Real-time security early warning method based on complex event processing
A complex event processing and security early warning technology, applied in the fields of electrical digital data processing, computer security devices, special data processing applications, etc., can solve the problems of conservative event processing, missed event reporting, single security log of security early warning processing methods, etc., to achieve Real-time analysis and early warning, the effect of improving flexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0051] In order to make the technical means, creative features, goals and effects achieved by the present invention easy to understand, the present invention will be further described below in conjunction with specific embodiments.
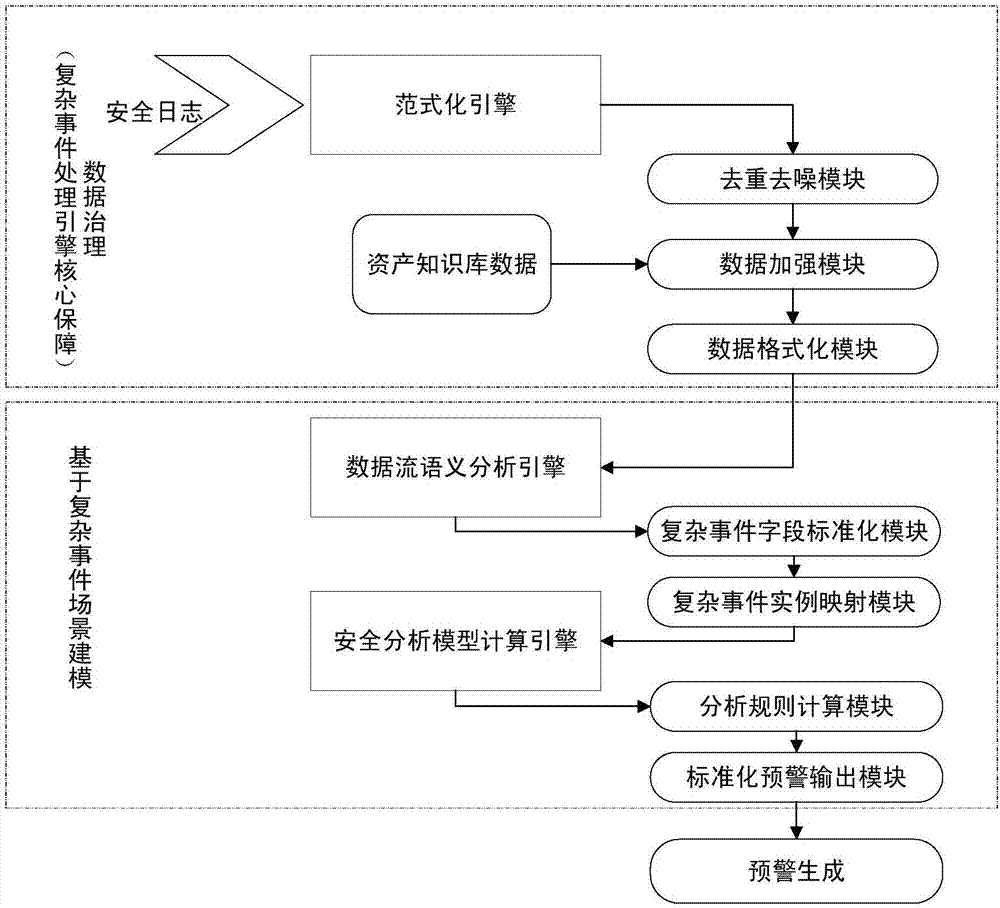
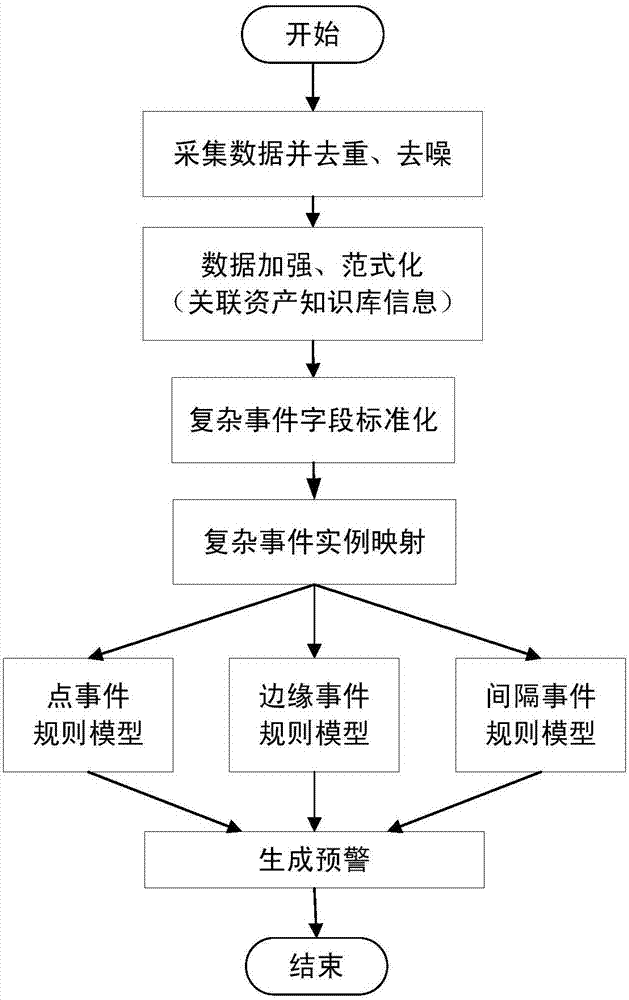
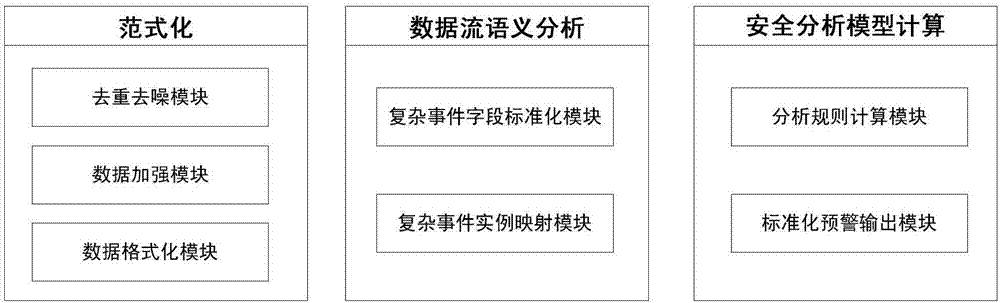
[0052] see Figure 1 to Figure 3 , a kind of real-time safety warning method based on complex event processing of the present invention, comprises the following steps:
[0053] (1) The collected data enters the security warning framework in real time for deduplication and denoising, and dynamic data (real-time data) is associated with static data (asset data) for normalization;
[0054] (2) The normalized data is extracted according to the semantic context and mapped into complex event fields to prepare for early warning generation;
[0055] (3) Establish a model in combination with scene rules, analyze data, and generate real-time early warning events.
[0056] On the basis of using CEP, Kafka, Storm, Esper and other open source technology fram...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com