Intelligent security event association analysis system for threat scene
A technology for correlation analysis and security events, applied in transmission systems, digital transmission systems, electrical components, etc., it can solve the problems of scattered data sources, lack of correlation and comprehensive analysis, and inability to form a unified view of enterprise data, saving time.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
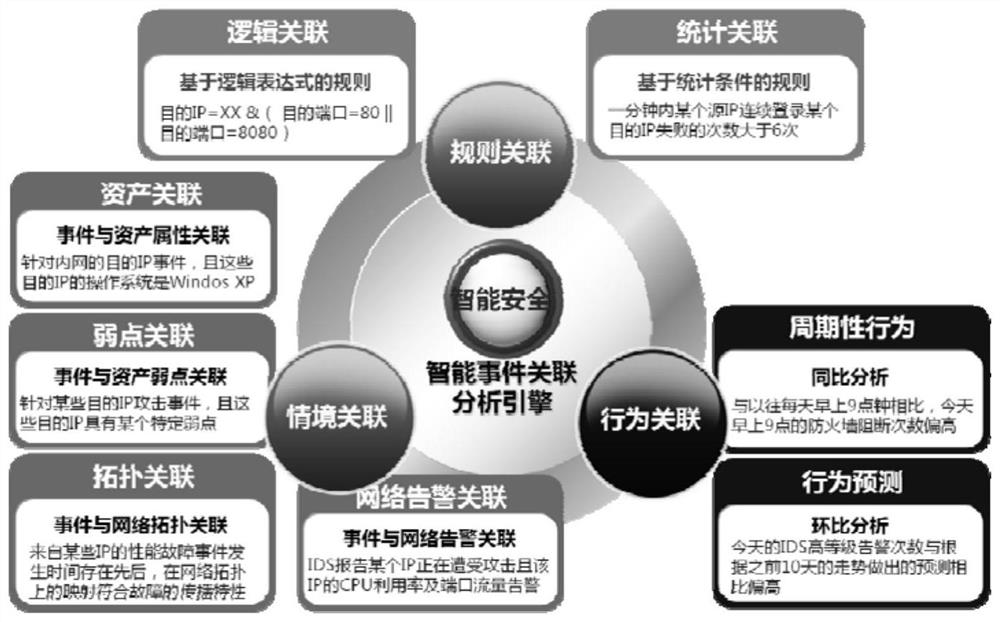
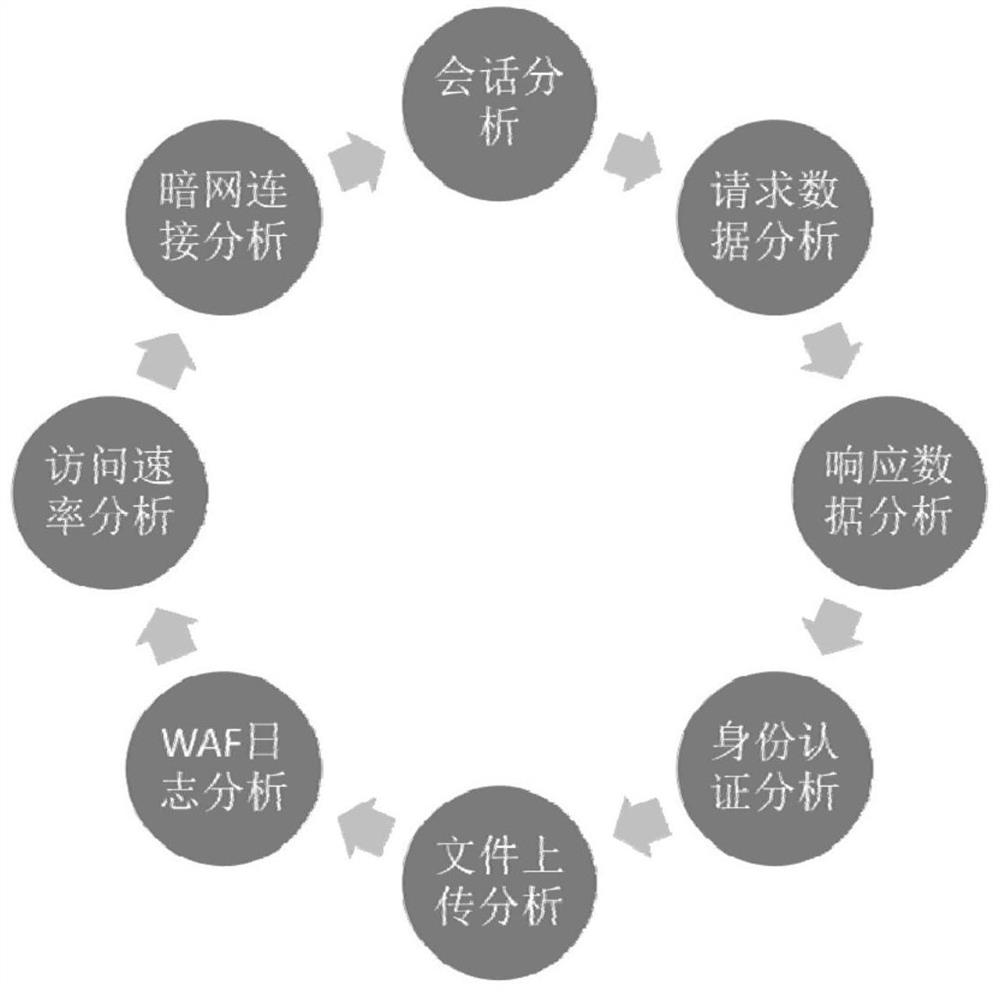
[0059] This application provides an intelligent security event correlation analysis system oriented to threat scenarios, including a mass-format event storage module, an analysis module, and a visual display module;
[0060] Using distributed massive log collection technology, it can support a single event collector and multiple event collectors at the same time. Use distributed collectors to further improve the performance of event collection. The mass-format event storage module supports a single event collector and multiple event collectors. With the help of hardware multi-core features, a parallel event pipeline collection method is used to collect massive log data, and an asynchronous non-blocking event collection method is adopted. Parallel pipeline processing of events. Greatly improved the performance of event collection and preprocessing;
[0061] With the help of the built-in distributed event access agent, the system can store massive events in parallel in a distr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com