Patents
Literature
100 results about "Security awareness" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Security awareness is the knowledge and attitude members of an organization possess regarding the protection of the physical, and especially informational, assets of that organization. Many organizations require formal security awareness training for all workers when they join the organization and periodically thereafter, usually annually.
System and method for assessing cybersecurity awareness
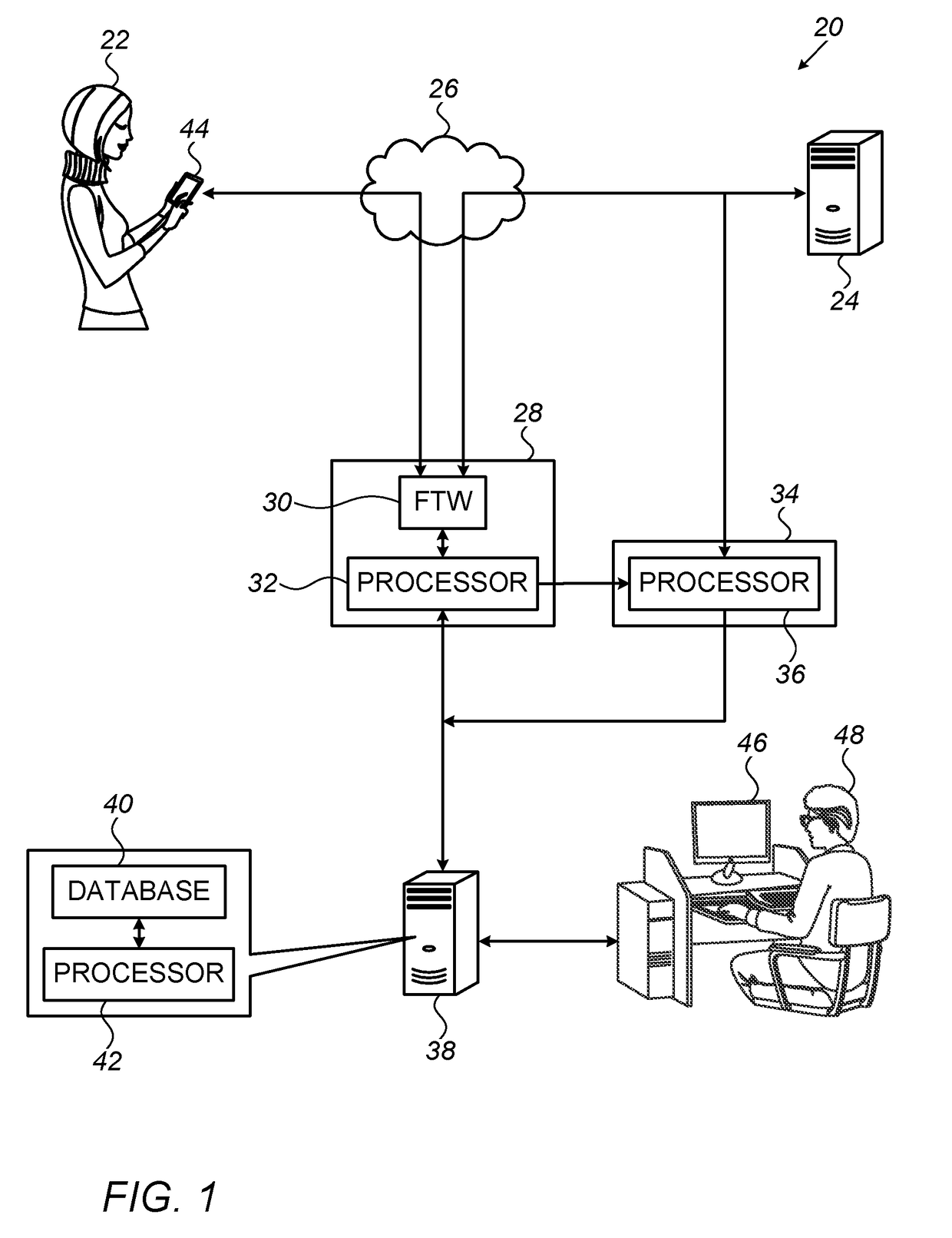
Described embodiments include a system that includes a monitoring agent, configured to automatically monitor usage of a computing device by a user, and a processor. The processor is configured to compute, based on the monitoring, a score indicative of a cyber-security awareness of the user, and to generate an output indicative of the score.
Owner:B G NEGEV TECH & APPL LTD
System and methods for protecting confidential information on network sites based on security awareness
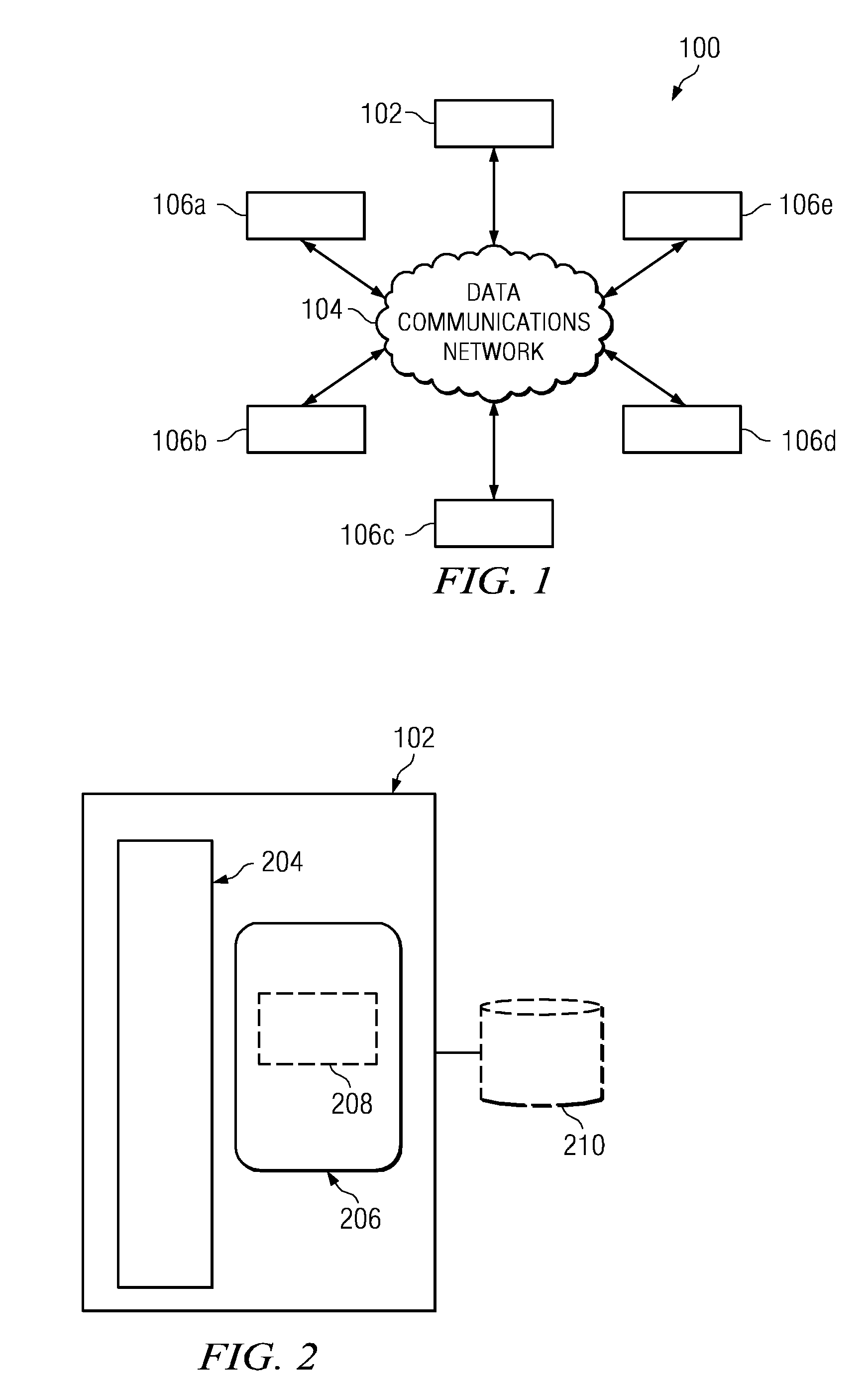
ActiveUS20090241168A1Effective and scalable network protectionPrevent leakageMemory loss protectionDigital data processing detailsSecurity awarenessNetwork interface
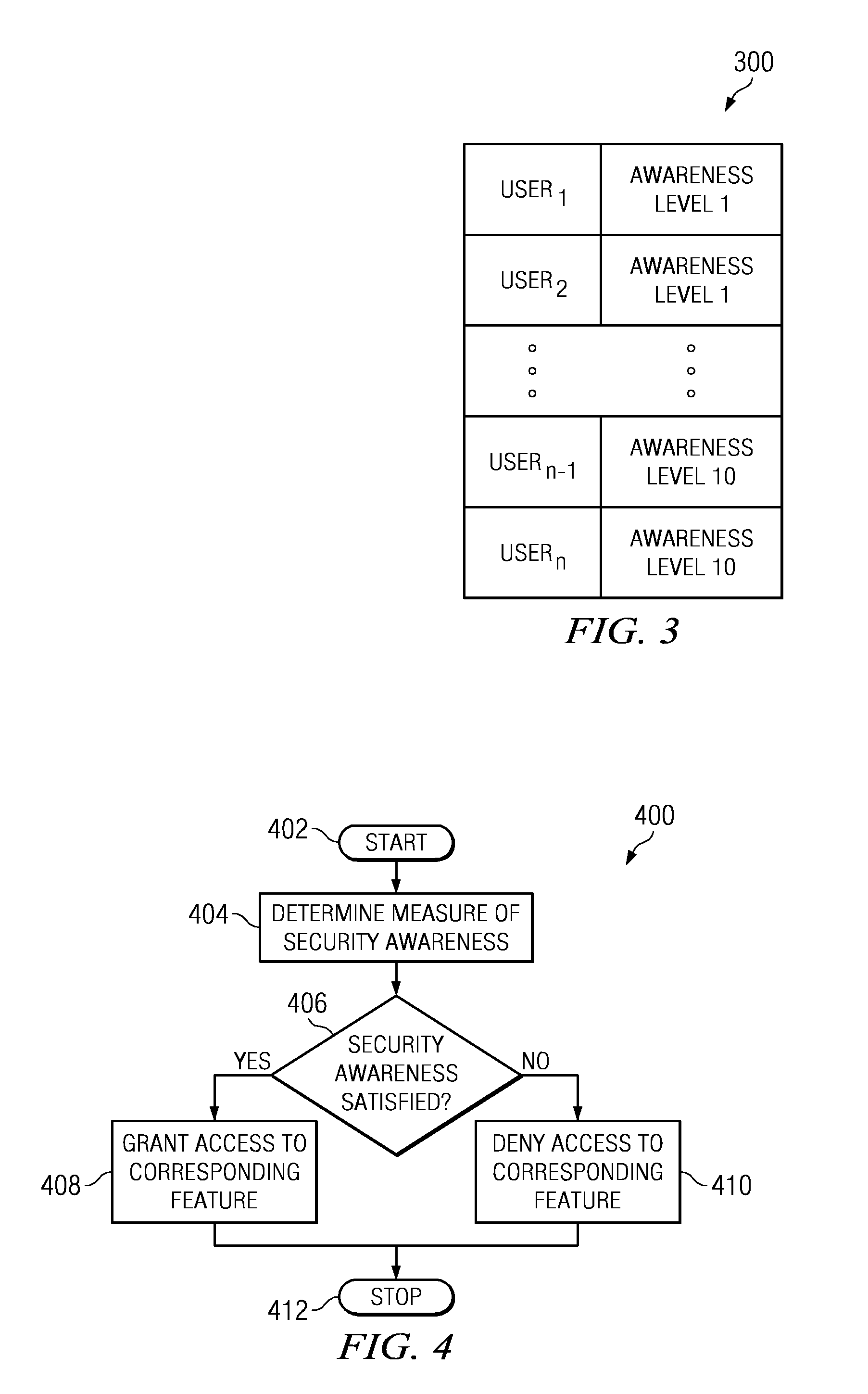
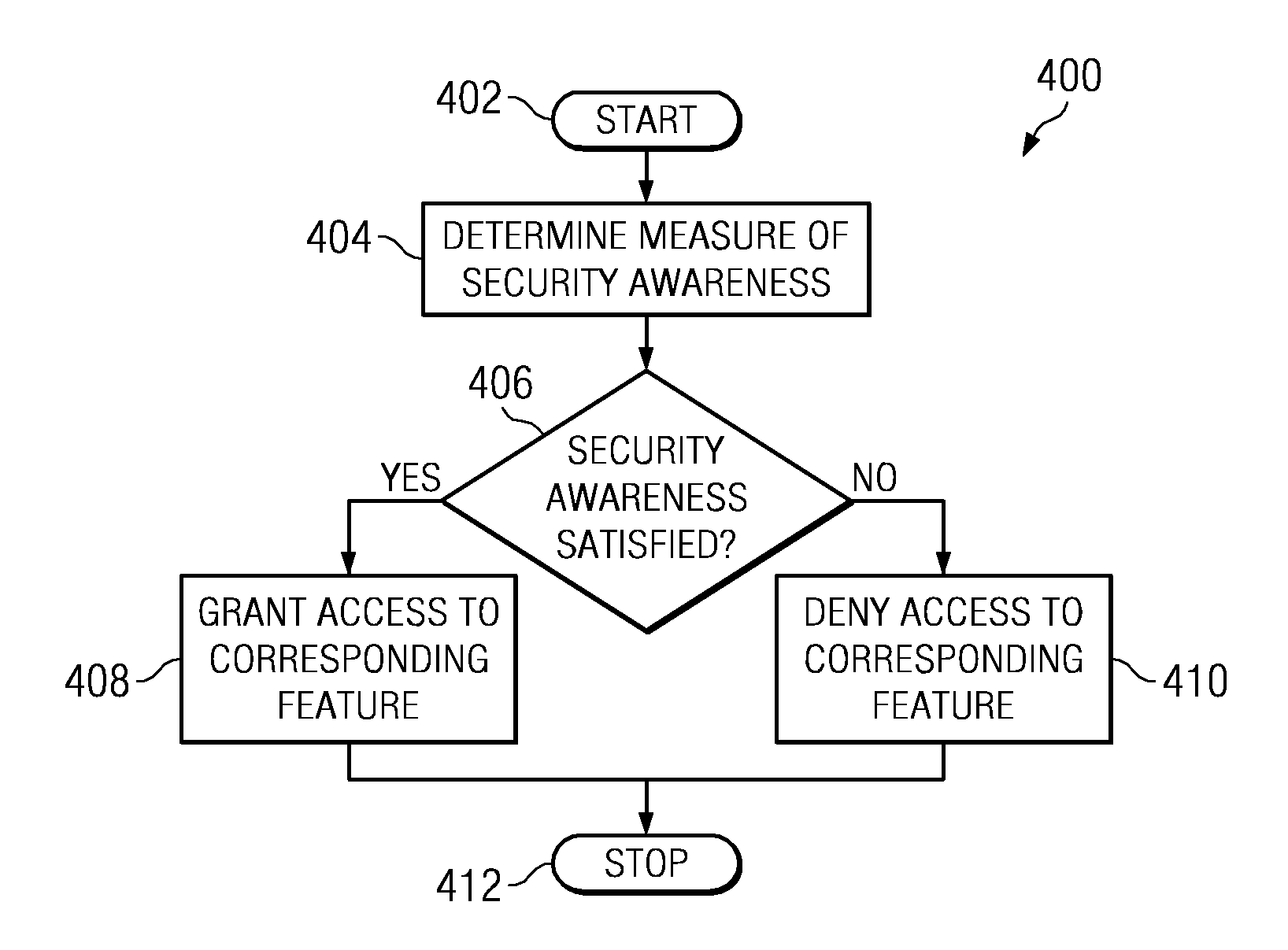
A system for protecting confidential information based upon user security awareness is provided. The system includes a network interface for connecting the system to a plurality of remotely-located network sites. The system also includes one or more processors on which at one or more data processing feature execute in response to a request received from a user of one of the remotely-located network sites. The system further includes a security-awareness module configured to execute in conjunction with the one or more processors for determining a measure of security awareness of the user, and for granting or denying the user access to the at least one data processing feature based upon the measure of security awareness.
Owner:IBM CORP
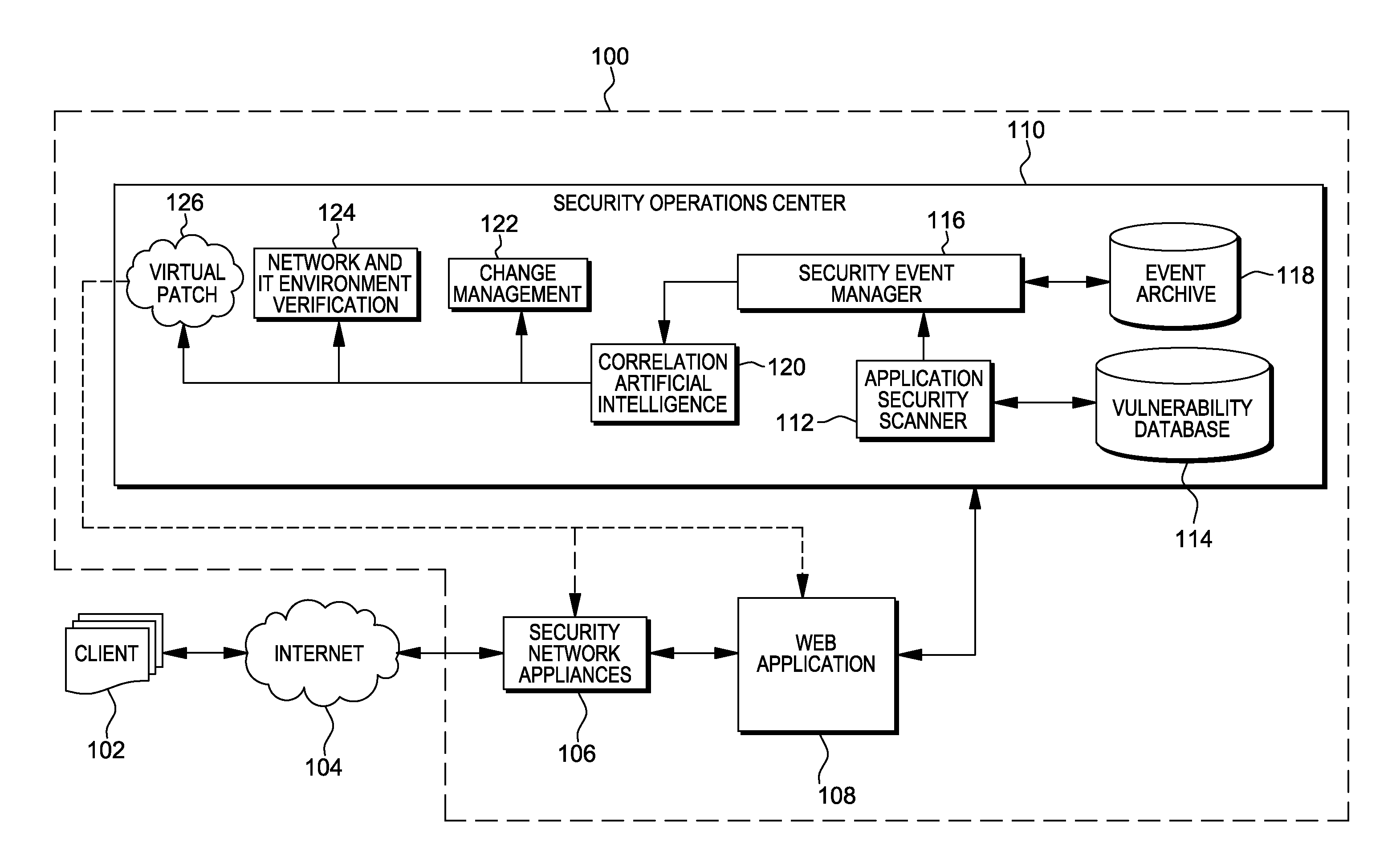
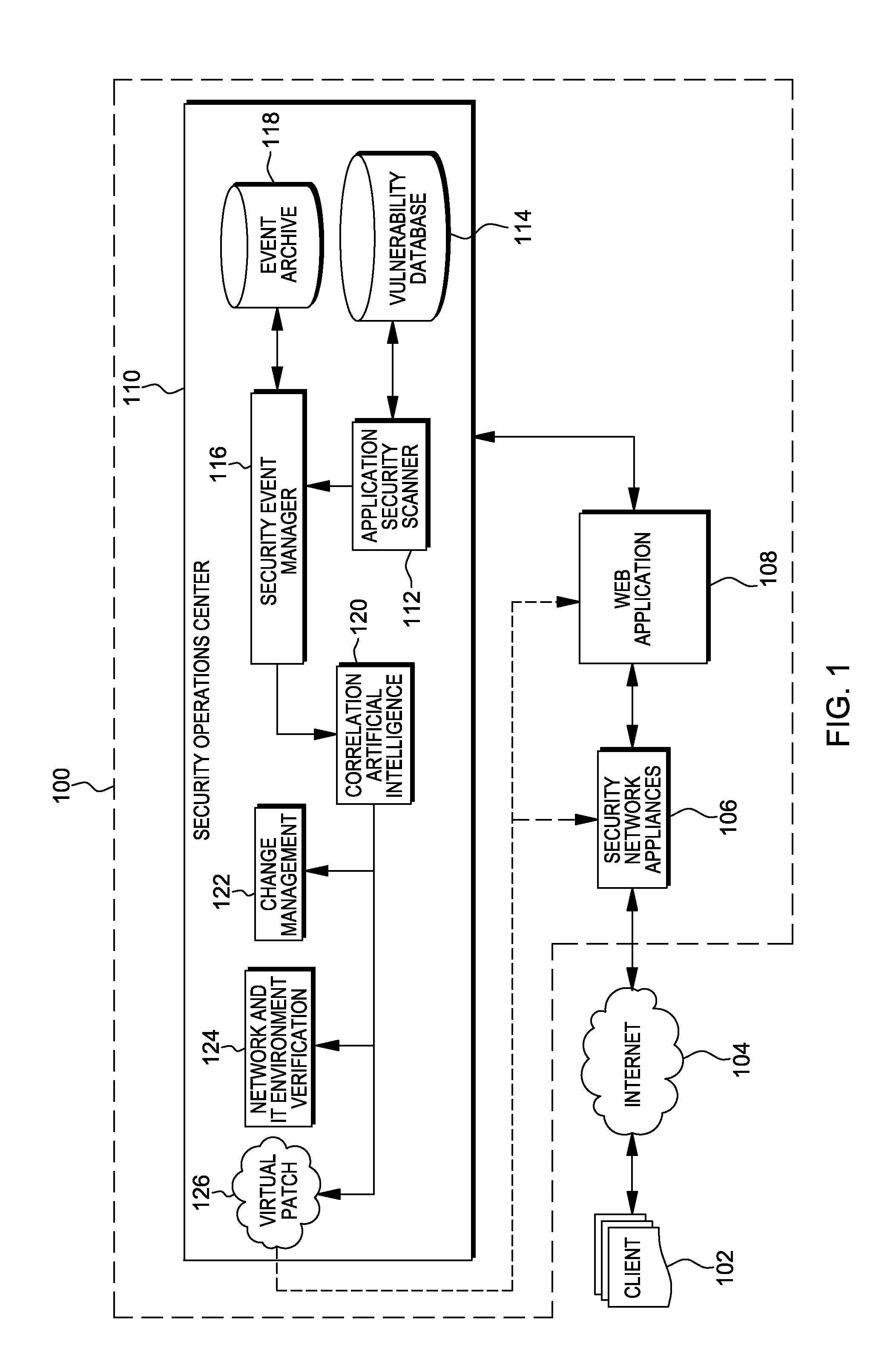
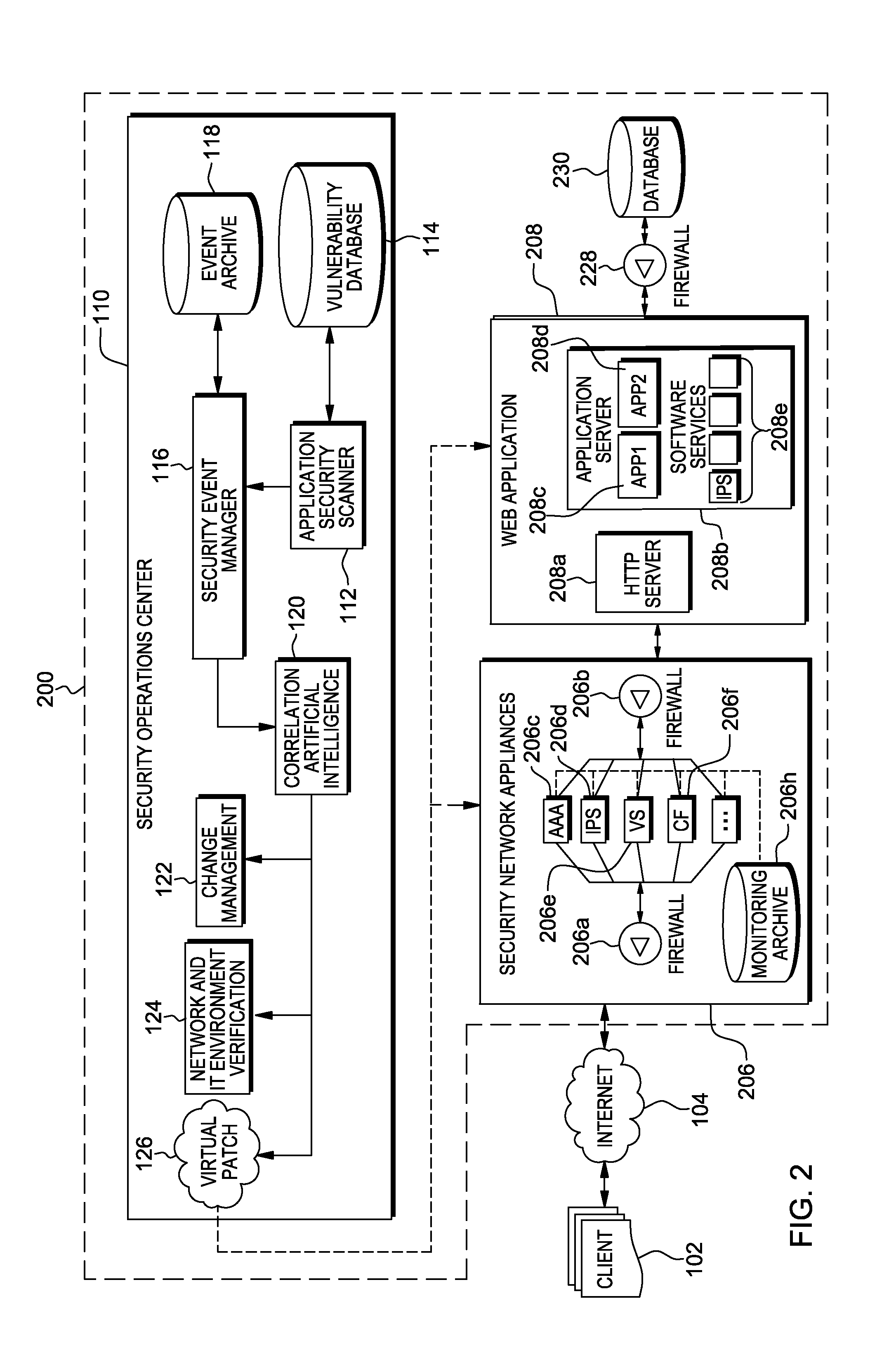
Web application exploit mitigation in an information technology environment
ActiveUS20130086688A1Improve protectionMemory loss protectionUnauthorized memory use protectionEnd to end securityProgram management
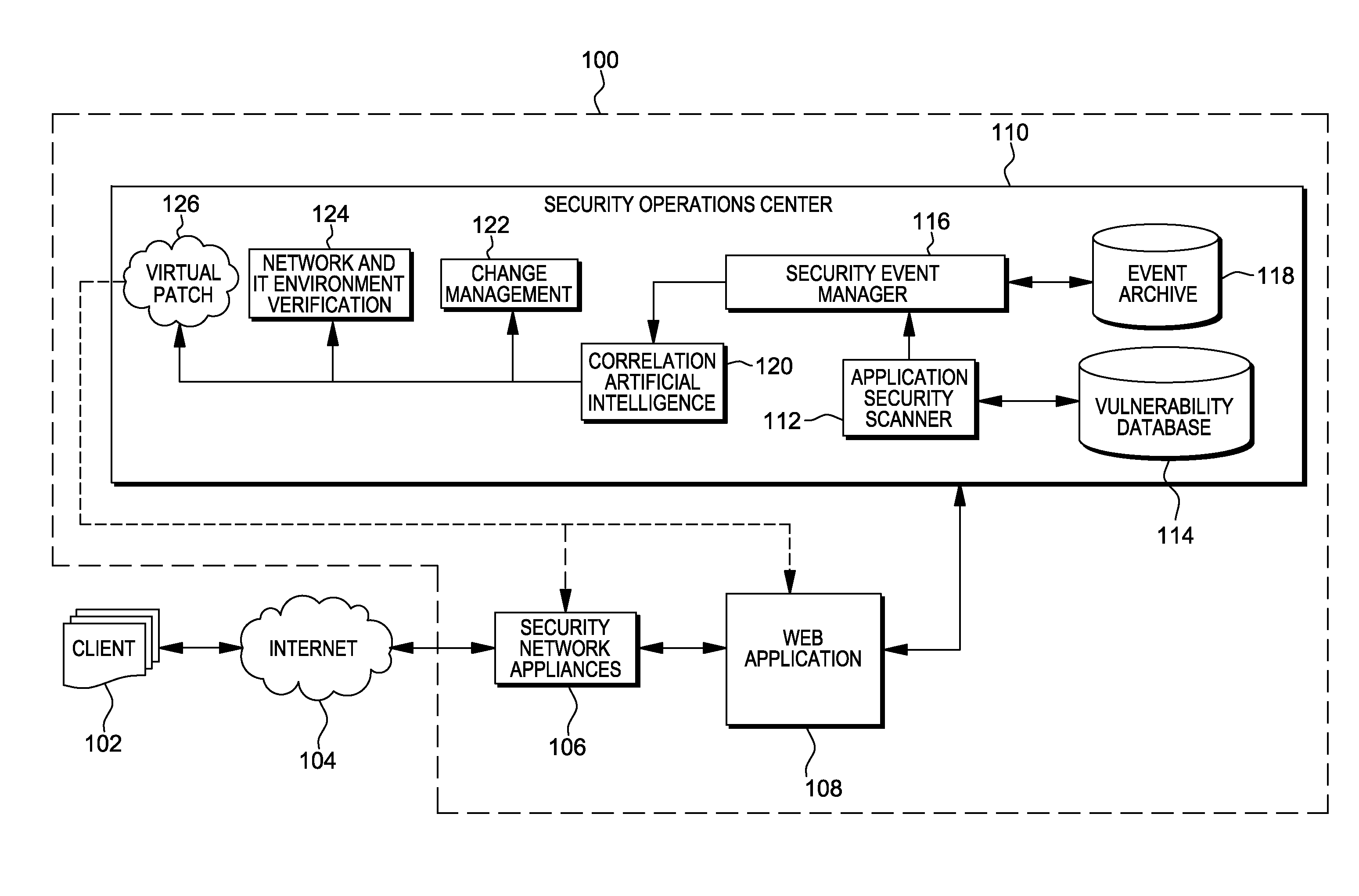
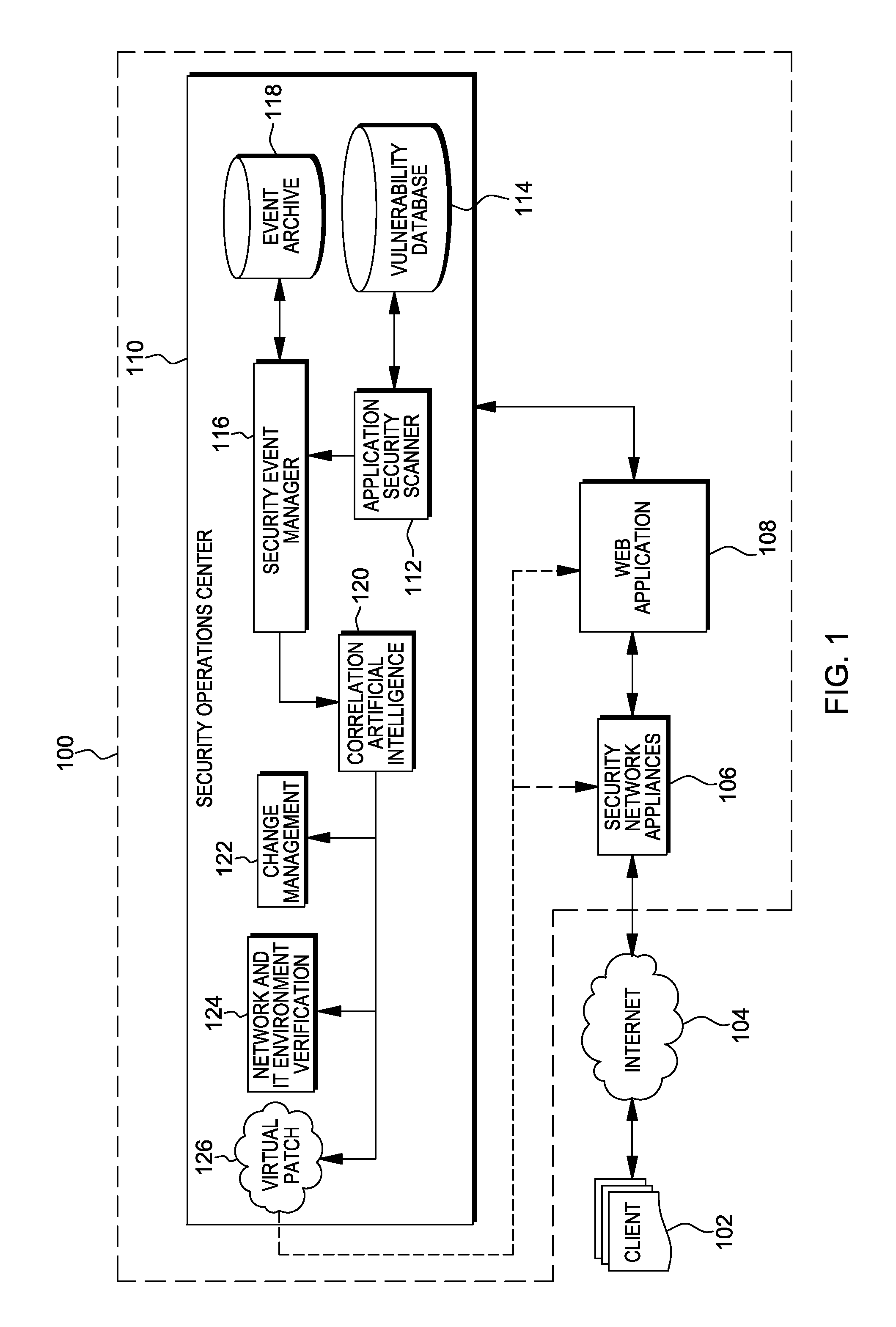
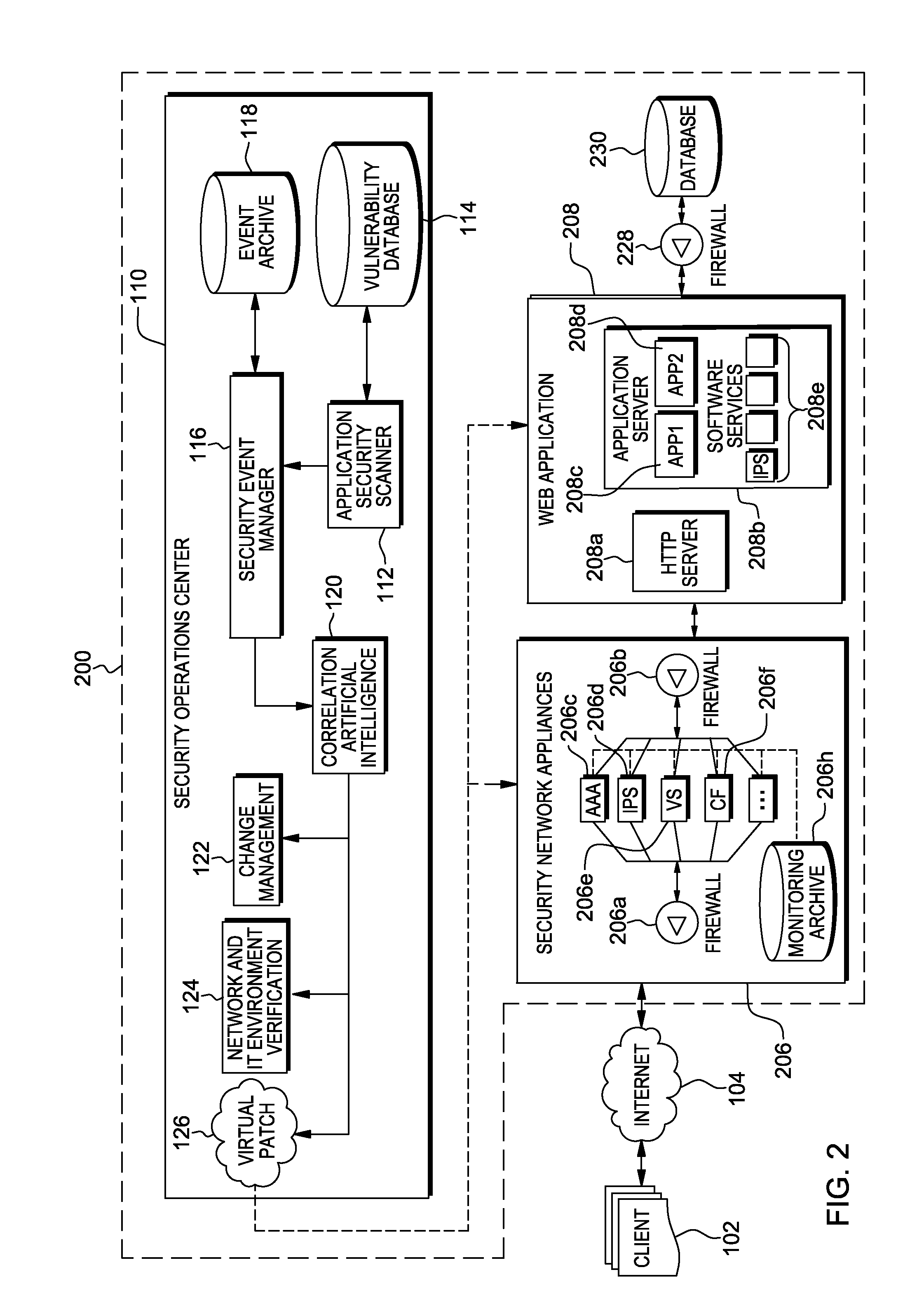
Methods, systems, and computer program products are provided herein for facilitating security in an information technology environment. Web application security vulnerabilities are discovered and addressed by means of virtual patches deployed to components of the information technology environment. An intelligent feedback loop is created to fill the void in the security of the web application when implemented in the specific information technology environment, thereby providing end-to-end security application management through dynamic, pre-emptive, and proactive security awareness and protection in the information technology environment. As new web application security vulnerabilities are discovered, the vulnerability is diagnosed and resolved to preemptively prevent exploitation of the security vulnerability.
Owner:FINJAN BLUE INC
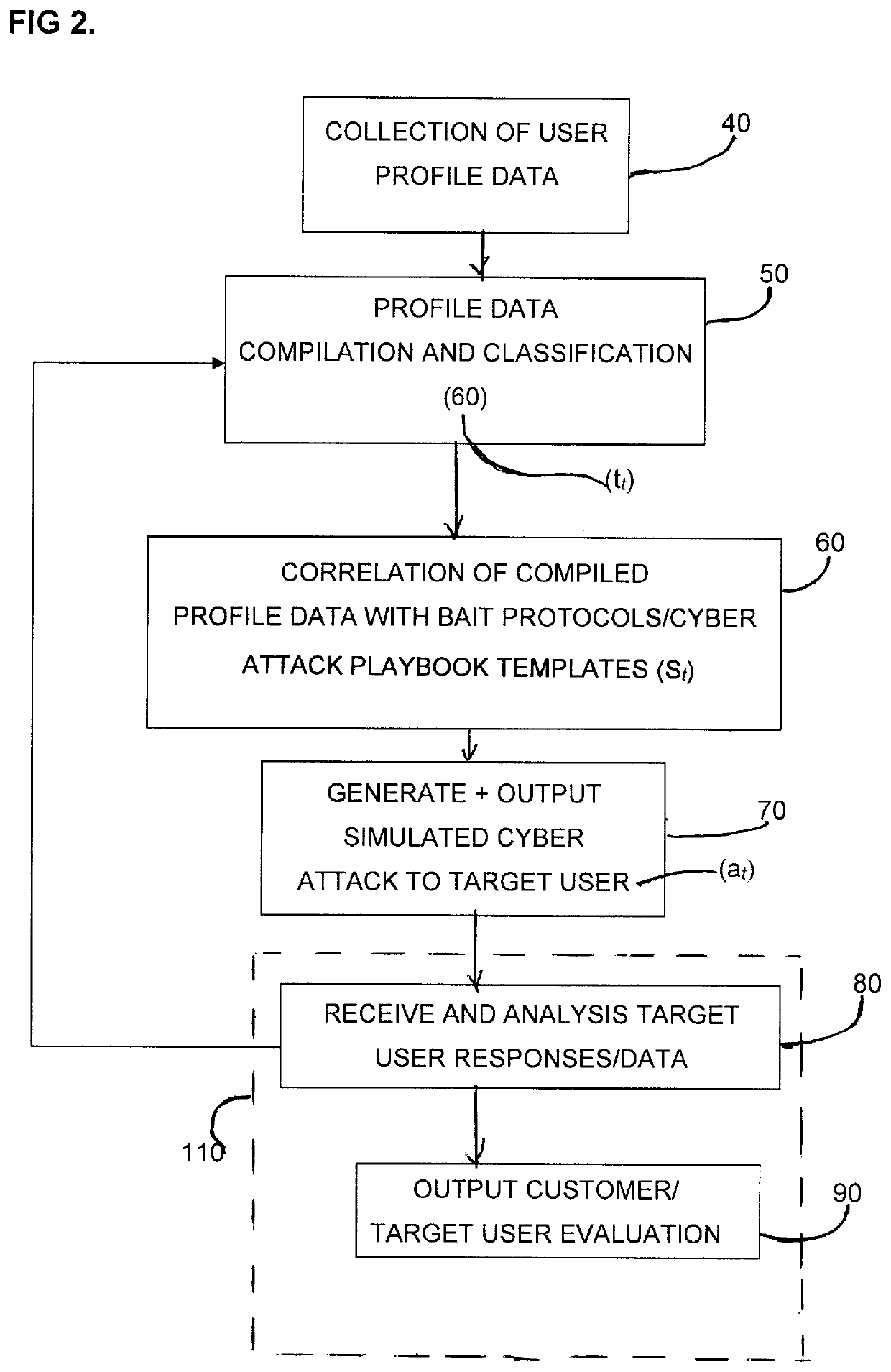
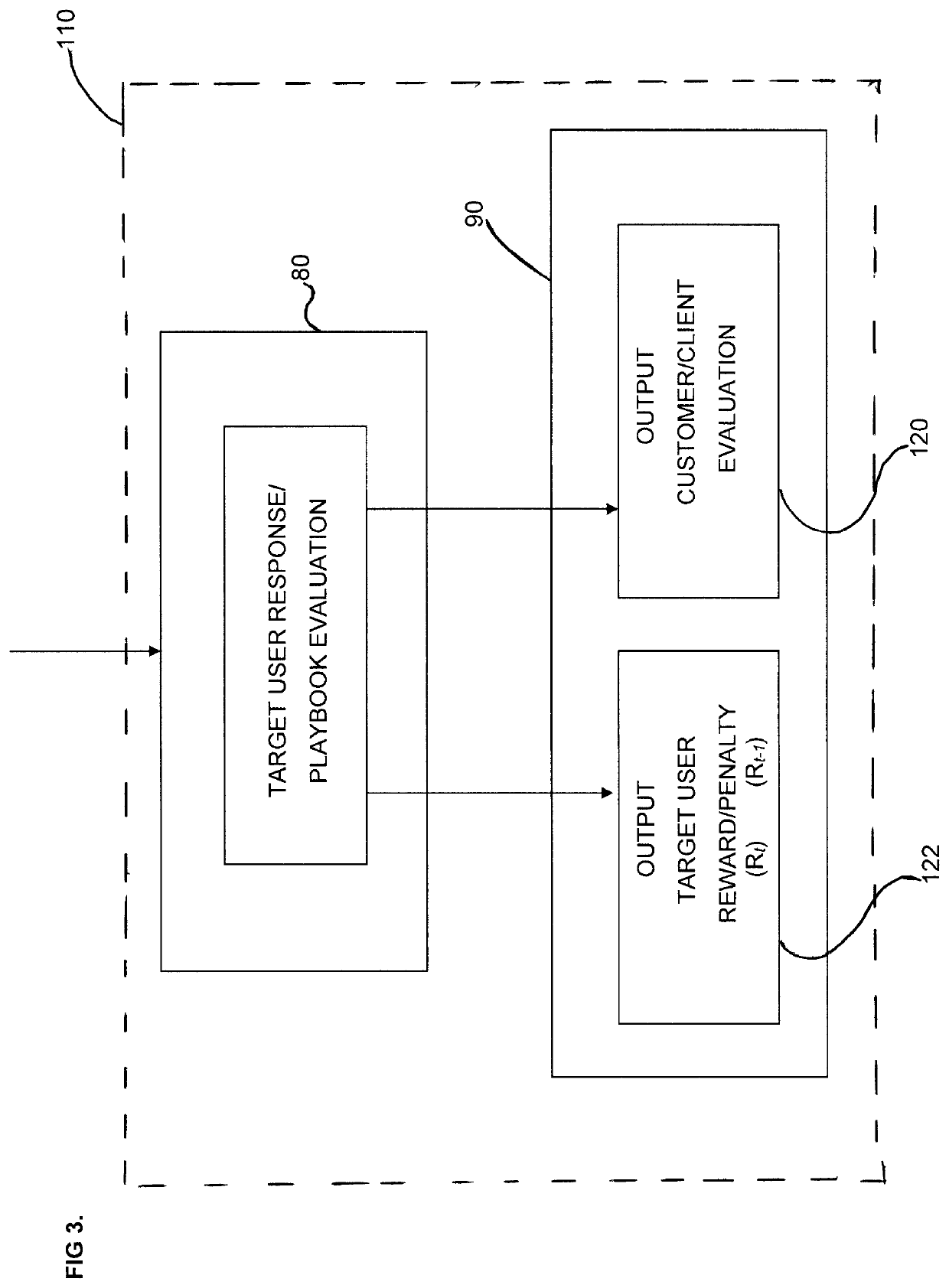
System and Method for Social Engineering Cyber Security Training
A system and method are provided for growing cyber security awareness relating to social engineering and administering anti-social engineering training. The system makes use of artificial intelligence (AI), cyber security strategies and / or gamification principles to help organizations better understand and prepare for potential social engineering security risks. One embodiment of the system includes a reinforcement learning (RL) module, which further includes a trained predictor and an agent that interacts with a target. The RL module receives as input a training dataset that includes information about the target. The trained predictor generates a bait for the target based on the input training dataset; and the agent delivers the generated bait as an attack on the target. The RL module outputs a playbook of the attack, which can be used to update the training dataset and the trained predictor for subsequent iterative attacks, and / or to recommend social engineering countermeasures to the target.
Owner:UNIVERSITY OF WINDSOR
Protecting confidential information on network sites based on security awareness
ActiveUS8365246B2Memory loss protectionDigital data processing detailsInternet privacySecurity awareness
A system for protecting confidential information based upon user security awareness is provided. The system includes a network interface for connecting the system to a plurality of remotely-located network sites. The system also includes one or more processors on which at one or more data processing feature execute in response to a request received from a user of one of the remotely-located network sites. The system further includes a security-awareness module configured to execute in conjunction with the one or more processors for determining a measure of security awareness of the user, and for granting or denying the user access to the at least one data processing feature based upon the measure of security awareness.
Owner:IBM CORP
Web application exploit mitigation in an information technology environment
ActiveUS8572750B2Improve protectionMemory loss protectionError detection/correctionEnd to end securityProgram management
Methods, systems, and computer program products are provided herein for facilitating security in an information technology environment. Web application security vulnerabilities are discovered and addressed by means of virtual patches deployed to components of the information technology environment. An intelligent feedback loop is created to fill the void in the security of the web application when implemented in the specific information technology environment, thereby providing end-to-end security application management through dynamic, pre-emptive, and proactive security awareness and protection in the information technology environment. As new web application security vulnerabilities are discovered, the vulnerability is diagnosed and resolved to preemptively prevent exploitation of the security vulnerability.
Owner:FINJAN BLUE INC
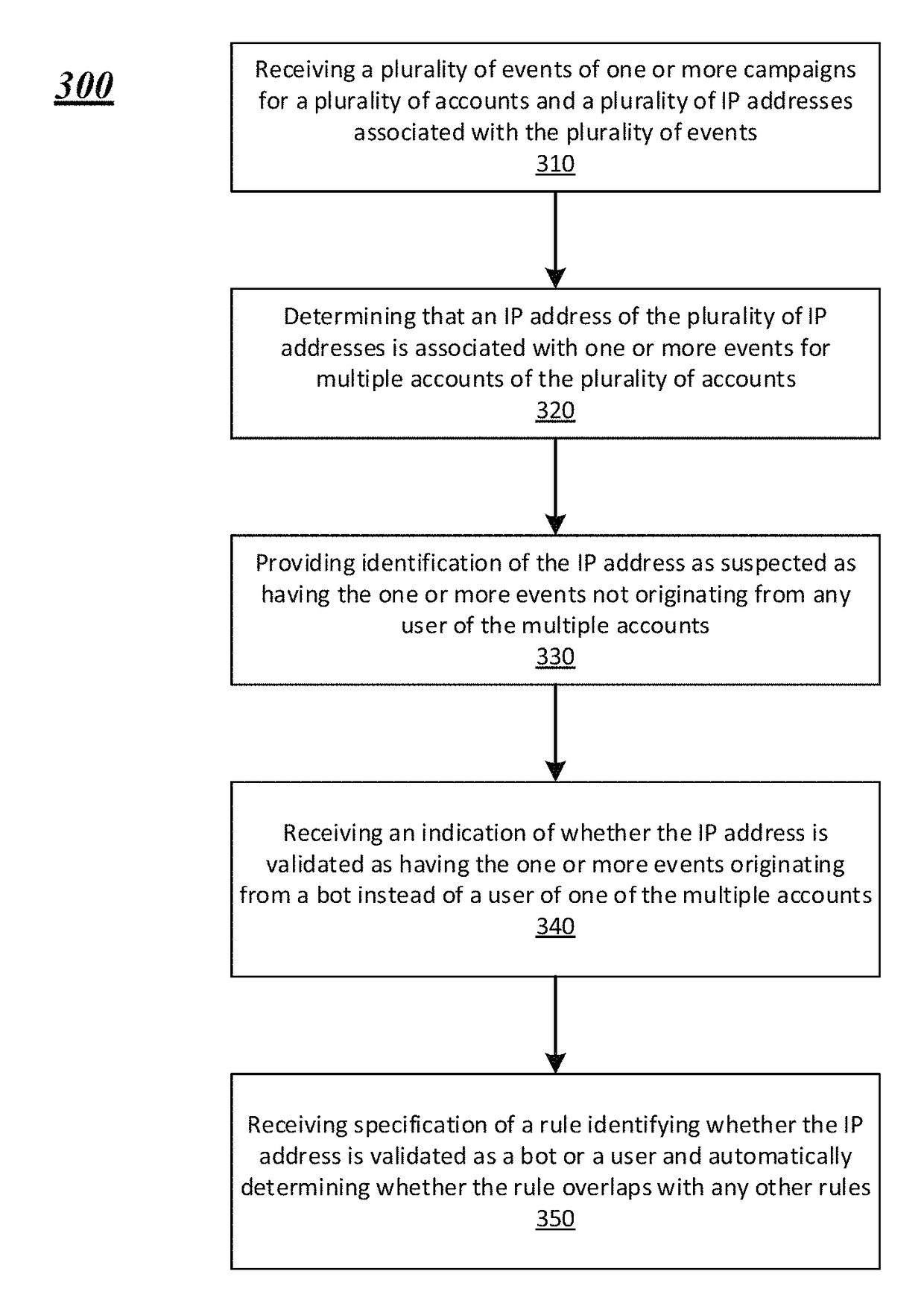
Systems and methods for discovering suspect bot IP addresses and using validated bot IP address to ignore actions in a simulated phishing environment
Methods, systems and apparatus are provided which allow a server of a security awareness system to associate IP addresses with events representing user interactions with simulated phishing campaigns. The server receives a plurality of events related to one or more simulated phishing campaigns for a plurality of accounts. The server determines if an IP address of the plurality of IP addresses is associated with one or more events for multiple accounts of the plurality of accounts. Based upon this determination, the server provides identification of the IP address as suspected as having the one or more events associated with it not originating from any user of the multiple accounts. The server receives an indication of whether the IP address is validated as having the one or more events originating from a bot instead of a user of one of the multiple accounts.
Owner:KNOWBE4 INC
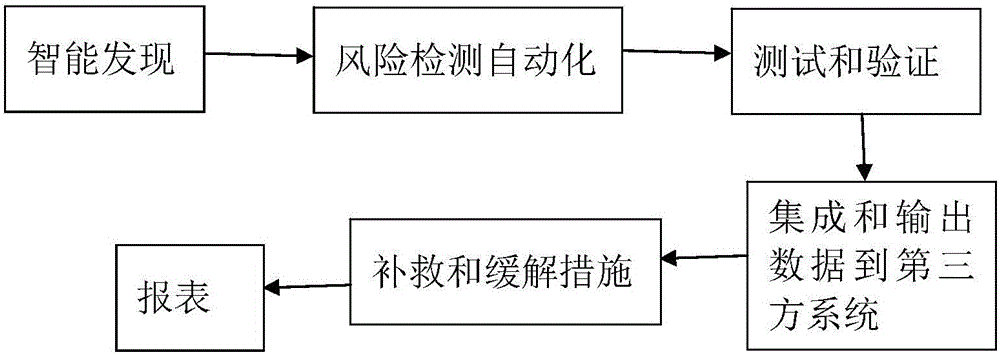
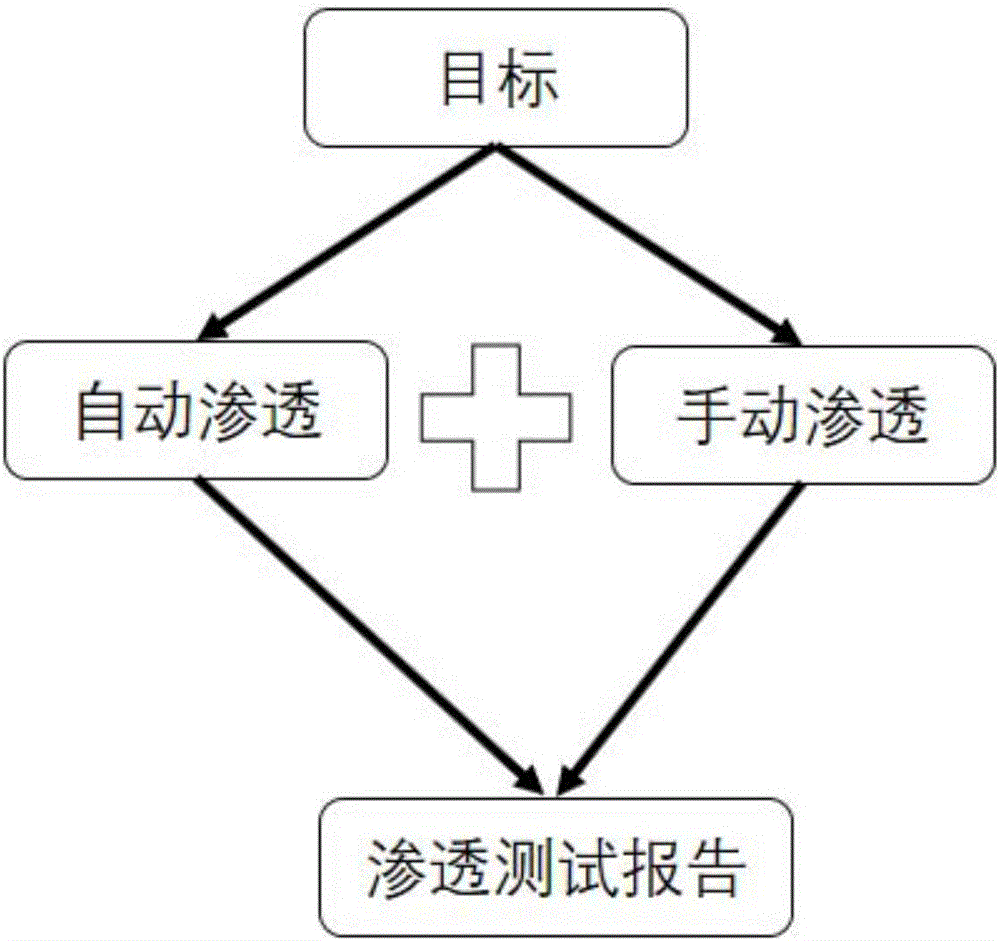
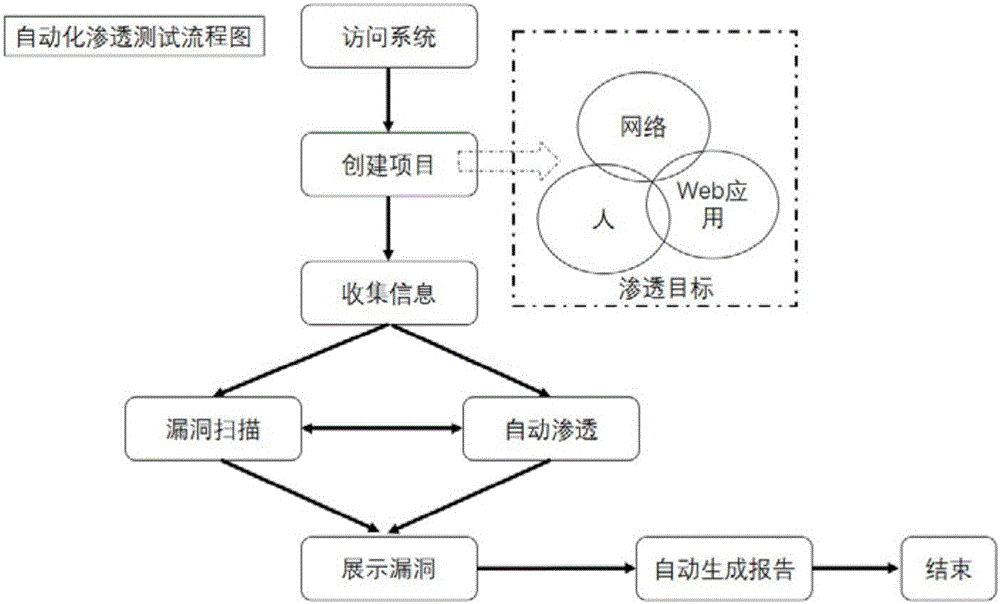
Automatic penetration testing method and system
InactiveCN105827642ARaise security awarenessImprove inspection efficiencyData switching networksEngineeringVulnerability
The invention discloses an automated penetration testing method and system, including an automatic penetration method and a manual penetration method; in the manual penetration method, it is necessary to select a penetration mode for automatic penetration; the penetration mode includes loophole penetration, brute force cracking, and WEB penetration and social engineering tests. The present invention has the advantages of loophole hazard display, comprehensive coverage inspection, and automatic penetration. By utilizing the discovered loopholes, the present invention displays the hazards caused by the loopholes, deters development and operation and maintenance personnel, forms indirect security awareness education for them, and improves personnel security. Security awareness; comprehensive coverage inspection, through security inspection of networks, applications, and personnel; through automated penetration, improve the efficiency and comprehensiveness of security personnel inspections.
Owner:SHENZHEN ANLUO TECH CO LTD
Systems and methods for artificial model building techniques
ActiveUS10009375B1Avoid actionSame effectPlatform integrity maintainanceTransmissionHyperlinkRequest - action
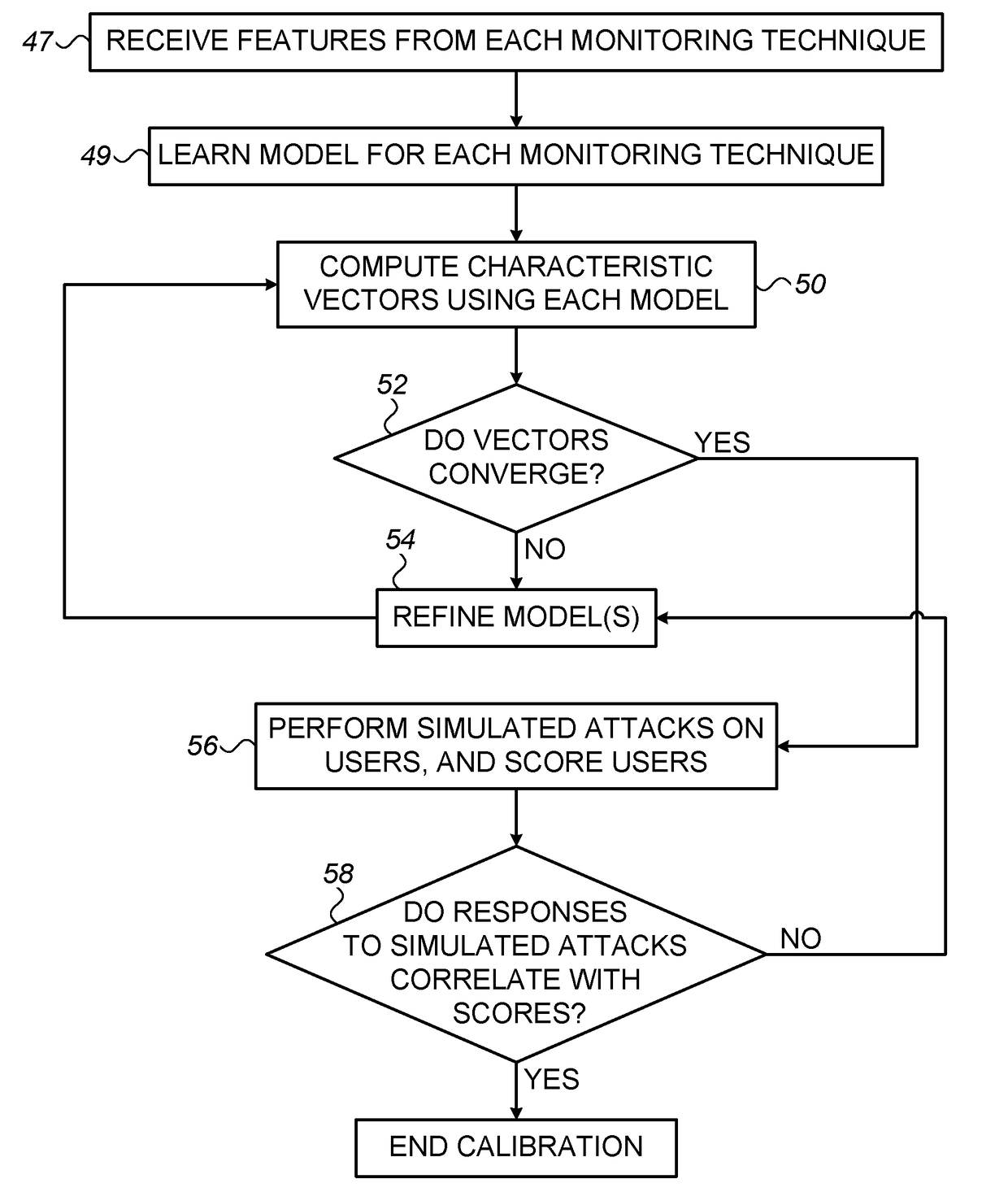
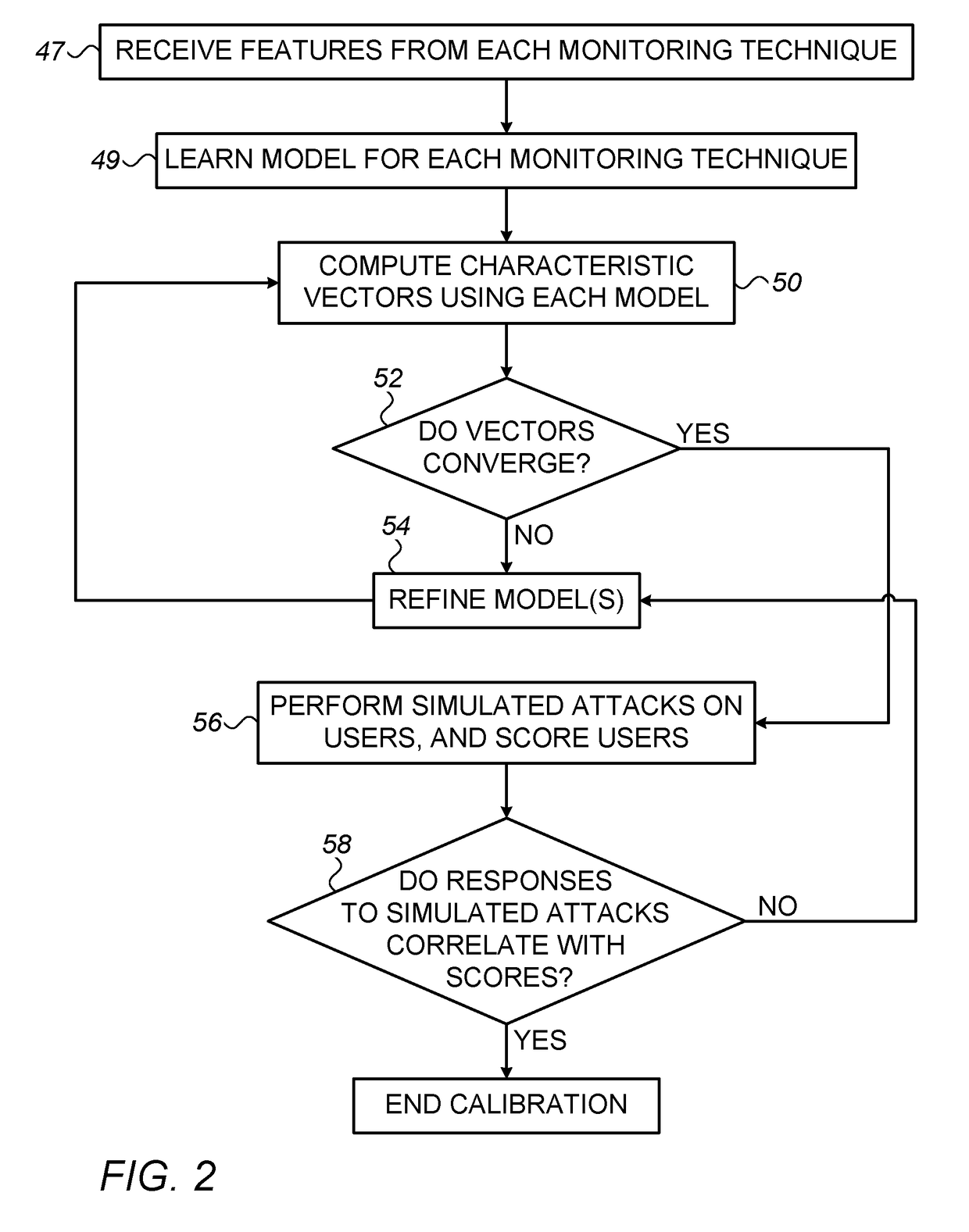
Embodiments disclosed describe a security awareness system may adaptively learn the best design of a simulated phishing campaign to get a user to perform the requested actions, such as clicking a hyperlink or opening a file. In some implementations, the system may adapt an ongoing campaign based on user's responses to messages in the campaign, along with the system's learned awareness. The learning process implemented by the security awareness system can be trained by observing the behavior of other users in the same company, other users in the same industry, other users that share similar attributes, all other users of the system, or users that have user attributes that match criteria set by the system, or that match attributes of a subset of other users in the system.
Owner:KNOWBE4 INC
Systems and methods for creating and commissioning a security awareness program
Methods, systems and apparatus for implementing a security awareness program are provided which allow a device of a security awareness system to receive attributes of an implementation of a security awareness program from an entity, such as a company. Responsive to the attributes, the device determines a configuration for each of a baseline simulated phishing campaign, electronic based training of users of the entity for security awareness and one or more subsequent simulated phishing campaigns. The device initiates execution of the baseline simulated phishing campaign to identify a percentage of users of the entity that are phish-prone.
Owner:KNOWBE4 INC
Systems and methods for determining individual and group risk scores
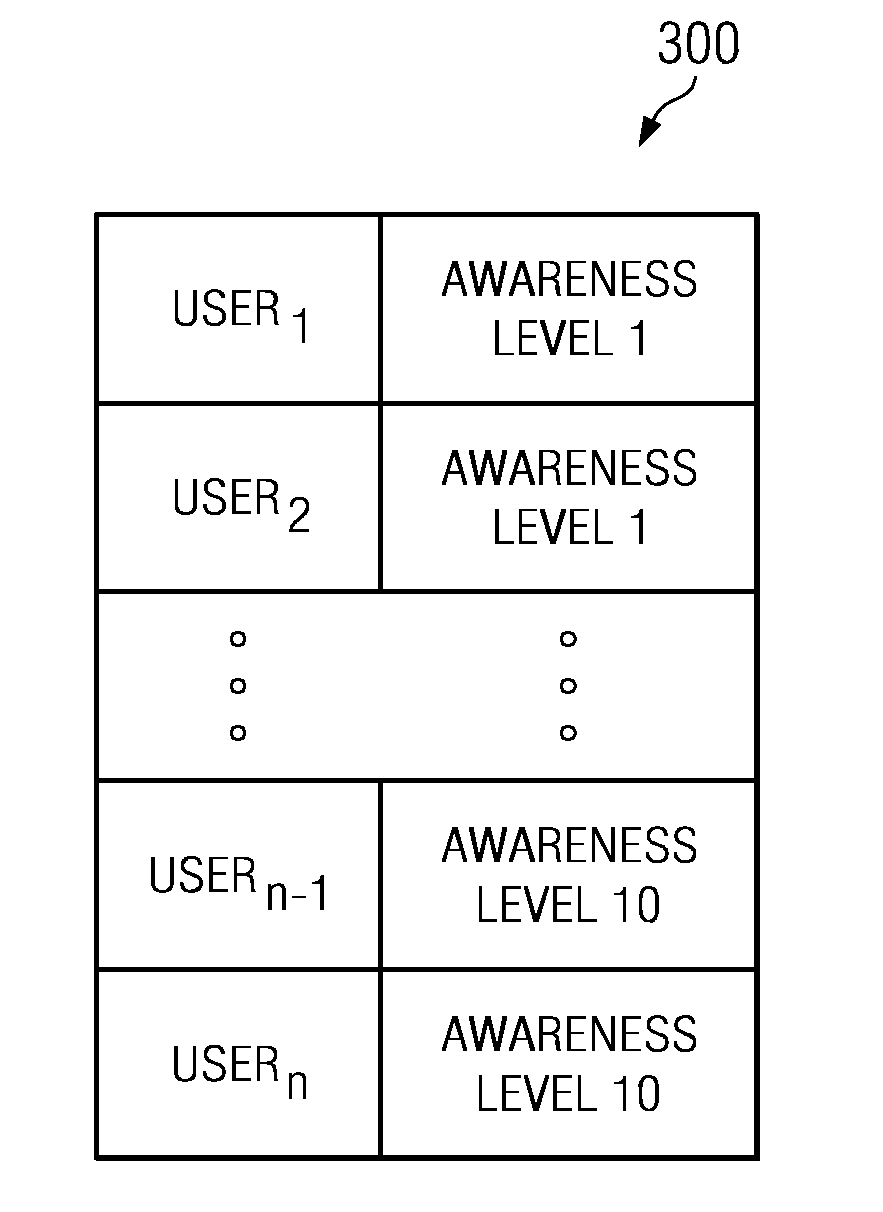
Embodiments disclosed herein describe a server, for example a security awareness server or an artificial intelligence machine learning system that establishes a risk score or vulnerable for a user of a security awareness system, or for a group of users of a security awareness system. The server may create a frequency score for a user, which predicts the frequency at which the user is to be hit with a malicious attack. The frequency score may be based on at least a job score, which may be represented by a value that is based on the type of job the user has, and a breach score that may be represented by a value that is based on the user's level of exposure to email.
Owner:KNOWBE4 INC
Systems and methods for using attribute data for system protection and security awareness training
ActiveUS20190034623A1Improve security awareness trainingEnhance anti-phishing capability of systemHardware monitoringPlatform integrity maintainanceData fileSystem protection
The present disclosure describes a system for saving metadata on files and using attribute data files inside a computing system to enhance the ability to provide user interfaces based on actions associated with non-executable attachments like text and document files from untrusted emails, to block execution of potentially harmful executable object downloads and files based on geographic location, and to a create a prompt for users to decide whether to continue execution of potentially harmful executable object downloads and files. The system also records user behavior on reactions to suspicious applications and documents by transmitting a set of attribute data in an attribute data file corresponding to suspicious applications or documents to a server. The system interrupts execution of actions related to untrusted phishing emails in order to give users a choice on whether to proceed with actions.
Owner:KNOWBE4 INC
Systems and methods for discovering and alerting users of potentially hazardous messages
This disclosure generally revolves around providing users with advance warning that a message that they have received may be suspicious. The user may not be aware of known threats, may not recognize threats in real time, or may not be aware of new threats, and therefore may unintentionally interact with a hazardous message. A security awareness system, on the other hand, is aware of known threats and may become aware of new threats more quickly than users can be trained to identify them. The system may notify the user when one of these threats are found in their messages. The disclosure further provides systems and methods for updating the security awareness training for users for new threats that appear.
Owner:KNOWBE4 INC
System and methods for spoofed domain identification and user training
Systems and methods are disclosed that minimize ongoing risk to an organization from user behaviors which magnify the severity of a spoofed domain. Systems and method are provided which enable an entity and users of an entity to identify potential harmful domains, combining search, discovery, reporting, the generation of risk indicators, end-user risk assessments, and training into a security awareness system.
Owner:KNOWBE4 INC
Intrusion process layering online risk assessment method
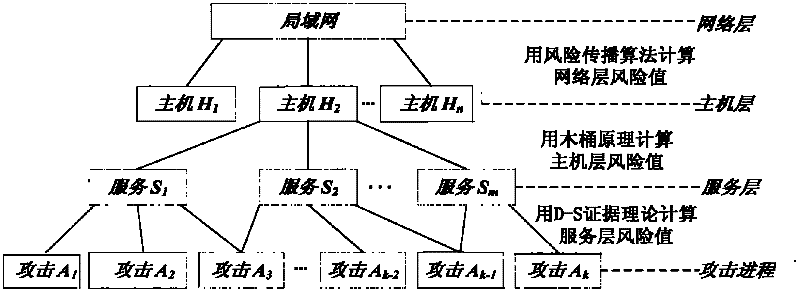
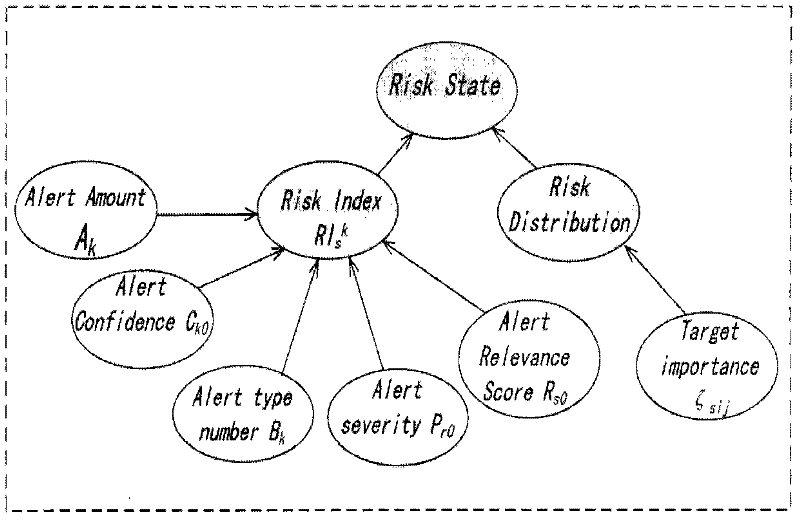
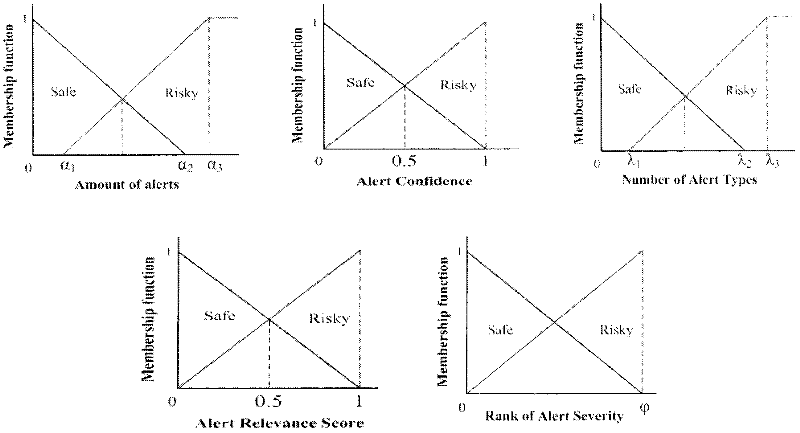
InactiveCN102394766AImprove adaptabilityImprove toleranceData switching networksRisk statusSecurity awareness
The invention discloses an intrusion process layering online risk assessment system and a method, which are used for assessing the risk condition produced on three layers of the service, the host and the network of an occurrent intrusion process in real time. In the invention, on the layer of the service, an evidence theory is used for fusing multi vectors in an alarm thread to compute a risk index, wherein the vectors can response risk change conditions, the objective condition of intrusion risks is reflected by the risk index, and simultaneously, with target risk distribution reflected by subjective safety awareness, the risk condition of a target is comprehensively assessed; on the layer of the host, a risk assessment method based on a cask principle is provided; and on the layer of the network, a safety dependence network concept is provided, and an improved risk spreading algorithm is utilized so as to complete the risk assessment of the layer of the network. According to the invention, the alarm processes of alarm verification, aggregation and correlation as well as alarm confidence learning are closely combined with the risk assessment, so that the subjectivity, the fuzziness, the uncertainty and other problems in the risk assessment are better processed.
Owner:穆成坡
Method and device for processing web-side access
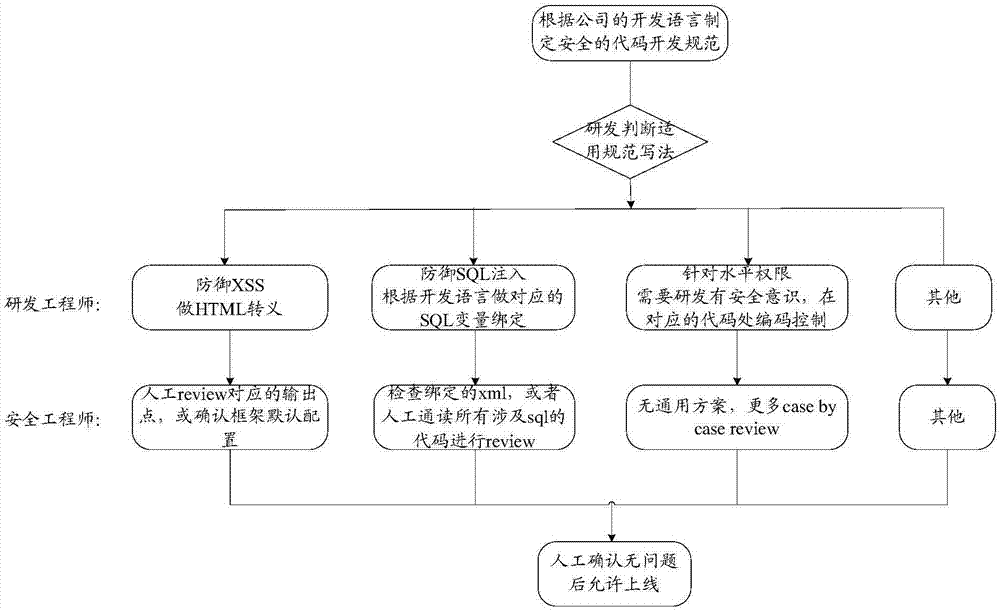
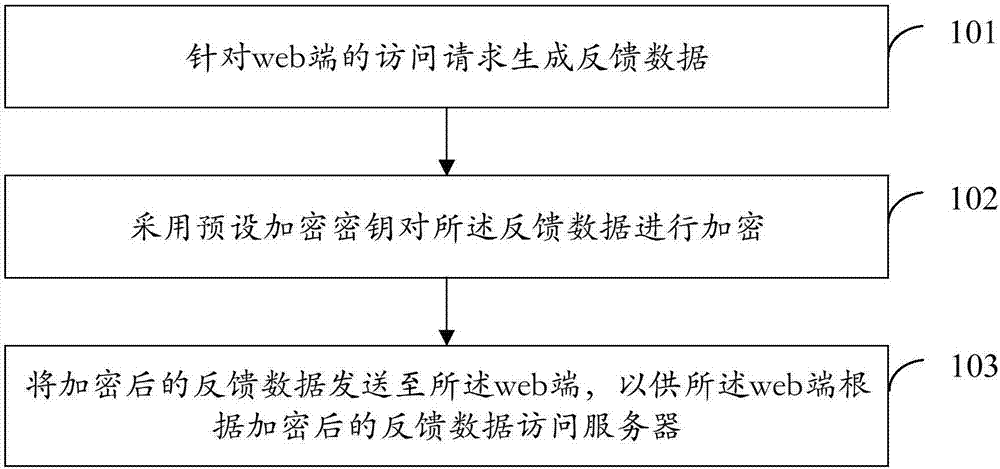
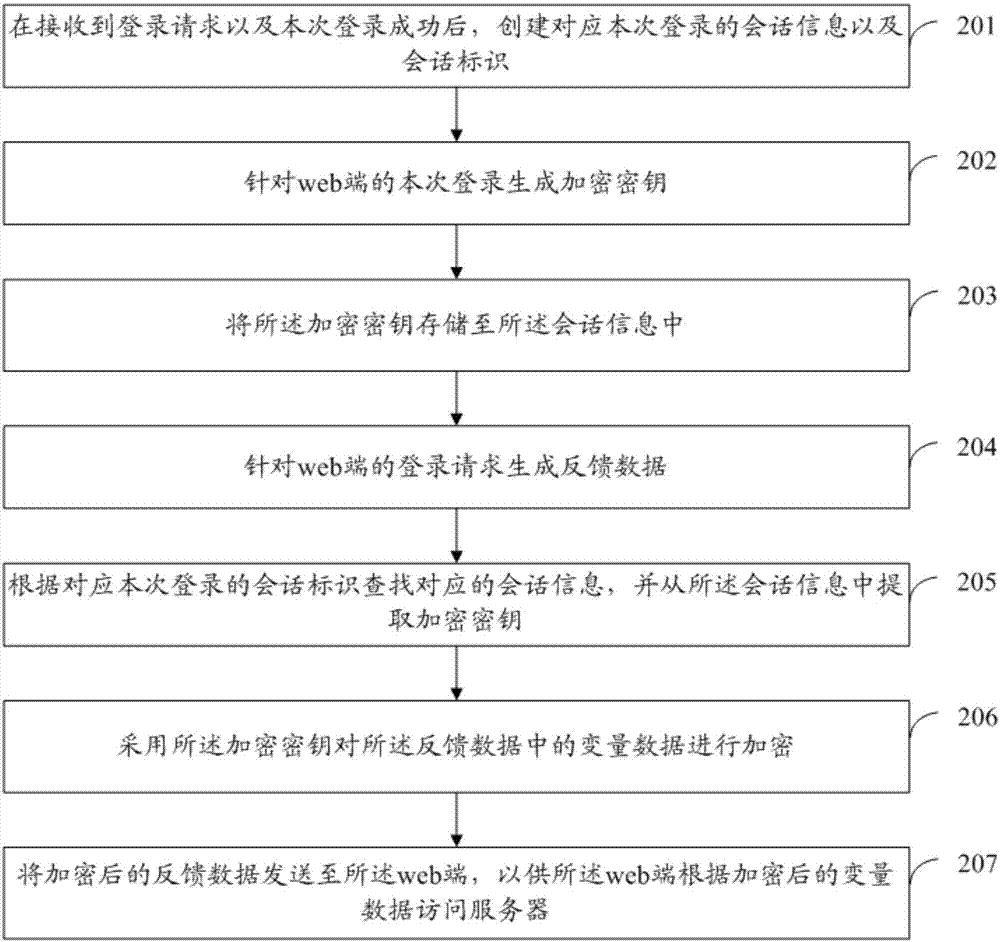
InactiveCN107294921AReduced Security Awareness RequirementsSolve web security issuesKey distribution for secure communicationDigital data protectionSecurity awarenessDEVS
The application provides a method and a device for processing web-side access. The method includes the following steps: generating feedback data for an access request at a Web side; using a preset encryption key to encrypt the feedback data; and sending the encrypted feedback data to the web side to enable the Web side to access a server according to the encrypted feedback data. According to the scheme of the application, if the variable data in the feedback data in encrypted, attackers are unable to construct new access parameters by modifying the variable data of the system, so that the security of Web is improved, and all kinds of security attacks due to horizontal permission vulnerabilities are eradicated; and meanwhile, the requirement on security awareness of development personnel in the research and development stage of a business system is lowered, and the manpower cost is reduced.
Owner:ALIBABA GRP HLDG LTD
Personnel dressing detection method, processing terminal and storage medium
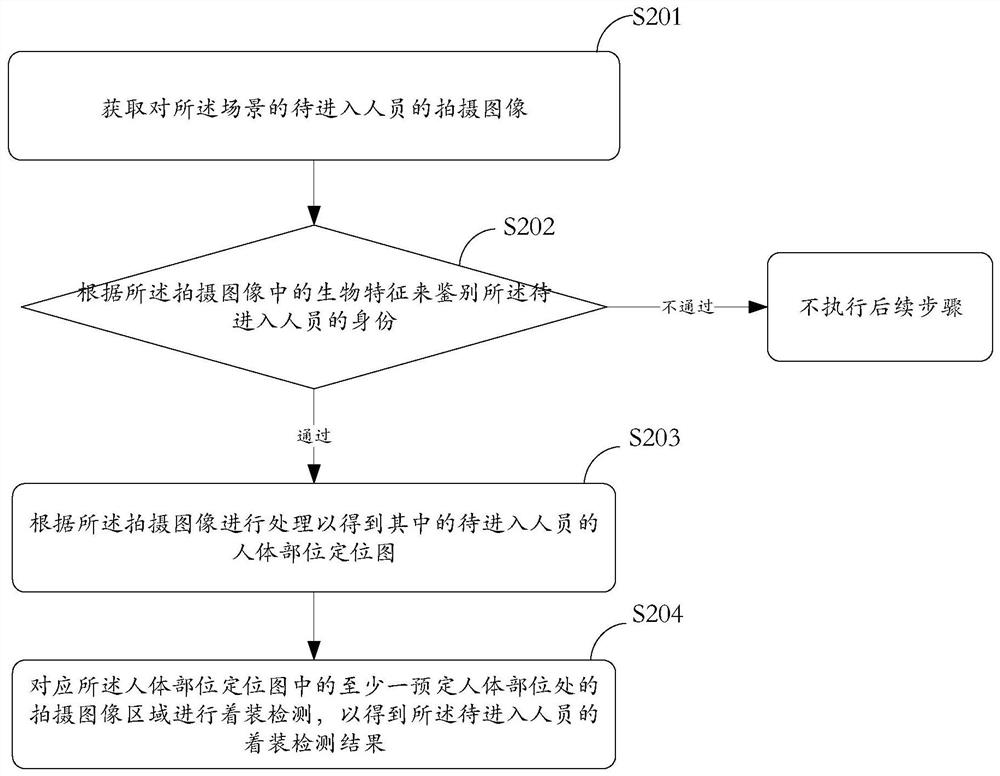
ActiveCN111626210ARemind and raise security awarenessRaise security awarenessMultiple biometrics useHuman bodySecurity awareness
A personnel dressing detection method, a processing terminal and a storage medium are applied to scenes with dressing requirements. Specifically, the method comprises the following steps: acquiring ashot image of a to-be-entered person in a scene; processing according to the shot image to obtain a human body part positioning map of the to-be-entered person; and performing dressing detection corresponding to the shot image area of at least one predetermined human body part in the human body part positioning graph to obtain a dressing detection result of the to-be-entered person. According to the invention, the dressing detection result of the to-be-entered person in the scene is automatically detected; the method is simple, efficient and accurate, personnel dressing can be further supervised by utilizing the dressing detection result so as to remind and improve the safety awareness of related personnel, and personnel who do not pass the dressing detection result may be strange personnel and can be discriminated so as to limit the behavior of the strange personnel, so that the safety level of a scene is improved; in addition, the dressing detection result can also be used for beingmatched with the dressing person, and if necessary, the matching result can be sent to a manager or the dressing person.
Owner:SHANGHAI TECH UNIV
Network information security awareness education method and device, storage medium
InactiveCN109067637ASolve the strong and weakImprove training effectData switching networksRelevant informationSecurity awareness
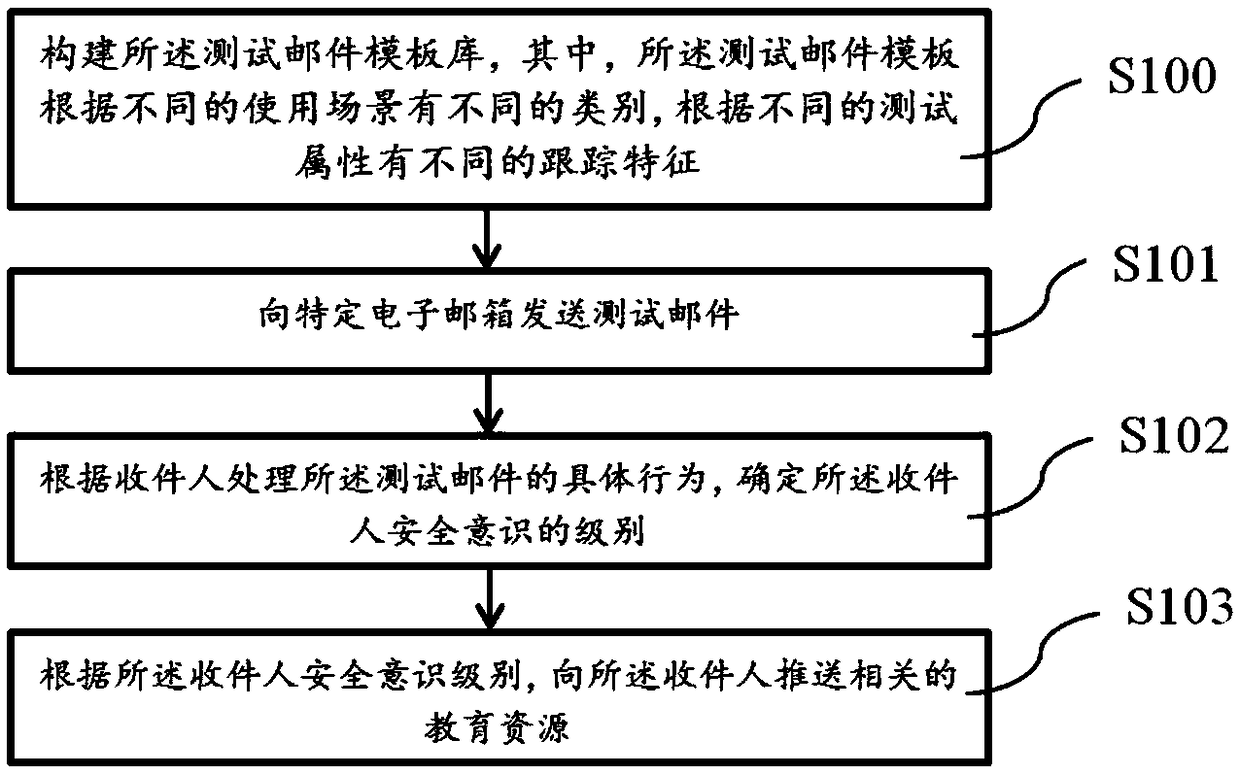
The invention discloses a network information security awareness education method and device and a storage medium, wherein, the method comprises the following steps of: constructing a test mail template database,wherein, the test mail template has different categories according to different use scenes and has different tracking characteristics according to different test attributes; sending test mails to specific e-mailboxes; determining a level of security awareness of the recipient according to a specific behavior of the recipient in processing the test mail; according to the recipient's security awareness level, relevant information security awareness education resources are pushed to the recipient. The technical proposal disclosed by the invention solves the technical problem that in the prior art, the safety consciousness of each e-mail user can not be known in time, and further solves the technical problem that the recipient of the e-mail can not be fully aware of the network information in time and pertinently in the related technology.
Owner:海南首联信通科技有限公司
Systems and methods for determining a job score from a job title
ActiveUS10992699B1Allocation is accurateImpact the amount of inbound and outbound communicationEnsemble learningBiological modelsAttackSecurity awareness
Embodiments disclosed herein describe a server, for example a security awareness server or an artificial intelligence machine learning system that establishes a job score for a user based on the user's job title. In embodiments, the vulnerability of a user to malicious cybersecurity attacks, the propensity for the user to engage with a malicious attack, and the severity of a malicious attack likely to be sent to the user and the severity of the harm to the user's organization is the user engages with the malicious attack is represented in a user risk score. The risk score for a user of a security awareness system, or for a group of users of a security awareness system, may be calculated based on one or more of a frequency score for the user, a propensity score for the user, a severity score for the user, and a job score for the user.
Using smart groups for computer-based security awareness training systems
This disclosure describes embodiments of an improvement to the static group solution because all the administrator needs to do is specify the criteria they care about. Unlike static groups, where the administrator needs to keep track of the status of individual users and move them between static groups as their status changes, smart groups allows for automatic identification of the relevant users at the moment that action needs to be taken. This feature automates user management for the purposes of enrollment in either phishing and training campaigns. Because the smart group membership is determined as the group is about to be used for something, the smart group membership is always accurate and never outdated. The query that determines the smart group membership gets run at the time when you are about to do a campaign or perform some other action that needs to know the membership of the smart group.
Owner:KNOWBE4 INC
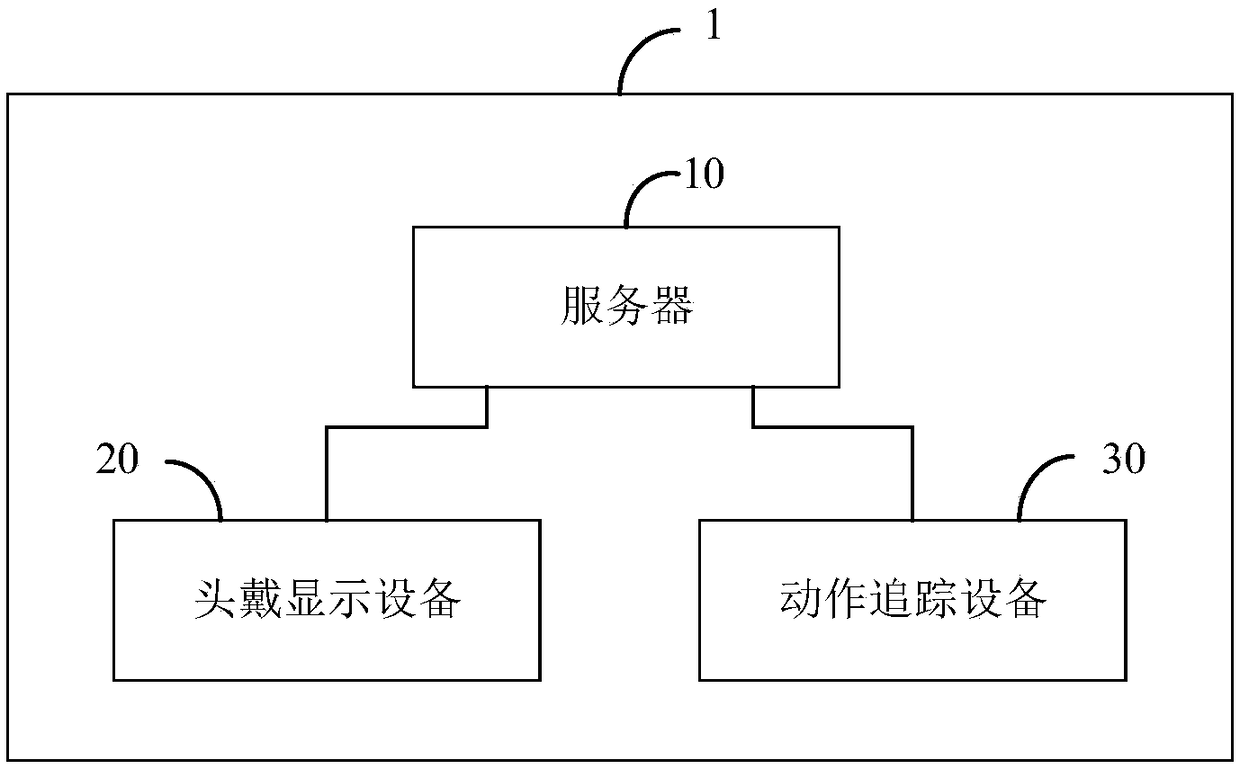
Electric shock accident simulation system
InactiveCN108922302ARaise security awarenessA correct understanding of destructive powerInput/output for user-computer interactionCosmonautic condition simulationsDisplay deviceSecurity awareness
The invention is applicable to the technical field of virtual reality, and provides an electric shock accident simulation system. The electric shock accident simulation system comprises a server, a head-mounted display device and an action tracking device; a power training virtual scene is sent to the head-mounted display device through the server, and the head-mounted display device displays thepower training virtual scene; initial information of a person is acquired by the action tracking device, and the initial information of the person is sent to the server; the server obtains action information according to the initial information, and determines whether the action information satisfies a preset electric shock triggering condition; if the action information satisfies the preset electric shock triggering condition, an electric shock accident virtual scene is sent to the head-mounted display device, and the head-mounted display device displays the electric shock accident virtual scene. According to the invention, the electric shock accident virtual scene is sent to the head-mounted display device of the person when the action information satisfies the preset electric shock triggering condition, so that the person is in a scene of the electric shock accident, thereby correctly understanding the destructive power and harmfulness of the electric power accidents; and the security awareness of the person is improved.
Owner:STATE GRID CORP OF CHINA +1
Systems and methods for artificial model building techniques
ActiveUS10264018B1Avoid actionSame effectPlatform integrity maintainanceTransmissionHyperlinkRequest - action
Embodiments disclosed describe a security awareness system may adaptively learn the best design of a simulated phishing campaign to get a user to perform the requested actions, such as clicking a hyperlink or opening a file. In some implementations, the system may adapt an ongoing campaign based on user's responses to messages in the campaign, along with the system's learned awareness. The learning process implemented by the security awareness system can be trained by observing the behavior of other users in the same company, other users in the same industry, other users that share similar attributes, all other users of the system, or users that have user attributes that match criteria set by the system, or that match attributes of a subset of other users in the system.
Owner:KNOWBE4 INC
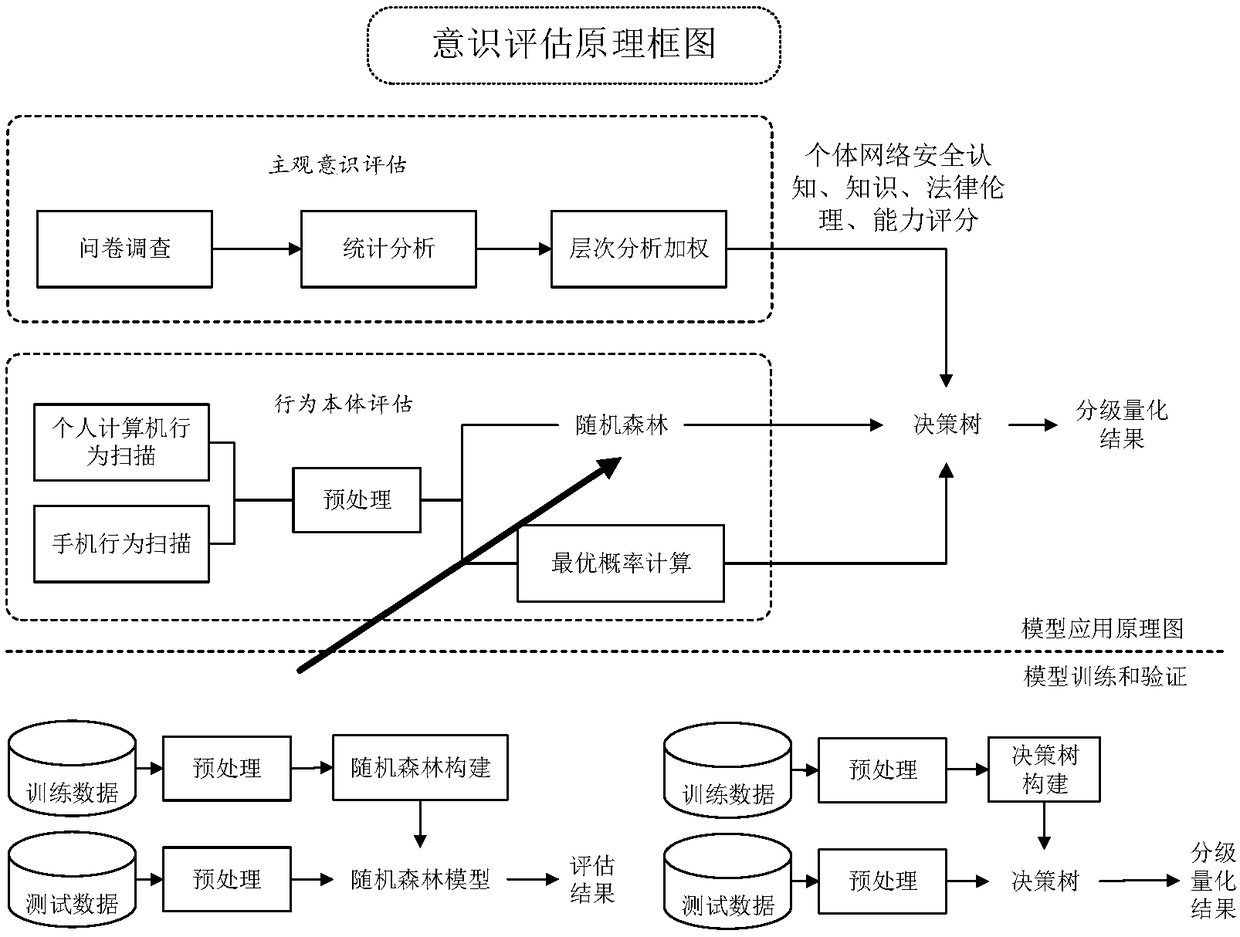
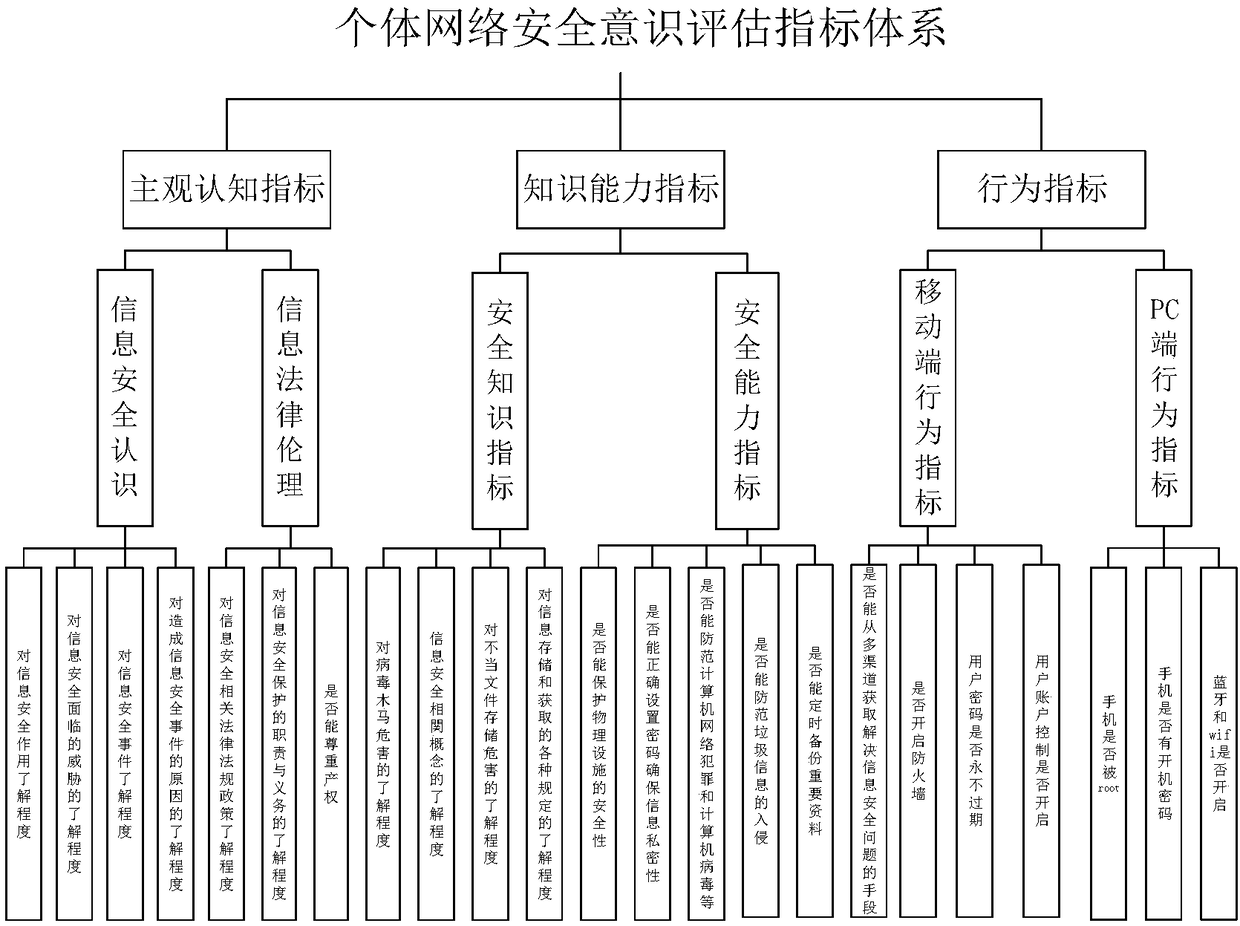
Individual network security awareness grading quantitative evaluation method
The invention provides an individual network security awareness grading quantitative evaluation method for the problems of fuzzy definition of network security awareness and lack of an effective assessment system and method at present. The method comprises three parts including subjective consciousness assessment, behavior ontology assessment and assessment decision making. In the subjective consciousness assessment part, individual information is obtained through questionnaire survey; four dimensions including information security awareness, information legal ethics, information security knowledge and information security capability are scored through an analytic hierarchy process; and scores of an individual user in the four dimensions are obtained. In the behavior ontology assessment part, computer and mobile phone user behaviors are scanned; a direct distance with the optimal user behavior is calculated; and the security levels of the user behaviors are judged through a random forest algorithm. By fusing the subjective consciousness assessment and the behavior ontology assessment, the individual network space security awareness level is assessed. An experimental result shows that the method can realize individual network security awareness grading quantization in combination with a machine learning method, the granularity is reduced from high to low and is not less than the4 level, and the grading accuracy is more than 95%. The method can be used for improving the comprehensiveness and universality of an individual network security awareness grading quantitative model,and has a certain practical value.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
EHS transparent management system and method based on AI technology
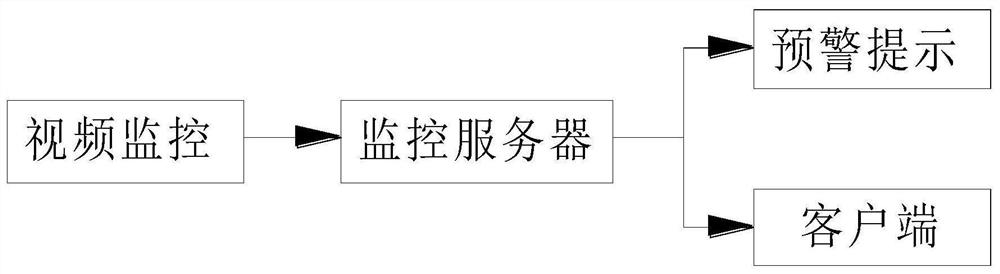
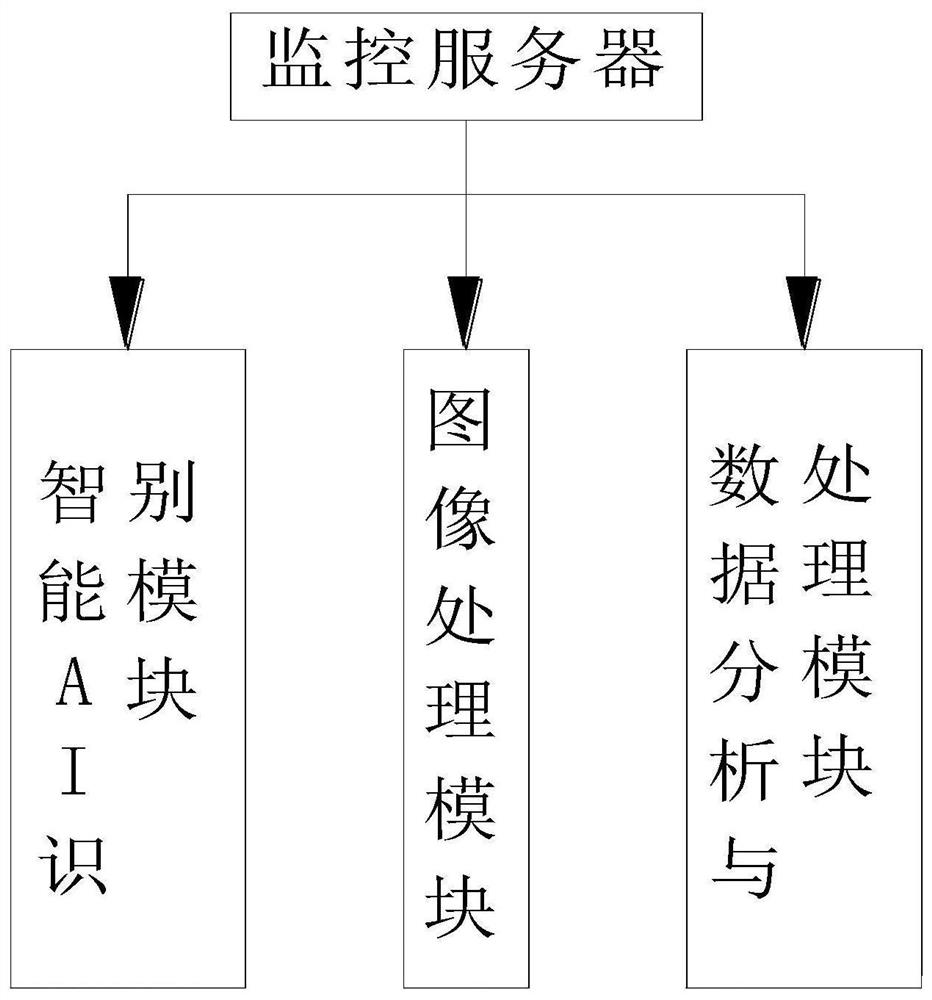
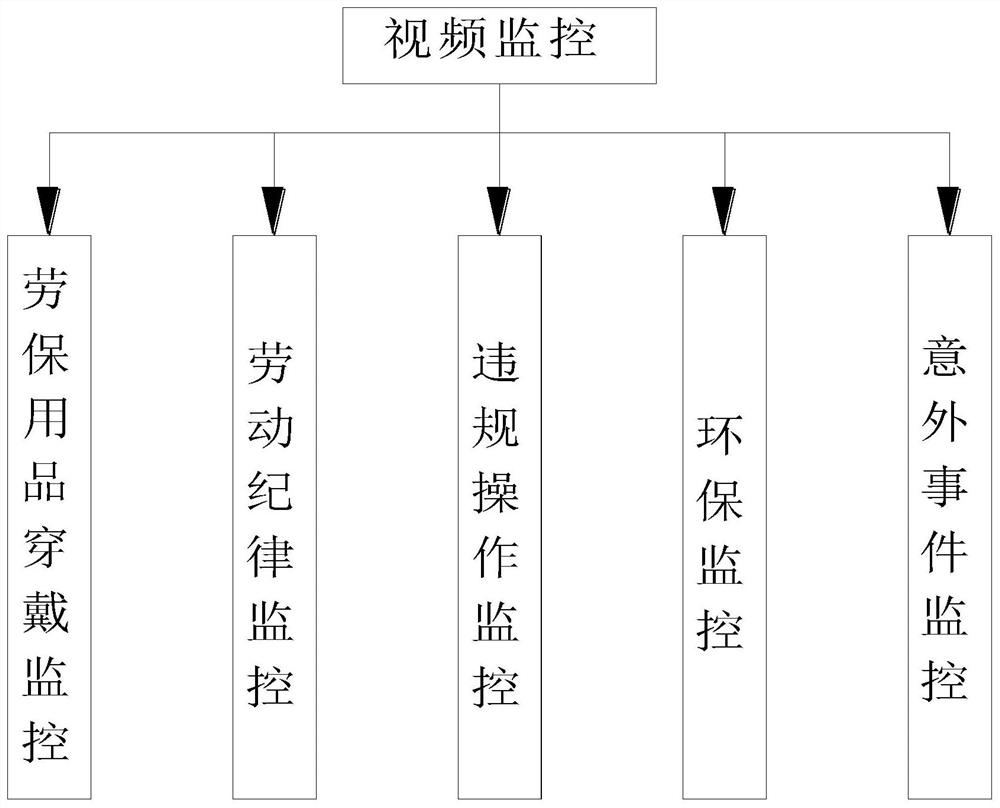
PendingCN112488483AImprove computing efficiencyImprove the ability to distinguishOffice automationResourcesVideo monitoringSecurity awareness
The invention relates to the technical field of safety management, and discloses an EHS transparent management system and method based on the AI technology, and the system comprises a video monitor, amonitoring server, an early warning prompt, and a client, the video monitor is connected with the monitoring server, the early warning prompt is connected with the monitoring server, and the client is connected with the monitoring server; the video monitoring realizes real-time monitoring on whether personnel activities in a production area operate according to a standardized process, preset parameter values are set in the monitoring server, real-time identification and detection are performed on wearing and behaviors of workers according to a real-time video monitored by applying the video monitoring, and the client is used for enabling managers to know monitoring conditions in real time. The early warning prompt gives an early warning prompt for dangerous behaviors which do not meet thestandard requirements; the problems that in the prior art, safety awareness of on-duty personnel in a factory workshop is not high, production operation behaviors of the personnel are not standard, precautionary measures in a factory are not enough, and therefore safety accidents are prone to being caused are solved.
Owner:上上德盛集团股份有限公司
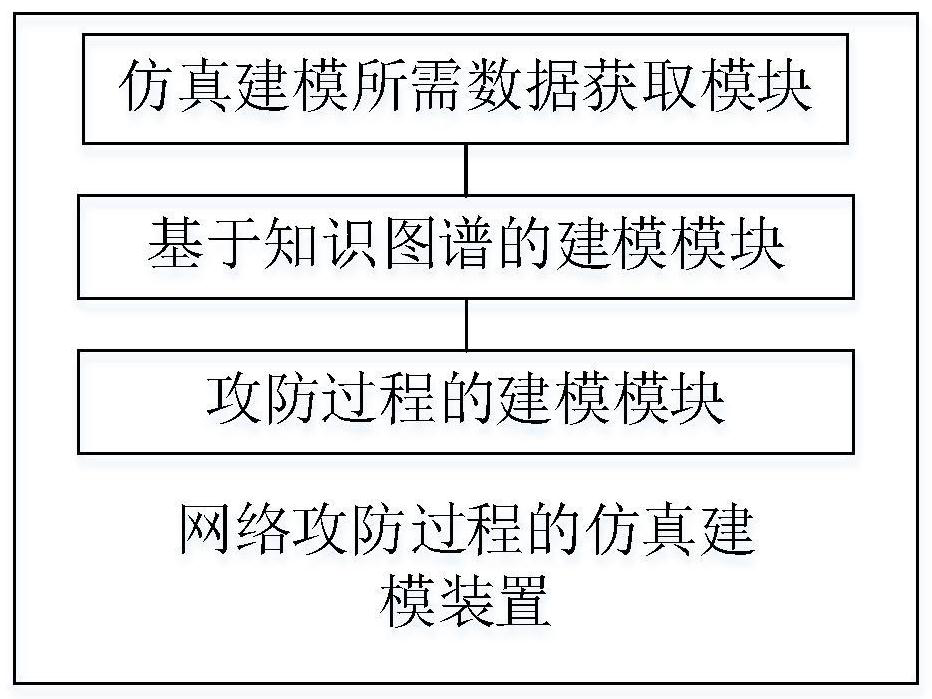
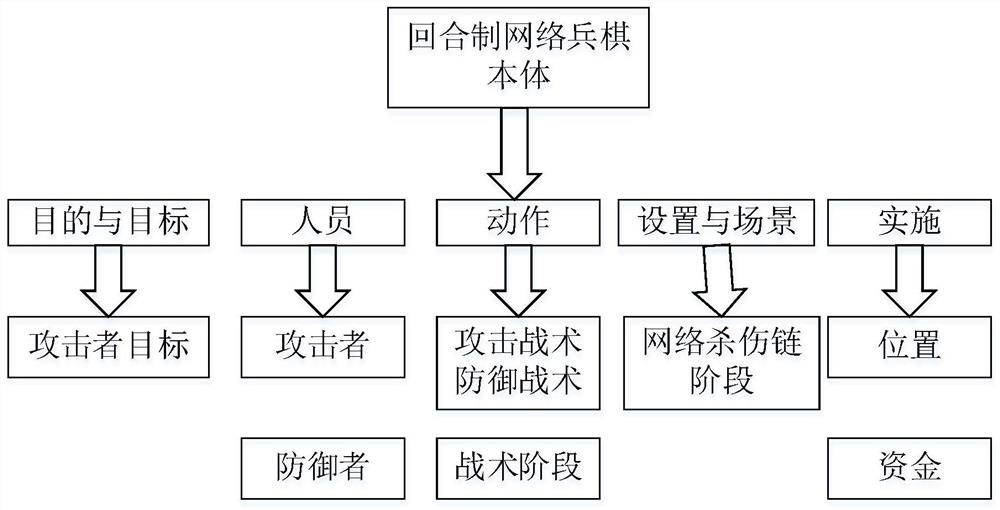
Simulation modeling method and device for network attack and defense process and network turn war chess
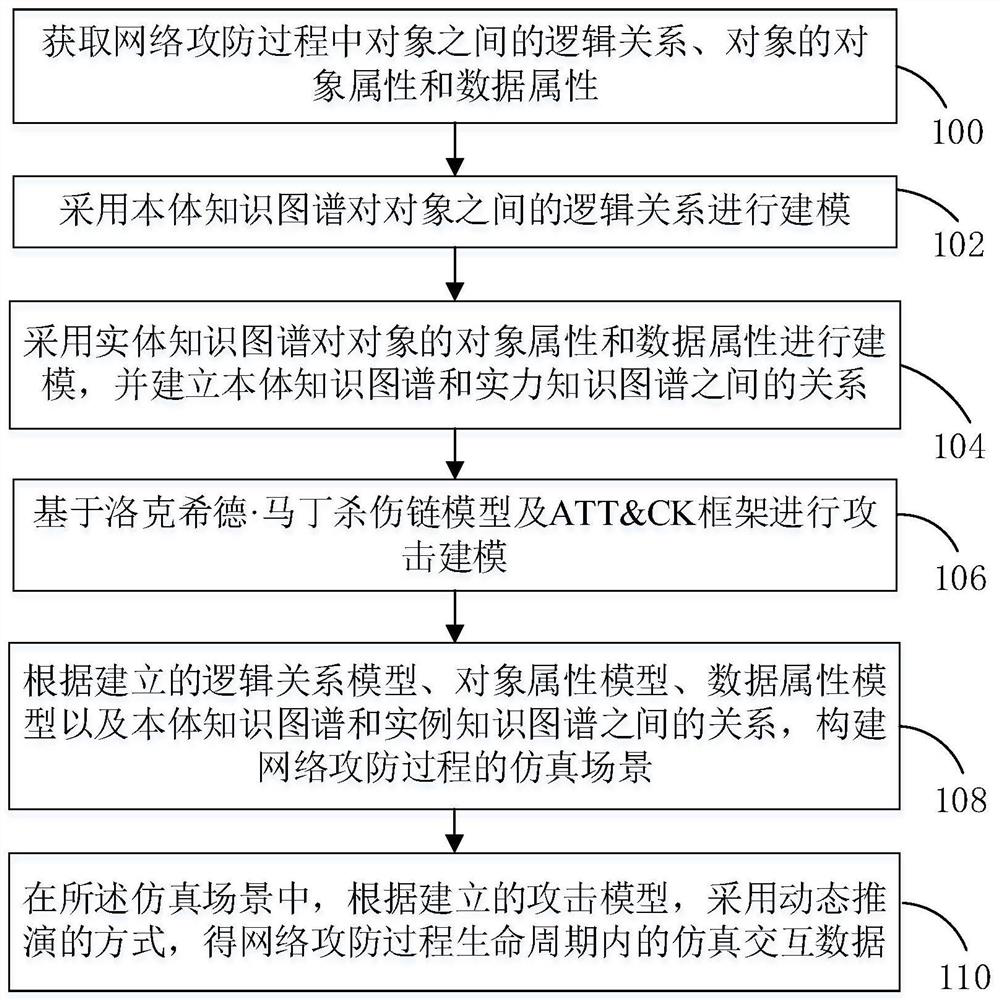
ActiveCN113536573ATo achieve the purpose of education and trainingImprove securityData processing applicationsBoard gamesPathPingAttack
The invention relates to a simulation modeling method and device for a network attack and defense process and network turn war chess. The method comprises the following steps: acquiring a logical relationship between objects in a network attack and defense process, and object attributes and data attributes of the objects, wherein the objects comprise attackers, defenders, attack and defense steps, attack and defense modes, attack effects and resource consumption; carrying out network attack and defense combat simulation based on an attack path of a Lokhide-Martin killer chain model and an ATTCK framework by adopting a network round system game mode, and taking a knowledge graph as a data structure organization mode, so that game participants, namely, attackers, defenders and audiences can learn the network attack paradigm and understand the application stage and the generation effect of the attack defense technical means, finally the purpose of educational training is achieved, the network attack and defense safety awareness and interest of participants are improved, and technical support is provided for attack and defense technique and tactical effect evaluation.
Owner:NAT UNIV OF DEFENSE TECH
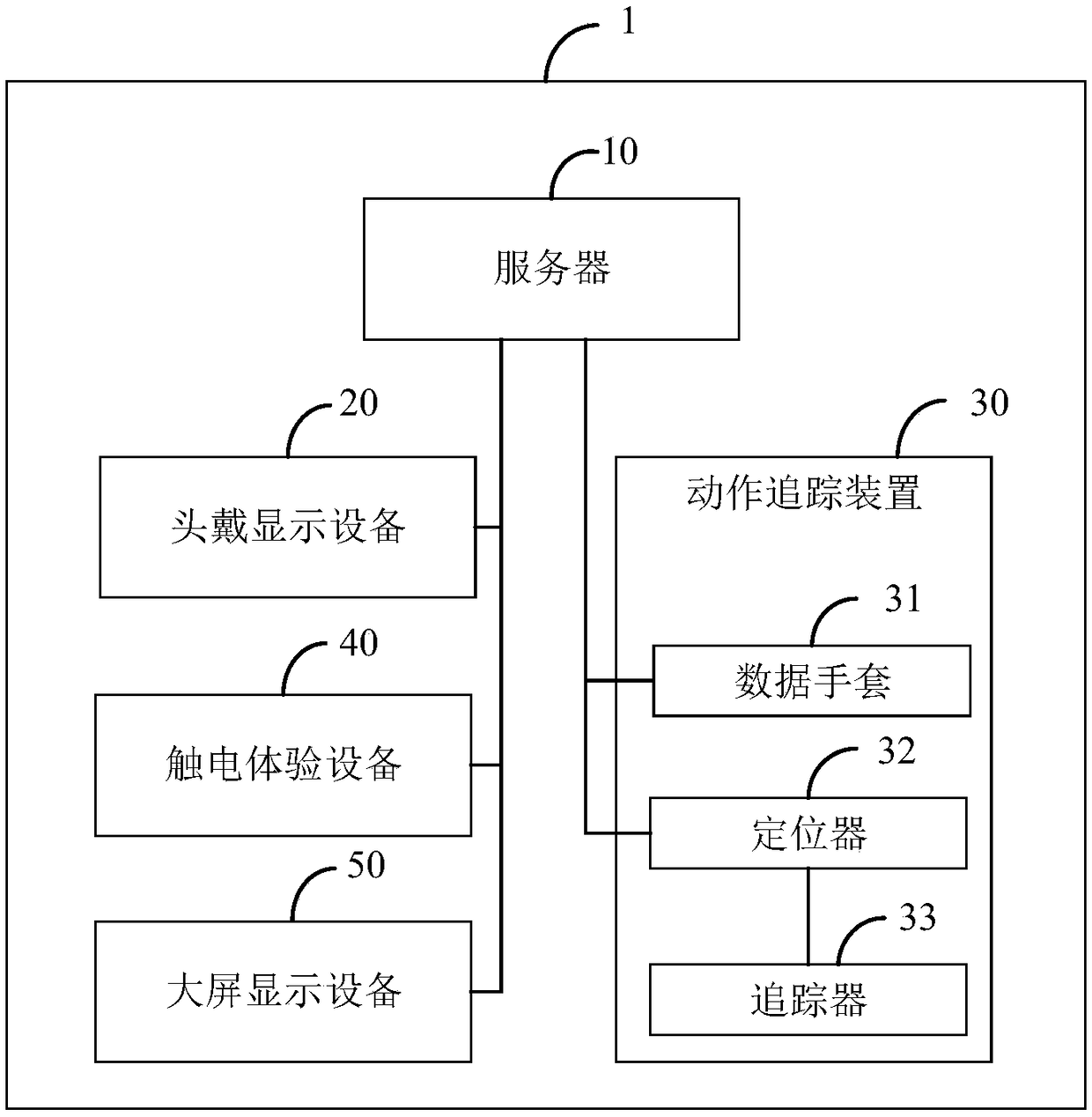
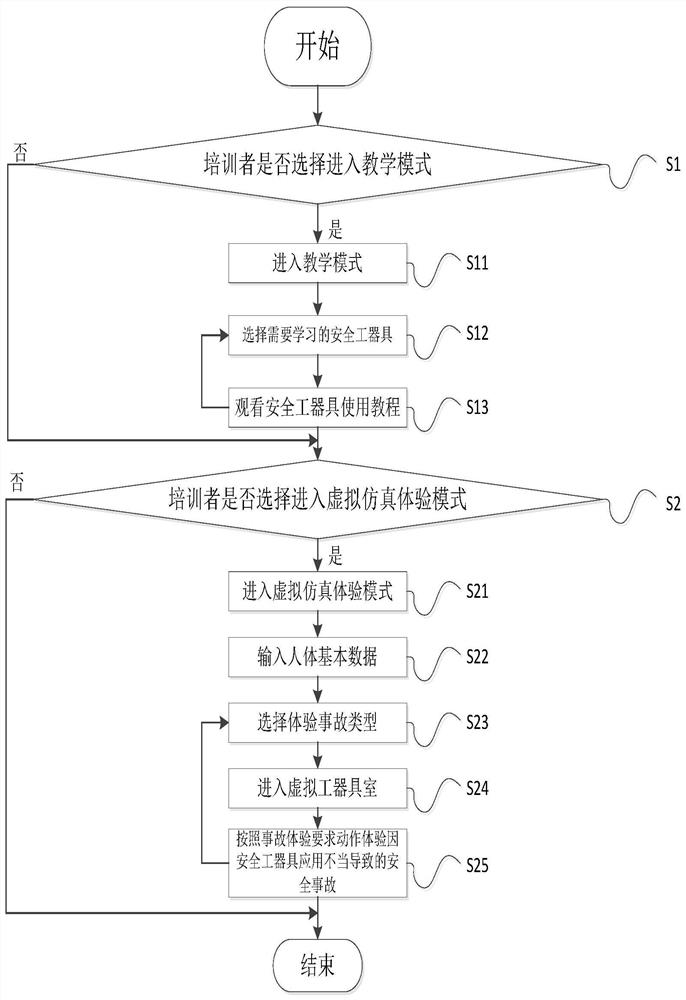
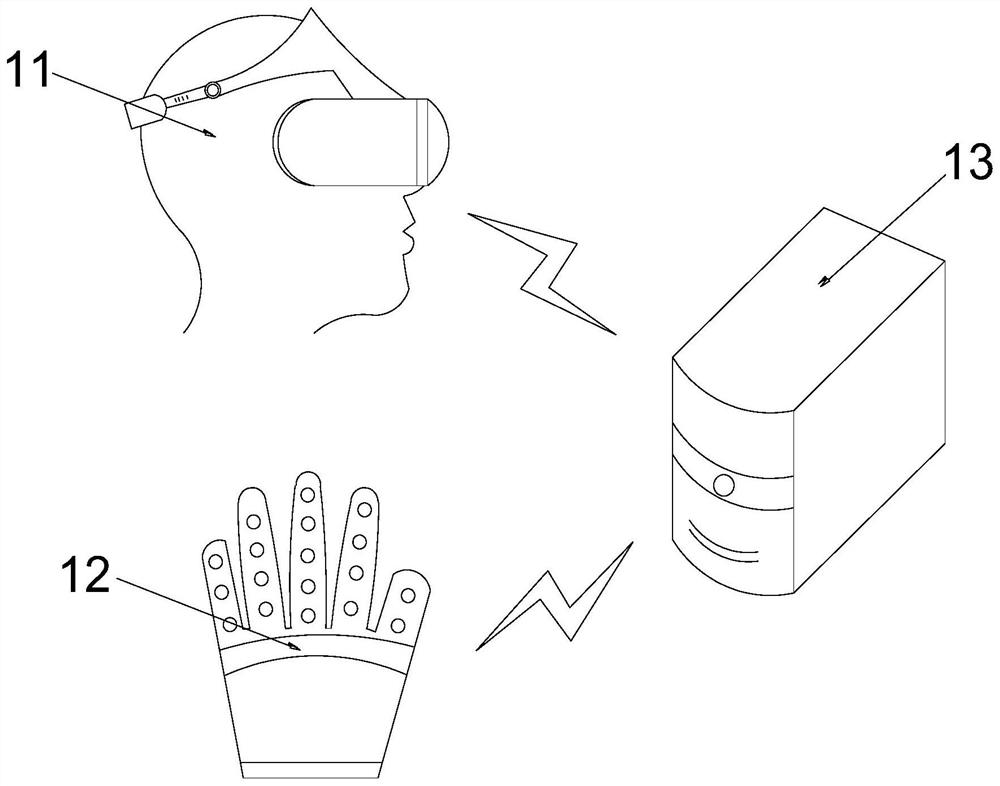
Safety tool training system and method based on virtual technology
InactiveCN111882942AImprove securityHas a warning effectCosmonautic condition simulationsData processing applicationsAnimationSimulation
The invention discloses a safety tool training system and method based on a virtual technology, relates to the technical field of power system simulation training, enables a trainee to learn and master the use key points of safety tools through the cooperation of VR equipment and a plurality of virtual tools in a data server, and breaks through a conventional training mode, a trainee learns and better masters the use key points of the safety tools in an animation and virtual simulation experience mode, the experience of electric shock accidents caused by improper use of the safety tools is setin the operation process, safety skills and safety awareness are enhanced, the whole training and learning process is easy to operate, the system is not limited by places and weather, achieves the learning and use of various types of safety tools in one training course, reduces the investment of manpower and material resources, simulates the real operation process under the condition that no trainee or safety tool exists, guarantees the safety of the training process, and improves the training effect.
Owner:ZHEJIANG LANDI ELECTRIC POWER TECH CO LTD
Miner safety behavior competence evaluation system
InactiveCN102737348AReduce coal mine accidentsConvenient and quick comprehensive evaluationData processing applicationsClimate change adaptationState of artSafety knowledge
The invention provides a miner safety behavior competence evaluation system, relating to an evaluation system. A region is divided by vertically arranged and crossed spacer plates into in a safety physiological data collection area, a safety competence data collection area, an individual psychological data collection area and a character data collection area. An upper middle position in the areas is provided with a safety behavior competence data integration evaluation apparatus. Four measuring tables are arranged in the above four areas respectively. The measuring tables have functions of zero dimension processing of collected data, operation and output. The four areas respectively measure kinesthesis position identification, sense of balance, movement of multiple parts, perception, memory, comprehension, judgment, reaction, safety consciousness, safety knowledge and skills, temperament, and character of miners. The safety behavior competence data integration evaluation apparatus carries out comprehensive calculation and provides a comprehensive score. According to the invention, a problem that carrying out integrated evaluation on the safety behavior competence of the miners is difficult in the prior art is solved.
Owner:CHINA UNIV OF MINING & TECH (BEIJING)
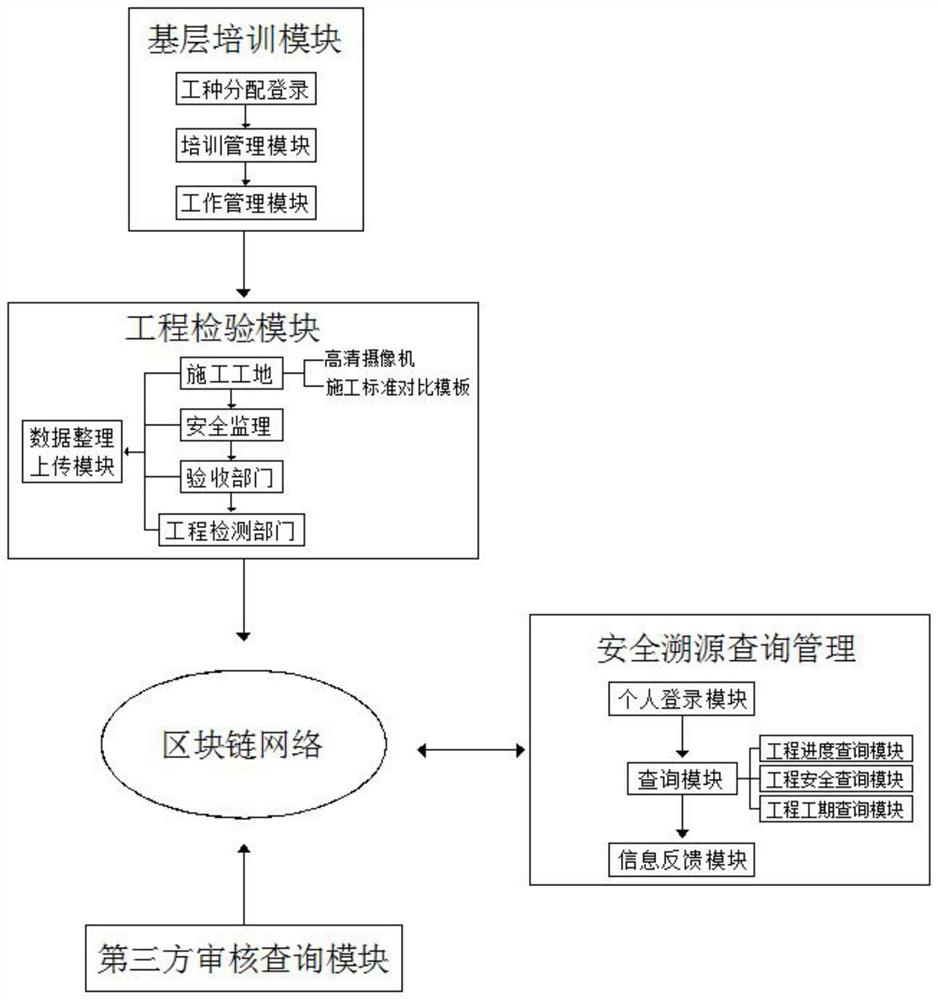
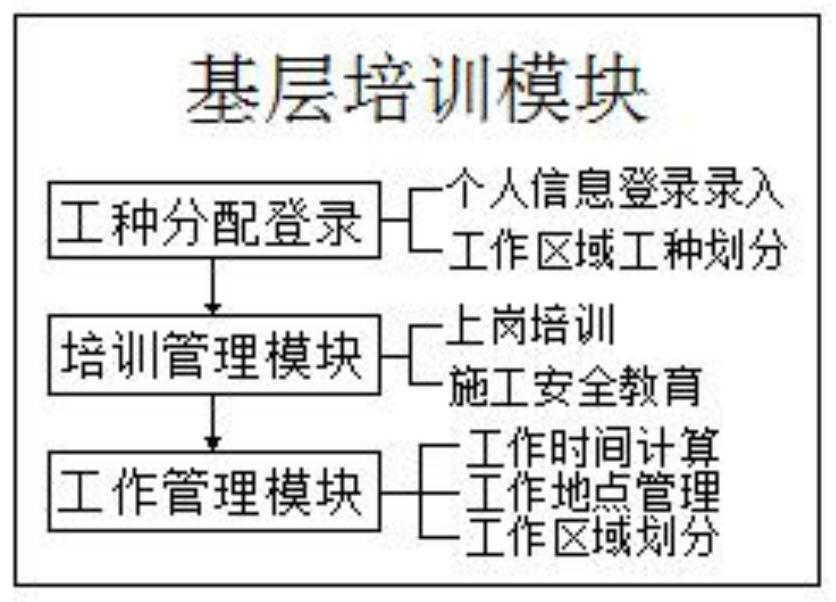
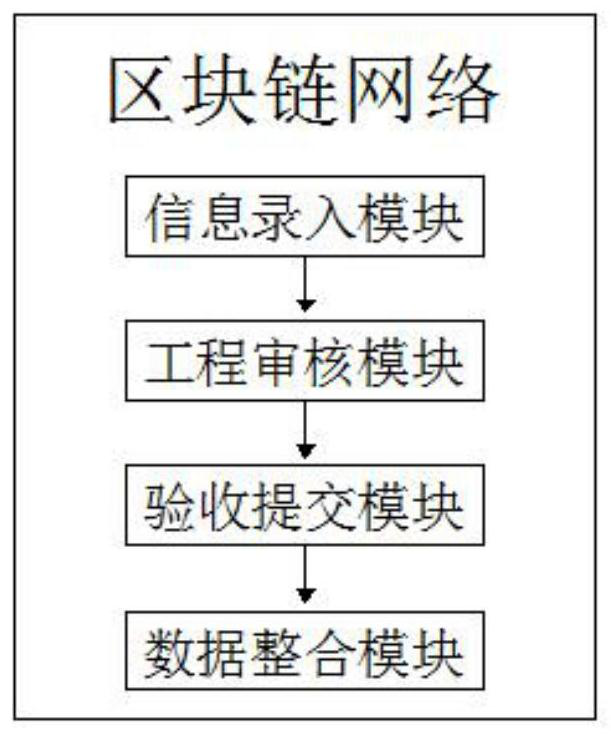
Engineering safety supervision traceability system based on block chain
InactiveCN111768172AImprove authorityGuaranteed accuracyDatabase distribution/replicationClosed circuit television systemsThird partyChain network
The invention discloses an engineering safety supervision traceability system based on a block chain. The system comprises a basic training module, an engineering inspection module, a block chain network, a security traceability query management module and a third-party auditing query module; the output end of the basic training module is connected with the input end of the engineering inspectionmodule, and the output end of the engineering inspection module is connected with the input end of the block chain network. According to the engineering safety supervision traceability system based ona block chain, firstly, the system carries out work type distribution, training management and work management on construction workers; workers are helped to improve the working efficiency in the working process; the safety awareness is increased, normal operation of a project is facilitated, potential safety hazards are avoided, the authority of the supervision system is increased due to the addition of the third party, the accuracy of project acceptance check is helped to be guaranteed, the problem that a project party cannot modify the project is solved, the safety of the project is also improved, and loss of owners or users caused by bean curd residue projects is avoided.
Owner:JIANGSU RONGZE INFORMATION TECH CO LTD
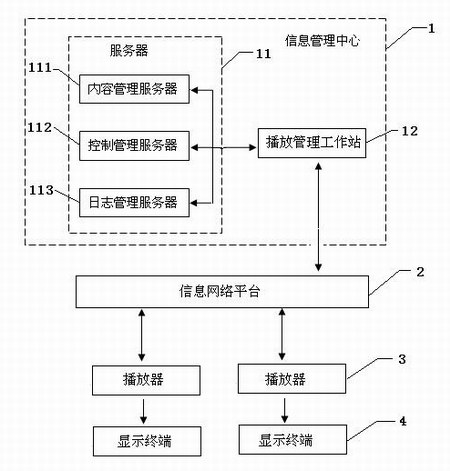
Network television management system for safety in production
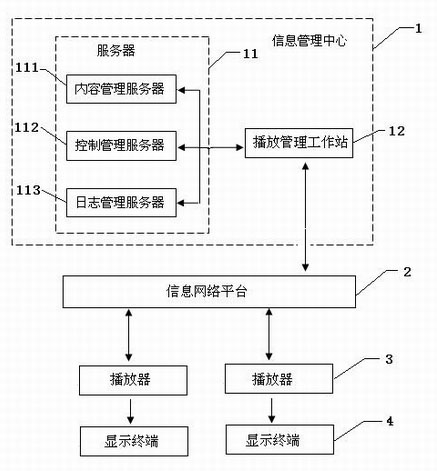
InactiveCN101895546AGuaranteed uptimeAvoid partial service failureTelevision system detailsColor television detailsInformation networksCrowds
The invention discloses a network television management system for safety in production, which comprises an information management center, an information network platform, at least one player and a display terminal connected with the player. The network television management system for safety in production can reveal the law on safety in production, popularize the elementary knowledge of laws and rules and reinforce safety awareness according to different displayed contents set by different enterprises in an audio and video illustration mode, greatly enhances the management level of the enterprise managers and the safety awareness of the audiences, lays a good foundation in promoting the stability and the improvement of safety in production, and simultaneously saves a large amount of training cost for industrial and mining enterprises.
Owner:CTV SCREEN BEIJING FILM CENT
System and methods for reverse vishing and point of failure remedial training
ActiveUS20190297110A1Avoid actionPrevent fraudMessaging/mailboxes/announcementsTransmissionTelecommunicationsPhishing
Embodiments of the disclosure describe a simulated phishing campaign manager that communicates a simulated phishing communication that includes at least the telephone number and reference identifier, to a device of a user. The content of the simulated phishing communication may prompt the user to call the telephone number identified in the simulated phishing communication. The security awareness system may select a telephone number and a reference identifier to use for the simulated phishing communication, the combination of which may be later used to identify a specific user if they respond to the message. Each of a plurality of users may have a unique combination of telephone number and reference identifier. The telephone number may be selected based on the geographic location of the user, or the telephone number may be selected to correspond to content in a simulated phishing communication.
Owner:KNOWBE4 INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com