Patents
Literature
857 results about "Sorting algorithm" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer science, a sorting algorithm is an algorithm that puts elements of a list in a certain order. The most frequently used orders are numerical order and lexicographical order. Efficient sorting is important for optimizing the efficiency of other algorithms (such as search and merge algorithms) that require input data to be in sorted lists. Sorting is also often useful for canonicalizing data and for producing human-readable output. More formally, the output of any sorting algorithm must satisfy two conditions...
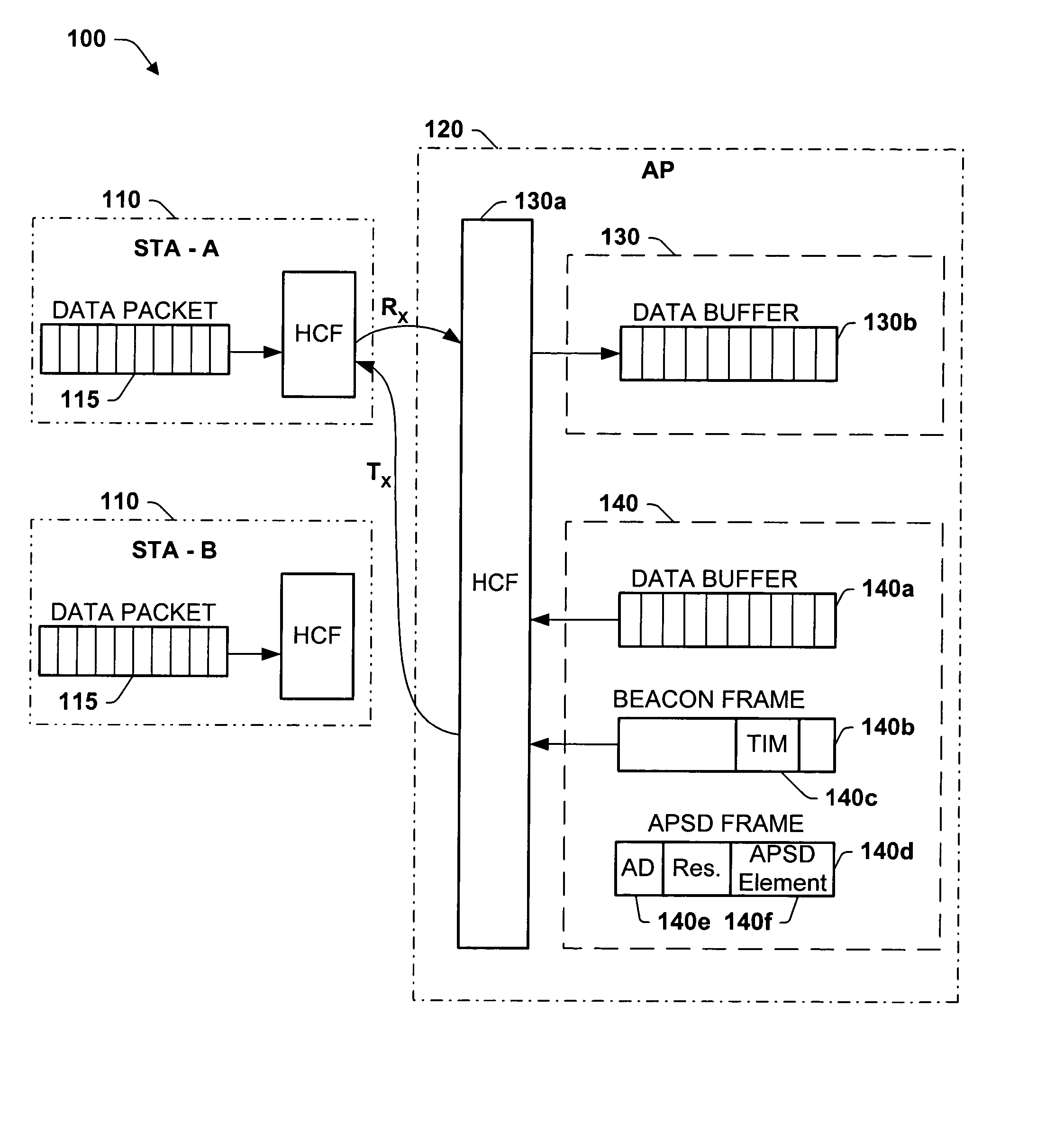
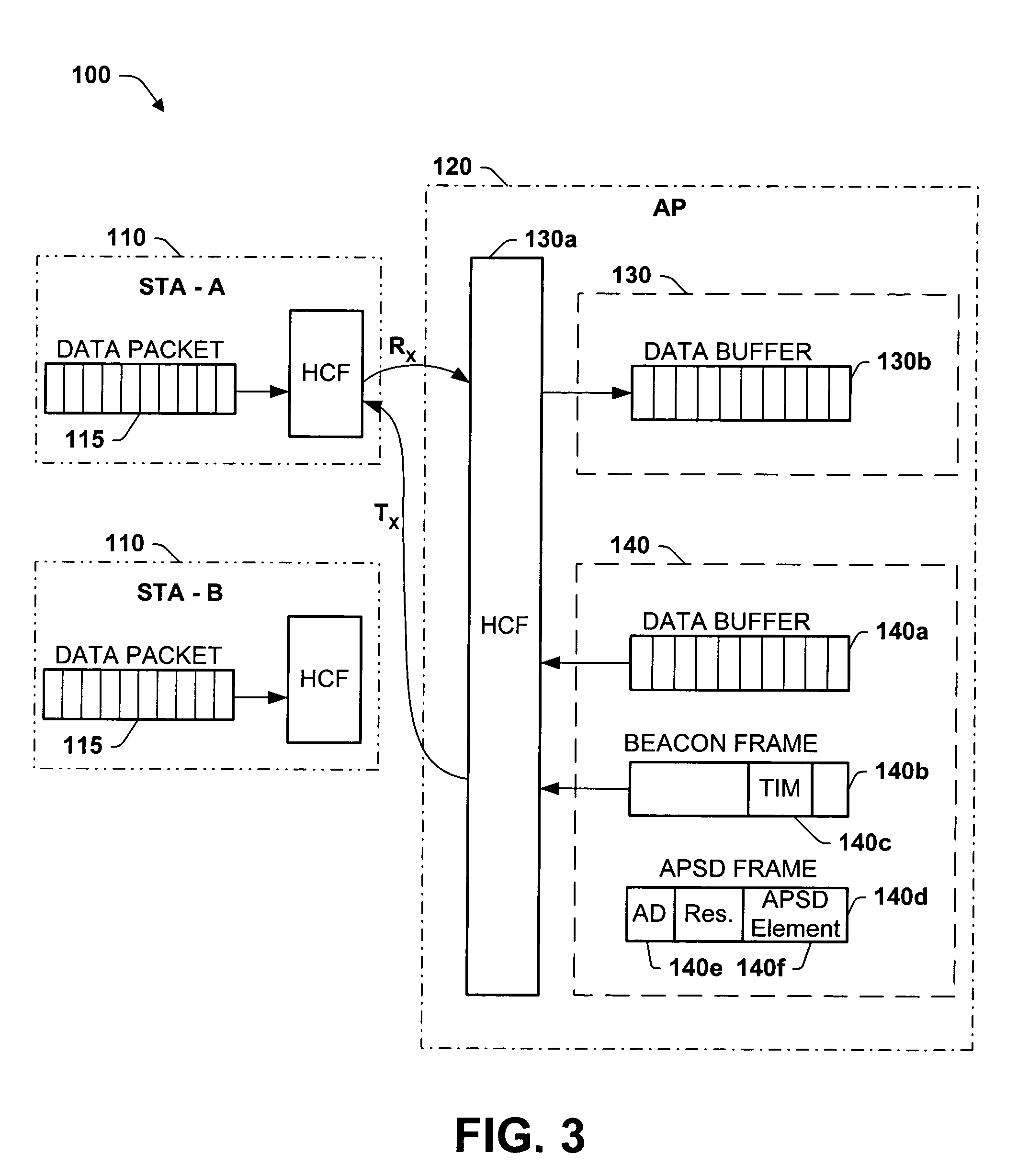
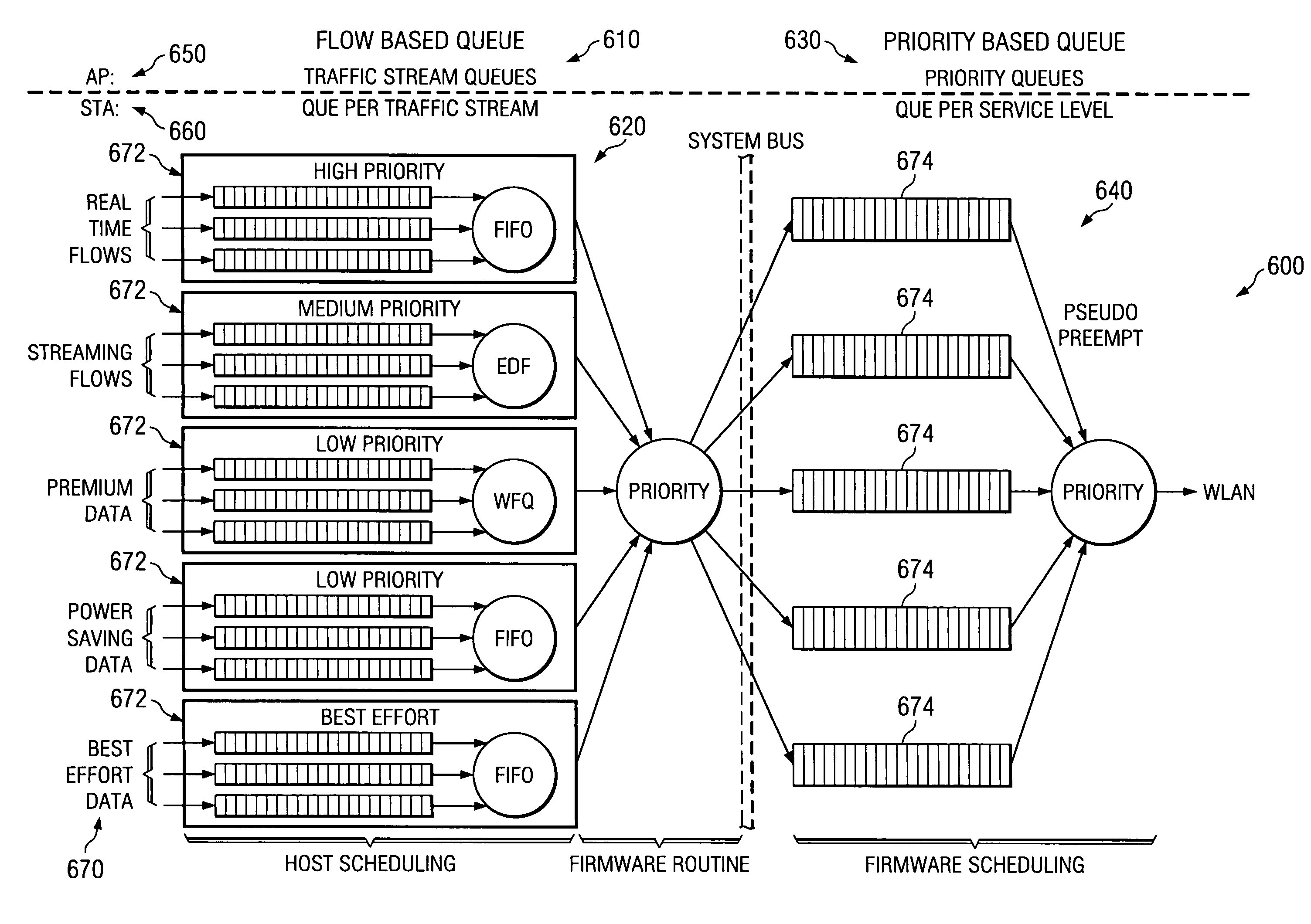
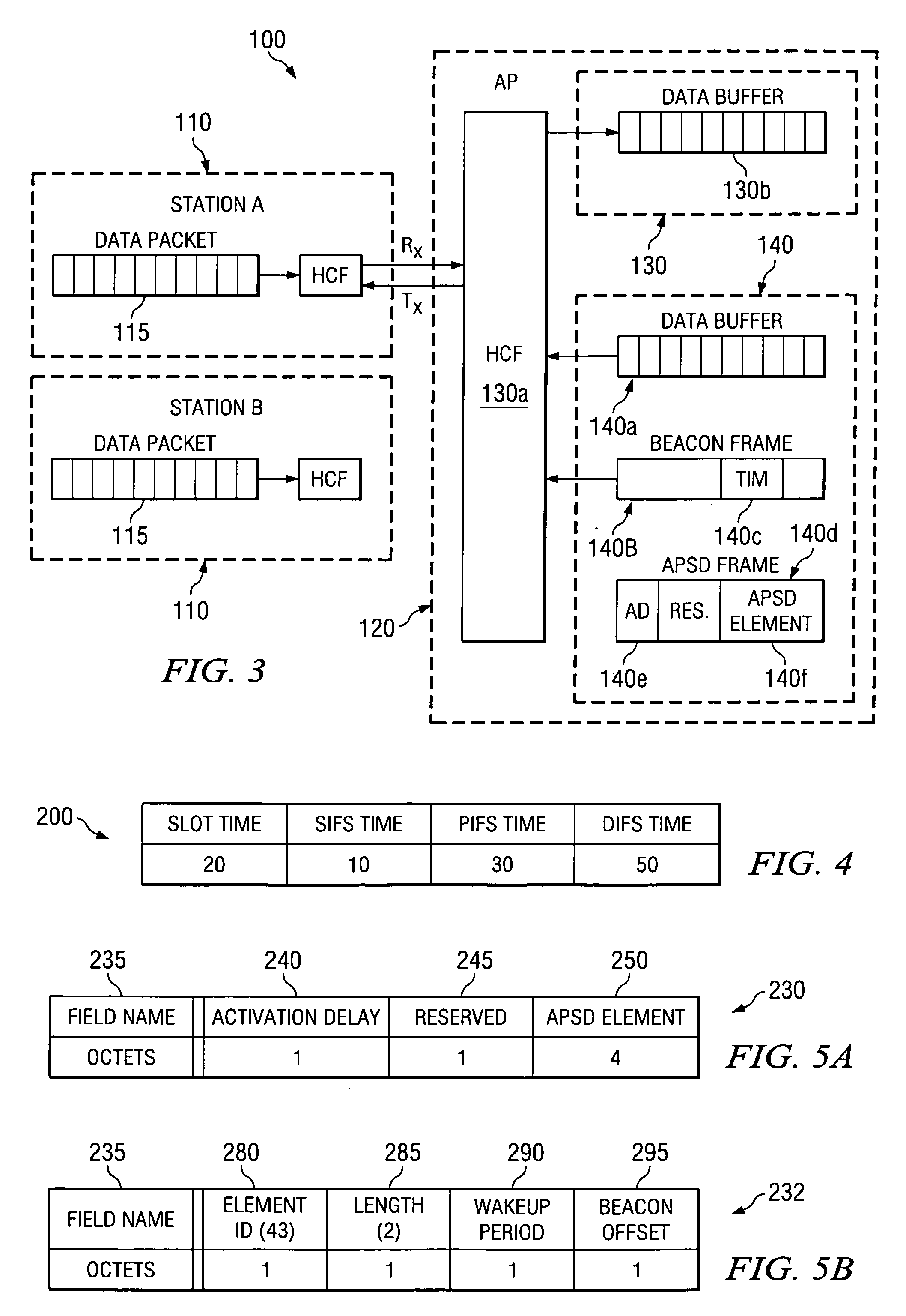
Optimal power saving scheduler for 802.11e APSD
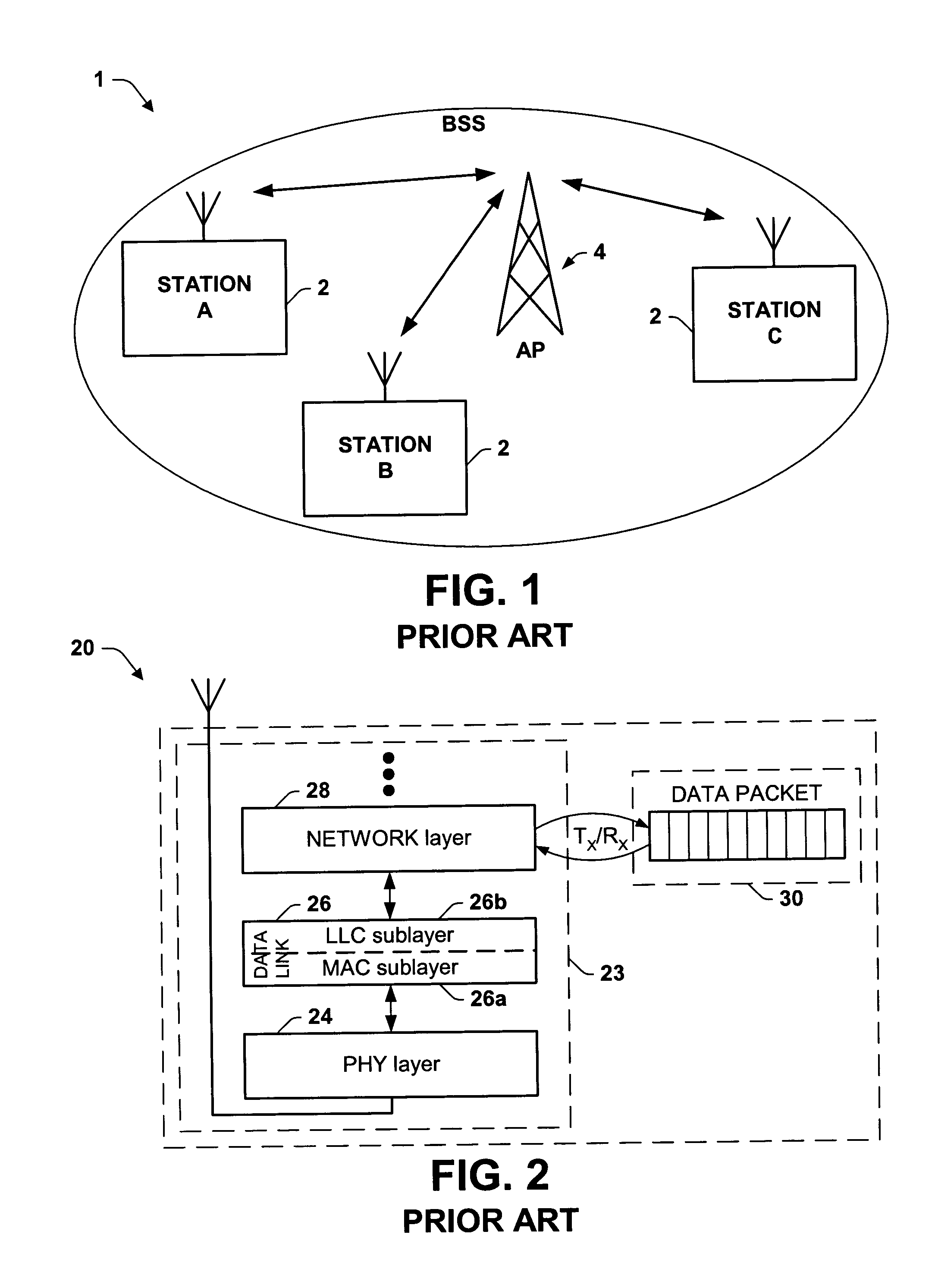
A new system and method is described, utilizing a scheduler based on a transmission power consumption calculation and prioritizing algorithm. The system utilizes the (APSD) protocol specified in the 802.11e draft for saving power in wireless local area networks. The system comprises an access point having a priority queue, one or more stations, an APSD frame comprising an association ID for identifying one of the stations and a scheduled wake-up time for the identified station. An algorithm is employed for calculating the total transmission power consumption of downlink data for the stations. The AP originates and transmits to the one or more stations the APSD frame of the scheduled activation delay time. The current data to be transmitted to each station is accessed by the algorithm to determine the total transmission power consumption to each station. A priority queue in the AP is ordered from the lowest to the highest receiving power consumption, assigning the highest priority to the lowest power consumption transmission to minimize total power consumption to the PS stations in the AP queue.
Owner:TEXAS INSTR INC
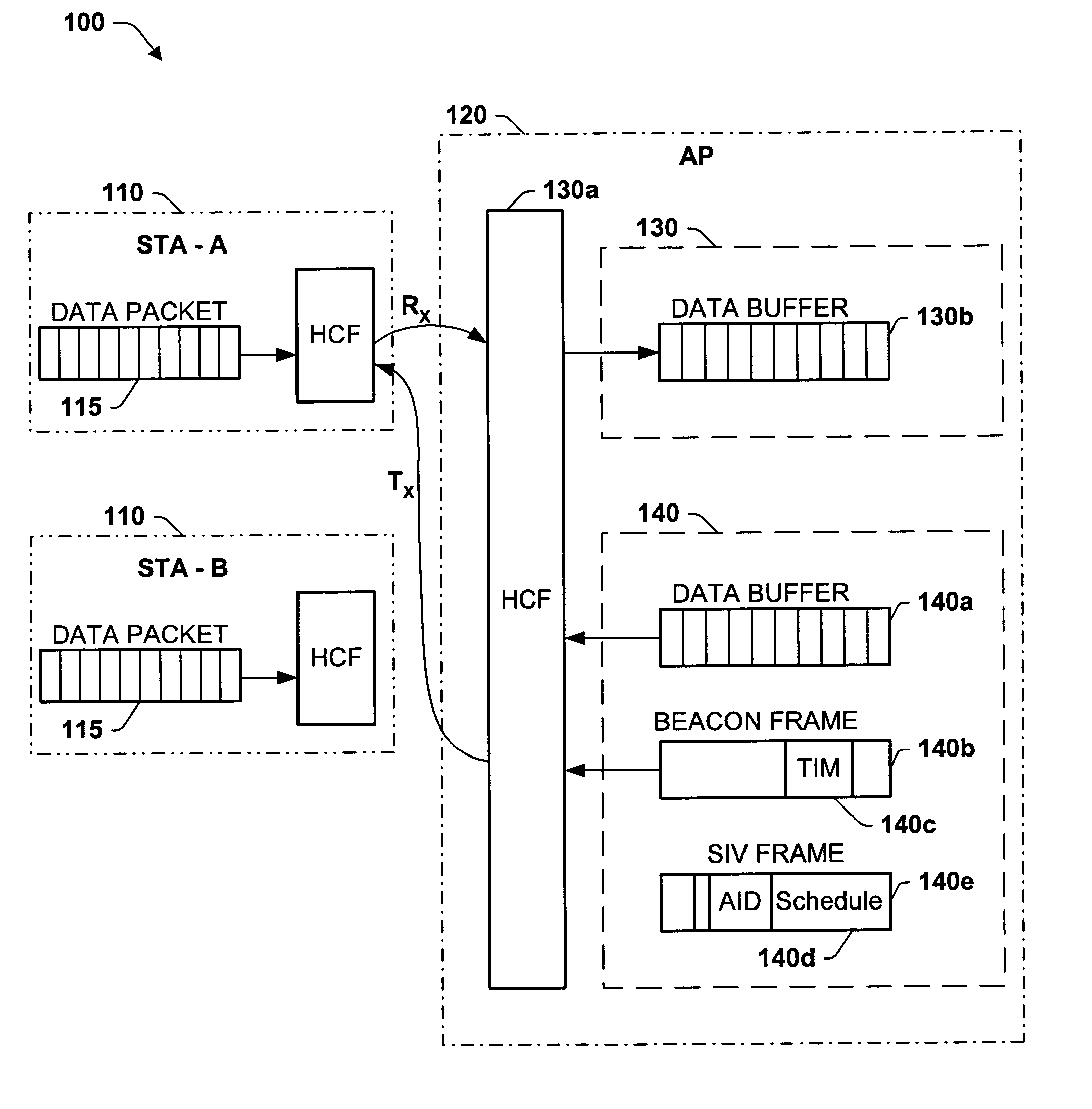
Optimal power saving scheduler for schedule information vector
ActiveUS20050003794A1Minimize timeSave powerEnergy efficient ICTError preventionSorting algorithmData transmission time
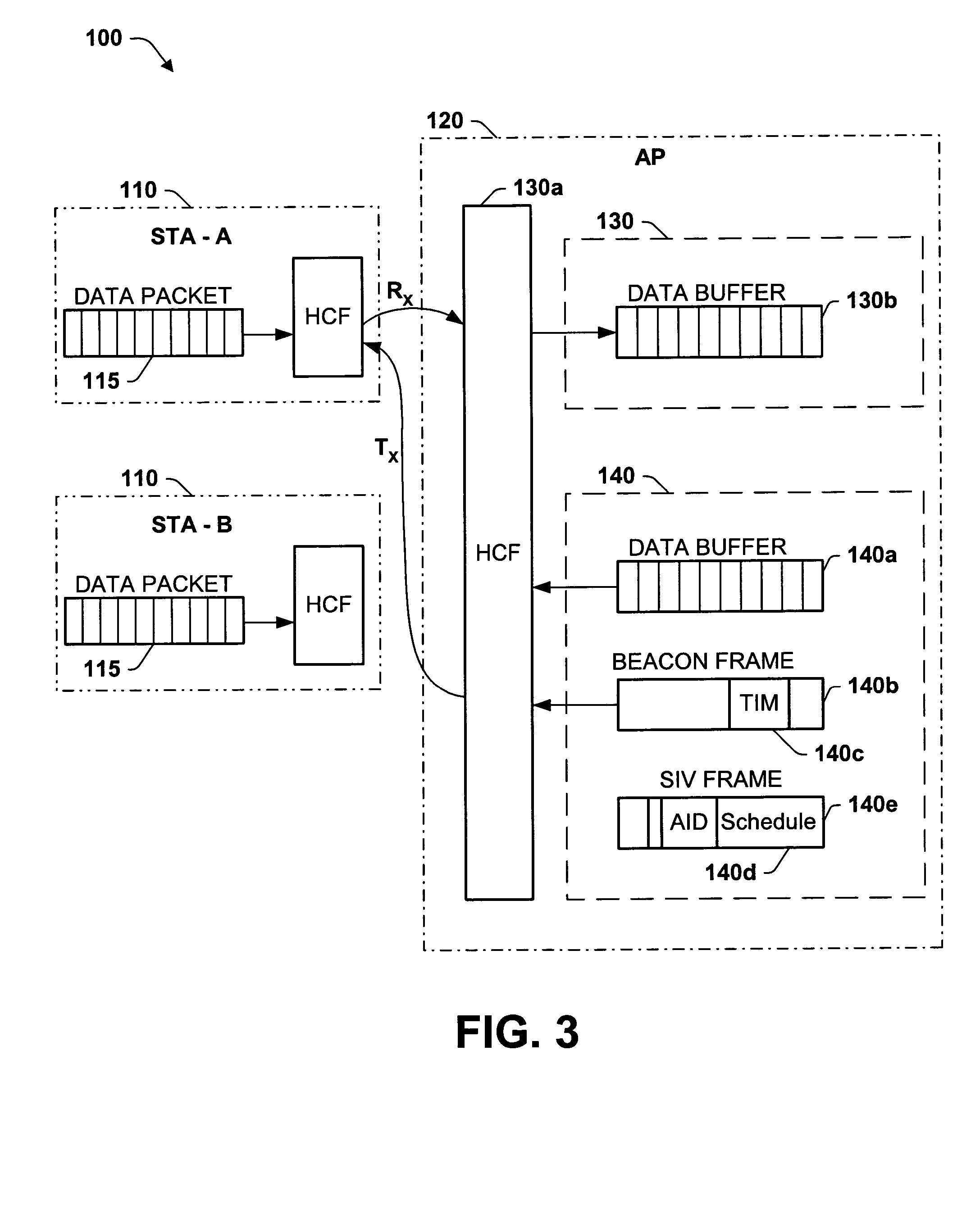
A new system and method is described, utilizing a scheduler based on a transmission time calculation and prioritizing algorithm. The system utilizes a Schedule Information Vector (SIV) protocol for saving power in wireless local area networks. The system comprises an access point having a priority queue, one or more stations, an SIV frame comprising an association ID for identifying one of the stations and a scheduled wake-up time for the identified station. An algorithm is employed for calculating the transmission time of downlink data for the stations. The access point originates and transmits to the one or more stations the SIV frame of the scheduled wake-up times. The current data to be transmitted to each station is accessed by the algorithm to determine the total transmission time to each station. A priority queue in the access point is ordered from the shortest to the longest transmission, assigning the highest priority to the shortest power save transmission to minimize the total power consumption of the network.
Owner:TAHOE RES LTD
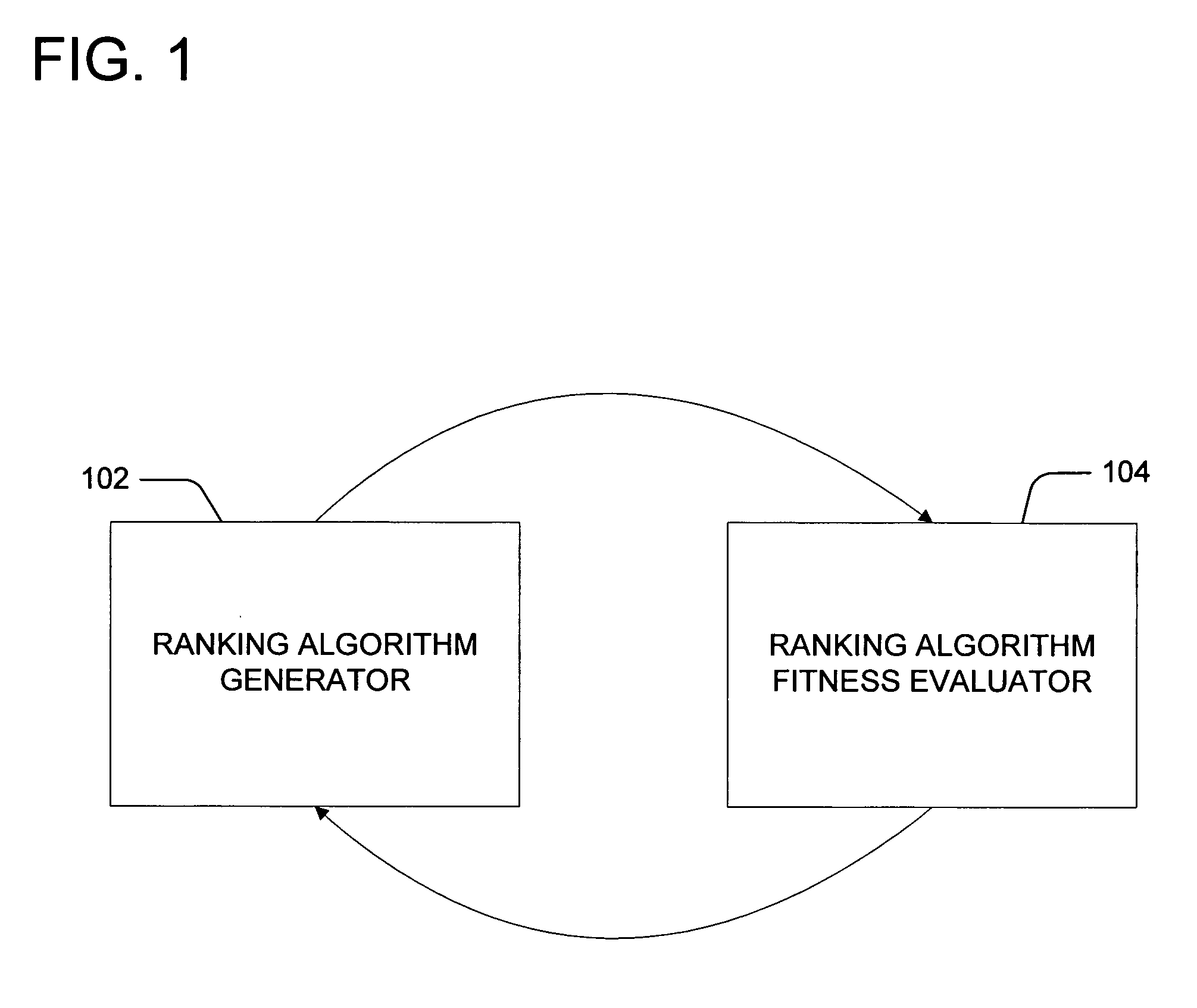
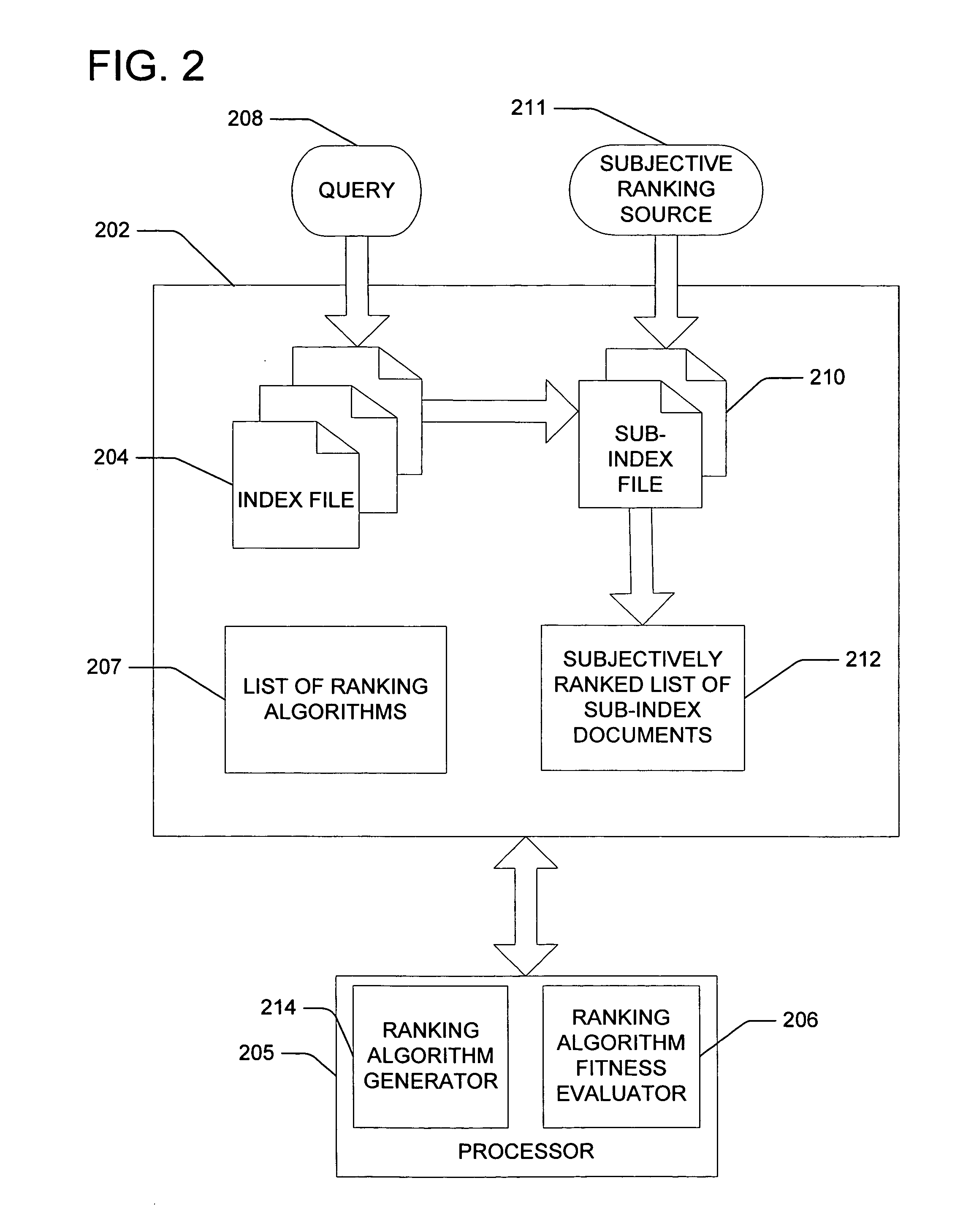
Machine directed improvement of ranking algorithms
InactiveUS7243102B1Easy to processEnhanced informationData processing applicationsDigital data information retrievalSorting algorithmAlgorithm
Improving ranking algorithms for information retrieval. The ranking algorithms operate on search results obtained from a search engine. Input information including information describing a first ranking algorithm, a first score associated with the first ranking algorithm, a second ranking algorithm, a second score associated with the second ranking algorithm, and causal information relating a difference between the first ranking algorithm and the second ranking algorithm with a difference between the first score and the second score is received. An optimizing algorithm is applied to the received input information to identify an optimal ranking algorithm having an optimal score. The optimal ranking algorithm is defined by a plurality of parameters and a plurality of weights associated with the plurality of parameters.
Owner:MICROSOFT TECH LICENSING LLC
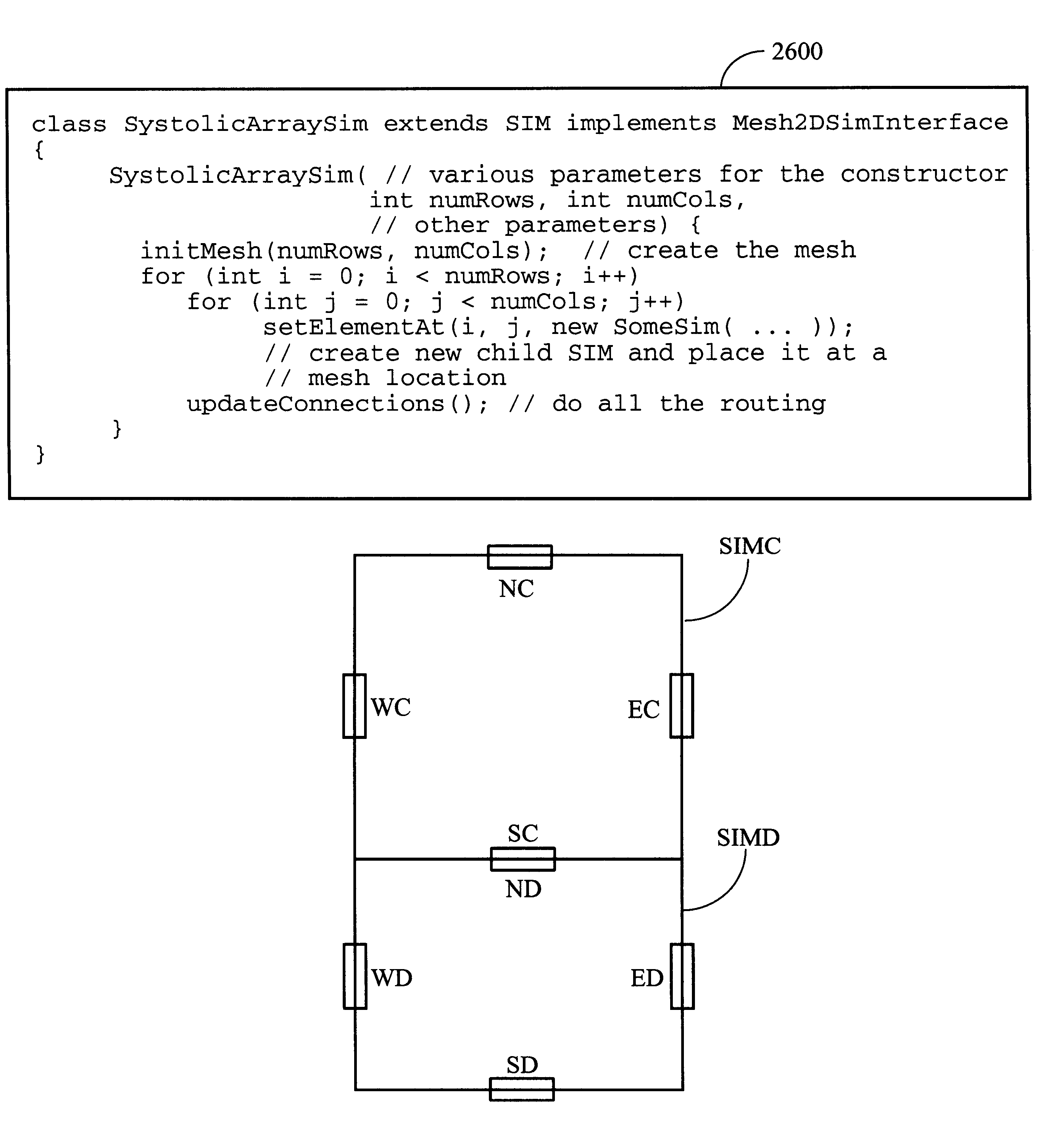
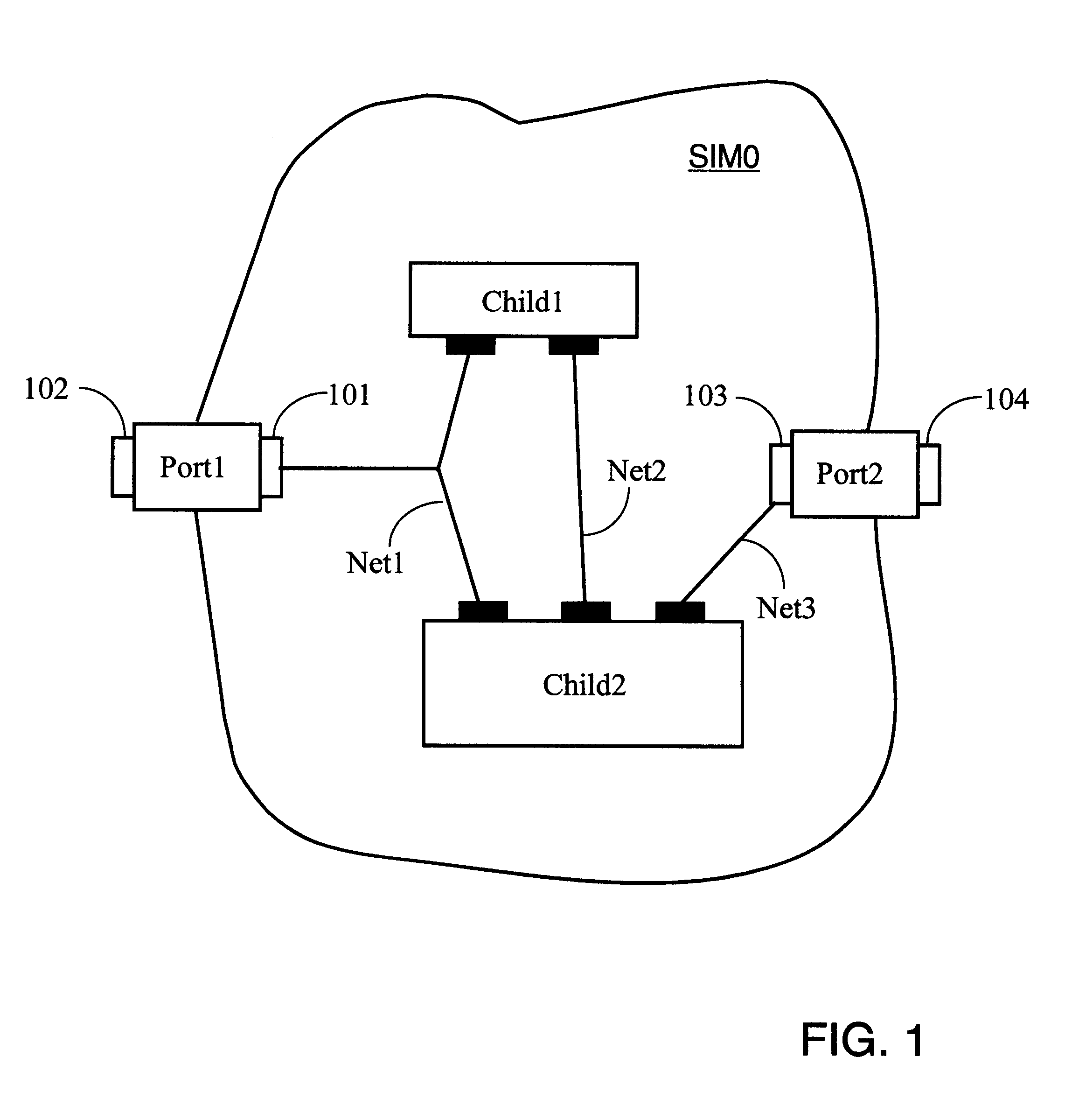
Hetergeneous method for determining module placement in FPGAs
InactiveUS6457164B1Reduce deliverySpeed up the implementation processElectronic switchingComputer programmed simultaneously with data introductionGrid patternSorting algorithm
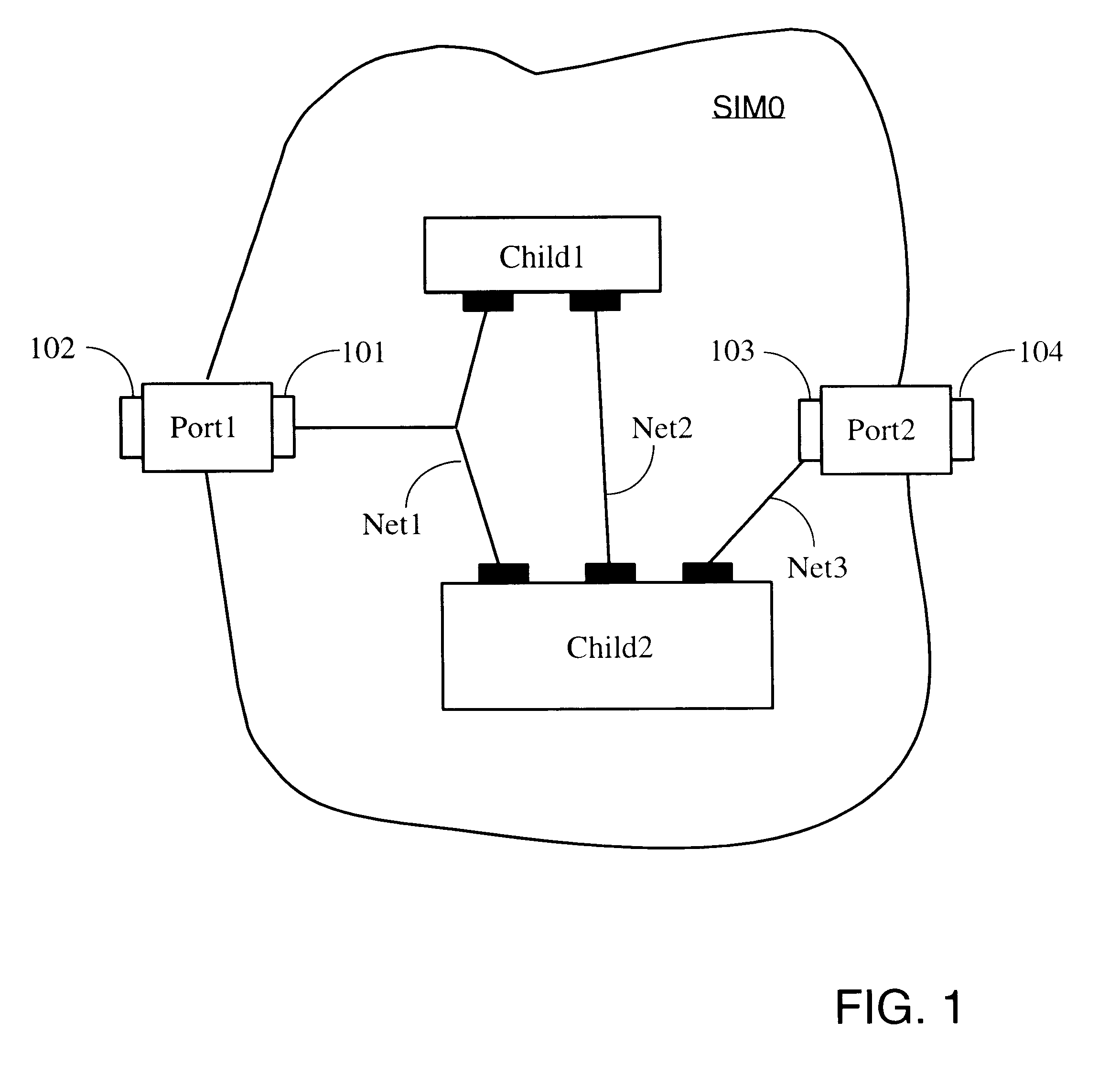
The invention provides parametric modules called Self Implementing Modules (SIMs) for use in programmable logic devices such as FPGAS. The invention further provides tools and methods for generating and using SIMs. SIMs implement themselves at the time the design is elaborated, targeting a specified FPGA according to specified parameters. In one embodiment, a SIM references or includes one or more floorplanners each of which may employ one or more placement algorithms. Such placement algorithms might include, for example: a linear ordering algorithm that places datapath logic bitwise in a regular linear pattern; a rectangular mesh algorithm that implements memory in a grid pattern in distributed RAM; a columnar algorithm for counters and other arithmetic logic; or a simulated annealing algorithm for random logic such as control logic. Therefore, a design including more than one SIM can utilize a plurality of placement algorithms at the same or different levels of hierarchy. The design as a whole can therefore utilize a non-uniform global placement strategy.
Owner:XILINX INC
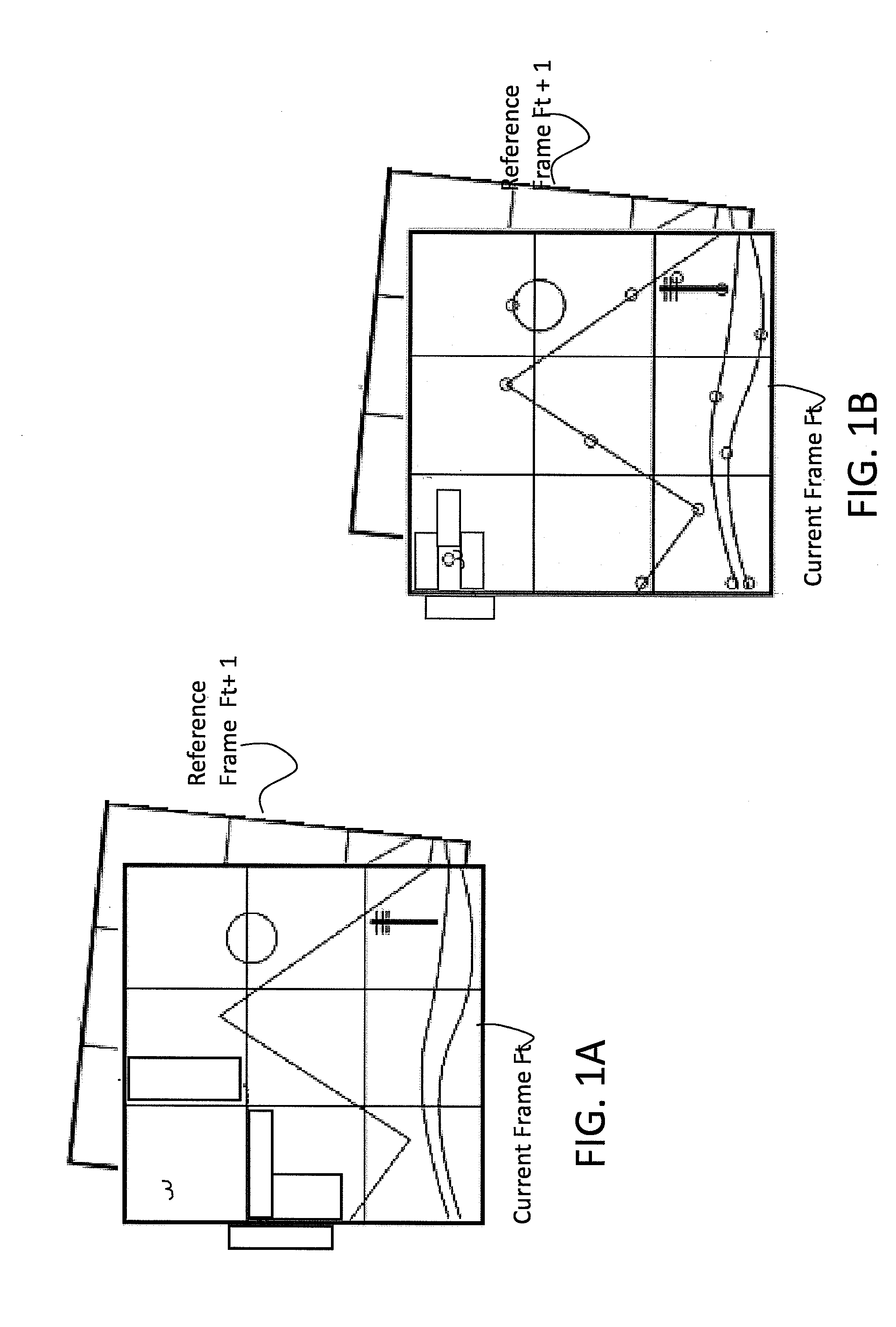
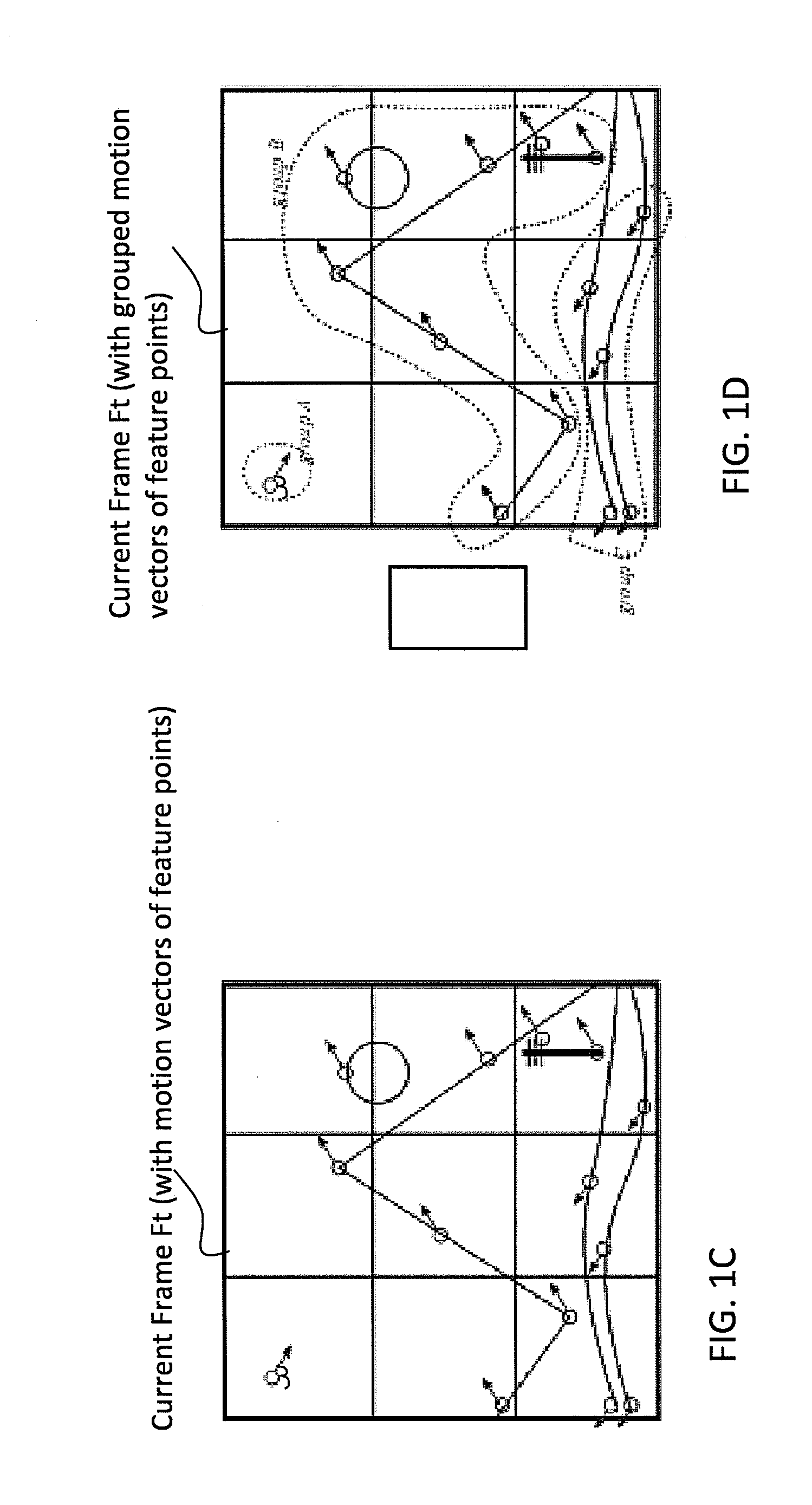
Digital image stabilization device and method
ActiveUS20120162454A1Improve efficiencyEfficient processingImage enhancementTelevision system detailsSorting algorithmObject based
A method of Digital Image Stabilization (DIS) including a feature point sorting algorithm for selecting optimal feature points, and a computationally efficient tile-vector based search algorithm for deriving motion vectors of the selected feature points, and a feature point motion vector grouping / comparison process for grouping pairs of the selected feature points based on their vector magnitude ratio and their angular difference.A Digital Image Stabilization method including selecting a Principal transform representing a stationary / background object in the scene of a video frame, based on scoring each of a plurality of transforms of tile motion vector (Tile MV) groups and of feature point motion vector (FP MV) groups, and excluding large moving objects based on the history of the stationary (background) group and the history of each of the plurality motion vector groups.
Owner:SAMSUNG ELECTRONICS CO LTD
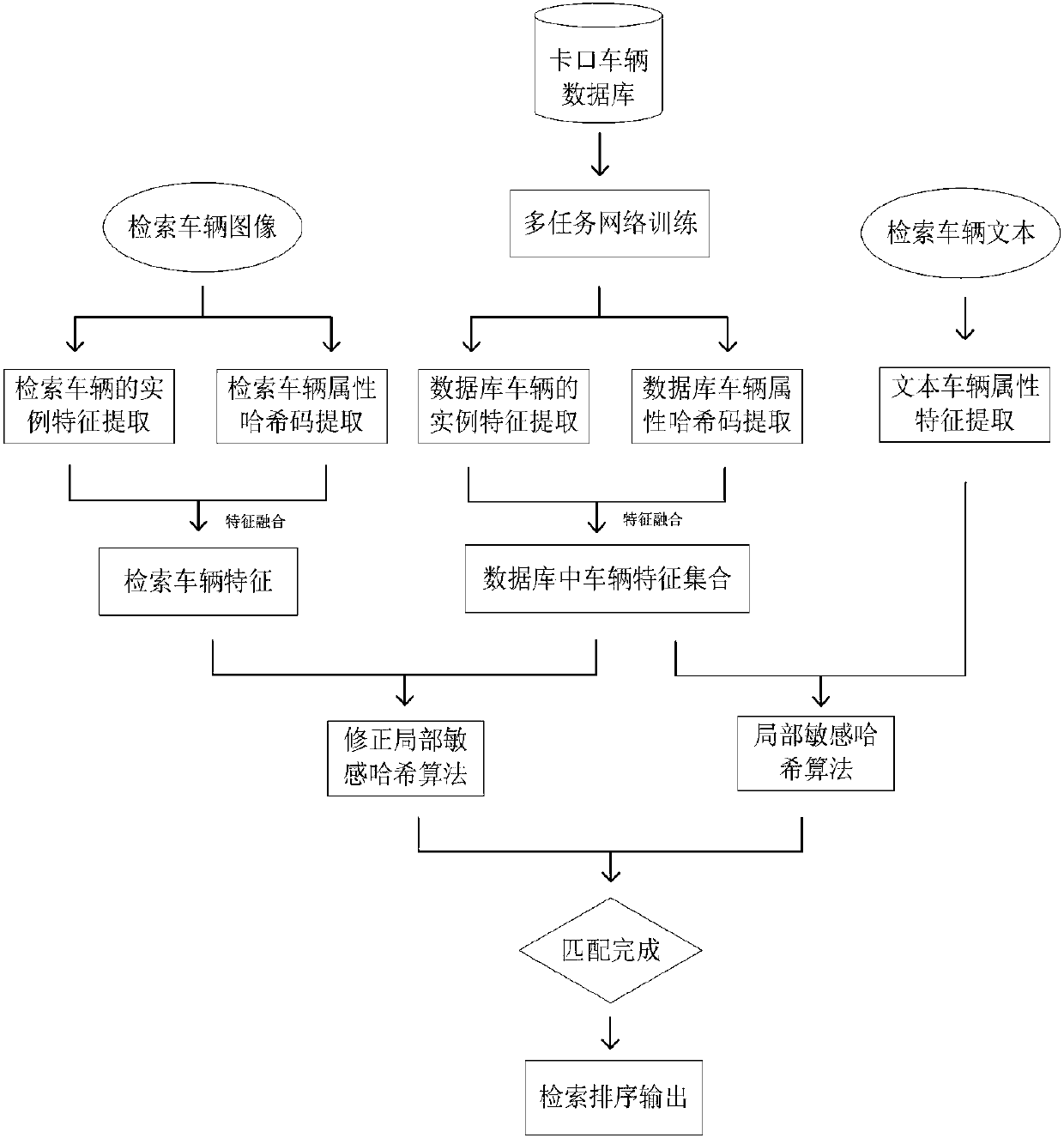
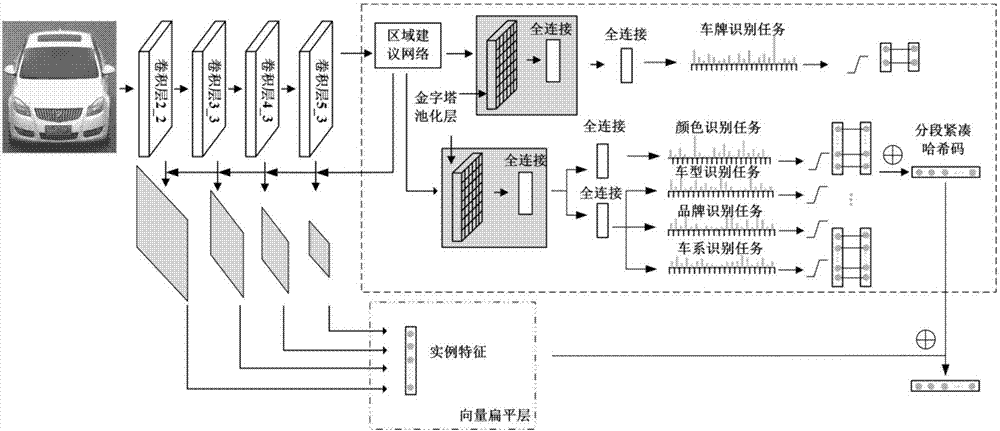
Modified local sensitive hash vehicle retrieval method based on multitask deep learning
ActiveCN108108657AAchieve retrievalRealize adaptive feature extractionCharacter and pattern recognitionNeural architecturesSorting algorithmAlgorithm
The invention discloses a modified local sensitive hash vehicle retrieval method based on multitask deep learning. A multitask end-to-end convolution neural network is used to identify a vehicle model, a vehicle system, a vehicle logo, a color and a license plate simultaneously in a subsection parallel mode. A network module for extracting vehicle image example features based on a characteristic pyramid and an algorithm by using a modified local sensitive hash sorting algorithm to sort the vehicle characteristics in a database, and a cross-modal text retrieval method when a retrieval vehicle image can not be acquired are included. The multitask end-to-end convolution neural network and the modified local sensitive hash vehicle retrieval method are provided, the automation level and the intelligence level of vehicle retrieval can be improved effectively, little storage space is used, and image retrieval requirements in a big data era are met by using a quicker retrieval speed.
Owner:ZHEJIANG UNIV OF TECH
A method for implementing a question answering system based on a question-answer pair
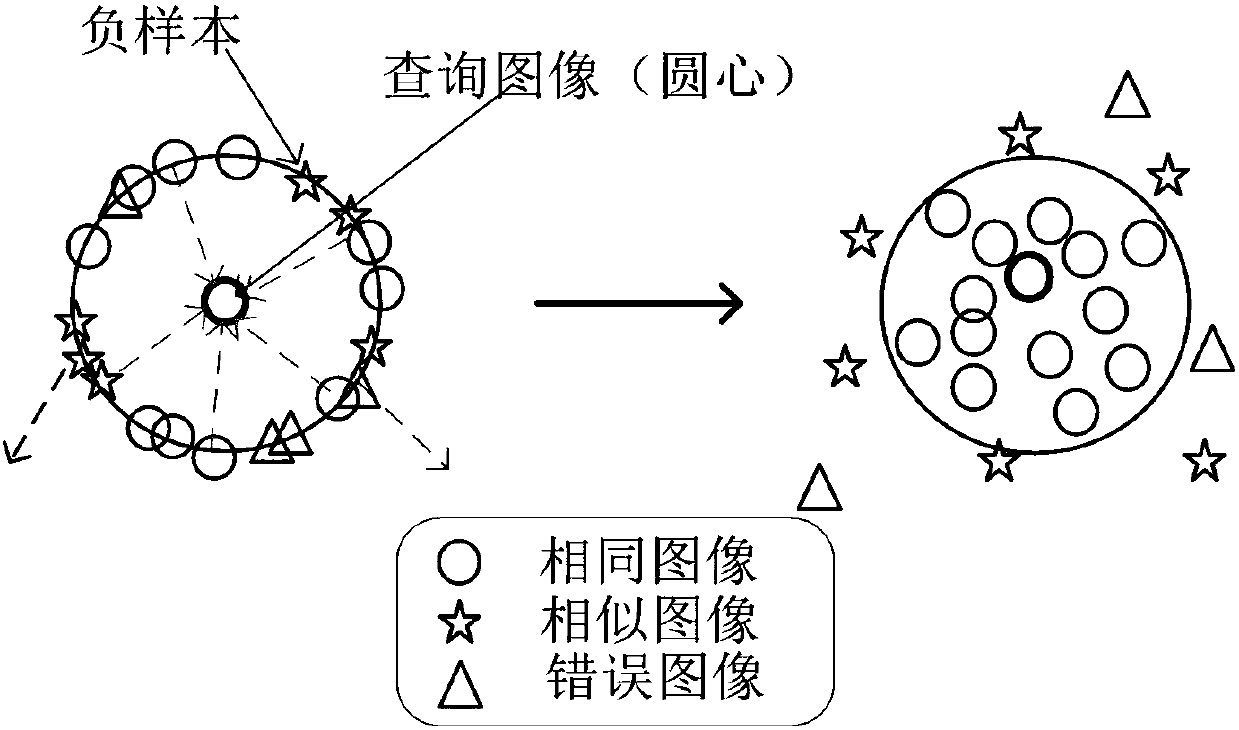
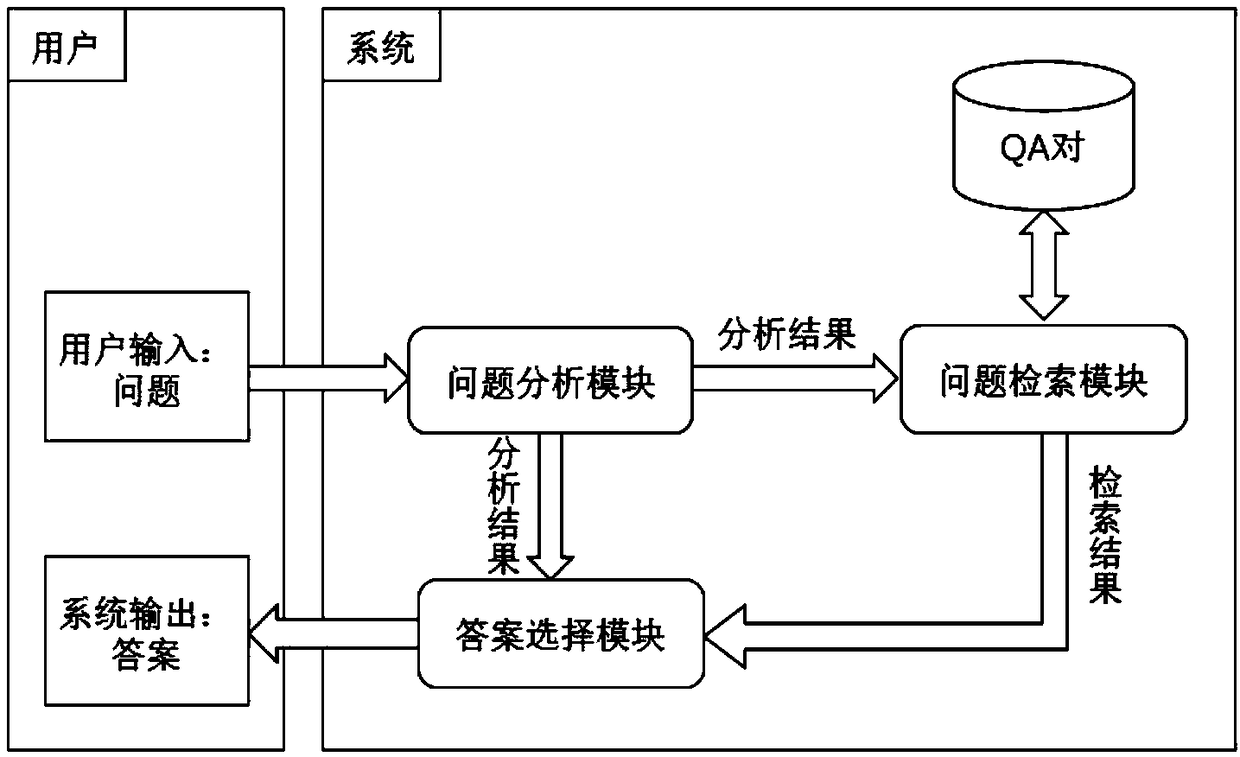
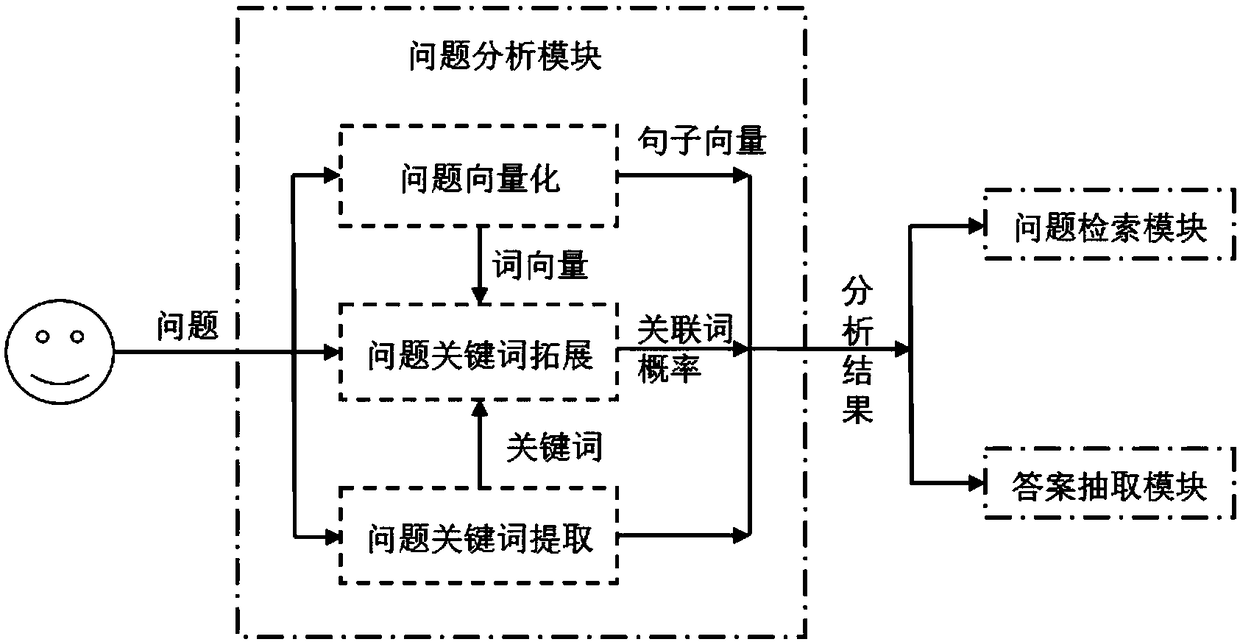
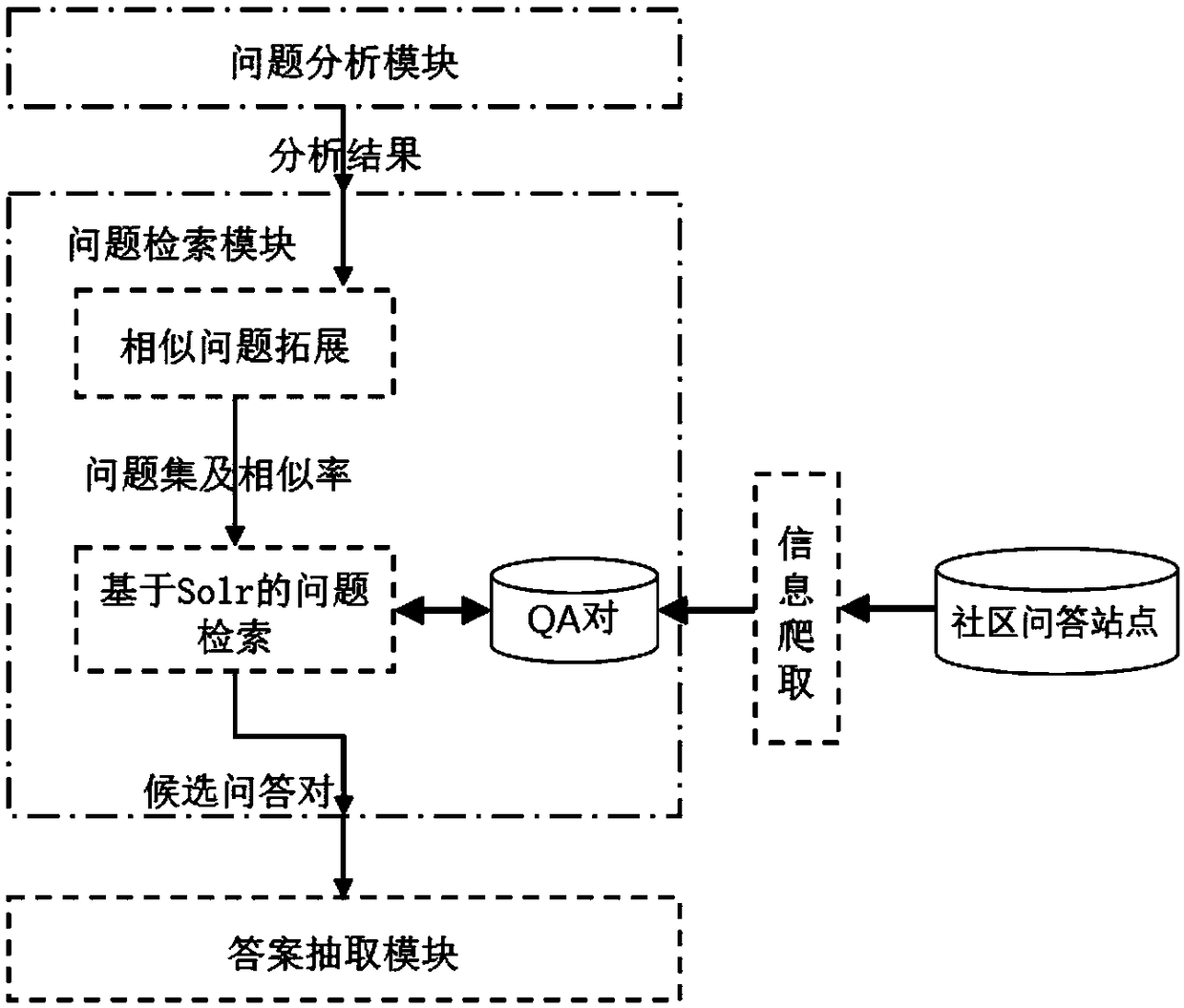
ActiveCN109271505AImprove accuracyText database queryingSpecial data processing applicationsSorting algorithmSingle best answer
A method for implementing a question answering system based on a question-answer pair comprises the following steps: question analysis, question retrieval and answer selection. After a user submits aquestion expressed in natural language to the question answering system, the question answering system uses question vectorization, keyword extraction, keyword extension and other natural language processing techniques to understand the questioning intent of a user, and then uses the engine searching method in the question-answer pair database to obtain the question-related candidate question-answer pair set, and uses a matching algorithm and sorting algorithm to accurately select the best answer from the candidate sets. The invention obtains the function of the matching degree score between the question and the answer by learning by synthesizing different algorithms and models, the method of choosing the best answer from the candidate question-answer pairs is realized, and an answer selection method based on convolution neural network and Xgboost feature fusion is completed, which provides a better method for the answer selection of the question answering system.
Owner:深圳智能思创科技有限公司
Optimal power saving scheduler for 802.11e APSD
ActiveUS7245946B2Save trafficSave powerEnergy efficient ICTPower managementSorting algorithmDelayed time
A new system and method is described, utilizing a scheduler based on a transmission power consumption calculation and prioritizing algorithm. The system utilizes the (APSD) protocol specified in the 802.11e draft for saving power in wireless local area networks. The system comprises an access point having a priority queue, one or more stations, an APSD frame comprising an association ID for identifying one of the stations and a scheduled wake-up time for the identified station. An algorithm is employed for calculating the total transmission power consumption of downlink data for the stations. The AP originates and transmits to the one or more stations the APSD frame of the scheduled activation delay time. The current data to be transmitted to each station is accessed by the algorithm to determine the total transmission power consumption to each station. A priority queue in the AP is ordered from the lowest to the highest receiving power consumption, assigning the highest priority to the lowest power consumption transmission to minimize total power consumption to the PS stations in the AP queue.
Owner:TEXAS INSTR INC
Heterogeneous method for determining module placement in FPGAs
InactiveUS6243851B1Reduce deliverySpeed up the implementation processElectronic switchingComputer aided designSorting algorithmGrid pattern
The invention provides parametric modules called Self Implementing Modules (SIMs) for use in programmable logic devices such as FPGAs. The invention further provides tools and methods for generating and using SIMs. SIMs implement themselves at the time the design is elaborated, targeting a specified FPGA according to specified parameters. In one embodiment, a SIM references or includes one or more floorplanners each of which may employ one or more placement algorithms. Such placement algorithms might include, for example: a linear ordering algorithm that places datapath logic bitwise in a regular linear pattern; a rectangular mesh algorithm that implements memory in a grid pattern in distributed RAM; a columnar algorithm for counters and other arithmetic logic; or a simulated annealing algorithm for random logic such as control logic. Therefore, a design including more than one SIM can utilize a plurality of placement algorithms at the same or different levels of hierarchy. The design as a whole can therefore utilize a non-uniform global placement strategy.
Owner:XILINX INC
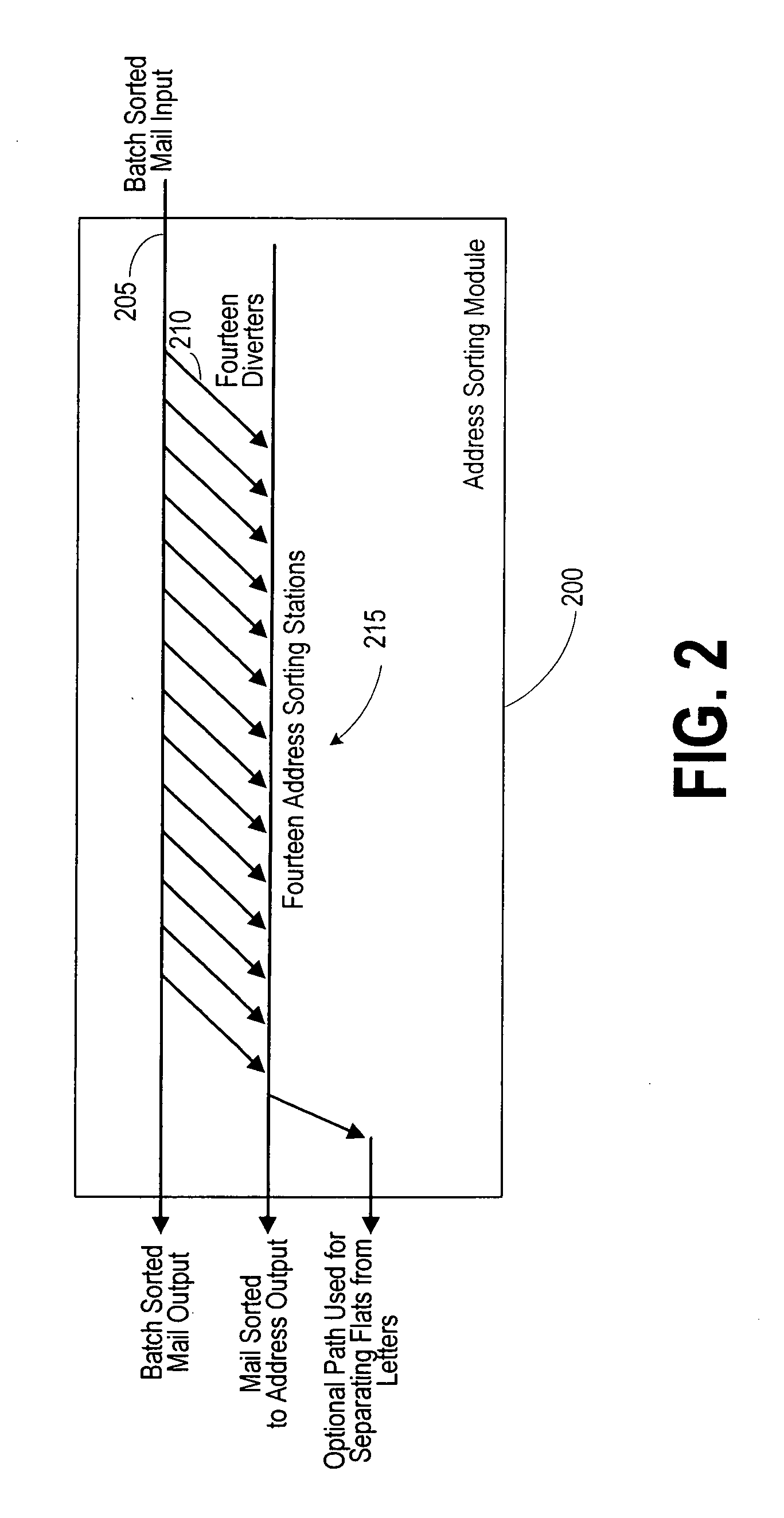
Mail sorter, method, and software product for a two-step and one-pass sorting algorithm
InactiveUS20080011653A1Short working hoursReduce path lengthSeparation devicesCharacter and pattern recognitionSorting algorithmSoftware product line
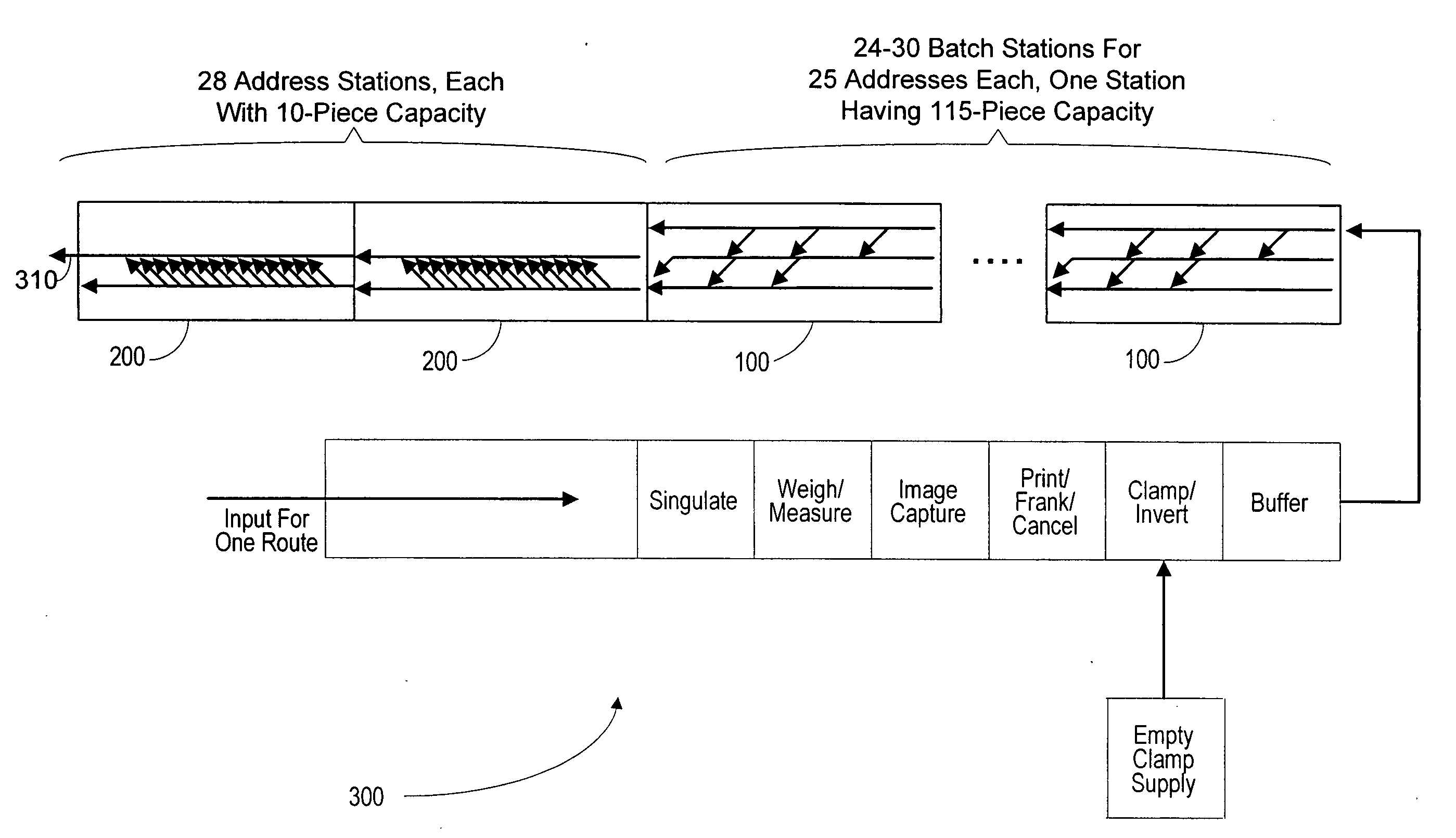
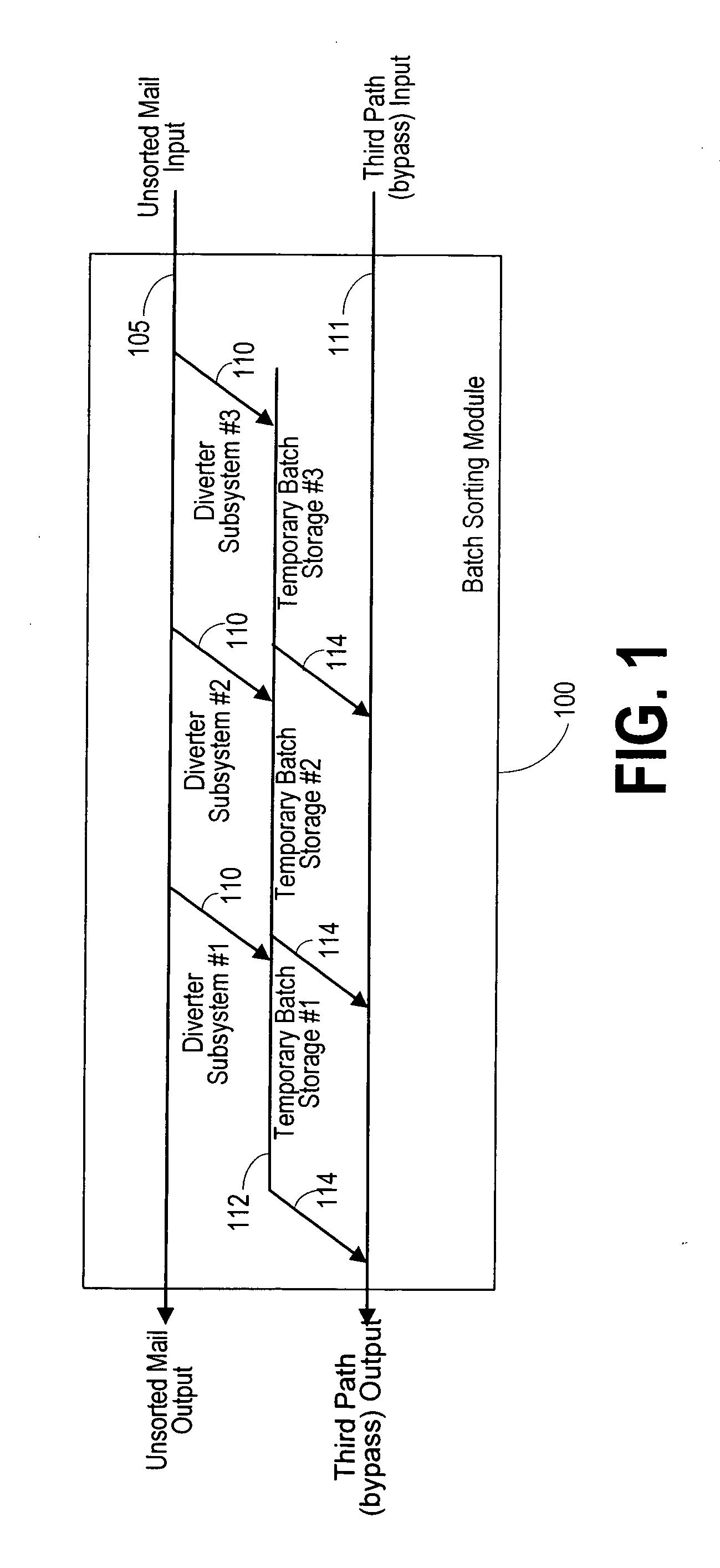
A sorter, method, and software product are used for sorting objects into a sequence of destination addresses, in at most a single pass through the sorter. In a first stage of the single pass through the sorter, the objects are sorted into a plurality of batches corresponding to groups of the destination addresses. The batches are then eventually advanced from the first stage to a second stage of the single pass through the sorter. During that second stage, objects in each of the batches are sorted into the sequence of destination addresses.
Owner:LOCKHEED MARTIN CORP
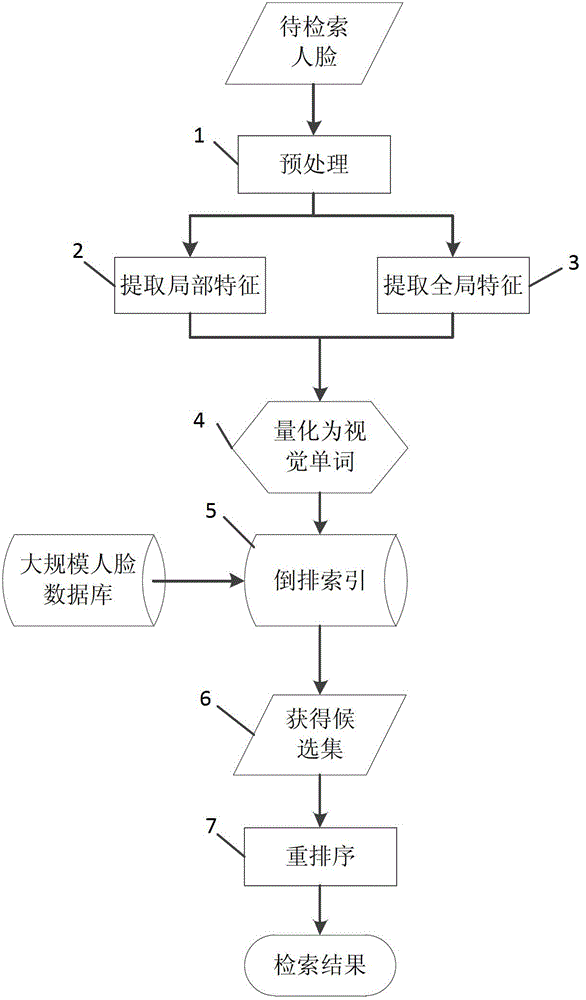
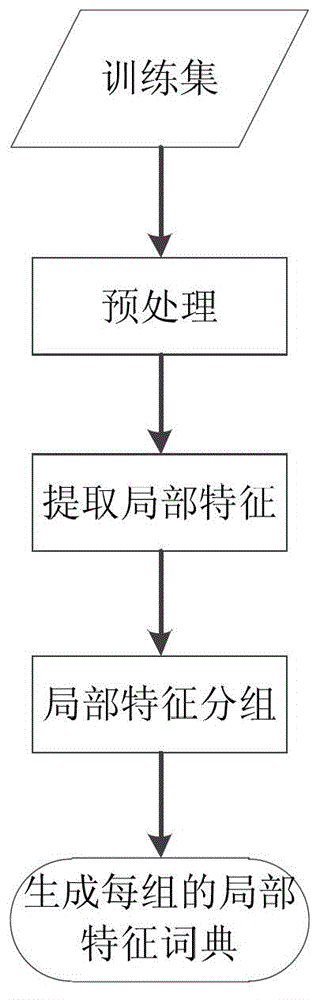
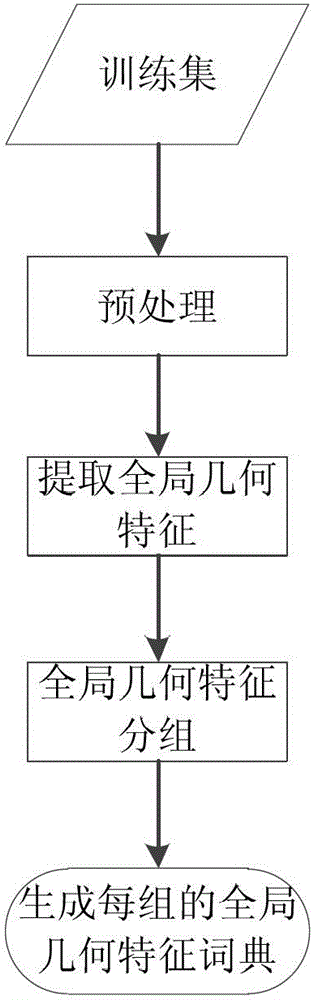
Large-scale human face image searching method
InactiveCN102982165AImprove scalabilityAvoid linear searchCharacter and pattern recognitionSpecial data processing applicationsSorting algorithmResearch efficiency
The invention discloses a large-scale human face image searching method. The method comprises the following steps of preprocessing human face images; extracting local characteristics from the human face images; extracting overall geometrical characteristics from the human face images; quantifying the local characteristics; quantifying the overall geometrical characteristics; establishing a reverse index; searching a candidate human face image set; and re-arranging the candidate human face image set. By the method, an index for a large-scale human face image database can be established, quick human face research is realized, and the research efficiency is realized. In addition, the accuracy of human face research is improved by embedding an auxiliary information characteristic quantifying and candidate human face image set re-arranging algorithm. Effective and accurate large-scale human face image search is realized by the method, so that the method has higher use value.
Owner:NANJING UNIV
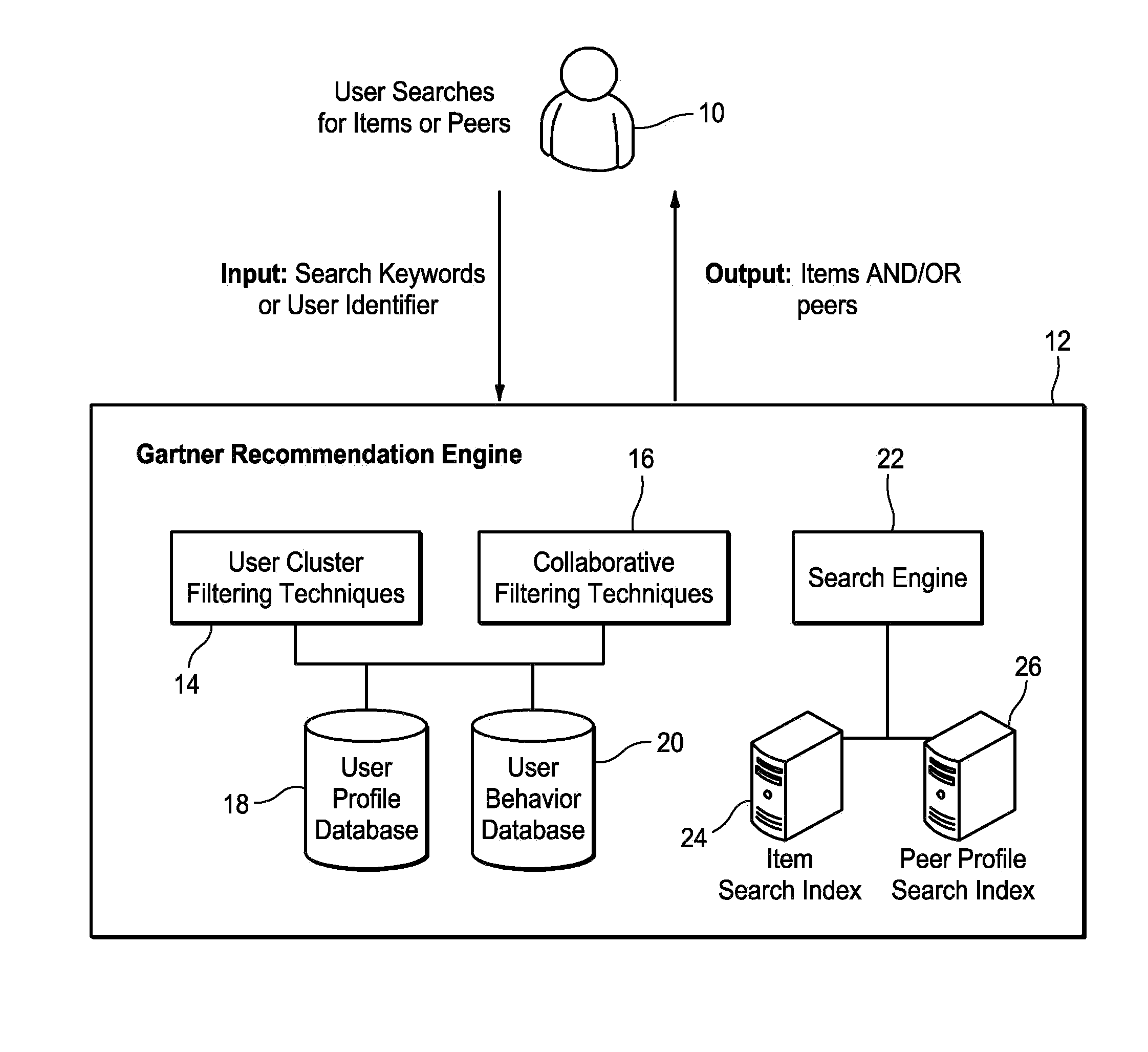
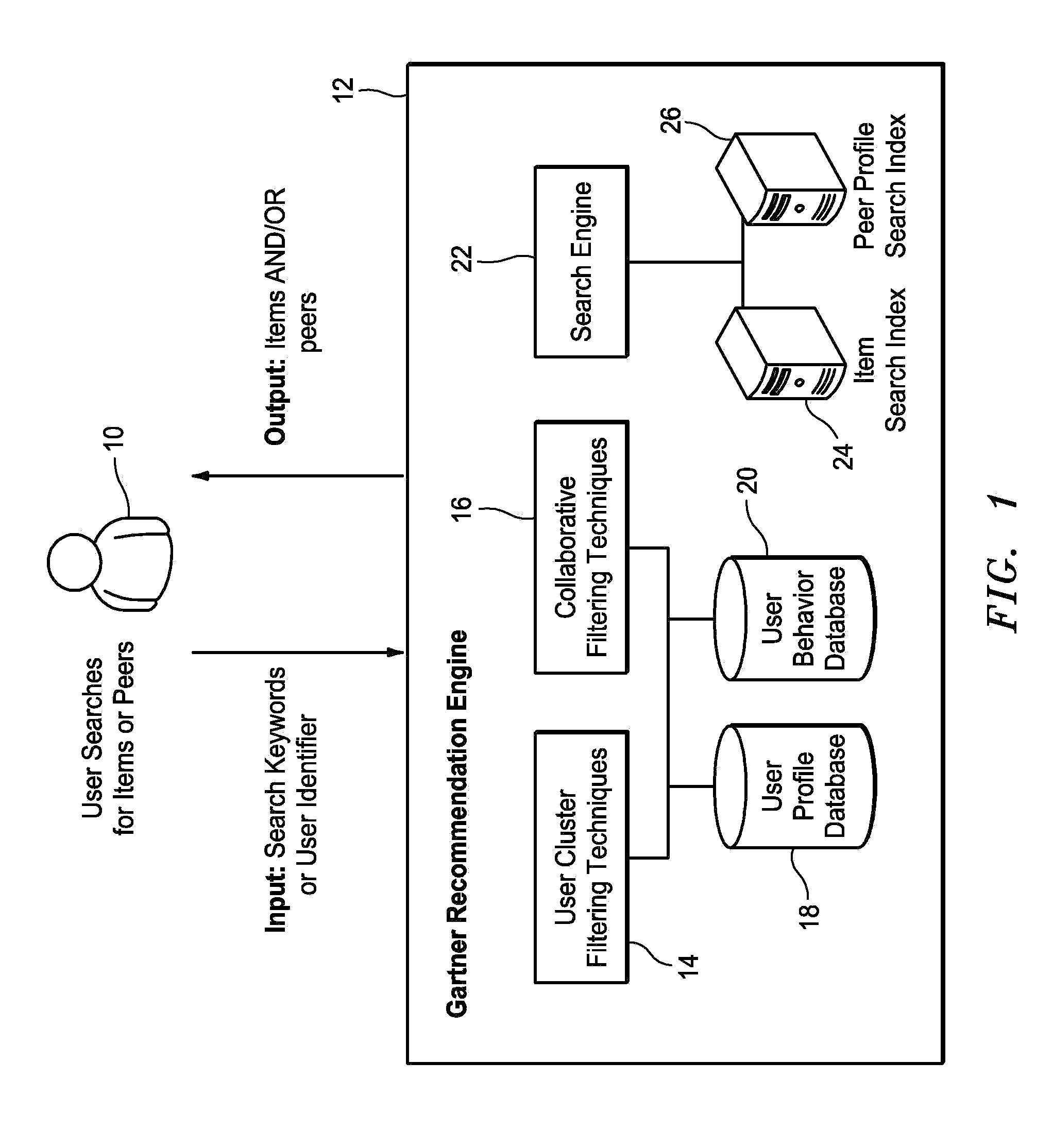
Bi-model recommendation engine for recommending items and peers
InactiveUS20110191311A1Improve future recommendationDigital data information retrievalDigital data processing detailsSorting algorithmFilter algorithm
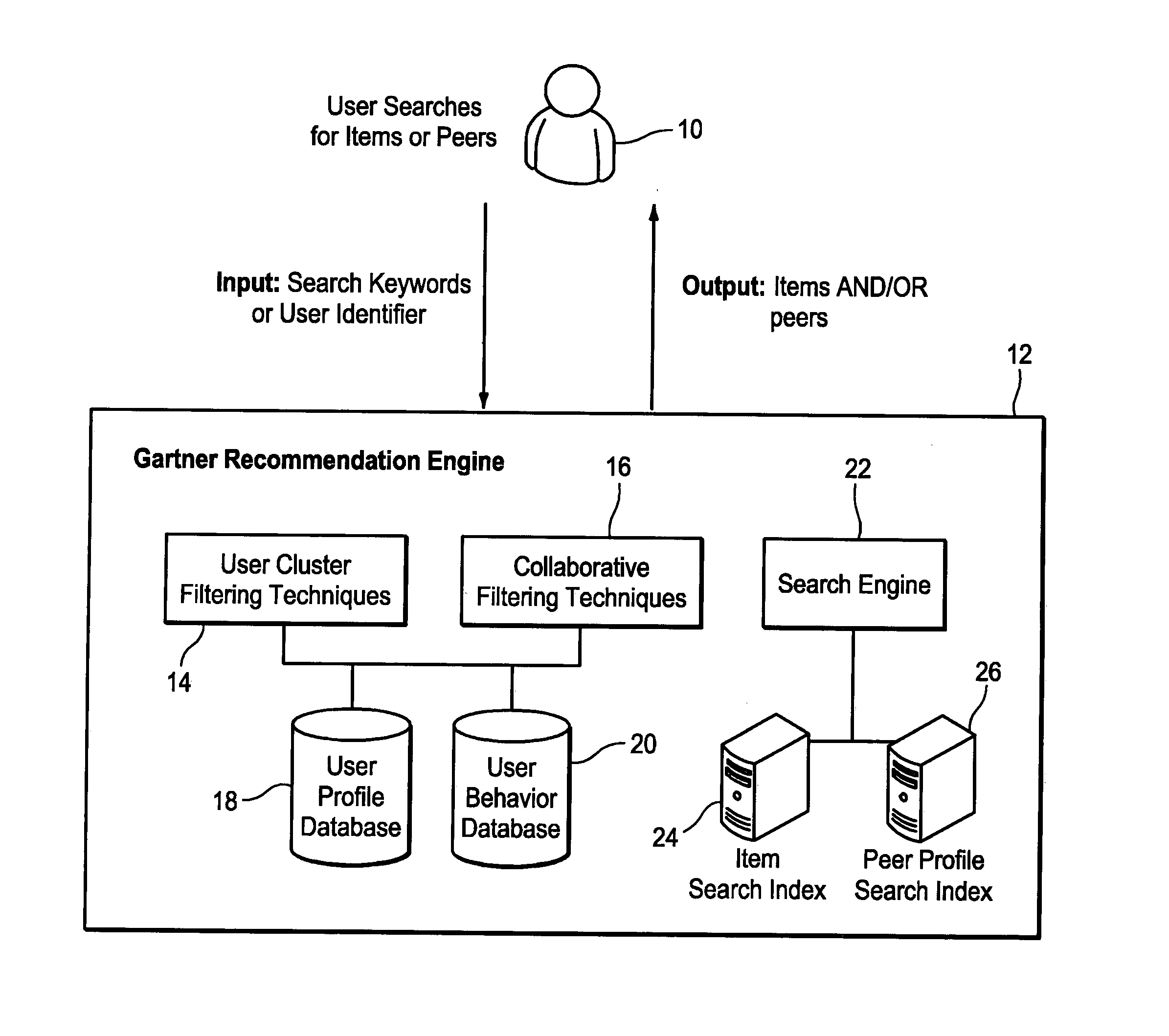
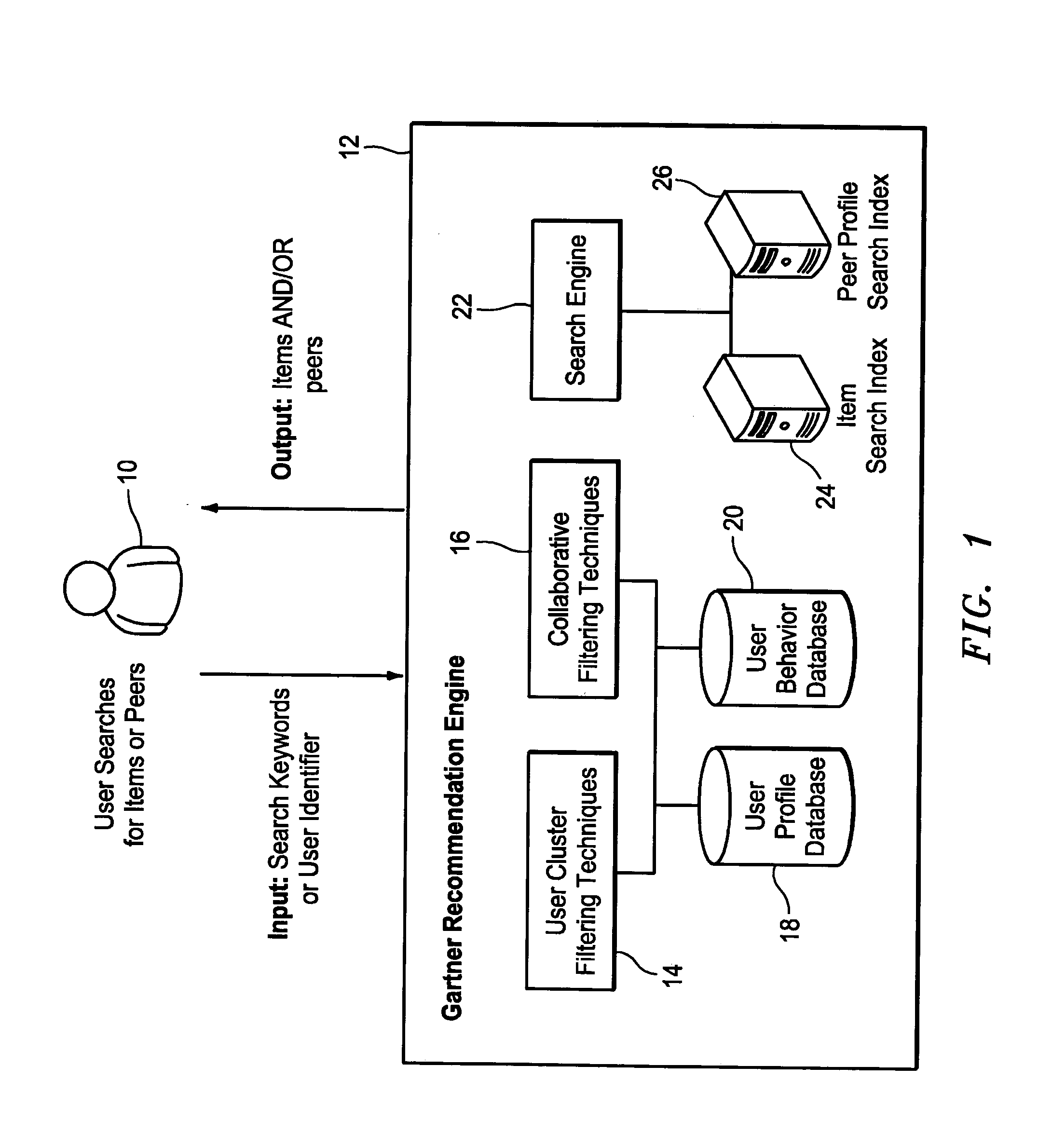
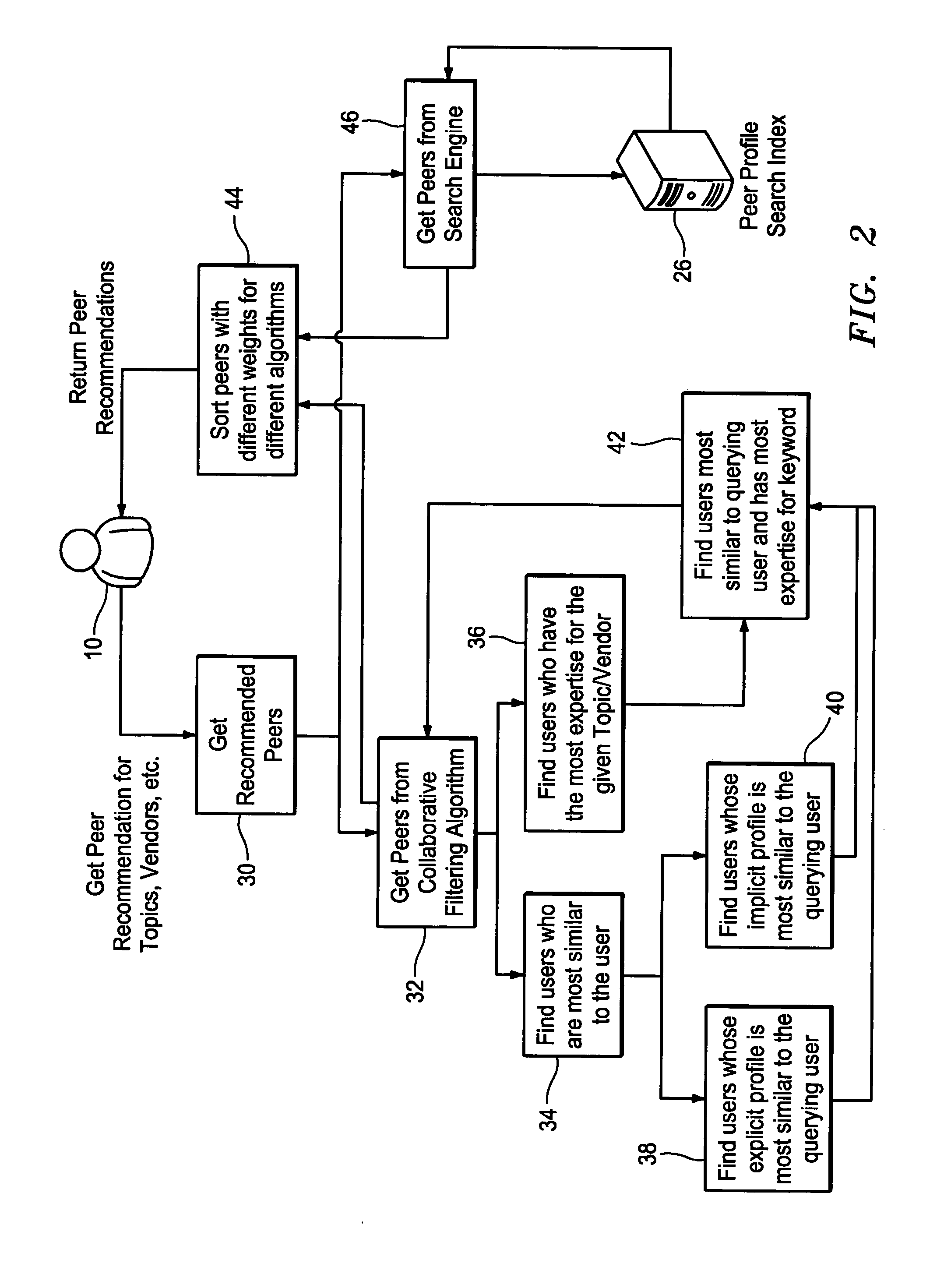
A networked peer and item recommendation system makes recommendations to users such as documents of interest and peers with whom the users may want to connect. User profile information is maintained in a profiles database. A log enables the collection of user behavior information. A cluster filtering algorithm determines a cluster that a querying user belongs to. A collaborative filtering algorithm locates other users having implicit and explicit profiles in the database that are similar to the profile of the querying user. A search engine returns items based on a keyword provided by the querying user. A sorting algorithm sorts the items returned by the cluster filtering algorithm, collaborative filtering algorithm and search engine for presentation to the querying user. Potential peers are also presented to the querying user. The items and potential peers presented are those most likely to be of help to the querying user.
Owner:GARTNER INC
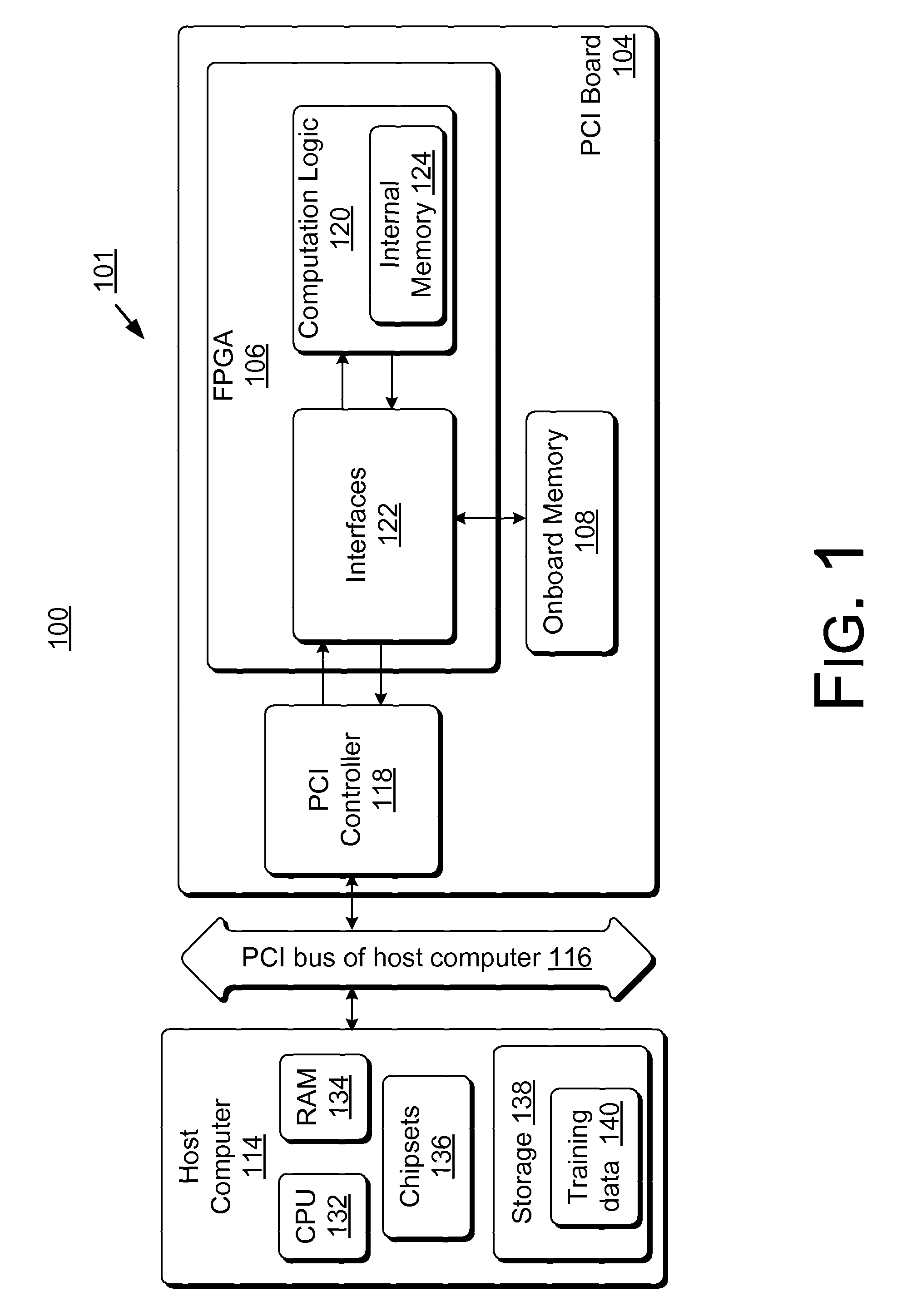
Field-programmable gate array based accelerator system
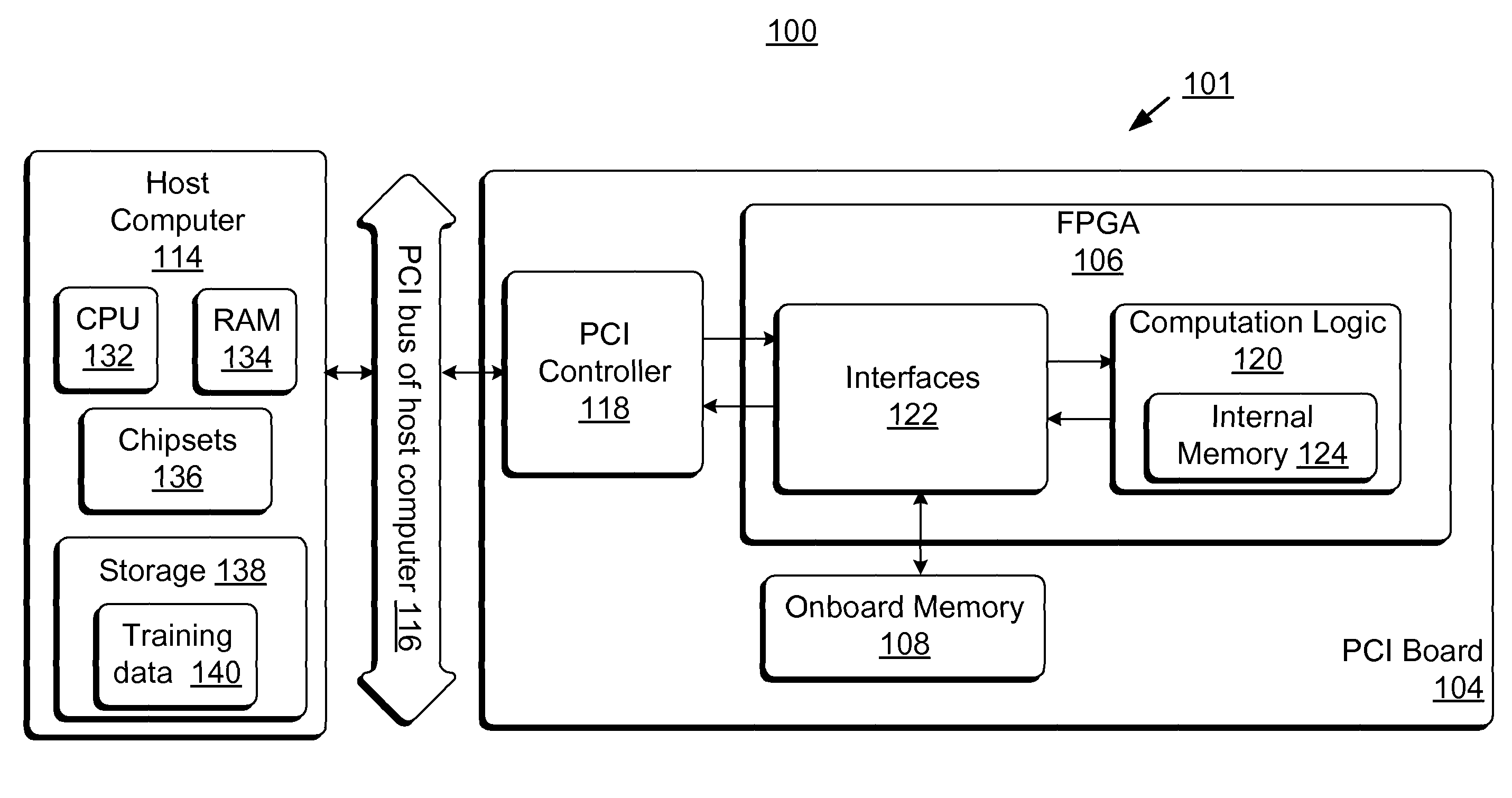
ActiveUS8131659B2Less timeLess costDigital computer detailsDigital dataHidden layerArithmetic logic unit
Accelerator systems and methods are disclosed that utilize FPGA technology to achieve better parallelism and processing speed. A Field Programmable Gate Array (FPGA) is configured to have a hardware logic performing computations associated with a neural network training algorithm, especially a Web relevance ranking algorithm such as LambaRank. The training data is first processed and organized by a host computing device, and then streamed to the FPGA for direct access by the FPGA to perform high-bandwidth computation with increased training speed. Thus, large data sets such as that related to Web relevance ranking can be processed. The FPGA may include a processing element performing computations of a hidden layer of the neural network training algorithm. Parallel computing may be realized using a single instruction multiple data streams (SIMD) architecture with multiple arithmetic logic units in the FPGA.
Owner:MICROSOFT TECH LICENSING LLC
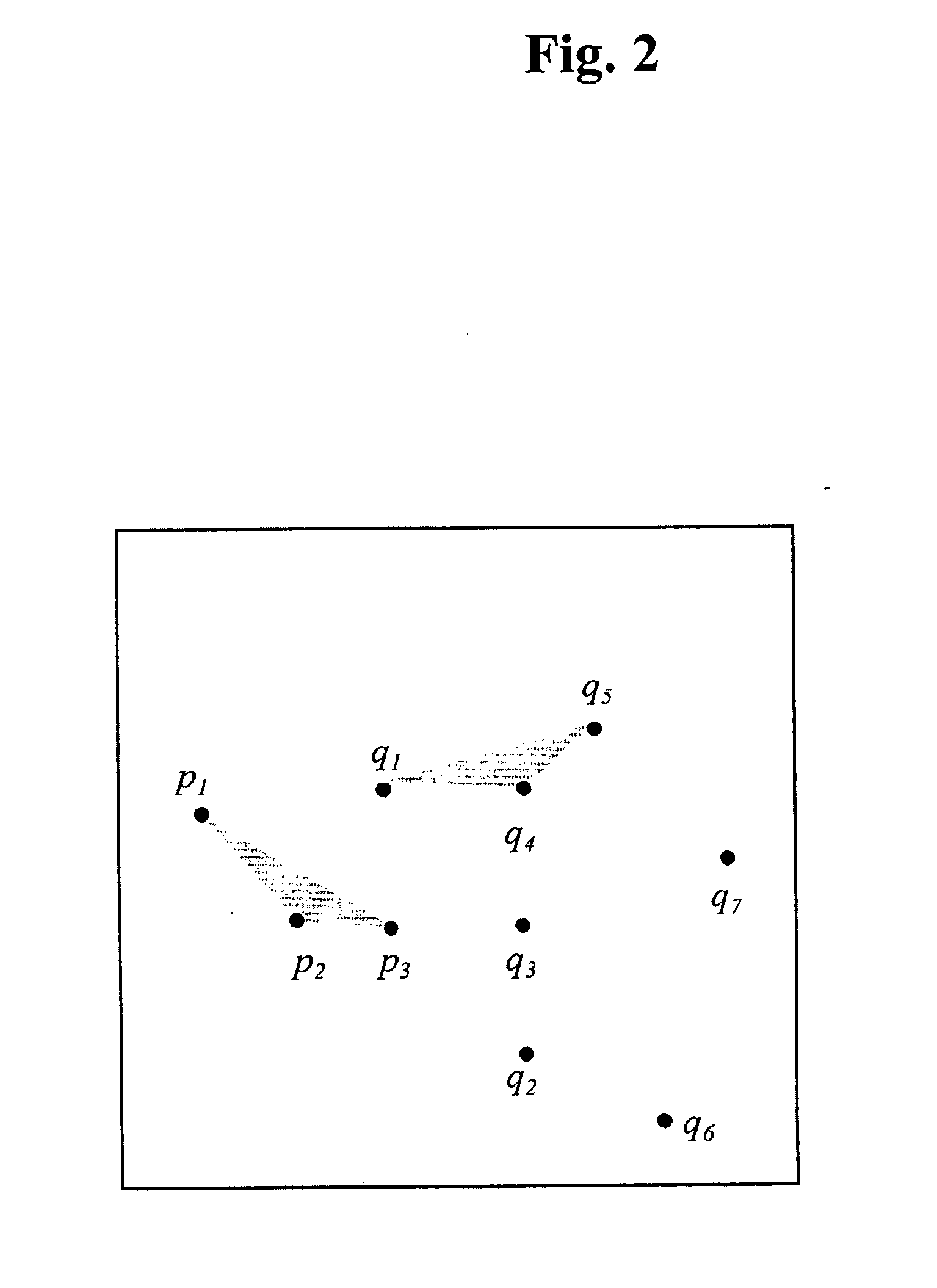
Distance sorting algorithm for matching patterns
The invention provides methods and systems for performing a matching function between a first pattern and a second pattern. This technique involves creating a set of all distance measurements between pairs of points in the first pattern and all distance measurements between pairs of points in the second pattern. This set is then partitioned into subsets of nearly equal distance elements. Those subsets containing at least one element derived from each pattern determine possible line segment matches which are then analyzed mathematically to determine the partial transform that maps the associated points of the first pattern into the points of the second pattern. The resulting set of partial transforms is then reviewed to determine matched line segments between the two patterns.
Owner:THE JOHN HOPKINS UNIV SCHOOL OF MEDICINE
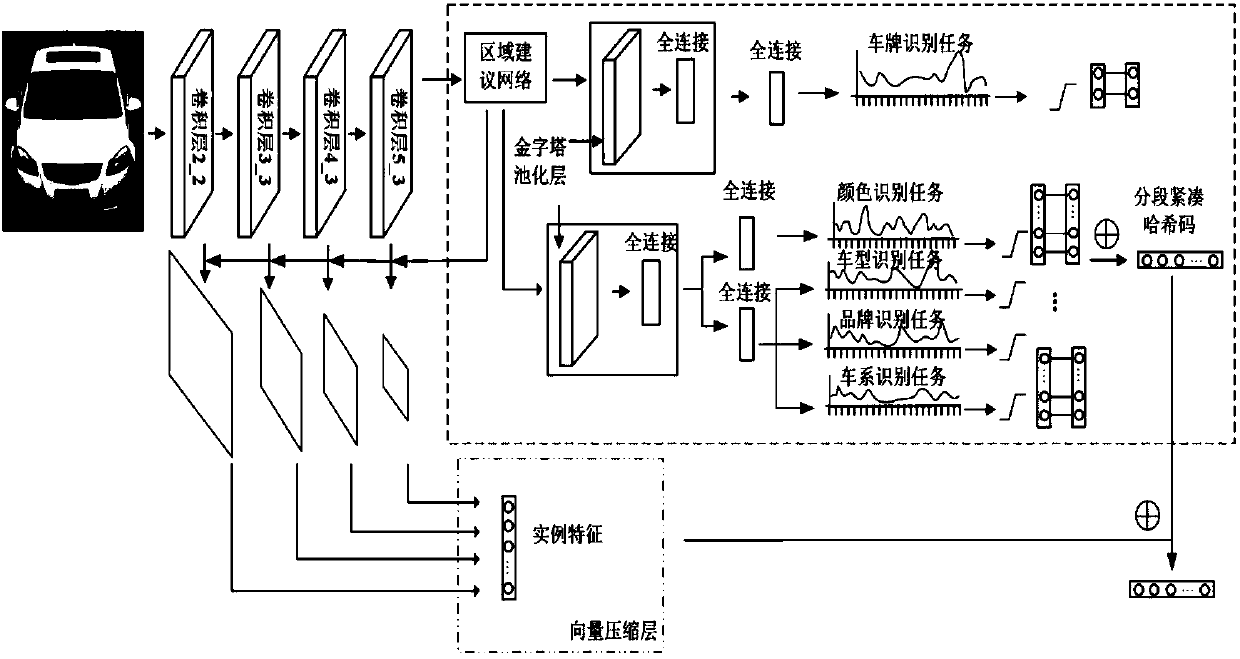
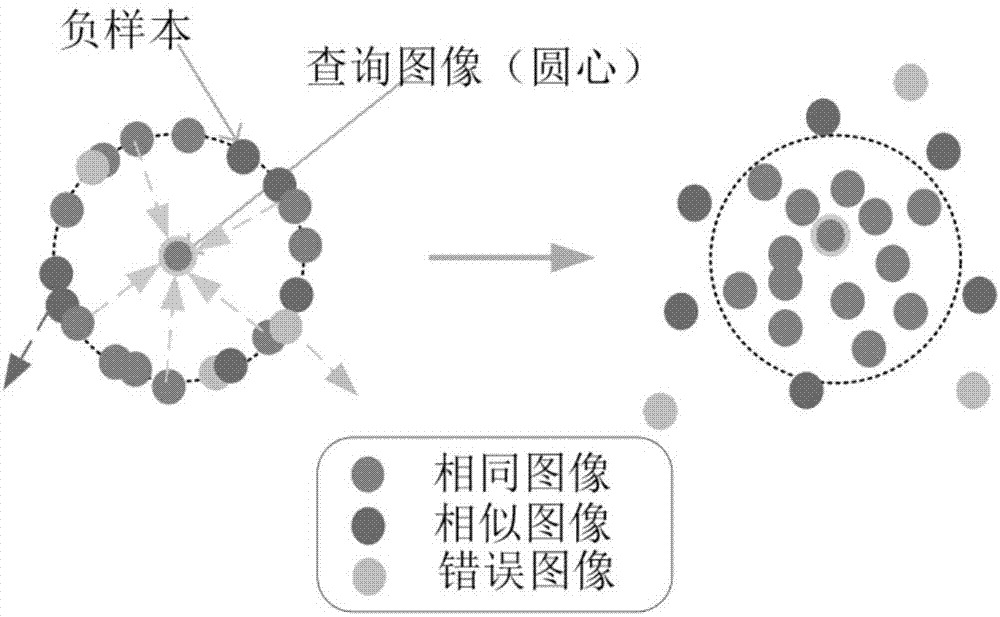
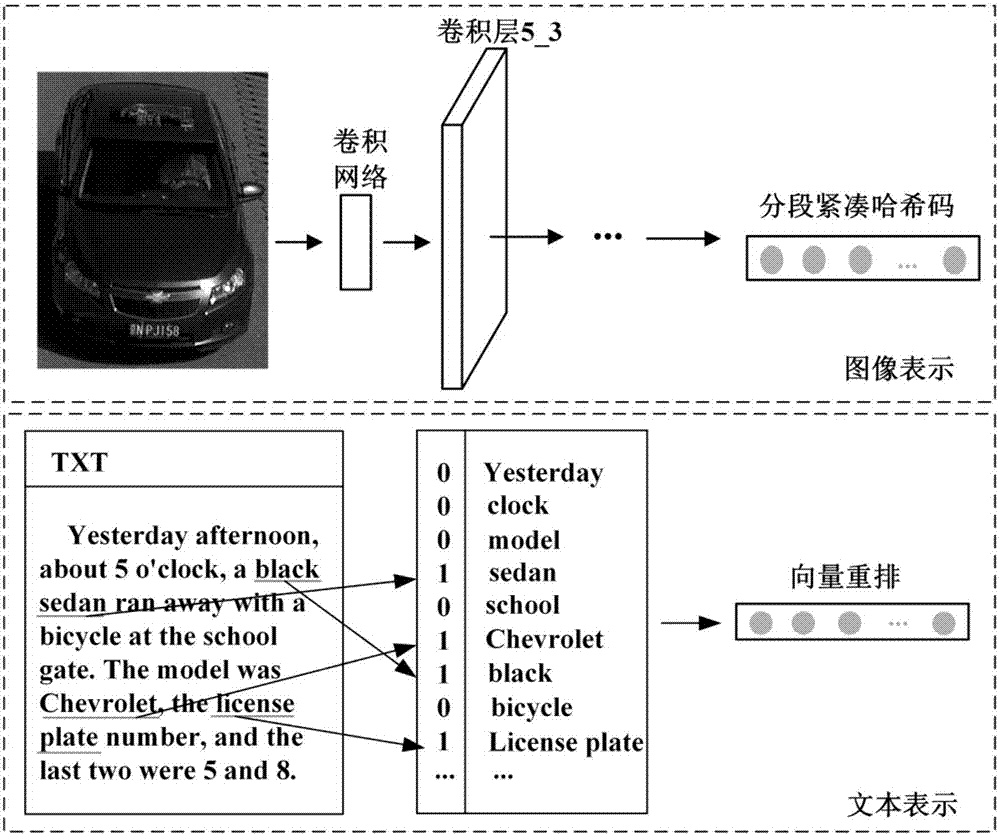
Fast hash vehicle retrieval method based on multi-task deep learning
ActiveCN107885764ASolve the problem of weak generalization abilityMaximize sharingCharacter and pattern recognitionNeural architecturesSorting algorithmSemantics
The invention provides a fast hash vehicle retrieval method based on multi-task deep learning. The fast hash vehicle retrieval method includes a multi-task deep convolutional neural network used for deep learning and training recognition, a segmented compact hash code and instance feature fusion method for improving the retrieval accuracy and the practicality of the retrieval method, a local sensitive hash reordering algorithm for improving the retrieval performance and a cross-modal retrieval method for improving the robustness and accuracy of a retrieval engine. In the fast hash vehicle retrieval method, firstly, a method for segmented learning of hash codes through a multi-task deep convolutional network is proposed, image semantics and image representation are combined, the connectionbetween related tasks is used for improving the retrieval accuracy and refining image features, and at the same time, minimizing image coding is used for making learned vehicle features more robust; secondly, a feature pyramid network is used for extracting the instance features of vehicle images; then, a local sensitive hash reordering method is used for retrieving the extracted features; and finally, a cross-modal assisted vehicle retrieval method is used for the special case in which target images of inquired vehicles cannot be obtained.
Owner:ENJOYOR COMPANY LIMITED
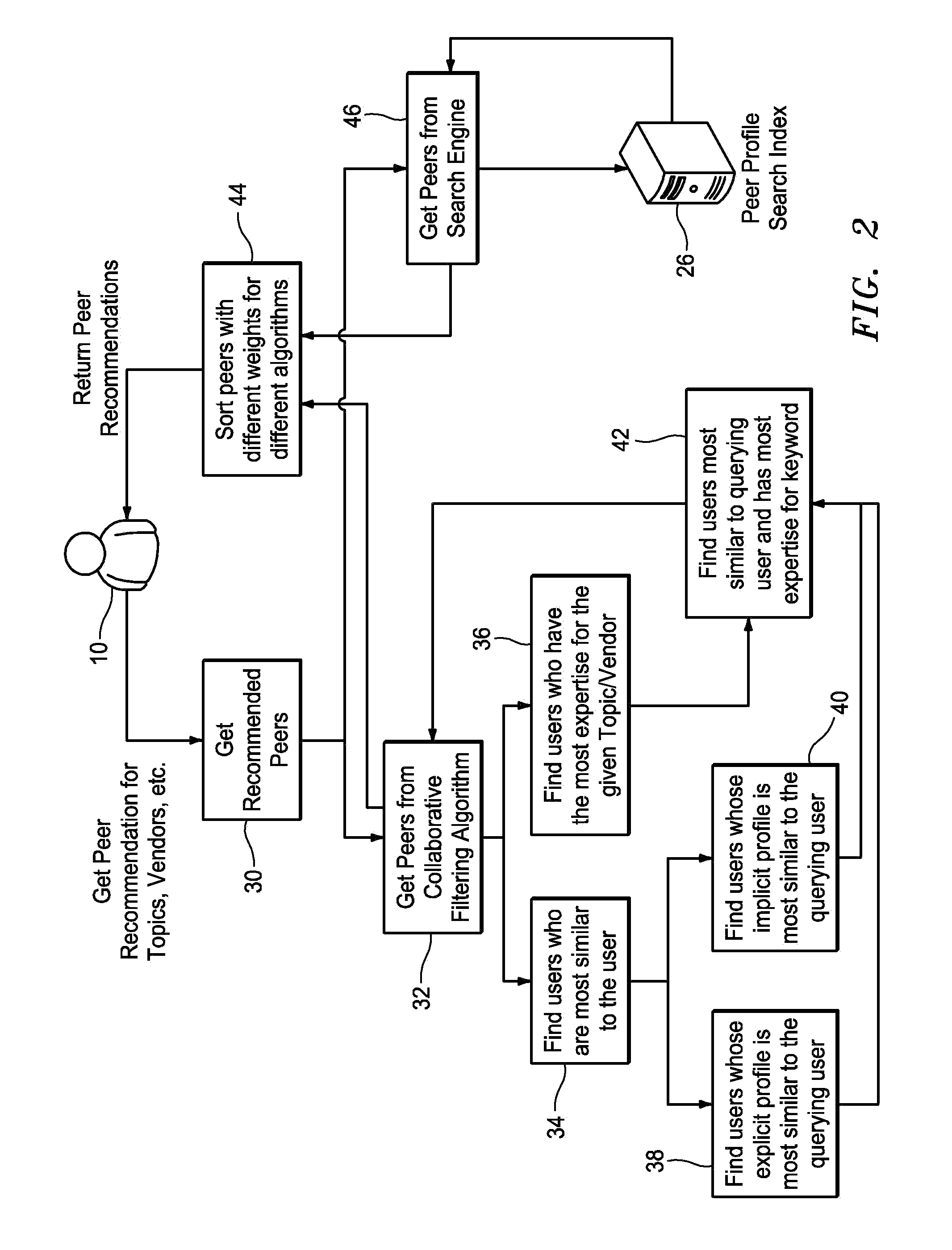
Bi-model recommendation engine for recommending items and peers
ActiveUS20130159325A1Improve future recommendationDigital data information retrievalDigital data processing detailsSorting algorithmFilter algorithm
A networked peer and item recommendation system makes recommendations to users such as documents of interest and peers with whom the users may want to connect. User profile information is maintained in a profiles database. A log enables the collection of user behavior information. A cluster filtering algorithm determines a cluster that a querying user belongs to. A collaborative filtering algorithm locates other users having implicit and explicit profiles in the database that are similar to the profile of the querying user. A dynamic expert verification algorithm is associated with the collaborative filtering algorithm to verify the qualifications of users and produce bias towards users with higher quality interactions. A search engine returns items based on a keyword provided by the querying user. A sorting algorithm sorts the items returned by the cluster filtering algorithm, collaborative filtering algorithm and search engine for presentation to the querying user.
Owner:GARTNER INC
Data communication method and apparatus utilizing programmable channels for allocation of buffer space and transaction control
InactiveUS20060179182A1Easy to adaptEfficient configurationError preventionTransmission systemsSorting algorithmIntegrated circuit
A control mechanism for data bus communications employs channels to which bus transactions are assigned, each channel having independent flow control. The control mechanism enforces an ordering algorithm among channels, whereby at least some transactions may pass other transactions. Channel attributes are programmable to vary the ordering conditions. Preferably, each channel is allocated its own programmable buffer area. The control mechanism independently determines, for each channel, whether buffer space is available and enforces flow control independently for each channel accordingly. Flow control is preferably credit-based, credits representing buffer space or some other capacity of a receiver to receive data. Preferably, the flow control mechanism comprises a central interconnect module controlling internal communications of an integrated circuit chip.
Owner:IBM CORP
Leaf sequencing algorithm for moving targets
ActiveUS7796731B2Undesirable effectHandling using diaphragms/collimetersX-ray/gamma-ray/particle-irradiation therapySorting algorithmIntensity modulation
A method of providing intensity modulated radiation therapy to a moving target is disclosed. The target moves periodically along a trajectory that is projected onto a multi-leaf collimator (MLC) plane. The MLC plane is divided into thin slices parallel to the movement of the target. The present invention optimizes the leaf sequence such that, within each slice, if a point receives radiation, all other points in that slice that receive the same amount or more fluence are also receiving radiation at the same time.
Owner:VARIAN MEDICAL SYST INT AG
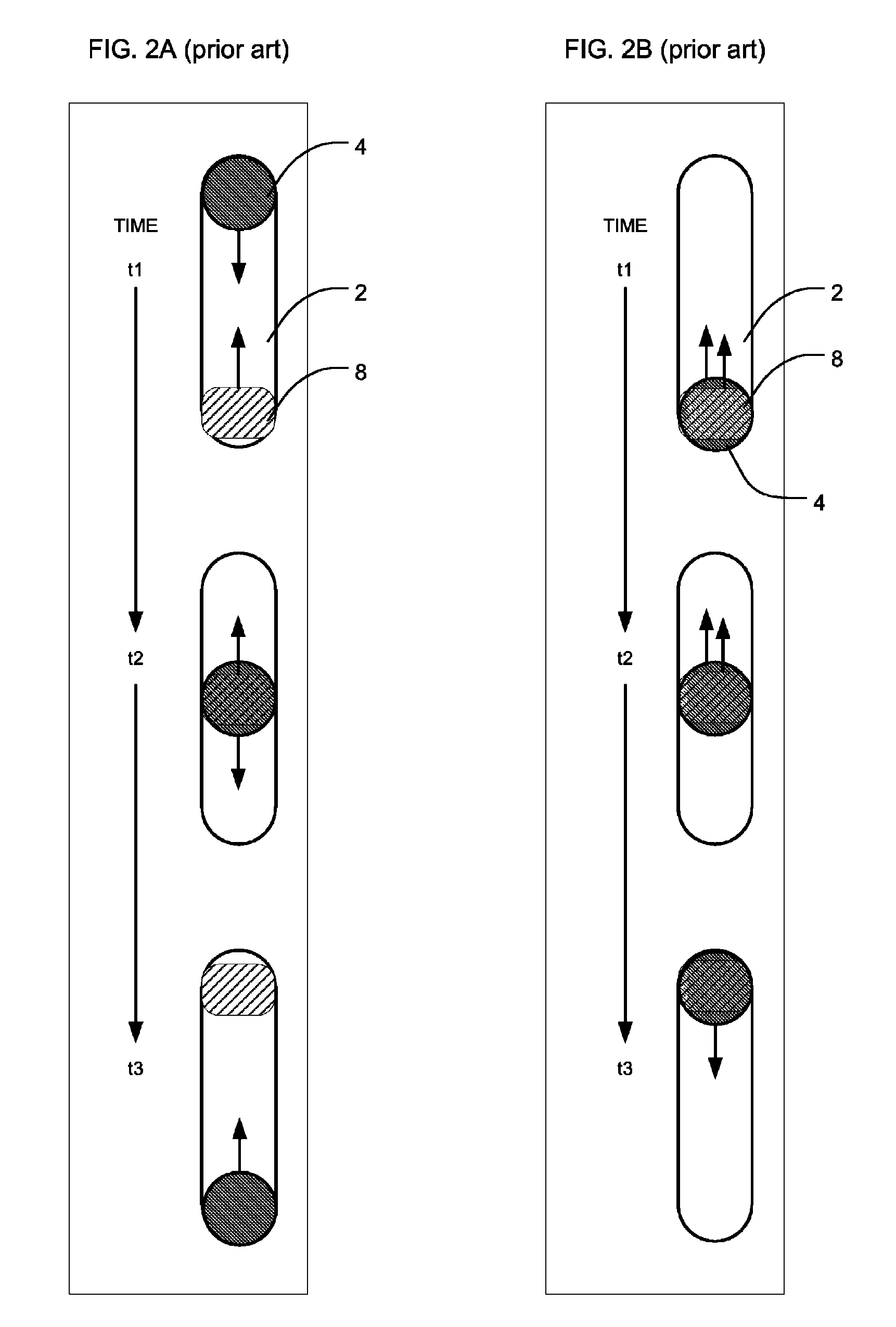
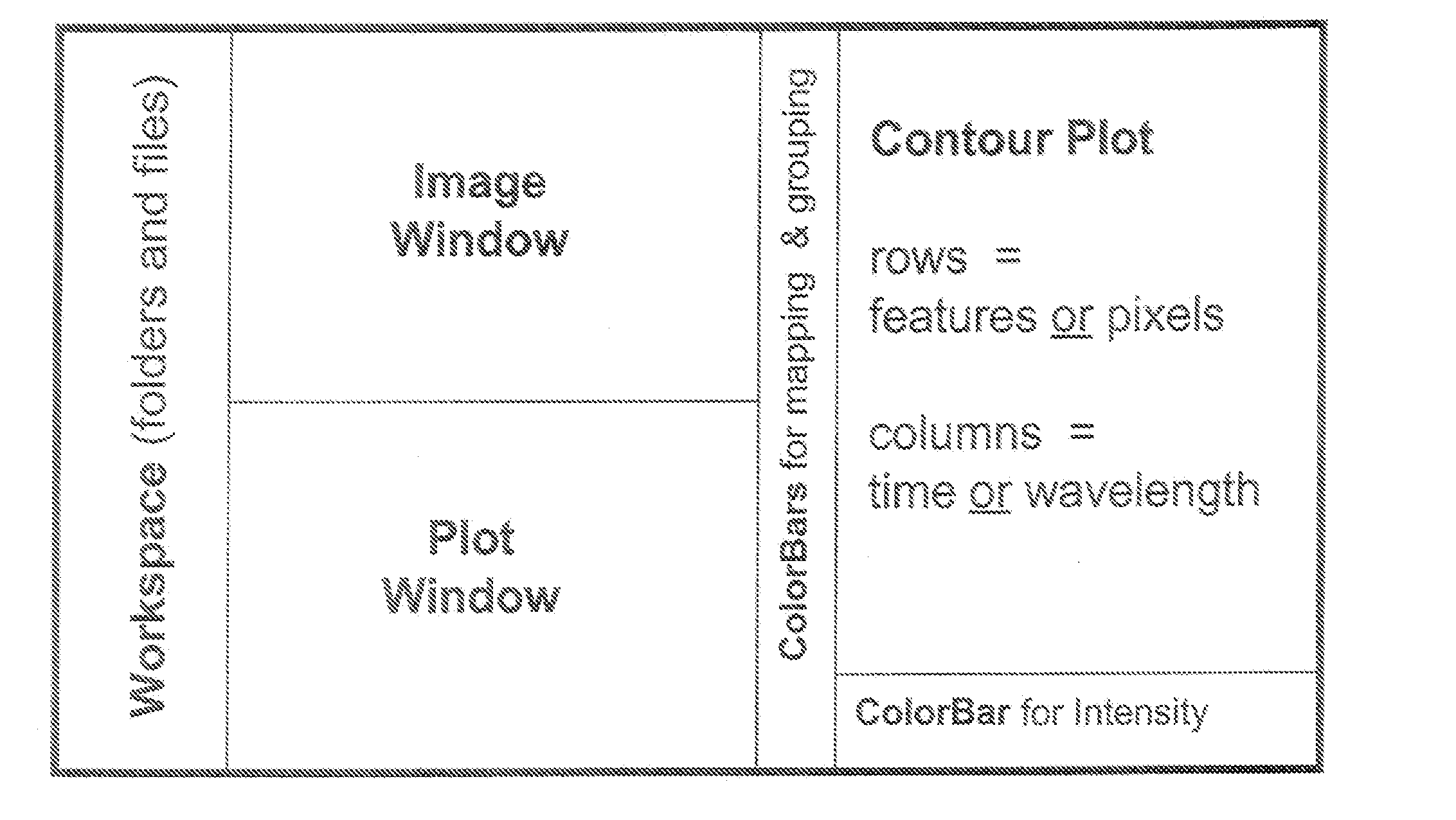
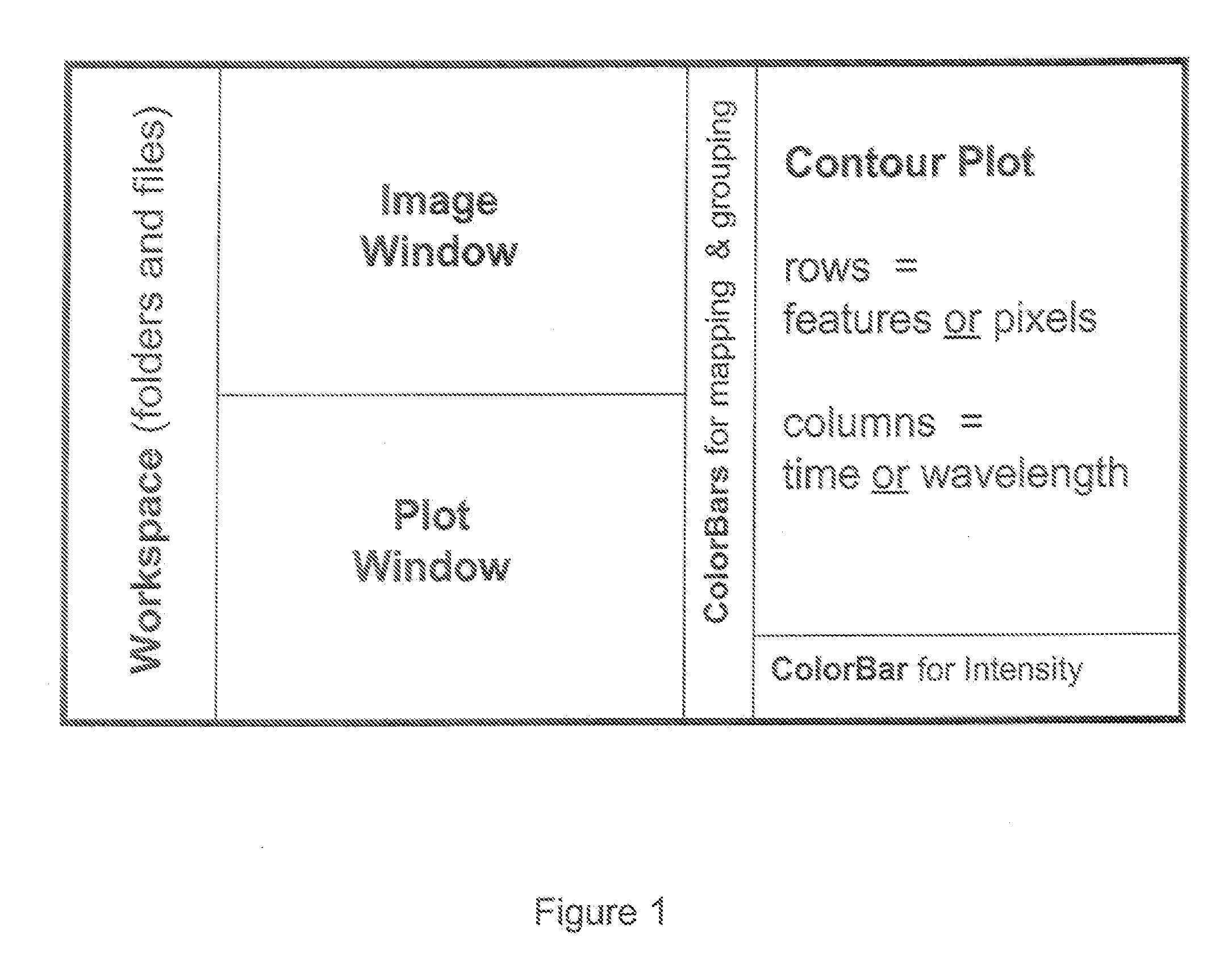
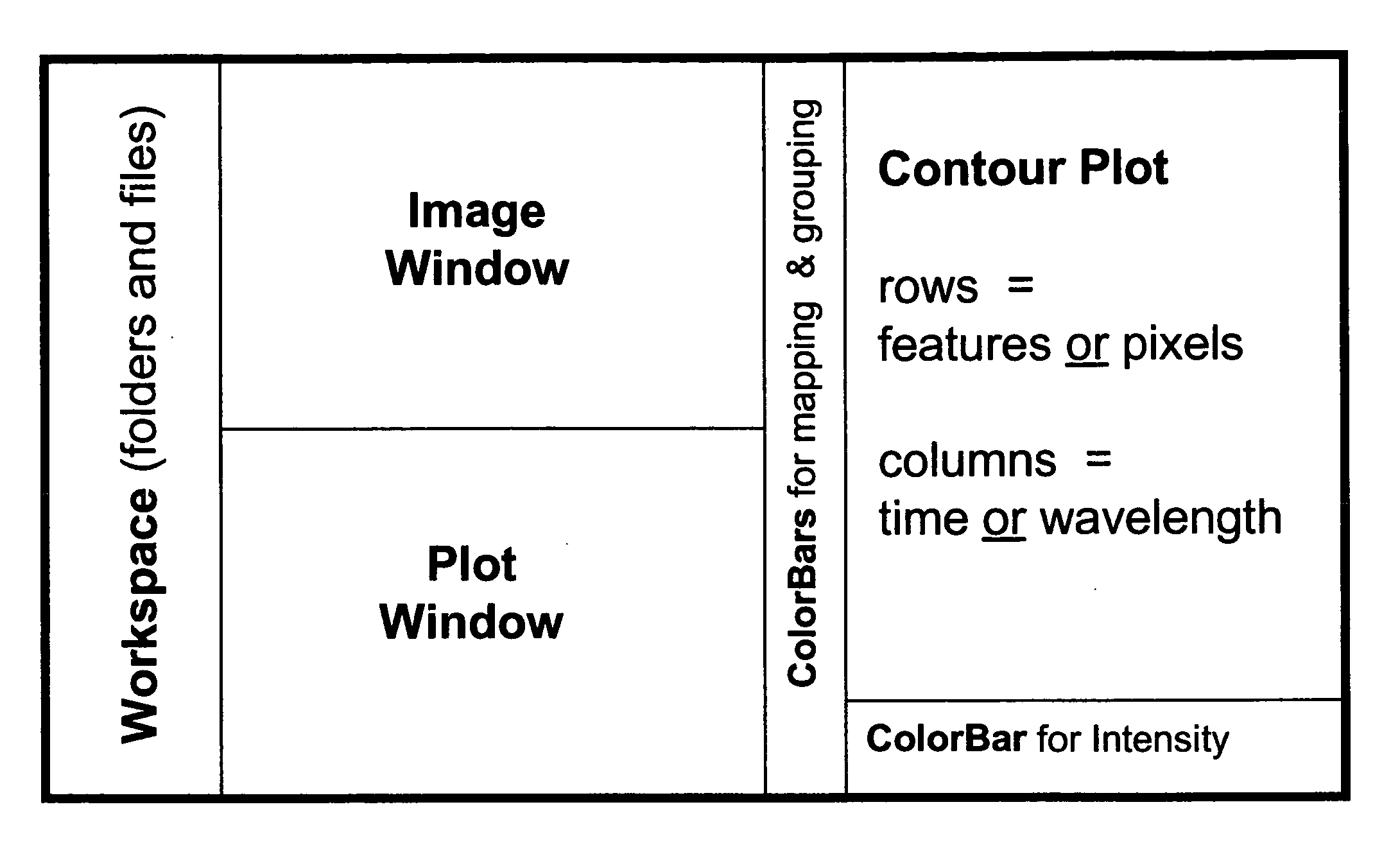
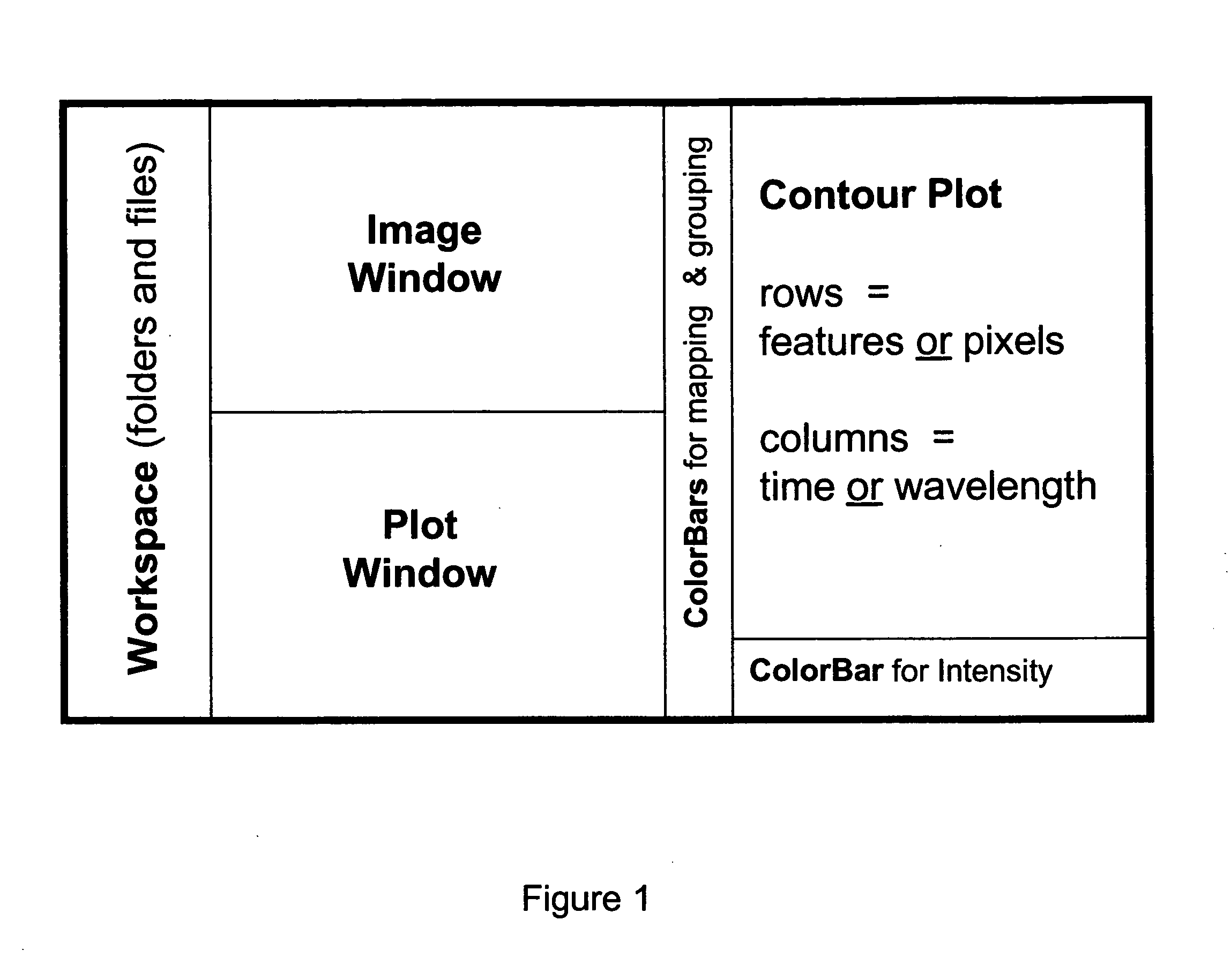
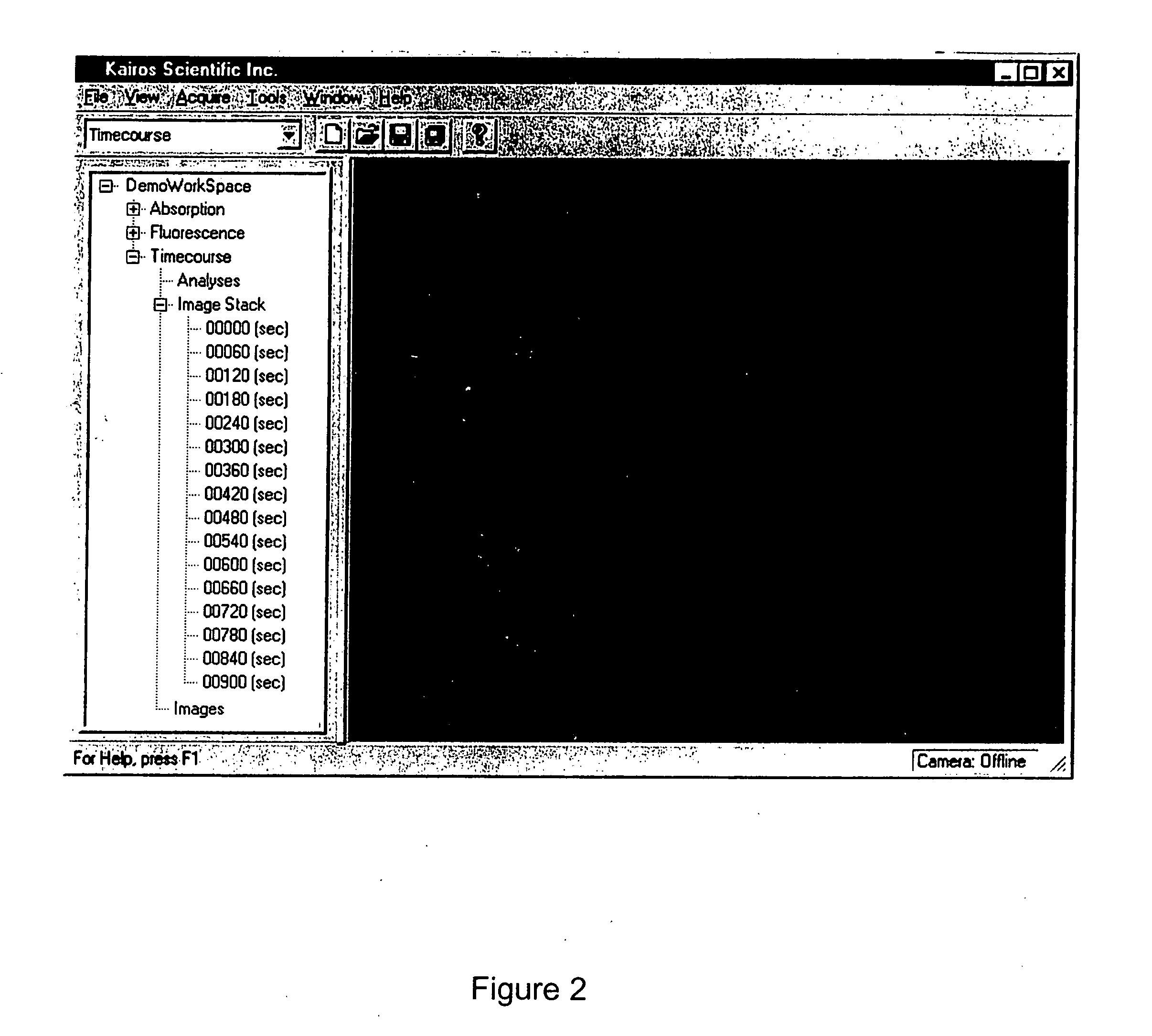
Visualization and Processing of Multidimensional Data Using Prefiltered and Sorting Criteria
InactiveUS20070217689A1Rapidly and efficiently extracting useful informationFacilitates independent sorting backcoloringImage enhancementImage analysisDigital imagingSorting algorithm
Complex multidimensional datasets generated by digital imaging spectroscopy can be organized and analyzed by applying software and computer-based methods comprising sorting algorithms. Combinations of these algorithms to images and graphical data, allow pixels or features to be rapidly and efficiently classified into meaningful groups according to defined criteria. Multiple rounds of pixel or feature selection may be performed based on independent sorting criteria. In one embodiment sorting by spectral criteria (e.g., intensity at a given wavelength) is combined with sorting by temporal criteria (e.g., absorbance at a given time) to identify microcolonies of recombinant organisms harboring mutated genes encoding enzymes having desirable kinetic attributes and substrate specificity. Restriction of the set of pixels analyzed in a subsequent sort based on criteria applied in an earlier sort (“sort and lock” analyses) minimize computational and storage resources. User-defined criteria can also be incorporated into the sorting process by means of a graphical user interface that comprises a visualization tools including a contour plot, a sorting bar and a grouping bar, an image window, and a plot window that allow run-time interactive identification of pixels or features meeting one or more criteria, and display of their associated spectral or kinetic data. These methods are useful for extracting information from imaging data in applications ranging from biology and medicine to remote sensing.
Owner:KAIROS SCI
Visualization and processing of multidimensional data using prefiltering and sorting criteria
InactiveUS20050114801A1Rapidly and efficiently extracting useful informationFacilitates independent sortingImage enhancementDrawing from basic elementsSorting algorithmDigital imaging
Complex multidimensional datasets generated by digital imaging spectroscopy can be organized and analyzed by applying software and computer-based methods comprising sorting algorithms. Combinations of these algorithms to images and graphical data, allow pixels or features to be rapidly and efficiently classified into meaningful groups according to defined criteria. Multiple rounds of pixel or feature selection may be performed based on independent sorting criteria. In one embodiment sorting by spectral criteria (e.g., intensity at a given wavelength) is combined with sorting by temporal criteria (e.g., absorbance at a given time) to identify microcolonies of recombinant organisms harboring mutated genes encoding enzymes having desirable kinetic attributes and substrate specificity. Restriction of the set of pixels analyzed in a subsequent sort based on criteria applied in an earlier sort (“sort and lock” analyses) minimize computational and storage resources. User-defined criteria can also be incorporated into the sorting process by means of a graphical user interface that comprises a visualization tools including a contour plot, a sorting bar and a grouping bar, an image window, and a plot window that allow run-time interactive identification of pixels or features meeting one or more criteria, and display of their associated spectral or kinetic data. These methods are useful for extracting information from imaging data in applications ranging from biology and medicine to remote sensing.
Owner:YANG MARY M +5
Integrative searching result sequencing system and method
ActiveCN101079033AIncrease flexibilityMeet individual needsSpecial data processing applicationsPersonalizationSorting algorithm
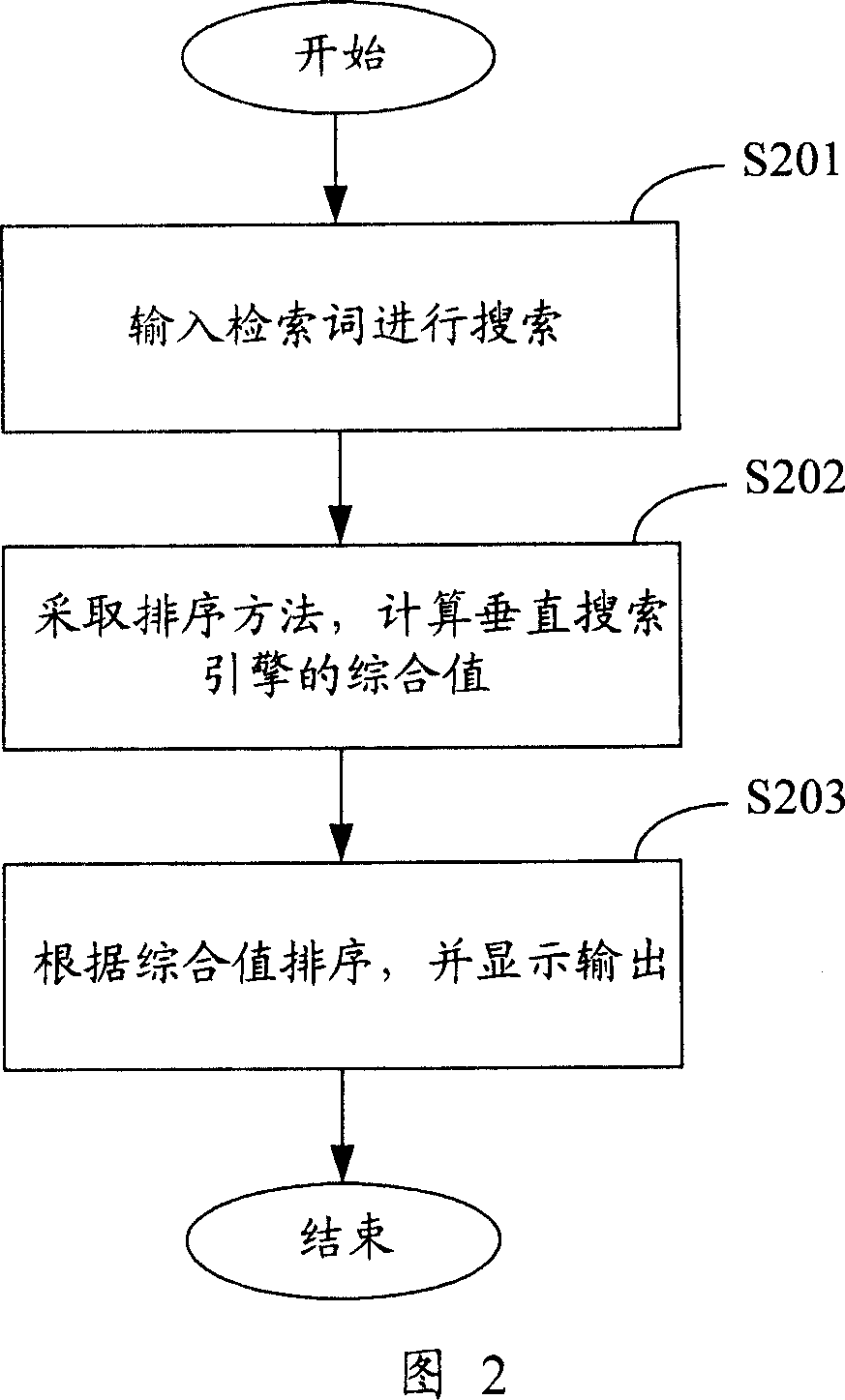
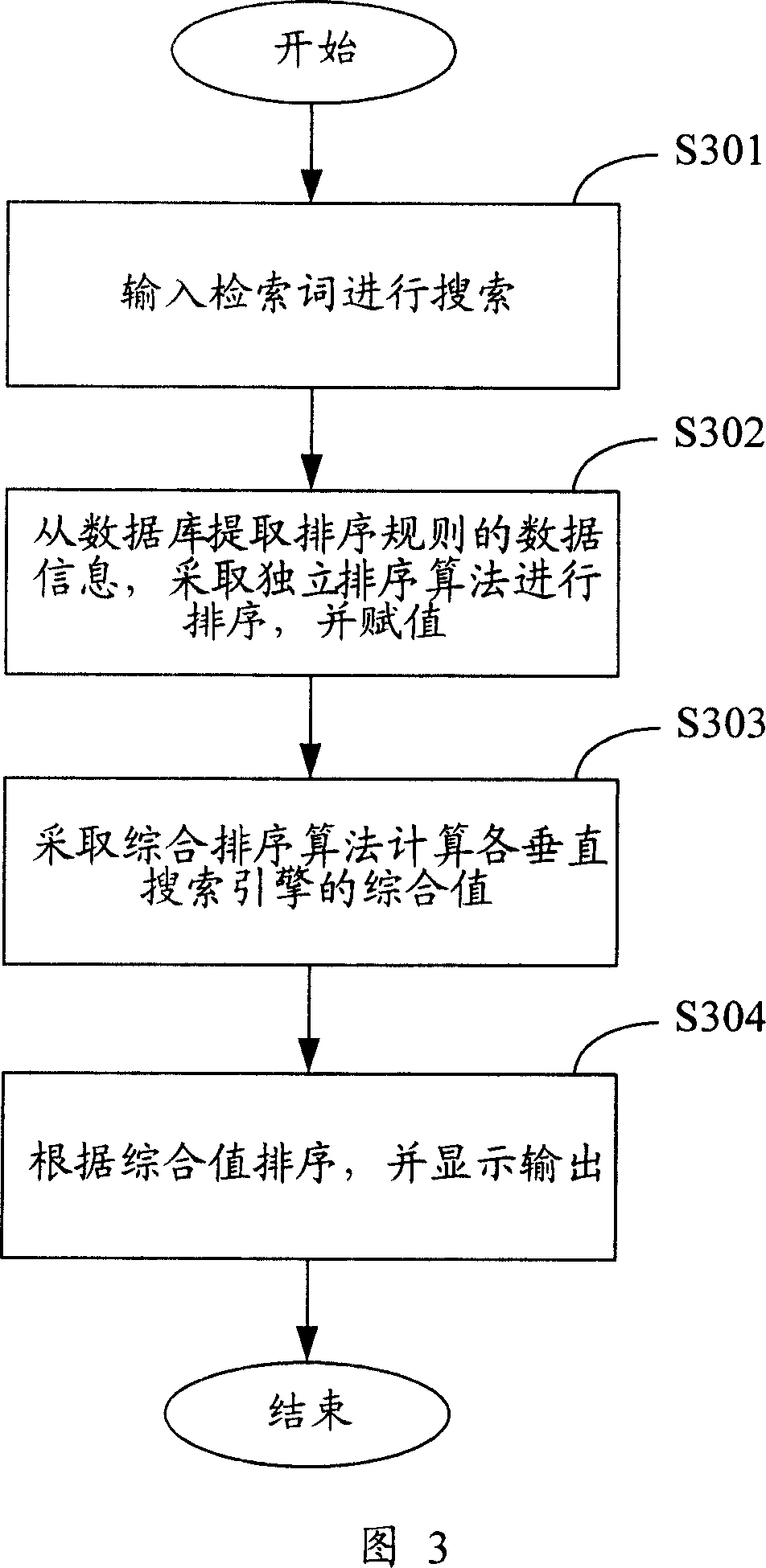
The invention discloses an ordering system of comprehensive searching result and method in data treating domain, which comprises the following steps: A, inputting term to the comprehensive searching engine; searching; getting all vertical searching engine result; B, extracting data information from the data bank with the ordering module; adopting sort algorithm; calculating each comprehensive value of vertical searching engine in the searching result; C, comparing comprehensive value of each vertical searching engine; ordering for the vertical searching engine; displaying the final ordering information; outputting. This invention can enhance flexibility for comprehensive searching result, which can meet personalized demand of the users.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
Sorting method of vehicle-mounted laser scanning point cloud data of urban ground objects
InactiveCN103390169AHigh degree of adaptabilityHigh degree of automationCharacter and pattern recognitionElectromagnetic wave reradiationSorting algorithmLaser scanning
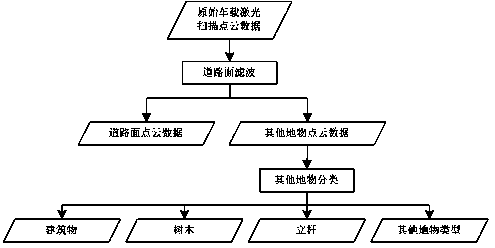
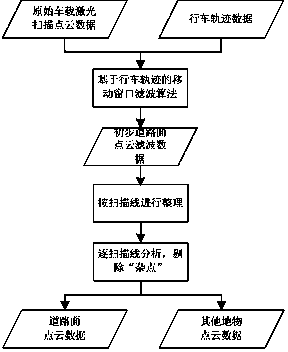
The invention provides a sorting method of vehicle-mounted laser scanning point cloud data of urban ground objects. The method mainly comprises two steps as follows: original vehicle-mounted laser scanning point cloud data are subjected to road surface filtering in combination of vehicle tracking data, and point cloud data of a road surface are separated from point cloud data of other ground objects; and the obtained point cloud data of other ground objects are further identified to be different ground object types. In the road surface filtering algorithm, the vehicle tracking data are combined, and a histogram statistic and analytical method is introduced, so that the self-adaption degree, the automation degree and the accuracy of the filtering algorithm of the road surface in an urban environment are improved greatly; and in the sorting algorithm of other ground objects, a point cloud feature image sorting method based on the maximum elevation value is improved, mistakenly sorted point cloud data are corrected with a cellular automaton technology, and a new thought and method are provided for the sorting algorithms of vehicle-mounted laser scanning point cloud data.
Owner:WUHAN UNIV
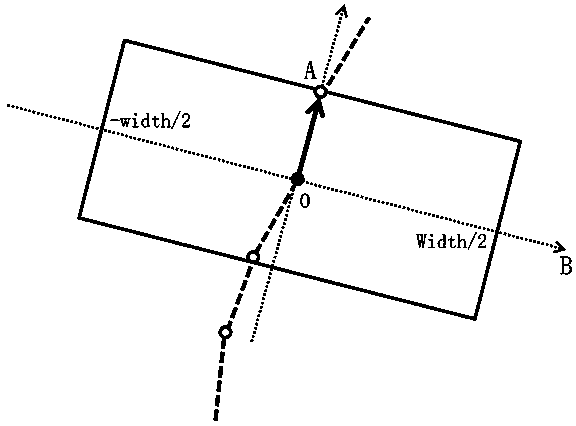
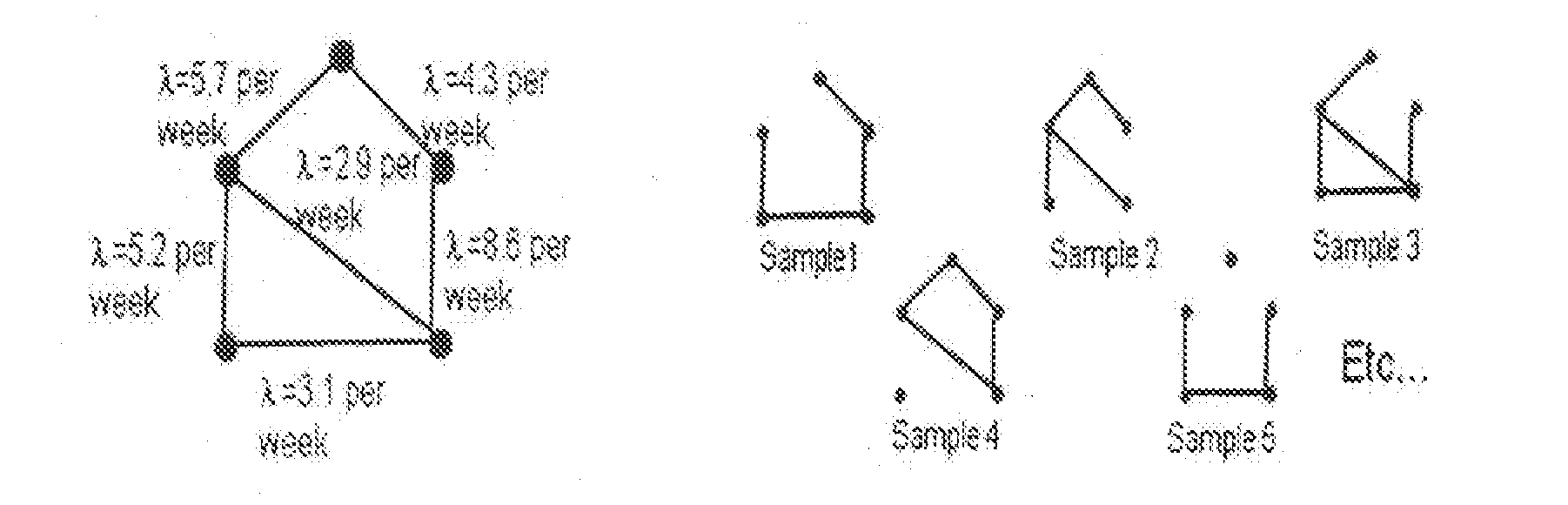
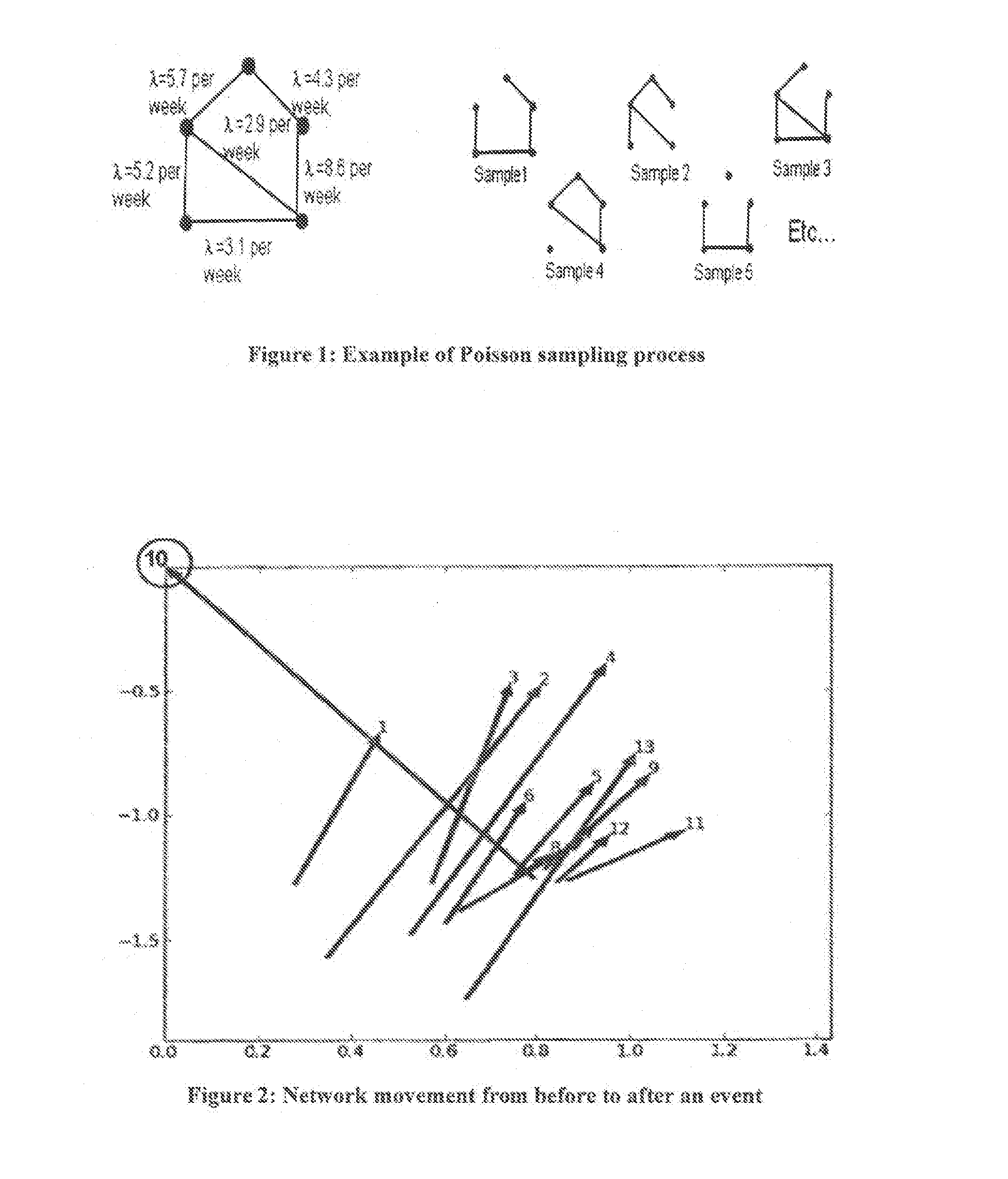
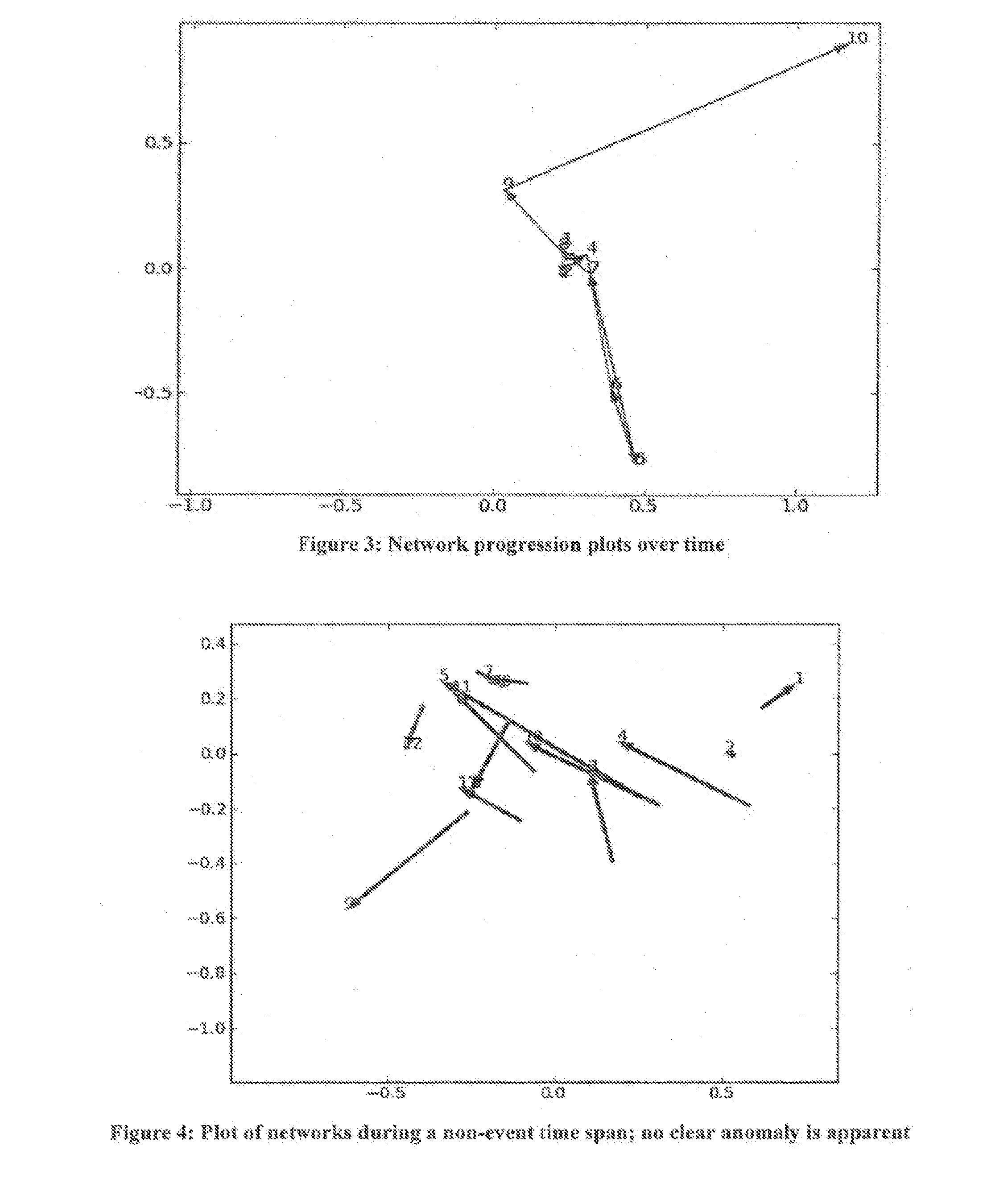
Method and apparatus for identifying a threatening network
A system and method for identifying a threatening network is provided. The system comprises a network movement before / after algorithm that provides a graphical plot of changes in networks' communications activity from before to after a key event occurs, so that an analyst is able to identify anomalous behavior; a network progression algorithm that provides a graphical plot to analyze behavior in small increments of time without specification or emphasis upon a particular event, so that the analyst is able to see a trend in behavioral changes; a statistical network anomaly ranking algorithm that provides as output a ranked list of the networks; and an anomaly trend graphs algorithm that analyzes and visualizes the networks' anomaly scores over time, so that the analyst is able to see which networks are consistently suspicious, which networks accumulate more suspiciousness in response to an event, and which networks are trending toward more suspiciousness.
Owner:21ST CENTURY TECH
Computer-Implemented Method For Enhancing Product Sales
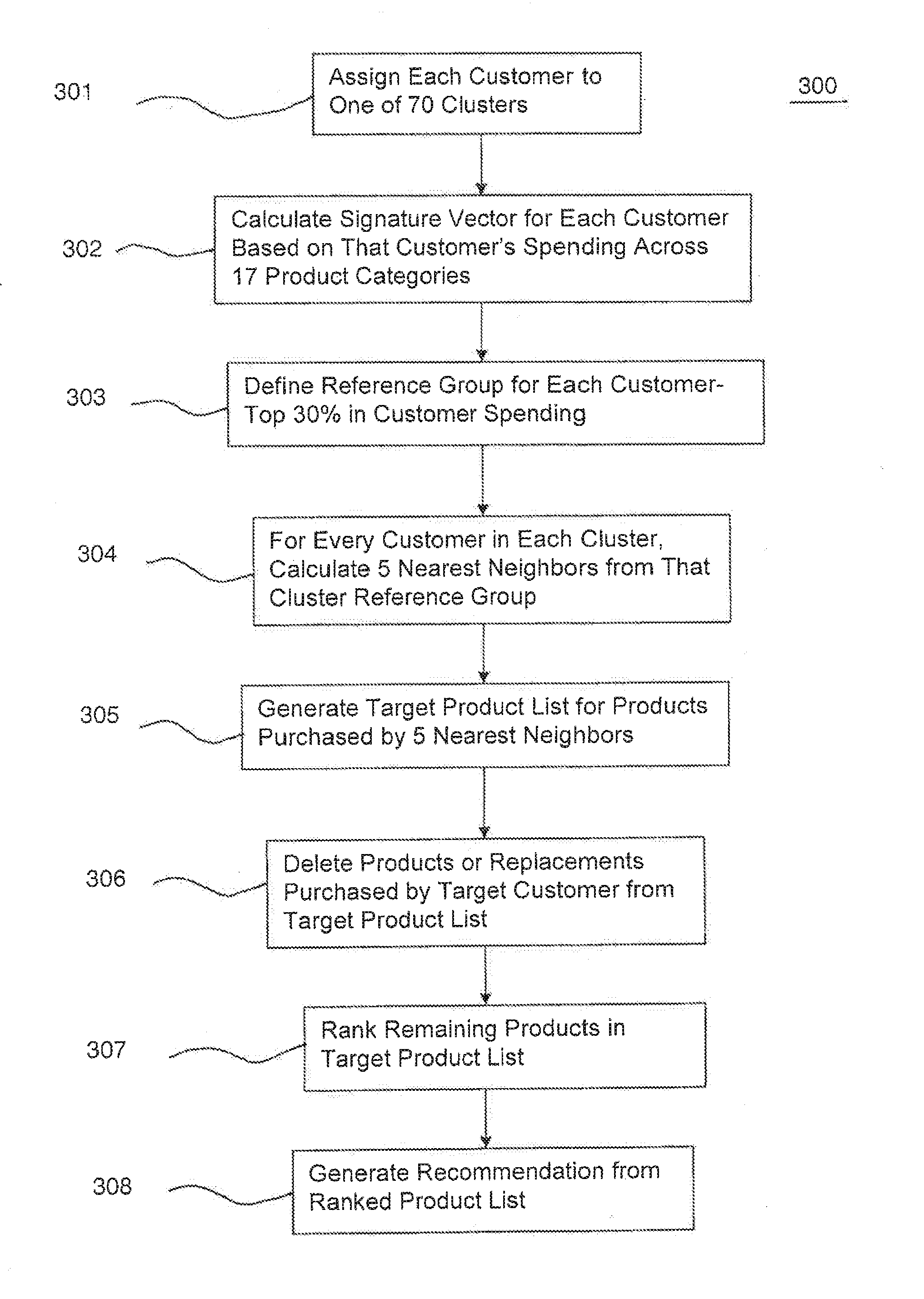
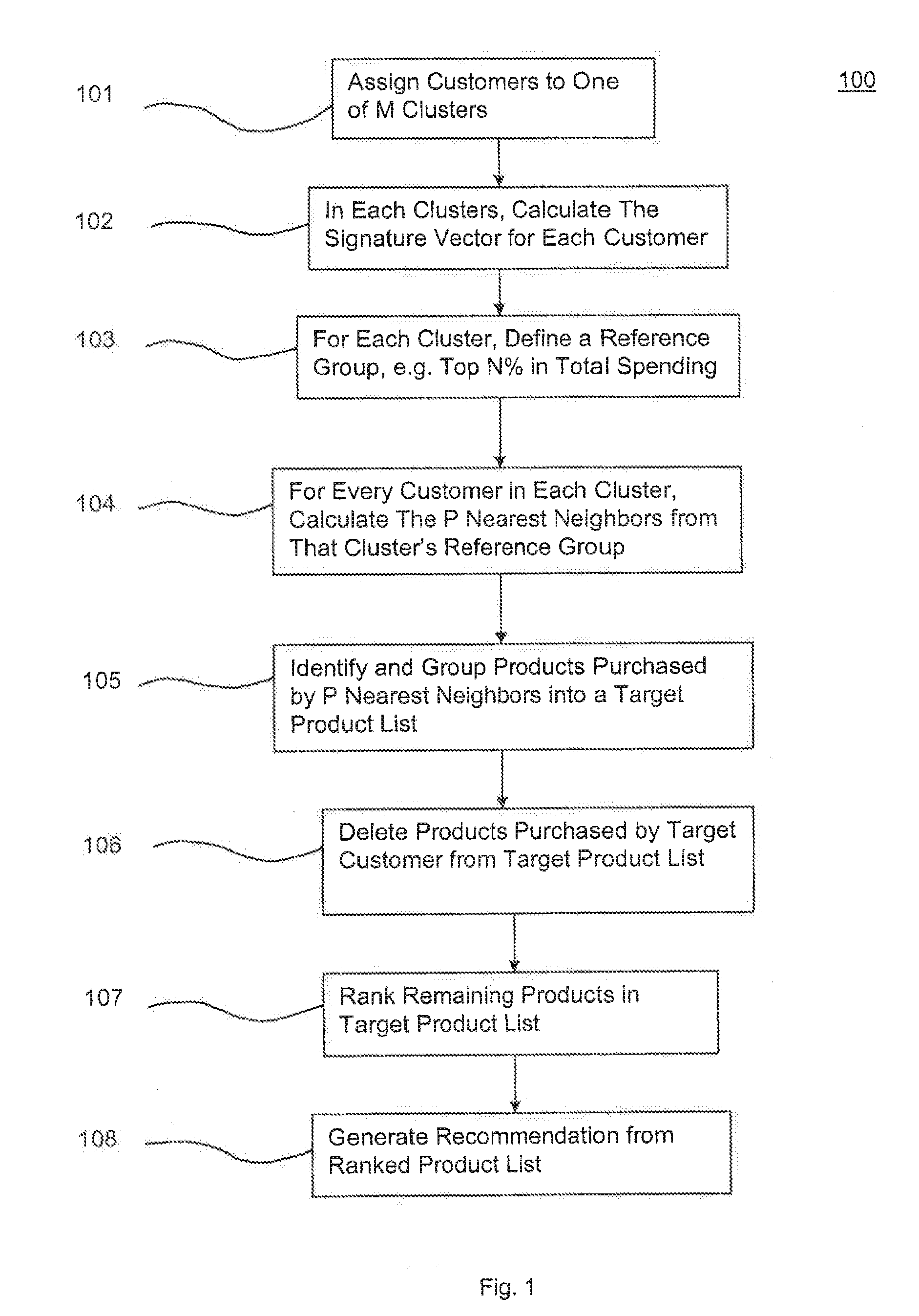
InactiveUS20110213661A1Fuzzy logic based systemsBuying/selling/leasing transactionsSorting algorithmNear neighbor
A computer-implemented method for providing product recommendations to customers is disclosed. For each customer for whom a product recommendation is desired, hereinafter “the target customer”, a group of other customers, hereinafter “a group of nearest neighbors” is identified using an algorithm that examines each customer's previous spending across a plurality of different product categories and optionally, one or more demographic attributes, and then selects those customers whose attributes most nearly matches that of the target customer. The products purchased by these nearest neighbors that have not been purchased by the target customer are then ranked using a ranking algorithm that weights such purchased products based on the frequency of their purchase and the number of nearest neighbors purchasing such products. A product recommendation for the target customer is formed by selecting a predetermined number of the highest ranked products purchased by the nearest neighbors.
Owner:OPERA SOLUTIONS
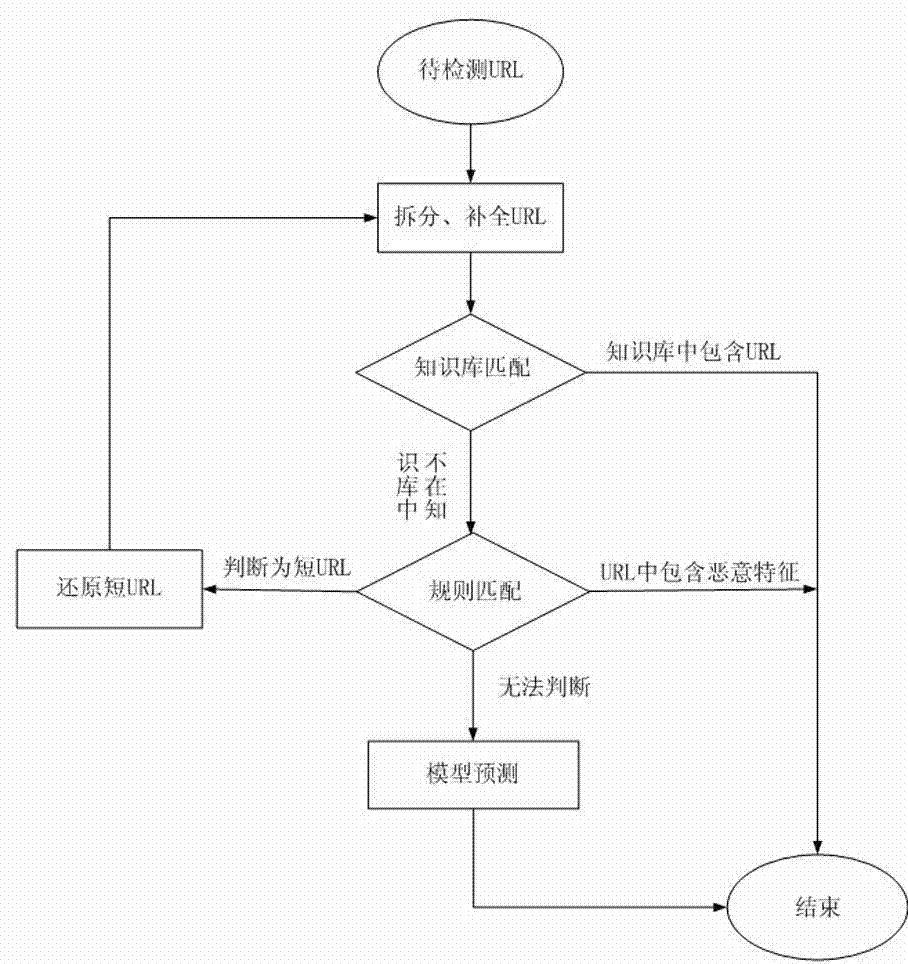
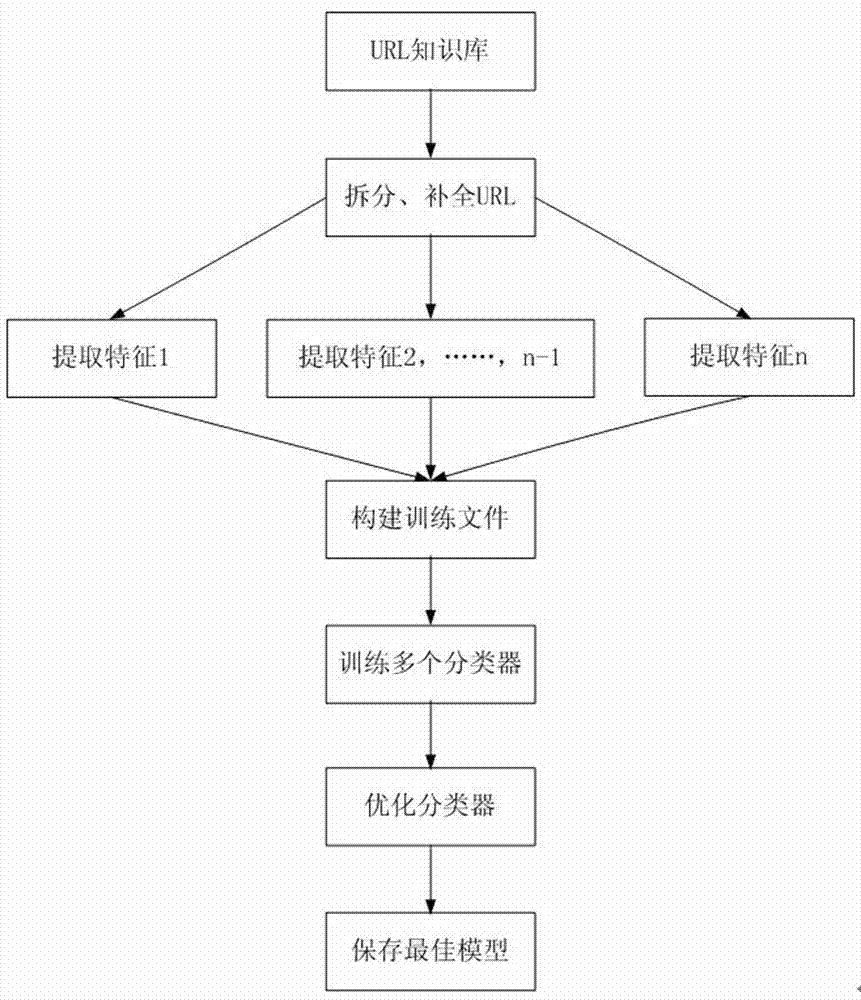
Malicious URL detection method and implement system thereof
The invention discloses a malicious URL detection method and a system. The method comprises the steps of splitting a URL to be detected into character strings according to a URL grammar and a semantic structure in the RFC1738 standard; analyzing, completing and modifying the character strings which are obtained by splitting; aiming at a new URL formed by the processed character strings, traversing and matching a URL knowledge base; judging whether the new URL contains malicious features and belongs to a short URL according to rules, and if the new URL belongs to the short URL, restoring the short URL into a long URL; finally, extracting the features from the URL knowledge base, applying a sorting algorithm training model through machine learning, and predicting the malicious property of the URL. By applying the method and the system, the flexibility and eversporting property of URL forms are solved, a newly-emerging malicious website can be recognized, the harm from the malicious URL can be effectively resisted, and the safety performance of user information can be substantially improved.
Owner:JIANGSU PAYEGIS INFORMATION SECURITY TECH CO LTD
Adaptive hierarchy structure ranking algorithm
InactiveUS20070162448A1Digital data information retrievalDigital data processing detailsSorting algorithmPaper document
The present invention is a method for ranking a plurality of documents during a search query utilizing a hierarchical keyword ranking scheme. The present invention utilizes an algorithm which determines a level value for each searched page in the plurality of documents. The algorithm then ranks each page from the plurality of documents by extracting keywords from each document and determining a page keyword rank for each searched page. Next, a hierarchical keyword rank is determined based upon the level value and the page keyword rank for each page. This hierarchical keyword rank is used to rank order the searched documents in order of importance.
Owner:JAIN ASHISH +1
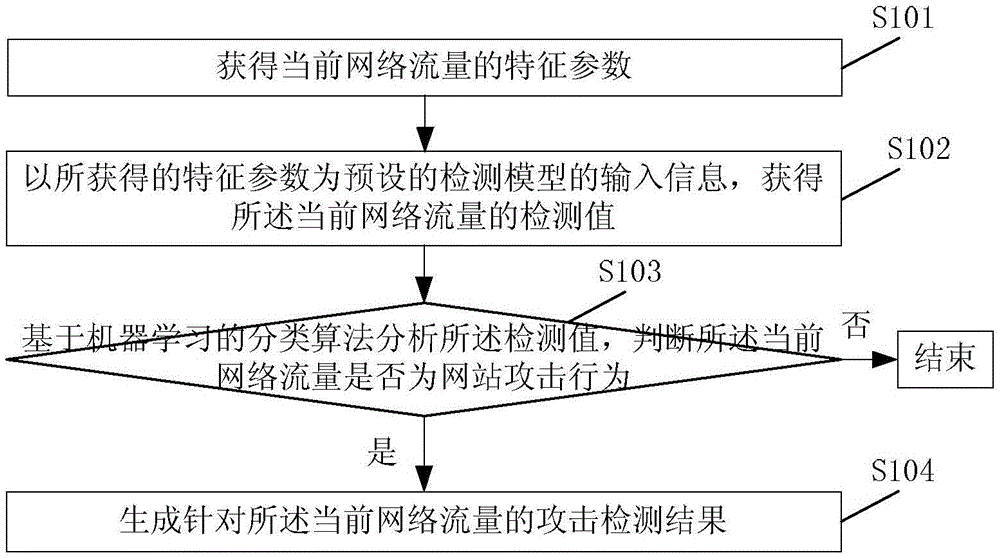
Method and device for detecting website attack behaviors based on machine learning
The embodiment of the invention discloses a method and a device for detecting website attack behaviors based on machine learning, applied to a server. The method comprises the steps of acquiring the feature parameters of a current network flow, using the acquired feature parameters as the input information of a preset detection model, and acquiring the detection value of the current network flow, wherein the detection value is the feature value used for representing that the current network flow is the website attack behavior, the detection model is the one aiming at the feature parameters; updating the detection model according to the acquired feature parameters in the case of meeting preset updating conditions; analyzing the detection value based on the sorting algorithm of machine learning for judging whether the current network flow is the website attack behavior; and if yes, generating the attack detection result aiming at the current network flow. With the application of the method, the network environment which develops quickly can be adapted, and the detection rate of the website attack behaviors can be improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM +1
Data processing method based on knowledge map
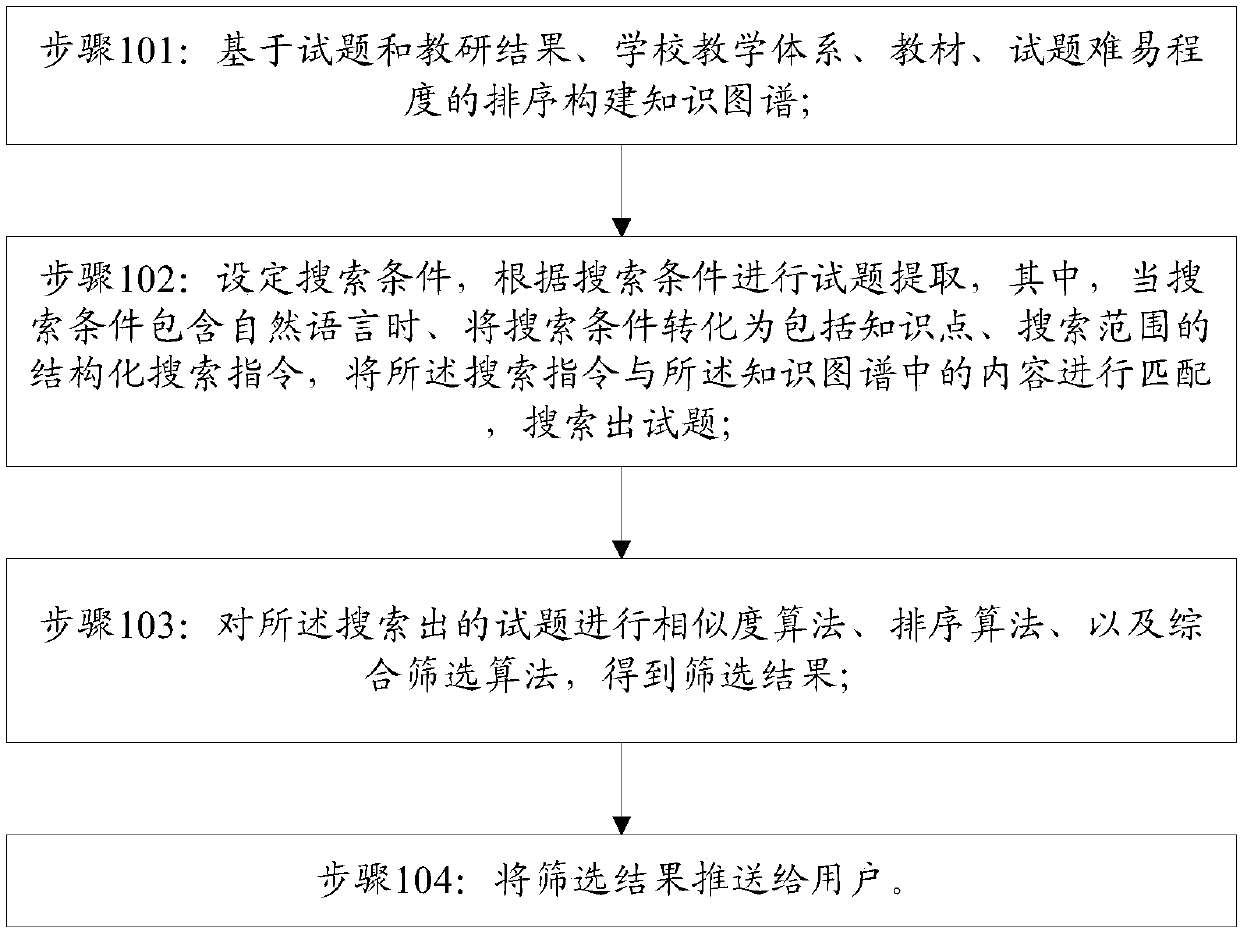
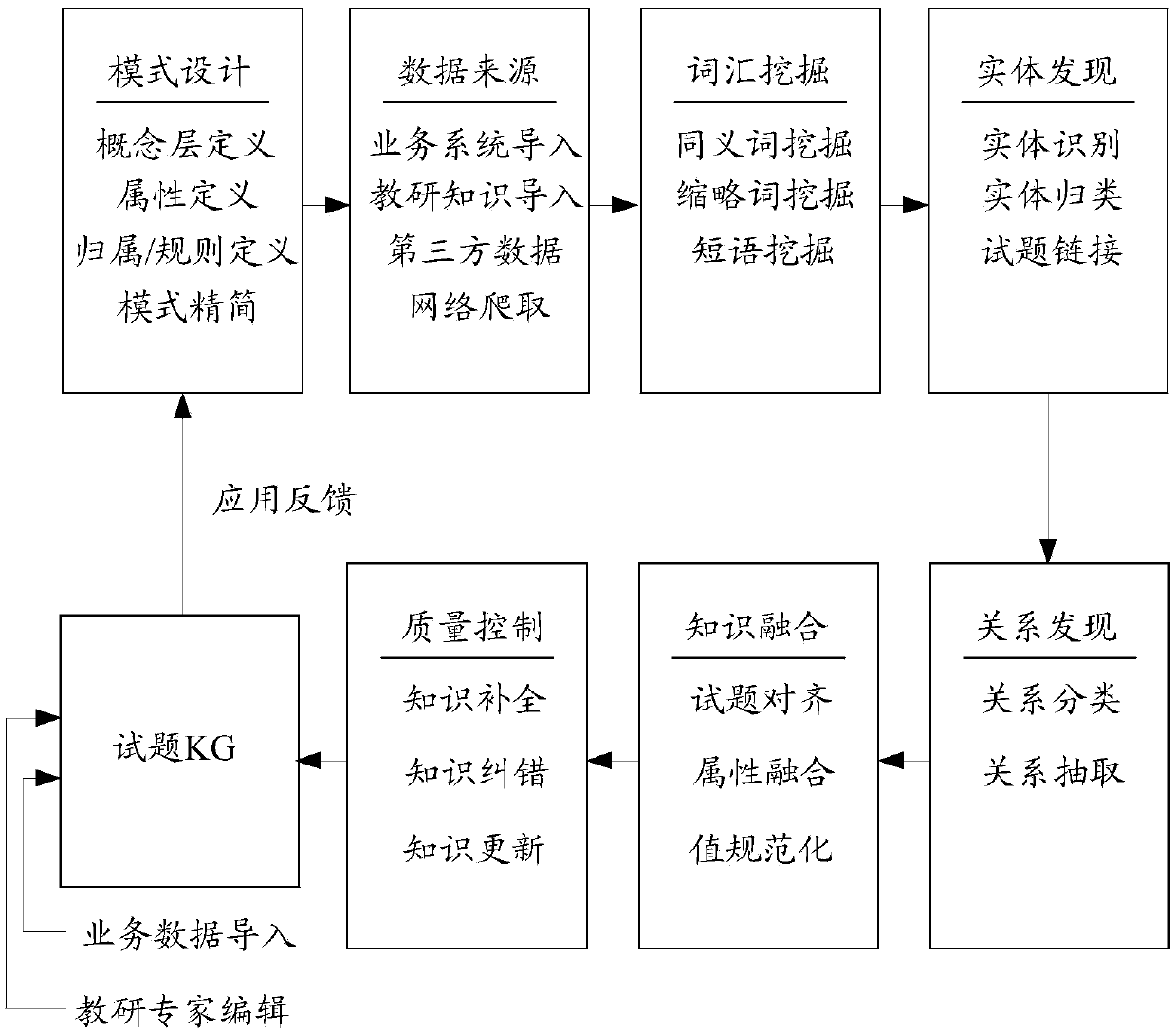
ActiveCN109255031ASimplify the search processImprove the efficiency of searching for test questionsText database clustering/classificationSemantic tool creationSorting algorithmScreening algorithm
The invention discloses a data processing method based on a knowledge map, which comprises the following steps: constructing a knowledge map based on the sorting of examination questions and teachingand research knowledge, school teaching, teaching materials and the difficulty degree of examination questions to obtain a knowledge base; setting search conditions and extracting test questions according to the search conditions, wherein, when the search conditions contain natural language, the search conditions are converted into structured search instructions including knowledge points and search ranges, and the search instructions are matched with the contents in the knowledge map to search out the test questions; carrying out similarity algorithm, sorting algorithm and comprehensive screening algorithm on the searched test questions to obtain a screening result; pushing the filter results to the user. The invention simplifies the retrieval process of the test questions and improves the efficiency of searching the test questions by establishing the knowledge map of the test questions and searching based on the knowledge points when searching.
Owner:苏州友教习亦教育科技有限公司
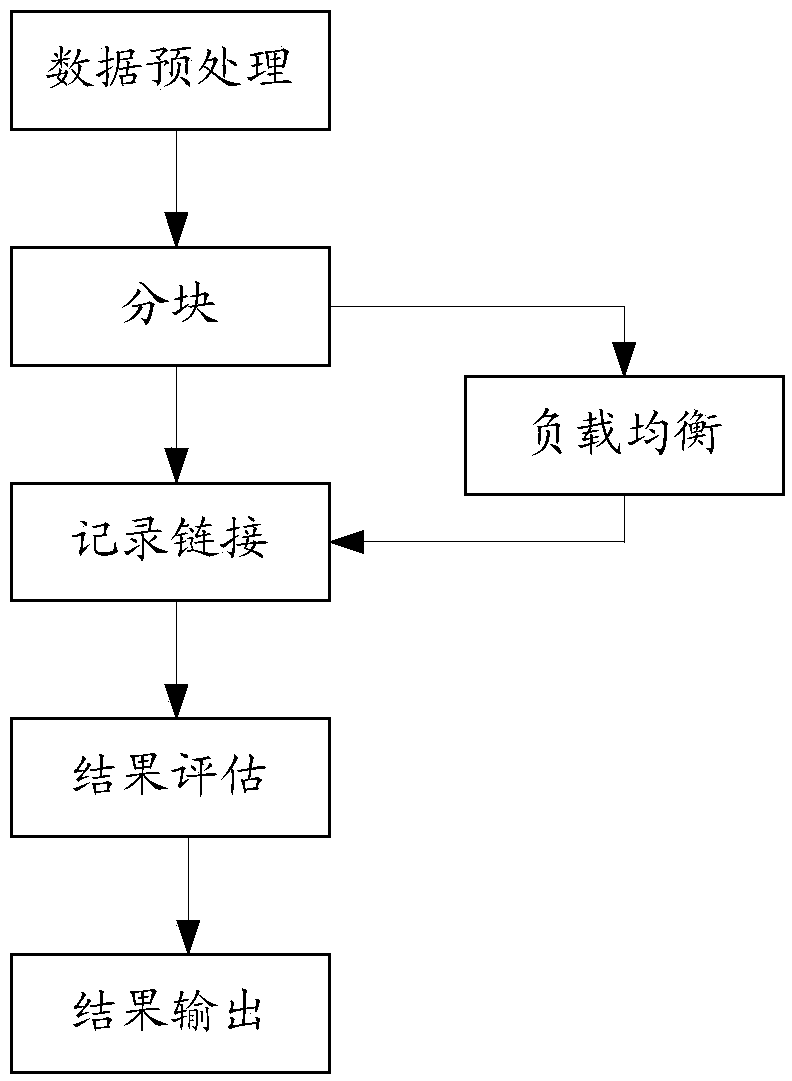
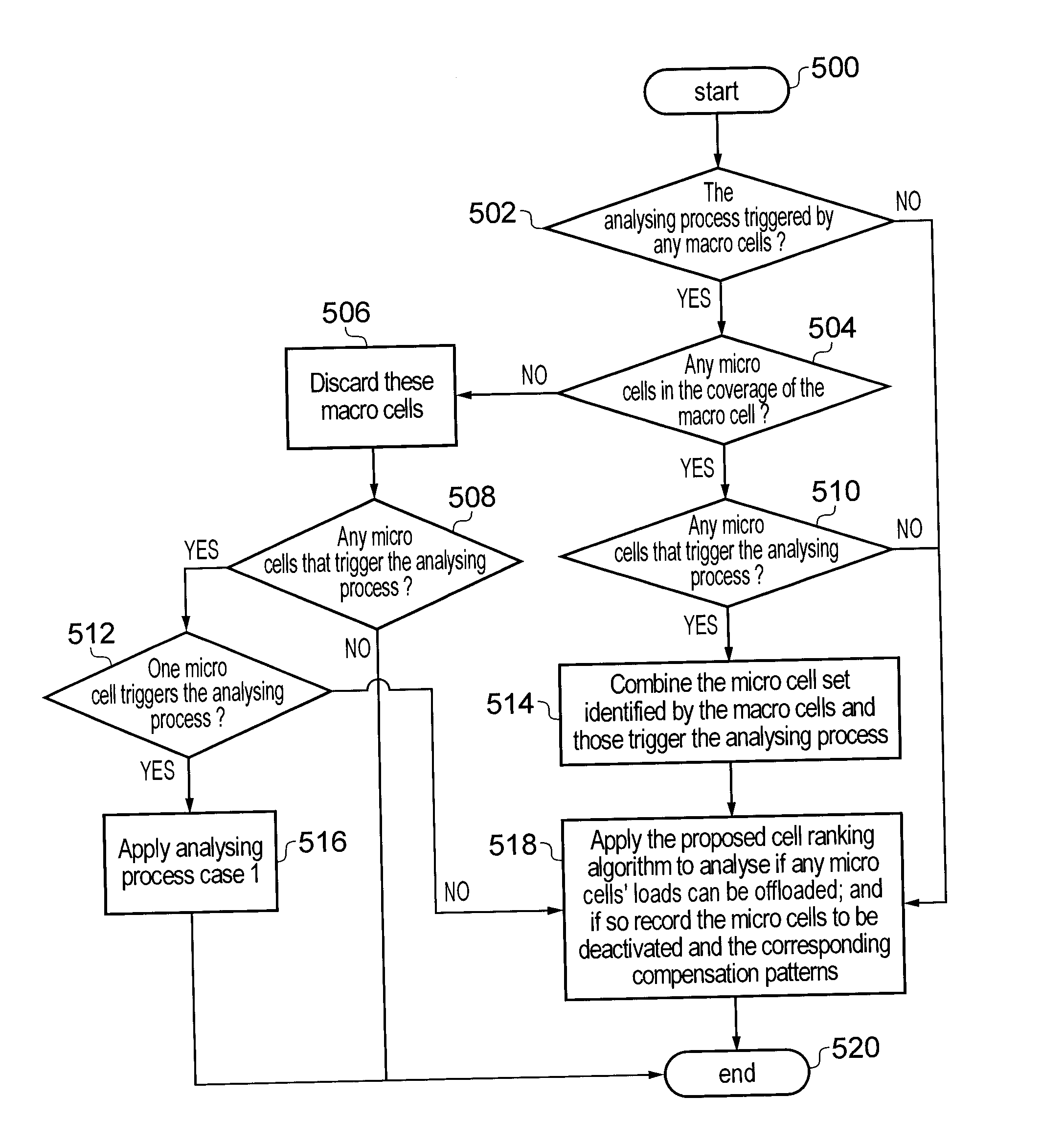
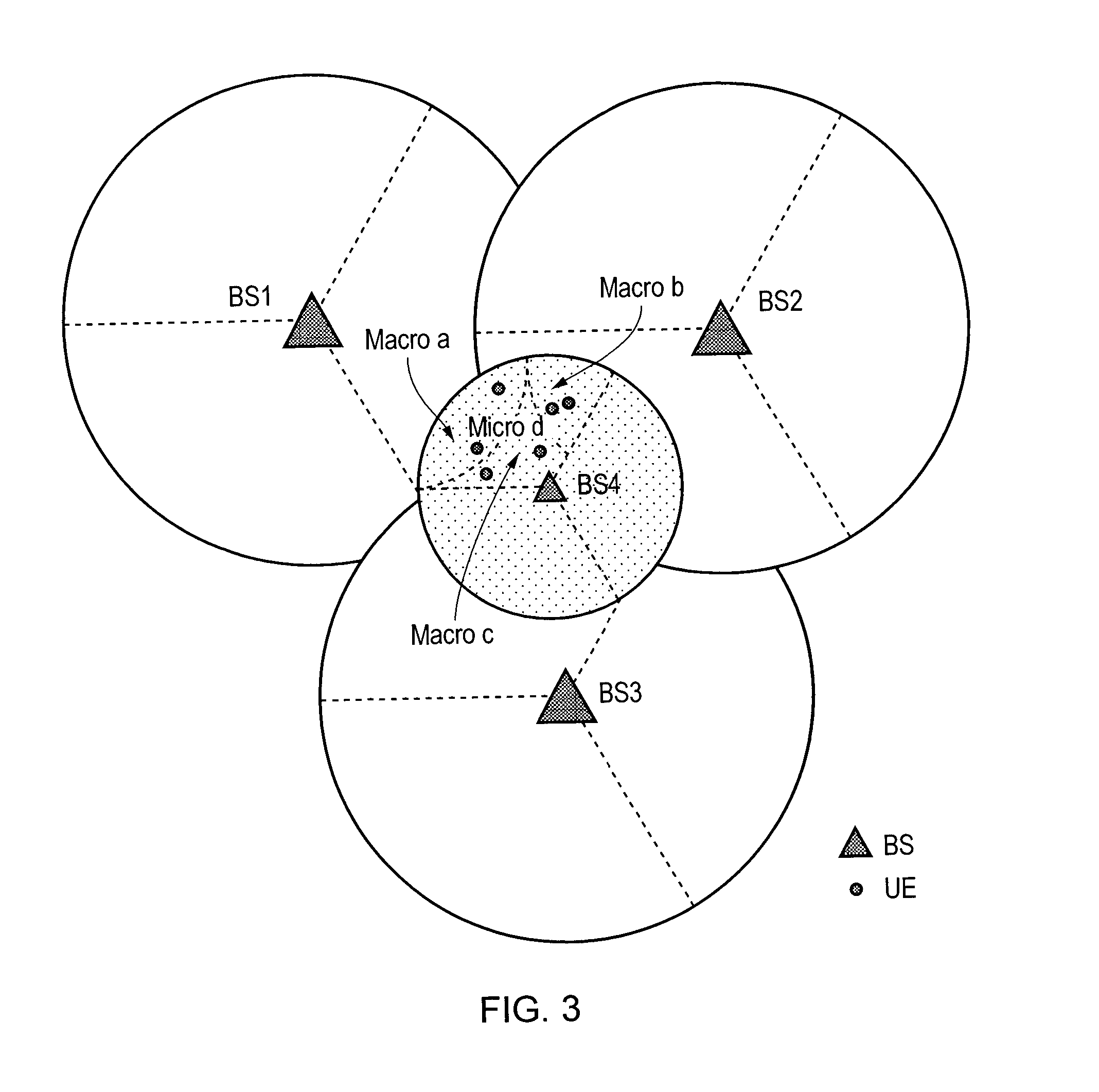
Deactivation of micro cells in cellular wireless networks
InactiveUS20130294272A1Avoid OverloadingSave energyPower managementError preventionQuality of serviceSorting algorithm
A cell ranking algorithm for power saving in a cellular wireless network having a heterogeneous network structure of macro and micro cells. The algorithm determines when and which micro cells in the network can be deactivated, by which the power consumption of the network can be reduced. A micro cell (Micro d) having a traffic load below a threshold value is deactivated and its load is assigned to adjacent macro cells (Macro a, Macro b) acting as compensation cells. The proposed algorithm is based on the comprehensive consideration of factors that have influence on the power saving of the network and the balance between the traffic load (or quality of service) and the energy saving.
Owner:FUJITSU LTD
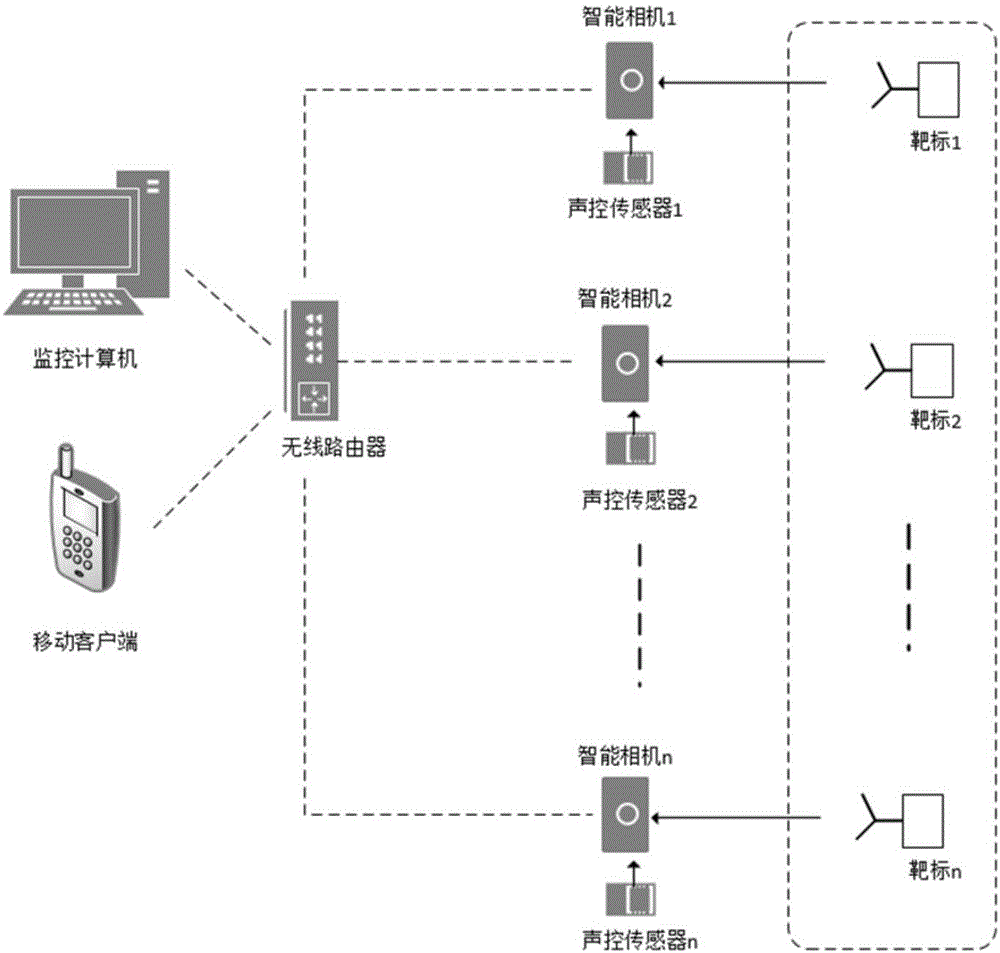
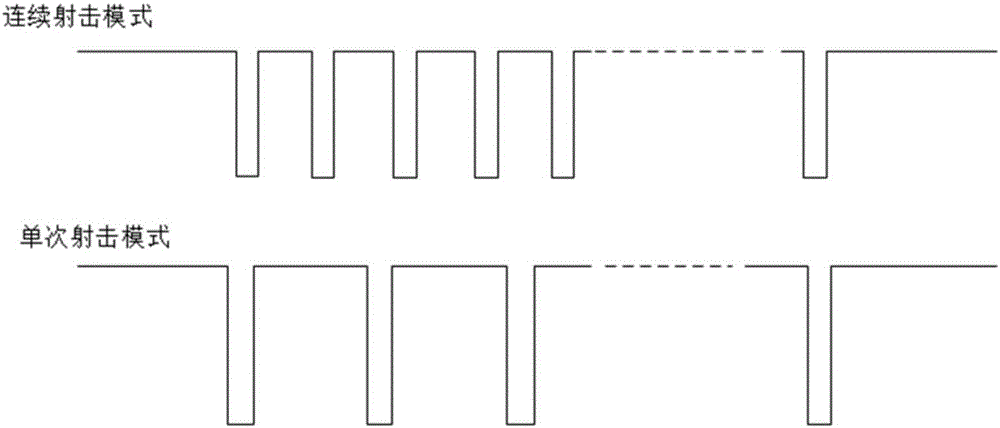
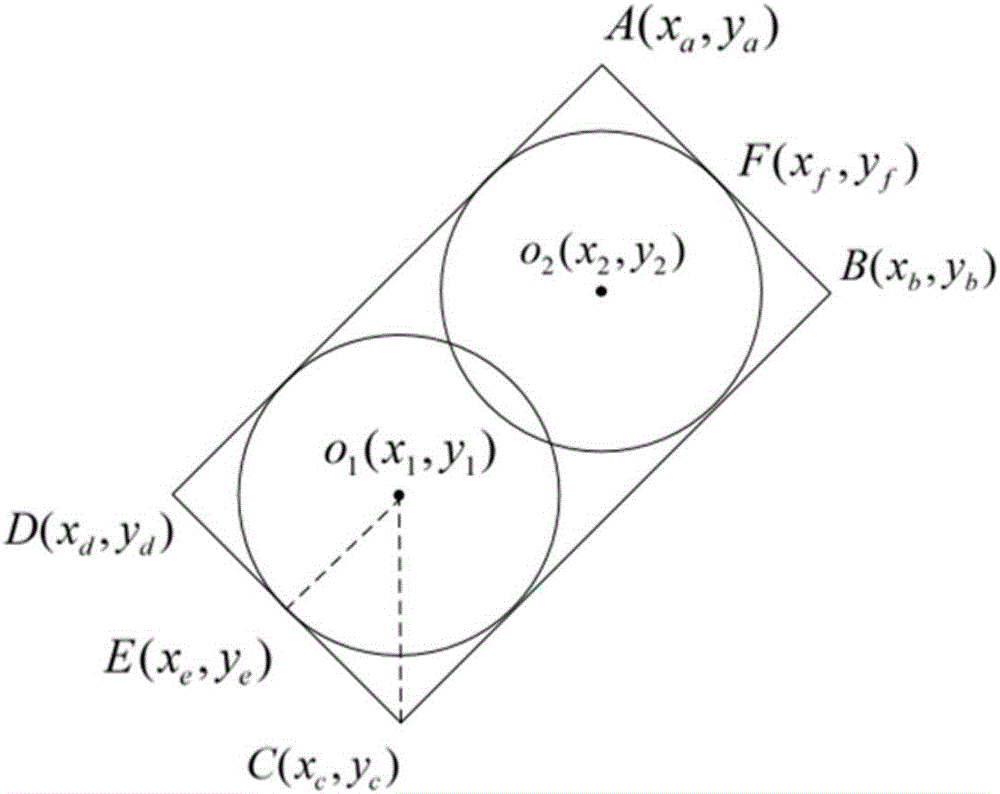
Intelligent target scoring system and method based on multi-bullet-hole mode recognition algorithm
InactiveCN106802113ADistinguish between shooting modesControl tasks are simpleImage enhancementImage analysisCorrection algorithmSorting algorithm
The invention provides an intelligent target scoring system and method based on a multi-bullet-hole mode recognition algorithm. The system comprises a sound control sensor, a swarm intelligence camera, a supervisory control computer and a mobile client. The intelligence camera is arranged in front of targets. Shooting signals trigger the intelligence camera to collect images through the sound control sensor. A target surface positioning correction algorithm, a multi-bullet-hole recognition sorting algorithm and a target scoring algorithm are used for acquiring the bullet hole type and shooting scoring information in real time, and then the information is uploaded to the supervisory control computer and the mobile client through an internal WIFI module. The mobile client conducts voice target scoring, the supervisory control computer displays the shooting scoring information of each shooter in real time, and a user interface is provided for performing statistical query and intelligent management on the shooting information. According to the intelligent target scoring system and method, shooting target scoring of each target is independent and does not depend on the supervisory control computer, the structure is simple, and safety and reliability are achieved; and meanwhile, the provided mode recognition method is high in antijamming capability, the bullet hole recognition rate is high and real-time performance and accuracy can be achieved.
Owner:XI AN JIAOTONG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com