Patents
Literature
128results about How to "Good for load balancing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
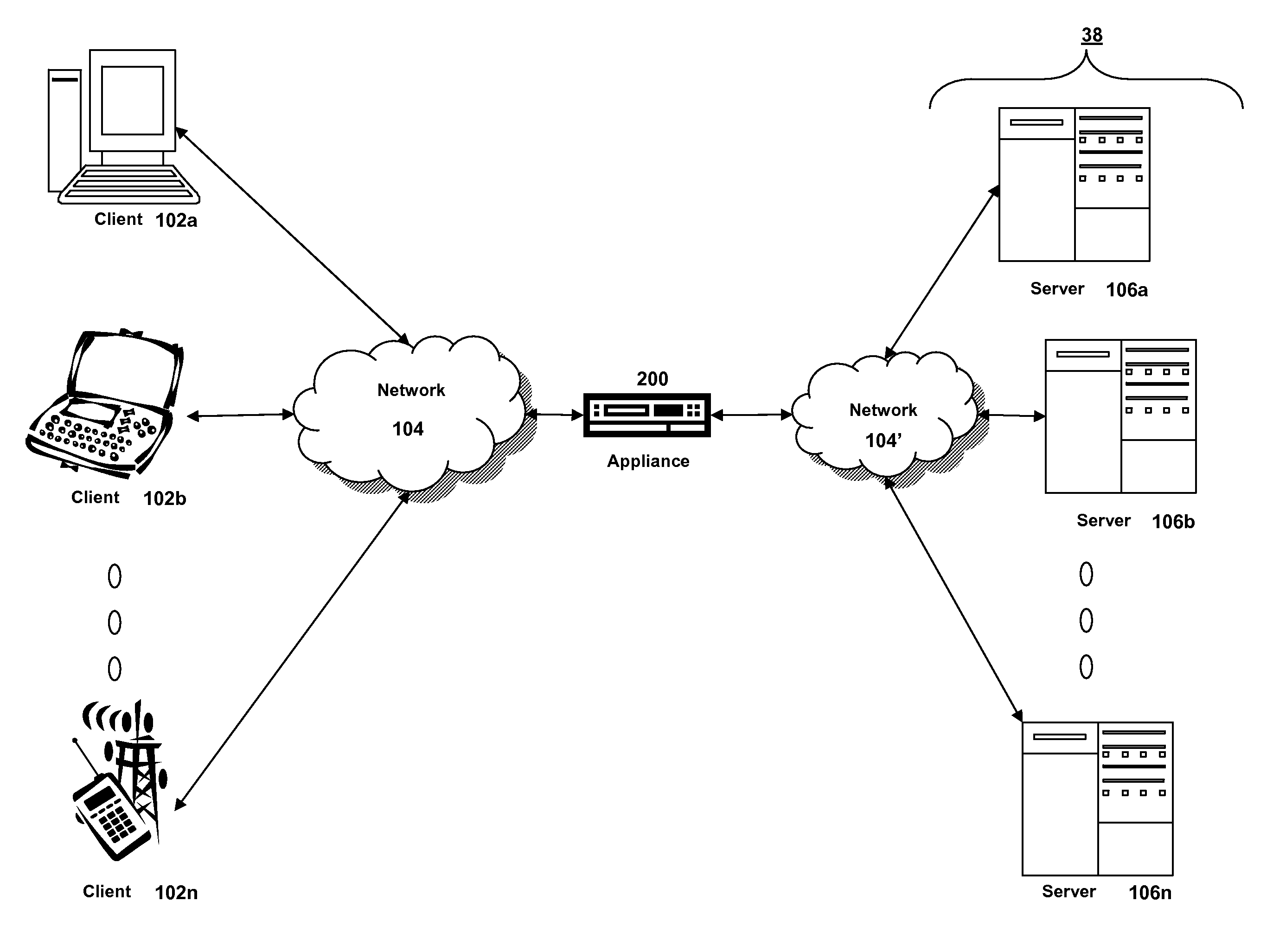
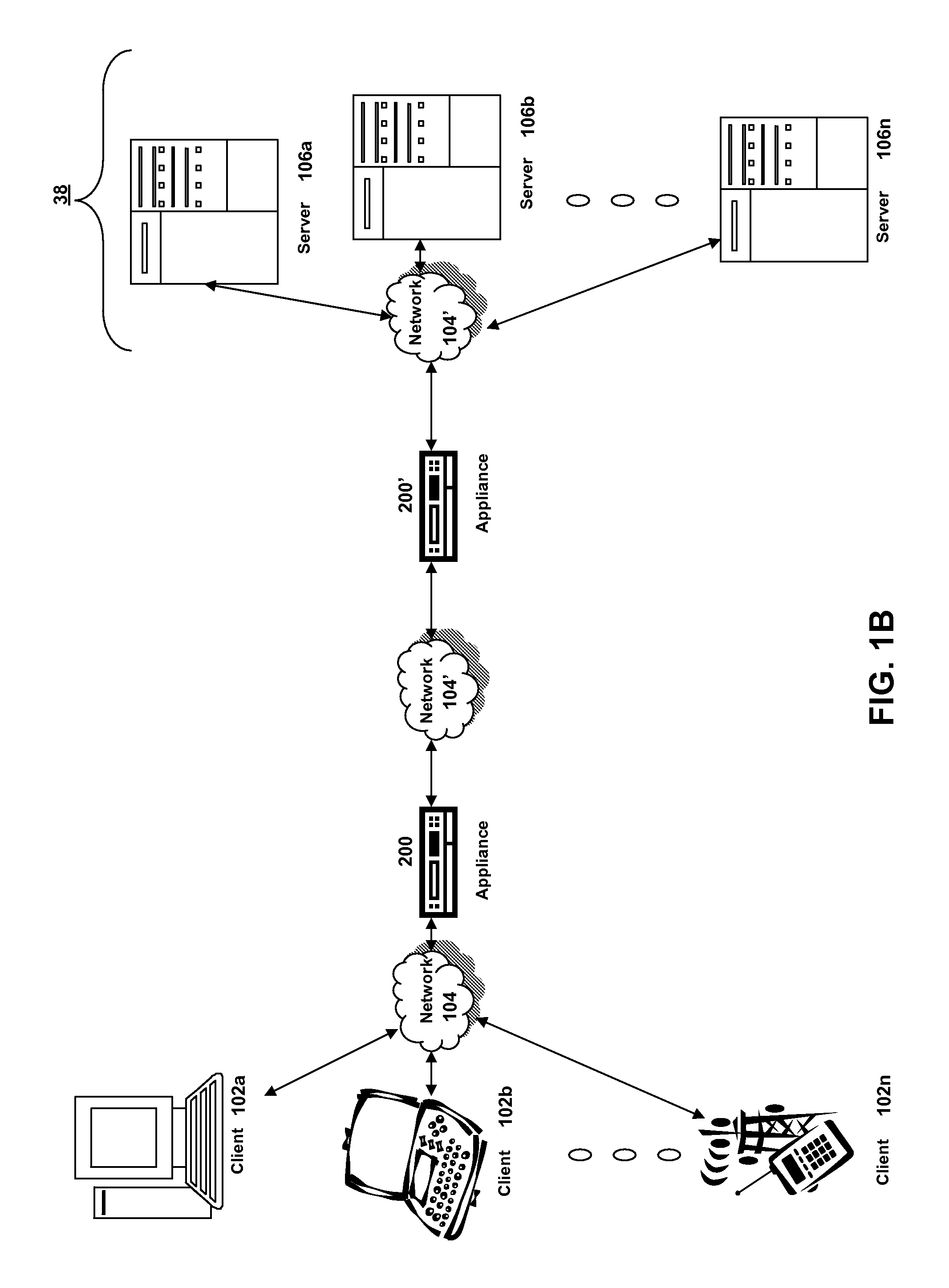
Systems and Methods for Load Balancing Based on User Selected Metrics
ActiveUS20080225710A1Good for load balancingGood flexibilityError preventionTransmission systemsDevice MonitorSimple Network Management Protocol
The present invention provides improvements to load balancing by providing a load balancing solution that allows a user to select metrics, weights and thresholds from metrics collected or determined by a load balancing appliance as well as metrics obtained from another device, such as a server running the service. The systems and methods described providing a load balancing technique in which load balancing decisions can be made based on metrics known by another device monitoring such metrics. The load balancing appliance uses a network management protocol and communication model, such as a Simple Network Management Protocol (SNMP), to identify and collect metrics from a server, service or other device. These metrics are available on the load balancing appliance with appliance determined metrics. Via a configuration interface of the appliance, a user can select one or more appliance determined metrics and / or the metrics obtained via the network management protocol to determine the load of a service.
Owner:CITRIX SYST INC
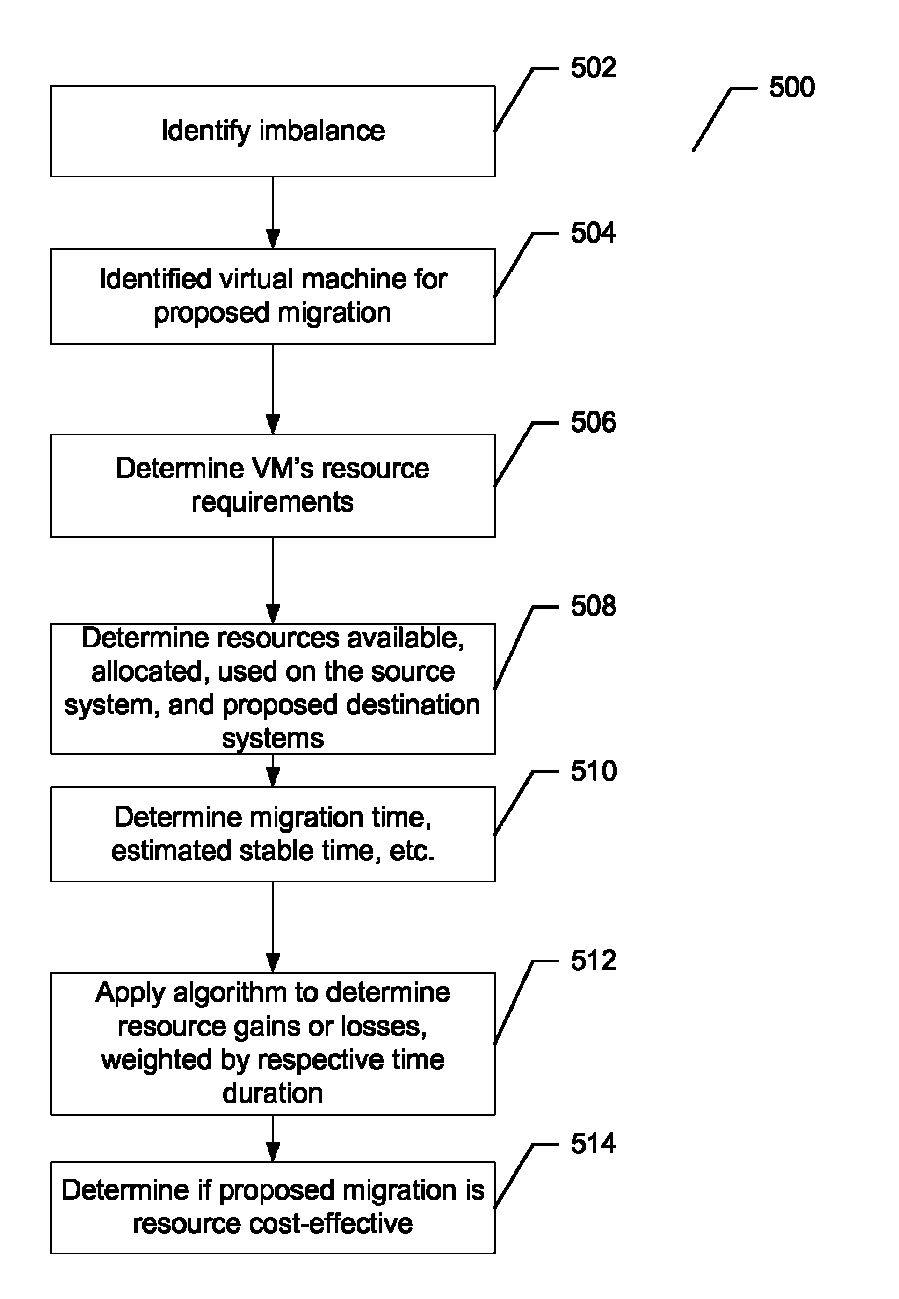
Method and system for determining a cost-benefit metric for potential virtual machine migrations
ActiveUS8095929B1Good for load balancingDigital computer detailsMultiprogramming arrangementsCost effectivenessProtection system
A cost-benefit metric for load balancing virtual machines is used to estimate a net gain in resource availability achieved by a proposed virtual machine migration. The cost-benefit metric can be used together with any other known metrics to evaluate candidate migrations. The metric takes into account stability of loads as well as migration cost, hence can protect a system from thrashing, i.e., frequently migrating virtual machines without gaining resource availability.
Owner:VMWARE INC
Load Balanced Routing for Low Power and Lossy Networks
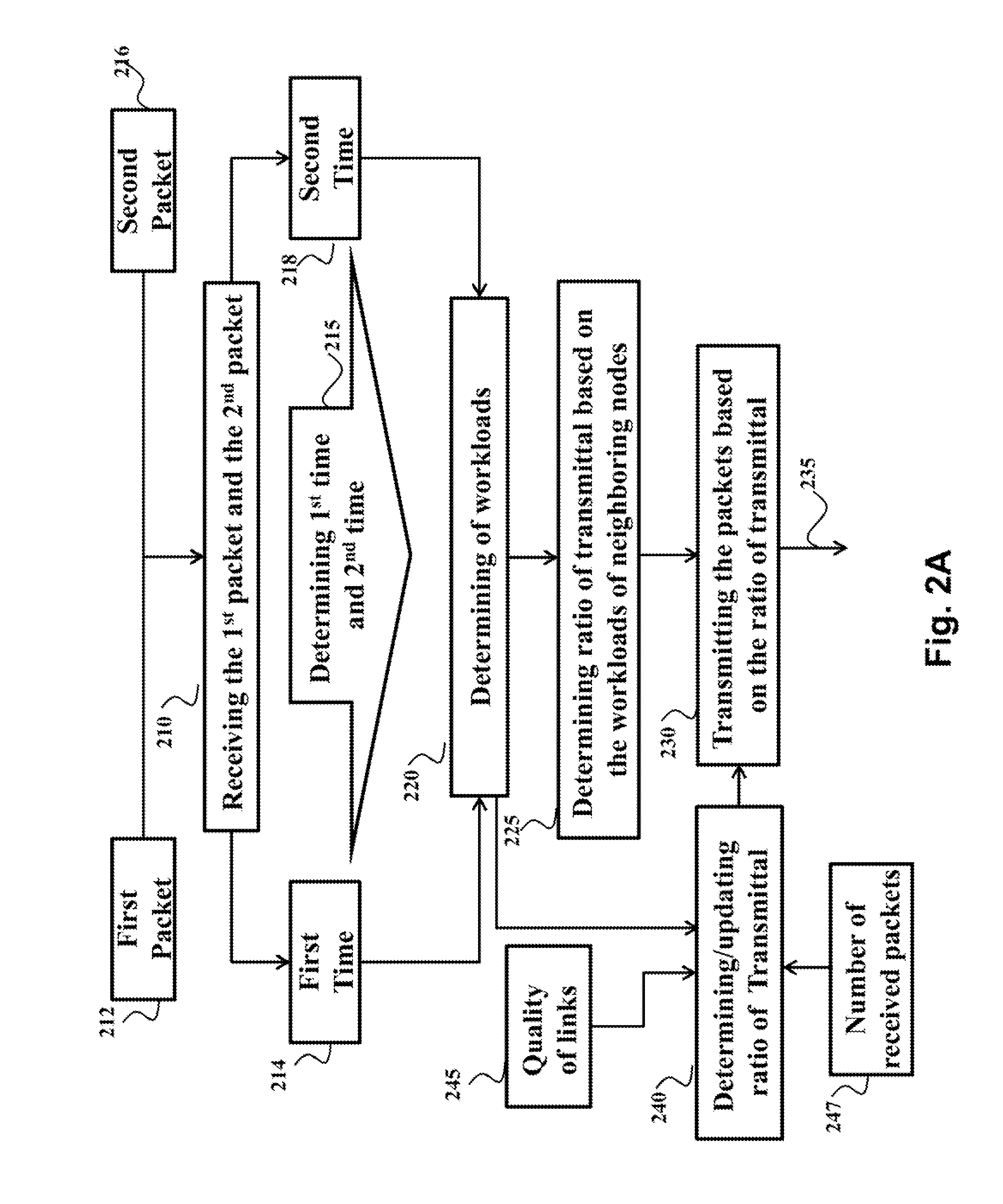
InactiveUS20140204759A1Small workloadHeavy workloadError preventionTransmission systemsLoad balanced routingWorkload
A node includes a receiver for receiving a first packet from a first node at a first time and a second packet from a second node at a second time, a processor for determining the first time and the second time and for comparing the first time with the second time to produce a ratio of workloads of the first node and the second node, and a transmitter for transmitting packets to the first and the second nodes based on the ratio.
Owner:MITSUBISHI ELECTRIC RES LAB INC
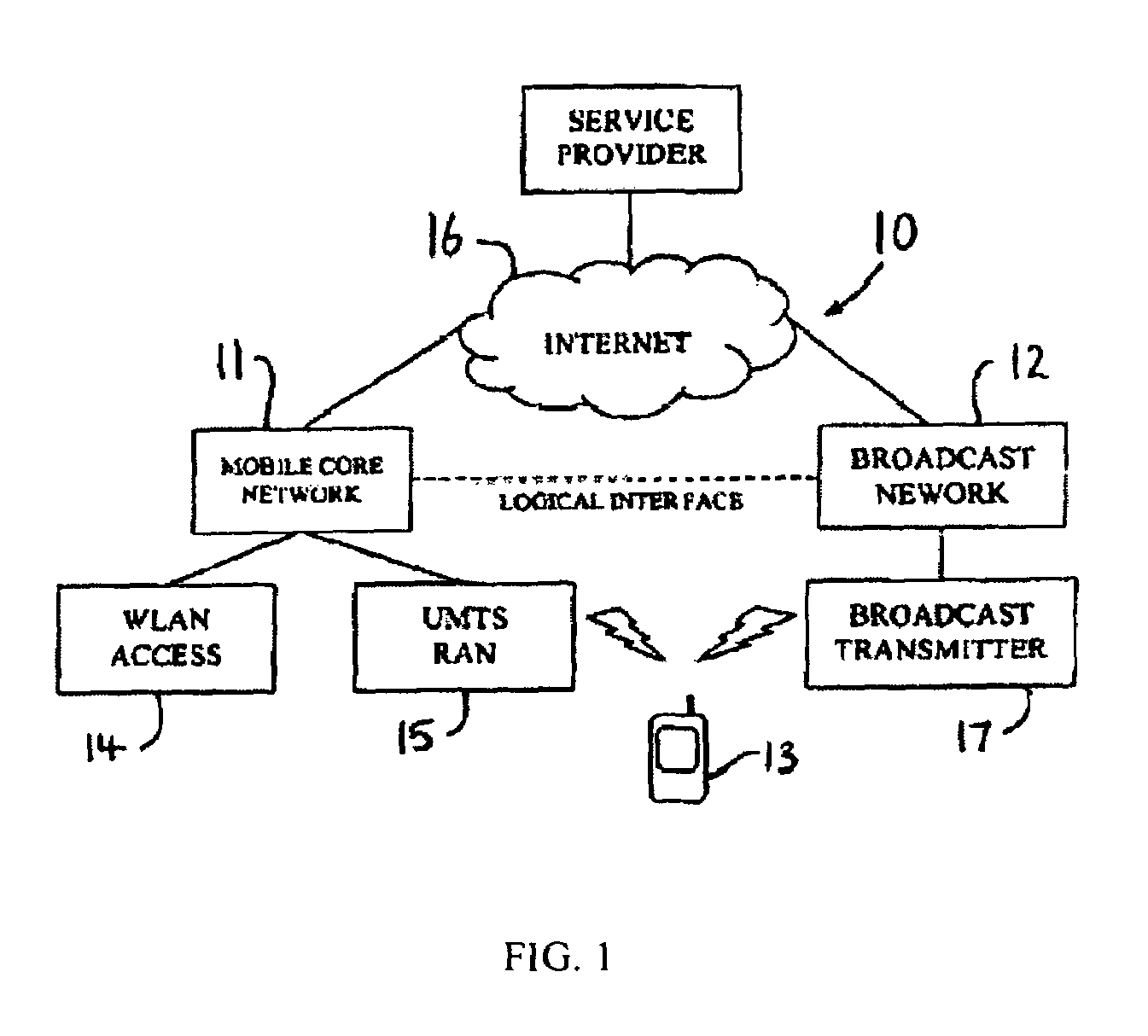
Method of discovering multi-mode mobile terminals
ActiveUS20060166699A1Convenient intercommunicationEasily informedNetwork traffic/resource managementAssess restrictionTelecommunicationsHeterogeneous network
A method of discovering multi-mode mobile terminals (13) in a heterogeneous network environment, each multi-mode mobile terminal (13) having at least one interface for sending packet data to and / or receiving packet data from a home radio communication network (11) and a foreign radio communication network (12), said home radio communication network having a different access technology from said foreign radio communication network, each multi-mode mobile terminal (13) performing the steps of: (a) listening to said foreign radio communication network (12); (b) receiving and storing a foreign network indicator for indicating presence of said foreign radio communication network (12); and (c) transmitting said foreign network indicator to said home radio communication network (11); whereby said home radio communication network (11) may store a database comprising a mapping between a multi-mode mobile terminal identity, a home network indicator and a foreign network indicator, to facilitate interworking of said home and foreign radio communication networks.
Owner:DOLBY LAB LICENSING CORP
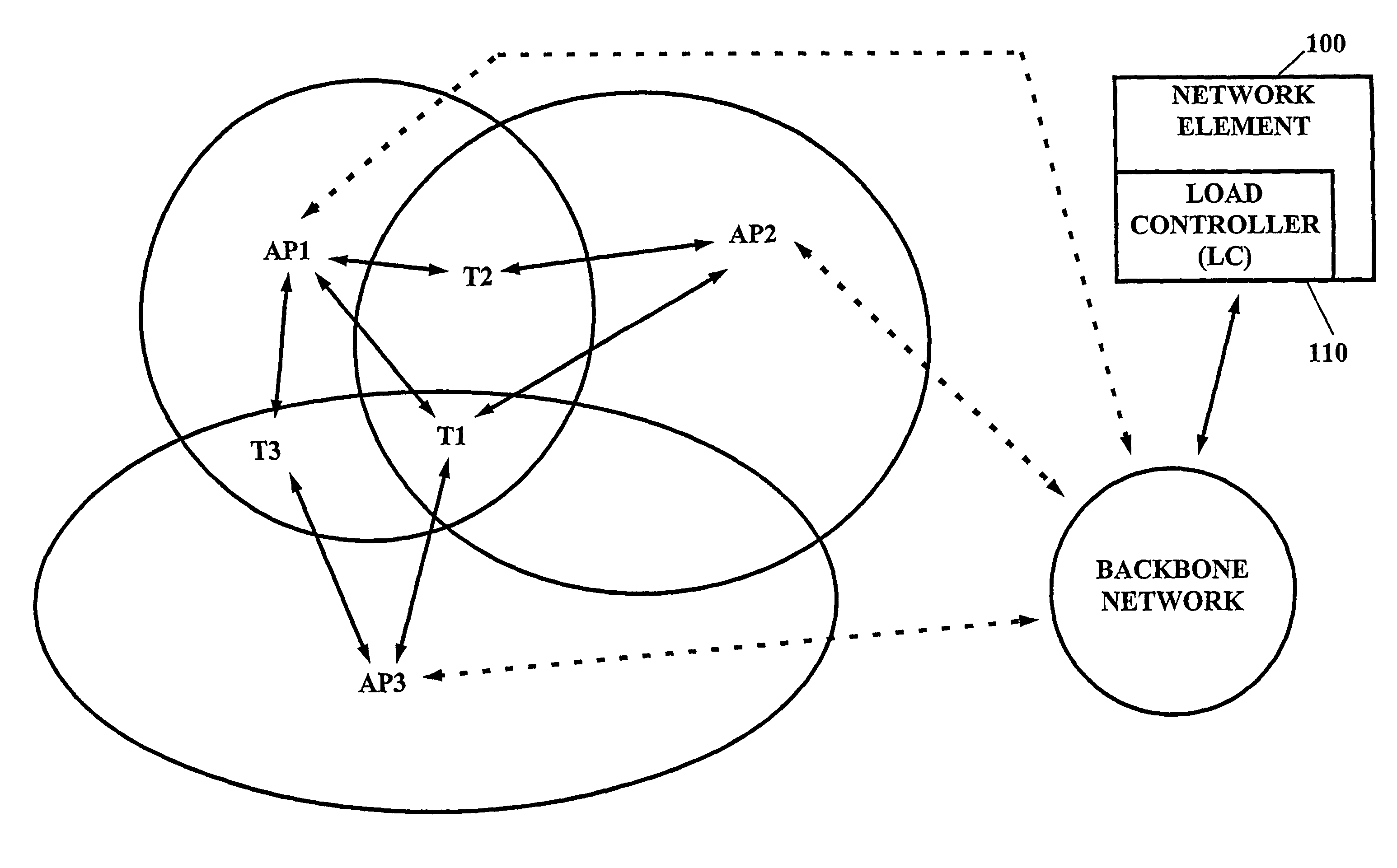
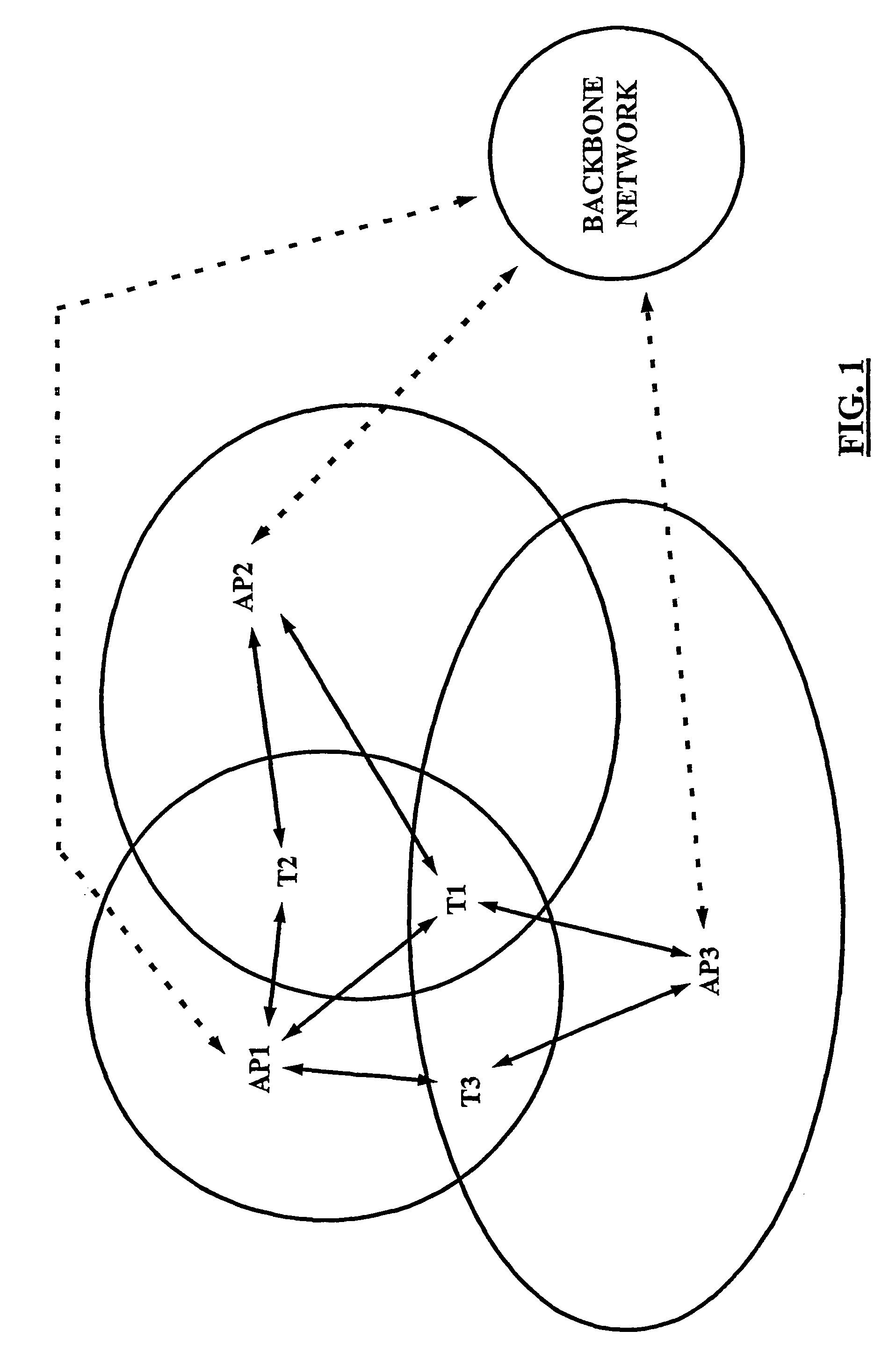
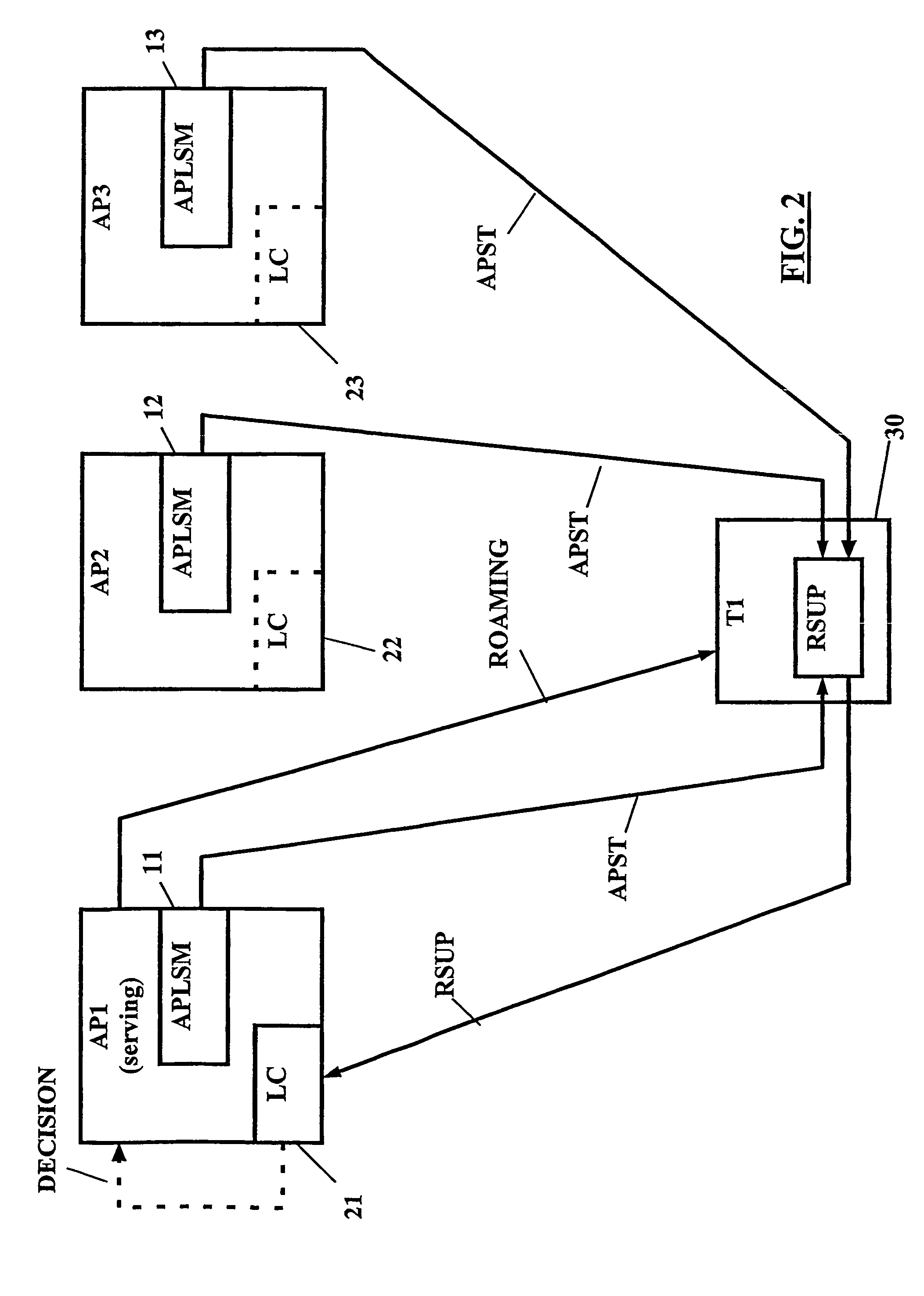
Load balancing in wireless communication network
InactiveUS20050208950A1Improve load balanceGood for load balancingNetwork traffic/resource managementAssess restrictionTelecommunicationsProcess information
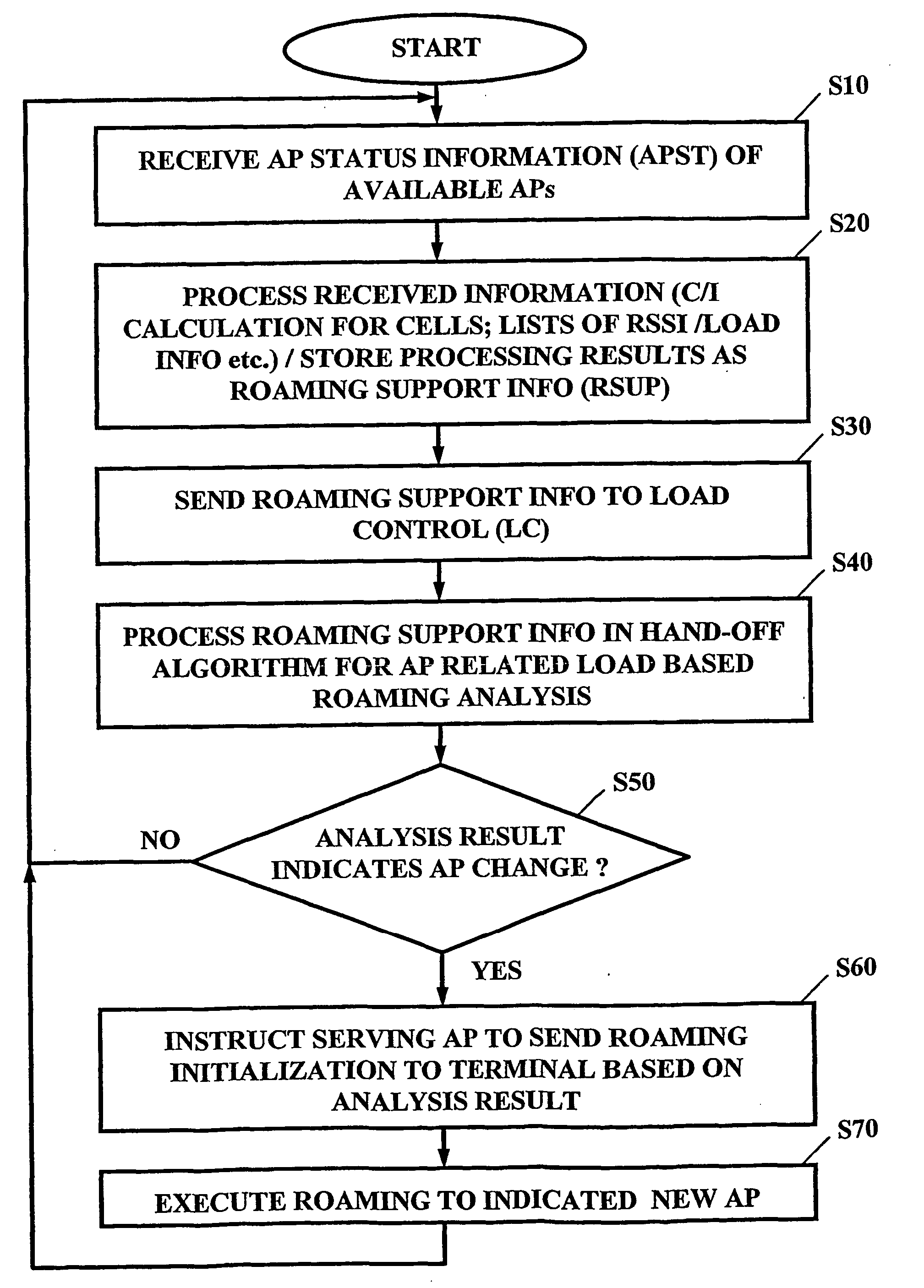
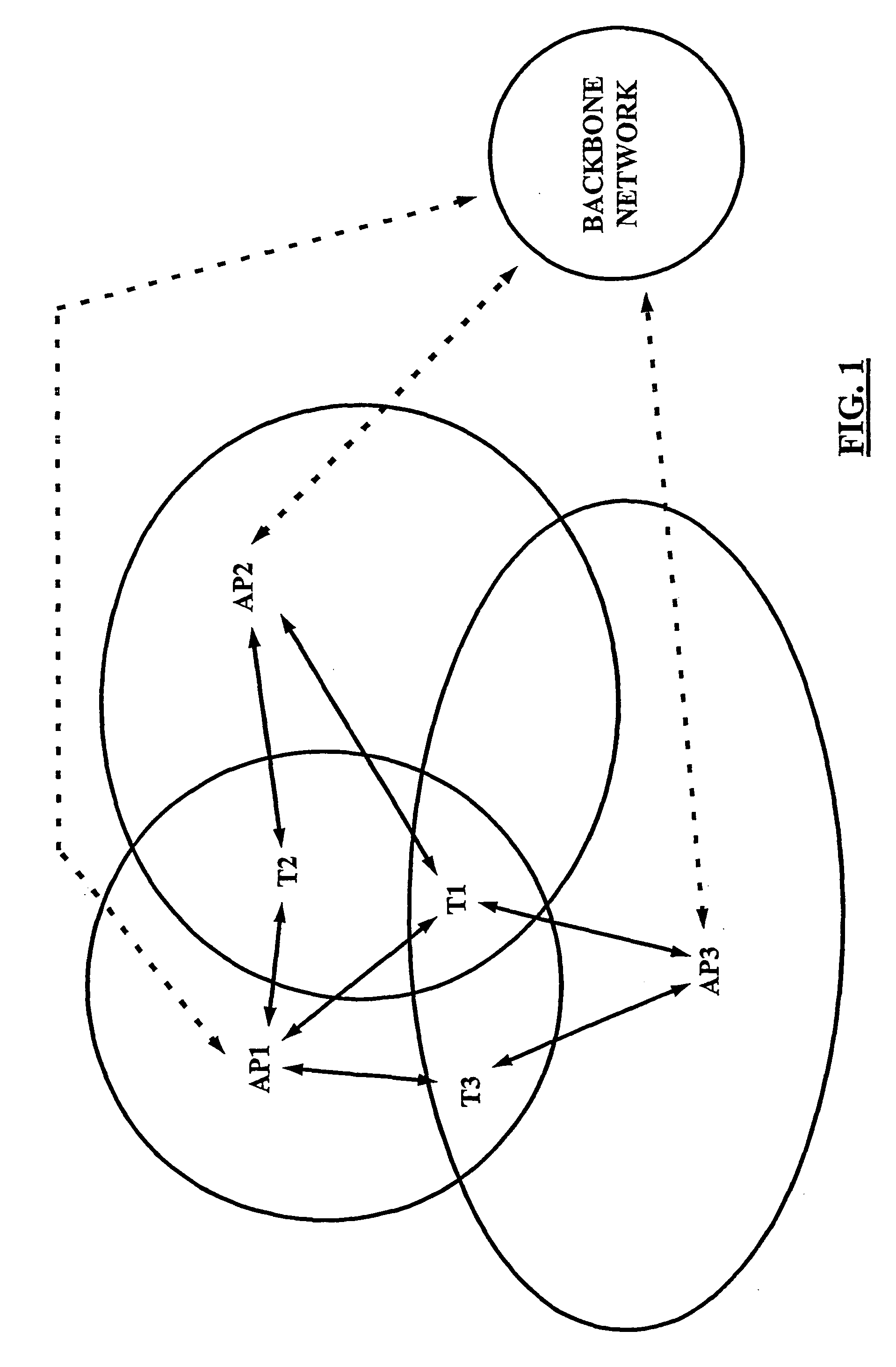
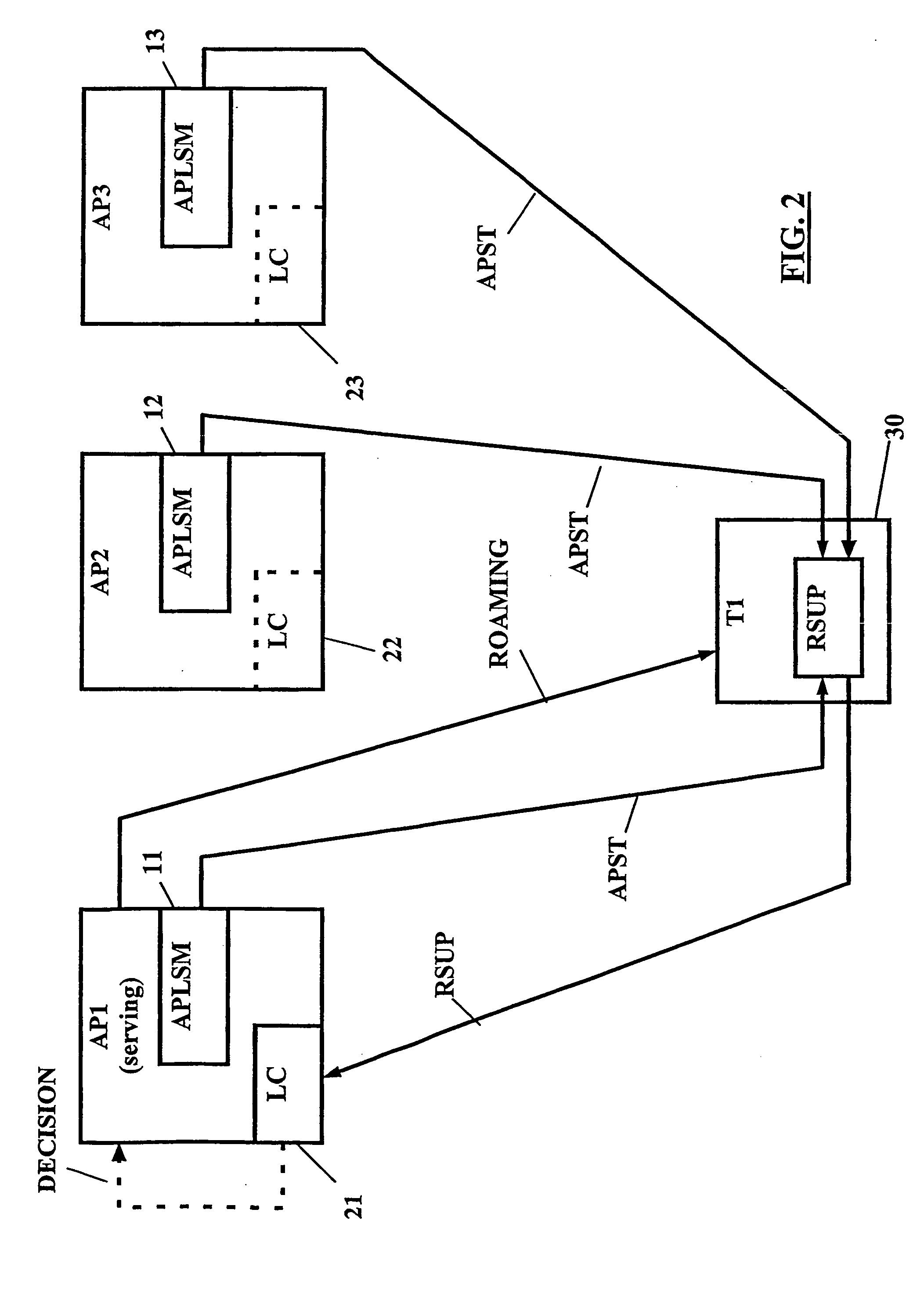
For load balancing in a wireless communication network comprising at least one subscriber terminal (T1, T2, T2) and a plurality of access points (AP1, AP2, AP3), a load control device (21; 110) is used which is located outside of said subscriber terminal, wherein said load control device is adapted to process information related to a load in said wireless communication network and to instruct roaming of said subscriber terminal from an associated access point to another one of said plurality of access points. Access point status information (APST) determined in said plurality of access points (S10; S110) is received and communication status information related to said plurality of access points (S20; S120) is determined. The subscriber terminal processes (S20; S120) these information into roaming support information (RSUP), which are in turn processed (S40; S160) in said load control device an access point related load based roaming analysis. On this basis, it is decided (S50; S170) by the load control device, whether said subscriber terminal is to be associated with another one of said plurality of access points.
Owner:NOKIA TECHNOLOGLES OY
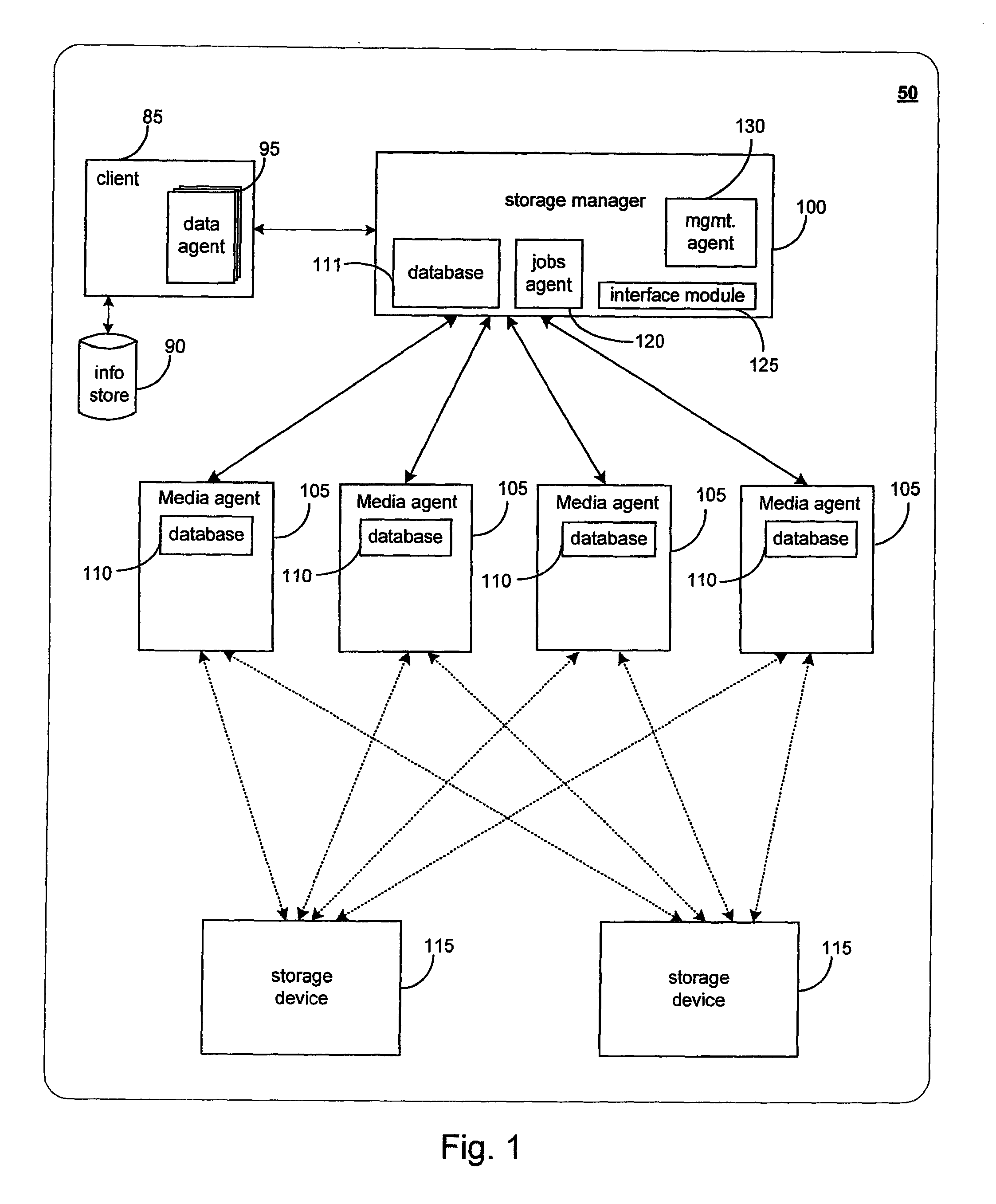
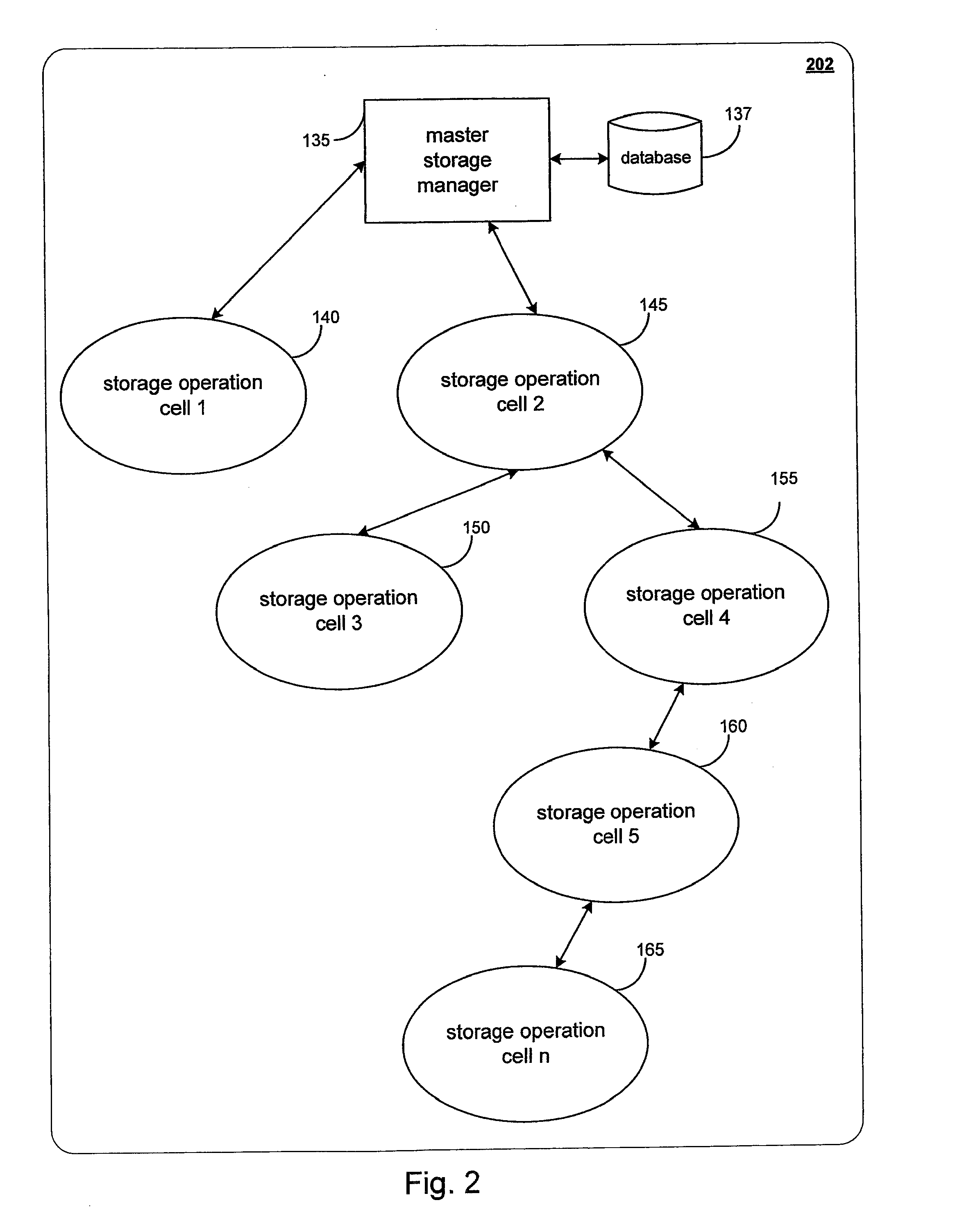
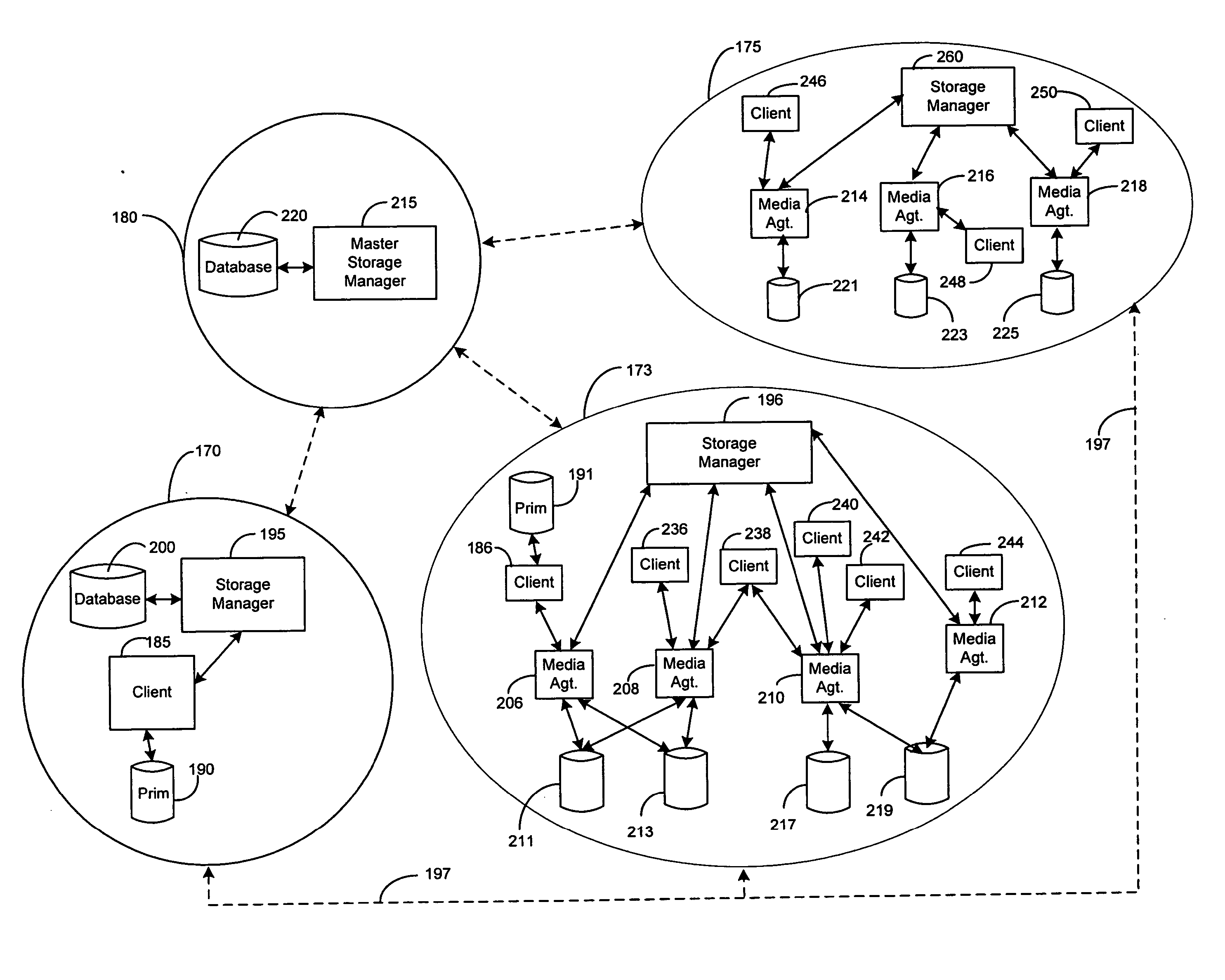
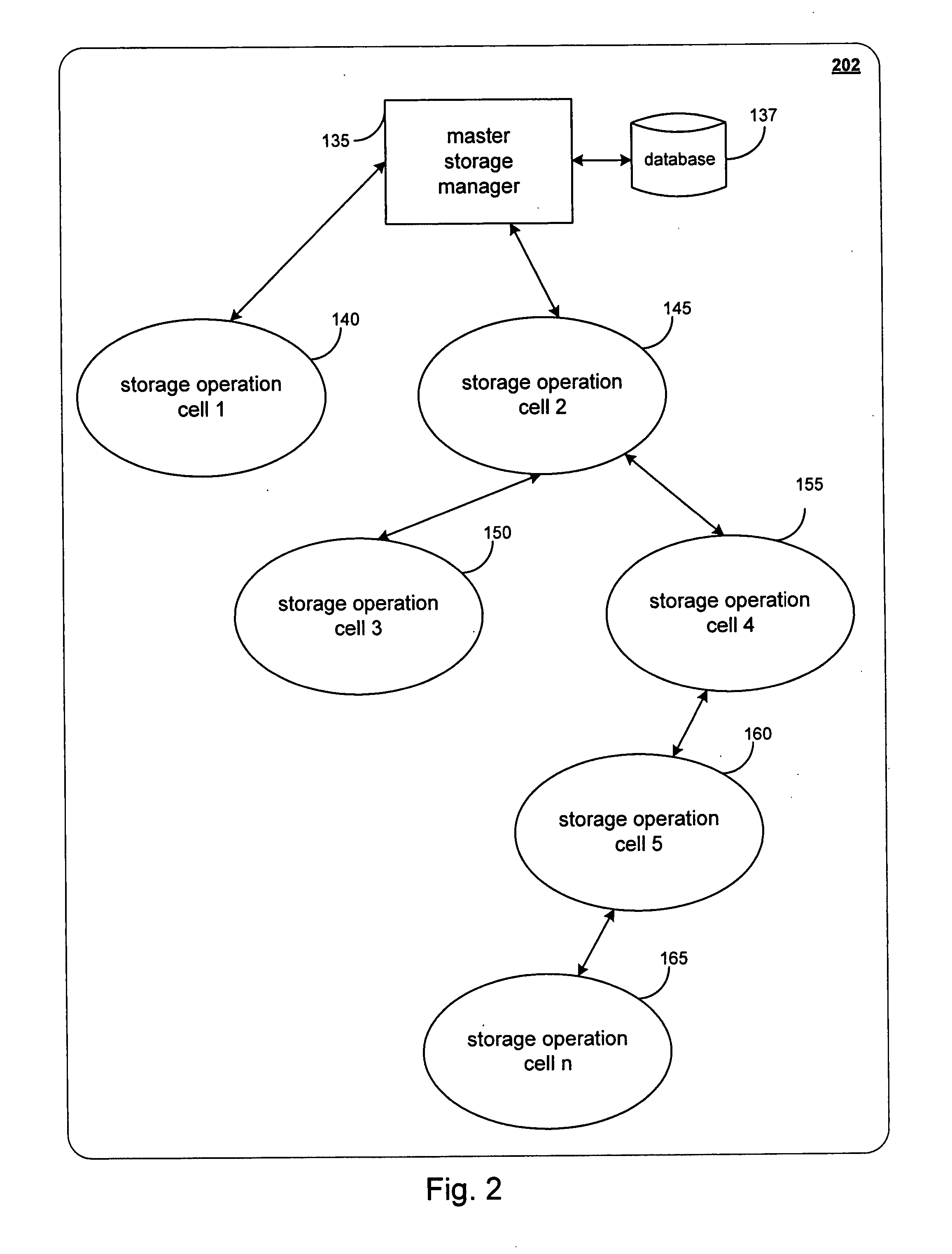
Systems and Methods for Migrating Components in a Hierarchical Storage Network
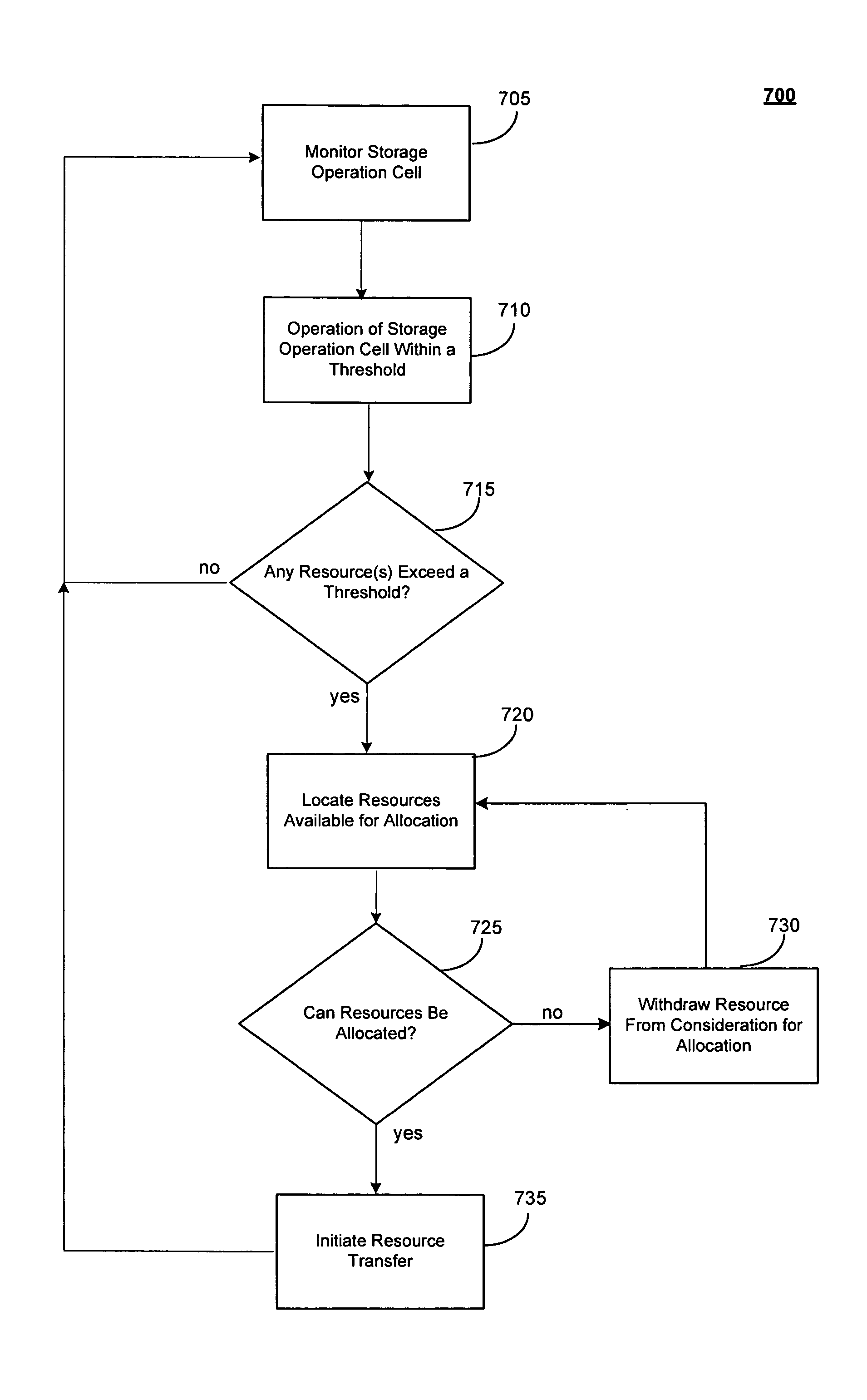
InactiveUS20110010518A1Improve performancePromote recoveryResource allocationError detection/correctionFailoverOperational system
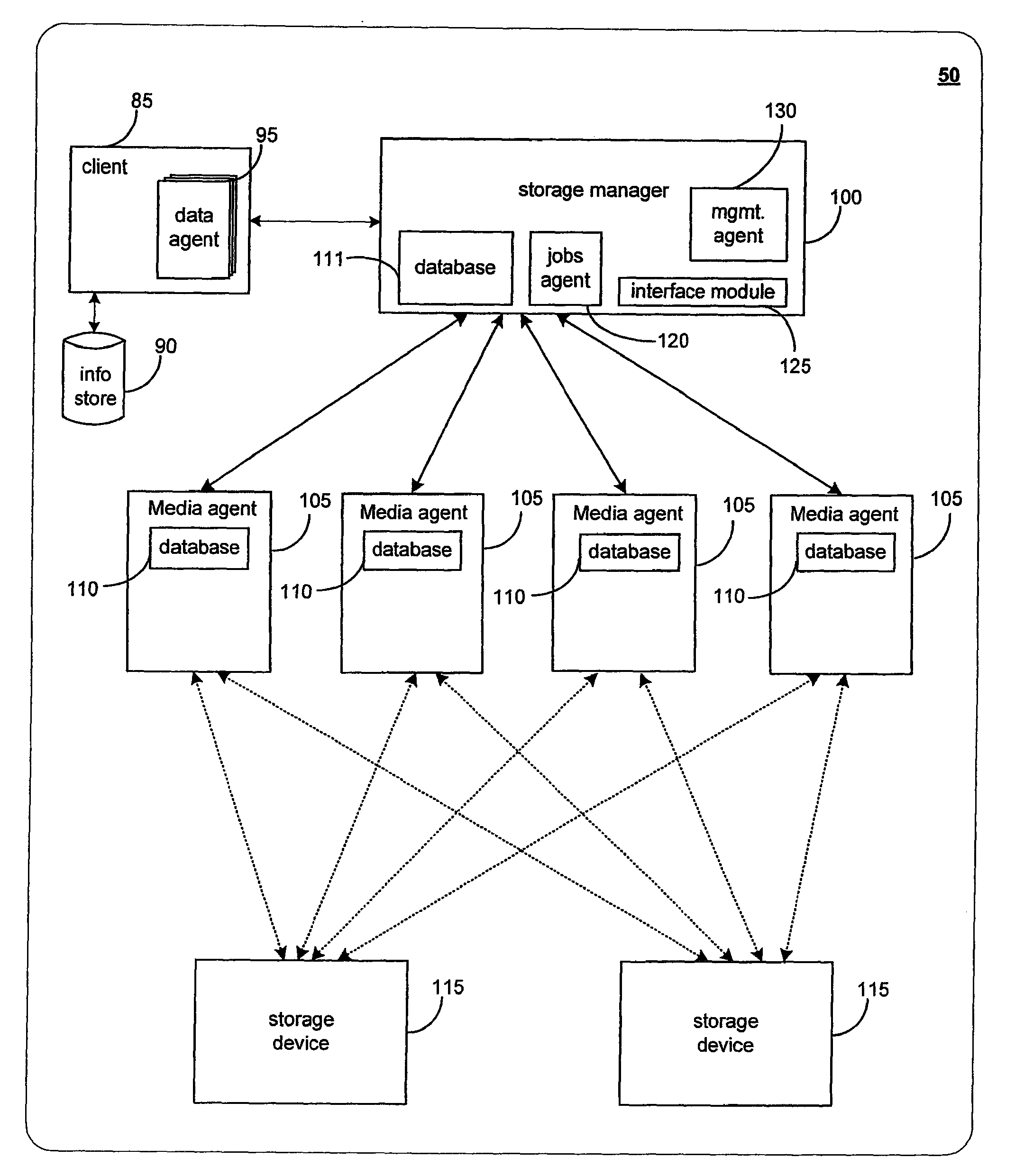
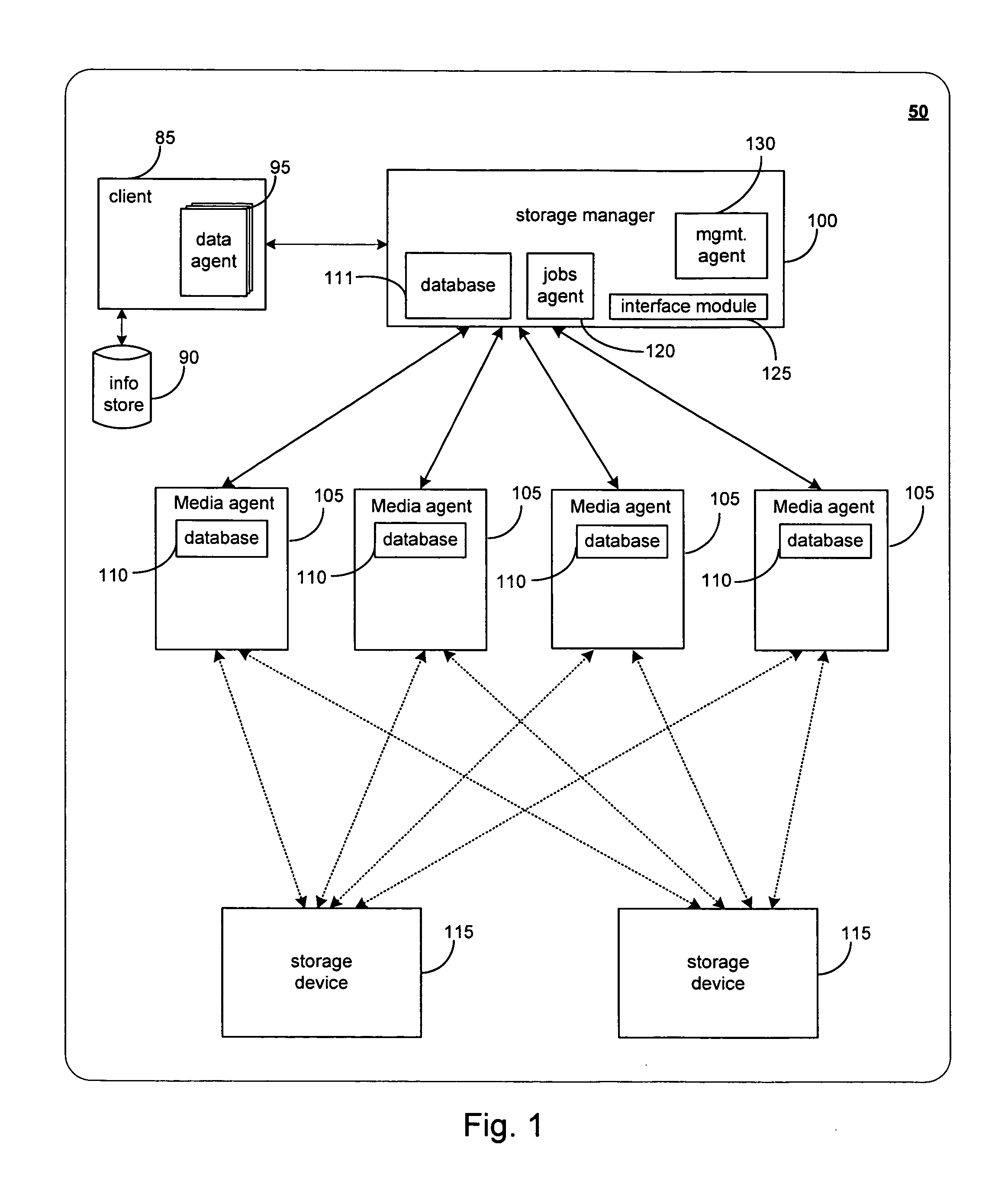
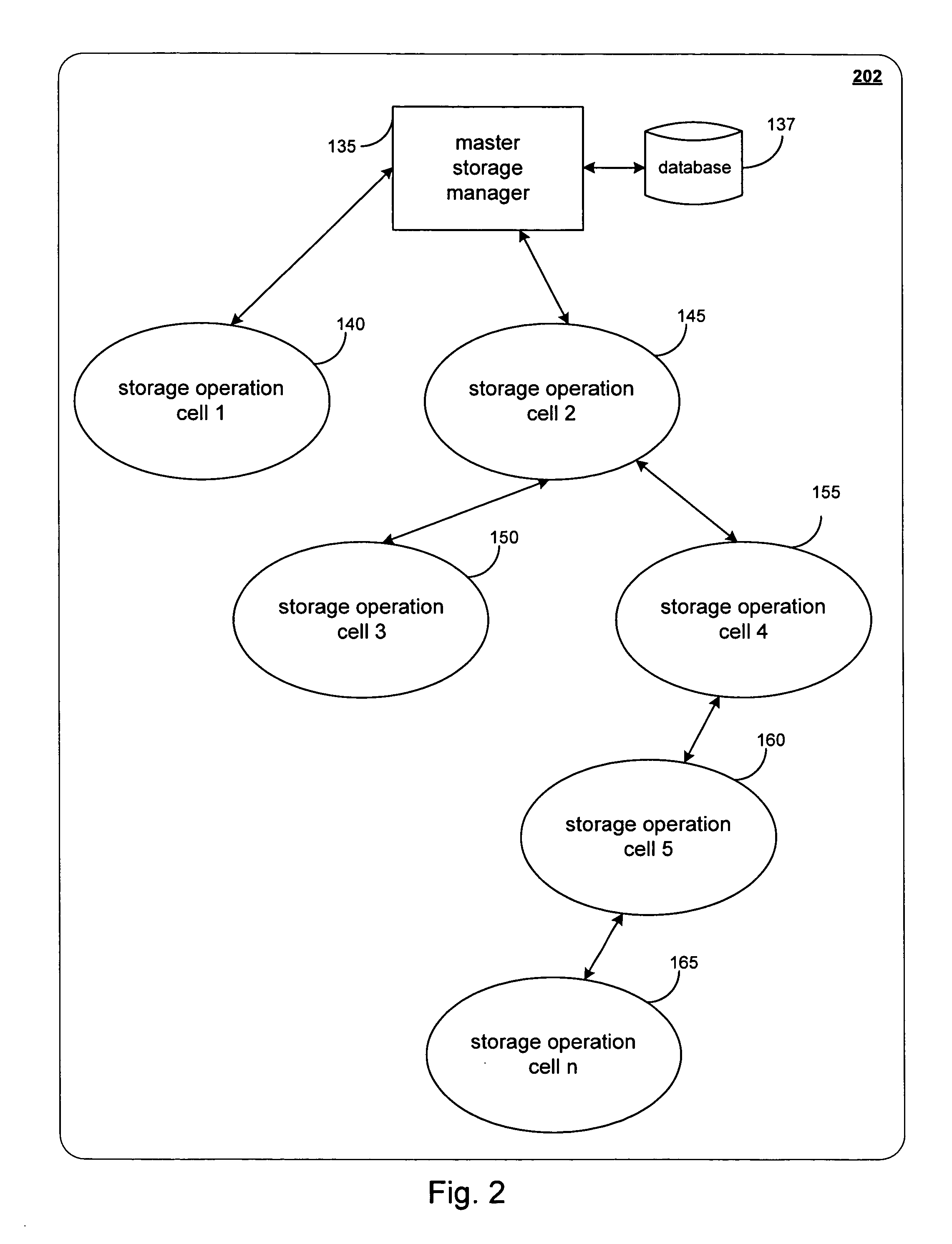
System and methods for selectively or automatically migrating resources between storage operation cells are provided. In accordance with one aspect of the invention, a management component within the storage operation system may monitor system operation and migrate components from storage operation cell to another to facilitate failover recovery, promote load balancing within the system and improve overall system performance as further described herein. Another aspect of the invention may involve performing certain predictive analyses on system operation to reveal trends and tendencies within the system. Such information may be used as the basis for potentially migrating components from one storage operation cell to another to improve system performance and reduce or eliminate resource exhaustion or congestion conditions.
Owner:COMMVAULT SYST INC
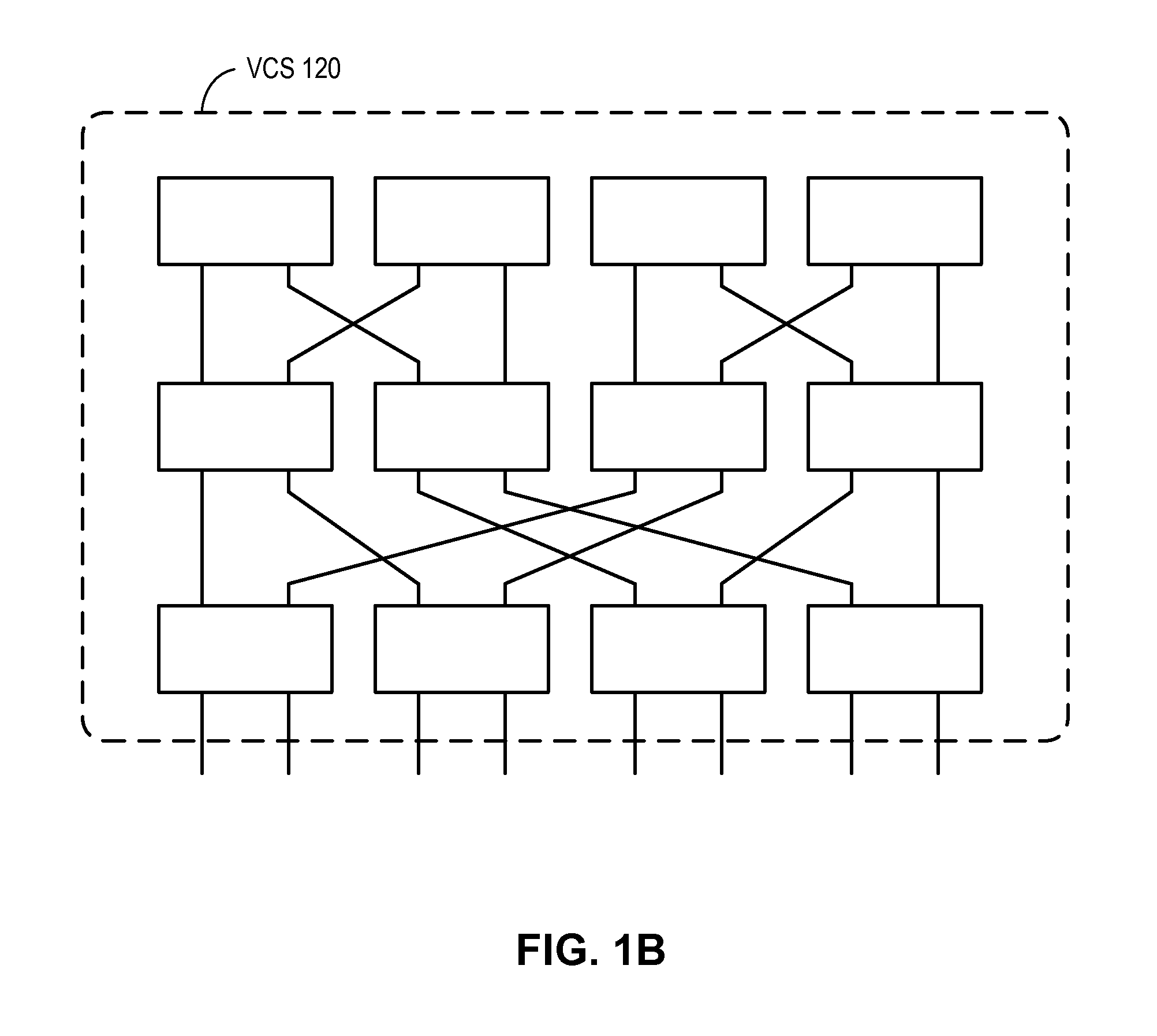
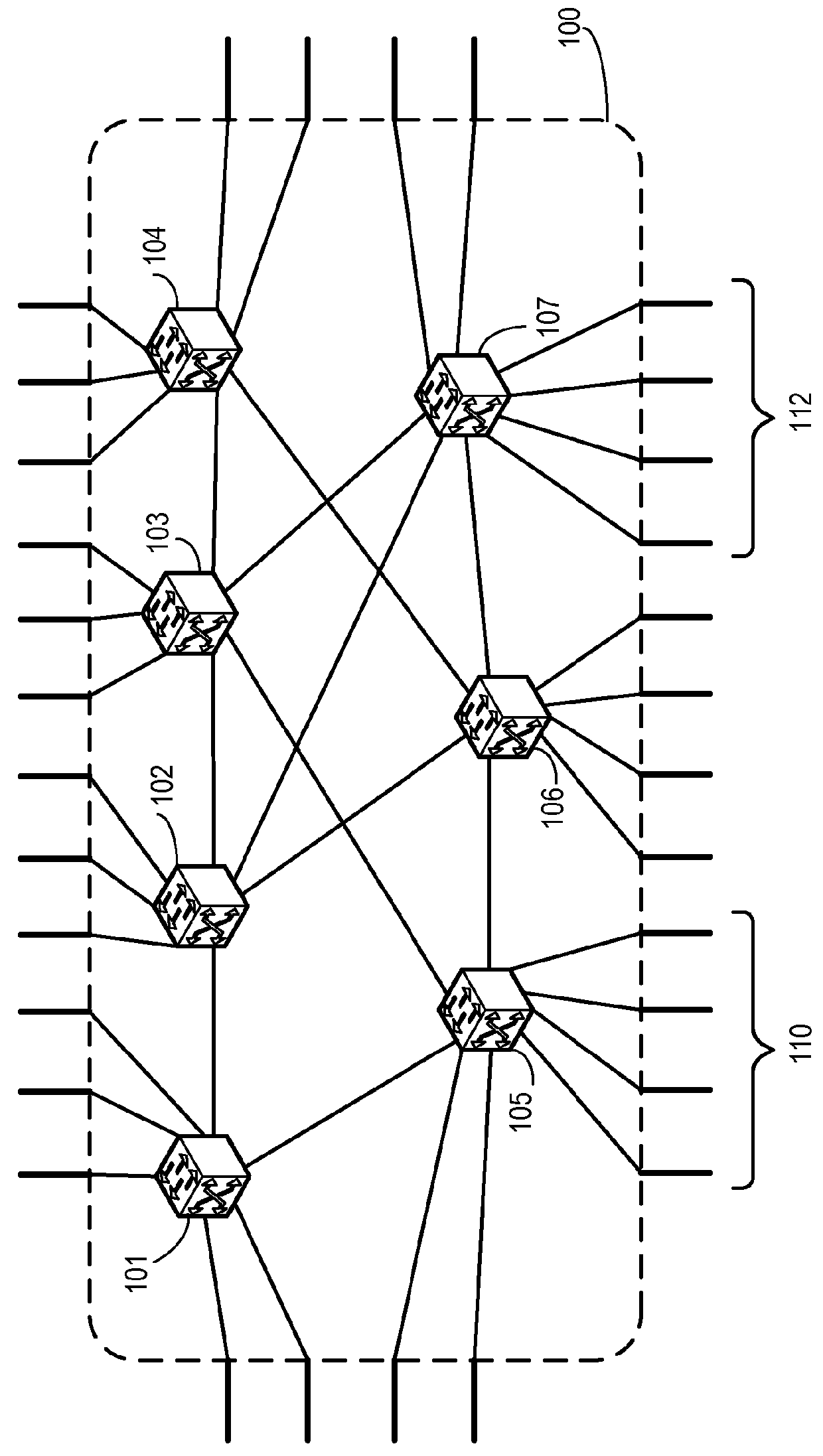
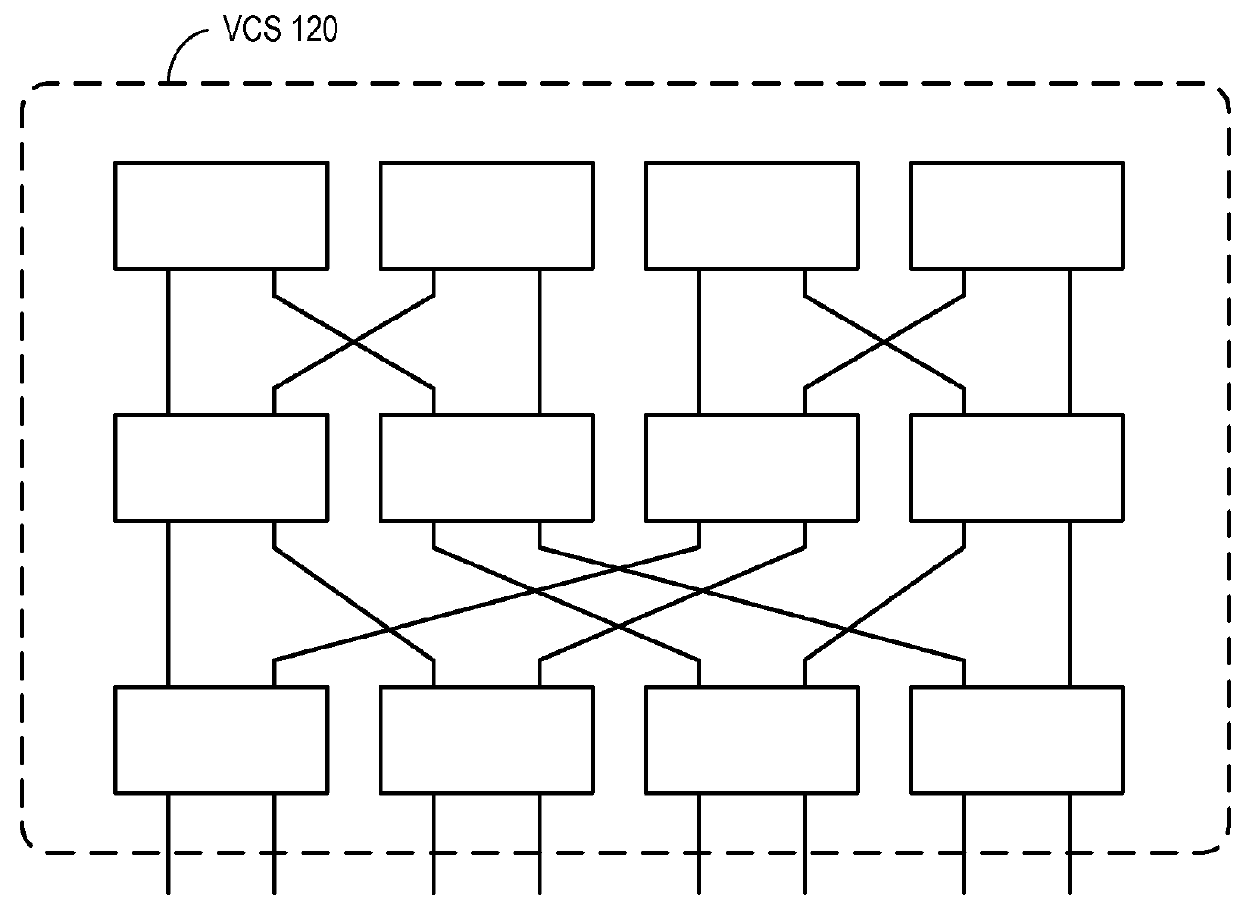
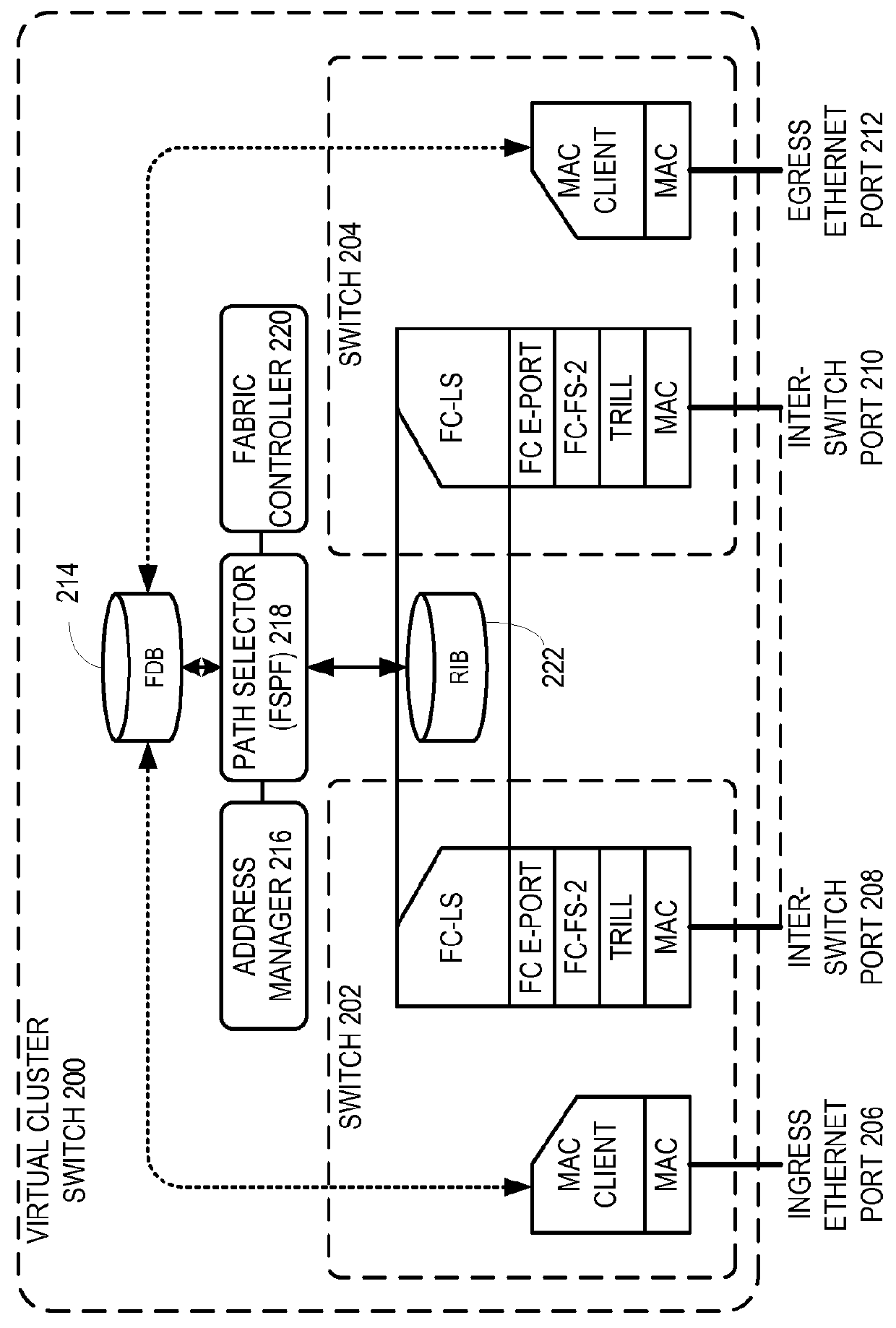
Traffic management for virtual cluster switching
ActiveUS20110299391A1Enhanced transmission selectionGood for load balancingError preventionTransmission systemsTraffic capacityVirtual cluster
One embodiment of the present invention provides a switch system. The switch includes one or more ports on the switch configured to transmit packets encapsulated based on a first protocol. The switch further includes a traffic management mechanism and a control mechanism. During operation, the control mechanism forms a logical switch based on a second protocol, receives an automatically assigned identifier for the logical switch without requiring manual configuration of the identifier, and joins a virtual cluster switch.
Owner:AVAGO TECH INT SALES PTE LTD
Multitask process monitoring method and system in distributed system environment
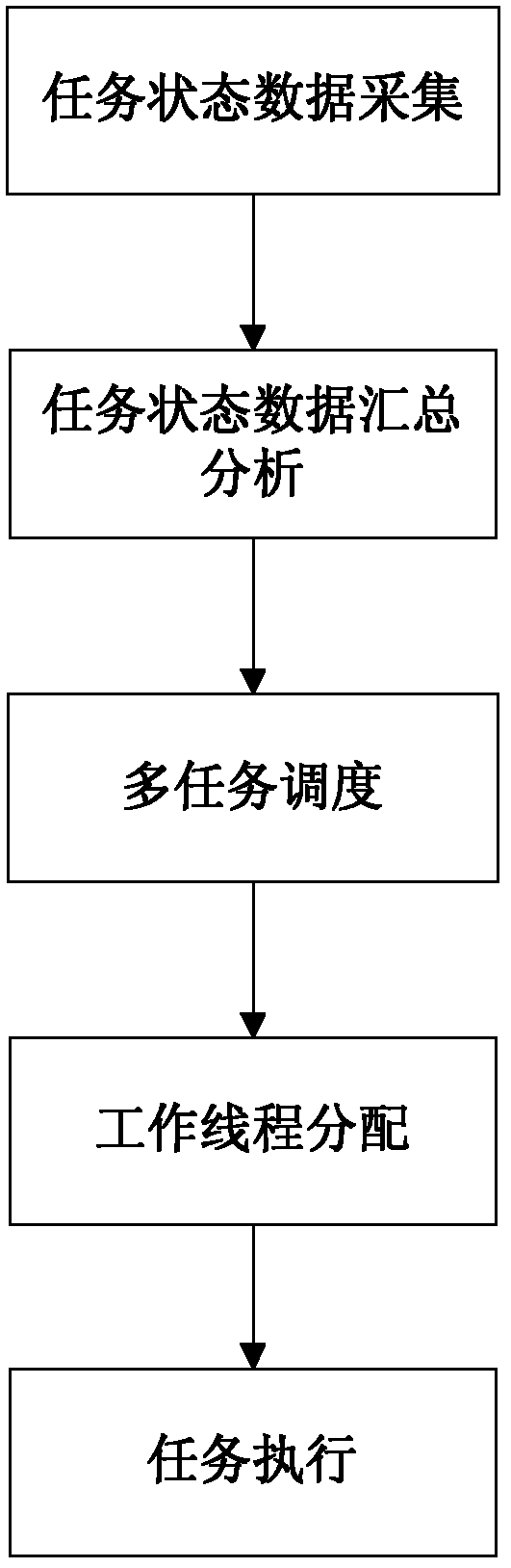
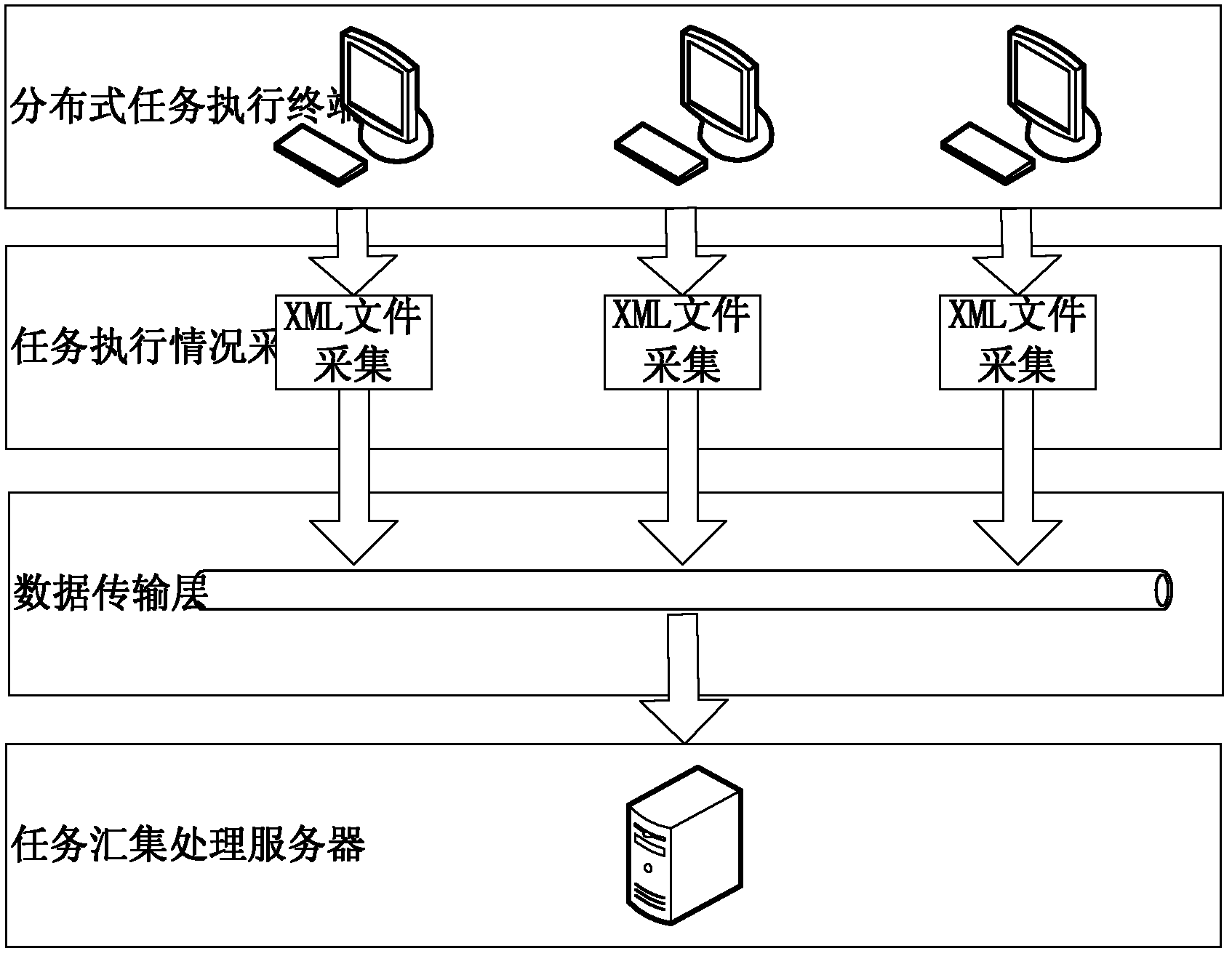
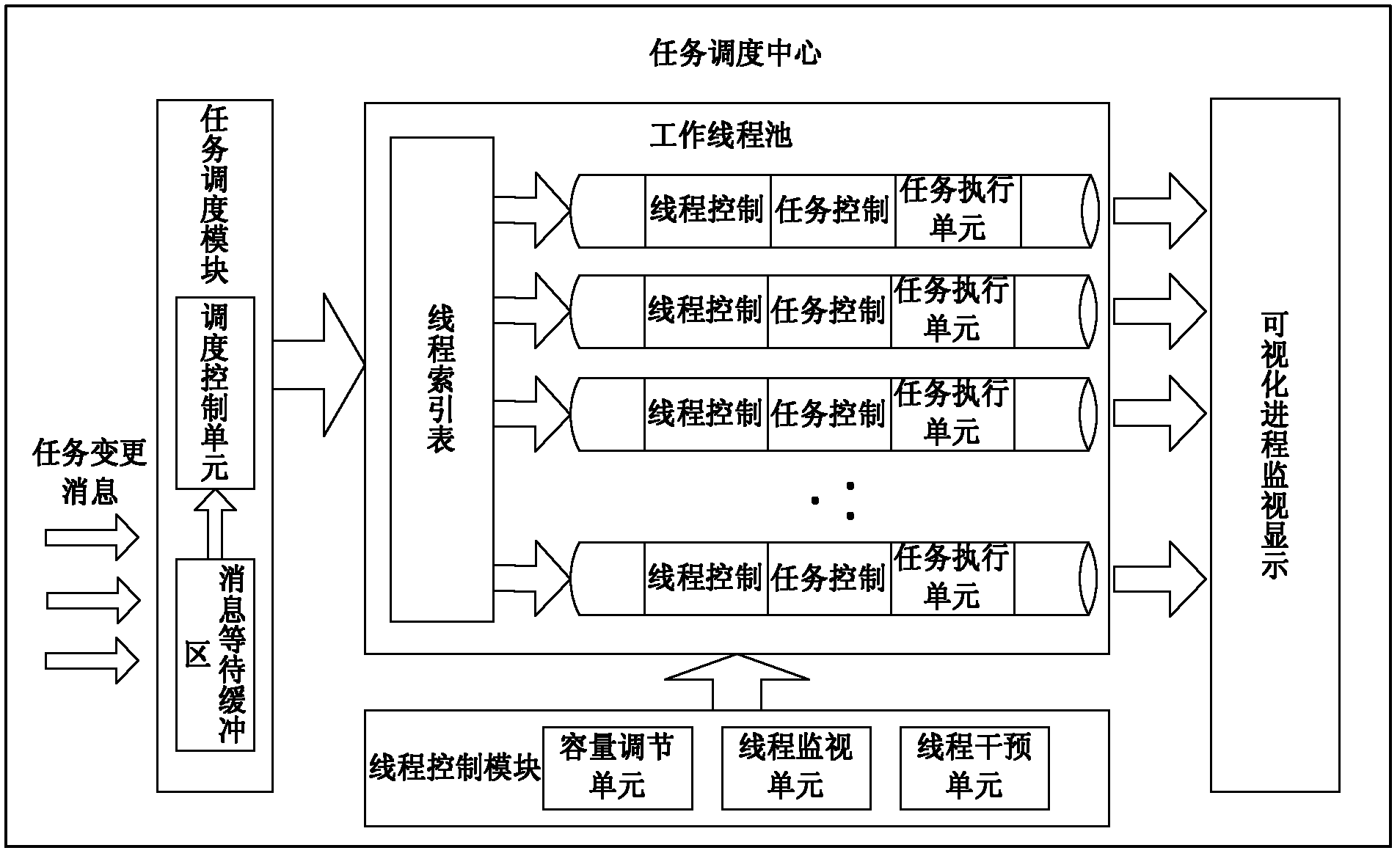
ActiveCN102360310AEfficient parallel processingGood for load balancingResource allocationFiltrationMonitoring system
The invention discloses a multitask process monitoring method in the distributed system environment. The method comprises the following steps that: five states of the task execution process of each task execution terminal in the distributed system environment are monitored; an XML (eXtensible markup language) format description file is transported to a task collecting and processing server, the task execution conditions after filtration are written in a database and simultaneously task change information is sent to notify a task scheduling center; the task scheduling center directly submits the information to a task scheduling module after receiving the task change information and the task scheduling module adds the received information to information waiting queues; a scheduling control unit searches for a thread index table for threads of execution of the task and gives the threads of execution to the threads to be executed; and a thread control module monitors a plurality of threads in a work thread pool in real time in the system operation process. The invention also discloses a multitask process monitoring system. The system comprises a plurality of distributed task execution terminals, the task collecting and processing server and the task scheduling center.
Owner:THE 28TH RES INST OF CHINA ELECTRONICS TECH GROUP CORP
Method and device for controlling carrier frequency of multi-carrier/subdistrict system
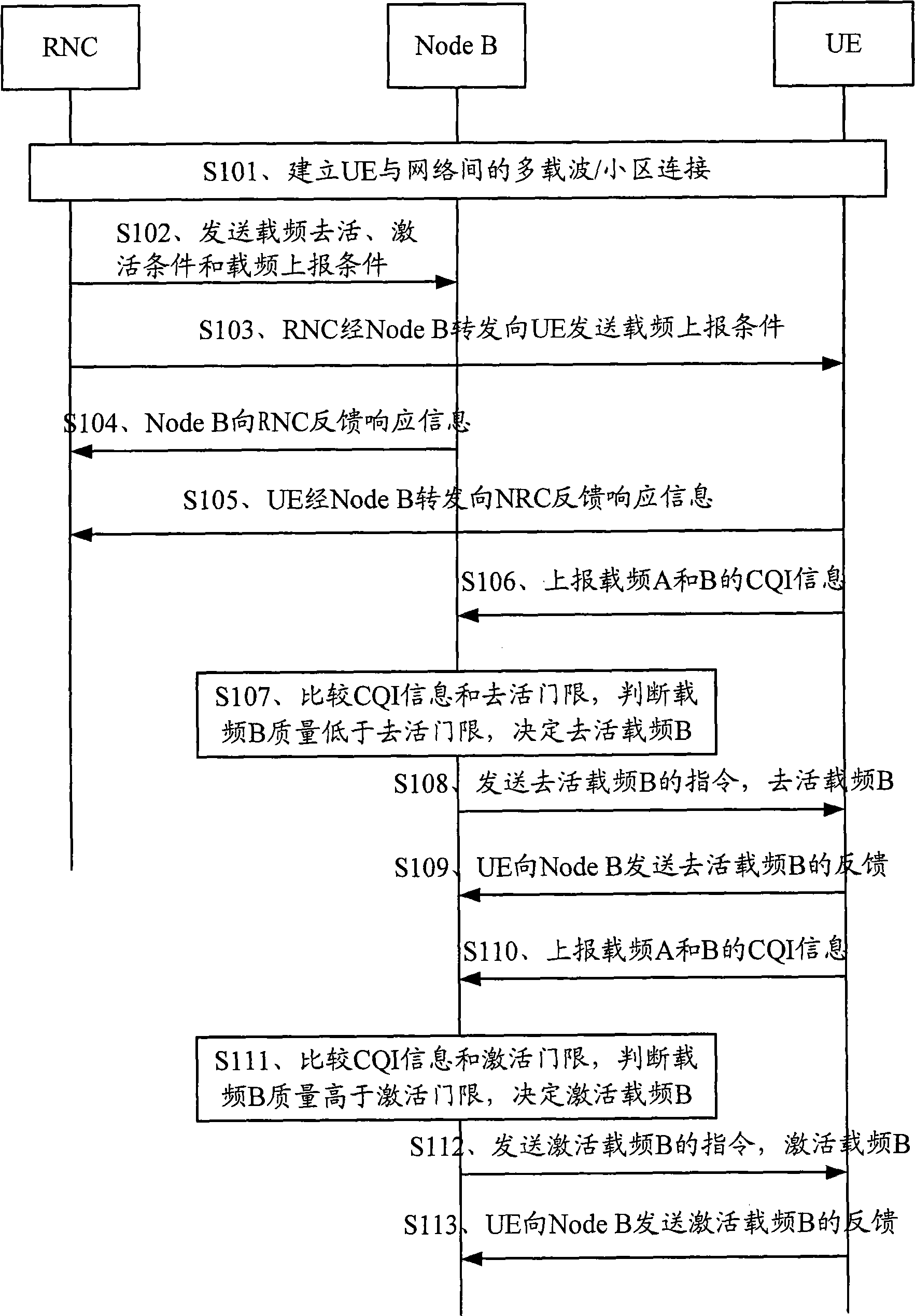
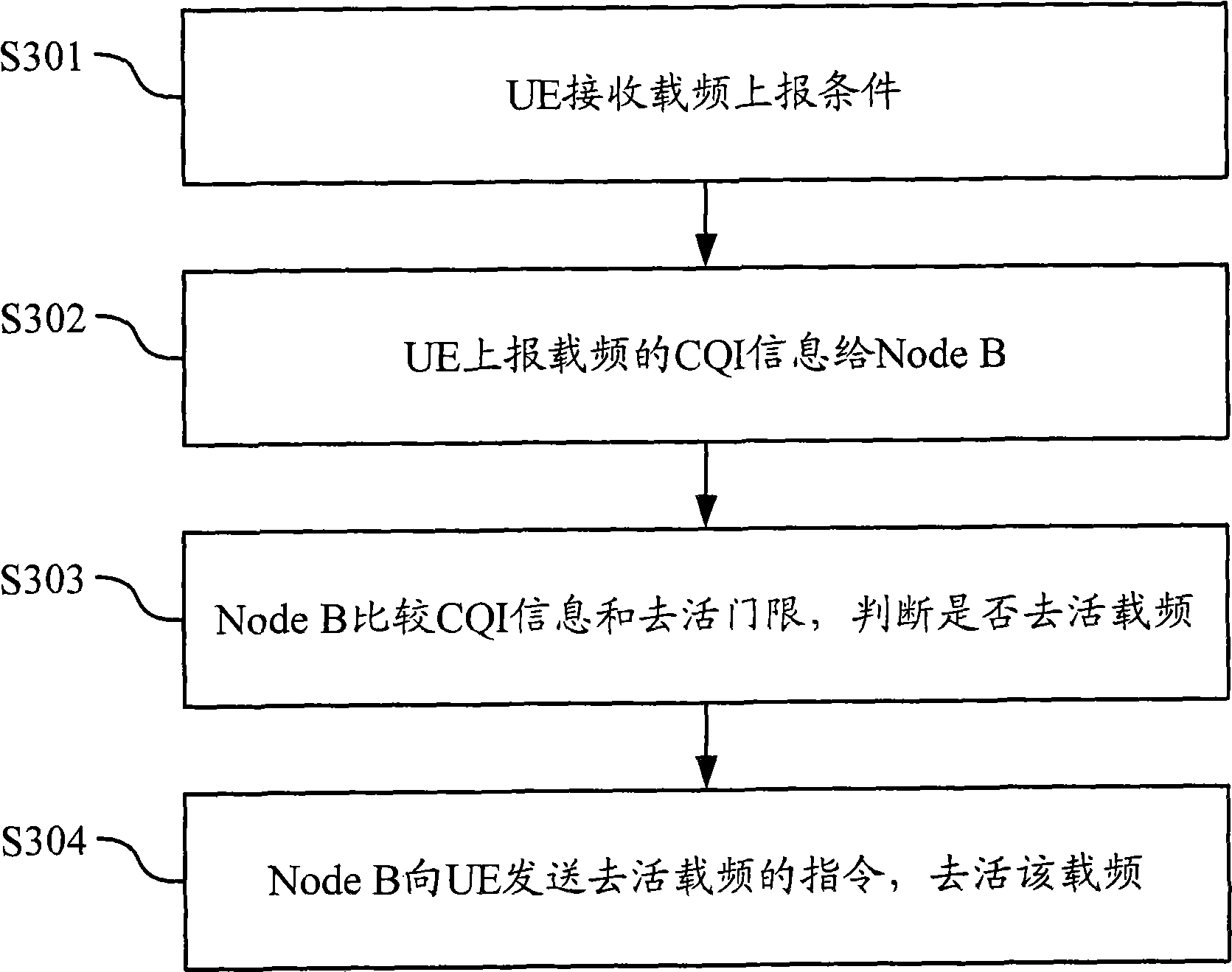
ActiveCN101547477AQuality improvementImprove experienceNetwork traffic/resource managementSignal allocationSystem capacityEngineering
The embodiment of the invention discloses a method and a device for controlling the carrier frequency of a multi-carrier / subdistrict system. The method comprises the following steps: receiving the signal path quality indicating CQI information of the carrier frequency, which is reported by a terminal; carrying out deactivation or activation judgment for the carrier frequency according to the signal path quality indicating CQI information; and ordering the terminal to deactivate or activate the carrier frequency according to the judgment result. The method flexibly activates and deactivates a certain carrier frequency according to carrier frequency quality reporting and threshold comparison in the multi-carrier / subdistrict system, thereby enhancing the system capacity and having better load balancing effect.
Owner:HUAWEI TECH CO LTD
Systems and methods for migrating components in a hierarchical storage network
ActiveUS20070198797A1Improve performancePromote recoveryResource allocationError detection/correctionFailoverLoad Shedding
System and methods for selectively or automatically migrating resources between storage operation cells are provided. In accordance with one aspect of the invention, a management component within the storage operation system may monitor system operation and migrate components from storage operation cell to another to facilitate failover recovery, promote load balancing within the system and improve overall system performance as further described herein. Another aspect of the invention may involve performing certain predictive analyses on system operation to reveal trends and tendencies within the system. Such information may be used as the basis for potentially migrating components from one storage operation cell to another to improve system performance and reduce or eliminate resource exhaustion or congestion conditions.
Owner:COMMVAULT SYST INC
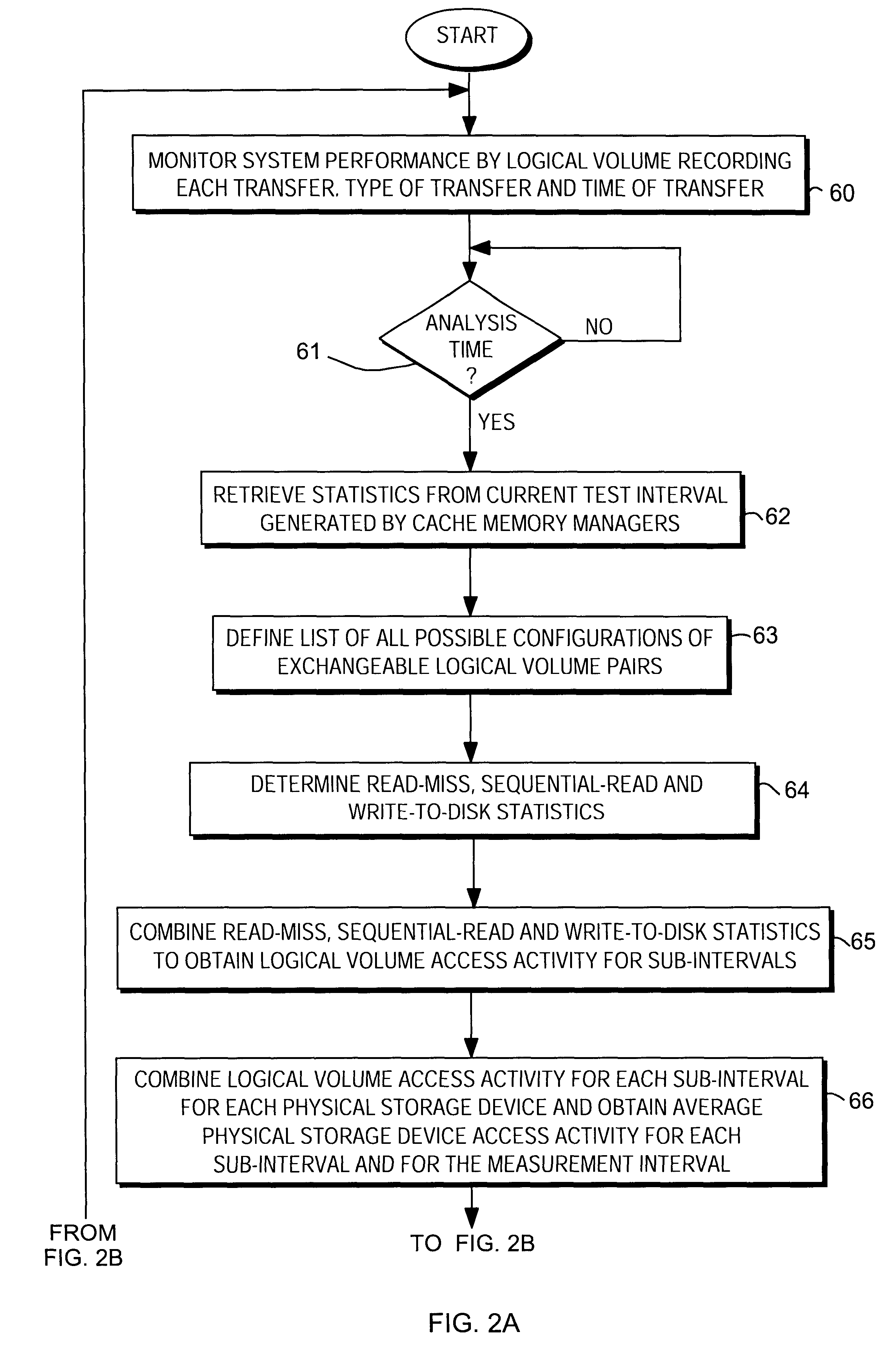
Load balancing on disk array storage device
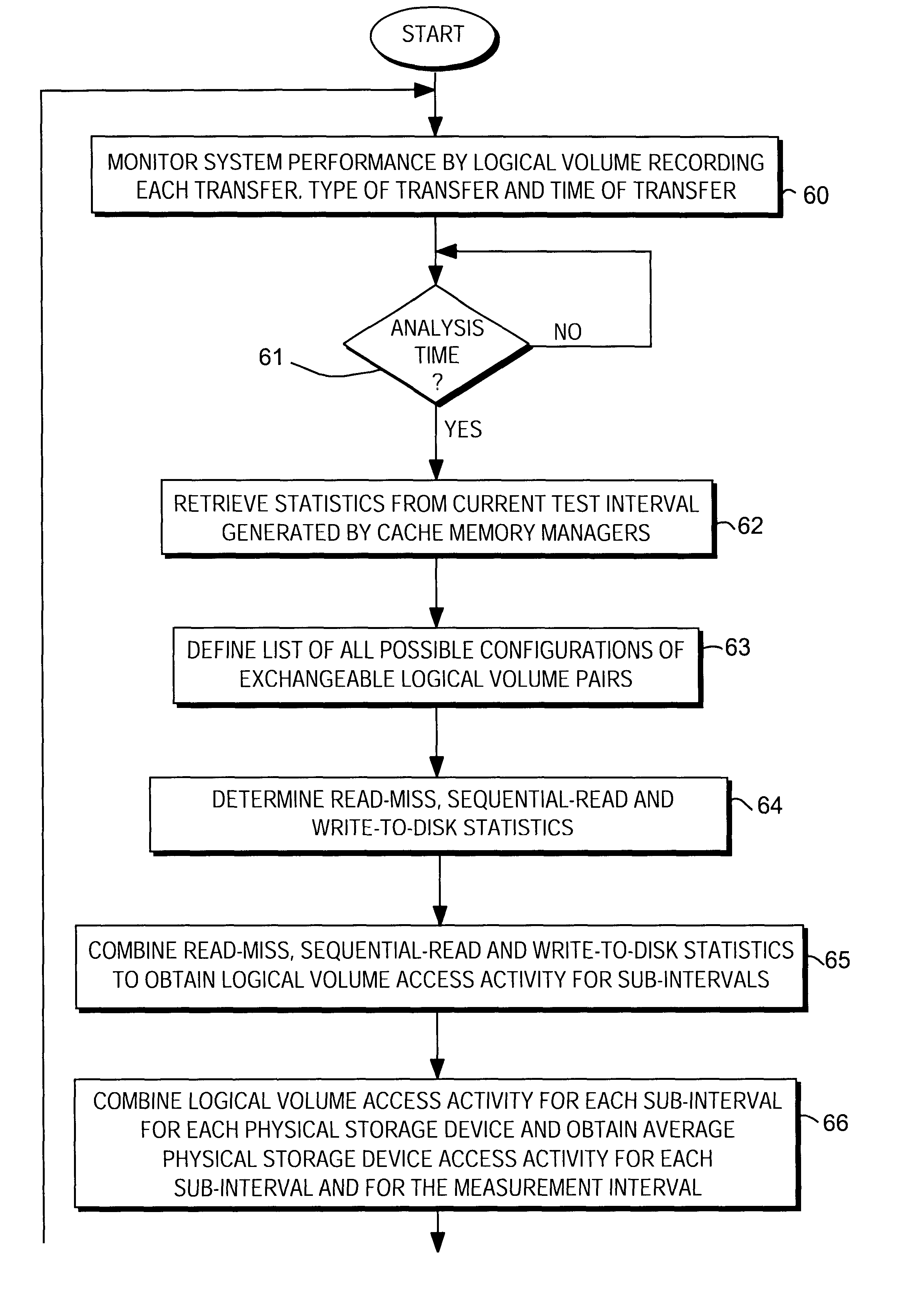
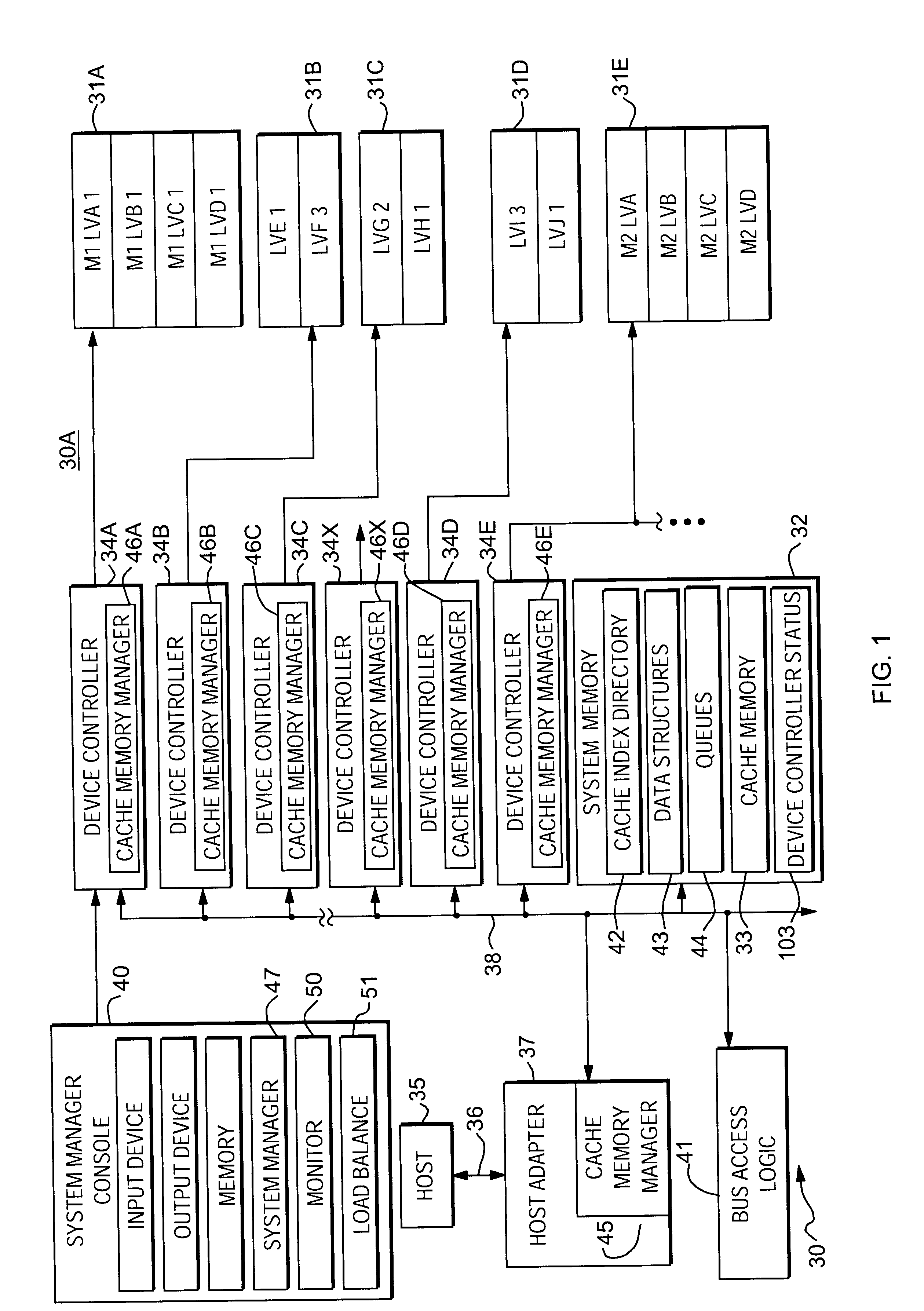
InactiveUS6711649B1Reduce imbalanceGood for load balancingInput/output to record carriersMemory loss protectionStatistical analysisDisk array
Load balancing of activities on physical disk storage devices is accomplished by monitoring reading and writing operations to blocks of contiguous storage locations on the physical disk storage devices. A list of exchangeable pairs of blocks is developed based on size and function. Statistics accumulated over an interval are then used to obtain access activity values for each block and each physical disk drive. A statistical analysis leads to a selection of one block pair. After testing to determine any adverse effect of making that change, the exchange is made to more evenly distribute the loading on individual physical disk storage devices.
Owner:EMC IP HLDG CO LLC
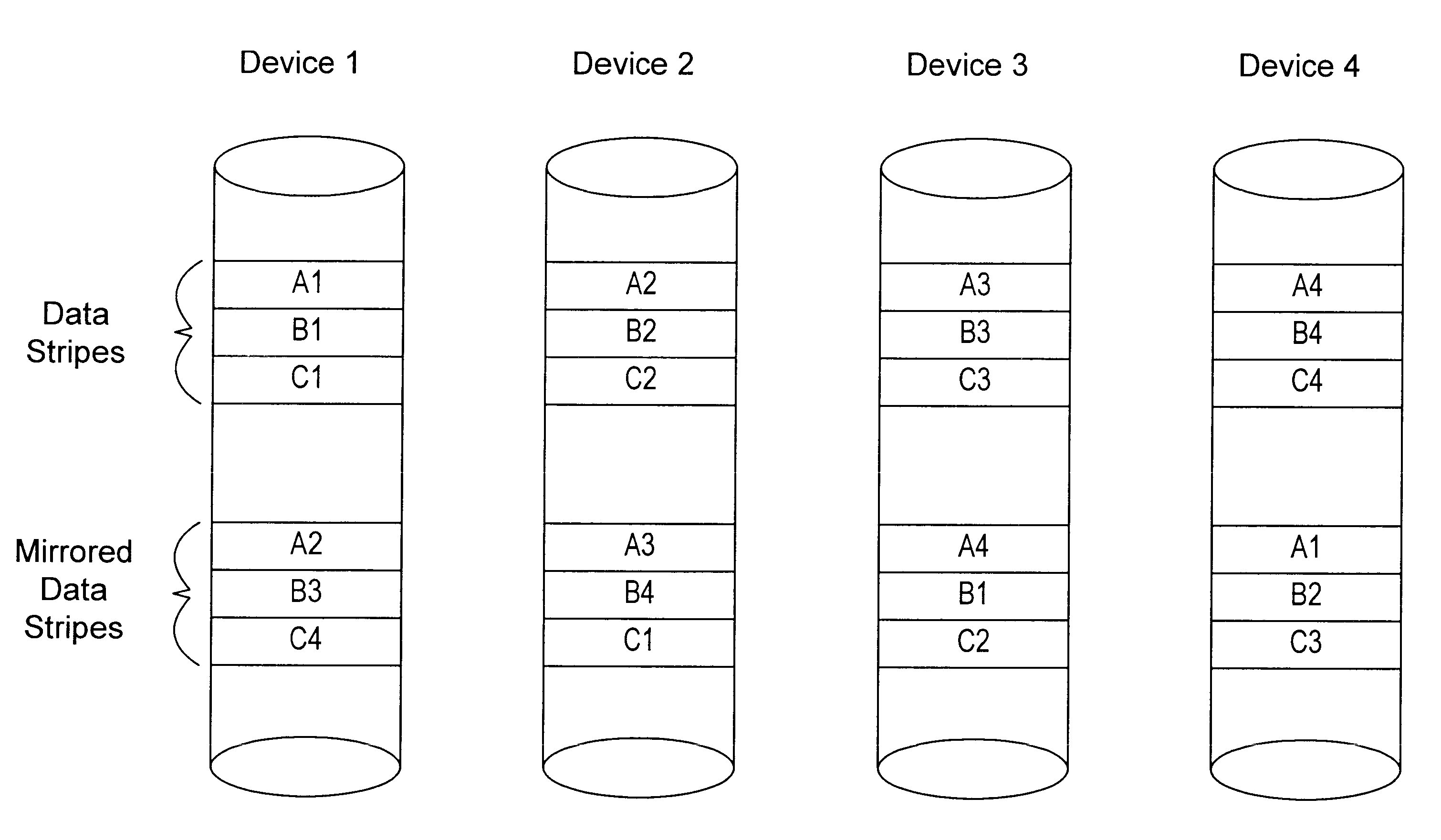
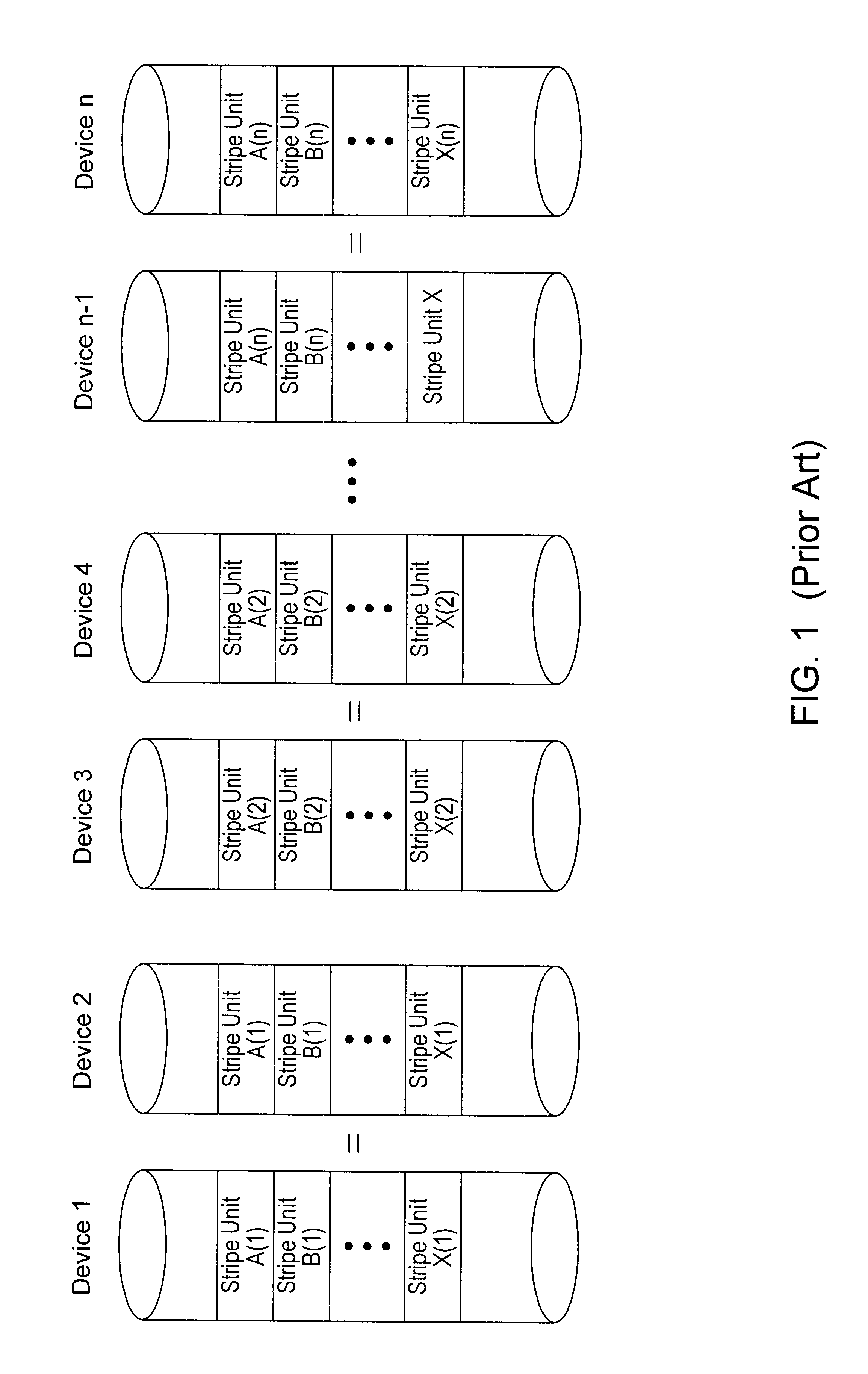
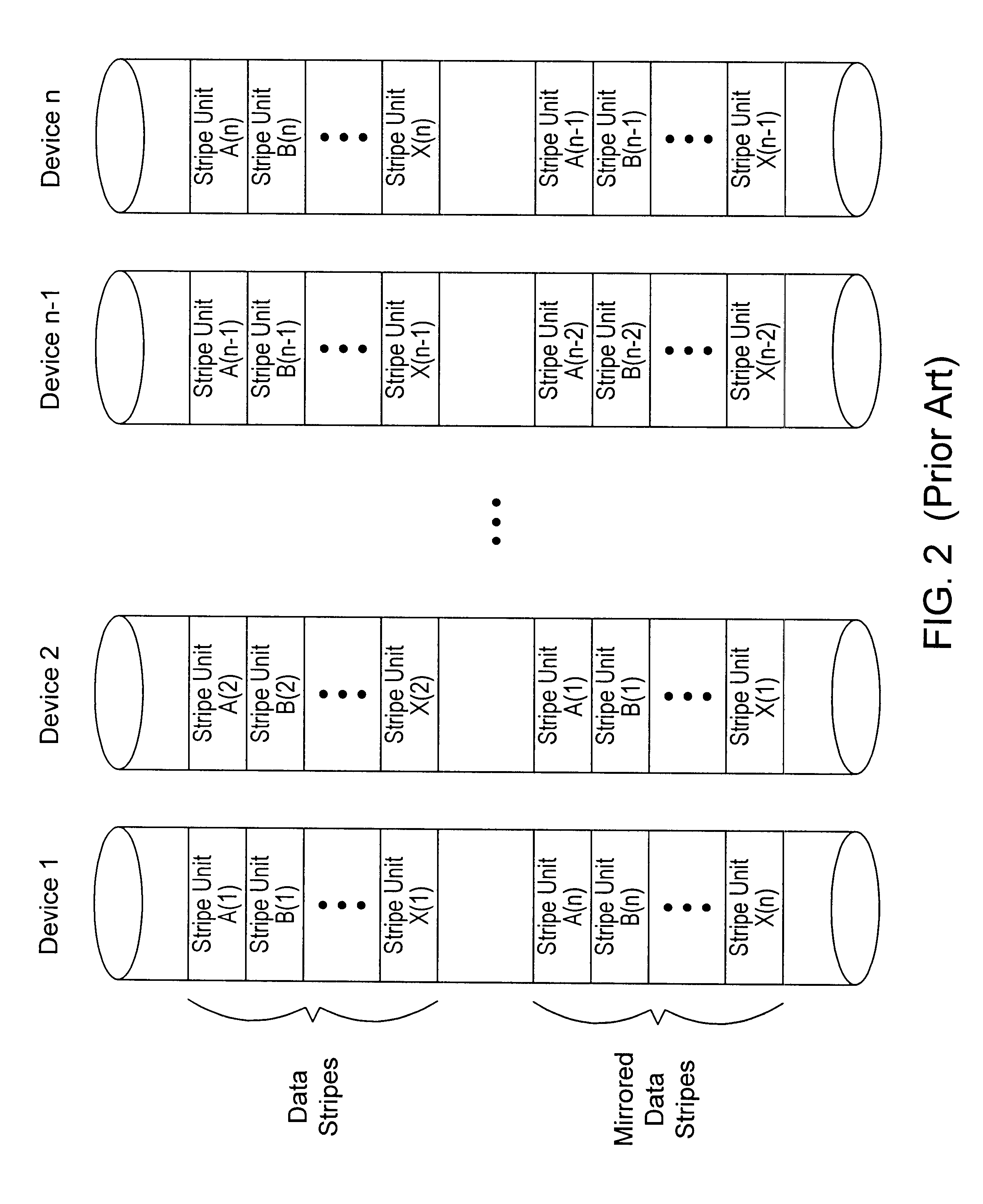
Load balancing configuration for storage arrays employing mirroring and striping
InactiveUS6425052B1Good for load balancingInput/output to record carriersMemory systemsDistributed computing
Owner:ORACLE INT CORP
Systems and methods for migrating components in a hierarchical storage network
InactiveUS20070260834A1Promote recoveryGood for load balancingResource allocationError detection/correctionFailoverLoad Shedding
System and methods for selectively or automatically migrating resources between storage operation cells are provided. In accordance with one aspect of the invention, a management component within the storage operation system may monitor system operation and migrate components from storage operation cell to another to facilitate failover recovery, promote load balancing within the system and improve overall system performance as further described herein. Another aspect of the invention may involve performing certain predictive analyses on system operation to reveal trends and tendencies within the system. Such information may be used as the basis for potentially migrating components from one storage operation cell to another to improve system performance and reduce or eliminate resource exhaustion or congestion conditions.
Owner:COMMVAULT SYST INC
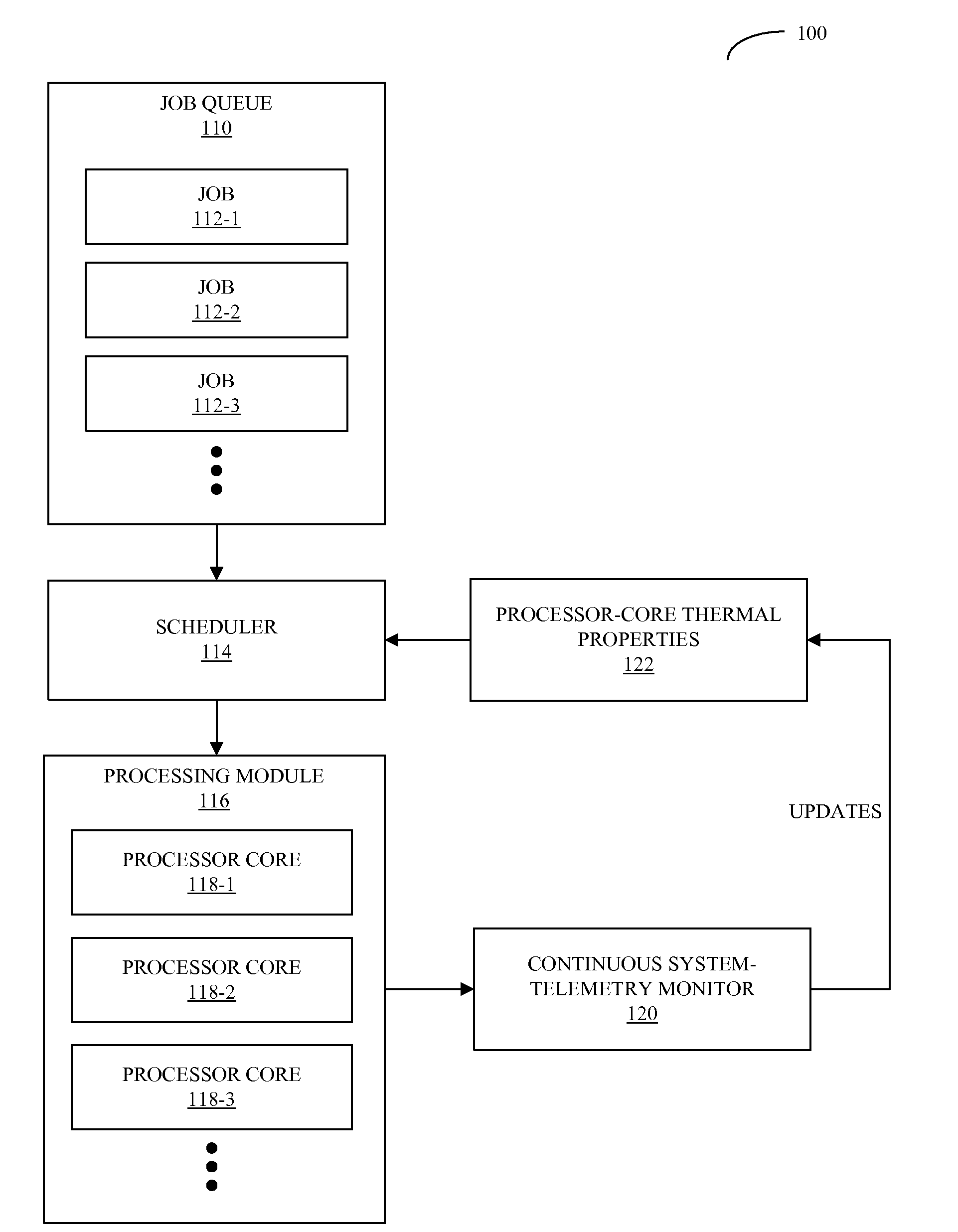
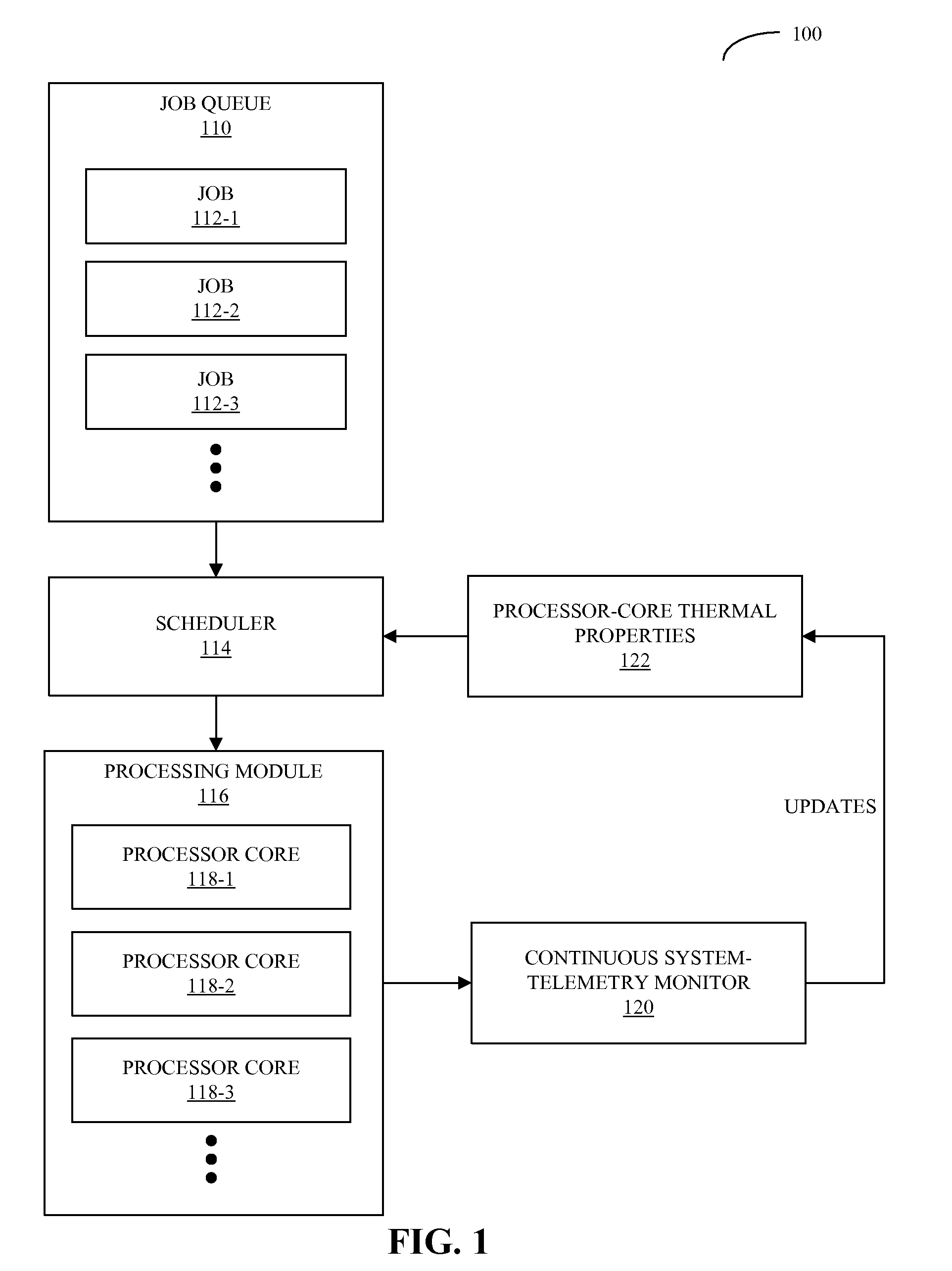
Workload scheduling in multi-core processors
ActiveUS20090271141A1Cancel noiseReduces spatial and temporal thermal variationThermometer detailsEnergy efficient ICTThermal variationComputerized system
A computer system that schedules loads across a set of processor cores is described. During operation, the computer system receives thermal measurements from sensors associated with the set of processor cores, and removes noise from the thermal measurements. Then, the computer system analyzes thermal properties of the set of processor cores based on the thermal measurements. Next, the computer system receives a process to be executed, and schedules the process to be executed by at least one of the processor cores based on the analysis. This scheduling is performed in a manner that reduces spatial and temporal thermal variations in the integrated circuit.
Owner:ORACLE INT CORP
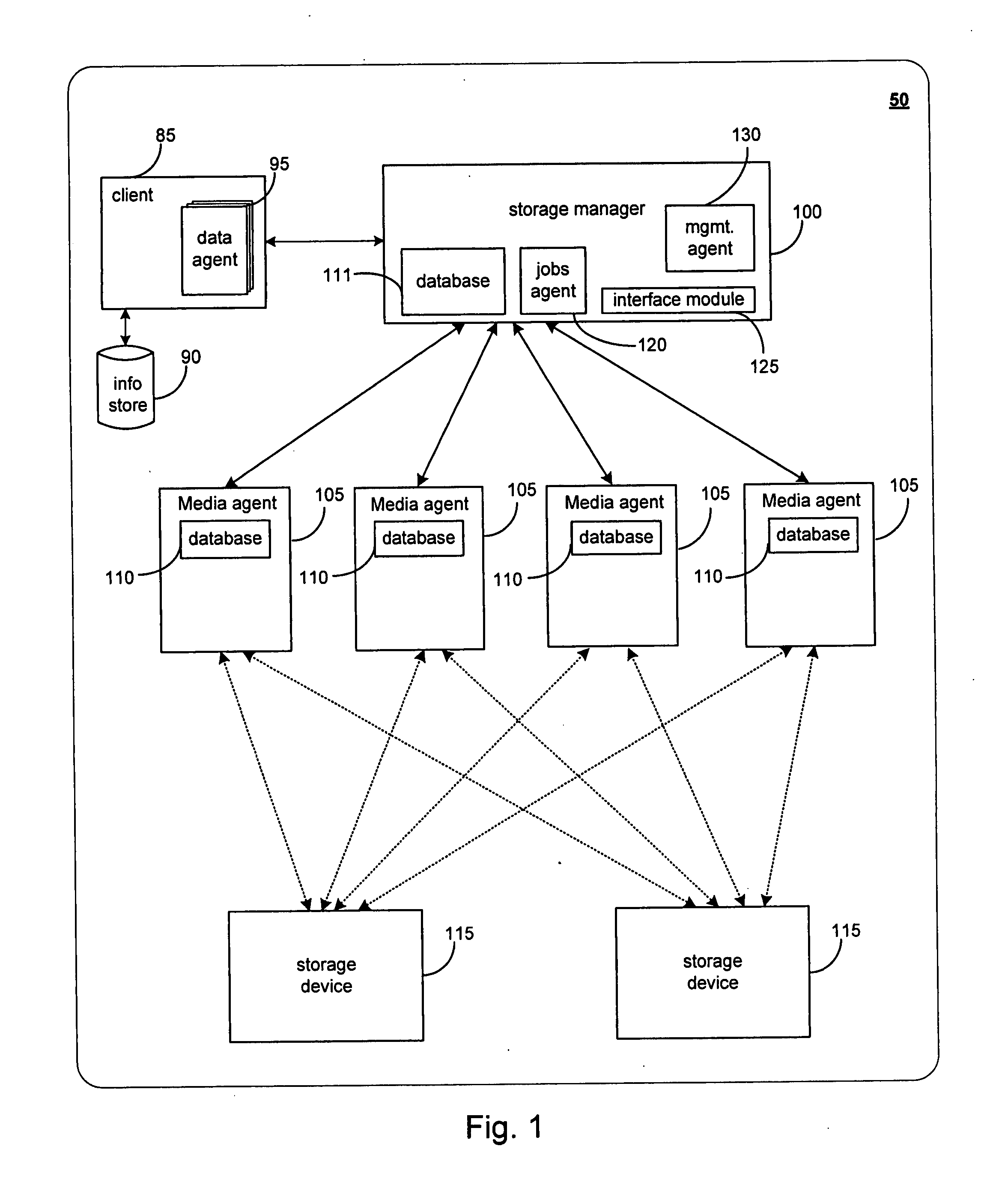
Systems and methods for load balancing based on user selected metrics
ActiveUS8291108B2Good for load balancingGood flexibilityDigital computer detailsProgram controlDevice MonitorSimple Network Management Protocol
Owner:CITRIX SYST INC
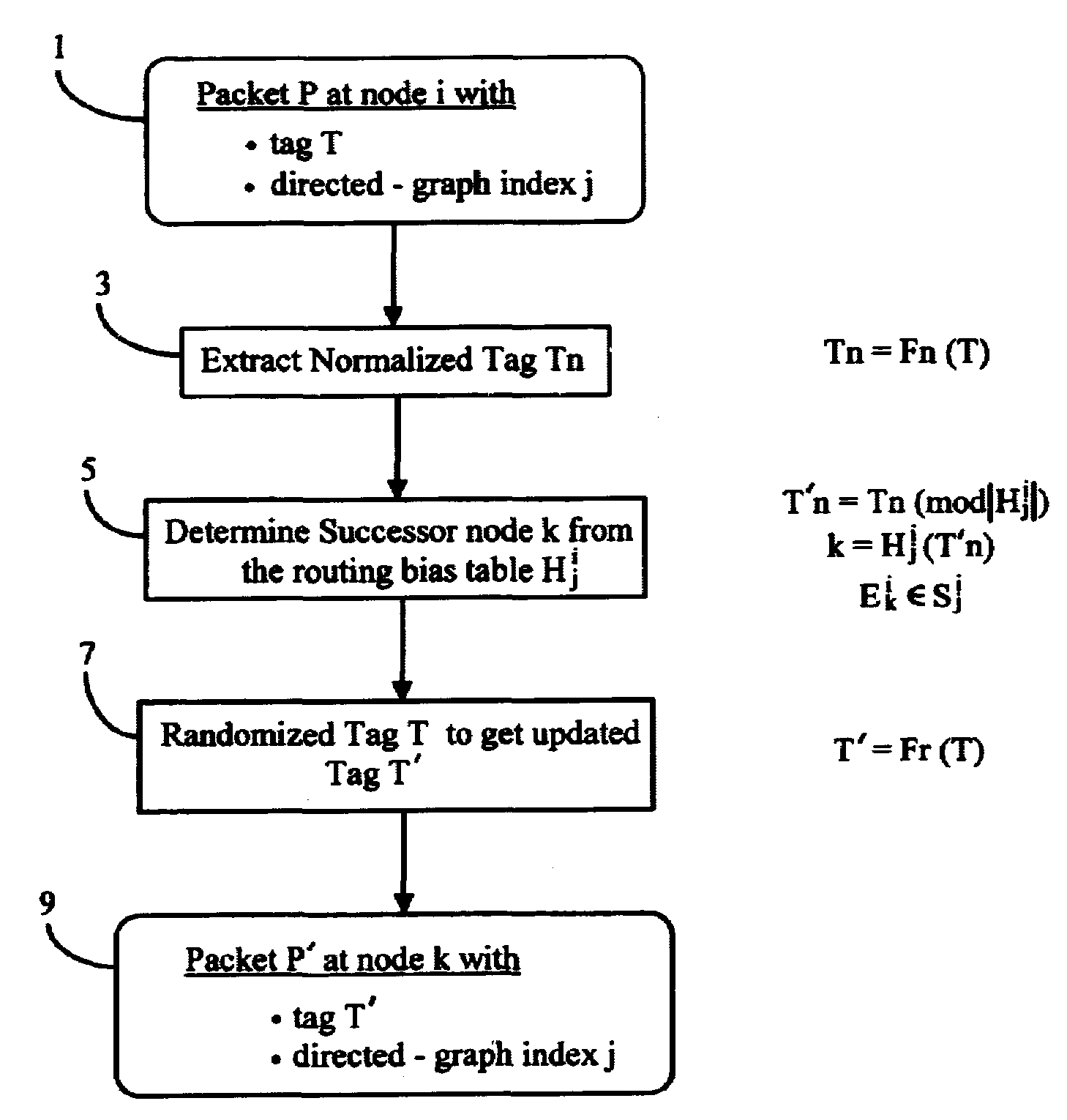
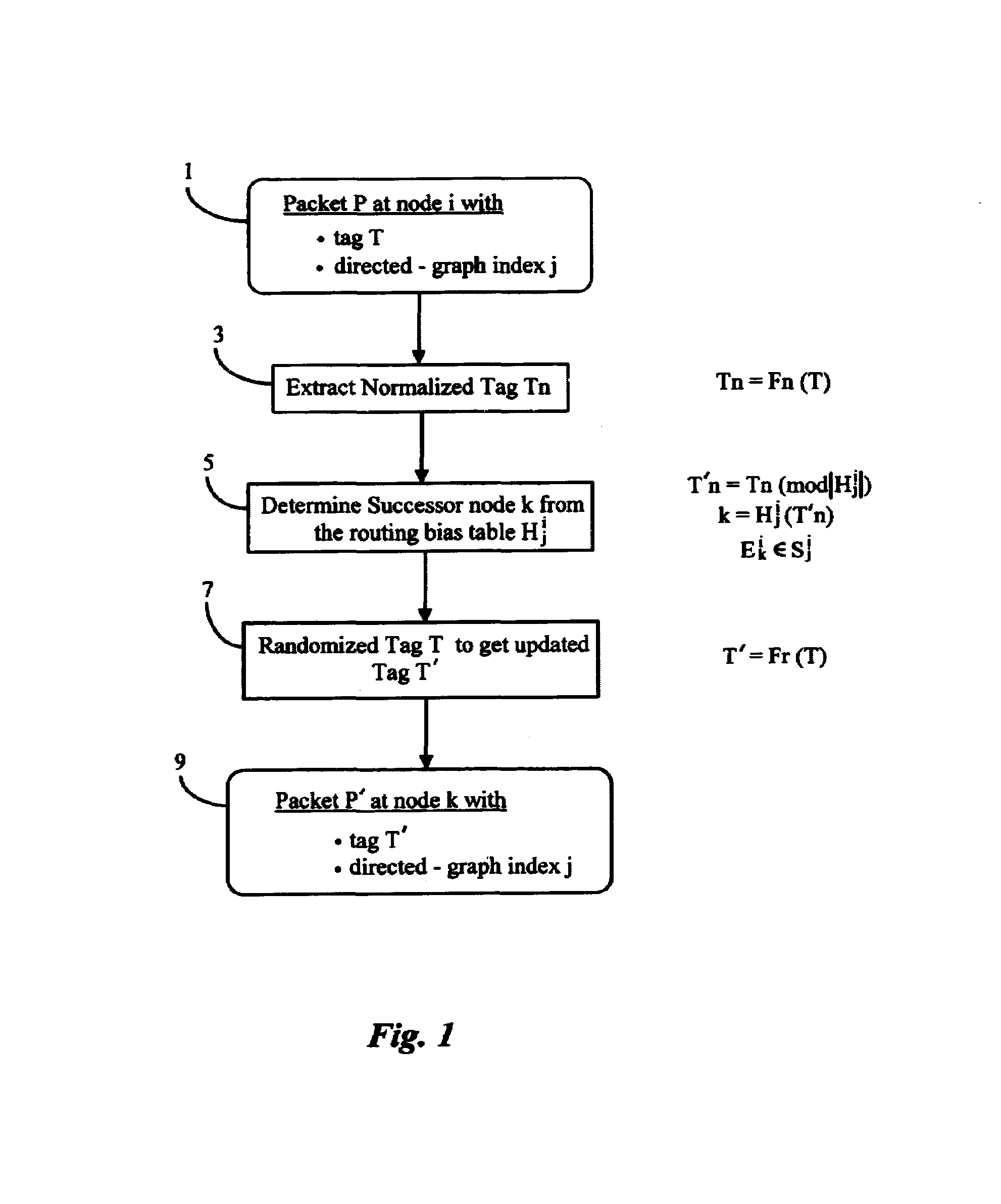
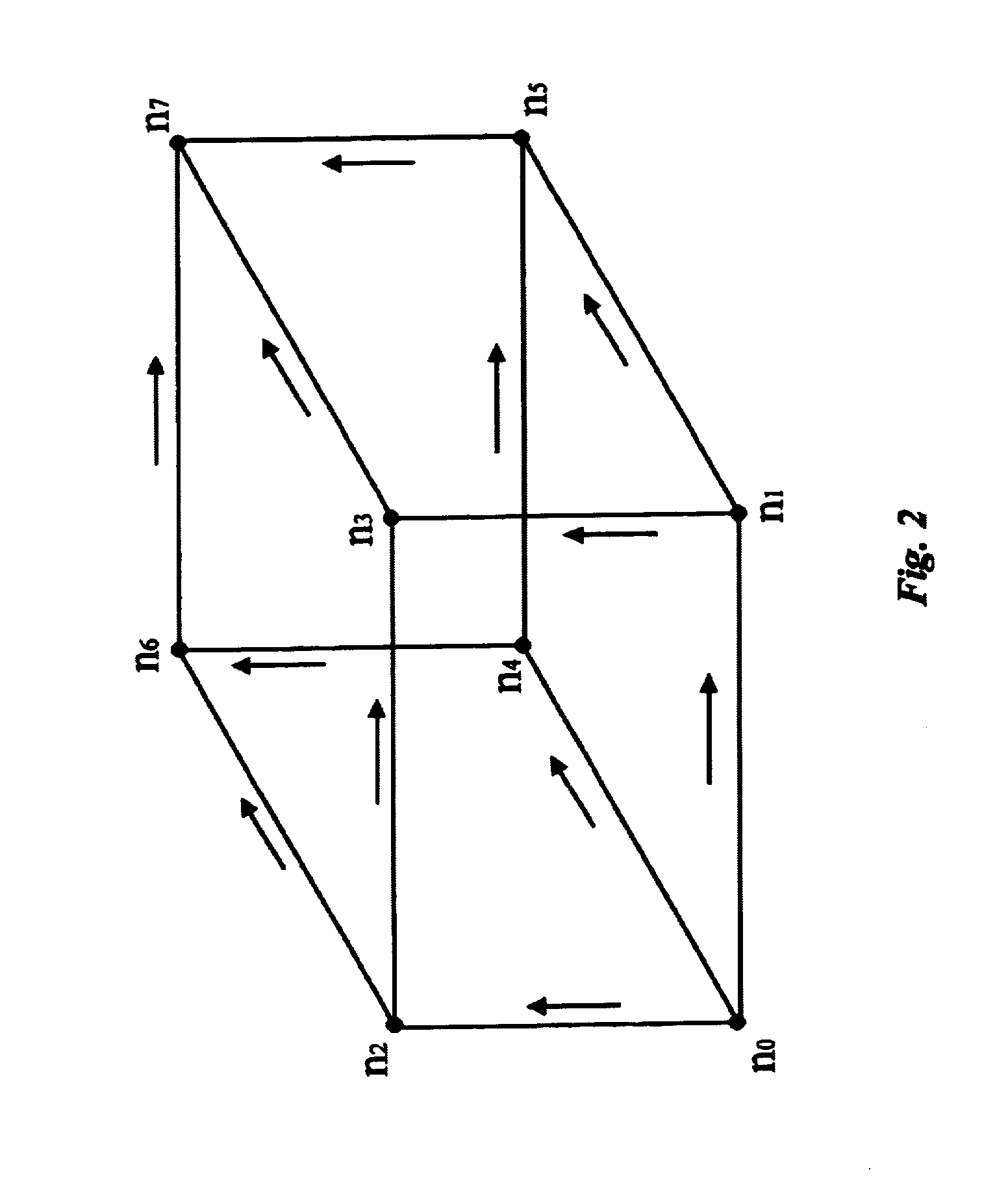
Method for load-balancing with FIFO guarantees in multipath networks
InactiveUS7002958B1Reduce stepsGood for load balancingData switching by path configurationComputer scienceDistributed computing
A method for routing packets in a multipath network of nodes balances the loading of system resources while guaranteeing a FIFO network (i.e., First In First Out). Acyclic directed graphs based on local network information are used at each node with routing bias tables that allow for local preferences. A randomizing function may be used throughout the network to allow uniform utilization of system resources. A normalizing function may be used throughout the network to reduce bit operations in routing packets.
Owner:PLURIS
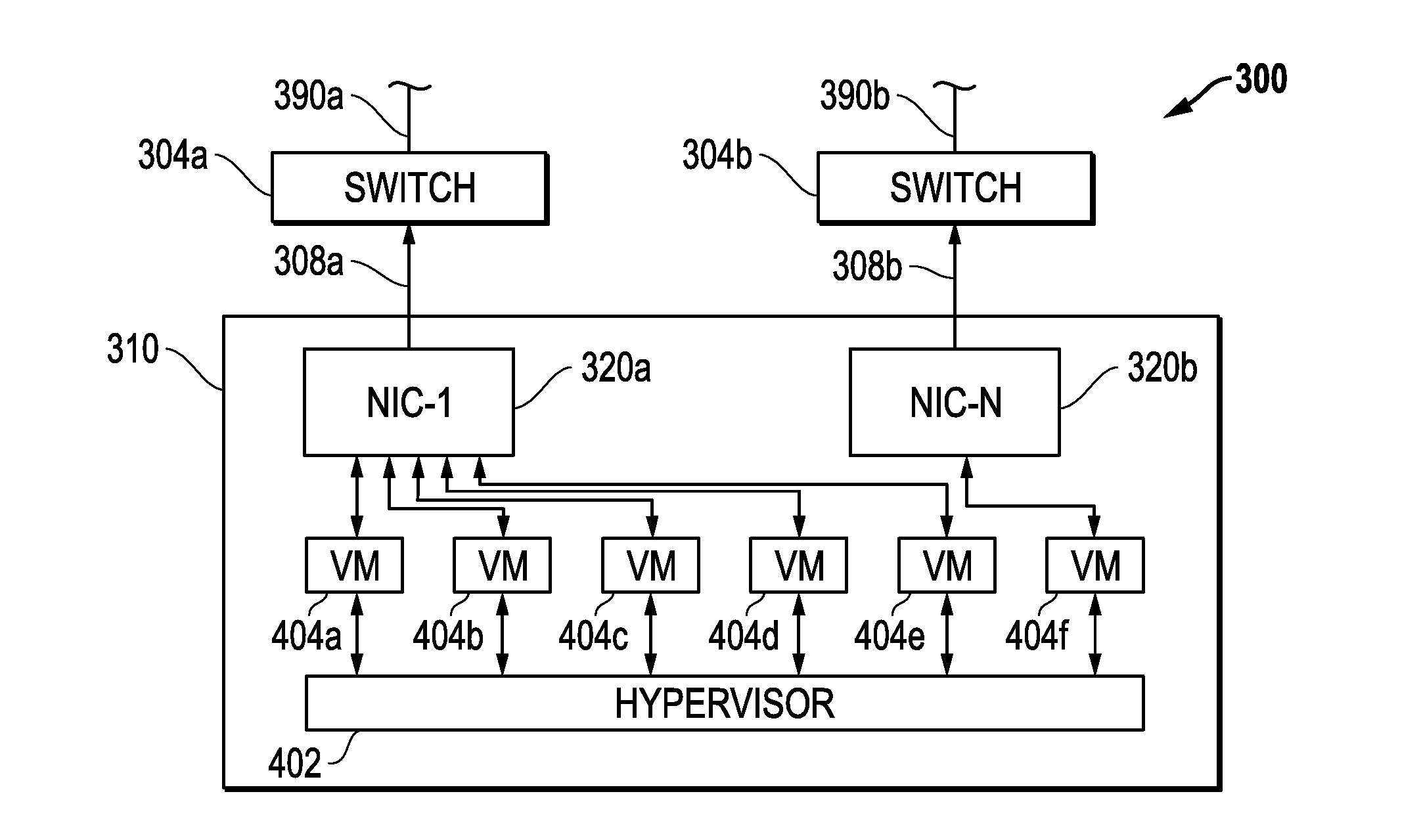
Systems And Methods For Native Network Interface Controller (NIC) Teaming Load Balancing
ActiveUS20150029848A1Enhance NIC teaming load balancingReduce decreaseError preventionFrequency-division multiplex detailsHandling systemNetwork switch
Systems and methods are provided that may be employed in a network environment to implement load balancing for multi-network interface controller (NIC) teaming applications using pause frame flow control communications received at an information handling system in situations where a given data path through a given NIC of the information handling system and a corresponding network switch is heavily loaded or otherwise congested relative to one or more other more lightly loaded data paths through other NICs of the information handling system and their corresponding network switches.
Owner:DELL PROD LP
Method of discovering multi-mode mobile terminals
ActiveUS7596385B2Convenient intercommunicationEasily informedNetwork traffic/resource managementAssess restrictionTelecommunicationsHeterogeneous network
Owner:DOLBY LAB LICENSING CORP
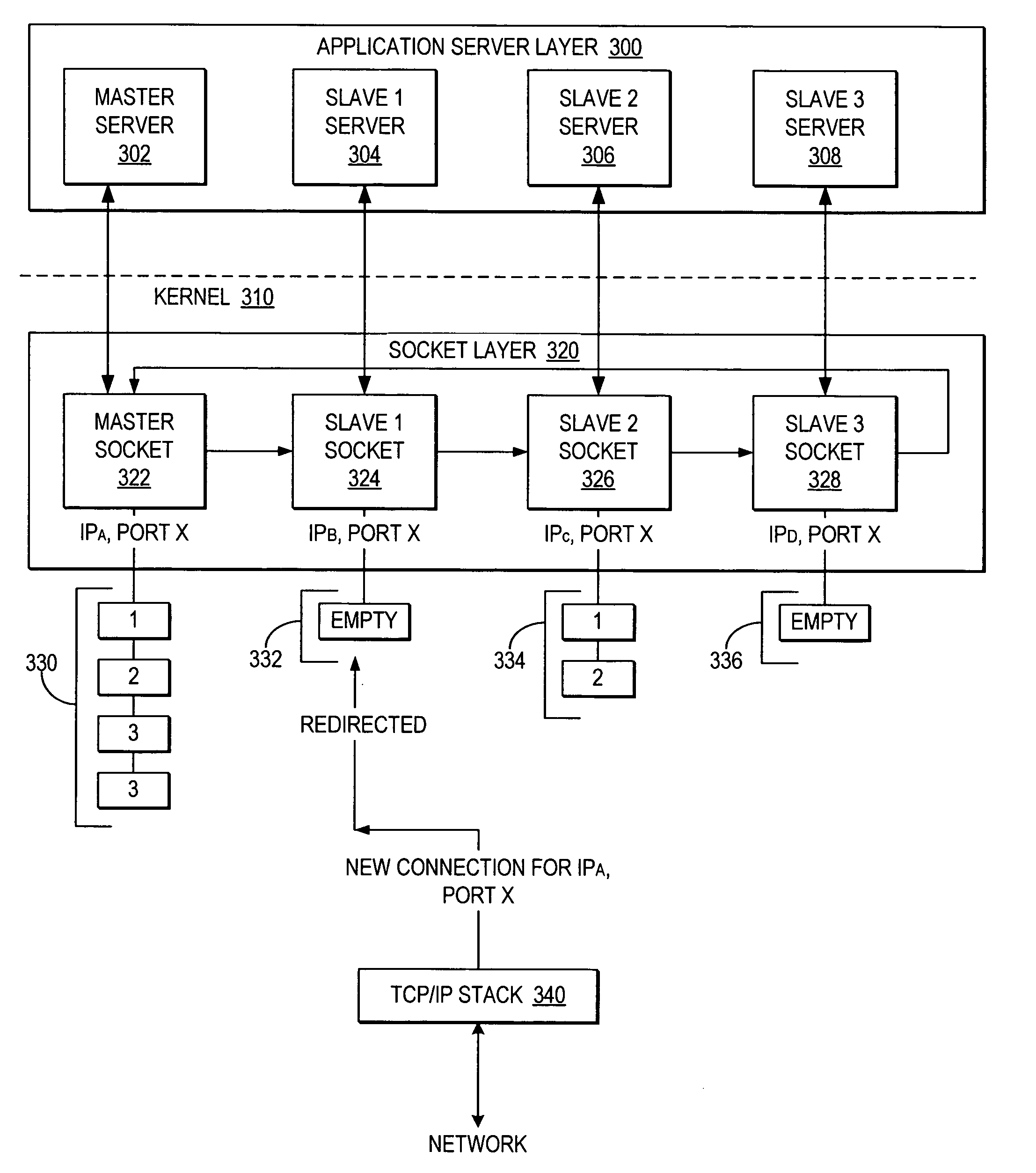
Redirecting client connection requests among sockets providing a same service
InactiveUS20050165932A1Improve load balanceGood for load balancingDigital computer detailsMultiprogramming arrangementsClient-sideServer system
A method, system, and program for redirecting client connection requests among sockets providing a same service are provided. An application requests multiple sockets from a kernel. In addition, the application generates a socket call option to bind the sockets to a particular port number and passes a list of the sockets to the kernel, where the list indicates that the sockets will all provide access to server systems providing the same service. In response, the kernel sets up the sockets, bound to the same port, and set to reference one another. Then, when a connection request is received for a first socket in the list with a queue that is full, the kernel redirects the connection request to a second socket in the list with available queue space. Thus, rather than drop the connection request from the first socket when it lacks available queue space, the connection request is redirected to another socket providing access to the same service.
Owner:IBM CORP
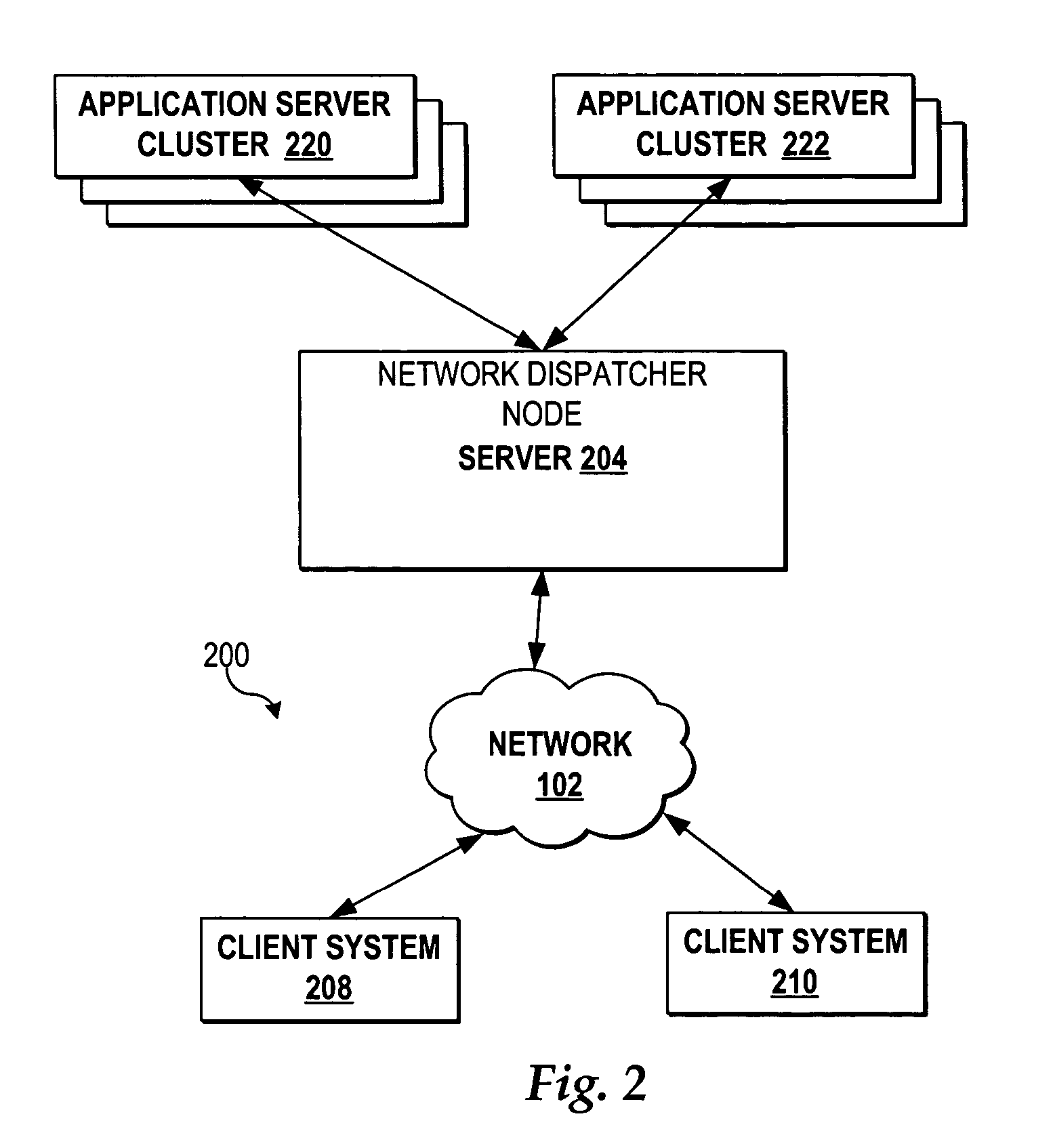
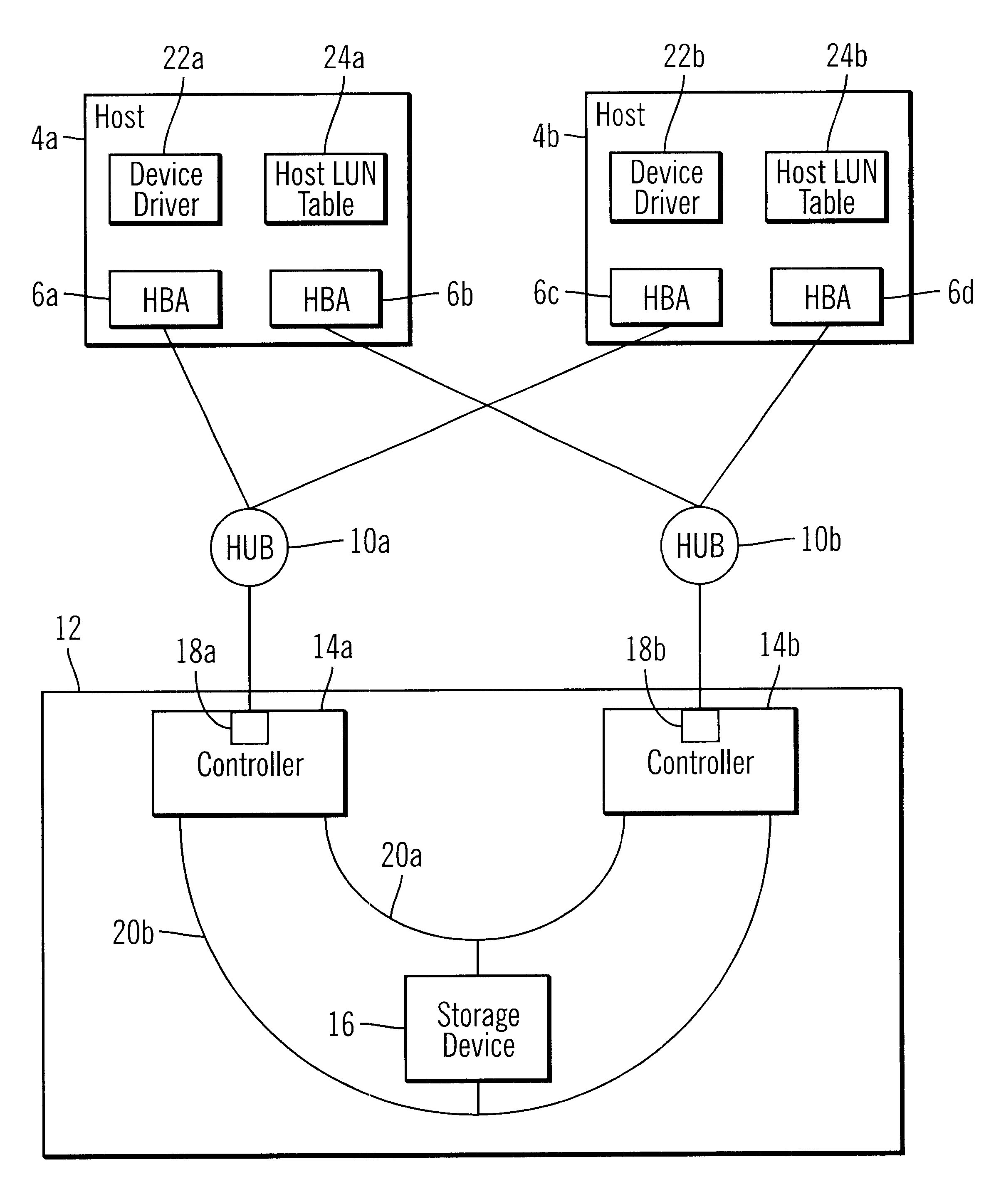
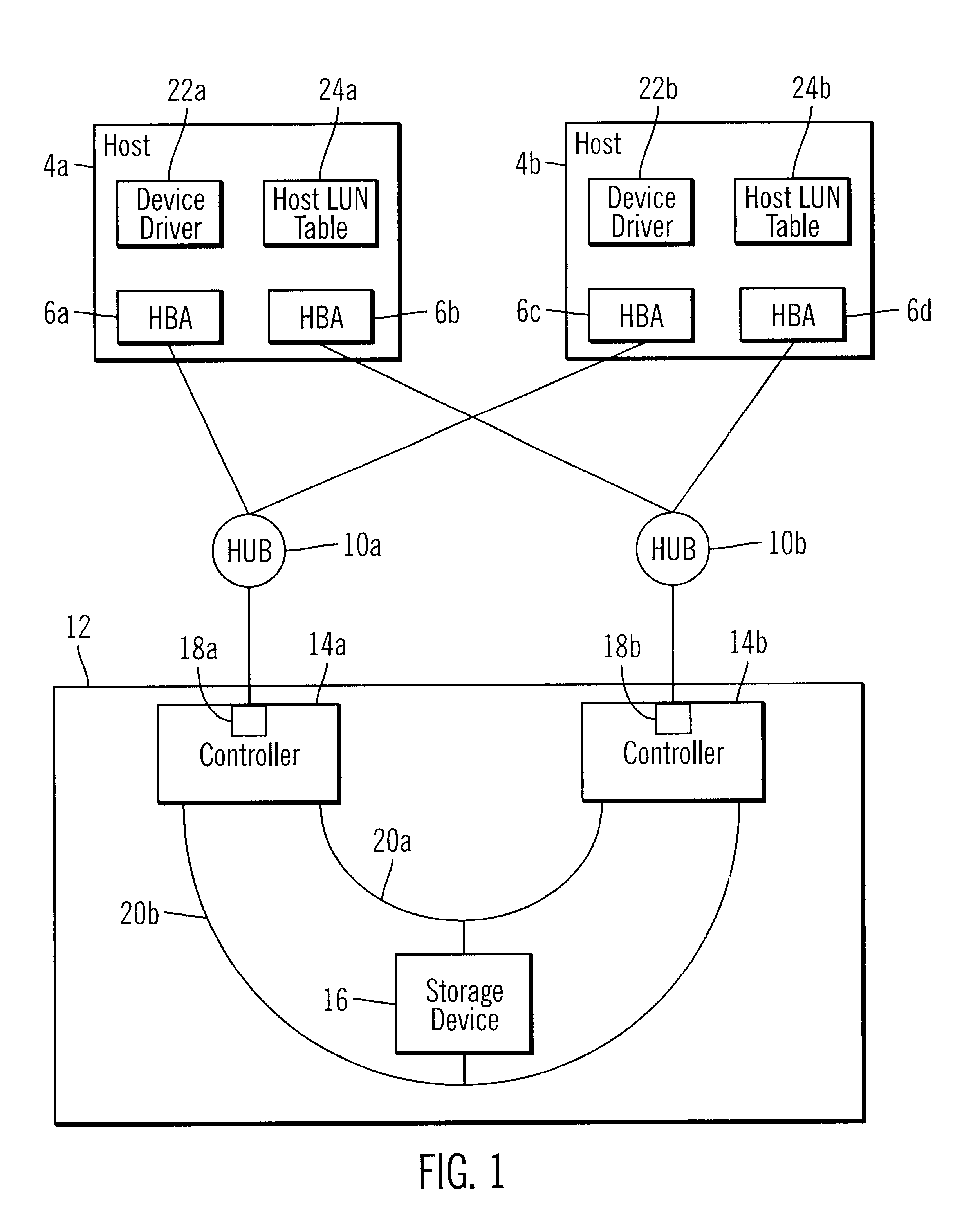
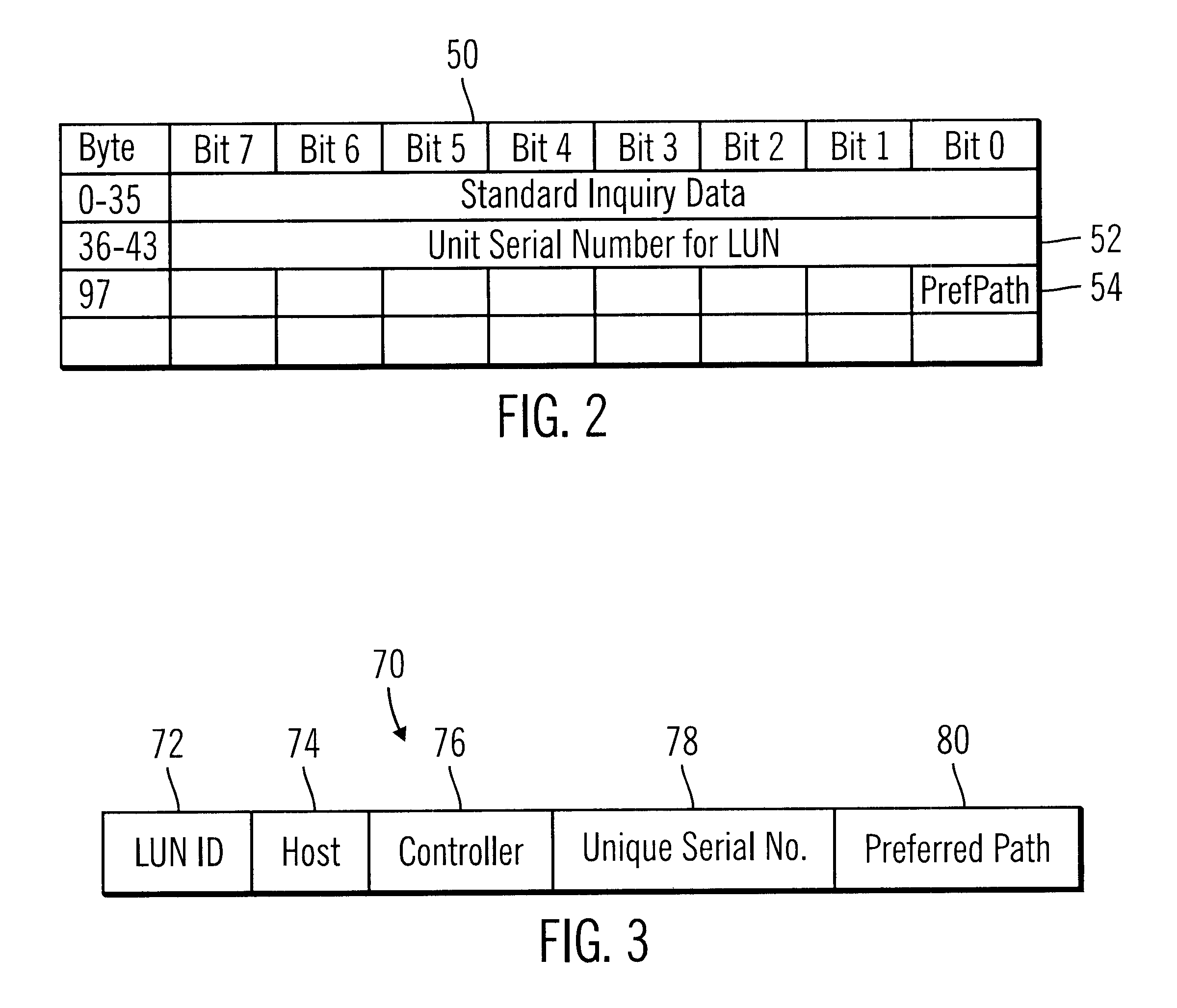
Method, system, program, and data structure for selecting a preferred path to a storage device
InactiveUS6601128B1Minimizes I/O processingEqually distributedInput/output to record carriersError detection/correctionPathPingControl store
Disclosed is a method, system, program, and data structure for selecting a path to one of at least two controllers. Each controller is capable of providing access to storage areas, such as Logical Unit Numbers (LUNs). Path information is received from the controllers indicating a preferred controller to use to access each storage area. An input / output (I / O) command directed to a target storage area is processed and the I / O command is directed to the controller indicated in the path information as the preferred controller for the target storage area. The controller receiving the I / O command executes the I / O command against the target storage area. The path information to the storage controllers providing access to the storage areas is encoded with information designating one controller as the preferred controller and another as a non-preferred controller. The encoded path information is returned to a requesting computer. The requesting computer initially sends an input / output (I / O) command to the preferred controller and sends the I / O command to the non-preferred controller if the preferred controller cannot execute the I / O command.
Owner:IBM CORP
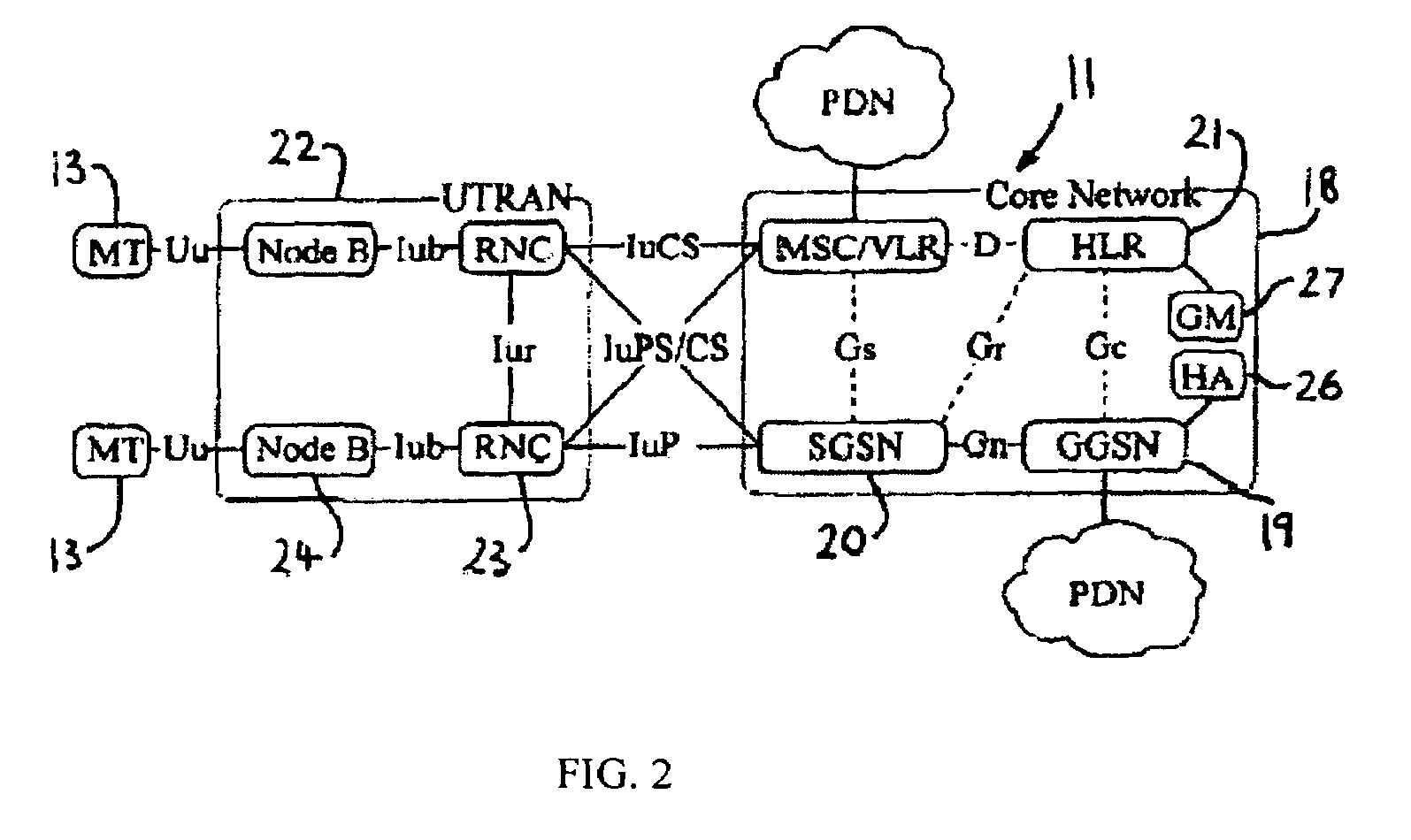
Hierarchy Encoding Apparatus and Hierarchy Encoding Method
InactiveUS20080069088A1Efficient reduction of signaling loadFrequent relocation can be preventedAssess restrictionCode division multiplexRadio access networkResource management
The present invention relates to a method and base station in a mobile communication system for relocating from a controlling base station to another base station within a mobile communication network resource management control functionality of shared channels in a plurality of cells, each cell being controlled by a base station, wherein each of the shared channels is shared by a plurality of mobile terminals within a cell. Further, the present invention relates to a mobile communication system. To enable controlling network element relocation for distributed radio access network the present invention suggests estimating at the controlling base station the signaling load between the controlling base station and each reporting base station or the processing load at each reporting base station, determining whether to relocate resource management control functionality for at least a part of said plurality of cells and performing the relocation if it has been decided to relocate same.
Owner:PANASONIC CORP
Ray shooting method utilizing geometrical stencils
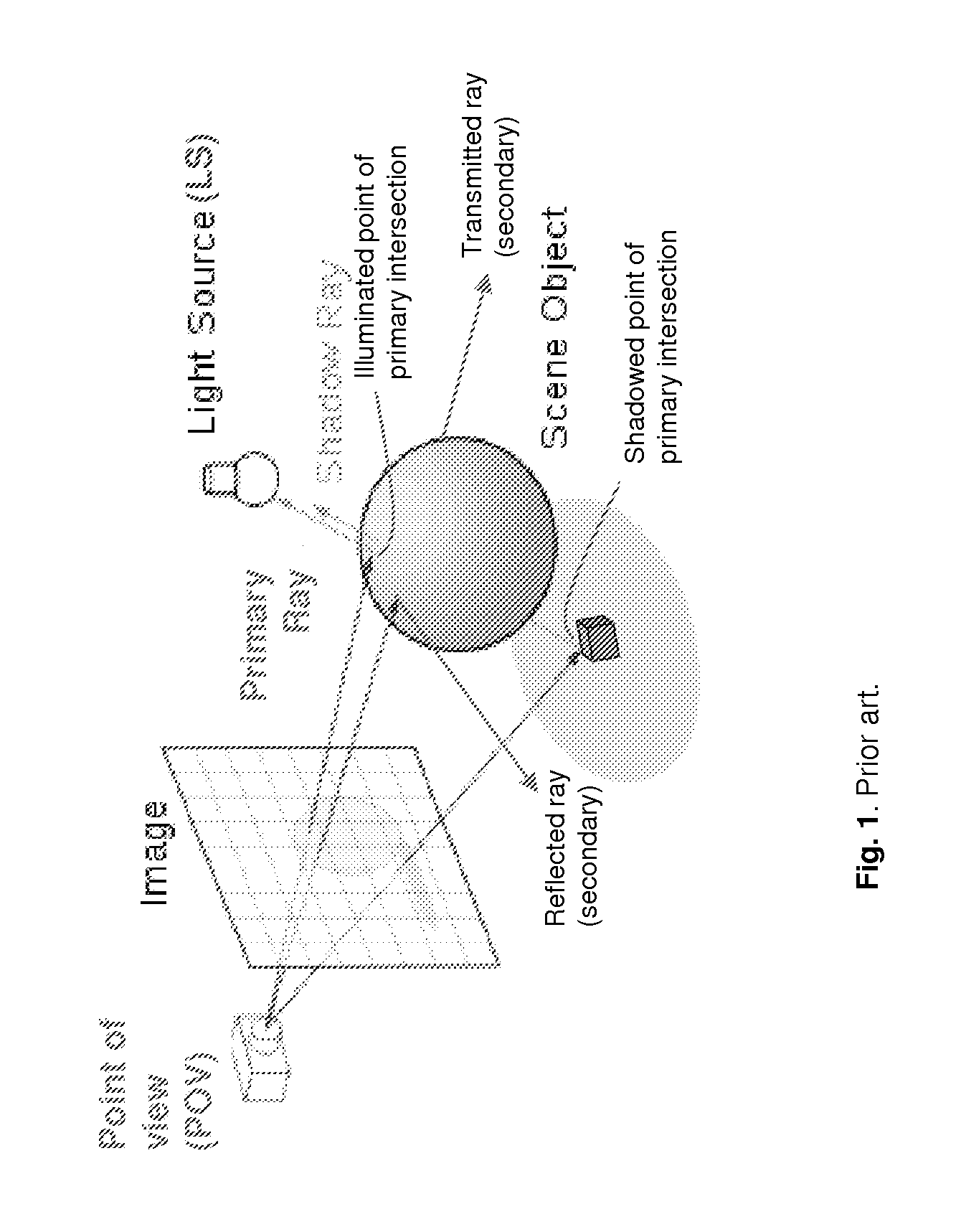
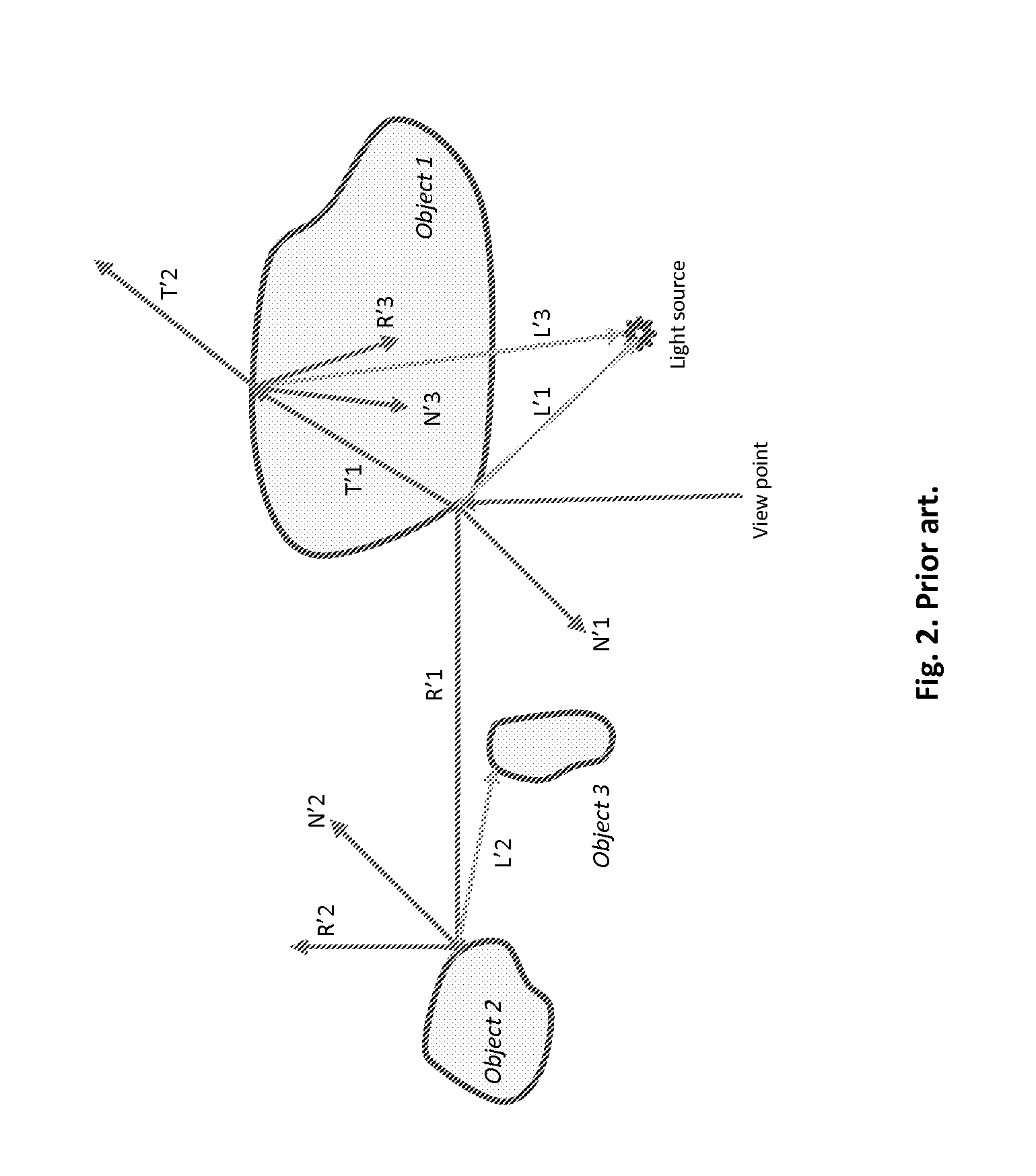
ActiveUS20140375641A1Effective trackingCut down high traversalDetails involving 3D image dataProgram controlVisibilityViewpoints
Aspects comprise a ray shooting method based on the data structure of a uniform grid of cells, and on local stencils in cells. The high traversal and construction costs of accelerating structures are cut down. The object's visibility from the viewpoint and from light sources, as well as the primary workload and its distribution among cells, are gained in the preprocessing stage and cached in stencils for runtime use. In runtime, the use of stencils allows a complete locality at each cell, for load balanced parallel processing.
Owner:SNAP INC
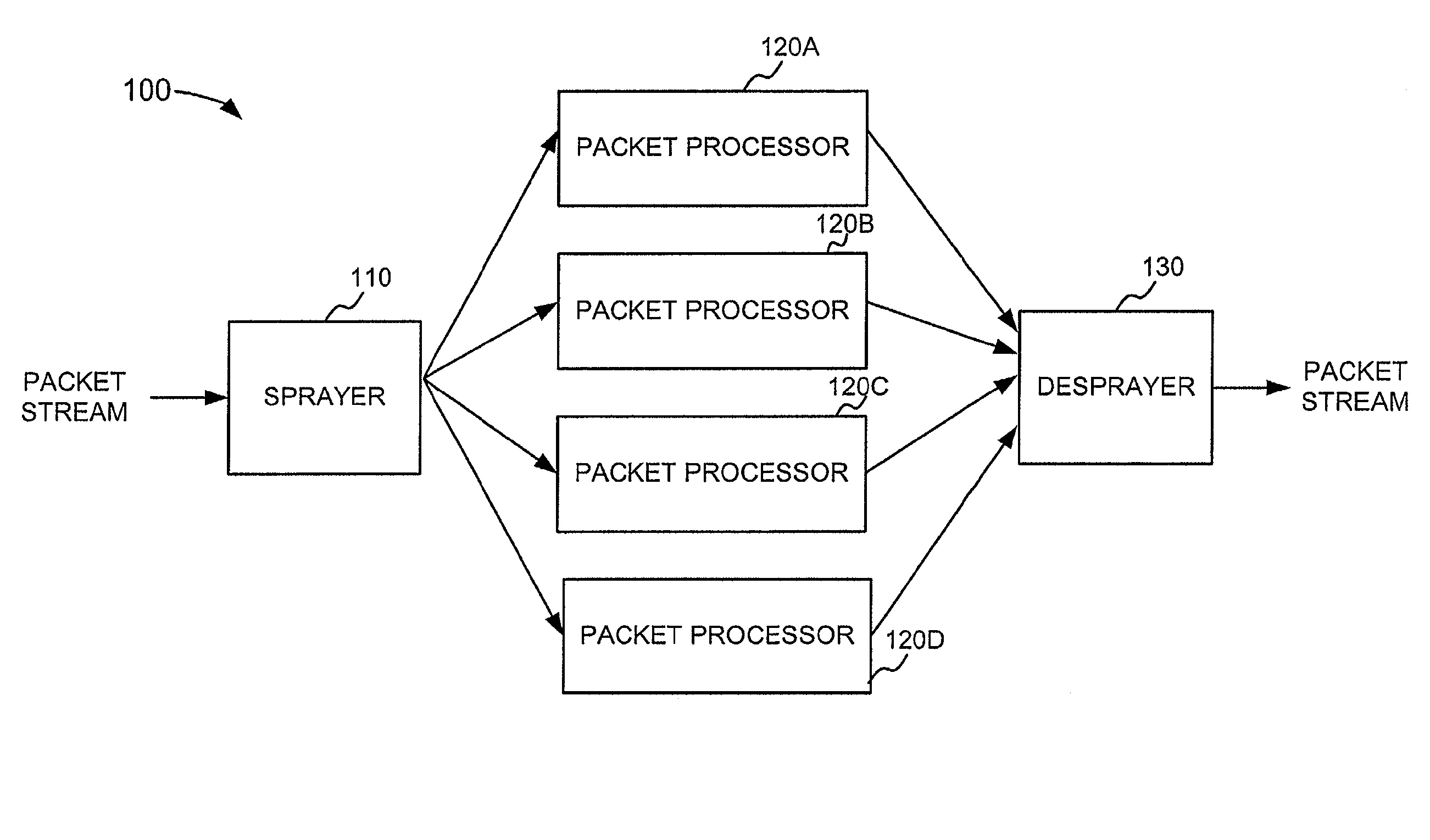
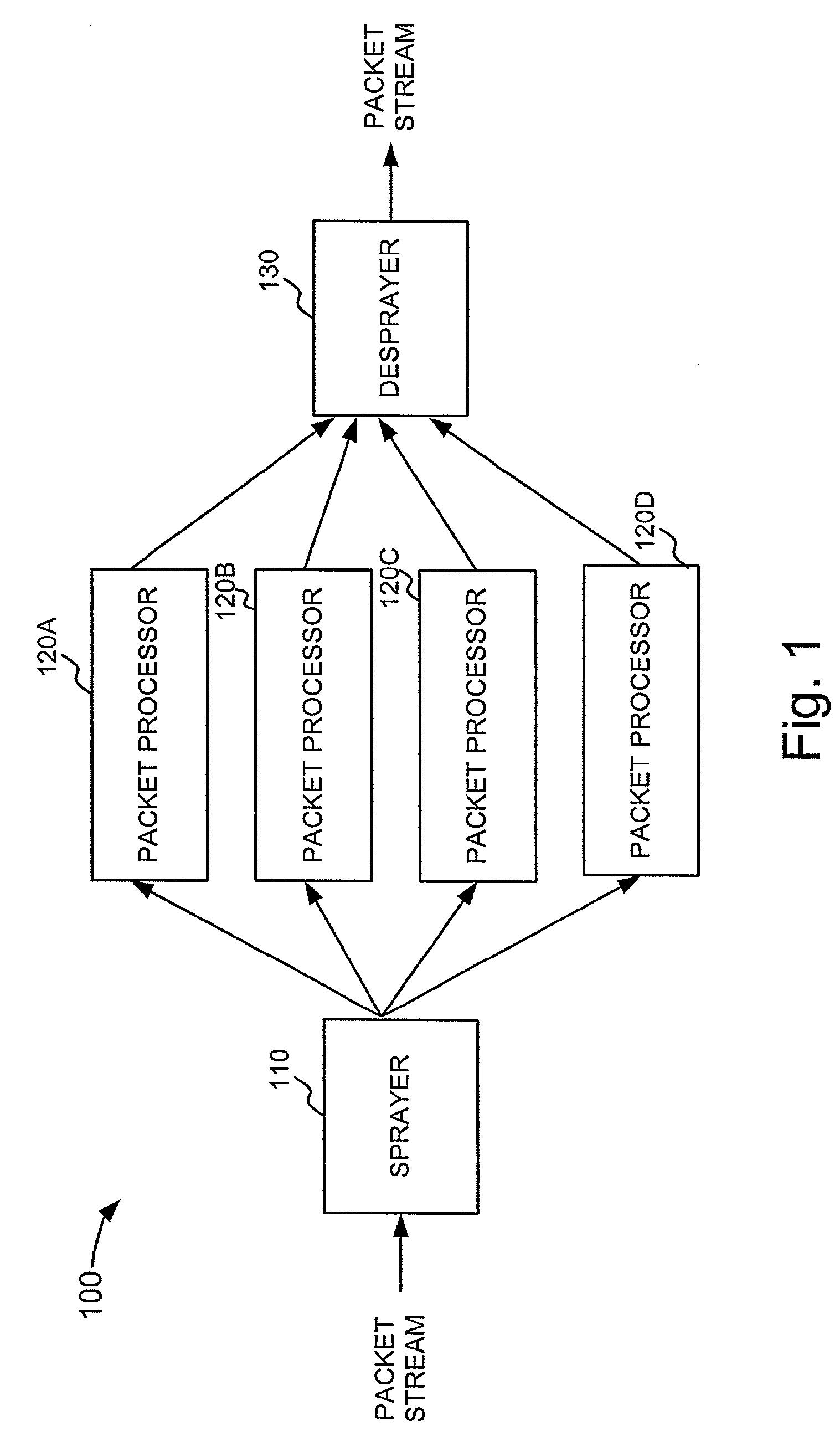
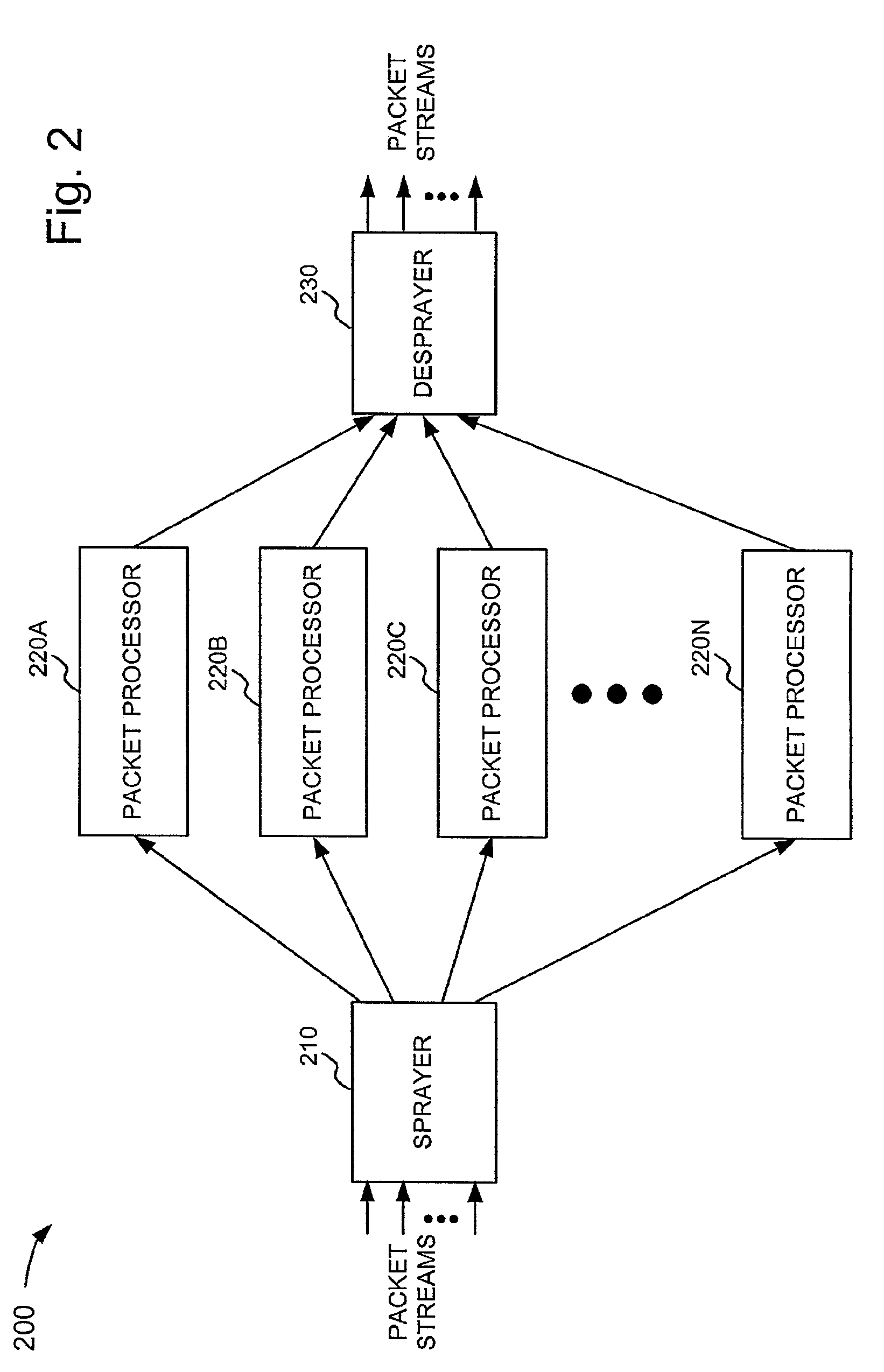
Packet spraying for load balancing across multiple packet processors
InactiveUS7782782B1Good for load balancingError preventionTransmission systemsPacket processingReal-time computing
A network device includes multiple packet processing engines implemented in parallel with one another. A spraying component distributes incoming packets to the packet processing engines using a spraying technique that load balances the packet processing engines. In particular, the spraying component distributes the incoming packets based on queue lengths associated with the packet processing engines and based on a random component. In one implementation, the random component is a random selection from all the candidate processing engines. In another implementation, the random component is a weighted random selection in which the weights are inversely proportional to the queue lengths.
Owner:JUMIPER NETWORKS INC
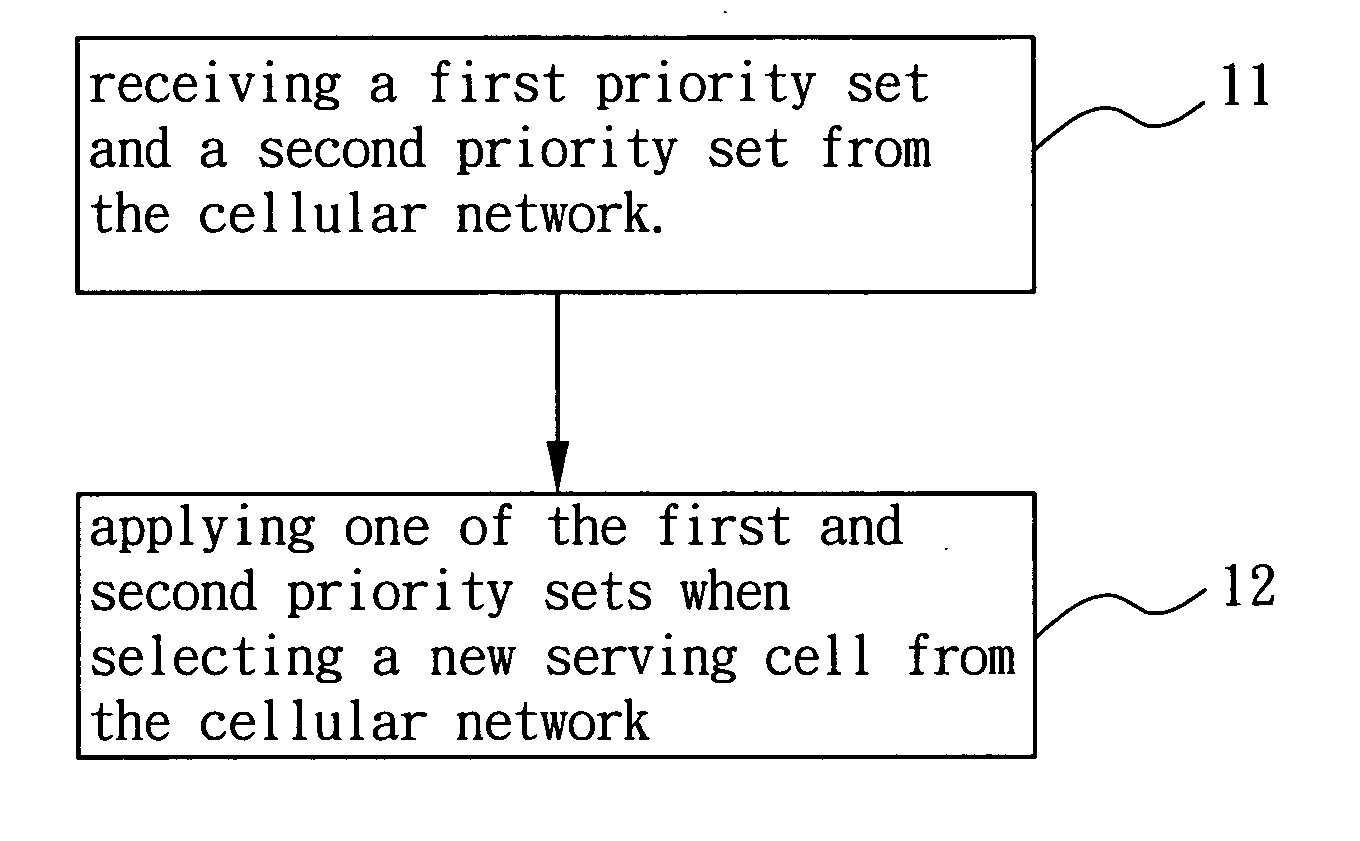
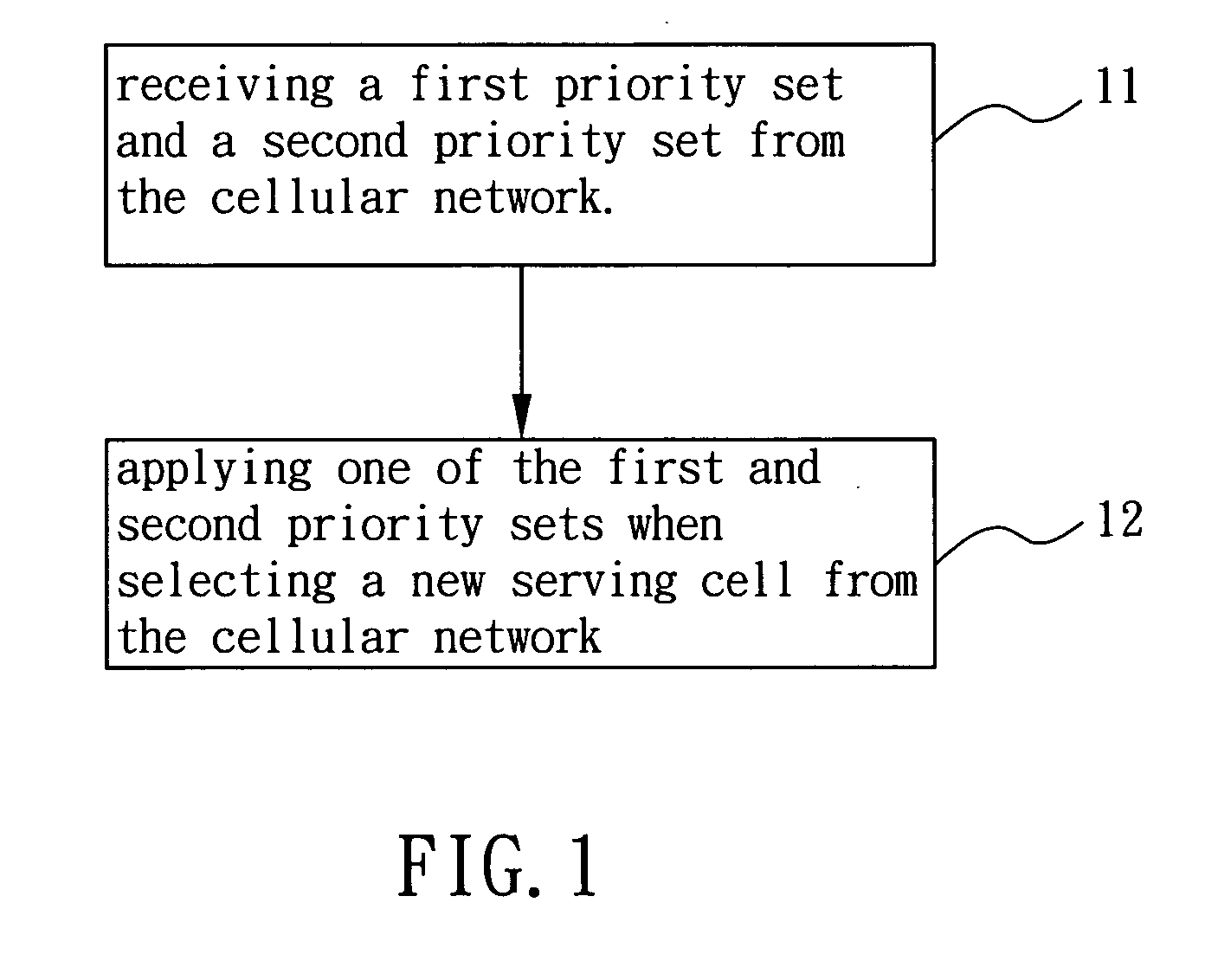
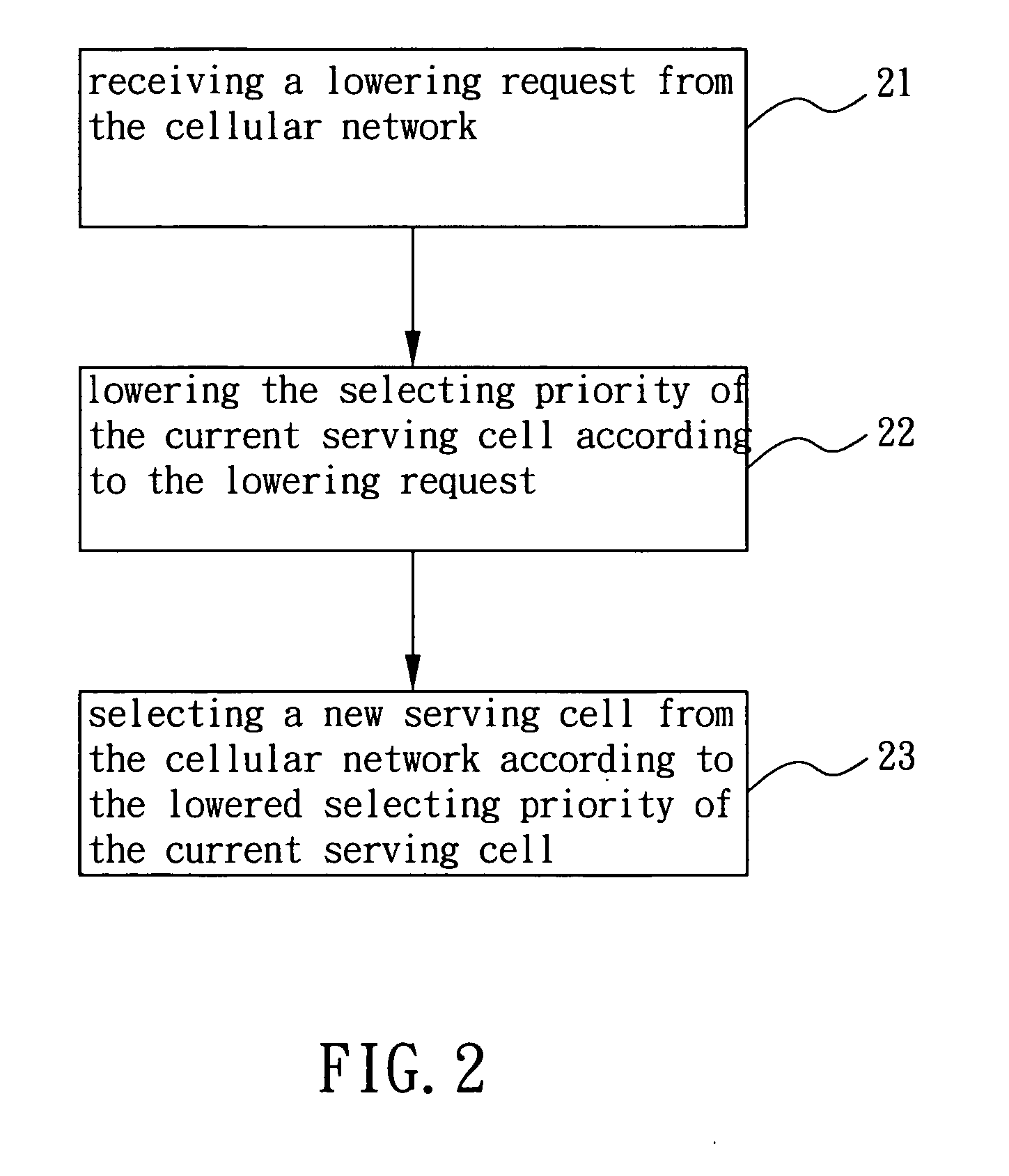
Method for improving cell load balance in cellular network and associated user equipment
InactiveUS20100291941A1Improve load balanceGood for load balancingWireless communicationRadio accessCellular network
A method for improving cell load balance in a cellular network and an associated user equipment (UE) are provided to improve cell load balance of the cellular network in a more flexible and effective manner. The method is used in the UE, and comprises receiving a first priority set and a second priority set from the cellular network and applying one of the first and second priority sets when selecting a new serving cell from the cellular network. Each of the first and second priority sets assigns a selecting priority to at least one carrier frequency or radio access frequency of the cellular network
Owner:HTC CORP
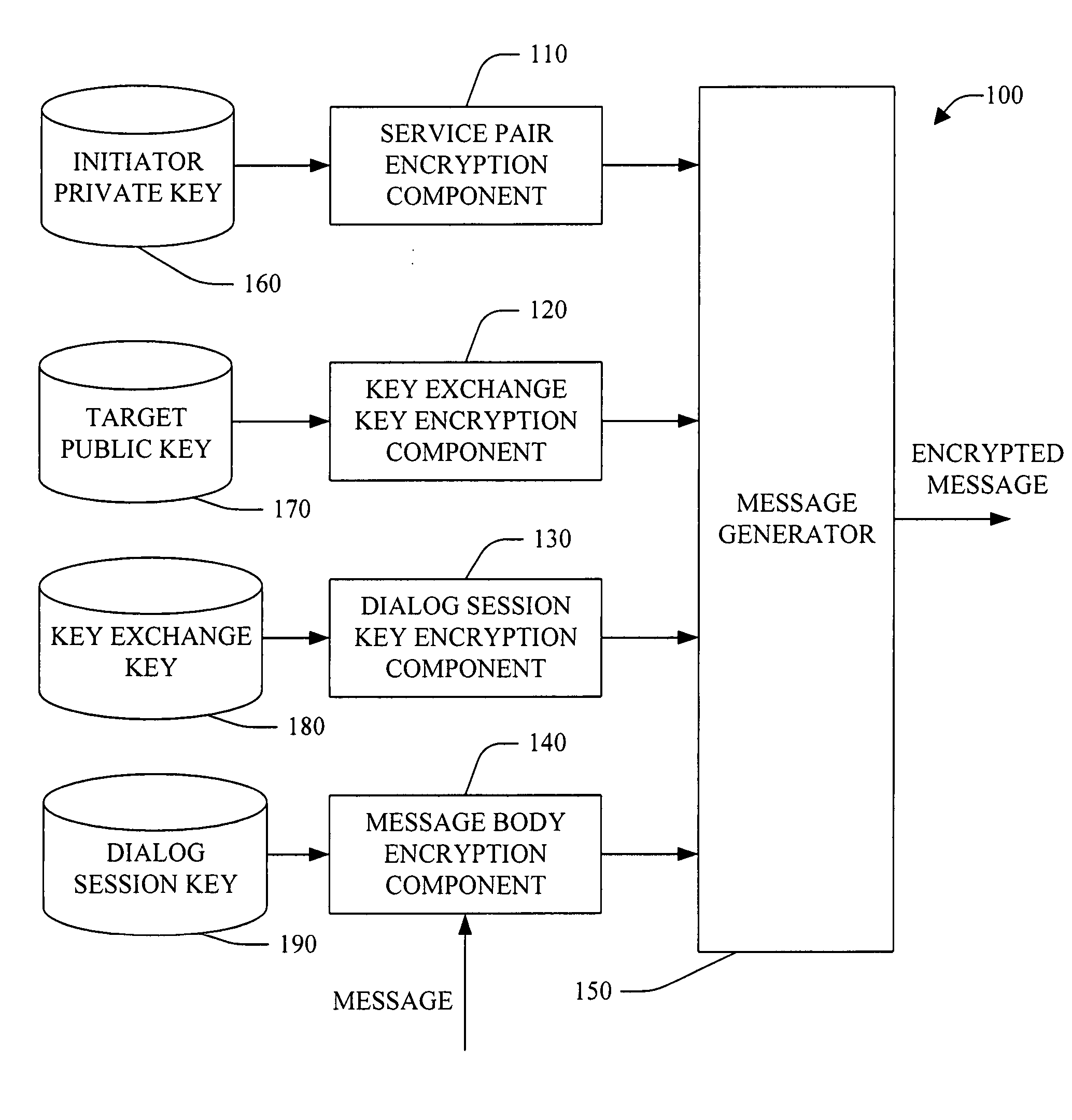
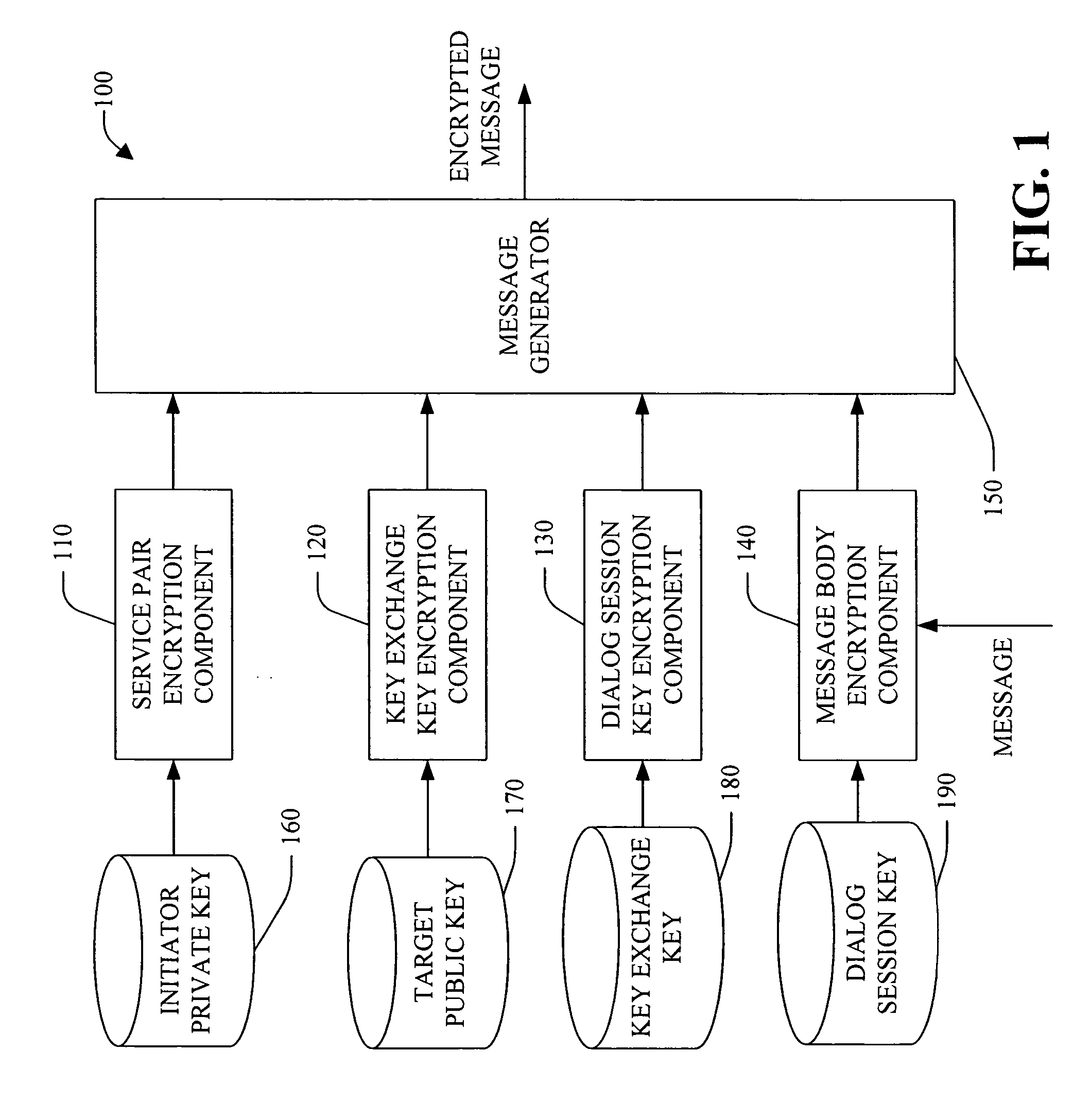
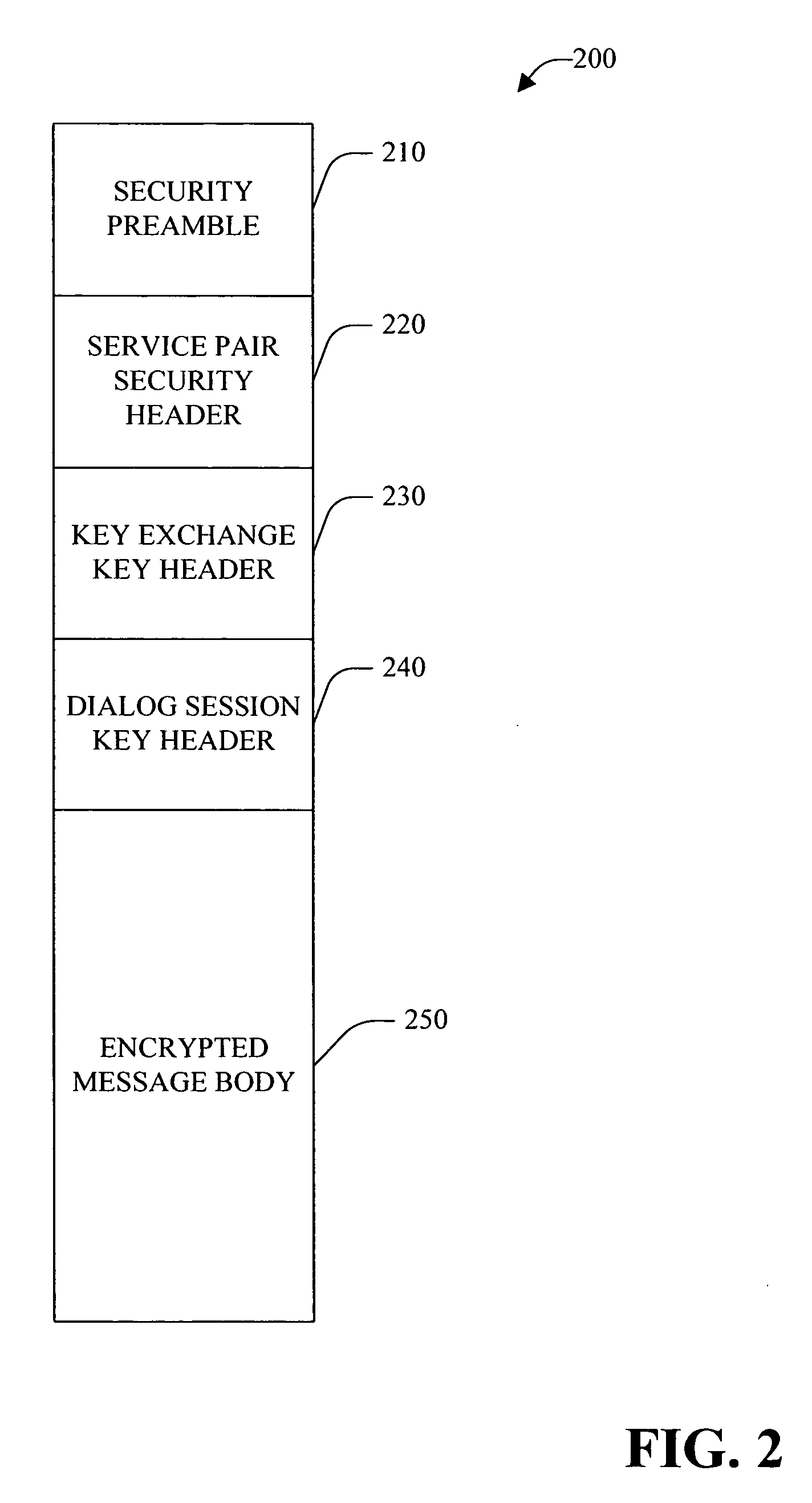
Session key exchange key
InactiveUS20050232426A1Reduce processing timeIncrease flexibilityKey distribution for secure communicationMultiple keys/algorithms usageKey exchangeSecure communication
A system and method for employing a key exchange key to facilitate secure communication is provided. The key exchange key can be employed, for example, to encrypt and / or decrypt dialog session key(s) that are used to encrypt and / or decrypt message(s) that form a dialog between an initiator system and target system. In one example, a key exchange key is unique to a service pair, while a dialog session key is unique to a particular dialog between the service pair. The system can facilitate end-to-end encryption of message data in a dialog—the message data is encrypted at one dialog endpoint and not decrypted until it reaches the other dialog endpoint. The system can be employed to facilitate secure dialog with minimal performance overhead when compared with conventional system(s). Optionally, the system can facilitate load balancing (e.g., among deployed instances of a service). In this example, secured dialogs to a service can be location transparent so that a dialog targeted to a service can be able to talk to any instance of the same service transparently without any additional security setup. The system employs both public key / private key asymmetric encryption technique(s) and symmetric encryption technique(s) to authenticate and secure information exchanged between an initiator system and a target system.
Owner:MICROSOFT TECH LICENSING LLC
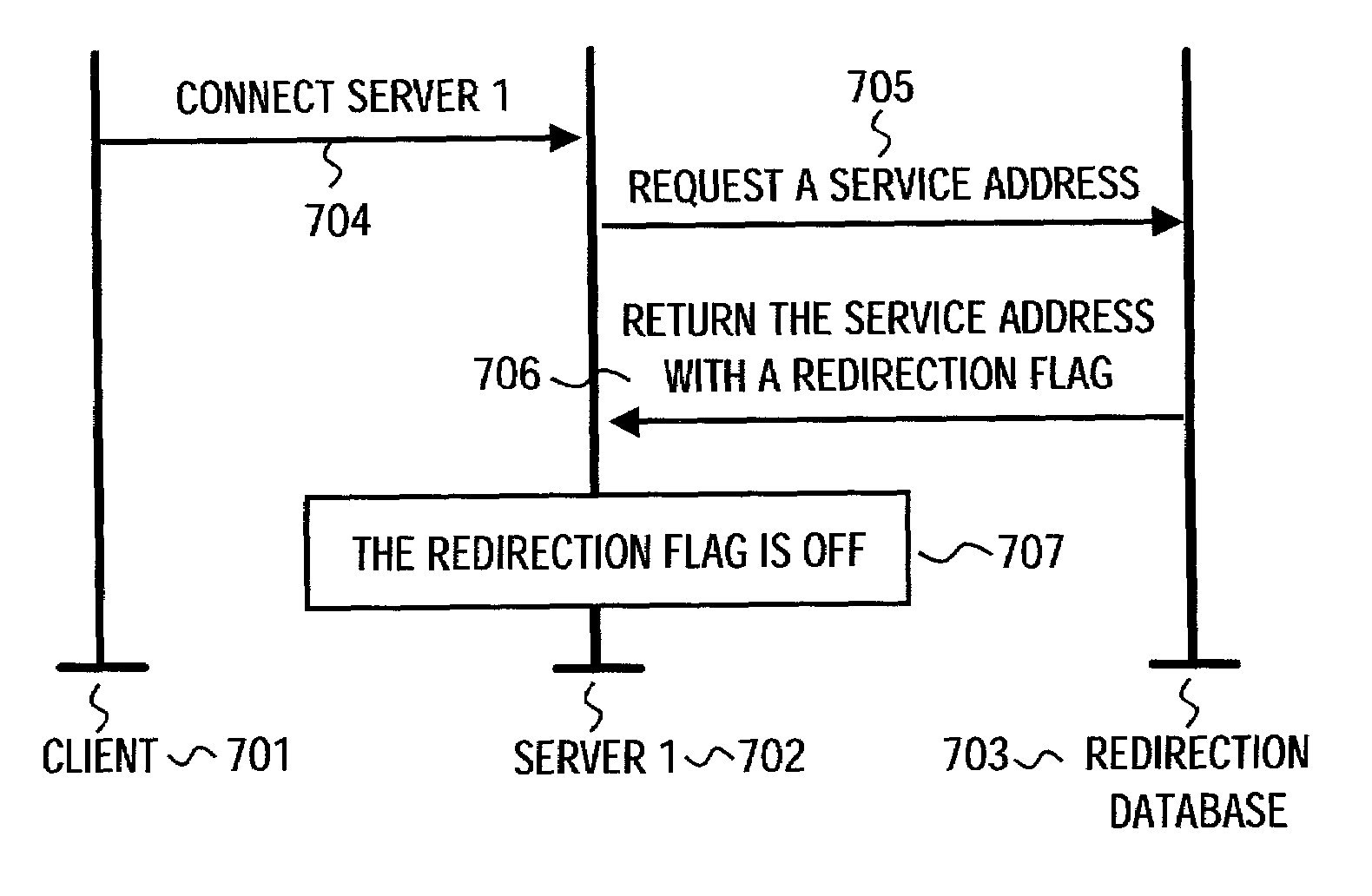
Method for assisting load balancing in a server cluster by rerouting IP traffic, and a server cluster and a client, operating according to same
ActiveUS7003575B2Good for load balancingImprove balanceMultiple digital computer combinationsProgram controlTraffic capacityTelecommunications link
An invention enables network traffic rerouting, while avoiding the necessity of traffic to pass via a cluster's master node. By doing so, neither the master node, nor its communication link become a critical failure or load point, thus disrupting the cluster performance. At first a client sends a packet a certain server of the cluster. If the client is redirected, said server adds a redirection header, defined by a new redirection protocol, to the packet, and returns the packet to the client. A service address and a redirection flag are placed in the header. The client receives the packet with the redirection header and connects to the target server whose address is in the header. From then on, the target server handles the client's packet and the whole transmission related to it.
Owner:MAVENIR SYSTEMS
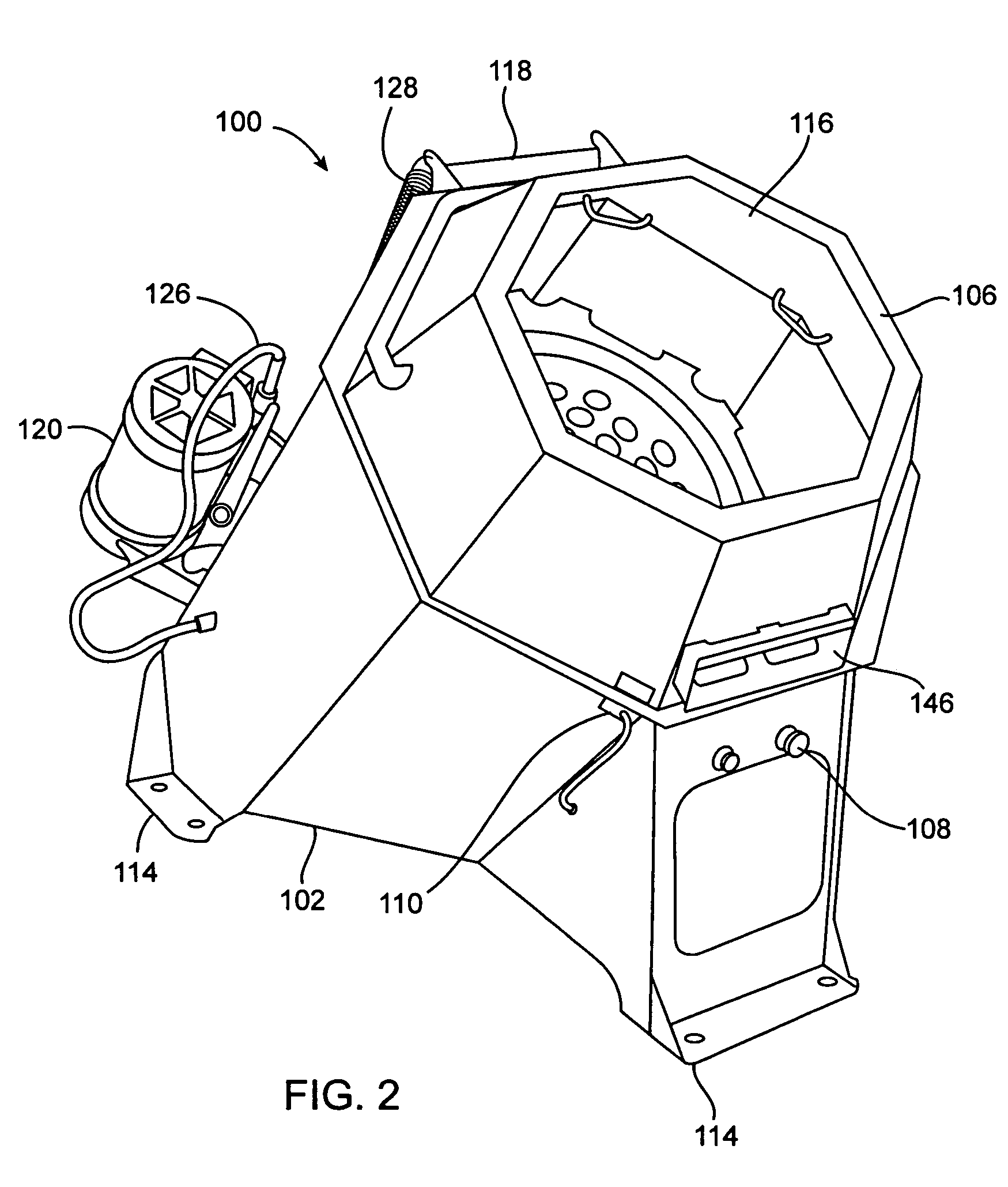
Canted manually loaded produce dryer
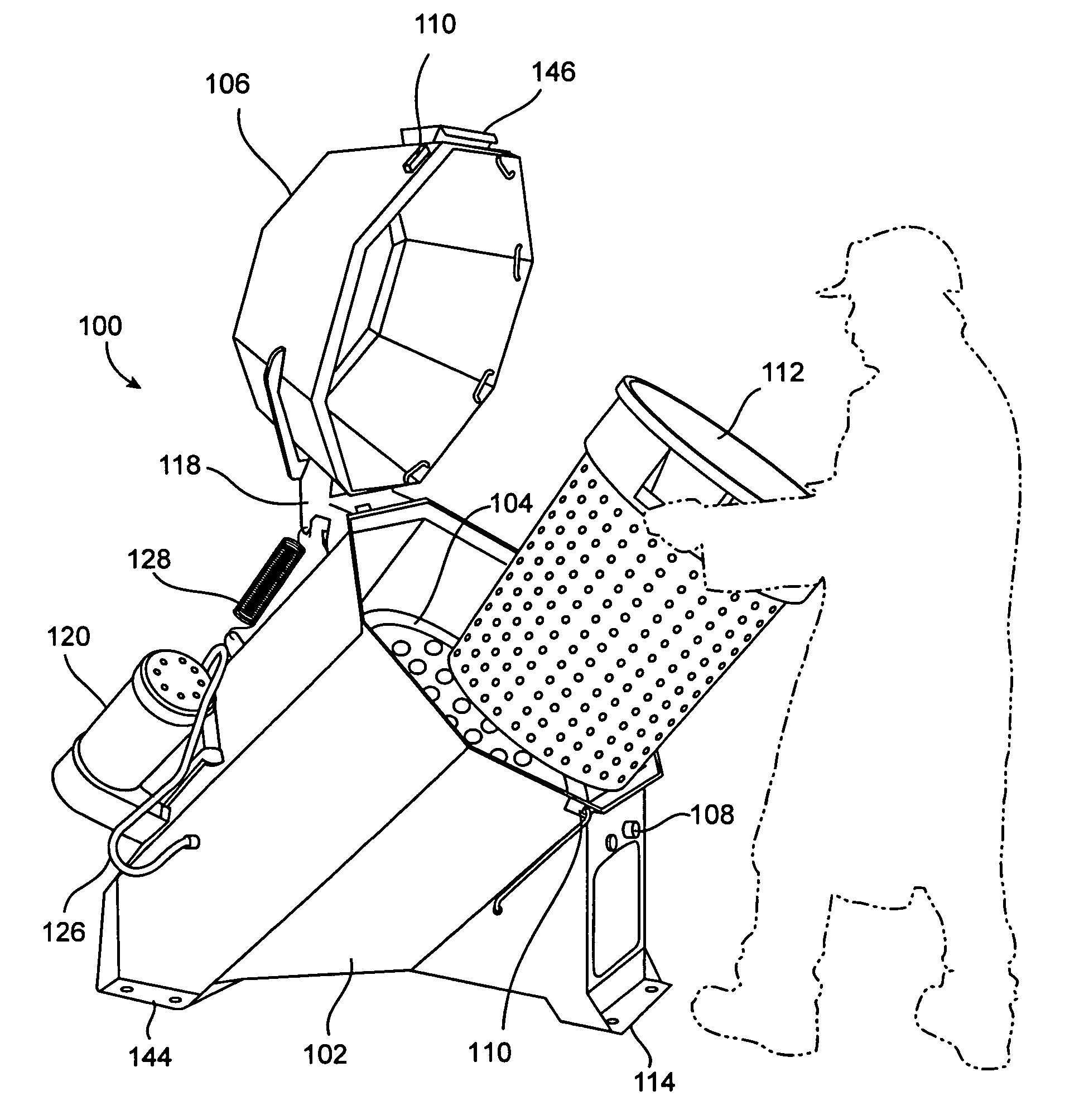
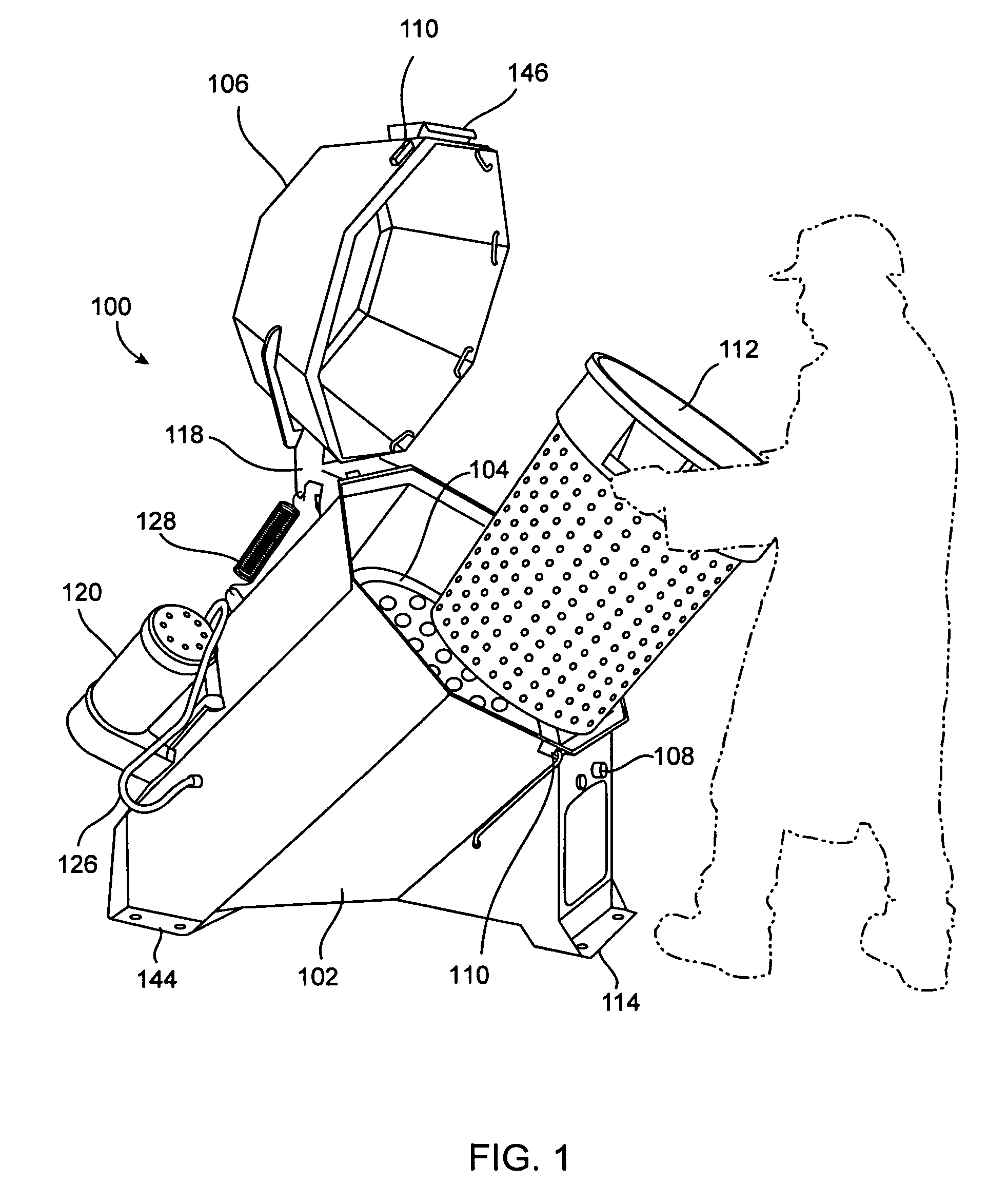
InactiveUS7028415B2Easy to adaptGood for load balancingDrying solid materials without heatDrying machinesEngineering
A drying apparatus for use with many kinds of objects, but is particularly suited for use in drying most kinds of produce and vegetables including leaf vegetables. In one embodiment, the dryer includes a canted drum design which provides a number of benefits and advantages over prior art designs. The canted design allows the use of a spin drying method that breaks up clumps of material in the dryer and assists in the even distribution of material, thereby improving load balance. The canted design provides ergonomic advantages to the operator when loading and unloading the dryer, and, the canted design allows easy access to the drive system for maintenance and repairs.
Owner:HEINZEN LLC
Load balancing in wireless communication network
InactiveUS7509129B2Good for load balancingImprove throughputNetwork traffic/resource managementAssess restrictionTelecommunicationsProcess information
For load balancing in a wireless communication network comprising at least one subscriber terminal (T1, T2, T2) and a plurality of access points (AP1, AP2, AP3), a load control device (21; 110) is used which is located outside of said subscriber terminal, wherein said load control device is adapted to process information related to a load in said wireless communication network and to instruct roaming of said subscriber terminal from an associated access point to another one of said plurality of access points. Access point status information (APST) determined in said plurality of access points (S10; S110) is received and communication status information related to said plurality of access points (S20; S120) is determined. The subscriber terminal processes (S20; S120) these information into roaming support information (RSUP), which are in turn processed (S40; S160) in said load control device an access point related load based roaming analysis. On this basis, it is decided (S50; S170) by the load control device, whether said subscriber terminal is to be associated with another one of said plurality of access points.
Owner:NOKIA TECHNOLOGLES OY
Traffic management for virtual cluster switching
ActiveUS9231890B2Good for load balancingEnhanced transmission selectionData switching networksTraffic capacityVirtual cluster
One embodiment of the present invention provides a switch system. The switch includes one or more ports on the switch configured to transmit packets encapsulated based on a first protocol. The switch further includes a traffic management mechanism and a control mechanism. During operation, the control mechanism forms a logical switch based on a second protocol, receives an automatically assigned identifier for the logical switch without requiring manual configuration of the identifier, and joins a virtual cluster switch.
Owner:AVAGO TECH INT SALES PTE LTD
Multithreading processor and multithreading processing method
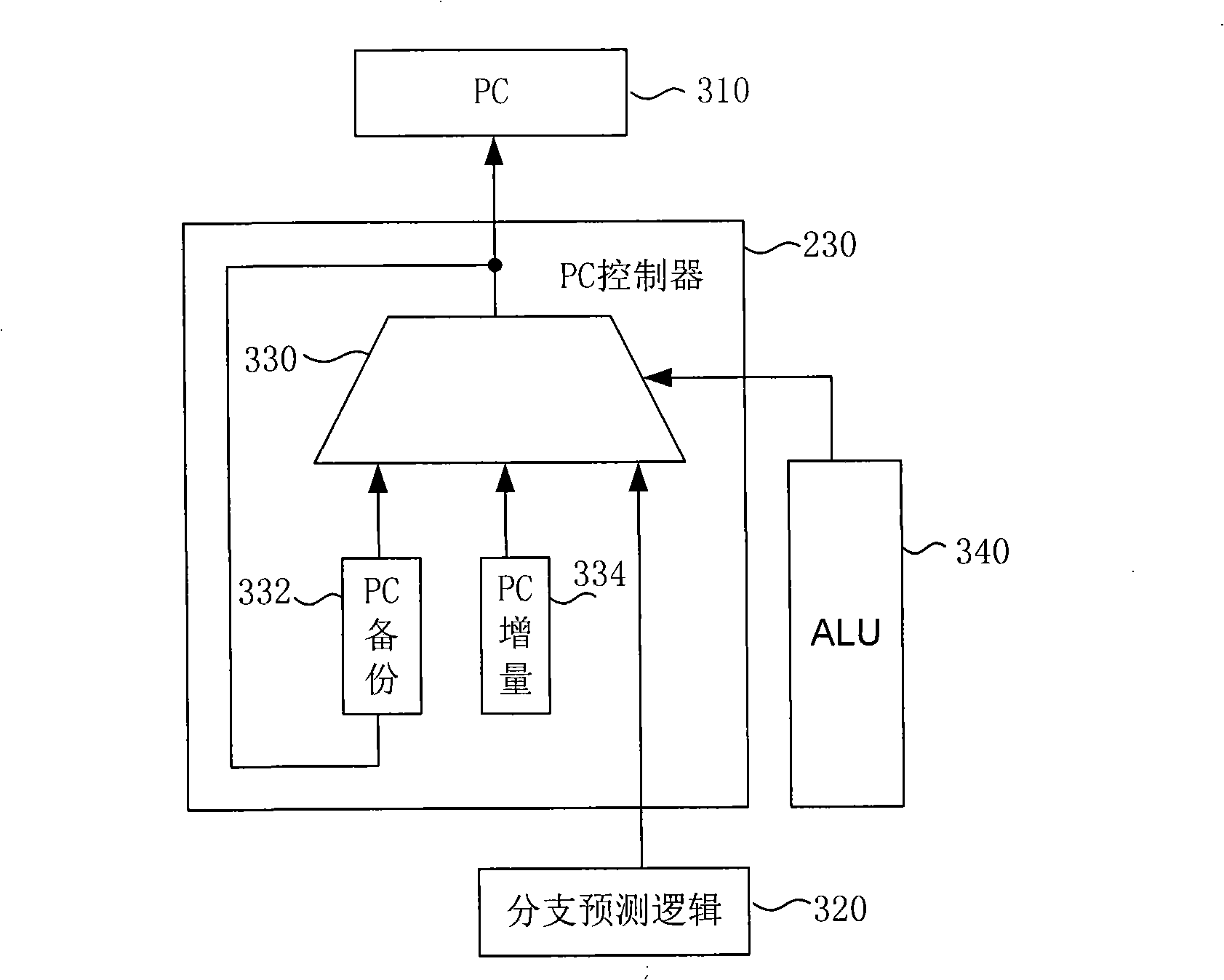
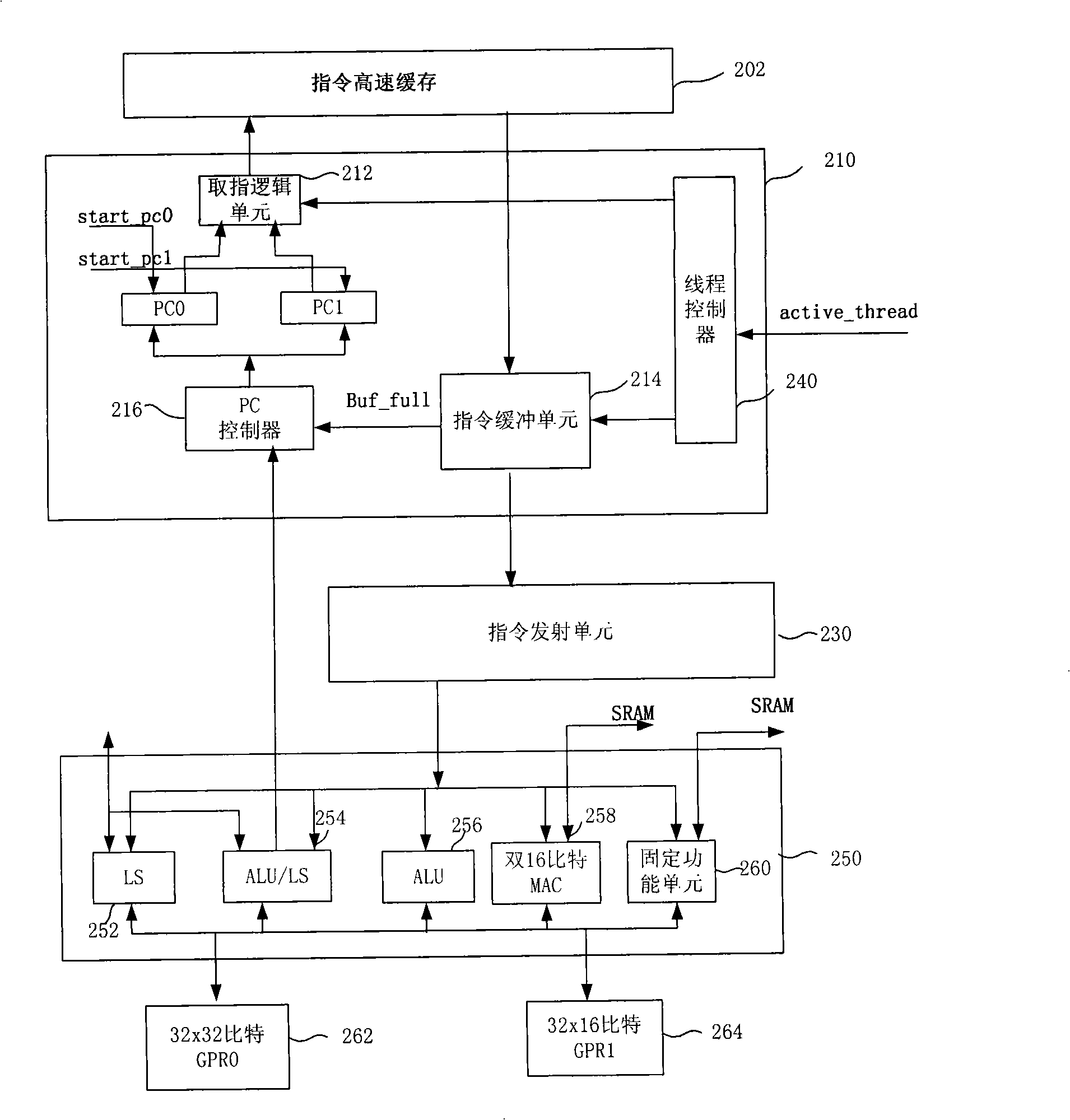
InactiveCN101344842AEfficient use ofLow costConcurrent instruction executionDual coreApplication software
The invention discloses a processor for parallel processing of a plurality of threads and a method for the processor to process a plurality of threads parallelly. The threads can come from different applications in the processor for parallel processing of a plurality of threads. The processor comprises a structural memory, which provides independent instructions and data storage for a plurality of threads; an instruction issuance unit, which reads the instructions of a plurality of threads and issues the instructions to an execution engine; the execution engine, which, shared by a plurality of threads, executes the instructions from the instruction issuance unit. The processor and the method of the invention avoid the necessity of execution pipeline reproduction in dual core proposals, allow better utilization of hardware resources and achieve better load equilibrium among a plurality of processed threads, thereby greatly lowering the chip cost.
Owner:苏州简约纳电子有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com