Method for dynamically setting password by setting graphic per se in grid digital array
A digital array and graphics technology, applied in digital data authentication, electronic digital data processing, computer security devices, etc., can solve problems such as account password leakage, password leakage, invasion, etc., to protect password security, prevent sudden attacks, and prevent strong effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0039] 1. The user applies for registration of an account through the client of the computer server as usual, and the client gives the user's account or account number after confirmation, such as: YNKM123;
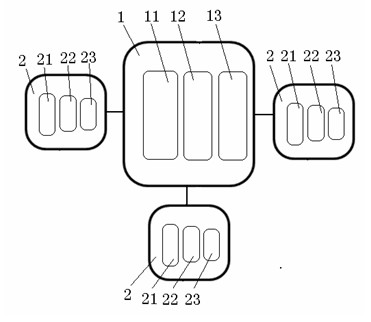
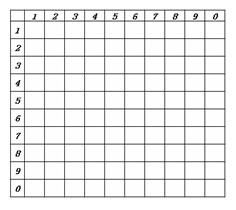
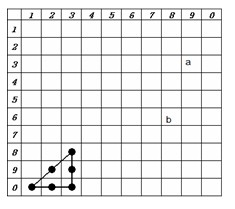
[0040] 2. The user clicks the "Graphic Password" option on the client terminal, and the grid is displayed in a grid array with blank spaces and a horizontal and vertical coordinates of 10×10 (such as figure 2 ), the user defines a triangle in the grid array diagram, the triangle is composed of six reference points and three lines connecting the reference points, and the hypotenuse of the triangle faces left, such as image 3 , select the upper acute corner point ① of the triangle as the anchor point of the triangle, start from the anchor point ①, and determine the arrangement order of the reference points to the lower left, right, and upward, as ①~⑥, such as Figure 4 , the initial position coordinates of the positioning point are: abscissa 3, ordinate 8, and at the same ...
Embodiment 2
[0043] When a user uses a network account, the following login verification is performed:
[0044] A. The user clicks the "graphic password" option on the client terminal, and the horizontal and vertical coordinate grid number array with numbers in the grid is displayed, such as Figure 5 , the abscissa 3 and ordinate 8 of the anchor point ① of the triangle set by the user according to Example 1, in Figure 4 Copy out the triangle;
[0045] B. In the abscissa and ordinate grid number array of A above, the user obtains the number 4 in the corresponding grid according to the abscissa 9 and ordinate 3 of the counting point a, and the counting order is determined from ① to ⑥ in sequence Number 4 to ④ in the triangle, then the position ④ in the triangle is the ordinate point, and the ordinate point is the number 2 in the grid where the position ④ is located is the next new ordinate of the triangle anchor point ①, and the ordinate point is the next new ordinate of the triangle anch...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com