Attribute-based access control model and cross domain access method thereof
A technology of access control and attributes, applied in transmission systems, electrical components, etc., to achieve the effect of access control
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
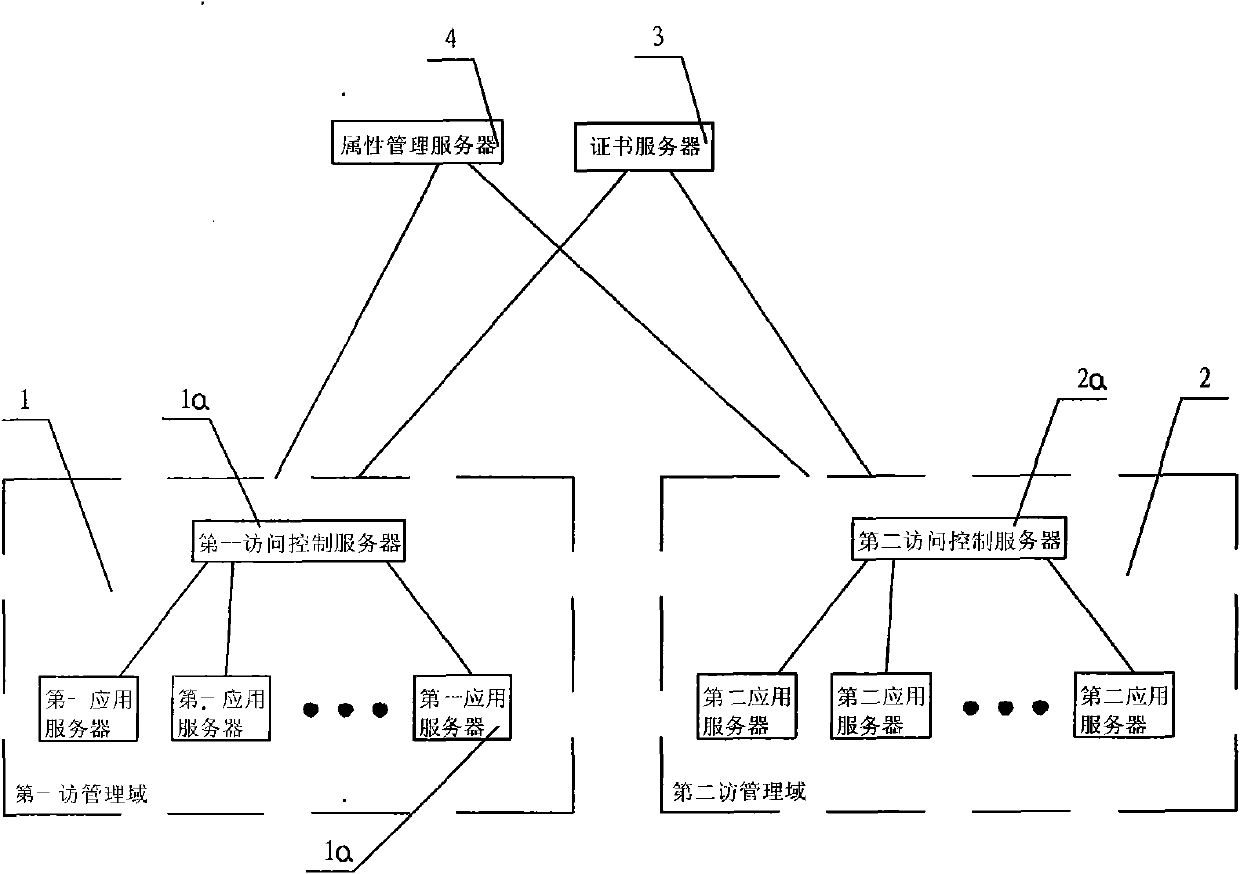
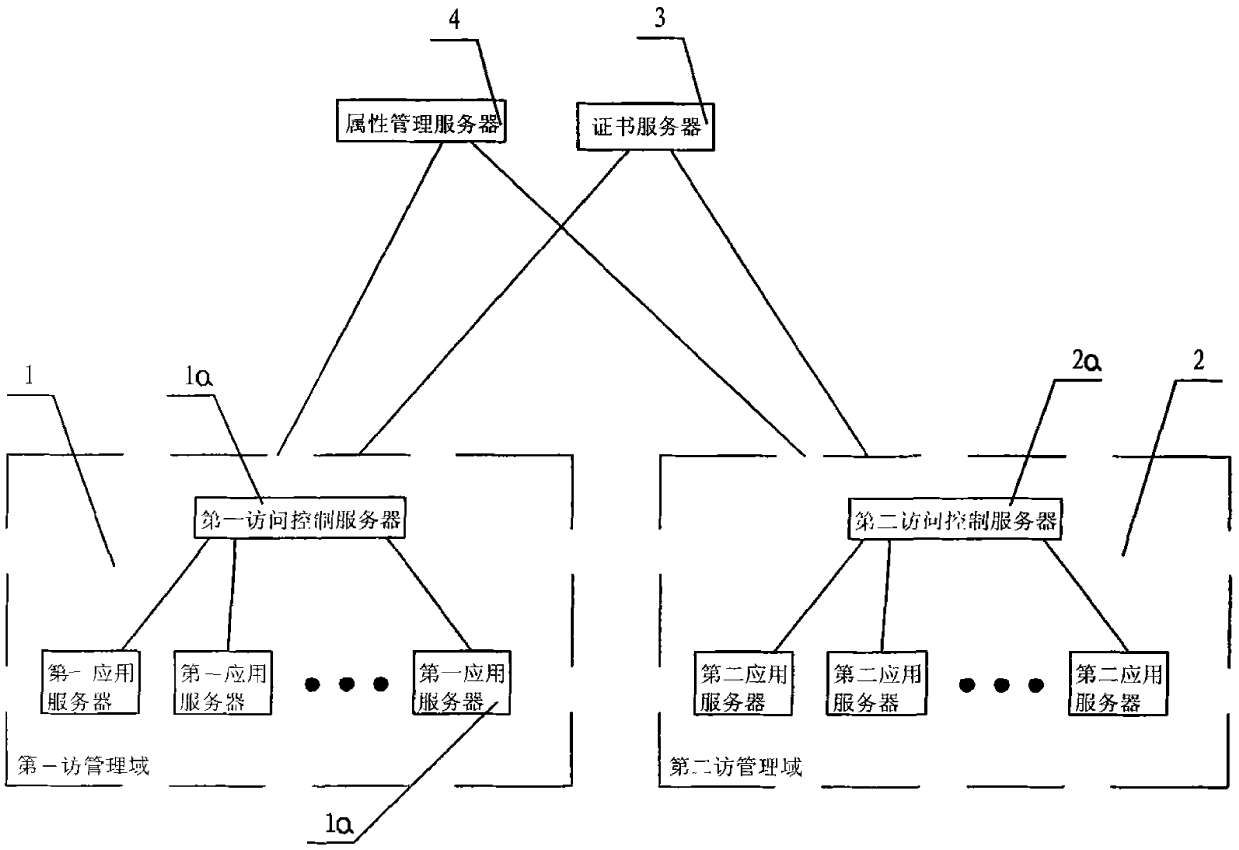
[0062] Such as figure 1 As shown, an attribute-based access control model described in the present invention, in order to simplify the description of the method, two management domains, the first management domain 1 and the second management domain 2, are used as examples for illustration. Including a first management domain 1 and a second management domain 2 connected to the Internet, wherein the first management domain 1 is provided with a first access control server 1a, and the first access control server 1a is connected with at least one first application Server 1b, wherein the second management domain 2 is provided with a second access control server 2a, the second access control server 2a is connected to at least one second application server 2b, the key lies in: it also includes a certificate server 3 and an attribute management server 4;
[0063] Where certificate server 3 is used for:
[0064] I. By issuing server certificates to the first access control server 1a a...
Embodiment 2
[0127] A cross-domain access method based on an attribute-based access control model, the key of which is:
[0128] Step 1. The certificate server issues server certificates to the first management domain 1 and the first management domain 2, respectively, for maintaining the trust chain relationship between the first access control server 1a and the second access control server 2a;
[0129] Step 2, the user logs in to the first management domain 1 through the first application server 1b, the first access control server 1a issues an attribute certificate containing a digital signature to the user, and the user downloads the attribute certificate to the local disk of the first application server 1b for storage;
[0130] Step 3. When the user logs in to the second management domain 2 and anonymously accesses resources under the second management domain 2, submit the attribute certificate issued by the first management domain 1 to the second management domain 2;
[0131] Step 4, t...
Embodiment 3
[0134] A cross-domain access method based on an attribute-based access control model, the key of which is:
[0135] Step 1. The certificate server issues server certificates to the first management domain 1 and the first management domain 2, respectively, for maintaining the trust chain relationship between the first access control server 1a and the second access control server 2a;
[0136] Step 2: The user logs in to the first management domain 1 through the first application server 1b, and the certificate server and the first access control server 1a issue to the user a user certificate encrypted with a private key and an attribute certificate containing a digital signature respectively. The certificate is downloaded to the local disk of the first application server 1b for storage;
[0137] Step 3: When the user transparently accesses resources under the second management domain 2, submit the user certificate and the attribute certificate to the second management domain 2 at...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com