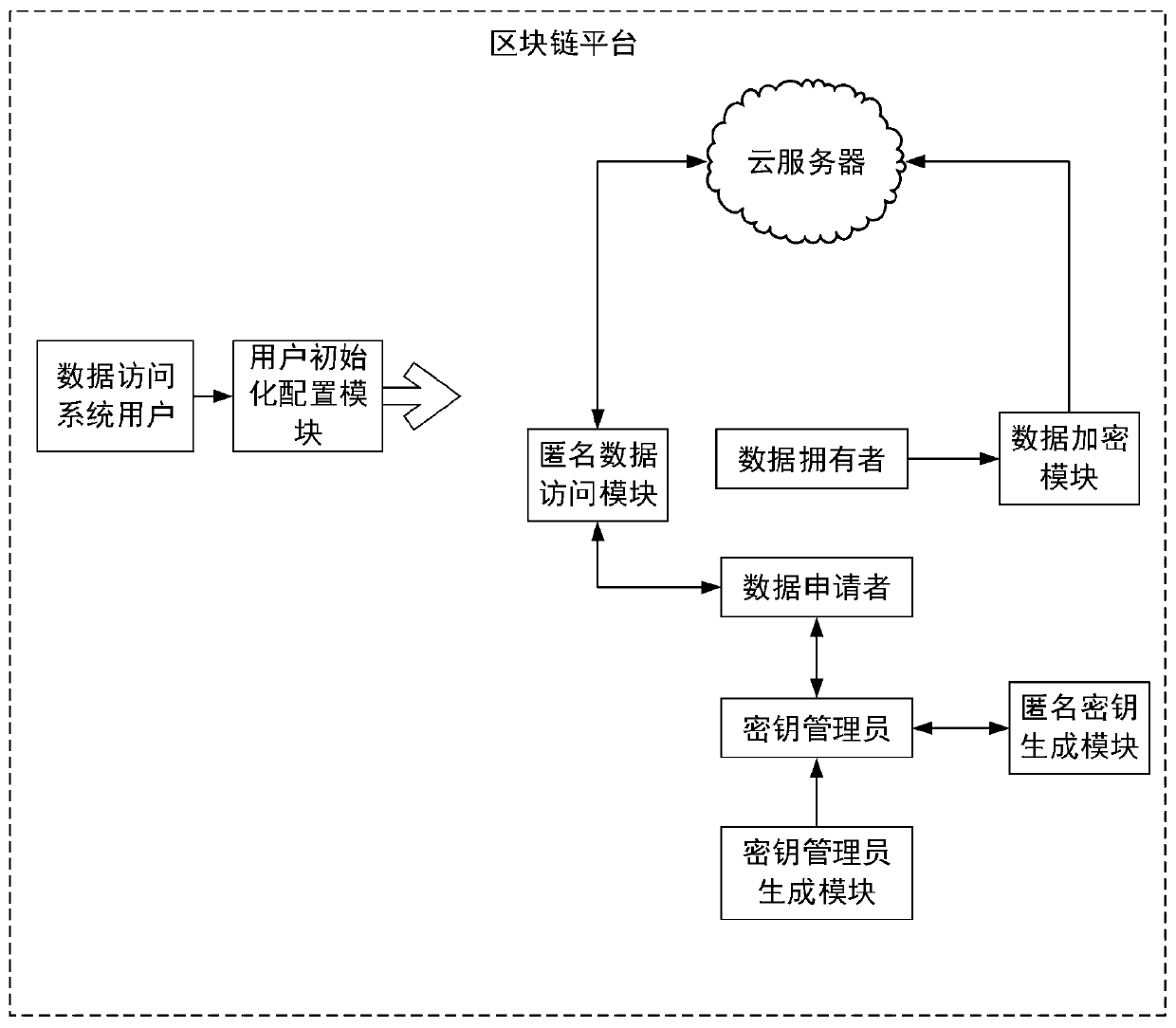
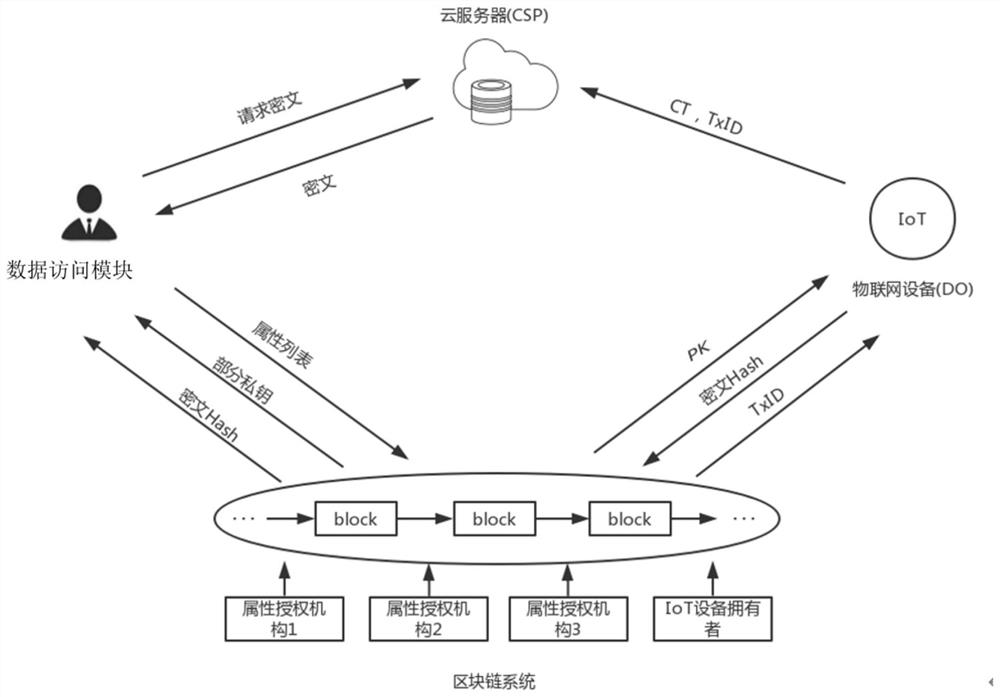
Data access control method and system in large-scale cloud storage based on block chain
ActiveCN110493347APrivacy protectionAchieve self-managementKey distribution for secure communicationUser identity/authority verificationPlaintextPassword
The invention belongs to the technical fields of cloud storage, access control and blocks chains, and particularly relates to a data access control method and a data access control system in large-scale cloud storage based on a block chain. The method comprises the steps: registering all participants as nodes of a block chain platform; selecting a key administrator by utilizing an authority proving mechanism and executing an attribute password scheme of a (t, n) threshold multi-attribute authority ciphertext strategy; initiating an anonymous key generation transaction between key managers to generate an attribute private key for the applicant; the data owner uploads the encrypted data to the cloud storage server under the constructed data access strategy; the applicant anonymously sends adata access request to the cloud storage server, and the server verifies whether the user identity attribute is revoked and returns a result after successful pre-decryption; and the user decrypts thereceived pre-decrypted ciphertext to obtain a final plaintext. The invention provides a centerless fine-grained access control method for large-scale cloud storage data, and the centerless fine-grained access control method has good expansibility and user privacy guarantee.
Owner:上海宇讷科技有限公司
System and method to enable PKI- and PMI-based distributed locking of content and distributed unlocking of protected content and/or scoring of users and/or scoring of end-entity access means—added
ActiveUS9270663B2Key distribution for secure communicationUser identity/authority verificationTrust relationshipApplication software
A central server configured with an Attribute Authority (“AA”) acting as a Trusted Third Party mediating service provider and using X.509-compatible PKI and PMI, VPN technology, device-side thin client applications, security hardware (HSM, Network), cloud hosting, authentication, Active Directory and other solutions. This ecosystem results in real time management of credentials, identity profiles, communication lines, and keys. It is not centrally managed, rather distributes rights to users. Using its Inviter-Invitee protocol suite, Inviters vouch for the identity of Invitees who successfully complete the protocol establishing communication lines. Users establish and respond to authorization requests and other real-time verifications pertaining to accessing each communication line (not end point) and sharing encrypted digital files. These are auditable, brokered, trusted-relationships where such relationships / digital agreements can each stand-alone (for privacy) or can leverage build-up of identity confidence levels across relationships. The service is agnostic to how encrypted user content is transported or stored.
Owner:T CENT
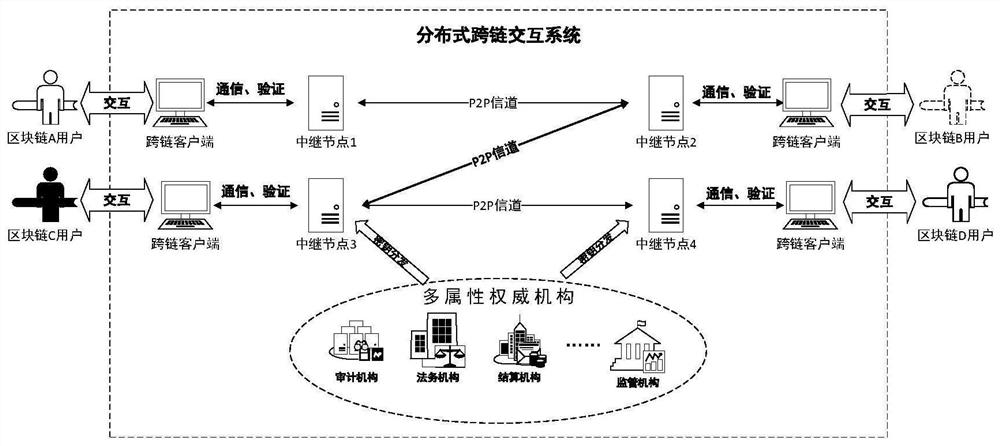
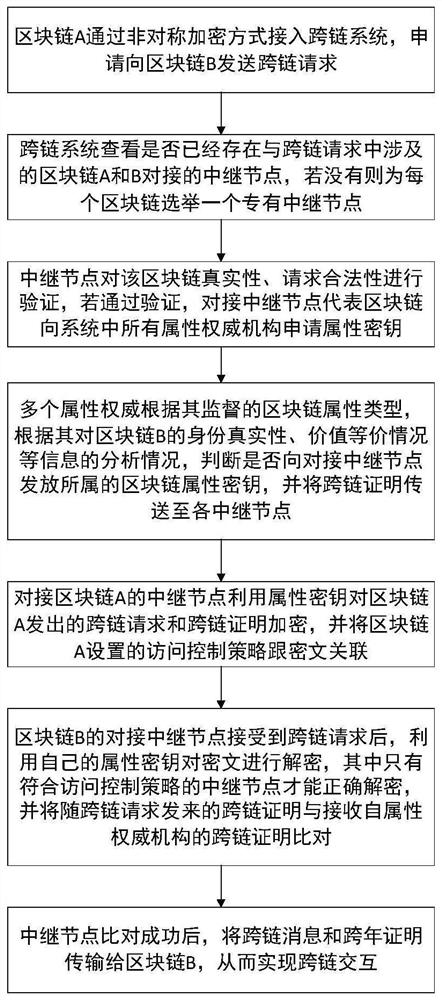
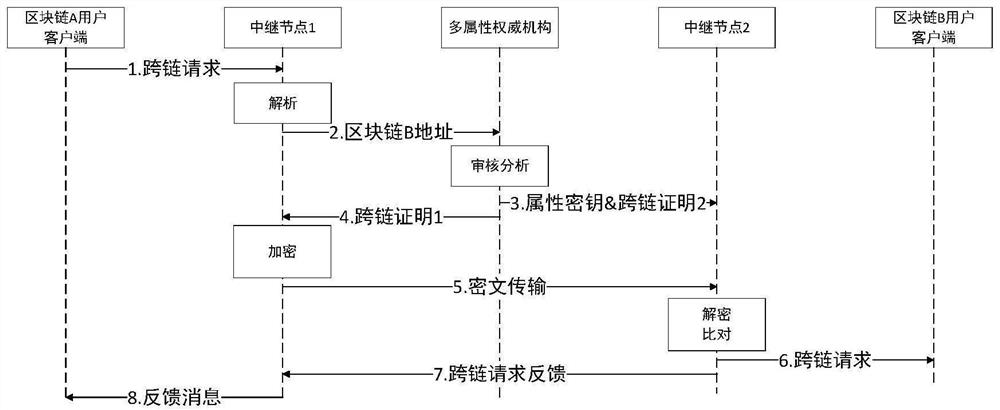
Distributed cross-chain system and cross-chain information interaction and system access control mechanism
ActiveCN112003889AImprove securityMeet the needs of cross-chain message brokersUser identity/authority verificationTrunkingEngineering
The invention discloses a distributed cross-chain system and a cross-chain information interaction and system access control mechanism. The distributed cross-chain system comprises a plurality of cross-chain clients, a cross-chain relay node, an attribute authority mechanism and a point-to-point encryption channel. The access control mechanism comprises the steps that a relay node verifies a blockchain user; the relay node adapts to the block chain attribute and agents the cross-chain message and encryption transmission of the block chain attribute, the attribute authority mechanism issues anattribute key and a cross-chain certificate to the relay node, a target block chain peer-to-peer relay node receives the encrypted file and decrypts and compares the cross-chain certificate, and finally the cross-chain message is received by a target block chain user so as to realize cross-chain communication. According to the invention, the relay node can be flexibly set to meet the cross-chainmessage proxy requirement of the specific block chain; high flexibility and expandability are realized, meanwhile, a decentralized attribute revocable and updatable attribute cryptographic mechanism is utilized, a fine-grained access control strategy is provided for cross-chain communication of the block chain, and the safety of a cross-chain system of the block chain is improved.
Owner:NANJING UNIV OF POSTS & TELECOMM
Safely outsourced attribute-based encryption method
ActiveCN102769620AReduce the burden onReduce overheadData switching networksSecuring communicationKey distributionKey generation
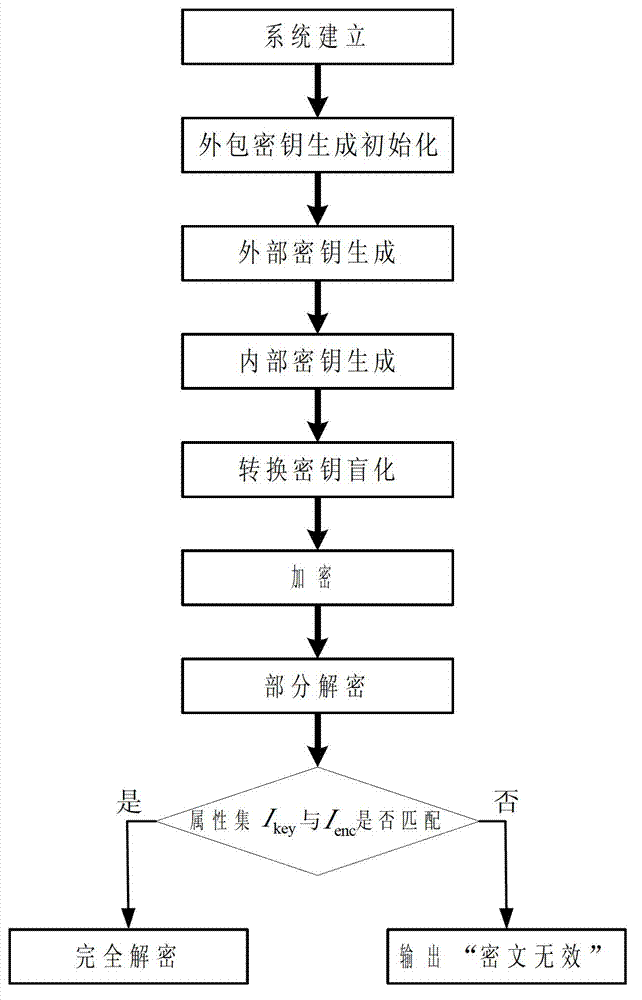
The invention discloses a safely outsourced attribute-based encryption method, which supports outsourcing for secret key distribution and decryption. The method comprises the following steps: (1) system establishing; (2) initialization of outsourcing secret key generation; (3) generation of an external secret key; (4) generation of an internal secret key; (5) blinding of conversion secret key; (6) encryption; (7) partial decryption; and (8) complete decryption. The safely outsourced encryption method has the advantages of simple construction process and high transmission efficiency and can be used for realizing fine-grained resource access control under a cloud computing environment, and a large amount of expenditure is saved for attribute authorities and users.
Owner:GUANGZHOU UNIVERSITY
Fine-grained data access control method based on fragmenting of secret keys
ActiveCN104022869AImprove securityImprove confidentialityKey distribution for secure communicationAttribute authorityFine grain
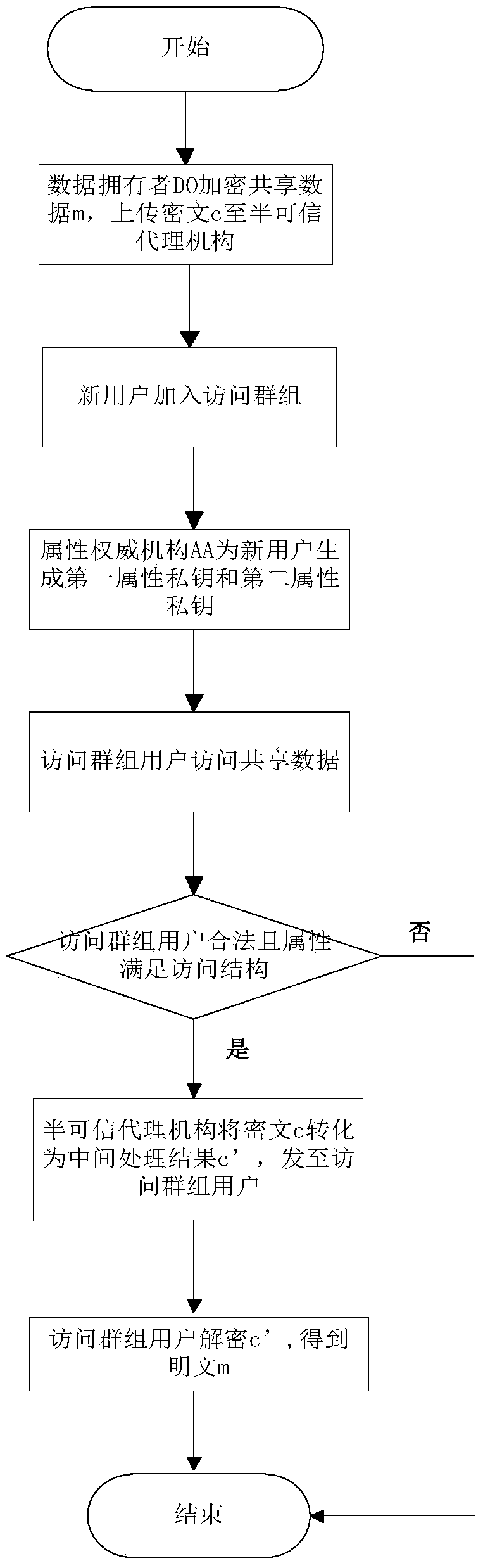
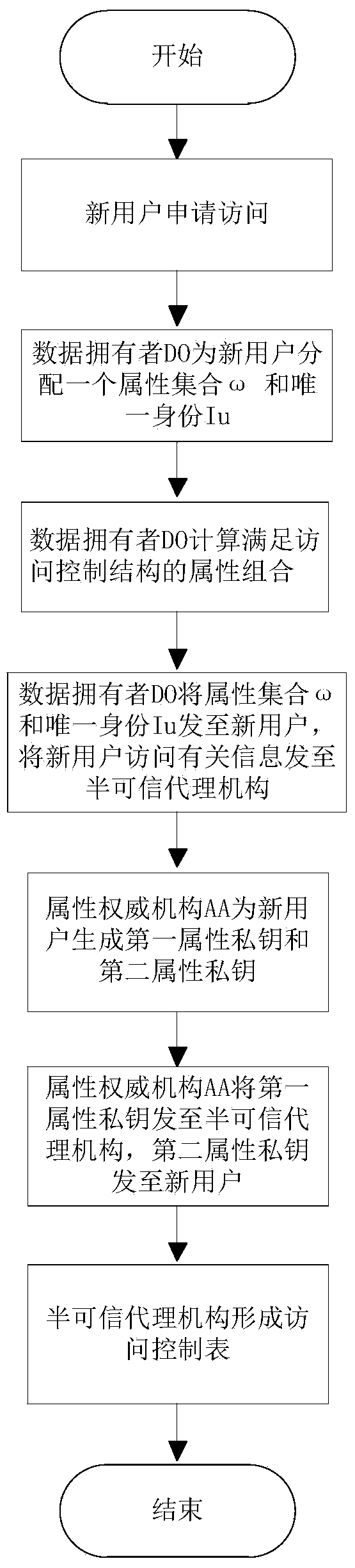
The invention discloses a fine-grained data access control method based on fragmenting of secret keys. The method mainly solves the problems that the safety is low and the calculation amount is large in the prior art. The method comprises the implementation steps that (1) a data owner encrypts shared data to obtain a cryptograph; (2) an attribute authority generates two attribute private keys for an access group user and sends the two attribute private keys to a semi-trusted agency and the access group user respectively; (3) when the access group user meets the requirement of an access control structure, the semi-trusted agency converts the cryptograph into an intermediate result through the first attribute private key, and the access group user decrypts the intermediate result through the second attribute private key to obtain the shared data; (4) the attribute private key fragmenting technology is adopted to control the access group user to obtain an incomplete attribute private key, so that the owner does not need to encrypt the shared data again after executing the undoing operation. By means of the method, fine-grained access control can be provided for the shared data, and the safety of the shared data can be improved. The method can be applied to access of the shared data under cloud shared data access control.
Owner:XIDIAN UNIV
Cloud storage outsourced decryption attribute-based encryption method capable of limiting access times
ActiveCN109639677ASecure outsourcing decryption serviceKey distribution for secure communicationUser identity/authority verificationAccess structureCryptographic hash function
The invention discloses a cloud storage outsourced decryption attribute-based encryption method capable of limiting access times, wherein a data user generates a corresponding conversion key accordingto a decryption key distributed by an attribute authority mechanism; the conversion key is outsourced to a cloud server when a decryption service needs to be outsourced; and a conversion ciphertext returned by the cloud server is subjected to outsourced decryption verification. In the method, an access structure of LSSS is adopted, a verifiable random function (VRF) is used to limit the access times of the user, a decryption operation of the client is outsourced to the cloud by using an outsourcing computing technology, a secure decryption outsourcing service is realized by using a key blinding technology, and the correctness of the outsourced decryption is verified through a verification token generated by using a cryptographic hash function. The fine-grained access control mode capableof limiting the access times of the users in a fixed time realizes public verification of the correctness of outsourced decryption in the attribute-based encryption.
Owner:GUANGDONG UNIV OF TECH +1
Distributed cross-domain authorization and access control method based on attribute password
ActiveCN108418784AAvoid bottlenecksAvoid security issuesKey distribution for secure communicationPasswordSecret code
The invention provides a distributed cross-domain authorization and access control method based on an attribute password. The method is mainly used for solving the problems of cross-domain authorization and access control under a large-scale distributed environment. The invention designs a hierarchical attribute-based encryption with controlled key delegation and attribute authorities, supportingdecentralized and controlled security authorization for users of a plurality of domains, preventing abuse of the key delegation, and accordingly achieving non-interactive access control. The method also supports decoding of an external packet, and supports the authorization to the light-weight users for accessing the system.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
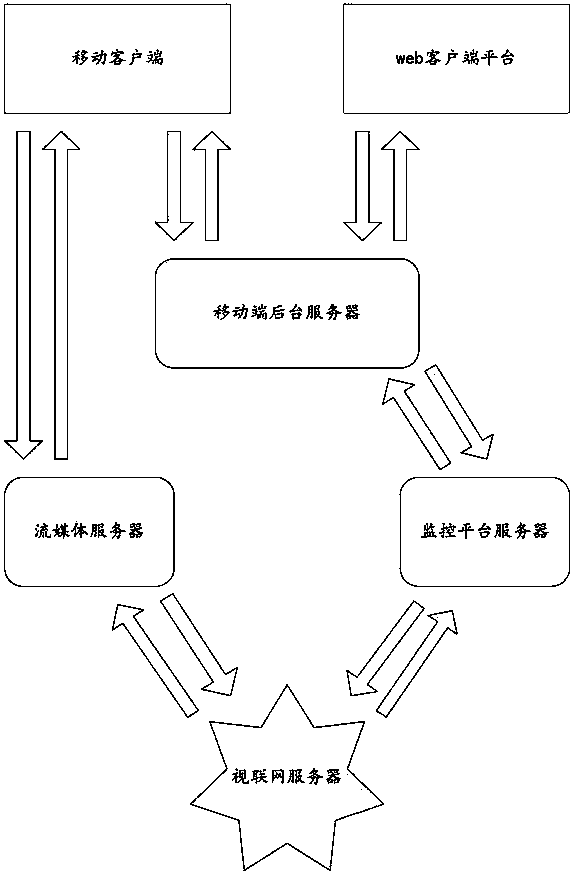
Method and device for obtaining surveillance video of internet of videos
ActiveCN109348171AImprove the efficiency of watching surveillance videoReduce human resource costsClosed circuit television systemsSelective content distributionMobile endTerminal equipment
The embodiment of the invention provides a method and a device for obtaining a surveillance video, which are applied to internet of videos. The method comprises the following steps: a mobile terminaldevice sends a first surveillance video list obtaining request to a background server; the mobile-terminal background server recognizes target user attribute authority corresponding to target user information; the mobile-terminal background server sends a second surveillance video list obtaining request to a monitoring platform server; the monitoring platform server searches a surveillance video list corresponding to the user attribute authority and returns to the mobile-terminal background server; the mobile-terminal background server sends a surveillance video list to the mobile terminal device; the mobile terminal device shows the surveillance video list and receives a selection operation of a user based on the surveillance video list; the mobile terminal device sends the first surveillance video obtaining request to a stream media server so as to obtain the surveillance video data through the stream media server. The method and the device for obtaining a surveillance video in the invention can make the user watch the surveillance video conveniently and reduces the manpower resource required for audit.
Owner:VISIONVERA INFORMATION TECH CO LTD
Outsourcing attribute encryption method supporting attribute cancellation
InactiveCN106452735AReduce computational overheadGood encryptionKey distribution for secure communicationPublic key for secure communicationCloud storageComputer science
The invention provides an outsourcing attribute encryption method supporting attribute cancellation. A part of secret key generation and ciphertext decryption operation is given to an outsourcing mechanism for completion, and a version number is set for a private key of a user to support the attribute cancellation. Secret key generation is completed by an attribute authority and an outsourcing secret key generation mechanism together, and decryption operation is completed by a cloud storage provider and the user together. When a secret key is generated, the attribute authority sends correlation data to the outsourcing secret key generation mechanism, the outsourcing secret key generation mechanism returns a part of the generated secret key to the attribute authority, and the attribute authority calculates a correlation result so as to obtain a conversion secret key. When some attributes of a certain user are cancelled, the version number of the private key of the user is updated, an upgraded secret key is generated and sent to the user to enable the user to update his private key, at the same time, the conversion secret key corresponding to the user on the cloud storage provider is updated, and thus the purpose of attribute cancellation of the user is realized.
Owner:GUANGDONG UNIV OF TECH
Attribute-based digital signature system
ActiveUS20130073860A1Easy to processEasy to combineKey distribution for secure communicationUser identity/authority verificationDigital signatureRevocation
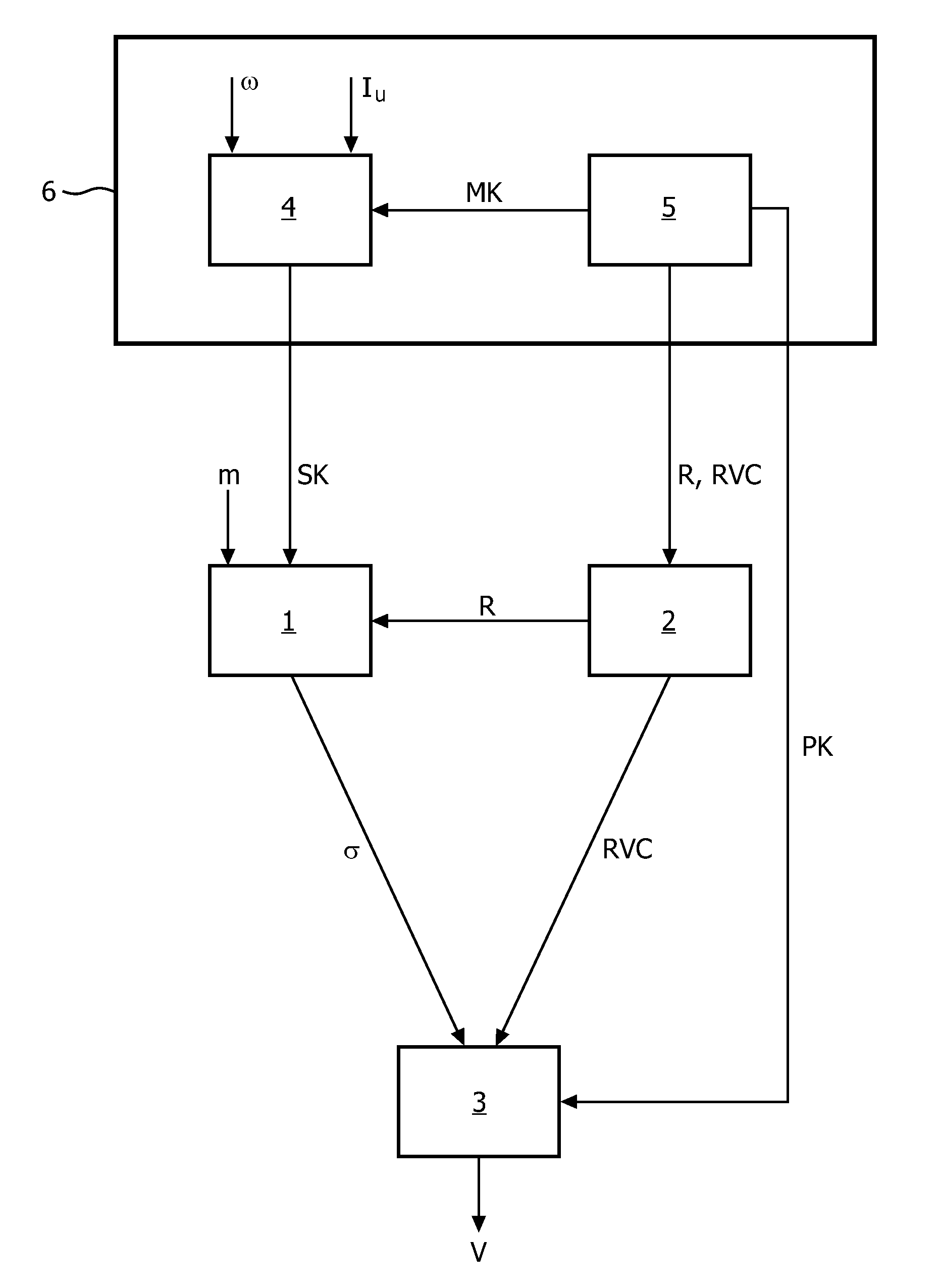
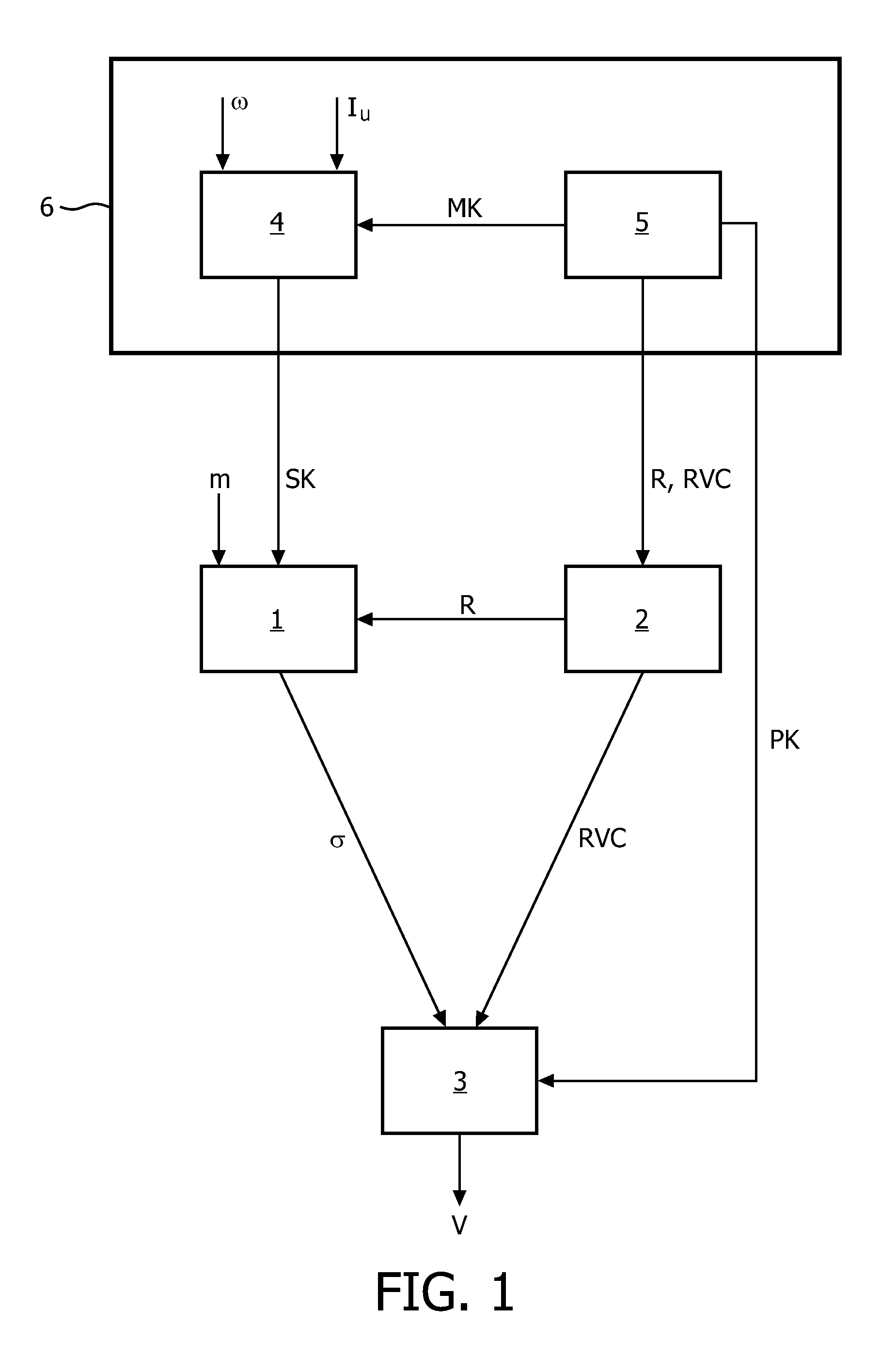
An attribute-based digital signature system comprises a signature generation unit (1) for signing a message (m) by generating a signature (σ) based on a user secret key (SK) associated with a set of user attributes, wherein the signature generation unit (1) is arranged for combining the user secret key (SK) with revocation data (R) to form at least part of the signature (σ), wherein the revocation data (R) complements respective ones of a plurality of valid user secret keys and wherein the revocation data (R) prevents a revoked user secret key (SK) from being used to validly sign a message (m) with the set of user attributes. The system further comprises a revocation unit (2) for selectively removing at least part of the signing capability of a to-be-revoked user secret key (SK), by generating updated revocation data (R), wherein the updated revocation data (R) is based on at least part of the to-be-revoked user secret key (SK). A plurality of attribute authorities 301 may independently issue cryptographic keys.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
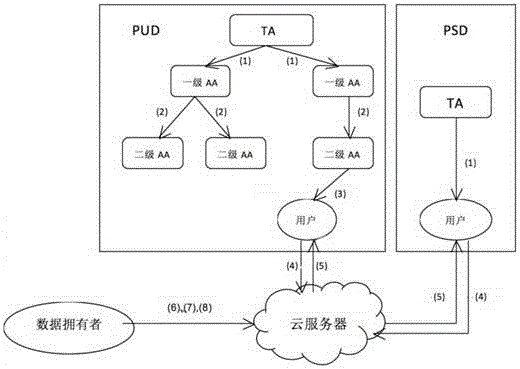
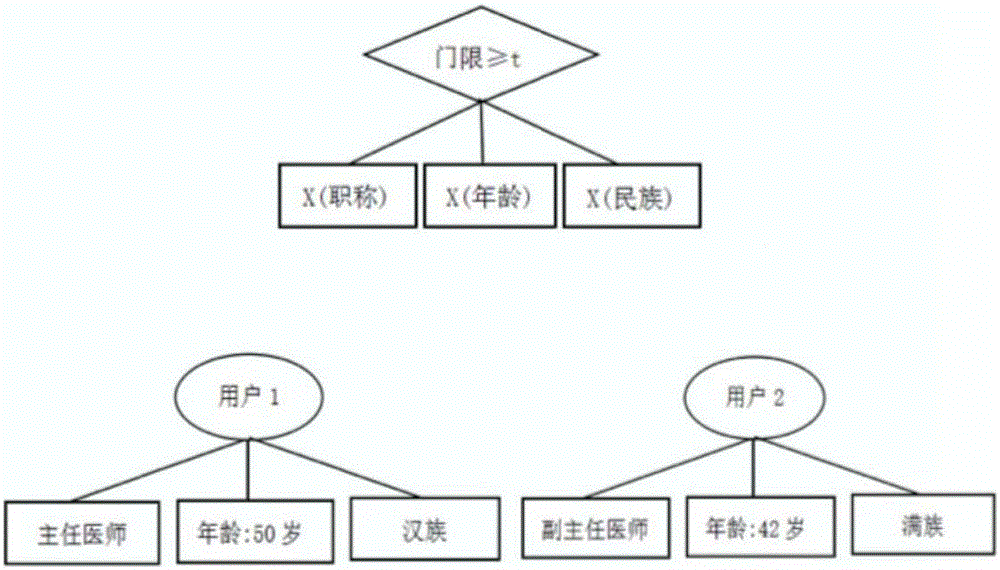
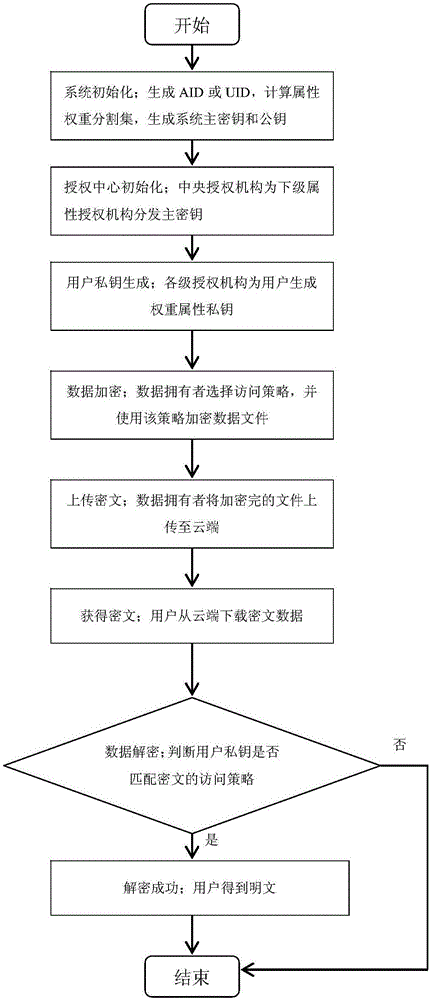
Attribute-based multi-mechanism hierarchical ciphertext-policy weight encryption method under cloud environment
ActiveCN106059763ABuild safe and reliableKey distribution for secure communicationPlaintextAttribute weight
The invention discloses an attribute-based multi-mechanism hierarchical ciphertext-policy weight encryption method under a cloud environment. The method comprises steps: a central authority mechanism generates a global identifier AID or UID for a subordinate attribute authority mechanism or a user, and calculates an attribute weight segmentation set for each attribute in a system; the central authority mechanism randomly selects a bilinear pairing and a bilinear group, generates a system main key MK and a public key PK, retains the MK and publishes the PK; the central authority mechanism distributes the main key or a weight attribute private key for the subordinate attribute authority mechanism or the user; a data owner selects an access policy, encrypts a file and uploads the file to a cloud server; the user requests the cloud server for accessing to the encrypted file, the cloud server returns back a ciphertext CT, the user decrypts the file through the weight attribute private key, and if the attribute in the private key satisfies the access policy, the user obtains a plaintext. With the method provided by the invention, a graded hierarchical multiple-authority mechanism is established, and the authorities of different grades can be in charge of different attributes and distribute private key components.
Owner:NANJING UNIV OF POSTS & TELECOMM
Weight attribute-based encryption method based on hierarchical authorities
ActiveCN108881291AImprove securityIncrease flexibilityKey distribution for secure communicationPlaintextData file
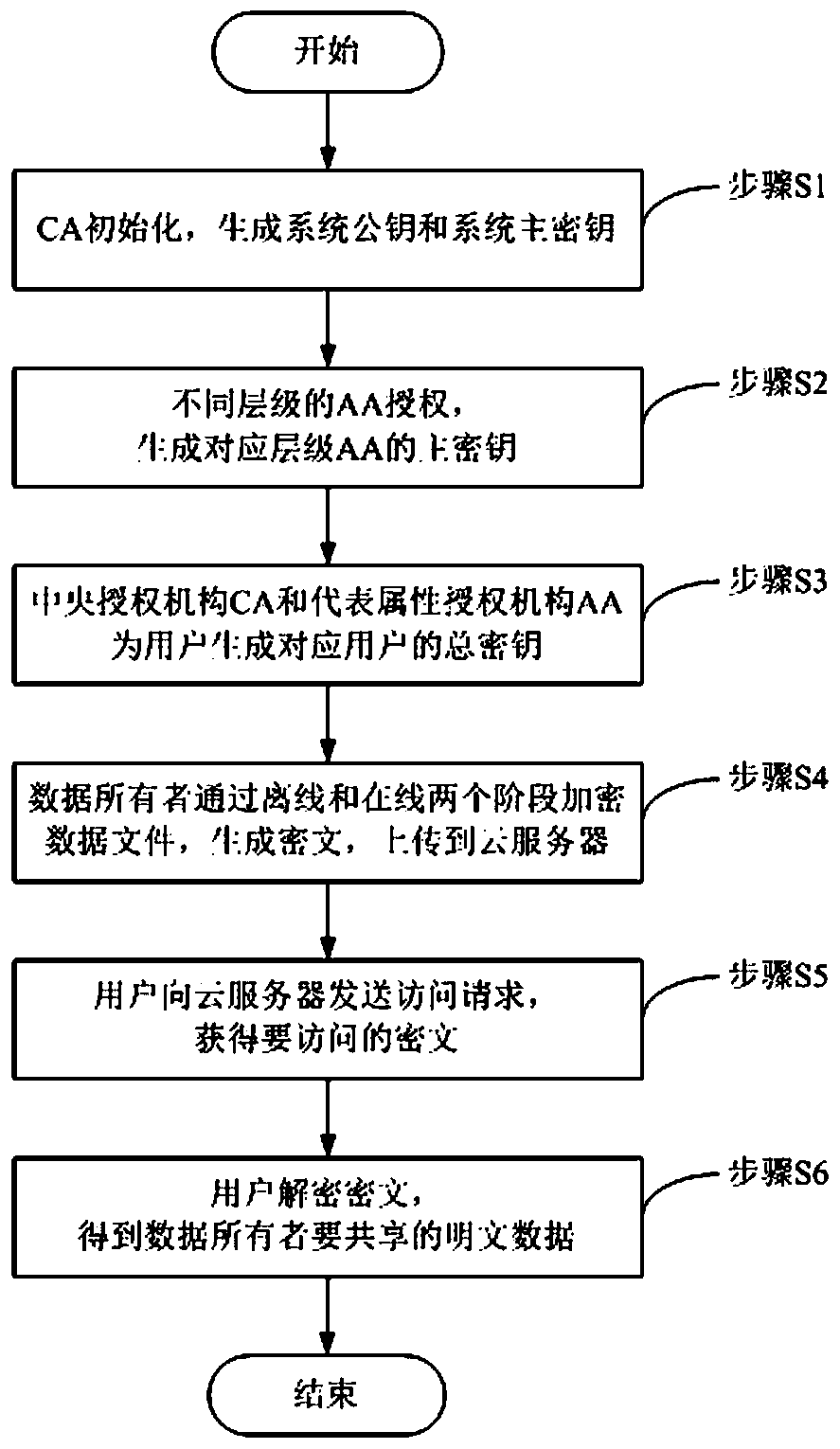
A weight attribute-based encryption method based on hierarchical authorities is disclosed. A system public key and a system master key are generated when a central authority (CA) is initialized, master keys of corresponding levels of representative attribute authorities (AAs) are generated by authorization of different levels of AAs, the CA and the representative AAs generate total keys of corresponding users for the users, a data owner encrypts a data file through two stages of on-line encryption and off-line encryption, a cipher text is generated and uploaded to a cloud server for storage, auser sends an access request to the cloud server to obtain the cipher text data stored in the cloud server, and the user decrypts the cipher text data obtained from the cloud server to obtain the plain text data to be shared by the data owner. By introducing the hierarchy and attribute weights of the authorities, the encryption system has better flexibility in the cloud storage environment, finer-grained access control can be implemented, and the security of the stored data is improved.
Owner:上海汉枫电子科技有限公司
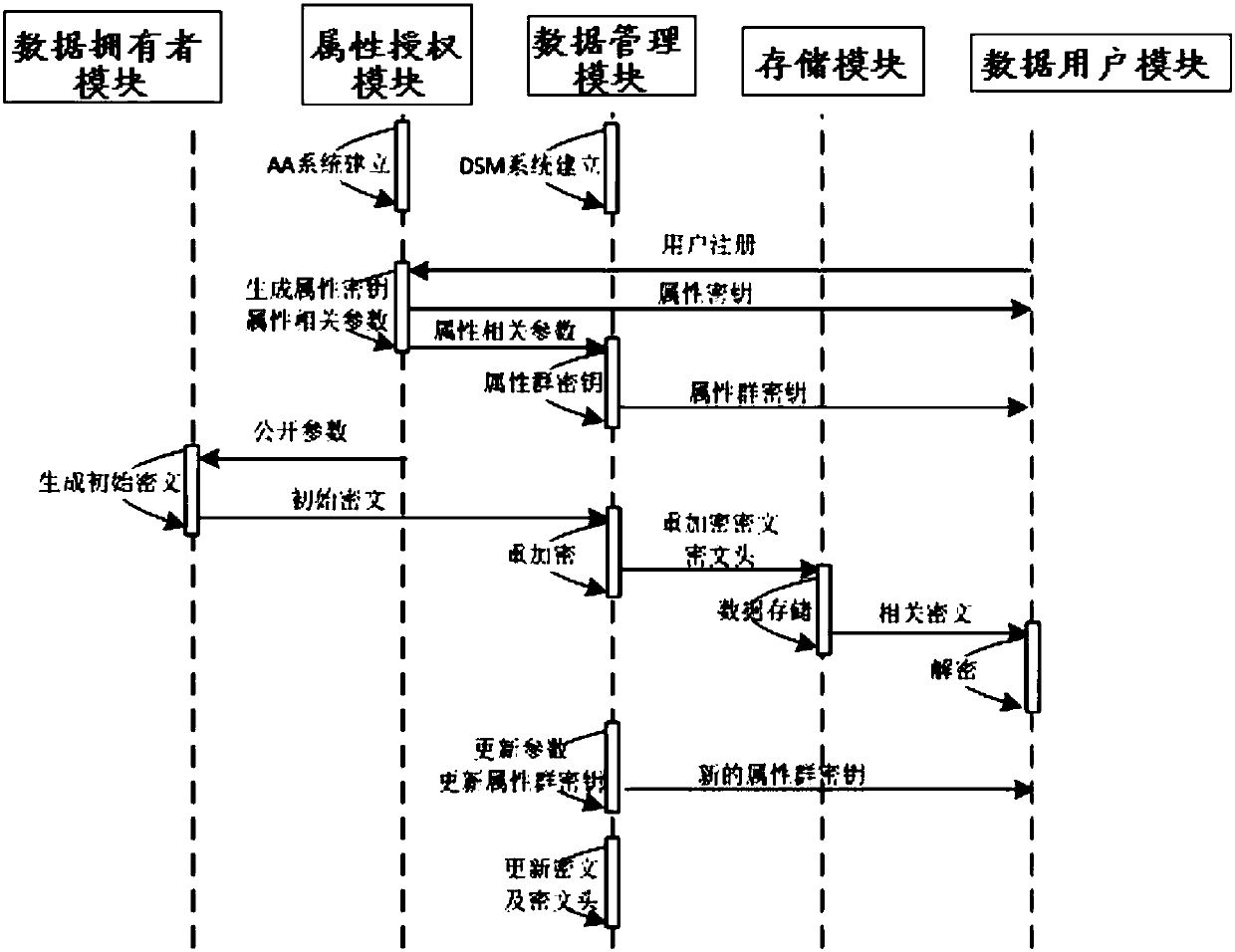
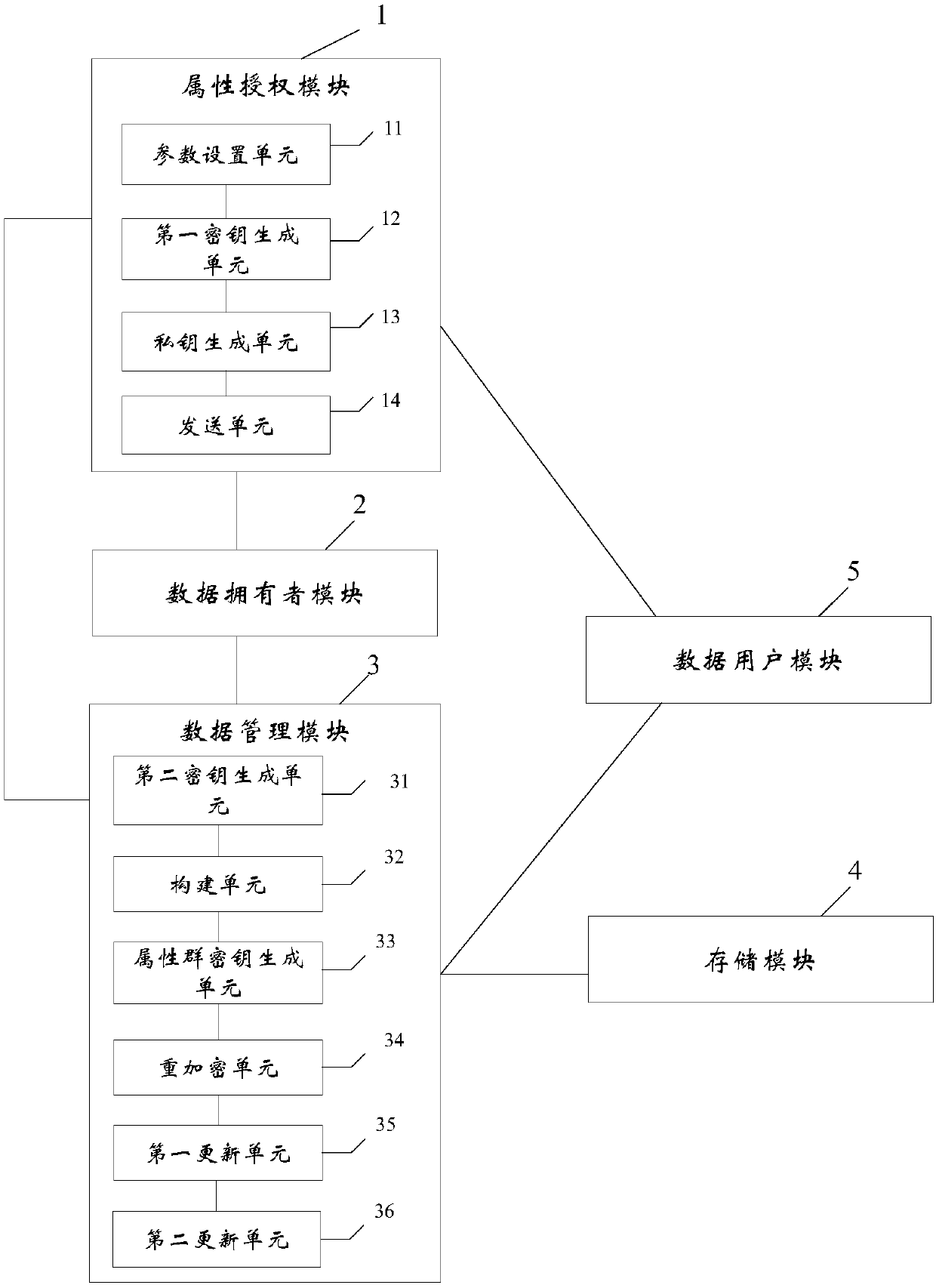
Revocable attribute-based encryption system and method for cloud storage
ActiveCN108200181ALighten the computational burdenConstant lengthKey distribution for secure communicationMultiple keys/algorithms usagePlaintextData access
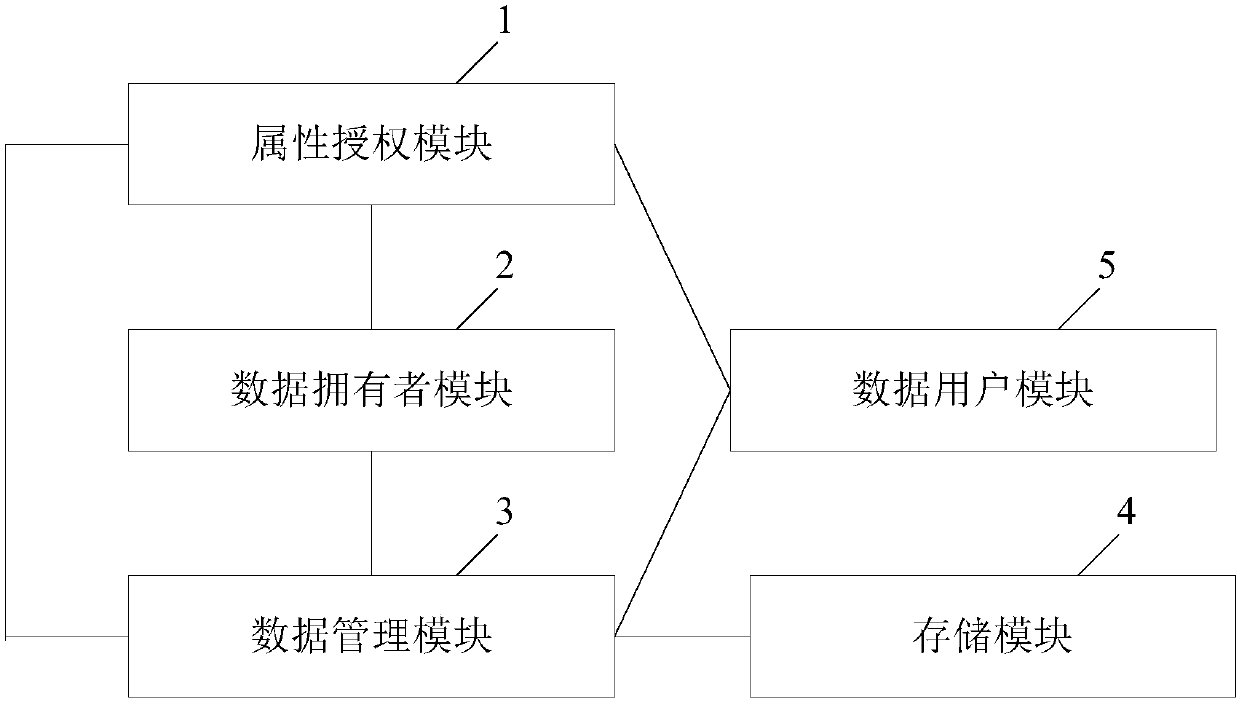
The invention discloses a revocable attribute-based encryption system and method for cloud storage. An attribute authorization module generates a public key and a main private key of an encryption system, and an attribute private key and an attribute group initial key of a data user; a data owner module constructs a data access structure, and obtain initial ciphertext by encrypting the plaintext;a data management module generates a attribute group key through the constructed key encryption key tree, performs re-encryption processing on the initial ciphertext to generate a ciphertext file anda ciphertext header of the ciphertext file, and stores the ciphertext file via a storage module; the data management module can also update the attribute group key after the data user module attributeis revoked, and process to obtain an updated ciphertext file. The data user module accesses the ciphertext file and decrypts the ciphertext file to obtain a plaintext corresponding to the ciphertextfile. Therefore, the attribute-level user revocation capability is implemented, the collusion attack between a revoking user and a non-revoking user can be resisted, and fixed-length ciphertext lengthand higher efficiency are achieved.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
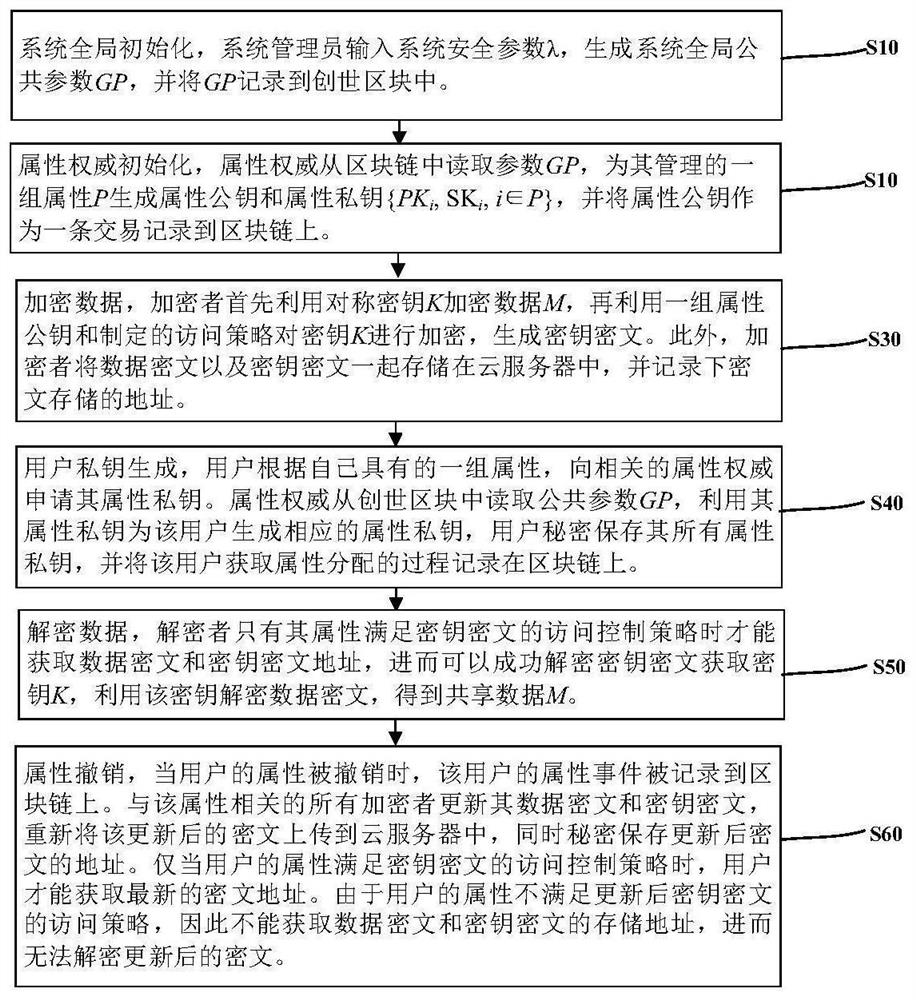
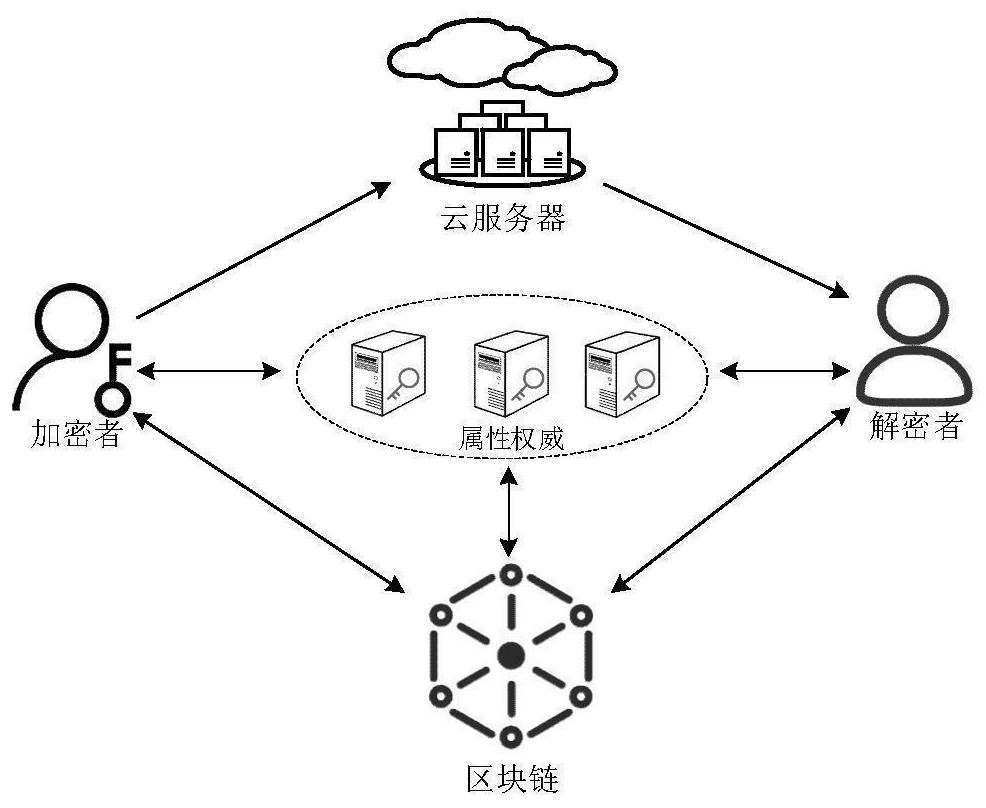
Multi-authority attribute-based encryption method based on blockchain
ActiveCN113193953AImplement fine-grained authorizationImprove management efficiencyKey distribution for secure communicationUser identity/authority verificationEngineeringKey management
The invention provides a multi-authority attribute-based encryption method based on a blockchain, which comprises the following steps of: globally initializing a system, generating a system general parameter (GP), and recording the GP into a genesis block; initializing attribute authority, wherein all the attribute authority generates a group of attribute public and private keys by using the GP; encrypting data, wherein an encryptor generates a data ciphertext and a key ciphertext by using symmetric encryption and attribute encryption algorithms; generating a user private key, wherein the attribute authority generates a group of attribute private keys for the user; decrypting the data, wherein the user decrypts the ciphertext by using the attribute private key to obtain shared data; and revoking the attribute, wherein due to user attribute revocation, an attribute set does not meet an access strategy, and a updated ciphertext address cannot be obtained. According to the invention, the blockchain is utilized to record the time sequence attribute state of the user, so that distributed distribution, storage and revocation of the attribute private key are realized, the key management efficiency of a distributed attribute-based encryption mechanism is improved, and the security of data sharing in a distributed environment is enhanced.
Owner:NANTONG UNIVERSITY
Traceable layered multi-authorization ciphertext policy attribute base authentication method
ActiveCN110113156AWon't leakSafety protectionKey distribution for secure communicationUser identity/authority verificationUser privacyAuthorization
The invention relates to a traceable layered multi-authorization ciphertext policy attribute base authentication method. A central authorization mechanism generates a main public / private key of a system, a private key of a zero-level authorization mechanism and a private key of a signer; the upper-level attribute authorization mechanism authorizes the next-level attribute authorization mechanism,and the attribute authorization mechanisms of different levels can generate attribute keys for signers according to the managed attribute sets and then send the attribute keys to the signers; a signerin the system owns a private key and an attribute key, signs a message by using the attribute key of the signer, and sends signature information of the message to a verifier; the verifier verifies whether the signature is valid or not by using the attribute public key of the signer; when there is a dispute in the system, the tracker is responsible for recovering the identity information of the signer from the signature. According to the method, the privacy of the user can be protected, collusion attacks of multiple authorization mechanisms can be resisted, and the method is safe and efficient.
Owner:FUJIAN NORMAL UNIV
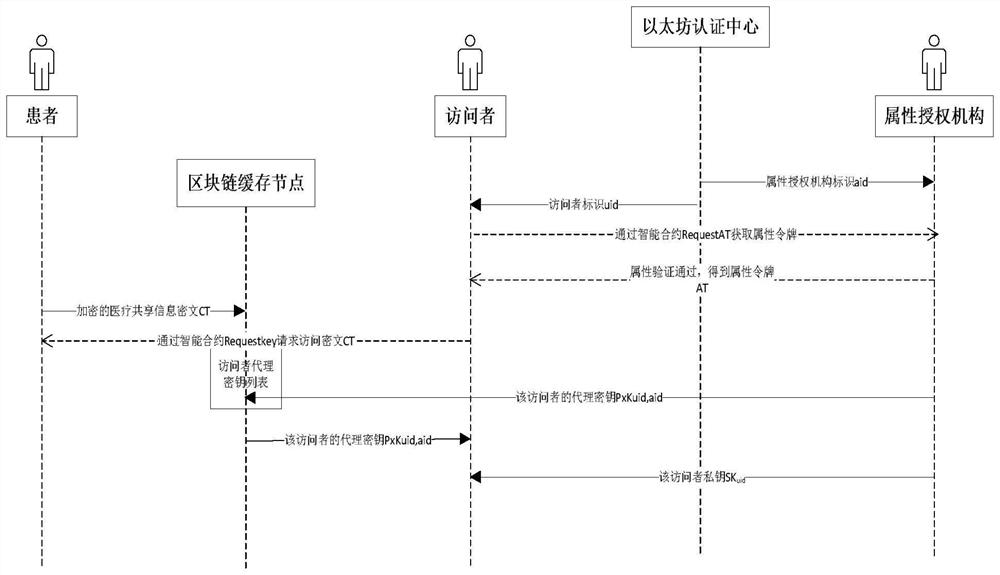
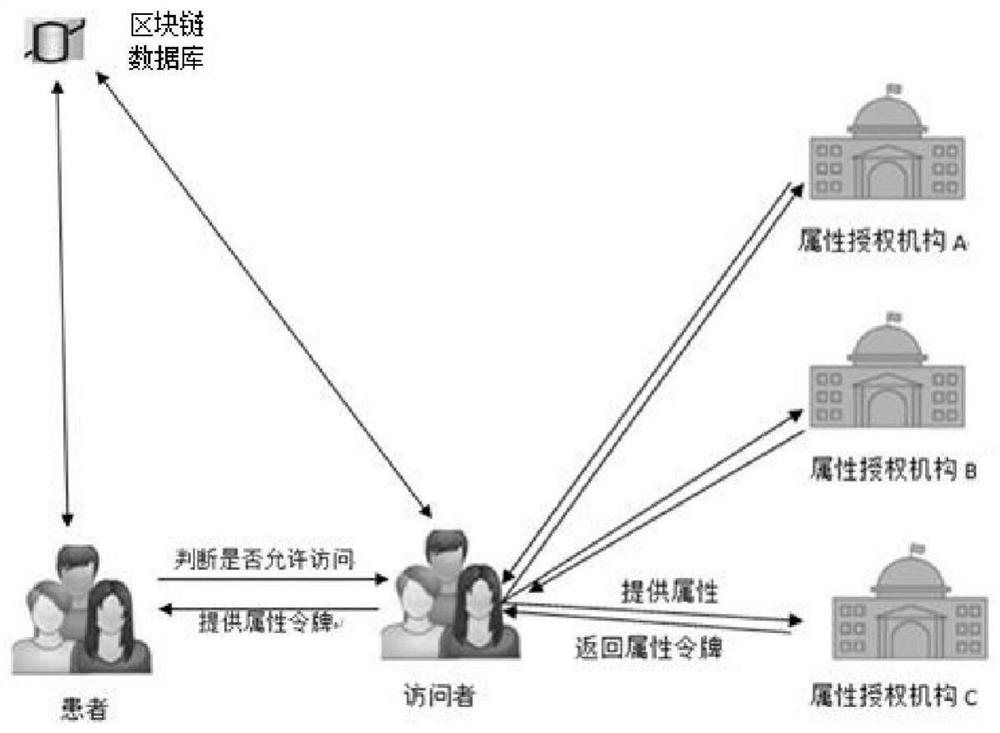
Medical information attribute encryption access control method based on block chain
ActiveCN111901302AImplement access controlAchieve retrospective accountabilityUser identity/authority verificationDigital data protectionInformation accessData information
The invention discloses a medical information attribute encryption access control method based on a block chain. The method comprises the following steps that a patient performs attribute encryption based on a ciphertext strategy on personal medical data and stores the personal medical data to the block chain; a visitor provides corresponding attributes for a plurality of attribute authorization mechanisms through a smart contract and waits for verification, and if the verification succeeds, the visitor is also granted an attribute token through the smart contract; when the patient has enoughattribute tokens, data information access is requested to the patient through the smart contract; and if the patient judges that the attribute set of the visitor meets the formulated access strategy,the visitor has permission to access the medical data information of the patient. According to the method, access control of a plurality of attribute authorization mechanisms and traceability responsibility asking of the attribute authorization mechanisms can be realized, and a patient can autonomously control medical data access.
Owner:矩阵纵横(北京)科技有限公司
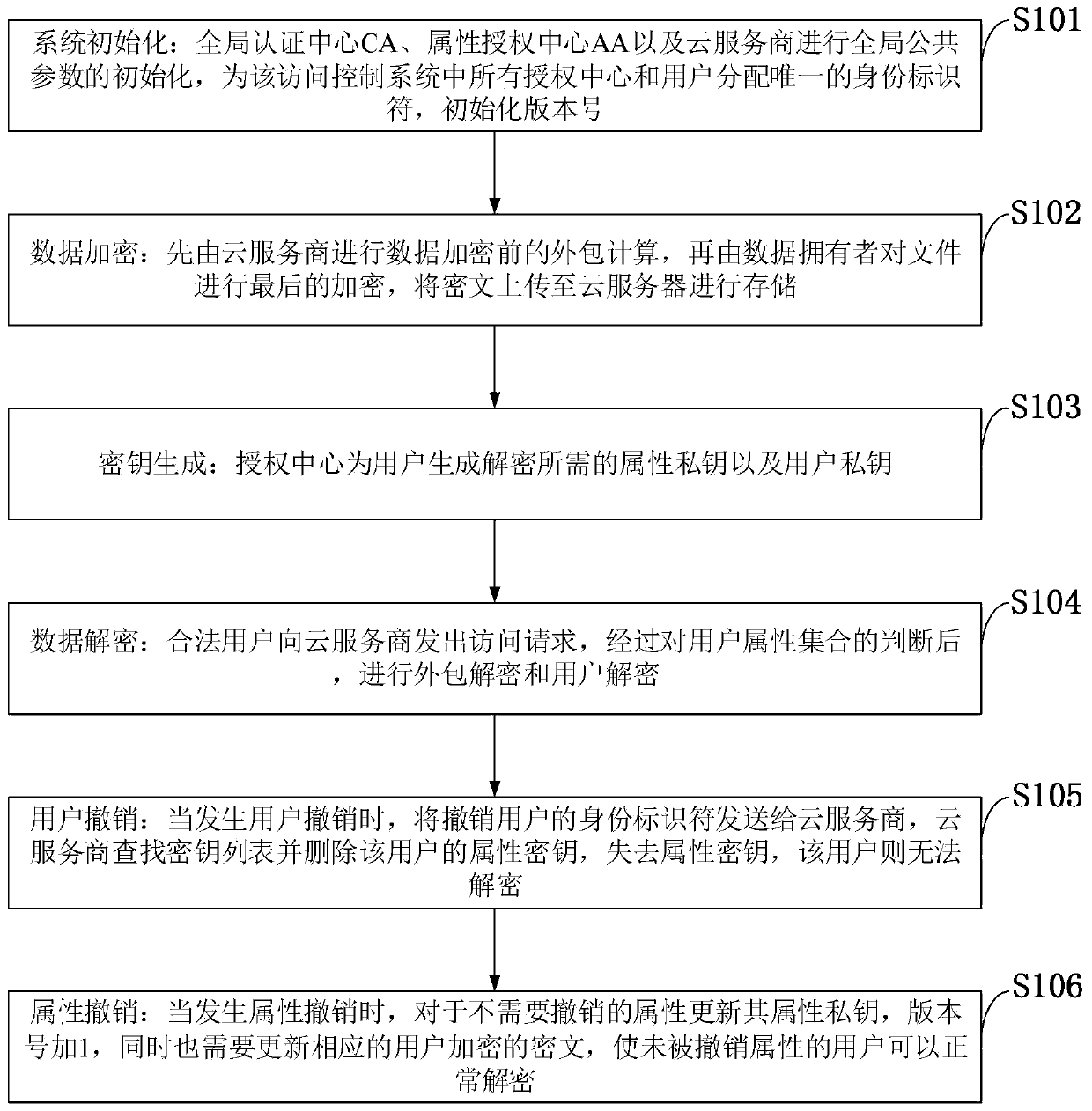
Multi-authorization center access control method and system and cloud storage system
InactiveCN110602063ALighten the computational burdenAvoid Collusion AttacksTransmissionUser PrivilegeCloud storage system
The invention belongs to the technical field of information security, and discloses a multi-authorization center access control method and system and a cloud storage system, and the method comprises the steps: system initialization: initializing a global authentication center CA and an attribute authorization center AA; data encryption: outsourcing encryption and user encryption performed by a cloud service provider; key generation: an attribute authorization center AA allocates an attribute private key related to the attribute and a user decryption key to the user; the user sends a file access request to the cloud service provider, and the process comprises outsourcing decryption of the cloud service provider and final decryption of the user; some users in the system are revoked; certainattributes in the system are revoked. The method has the advantages of high system efficiency, reduction of user computing burden, support of multiple authorization centers, dynamic change of user permission and the like, and can be used in a cloud storage system to guarantee the data privacy security of users, reduce the computing overhead of the users and improve the system efficiency.
Owner:XIDIAN UNIV
Partial strategy hiding access control method and system and wireless communication system
ActiveCN111695095AReduce stepsReduce computational overheadKey distribution for secure communicationDigital data protectionCommunications systemInternet privacy
The invention belongs to the technical field of wireless communication, and discloses a partial strategy hiding access control method and system and a wireless communication system. A central authorization center generates global public parameters, a system master key and a user global unique identity identifier; the attribute authorization center generates an attribute authorization center publicand private key pair, and generates a user agent key and a decryption key; the data owner formulates an access control strategy according to a sharing demand, embeds the access control strategy intothe ciphertext, and uploads the partially hidden access control strategy and the ciphertext to the cloud together; the cloud service provider judges whether the data requester meets the partially hidden access control strategy or not; the data user uses the decryption key to complete final authentication; when user revocation occurs, the cloud service provider deletes the proxy key corresponding to the revoked user; and when attribute revocation occurs, the cloud service provider updates the corresponding proxy key and ciphertext. According to the invention, the authentication efficiency is high under the same security strength.
Owner:XIDIAN UNIV
Privacy protection method for storing shared data in mobile cloud
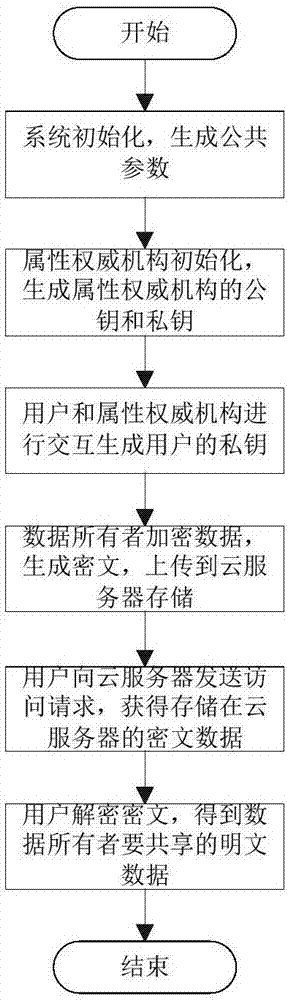
InactiveCN107968780AChange the privacy protection attribute encryption methodSmall amount of calculationTransmissionPlaintextMobile cloud
The invention discloses a privacy protection method for storing shared data in a mobile cloud. The privacy of a data owner is effectively protected through strategy semi-hiding. A public key and a private key are generated when an attribute authority is initialized, the data owner encrypts the data by using the public key generated by the attribute authority, thereby generating ciphertext and uploading the ciphertext to a cloud server to store; a user and the attribute authority are interacted to generate a private key of the user; when the user sends an access request to the cloud server andacquires the ciphertext data stored at the cloud server by the data owner, the decryption is performed through plaintext data to be shared by the data owner and the related operation is performed. Through the privacy protection method disclosed by the invention, the protection of the privacy of the data owner can be well protected, the calculated quantity of the data owner in the traditional hiding access scheme is greatly reduced, and the method is suitable for the situation that the encryption strategy in the mobile terminal application is far less than the system attribute.
Owner:SHANGHAI MARITIME UNIVERSITY
Attribute encryption access control system and method based on block chain
ActiveCN112804064AControl fine-grained access controlKey distribution for secure communicationUser identity/authority verificationThe InternetData access
The embodiment of the invention relates to an attribute encryption access control system and method based on a block chain. The system comprises: a block chain system which comprises a plurality of attribute authorization mechanisms and is used for generating public parameters and master key data after initialization operation and sending the public parameters; a data accessor which interacts with the block chain system; Internet-of-Things equipment which interacts with the block chain system; and a cloud server which interacts with the data accessor and the Internet-of-Things equipment, and is used for receiving and storing the ciphertext data and the transaction number data sent by the Internet-of-Things equipment, and receiving a request ciphertext instruction sent by the data accessor. According to the multi-centralization and non-tampering characteristics of the block chain, a trusted third party can enable a plurality of attribute authorization mechanisms and data owners to participate in attribute endorsement auditing by using the alliance chain, and the ciphertext hash value is stored; and the attribute-based fine-grained access control of the user is realized through an attribute encryption and symmetric encryption hybrid mechanism of a hidden ciphertext strategy.
Owner:XIAN UNIV OF POSTS & TELECOMM
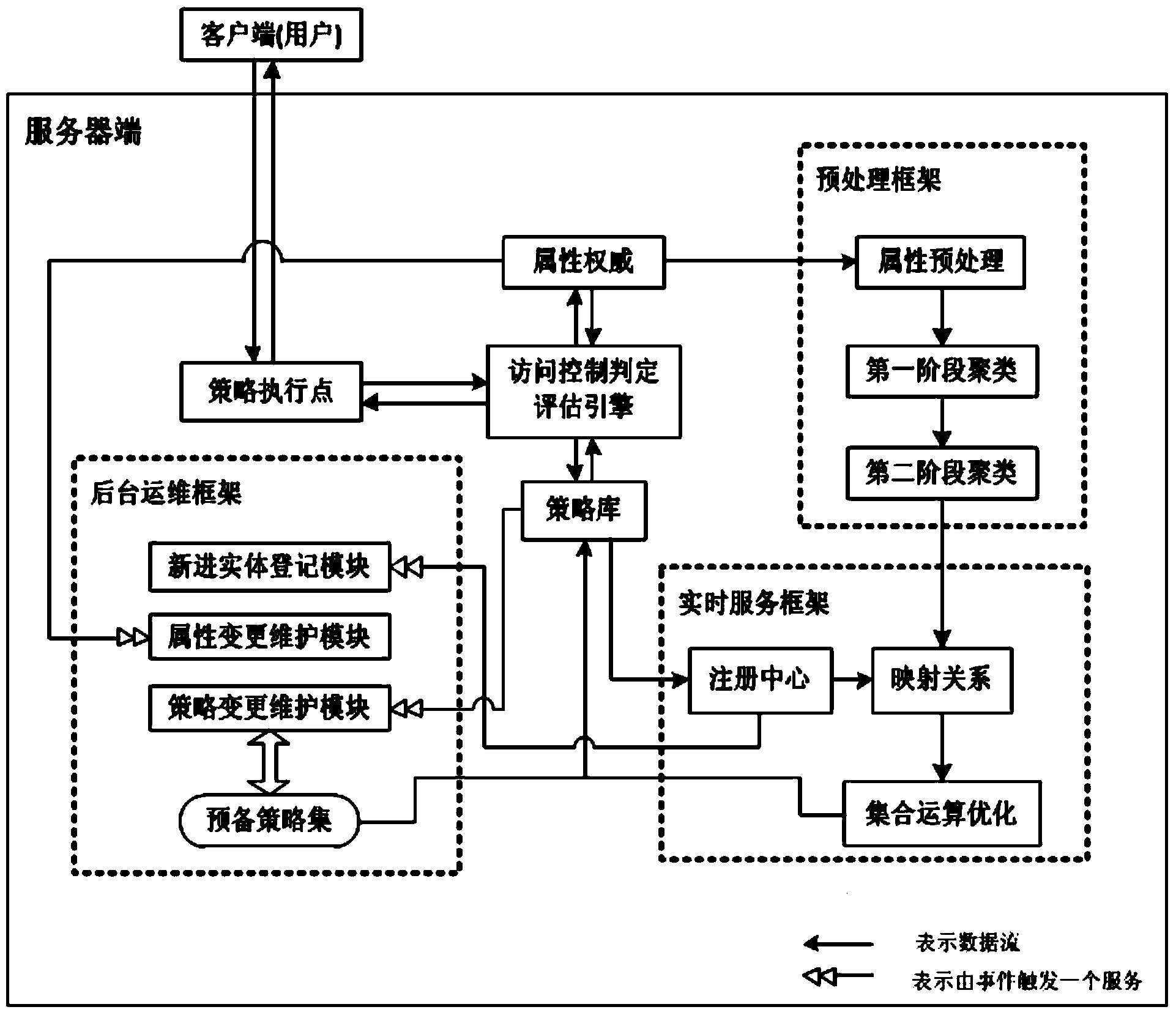
Access control determination engine optimization system and method based on big data
InactiveCN103902742ASatisfy securityReduce workloadRelational databasesTransmissionStrategy executionReal time services
An access control determination engine optimization system based on big data is composed of a client terminal and a server terminal. The server terminal is used for conducting decision evaluation, authorization and execution on a request sent by the client terminal. The access control determination engine optimization system comprises an original access control determination engine, an infrastructure portion of the original access control determination engine, a preprocessing frame, a real-time service frame and a background operation and maintenance frame, wherein the original access control determination engine and the infrastructure portion of the original access control determination engine comprise an access control determination evaluation engine module, a strategy execution point, an attribute authority module and a strategy library module, the preprocessing frame is used for processing required before deployment of the access control determination engine, and comprises an attribute preprocessing module, a first-stage clustering module and a second-stage clustering module, the real-time service frame is used for processing a real-time request generated when the server terminal runs, and comprises a registration center module, a mapping relation module and a set operation optimization module, and the background operation and maintenance frame comprises a recent entity registration module, an attribute change and maintenance module, a strategy change and maintenance module and a preparation strategy set module. The access control determination engine optimization system has the advantages of being efficient and high in availability, safety and universality.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Resource efficient security data sharing method and system
ActiveCN108540280AReduce computational overheadQuick responseKey distribution for secure communicationEncryption apparatus with shift registers/memoriesAccess structureOriginal data
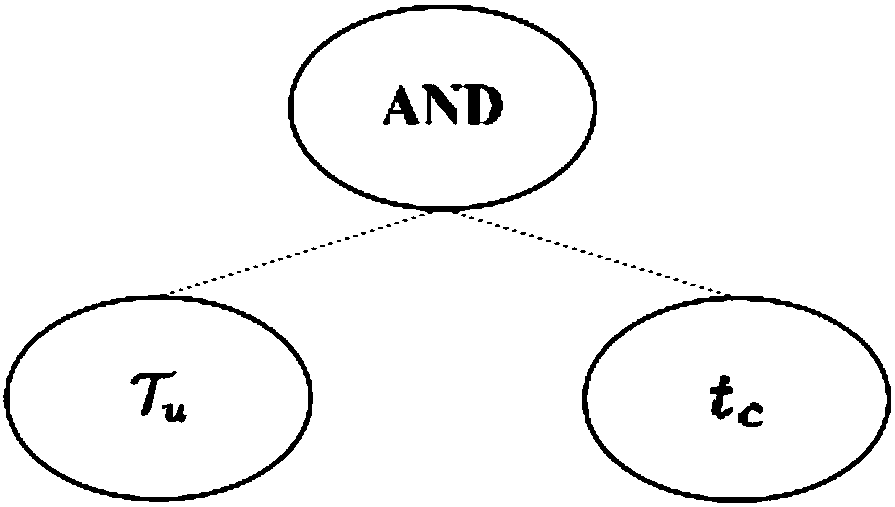
The invention provides a resource efficient security data sharing method and system. The method comprises the steps that an issuer preprocesses original data to obtain metadata M, wherein the metadataM is encrypted through utilization of a fog node symmetrical encryption scheme, a symmetrical key is protected by a set access structure, the accurate symmetrical key only can be obtained through decryption of a decryption server when an attribute set S of a subscriber satisfies the access structure corresponding to a target ciphertext, and further the metadata M is restored; the symmetrical keyand attributes are managed by an attribute authority; the access structure is an access tree gamma established by the issuer, non-leaf nodes of the access tree gamma are threshold gates, leaf nodes are associated with attribute values, and the access tree gamma comprises a left subtree gamma <c> and a right substree t <c>; the left subtree gamma <c> is determined by the issuer and corresponds to the ciphertext; and the right substree t <c> is the lead node for describing a time stamp. According to the method and the system, different security demands are realized, the computing cost is clearlyreduced, and the efficient user revocation is realized.
Owner:SHANGHAI JIAO TONG UNIV +2
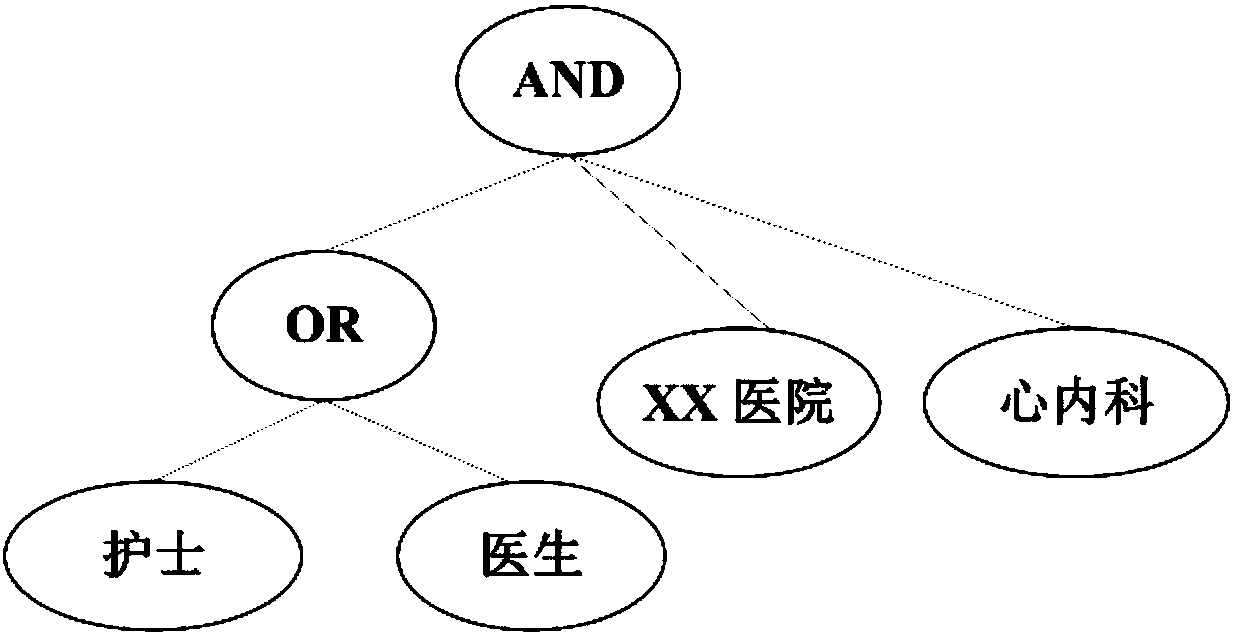
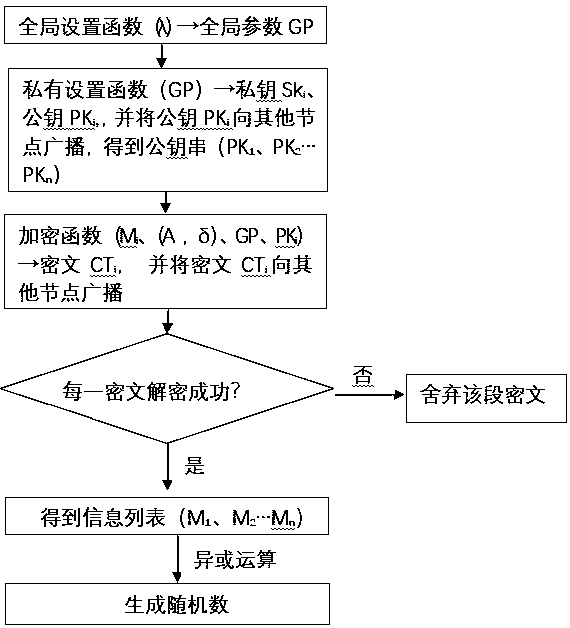
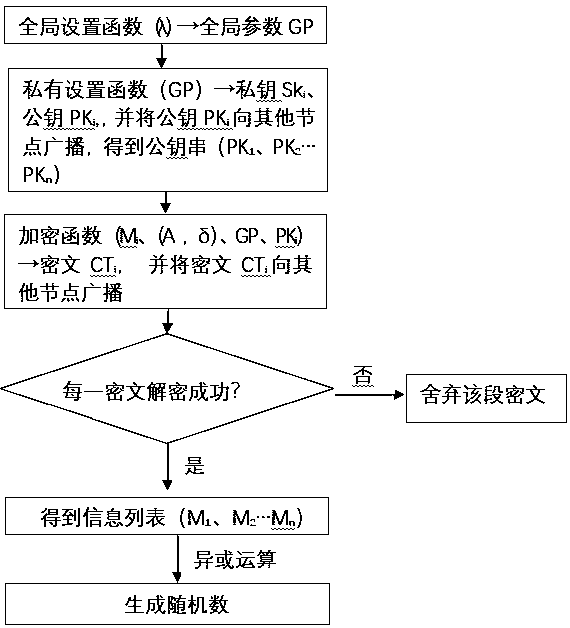
Distributed verifiable random number generation method based on CP-ABE
ActiveCN109981263AImprove fault toleranceImprove cheating resistanceKey distribution for secure communicationPublic key infrastructure trust modelsThird partyPassword
The invention belongs to the technical field of passwords, and particularly relates to a distributed verifiable random number generation method based on CP-ABE. Based on a distributed random number generation system, a multi-attribute authorization center CP-ABE is taken a basic framework, and multiple nodes participate in attribute distribution, secret key generation, information encryption, secret text list broadcasting and decryption, a random number is generated, so that a highly-centralized third-party verifiable distributed random number generation scheme is realized. In the whole process, through mutual verification of multiple users and a preset standard value t / n, it can be effectively avoided that the disguising node provides false information or does not provide information, andtherefore the safety and the stability of the system are guaranteed.
Owner:FUDAN UNIV
Distributed attribute-based encryption method supporting fine-grit attribute revocation on lattice
ActiveCN108880801ASolve the leakage problemImprove securityKey distribution for secure communicationImage extractionInformation security
The invention discloses a distributed attribute-based encryption method supporting fine-grit attribute revocation on lattice, and belongs to the field of the information security. The method comprisesthe following steps: at the system initialization stage: the linear secret sharing is performed on a target vector at a system initialization stage, a sub-secret sharing value is served as a privatekey of a corresponding attribute authorization mechanism, and the attribute authorization mechanism establishes the corresponding binary revocation tree for the managed system attribute; at the user attribute key and the update key generation stage: the attribute authorization mechanism obtains the secondary sub-secret sharing value of the user attribute by using secondary linear secret sharing, and the computes the user attribute key and the user attribute update key through a primary image extraction algorithm and a left-sampling algorithm; at the encryption stage: an encryption party computes the ciphertext of the message by using the Gaussian noise, the encrypted and preprocessed noise vector and the system public parameter; at the decryption: a decryption party decrypts the ciphertextby using the user attribute key and the user attribute update key. The method disclosed by the invention is high in security, flexible in access policy and supports the fine-grit attribute permissionrevocation.
Owner:芽米科技(广州)有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com