System and method of managing network security risks
a network security and risk management technology, applied in the field of managing threats to network security, can solve problems such as compromise network security, and many administrators, however, have neither the time nor the experience to maintain up-to-date knowledge of network security threats
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
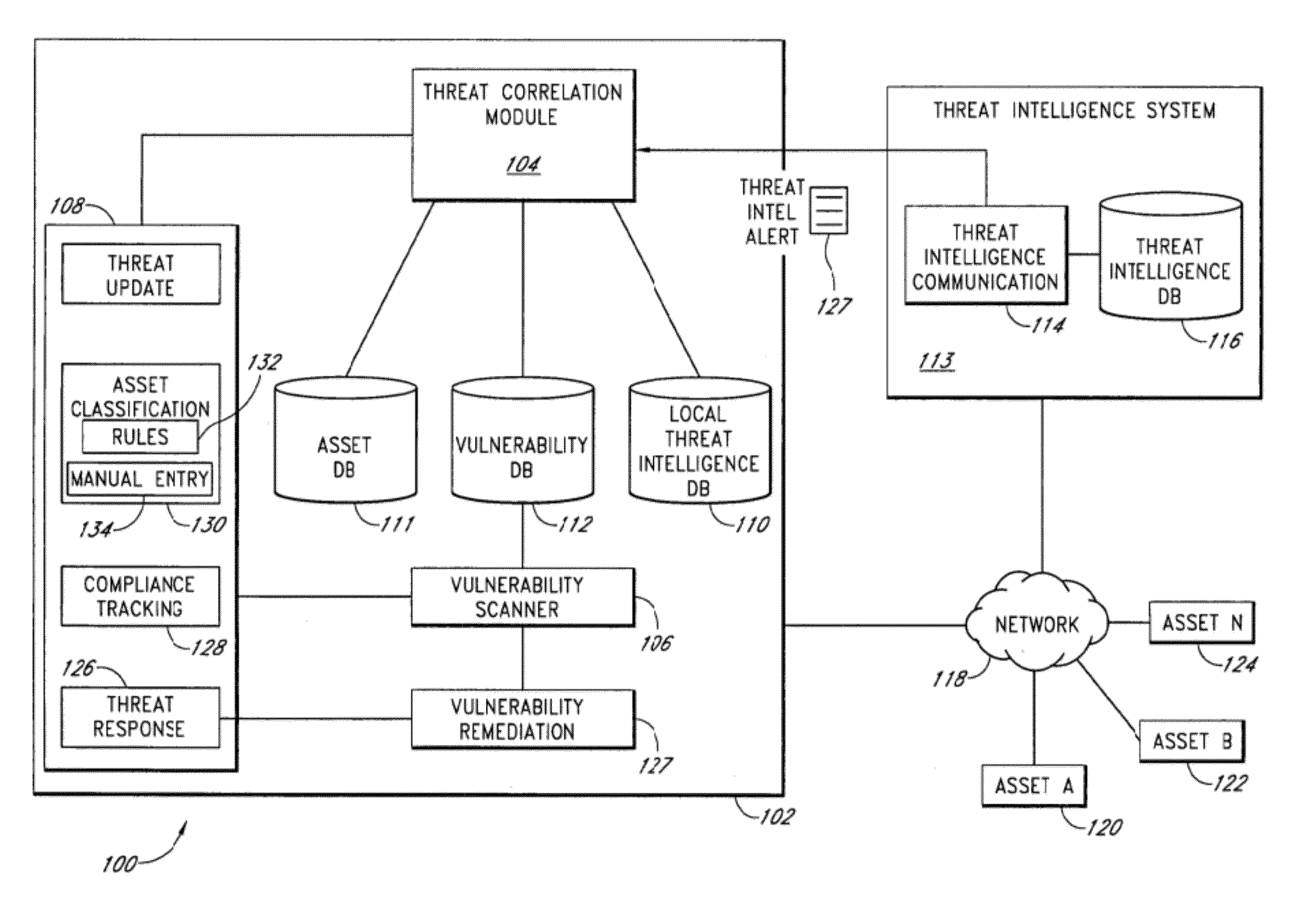
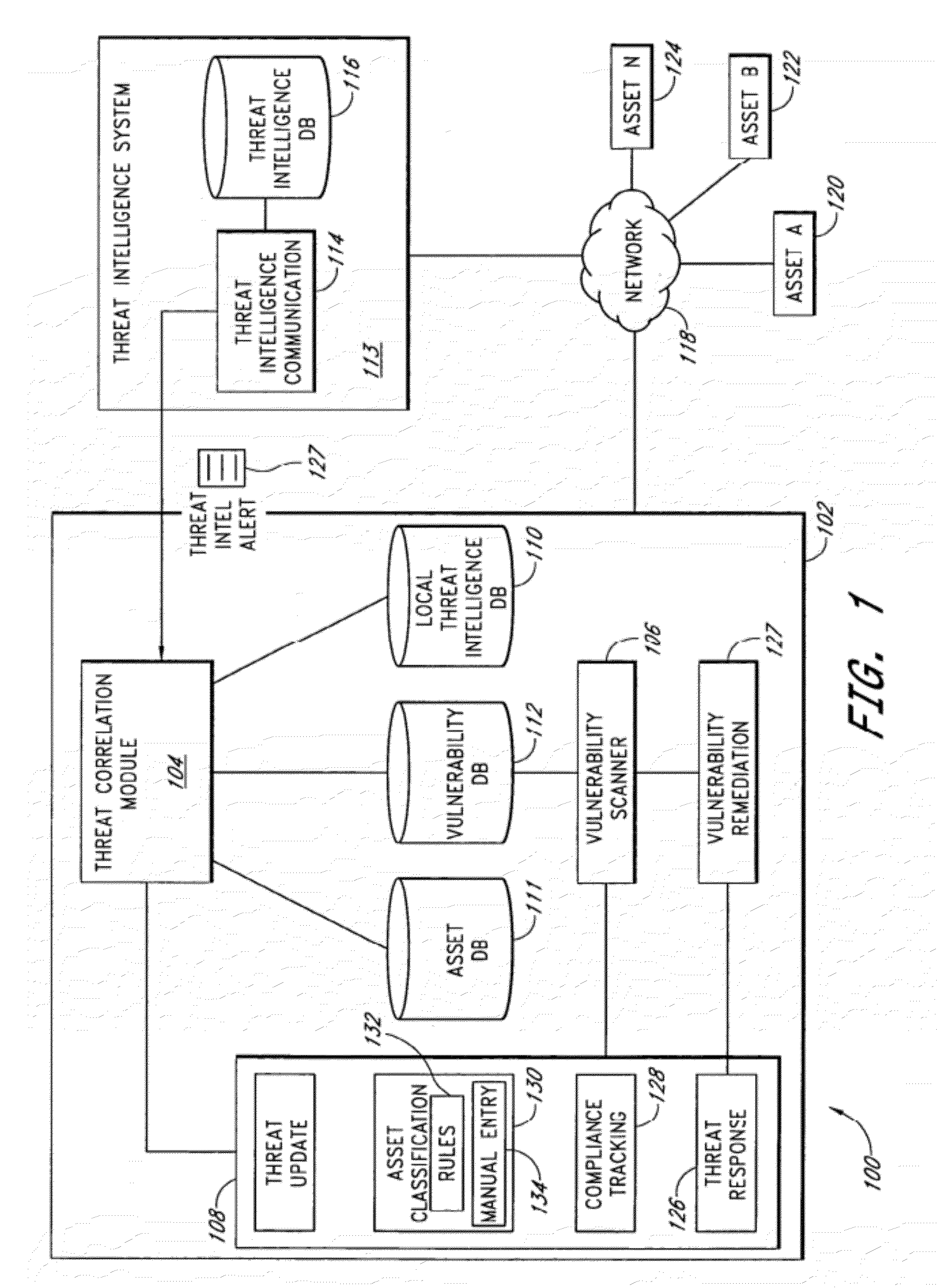
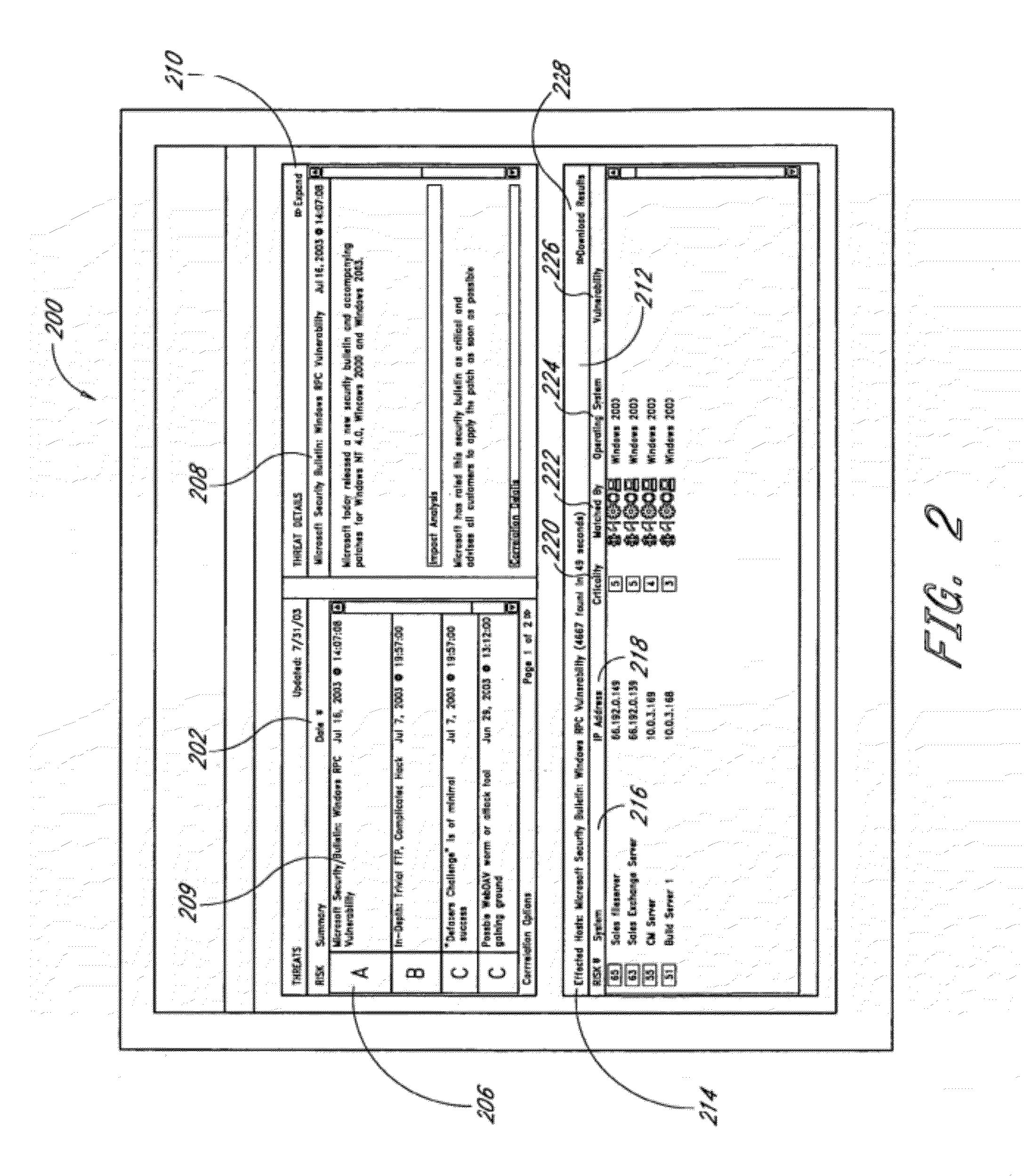
[0022]Computer networks are exposed to a number of vulnerabilities to network security. Such vulnerabilities include open ports, flawed email application programs and other flawed application programs that can provide unauthorized access to a network node, trojan horses, worms, viruses, and the like. Many of these vulnerabilities, such as trojan horses, worms, and viruses, can cause damage or data loss to a computer system simply by existing and being activated on a computer system. Other vulnerabilities, such as holes created by flawed email or other flawed application programs, can provide means for individuals to gain unauthorized access to a computer system. Individuals that gain unauthorized access to a computer system may willfully or unwittingly view secret information, delete files, alter the settings of a computer network, or otherwise compromise the security of a computer network. For this reason, many administrators desire to detect network vulnerabilities and fix them be...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com