Intrusion process layering online risk assessment method
A risk assessment and hierarchical technology, applied in the direction of digital transmission systems, electrical components, transmission systems, etc., to achieve the effects of increasing adaptability, increasing tolerance, and reducing the risk of false alarms causing false responses
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] The present invention will be further described below in conjunction with accompanying drawing and specific examples:
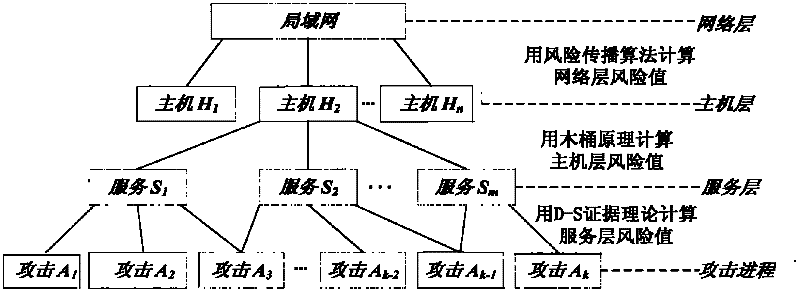
[0024] The protected network system is composed of various hosts, on which the operating system and various application network service programs are running: the first level of risk assessment is carried out at the application service level of each host; the second level is at the level of each host above; finally, at the network level, forming such figure 1 The risk assessment tree shown.
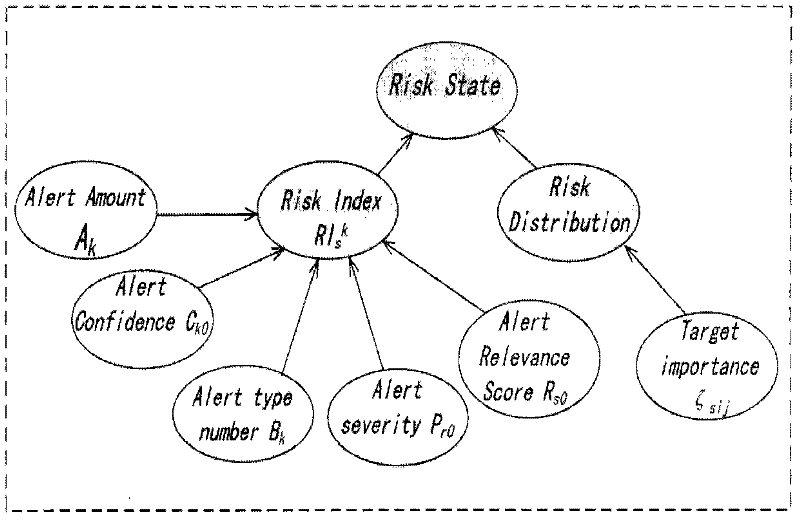
[0025] Definition 1. The risk index RI (risk index) is the degree of danger caused by the intrusion process to a specific target.
[0026] Definition 2. Target risk distribution (risk distribution). Risk distribution refers to the distribution of high, medium and low risk ranges that the target system can tolerate.
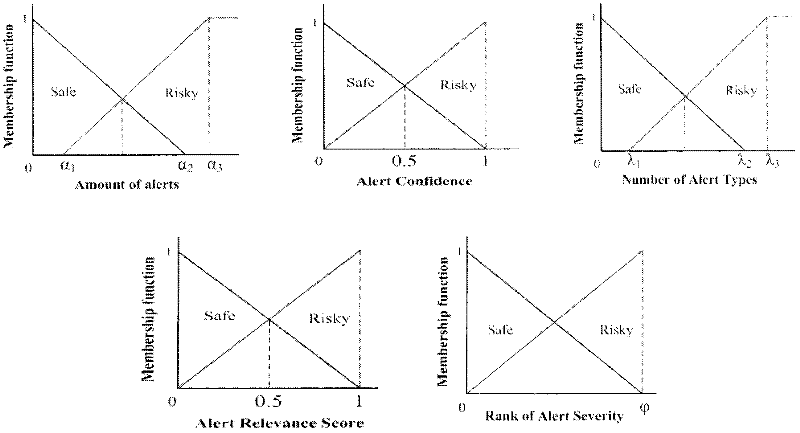
[0027] Step A: Risk assessment at the service level
[0028] Suppose there are m hosts H on the protected network i (i=1, 2,..., m), each operatin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com