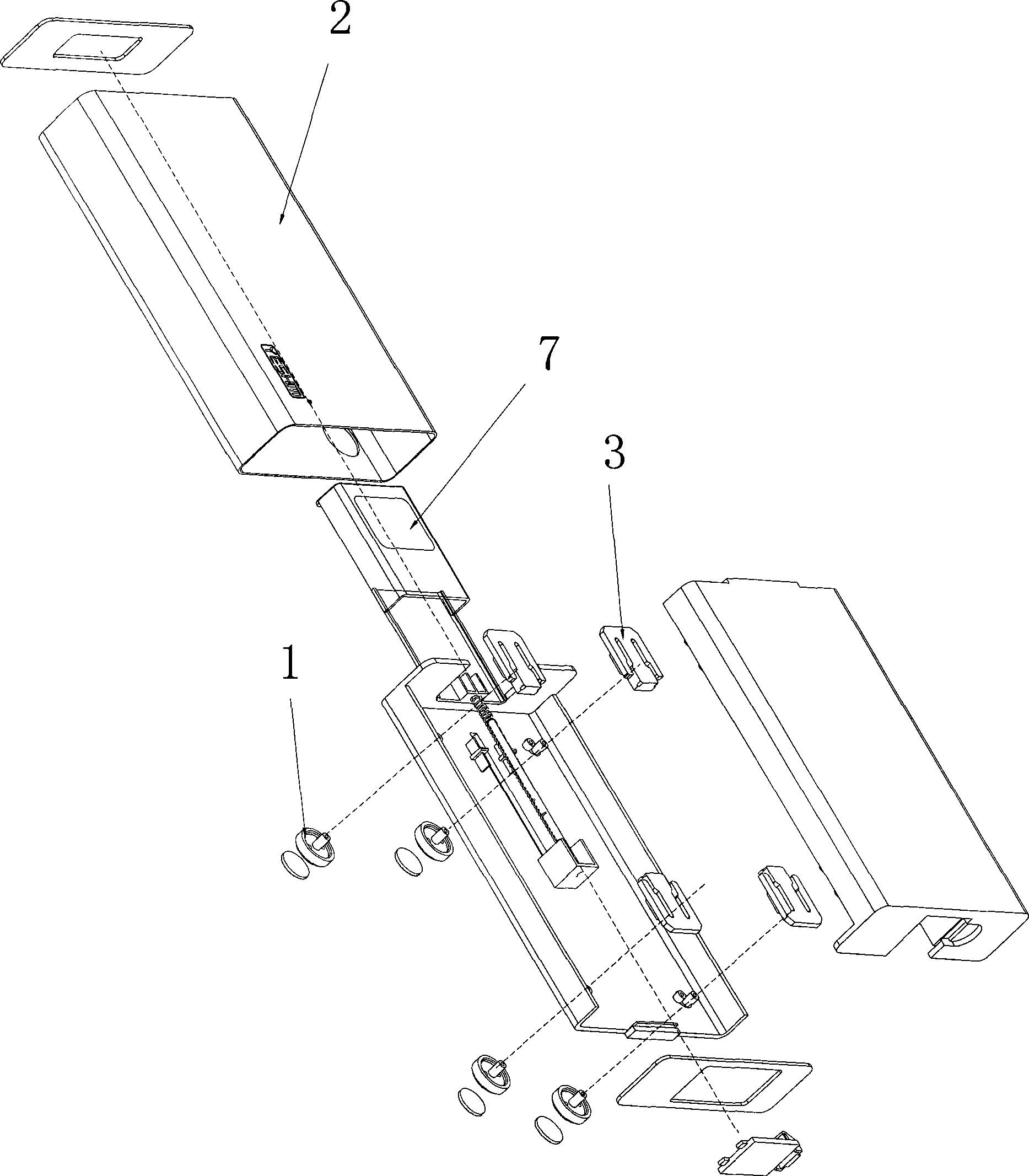
Patents
Literature
169results about How to "Improve authority" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
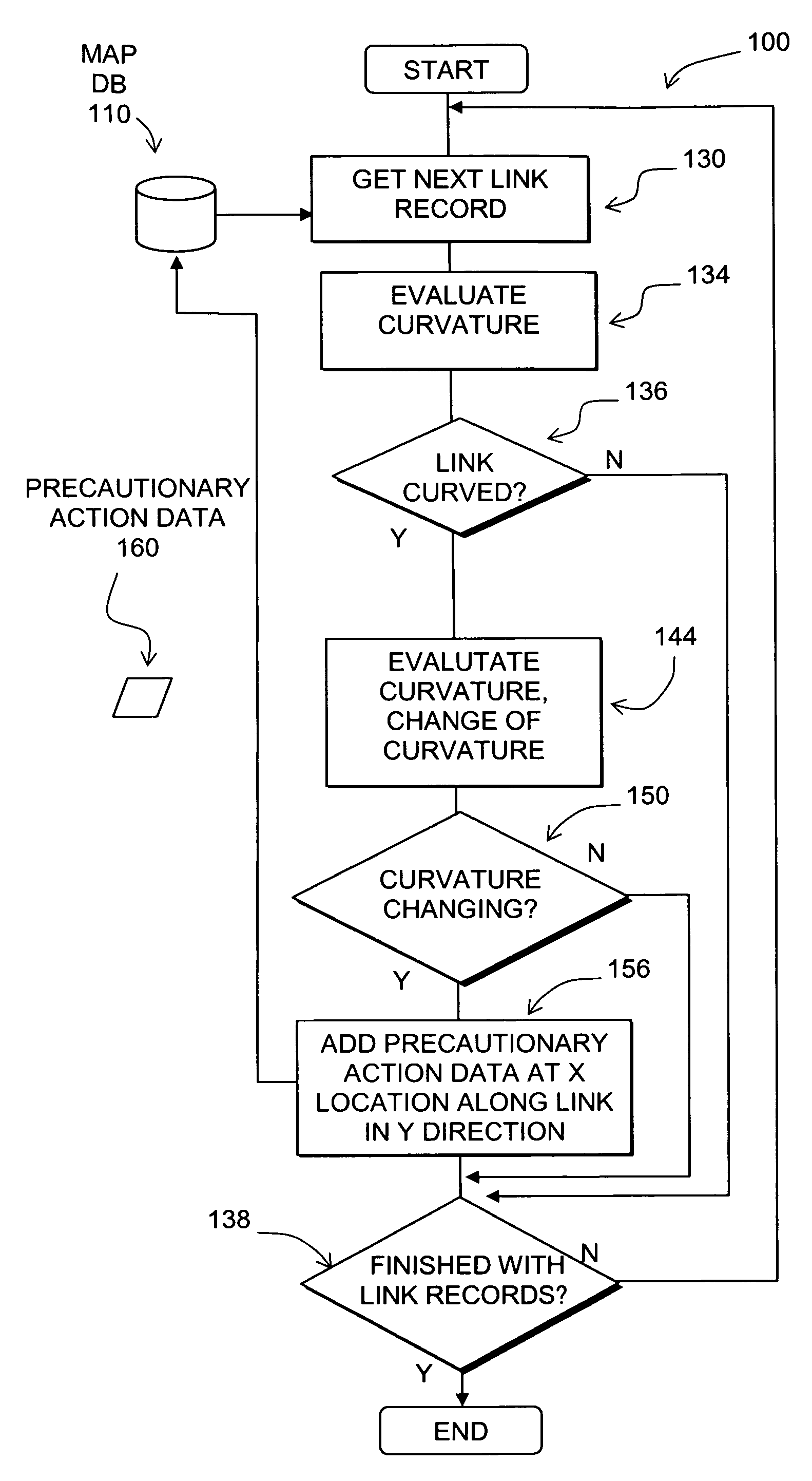
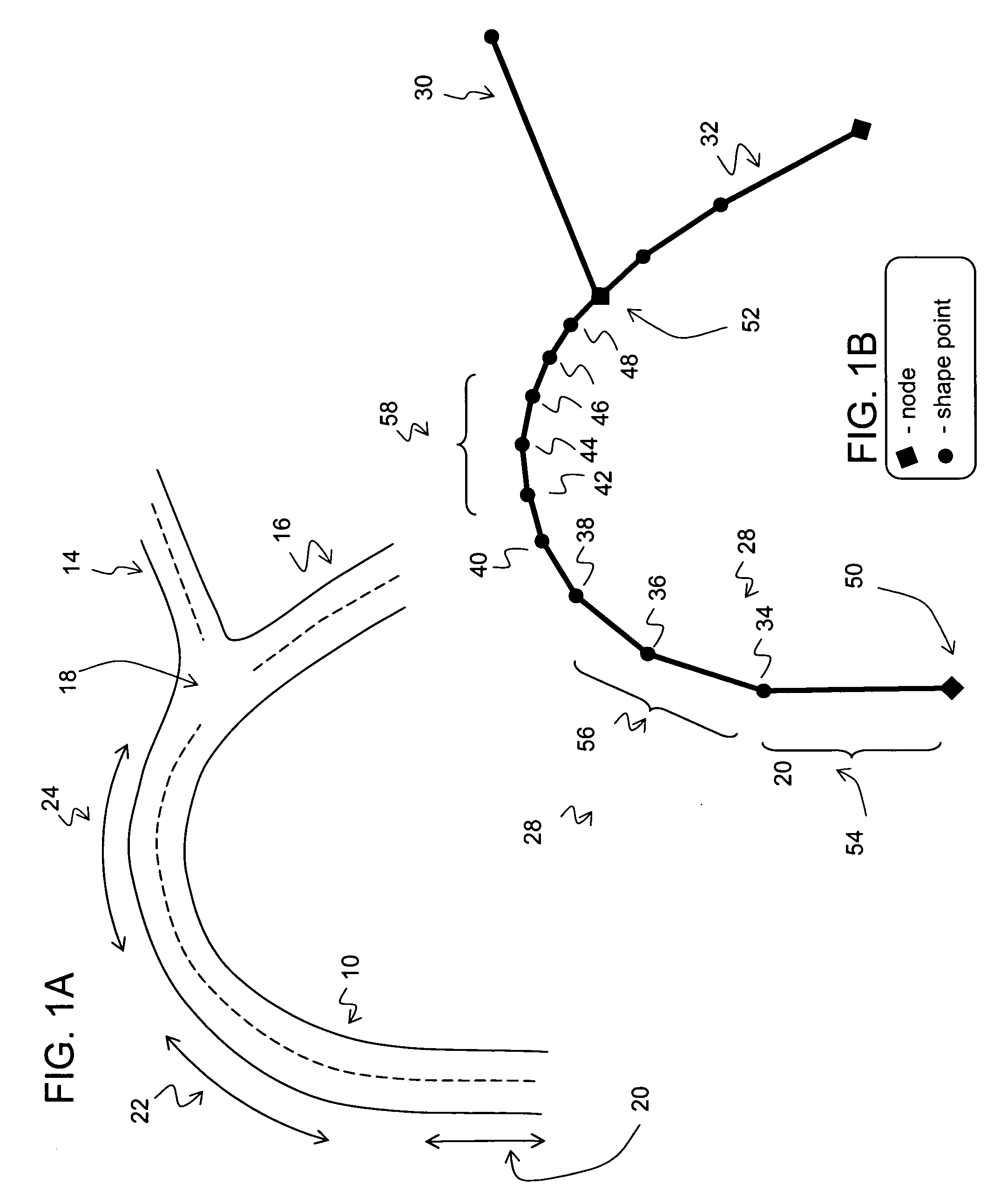
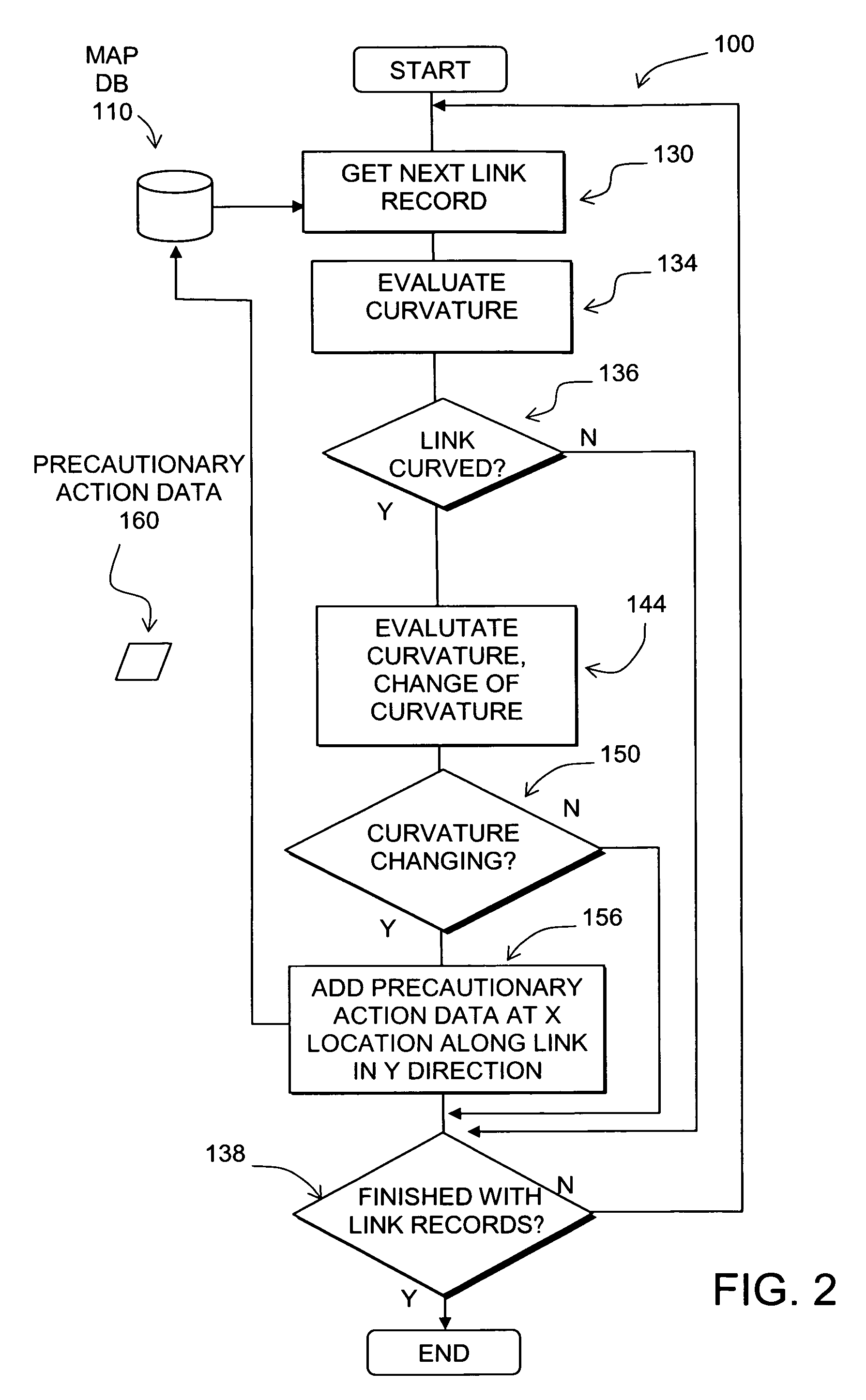
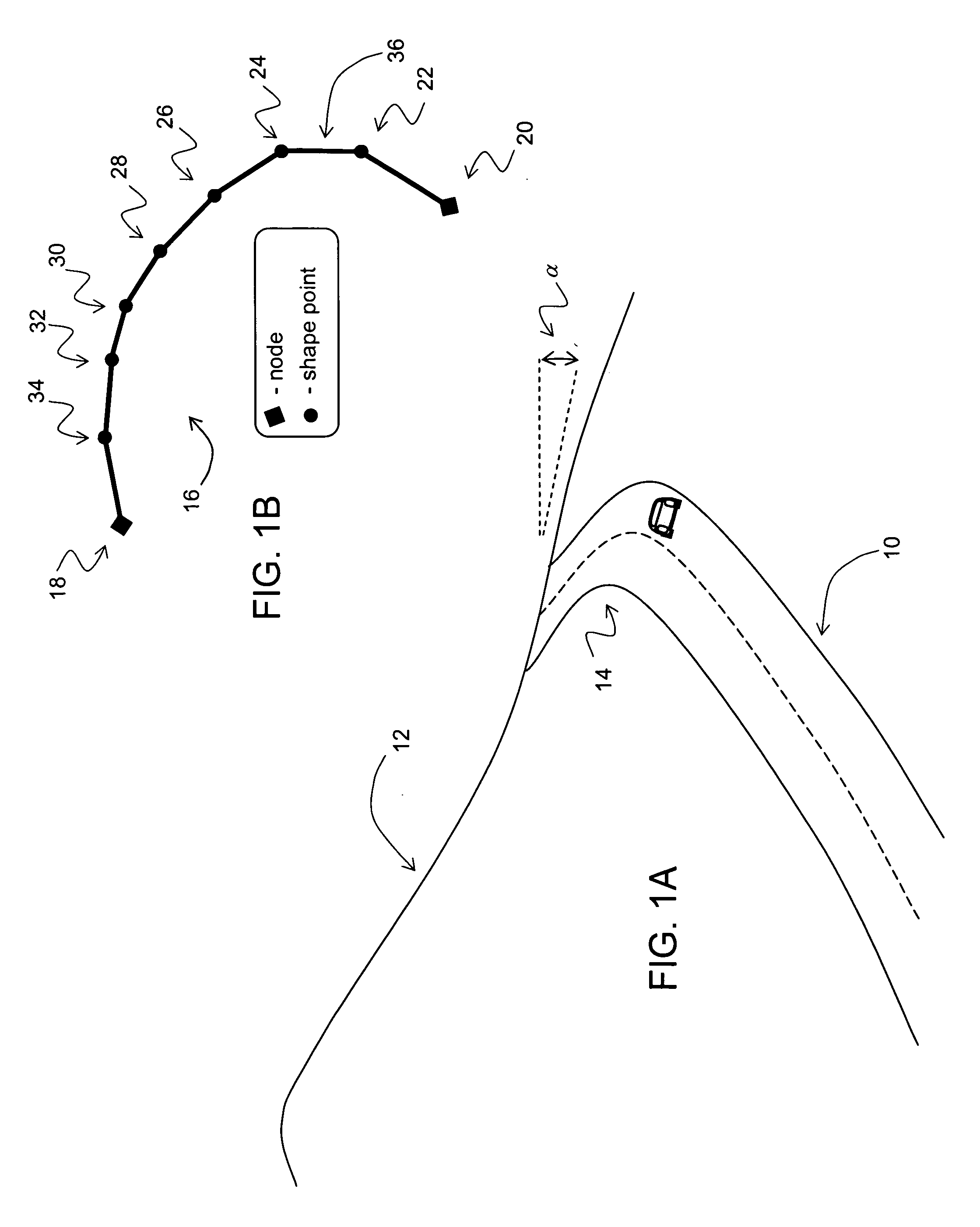
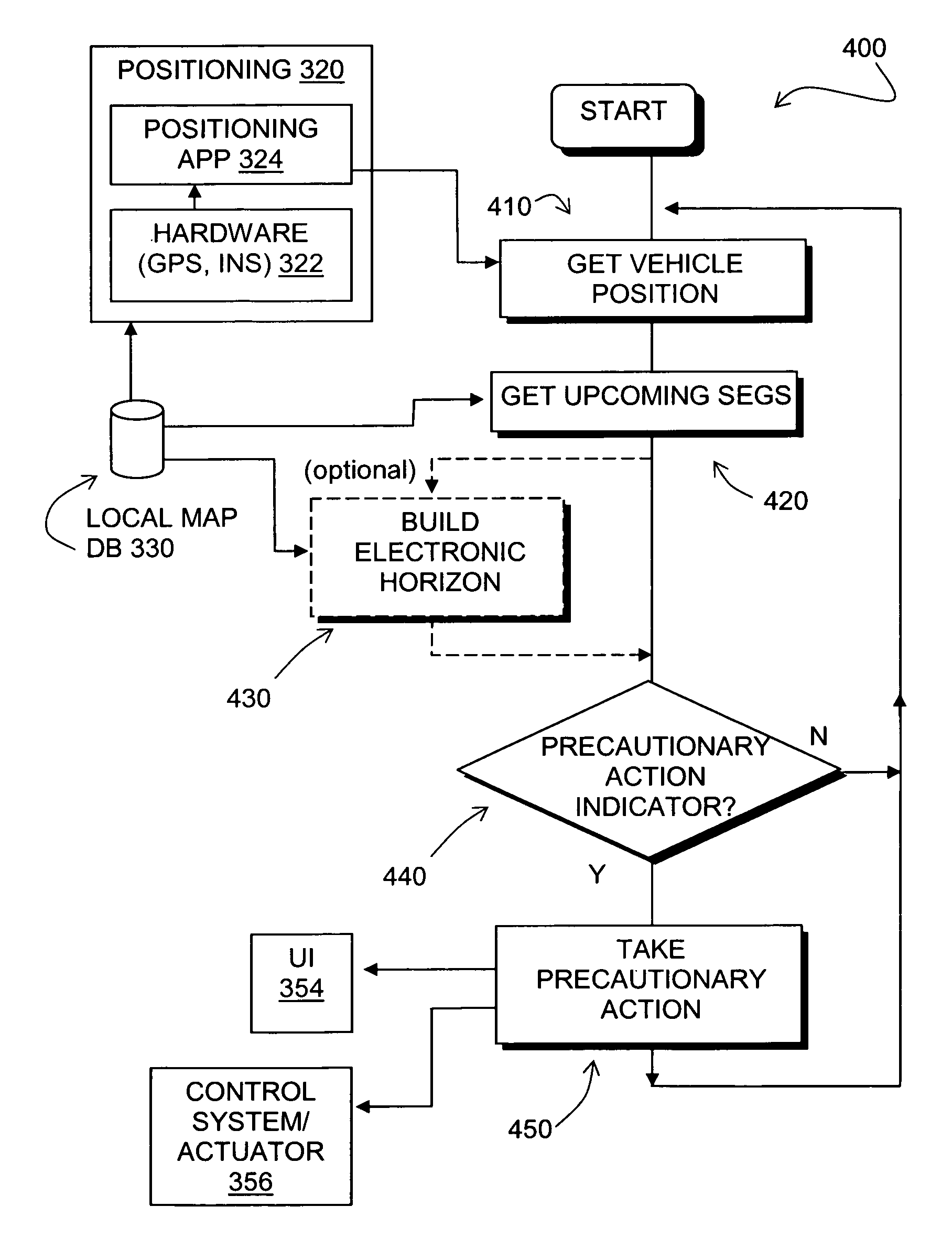
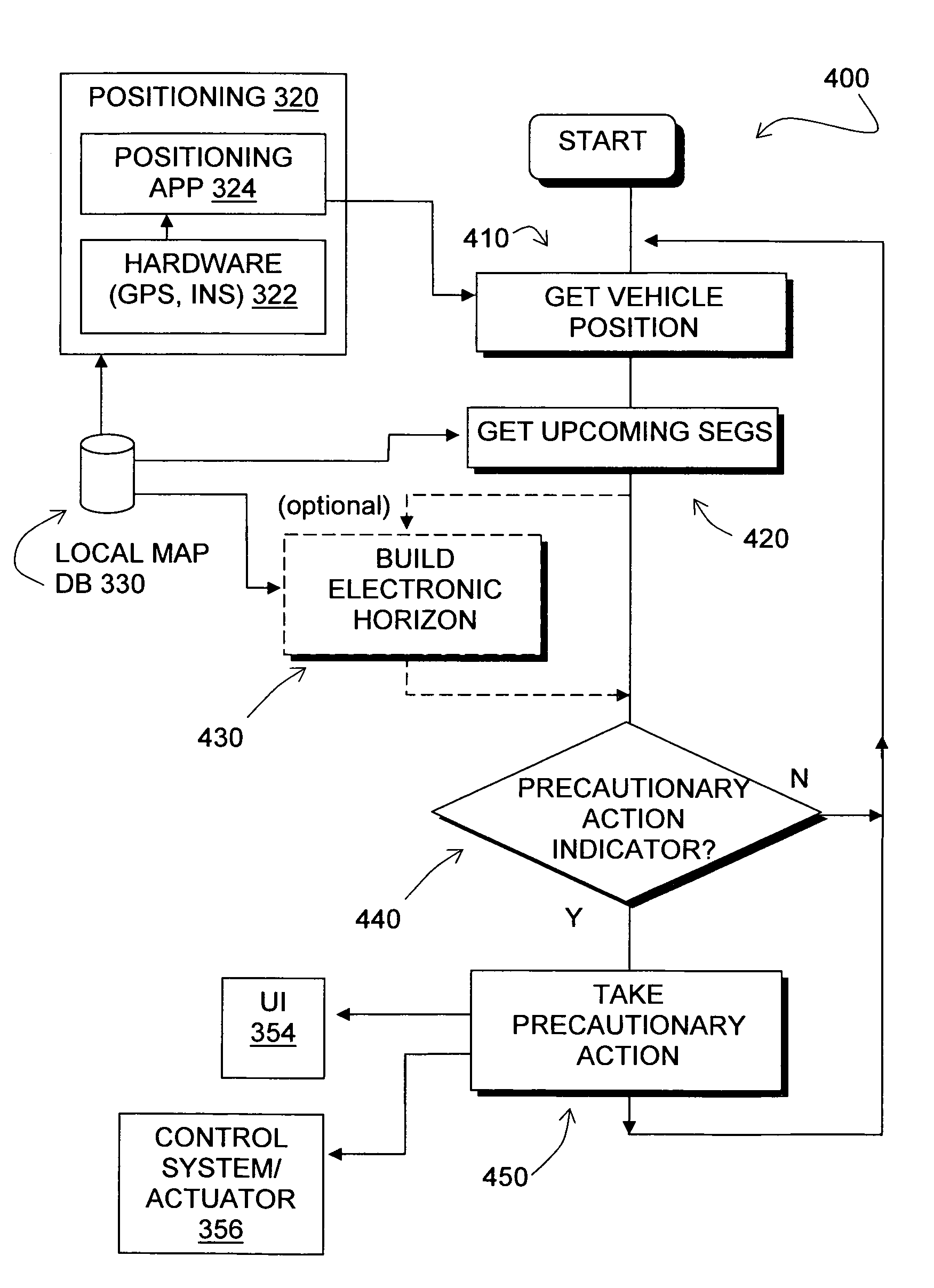
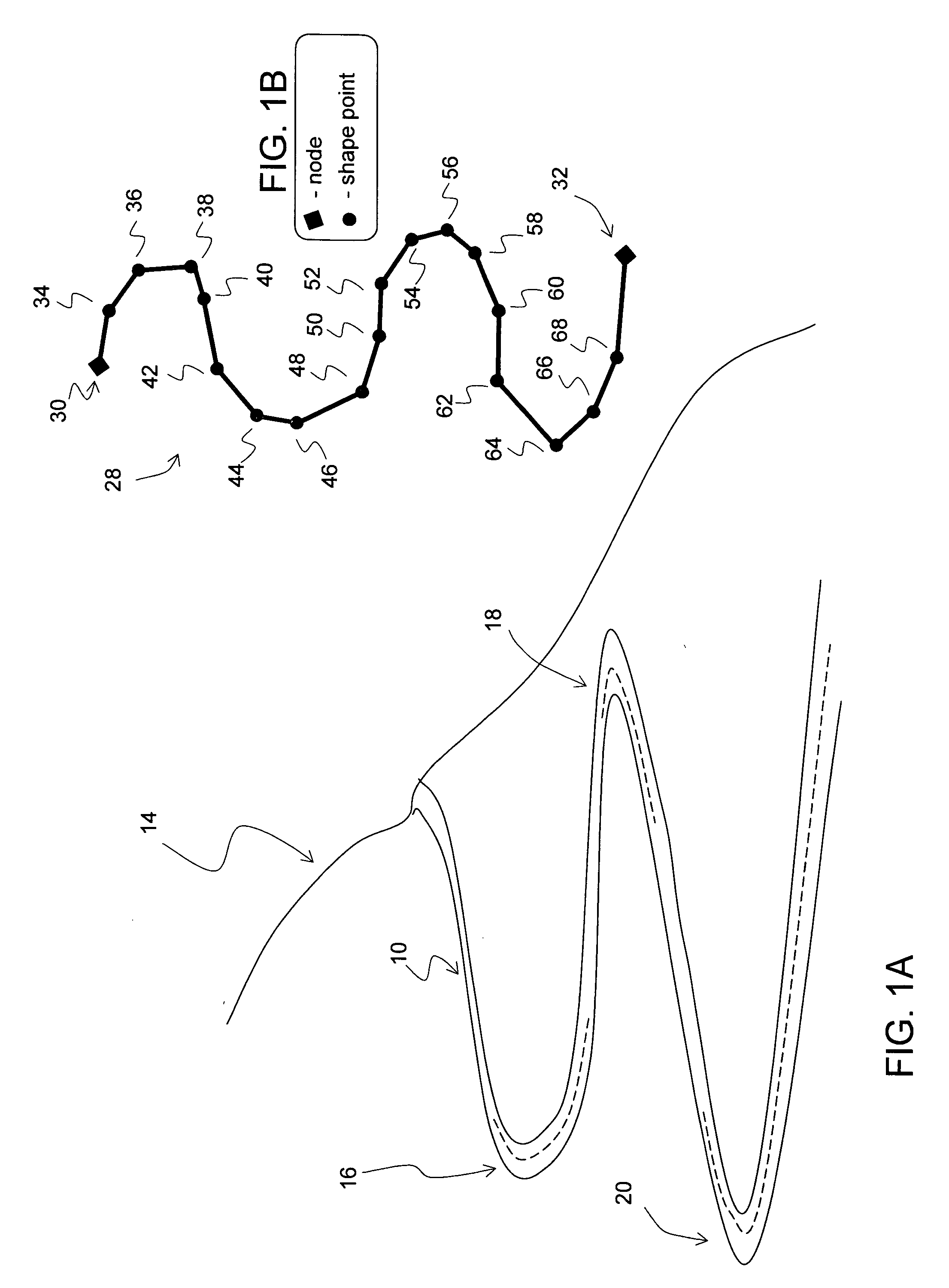
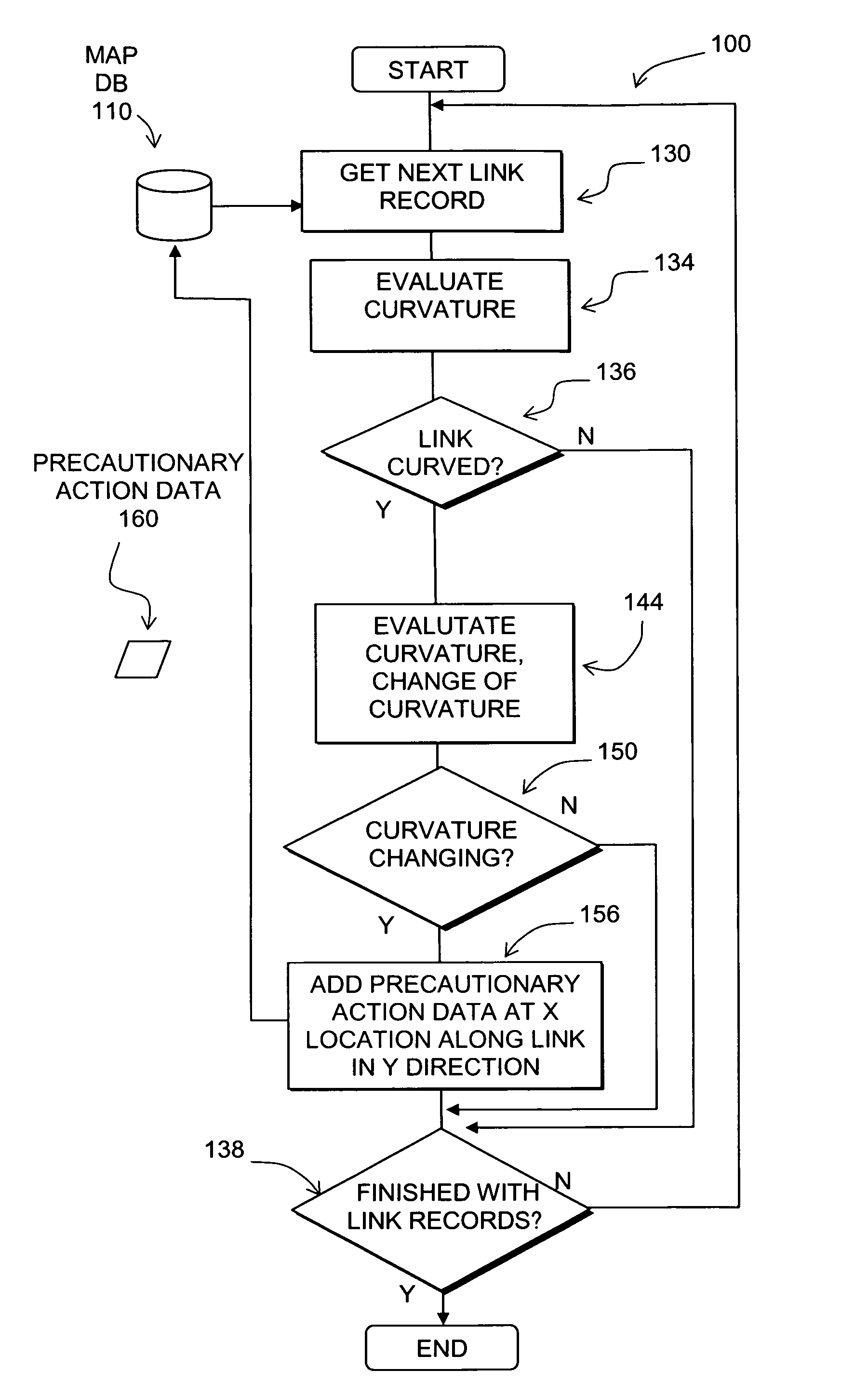
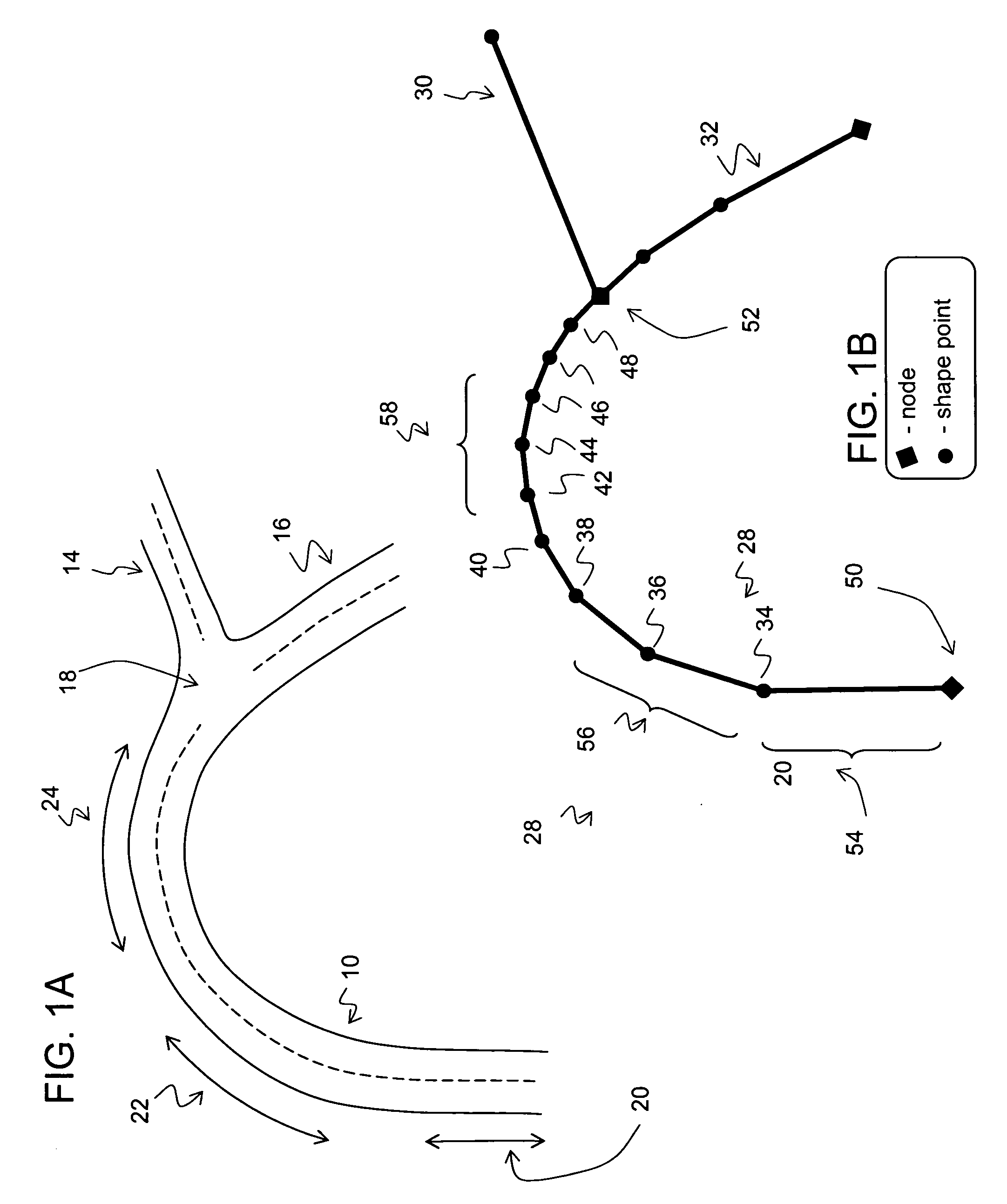
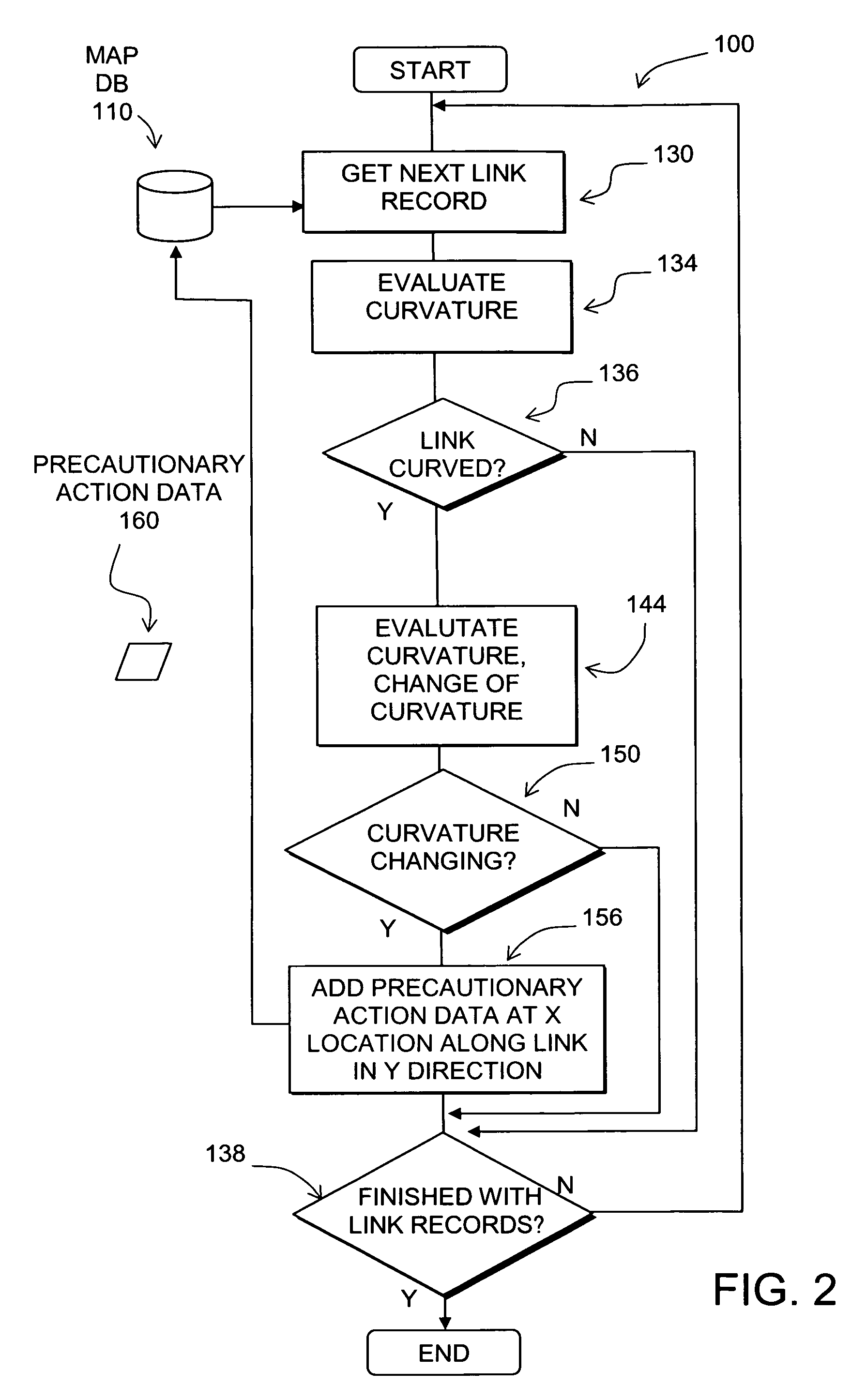
Data mining in a digital map database to identify decreasing radius of curvature along roads and enabling precautionary actions in a vehicle
ActiveUS20090300067A1Increasing control authorityHigh sensitivityInstruments for road network navigationRoad vehicles traffic controlRoad networksPositioning system
Owner:HERE GLOBAL BV
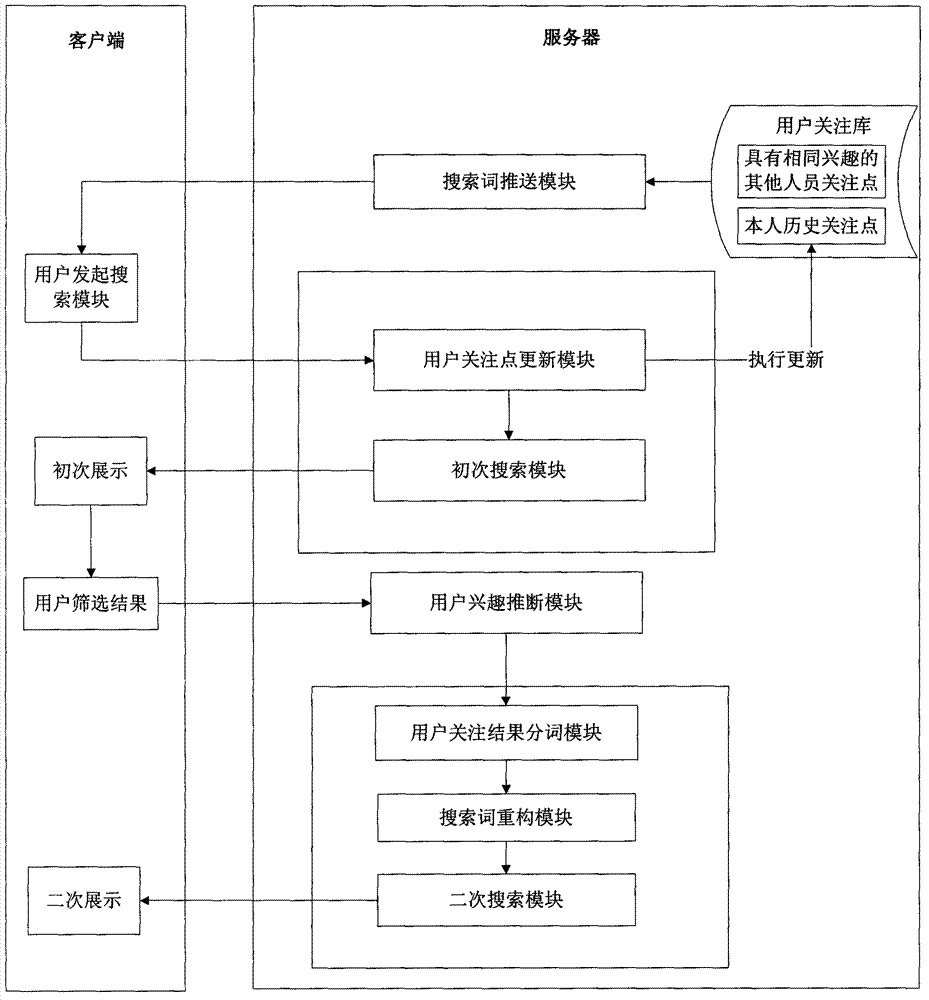
User-oriented information search engine system and method
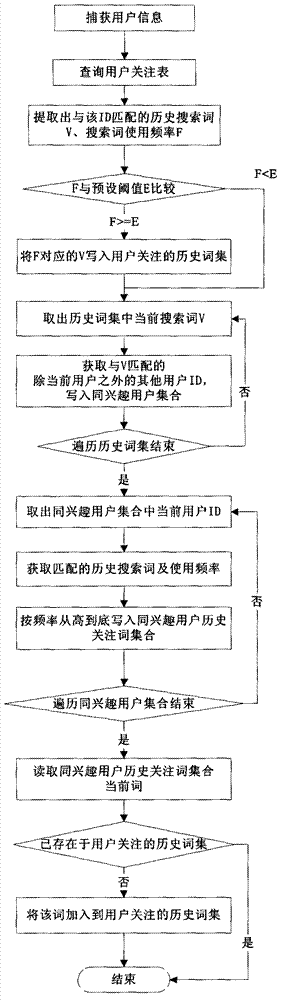
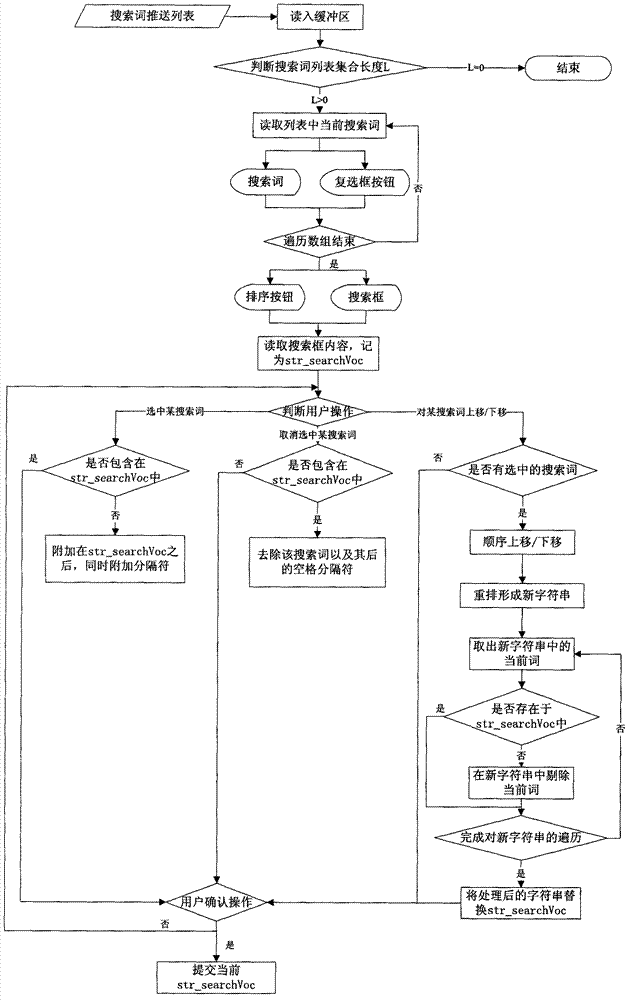
ActiveCN102930022AIn line with true intentionsImplement refactoringSpecial data processing applicationsSearch wordsInformation searching
The invention discloses a user-oriented information search engine system and a method. The system comprises eight modules of a search term pushing module, a user initiating search module, a user concern updating module, a primary search module, a user interest deducing module, a user concern result word segmentation module, a search word refactoring module and a secondary search module. The method includes analyzing and pushing user selectable search words, performing user initiating search, updating user concerns, executing the primary search, deducing user interests, performing word segmentation for user concern results, refactoring the search words and executing the secondary search. Accordingly, the system has the advantages of being complete in inquiring range and high in inquiring accuracy. Besides, by means of the system, the select input and automatic sequencing of the search words can be achieved, the accuracy of following inquiring results can be improved through the interactive operation, and a flexible, convenient and intelligent interactive interface is provided for the user to execute information search.
Owner:CHINA ACAD OF LAUNCH VEHICLE TECH
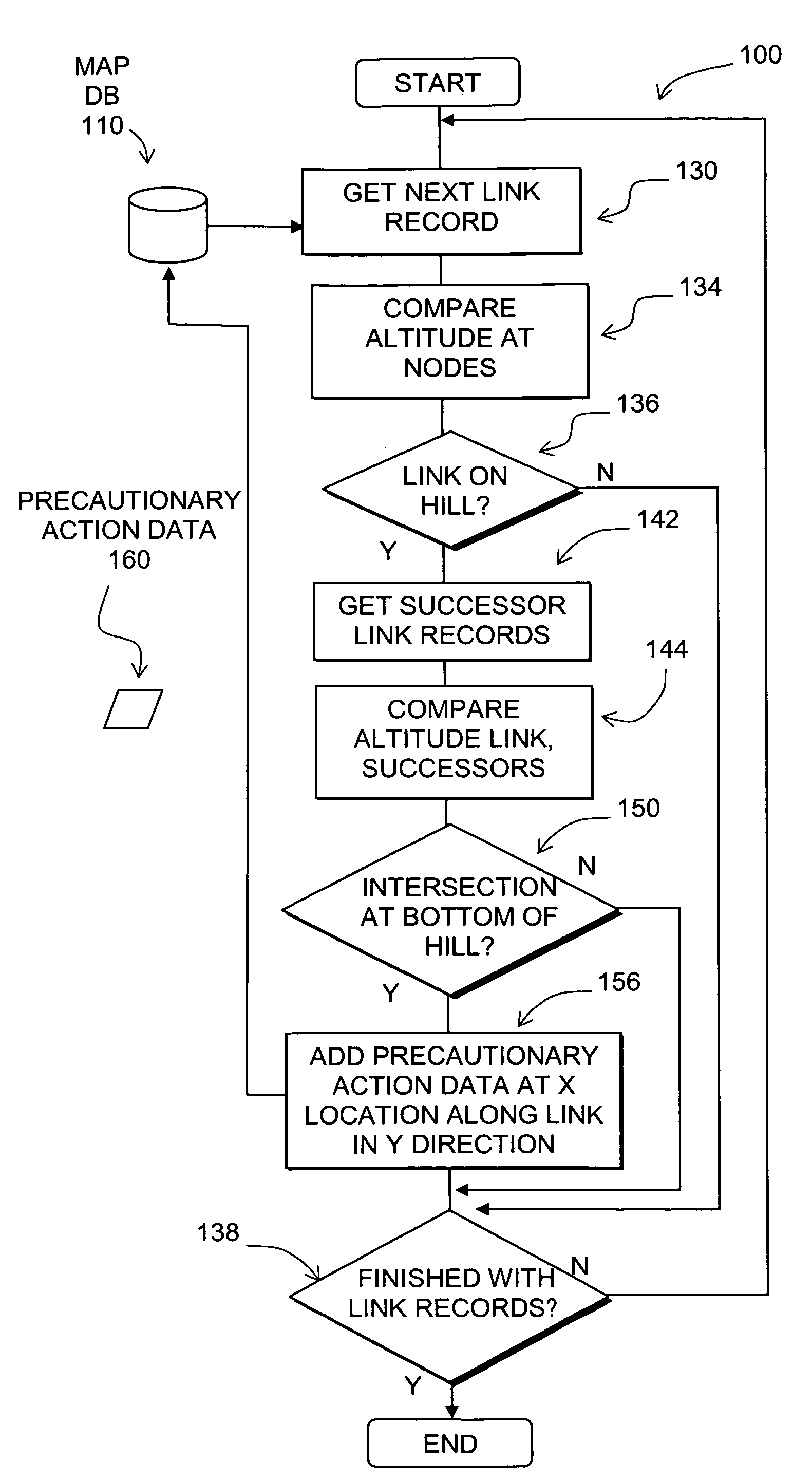
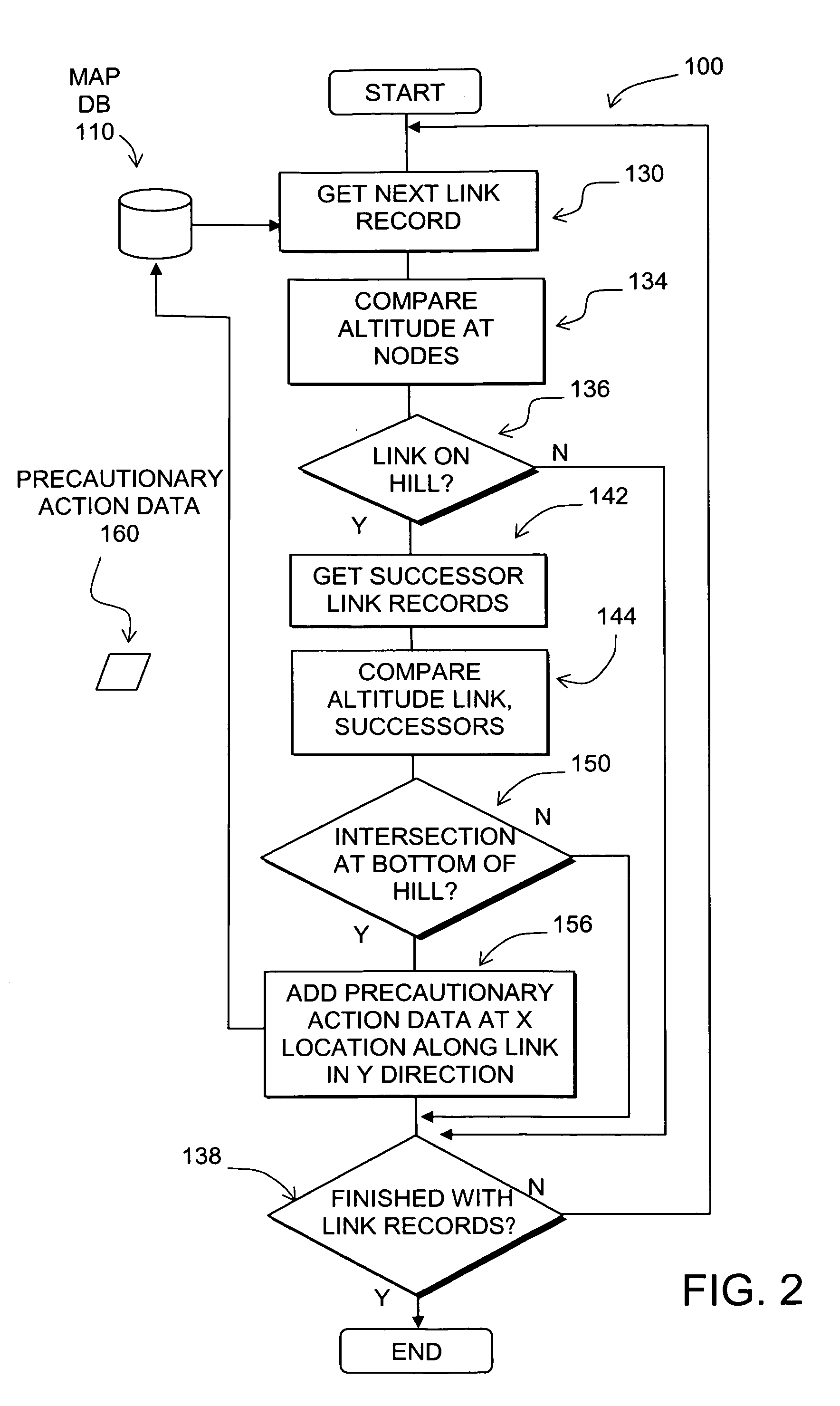
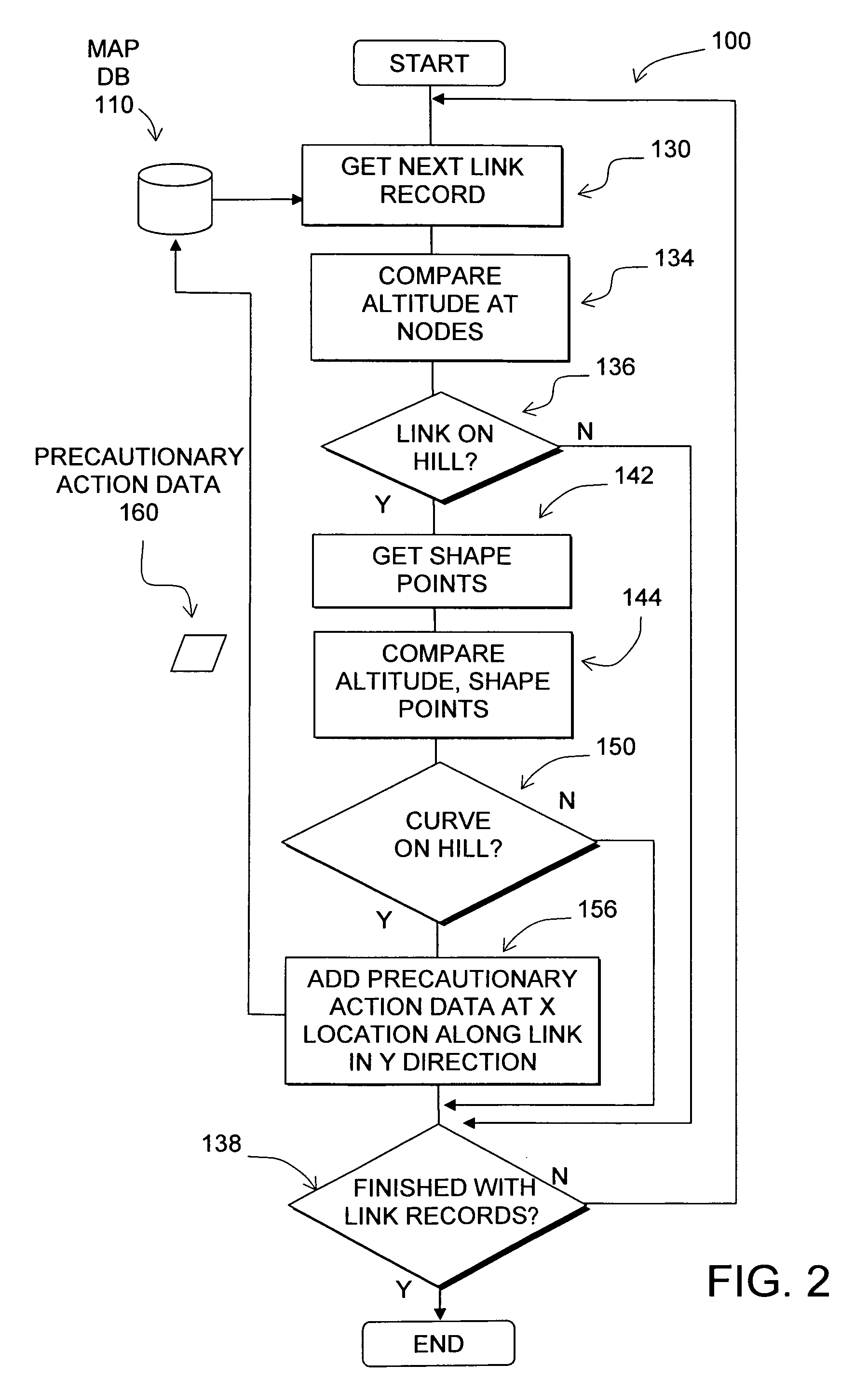
Data mining in a digital map database to identify intersections located at hill bottoms and enabling precautionary actions in a vehicle
ActiveUS20090300053A1Increasing control authorityHigh sensitivityAnalogue computers for vehiclesInstruments for road network navigationRoad networksPositioning system
Disclosed is a feature for a vehicle that enables taking precautionary actions in response to conditions on the road network around or ahead of the vehicle, in particular, an intersection located at the bottom of a hill. A database that represents the road network is used to determine locations where an intersection of roads is located at the bottom of a hill. Then, precautionary action data is added to the database to indicate a location at which a precautionary action is to be taken about the intersection of roads located at the bottom of a hill. A precautionary action system installed in a vehicle uses this database, or a database derived therefrom, in combination with a positioning system to determine when the vehicle is at a location that corresponds to the location of a precautionary action. When the vehicle is at such a location, a precautionary action is taken by a vehicle system as the vehicle is approaching an intersection located at the bottom of a hill.
Owner:HERE GLOBAL BV
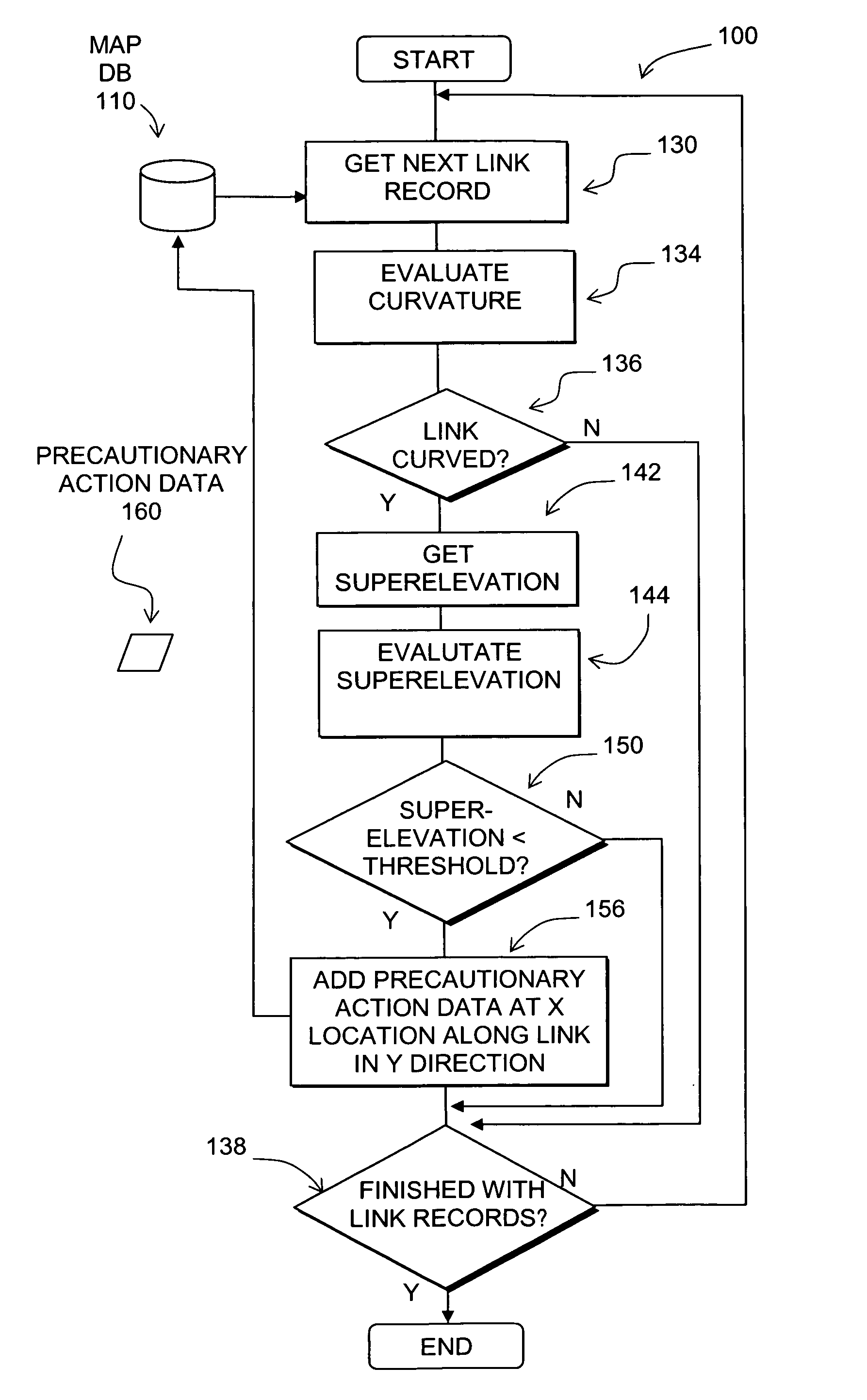
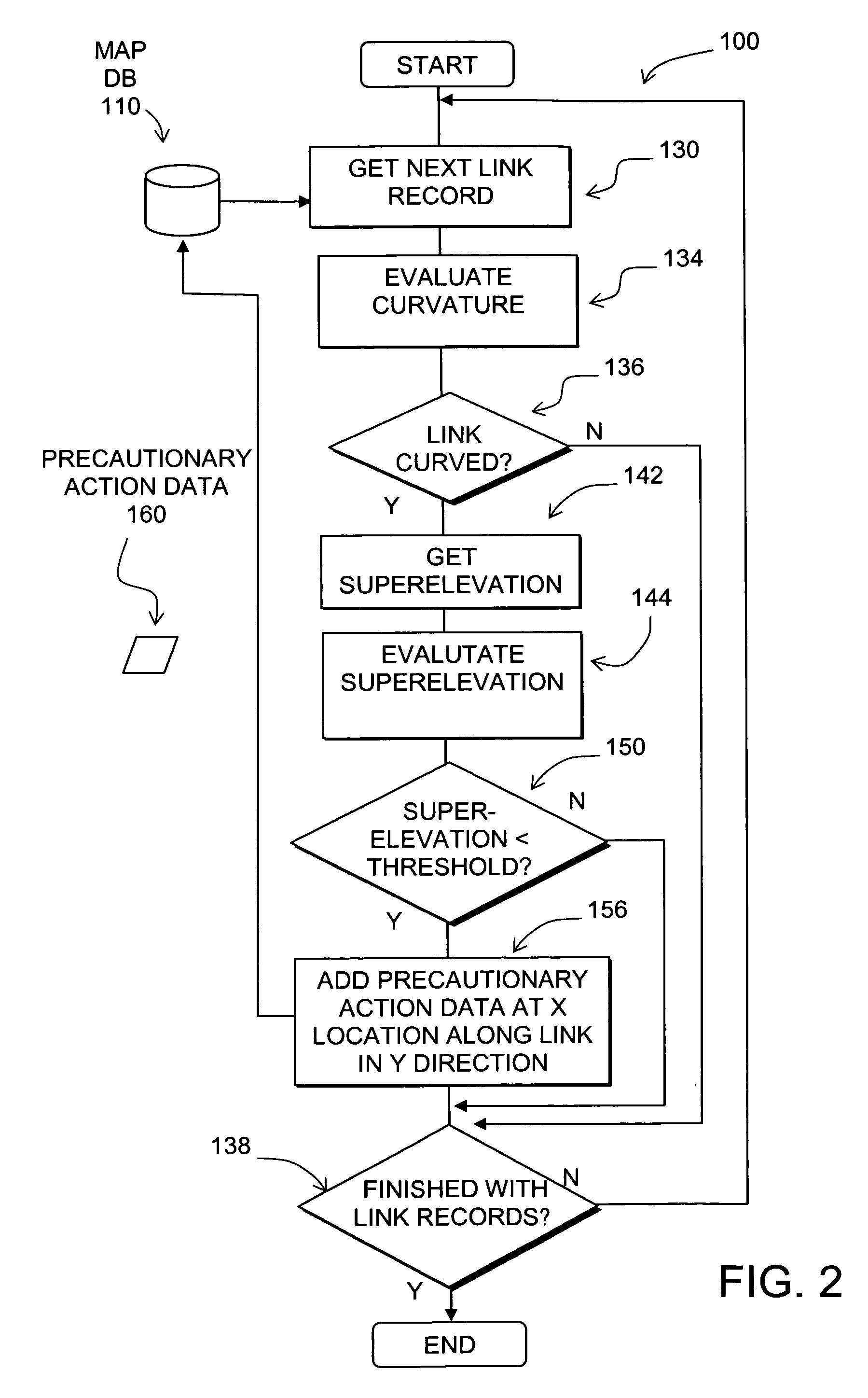
Data mining in a digital map database to identify insufficient superelevation along roads and enabling precautionary actions in a vehicle
ActiveUS20090299630A1Increasing control authorityHigh sensitivityInstruments for road network navigationDigital data processing detailsRoad networksPositioning system
Disclosed is a feature for a vehicle that enables taking precautionary actions in response to conditions on the road network around or ahead of the vehicle, in particular, a curved portion of a road with insufficient superelevation. A database that represents the road network is used to determine locations where curved sections of roads have insufficient superelevation (banking), i.e., where the superelevation is below a threshold. Then, precautionary action data is added to the database to indicate a location at which a precautionary action is to be taken about the location of insufficient superelevation. A precautionary action system installed in a vehicle uses this database, or a database derived therefrom, in combination with a positioning system to determine when the vehicle is at a location that corresponds to the location of a precautionary action. When the vehicle is at such a location, a precautionary action is taken by a vehicle system as the vehicle is approaching a location of insufficient superelevation.
Owner:HERE GLOBAL BV
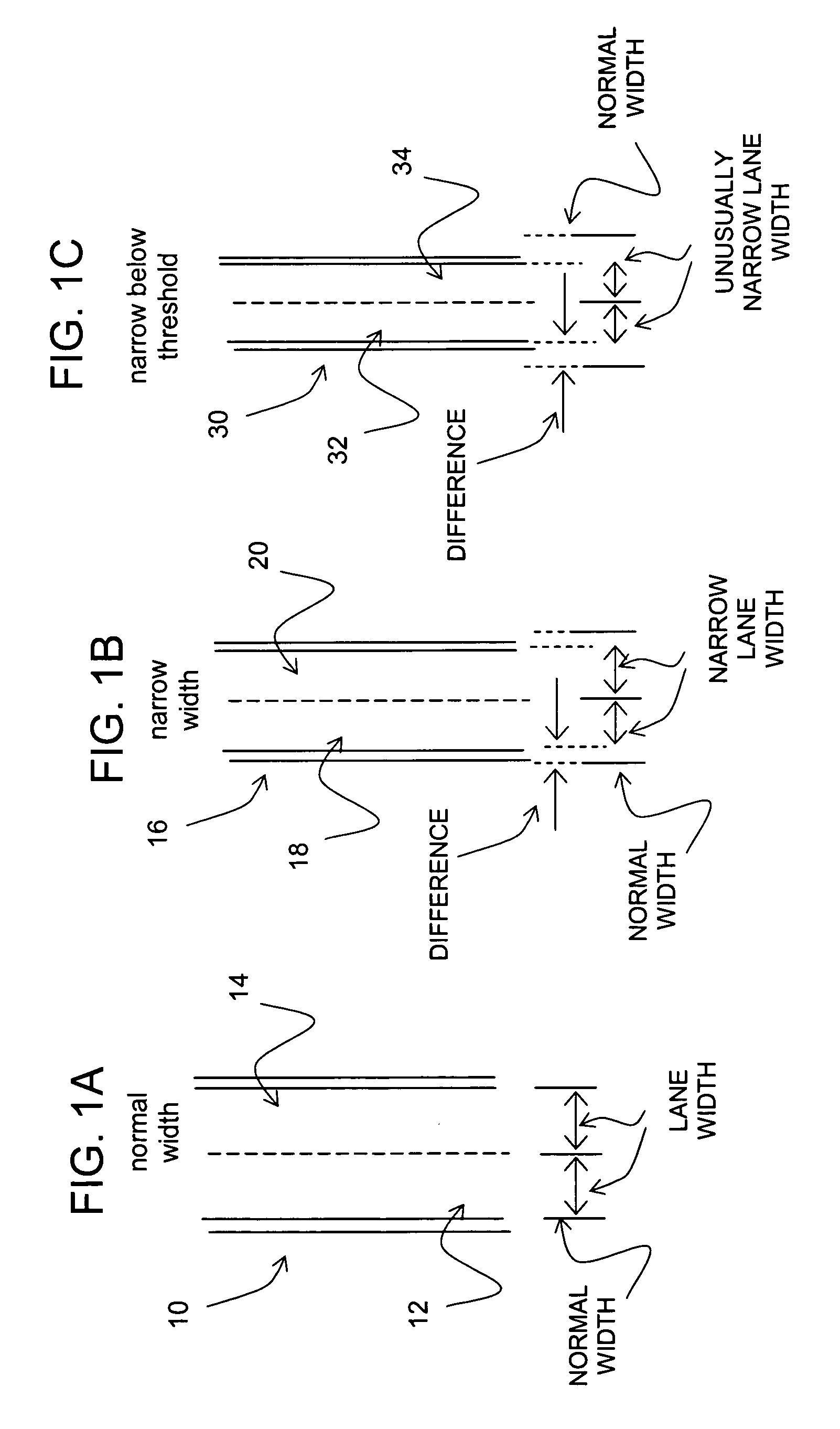
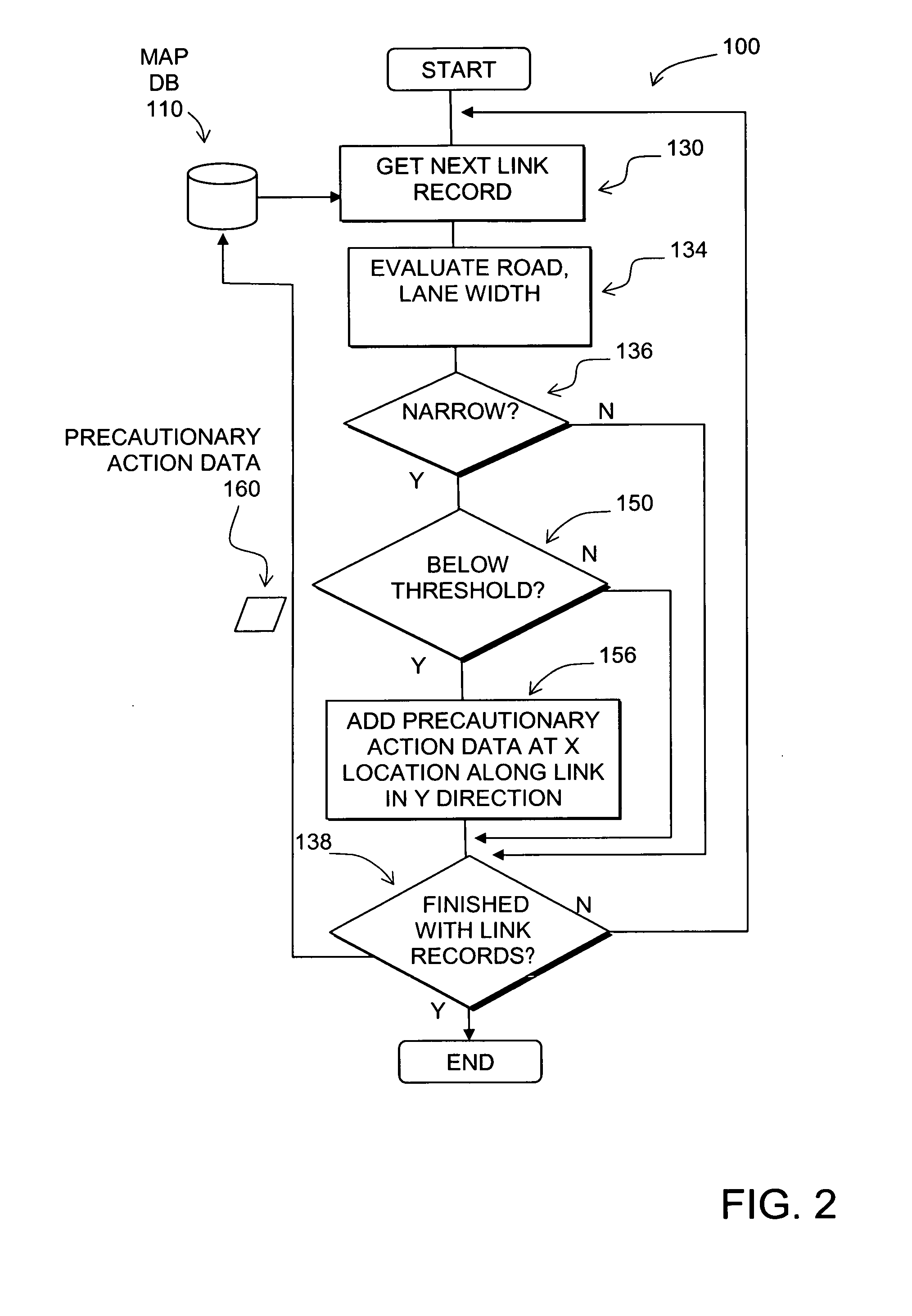
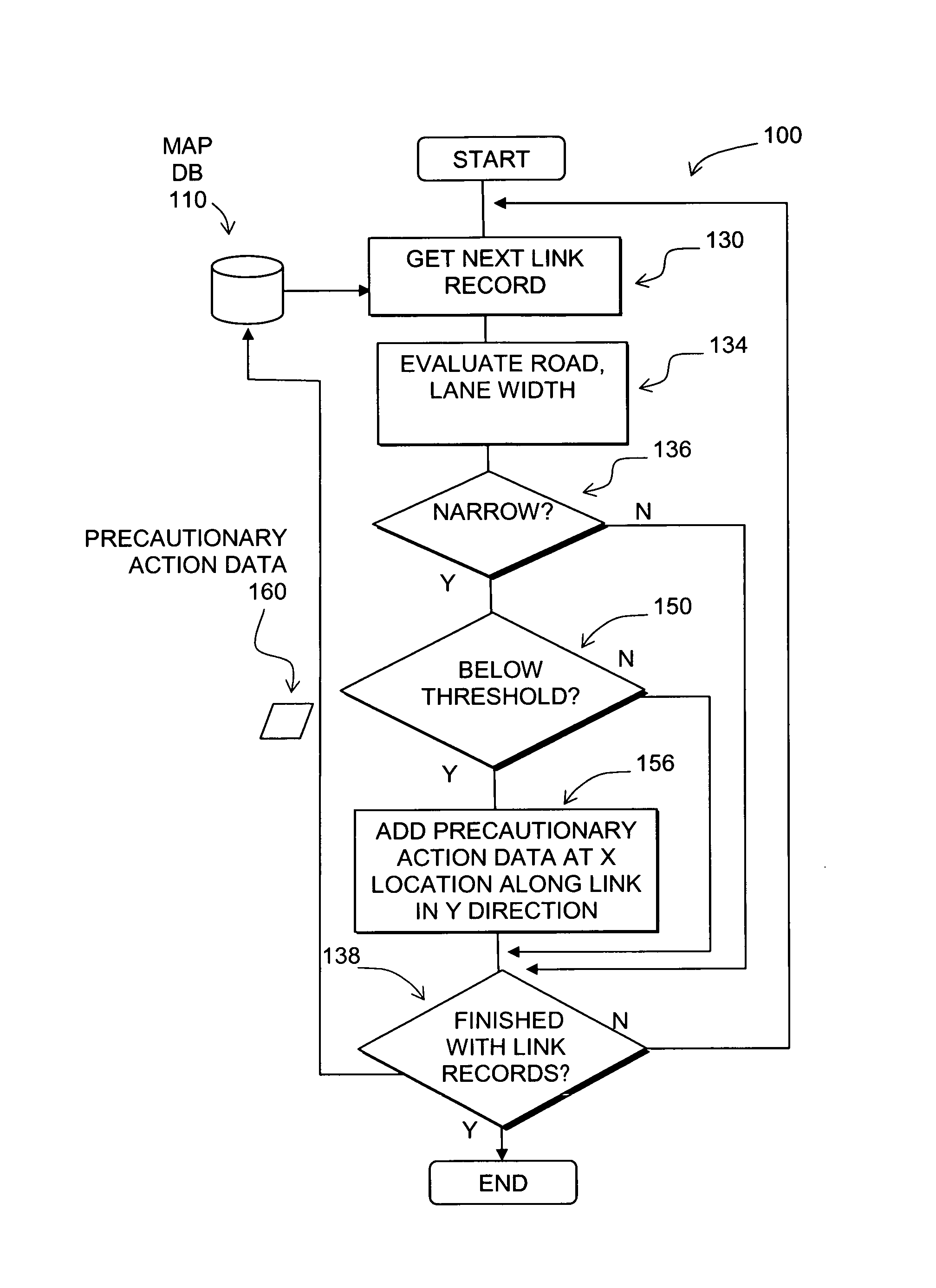
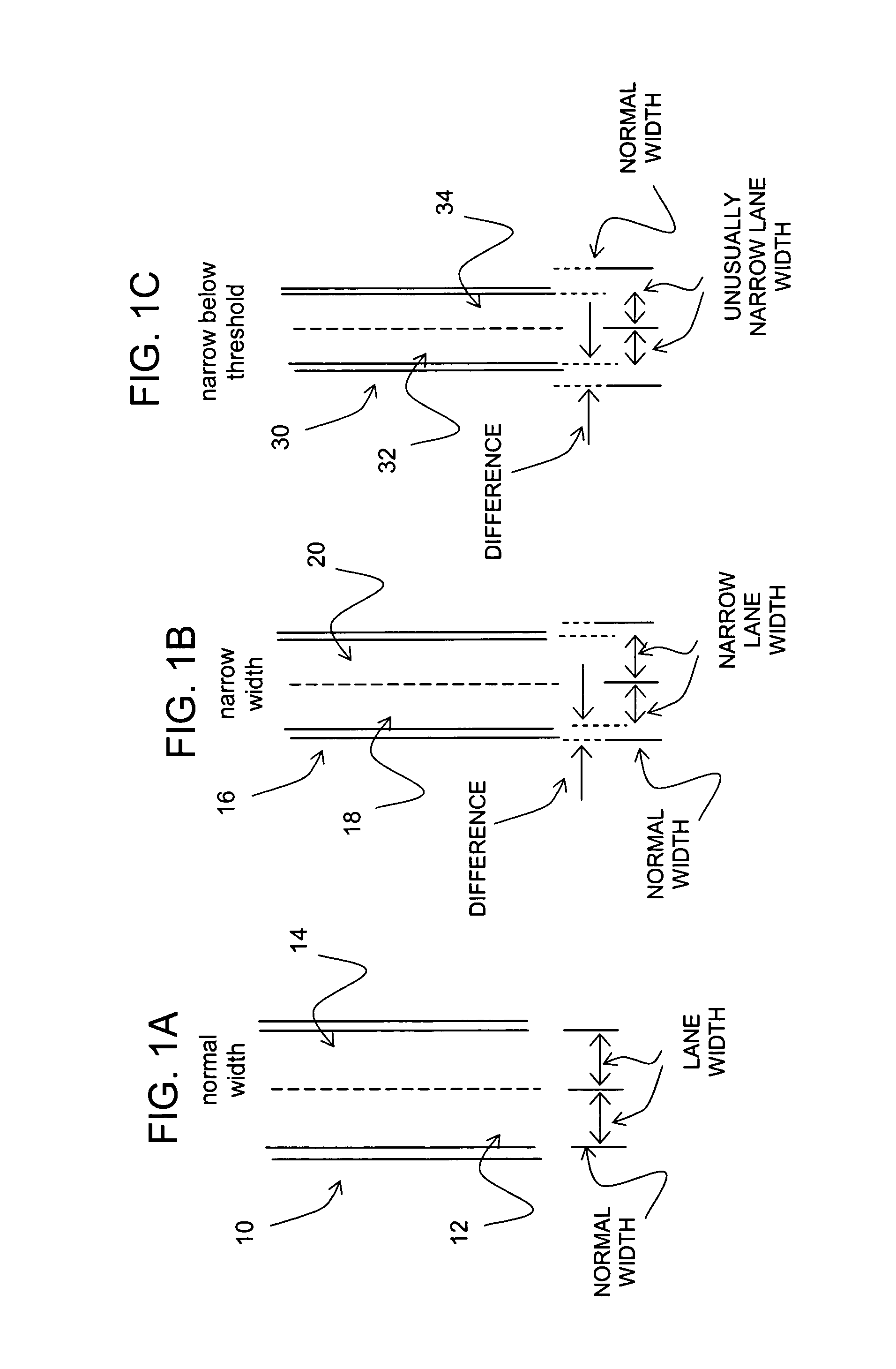
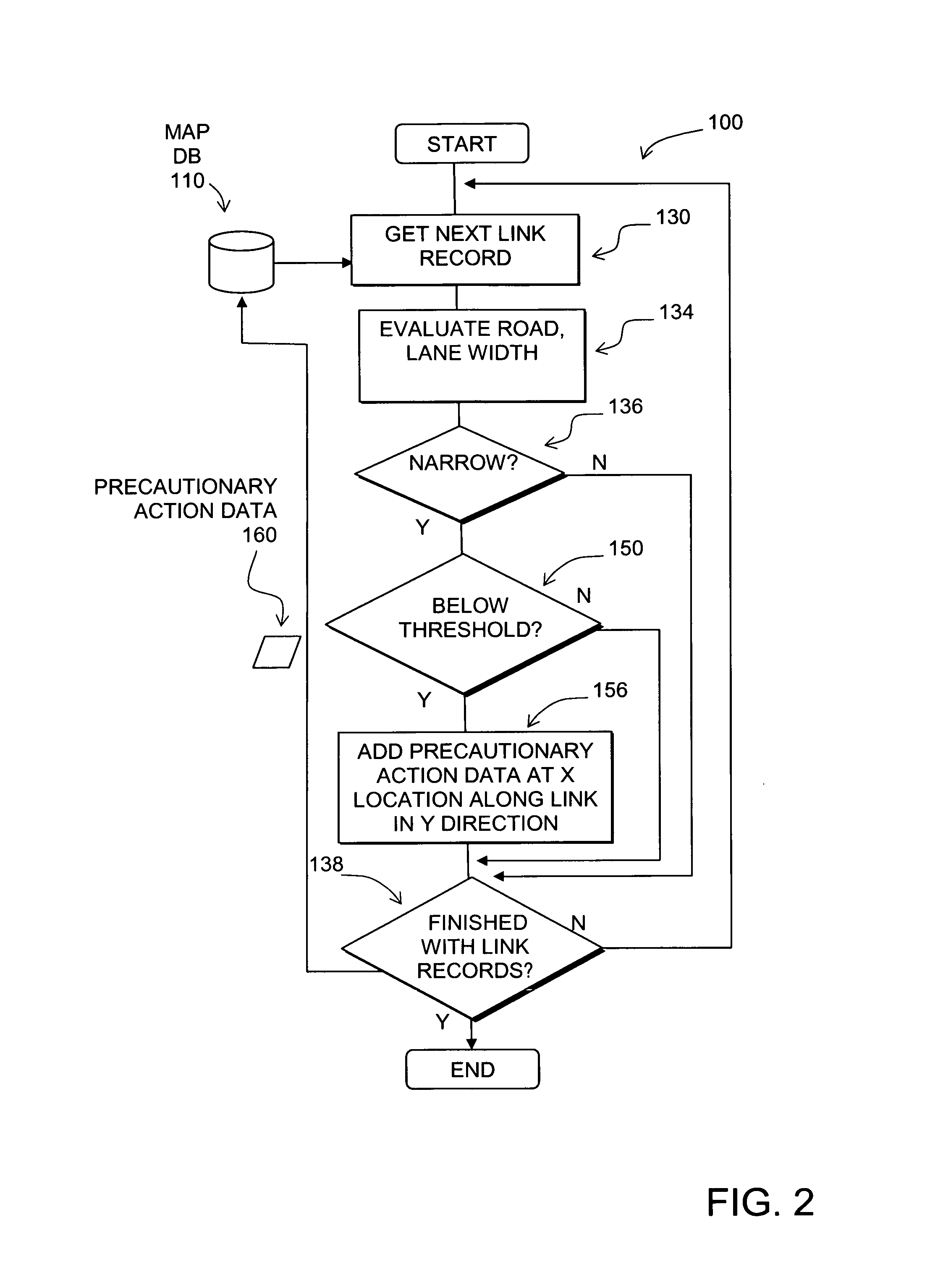
Data mining in a digital map database to identify unusually narrow lanes or roads and enabling precautionary actions in a vehicle
ActiveUS20090299626A1Increasing control authorityHigh sensitivityInstruments for road network navigationRoad vehicles traffic controlRoad networksComputer science
Disclosed is a feature for a vehicle that enables taking precautionary actions in response to conditions on the road network around or ahead of the vehicle, in particular, an unusually narrow road width or lane width. A database that represents the road network is used to determine locations where an unusually narrow road width or lane width exists along roads. Then, precautionary action data is added to the database to indicate a location at which a precautionary action is to be taken about the location where the unusually narrow road width or lane width exists. A precautionary action system installed in a vehicle uses this database, or a database derived therefrom, in combination with a positioning system to determine when the vehicle is at a location that corresponds to the location of a precautionary action. When the vehicle is at such a location, a precautionary action is taken by a vehicle system as the vehicle is approaching a location where the unusually narrow road width or lane width exists.
Owner:HERE GLOBAL BV
Data mining in a digital map database to identify curves along downhill roads and enabling precautionary actions in a vehicle
ActiveUS20090299617A1Increasing control authorityHigh sensitivityAnalogue computers for vehiclesInstruments for road network navigationRoad networksPositioning system
Disclosed is a feature for a vehicle that enables taking precautionary actions in response to conditions on the road network around or ahead of the vehicle, in particular, a curve along a downhill road segment. A database that represents the road network is used to determine locations where a curve is located along a downhill road segment. Then, precautionary action data is added to the database to indicate a location at which a precautionary action is to be taken about the location of the curve along the downhill road segment. A precautionary action system installed in a vehicle uses this database, or a database derived therefrom, in combination with a positioning system to determine when the vehicle is at a location that corresponds to the location of a precautionary action. When the vehicle is at such a location, a precautionary action is taken by a vehicle system as the vehicle is approaching a location of the curve in the downhill road segment.
Owner:HERE GLOBAL BV
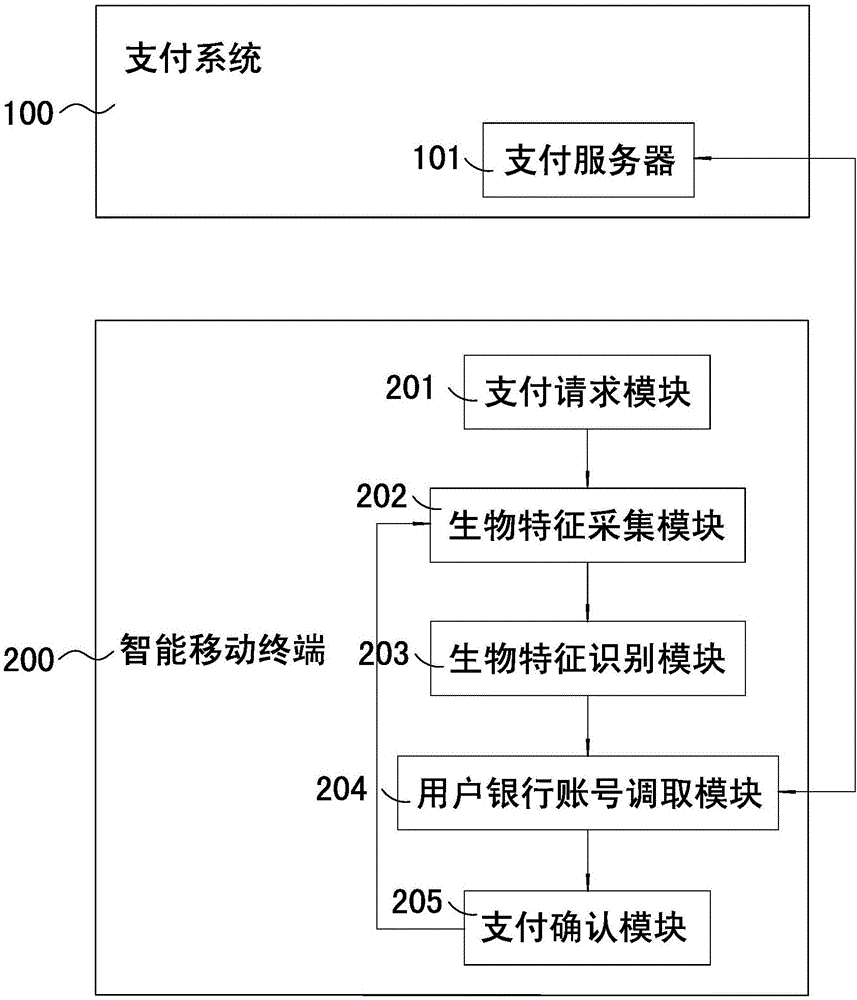
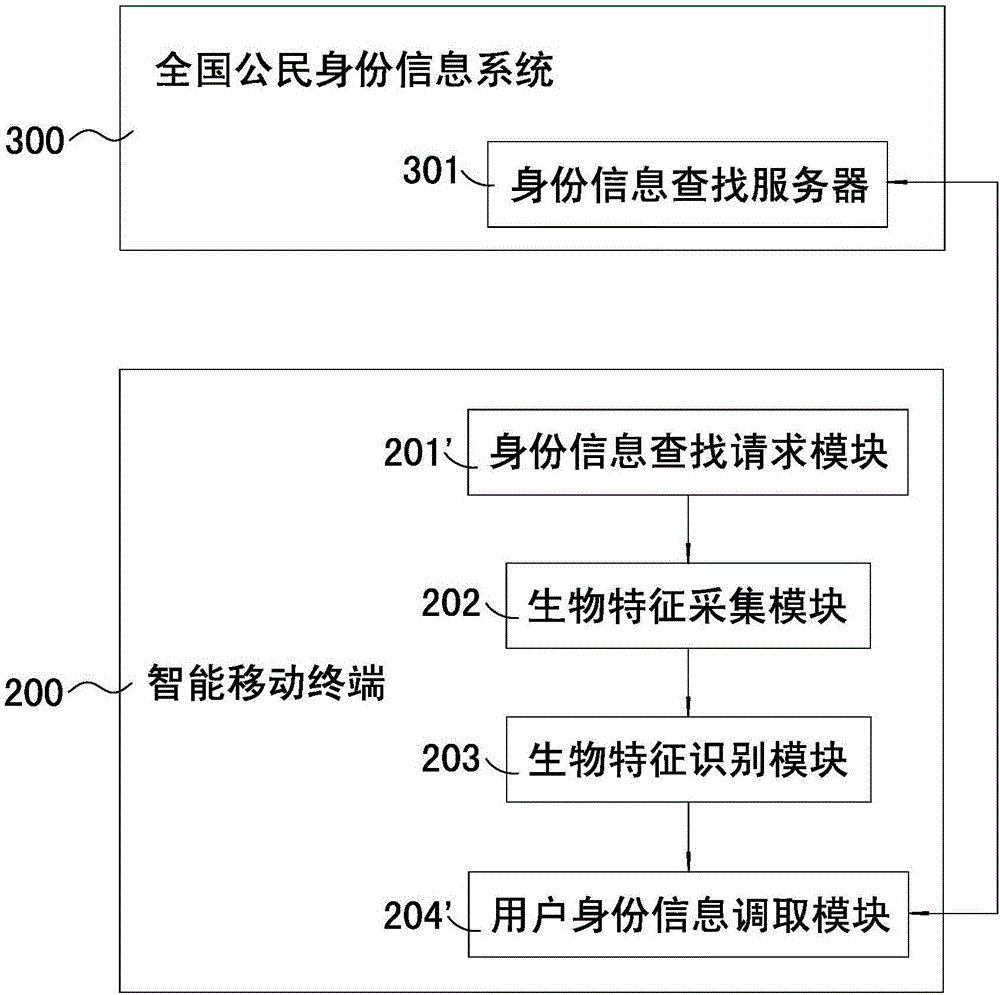
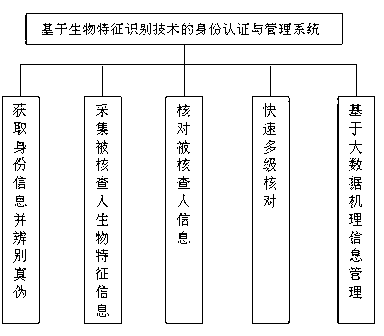
Payment and identity authentication systems based on biometric feature recognition
InactiveCN106296199AImprove accuracyImprove reliabilityBiometric pattern recognitionProtocol authorisationPalm printBank account
The invention discloses payment and identity authentication systems based on biometric feature recognition. The payment system based on the biometric feature recognition comprises a payment system and a smart mobile terminal, wherein the payment system comprises a payment server for storing user bank account information which is bound with biometric feature information of a user; and the smart mobile terminal comprises a payment request module, a biometric feature acquisition module, a biometric feature recognition module, a user bank account calling module and a payment confirmation module. The payment system based on the biometric feature recognition has the effects that when the payment system is used for making a payment, the user can make a rapid payment by inputting a voiceprint, irises, a palm print, a vein, ears, a gait or retinas without carrying any cash, bank card, consumer card or mobile phone no matter where the user is, so that a conventional payment mode is broken, and the restraints of the cash, cards and electronic equipment are broken. A checker can rapidly check user identity information by using the identity authentication system, and the user does not need to take out any identity card, so that high practicability and a good use effect are achieved.
Owner:刘洪文
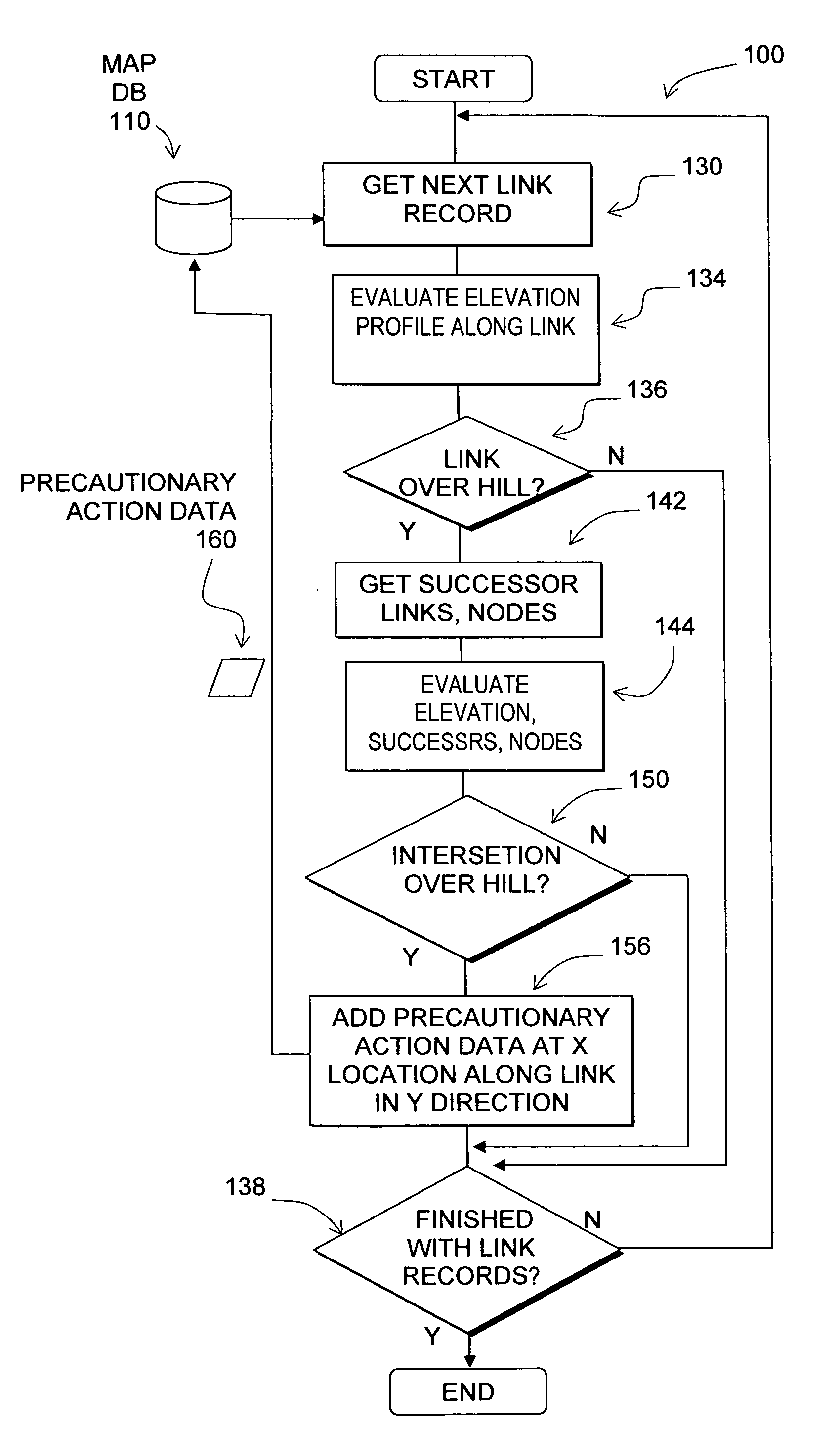
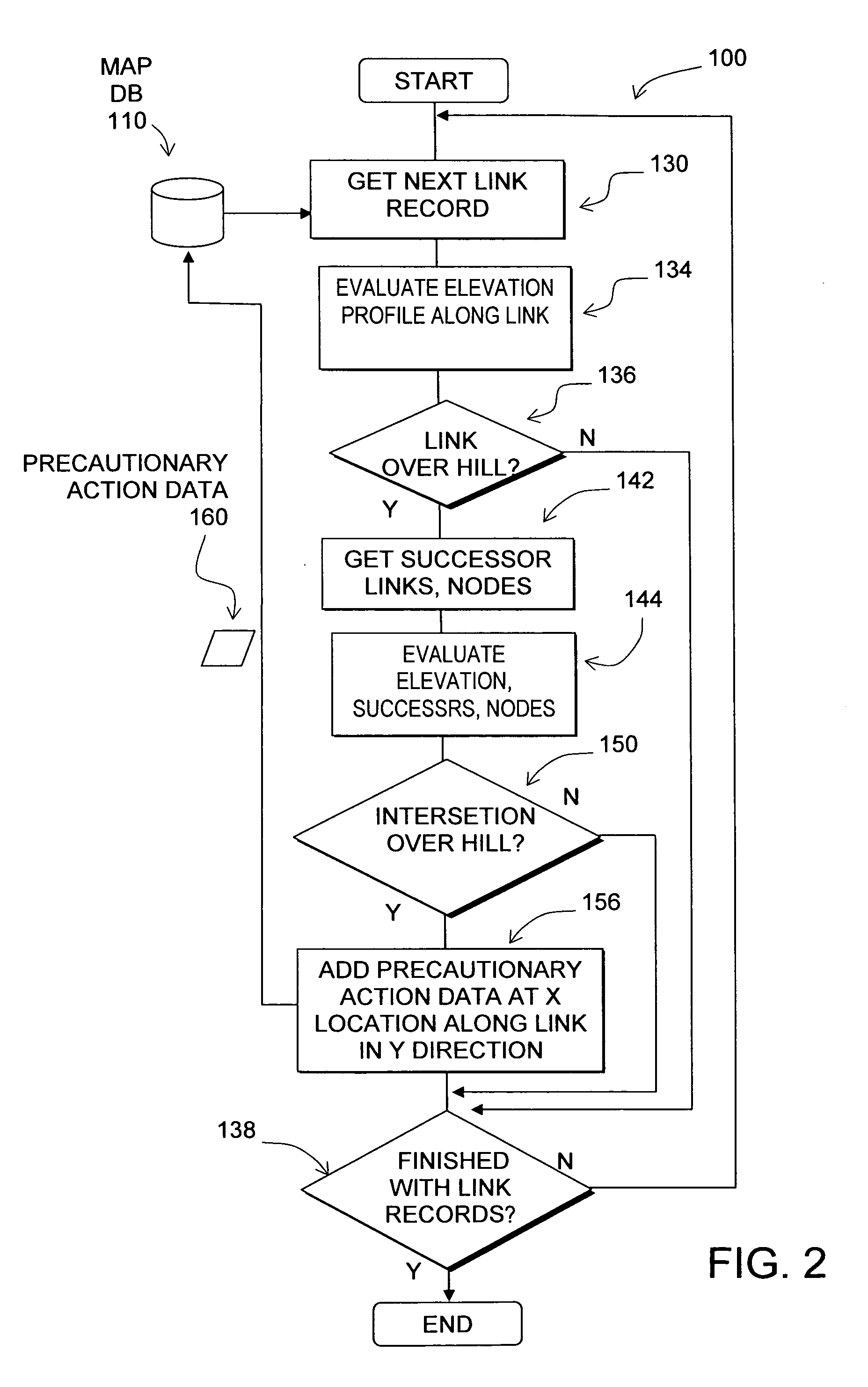
Data mining in a digital map database to identify intersections located over hills and enabling precautionary actions in a vehicle
InactiveUS20090299616A1Improve authorityHigh sensitivityAnalogue computers for vehiclesInstruments for road network navigationRoad networksPositioning system
Disclosed is a feature for a vehicle that enables taking precautionary actions in response to conditions on the road network around or ahead of the vehicle, in particular, an intersection located over a hilltop along a section of road. A database that represents the road network is used to determine locations where an intersection located over a hilltop is located along a section of road. Then, precautionary action data is added to the database to indicate a location at which a precautionary action is to be taken about the intersection located over a hilltop located along the section of road. A precautionary action system installed in a vehicle uses this database, or a database derived therefrom, in combination with a positioning system to determine when the vehicle is at a location that corresponds to the location of a precautionary action. When the vehicle is at such a location, a precautionary action is taken by a vehicle system as the vehicle is approaching an intersection located over a hilltop.
Owner:HERE GLOBAL BV
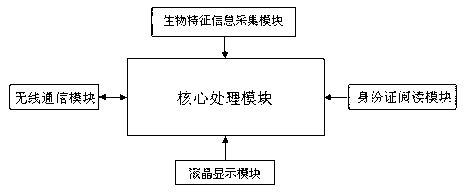
Identity authentication method based on biological feature information
InactiveCN103714315AImprove accuracyImprove authorityCharacter and pattern recognitionRecord carriers used with machinesData informationNetwork packet
The invention discloses an identity authentication method based on biological feature information. The method includes: Step 1, erecting a data server in a management background; Step 2, collecting biological feature information of a user through an identity authentication device, and generating an authentication information data packet to be sent to the data server of the management background for storage; Step 3, in identity authentication of the user, the identity authentication device firstly collecting electronic data information in an identity card of the user, and then reading corresponding fingerprint line information and face feature information; and Step 4, the identity authentication device collecting fingerprint line information and face feature information, and then performing analysis and comparison with the fingerprint line information and the face feature information transmitted by the data server. If the biological feature information of the two is identical, the identity authentication is passed, and otherwise the identity authentication fails. The identity authentication method uses various biological feature information recognition technologies to perform identity authentication, and is high in security and strong in reliability.
Owner:南京译海网络科技股份有限公司
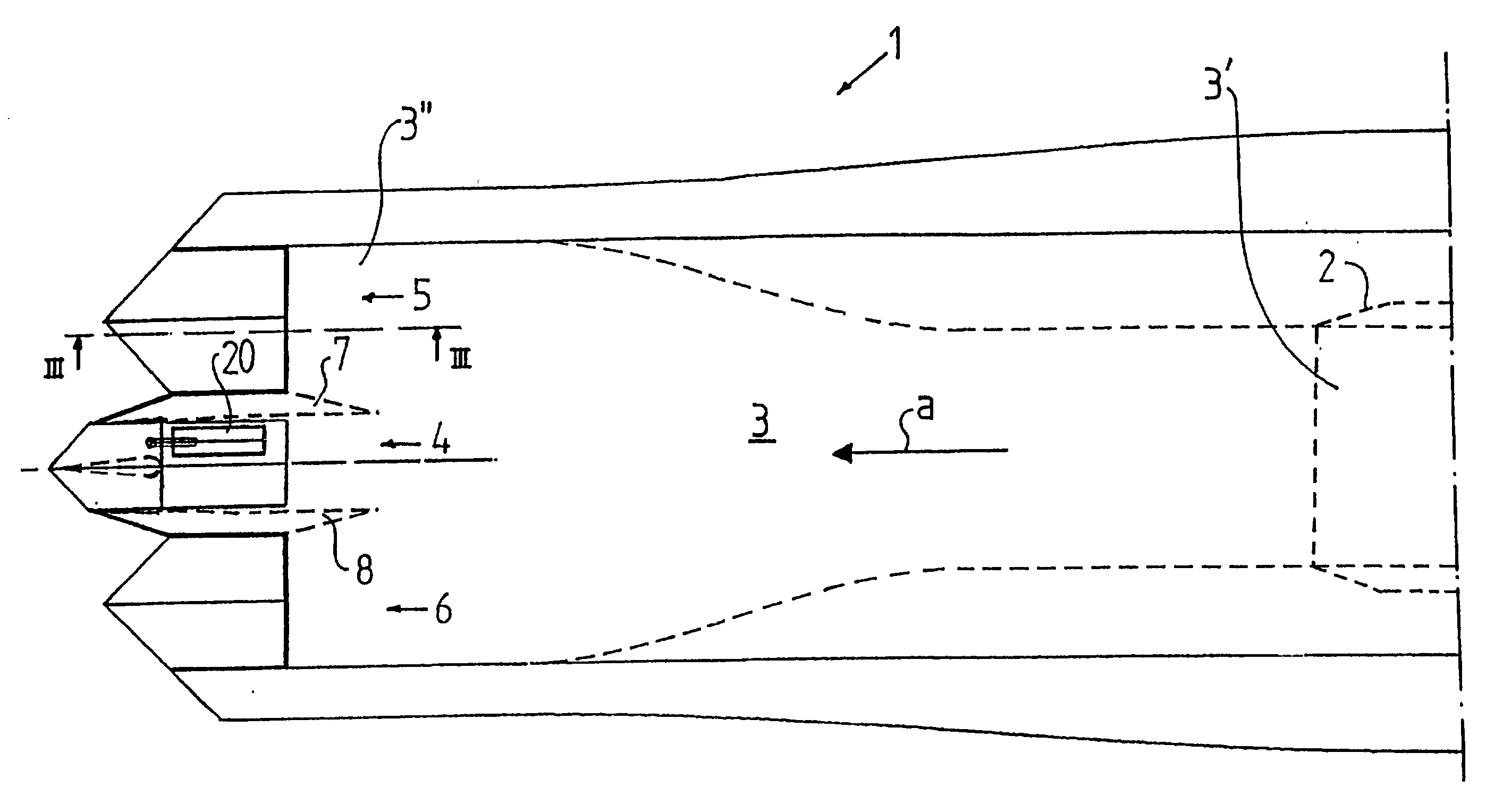
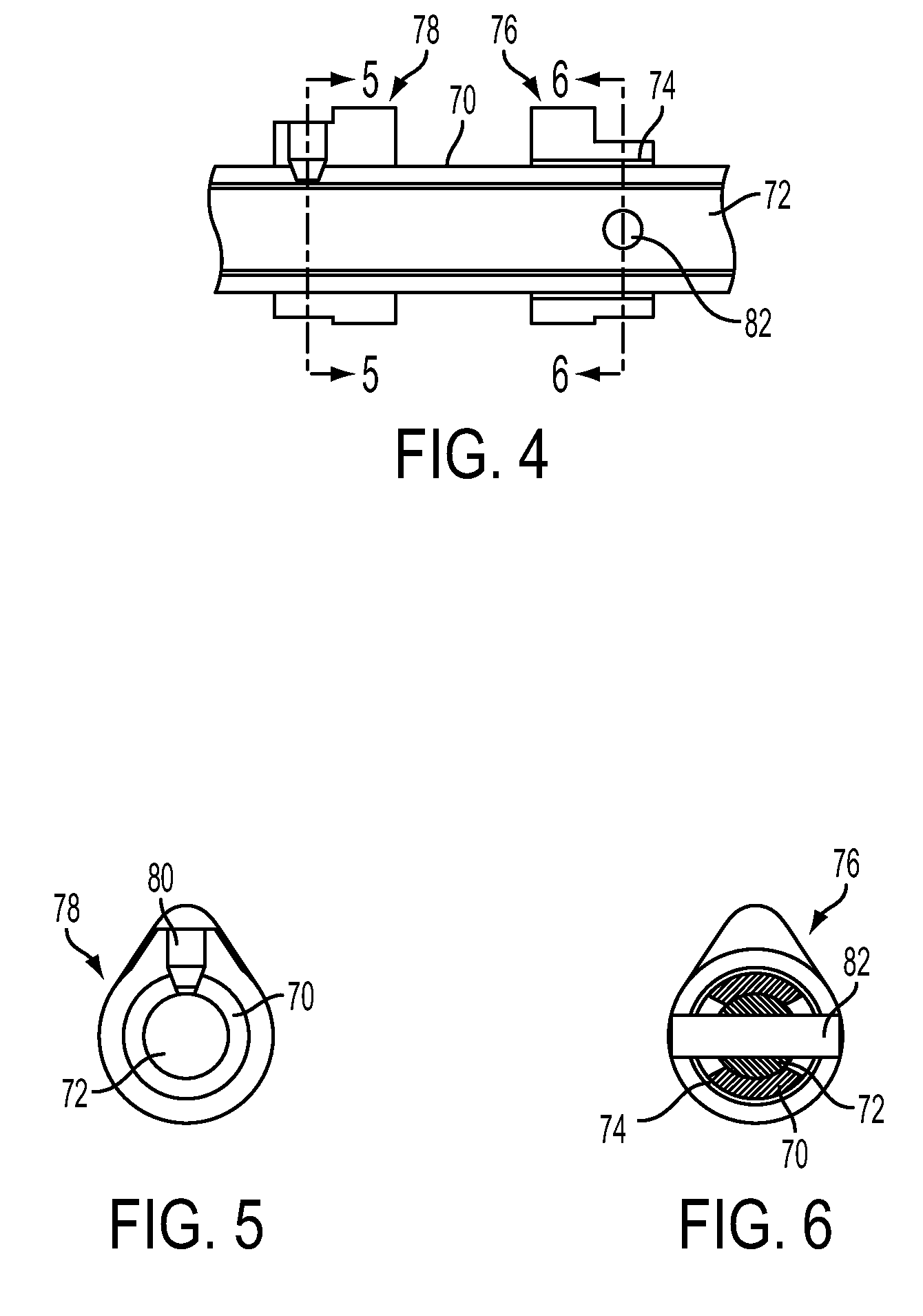
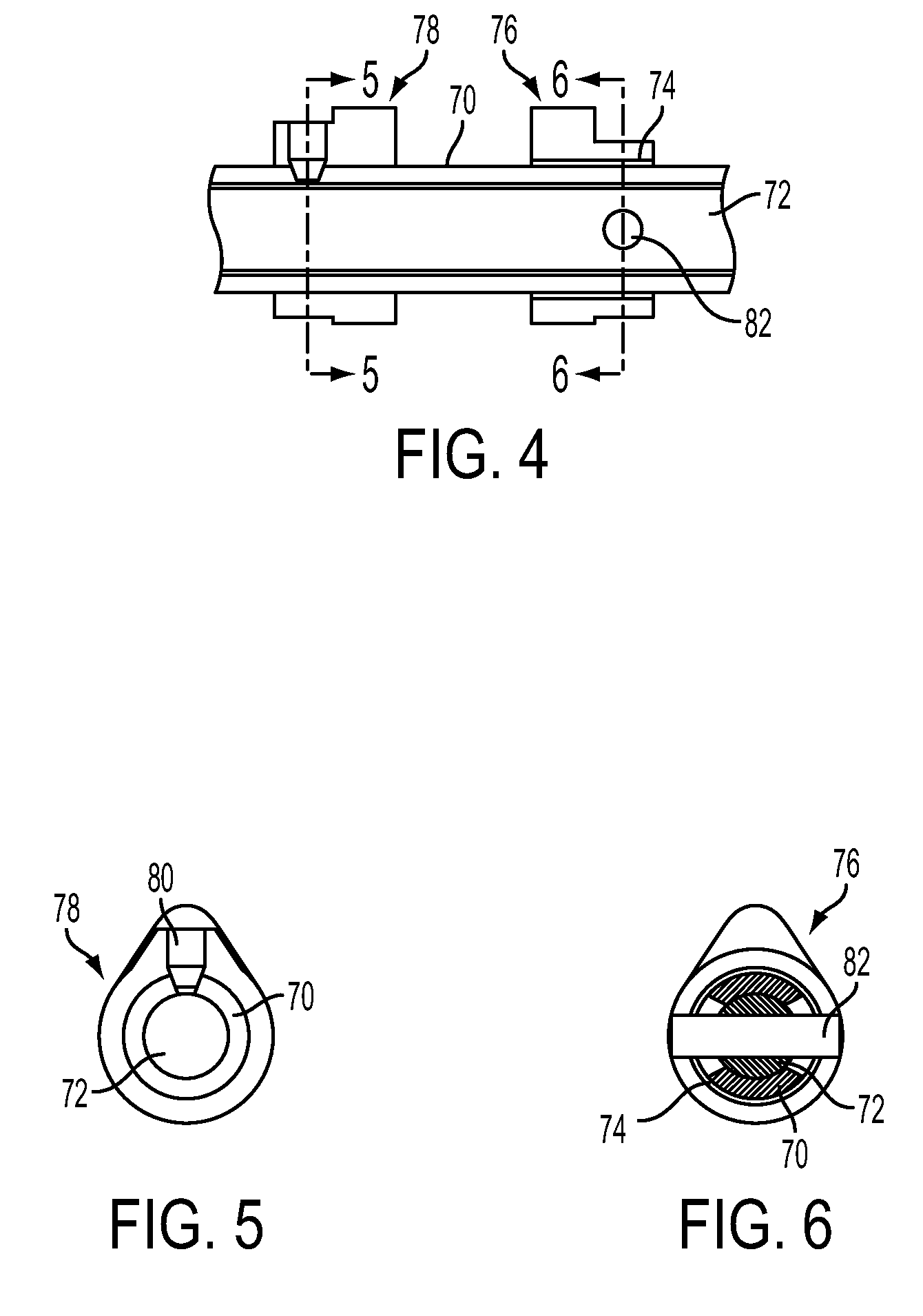
Outlet device for a jet engine
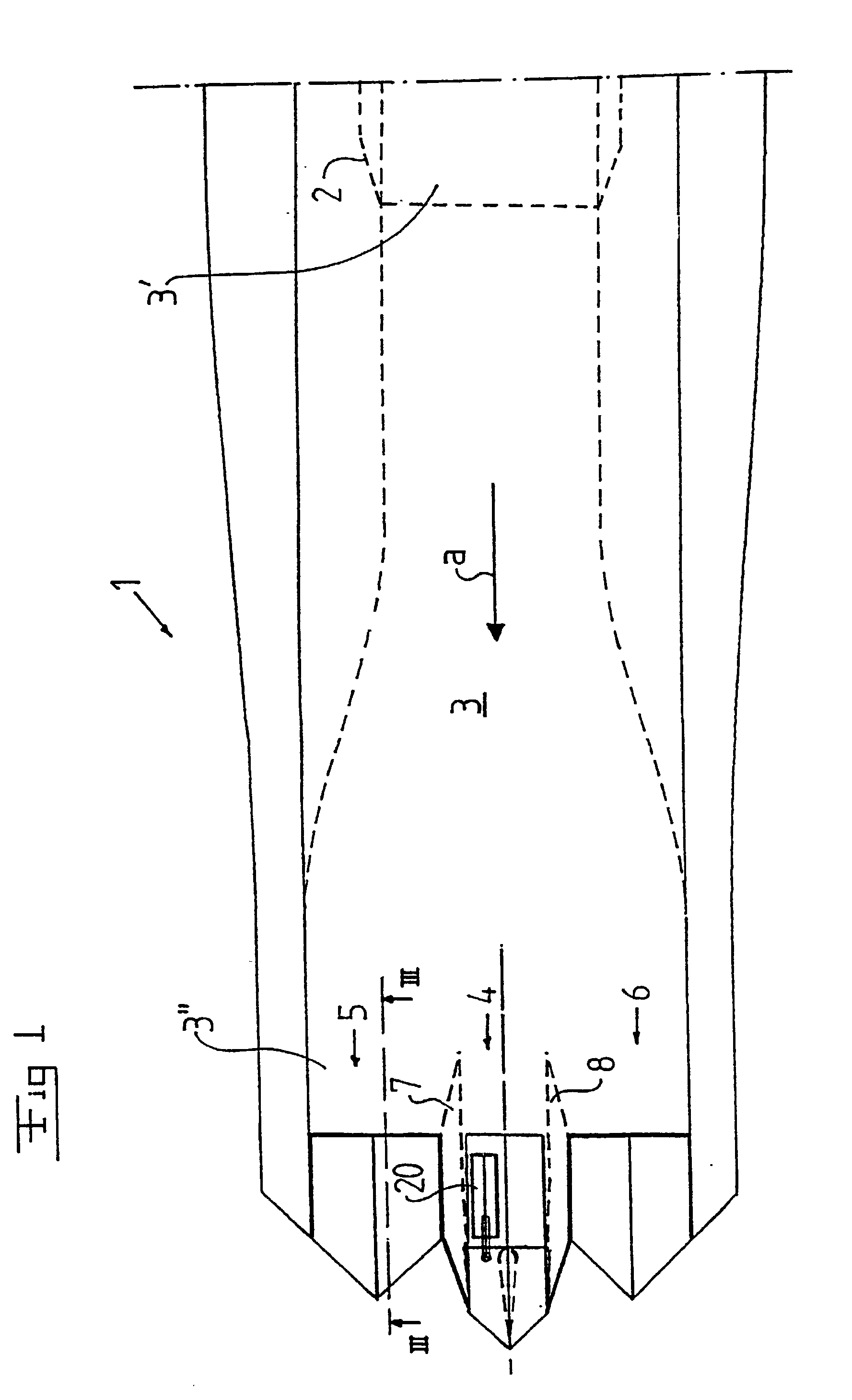
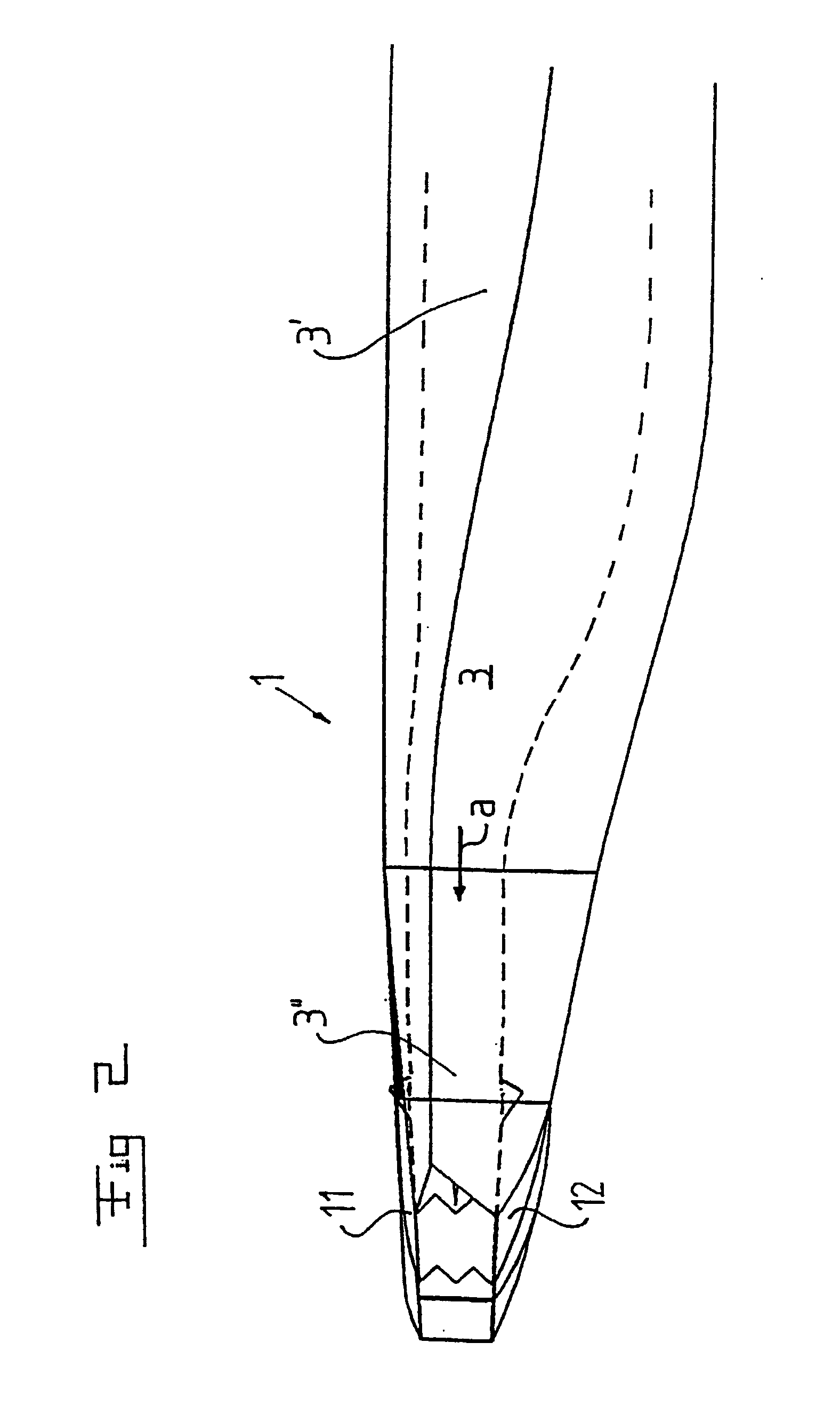
InactiveUS20020189232A1Improve authoritySimple designSpraying apparatusJet propulsion plantsJet engineAirplane
An outlet device for a jet engine (2) includes an outlet channel (3), which has an upstream end (3') for being connected to the jet engine and a downstream end (3'') and which defines a main flow direction (a) for a jet from the jet engine. The outlet channel has in the proximity of the downstream end an elongated shape, seen in a section across the flow direction, and includes at least two outlet portions (4, 5, 6), which are separated from each other, for a respective outlet flow of said jet. A first outlet portion (5, 6) includes means for controlling the outlet direction of the outlet flow in a first plane and a second outlet portion (4) includes means for controlling the outlet direction of the outlet flow in a second plane, which forms an angle to the first plane. An aircraft may include such an outlet device.
Owner:SAAB AB
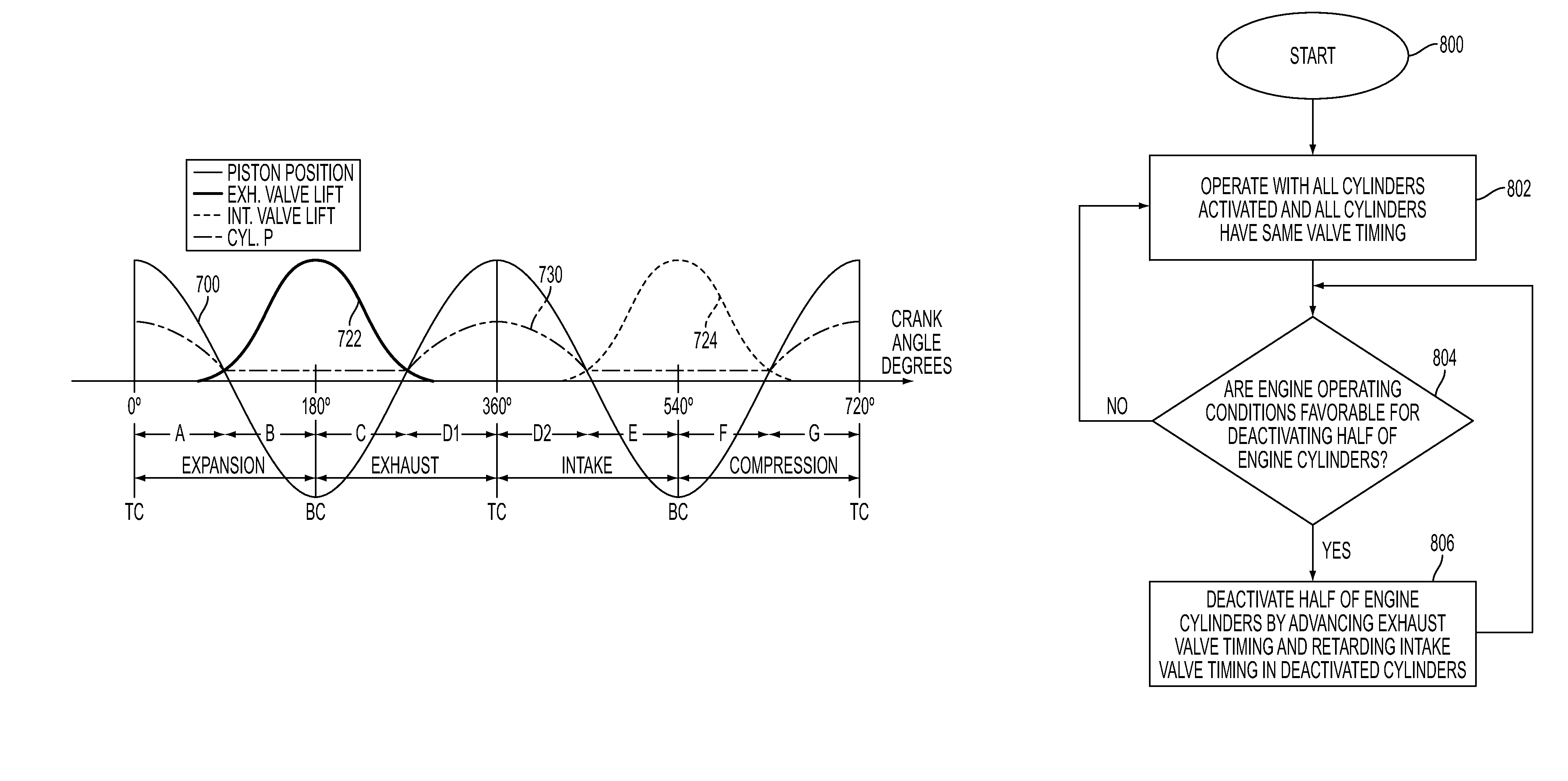
Adjusting valve timing to deactivate engine cylinders for variable displacement operation
ActiveUS20100175645A1Facilitate smooth transitionEffectively disableValve arrangementsYielding couplingVariable displacementExhaust valve
An internal combustion engine having two cylinder banks and adjustable camshaft timing is disclosed in which the camshafts in one cylinder bank are adjusted so that there is no net flow from the cylinders to effectively disable the cylinder bank. In particular, exhaust valve timing is advanced so that the maximum valve lift occurs approximately at bottom center between expansion and exhaust strokes and intake valve timing is advanced so that maximum valve lift occurs approximately at bottom center between intake and compression strokes. Also disclosed is an engine in which an intake and an exhaust camshaft on a single bank are coaxial with valve timings adjusted by rotating the inner of the two camshafts with respect to the outer of the two camshafts.
Owner:FORD GLOBAL TECH LLC
Adjusting valve timing to deactivate engine cylinders for variable displacement operation
ActiveUS8042504B2Effectively disableImprove authorityValve arrangementsYielding couplingExhaust valveExternal rotation
An internal combustion engine having two cylinder banks and adjustable camshaft timing is disclosed in which the camshafts in one cylinder bank are adjusted so that there is no net flow from the cylinders to effectively disable the cylinder bank. In particular, exhaust valve timing is advanced so that the maximum valve lift occurs approximately at bottom center between expansion and exhaust strokes and intake valve timing is advanced so that maximum valve lift occurs approximately at bottom center between intake and compression strokes. Also disclosed is an engine in which an intake and an exhaust camshaft on a single bank are coaxial with valve timings adjusted by rotating the inner of the two camshafts with respect to the outer of the two camshafts.
Owner:FORD GLOBAL TECH LLC
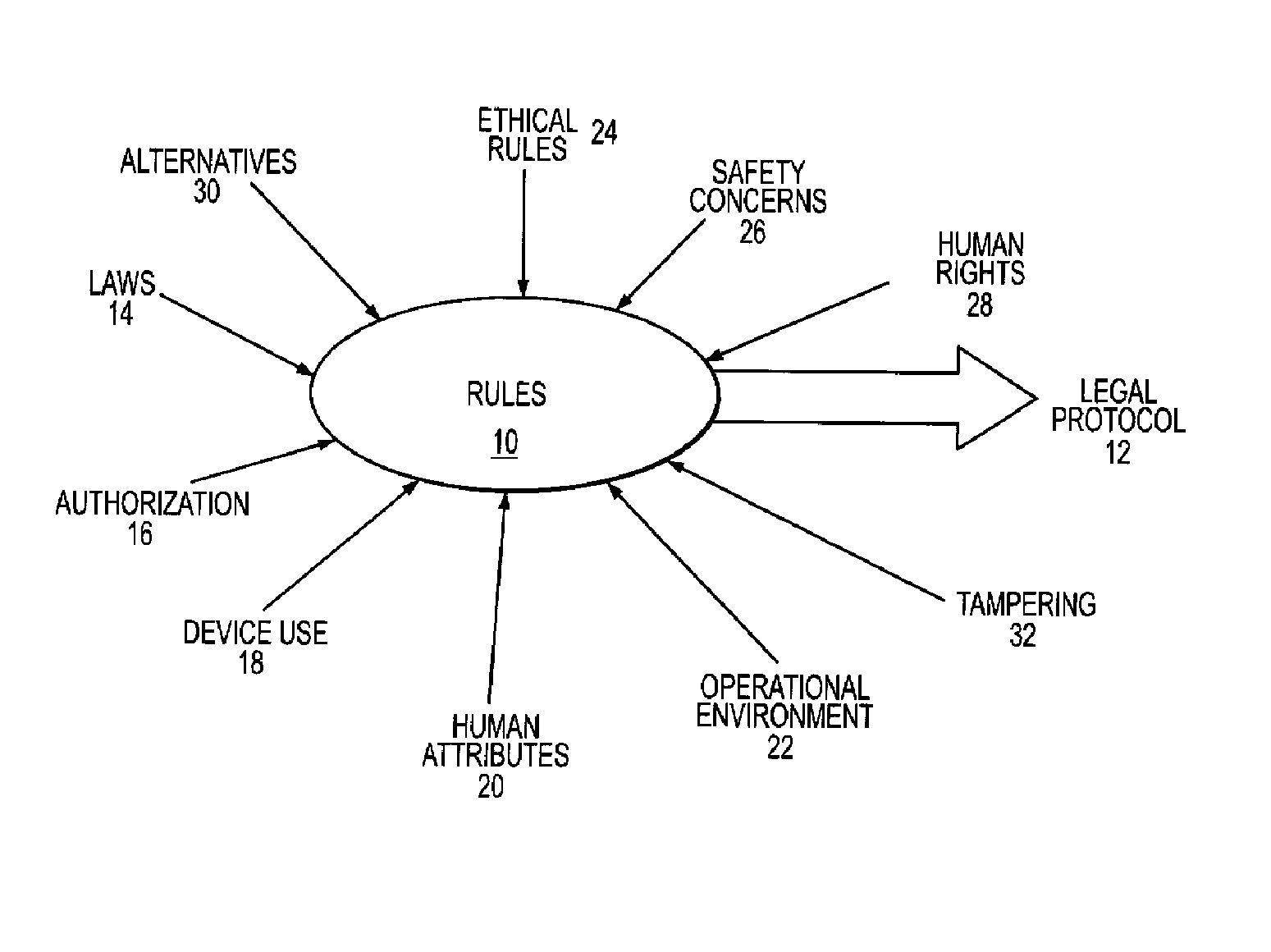
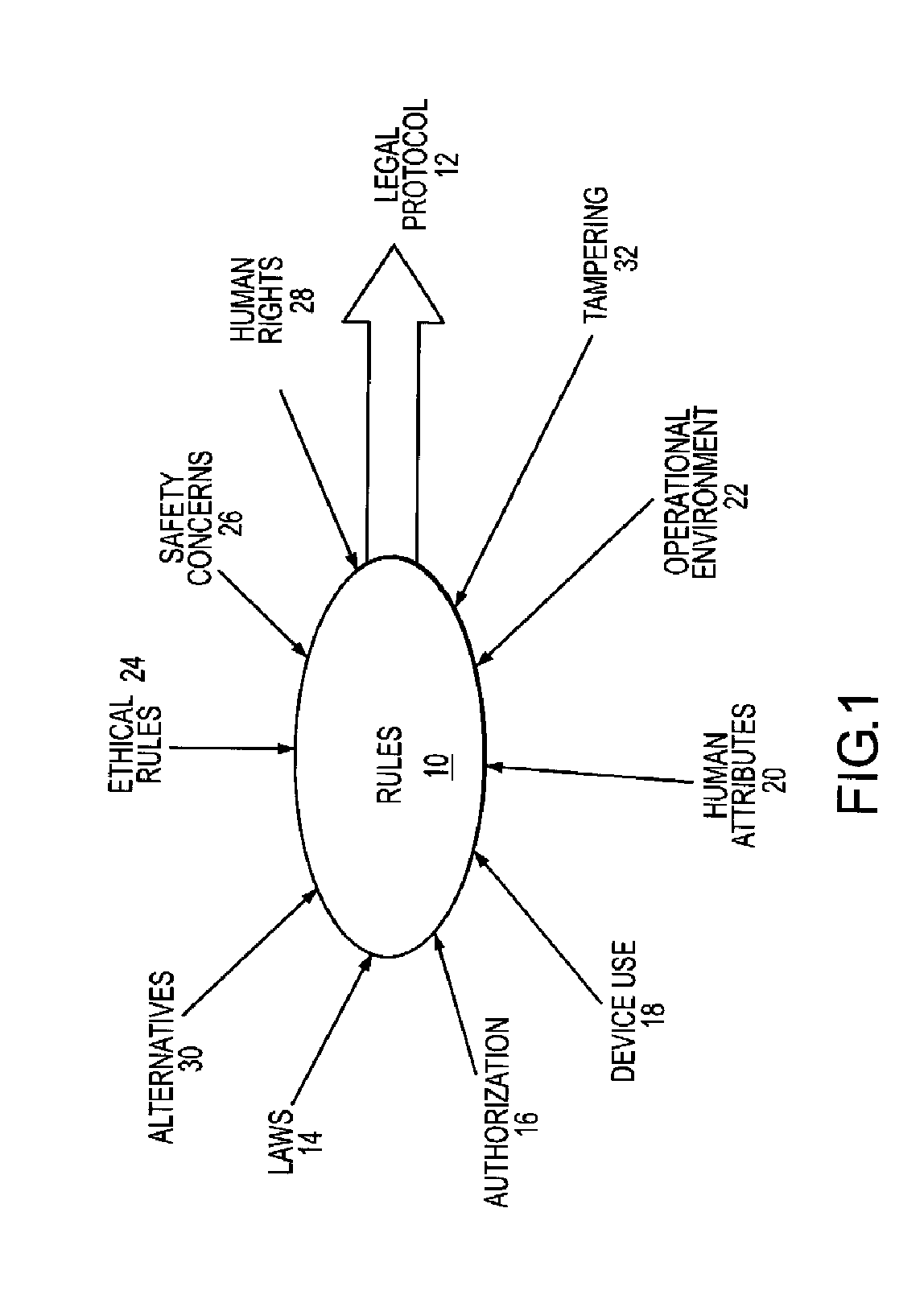
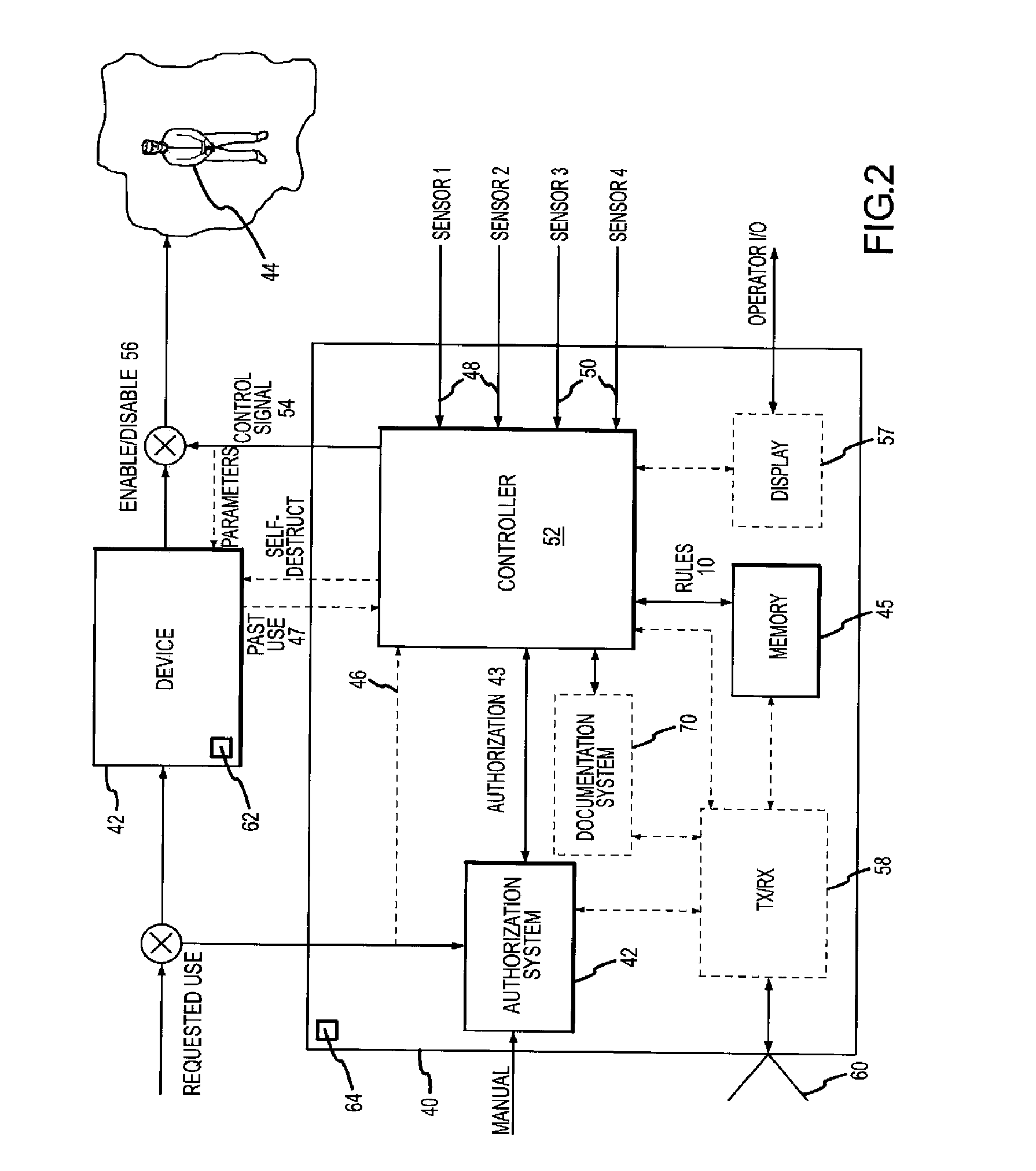
Safeguard System for Ensuring Device Operation in Conformance with Governing Laws
ActiveUS20100269674A1Guaranteed usageImprove authoritySafety arrangementSighting devicesProtective systemAuthorization
A safeguard system ensures device operation in conformance with governing laws for devices such as directed energy weapons or surveillance systems, whose misuse may discomfort, harm or otherwise violate the legal rights of a person. A legal protocol is defined by rules embodying the laws that govern the use of the device and requires as inputs an authorization to use the device and input condition(s) relating to at least one of a use of the device, an attribute of a human target of the device and an operational environment of the device and human target. The safeguard system applies the rules to the authorization and input condition(s) to generate a control signal that ensures the device is used in conformance with the legal protocol. A documentation system records the authorization, input condition(s) applied rules, and control signal.
Owner:RAYTHEON CO
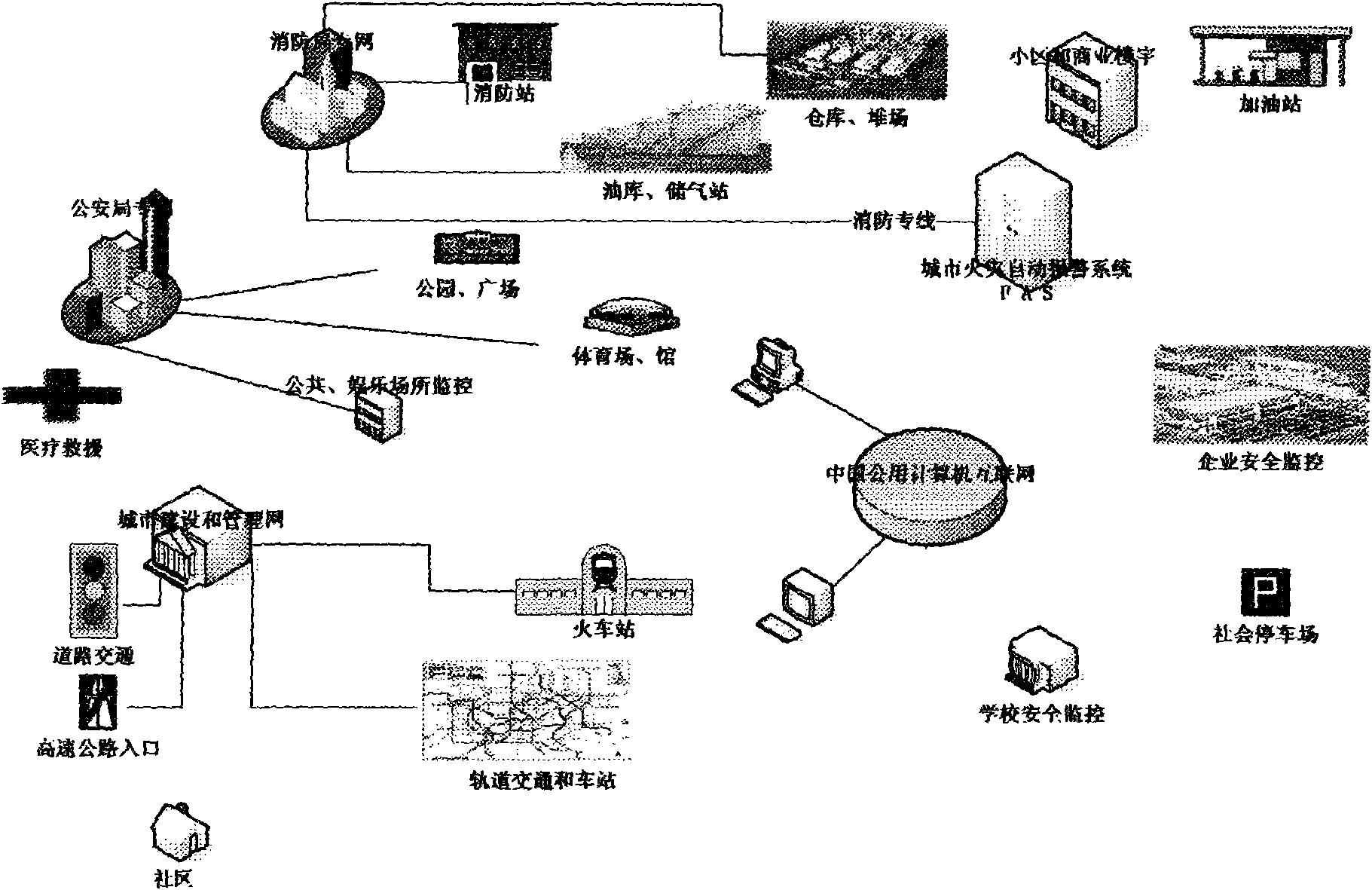
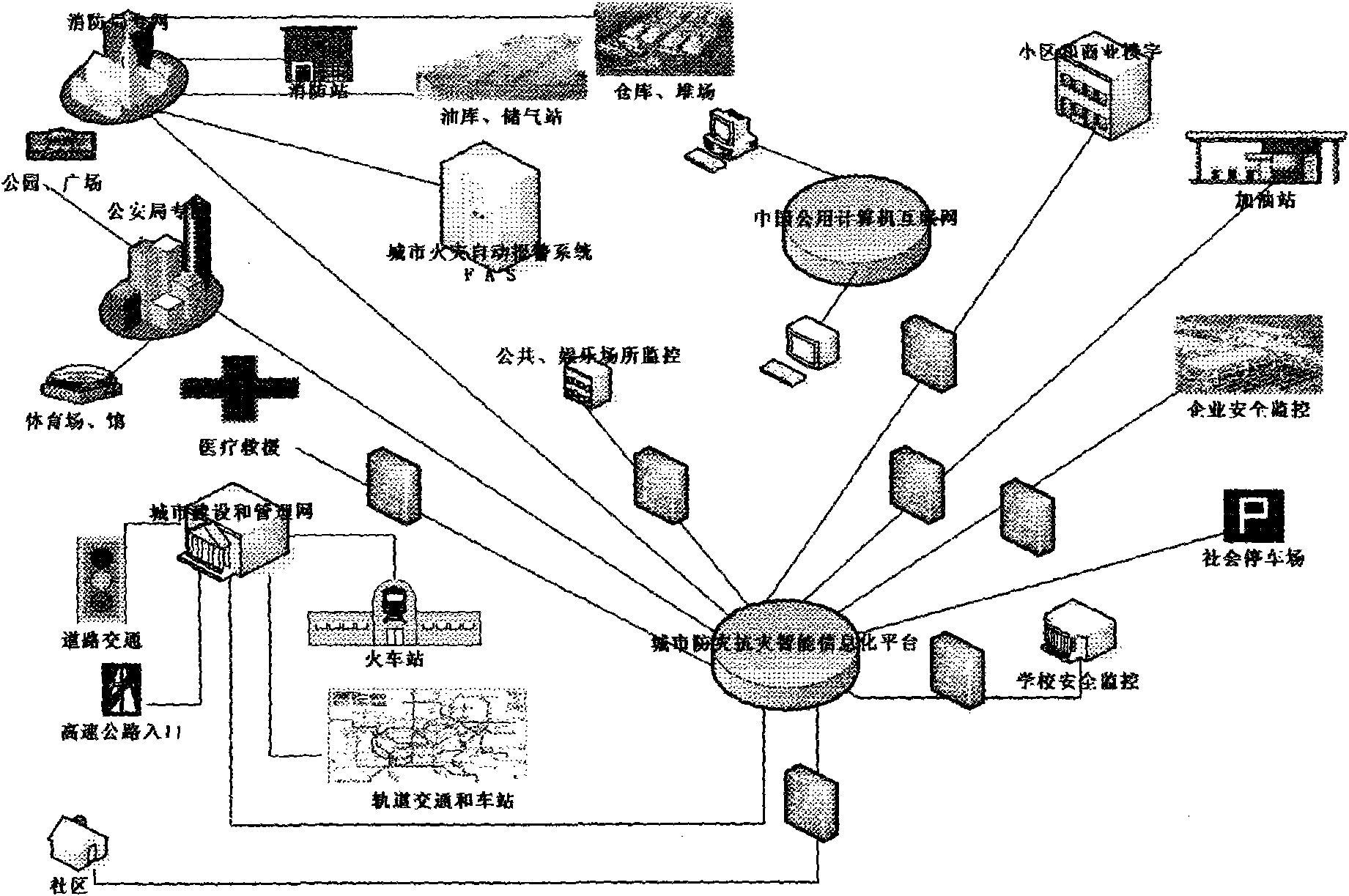
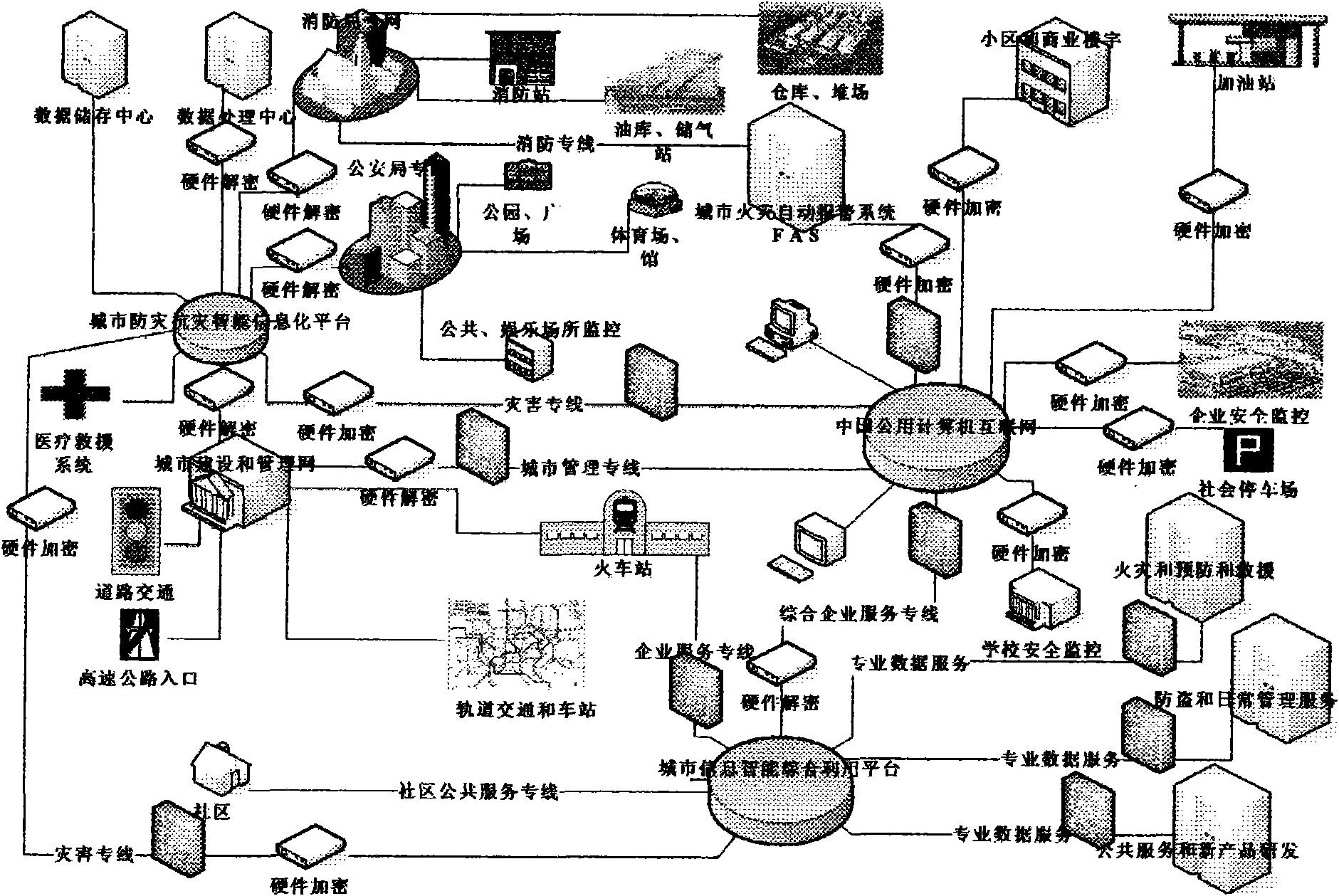
Construction method for urban disaster prevention and fighting informationalized rescue command comprehensive intelligent platform
InactiveCN101539951AUse timeImprove accuracyData switching by path configurationClosed circuit television systemsVideo monitoringDisaster area
The invention relates to a construction method for an urban disaster prevention and fighting informationalized rescue command comprehensive intelligent platform. The method organically integrates the telemetry and remote-sensing devices for video monitoring and fire detection and alarm, the CHINANET, and the acoustic and optical analysis and data transmission techniques. Through the establishment of a local area network which is connected with the CHINANET and is specialized in disaster prevention and rescue handling, the platform realizes the real-time acquisition of a great amount of disaster area information (including the information about the disaster occurrence process) in a most economical mode within the shortest time, shares the real-time information with related experts and technical staff for analysis and treatment in a safe mode, and provides a brand-new informationalized solution for the disaster cause analysis, process recording and rescue handling. The invention also provides a practical solution for the wider practical and daily application of the system. Simultaneously, the method related to data acquisition and processing also breaks an inherent data source, acquisition and transmission mode of the optical analysis.
Owner:徐东伟
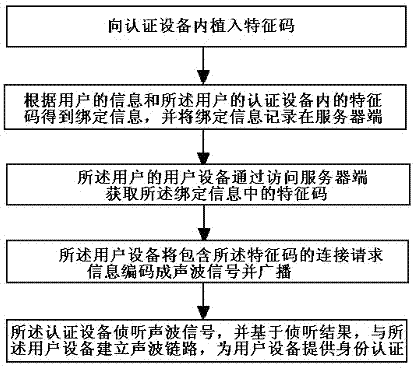
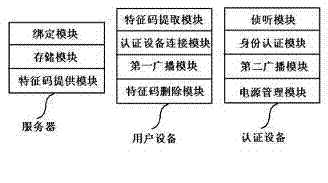
Identity authentication method and system based on sound wave communications
ActiveCN103905200AAvoid safety hazardsStrengthen trusted identity authenticationUser identity/authority verificationDigital data authenticationUser deviceDevice Monitor
The invention relates to the technical field of network security, and provides an identity authentication method and system based on sound wave communications. The method includes the steps that 1, feature codes are implanted into an authentication device; 2, binding information is obtained according to user information and the feature codes in the authentication device of a user, and the binding information is recorded in a server-side; 3, user equipment of the user has access to the server-side to obtain the feature codes in the binding information; 4, the user equipment encodes connecting request information containing the feature codes into sound wave signals and broadcasts the sound wave signals; 5, the authentication device monitors the sound wave signals, a sound wave link is established between the authentication device and the user equipment according to a monitoring result, and identity authentication is provided to the user equipment. According to the identity authentication method and system based on sound wave communications, common potential safety hazards of existing sound wave equipment are avoided, trusted identity authentication of each service system can be enhanced, the authority and the security of data of each service system are improved, power consumption of the authentication device is saved, and meanwhile user experience is improved.
Owner:BEIJING ZHONGJIN GUOXIN TECH
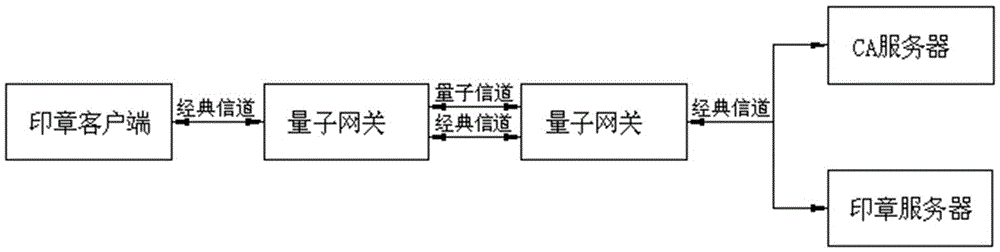
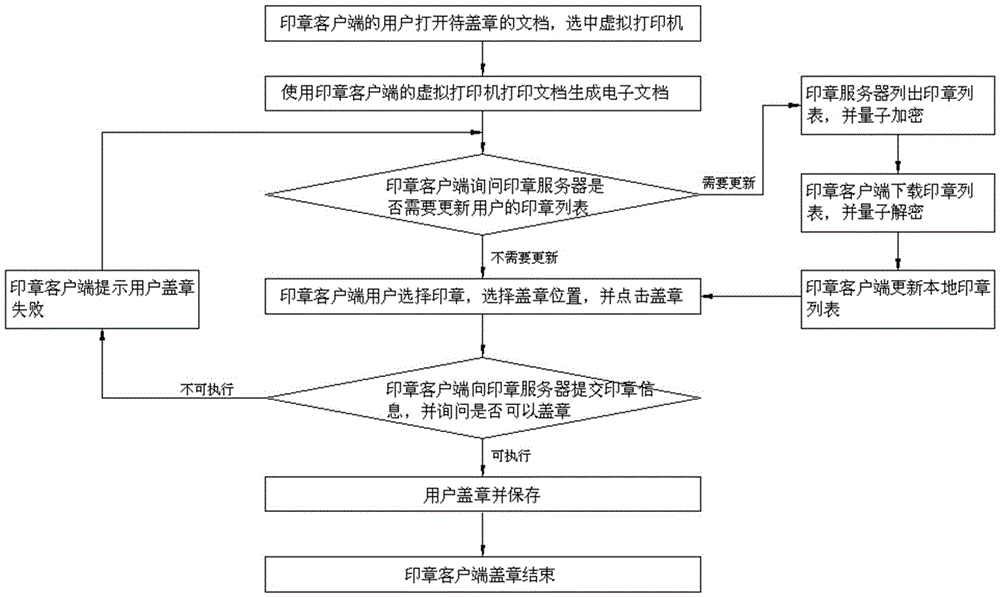
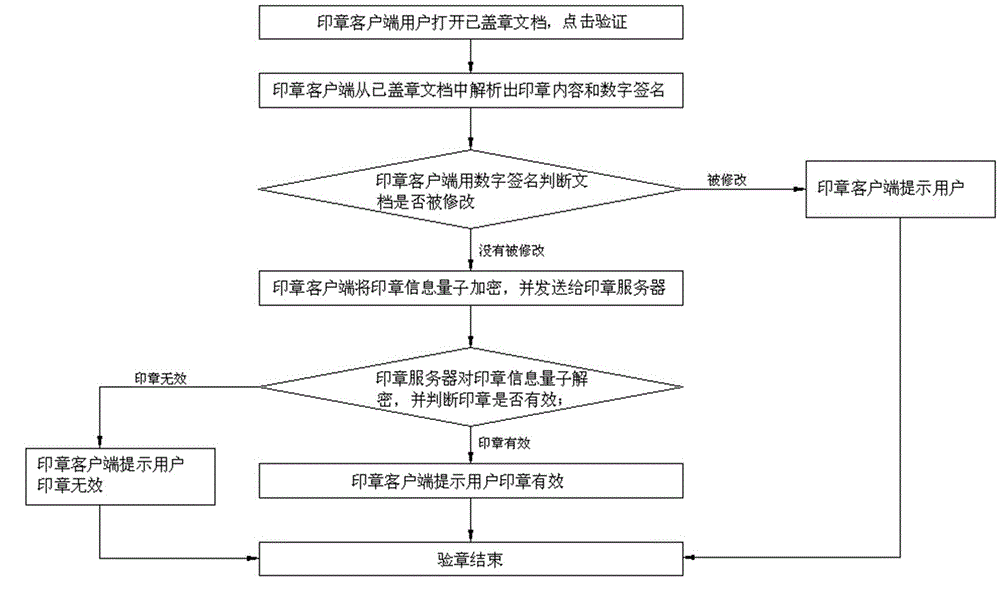
Quantum seal stamping and verifying system, and configuration, stamping process and verifying method thereof
ActiveCN105119941AGuaranteed absolute security transmissionImprove reliabilityKey distribution for secure communicationValidation methodsQuantum channel
A quantum seal stamping and verifying system provided by this invention comprises a seal client, a quantum gateway of the seal client, a server quantum gateway, a CA (Certification Authority) server and a seal server; the seal client is connected with the quantum gateway of the seal client through a classical channel; the seal server and the CA server are connected with the quantum gateway of the seal server through the classical channel; the quantum gateway of the seal client and the quantum gateway of the seal server are connected with a quantum channel through the classical channel. The invention provides a quantum seal stamping and verifying system, and a configuration, a stamping process and a verifying method thereof, wherein the system is difficult to be cracked and is capable of greatly improving the validity and the authority of the seal.
Owner:ZHEJIANG SHENZHOU QUANTUM NETWORK TECH CO LTD
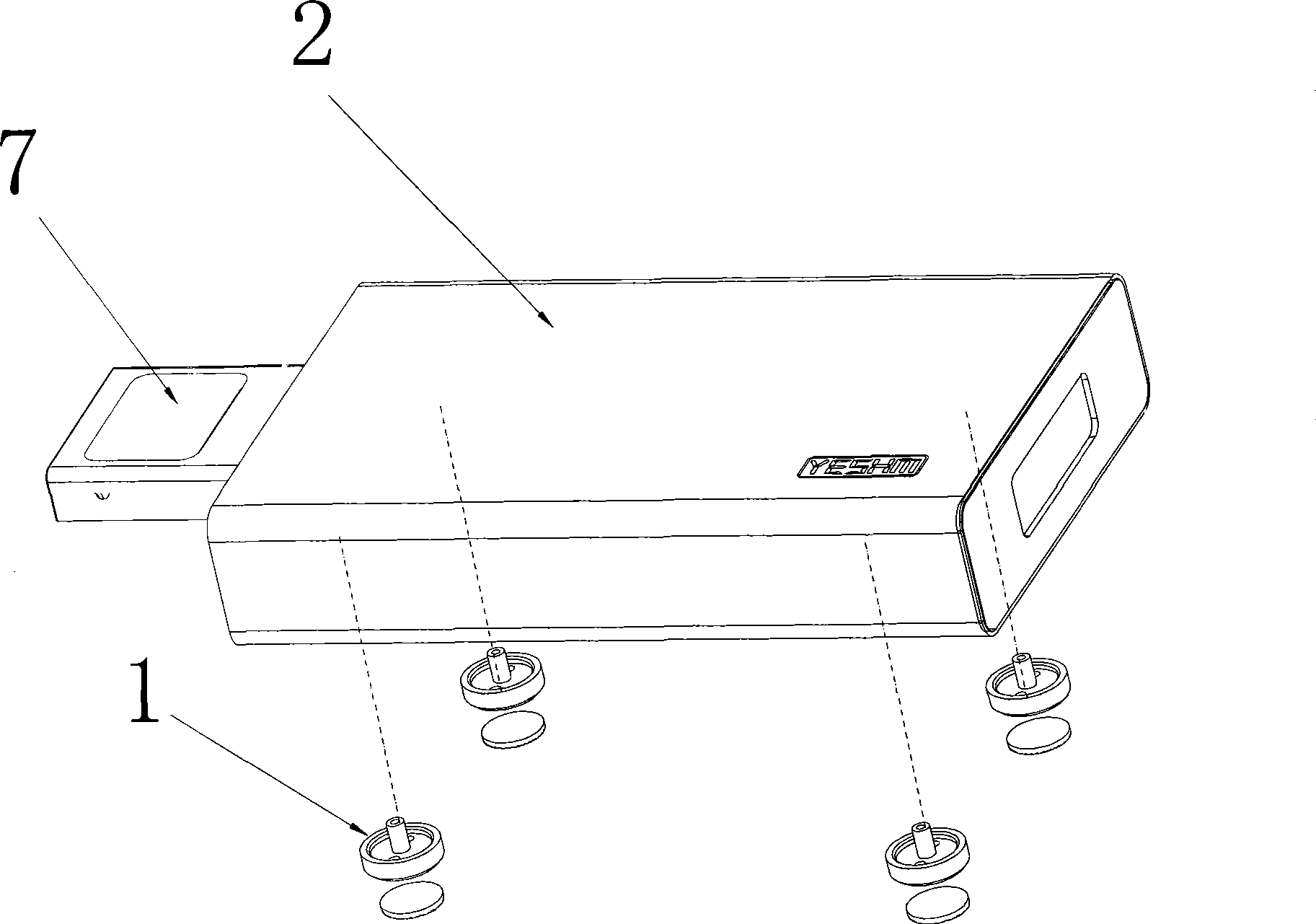
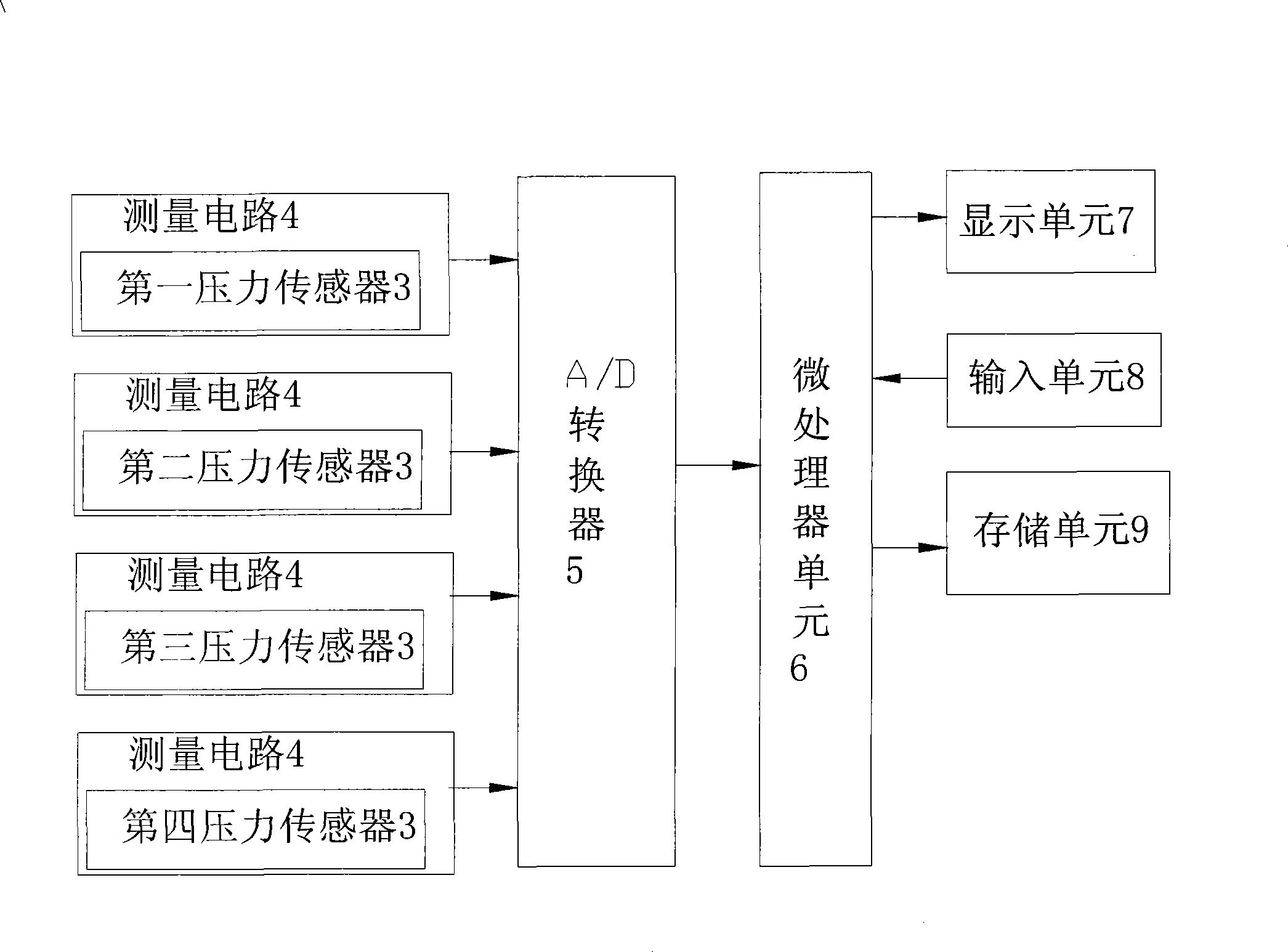
Balancing capacity measurement method as well as instrument and electronic scale with function for measuring balancing capacity
InactiveCN101433459AImprove accuracyImprove authoritySurgeryVaccination/ovulation diagnosticsCapacity valueElectric signal
The invention provides a method for measuring balanced capacity, which is characterized in that: a user stands on a bearing panel(2) by one foot, pressure sensors(3) arranged on a plurality of support legs(1) on the bottom of the bearing panel(2) can induce the center-of-gravity shift of the user, and convert the center-of-gravity shift into electric signal which is input to a microprocessor unit(6) for processing, and the microprocessor unit(6) can work out a balanced capacity value of the user. A balanced capacity measuring device and an electric scale with the balanced capacity measuring function can be manufactured by the method; moreover, the method has the advantages of scientific and reasonable measurement, high accuracy and authoritativeness, convenient use and strong interestingness.
Owner:ZHONGSHAN YESHM COMMODITIES
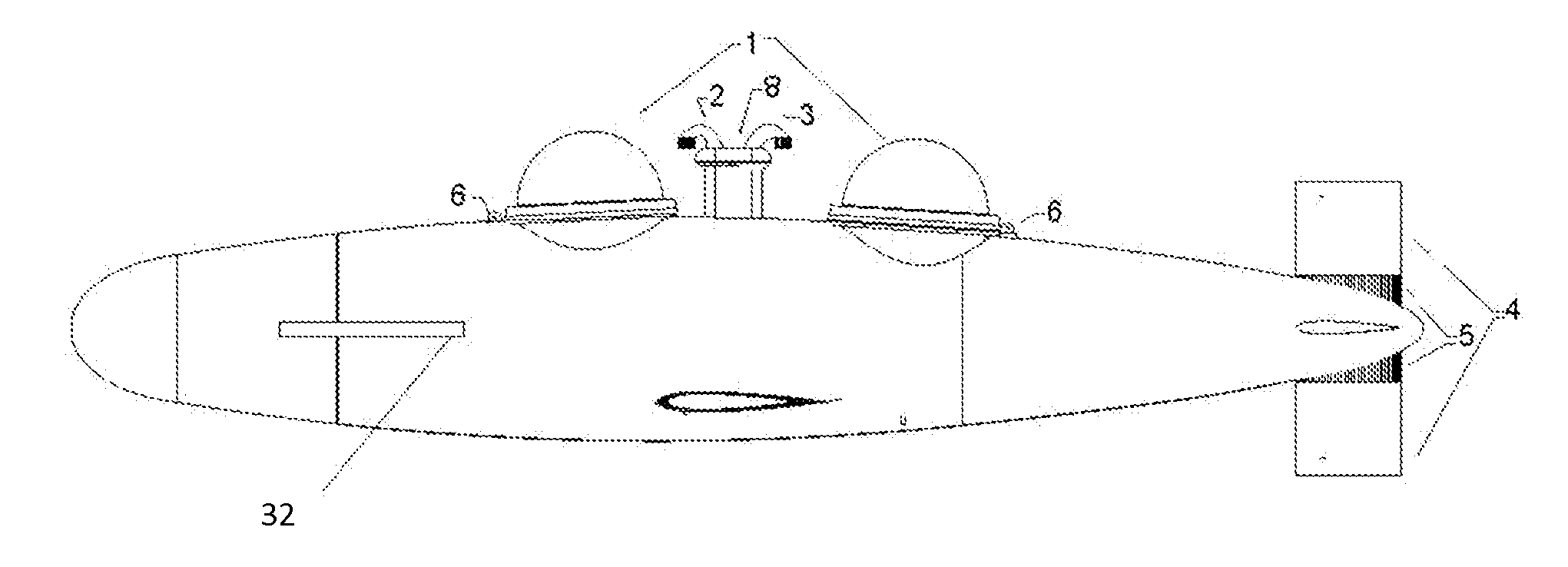
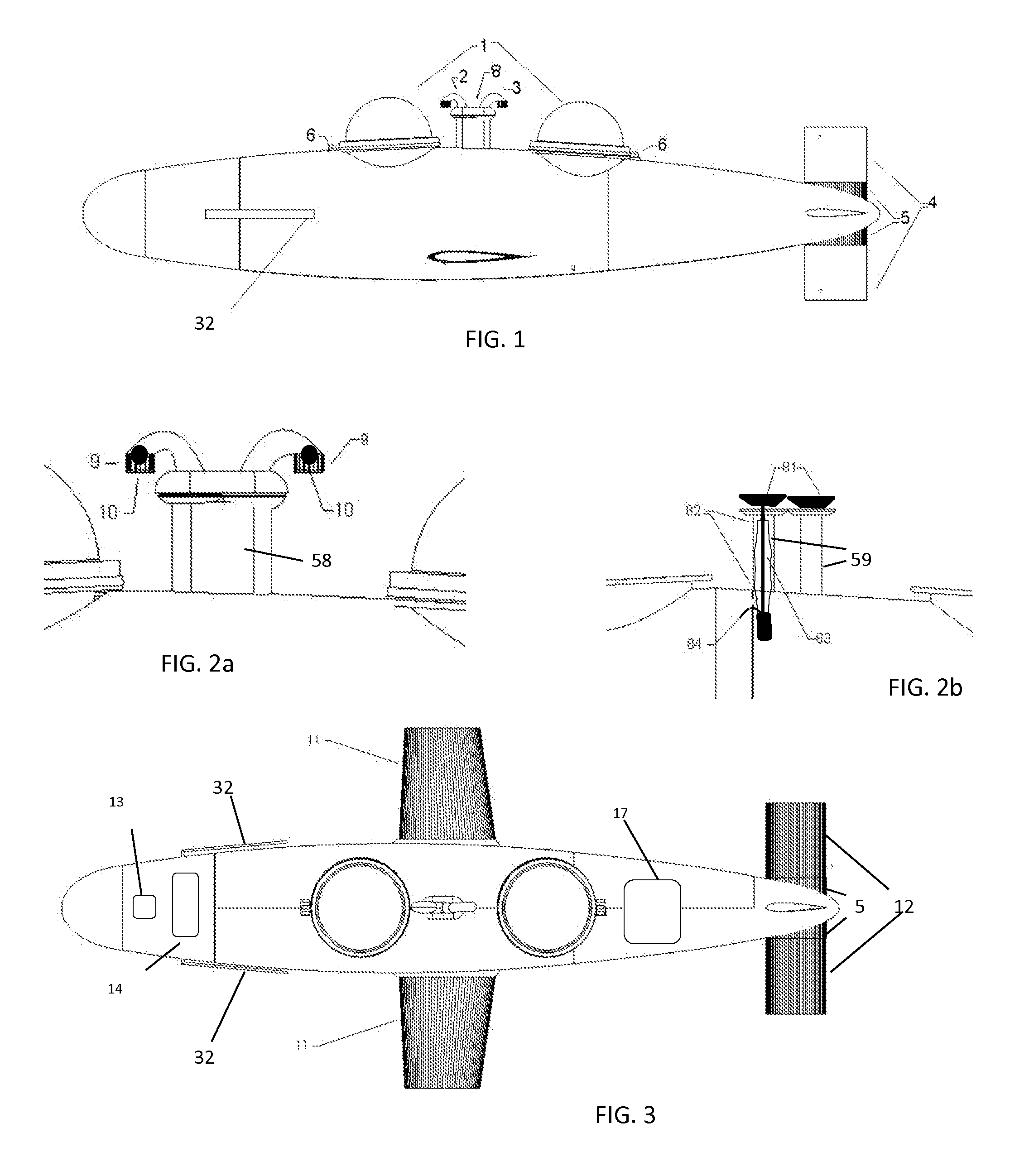
Towable pressurized dry personal submersible using surface air replenishment
InactiveUS20140090590A1Lower costMinimize dragUnderwater vesselsUnderwater equipmentAirplaneRapid transit
A submersible able to maintain one atmosphere of pressure throughout its operating envelope with the capacity to maintain a habitable atmosphere through its capability of rapid transit between underwater operating areas and the water's surface so as to replenish habitable air via a system of ducting, valves, and fans. The submersible is comprised of a towing and stability system that can vary stability about the submersible's longitudinal axis by selectively clutching or declutching the submersible's minimally stable crew compartment to the submersible's more stable bow hull, as controlled by the submersible's operator. The towing and stability system also provides the ability to propel the submersible underwater along a path of the operator's selection by aligning the tow vector within proximity of the center of gravity and then steering the submersible in three dimensions by articulating a plurality of hydroplanes which enact moments upon the submersible, thereby controlling its path.
Owner:MAURER RICHARD ROSS
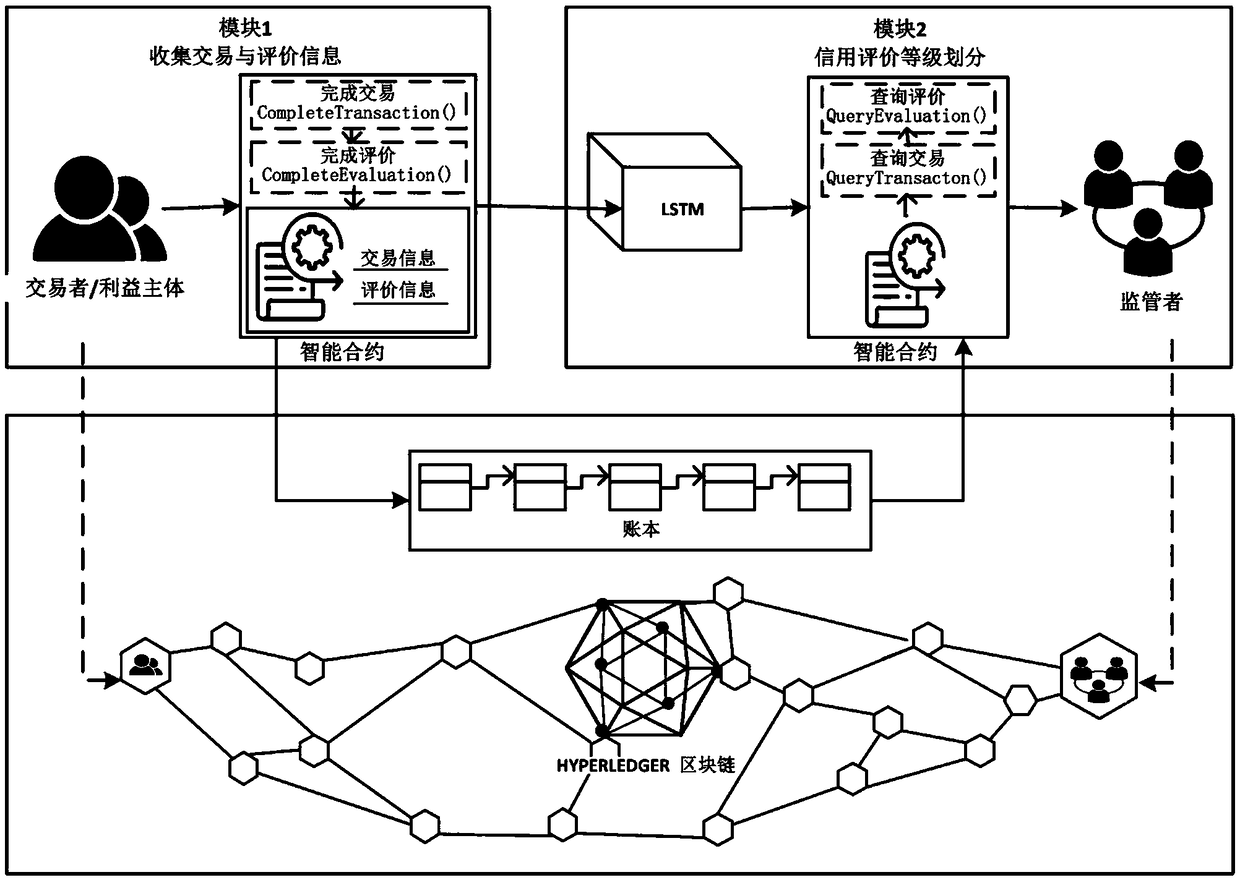
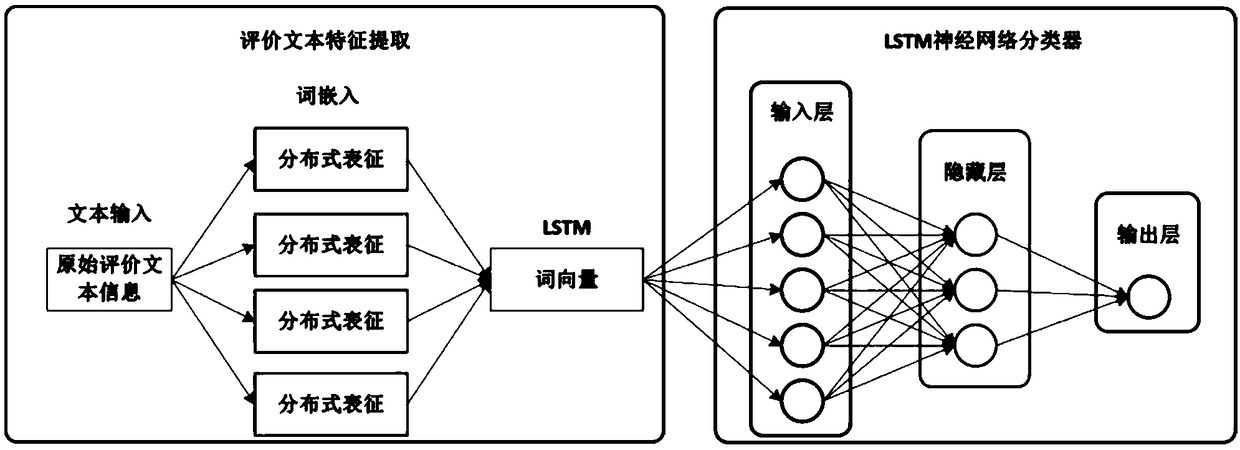
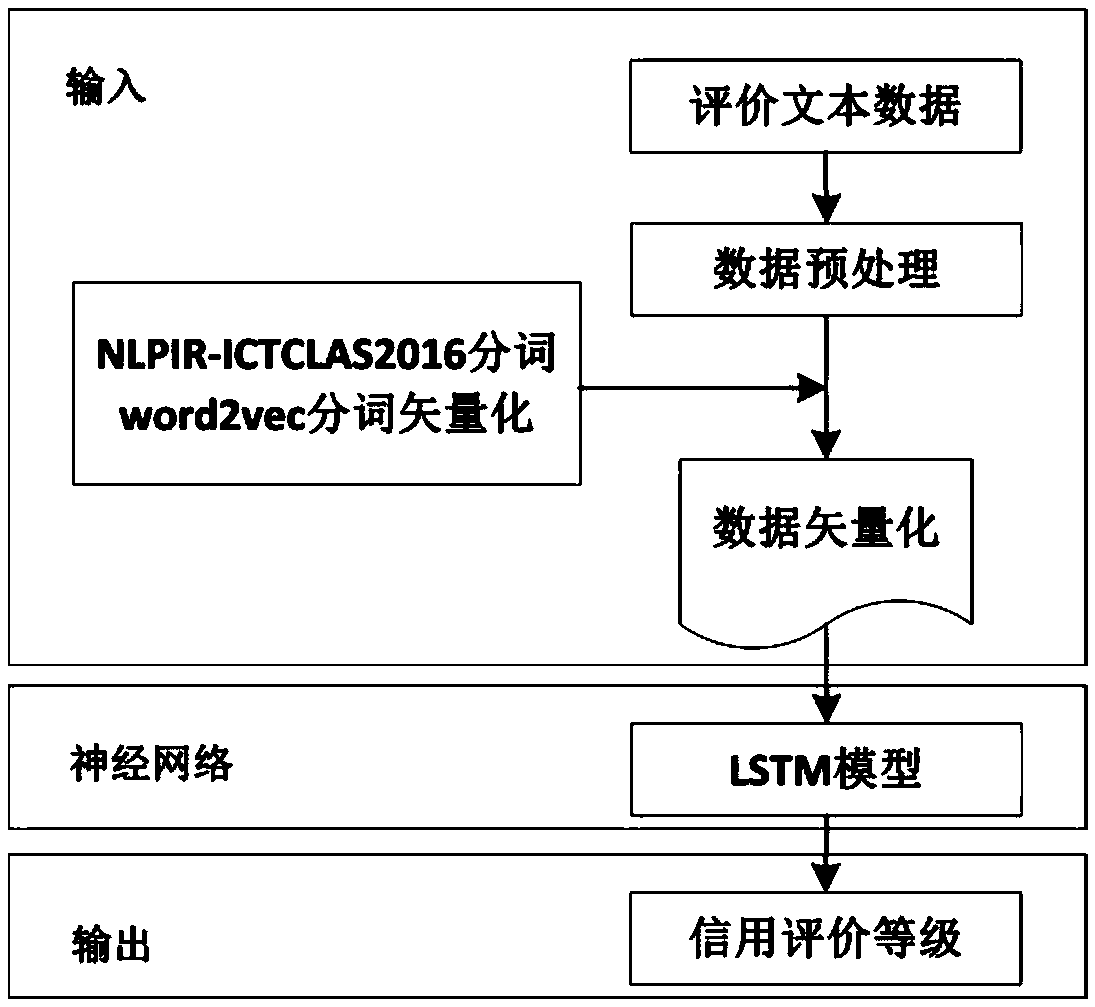
Block chain-based food safety multi-interest subject credit evaluation method
InactiveCN108717606AEasy to supervise and manageReduce regulatory costsResourcesCommerceFood supplySmart contract
The invention provides a block chain-based good safety multi-interest subject credit evaluation method. According to the method, a Hyperledger block chain is taken as a bottom support technology of the credit evaluation method, multi-interest subjects (traders) on food supply chains and supervisors are endowed with different identity authorities, and the traders are endowed with identity anonymityand evaluation result publicity and transparency during the evaluation; and the supervisors collect evaluation information, for transactions, of the multi-interest subjects on the food supply chainsthrough intelligent contracts, carry emotion analysis on the fed back evaluation information by adoption of a deep learning algorithm long and short term memory (LSTM) model, and feed credit evaluation results back to both parties of the transactions. According to the method, the efficiency and correctness of traditional credit evaluation systems are improved and the effectiveness of food safety supervision is enhanced.
Owner:BEIJING TECHNOLOGY AND BUSINESS UNIVERSITY
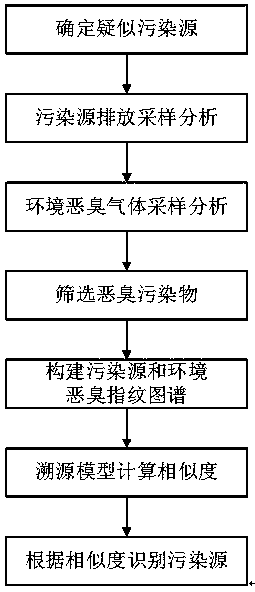
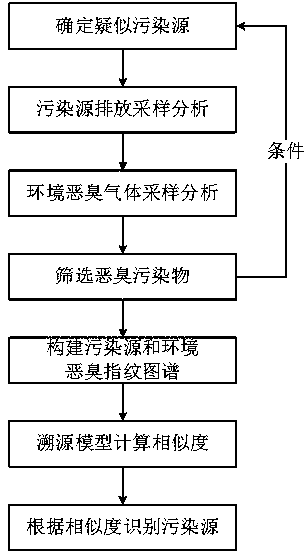
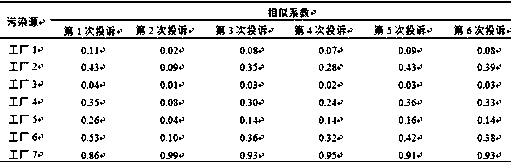
Stink fingerprint spectrum based stink pollution source tracing method and application thereof
ActiveCN108760912AAccurate identificationOvercoming technical deficienciesComponent separationEnvironmental stewardshipSource tracing
The invention relates to a stink fingerprint spectrum based stink pollution source tracing method. The method comprises the following steps: A, determining a suspected pollution source; B, discharging, sampling, analyzing the pollution source; C, sampling and analyzing an environment stink gas; D, screening a stink pollutant; E, constructing a pollution source and environment stink fingerprint spectrum; F, calculating the similarity through a source tracing mode; and G, identifying the pollution source according to the similarity. The stink fingerprint spectrum is constructed through the fingerprint spectrum technology and the odor threshold of a stink substance, the similarity coefficient of the pollution source and environment stink fingerprint spectrum is calculated by using an includedangle cosine method, so that the possible source of the stink pollution is judged, the source of the stink pollution is rapidly and accurately identified, the difficult problem of tracing the sourceof the stink pollution is solved, the technical defect of complaint management of the stink pollution is overcome, and the effectiveness and the authority in supervision and law enforcement of the stink pollution of the environmental management department are improved.
Owner:天津市生态环境科学研究院(天津市环境规划院 +1
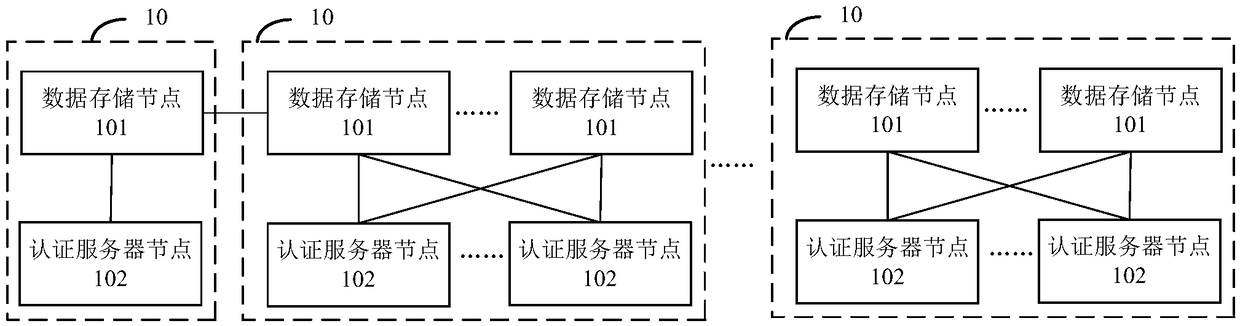
Whole-network unified online authentication method and system based on block chain
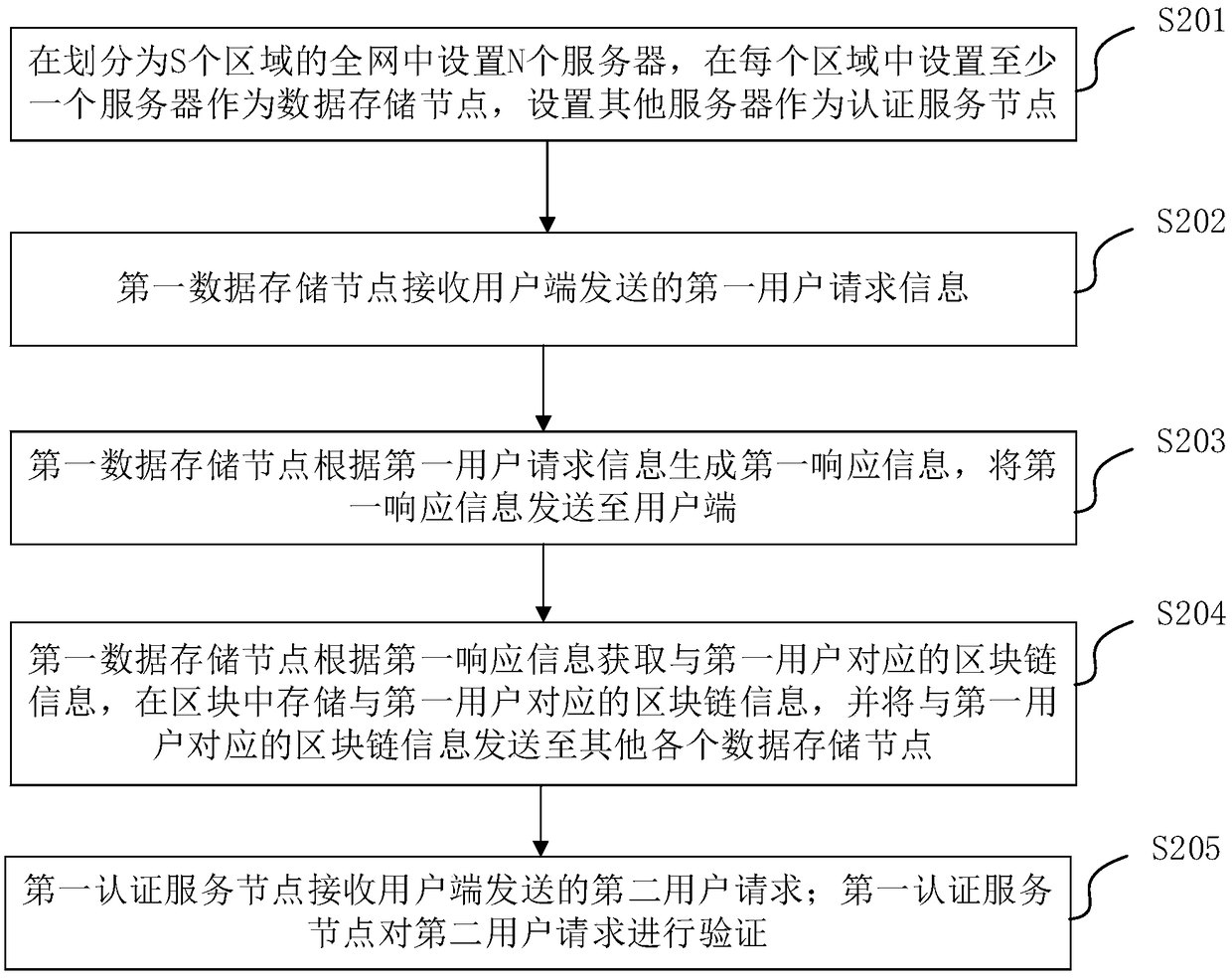
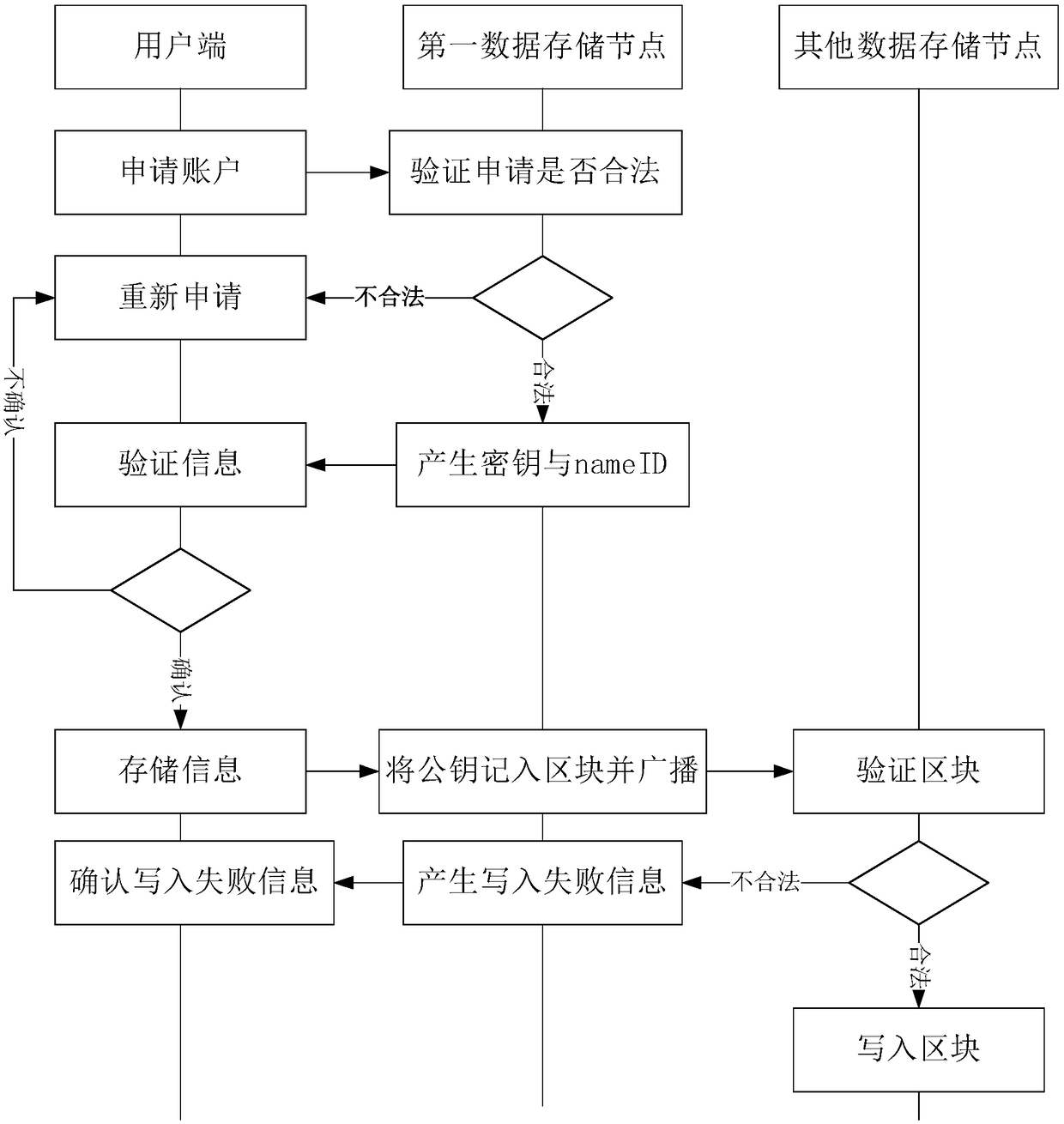
The invention provides a whole-network unified online authentication method and system based on a block chain. The method comprises the following steps that N servers are arranged in the whole networkdivided into S areas, and at least one server is arranged in each area to serve as a data storage node, wherein other servers are set as authentication service nodes; a first data storage node receives first user request information sent by a user side; the first data storage node generates first response information according to the first user request information, and sends the first response information to the user side; the first data storage node acquires block chain information corresponding to a first user according to the first response information, stores the block chain information corresponding to the first user in a block, and sends the block chain information corresponding to the first user to other data storage nodes; and the first authentication service node receives a second user request sent by the user side, and verifies the second user request.
Owner:BEIJING INFORMATION SCI & TECH UNIV
Motor vehicle headlamp luminous intensity distribution property self-adaption detection method based on camera method
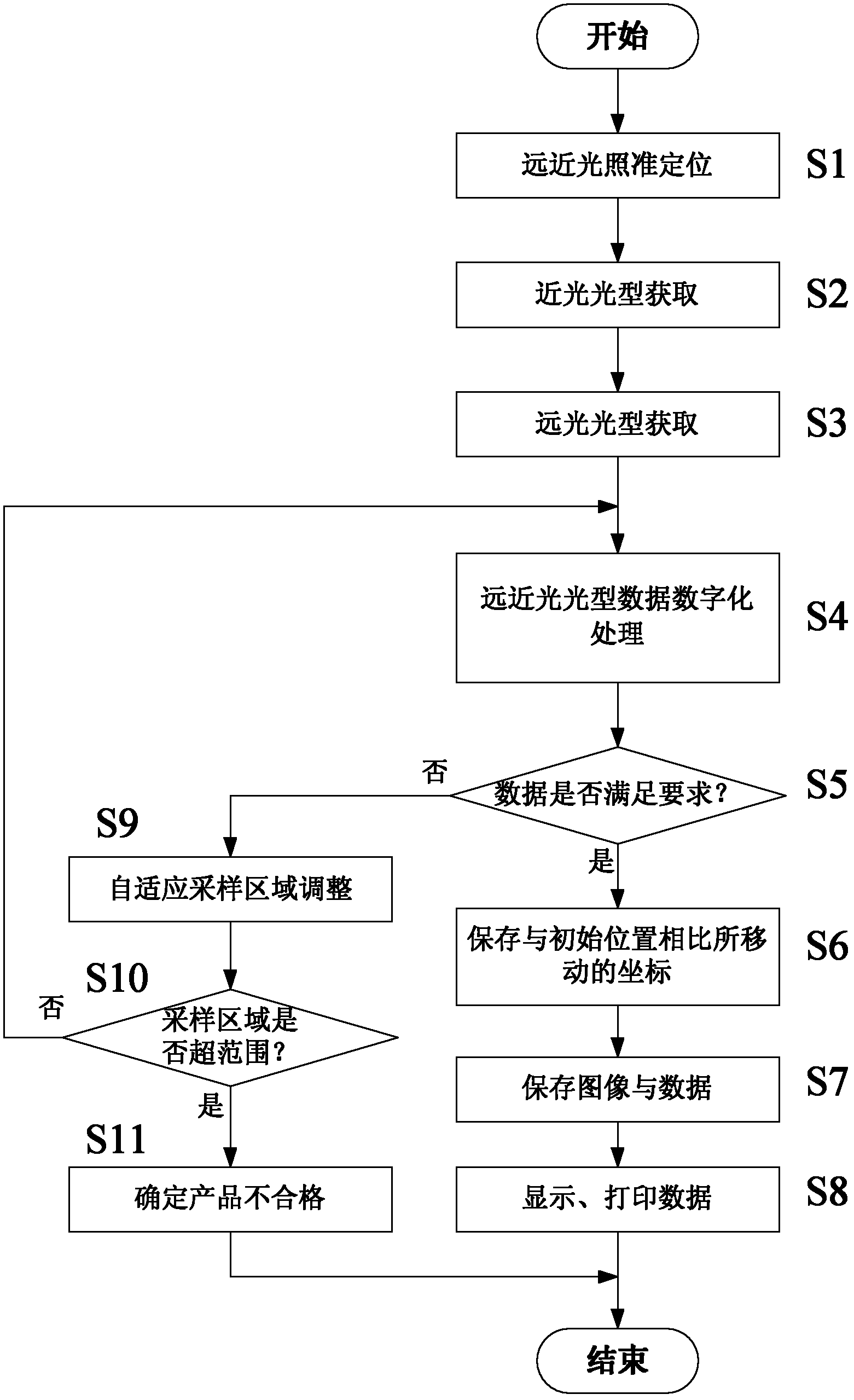
InactiveCN102323044AShorten the timeImprove authorityTesting alignment of vehicle headlampsLuminous intensityComputer vision
The invention discloses a motor vehicle headlamp luminous intensity distribution property self-adaption detection method based on camera method, which comprises the following steps of: performing quasi-positioning on far and near illumination; acquiring the light type of lower beams, acquiring the light type of upper beams; digitally processing light type data of upper and lower beams; judging whether the data meets a certain requirement or not; storing coordinates of movement compared with an initial position; storing images and the data; printing and displaying data; carrying out self-adaption sampling region adjustment; judging whether the sampling region surpasses a certain range or not; determining whether a product is qualified, and the like. By adopting the motor vehicle headlamp luminous intensity distribution property self-adaption detection method based on camera method, all possible measurement can be realized by performing one-step collimation of the motor vehicle headlamp luminous intensity distribution property self-adaption detection system in the prior art; and if a lamp at a collimation position is unqualified, other positions where the lamp is qualified can be searched through software without collimating or testing once again, so that the detection testing time can be shortened, and the possibility of passed inspection and the authority and accuracy of detection can be increased.
Owner:TIANJIN INTERNAL COMBUSTION ENGINE RES INST
SIP-based integrated interconnection management system of internet of things
InactiveCN101877718AExtensionMobile allowedNetwork topologiesWireless network protocolsComputer networkThe Internet
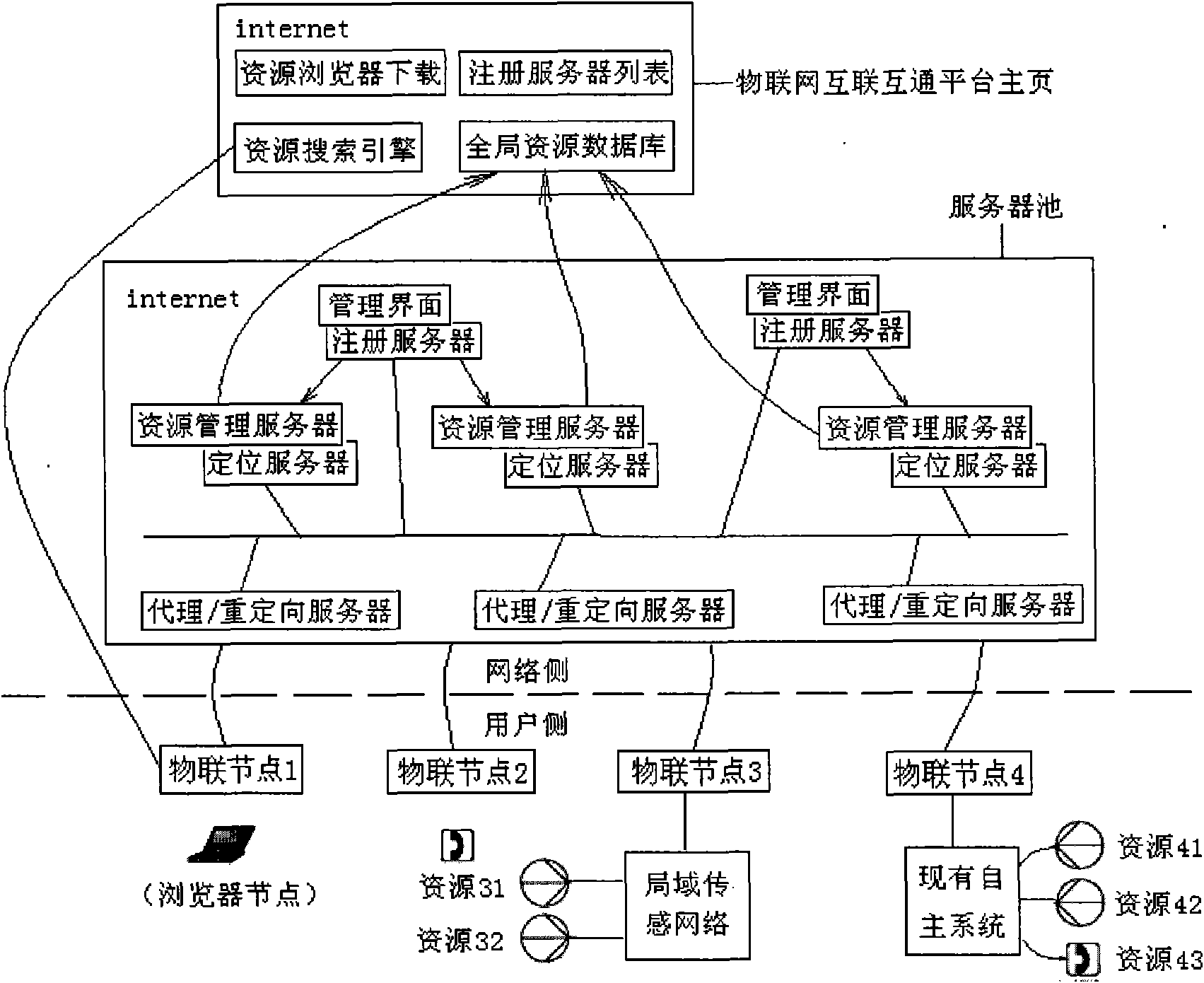
The invention relates to an SIP-based integrated interconnection management system of the internet of things, comprising an integrated interconnection management platform and a things connection node set which interact with each other through the extended SIP, wherein the integrated interconnection management platform is used for managing the global resource database, the things connection nodes and register of the things connection nodes, providing the resource search service and dynamically establishing mutual access among a plurality of things connection nodes in the things connection node set. The invention relates to a special things connection node called browser node. A plurality of resources of the internet of things can be simultaneously accessed in a window of browser users by operating software of a resource browser of the internet of things on the computer, thus ensuring immediate establishment of an application system of the internet of things to be possible. In the invention, the existing resources which are not in the application system of the internet of things or a local sensor network system can be brought into the integrated interconnection management system of the internet of things by consistent means by utilizing the extended SIP.
Owner:蒋涵民
Data mining in a digital map database to identify unusually narrow lanes or roads and enabling precautionary actions in a vehicle
ActiveUS9182241B2Improve authorityHigh sensitivityInstruments for road network navigationRoad vehicles traffic controlRoad networksPositioning system
Disclosed is a feature for a vehicle that enables taking precautionary actions in response to conditions on the road network around or ahead of the vehicle, in particular, an unusually narrow road width or lane width. A database that represents the road network is used to determine locations where an unusually narrow road width or lane width exists along roads. Then, precautionary action data is added to the database to indicate a location at which a precautionary action is to be taken about the location where the unusually narrow road width or lane width exists. A precautionary action system installed in a vehicle uses this database, or a database derived therefrom, in combination with a positioning system to determine when the vehicle is at a location that corresponds to the location of a precautionary action. When the vehicle is at such a location, a precautionary action is taken by a vehicle system as the vehicle is approaching a location where the unusually narrow road width or lane width exists.
Owner:HERE GLOBAL BV
Data mining in a digital map database to identify decreasing radius of curvature along roads and enabling precautionary actions in a vehicle
ActiveUS8698649B2Improve authorityHigh sensitivityInstruments for road network navigationArrangements for variable traffic instructionsRoad networksComputer science
Owner:HERE GLOBAL BV
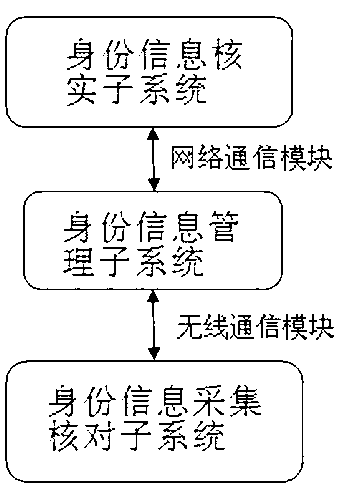
Identity authentication and management system based on biological feature identification technology
InactiveCN103226703AImprove speedImprove accuracy and authorityCharacter and pattern recognitionComputer securityManagement system
The invention provides an identity authentication and management system based on a biological feature identification technology. The system is characterized by comprising an identity information collection and verification subsystem, an identity information management subsystem and an identity information verification subsystem, wherein the identity information collection and verification subsystem is connected with the identity information management subsystem through 3G communication; and the identity information verification subsystem is connected with the identity information management subsystem through a network. According to the identity authentication and management system, the authenticity of an identity card is distinguished by using the relevant biological feature identification technology in combination with the identity information, whether the biological feature information of a person to be verified accords with the information of the identity card is judged through comparison, and the identity information of citizens and the relevant biological feature information and previous authentication result of the person to be verified are processed, analyzed and managed by using a big data mechanism, so that the authentication rapidity is improved, and the accuracy and authority of identity authentication are improved through multi-level verification.
Owner:QINGDAO UNIV OF SCI & TECH
Method and apparatus for determining address information in home page of official website
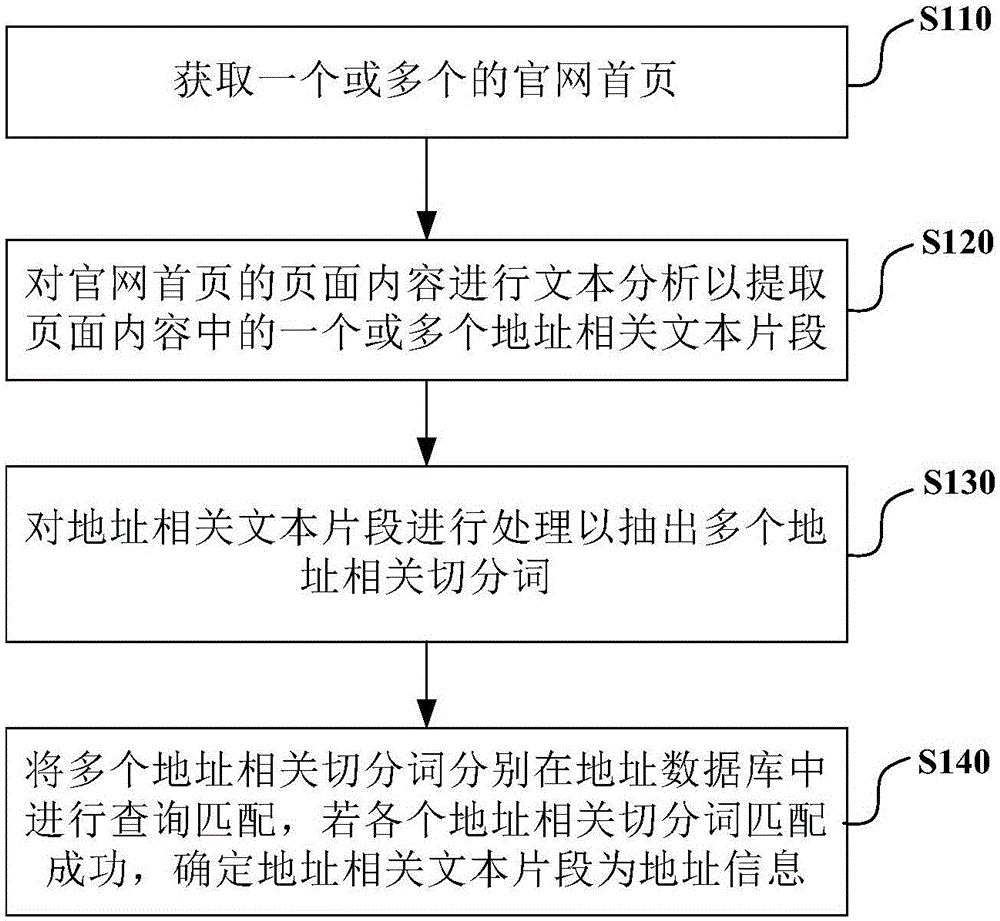
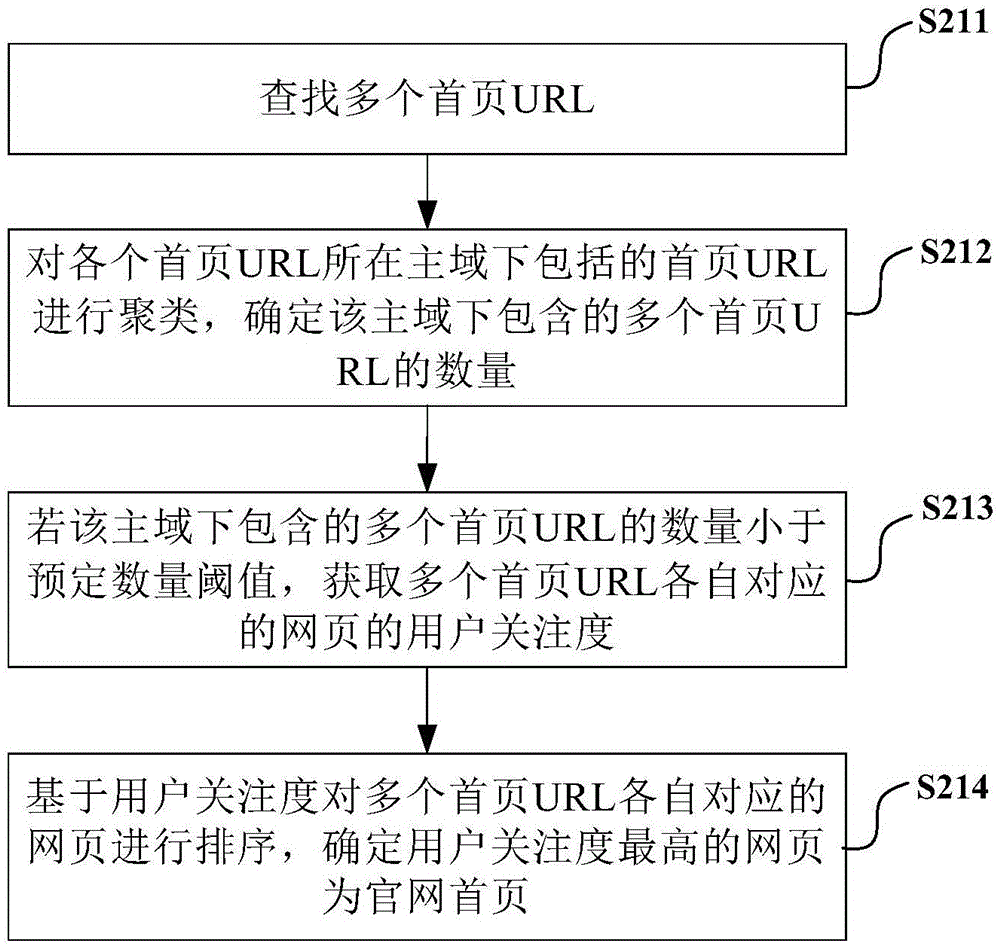
InactiveCN105069076AImprove authorityImprove accuracySpecial data processing applicationsWeb data retrieval using information identifiersHome pageWorld Wide Web
The present invention provides a method for determining address information in a home page of an official website. The method comprises: acquiring one or more home pages of an official website; performing text analysis on a page content of the home page of the official website so as to extract one or more address related text segments in the page content; performing processing on the address related text segment so as to extract a plurality of address related segmenting words; and respectively performing query and matching on the plurality of address related segmenting words in an address database, and if each address related segmenting word is matched successfully, determining that each address related text segment is address information. According to the embodiment of the present invention, the home page of the official website is determined in a large number of home pages, and the address information is determined based on the page content of the home page of the official website, so that the address information with relatively high authority and validity in the official website can be rapidly acquired, and strong guarantee is provided for a manner of detecting POI data based on the address information in the official website.
Owner:BEIJING QIHOO TECH CO LTD +1
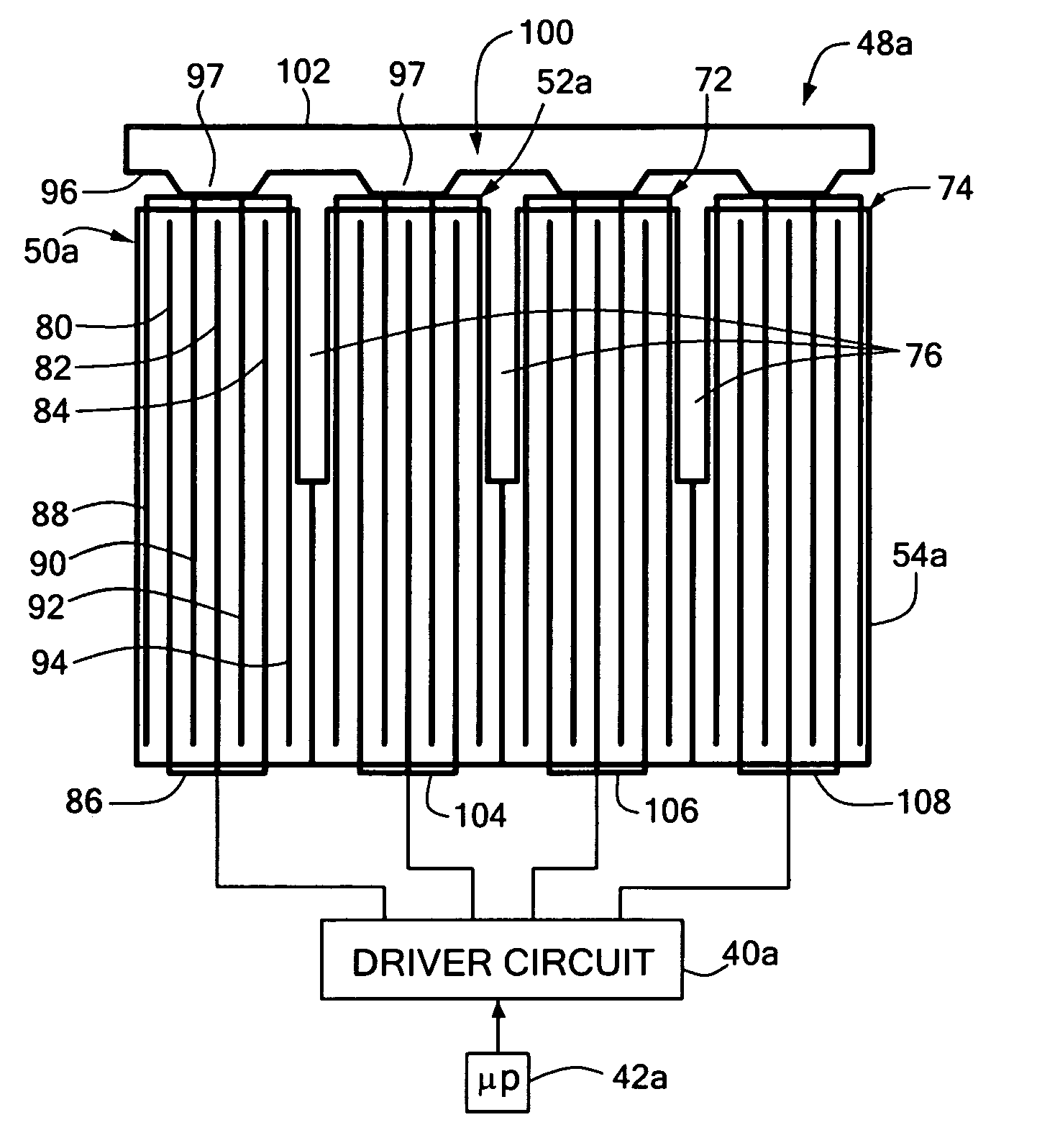
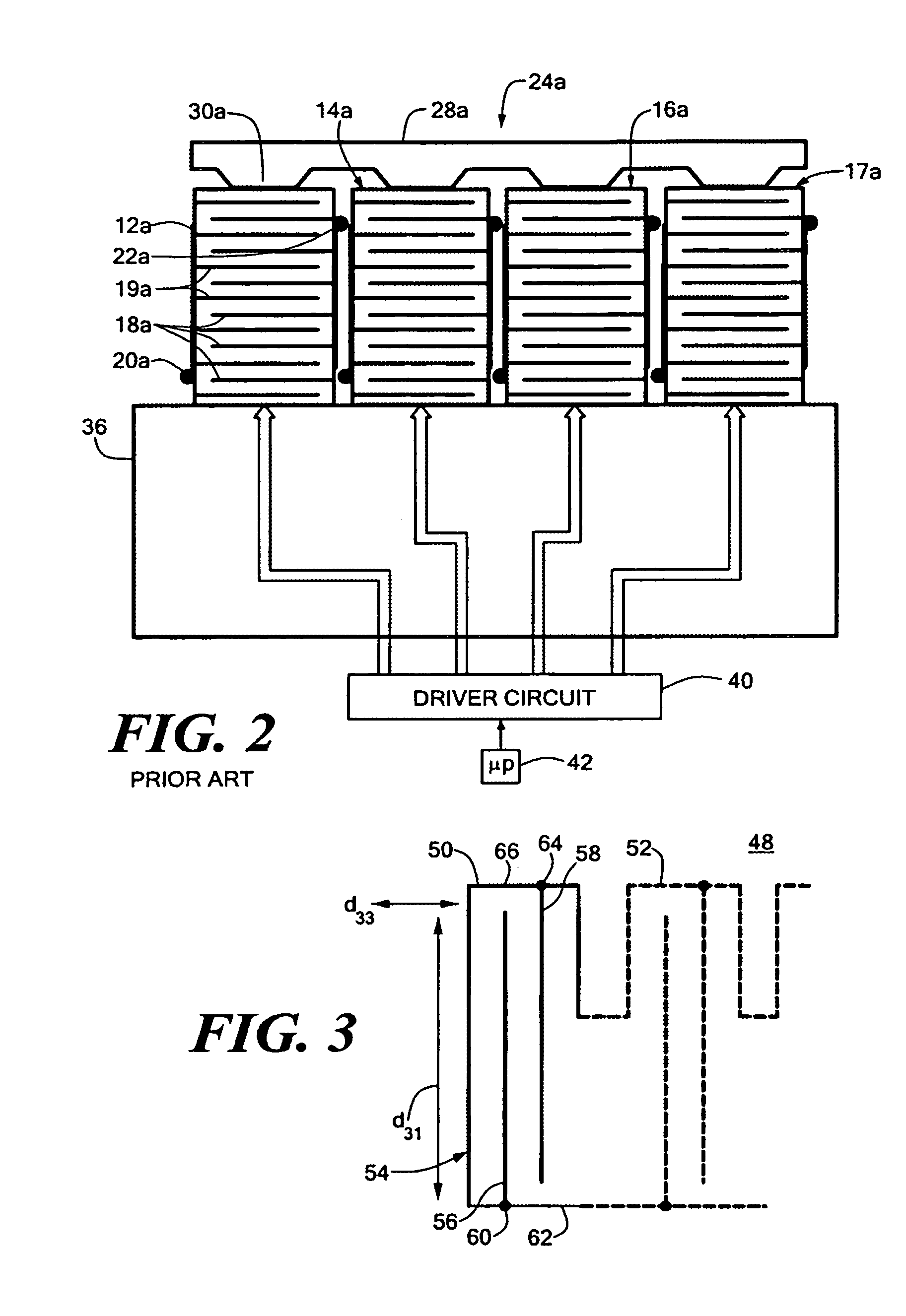
Transverse electrodisplacive actuator array
A transverse electrodisplacive actuator array for controlling the optical phasing of a reflective surface includes a support structure; a plurality of electrodisplacive actuator elements extending from a proximate end at the support structure to a distal end; each actuator element including at least one addressable electrode and one common electrode spaced from the addressable electrode and extending along the direction of said proximate and distal ends along the transverse d31 strain axis; a reflective member having a reflective surface and a mounting surface mounted on the actuator elements; and a plurality of addressable contacts and at least one common contact for applying voltage to the addressable and common electrodes to induce a transverse strain in addressed actuator elements to effect an optical phase change in the reflective surface at the addressed actuator elements.
Owner:NORTHROP GRUMMAN SYST CORP
Distributed authentication method based on pre-shared key
InactiveCN105323754AEnsure safetyThe authentication result is reliableSecurity arrangementAccess networkEphemeral key
The invention discloses a distributed authentication method based on a pre-shared key (PSK). The method comprises the following steps that the PSK is acquired before a request access network node accesses the network and a success access network node is selected to be an authentication node so as to carry out bidirectional authentication; during each bidirectional authentication, two parties generate random numbers respectively; according to the PSK and the random numbers, a temporary key and a verification key are generated and are used for encrypting an authentication interaction message and verifying an identity of an opposite side respectively; the two parties locally maintain one identification sequence number which is used for identifying an effective bidirectional authentication; during a bidirectional authentication process, one party recovers the temporary key and the verification key of the opposite side according to the PSK and the random number of the opposite side, receives and decrypts the opposite side identification sequence number and then compares with a local identification sequence number; whether a replay attack prevention condition is satisfied is verified; if the replay attack prevention condition is not satisfied, the bidirectional authentication is invalid; if the replay attack prevention condition is satisfied, the recovered verification key of the opposite side is sent to the opposite side; after receiving and decrypting, the opposite side verifies whether the verification key is the same with the verification key generated by the opposite side itself; if the verification key is not the same with the verification key generated by the opposite side itself, the authentication is failed; and if the verification key is the same with the verification key generated by the opposite side itself, the identity of one party is valid.
Owner:BEIJING XINWEI TELECOM TECH +1
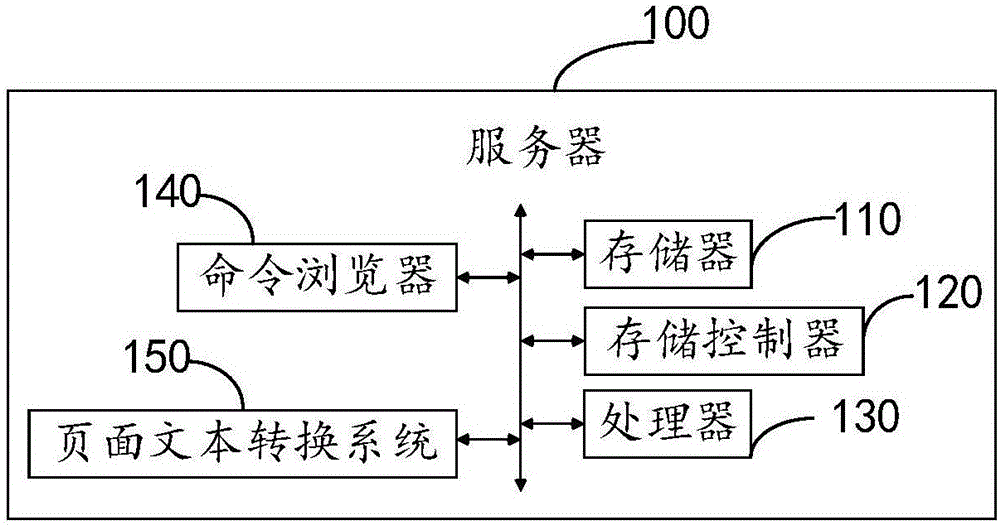
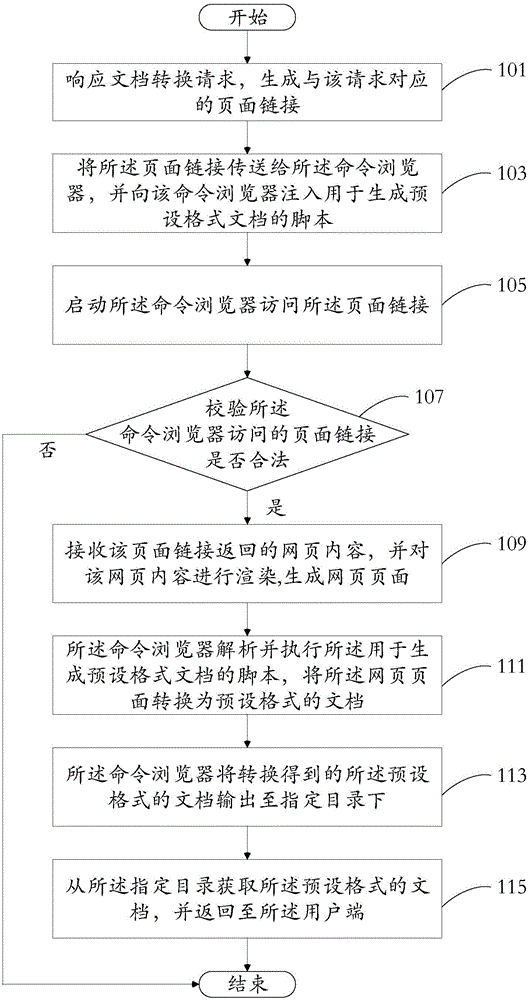
Page text conversion method and system
InactiveCN106354700AImprove reading experienceImprove authorityNatural language data processingSpecial data processing applicationsNetwork communicationDocumentation
The embodiment of the invention provides a page text conversion method and system, and belongs to the technical field of network communication. The method comprises the steps that 1, a document conversion request sent by a user side is responded, a page link corresponding to the request is generated and transmitted to a command browser, and a script used for generating a document with a default format is injected into the command browser; 2, the command browser is started to access the page link, and the received web content returned by the page link is rendered to generate a web page; 3, the command browser analyzes and executes the script to convert the web page into the document with the default format. According to the method and system, the condition that a dynamic complex HTML text is converted into the document, such as a PDF document, with the default format is supported, the content of documents viewed by the user is richer, and the user experience is improved.
Owner:GUANGZHOU AIJIUYOU INFORMATION TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com