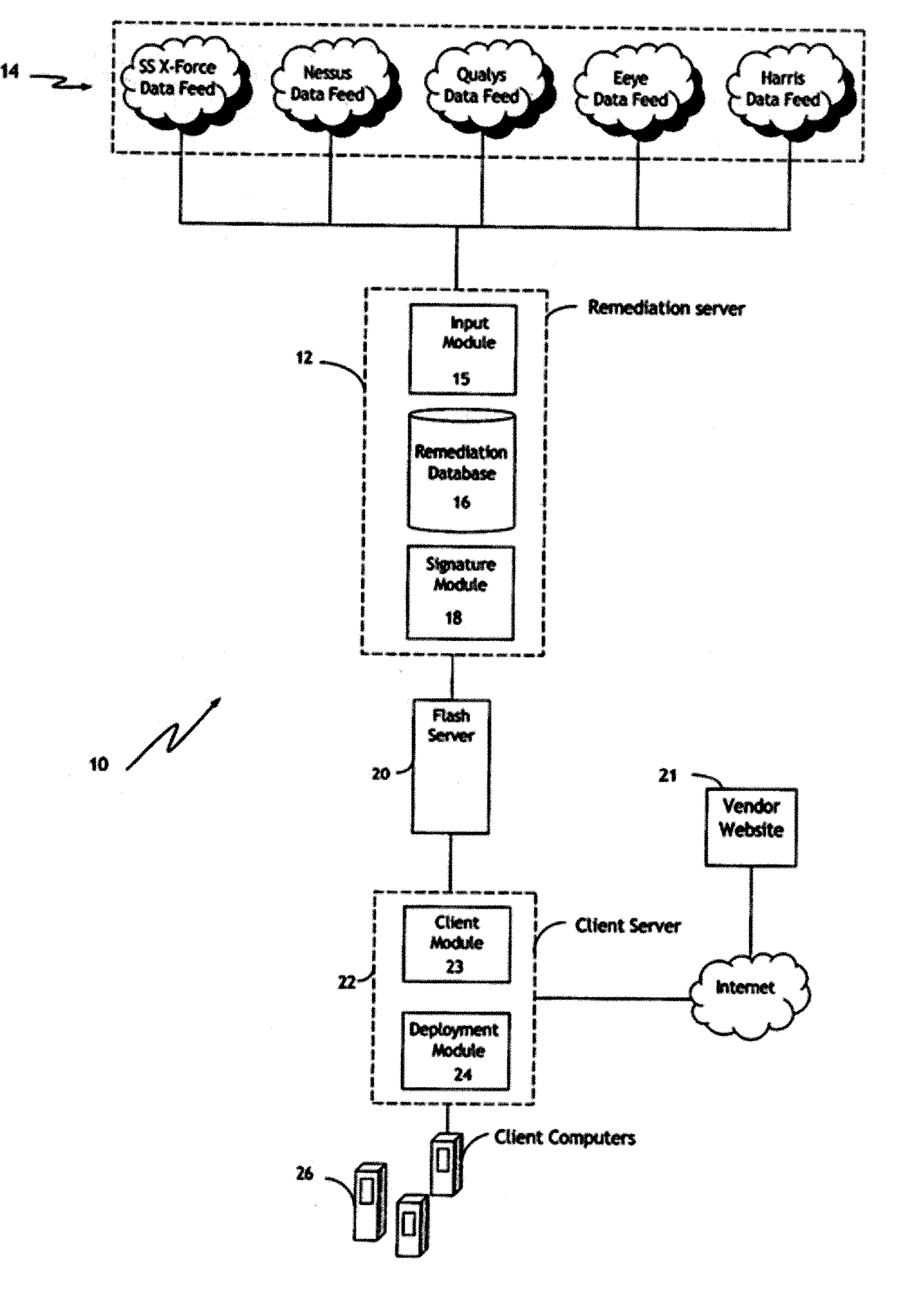
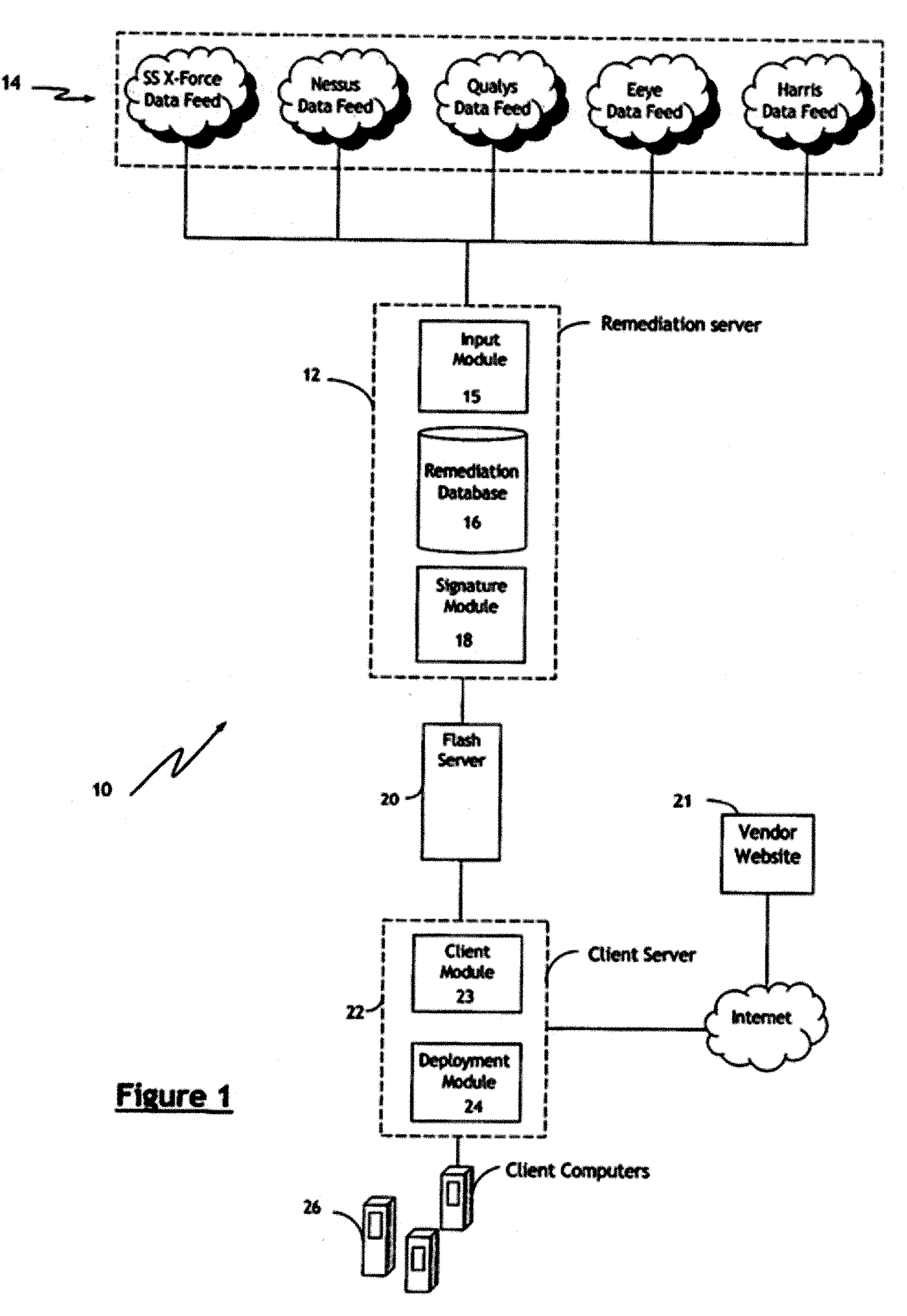
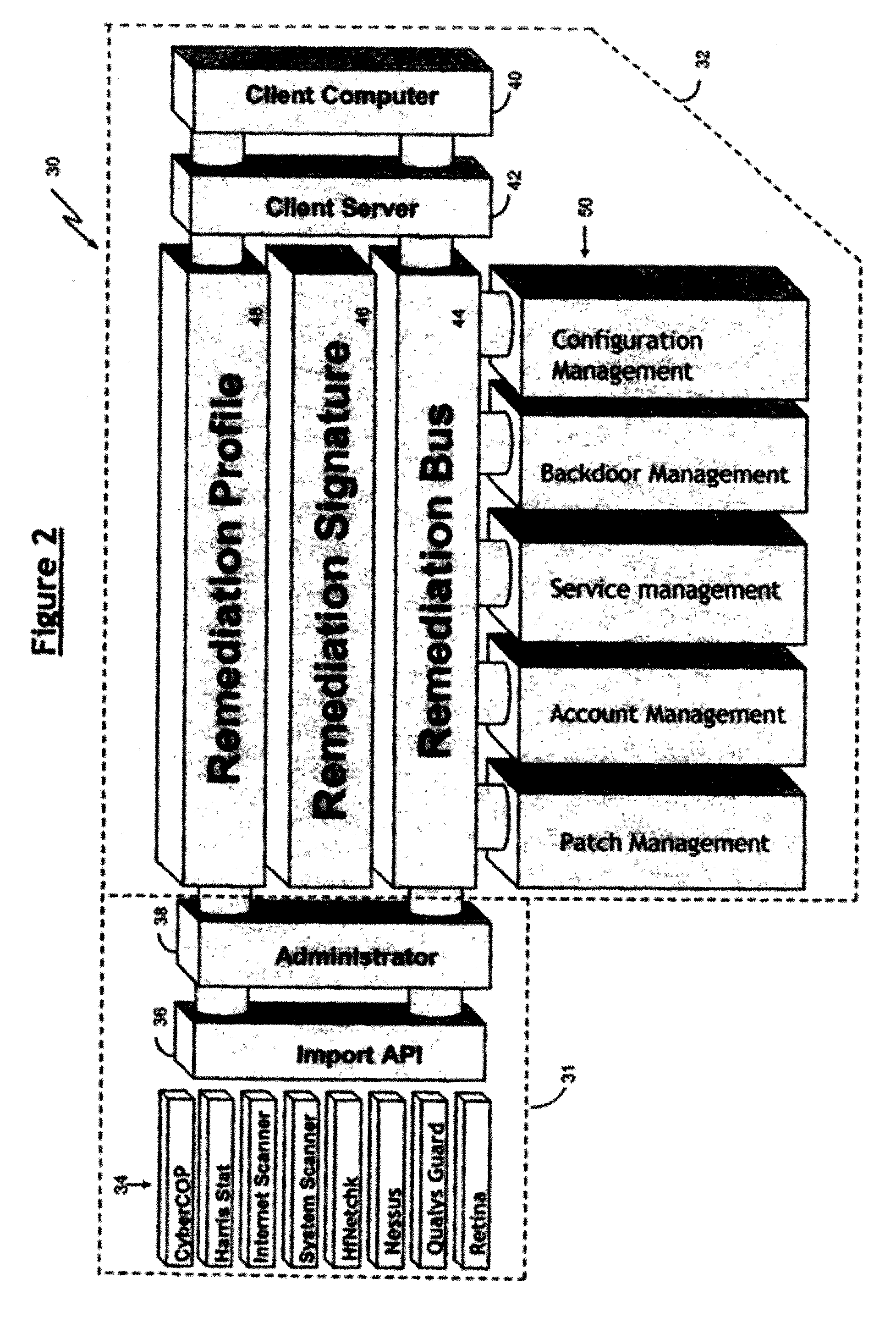
Automated Computer Vulnerability Resolution System
a vulnerability resolution and automatic technology, applied in the field of automatic computer vulnerability resolution system, can solve the problems of increasing burden on the maintenance team of increasing the burden of maintaining security for these computer systems and/or networks, and increasing the complexity of the computer system and the application running thereon
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
CROSS-REFERENCE TO RELATED APPLICATIONS
[0001] This application claims priority from U.S. Provisional Application serial no. 60 / 345,689 filed on December 31, 2001.
STATEMENT REGARDING FEDERALLY SPONSORED RESEARCH OR DEVELOPMENT
[0002] Not applicable.
REFERENCE TO A MICROFICHE APPENDIX
[0003] Not applicable.
FIELD OF THE INVENTION
[0004] The invention relates generally to a method and system for resolving security vulnerabilities in computers and, more particularly, to a vulnerability resolution system in which computer security vulnerability information from one or more sources can be aggregated and comprehensive remediation updates can be generated for managed automated distribution to target client computers.
BACKGROUND OF THE INVENTION
[0005] Computers, computer systems, and the applications running thereon are becoming increasingly complex. In addition, with the advent of the Internet and other modern networking technology, computers have become increasingly interconnected and remote ac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com