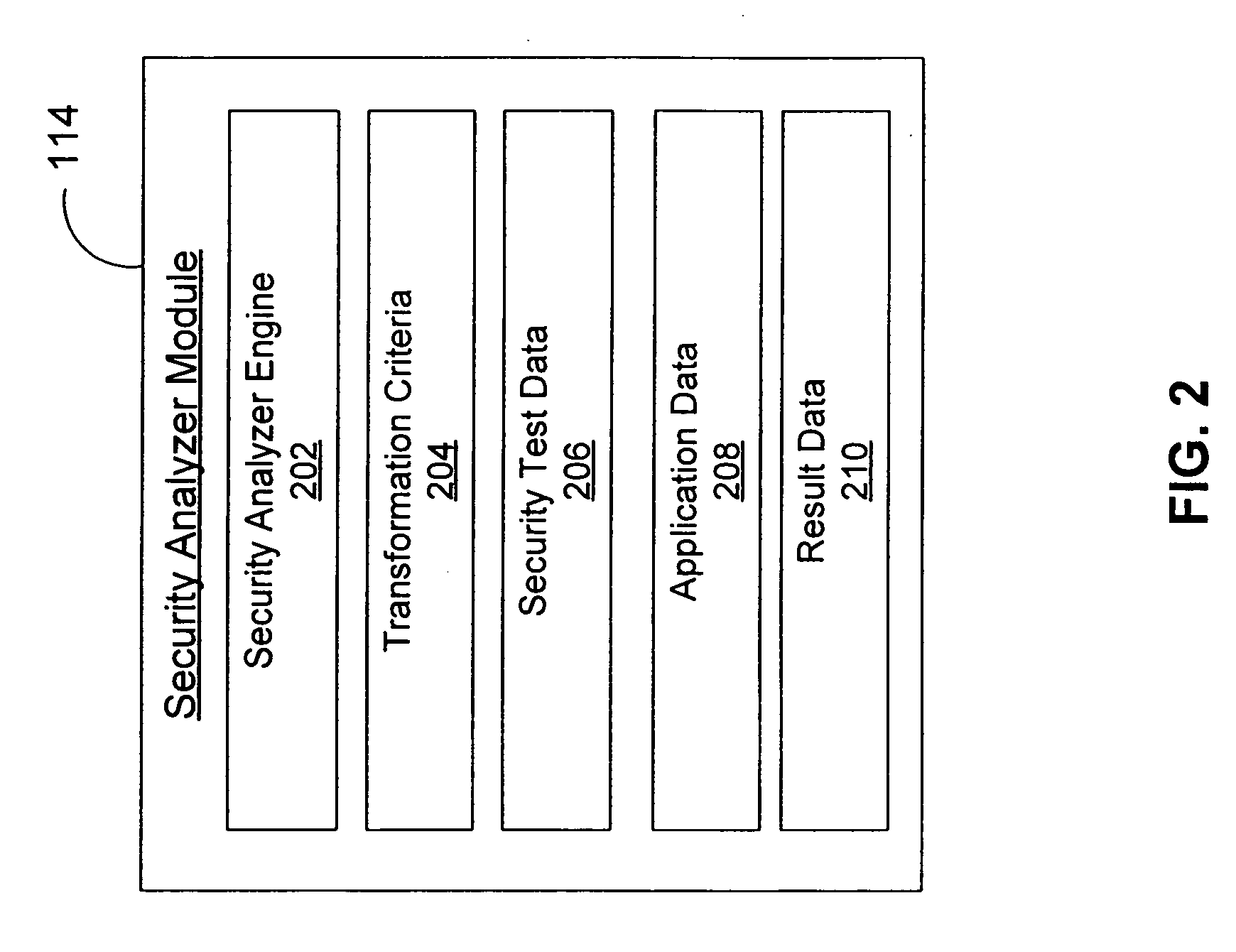
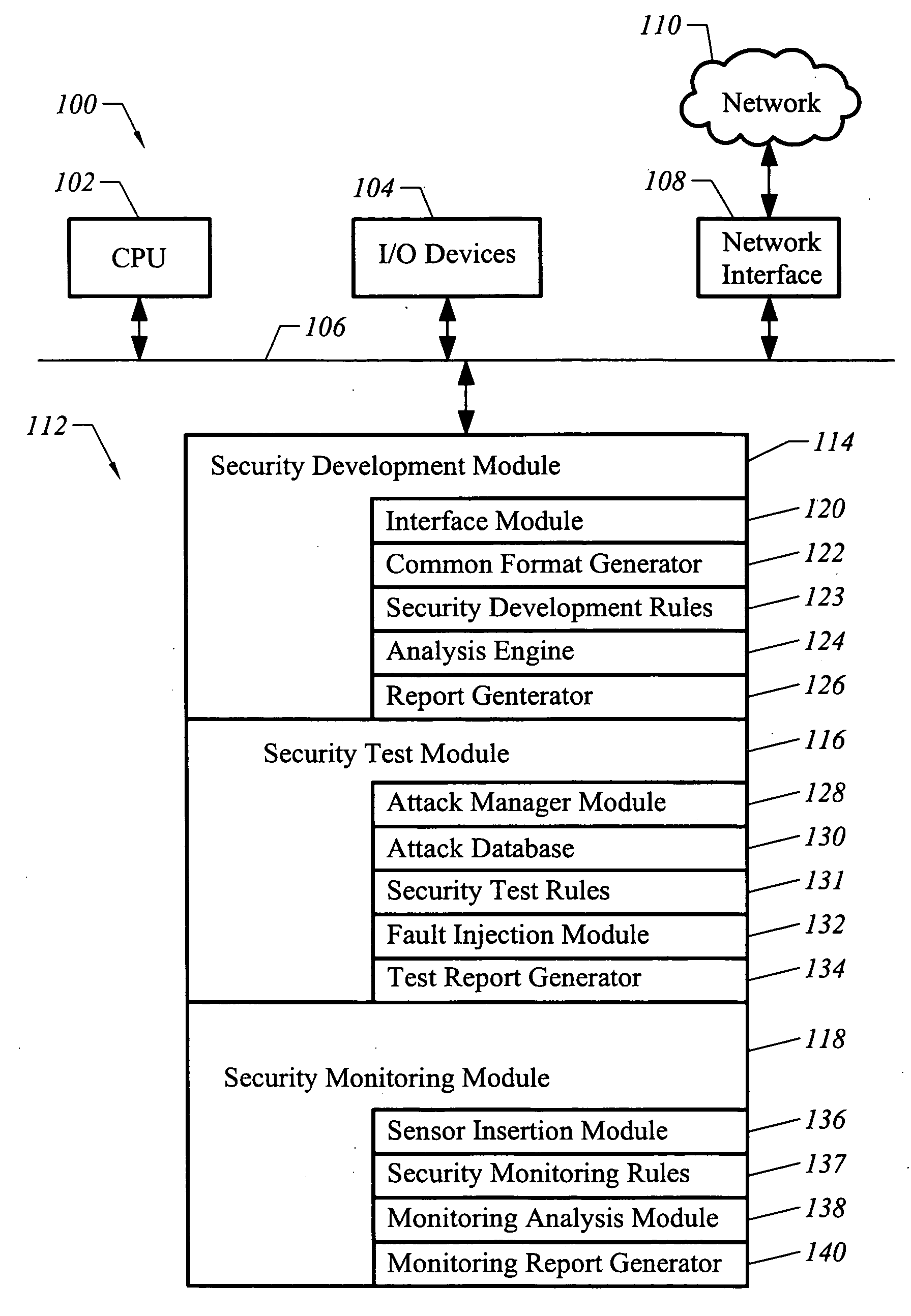
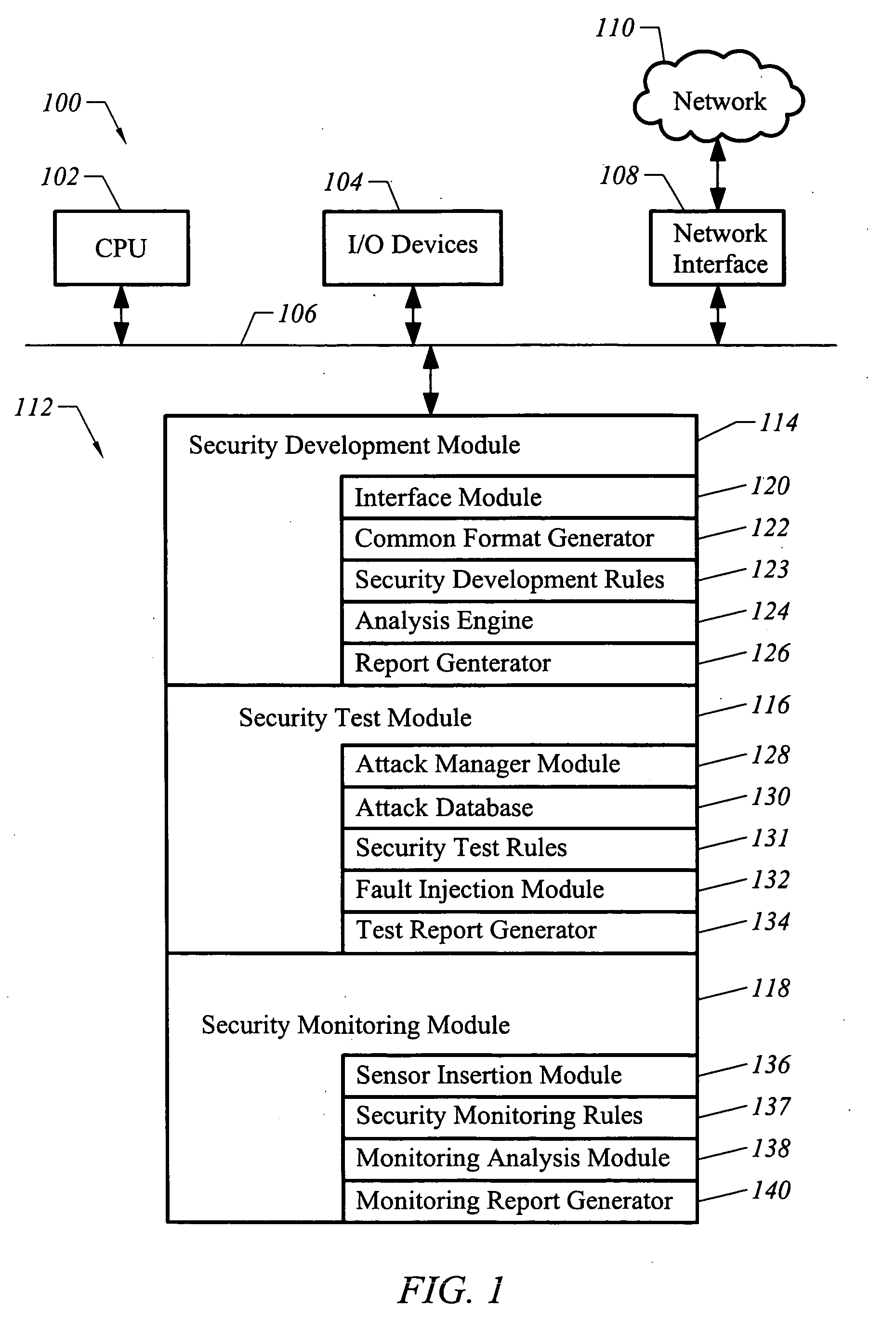
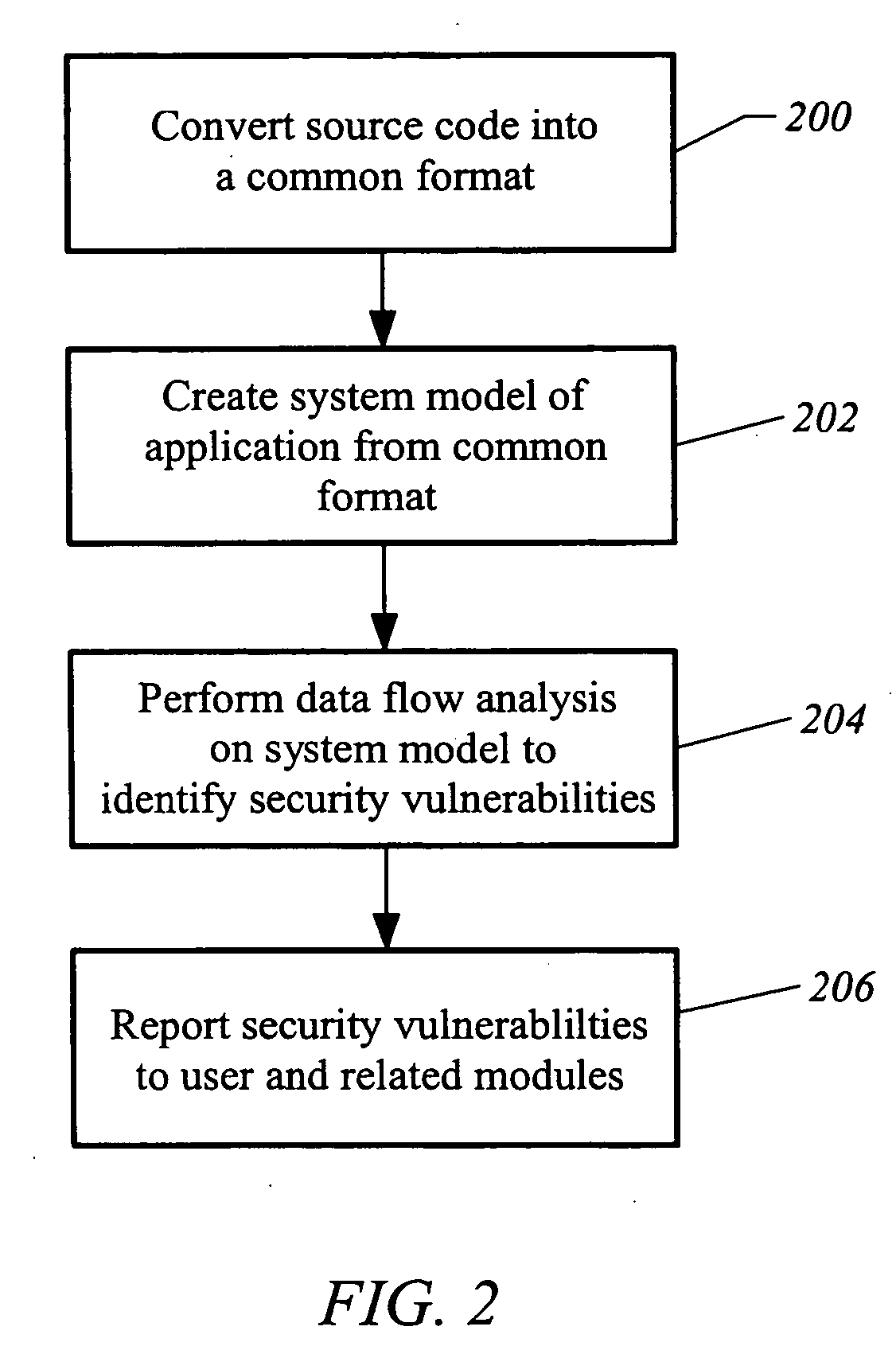
Patents
Literature
872 results about "Security bug" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
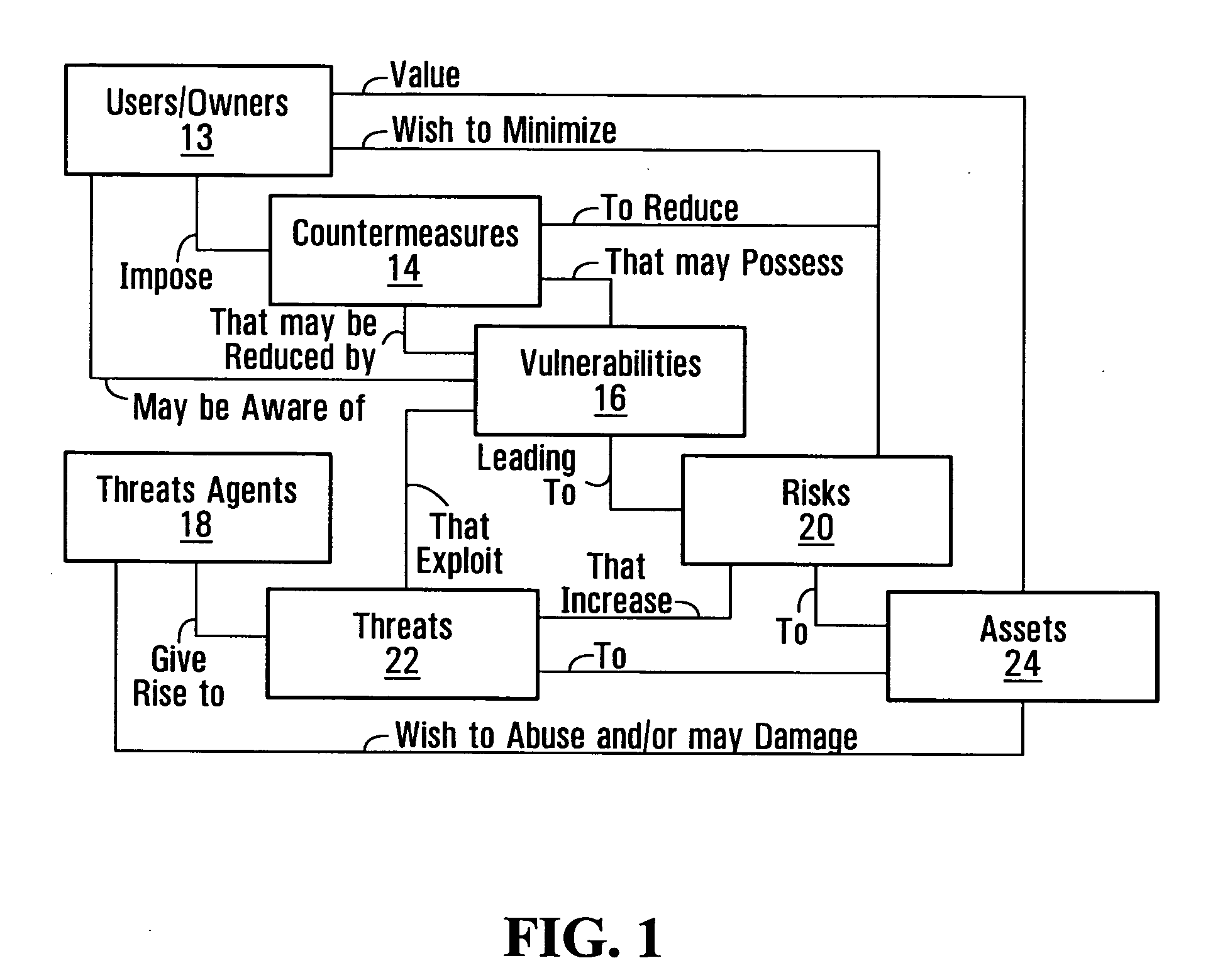
A security bug or security defect is a software bug that can be exploited to gain unauthorized access or privileges on a computer system. Security bugs need not be identified nor exploited to qualify as such.
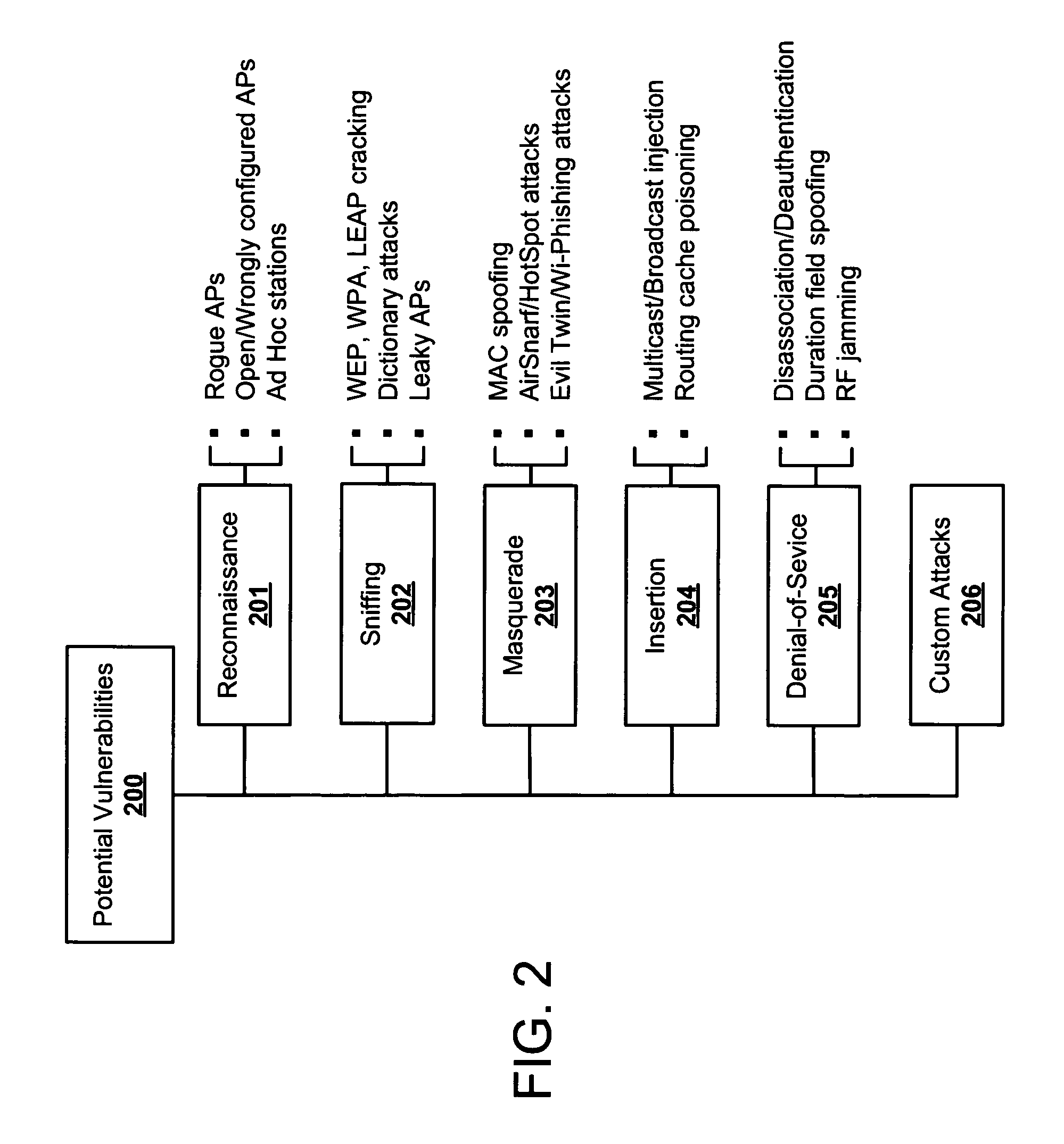
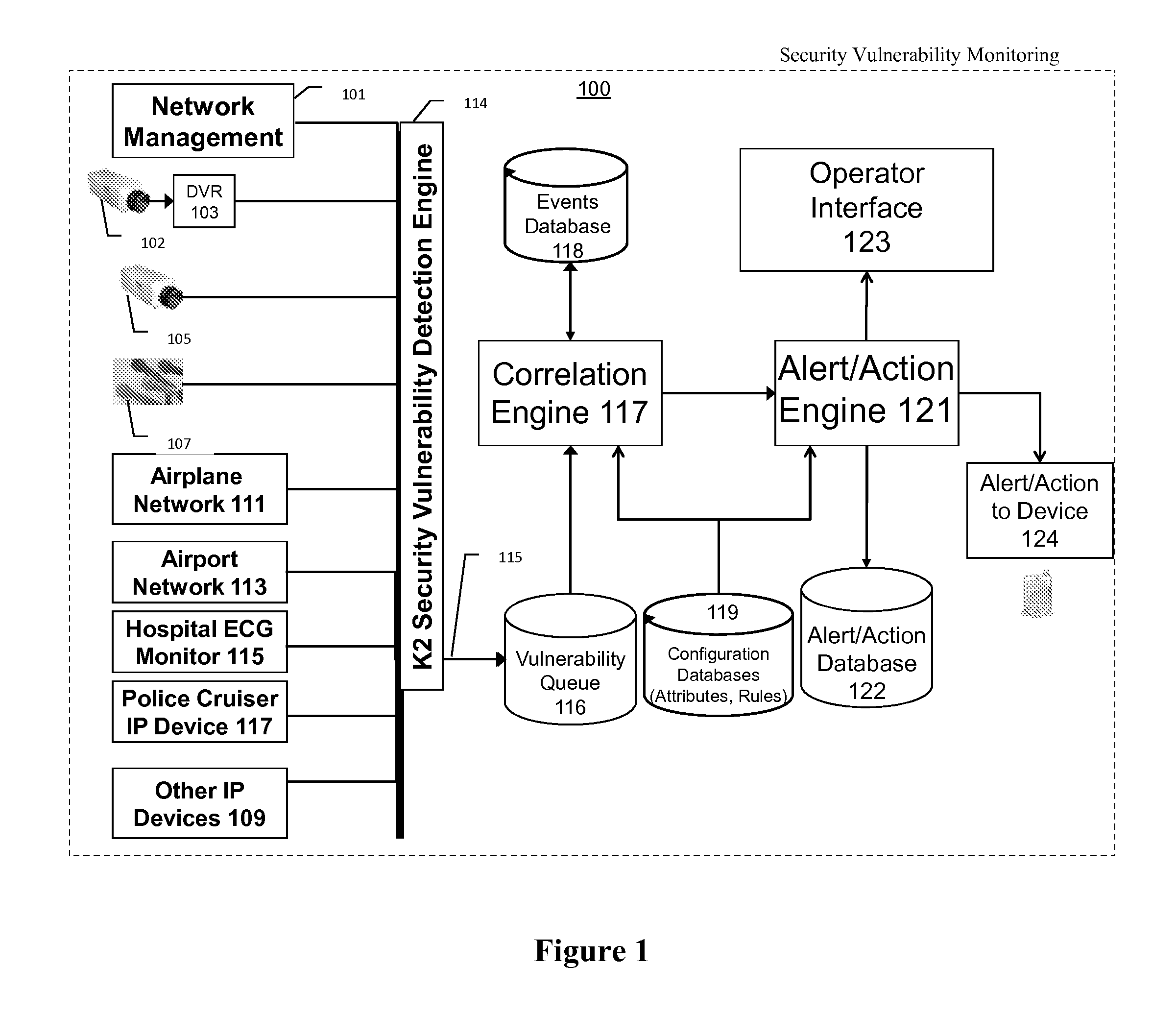
Systems and methods for wireless vulnerability analysis
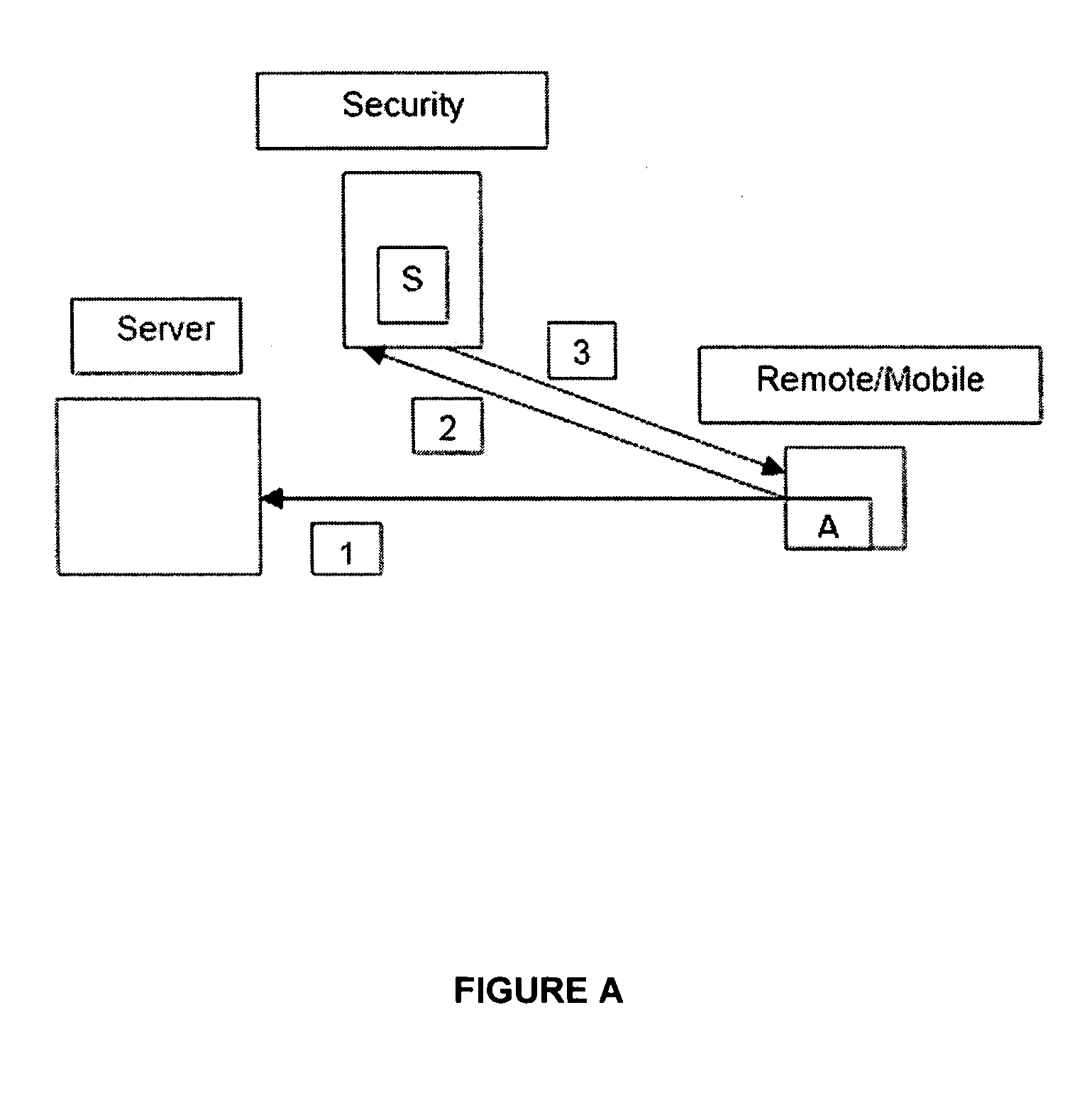
ActiveUS20070142030A1Memory loss protectionUnauthorised/fraudulent call preventionComputer networkVulnerability
Security vulnerability assessment for wireless networks is provided. Systems and methods for security vulnerability assessment simulate an attack upon the wireless network, capture the response from the wireless network, and identify a vulnerability associated with the wireless network after analyzing the response from the wireless network.
Owner:EXTREME NETWORKS INC
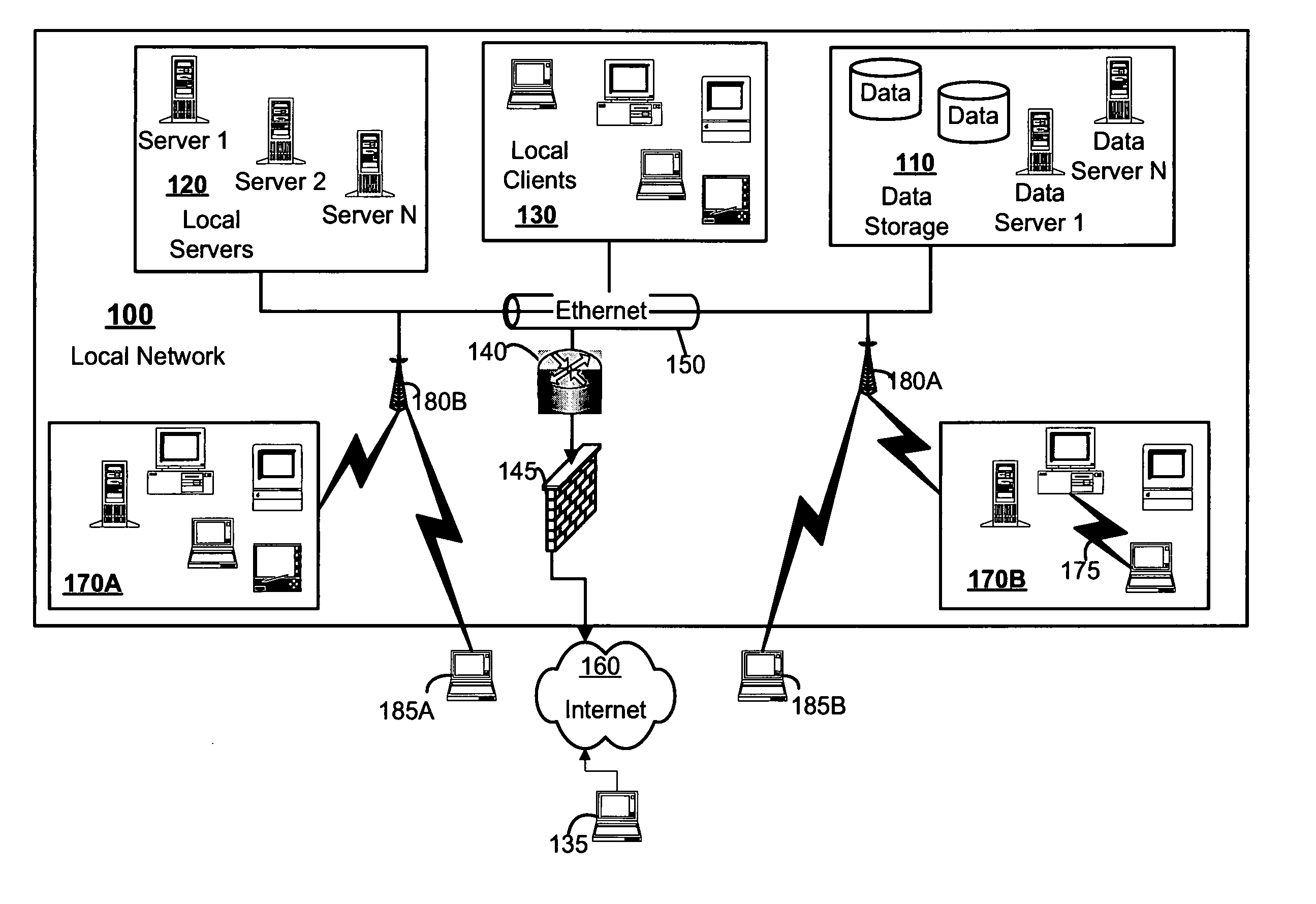
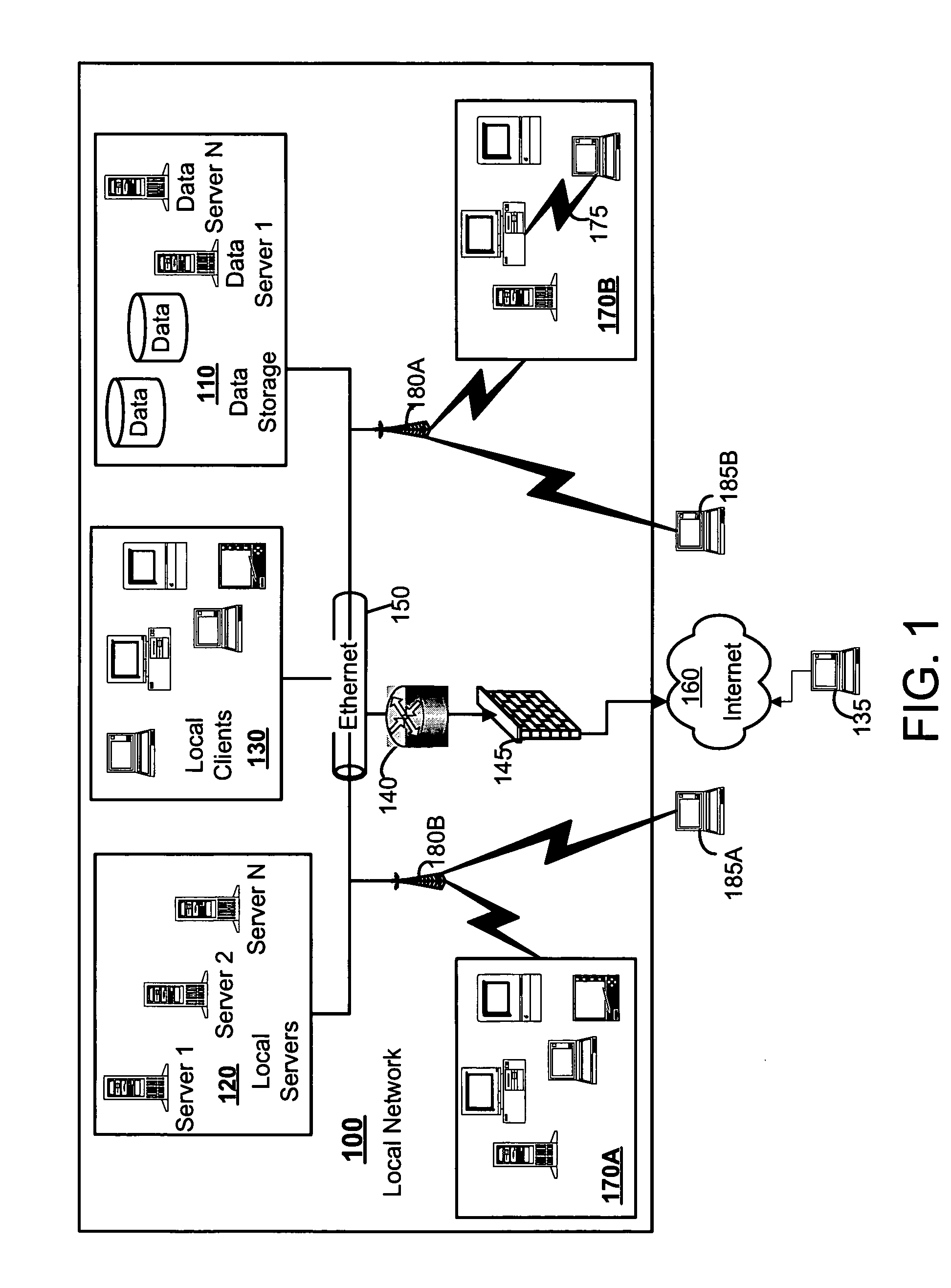
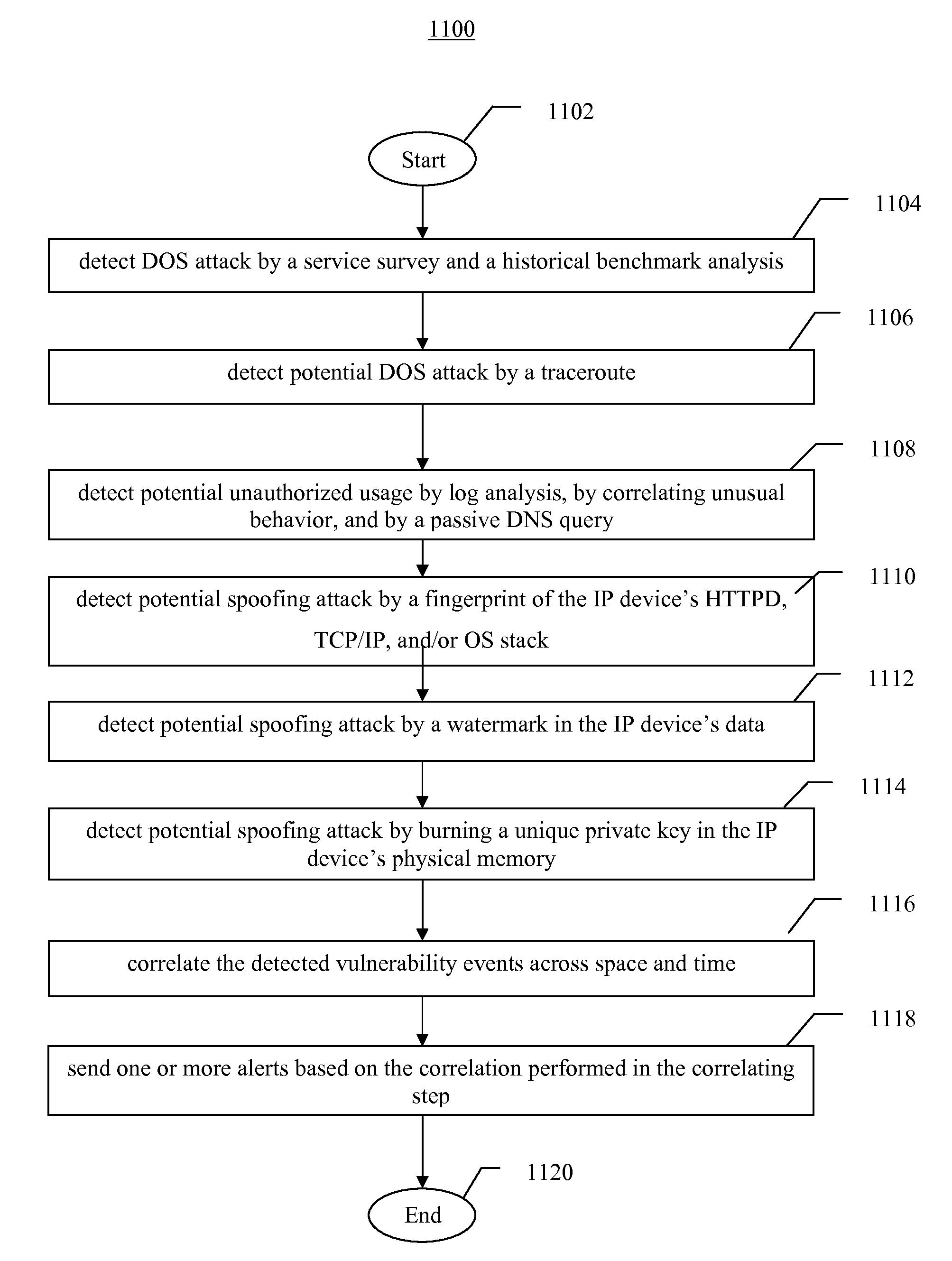
Systems, methods, and devices for detecting security vulnerabilities in IP networks
InactiveUS20100262688A1Detect and prevent spoofingEasy to addMemory loss protectionDigital data processing detailsBaseline dataData stream
This invention is a system, method, and apparatus for detecting compromise of IP devices that make up an IP-based network. One embodiment is a method for detecting and alerting on the following conditions: (1) Denial of Service Attack; (2) Unauthorized Usage Attack; and (3) Spoofing Attack. A survey of services running on the IP device, historical benchmark data, and traceroute information may be used to detect a possible Denial of Service Attack. A detailed log analysis and a passive DNS compromise system may be used to detect a possible unauthorized usage. Finally, a fingerprint of the IP device or its configuration settings, a watermark inserted in the data-stream, and a private key burned into the IP devices' physical memory may be used to detect a possible spoofing attack. The present invention may be used to help mitigate intrusions and vulnerabilities in IP networks.
Owner:HUSSAIN DANIAR +1
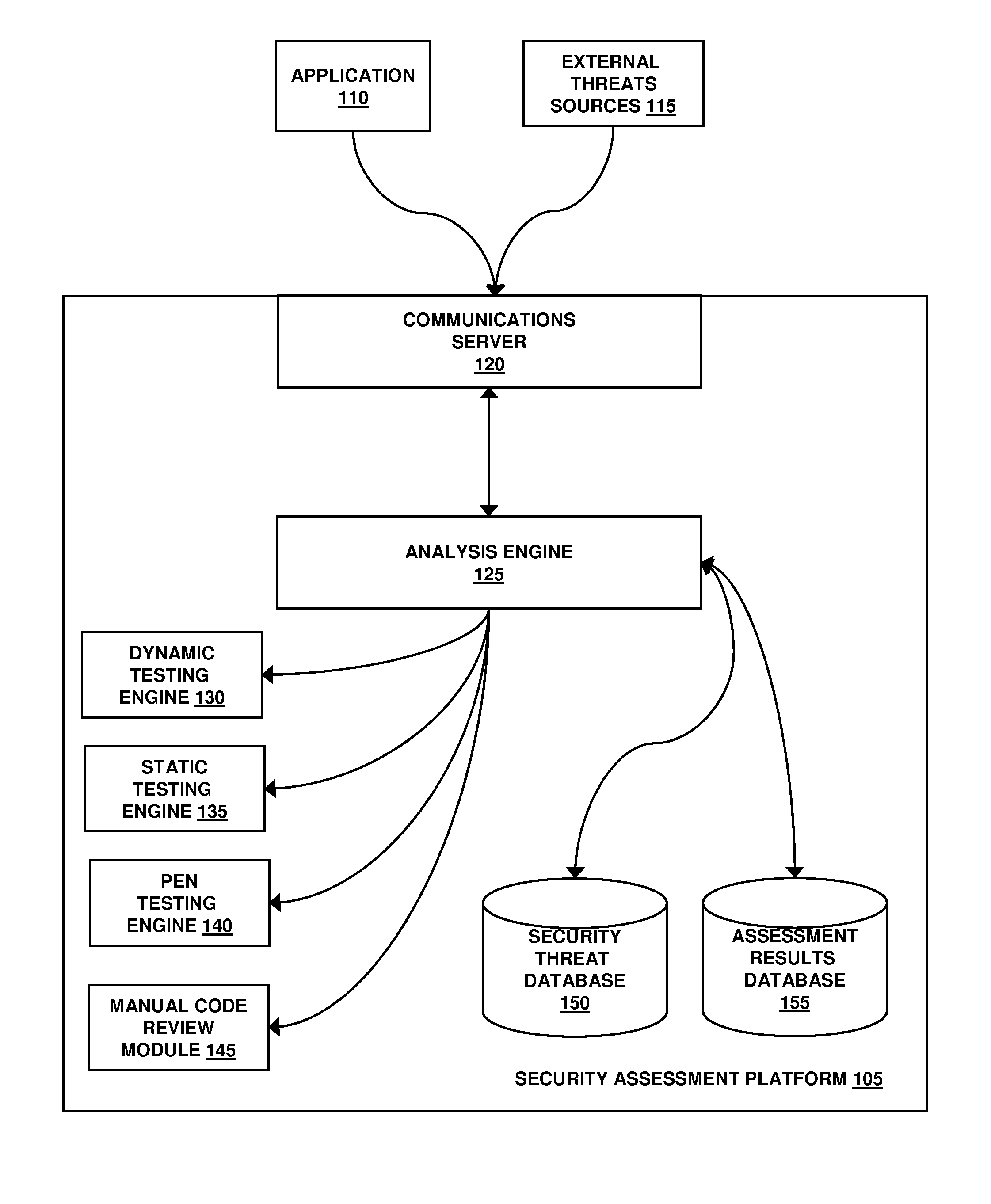
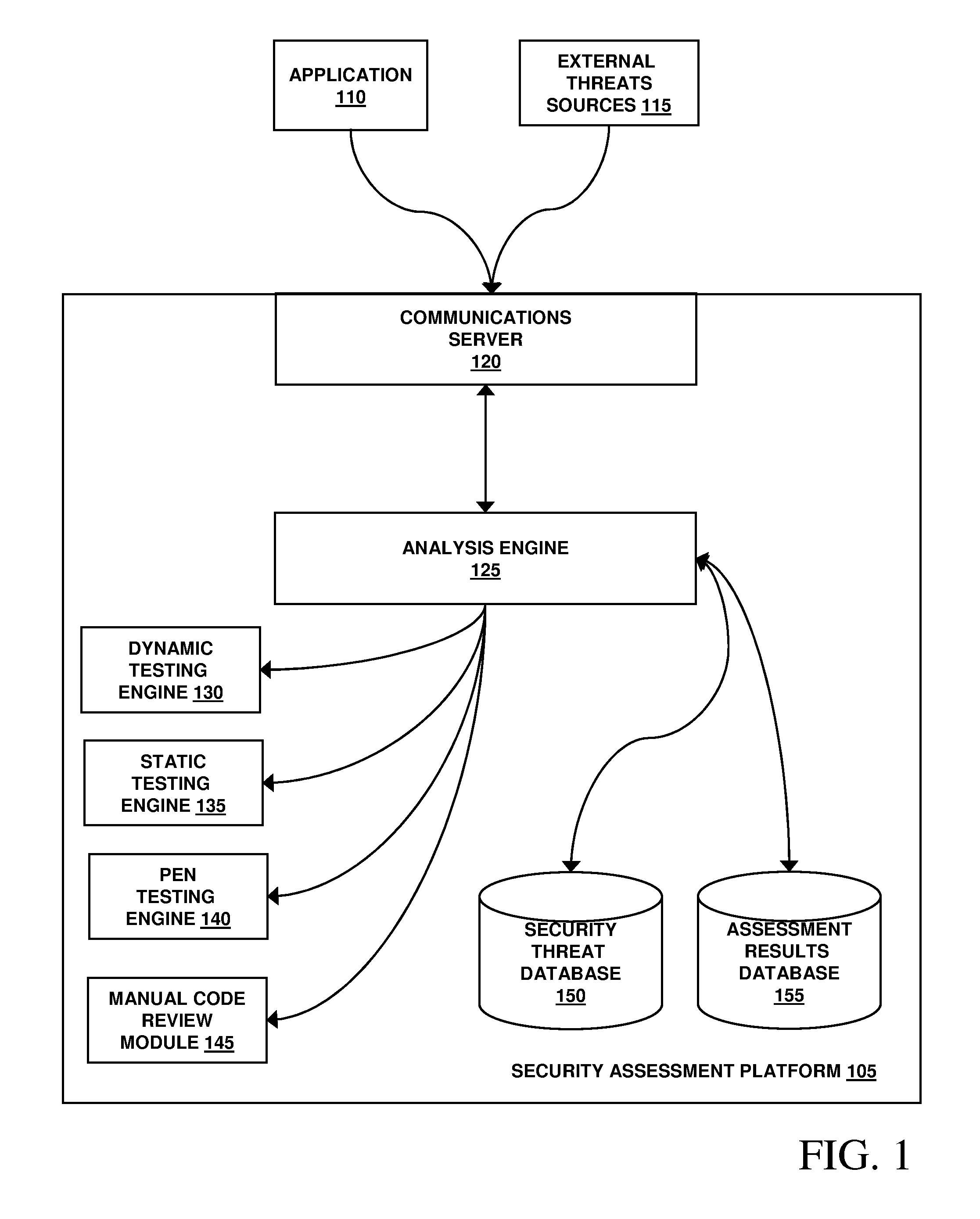
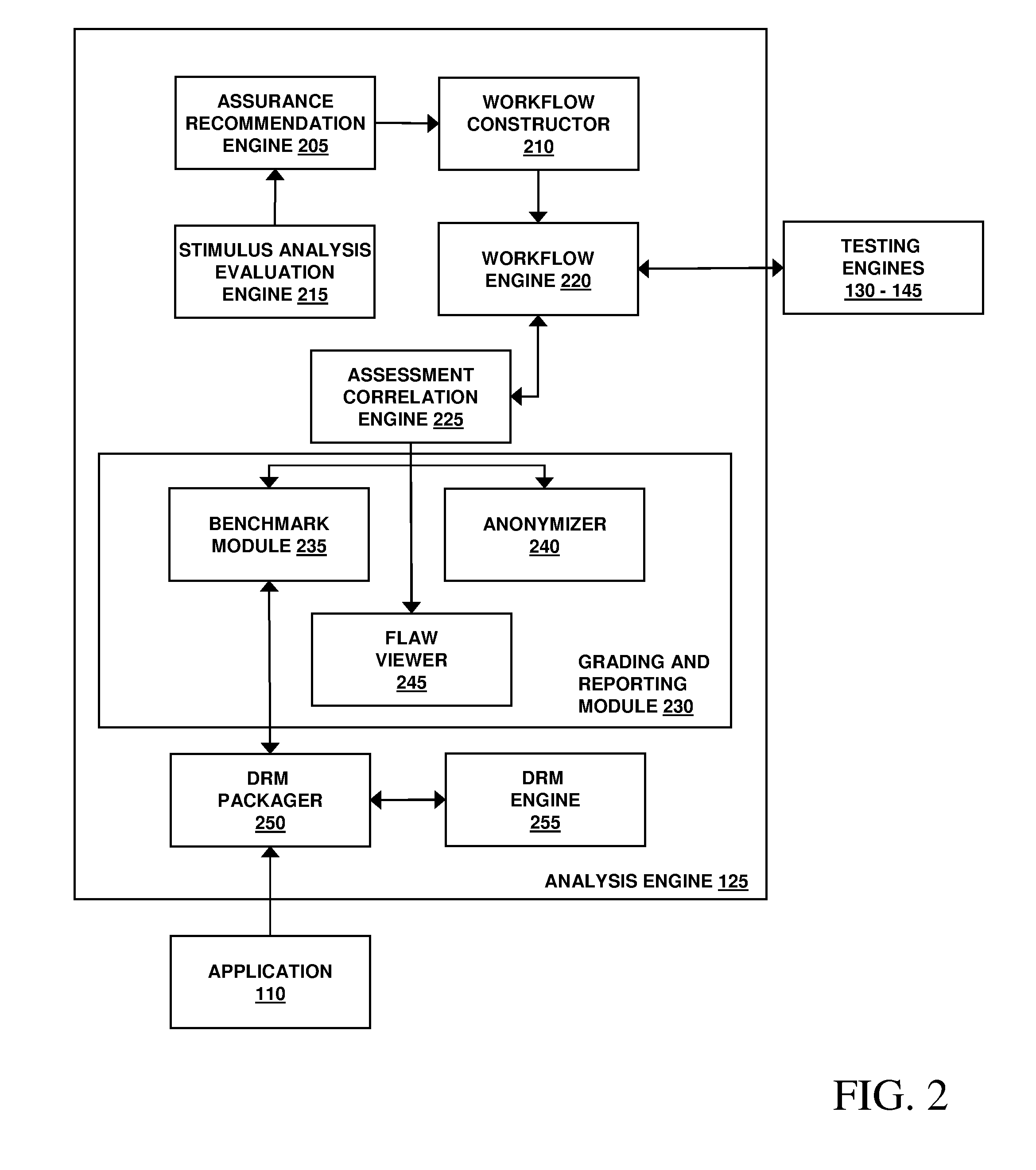
Assessment and analysis of software security flaws in virtual machines
ActiveUS20120072968A1Facilitates benchmarkingFacilitates security assessment and vulnerability testingMemory loss protectionError detection/correctionSoftware engineeringSecurity analysis
Security analysis and vulnerability testing results are “packaged” or “bound to” the actual software it describes. By linking the results to the software itself, downstream users of the software can access information about the software, make informed decisions about implementation of the software, and analyze the security risk across an entire system by accessing all (or most) of the reports associated with the executables running on the system and summarizing the risks identified in the reports.
Owner:VERACODE
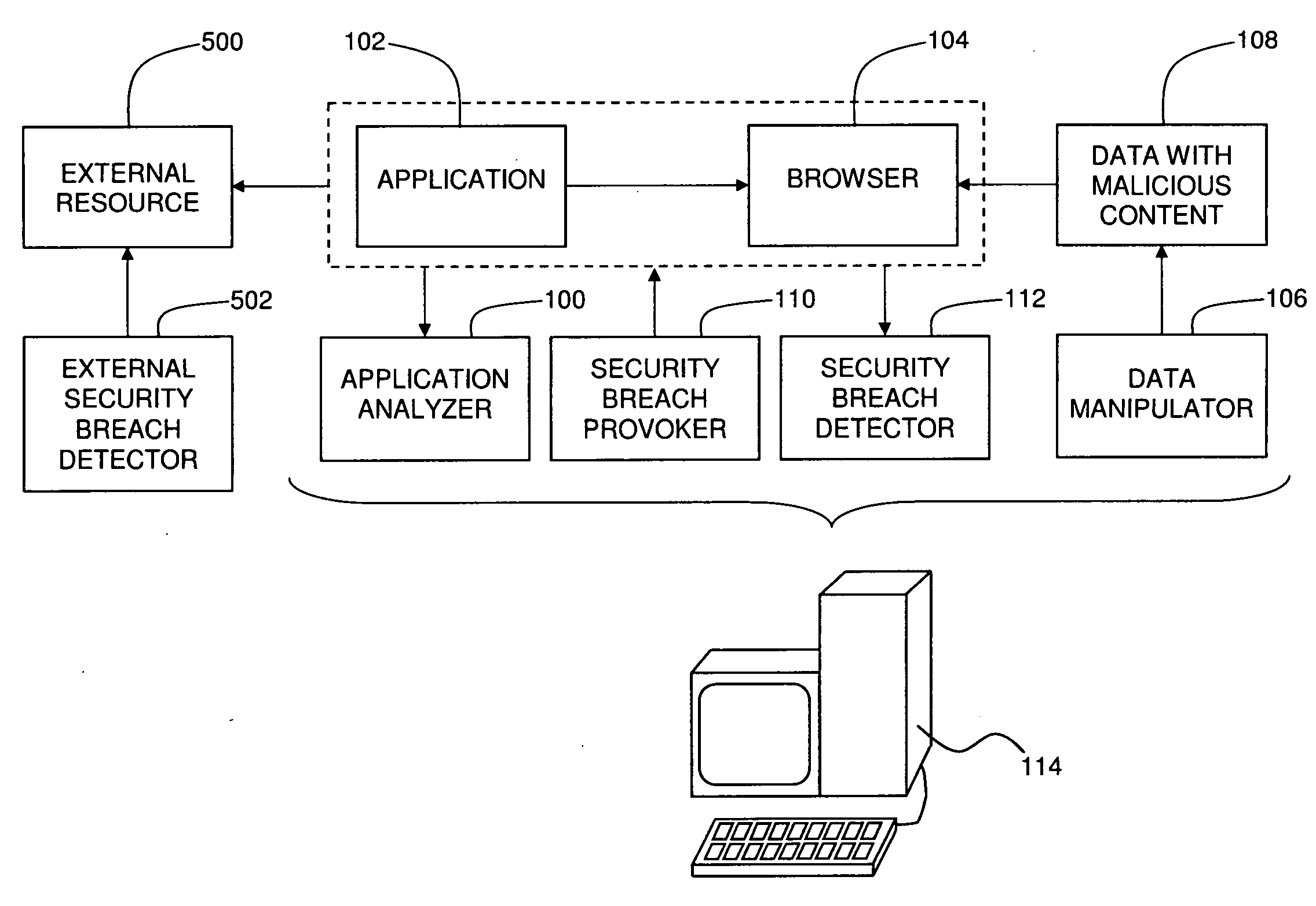
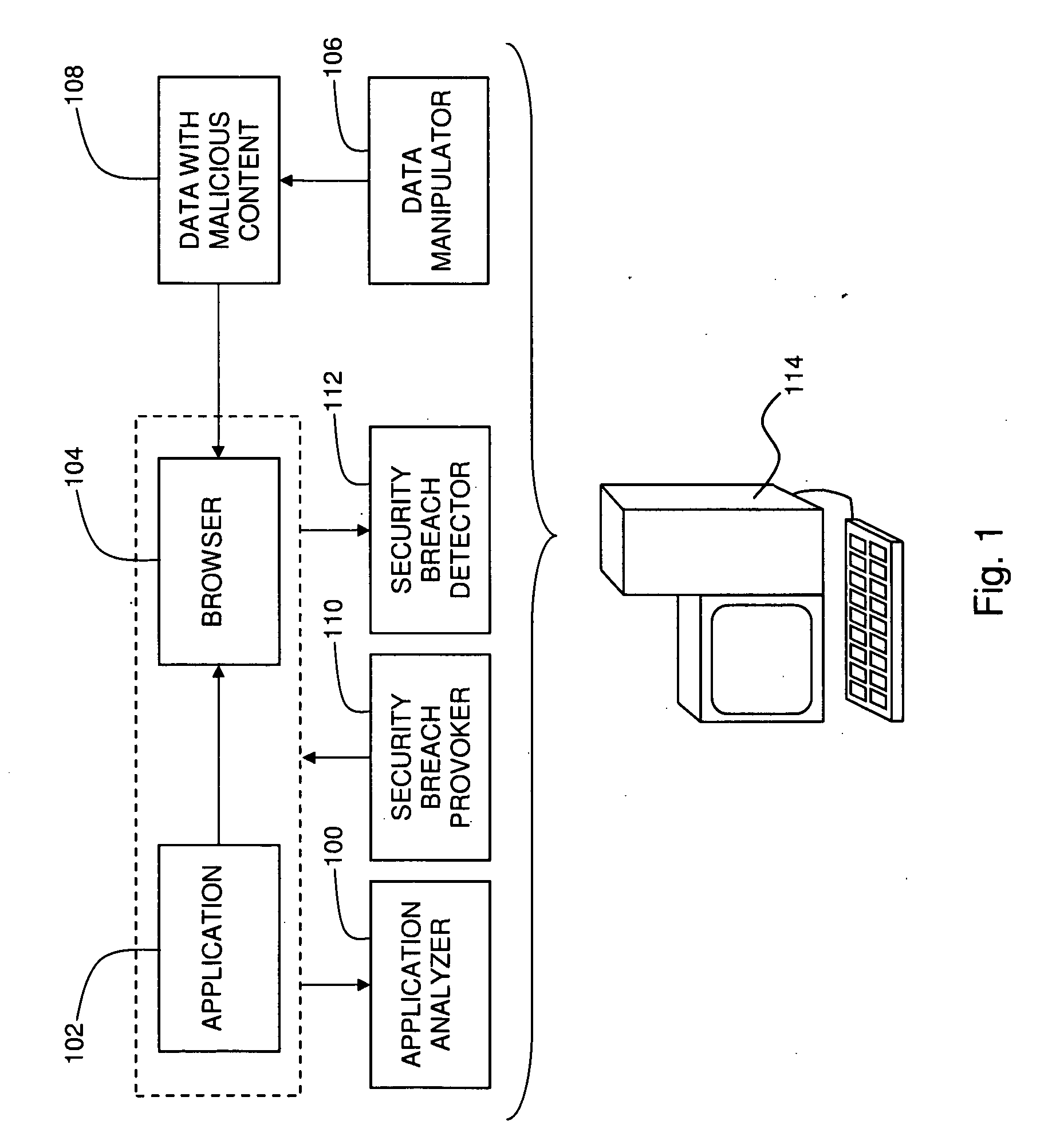
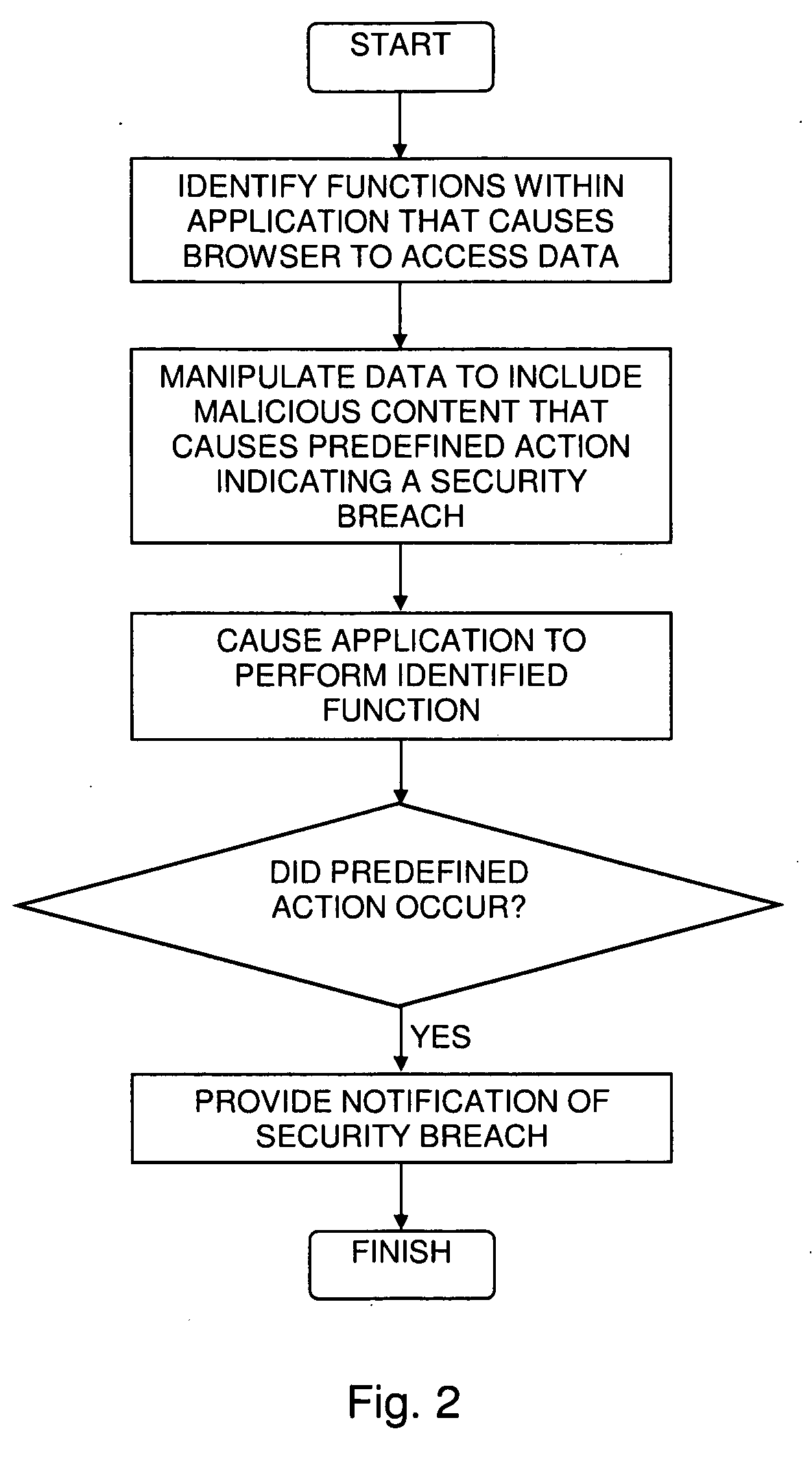
Identifying Security Breaches Caused by Web-Enabled Software Applications
Identifying a security breach caused when a computer-based software application uses a computer-based web browser application, including identifying at least one function within a computer-based software application that causes a computer-based web browser application to access data from a source that is external to the software application, at least partially replacing the data with malicious content that is configured to cause a predefined action to occur when the malicious content is accessed by the web browser application, where the predefined action is associated with a known security breach when the predefined action occurs subsequent to the malicious content being accessed by the web browser application, causing the software application to perform the function, and determining whether the predefined action is performed.
Owner:IBM CORP
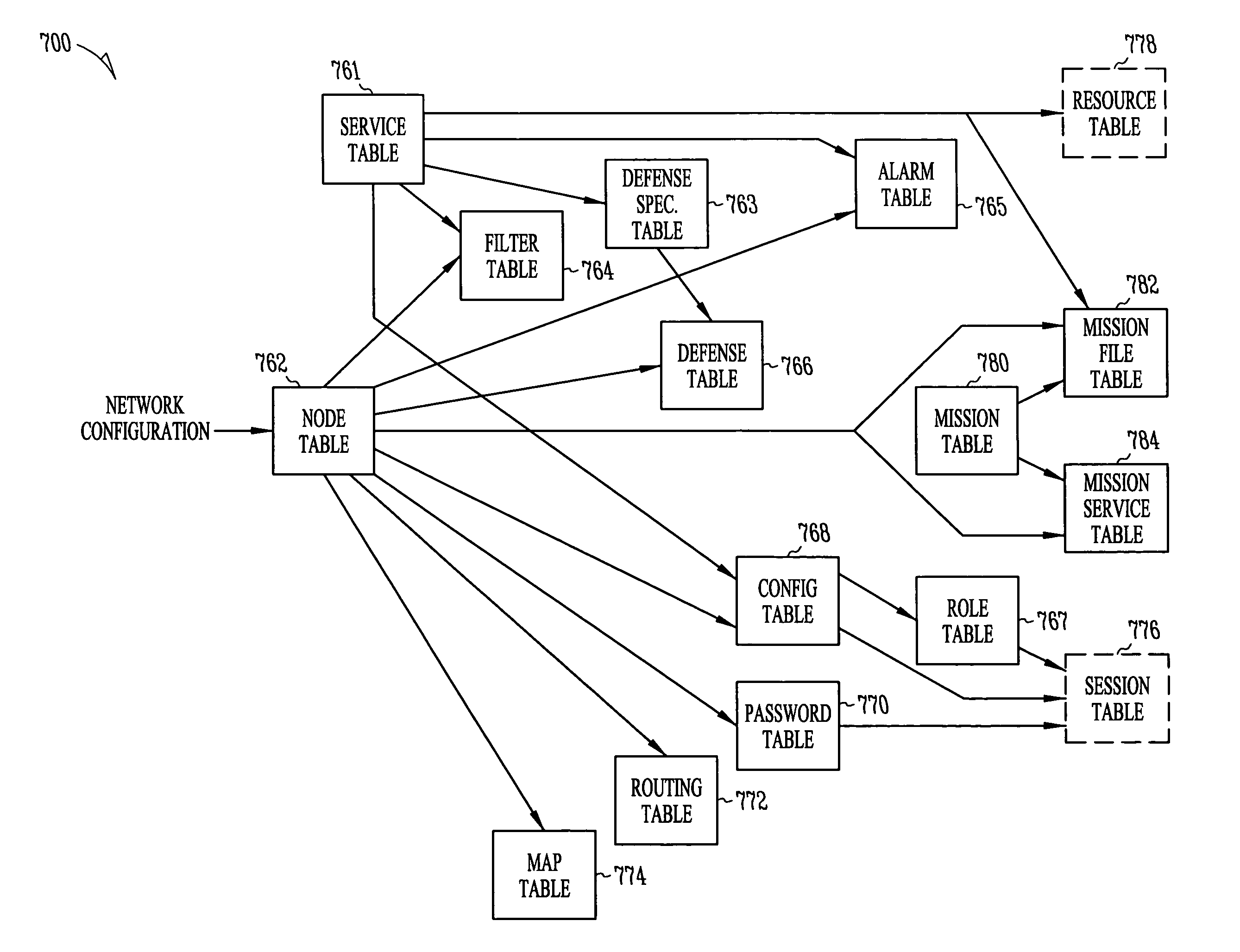
Network security modeling system and method
InactiveUS7315801B1Analogue computers for electric apparatusDigital computer detailsNetwork security policyVulnerability
A network security modeling system which simulates a network and analyzes security vulnerabilities of the network. The system includes a simulator which includes a network vulnerabilities database and a network configuration module having network configuration data. The simulator determines vulnerabilities of the simulated network based on the network configuration data and the vulnerabilities database.
Owner:MCAFEE LLC
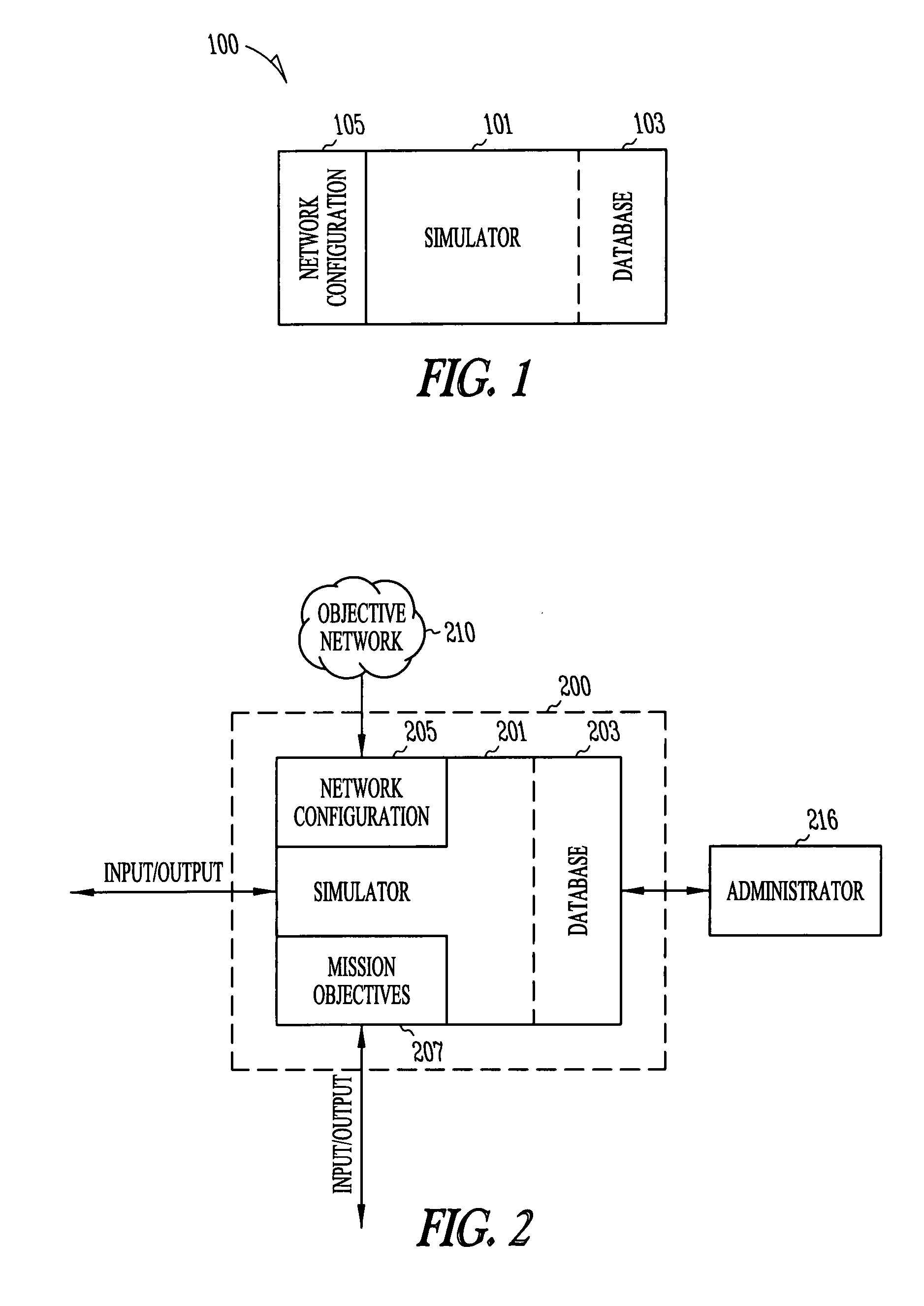
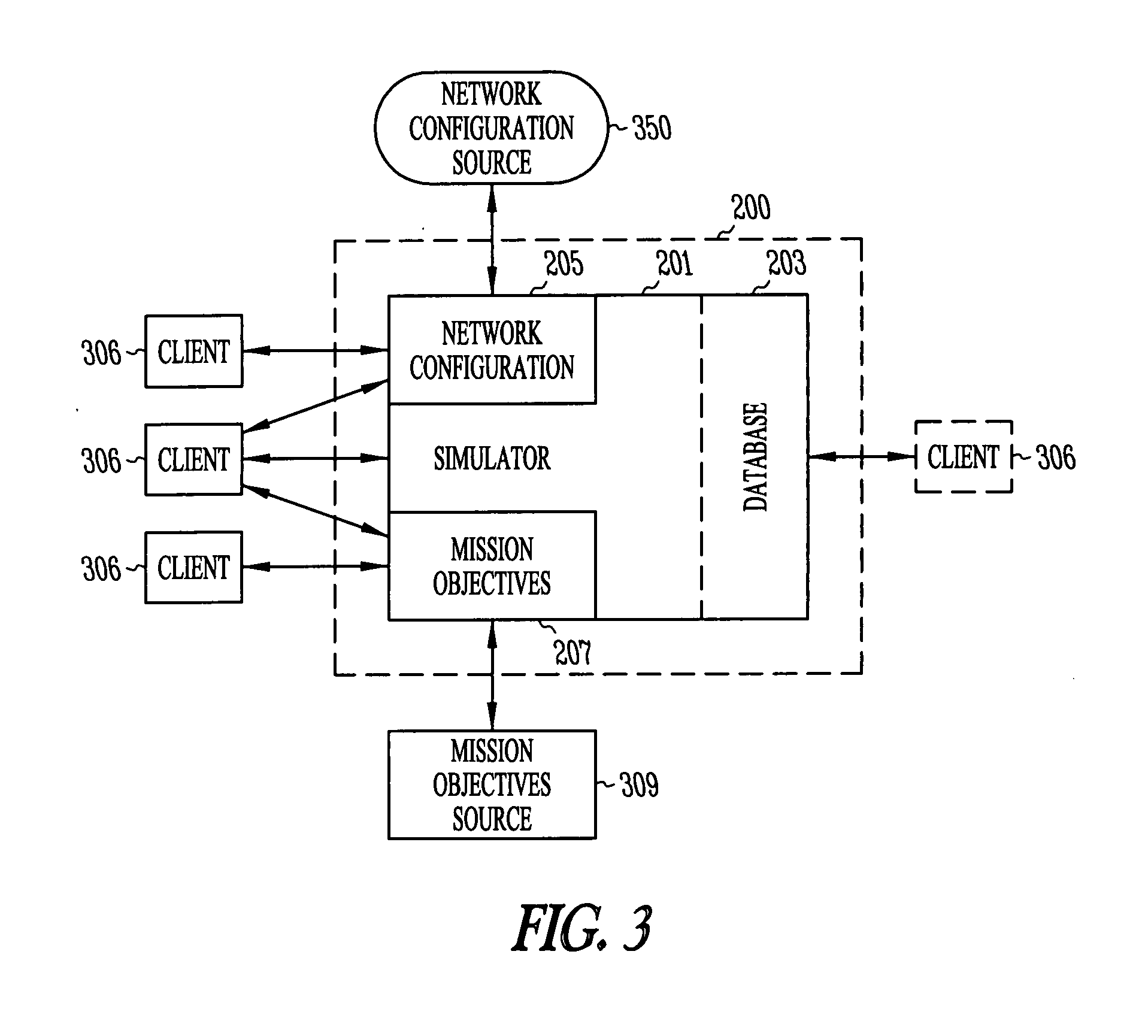
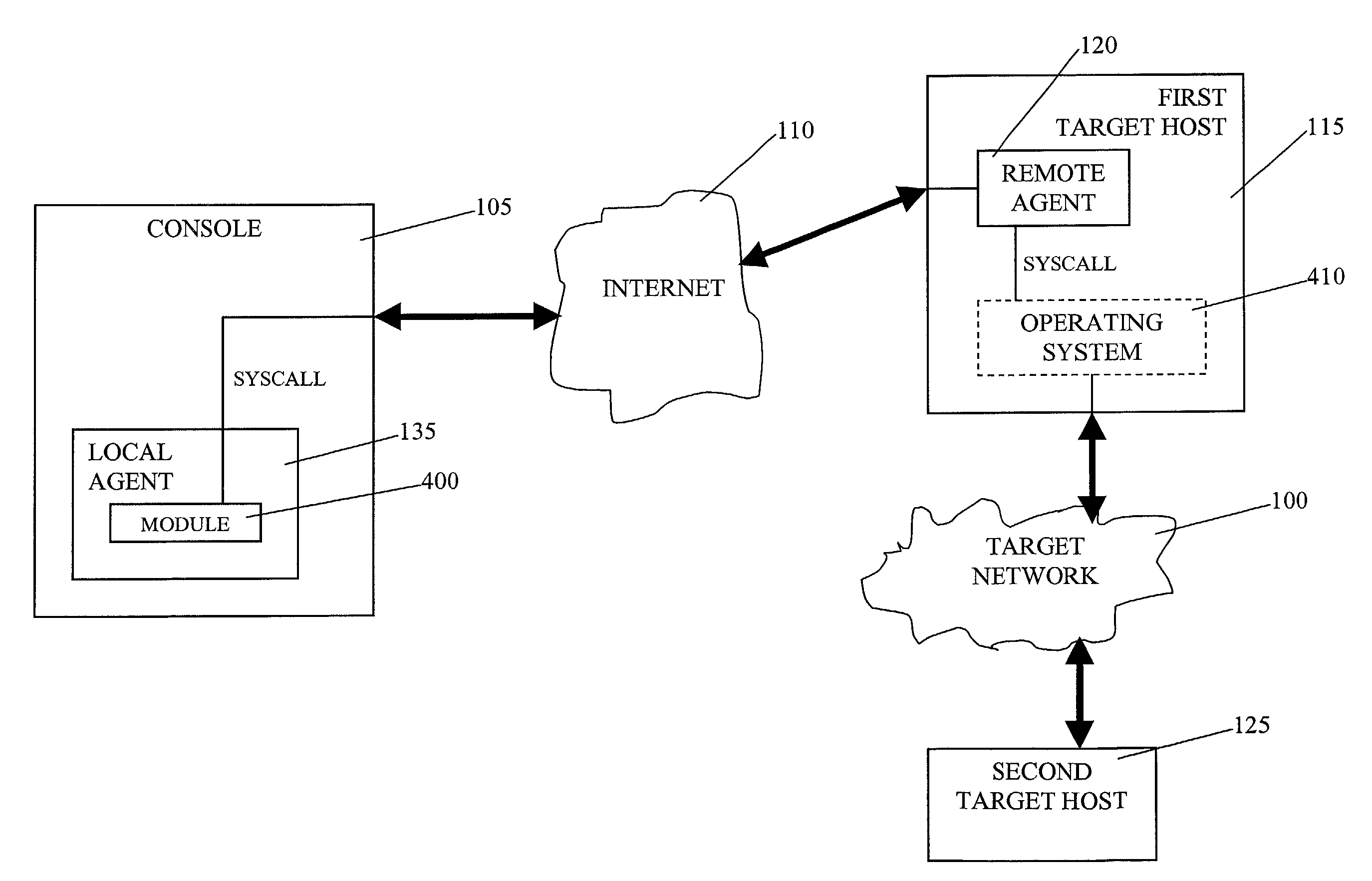
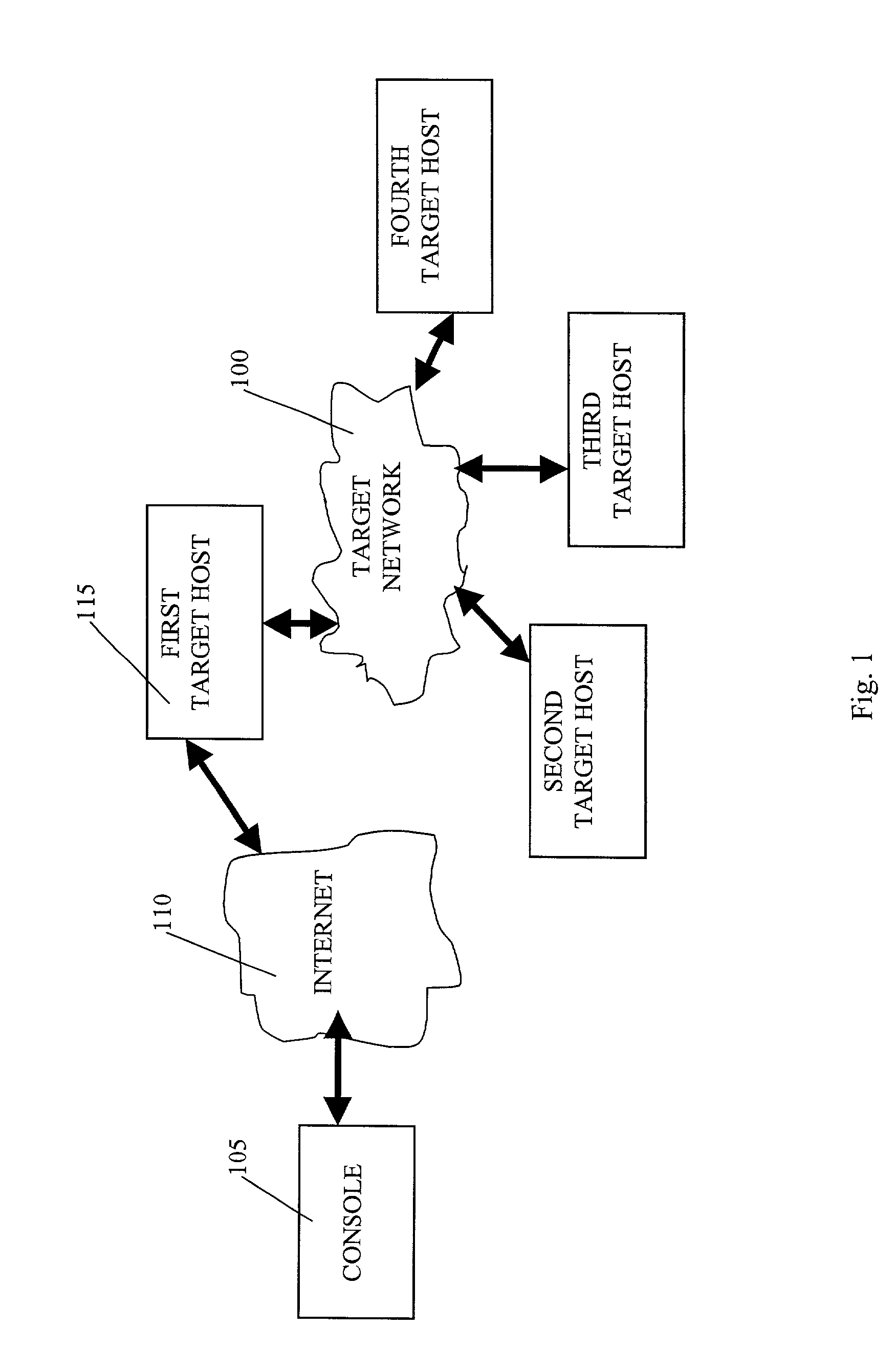
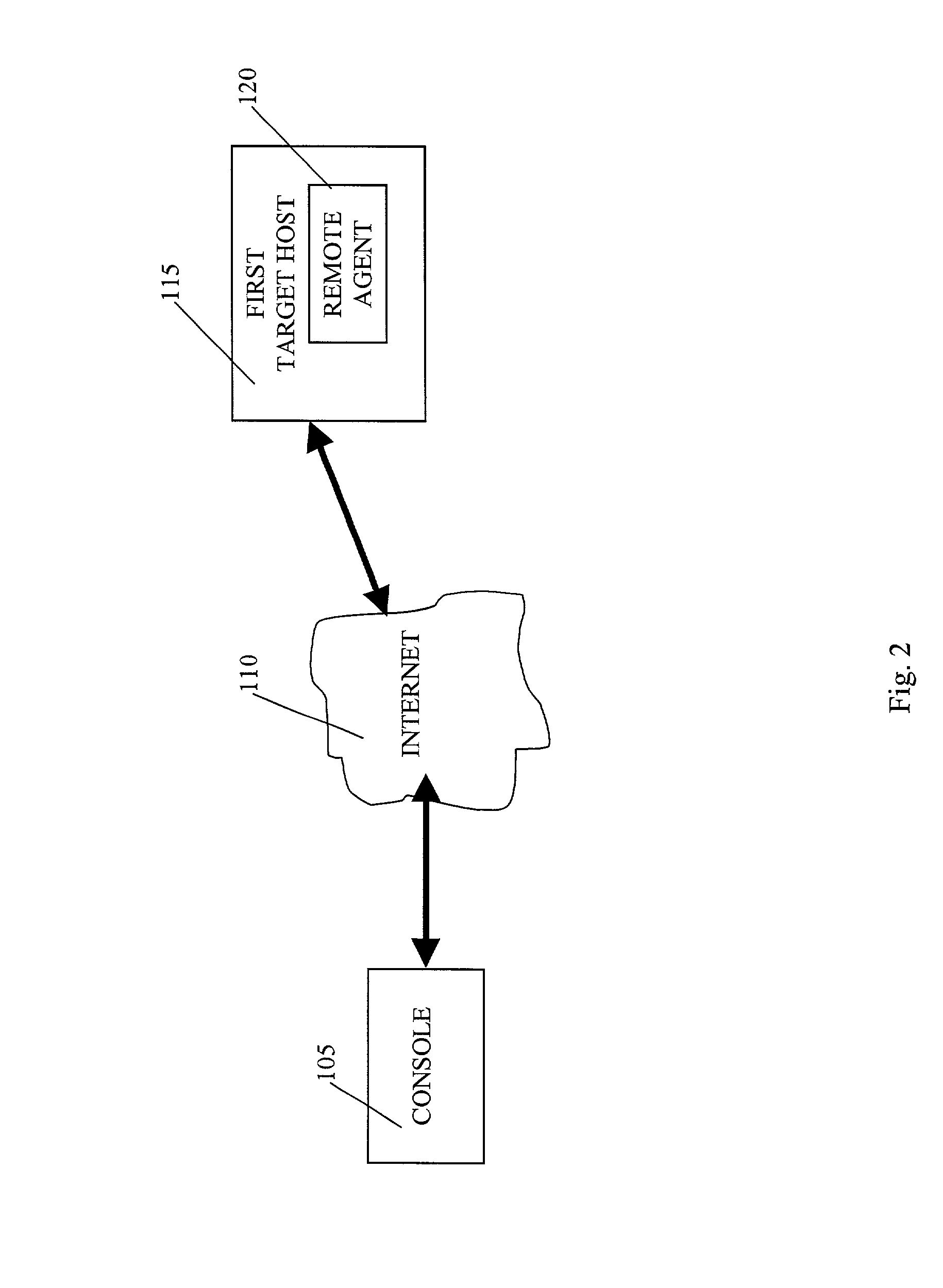
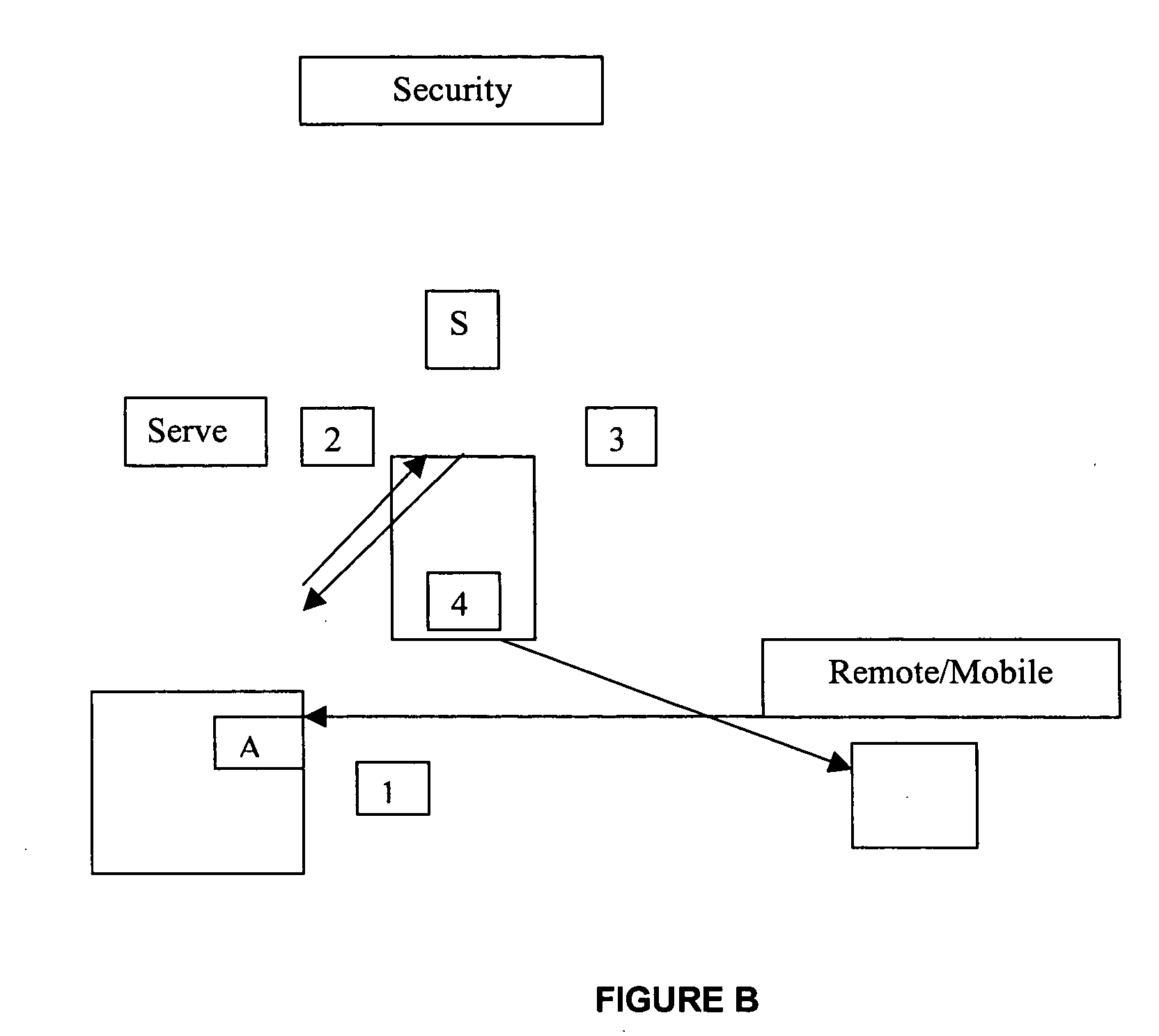
Automated computer system security compromise
A system is provided for performing penetration testing of a target computer network by installing a remote agent in the target computer network. The system includes a local agent provided in a computer console and configured to receive and execute commands. A user interface is provided in the console and configured to send commands to and receive information from the local agent, process the information, and present the processed information. A database is configured to store the information received from the local agent. A network interface is connected to the local agent and configured to communicate with the remote agent installed in the target computer network via a network. Security vulnerability exploitation modules are provided for execution by the local agent and / or the remote agent.
Owner:FORTRA LLC
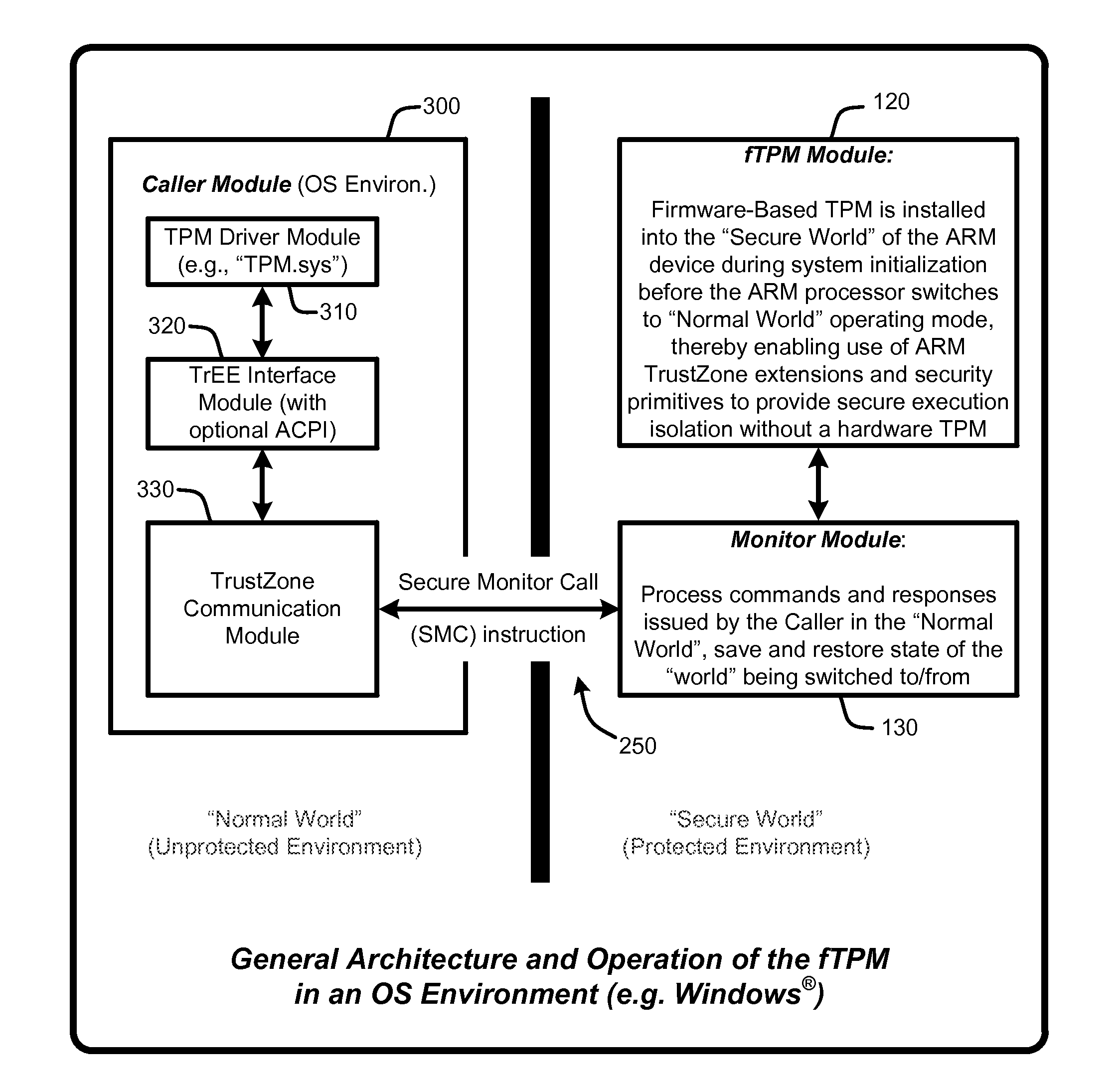
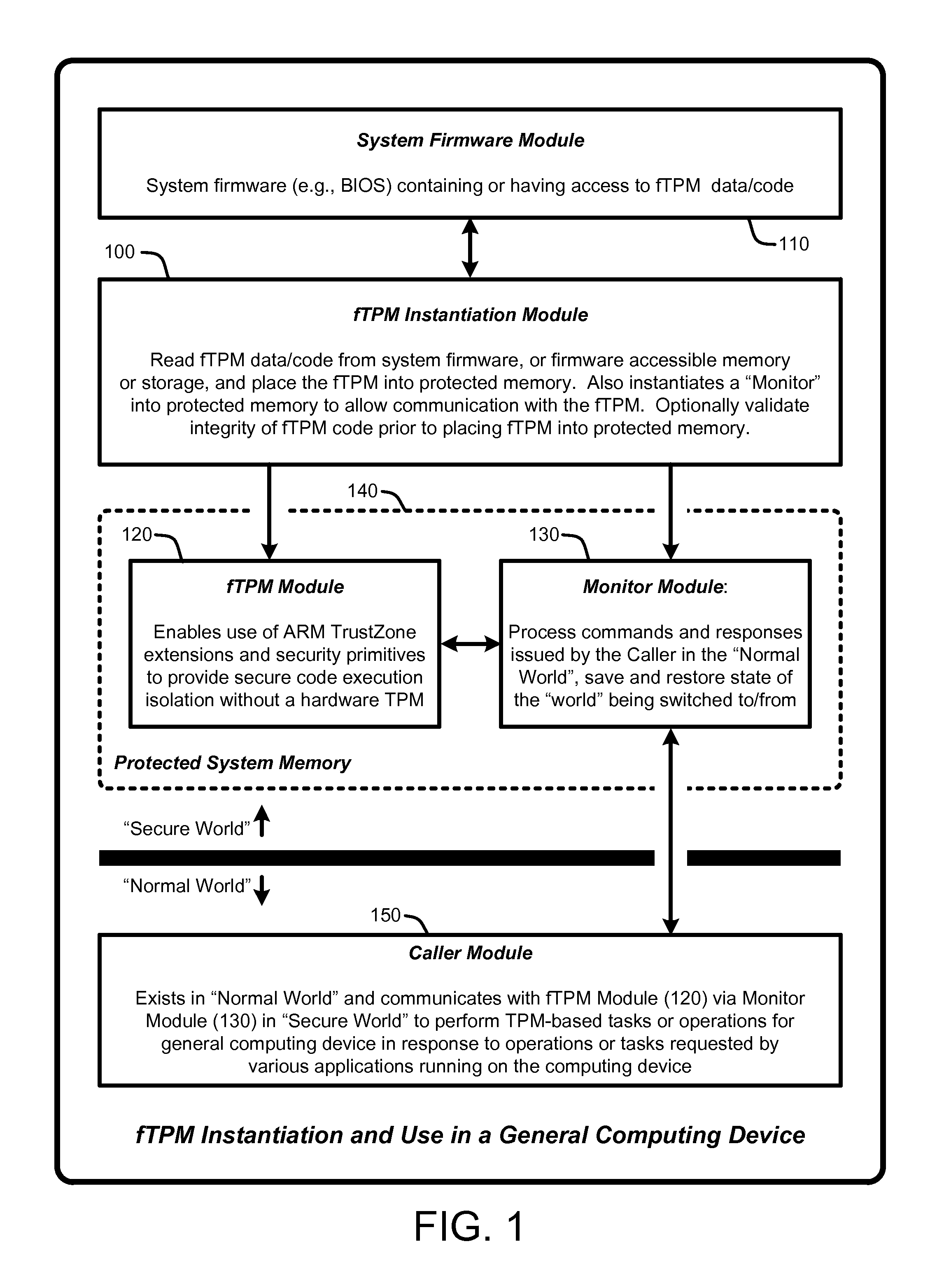
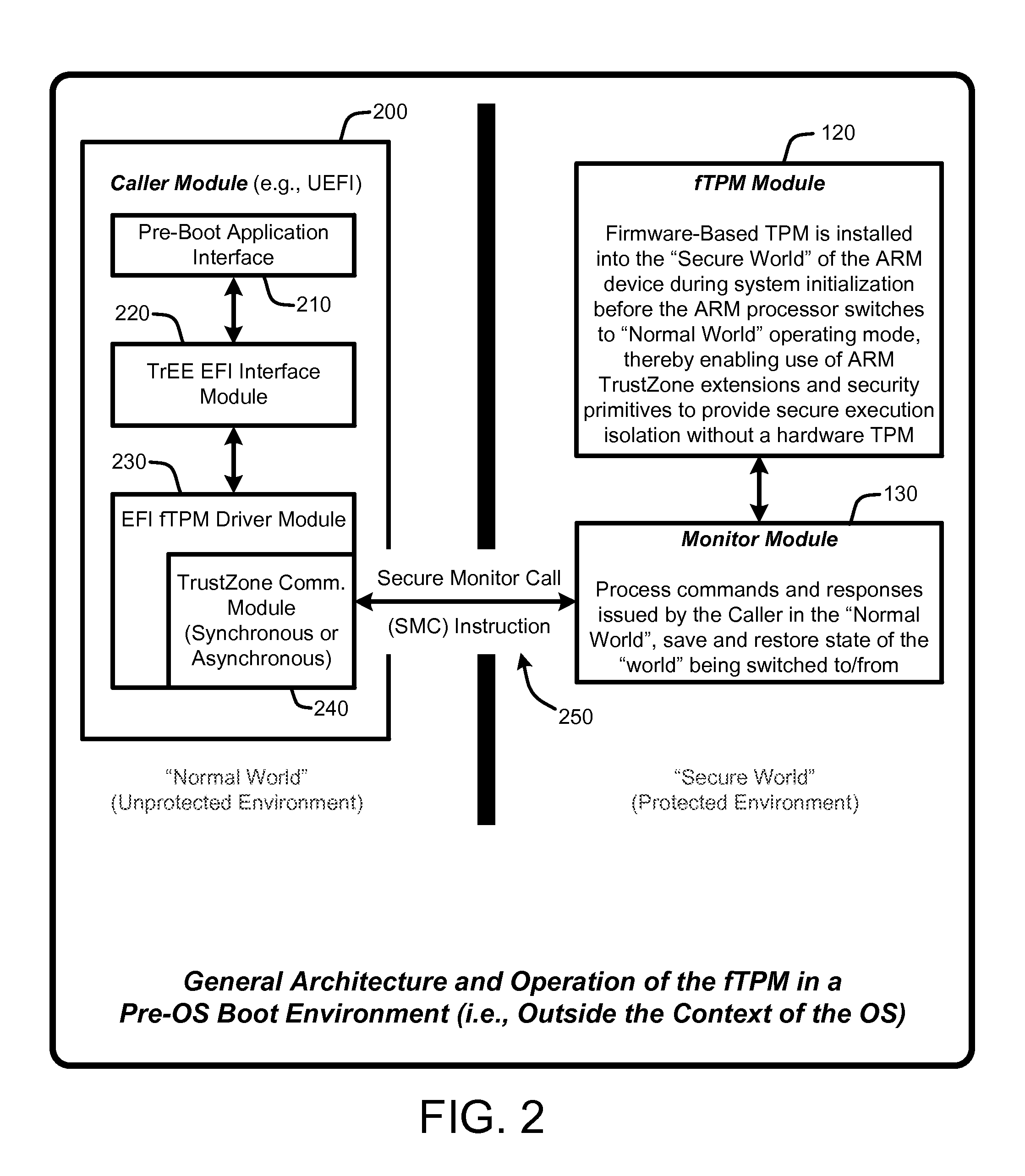
Firmware-based trusted platform module for arm processor architectures and trustzone security extensions
ActiveUS20130031374A1Increase costReduce system costDigital data processing detailsUnauthorized memory use protectionTrusted Platform ModuleSafe handling
A “Firmware-Based TPM” or “fTPM” ensures that secure code execution is isolated to prevent a wide variety of potential security breaches. Unlike a conventional hardware based Trusted Platform Module (TPM), isolation is achieved without the use of dedicated security processor hardware or silicon. In general, the fTPM is first instantiated in a pre-OS boot environment by reading the fTPM from system firmware or firmware accessible memory or storage and placed into read-only protected memory of the device. Once instantiated, the fTPM enables execution isolation for ensuring secure code execution. More specifically, the fTPM is placed into protected read-only memory to enable the device to use hardware such as the ARM® architecture's TrustZone™ extensions and security primitives (or similar processor architectures), and thus the devices based on such architectures, to provide secure execution isolation within a “firmware-based TPM” without requiring hardware modifications to existing devices.
Owner:MICROSOFT TECH LICENSING LLC
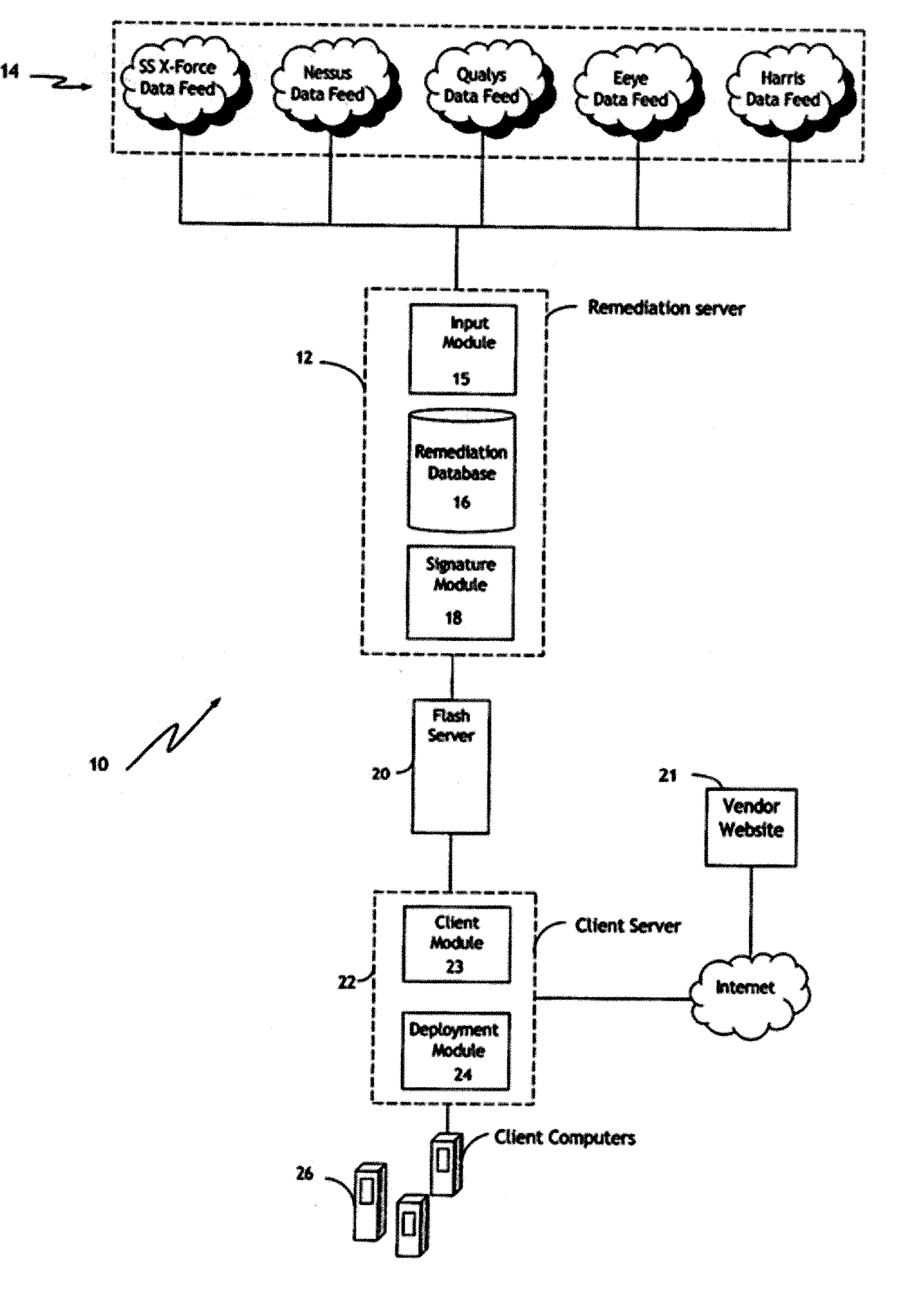
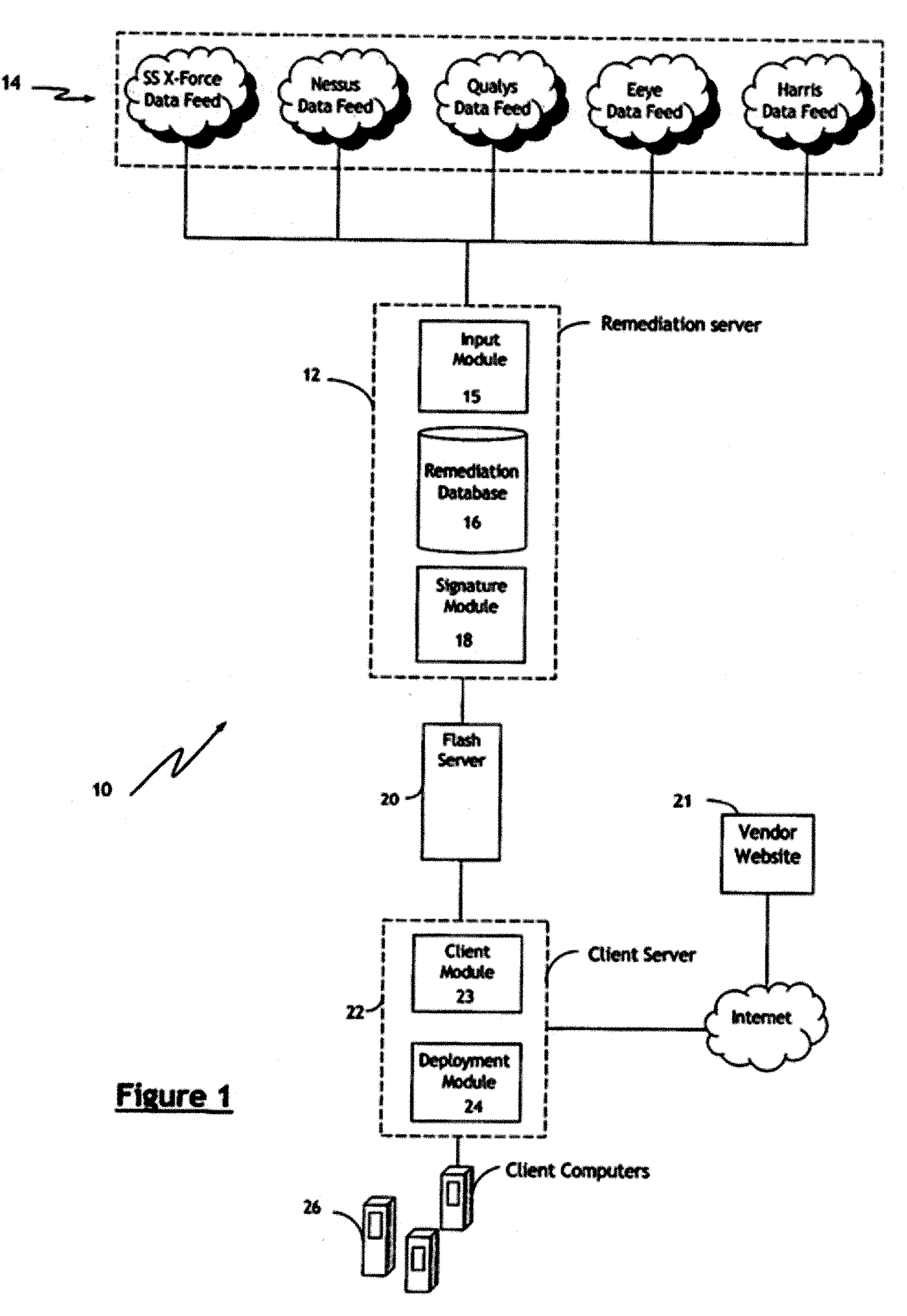
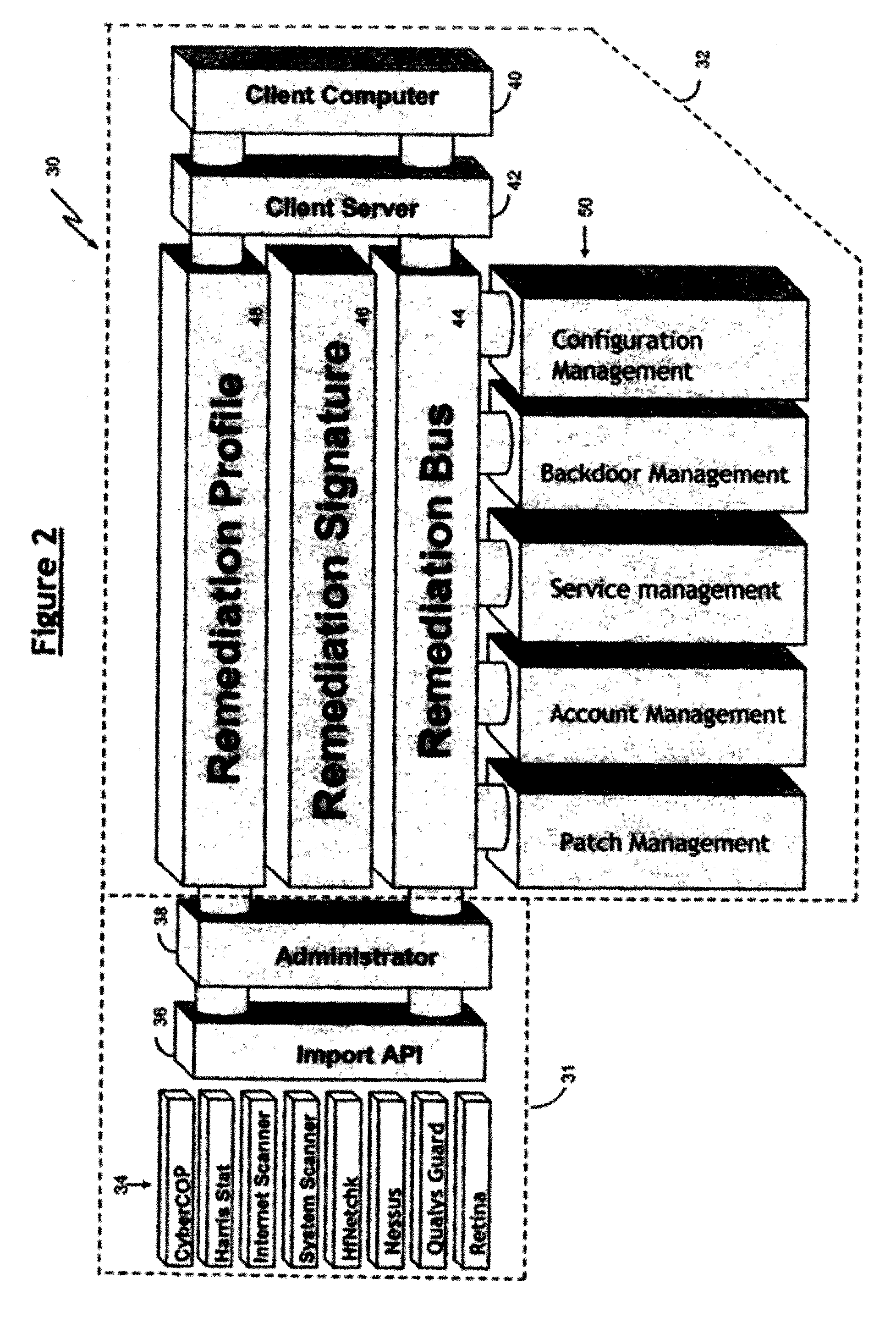
Automated Computer Vulnerability Resolution System
Abstract of the Disclosure A system and process for addressing computer security vulnerabilities. The system and process generally comprise aggregating vulnerability information on a plurality of computer vulnerabilities; constructing a remediation database of said plurality of computer vulnerabilities; constructing a remediation signature to address the computer vulnerabilities; and deploying said remediation signature to a client computer. The remediation signature essentially comprises a sequence of actions to address a corresponding vulnerability. A managed automated approach to the process is contemplated in which the system is capable of selective deployment of remediation signatures; selective resolution of vulnerabilities; scheduled deployment of remediation signatures; and scheduled scanning of client computers for vulnerabilities.
Owner:MCAFEE LLC
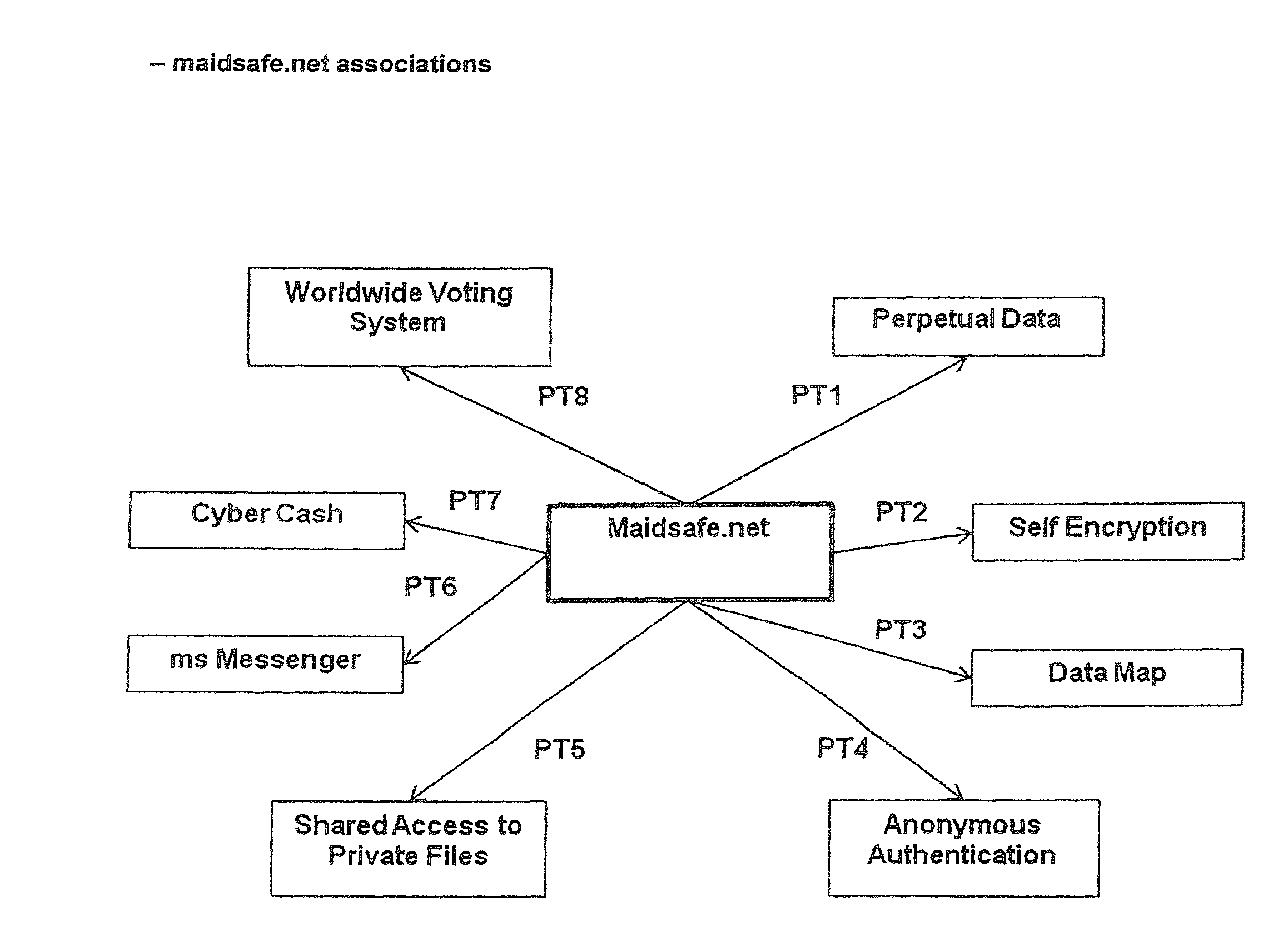
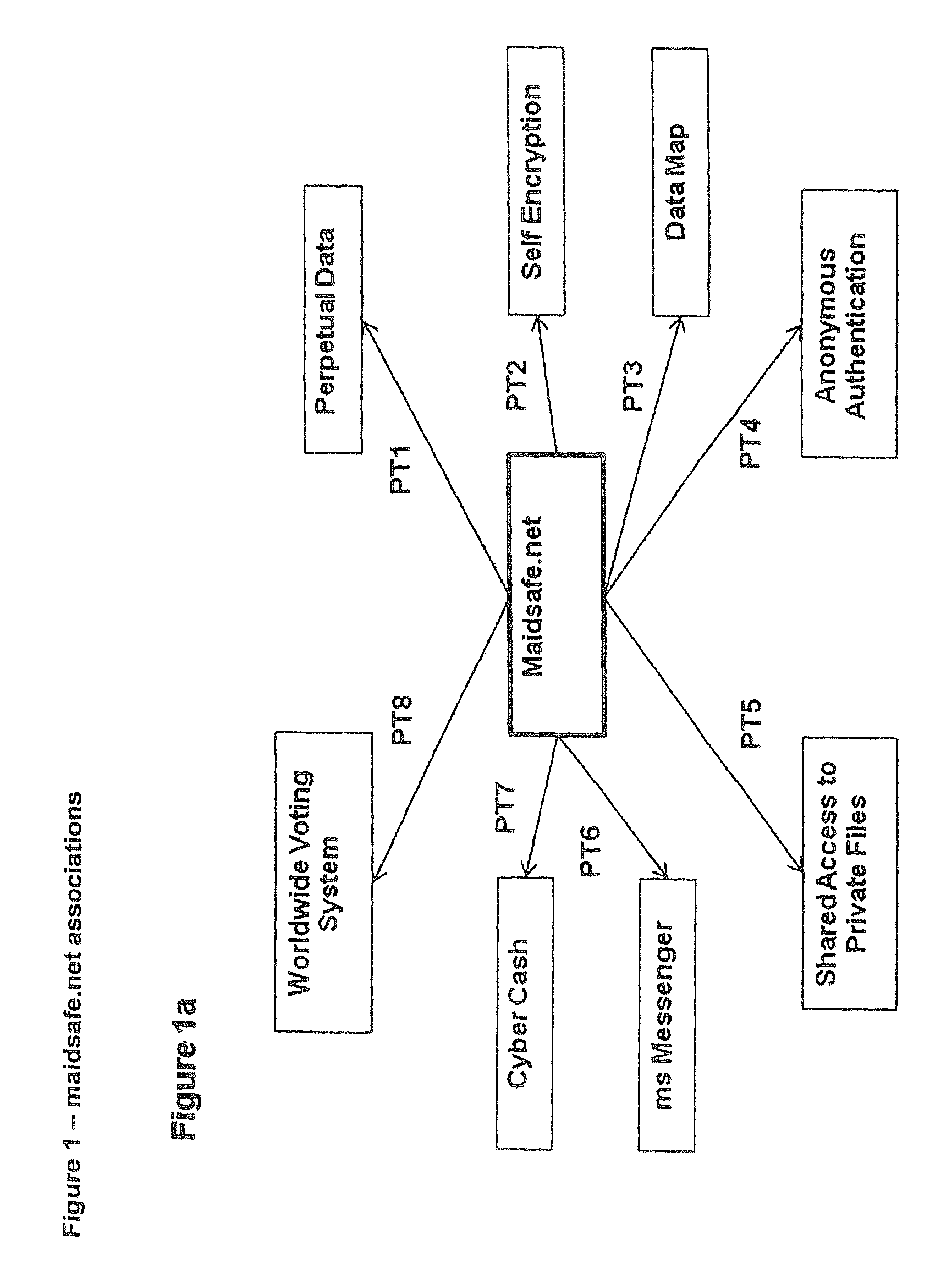
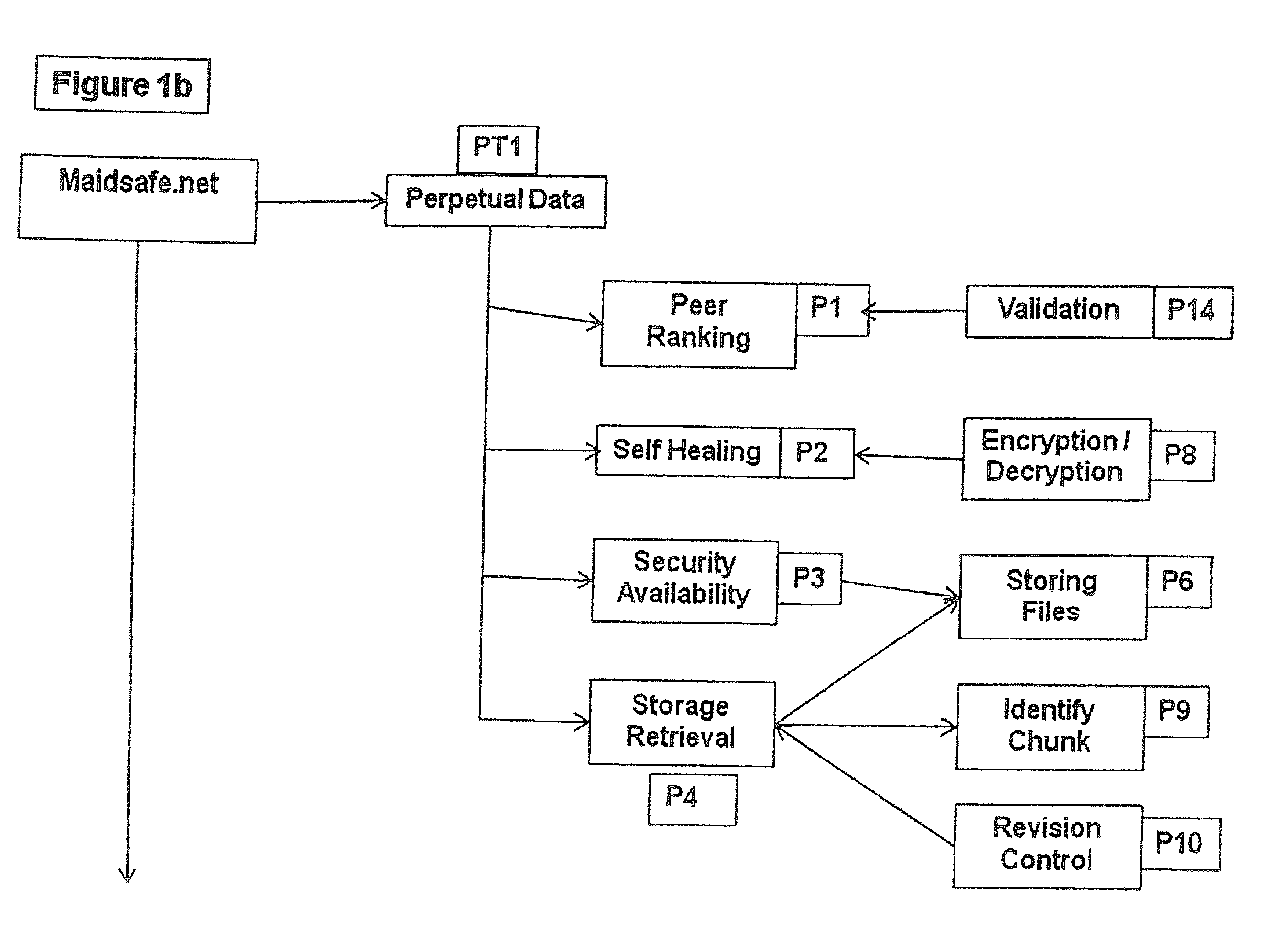
Maidsafe.net
InactiveUS20100064354A1Maintain validityEasy to set upDigital data processing detailsAnalogue secracy/subscription systemsSecure communicationVendor lock-in
This invention is a network that is defined by its novel approach to privacy, security and freedom for its users. Privacy by allowing access anonymously, security by encrypting and obfuscating resources and freedom by allowing users to anonymously and irrefutably be seen as genuine individuals on the network and to communicate with other users with total security and to securely access resources that are both their own and those that are shared by others with them. Further, this invention comprises a system of self healing data, secure messaging and a voting system to allow users to dictate the direction of development of the network, whereby adoption or denial of proposed add-ons to the network will be decided. System incompatibilities and security breaches on networks and the Internet are addressed by this invention where disparity and tangents of development have had an undue influence. The functional mechanisms that this invention provides will restore open communications and worry-free access in a manner that is very difficult to infect with viruses or cripple through denial of service attacks and spam messaging, plus, it will provide a foundation where vendor lock-in need not be an issue.
Owner:UNIV OF CALIFORNIA IRVINE
Method and system for enforcing secure network connection
InactiveUS20050278777A1Blocking in networkDigital data processing detailsUser identity/authority verificationNetwork connectionSecurity policy
The invention is a system and method for enforcing remote users to use secure network connections. Every time a user connects to the network, its network connection is verified for security vulnerabilities and a security policy applies to every network connection based on the number and severity of security vulnerabilities identified for this particular user on this particular network connection.
Owner:HACKERPROOF SECURITY
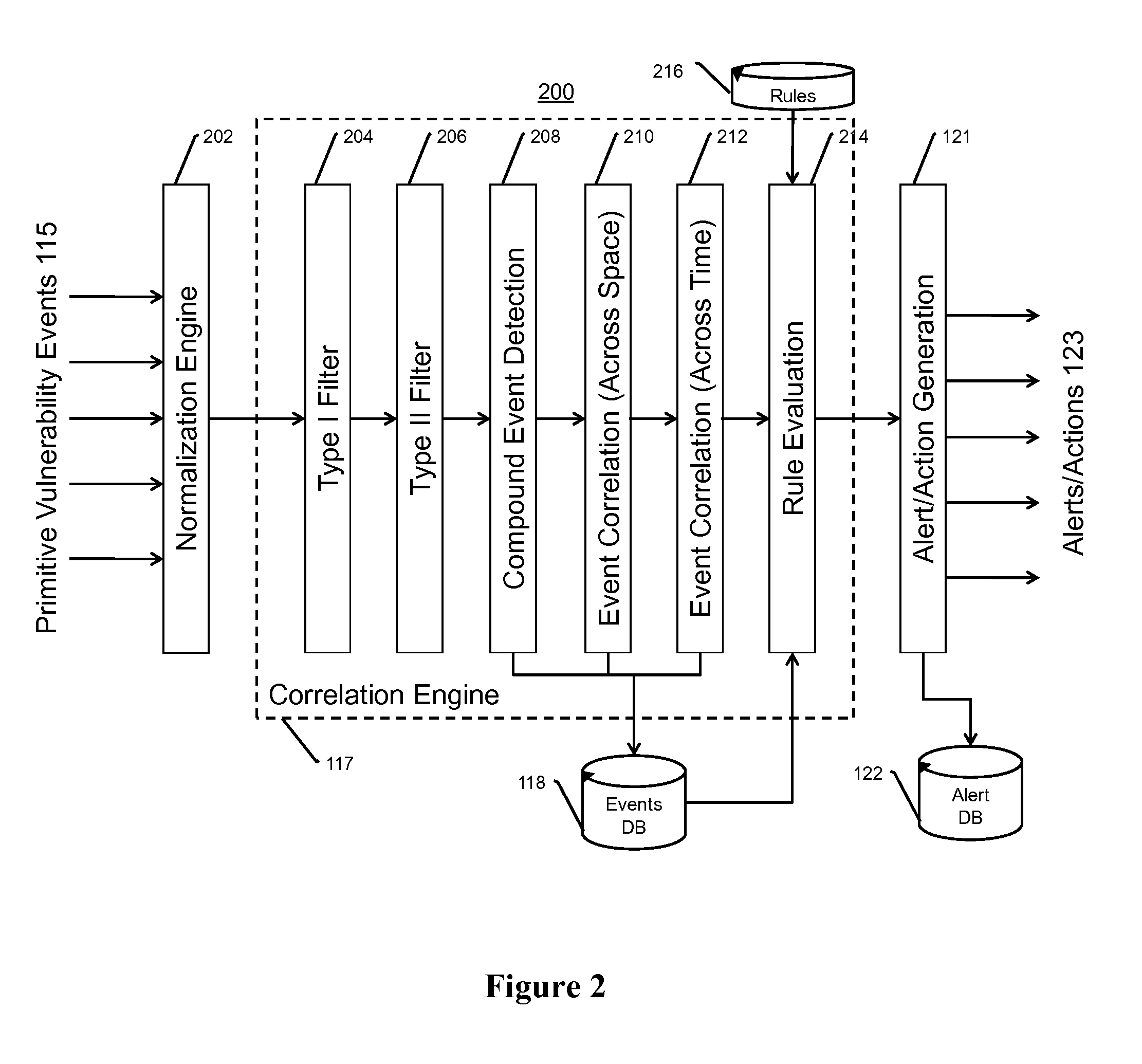
Network security testing
ActiveUS7325252B2Improve viewing effectShort working hoursMemory loss protectionError detection/correctionSecurity solutionWork period
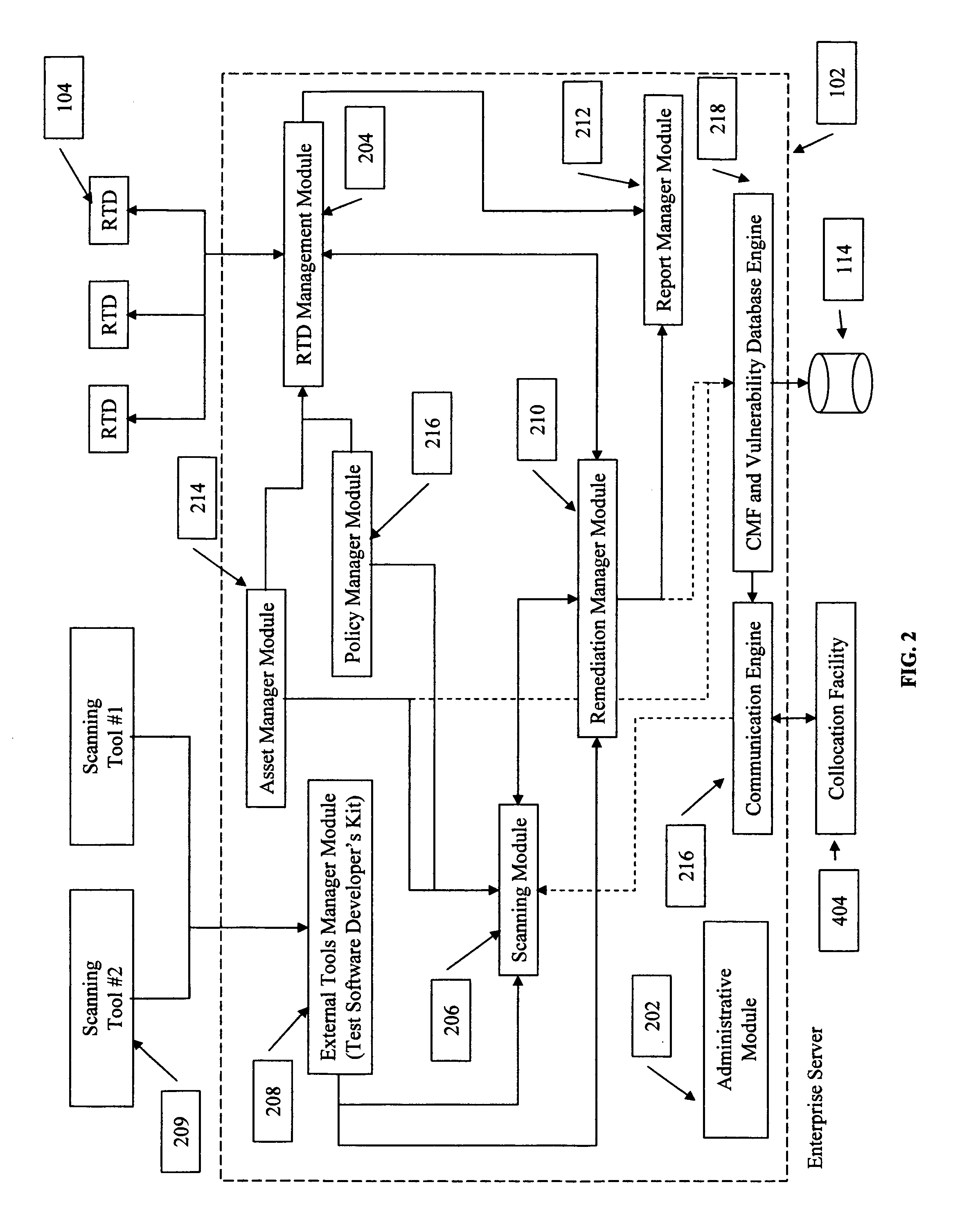
To answer the security needs of the market, a preferred embodiment was developed. A preferred embodiment provides real-time network security vulnerability assessment tests, possibly complete with recommended security solutions. External vulnerability assessment tests can emulate hacker methodology in a safe way and enable study of a network for security openings, thereby gaining a true view of risk level without affecting customer operations. Because this assessment can be performed over the Internet, both domestic and worldwide corporations benefit. A preferred embodiment's physical subsystems combine to form a scalable holistic system that can be able to conduct tests for thousands of customers any place in the world. The security skills of experts can be embedded into a preferred embodiment systems and automated the test process to enable the security vulnerability test to be conducted on a continuous basis for multiple customers at the same time. A preferred embodiment can reduce the work time required for security practices of companies from three weeks to less than a day, as well as significantly increase their capacity. Component subsystems typically include a Database, Command Engine, Gateway, multiple Testers, Report Generator, and an RMCT.
Owner:ALERT LOGIC
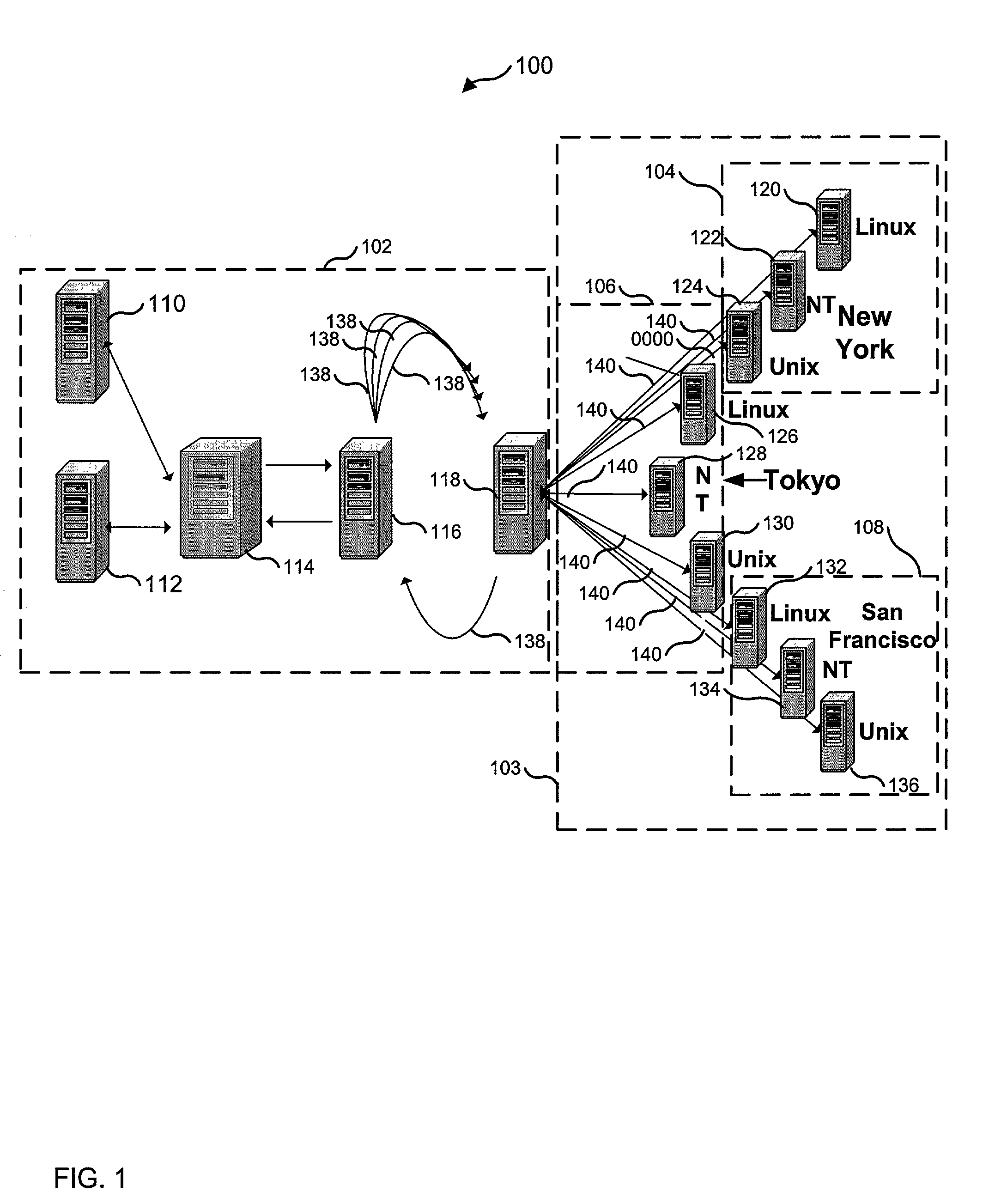
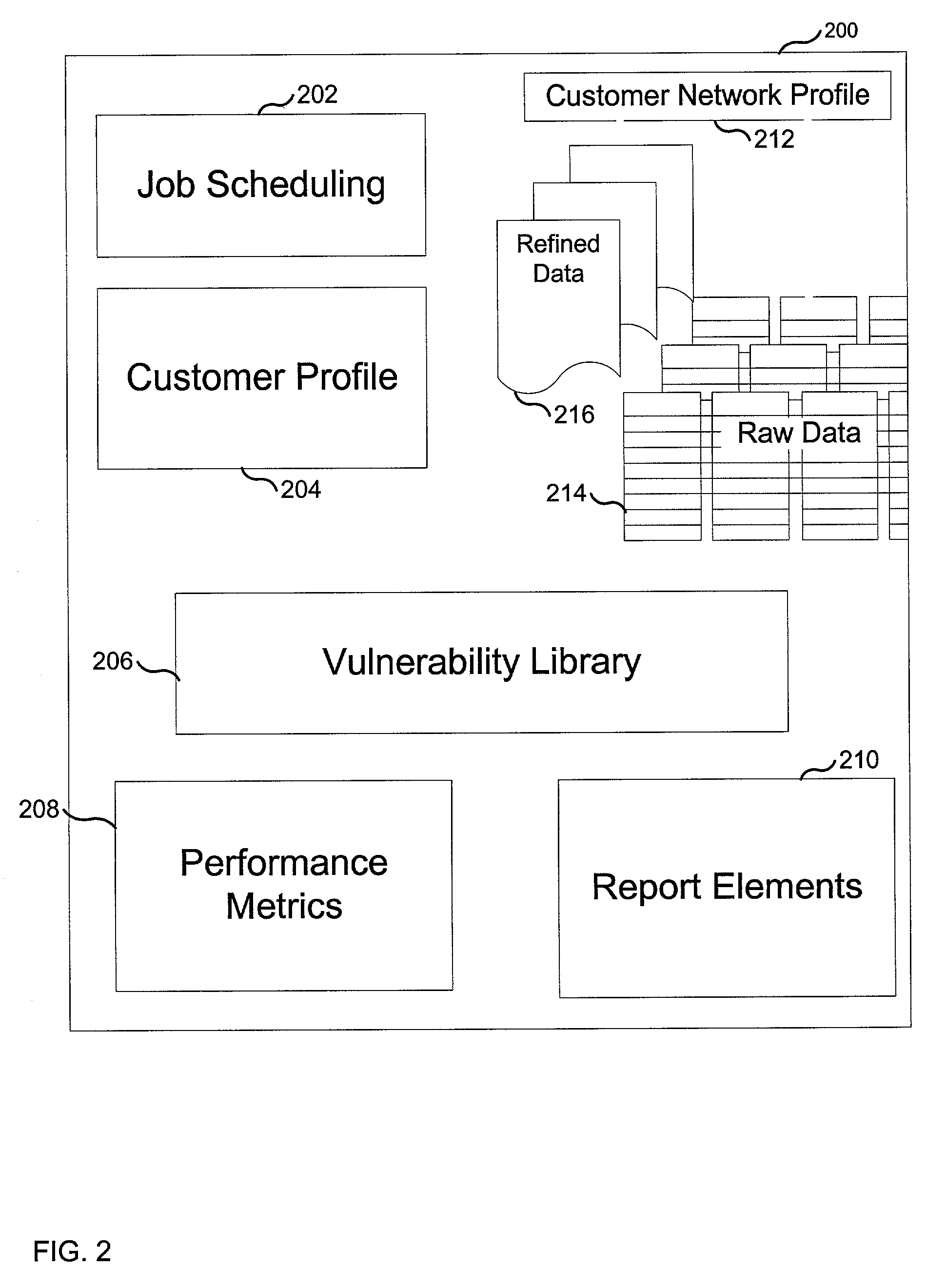
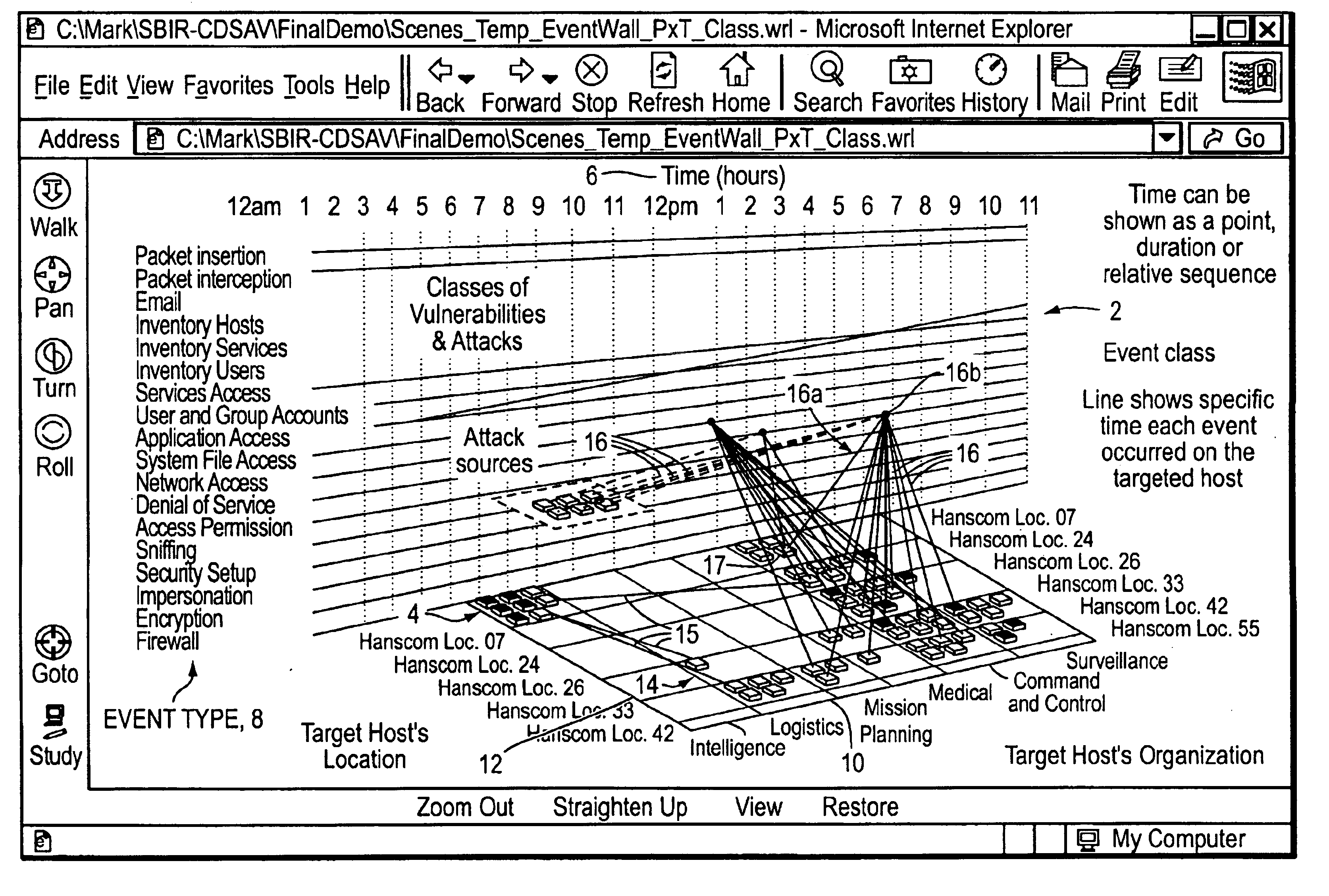
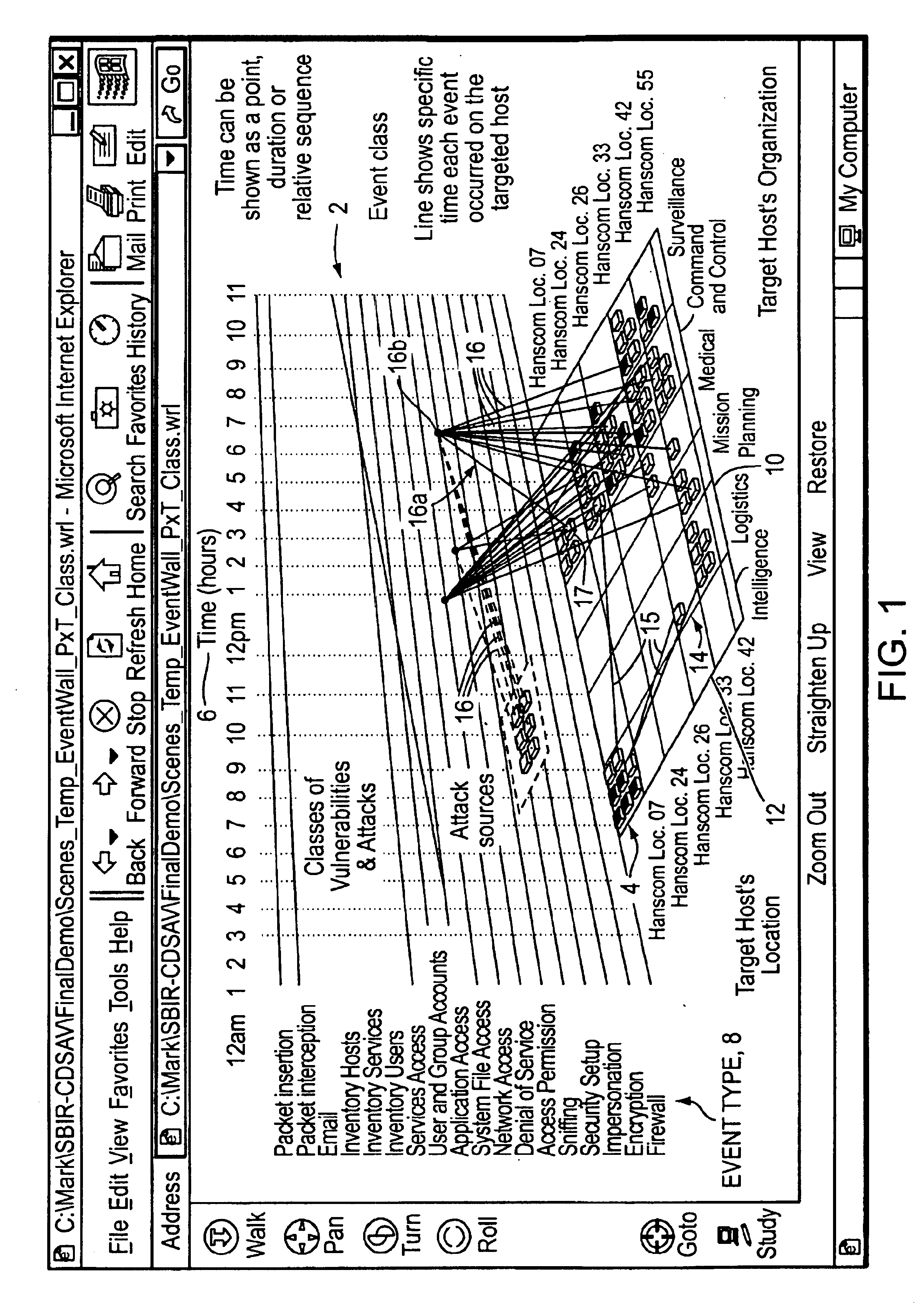
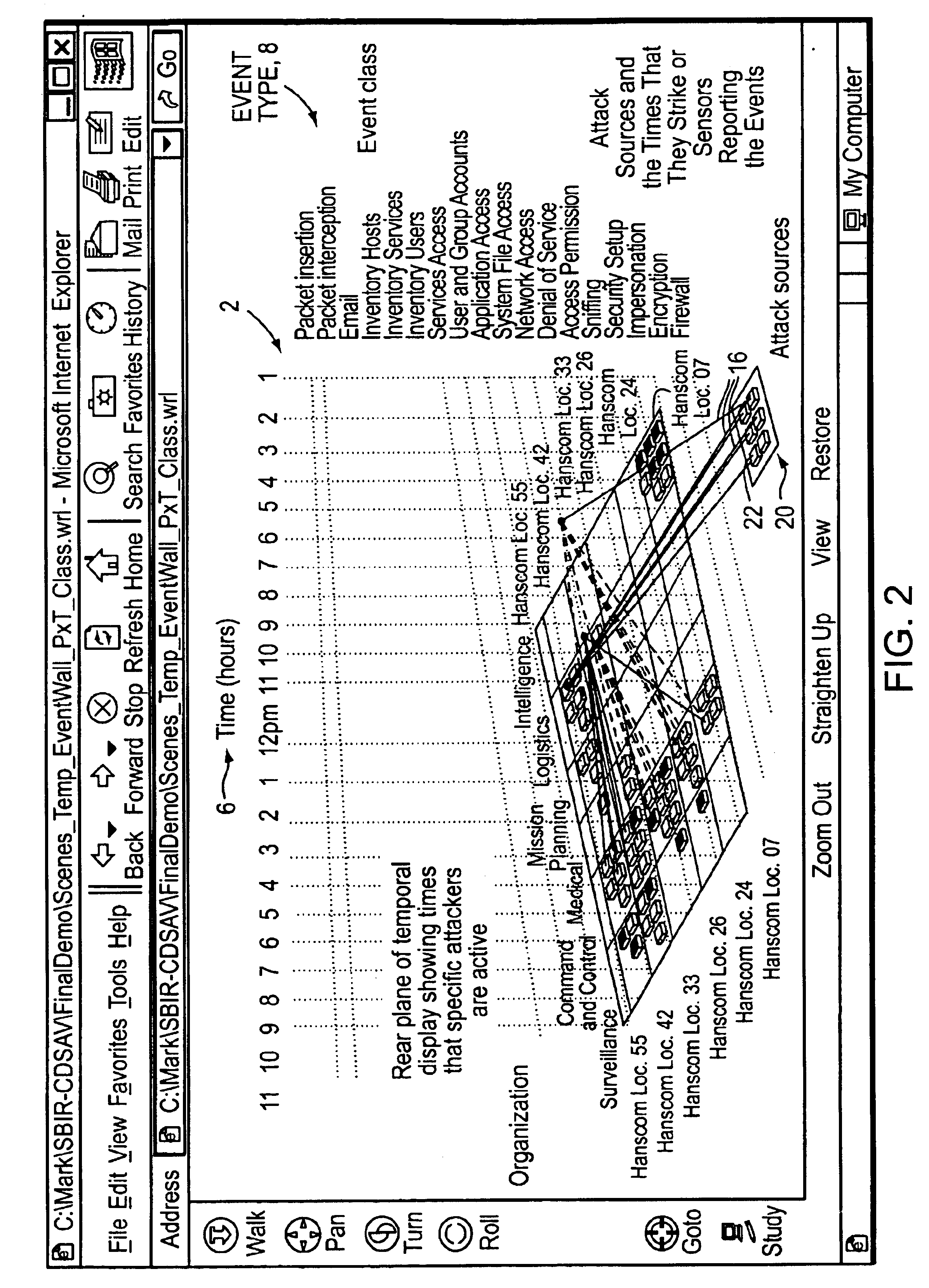
Visualizing security incidents in a computer network
InactiveUS6906709B1Enhanced Situational AwarenessFacilitate human perceptionTransmission3D-image renderingDatabase interfaceBusiness function
A method of visualizing the impact of security flaws or breaches in a network. A 3-D visualization tool that simulates 3-D space on a monitor interfaces with a security database which relationally associates security events with the network elements affected thereby. The security events are visually depicted in a first section of simulated 3-D space and the network elements are depicted in a second section of simulated 3-D space. Relationship lines are drawn between displayed categories of security events and the displayed network elements in order to aid an analyst to visualize the impact of security breaches on the organization. Various other properties of the network elements may also be displayed such as the role of the network device within the organization, and the business functions of the organization.
Owner:APPLIED VISION
Method to generate a quantitative measurement of computer security vulnerabilities
InactiveUS20060101518A1Memory loss protectionError detection/correctionCollocationSecurity management
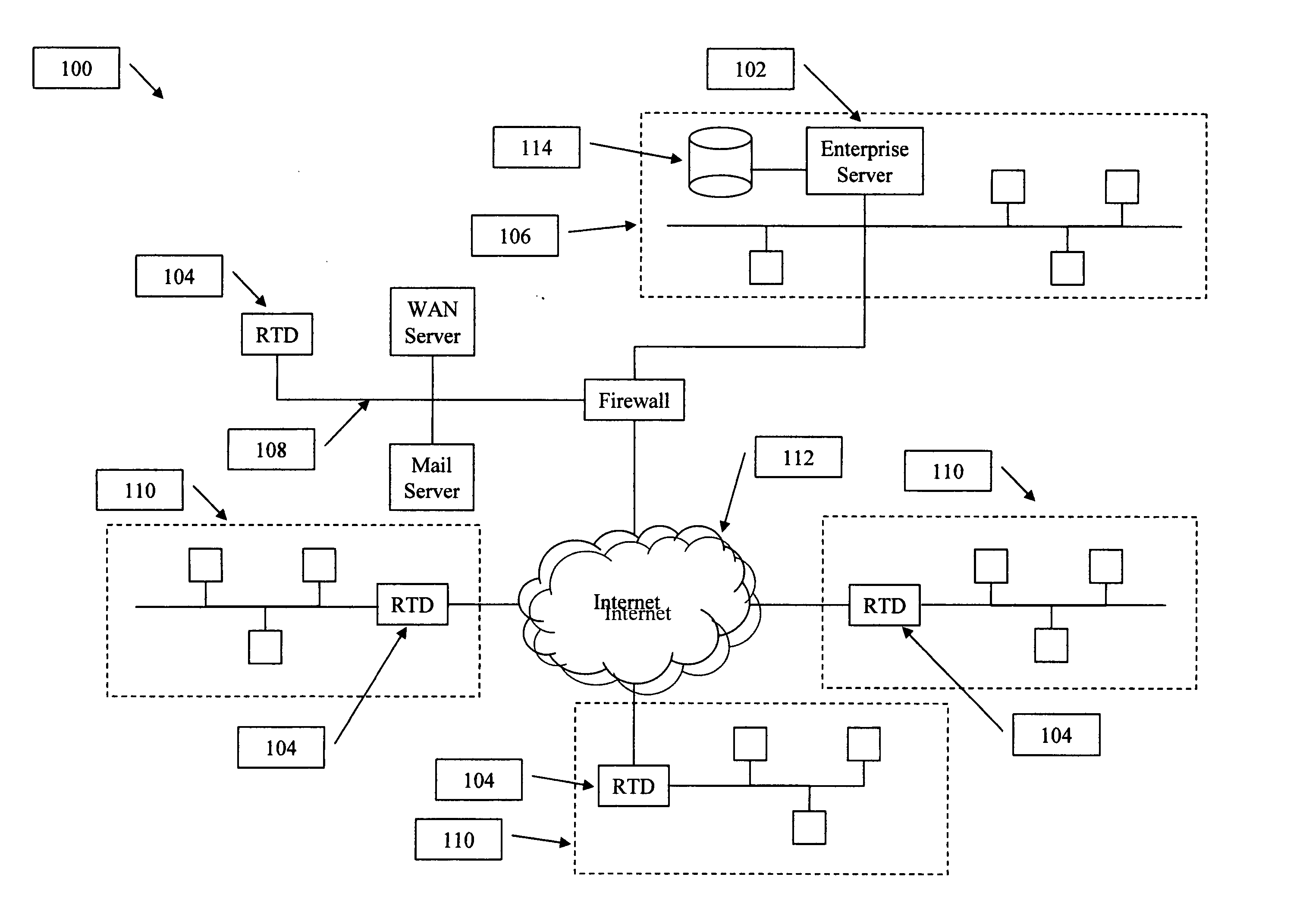
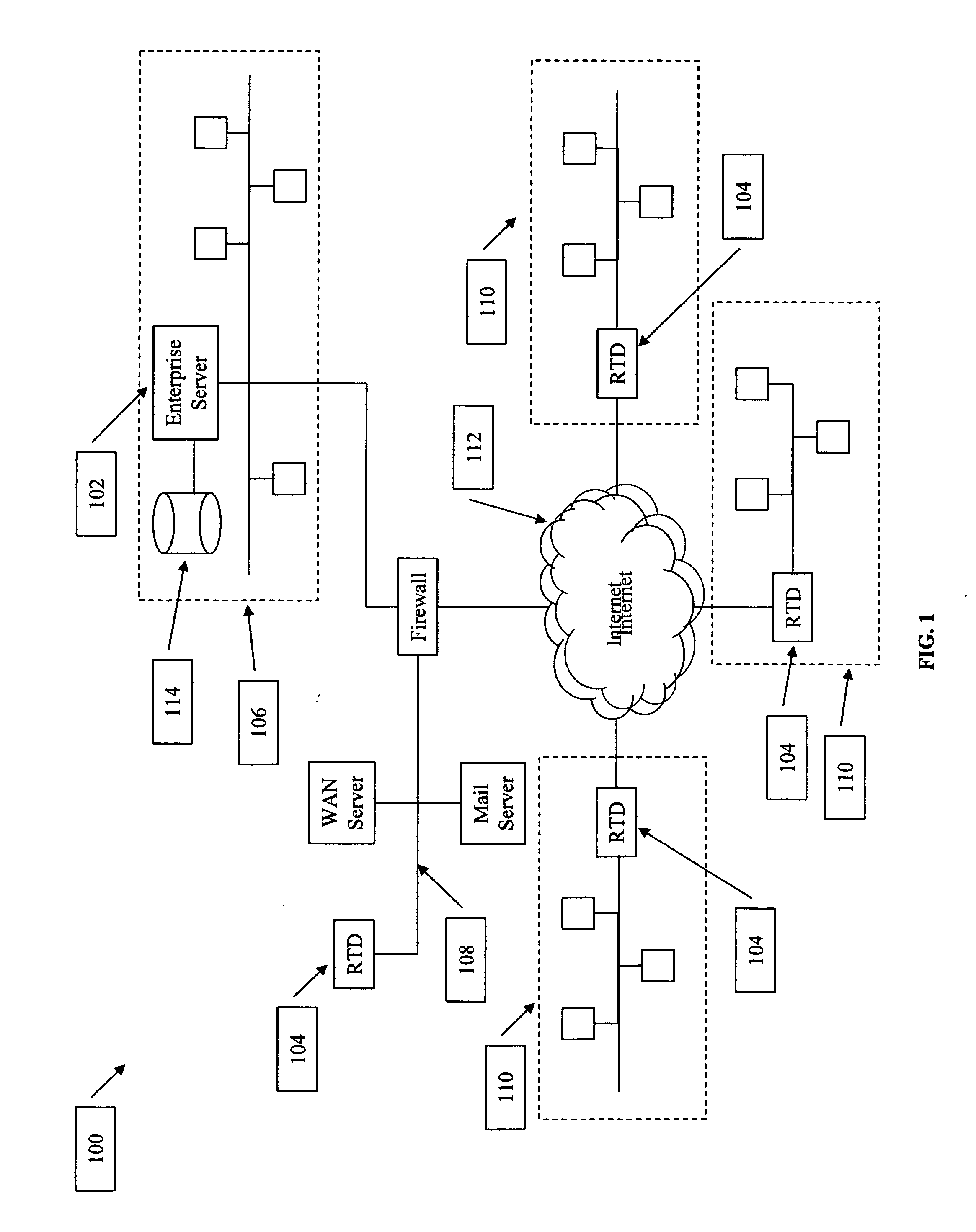
The present invention provides a system and method to provide a measurement of the risk that a computer network may have to computer security threats. The system includes a collocation facility that is coupled to a plurality of computer security management systems. Some or all of the vulnerability information is reported to the collocation facility. At the collocation facility, this information is compared to a standard. This comparison yields a number or other measurement of that organization's risk in its computer security. The collocation facility can then report this measurement to any information user that wishes to know what the vulnerability is for that organization.
Owner:SCHUMAKER TROY T +1
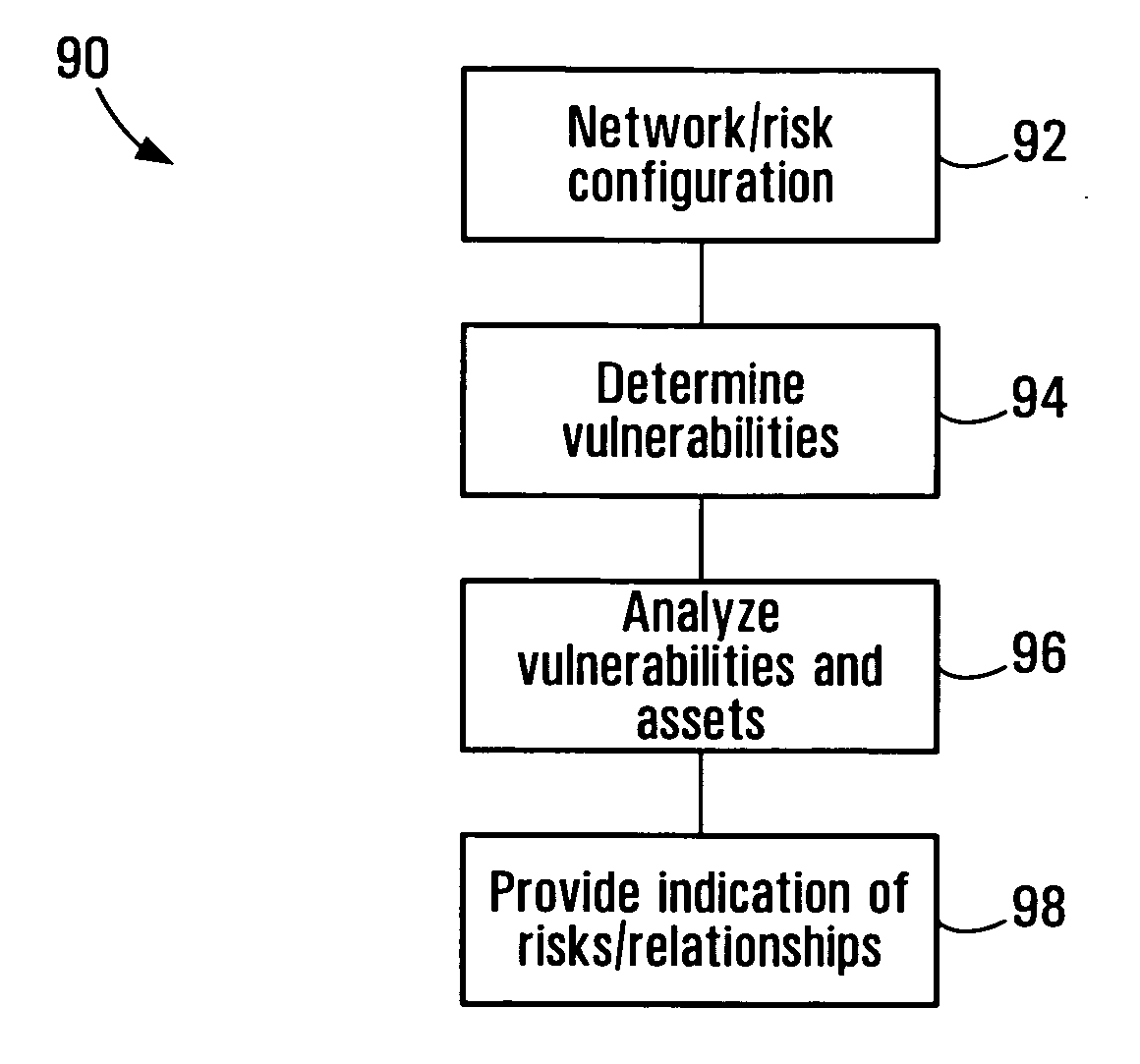
Information system service-level security risk analysis
Information system service-level security risk analysis systems, methods, and Graphical User Interfaces are disclosed. Assets of an information system that have relationships with a service provided by the information system are identified, and at least one security risk to the service is determined by analyzing security vulnerabilities associated with the identified assets. A consolidated representation of the service is provided, and includes an indication of the determined security risk(s) and an indication of a relationship between the service and at least one of the identified assets. The security risk indication may include indications of multiple security parameters. Security risks may be represented differently depending on whether they arise from a security vulnerability of an asset that has a relationship with the service or a security vulnerability of an asset that has a relationship with the service only through a relationship with an asset that has a relationship with the service.
Owner:ALCATEL LUCENT SAS
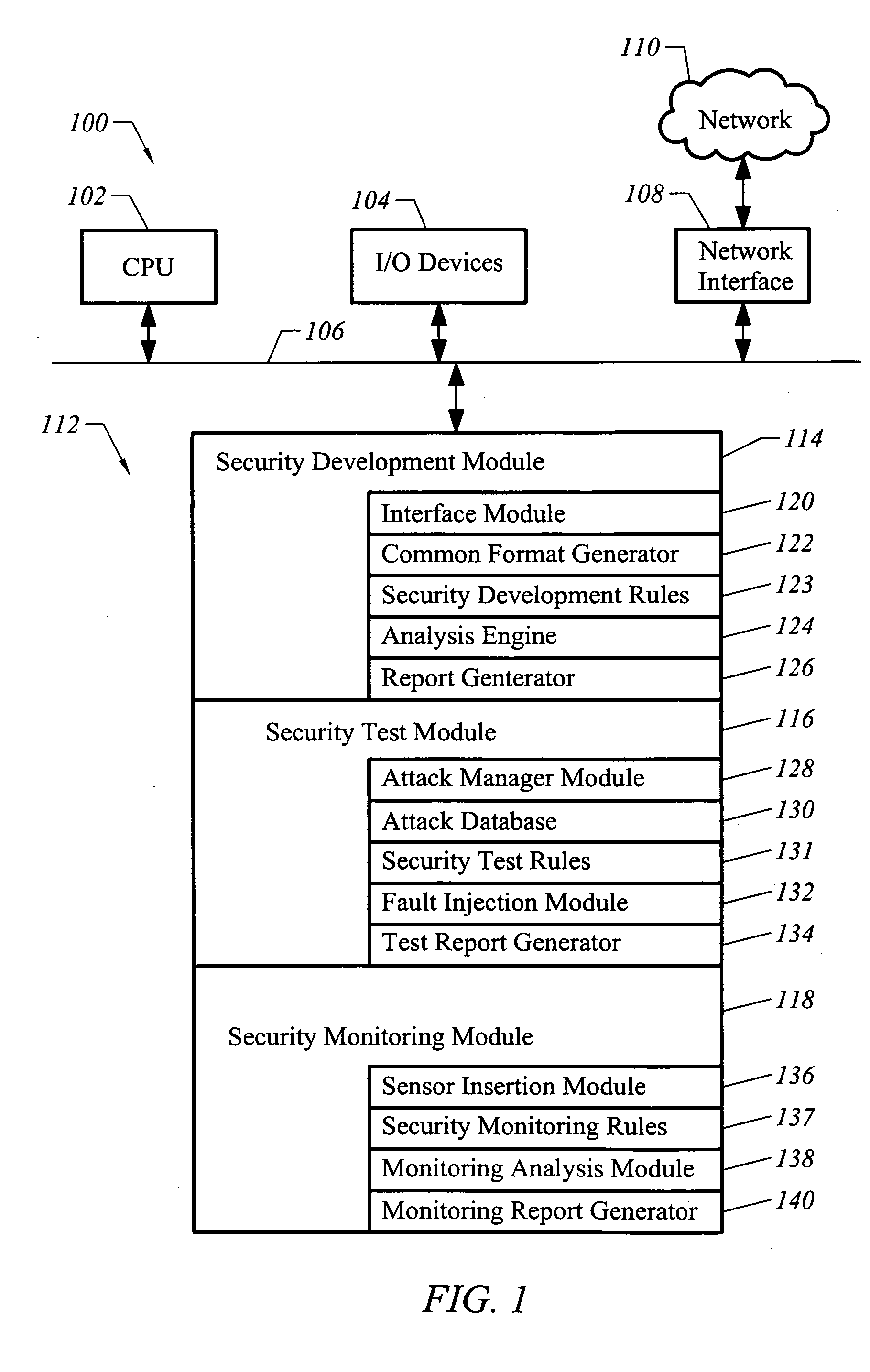
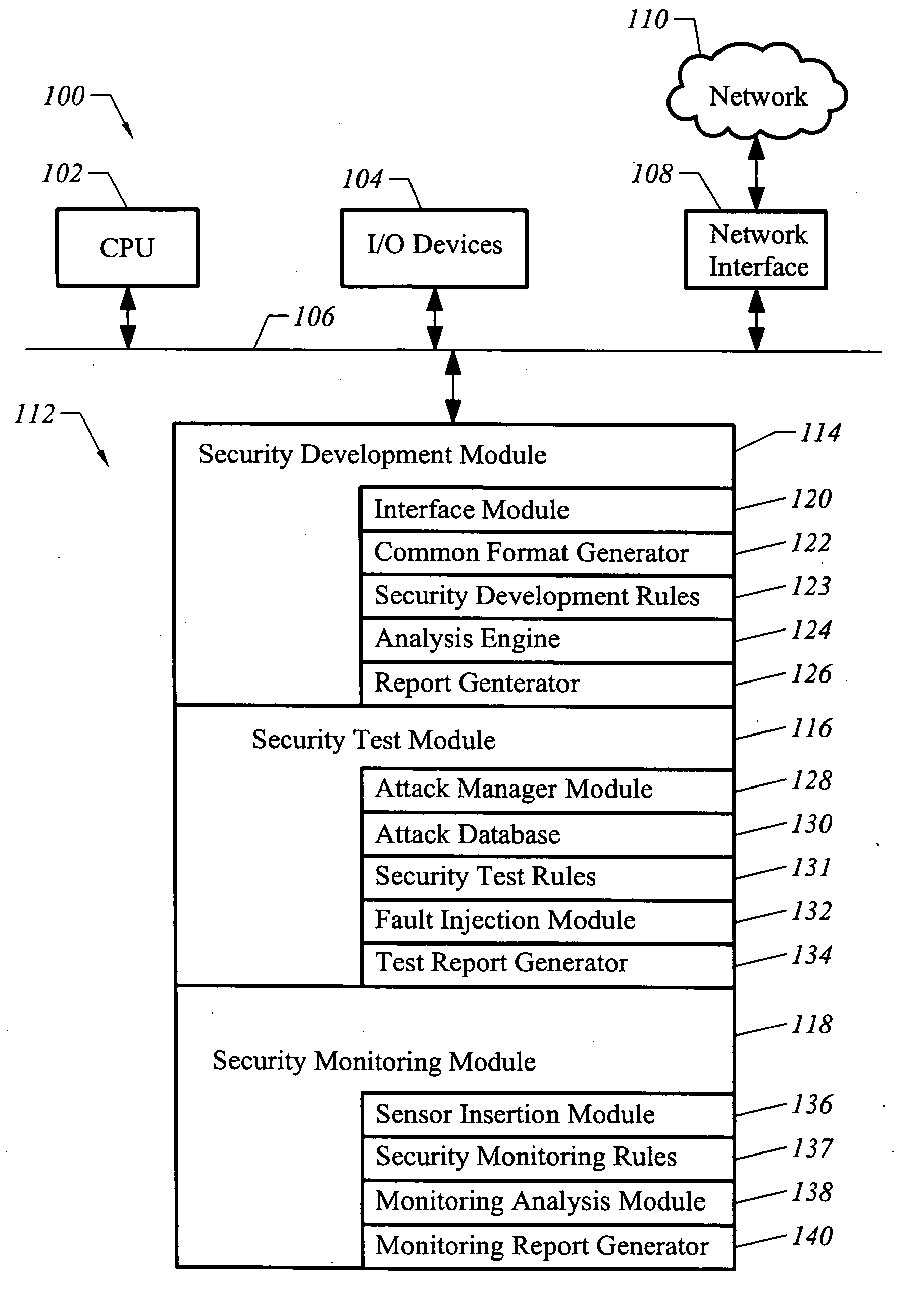
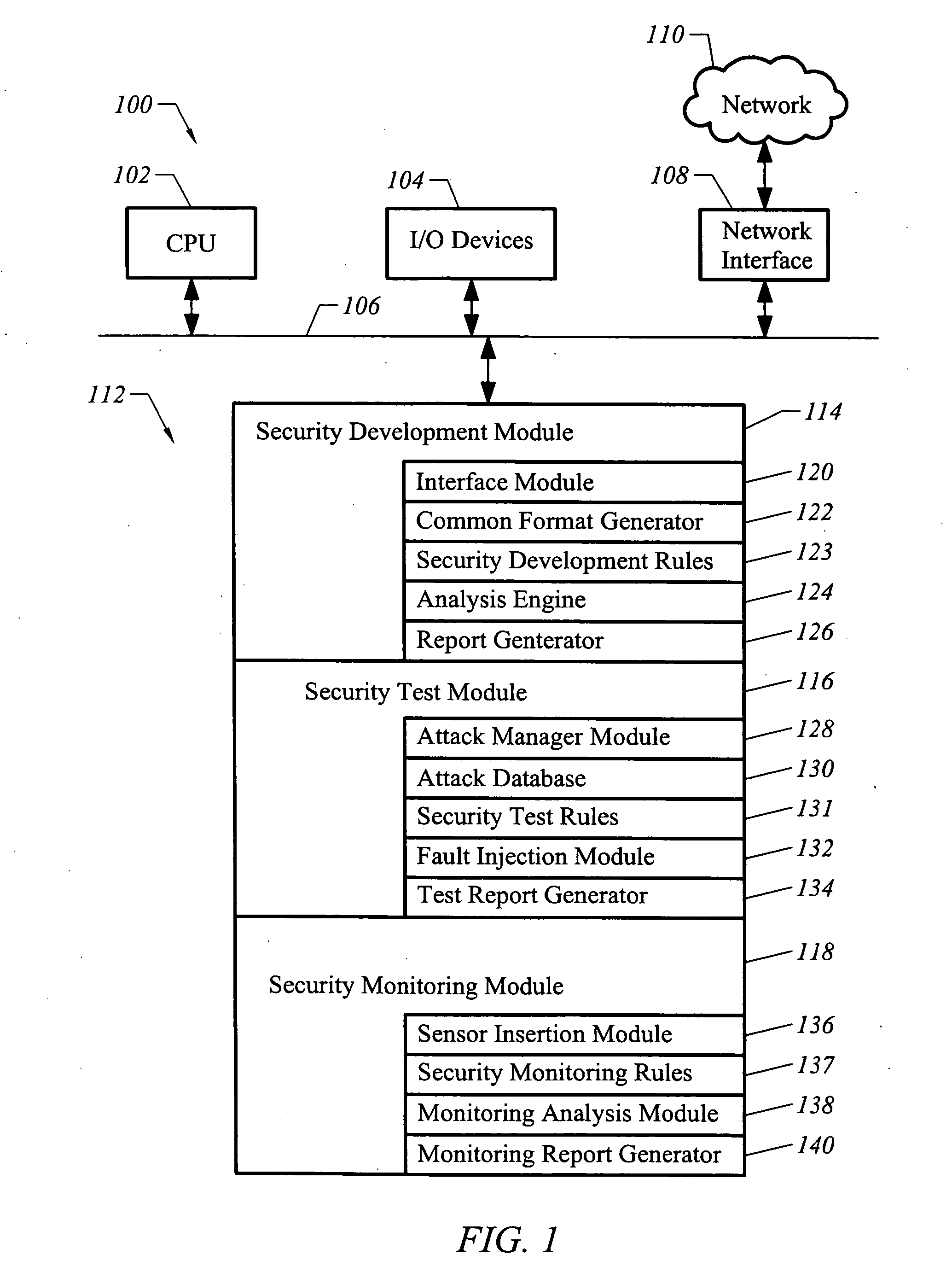
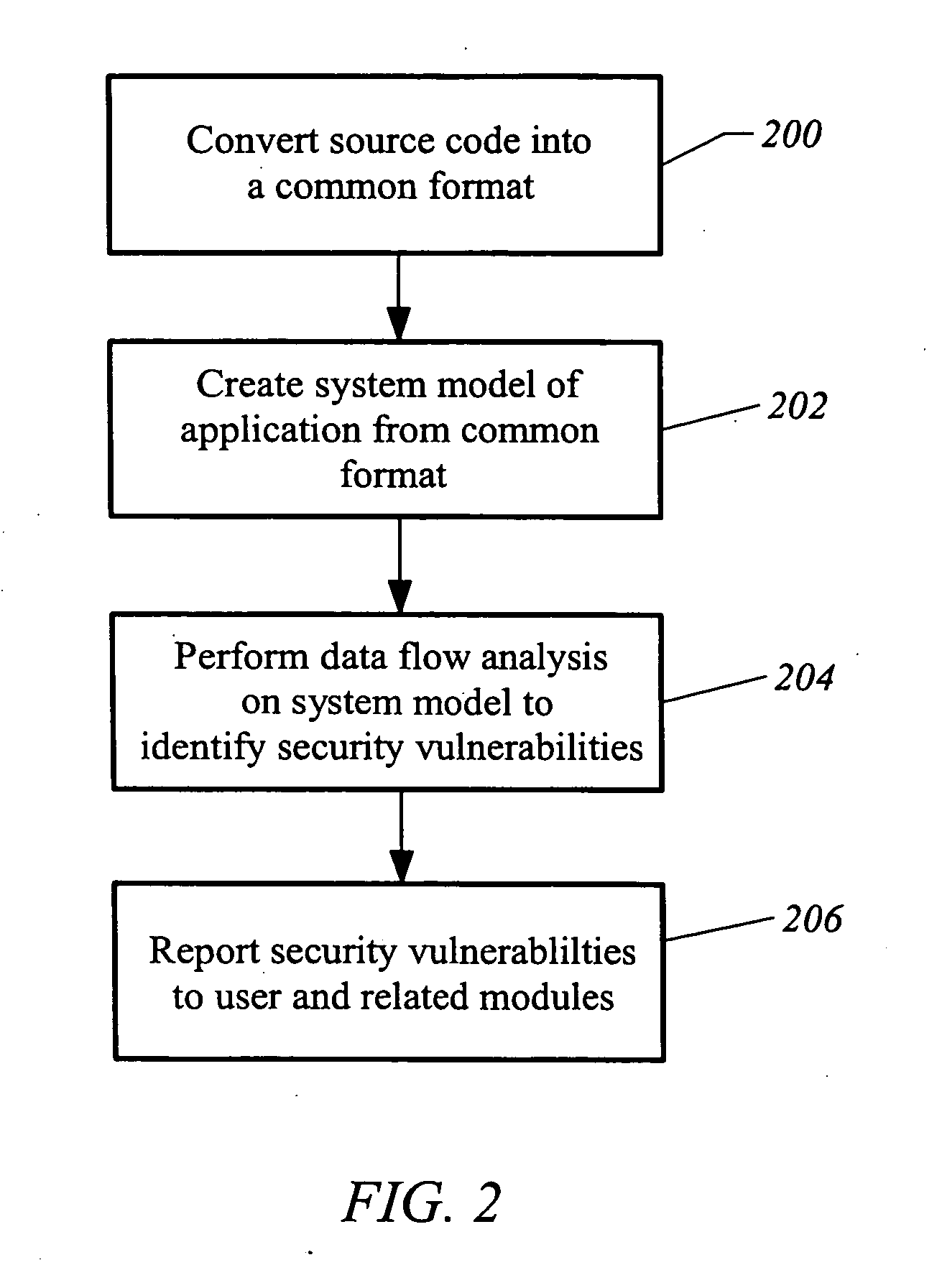
Apparatus and method for developing secure software
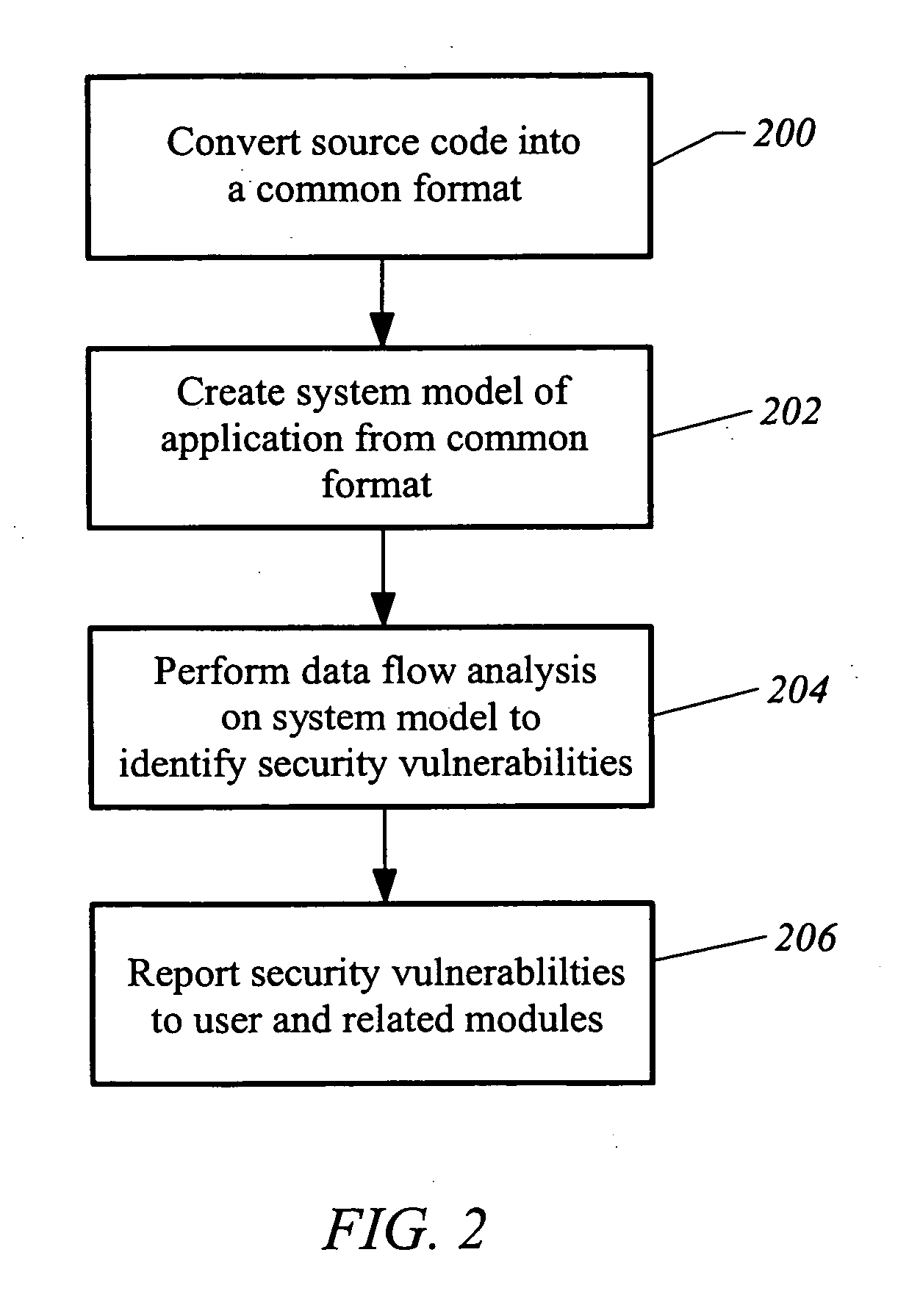
ActiveUS20050273854A1Memory loss protectionDigital data processing detailsProgram instructionSecurity bug
A computer readable medium includes executable instructions to analyze program instructions for security vulnerabilities. The executable instructions convert diverse program instruction formats to a common format. A system model is derived from the common format. A static analysis is performed on the system model to identify security vulnerabilities. Security vulnerabilities are then reported.
Owner:MICRO FOCUS LLC
System and method of managing network security risks
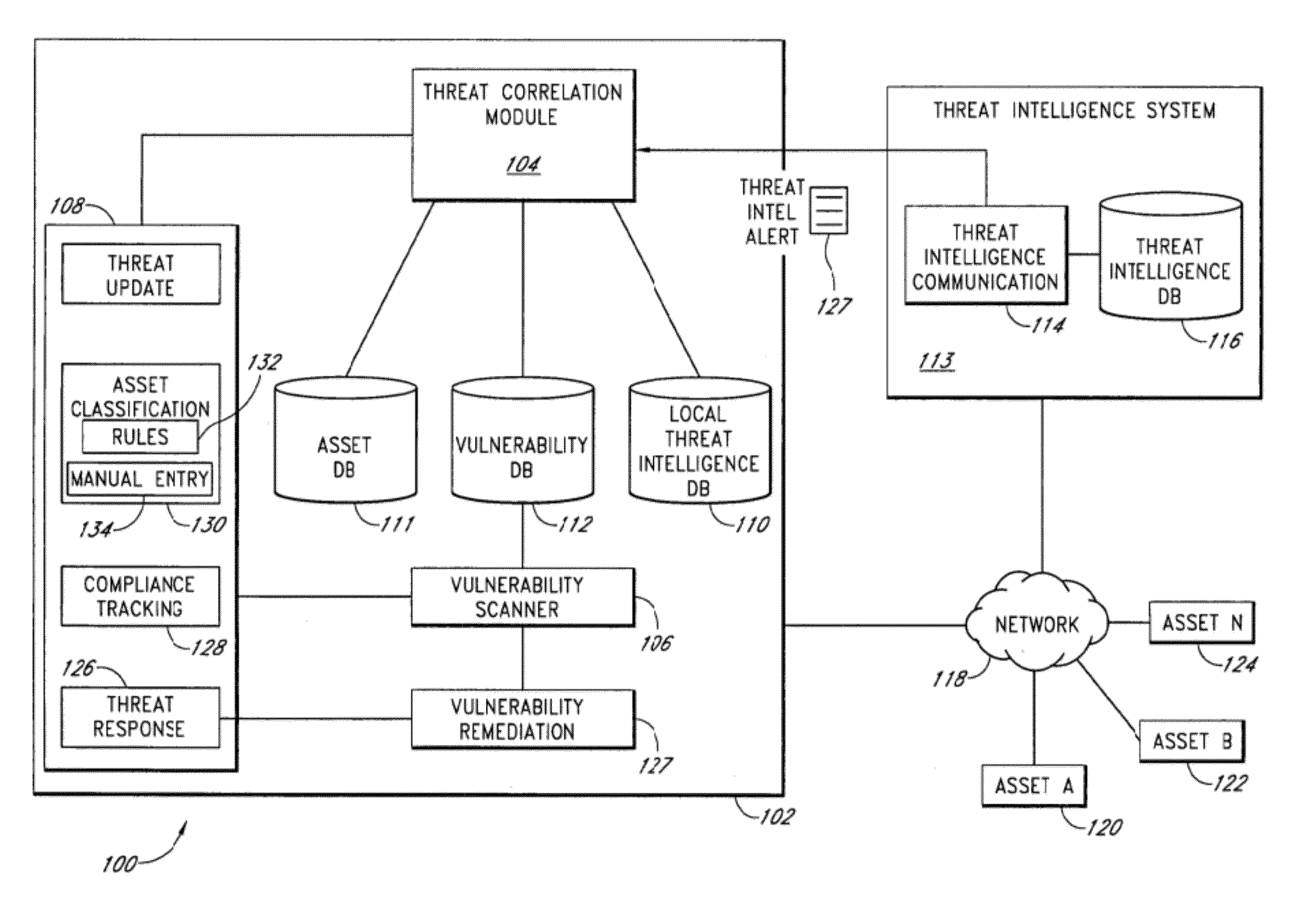
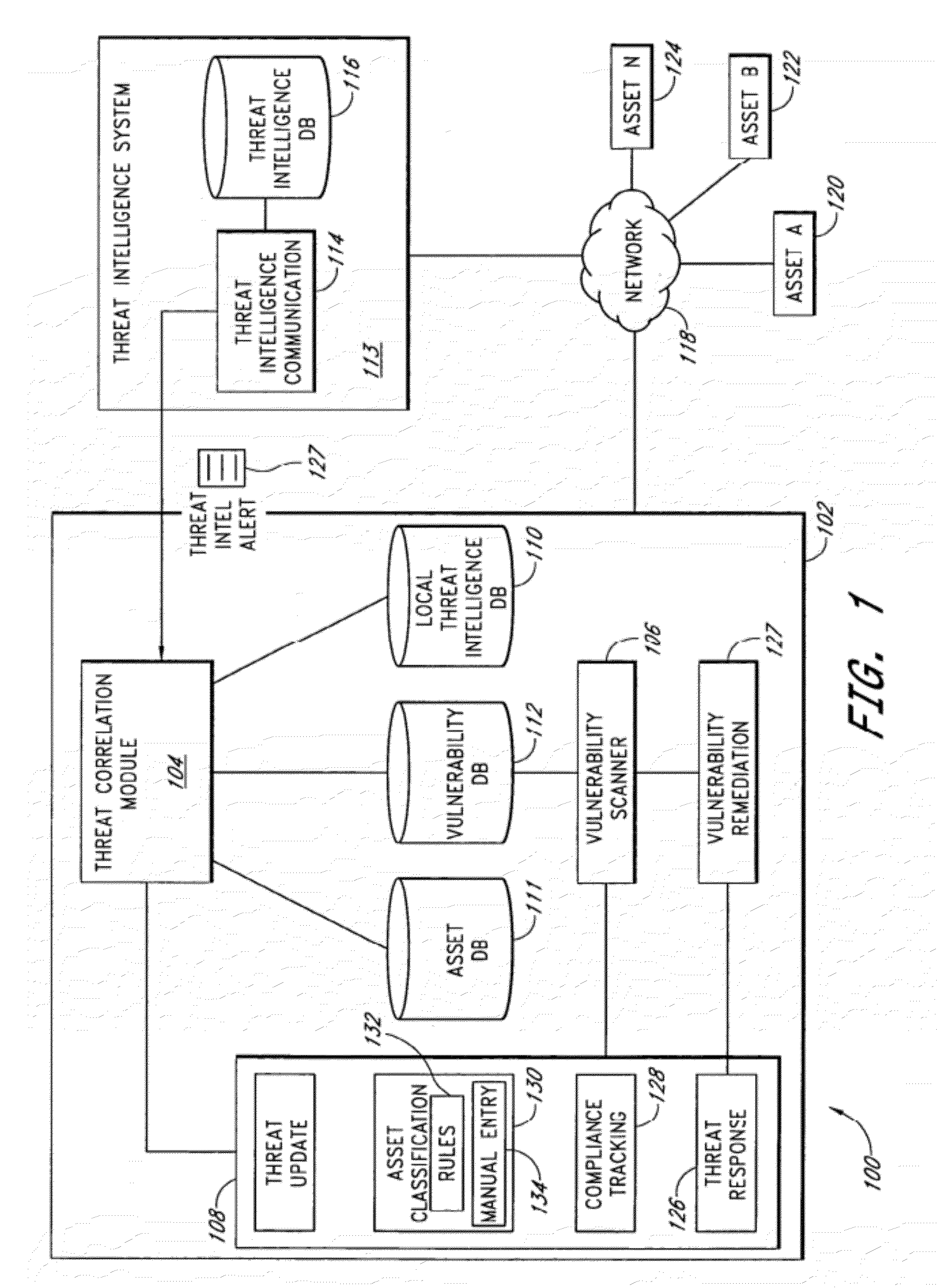
InactiveUS20120185945A1Memory loss protectionError detection/correctionThreat intelligencePreventive action
A security risk management system comprises a vulnerability database, an asset database, a local threat intelligence database and a threat correlation module. The vulnerability database comprises data about security vulnerabilities of assets on a network gathered using active or passive vulnerability assessment techniques. The asset database comprises data concerning attributes of each asset. The threat correlation module receives threat intelligence alerts that identify attributes and vulnerabilities associated with security threats that affect classes of assets. The threat correlation module compares asset attributes and vulnerabilities with threat attributes and vulnerabilities and displays a list of assets that are affected by a particular threat. The list can be sorted according to a calculated risk score, allowing an administrator to prioritize preventive action and respond first to threats that affect higher risk assets. The security risk management system provides tools for performing preventive action and for tracking the success of preventive action.
Owner:MCAFEE INC
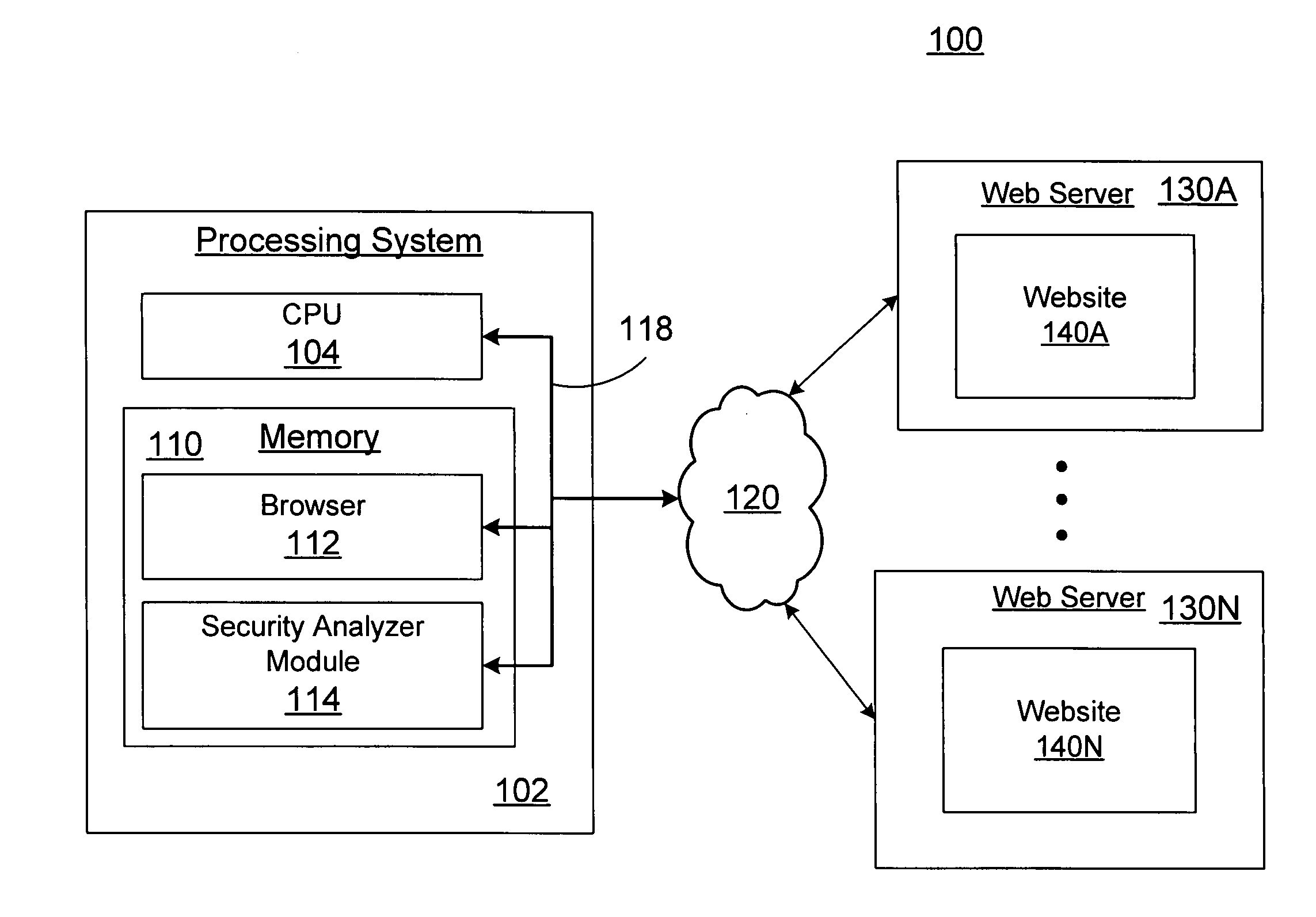
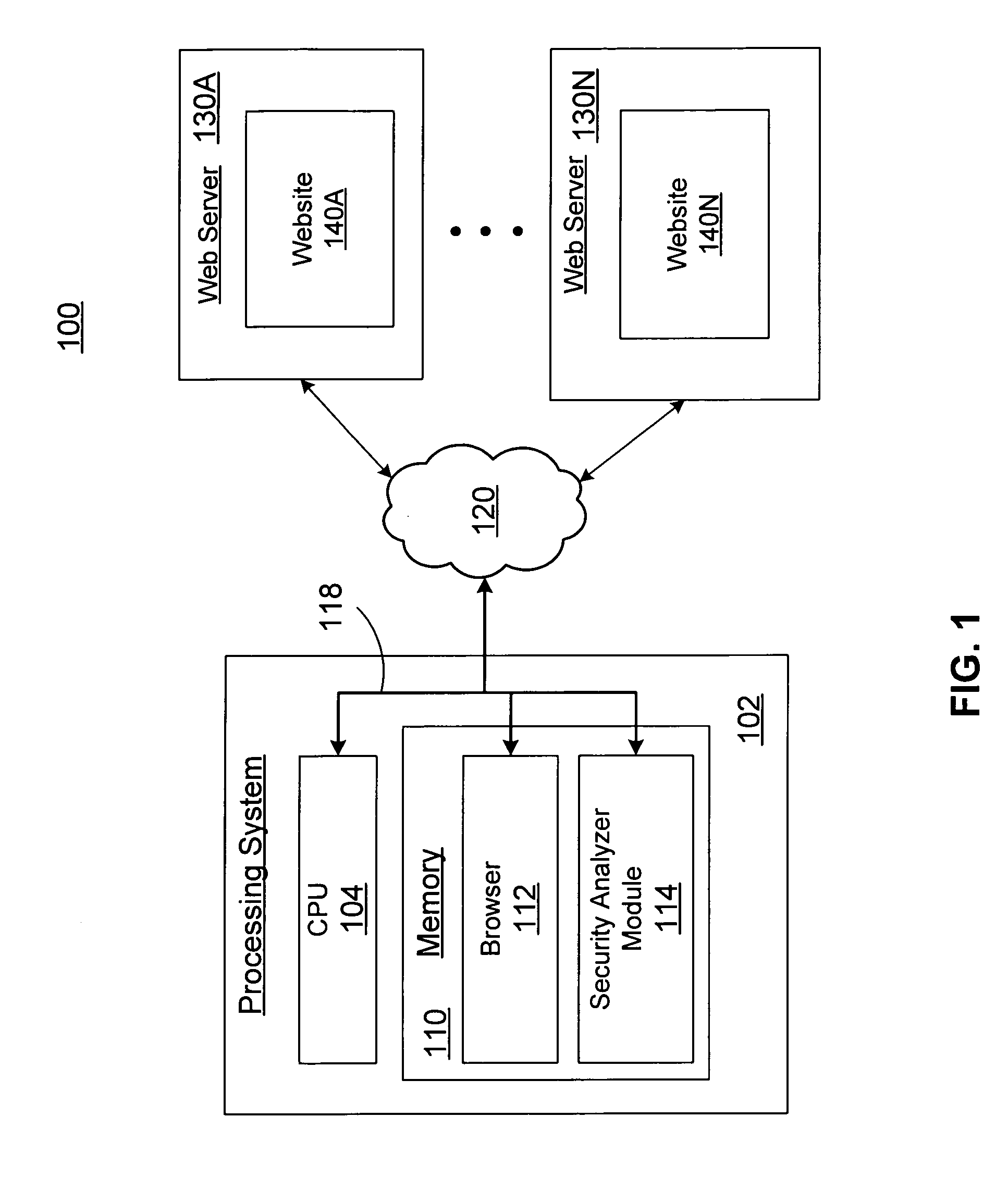
Internet security analysis system and process
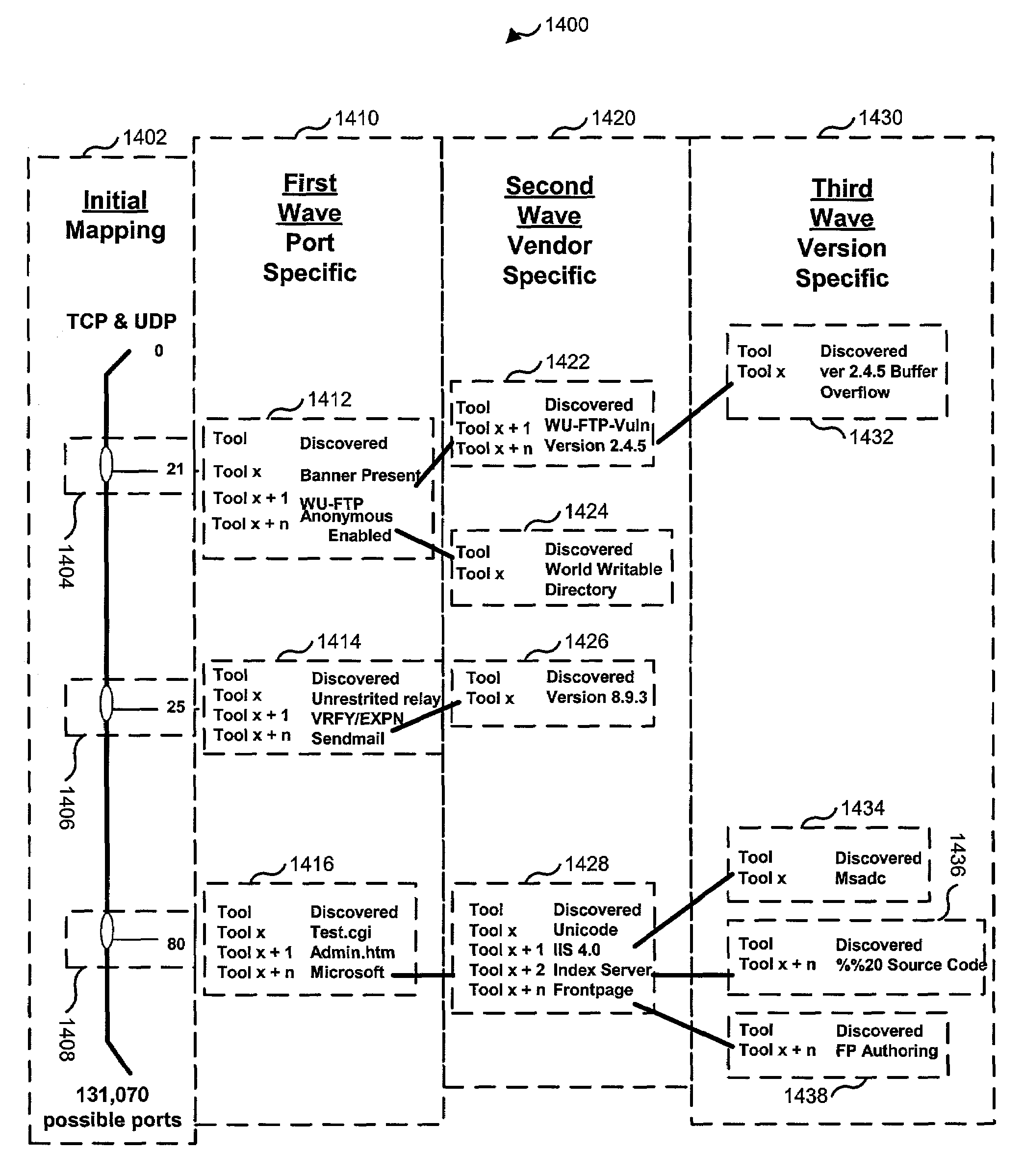
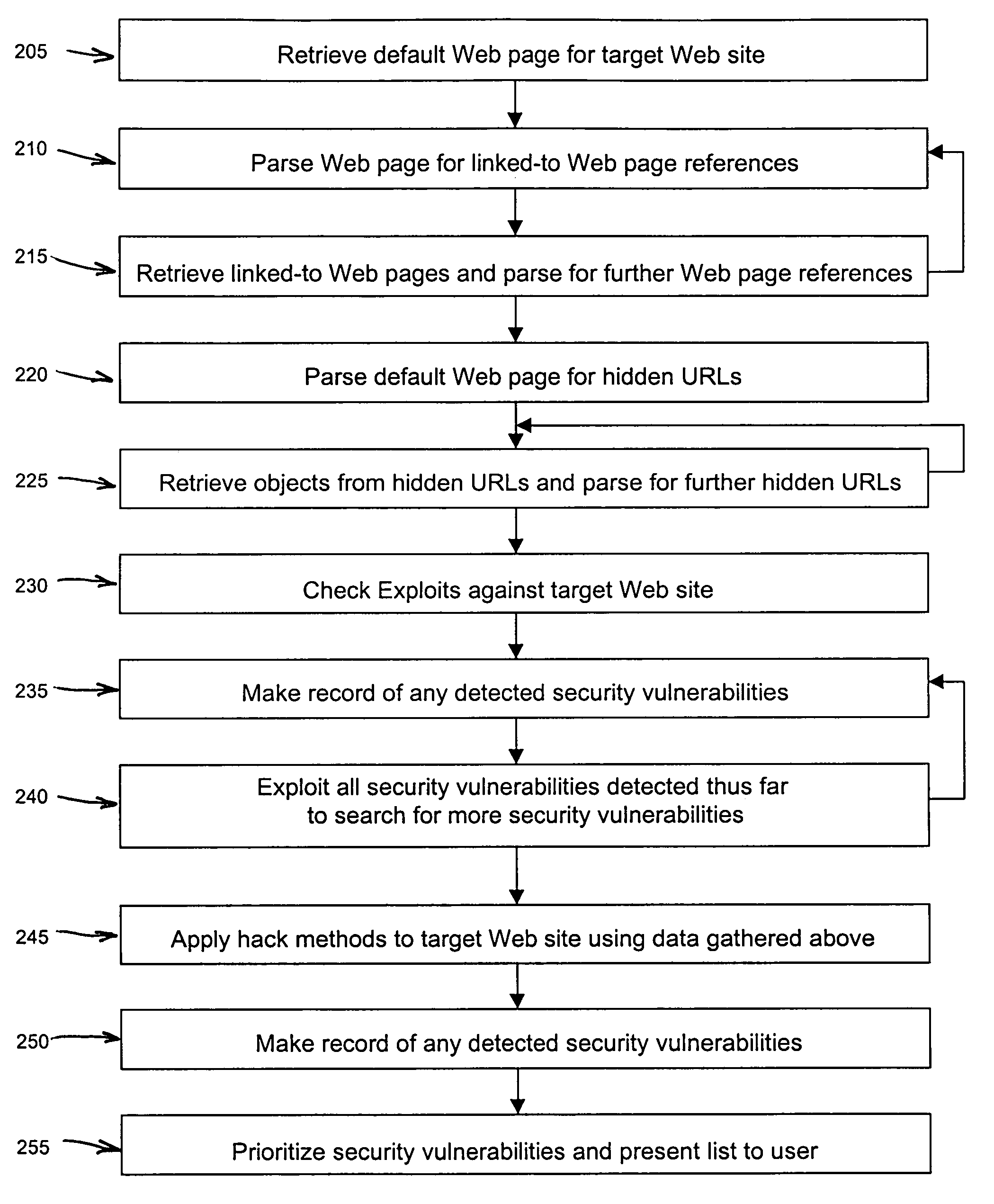
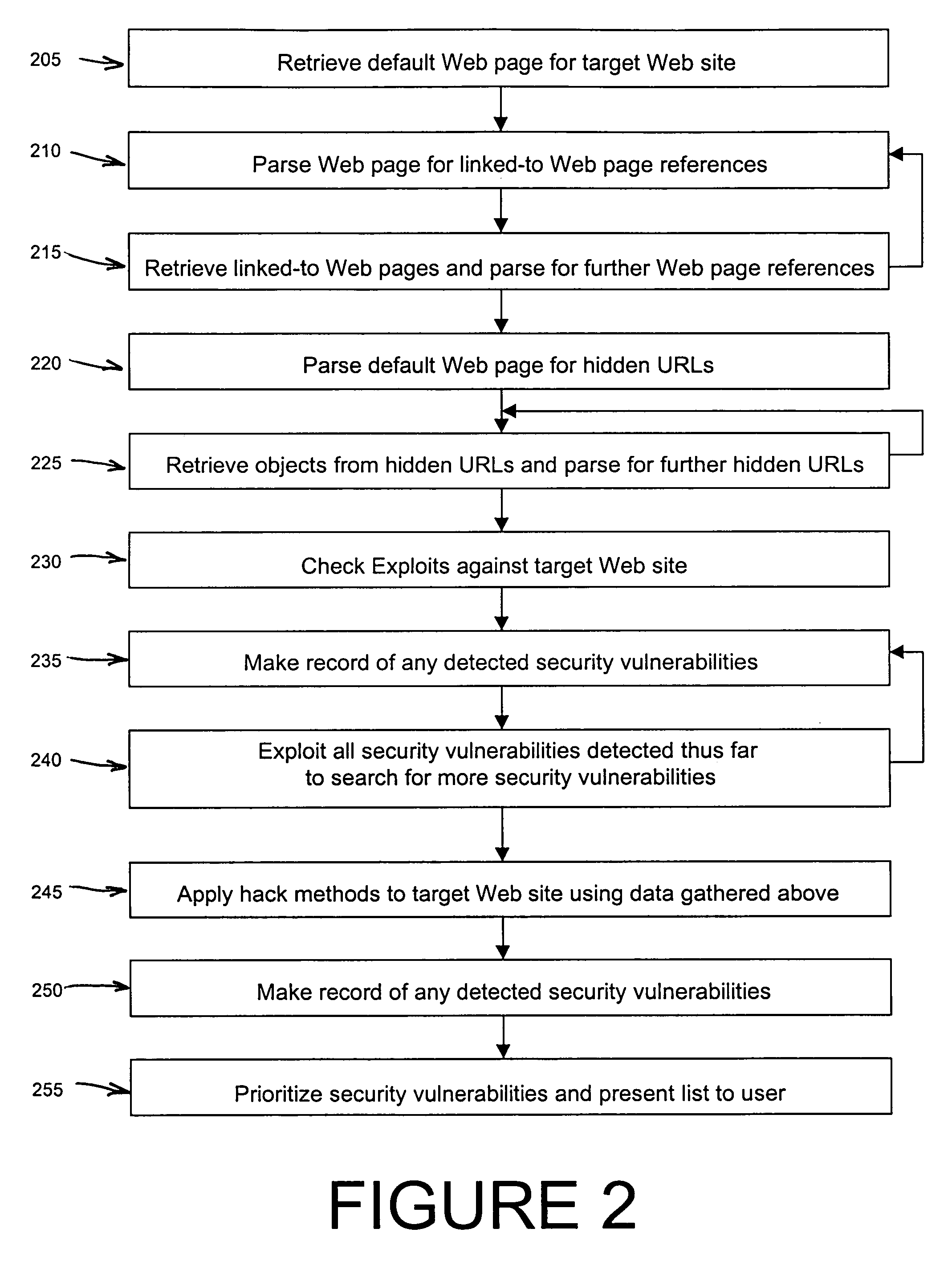
InactiveUS6996845B1Memory loss protectionUnauthorized memory use protectionWeb siteSecurity analysis
An automated Web security analysis system and process identifies security vulnerabilities in a target Internet Web site by parsing through the target Web site to search for a predetermined list of common security vulnerabilities. The process is recursive, exploiting information gathered throughout the process to search for additional security vulnerabilities. A prioritized list of detected security vulnerabilities is then presented to a user, including preferably a list of recommendations to eliminate the detected security vulnerabilities.
Owner:SPI DYNAMICS HEADQUARTERS
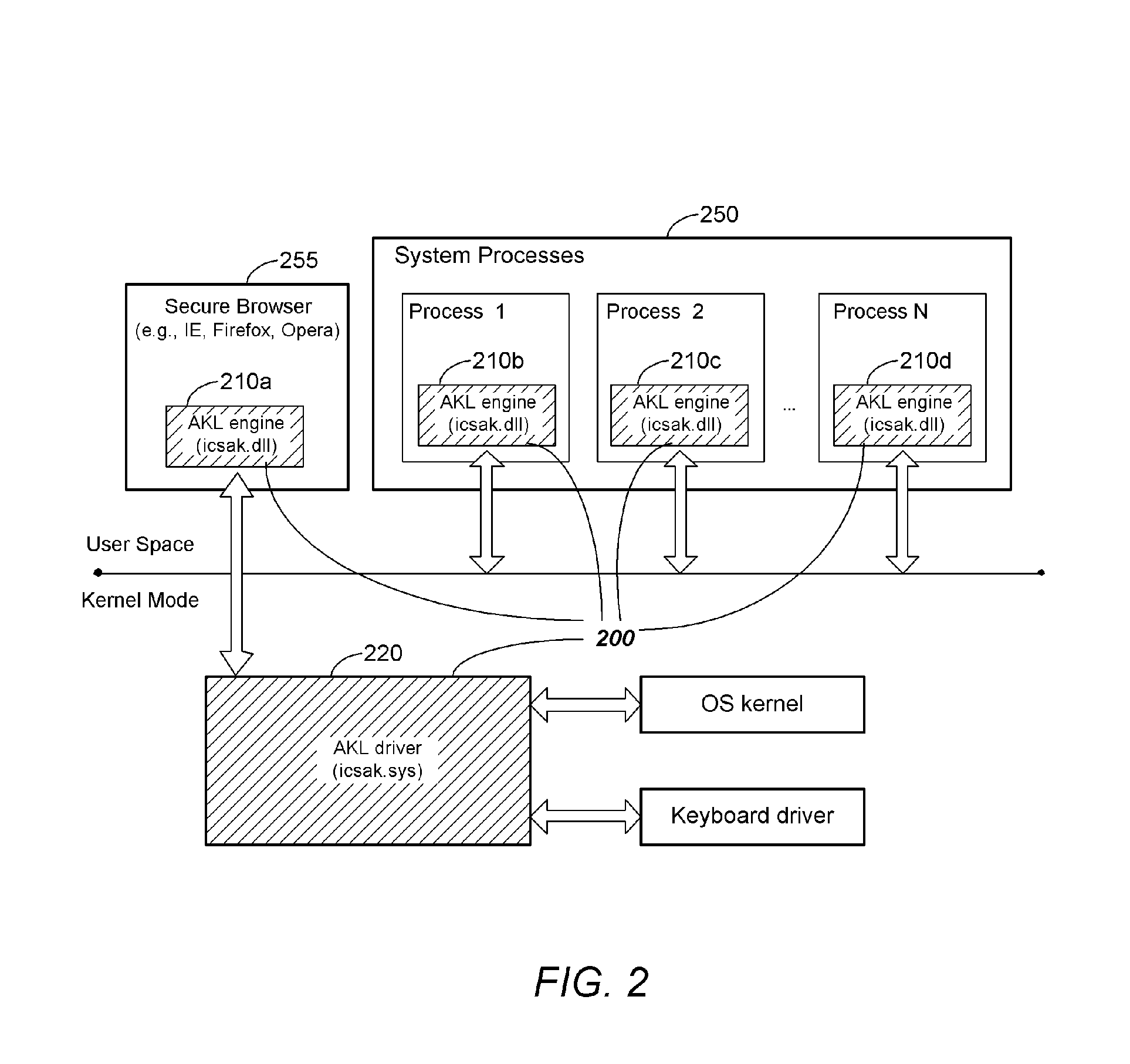
System and Methodology Protecting Against Key Logger Spyware
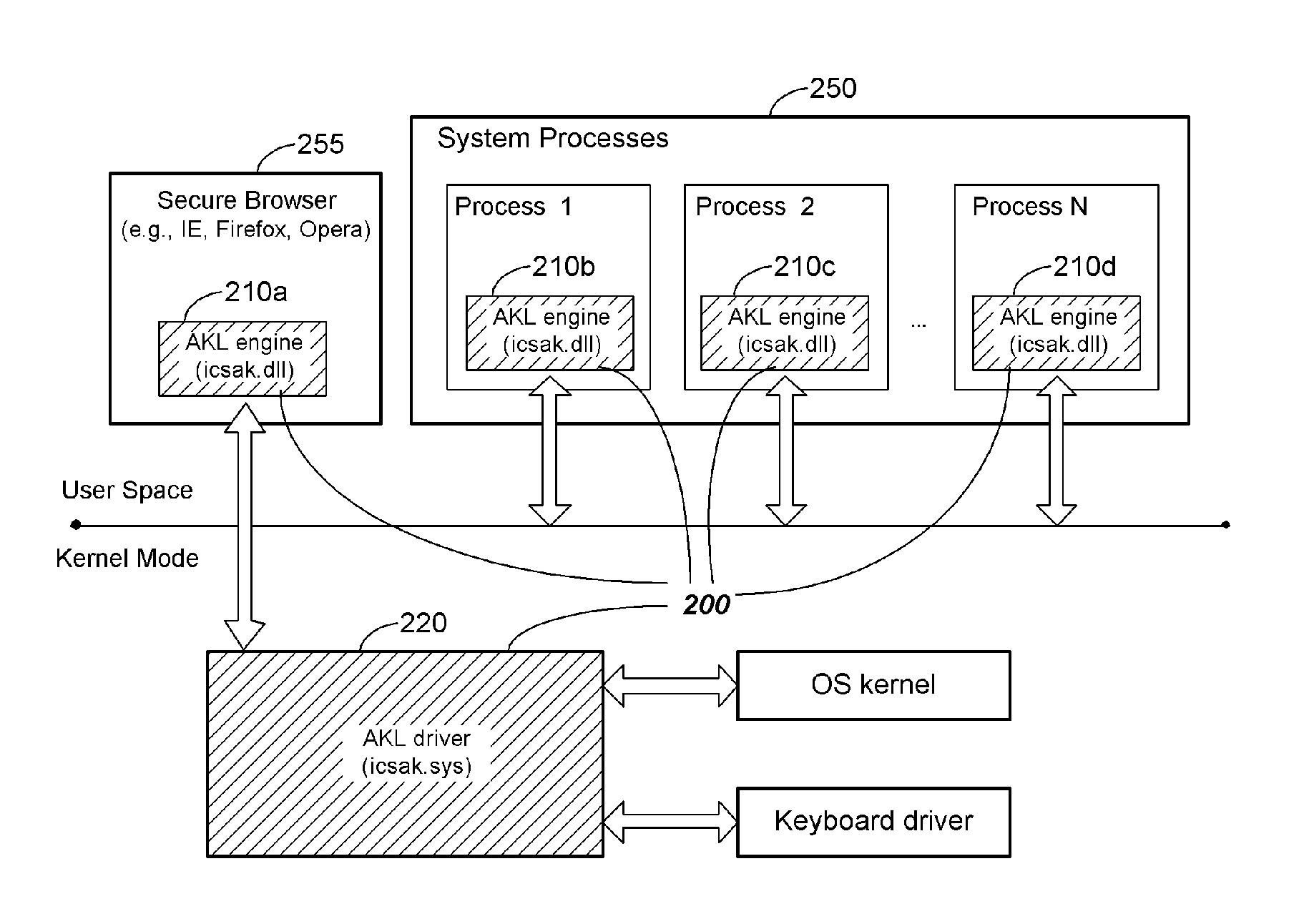
InactiveUS20070240212A1Prevent theftMemory loss protectionError detection/correctionUser inputVulnerability
System and methodology protecting against key logger software (spyware) is described. In one embodiment, for example, a method is described for protecting a computer system from security breaches that include unauthorized logging of user input, the method comprises steps of: specifying a particular application to be protected from unauthorized logging of user input; identifying additional system processes that may serve as a source of unauthorized logging of user input; injecting into the particular application and each identified system process an engine capable of detecting and blocking attempts at unauthorized logging of user input; and upon detection of an attempt at unauthorized logging of user input, blocking the attempt so that user input for the particular application remains protected from unauthorized logging.
Owner:CHECK POINT SOFTWARE TECH INC
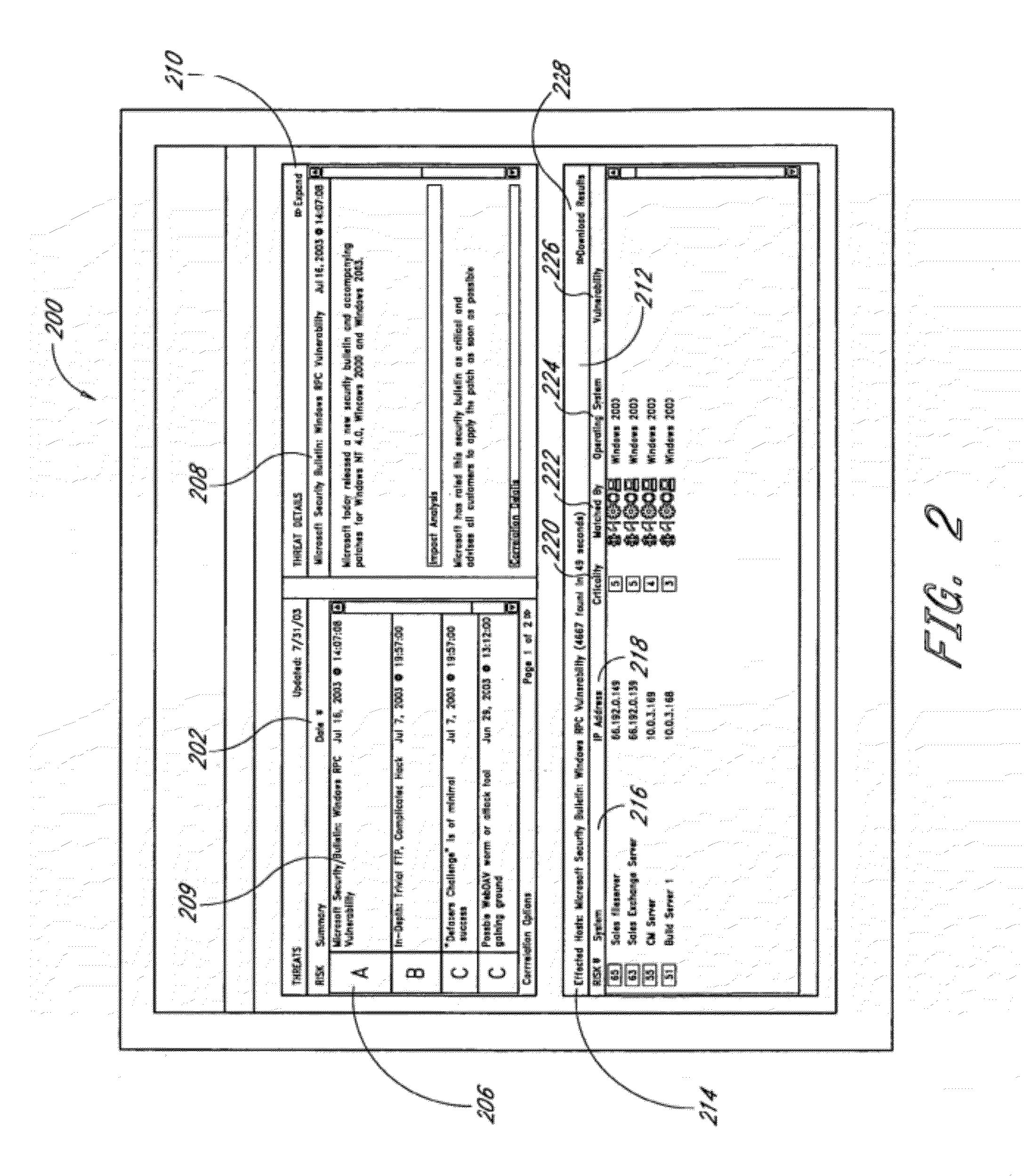
Systems and methods of associating security vulnerabilities and assets
ActiveUS20070067846A1Accurate assessmentMemory loss protectionError detection/correctionGraphicsGraphical user interface
Systems and methods of associating security vulnerabilities and assets, and related Graphical User Interfaces (GUIs) and data structures, are disclosed. A definition of a security vulnerability, which includes multiple asset characteristics such as an asset platform that may be exploited via the security vulnerability and an asset platform that is affected when the exploited asset platform is exploited via the security vulnerability, is compared with definitions of one or more assets of an information system. An association between the security vulnerability and an asset is made if the definition of the asset includes a first asset characteristic of the security vulnerability definition and either the definition of the asset or the definition of another asset that has a relationship with the asset includes a second asset characteristic of the security vulnerability definition. The security vulnerability definition may also identify an asset platform that protects against the vulnerability.
Owner:ALCATEL LUCENT SAS
Security vulnerability information aggregation
InactiveUS20070067848A1Memory loss protectionError detection/correctionGraphicsGraphical user interface
Security vulnerability information aggregation techniques are disclosed. Vulnerability information associated with one or more security vulnerabilities is obtained from multiple sources and aggregated into respective unified vulnerability definitions for the one or more security vulnerabilities. Aggregation may involve format conversion, content aggregation, or both in some embodiments. Unified vulnerability definitions may be distributed to vulnerability information consumers in accordance with consumer-specific policies. Storage of vulnerability information received from the sources may allow the aggregation process to be performed on existing vulnerability information “retro-actively”. Related data structures and Graphical User Interfaces (GUIs) are also disclosed.
Owner:NOKIA TECHNOLOGLES OY
Methods and systems for controlling access to computing resources based on known security vulnerabilities
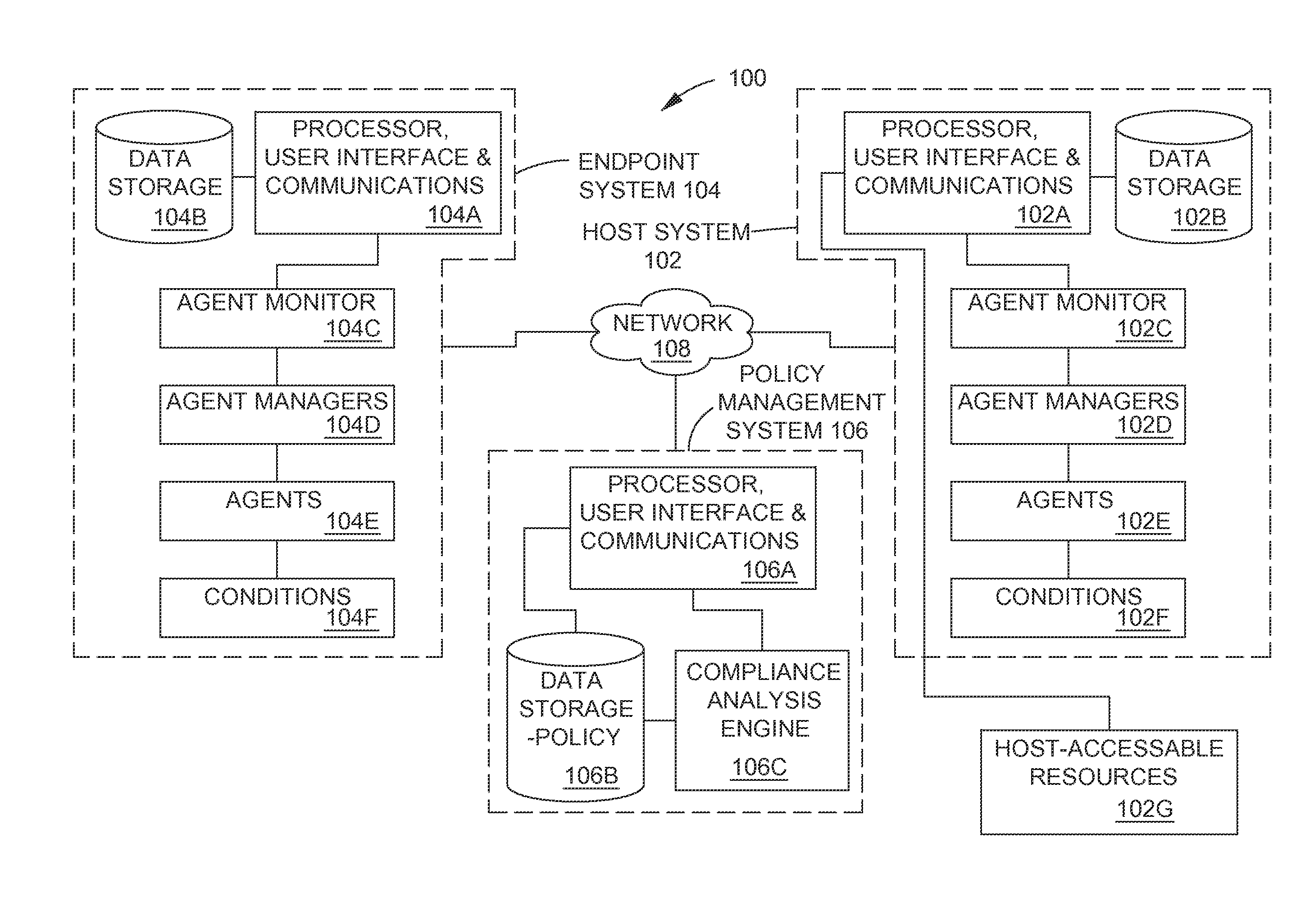
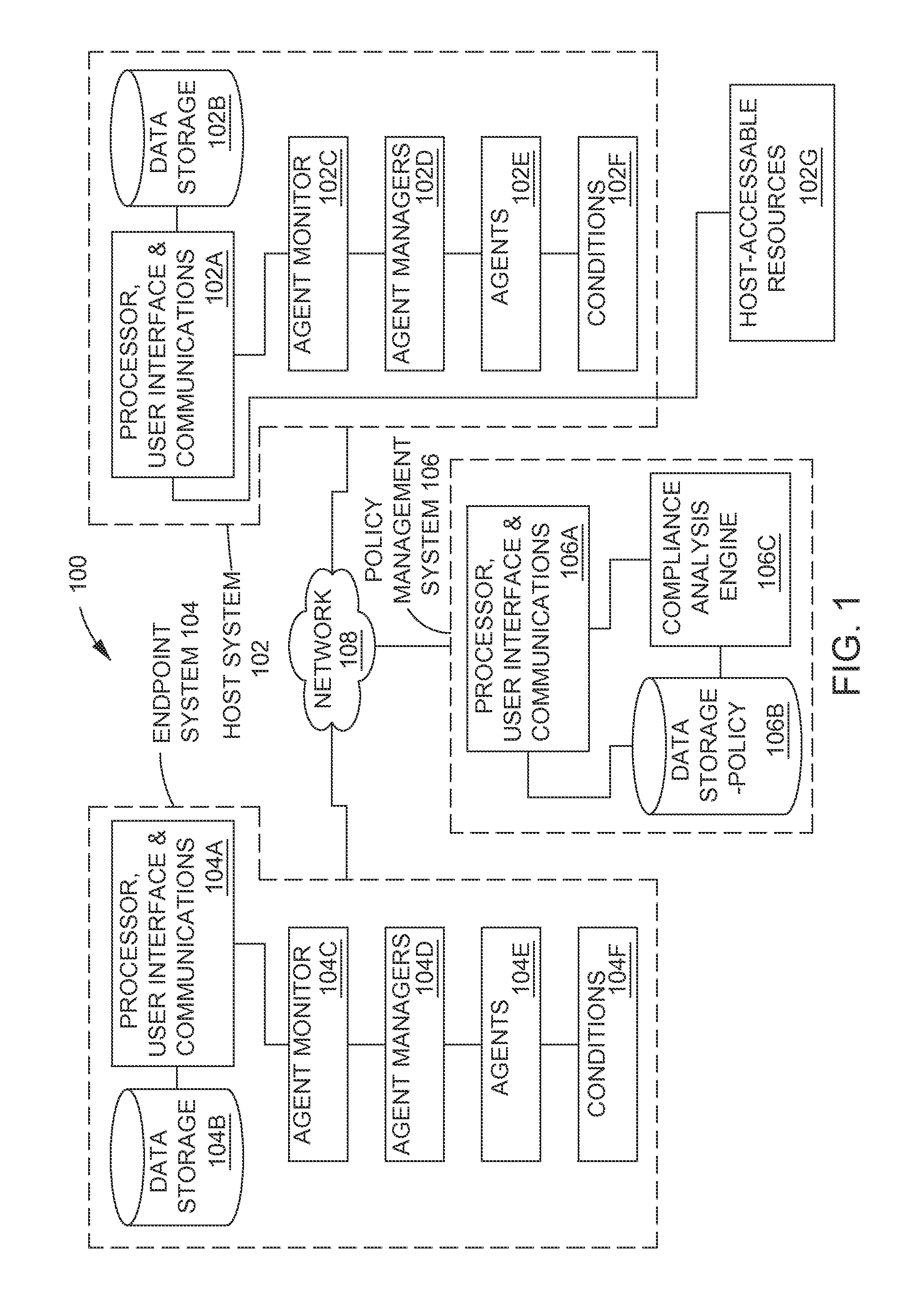
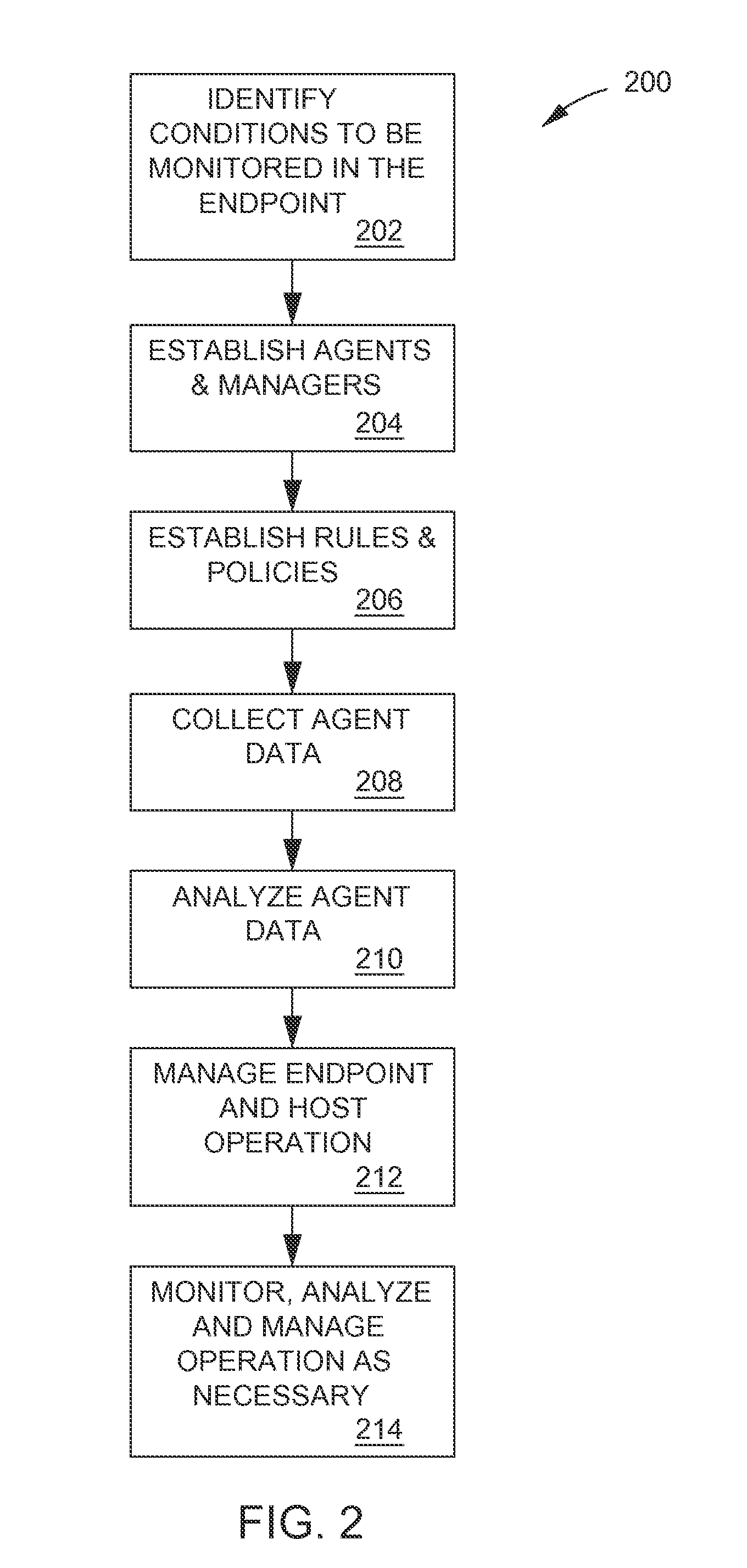
ActiveUS20130254833A1Error detection/correctionPlatform integrity maintainanceEngineeringVulnerability (computing)
Methods and systems are provided for fine tuning access control by remote, endpoint systems to host systems. Multiple conditions / states of one or both of the endpoint and host systems are monitored, collected and fed to an analysis engine. Using one or more of many different flexible, adaptable models and algorithms, an analysis engine analyzes the status of the conditions and makes decisions in accordance with pre-established policies and rules regarding the security of the endpoint and host system. Based upon the conditions, the policies, and the analytical results, actions are initiated regarding security and access matters. In one described embodiment of the invention, the monitored conditions include software vulnerabilities.
Owner:TAASERA LICENSING LLC
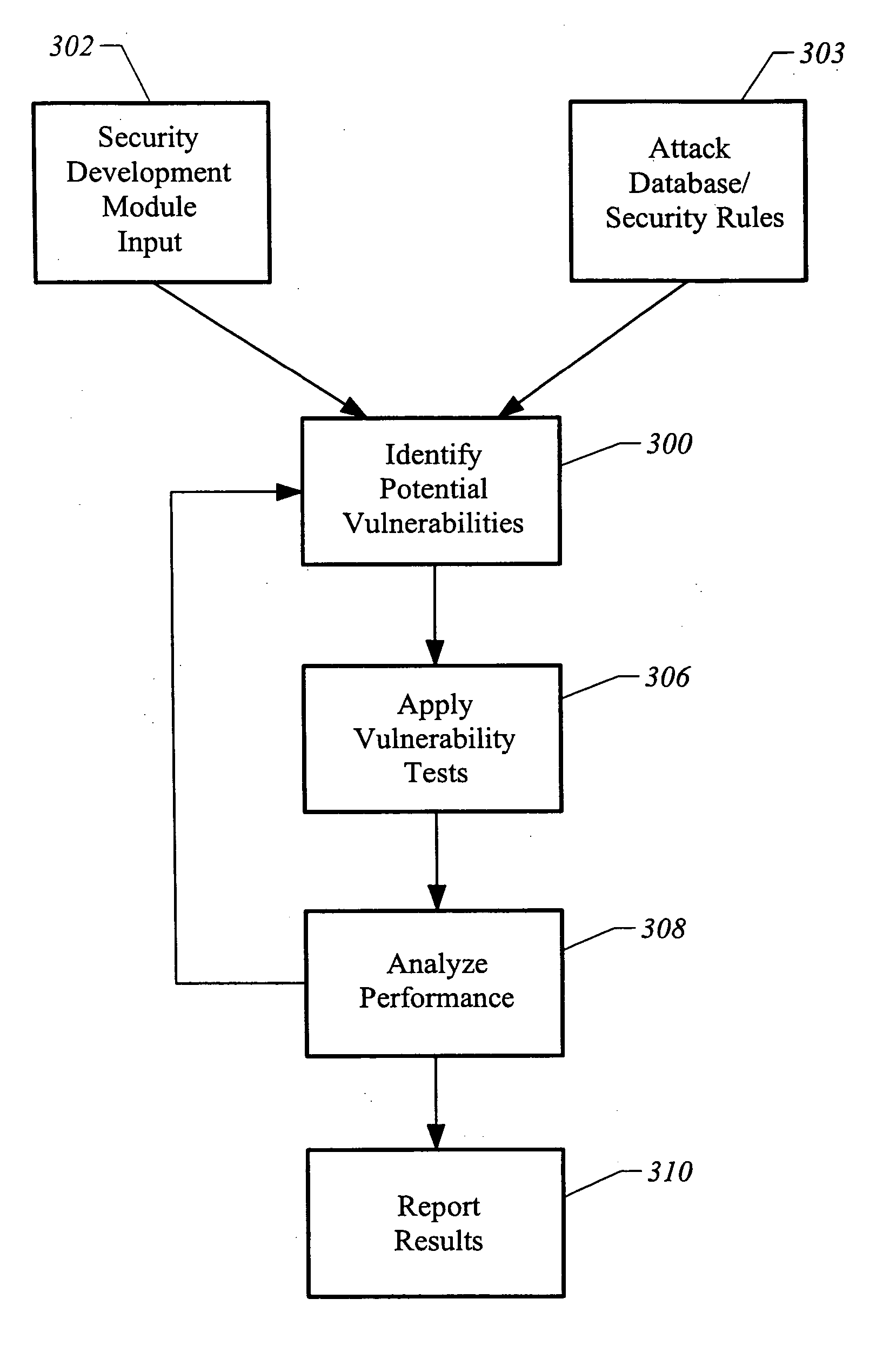
Apparatus and method for testing secure software
InactiveUS20050273859A1Memory loss protectionError detection/correctionProgram instructionPerformance results
A computer readable medium includes executable instructions to analyze program instructions for security vulnerabilities. Executable instructions identify potential security vulnerabilities within program instructions based upon input from an attack database and information derived during a static analysis of the program instructions. Vulnerability tests are applied to the program instructions in view of the security vulnerabilities. Performance results from the vulnerability tests are analyzed. The performance results are then reported.
Owner:FORTIFY SOFTWARE
System for detecting vulnerabilities in web applications using client-side application interfaces
ActiveUS20060195588A1Memory loss protectionUnauthorized memory use protectionNetwork serviceUser defined
An improved method and apparatus for client-side web application analysis is provided. Client-side web application analysis involves determining and testing, using client-side application interfaces and the like, data input points and analyzing client requests and server responses. In one embodiment, a security vulnerability analyzer is employed to analyze web page content for client-side application files, such as Flash files and Java applets, extract web addresses and data parameters embedded in the client-side application file, and modify the data parameters according to user-defined test criteria. The modified data parameters are transmitted as part of a request to a respective web server used to service the client-side application files. The security vulnerability analyzer analyzes the response from the server to ascertain if there are any security vulnerabilities associated with the interface between the client-side application file and the web server.
Owner:SYNOPSYS INC
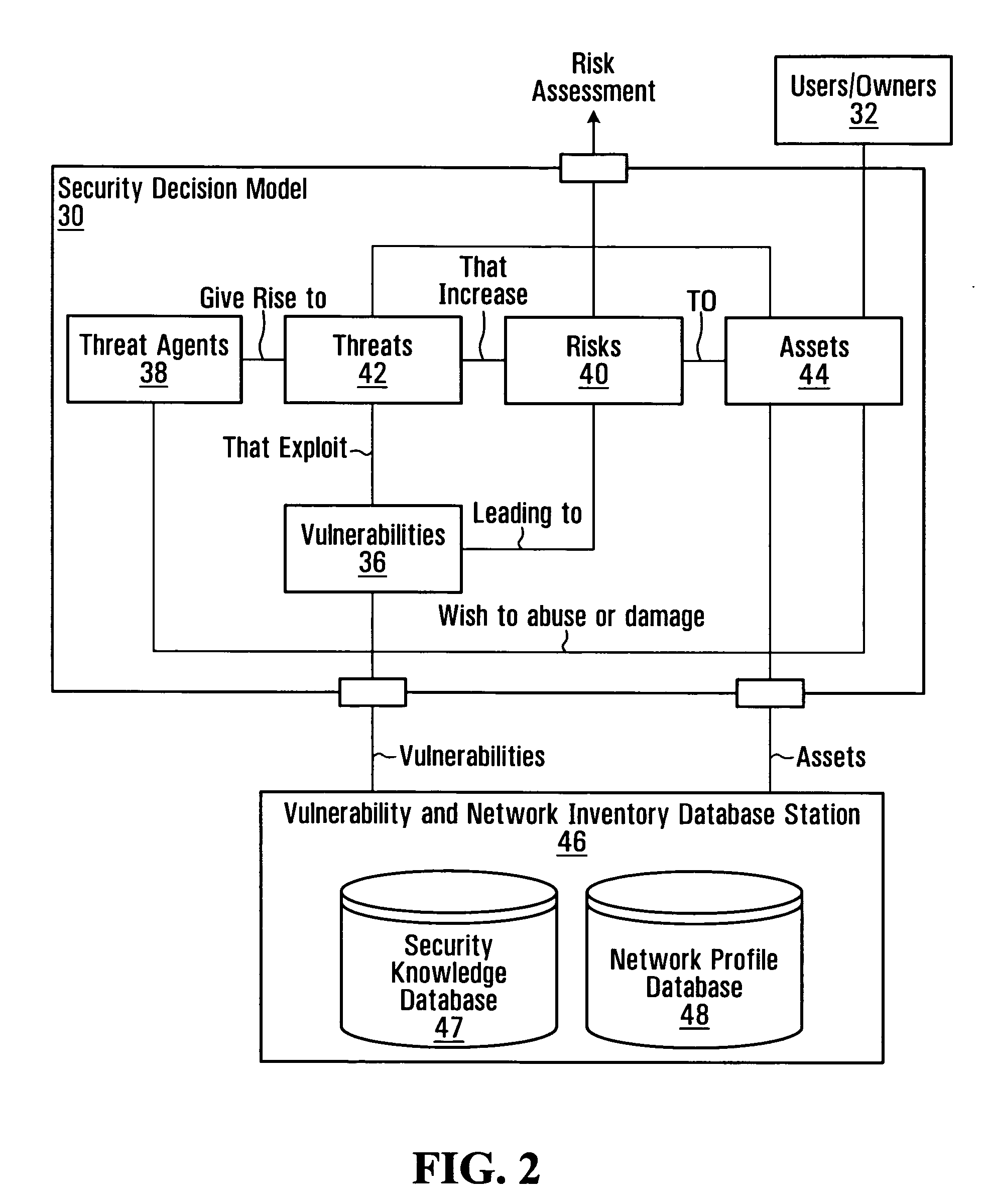
Apparatus and method for developing, testing and monitoring secure software
InactiveUS20050273860A1Memory loss protectionError detection/correctionProgram instructionSafety testing
A method of analyzing program instructions for security vulnerabilities includes applying a static analysis to program instructions during a development phase of the program instructions to identify security vulnerabilities. The security vulnerabilities are used to apply a security test to the program instructions during a testing phase of the program instructions. The security vulnerabilities are analyzed to develop security monitoring criteria to apply to the program instructions during a deployment phase of the program instructions.
Owner:FORTIFY SOFTWARE
Security vulnerability monitor
InactiveUS20050005152A1Digital data processing detailsAnalogue secracy/subscription systemsOperational systemPersonal computer
A method and apparatus for automatically determining whether a security vulnerability alert is relevant to a device (e.g., personal computer, server, personal digital assistant [PDA], etc.), and automatically retrieving the associated software patches for relevant alerts, are disclosed. The illustrative embodiment intelligently determines whether the software application specified by a security vulnerability alert is resident on the device, whether the version of the software application on the device matches that of the security vulnerability alert, and whether the device's hardware platform and operating system match those of the security vulnerability alert.
Owner:AVAYA INC
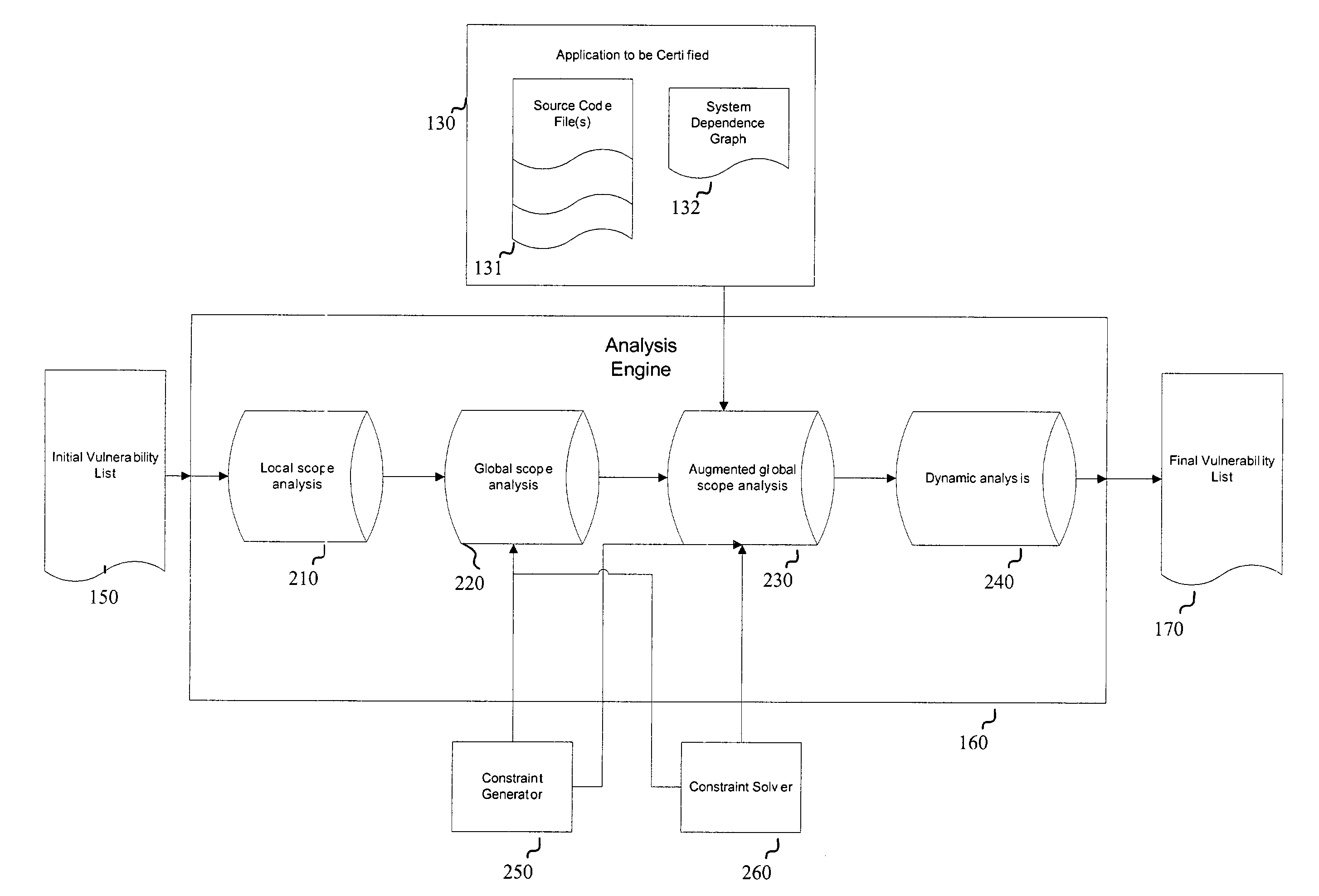
Systems and methods for detecting software security vulnerabilities
ActiveUS7392545B1Memory loss protectionUnauthorized memory use protectionApplication softwareVulnerability
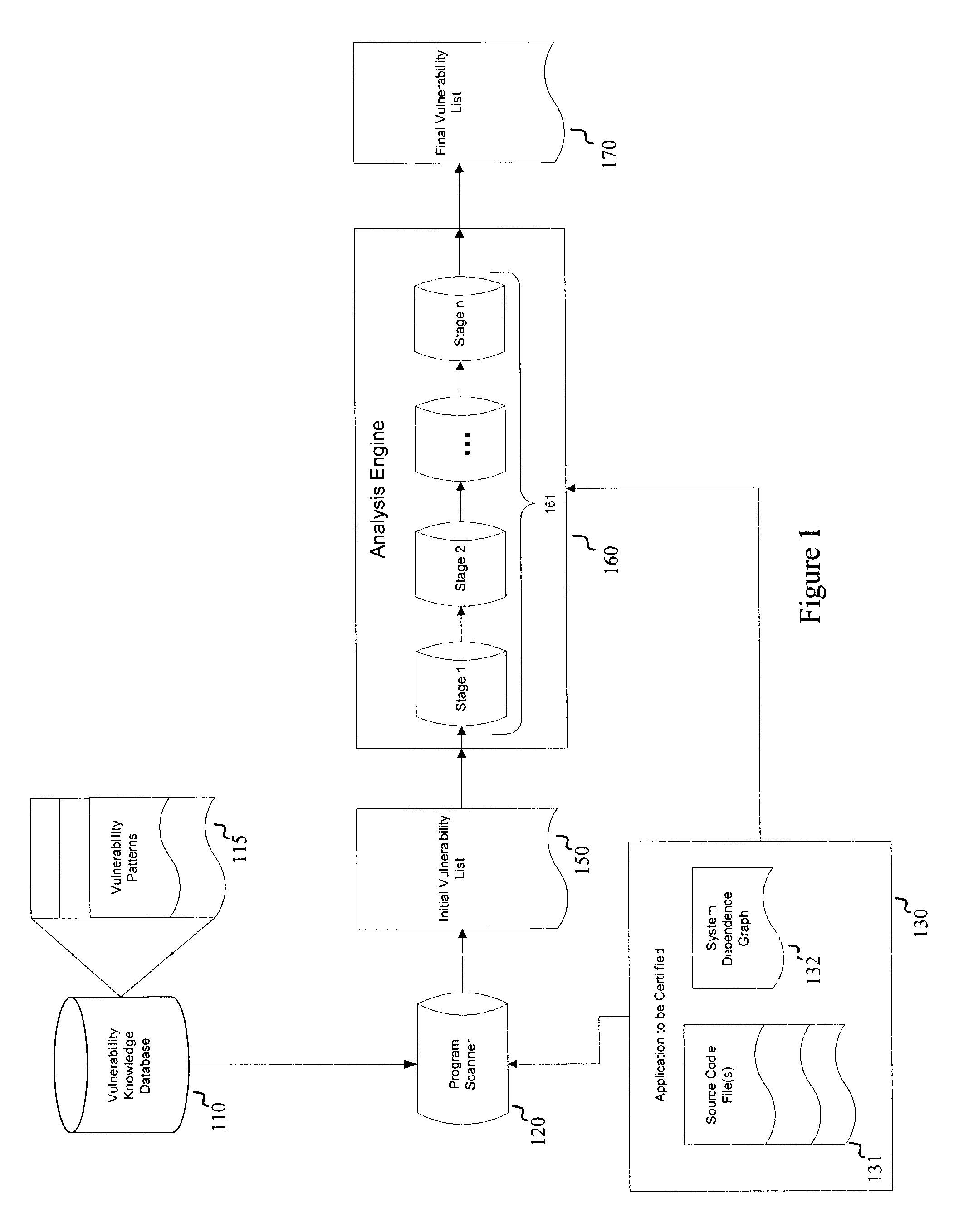
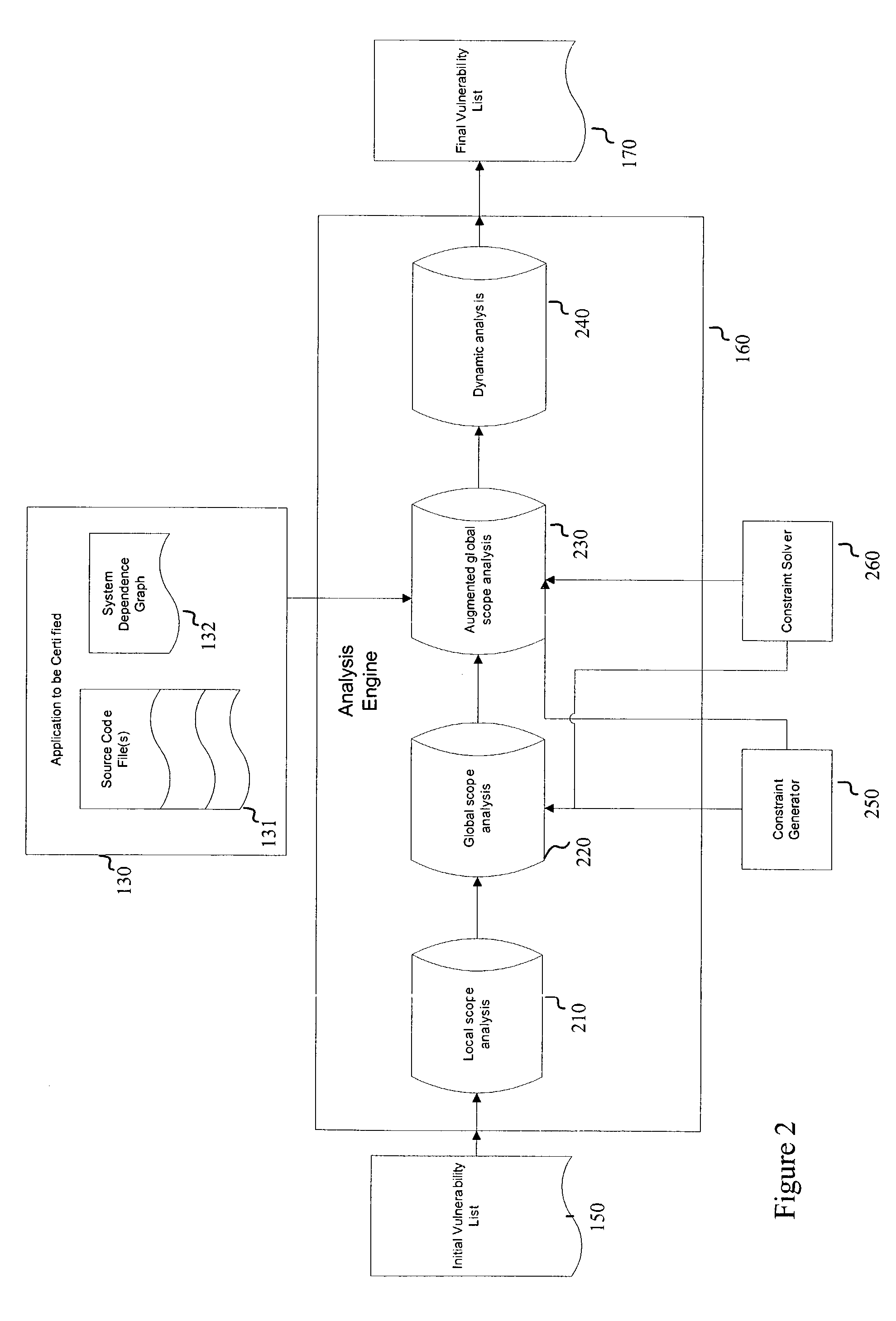
Embodiments of the present invention relate to systems and methods for static analysis of a software application. According to an embodiment, a system includes a program scanner coupled to an analysis engine. The program scanner is configured to identify one or more vulnerability patterns in a software program and to output an initial potential vulnerability list. The analysis engine is configured to apply one or more rules to a potential vulnerability to determine whether the potential vulnerability is a vulnerability.
Owner:SYNOPSYS INC
Method and system for identifying, fixing, and updating security vulnerabilities
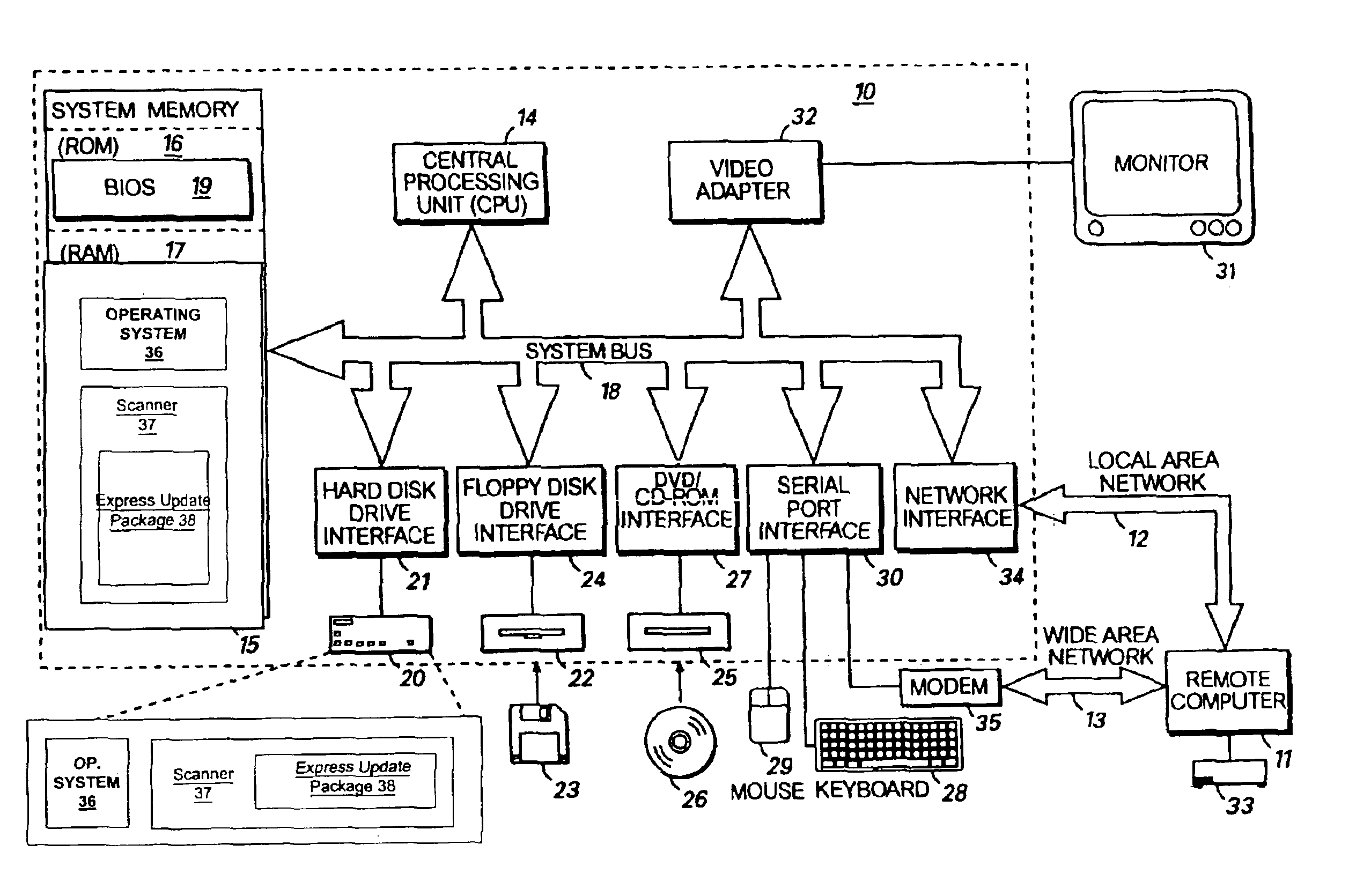
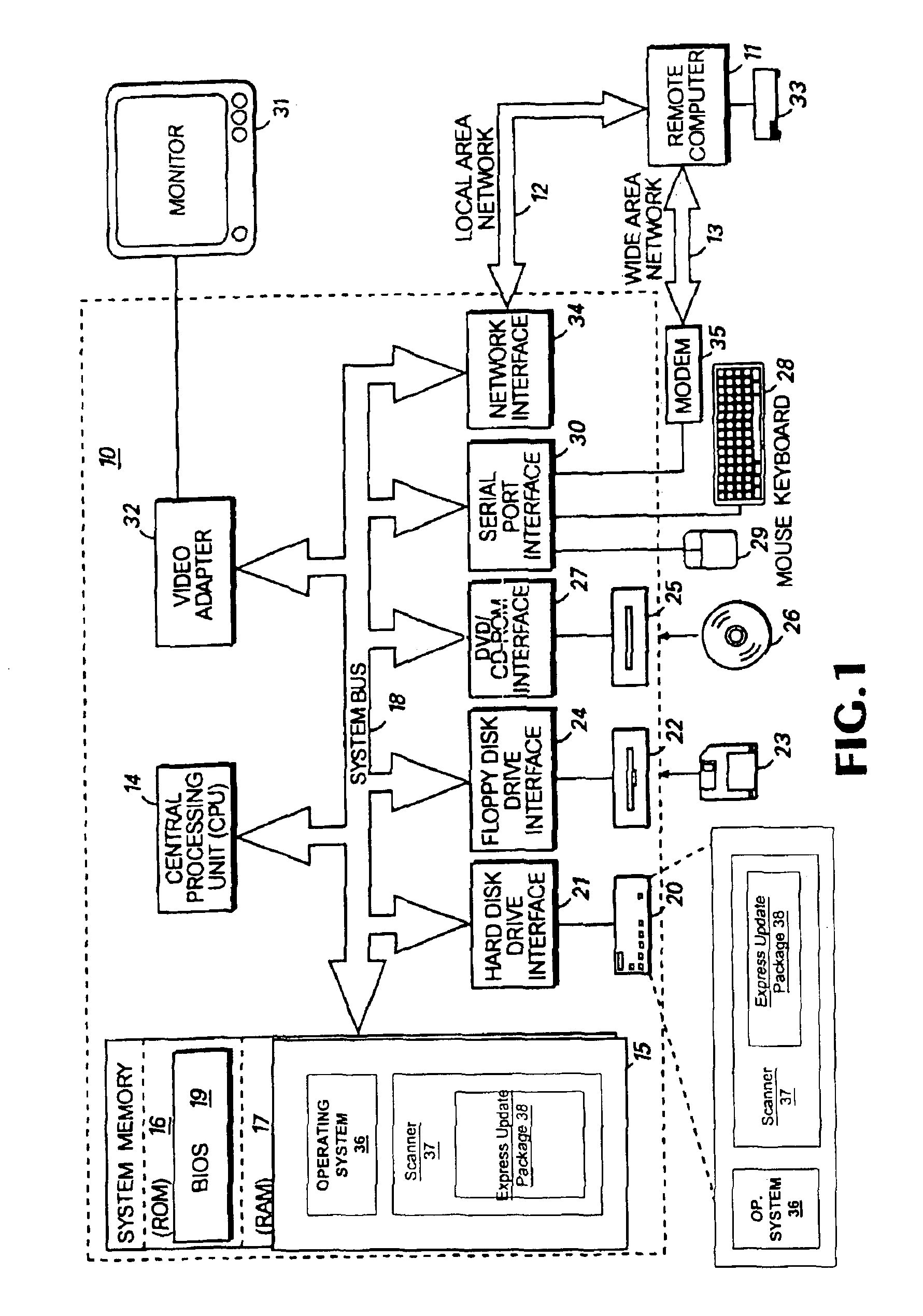
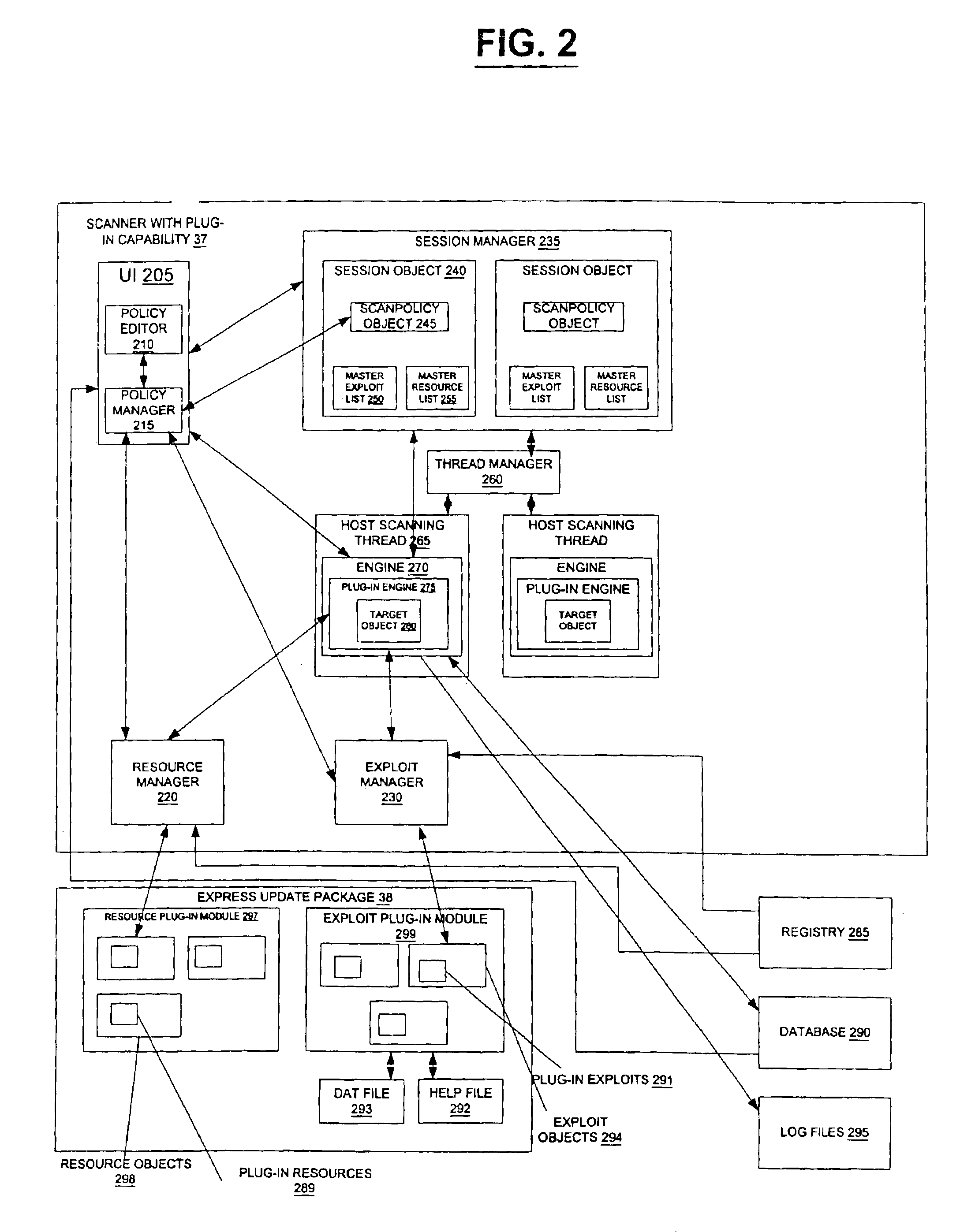
InactiveUS6907531B1Easy to useError preventionMemory loss protectionOperational systemSystem identification
A method and system identifies, fixes, and updates security vulnerabilities in a host computer or host computers. The present invention can communicate between a scanner with plug-in capability, an operating system, and an express update package.The architectural set-up can allow exploits within the scanner and exploits in the express update package to function with no knowledge of each other. The user also needs no knowledge of whether the exploits are within the scanner or the express update package. Mutual authentication procedures can enable the scanner to load only legitimate express update packages, and can provide that express update packages can only be loaded into legitimate scanners.
Owner:FINJAN BLUE INC
Assessment and analysis of software security flaws
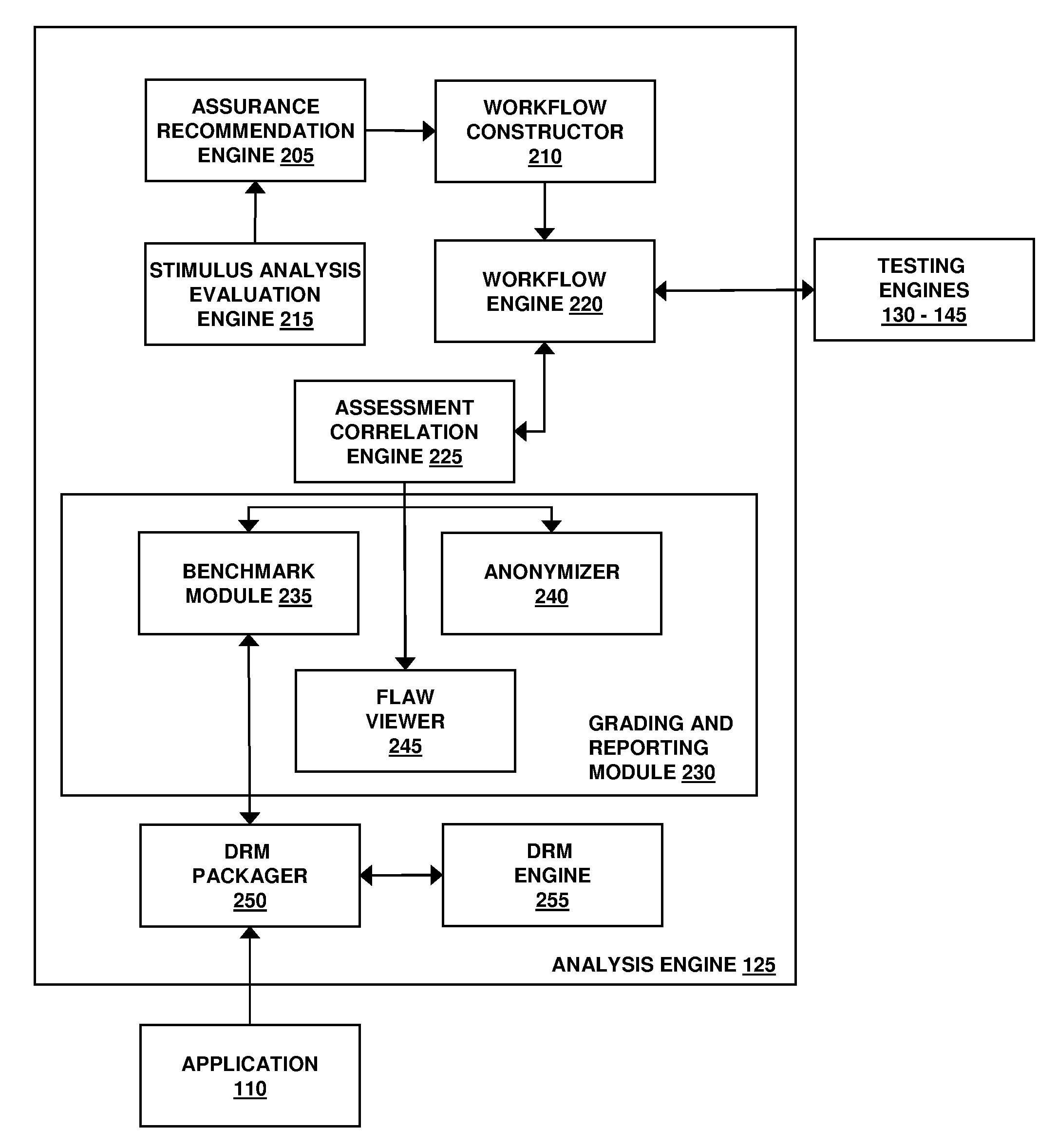
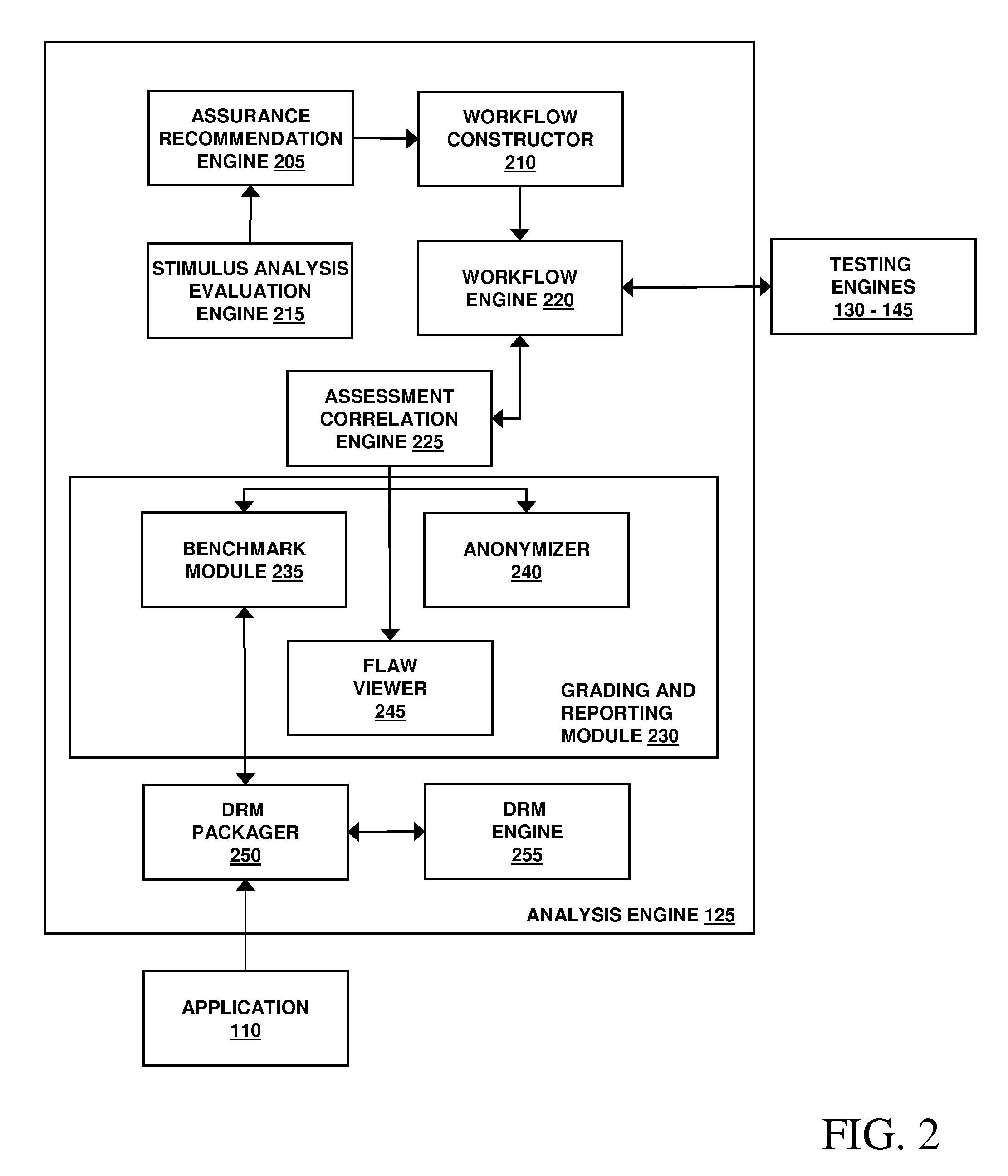
InactiveUS20100281248A1Facilitates security assessment and vulnerability testingFacilitates benchmarkingMemory loss protectionDigital data processing detailsSecurity assessmentProgram planning
Security assessment and vulnerability testing of software applications is performed based at least in part on application metadata in order to determine an appropriate assurance level and associated test plan that includes multiple types of analysis. Steps from each test are combined into a “custom” or “application-specific” workflow, and the results of each test may then be correlated with other results to identify potential vulnerabilities and / or faults.
Owner:VERACODE
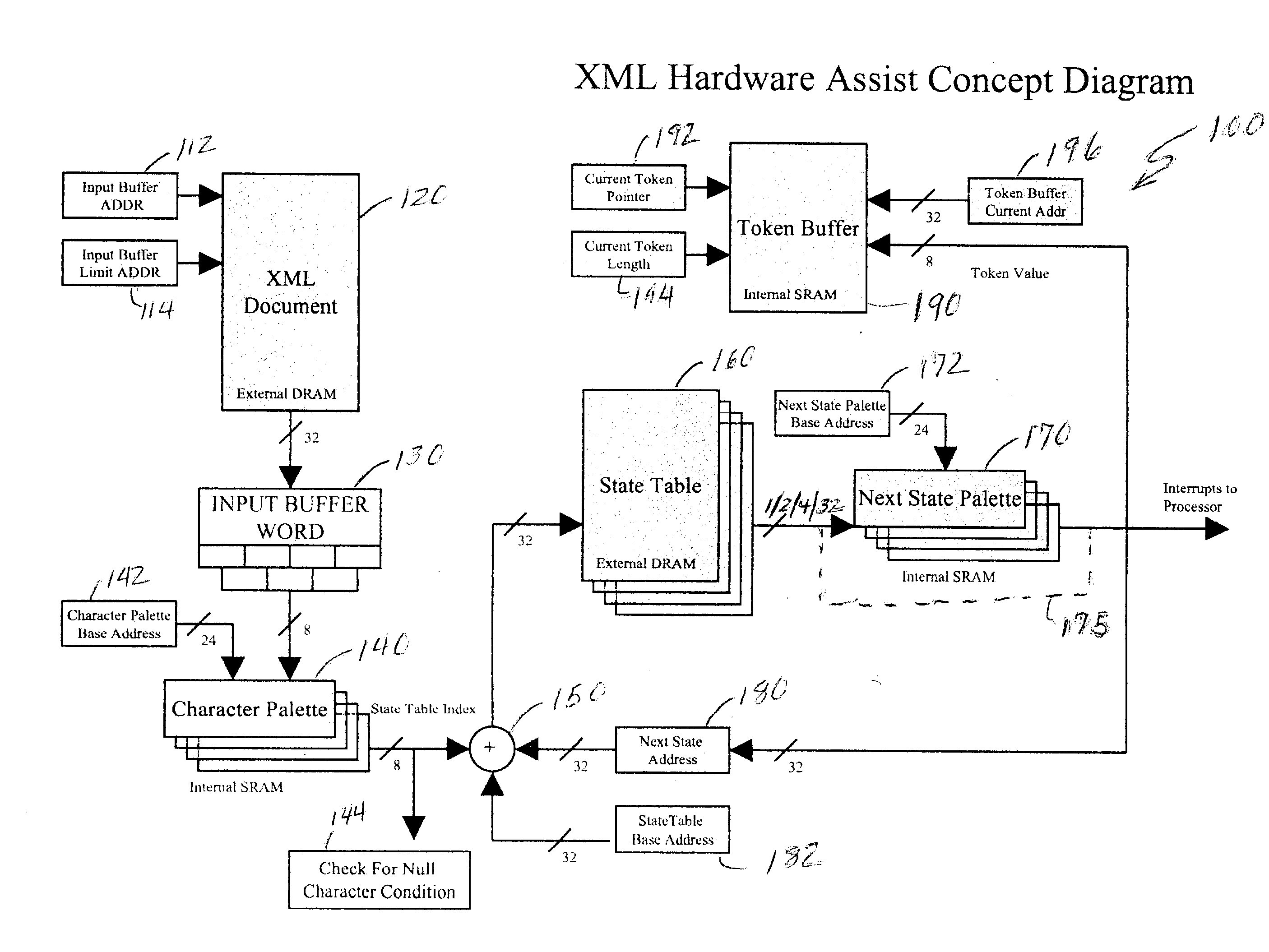
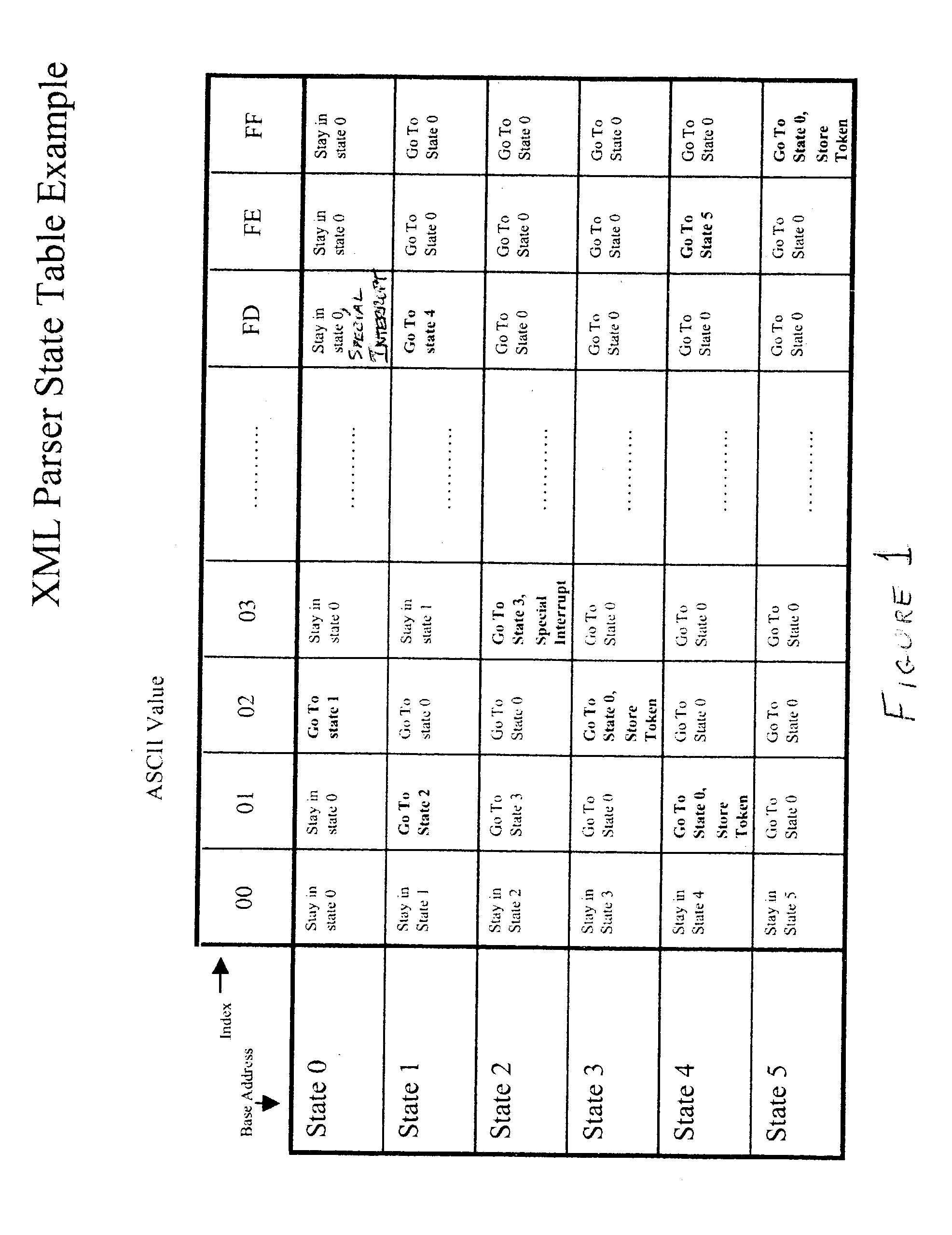
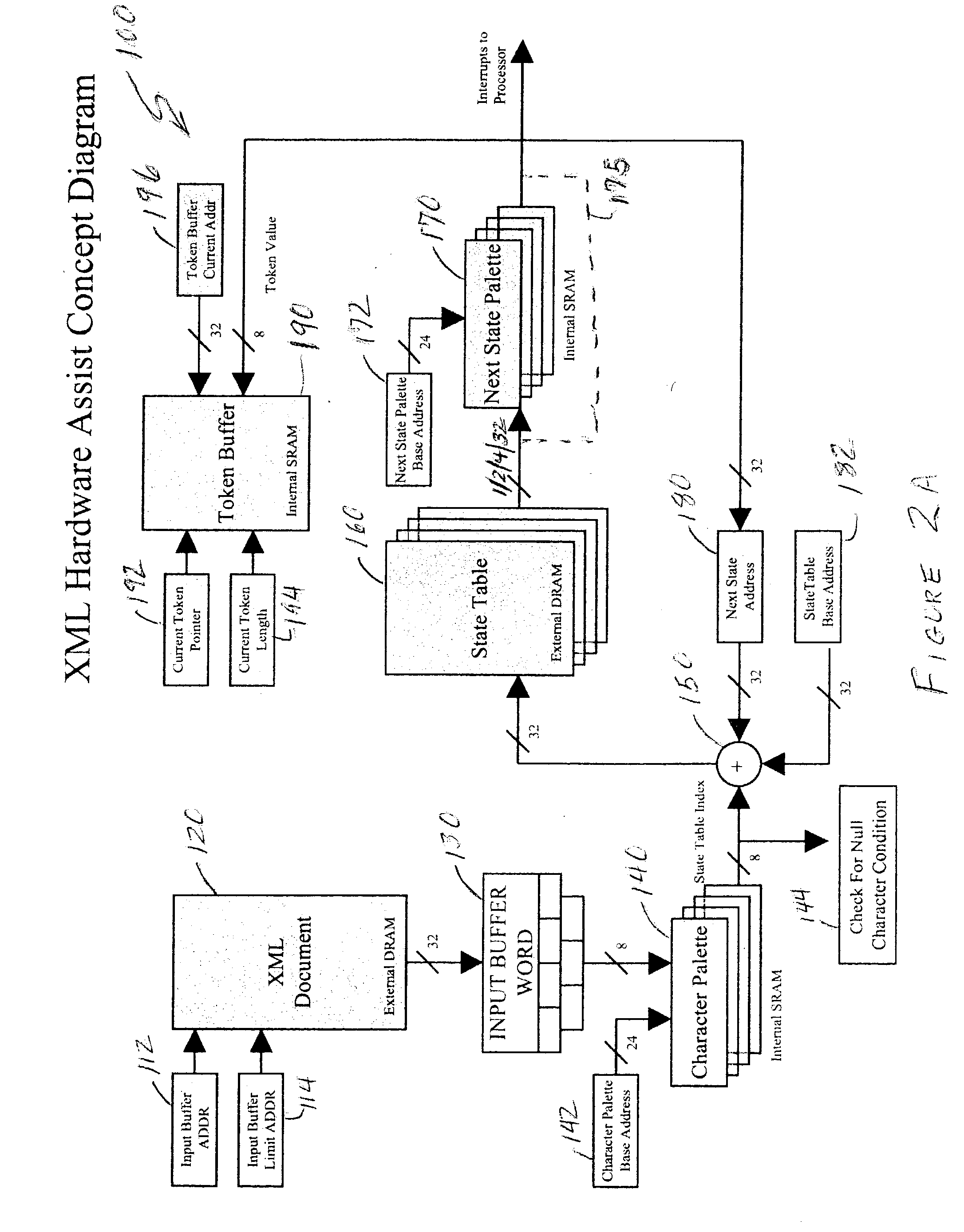
Intrusion detection accelerator
InactiveUS20040083387A1Memory loss protectionDigital computer detailsNetwork controlHardware acceleration
Signatures of character strings in a document which may indicate a possible intrusion into or attack on a networked computer system or node thereof or other security breach are detected at high speed using a hardware accelerator within the environment of a hardware parser accelerator. An interrupt or exception can thus be issued to a host CPU before a command which may constitute such a security breach, intrusion or attack can be made executable by parsing of a document. The CPU can initiate network control measures to prevent or limit the intrusion.
Owner:LOCKHEED MARTIN CORP
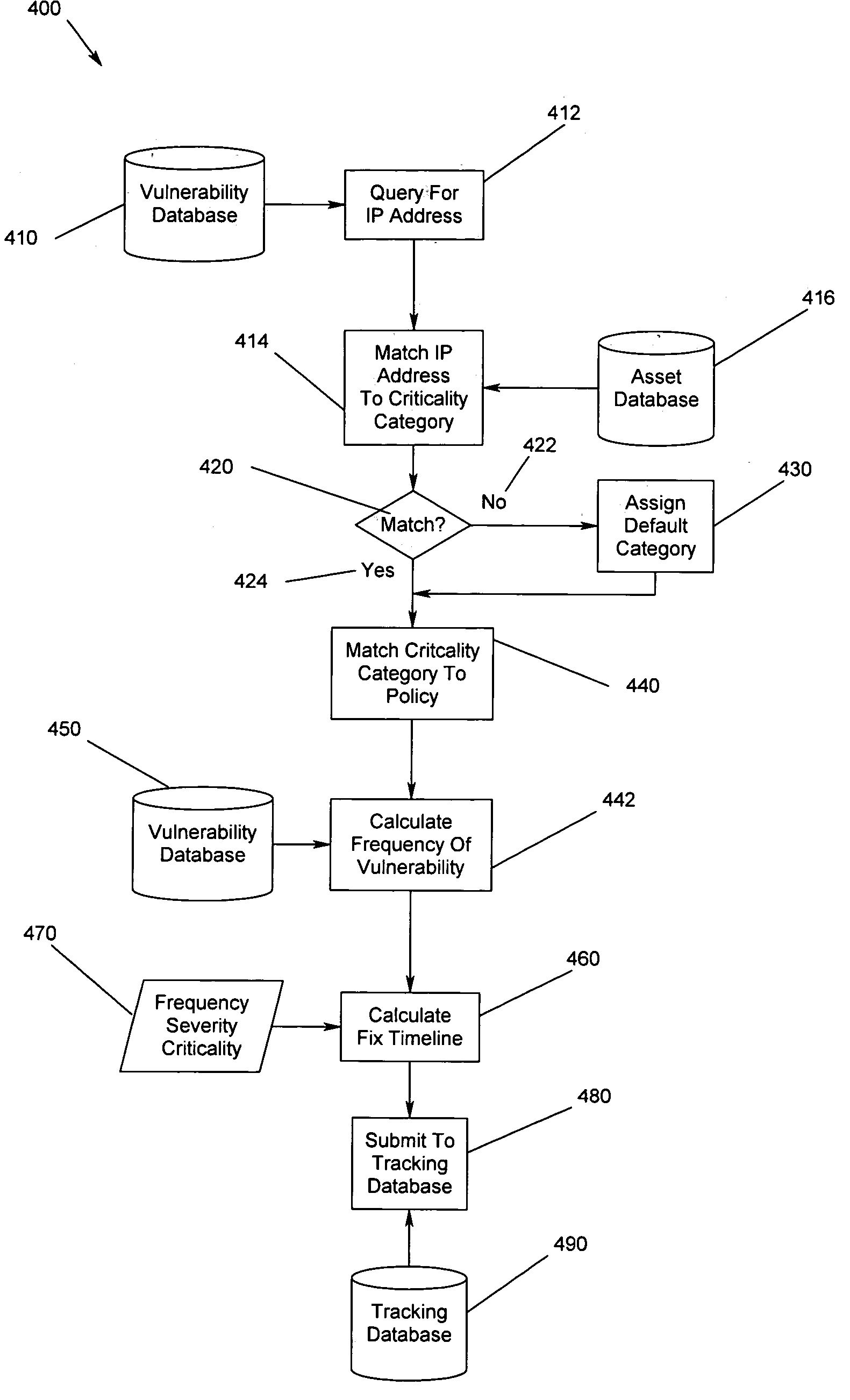
Method, apparatus and program storage device for providing automated tracking of security vulnerabilities
InactiveUS20050160480A1Memory loss protectionUnauthorized memory use protectionVulnerability factorOperating system
A method, apparatus and program storage device for providing automated tracking of security vulnerabilities is disclosed. Security problems are reported, aged and tracked. A time to fix the vulnerability identified by the vulnerability assessment of the system is based on the determined vulnerability score. The vulnerability factor is based upon consideration of a plurality of identified parameters.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com