Patents
Literature
493 results about "Security analysis" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Security analysis is the analysis of tradeable financial instruments called securities. It deals with finding the proper value of individual securities (i.e., stocks and bonds). These are usually classified into debt securities, equities, or some hybrid of the two. Tradeable credit derivatives are also securities. Commodities or futures contracts are not securities. They are distinguished from securities by the fact that their performance is not dependent on the management or activities of an outside or third party. Options on these contracts are however considered securities, since performance is now dependent on the activities of a third party. The definition of what is and what is not a security comes directly from the language of a United States Supreme Court decision in the case of SEC v. W. J. Howey Co.. Security analysis is typically divided into fundamental analysis, which relies upon the examination of fundamental business factors such as financial statements, and technical analysis, which focuses upon price trends and momentum. Quantitative analysis may use indicators from both areas.
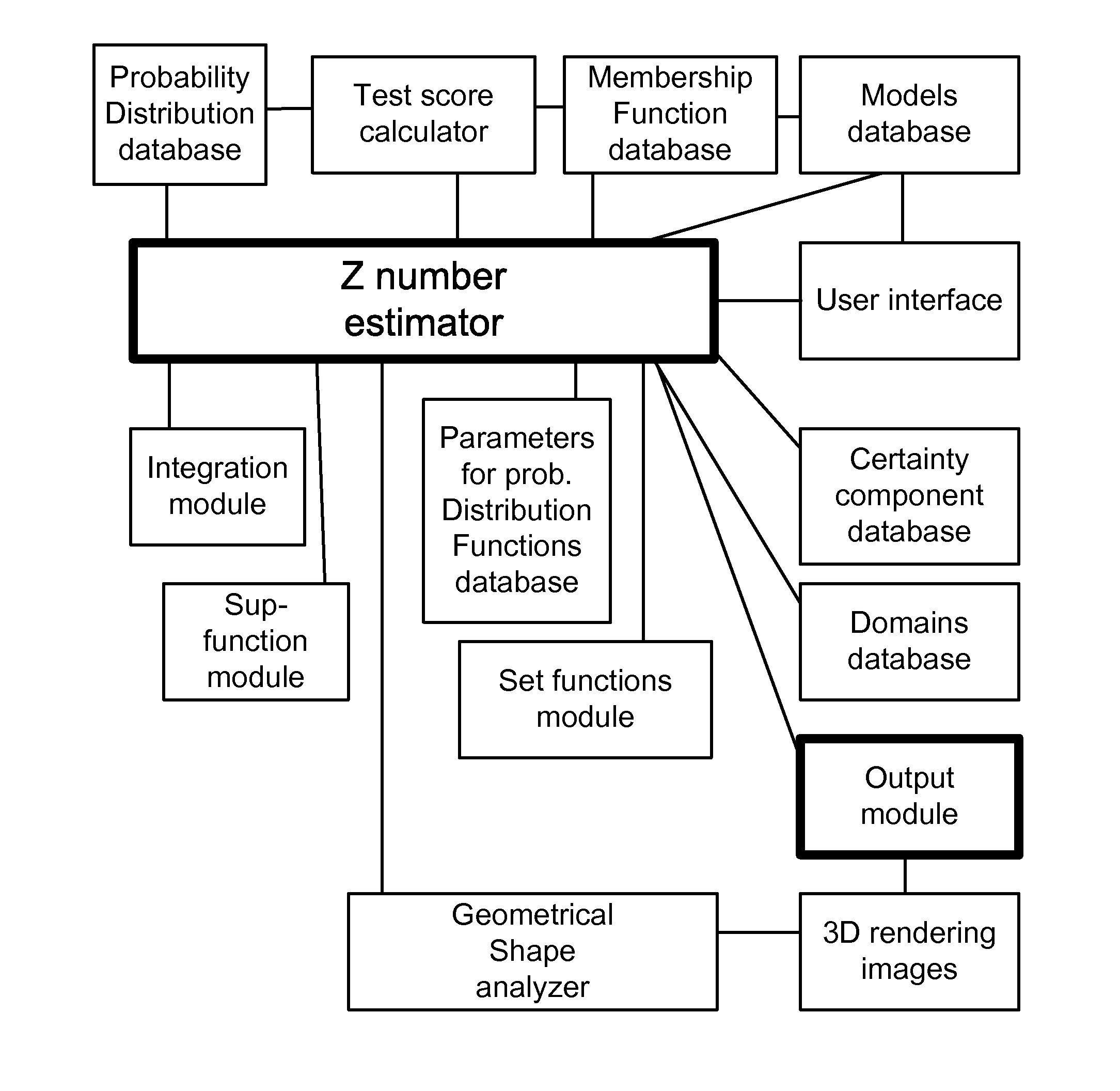
Application of Z-Webs and Z-factors to Analytics, Search Engine, Learning, Recognition, Natural Language, and Other Utilities
Here, we introduce Z-webs, including Z-factors and Z-nodes, for the understanding of relationships between objects, subjects, abstract ideas, concepts, or the like, including face, car, images, people, emotions, mood, text, natural language, voice, music, video, locations, formulas, facts, historical data, landmarks, personalities, ownership, family, friends, love, happiness, social behavior, voting behavior, and the like, to be used for many applications in our life, including on the search engine, analytics, Big Data processing, natural language processing, economy forecasting, face recognition, dealing with reliability and certainty, medical diagnosis, pattern recognition, object recognition, biometrics, security analysis, risk analysis, fraud detection, satellite image analysis, machine generated data analysis, machine learning, training samples, extracting data or patterns (from the video, images, and the like), editing video or images, and the like. Z-factors include reliability factor, confidence factor, expertise factor, bias factor, and the like, which is associated with each Z-node in the Z-web.
Owner:Z ADVANCED COMPUTING
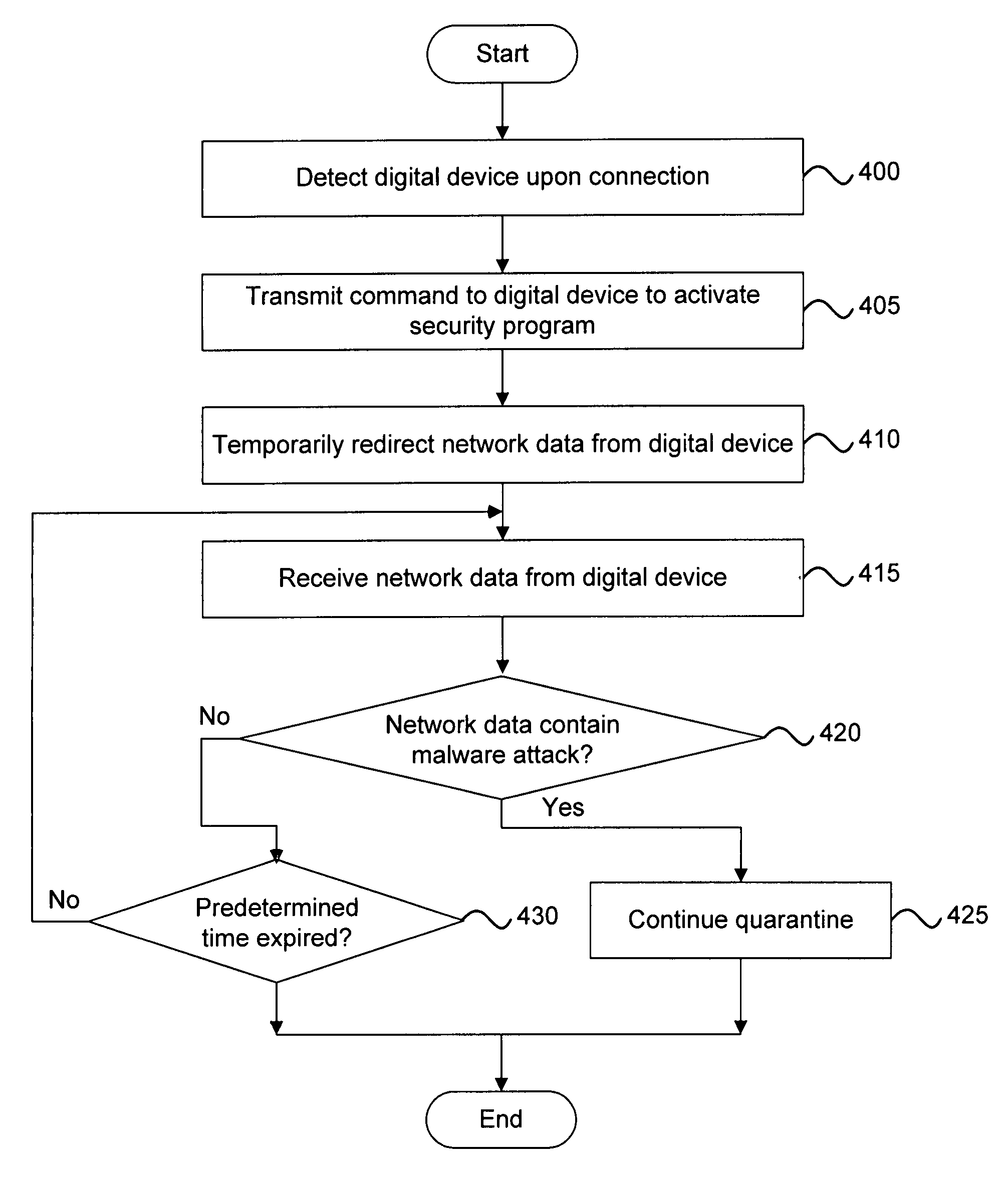
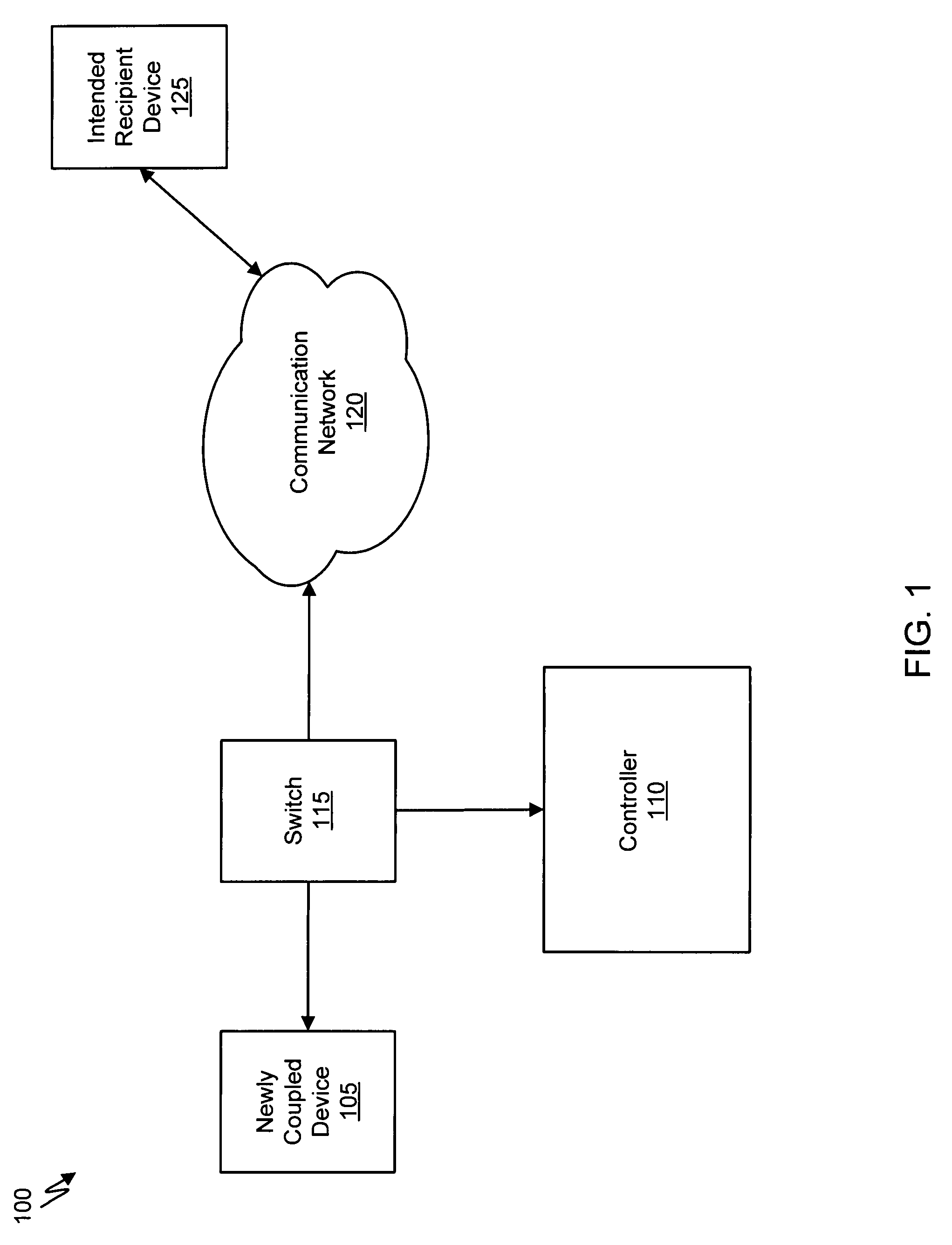
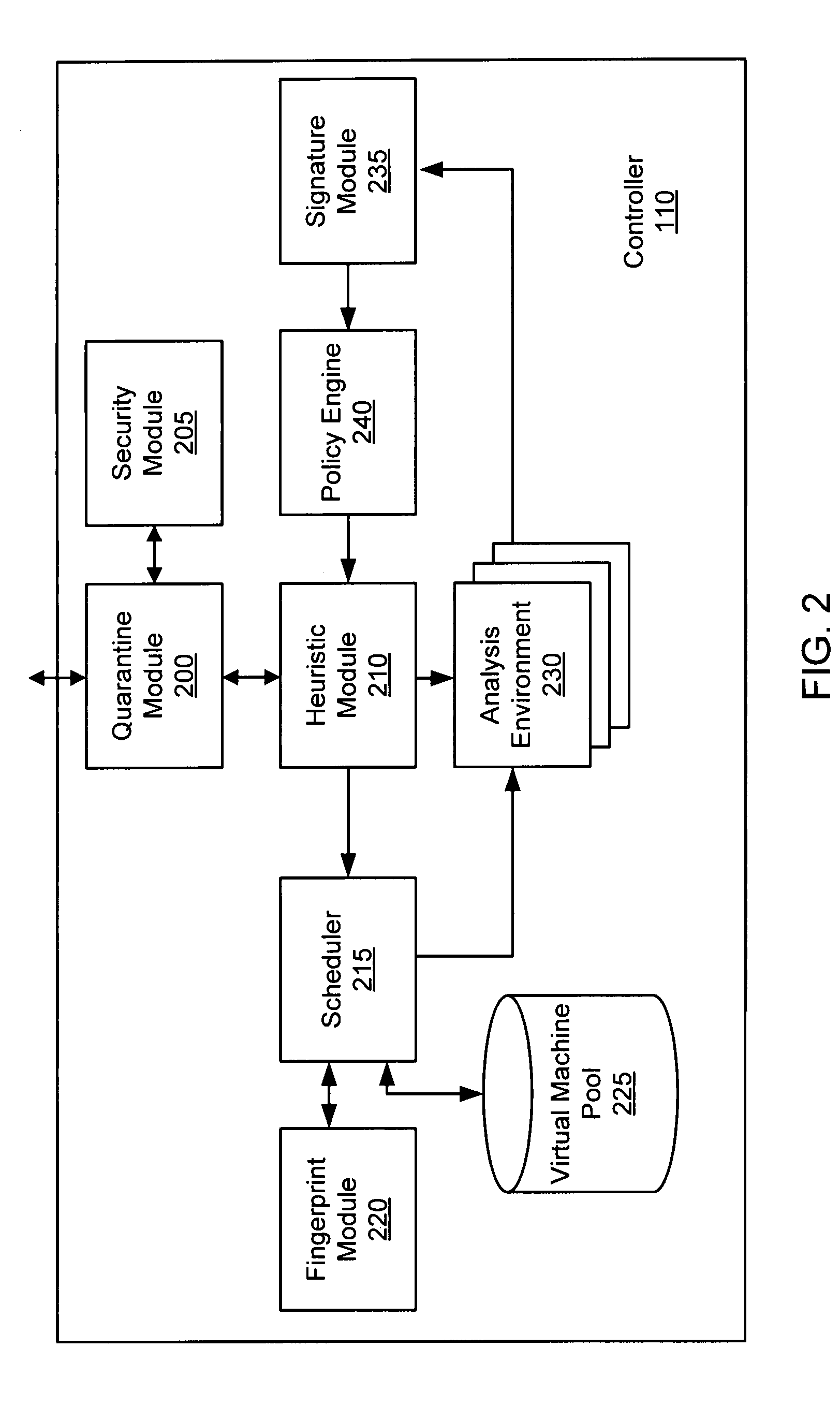
Malware containment and security analysis on connection
Systems and methods for malware containment and security analysis on connection are provided. Digital devices are quarantined for a predetermined period of time upon connection to the communication network. When a digital device is quarantined, all network data transmitted by the digital device is directed to a controller which then analyzes the network data to identify unauthorized activity and / or malware within the newly connected digital device. An exemplary method to contain malware includes detecting a digital device upon connection with a communication network, quarantining network data from the digital device for a predetermined period of time, transmitting a command to the digital device to activate a security program to identify security risks, and analyzing the network data to identify malware within the digital device.
Owner:FIREEYE SECURITY HLDG US LLC
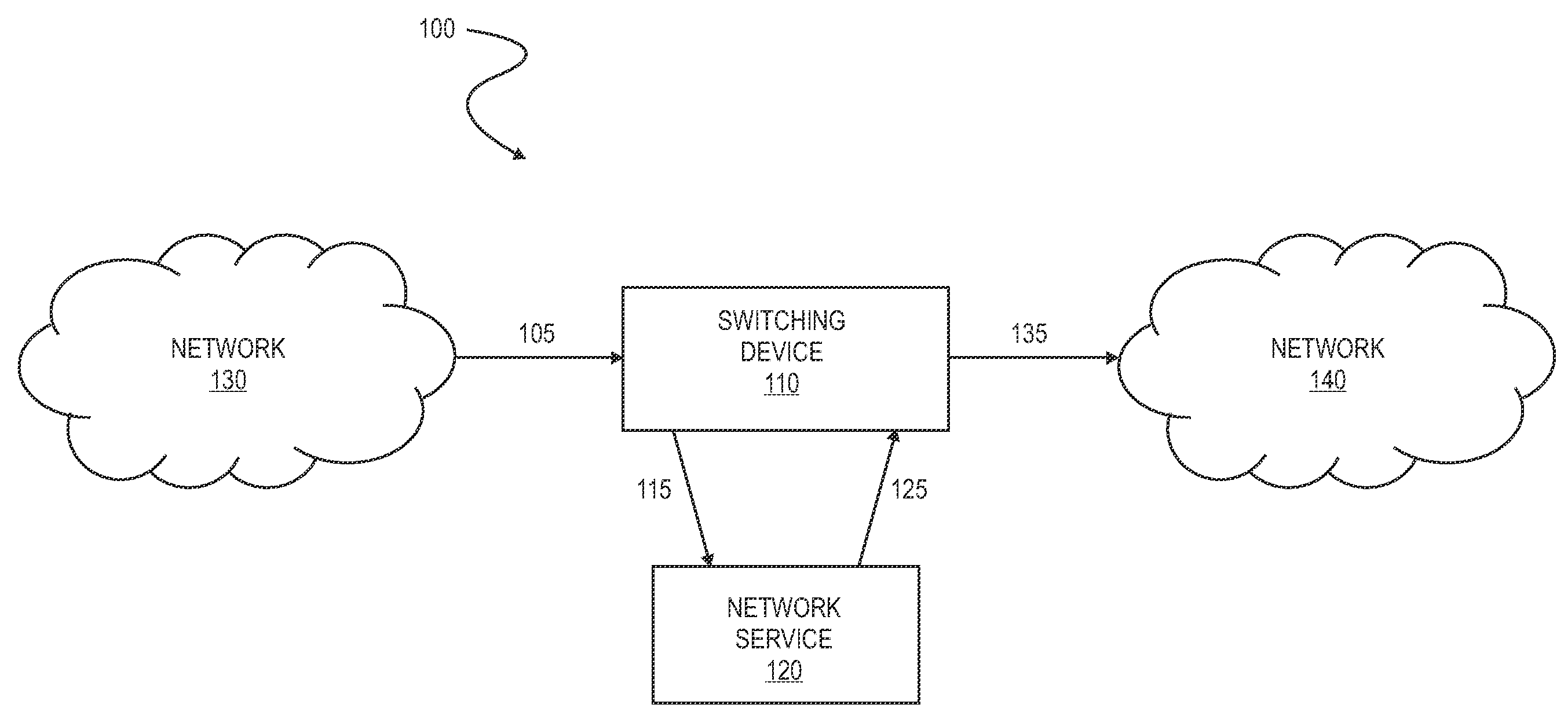
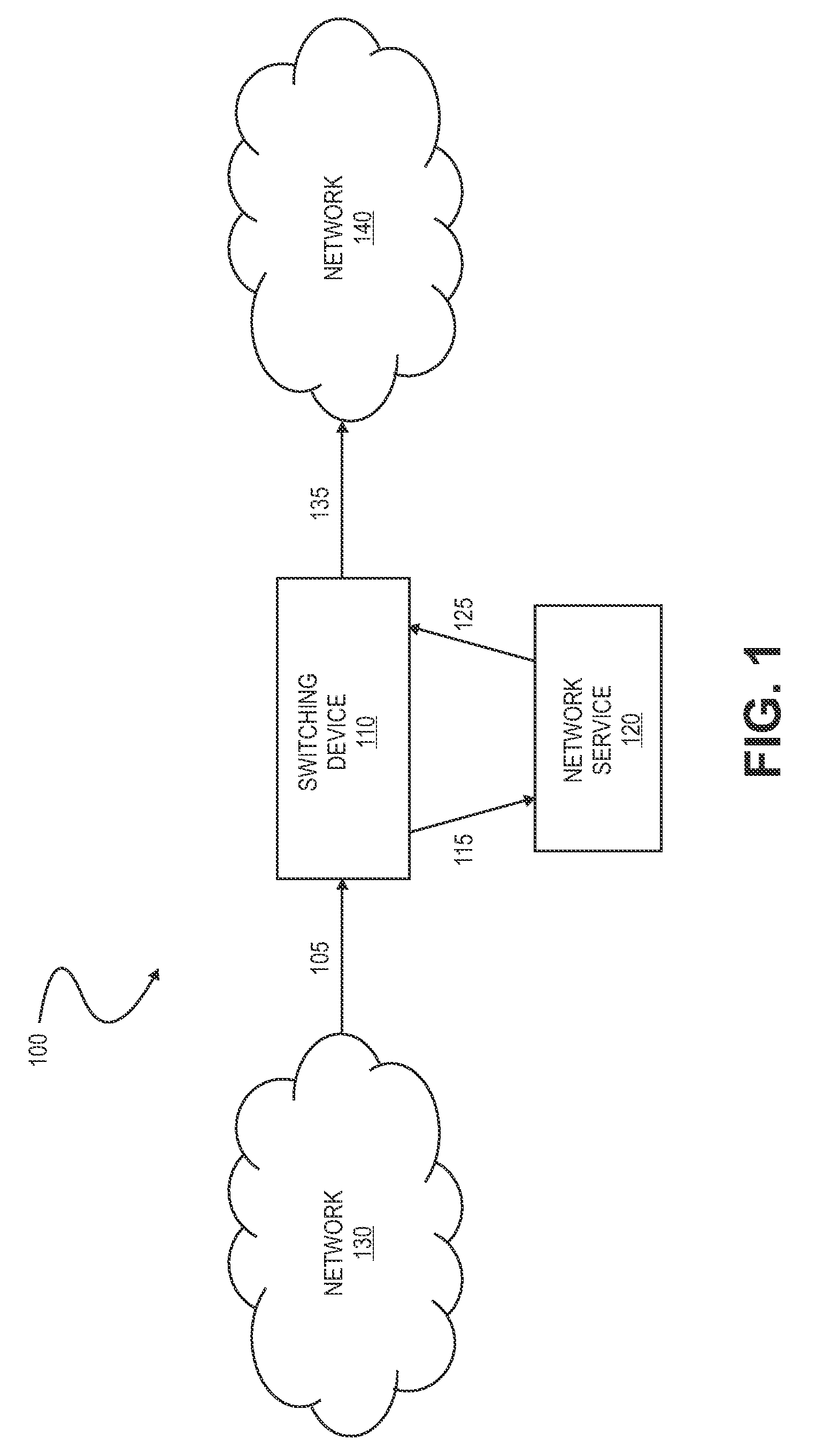
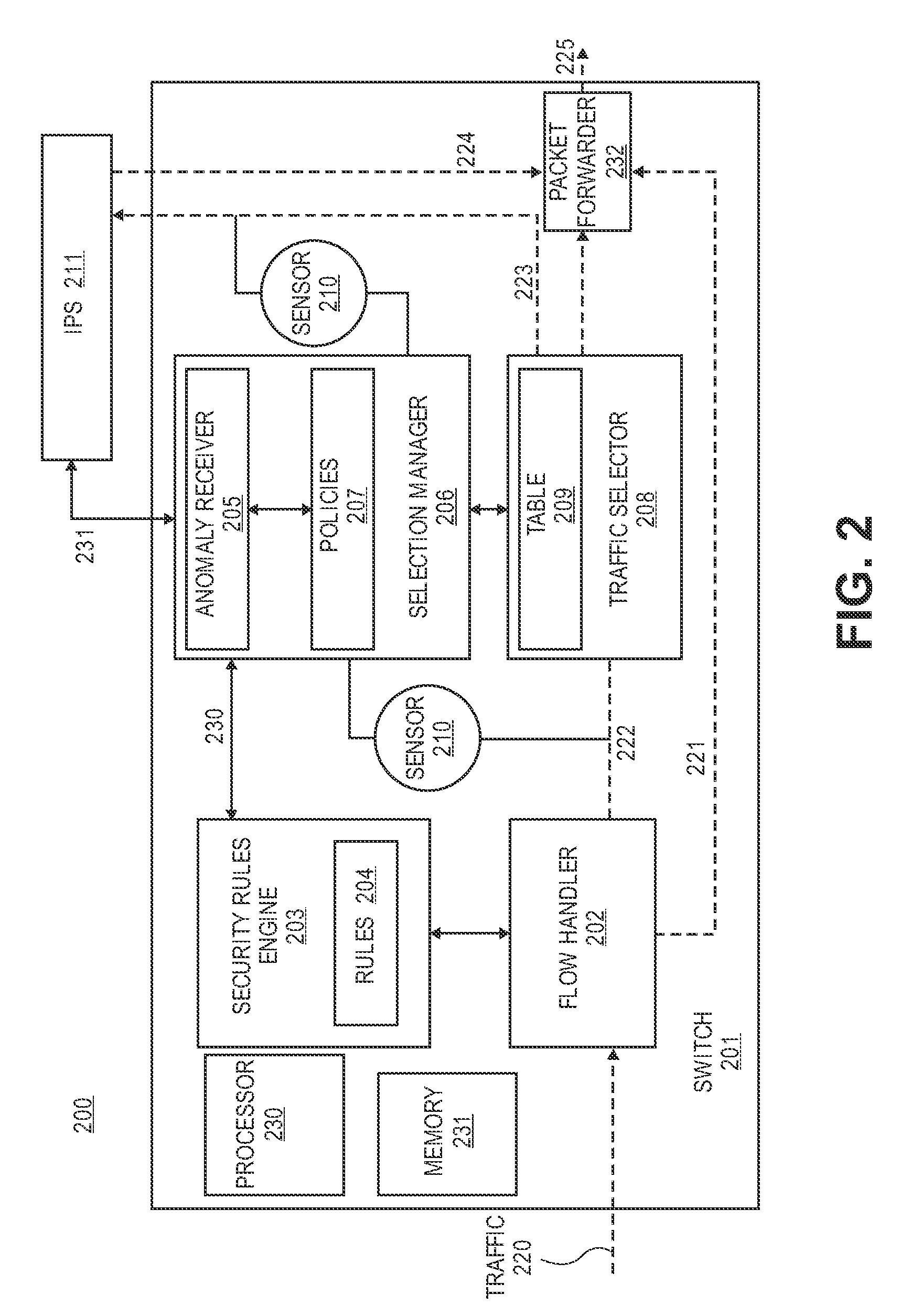
Method and mechanism for port redirects in a network switch
ActiveUS20090003317A1Memory loss protectionError detection/correctionNetwork switchSecurity analysis
A method for selectively redirecting a data packet to a port on a switching device which is associated with a corresponding network service. In one embodiment, the data packet is redirected to an intrusion prevention service (IPS) for security analysis of the data packet. In another embodiment, the switching device performs a data link layer redirecting of the data packet based at least in part on whether the data packet is to be flooded from the switching device.
Owner:EXTREME NETWORKS INC
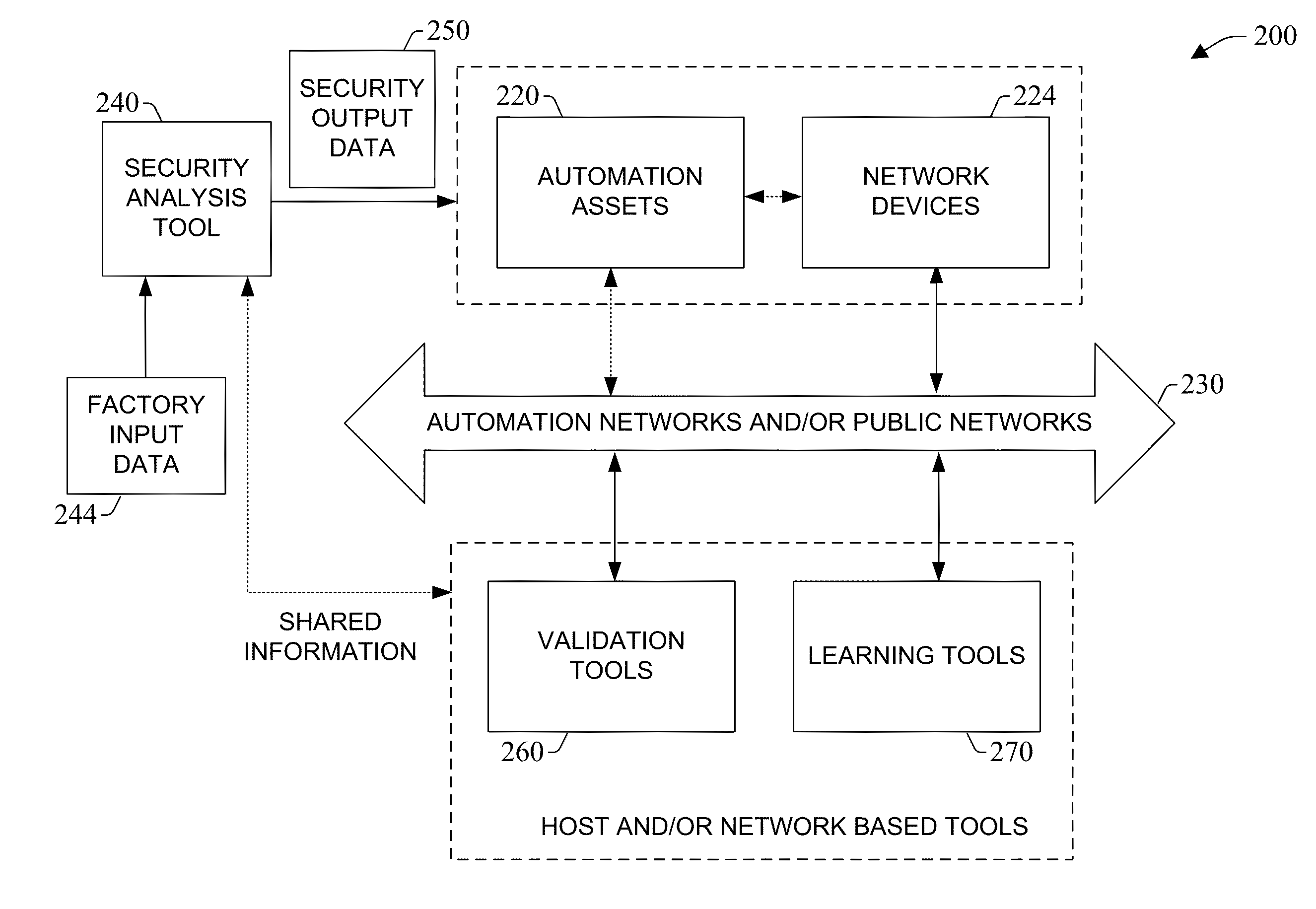
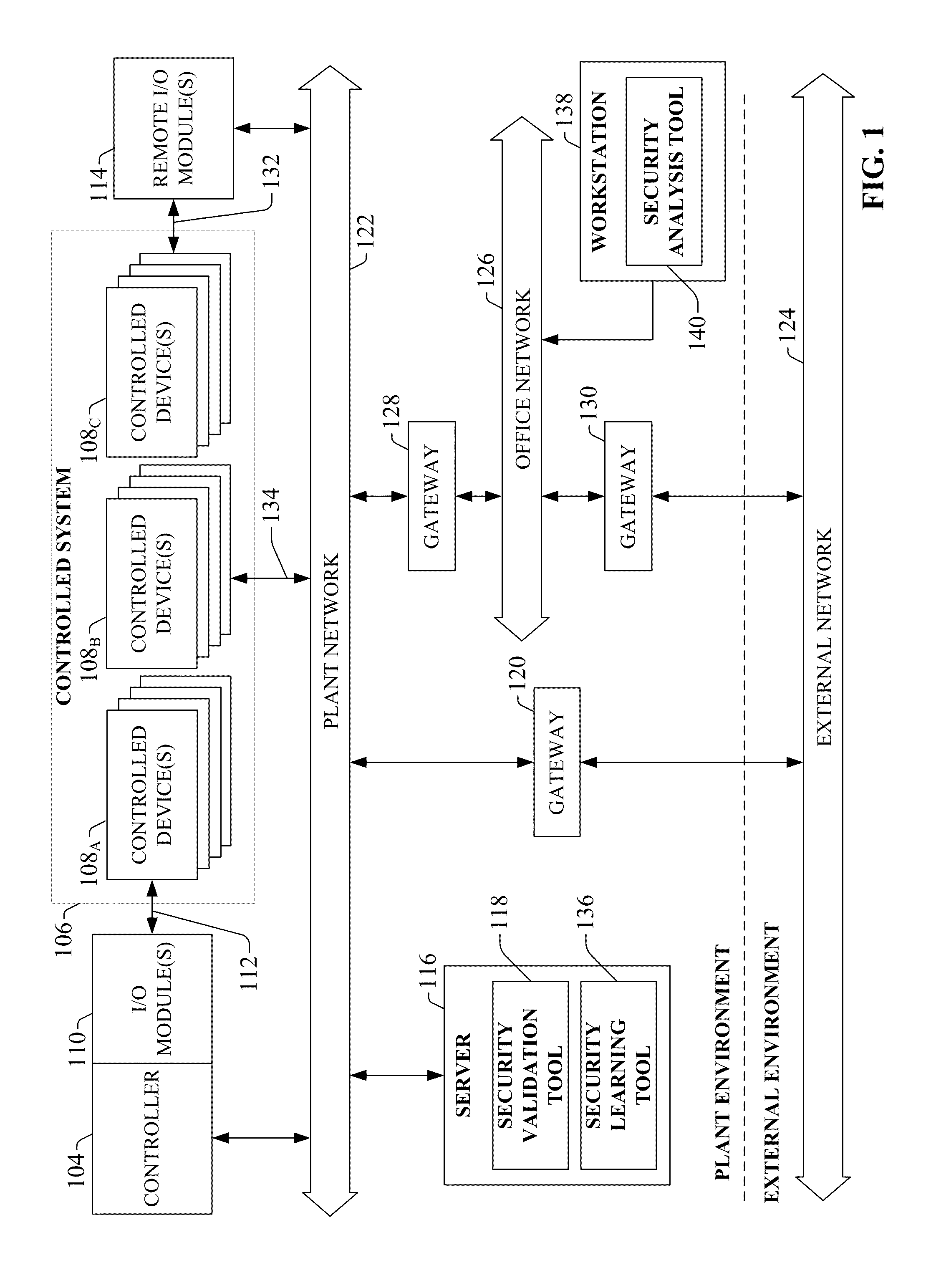
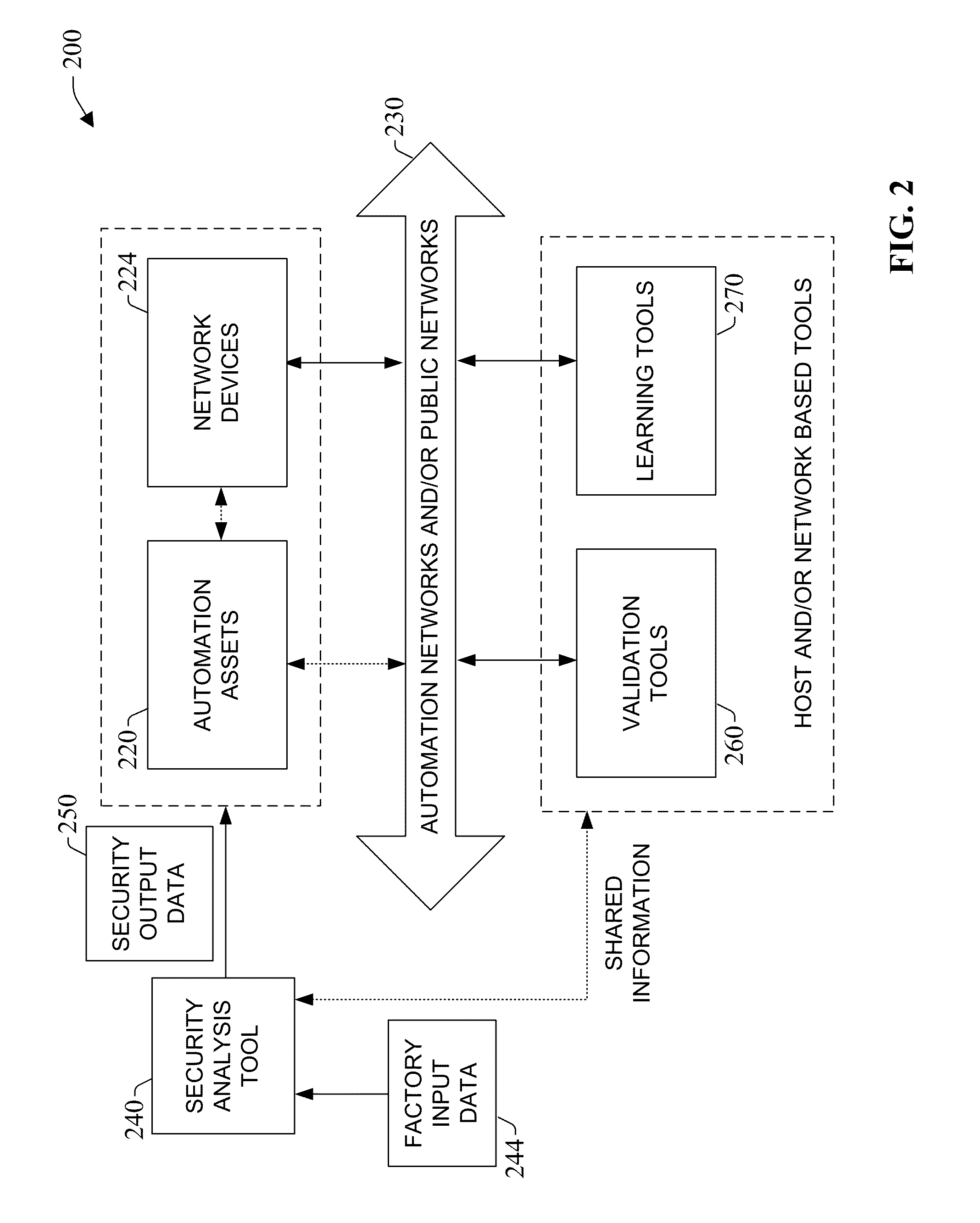
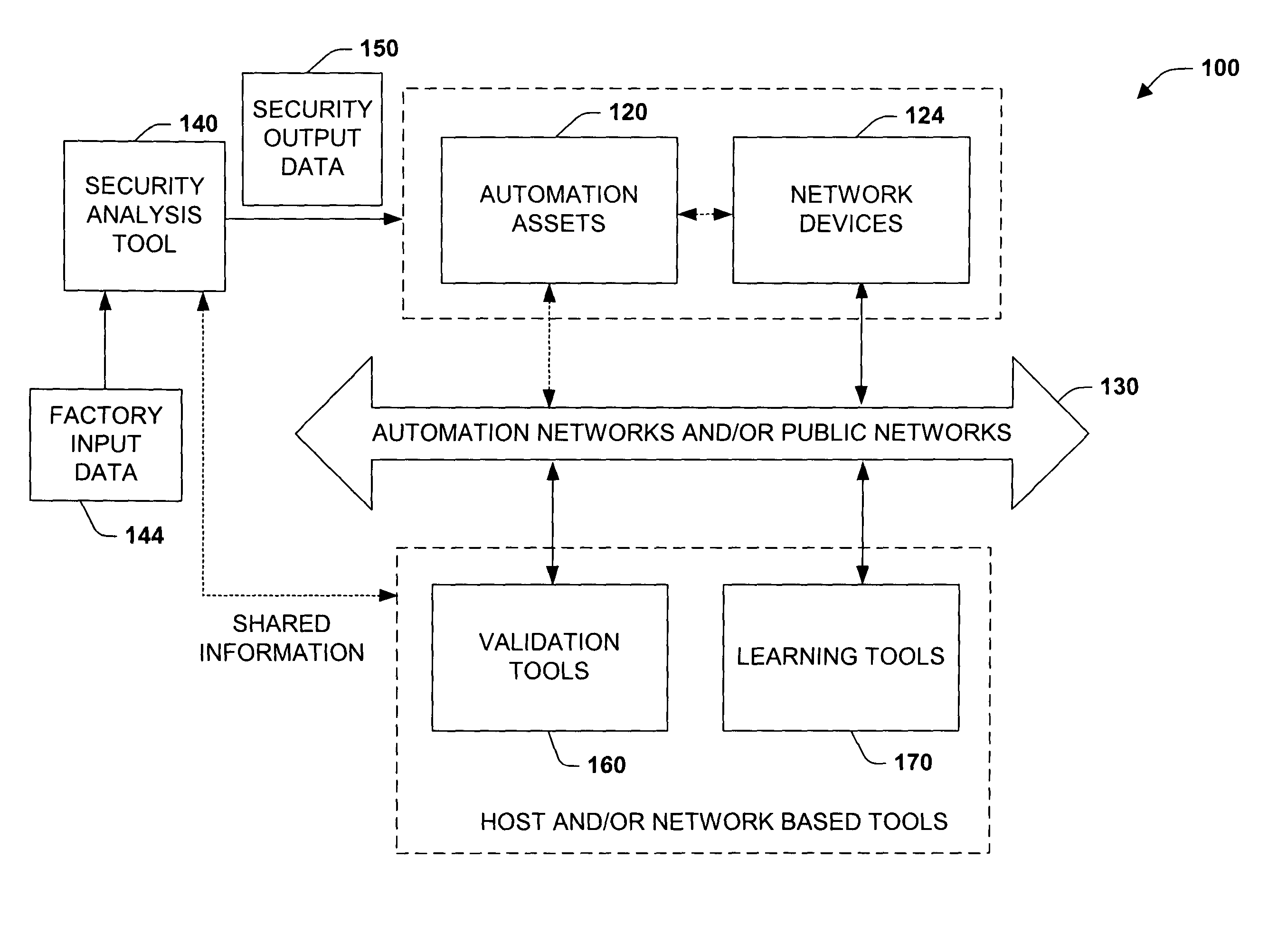
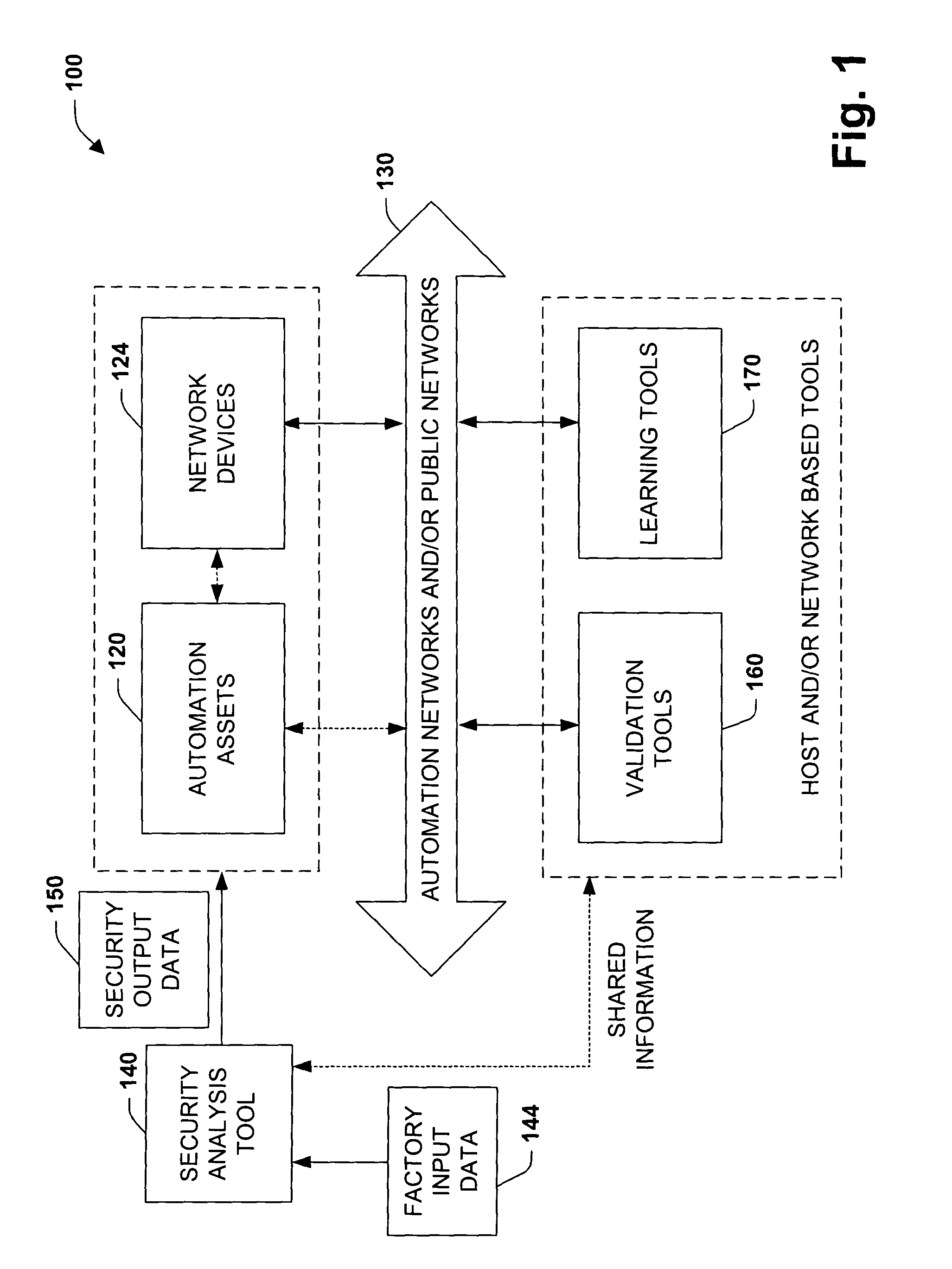
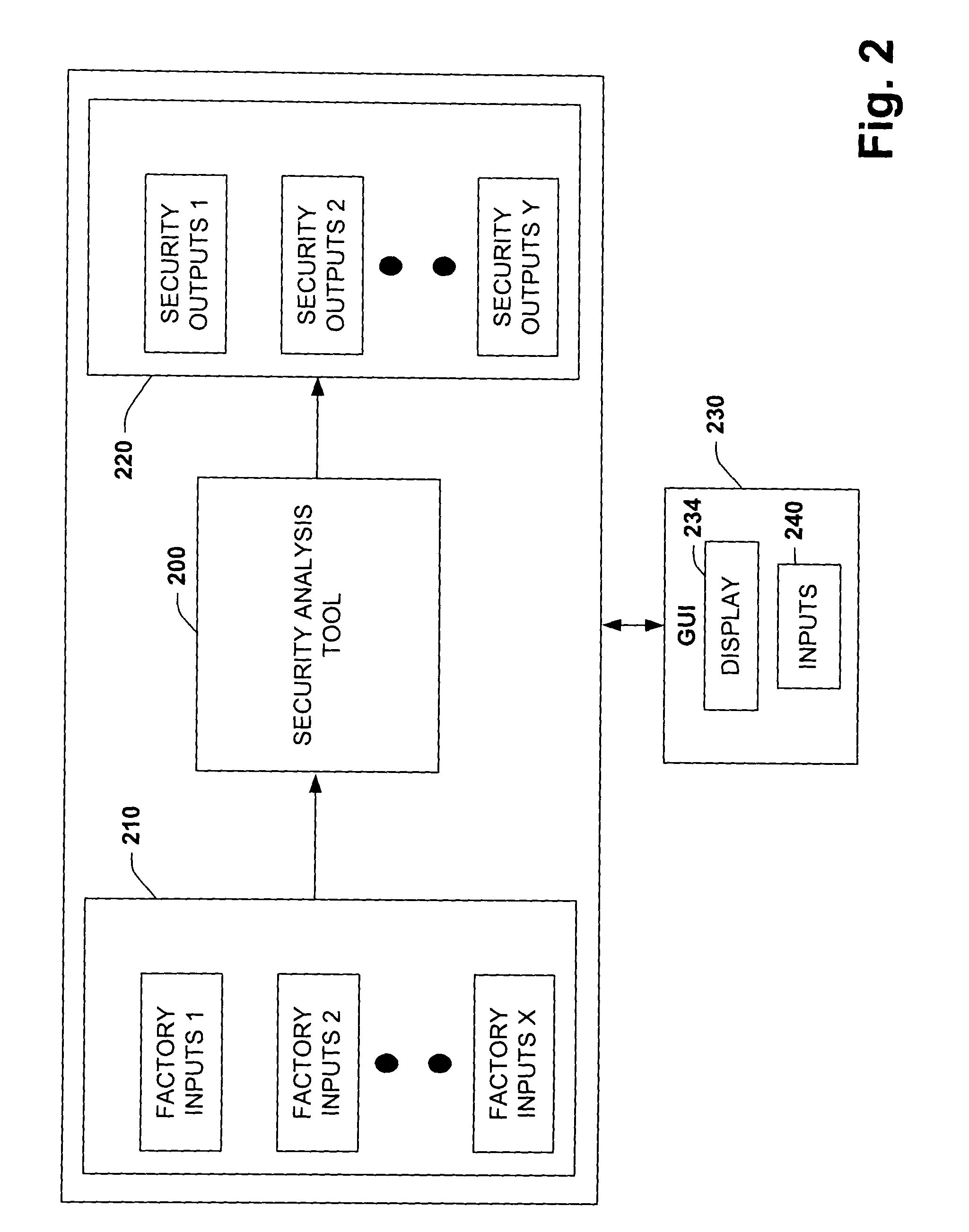
System and methodology providing automation security analysis and network intrusion protection in an industrial environment
ActiveUS20130031037A1Improve integrityFacilitate privacyProgramme controlComputer controlGuidelineEngineering
The present invention relates to a system and methodology facilitating automation security in a networked-based industrial controller environment. Various components, systems and methodologies are provided to facilitate varying levels of automation security in accordance with security analysis tools, security validation tools and / or security learning systems. The security analysis tool receives abstract factory models or descriptions for input and generates an output that can include security guidelines, components, topologies, procedures, rules, policies, and the like for deployment in an automation security network. The validation tools are operative in the automation security network, wherein the tools perform security checking and / or auditing functions, for example, to determine if security components are in place and / or in suitable working order. The security learning system monitors / learns network traffic patterns during a learning phase, fires alarms or events based upon detected deviations from the learned patterns, and / or causes other automated actions to occur.
Owner:ROCKWELL AUTOMATION TECH
Security analysis system
An improved securities analysis system includes a data conversion device for converting both technical and fundamental data about a security into a unified format for analysis by an analysis process engine. The analysis process engine processes the disparate data in accordance with a set of rules and the results are forwarded to a display for viewing or used in further analysis.
Owner:WINDOW ON WALLSTREET
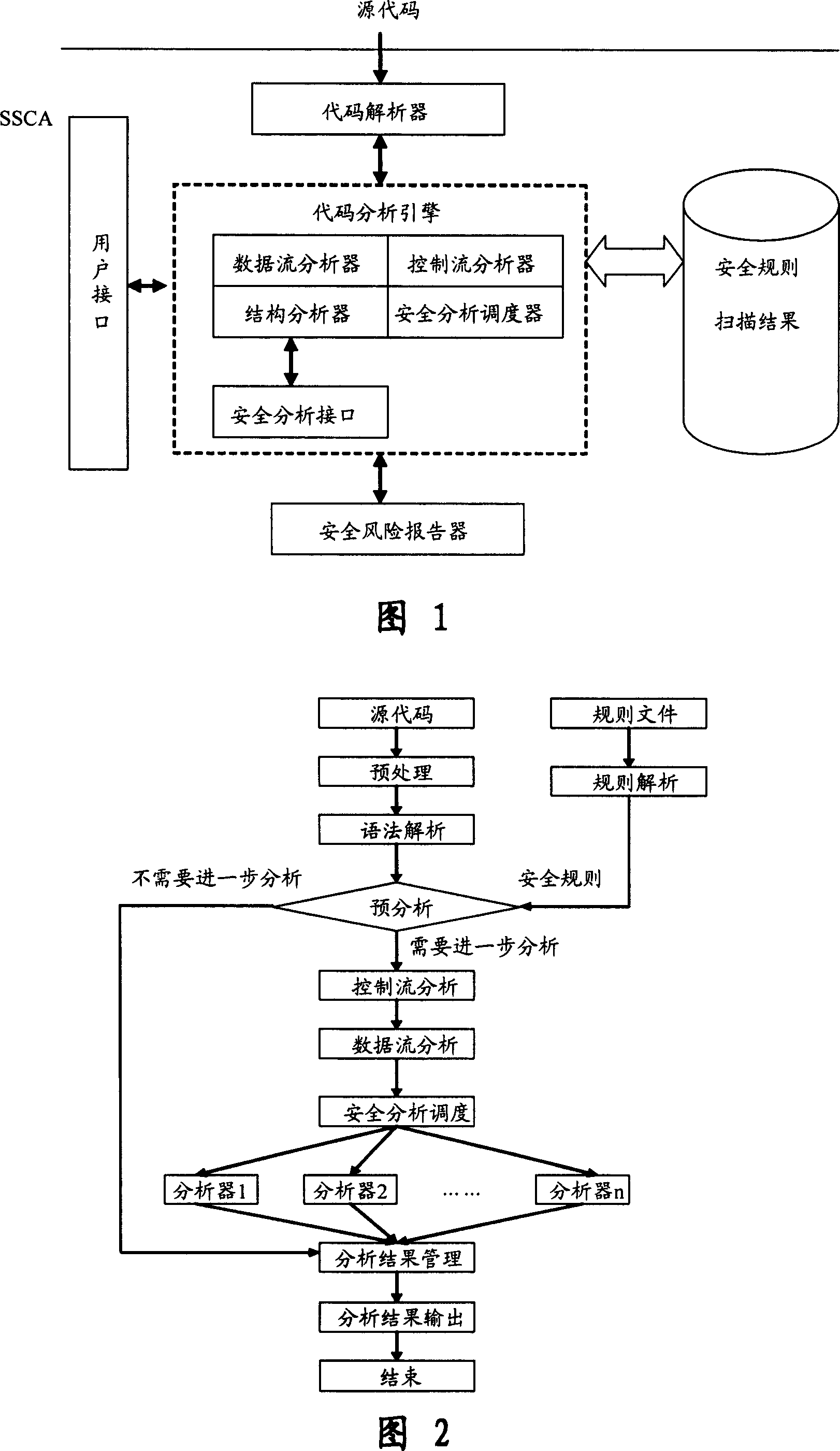
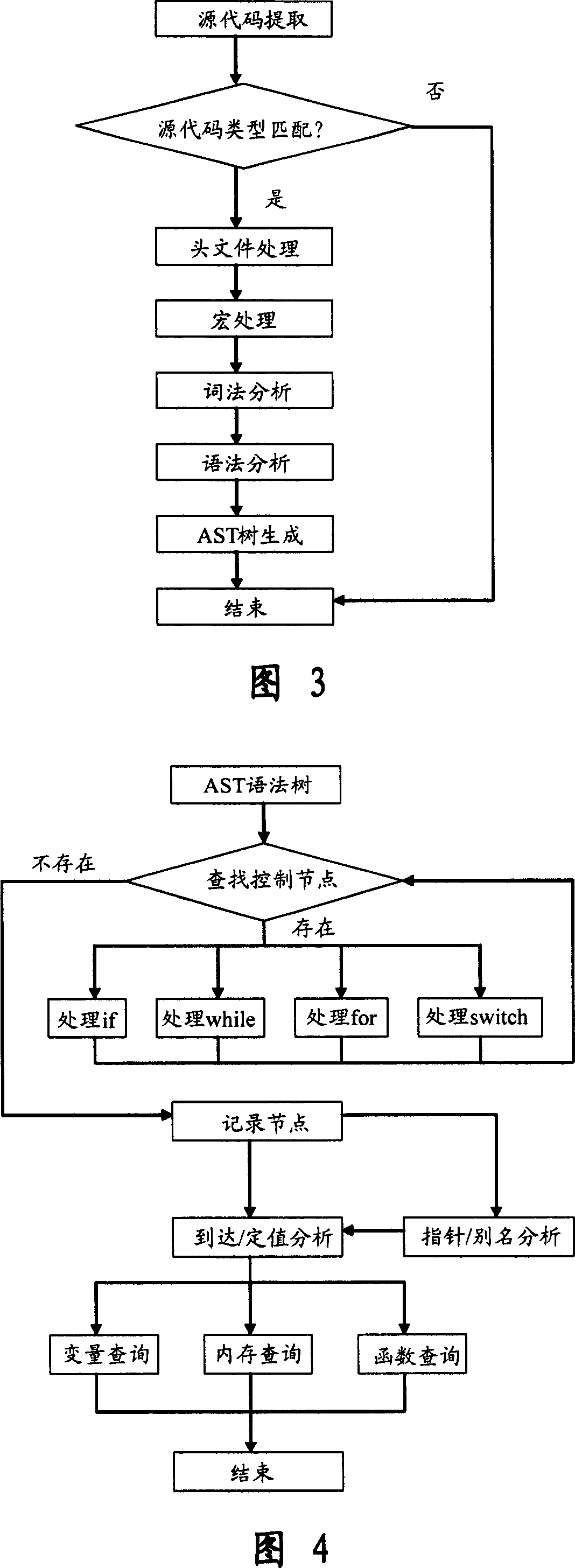
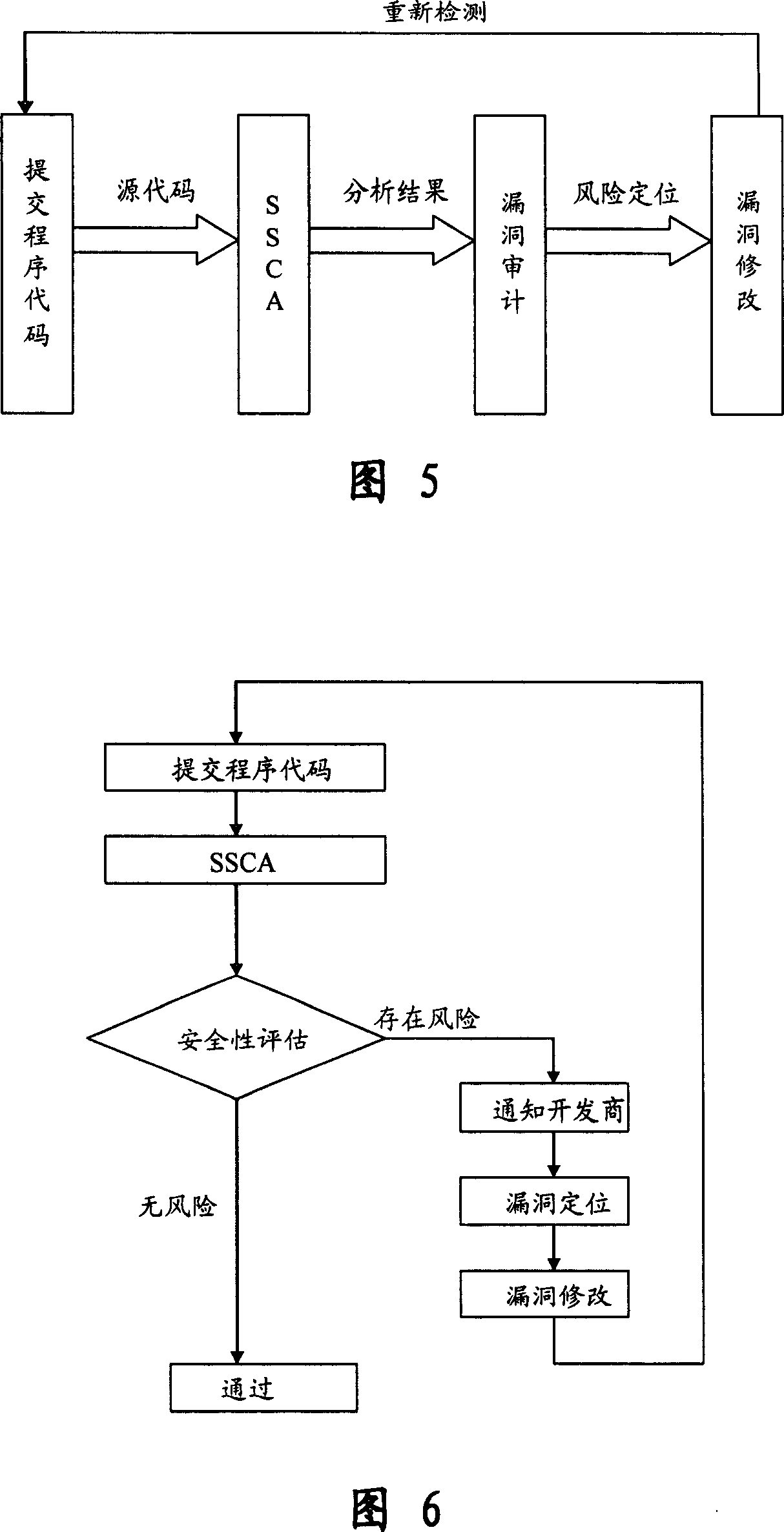
Software safety code analyzer based on static analysis of source code and testing method therefor
InactiveCN101017458AImprove accuracySupport for expansionSoftware testing/debuggingStatic timing analysisStructure analysis
This invention relates to one software analyzer and its test method based on source codes static analysis, wherein the analysis device comprises five function modules of code analysis device, codes analysis engine, safety risk report device, safety rules database and user interface; this invention gets programs safety risk to user according to the source program and grammar and meanings and delivers the safety leak to the user for audit and evaluation.
Owner:深圳北邮网络科技有限公司
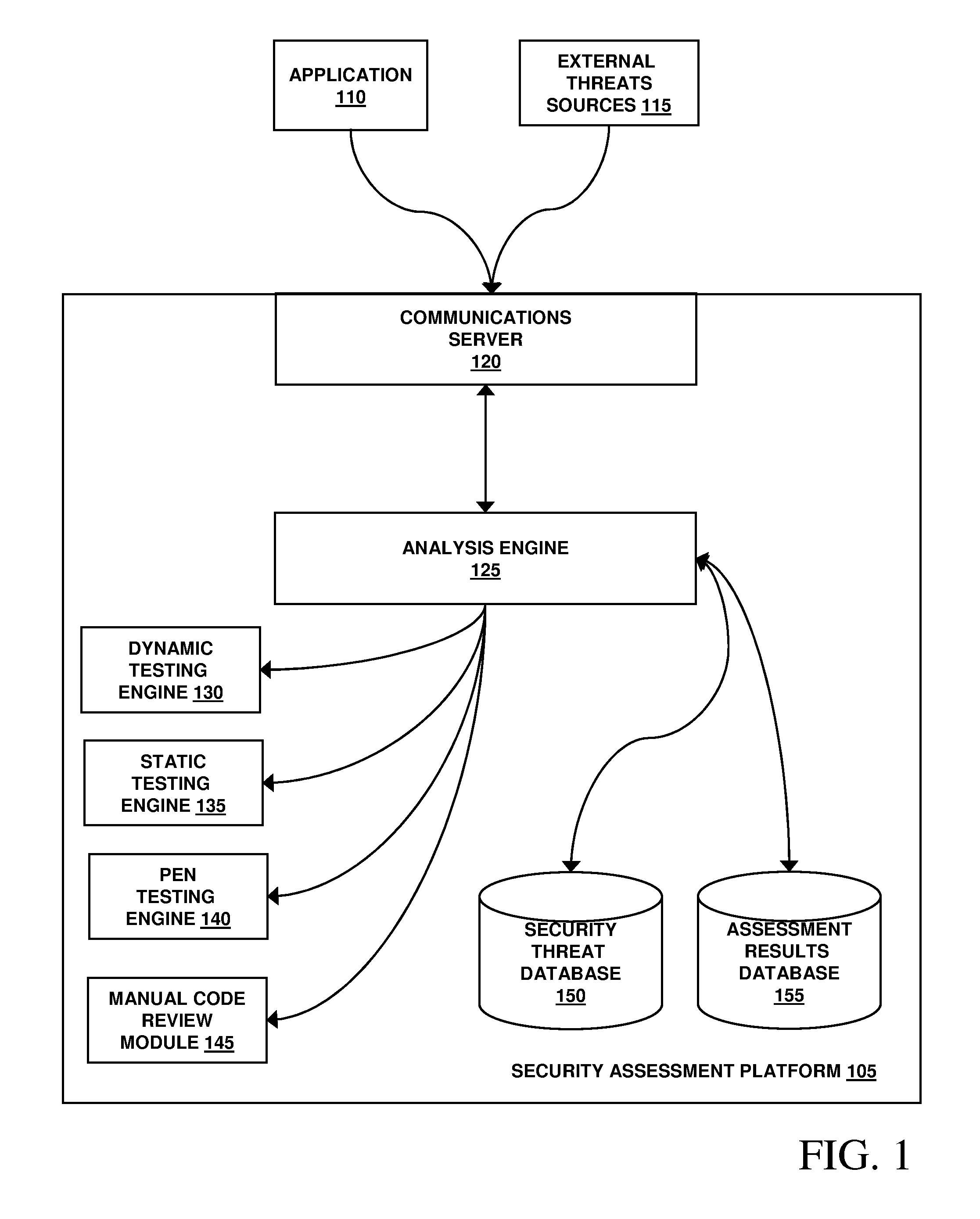
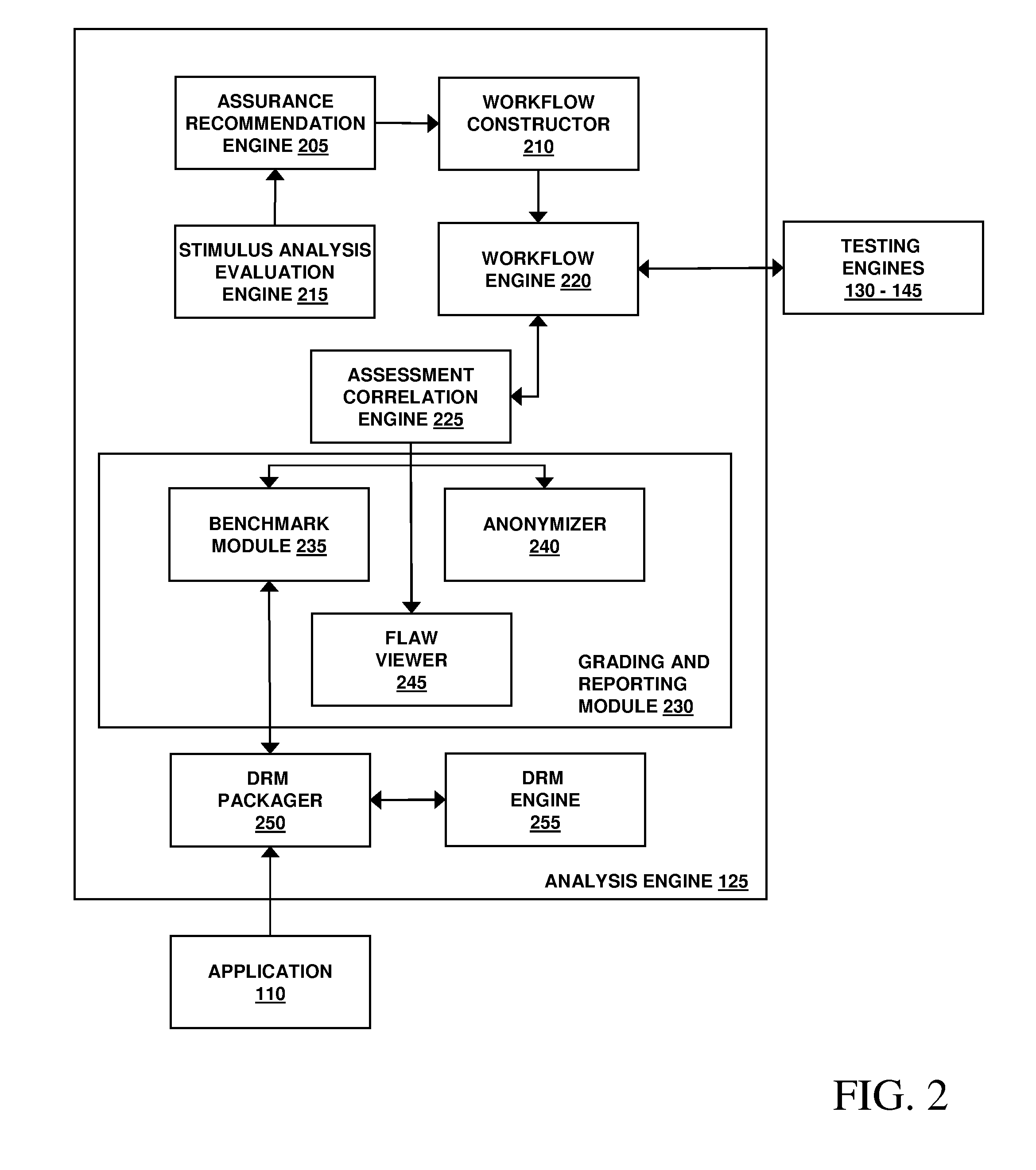
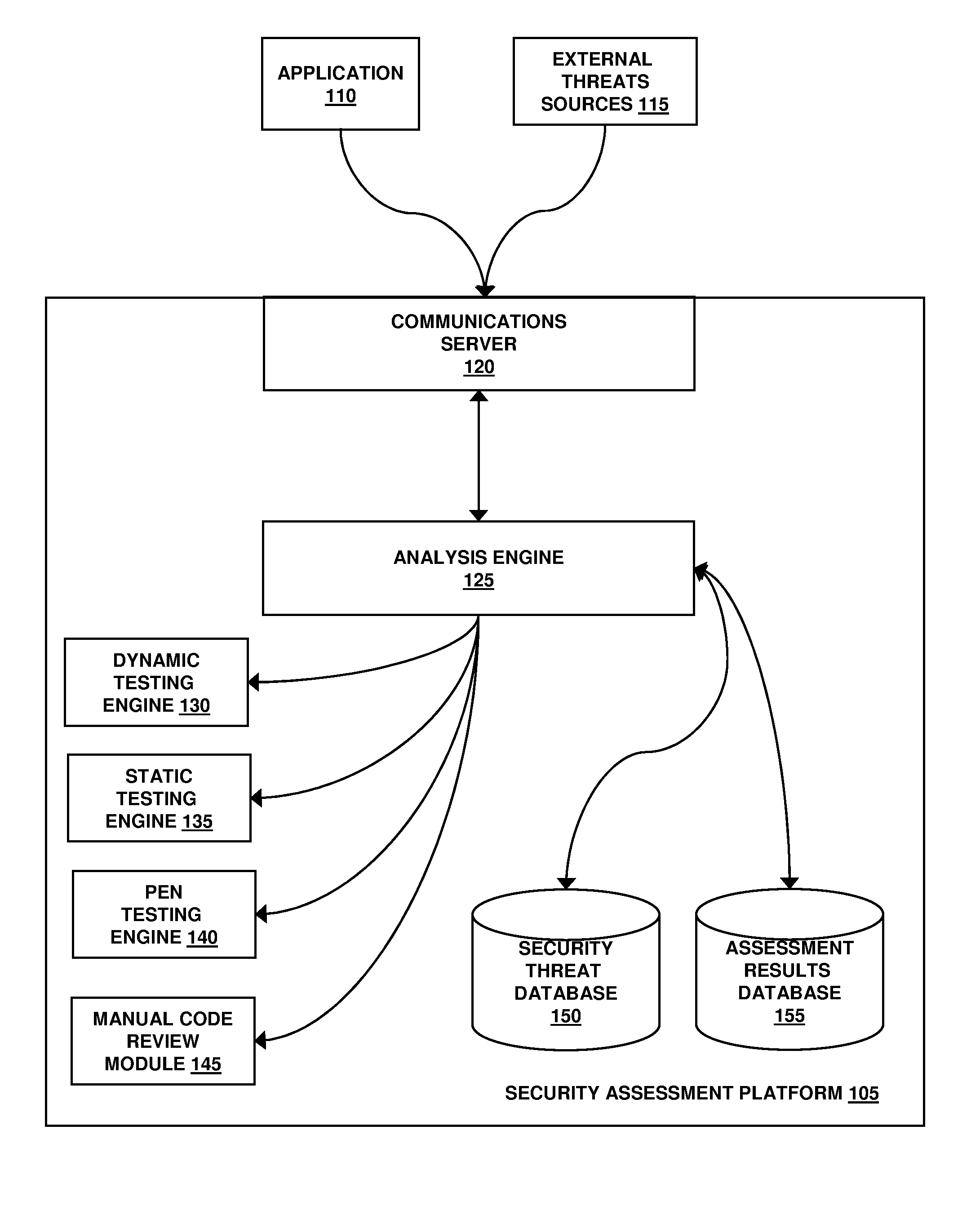
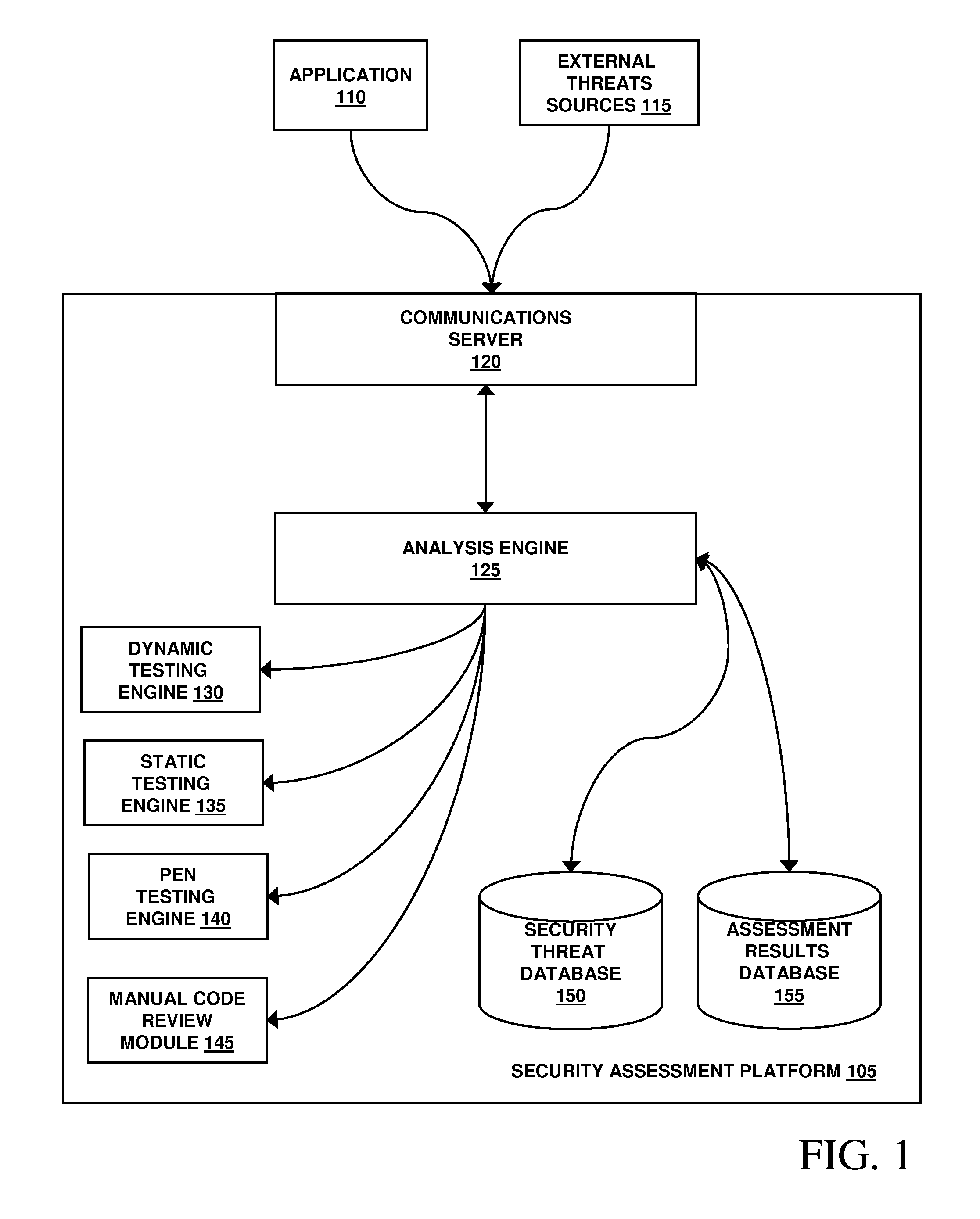
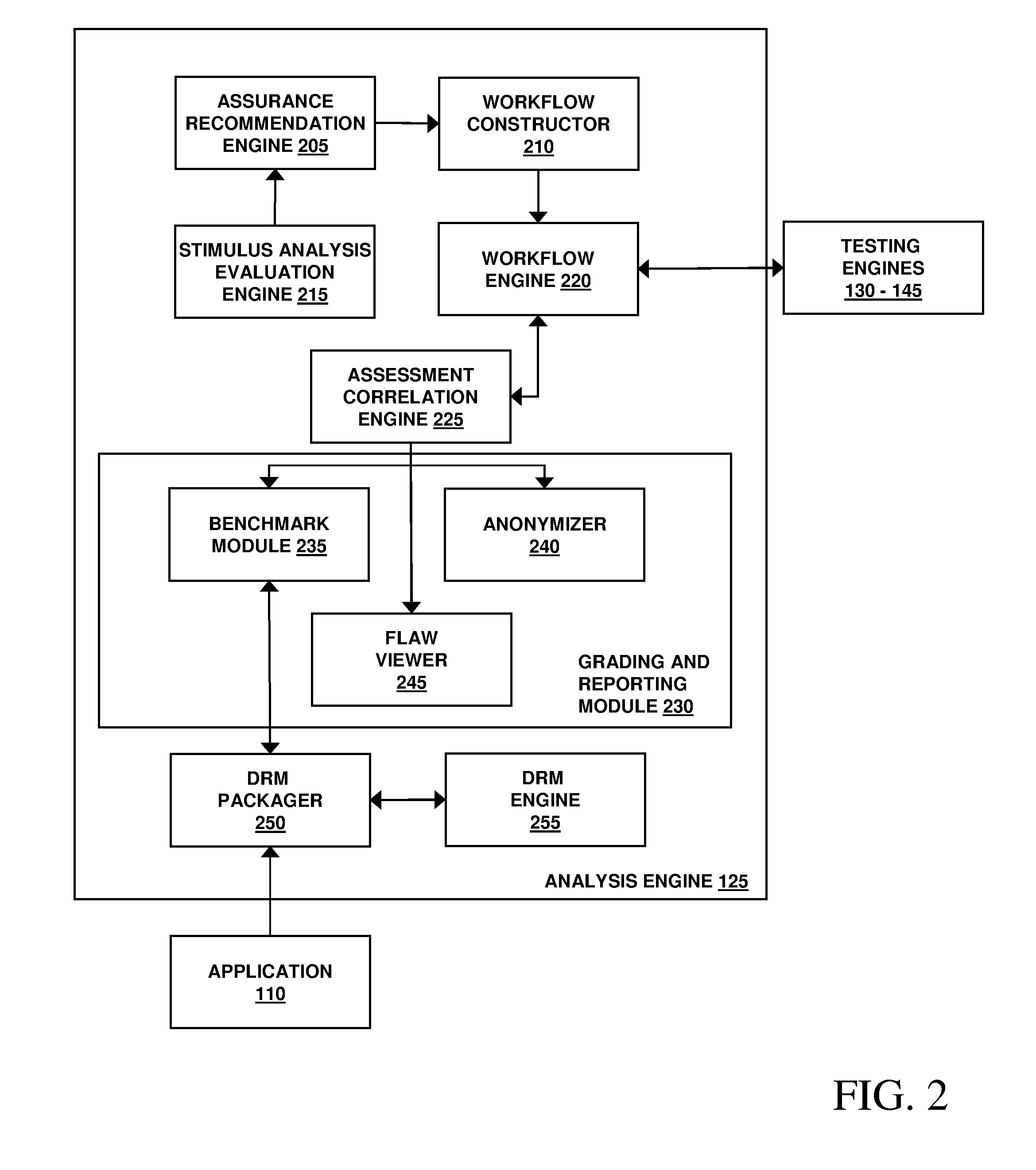
Assessment and analysis of software security flaws in virtual machines
ActiveUS20120072968A1Facilitates benchmarkingFacilitates security assessment and vulnerability testingMemory loss protectionError detection/correctionSoftware engineeringSecurity analysis
Security analysis and vulnerability testing results are “packaged” or “bound to” the actual software it describes. By linking the results to the software itself, downstream users of the software can access information about the software, make informed decisions about implementation of the software, and analyze the security risk across an entire system by accessing all (or most) of the reports associated with the executables running on the system and summarizing the risks identified in the reports.
Owner:VERACODE
System and method for medical device security, data tracking and outcomes analysis
InactiveUS20170068792A1Easy to createImprove equipment qualitySurgical needlesVaccination/ovulation diagnosticsPersonalizationGuideline
The present invention creates an objective methodology of quantitative accountability for medical device manufacturers, vendors, clinical providers, patients, and payers. In one embodiment, the standardized data received and stored in the medical device database can in turn be used for a variety of applications related to decision support (e.g., medical device selection), education and training (e.g., procedural performance), cost efficacy, evidence based medicine and best practice guidelines, personalized medicine, and comparative performance / safety analytics.
Owner:REINER BRUCE
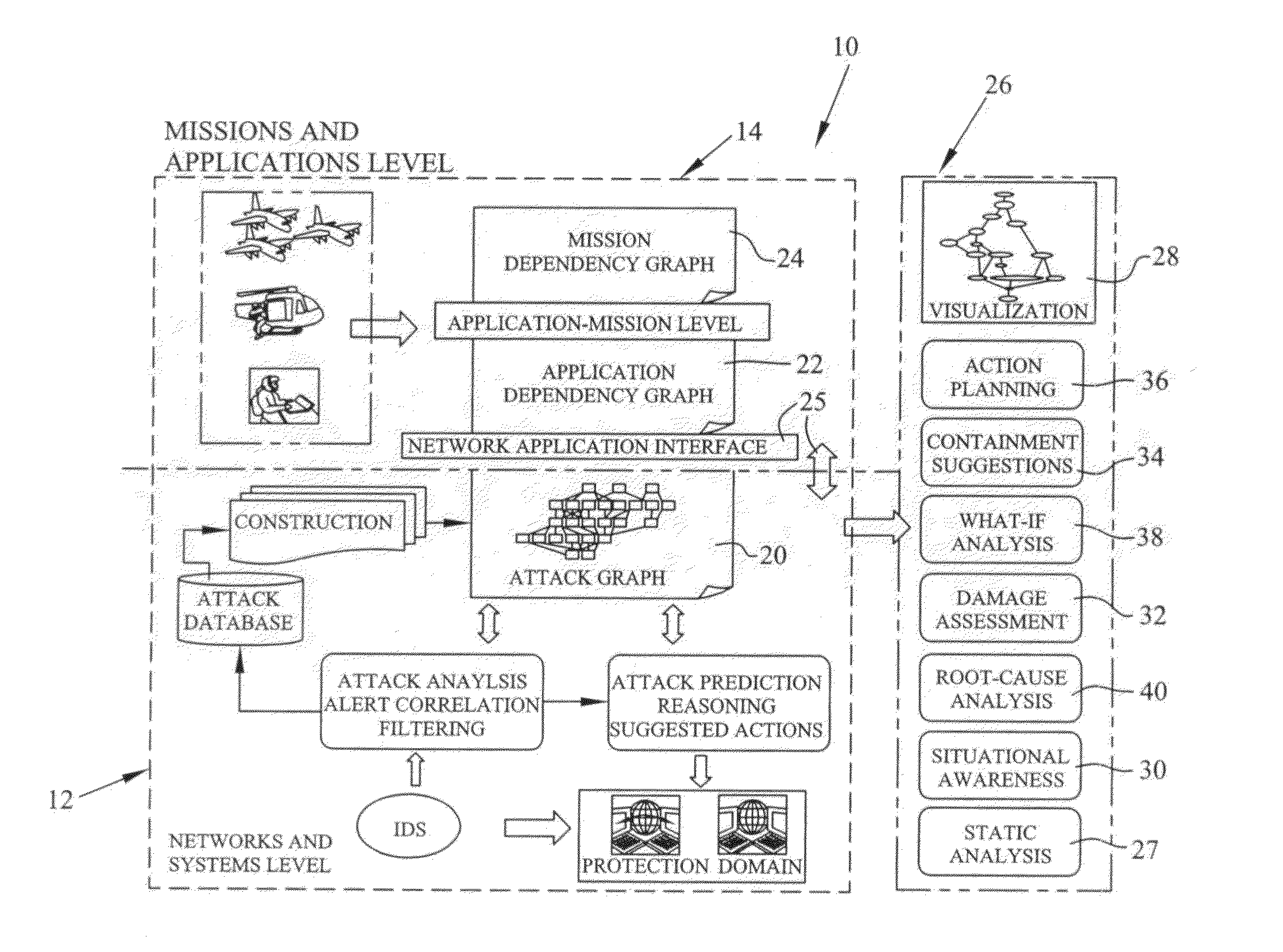
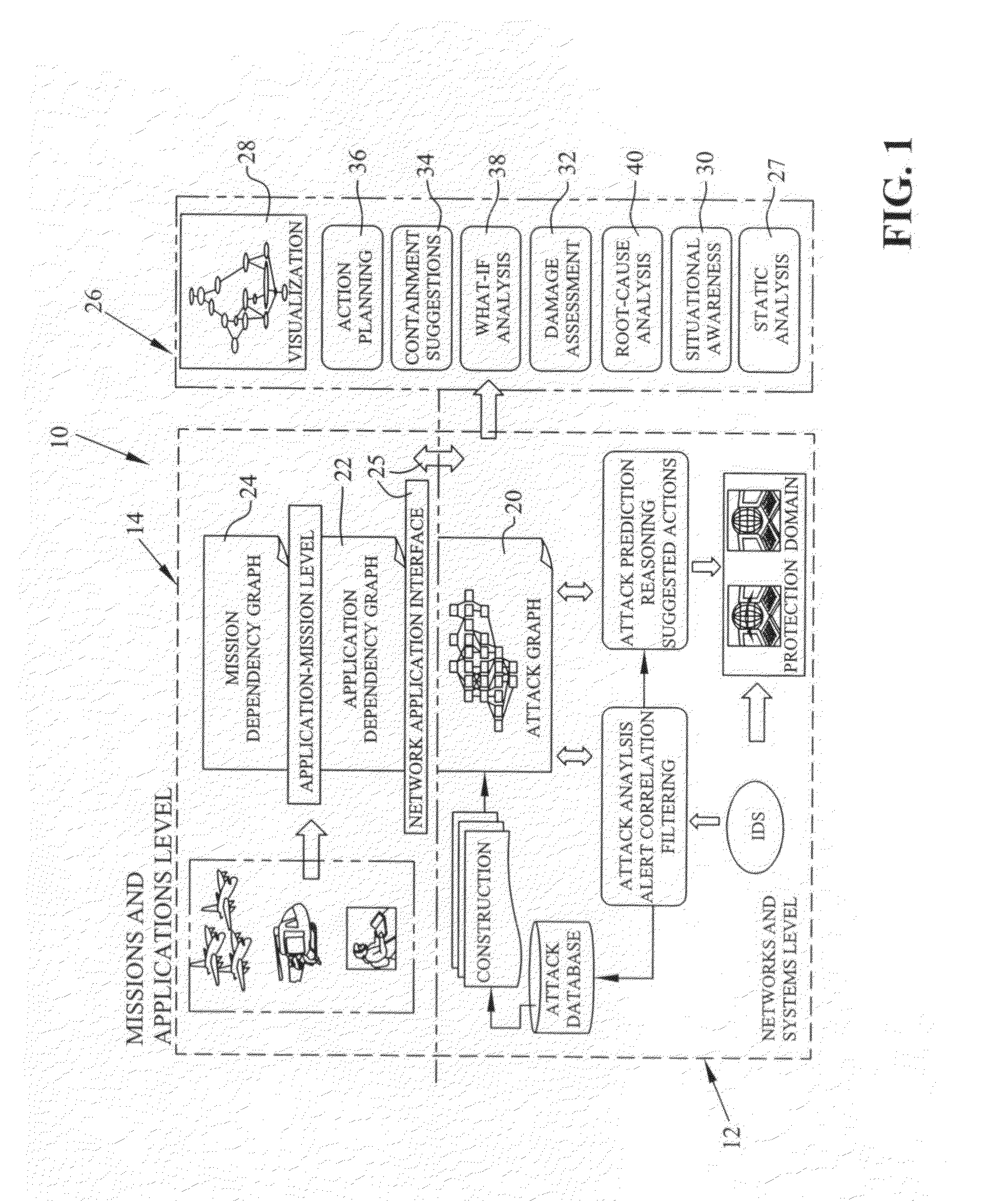
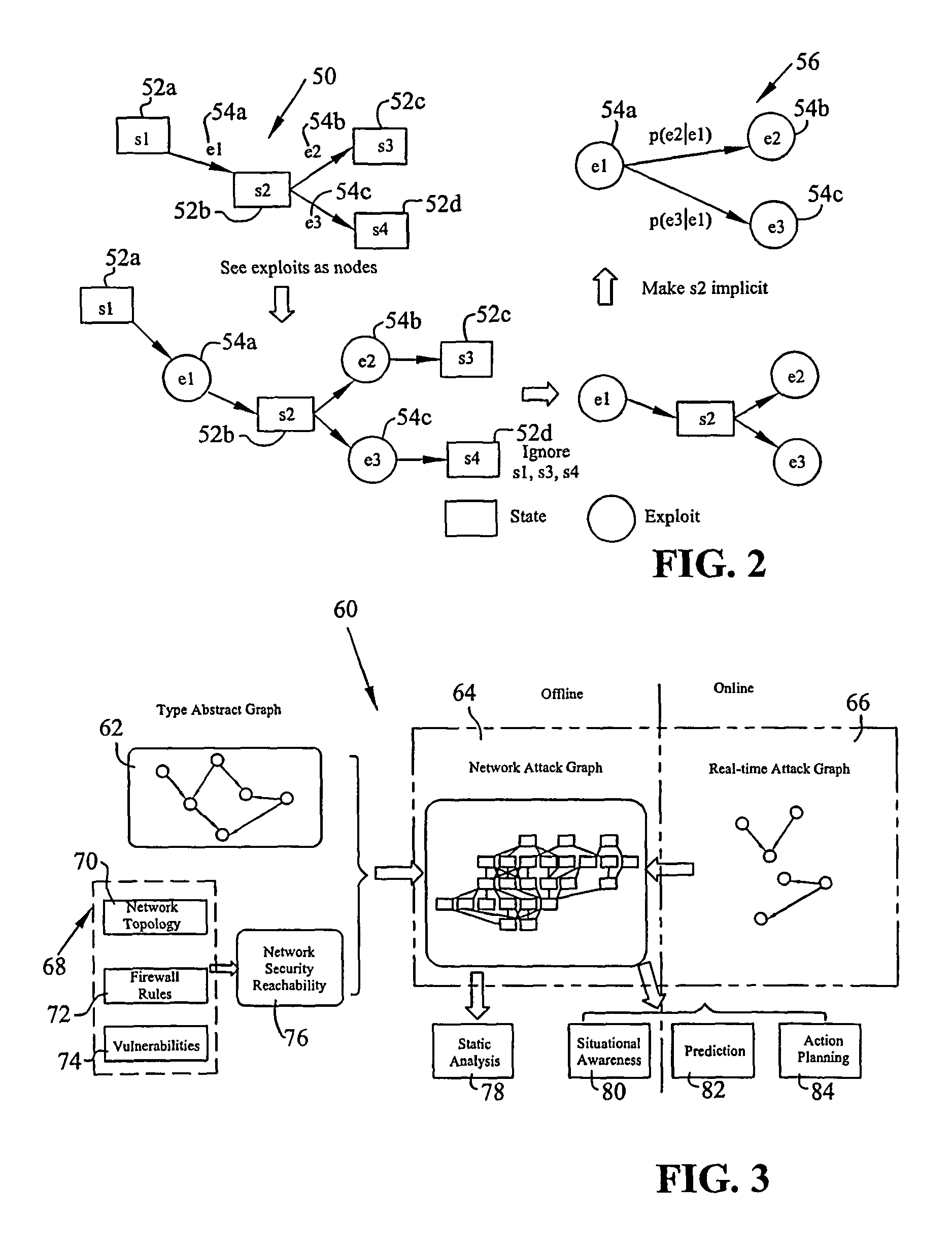
Graphical models for cyber security analysis in enterprise networks
ActiveUS8881288B1Accurate and efficientReduce and compress redundancyMemory loss protectionError detection/correctionGraphicsGaussian network model
A method of generating graphical models for providing security analysis in computer networks that in one embodiment includes the steps of generating a type abstract graph independent of particular networks that models abstract dependency relationships among attributes and exploits; generating network-specific attack graphs by combining the type abstract graph with specific network information; monitoring an intruder alert; and generating a real-time attack graph by correlating the intruder alert with the network-specific attack graph. The real-time attack graph can be generated using reachability checking, bridging, and exploit prediction based on consequence alerts and may further include the step of calculating the likelihood of queries using a Bayesian network model. The method may also include the steps of inferring unobserved attacks that may have been missed by intrusion detection sensors, and projecting on which hosts and using what exploits additional intruder attacks may occur. The method may further include the step of comparing alternate actions by computation, wherein the alternate actions include the step of patching some vulnerabilities, and wherein the specific network information includes network topology. The specific network information may also include firewall rules.
Owner:INTELLIGENT AUTOMATION LLC
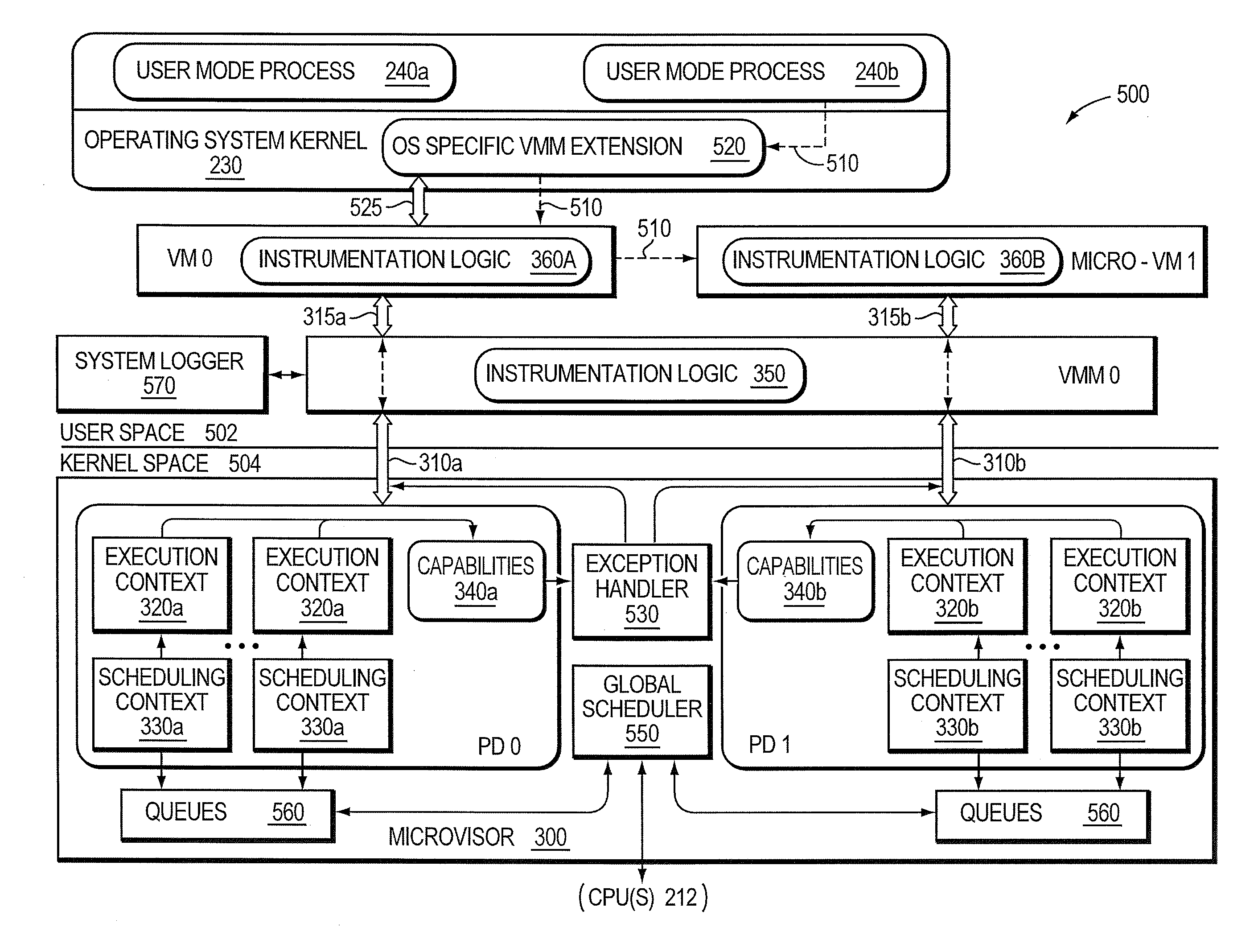
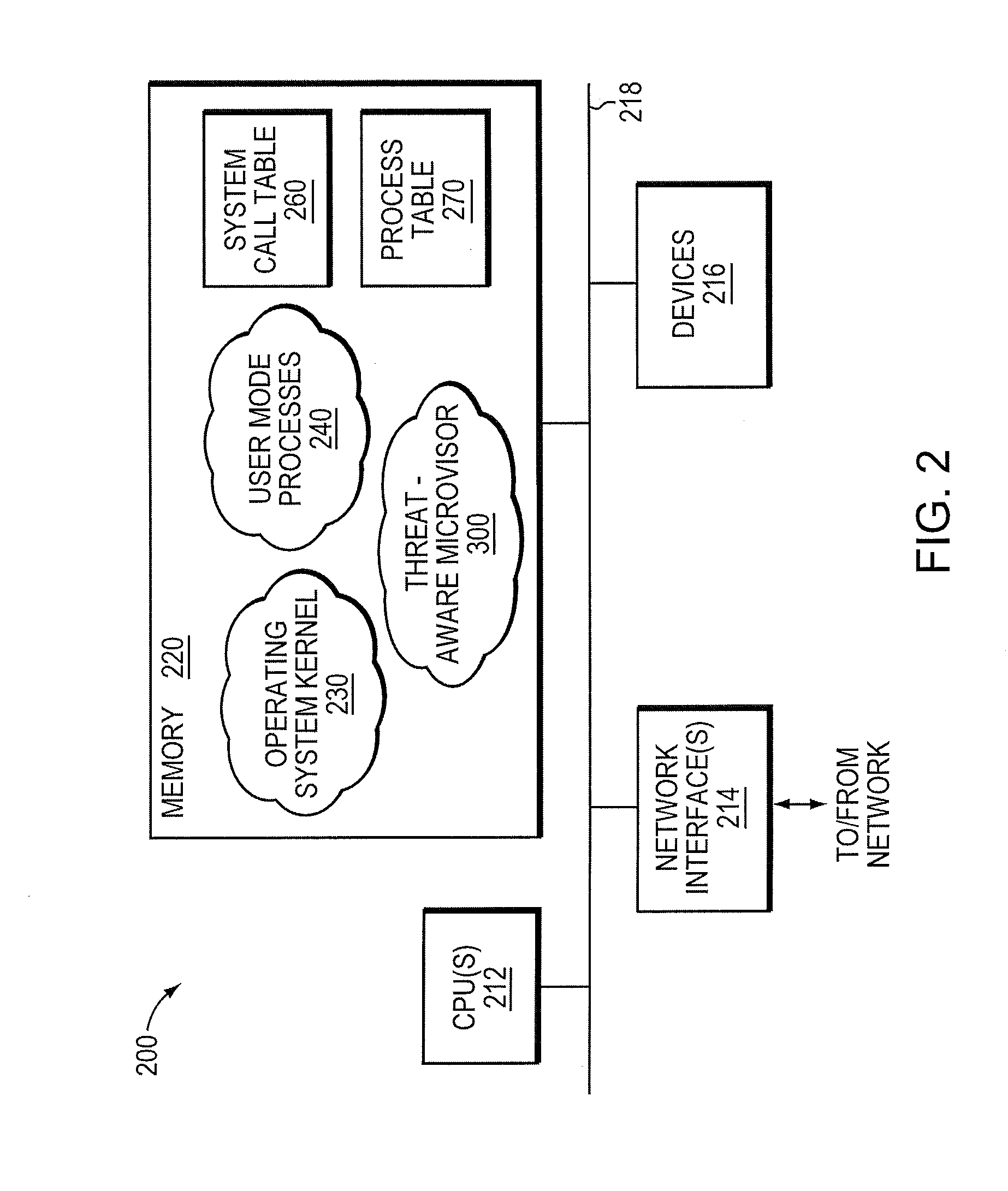
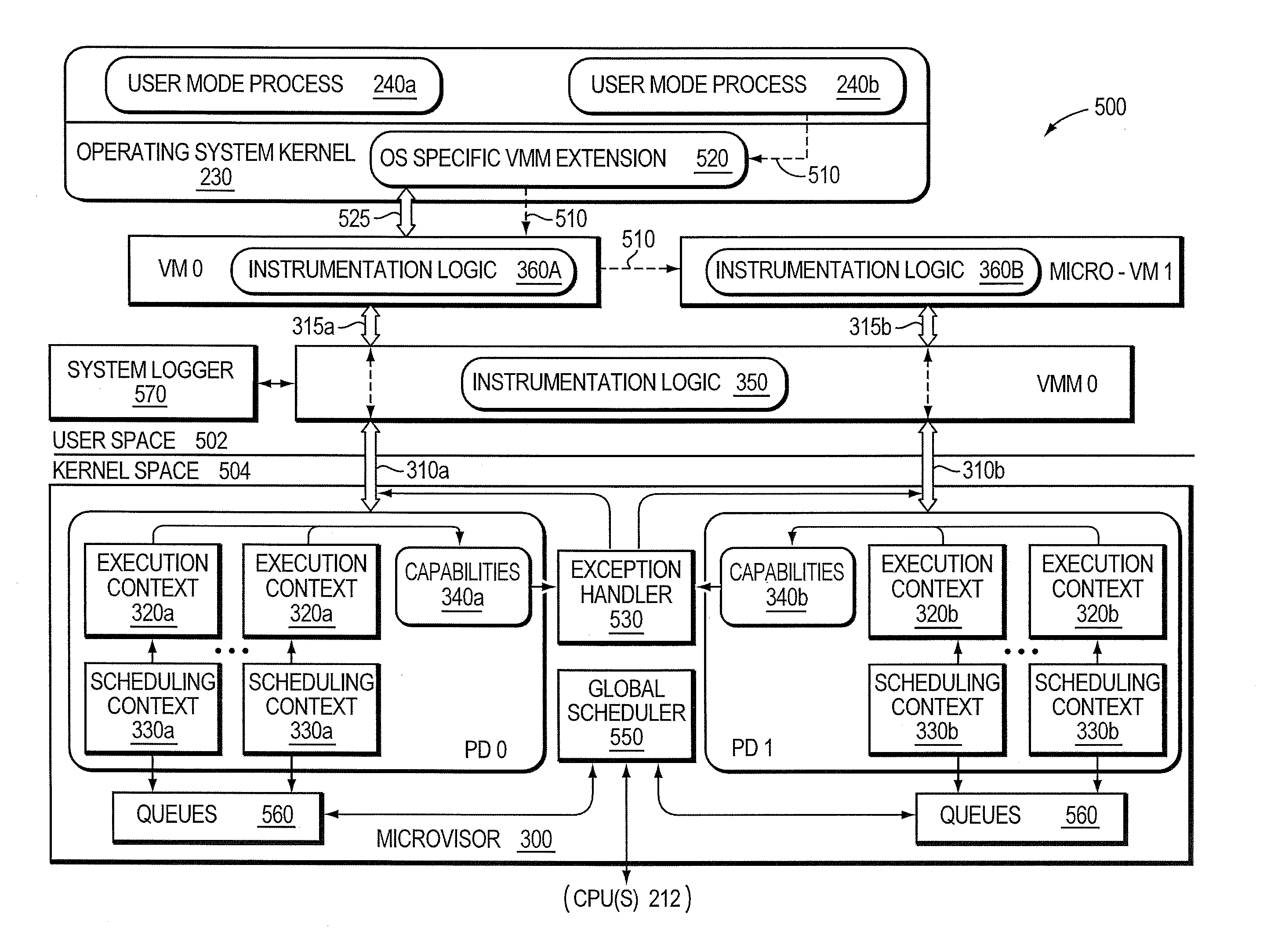
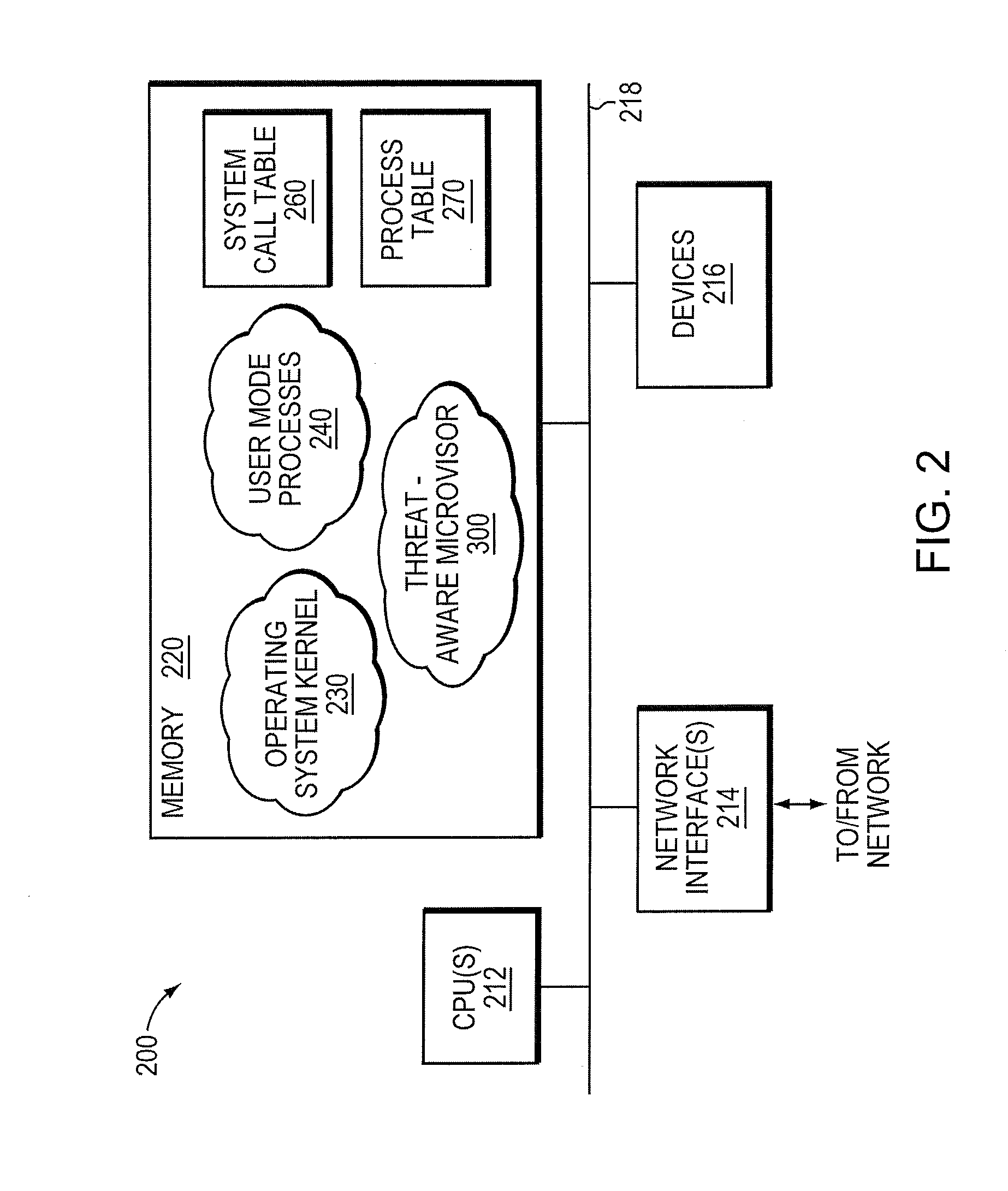
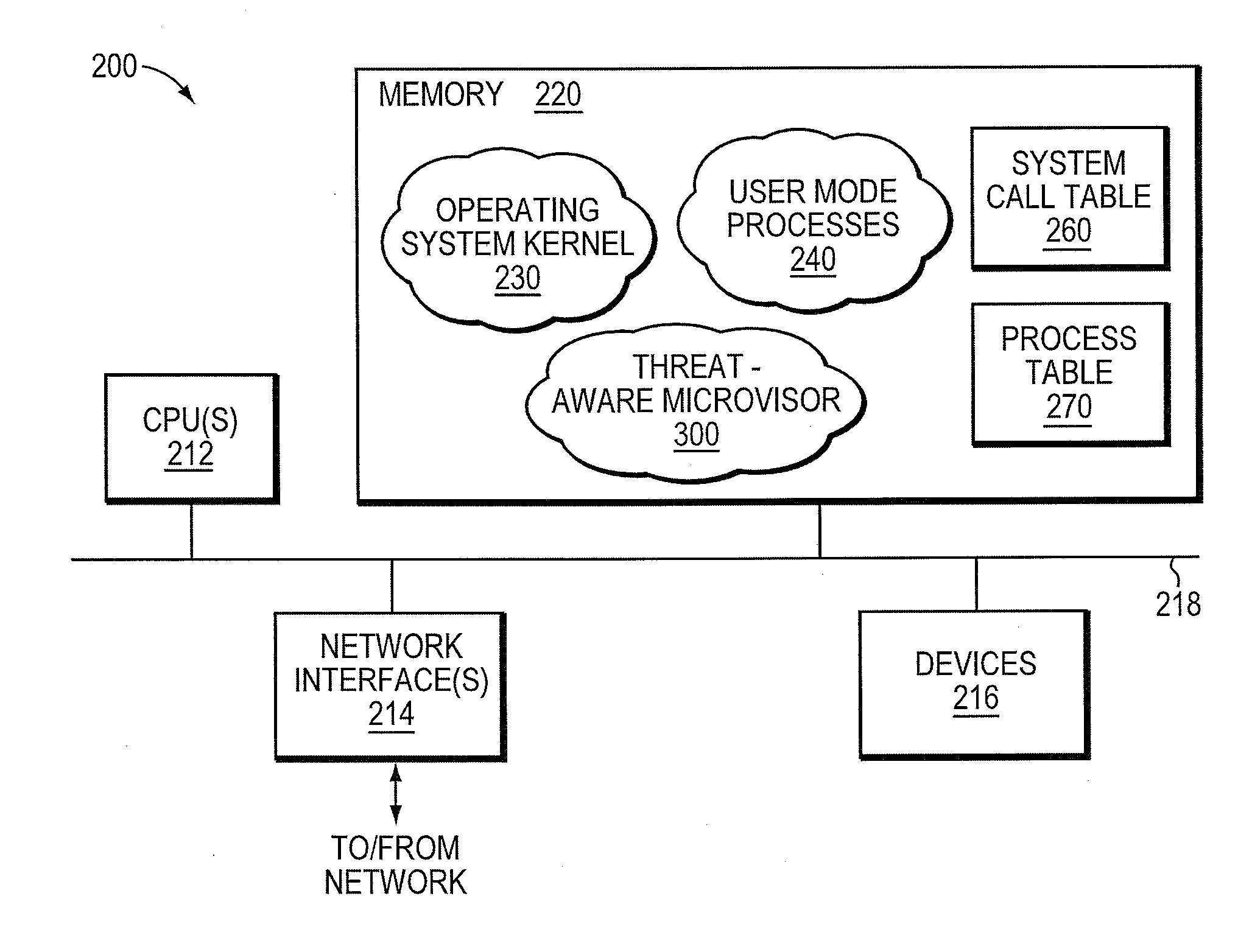
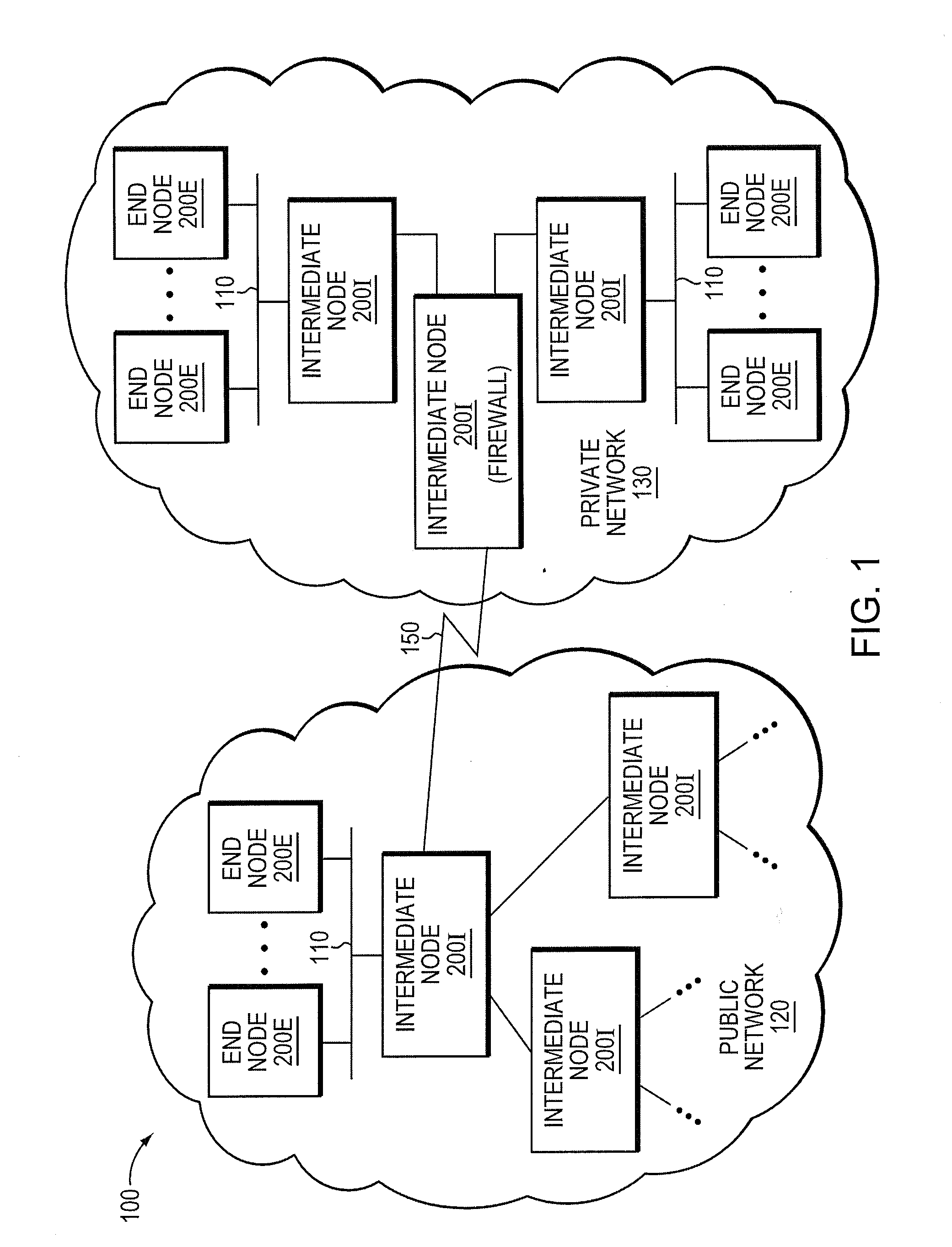
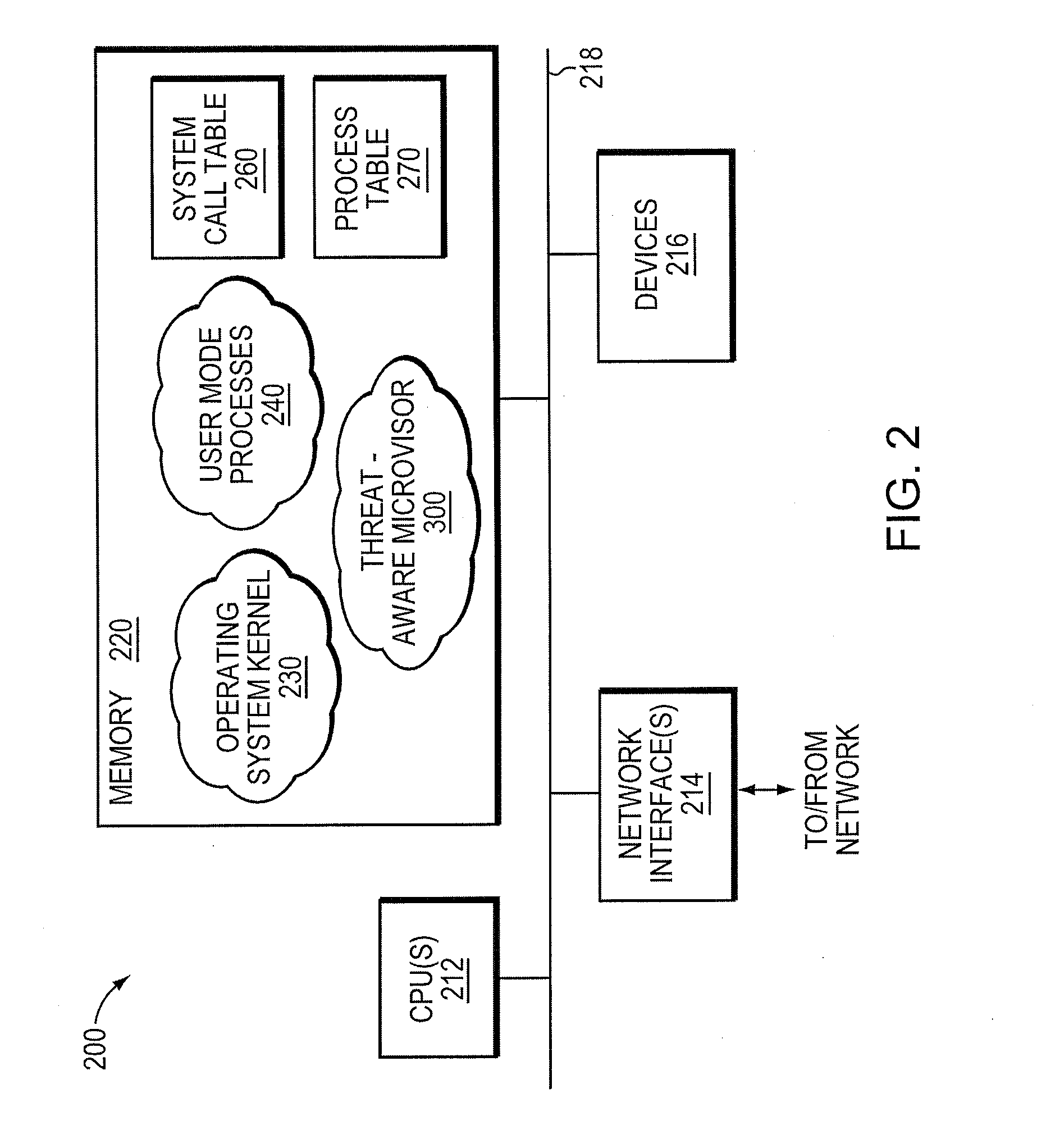
Micro-virtualization architecture for threat-aware microvisor deployment in a node of a network environment
ActiveUS20150199532A1Digital data processing detailsAnalogue secracy/subscription systemsVirtualizationSecurity analysis
A micro-virtualization architecture deploys a threat-aware microvisor as a module of a virtualization system configured to facilitate real-time security analysis, including exploit detection and threat intelligence, of operating system processes executing in a memory of a node in a network environment. The micro-virtualization architecture organizes the memory as a user space and kernel space, wherein the microvisor executes in the kernel space of the architecture, while the operating system processes, an operating system kernel, a virtual machine monitor (VMM) and its spawned virtual machines (VMs) execute in the user space. Notably, the microvisor executes at the highest privilege level of a central processing unit of the node to virtualize access to kernel resources. The operating system kernel executes under control of the microvisor at a privilege level lower than a highest privilege level of the microvisor. The VMM and its spawned VMs execute at the highest privilege level of the microvisor.
Owner:MANDIANT +1
Application of Z-webs and Z-factors to analytics, search engine, learning, recognition, natural language, and other utilities
ActiveUS8873813B2Character and pattern recognitionFuzzy logic based systemsMedical diagnosisConfidence factor
Here, we introduce Z-webs, including Z-factors and Z-nodes, for the understanding of relationships between objects, subjects, abstract ideas, concepts, or the like, including face, car, images, people, emotions, mood, text, natural language, voice, music, video, locations, formulas, facts, historical data, landmarks, personalities, ownership, family, friends, love, happiness, social behavior, voting behavior, and the like, to be used for many applications in our life, including on the search engine, analytics, Big Data processing, natural language processing, economy forecasting, face recognition, dealing with reliability and certainty, medical diagnosis, pattern recognition, object recognition, biometrics, security analysis, risk analysis, fraud detection, satellite image analysis, machine generated data analysis, machine learning, training samples, extracting data or patterns (from the video, images, and the like), editing video or images, and the like. Z-factors include reliability factor, confidence factor, expertise factor, bias factor, and the like, which is associated with each Z-node in the Z-web.
Owner:Z ADVANCED COMPUTING
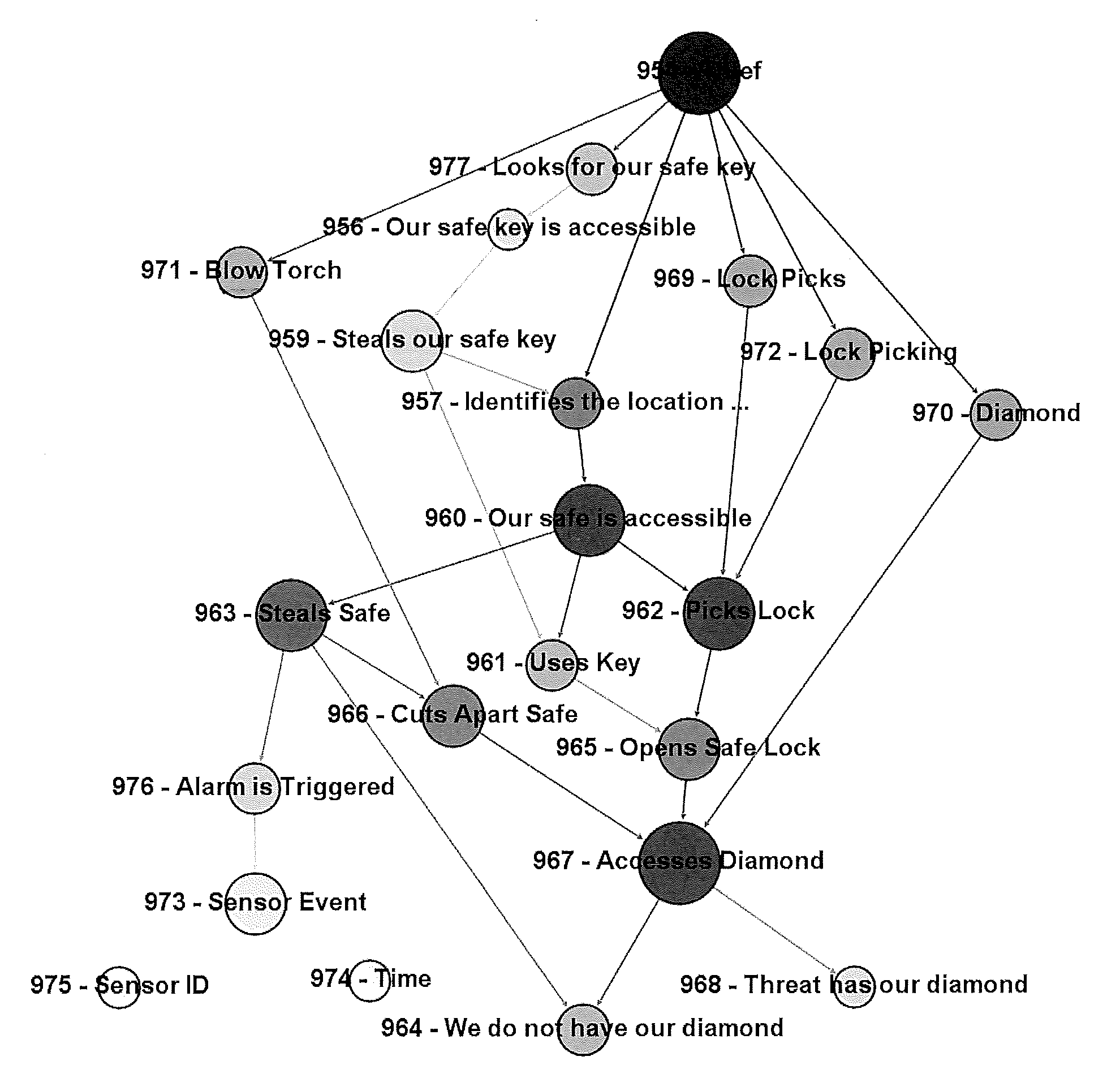
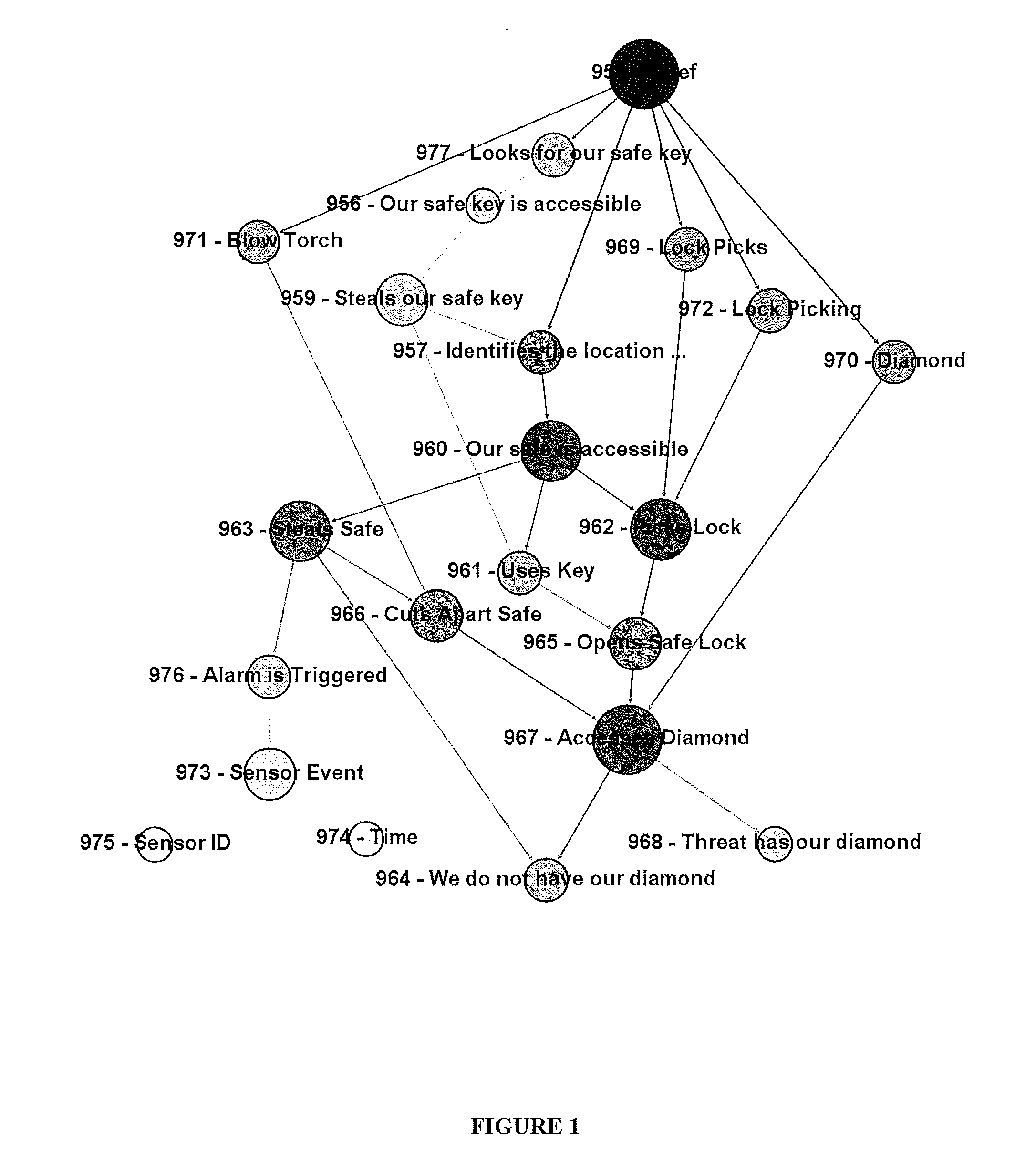
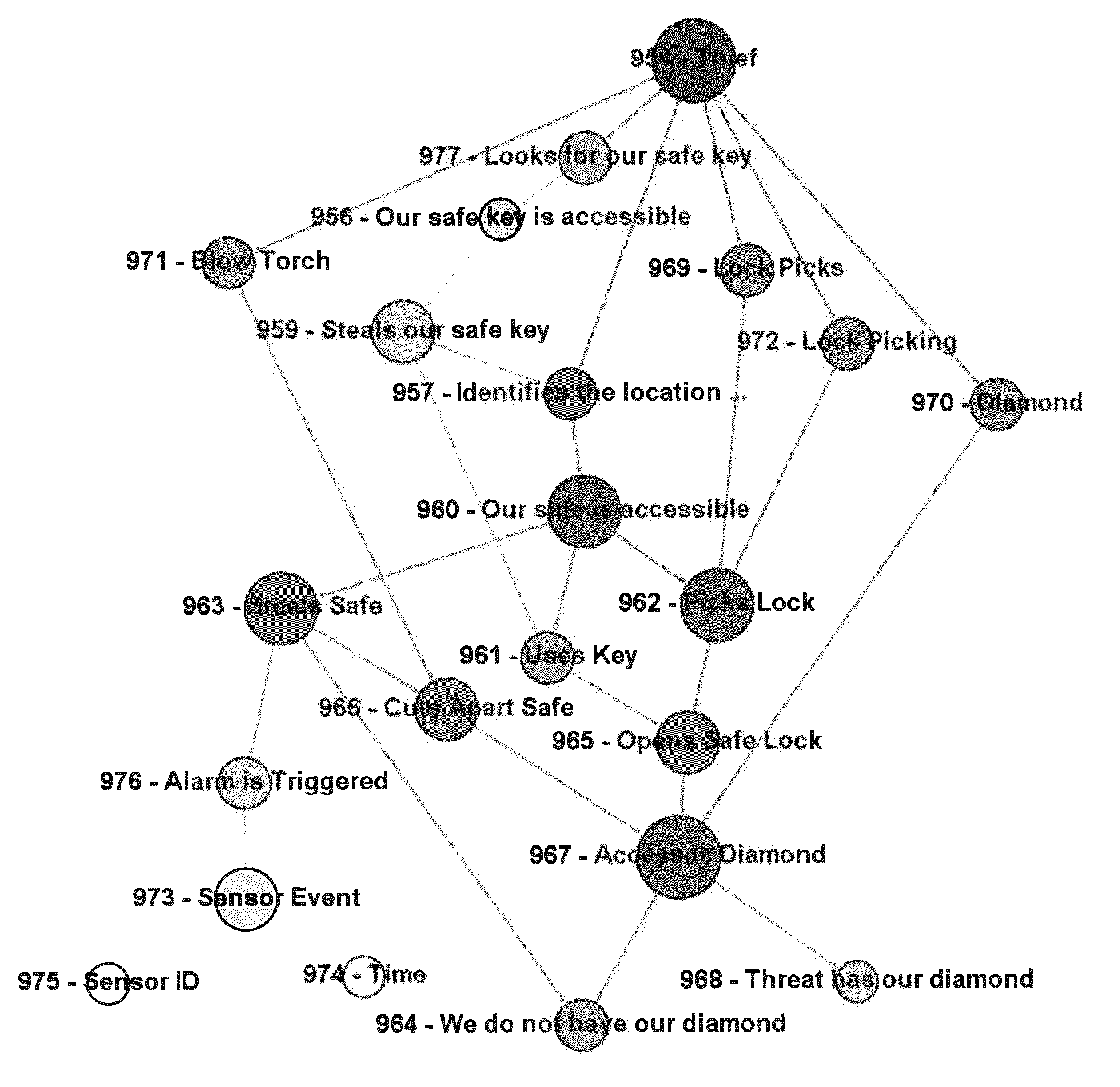
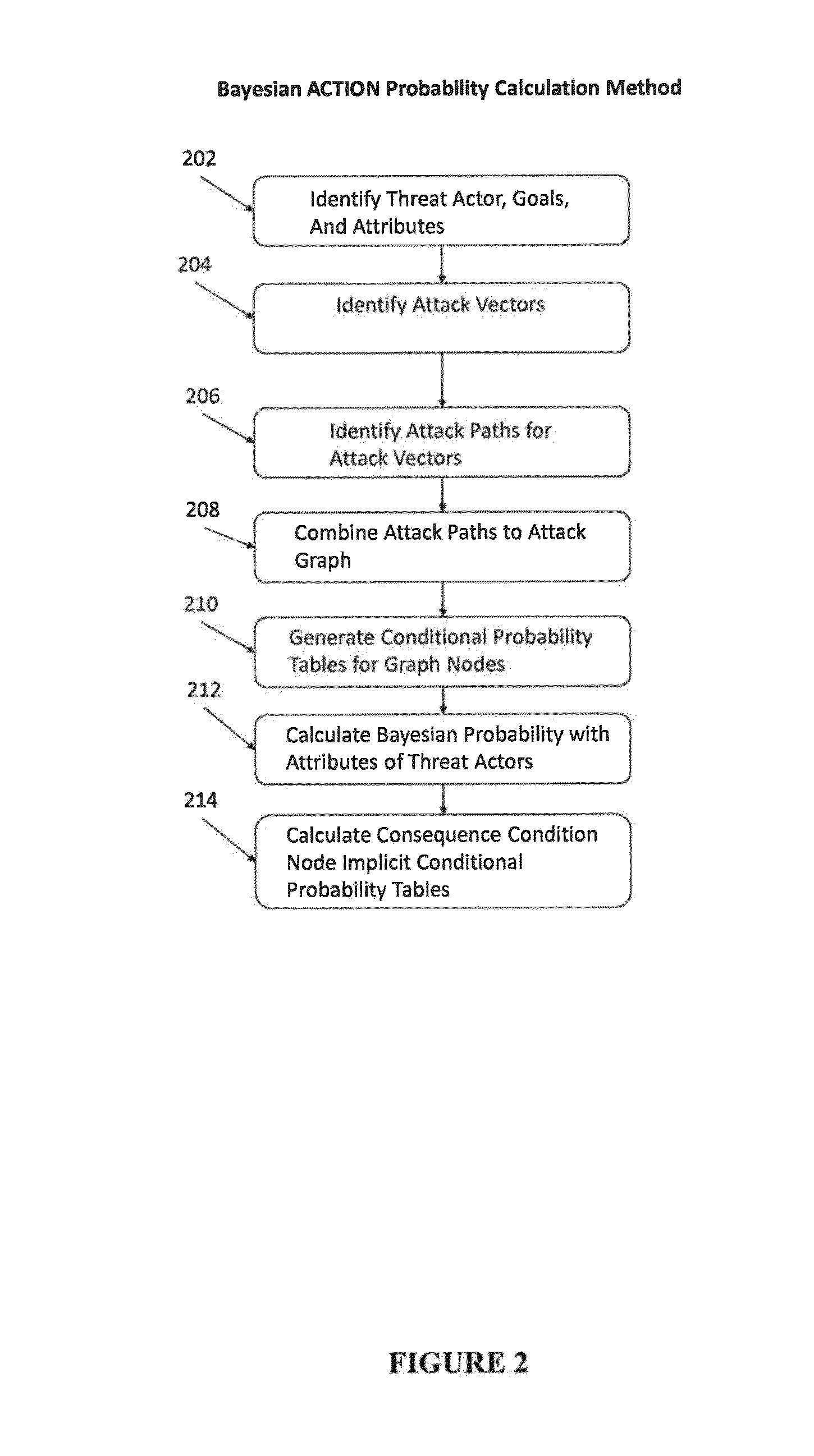
System and Method for Cyber Security Analysis and Human Behavior Prediction
ActiveUS20160205122A1Simple conditionsMemory loss protectionError detection/correctionHuman behaviorAttack graph
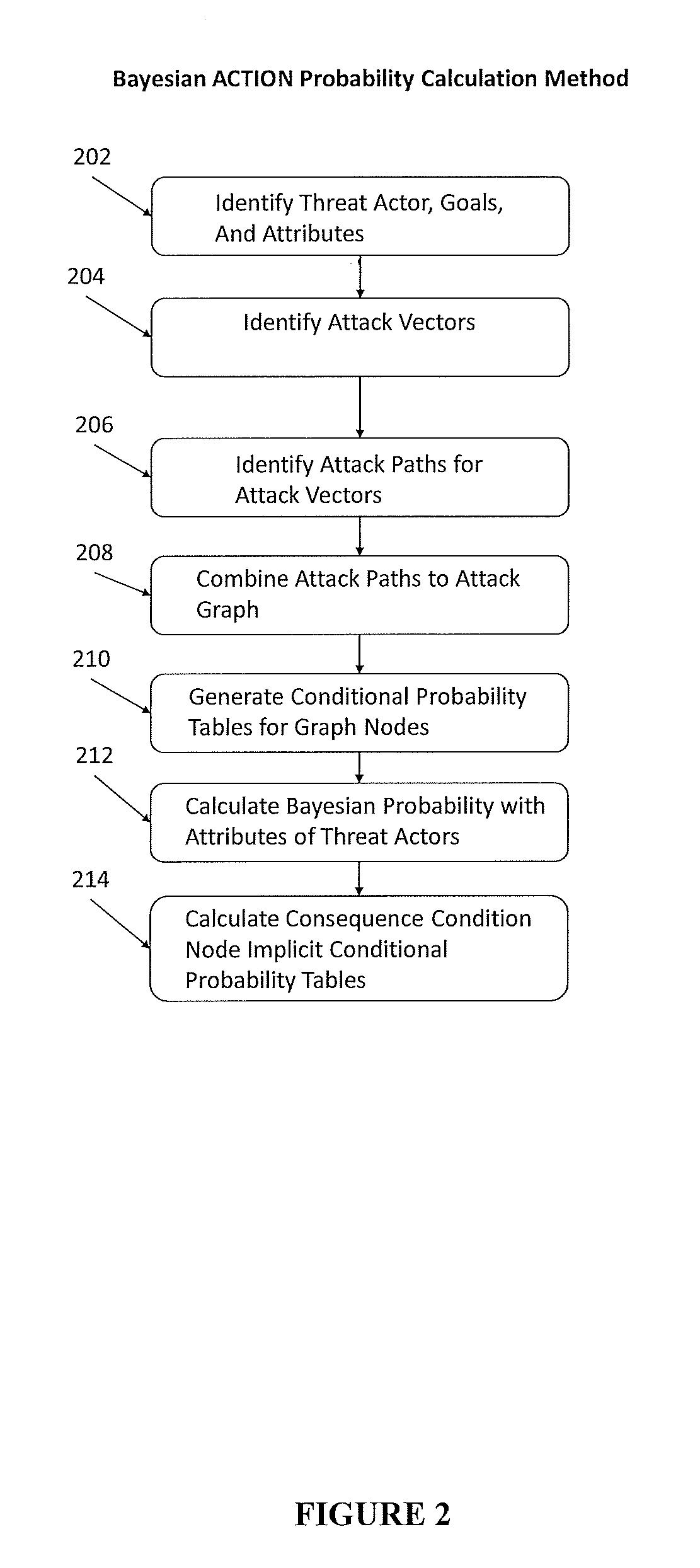
An improved method for analyzing computer network security has been developed. The method first establishes multiple nodes, where each node represents an actor, an event, a condition, or an attribute related to the network security. Next, an estimate is created for each node that reflects the ease of realizing the event, condition, or attribute of the node. Attack paths are identified that represent a linkage of nodes that reach a condition of compromise of network security. Next, edge probabilities are calculated for the attack paths. The edge probabilities are based on the estimates for each node along the attack path. Next, an attack graph is generated that identifies the easiest conditions of compromise of network security and the attack paths to achieving those conditions. Finally, attacks are detected with physical sensors on the network, that predict the events and conditions. When an attack is detected, security alerts are generated in response to the attacks.
Owner:BASSETT GABRIEL
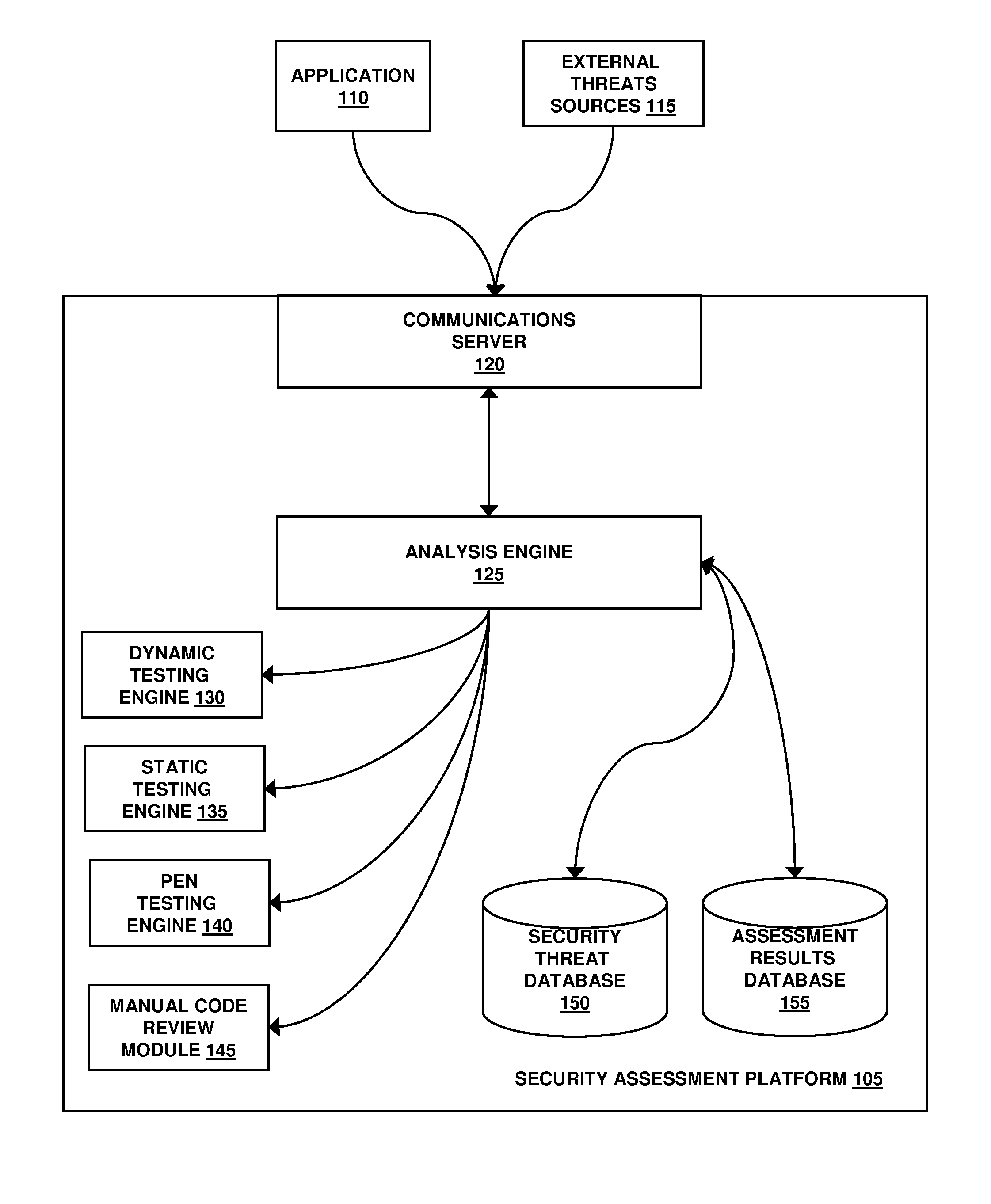
Assessment and analysis of software security flaws
ActiveUS20110173693A1Facilitates benchmarkingFacilitates security assessment and vulnerability testingMemory loss protectionDigital data processing detailsSoftware engineeringSecurity analysis
Security analysis and vulnerability testing results are “packaged” or “bound to” the actual software it describes. By linking the results to the software itself, downstream users of the software can access information about the software, make informed decisions about implementation of the software, and analyze the security risk across an entire system by accessing all (or most) of the reports associated with the executables running on the system and summarizing the risks identified in the reports.
Owner:VERACODE
Micro-virtualization architecture for threat-aware microvisor deployment in a node of a network environment
ActiveUS9292686B2Digital data protectionPlatform integrity maintainanceVirtualizationOperational system
A micro-virtualization architecture deploys a threat-aware microvisor as a module of a virtualization system configured to facilitate real-time security analysis, including exploit detection and threat intelligence, of operating system processes executing in a memory of a node in a network environment. The micro-virtualization architecture organizes the memory as a user space and kernel space, wherein the microvisor executes in the kernel space of the architecture, while the operating system processes, an operating system kernel, a virtual machine monitor (VMM) and its spawned virtual machines (VMs) execute in the user space. Notably, the microvisor executes at the highest privilege level of a central processing unit of the node to virtualize access to kernel resources. The operating system kernel executes under control of the microvisor at a privilege level lower than a highest privilege level of the microvisor. The VMM and its spawned VMs execute at the highest privilege level of the microvisor.
Owner:MANDIANT +1
Threat-aware microvisor
ActiveUS20150199513A1Memory loss protectionError detection/correctionOperational systemComputer module
A threat-aware microvisor is configured to facilitate real-time security analysis, including exploit detection and threat intelligence, of operating system processes executing on a node of a network environment. The microvisor may be embodied as a module disposed or layered beneath (underlying) an operating system kernel executing on the node to thereby control privileges (i.e., access permissions) to kernel resources, such as one or more central processing units (CPUs), network interfaces, memory, and / or devices, of the node. Illustratively, the microvisor may be configured to control access to one or more of the resources in response to a request by an operating system process to access the resource.
Owner:FIREEYE SECURITY HLDG US LLC
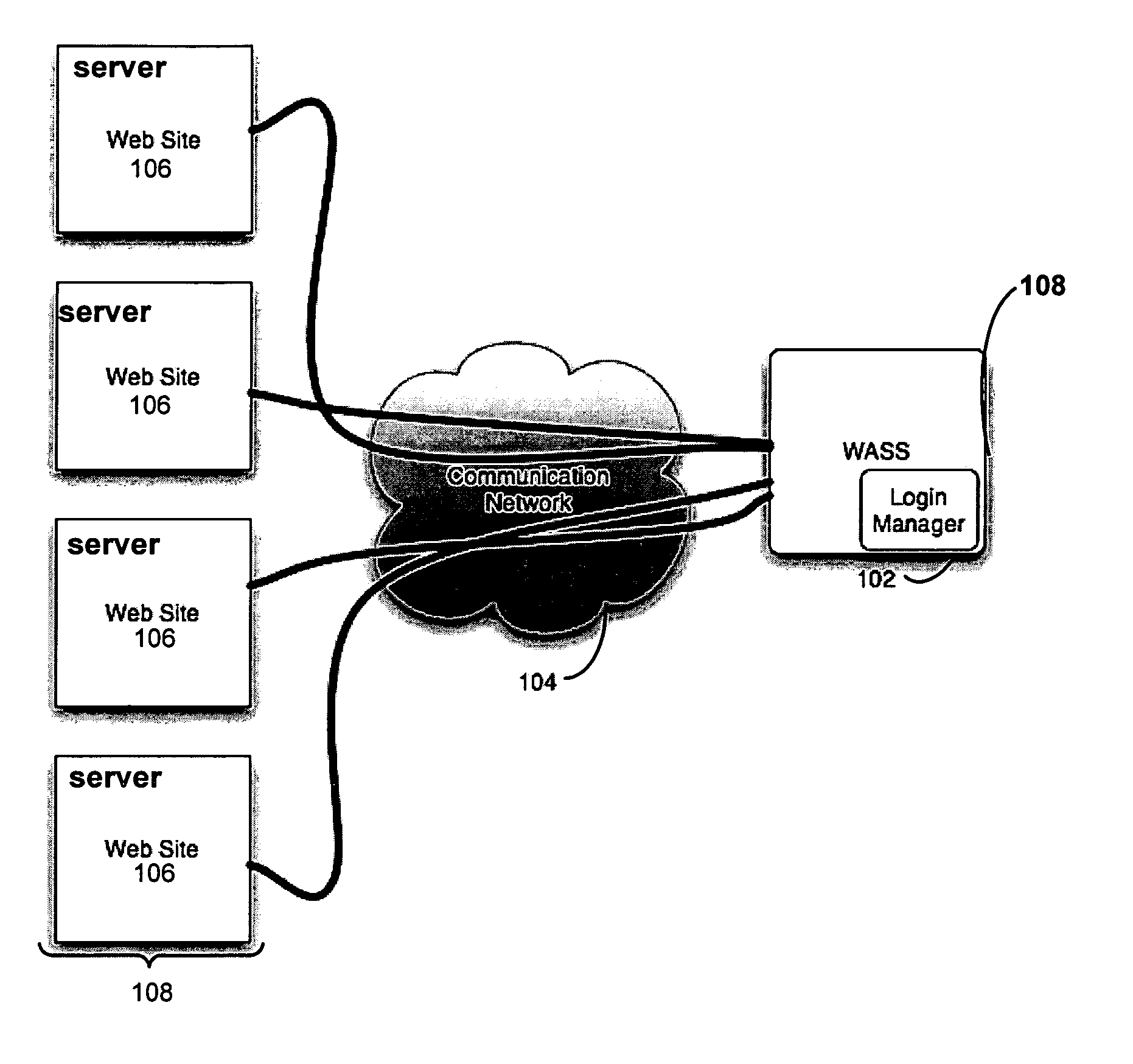
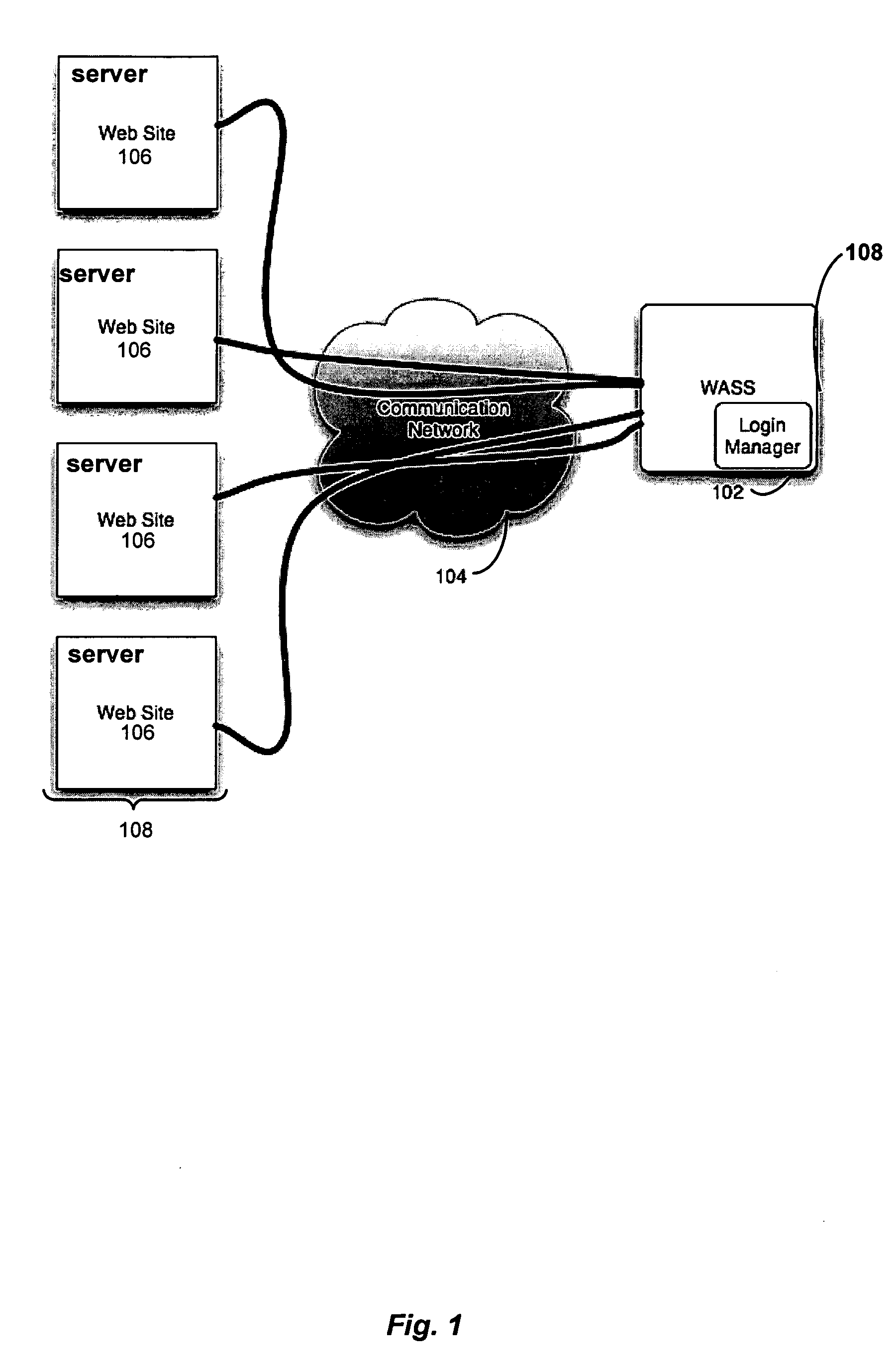
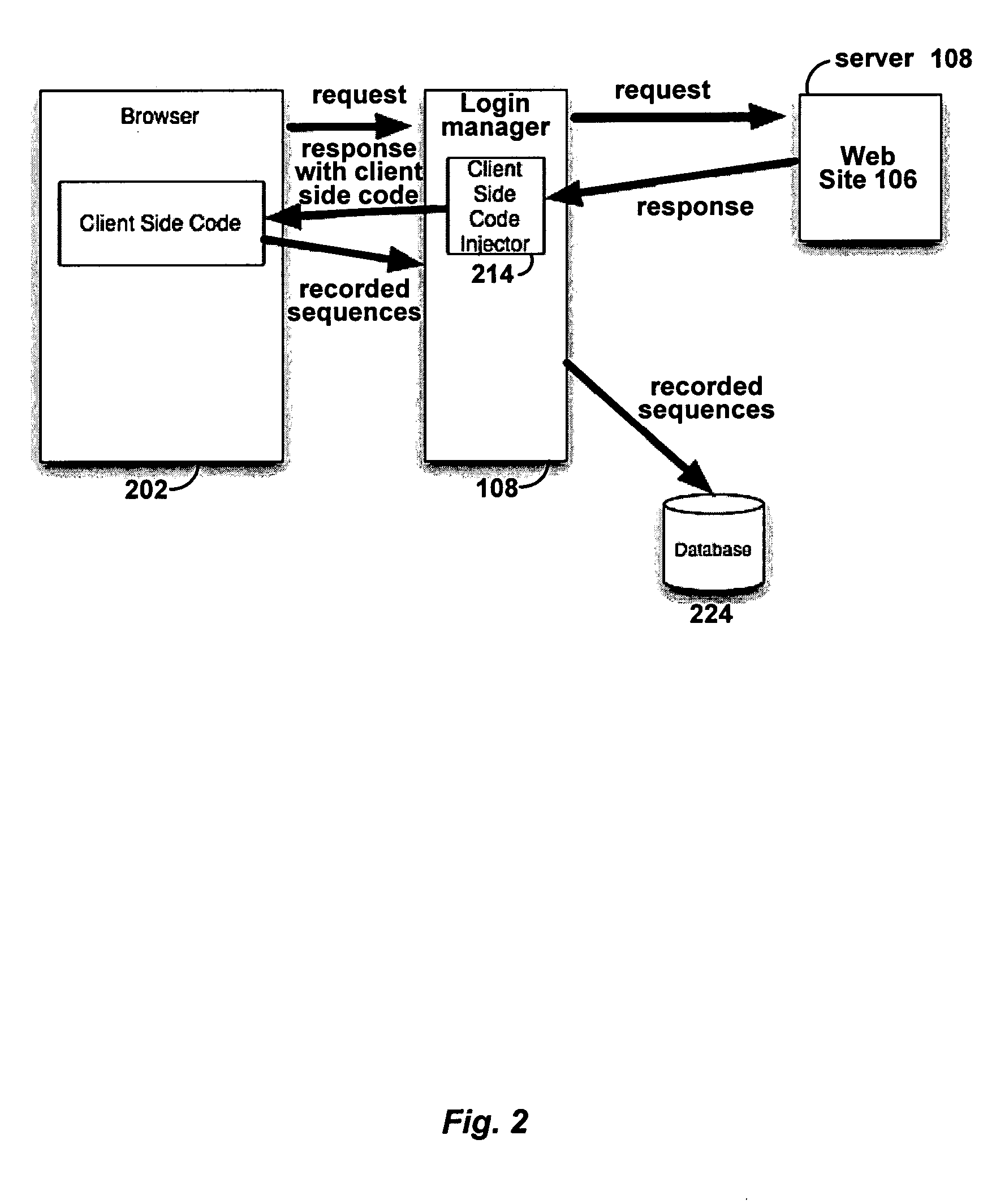
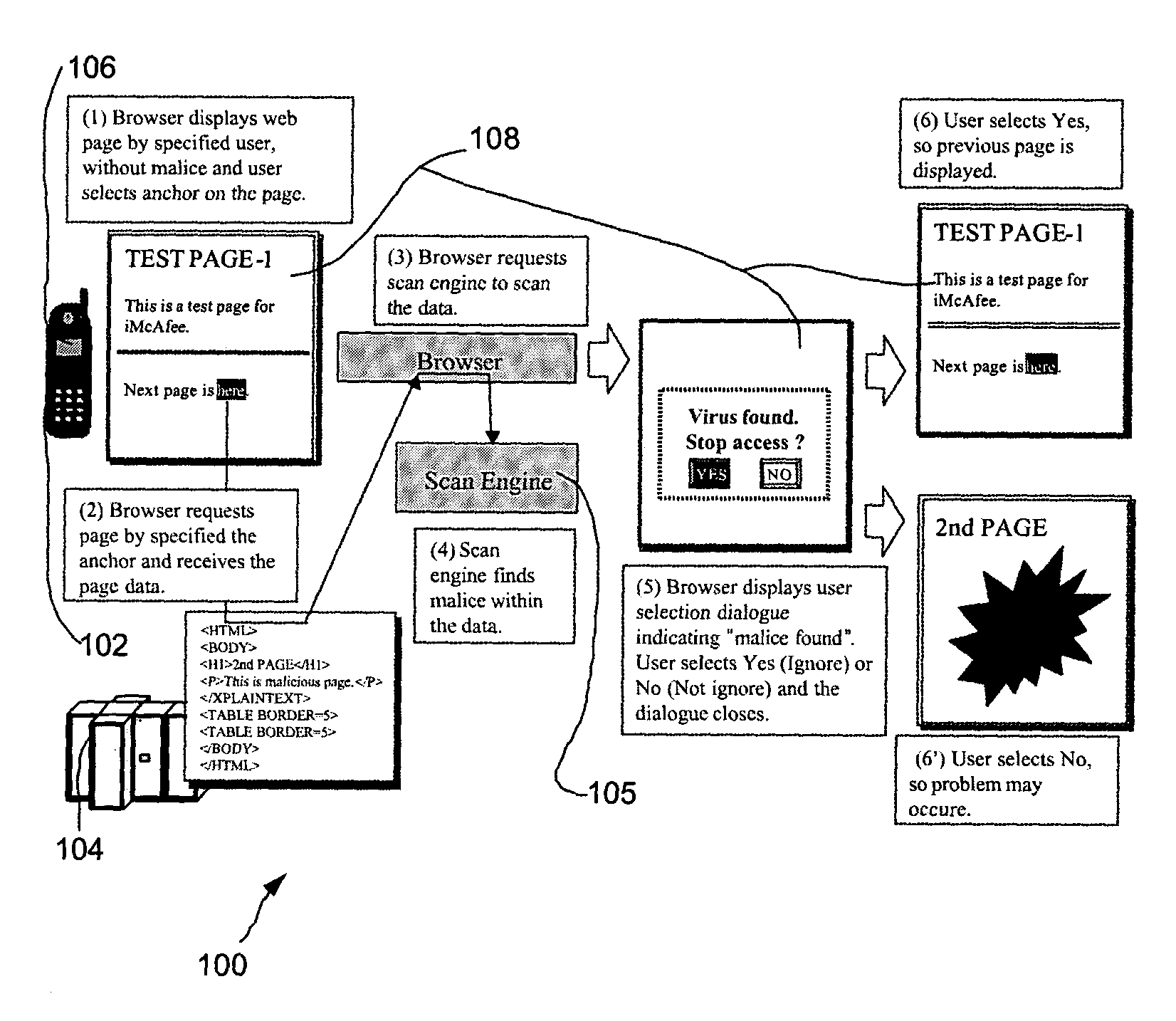
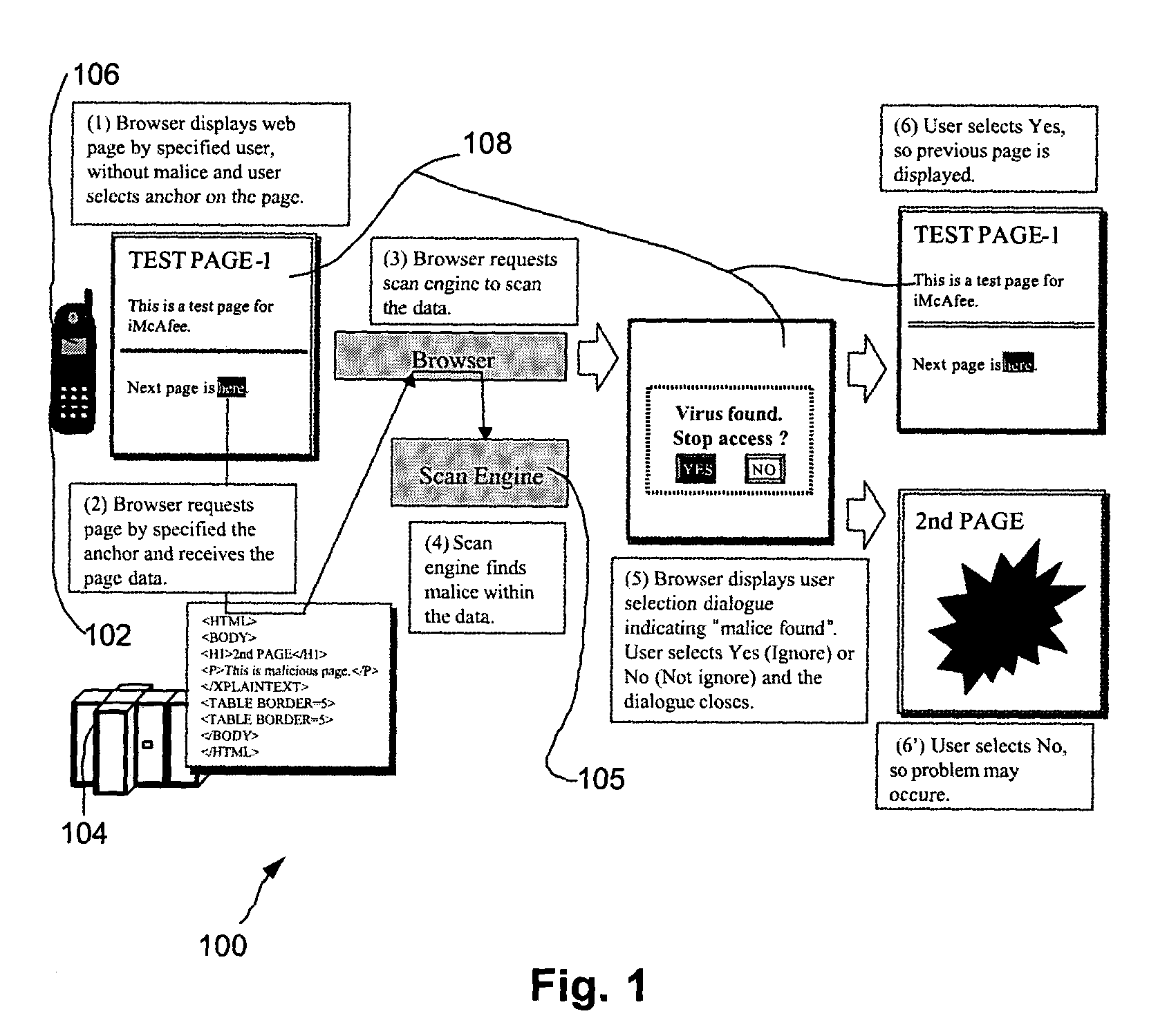
Automated login session extender for use in security analysis systems
ActiveUS20060048214A1Digital data processing detailsUser identity/authority verificationWeb siteProgram security
A web application security scanner (WASS) includes a login manager configured to perform an automated login to a web site. The automated login may be performed when the login manager detects that a login session has ended. The login manager is configured to determine credentials for the web site to allow the WASS to access the web site. The WASS may then use the credentials to continue scanning the web site. Thus, previously unscannable web pages may be accessed in the web site because of the automated login process.
Owner:SYNOPSYS INC
System and method for cyber security analysis and human behavior prediction
ActiveUS9292695B1Attacked easilyError detection/correctionPlatform integrity maintainanceHuman behaviorAttack graph
A method for analyzing computer network security has been developed. The method first establishes multiple nodes, where each node represents an actor, an event, a condition, or an attribute related to the network security. Next, an estimate is created for each node that reflects the case of realizing the event, condition, or attribute of the node. Attack paths are identified that represent a linkage of nodes that reach a condition of compromise of network security. Next, edge probabilities are calculated for the attack paths. The edge probabilities are based on the estimates for each node along the attack path. Finally, an attack graph is generated that identifies the easiest conditions of compromise of network security and the attack paths to achieving those conditions.
Owner:BASSETT GABRIEL
Internet security analysis system and process
InactiveUS6996845B1Memory loss protectionUnauthorized memory use protectionWeb siteSecurity analysis
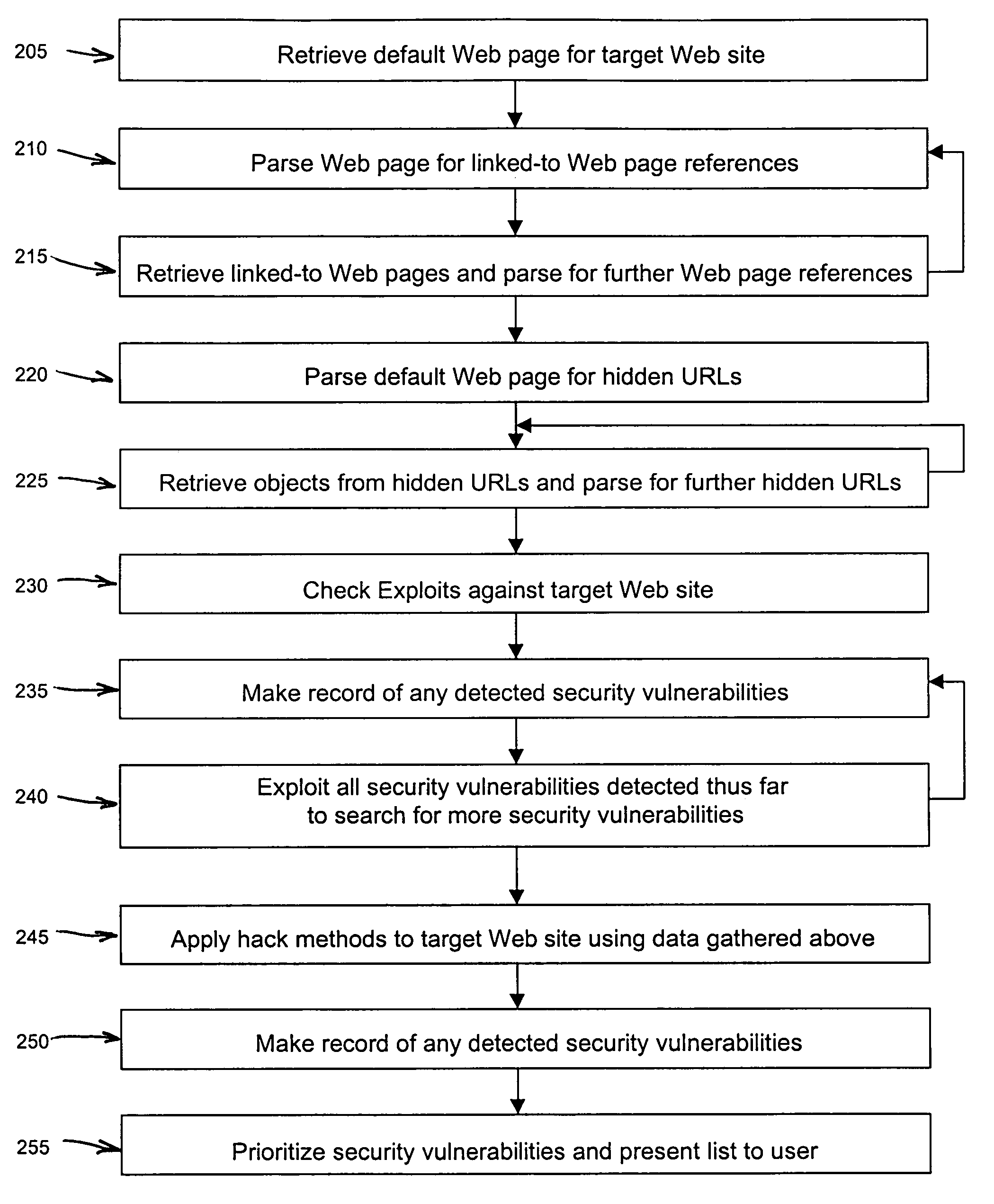
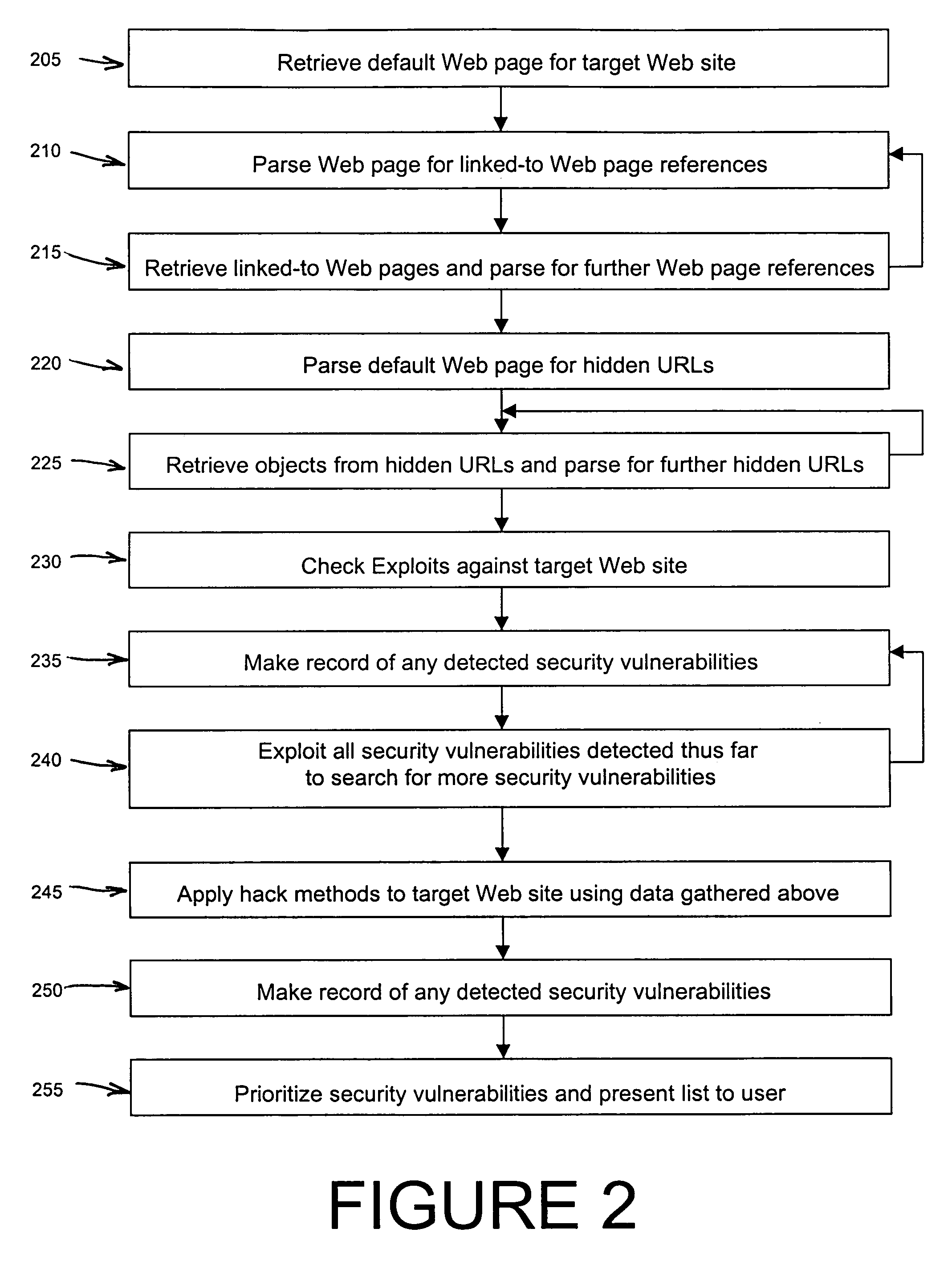
An automated Web security analysis system and process identifies security vulnerabilities in a target Internet Web site by parsing through the target Web site to search for a predetermined list of common security vulnerabilities. The process is recursive, exploiting information gathered throughout the process to search for additional security vulnerabilities. A prioritized list of detected security vulnerabilities is then presented to a user, including preferably a list of recommendations to eliminate the detected security vulnerabilities.
Owner:SPI DYNAMICS HEADQUARTERS
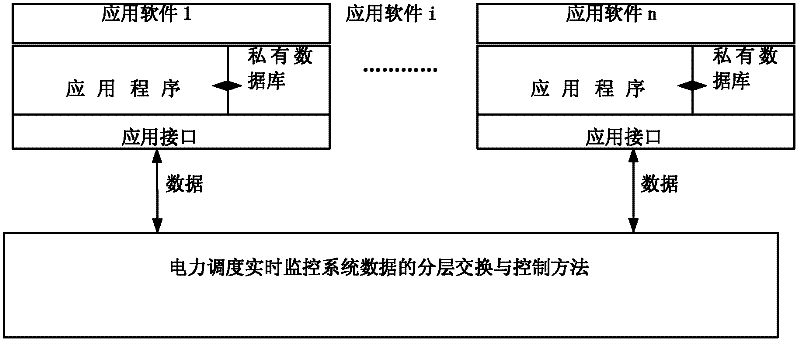
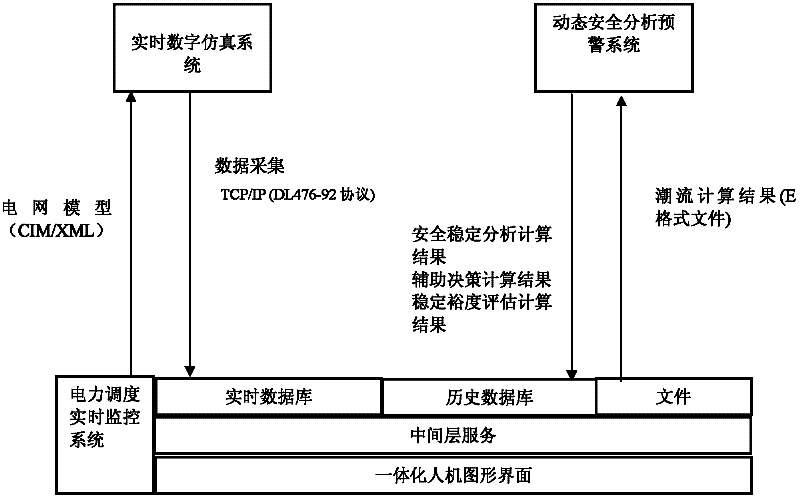
Layered exchange and control method for real-time monitoring system data by power dispatching
ActiveCN102215253AAchieve sharingRealize layered maintenanceCircuit arrangementsTransmissionHuman–machine interfaceElectric power system
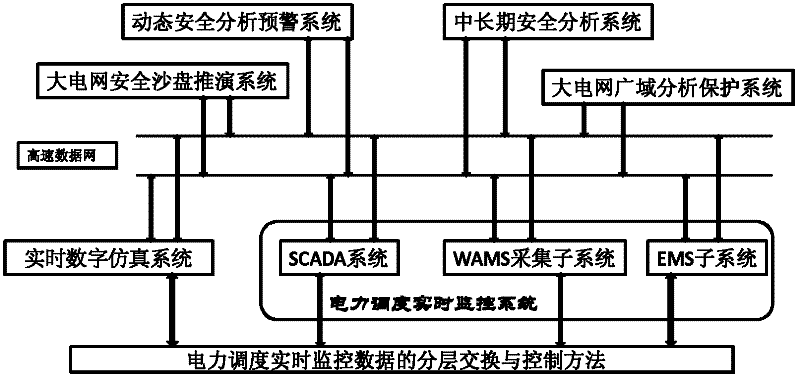
The invention provides a layered exchange and control method for real-time monitoring system data by power dispatching. A CIM / XML (common information module) / (extensible markup language) interface, a CIM / E interface and other models of the electric power subsystems are processed and combined to establish a device model of the large power grid, therefore, perfect interaction of various application data including SCADA (supervisory control and data acquisition) real-time data, WAMS (wide area measurement system) data, EMS (enhanced message service) advanced application data and dynamic security analysis warning information can be realized, and power system control commands among the systems can be smoothly transmitted and executed. A data acquisition and exchange function can support multiple communication protocols, multi-application, multi-type and large amounts of data, satisfy the real-time requirements of all transmission environments, and provide comprehensive multi-scale real-time operation information of the power grid for other application analysis systems. A close integration mode is used to realize application integration and each subsystem and application can be monitored and managed, so a uniform access interface and a man-machine interface can be ensured to provide for each application system.
Owner:CHINA ELECTRIC POWER RES INST +1
API system, method and computer program product for accessing content/security analysis functionality in a mobile communication framework
InactiveUS7392043B2Network traffic/resource managementMemory loss protectionOperational systemSecurity analysis
A system, method and computer program product are provided for accessing security or content analysis functionality utilizing a mobile communication device. Included is an operating system installed on a mobile communication device capable of communicating via a wireless network. Further provided is an application program installed on the mobile communication device and executed utilizing the operating system for performing tasks. A scanning subsystem remains in communication with the application program via an application program interface. Such scanning subsystem is adapted for accessing security or content analysis functionality in conjunction with the tasks performed by the application program.
Owner:NTT DOCOMO INC +1
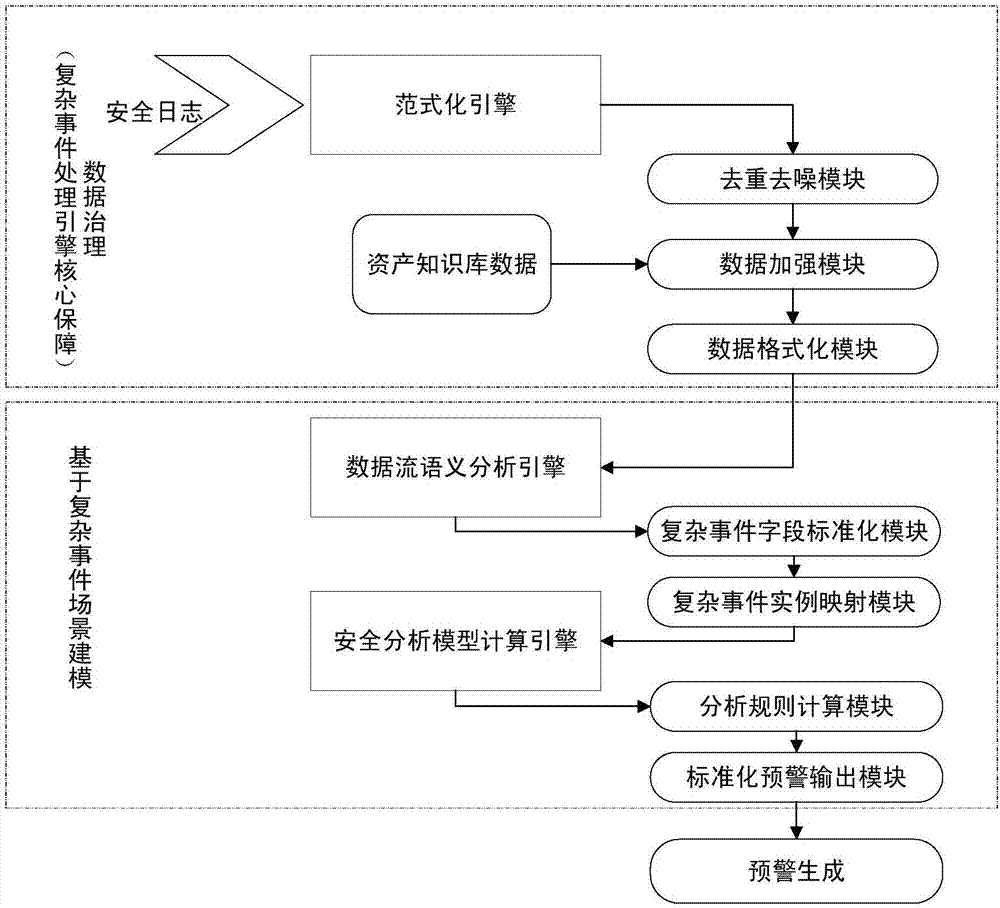
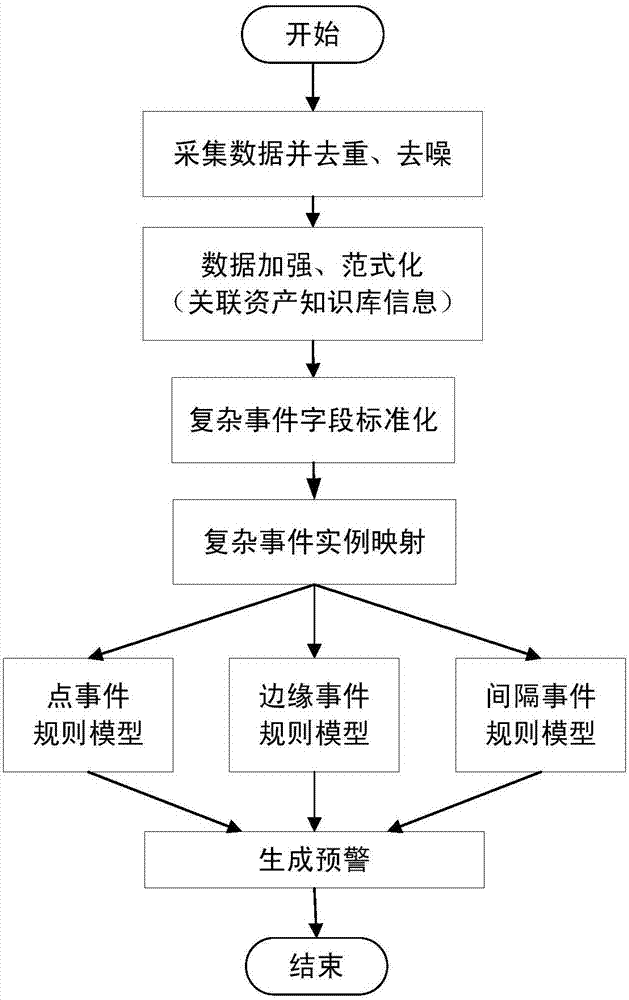
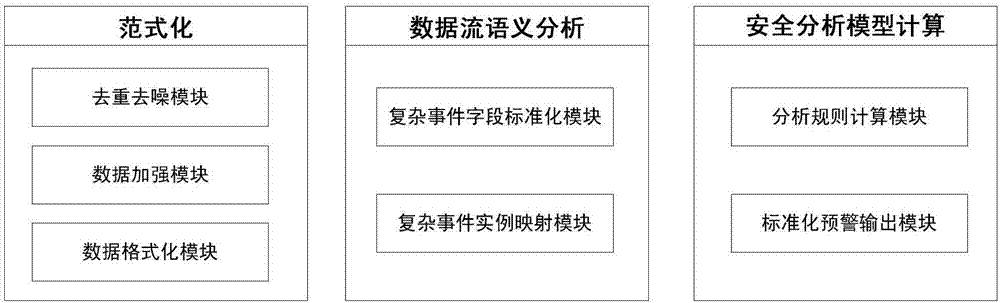
Real-time security early warning method based on complex event processing
ActiveCN107147639AReal-time analysis and early warningIncrease flexibilityPlatform integrity maintainanceTransmissionStreaming dataComplex event processing
The invention discloses a real-time security early warning method based on complex event processing. The method specifically comprises the following steps: step (1), using a formalized engine to perform log field segmentation on collected security data, performing normalization on fields according to field requirements, and associating knowledge base information according to the fields that are expected to be outputted; step (2), using a data flow semantic analysis engine to perform data context analysis according to a complex event instance to be modeled as a scene, and analyzing mapping stream data based on a standardized analysis field template; and step (3), using a security analysis model calculation engine, in an analysis rule calculation module, analyzing according to scenes based on a point event, an edge event and an interval event, and generating an early warning event. The real-time security early warning method based on the complex event processing provided by the invention realizes the multi-angle association analysis of original log data through a configurable normalization rule, a semantic recognition rule and a security analysis rule, and discovers unknown threats and carries out early warning timely.
Owner:STATE GRID CORP OF CHINA +3
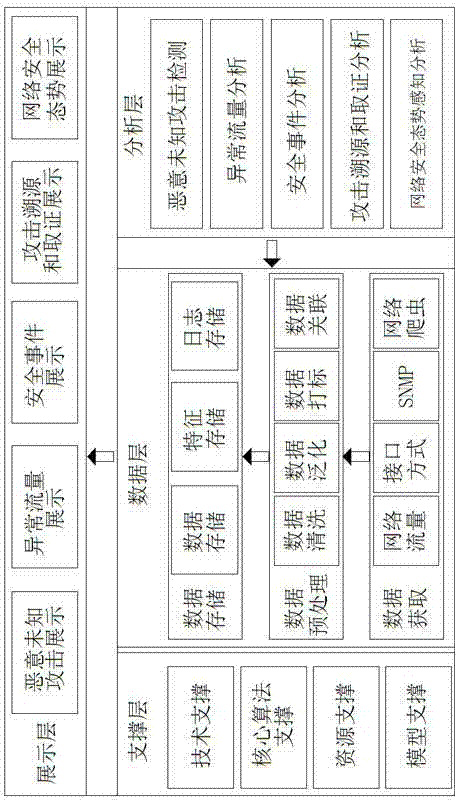
Security analysis framework based on network traffic meta data
InactiveCN104753946ATimely implementation managementControl in timeData switching networksSecurity analysisNetwork security situation awareness
The invention discloses a security analysis framework based on network traffic meta data. The framework comprises a data layer, an analysis layer, a supporting layer and a displaying layer; the meta data of users, application, location, operation and time relevant to network traffic are acquired, compressed and stored, by means of the key technology, core algorithm, assistant resource and model database of the supporting layer, the secure analysis and displaying of the network meta data are implemented. According to the framework, the network traffic is acquired, the traffic meta data are extracted, the suspected malicious attacks existing in the network traffic are detected by the big data technology, the accuracy of malicious attack detection can be improved, the emergency responding time can be prolonged, and the security of the IT environment is guaranteed effectively; the theoretical basis and guidance are provided for deep security analysis of the network big data, and the significant value can be brought to malicious unknown attack detection, attack tracing and forensic analysis, network security situation awareness and other aspects.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
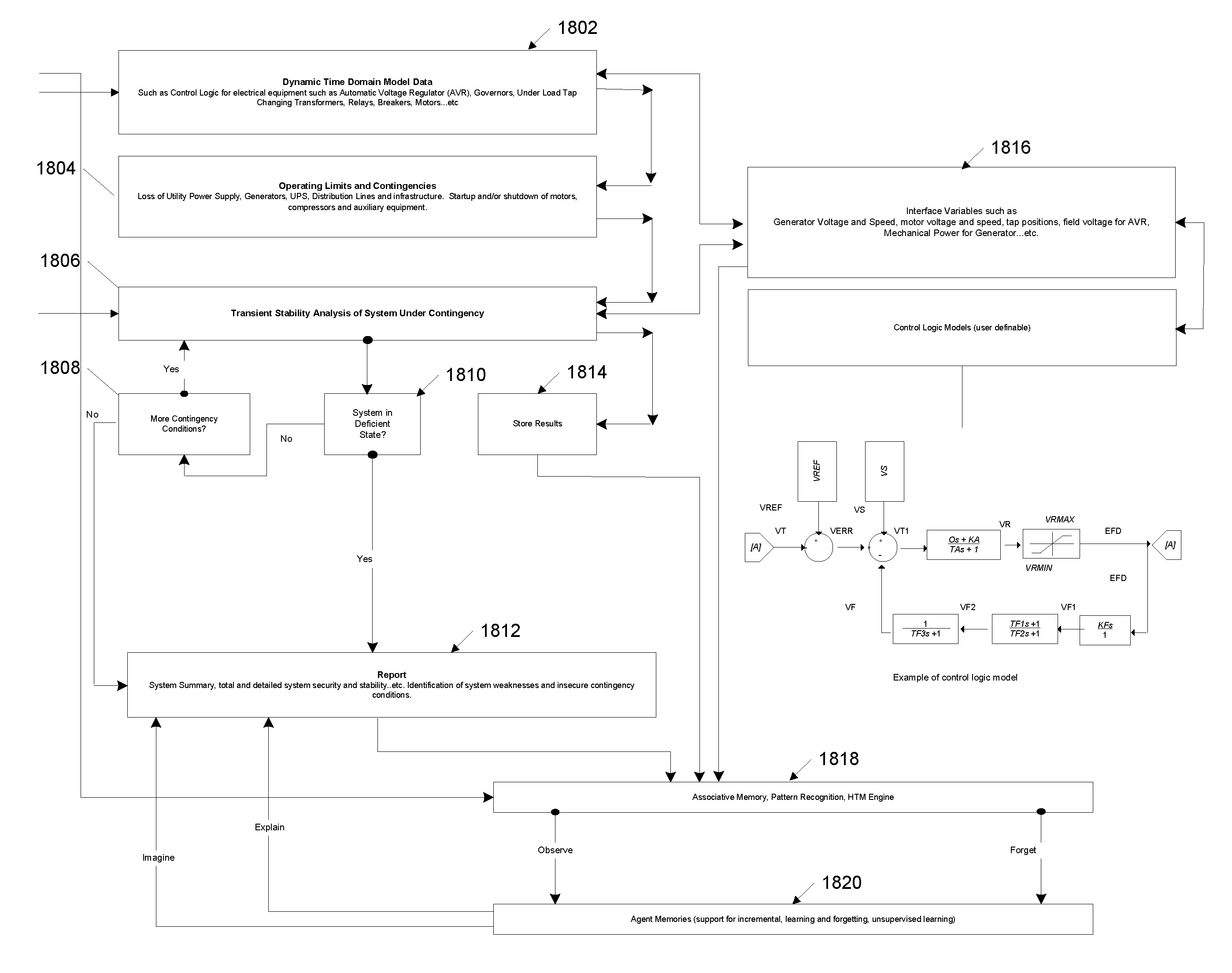
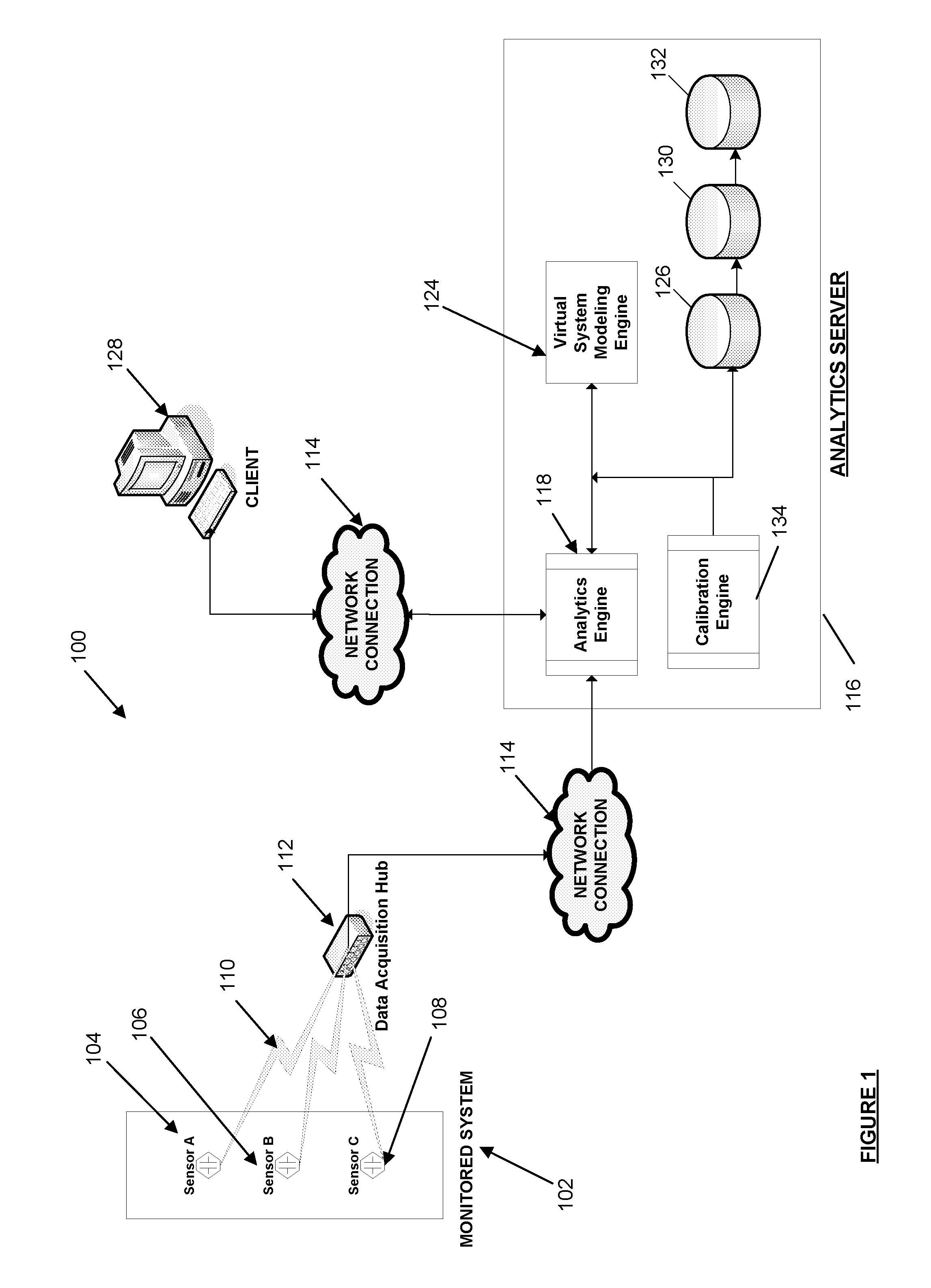
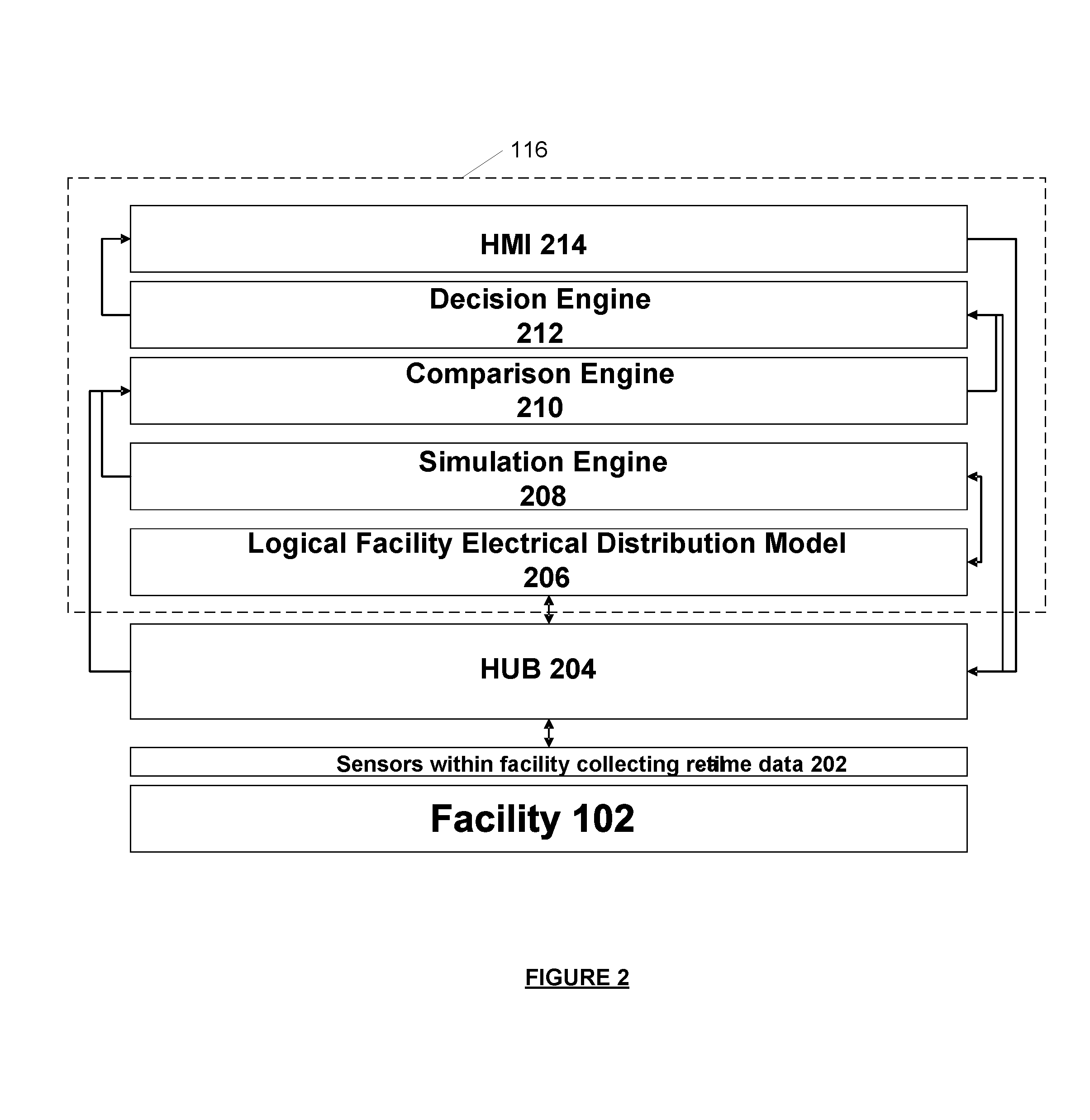
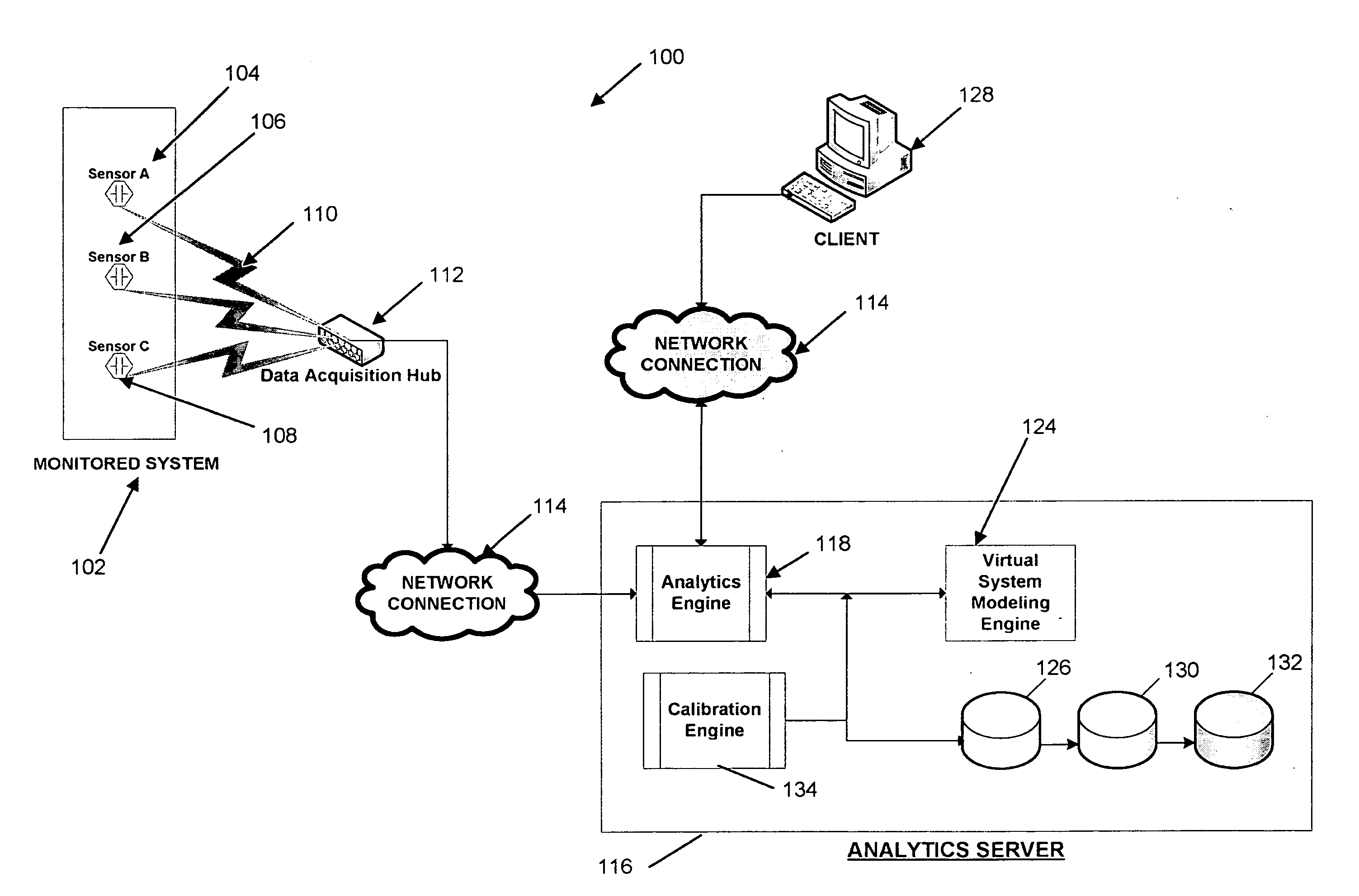
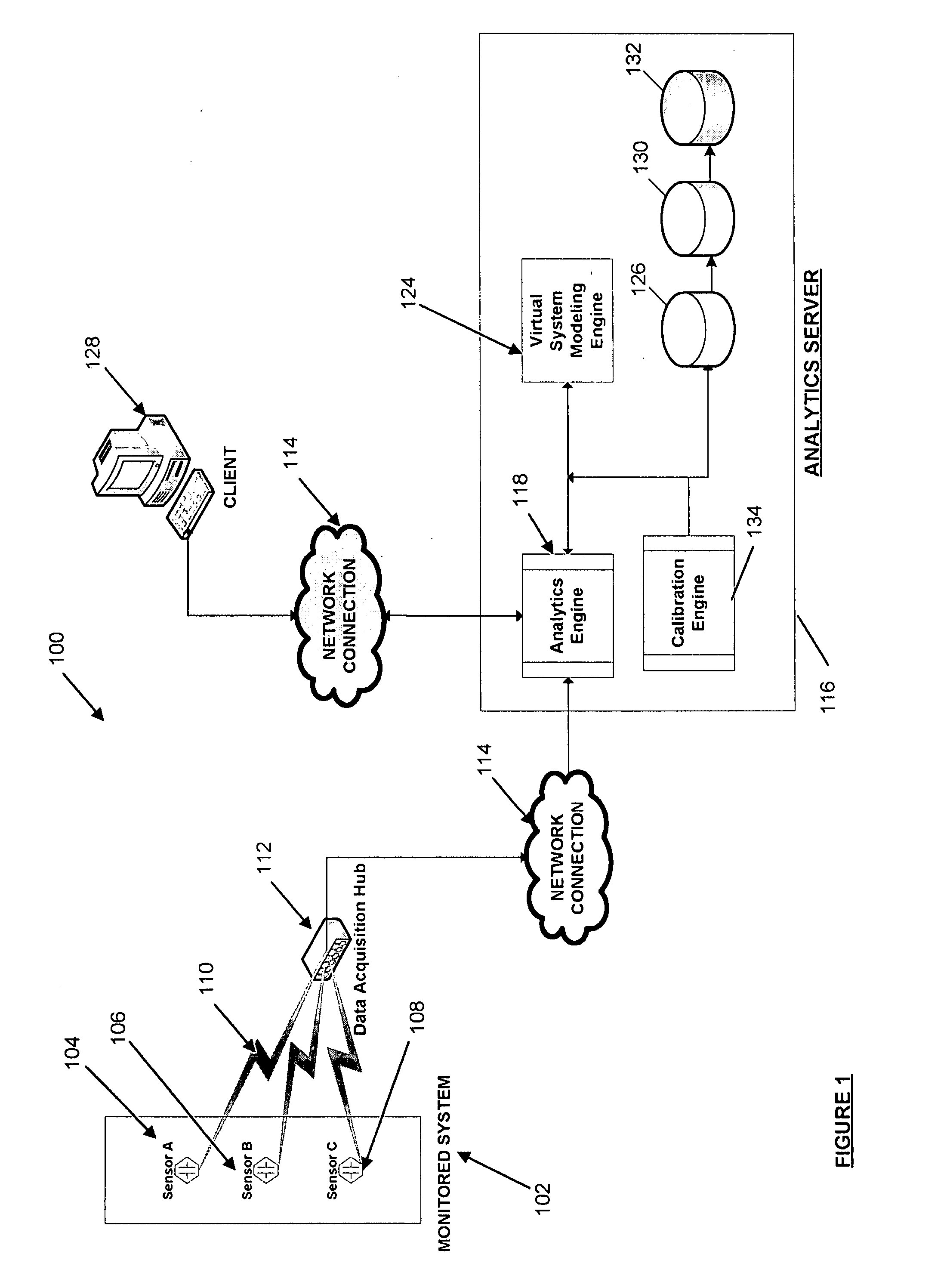
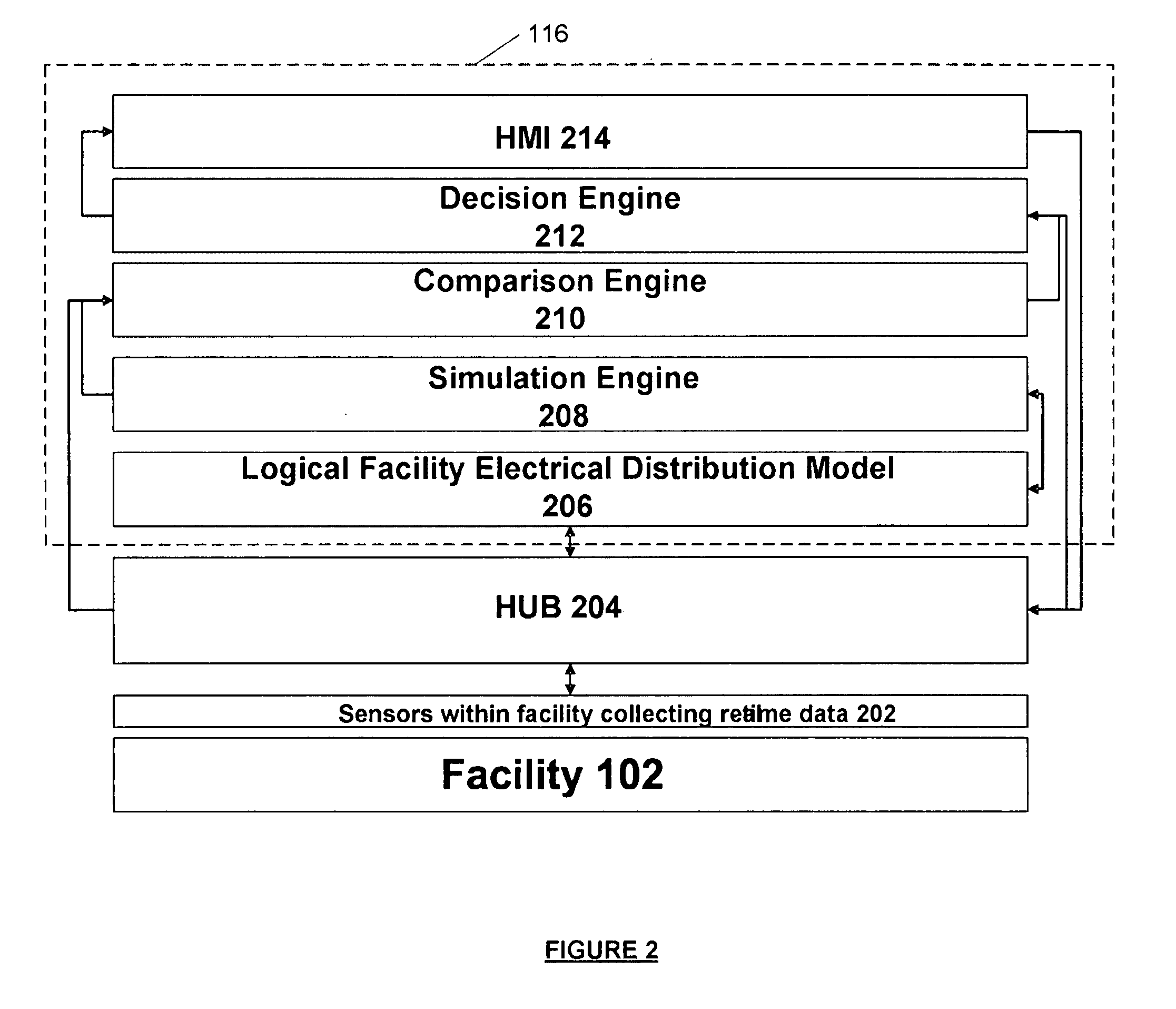
Systems and methods for predictive monitoring including real-time strength and security analysis in an electrical power distribution system
InactiveUS7840395B2Error preventionFrequency-division multiplex detailsReal-time dataDistribution system
A system for performing real-time failure mode analysis of a monitored system is disclosed. The system includes a data acquisition component, an analytics server and a client terminal. The data acquisition component is communicatively connected to a sensor configured to acquire real-time data output from the monitored system. The analytics server is communicatively connected to the data acquisition component and is comprised of a virtual system modeling engine, an analytics engine and a machine learning engine.
Owner:POWER ANALYTICS CORP
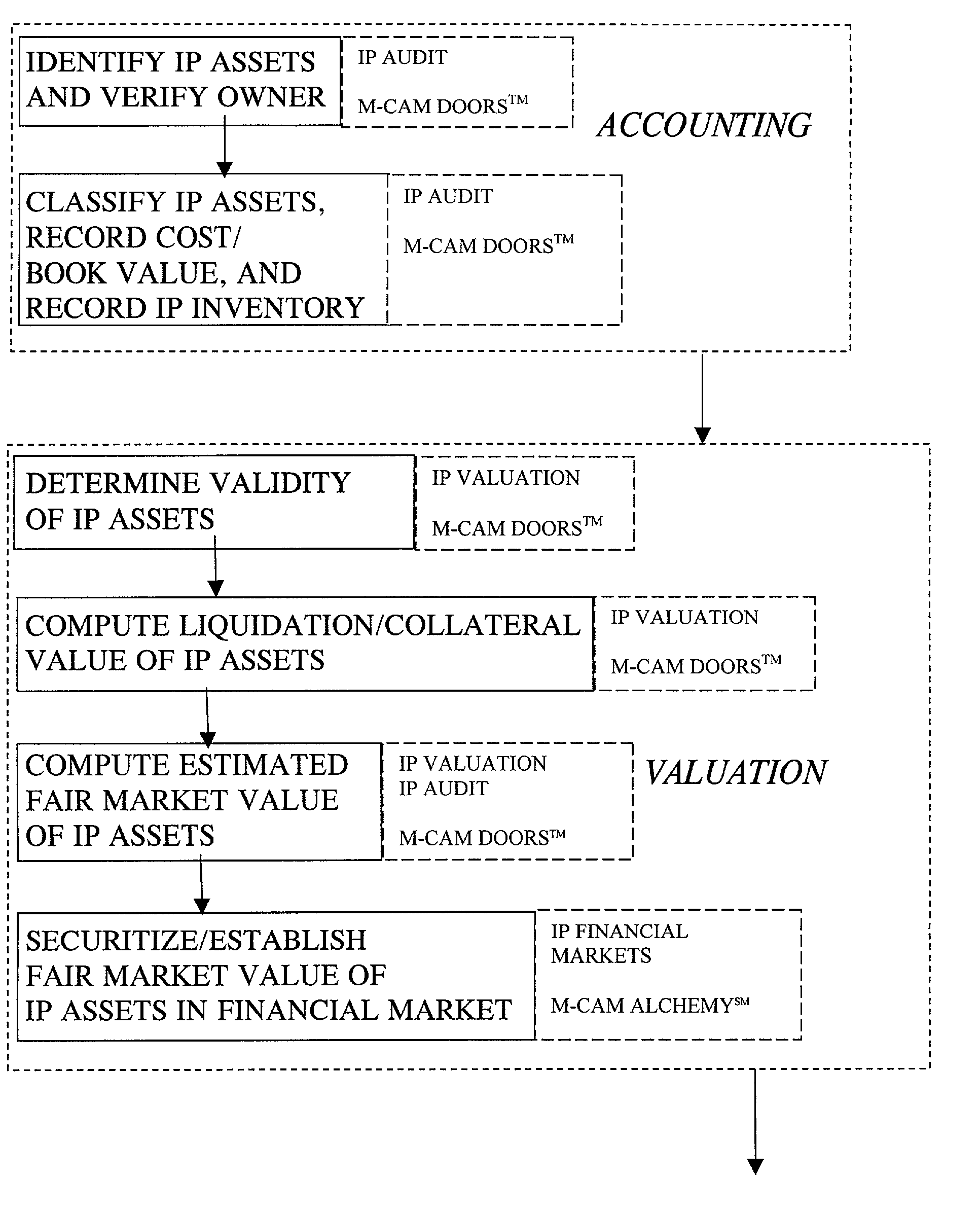
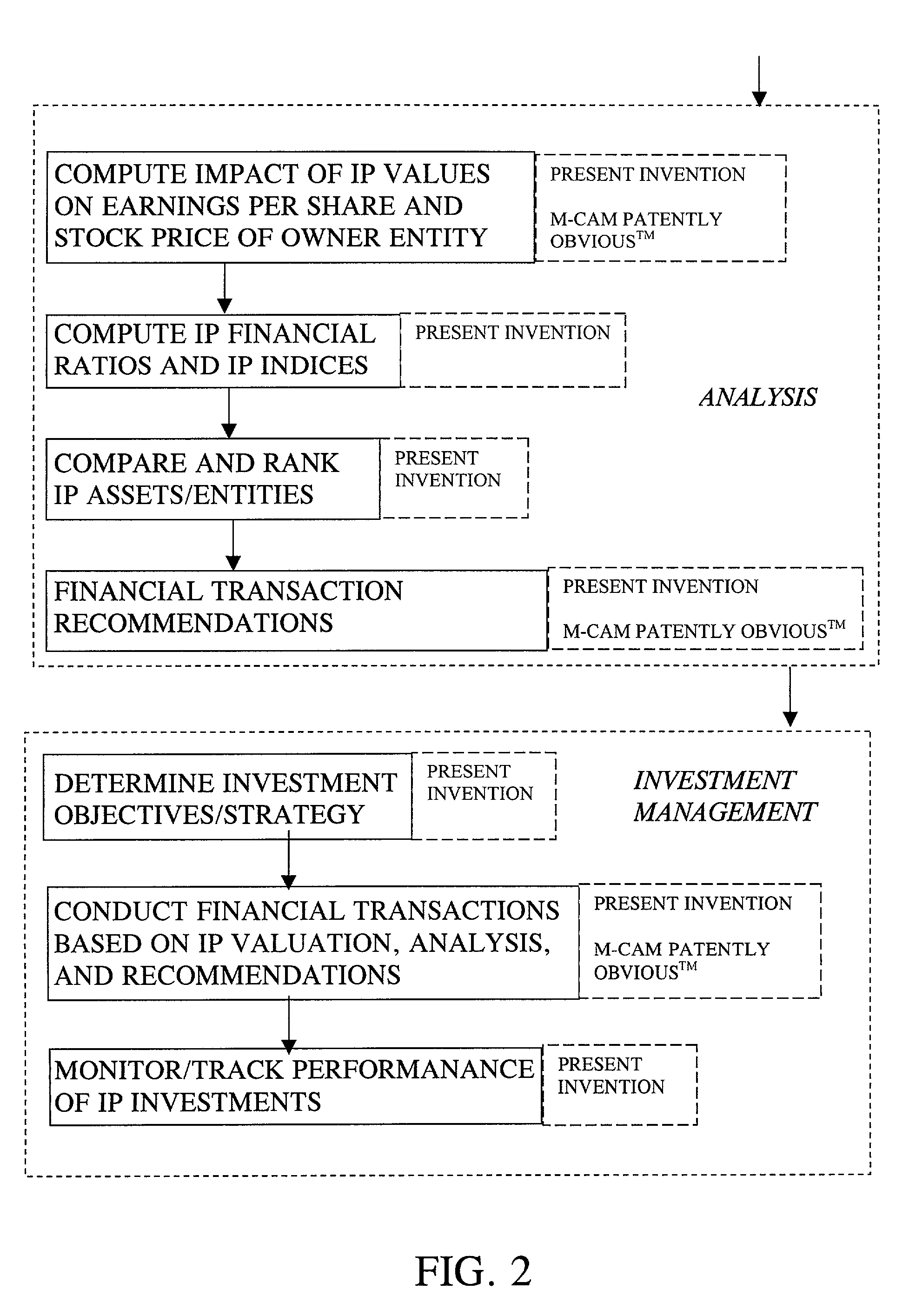
Intellectual property investment process
InactiveUS20020099637A1Facilitate fair market valueEnhance traditional financial recommendationFinanceSpecial data processing applicationsIntellectual propertyCombined use
A process for investment in intellectual property, comprising providing an accounting for an intellectual property investment; providing a valuation with respect to the intellectual property investment; performing financial analysis related to the intellectual property investment and making a recommendation based upon the financial analysis; and managing the investment based upon the accounting, valuation, and analysis for the investment. The financial analysis includes computing one or more financial ratios or indices, comparing financial information relating to the IP investments to one or more other IP investments, and making a financial transaction recommendation with respect to the IP investment. The analysis and recommendation process may stand alone or may be used in conjunction with pre-existing, non-IP-based securities analysis and recommendation / estimation processes.
Owner:WILKINSON WILLIAM T
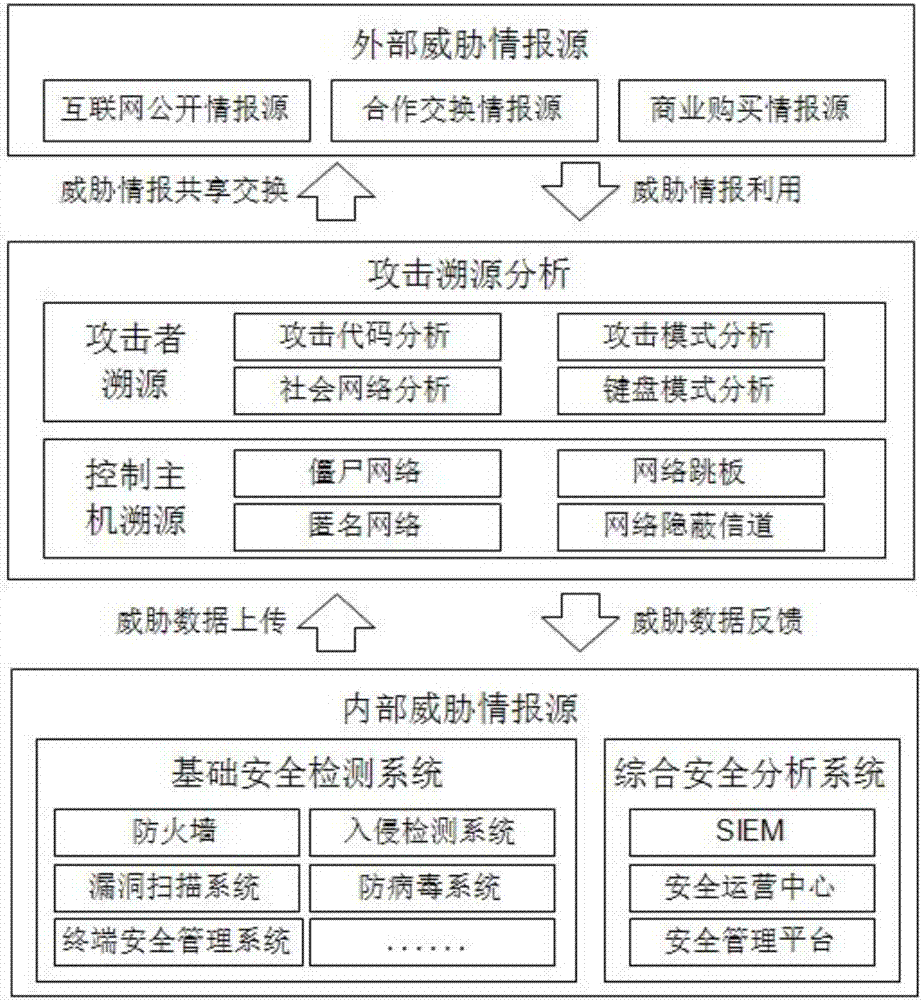
Threat intelligence analysis system for attack tracing
InactiveCN107046543AEasy to distinguishImprove generalizationTransmissionIntelligence analysisSecurity analysis
The invention discloses a threat intelligence analysis system for attack tracing. The system comprises an internal threat intelligence collection module, an external threat intelligence collection module and an attack tracing analysis module; the internal threat intelligence collection module comprises a security detection module and a security analysis module; the attack tracing analysis module comprises attacker tracing and attack host tracking; threat intelligence obtained by the internal threat intelligence collection module and the external threat intelligence collection module is uploaded to the attack tracing analysis module, the attack tracing analysis module performs attacker tracing and attack host tracking on the threat intelligence and feeds back the result to the security detection module and the security analysis module; and meanwhile, the result is performed with threat intelligence sharing and exchange with an external cooperation mechanism. The threat intelligence analysis system disclosed by the invention can not only singly and quickly accomplish threat intelligence analysis and detection, but also can provide prediction for the attacks of enterprises, the method is orientated to attack tracing, and the attack mode is analyzed from the source so as to better identify the identity of the attacker.
Owner:STATE GRID CORP OF CHINA +3
Assessment and analysis of software security flaws in virtual machines
ActiveUS8613080B2Facilitates security assessment and vulnerability testingFacilitates benchmarkingMemory loss protectionDigital data processing detailsSoftware engineeringSecurity analysis
Security analysis and vulnerability testing results are “packaged” or “bound to” the actual software it describes. By linking the results to the software itself, downstream users of the software can access information about the software, make informed decisions about implementation of the software, and analyze the security risk across an entire system by accessing all (or most) of the reports associated with the executables running on the system and summarizing the risks identified in the reports.
Owner:VERACODE
Systems and methods for predictive monitoring including real-time strength and security analysis in an electrical power distribution system
InactiveUS20070286089A1Error preventionFrequency-division multiplex detailsReal-time dataData acquisition
A system for performing real-time failure mode analysis of a monitored system is disclosed. The system includes a data acquisition component, an analytics server and a client terminal. The data acquisition component is communicatively connected to a sensor configured to acquire real-time data output from the monitored system. The analytics server is communicatively connected to the data acquisition component and is comprised of a virtual system modeling engine, an analytics engine and a machine learning engine.
Owner:POWER ANALYTICS CORP
Integral electricity market operation system
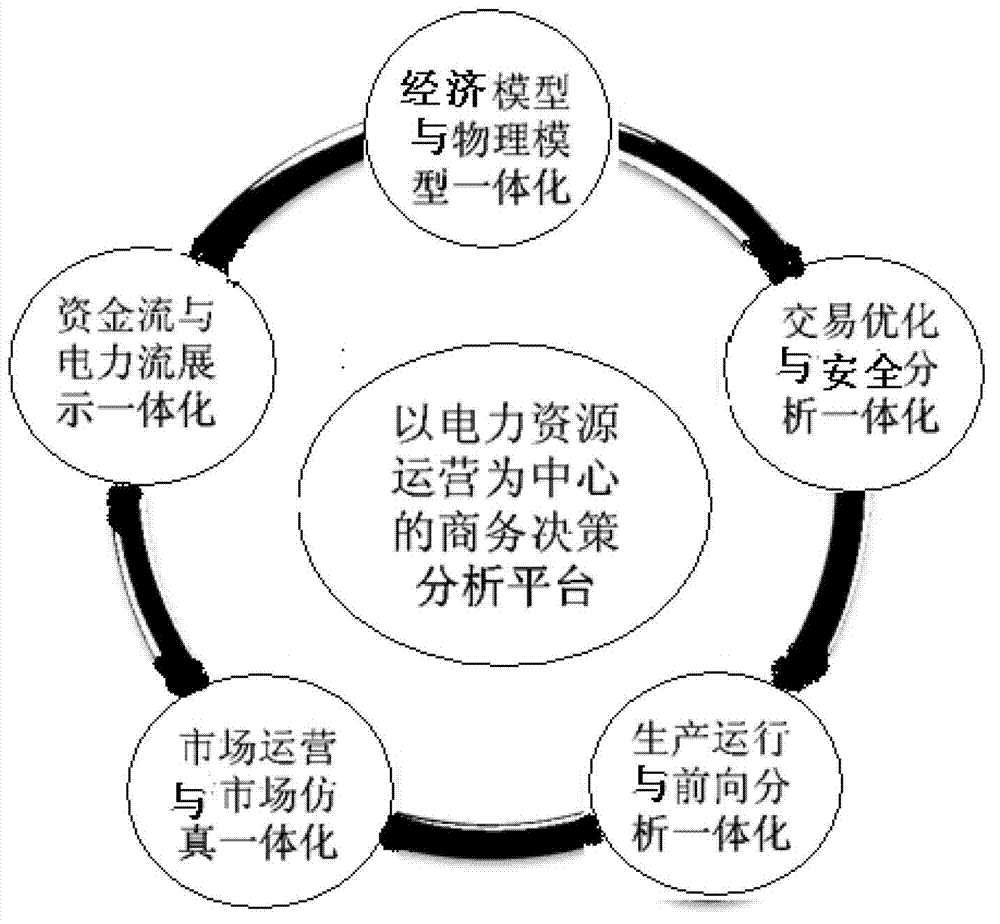
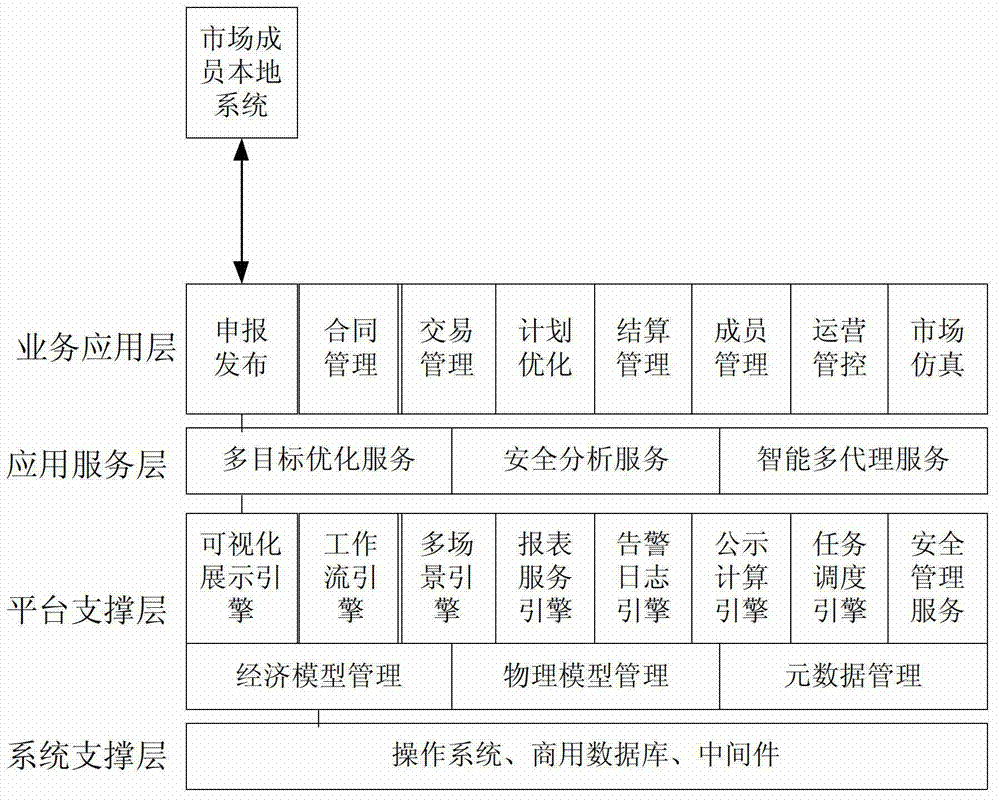
InactiveCN102903063ARealize organic integrationAutomatically meet safe operation requirementsData processing applicationsMarket simulationElectricity trade
The invention relates to an integral electricity market operation system. The system comprises a system supporting layer, a platform supporting layer, an application service layer and a business application layer, wherein the system supporting layer is used for providing operation environment and development environment for the electricity market operation system; the platform supporting layer is used for managing a power gird physical model, a market economic model and a dynamic data model and providing sharing platform supporting for application; the application service layer is used for providing service for trade management, planning optimization, operational control and market simulation; and the business application layer is used for providing service for electricity market operation. By the aid of the system, the design of an integral electricity market operation system frame of multi-cycle electricity trade decision and management and the design of an integral electricity market operation system frame of integrity of the economic model and the physical model, integrity of the trade optimization and safety analysis, integrity of production operation and forward analysis, integrity of market operation and the market simulation and integrity of capital flow and electricity flow display are supported, a business decision analysis platform is constructed and the electricity source operation serves as the center.
Owner:CHINA ELECTRIC POWER RES INST +1
Detection device and method for security vulnerability of software
InactiveCN102541729ASatisfy attentionImprove use valueSoftware testing/debuggingSystems managementGoal system
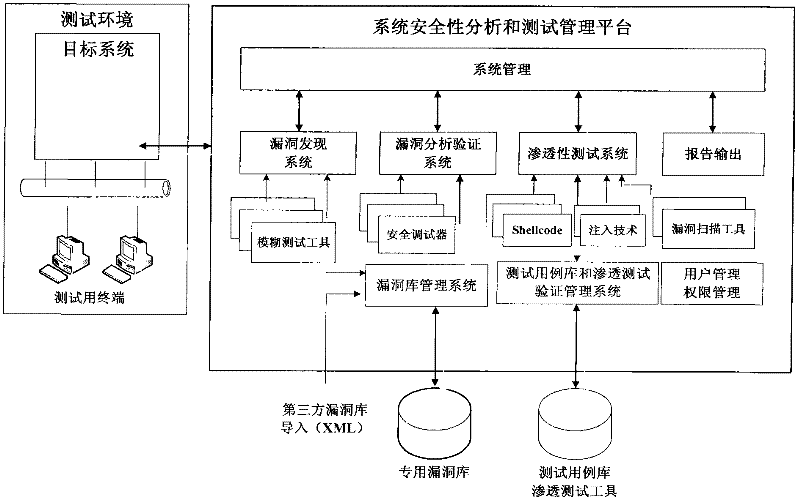
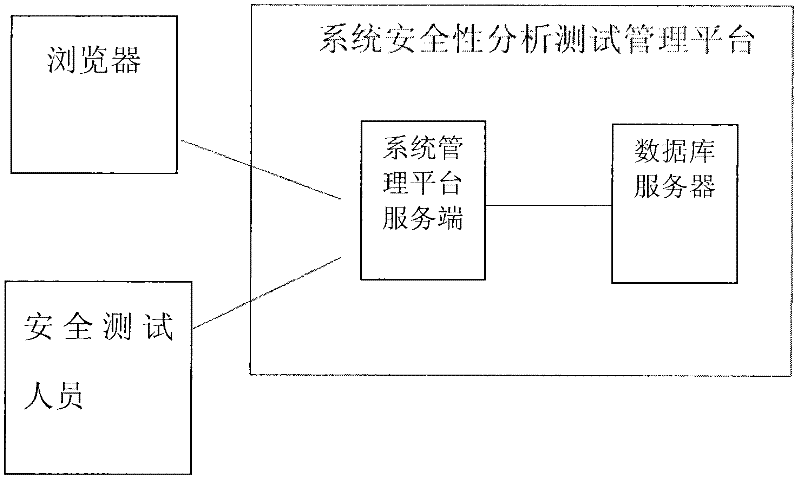
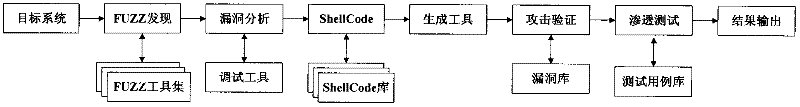
The invention relates to the field of computers, in particular to a detection device and method for a security vulnerability of a dedicated information system. According to the detection device and method disclosed by the invention, a tester can not only access a target system to a testing network but also access the detection device to a production system by connecting a test terminal with the target system, wherein the target system is located in the production system. As the core of the detection device, a system security analysis and test management platform comprises a vulnerability discovering system, a vulnerability authenticating and analyzing system, a permeability testing system, a vulnerability library, a test case library, a report outputting system, a user and permission management system, a system management platform and the like. When the detection device and method for the security vulnerability of the software, provided by the invention, are adopted, the vulnerability can be found before the application of the software, and corresponding strategies can be provided, so that the detection device and method meet the requirement on the emphasis on information security in the current society in a better manner; and moreover, the detection device and method have a higher application value.
Owner:AVIATION IND INFORMATION CENT
System and methodology providing automation security analysis, validation, and learning in an industrial controller environment
ActiveUS8909926B2Improve integrityFacilitate privacyComputer controlUser identity/authority verificationGuidelineEngineering
The present invention relates to a system and methodology facilitating automation security in a networked-based industrial controller environment. Various components, systems and methodologies are provided to facilitate varying levels of automation security in accordance with security analysis tools, security validation tools and / or security learning systems. The security analysis tool receives abstract factory models or descriptions for input and generates an output that can include security guidelines, components, topologies, procedures, rules, policies, and the like for deployment in an automation security network. The validation tools are operative in the automation security network, wherein the tools perform security checking and / or auditing functions, for example, to determine if security components are in place and / or in suitable working order. The security learning system monitors / learns network traffic patterns during a learning phase, fires alarms or events based upon detected deviations from the learned patterns, and / or causes other automated actions to occur.
Owner:ROCKWELL AUTOMATION TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com