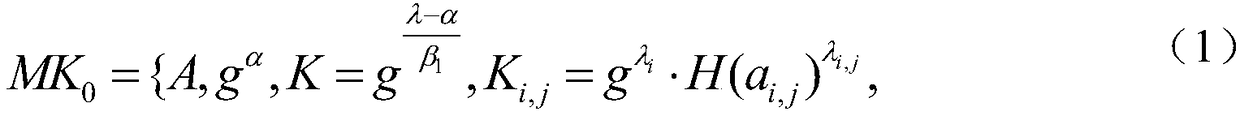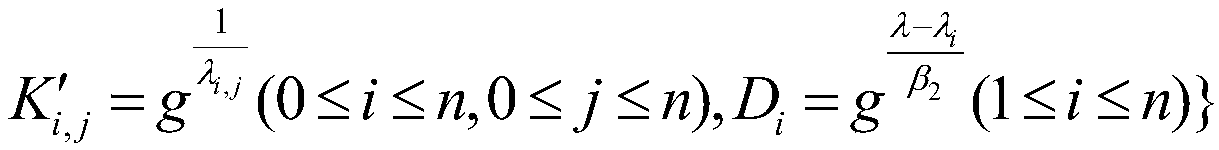Patents
Literature
170 results about "XML Encryption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
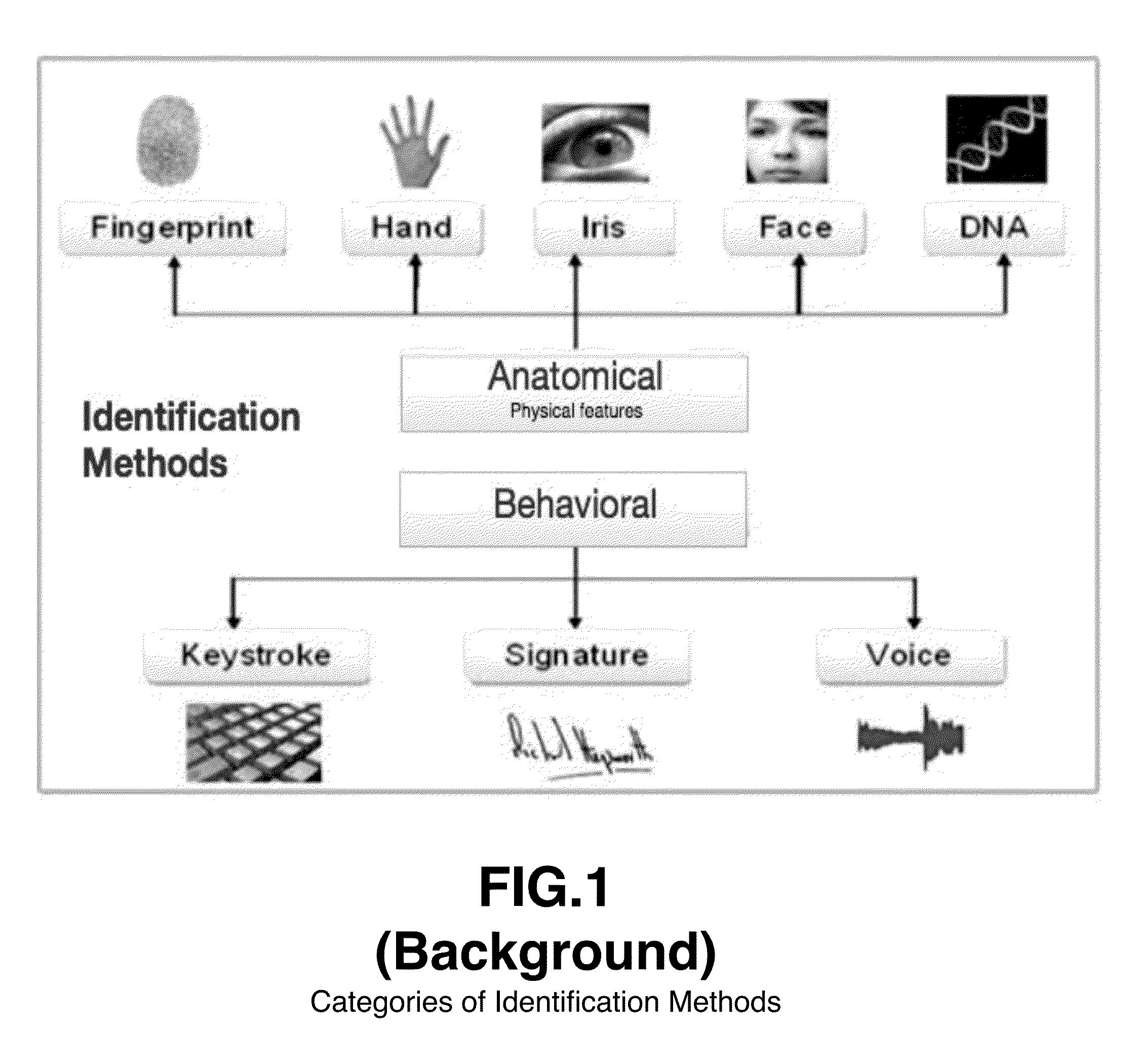
XML Encryption, also known as XML-Enc, is a specification, governed by a W3C recommendation, that defines how to encrypt the contents of an XML element. Although XML Encryption can be used to encrypt any kind of data, it is nonetheless known as "XML Encryption" because an XML element (either an EncryptedData or EncryptedKey element) contains or refers to the cipher text, keying information, and algorithms.
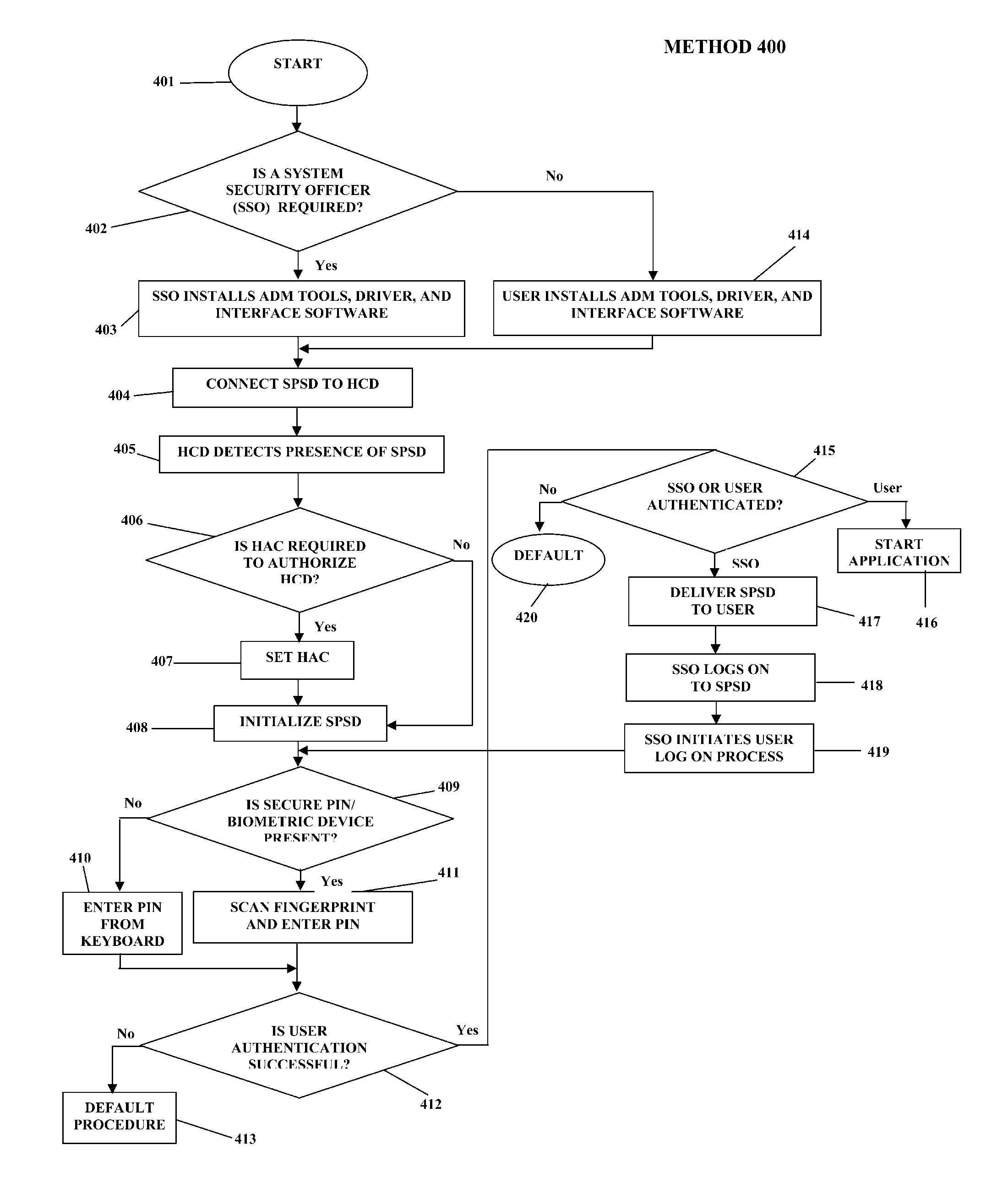
Portable data encryption device with configurable security functionality and method for file encryption
ActiveUS9049010B2Mitigates and eliminates vulnerabilityKey distribution for secure communicationUser identity/authority verificationPlaintextComputer hardware
A portable encryption device with logon access controlled by an encryption key, with an on board cryptographic processor for reconstituting the encryption key from a plurality of secrets generated by a secret sharing algorithm, optionally shrouded with external secrets using an invertible transform resistant to quantum computing attacks. Another embodiment provides file decryption controlled by a file encryption key, with the on board cryptographic processor reconstituting the file encryption key from a version of the file encryption key which has been shrouded with a network authorization code. A method for encryption of a plaintext file by hashing, compressing, and encrypting the plaintext file, hashing the ciphertext, hashing the plaintext hash and the ciphertext hash, and sealing the ciphertext together with the resulting hash. A portable encryption device for performing the method is also disclosed.
Owner:SPYRUS
Combined hardware and software based encryption of databases
InactiveUS6963980B1Increase flexibilityImprove performanceUser identity/authority verificationUnauthorized memory use protectionTamper proof hardwareRelational database
A relational database system for encryption of individual data elements comprising a encryption devices of at least two different types, the types being tamper-proof hardware and software implemented. The encryption processes of the system are of at least two different security levels, differing in the type of encryption device holding the process keys for at least one of the process key categories and also differing in which type of device executing the algorithm of the process. Each data element to be protected is assigned an attribute indicating the usage of encryption process of a certain security level.
Owner:PROTEGRITY CORP
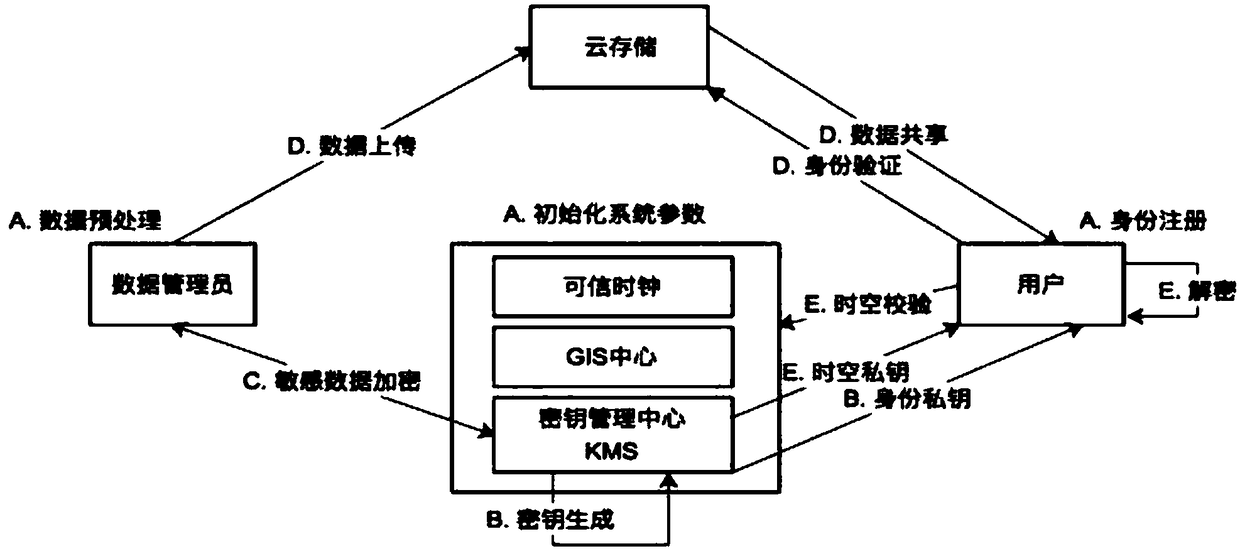
File security sharing method and system based on blockchain cloud storage
ActiveCN108259169AEasy to share remotelyFrequent migrationKey distribution for secure communicationXML EncryptionCloud data
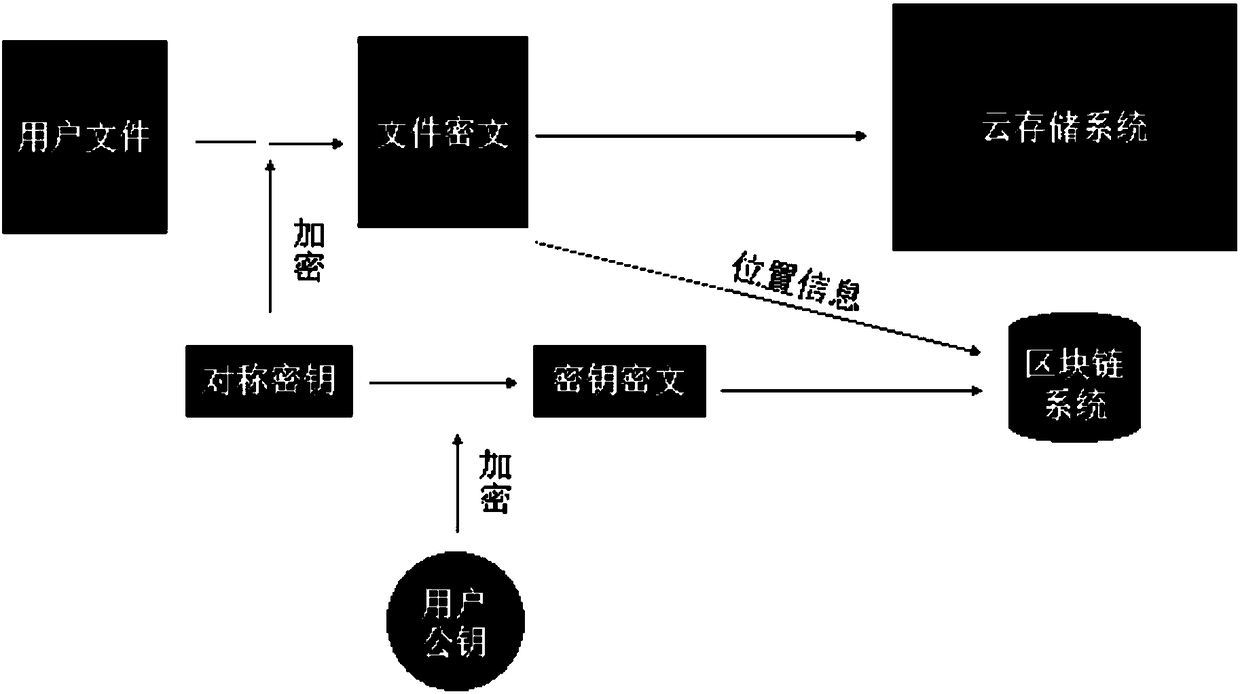
The invention is applicable to the field of data storage technology improvement, and provides a file security sharing method based on blockchain cloud storage. The method includes the steps as follows: S1, performing data encryption on a file by using a symmetric encryption algorithm, and storing a data ciphertext in a cloud disk; S2, enabling a user to generate a key ciphertext by using a symmetric key for decrypting the data ciphertext through encryption, and storing the storage locations of the key ciphertext and the data ciphertext together on a blockchain as a part of metadata; and S3, performing proxy re-encryption on the stored file data by using a new key, and securely sharing the data through the new key and the re-encrypted new ciphertext. Through the implementation of a cloud security storage and sharing mechanism for a private file under a decentralized storage architecture of the blockchain, the data stored in the cloud by the user can only be accessed through a private key, when the own encrypted data needs to be shared to other users, the own original key of an owner cannot be exposed to other people, and the process of downloading all cloud data, re-encrypting the data by using a shared key, and then uploading the data in sequence is not required.
Owner:PEKING UNIV SHENZHEN GRADUATE SCHOOL +1
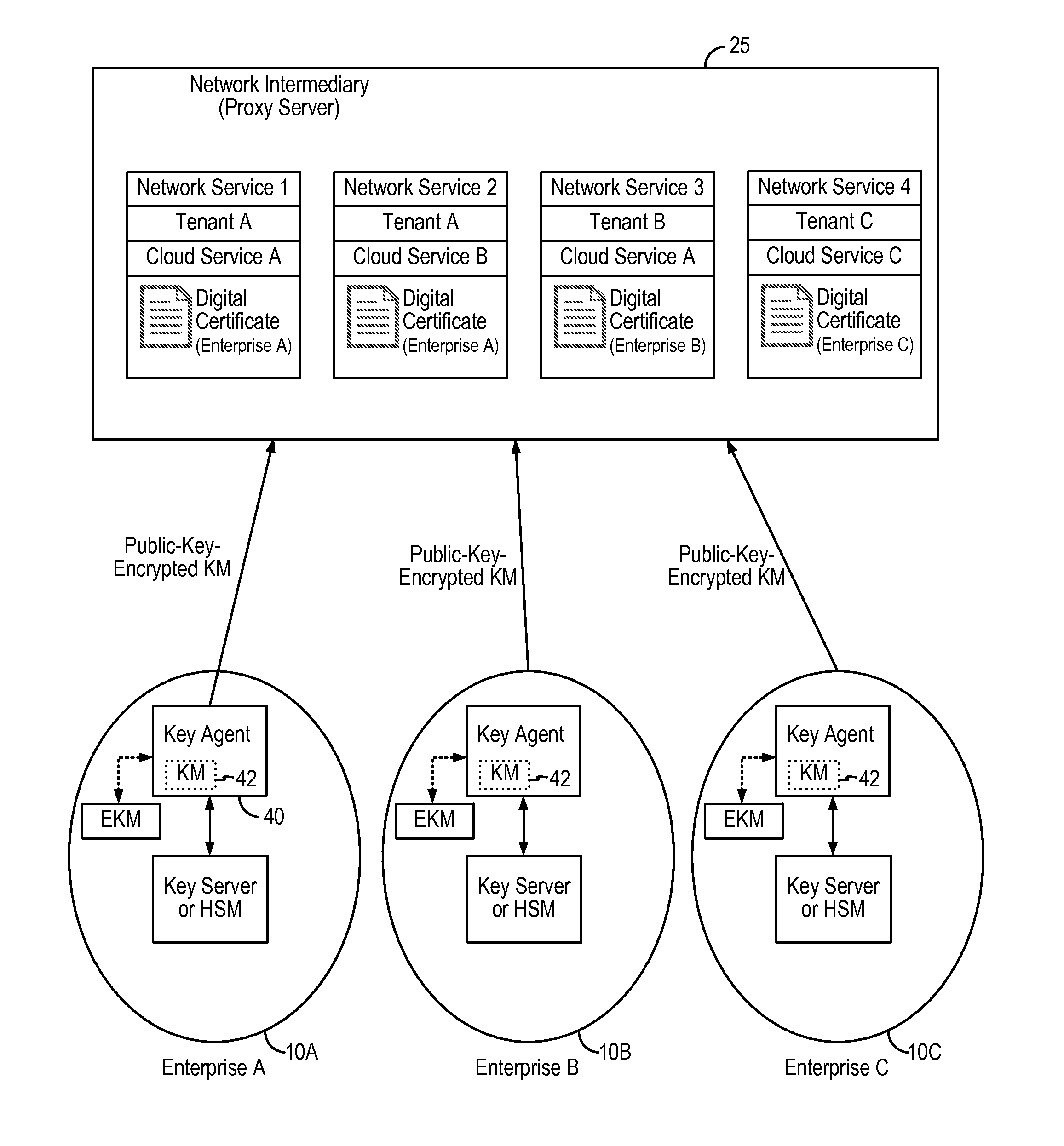
Encryption in the cloud using enterprise managed keys
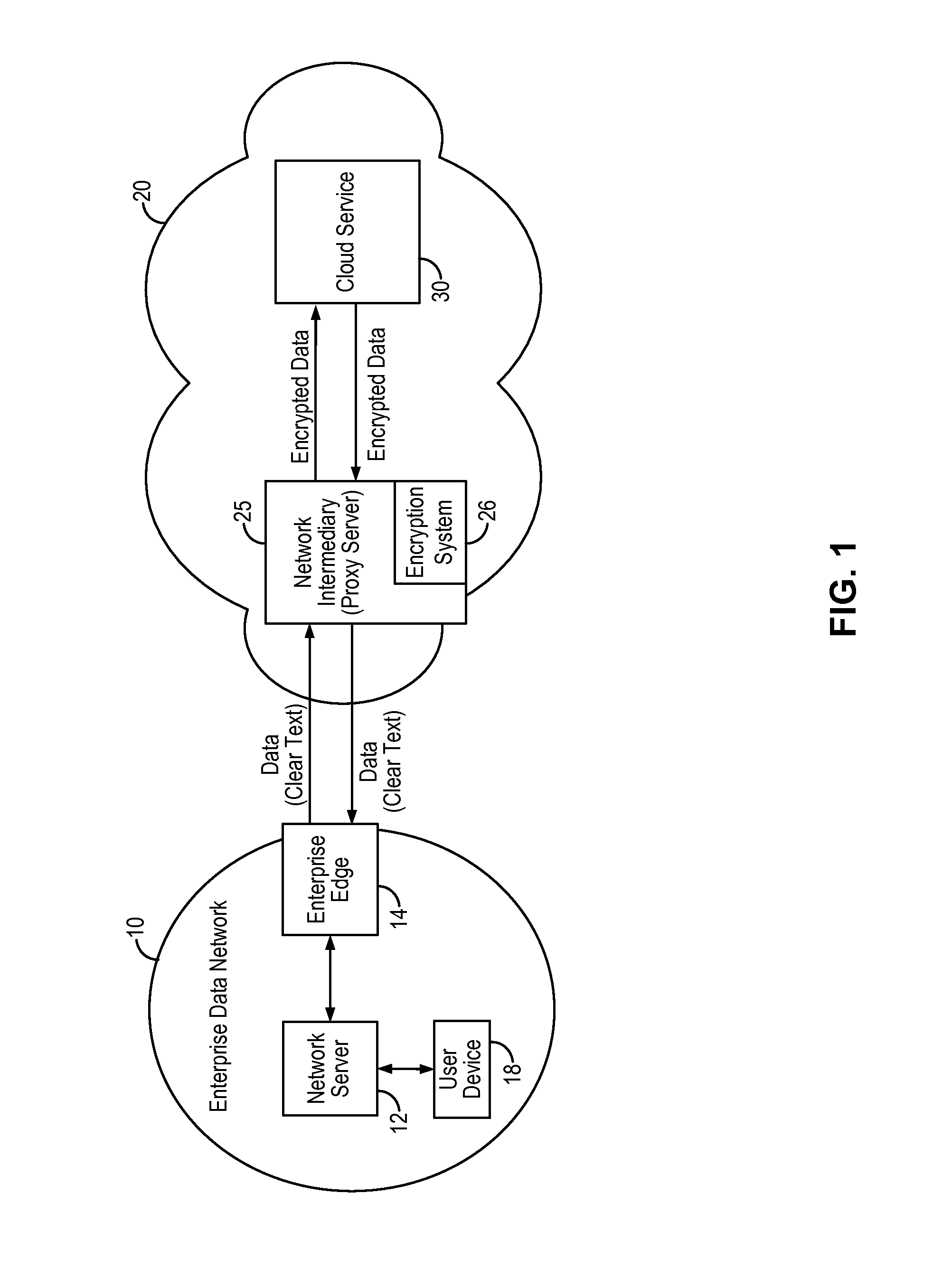
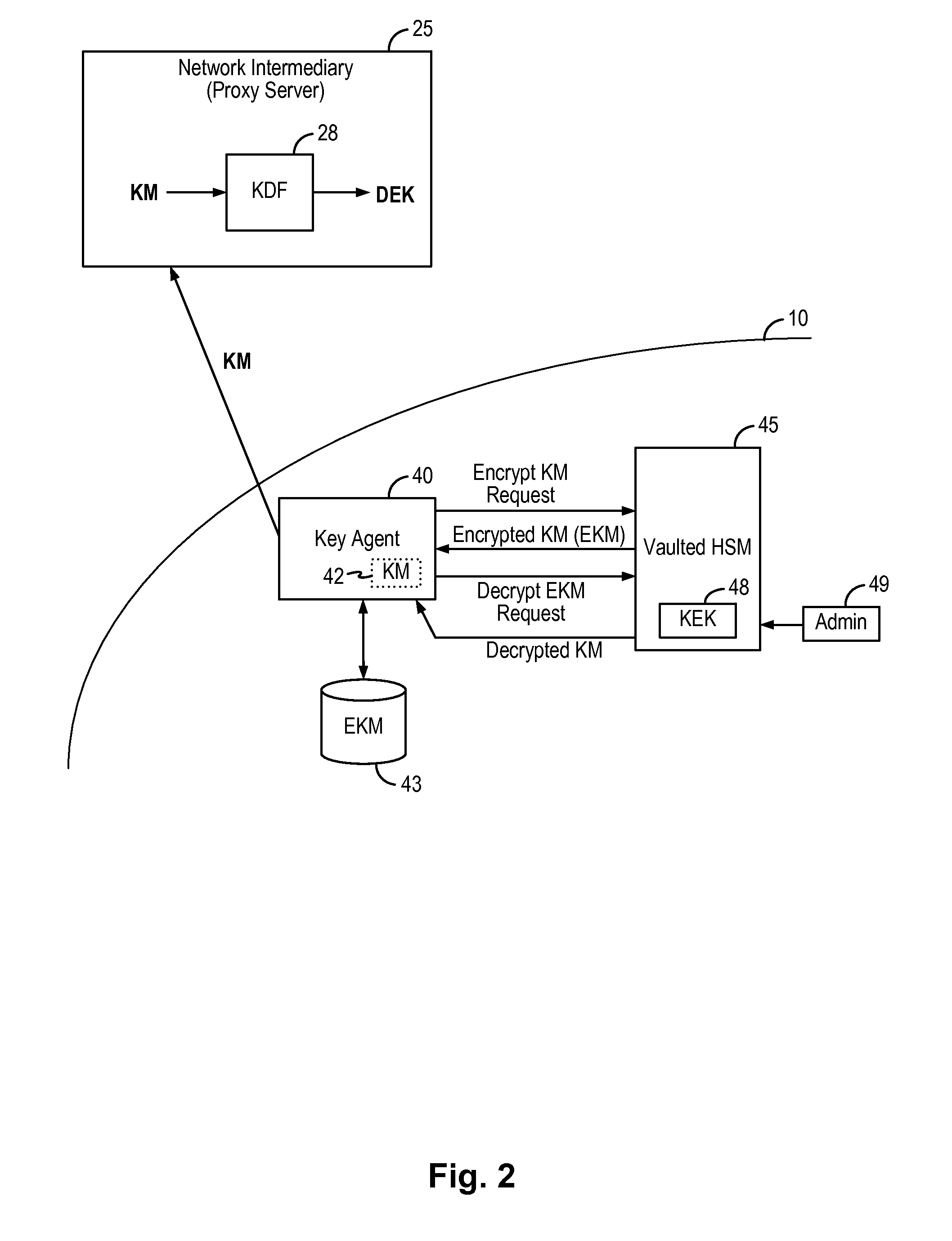
An encryption key management system and method implements enterprise managed encryption key for an enterprise using encryption for cloud-based services. In some embodiments, the enterprise deploys a key agent on the enterprise data network to distribute encryption key material to the network intermediary on a periodic basis. The network intermediary receives the encryption key material from the enterprise and stores the encryption key material in temporary storage and uses the received encryption key material to derive a data encryption key to perform the encryption of the enterprise's data. In this manner, the enterprise can be provided with the added security assurance of maintaining and managing its own encryption key while using cloud-based data storage services. The encryption key management system and method can be applied to ensure that the enterprise's one or more encryption keys do not leave the enterprise's premises.
Owner:SKYHIGH SECURITY LLC
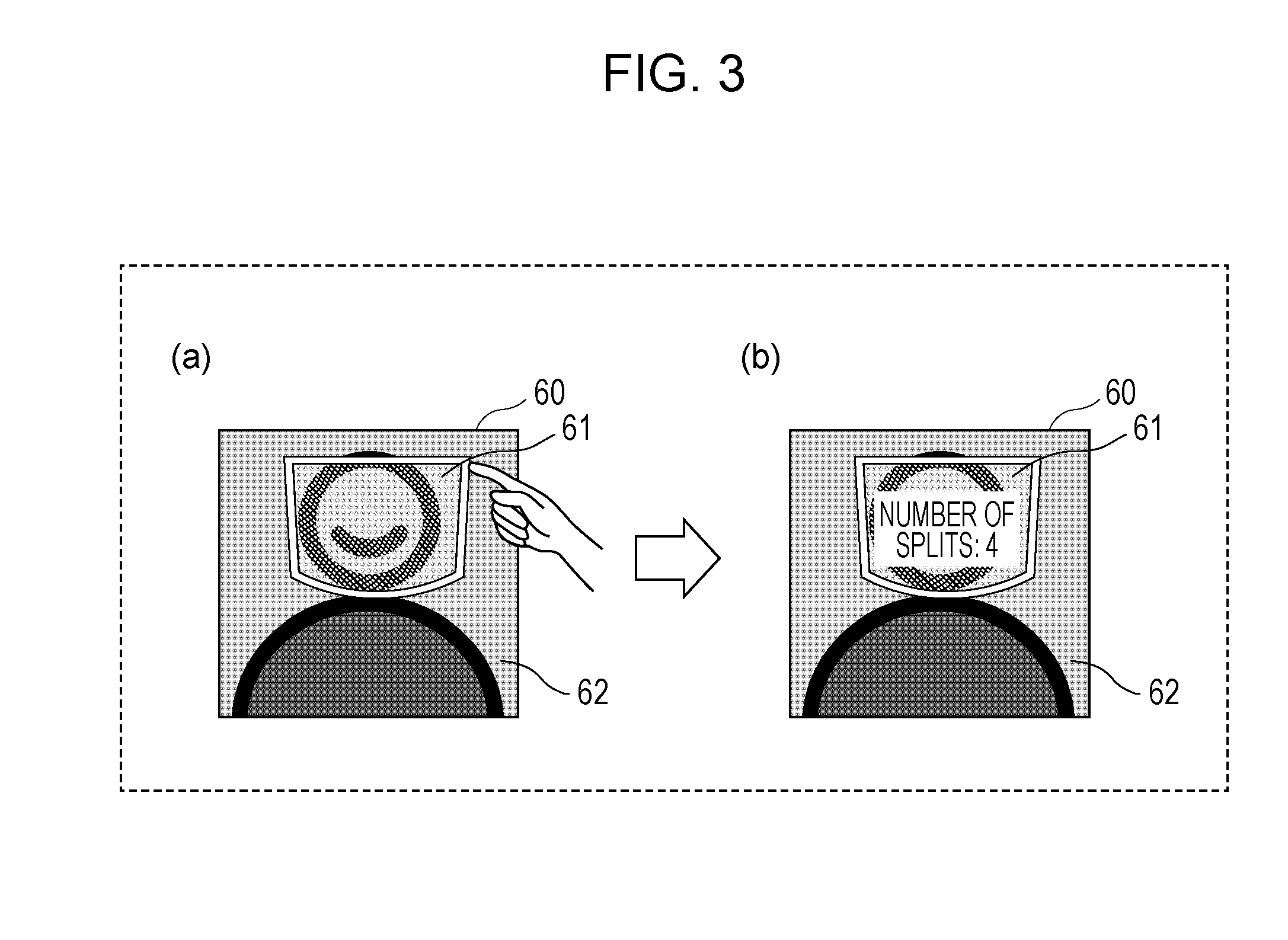
Encryption method, encryptor, and encryption system for encrypting electronic data by splitting electronic data
ActiveUS20160119134A1Improve confidentialityEasy to implementKey distribution for secure communicationUser identity/authority verificationXML EncryptionElectronic data
An encryption method includes displaying encryption target data on a display screen as an image, performing first acceptance in which designation of an at least partial region of the displayed image is accepted, performing second acceptance in which designation regarding splitting of the designated at least partial region is accepted, and splitting data that is included in the encryption target data and corresponds to the designated at least partial region in accordance with the designation regarding the splitting under a secret sharing scheme.
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
Format-Preserving Encryption Via Rotating Block Encryption
Methods and systems are described for format-preserving encryption. Format-preserving encryption on an entire format F may be achieved by performing format-preserving encryption on one or more subsets of F and then applying one or more permutation rounds in such a way that all elements of F enter a subset to be encrypted. A predetermined number of encryption rounds and a predetermined number of permutation rounds may be interleaved until all elements are thoroughly mixed. The resultant output data may be saved in a database in the same format as the original input data, meet all constraints of the database, and pass all validity checks applied by software supporting the database.
Owner:CA TECH INC
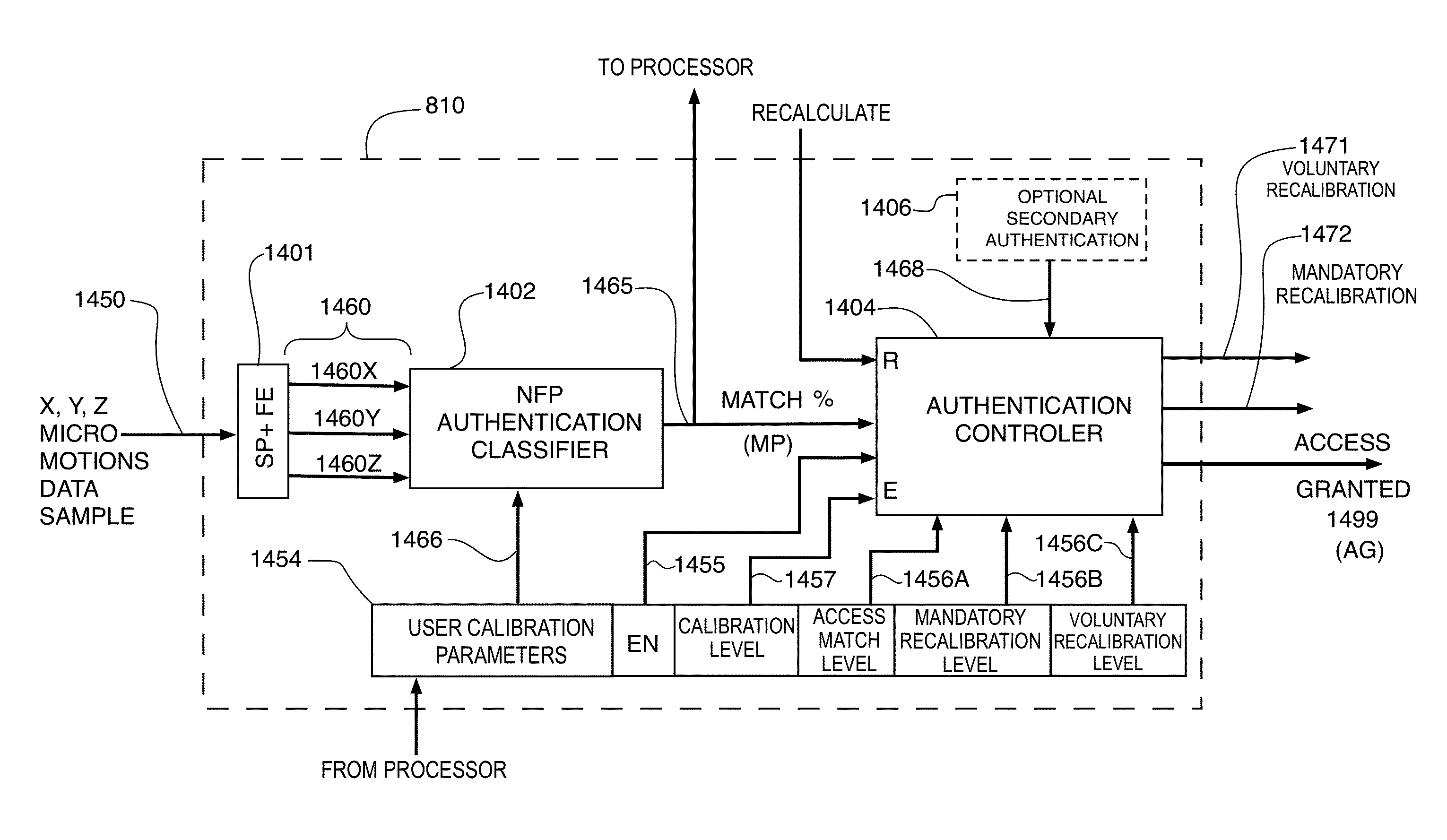
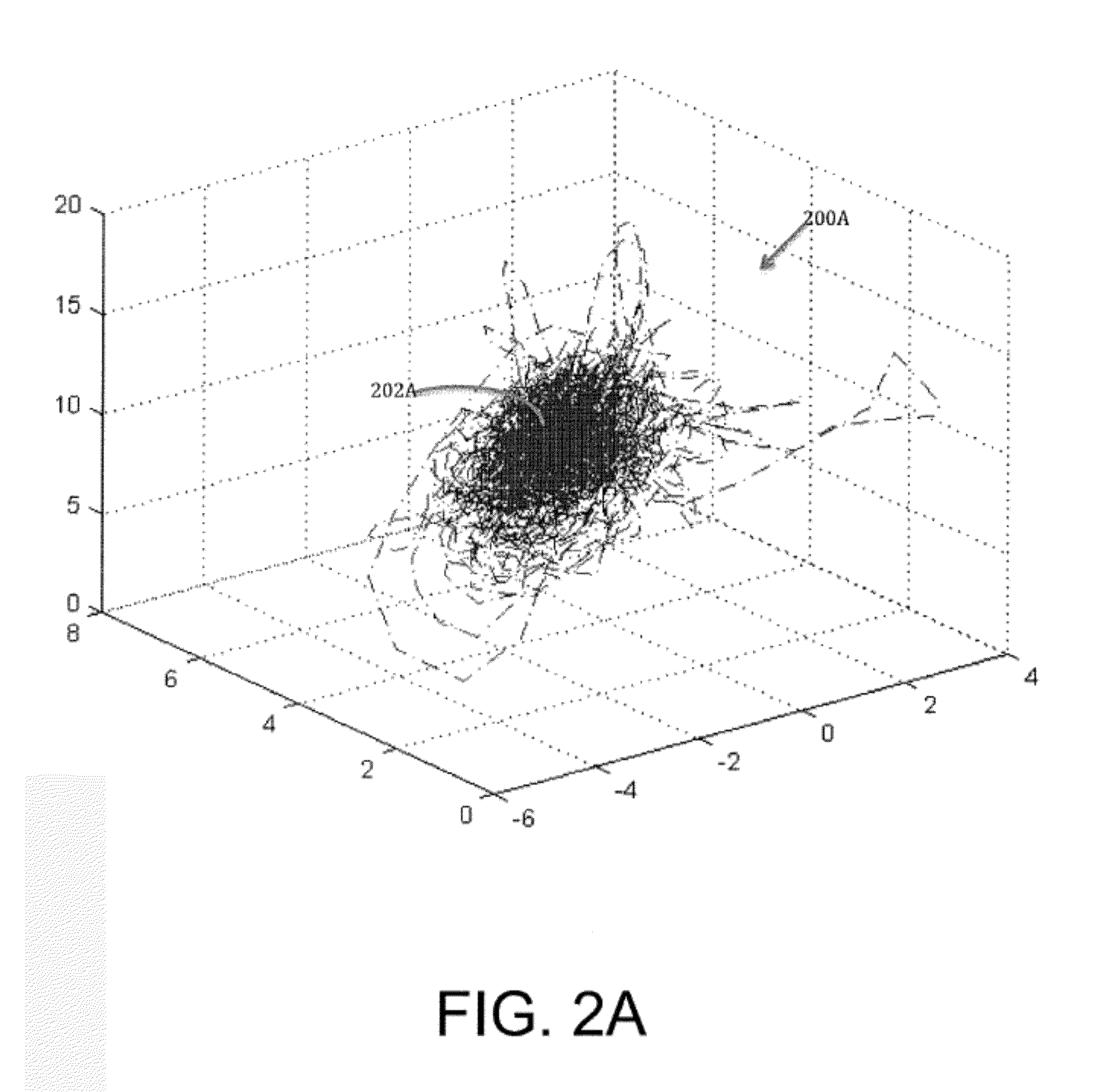
Data encryption/decryption using neuro and neuro-mechanical fingerprints
ActiveUS20160234174A1Exclude influenceEasy to useKey distribution for secure communicationEncryption apparatus with shift registers/memoriesXML EncryptionMulti dimensional
In accordance with one embodiment, a method for securing data is disclosed. The method includes sensing multi-dimensional motion of a body part of a user to generate a multi-dimensional signal; in response to the multi-dimensional signal and user calibration parameters, generating a neuro-mechanical fingerprint; and encrypting data with an encryption algorithm using the neuro-mechanical fingerprint as a key.
Owner:AERENDIR MOBILE INC
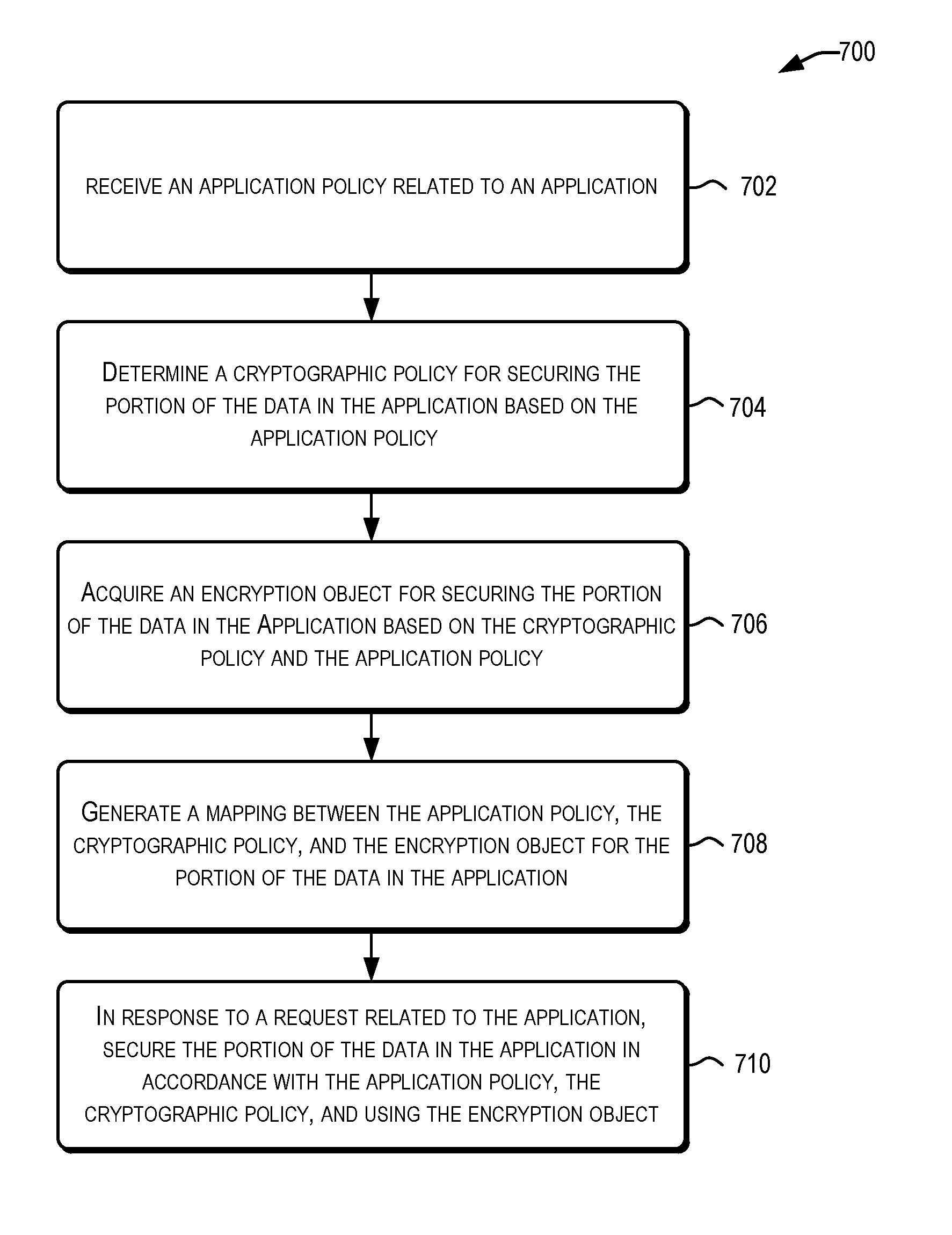
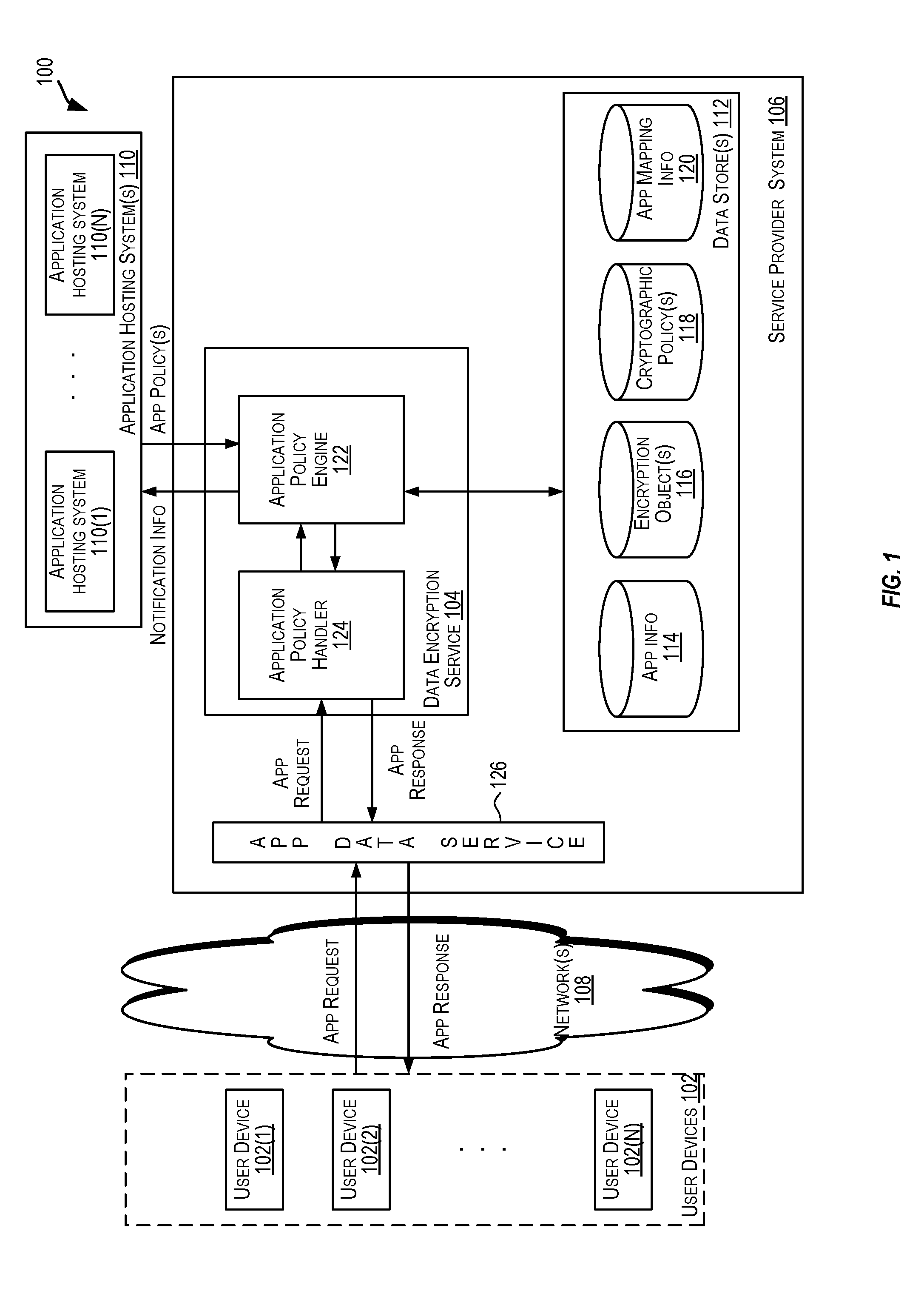
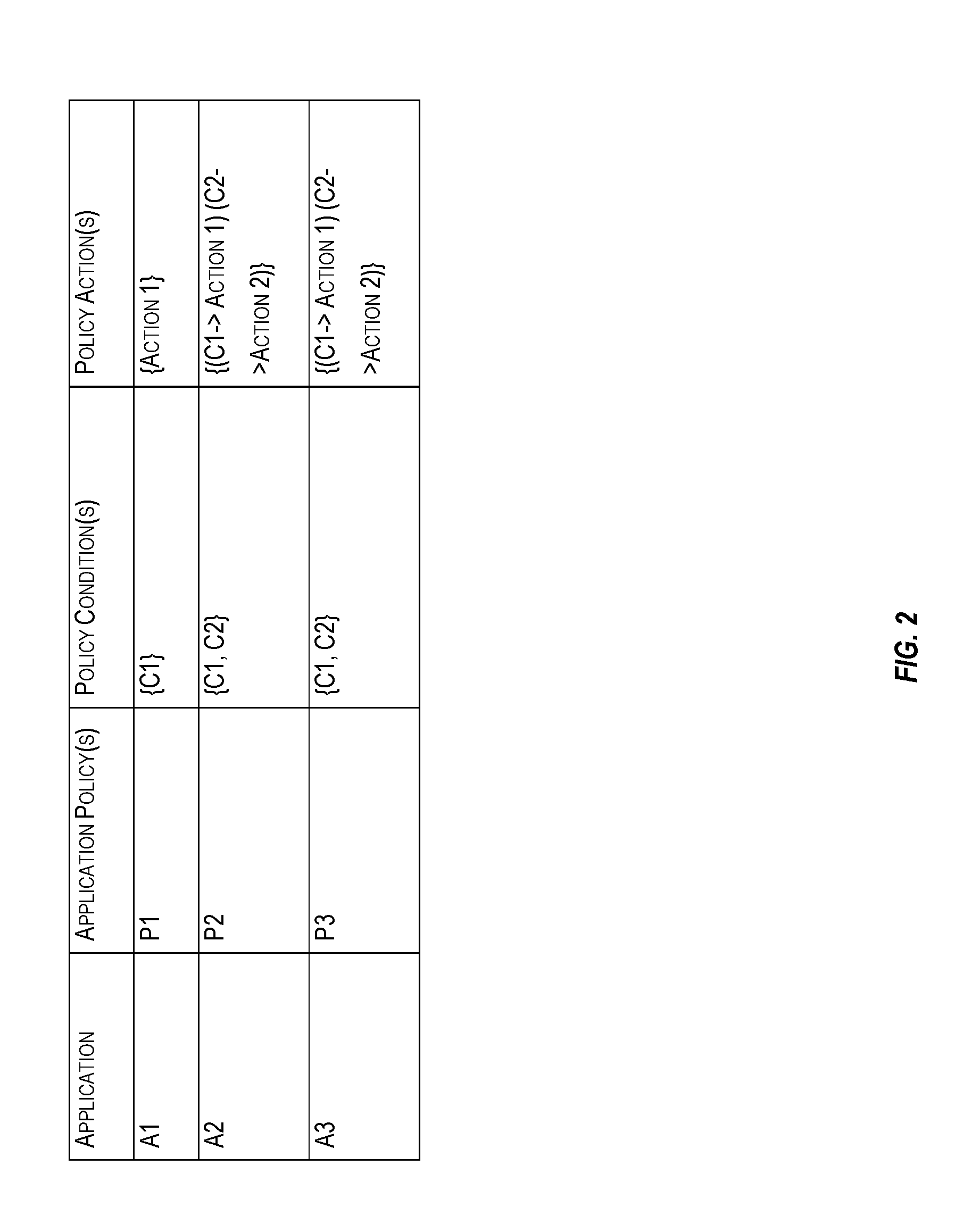
Data encryption service
ActiveUS20170006064A1User identity/authority verificationComputer security arrangementsPassword policyInternet privacy
A centralized framework for managing the data encryption of resources is disclosed. A data encryption service is disclosed that provides various services related to the management of the data encryption of resources. The services may include managing application policies, cryptographic policies, and encryption objects related to applications. The encryption objects may include encryption keys and certificates used to secure the resources. In an embodiment, the data encryption service may be included or implemented in a cloud computing environment and may provide a centralized framework for effectively managing the data encryption requirements of various applications hosted or provided by different customer systems. The disclosed data encryption service may provide monitoring and alert services related to encryption objects managed by the data encryption service and transmit the alerts related to the encryption objects via various communication channels.
Owner:ORACLE INT CORP
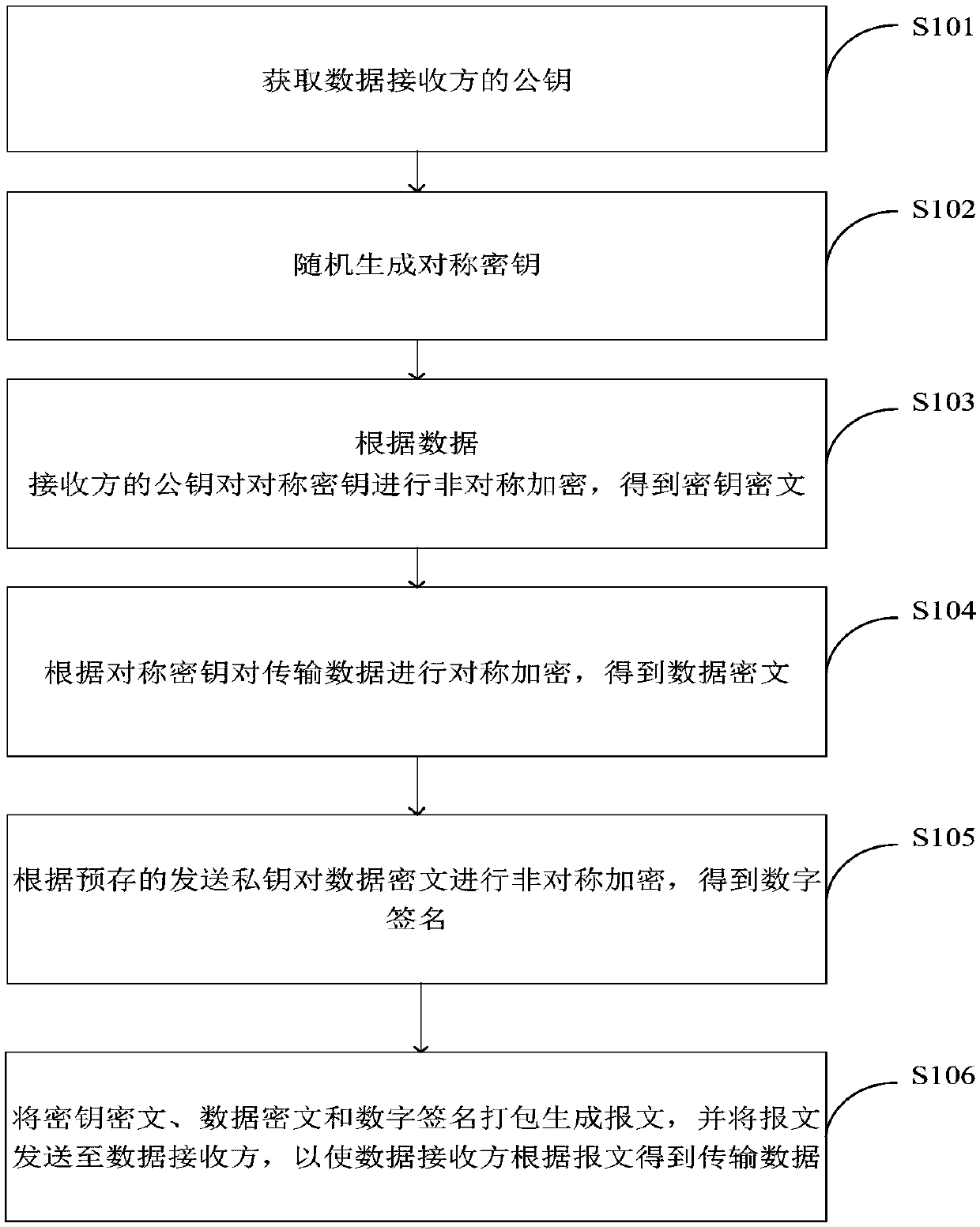
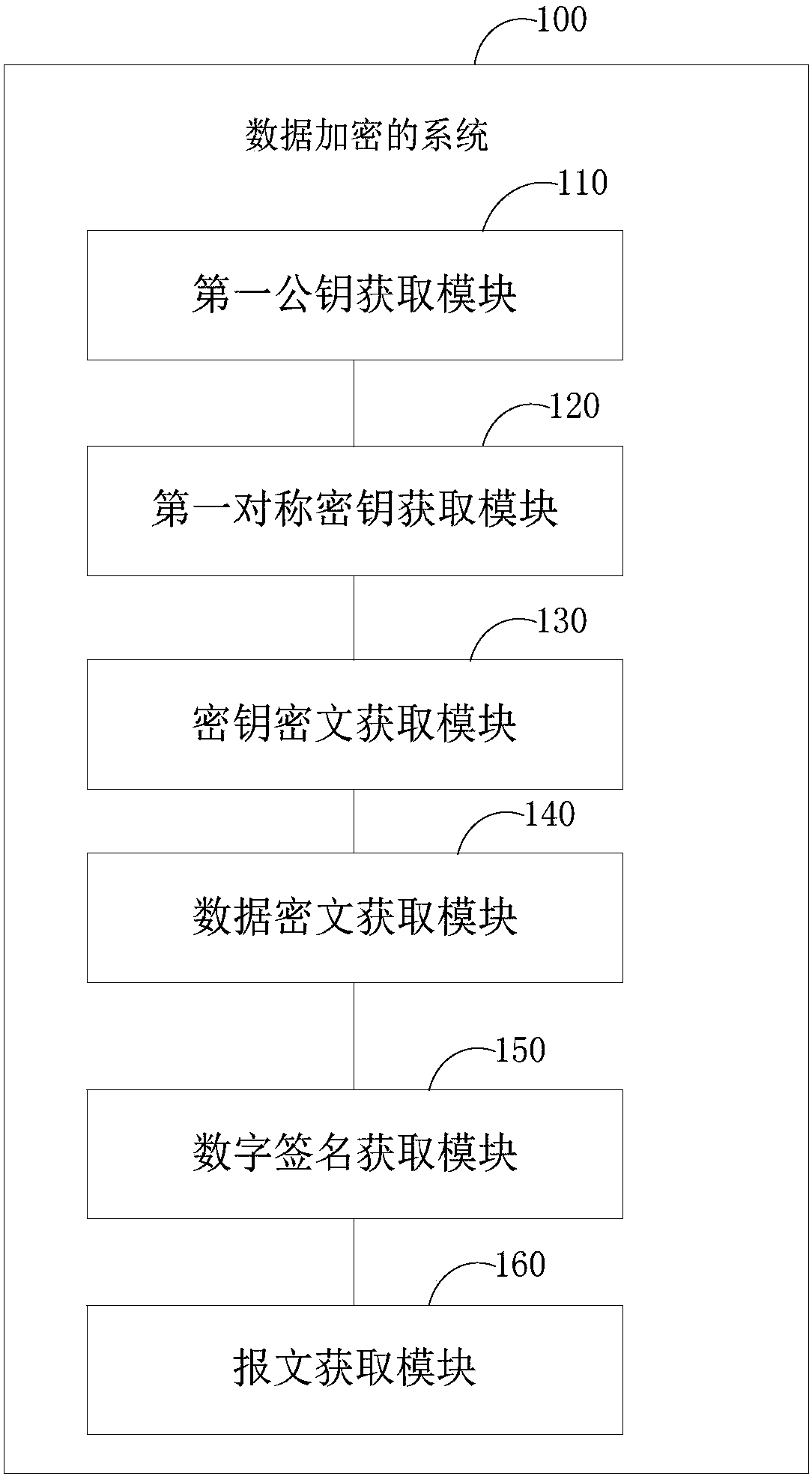
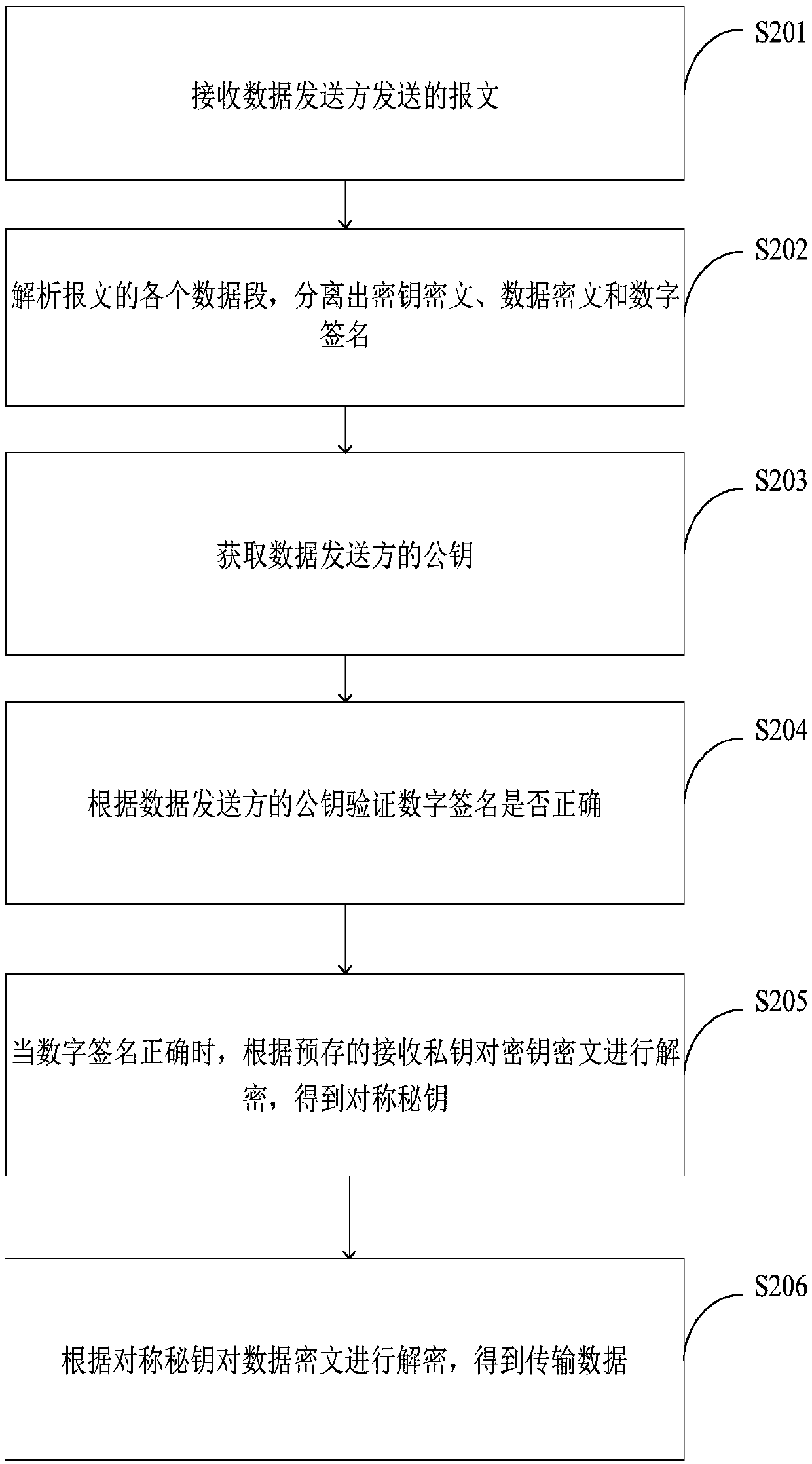
Data encryption method and system, data decryption method and system and terminal equipment
InactiveCN109802825AImprove securityGuaranteed reliabilityKey distribution for secure communicationPublic key for secure communicationCiphertextDigital signature
The method is suitable for the technical field of data encryption. The invention provides a data encryption method and system, data decryption method and system and terminal equipment. During data encryption, the data receiver obtains a public key of the data receiver to achieve RANDOM GENERATION OF SYMMETRIC KEYS, the symmetric key is encrypted according to the public key of the data receiver sothat Key ciphertext is acquired. the transmission data is encrypted according to the symmetric key to obtain a data ciphertext, the data ciphertext is encrypted according to a pre-stored sending private key to obtain a digital signature, the key ciphertext is packaged the data ciphertext and the digital signature to generate a message, the message is snet to a data receiver, and when the data is decrypted, the transmission data is acquired by the data receiver according to the message. Therefore, the problem that when the encrypted data sent by the data sender is maliciously attacked by the man-in-the-middle, the sender and the receiver of the data cannot know whether the encrypted data is attacked or not, so that the security of data transmission is low is effectively solved.
Owner:金证财富南京科技有限公司
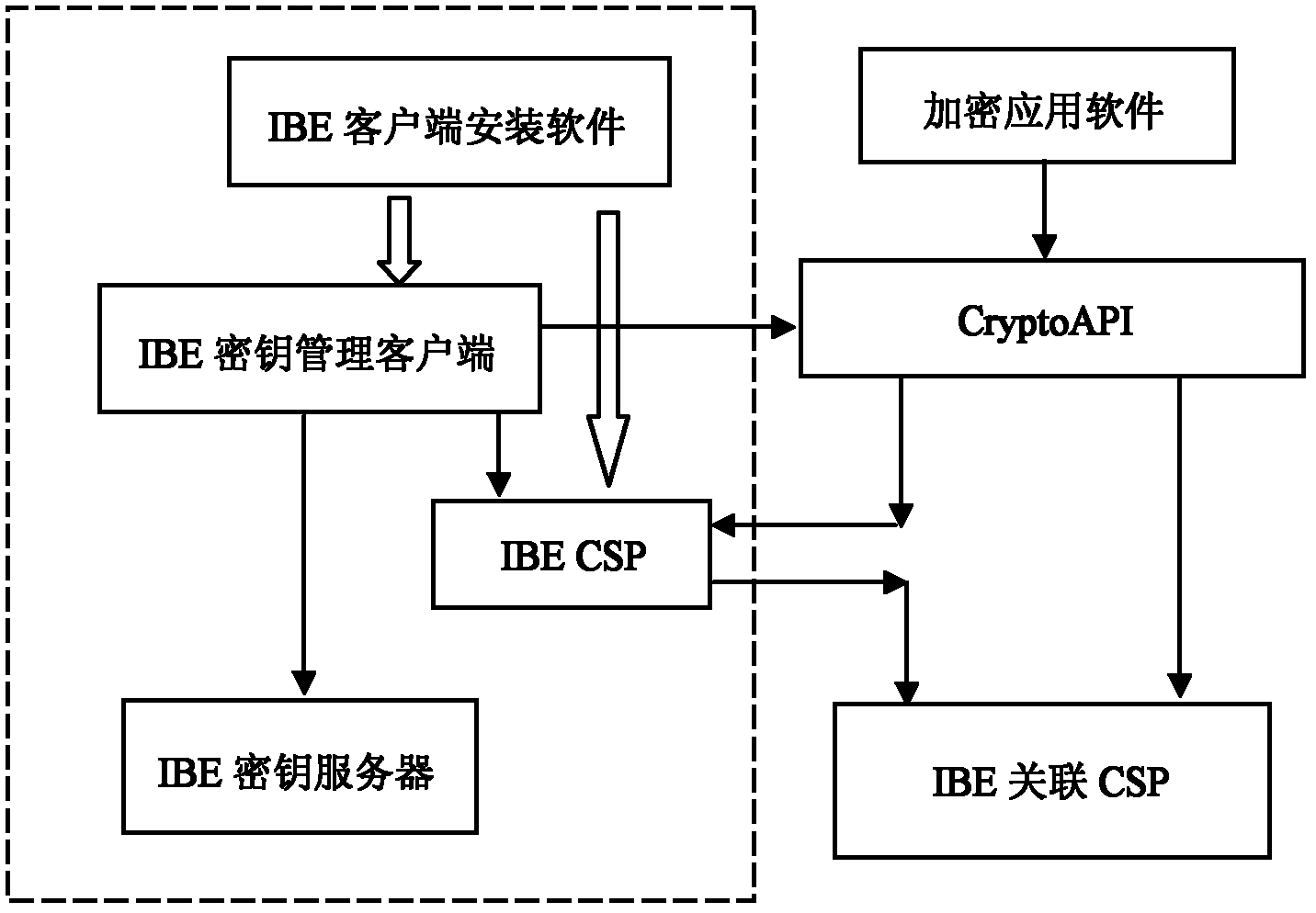
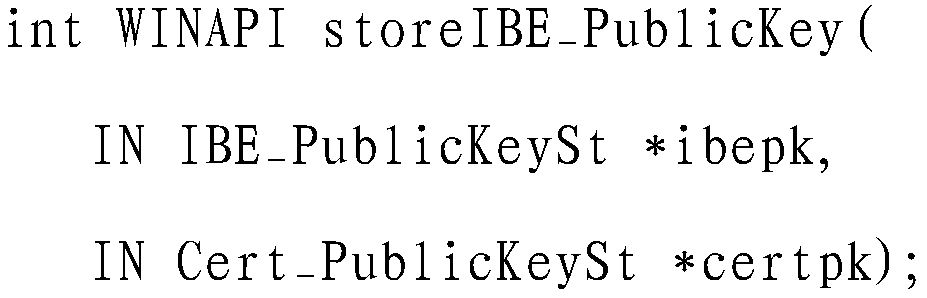
IBE (Internet Booking Engine) data encryption system based on medium digital certificate
InactiveCN102255729ASolve technical difficultiesPublic key for secure communicationUser identity/authority verificationThe InternetXML Encryption
The invention relates to an IBE (Internet Booking Engine) data encryption system based on a medium digital certificate, and comprises four components: an IBE CSP (Cryptographic Service Provider), an IBE key management client, an IBE key server and an IBE client installing software, wherein the IBE CSP is the core and key of the IBE data encryption system. The IBE data encryption system is used for enabling the system and the application which do not support an IBE encryption process to utilize the IBE process to encrypt and decrypt. In the IBE data encryption system, the medium digital certificate is taken as a bridge, an asymmetric key algorithm which is supported by RSA (Rivest Shamir Adleman), ECC (Elliptic Curves Cryptography) or other X509 certificate is provided by a register, but actually a Windows CSP of the IBE algorithm is realized, the data encryption and decryption operations based on the RSA, ECC or other asymmetric key algorithms are automatically converted into the corresponding data encryption and decryption operations based on the IBE algorithm.
Owner:WUHAN UNIV OF TECH +1
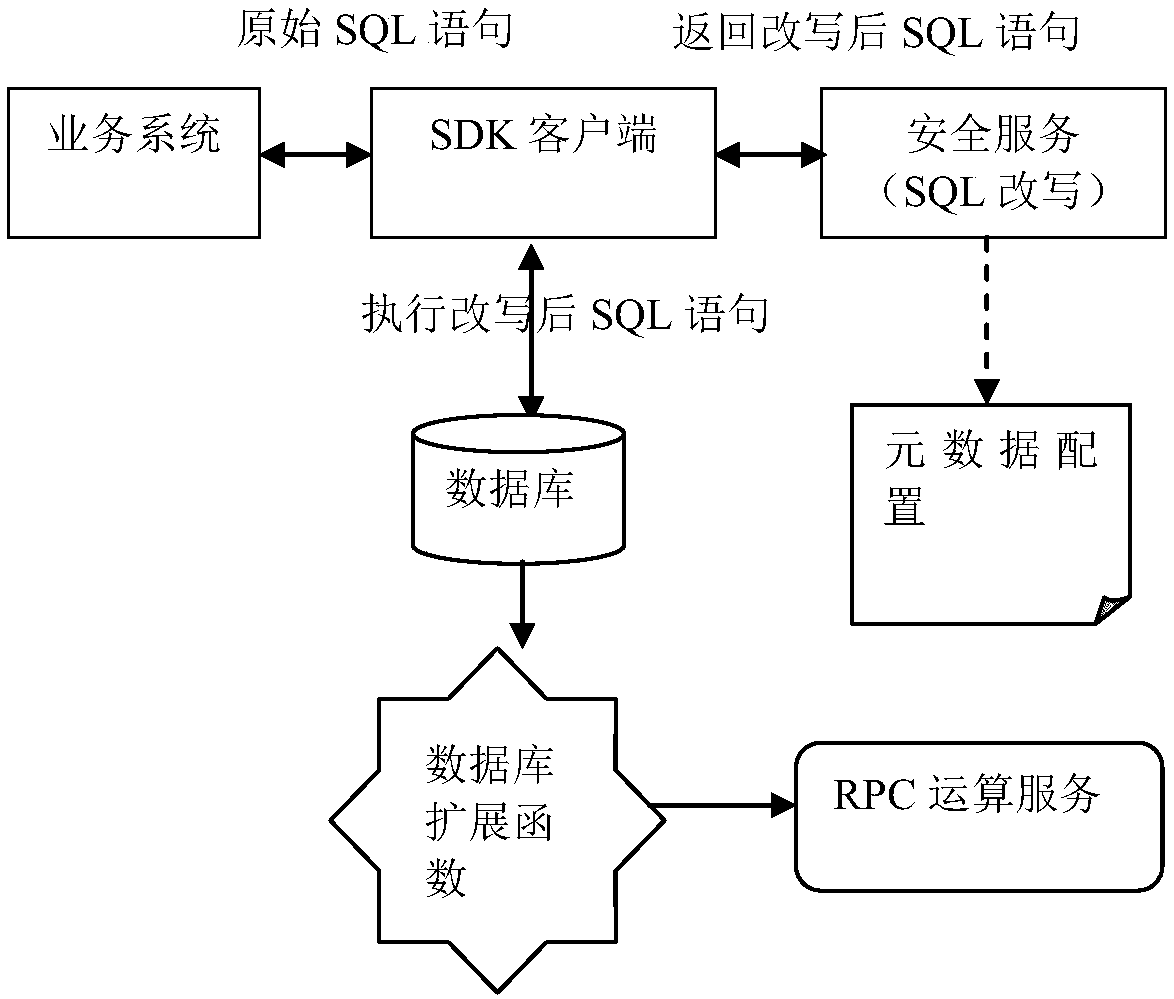
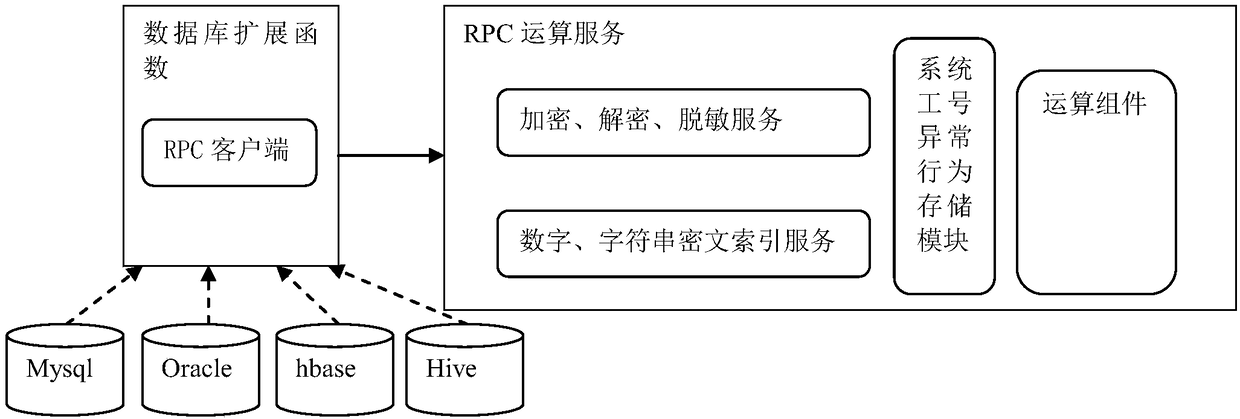
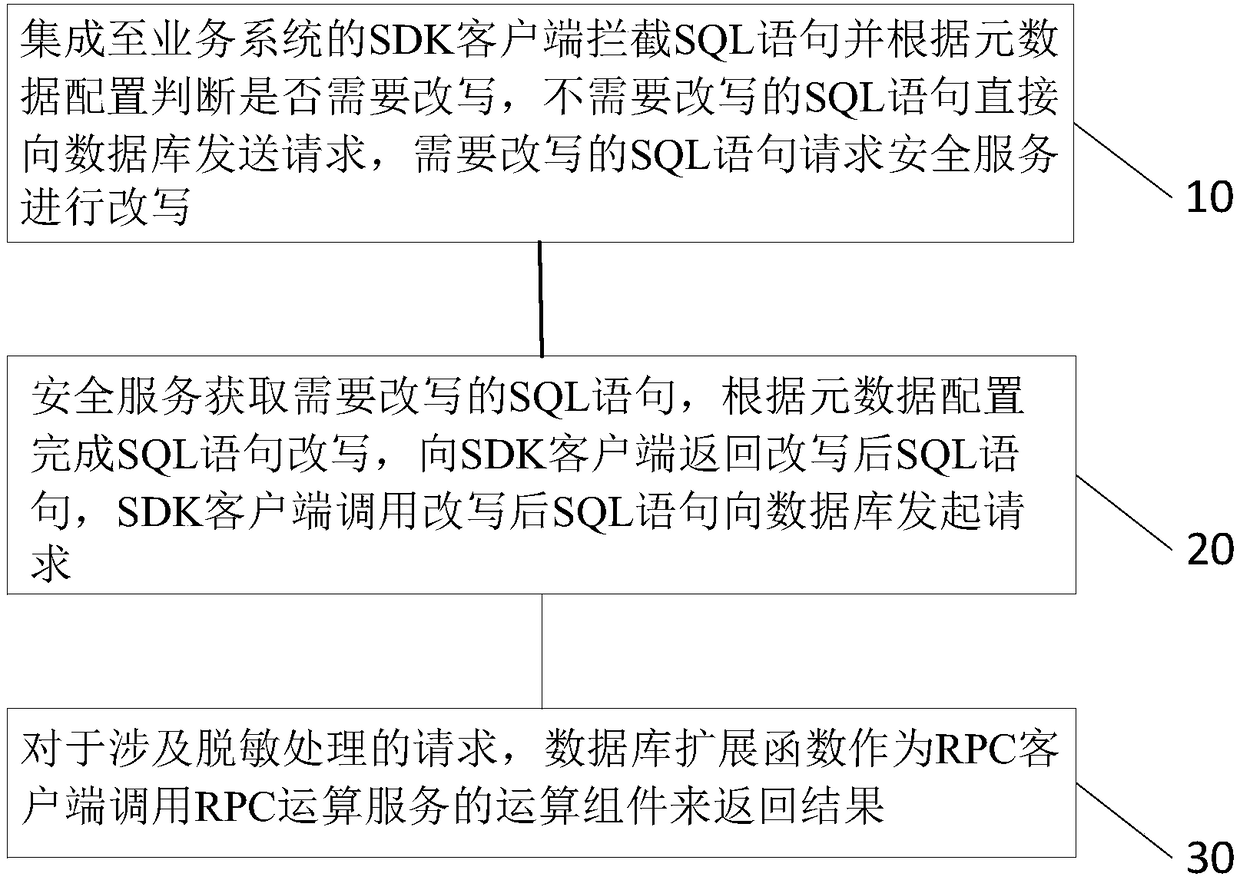
Data encryption/decryption and desensitization operation engine and working method thereof
The invention relates to a data encryption / decryption and desensitization operation engine, a working method thereof and a computer readable storage medium. The working method of the data encryption / decryption and desensitization operation engine comprises the following steps of: 10, intercepting SQL statements by an SDK client integrated to a business system, judging whether the SQL statements need to be rewritten or not according to a metadata configuration, directly sending requests to a database by the SQL statements not needing to be rewritten, and requesting a security service by the SQLstatements needing to be rewritten so as to be rewritten; 20, obtaining the SQL statements needing to be rewritten by the security service, completing SQL statement rewriting according to the metadata configuration, returning the rewritten SQL statements to the SDK client, and calling the rewritten SQL statements to initiate a request to the database by the SDK client; and 30, for the request involved in desensitization processing, taking a database expansion function as an RPC client to call an operation component of an RPC operation service so as to return a result. By using a client SDK mode, the business unavailability risk, caused by stability, of transparent data encryption gateway agency mode is avoided.
Owner:SHENZHEN TIANYUAN DIC INFORMATION TECH CO LTD
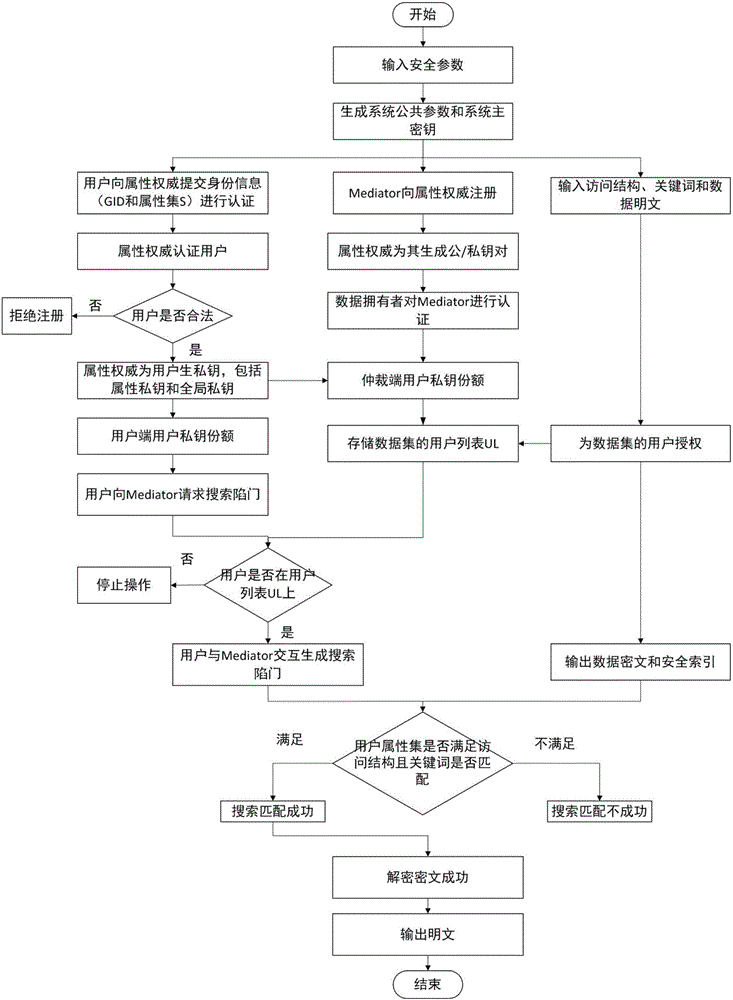
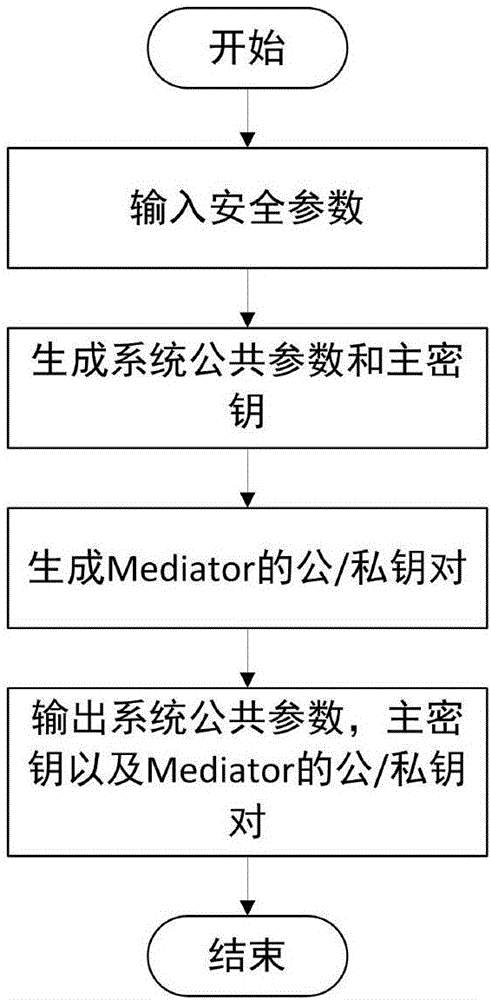
Mediated and searchable encryption method
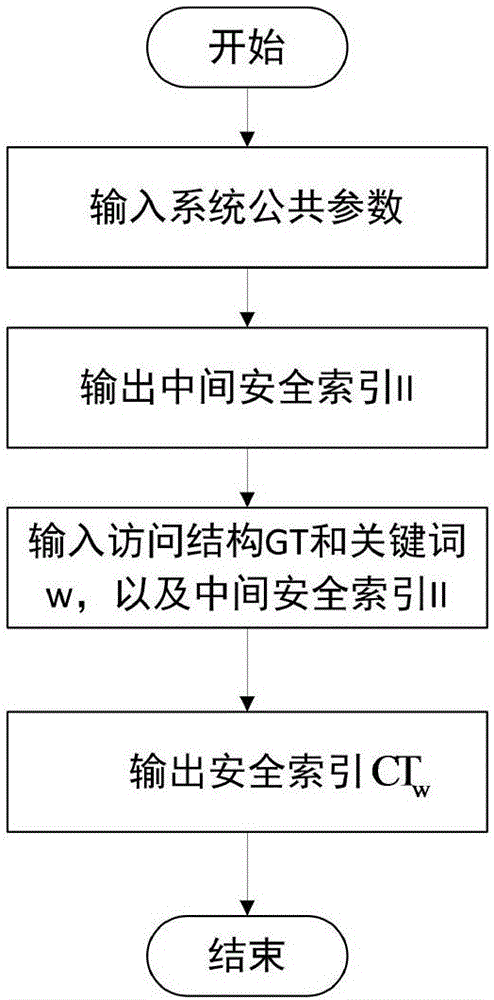
ActiveCN106850652AEfficient undoImprove decryption efficiencyKey distribution for secure communicationOnline and offlineXML Encryption
The invention relates to a mediated and searchable encryption method. The method comprises the following steps: S1, system initialization; S2, keyword encryption; S3, data encryption; S4, user key generation; S5, search Trapdoor generation; S6, data searching; S7, data decryption; and S8, user revocation. The mediated and searchable encryption method provided by the invention has the advantages that online and offline encryption and mediated encryption can be achieved, the method is applicable to a mobile cloud computing environment, and user permissions can be revoked instantly.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
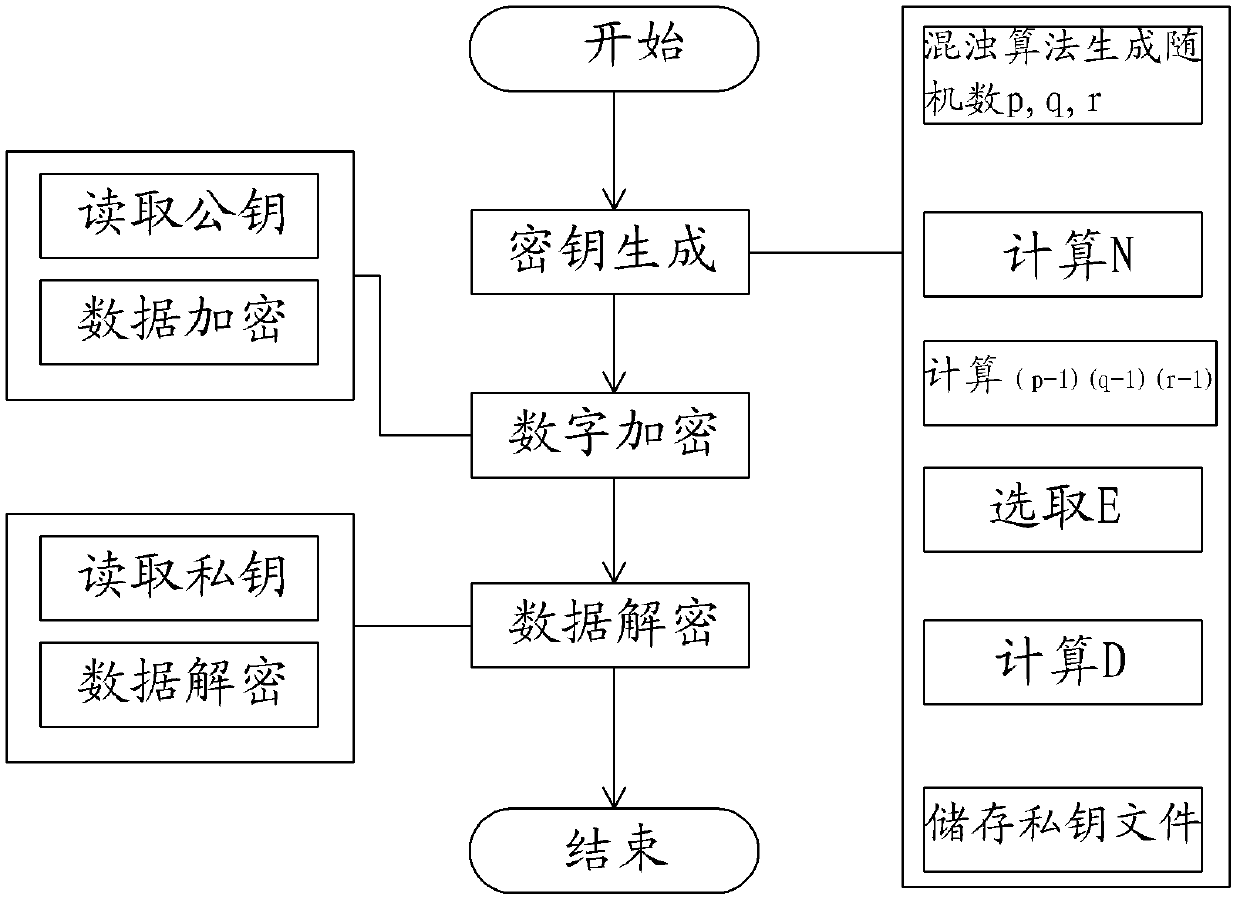
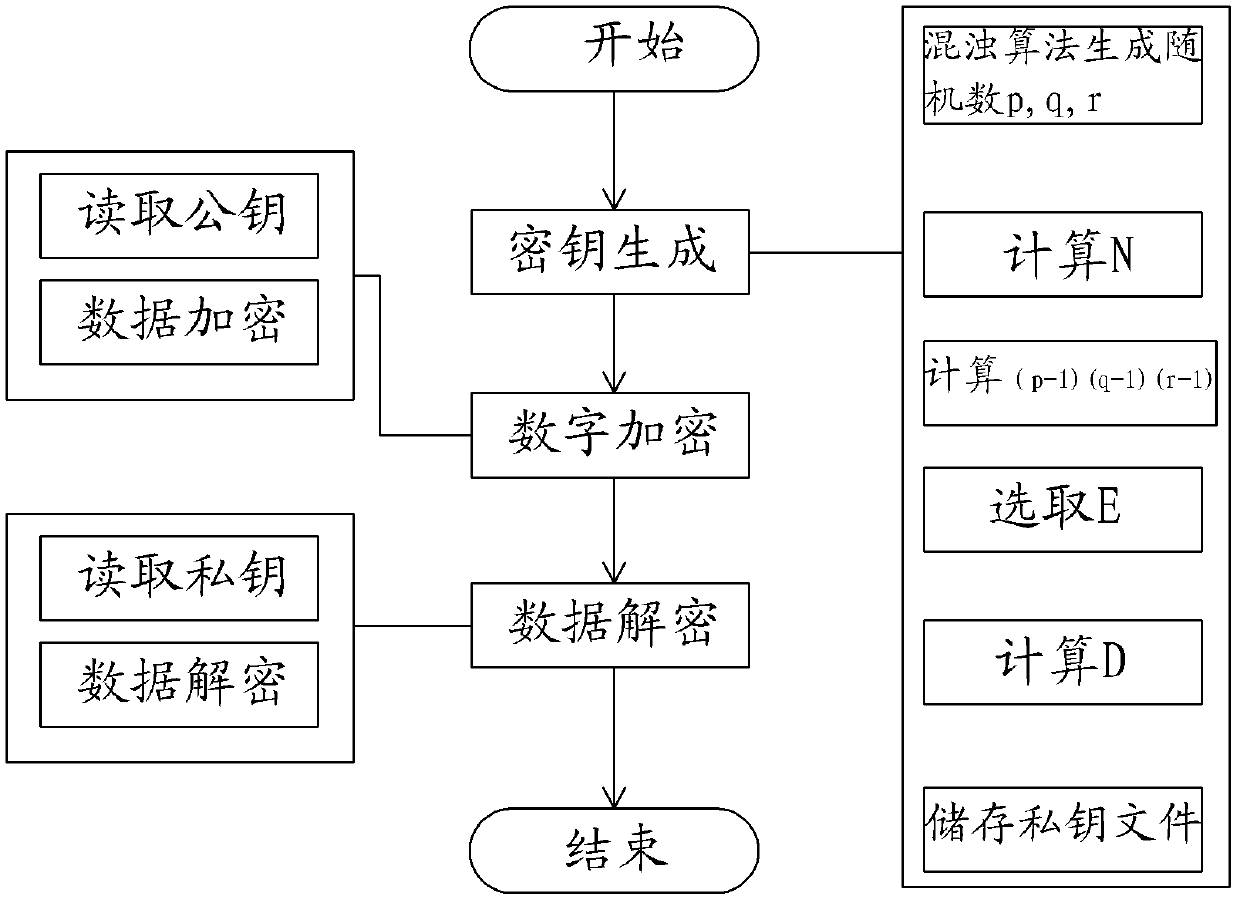
Digital rights management method based on N RSA (Rivest Shamir Adleman) encryption algorithms based on chaotic algorithm
InactiveCN102437912AImprove securityIncrease opennessSecuring communicationXML EncryptionDigital rights management
The invention relates to a digital rights management method based on N RSA (Rivest Shamir Adleman) encryption algorithms based on a chaotic algorithm, comprising three steps of privet key generation, data encryption and data decryption. The method comprises the specific steps of: utilizing the chaotic algorithm as the RSA encryption algorithm to generate prime numbers and combining the generated prime numbers to form a public key and a privet key; and then utilizing the public key and the privet key to encrypt and decrypt contents of files. As the chaotic algorithm process provided by the invention has the characteristics of randomness, balance and stability, the generated prime numbers have good quality and fast speed and are uniformly distributed; the calculation of the prime numbers is operated in the class of the prime numbers and is convenient; the response speed of the calculation is fast and results are reliable and accurate; in the encryption process and the decryption process, the length of the privet key is long enough through encrypting and decrypting data of the privet key and the public key; meanwhile, the encryption speed of the data is faster, so that the encryption and the decryption are assured; and meanwhile, the privet key is not easy to crack, so that the practical applicability and the openness of the algorithm are greatly enhanced.
Owner:厦门博鼎智文传媒科技有限公司
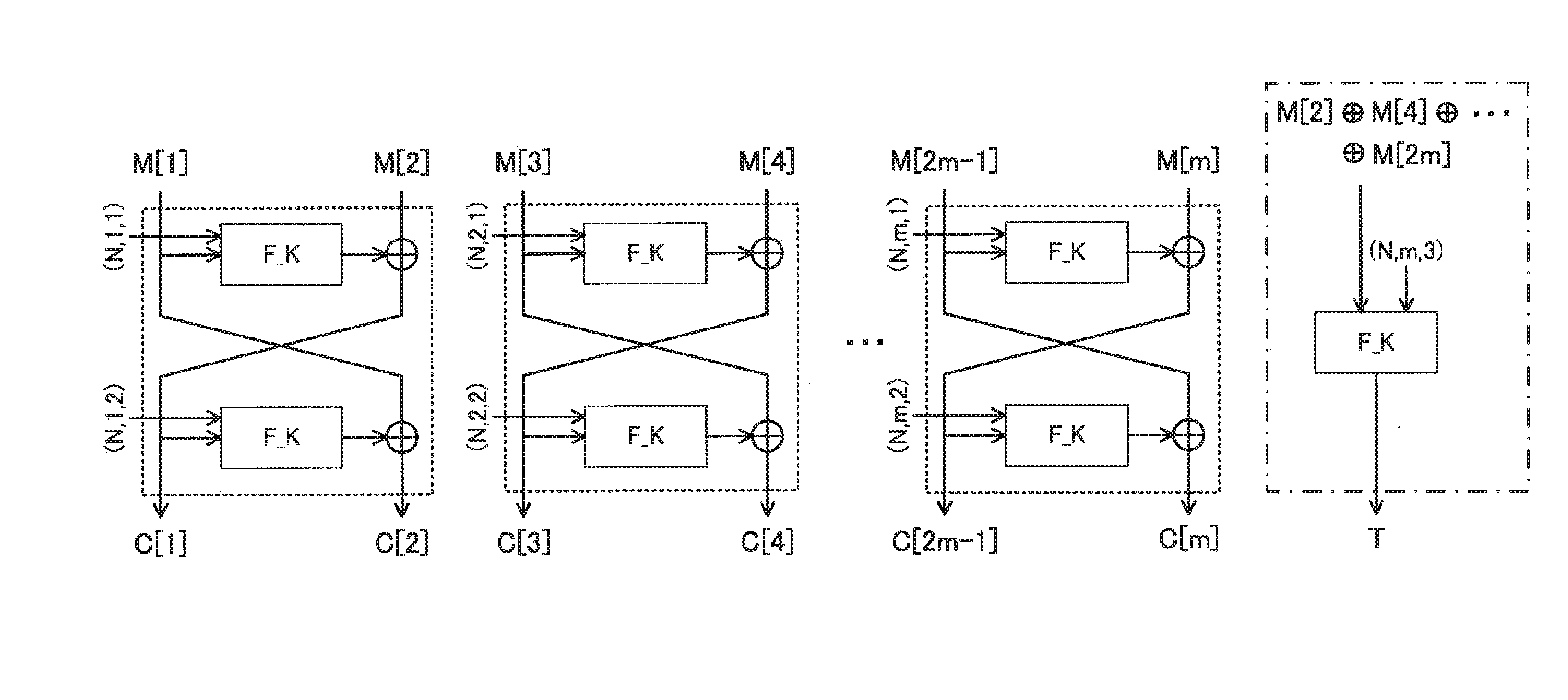
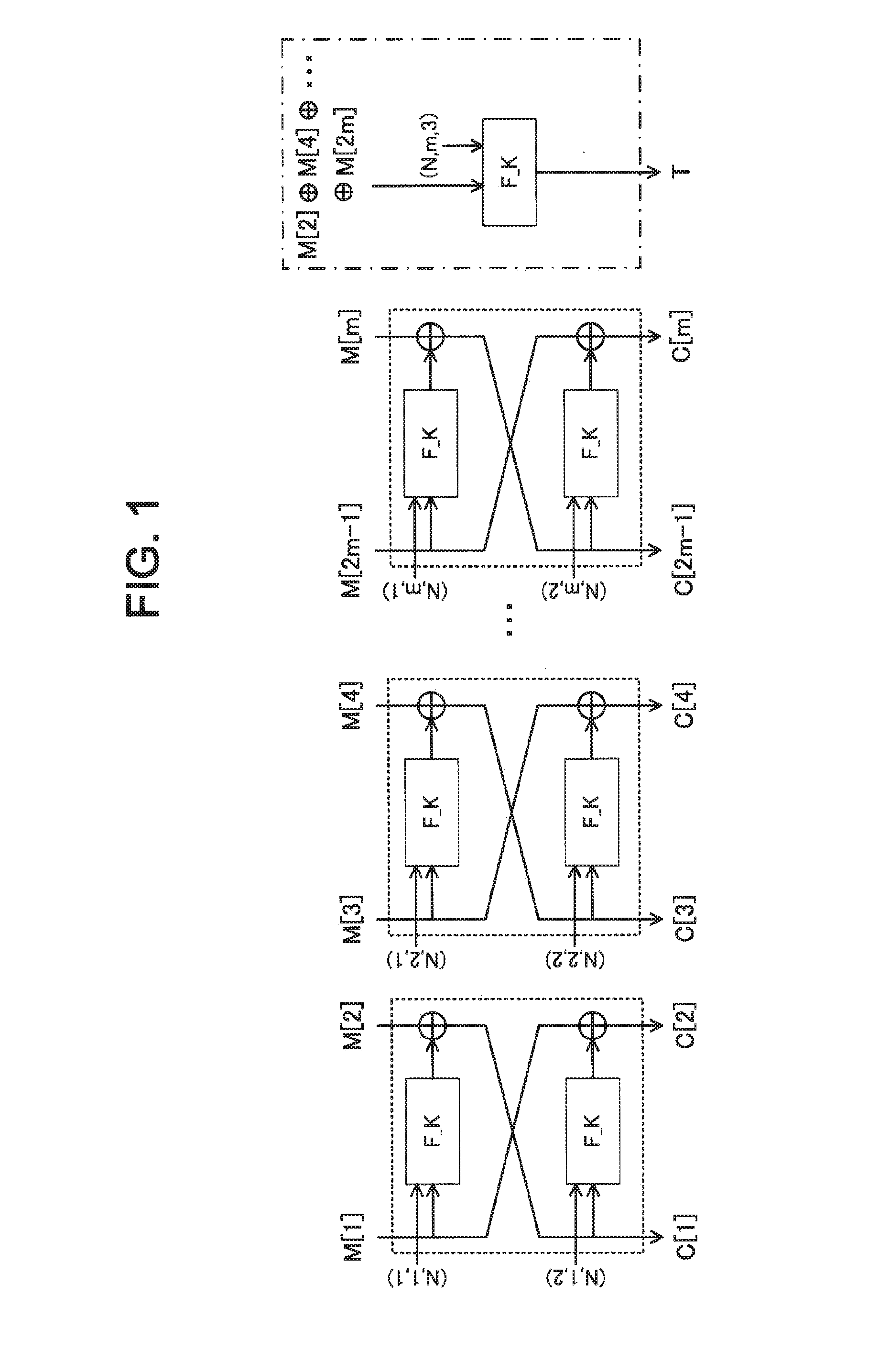
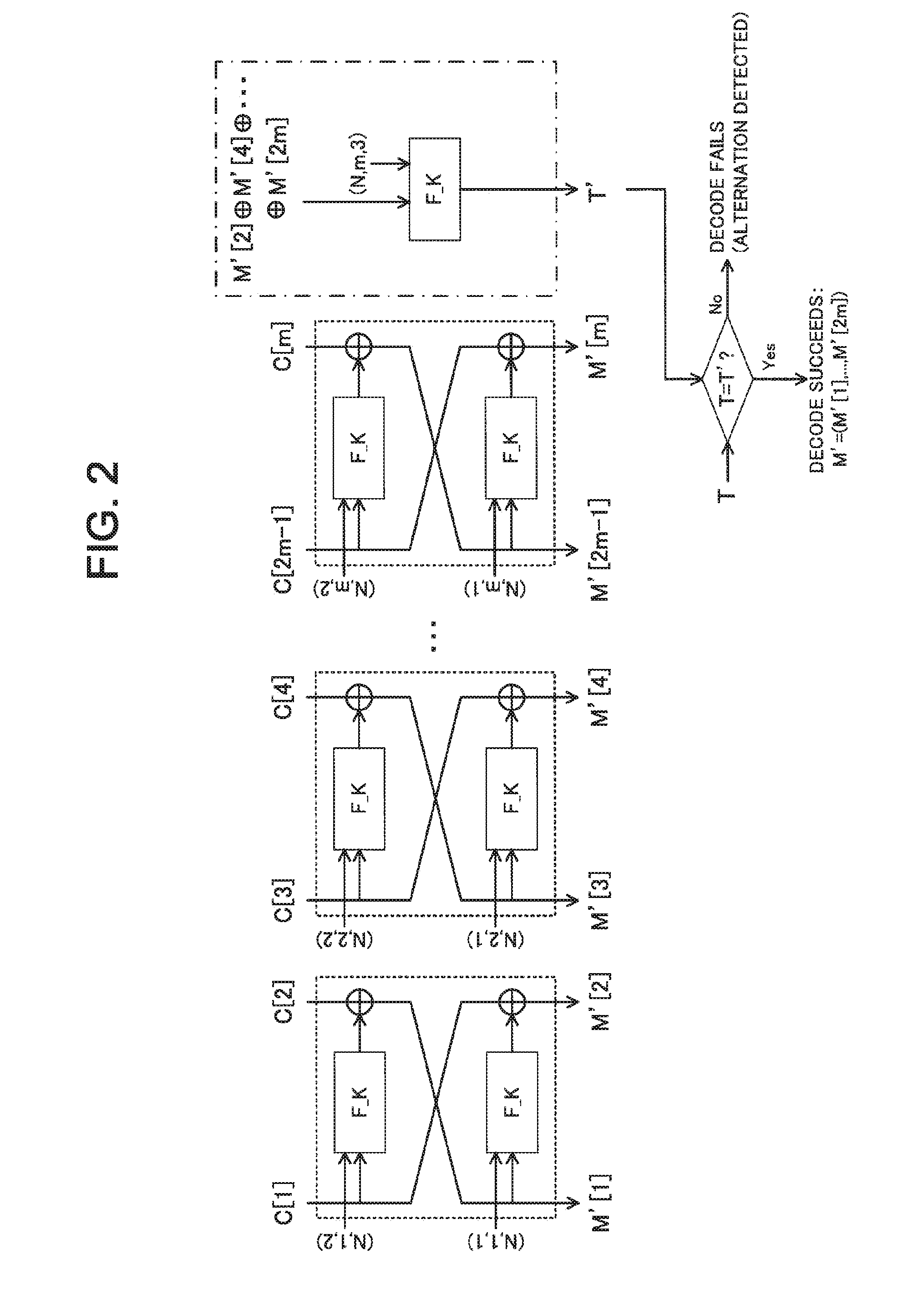
Authenticated encryption device, authenticated encryption method, and program for authenticated encryption
ActiveUS20160173276A1Encryption apparatus with shift registers/memoriesUser identity/authority verificationPlaintextAlgorithm
To achieve one-pass and one-rate authenticated encryption capable of performing parallel processings and totally performing encryption and decode processings by only one encryption function. An authenticated encryption device comprises an authenticated encryption means for applying a two-round Feistel structure using an encryption function assigned with an auxiliary variable for a round function per two blocks to an input plaintext or encrypted text thereby to generate an encrypted text or decoded plaintext. The authenticated encryption means finds an encrypted text chunk CC[i]=(C[i_1], C[i_2]) corresponding to an i-th plaintext chunk MC[i]=(M[i_1], M[i_2]) when dividing a plaintext into chunks per two blocks as:C[i_1]=F_K((N,Tw_i_1),M[i_1]) xor M[i_2],C[i_2]=F_K((N,Tw_i_2),C[i_1]) xor M[i_1].
Owner:NEC CORP
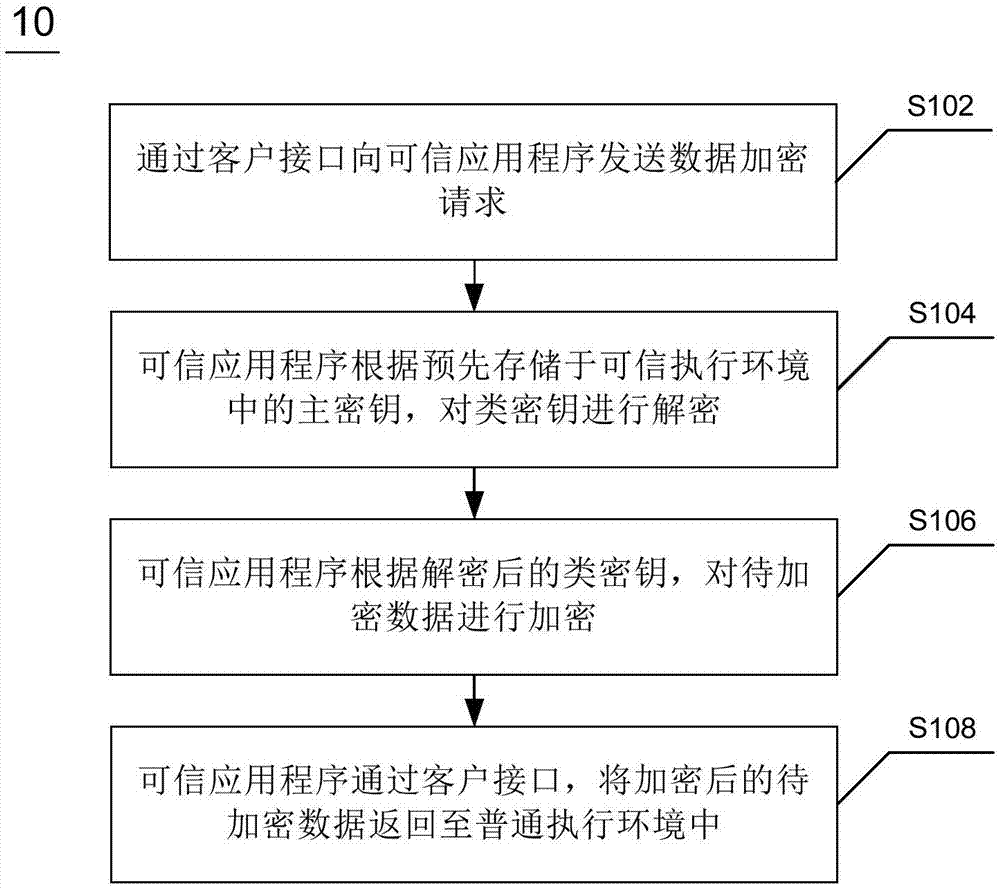
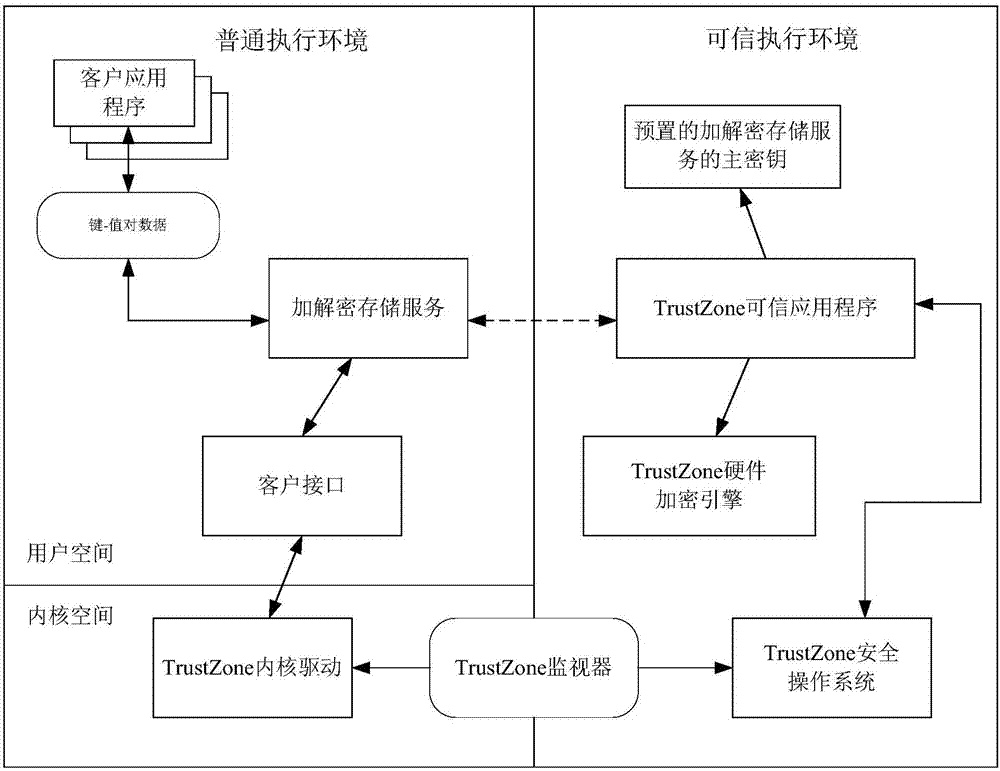
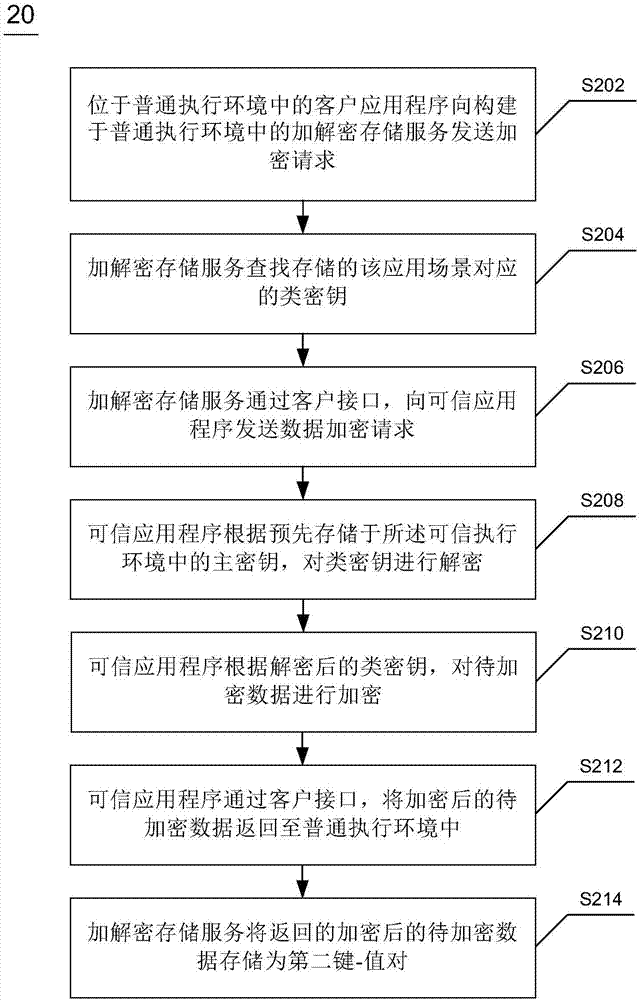
TrustZone-based data encryption and decryption methods and apparatuses, and terminal device
ActiveCN106997439AImprove encryption securityImprove securityKey distribution for secure communicationDigital data protectionTerminal equipmentXML Encryption
The invention discloses TrustZone-based data encryption and decryption methods and apparatuses, and a terminal device. The encryption method comprises the steps of sending a data encryption request to a trusted application in a trusted execution environment through a client interface between a general execution environment and the trusted execution environment, wherein the data encryption request comprises a class key and to-be-encrypted data; decrypting the class key according to a main key pre-stored in the trusted execution environment by the trusted application; encrypting the to-be-encrypted data according to the decrypted class key by the trusted application; and returning the encrypted to-be-encrypted data to the general execution environment through the client interface by the trusted application. The encryption method has high security performance and expandability.
Owner:北京元心君盛科技有限公司
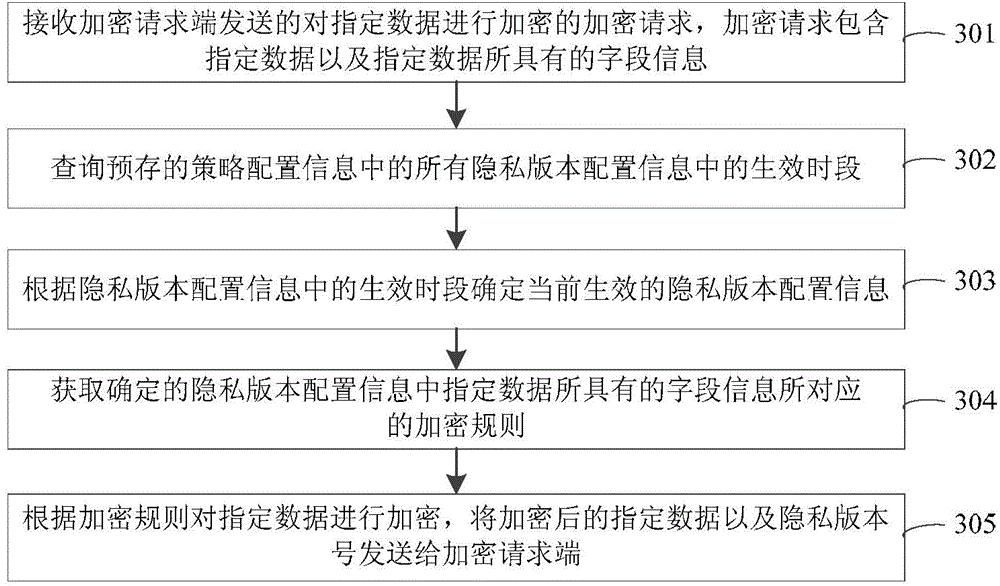
Data encryption method, device, equipment and system and data decryption method, device, equipment and system
ActiveCN104601325ASolve the problem of low securityImprove securityUser identity/authority verificationDigital data protectionXML EncryptionData decryption
The embodiment of the invention provides a data encryption method, device, equipment and system and a data decryption method, device, equipment and system, and relates to the field of data security. The data encryption method comprises the following steps: receiving an encryption request for encrypting specified data; acquiring an encryption rule corresponding to field information in pre-stored currently-effective privacy version configuration information; and encrypting the specified data according to the searched encryption rule. The specified data is encrypted through the preconfigured currently-effective privacy version configuration information. The problem of low security of encryption and decryption methods provided in the prior art is solved. The effective privacy version configuration information is updated automatically along with time, so that the probability of forced cracking of encrypted data can be lowered to a great extent, and the security during data encryption or decryption can be enhanced greatly.
Owner:HUAWEI TECH CO LTD
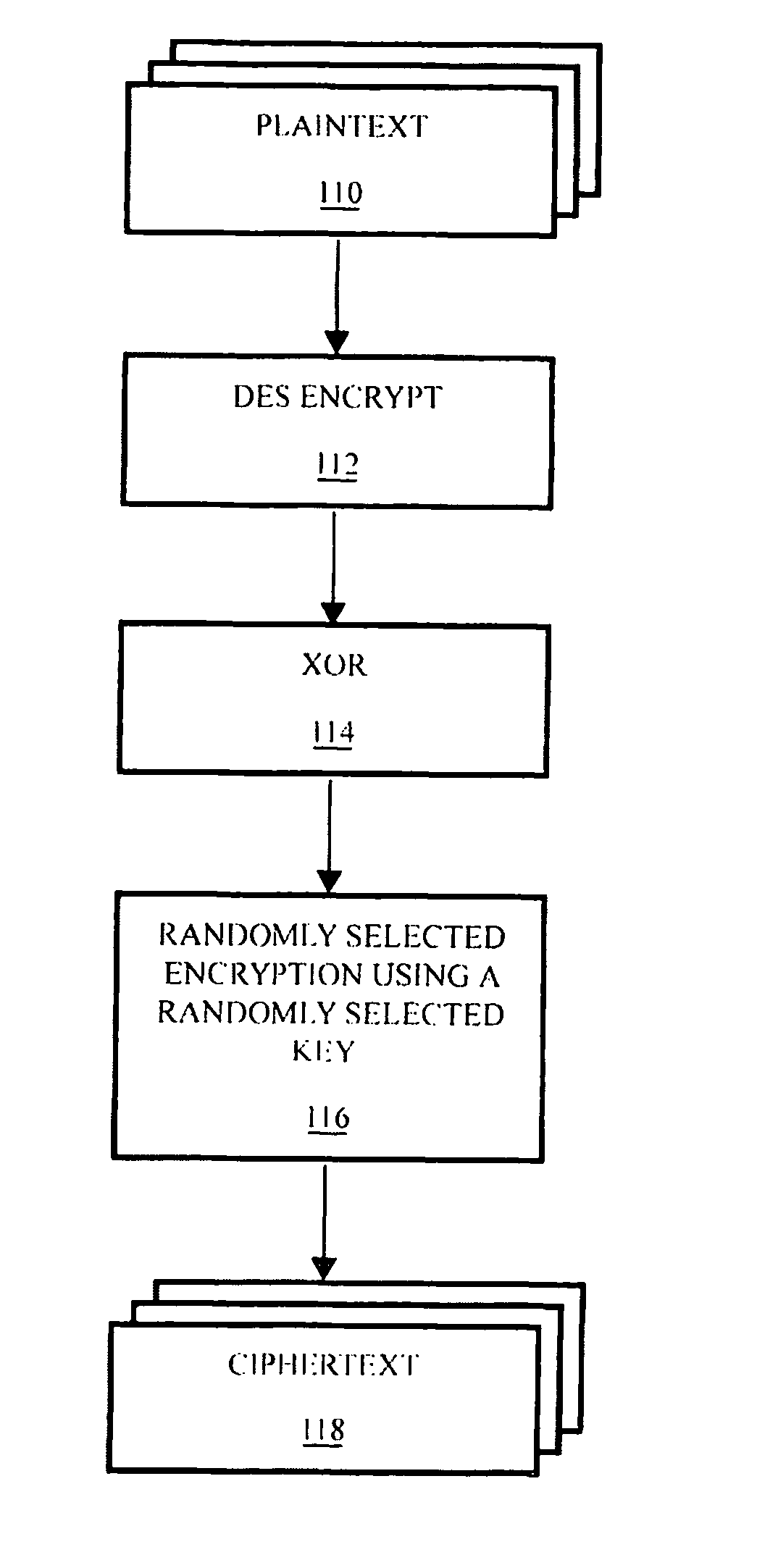
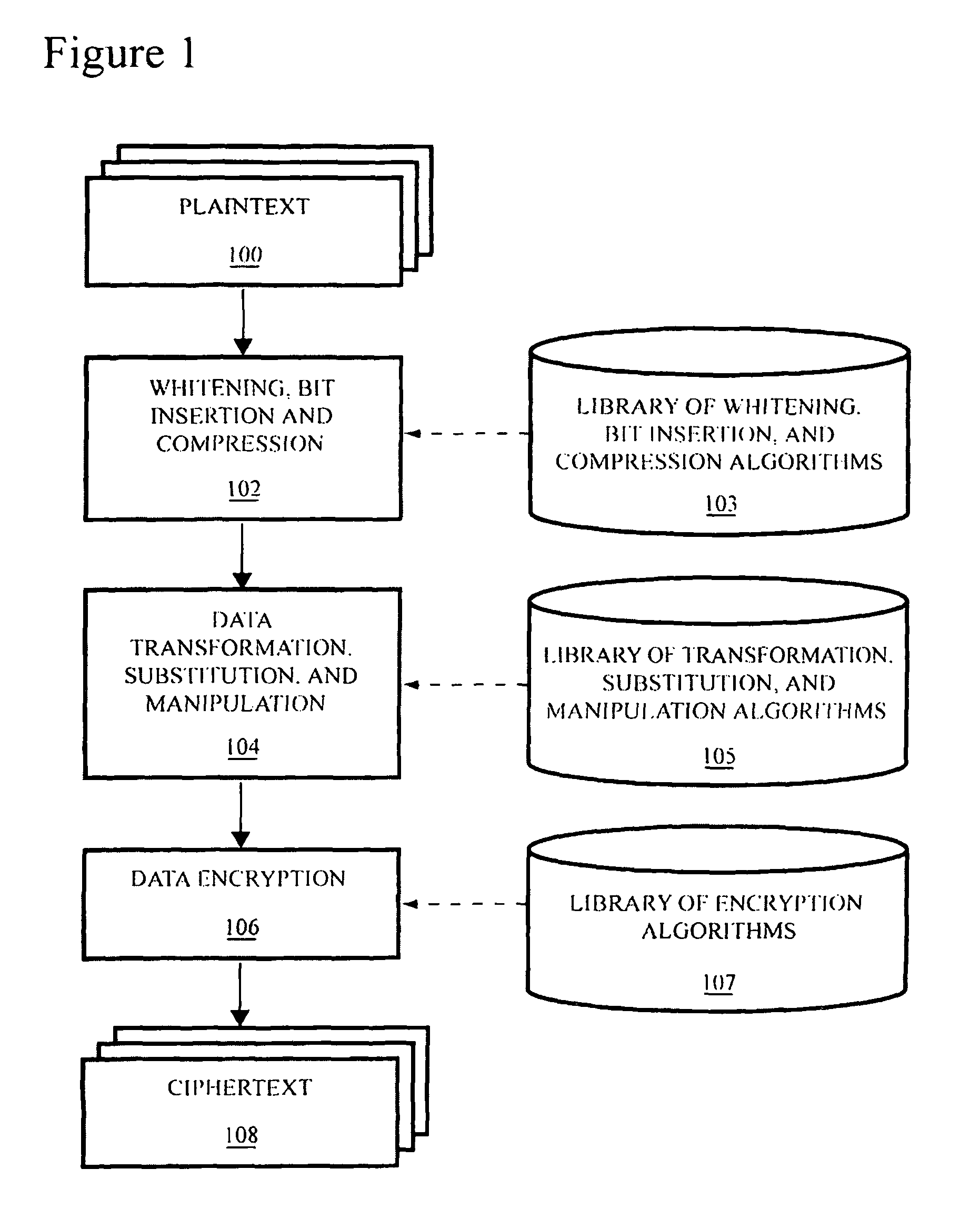
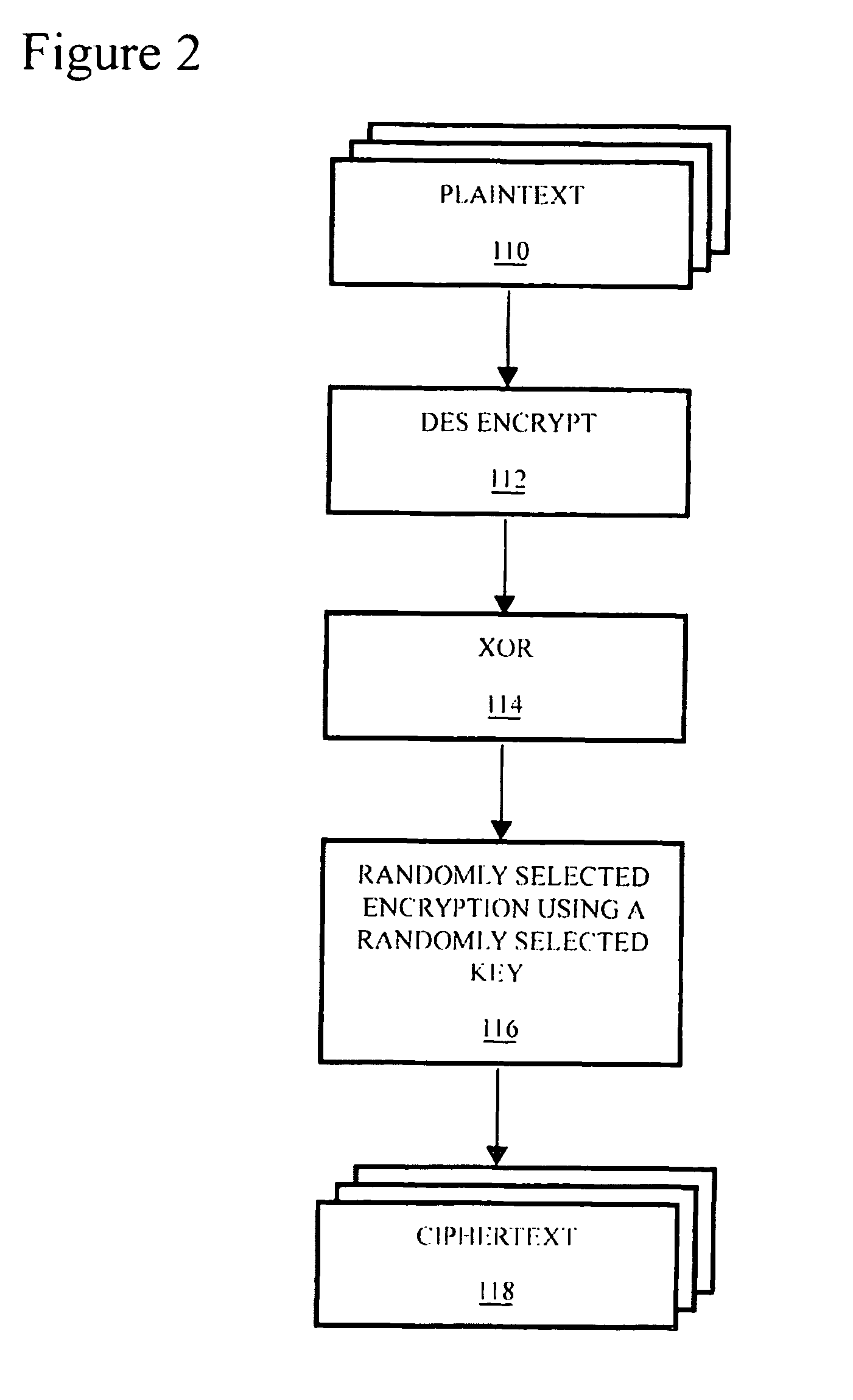
Method and system for securing data utilizing reconfigurable logic
A method is provided for securing data sets by dynamically hopping amongst a variety of data encryption and / or manipulation protocols. Such dynamic protocol hopping can be implemented in reconfigurable logic, or some combination of reconfigurable logic and fixed circuitry or software. The encryption and / or manipulation protocol applied to the data set is selected from among a plurality of encryption protocols in an, optionally upgradeable, library of protocols. Preferably, the selection can be driven by a random number generator. More preferably, the number of encryption protocols available can be extended using a logic-stretching engine. An apparatus is also provided for securing data, including a memory that contains data describing encryption protocols, a communications interface that is configured to receive data, and a processor that reads from the memory one of the encryption protocols and encrypts the received data based on the encryption protocol. Preferably, the apparatus also includes a random number generator, and the processor selects the encryption protocol to read, and encryption parameters to use, based on the output of the random number generator.
Owner:ADVANCED COMM CONCEPTS
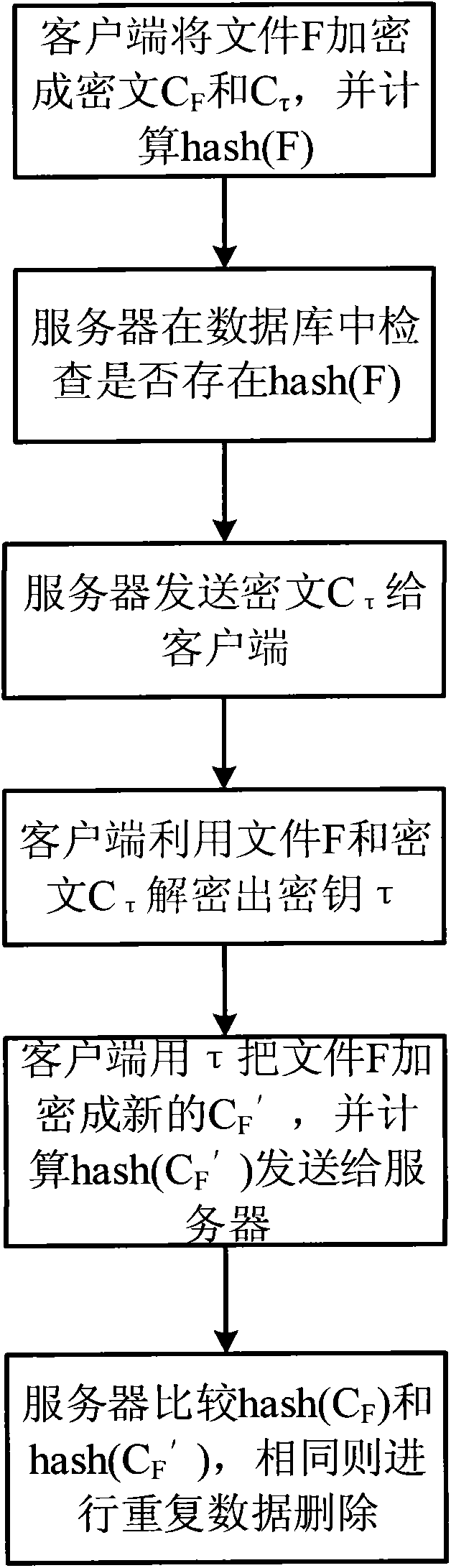
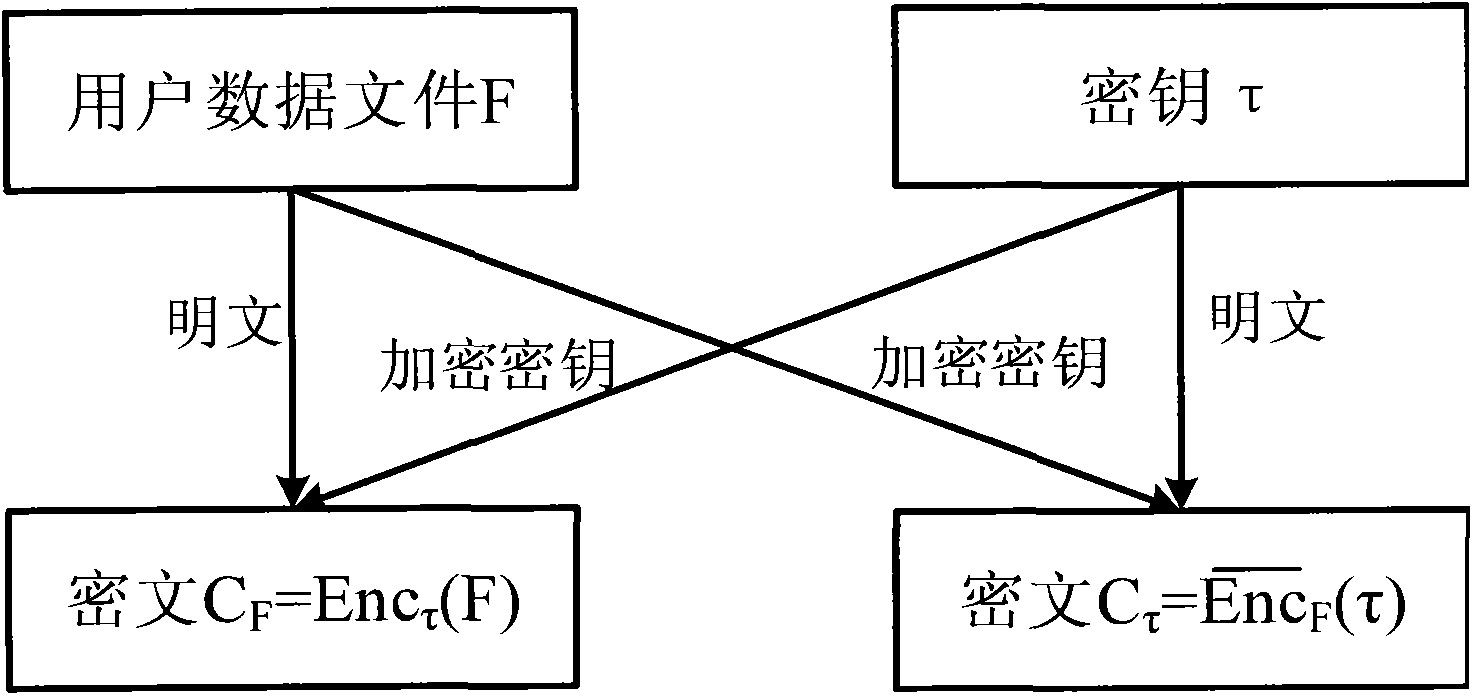
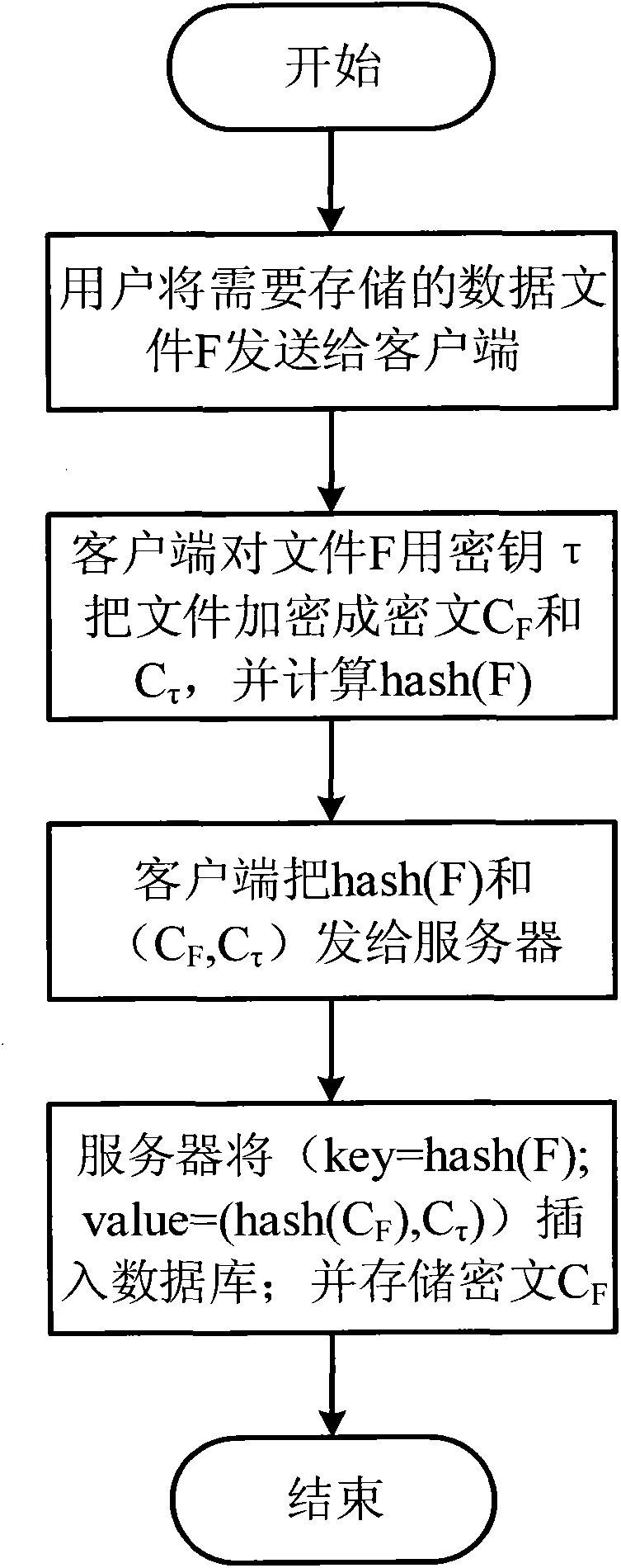
Safe method for repeated data deleting
InactiveCN103731423AEnsure safetyEncryption apparatus with shift registers/memoriesComputer hardwareCiphertext
The invention discloses a safe method for repeated data deleting. The method comprises the steps that a client side encrypts files which need to be stored through the same secret key with different encryption algorithms; a server judges whether the files are stored through the Hash values of the files first; the client side decrypts a secret key through a ciphertext returned by the server, and then encryption is carried out with another encryption algorithm; and the server carries out two-time encryption with the same encryption algorithm by comparing the files to judge whether repeated date deleting is carried out. The advantage of a repeated data deleting technology is guaranteed, user data privacy is guaranteed, and an external attacker and an unreliable cloud storage serve provider are prevented.
Owner:BEIJING SAFE CODE TECH
Ciphertext domain multi-bit reversible information hiding method
InactiveCN105634732AImplement encryptionEfficient extractionKey distribution for secure communicationImage data processing detailsLearning with errorsCiphertext
The invention provides a ciphertext domain multi-bit reversible information hiding method capable of effectively ensuring large volume embedment of data, reversible recovery of carrier data and undetectability of embedded information on the premise of meeting separable steganography. The method comprises the following steps: 1, parameter setting and data pre-processing; 2, encryption and information embedment; and 3, decryption and information extraction. By recoding ciphertext data based on an R-LWE (Ring Learning with Errors) public key cipher algorithm, a user can embed multi-ary information based on ciphertext domain operation to realize data encryption. After the information is embedded, the user can effectively extract the hidden information with a steganographic key and recover the data before encryption without errors by using a decryption key. Compared with the existing ciphertext domain steganography, the method has the advantages that error-free decryption of the embedded ciphertext and effective extraction of the hidden information can be realized, and the decryption and extraction processes are separable.
Owner:ENG UNIV OF THE CHINESE PEOPLES ARMED POLICE FORCE
Data encryption and decryption and key distribution method and device, equipment and readable storage medium
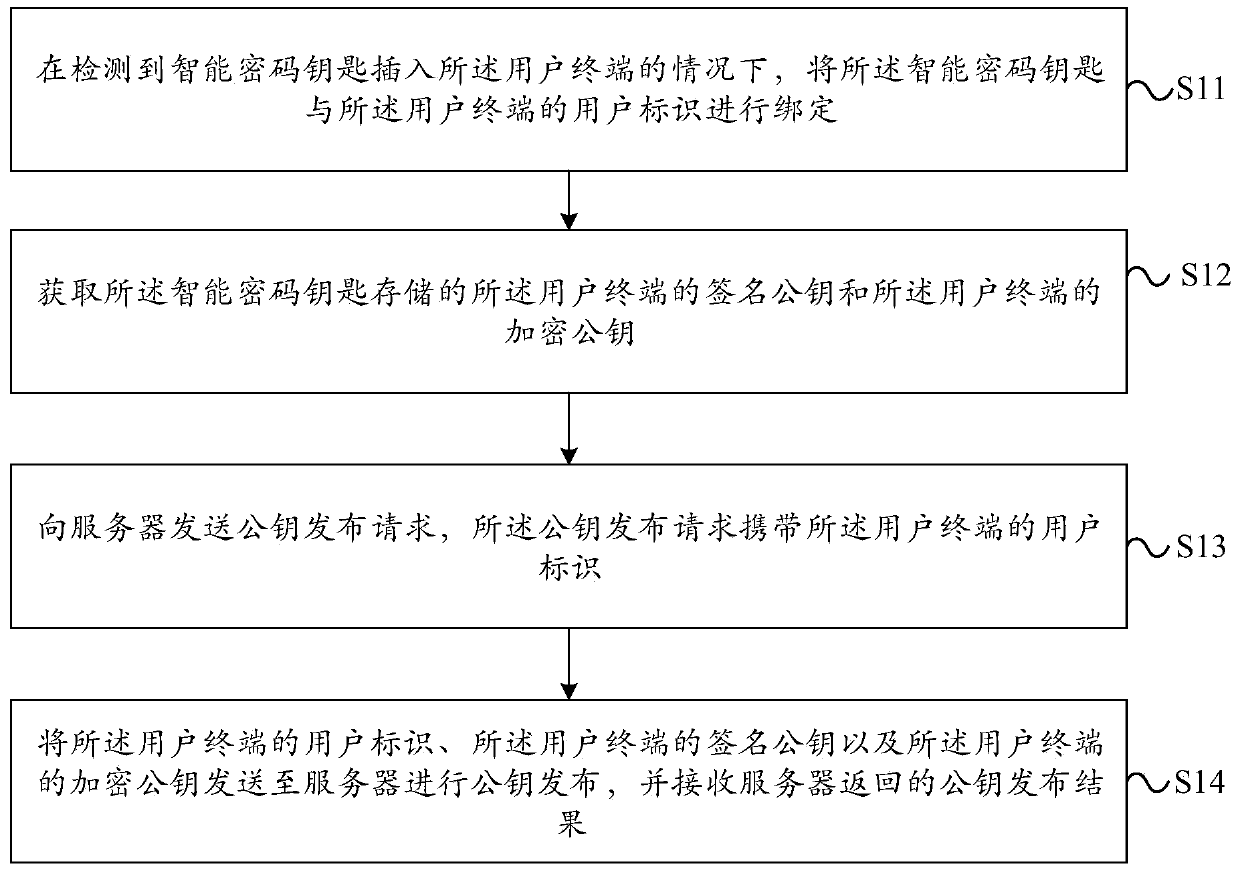
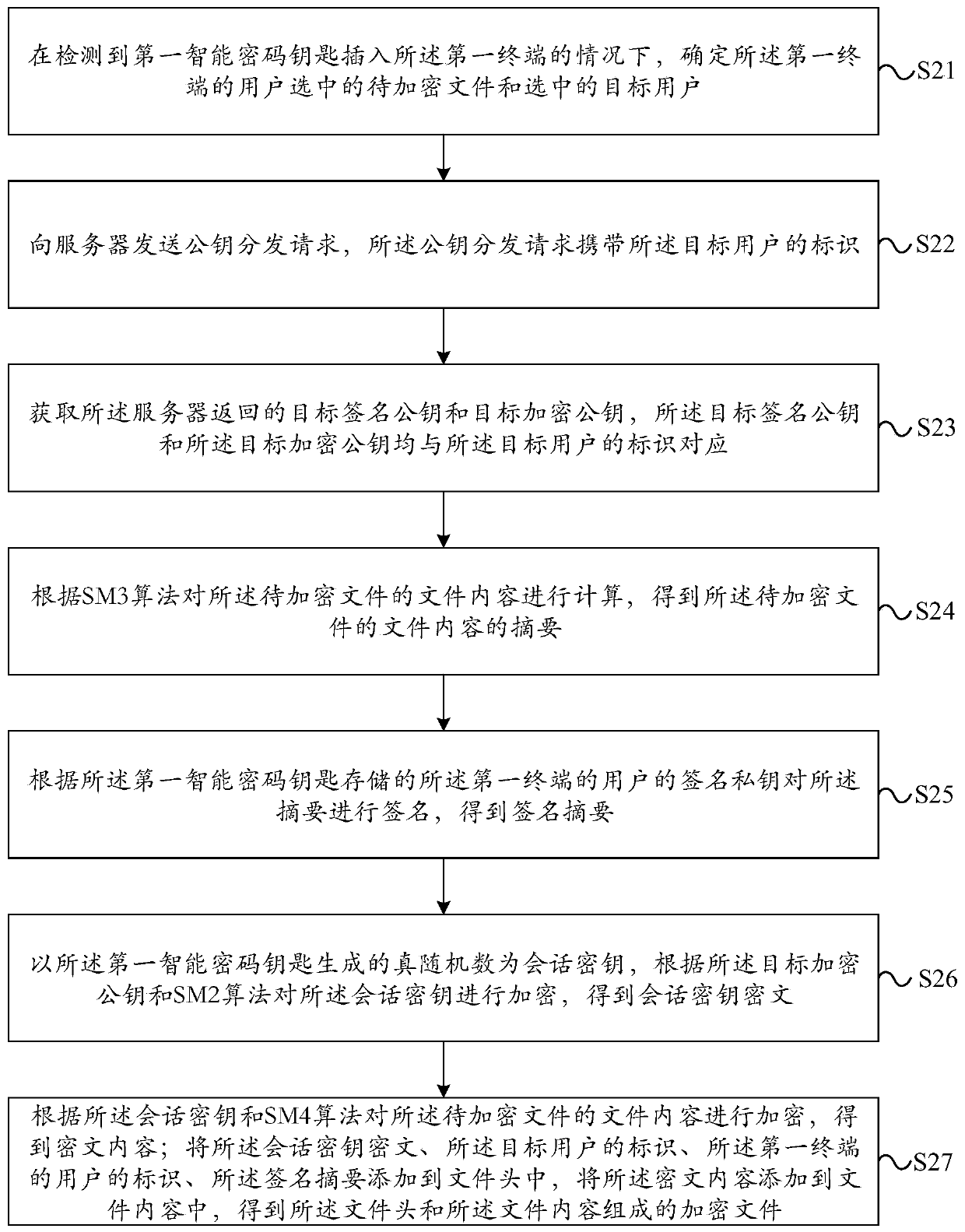
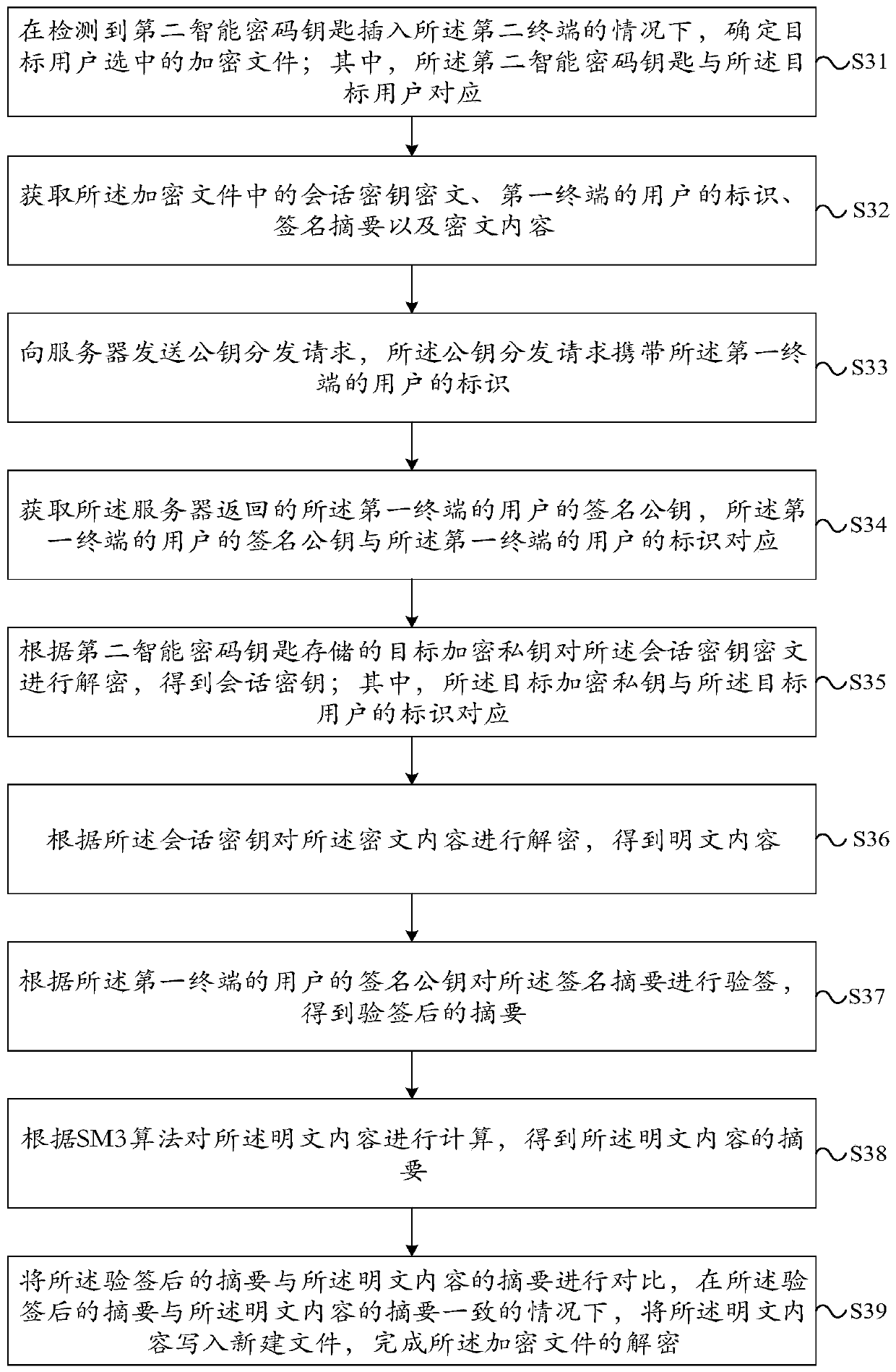
ActiveCN110474898AImprove leakageEasy to crackUser identity/authority verificationPasswordCiphertext
The embodiment of the invention provides a data encryption method, the method is applied to a first terminal, and the method comprises the steps: determining a to-be-encrypted file selected by a userof the first terminal and a selected target user under the condition that a first intelligent password key is detected to be inserted into the first terminal; calculating the file content of the to-be-encrypted file according to an SM3 algorithm to obtain an abstract of the file content of the to-be-encrypted file; signing the abstract according to a signature private key of a user of the first terminal stored in the first intelligent password key to obtain a signature abstract; taking a true random number generated by the first intelligent password key as a session key, and encrypting the session key according to the target encryption public key and an SM2 algorithm to obtain a session key ciphertext; encrypting the file content of the to-be-encrypted file according to the session key andan SM4 algorithm to obtain ciphertext content; therefore, the security of the encrypted data is improved.
Owner:北京明朝万达科技股份有限公司
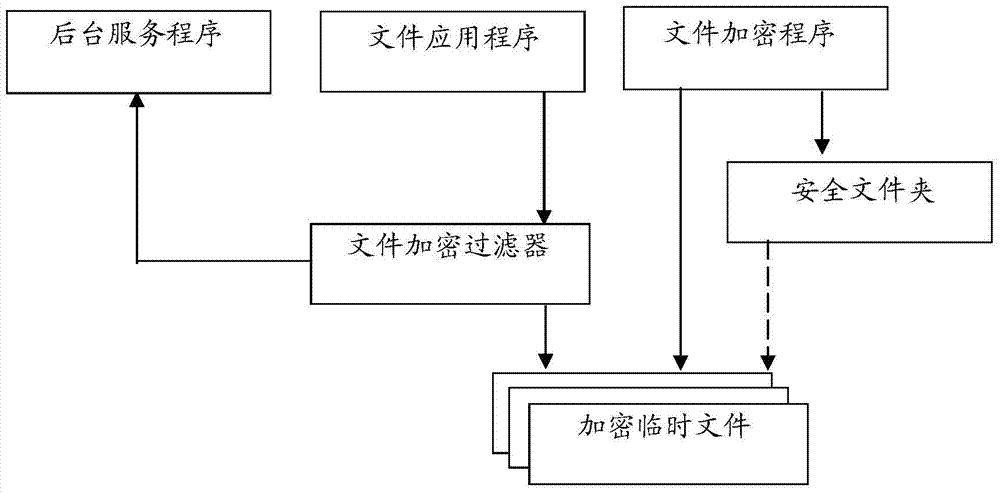
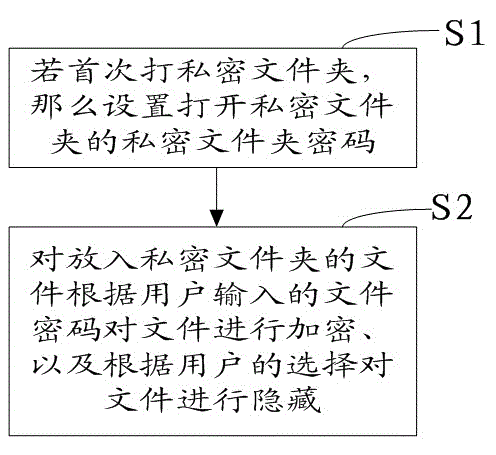
File encryption system
The invention relates to a file encryption system, comprising a safety folder, a file encryption program and a file encryption filter. The file encryption program generates a temporary file, namely an encrypted temporary file, corresponding to an opened file on a permanent storage medium of a computer in a form of a ciphertext when a user opens a currently browsed file in currently browsed safety folder by using a cursor through a human-computer interface of the file encryption program in a double-click manner; a new temporary file, namely an encrypted temporary file, which relates to file content of the selected opened file and is generated in the process that a file application program processes the opened file, also exists in the form of the ciphertext; the file encryption filter automatically carries out corresponding decryption and encryption treatment on the file content when the file application program carries out reading and writing operations on the encrypted temporary files. Thus, leakage of sensitive information due to the fact that the file content of the opened file exists on the permanent storage medium in a form of a cleartext is avoided.
Owner:WUHAN UNIV OF TECH
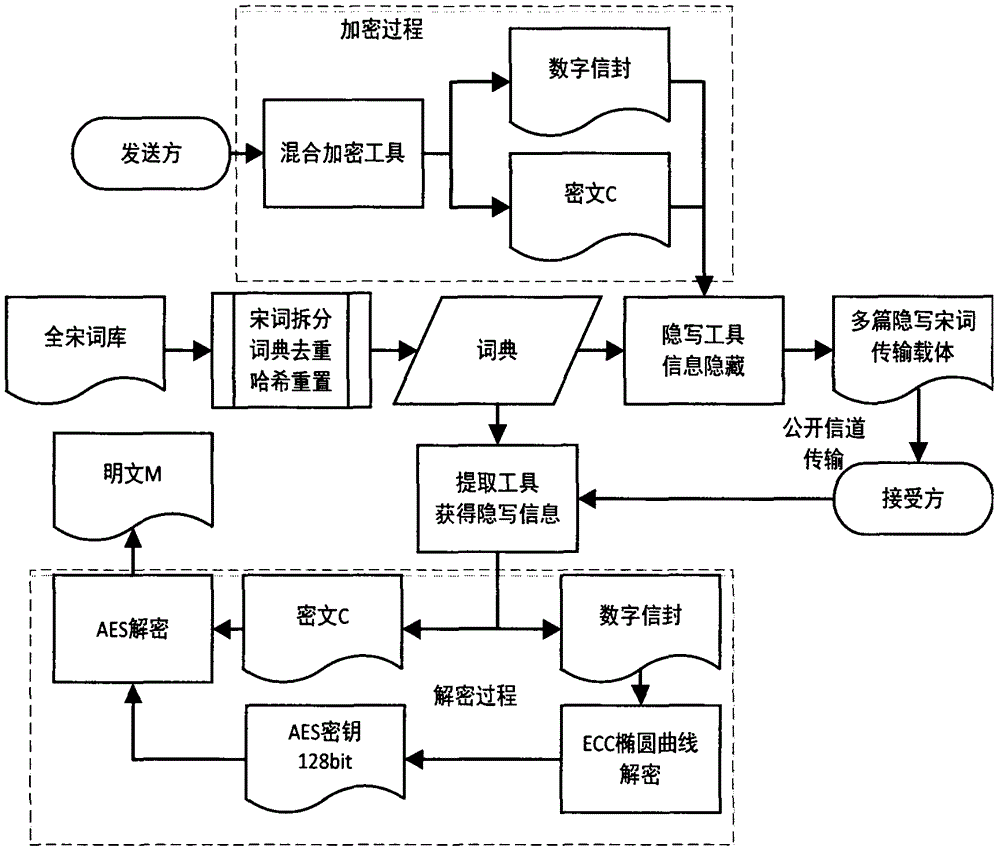
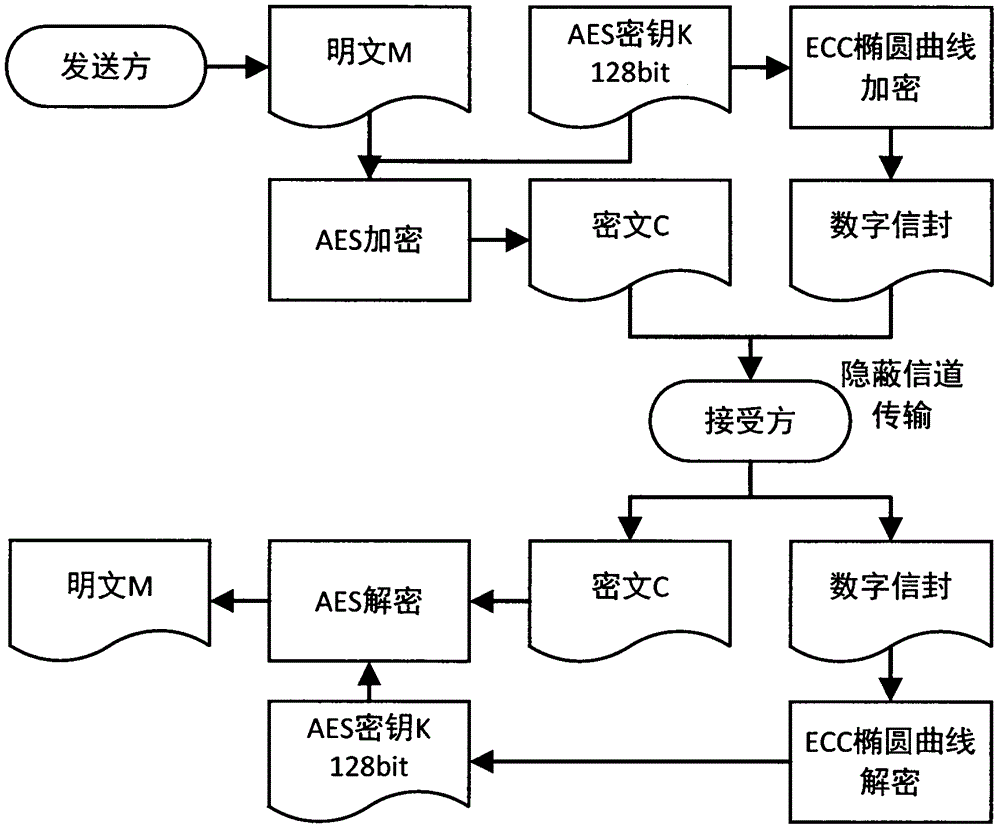
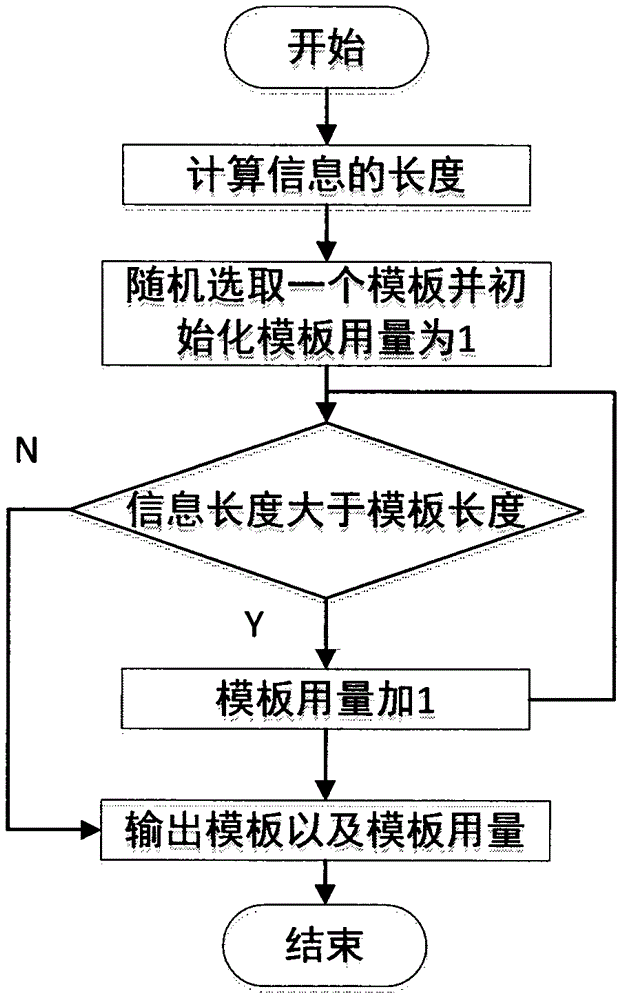
Song ci poetry text message hiding technology based on hybrid encryption
InactiveCN106254074AAchieve covert communicationSafety managementEncryption apparatus with shift registers/memoriesPublic key for secure communicationCiphertextXML Encryption
The invention provides a Song ci poetry text message hiding technology based on hybrid encryption, which belongs to the information hiding and data security directions in the field of computers. The Song ci poetry text message hiding technology comprises the steps of encrypting secret information to be hidden by using an advanced encryption standard (AES) in a hybrid manner, encrypting an AES secret key by using an elliptic curve cryptography (ECC) algorithm, passing all information after encryption processing through a 140 tune name template library of the complete collection of Song ci poetry, and hiding the information by means of the system which is composed of templates, a dictionary, a steganographic device and an extractor, wherein the system can generate steganographic Song ci poetry through a random selection or template designation method according to the length of a cryptograph, and the sentence length, grammatical style and intonation sentence pattern of the steganographic Song ci poetry conform to the original Song ci poetry completely, thereby achieving the purposes of obfuscating attackers and ensuring secure transmission of the hidden information. The Song ci poetry text message hiding technology disclosed by the invention can solve the security problem of data transmission in channels, can provide double security measures of information hiding and data encryption, and has high practical application value.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
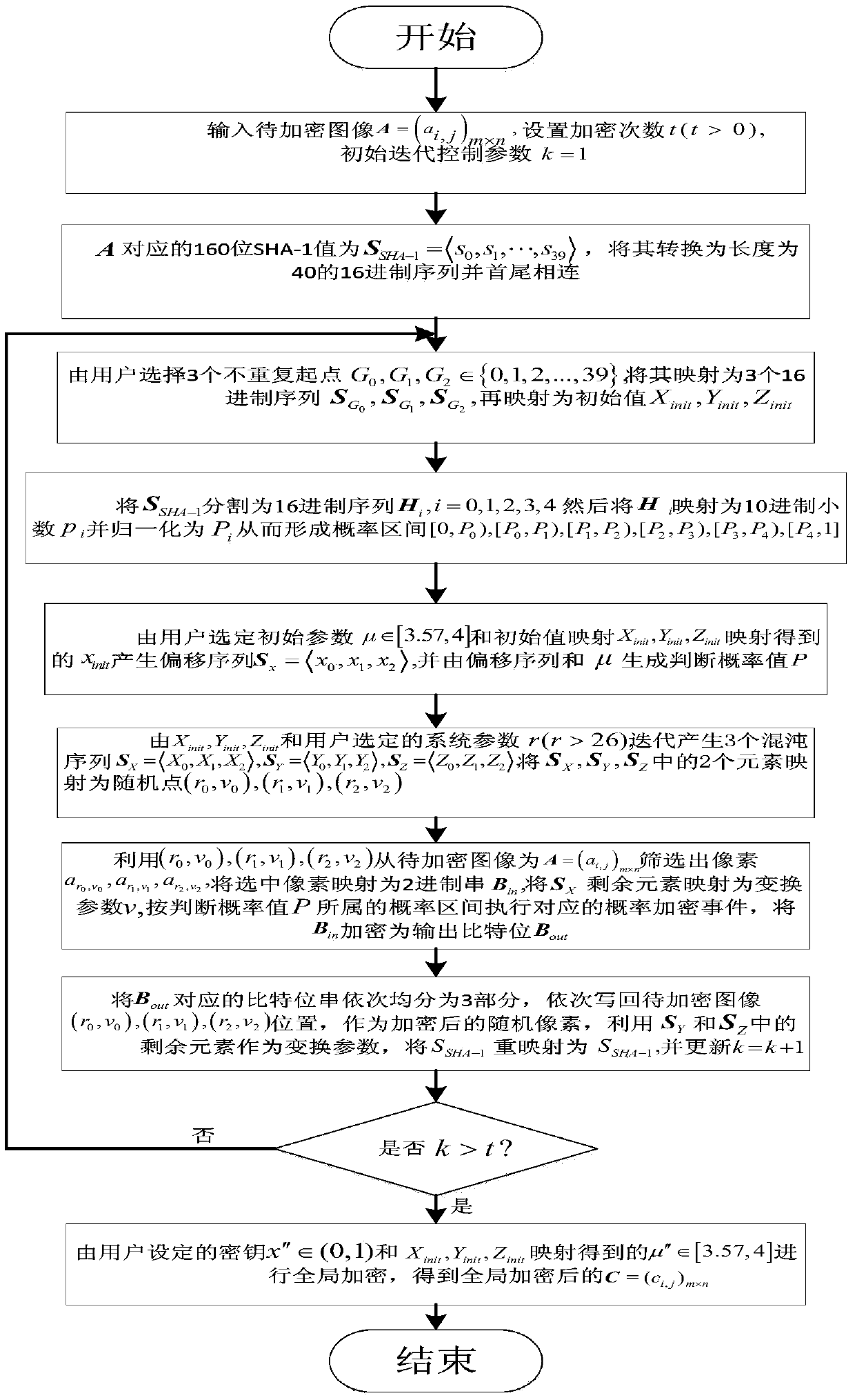
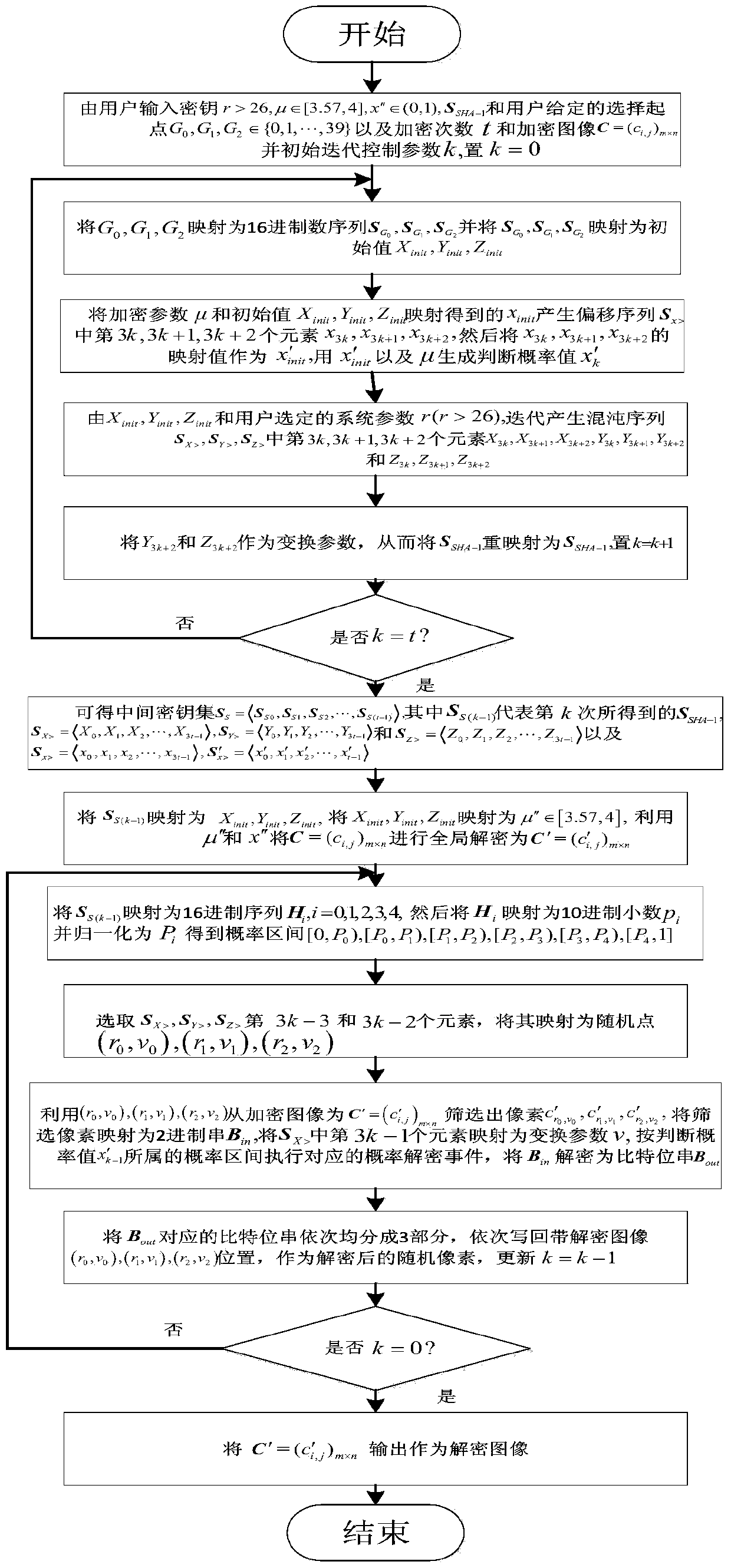
Image encryption and decryption method based on improved Joseph traversal and generalized Henon mapping
ActiveCN103929563AIncrease the number of replacements generatedEnsure safetySecuring communicationPictoral communicationComputer hardwareCoupling
The invention provides an image encryption and decryption method based on improved Joseph traversal and generalized Henon mapping. An SHA-1 value of an image to be encrypted and encryption parameters selected by a user are combined to serve as a secret key, generalized Henon mapping is driven to randomly disturb the initial position, the counting-off interval and the counting-off direction of Joseph traversal mapping used for position point permutation, so that different encryption images and encryption parameters correspond to different position point permutation processes in essence; coupling of all the encryption steps is enhanced, different encryption processes are started according to different images to be encrypted, so that selective plain text attacks are effectively resisted, and the image encryption and decryption method has large secret key space and is easy to implement and low in cost.
Owner:江苏瀚洋精工科技有限公司
Encryption-domain reversible information hiding method based on classified scrambling and hiding information classification
InactiveCN107103631AAdd classification scrambling encryptionAchieve protectionImage codingPictoral communicationPattern recognitionXML Encryption
Provided is an encryption-domain reversible information hiding method based on classified scrambling and hiding information classification. Variable pixels and fixed pixels are classified into blocks and scrambled in a classified way to reserve a hidden space of an encryption image; during image encryption, the image is divided into variable pixels and fixed pixels, bitwise XOR and scrambling encryption are carried out by taking the pixel as unit, and pixel values and positions are protected by encryption; at the same time, a block classification matrix serves as a part of an image encryption key, and further the possibility of leakage of content of the encryption image is further reduced; and during information hiding, the information to be hidden is divided into disclosed, authorized and private types according to functions, and protection of different levels is realized by using different encryption methods. During information extraction, the information can be extracted correctly by obtaining corresponding authorization, and the private information is very hard to obtain without a hidden secret key; and during image decryption, the encryption image the same with an original image can be obtained via an encryption key only. An algorithm is easy to realize, and the steganographic capacity is large.
Owner:SOUTHWEST JIAOTONG UNIV
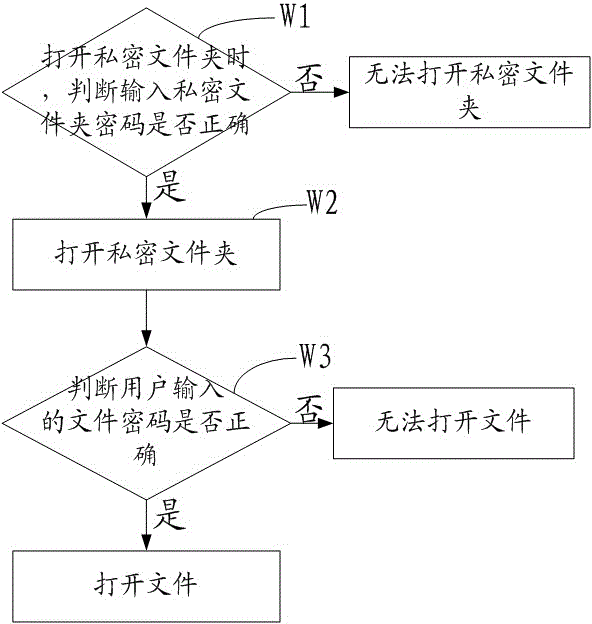
File encryption and decryption method and system
The invention provides a file encryption and decryption method and system. The encryption and decryption method comprises encryption steps and decryption steps, wherein the encryption steps are as follows: A, if a private file folder is opened for the first time, a private file folder password for opening the private file folder is set; B, with regard to a file put in the private file folder, the file is encrypted according to a file password input by a user and is hidden according to option of the user. The decryption steps are as follows: (1) when a private file folder is opened, the password of the private file folder is need to be input; if the input password is correct, the step (2) is executed, otherwise the private file folder cannot be opened; (2) the private file folder is opened; (3) the user is prompted to input the password of a file selected by the user; if the input password is correct, the file is opened, otherwise the file cannot be opened. The file encryption and decryption method and system have the benefits that the problem of disclosure of private files, probably existing in the current mobile terminals, is solved through multiple encryptions and file hiding.
Owner:SHENZHEN KENXINDA TECH
Image encryption and decryption method based on probability interval division and dynamic probability events
ActiveCN105577354AIncrease tight couplingImprove securityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesPattern recognitionProbabilistic encryption
The invention provides an image encryption and decryption method based on probability interval division and dynamic probability events. The method comprises steps of during encryption, firstly mapping secret key parameters and SHA-1 values of to-be-encrypted images to different probability encryption sections; carrying out random screening on to-be-encrypted pixels based on the secret key parameters and the SHA-1 values; and executing and writing different probability encryption events into corresponding pixel positions according to the probability sections where the probability encryption events fall. In order to improve safety, an SHA-1 value remapping process is added for dividing the probability sections, screening the to-be-encrypted pixels and carrying out stochastic disturbance on encryption; and by adding an overall situation encryption process related to SHA-1 update values and user secret keys, performance of an image encryption algorithm is enhanced. The method also comprises steps of during decryption, firstly recovering encrypted parameters; then finishing overall decryption; and at last executing inverse decryption operation on randomly screened pixels. Compared with the prior art, different pixels and secret keys correspond to different encryption processes, so the method is highly safe.
Owner:SHAANXI NORMAL UNIV
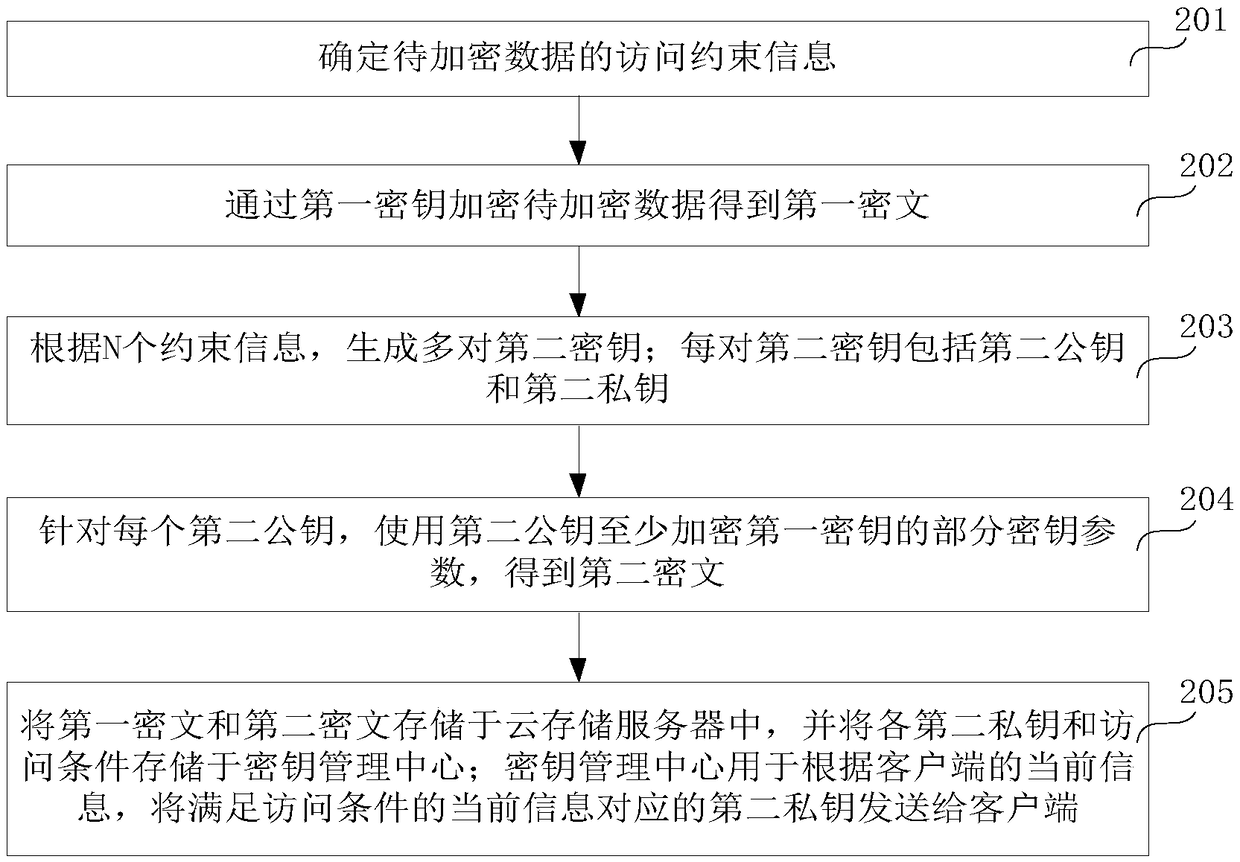
Data encryption and decryption method and device
ActiveCN108667605AEnsure safetyImprove securityKey distribution for secure communicationMultiple keys/algorithms usageCiphertextXML Encryption
Embodiments of the invention relate to the technical field of cryptography, and in particular to a data encryption and decryption method and a data encryption and decryption device, used to improve data security in the sharing process. The method comprises: determining access constraint information of the data to be encrypted, wherein the access constraint information includes N constraint information; encrypting the data to be encrypted by the first key to obtain a first ciphertext, wherein the first key is a symmetric key; generating a plurality of pairs of second keys according to the N constraint information; encrypting at least a partial key parameter of the first key using the second public key for each second public key to obtain a second ciphertext, wherein the second private key corresponding to the second public key is used to decrypt the second ciphertext; storing the first ciphertext and the second ciphertext in the cloud storage server, and storing each second private keyand access condition in the key management center, wherein the key management center is configured to send the second private key corresponding to the current information satisfying the access condition to the client according to the current information of the client. In this way, the security of shared data may be improved.
Owner:RAJAX NETWORK &TECHNOLOGY (SHANGHAI) CO LTD
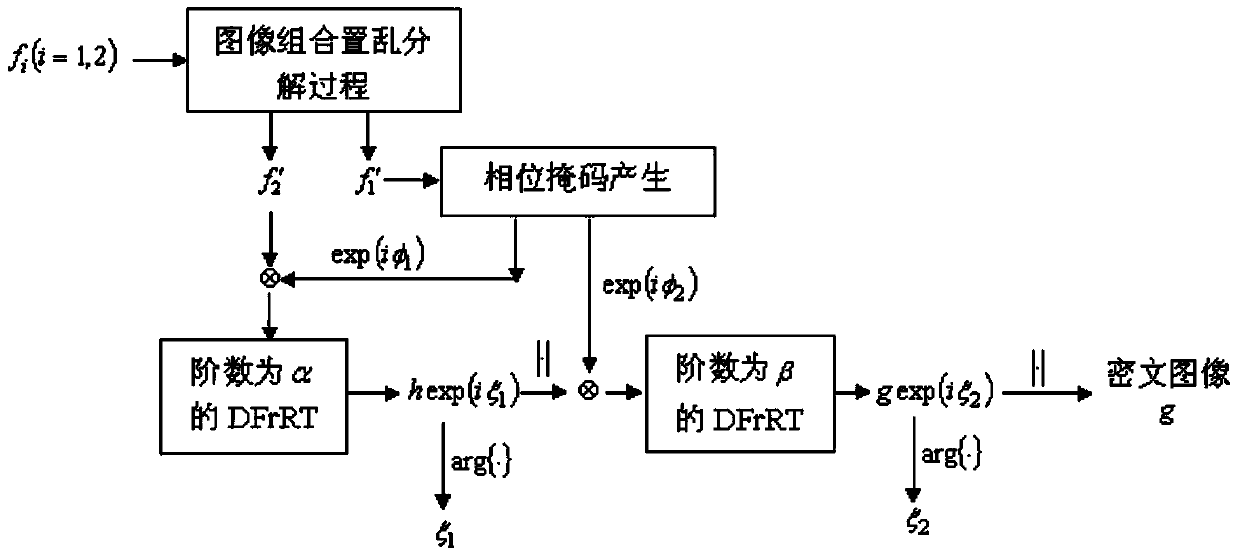
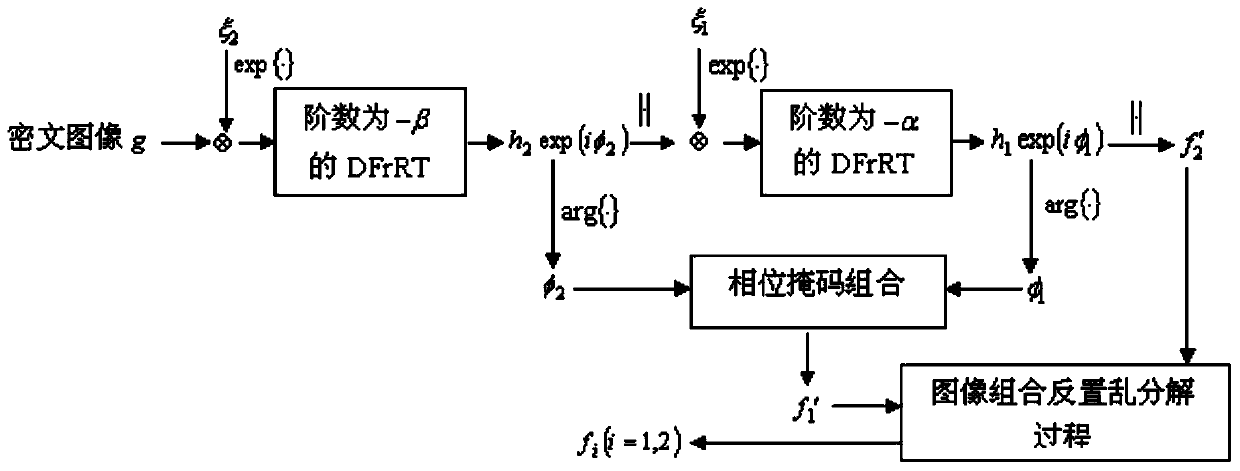
Asymmetric double-image encryption and decryption method based on chaos and cascade DFrRT
InactiveCN104050623AAdd nonlinearityIncrease disorderImage data processing detailsPlaintextCiphertext
The invention discloses an asymmetric double-image encryption method based on chaos and cascade DFrRT. The encryption method comprises the steps that two original gray level images are normalized and connected into an extension image in the horizontal direction; next, the extension image is scrambled by i times of cat mapping, and then the extension image is decomposed into two new images; two phase masks are generated through the image f'1, and the image f'2 and one phase mask are subjected to convolution; Logistic mapping is conducted on an obtained complex matrix, and a conversion result is obtained through DFrRT conversion with the order of alpha; the amplitude of the complex matrix is extracted, and the amplitude and the other phase mask are subjected to convolution; Logistic mapping is conducted on an obtained second complex matrix, and a conversion result is obtained through DFrRT conversion with the order of beta; the amplitude of the second complex matrix is extracted, and then a final ciphertext image is obtained. The invention further discloses a corresponding decryption method. By means of the asymmetric double-image encryption and decryption method, the nonlinearity and disorder of a plaintext image in a spatial domain and a transformation domain are enhanced, and conventional attacks can be well resisted.
Owner:XIAN UNIV OF TECH
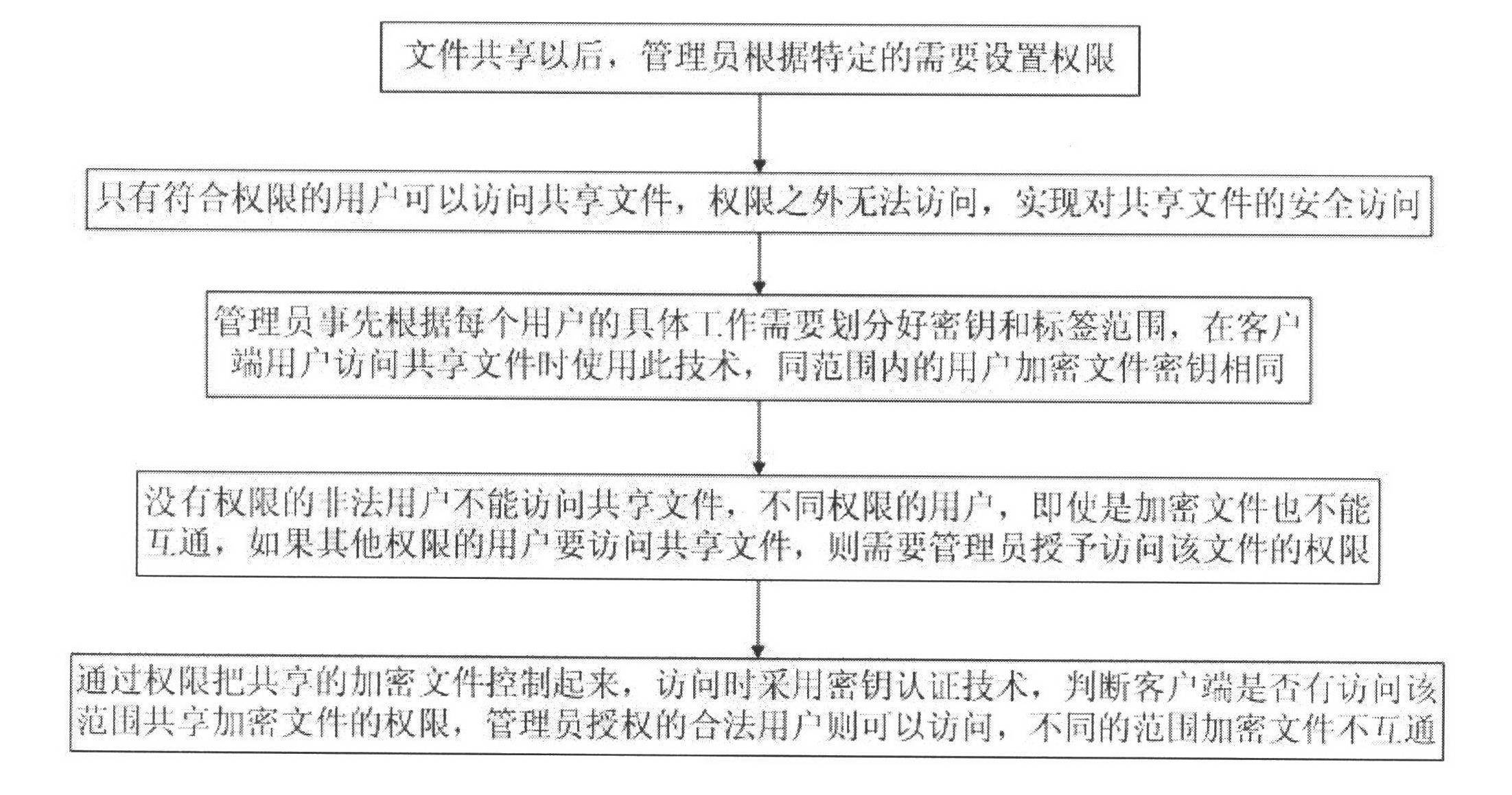
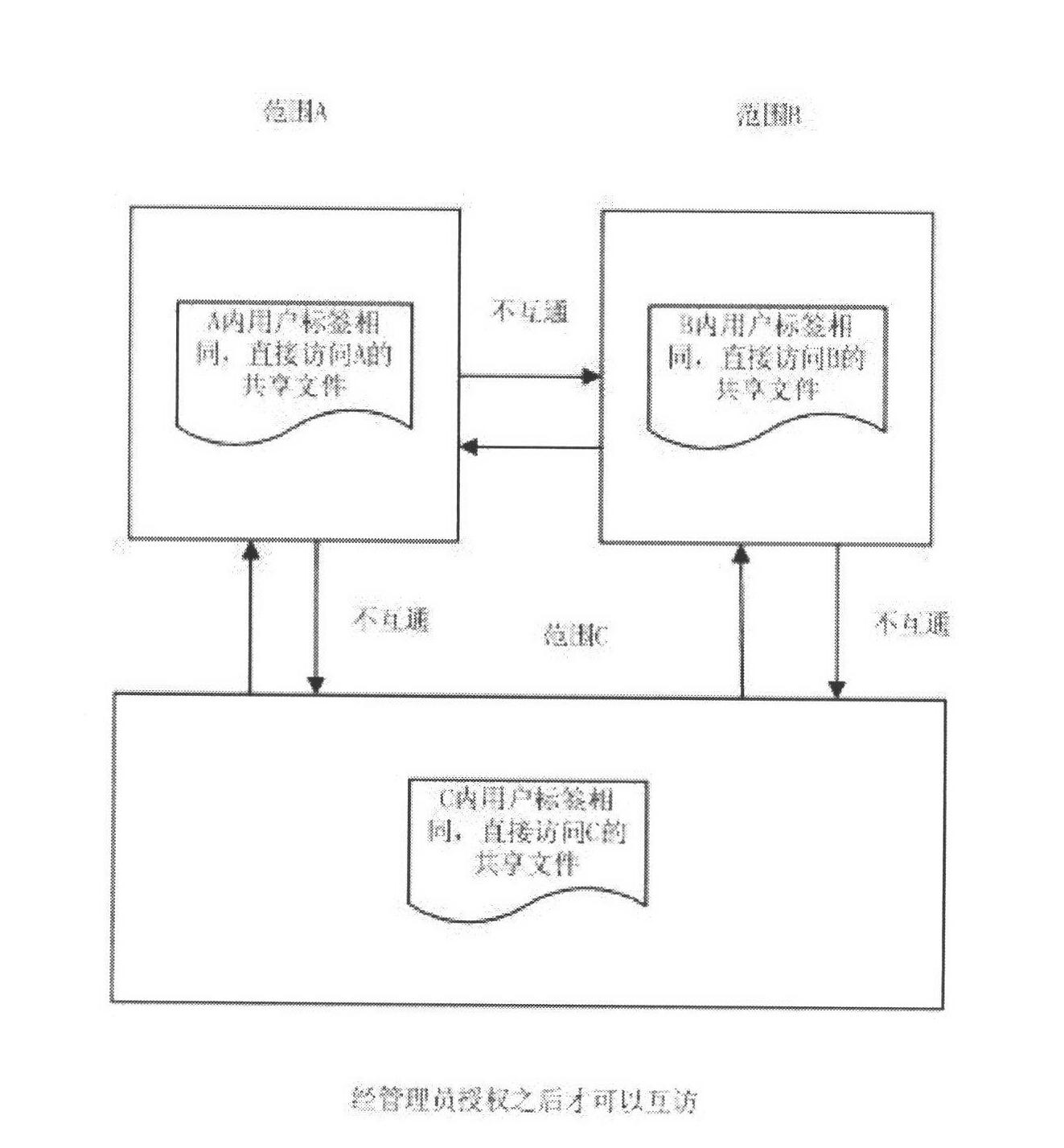
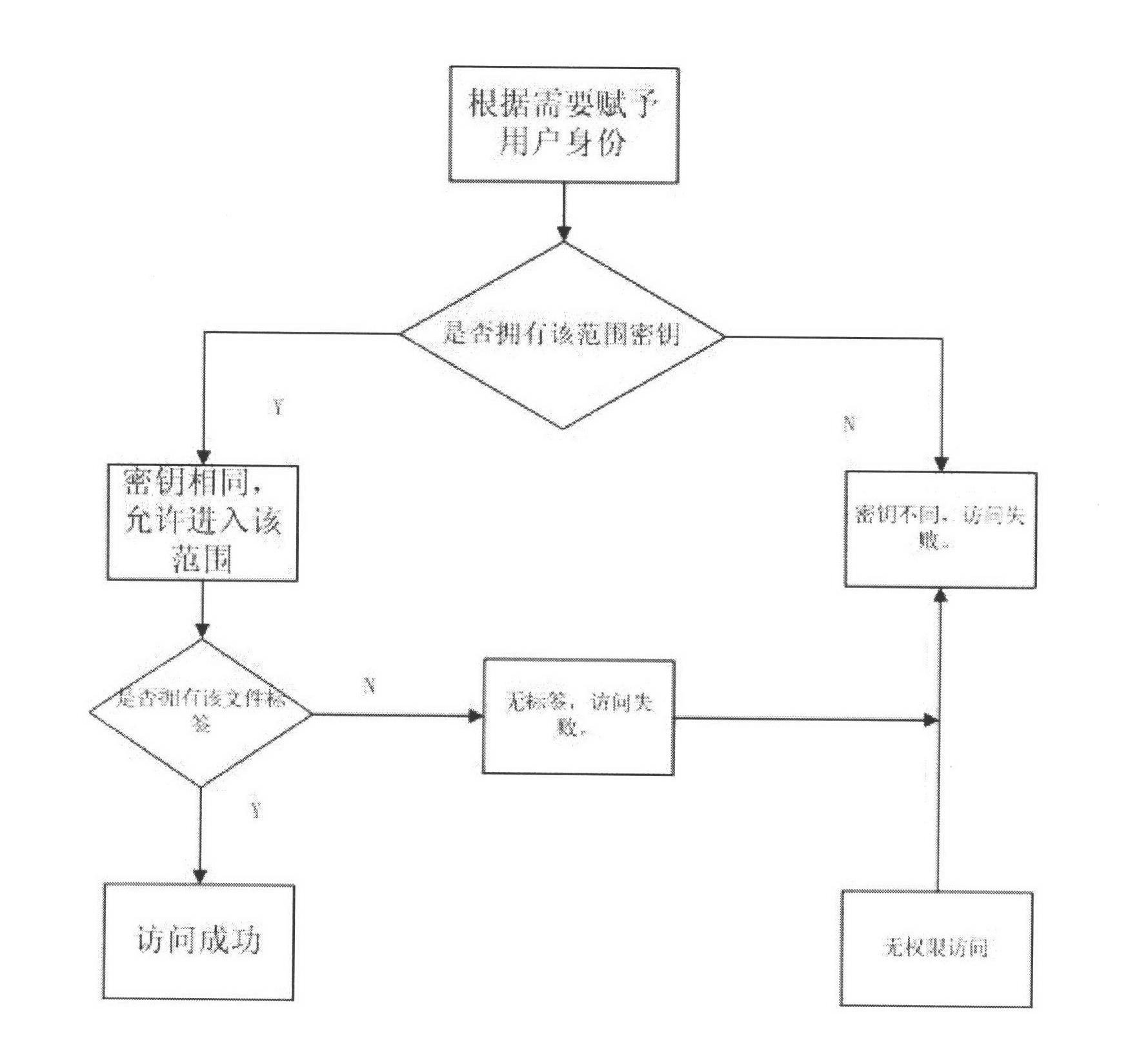
Shared file authority control method
InactiveCN102611686AEnsure safetyDigital data protectionTransmissionXML EncryptionKey authentication
The invention discloses a shared file authority control method which is characterized by comprising the following steps: after a file is shared, an administrator sets authority according to the specific need; only the user conforming to the authority can access the shared file so as to realize the secure access to the shared file; the administrator firstly divides the key and label range according to the concrete working need of each user, and the user encrypted files in the same range share the same key; an illegal user without the authority can not access the shared file; if a user with other authority is to access the shared file, the administrator needs to grant the authority for accessing the file; and when in access, a key authentication technology is adopted to judge whether a client has the authority for accessing the shared encrypted file in the range, wherein the encrypted files in different ranges are not interoperable. Through the invention, based on file encryption, effective control on the authority of the shared file is realized, and the users in the authority range can access the shared encrypted file while the users outside the range can not access the shared encrypted file, thereby ensuring the security of the enterprise information.
Owner:WUXI CINSEC INFORMATION TECH
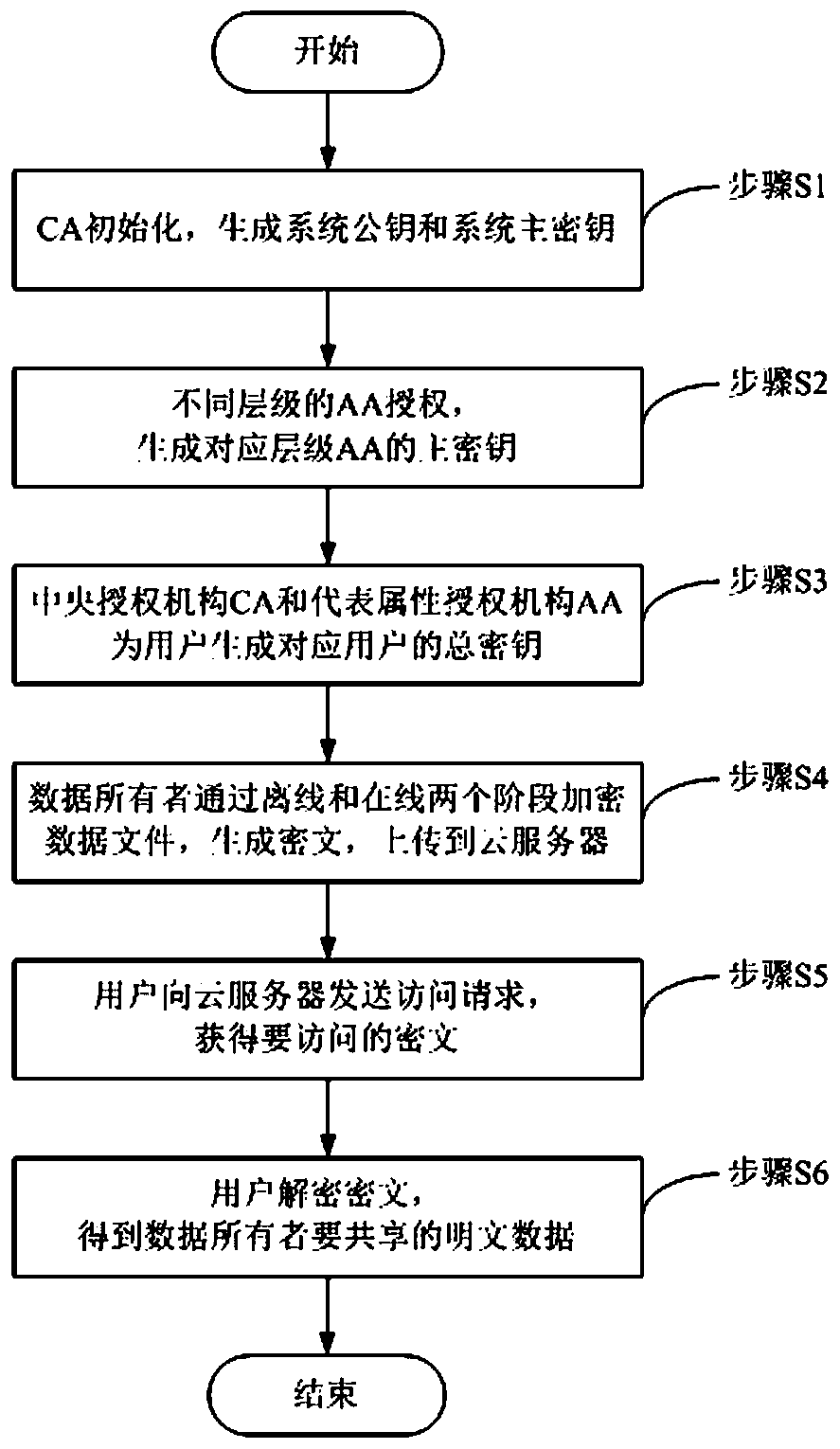
Weight attribute-based encryption method based on hierarchical authorities
ActiveCN108881291AImprove securityIncrease flexibilityKey distribution for secure communicationPlaintextData file
A weight attribute-based encryption method based on hierarchical authorities is disclosed. A system public key and a system master key are generated when a central authority (CA) is initialized, master keys of corresponding levels of representative attribute authorities (AAs) are generated by authorization of different levels of AAs, the CA and the representative AAs generate total keys of corresponding users for the users, a data owner encrypts a data file through two stages of on-line encryption and off-line encryption, a cipher text is generated and uploaded to a cloud server for storage, auser sends an access request to the cloud server to obtain the cipher text data stored in the cloud server, and the user decrypts the cipher text data obtained from the cloud server to obtain the plain text data to be shared by the data owner. By introducing the hierarchy and attribute weights of the authorities, the encryption system has better flexibility in the cloud storage environment, finer-grained access control can be implemented, and the security of the stored data is improved.
Owner:上海汉枫电子科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com