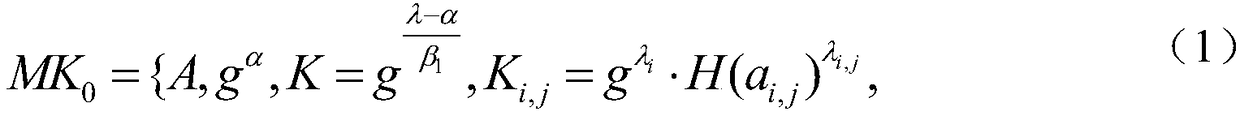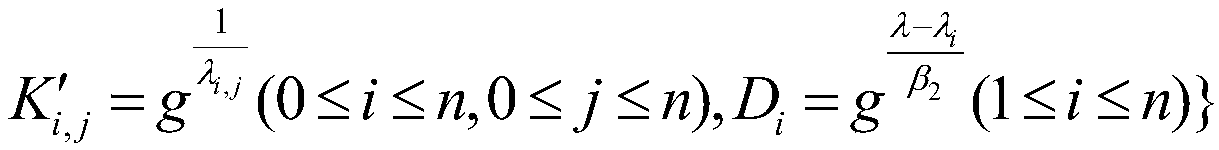Weight attribute-based encryption method based on hierarchical authorities
A technology of attribute-based encryption and authorization authority
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
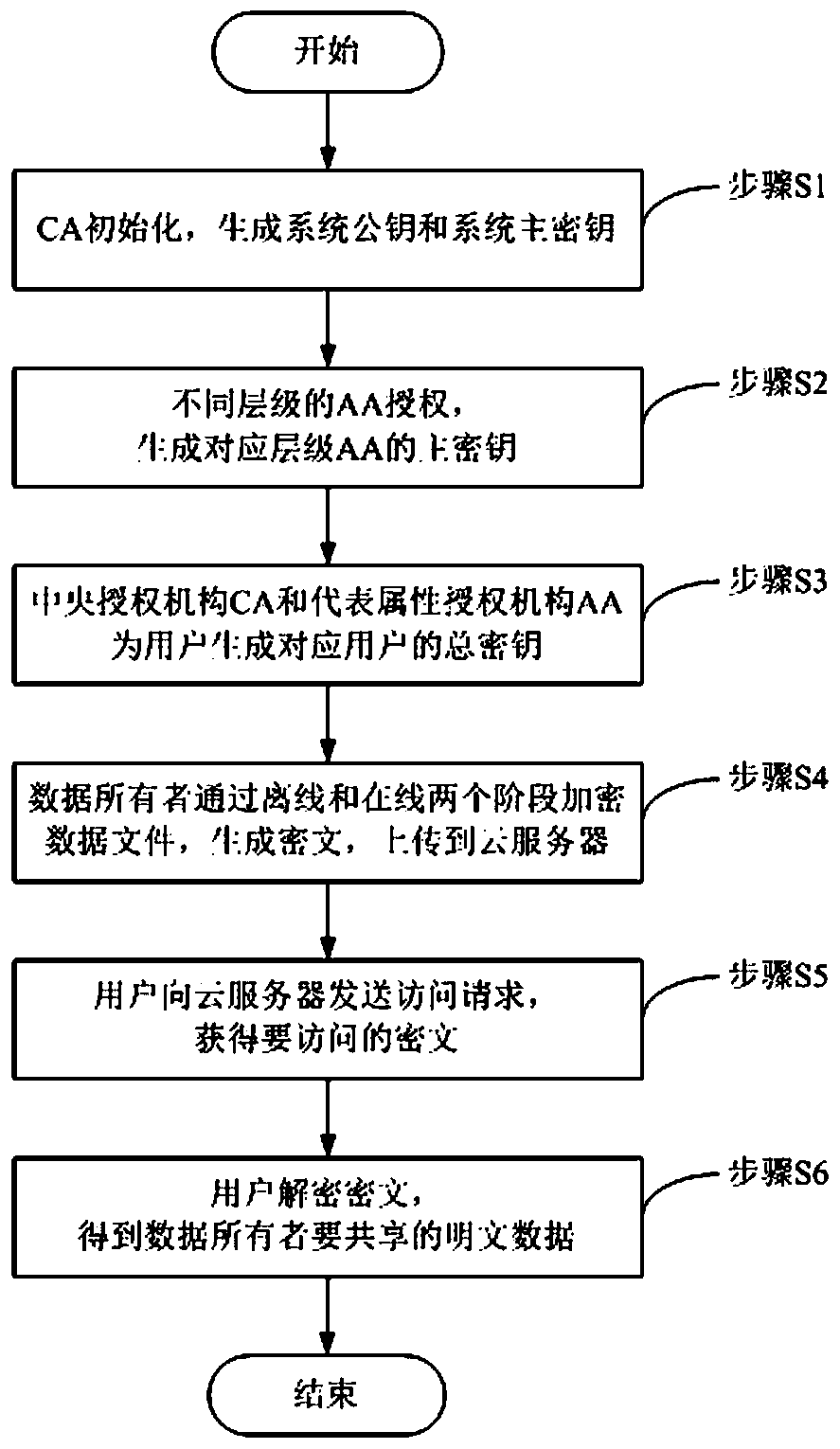
[0066] based on the following figure 1 Preferred embodiments of the present invention will be described in detail.
[0067] like figure 1 As shown, the present invention provides a kind of weight attribute base encryption method based on hierarchical authority, comprising the following steps:
[0068] Step S1, when the central authority CA is initialized, a system public key and a system master key are generated;
[0069] Step S2, authorize the representative attribute authority AA of different levels, and generate the master key of the representative attribute authority AA of the corresponding level;
[0070] Step S3, the central authority CA and the representative attribute authority AA distribute the user system private key and the user private key to the user, and the combination of the two generates the user's total key; wherein, AA generally refers to AA of different levels;
[0071] Step S4, the data owner encrypts the data file through two stages of online encryptio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com