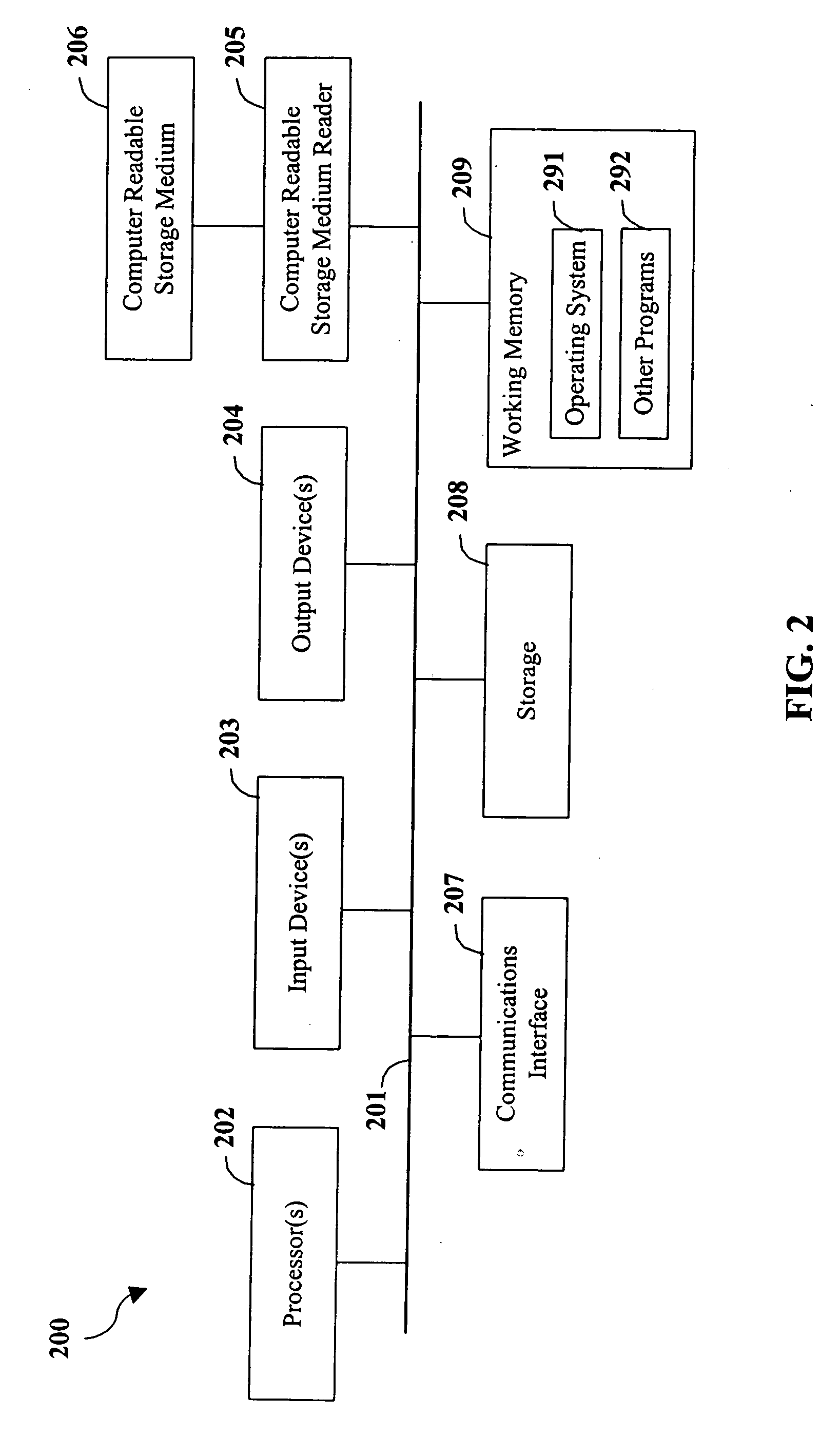
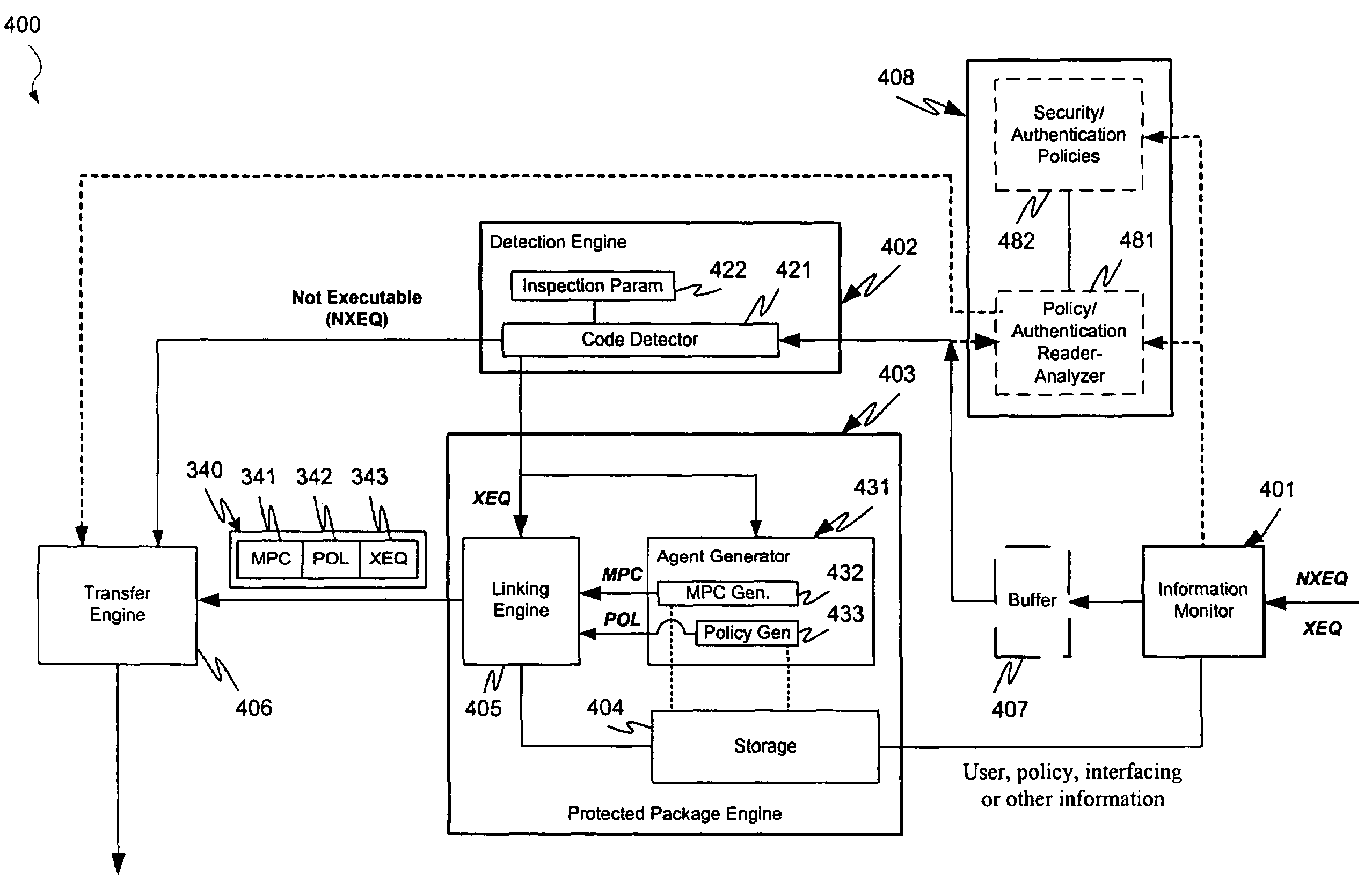
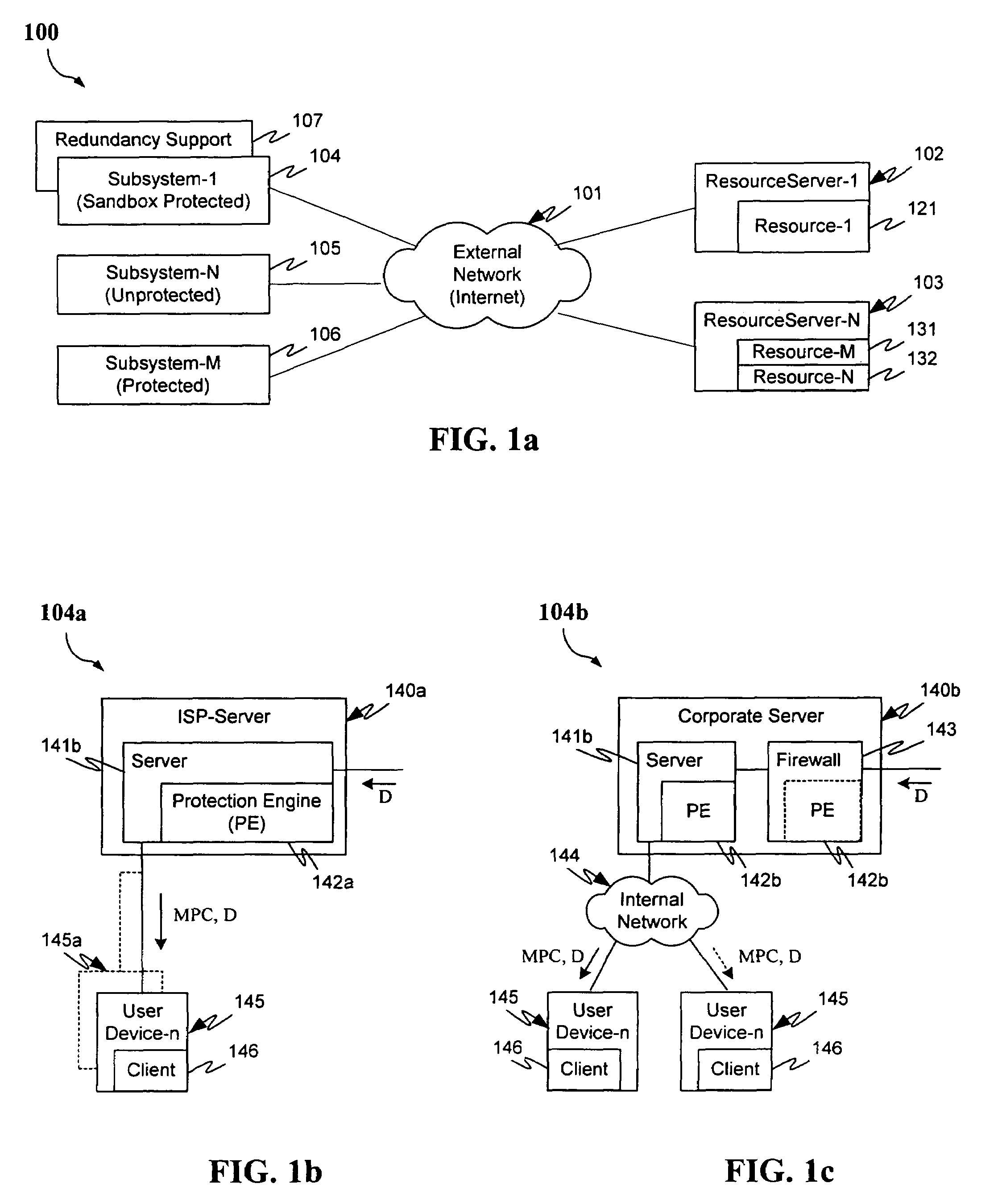
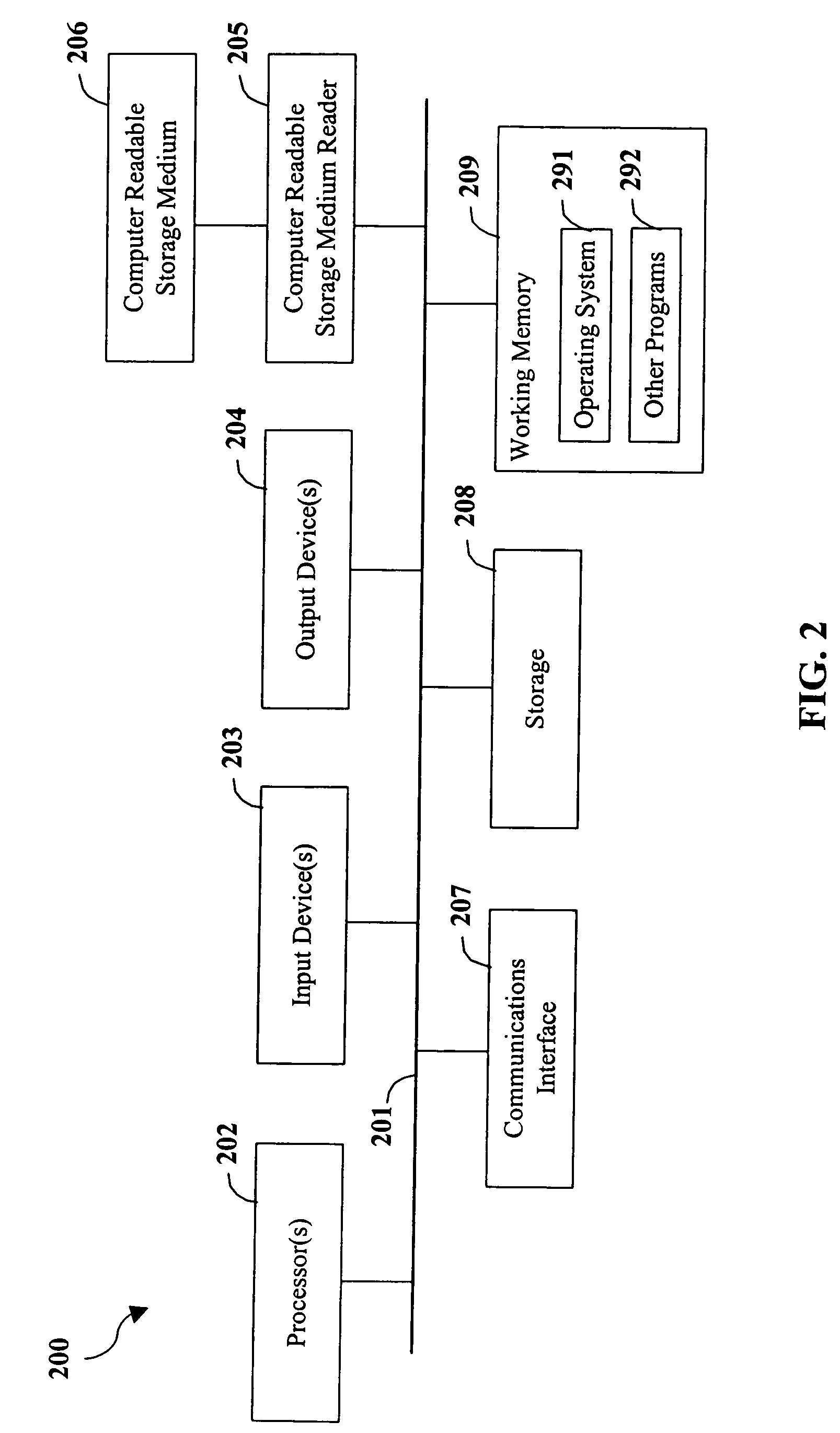
Patents
Literature
86 results about "Mobile code" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
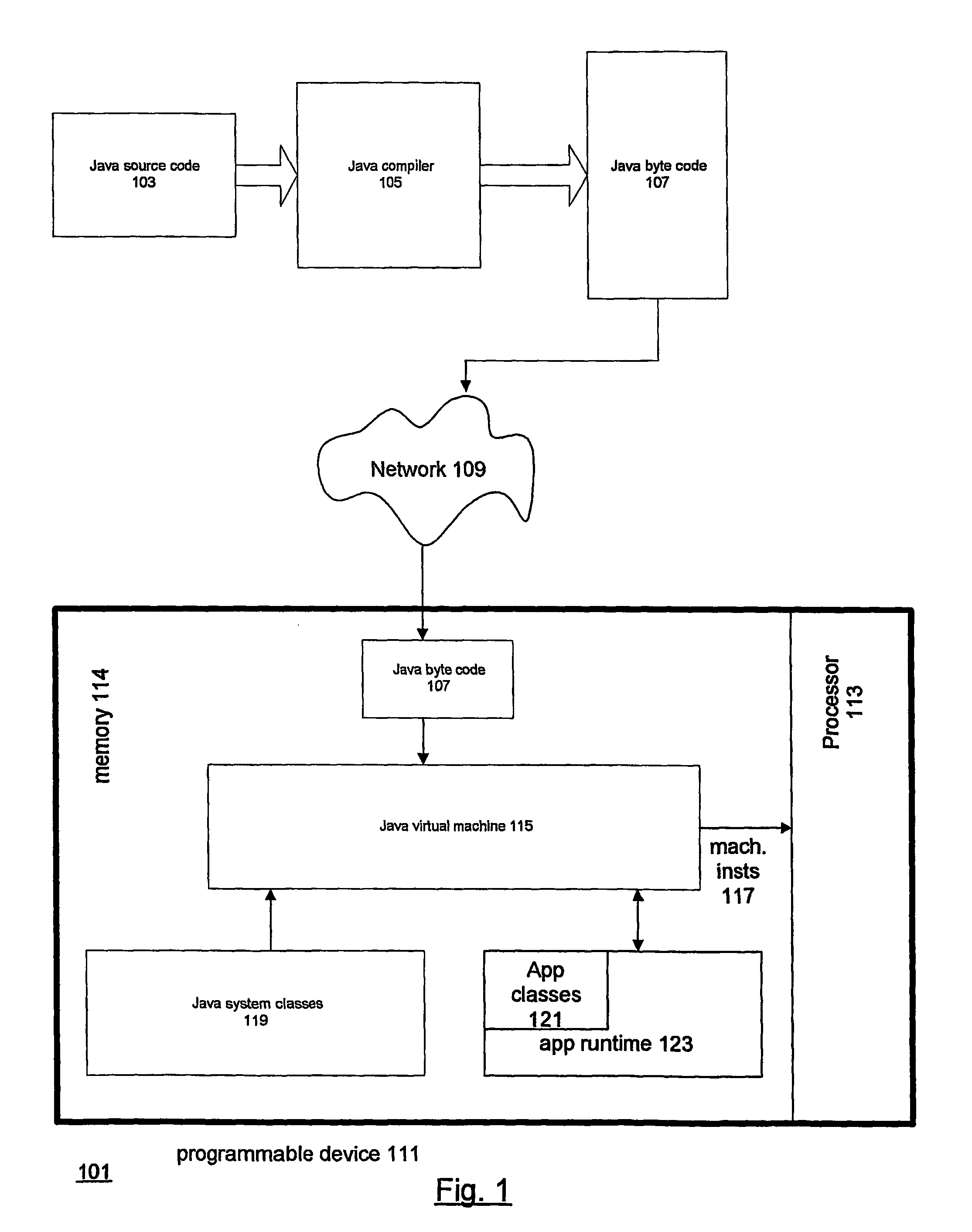
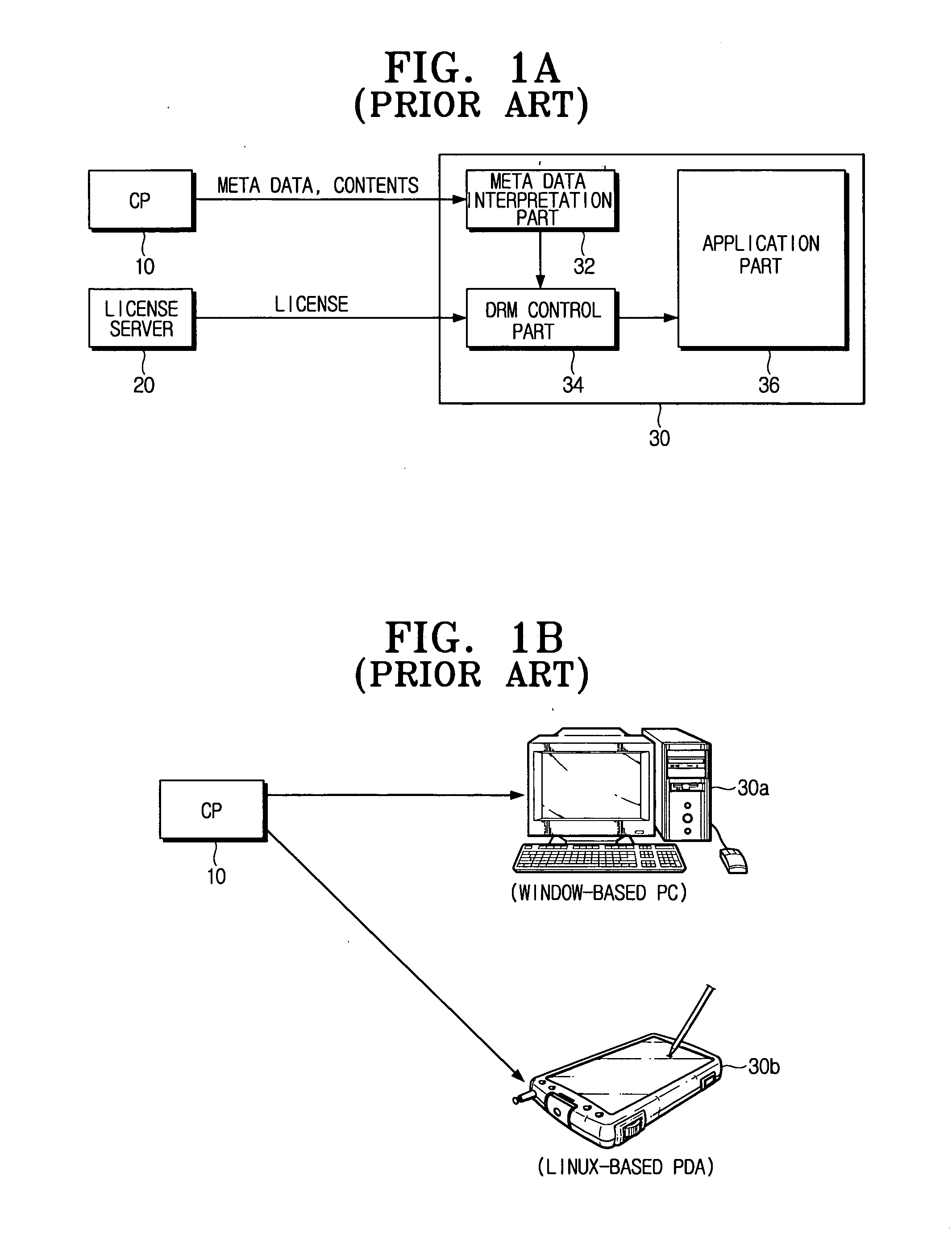
In computer science, mobile code is software transferred between systems, e.g. transferred across a network, and executed on a local system without explicit installation by the recipient. Examples of mobile code include scripts, Java applets, ActiveX controls, Flash animations, Shockwave movies, and macros embedded within Microsoft Office documents. Mobile code can also download and execute in the client workstation via email. Mobile code may download via an email attachment or via an HTML email body. For example, the ILOVEYOU, TRUELOVE, and AnnaK email viruses/worms all were implemented as mobile code. In almost all situations, the user is not aware that mobile code is downloading and executing in their workstation. Mobile code technologies can be used to support three different paradigms: Code on demand, Remote evaluation, and Mobile agents. Mobile code can also be encapsulated or embedded in other file formats not traditionally associated with executable code. An example of this form of encapsulation is the presence of JavaScript in a PDF.
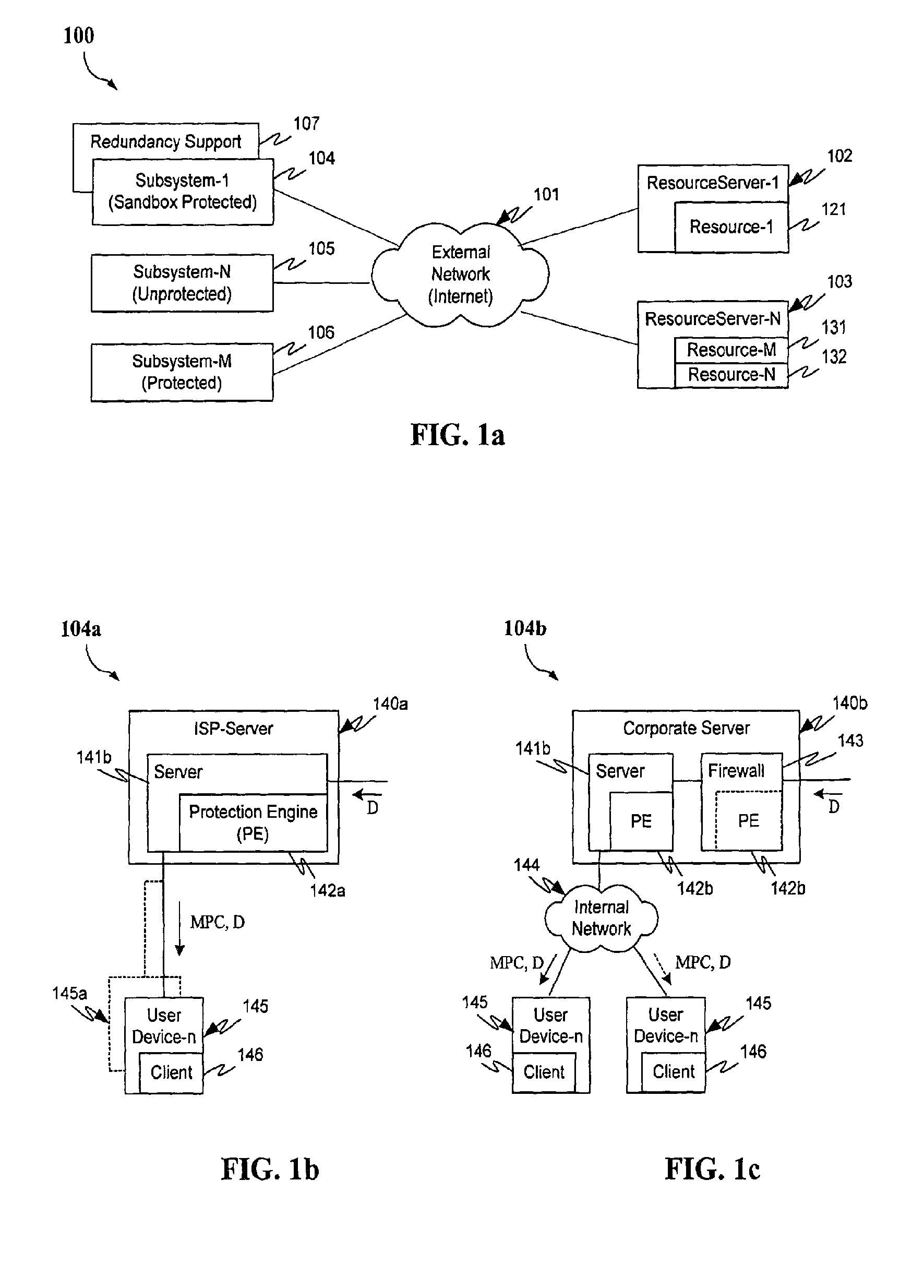
Malicious mobile code runtime monitoring system and methods
InactiveUS7058822B2Minimization requirementsEasy to updateMemory loss protectionDigital data processing detailsVisual BasicMonitoring system
Owner:FINJAN LLC
Secure internet applications with mobile code
InactiveUS6907530B2Easy accessUser identity/authority verificationUnauthorized memory use protectionThe InternetMobile code
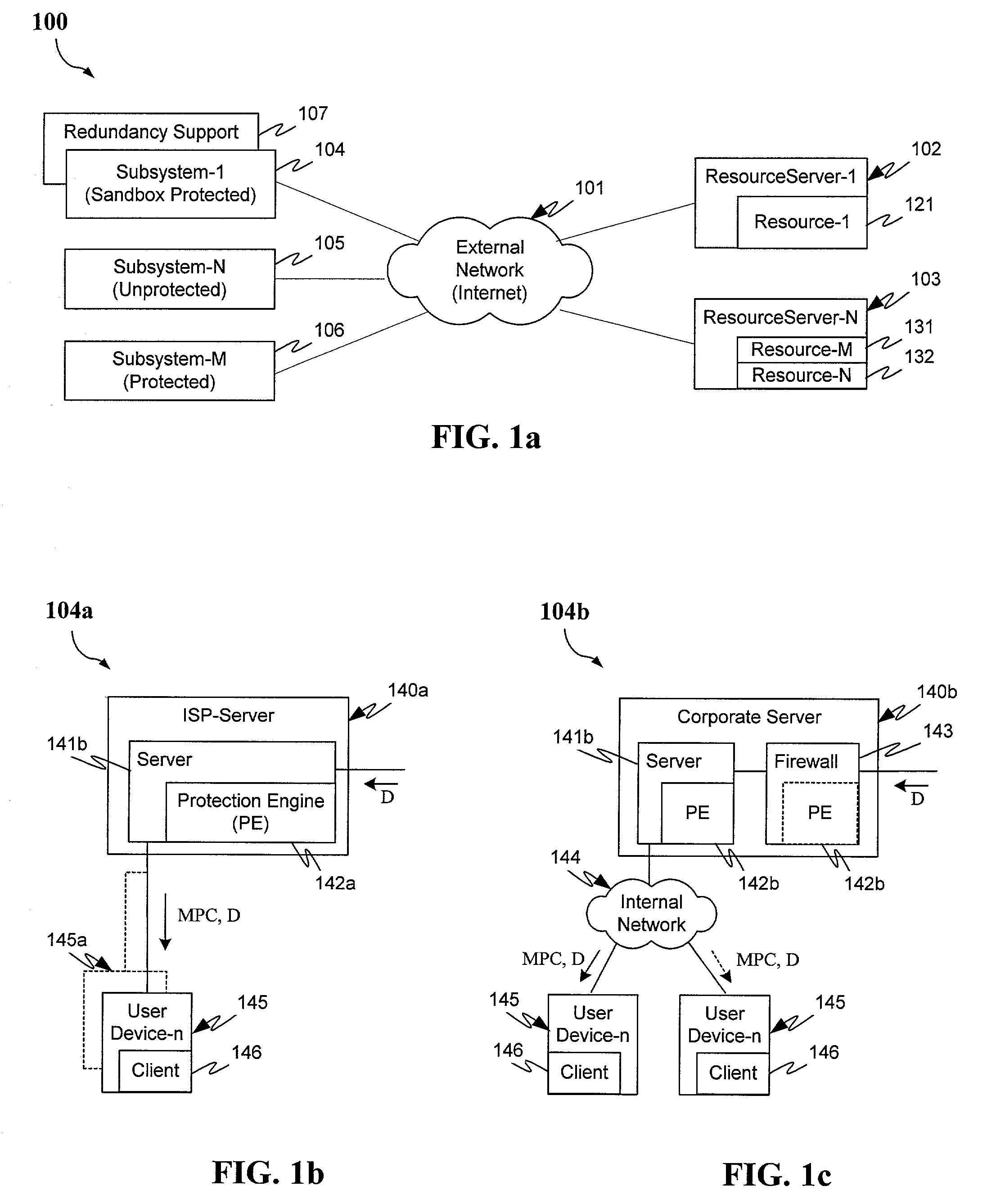
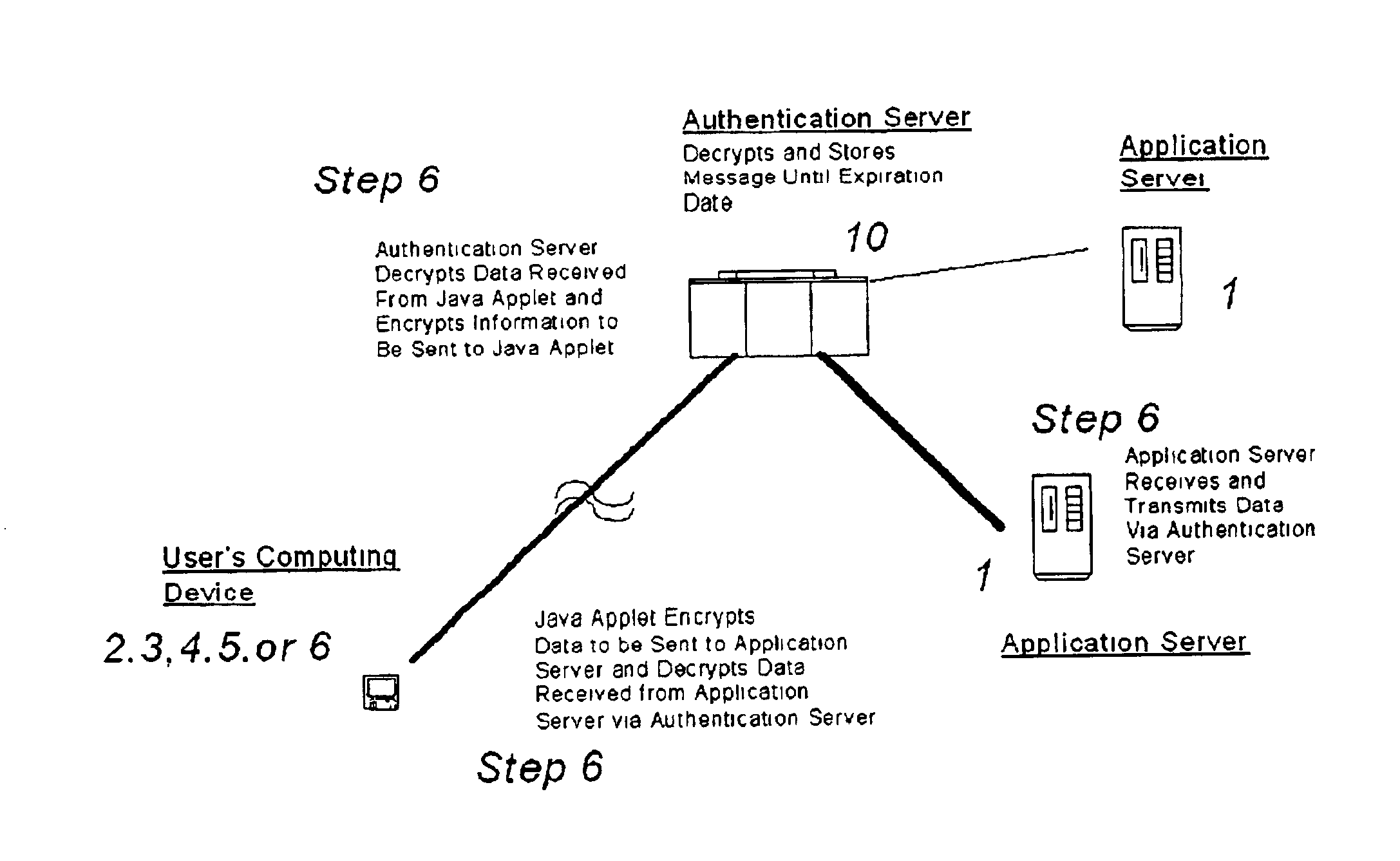
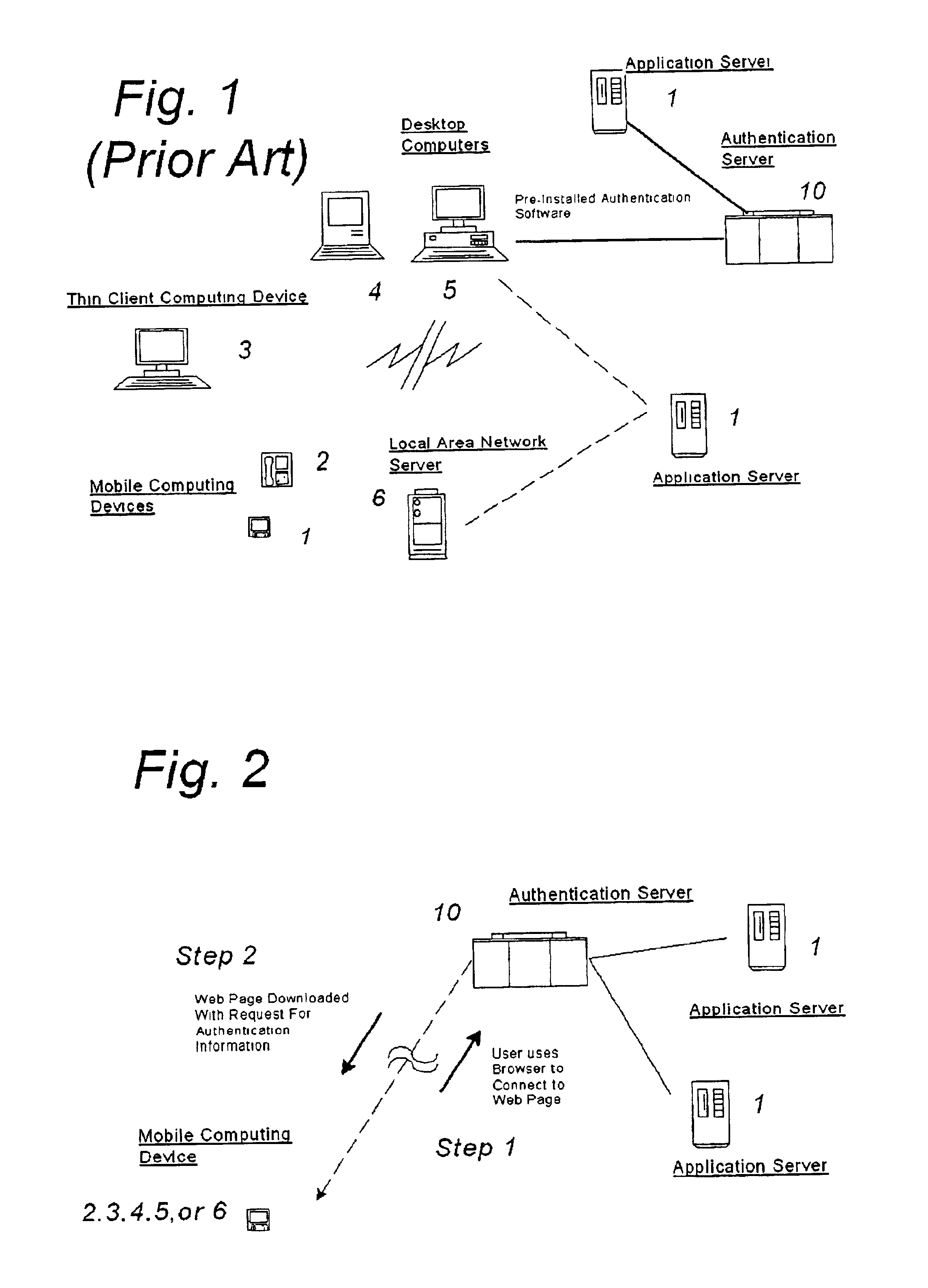
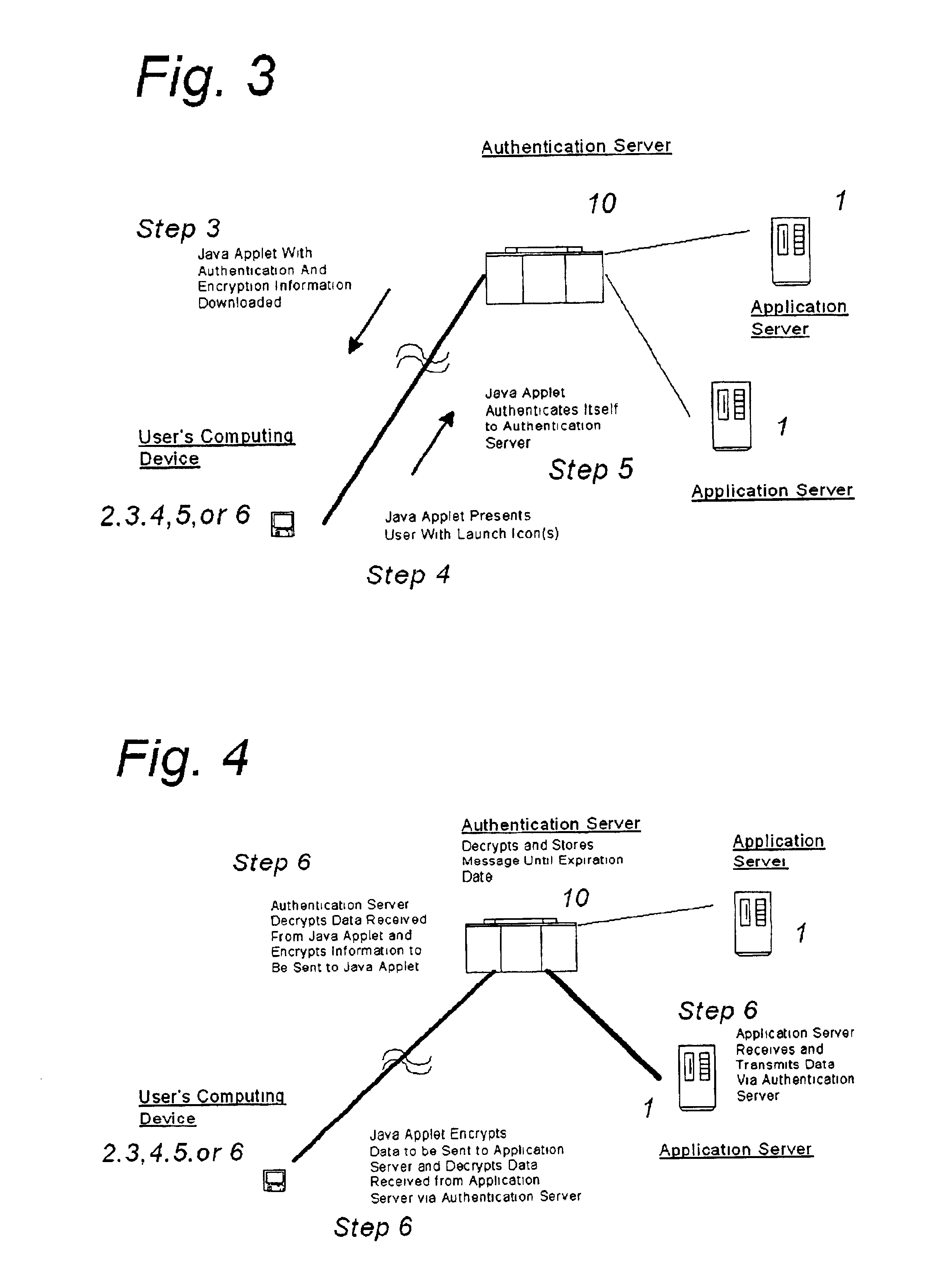
A system and method for securing pathways to a remote application server involves a gateway or authentication server, and a mobile code authentication and encryption client available for download from the gateway or authentication server. Upon connection of a user's computing device to the authentication server over the open network, the authentication server requests authentication information, such as a password, from the user, and upon authentication of the user by the authentication server, the authentication server downloads the mobile code authentication and encryption client to the user's computing device. The authentication and encryption client then authenticates itself to authentication server, after which a secure communications channel between the user's computing device and the authentication server is opened, the secure communications channel permitting transfer of data between the user's computing device and an application server. The system and method do not require pre-installation or any certificates or other authentication and encryption software on the user's computing device, enabling the system and method to be used with thin-client and mobile computing devices, as well as with conventional computers.
Owner:SSL SERVICES
Method and apparatuses for secure, anonymous wireless LAN (WLAN) access
ActiveUS8285992B2Digital data processing detailsUser identity/authority verificationWeb browserWeb service
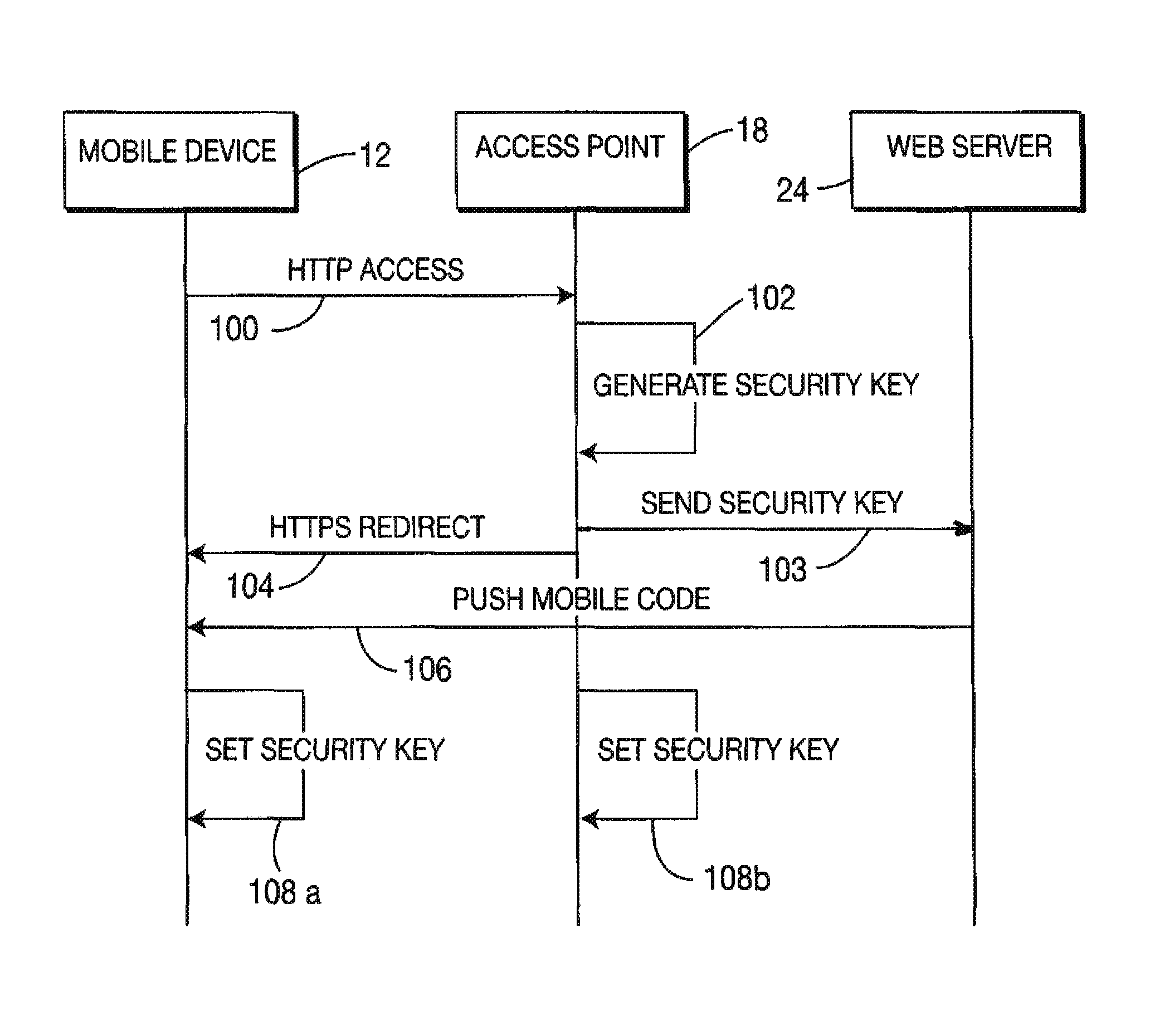
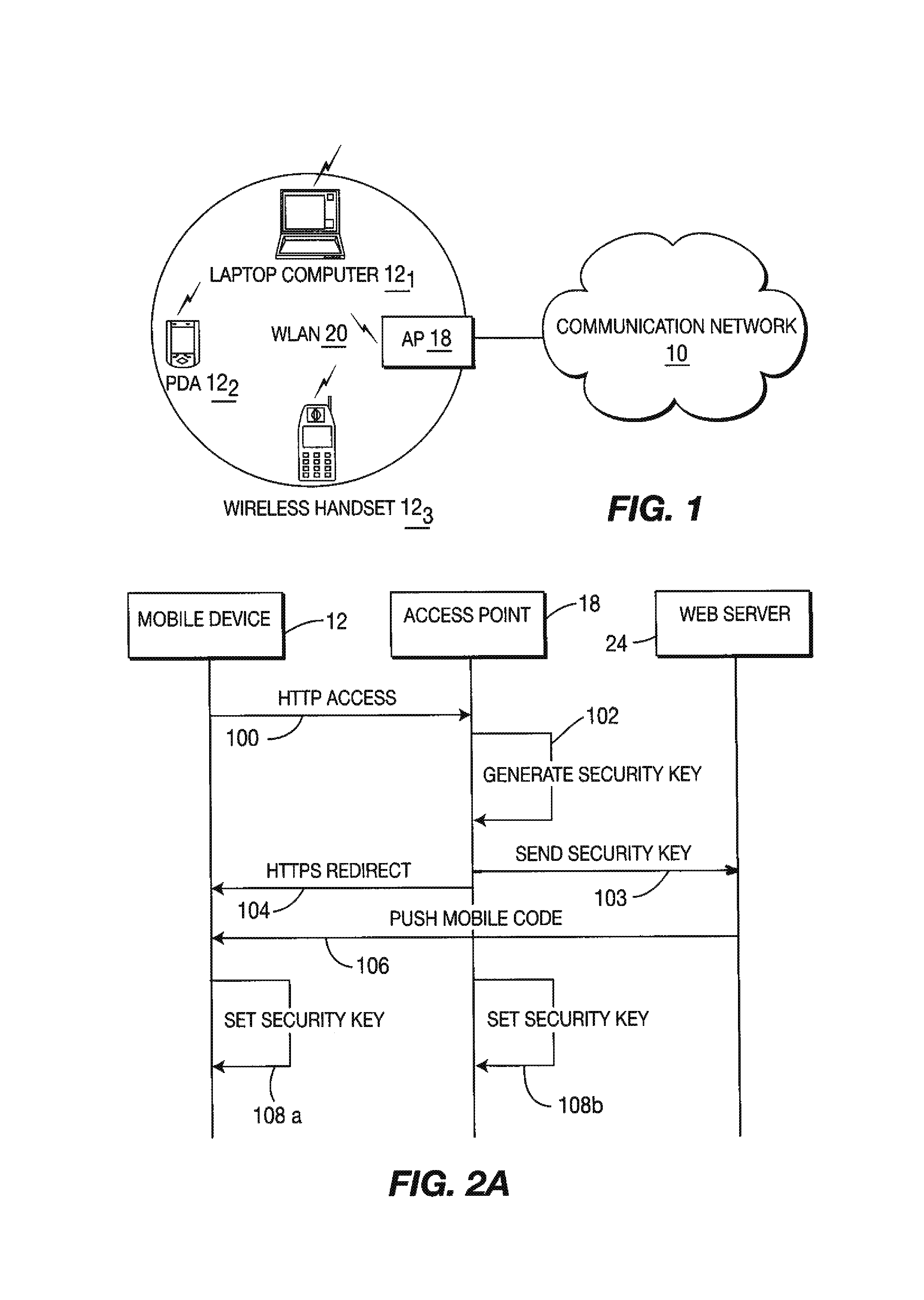
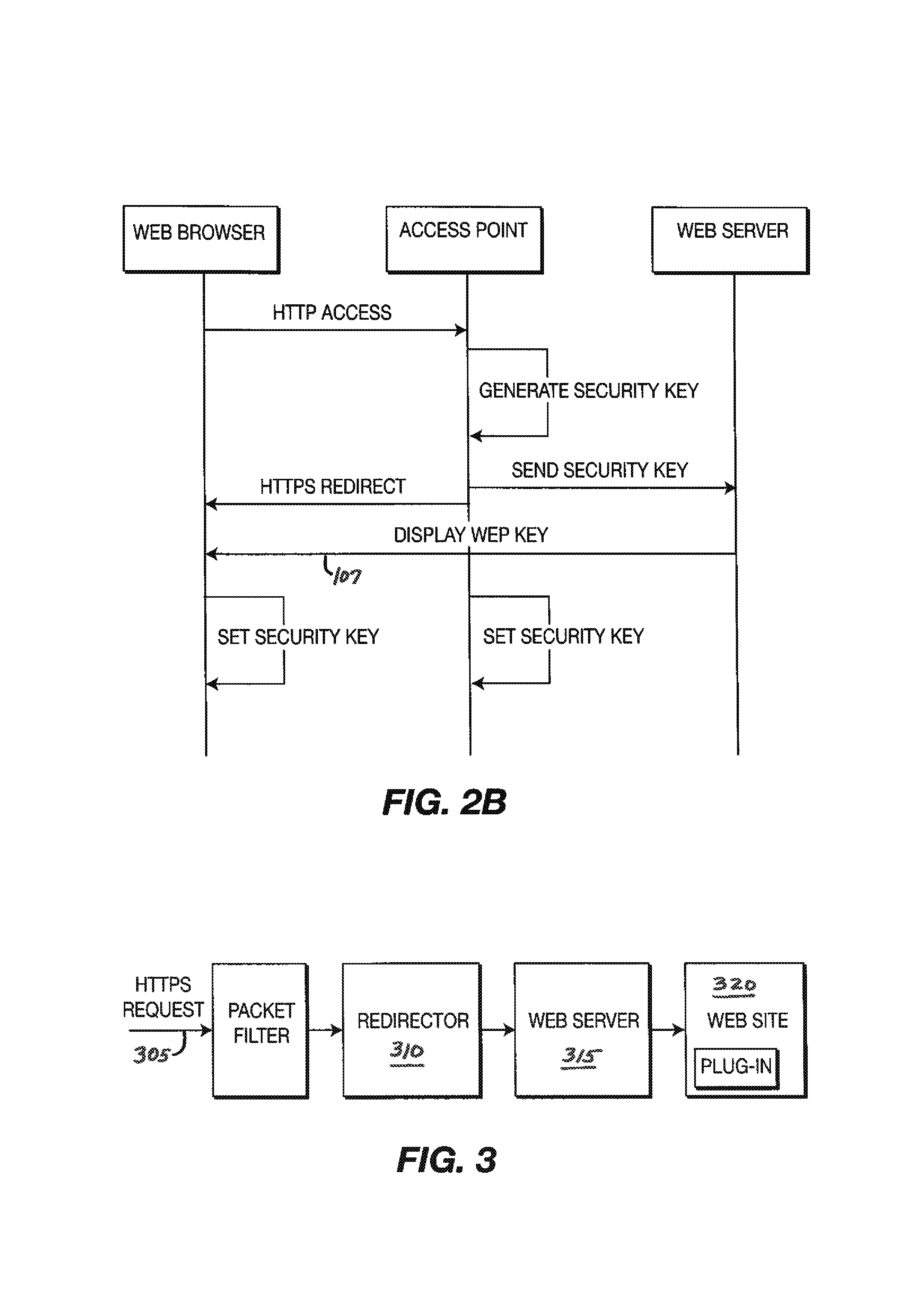
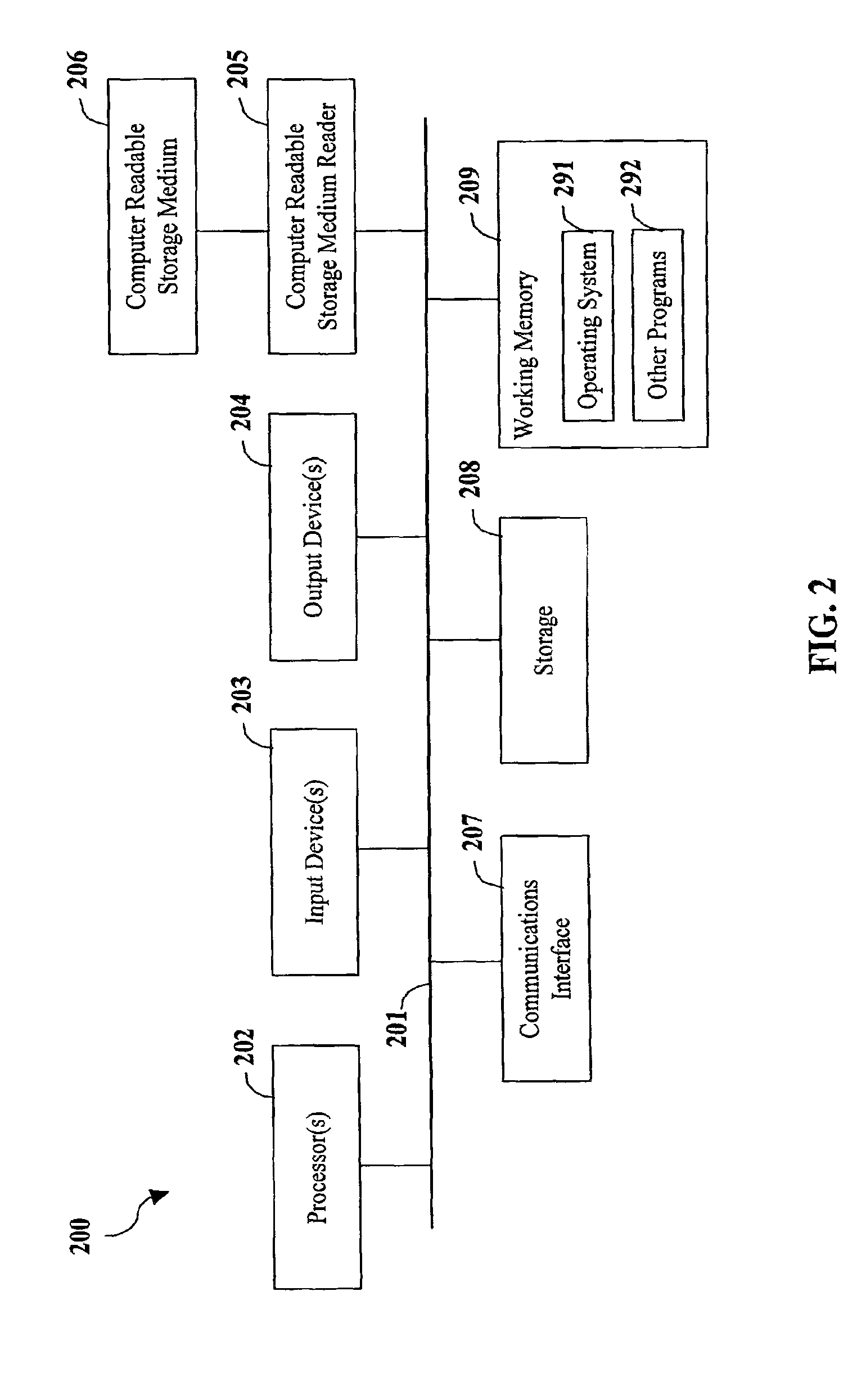
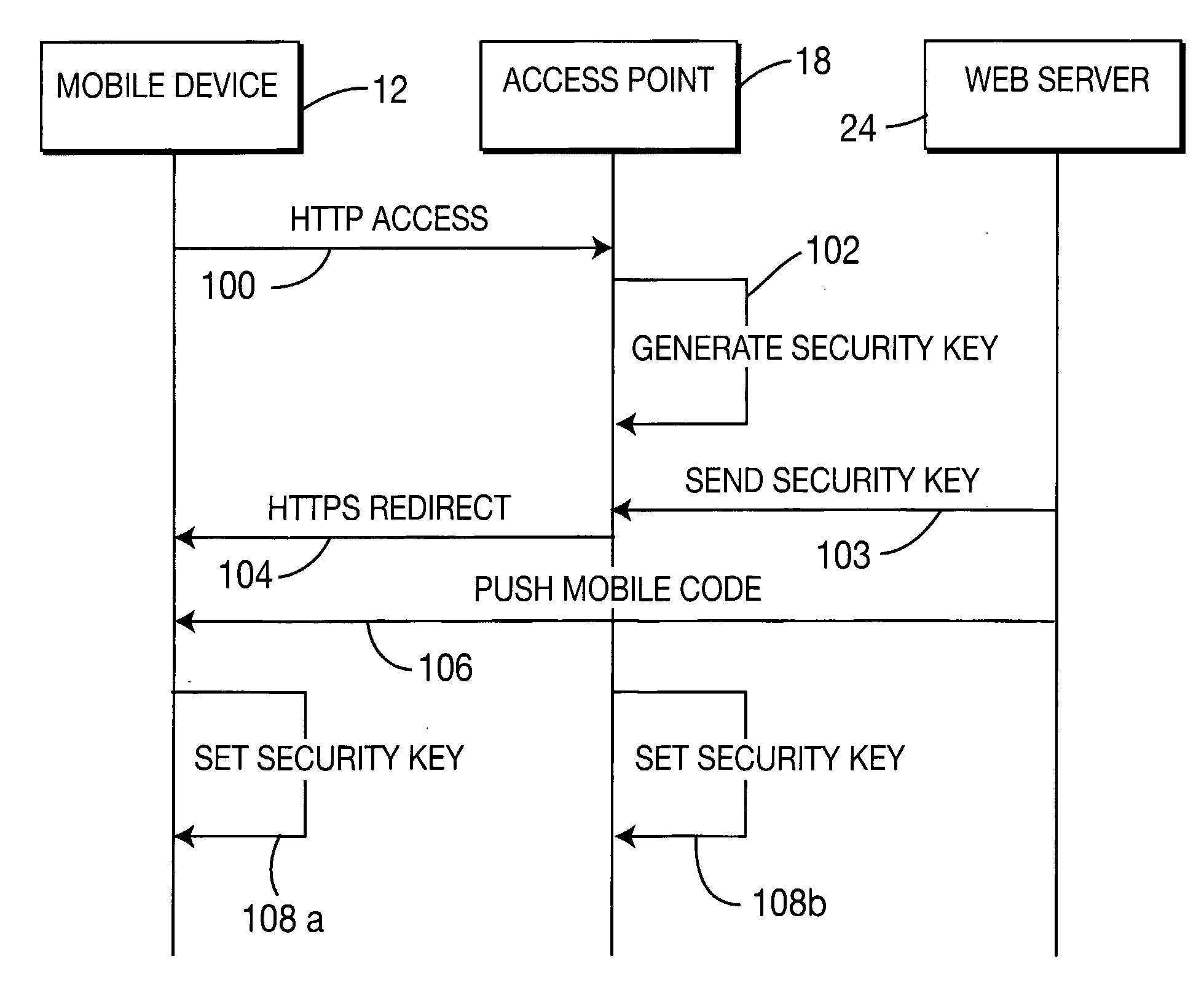
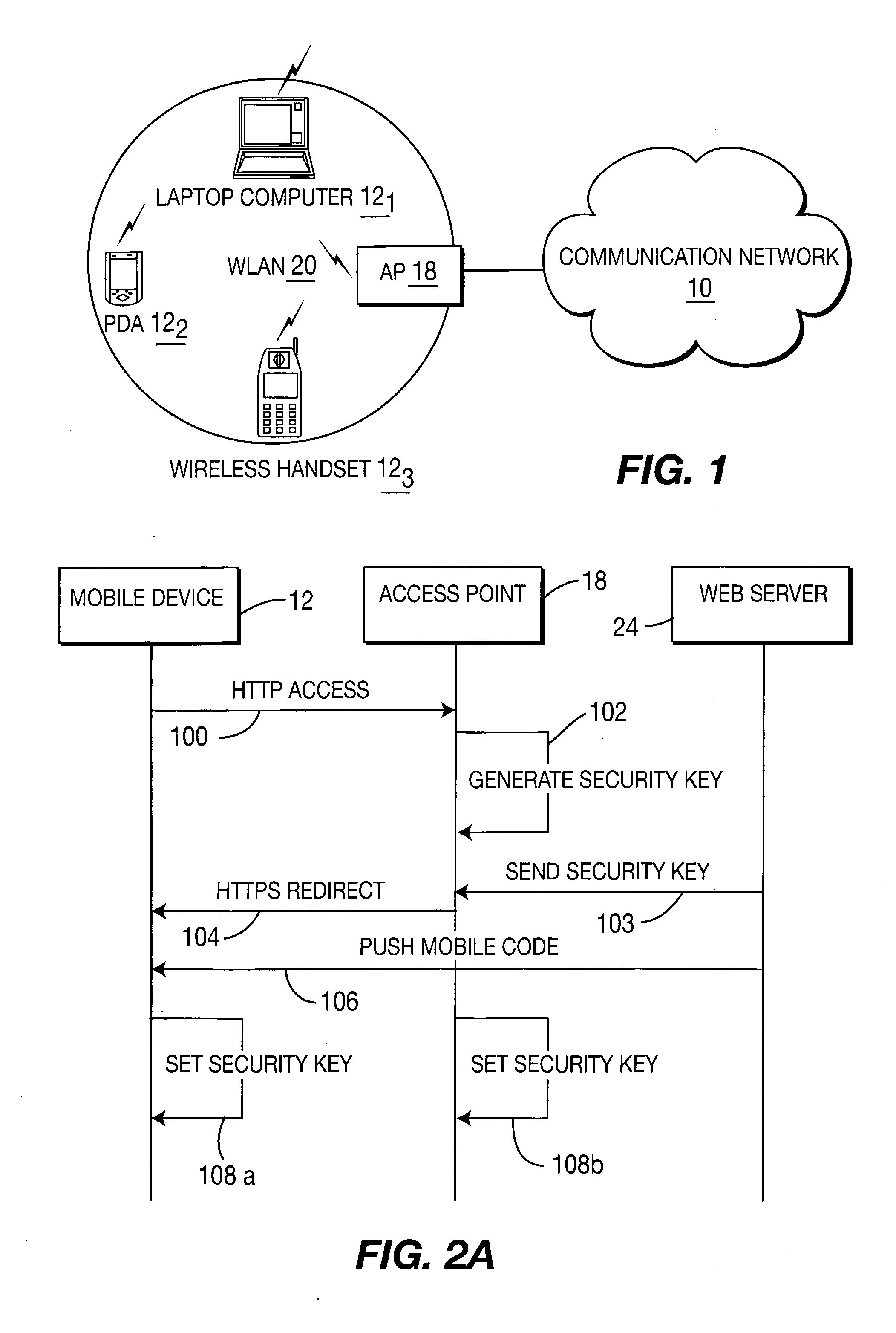
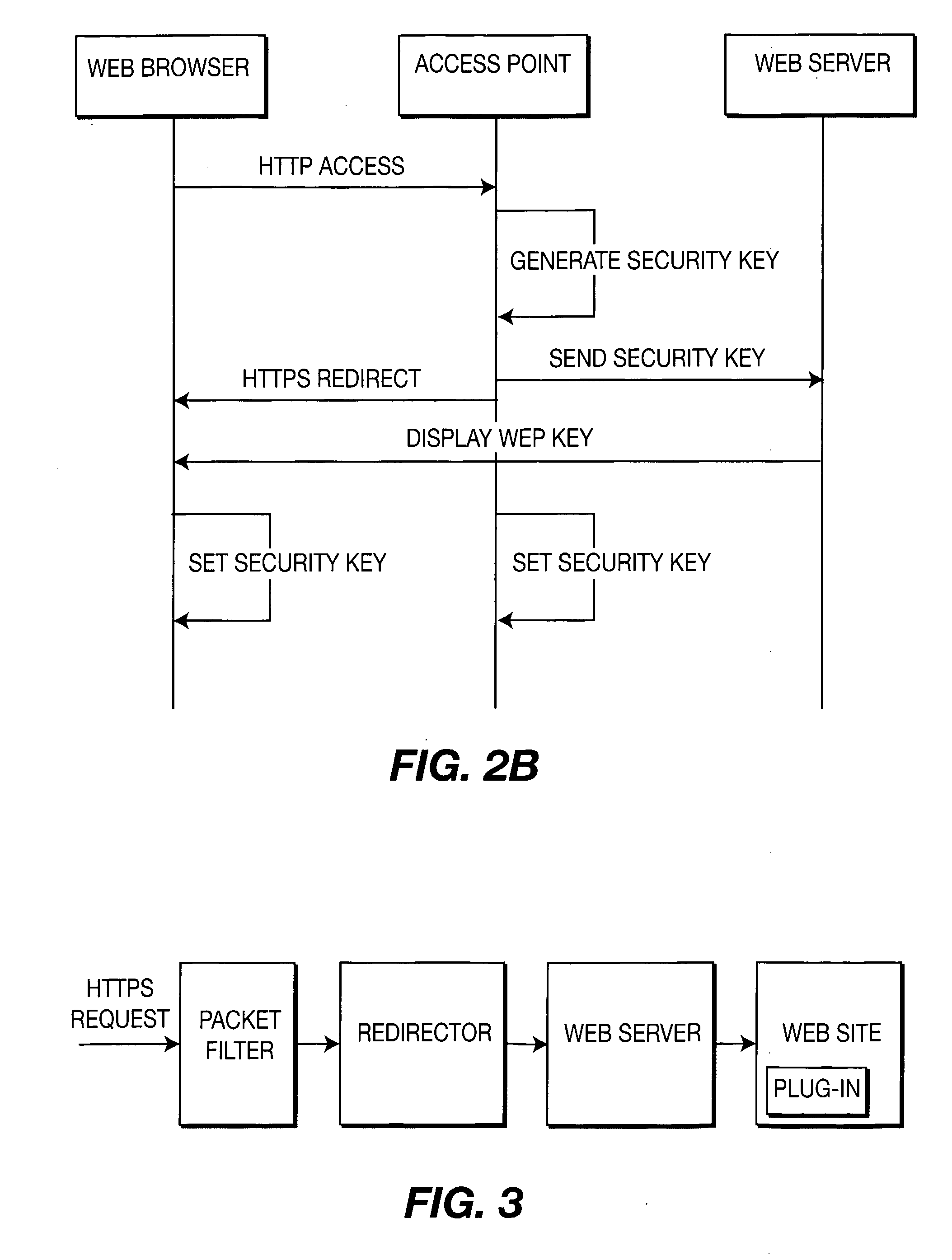
A method and system for providing secure, anonymous access to a wireless local area network, including configuring an access point to drop packets except packets exhibiting an URL access protocol like HTTP and HTTPS, intercepting a URL access request by an access point from a mobile device via a web browser, re-directing the URL access request to a web server by the access point generating a security key by one of the access points and the web server, communicating the generated security key to the said web server securely by the access point or vice versa and setting the security key by the access point is described. A mobile device including means for forwarding a request for secure access to a wireless local area network via a URL access request, means for receiving a mobile code or a signal for displaying a security key and means for setting the security key is also described.
Owner:THOMSON LICENSING SA
System and method for providing context information
InactiveUS7552265B2Digital computer detailsElectrographic process apparatusAdministrative domainData source
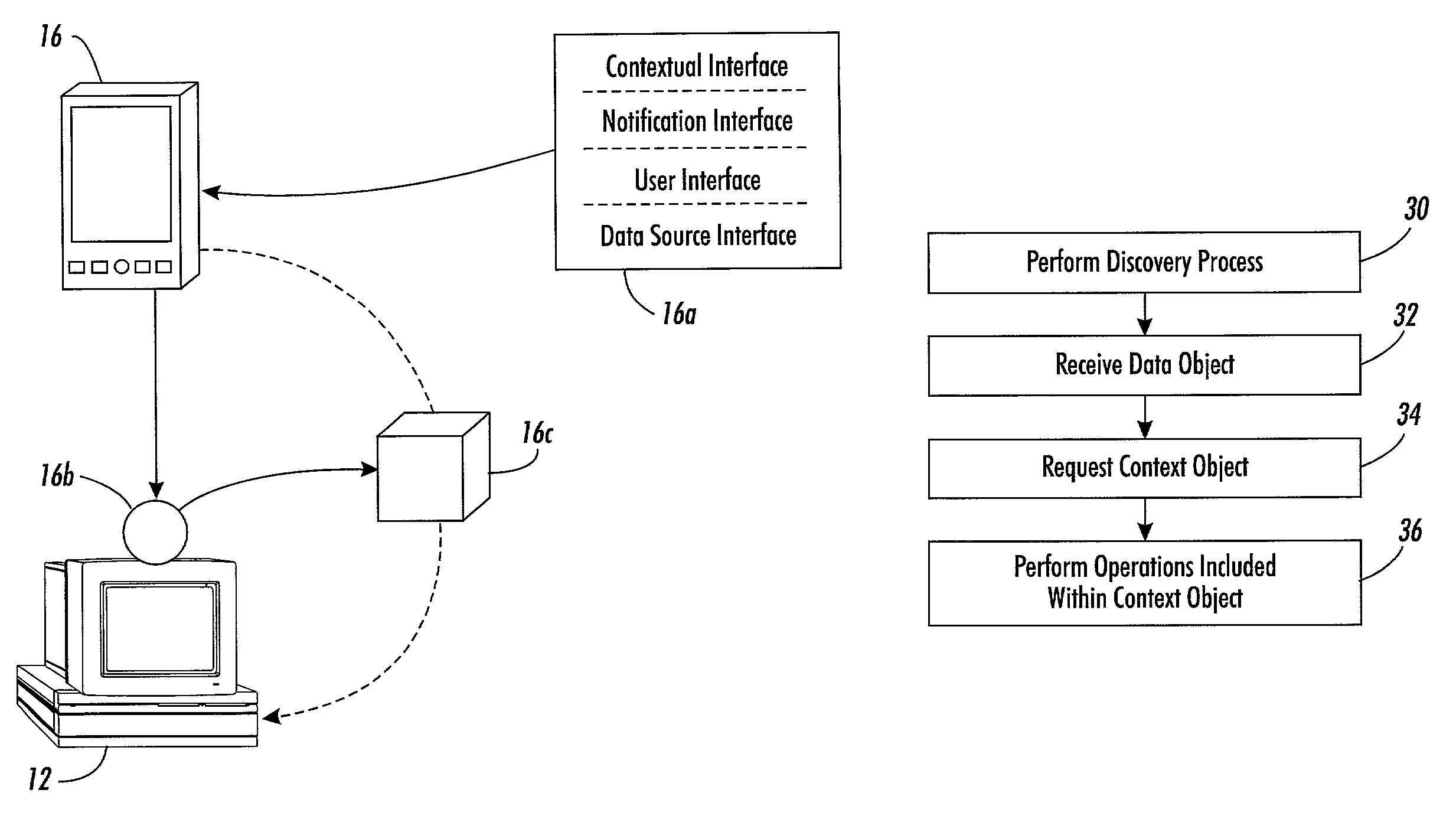
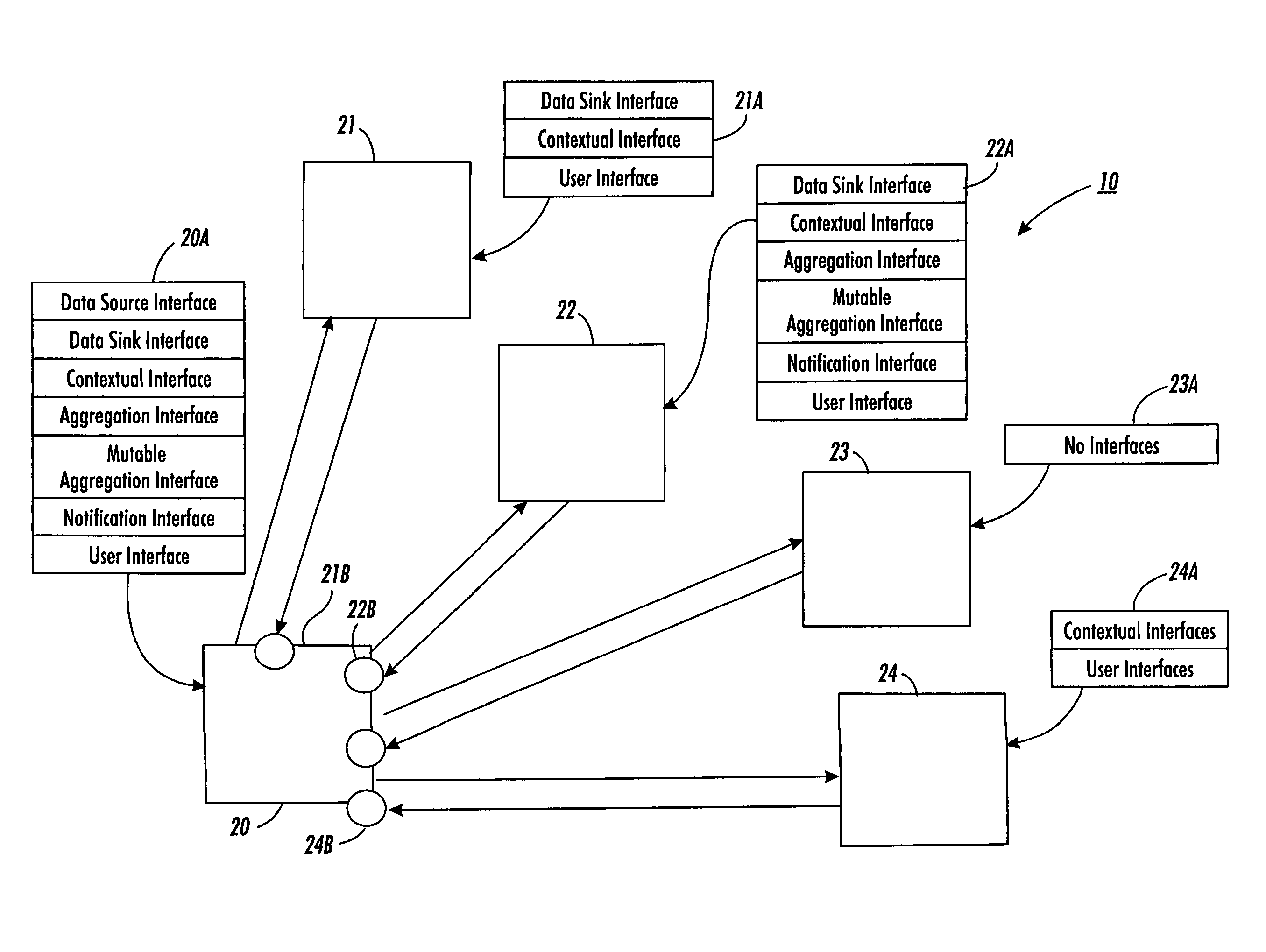
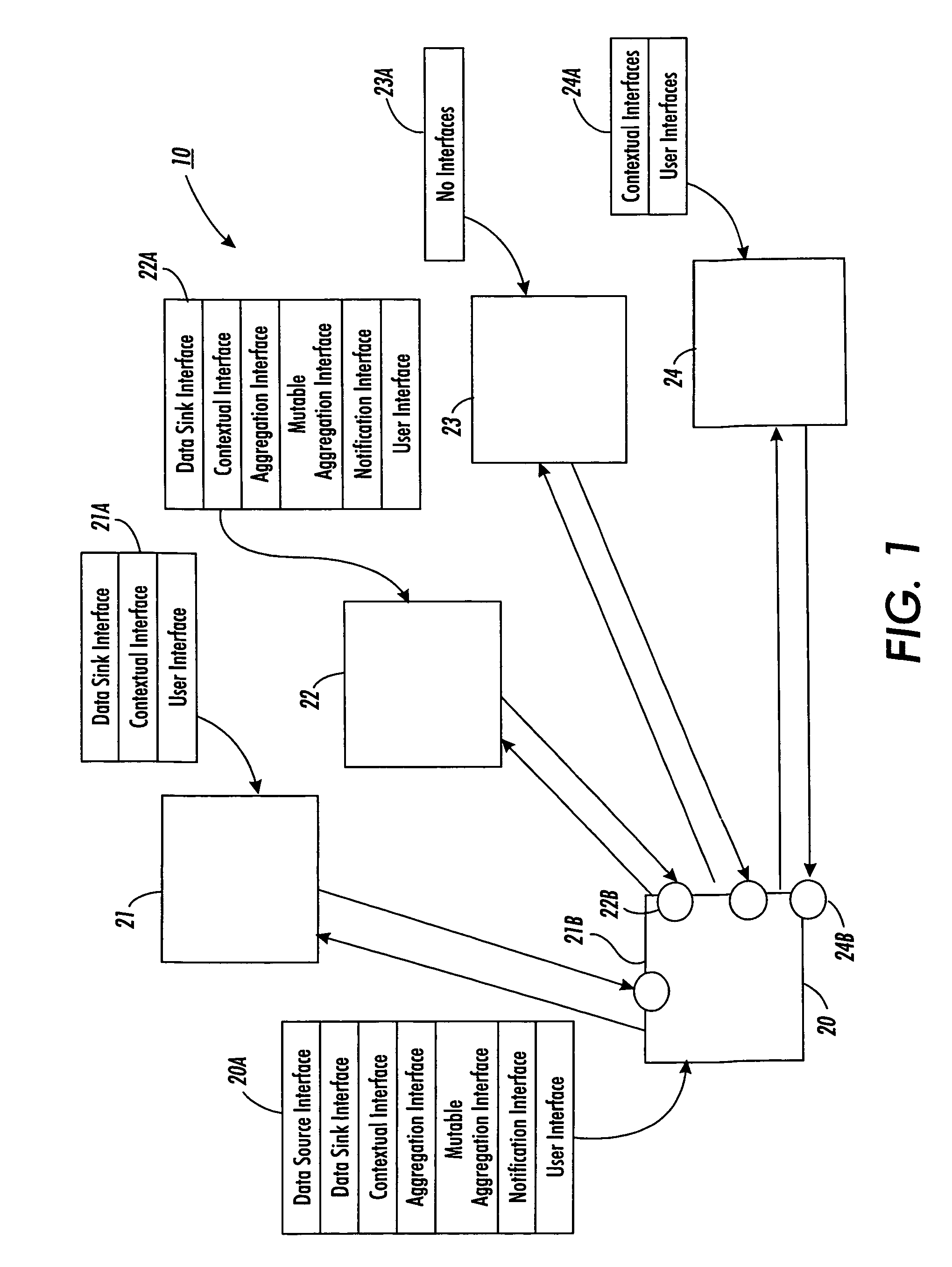
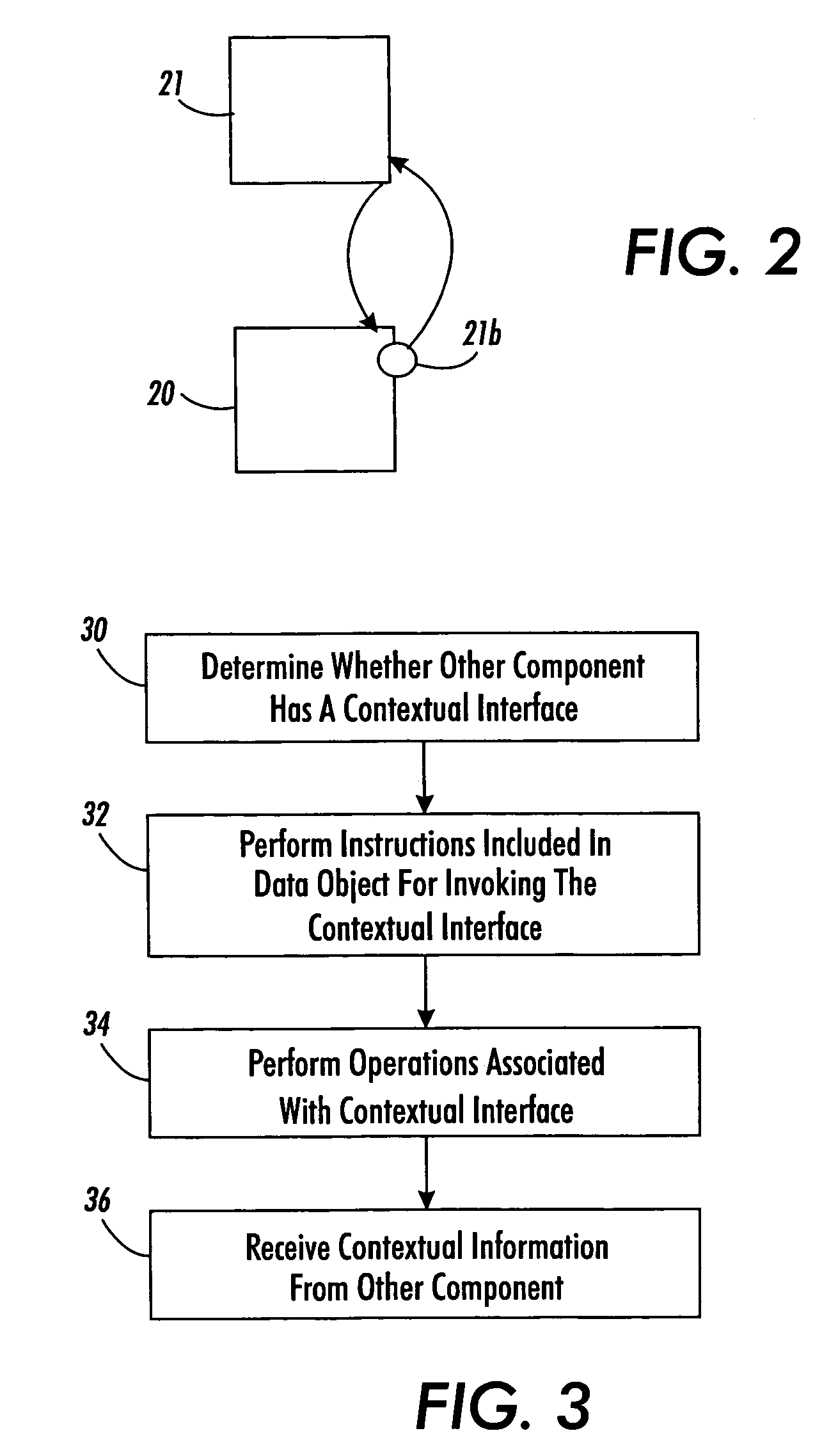
Systems and methods for enabling arbitrary components to transfer current, contextual data between each other without requiring prior knowledge of each other. The contextual data may include executable computer language instructions or a type, operating status, identity, location, administrative domain or environment information of the components or its users. The system includes a set of arbitrary components associated with one or more universal interfaces. The one or more universal interfaces may include mobile code, a contextual interface, a notification interface, a user interface and a data source interface. A first component at least has a universal contextual interface. A second component may invoke the universal contextual interface and execute associated instructions to transfer contextual data between the first component and the second component.
Owner:GULA CONSULTING LLC
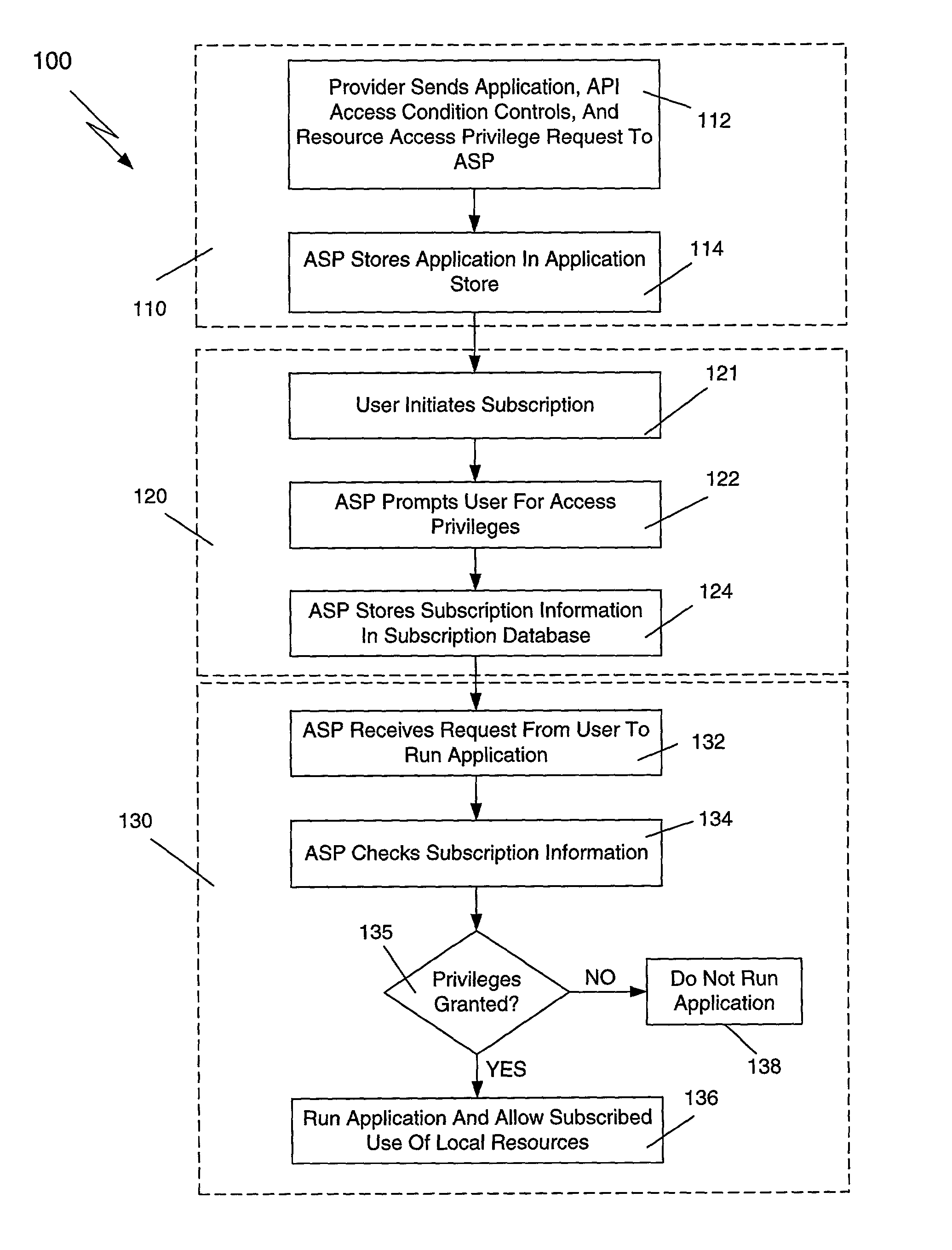
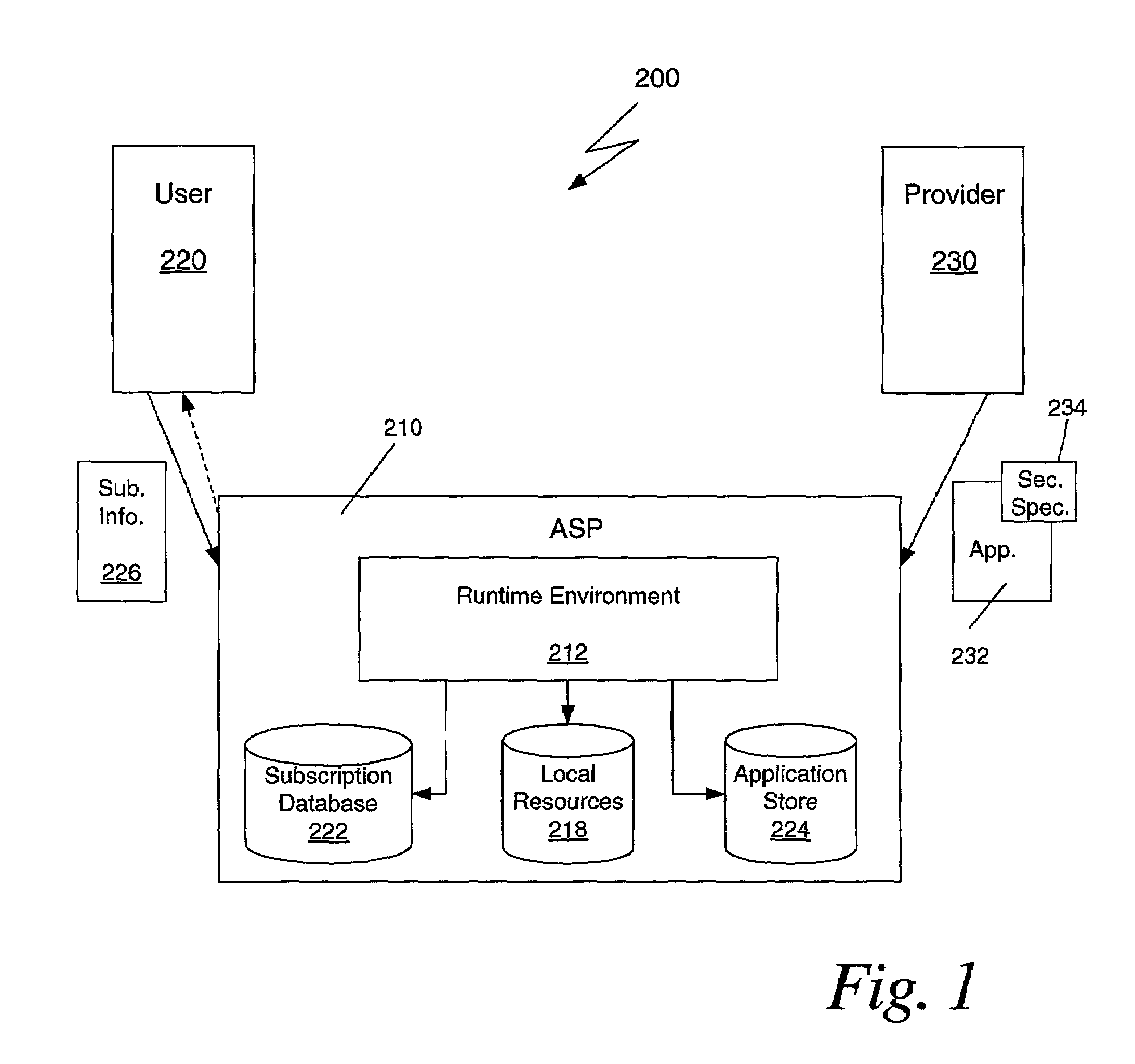
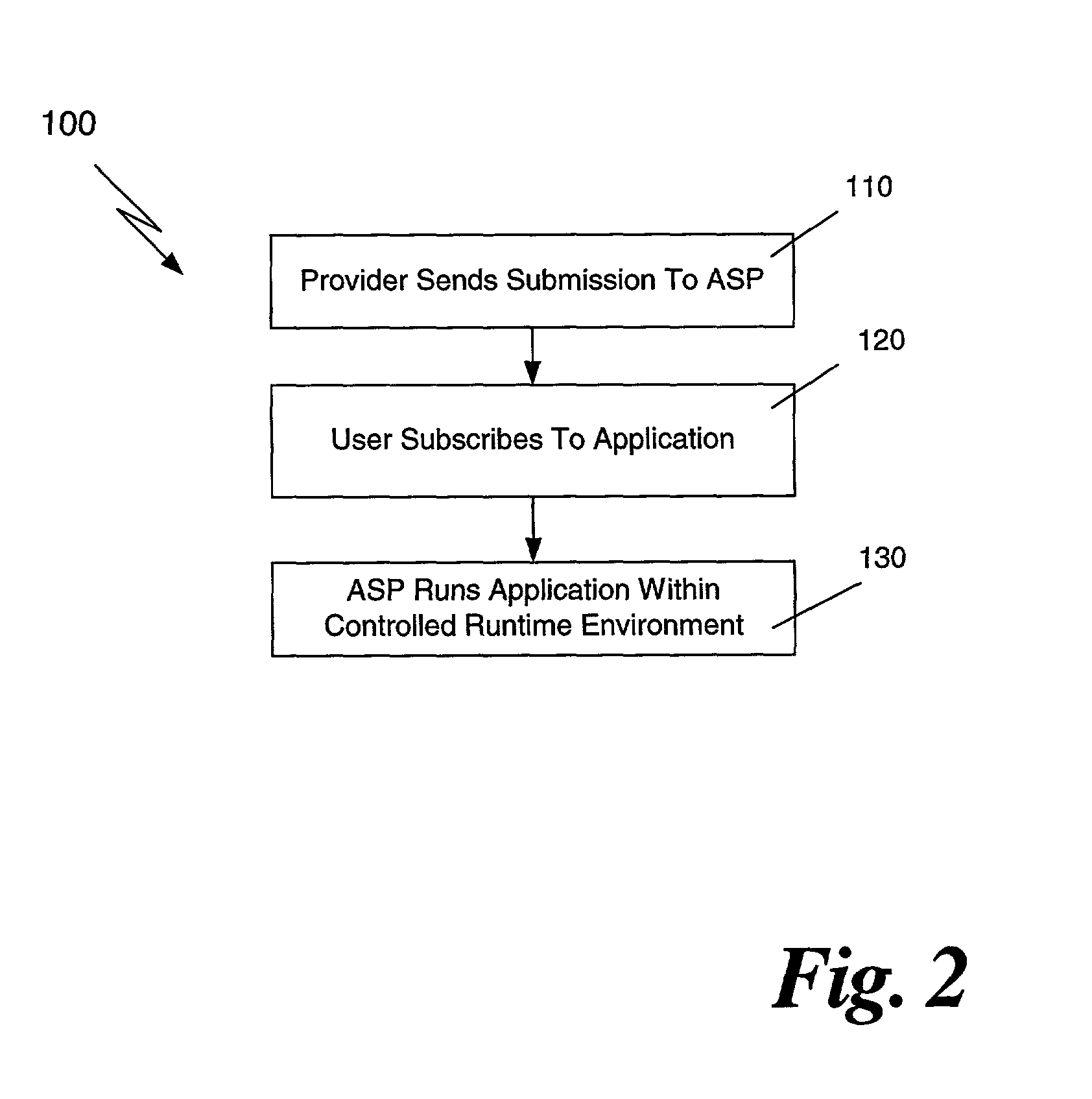
Mobile code security architecture in an application service provider environment
ActiveUS7096491B2Random number generatorsUnauthorized memory use protectionSecurity specificationResource based
A method is disclosed for providing mobile code software applications to users via an application service provider (ASP). The ASP receives a mobile code application, such as a Java application, from a provider, along with a security specification. The security specification defines access privileges requested to execute the application, including privileges to execute functions performed by the application and privileges to access local resources of the ASP. The ASP receives a subscription to the application from a user. The subscription includes subscription information granting or denying privileges, and specifying parameters for the privileges, requested in the security specification. The ASP executes the application at runtime by determining for each executable function whether the user has authorized the requested privilege. Those functions authorized by the user are executed in one embodiment. During runtime the ASP limits the application's access to local resources based on the privileges granted by the user.
Owner:ENT SERVICES DEV CORP LP
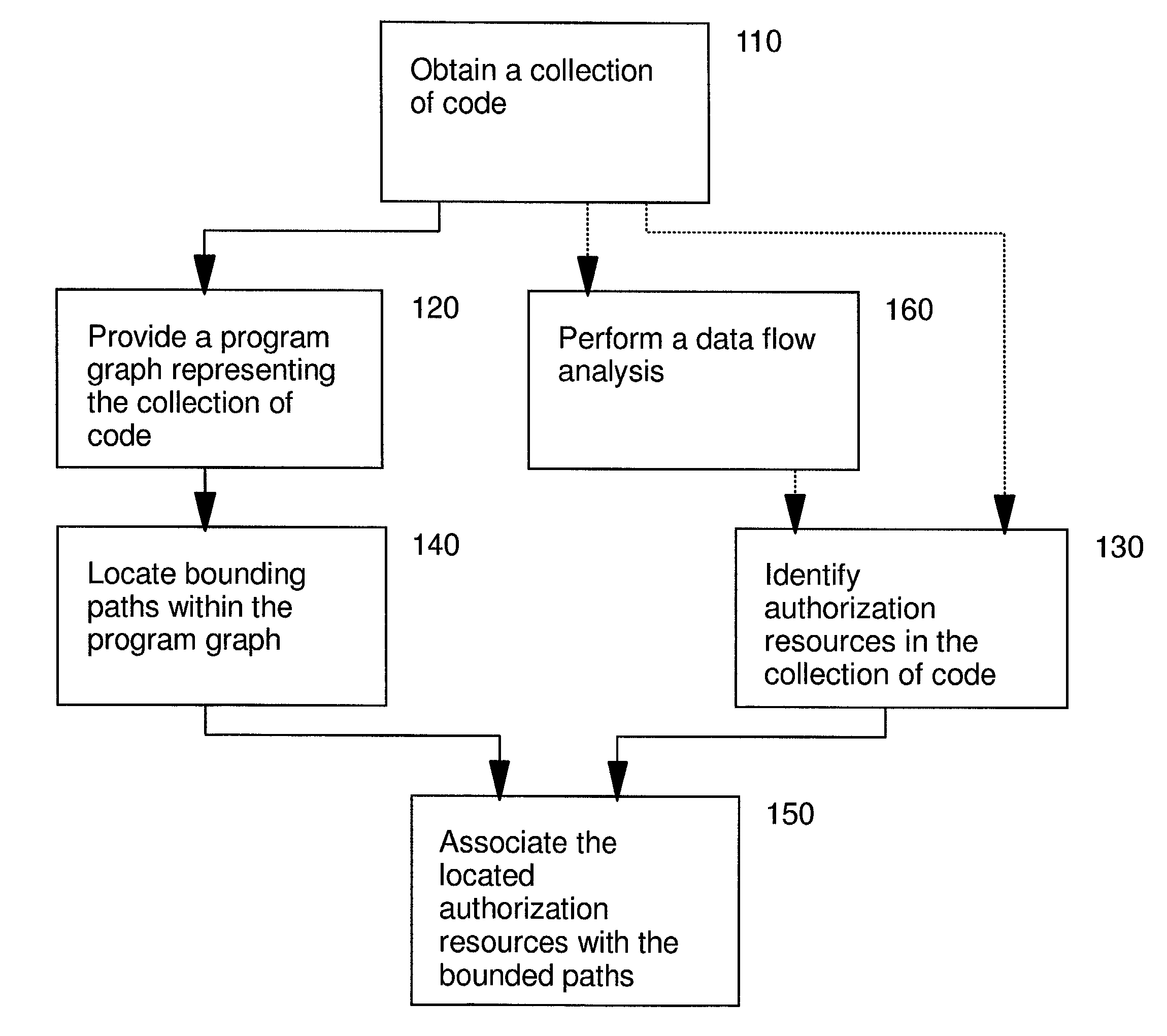
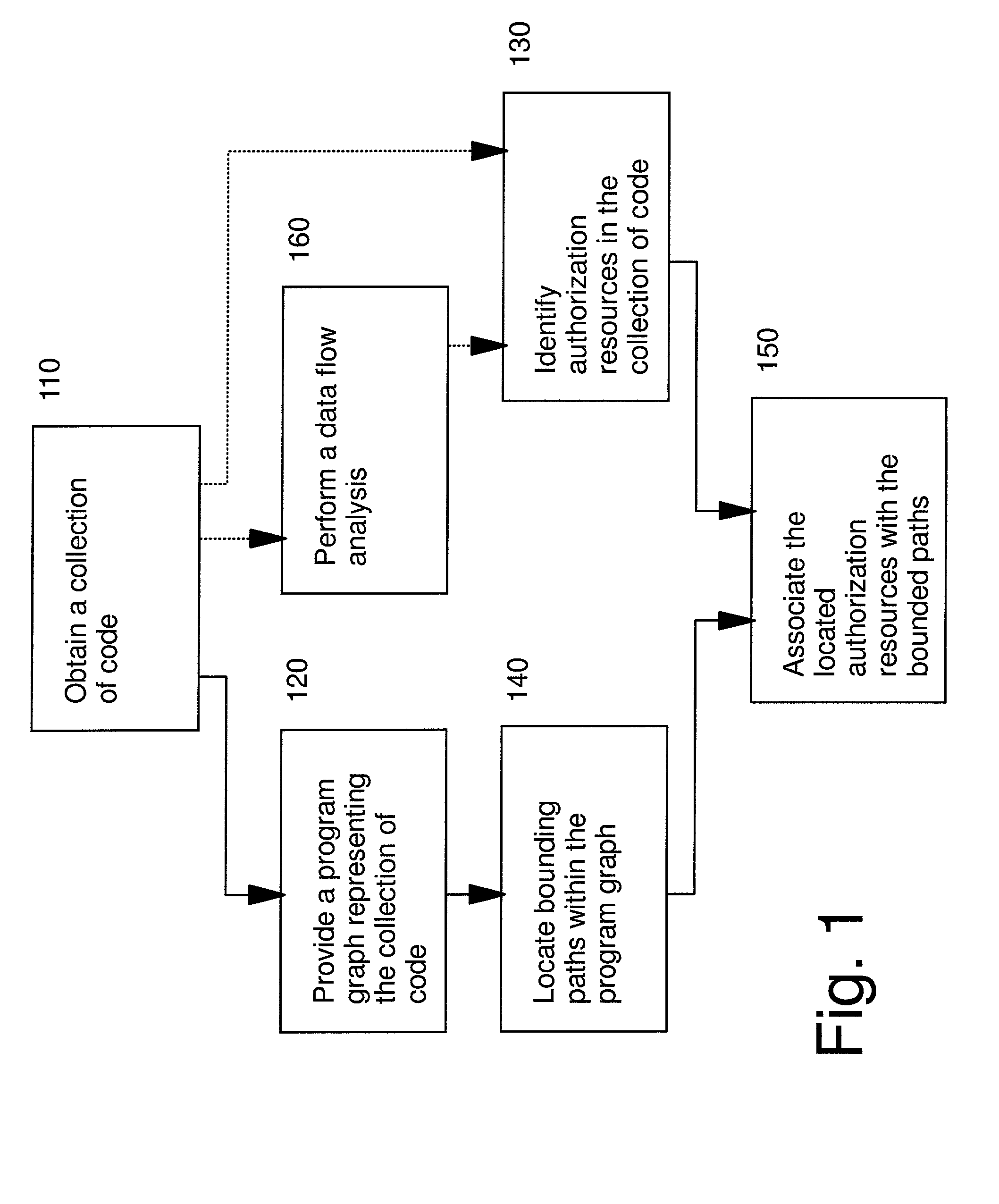
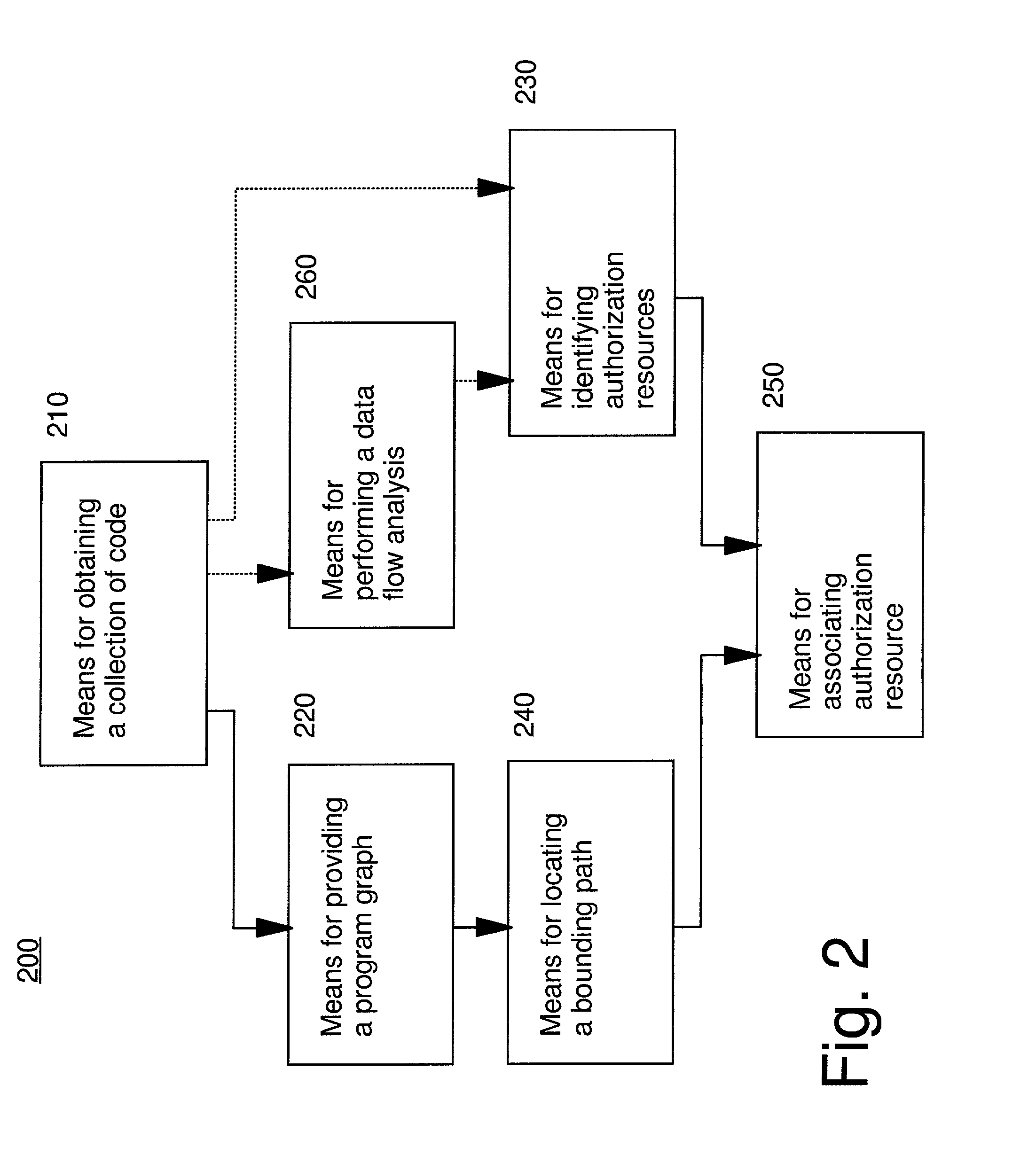
Automated program resource identification and association
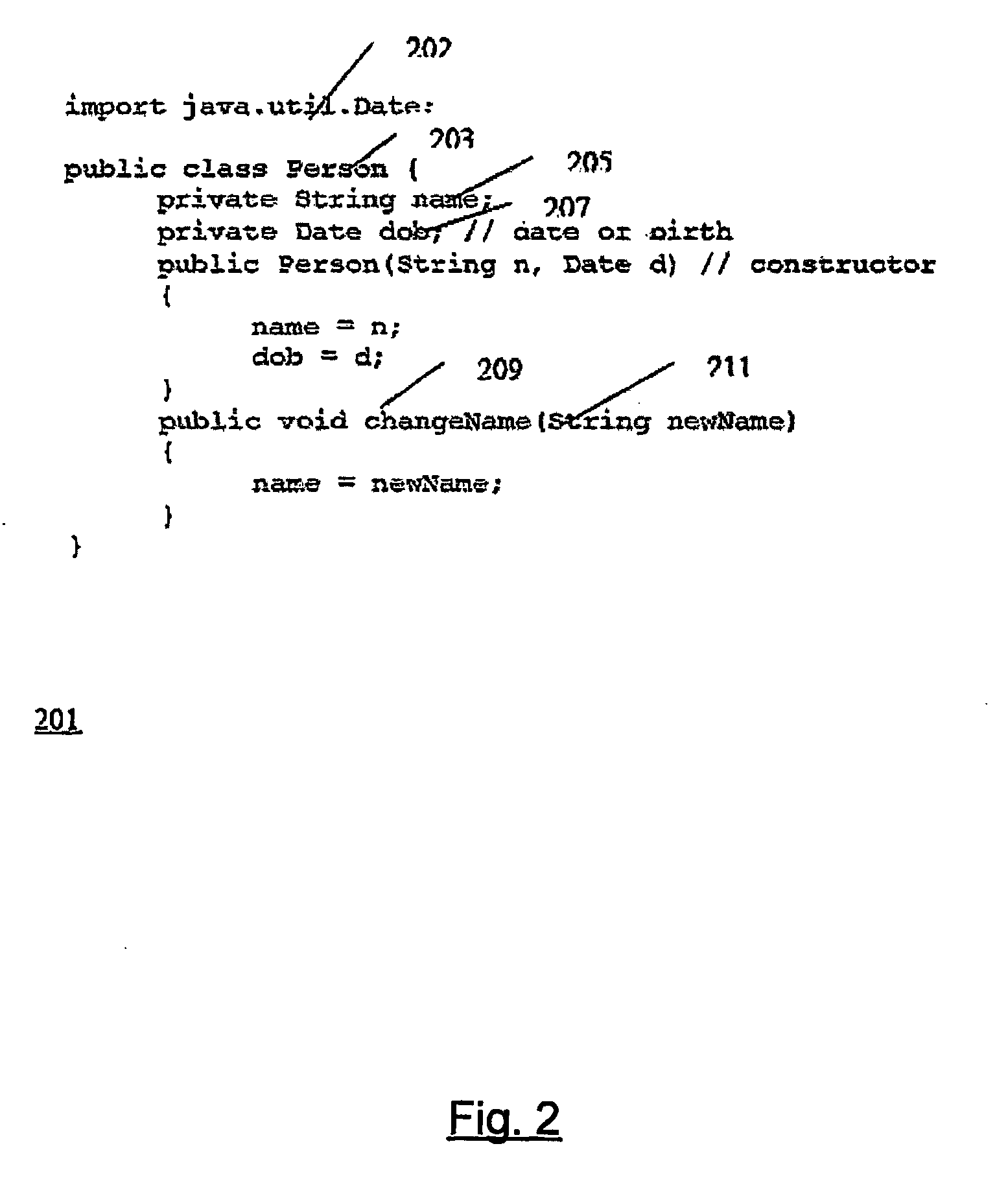
This invention provides methods and apparatus for determining a set of authorization usage for collection of code. By using a program graph, the present invention identifies the code within in bounded paths in the program graph that use authorization. The level of precision is able to identify authorization usage to the level of basic blocks, methods, classes or other collections of code. By using the analysis technique described in this invention, we can determine the authorizations needed by collections code, including Java applets, servlets, and Enterprise JavaBeans. By using the present invention, it is possible, prior to loading the mobile code, to prompt the administrator or end-user to authorize or deny the code access to restricted the resources, or determine whether authorization testing will be required.
Owner:IBM CORP
Malicious mobile code runtime monitoring system and methods
InactiveUS20060026677A1Minimizing serverMinimizing client resource requirementMemory loss protectionError detection/correctionVisual BasicMonitoring system
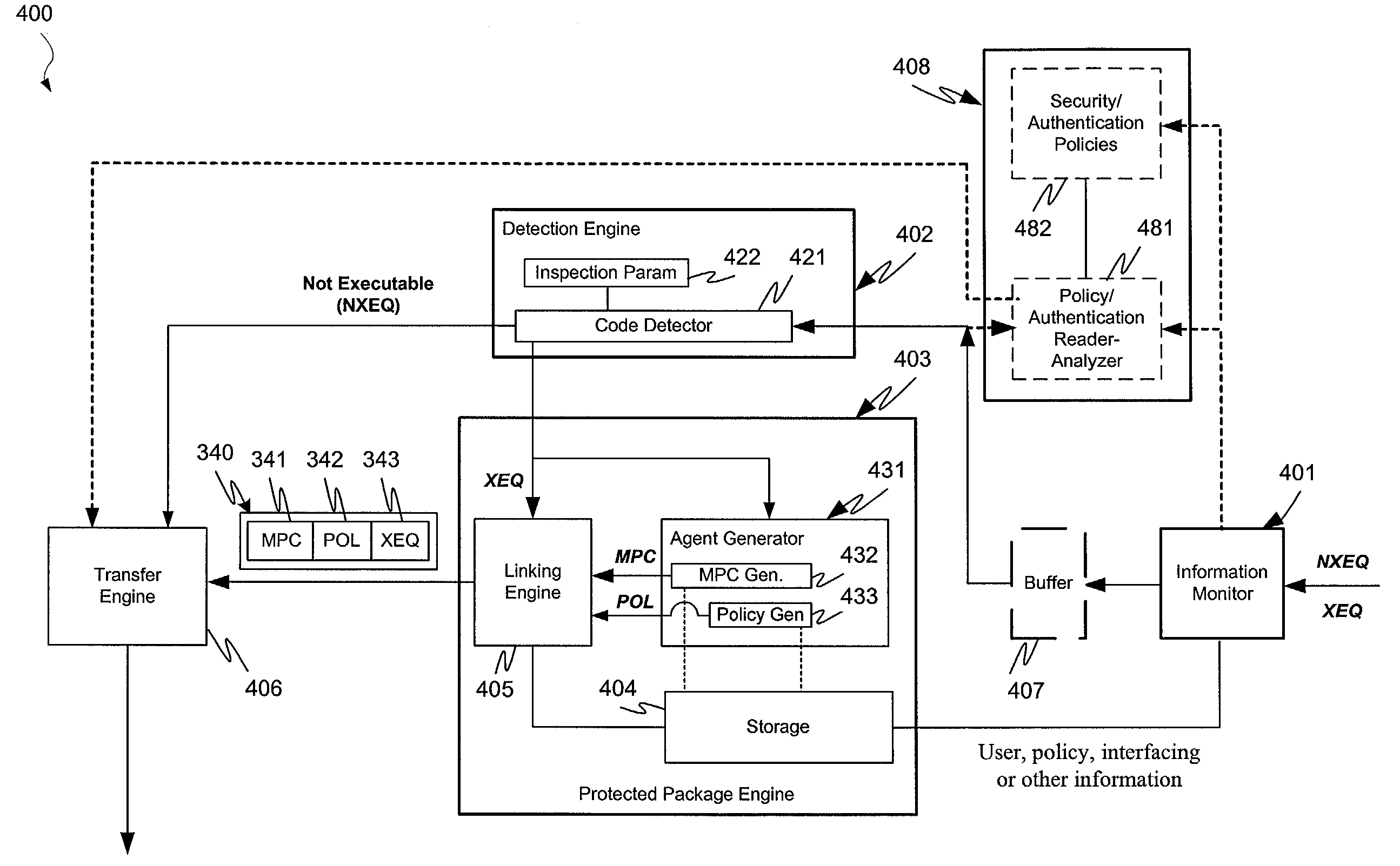
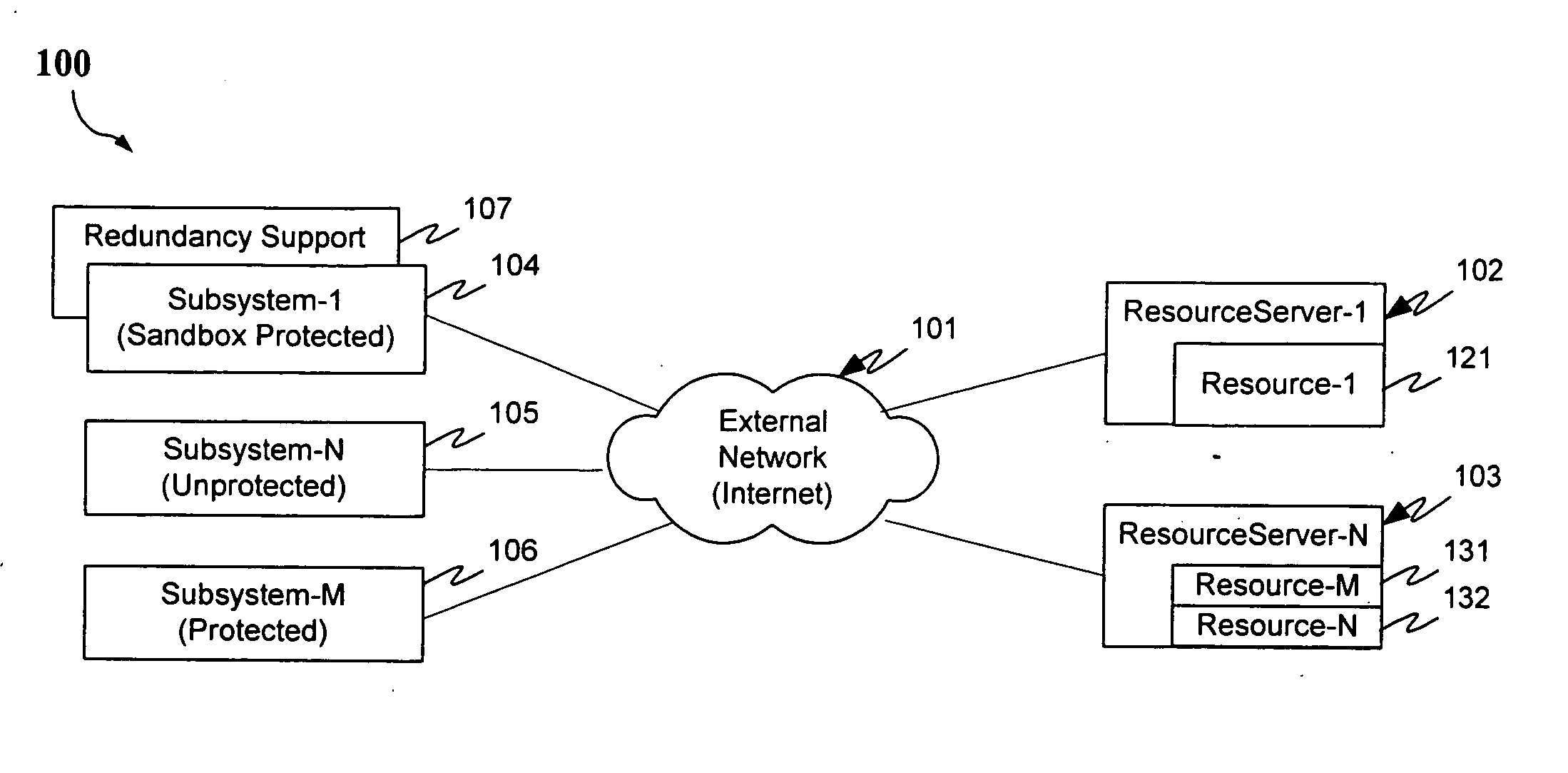
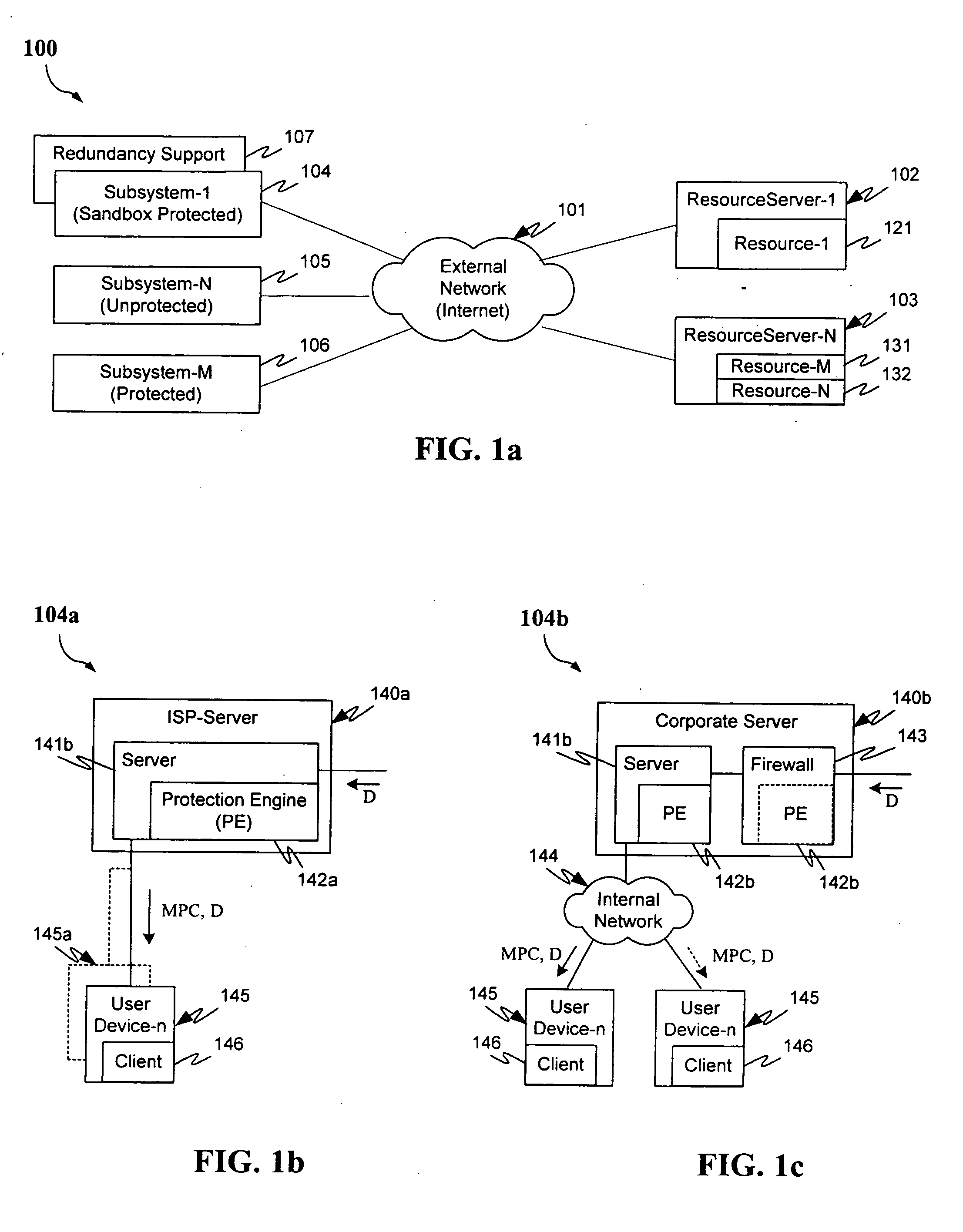
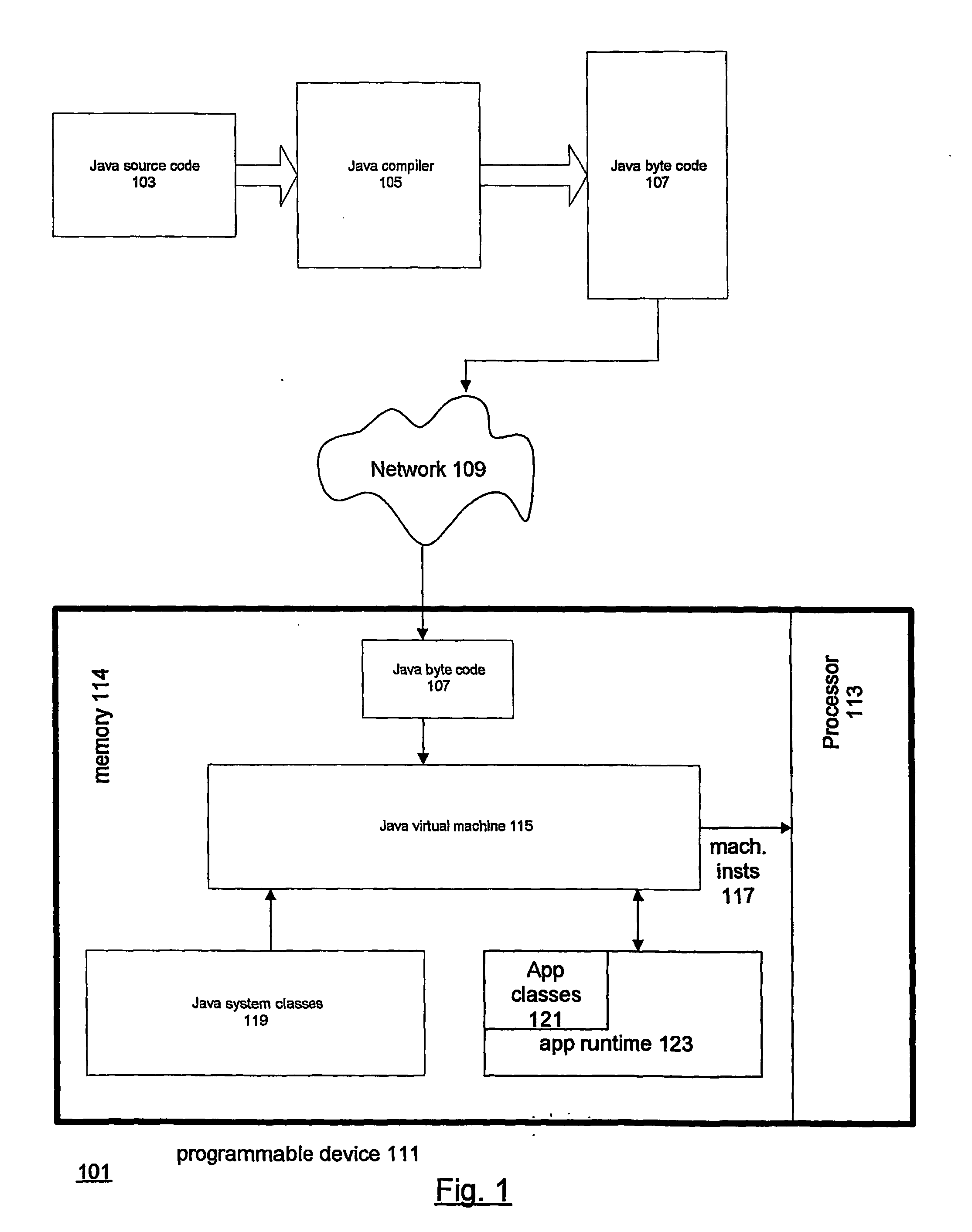
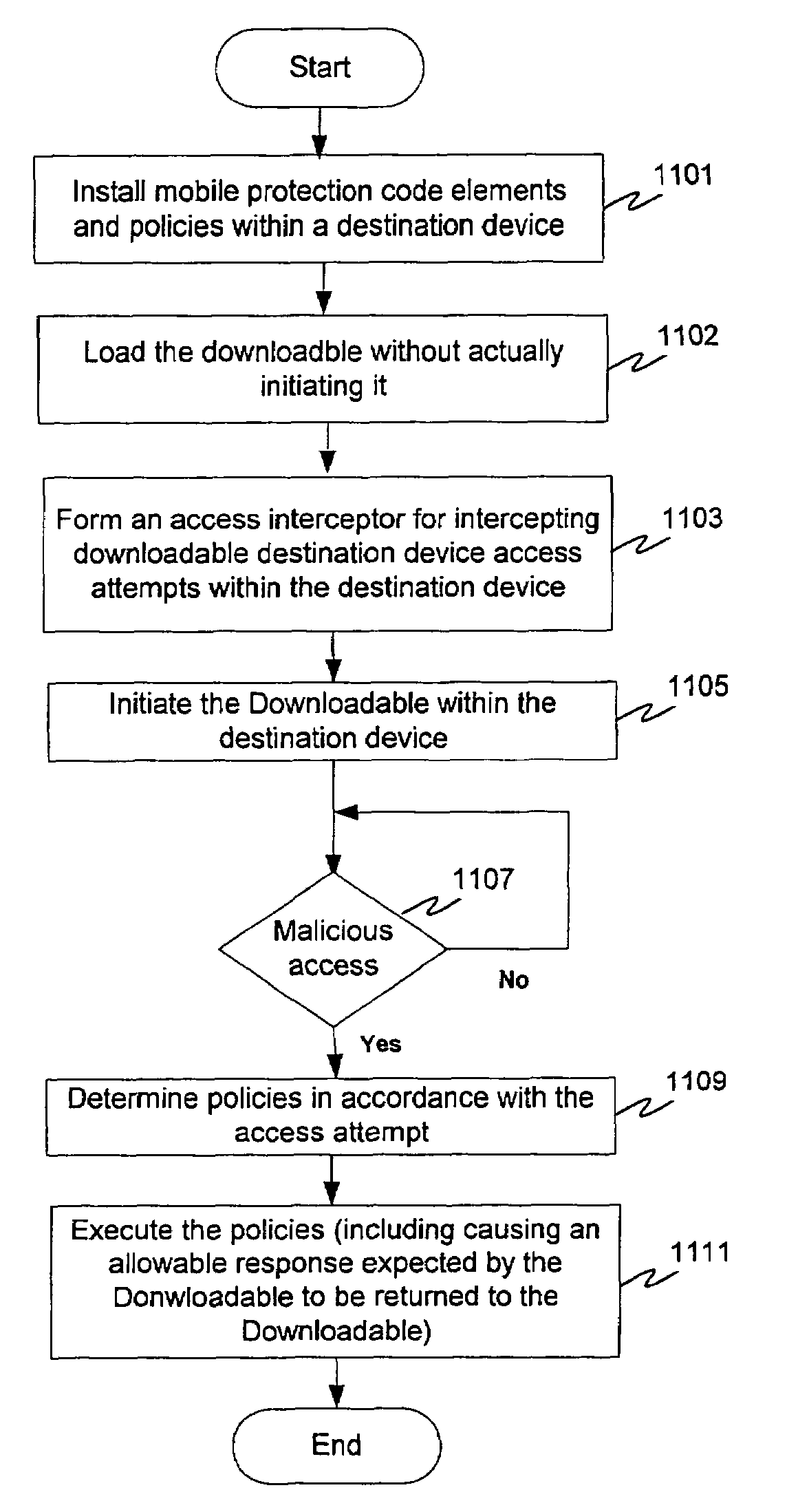
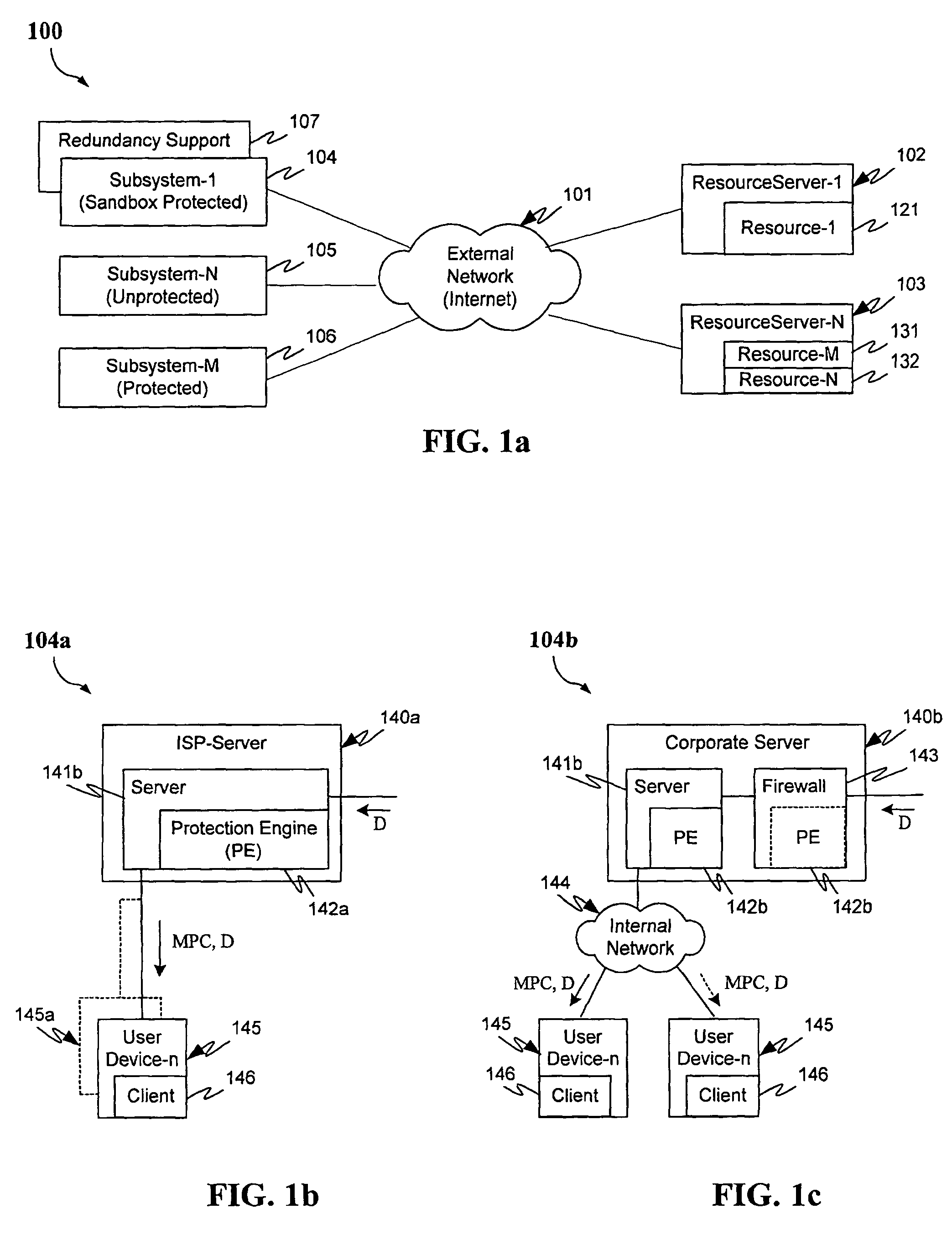
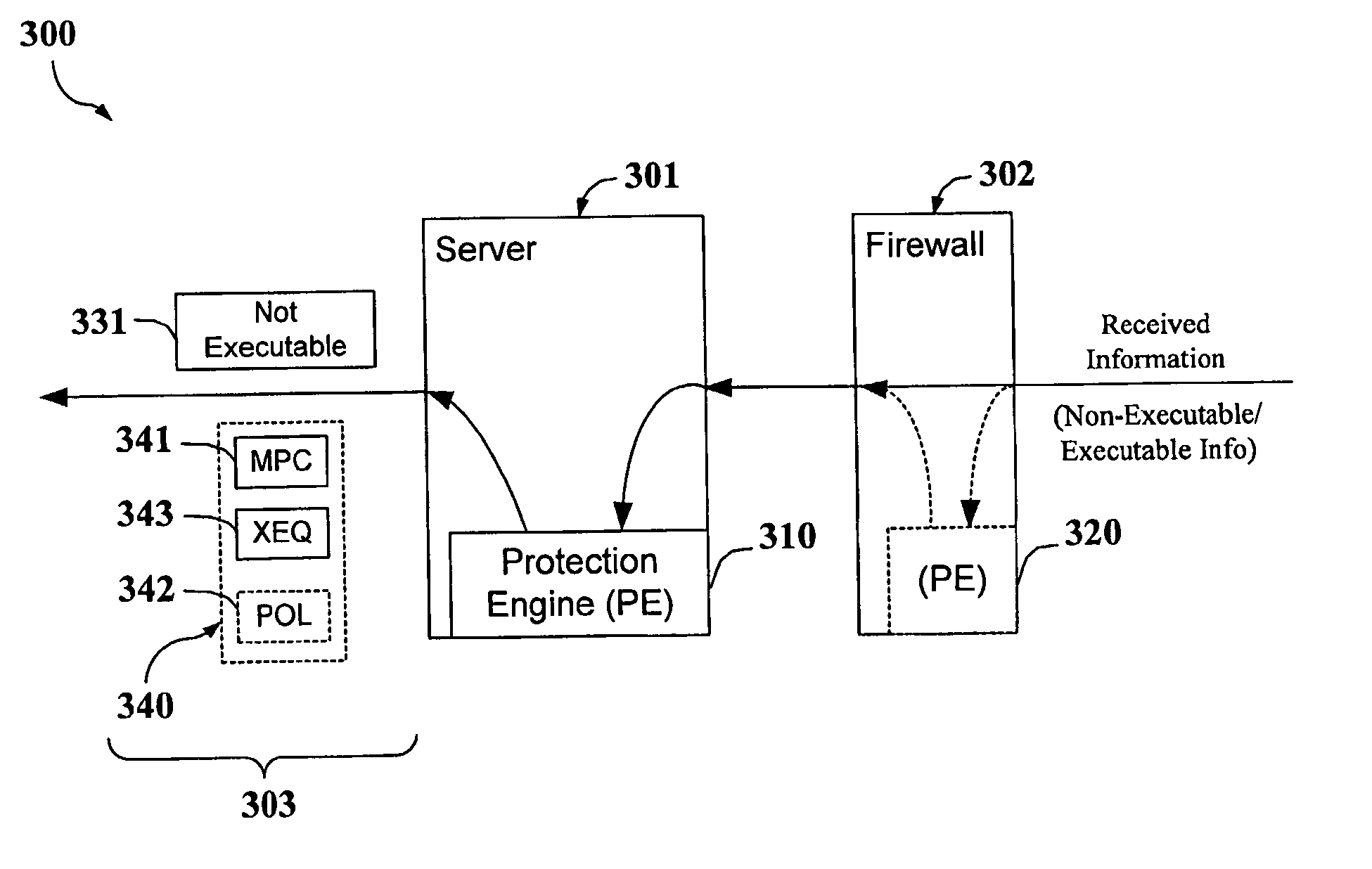
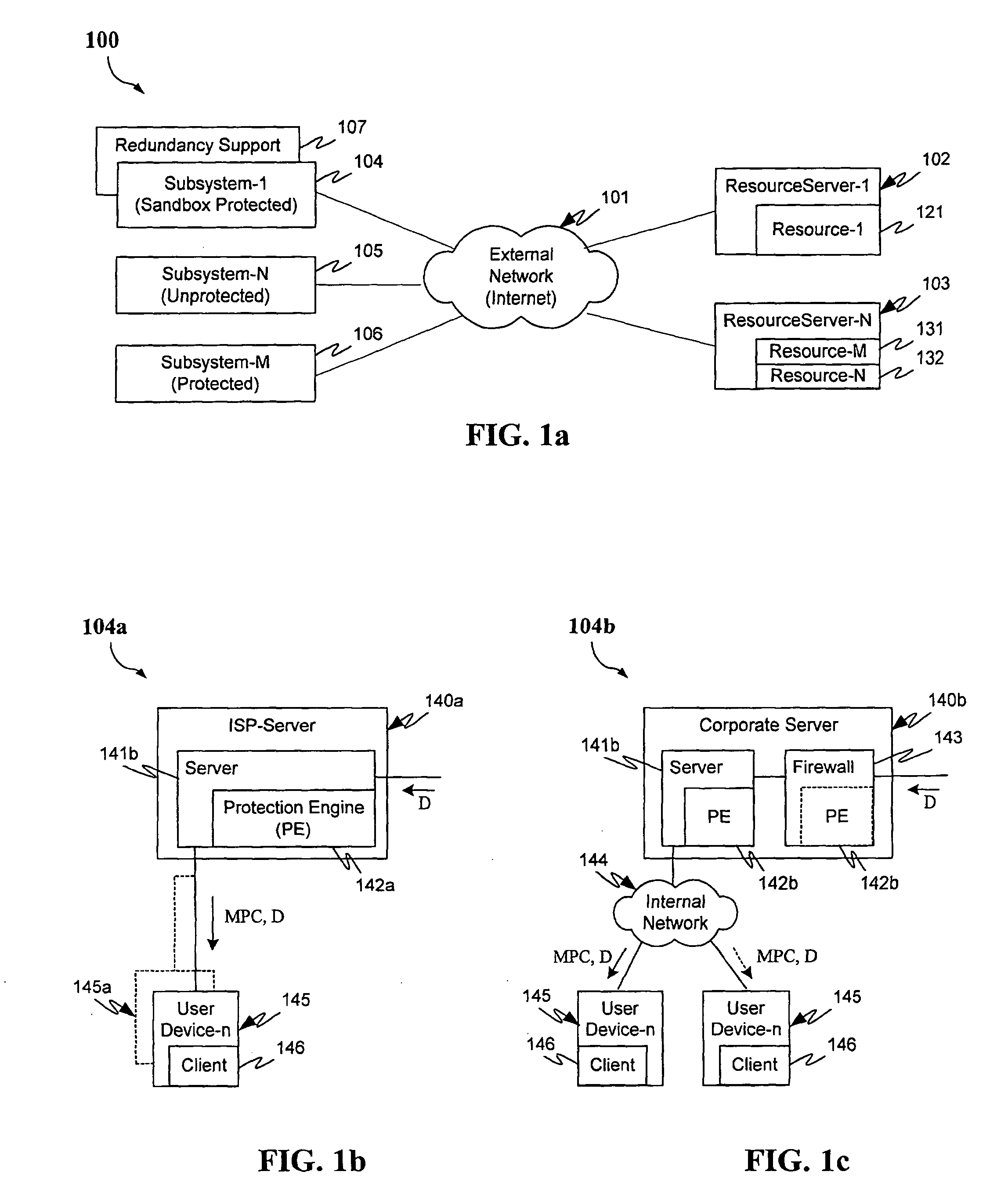
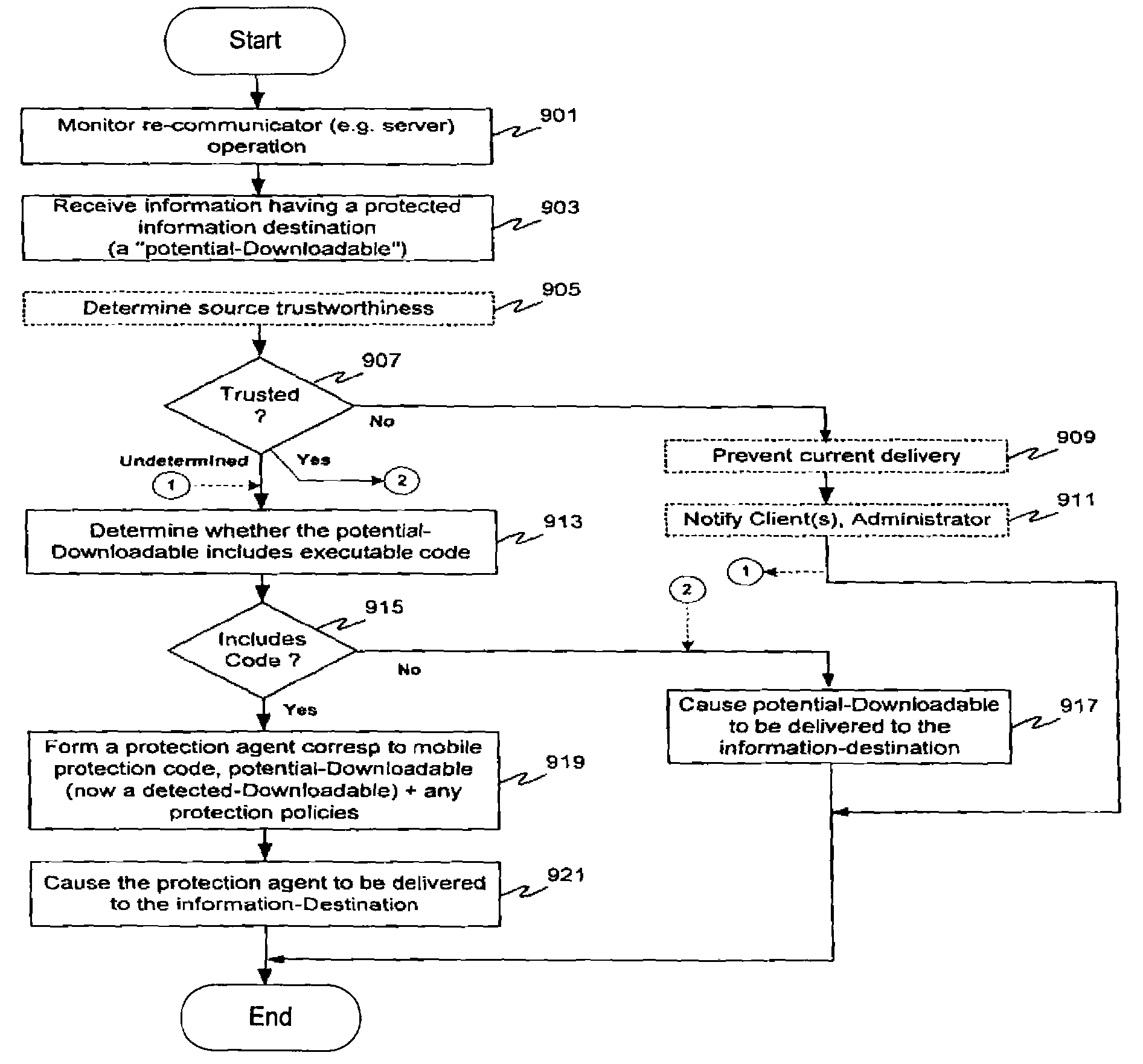
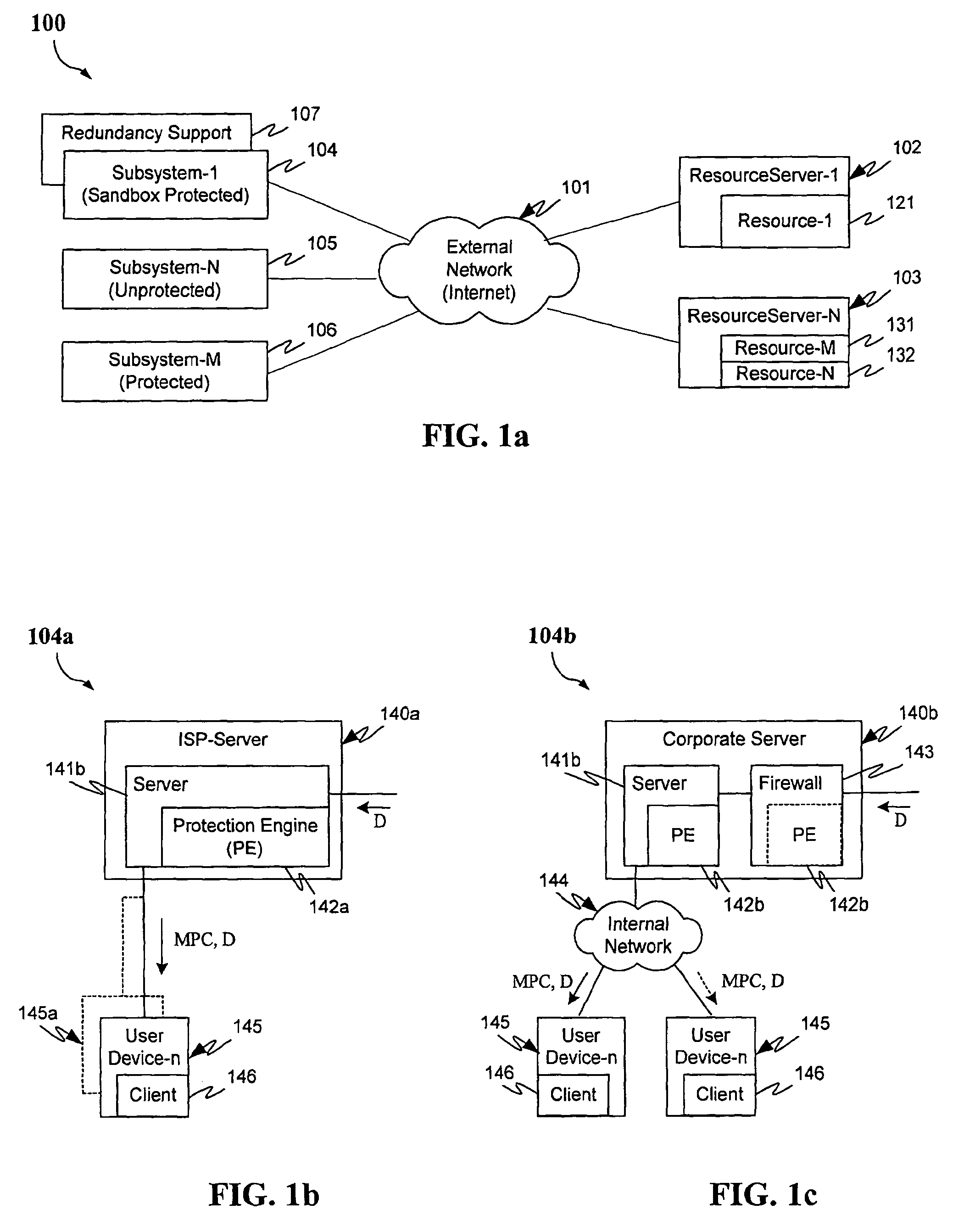
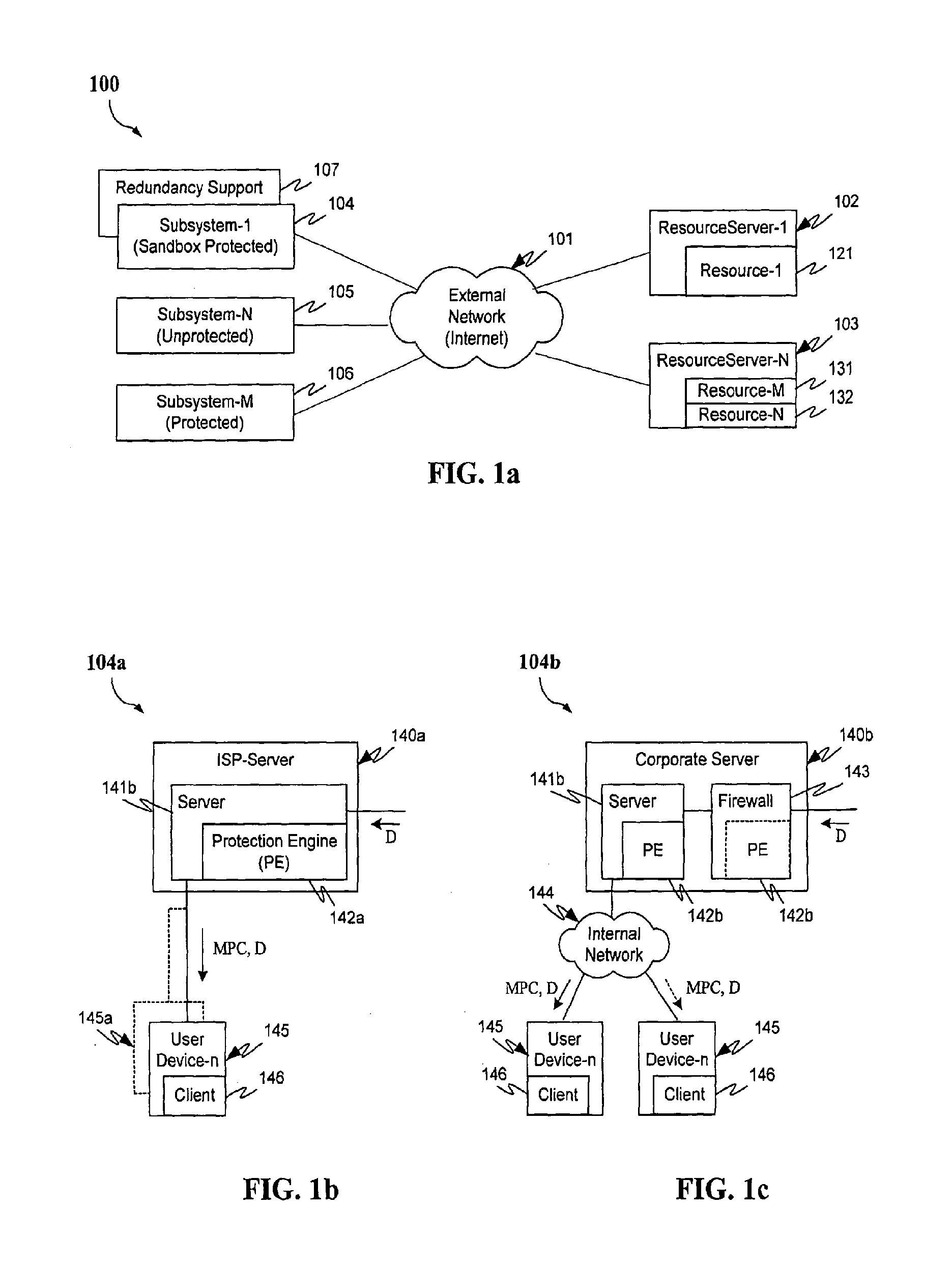
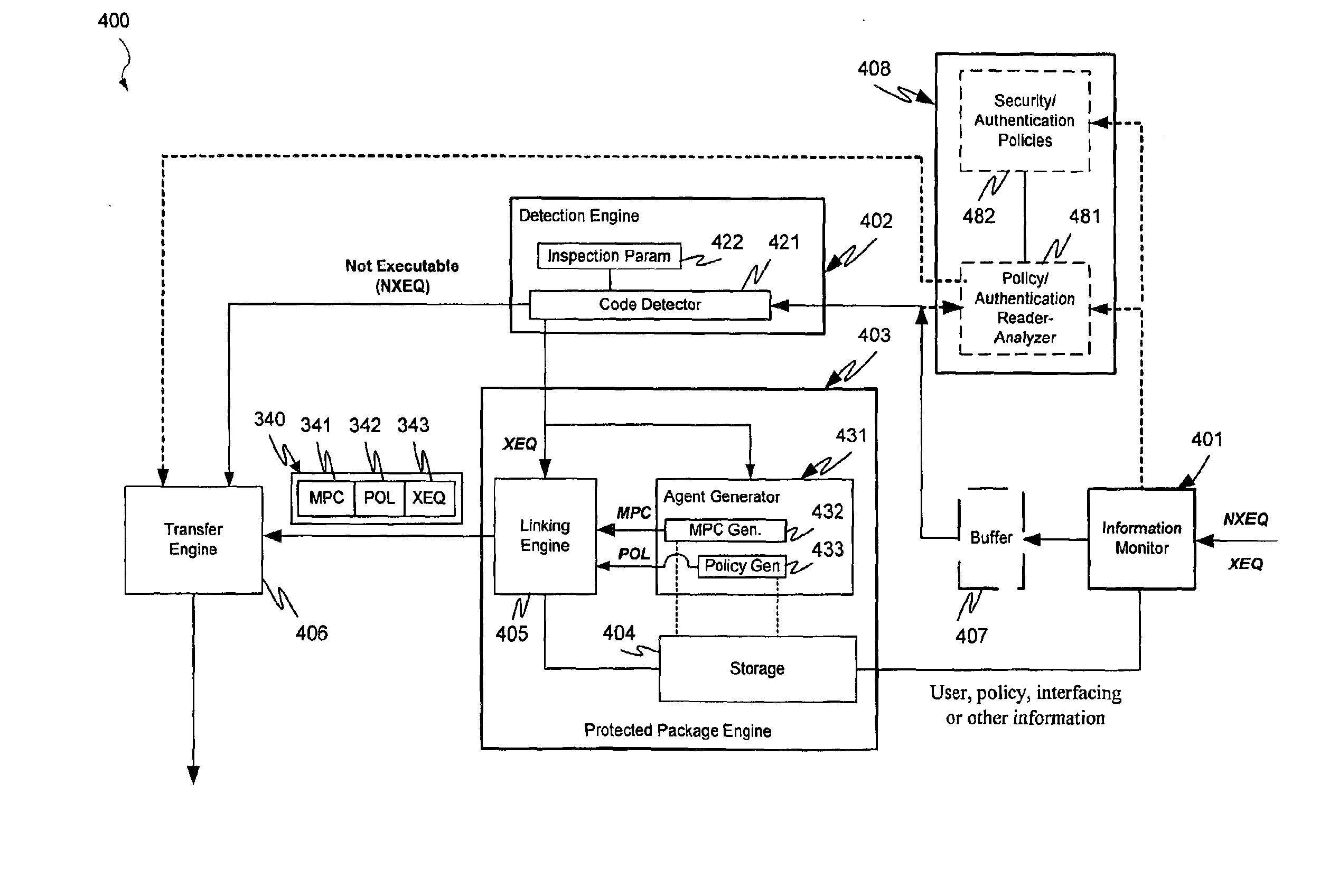
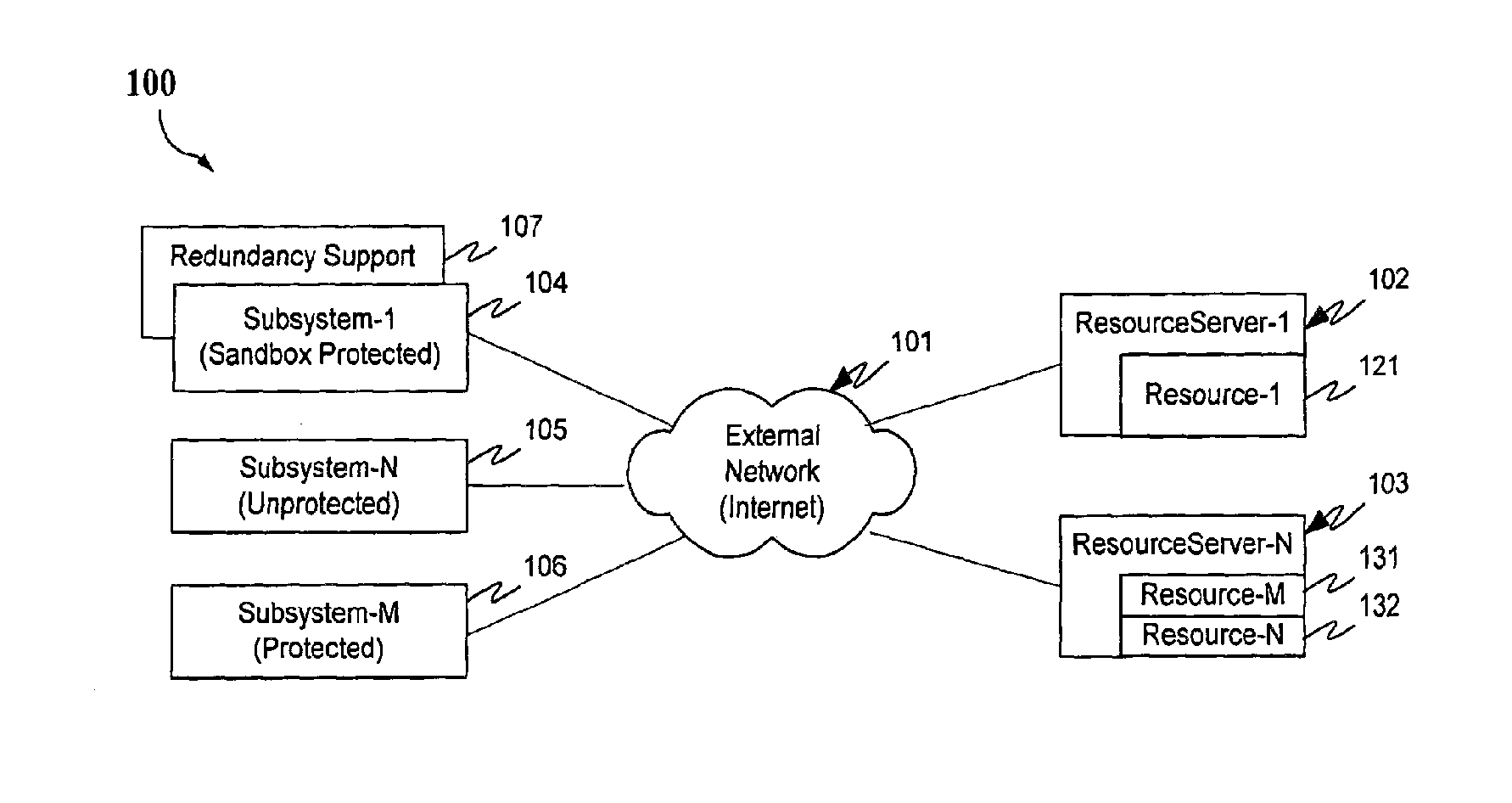
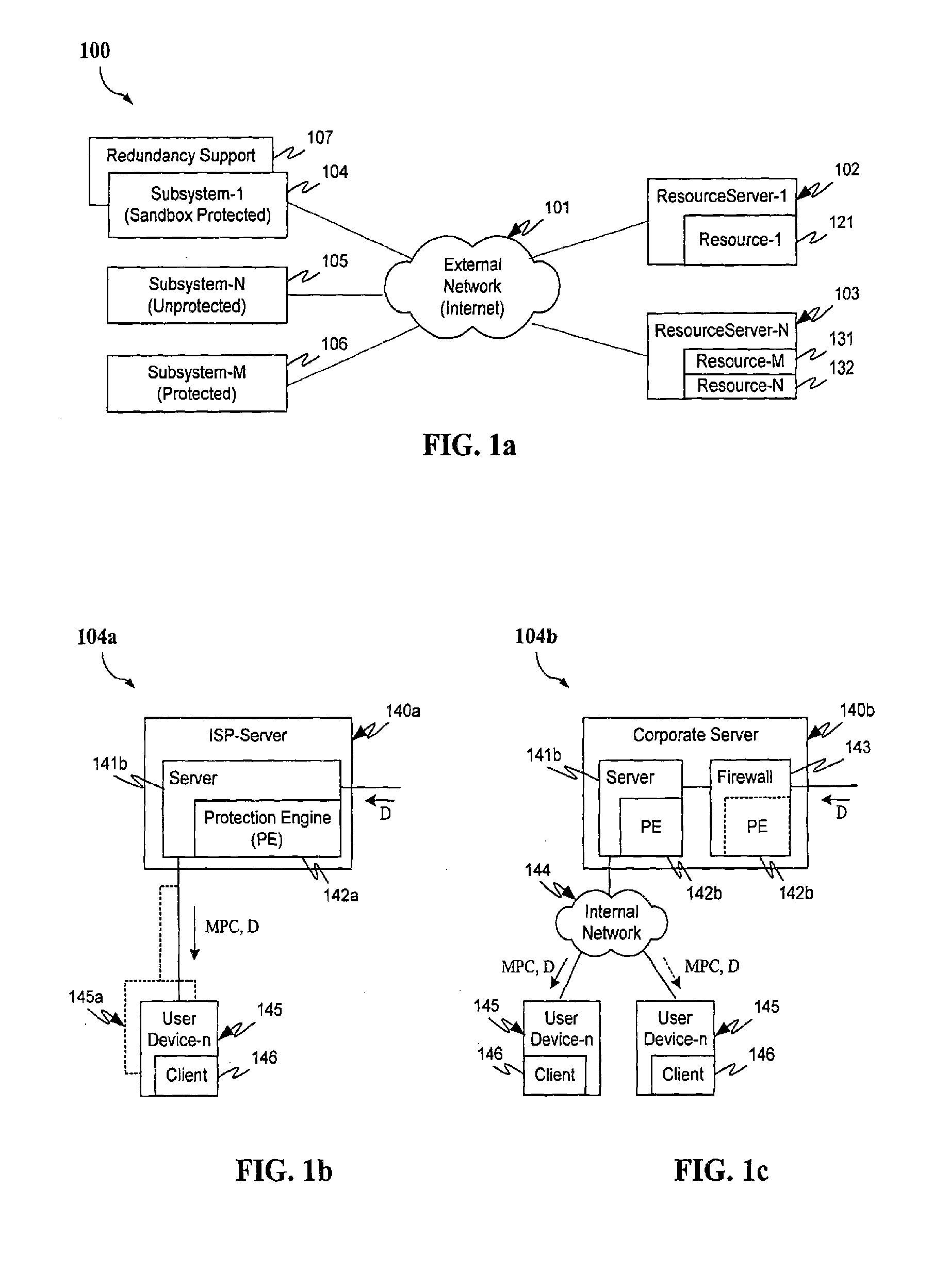
Protection systems and methods provide for protecting one or more personal computers (“PCs”) and / or other intermittently or persistently network accessible devices or processes from undesirable or otherwise malicious operations of Java™ applets, ActiveX™ controls, JavaScript™ scripts, Visual Basic scripts, add-ins, downloaded / uploaded programs or other “Downloadables” or “mobile code” in whole or part. A protection engine embodiment provides, within a server, firewall or other suitable “re-communicator,” for monitoring information received by the communicator, determining whether received information does or is likely to include executable code, and if so, causes mobile protection code (MPC) to be transferred to and rendered operable within a destination device of the received information, more suitably by forming a protection agent including the MPC, protection policies and a detected-Downloadable. An MPC embodiment further provides, within a Downloadable-destination, for initiating the Downloadable, enabling malicious Downloadable operation attempts to be received by the MPC, and causing (predetermined) corresponding operations to be executed in response to the attempts, more suitably in conjunction with protection policies.
Owner:FINJAN LLC
Malicious mobile code runtime monitoring system and methods
InactiveUS7647633B2Minimization requirementsEasy to updateMemory loss protectionDigital data processing detailsVisual BasicMonitoring system
Protection systems and methods provide for protecting one or more personal computers (“PCs”) and / or other intermittently or persistently network accessible devices or processes from undesirable or otherwise malicious operations of Java™ applets, ActiveX™ controls, JavaScript™ scripts, Visual Basic scripts, add-ins, downloaded / uploaded programs or other “Downloadables” or “mobile code” in whole or part. A protection engine embodiment provides, within a server, firewall or other suitable “re-communicator,” for monitoring information received by the communicator, determining whether received information does or is likely to include executable code, and if so, causes mobile protection code (MPC) to be transferred to and rendered operable within a destination device of the received information, more suitably by forming a protection agent including the MPC, protection policies and a detected-Downloadable. An MPC embodiment further provides, within a Downloadable-destination, for initiating the Downloadable, enabling malicious Downloadable operation attempts to be received by the MPC, and causing (predetermined) corresponding operations to be executed in response to the attempts, more suitably in conjunction with protection policies.
Owner:FINJAN LLC
System and methods for securely permitting mobile code to access resources over a network
InactiveUS6993588B2Avoid attackElectric signal transmission systemsDigital data processing detailsNetwork connectionMobile code
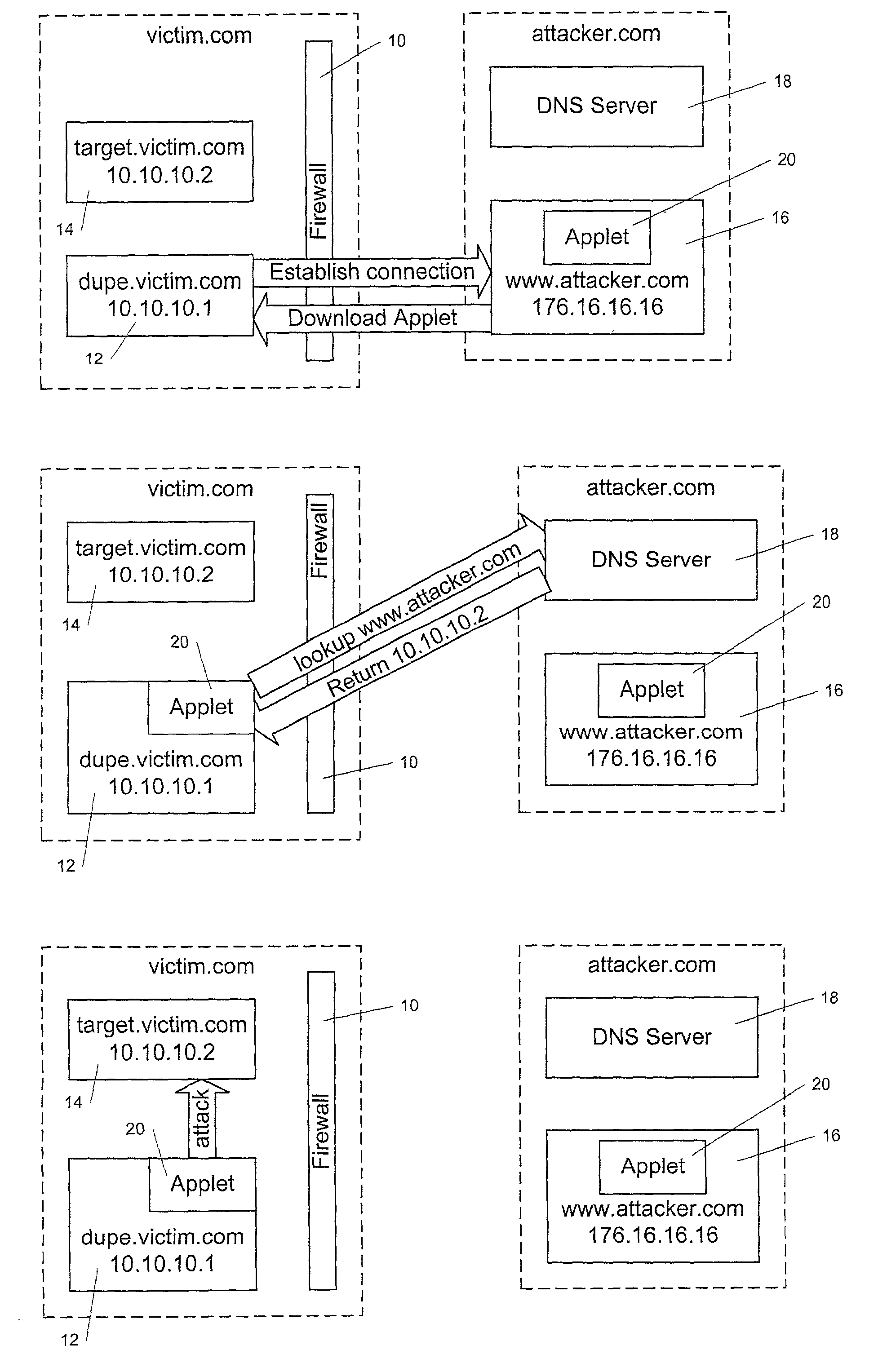
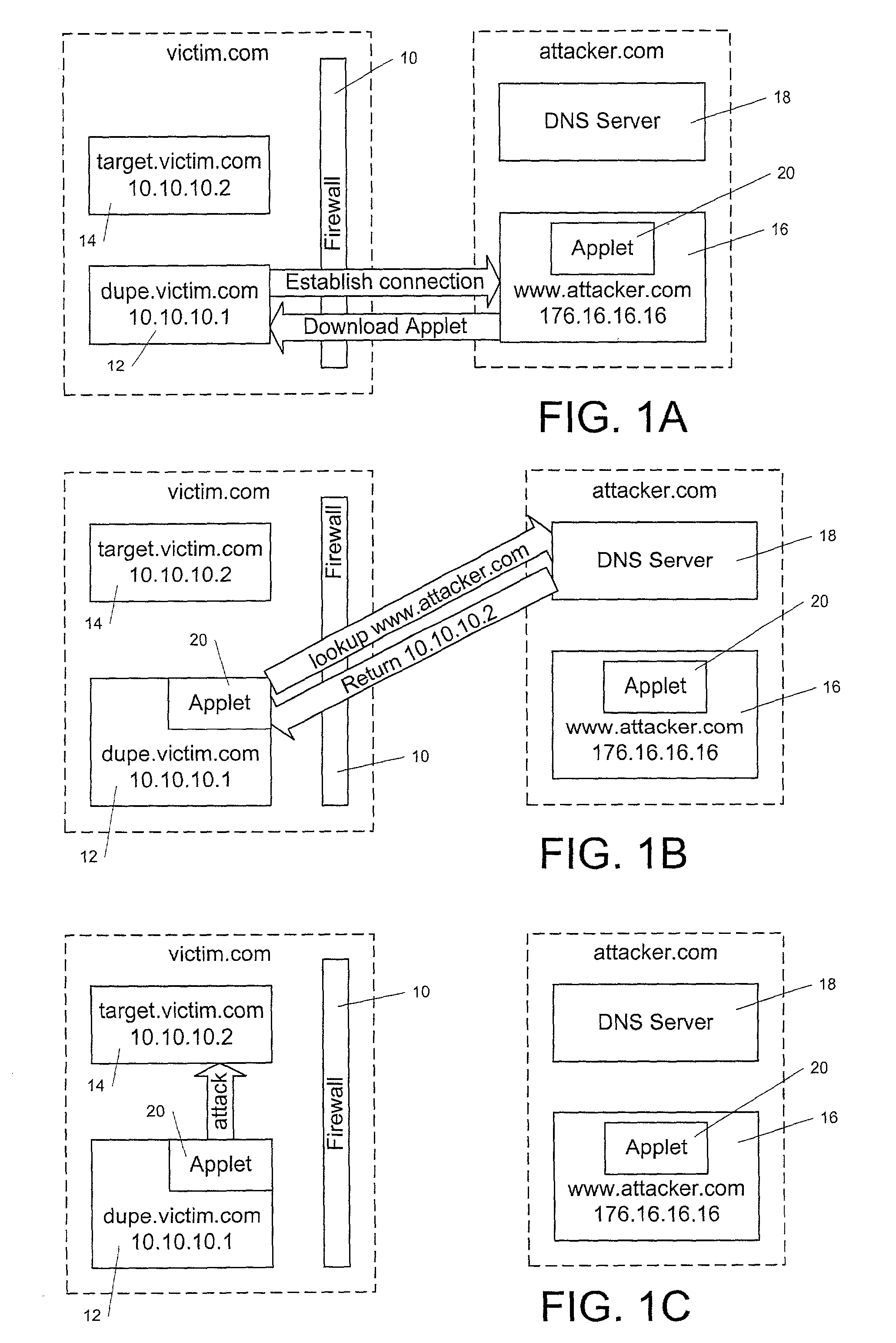
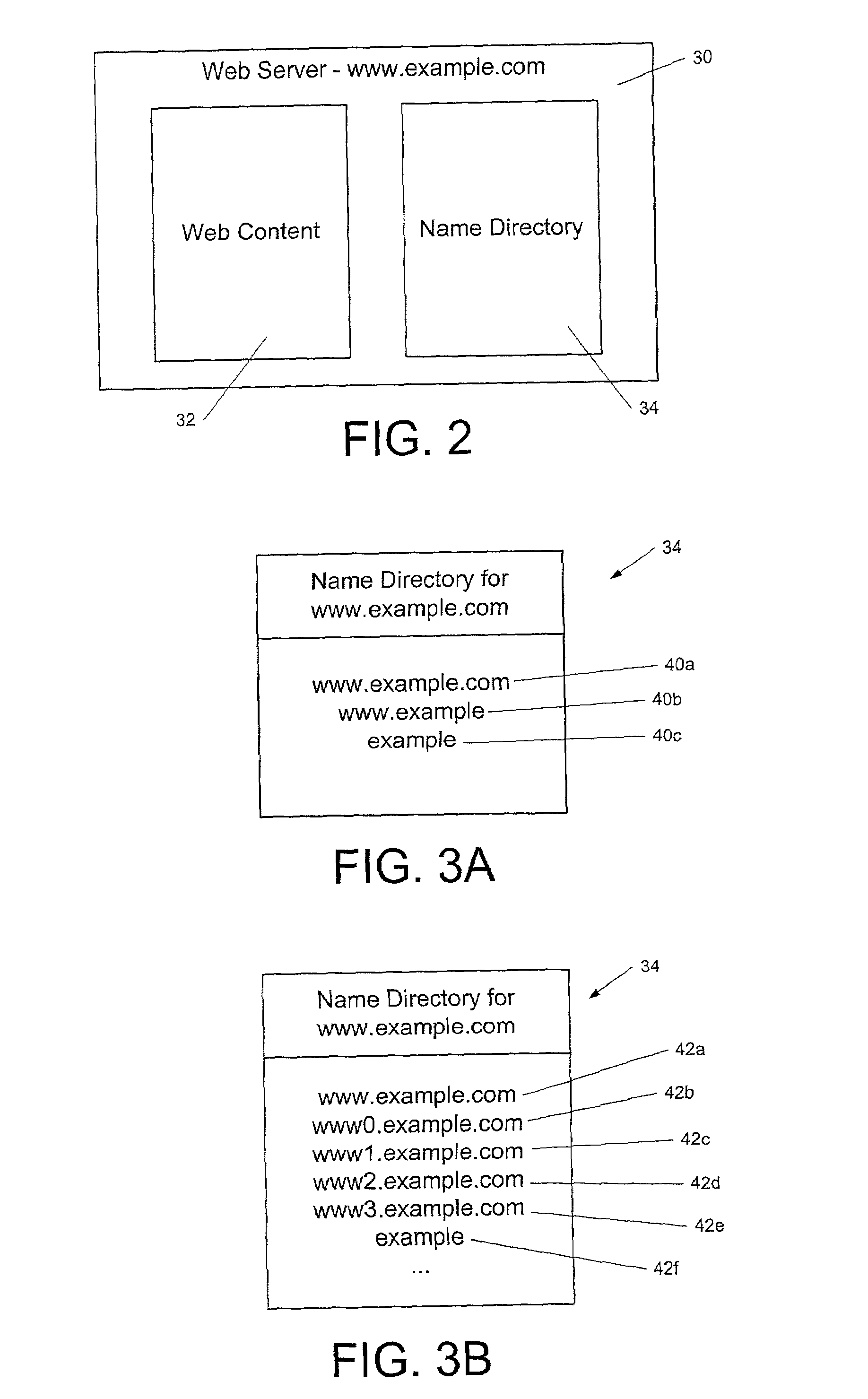
A system and methods are disclosed that permit mobile code, such as an applet, to create a network connection with a content server on a network, without exposing the client computer that is running the applet, or other computers with which the client computer may communicate, to a DNS spoofing attack. This is achieved in accordance with the principles of the present invention by using network restriction software in the execution engine or runtime system under which the applet executes. When the applet attempts to create a network connection to a content server, the network restriction software checks a “name directory” on the content server for the presence of an entry whose name corresponds to the name of the computer from which the applet was downloaded. If such an entry is present, then the network restriction software permits the network connection between the applet and the content server to be created. If not, the applet may not create a network connection with the content server. Additionally, address checks may be applied to assist in preventing DNS spoofing attacks from succeeding.
Owner:SCSK CORP
Protecting mobile code against malicious hosts cross references to related applications
ActiveUS20060026430A1User identity/authority verificationUnauthorized memory use protectionProgramming languageMobile code
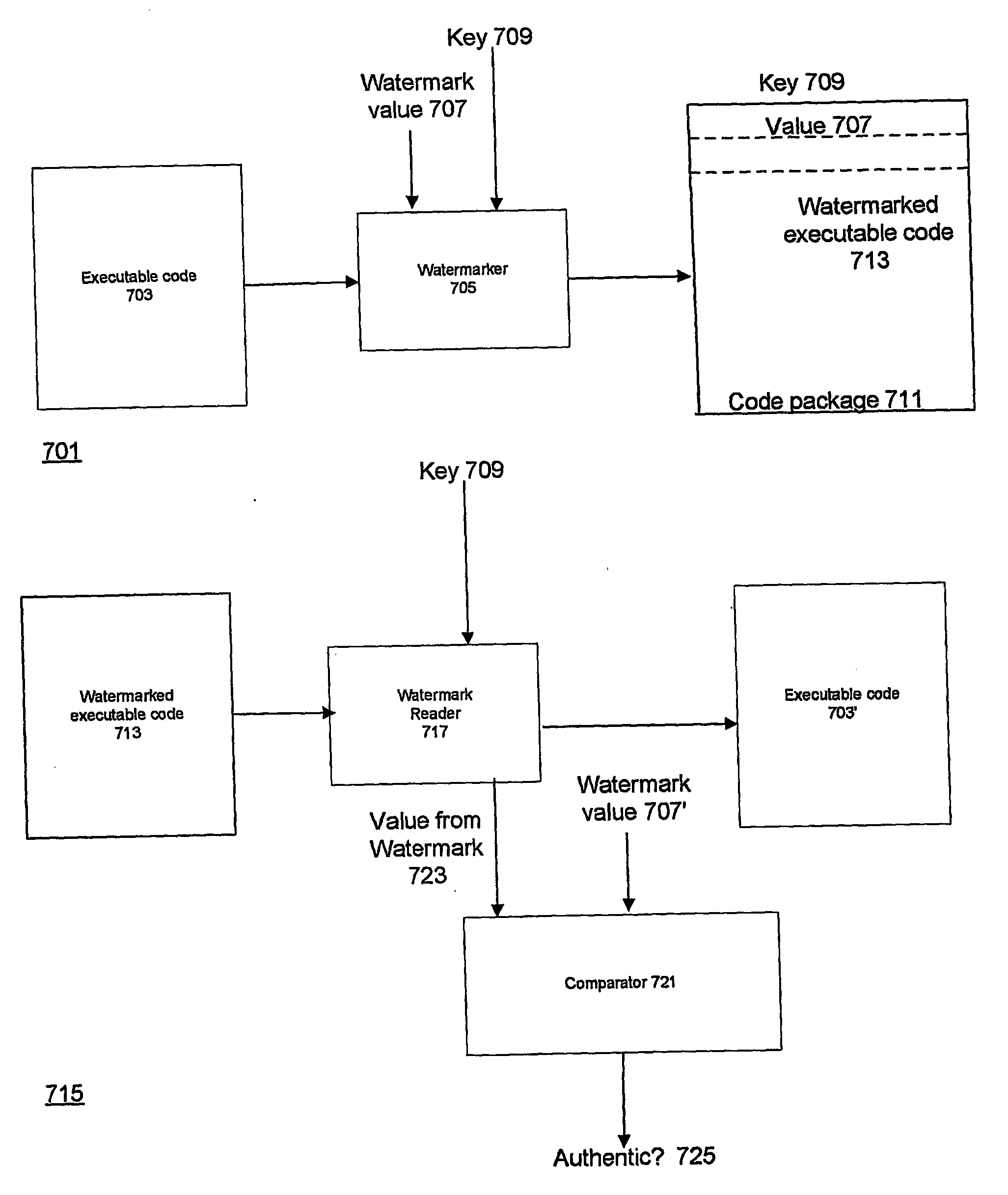
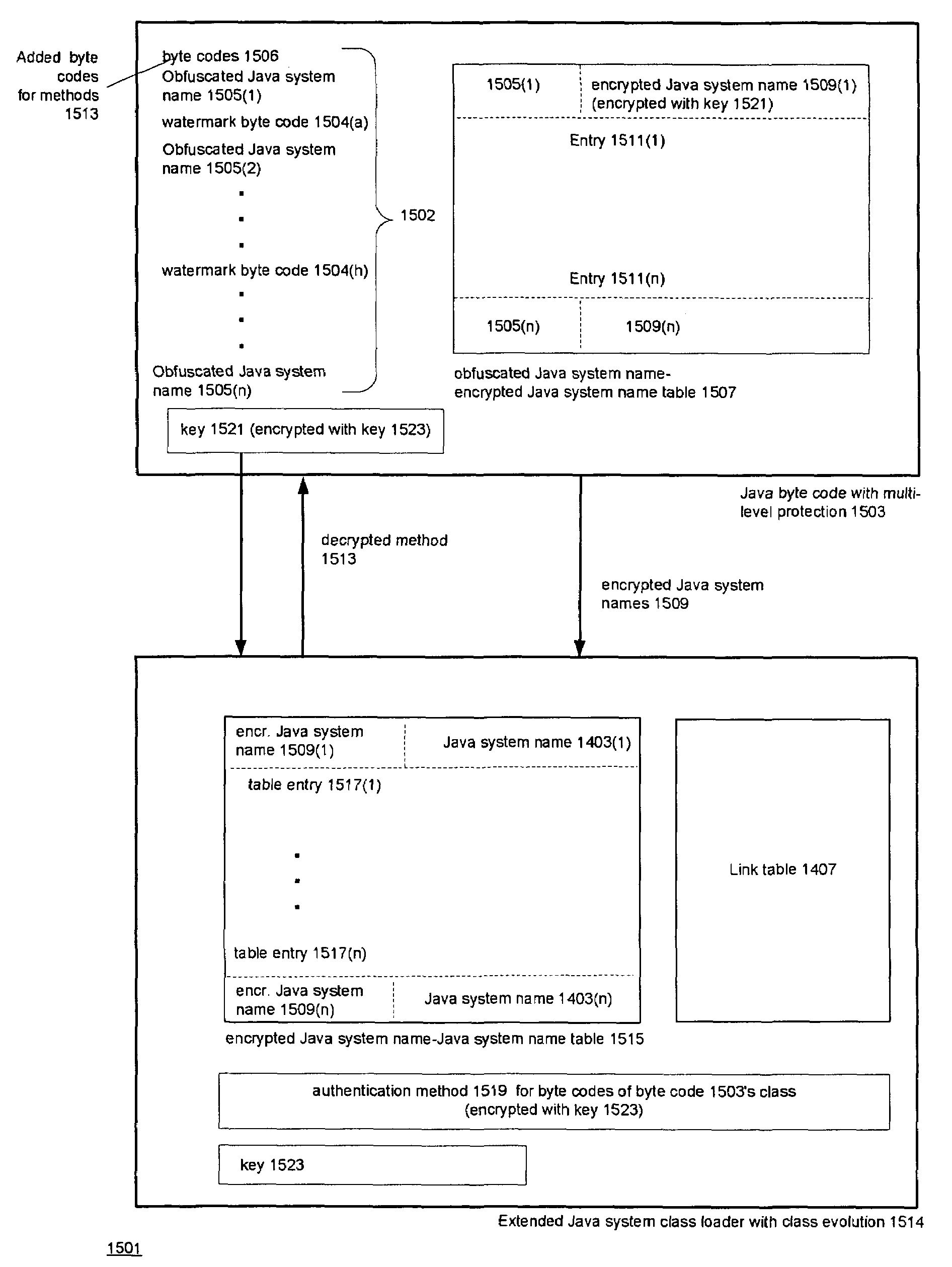
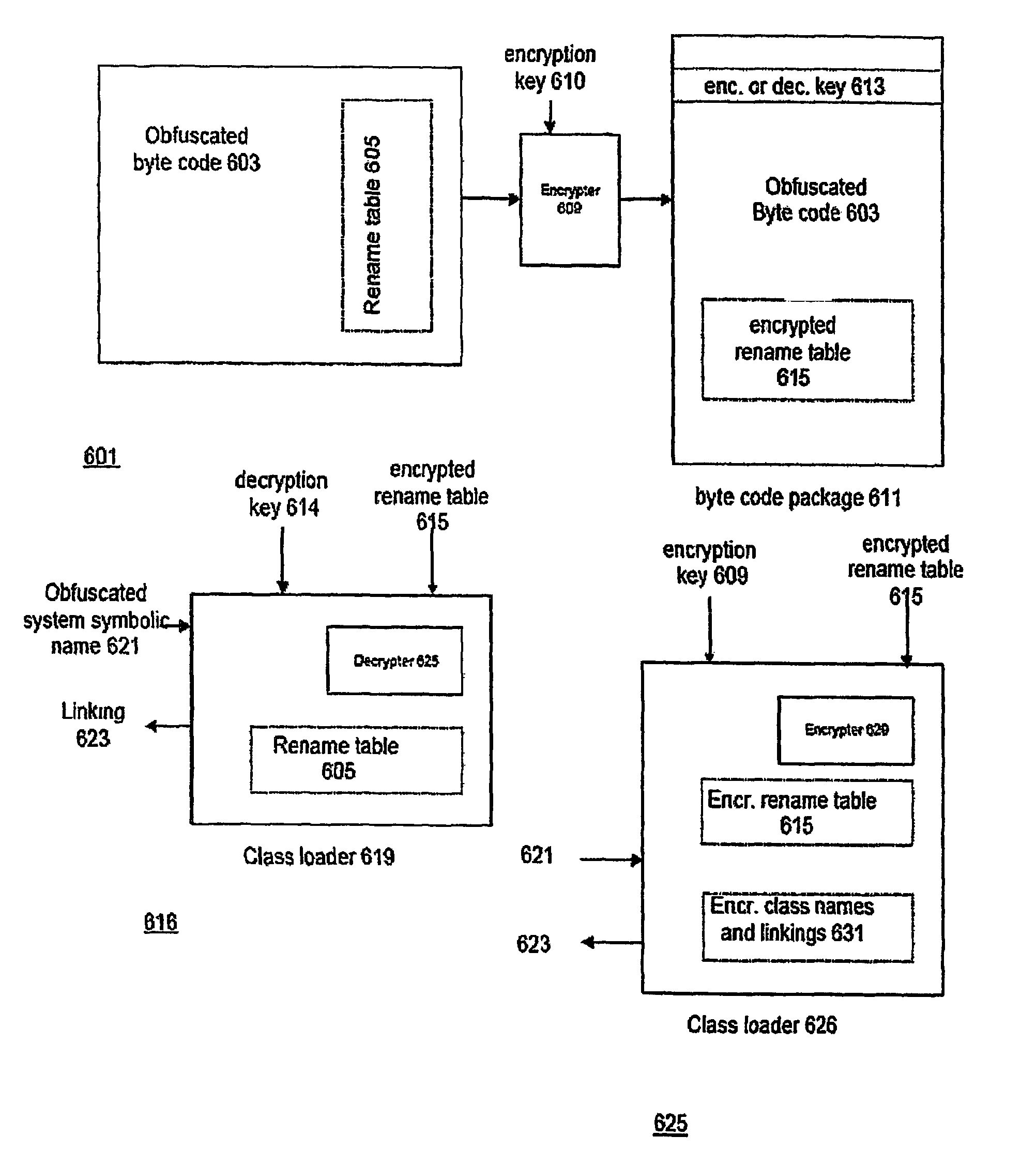
Techniques for using a class loader to protect mobile code against a malicious host. The techniques include using the class loader to extend a class used by the mobile code such that a method is added to the code which authenticates the mobile code. When executed, the method provides a dynamic watermark that authenticates the code. The method may be encrypted until it is added to the code. One such method uses a static watermark in the code to determine whether the code has been modified. The techniques also include using a class loader to extend the class such that obfuscated symbolic names in the program that correspond to symbolic names defined by the class can be resolved. A way of doing this is to include a first association between the obfuscated symbolic names and encrypted forms of the corresponding symbolic names in the program and to make a second association between the encrypted forms of the corresponding symbolic names and information used to resolve the symbolic names defined in the class. The loader then uses the first and second associations to resolve the obfuscated names.
Owner:FRAUNHOFER GESELLSCHAFT ZUR FOERDERUNG DER ANGEWANDTEN FORSCHUNG EV
Method and system for protecting a computer and a network from hostile downloadables
InactiveUS7613926B2Minimization requirementsEasy to updateMemory loss protectionUser identity/authority verificationVisual BasicPersonal computer
Protection systems and methods provide for protecting one or more personal computers (“PCs”) and / or other intermittently or persistently network accessible devices or processes from undesirable or otherwise malicious operations of Java™ applets, ActiveX™ controls, JavaScript™ scripts, Visual Basic scripts, add-ins, downloaded / uploaded programs or other “Downloadables” or “mobile code” in whole or part. A protection engine embodiment provides, within a server, firewall or other suitable “re-communicator,” for monitoring information received by the communicator, determining whether received information does or is likely to include executable code, and if so, causes mobile protection code (MPC) to be transferred to and rendered operable within a destination device of the received information, more suitably by forming a protection agent including the MPC, protection policies and a detected-Downloadable. An MPC embodiment further provides, within a Downloadable-destination, for initiating the Downloadable, enabling malicious Downloadable operation attempts to be received by the MPC, and causing (predetermined) corresponding operations to be executed in response to the attempts, more suitably in conjunction with protection policies.
Owner:FINJAN LLC
Security gateway and method for forwarding webpage by using security gateway
InactiveCN102469113AReduce computational overheadAccurate detectionTransmissionSpecial data processing applicationsMobile codeUniform resource locator
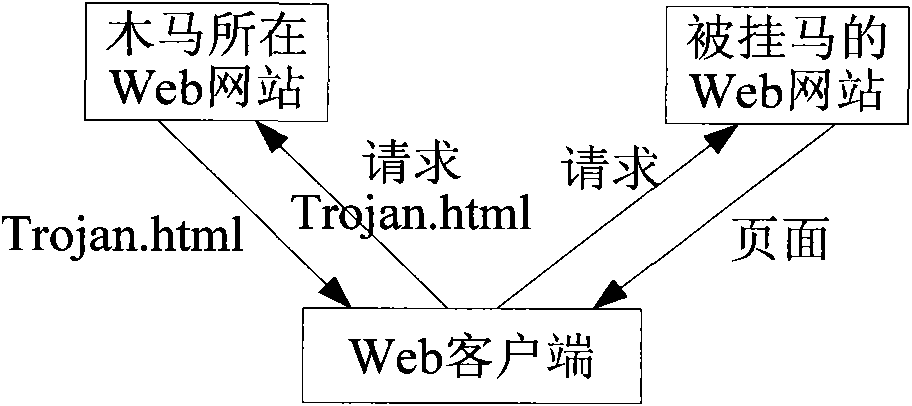
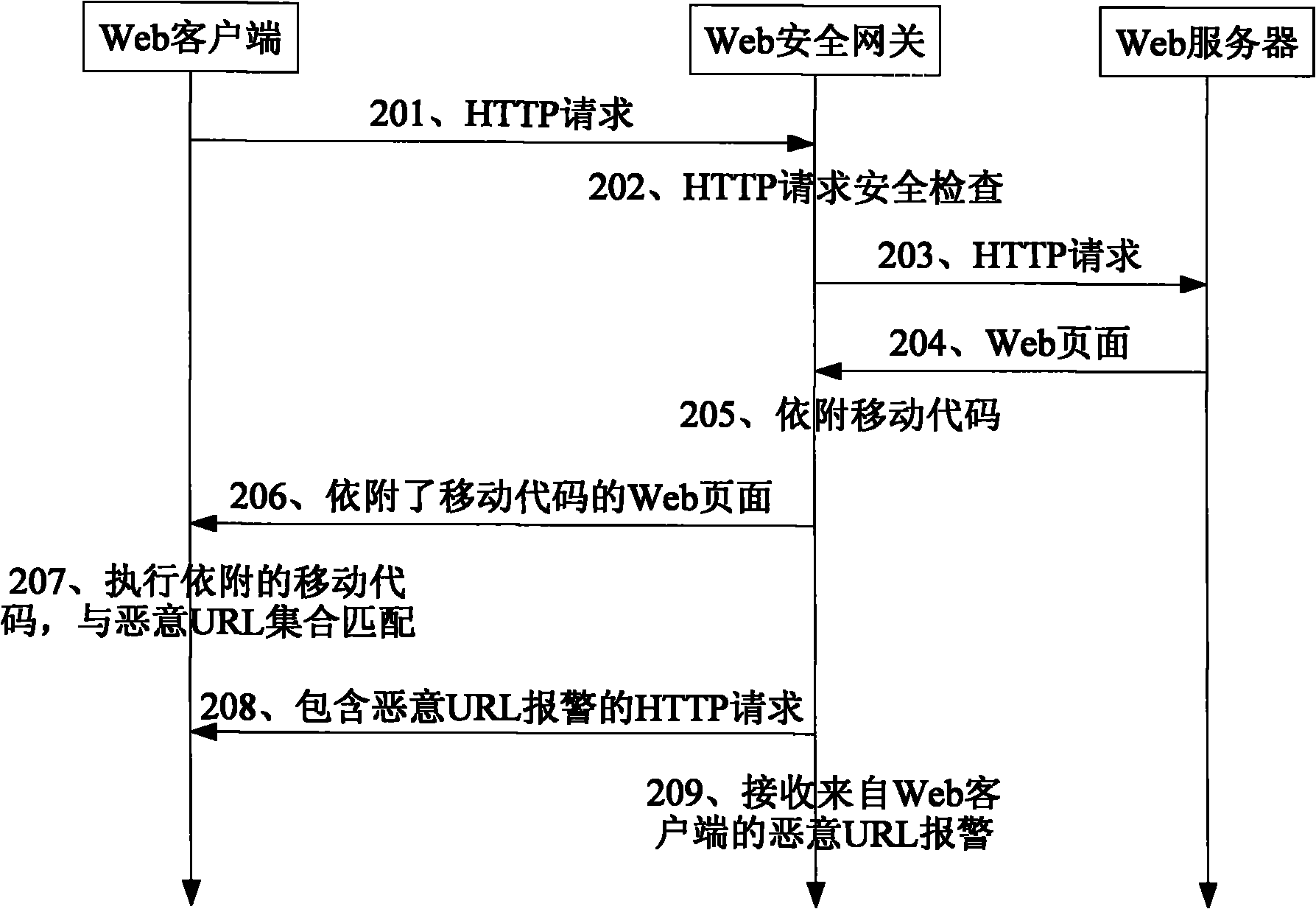
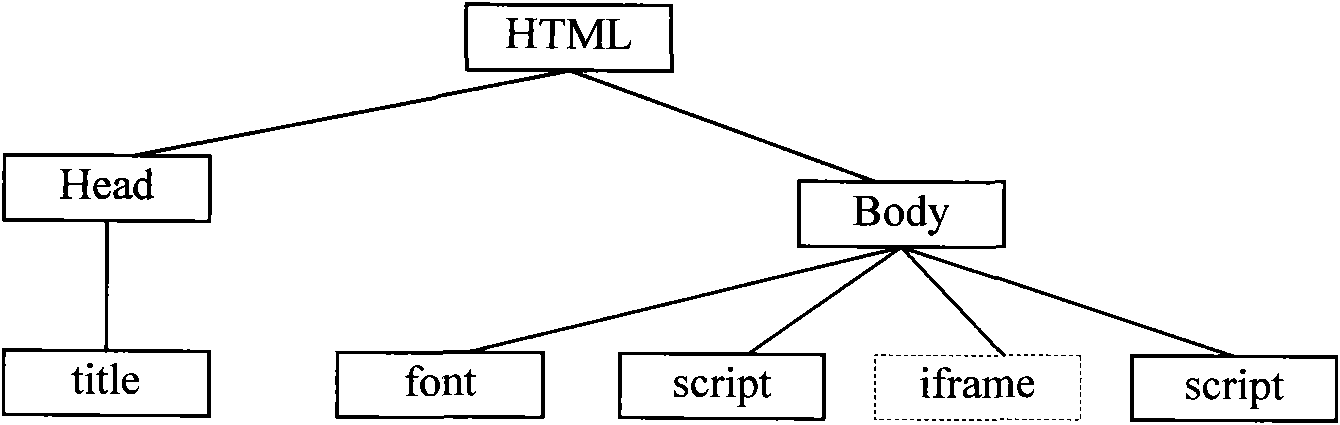
The invention discloses a security gateway and a method for forwarding a webpage by using the security gateway. The method comprises the following steps of: attaching a pre-generated mobile code to a Web page to be forwarded after the Web page requested by a client is acquired from a server; setting the mobile code to ensure that a corresponding document object model corresponding to the web page to which the mobile code is attached is traversed, extracting a uniform resource locator (URL) from a specified hypertext markup language (HTML) label and matching the extracted URL with a preset malicious URL set during execution; adding a command statement into the Web page to which the mobile code is attached; setting the command statement to ensure that the execution of the mobile code is triggered when the Web page is loaded; and forwarding the Web page to which the mobile code is attached and into which the statement is added to the client. By the method, malicious URL hidden in the Web page can be accurately detected under the condition that computation overhead of the security gateway is not increased.
Owner:BEIJING VENUS INFORMATION TECH +1
Method and system for protecting a computer and a network from hostile downloadables
InactiveUS20060149968A1Minimizing serverMinimizing client resource requirementMemory loss protectionError detection/correctionVisual BasicPersonal computer
Protection systems and methods provide for protecting one or more personal computers (“PCs”) and / or other intermittently or persistently network accessible devices or processes from undesirable or otherwise malicious operations of Java™ applets, ActiveX™ controls, JavaScript™ scripts, Visual Basic scripts, add-ins, downloaded / uploaded programs or other “Downloadables” or “mobile code” in whole or part. A protection engine embodiment provides, within a server, firewall or other suitable “re-communicator,” for monitoring information received by the communicator, determining whether received information does or is likely to include executable code, and if so, causes mobile protection code (MPC) to be transferred to and rendered operable within a destination device of the received information, more suitably by forming a protection agent including the MPC, protection policies and a detected-Downloadable. An MPC embodiment further provides, within a Downloadable-destination, for initiating the Downloadable, enabling malicious Downloadable operation attempts to be received by the MPC, and causing (predetermined) corresponding operations to be executed in response to the attempts, more suitably in conjunction with protection policies.
Owner:FINJAN LLC
Extensible Ubiquitous Secure Operating Environment
InactiveUS20080244689A1Secures user session activityPlatform integrity maintainanceSpecial data processing applicationsOperational systemSecure state
The present invention provides a portable and secure computer operating system, and applications that can be used securely on virtually any computer system regardless of its security state (i.e., regardless of the presence of computer viruses, Trojan code, keylogging software, or any other malicious mobile code that may exist on host computer system). The present invention is embodied within three (3) components including 1) the client desktop or server software, 2) the appliance-based management server, and 3) the media (i.e., including but not limited to USB thumb drive or CDROM) on which the client desktop or server software is installed.
Owner:DALTON CURTIS EVERETT
Malicious mobile code runtime monitoring system and methods
InactiveUS8079086B1Minimization requirementsEasy to updateMemory loss protectionUser identity/authority verificationVisual BasicMonitoring system
Protection systems and methods provide for protecting one or more personal computers (“PCs”) and / or other intermittently or persistently network accessible devices or processes from undesirable or otherwise malicious operations of Java TN applets, ActiveX™ controls, JavaScript™ scripts, Visual Basic scripts, add-ins, downloaded / uploaded programs or other “Downloadables” or “mobile code” in whole or part. A protection engine embodiment provides, within a server, firewall or other suitable “recommunicator,” for monitoring information received by the communicator, determining whether received information does or is likely to include executable code, and if so, causes mobile protection code (MPC) to be transferred to and rendered operable within a destination device of the received information, more suitably by forming a protection agent including the MPC, protection policies and a detected-Downloadable. An MPC embodiment further provides, within a Downloadable-destination, for initiating the Downloadable, enabling malicious Downloadable operation attempts to be received by the MPC, and causing (predetermined) corresponding operations to be executed in response to the attempts, more suitably in conjunction with protection policies.
Owner:FINJAN LLC
System and method for enabling communication among arbitrary components
InactiveUS7296042B2Data processing applicationsDigital data processing detailsCommunications systemData source
Methods and systems for enabling arbitrary components to communicate with each other. The communication system includes a first set of components associated with one or more universal interfaces that include mobile code. The one or more universal interfaces comprise a data source interface, a data sink interface, an aggregation interface, a mutable aggregation interface, a context interface, a notification interface or a user interface. Further, the universal interfaces associated with the first set of components can be provided to and implemented by a second set of components to enable the second set of components to communicate with the first set of components despite the first set and the second set of component utilizing different communication mediums or protocols.
Owner:THINKLOGIX LLC
Protecting mobile code against malicious hosts
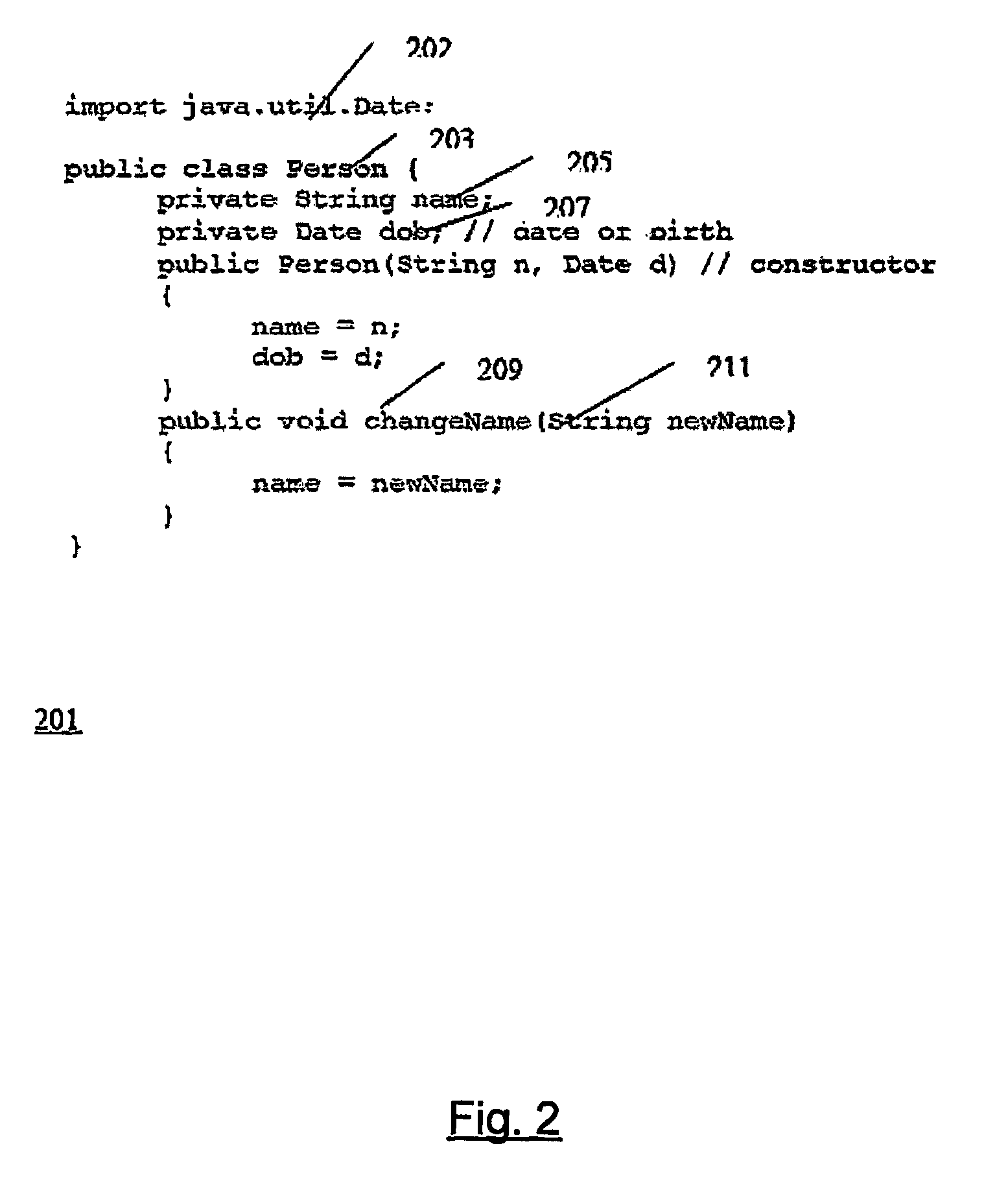
Techniques for using a class loader to protect mobile code against a malicious host. The techniques include using the class loader to extend a class used by the mobile code such that a method is added to the code which authenticates the mobile code. When executed, the method provides a dynamic watermark that authenticates the code. The method may be encrypted until it is added to the code. One such method uses a static watermark in the code to determine whether the code has been modified.The techniques also include using a class loader to extend the class such that obfuscated symbolic names in the program that correspond to symbolic names defined by the class can be resolved. A way of doing this is to include a first association between the obfuscated symbolic names and encrypted forms of the corresponding symbolic names in the program and to make a second association between the encrypted forms of the corresponding symbolic names and information used to resolve the symbolic names defined in the class. The loader then uses the first and second associations to resolve the obfuscated names.The class extension techniques may be combined with obfuscation of names defined in the program and static watermarking to provide layered protection of the mobile code. The obfuscation and definition of the first association are done prior to execution of the program and the class extension is done on execution of the program. The disclosed techniques are particularly well-adapted for use with the byte codes produced by Java language compilers from Java language programs.
Owner:FRAUNHOFER GESELLSCHAFT ZUR FOERDERUNG DER ANGEWANDTEN FORSCHUNG EV
Malicious Mobile Code Runtime Monitoring System and Methods
InactiveUS20120117651A1Minimization requirementsEasy to updateMemory loss protectionError detection/correctionVisual BasicMonitoring system
Owner:FINJAN LLC
Corporate business tax web site
InactiveUS20060085304A1Improve scalabilityComplete banking machinesFinanceMobile codeDigital identity
A Corporate Business Income tax web site where a user enters the tax information into a web site using a web browser; the web site calculates the tax due or downloads mobile code and the mobile calculates the tax due; the corporate tax data is transferred to the taxing agency; an acknowledgment is received back from the taxing agency; the information in the acknowledgment is sent to the user. Also, a web site where the user who E-Files the tax return is verified using a digital ID.
Owner:BUARQUE DE MACEDO MICHAEL CARLOS +1
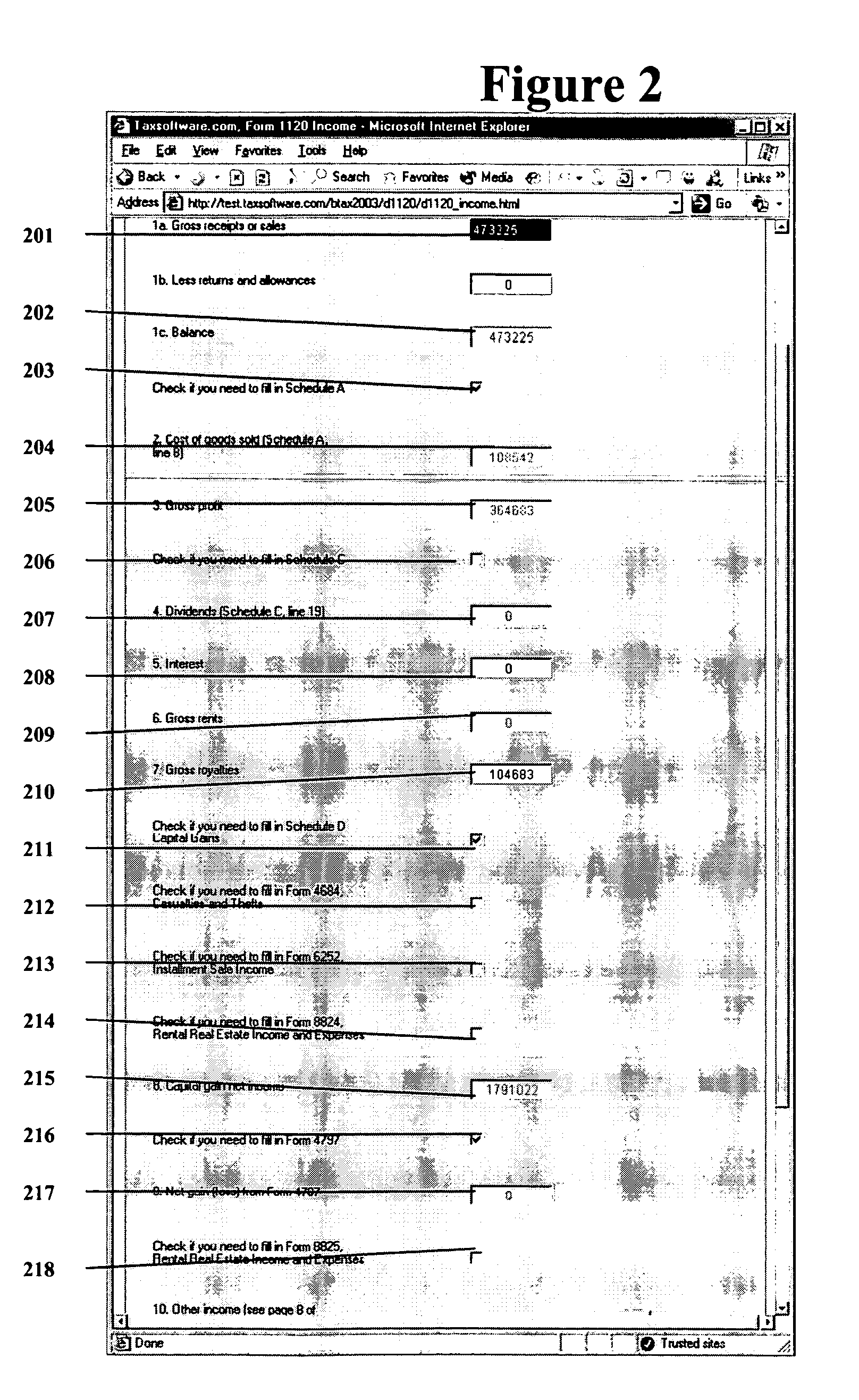
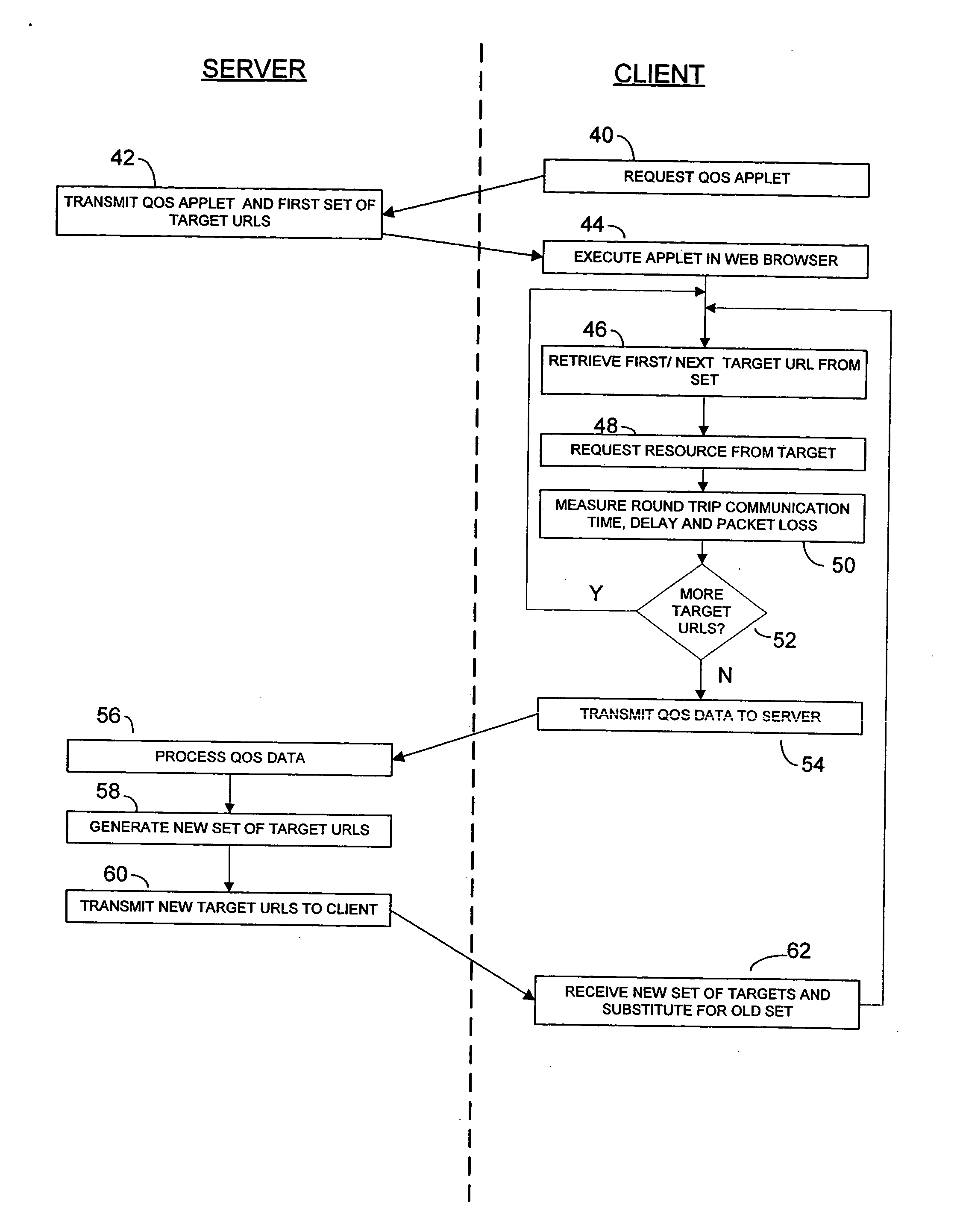
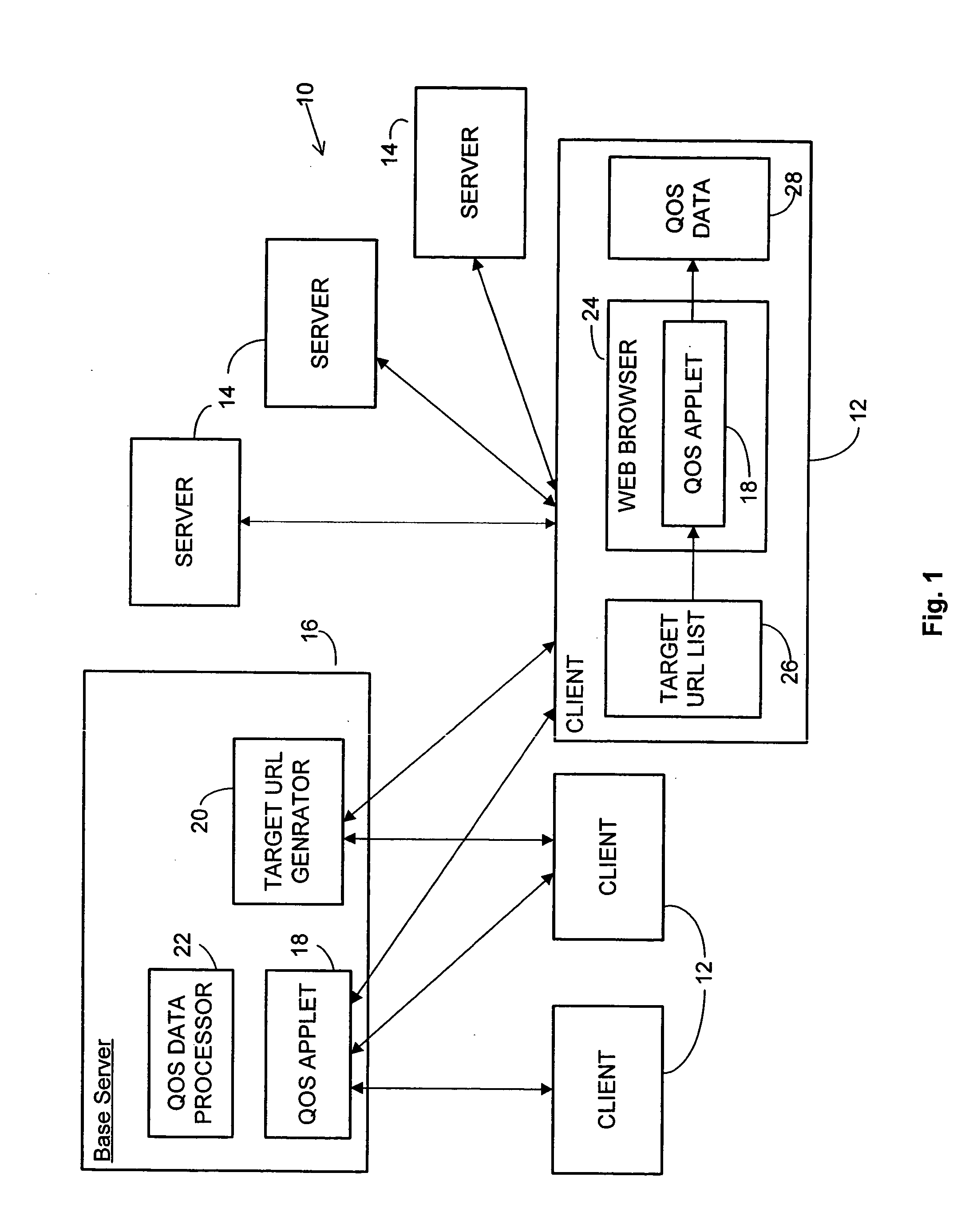
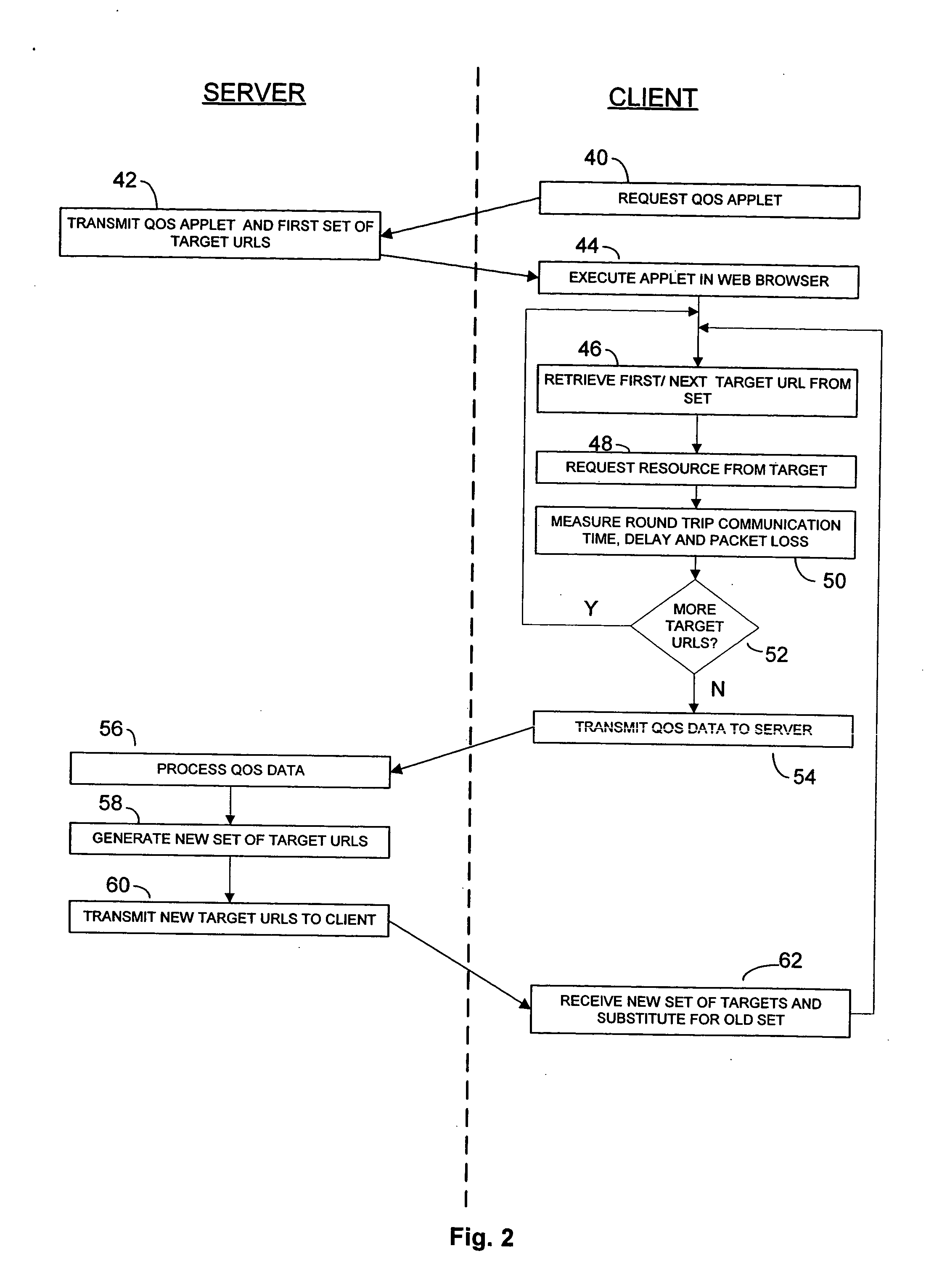
Method and system for using mobile code to measure quality of service over a network
InactiveUS20050091378A1Efficient and cost-effectiveMultiple digital computer combinationsData switching networksQuality of serviceWeb browser
The invention is a method for using mobile code such as an applet to conduct quality of service measurements of network paths in client applications such as web browsers. A client computer downloads the mobile code from a base server as well as a list of target host URLs from the base server. When executed, the mobile code accesses each of the target URLs and measures quality of service (QoS) data such as round-trip time, delays, loss of packets, etc. for each URL. The mobile code compiles this QoS data and transmits it back to the base server for processing and analysis. The base server may then transmit a second set of target URLs, which set may be generated randomly, previously selected, or selected based upon the QoS data received from the mobile code. In addition, the client may use the QoS measurements to determine which of the target URLs represents the better or best path of communications for the client, and may re-establish communications over that path accordingly. When many clients retrieve and run the mobile code and send QoS results back to the base server, the base server will eventually compile a comprehensive set of QoS statistics for widespread Internet traffic in a cost-effective and efficient manner.
Owner:NONNENMACHER JORG
Protecting mobile code against malicious hosts
ActiveUS7877613B2User identity/authority verificationUnauthorized memory use protectionProgramming languageMobile code
Techniques for using a class loader to protect mobile code against a malicious host. The techniques include using the class loader to extend a class used by the mobile code such that a method is added to the code which authenticates the mobile code. When executed, the method provides a dynamic watermark that authenticates the code. The method may be encrypted until it is added to the code. One such method uses a static watermark in the code to determine whether the code has been modified. The techniques also include using a class loader to extend the class such that obfuscated symbolic names in the program that correspond to symbolic names defined by the class can be resolved. A way of doing this is to include a first association between the obfuscated symbolic names and encrypted forms of the corresponding symbolic names in the program and to make a second association between the encrypted forms of the corresponding symbolic names and information used to resolve the symbolic names defined in the class. The loader then uses the first and second associations to resolve the obfuscated names.
Owner:FRAUNHOFER GESELLSCHAFT ZUR FOERDERUNG DER ANGEWANDTEN FORSCHUNG EV
Malicious mobile code runtime monitoring system and methods
InactiveUS9219755B2Minimization requirementsEasy to updatePlatform integrity maintainanceTransmissionVisual BasicMonitoring system
Protection systems and methods provide for protecting one or more personal computers (“PCs”) and / or other intermittently or persistently network accessible devices or processes from undesirable or otherwise malicious operations of Java TN applets, ActiveX™ controls, JavaScript™ scripts, Visual Basic scripts, add-ins, downloaded / uploaded programs or other “Downloadables” or “mobile code” in whole or part. A protection engine embodiment provides for monitoring information received, determining whether received information does or is likely to include executable code, and if so, causes mobile protection code (MPC) to be transferred to and rendered operable within a destination device of the received information. An MPC embodiment further provides, within a Downloadable-destination, for initiating the Downloadable, enabling malicious Downloadable operation attempts to be received by the MPC, and causing (predetermined) corresponding operations to be executed in response to the attempts.
Owner:FINJAN LLC
Malicious Mobile Code Runtime Monitoring System and Methods
InactiveUS20150288720A1Minimizing serverMinimizing client resource requirementPlatform integrity maintainanceTransmissionVisual BasicMonitoring system
Protection systems and methods provide for protecting one or more personal computers (“PCs”) and / or other intermittently or persistently network accessible devices or processes from undesirable or otherwise malicious operations of Java TN applets, ActiveX™ controls, JavaScript™ scripts, Visual Basic scripts, add-ins, downloaded / uploaded programs or other “Downloadables” or “mobile code” in whole or part. A protection engine embodiment provides for monitoring information received, determining whether received information does or is likely to include executable code, and if so, causes mobile protection code (MPC) to be transferred to and rendered operable within a destination device of the received information. An MPC embodiment further provides, within a Downloadable-destination, for initiating the Downloadable, enabling malicious Downloadable operation attempts to be received by the MPC, and causing (predetermined) corresponding operations to be executed in response to the attempts.
Owner:FINJAN LLC
Method and Apparatuses for Secure, Anonymous Wireless Lan (WLAN) Acess
ActiveUS20090070859A1Digital data processing detailsUser identity/authority verificationWeb browserWeb service
A method and system for providing secure, anonymous access to a wireless local area network, including configuring an access point to drop packets except packets exhibiting an URL access protocol like HTTP and HTTPS, intercepting a URL access request by an access point from a mobile device via a web browser, re-directing the URL access request to a web server by the access point generating a security key by one of the access points and the web server, communicating the generated security key to the said web server securely by the access point or vice versa and setting the security key by the access point is described. A mobile device including means for forwarding a request for secure access to a wireless local area network via a URL access request, means for receiving a mobile code or a signal for displaying a security key and means for setting the security key is also described.
Owner:THOMSON LICENSING SA
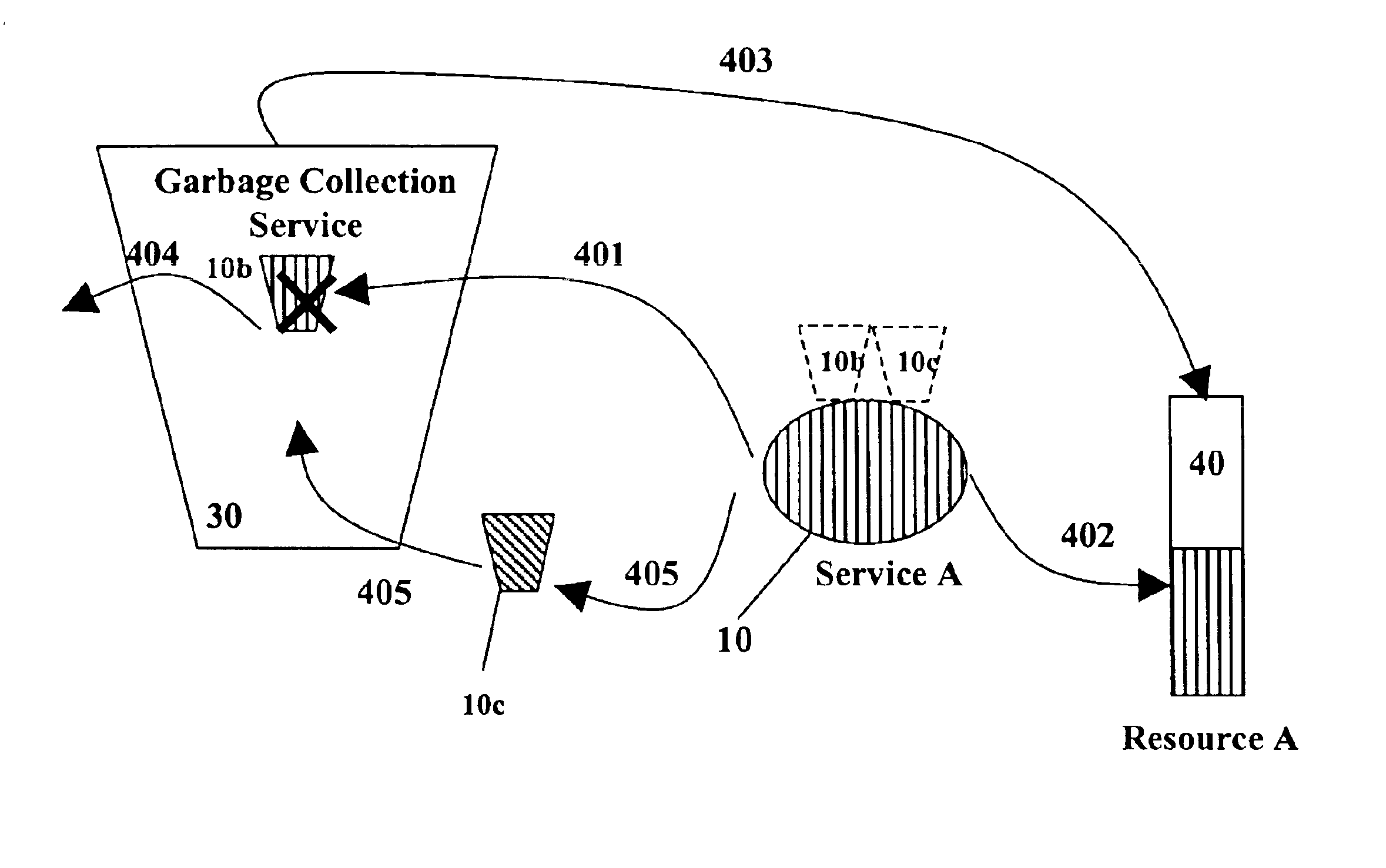
Method and system for multimode garbage collection
InactiveUS6961740B2Data processing applicationsMemory adressing/allocation/relocationRefuse collectionWaste collection
This invention is a method and system for improved garbage collection in a distributed computing system. Garbage collection is the process of releasing resources that are no longer being utilized by the objects to which those resources are allocated. Specifically, a garbage collection system and method are described that allow for different types of garbage collection to be used at different times and / or on different objects or resources in the system. In the preferred embodiment, the garbage collection routines are contained in separate mobile code module that can be changed dynamically interchanged to provide different garbage collection algorithms.
Owner:GLOBAL INFO TEK
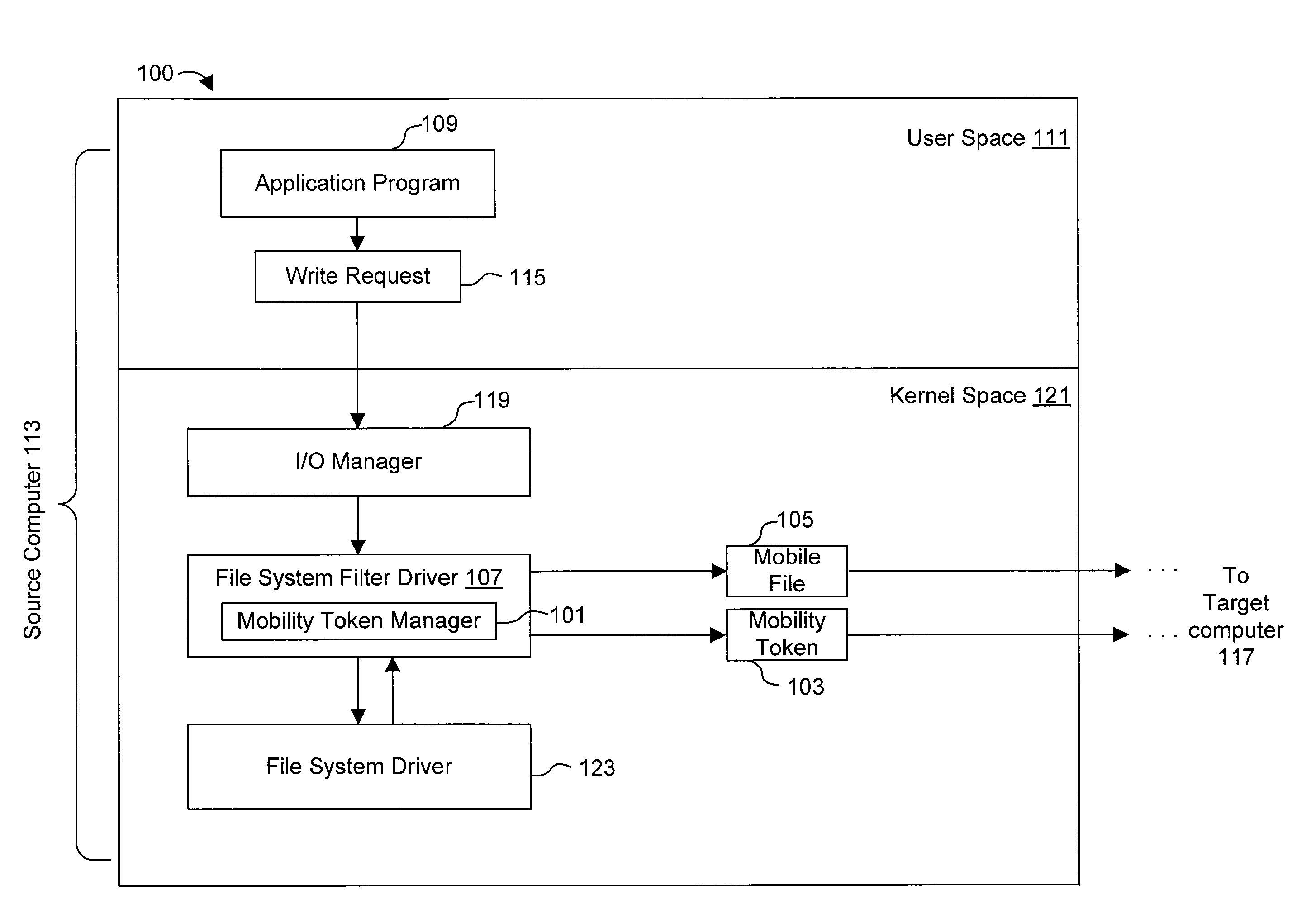
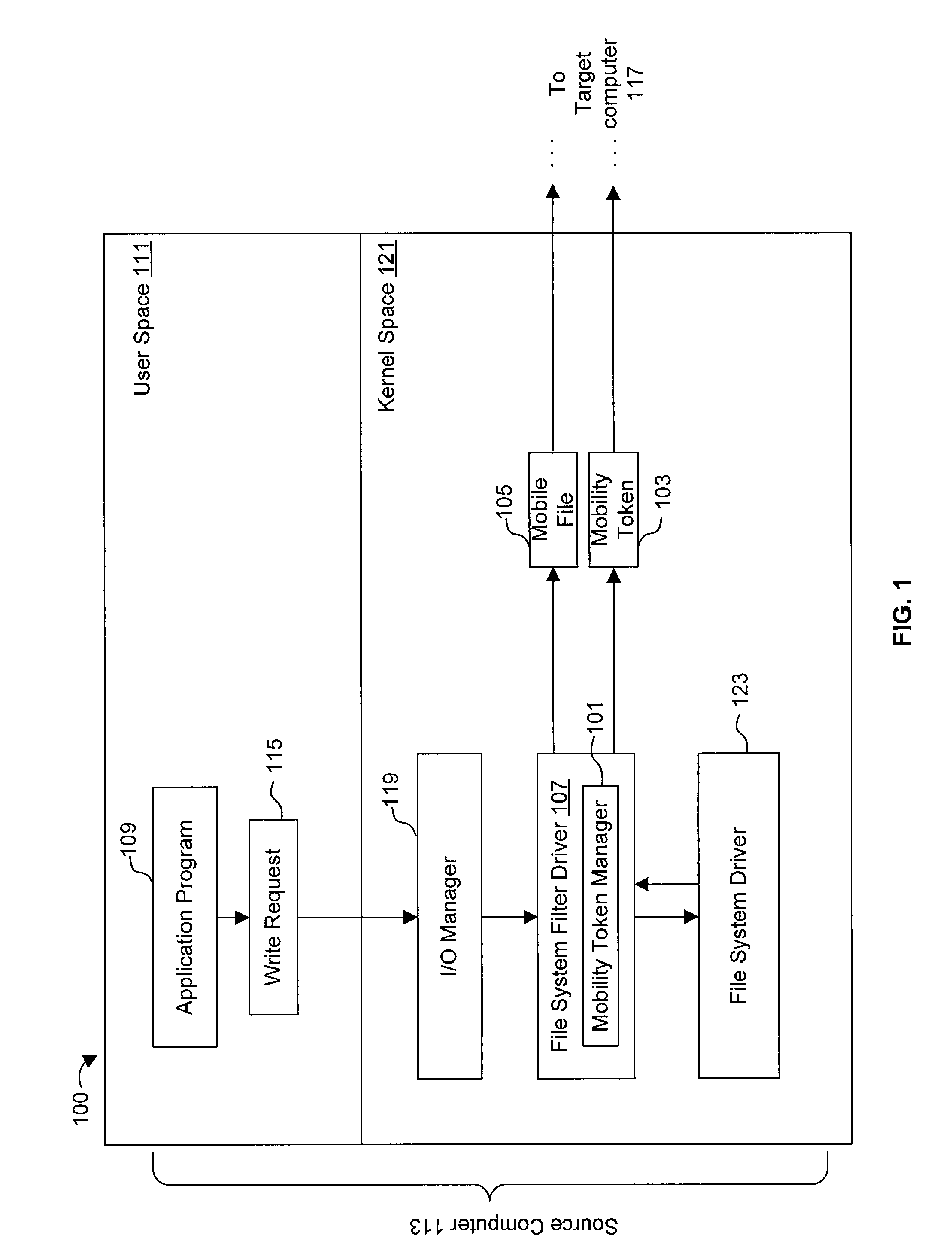
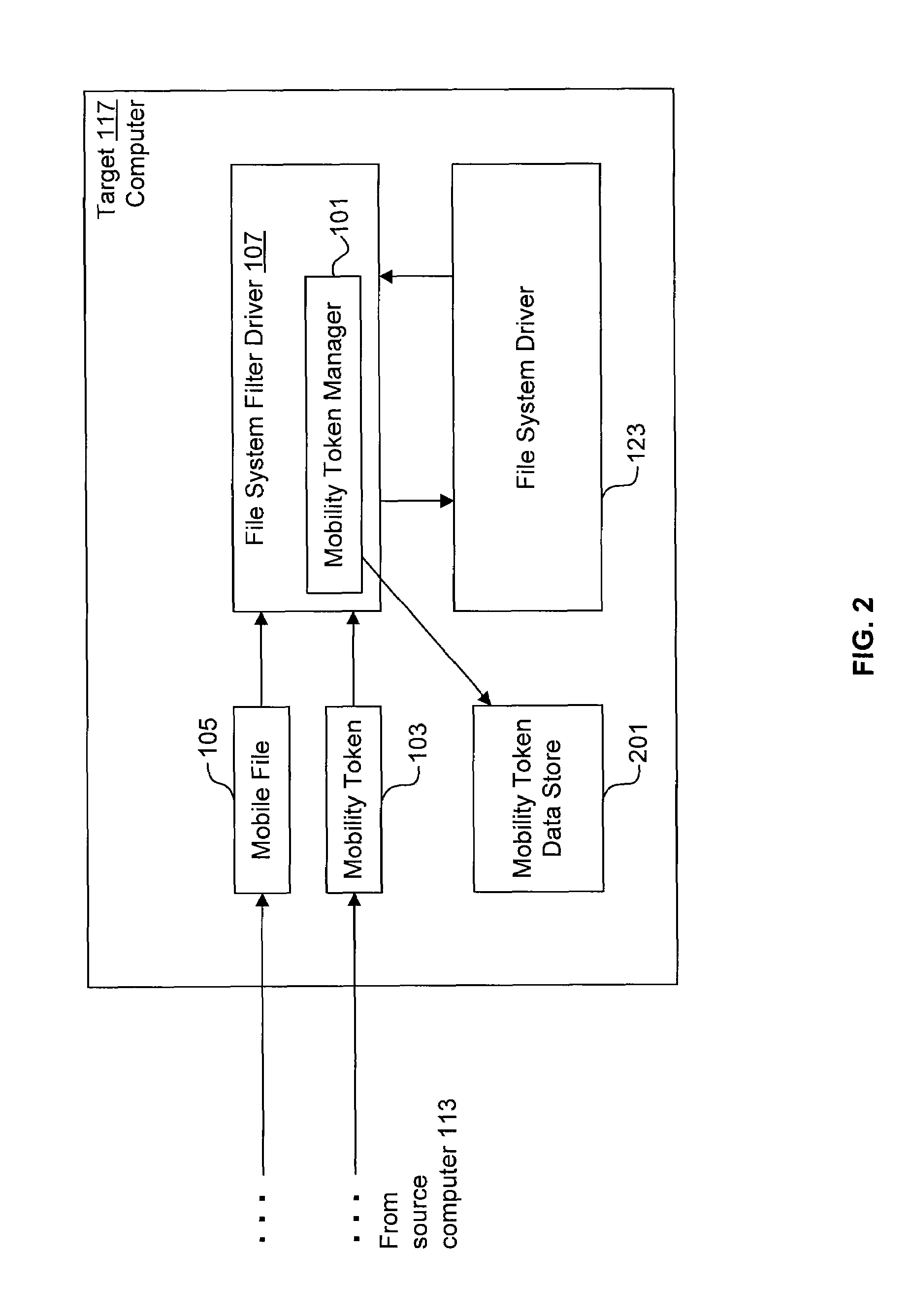
Using mobility tokens to observe malicious mobile code
ActiveUS7337327B1Unauthorized memory use protectionHardware monitoringRelevant informationMobile code
One or more mobility token managers (101) track movement of files (105) within a network. A mobility token manager (101) on a source computer (113) detects an attempt to write a file (105) to a target computer (117). Responsive to the detection, the mobility token manager (101) writes a mobility token (103) containing data concerning at least the file (105) and the write operation to the target computer (117). A mobility token manager (101) on the target computer (117) detects that the mobility token (103) is being written to the target computer (117). The mobility token manager (101) on the target computer (117) reads the mobility token (103), and determines relevant information concerning the file (105) associated with the mobility token (103).
Owner:CA TECH INC
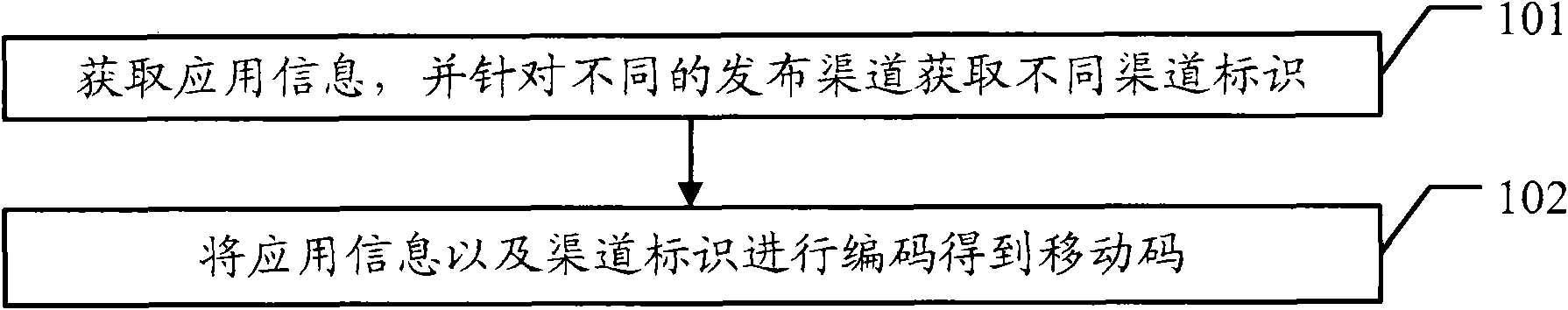
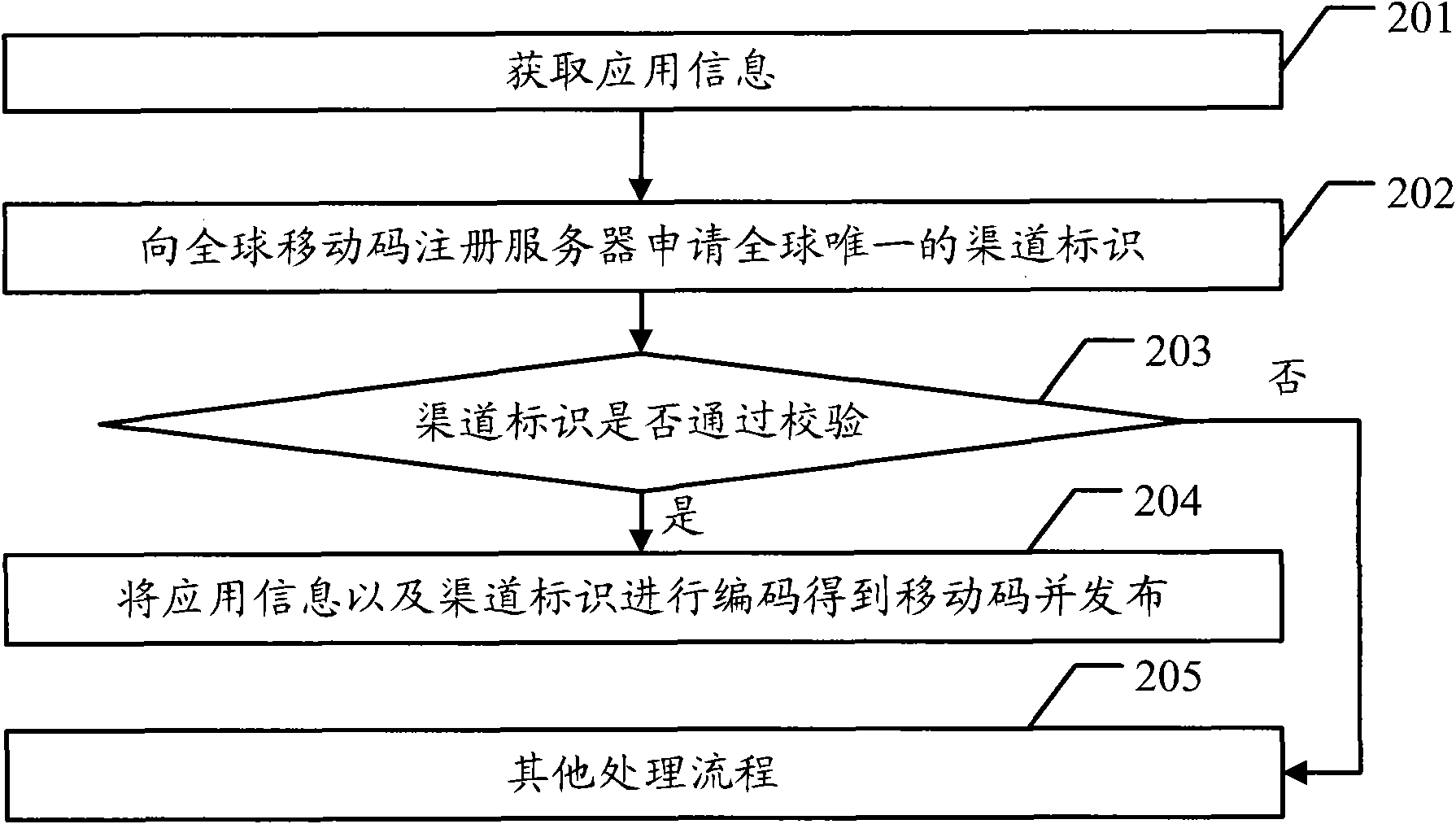
Data generation method, data transmission method and related equipment
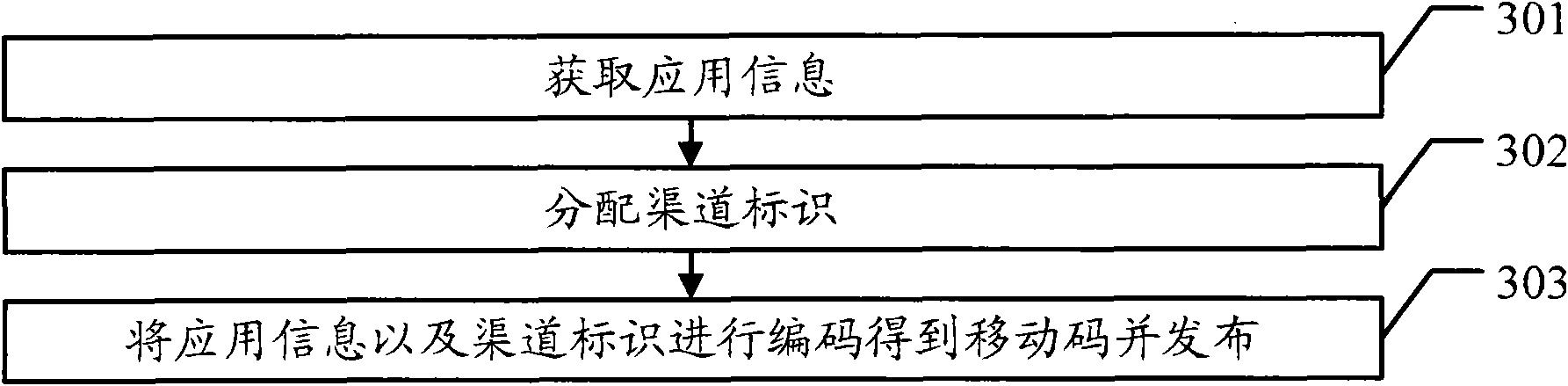
The embodiment of the invention discloses a data generation method, a data transmission method and related equipment, which can promote the service development of a mobile code. The data generation method comprises the following steps of: acquiring application information, and acquiring different channel identifiers for different release channels; and coding the application information and the channel identifiers to obtain the mobile code. The embodiment of the invention also provides the data transmission method and the related equipment. The embodiment of the invention can effectively promote the service development of the mobile code.
Owner:HUAWEI DEVICE CO LTD
Contents player and playing method, mobile code providing device and providing method applied to DRM system
InactiveUS20060149961A1Program/content distribution protectionSpecial data processing applicationsMobile codeDigital rights management
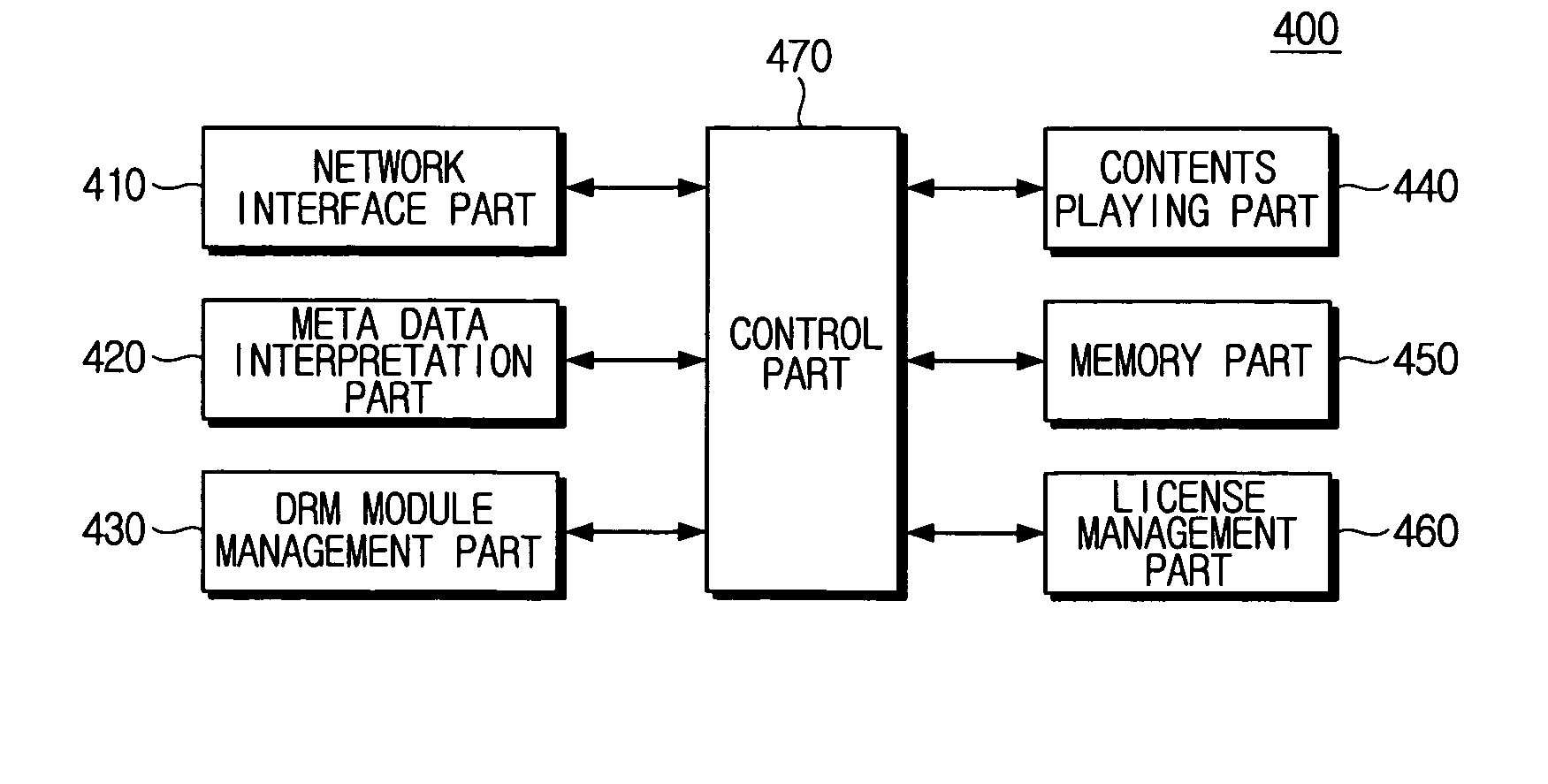
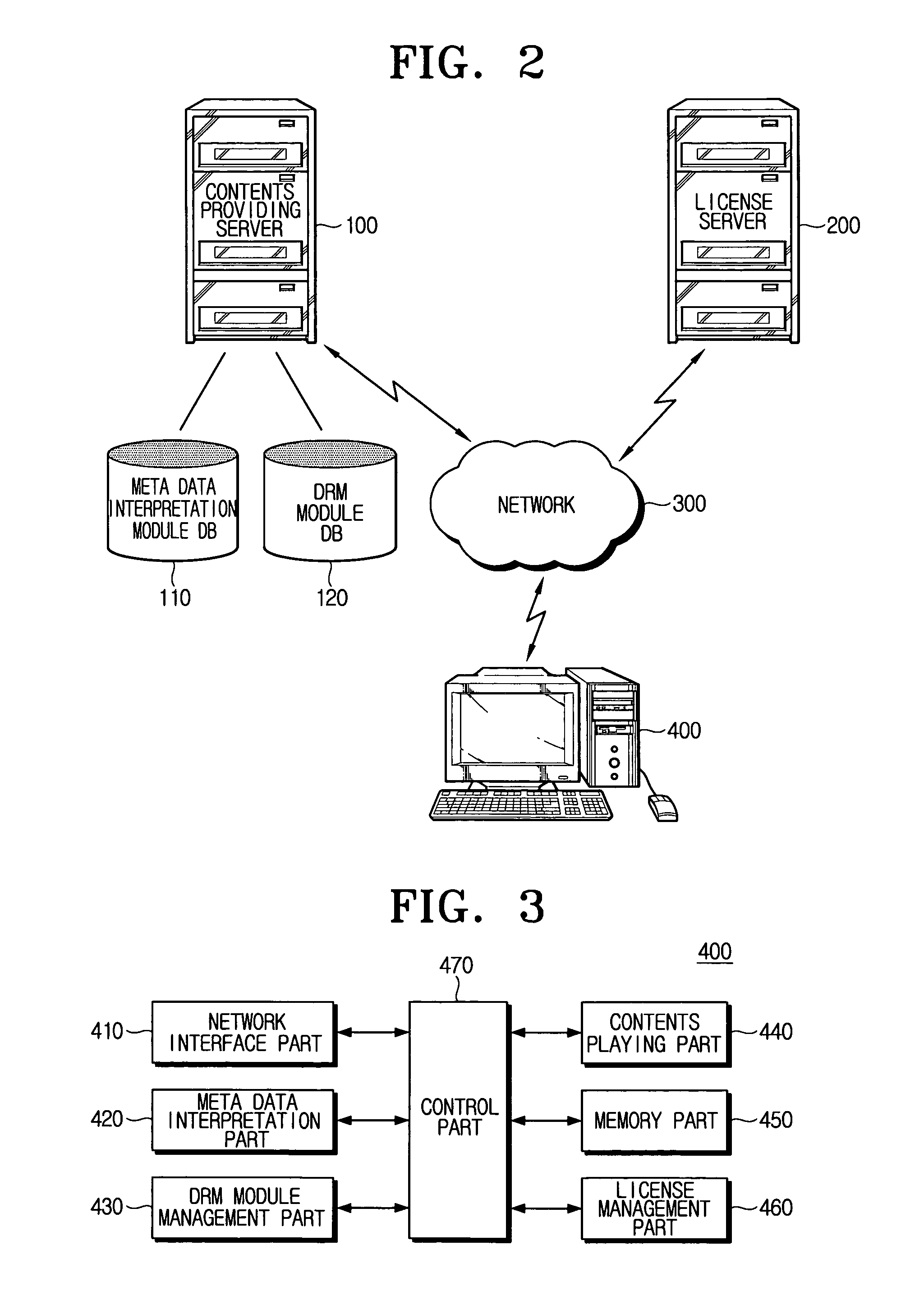
A contents player, a method for playing contents, a mobile code providing device and a method for providing a mobile code, that are applied to a digital rights management (DRM) system. The contents player applied to the DRM system, according to an embodiment of the present invention, includes a network interface part which receives the contents and additional data regarding the contents; a DRM module management part which demodulates the contents by a predetermined DRM module and if the DRM module capable of demodulating the contents does not exist, updates the DRM module through the network interface part; and a contents playing part which plays the demodulated contents. Accordingly, all the contents provided by a content provider can be used regardless of the DRM technology applied to the contents and a platform of a demodulator.
Owner:SAMSUNG ELECTRONICS CO LTD
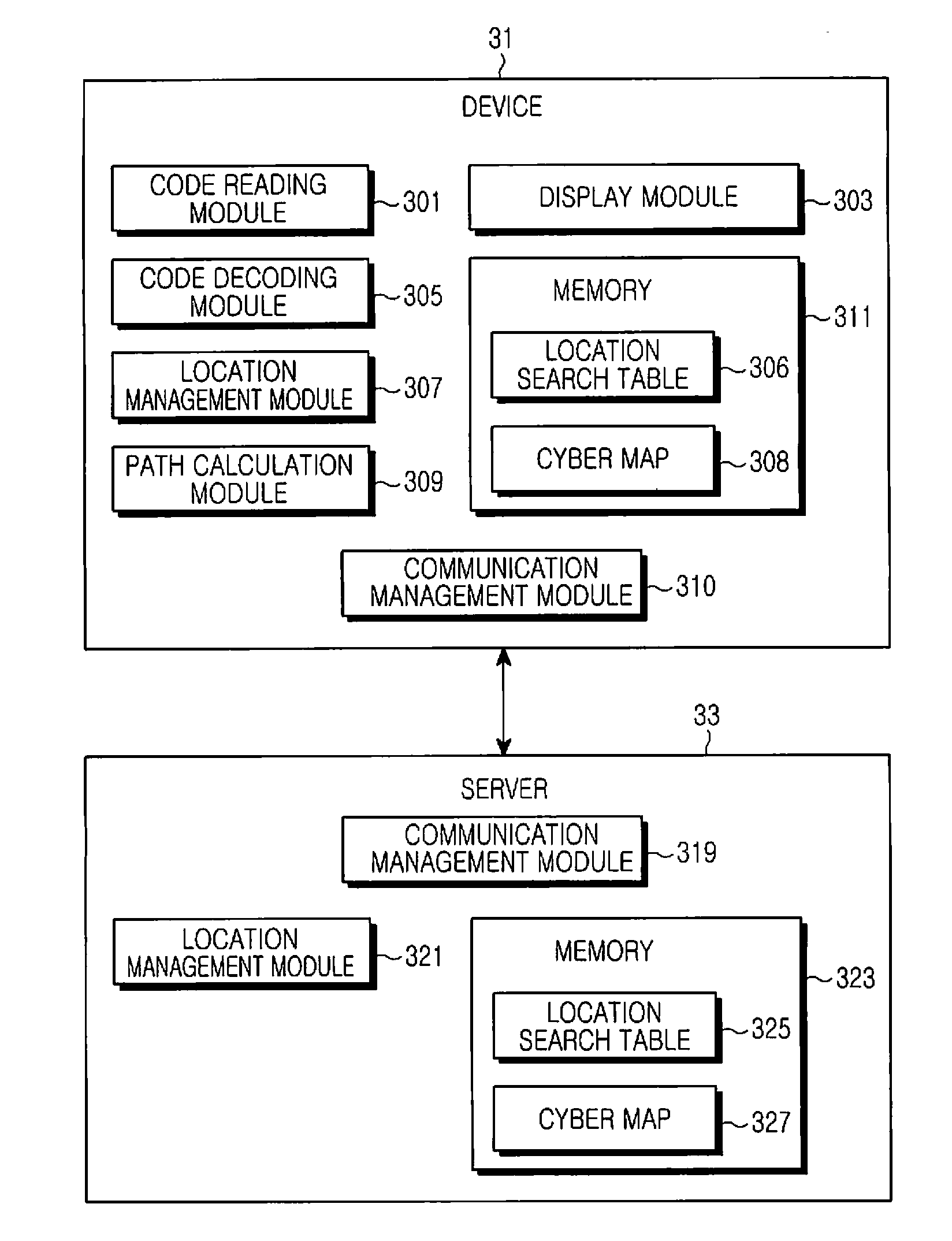
System and method for providing location information service using mobile code
InactiveUS20110059750A1Accurate detectionPosition fixationWireless commuication servicesMobile codeOutput device
An apparatus and method for providing a location information service using a mobile code in a Mobile Station (MS). The method includes scanning, by an input device of the MS, a mobile code; analyzing identifier information of the scanned mobile code; determining whether the identifier information corresponds to other information stored in the MS; if the identifier information corresponds to other information stored in the MS, acquiring location information, to be matched on a first cyber map in the MS, corresponding to the identifier information; matching the acquired location information on the first cyber map and displaying the matched first cyber map on an output device of the MS; and calculating a moving distance and a path using at least one location corresponding to the acquired location information.
Owner:SAMSUNG ELECTRONICS CO LTD
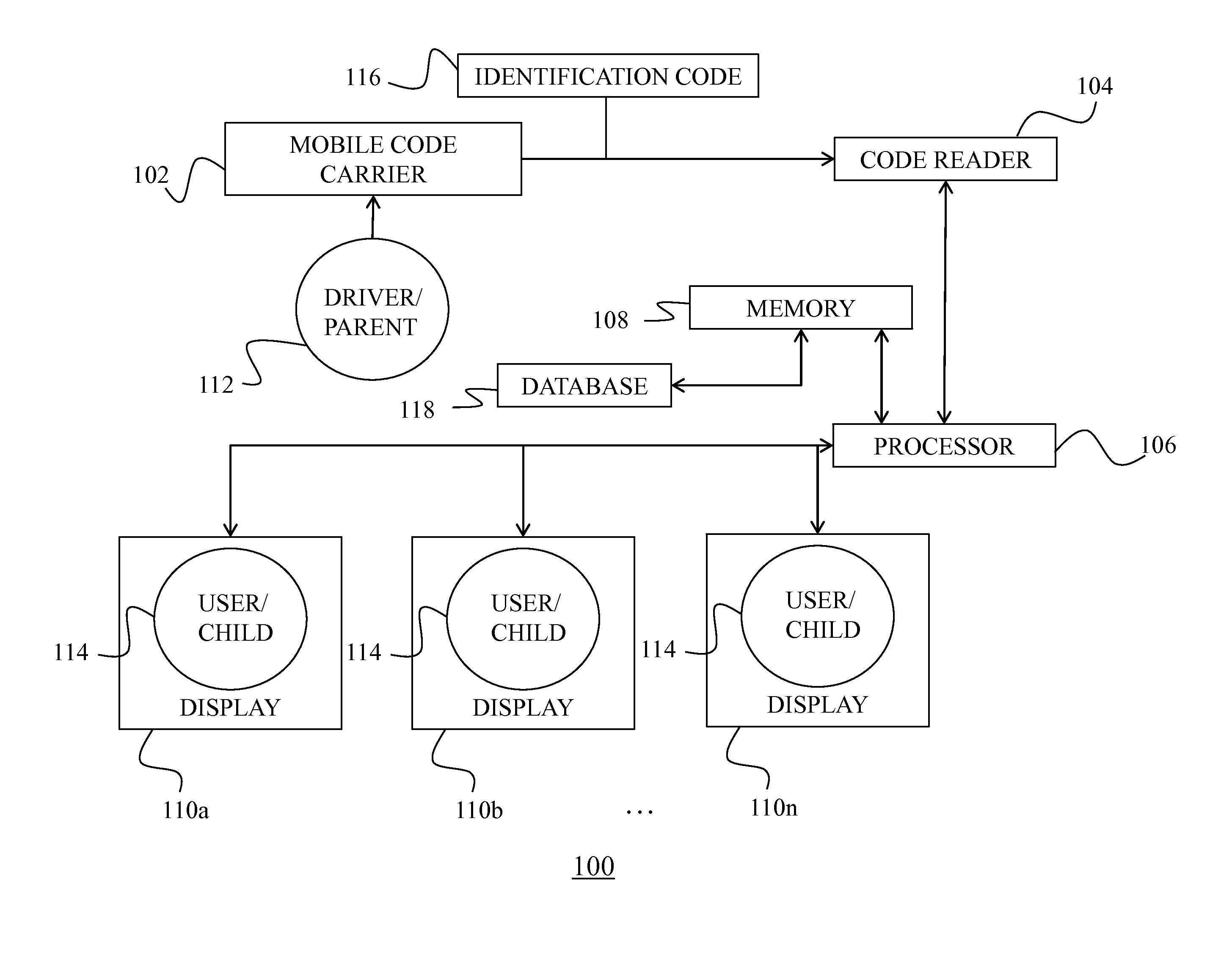
Driver/parent arrival notification system and method of notification
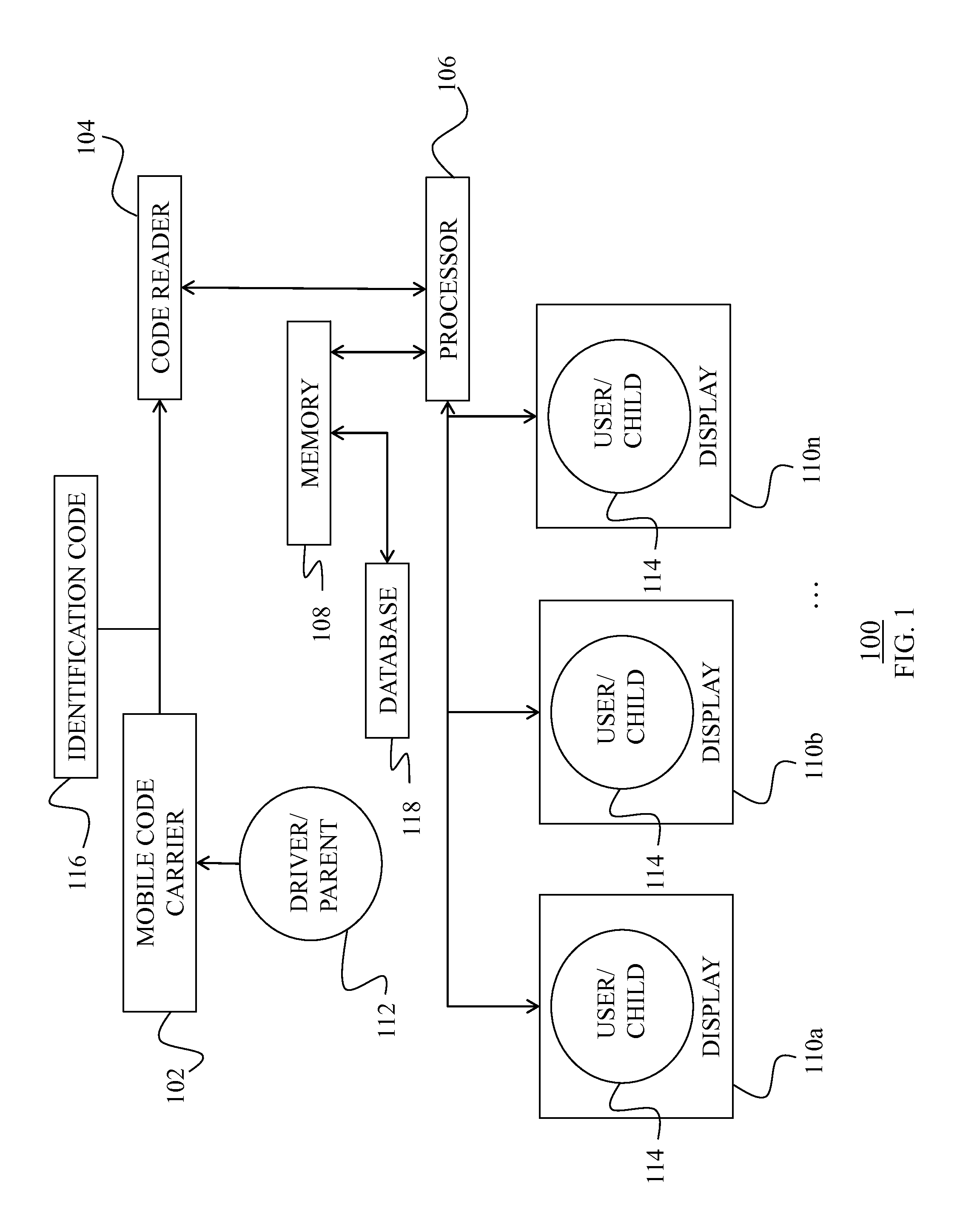
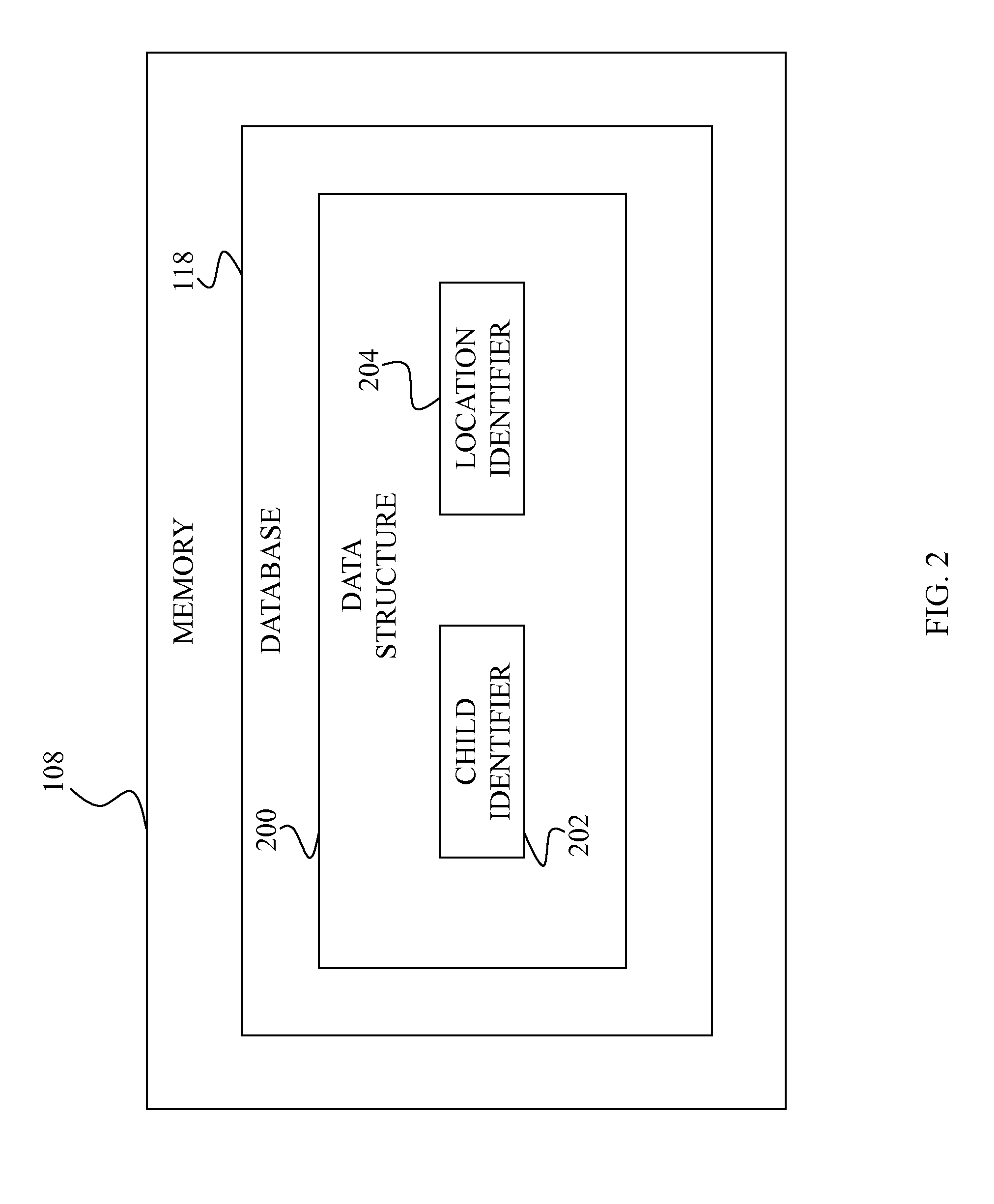
ActiveUS20130256396A1Low costEfficiently provideResourcesSpecial data processing applicationsDriver/operatorDisplay device
A system for providing a user / child with the arrival status of a driver / parent and method therefore includes providing a mobile code carrier, a code reader that identifies a code stored on the code carrier, a processor communicatively coupled to the code reader, a memory communicatively coupled to the processor storing a data base that includes a data structure, and a plurality of displays each communicatively coupled to the processor and located in one of a plurality of disparate locations within a building. The method further includes identifying the code, associating the code with a target and at least one location within the building, and displaying to one of the plurality of displays where the target is located a message indicating that the driver / parent has arrived.
Owner:DISCOVERY SCHOOLS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com