Data encryption method and system, data decryption method and system and terminal equipment
A technology of data encryption and data ciphertext, which is applied to transmission systems, public keys and key distribution of secure communications, and can solve the problems of low data transmission security and inability to know whether encrypted data has been attacked, and achieves security and safety. Effects of Integrity Assurance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
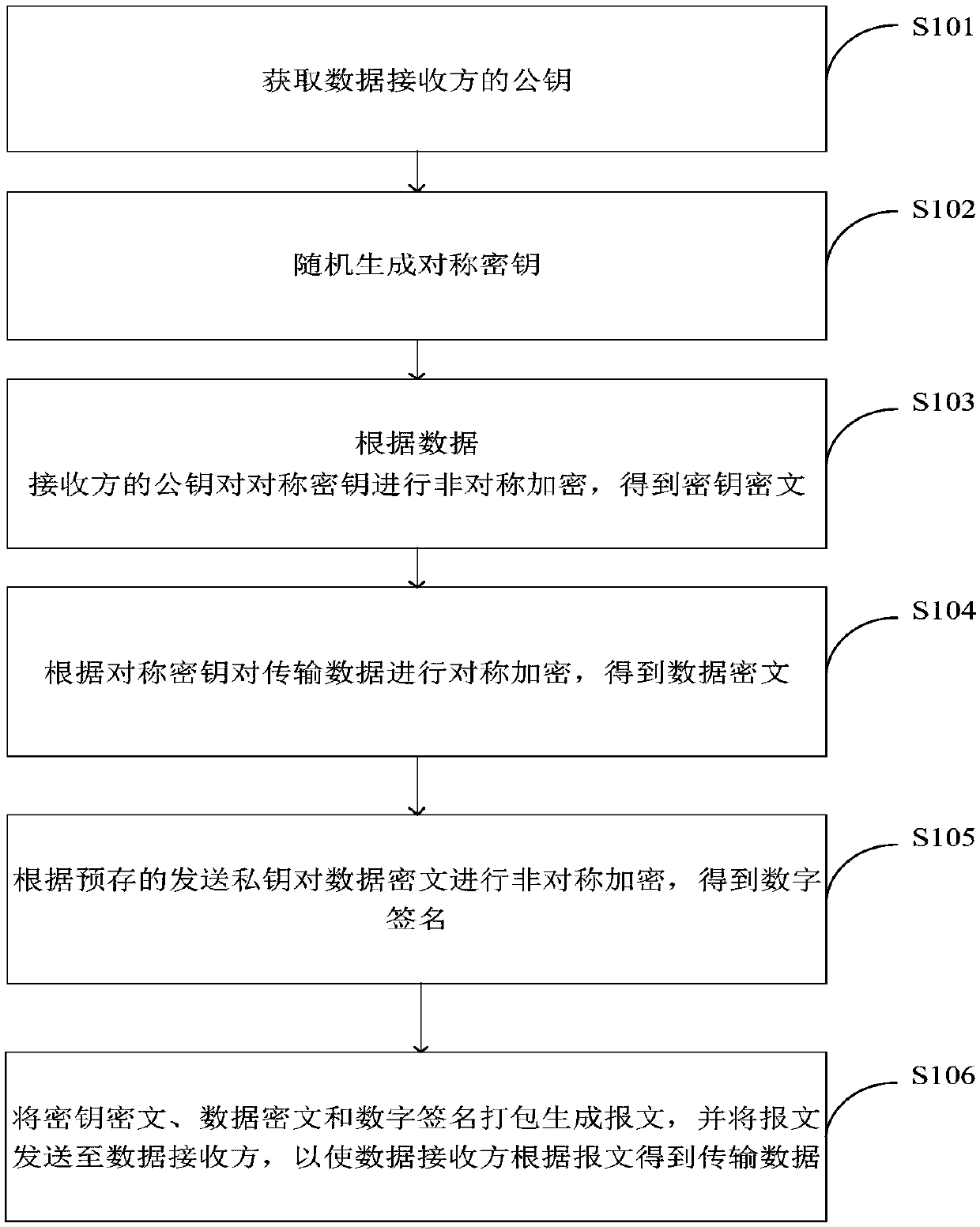
[0046] figure 1 It shows the implementation process of the data encryption method provided by an embodiment of the present invention, which is applied to the data sender, and the process is described in detail as follows:
[0047] In step S101, the public key of the data receiver is obtained.
[0048] In one embodiment, the public key certificate of the data recipient is obtained, and when the public key certificate is updated, the validity of the public key certificate is verified, and if the public key certificate is legal, the public key of the data recipient is obtained.
[0049] In one embodiment, the data encrypted transmission involves a data sender and a data receiver, the data sender sends encrypted data and the data receiver receives encrypted data.
[0050] In one embodiment, the data sender generates a password pair through an asymmetric encryption algorithm, and the password pair includes a public key and a sending private key.
[0051] In one embodiment, the da...
Embodiment 2
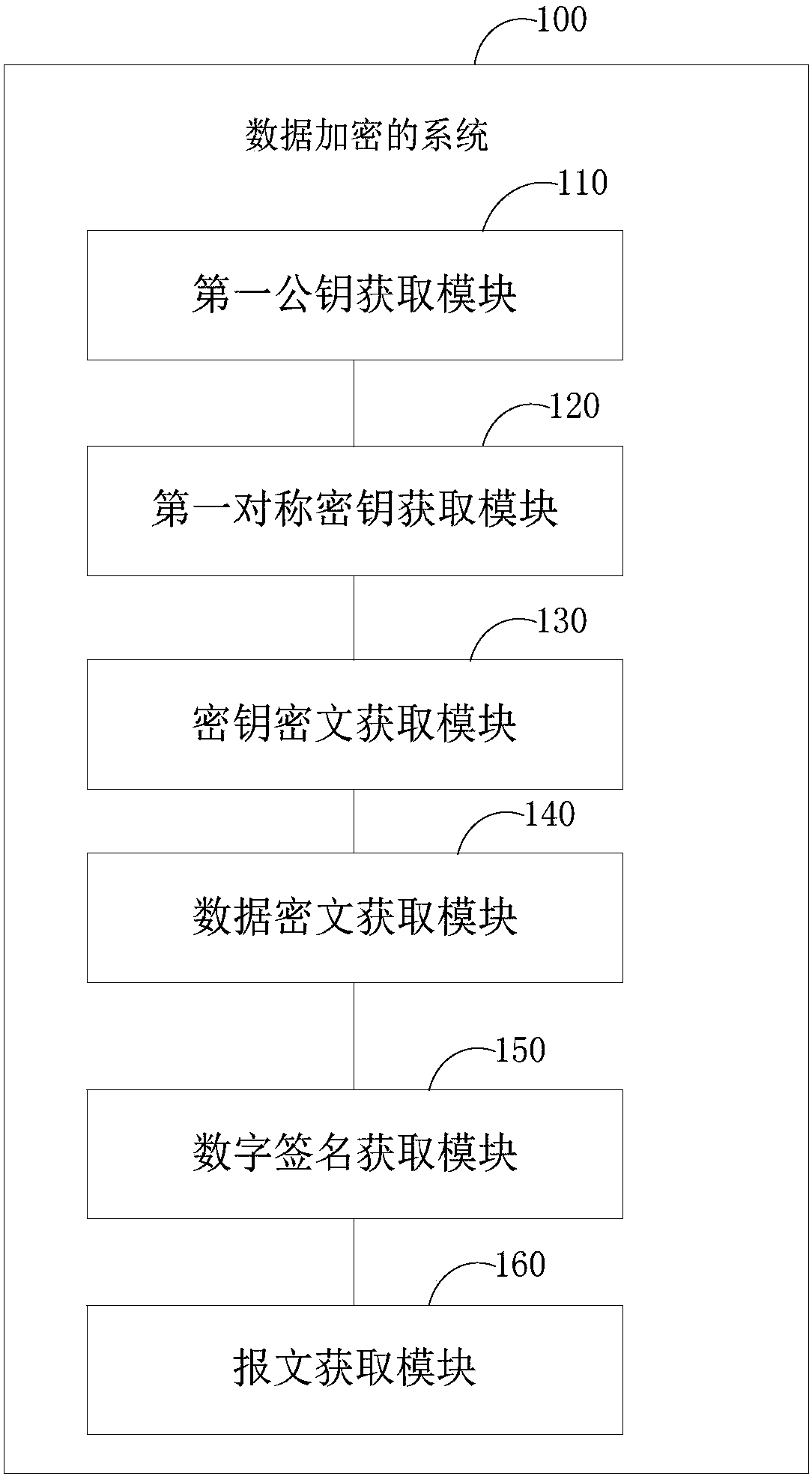
[0084] Such as figure 2 As shown, the data encryption system 100 provided by an embodiment of the present invention is applied to the data sender to perform figure 1 The method step in the corresponding embodiment, it comprises:
[0085] The first public key acquisition module 110 is used to acquire the public key of the data recipient;
[0086] A first symmetric key acquisition module 120, configured to randomly generate a symmetric key;
[0087] The key ciphertext acquisition module 130 is used to asymmetrically encrypt the symmetric key according to the public key of the data receiver to obtain the key ciphertext;
[0088] A data ciphertext acquisition module 140, configured to perform symmetric encryption on the transmission data according to the symmetric key to obtain the data ciphertext;
[0089] The digital signature acquisition module 150 is used to asymmetrically encrypt the data ciphertext according to the pre-stored sending private key to obtain the digital sig...
Embodiment 3
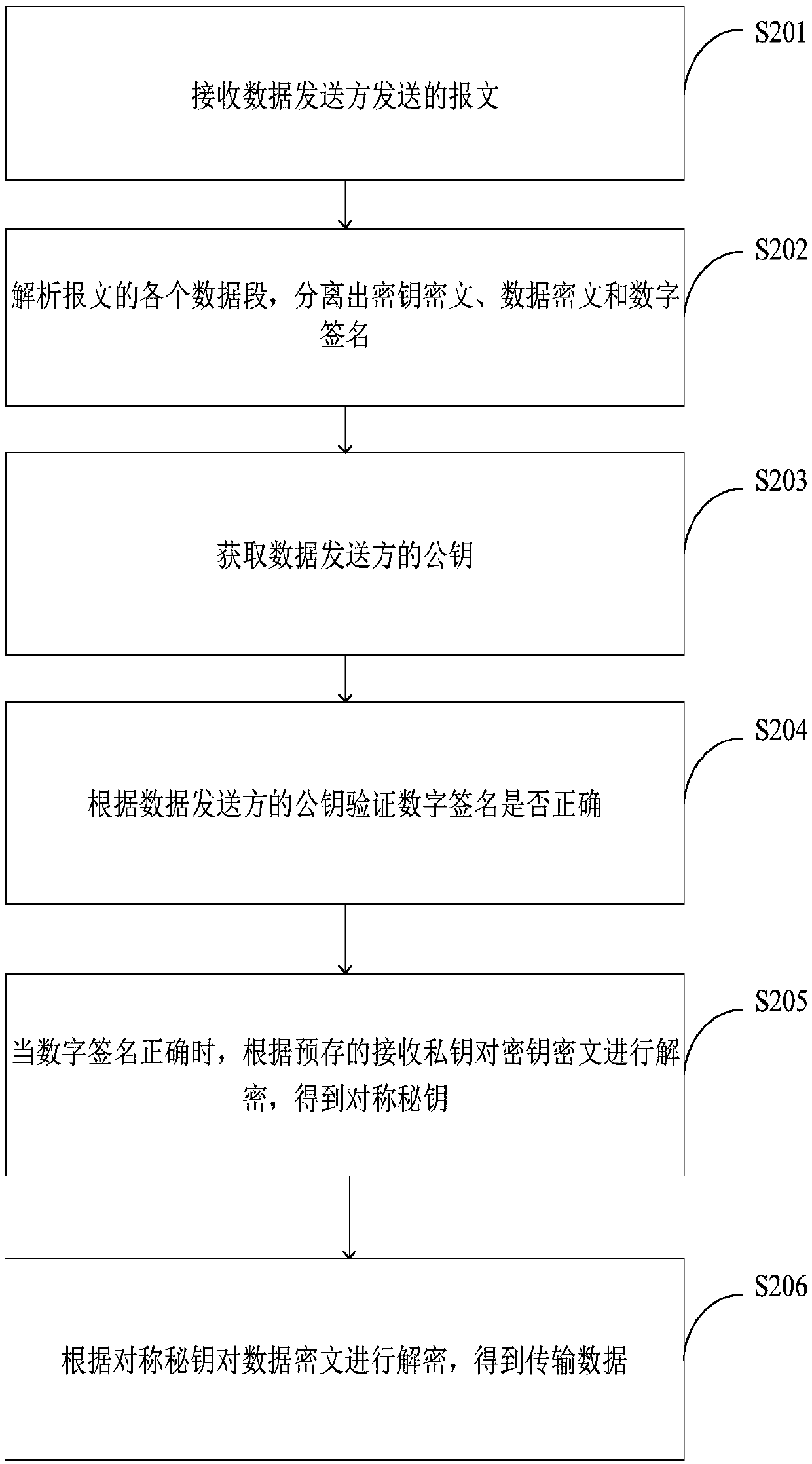
[0100] image 3 It shows the implementation process of the data decryption method provided by one embodiment of the present invention, which is applied to the data receiver, and the process is described in detail as follows:
[0101] In step S201, a message sent by a data sender is received.
[0102] In one embodiment, before step S201, it also includes:
[0103] The data sender obtains the public key of the data receiver, randomly generates a symmetric key, and performs asymmetric encryption on the symmetric key according to the public key of the data receiver to obtain the key ciphertext; the data sender encrypts the transmitted data according to the symmetric key. Symmetric encryption to obtain the data ciphertext; the data sender asymmetrically encrypts the data ciphertext according to the pre-stored sending private key to obtain a digital signature; the data sender packs the key ciphertext, data ciphertext and digital signature to generate a message, And send the messag...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com