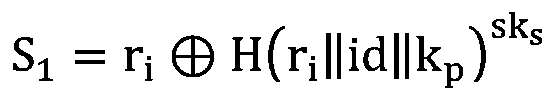Patents
Literature
60 results about "Password policy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A password policy is a set of rules designed to enhance computer security by encouraging users to employ strong passwords and use them properly. A password policy is often part of an organization's official regulations and may be taught as part of security awareness training. Either the password policy is merely advisory, or the computer systems force users to comply with it. Some governments have national authentication frameworks that define requirements for user authentication to government services, including requirements for passwords.
Cryptographic policy enforcement
ActiveUS20050166066A1User identity/authority verificationUnauthorized memory use protectionPassword policyData stream
Owner:MCAFEE LLC
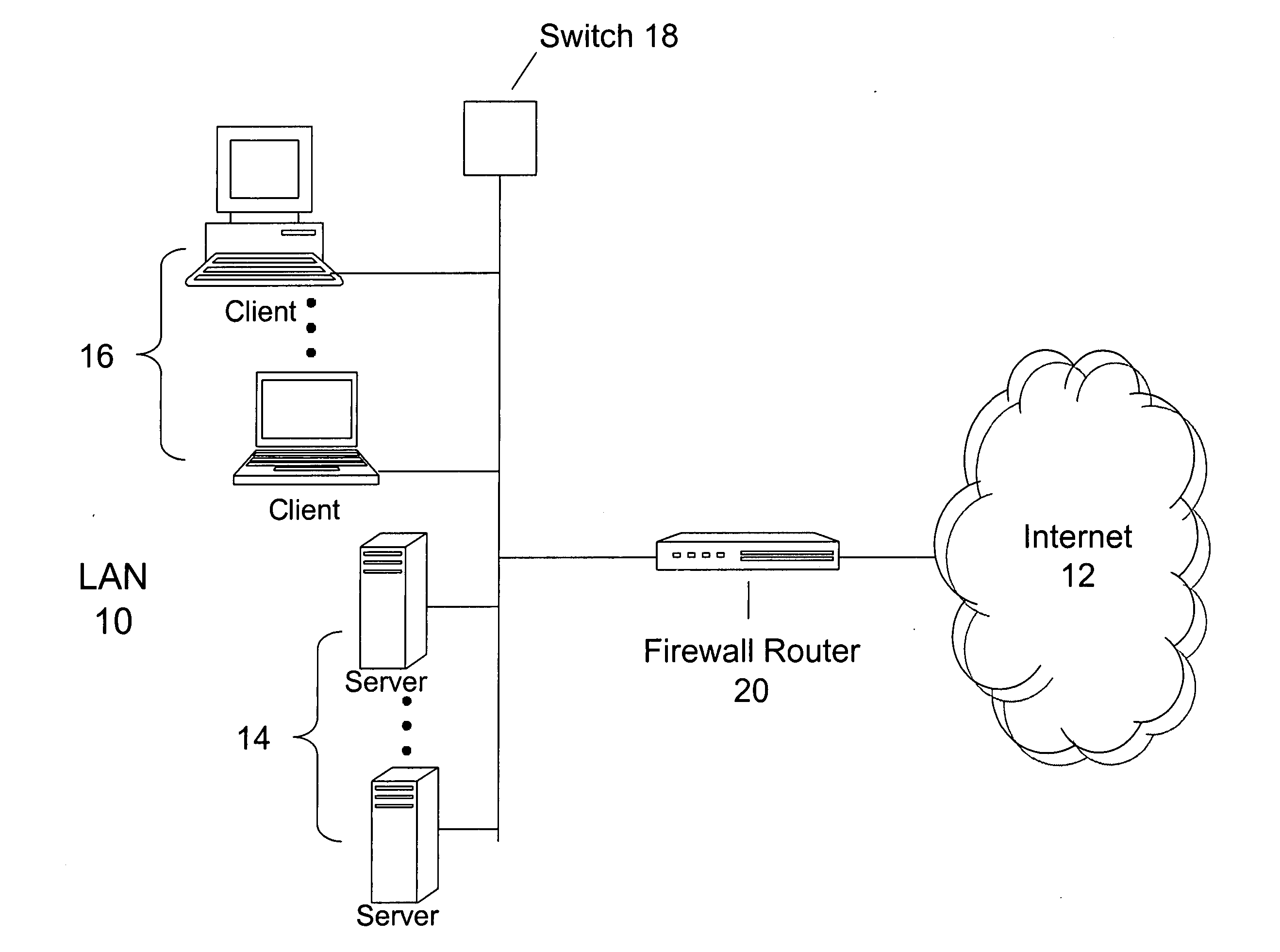
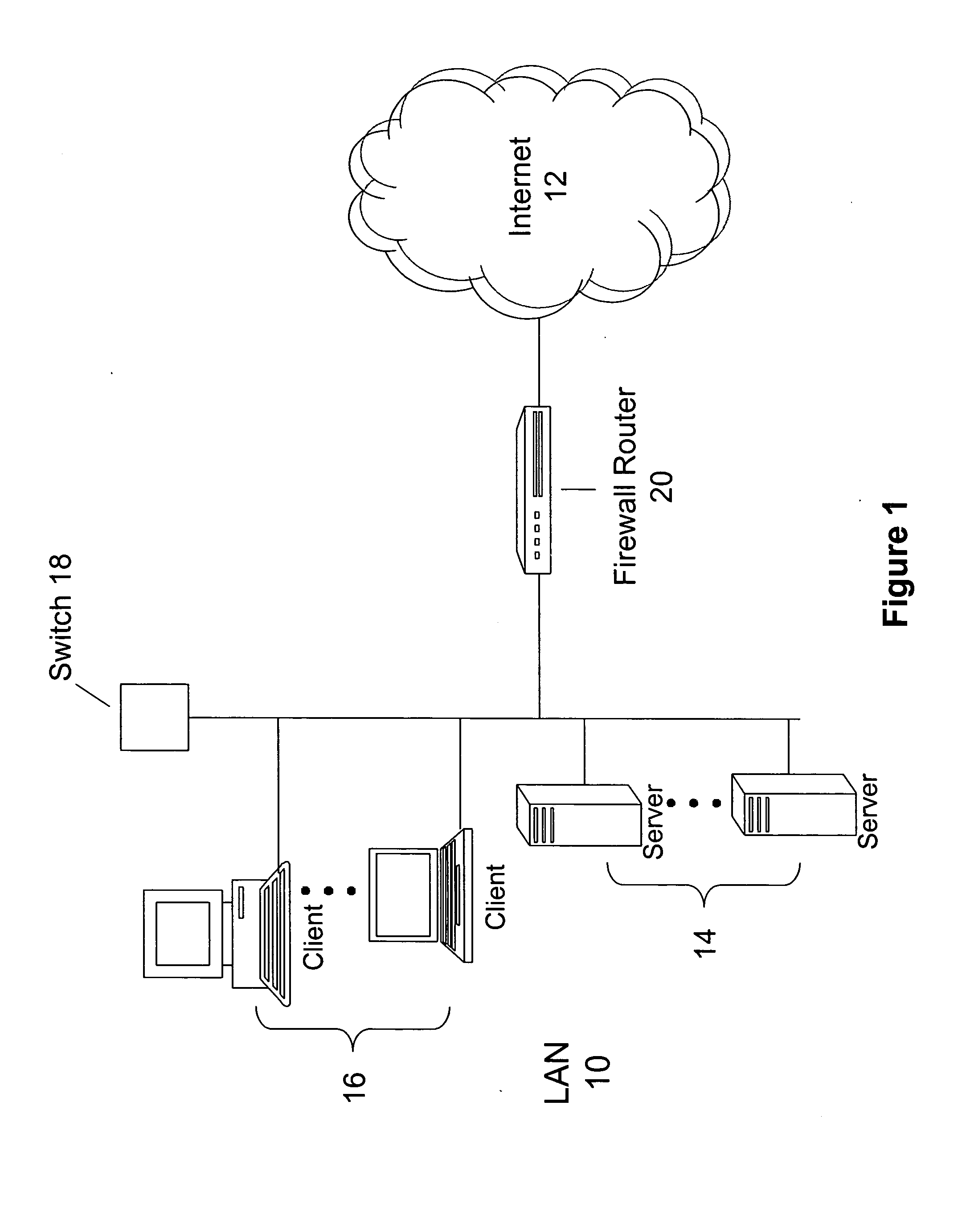
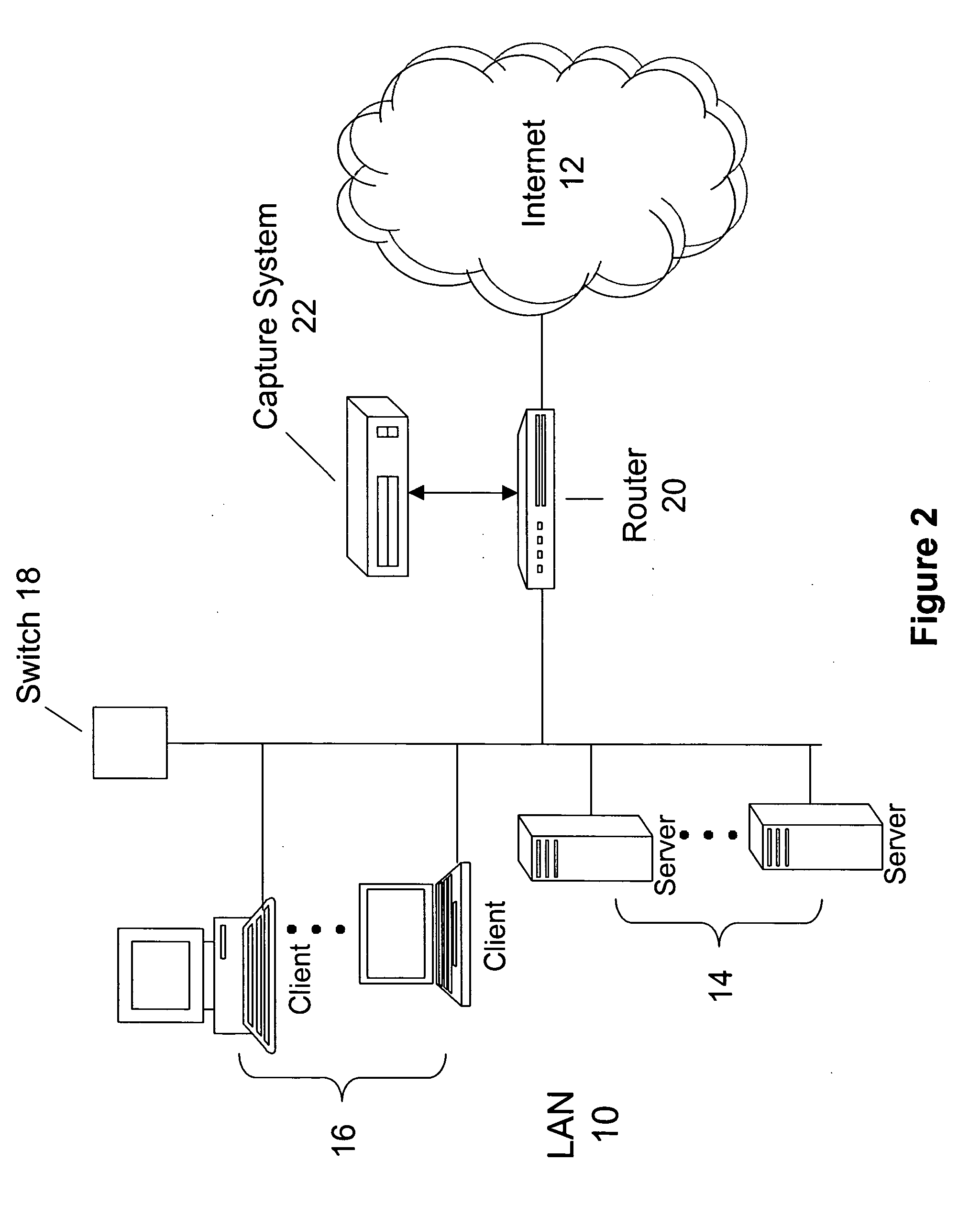
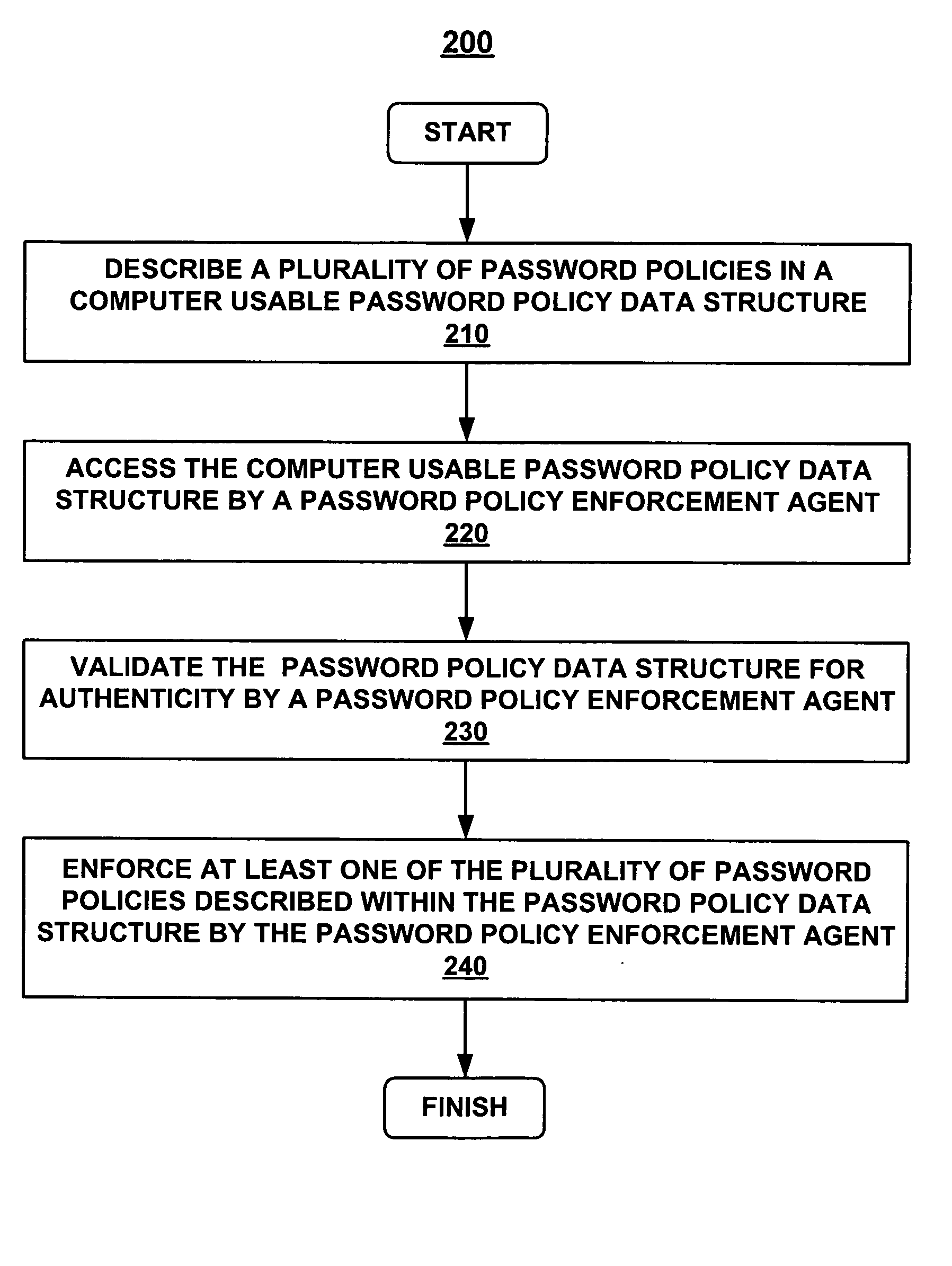
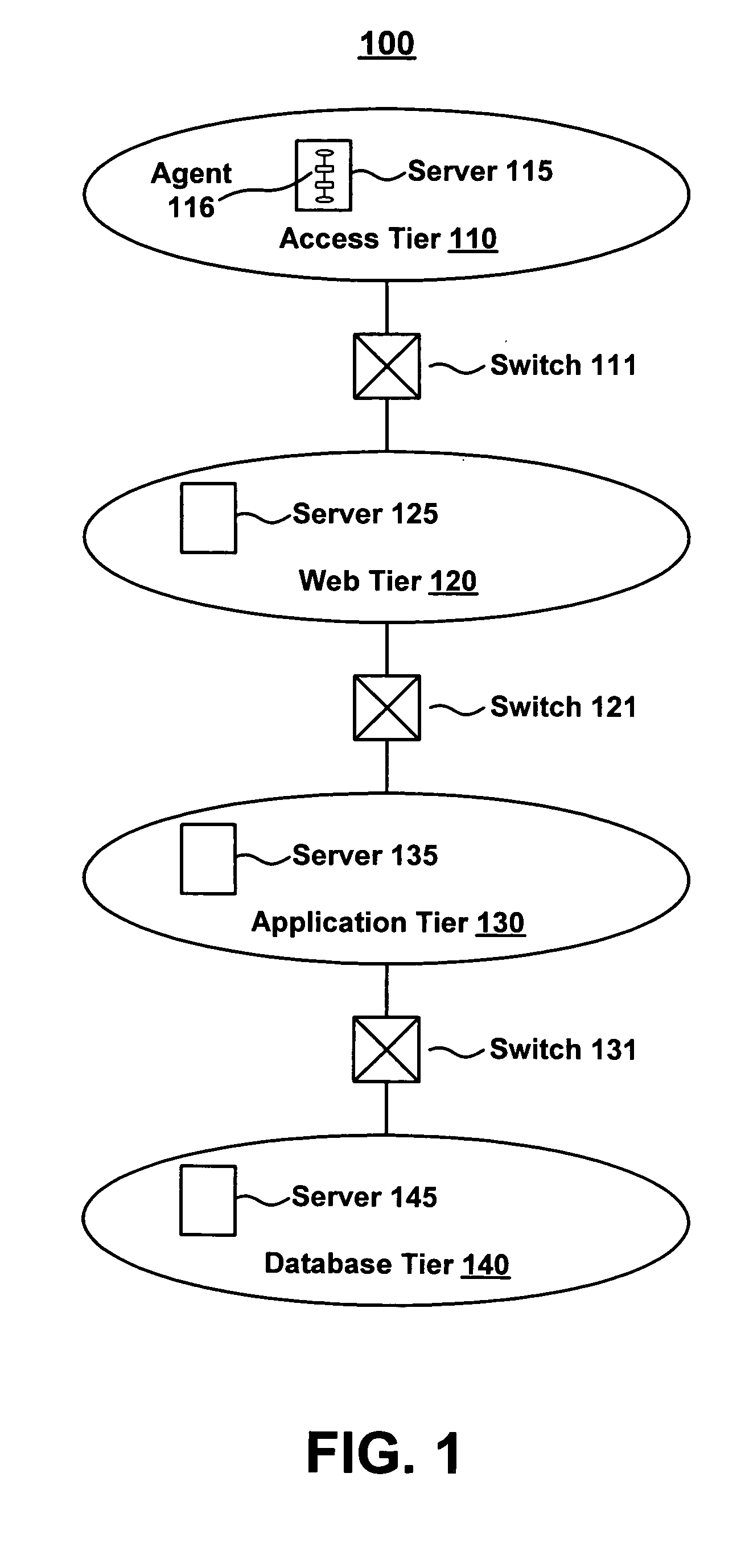
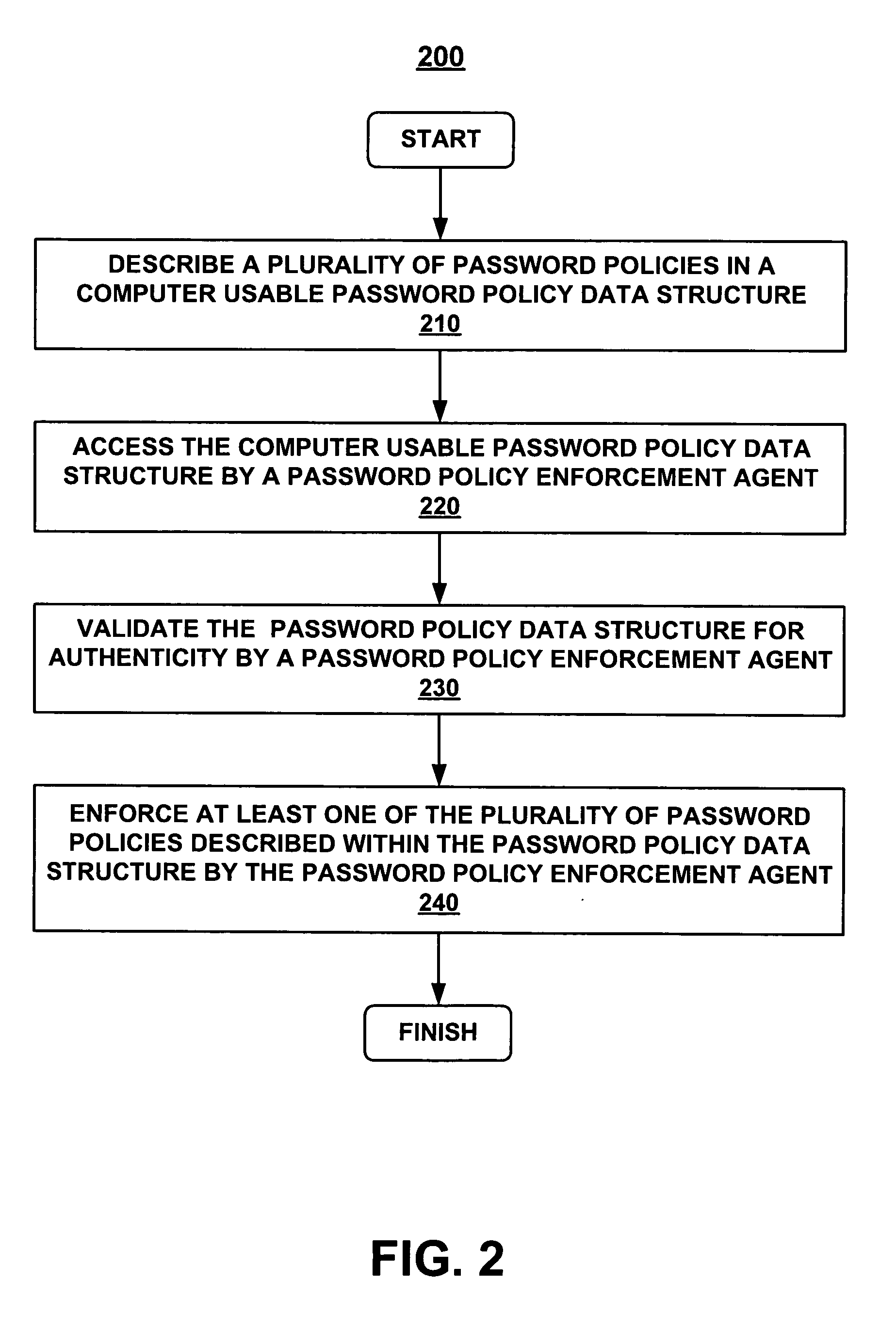
Method and system for establishing a consistent password policy
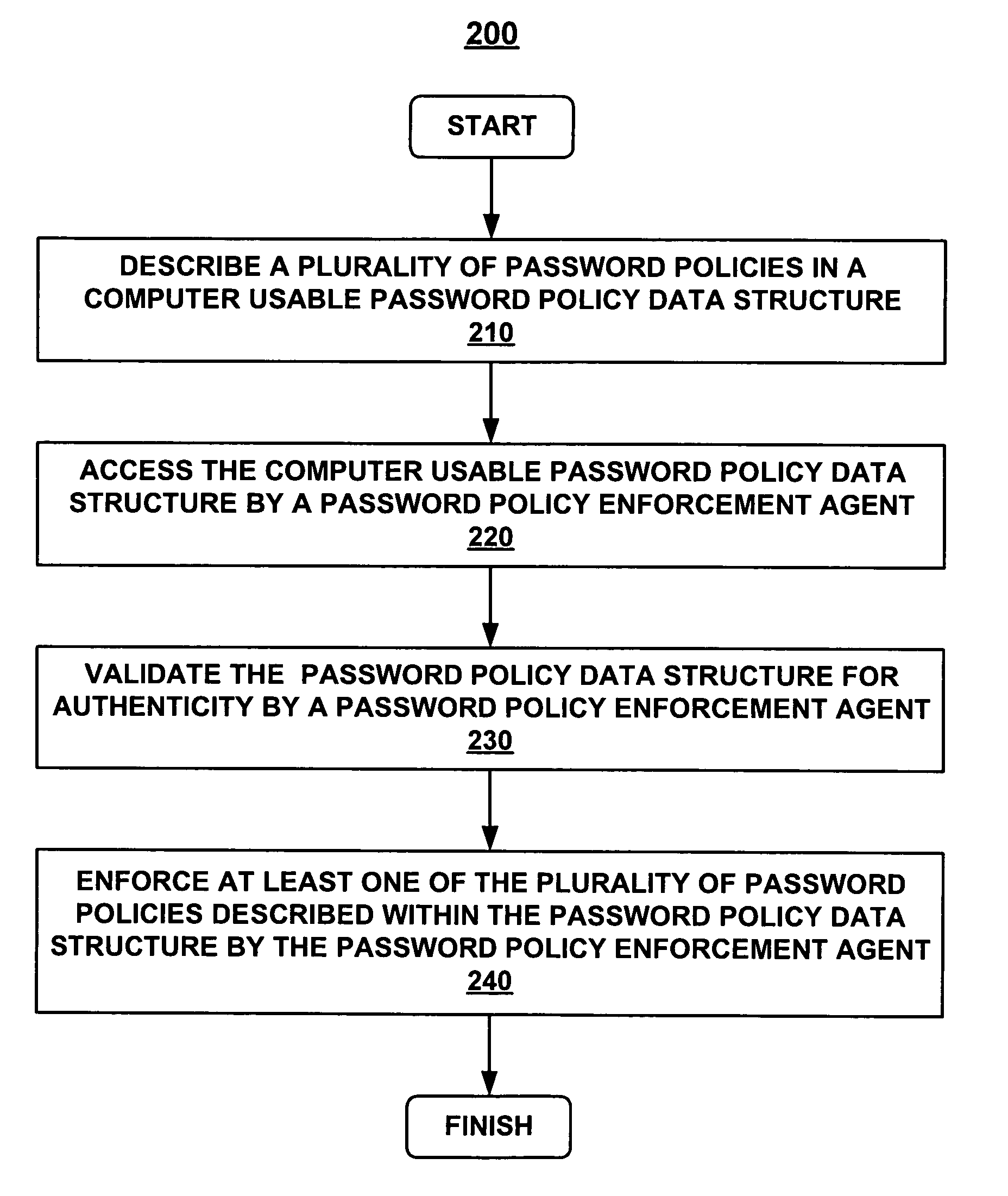
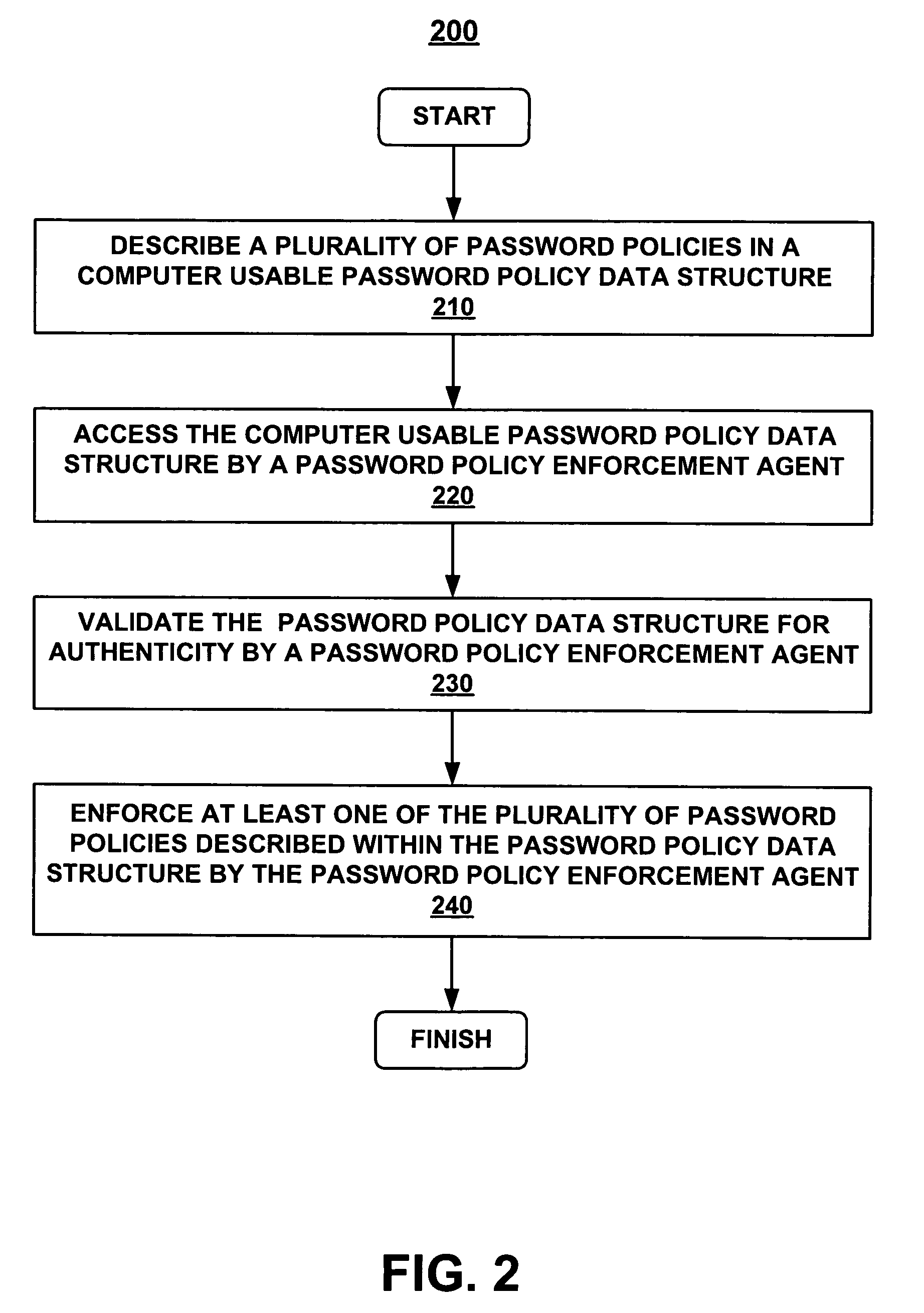
Methods and systems for establishing a consistent password policy. A plurality of password policies is described in a computer usable password policy data structure. The computer usable password policy data structure is accessed by a password policy enforcement agent. Optionally, the computer usable password policy data structure is validated for authenticity by the password policy enforcement agent. Optionally, the password policy enforcement agent can report back to a centralized configuration and aggregation point repository in order to provide a consistent view of policy enforcement.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP +1
Methods, systems, and computer program products that centrally manage password policies
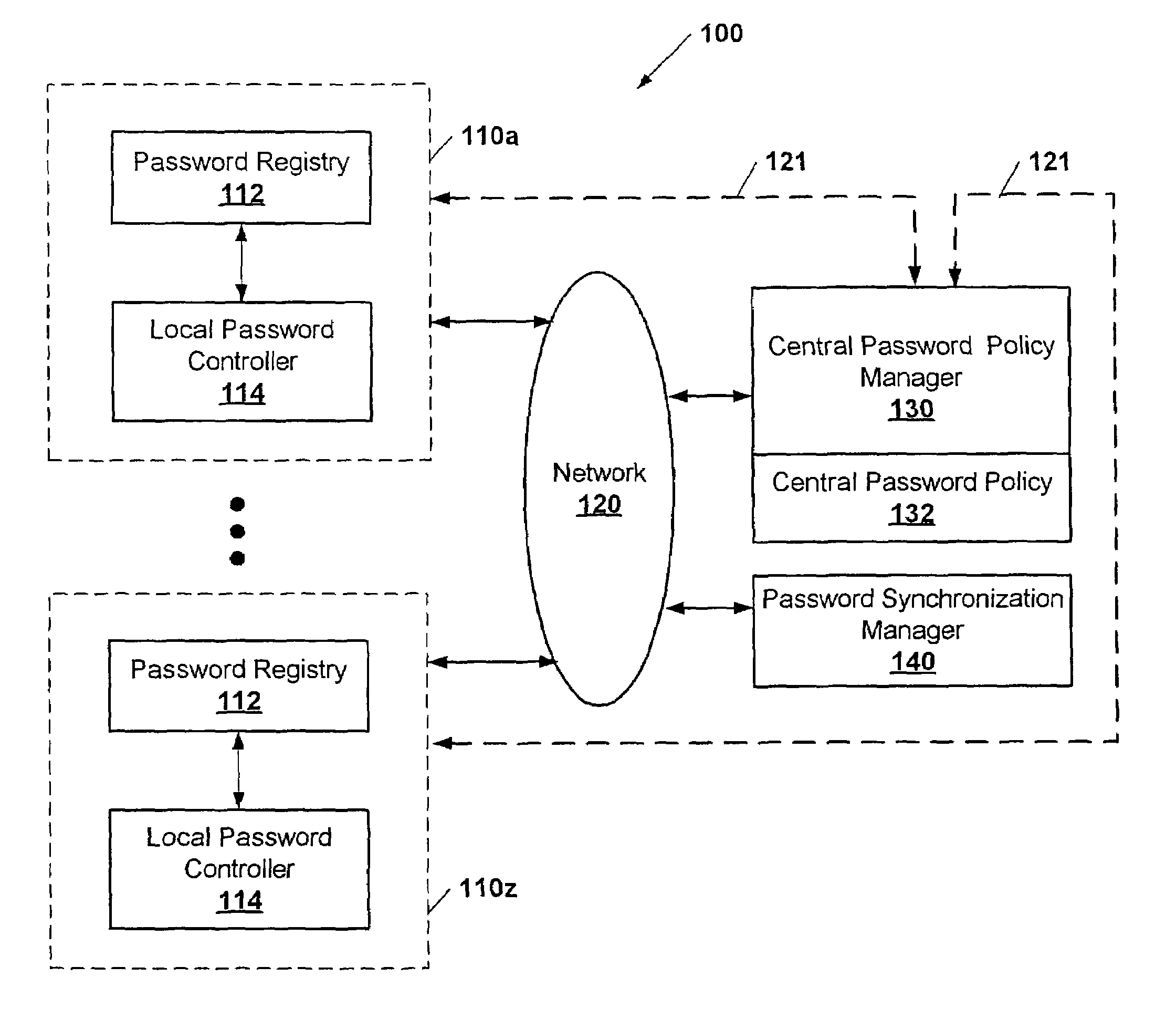
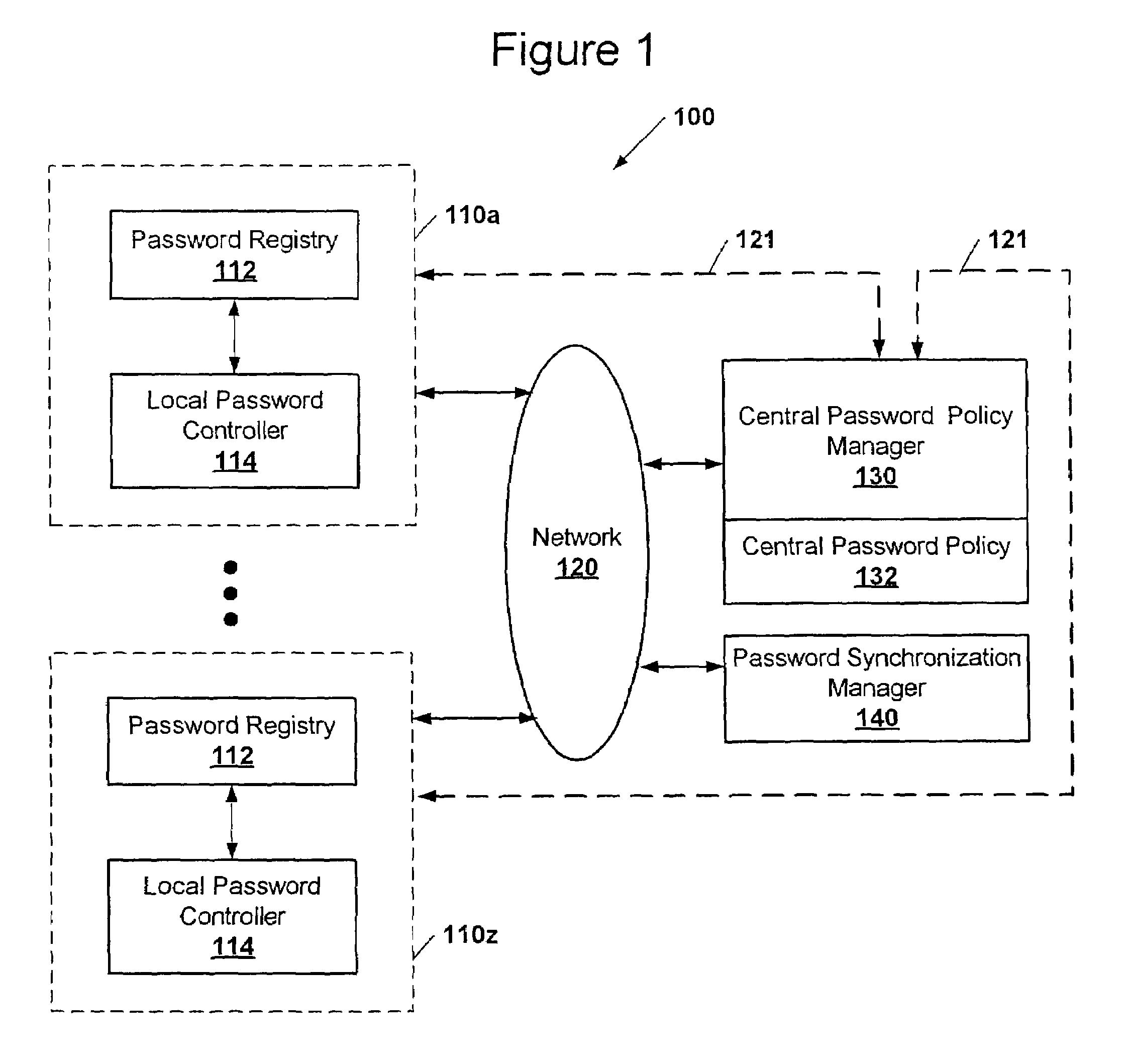
ActiveUS7530097B2Uniform levelDigital data processing detailsMultiple digital computer combinationsData processing systemPassword policy
A method of controlling password changes in a system having a plurality of data processing systems having separate password registries. Contents of passwords in the password registries of the data processing systems are controlled using password content policies that are centrally shared between the plurality of data processing systems.
Owner:IBM CORP
Server, method and program product for management of password policy information
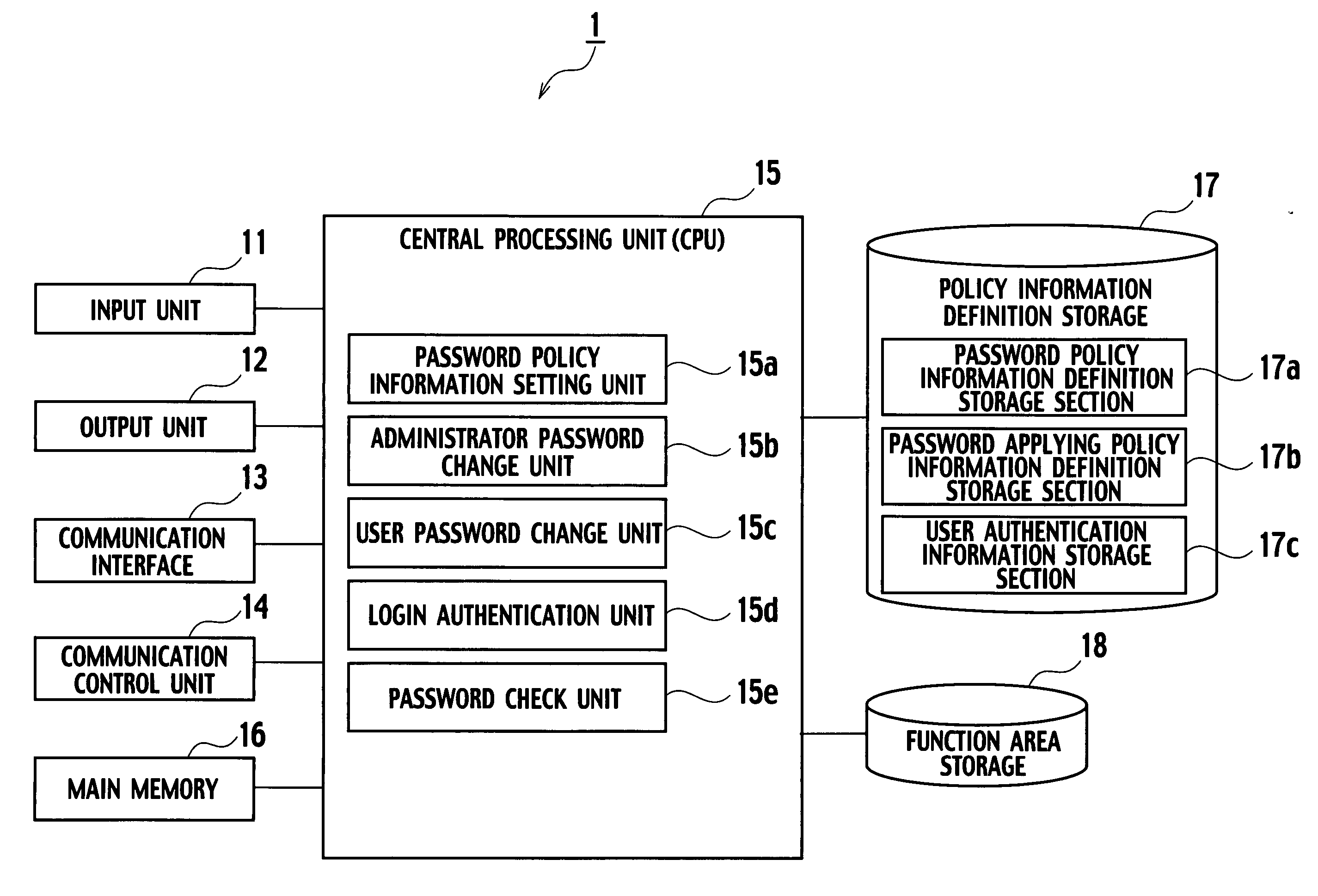
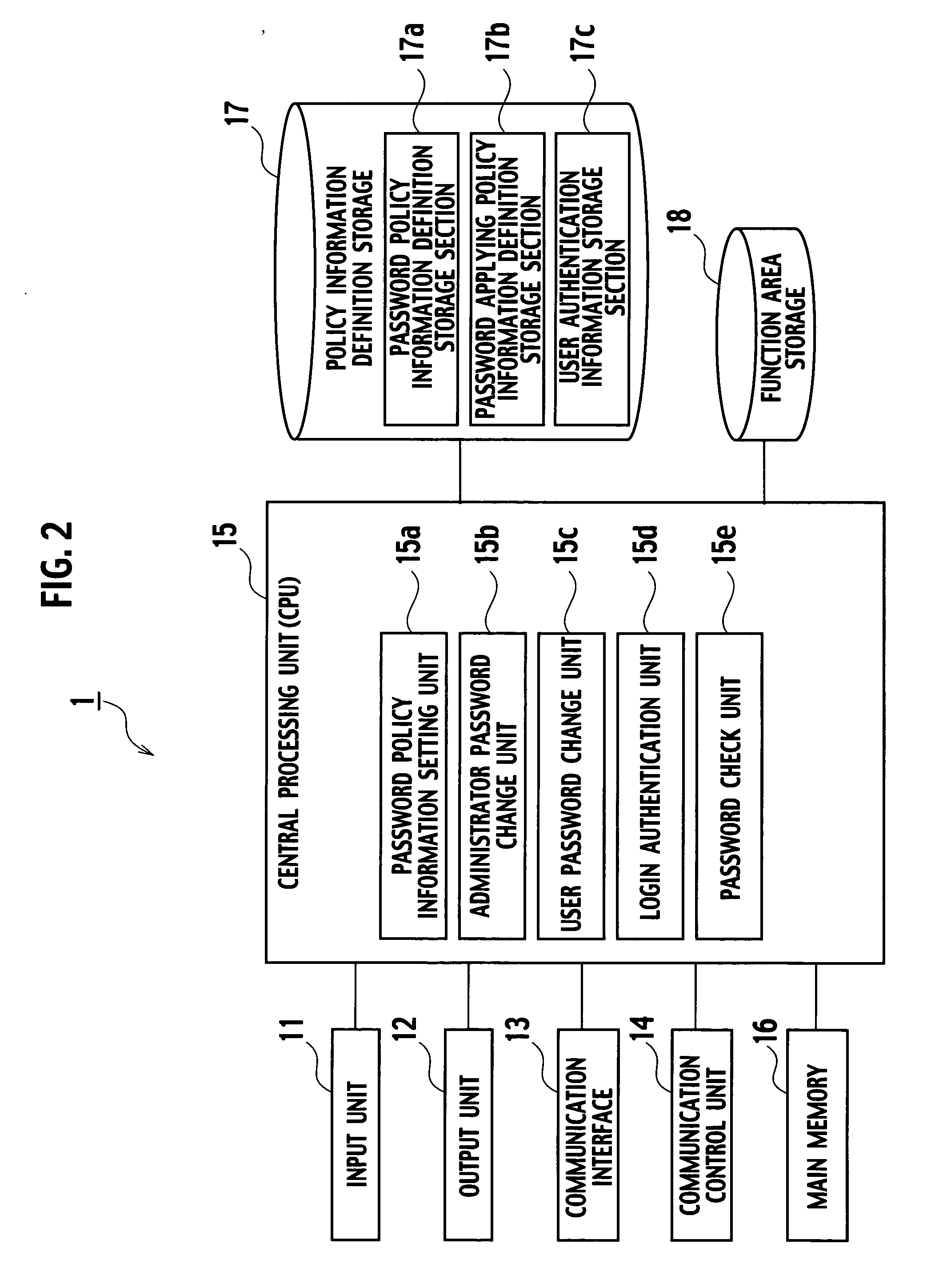
InactiveUS20060259960A1Random number generatorsUser identity/authority verificationPassword policyPassword
A password policy information management server 1 according to an embodiment of the present invention includes: a password policy information definition storage section 17a storing the password policy information; a password applying policy information definition storage section 17b storing password applying policy information including timing information; password policy information setting unit 15a configured to allow the administrator of the information system to set each password policy information; a password check unit 15e configured to check validity of the password; and an administrator password change unit 15b configured to request validity checking of a new password to the password check unit 15e according to timing defined by the password applying policy information stored in the password applying policy information definition storage section 17b.
Owner:KK TOSHIBA +1
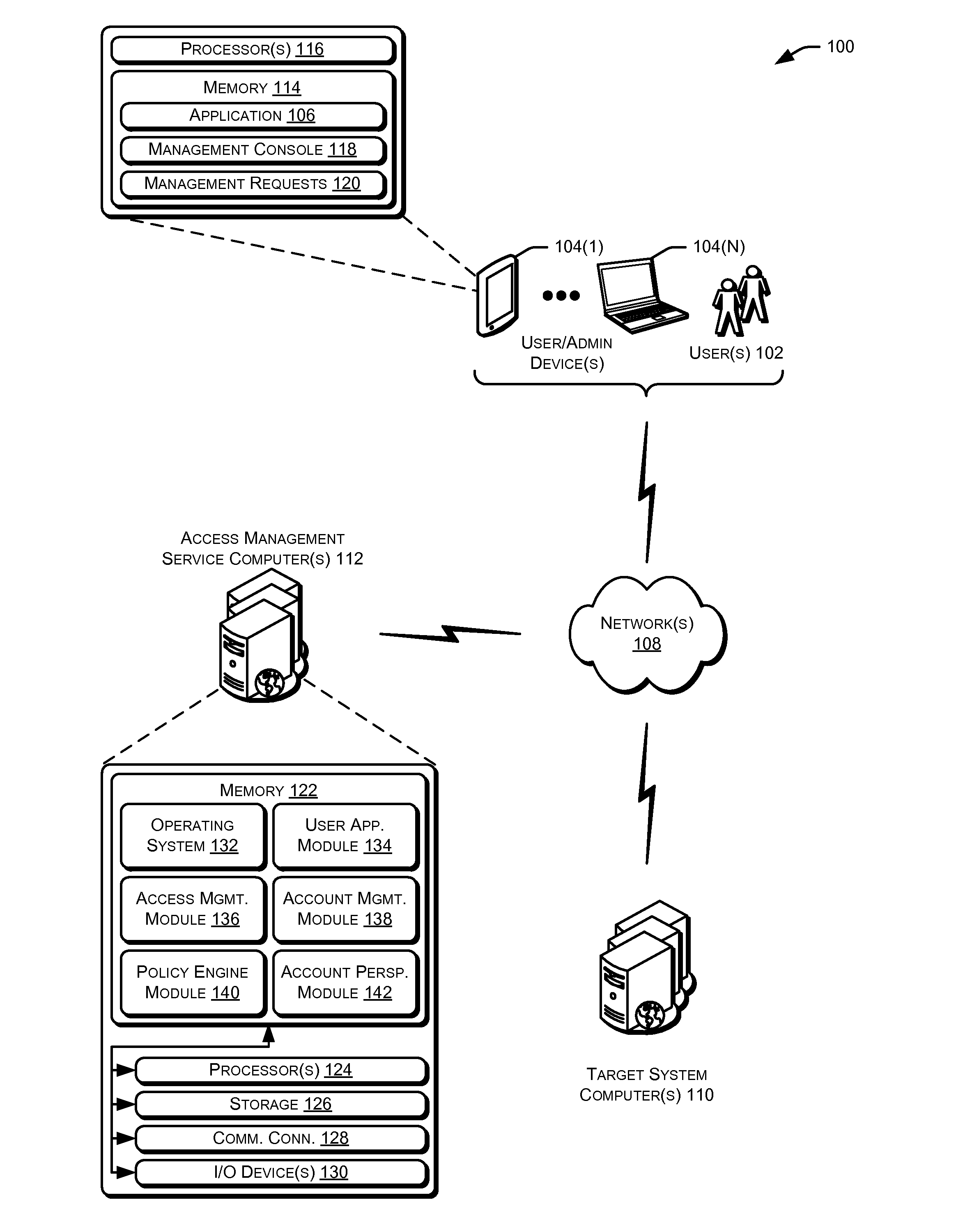
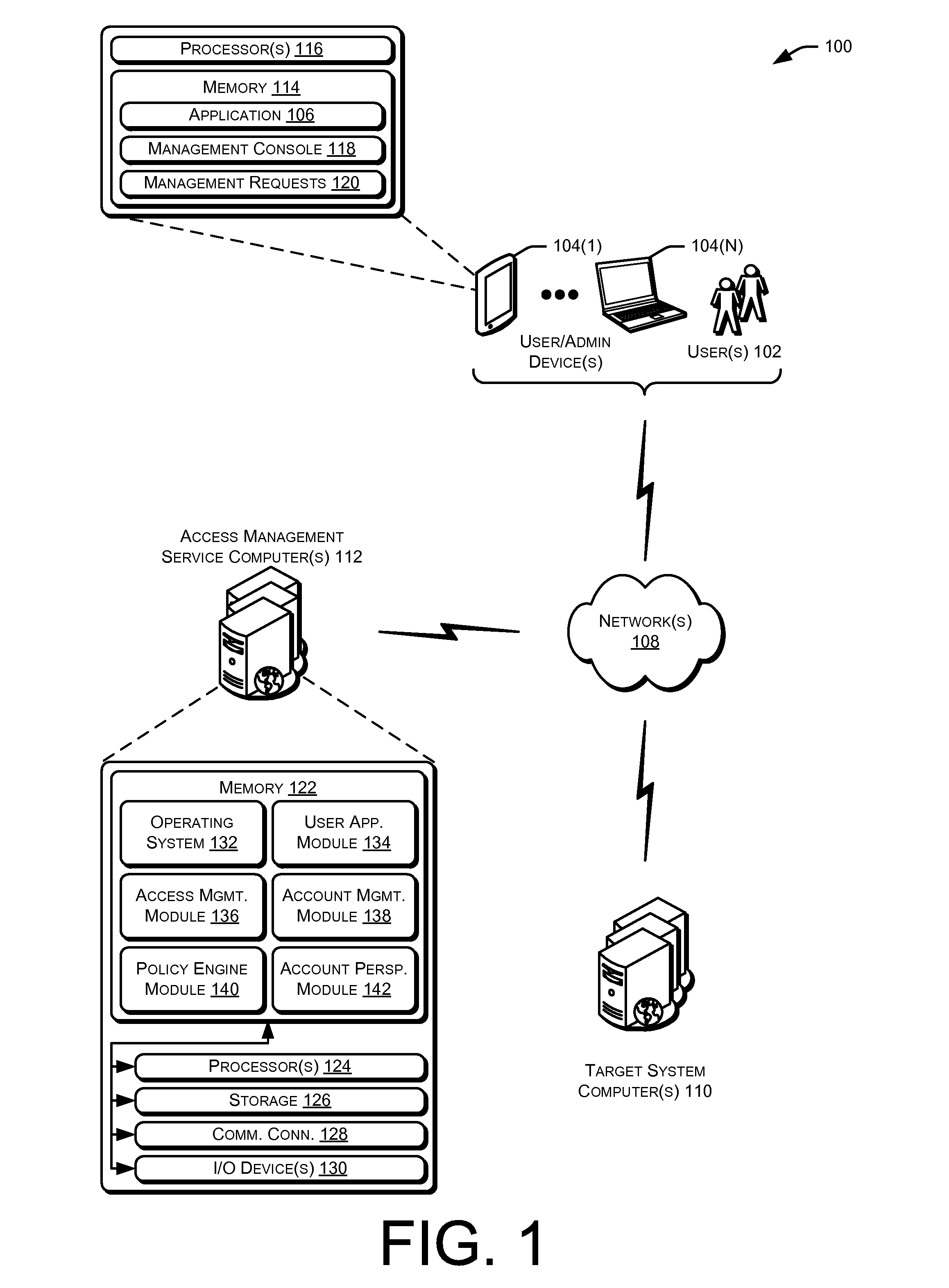
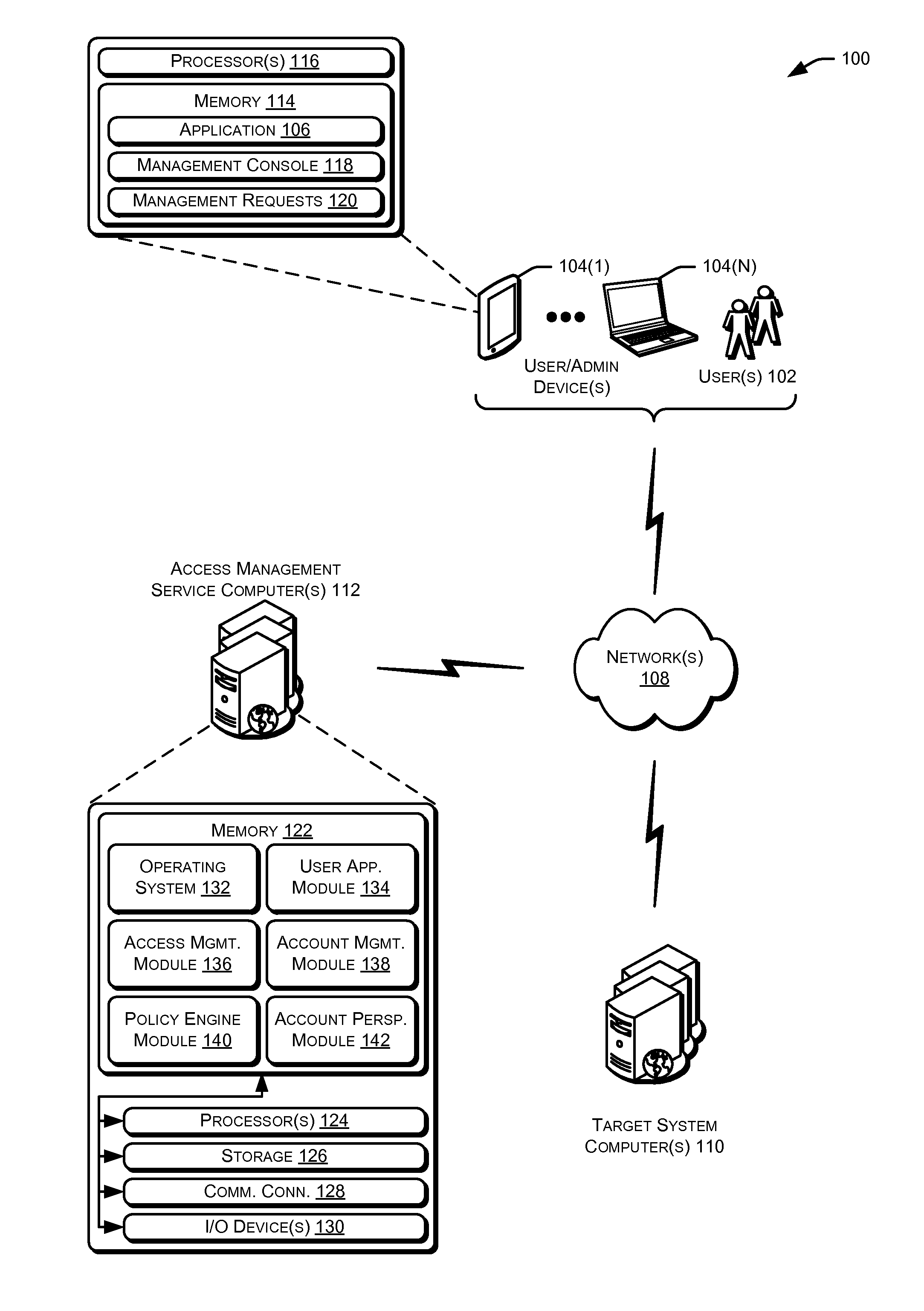
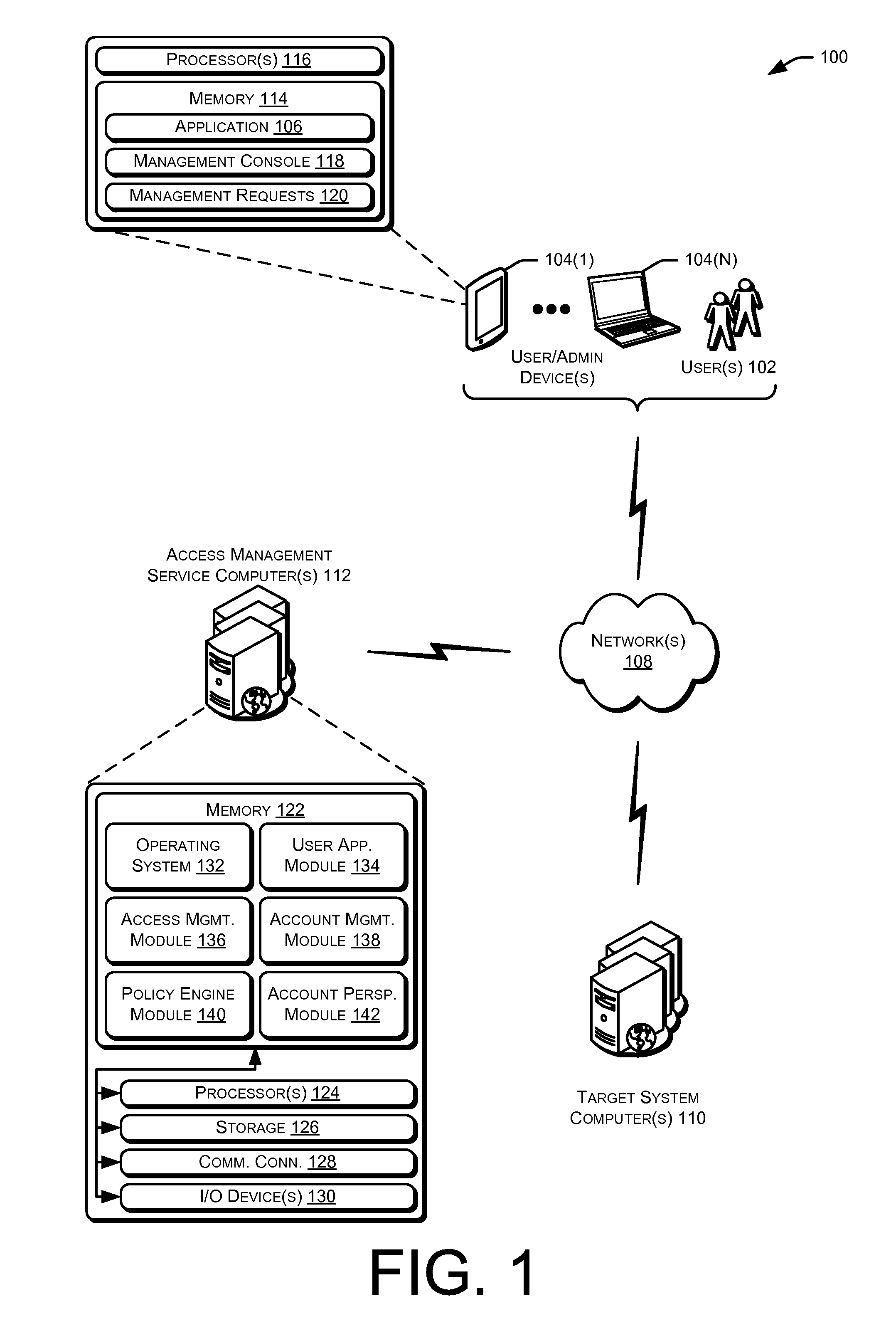
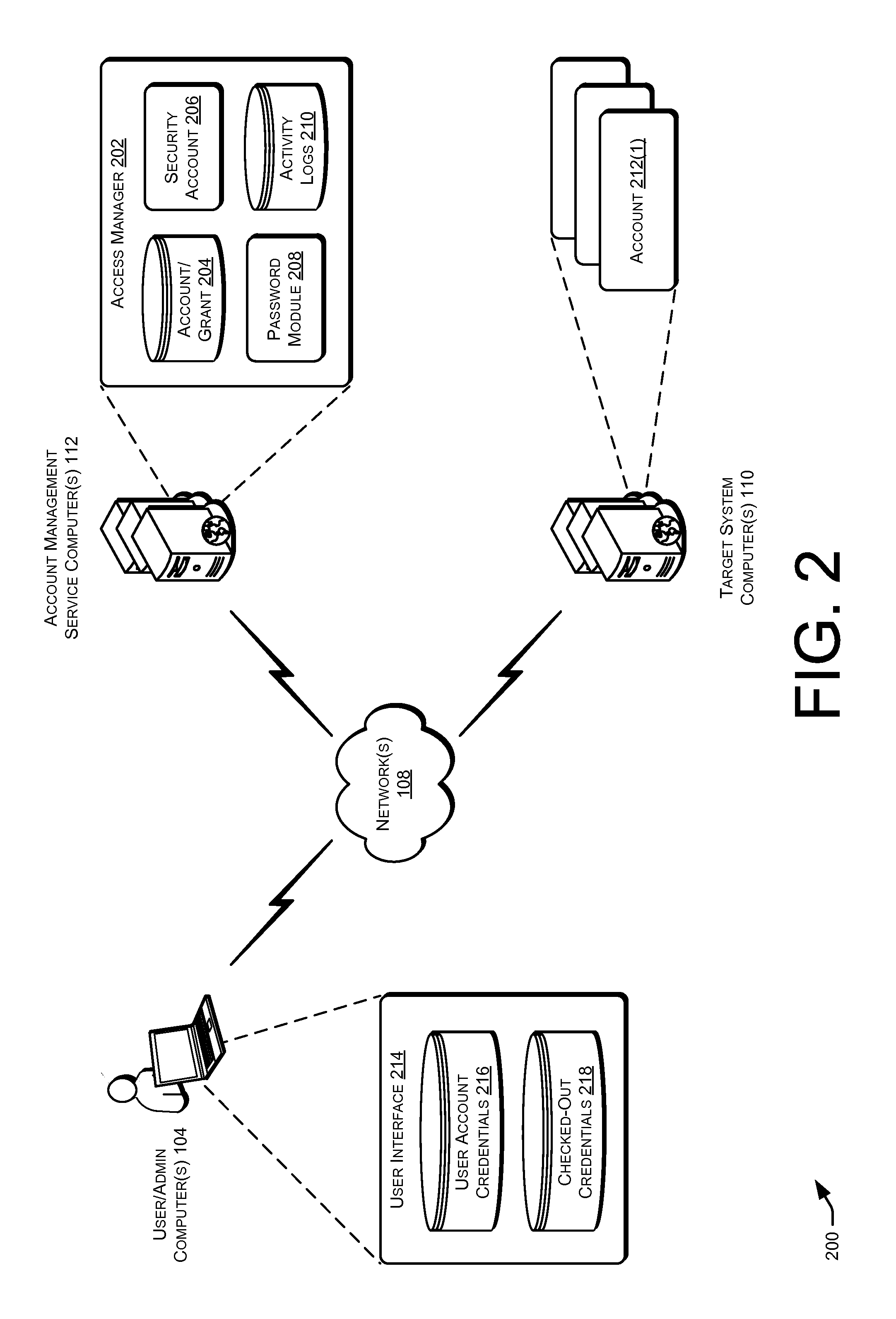
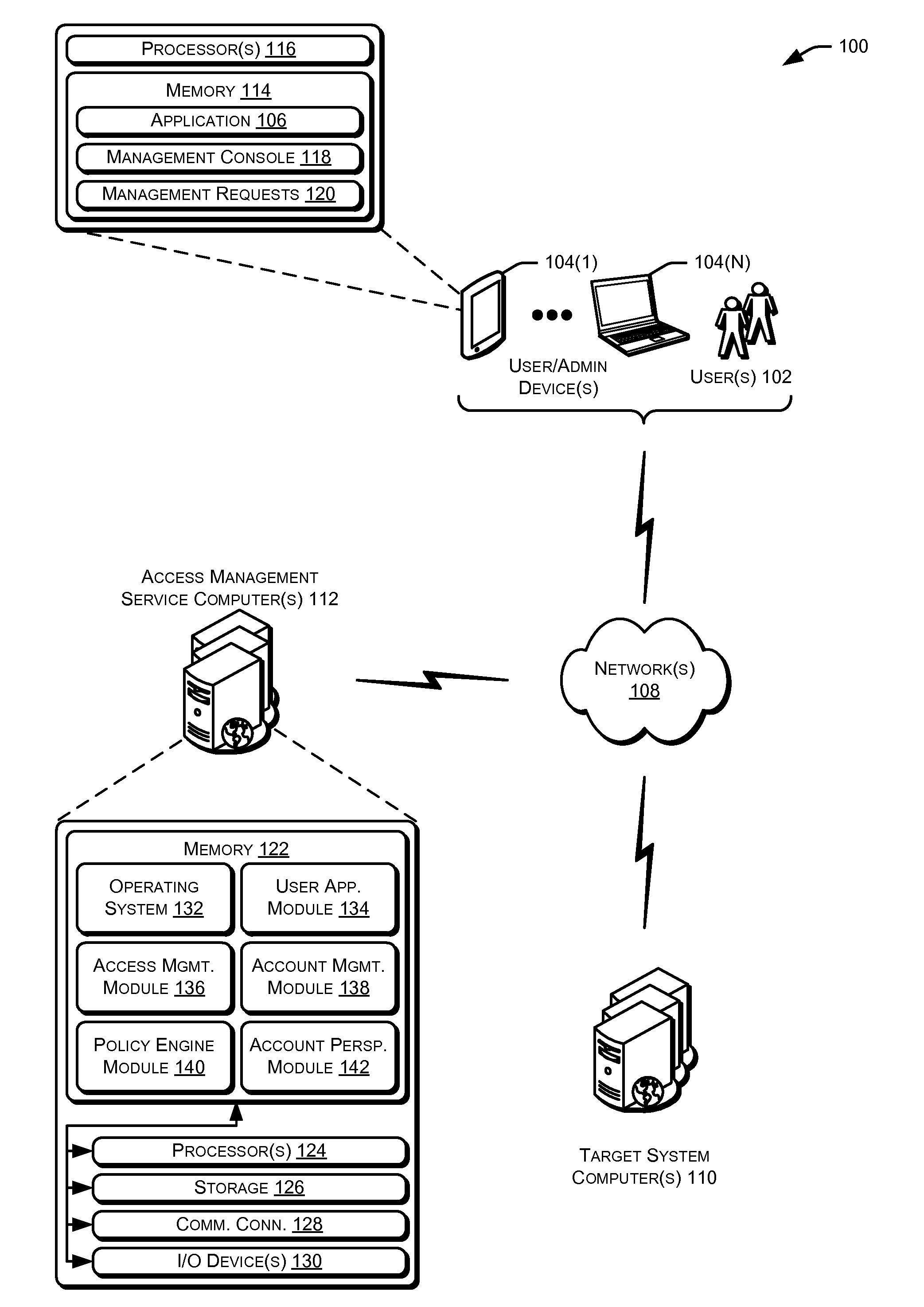
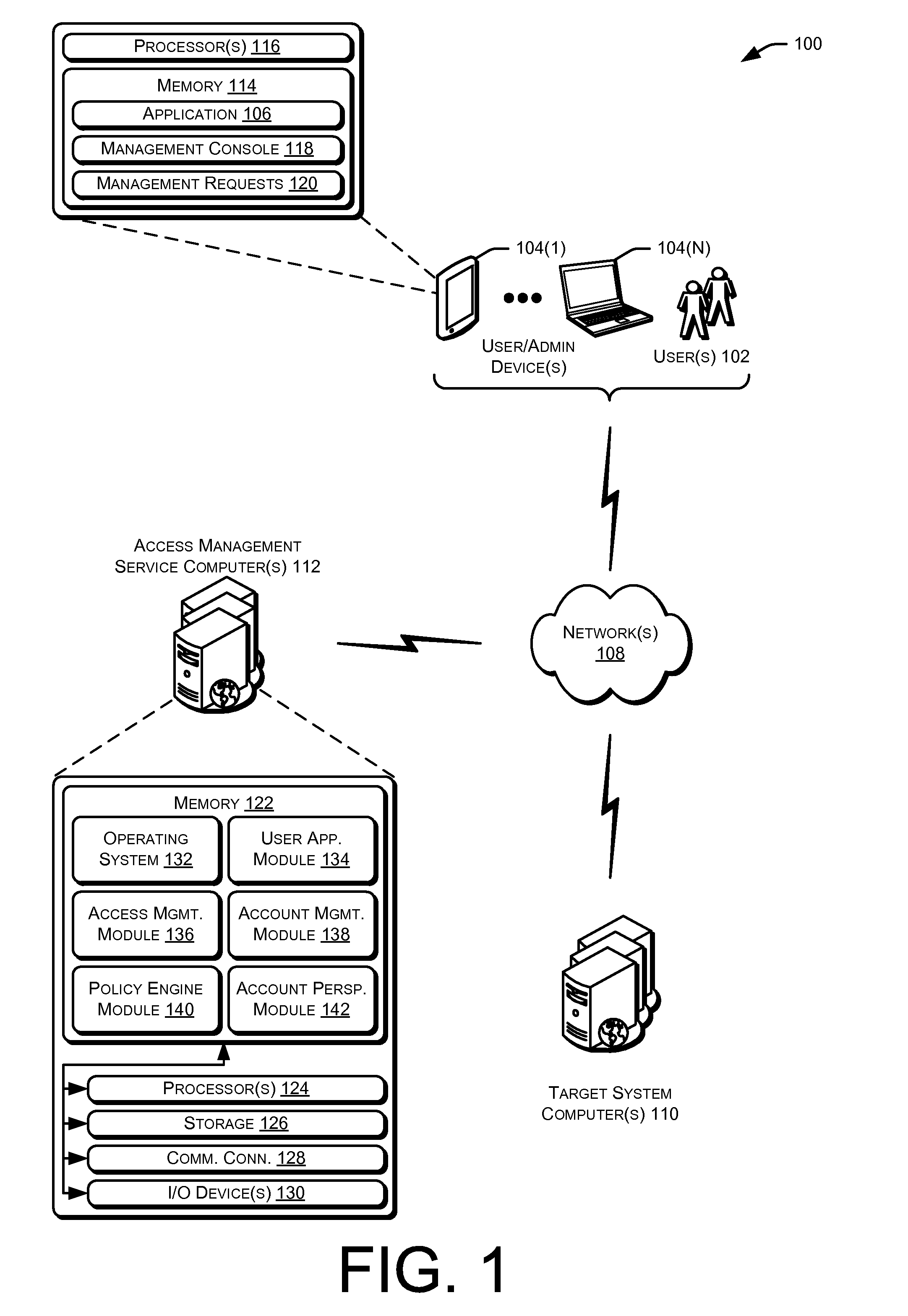
Privileged account manager, access management
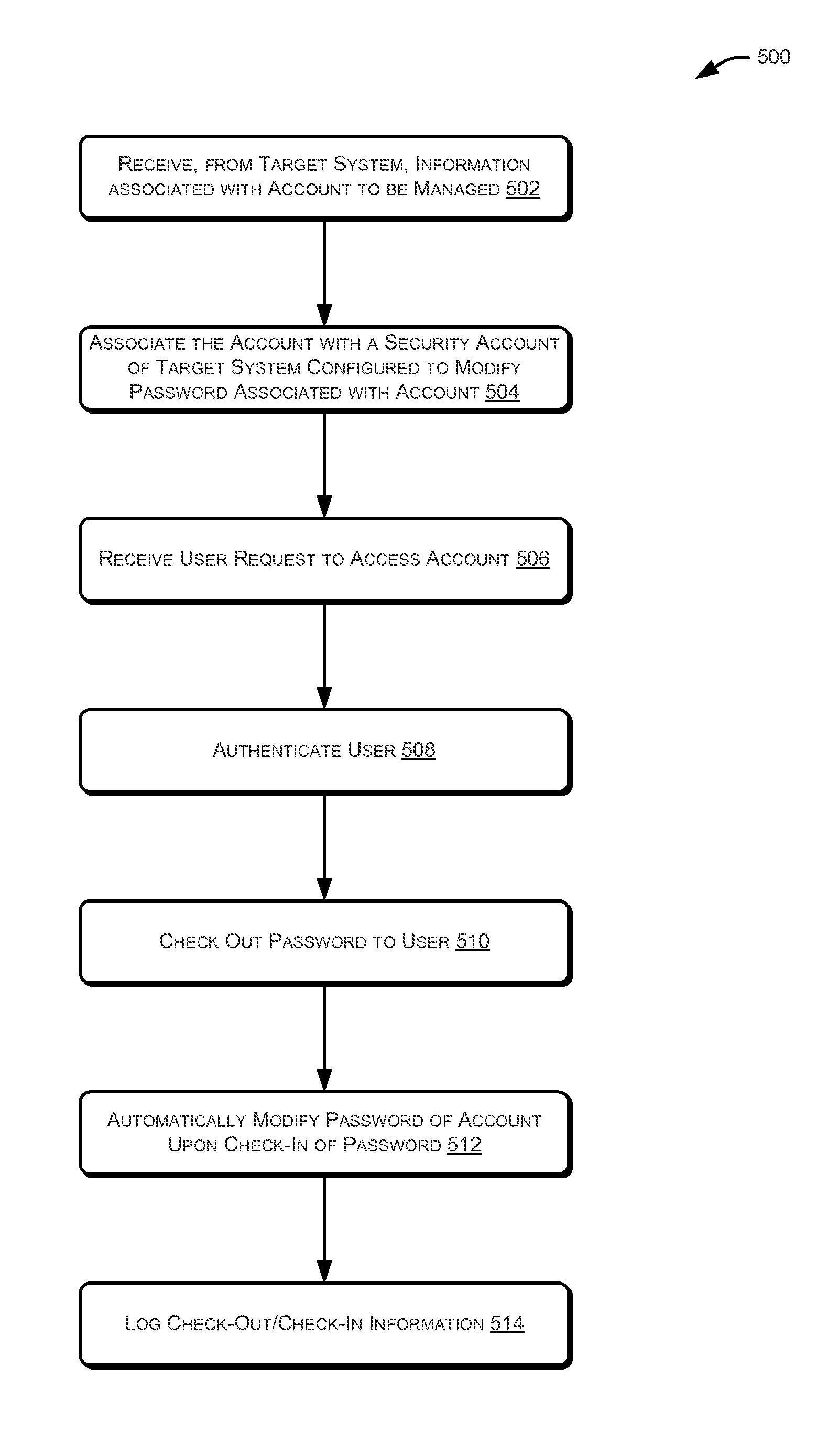
ActiveUS20130086658A1Digital data processing detailsMultiple digital computer combinationsPassword policyInternet privacy
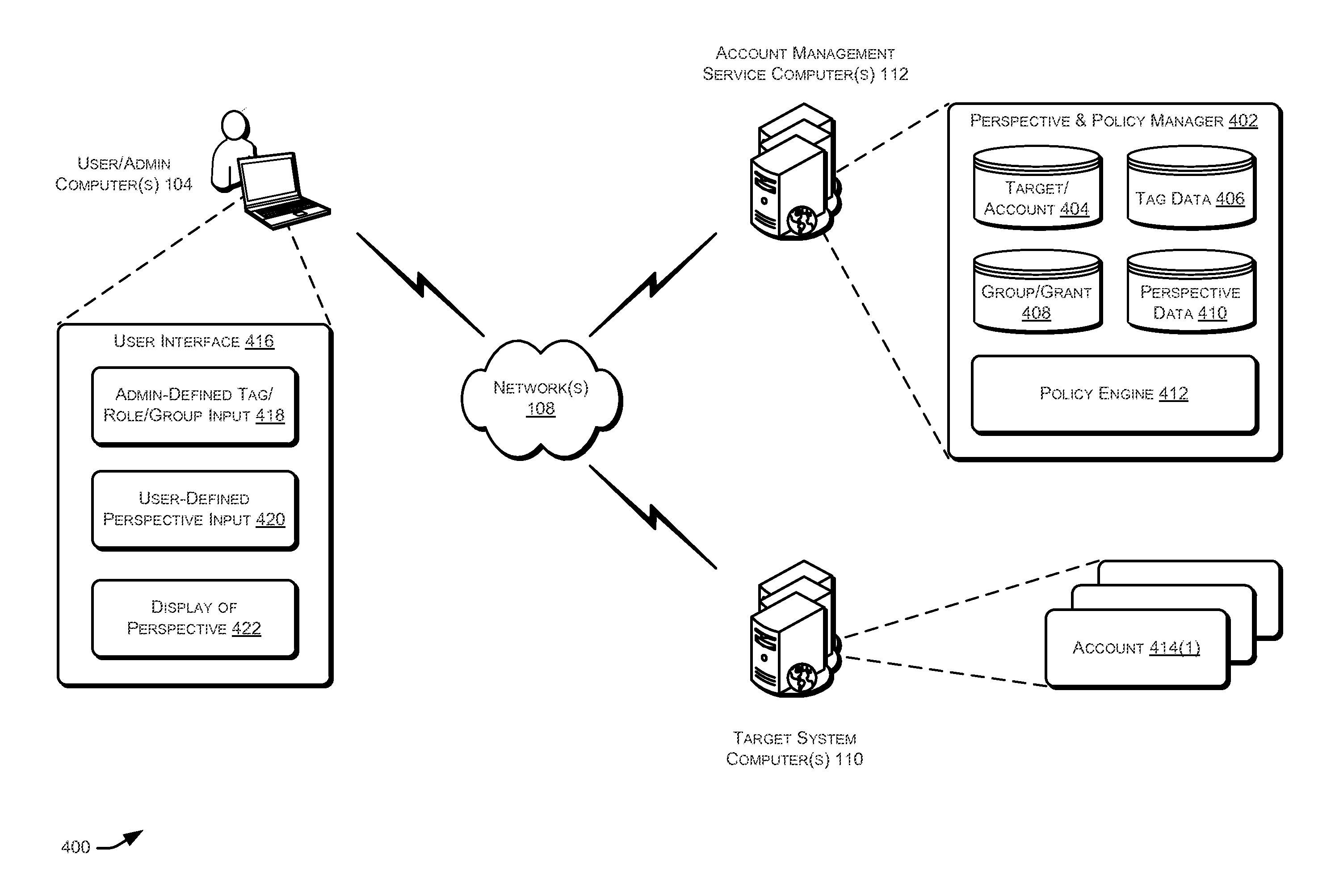
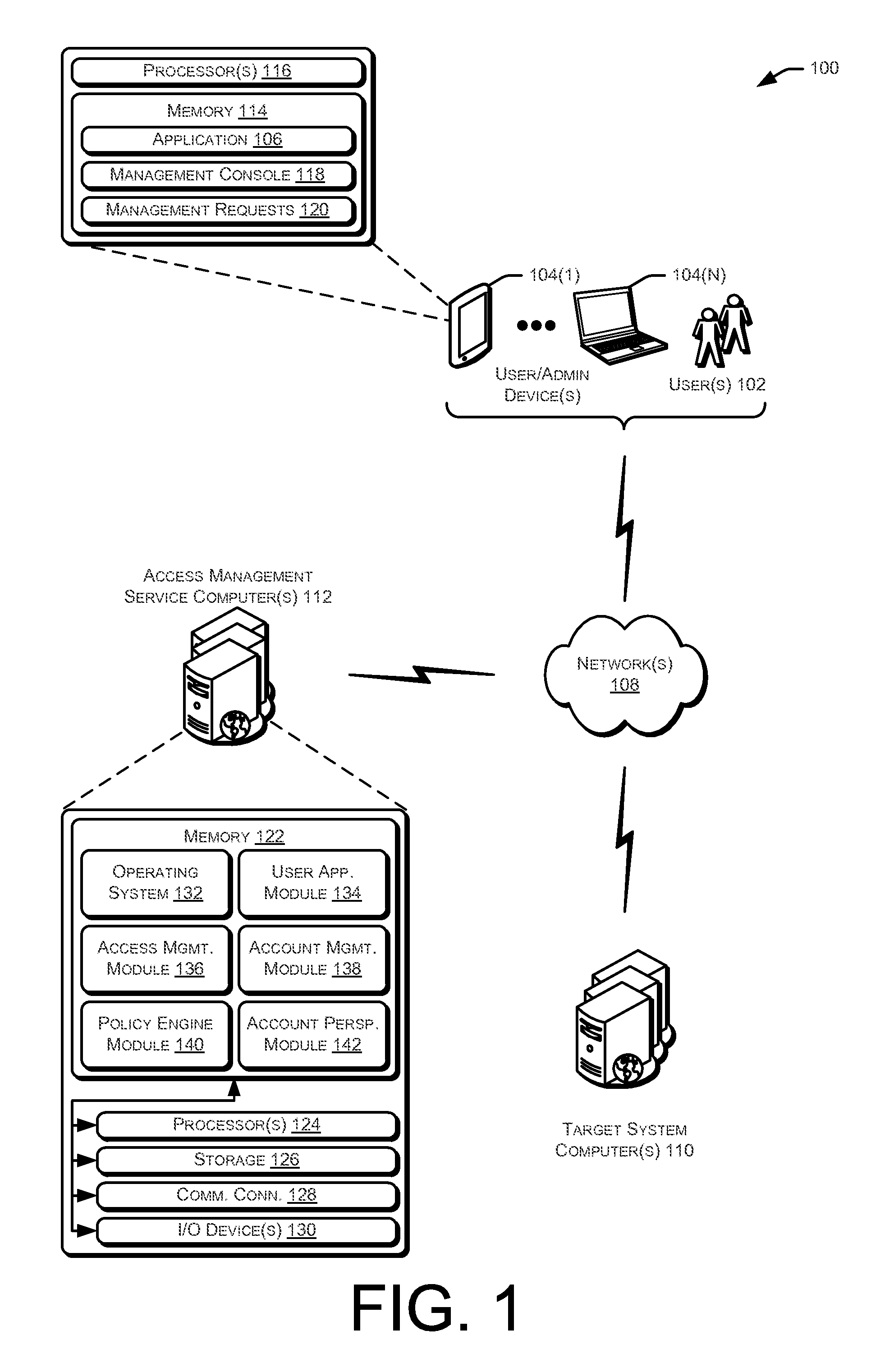
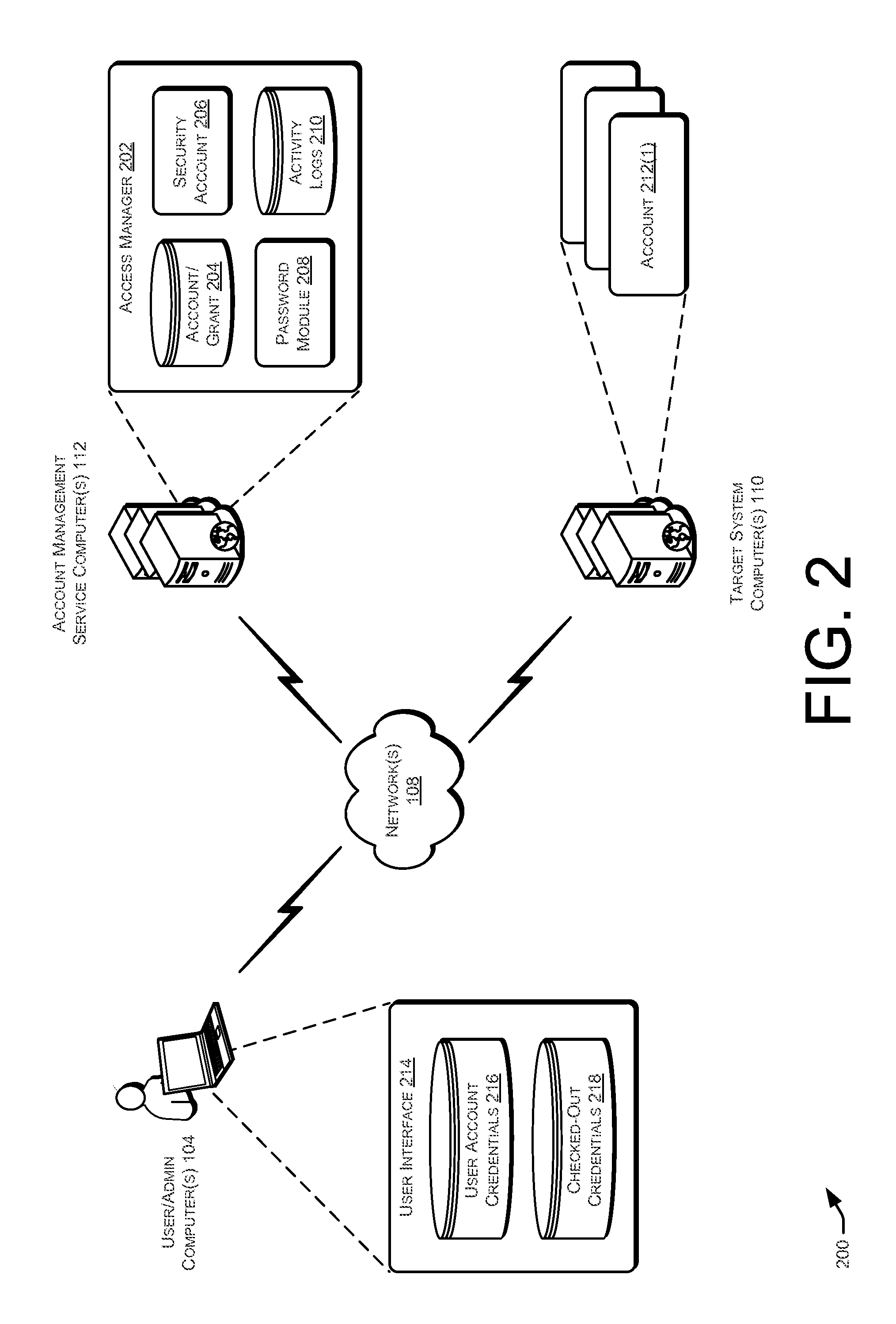
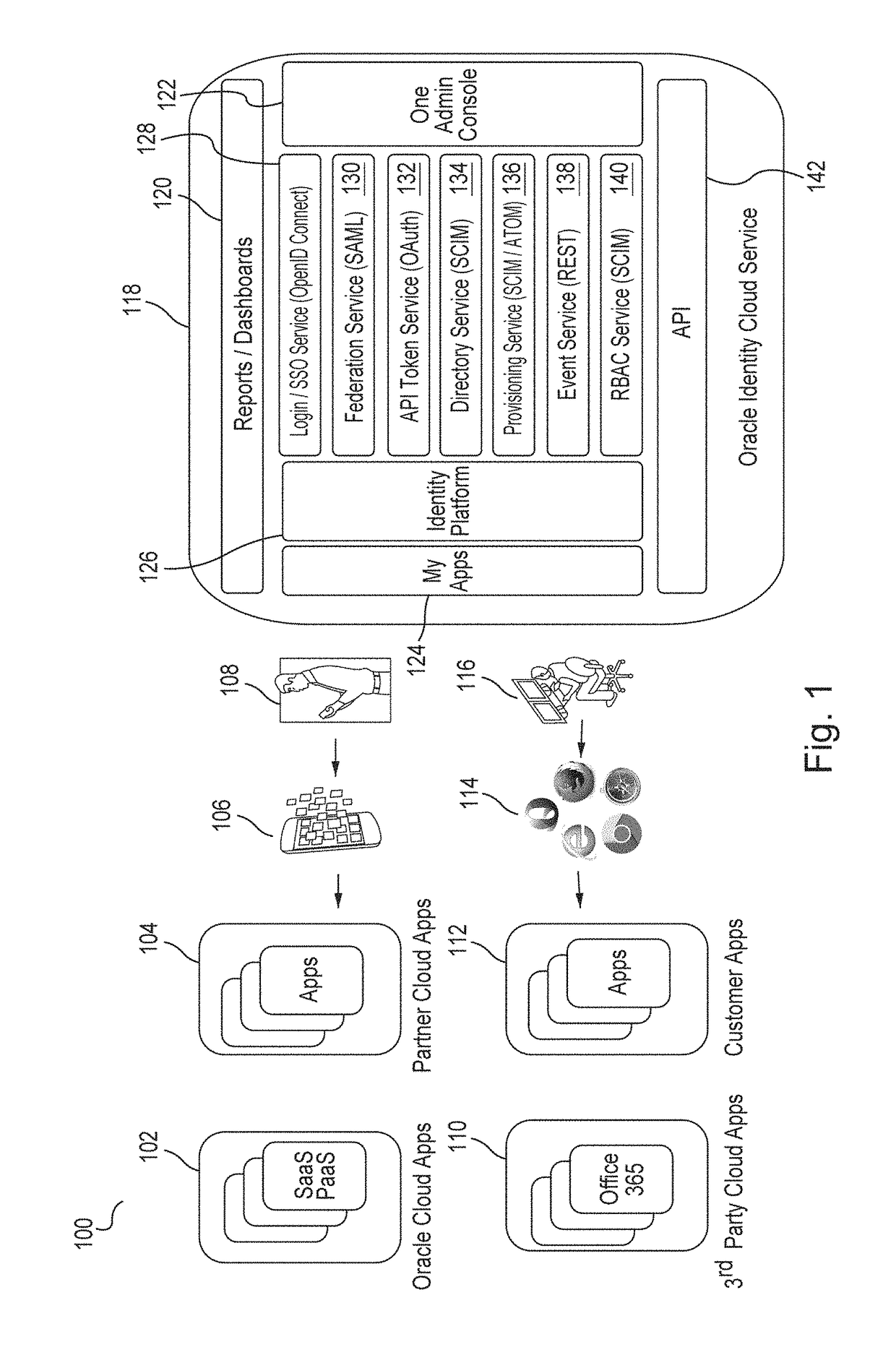
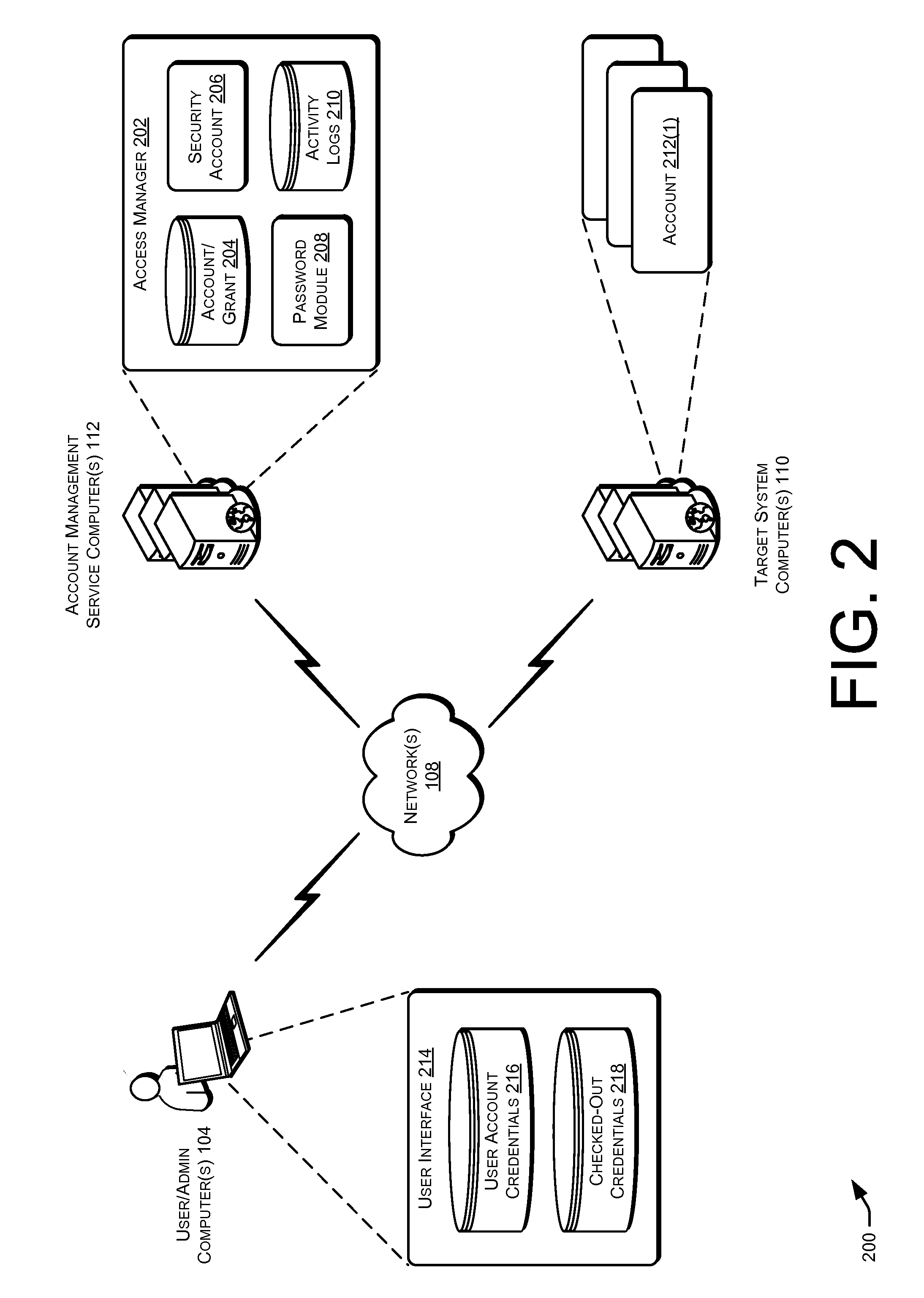
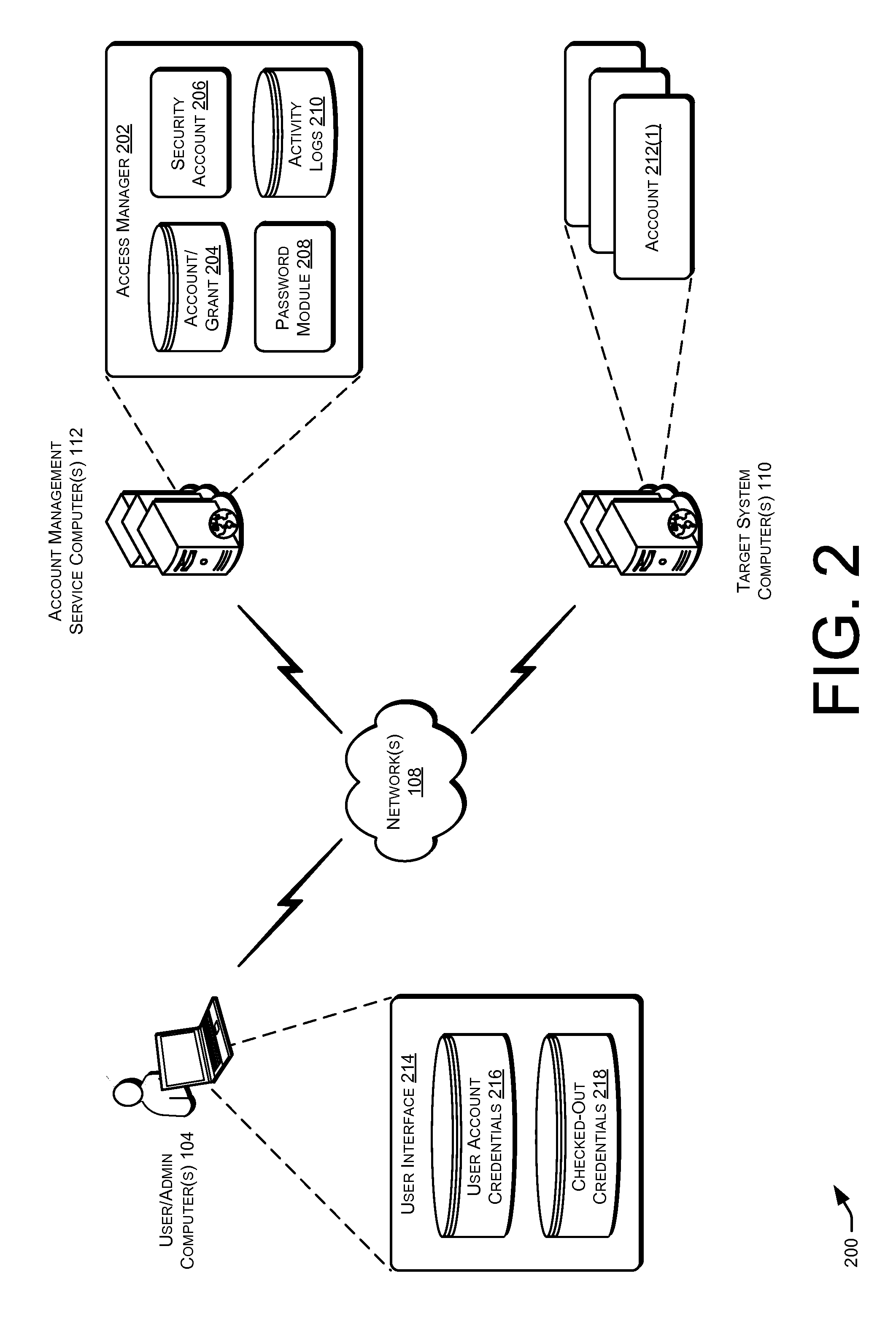
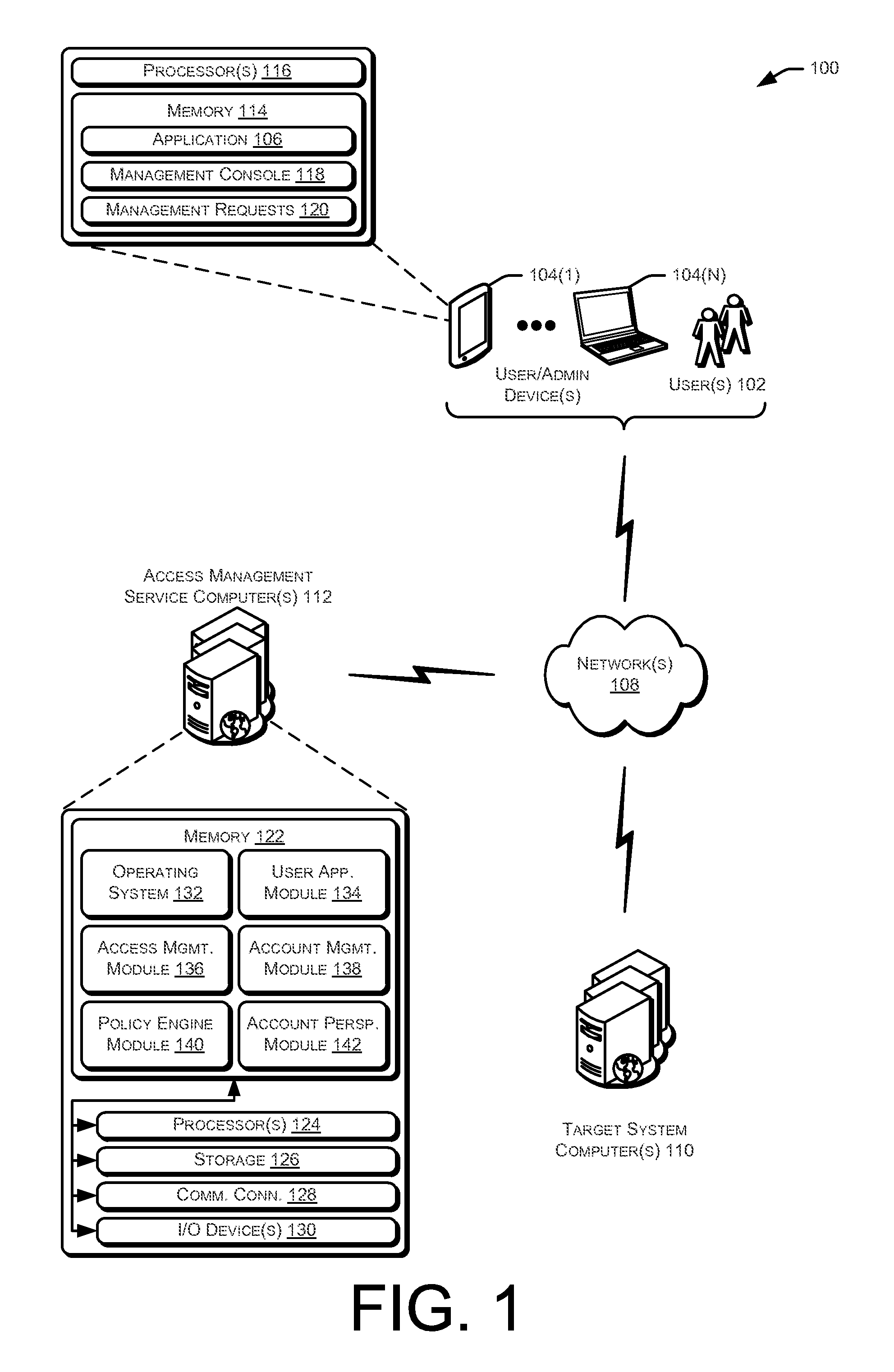
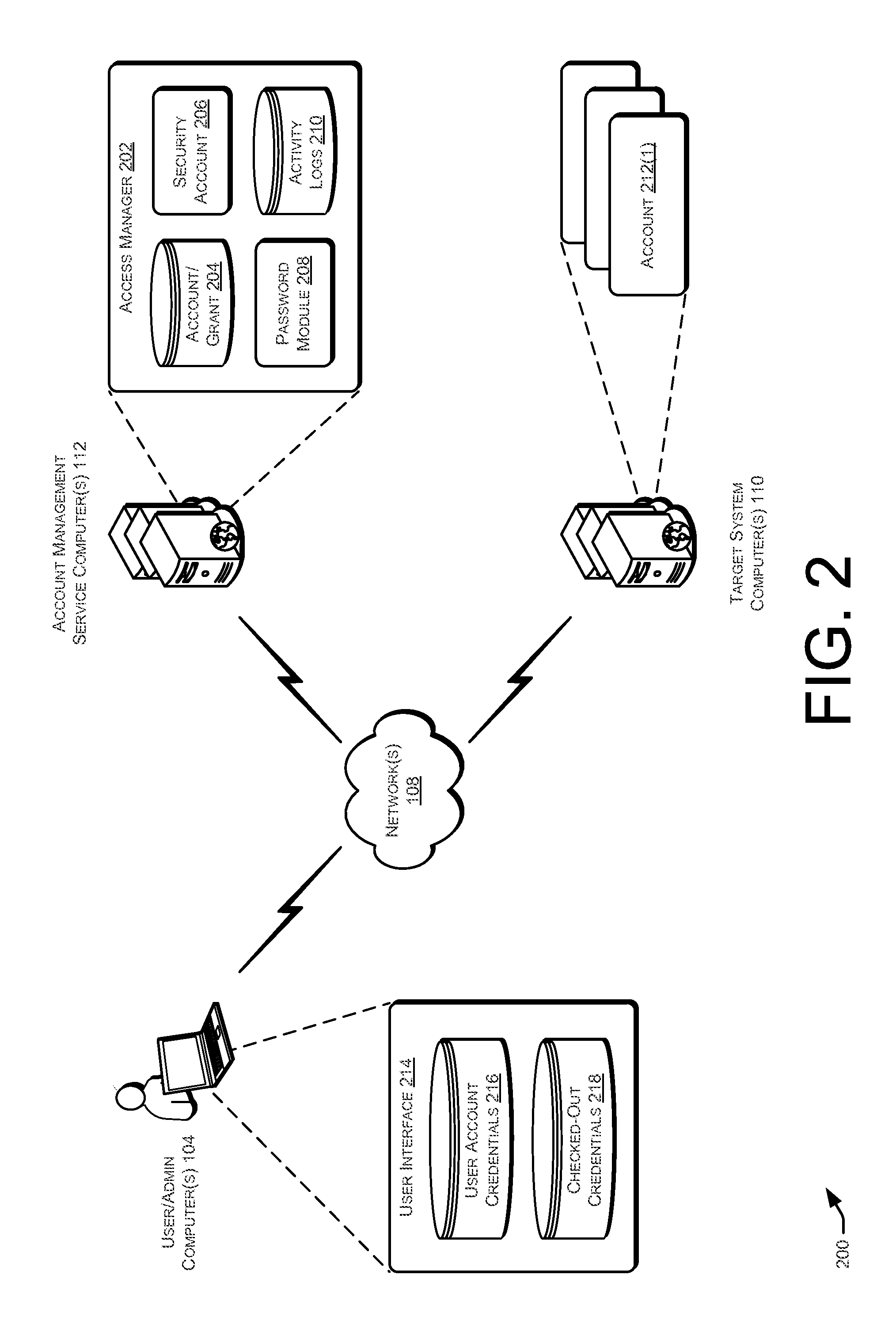
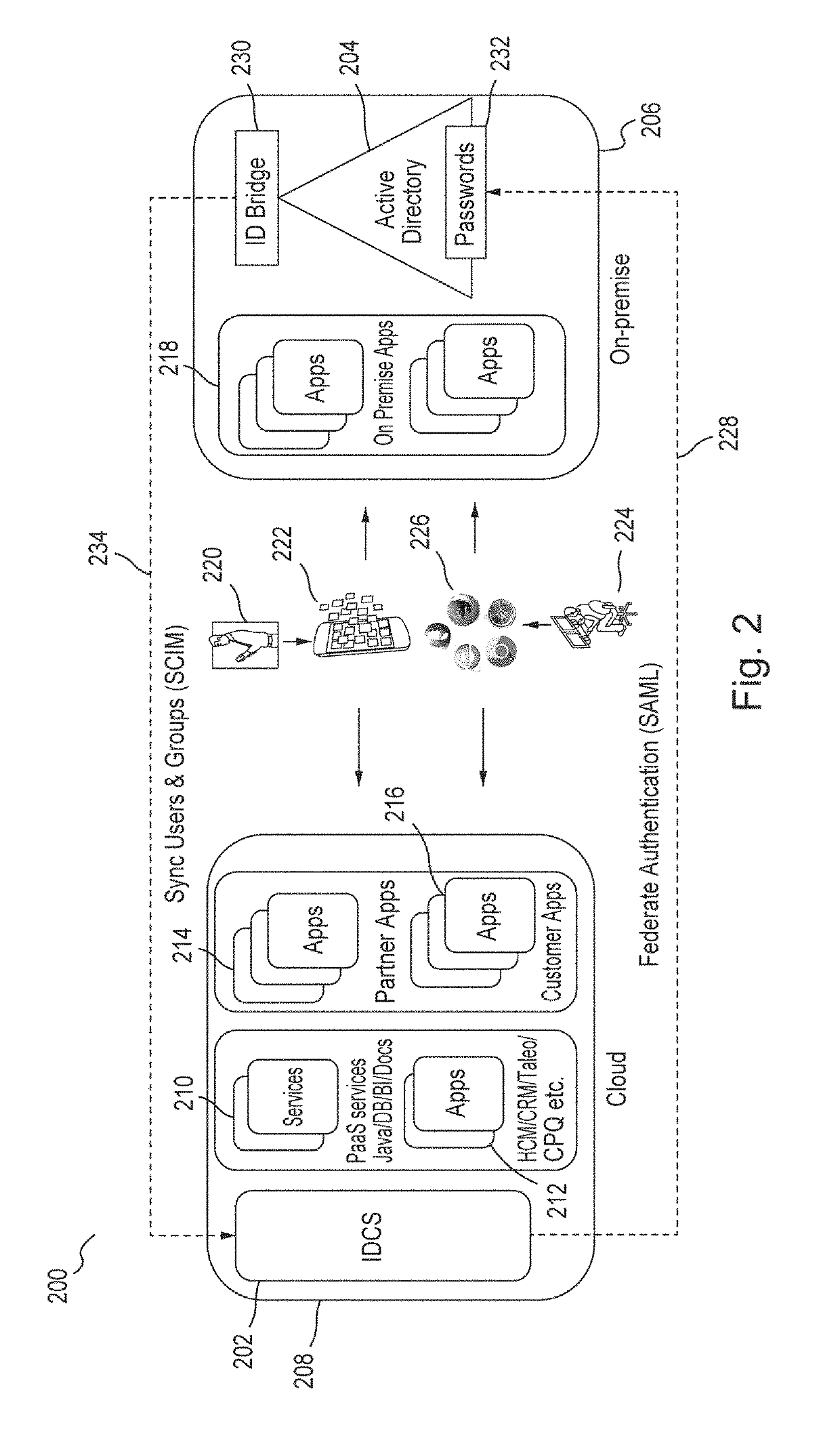
Techniques for managing accounts are provided. An access management system may check out credentials for accessing target systems. For example a user may receive a password for a period of time or until checked back in. Access to the target system may be logged during this time. Upon the password being checked in, a security account may modify the password so that the user may not log back in without checking out a new password. Additionally, in some examples, password policies for the security account may be managed. As such, when a password policy changes, the security account password may be dynamically updated. Additionally, in some examples, hierarchical viewing perspectives may be determined and / or selected for visualizing one or more managed accounts. Further, accounts may be organized into groups based on roles, and grants for the accounts may be dynamically updated as changes occur or new accounts are managed.
Owner:ORACLE INT CORP
User authentication using kerberos with identity cloud service
ActiveUS20180337914A1Key distribution for secure communicationSynchronising transmission/receiving encryption devicesPassword policyPassword
Embodiments authenticate a user in response to receiving from a Kerberos key distribution center (“KDC”) a request to authenticate the user that includes a user identification (“ID”). Embodiments retrieve a user record corresponding to the user ID, the user record including a principal key. Embodiments decrypt the principal key using a tenant-specific encryption key and encrypt the decrypted principal key using a Kerberos master key to generate an encrypted principal key. Embodiments retrieve a password policy corresponding to the user ID. Based on the retrieved password policies, embodiments construct password state attributes and return to the KDC the encrypted principal key, the password policy and the password state attributes.
Owner:ORACLE INT CORP
Privileged account manager, managed account perspectives
ActiveUS20130086060A1Digital data processing detailsDigital data authenticationPassword policyPassword
Techniques for managing accounts are provided. An access management system may check out credentials for accessing target systems. For example a user may receive a password for a period of time or until checked back in. Access to the target system may be logged during this time. Upon the password being checked in, a security account may modify the password so that the user may not log back in without checking out a new password. Additionally, in some examples, password policies for the security account may be managed. As such, when a password policy changes, the security account password may be dynamically updated. Additionally, in some examples, hierarchical viewing perspectives may be determined and / or selected for visualizing one or more managed accounts. Further, accounts may be organized into groups based on roles, and grants for the accounts may be dynamically updated as changes occur or new accounts are managed.
Owner:ORACLE INT CORP
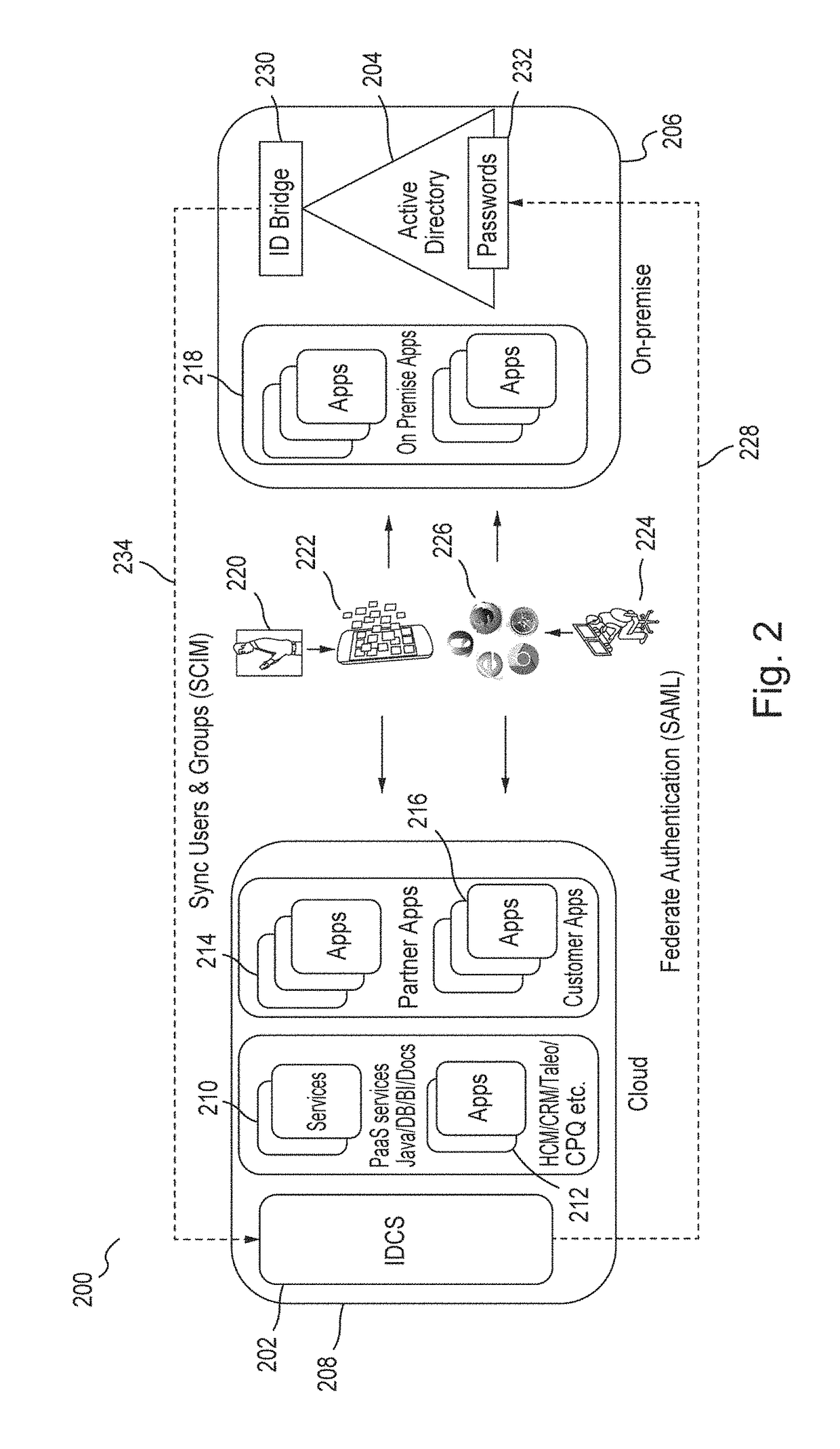
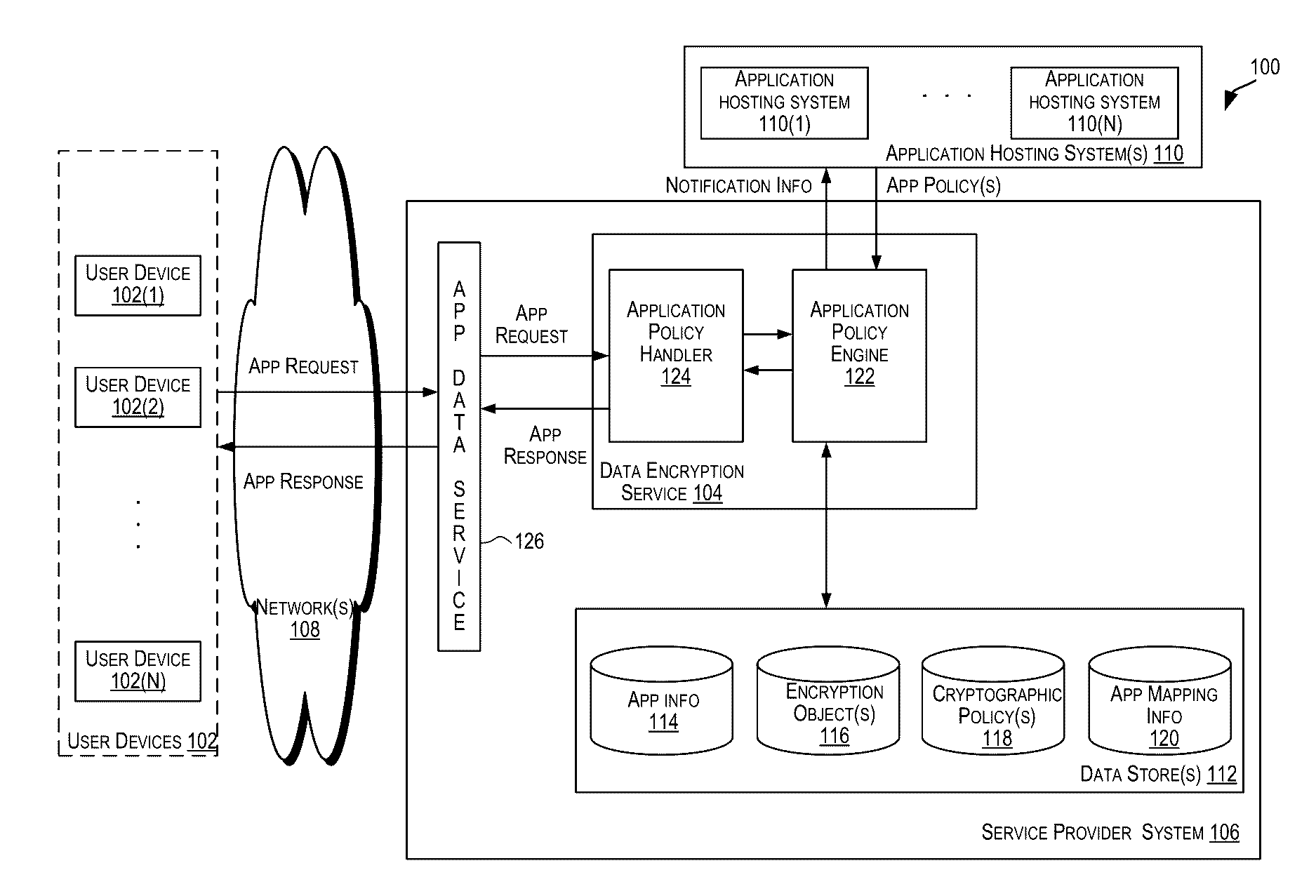
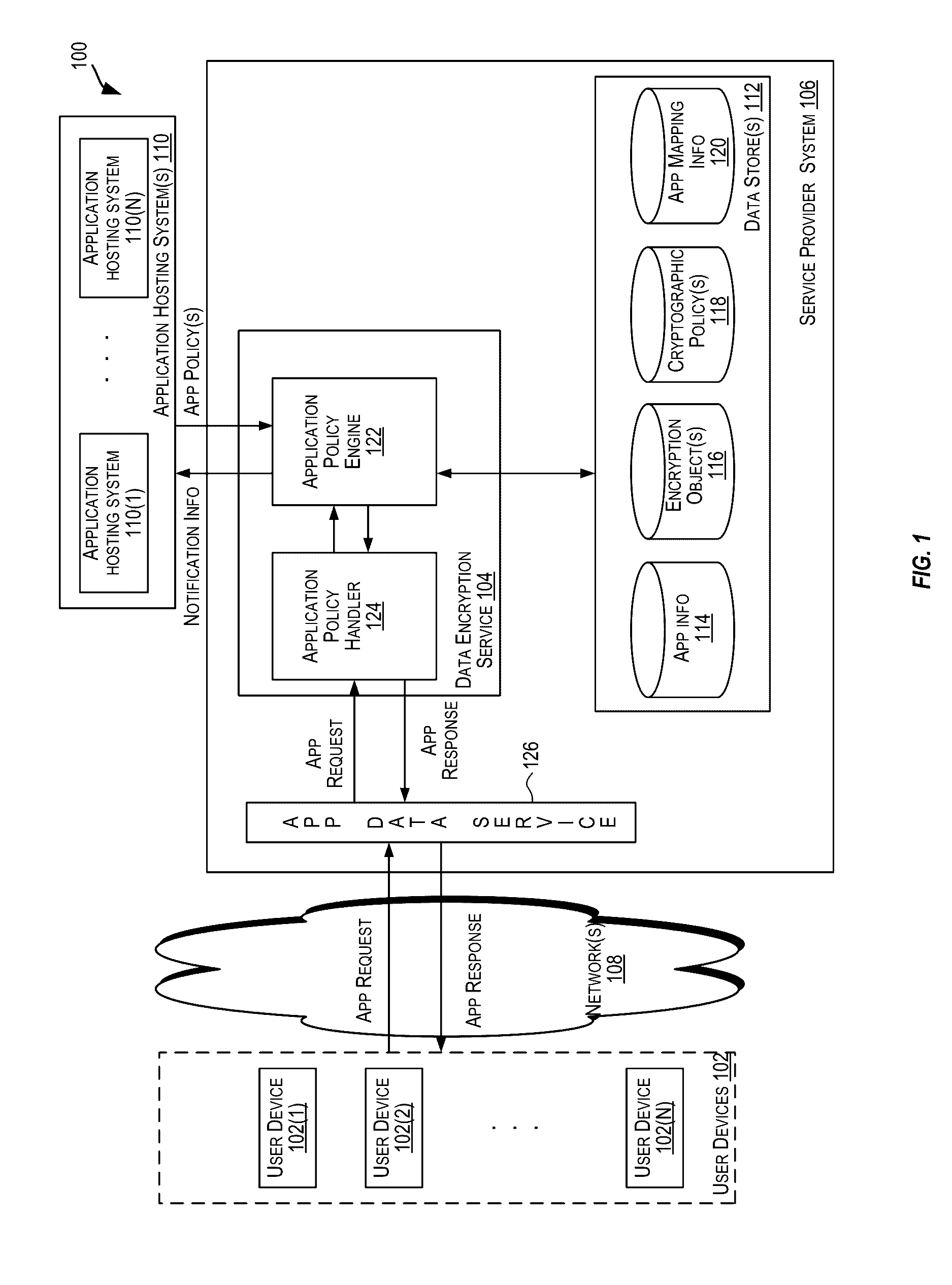
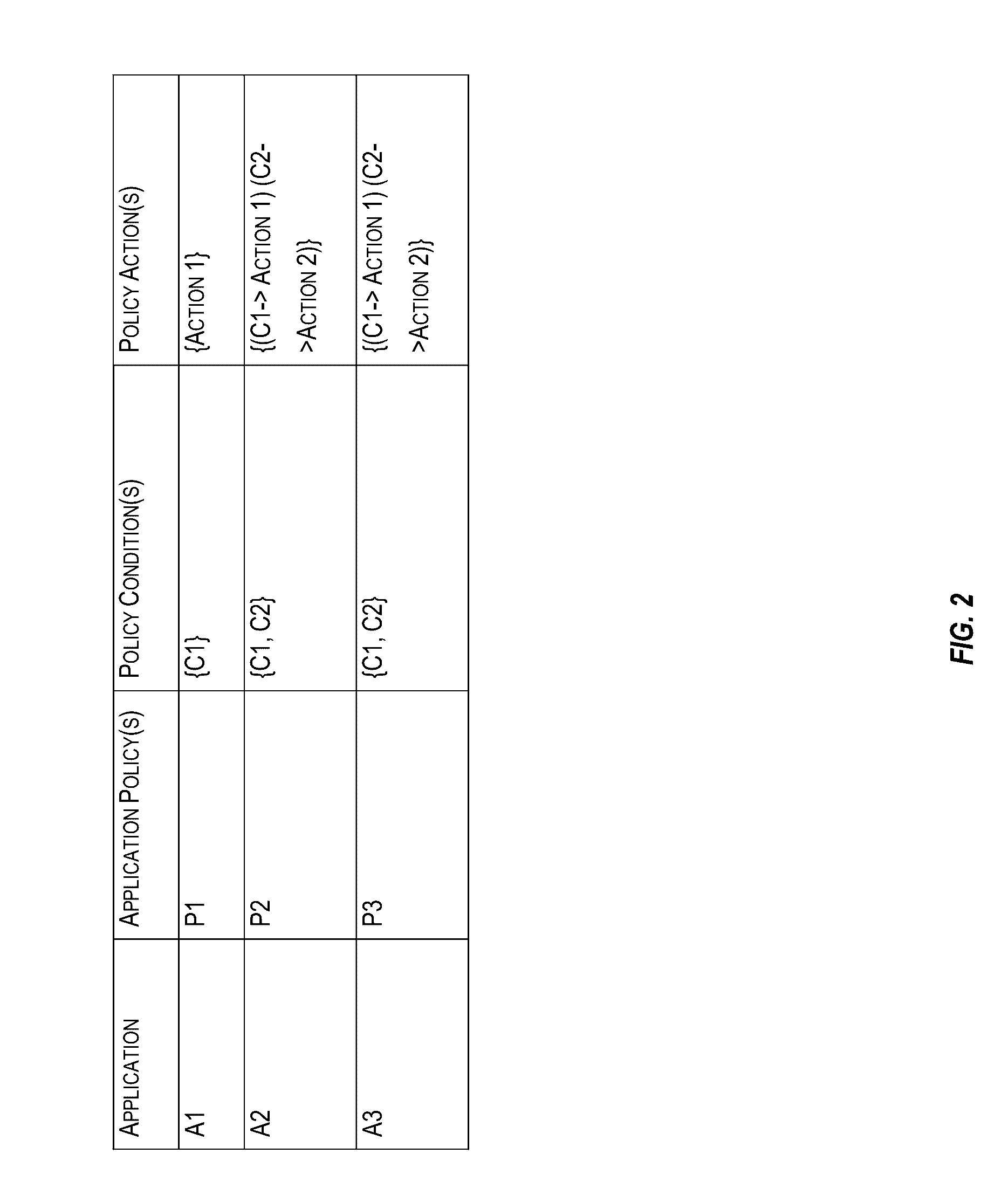
Data encryption service
ActiveUS20170006064A1User identity/authority verificationComputer security arrangementsPassword policyInternet privacy
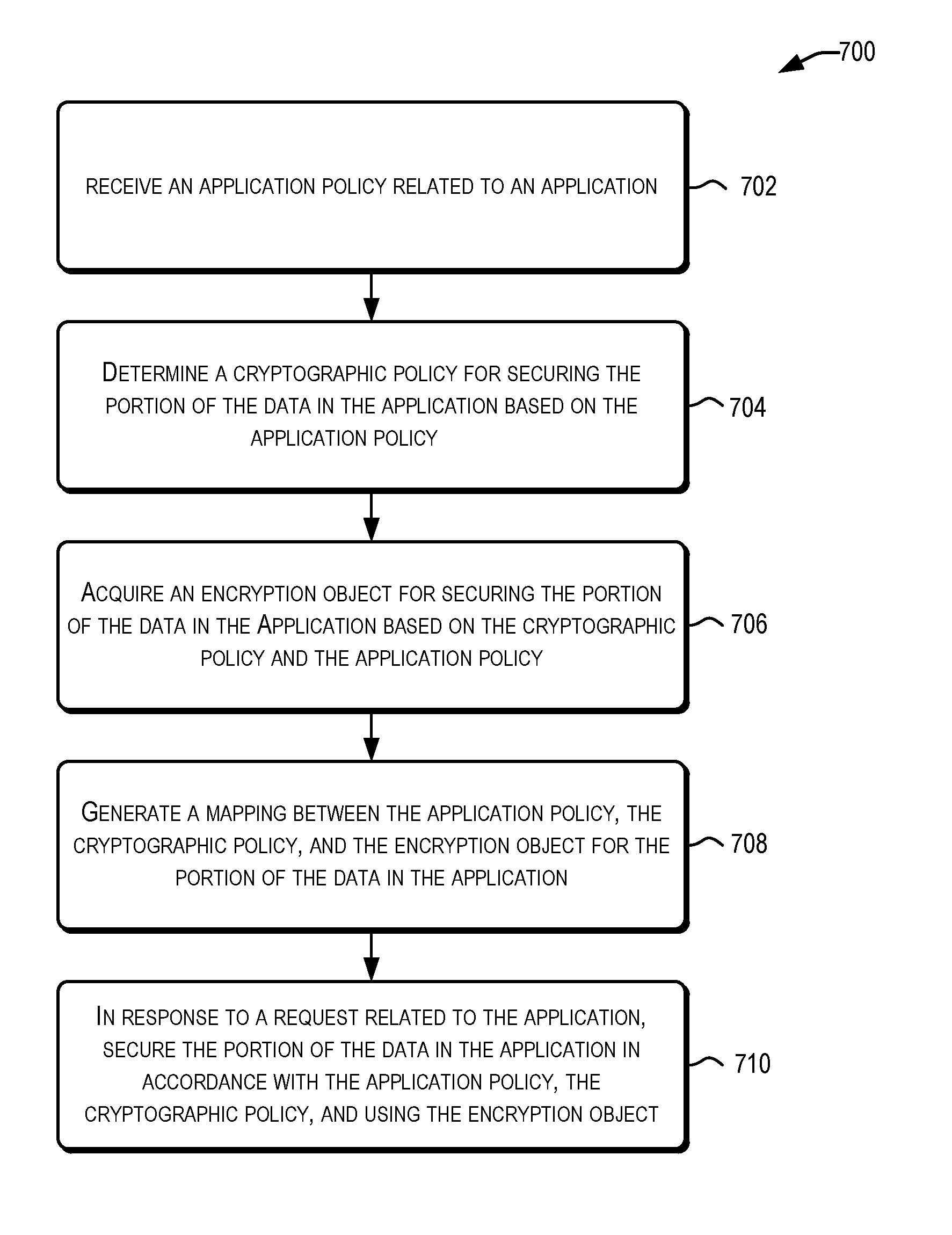
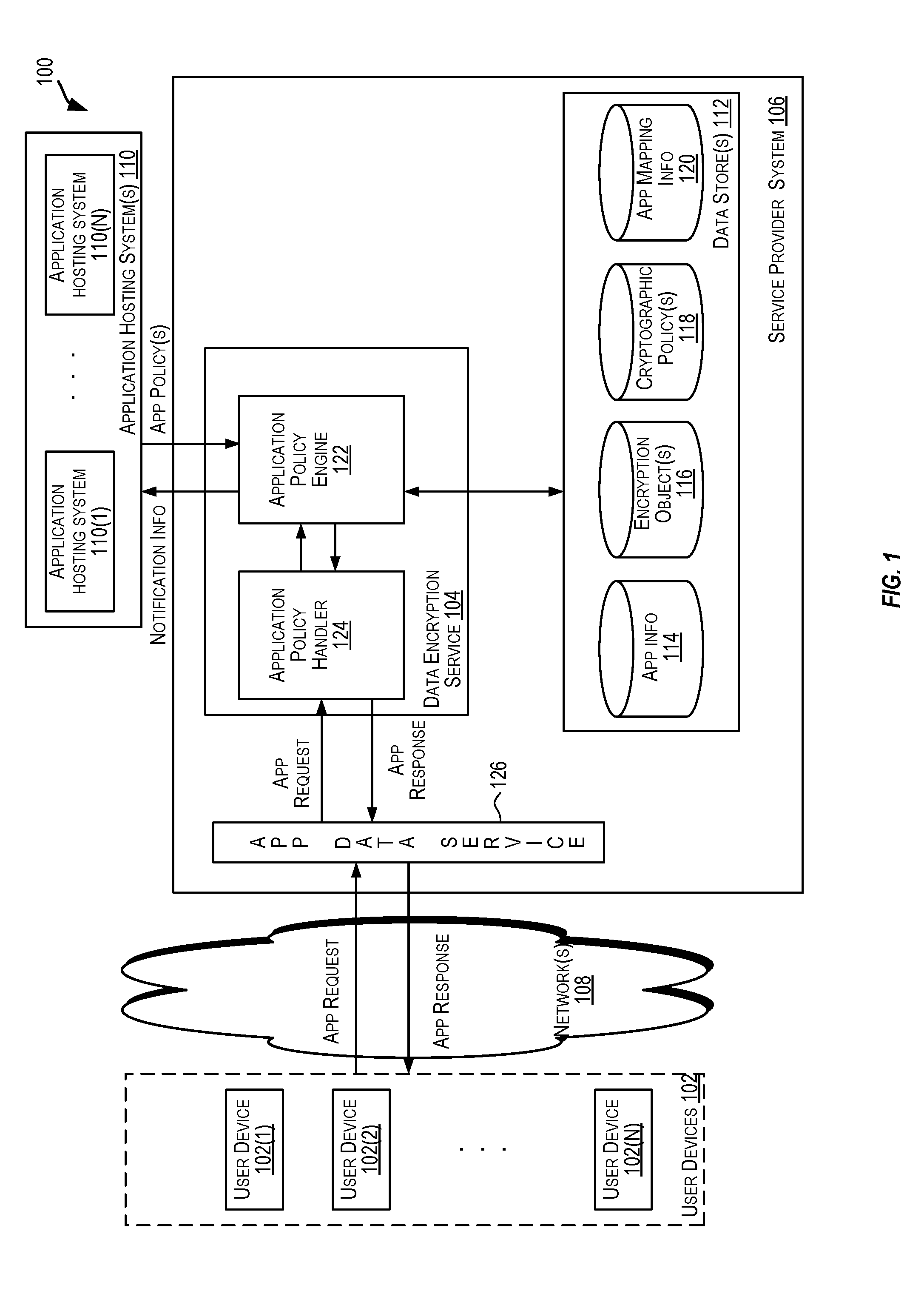
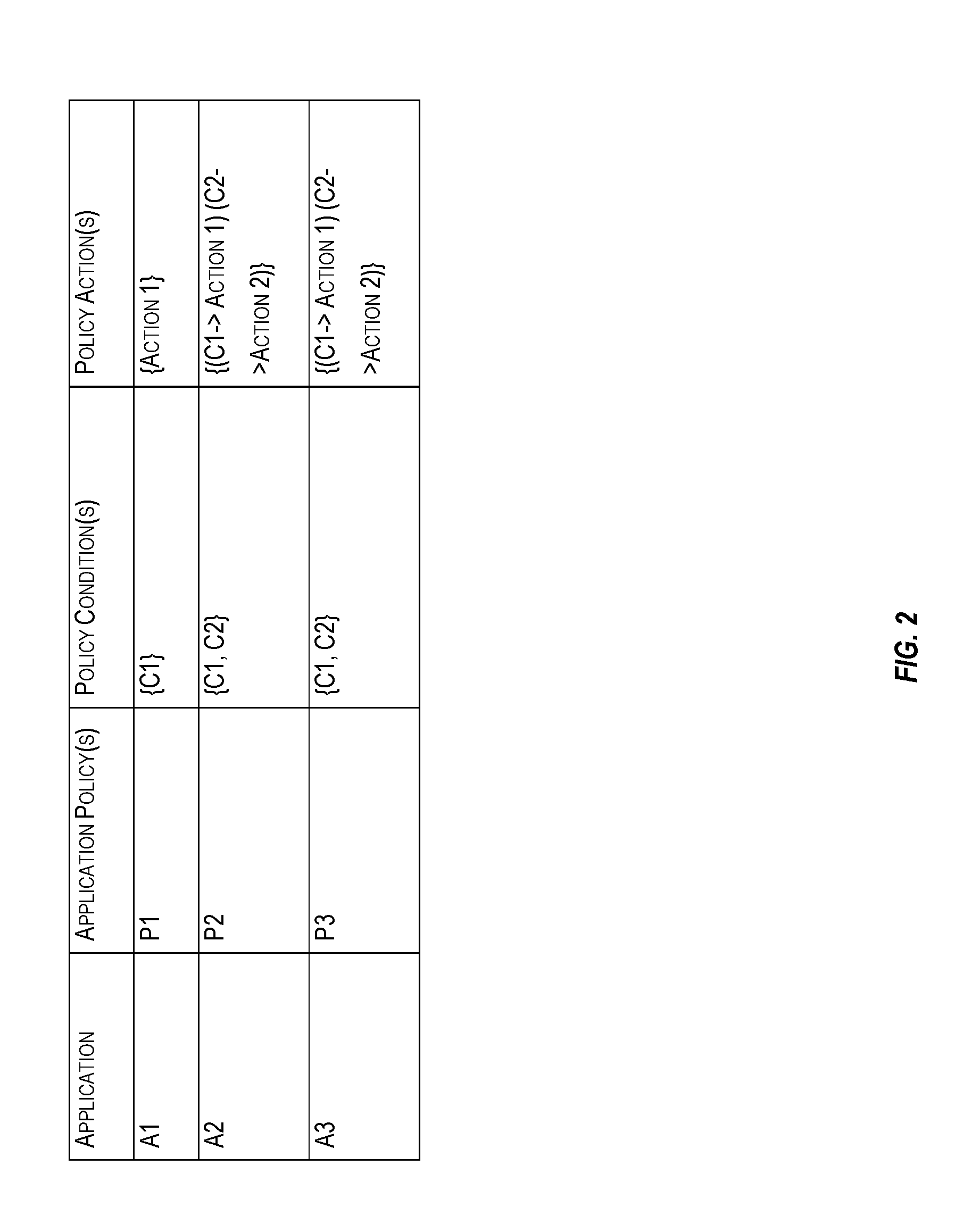
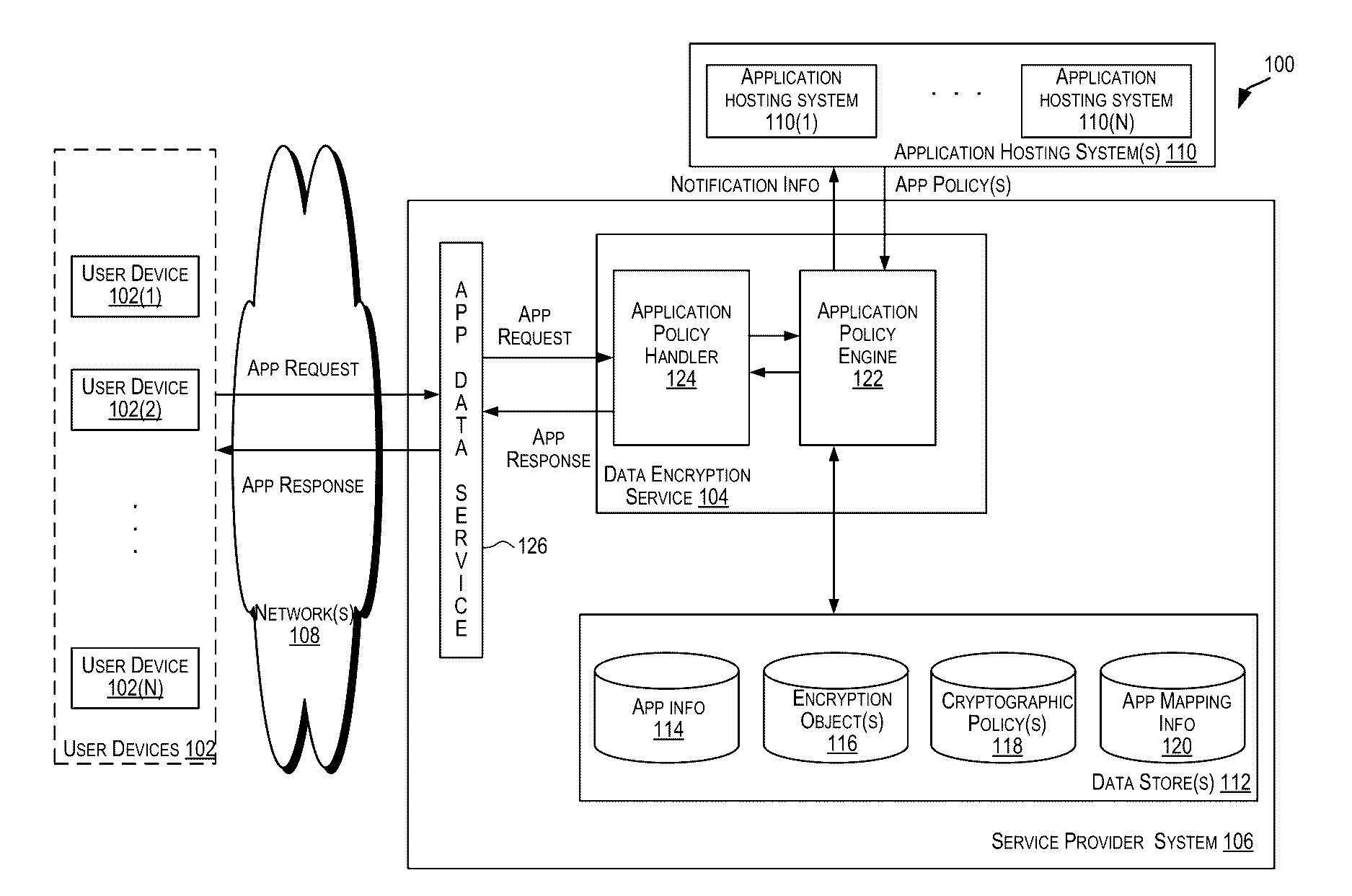
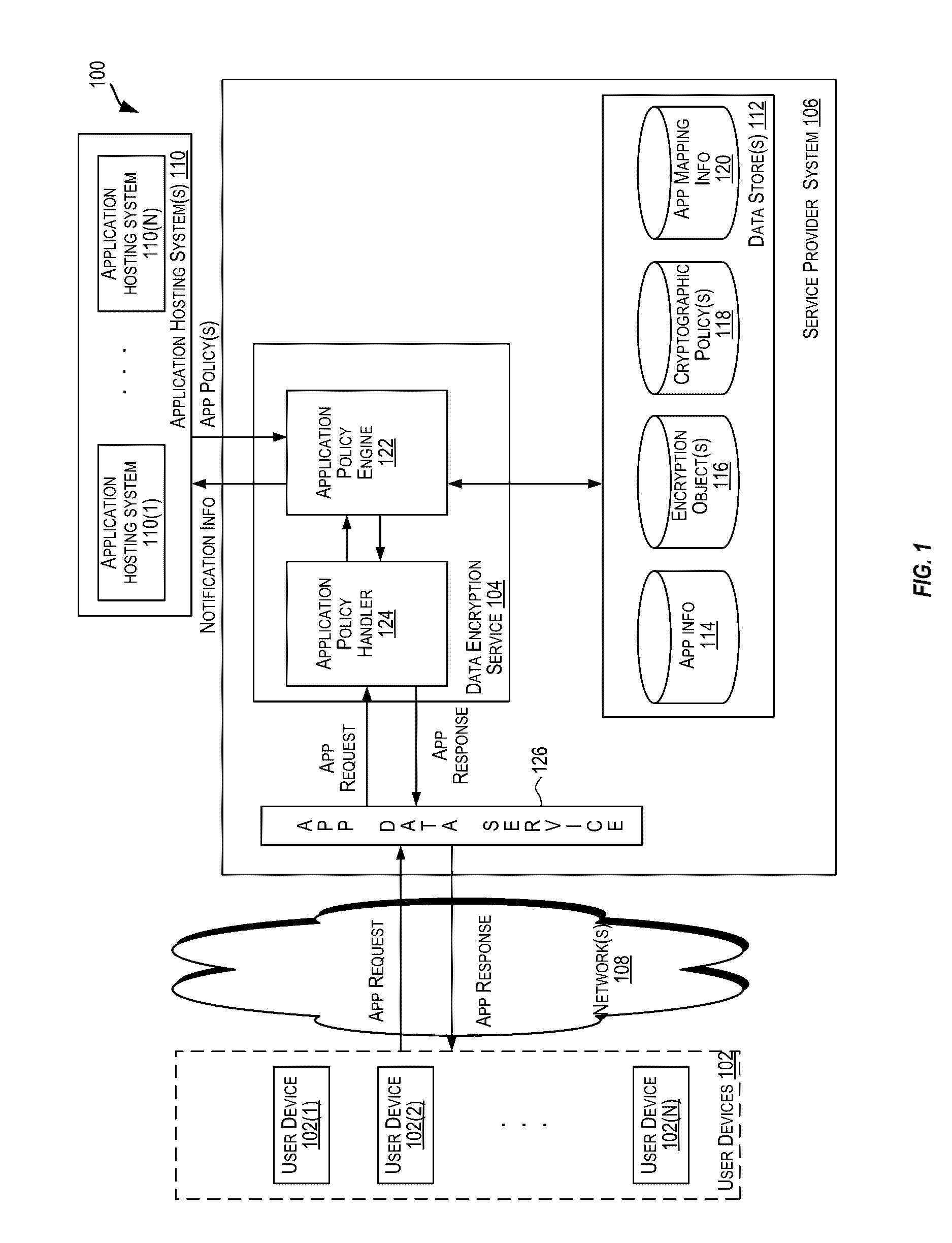
A centralized framework for managing the data encryption of resources is disclosed. A data encryption service is disclosed that provides various services related to the management of the data encryption of resources. The services may include managing application policies, cryptographic policies, and encryption objects related to applications. The encryption objects may include encryption keys and certificates used to secure the resources. In an embodiment, the data encryption service may be included or implemented in a cloud computing environment and may provide a centralized framework for effectively managing the data encryption requirements of various applications hosted or provided by different customer systems. The disclosed data encryption service may provide monitoring and alert services related to encryption objects managed by the data encryption service and transmit the alerts related to the encryption objects via various communication channels.
Owner:ORACLE INT CORP
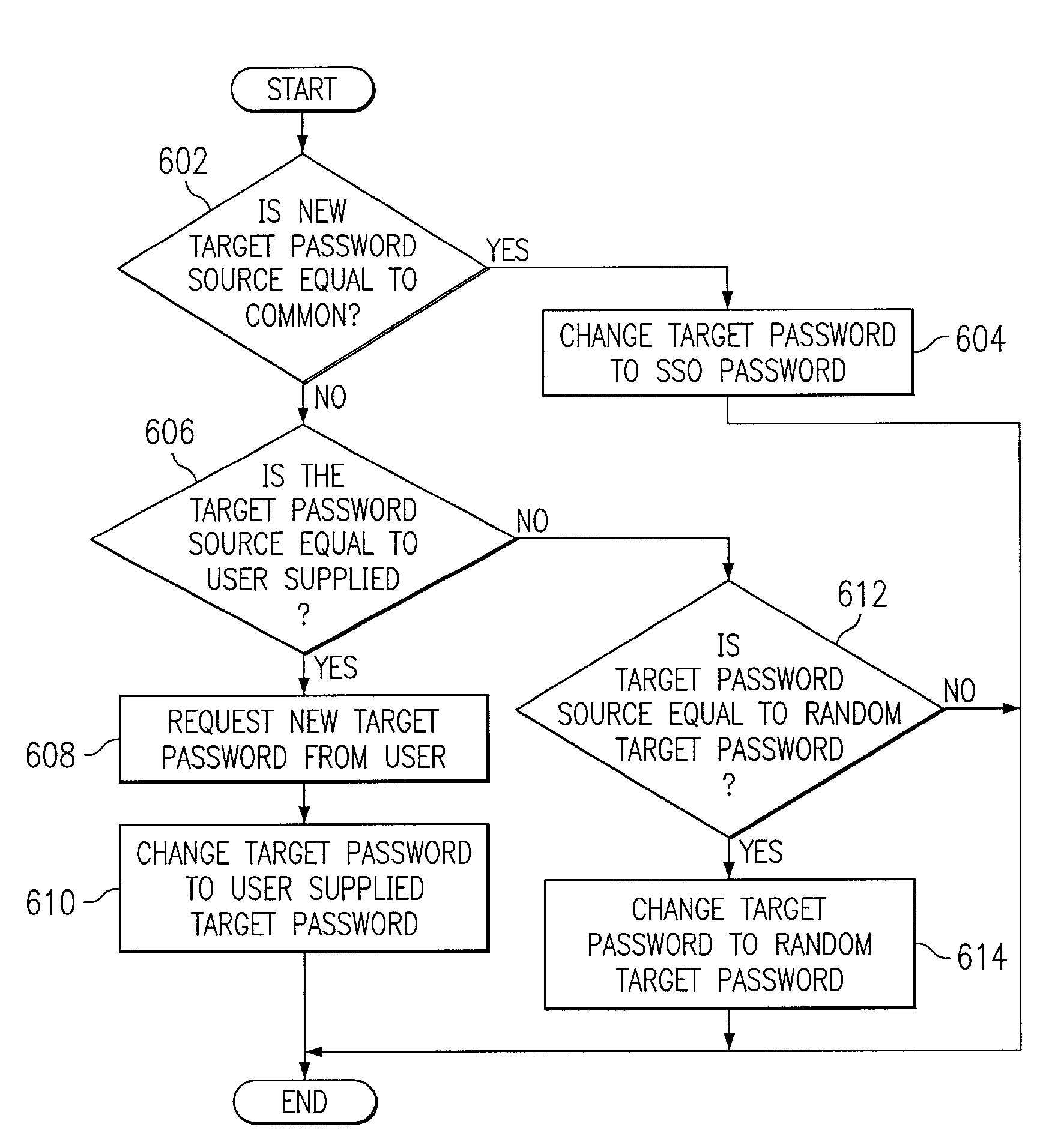
Incorporating password change policy into a single sign-on environment
ActiveUS7260838B2Digital data processing detailsUser identity/authority verificationPassword policyPassword
Method, instructions and system for establishing and enforcing change password policy in a single sign-on environment. In response to receiving a change instruction identifying a first single sign-on password, the first single sign-on password is changed to create a second single sign-on password. Then a target password is retrieved. The target password is modified in a user selected manner to match the second single sign-on password to create a modified target password. The modified target password is stored. In response to a request from a user requesting access to an application, the modified target password is retrieved and the modified target password is provided to the requested application.
Owner:TREND MICRO INC
Privileged account manager, application account management
ActiveUS20130086628A1Digital data processing detailsMultiple digital computer combinationsPassword policyPassword
Techniques for managing accounts are provided. An access management system may check out credentials for accessing target systems. For example a user may receive a password for a period of time or until checked back in. Access to the target system may be logged during this time. Upon the password being checked in, a security account may modify the password so that the user may not log back in without checking out a new password. Additionally, in some examples, password policies for the security account may be managed. As such, when a password policy changes, the security account password may be dynamically updated. Additionally, in some examples, hierarchical viewing perspectives may be determined and / or selected for visualizing one or more managed accounts. Further, accounts may be organized into groups based on roles, and grants for the accounts may be dynamically updated as changes occur or new accounts are managed.
Owner:ORACLE INT CORP
Privileged account manager, dynamic policy engine
ActiveUS20130086065A1Digital data processing detailsDigital data authenticationManagement systemPassword policy
Techniques for managing accounts are provided. An access management system may check out credentials for accessing target systems. For example a user may receive a password for a period of time or until checked back in. Access to the target system may be logged during this time. Upon the password being checked in, a security account may modify the password so that the user may not log back in without checking out a new password. Additionally, in some examples, password policies for the security account may be managed. As such, when a password policy changes, the security account password may be dynamically updated. Additionally, in some examples, hierarchical viewing perspectives may be determined and / or selected for visualizing one or more managed accounts. Further, accounts may be organized into groups based on roles, and grants for the accounts may be dynamically updated as changes occur or new accounts are managed.
Owner:ORACLE INT CORP
Password complexity policy for externally controlled systems
InactiveUS20110239267A1Digital data processing detailsUser identity/authority verificationPassword policyCorporate policy
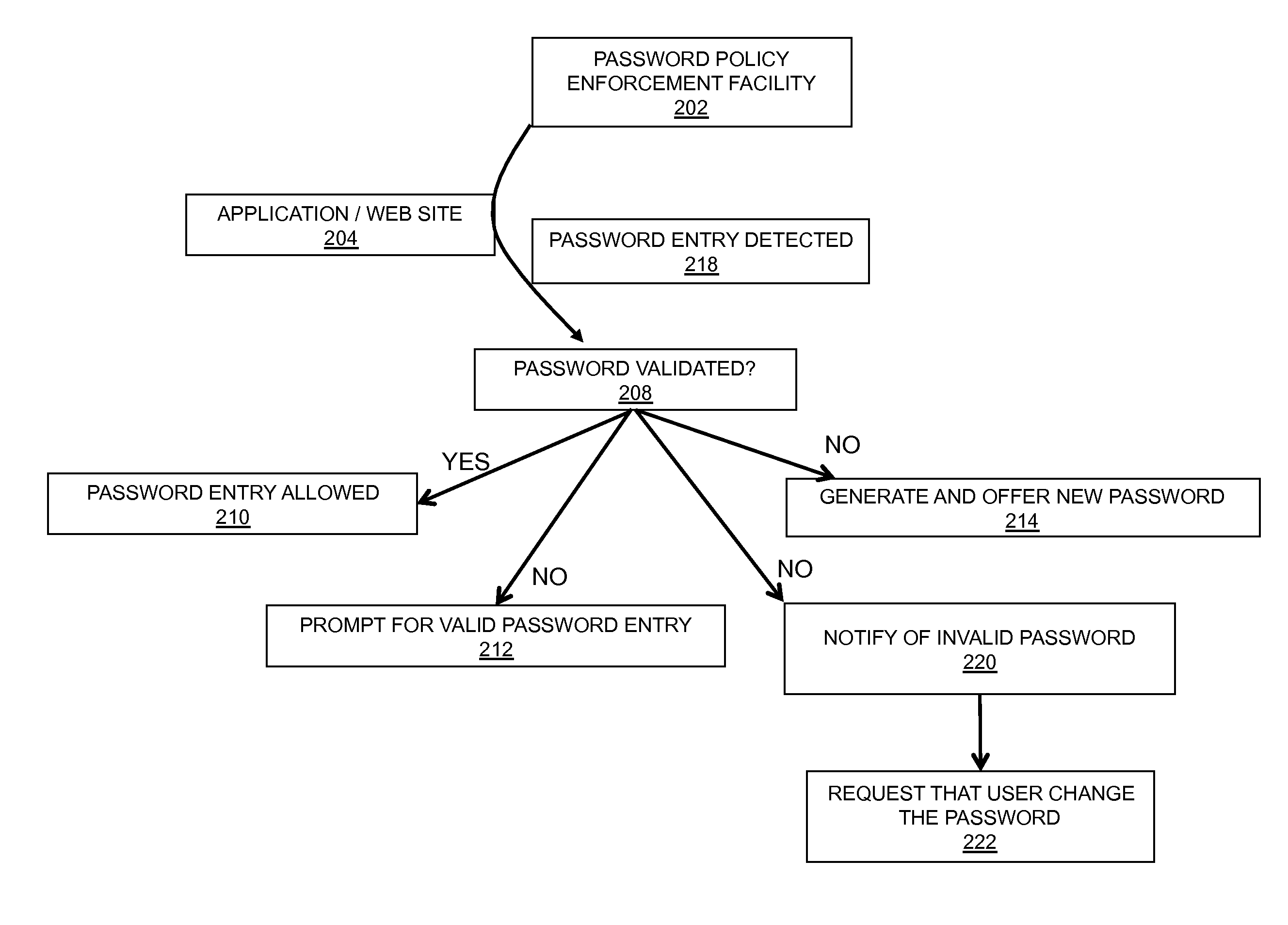
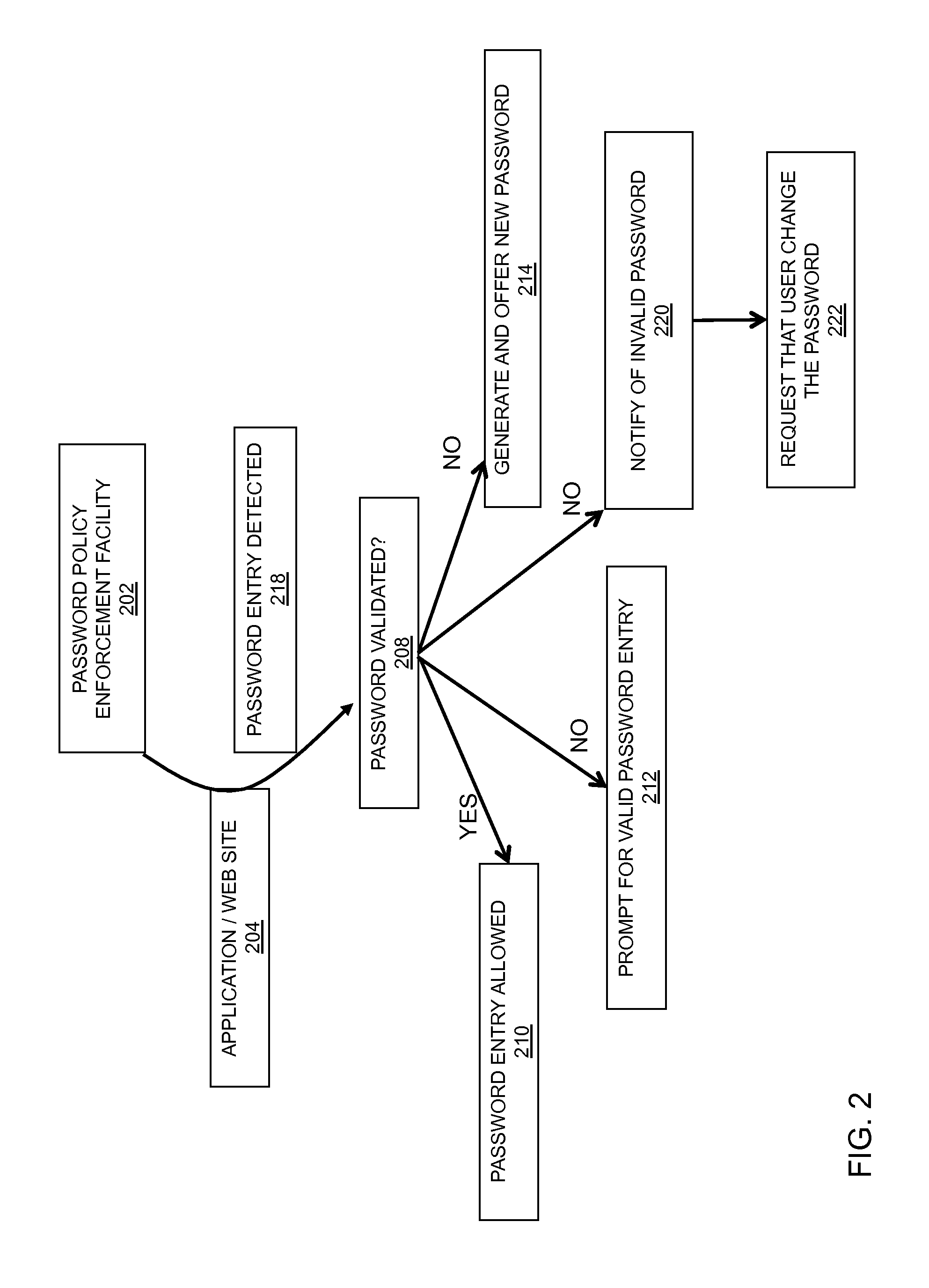
In embodiments of the present invention improved capabilities are described for password policy enforcement, such as passwords not normally in the administrative domain of the corporation, unlike common local policy enforcement. Password policy enforcement may include the steps of identifying a presentation of a software application user interface, wherein the presentation involves communicating the user interface over the Internet; evaluating the user interface for a presence of a user password field; and in response to a positive detection of the user password field, implementing a compliance process to ensure that any password entered into the user password field is compliant with a corporate policy relating to passwords.
Owner:SOPHOS
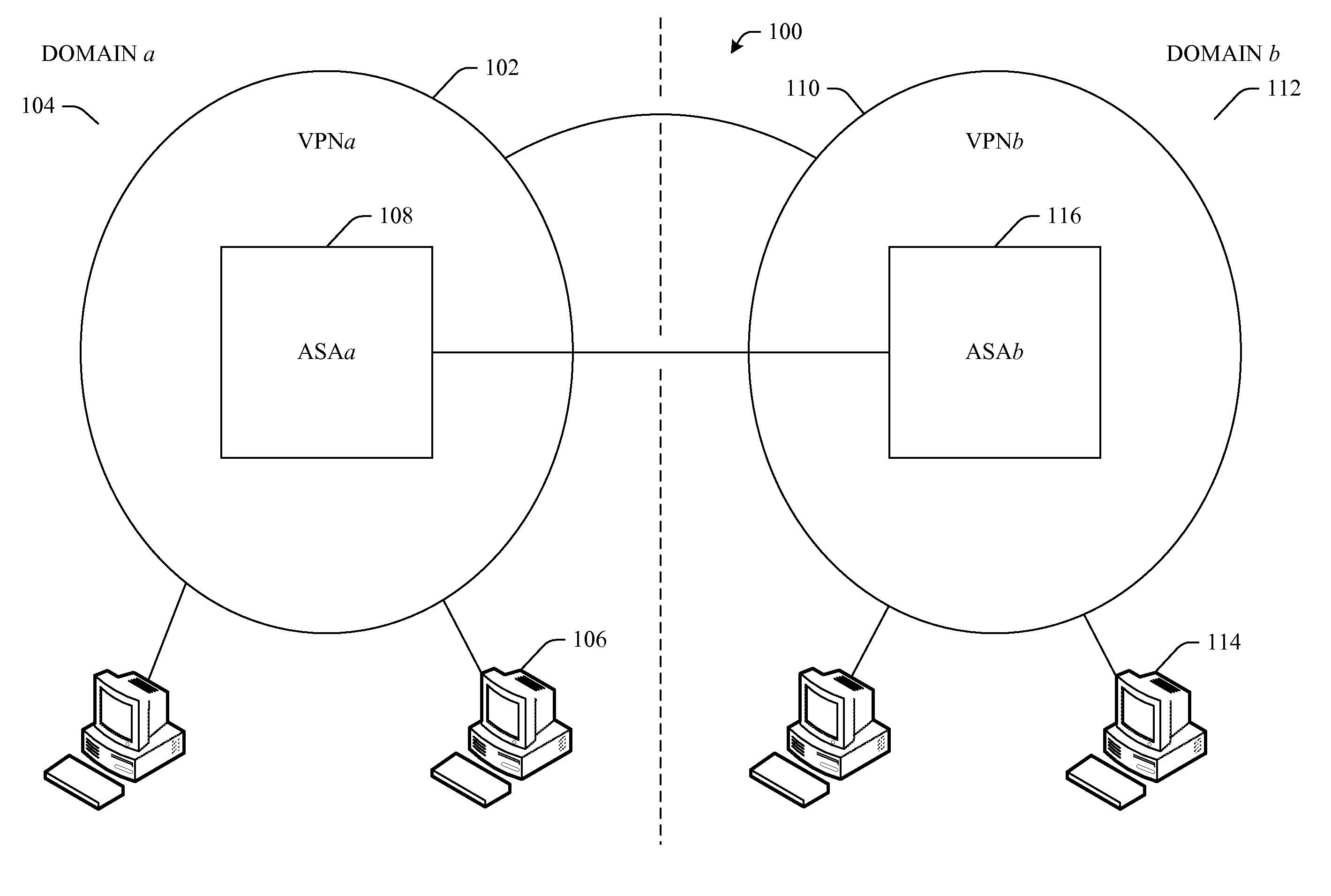
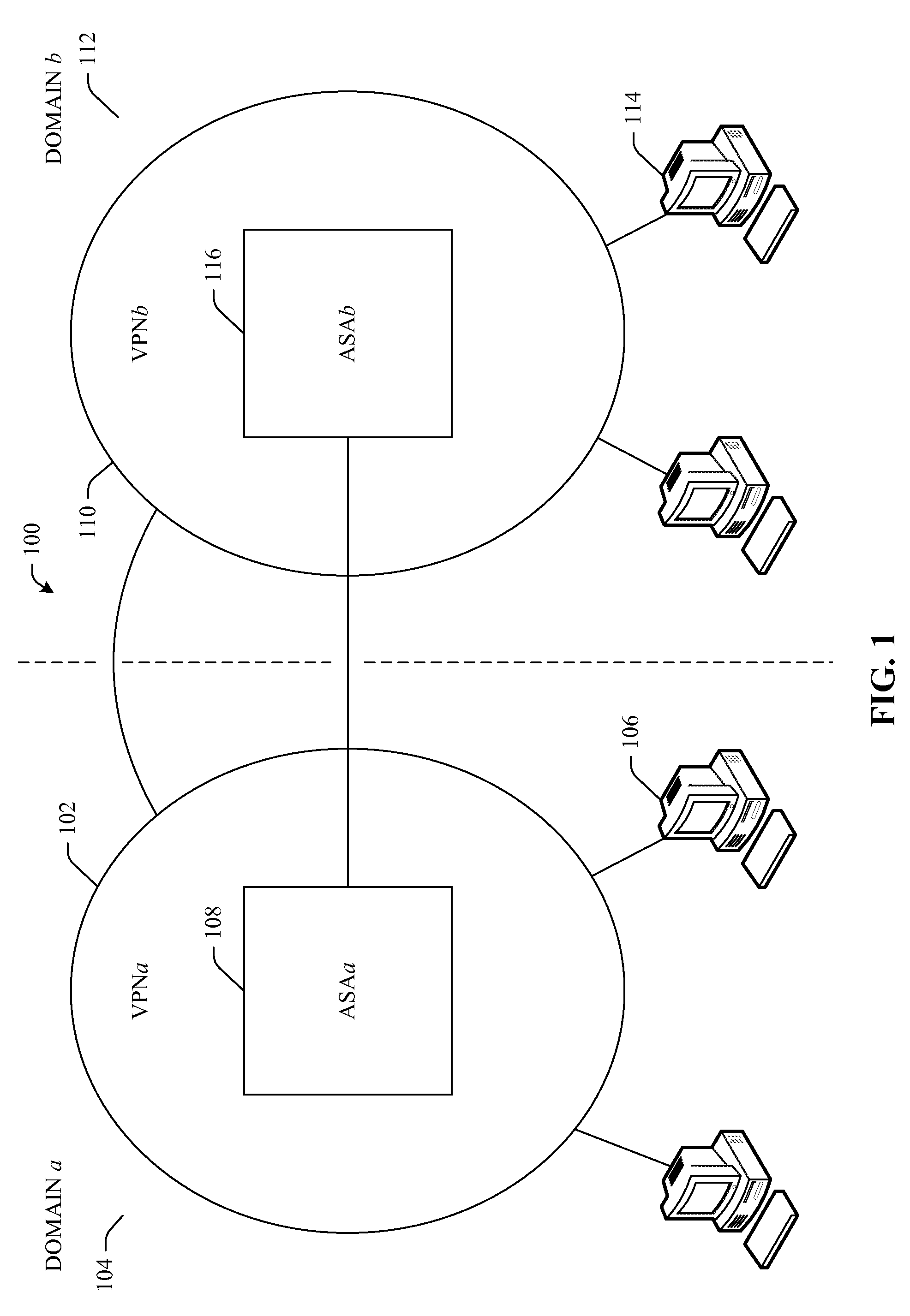
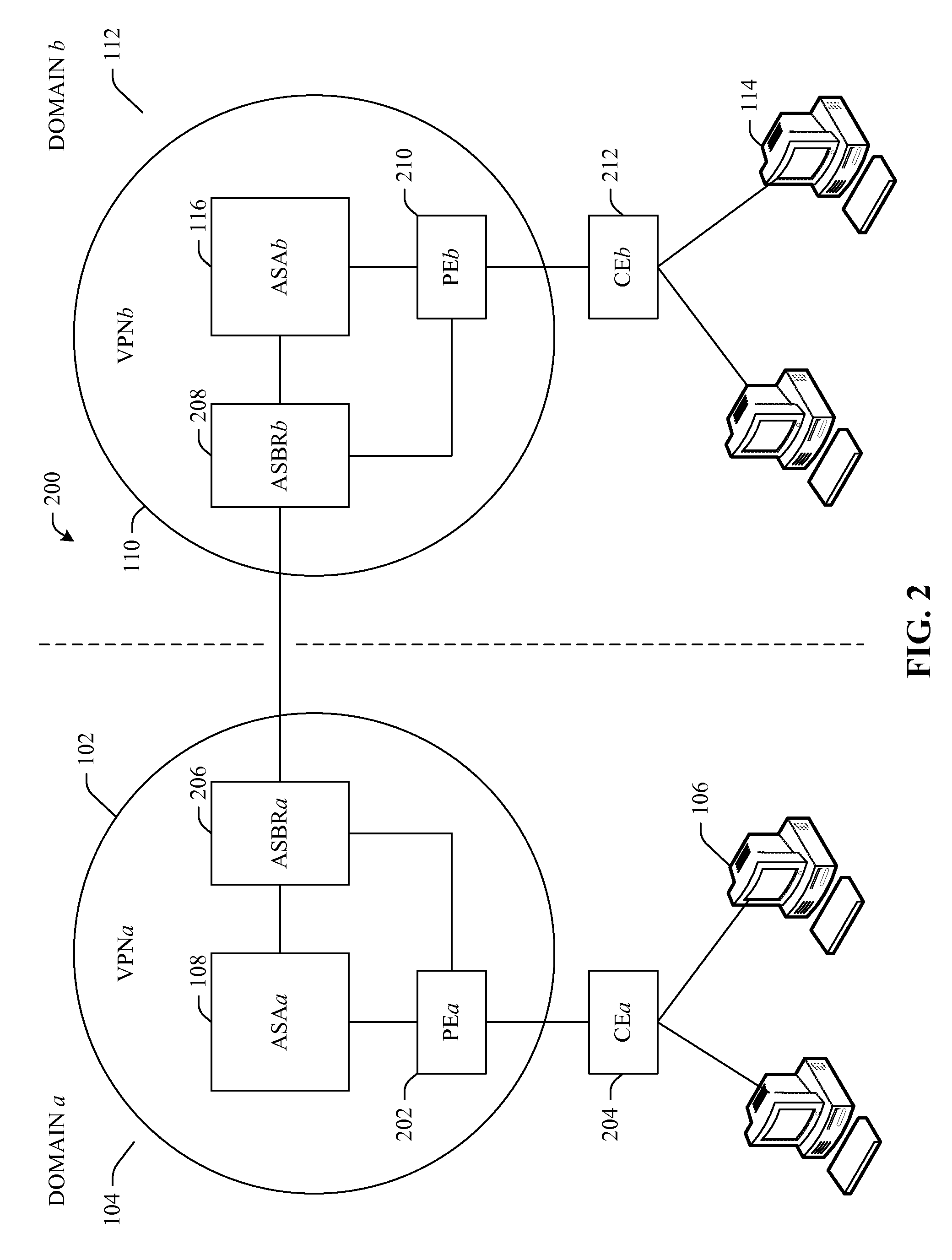
Multi-domain dynamic group virtual private networks
InactiveUS20080215880A1Data switching networksSecuring communicationSecure communicationPassword policy
Systems and / or methods of secure communication of information between multi-domain virtual private networks (VPNs) are presented. A dynamic group VPN (DGVPN) can reside in one domain and a disparate DGVPN can reside in a disparate domain. An administrative security authority (ASA) can be employed in each domain. Each ASA can generate and exchange respective keying material and crypto-policy information to be used for inter-domain communications when routing data from a member in one DGVPN to a member(s) in the disparate DGVPN, such that an ASA in one domain can facilitate encryption of data in accordance with the policy of the other domain before the data is sent to the other domain. Each ASA can establish a key server to generate the keying material and crypto-policy information associated with its local DGVPN, and such material and information can be propagated to intra-domain members.
Owner:CISCO TECH INC
Privileged account manager, access management
Owner:ORACLE INT CORP
Method for dynamically setting password by setting graphic per se in grid digital array
InactiveCN102148826AKeep your password safePrevent surprise attackUser identity/authority verificationDigital data authenticationGraphicsPassword policy
The invention provides a method for dynamically setting a password by setting a graphic per se in a grid digital array. The method comprises the following steps of: setting the graphic, a counting point and a password point per se in the grid array with abscissas and ordinates, setting a positioning point and reference point arrangement sequence per se in the graphic, simultaneously performing password counting in any one of the eight directions of the grid digital array, transmitting a counted password into a computer server and storing the password as a graphic password; and moving the self-set graphic into the grid digital array with the abscissas and the ordinates, obtaining an abscissa and ordinate point and the password point in the moved graphic according to the self-set counting point, and obtaining the password every time the graphic is moved until meeting the requirement of a network on password digits to dynamically finish password login by the easily-remembered graphic capable of preventing the password from being detected. By the method for dynamically obtaining the password and finishing the login, even though the graphic is the same, the same password cannot be obtained due to different graphic positioning points, different counting points and different password points. Therefore, the password security of a user can be greatly and effectively protected, and sudden attacks from bogusware such as Trojan and the like, and different kinds of snooping and harassing attacks in front of automatic teller machines are prevented; and the method is easy to remember and operate, and highly preventive.
Owner:王颢
Method and system for establishing a consistent password policy
Methods and systems for establishing a consistent password policy. A plurality of password policies is described in a computer usable password policy data structure. The computer usable password policy data structure is accessed by a password policy enforcement agent. Optionally, the computer usable password policy data structure is validated for authenticity by the password policy enforcement agent. Optionally, the password policy enforcement agent can report back to a centralized configuration and aggregation point repository in order to provide a consistent view of policy enforcement.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP +1
Computer-implemented method for generating passwords and computer program products of same
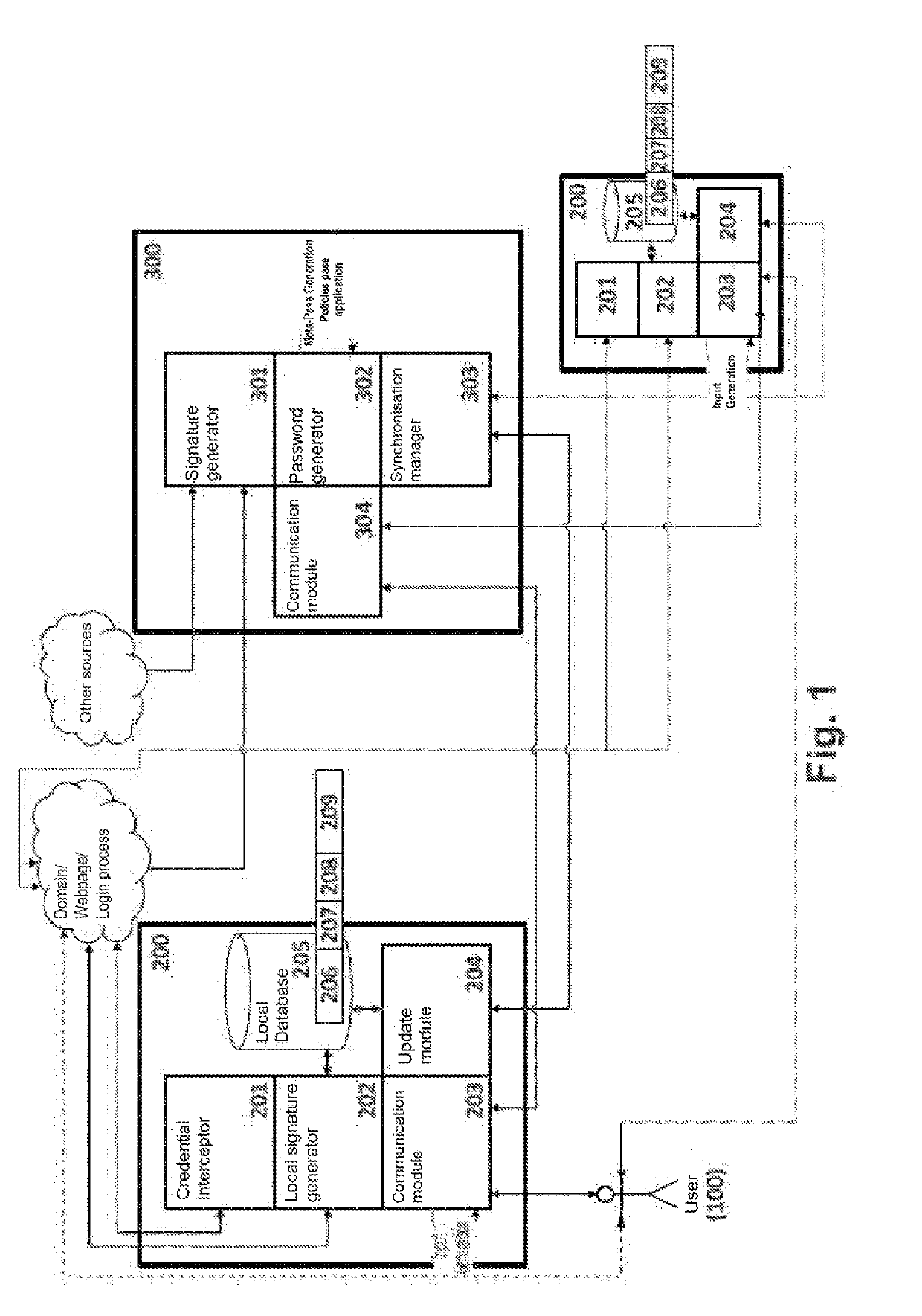
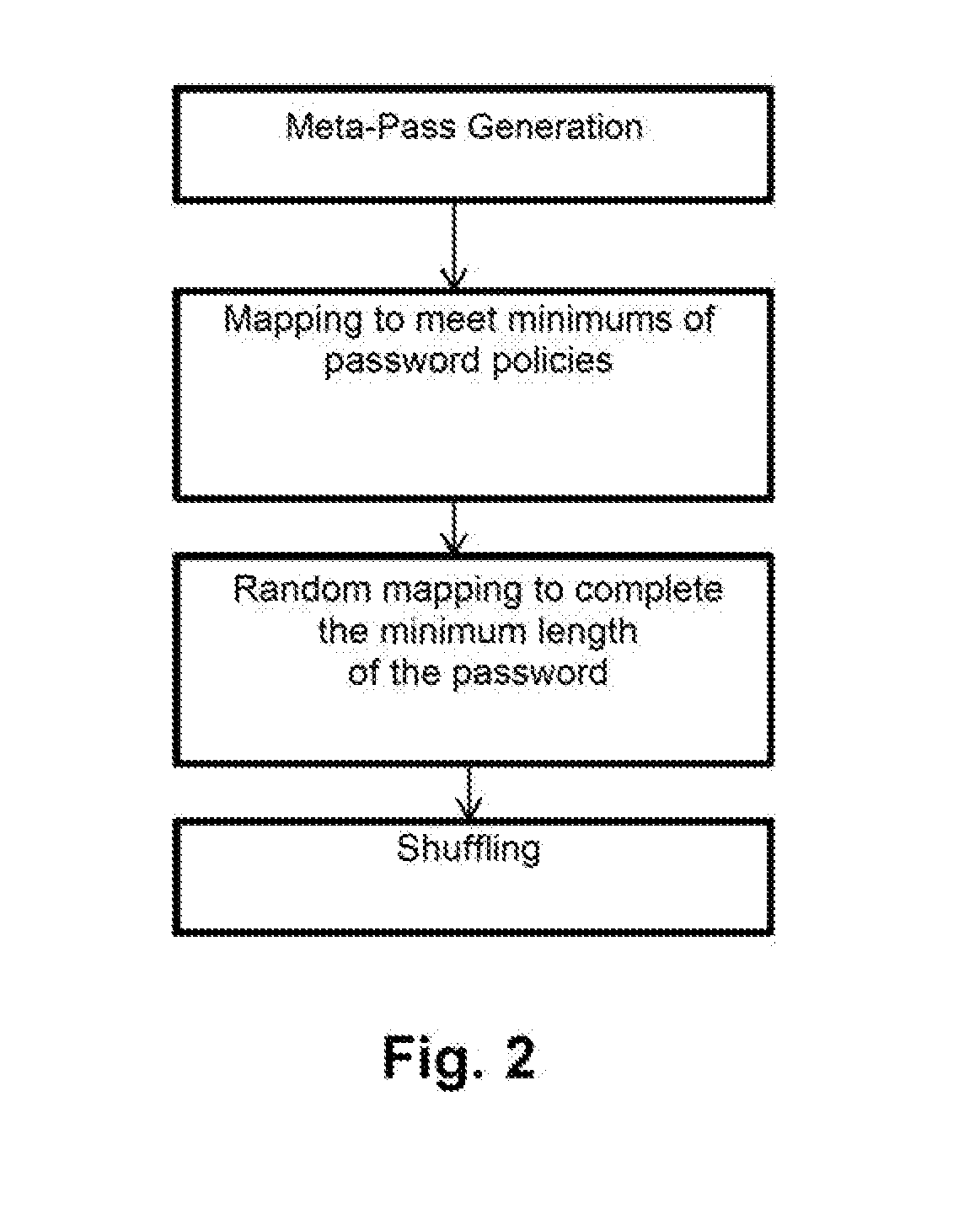
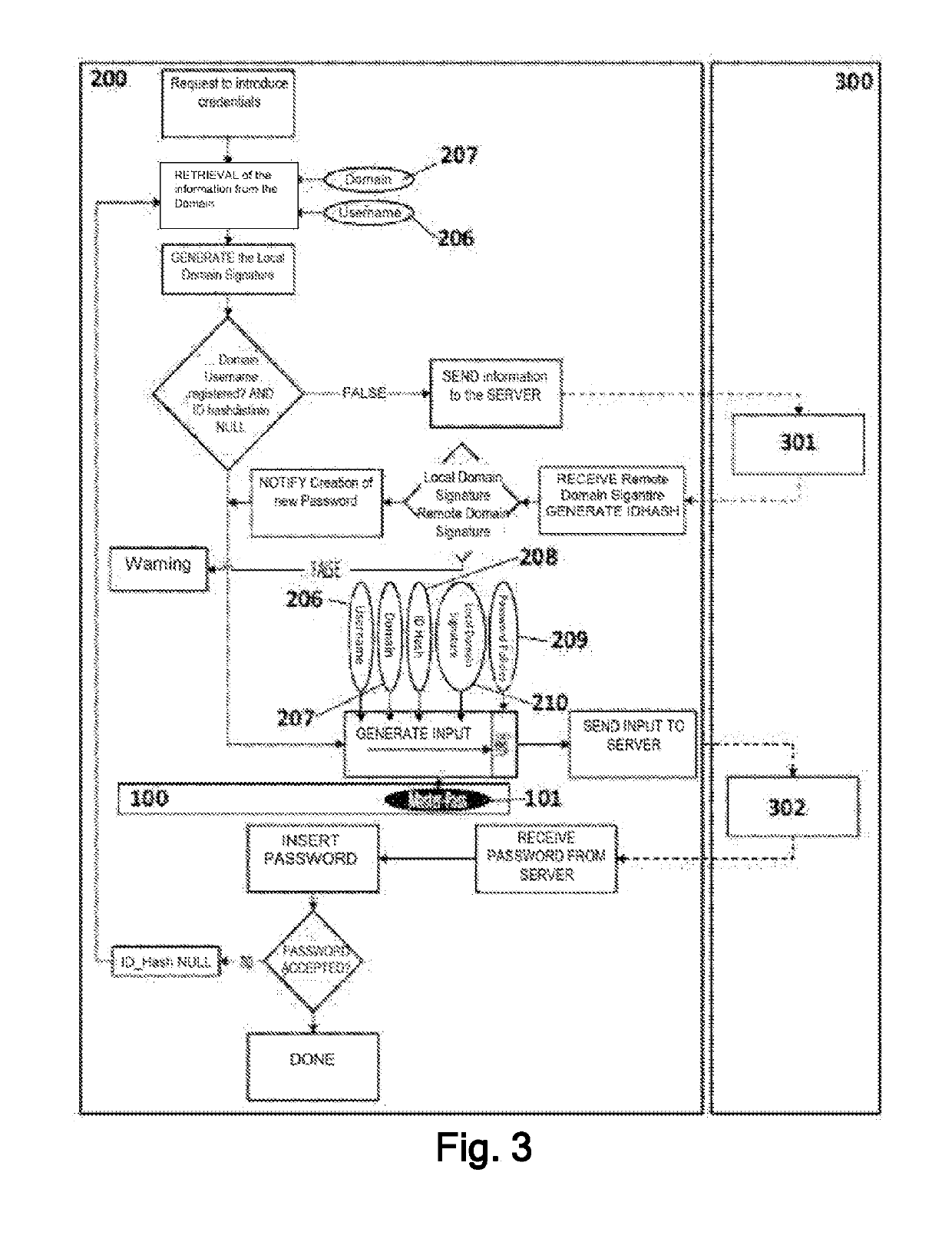
ActiveUS20190123898A1Prevents the permanent storage of the passwordsKey distribution for secure communicationSynchronising transmission/receiving encryption devicesPassword policyPassword
The invention relates to a computer-implemented method for generating passwords and to computer program products of same. The method comprises: accessing, by a user (100), by means of a first computation device (200), for the first time, a webpage or website identified by a web domain that requires the Identification of the user (100) on the webpage or website; and generating, by means of a password generator, a password required by the webpage or website, based on the use of a result obtained from the execution of a cryptographic function using password policies related to the domain, the use of a master password (101) known only to the user (100) and the use of an Id_Hash (208).
Owner:TELEFONICA CYBERSECURITY TECH SL
System for amending single point password
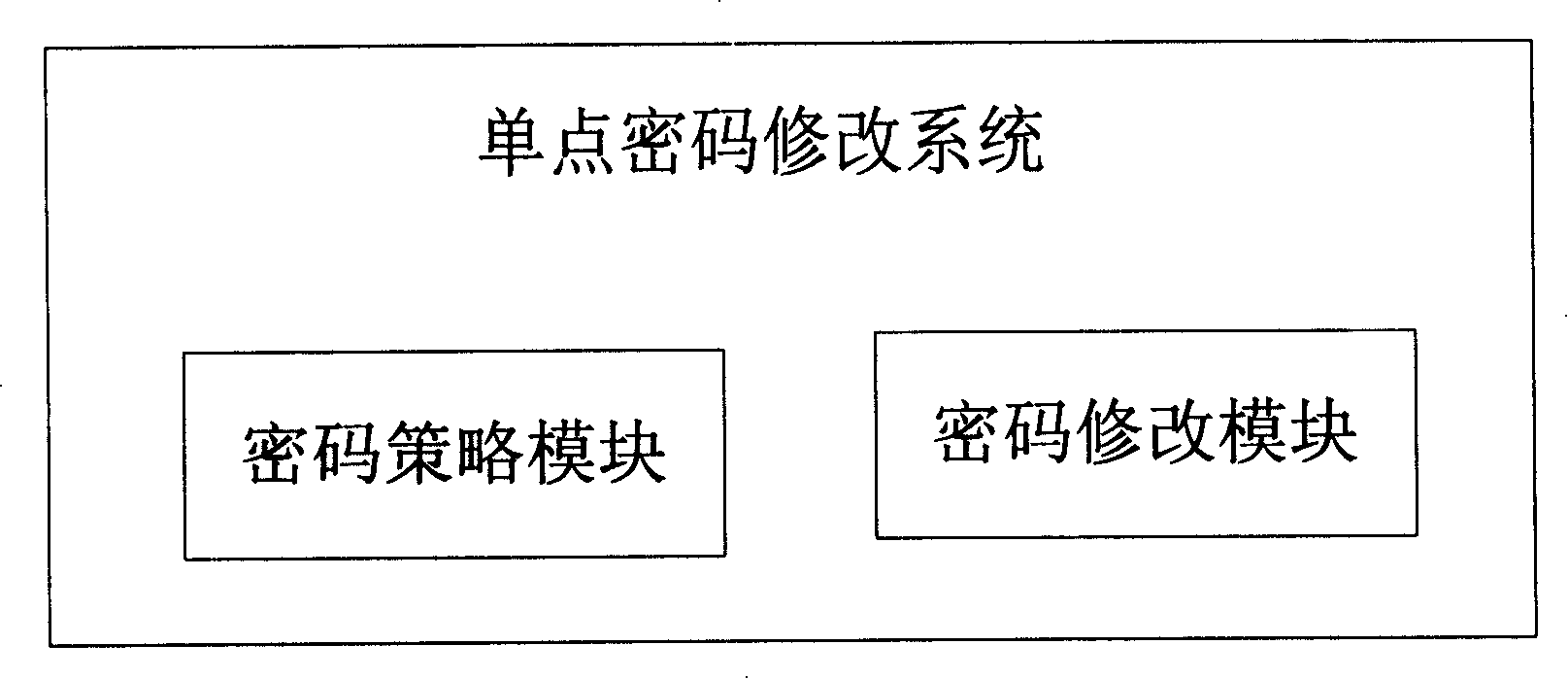
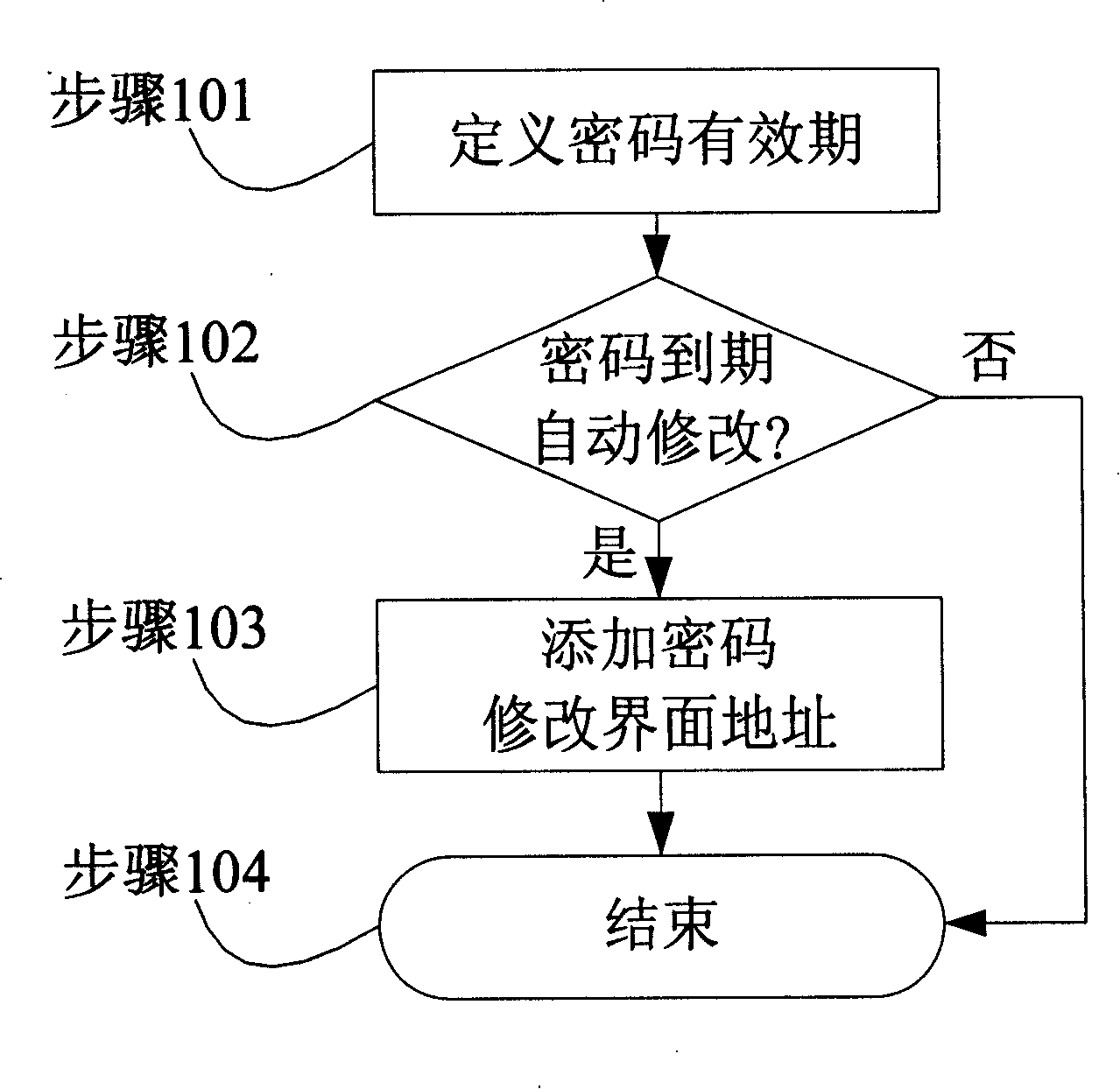
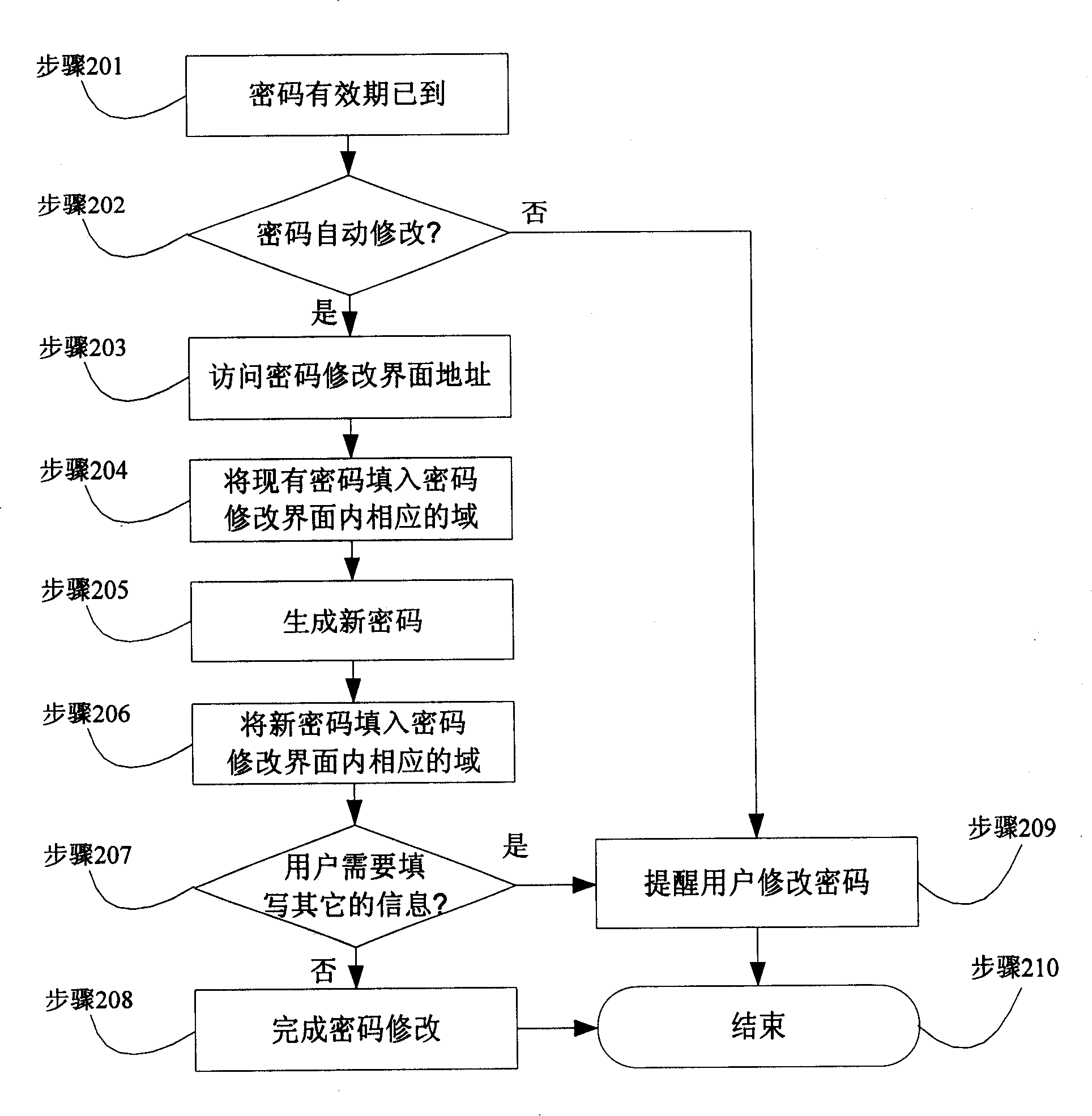
InactiveCN101207476AEncryption apparatus with shift registers/memoriesUnauthorized memory use protectionPassword policyPassword
The invention discloses a one-point password modifying system. The system comprises two modules of a password strategy module and a password modifying module. The password strategy module defines the validity period of the password, and modifies the interface visit address. The password modifying module reminds the user to modify the password when the validity period of the password is expired, and a new password is automatically generated. The prior password and the new password are filled into the corresponding domain in the modification interface of the password. If other information which needs the user to fill manually does not exist in the modification interface of the password, the password modifying module can automatically finish the password modification, or else, the user is reminded to continue to finish the modification work of the password.
Owner:吴琛
Monitoring and alert services and data encryption management
ActiveUS20170004312A1Digital data protectionMessaging/mailboxes/announcementsPassword policyData Applied
A centralized framework for managing the data encryption of resources is disclosed. A data encryption service is disclosed that provides various services related to the management of the data encryption of resources. The services may include managing application policies, cryptographic policies, and encryption objects related to applications. The encryption objects may include encryption keys and certificates used to secure the resources. In an embodiment, the data encryption service may be included or implemented in a cloud computing environment and may provide a centralized framework for effectively managing the data encryption requirements of various applications hosted or provided by different customer systems. The disclosed data encryption service may provide monitoring and alert services related to encryption objects managed by the data encryption service and transmit the alerts related to the encryption objects via various communication channels.
Owner:ORACLE INT CORP
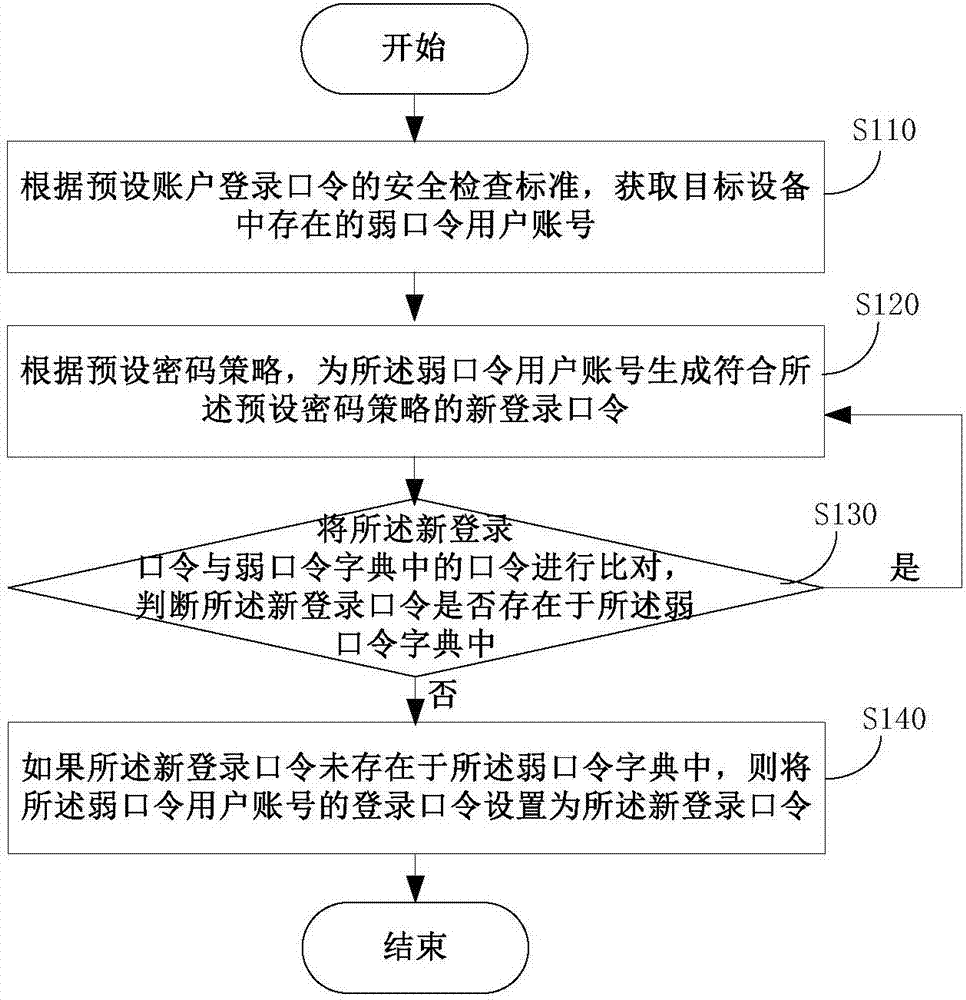
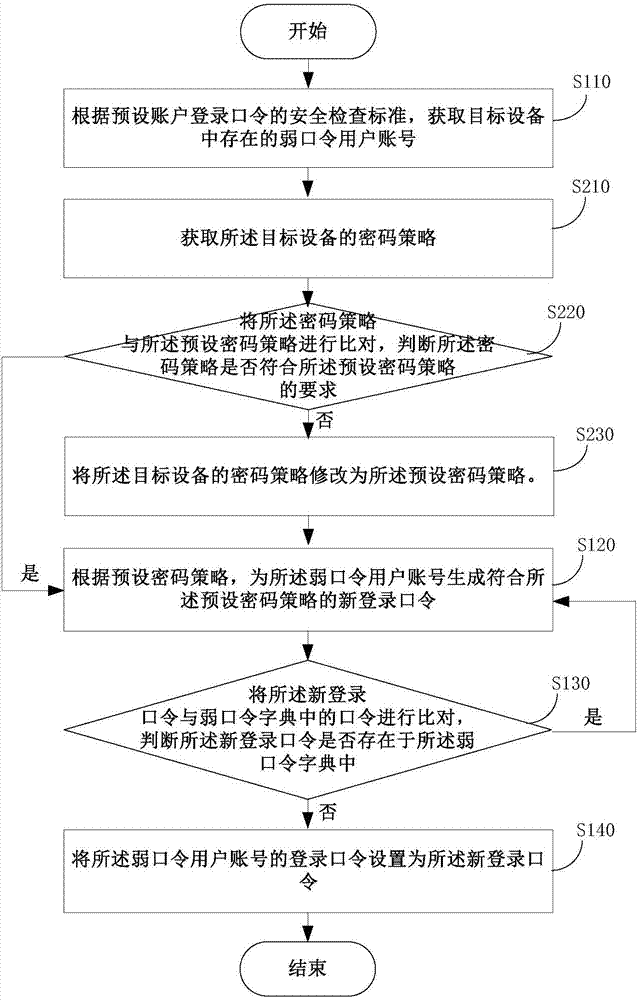
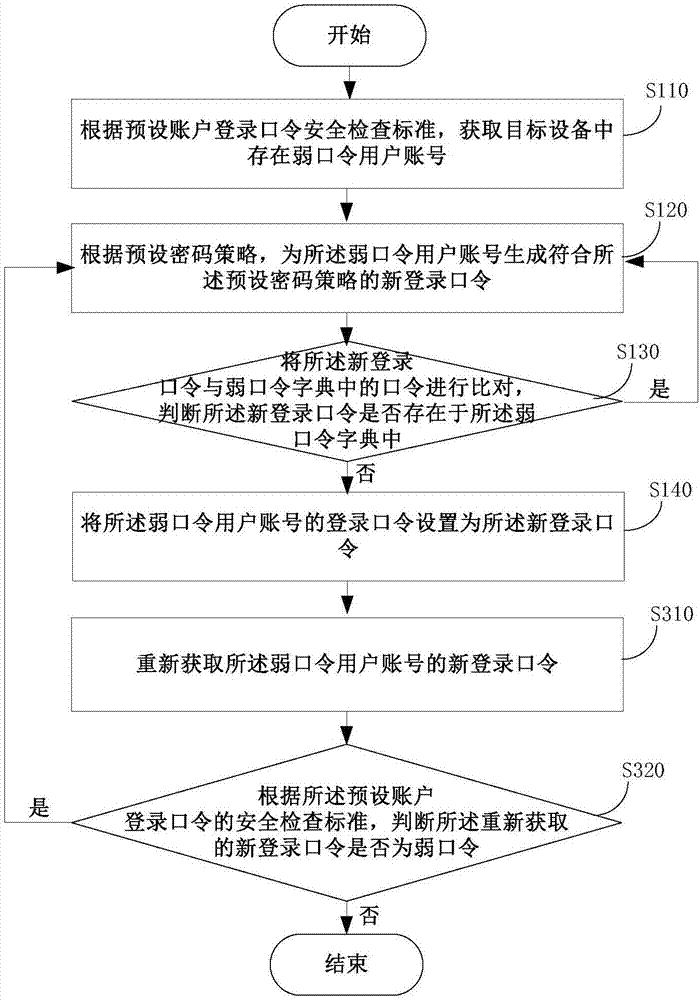
Method and device for managing device weak password
ActiveCN107196899AAccurate timingAvoid correctionTransmissionPassword policyApproaches of management
The invention discloses a method and a device for managing a device weak password. The method comprises steps: according to a preset account login password security check standard, a user account with a weak password in a target device is acquired; according to a preset password policy, a new login password meeting the preset password policy is generated for the user account with a weak password, weak password detection is carried out on the generated new login password, and if the new login password is not a weak password, the login password of the user account with the weak password is set to be the new login password. According to the method provided by the invention, weak password check and automatic repairing can be completed automatically, the work of a maintenance person can be lessened, the weak password in the device can be timely corrected, existence of a weak password in a network system is eliminated in a shortest time, and system data loss caused by a weak password and economic loss brought to an enterprise are further avoided.
Owner:ULTRAPOWER SOFTWARE +1
Data encryption service and customized encryption management
ActiveUS20170004313A1Efficient managementDigital data protectionMessaging/mailboxes/announcementsPassword policySecret code
A centralized framework for managing the data encryption of resources is disclosed. A data encryption service is disclosed that provides various services related to the management of the data encryption of resources. The services may include managing application policies, cryptographic policies, and encryption objects related to applications. The encryption objects may include encryption keys and certificates used to secure the resources. In an embodiment, the data encryption service may be included or implemented in a cloud computing environment and may provide a centralized framework for effectively managing the data encryption requirements of various applications hosted or provided by different customer systems. The disclosed data encryption service may provide monitoring and alert services related to encryption objects managed by the data encryption service and transmit the alerts related to the encryption objects via various communication channels.
Owner:ORACLE INT CORP
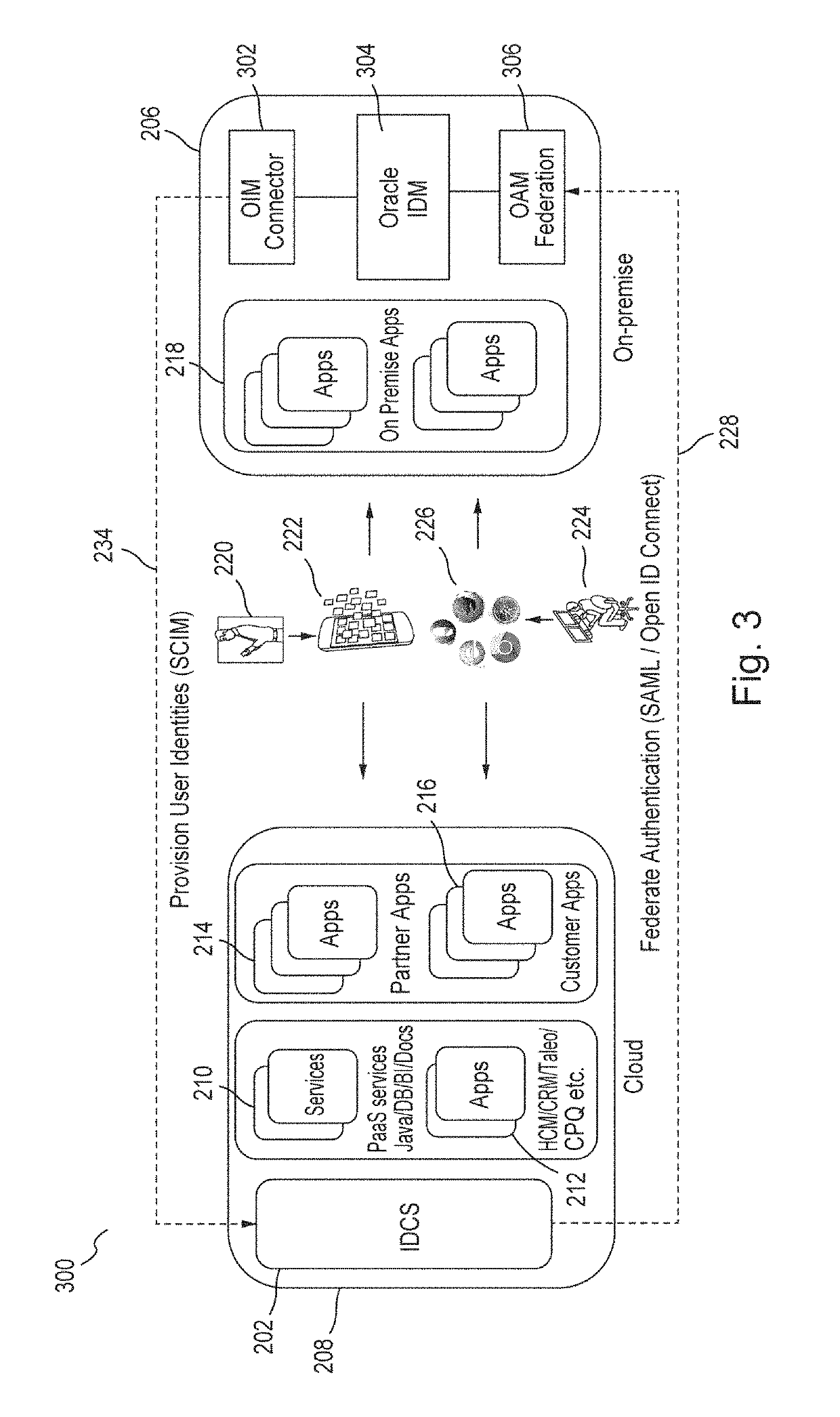
User authentication using kerberos with identity cloud service
ActiveUS10454915B2Key distribution for secure communicationSynchronising transmission/receiving encryption devicesPassword policyPassword
Embodiments authenticate a user in response to receiving from a Kerberos key distribution center (“KDC”) a request to authenticate the user that includes a user identification (“ID”). Embodiments retrieve a user record corresponding to the user ID, the user record including a principal key. Embodiments decrypt the principal key using a tenant-specific encryption key and encrypt the decrypted principal key using a Kerberos master key to generate an encrypted principal key. Embodiments retrieve a password policy corresponding to the user ID. Based on the retrieved password policies, embodiments construct password state attributes and return to the KDC the encrypted principal key, the password policy and the password state attributes.
Owner:ORACLE INT CORP
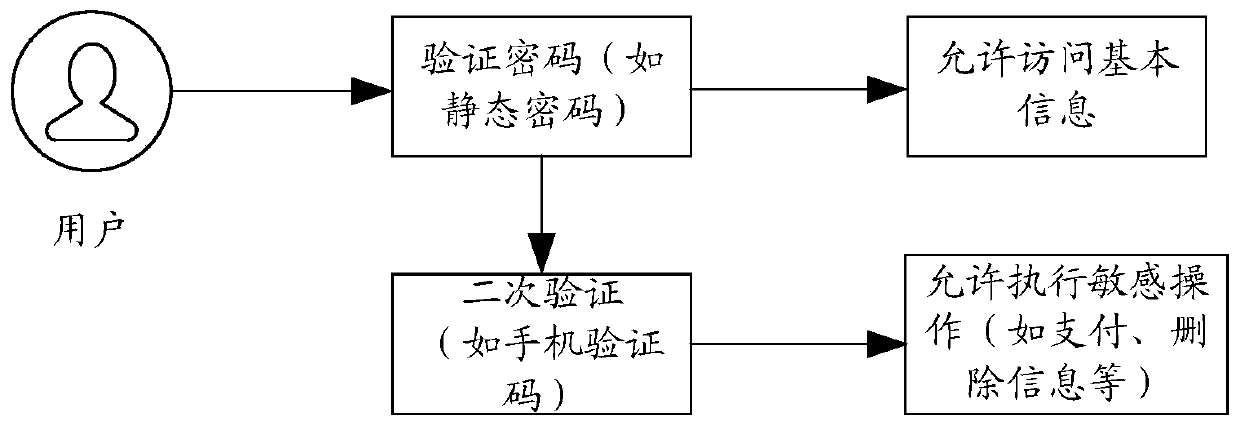
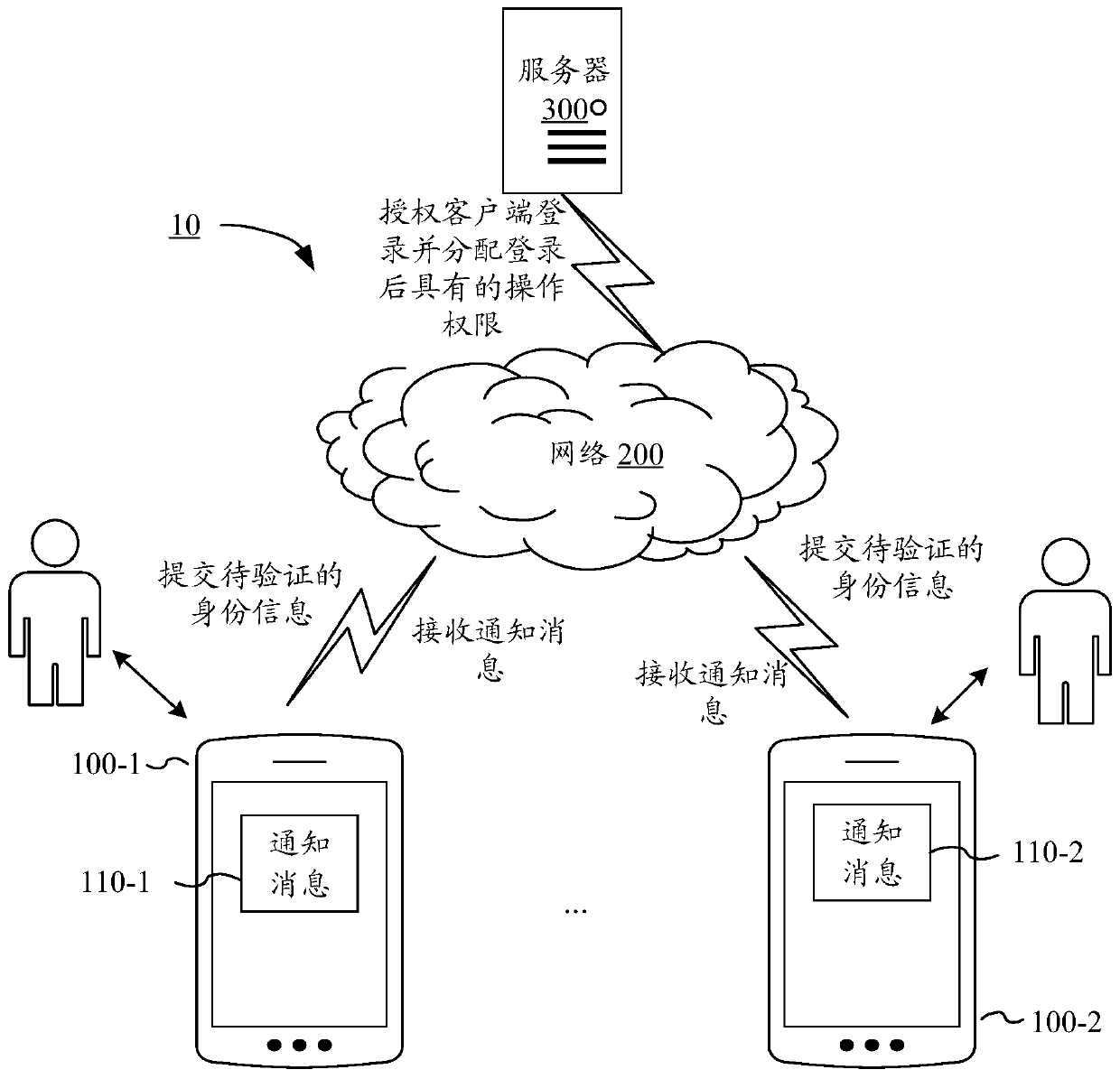
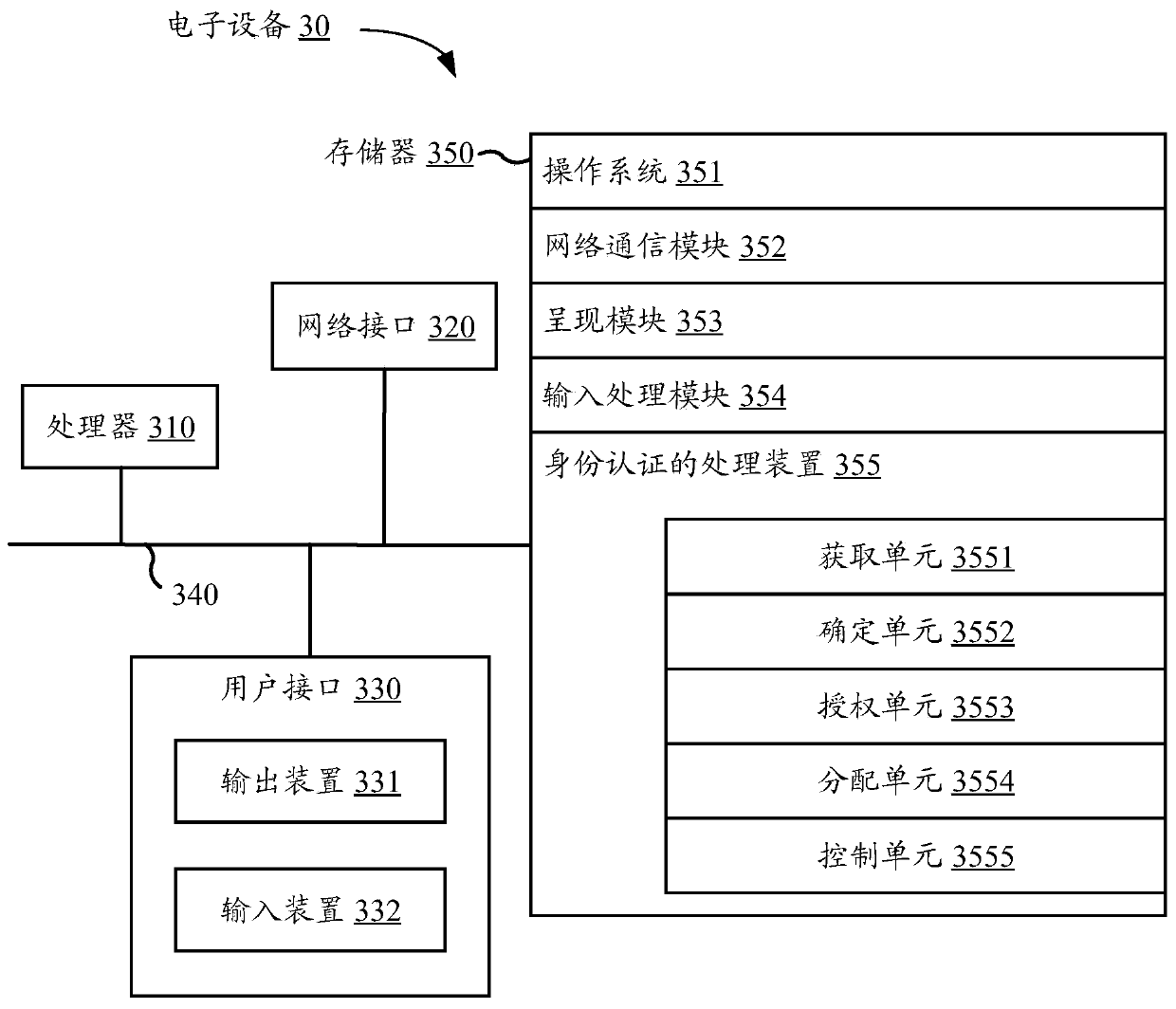
Identity authentication processing method and device, electronic equipment and storage medium
PendingCN110781468AImprove operating experienceImprove operational efficiencyDigital data authenticationThird partyPassword policy
The invention provides an identity authentication processing method and device, electronic equipment and a storage medium. The method comprises the following steps: acquiring identity information submitted by a client; determining a target password strategy for verifying the identity information in a plurality of password strategies; authorizing the client to log in a third-party application basedon the identity information when the identity authentication of the identity information based on the target password strategy is passed, and allocating an operation authority after the login of thethird-party application to the client based on the security classification corresponding to the target password strategy; and based on the operation authority, controlling the operation of the clientafter logging in the third-party application. According to the method and the device, the operation experience and the identity authentication efficiency of the user can be improved while the safety is ensured.
Owner:TENCENT TECH (SHENZHEN) CO LTD
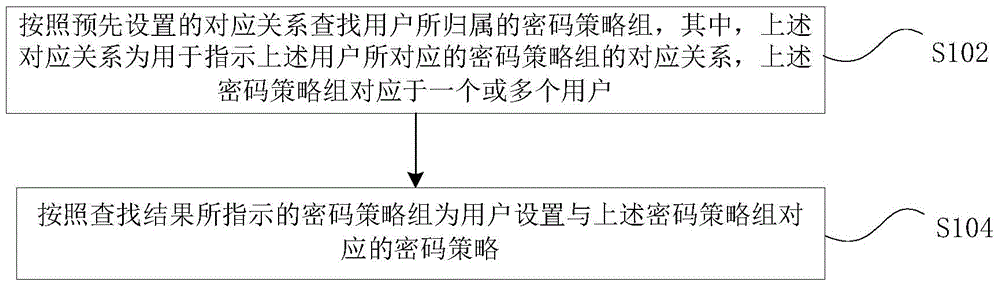
Password setting method and device
InactiveCN105809024ASolve the problem that the password policy is too singleDigital data authenticationPassword policyPassword
The present invention provides a password setting method and device, wherein the method includes: searching for the password policy group to which the user belongs according to the preset corresponding relationship, wherein the corresponding relationship is used to indicate the user's corresponding Correspondence of password policy groups, where the password policy groups correspond to one or more users; according to the password policy groups indicated by the search results, password policies corresponding to the password policy groups are set for users. The above-mentioned technical solution provided by the present invention solves the problem in the related art that the user password policies in the same information system are too single, and different levels of user password policies can be set for different levels of users.
Owner:航天信息软件技术有限公司
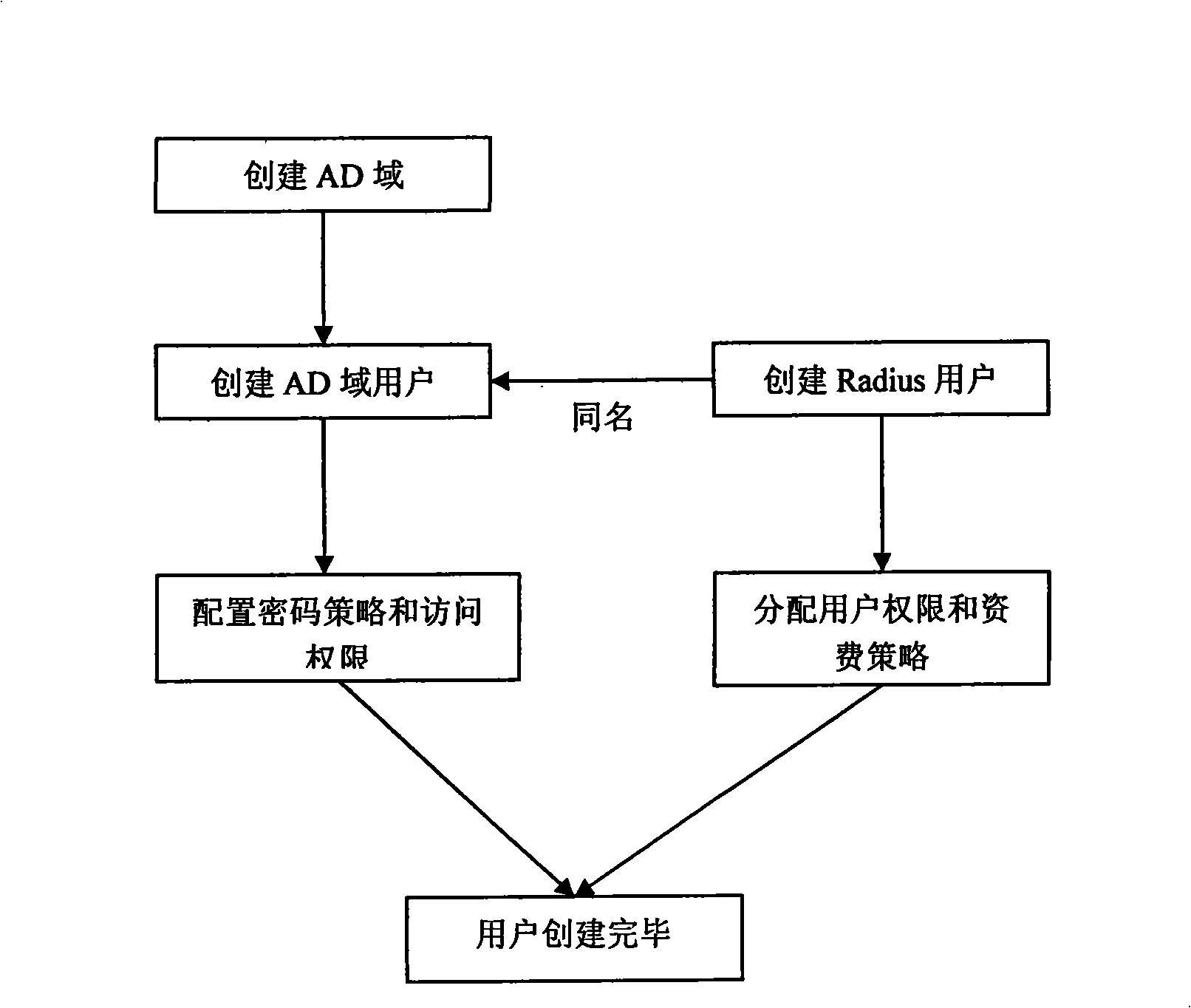
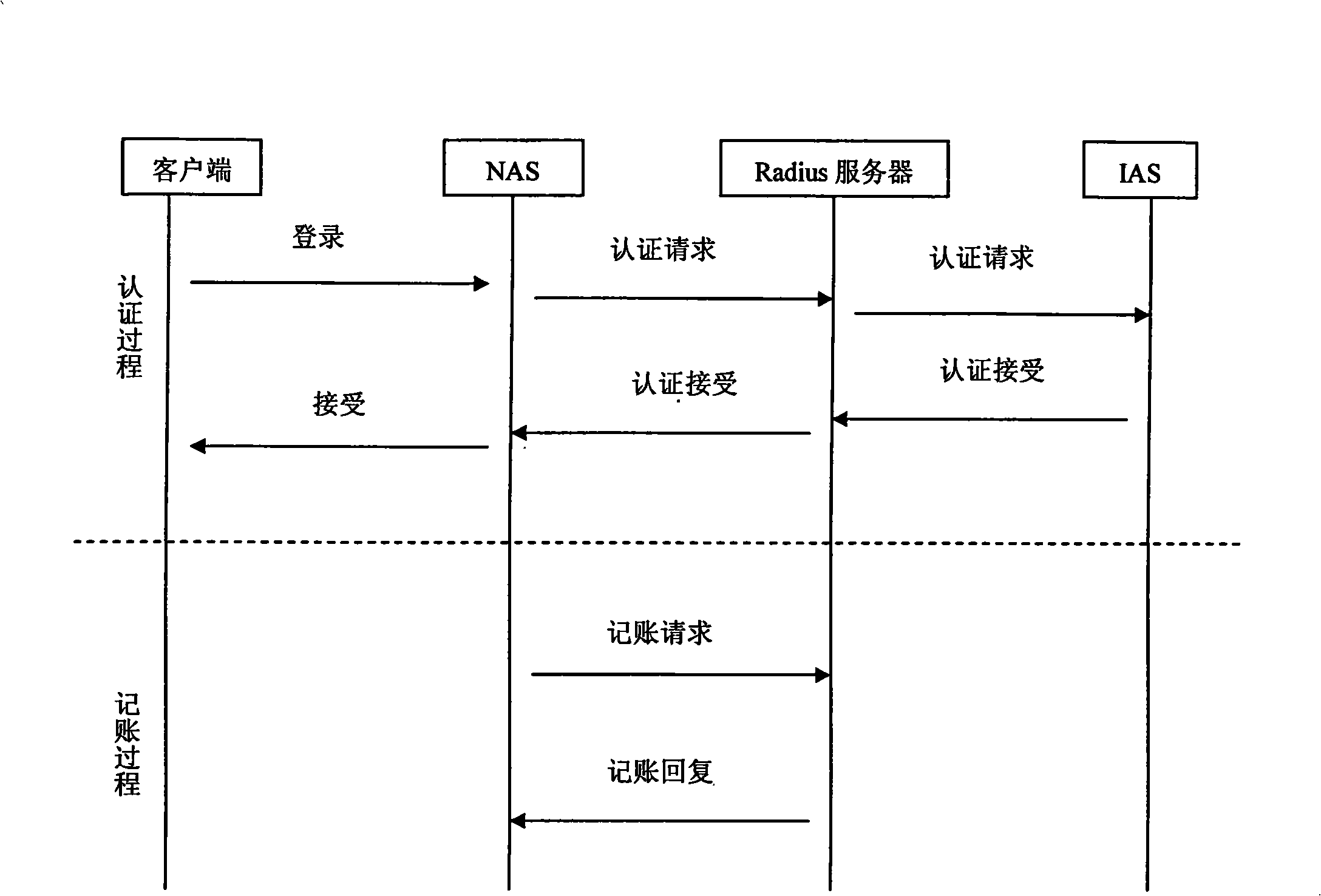
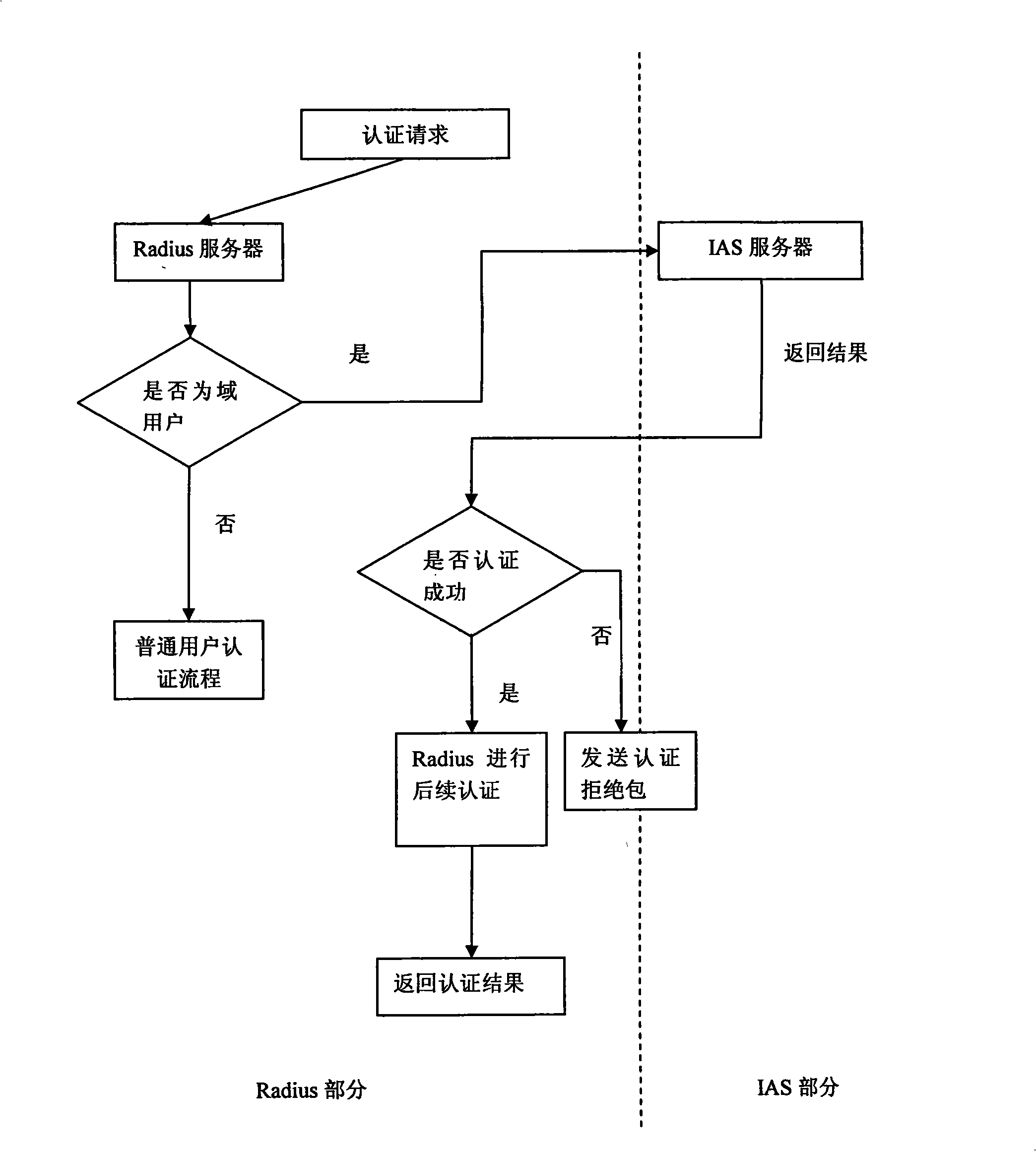
Method for implementing IAS system and Radius system integration
InactiveCN101296084AOne step to reachReduce workloadMetering/charging/biilling arrangementsUser identity/authority verificationSystem integrationPassword policy
The invention discloses a method for realizing integration of an IAS system and a Radius system, wherein, a domain user is established in the IAS system and configured with a password, a password strategy and authorization; a user having the same name with the domain user is established in the Radius system; when the user inputs an arbitrary password, the Radius system binds a pricing strategy and an authentication strategy for the user; the IAS system and the Radius system jointly authenticate the domain user. By adopting the method of the invention, the IAS system and the Radius system are integrated for finishing the treatment procedures synchronously, such as authentication and charging when the user logs in network or computer domain, which not only reduces the workload of login for the user, but also realizes one step login for the user, thus greatly enhancing the security, meeting the requirements for convenience and security of the login from enterprises and making a great progress over the prior art.
Owner:ZTE CORP
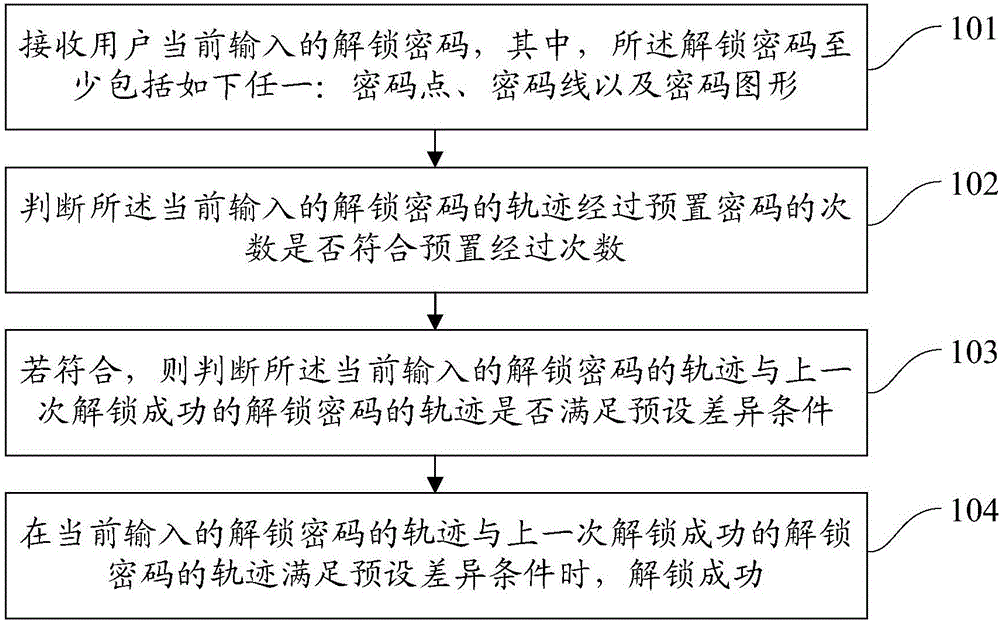
Unlocking method and intelligent terminal
InactiveCN106096376AReduced risk of crackingImprove securityDigital data authenticationGraphicsPassword policy
Embodiments of the invention provide an unlocking method and an intelligent terminal. The method comprises the steps of receiving an unlocking password currently input by a user, wherein the unlocking password at least comprises any one of the following information: a password point, a password line and a password graph; judging whether a frequency of passing a preset password by a track of the currently input unlocking password is a preset passing frequency or not; if yes, judging whether the track of the currently input unlocking password and a track of an unlocking password of previous successful unlocking meet a preset difference condition or not; and when the track of the currently input unlocking password and the track of an unlocking password of previous successful unlocking meet the preset difference condition, indicating that the unlocking is successful. According to the embodiments of the method and the terminal, the risk of cracking the unlocking password by others can be lowered, so that the security of the unlocking password can be improved.
Owner:VIVO MOBILE COMM CO LTD
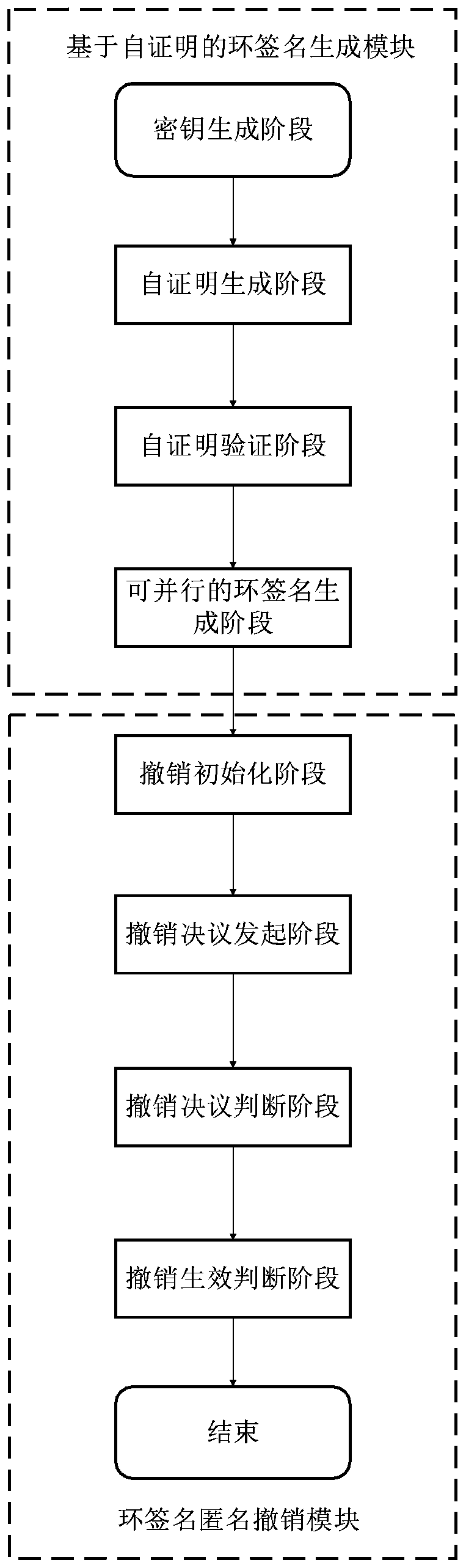
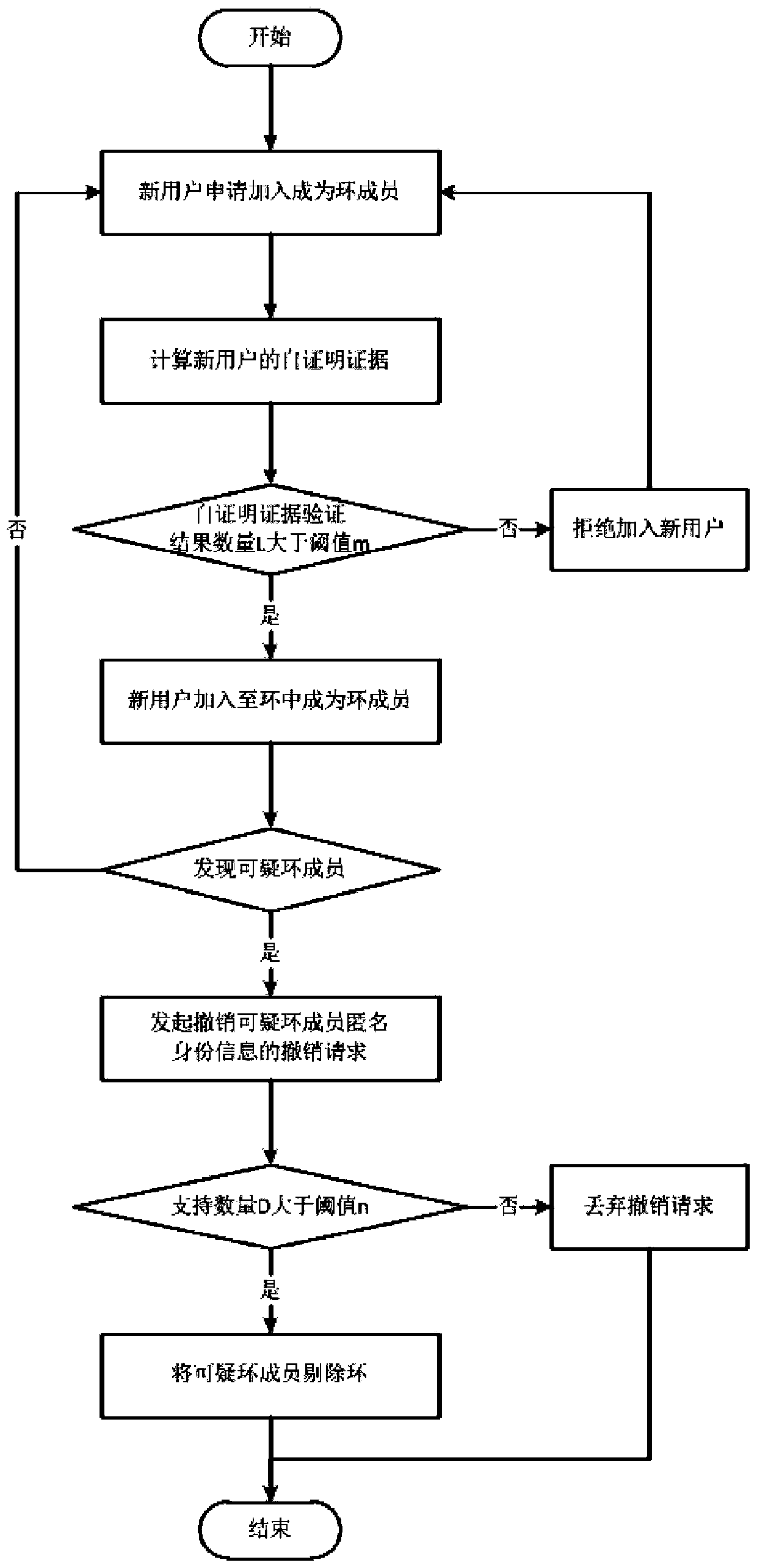
Anonymous revocation ring signature based on public chain and generation and revocation method of anonymous revocation ring signature
ActiveCN110190970AGenerate efficientlyGuaranteed not to discloseUser identity/authority verificationPassword policyPassword
The invention discloses an anonymous revocation ring signature based on a public chain and a generation and revocation method of the anonymous revocation ring signature, relating to the technical field of network security, the ring signature comprises a self-proving-based ring signature generation module and an anonymous identity cancellation module; the self-proving-based ring signature generation module comprises a key generation unit, a self-proving generation unit, a self-proving verification unit and a parallelizable ring signature generation unit, and the anonymous identity revocation module comprises a revocation initialization unit, a revocation initiation unit, a revocation judgment unit and a revocation effectiveness judgment unit. According to the invention, a ring signature parallel computing method based on cloud computing, an anonymous voting method based on ring signatures and a threshold password strategy are comprehensively used to realize efficient generation of ringsignatures of users on a public chain, conditional revocation of anonymous identities and security, fairness and credibility of a revocation process, so that the network security is improved.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
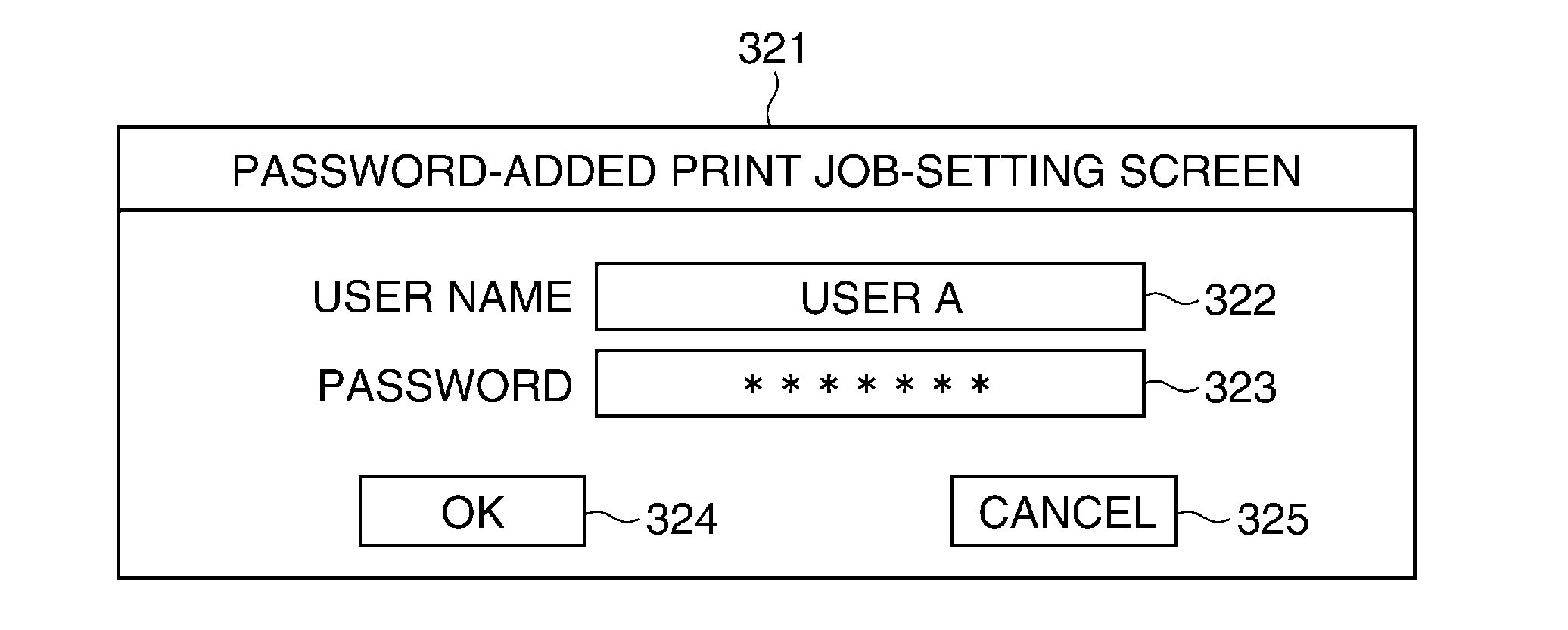
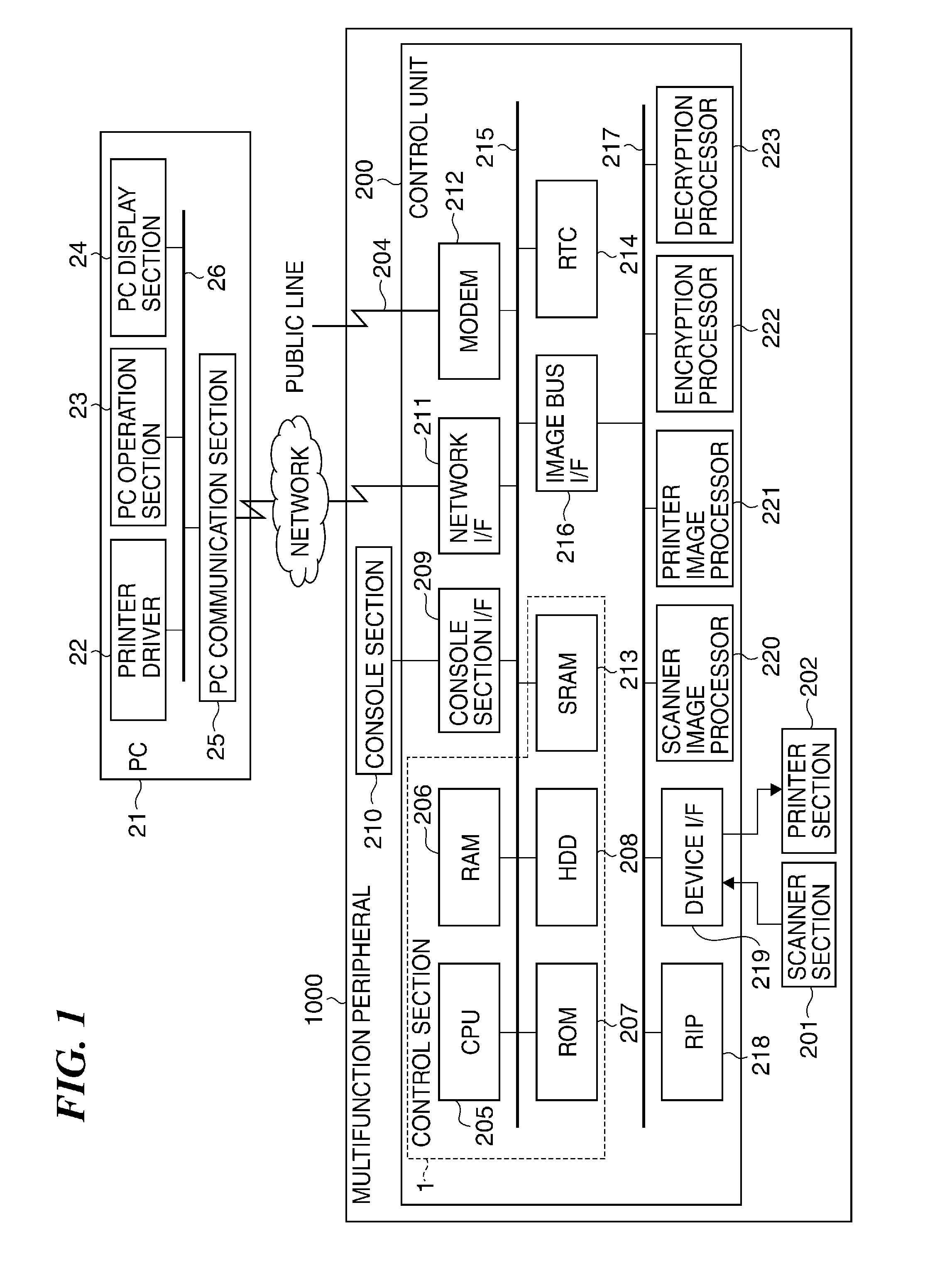
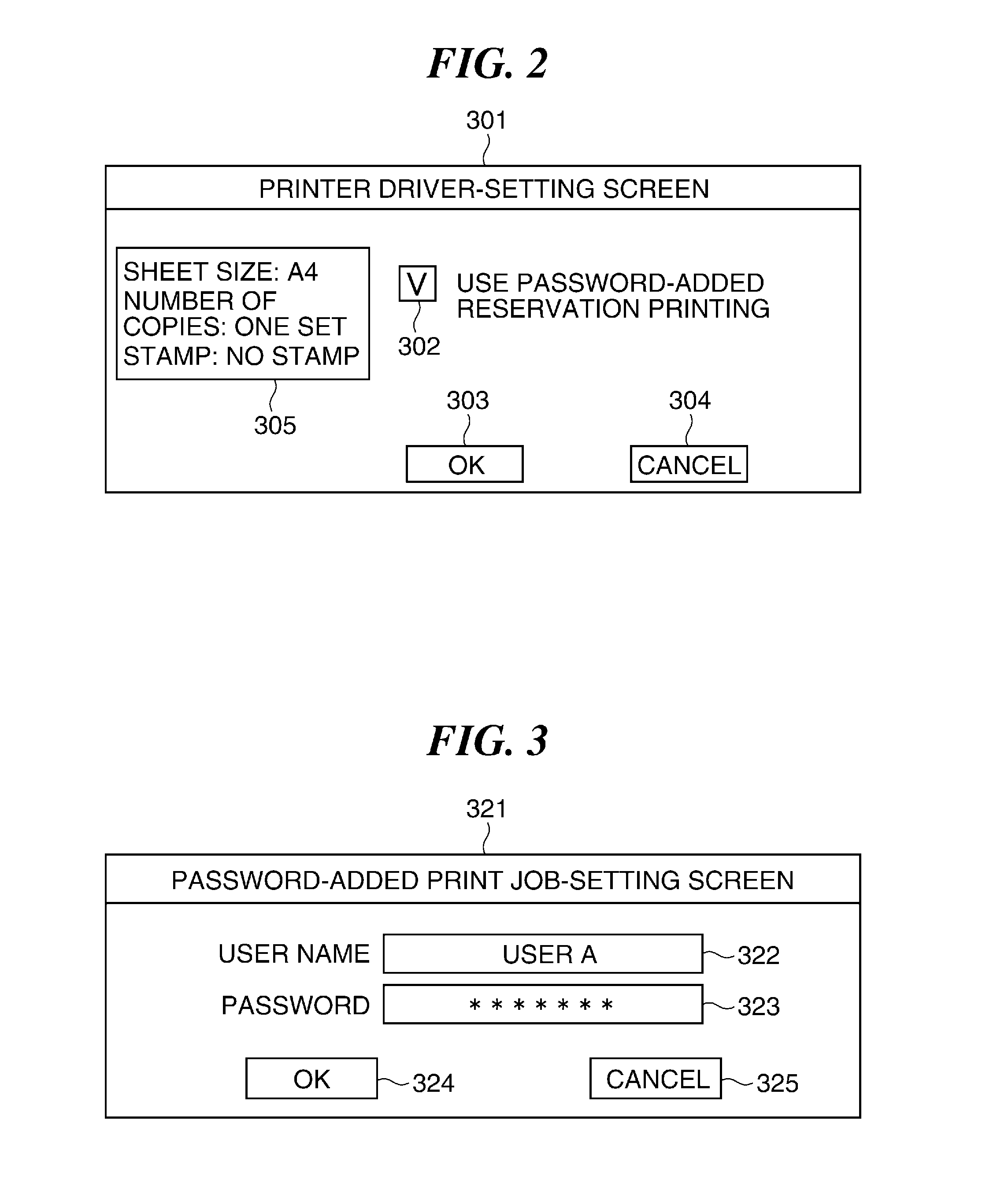
Image forming apparatus capable of reducing security risk, method of controlling image forming apparatus, system including image forming apparatus, and storage medium
ActiveUS20150128239A1Reduce security risksDigital data processing detailsMultiple digital computer combinationsPassword policyPassword
An image forming apparatus capable of notifying a user of violation of the information security policy or preventing execution of the job from being stopped. A password policy set via a password policy-setting screen. A password-added print job transmitted from a PC is stored in a storage device. A user inputs a password so as to execute processing of the password-added print job stored in the storage device. If the password input by the user matches the password added to the job, processing of the password-added print job is executed. It is determined whether or not the password added to the print job satisfies the password policy.
Owner:CANON KK
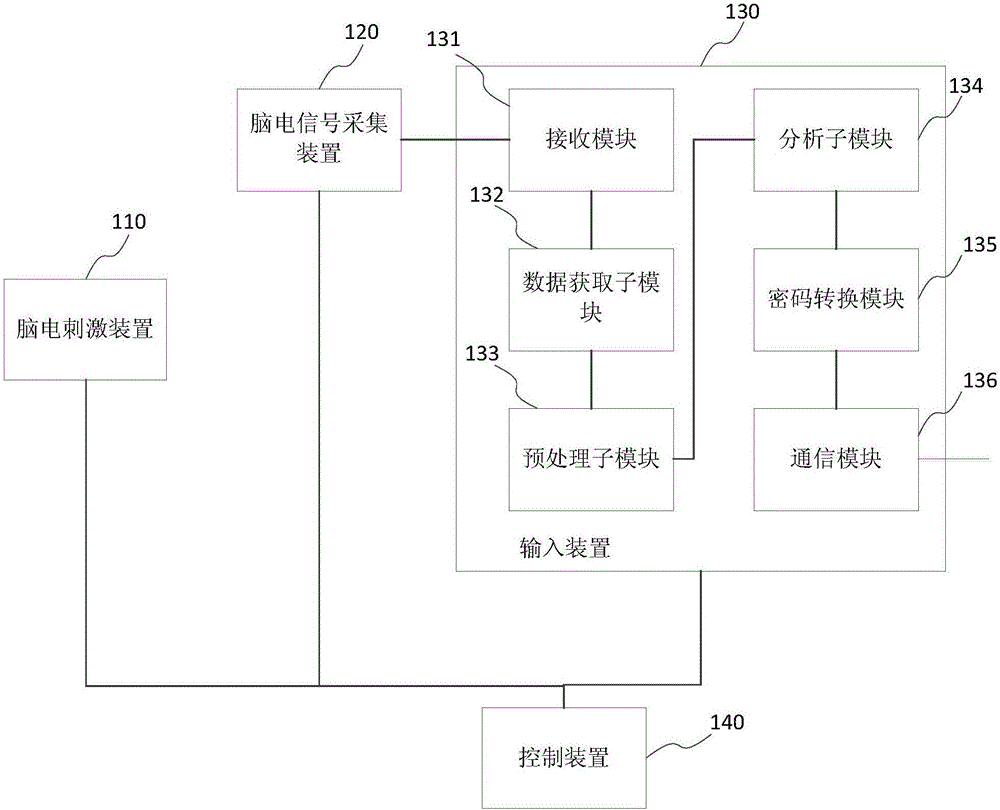
Password input device and method
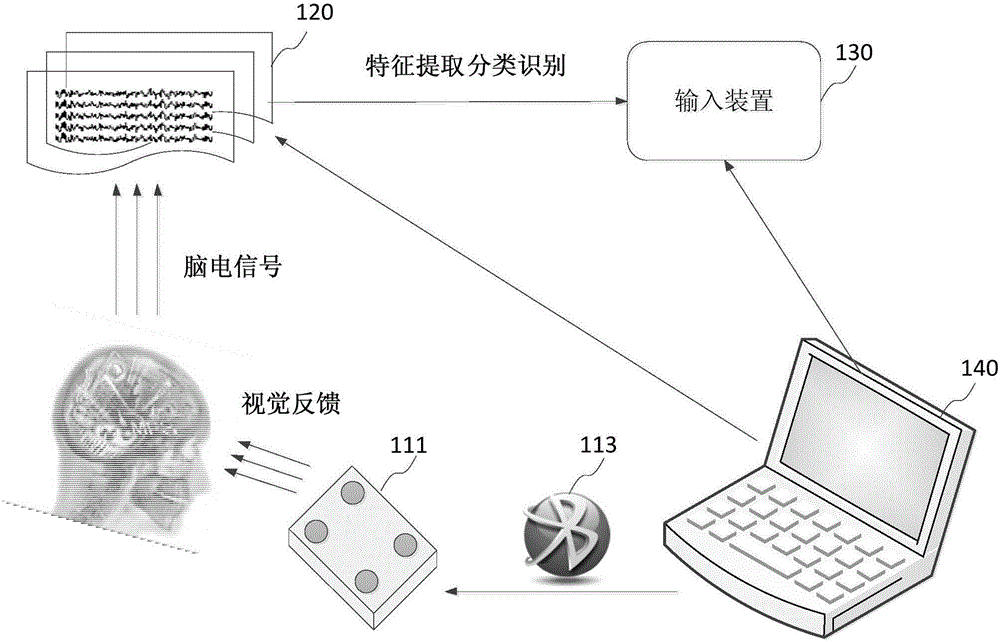
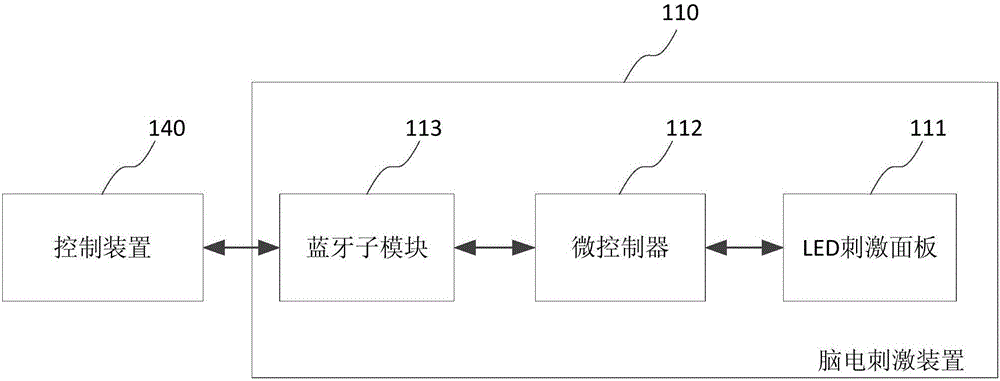
InactiveCN106774843AImprove securityNon-stationaryInput/output for user-computer interactionInternal/peripheral component protectionCrowdsVisual perception
The invention provides a password input device and a method, comprising a device of the electrical brain stimulation which provides a plurality of the visual stimuli of the different fixed frequencies; an electroencephalographic signal acquisition device collecting the EEG signal of the user through a lead, wherein the EEG signal is generated by which the user choose a gaze from a plurality of the visual stimuli of the different fixed frequencies according to the password and the password strategy; an input device connected with the EEG signal acquisition device which the steady - state visual is extracted to evoke the potential characteristics from the EEG signal, then is converted into the password and is transmitted to the encryption device. And the password strategy comprises the relationship between the password and the visual stimuli of a plurality of the different fixed frequencies. The password input device and the method are the encrypted input method for with a new bio-metric feature compared with a conventional password input mode, which utilizes the SSVP as the encryption means to remove the actual cryptographic input operation. The password input device and the method improve the security of the password input and require no training with the high recognition correctness and the wide range of the applicable population.
Owner:TONGJI UNIV
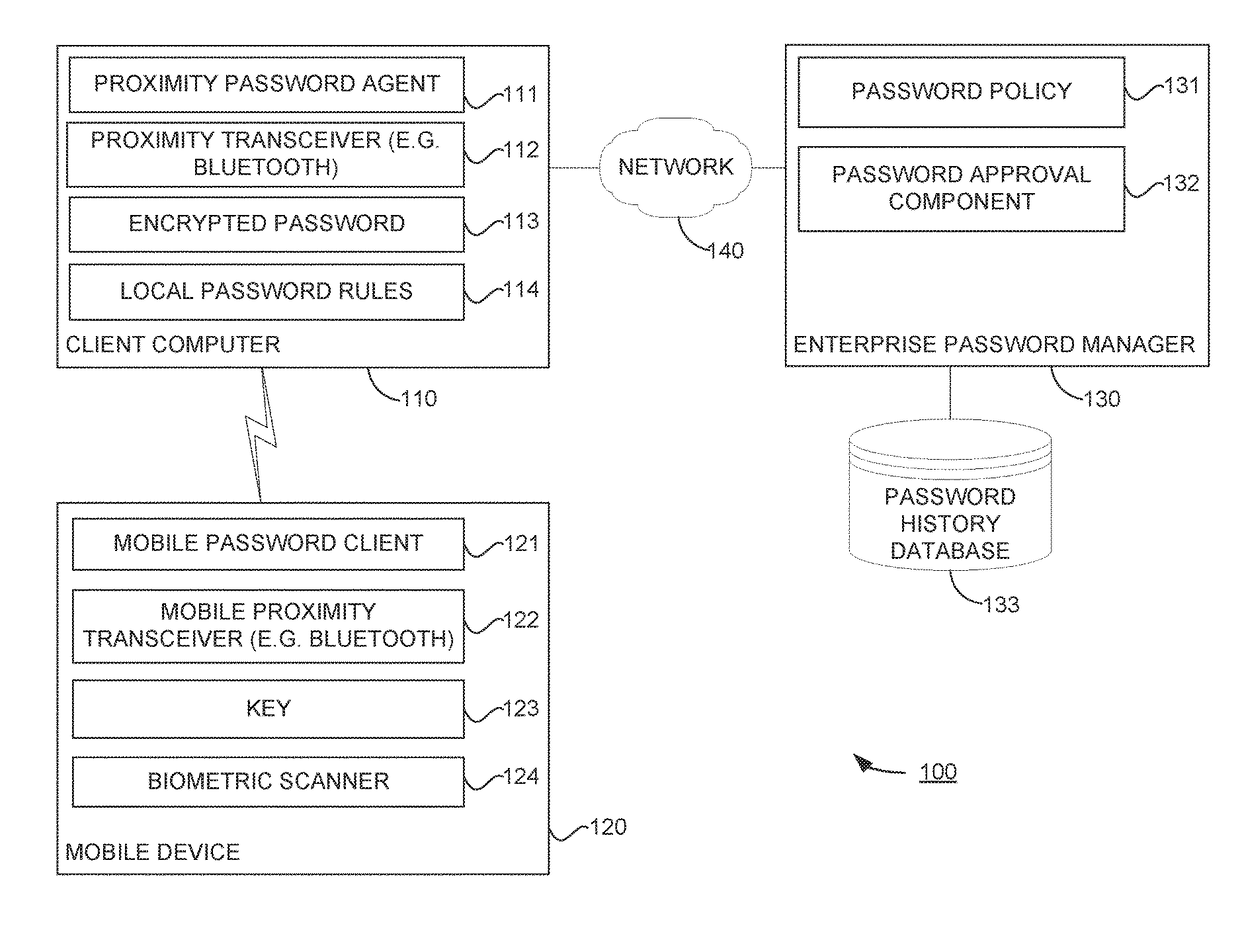
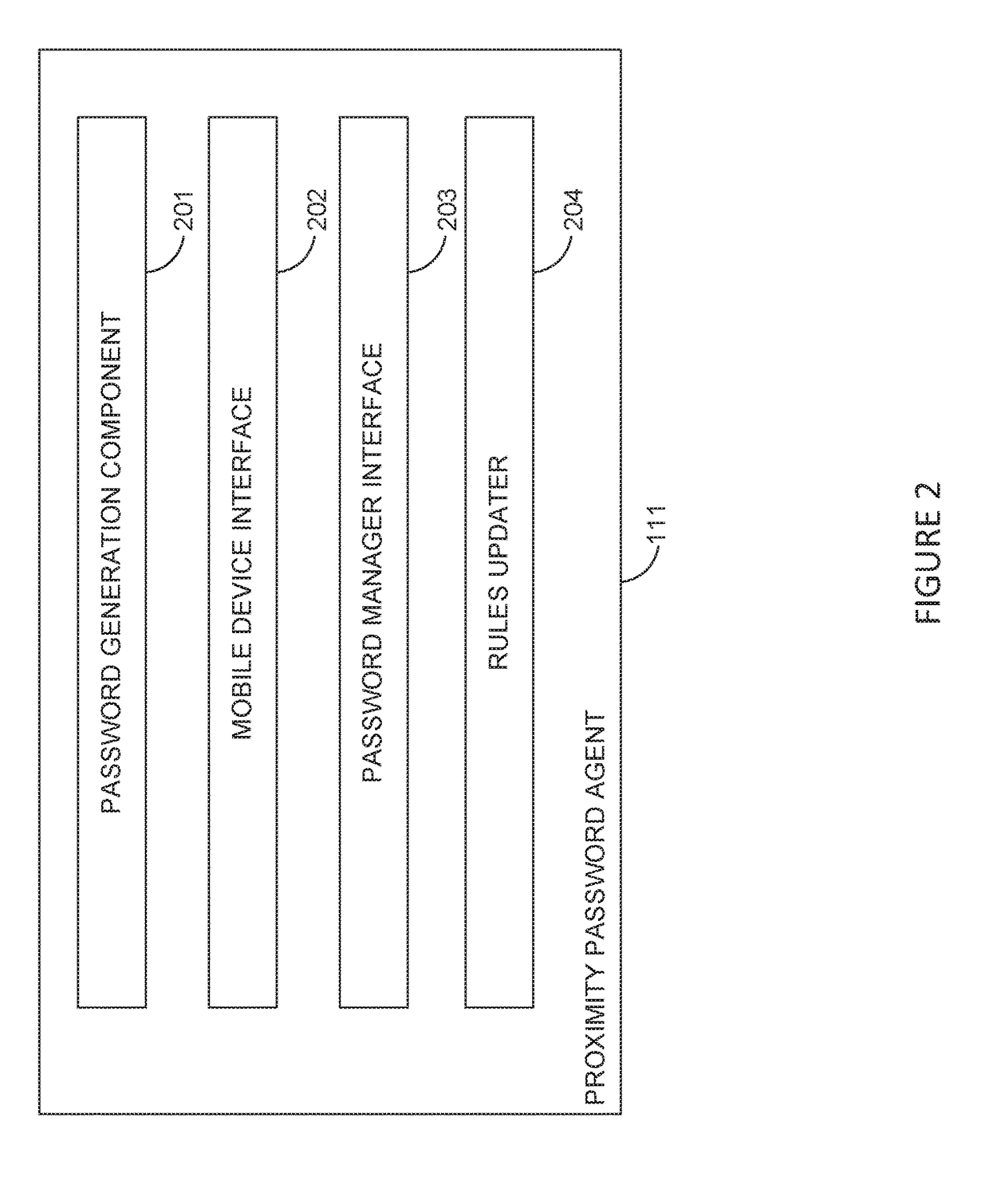
Systems and methods to enable automatic password management in a proximity based authentication
ActiveUS20180004934A1User identity/authority verificationDigital data authenticationAuthentication systemPassword policy
The present disclosure relates to changing a password in a proximity-based authentication system. After a successful proximity-based authentication, a password agent may determine that a password does not comply with an administrative password policy. The password agent may then generate a new password that does comply with the administrative password policy and submit a password change request to an administrator of that password policy, without any input by a user at these steps. The user can then request to view the password for input to a service using the same password, and after passing a biometric challenge may view the password.
Owner:CA TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com