Patents
Literature
2058 results about "Device Monitor" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
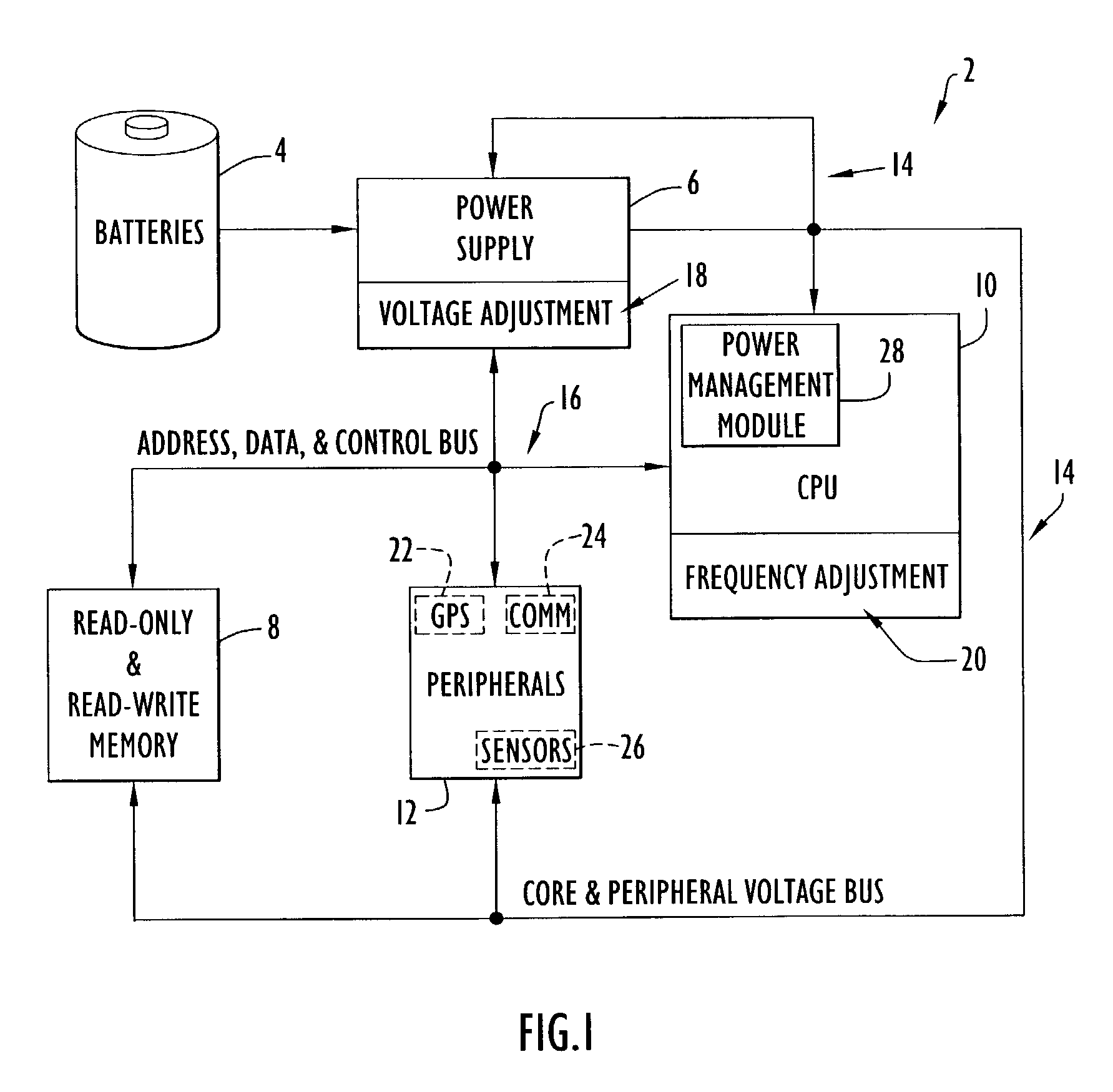
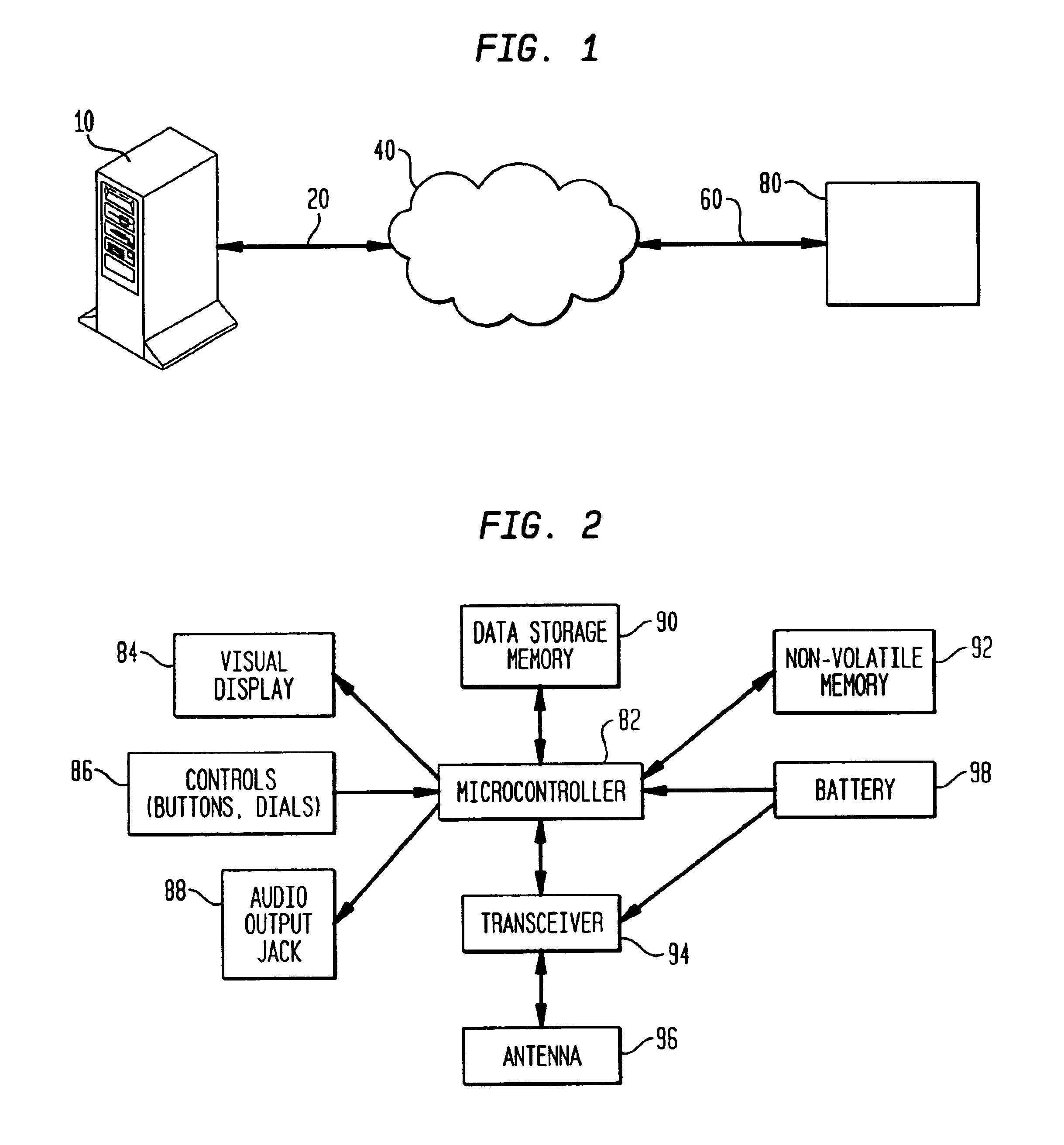
Method and apparatus for optimizing performance and battery life of electronic devices based on system and application parameters
InactiveUS7111179B1Reduce power consumptionExtending device operating lifeEnergy efficient ICTBatteries circuit arrangementsOperational systemElectrical battery
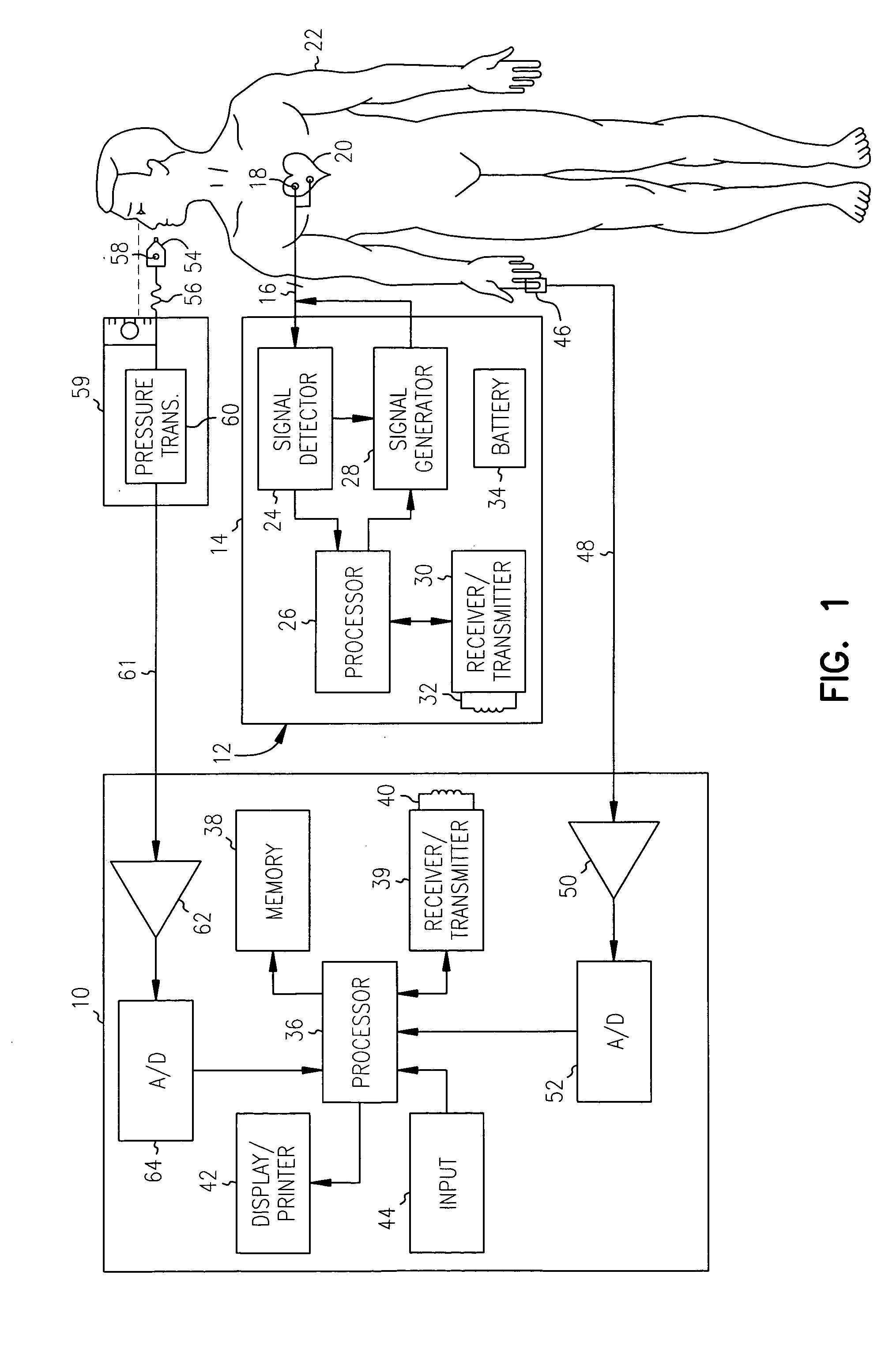
An electronic device (e.g., computer system, etc.) employing dynamic power management of the present invention adjusts power consumption in accordance with an analysis of parameters and events occurring over one or more time-periods. Preferably, the electronic device monitors microprocessor, operating system, peripheral and / or device-level events and adjusts run-time parameters, such as microprocessor clock frequency and voltage, to reduce power consumption with minimal perceived degradation in performance.
Owner:MOSAID TECH
Wireless multimedia player
InactiveUS6845398B1Network traffic/resource managementMultiple digital computer combinationsWireless mesh networkMultimedia servers
A wireless device, system and method for receiving and playing multimedia files streamed from a multimedia server over a wireless telecommunications network. A desired multimedia file is selected from one or more multimedia files stored in the multimedia server, which server is operatively connected to the wireless telecommunications network. Successive blocks of data from the desired multimedia file are streamed over the wireless telecommunications network in a digitized and compressed format and received by the wireless telecommunications device. The received blocks of data from the streamed multimedia file are temporarily stored in a buffer in the wireless device, decoded and decompressed, and successively played through an audio and / or video output in the wireless device. The wireless device monitors the blocks of data stored in the buffer and signals the wireless telecommunications network to increase the rate that the data blocks are transmitted over the wireless network in the event that the data stored in the buffer falls below a minimum threshold level.
Owner:LUCENT TECH INC
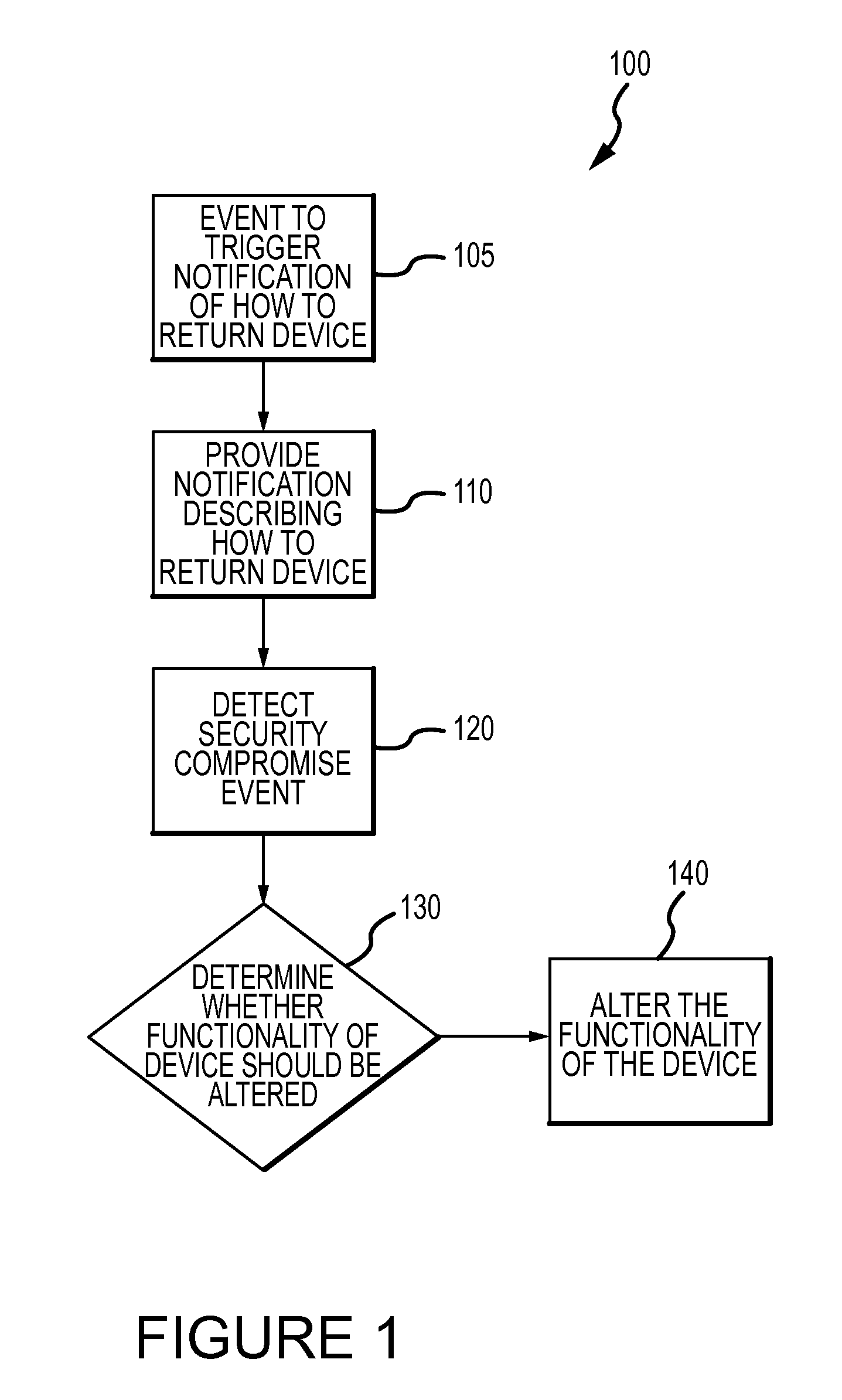
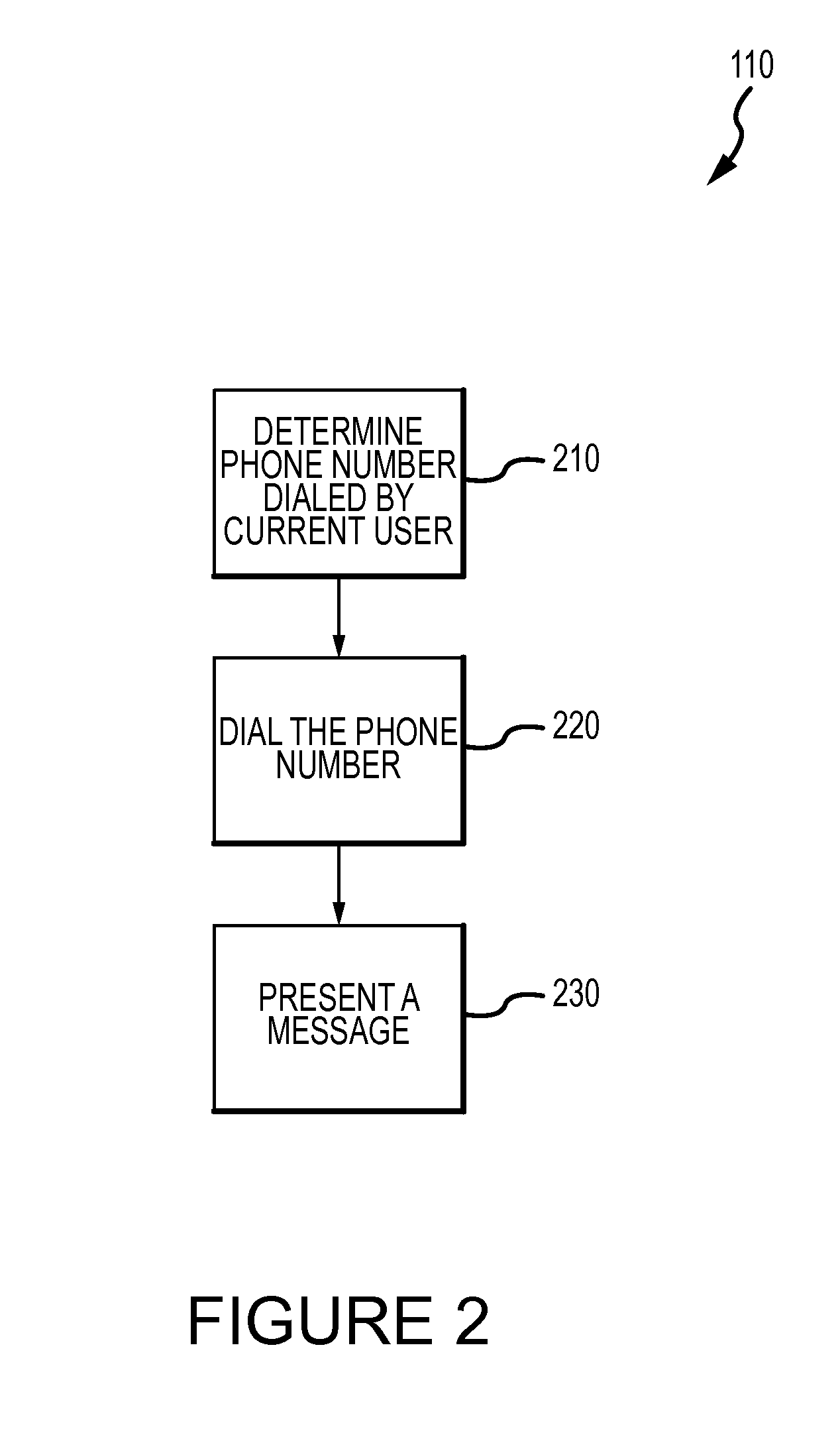
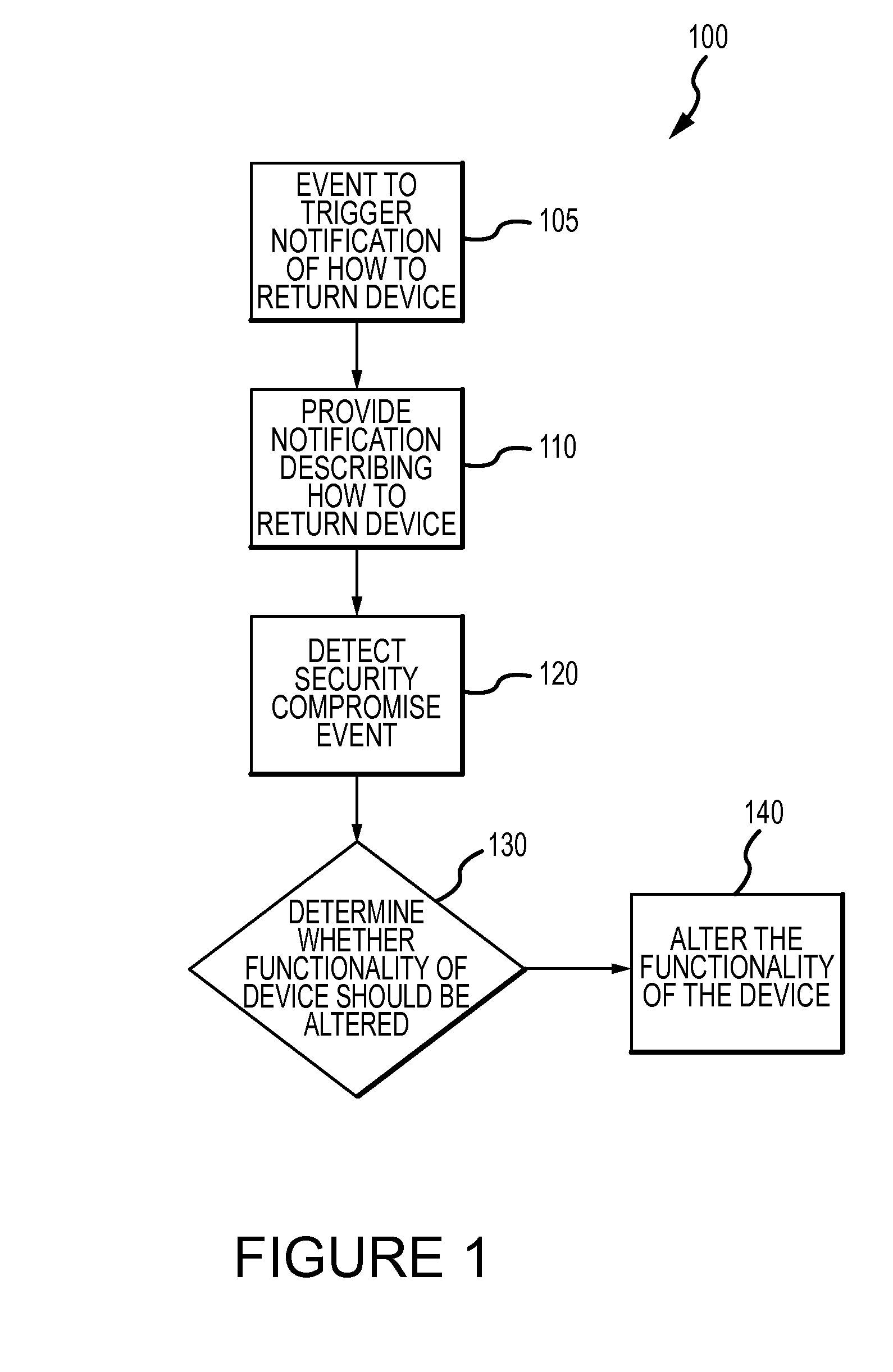
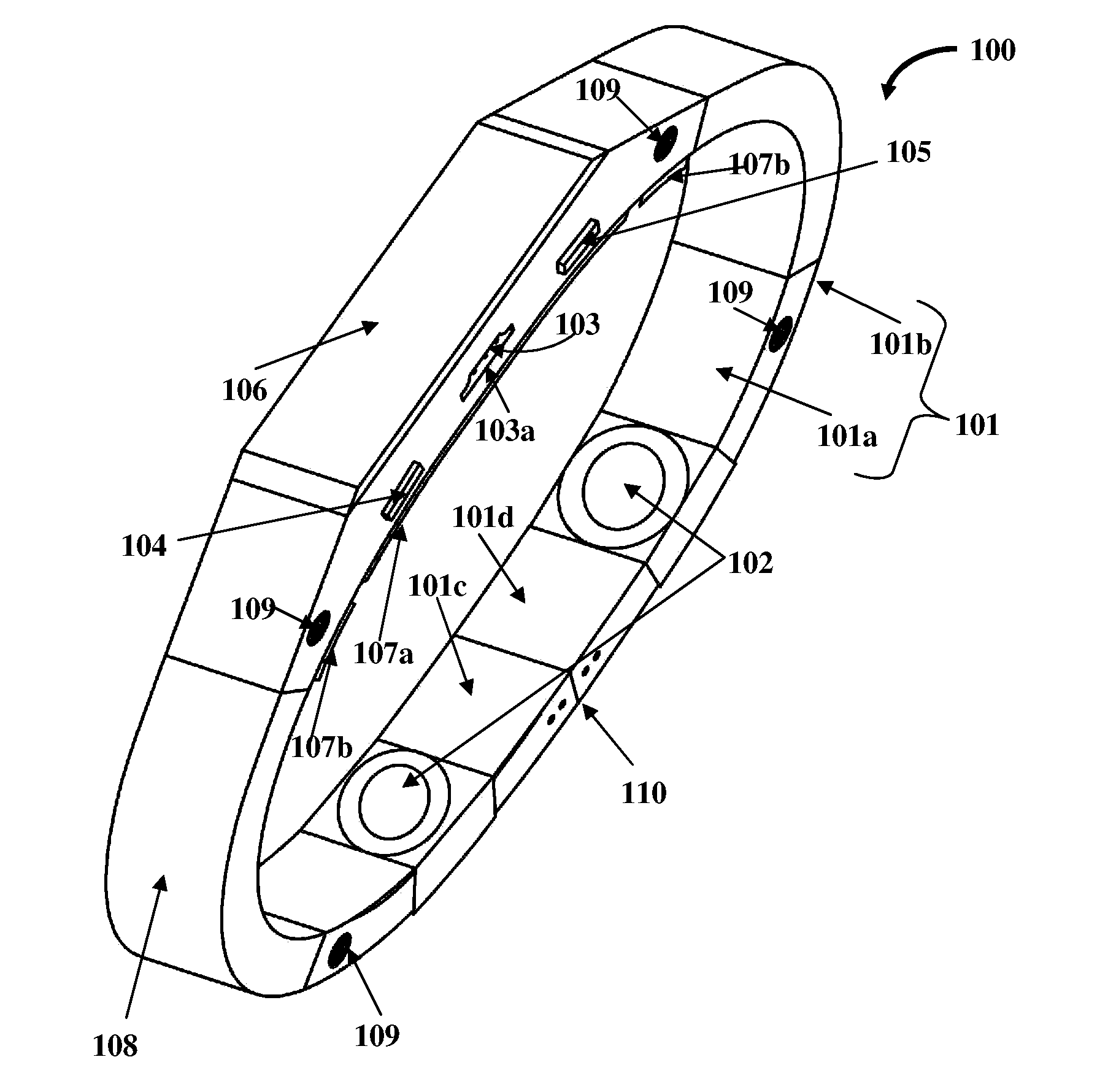
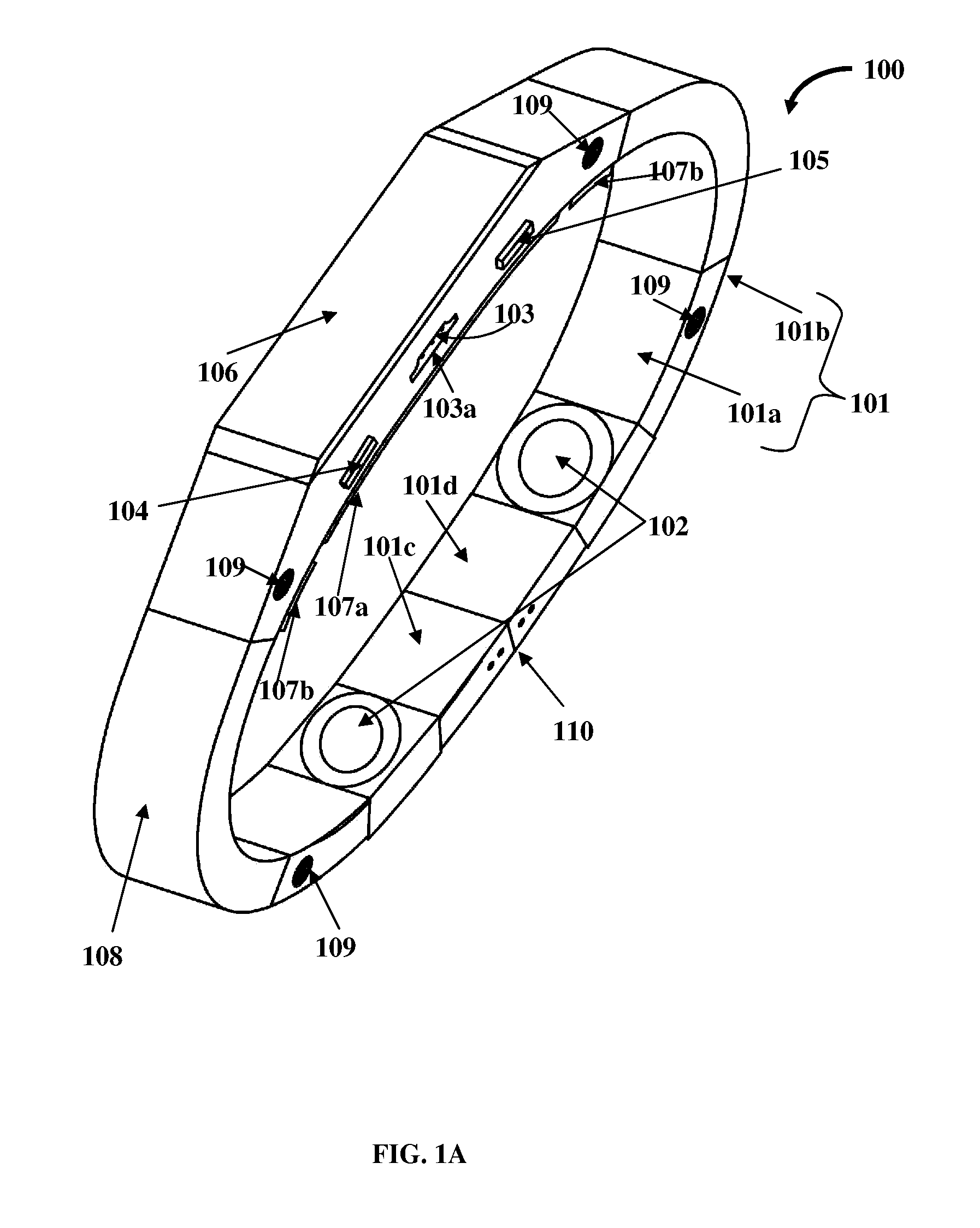
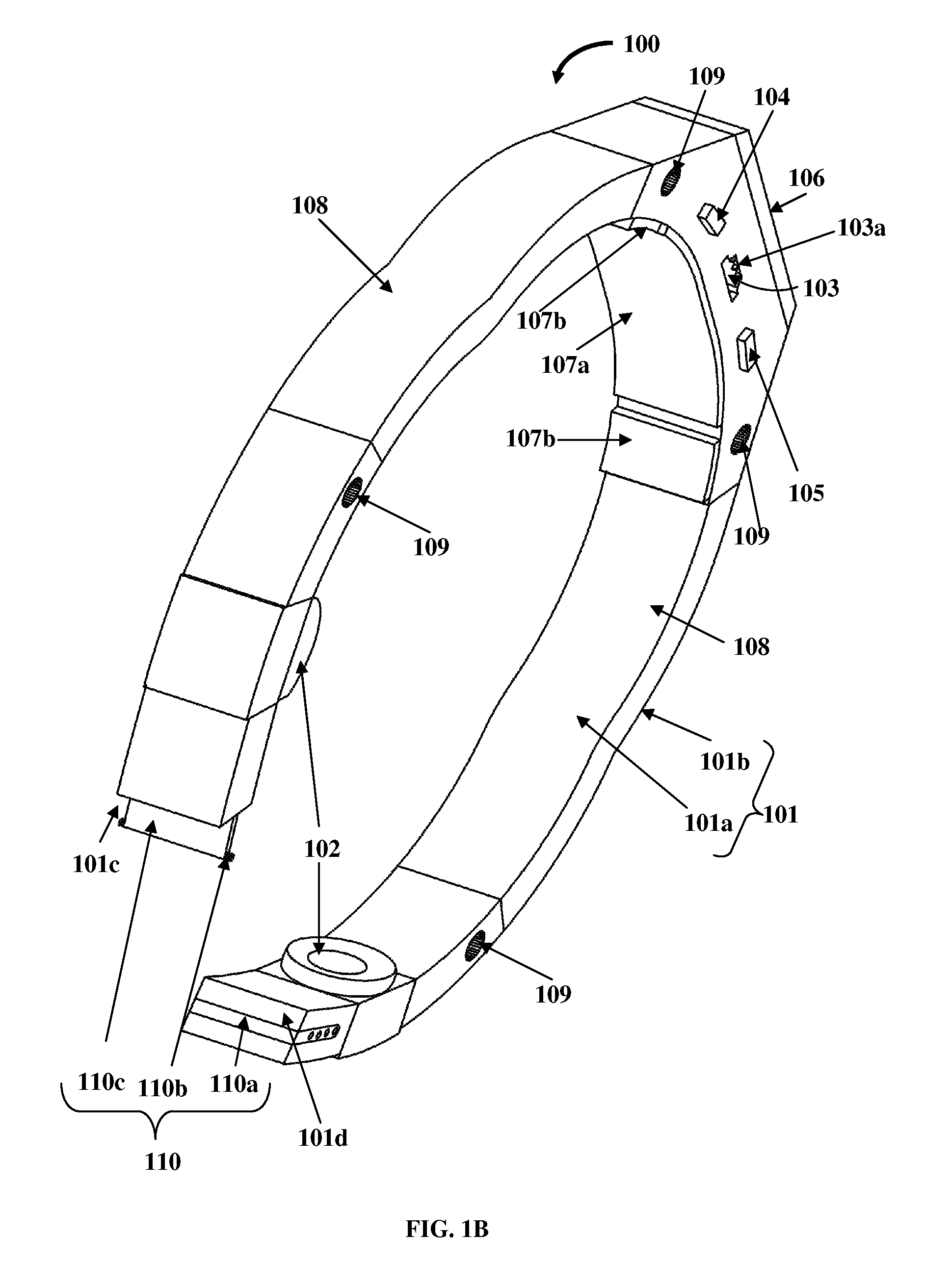
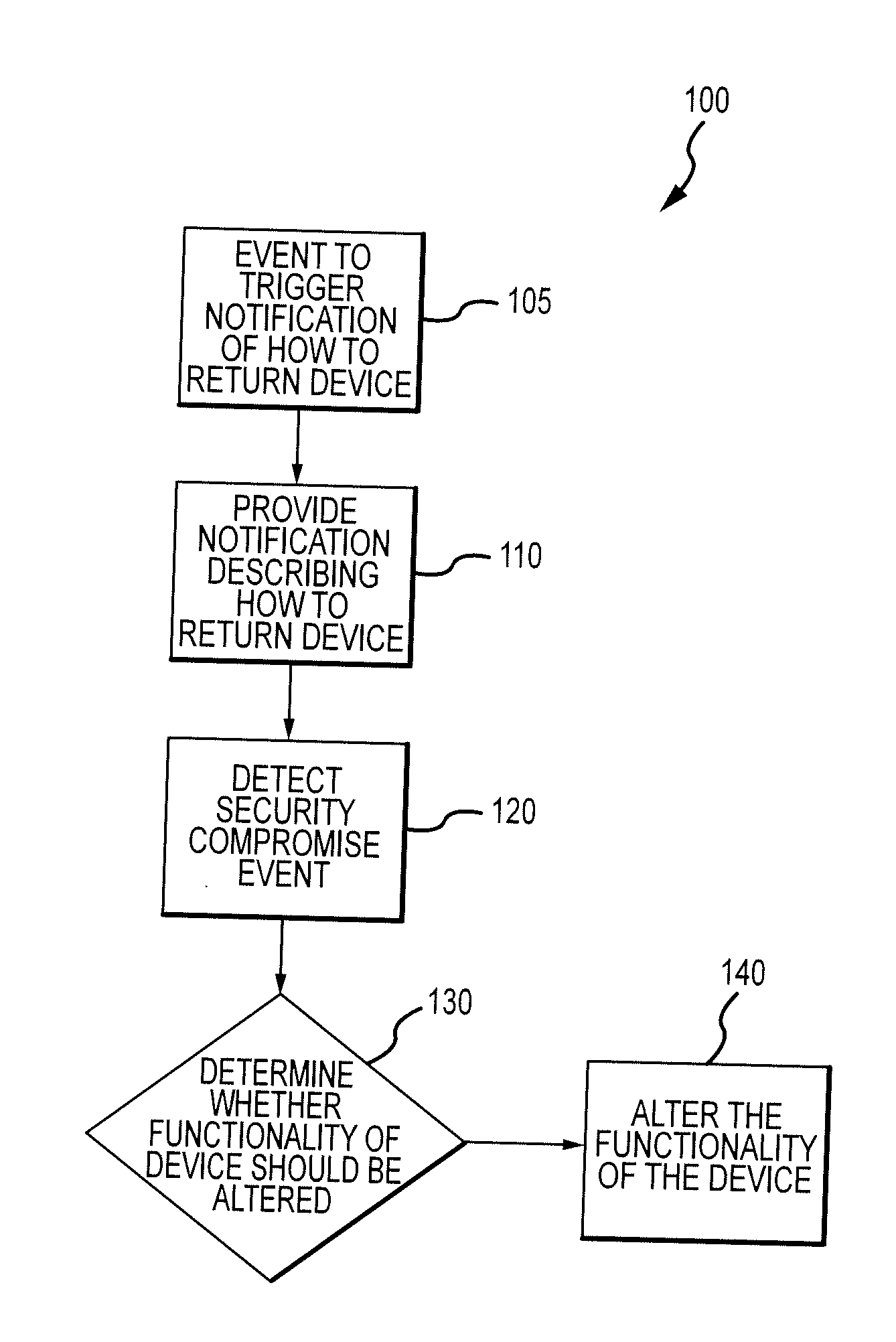
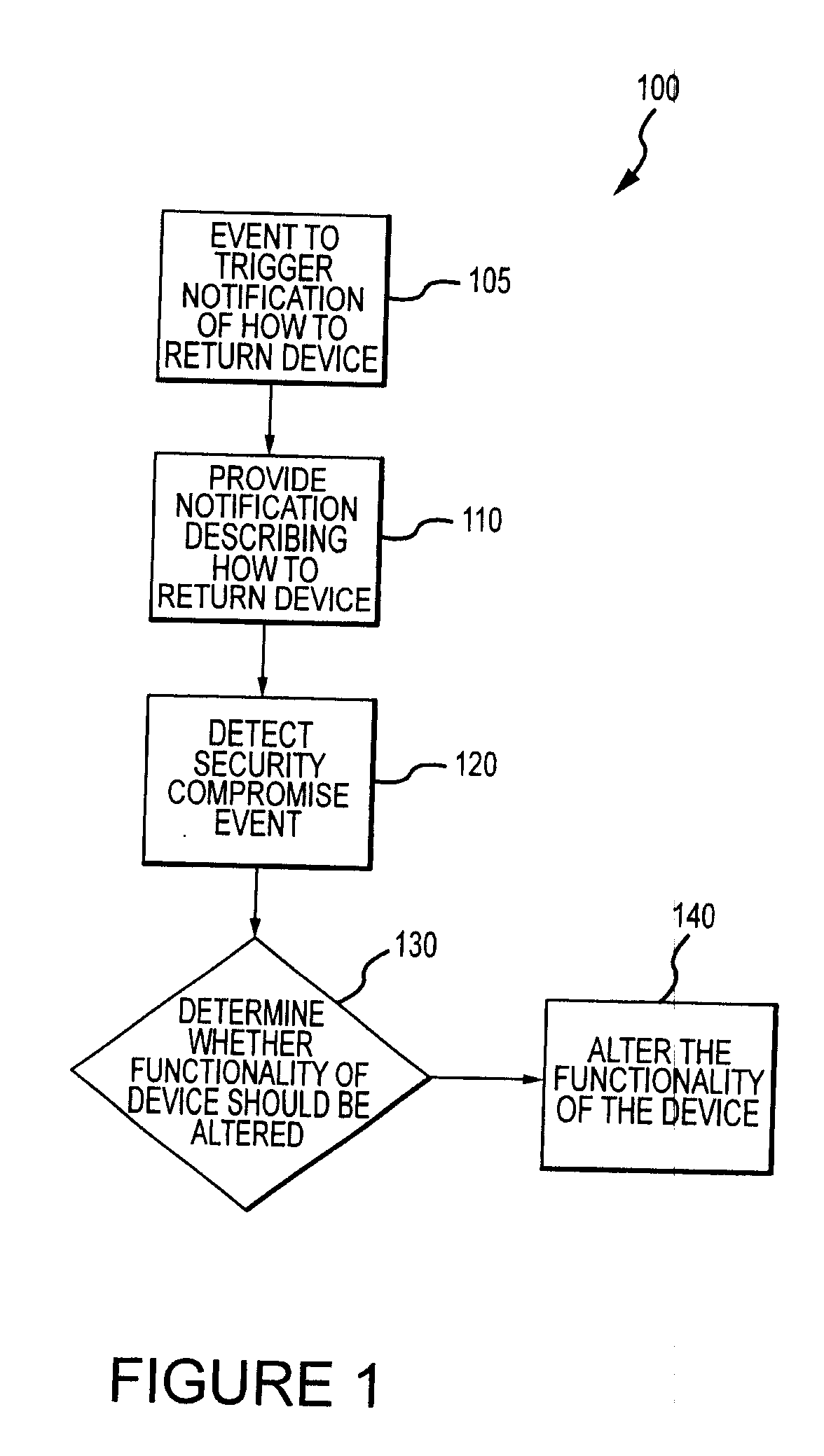
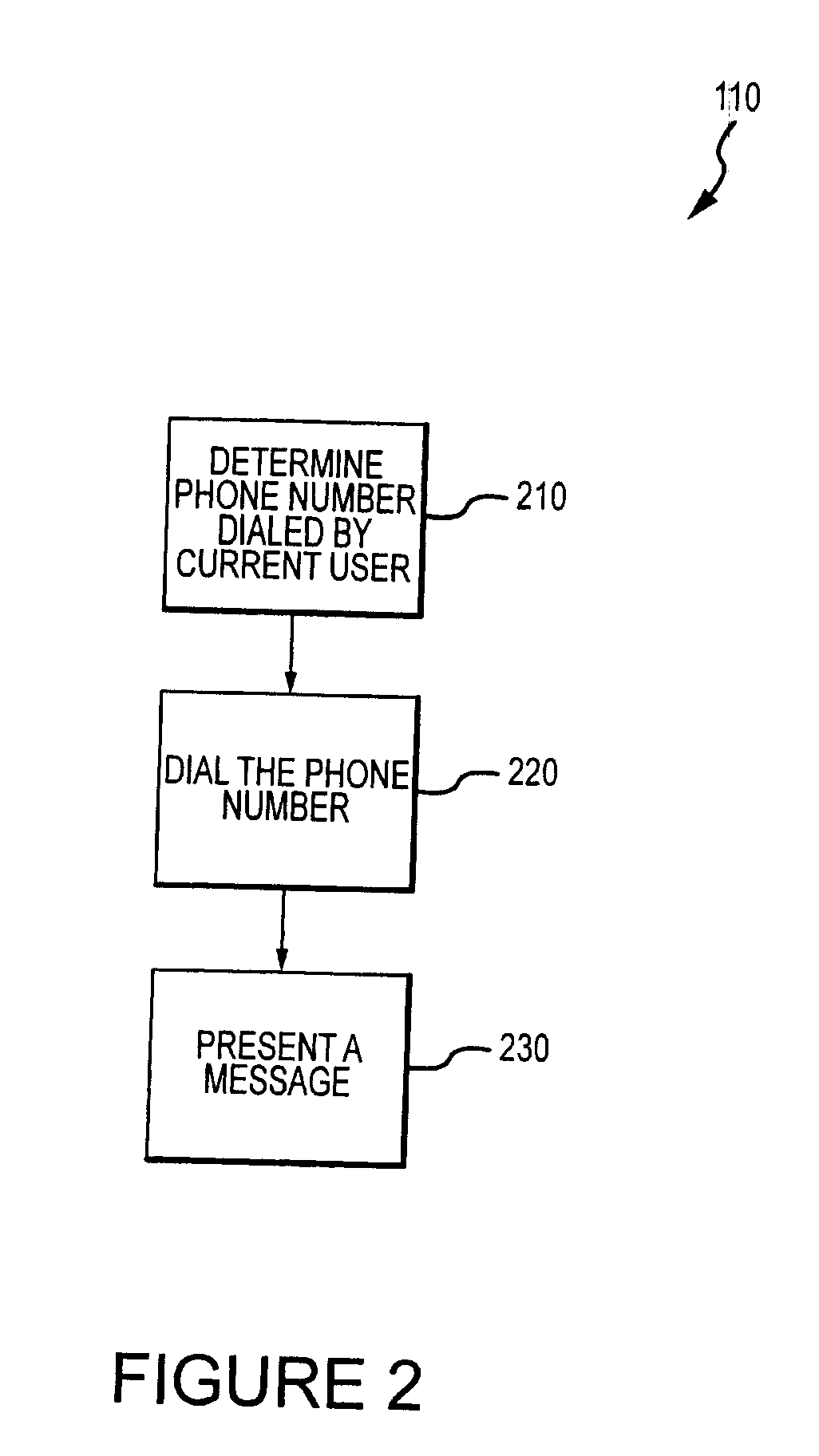
Method for mitigating the unauthorized use of a device
ActiveUS20090253410A1Raise the possibilityIncrease opportunitiesUnauthorised/fraudulent call preventionEavesdropping prevention circuitsDevice MonitorLocal environment
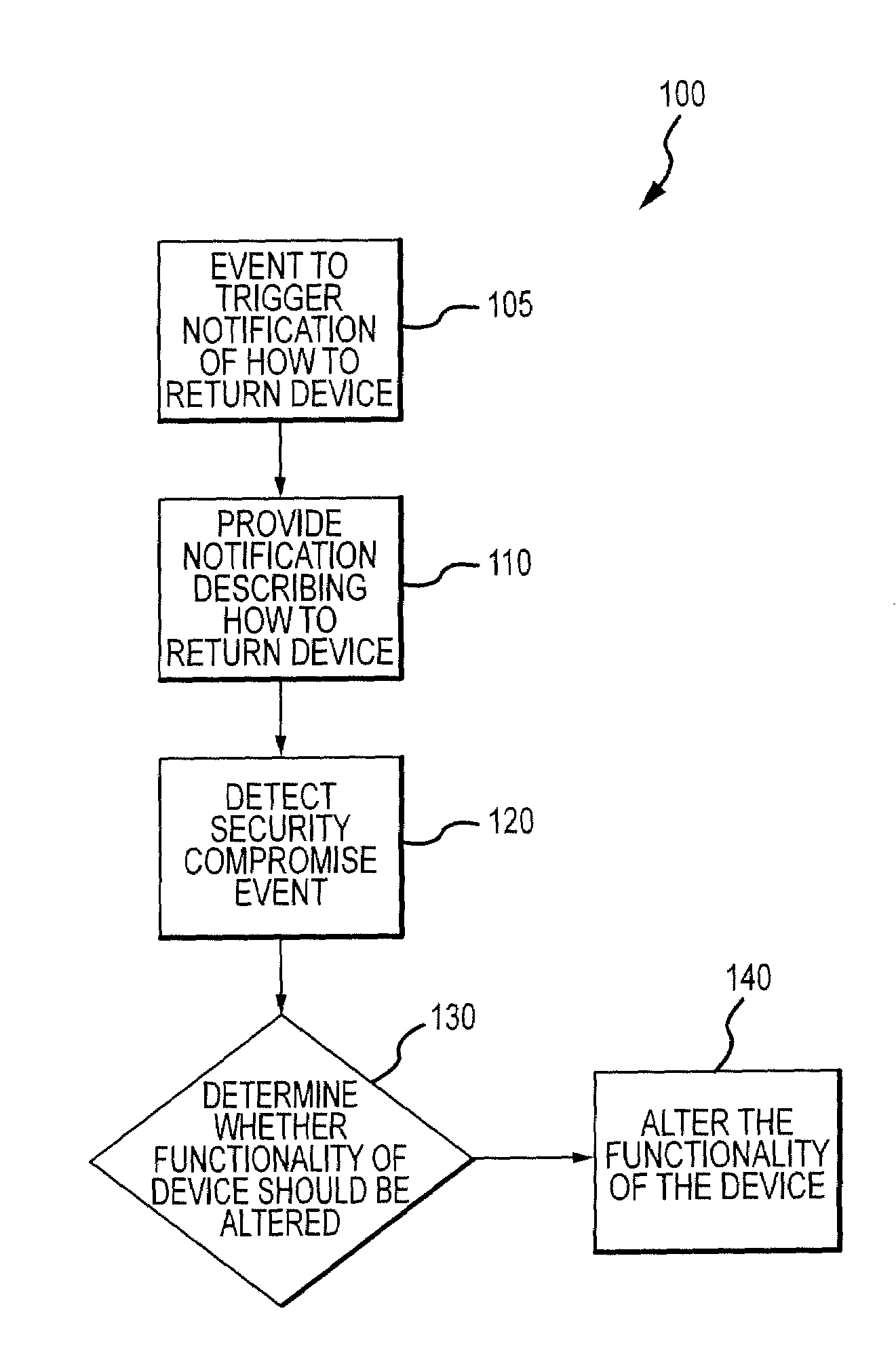
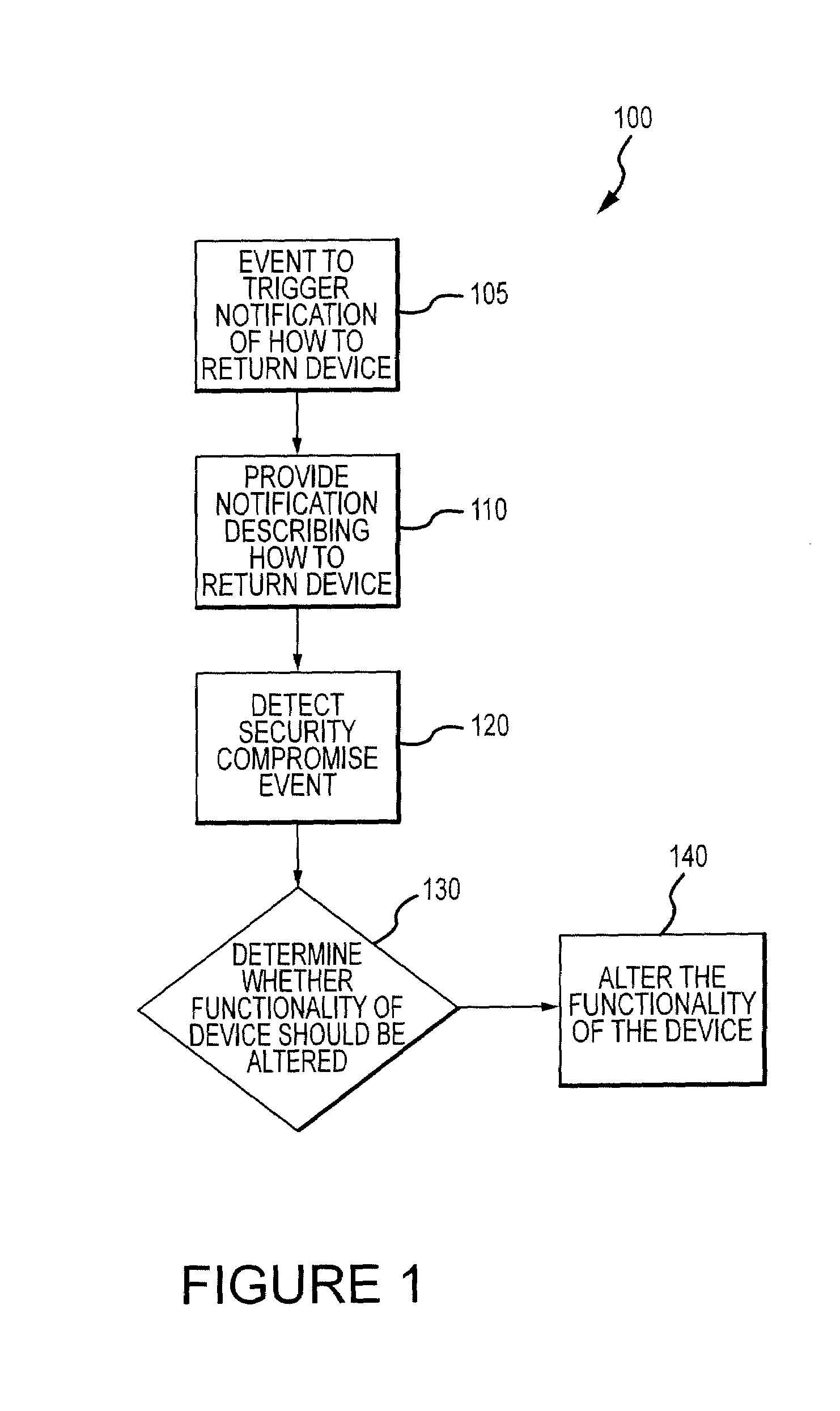
The invention is directed to systems and methods for detecting the loss, theft or unauthorized use of a device and / or altering the functionality of the device in response. In one embodiment, a device monitors its use, its local environment, and / or its operating context to determine that the device is no longer within the control of an authorized user. The device may receive communications or generate an internal signal altering its functionality, such as instructing the device to enter a restricted use mode, a surveillance mode, to provide instructions to return the device and / or to prevent unauthorized use or unauthorized access to data. Additional embodiments also address methods and systems for gathering forensic data regarding an unauthorized user to assist in locating the unauthorized user and / or the device.
Owner:BLANCCO TECH GRP IP OY
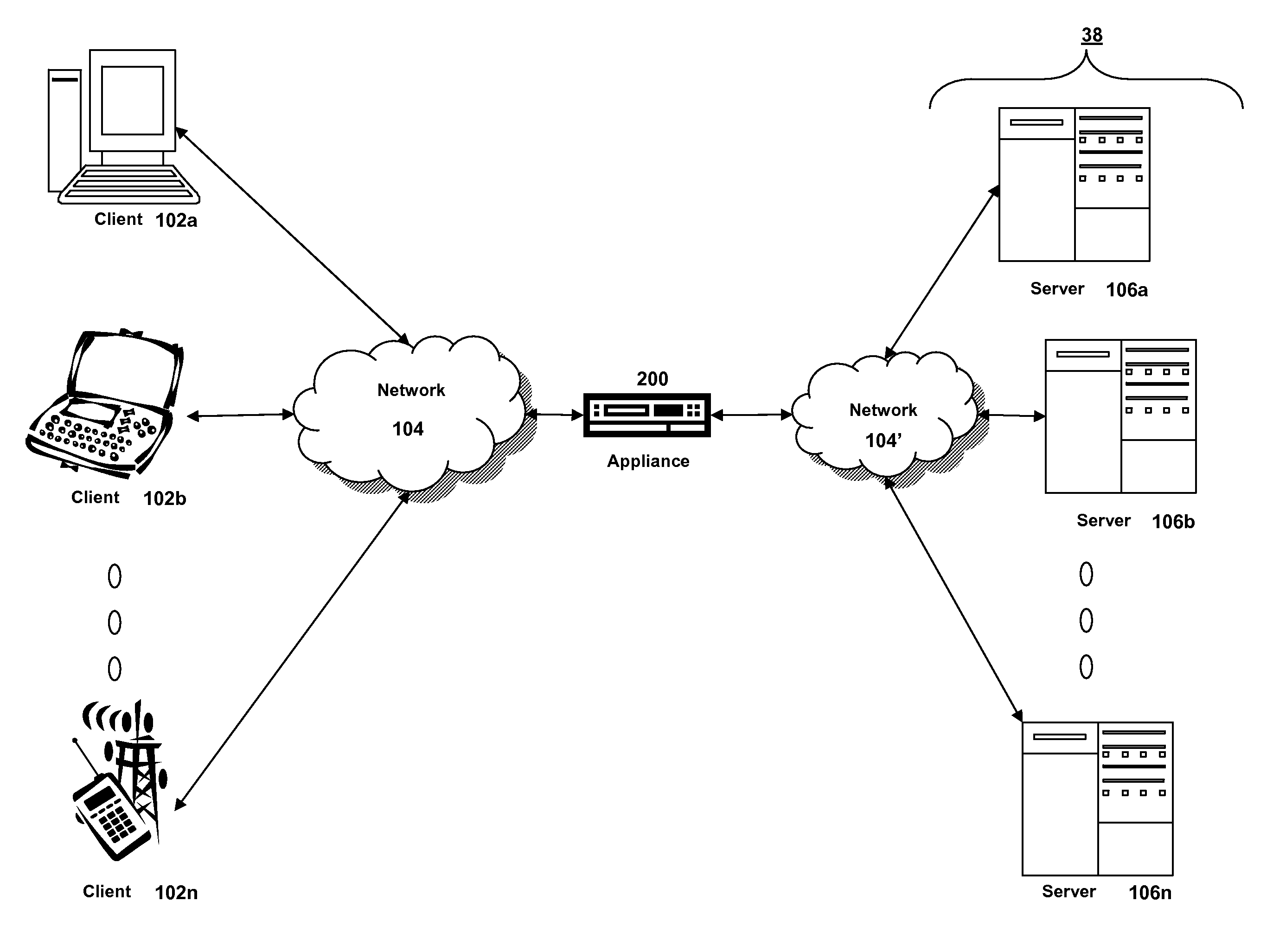
Systems and Methods for Load Balancing Based on User Selected Metrics
ActiveUS20080225710A1Good for load balancingGood flexibilityError preventionTransmission systemsDevice MonitorSimple Network Management Protocol
The present invention provides improvements to load balancing by providing a load balancing solution that allows a user to select metrics, weights and thresholds from metrics collected or determined by a load balancing appliance as well as metrics obtained from another device, such as a server running the service. The systems and methods described providing a load balancing technique in which load balancing decisions can be made based on metrics known by another device monitoring such metrics. The load balancing appliance uses a network management protocol and communication model, such as a Simple Network Management Protocol (SNMP), to identify and collect metrics from a server, service or other device. These metrics are available on the load balancing appliance with appliance determined metrics. Via a configuration interface of the appliance, a user can select one or more appliance determined metrics and / or the metrics obtained via the network management protocol to determine the load of a service.
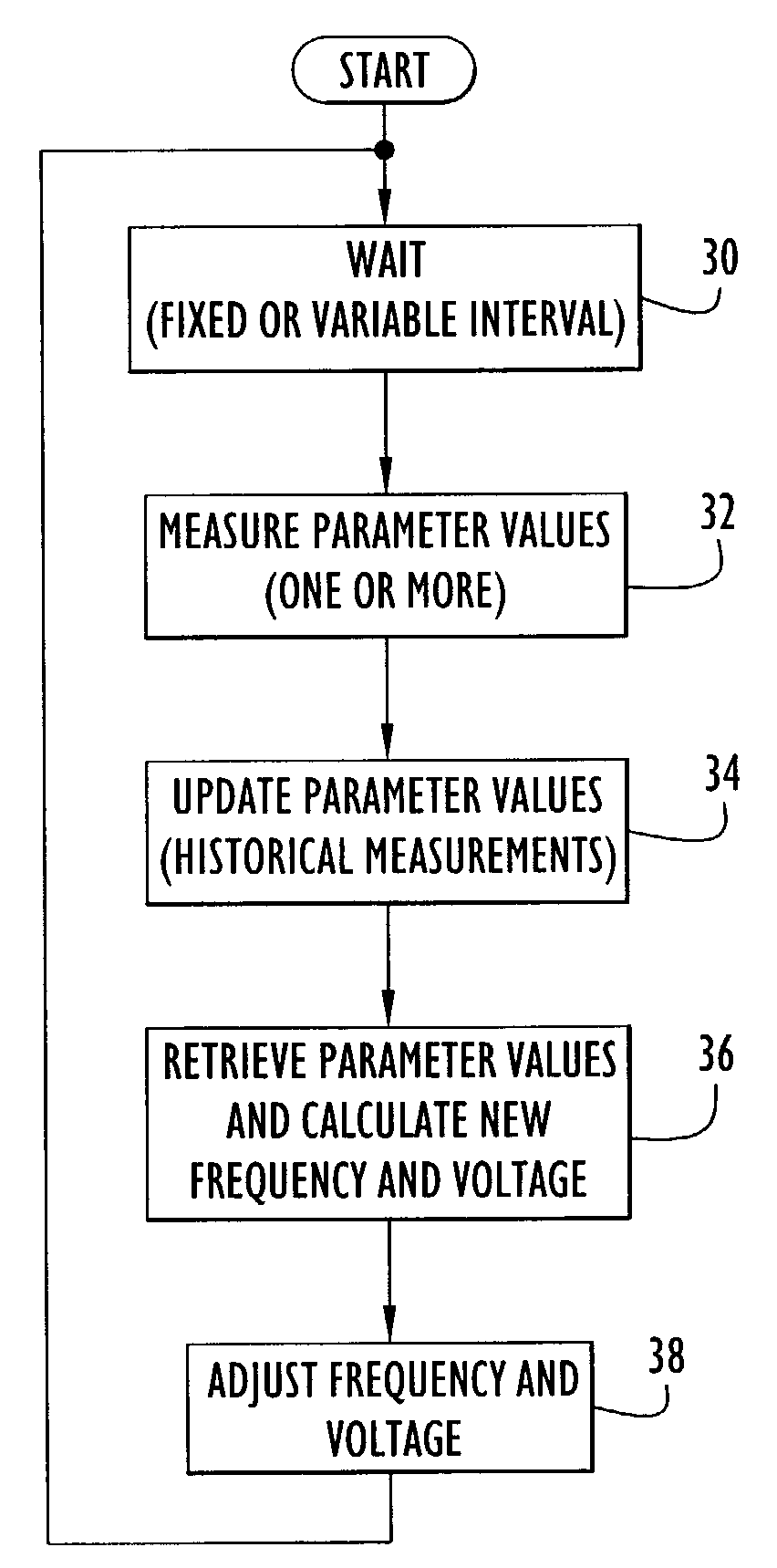
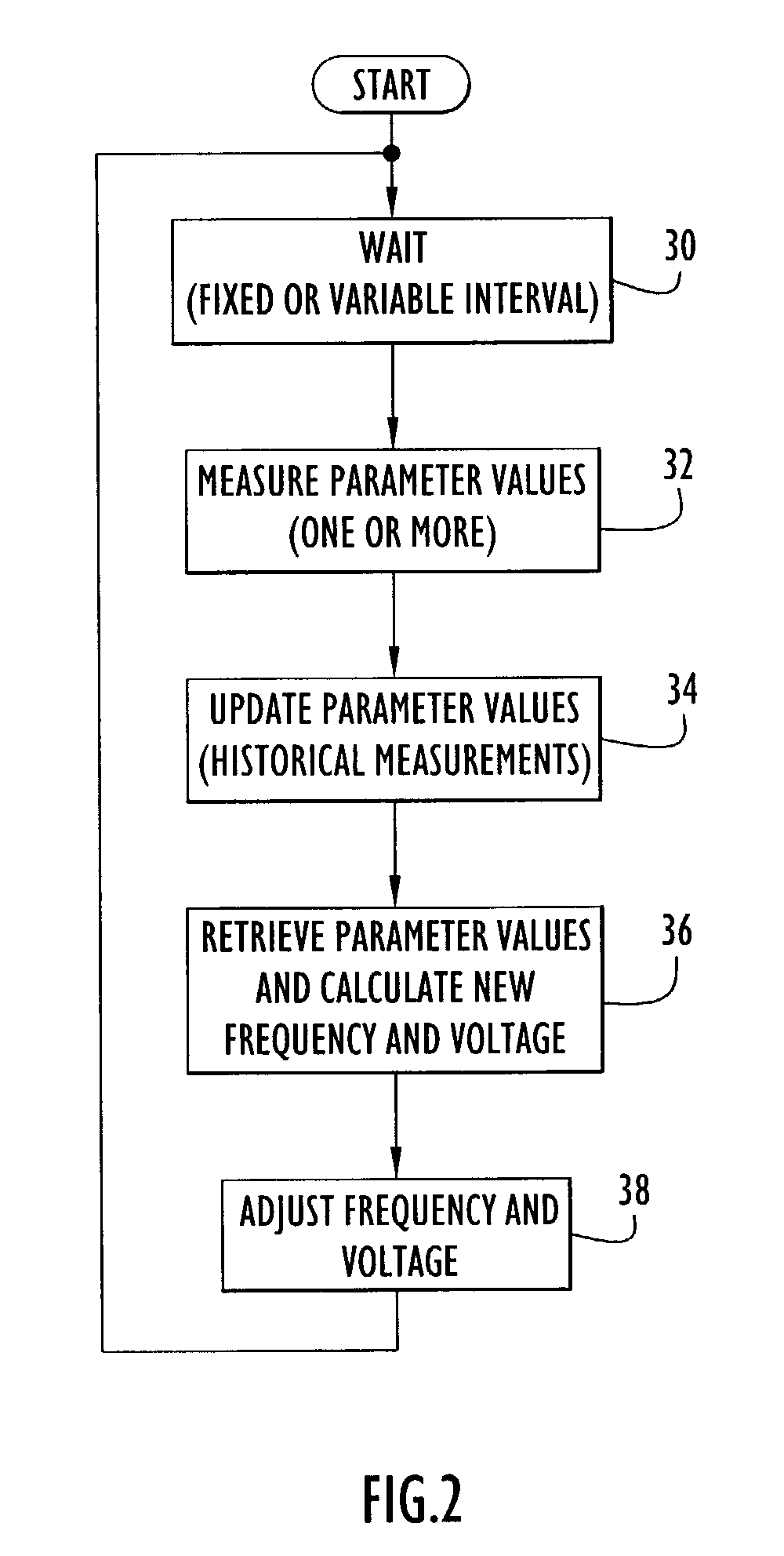
Owner:CITRIX SYST INC
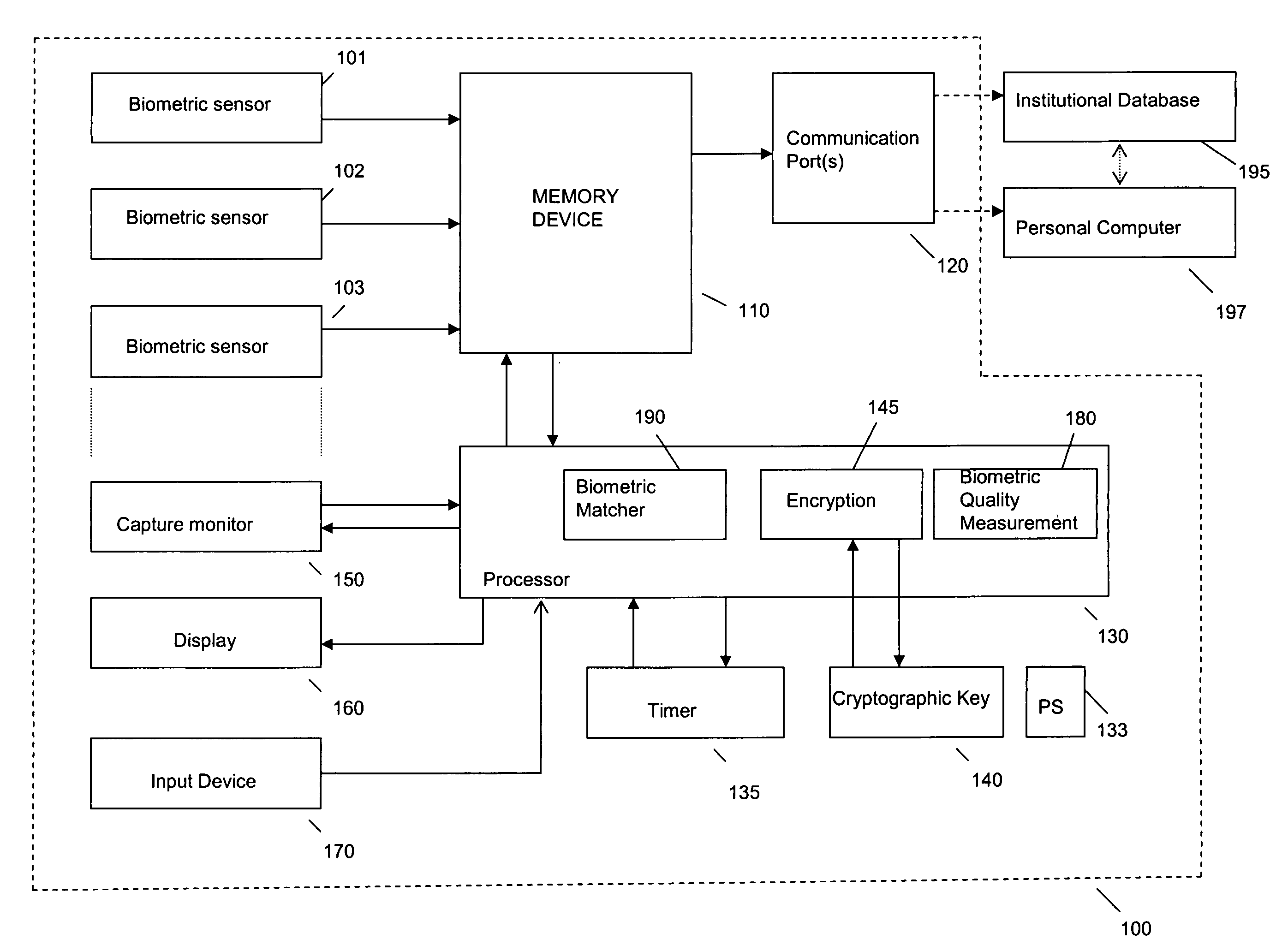
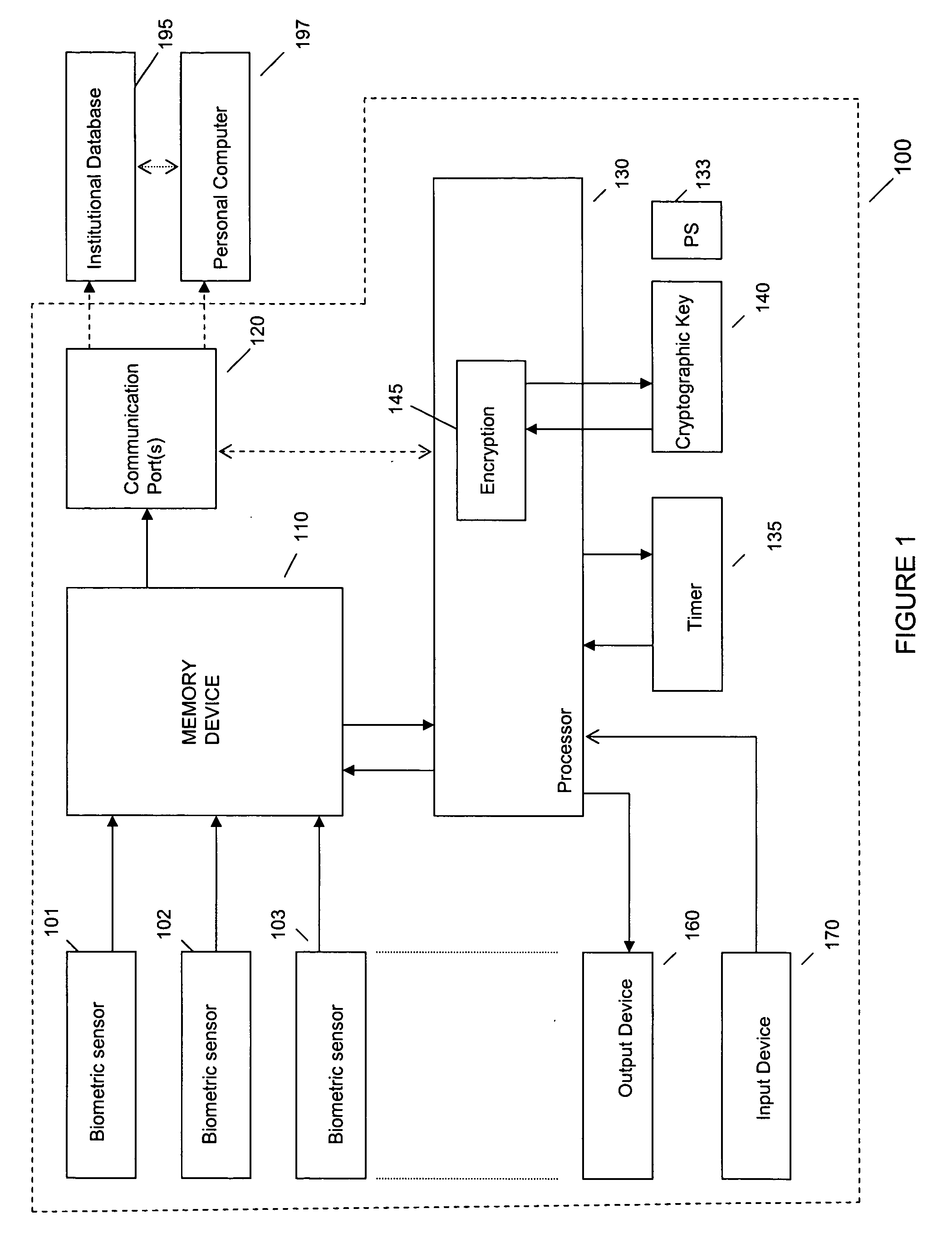
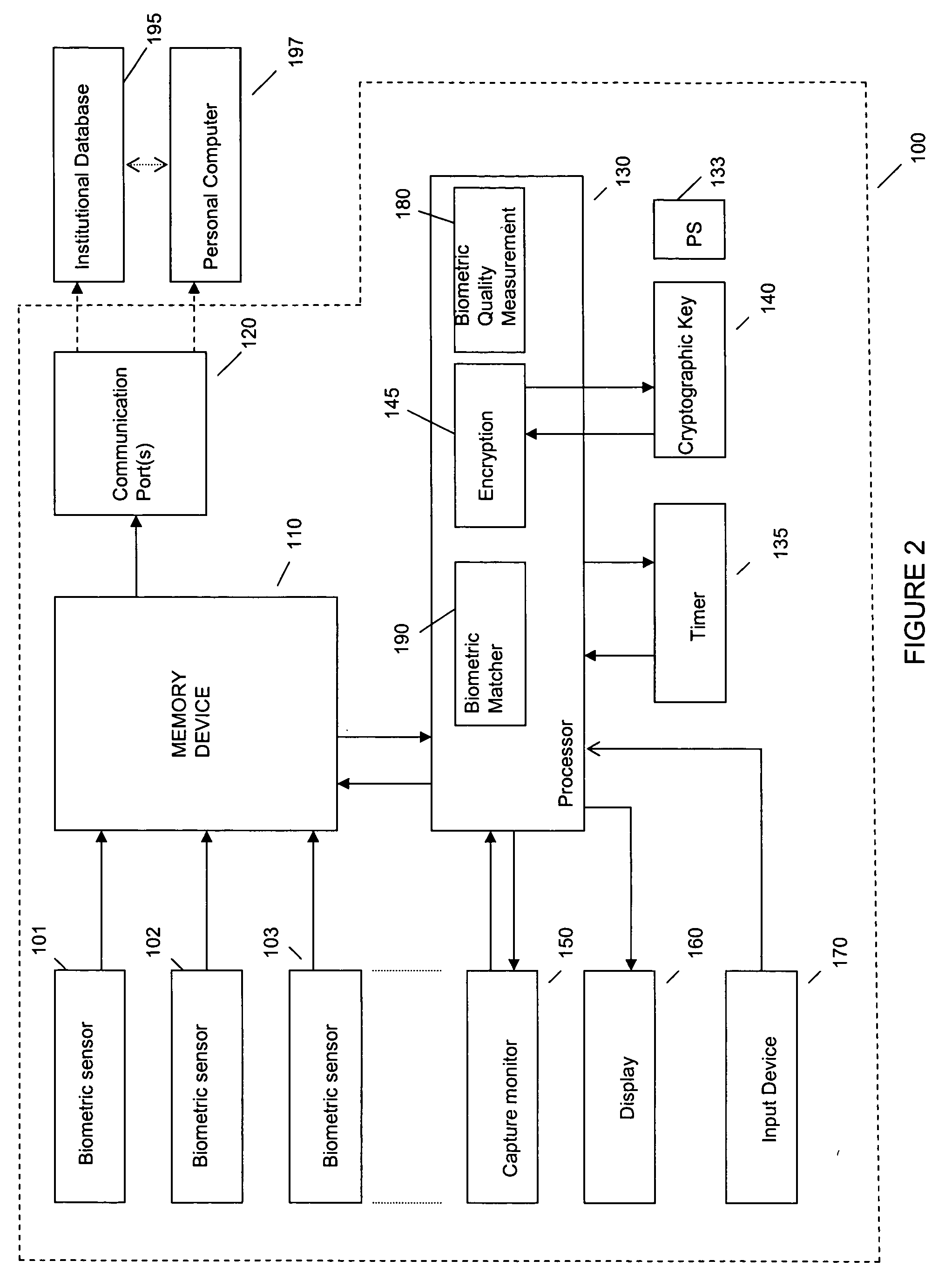
System and method for remote self-enrollment in biometric databases
InactiveUS20050229007A1Lower confidenceLow trustDigital data authenticationBiometric pattern recognitionBiometric dataDevice Monitor
A method and system is provided to provide enrollment of biometric data from individuals without the need for the enrollees to travel to a central location. The system and method provides for optionally detecting multiple types of biometric data, for example, fingerprints, facial scan, visual scan, iris scan, voice scan, or the like, to be captured at the point of enrollee use. During the biometric capture process, the biometric enrollment device monitors and establishes the identity of the enrollee and measures the quality of the biometric input as it occurs. If unacceptable quality is detected, then repeated biometric scans may be necessary, but is done at time of enrollment avoiding any need to send inaccurate information back to a service institution. When the enrollment process completes, the biometric data is encrypted, time stamped and either mailed back to the service institution or is transmitted back. The biometric device may remain with the user for subsequent use as an identification sensor which may authenticate a user with stored biometric information to authenticate a user's identity for a transaction or a request to access a service or equipment. The biometric enrollment device may also be embodied with another piece of equipment to authenticate use of that equipment.
Owner:IBM CORP
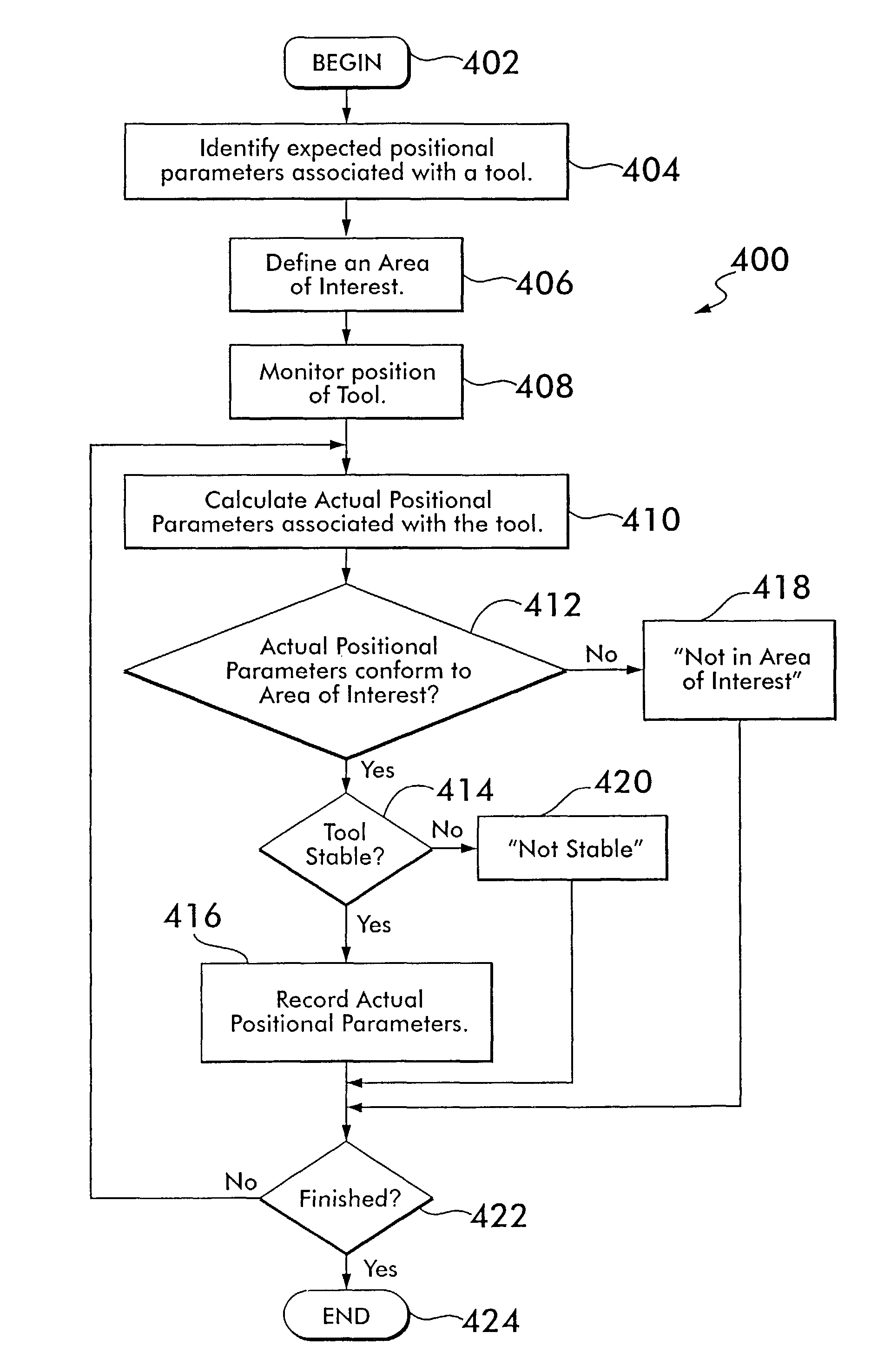
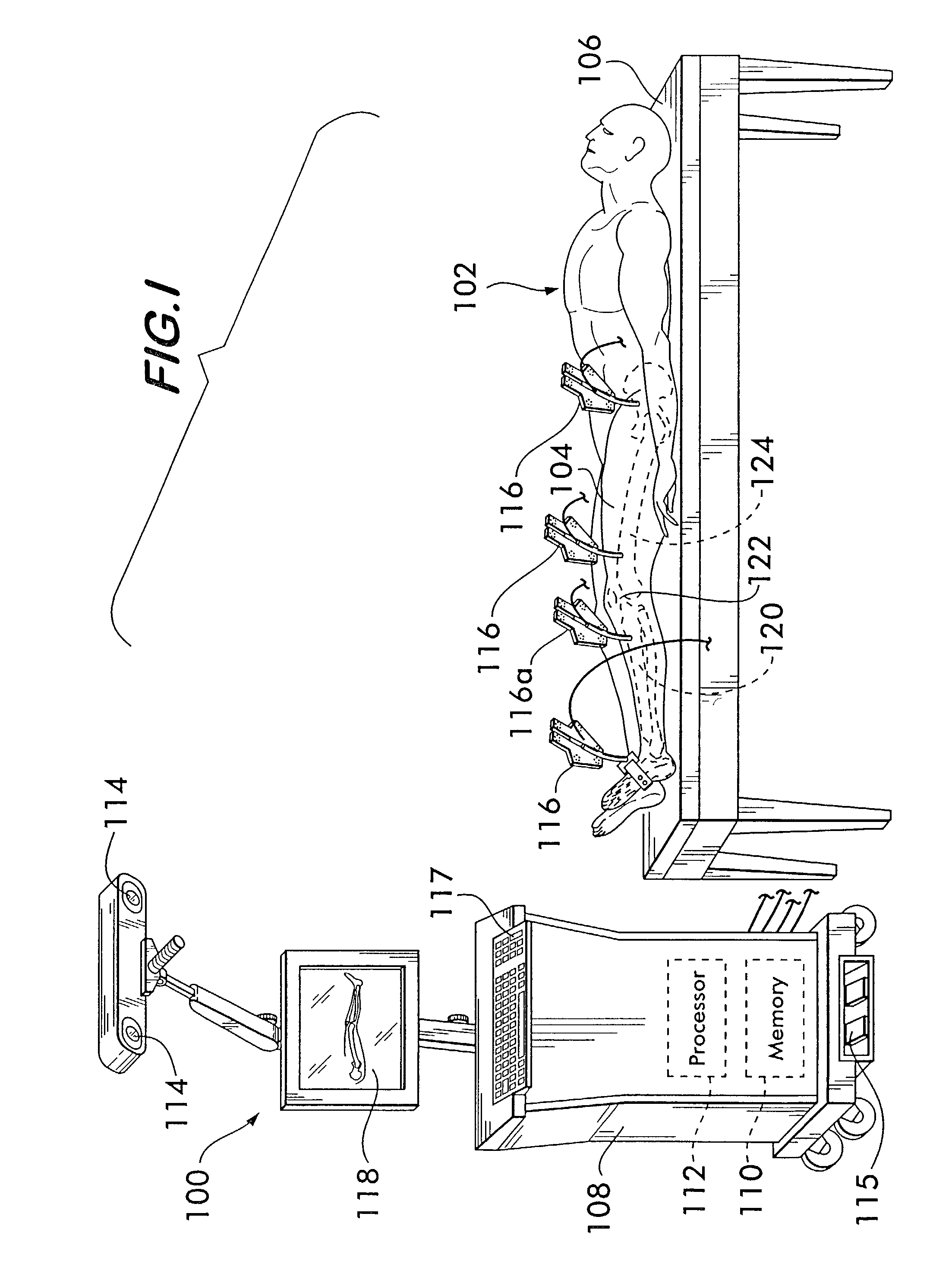
Recording localization device tool positional parameters
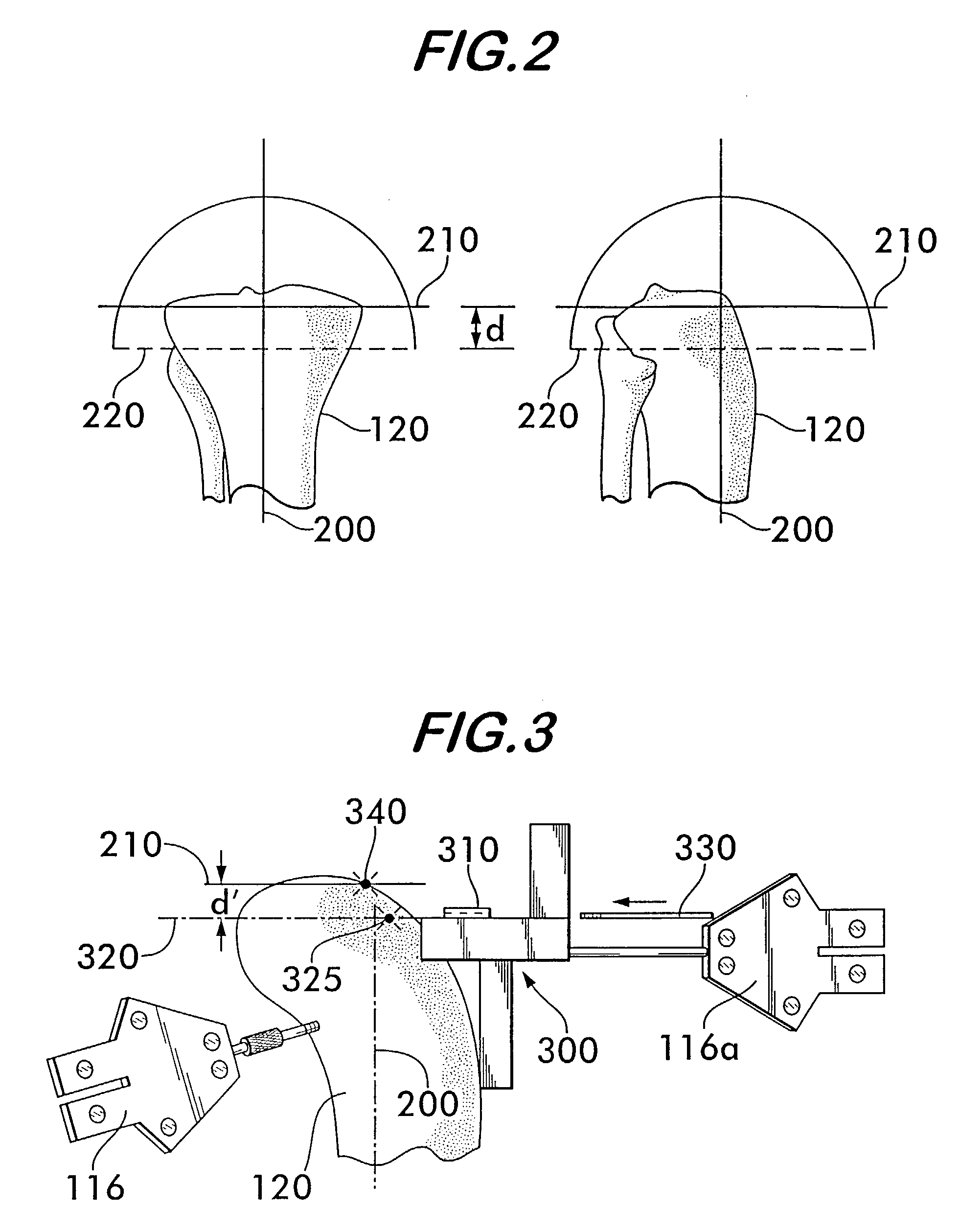
ActiveUS8355773B2Accurate recordAccurate positional parameterSurgical navigation systemsDiagnostic recording/measuringDevice MonitorLocation Equipment
Owner:AESCULAP AG
System for monitoring the unauthorized use of a device
ActiveUS20090247122A1Raise the possibilityIncrease opportunitiesUnauthorised/fraudulent call preventionEavesdropping prevention circuitsDevice MonitorLocal environment
The invention is directed to systems and methods for detecting the loss, theft or unauthorized use of a device and / or altering the functionality of the device in response. In one embodiment, a device monitors its use, its local environment, and / or its operating context to determine that the device is no longer within the control of an authorized user. The device may receive communications or generate an internal signal altering its functionality, such as instructing the device to enter a restricted use mode, a surveillance mode, to provide instructions to return the device and / or to prevent unauthorized use or unauthorized access to data. Additional embodiments also address methods and systems for gathering forensic data regarding an unauthorized user to assist in locating the unauthorized user and / or the device.
Owner:BLANCCO TECH GRP IP OY
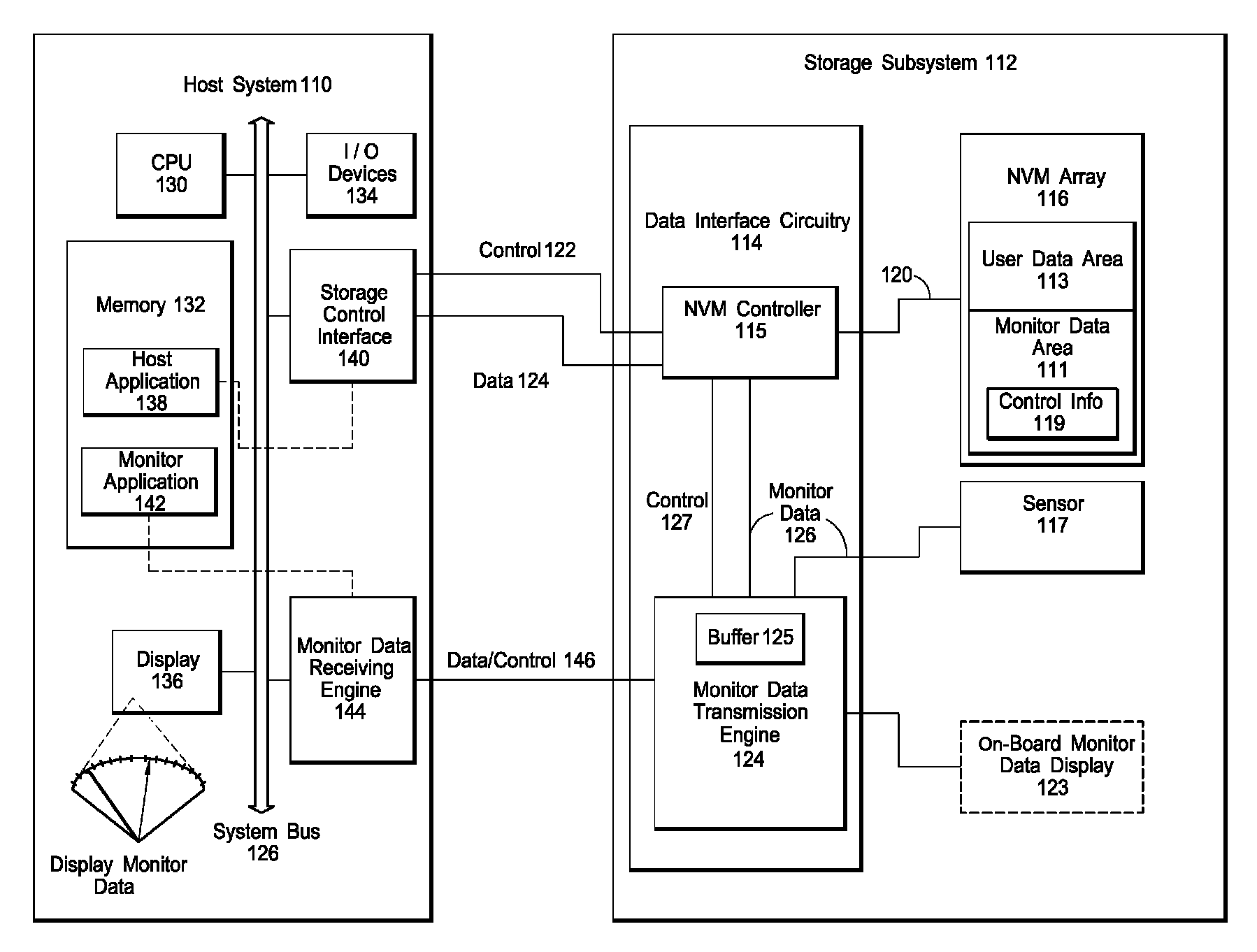
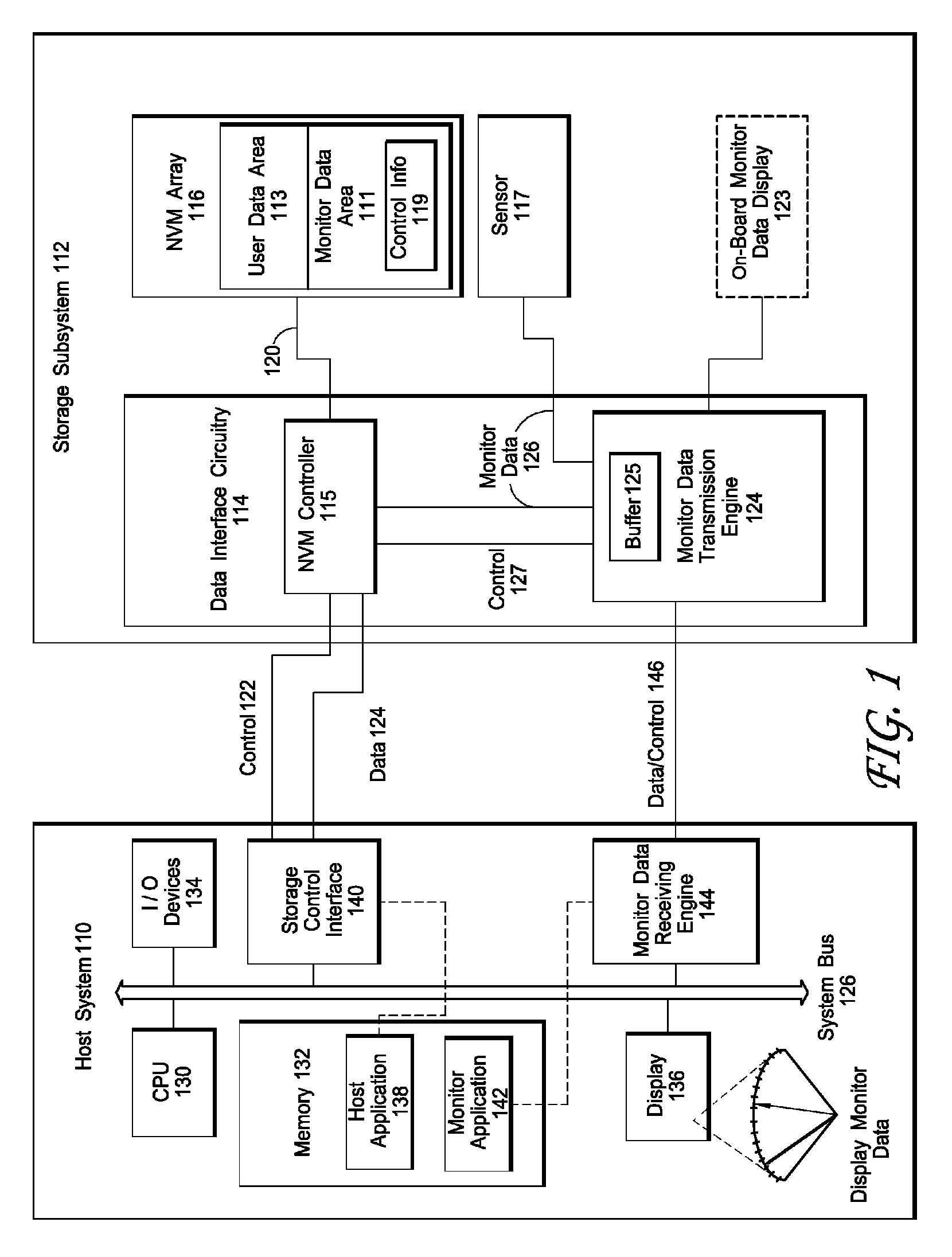
Interface for enabling a host computer to retrieve device monitor data from a solid state storage subsystem
ActiveUS7962792B2Reduce eliminateReduce the possibilityReliability/availability analysisInput/output processes for data processingSolid-state storageDevice Monitor
A non-volatile storage subsystem maintains, and makes available to a host system, monitor data reflective of a likelihood of a data error occurring. The monitor data may, for example, include usage statistics and / or sensor data. The storage subsystem transfers the monitor data to the host system over a signal interface that is separate from the signal interface used for standard storage operations. This interface may be implemented using otherwise unused pins / signal lines of a standard connector, such as a CompactFlash or SATA connector. Special hardware may be provided in the storage subsystem and host system for transferring the monitor data over these signal lines, so that the transfers occur with little or no need for host-software intervention. The disclosed design reduces or eliminates the need for host software that uses non-standard or “vendor-specific” commands to retrieve the monitor data.
Owner:WESTERN DIGITAL TECH INC
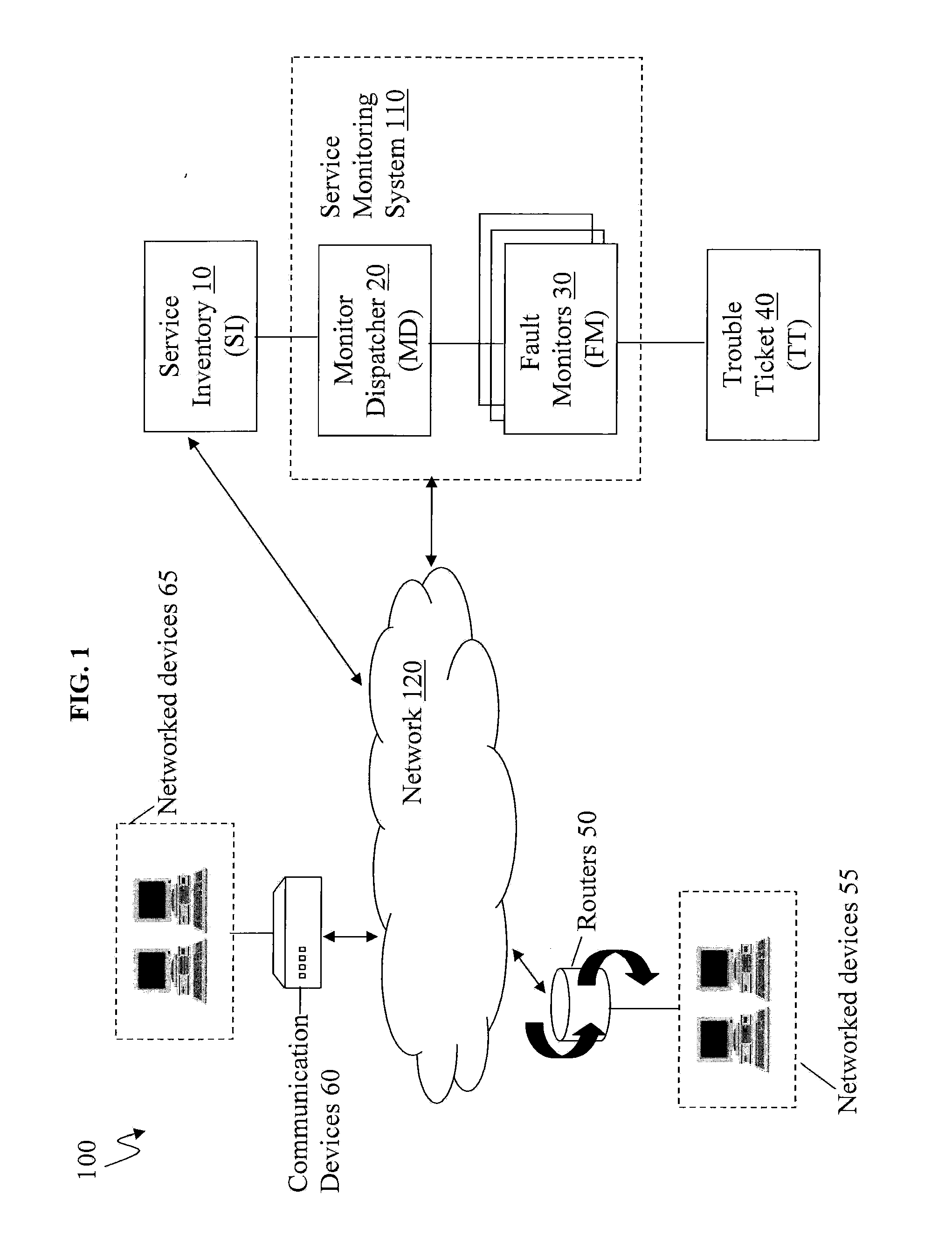
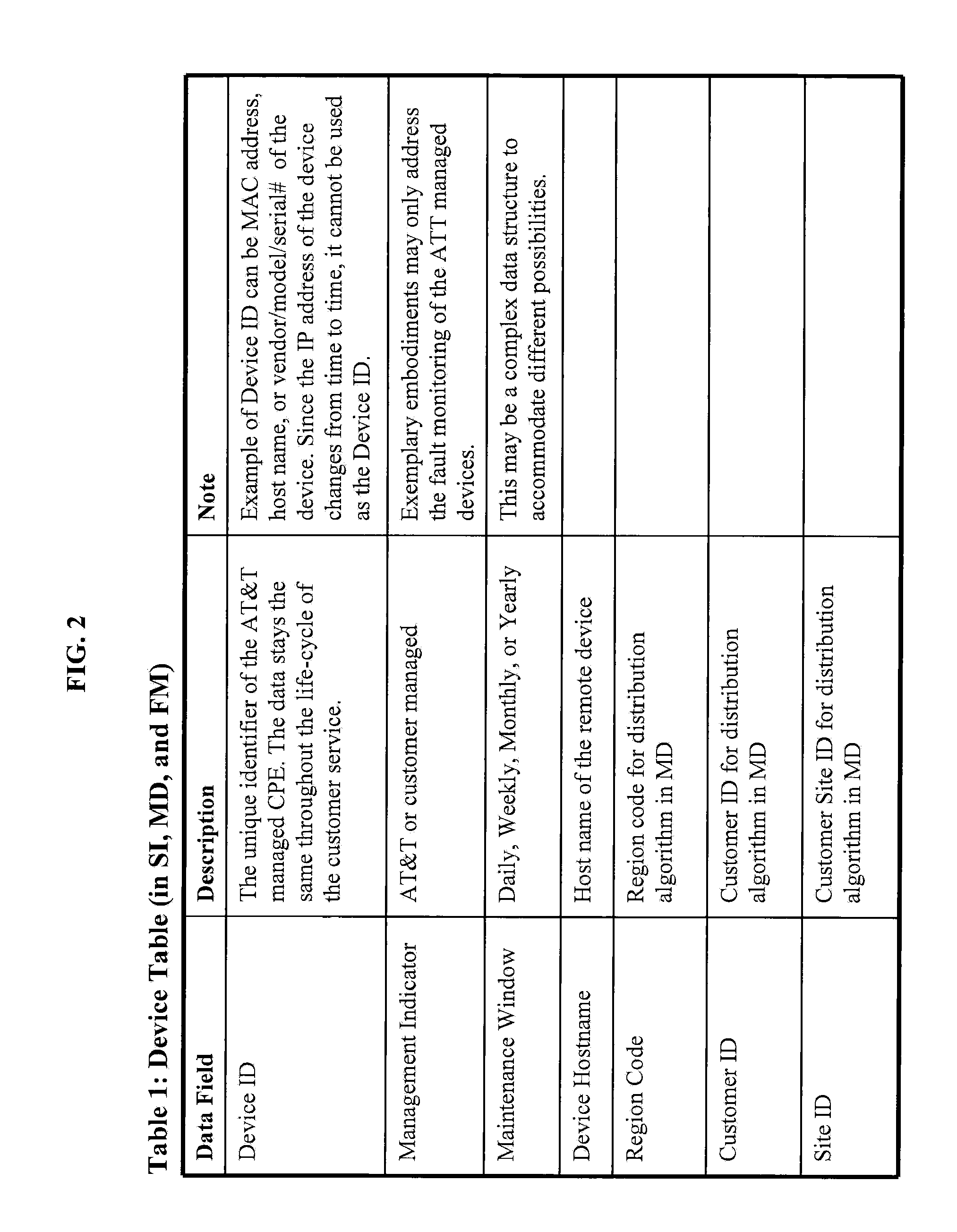
Scalable and Robust Mechanism for Remote IP Device Monitoring With Changing IP Address Assignment
A method is provided for monitoring devices with changing IP addresses. SNMP trap is received from a device at a first IP address to notify that a connection is up, and a SNMP poll is transmitted to the device to obtain an identifier. Predetermined consecutive SNMP GET requests are transmitted to the device in intervals. Responsive to failing to receive from the device predetermined consecutive SNMP GET responses equal to the predetermined consecutive SNMP GET requests, it is determined that there is a connection failure or a device failure and checked whether the device is in a maintenance window. If not in maintenance window, a trouble ticket is generated. Responsive to the failure, there is a predetermined waiting period for another SNMP trap from the device with a second IP address and the same identifier notifying that a connection is back up, and no trouble ticket is generated.
Owner:AT&T INTPROP I L P
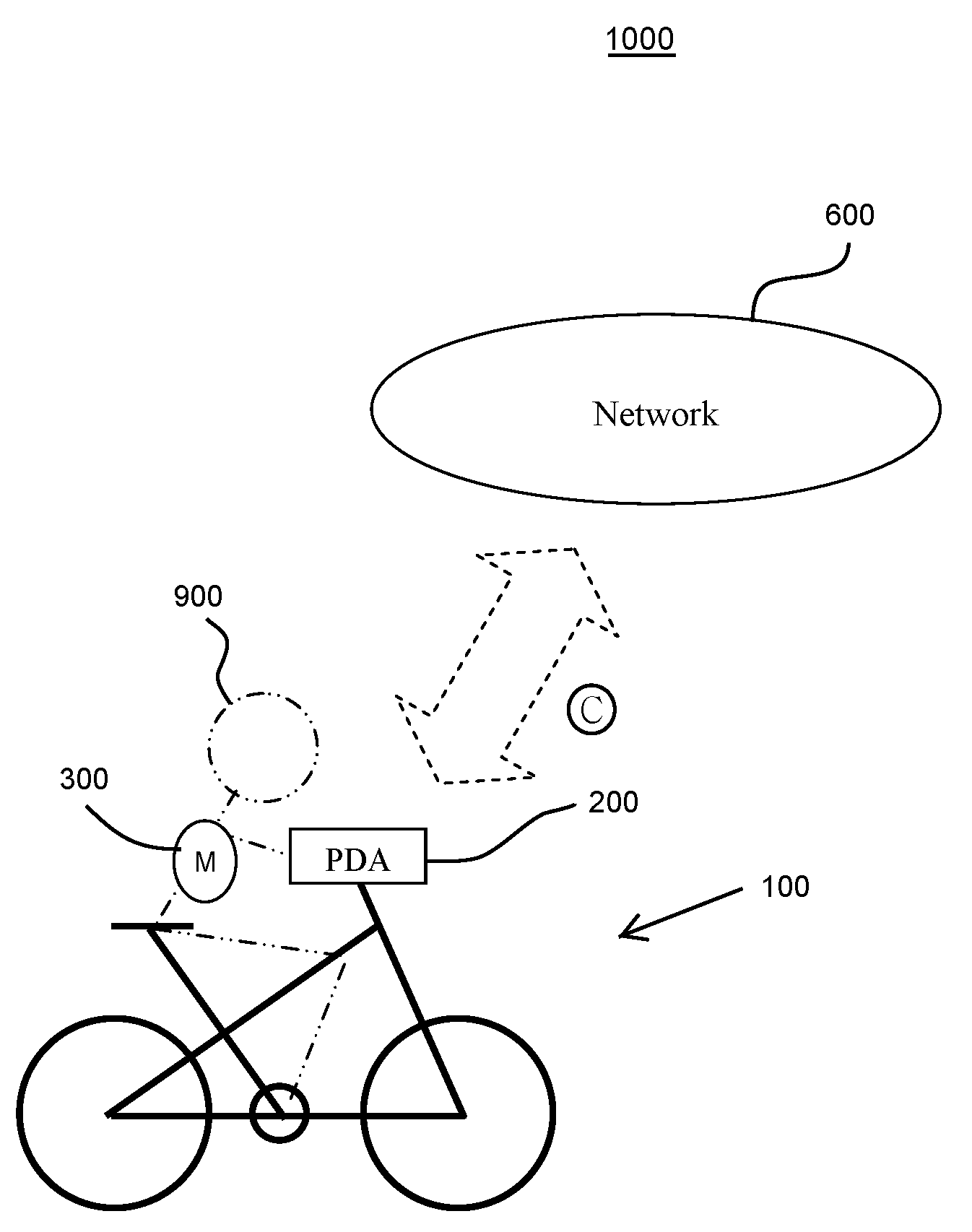
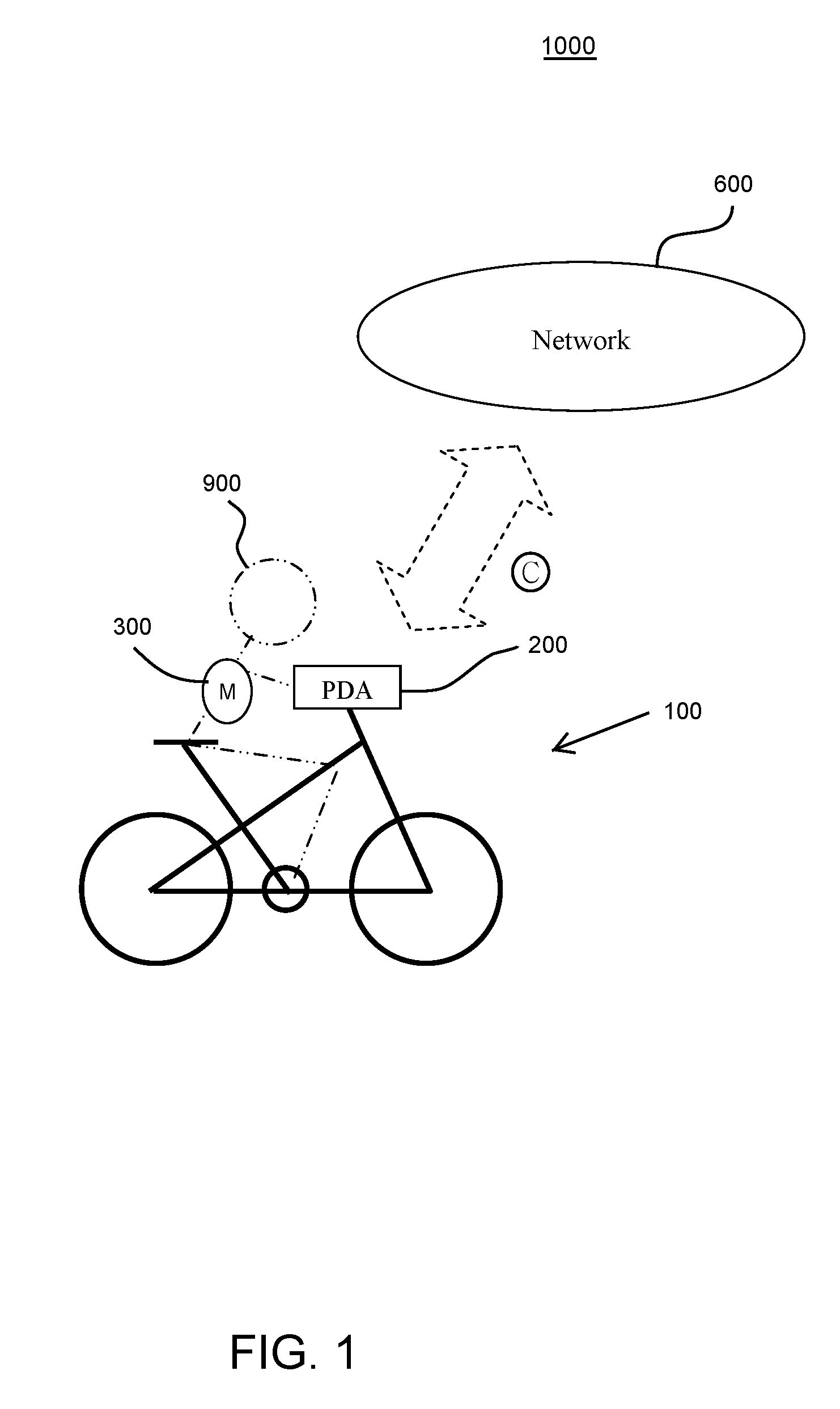
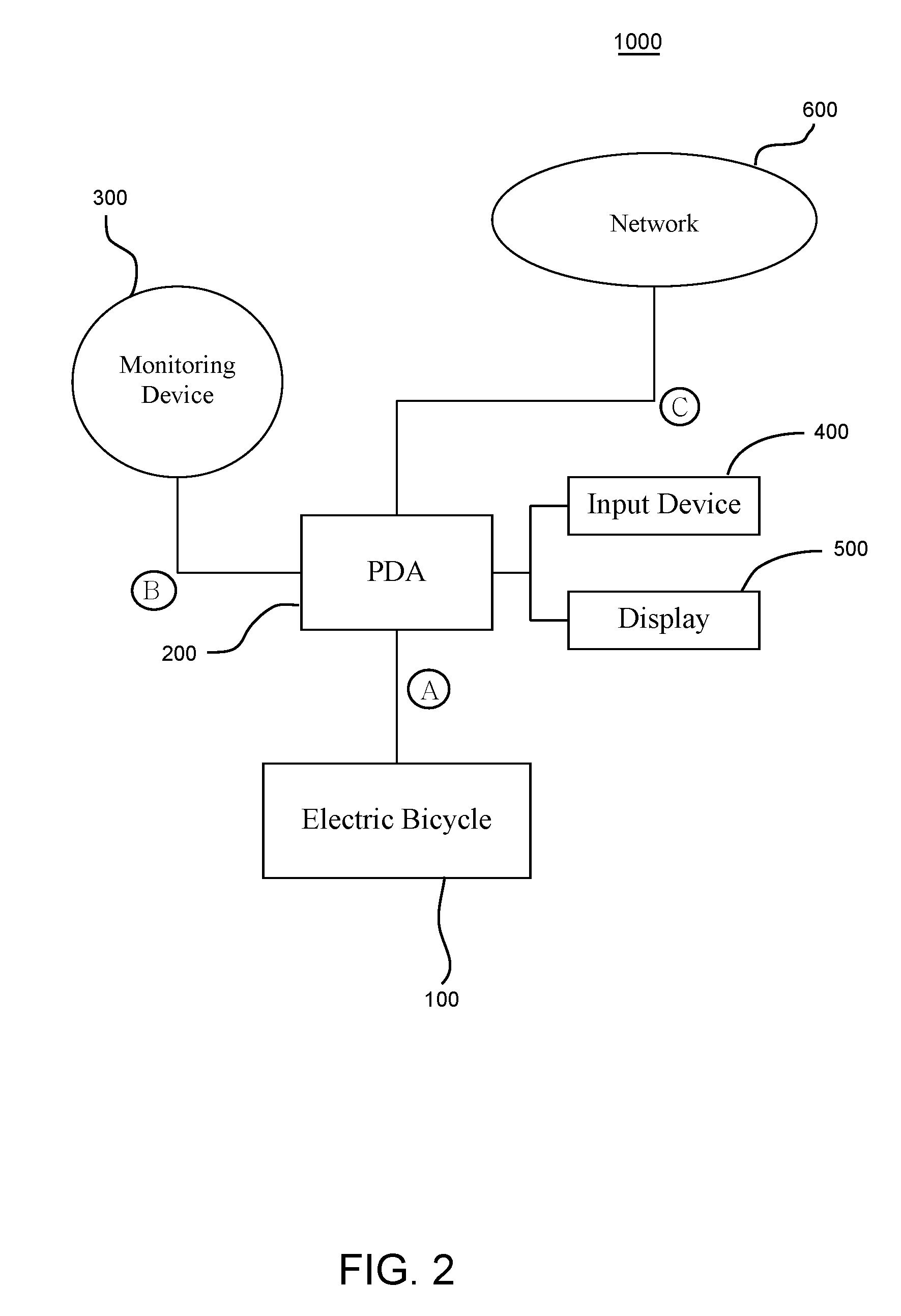
Electric bicycle with personal digital assistant
InactiveUS20090181826A1High levelGymnastic exercisingSatellite radio beaconingInformation processingData control
A control system for controlling an electric bicycle is provided, which includes an electric bicycle, an information processing unit, a monitoring device, an input device, and a display. The electric bicycle and the information processing unit exchange information with each other, and the information includes operation data on the electric bicycle, control data for the electric bicycle, exercise programs. The monitoring device monitors bodily condition of a bicycle rider, and communicates the monitored data with the information processing unit and the electric bicycle. Operations of the electrical bicycle are controlled by collected information and data. The operations of the electric bicycle include a power output level, gear shift, RPM, speed, and acceleration, and the operations of the electrical bicycle are controlled so as to keep a heart rate of the bicycle rider at a target heart rate.
Owner:TURNER JAMES R
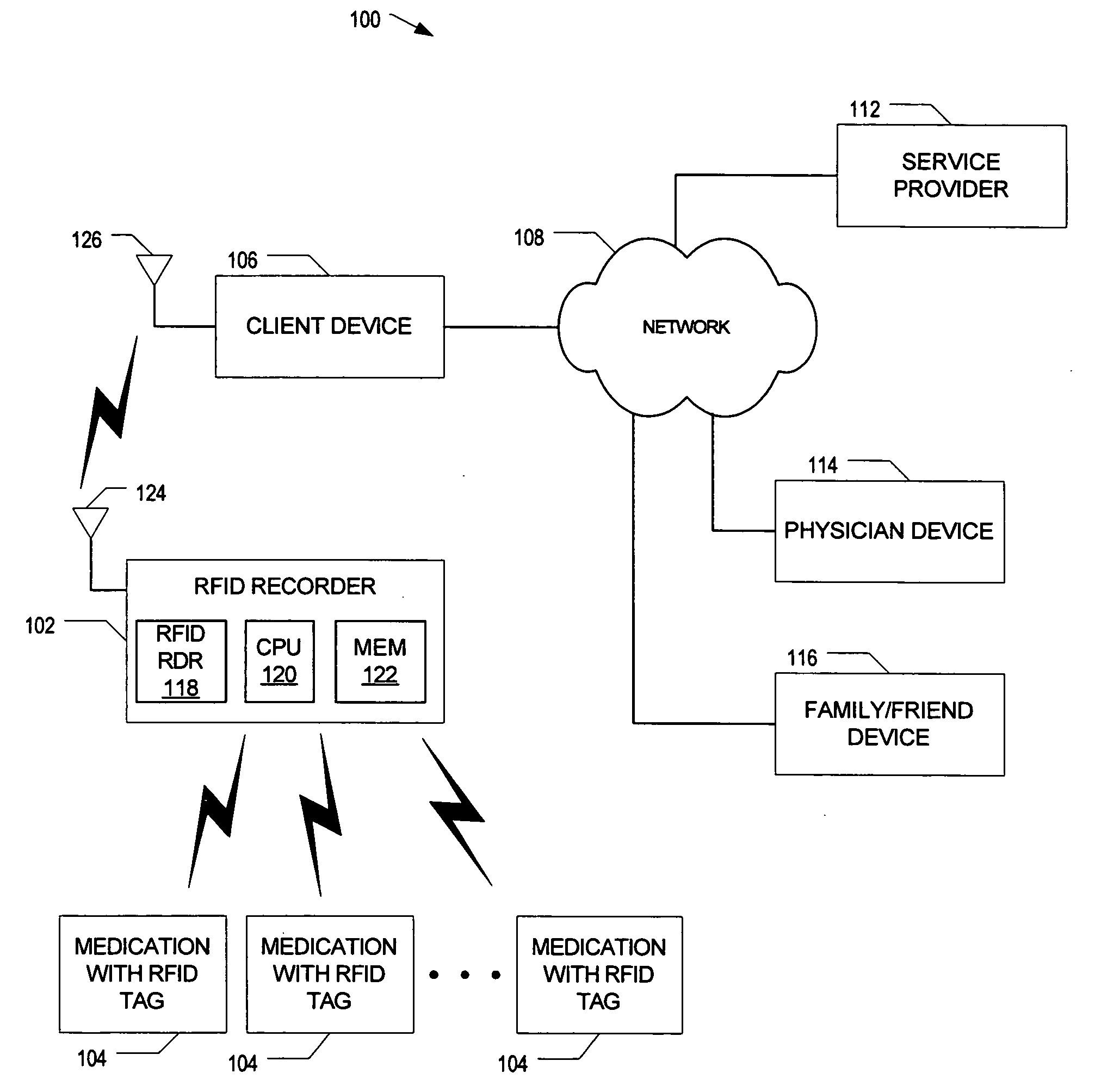
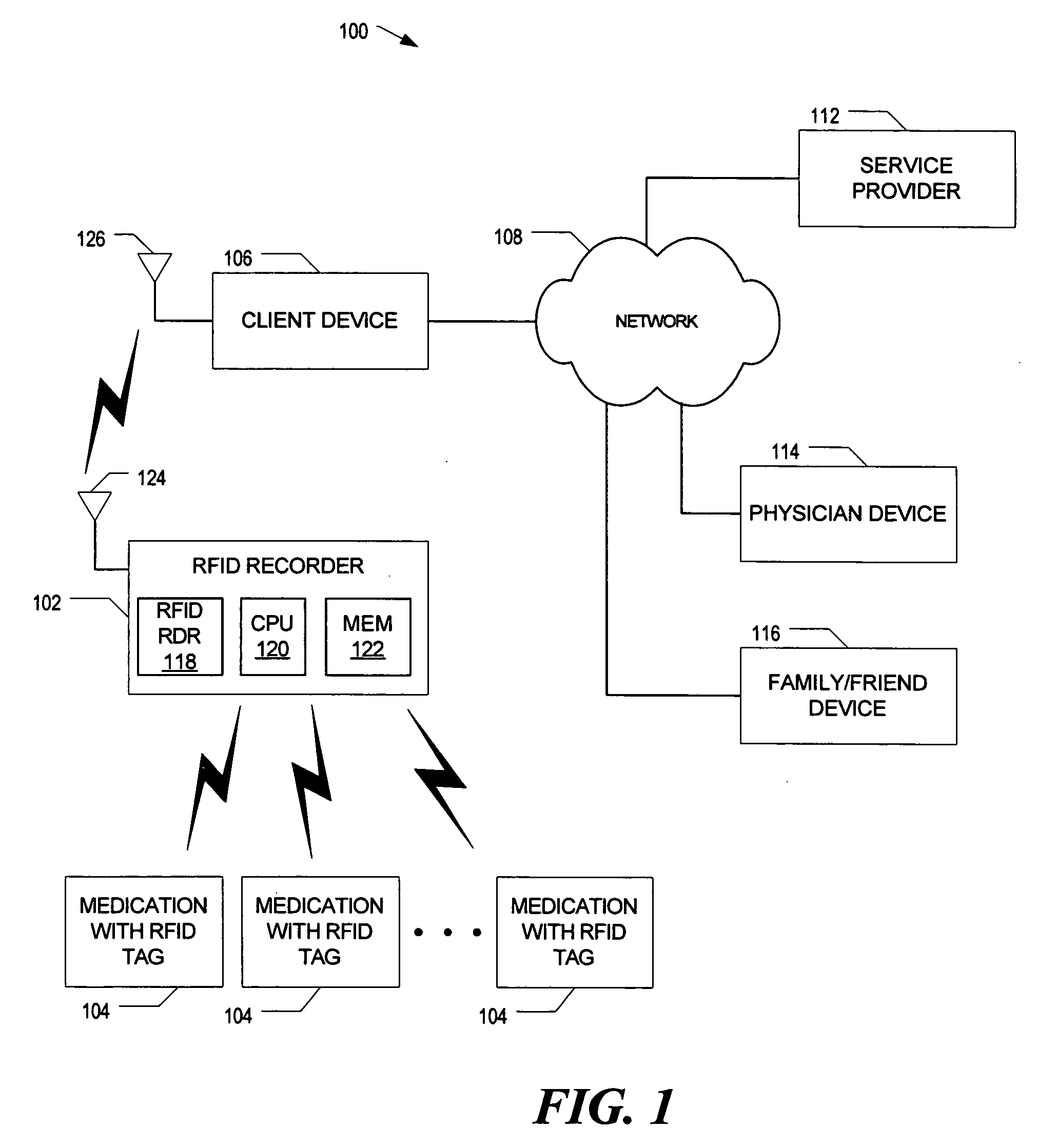
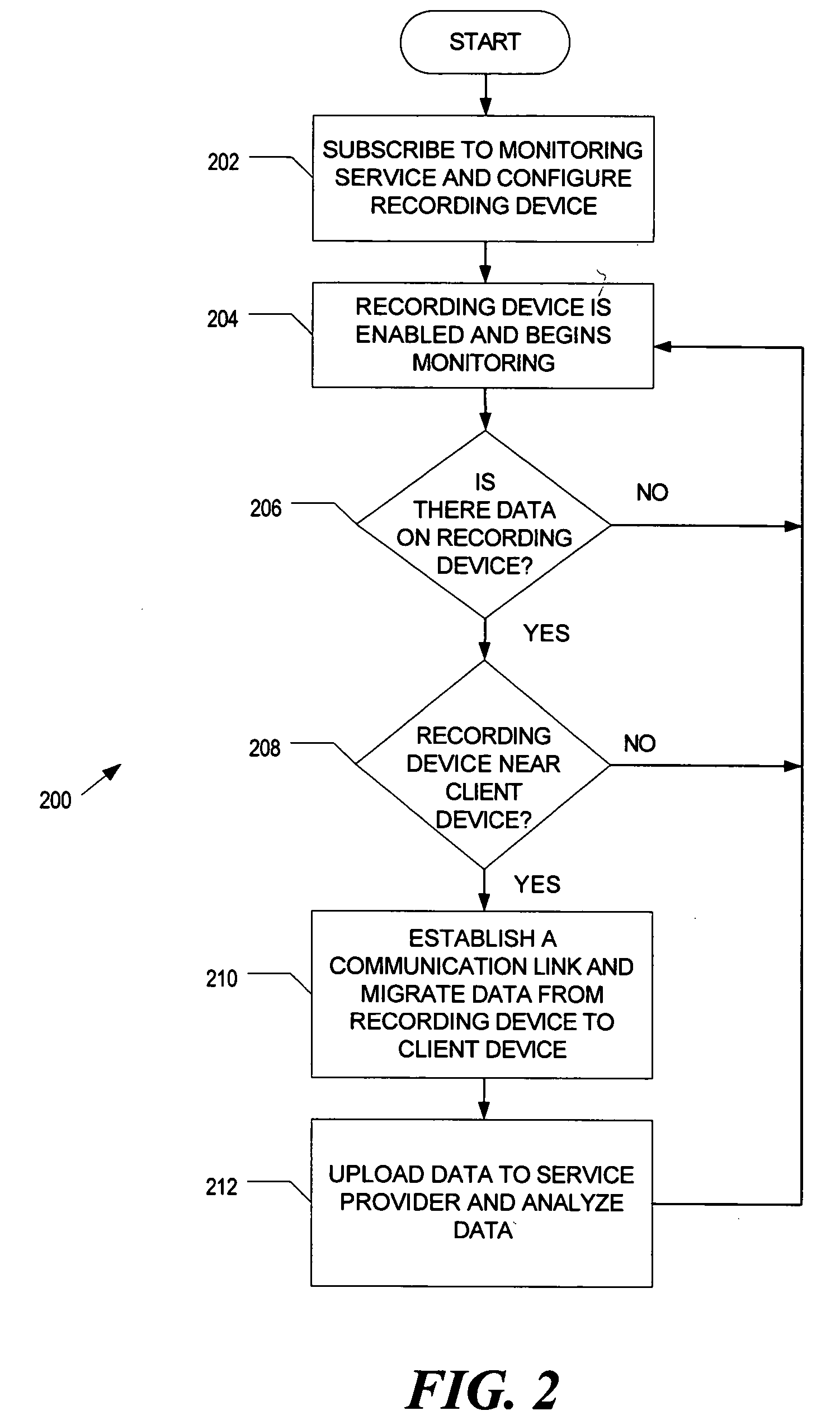
Radio frequency identification based system to track consumption of medication
InactiveUS20050285746A1Drug and medicationsCo-operative working arrangementsDevice MonitorRadio frequency
A radio frequency identification (RFID) based system to track consumption of medicine is disclosed. An RFID device monitors for a signal pattern indicative of an RFID tag contained within medication and determines a status based on a presence or absence of the signal pattern. The signal pattern includes a medication identifier and a signal level over time. A detected signal pattern is compared to stored ingestion profiles to distinguish between consumed and non-consumed medication.
Owner:INTEL CORP
Targeting of advertisements to users of an online service
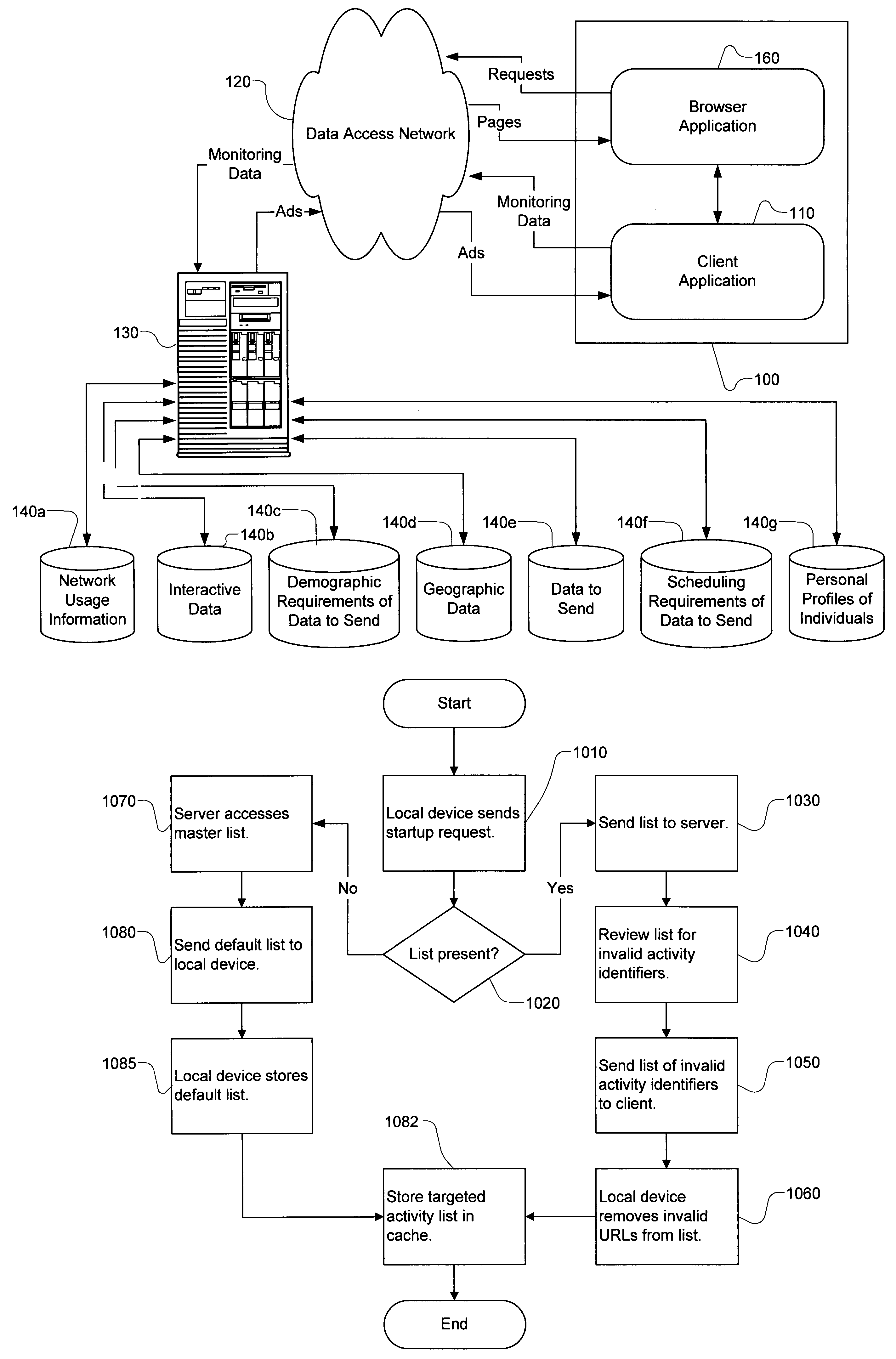
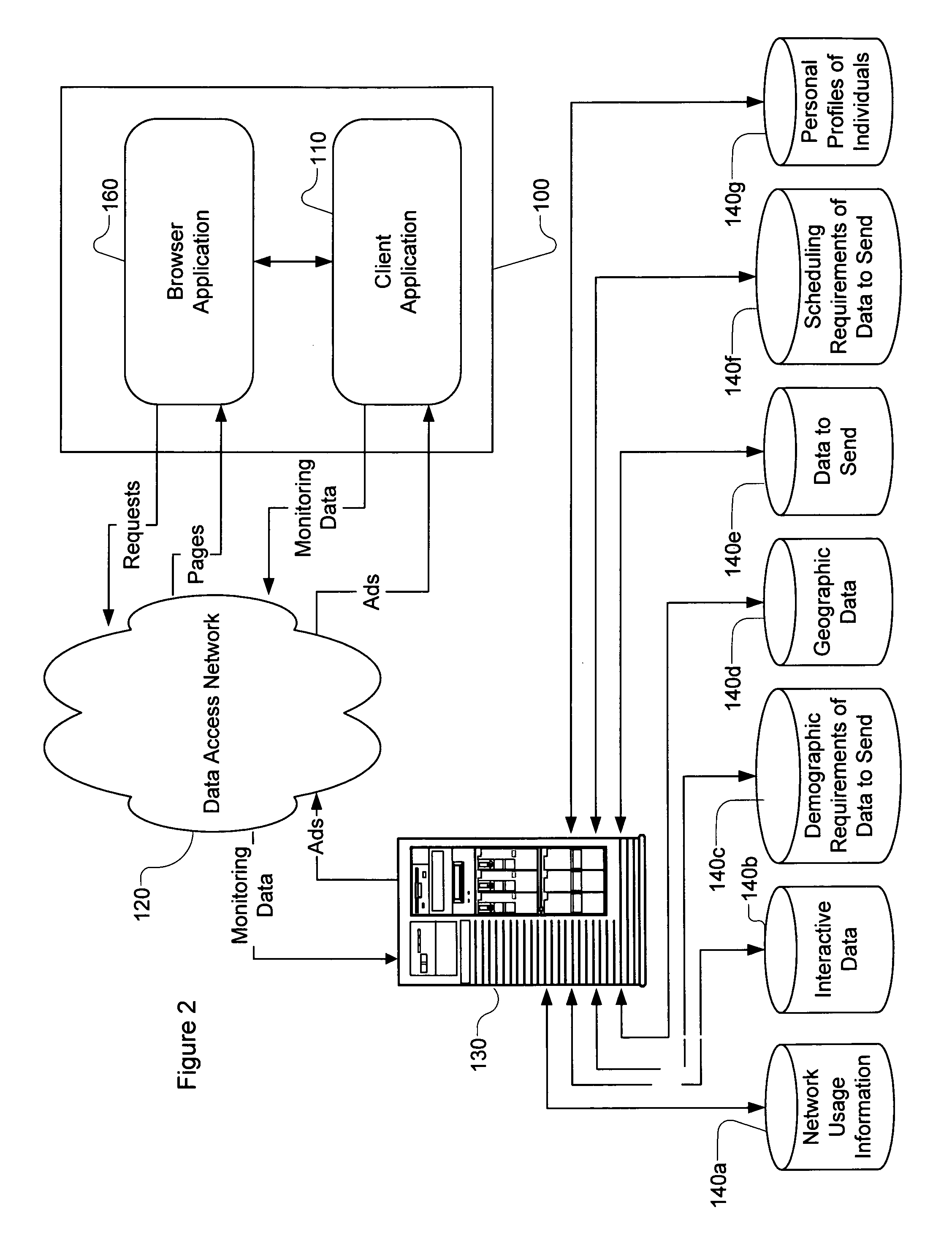
There is disclosed a server and local device that interface for selecting advertisements to be viewed by users of an online service based upon user activity. The local device preferably maintains a targeted activity list of activity identifiers and associated advertisements. The local device monitors the activity on the local device and compares the activity to the identifiers in the targeted activity list. If the activity matches one of the identifiers, the local device plays one or more advertisements.
Owner:SPEED TECH +1
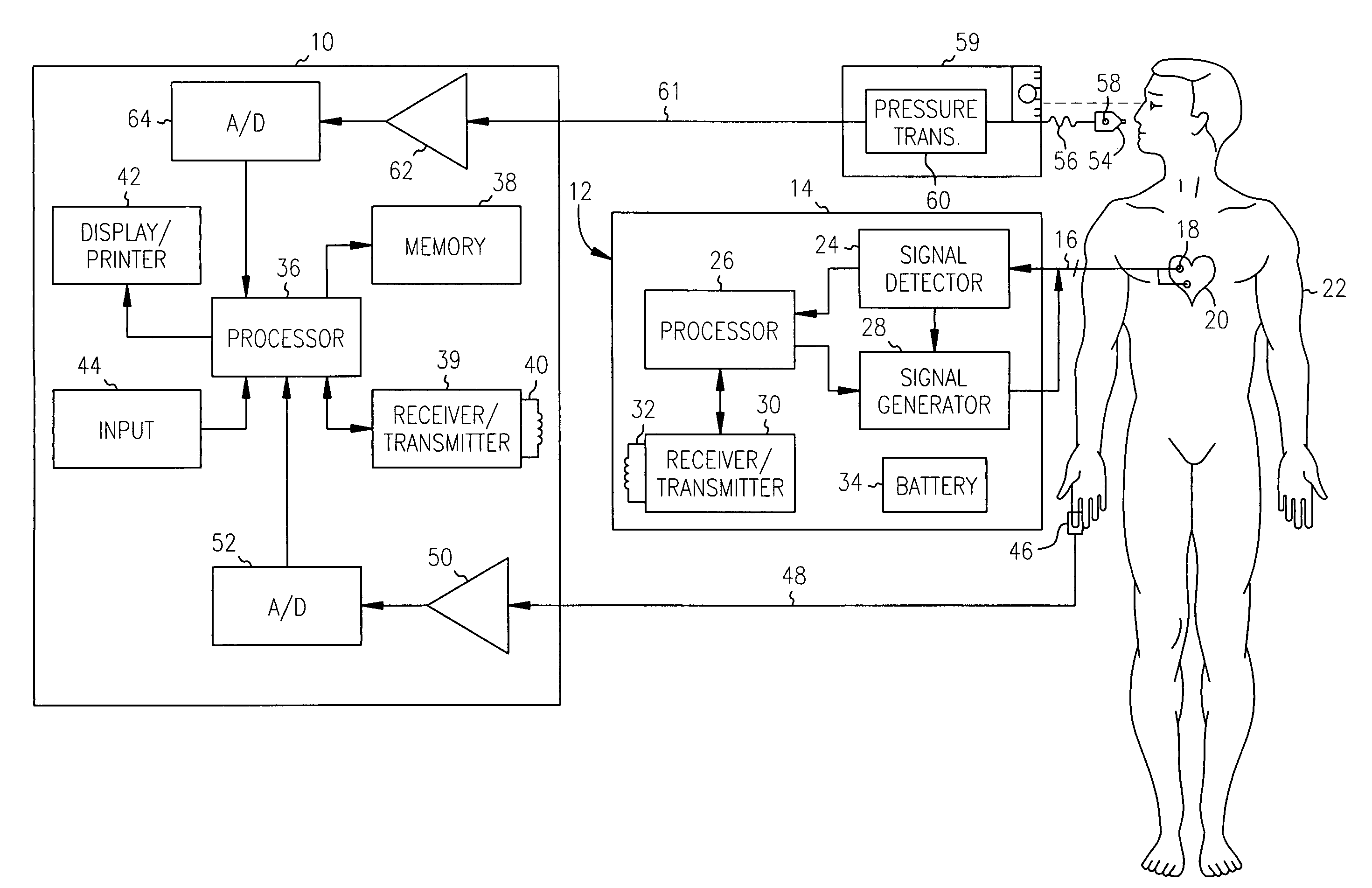
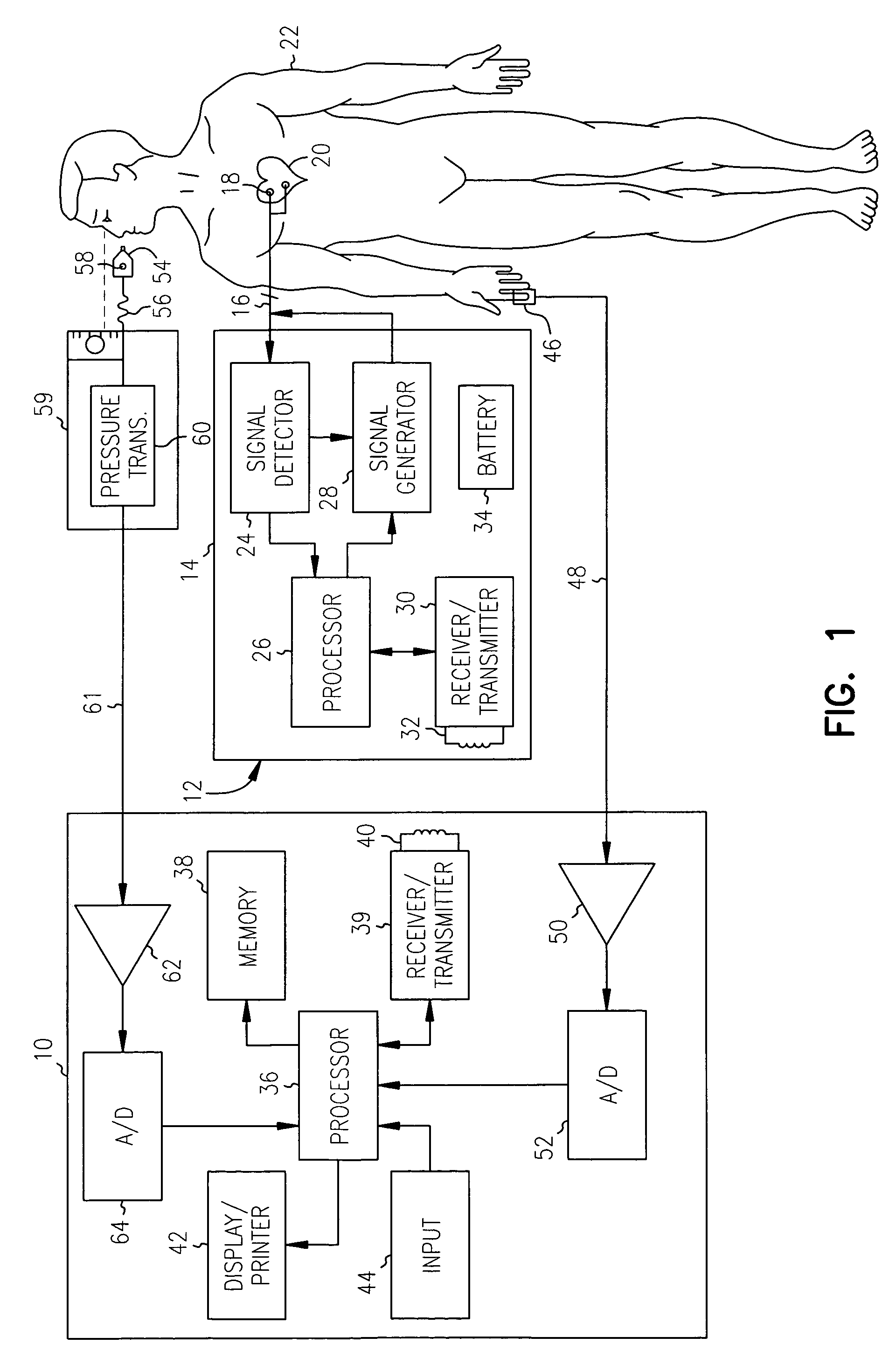
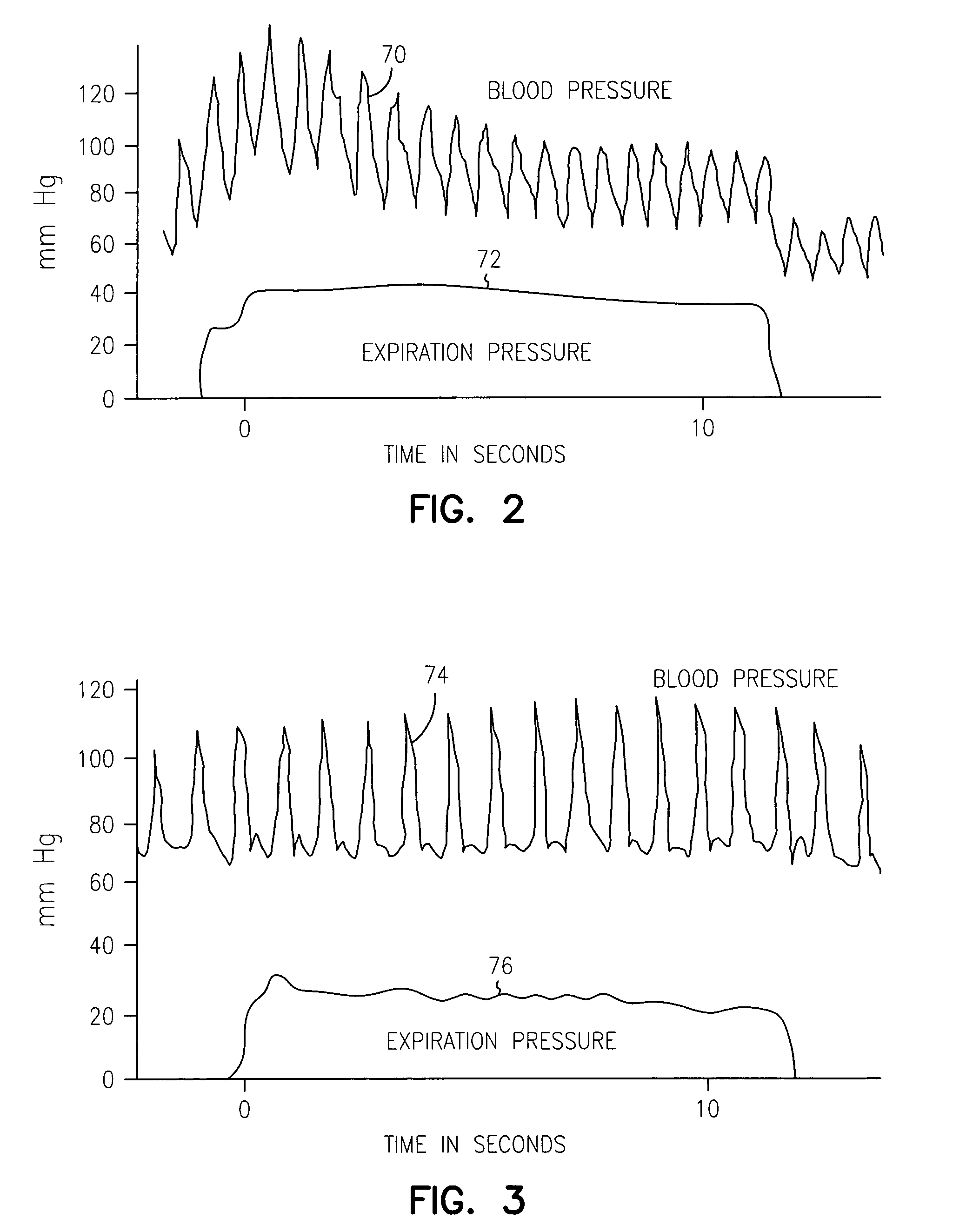
Non-invasive method and apparatus for cardiac pacemaker pacing parameter optimization and monitoring of cardiac dysfunction
InactiveUS20050043767A1Uniform peak amplitudeEasy to detectHeart stimulatorsCardiac dysfunctionAmplitude response
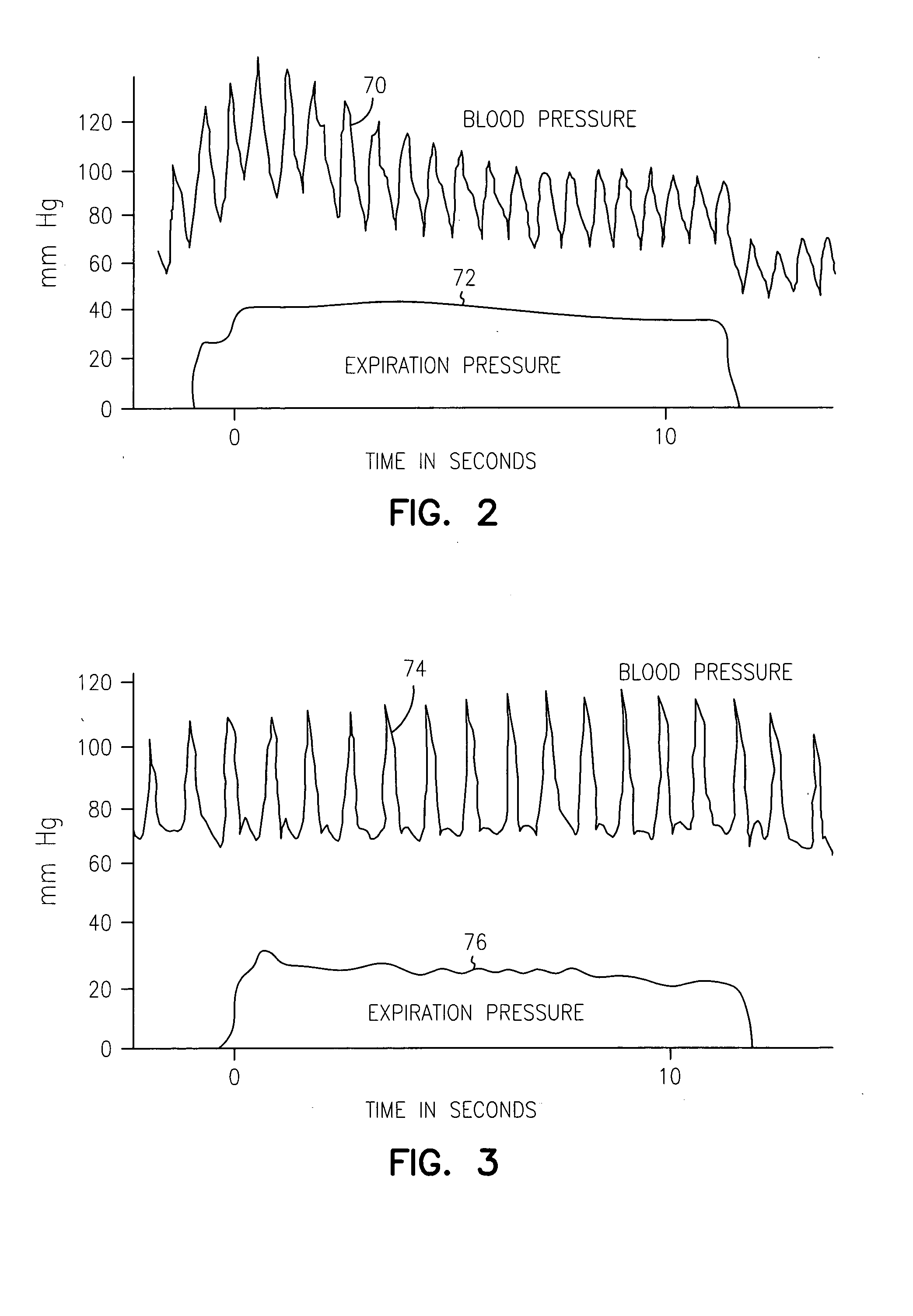
A plethysmogram signal is sensed from a patient and provided to a programmer device for monitoring the condition of the patient and for optimizing pacing parameters of a cardiac device implanted in the patient. The programmer device analyzes the plethysmogram signal for cardiac performance associated with different pacing parameters. The cardiac performance is indicated by, for example, a pulse amplitude response, a degree of pulsus alternans, or irregularity in the pressure pulses detected in an atrial fibrillation patient. The pacing parameters resulting in the best cardiac performance are selected as the optimum pacing parameters. In one embodiment, the programmer device monitors a Valsalva maneuver performed by a patient. Optimum pacing parameters are derived by analysis of the plethysmogram signals obtained during performance of the Valsalva maneuver while the patient is paced using different pacing parameters.
Owner:CARDIAC PACEMAKERS INC
Method for mitigating the unauthorized use of a device
ActiveUS20090253408A1Raise the possibilityIncrease opportunitiesUnauthorised/fraudulent call preventionEavesdropping prevention circuitsDevice MonitorLocal environment
The invention is directed to systems and methods for detecting the loss, theft or unauthorized use of a device and / or altering the functionality of the device in response. In one embodiment, a device monitors its use, its local environment, and / or its operating context to determine that the device is no longer within the control of an authorized user. The device may receive communications or generate an internal signal altering its functionality, such as instructing the device to enter a restricted use mode, a surveillance mode, to provide instructions to return the device and / or to prevent unauthorized use or unauthorized access to data. Additional embodiments also address methods and systems for gathering forensic data regarding an unauthorized user to assist in locating the unauthorized user and / or the device.
Owner:BLANCCO TECH GRP IP OY
Method and system for secure cashless gaming
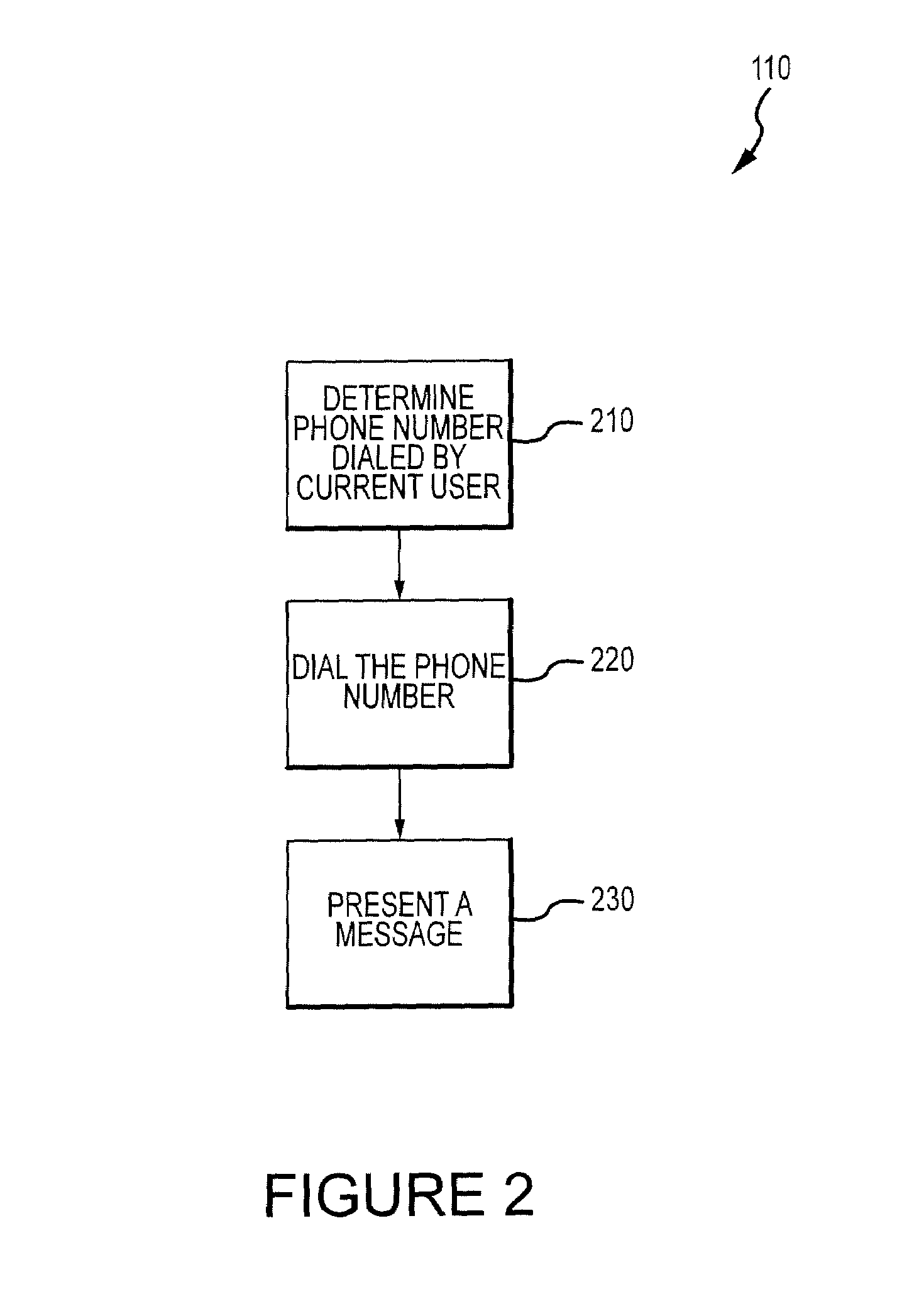
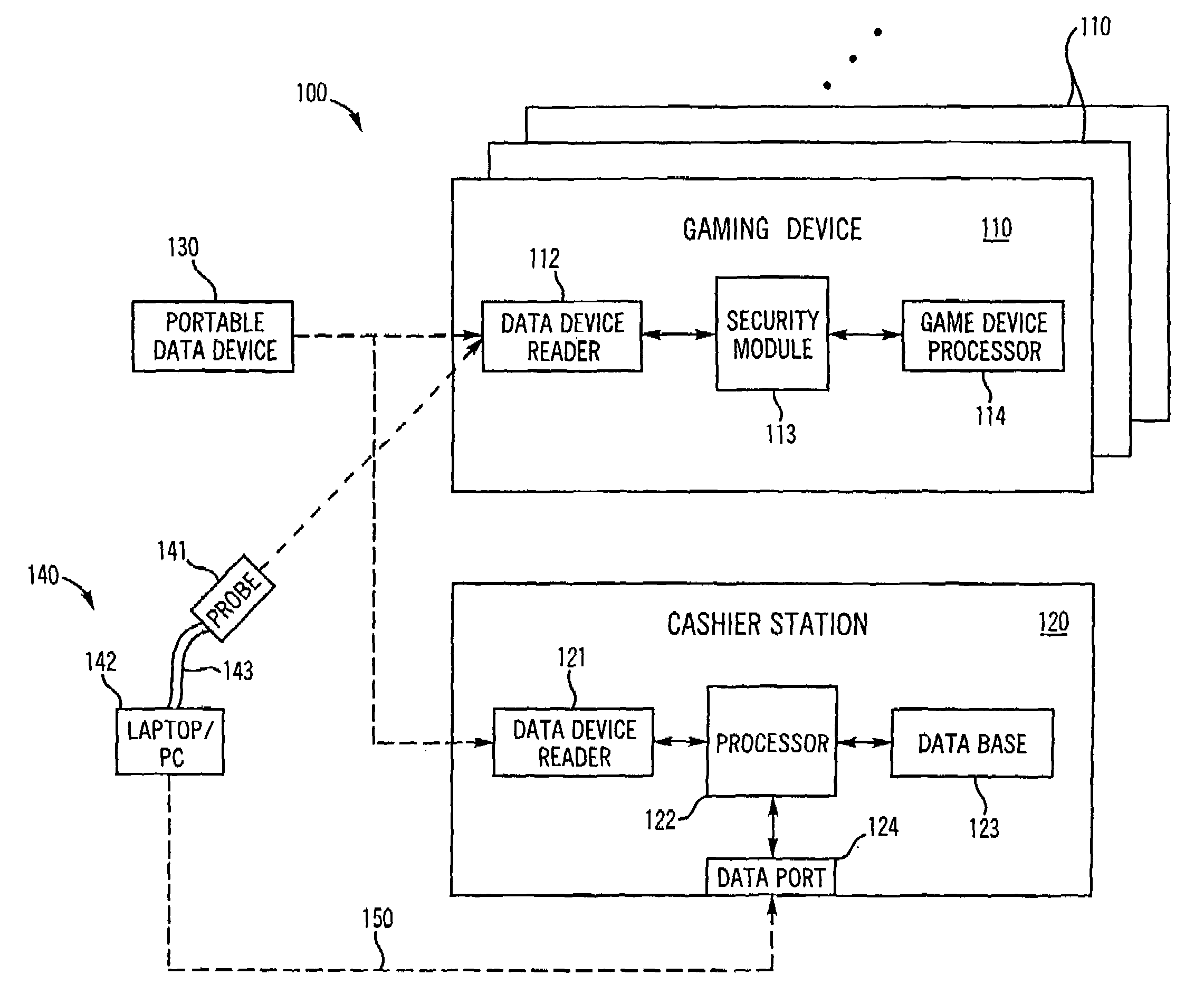
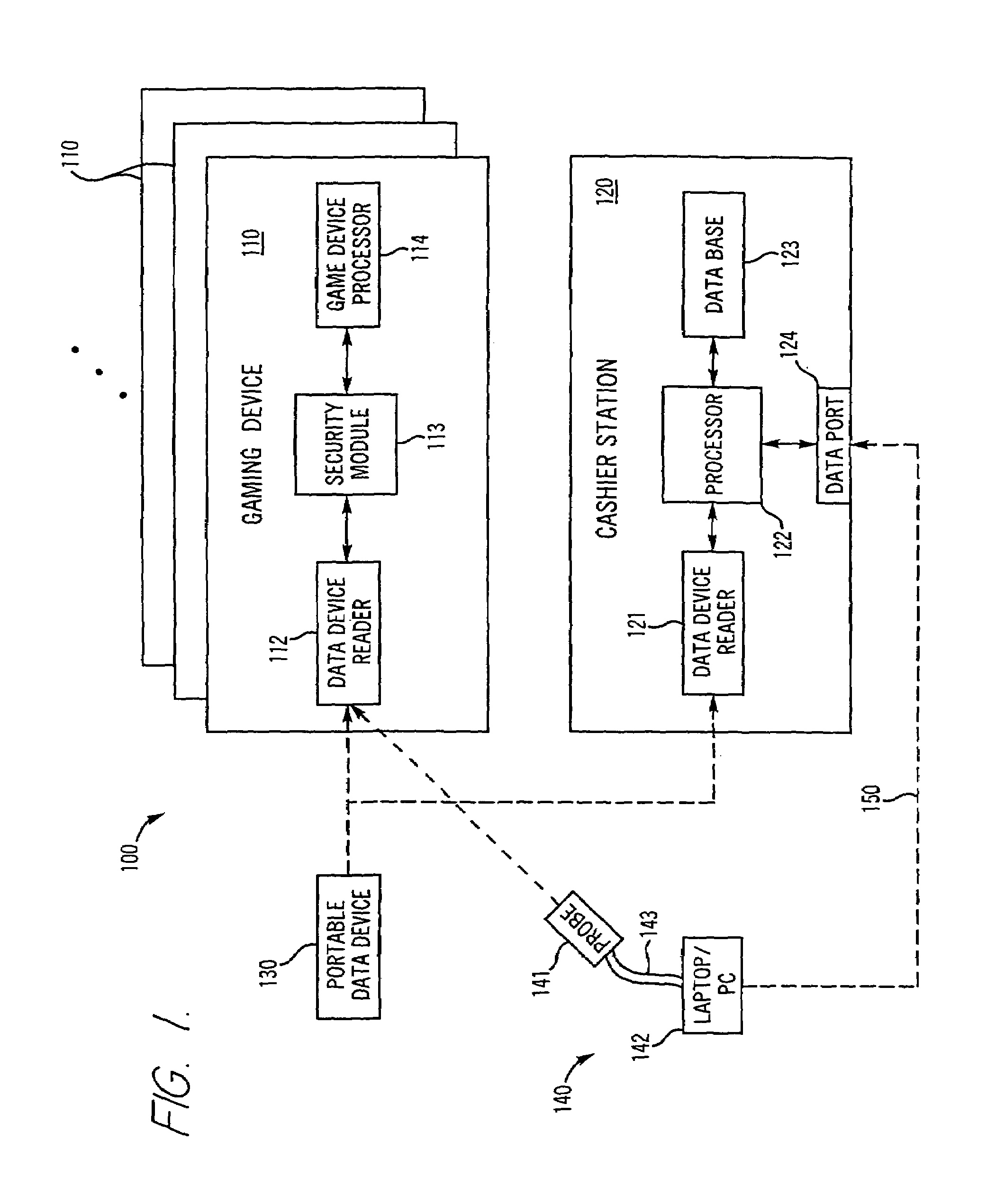
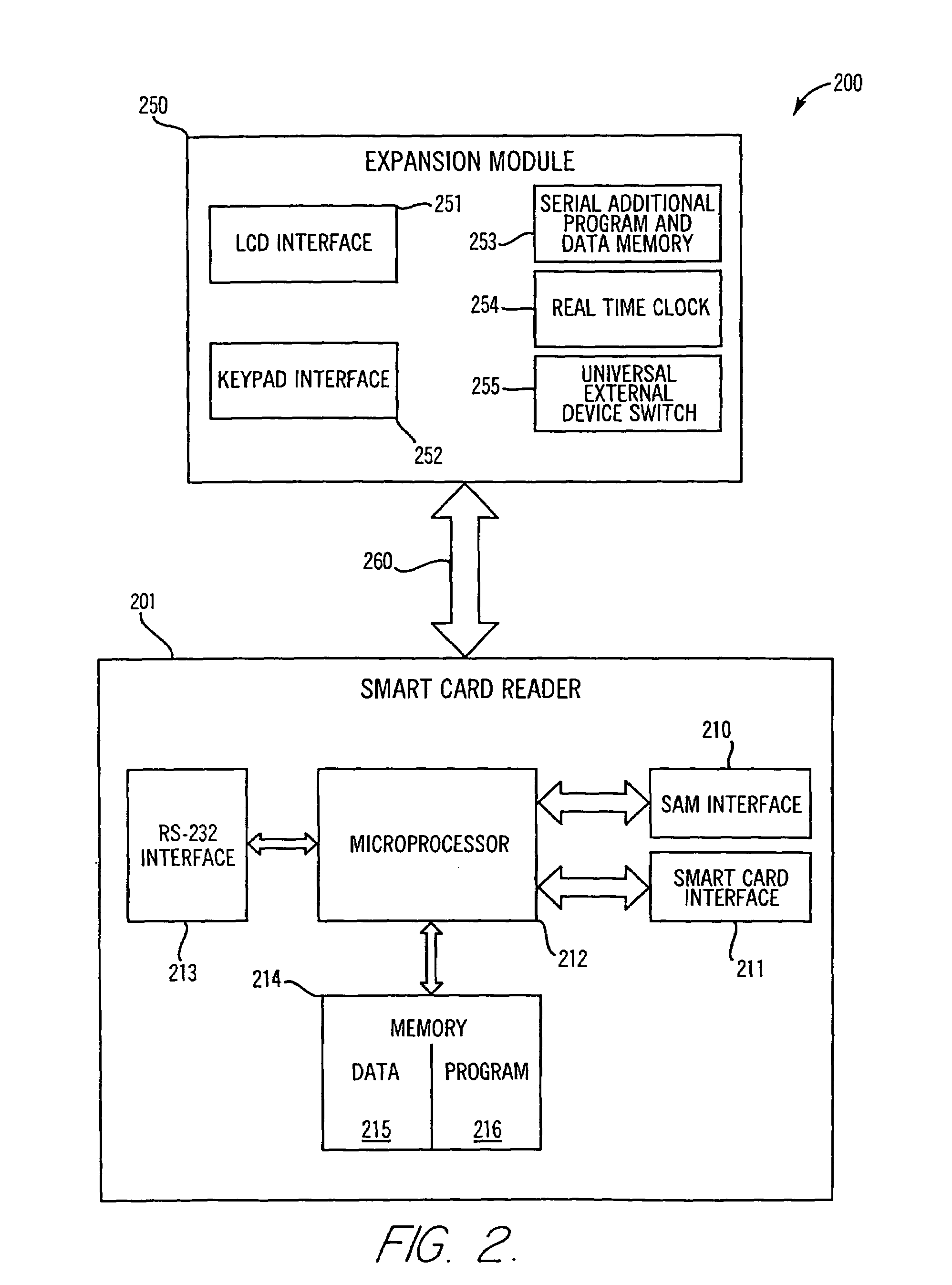
InactiveUS7036012B2Reduce needDigital data processing detailsUser identity/authority verificationData ingestionTransaction data
A secure cashless gaming system comprises a plurality of gaming devices which may or may not be connected to a central host network. Each gaming device includes an intelligent data device reader which is uniquely associated with a security module interposed between the intelligent data device reader and the gaming device processor. A portable data device bearing credits is used to allow players to play the various gaming devices. When a portable data device is presented to the gaming device, it is authenticated before a gaming session is allowed to begin. The intelligent data device reader in each gaming device monitors gaming transactions and stores the results for later readout in a secure format by a portable data extraction unit, or else for transfer to a central host network. Gaming transaction data may be aggregated by the portable data extraction unit from a number of different gaming devices, and may be transferred to a central accounting and processing system for tracking the number of remaining gaming credits for each portable data unit and / or player. Individual player habits can be monitored and tracked using the aggregated data. The intelligent data device reader may be programmed to automatically transfer gaming credits from a portable data device the gaming device, and continually refresh the credits each time they drop below a certain minimum level, thus alleviating the need for the player to manually enter an amount of gaming credits to transfer to the gaming device.
Owner:SMART CARD INTEGRATORS
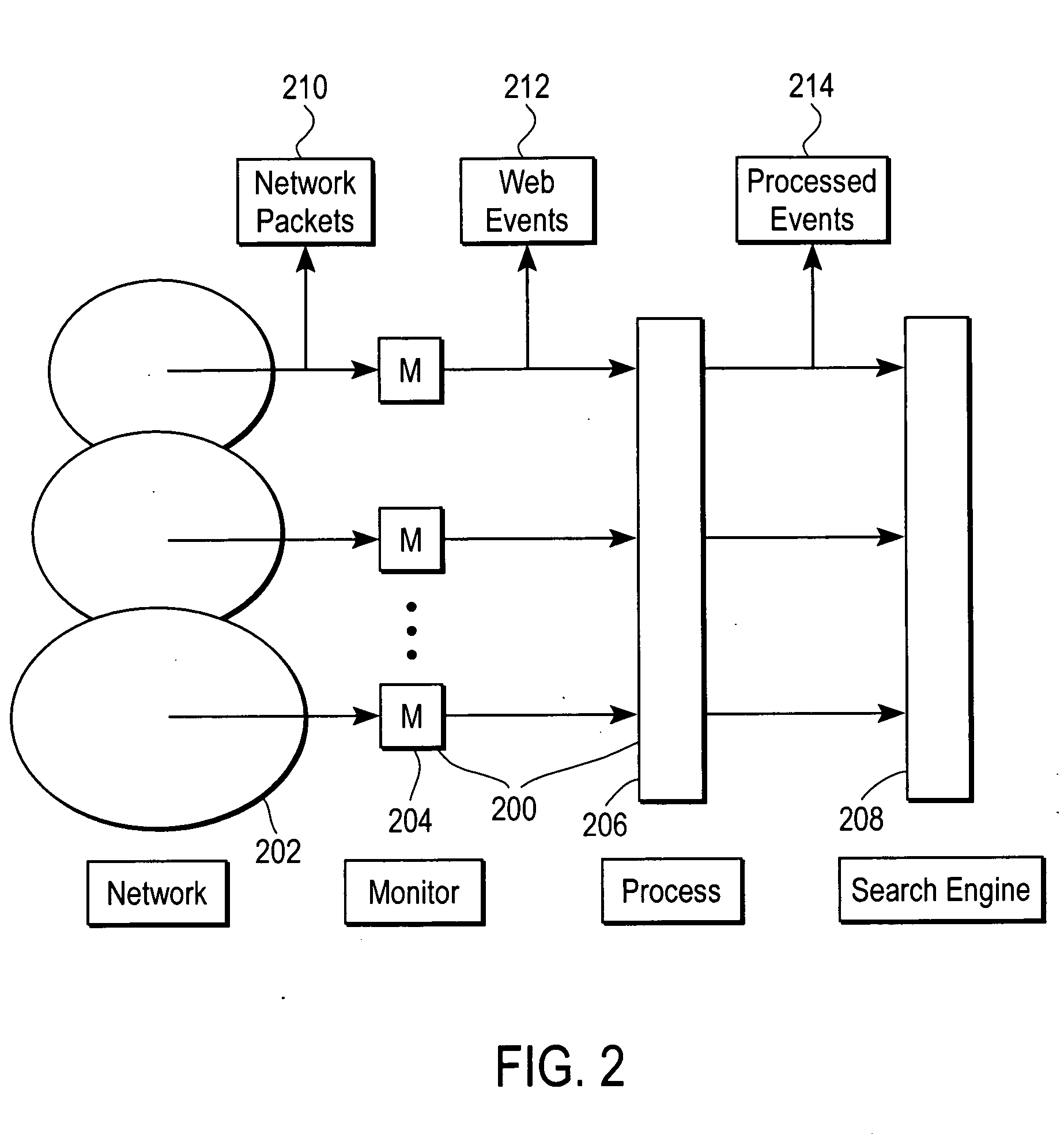
Network traffic monitoring for search popularity analysis
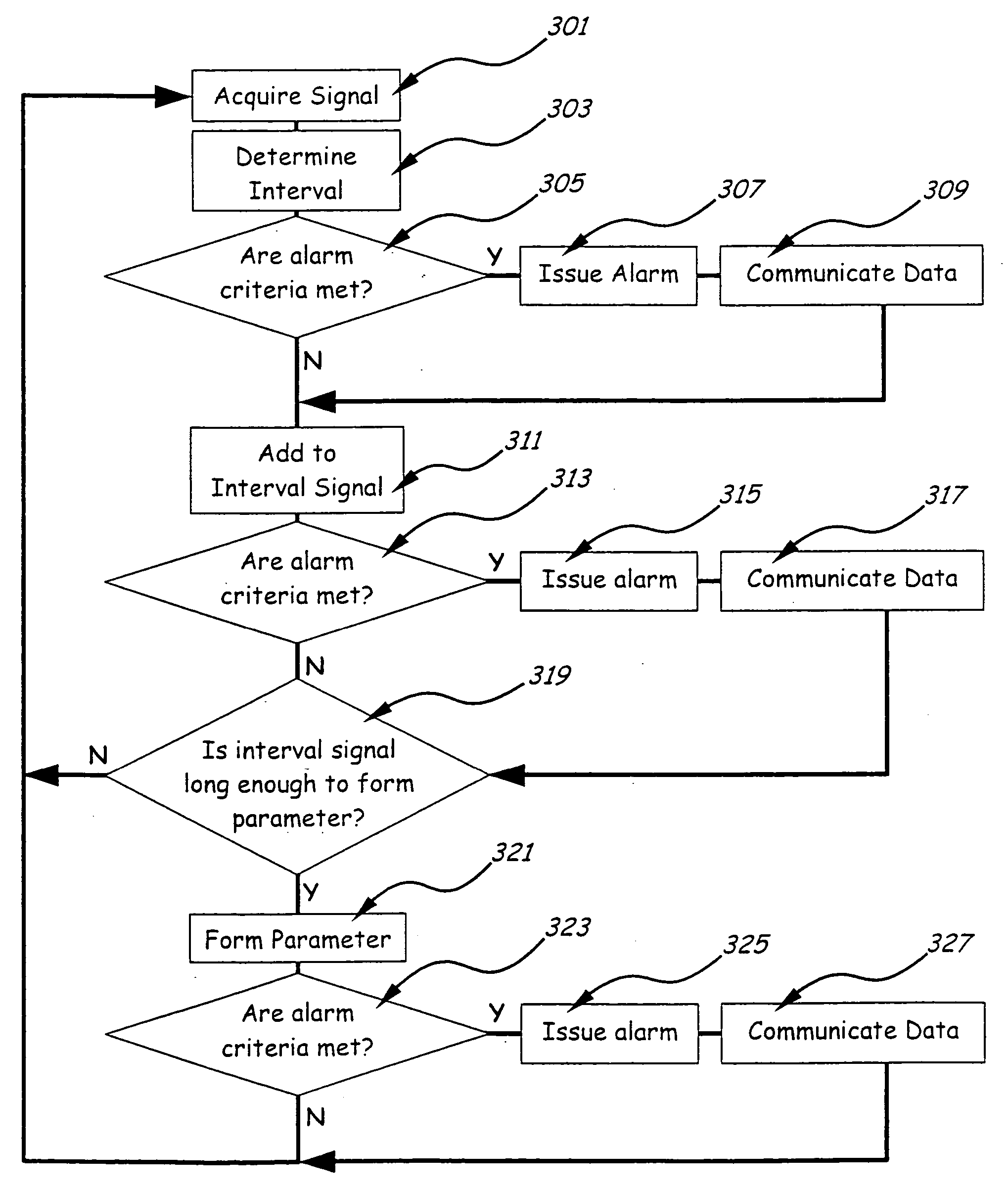
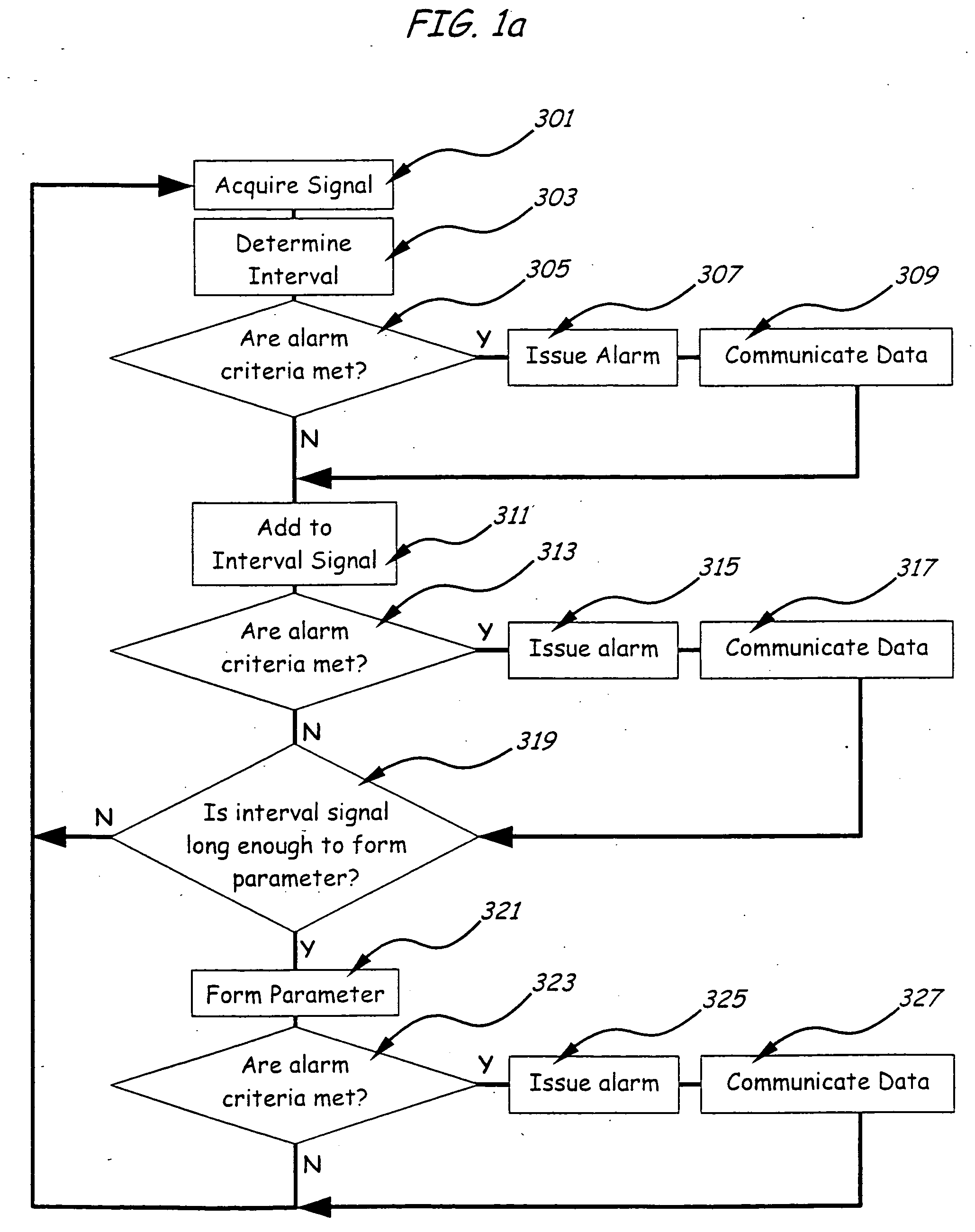
The popularity of web pages is monitored and used to rank the web pages retrieved in response to an Internet search. The popularity of a web page is proportionate to the number of visits to that web page. Web pages with greater popularity are ranked higher in priority. Furthermore, the score of a first web page is propagated to a plurality of second web pages to which the first web page is linked substantially in relative proportion to the popularity of the links from the first web page to each of the second web pages. Monitoring devices monitor TCP packets traversing the Internet and extract information from the TCP packets, such as the requested URI or URL, the client IP address, a server IP address and a server host name, and a referrer URI, if any. The extracted information is forwarded to a processing module that keeps track of the popularity of the web pages.
Owner:THE BOEING CO
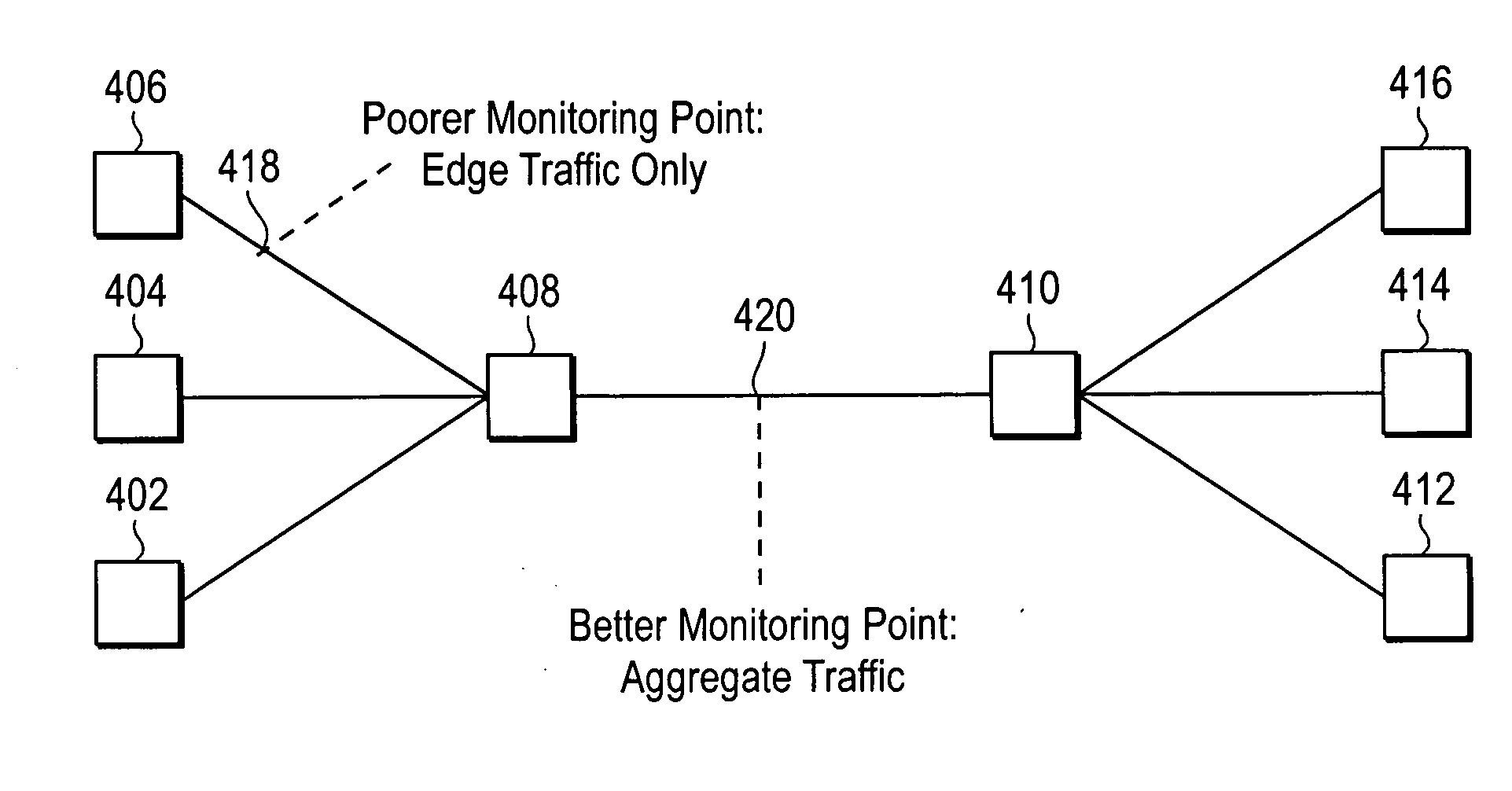
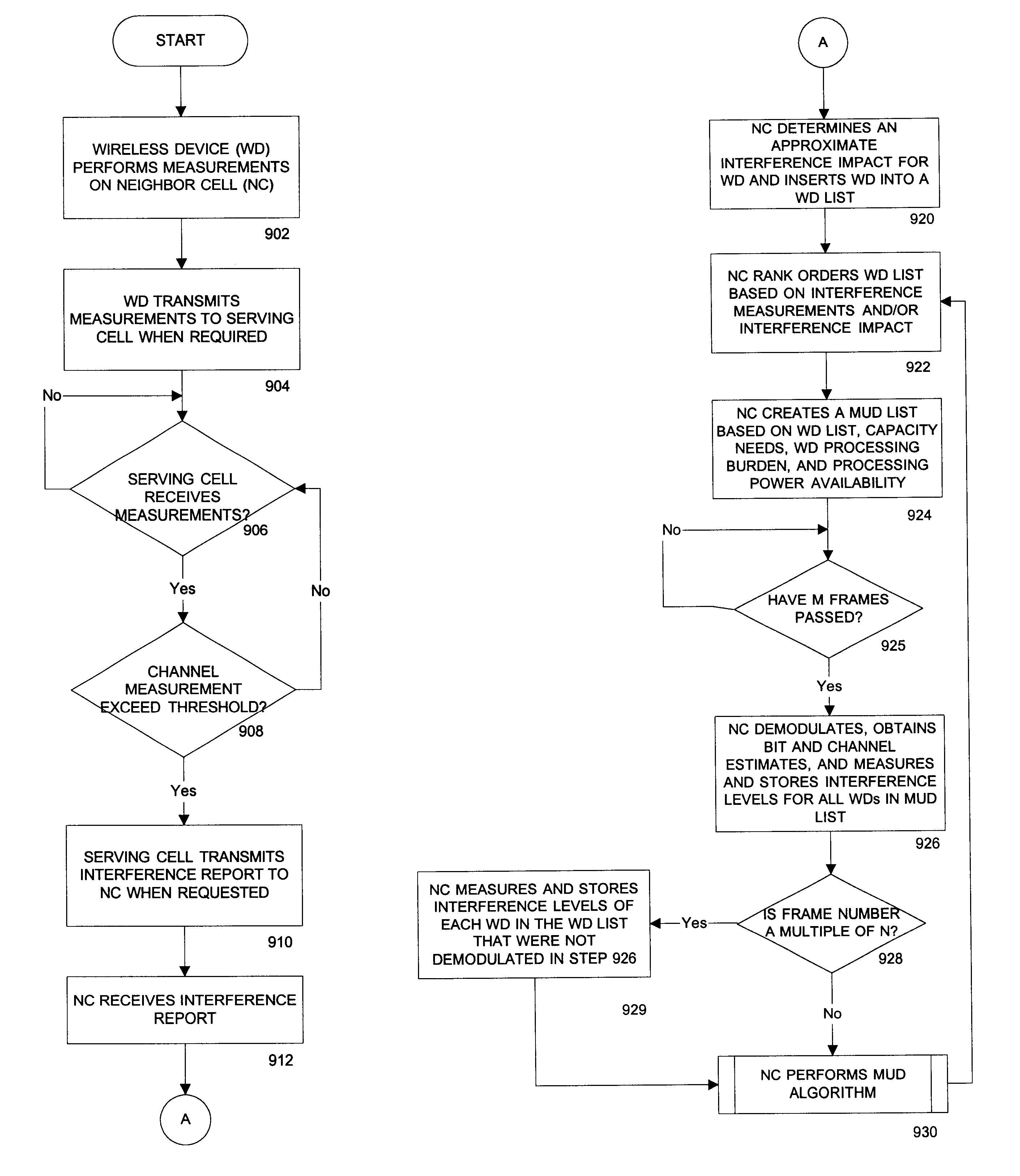
Methods and systems for reducing interference across coverage cells
InactiveUS6771934B2Error preventionLine-faulsts/interference reductionMulti user detectionDevice Monitor
Methods and systems are provided for reducing interference across coverage cells using base stations interconnected by a packet network. A wireless device monitors the channel signal strength of its serving cell and its neighboring cell. The serving cell collects measurements from the wireless devices within its cell and informs its neighboring cell when one of the wireless device may be causing significant interference to the neighboring cell. The neighboring cell collects this information and executes a multi-user detection and cancellation algorithm on a subset of these interfering wireless devices.
Owner:CISCO TECH INC
Method and apparatus for detecting vehicular collisions
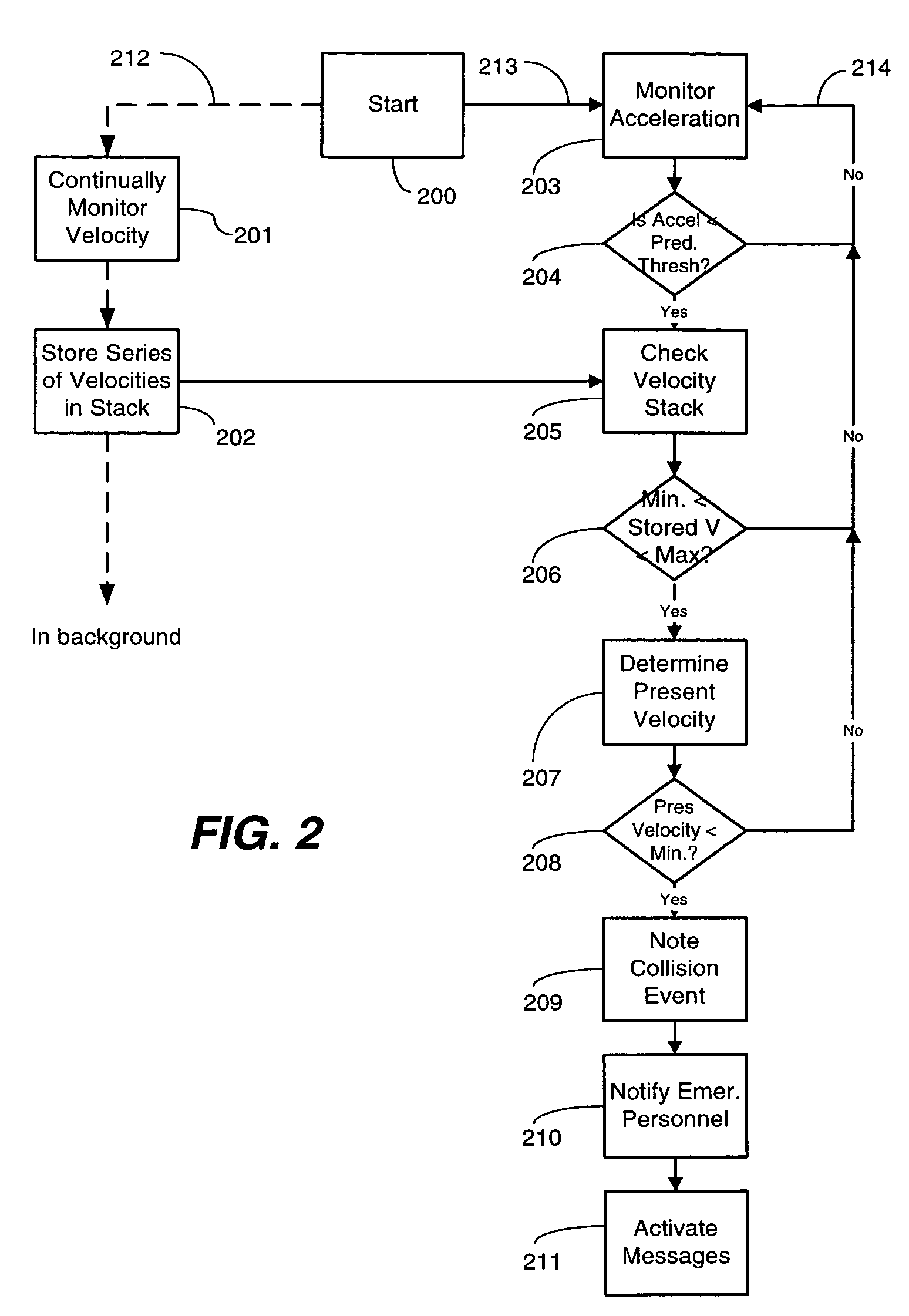
A portable electronic device, like a cellular telephone is capable of detecting collisions between vehicles and notifying the proper authorities. The device includes a microprocessor and memory, in addition to an accelerometer and global positioning systems receiver. The memory includes at least one filter for screening out false positives, which are false collision detections. In one embodiment, the device determines its velocity. It then checks to see if its velocity falls within a range associated with moving vehicles. If so, the device monitors the accelerometer. When acceleration values in excess of a predetermined threshold are detected, the device pauses and again checks its velocity. If the velocity has fallen from the range associated with moving vehicles to a range associated with a vehicle that has sustained a collision, the device notifies emergency personnel that a collision has occurred. Another filter includes an operability check of the keypad, coupled with a notification message that the authorities will be called if the keypad has not been actuated within a predetermined time. Another embodiment includes a detector capable of detecting a vehicular cradle, such that the notification only occurs when high acceleration values are detected in a vehicle.
Owner:CONTINENTAL AUTOMOTIVE SYST INC
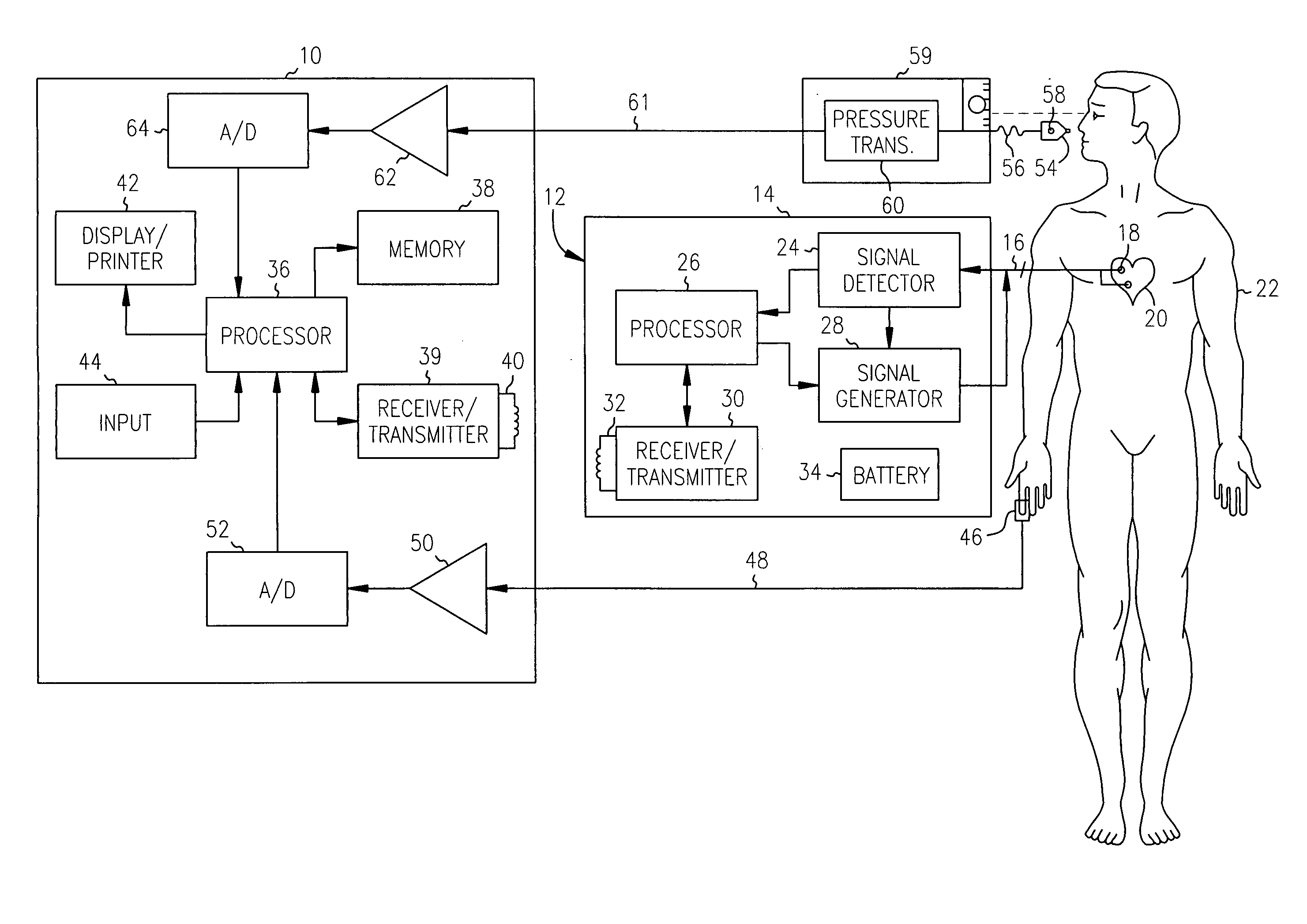
Noninvasive cardiovascular monitoring methods and devices
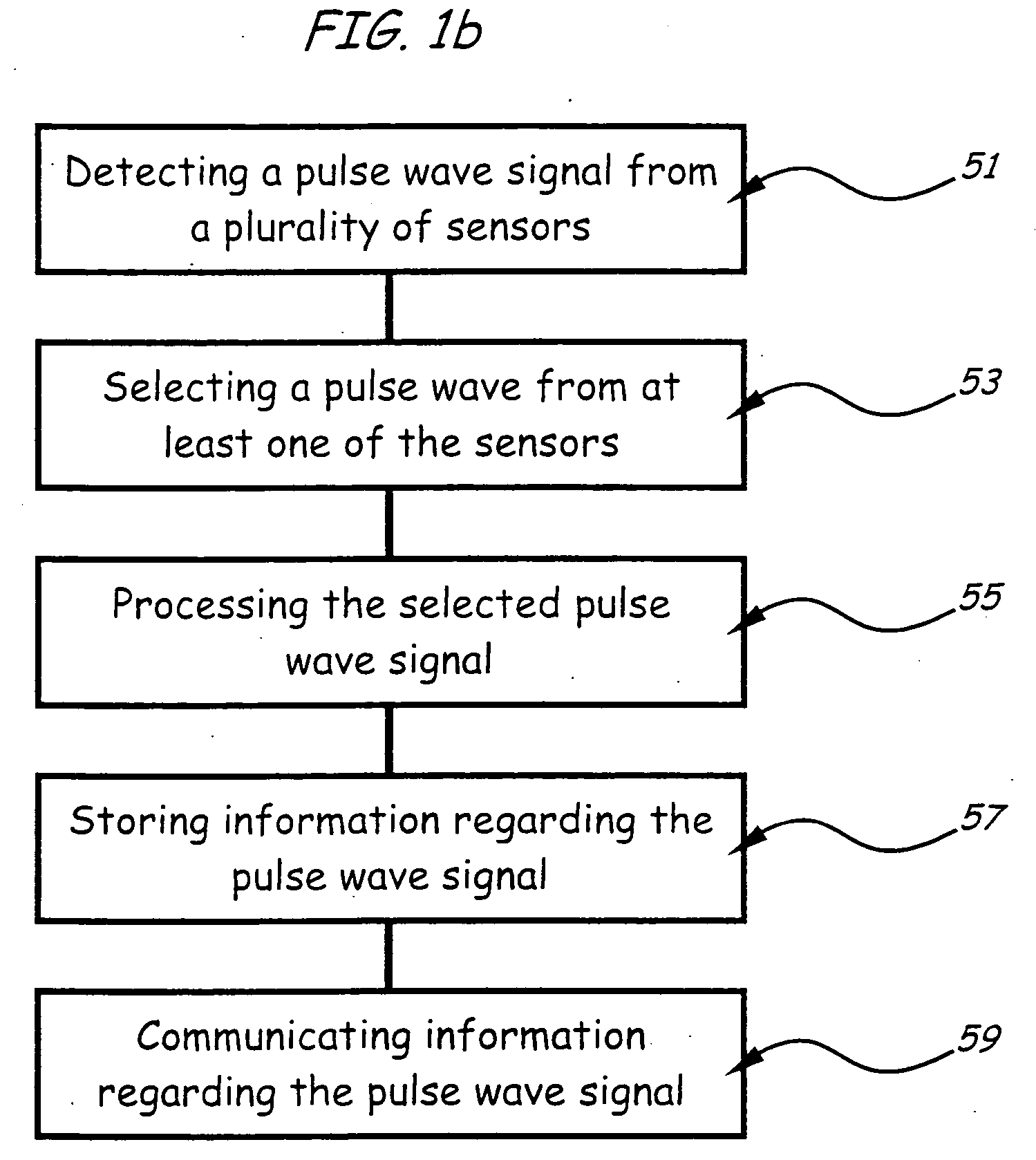
InactiveUS20050096557A1Facilitate signal acquisitionElectrocardiographySensorsPhysiologic StatesDevice Monitor
Monitoring the physiologic status of a human or animal subject includes detecting a blood vessel signal with a sensor. A physiologic time interval can be determined, and information related to the physiologic status of the subject can be analyzed and communicated.
Owner:VOSBURGH FREDERICK +2
Portable Physiological Data Monitoring Device
InactiveUS20120203076A1Diagnostic recording/measuringSensorsCommunication interfaceCommunication unit
A portable monitoring device and a method for monitoring and alerting physiological parameters of a patient are provided. The portable monitoring device comprises a housing, parameter sensing devices, a processing unit, and data communication units. The housing defines an inner surface for establishing physical contact with the patient's body part, and an outer surface opposing the inner surface. The parameter sensing devices acquire physiological data associated with the patient's physiological parameters. The processing unit processes the acquired physiological data and patient information. The data communication units, capable of synchronizing with responder devices, transmit the processed physiological data and the patient information to a base monitoring unit, a remote monitoring station, and / or responder devices via one or more transceivers and data communication interfaces for initiating relief measures. The portable monitoring device monitors the patient's physiological parameters and alerts the remote monitoring station for providing the relief measures to the patient.
Owner:THE ALARM BAND
System for monitoring the unauthorized use of a device
ActiveUS20090249460A1Raise the possibilityIncrease opportunitiesError detection/correctionVolume/mass flow measurementDevice MonitorLocal environment
The invention is directed to systems and methods for detecting the loss, theft or unauthorized use of a device and / or altering the functionality of the device in response. In one embodiment, a device monitors its use, its local environment, and / or its operating context to determine that the device is no longer within the control of an authorized user. The device may receive communications or generate an internal signal altering its functionality, such as instructing the device to enter a restricted use mode, a surveillance mode, to provide instructions to return the device and / or to prevent unauthorized use or unauthorized access to data. Additional embodiments also address methods and systems for gathering forensic data regarding an unauthorized user to assist in locating the unauthorized user and / or the device.
Owner:BLANCCO TECH GRP IP OY
Methods and systems for reducing interference across coverage cells
InactiveUS20030003906A1Reduce distractionsError preventionLine-faulsts/interference reductionMulti user detectionDevice Monitor
Methods and systems are provided for reducing interference across coverage cells using base stations interconnected by a packet network. A wireless device monitors the channel signal strength of its serving cell and its neighboring cell. The serving cell collects measurements from the wireless devices within its cell and informs its neighboring cell when one of the wireless device may be causing significant interference to the neighboring cell. The neighboring cell collects this information and executes a multi-user detection and cancellation algorithm on a subset of these interfering wireless devices.
Owner:CISCO TECH INC
Non-invasive method and apparatus for cardiac pacemaker pacing parameter optimization and monitoring of cardiac dysfunction
A plethysmogram signal is sensed from a patient and provided to a programmer device for monitoring the condition of the patient and for optimizing pacing parameters of a cardiac device implanted in the patient. The programmer device analyzes the plethysmogram signal for cardiac performance associated with different pacing parameters. The cardiac performance is indicated by, for example, a pulse amplitude response, a degree of pulsus alternans, or irregularity in the pressure pulses detected in an atrial fibrillation patient. The pacing parameters resulting in the best cardiac performance are selected as the optimum pacing parameters. In one embodiment, the programmer device monitors a Valsalva maneuver performed by a patient. Optimum pacing parameters are derived by analysis of the plethysmogram signals obtained during performance of the Valsalva maneuver while the patient is paced using different pacing parameters.
Owner:CARDIAC PACEMAKERS INC
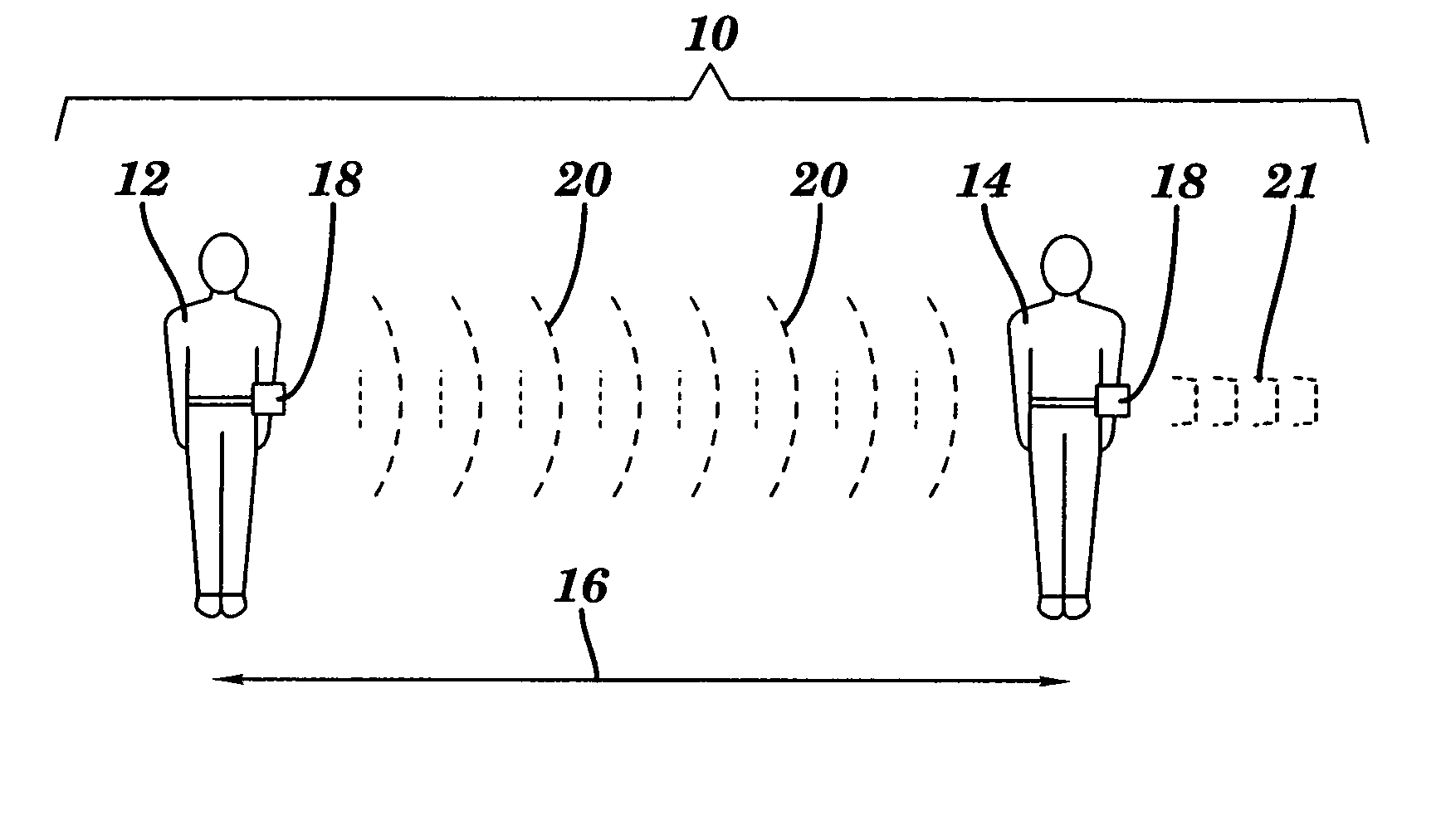
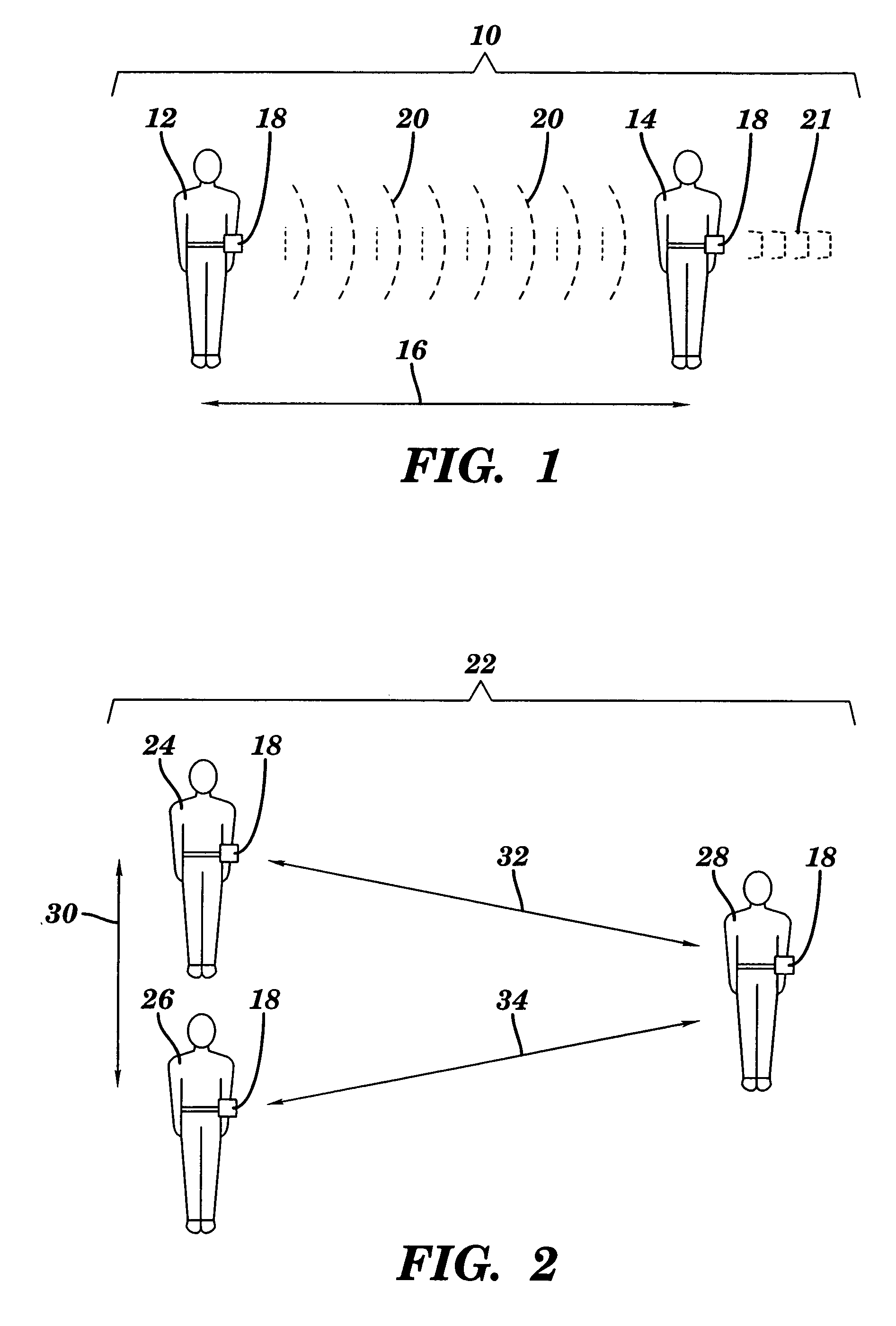
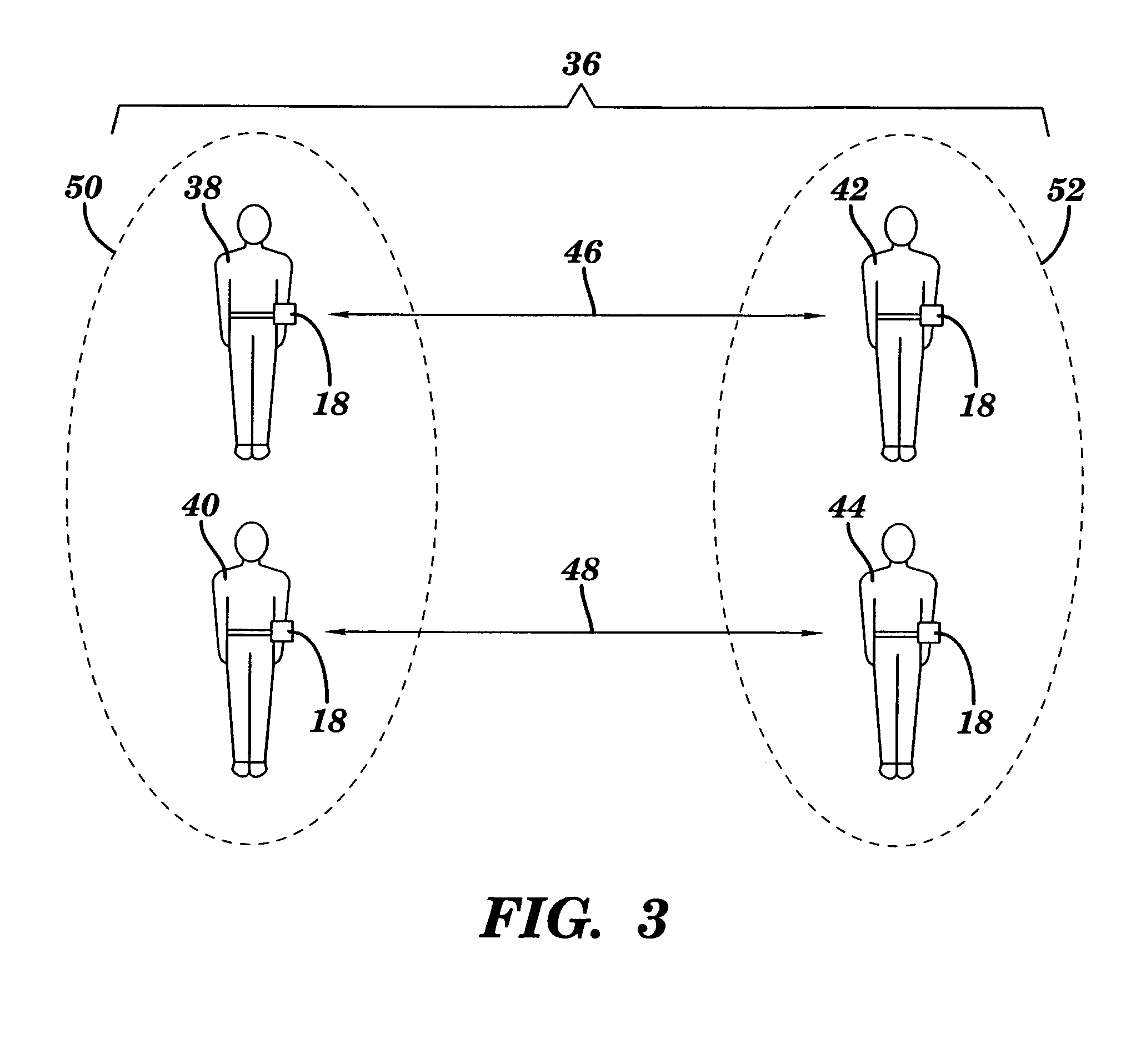
Methods and devices for monitoring the distance between members of a group
InactiveUS20050200487A1Improve survivabilityBreathing protectionBurglar alarm by hand-portable articles removalSurvivabilityDevice Monitor
Emergency workers and other personnel are often endangered by losing contact with other personnel, for example, firefighters working in hostile conditions. Methods and devices for improving the survivability and reducing the potential for injury or death of emergency personnel and others are provided. The methods and devices monitor the distance of members of a group to, among other things, minimize or prevent personnel from being separated from the group. Devices worn by members of a group monitor the distance between members by monitoring the characteristics of wireless communication, for example, signal strength, between members. If the distance between members exceeds or is less than a predetermined distance, an alarm is sounded to alert members to the potential for contact between members or loss of a member of the group. Though aspects of the invention may be used by emergency workers, such as firefighters and policemen, other aspects of the invention may be used to monitor objects or children, among others.
Owner:ODONNELL RYAN +2
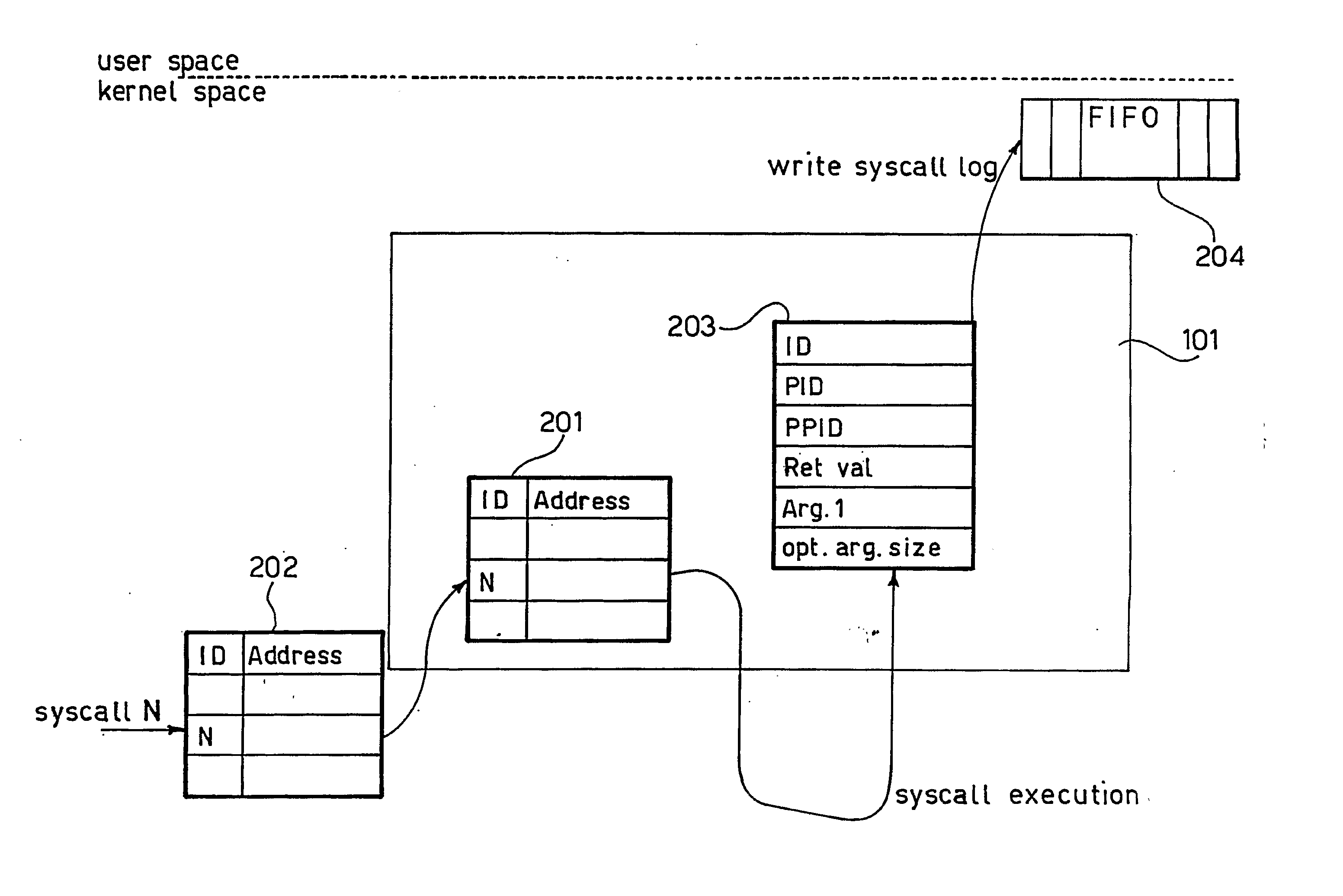
Method and apparatus for monitoring operation of processing systems, related network and computer program product therefor
InactiveUS20070107052A1Effective monitoringMemory loss protectionError detection/correctionFile systemDevice Monitor
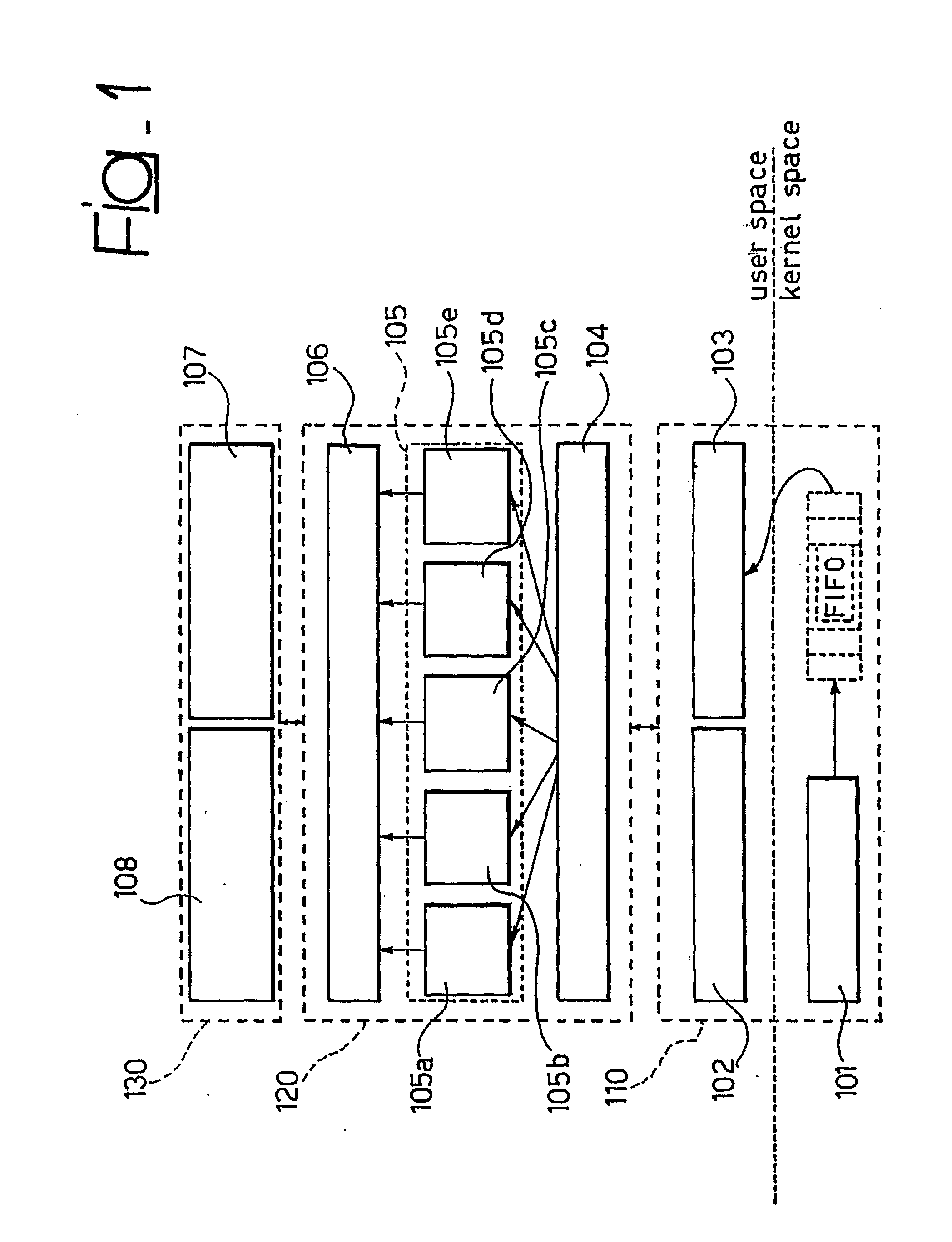
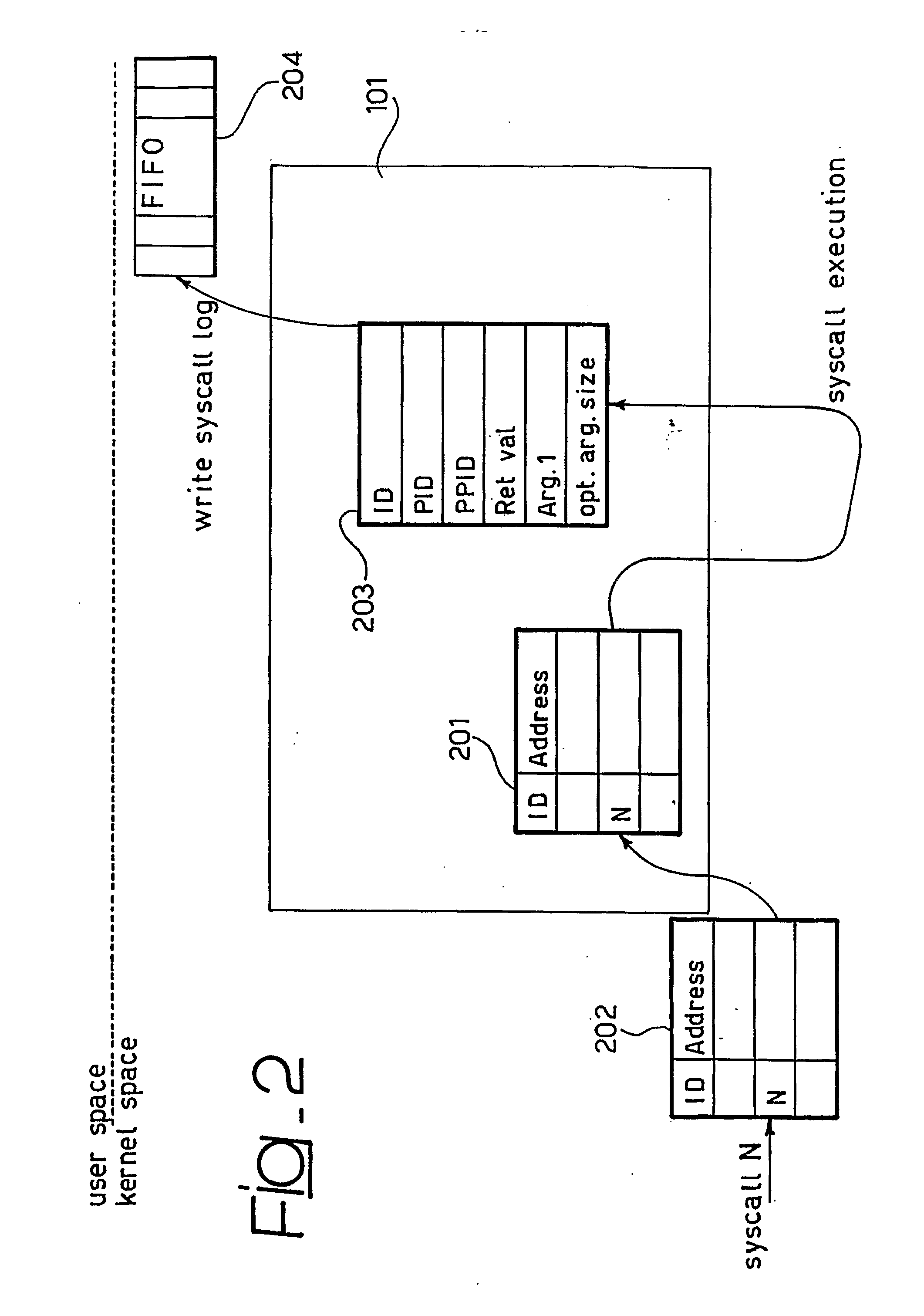
Apparatus for monitoring operation of a processing system includes a set of modules for monitoring operation of a set of system primitives that allocate or release the system resources and are used by different processes running on the system. Preferably, the modules include at least one application knowledge module tracking the processes running on the system and monitoring the resources used thereby, a network knowledge module monitoring connections by the processes running on the system, a file-system analysis module monitoring the file-related operations performed within the system, and a device monitoring module monitoring operation of commonly used modules with the system. A preferred field of application is in host-based intrusion detection systems.
Owner:TELECOM ITALIA SPA
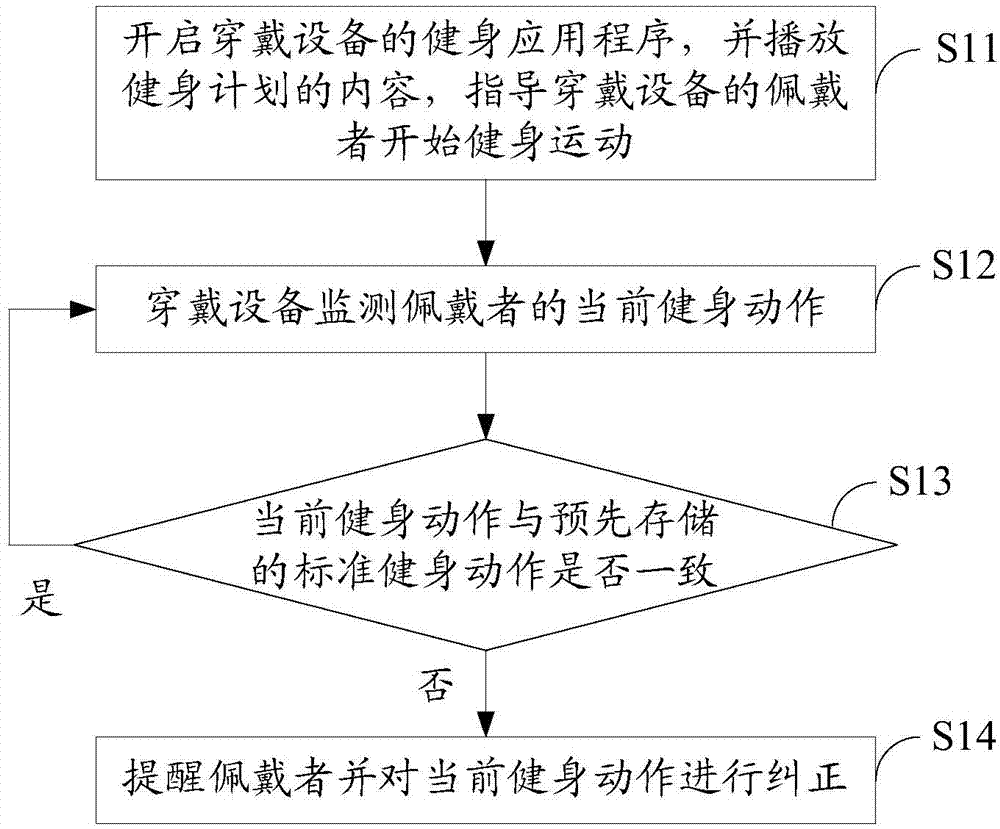
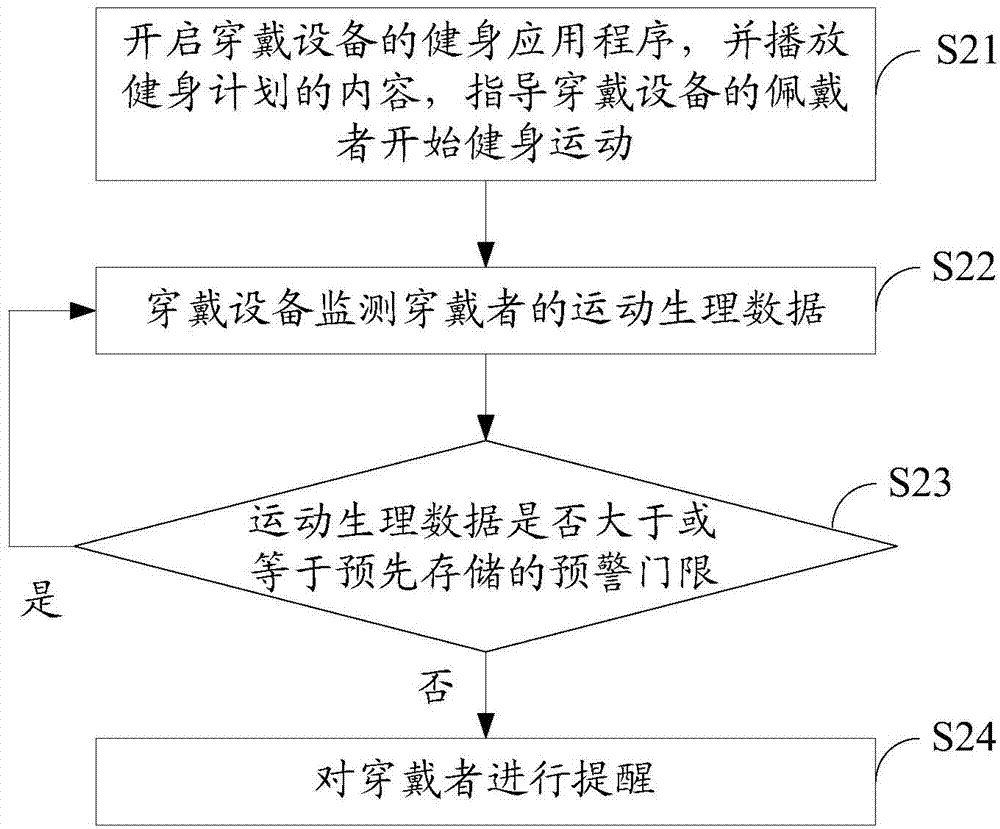
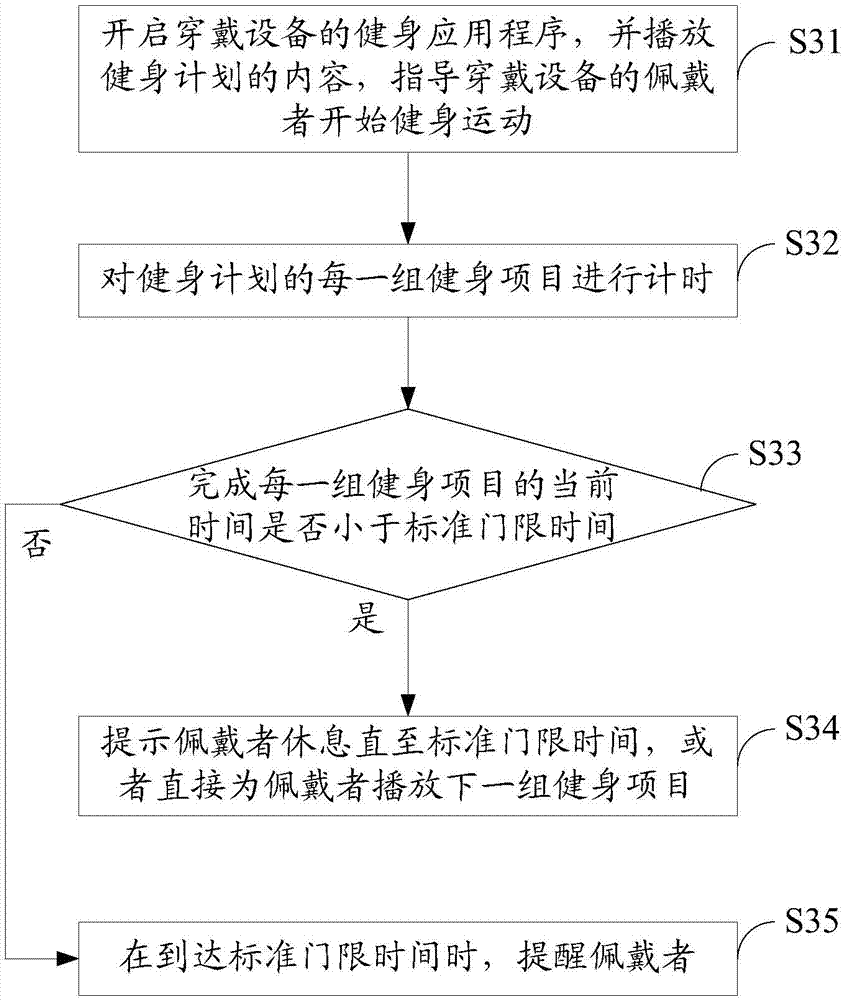
Wearable device and body building method based on same
InactiveCN104288983AMeet fitness needsCorrect irregular fitness movementsSport apparatusDevice MonitorEngineering
Owner:HUIZHOU TCL MOBILE COMM CO LTD
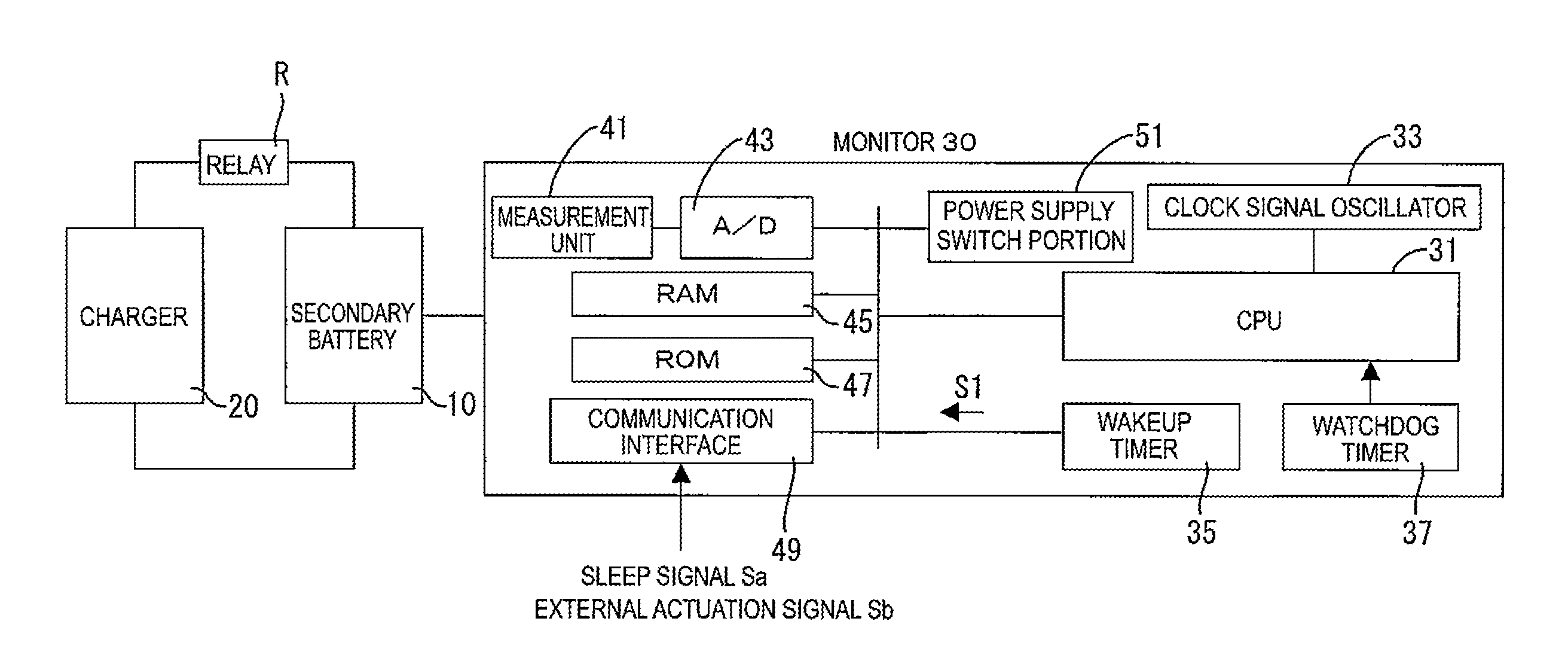
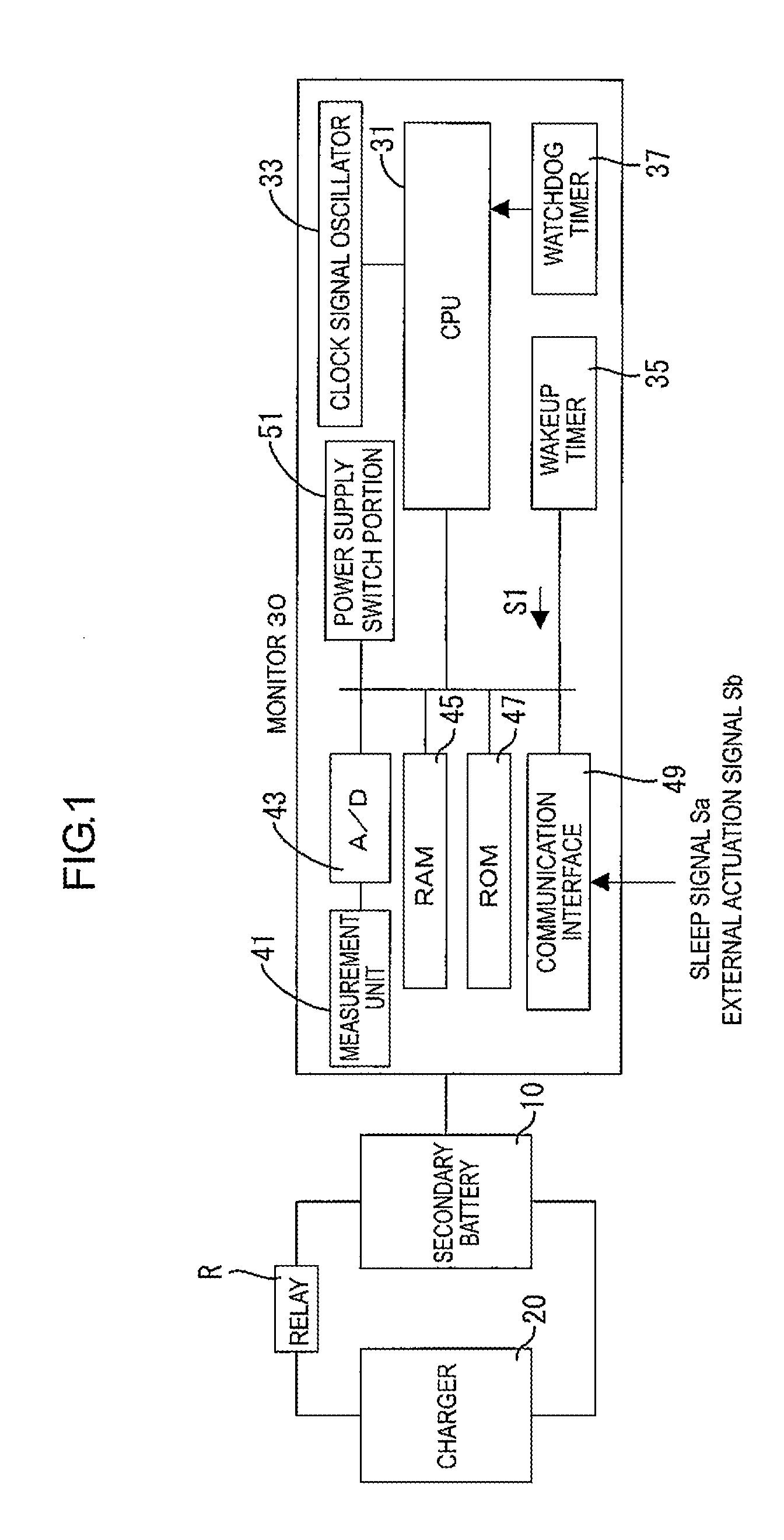
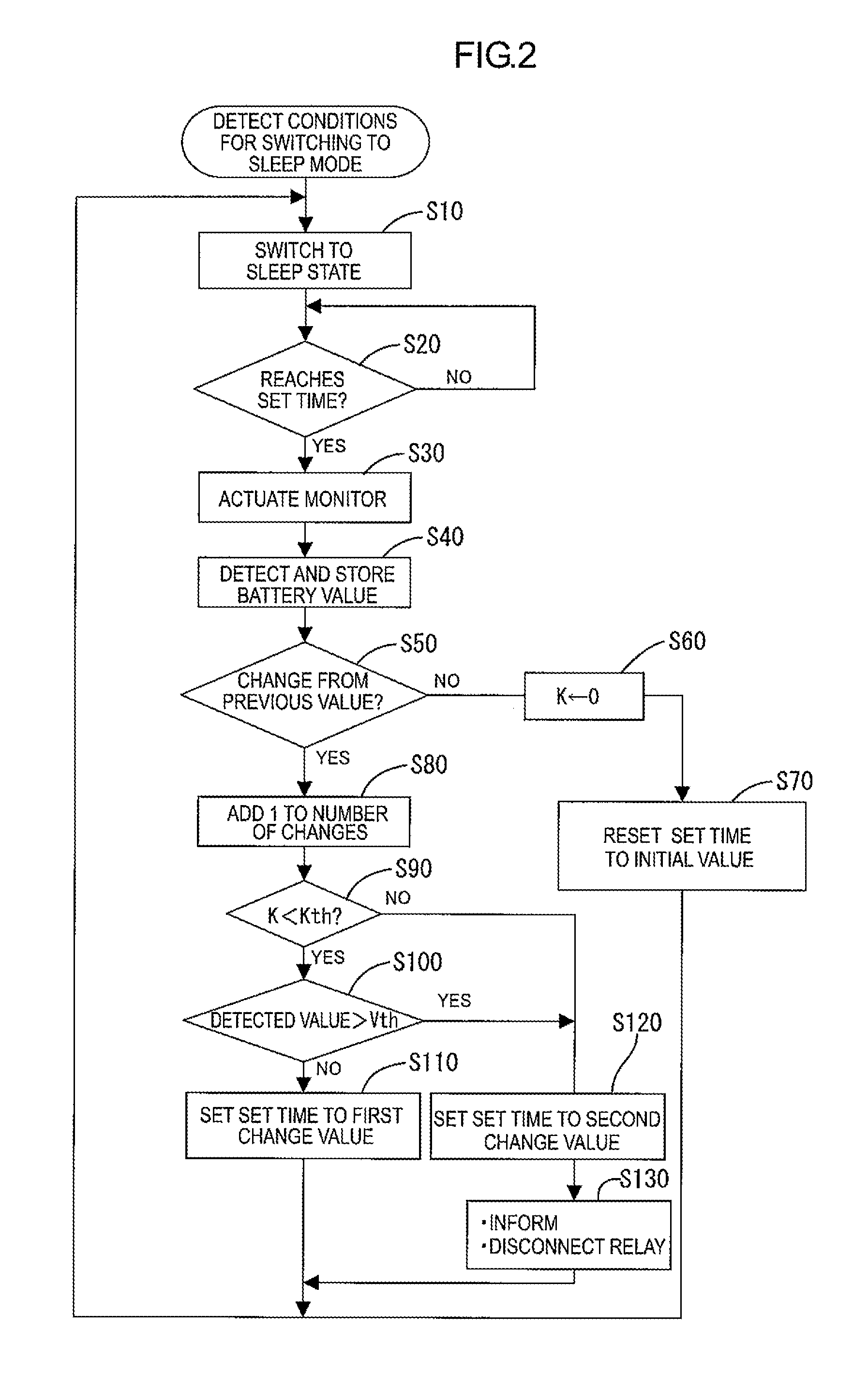
Electric storage device monitor
An electric storage device monitor includes a measurement unit detecting and obtaining a detected value, a power supply switch portion switching a power supply state of the monitor between a monitoring state and a low power consumption state, a wakeup timer to which an actuation time is set and starting counting time in response to switching to the low power consumption state and continuing counting time and outputting an actuation signal if reaching the actuation time, and a control unit. The switch portion switches from the low power consumption state to the monitoring state every time the wakeup timer outputs the actuation signal. The control unit controls the measurement unit to detect and obtain the detected value in the monitoring state, compares the detected value and a reference value, and changes the actuation time according to a comparison result of the detected value and the reference value.
Owner:GS YUASA INT LTD
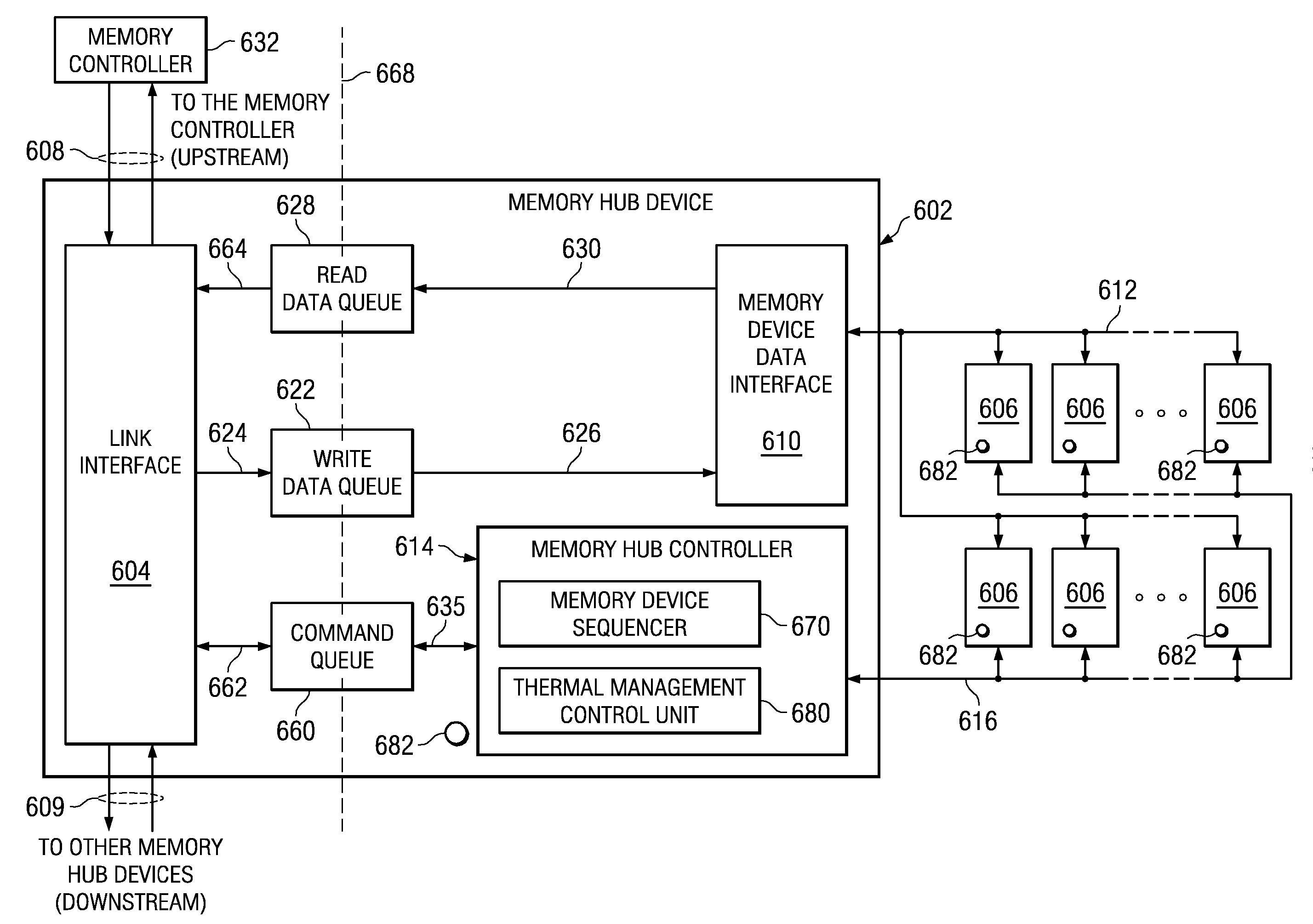
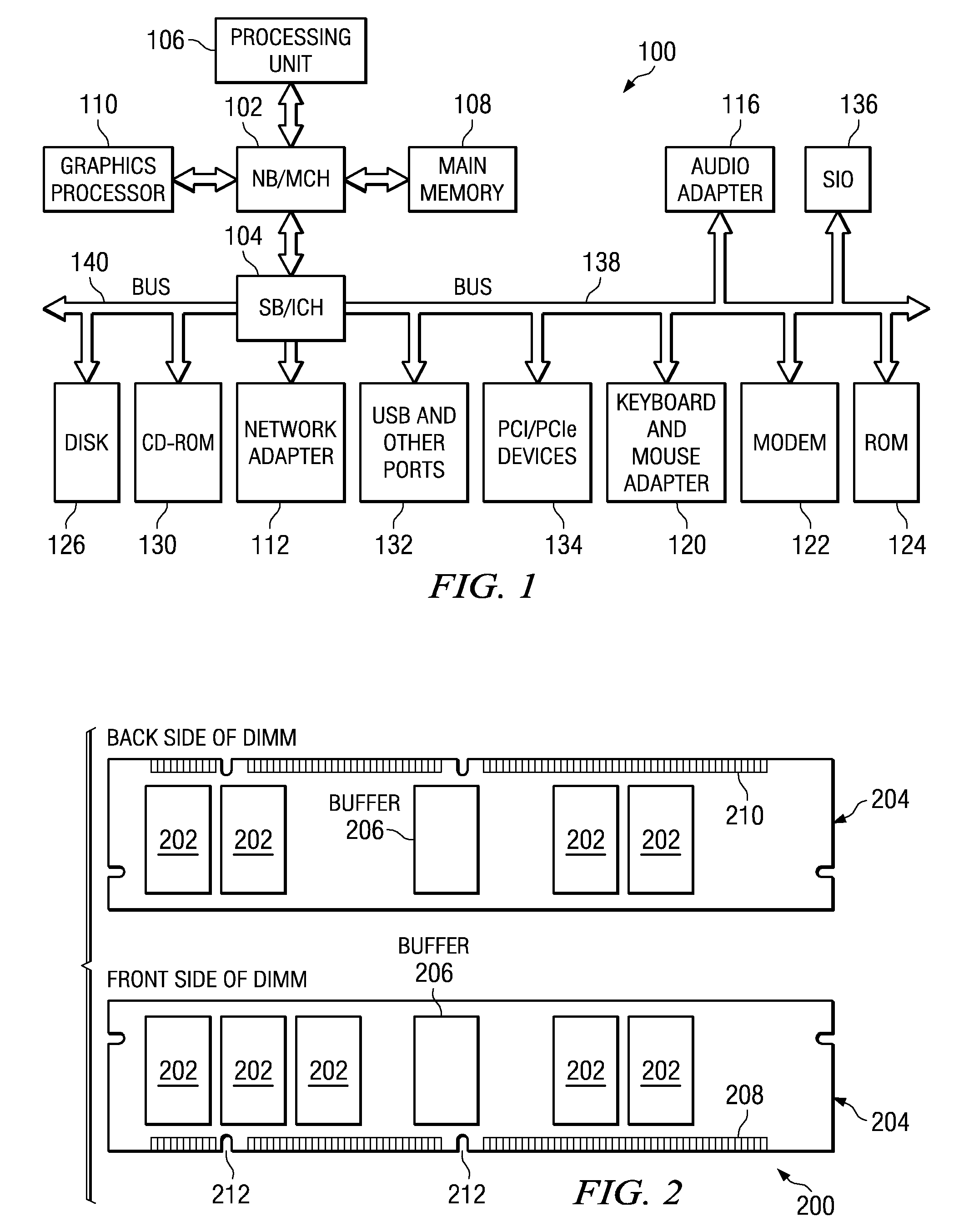
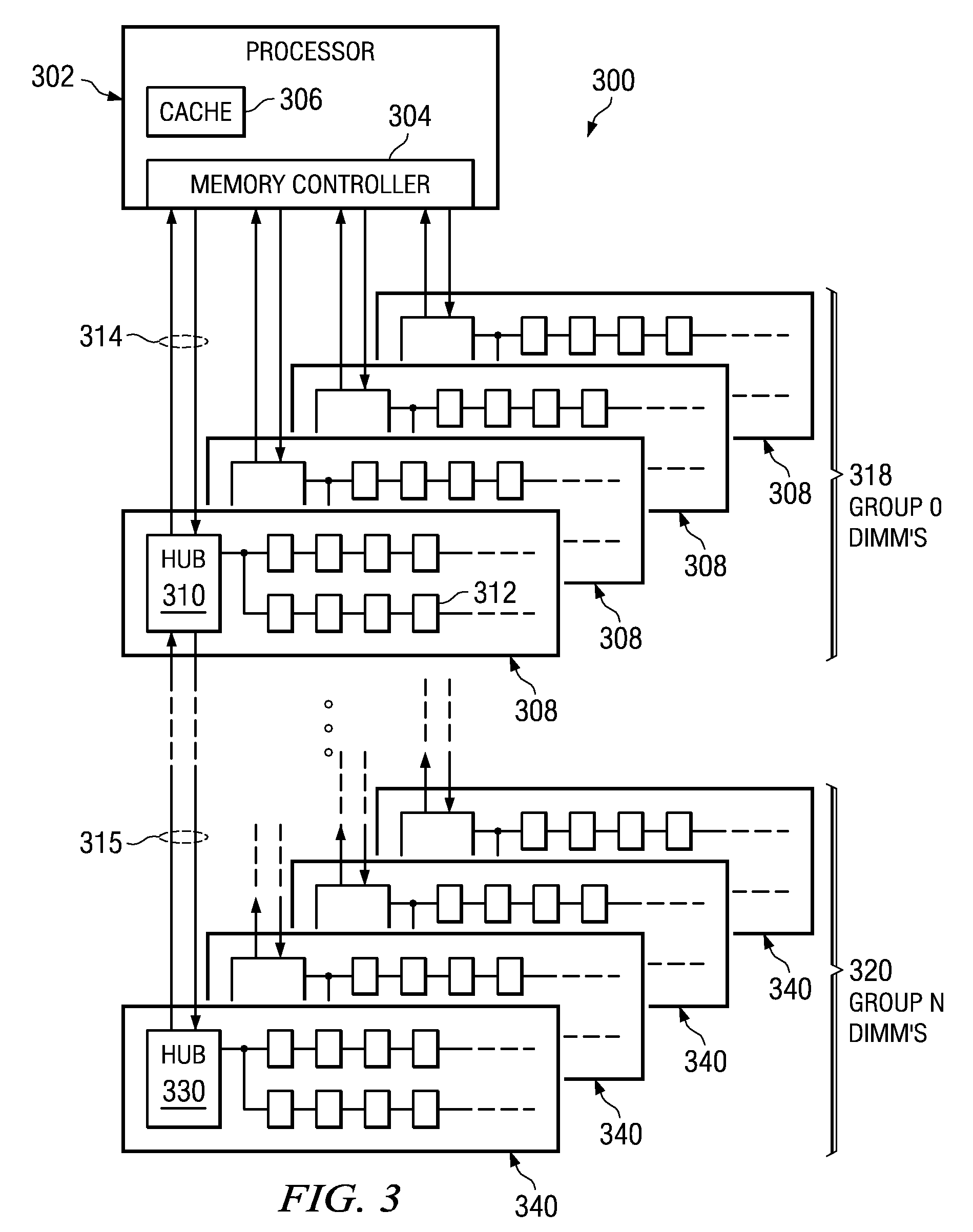
System to Enable a Memory Hub Device to Manage Thermal Conditions at a Memory Device Level Transparent to a Memory Controller
InactiveUS20090190427A1Increased memory bandwidthLower latencyEnergy efficient ICTDigital data processing detailsDevice MonitorComputer module
Owner:IBM CORP
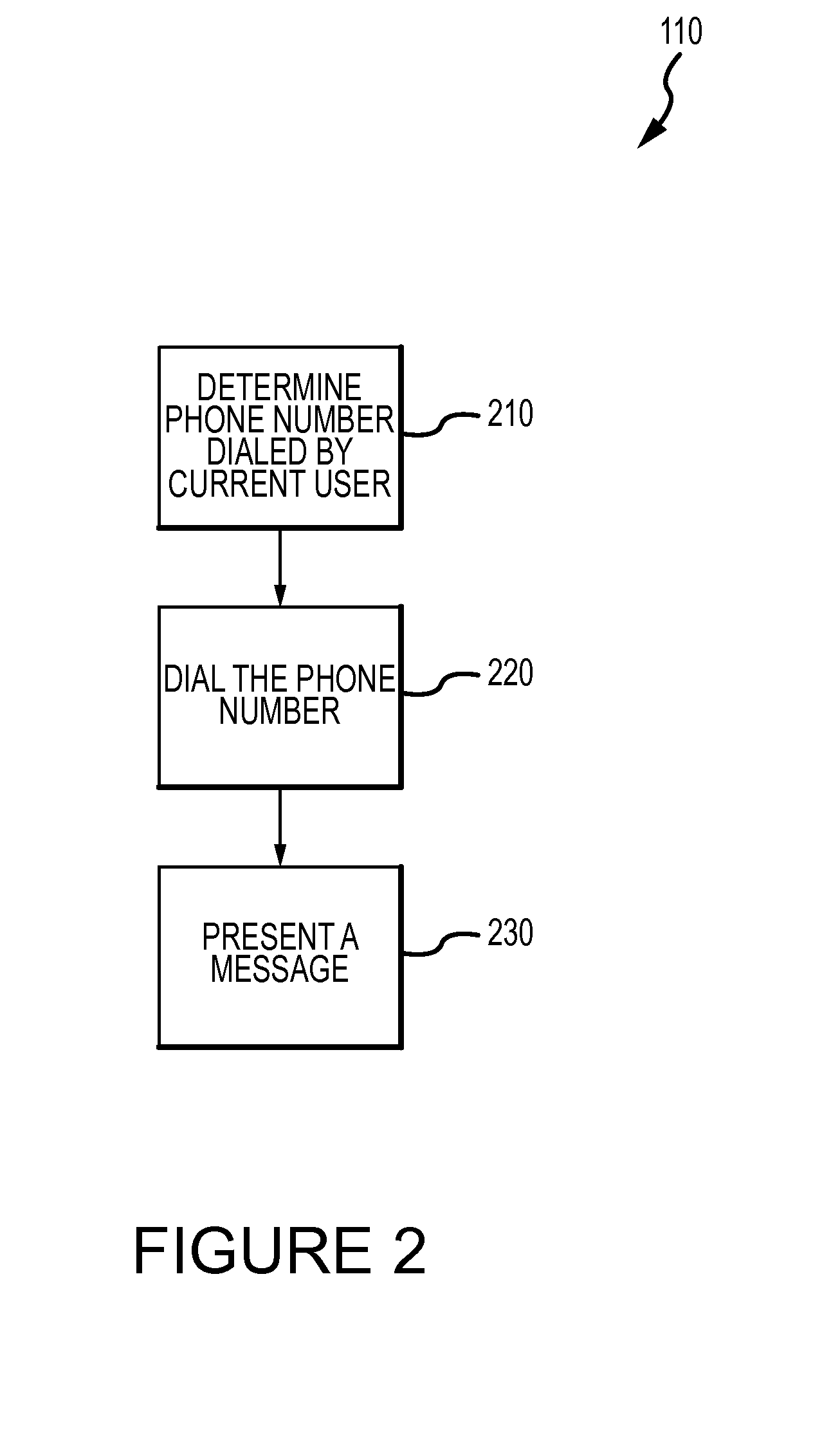
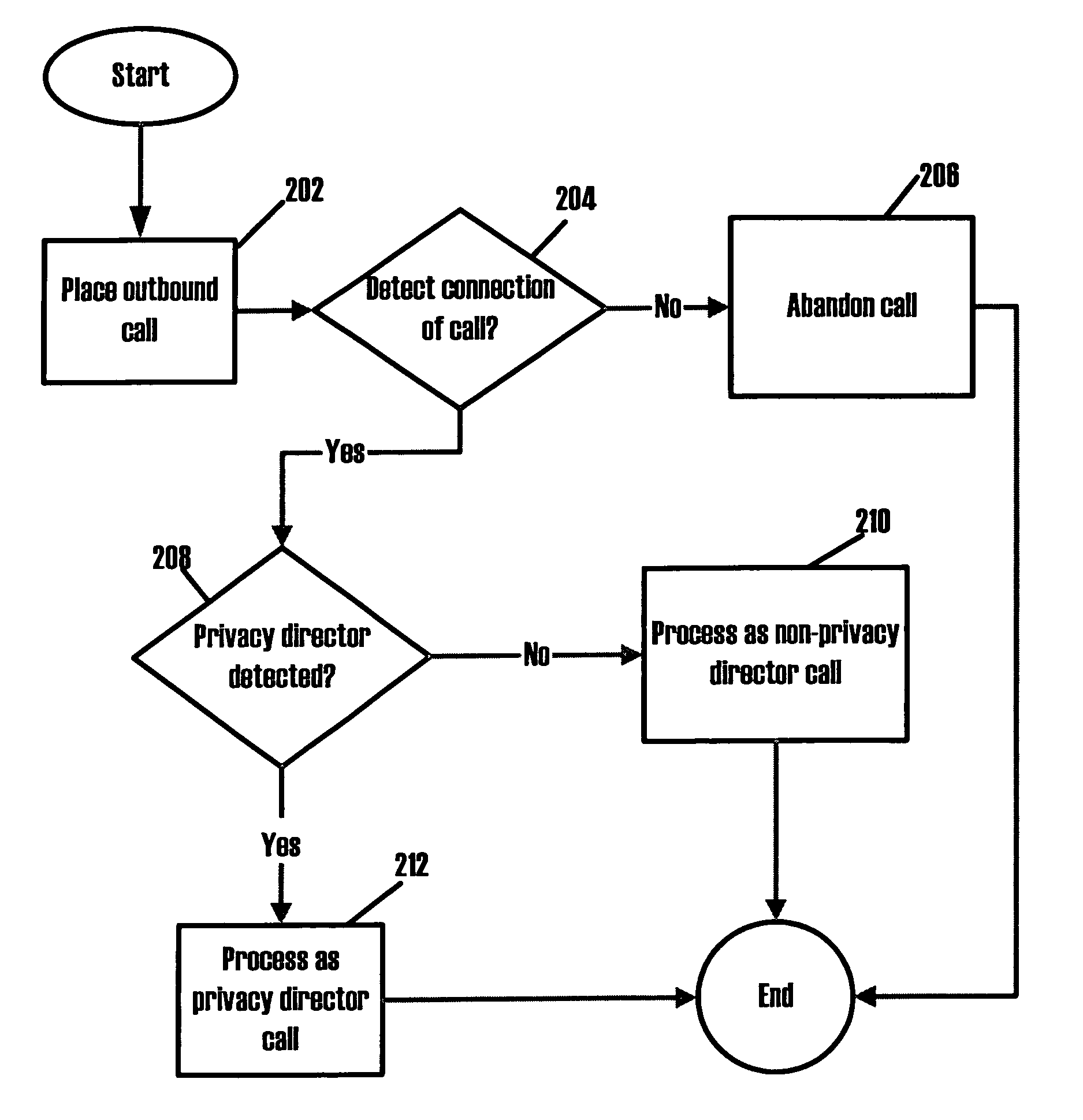
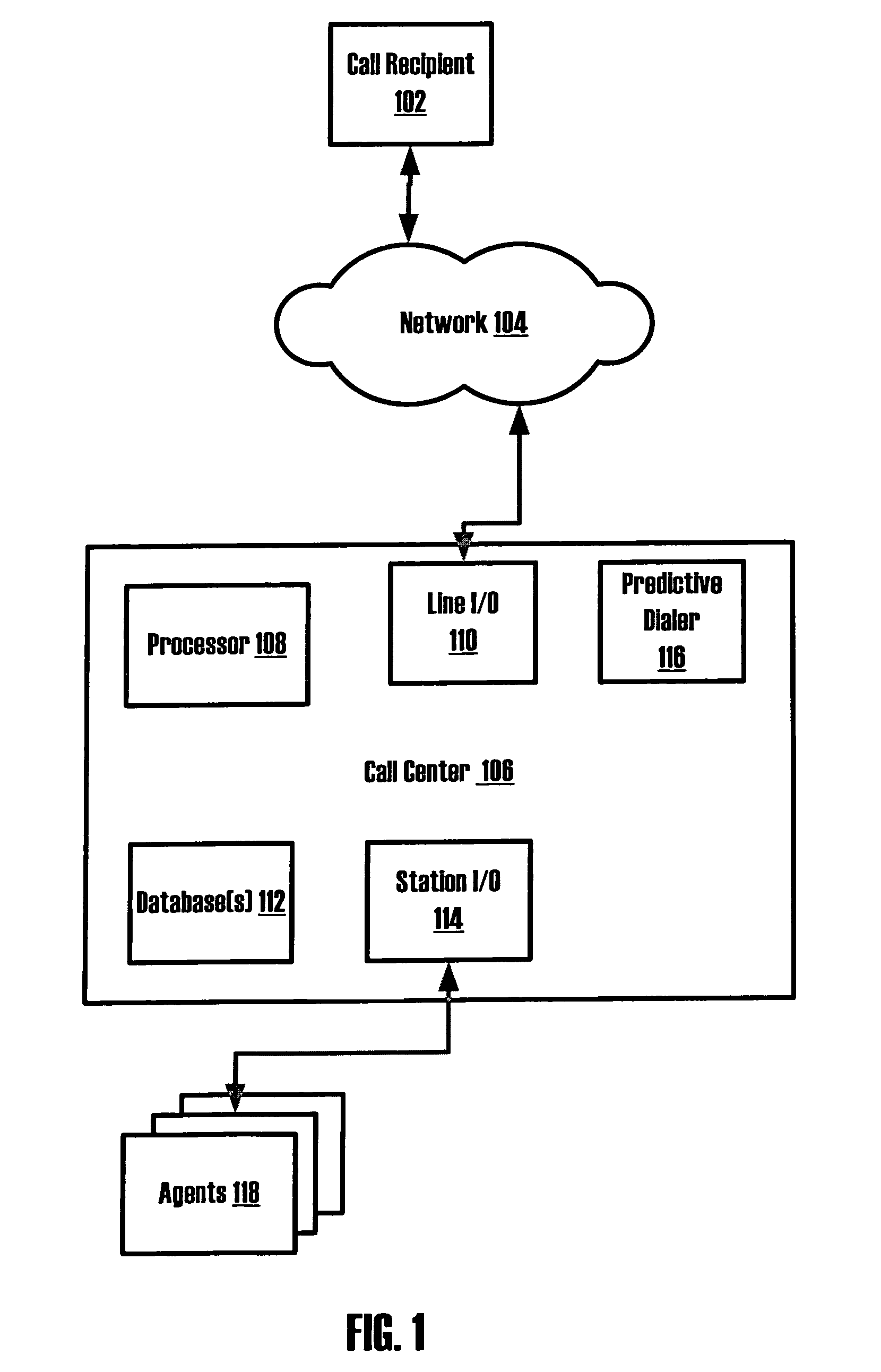
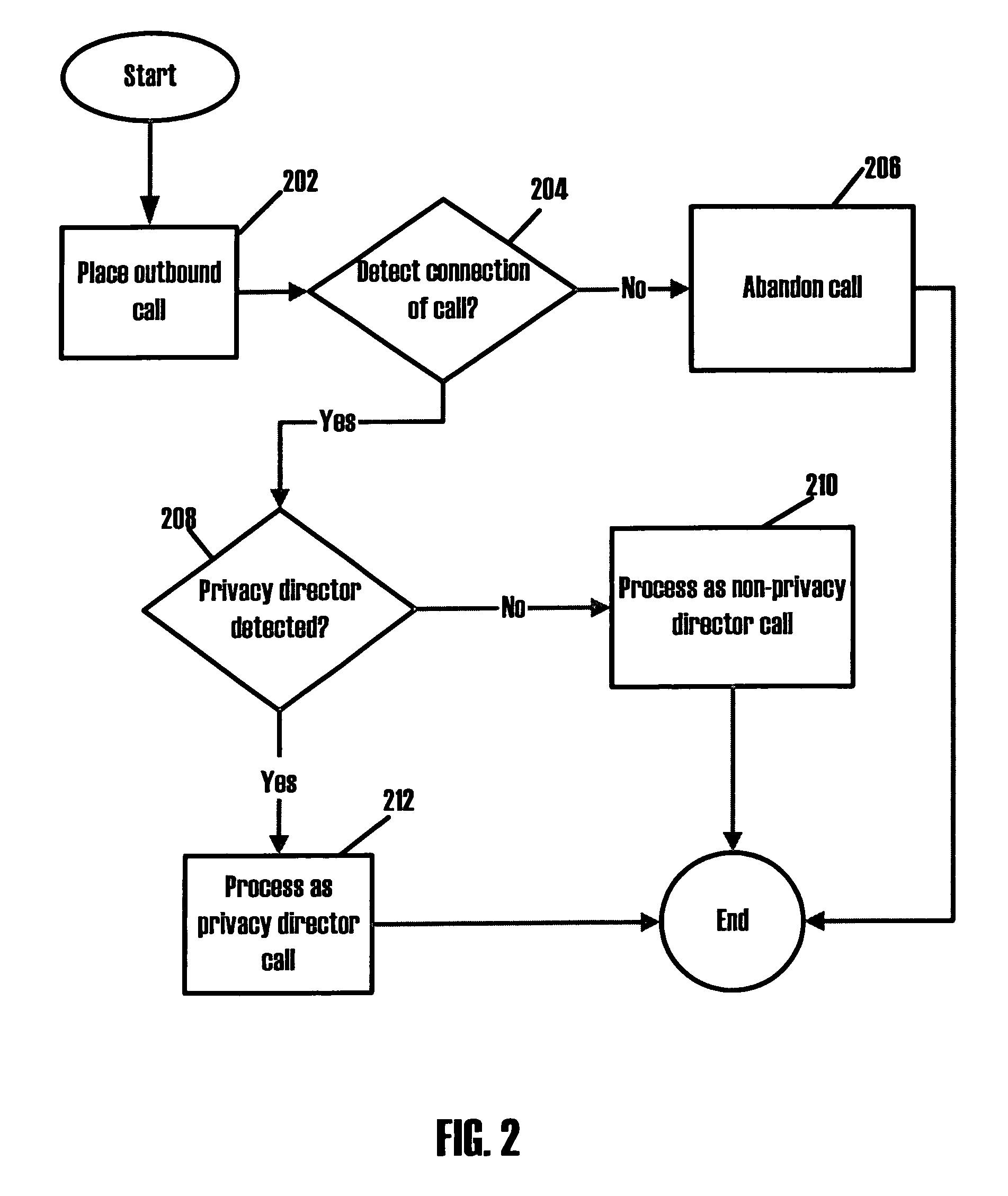
Systems and methods for detecting call blocking devices or services
Systems and methods for detecting call blocking devices or services. The devices monitor outbound call connections to determine if a connected call has been answered by a call blocking device or service rather than a person or answering machine. The verification is a comparison between the connection of an outbound call and a predefined parameter of data associated with that connection. For example, the predefined timing parameter may require detecting a connection before the first ring, or a connection occur within a predetermine period of time from when the outbound call is placed, or a connection occurring after a certain number of rings, etc. Which predefined parameter is associated with a particular outbound call may depend on the call blocking device or service the call center placing the outbound call expects to encounter on a particular connection attempt of a particular phone number. Once the call blocking device or service has been detected on a connected call, the call can be process as if a connection occurred including routing such calls to an available agent or other handling process customized to handle such calls such as automatically navigating prompts for voice or dialing responses from the privacy director systems.
Owner:NOBLE SYSTEMS CORPORATION
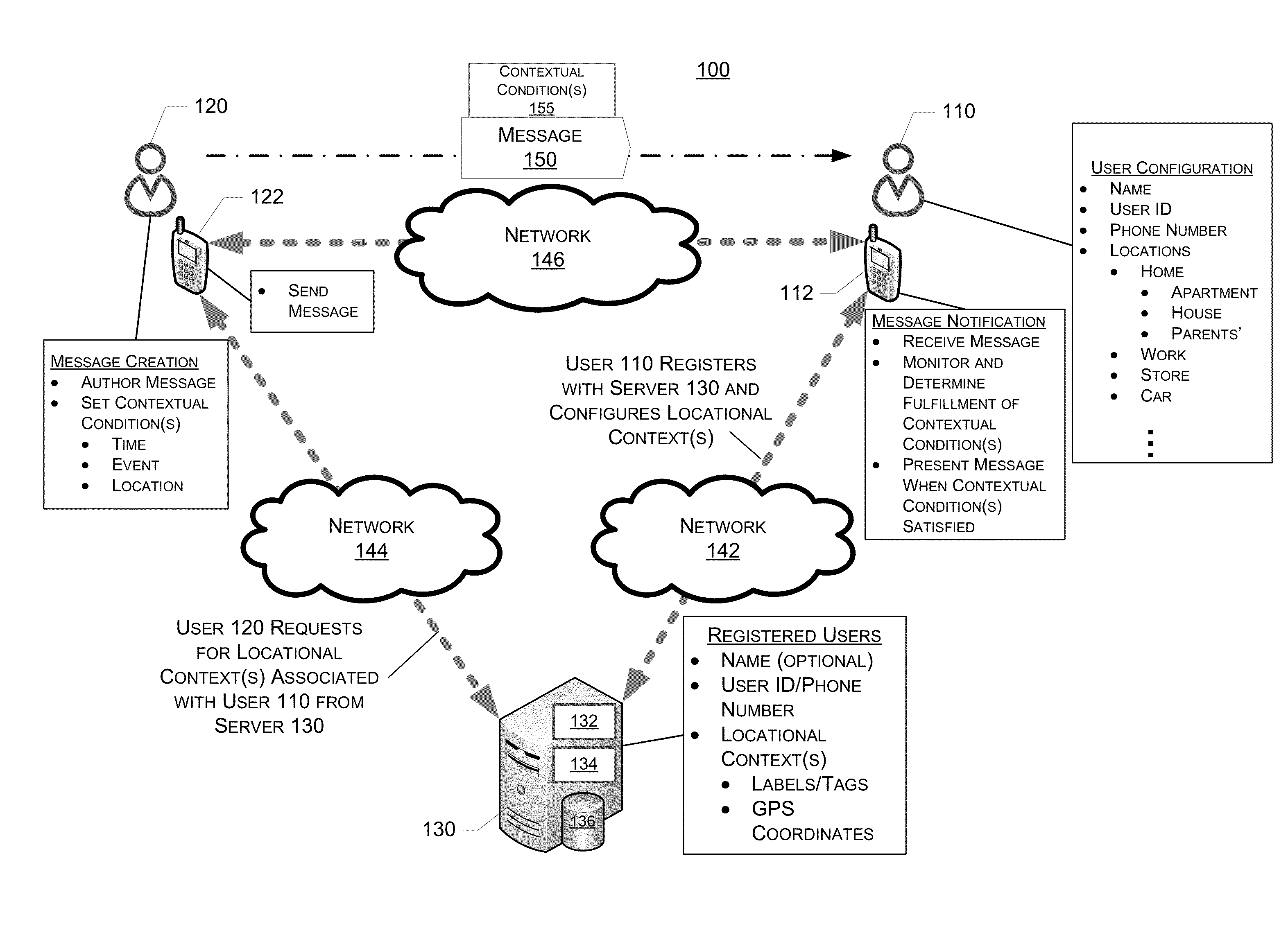
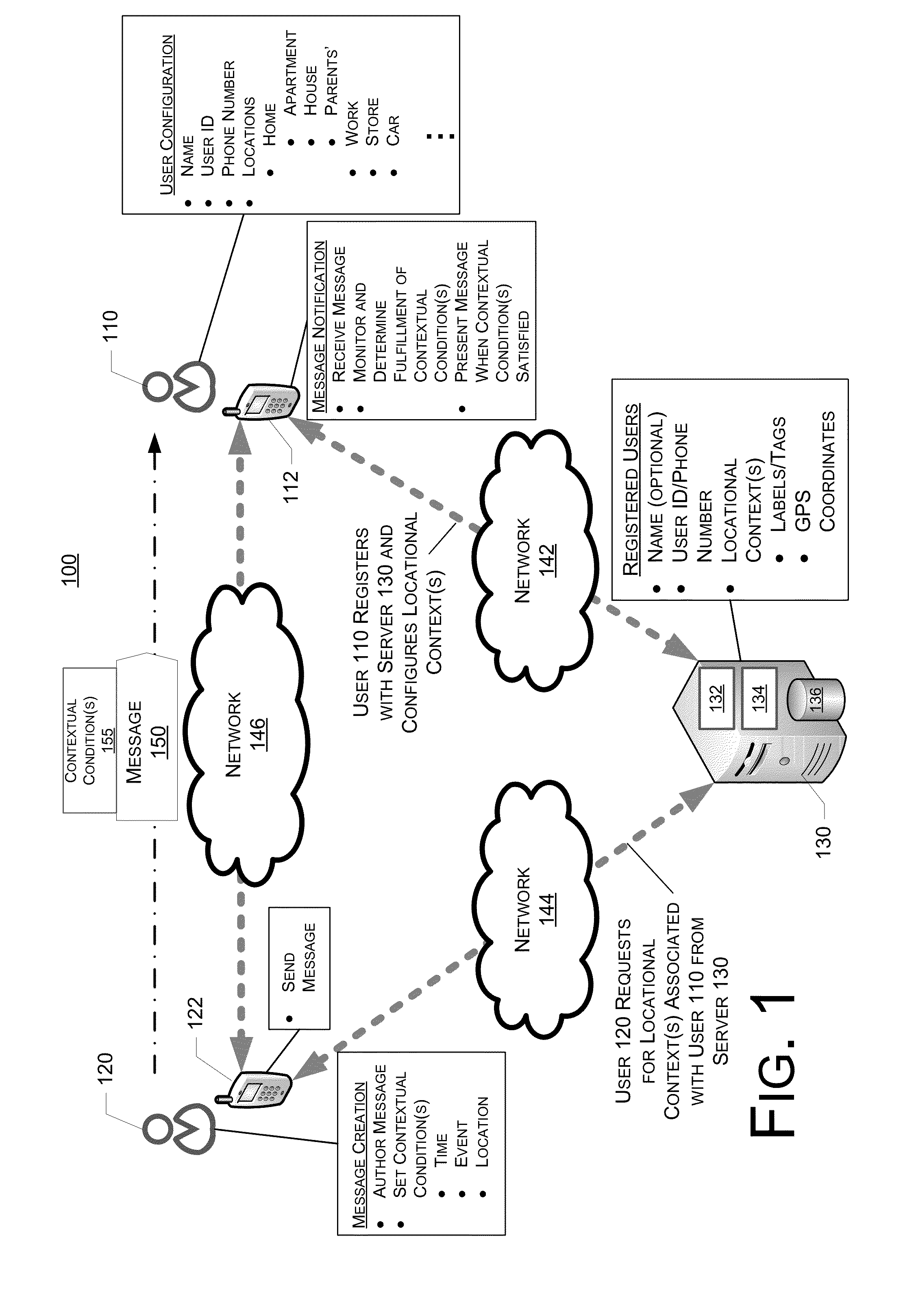
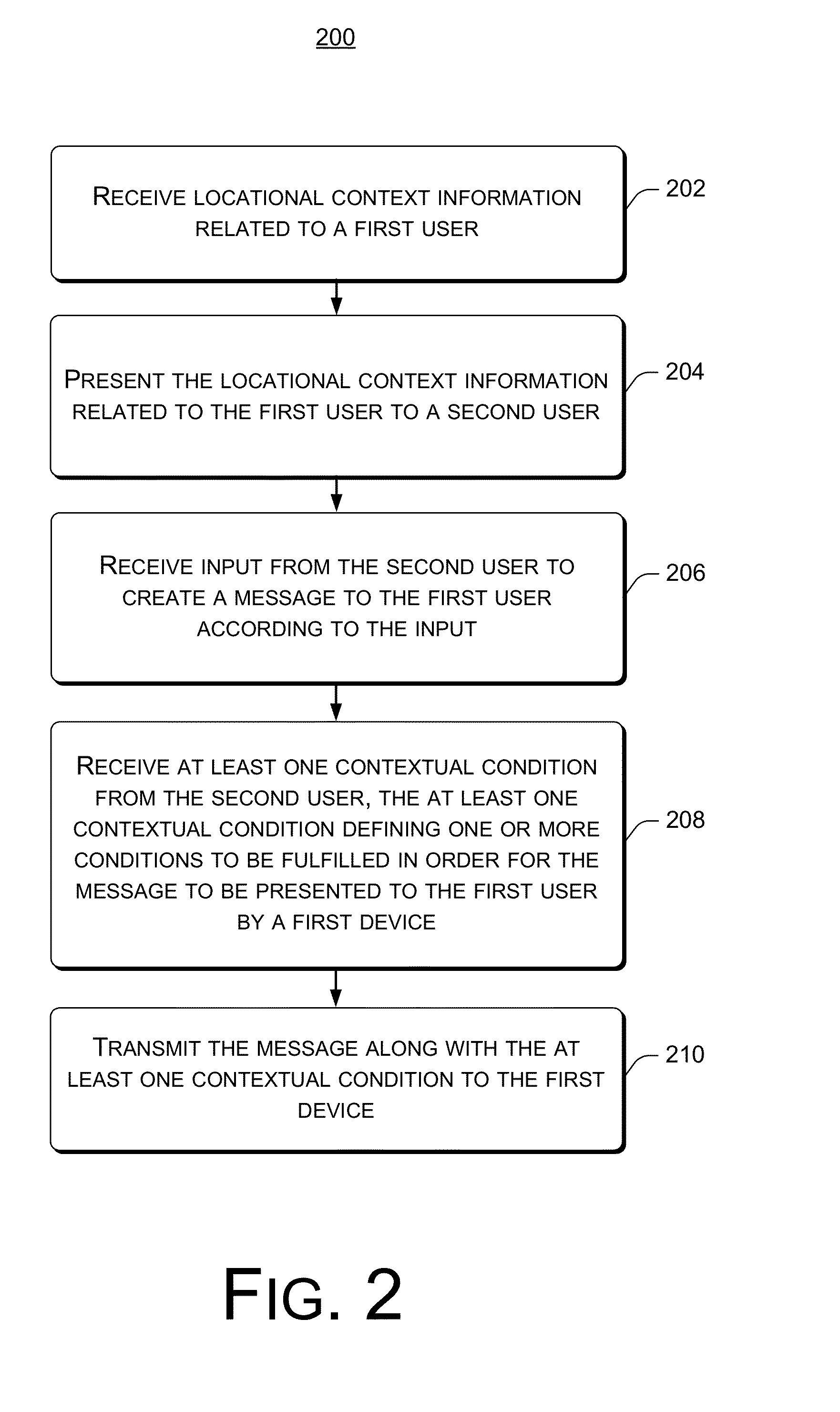
System, Method And Device For Creation And Notification Of Contextual Messages
System, method and device for the creation and notification of contextual messages are described. When creating or authoring a message, a sender can define a context in which the message is to be delivered to a recipient. Accordingly, after receiving the message, the recipient's device does not notify the recipient of the receipt of the message until the context is fulfilled. The recipient's device monitors conditions and determines whether the context is fulfilled, and notifies the recipient of the receipt of the message when the context is fulfilled. The recipient can configure common locations associated with the recipient and the information thereof is available in a non-specific way to a message sender for defining the context.
Owner:GROSSMAN BRENT
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com