Patents
Literature
224 results about "Administrative domain" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
An administrative domain is a service provider holding a security repository permitting to easily authenticate and authorize clients with credentials. This particularly applies to computer network security.
Transparent, look-up-free packet forwarding method for optimizing global network throughput based on real-time route status
ActiveUS20040032856A1Fast protection re-routingEfficient multicastingData switching by path configurationPrivate networkOSI model
A packet forwarding method for optimizing packet traffic flow across communications networks and simplifying network management. The invention provides look-up-free and packet-layer-protocol transparent forwarding of multi-protocol packet traffic among Layer-N (N=2 or upper in the ISO OSI model) nodes. The invention enables flexible and efficient packet multicast and anycast capabilities along with real-time dynamic load balancing and fast packet-level traffic protection rerouting. Applications include fast and efficient packet traffic forwarding across administrative domains of Internet, such as an ISP's backbone or an enterprise virtual private network, as well as passing packet traffic over a neutral Internet exchange facility between different administrative domains.
Owner:XENOGENIC DEV LLC
Method and apparatus for network distribution and provisioning of applications across multiple domains
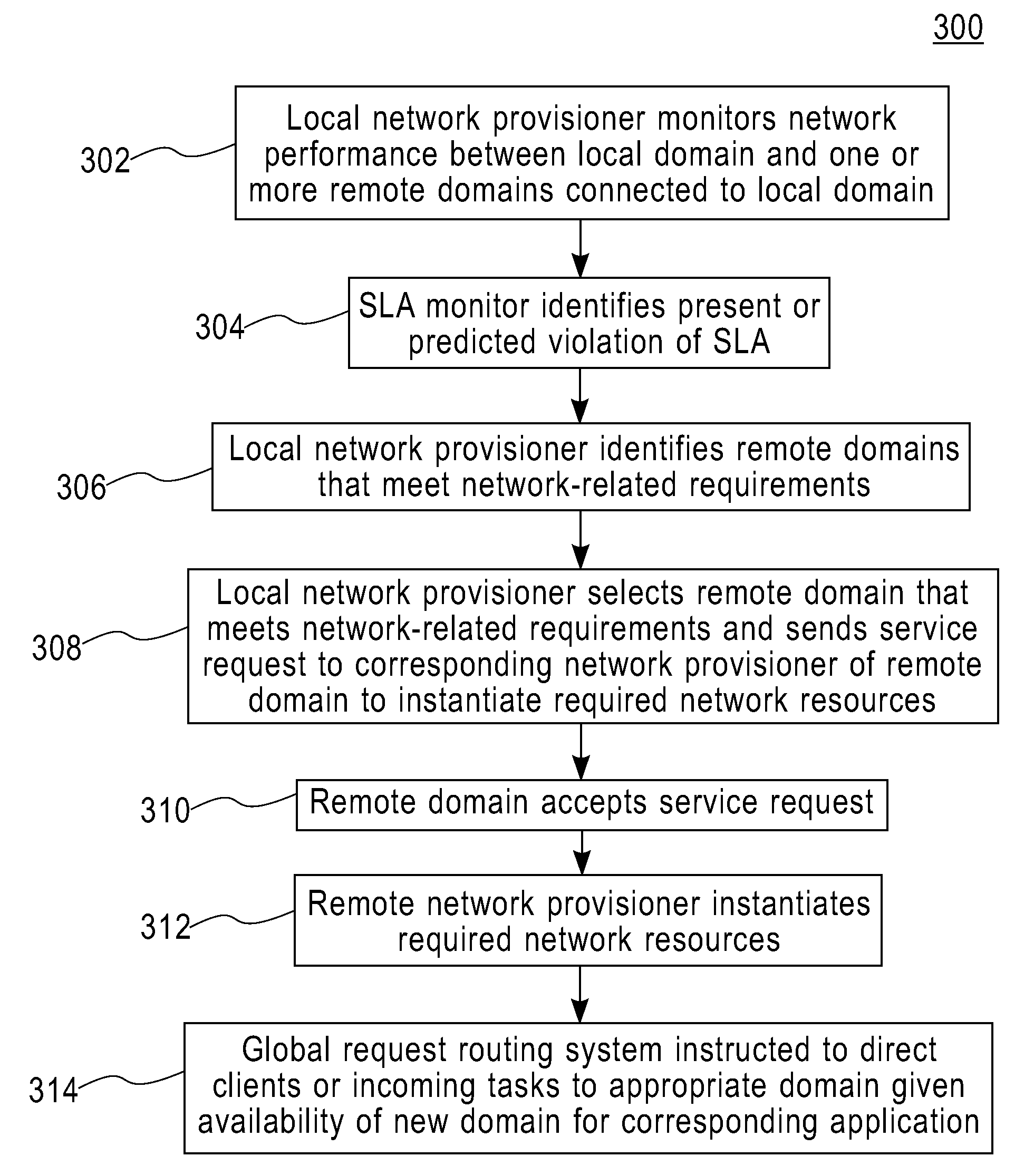
ActiveUS20080240150A1Error preventionTransmission systemsService-level agreementAdministrative domain
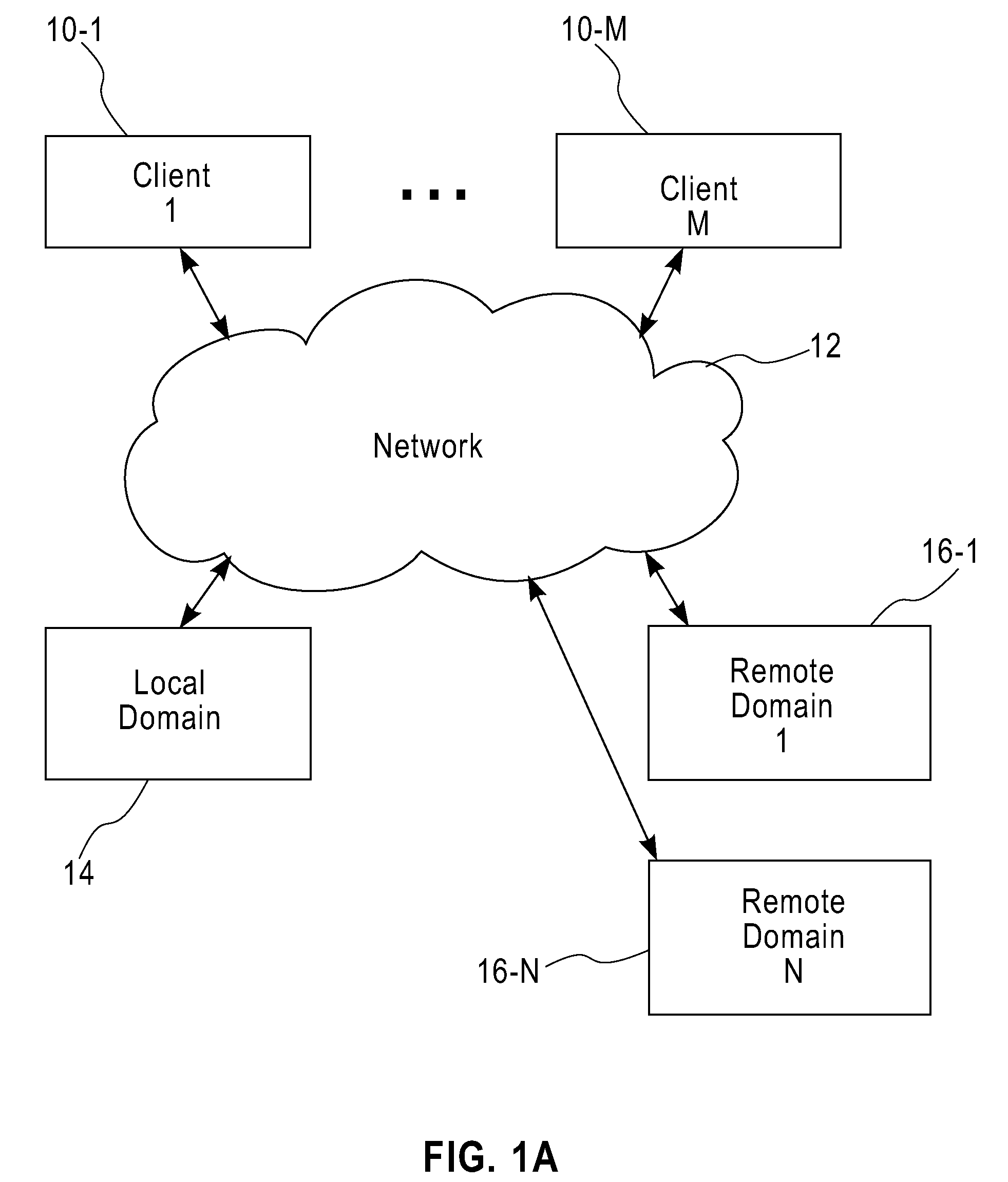
Techniques are disclosed for network distribution and provisioning of applications, such as transactional applications and parallel applications, across multiple administrative domains that ensure compliance with service level agreements. For example, a method of provisioning one or more resources in a distributed computing network to ensure compliance with a service level agreement associated with a computer application includes the following steps. Network performance is monitored between a local domain and one or more cooperating domains connected to the local domain by network paths. A present or predicted violation of the service level agreement is identified based on at least a portion of results of the monitoring step. One or more cooperating domains are selected that can effect compliance with the service level agreement by instantiating one or more network resources within at least one of the selected cooperating domains in response to a request from the local domain. Reconfiguration of the local domain is effectuated to allow the computer application to make use of the one or more newly instantiated network resources within the selected cooperating domain.
Owner:DAEDALUS BLUE LLC
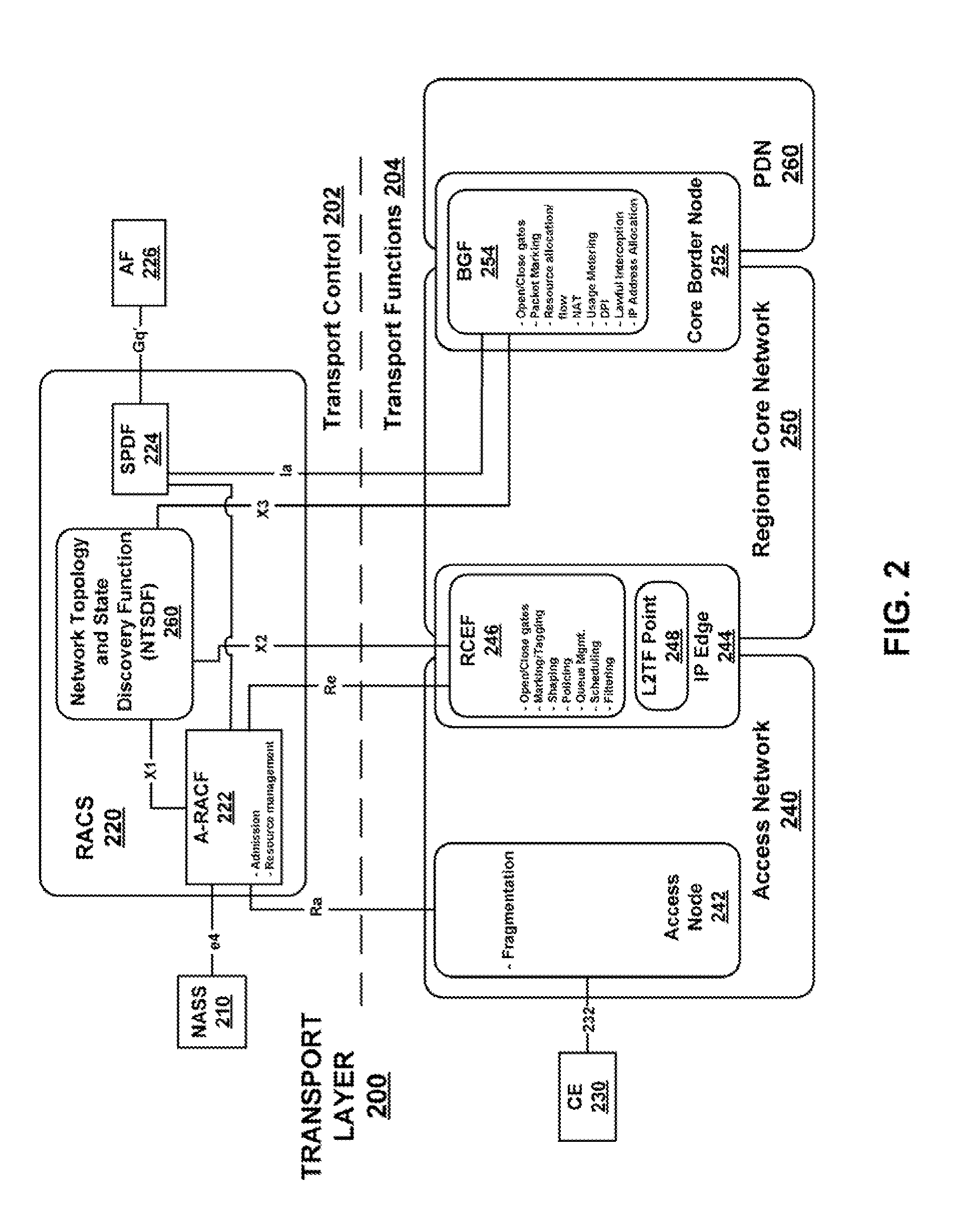
Topology discovery in heterogeneous networks
InactiveUS20090116404A1Data switching by path configurationResource Management SystemAdministrative domain
A Next Generation Network (NGN) resource management system and method includes a network topology discovery mechanism at the scale of an administrative domain. Information about nodes and links, such as bandwidth, delay, jitter, name and description of devices is collected and stored in a database by way of a protocol. The protocol is notifications-based, which involves each node device (e.g., a switch, router etc.) notifying its presence to its neighboring node.
Owner:TELEFON AB LM ERICSSON (PUBL)
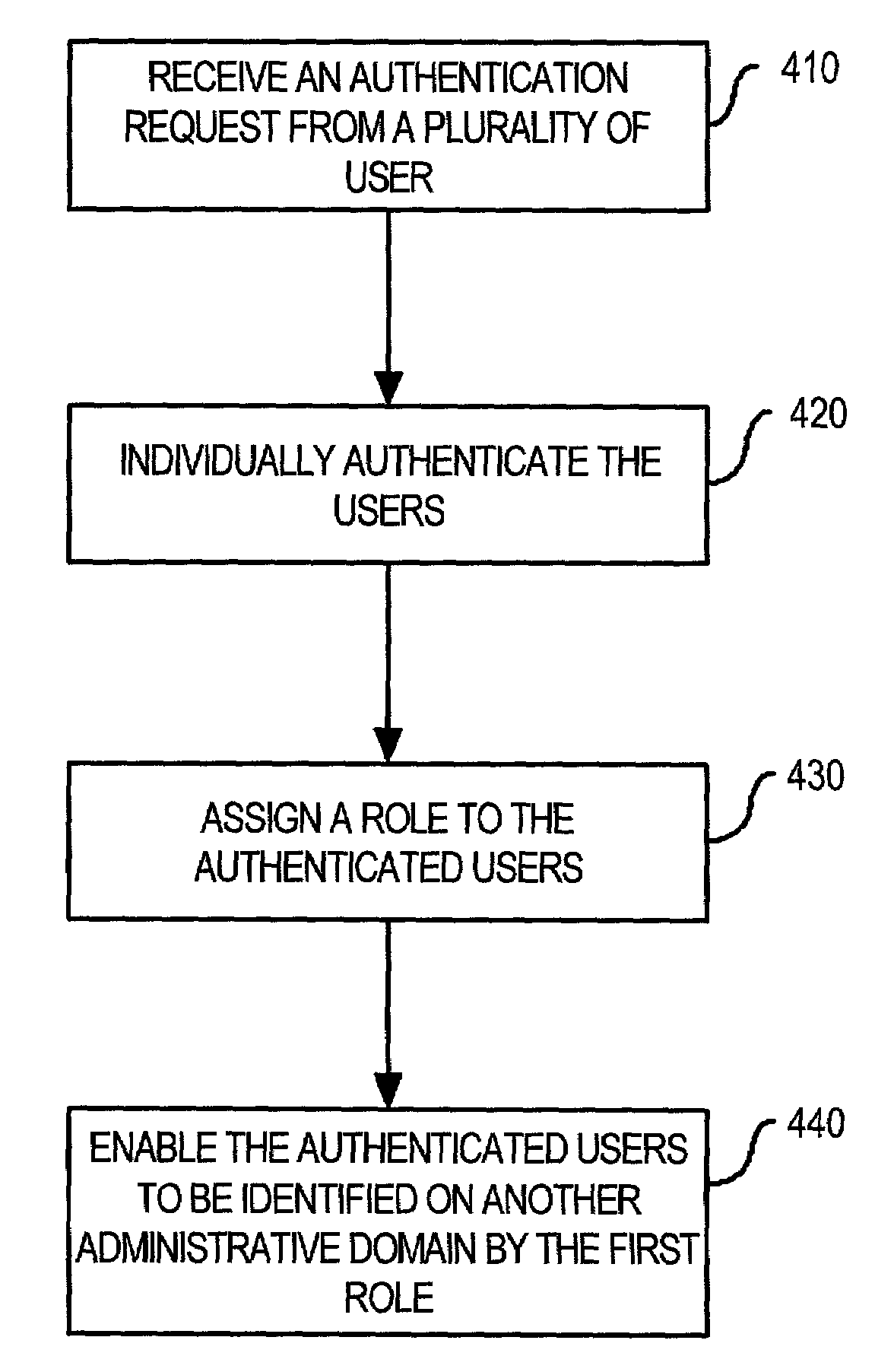
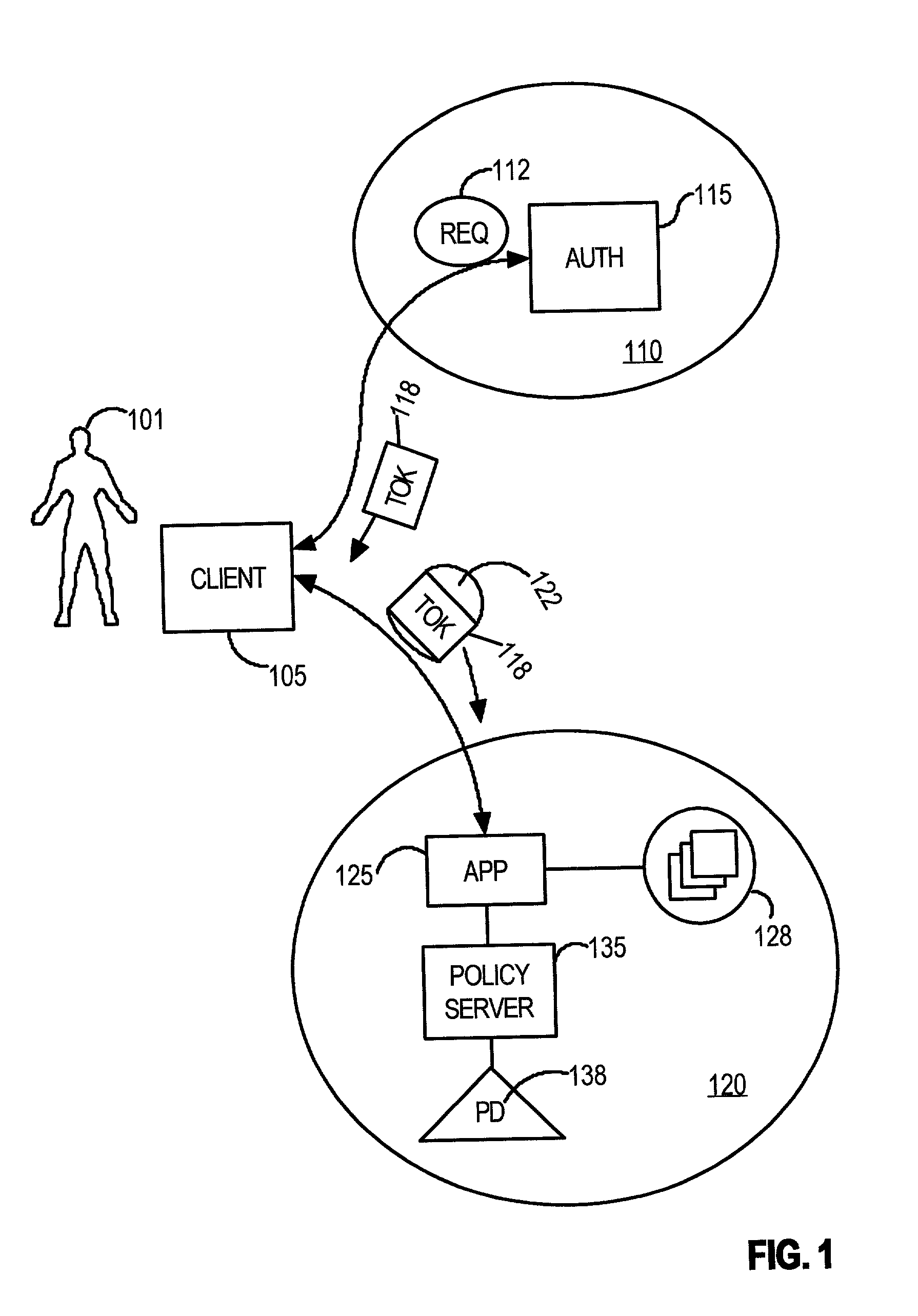
Method and apparatus for managing network resources for externally authenticated users
ActiveUS7010600B1Multiple digital computer combinationsTransmissionAdministrative domainWeb resource
A method is disclosed for managing network resources in multiple administrative domains. According to the method, a user is authenticated in a first administrative domain. A token is generated for the user that identifies the user as being assigned a role. The token is configured to identify the user by the role to a component of a second administrative domain. When the user requests a resource of the second administrative domain, its component examines the token and the role to determine whether to grant access to the resource. As a result, the second administrative domain may grant the user access to its resources without re-authenticating the user in the second administrative domain.
Owner:CISCO TECH INC
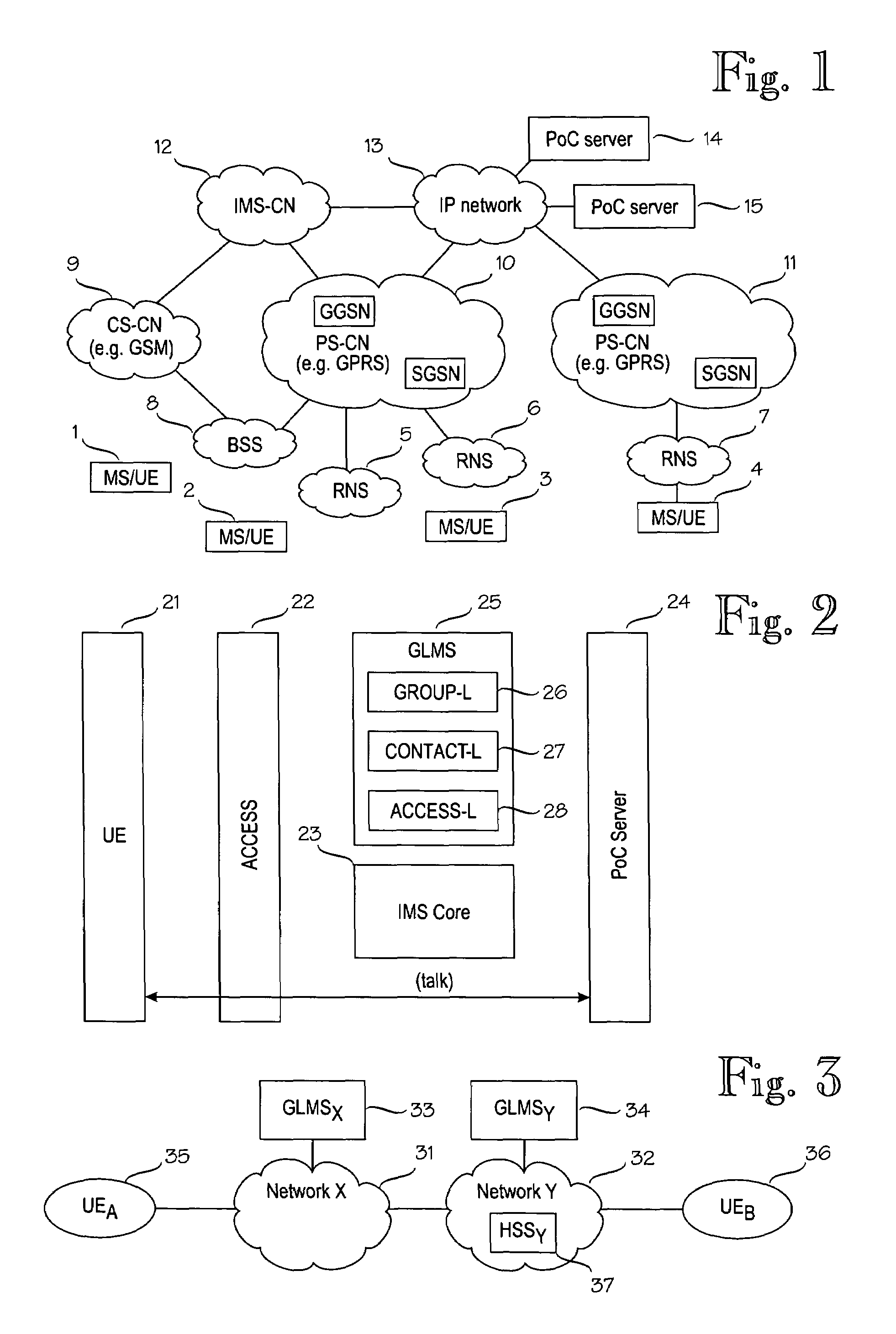
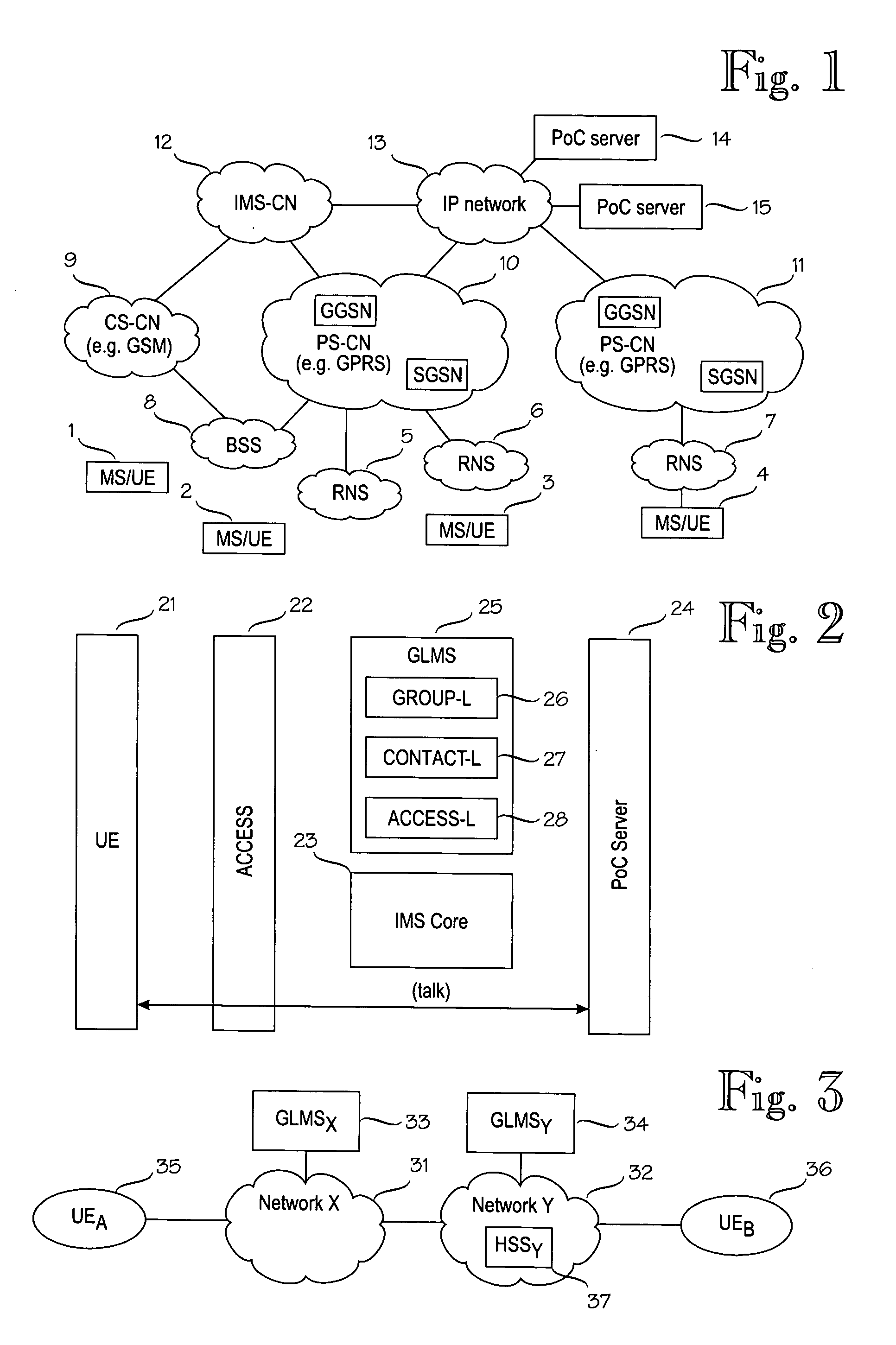
Group information management
ActiveUS7085365B2Improve user friendlinessReady adoptionSpecial service for subscribersMultiple digital computer combinationsCommunications systemAdministrative domain
A communication system including a first administrative subsystem and a second administrative subsystem providing group communication service. The system includes a first server for storing group and list management information of subscribers of the first administrative subsystem. The system also includes a second server for storing group and list management information of subscribers of the second administrative subsystem. Further, the system includes an interface for exchanging group and list management information between the first server and the second server. In addition, the system reduces ambiguity in group information management of integrated systems that include two or more administrative domains.
Owner:NOKIA TECHNOLOGLES OY
Transparent, look-up-free packet forwarding method for optimizing global network throughput based on real-time route status
ActiveUS7254138B2Improve performanceFast and efficient packet-level traffic protection re-routingError preventionTransmission systemsPrivate networkOSI model
Owner:XENOGENIC DEV LLC
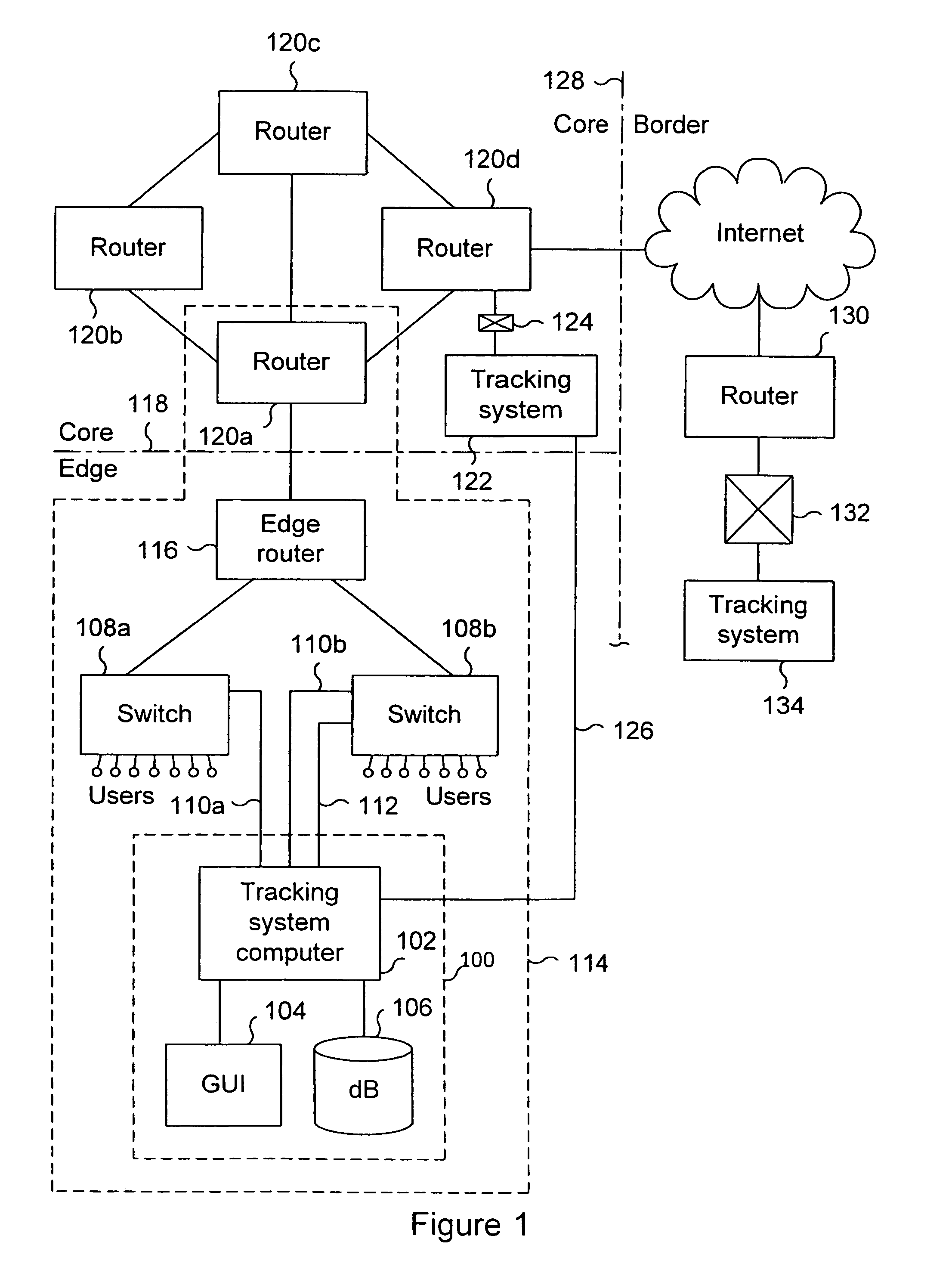
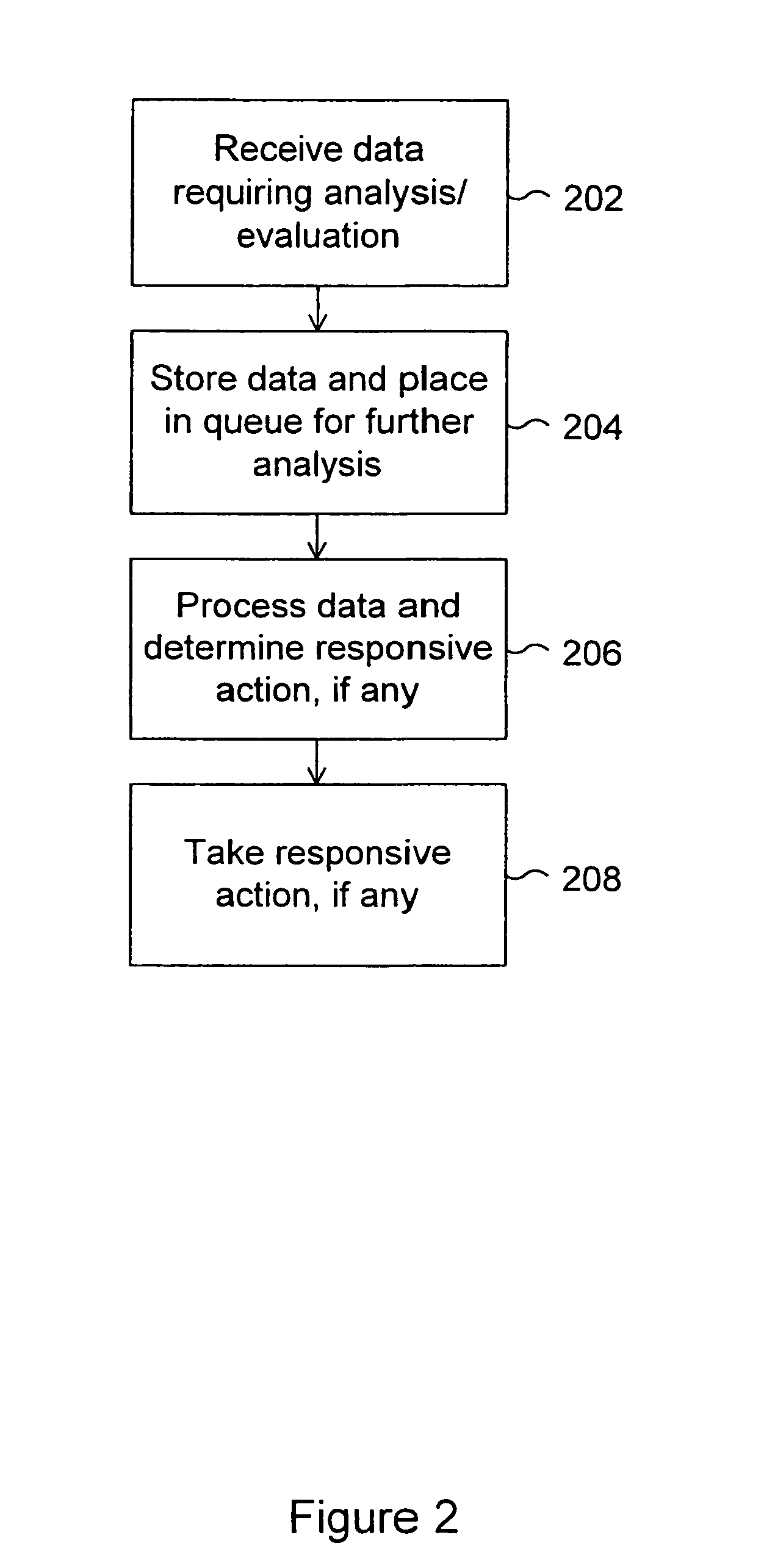
System and method for tracking the source of a computer attack
InactiveUS6971028B1Memory loss protectionDigital computer detailsAdministrative domainData placement
A system and method are disclosed for detecting and processing attacks on a computer network. Data indicating an attack may be taking place is received. The data is associated with an event. The data is placed in a selected one of a plurality of queues of data to be processed. The data in the queue is processed. Each queue is configured to store one or more sets of data, each set of data being associated with an event to be processed. An administrative domain may be notified that an attack may be taking place. The destination administrative domain may or may not be associated with other than the sending administrative domain. The source of an attack may be identified. Messages associated with an attack may be tracked back to identify a point of attack at which messages associated with the attack are entering a network.
Owner:CA TECH INC
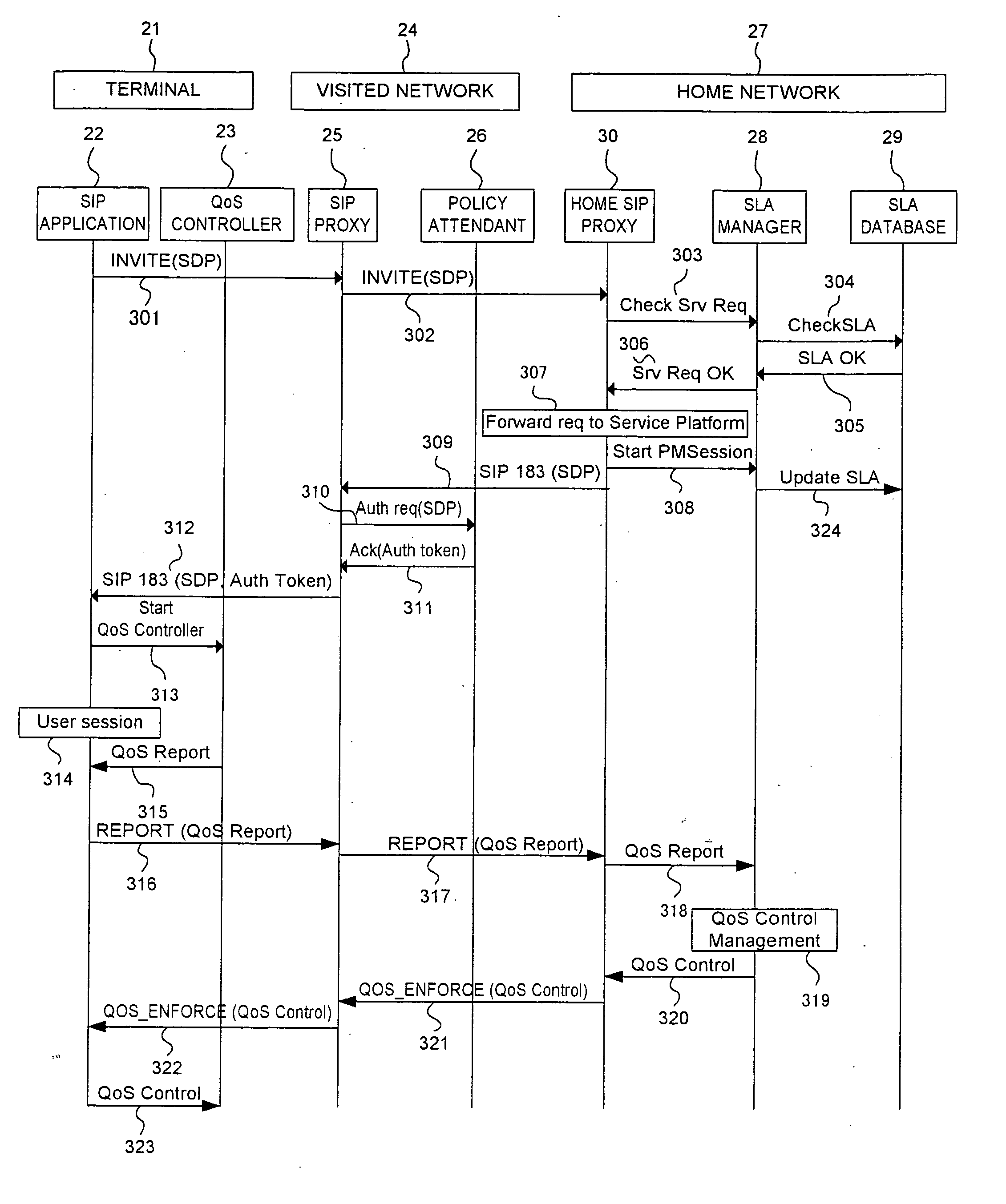
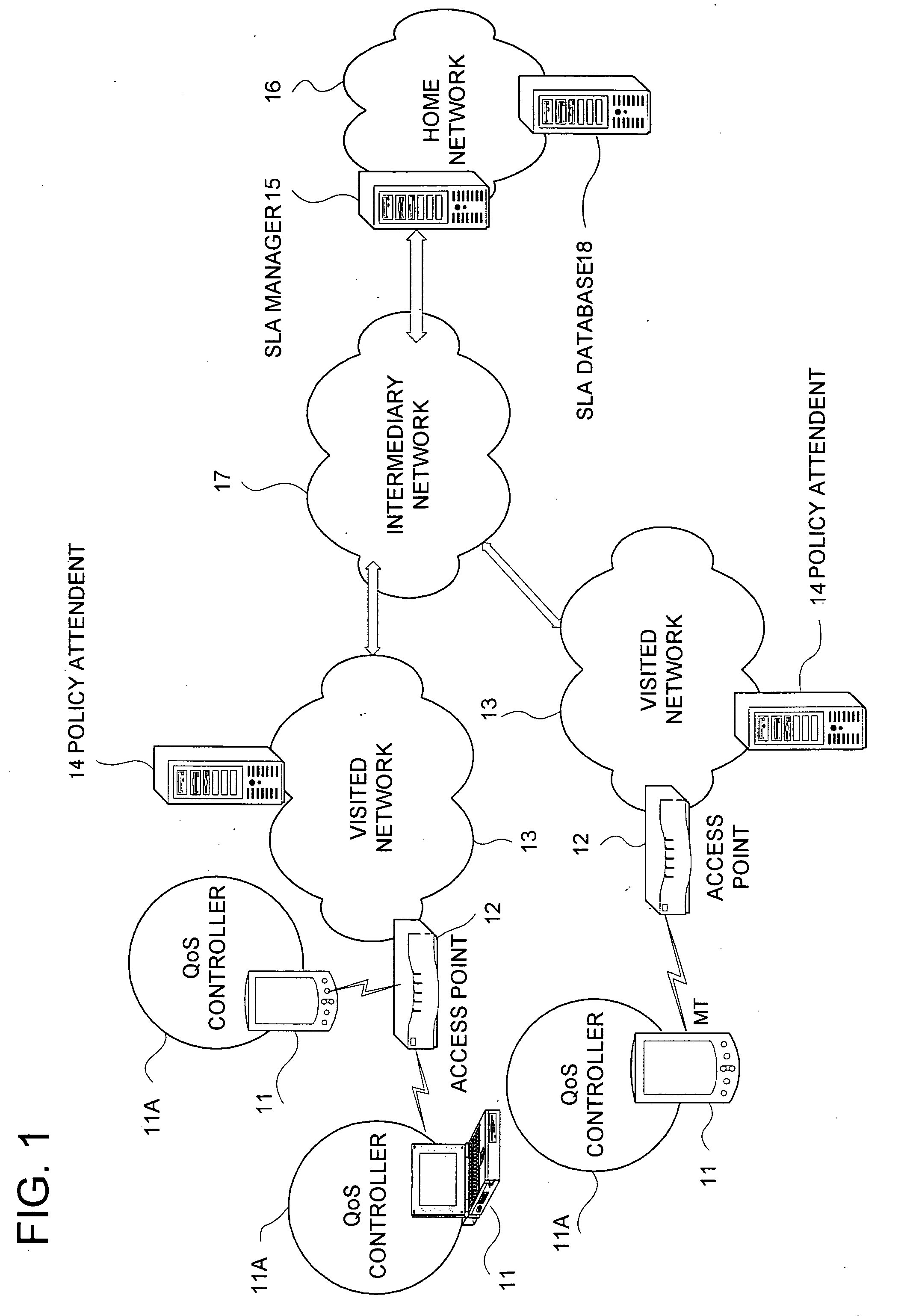
Communication system and communication method
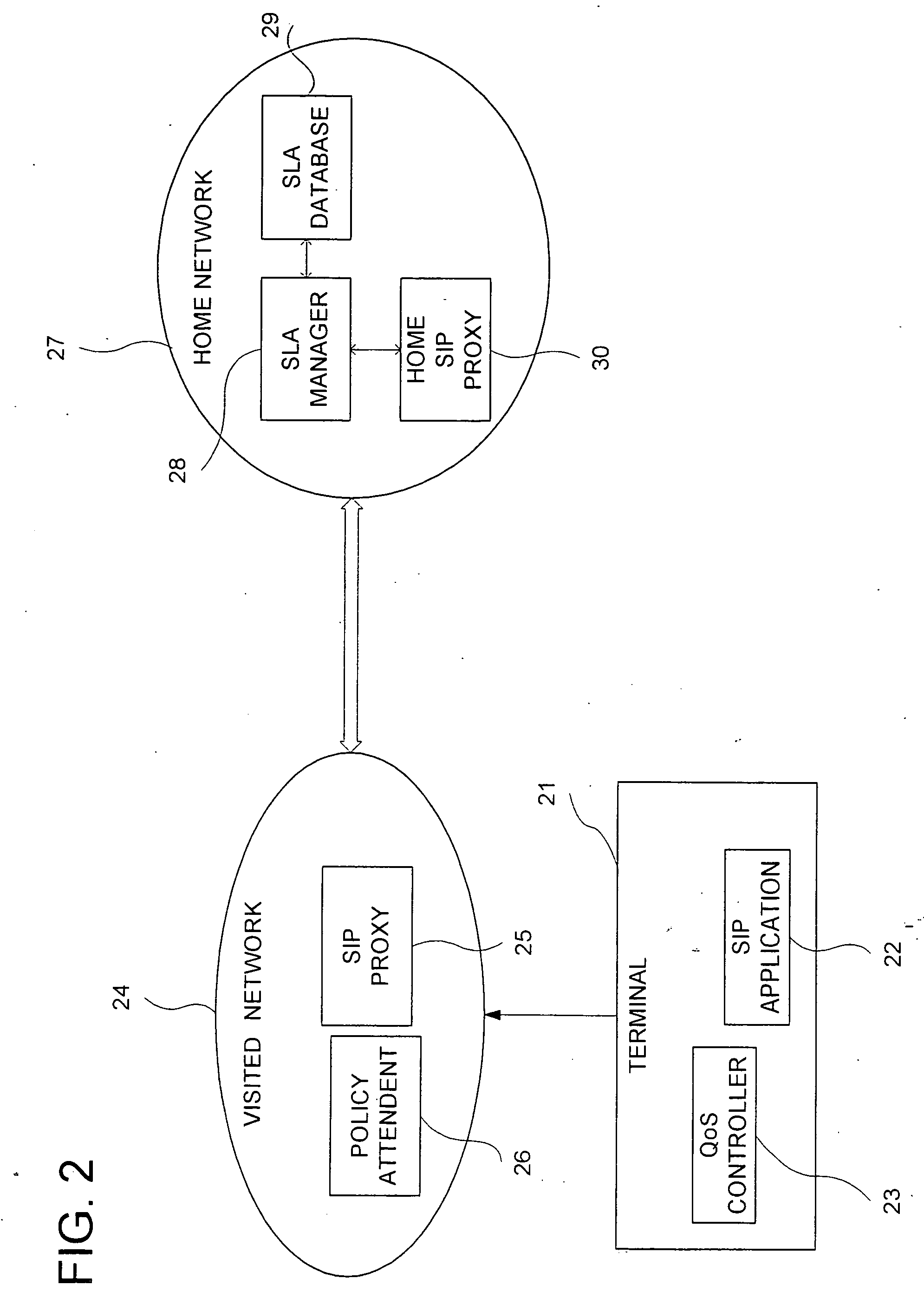
InactiveUS20060218302A1Not unnecessarily trafficError preventionTransmission systemsCommunications systemQos management
A technique for the end terminal provided with services to handle QoS process is disclosed. According to this technique, a terminal based QoS management scheme is implemented to achieve end-to-end QoS wherein the end terminal 21 is responsible for handling of the QoS related functions. In order for QoS management to be handled at terminal, the terminal needs to know the network conditions and external state of entities in order to know what action to be taken. For example, the terminal performs monitoring and usage collection. These performance data are then reported to a central server (SLA manager 28). The central server collects these data from all terminals within its administration domain. The central server also has access to information on the QoS to be given to individual terminals, such as service level. Based on the information, the central server decides what action to be taken by individual terminal and enforces these actions into the affected terminals.
Owner:PANASONIC CORP
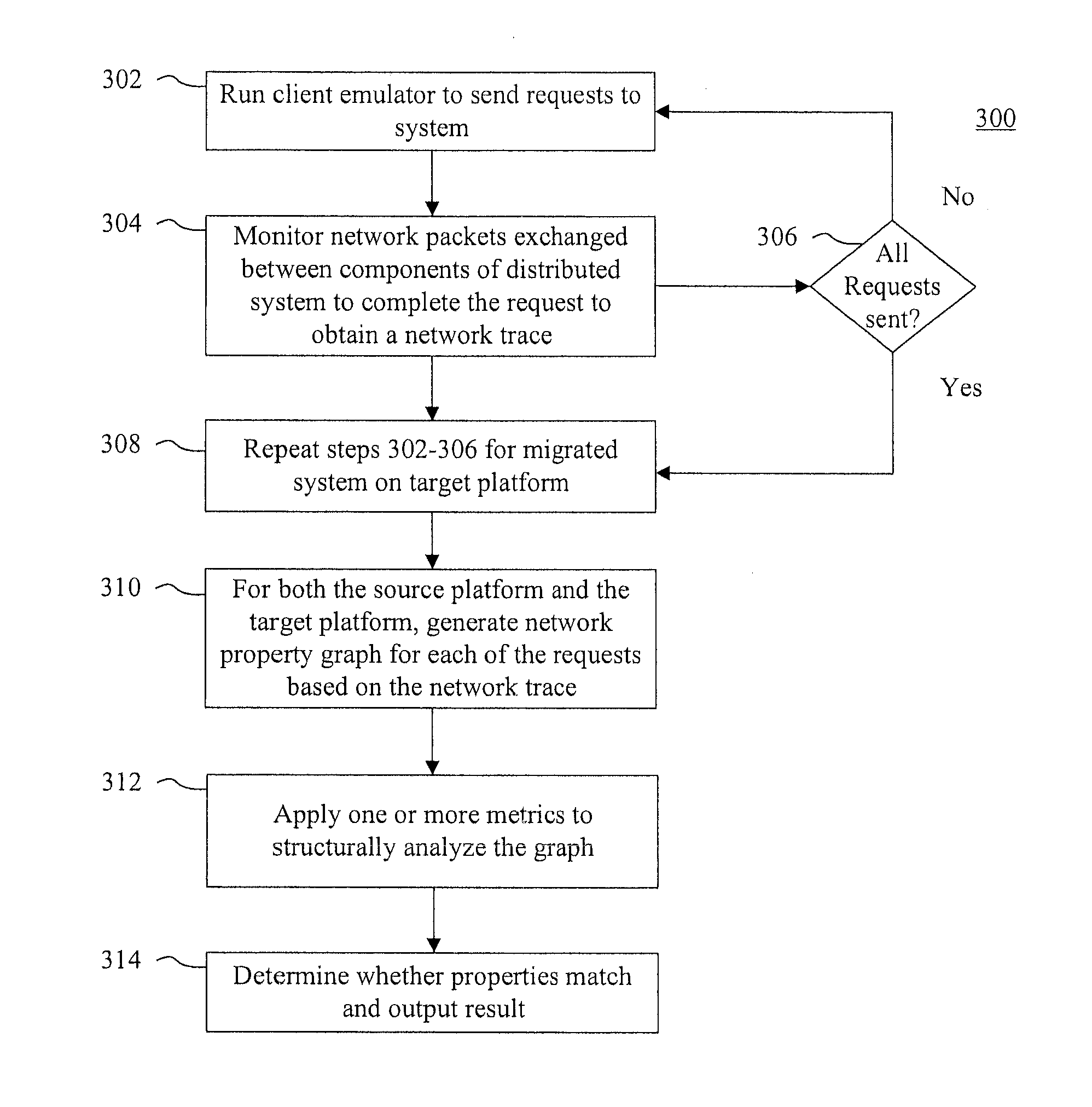
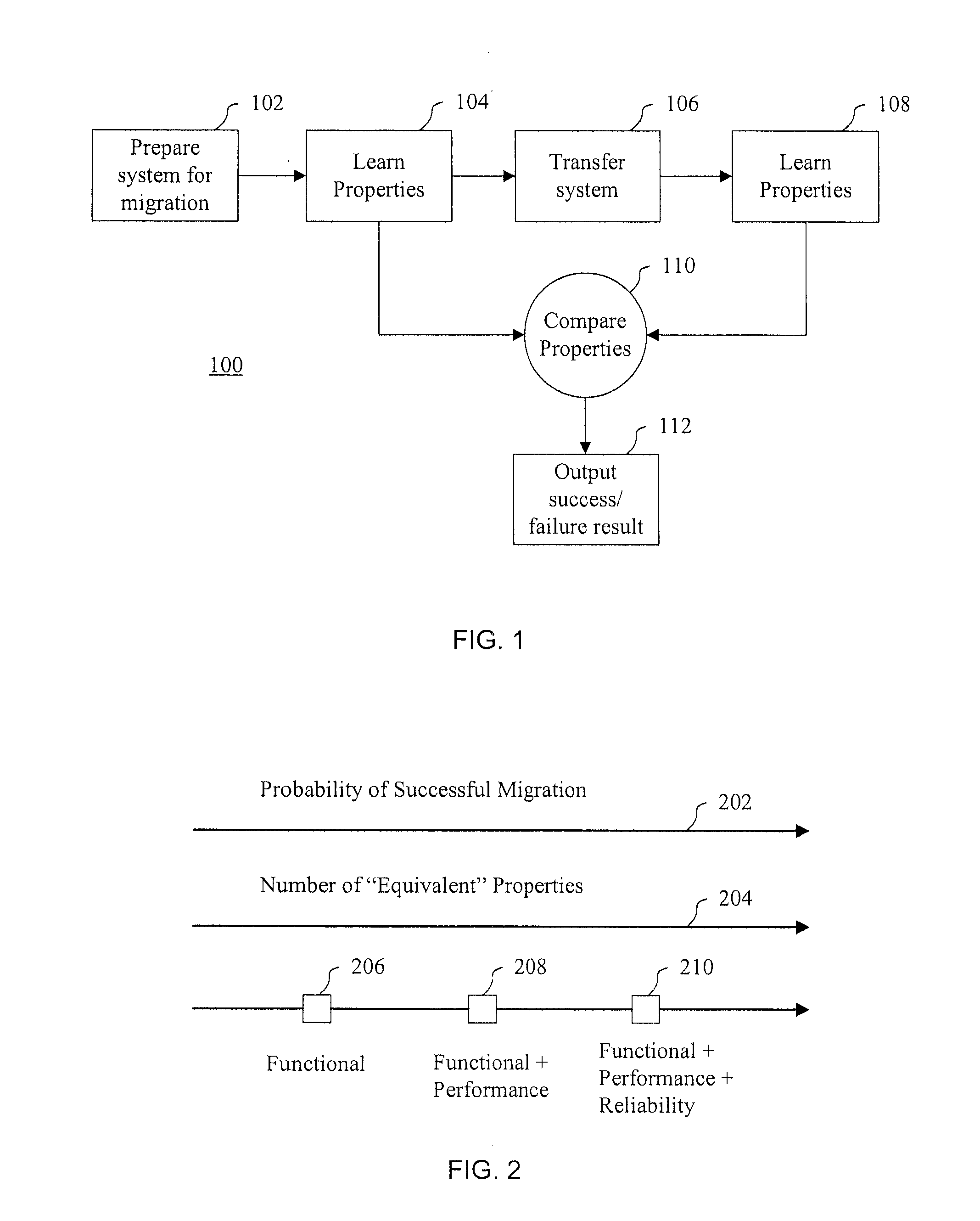
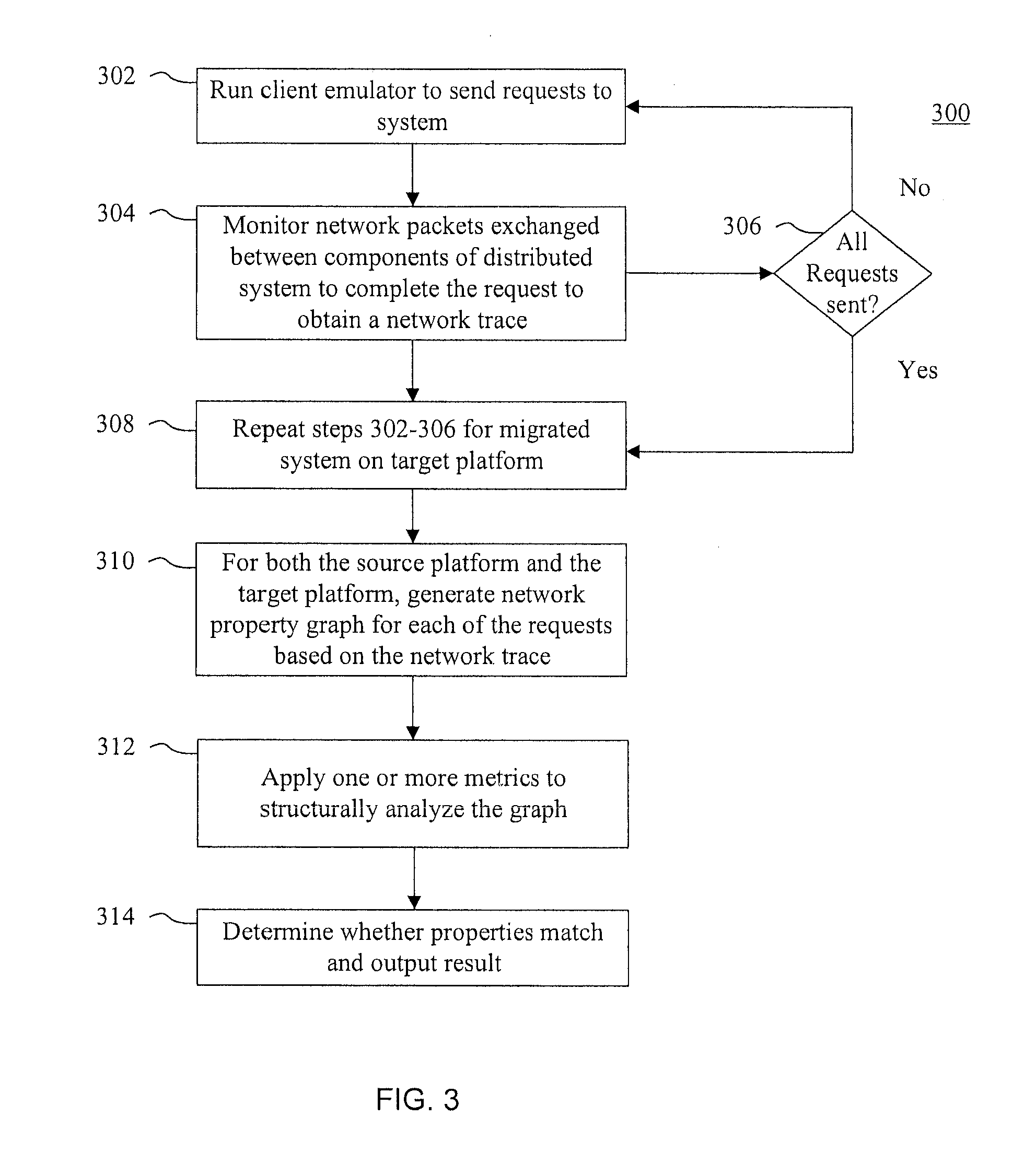
Methods and systems for migrating networked systems across administrative domains
ActiveUS20110276675A1Multiple digital computer combinationsProgram controlTransfer systemAdministrative domain
Systems and methods for determining whether networked system migrations are successful are disclosed. In accordance with one method, a first set of properties of the networked system on a source platform in a first administrative domain is determined. Further, the method includes transferring the networked system to a destination platform in a second administrative domain. In addition, a second set of properties of the transferred system on the destination platform is determined, where the first and second sets of properties include functional properties and at least one of: performance properties, security properties or reliability properties. The method also includes outputting an indication that the transfer of the system to the destination platform is successful in response to determining that one or more of the properties of the second set are equivalent to corresponding properties of the first set.
Owner:NEC CORP
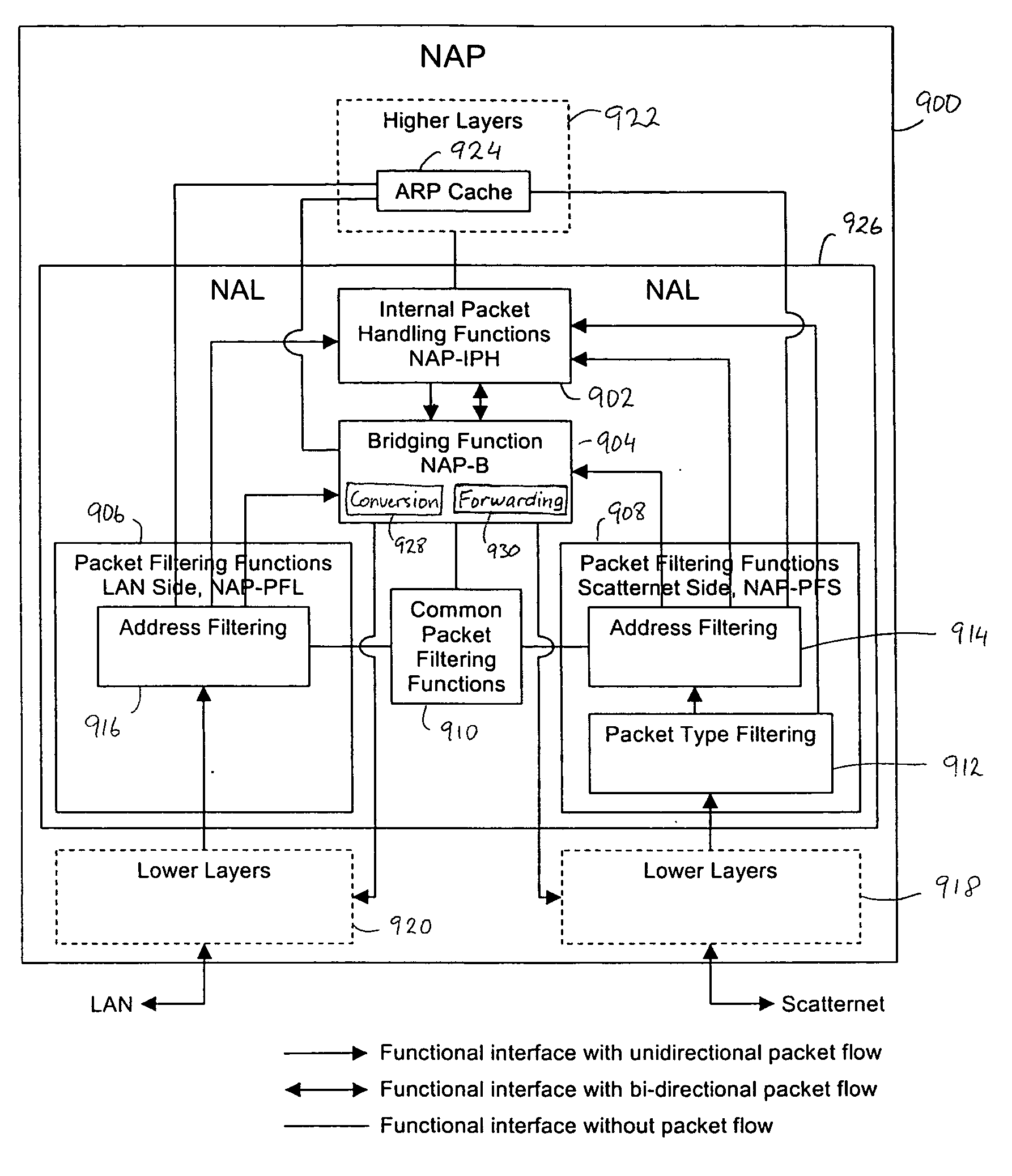
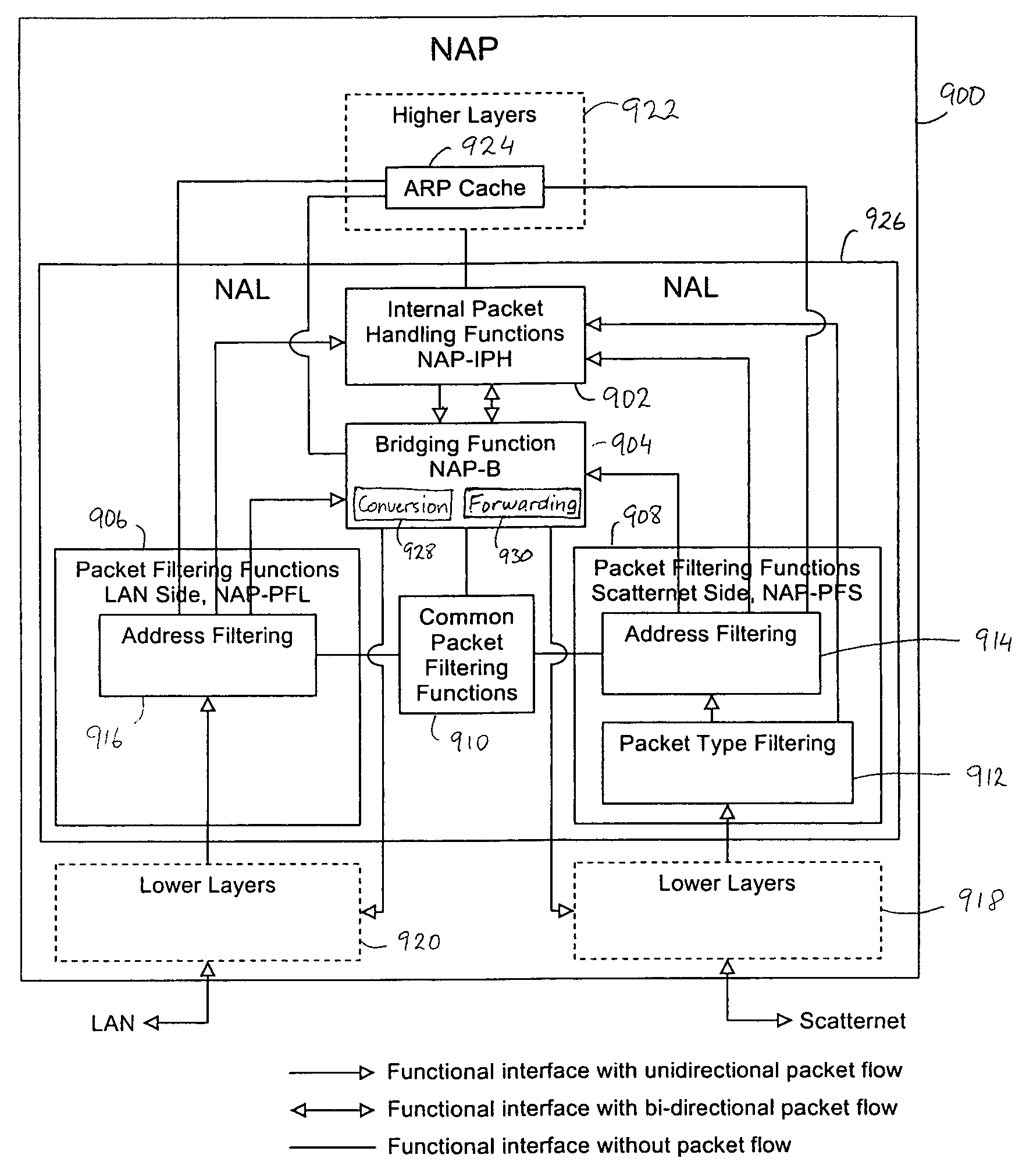
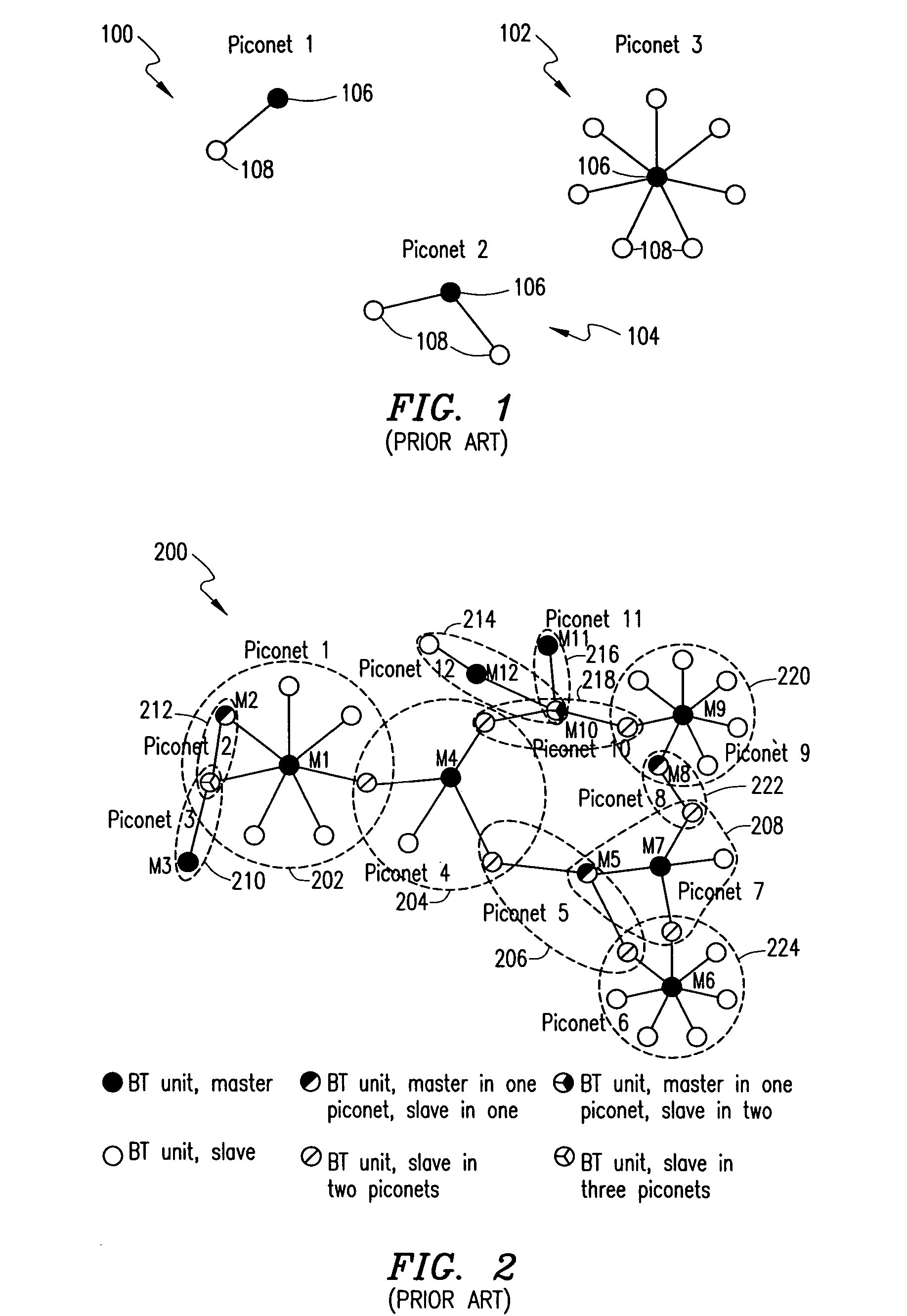
Bridging between a Bluetooth scatternet and an Ethernet LAN
InactiveUS20040167988A1Multiple digital computer combinationsNetworks interconnectionNetwork packetAdministrative domain
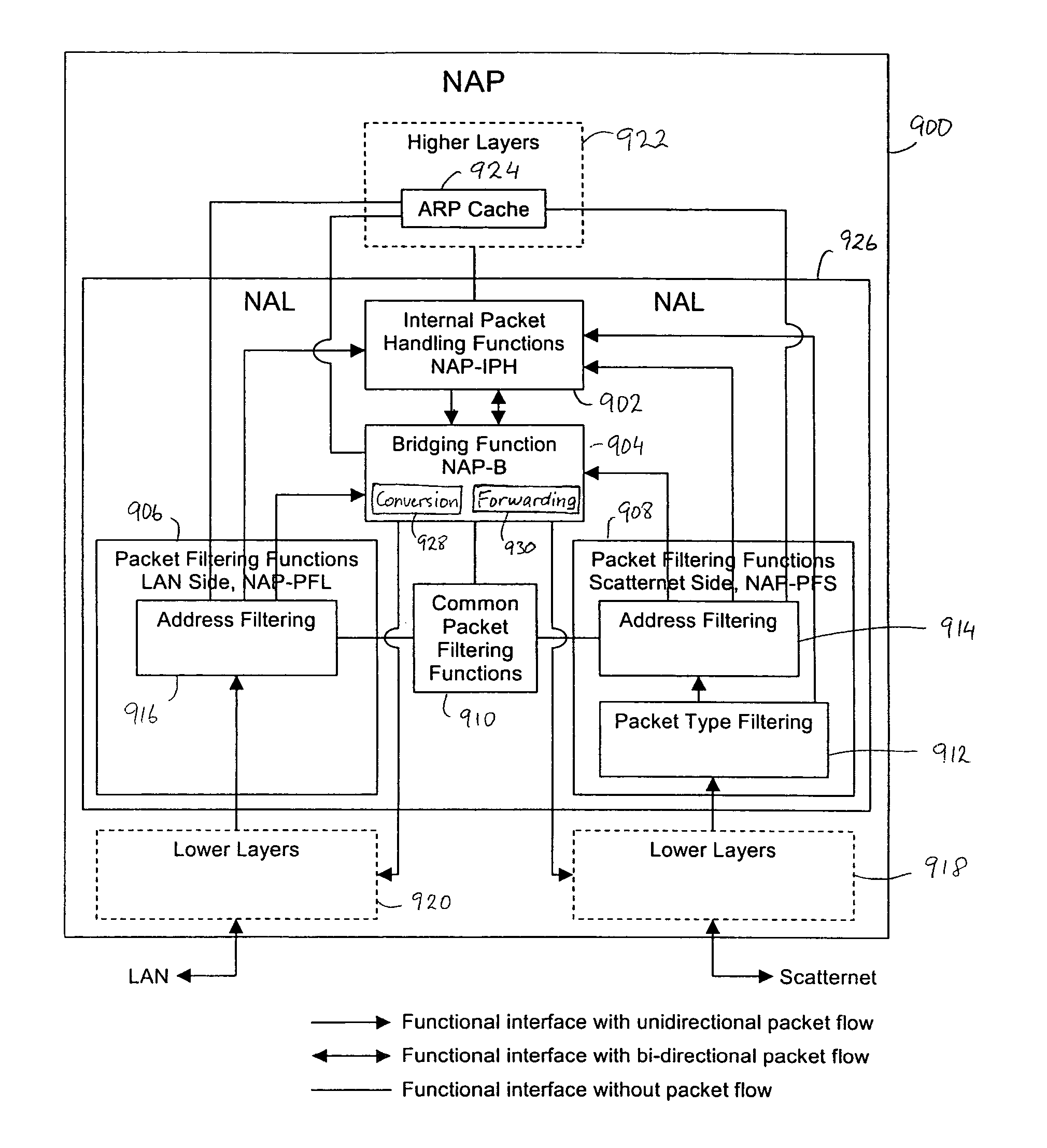
System and method are disclosed for bridging a point-to-point network such as a Bluetooth scatternet with a shared medium network such as an Ethernet LAN. The scatternet is connected to the LAN via a network access point (NAP). Data packets sent from the LAN to the scatternet are filtered at the NAP to eliminate unnecessary data packets from being sent to the scatternet. Only certain ones of the data packets are forwarded between the LAN and the scatternet. An inter-NAP protocol is used to exchange messages where two or more NAPs are connected to the LAN. Broadcast loops are prevented from occurring in the scatternet and the LAN by defining Administrative domains and NAP service areas (NAPSAs), and controlling the borders thereof according to a broadcast type of the data packets.
Owner:TELEFON AB LM ERICSSON (PUBL)
System and method for providing context information
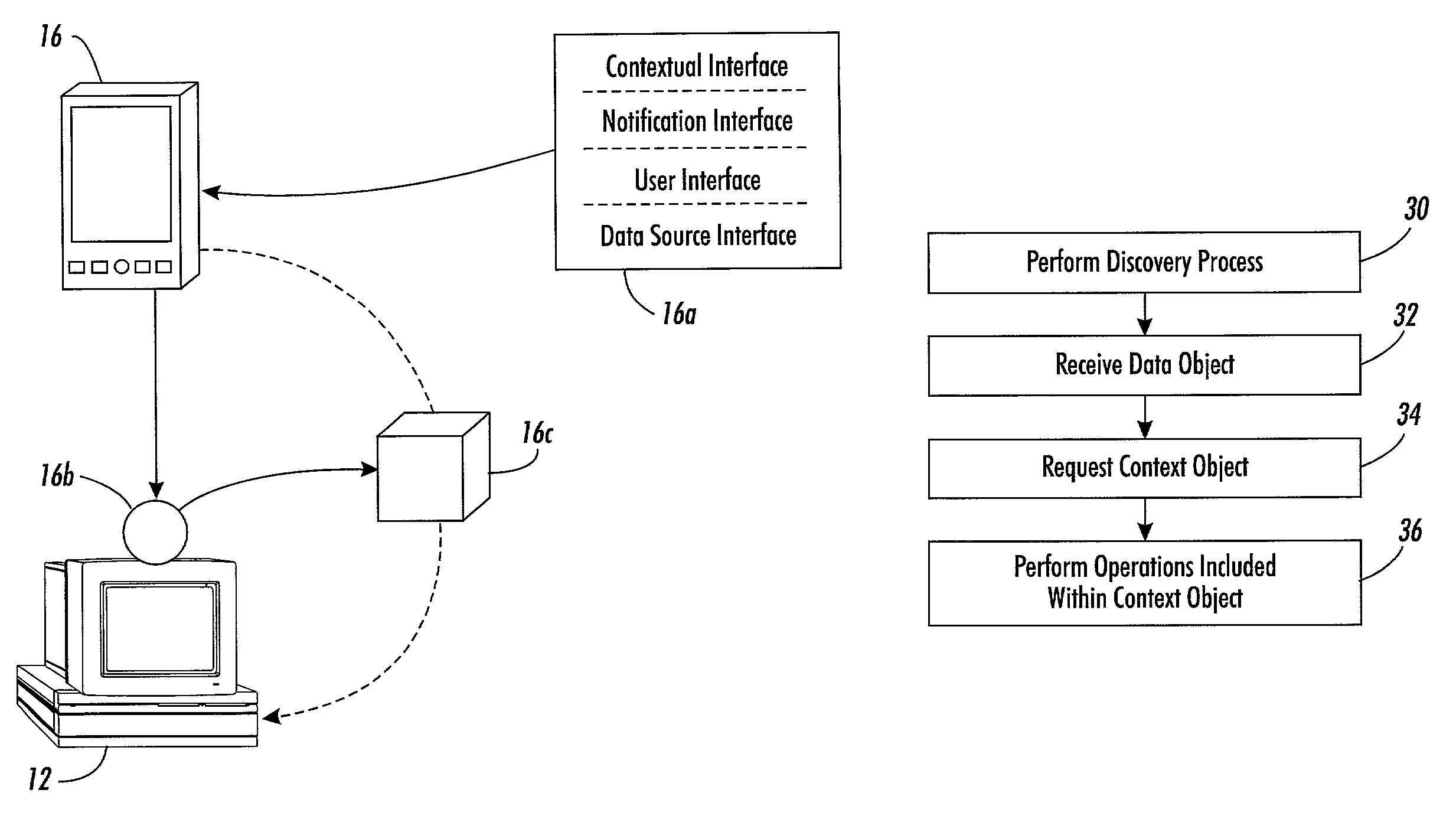
InactiveUS7552265B2Digital computer detailsElectrographic process apparatusAdministrative domainData source
Systems and methods for enabling arbitrary components to transfer current, contextual data between each other without requiring prior knowledge of each other. The contextual data may include executable computer language instructions or a type, operating status, identity, location, administrative domain or environment information of the components or its users. The system includes a set of arbitrary components associated with one or more universal interfaces. The one or more universal interfaces may include mobile code, a contextual interface, a notification interface, a user interface and a data source interface. A first component at least has a universal contextual interface. A second component may invoke the universal contextual interface and execute associated instructions to transfer contextual data between the first component and the second component.
Owner:GULA CONSULTING LLC
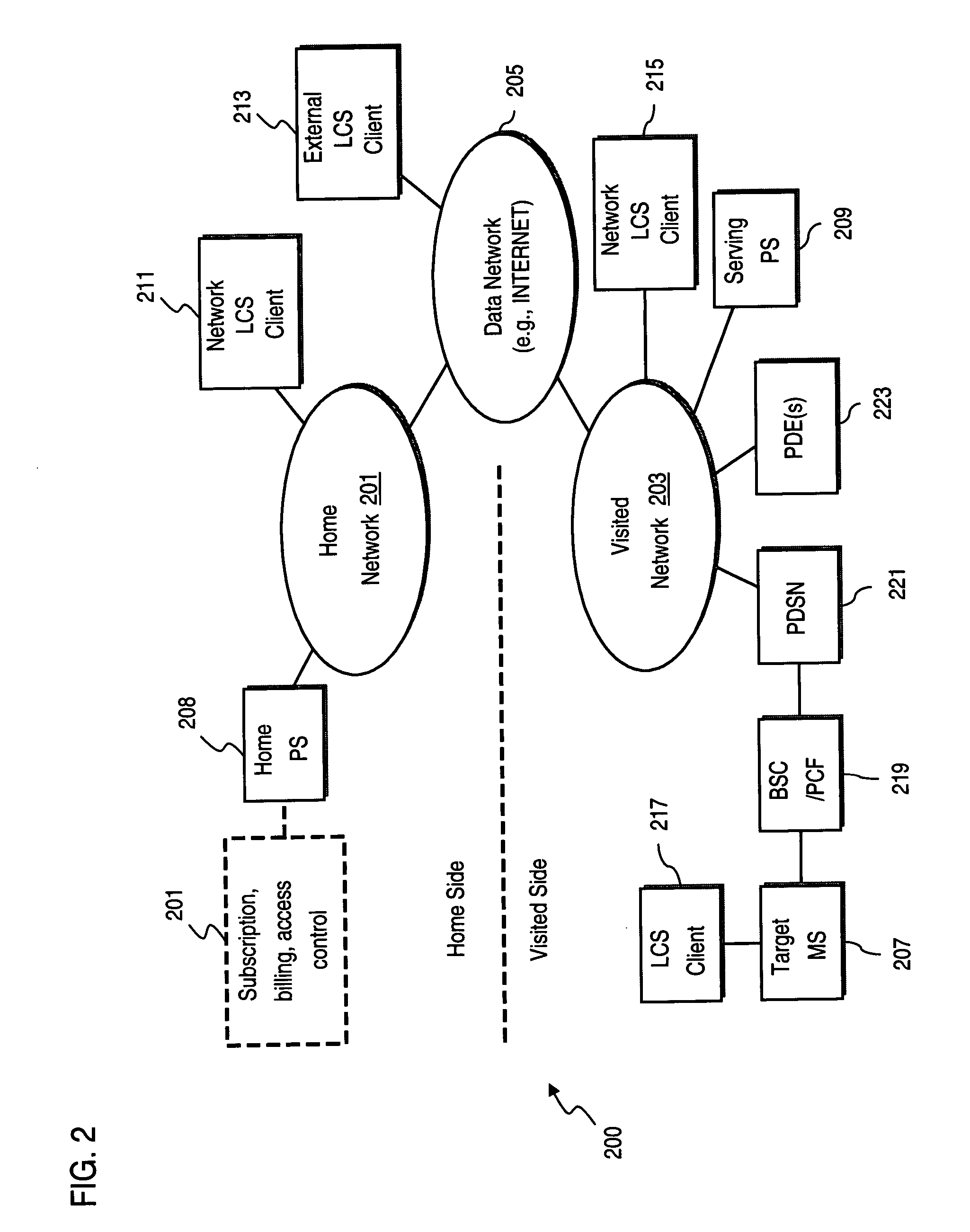
Signaling for administrative domain change during location tracking
ActiveUS20060274696A1Telephonic communicationRadio/inductive link selection arrangementsLocation trackingAdministrative domain
An approach provides signaling for administrative domain change during location tracking. Departure of a mobile node from a first administrative domain is detected during a position reporting session. It is determined whether a first, configured to determine position, within the first administrative domain is inaccessible. If inaccessible, signaling for a handoff is initiated for assignment of a second, configured to determine position, within a second administrative domain to continue the position reporting session.
Owner:NOKIA TECHNOLOGLES OY
Bridging between a bluetooth scatternet and an ethernet LAN
InactiveUS20040141511A1Network topologiesData switching by path configurationNetwork packetAdministrative domain
System and method are disclosed for bridging a point-to-point network such as a Bluetooth scatternet with a shared medium network such as an Ethernet LAN. The scatternet is connected to the LAN via a network access point (NAP). Data packets sent from the LAN to the scatternet are filtered at the NAP to eliminate unnecessary data packets from being sent to the scatternet. Only certain ones of the data packets are forwarded between the LAN and the scatternet. An inter-NAP protocol is used to exchange messages where two or more NAPs are connected to the LAN. Broadcast loops are prevented from occurring in the scatternet and the LAN by defining Administrative domains and NAP service areas (NAPSAs), and controlling the borders thereof according to a broadcast type of the data packets.
Owner:TELEFON AB LM ERICSSON (PUBL)
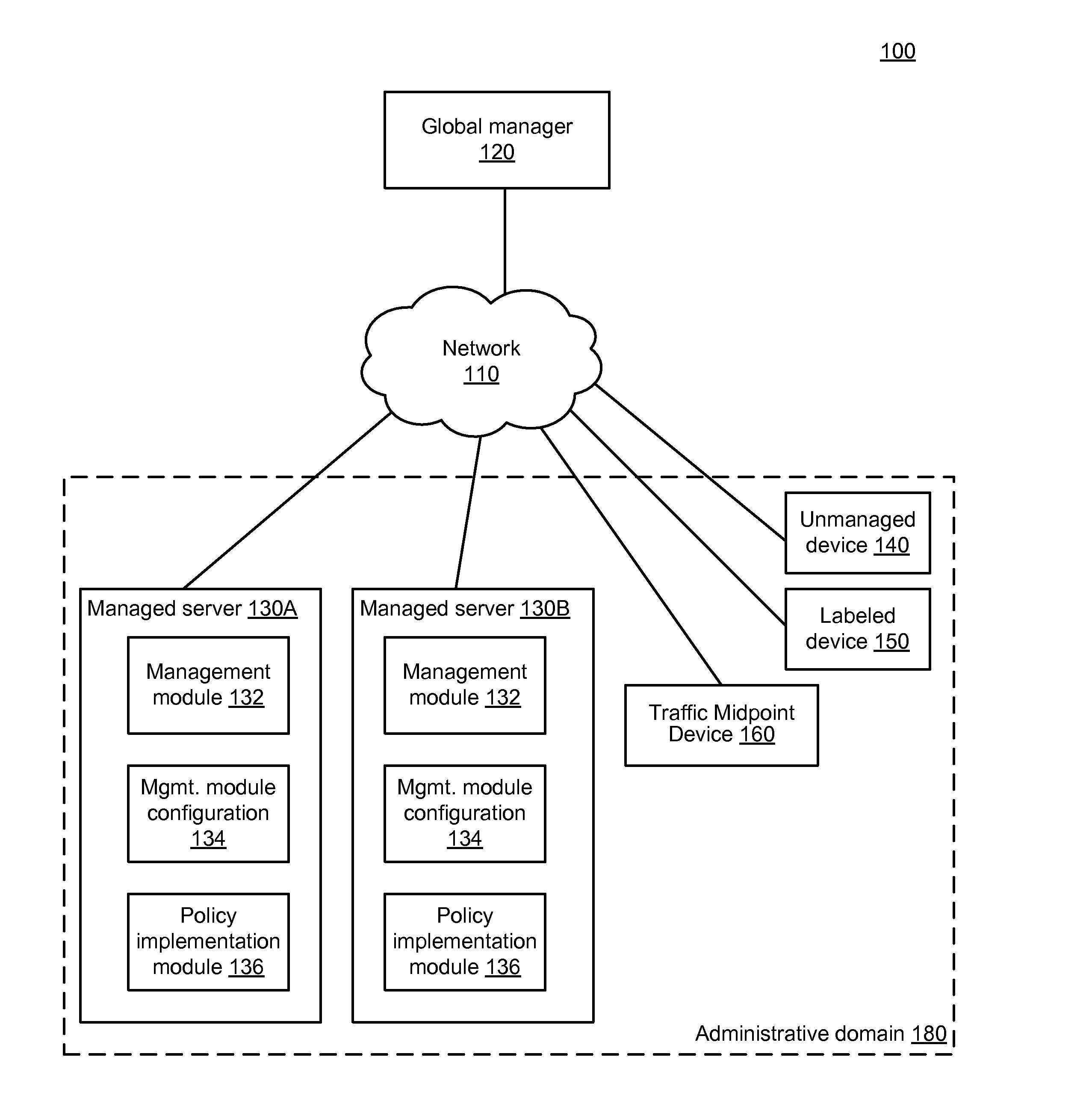
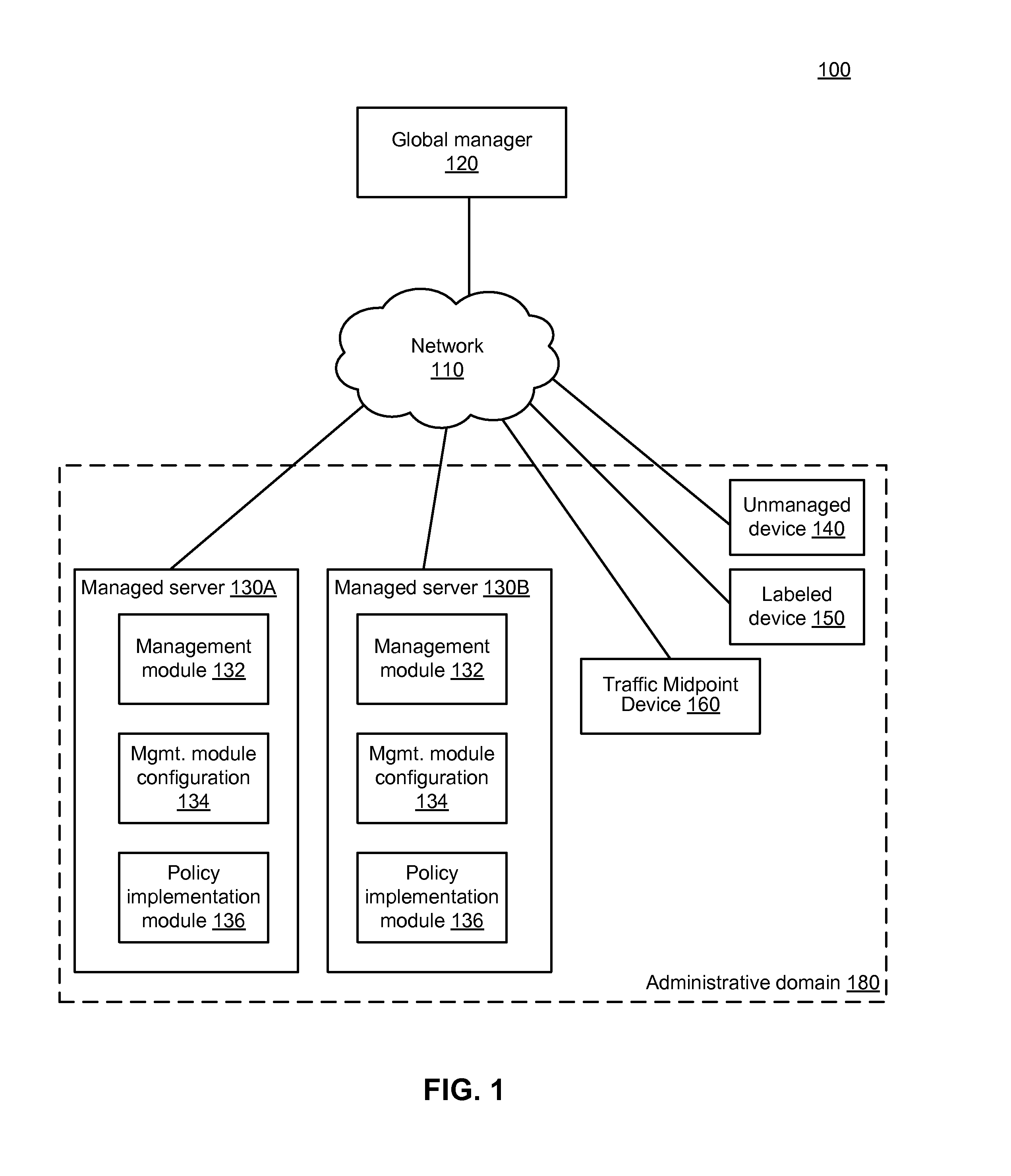
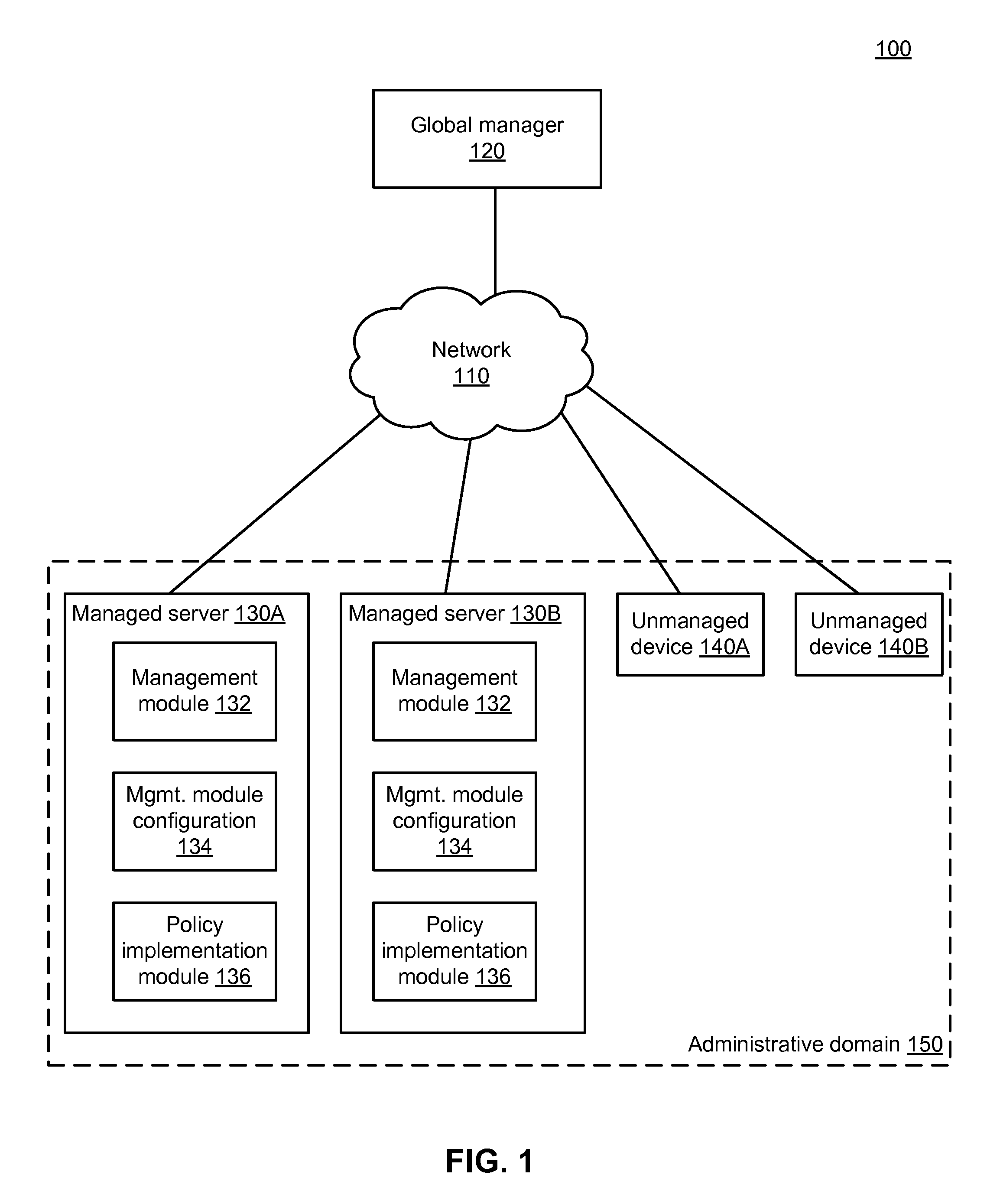
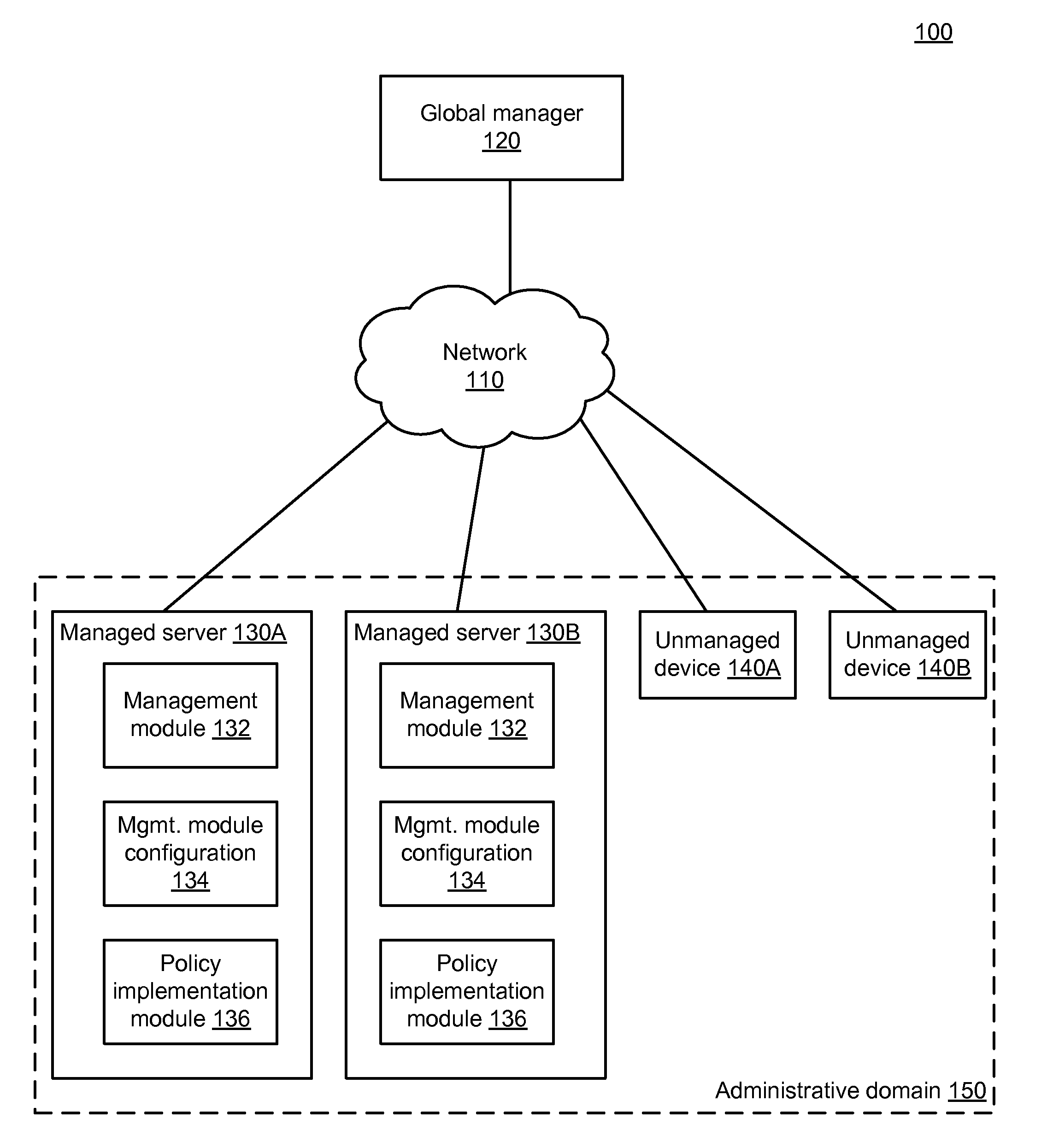
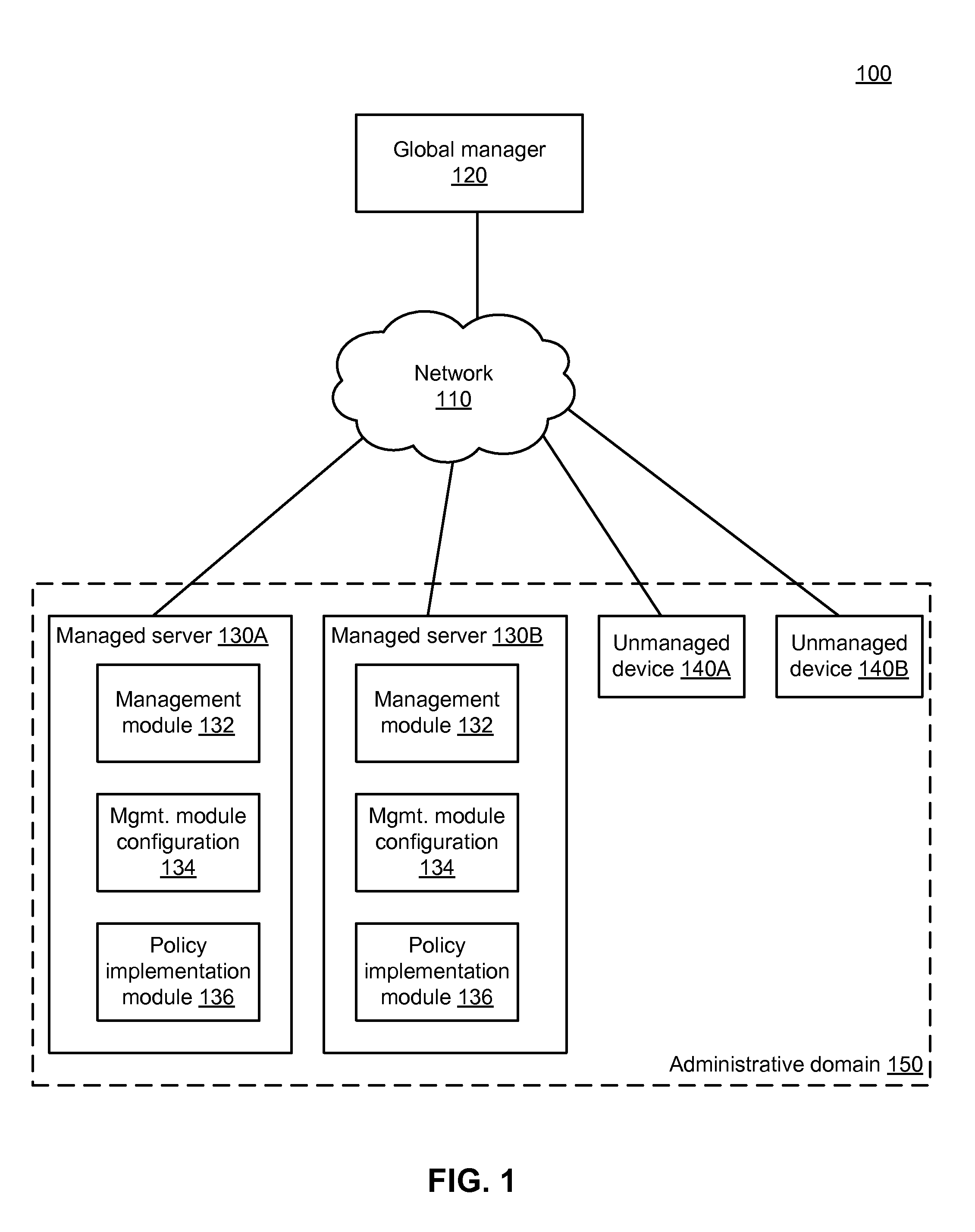
End-to-end policy enforcement in the presence of a traffic midpoint device
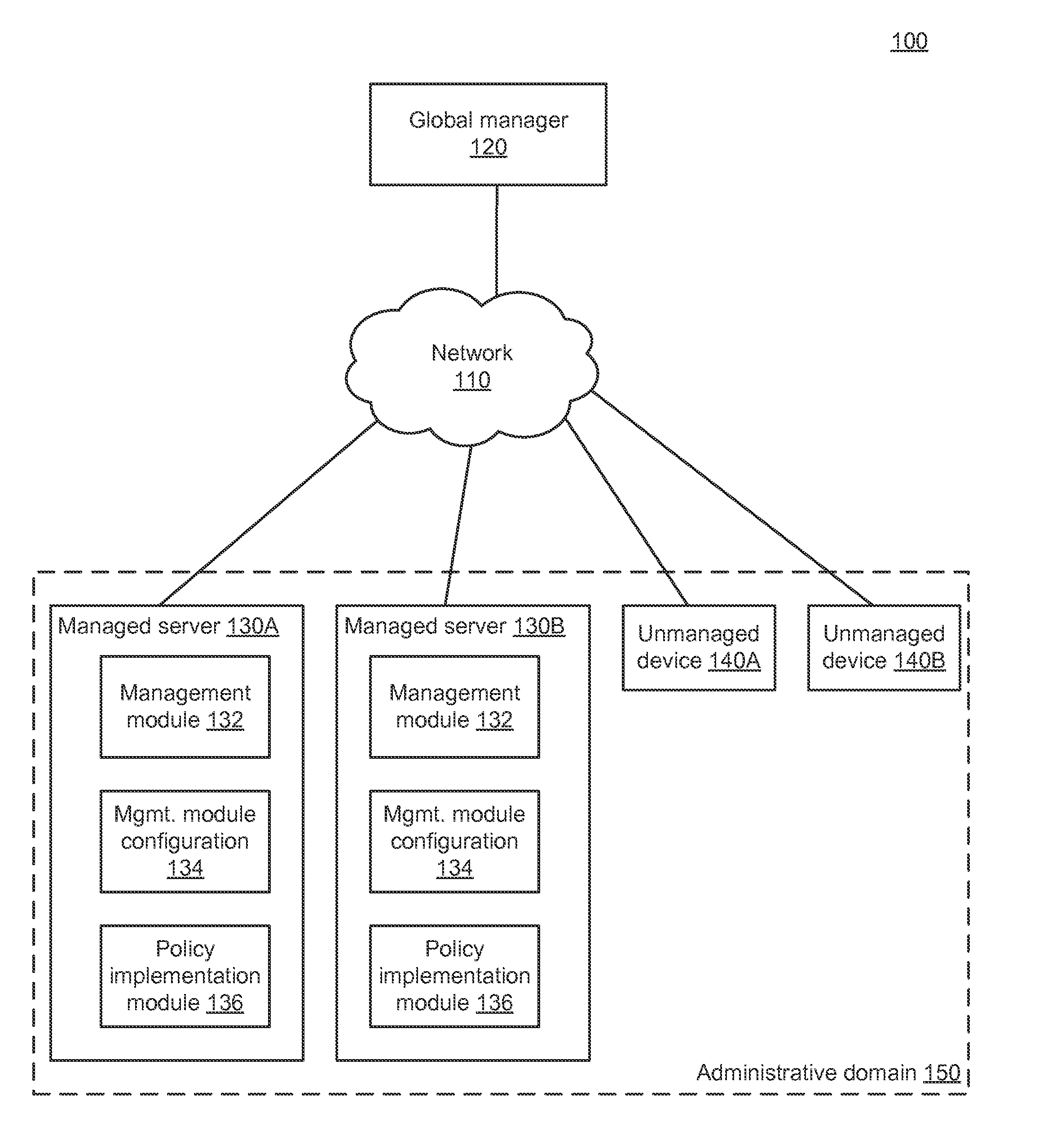
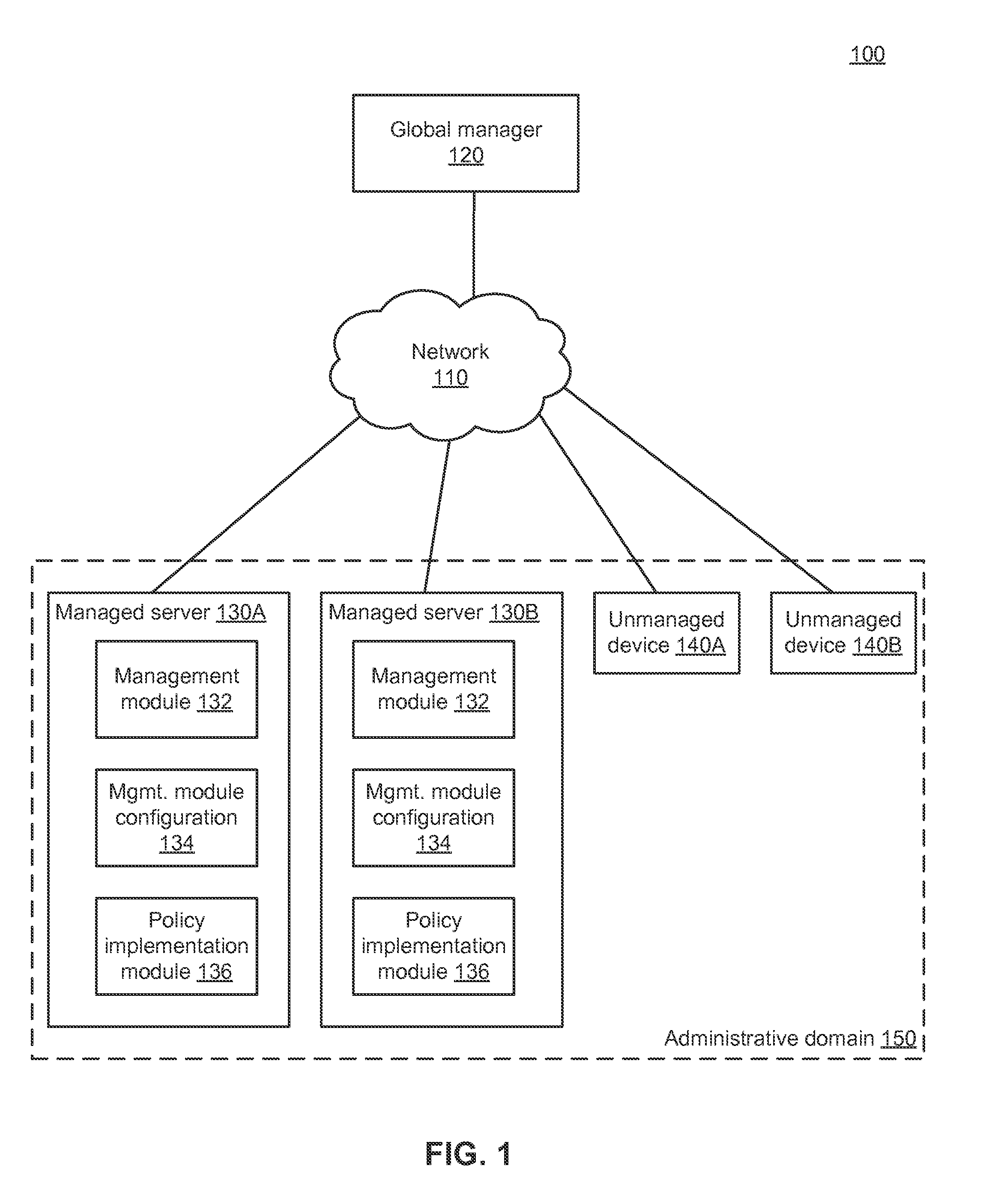
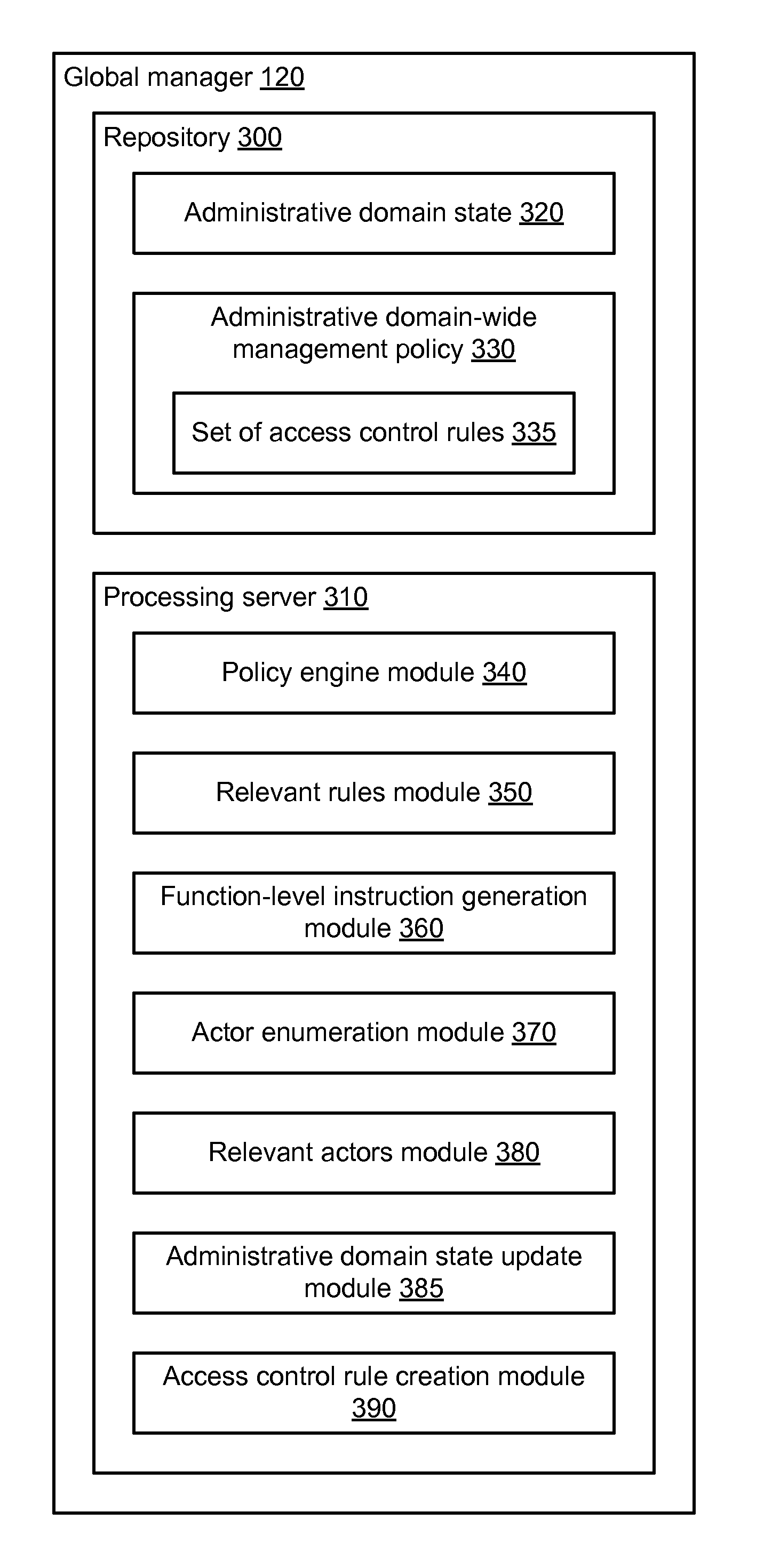
A global manager computer generates management instructions for a particular managed server within an administrative domain according to a set of rules. A global manager computer identifies a traffic midpoint device through which the provider managed server provides a service to a user device. The global manager determines a relevant rule from the set of rules that is applicable to communication between the provider managed server and the user device and generates a backend rule that is applicable to communication between the provider managed server and the traffic midpoint device. The global managed generates a backend function-level instruction including a reference to an actor-set authorized to communicate with the provider managed server to use the service. The global manager sends the backend function-level instruction to the provider managed server to configure the provider managed server to enforce the backend rule on communication with the actor-set including the traffic midpoint device.
Owner:ILLUMIO
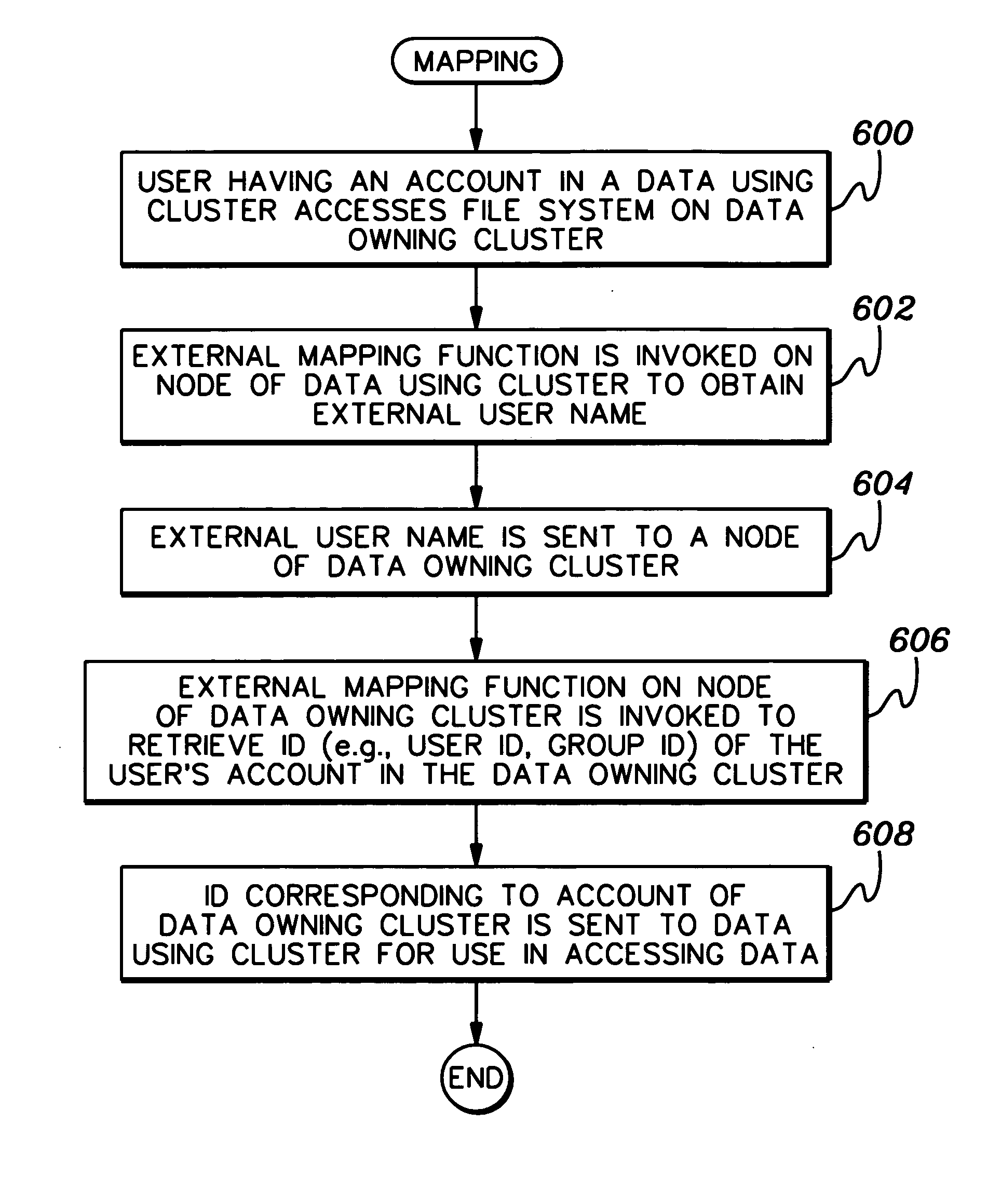
Employing an identifier for an account of one domain in another domain to facilitate access of data on shared storage media
InactiveUS20070011136A1Overcomes shortcomingDigital data information retrievalDigital data authenticationAdministrative domainApplication software
Access to data stored on shared storage media is facilitated by providing a user with uniform access to the user's data regardless from which administrative domain the user is accessing the data. An identifier for the user is created. The identifier corresponds to one account in one administrative domain, but is used in another administrative domain to access data owned by the user, but managed by the one administrative domain. This allows the user running an application in either administrative domain to access its data with the same permissions.
Owner:IBM CORP
Distributed network management using a logical multi-dimensional label-based policy model
ActiveUS20140310415A1Resource allocationError detection/correctionModel managementAdministrative domain
Management instructions for a particular managed server within an administrative domain are generated according to an administrative domain-wide management policy that comprises a set of one or more rules. The administrative domain includes a plurality of managed servers. A determination is made regarding which rules within the set of rules are relevant to the particular managed server. Function-level instructions are generated based on the rules that were determined to be relevant. A determination is made regarding which managed servers within the plurality of managed servers are relevant to the particular managed server. The function-level instructions and information regarding the managed servers that were determined to be relevant are sent to the particular managed server. The particular managed server uses the function-level instructions and information regarding the managed servers to configure a management module so that the configured management module implements the administrative domain-wide management policy.
Owner:ILLUMIO
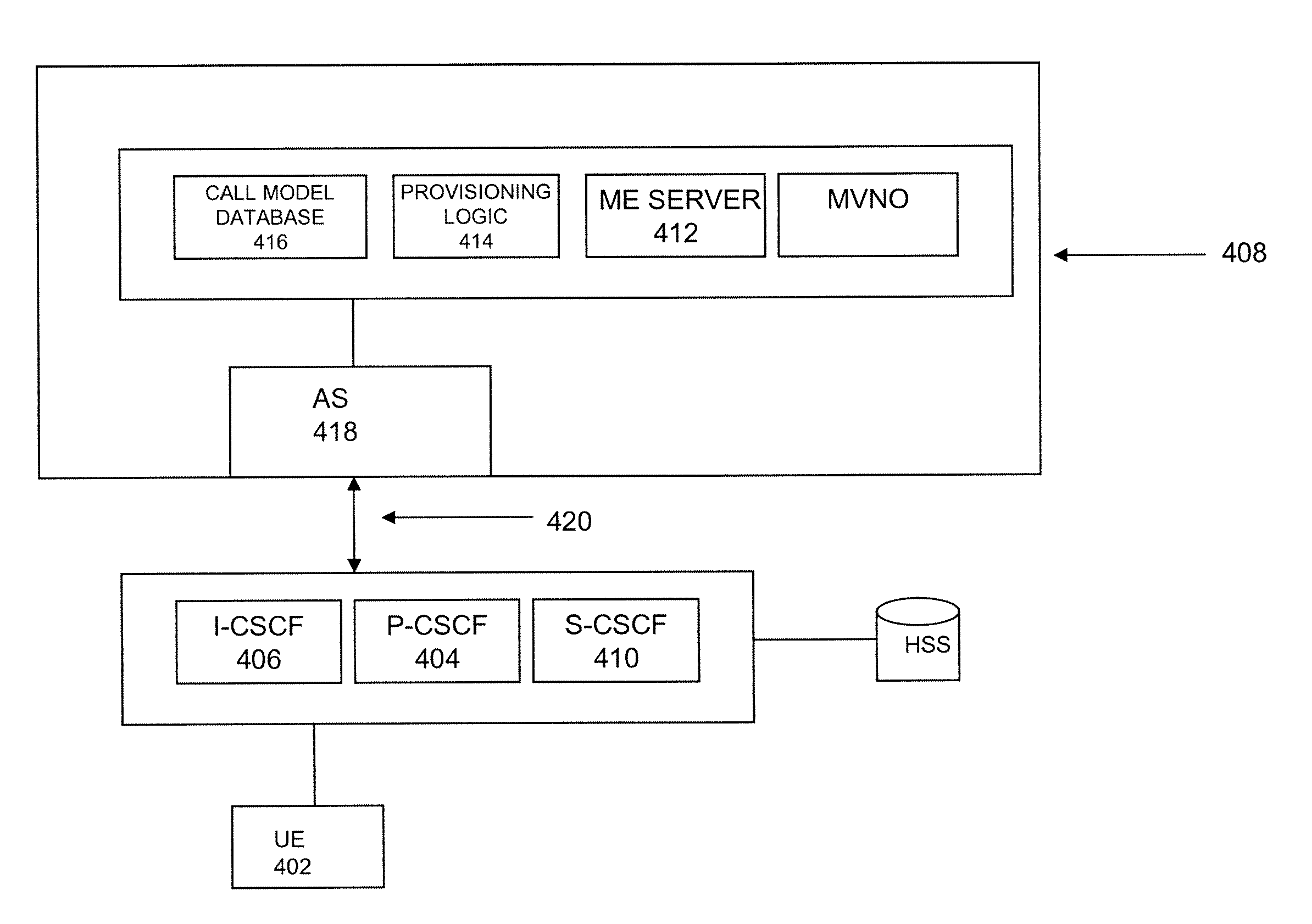
Method of avoiding or minimizing cost of stateful connections between application servers and S-CSCF nodes in an IMS network with multiple domains
ActiveUS20060291484A1Avoiding and minimizing costSpecial service for subscribersData switching by path configurationService domainApplication server
Methods of avoiding or minimizing cost of stateful connections between application servers (ASs) and S-CSCF nodes in an IMS network with multiple domains. S-CSCF service logic is provided and connected to a co-located AS. The IMS includes a network operator administration domain and an MVNO service domain, and the S-CSCF logic and AS are maintained in the same domain, e.g., the MVNO or network operator domain.
Owner:AYLUS NETWORKS
Method and system for routing calls over a packet switched computer network
ActiveUS20050201364A1Improve network efficiencyQuality improvementData switching by path configurationNetwork connectionsQuality of servicePathPing
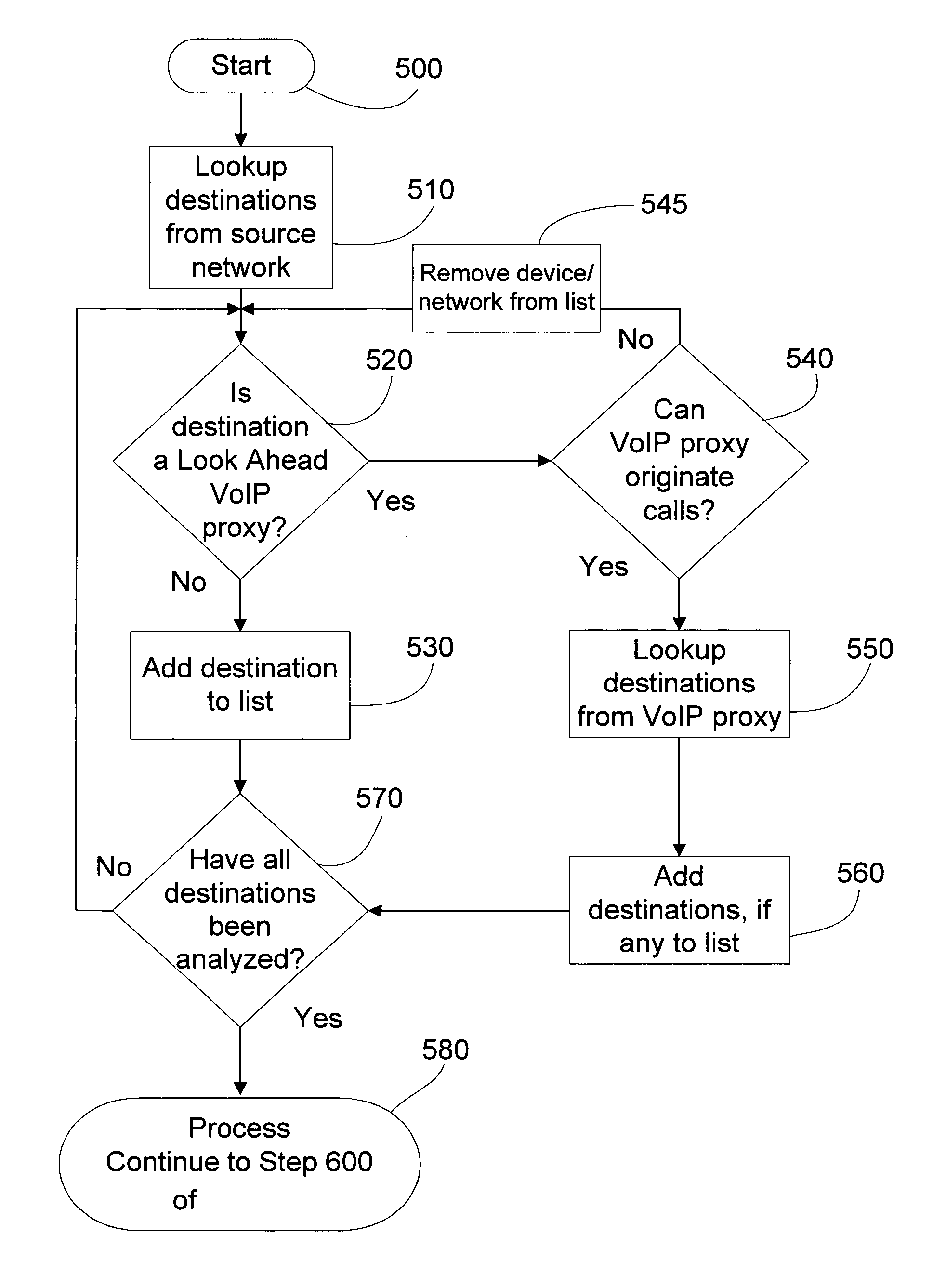
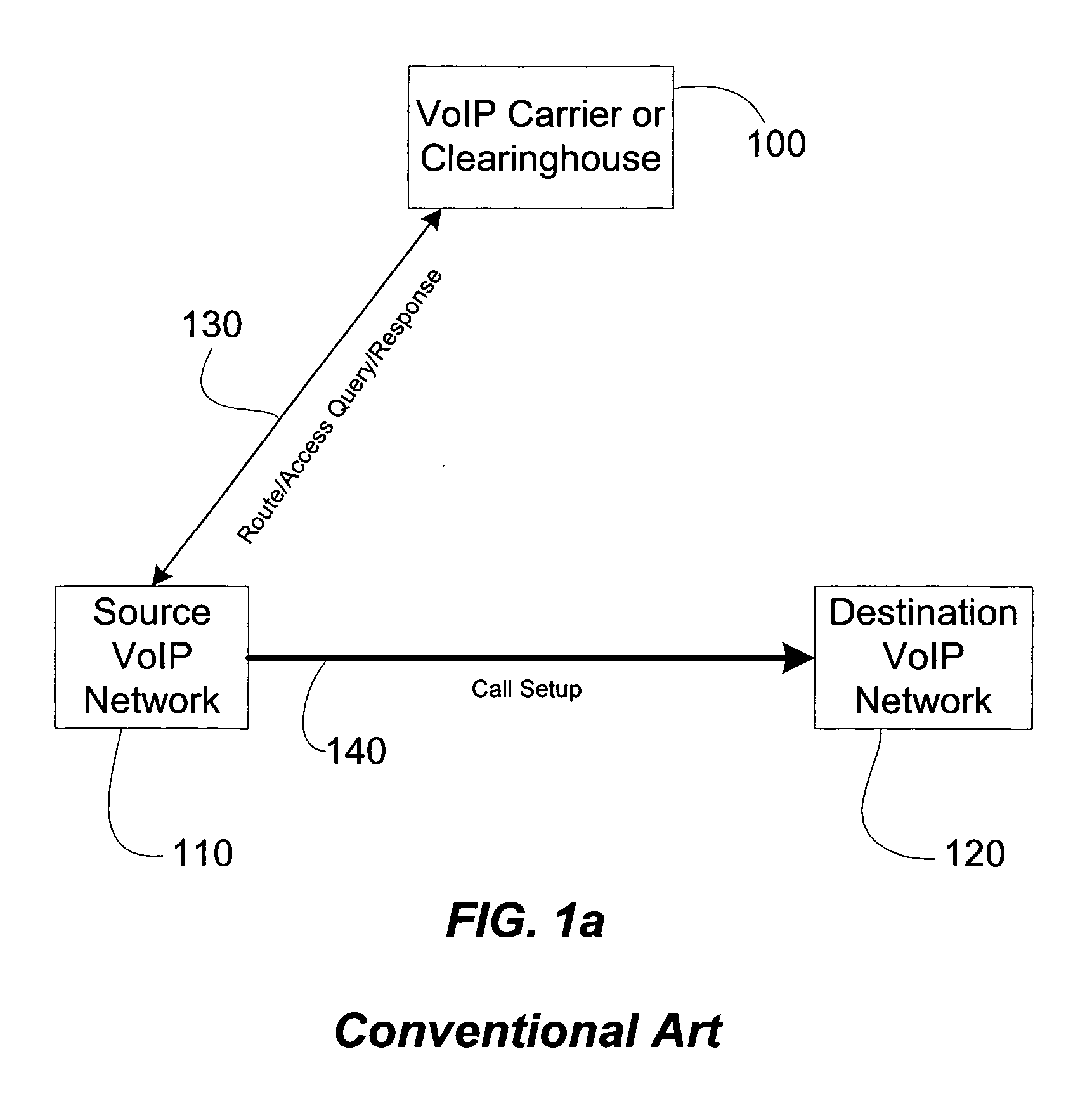
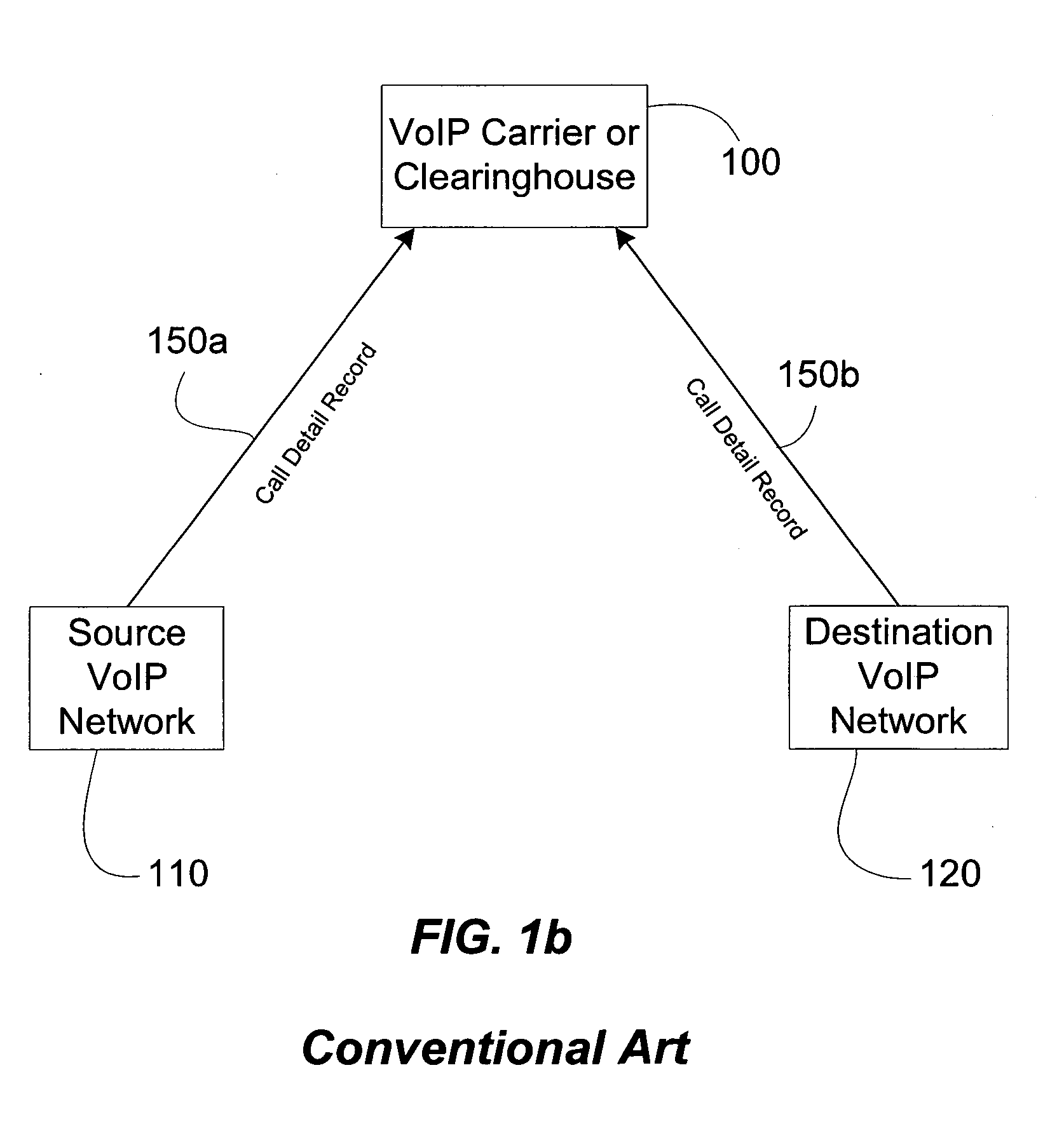
The present invention describes how a trusted network routing authority, such as a VoIP inter-exchange carrier or clearinghouse can provide routing and secure access control across multiple network domains with a single routing and admission request. This technology can improve network efficiency and quality of service when an Internet Protocol (IP) communication transaction, such as a Voice over IP (VoIP), must be routed across multiple devices or administrative domains. This technology defines the technique of performing multiple route look-ups at the source of the call path to determine all possible routes across intermediate domains to the final destination. The VoIP inter-exchange carrier or clearinghouse then provides routing and access permission tokens for the entire call path to the call source.
Owner:TRANSNEXUS
Automated generation of access control rules for use in a distributed network management system that uses a label-based policy model
ActiveUS20150128211A1TransmissionSpecial data processing applicationsAdministrative domainNetwork management
An access control rule authorizing communication between a plurality of managed servers within an administrative domain is determined. Communication information describing past communication between the plurality of managed servers is obtained. A subset of managed servers from the plurality of managed servers is identified by grouping the plurality of managed servers based on the obtained communication information. A group-level label set is determined to associate with the subset of managed servers. Role labels are determined for managed servers in the subset of managed servers. A managed server is associated with one role label. Based on the group-level label set and the role labels, an access control rule is generated authorizing communication between a first managed server of the subset of managed servers and a second managed server. The access control rule is stored as part of an administrative domain-wide management policy.
Owner:ILLUMIO
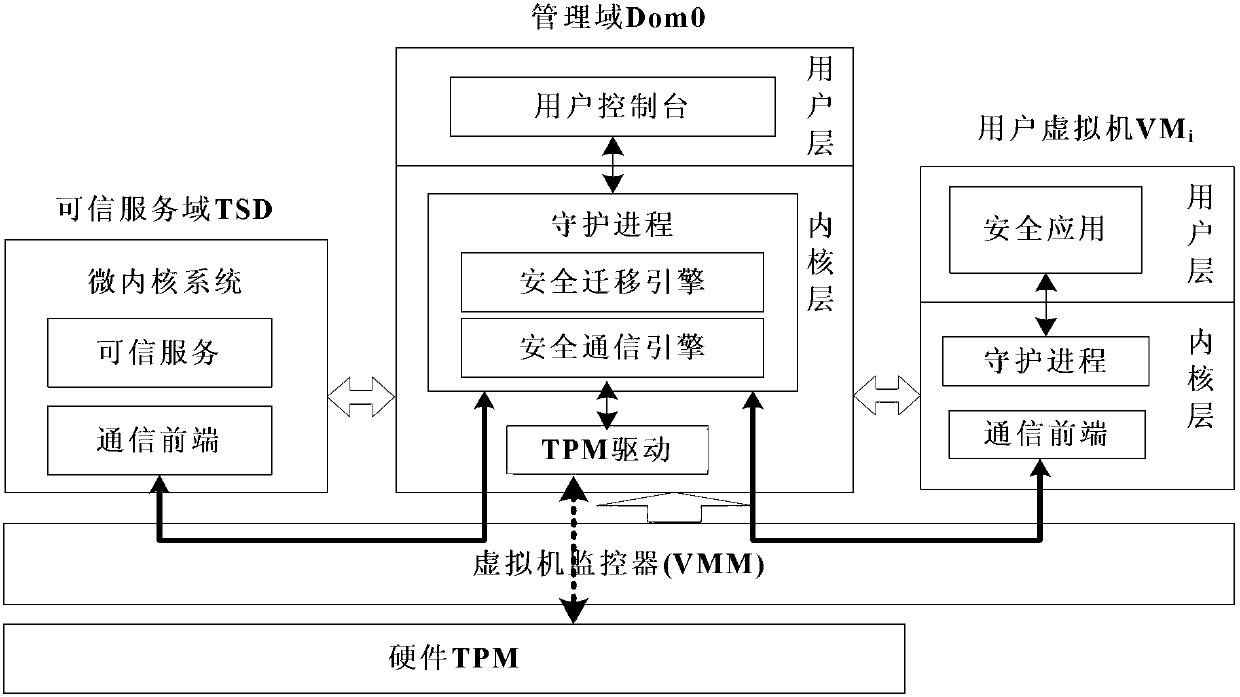
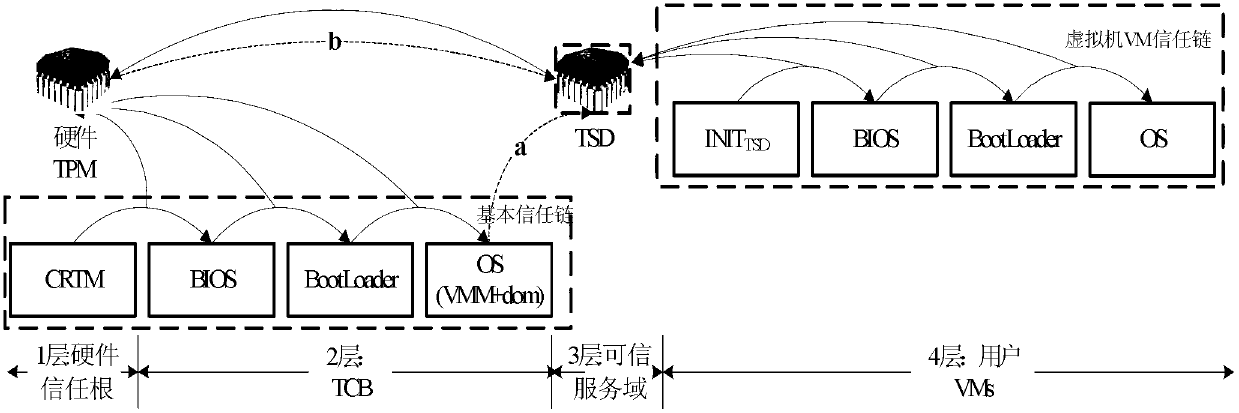
Dependable virtual platform and construction method thereof, data migration method among platforms
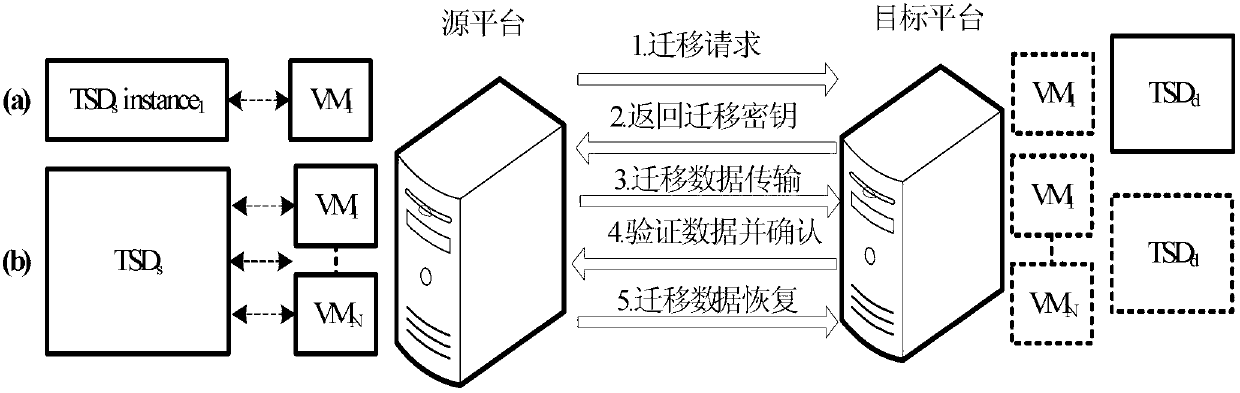
InactiveCN103139221AFlexible migrationQuick migrationTransmissionSecure communicationAdministrative domain
The invention discloses a dependable virtual platform and a construction method thereof, a data migration method among platforms. The dependable virtual platform comprises a hardware security chip, a virtual machine monitor (VMM), an administrative domain, a user domain and a dependable serving domain (TSD), wherein an expanded trust chain is used by the TSD for users to establish dependable operating environment. The construction method includes: building the TSD; then establishing secure communication mechanisms between the managing domain and the TSD and between the managing domain and a domestic user domain; accomplishing calls of security application of the user domain to a dependable function by the user domain through interaction with the managing domain, accomplishing transmission and treatments of dependable orders by the managing domain through the interaction of the TSD; interacting a source platform migration engine and a goal platform migration engine; migrating migration data which is produced and based on the hardware security chip and the TSD to a goal platform, and recovering data on the goal platform, accomplishing quick migration of the TSD and a virtual machine. The dependable virtual platform and the construction method thereof, the data migration method among platforms are capable of improving safety of dependable service and providing flexible operation and deployment mechanisms for the platforms.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Method and apparatus for selecting a certificate authority
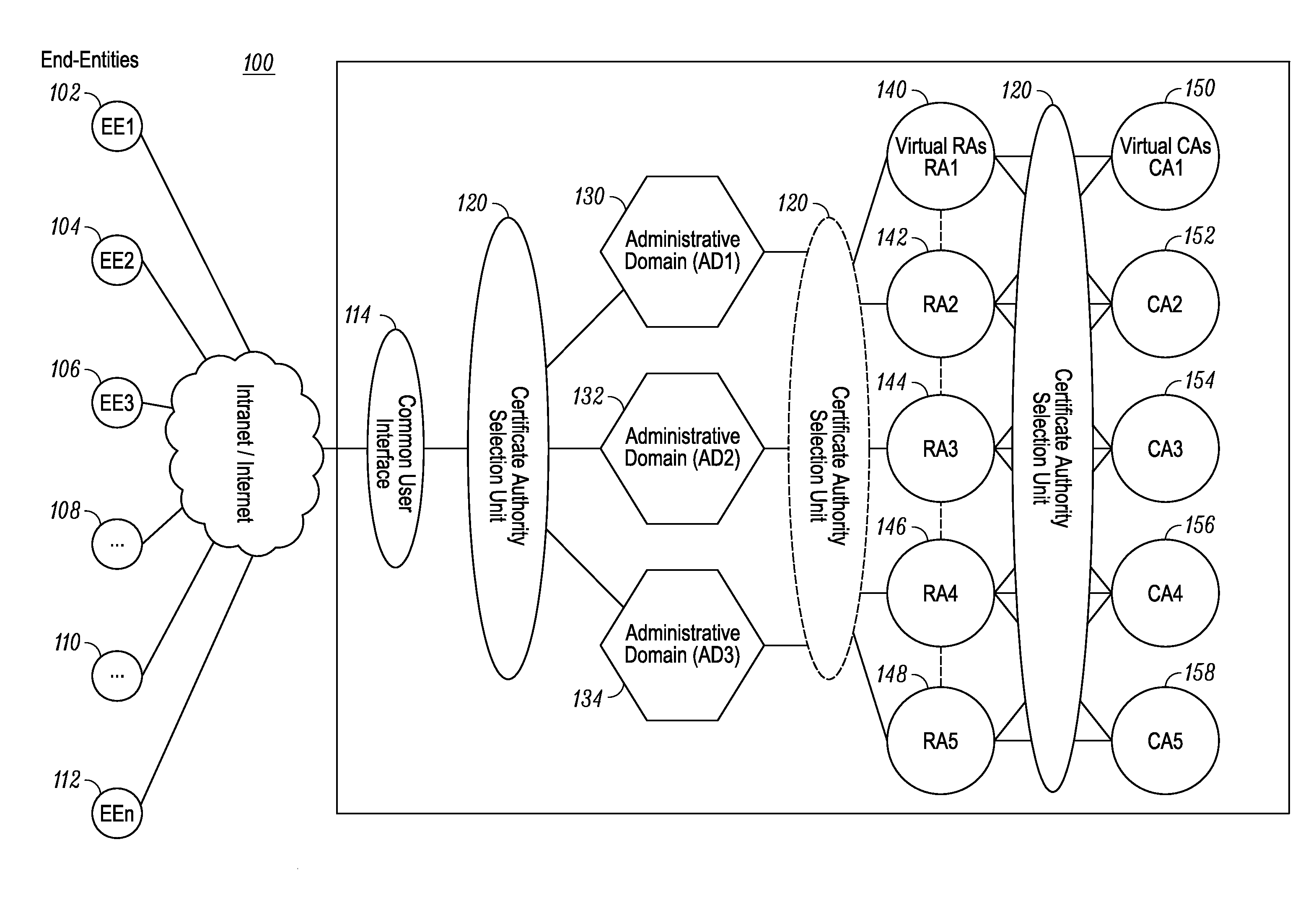
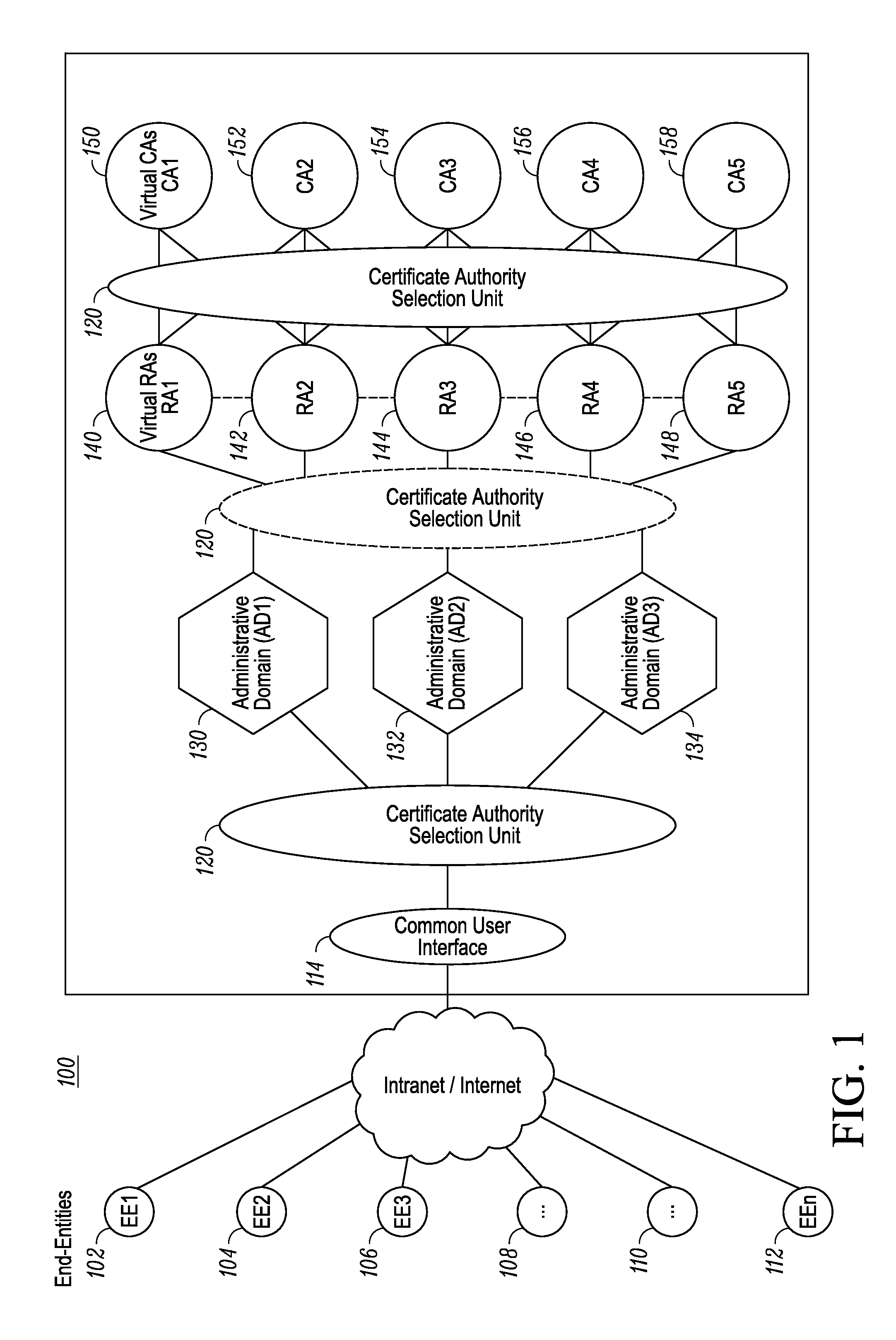
ActiveUS20110154024A1Digital data processing detailsMultiple digital computer combinationsCommunications systemAdministrative domain
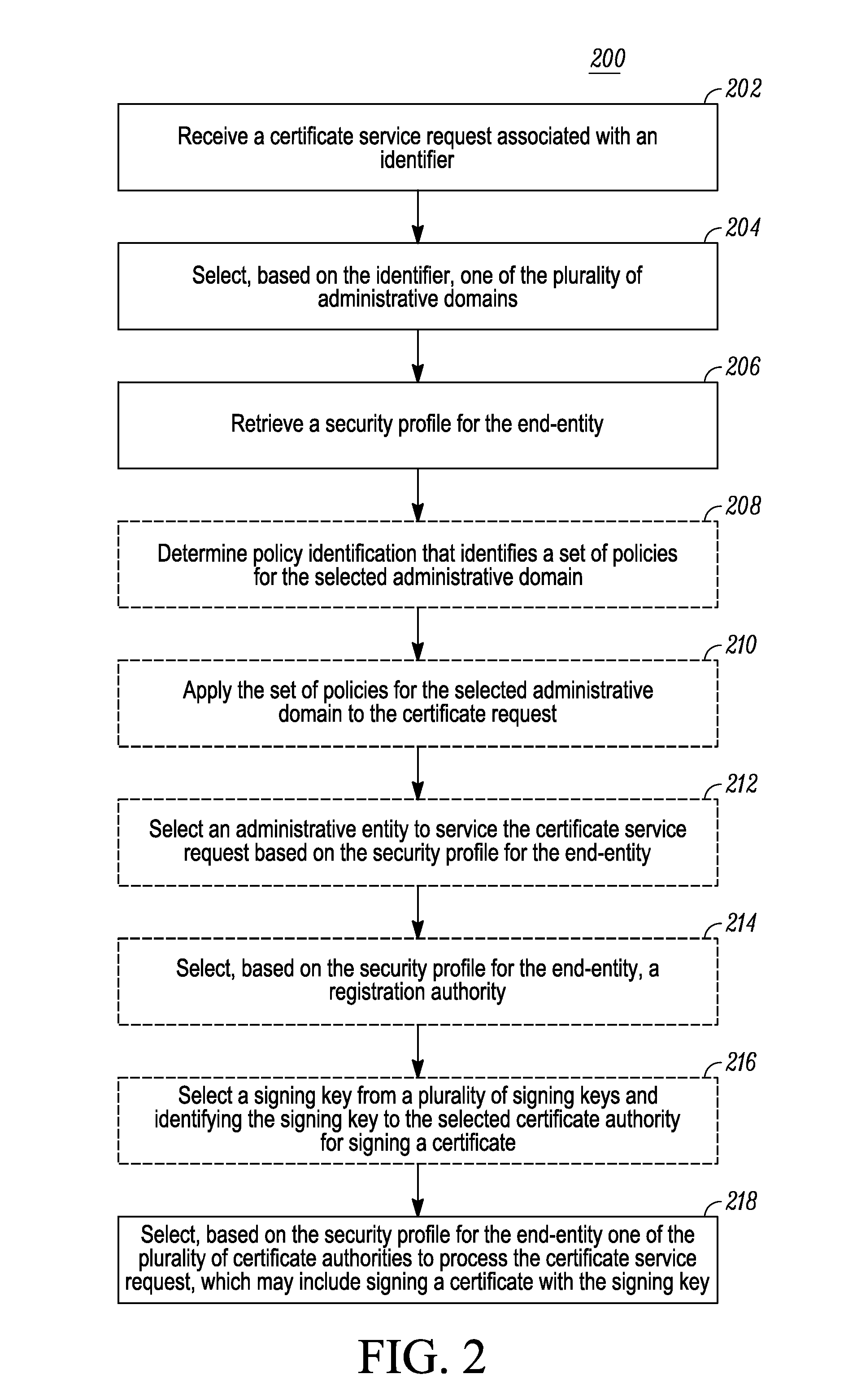
A certificate authority selection unit implements a method for selecting one of a plurality of certificate authorities servicing a plurality of administrative domains in a communication system. The method includes: receiving, from an end-entity via an interface, a certificate service request associated with an identifier; selecting, based on the identifier, one of the plurality of administrative domains in the communication system, wherein the plurality of administrative domains are serviced by a plurality of certificate authorities; retrieving a security profile for the end-entity; and selecting, based on the security profile for the end-entity, one of the plurality of certificate authorities to process the certificate service request.
Owner:MOTOROLA SOLUTIONS INC
Distributed Network Security Using a Logical Multi-Dimensional Label-Based Policy Model
ActiveUS20140373091A1Data switching networksSpecial data processing applicationsAdministrative domainMulti dimensional
A managed server (MS) within an administrative domain is quarantined. The administrative domain includes multiple MSs that use management instructions to configure management modules so that the configured management modules implement an administrative domain-wide management policy that comprises a set of one or more rules. The quarantined MS is isolated from other MSs. A description of the MS is modified to indicate that the MS is quarantined, thereby specifying a description of the quarantined MS. Cached actor-sets are updated to indicate the quarantined MS's changed state, thereby specifying updated actor-sets. A determination is made regarding which updated actor-sets are relevant to an other MS, thereby specifying currently-relevant updated actor-sets. A determination is made regarding whether the currently-relevant updated actor-sets differ from actor-sets previously sent to the other MS. Responsive to determining that the currently-relevant updated actor-sets are identical to the previously-sent actor-sets, no further action is taken.
Owner:ILLUMIO
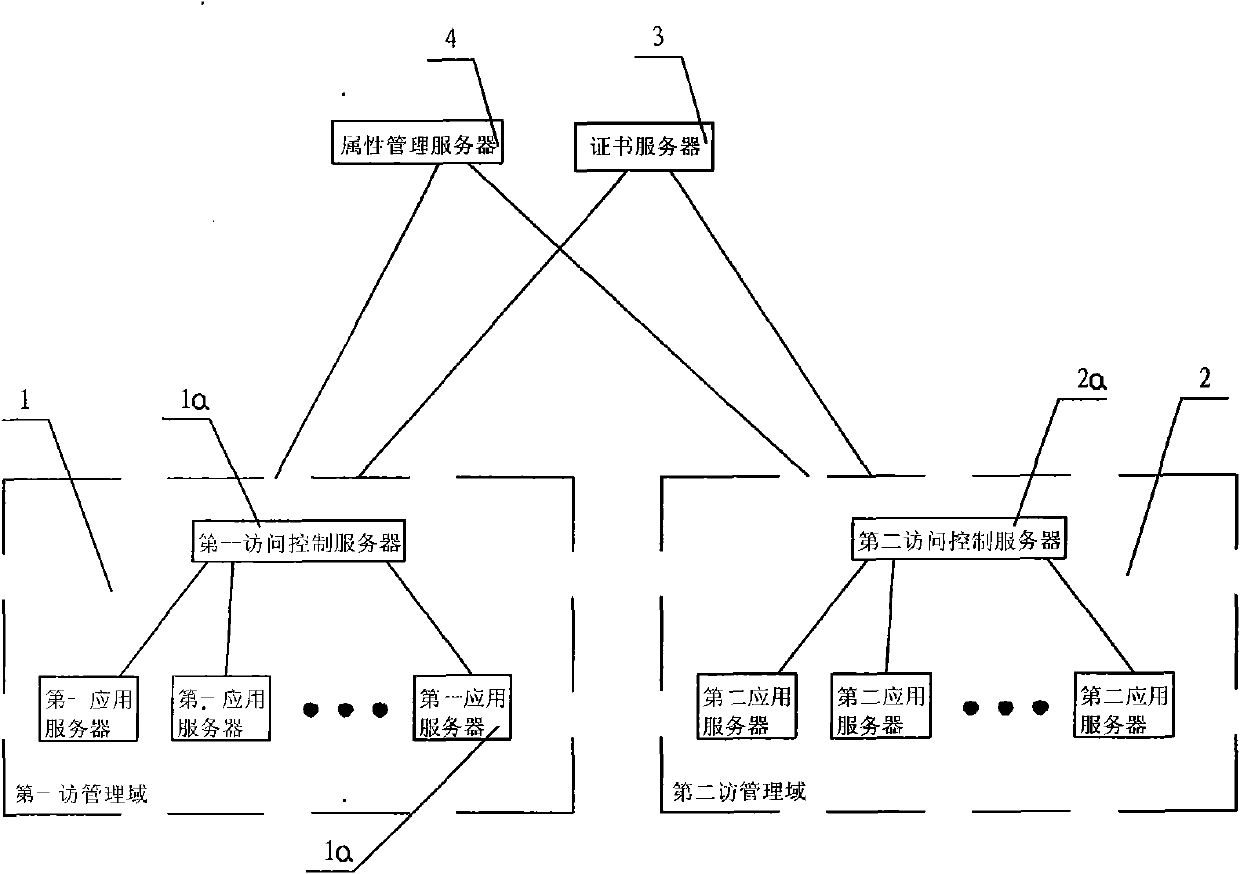
Attribute-based access control model and cross domain access method thereof
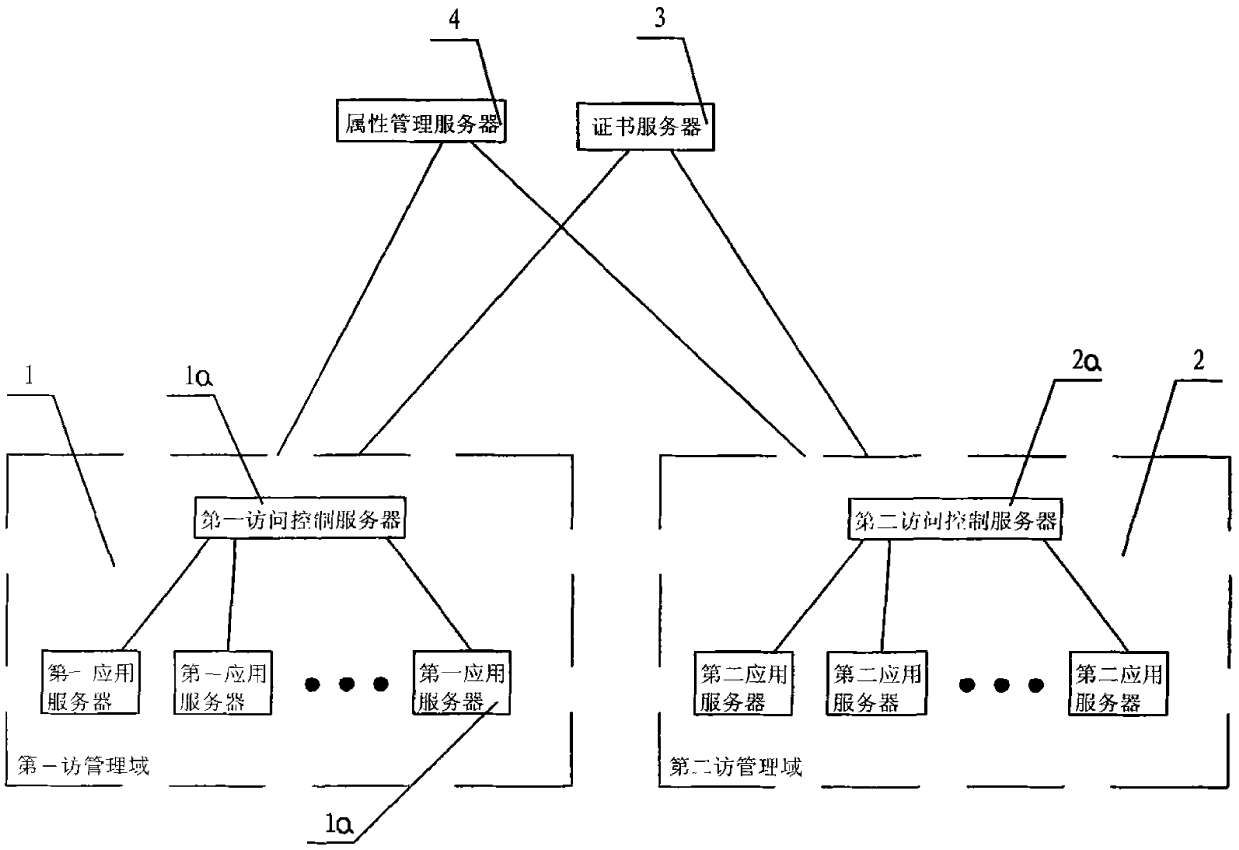
InactiveCN101997876ASolve the efficiency problem of user-role-permission assignmentImprove convenienceTransmissionAccess methodAdministrative domain
The invention discloses an attribute-based access control model and a cross domain access method thereof. The attribute-based access control model comprises a first management domain and a second management domain, and is characterized by comprising certificate servers and attribute management servers. The cross domain access method of the system comprises the following steps: the certificate servers are respectively used for awarding a server certificate for the first management domain and the second management domain; a user downloads an attribute certificate to a local disk for storage by logging on the first management domain; the user submits the attribute certificate to the second management domain; a second access control server verifies the attribute certificate; and the second access control server extracts an attribute value to judge the operation validity of the user. The attribute-based access control model and the cross domain access method thereof of the invention have the obvious advantages that the role of the user and the management domains can be considered as a single attribute of the user, the efficiency problem of user-role-authority valuation under the condition of complex role in a role-based access control (RBAC) model can be effectively solved, and the corresponding access control method is provided for an anonymous user in an open network environment.
Owner:CHONGQING UNIV
Routing optimization based switch method in local mobile administrative domain
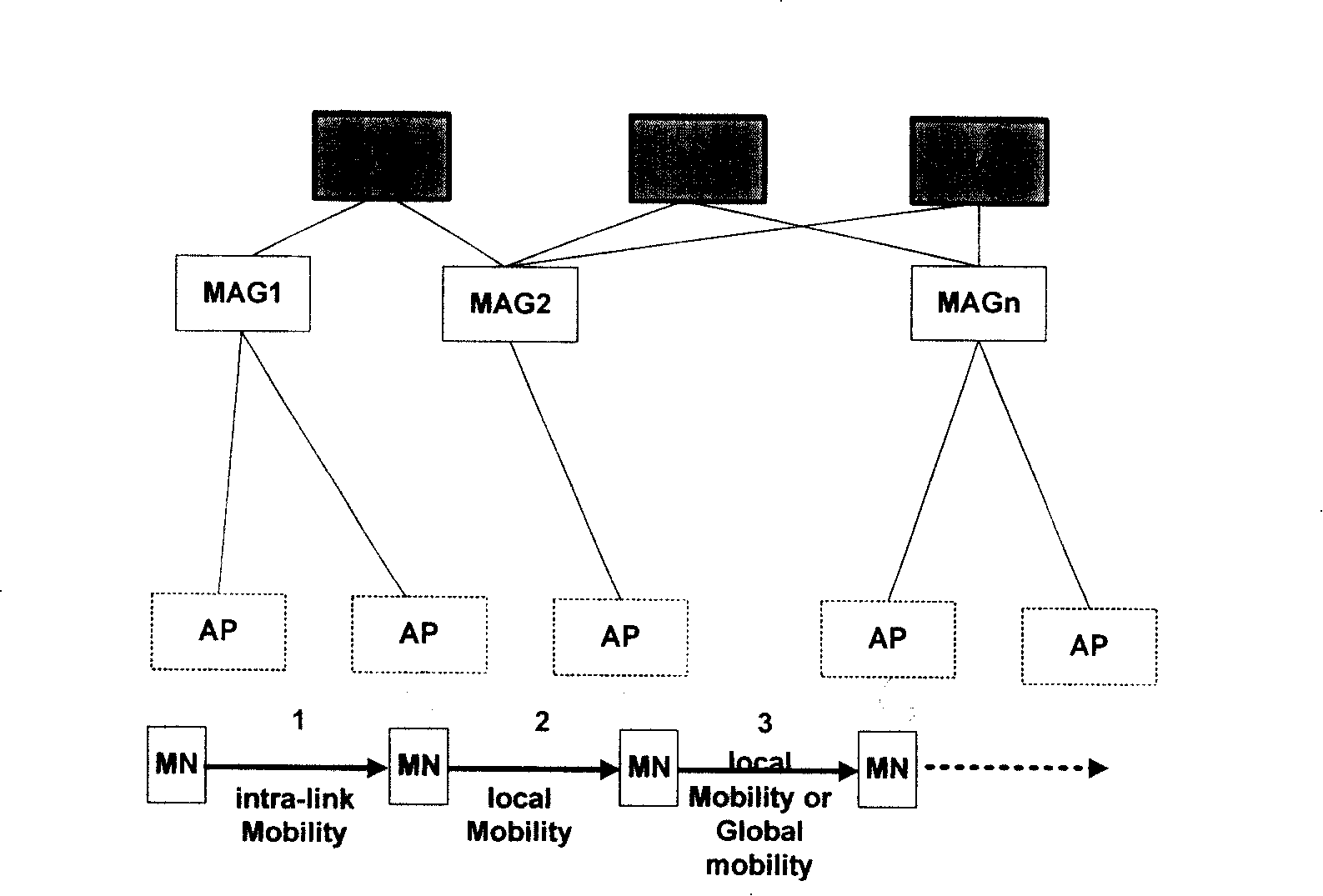
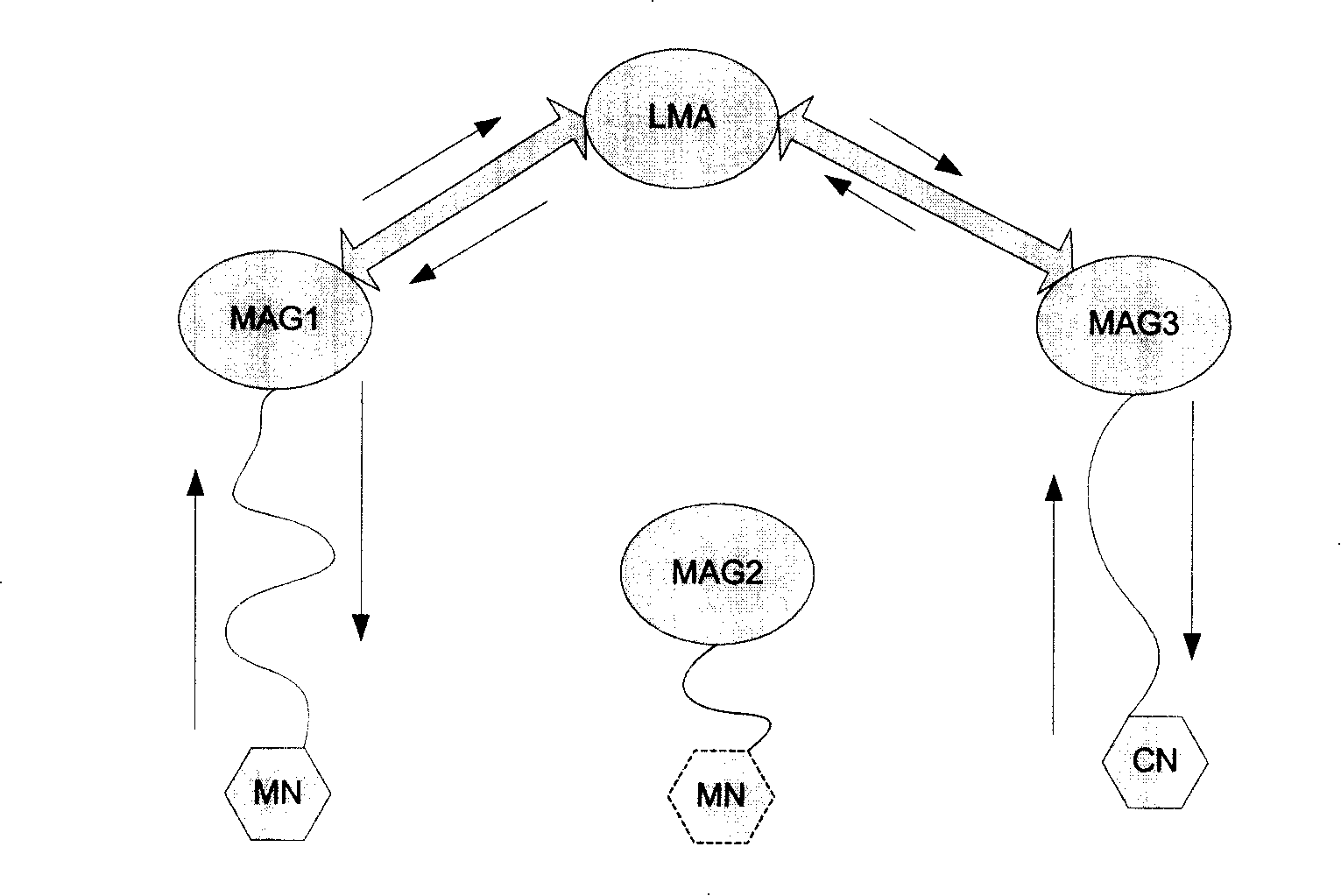
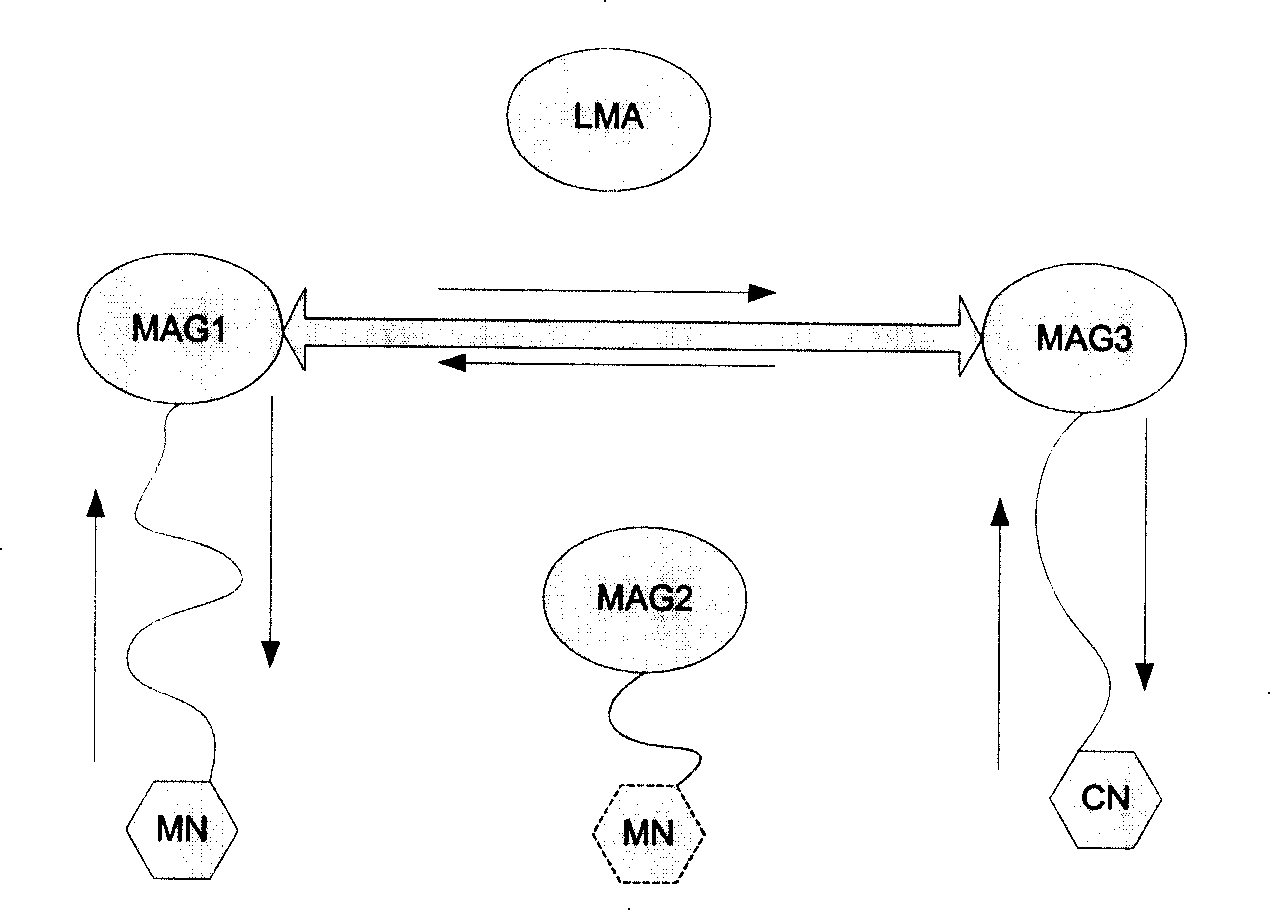
InactiveCN101179457AReduce transmission delayData switching by path configurationAdministrative domainTransmission delay
The invention provides a method for switching based on route optimization in a local mobile management domain, which is used during switching a mobile node (MN) in the local management domain. The method includes the following steps: when a target MAG detects MN switching is operated, a request for establishing a tunnel is put forward at once to establish a data communication channel between the MN and a source communication node (CN). The method for switching provided by the invention is capable of establishing a data communication channel as soon as possible between the MN and the CN after the MN is switched into a destination MAG, thus decreasing the transmission delay of uplink data in the MN.
Owner:HUAWEI TECH CO LTD
Bridging between a Bluetooth scatternet and an Ethernet LAN
System and method are disclosed for bridging a point-to-point network such as a Bluetooth scatternet with a shared medium network such as an Ethernet LAN. The scatternet is connected to the LAN via a network access point (NAP). Data packets sent from the LAN to the scatternet are filtered at the NAP to eliminate unnecessary data packets from being sent to the scatternet. Only certain ones of the data packets are forwarded between the LAN and the scatternet. An inter-NAP protocol is used to exchange messages where two or more NAPs are connected to the LAN. Broadcast loops are prevented from occurring in the scatternet and the LAN by defining Administrative domains and NAP service areas (NAPSAs), and controlling the borders thereof according to a broadcast type of the data packets.
Owner:TELEFON AB LM ERICSSON (PUBL)
Bridging between a bluetooth scatternet and an ethernet LAN
InactiveUS20040153520A1Network topologiesMultiple digital computer combinationsNetwork packetAdministrative domain
System and method are disclosed for bridging a point-to-point network such as a Bluetooth scatternet with a shared medium network such as an Ethernet LAN. The scatternet is connected to the LAN via a network access point (NAP). Data packets sent from the LAN to the scatternet are filtered at the NAP to eliminate unnecessary data packets from being sent to the scatternet. Only certain ones of the data packets are forwarded between the LAN and the scatternet. An inter-NAP protocol is used to exchange messages where two or more NAPs are connected to the LAN. Broadcast loops are prevented from occurring in the scatternet and the LAN by defining Administrative domains and NAP service areas (NAPSAs), and controlling the borders thereof according to a broadcast type of the data packets.
Owner:TELEFON AB LM ERICSSON (PUBL)
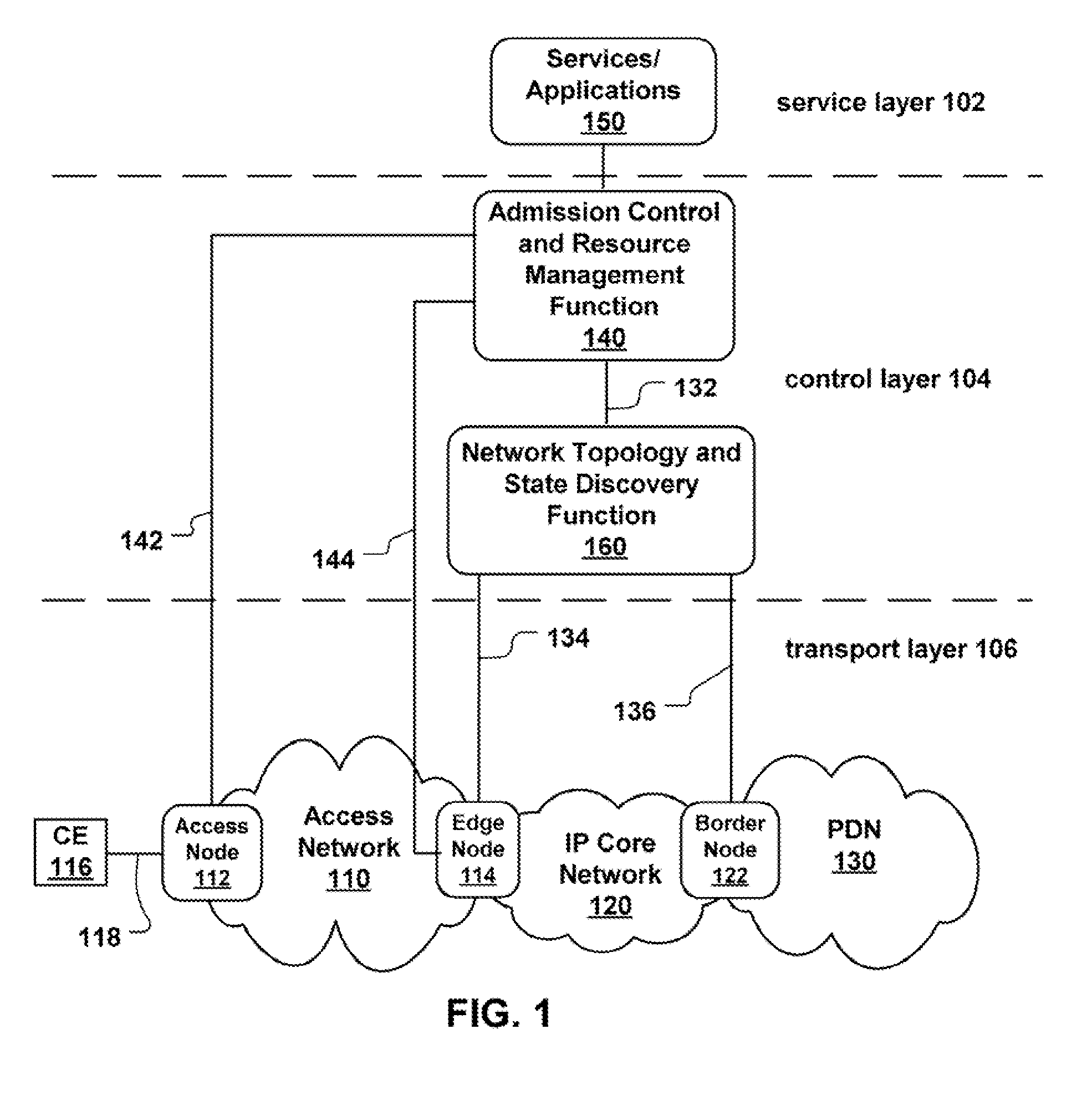
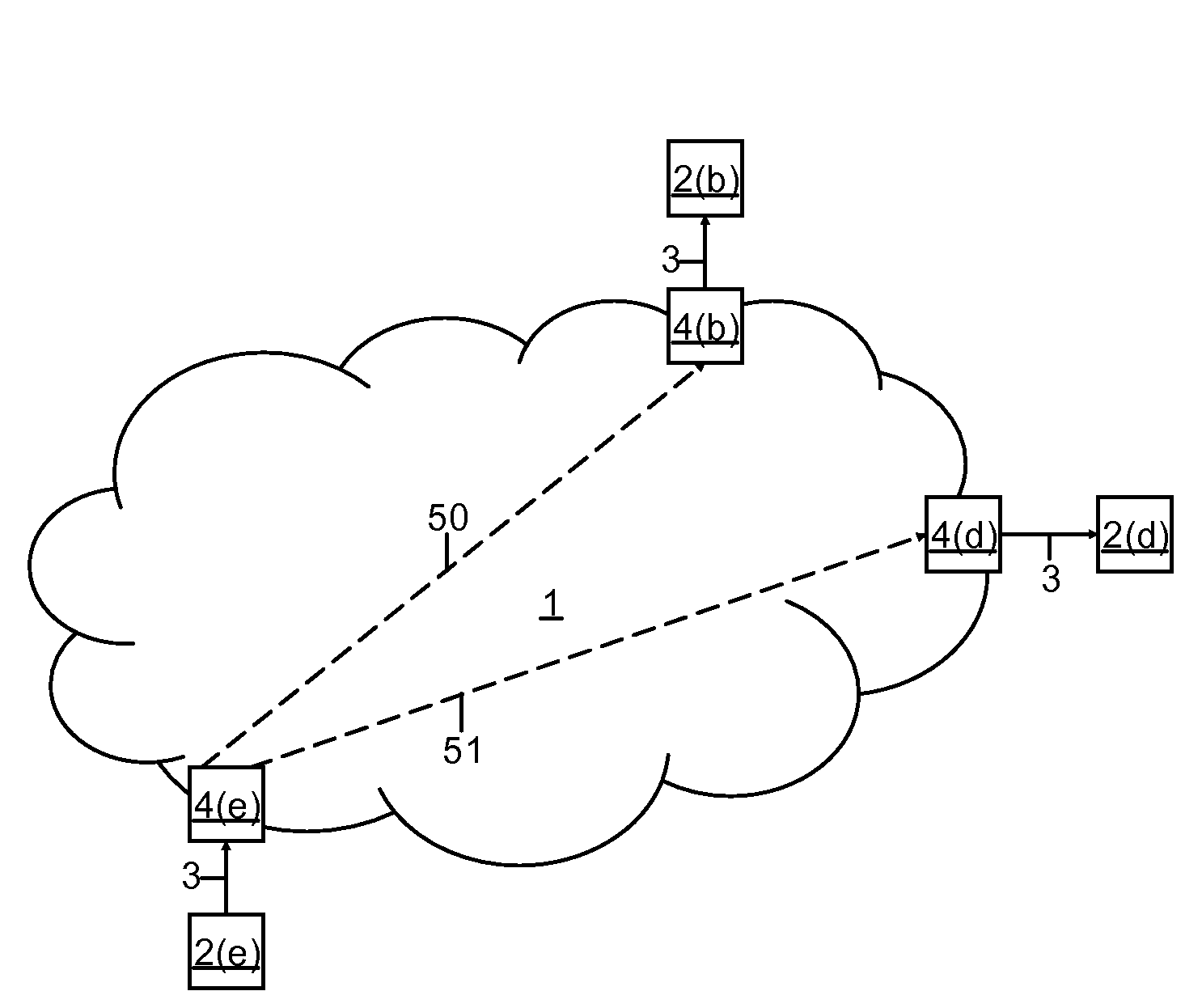
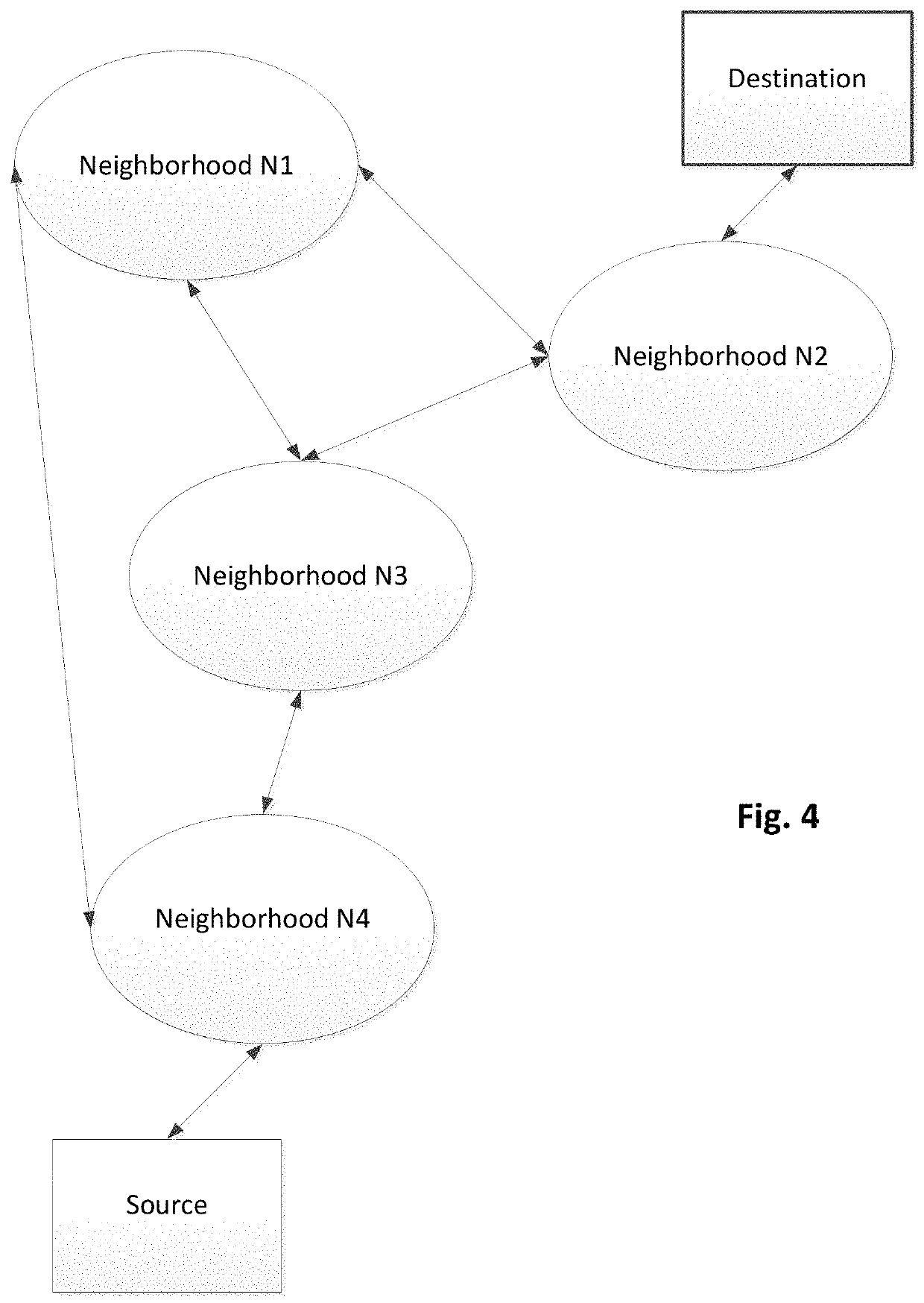
Network neighborhoods for establishing communication relationships between communication interfaces in an administrative domain
A method and apparatus form and / or define a network topology in a Layer 3 network with a plurality of nodes, where each node has at least one interface. To that end, the method defines a plurality of neighborhoods, and assigns at least one interface of each node to at least one of the neighborhoods. The method also assigns a communication role to each interface so that each communication role is effective relative to one of the plurality of neighborhoods. The method then enables communication between the interfaces of the plurality of nodes as a function of the neighborhoods and the communication roles.
Owner:128 TECH
System and method for realizing streaming media content service
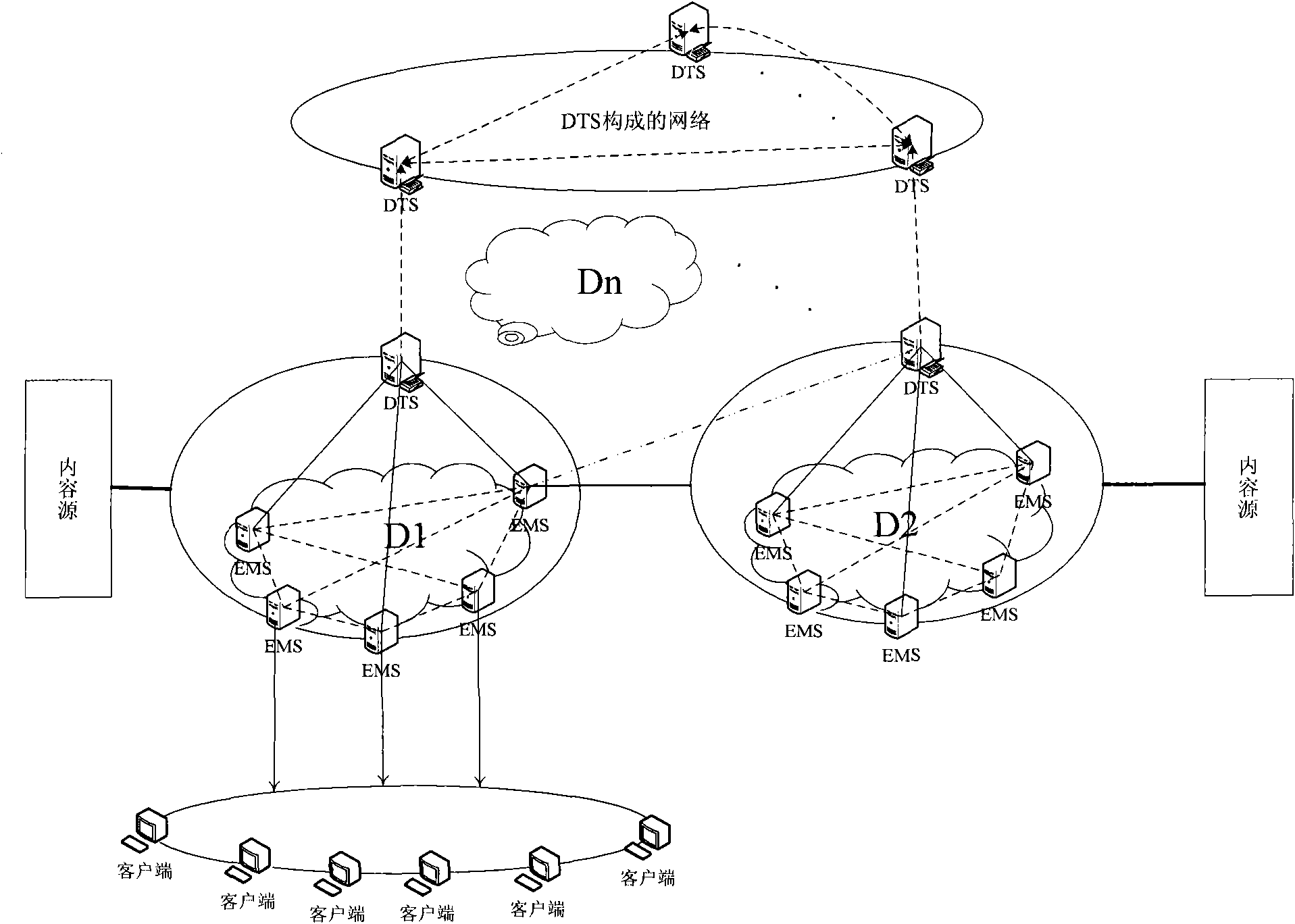
The invention discloses a system and a method for realizing streaming media content services. The invention combines P2P technique with CDN technique, connects a plurality of physical network administrative domains through communication networks and adopts constructing P2P network topology on EMSs in the domains. A DTS is also arranged in the domain, stores all storage content information of the EMSs in the domain and can fast find out the EMS storing certain media content when the searching delay of a DHT is larger. Besides, the DTS stores the information of cross-domain media content, and can fast locate the request to other domains when the media content requested by a user can not be found out in the domain. On one hand, the adoption of the invention resolves the poor expandability problem of the CDN system media capacity and user scale and reduces the effects of the bandwidth and the single point failure of a center node on other nodes in the system; and on the other hand, the arrangement of concentrative catalog servers guarantees the search time of nodes and ensures service quality.
Owner:BEIJING UNIV OF POSTS & TELECOMM +1
Method of avoiding or minimizing cost of stateful connections between application servers and S-CSCF nodes in an IMS network with multiple domains
ActiveUS7864936B2Avoiding and minimizing costSpecial service for subscribersData switching by path configurationApplication serverService domain
Owner:AYLUS NETWORKS
Group information management
ActiveUS20050232406A1Improve user friendlinessReady adoptionSpecial service for subscribersMultiple digital computer combinationsCommunications systemAdministrative domain
A communication system including a first administrative subsystem and a second administrative subsystem providing group communication service. The system includes a first server for storing group and list management information of subscribers of the first administrative subsystem. The system also includes a second server for storing group and list management information of subscribers of the second administrative subsystem. Further, the system includes an interface for exchanging group and list management information between the first server and the second server. In addition, the system reduces ambiguity in group information management of integrated systems that include two or more administrative domains.
Owner:NOKIA TECHNOLOGLES OY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com