Method and system for detecting voice spoofing attack of speakers on basis of deep learning
A technology of deception attack and detection method, applied in speech analysis, speech recognition, instruments, etc., can solve the problems of poor robustness, inability to accurately characterize the discriminative features of deceptive speech and real speech, and poor recognition effect, and improve the accuracy. , the effect of widening the gap and narrowing the gap
Active Publication Date: 2016-08-17
AISPEECH CO LTD
View PDF3 Cites 84 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
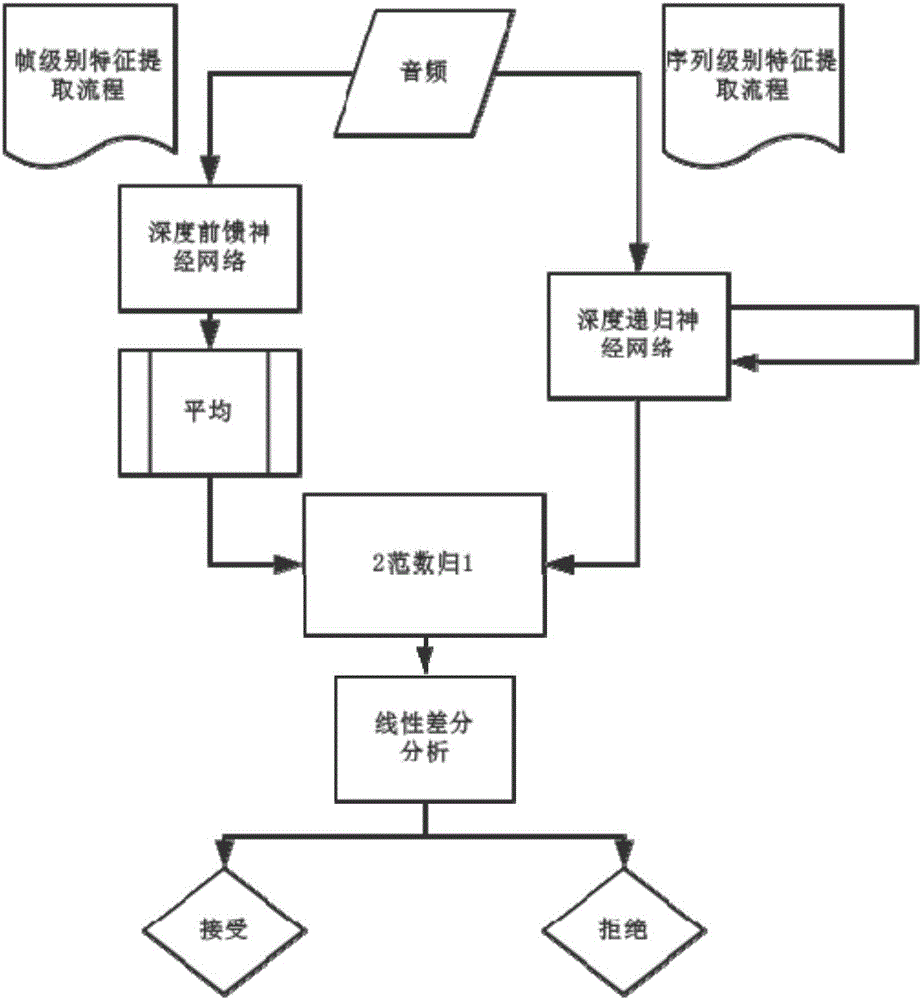
[0005] The present invention aims at the existing traditional voice spoofing attack detection method, which has the limitations of feature extraction that cannot accurately characterize the discriminative features between spoofed voice and real voice, dynamic features of lost voice signals, poor robustness, and poor recognition effect. In the feature extraction stage, the deep learning model is used to extract the feature vector, two different frameworks: frame-level feature representation based on deep feed-forward neural network And the sequence-level feature representation based on deep recurrent neural network, which can not only capture local features, but also grasp global information
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment 1
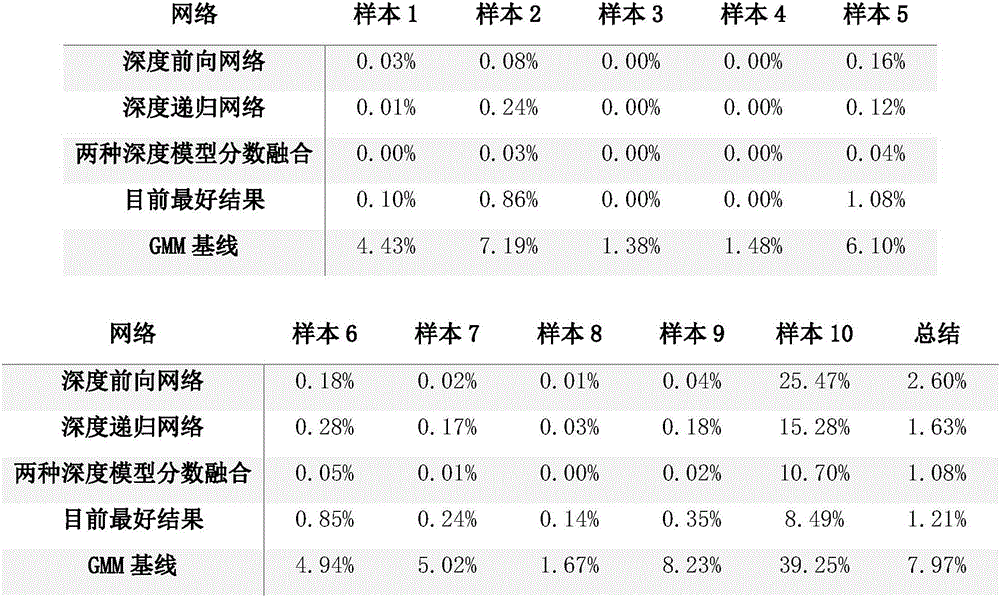
[0031] This example is tested with the newly released ASVSpoof2015 dataset, and compared with the existing baseline method, the results are shown in Table 1. It can be seen that the method proposed by the present invention can achieve the best result so far.
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
The invention discloses a method and a system for detecting voice spoofing attack of speakers on the basis of deep learning. The method includes constructing audio-frequency training sets, initializing deep feed-forward neural networks and deep recurrent neural networks and respectively training the deep feed-forward neural networks and the deep recurrent neural networks by the aid of multi-frame feature vectors and single-frame vector sequences of the training sets; respectively leading frame level and sequence level feature vectors of to-be-tested audio frequencies into two trained linear differential analysis models in test phases, weighting two obtained result grades to obtain scores and comparing the scores to predefined threshold values so as to discriminate voice spoofing. The method and the system have the advantages that local features can be captured, and global information can be grasped; the linear differential analysis models are used as classifiers in identification and verification phases, the voice spoofing attack can be judged by means of grade fusion, and accordingly the voice spoofing detection accuracy can be greatly improved.
Description
technical field [0001] The present invention relates to a technology in the field of intelligent speech, in particular to a method and system for detecting speaker speech spoofing attacks based on deep learning. Background technique [0002] Speech spoofing attack refers to the technology of forging the voice of a specific target to attack the automatic speaker recognition system. Speaker recognition technology has been widely used in many fields, such as: identity verification, Internet security, human-computer interaction, banking and securities systems, military criminal investigation, etc. In recent years, attacks on speaker recognition systems are mainly divided into four categories, namely imitation attacks, recording playback, speech synthesis, and speech conversion. Research shows that the main problem of traditional speech spoofing attack detection lies in feature extraction, and existing feature extraction methods have many shortcomings in terms of expressiveness ...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More IPC IPC(8): G10L15/06G10L15/14G10L15/16
CPCG10L15/063G10L15/14G10L15/16
Inventor 钱彦旻陈楠昕俞凯
Owner AISPEECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com