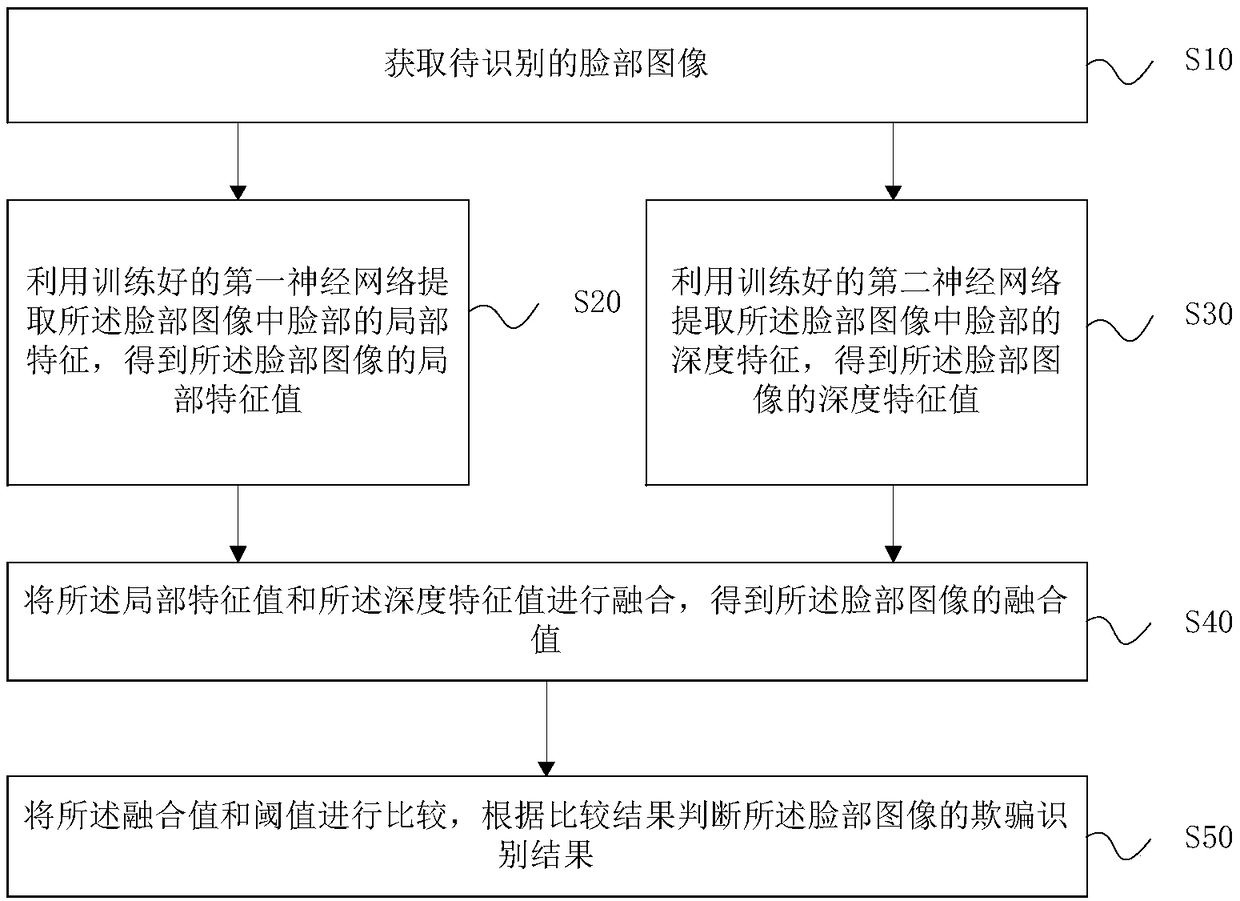
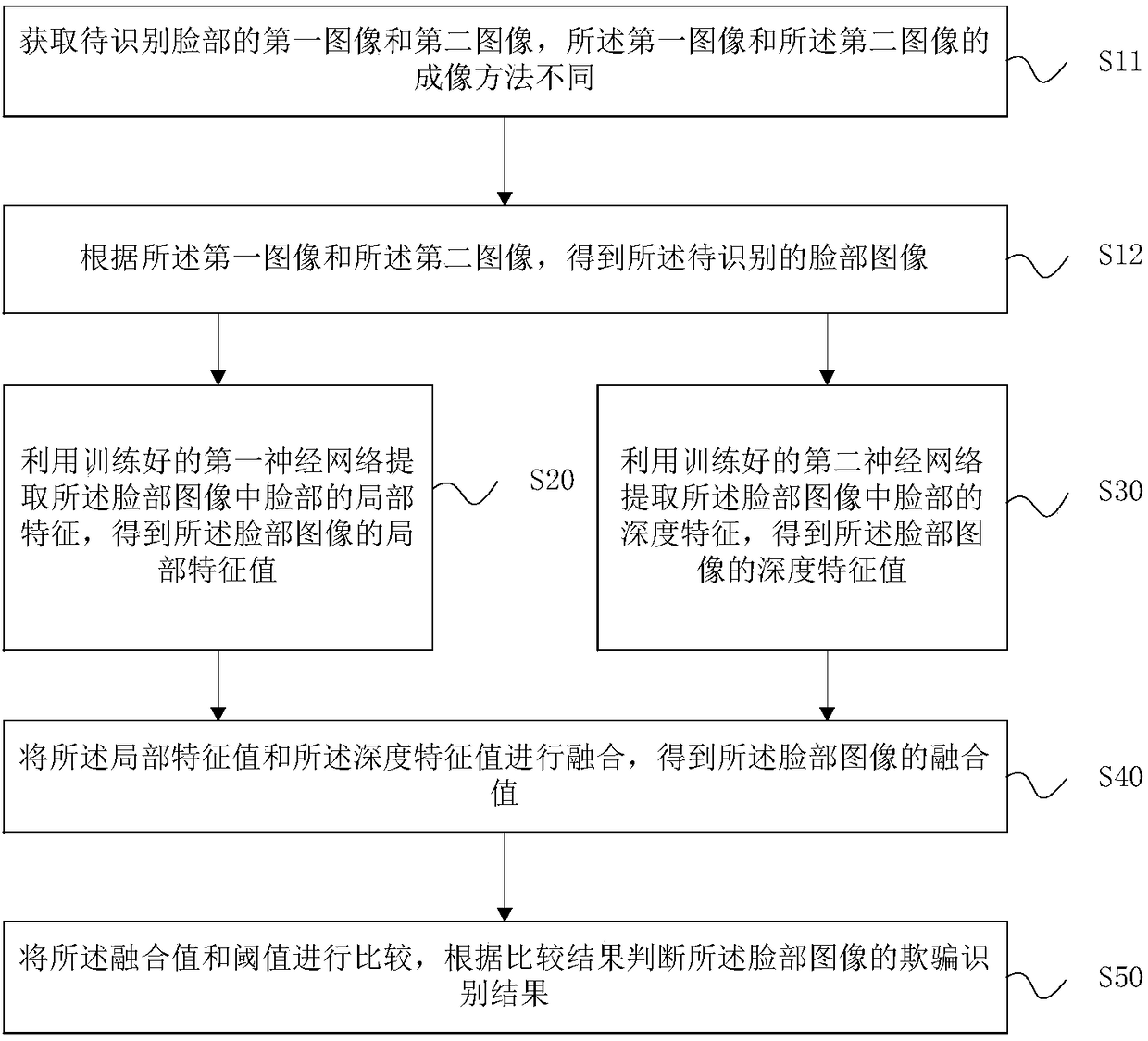
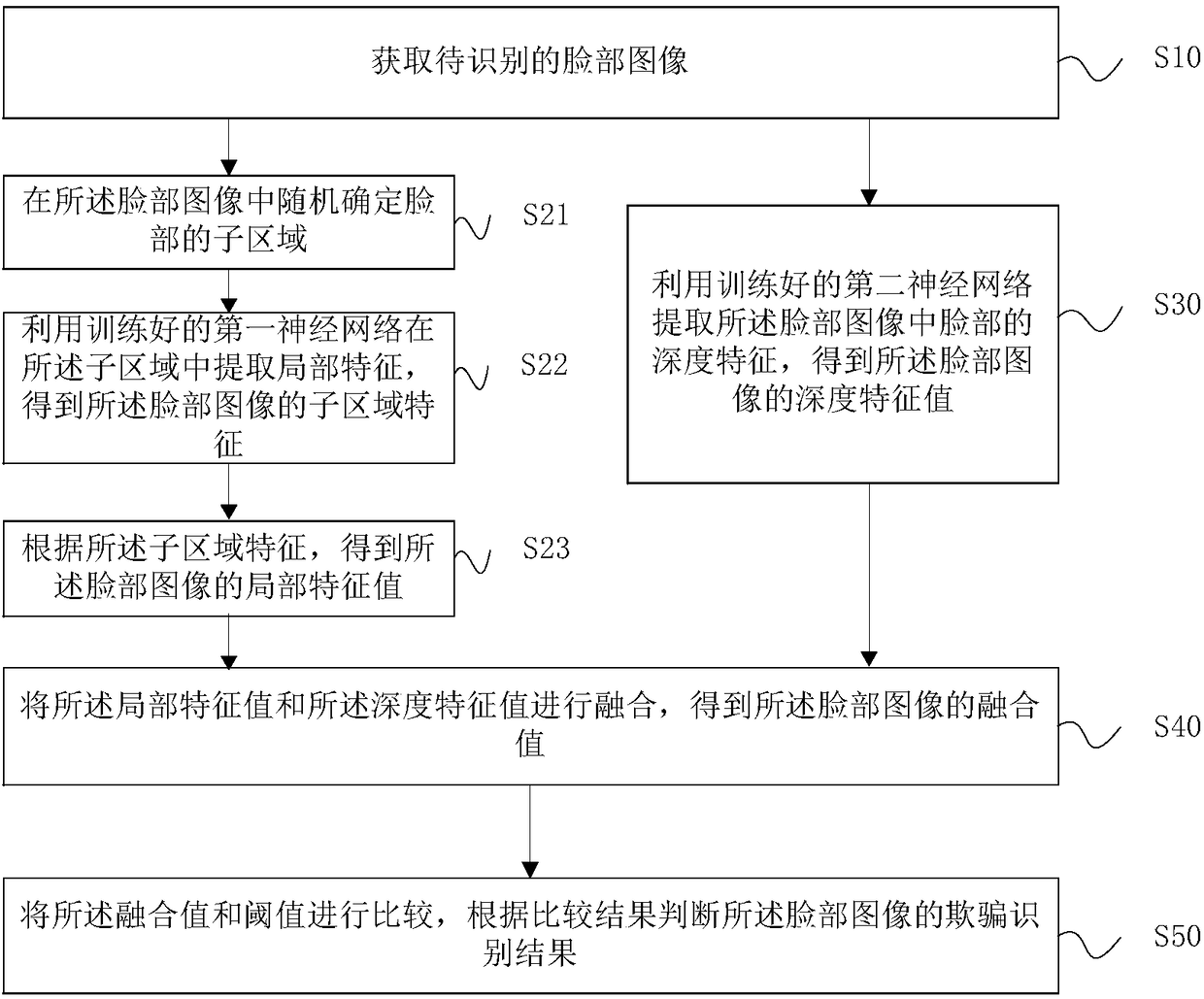
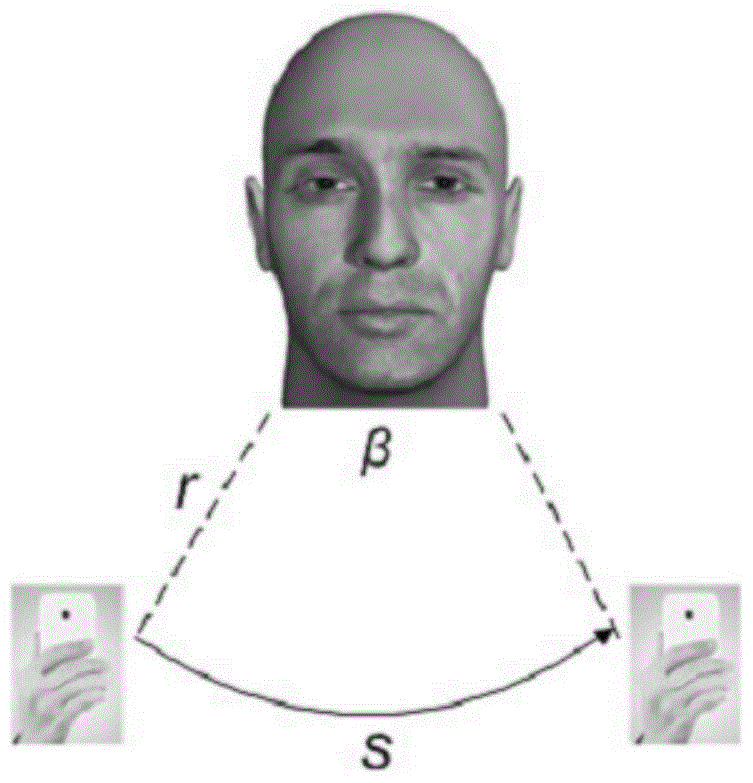
Patents
Literature
255 results about "Spoofing attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
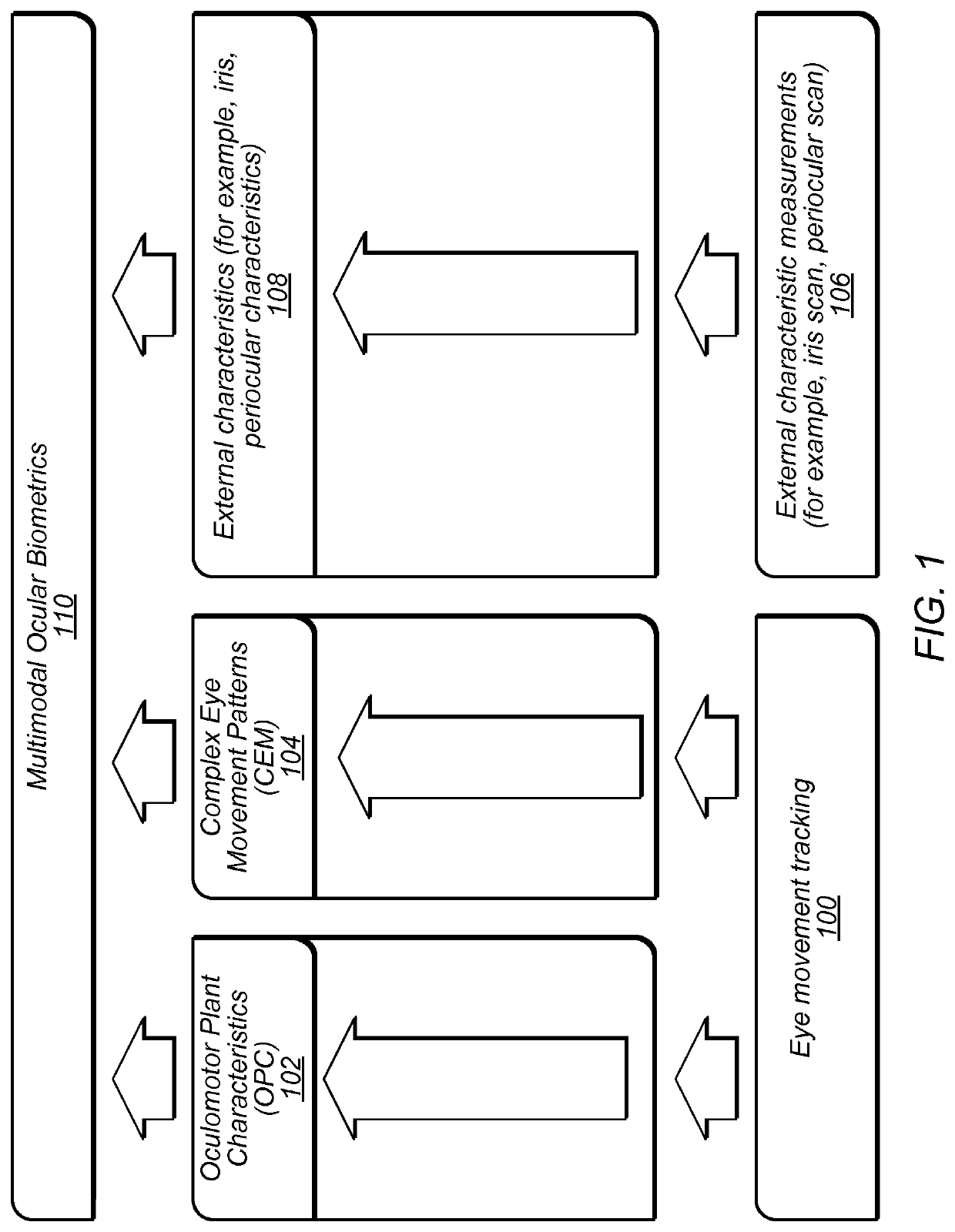
In the context of information security, and especially network security, a spoofing attack is a situation in which a person or program successfully identifies as another by falsifying data, to gain an illegitimate advantage.
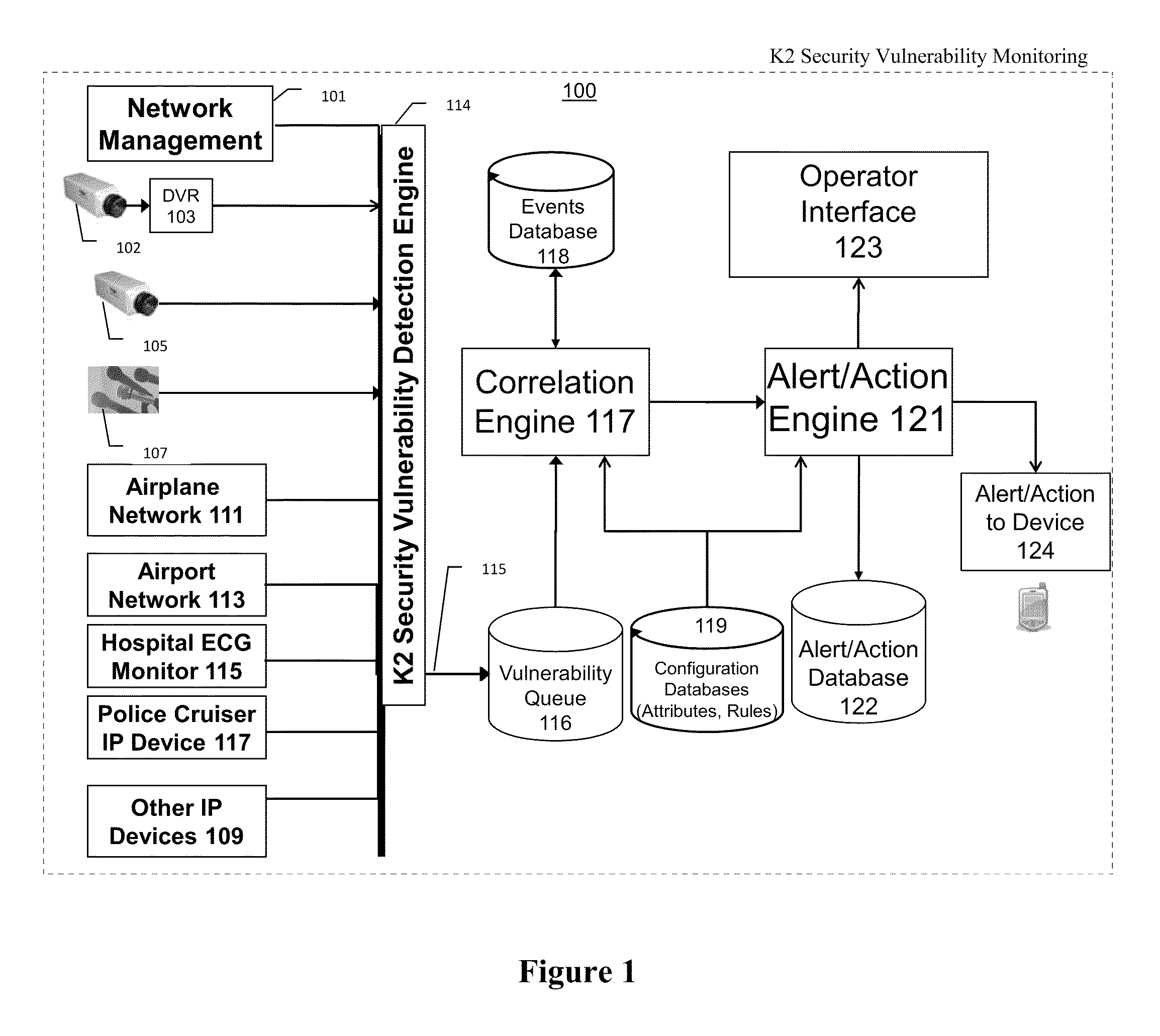
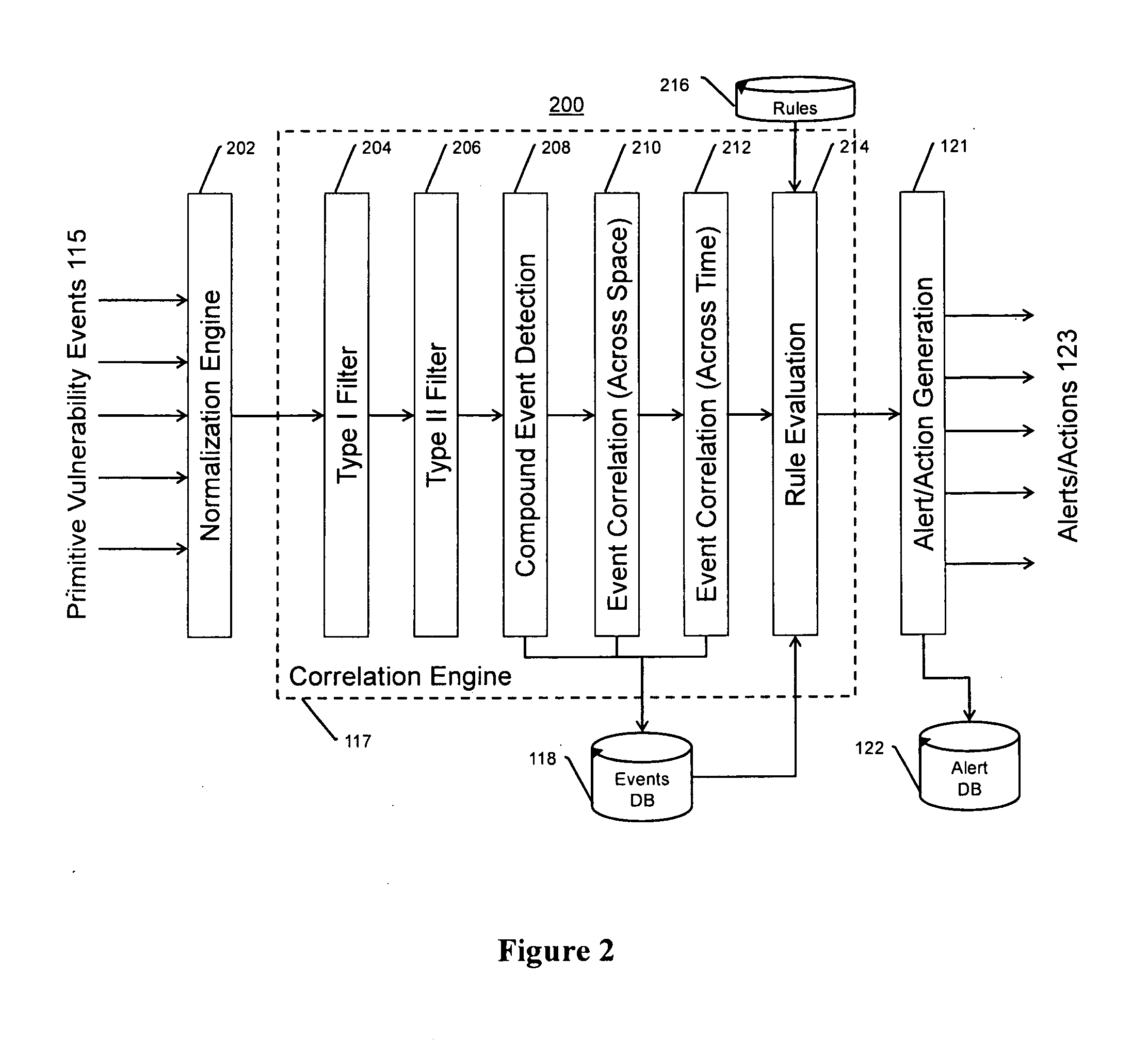
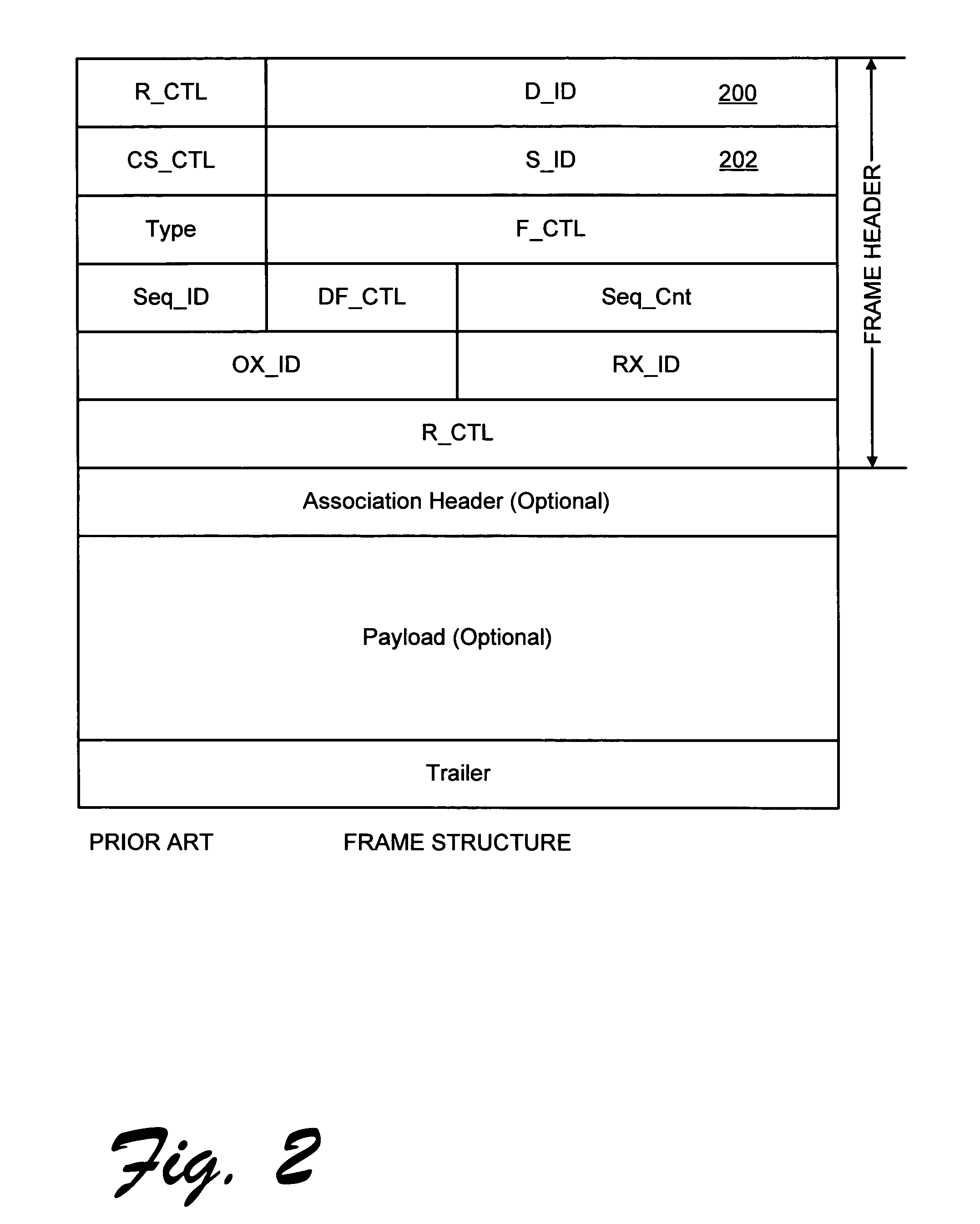
Systems, methods, and devices for detecting security vulnerabilities in IP networks
InactiveUS20100262688A1Detect and prevent spoofingEasy to addMemory loss protectionDigital data processing detailsBaseline dataData stream
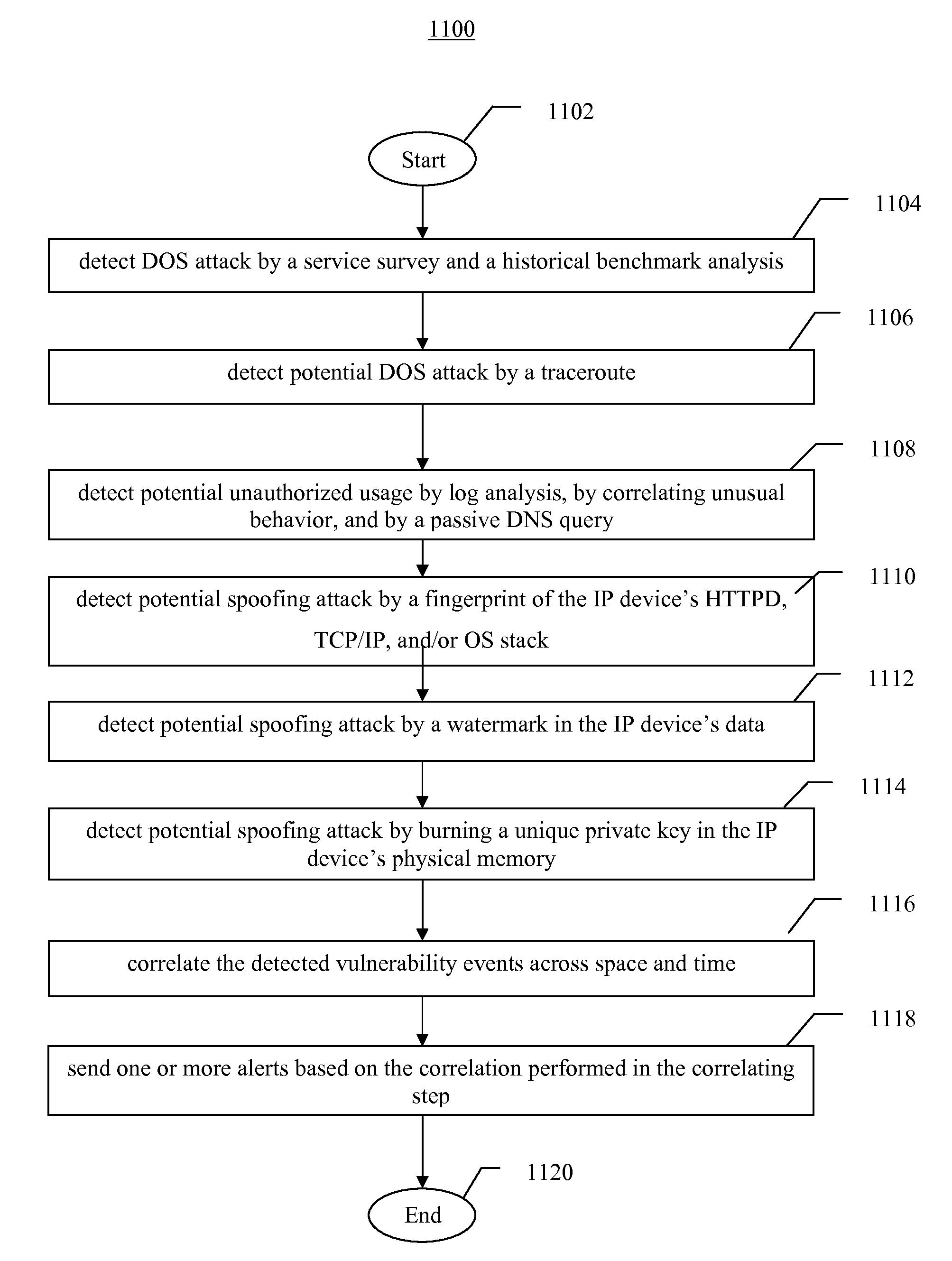
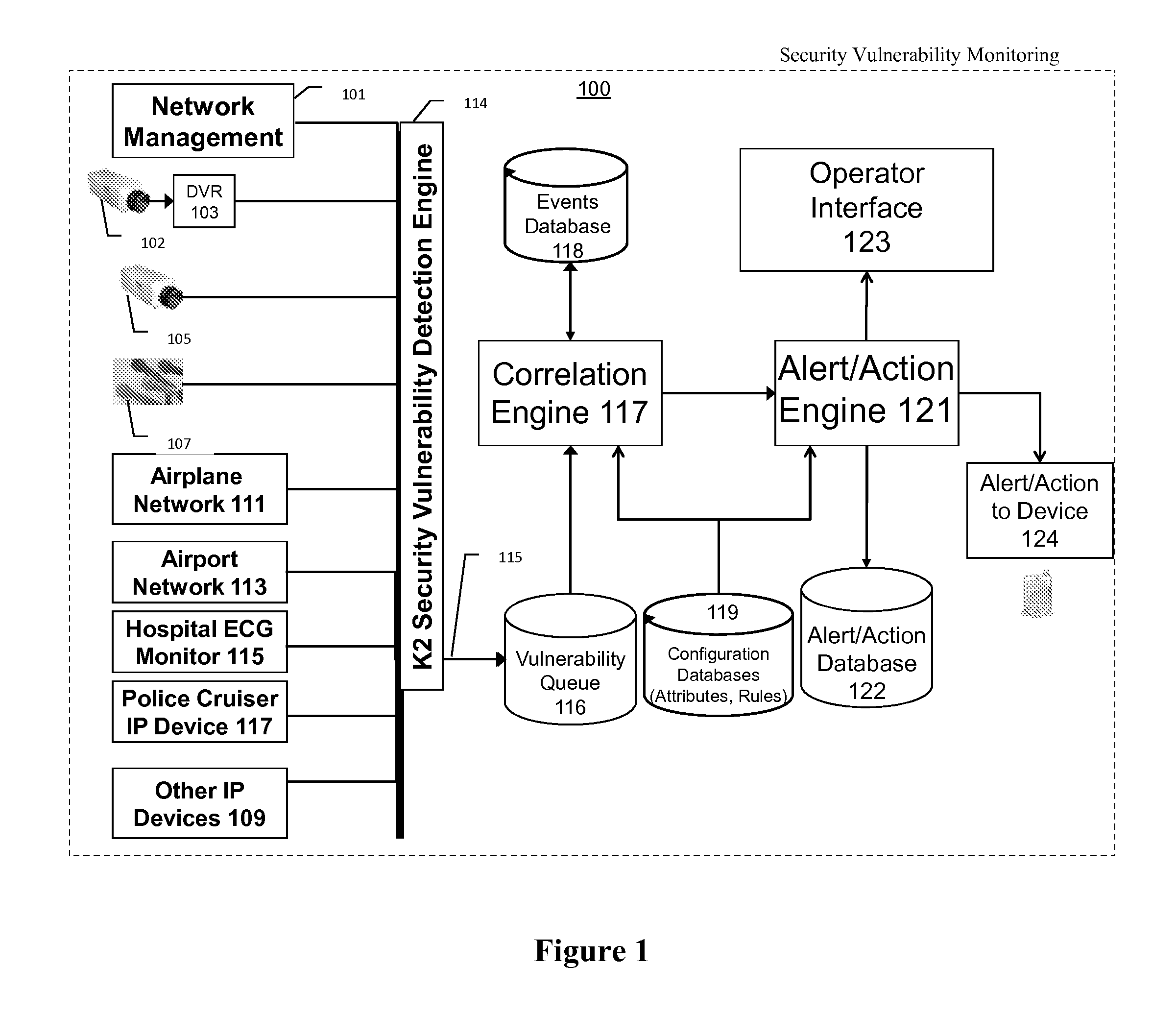
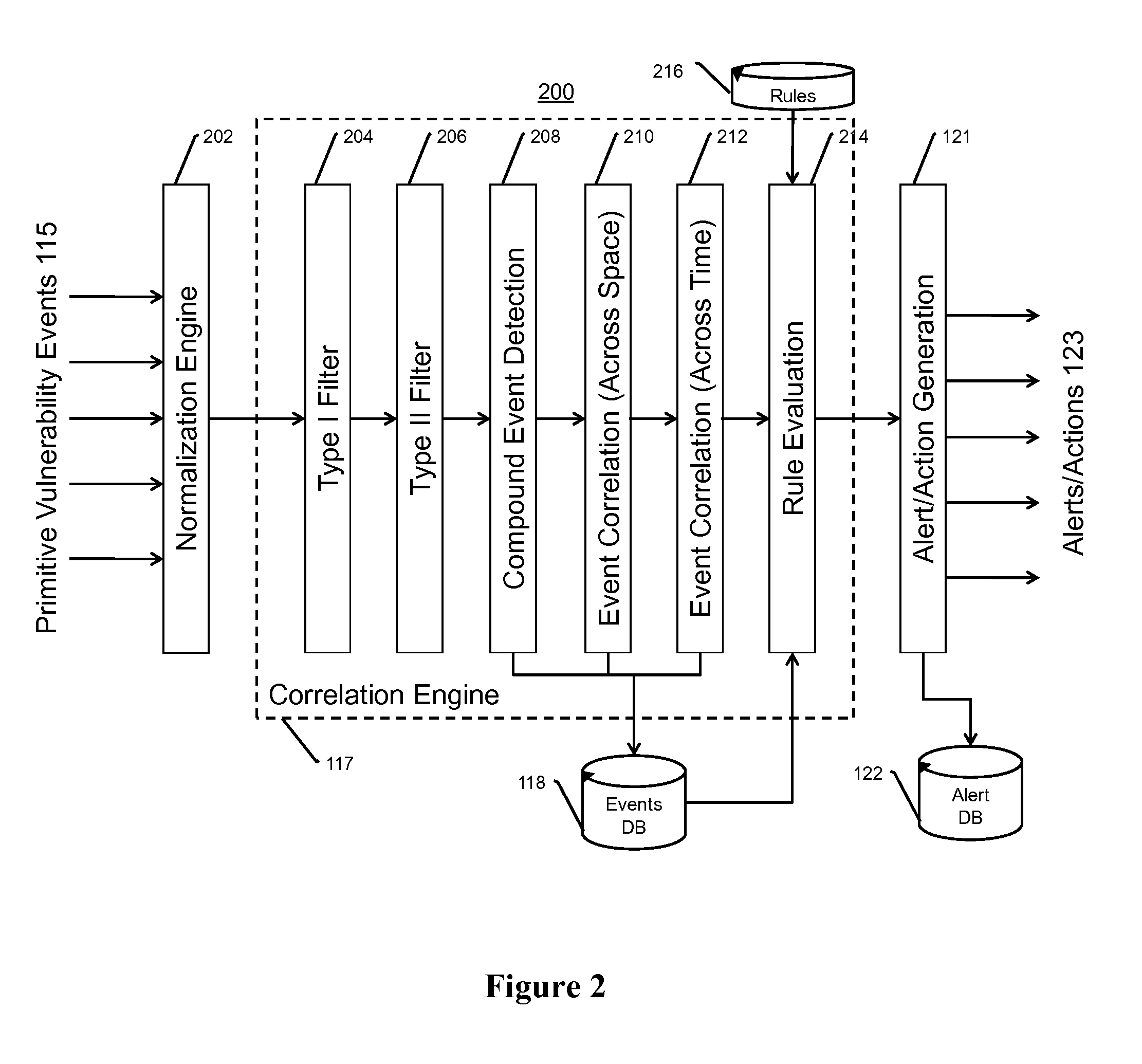
This invention is a system, method, and apparatus for detecting compromise of IP devices that make up an IP-based network. One embodiment is a method for detecting and alerting on the following conditions: (1) Denial of Service Attack; (2) Unauthorized Usage Attack; and (3) Spoofing Attack. A survey of services running on the IP device, historical benchmark data, and traceroute information may be used to detect a possible Denial of Service Attack. A detailed log analysis and a passive DNS compromise system may be used to detect a possible unauthorized usage. Finally, a fingerprint of the IP device or its configuration settings, a watermark inserted in the data-stream, and a private key burned into the IP devices' physical memory may be used to detect a possible spoofing attack. The present invention may be used to help mitigate intrusions and vulnerabilities in IP networks.
Owner:HUSSAIN DANIAR +1
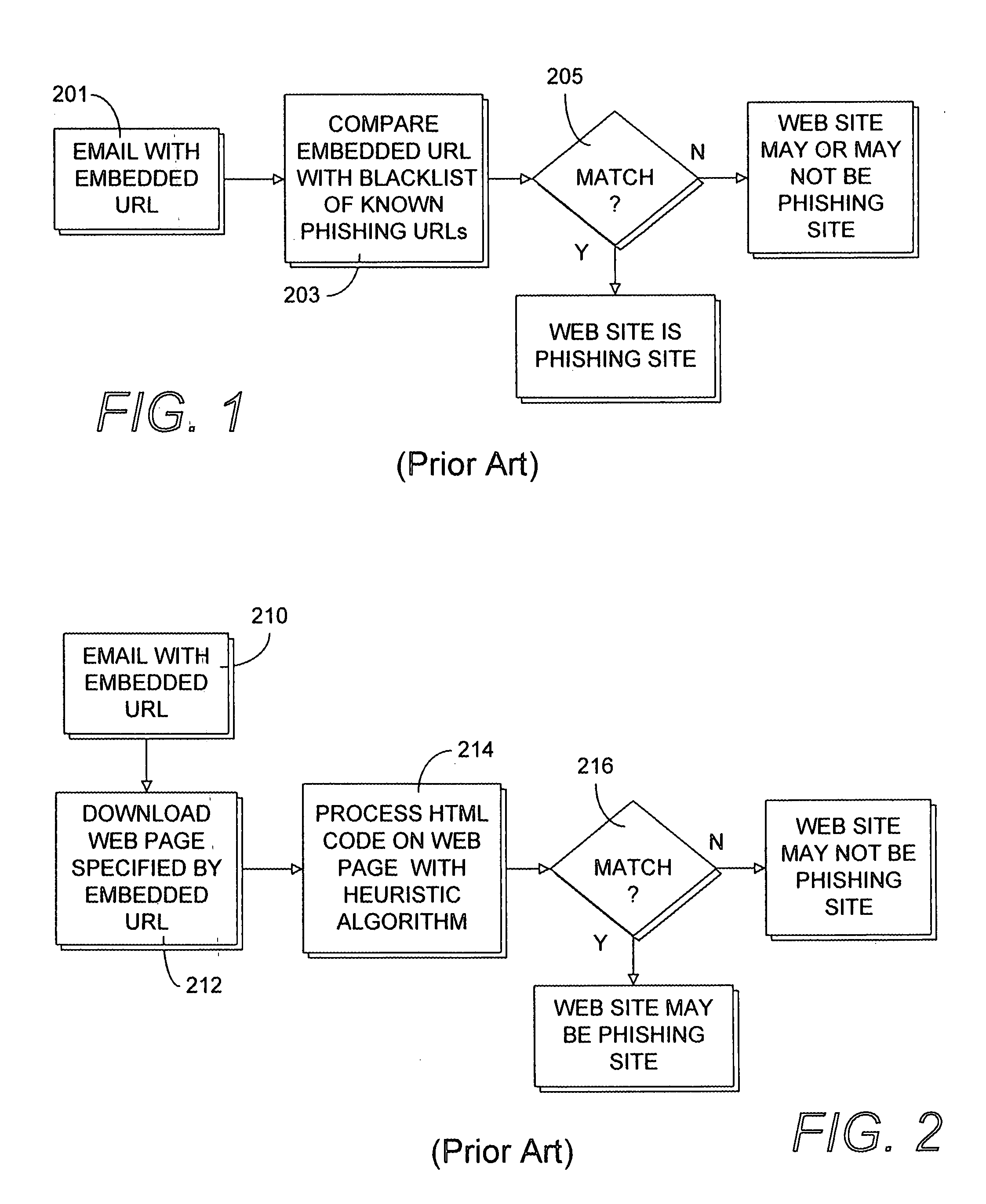
Protecting computer users from online frauds
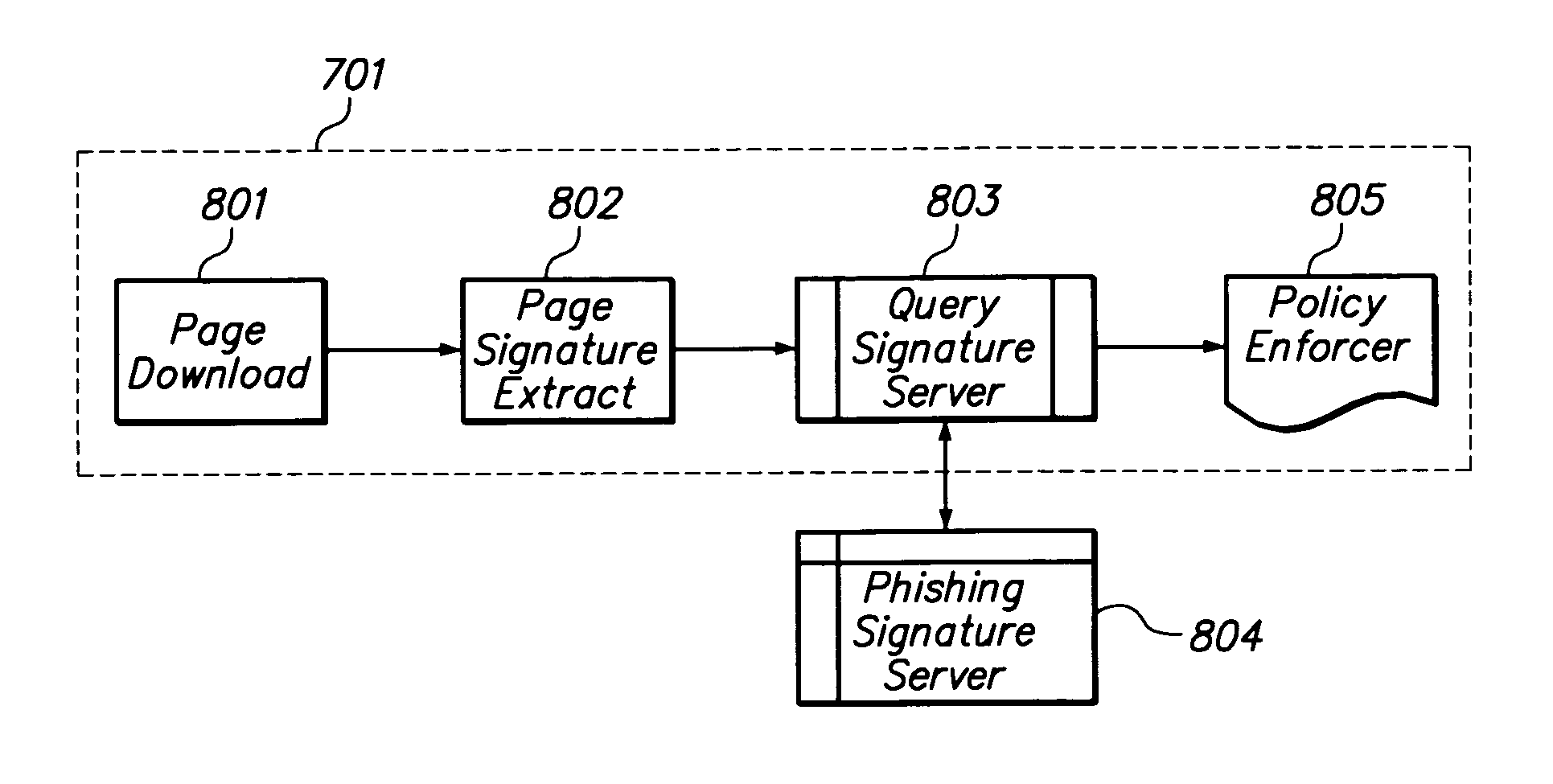
Protecting computer users from online frauds, such as phishing and pharming. A client computer may include a page signature extractor and a policy enforcer. The page signature extractor may encode a web page to generate its signature, which may be provided to a remote server computer for comparison with signatures of phishing pages. The client computer and the server computer may communicate using the DNS protocol. The policy enforcer may perform one or more predetermined actions when a match is found. Examples of such actions include replacing the web page with a blocking page, displaying a warning message, or both. The policy enforcer may be configured to determine if the web page is part of a phishing or pharming attack by comparing the URL of the web page to URLs of legitimate web pages.
Owner:TREND MICRO INC
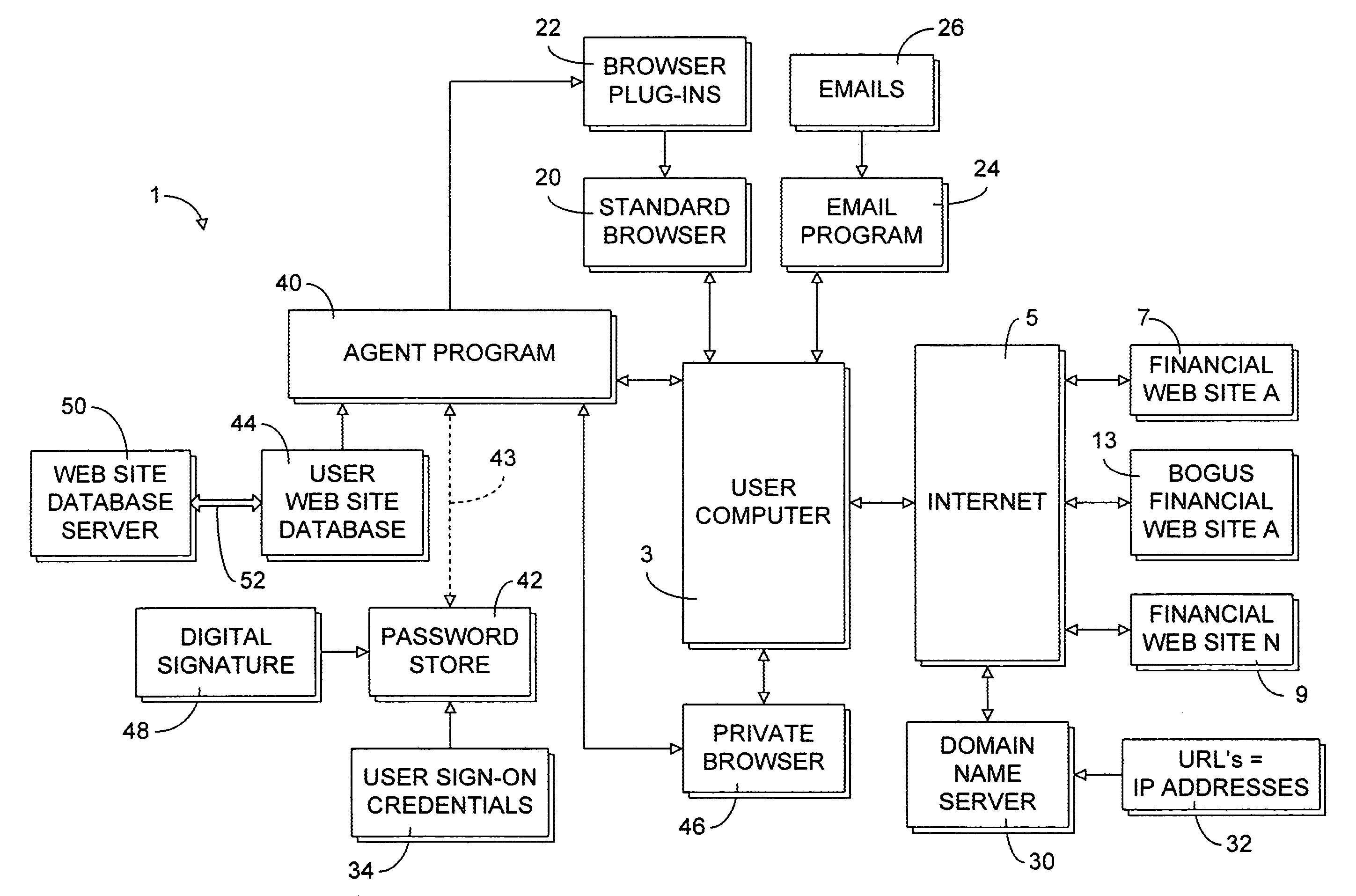
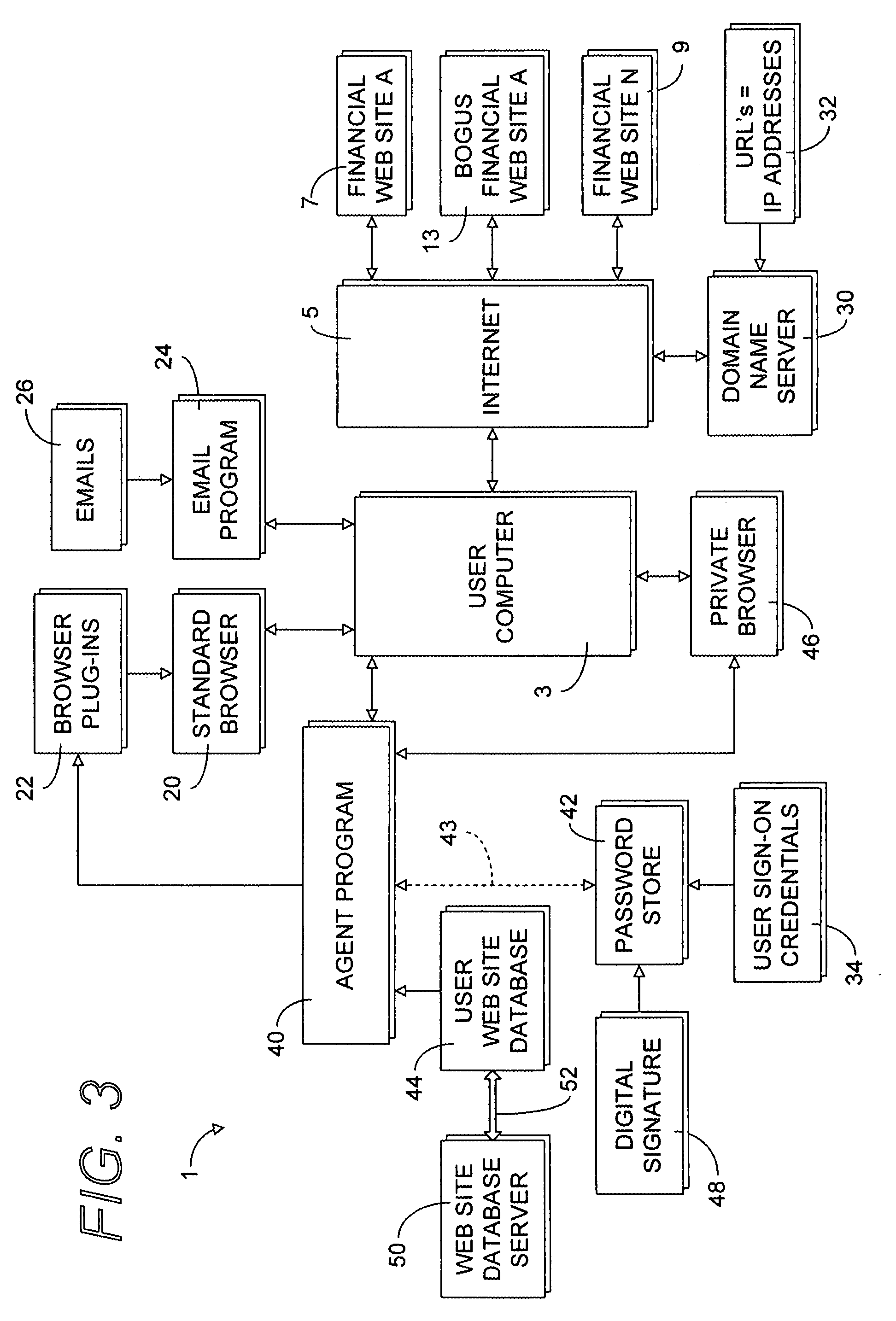
Secure web site authentication using web site characteristics, secure user credentials and private browser
ActiveUS20080028444A1Overcome deficienciesImprove approachDigital data information retrievalMemory loss protectionWeb siteIp address
A secure authentication process detects and prevents phishing and pharming attacks for specific web sites. The process is based on a dedicated secure hardware store for user sign-in credentials, a database of information about specific web sites, and a private secure browser. All user web activity is monitored by an agent program. The agent program checks to make sure that user attempts to send any sign-in credentials stored in secure hardware store of user sign-in credentials, to any web site accessed by the user, is allowed only if the IP address of the web site accessed by the user matches at least one of the IP addresses stored web site database associated with the sign-in credential the user is attempting to send. The process also detects mismatches between a URL and the actual IP address of the web site associated with the URL.
Owner:AURA SUB LLC +1
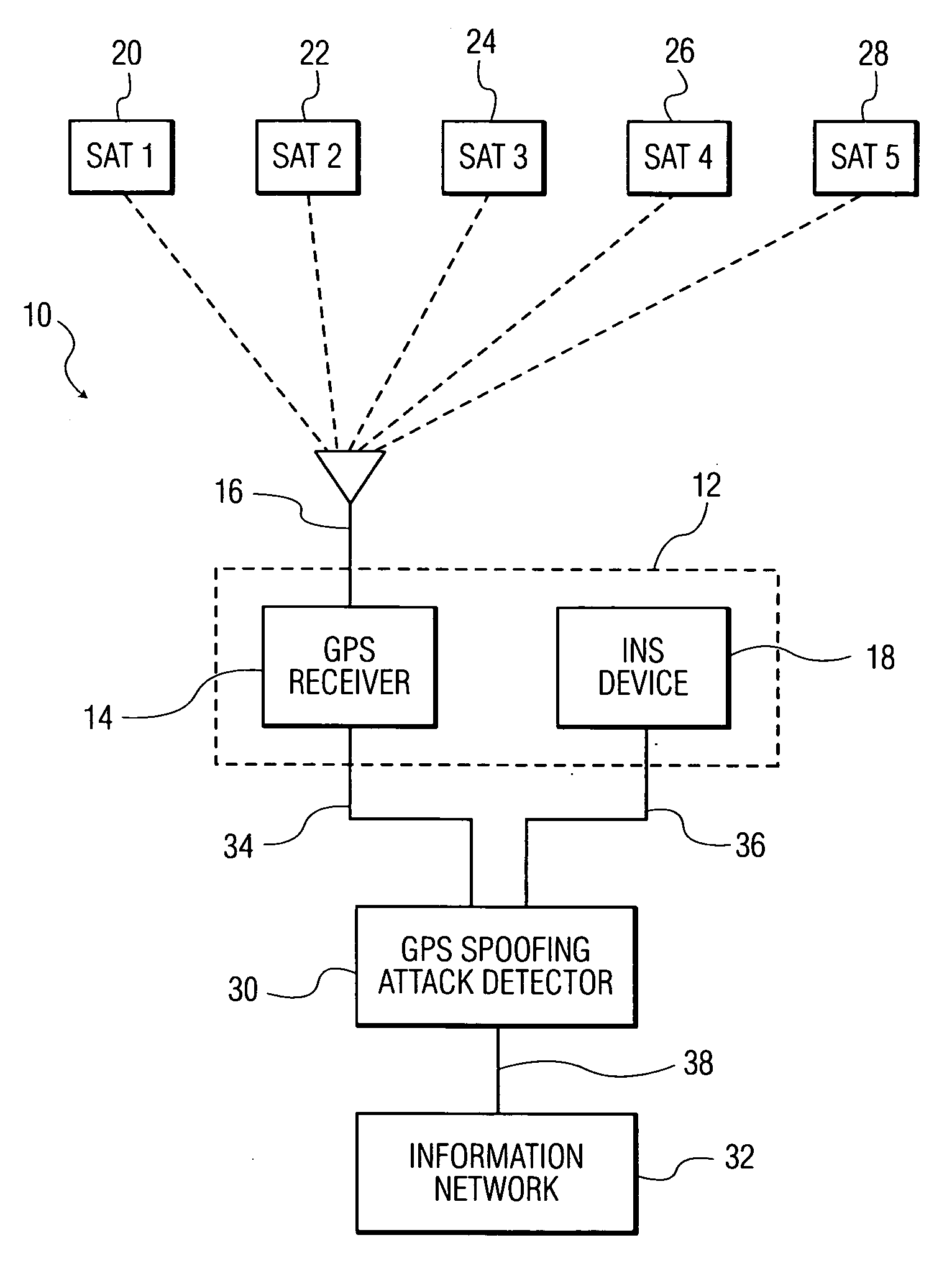
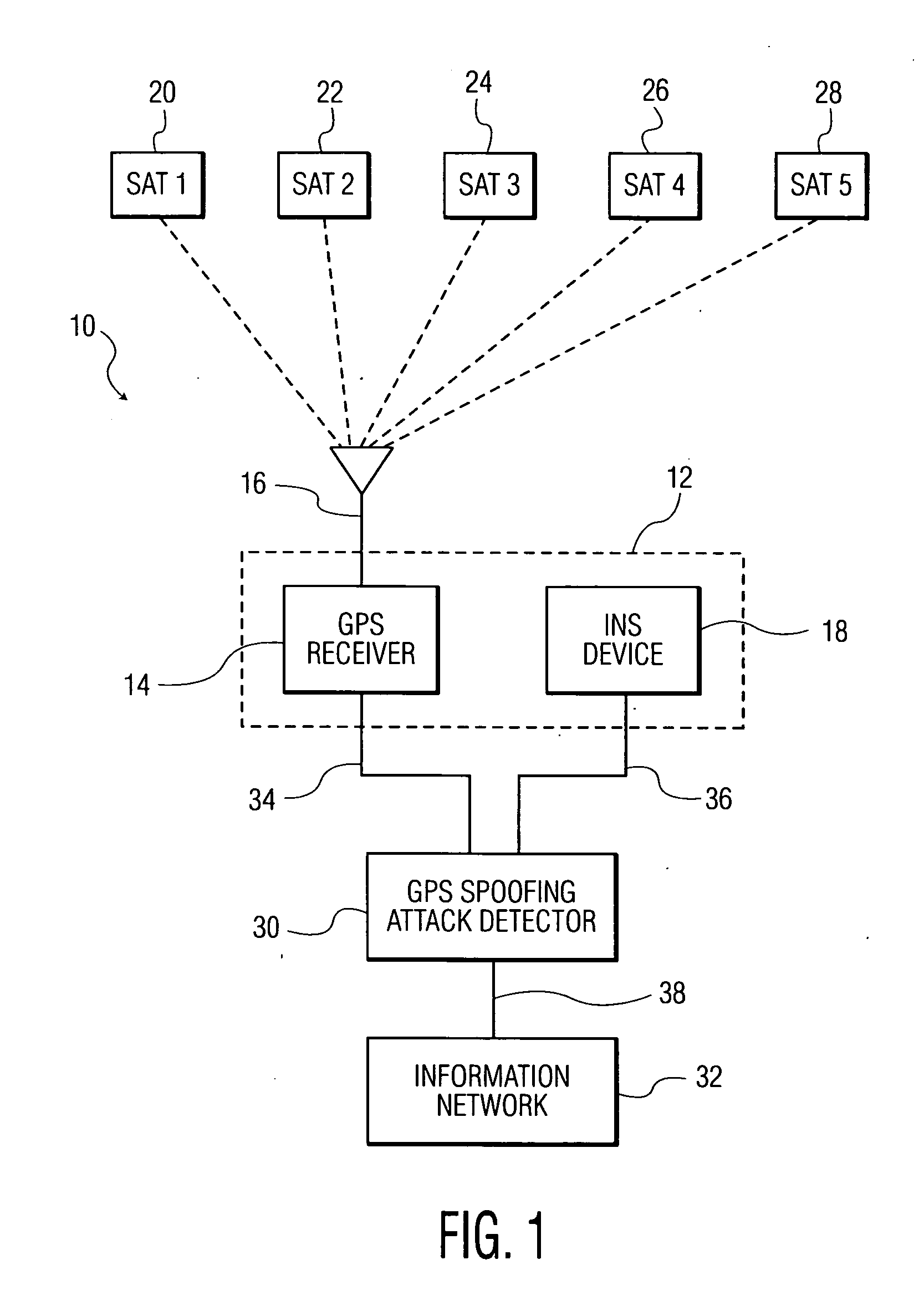
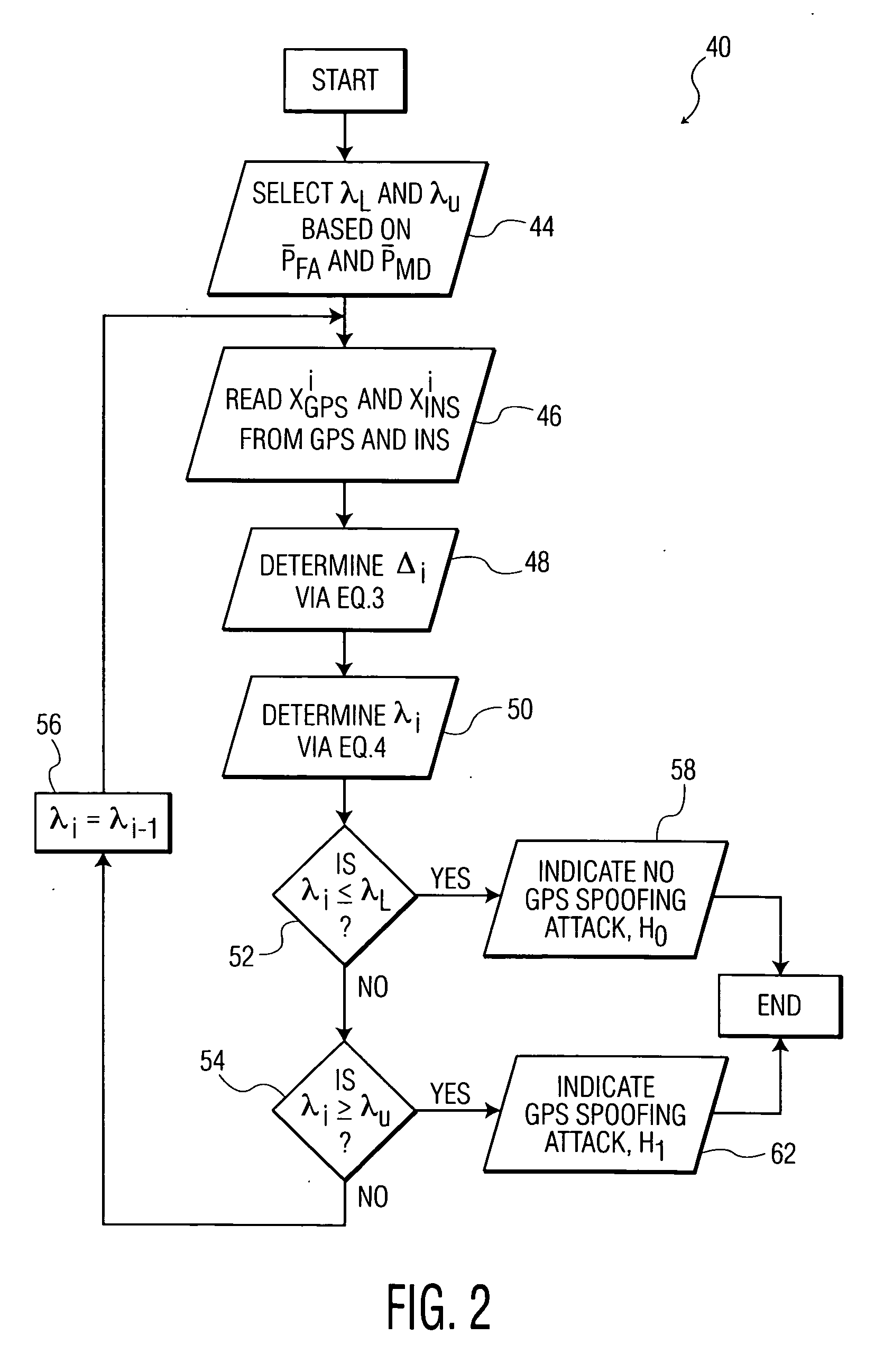
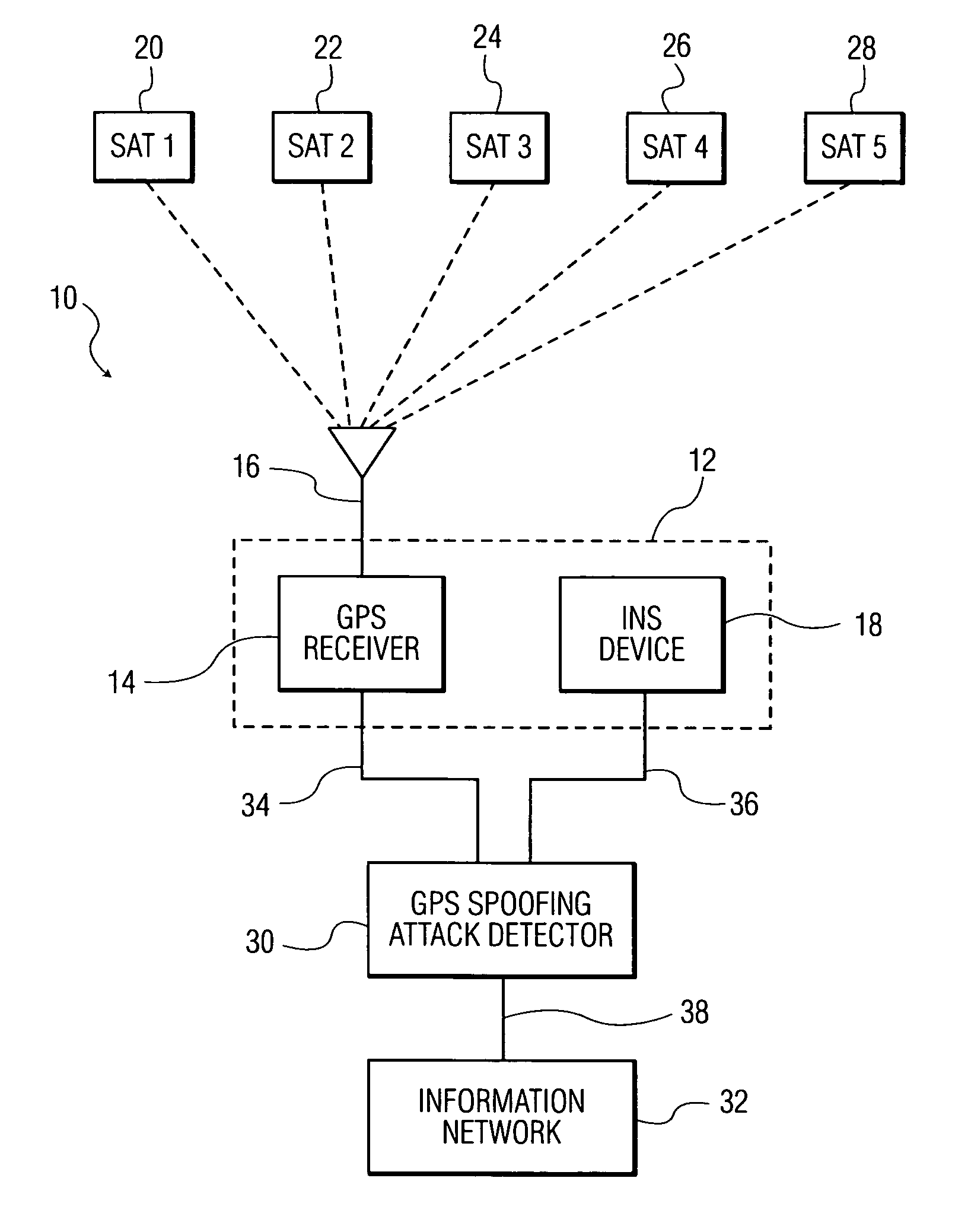
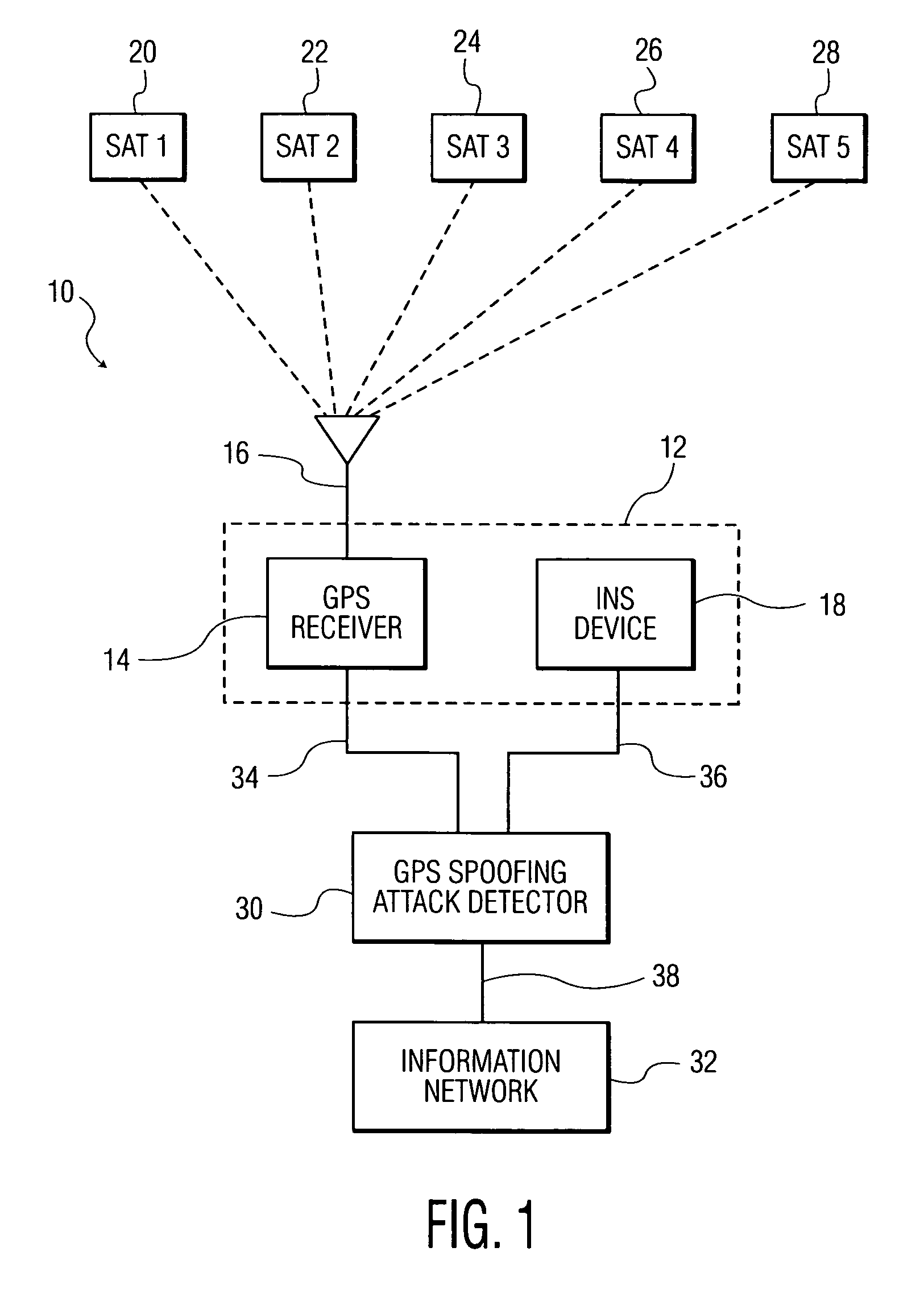
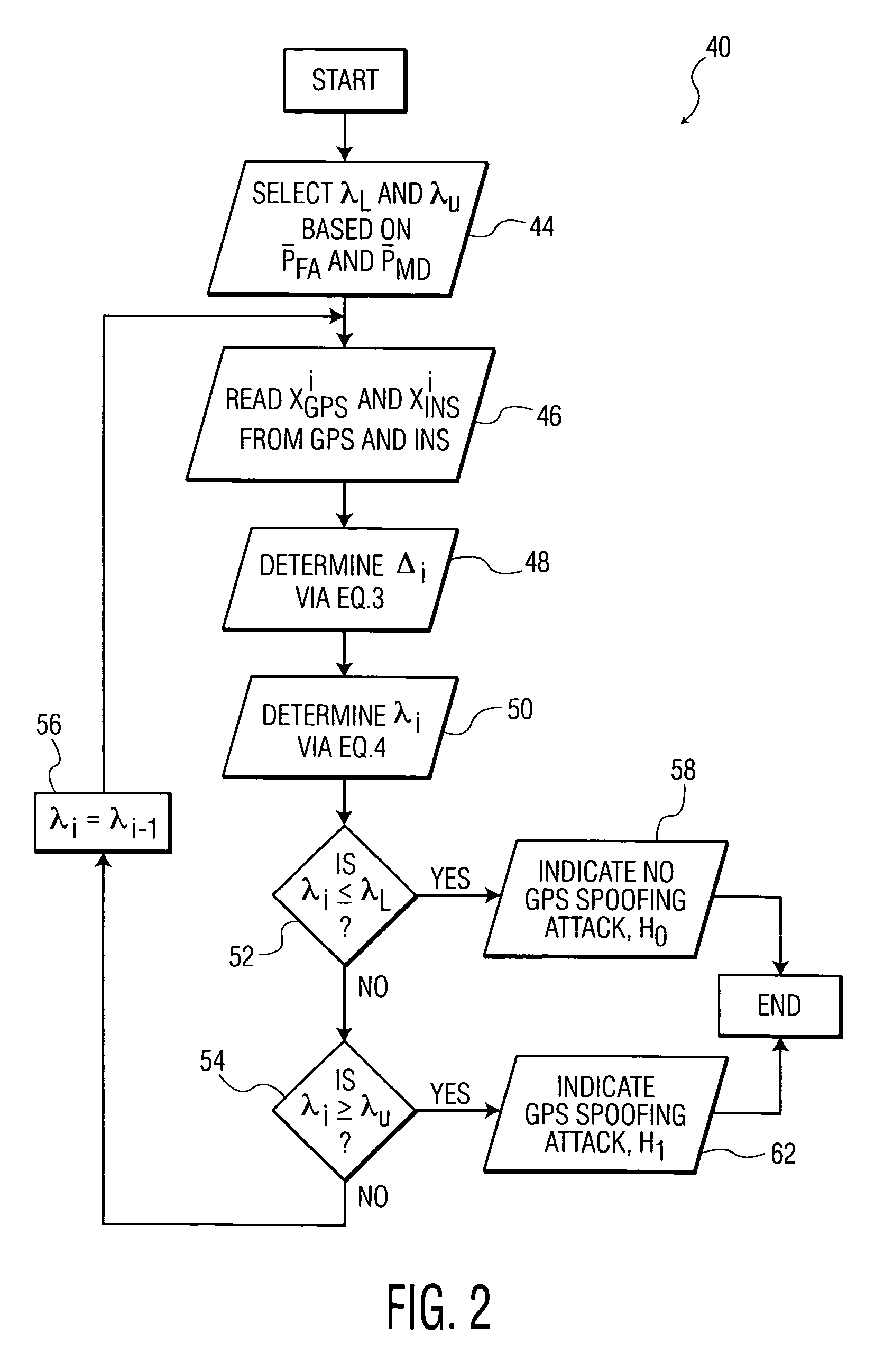
Methods and systems for detecting GPS spoofing attacks
ActiveUS20130002477A1Improve accuracyImprove efficiencySatellite radio beaconingGround truthNavigational system
A system and method for detecting global positioning system (GPS) spoofing attacks includes collecting GPS readings along with inertial navigational system (INS) readings as a ground truth, and sequentially testing the GPS readings and INS readings through the use of a sequential probability ratio testing (SPRT) process.
Owner:BAE SYST INFORMATION & ELECTRONICS SYST INTERGRATION INC
Method and apparatus for analyzing one or more firewalls
InactiveUS7016980B1Multiple digital computer combinationsProgram controlGraphicsGraphical user interface
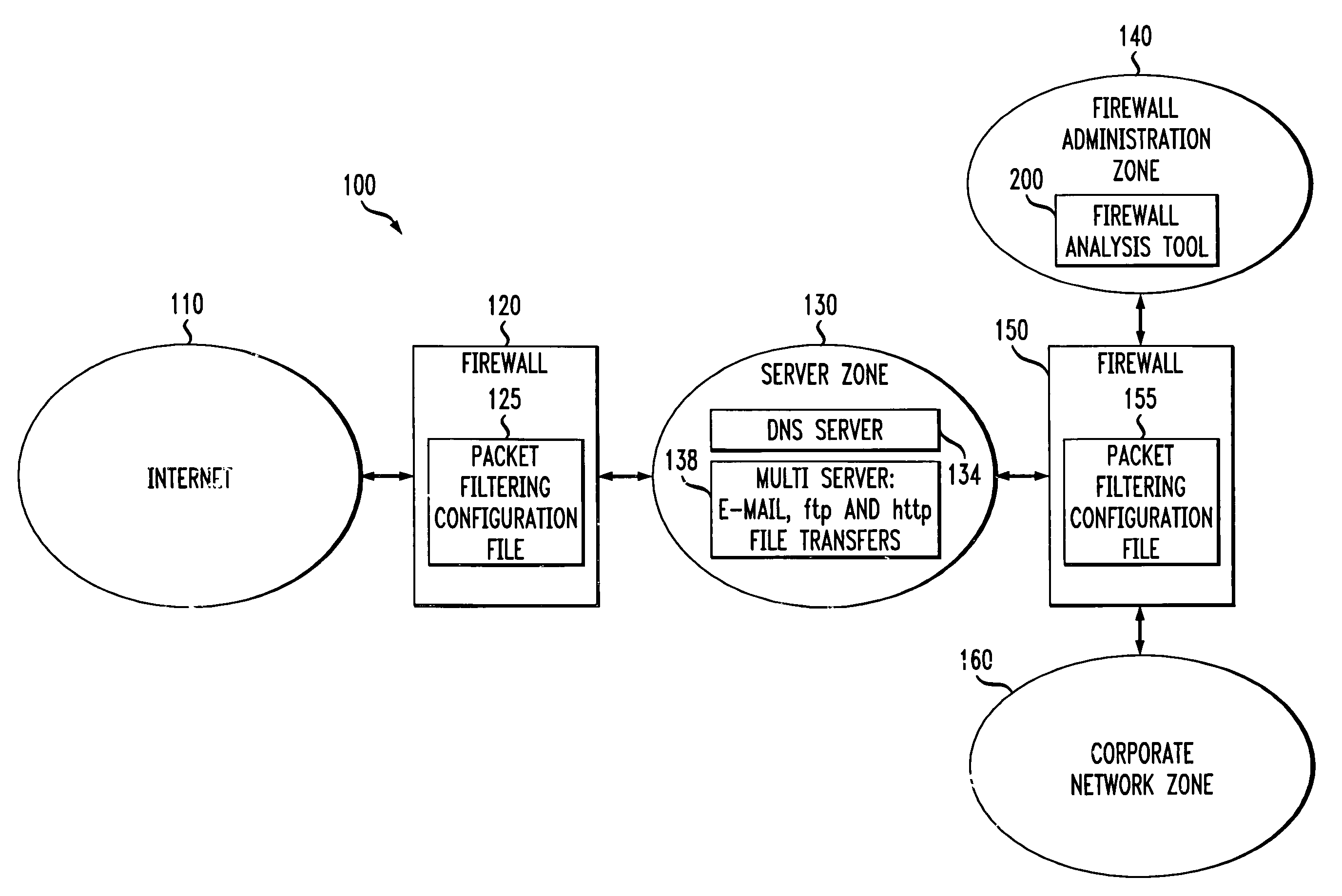
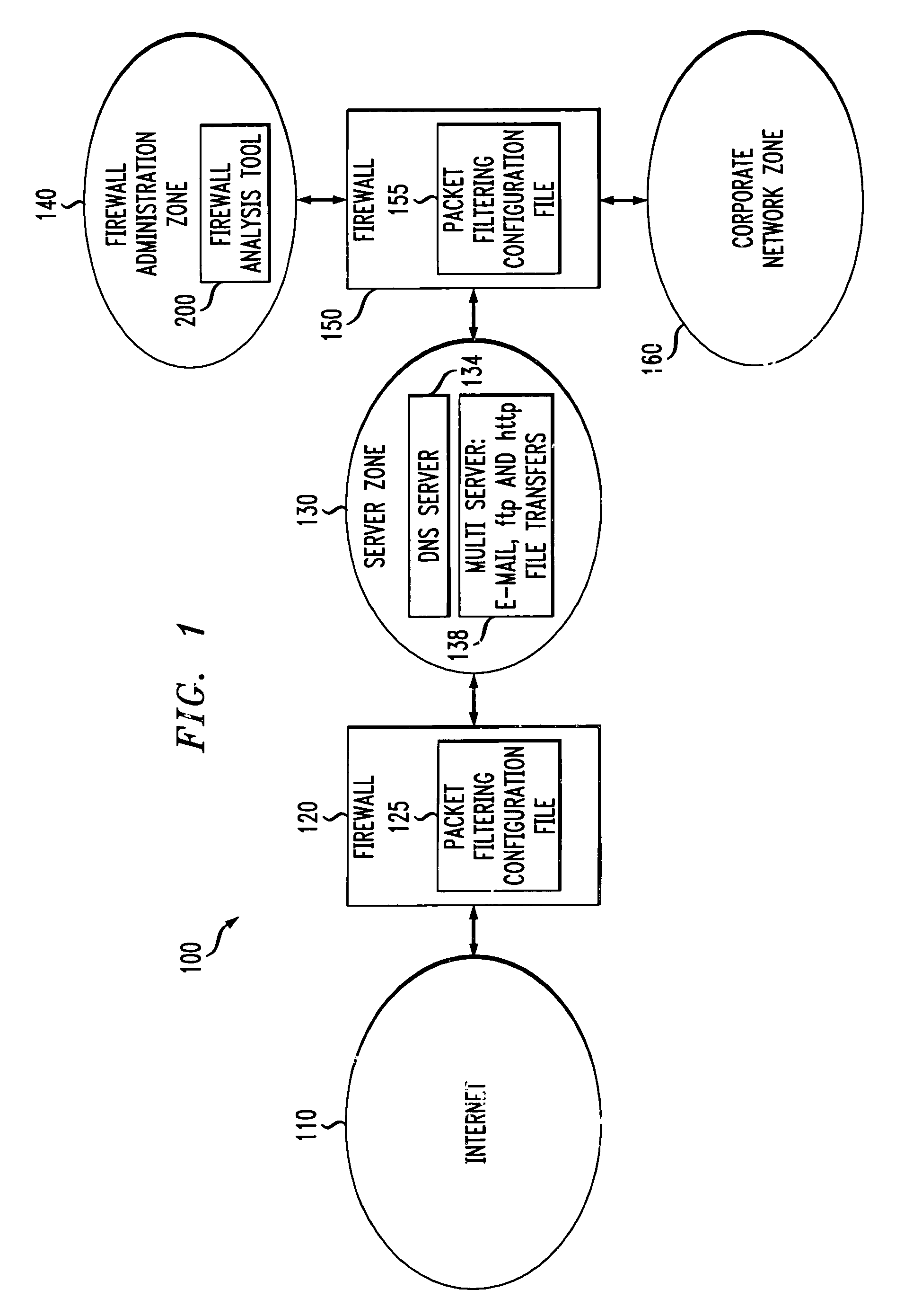
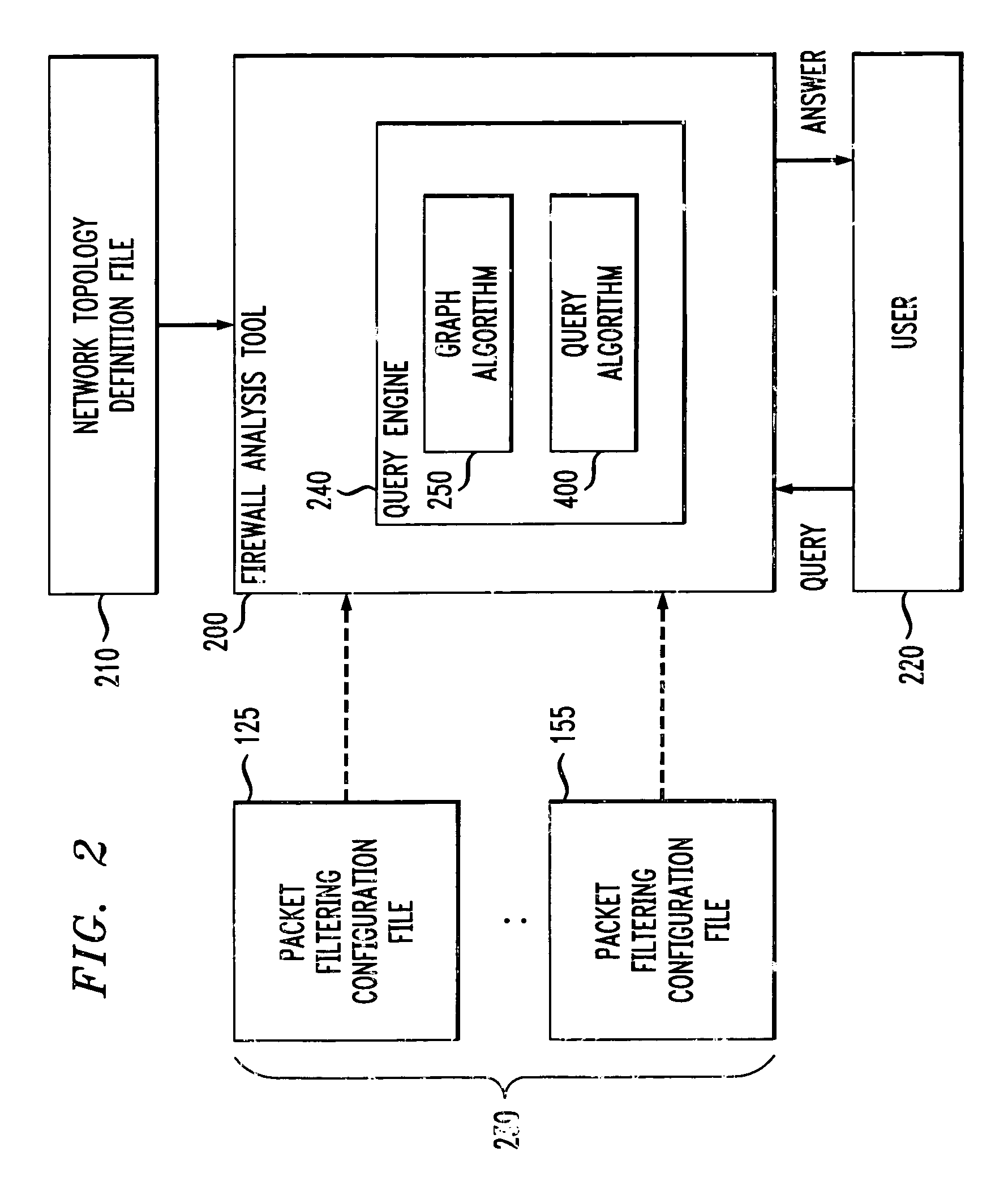
A method and apparatus are disclosed for analyzing the operation of one or more network gateways, such as firewalls or routers, that perform a packet filtering function in a network environment. Given a user query, the disclosed firewall analysis tool simulates the behavior of the various firewalls, taking into account the topology of the network environment, and determines which portions of the services or machines specified in the original query would manage to reach from the source to the destination. The relevant packet-filtering configuration files are collected and an internal representation of the implied security policy is derived. A graph data structure is used to represent the network topology. A gateway-zone graph permits the firewall analysis tool to determine where given packets will travel in the network, and which gateways will be encountered along those paths. In this manner, the firewall analysis tool can evaluate a query object against each rule-base object, for each gateway node in the gateway-zone graph that is encountered along each path between the source and destination. A graphical user interface is provided for receiving queries, such as whether one or more given services are permitted between one or more given machines, and providing results. A spoofing attack can be simulated by allowing the user to specify where packets are to be injected into the network, which may not be the true location of the source host-group.
Owner:ALCATEL-LUCENT USA INC
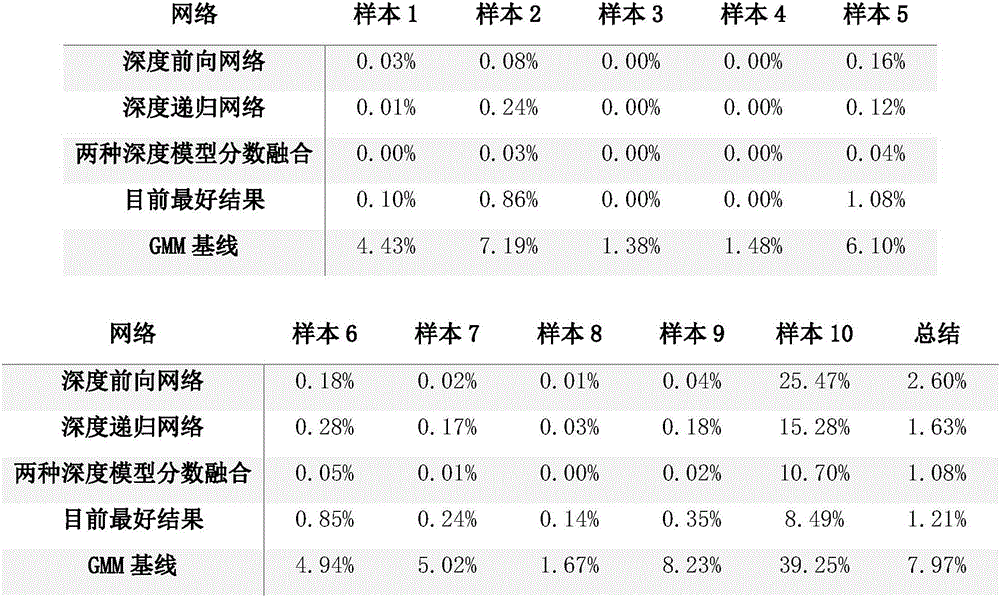
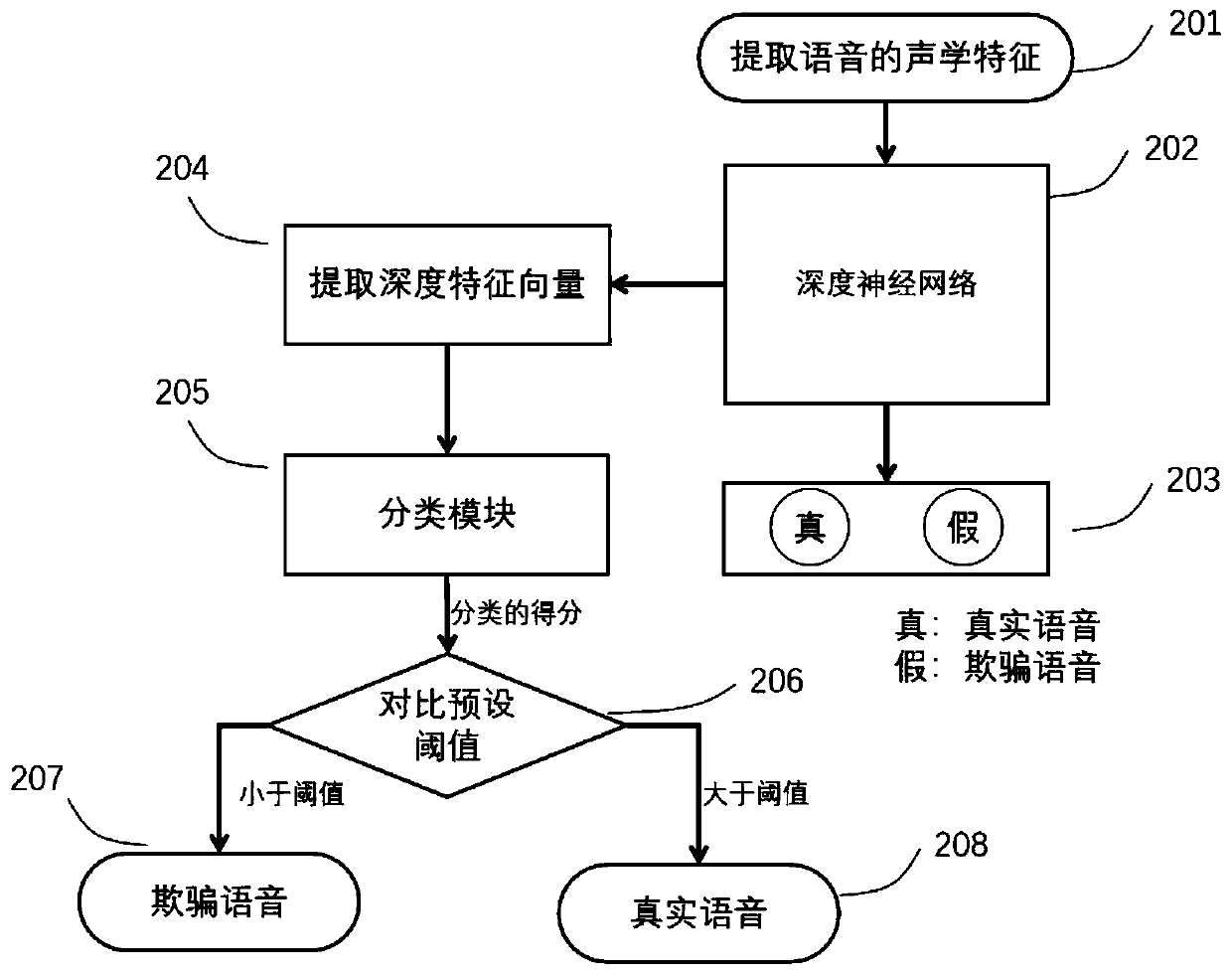
Method and system for detecting voice spoofing attack of speakers on basis of deep learning
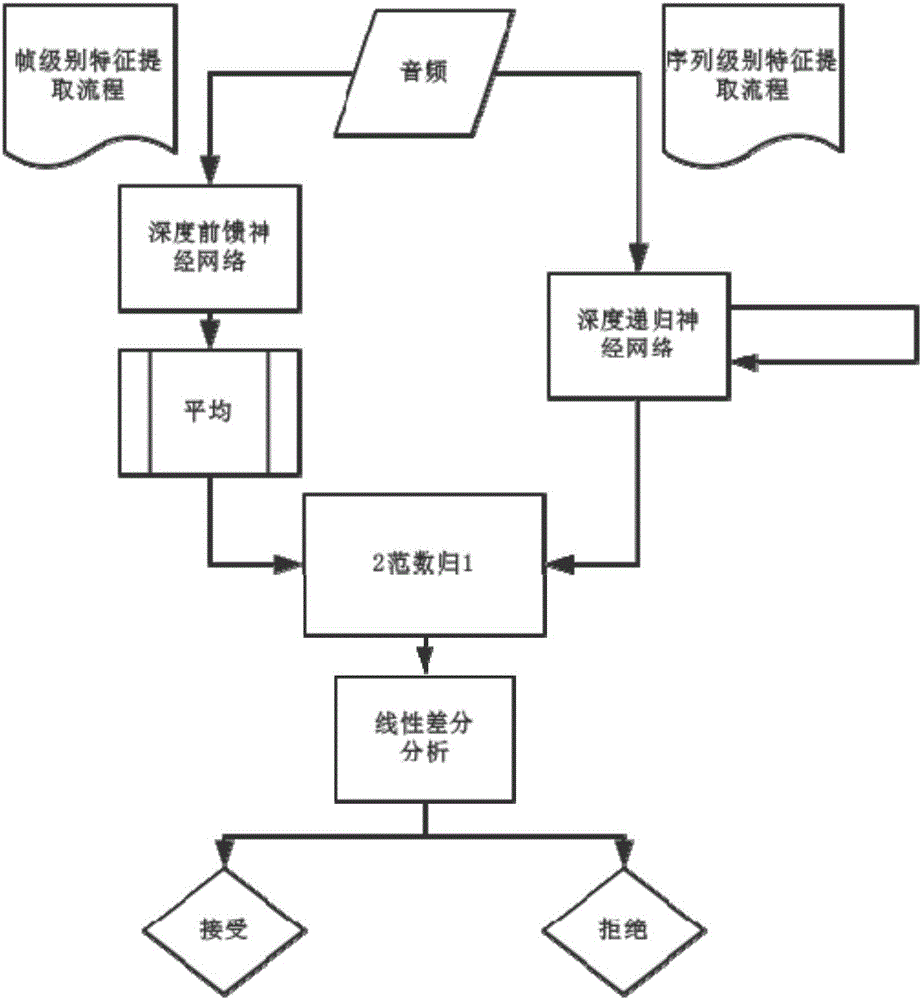
The invention discloses a method and a system for detecting voice spoofing attack of speakers on the basis of deep learning. The method includes constructing audio-frequency training sets, initializing deep feed-forward neural networks and deep recurrent neural networks and respectively training the deep feed-forward neural networks and the deep recurrent neural networks by the aid of multi-frame feature vectors and single-frame vector sequences of the training sets; respectively leading frame level and sequence level feature vectors of to-be-tested audio frequencies into two trained linear differential analysis models in test phases, weighting two obtained result grades to obtain scores and comparing the scores to predefined threshold values so as to discriminate voice spoofing. The method and the system have the advantages that local features can be captured, and global information can be grasped; the linear differential analysis models are used as classifiers in identification and verification phases, the voice spoofing attack can be judged by means of grade fusion, and accordingly the voice spoofing detection accuracy can be greatly improved.
Owner:AISPEECH CO LTD
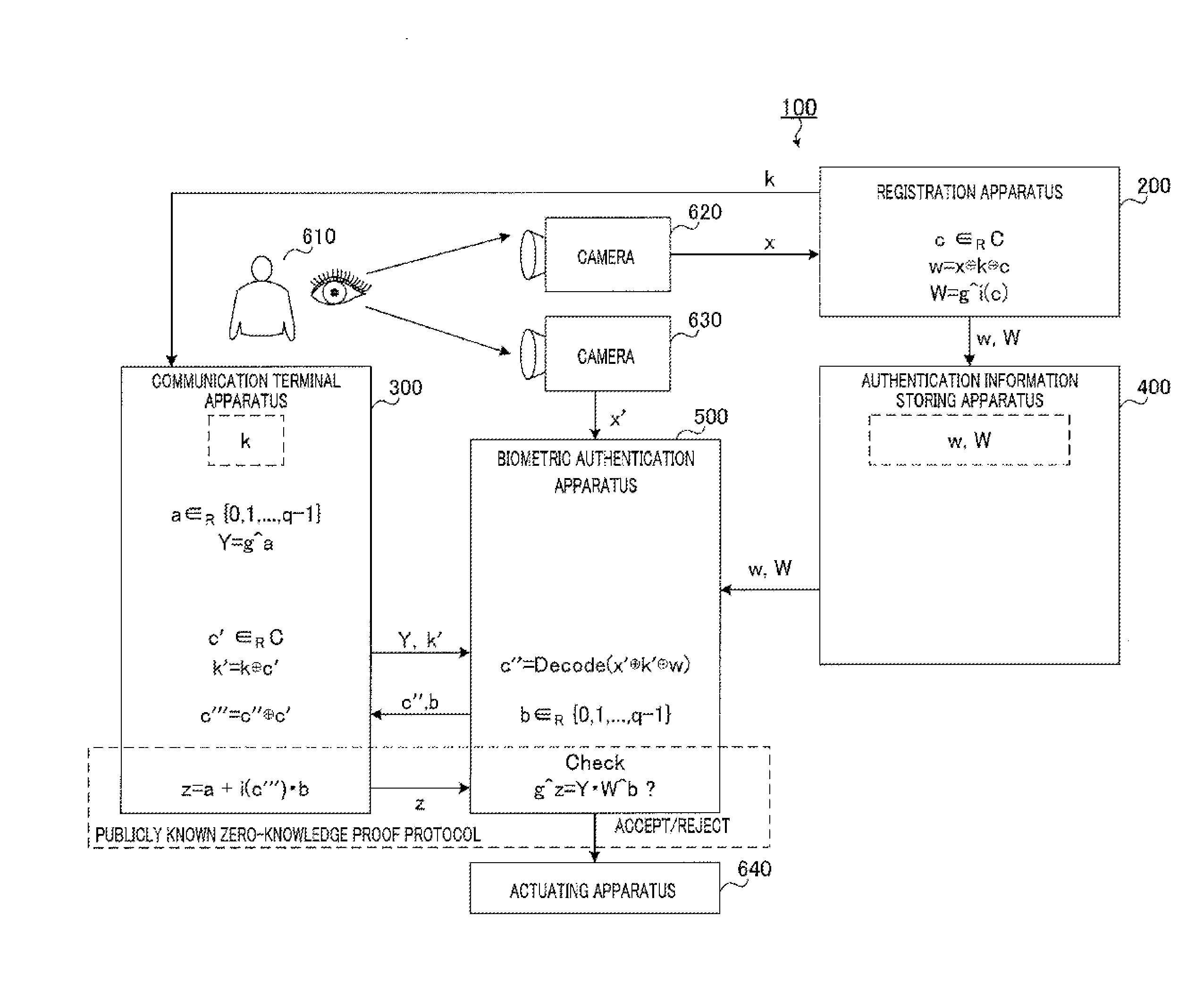
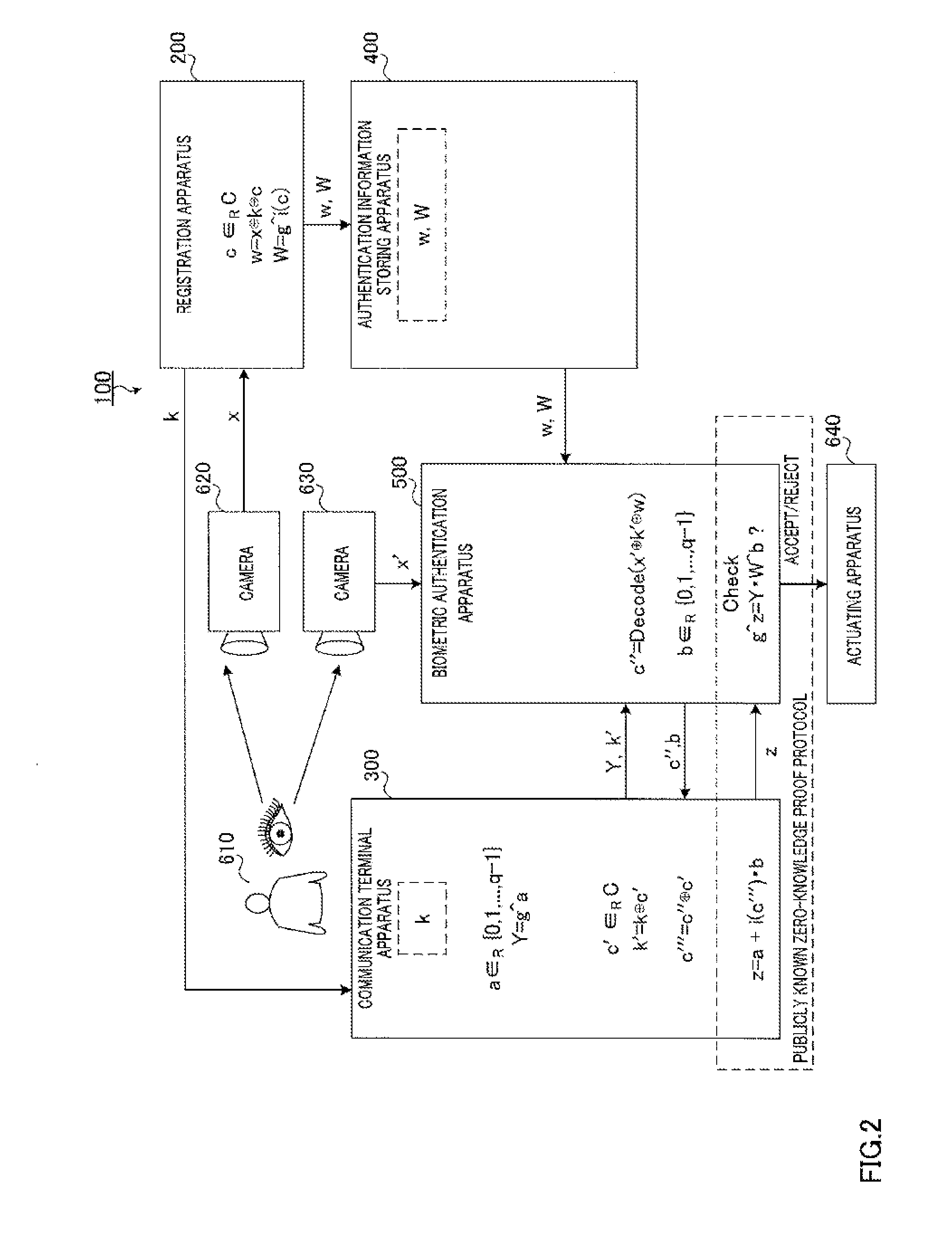
Biometric authentication system, communication terminal device, biometric authentication device, and biometric authentication method
ActiveUS20130174243A1Avoid attackDigital data processing detailsMultiple digital computer combinationsExclusive orTerminal equipment
Provided is a biometric authentication system capable of preventing spoofing attacks even if leakage of key information and a registration conversion template occurs. A communication terminal device (300) calculates secret key information k′ which is exclusive OR of key information k of the registration biological information and masked value c′ which is randomly selected from a predetermined error correction code group, and calculates verified information c′″ which is exclusive OR of sent information c″ and value c′. A biometric authentication device (500) calculates exclusive OR of authentication biological information, information k′, and registration conversion template w, as information c″, wherein the template w is exclusive OR of information x, information k, and authentication parameter c randomly selected from the code group; and performs biometric authentication on the basis of a degree of matching between information c′″ corresponding to information c″, and the parameter c.
Owner:PANASONIC CORP
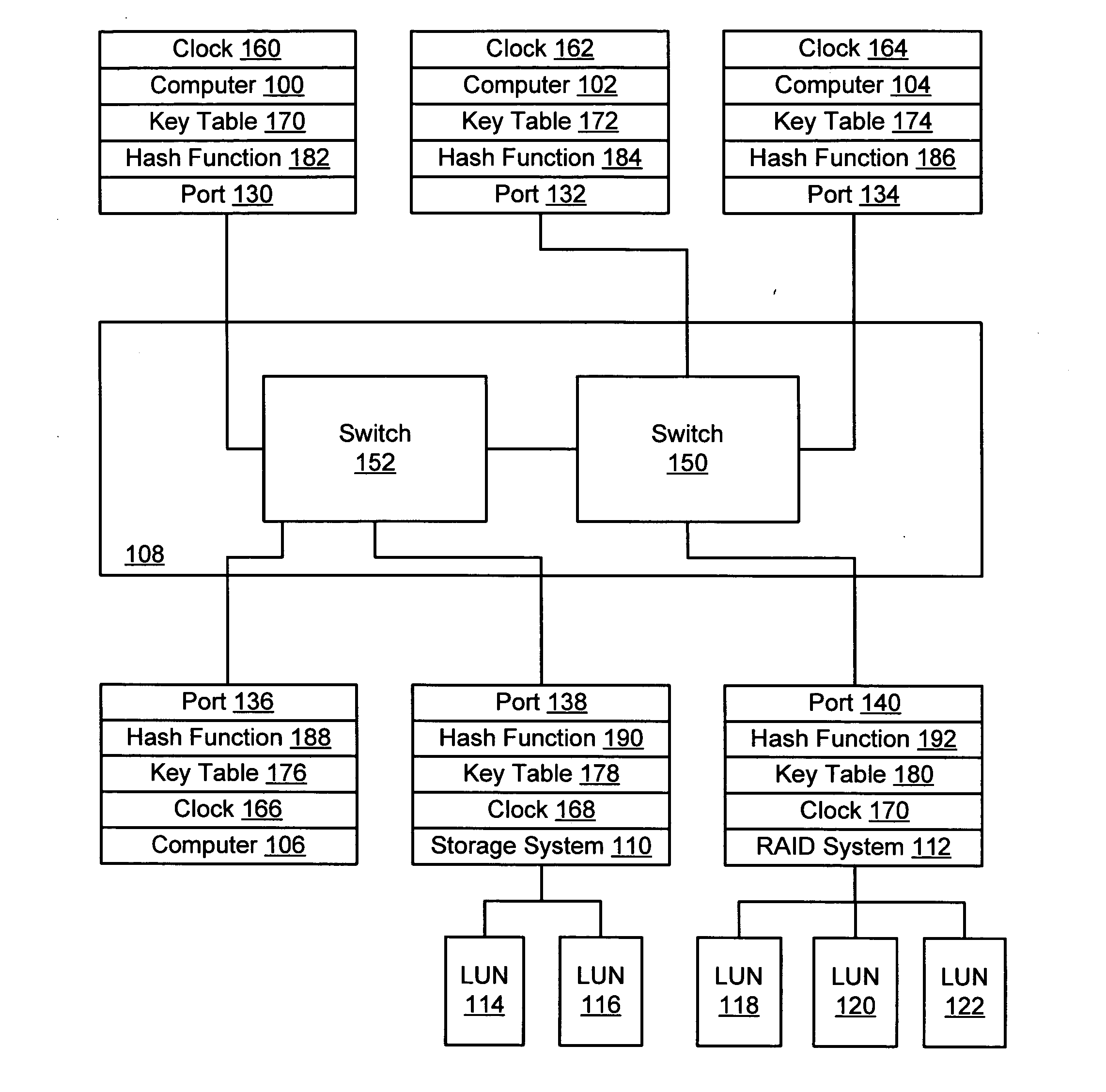
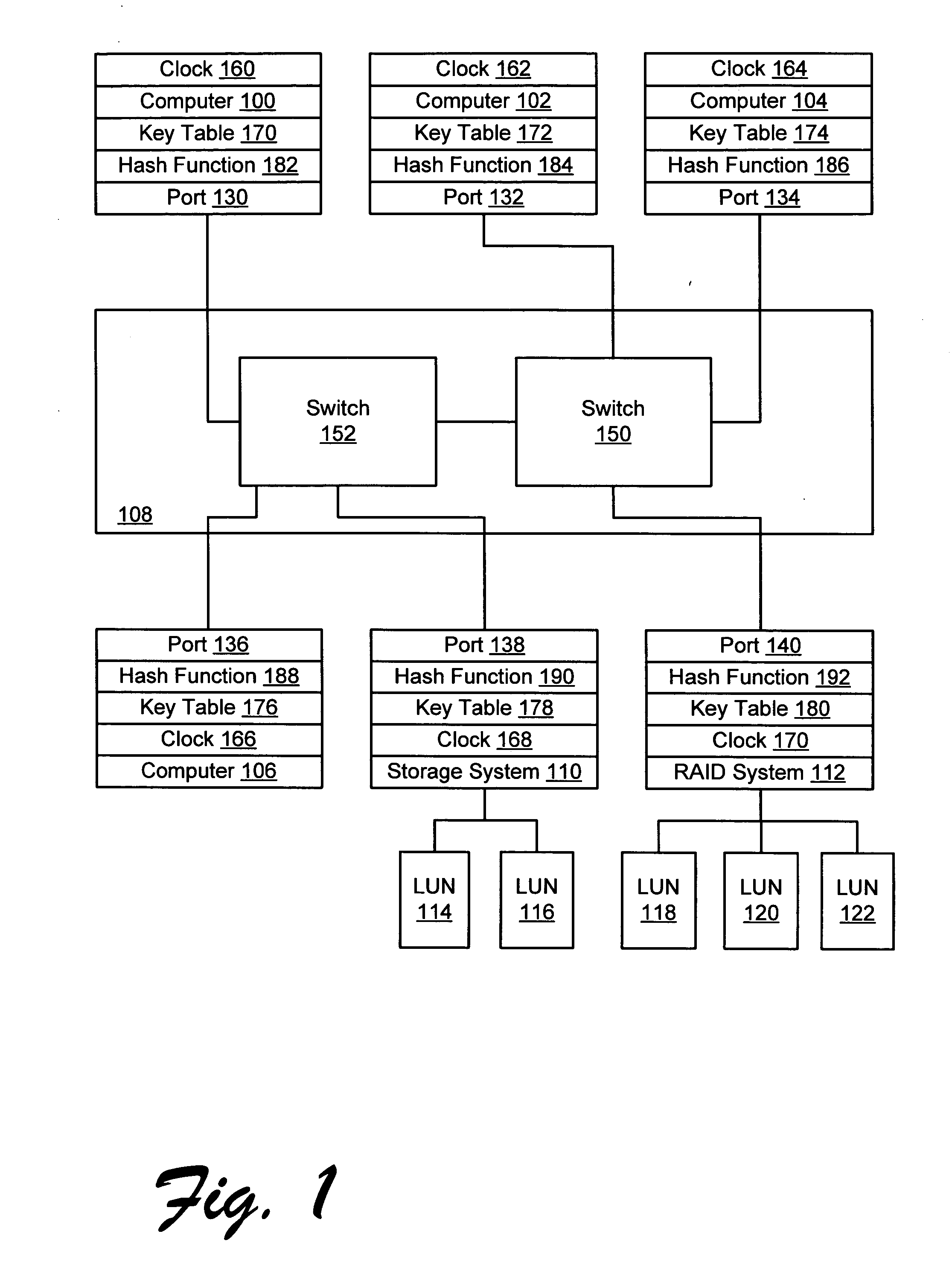
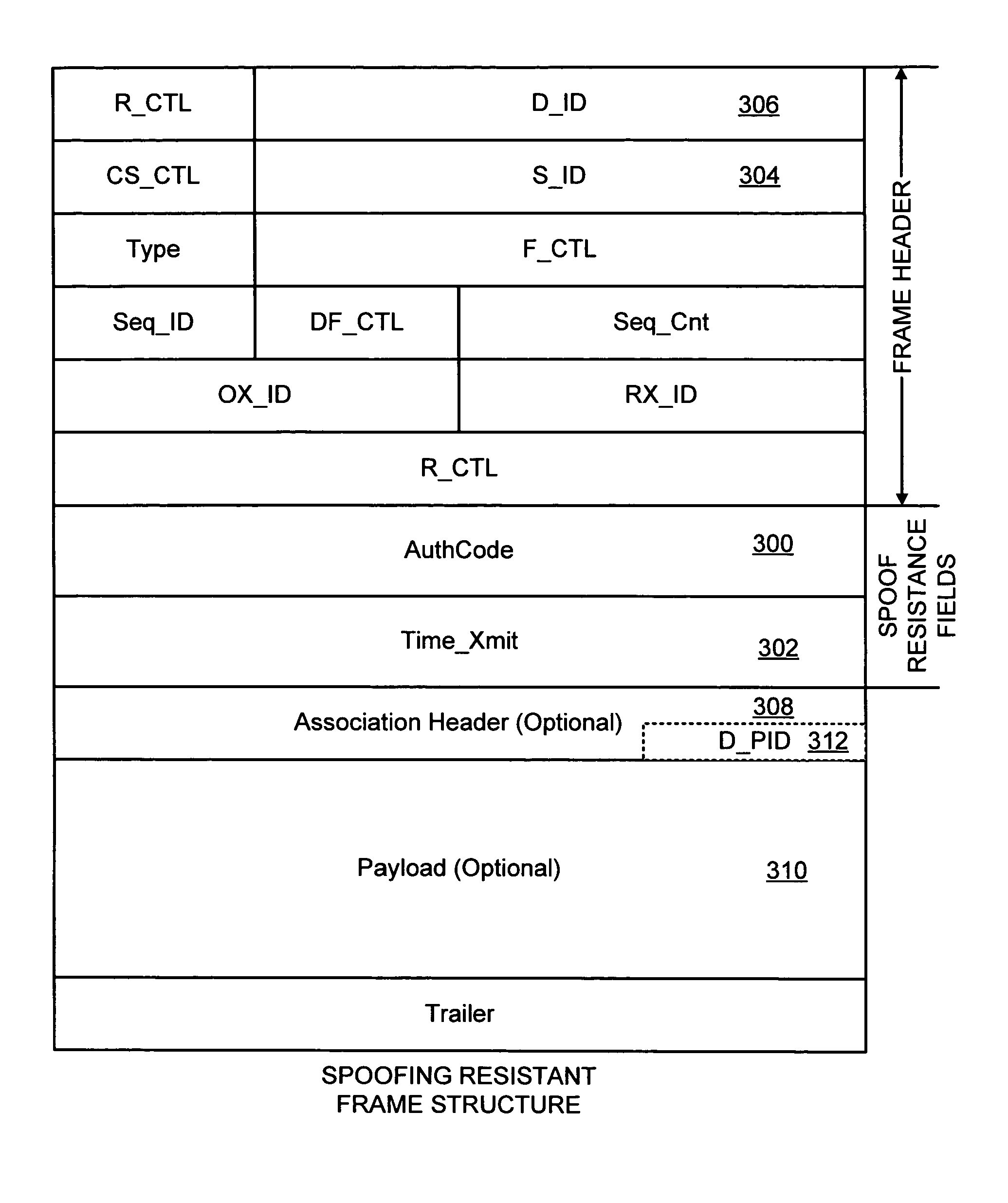
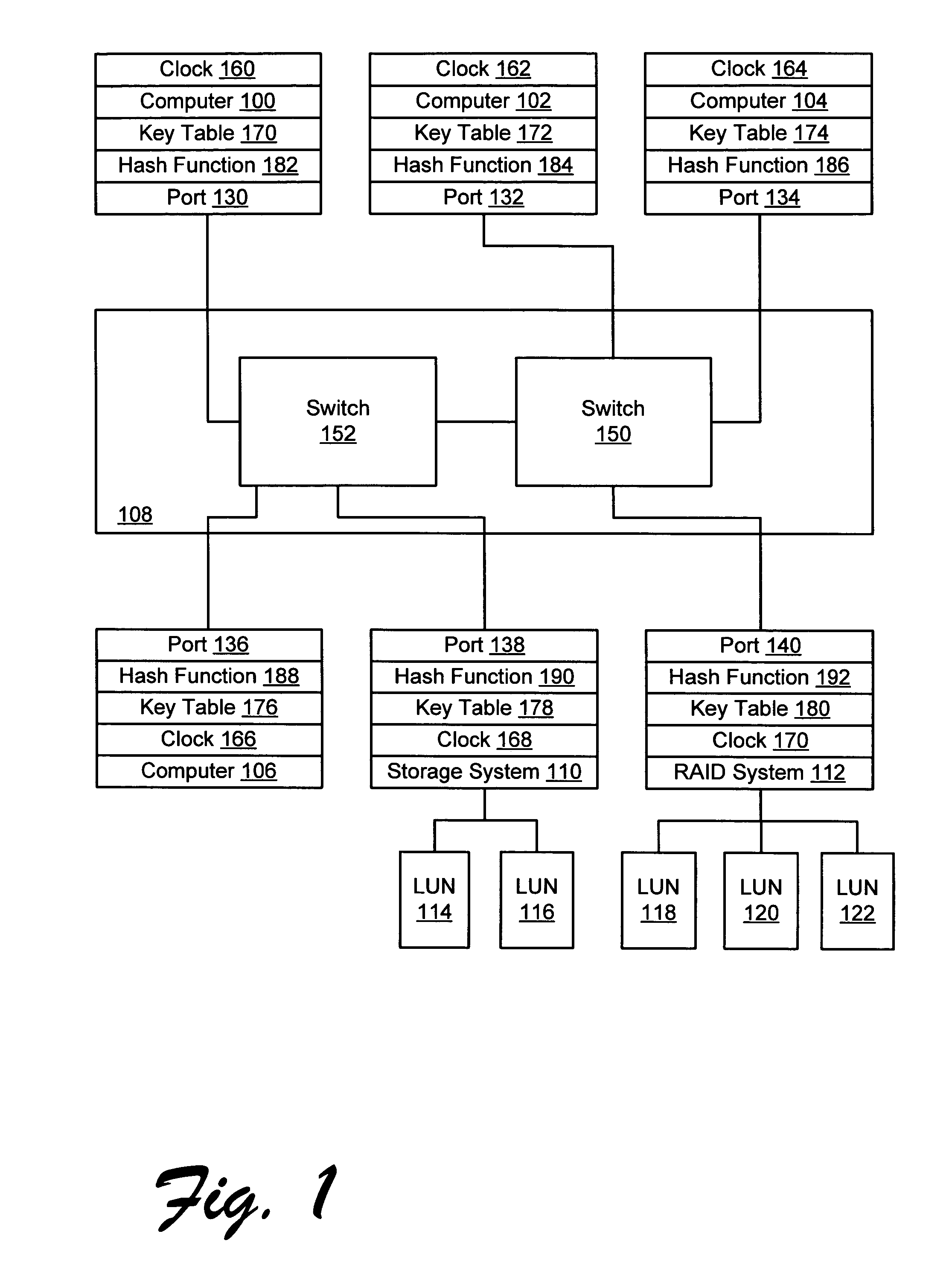
Apparatus and method for implementing spoofing-and replay-attack-resistant virtual zones on storage area networks
InactiveUS20050044354A1Digital data processing detailsUser identity/authority verificationHash functionStorage area network
A storage area network resistant to spoofing attack has several nodes each having a port, and storage area network interconnect interconnecting the ports. Each port is provided with a hash function generator for providing and verifying an authentication code for frames transmitted over the storage area network, and a key table for providing a key to the hash function generator. The authentication code is generated by applying a hash function to the key and to at least an address portion of each frame. In each node, the key is selected from that node's key table according to address information of the frame.
Owner:GOOGLE LLC
Methods and systems for detecting GPS spoofing attacks
ActiveUS8922427B2Improve efficiencyDetect identifyNavigation by speed/acceleration measurementsSatellite radio beaconingGround truthNavigation system
A system and method for detecting global positioning system (GPS) spoofing attacks includes collecting GPS readings along with inertial navigational system (INS) readings as a ground truth, and sequentially testing the GPS readings and INS readings through the use of a sequential probability ratio testing (SPRT) process.
Owner:BAE SYST INFORMATION & ELECTRONICS SYST INTEGRATION INC
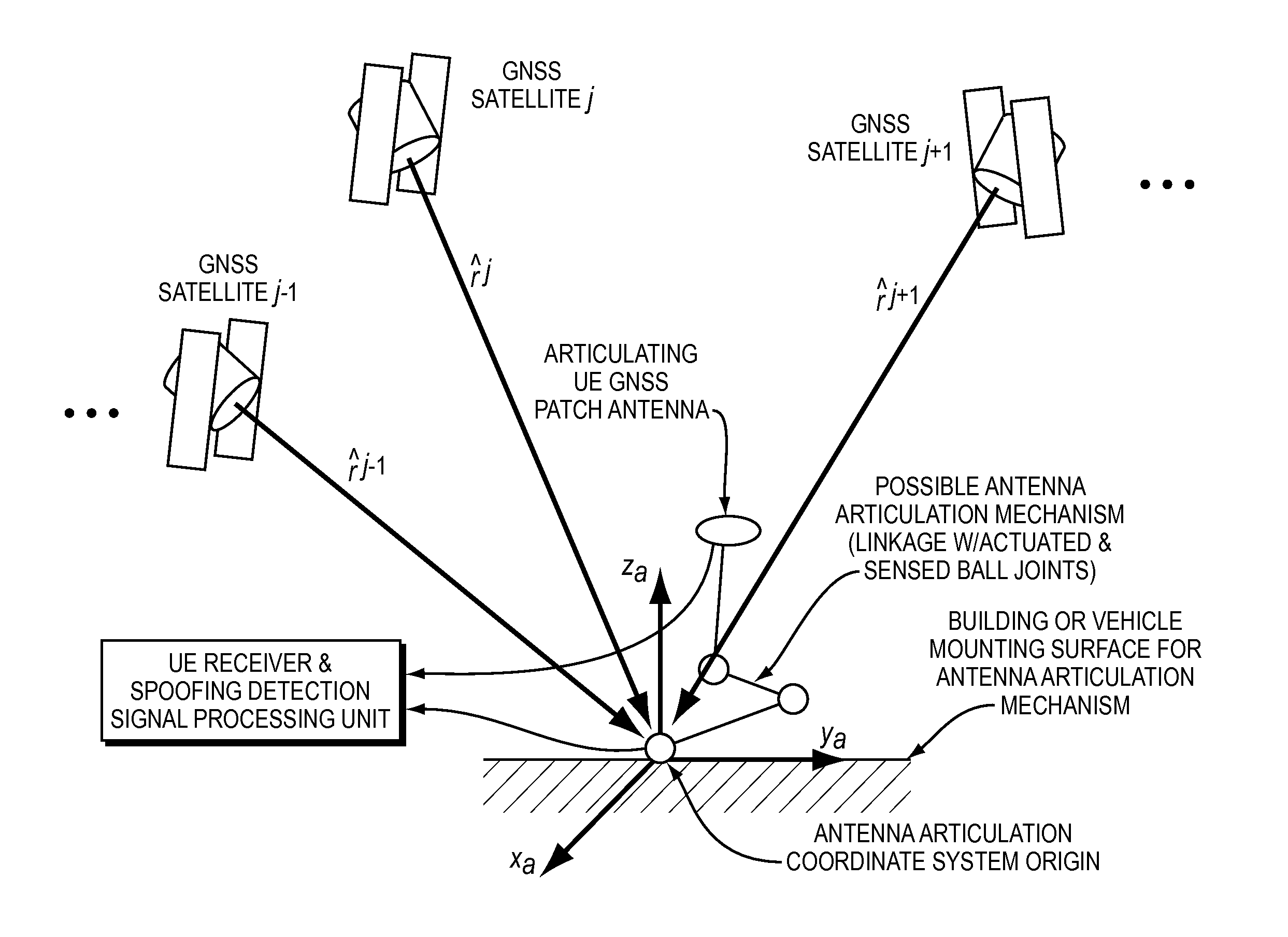
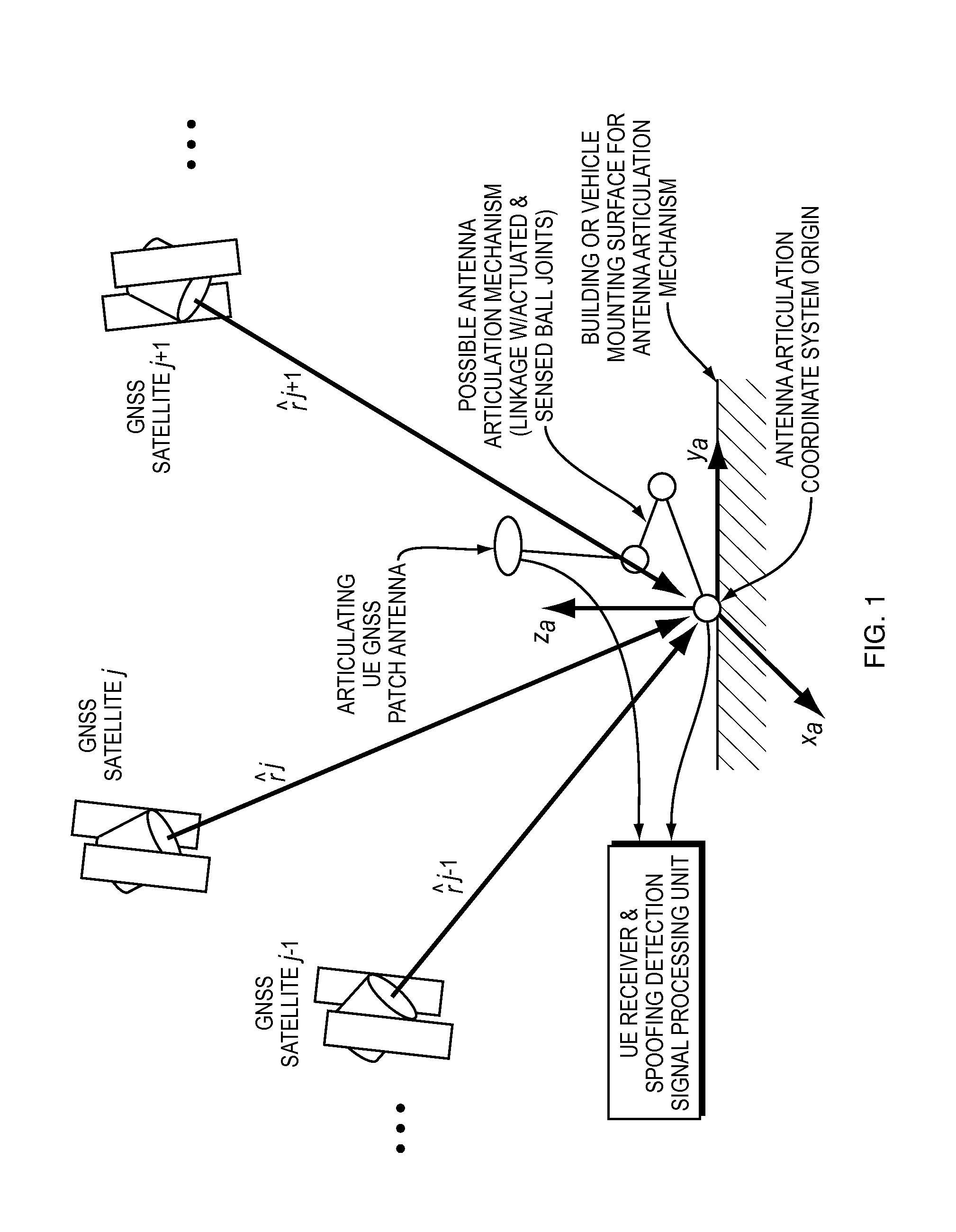
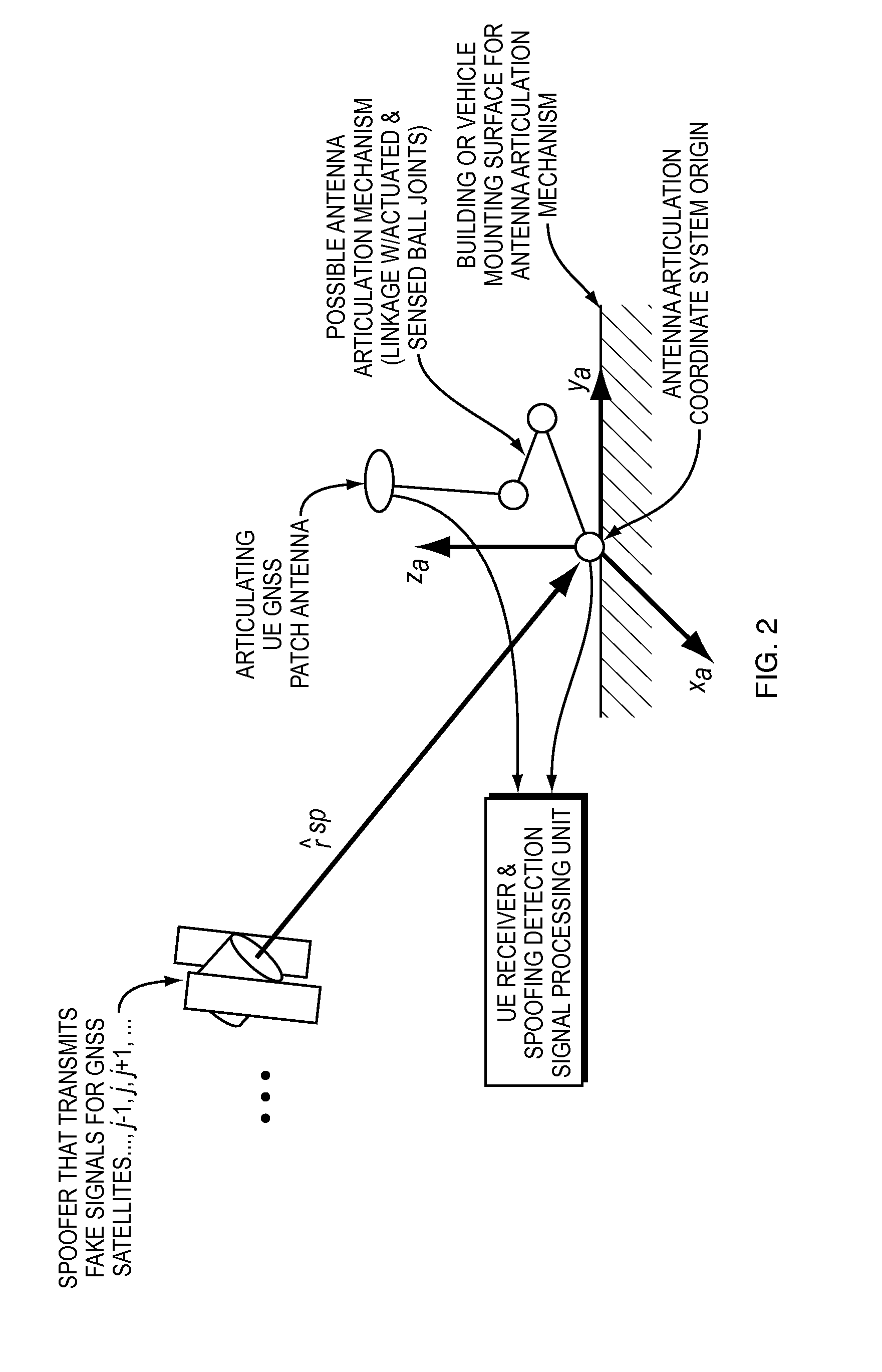
Methods and apparatus for detecting spoofing of global navigation satellite system signals using carrier phase measurements and known antenna motions
ActiveUS20150234053A1Simple signal processingCommunication jammingSatellite radio beaconingHypothesisFalse alarm
Methods and systems that can detect GNSS spoofing attacks and that do not require explicit or implicit knowledge of exact position or attitude and that provide hypothesis test statistics, threshold values, and probabilities of false alarm and missed detection.
Owner:CORNELL UNIVERSITY
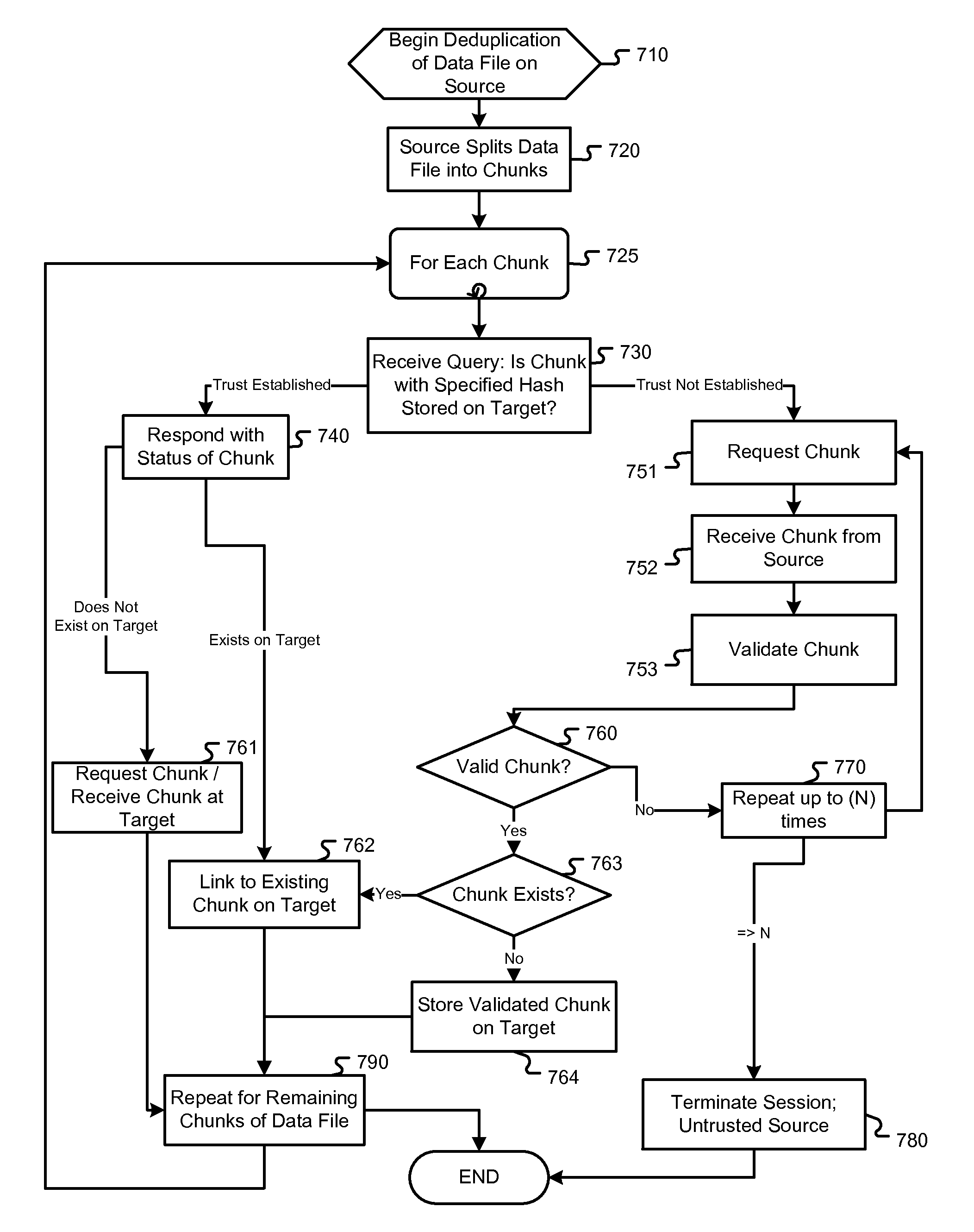
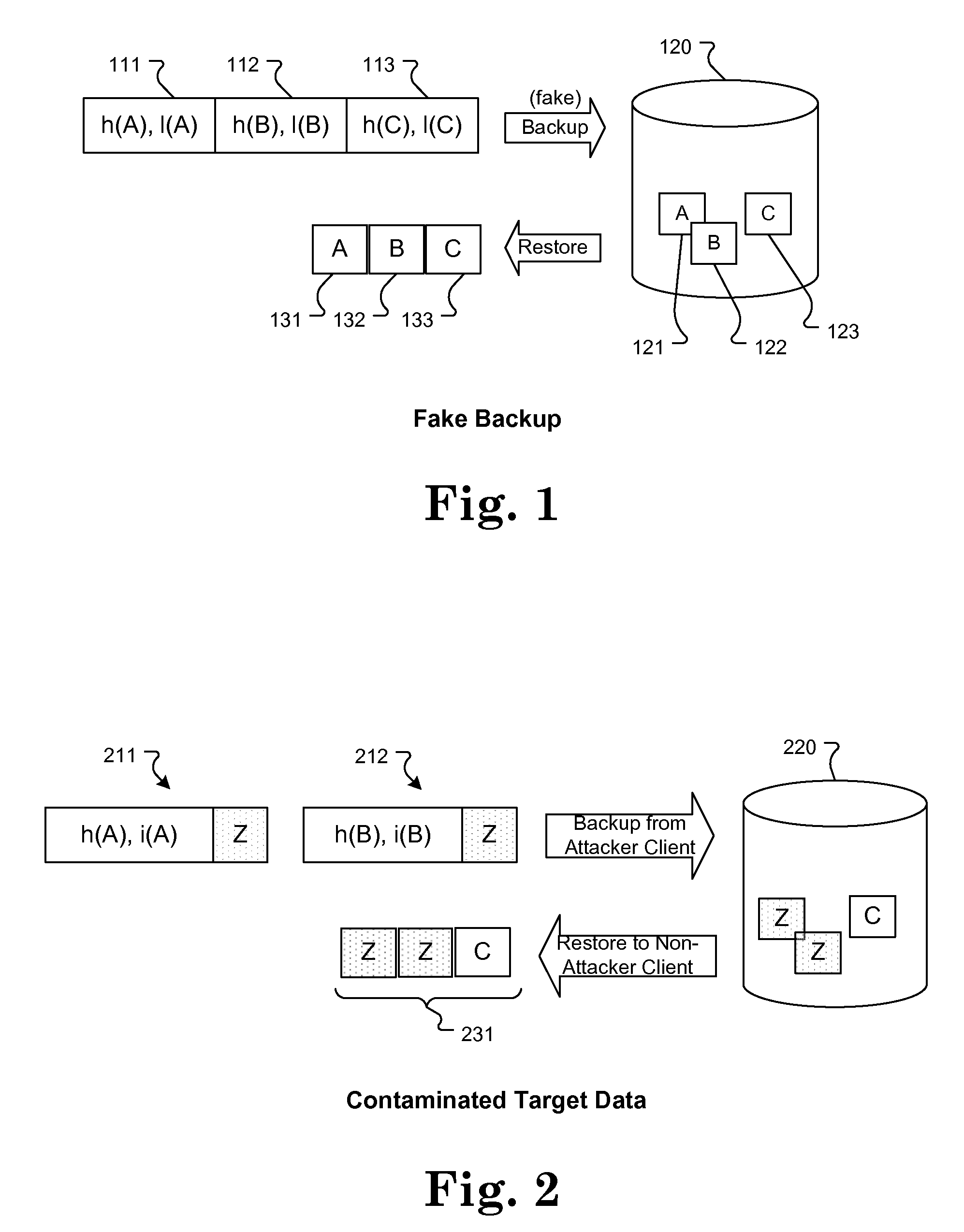
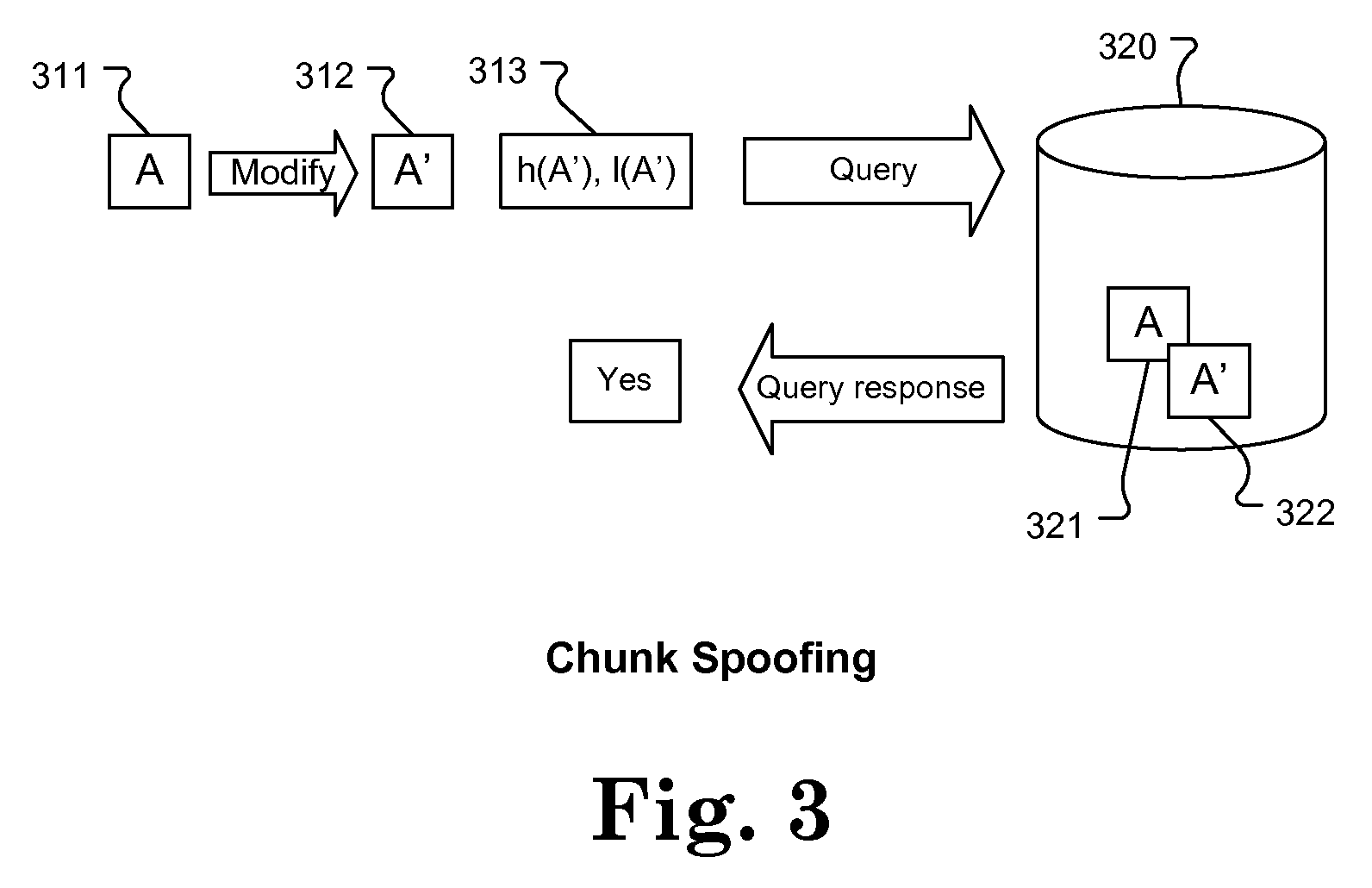
Approach for securing distributed deduplication software
The various embodiments of the present invention include techniques for securing the use of data deduplication activities occurring in a source-deduplicating storage management system. These techniques are intended to prevent fake data backup, target data contamination, and data spoofing attacks initiated by a source. In one embodiment, one technique includes limiting chunk querying to authorized users. Another technique provides detection of attacks and unauthorized access to keys within the target system. Additional techniques include the combination of validating the existence of data from the source by validating the data chunk, validating a data sample of the data chunk, or validating a hash value of the data chunk. A further embodiment involves the use of policies to provide authorization levels for chunk sharing and linking within the target. These techniques separately and in combination provide a comprehensive strategy to avoid unauthorized access to data within the target storage system.
Owner:AIRBNB
System for detecting change of name-to-IP resolution
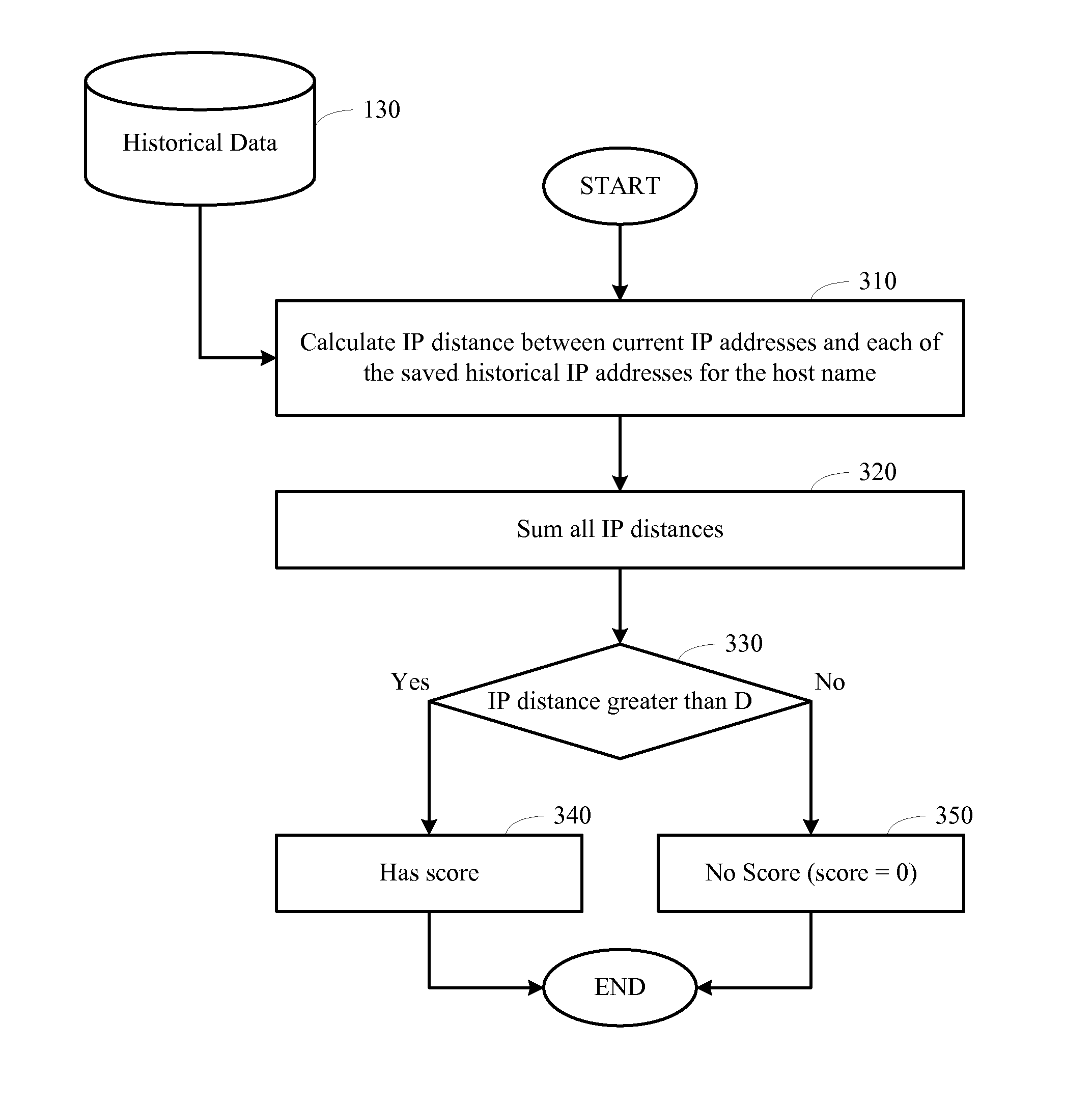
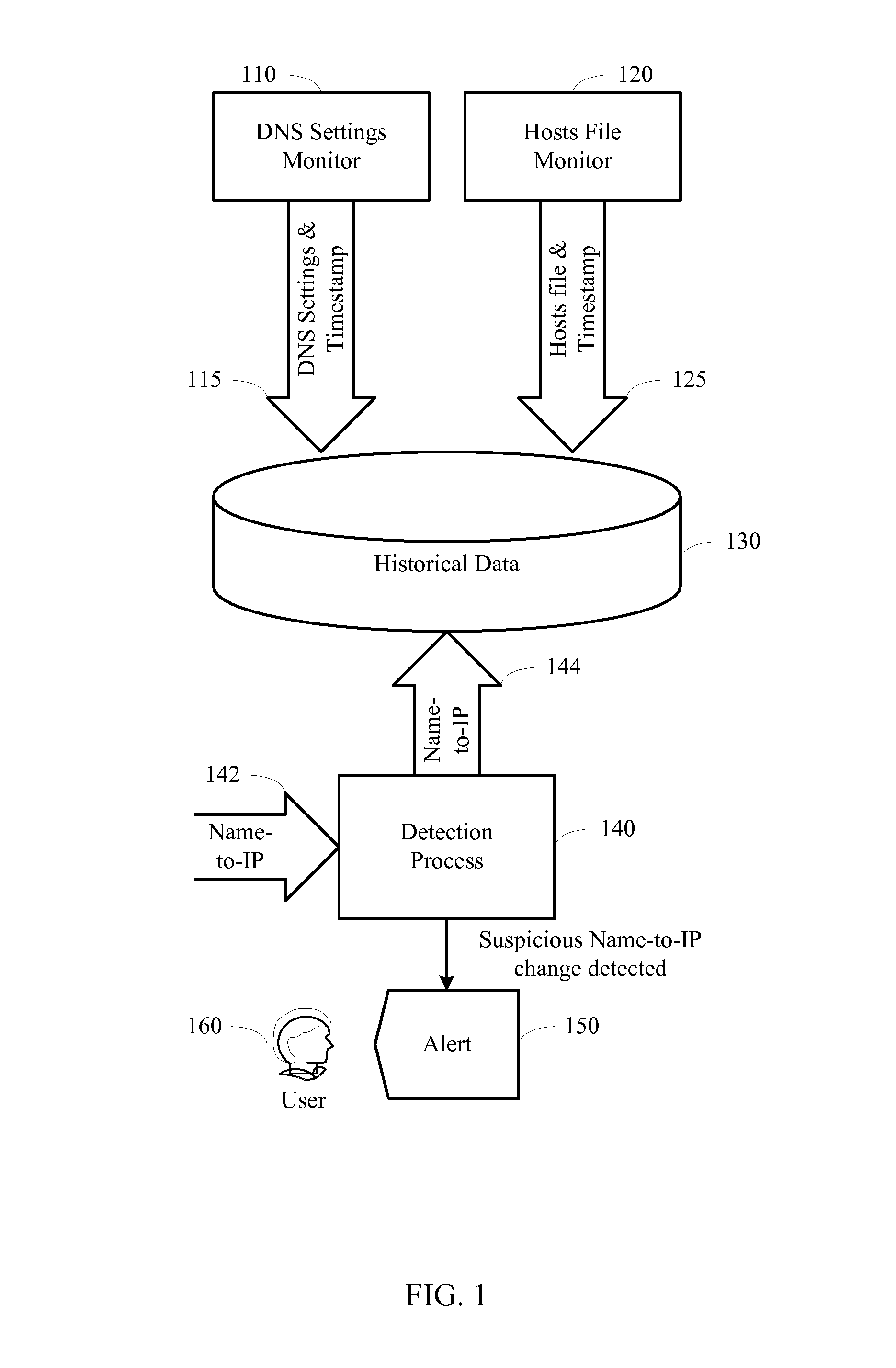
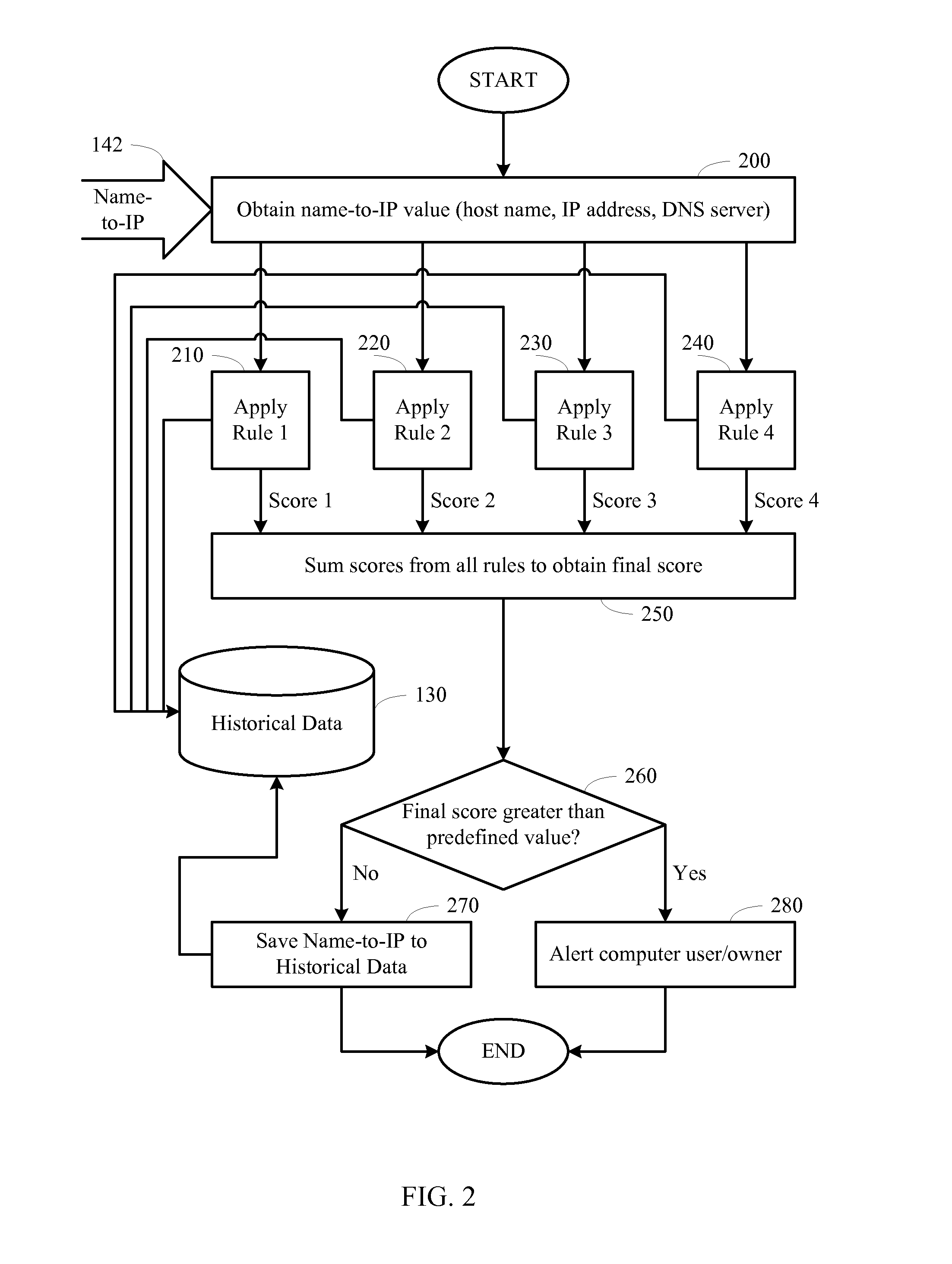
ActiveUS8316440B1Memory loss protectionUser identity/authority verificationIp addressTechnical standard
Detection for pharming attacks and specifically for changes in name-to-IP resolutions on a computer system using rules is described. The DNS settings and the Hosts file on a computer system are monitored and their modification information is saved as a part of the historical data over time. When an IP address is determined for a host name, various rules are applied to the IP address in connection with the saved historical data, such that each rule produces a score based on various criteria. Different rules may have different weights assigned to their scores. The scores of all the rules are summed up to produce a final score. If the final score is above a predefined value, then there is a suspicious change in the IP address, and an alert is sent. Otherwise, the host name and the IP address are saved as a part of the historical data.
Owner:TREND MICRO INC
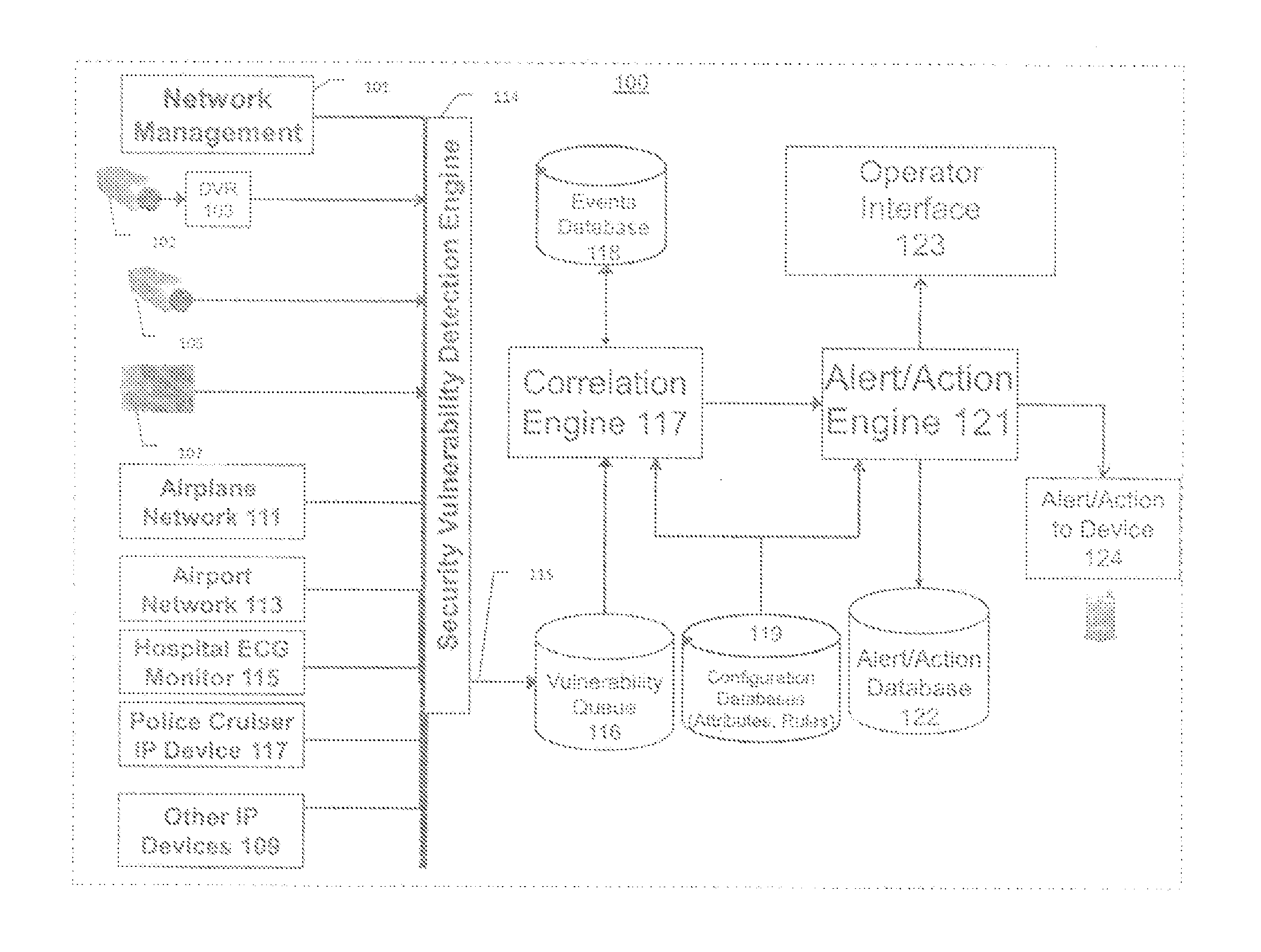
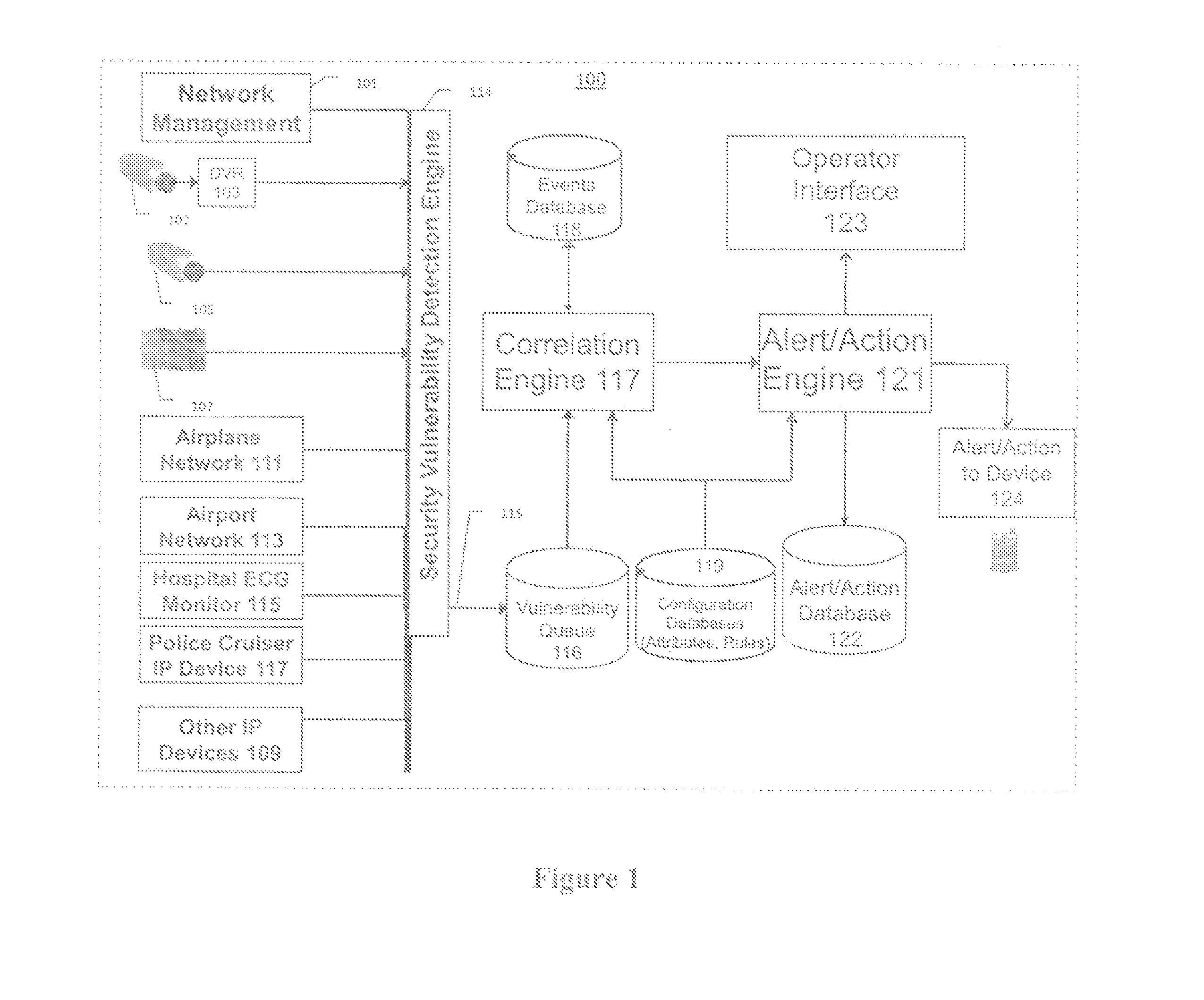
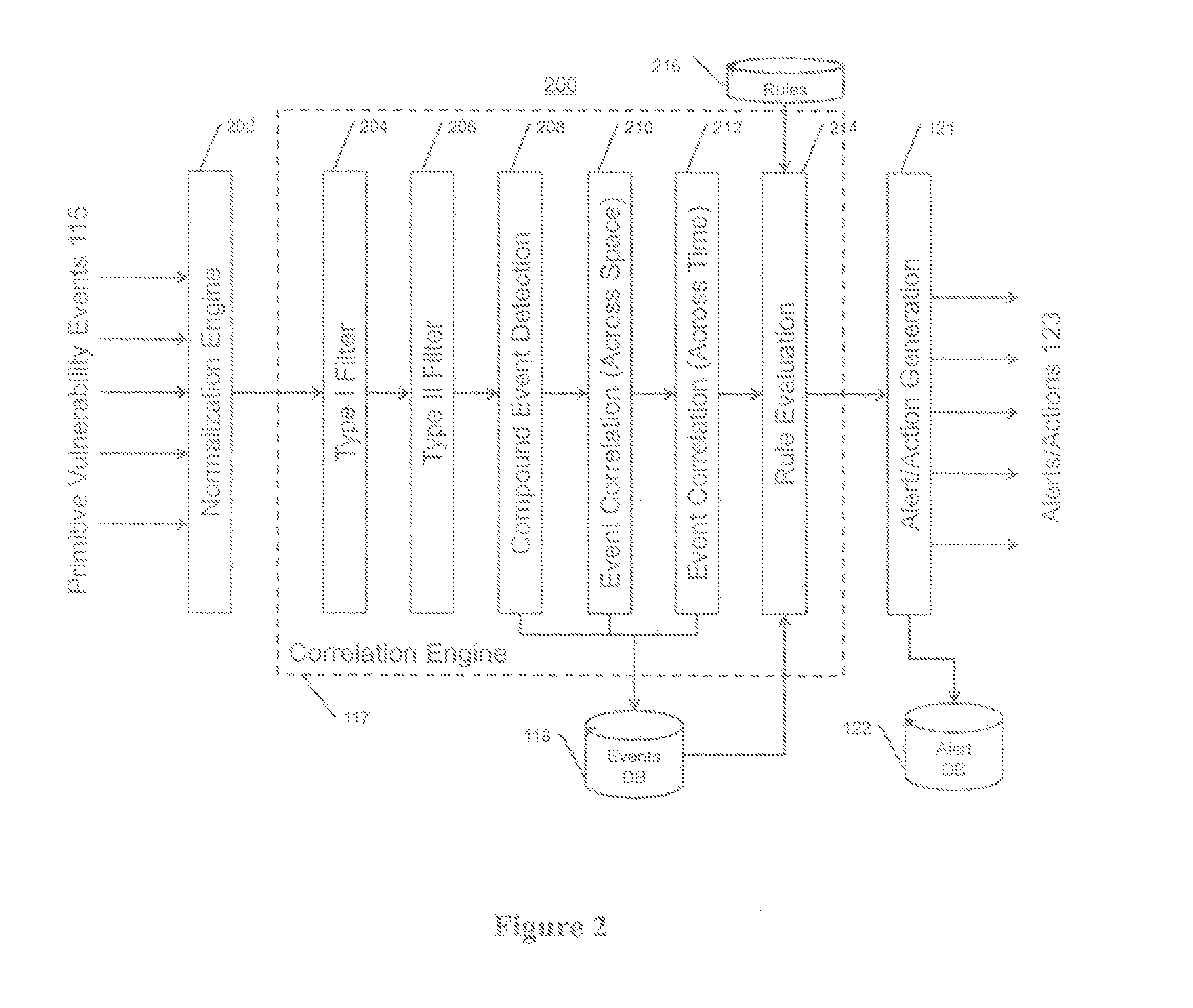
Systems, methods, and devices for detecting security vulnerabilities in IP networks
InactiveUS20100125663A1Easy to addMemory loss protectionError detection/correctionBaseline dataCamera image
This invention is a system, method, and apparatus for detecting compromise of IP devices that make up an IP-based network. One embodiment is a method for detecting and alerting on the following conditions: (1) Denial of Service Attack; (2) Unauthorized Usage Attack (for an IP camera, unauthorized person seeing a camera image); and (3) Spoofing Attack (for an IP camera, unauthorized person seeing substitute images). A survey of services running on the IP device, historical benchmark data, and traceroute information may be used to detect a possible Denial of Service Attack. A detailed log analysis and a passive DNS compromise system may be used to detect a possible unauthorized usage. Finally, a fingerprint (a hash of device configuration data) may be used as a private key to detect a possible spoofing attack. The present invention may be used to help mitigate intrusions and vulnerabilities in IP networks.
Owner:DNSSTUFF
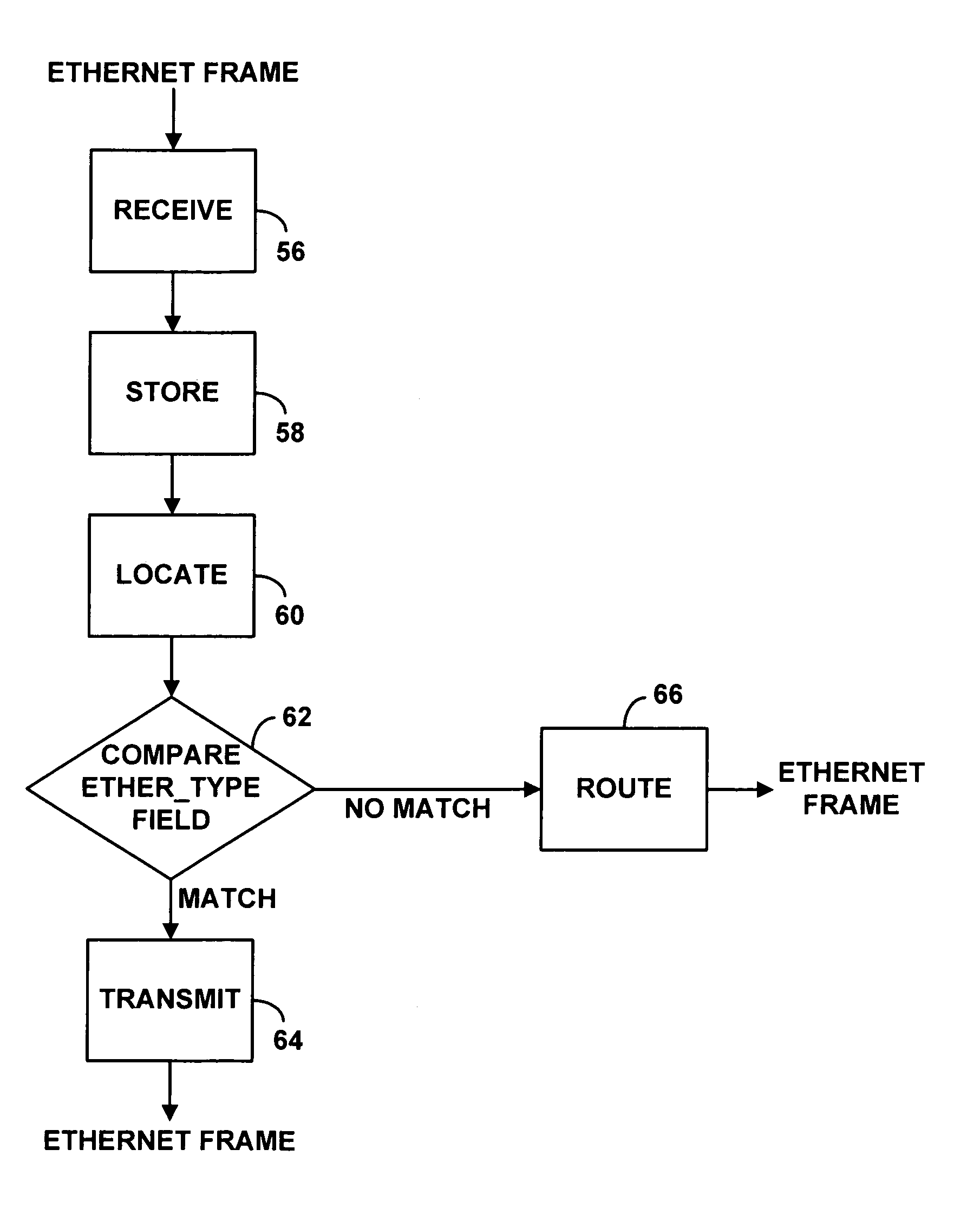
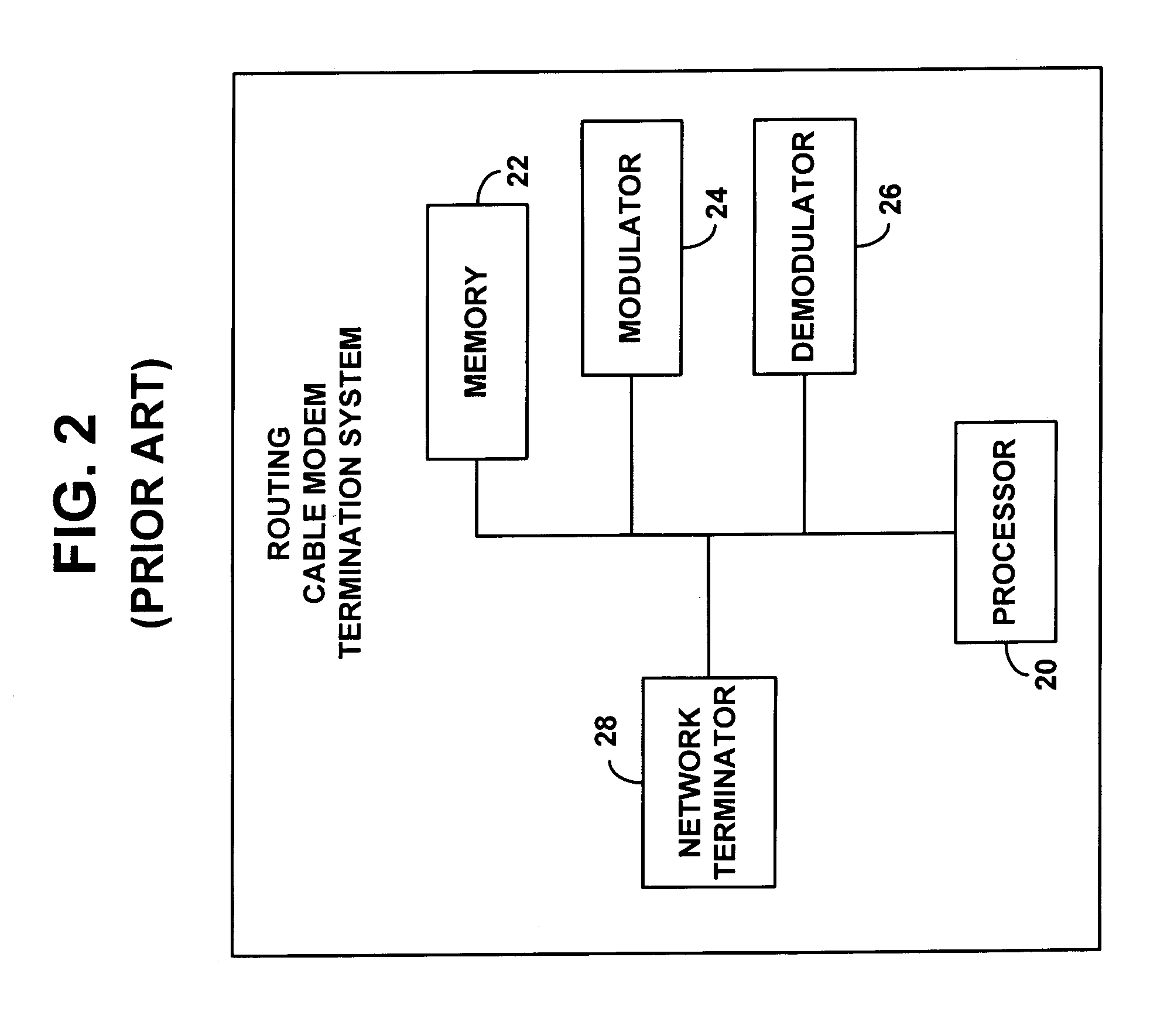
Method and apparatus for PPPoE bridging in a routing CMTS
InactiveUS7039049B1Reserved functionPrevent spoofing attacksBroadband local area networksTime-division multiplexPoint-to-Point ProtocolModem device
A routing Cable Modem Termination System (CMTS) configured to enable Point-to-Point Protocol over Ethernet (PPPoE). The routing CMTS may bridge Ethernet frames related to a PPPoE connection from a first network to a second network. Bridging Ethernet frames allows terminals in different networks to establish a PPPoE connection. A routing CMTS may also collect state information regarding PPPoE connections. The routing CMTS may use the state information to only bridge Ethernet frames related to valid PPPoE connections. It may act as a firewall to prevent spoofing attacks.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP +1
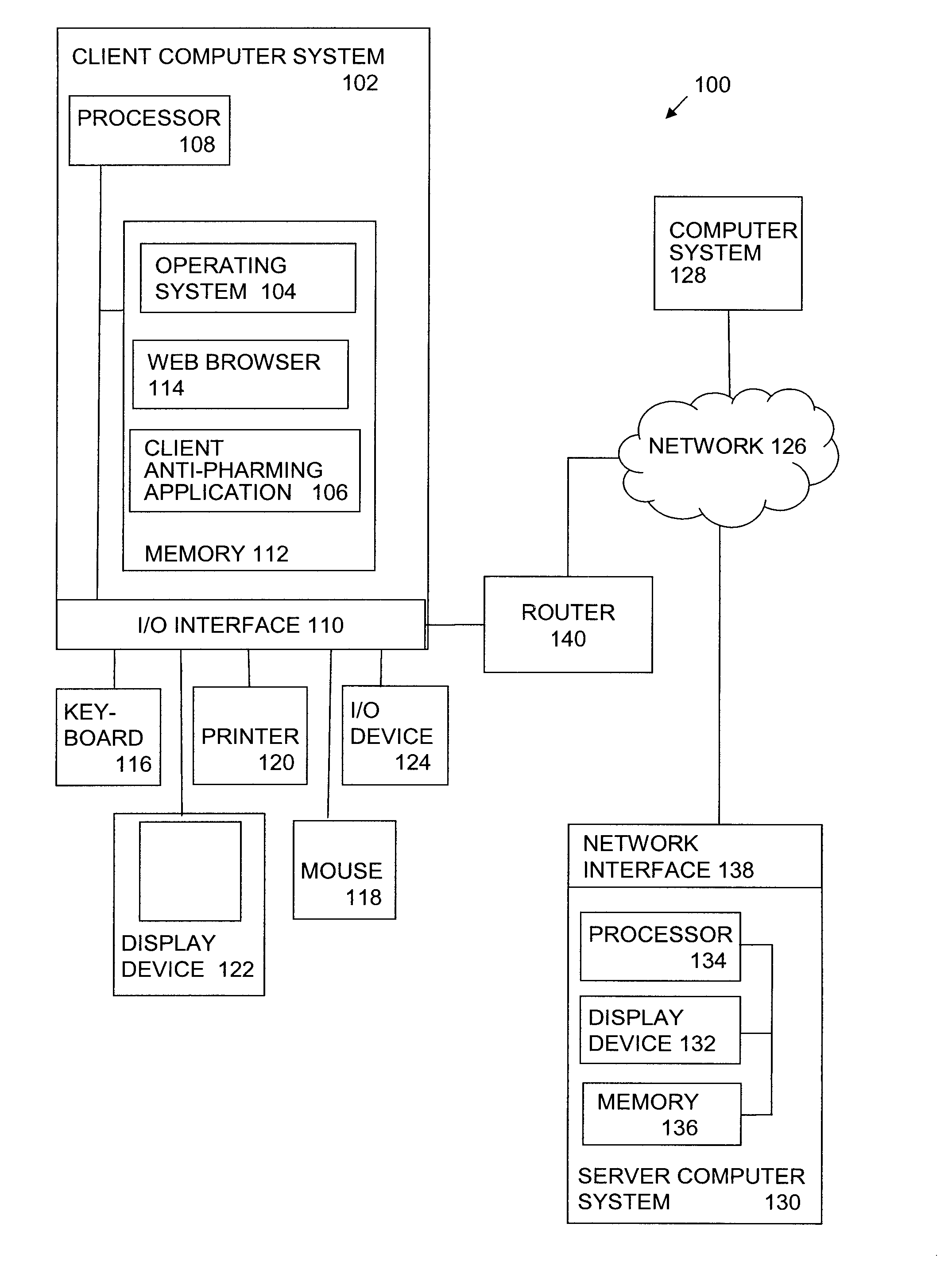
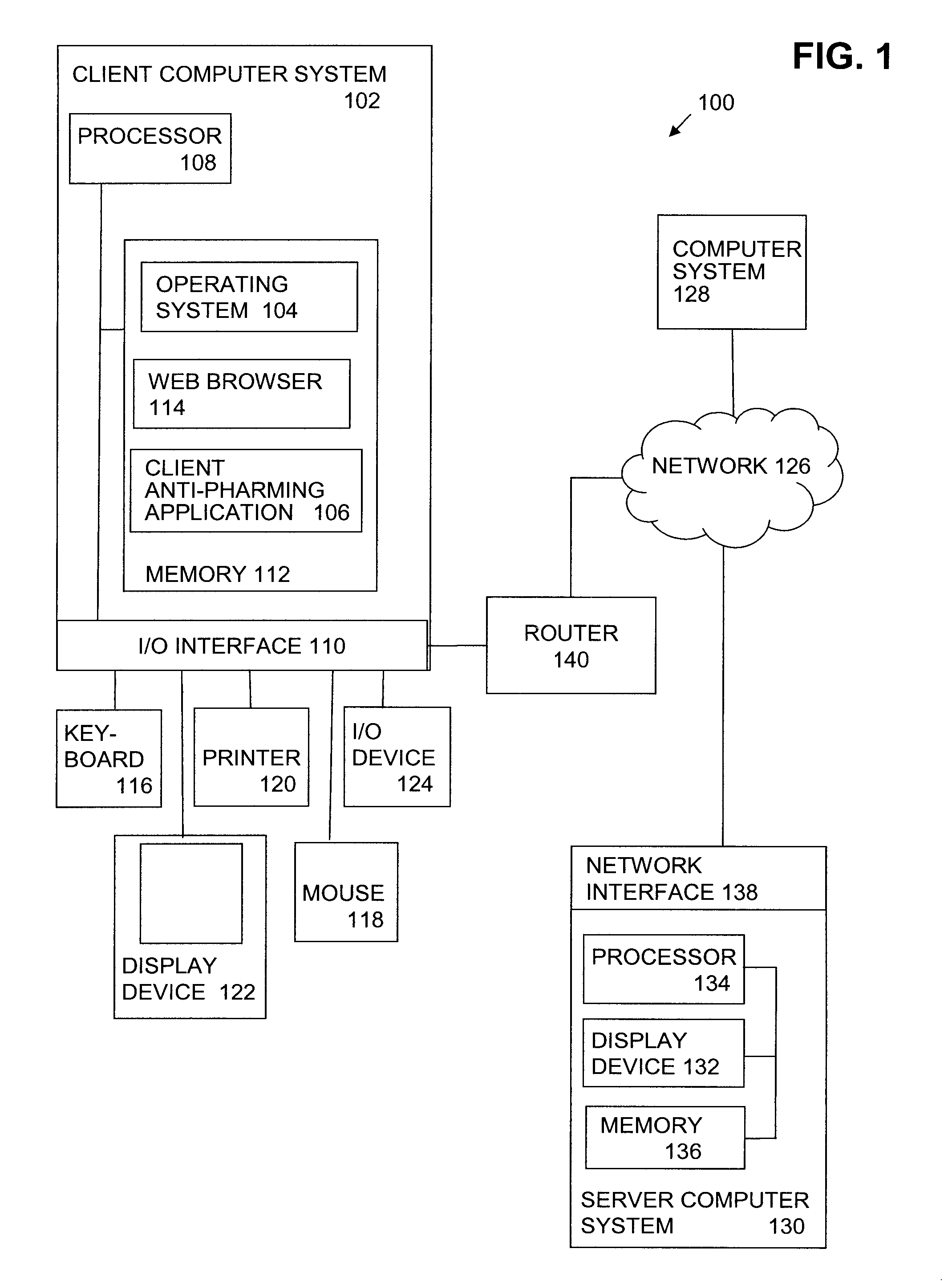
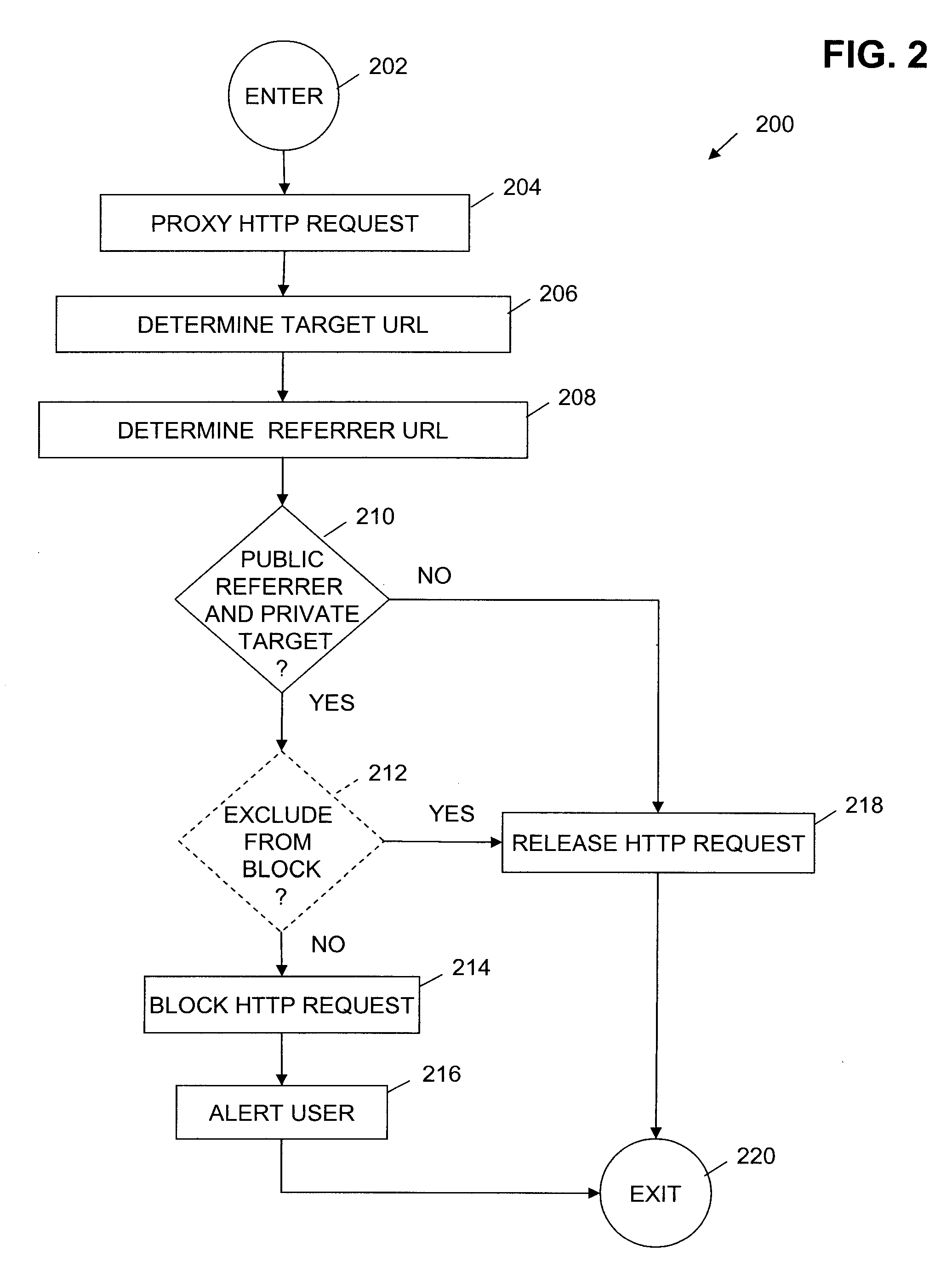
Client side protection against drive-by pharming via referrer checking
HTTP requests initiated from a web browser of a client computer system are proxied prior to release to a router, such as a home router. HTTP requests identifying a referrer URL corresponding to routable, public IP address and a target URL corresponding to a non-routable, private IP address are determined to be indicative of a drive-by pharming attack, and are blocked from sending to the router. HTTP requests not identifying a referrer URL corresponding to a routable, public IP address and a target URL corresponding to a non-routable, private IP address, the HTTP request are not determined to be indicative of a drive-by pharming attack, and are released for sending to the router. In some embodiments, an HTTP response received in response to a released HTTP request is proxied prior to release to the web browser. An HTTP response having content of type text / html or script is modified as indicated to prevent malicious activity and released to the web browser.
Owner:GEN DIGITAL INC
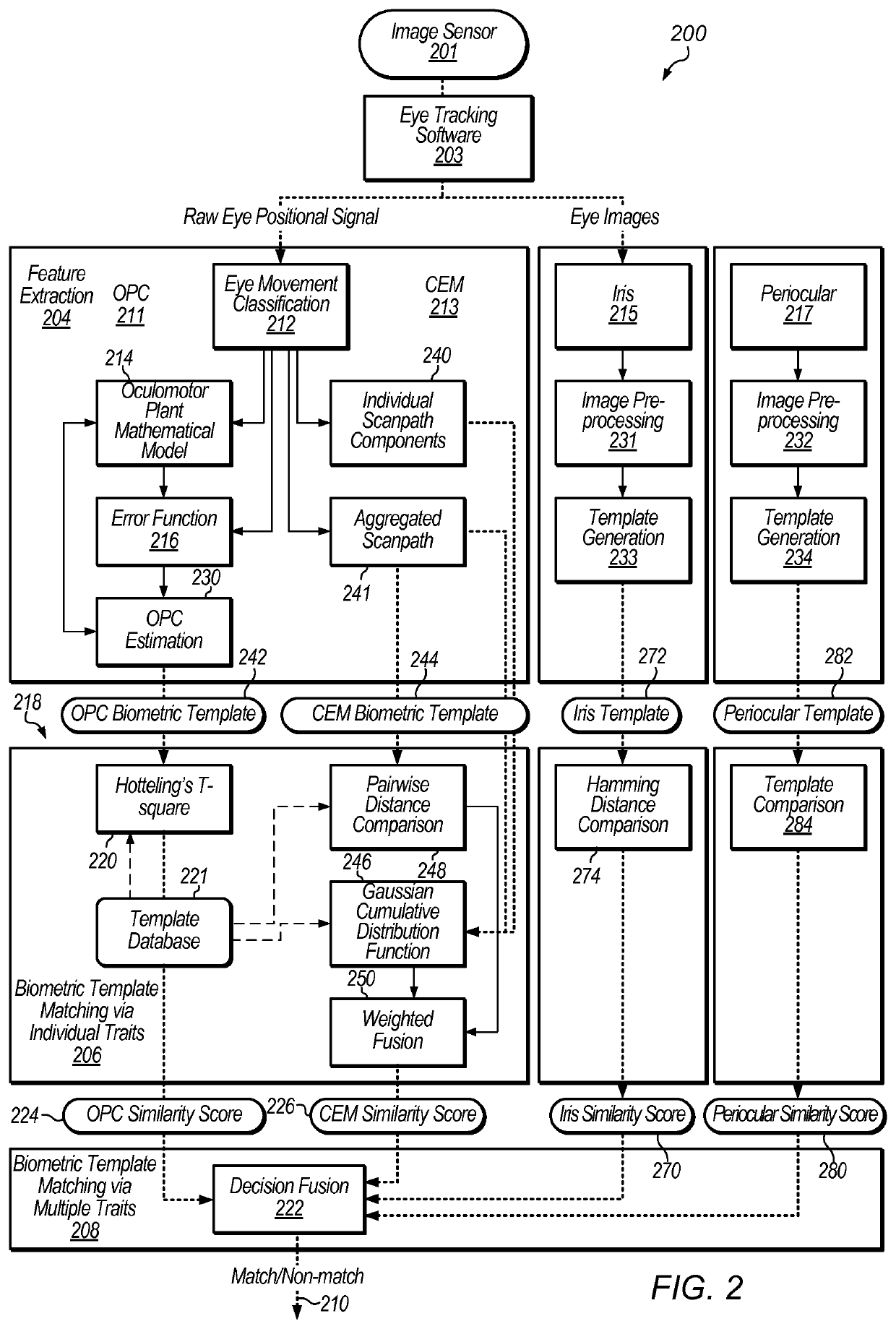
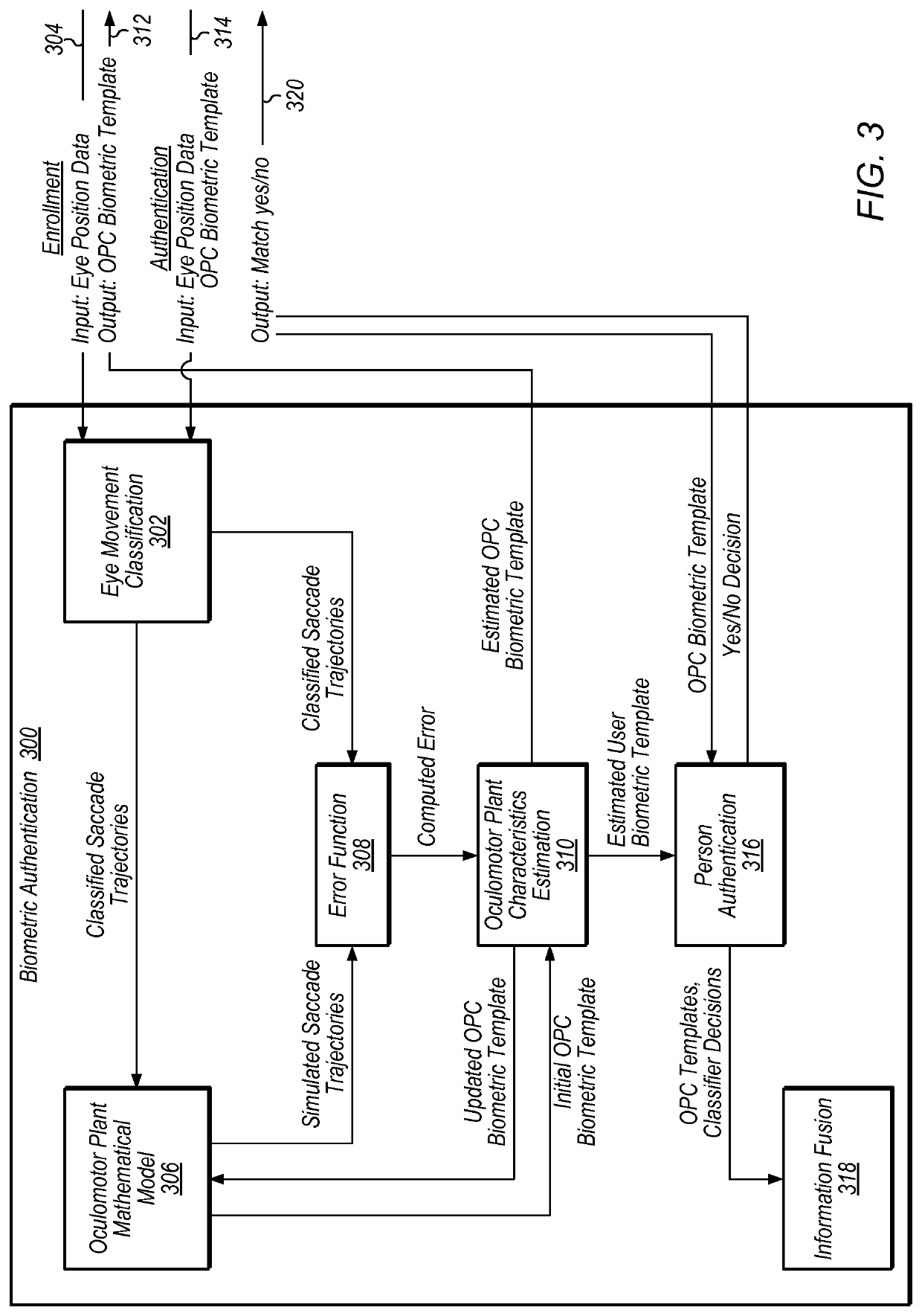
Detection of print-based spoofing attacks
ActiveUS20190392145A1Acquiring/recognising eyesDigital data authenticationFeature vectorSpoofing attack
A method of assessing the possibility of an iris print-attack includes measurement of the eye movement of a person. One or more values (e.g., a feature vector) are determined based on the measured eye movements. Based on the determined values, an assessment is made of whether or not the person is engaging in an iris print-attack.
Owner:TEXAS STATE UNIVERSITY
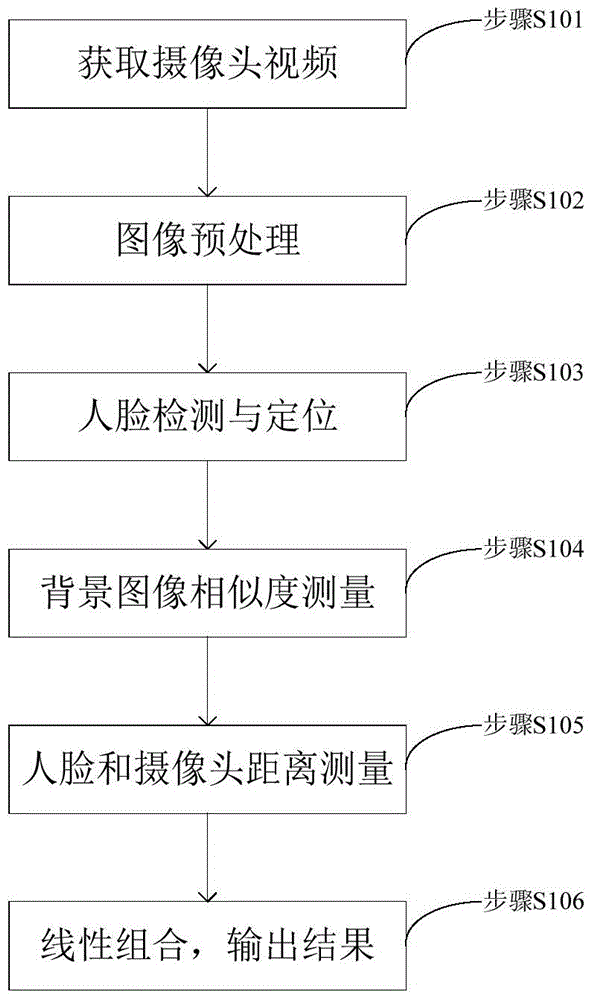
Living person detection method applied to face recognition
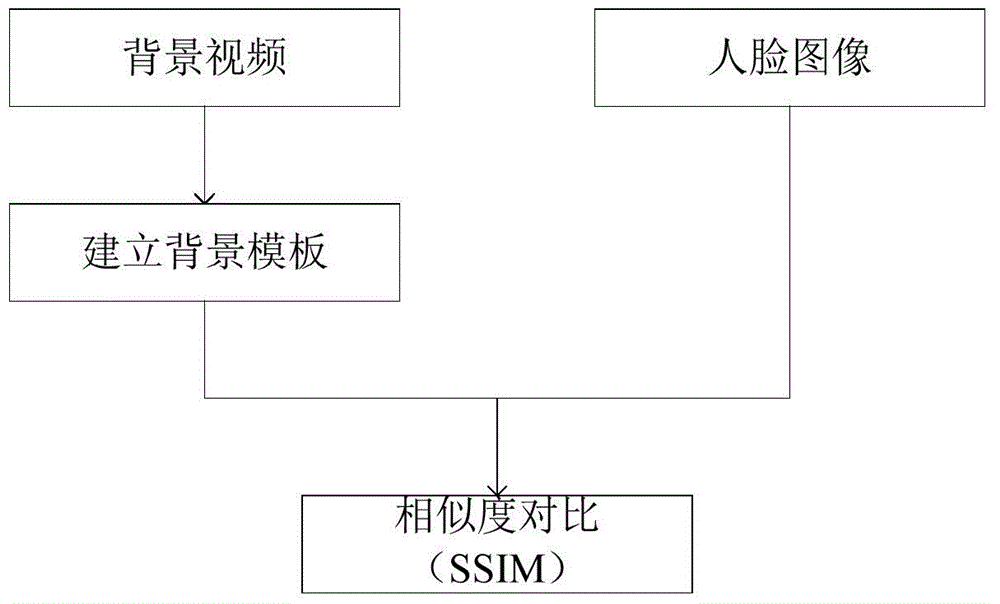
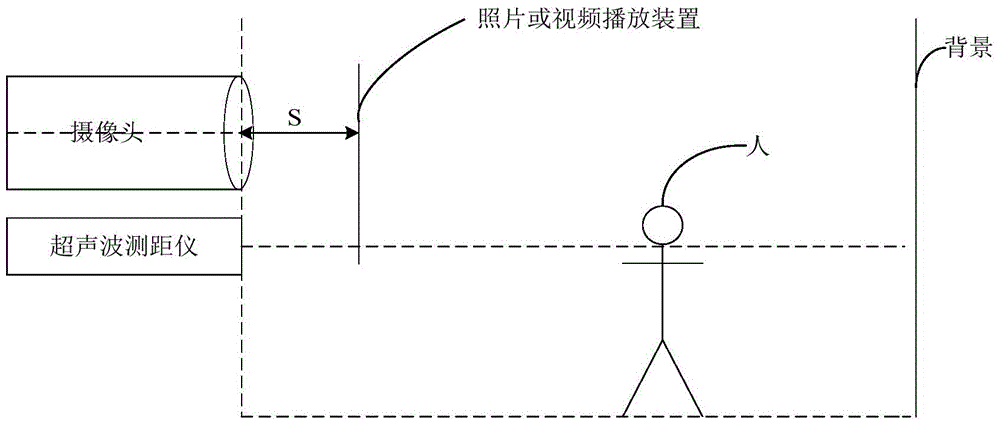
ActiveCN104915649ASolve the problem of spoofing facial recognition systemsIncrease success rateCharacter and pattern recognitionPattern recognitionFace detection
This invention discloses a living person detection method applied to face recognition. The method includes the following steps that: modeling is performed on the background of a current recognition environment; face detection is performed: the locations and sizes of faces are obtained and are adopted as the initial position of next face detection; the similarity between the background of inputted face images and a modeling background image is calculated through adopting an SSIM method; when the faces are detected, ultrasonic waves are utilized to measure the distance between a camera and an obstacle, and a classification probability value f is obtained through utilizing a logistic regression model; and an SSIM value and the value f are combined linearly, so that a final result R can be obtained, and when R is smaller than a certain threshold value, a spoofing attack is determined. The living person detection method applied to face recognition of the invention has the advantages of high success rate and excellent stability.
Owner:南京理工科技园股份有限公司
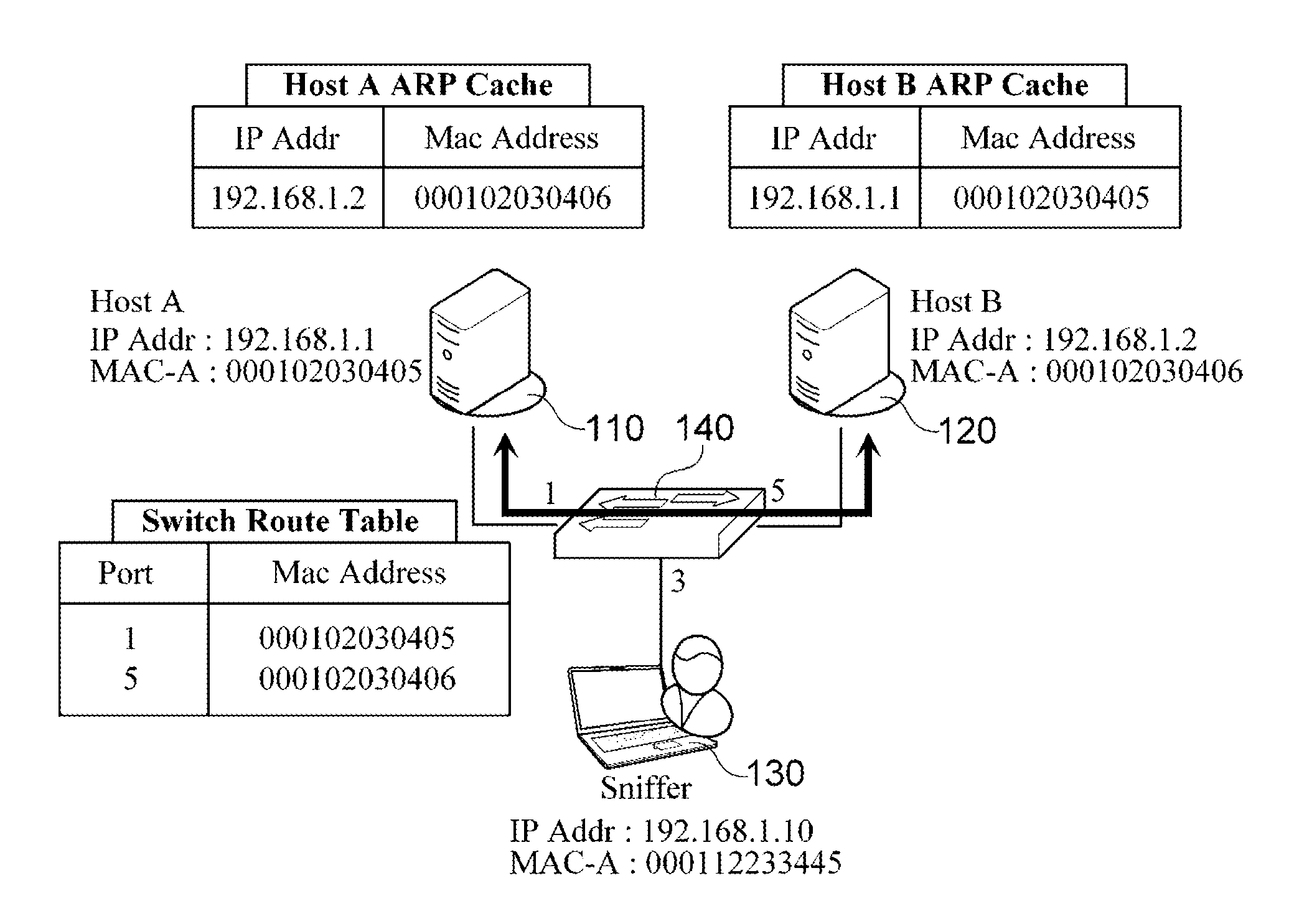
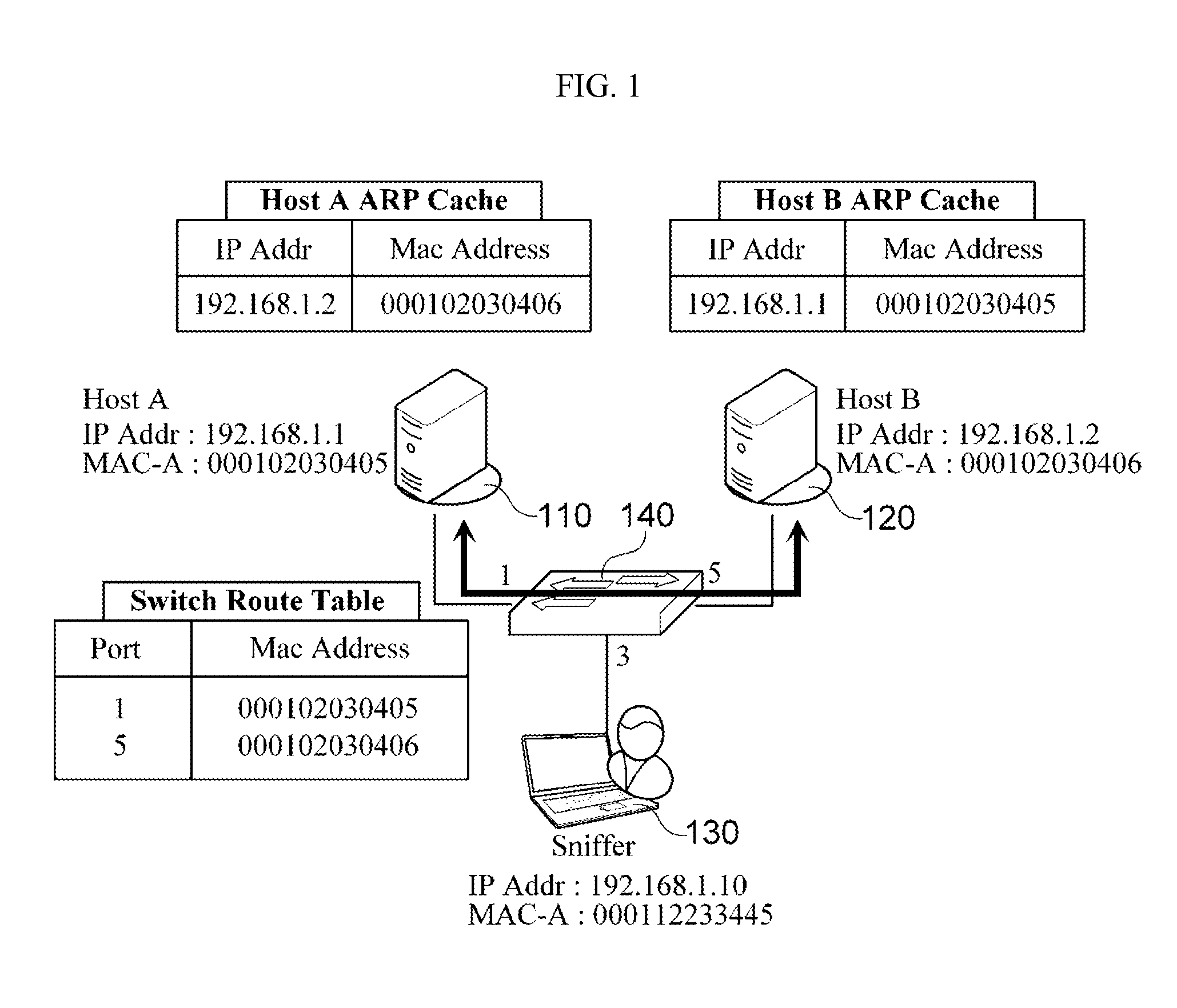
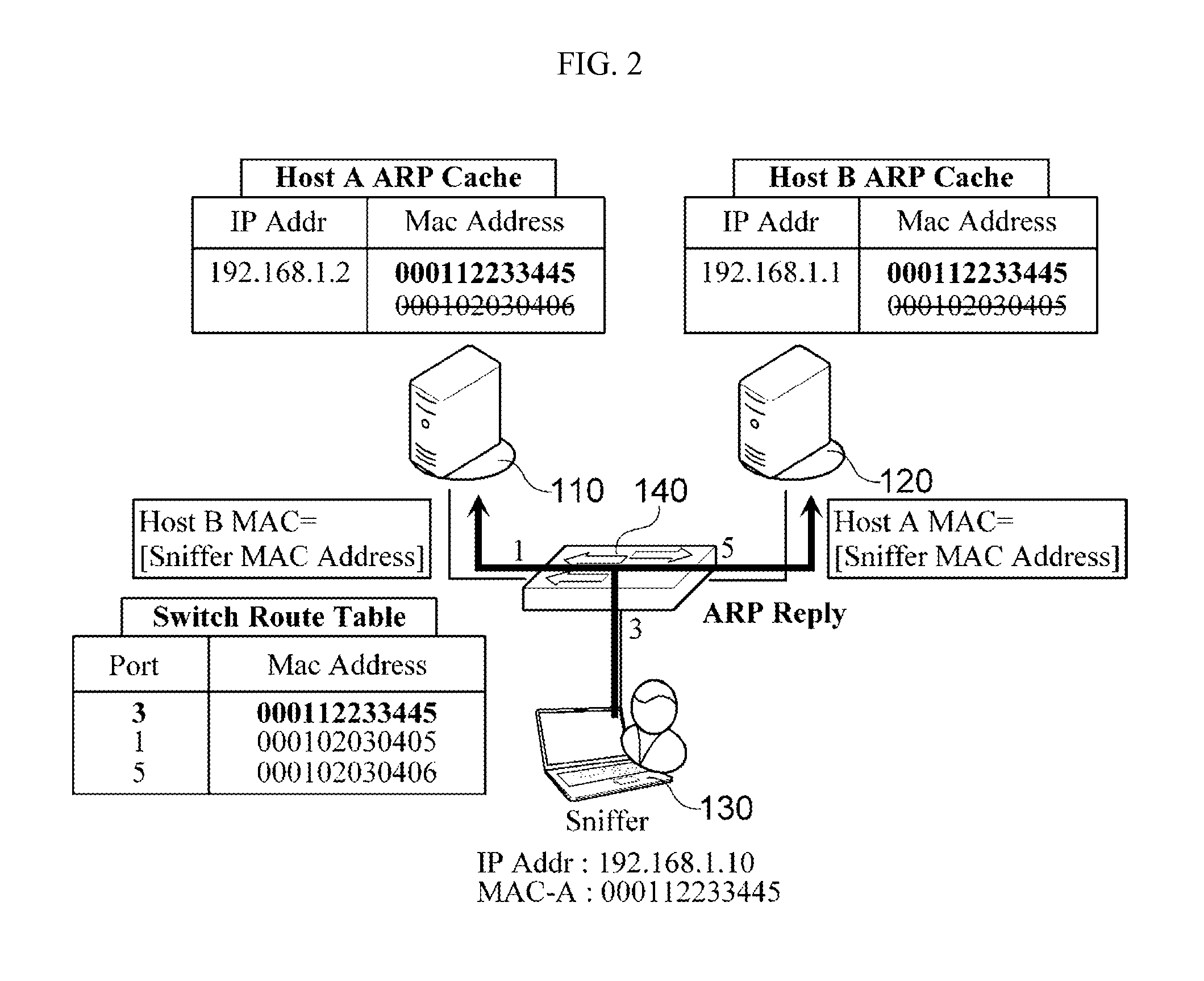
System and method for detecting address resolution protocol (ARP) spoofing
ActiveUS20130111589A1Easy to detectMemory loss protectionData taking preventionAddress Resolution ProtocolNetwork packet
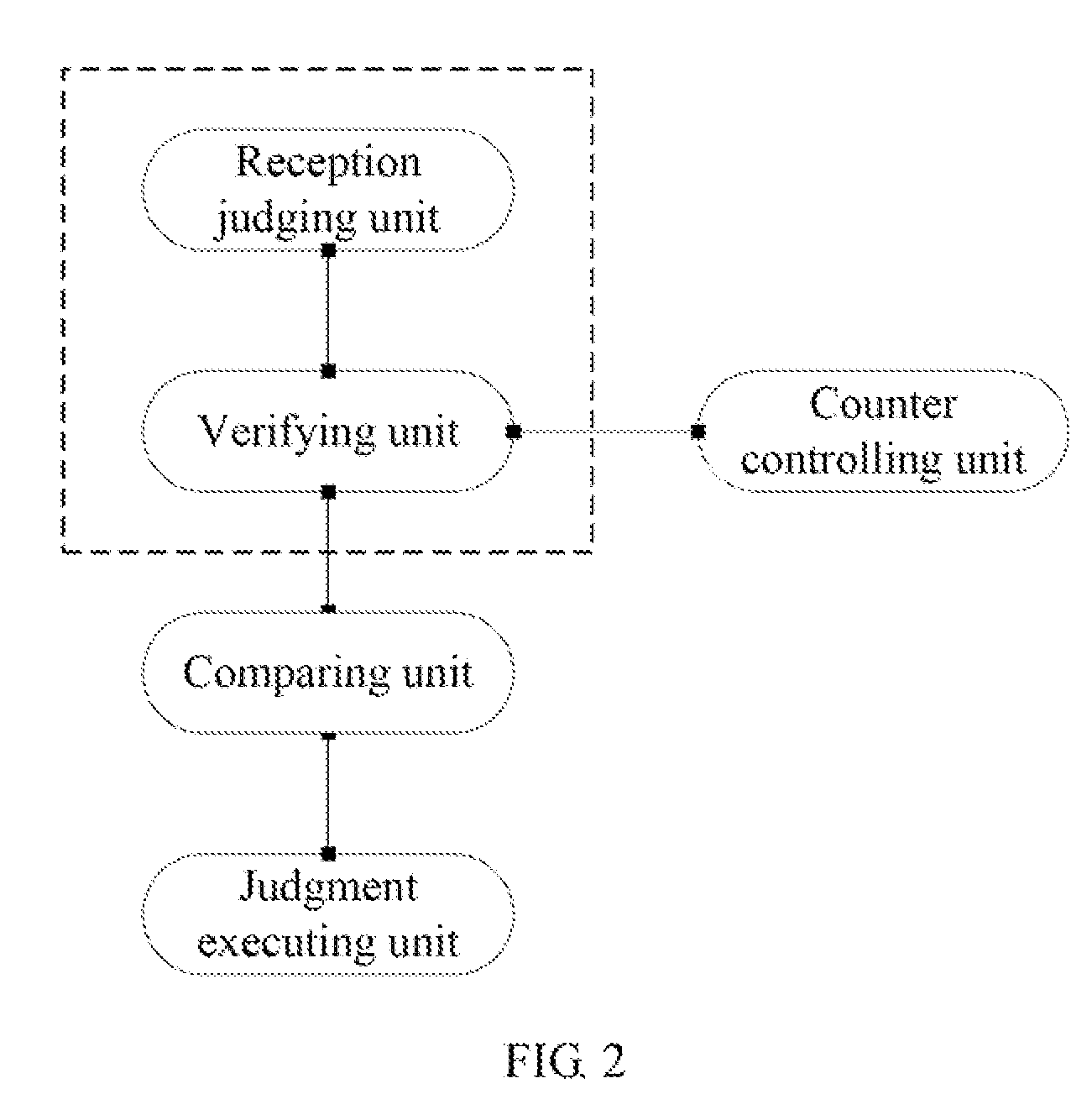
There are provided a system and method for detecting Address Resolution Protocol (ARP) attacks. The ARP spoofing attack detection system includes: a reception module which receives an ARP packet, and which determines whether the received ARP packet is an unsolicited ARP packet; a transmission module which creates, if the ARP packet is an unsolicited ARP packet, an ARP request packet corresponding to the unsolicited ARP packet, and which broadcasts the ARP request packet; and a detection module which determines, if an ARP response packet corresponding to the ARP request packet is received, whether an input port of the ARP response packet is identical to an input port of the unsolicited ARP packet, and which determines that an ARP spoofing attack has occurred if the input port of the ARP response packet is not identical to the input port of the unsolicited ARP packet.
Owner:SAMSUNG SDS CO LTD
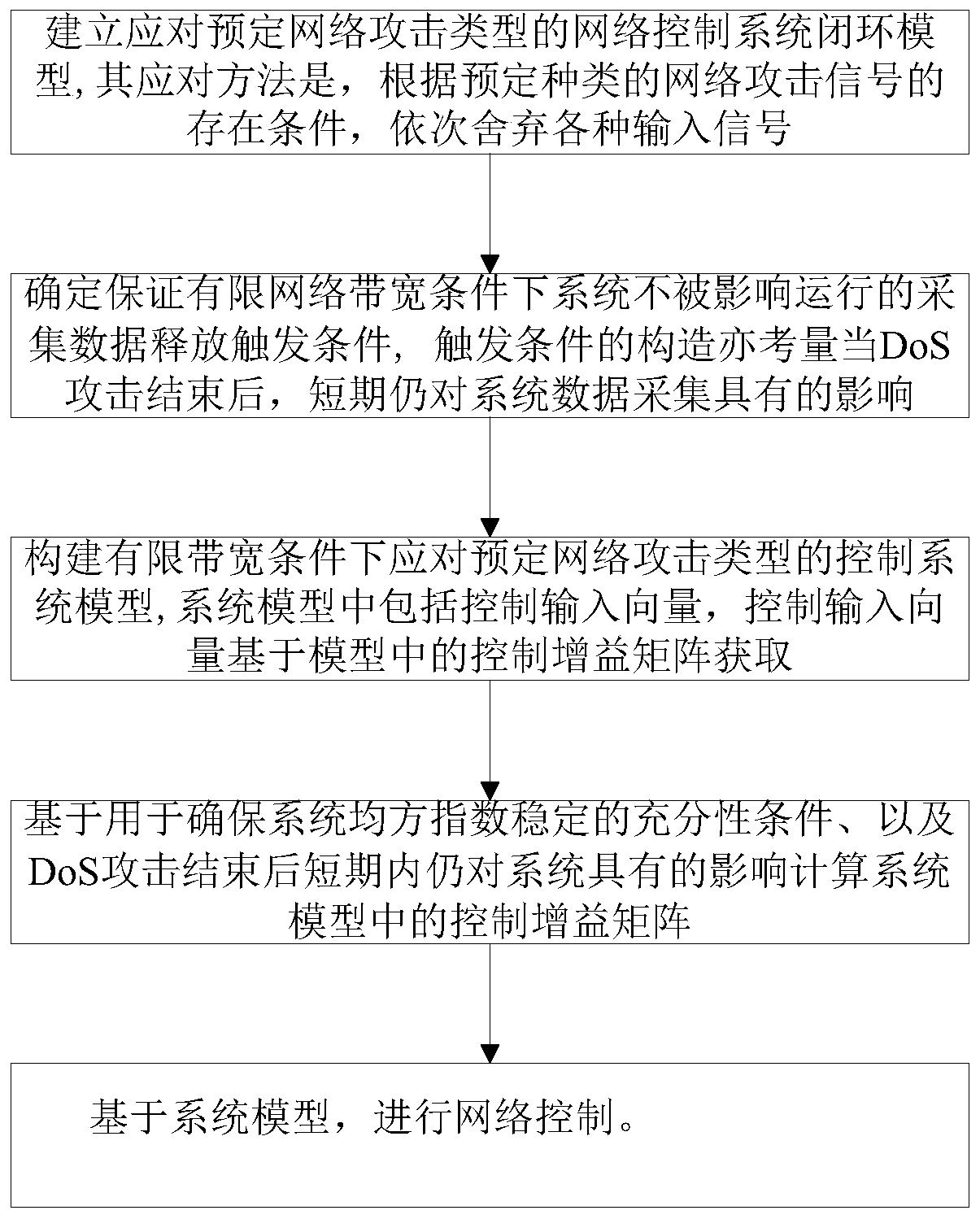
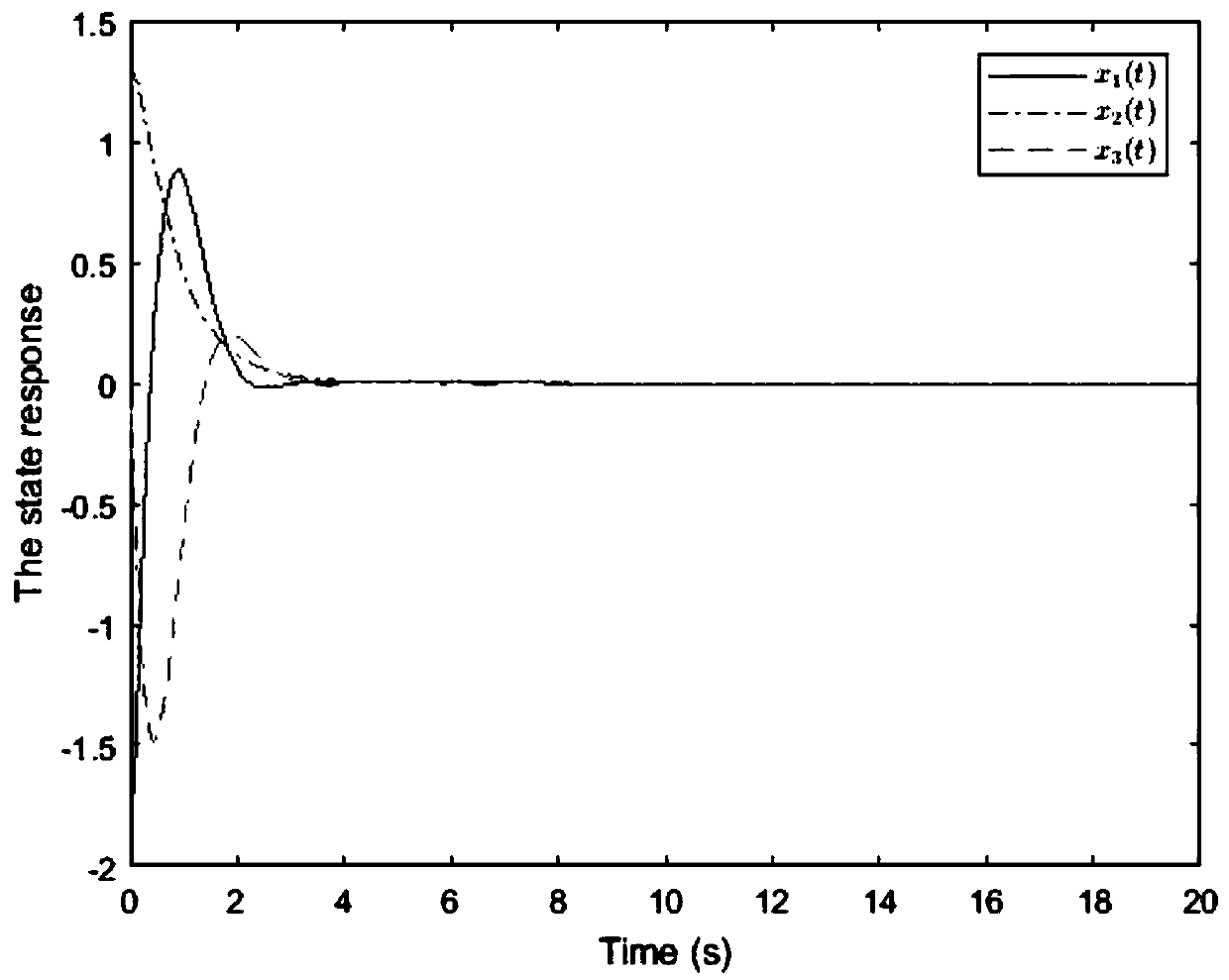
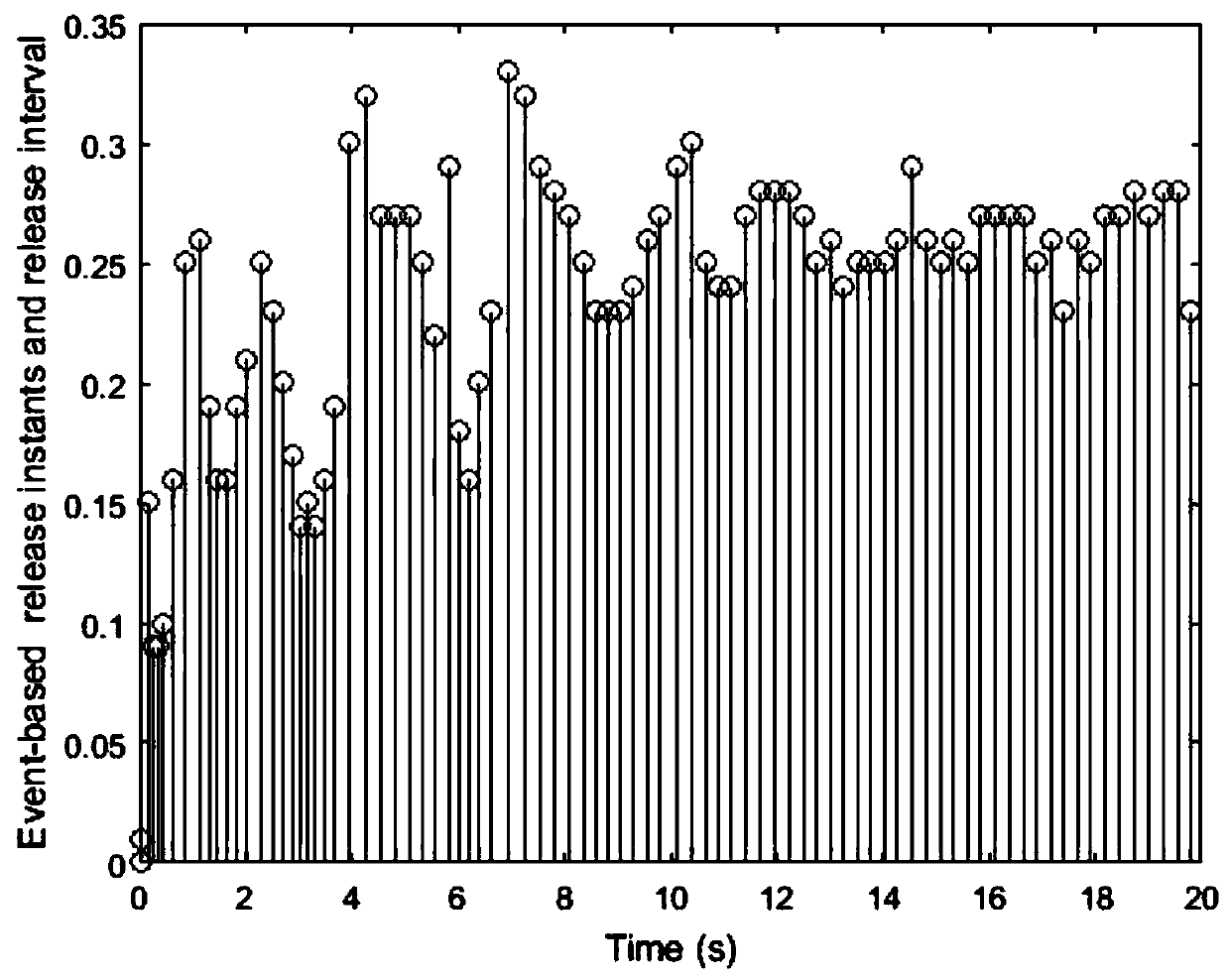
Security control method of event-driven network control system under multi-network attack
ActiveCN110213115AImprove stabilityReduce the number of transfersData switching networksLyapunov stabilityEvent trigger
The invention provides a security control method of an event-driven network control system under a multi-network attack. Considering the network transmission security problem, a random network spoofing attack, a replay attack and a DoS attack are sequentially introduced, and a system closed-loop model under the multi-network attack is established. Further considering the constraint of the limitednetwork bandwidth, an event trigger mechanism is introduced to screen and release sampling data meeting a preset event trigger condition to the network for transmission, thereby establishing a new switching system model on the basis of the system closed-loop model. Based on a switching system model, a Lyapunov stability theory is utilized to obtain a sufficiency condition for enabling the system to meet the stability of a mean square index, and a group of linear matrix inequalities is solved to obtain the gain of the state feedback controller. Compared with an existing controller design method, safe and stable operation of the network control system under the influence of multi-network attacks is guaranteed, meanwhile, the data transmission frequency is reduced, and limited network bandwidth resources are saved.
Owner:NANJING UNIV OF FINANCE & ECONOMICS
Method and apparatus for defending against arp spoofing attacks
ActiveUS20100107250A1Reliable and effective ARP verificationReduce signaling interactionMemory loss protectionDigital data processing detailsAddress Resolution ProtocolIp address
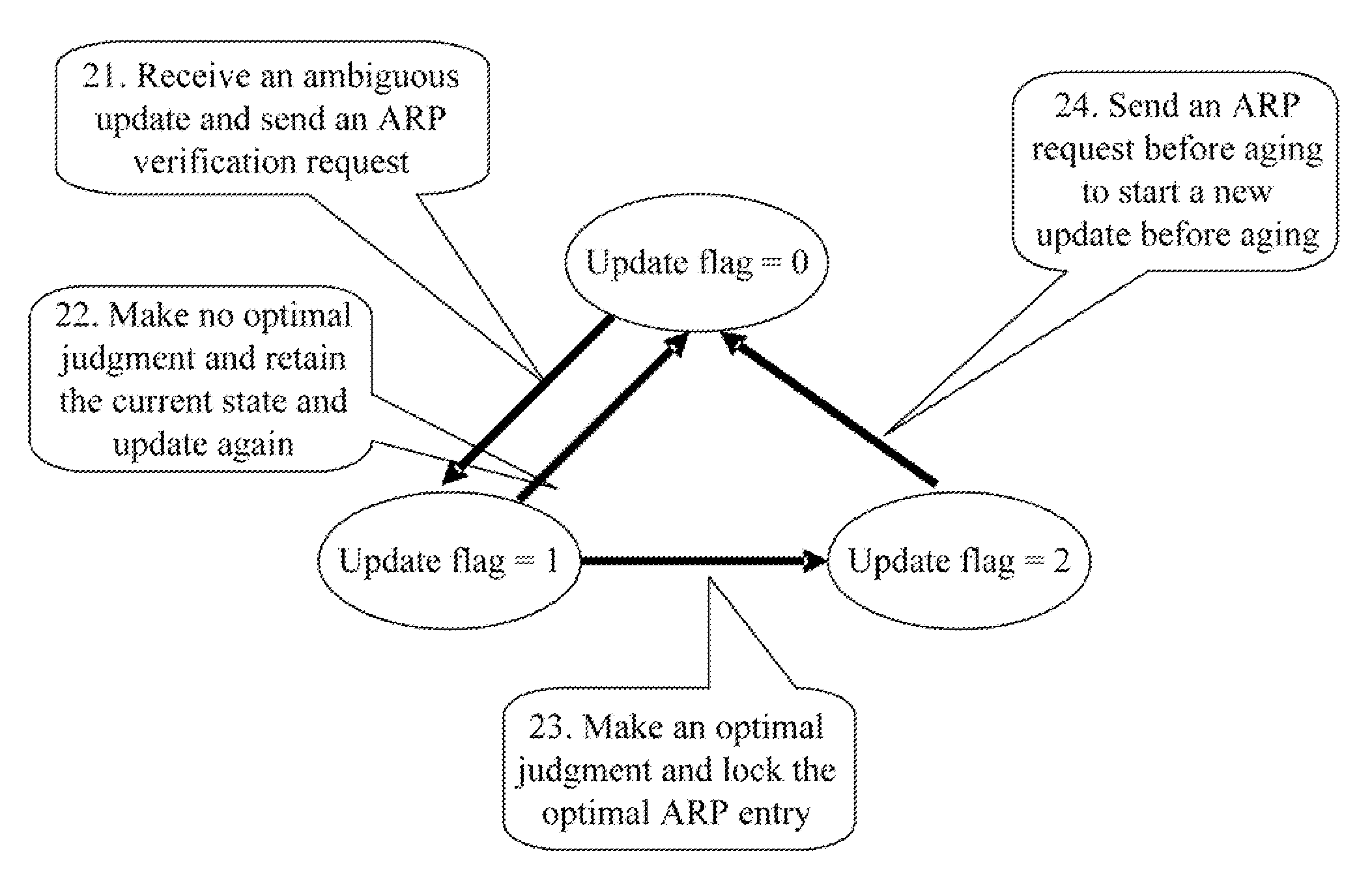
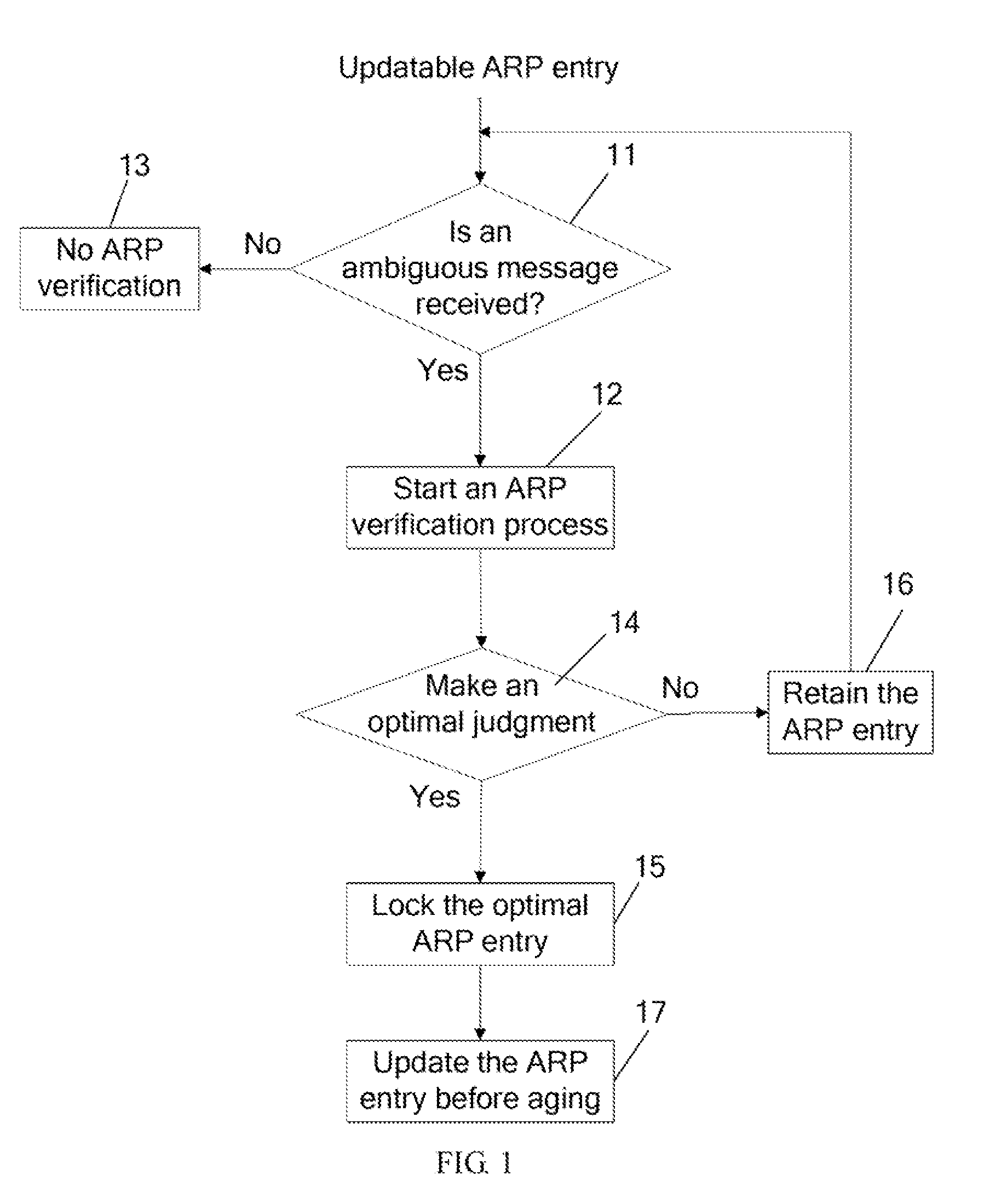
A method and an apparatus for defending against Address Resolution Protocol (ARP) spoofing attacks are disclosed. The method includes: when an ARP entry is updatable, judging whether the MAC address of a received ARP message is the same as the MAC address in the ARP entry, where the ARP message has the same Internet Protocol (IP) address as the ARP entry; if the MAC addresses are different, determining the received ARP message as an ambiguous ARP message and starting an ARP verification process, or else starting no ARP verification. In this way, when no address spoofing attacks occur, no verification messages are generated, and thus reducing signaling interactions and saving network resources; besides, spooling attacks possibly happening at any time are avoided, which effectively prevents address spoofing attacks via random scanning and protects the normal application of the real host.
Owner:HUAWEI TECH CO LTD
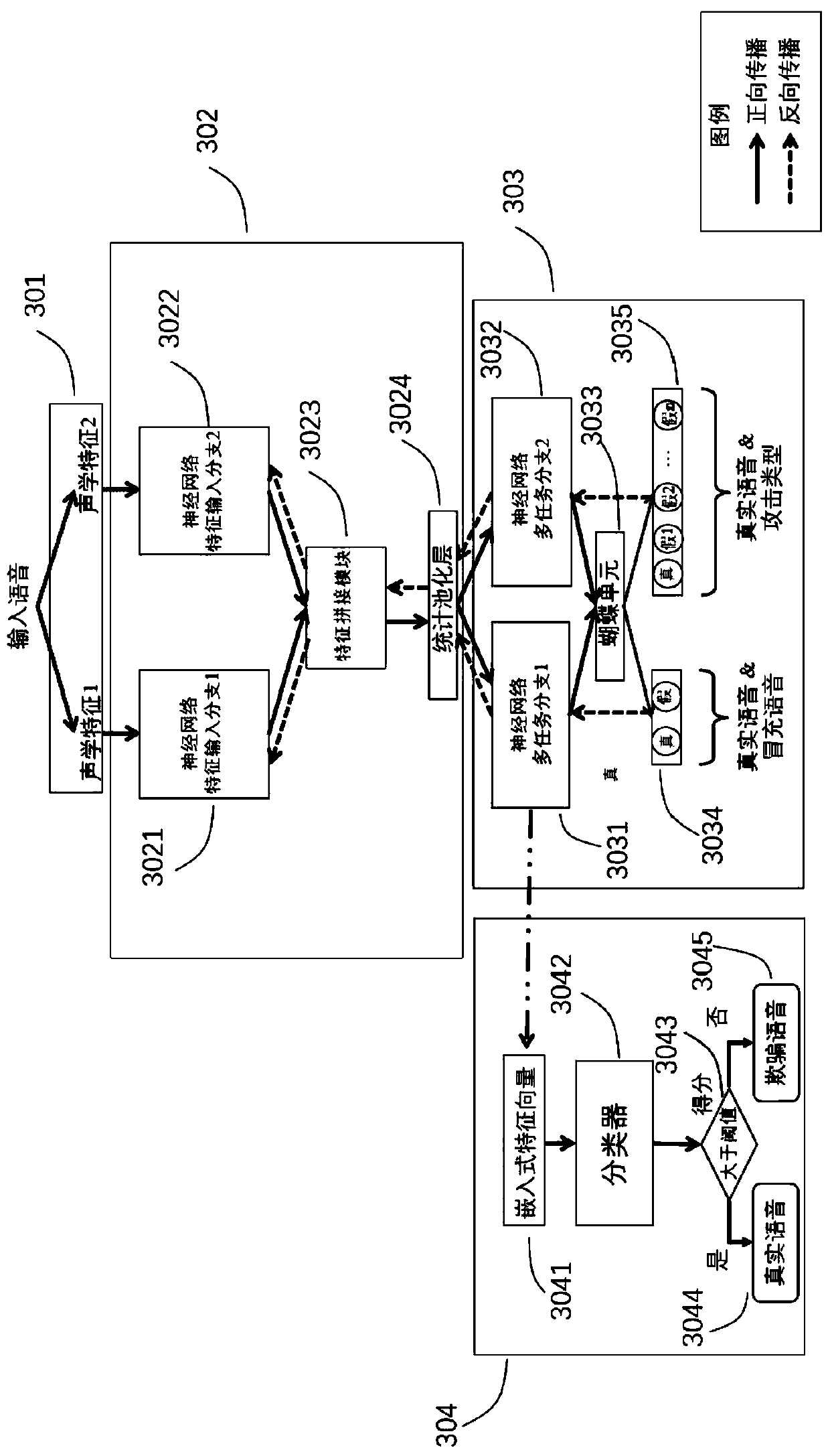
Deception voice detection method based on deep neural network
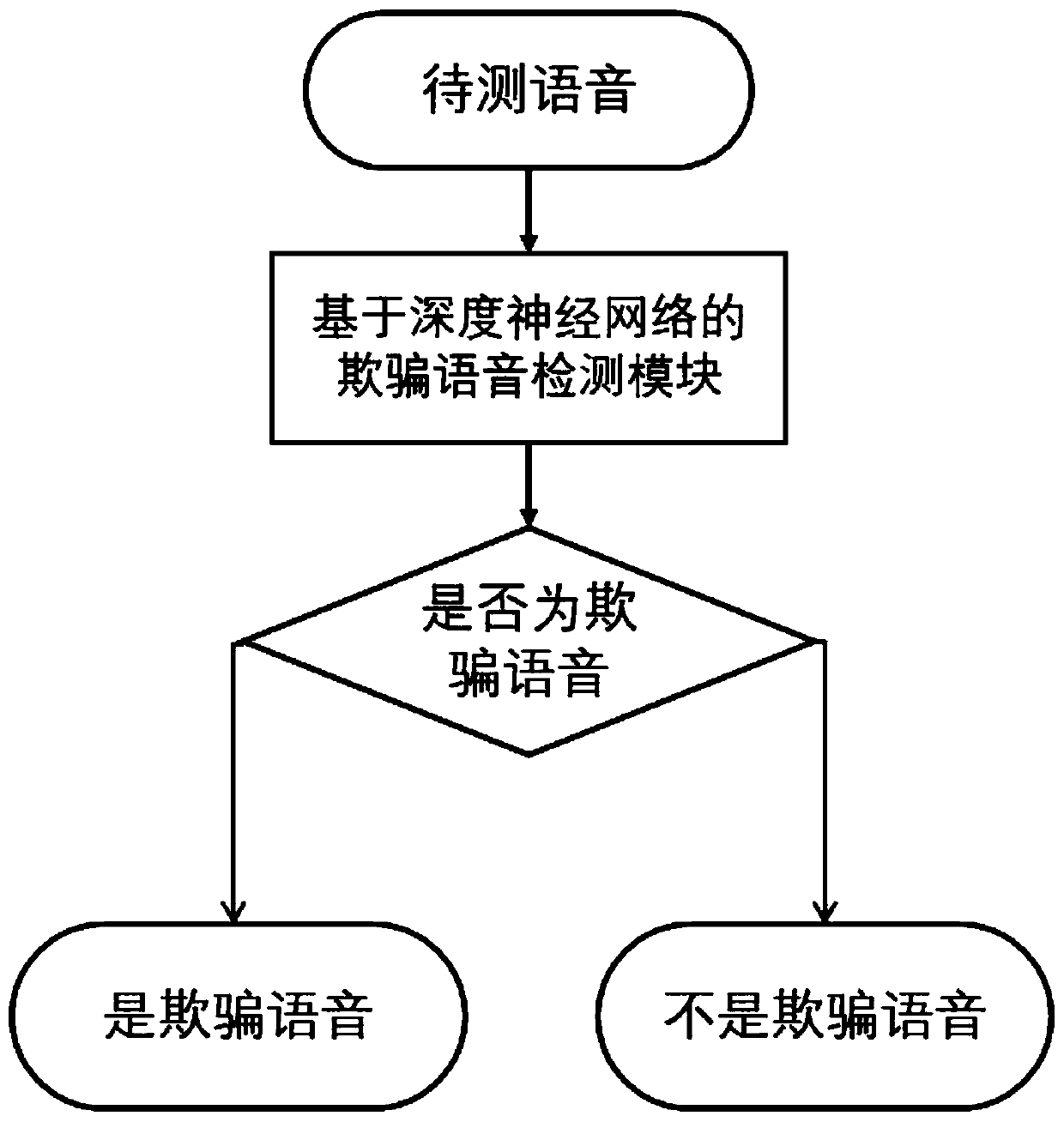
ActiveCN110491391AEfficient miningCompensation for RepresentationSpeech analysisVoice transformationSpeech sound
The invention discloses a deception voice detection method based on a deep neural network. The method comprises the following steps: A, training and building a deception voice detection model based onthe deep neural network according to voice data, with the known authenticity, of a user, wherein the deception voice detection model has network parameters; and B, performing classification judgmenton test voices to be tested in the trained deception voice detection model with the network parameters so as to judge whether the test voices are real voices or deceptive voices. The method has the following advantages: novel unknown voice synthesis, voice conversion, record playback and other deceptive attacks are supported.
Owner:XIAMEN UNIV
Apparatus and method for implementing spoofing-and replay-attack-resistant virtual zones on storage area networks
InactiveUS6973568B2Digital data processing detailsUser identity/authority verificationHash functionStorage area network
A storage area network resistant to spoofing attack has several nodes each having a port, and storage area network interconnect interconnecting the ports. Each port is provided with a hash function generator for providing and verifying an authentication code for frames transmitted over the storage area network, and a key table for providing a key to the hash function generator. The authentication code is generated by applying a hash function to the key and to at least an address portion of each frame. In each node, the key is selected from that node's key table according to address information of the frame.
Owner:GOOGLE LLC
Systems, methods, and devices for detecting security vulnerabilities in IP networks
ActiveUS8806632B2Easy to addMemory loss protectionError detection/correctionBaseline dataCamera image
This invention is a system, method, and apparatus for detecting compromise of IP devices that make up an IP-based network. One embodiment is a method for detecting and alerting on the following conditions: (1) Denial of Service Attack; (2) Unauthorized Usage Attack (for an IP camera, unauthorized person seeing a camera image); and (3) Spoofing Attack (for an IP camera, unauthorized person seeing substitute images). A survey of services running on the IP device, historical benchmark data, and traceroute information may be used to detect a possible Denial of Service Attack. A detailed log analysis and a passive DNS compromise system may be used to detect a possible unauthorized usage. Finally, a fingerprint (a hash of device configuration data) may be used as a private key to detect a possible spoofing attack. The present invention may be used to help mitigate intrusions and vulnerabilities in IP networks.
Owner:SECURENET SOLUTIONS GRP
Deception recognizing method and device of face image
InactiveCN108280418AImprove accuracyImprove robustnessSpoof detectionPattern recognitionSpoofing attack
Owner:BEIJING SENSING TECH CO LTD
Liveness detection method and system for face recognition on mobile platform
The invention provides a liveness detection method and system for face recognition on a mobile platform. The method includes the following steps that: a facial video containing of user photos at different angles as well as motion acceleration and rotation data of a mobile device in video recording are captured; the feature information of the correlation of head pose vector data and device movement vector data in the video are calculated and extracted; and whether the detected video is a real face or a face counterfeited from photos / videos is distinguished through a classifier. With the liveness detection method and system of the invention adopted, a face recognition-based identity recognition application on the mobile platform can resist photo and video-based spoofing attacks, and hardware devices which most mobile devices are not provided with are not needed to be adopted. The method and system have robustness for complex light conditions and can tolerate head rotation of the user in a use process.
Owner:李岩 +3
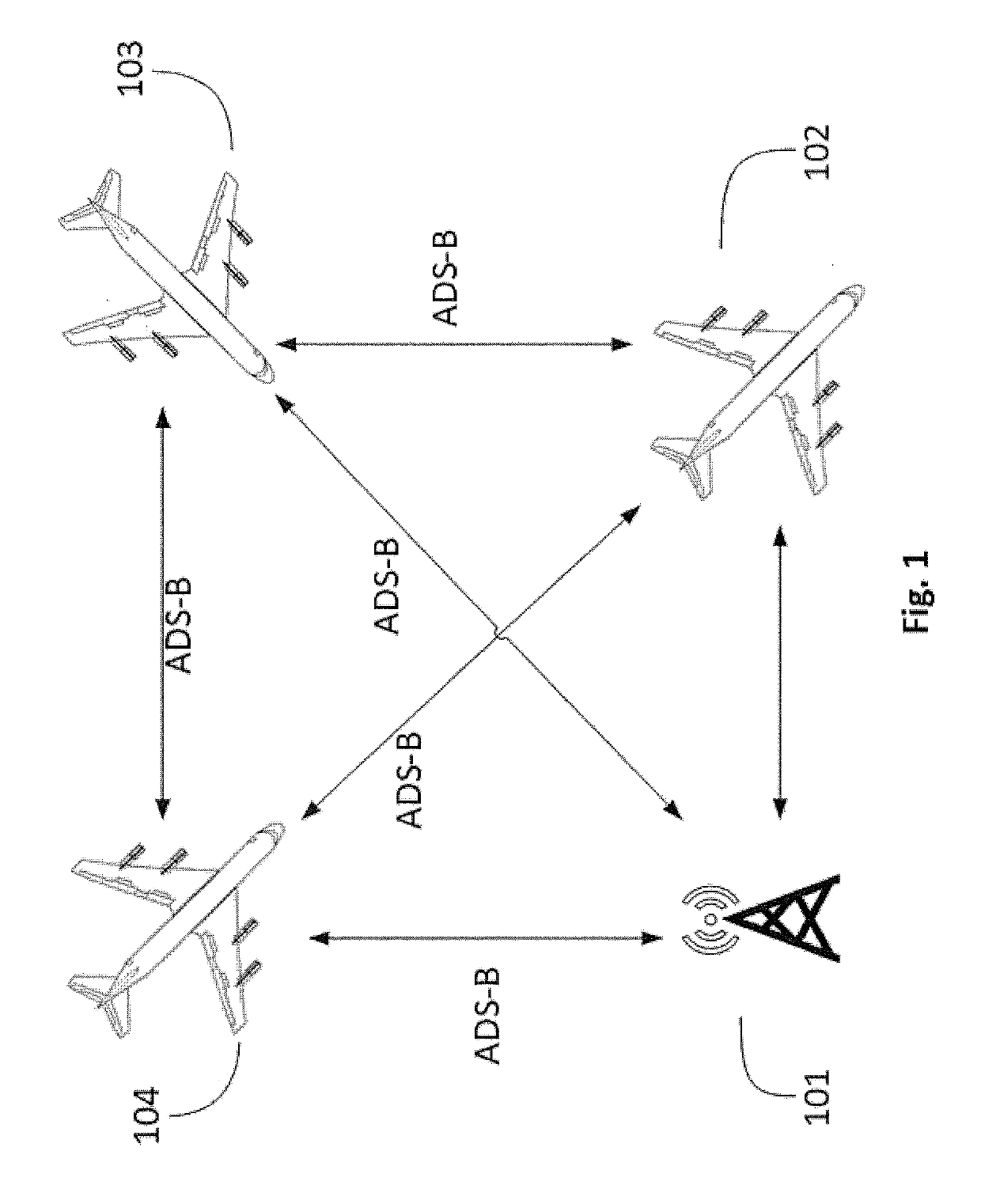
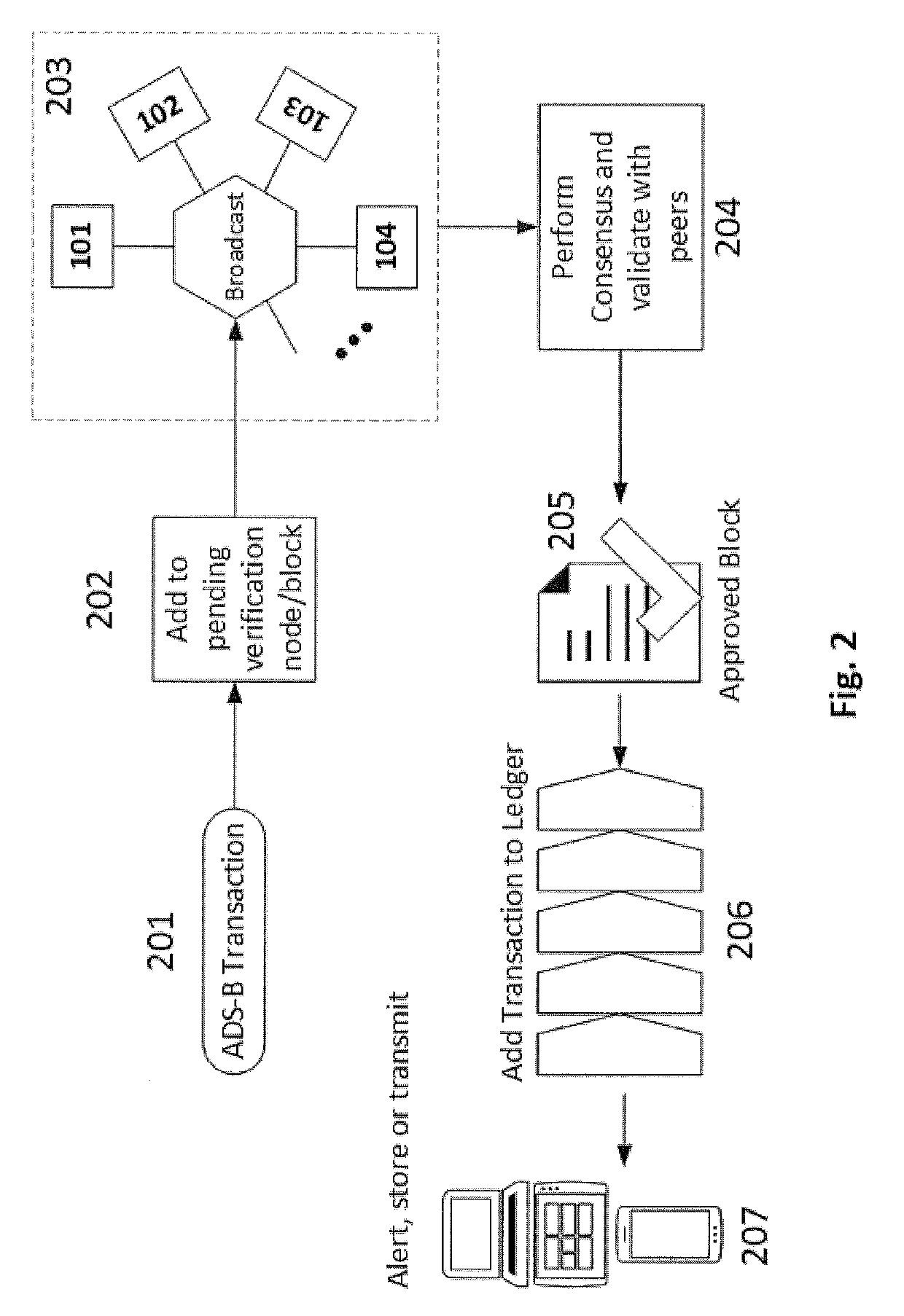
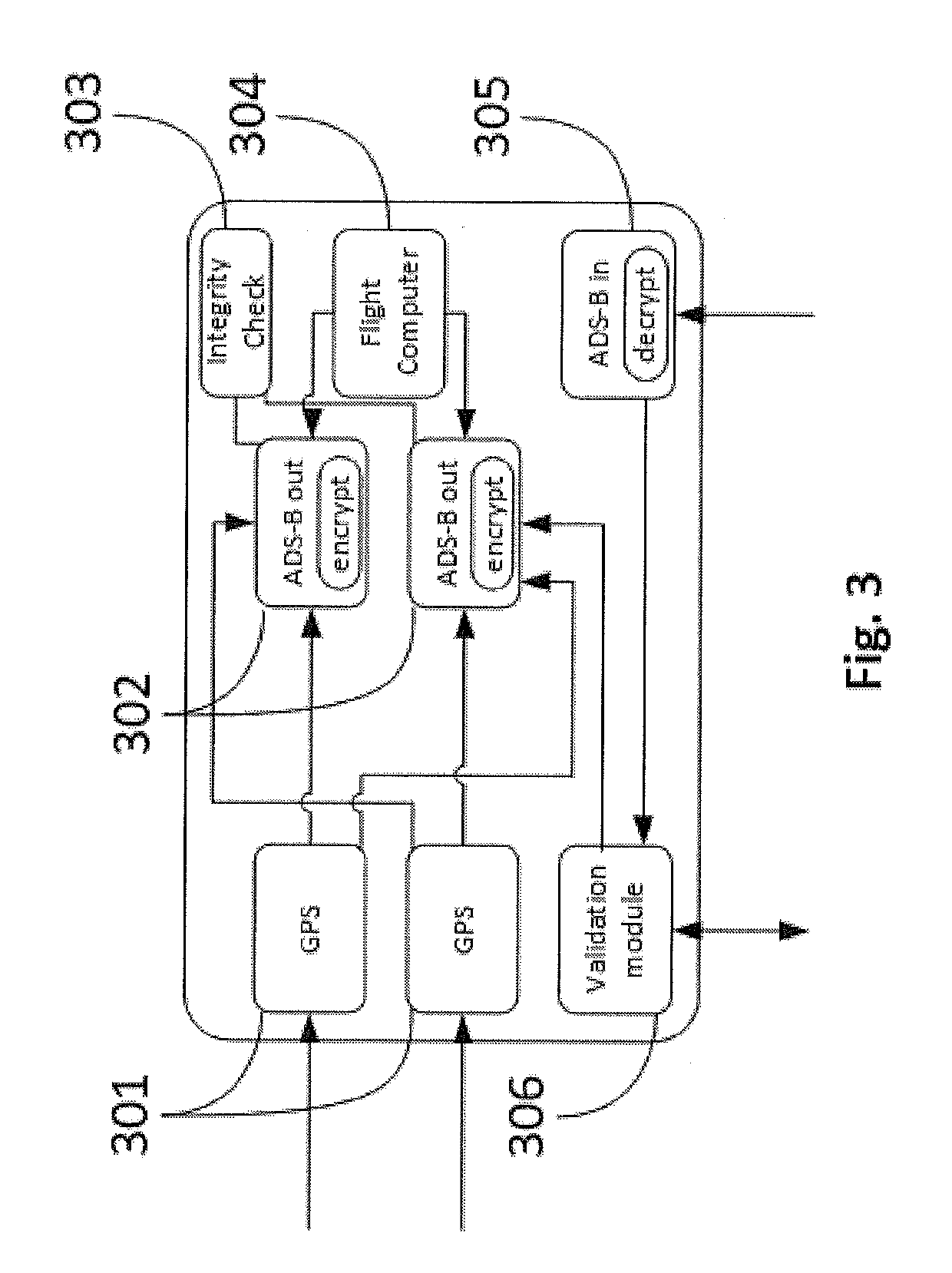
Method and network to implement decentralized validation and authentication mechanisms to prevent ads-b cyber-attacks
InactiveUS20190280871A1Improve securityOvercome disadvantagesEncryption apparatus with shift registers/memoriesUser identity/authority verificationCyber-attackEavesdropping
A method or network that addresses cybersecurity vulnerabilities in an ADS-B network by validating and authenticating ADS-B messages. Nodes of the network maintain a validated ledger of ADS-B transactions and use validated information from this ledger to improve security against common cybersecurity attacks including, but not limited to, denial of service attacks, jamming attacks, spoofing attacks, flooding attacks and eavesdropping.
Owner:ROBUST ANALYTICS INC
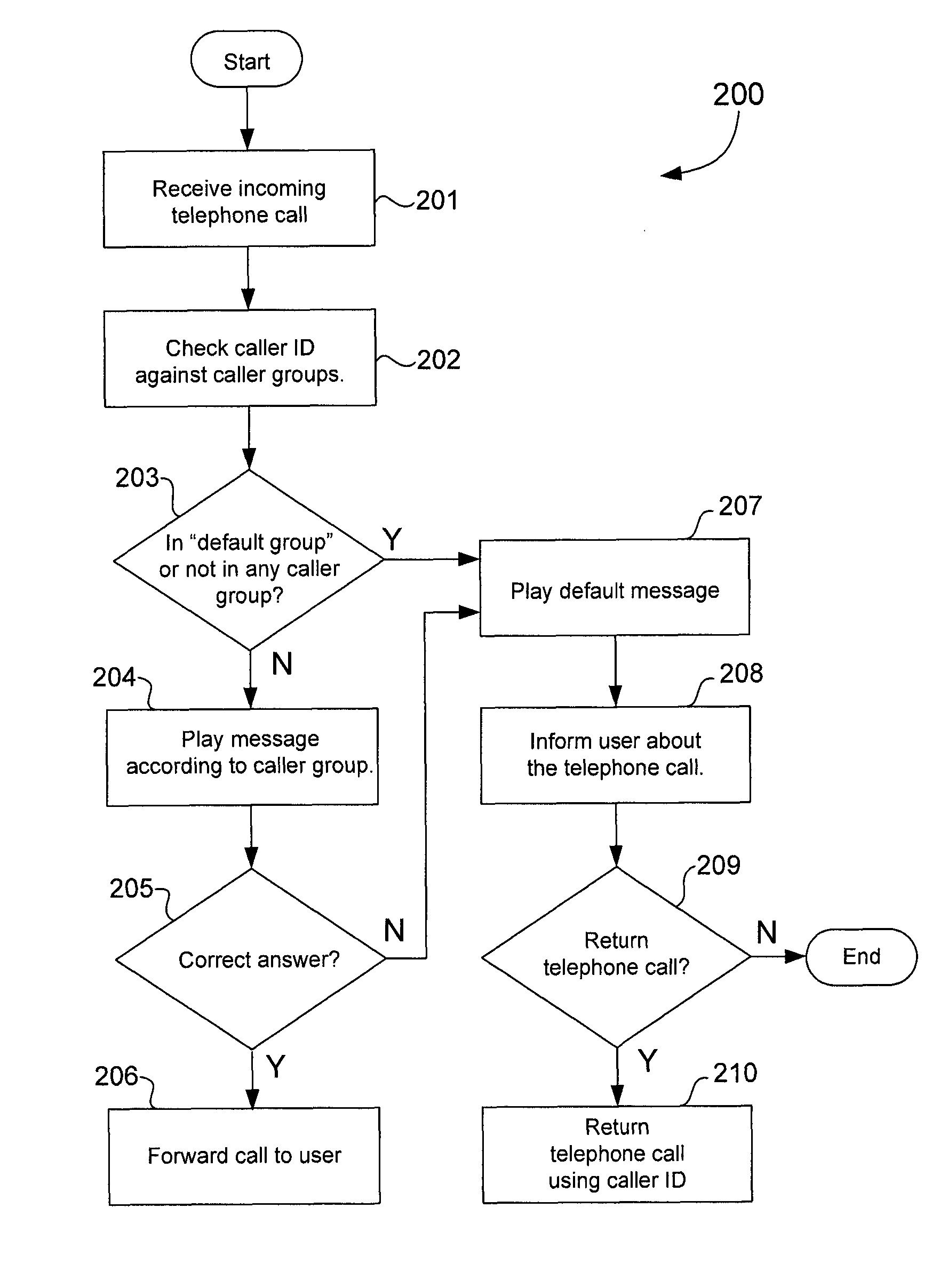
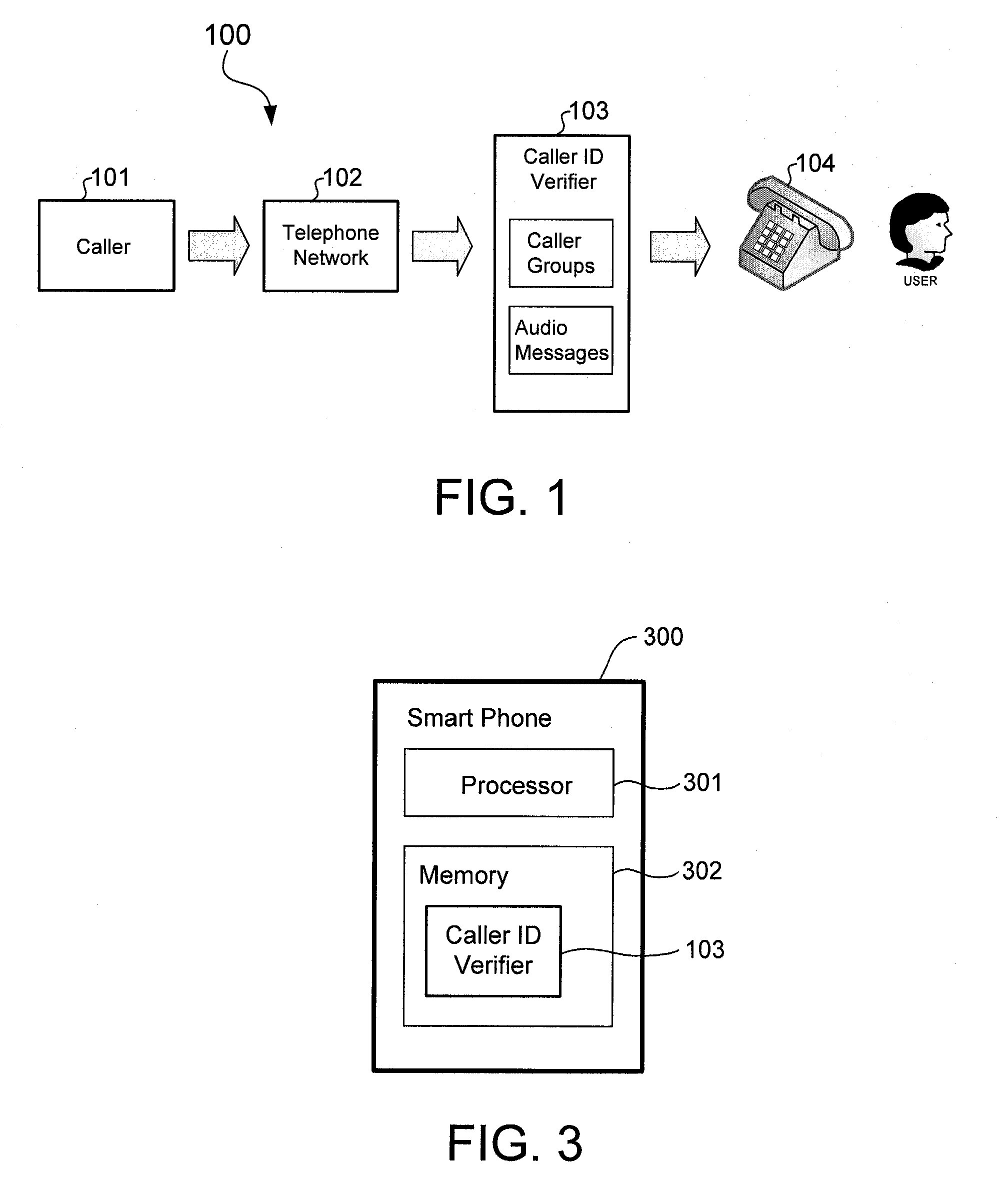
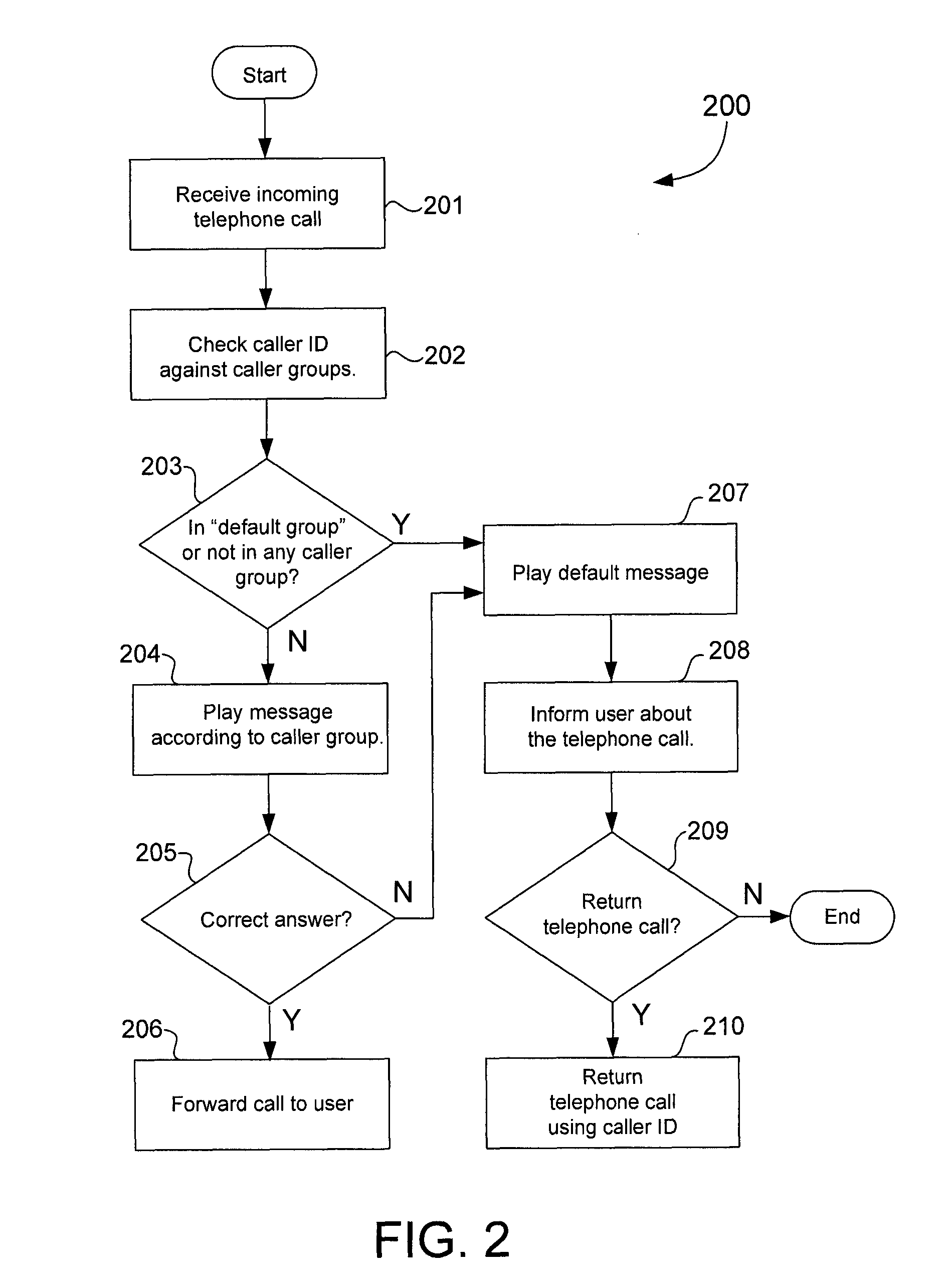
Techniques for protecting telephone users from caller ID spoofing attacks
ActiveUS8135119B1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsTelephone networkSpoofing attack
A caller ID verifier may be employed to protect telephone users against caller ID spoofing. The caller ID verifier may be implemented in a telephony apparatus, such as a smart phone, stand alone caller ID device, or telephone network infrastructure, for example. Telephone numbers of related callers may be grouped into caller groups. The caller ID verifier may be configured to play one of several audio messages depending on the caller group of the telephone number corresponding to the caller ID of the telephone call. An audio message may include a question. The caller ID verifier may forward the telephone call to the telephone user when the caller answers the question correctly. Otherwise, the caller ID verifier may terminate the telephone call and give the telephone user the option to return the telephone call using the caller ID.
Owner:TREND MICRO INC
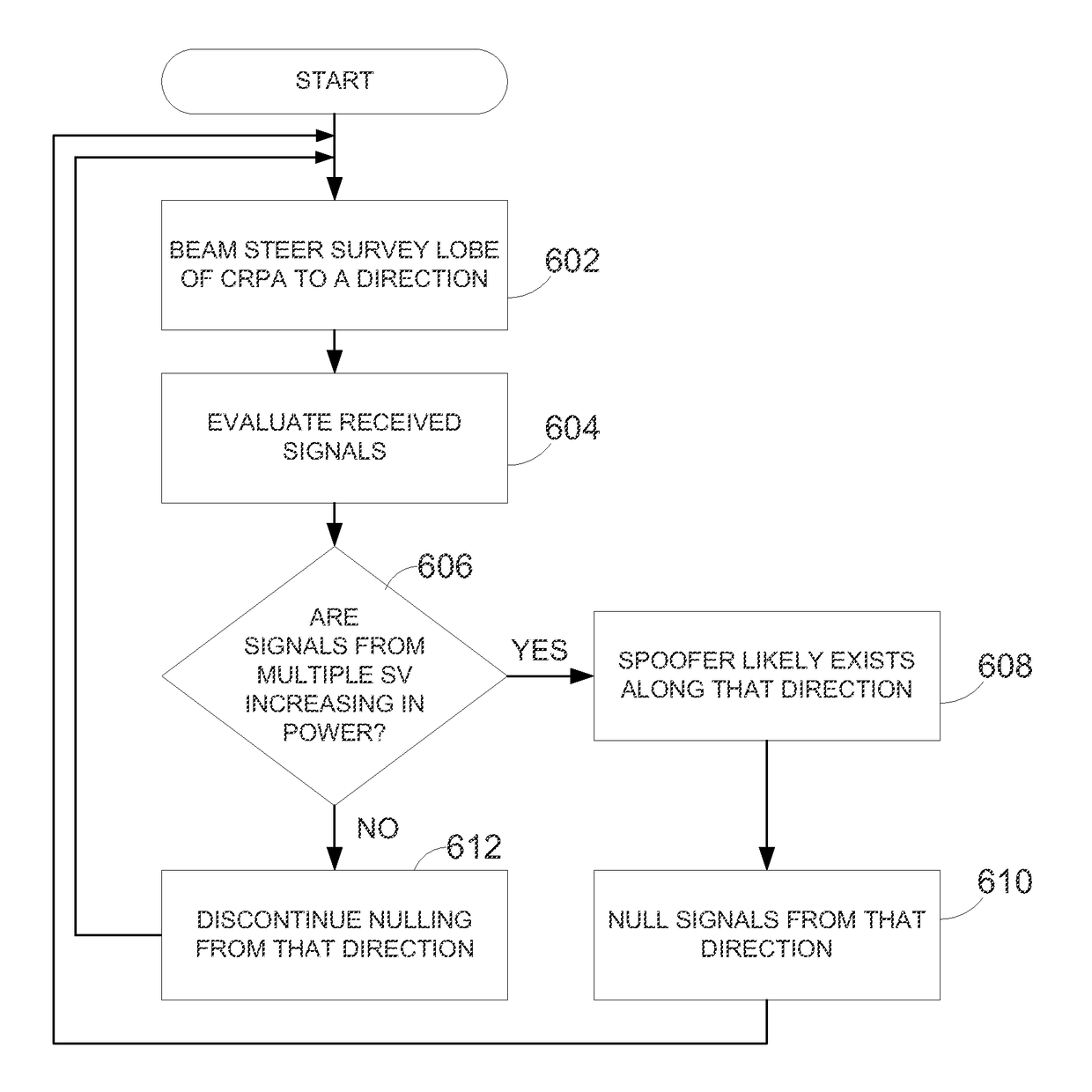
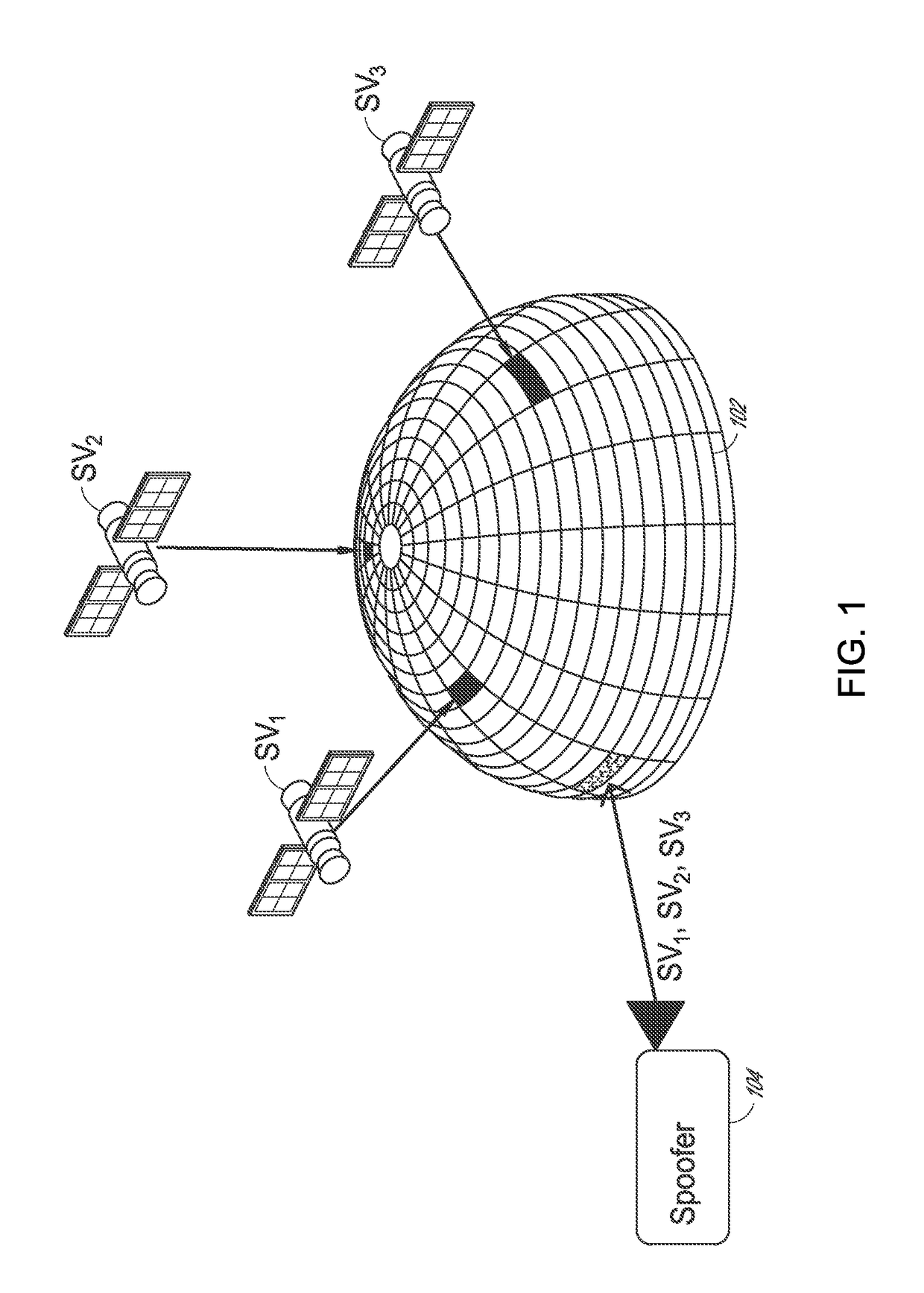
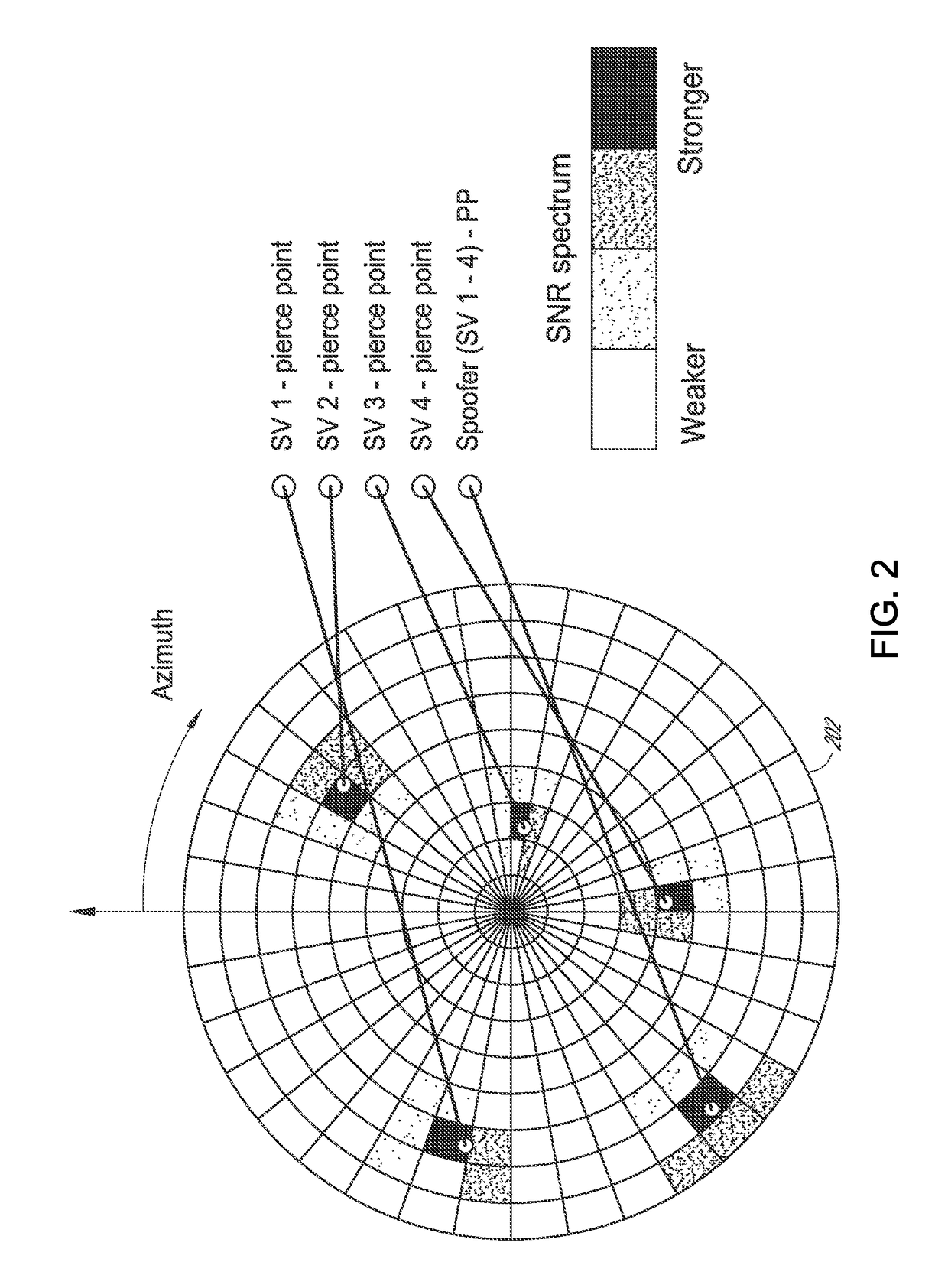
Global navigation satellite system spoofer identification technique
Disclosed is a technique that can provide one or more countermeasures against spoofers. A direction from which a spoofing attack occurs is identified. A beamformer can control an antenna pattern of a CRPA to null out signals from that direction, which can assist a GNSS receiver to avoid error induced by the spoofing attack. Further, after two or more observations, the location of the spoofer can be identified.
Owner:INTERSTATE ELECTRONICS
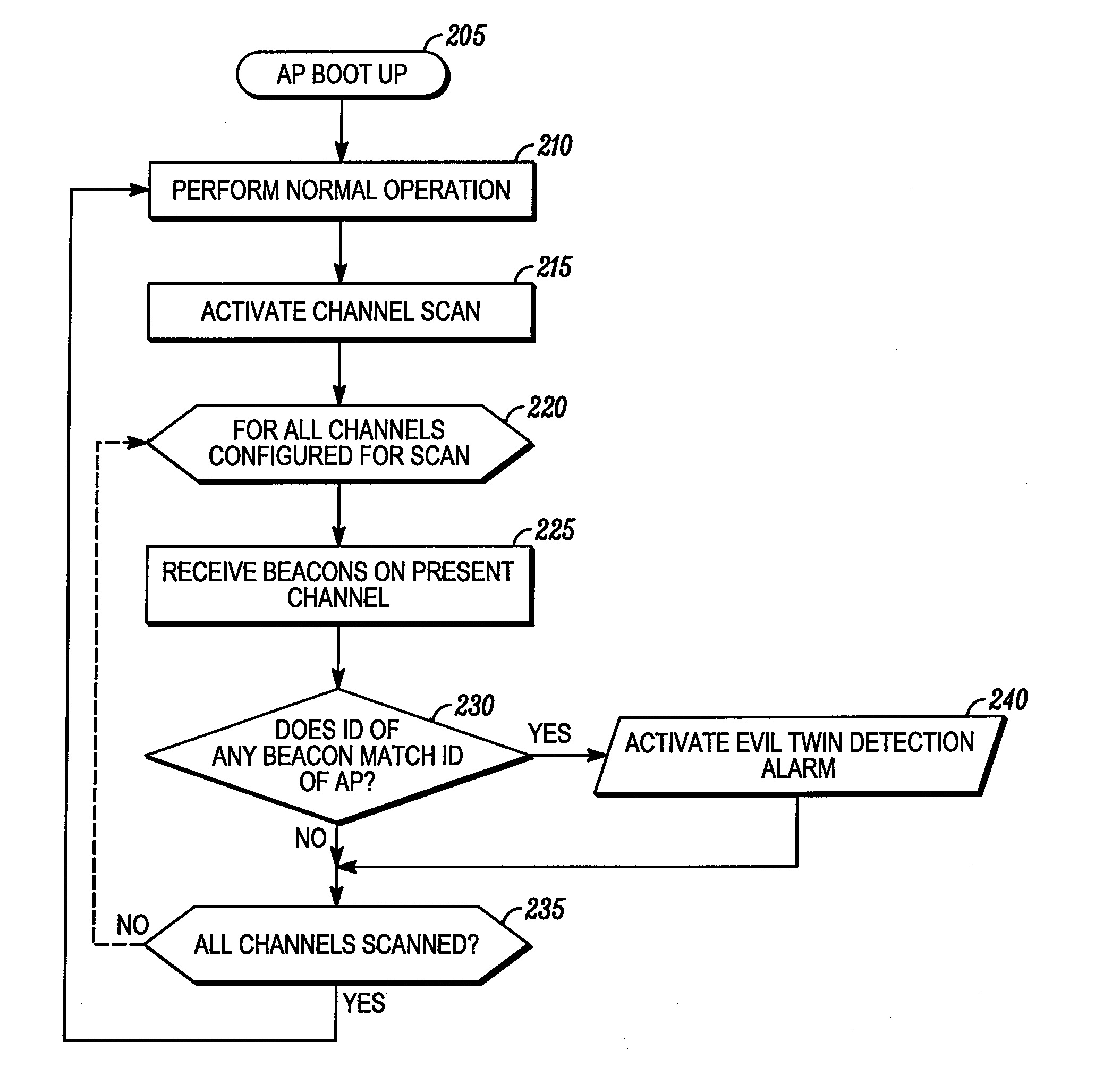
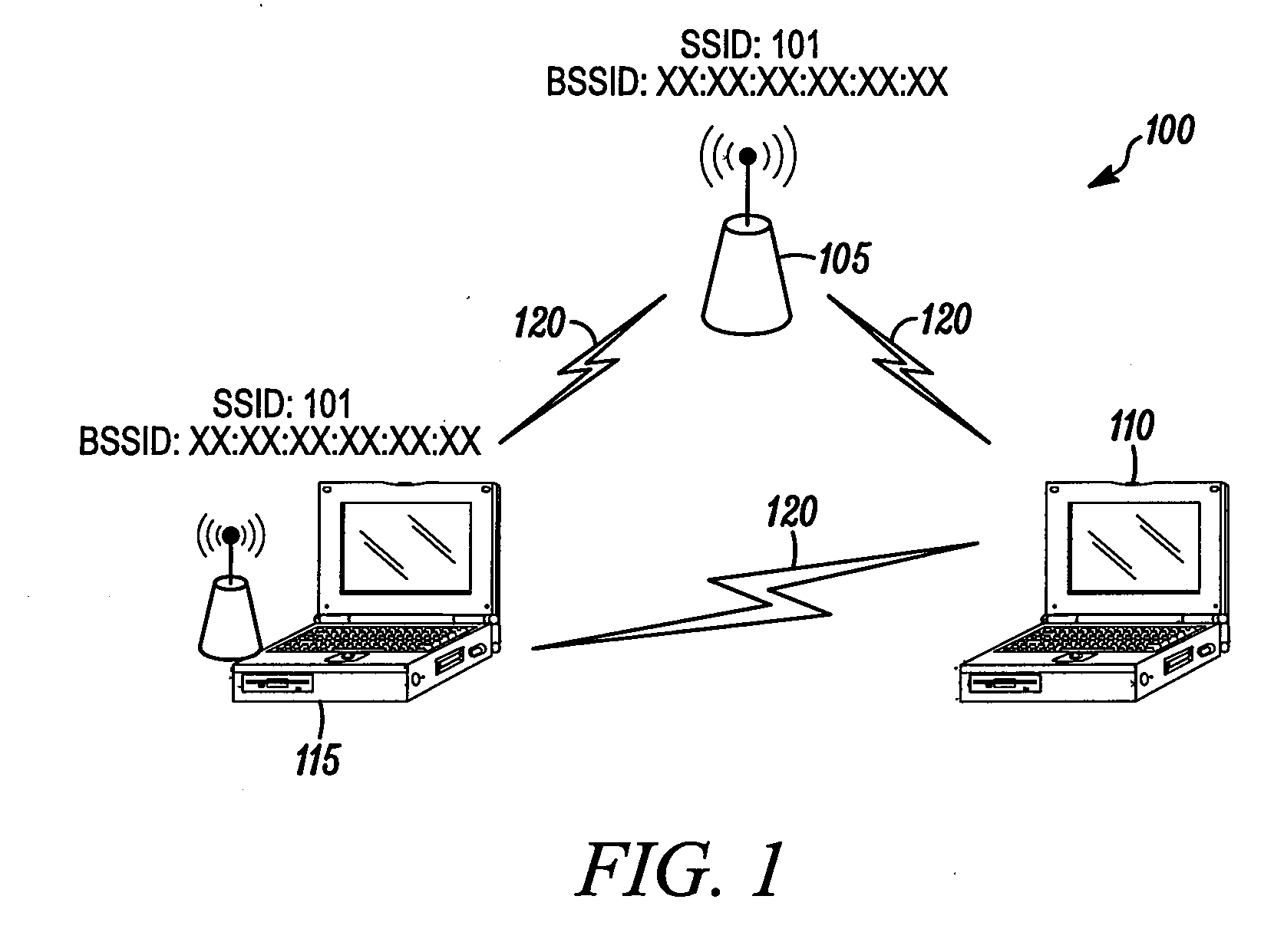
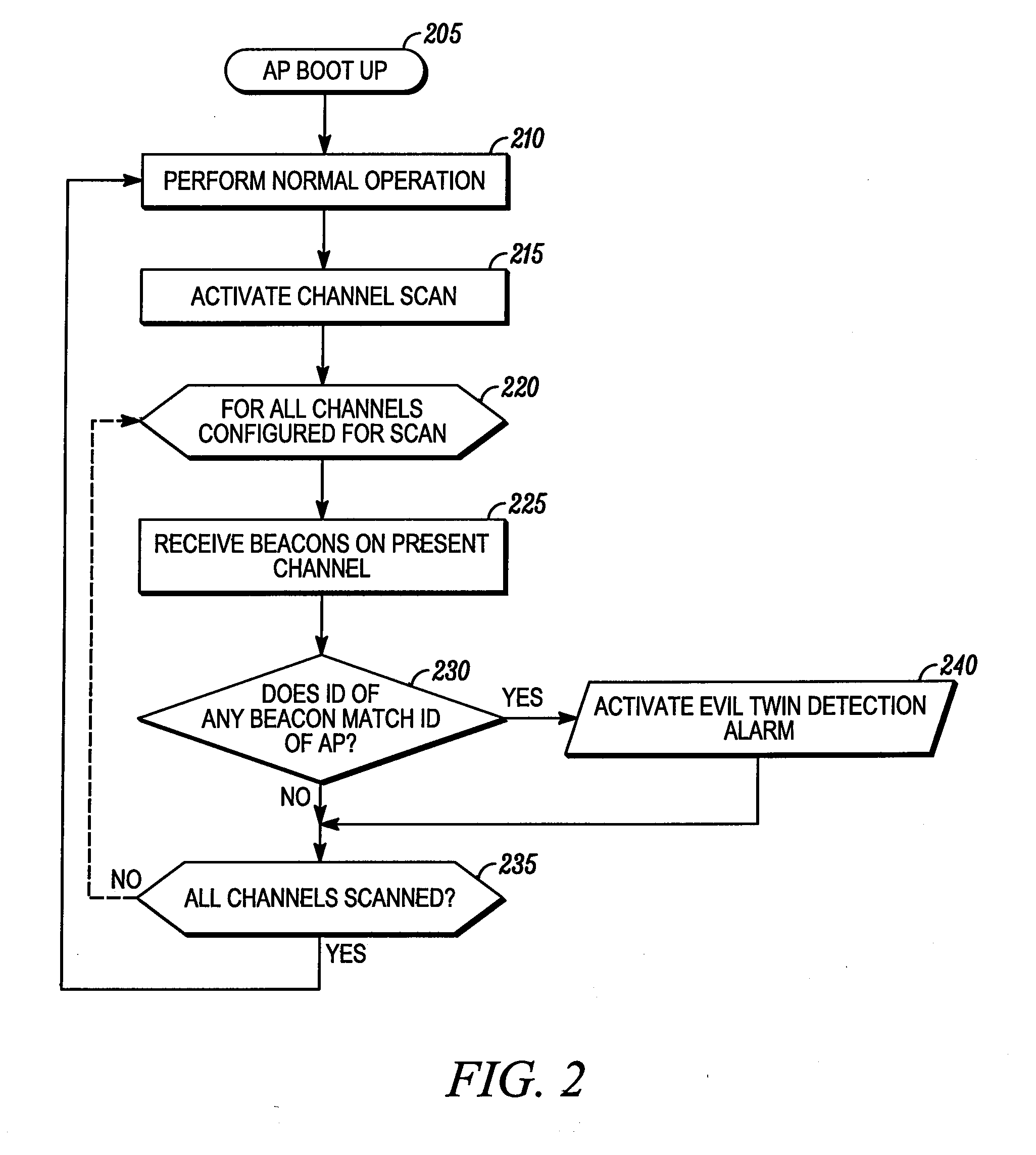
Method and device for detecting a spoofing attack in a wireless communication network
InactiveUS20110131651A1Memory loss protectionError detection/correctionTelecommunicationsSpoofing attack
A method and device enables detecting a spoofing attack in a wireless communication network (100). The method includes receiving at the primary access point (105) a beacon signal transmitted from an alternative access point (115), where the beacon signal includes an alternative access point identification. The primary access point (105) then compares the alternative access point identification with an actual identification of the primary access point (105). It is then determined at the primary access point that the alternative access point (115) is conducting a spoofing attack if the alternative access point identification matches the actual identification of the primary access point (105).
Owner:SYMBOL TECH INC
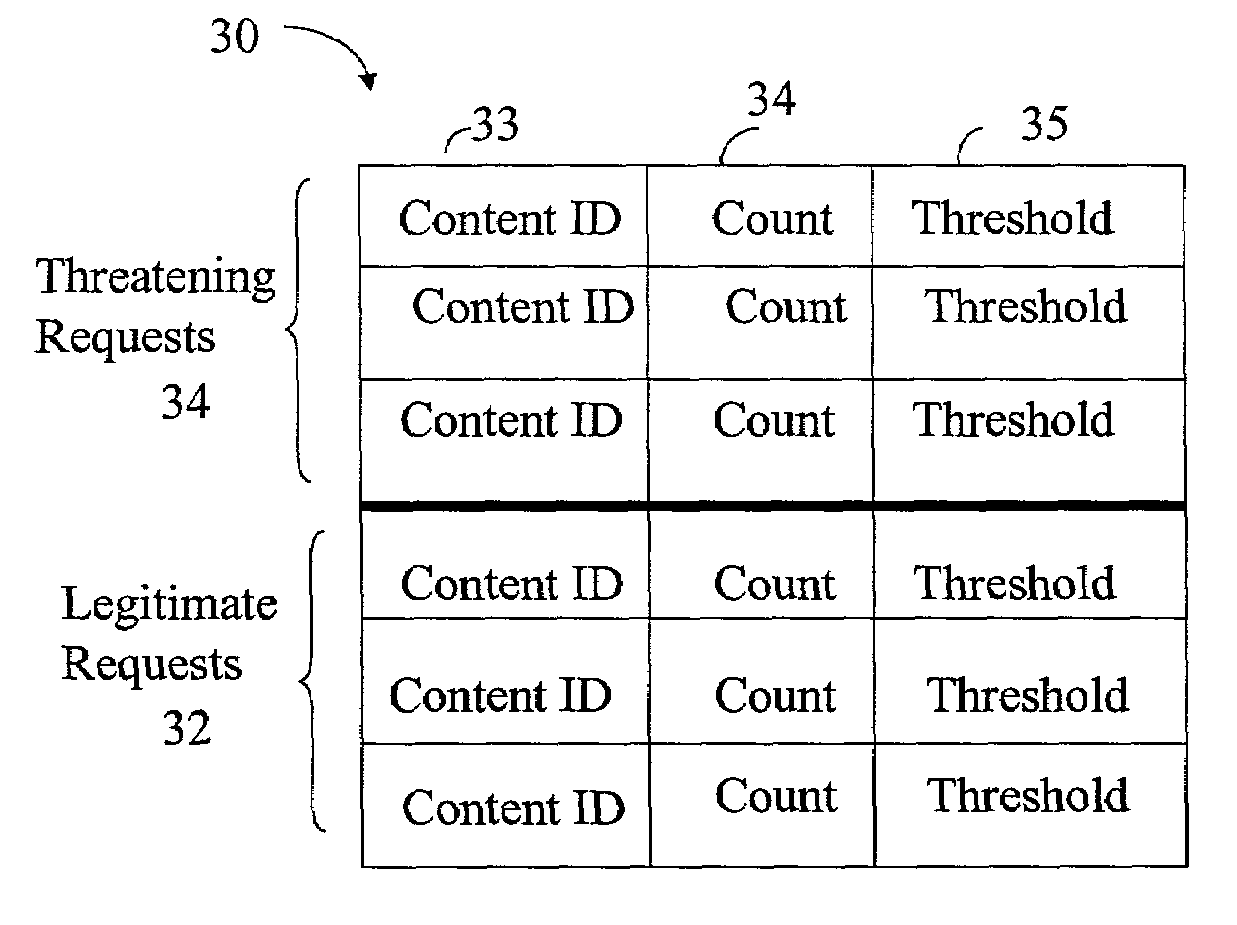
Method and apparatus for security management in a networked environment
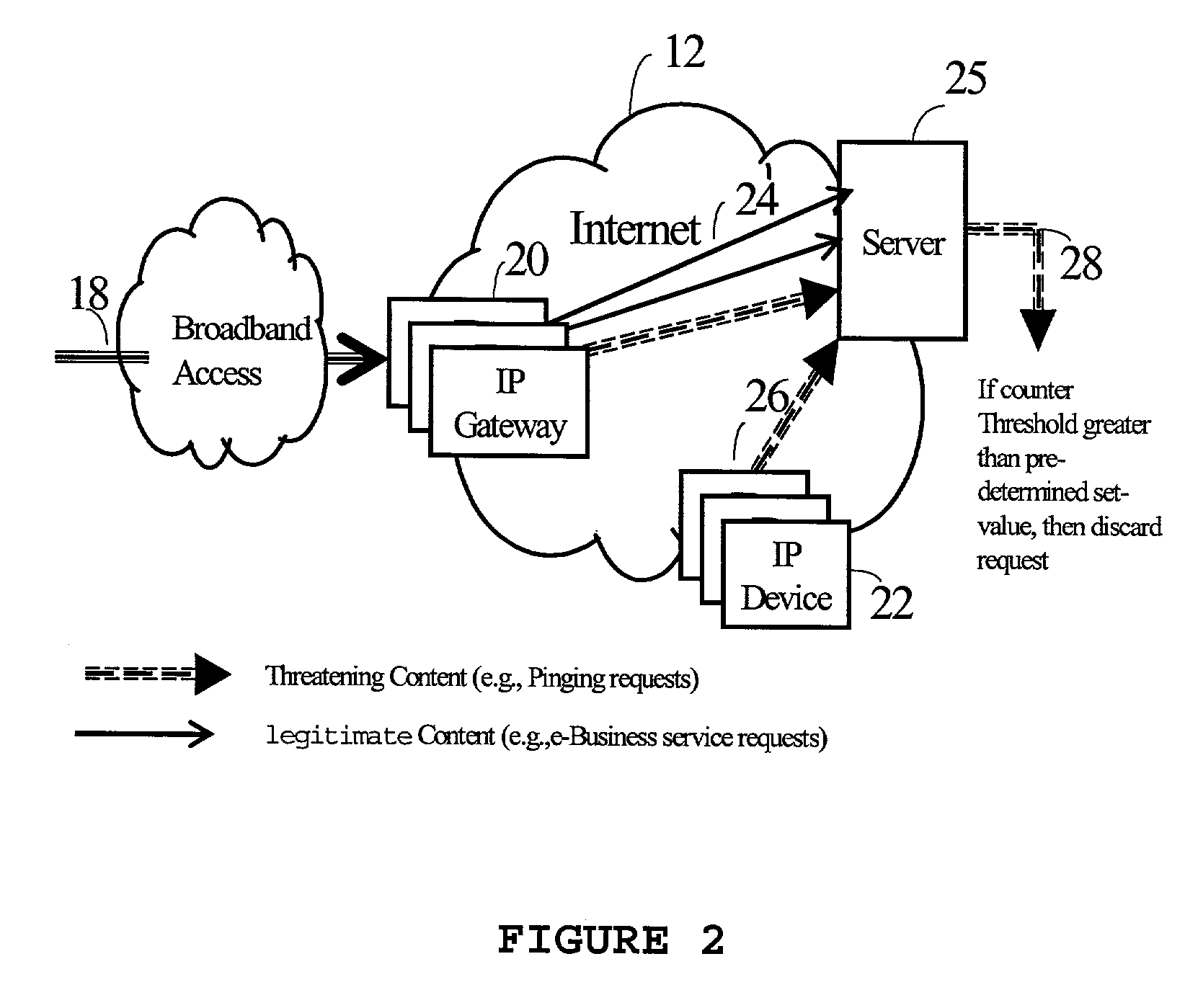
ActiveUS7246376B2Function increaseError preventionFrequency-division multiplex detailsSpecial eventsApplication software
In a networked environment, where multiple Internet Service Providers and multi-vendor equipment are involved in e-Business services and applications offering, the risk of overloading the Internet devices are real and security management is a challenge. Internet device traffic overloads could result from spoof attacks, (Denial-of-Service (DoS) or Distributed DoS (DDoS) attacks), device failures, special events, or widespread loads above engineered levels. To solve the problem of Internet security management for integrated optical and wireless devices, a new apparatus and functions running on IP devices are defined in this invention. Each Internet device includes counters and thresholding feature to manage the security attacks and prevent failure of the device being attacked.
Owner:RPX CLEARINGHOUSE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com