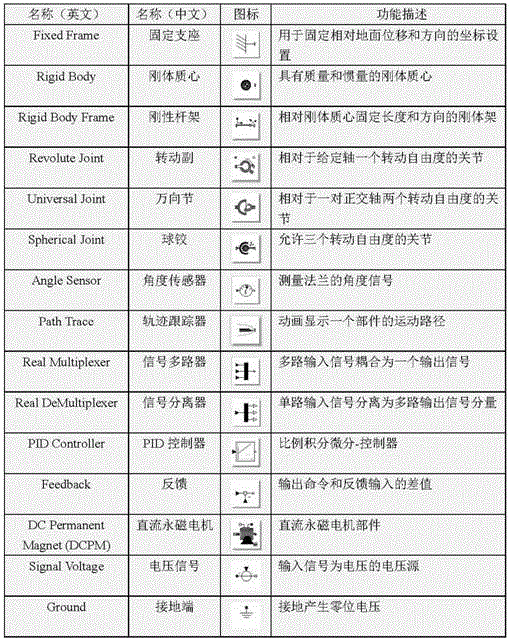
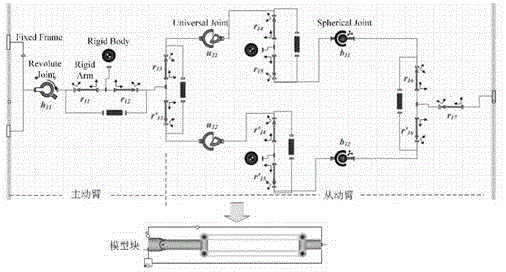
Patents
Literature
106 results about "Chain model" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The means-end chain model is a conceptual entity or structure which sets a connection between the user and the product.
Block chain based electronic copyright protection method
InactiveCN106250721AEffective circulationStrengthen supervisionProgram/content distribution protectionPasswordData operations
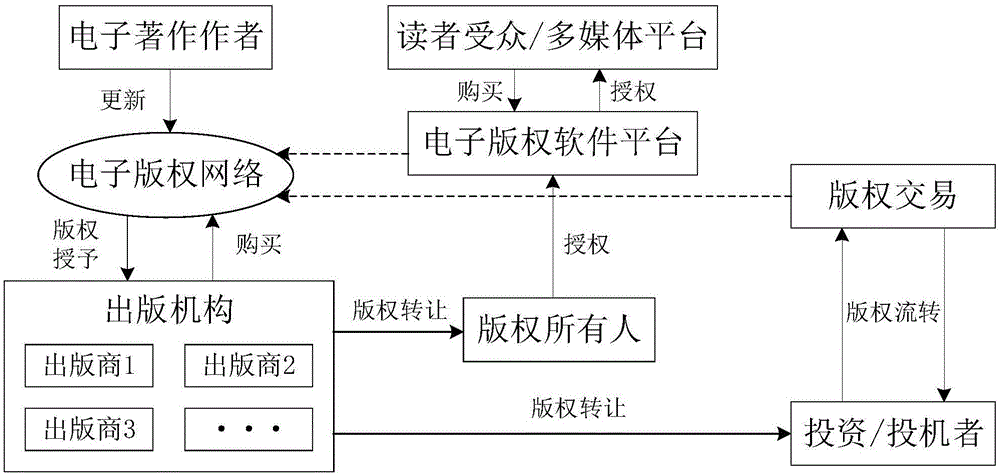
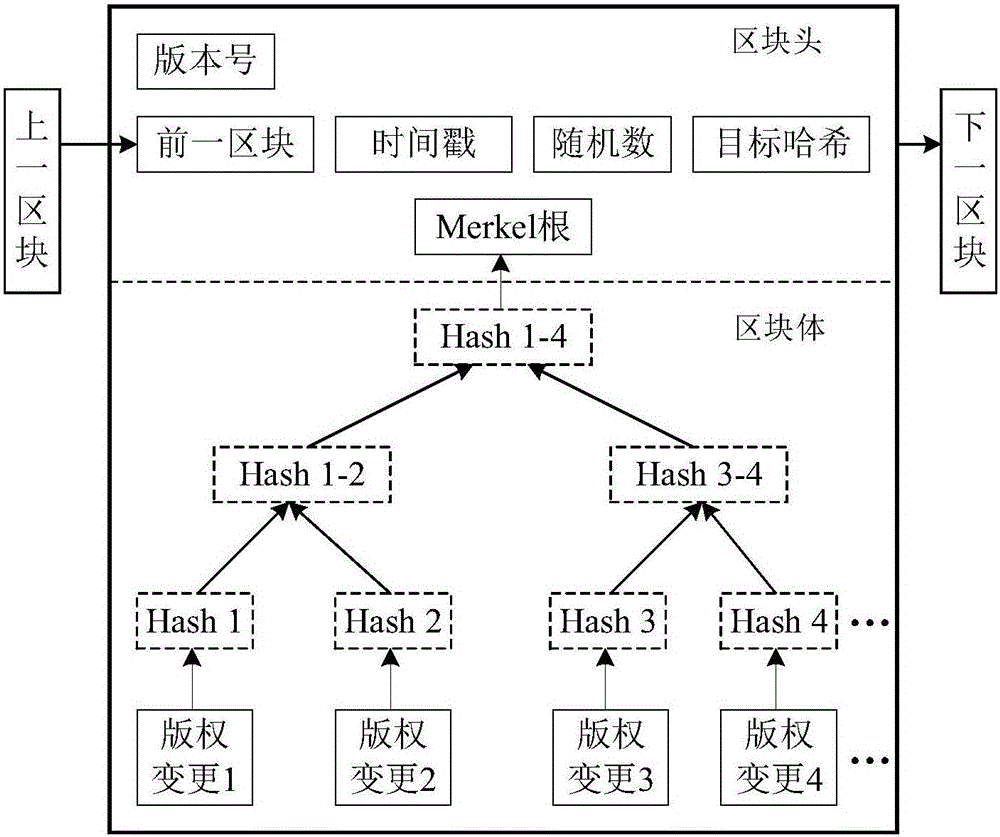
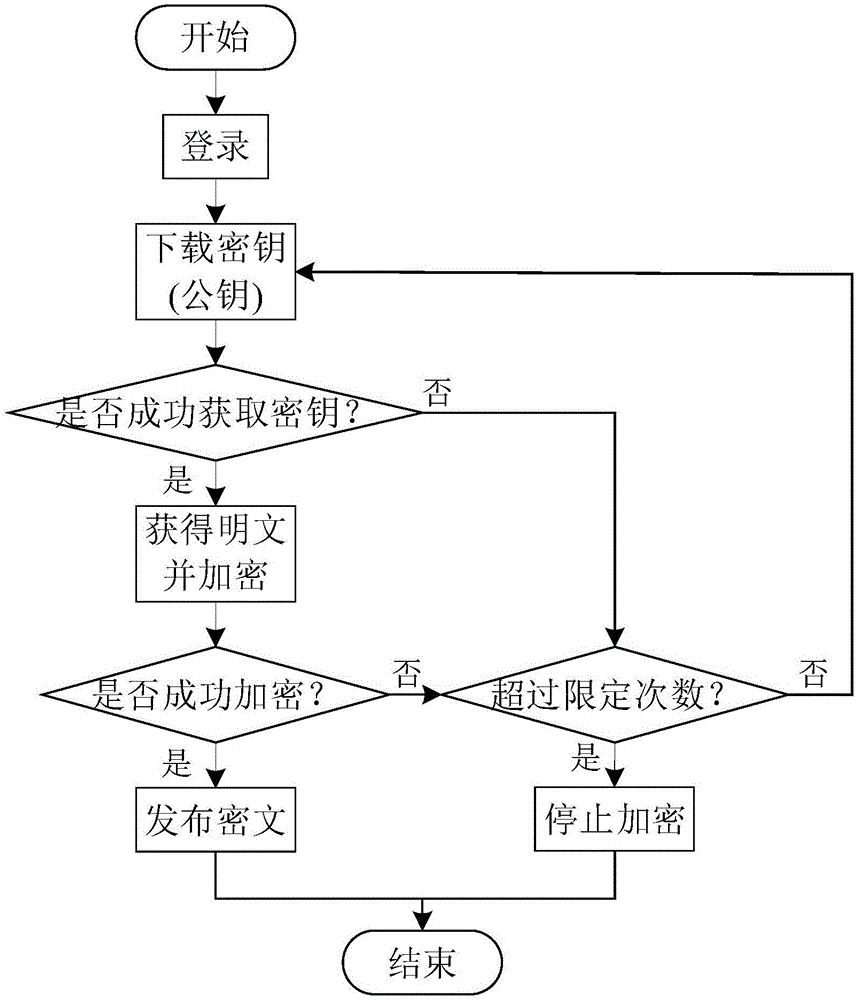
The invention discloses a block chain-based electronic copyright protection method, which utilizes a brand-new, decentralized, distributed architecture called block chain and gradually emerging with digital encrypted currencies such as bitcoins. Electronic copyright protection for data calculation methods. The blockchain model usually includes a data layer, a network layer, a consensus layer, etc., which are respectively responsible for completing the tasks of time-stamped data encapsulation, distributed networking propagation mechanism, and consensus algorithm of distributed nodes. At the same time, the application of elliptic curve encryption (ECC), an asymmetric encryption algorithm in the blockchain, requires the use of two different public and private key ciphers for encryption and decryption, which can greatly enhance the security of the copyright database sex. The complete model architecture of the block chain of the present invention makes it have very broad application prospects in the field of electronic copyright protection.
Owner:HANGZHOU YUNXIANG NETWORK TECH
Nonlinear adaptive control of resource-distribution dynamics
InactiveUS20060013132A1Improves controller performanceImprove performanceError preventionTransmission systemsReal systemsResource Management System
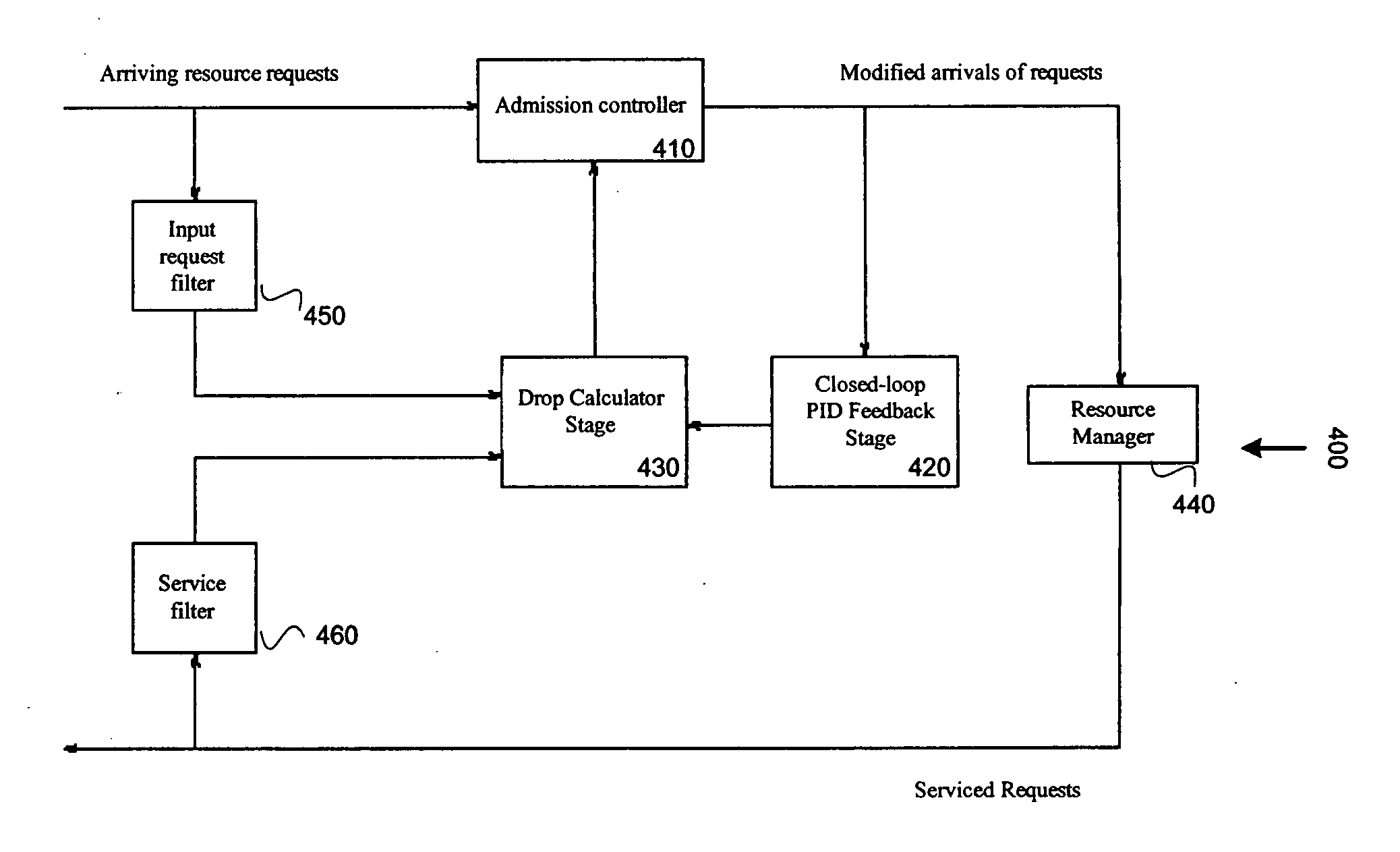
Nonlinear adaptive resource management systems and methods are provided. According to one embodiment, a controller identifies and prevents resource starvation in resource-limited systems. To function correctly, system processes require resources that can be exhausted when under high load conditions. If the load conditions continue a complete system failure may occur. Controllers functioning in accordance with embodiments of the present invention avoid these failures by distribution shaping that completely avoids undesirable states. According to one embodiment, a Markov Birth / Death Chain model of the resource usage is built based on the structure of the system, with the number of states determined by the amount of resources, and the transition probabilities by the instantaneous rates of observed consumption and release. A control stage is used to guide a controller that denies some resource requests in real systems in a principled manner, thereby reducing the demand rate and the resulting distribution of resource states.
Owner:CREATIVE TECH CORP
Distributed computing service platform for mobile network traffic
InactiveUS20150334094A1User identity/authority verificationHybrid transportMobile clientMobile ad hoc network
Described herein are systems, methods, and apparatus for processing network packet data in a distributed computing platform, such as a content delivery network, to provide services to mobile network operators and / or their mobile subscribers. According to the teachings hereof, distributed computing resources can be organized into a service platform to provide certain value-add services—such as deep packet inspection, transcoding, lawful intercept, or otherwise—using a service function chaining model. The platform resources are preferably located external to the mobile network, on the public Internet. The platform preferably operates on and processes traffic entering or exiting the mobile network. In some embodiments, the service platform is able to establish an encrypted channel between itself and the mobile client through the mobile network, e.g., using content provider key and certificate information available to the platform (but which may not be available to the mobile network operator).
Owner:AKAMAI TECH INC
Network threat detection method, device and network management equipment
ActiveCN107888607AMeet the needs of efficient and friendlyRealize automated detectionTransmissionNetwork managementChain model
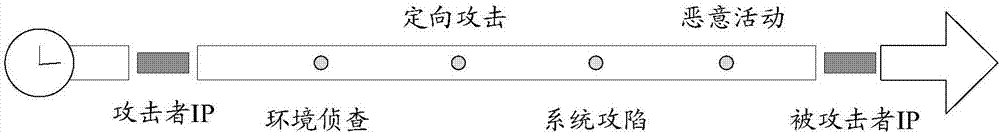
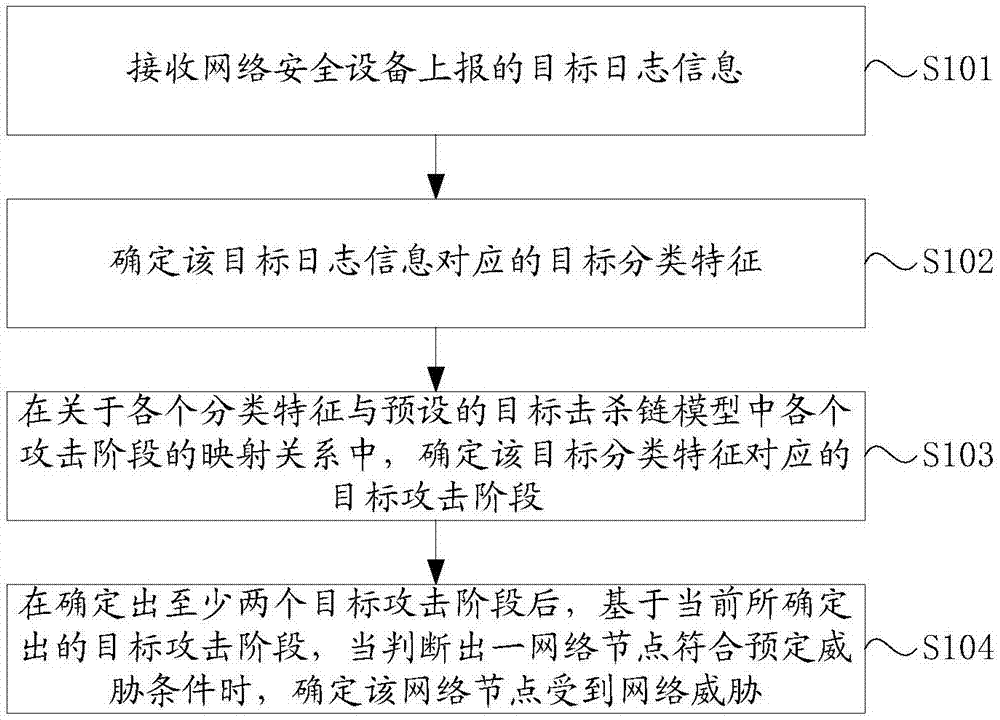
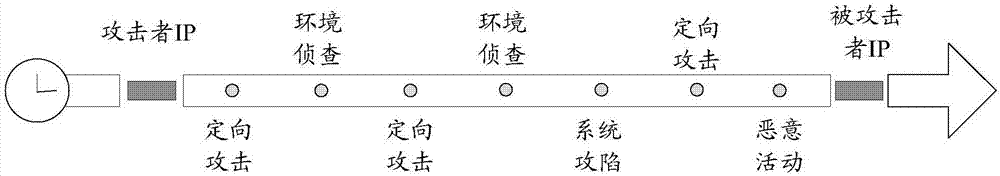
The application provides a network threat detection method and device, and network management equipment. The method comprises the following steps: receiving target log information reported by networksecurity equipment; determining a target classification feature corresponding to the target log information; determining a target attack stage corresponding to the target classification feature in a mapping relation about each classification feature and each attack state in a preset target kill chain model; and determining a fact that a network node is under network threat when judging that the network node meets the preset threat condition based on the currently determined each target attack stage after determining out at least two target attack stages, wherein the preset threat condition isas follows: generating the stage combination in forward sequence in the target kill chain model according to time order on a time shaft, and the stage combination comprises at least two attack stages.Through the scheme provided by the application, the problem of low detection efficiency in the prior art can be solved.
Owner:NEW H3C TECH CO LTD
Block chain model with the privacy protection function
ActiveCN108171511APrivacy protectionAttack resistanceKey distribution for secure communicationUser identity/authority verificationSource Data VerificationCiphertext
The invention discloses a block chain model with the privacy protection function. The block chain model is formed by a minimum trustrank administrator, a private part, and a public part. The minimum trustrank administrator is used for assisting in transaction; the private part is used for defining input information of all sides participating in transaction and sending and receiving of the information and defining relevant calculations during the transaction process and verification of relevant data during the transaction process; and the public part is used for ensuring fairness of the transaction. On the basis of currency encryption, a block chain is constructed by using a distributed anonymous mechanism, zero-knowledge verification, overtime penalties, and packaging methods. Realizationof currency generation and usage, and conversion into basic currency having the privacy protection function relays on zk-SNARK and related data in a ciphertext mode are verified, so that the user is able to realize data verification while the user information is not leaked.
Owner:广州京盛数码科技有限公司
Method and system for detecting malicious application of Android system
InactiveCN106874761ATo achieve effective identificationMake up for the lack of difficulty in detecting unknown applicationsPlatform integrity maintainanceApplication softwareSource code
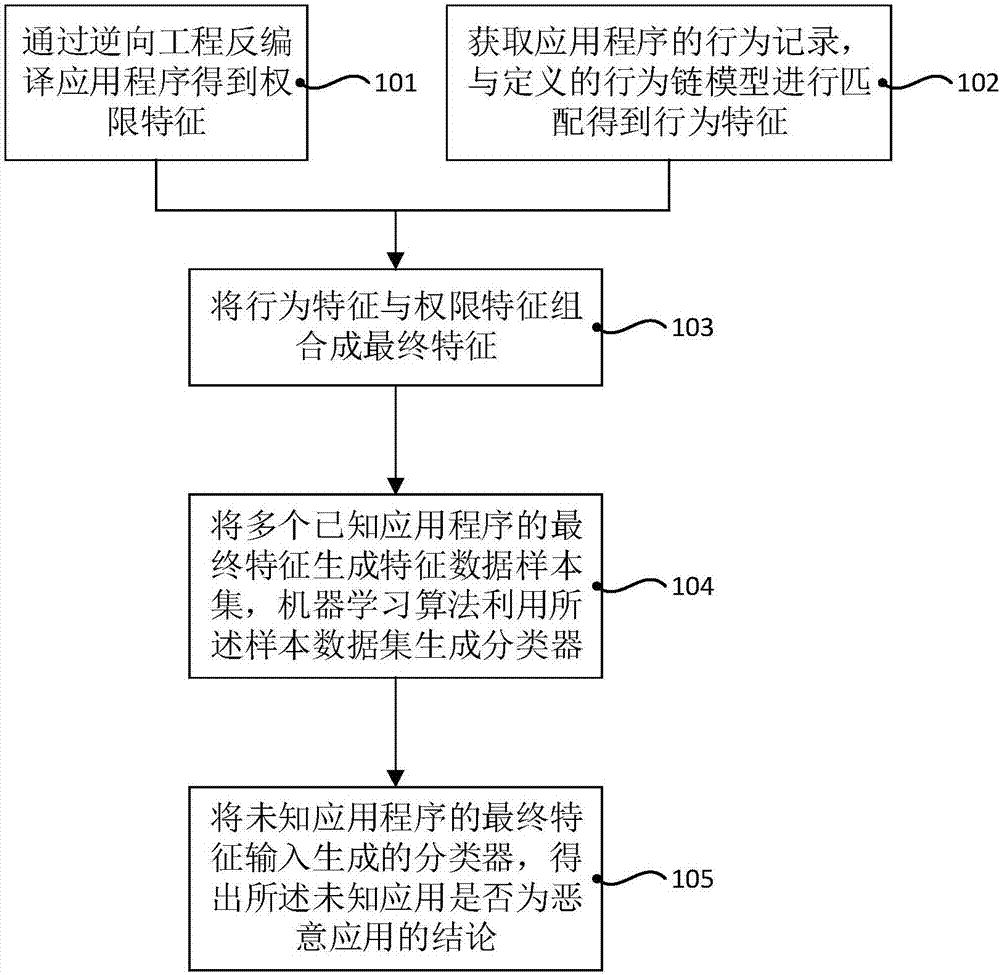
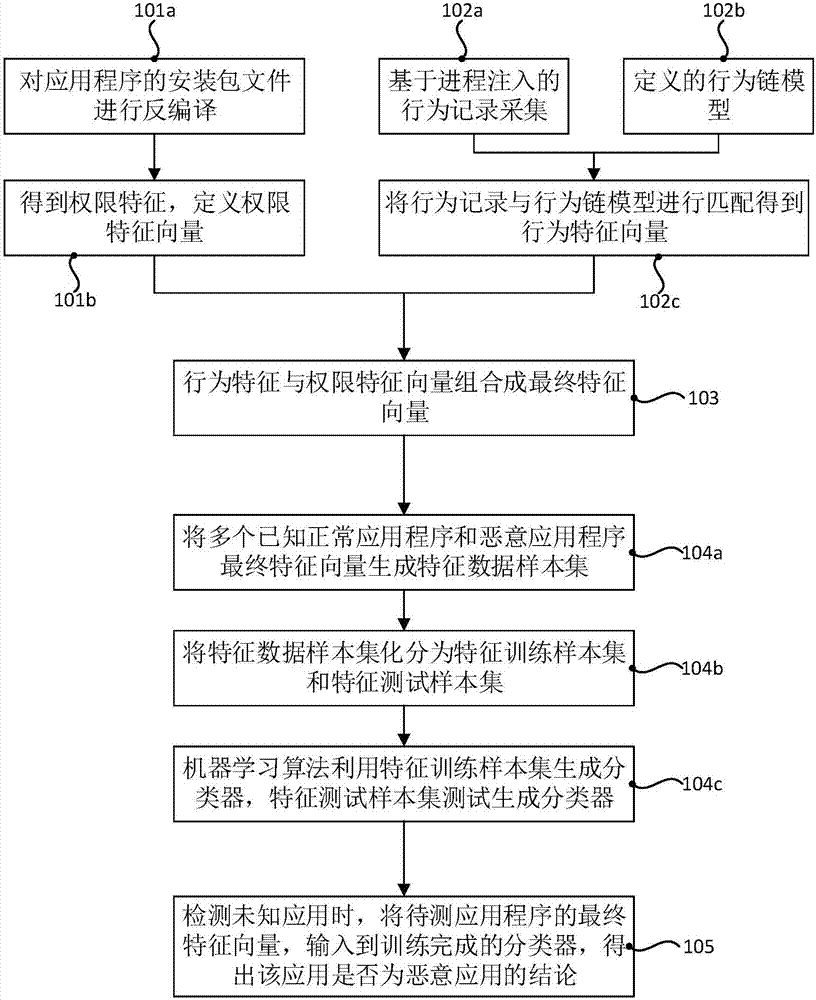
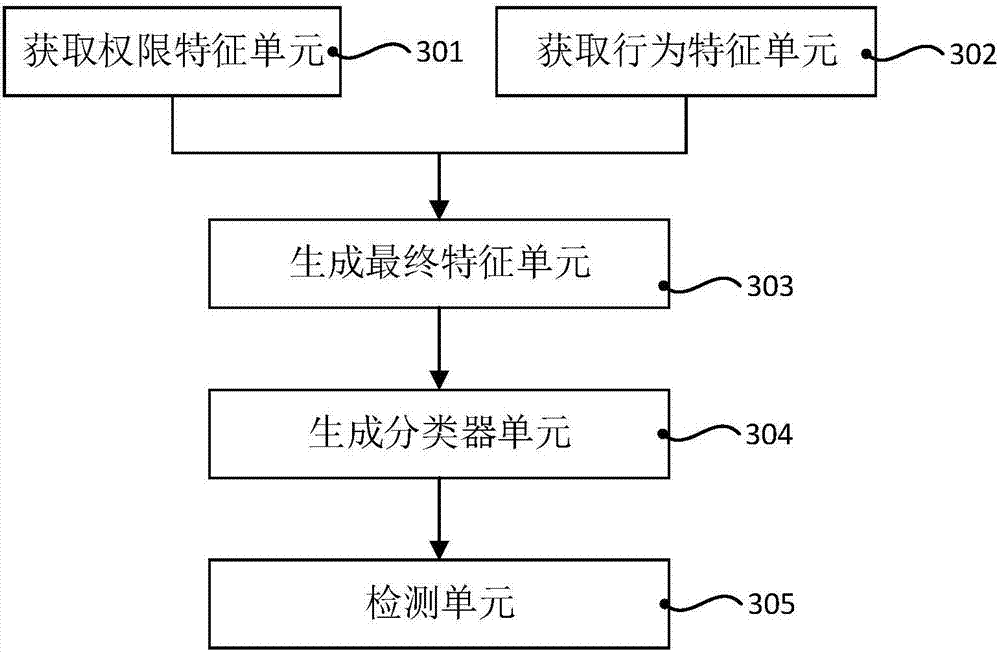
The invention discloses a method and a system for detecting a malicious application of an Android system. The method comprises the following steps: acquiring a privilege characteristic by a reverse engineering de-compilation application program; matching by a behavior chain model for dynamic behavior collection and definition, thereby acquiring a behavior characteristic; combining plentiful privilege characteristics with behavior characteristics, thereby generating a characteristic data sample set; adopting a machine learning algorithm for utilizing the characteristic data sample set to generate a classifier; and inputting the characteristics of an unknown application program to the classifier, thereby acquiring a conclusion indicating if the unknown application program belongs to the malicious application. The invention provides the behavior chain model on the basis of the reverse engineering and the dynamic behavior collection, and then the unknown application program is detected through the machine learning algorithm, so that the efficient recognition for the malicious application is realized, the accuracy is high and the detection method and system provided by the invention are high in efficiency, need not change the system source code and are high in availability.
Owner:BEIJING UNIV OF POSTS & TELECOMM
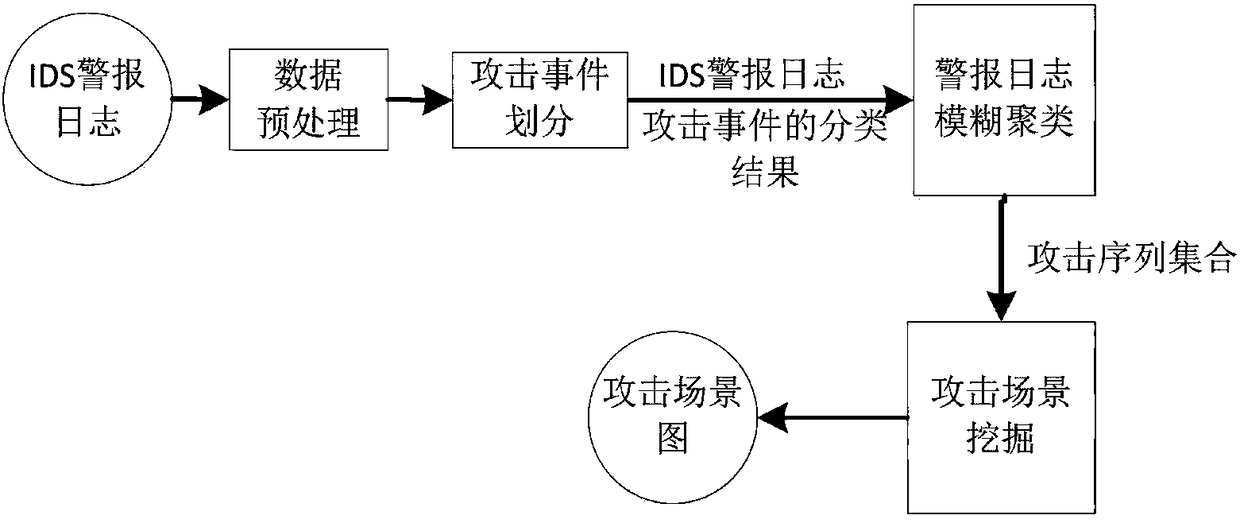
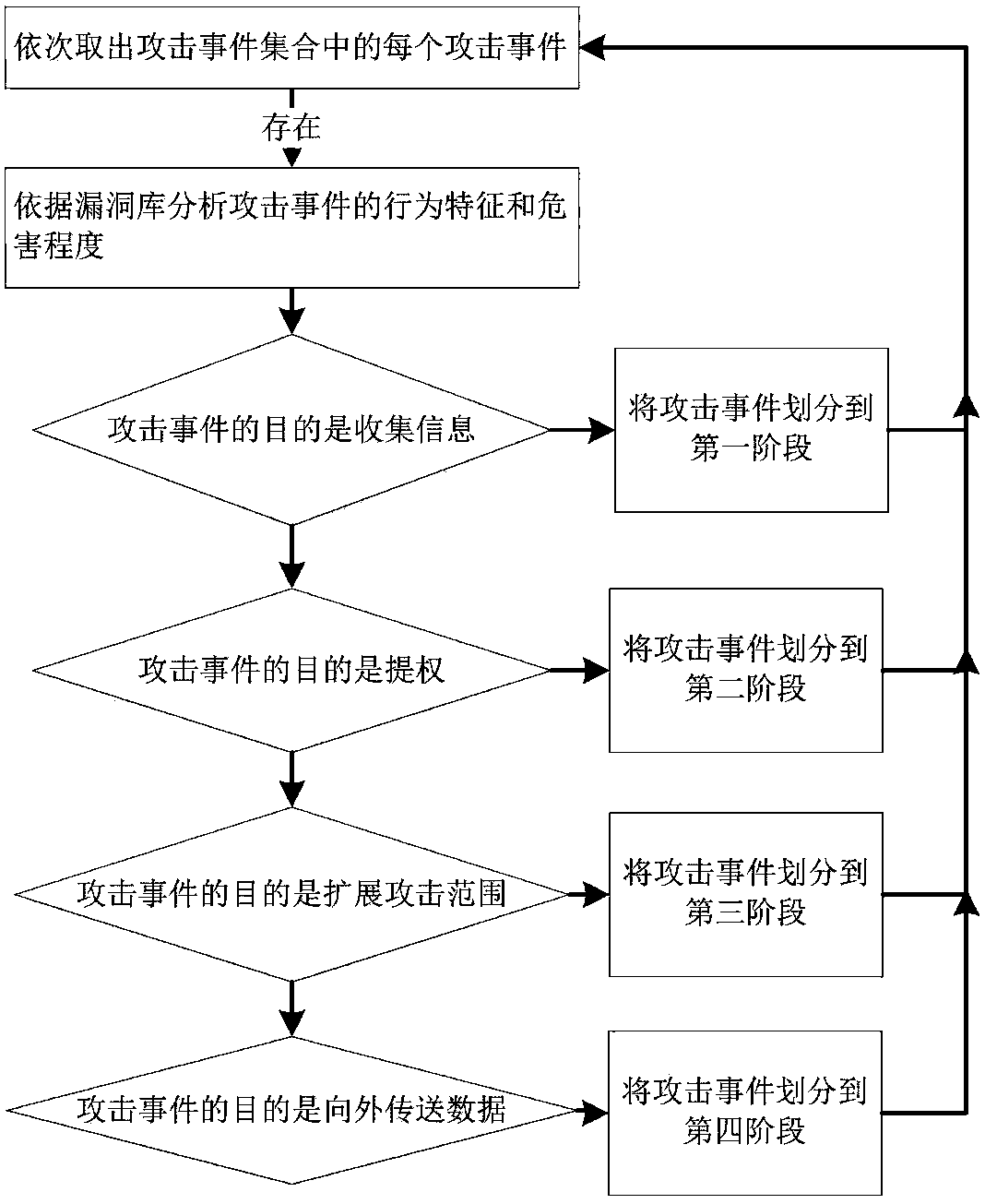
APT attack scene mining method based on intrusion kill chain and fuzzy clustering
ActiveCN108076040AImprove accuracyImprove relevanceTransmissionDirected graphTransition probability matrix
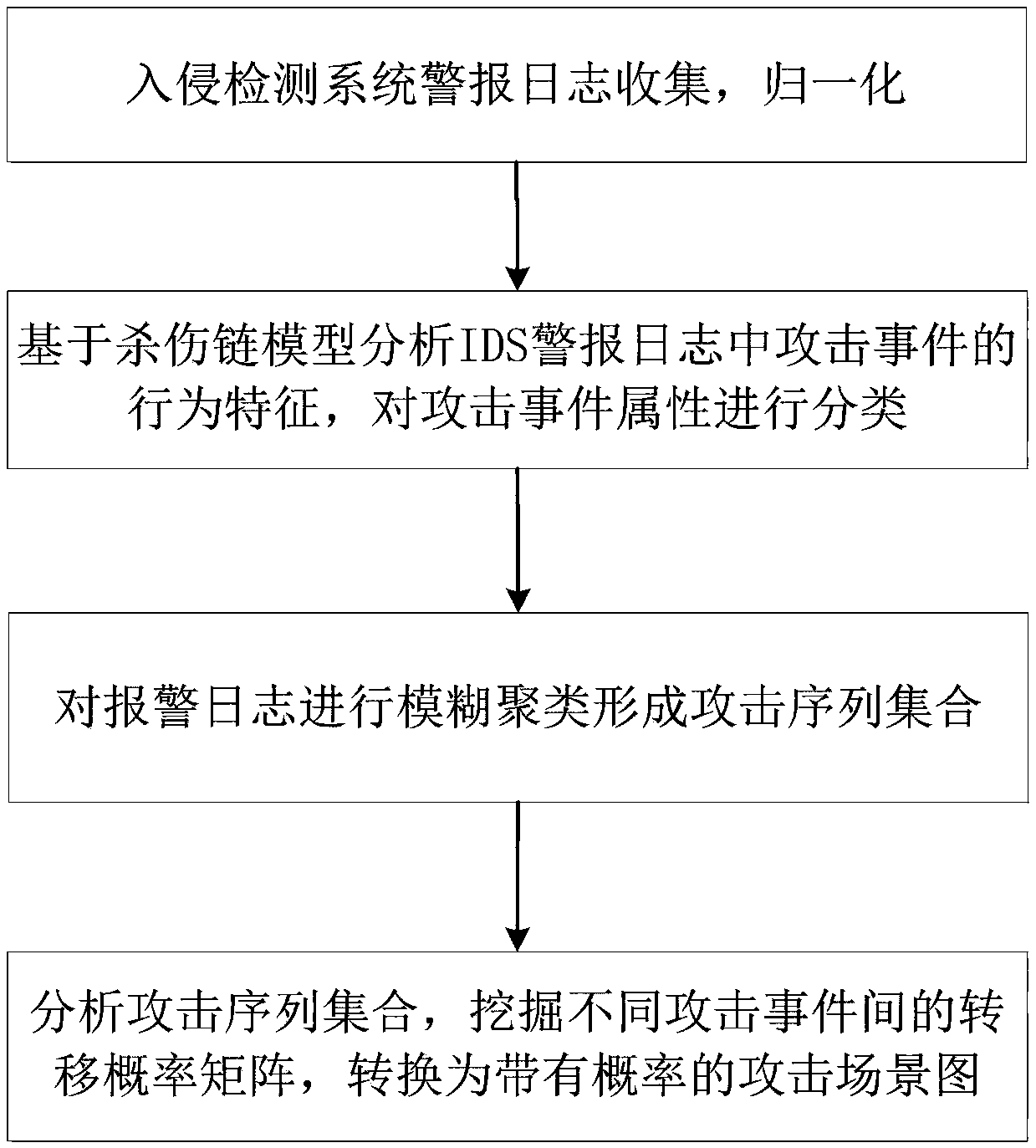
The invention discloses an APT attack scene mining method based on an intrusion kill chain and fuzzy clustering. The method can be used for mining an APT attack scene in an intrusion detection system(IDS) log. The method comprises the steps of collecting and normalizing alert of the intrusion detection system; analyzing behavior characteristics of attack events in alert logs based on an intrusionkill chain model and classifying the attack events; carrying out fuzzy clustering on the alert logs to form an attack sequence set; and analyzing the attack sequence set, deleting incomplete sequences, converting each attack sequence into a directed graph, mining a transition probability matrix among different attack events, and converting the transition probability matrix into an APT attack scene graph with the probability. According to the method, the APT attack graph in true alert can be mined, and the theoretical foundation for APT detection and defense is provided.
Owner:BEIJING UNIV OF POSTS & TELECOMM
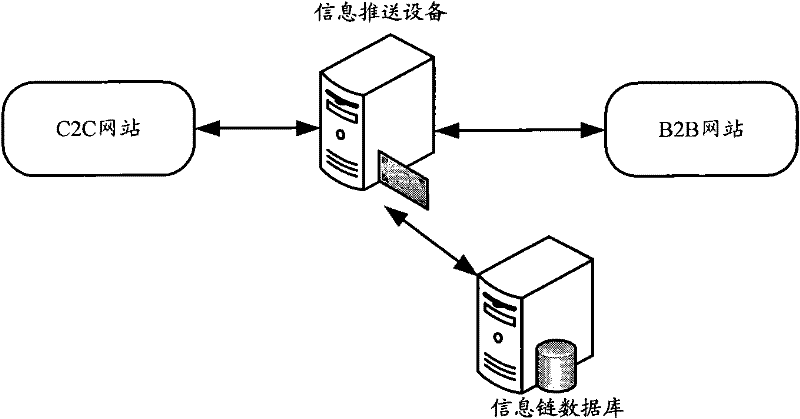
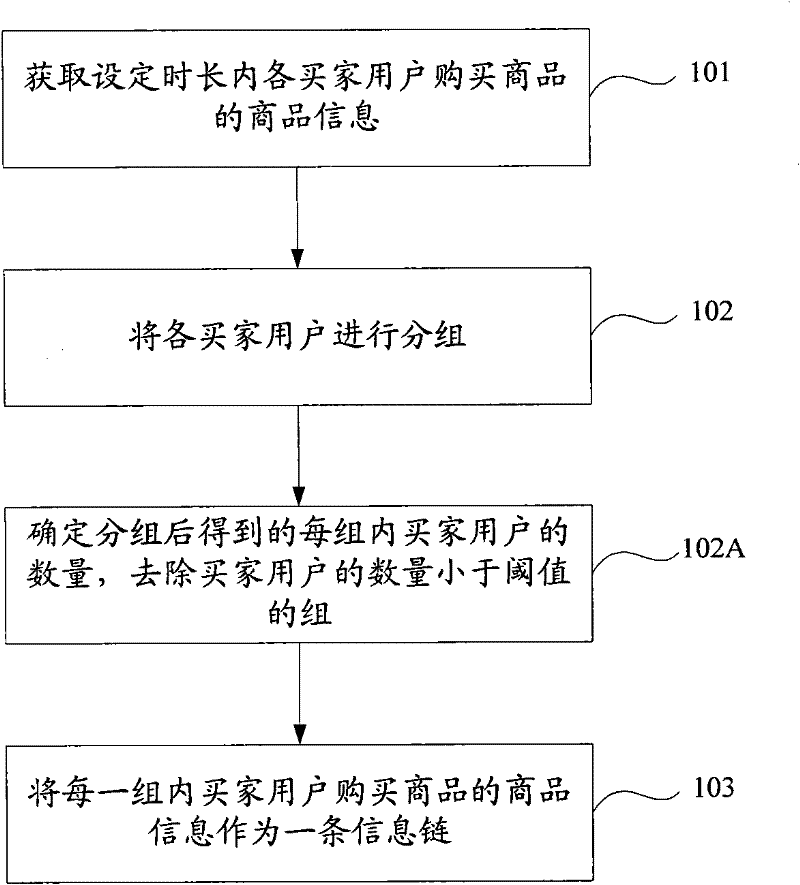
Information pushing method, system and equipment
ActiveCN102446326AAccurately obtainedImprove accuracySpecial data processing applicationsMarketingChain modelWorld Wide Web
The invention discloses an information pushing method, system and equipment. The information pushing method mainly comprises the following steps: inquiring information chains with higher correlation degree for commodity information corresponding to information ordering request of a seller user in a first website through an information chain model prestored in a database, determining the category of all inquired information contained in the information chains in a second website, and pushing the commodity information belonging to the category in the second website to the seller user in the first website, thus, the information pushing accuracy is improved, and the aim for actively recommending information between the two websites is achieved.
Owner:ALIBABA GRP HLDG LTD
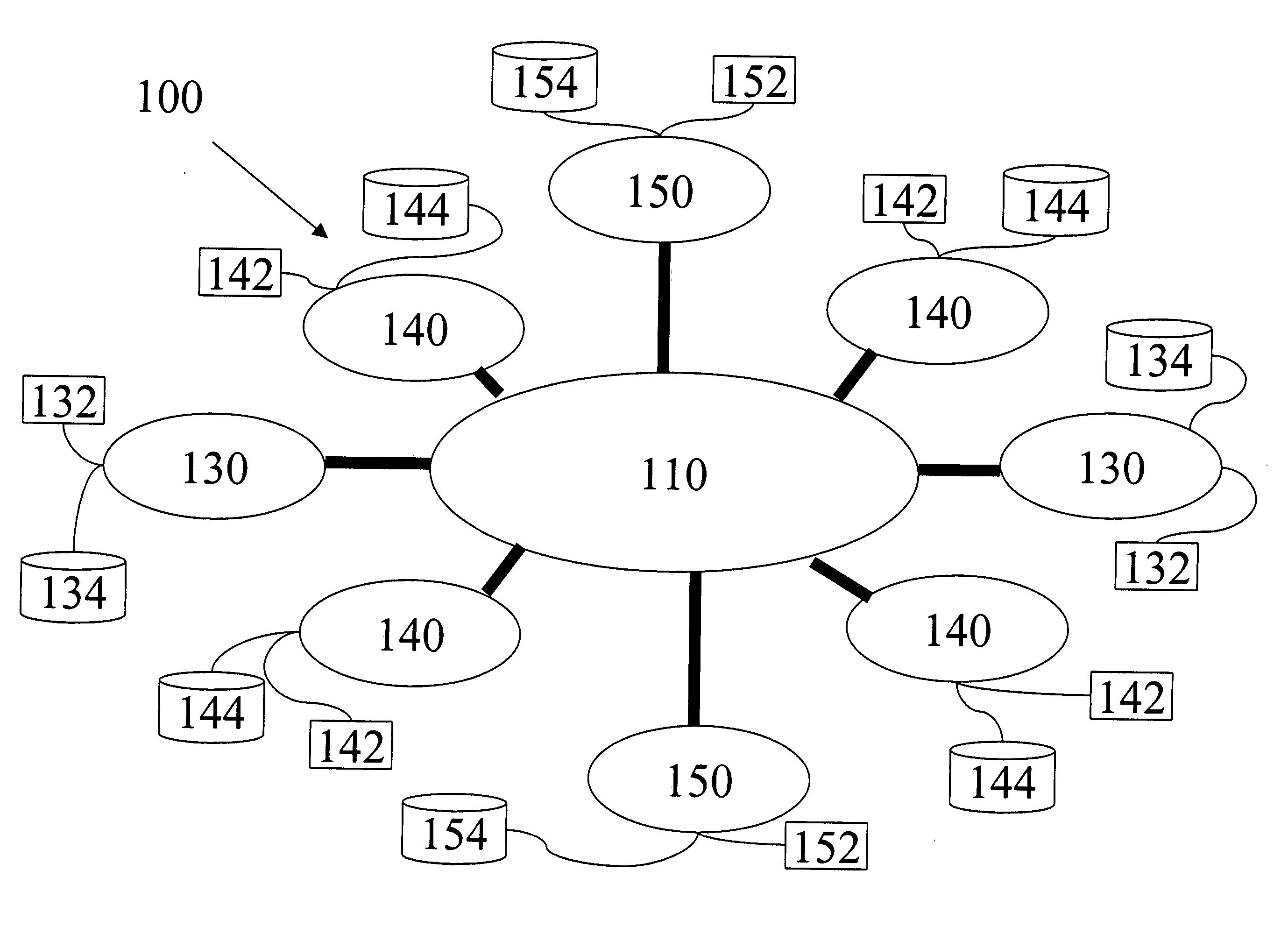
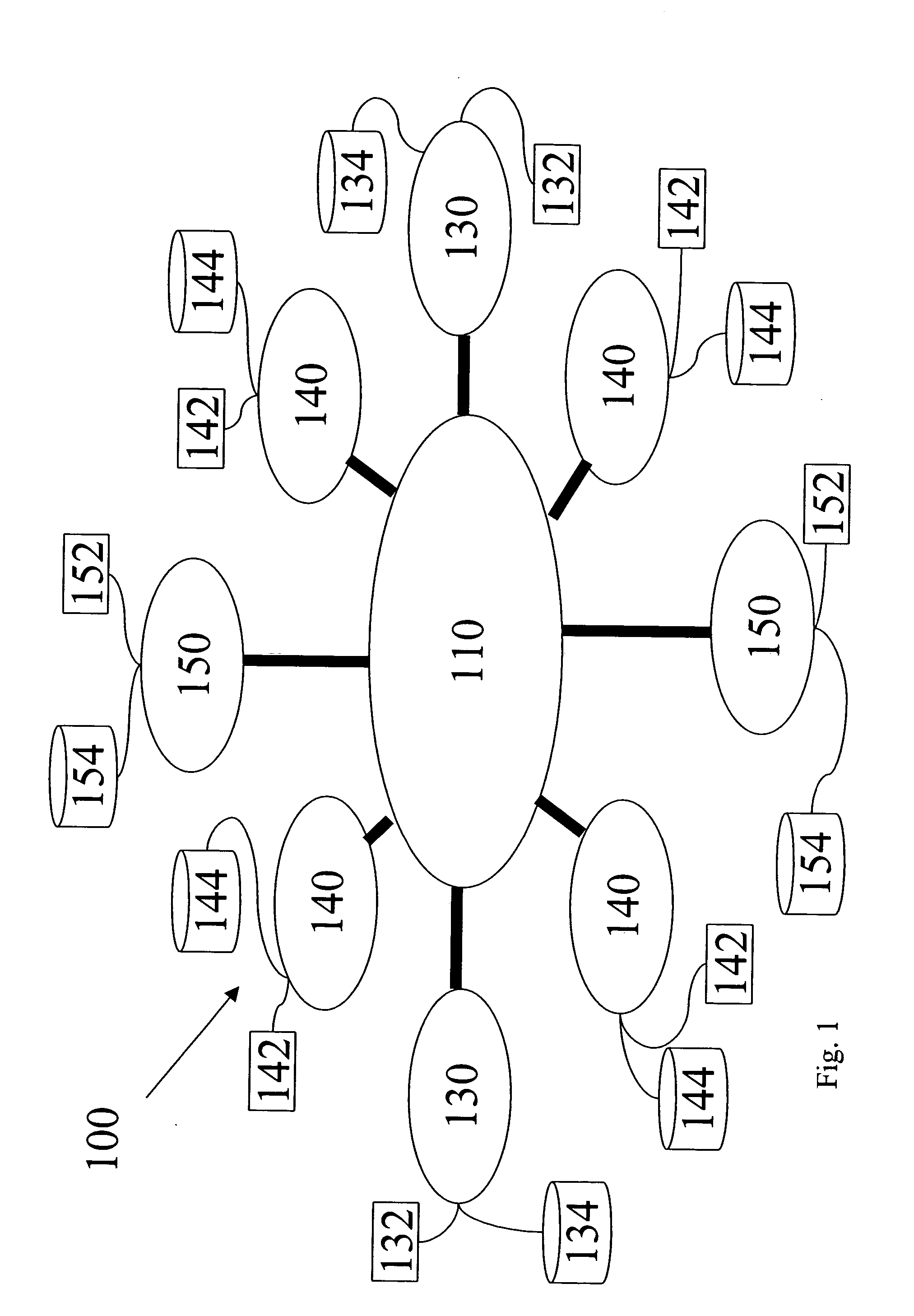
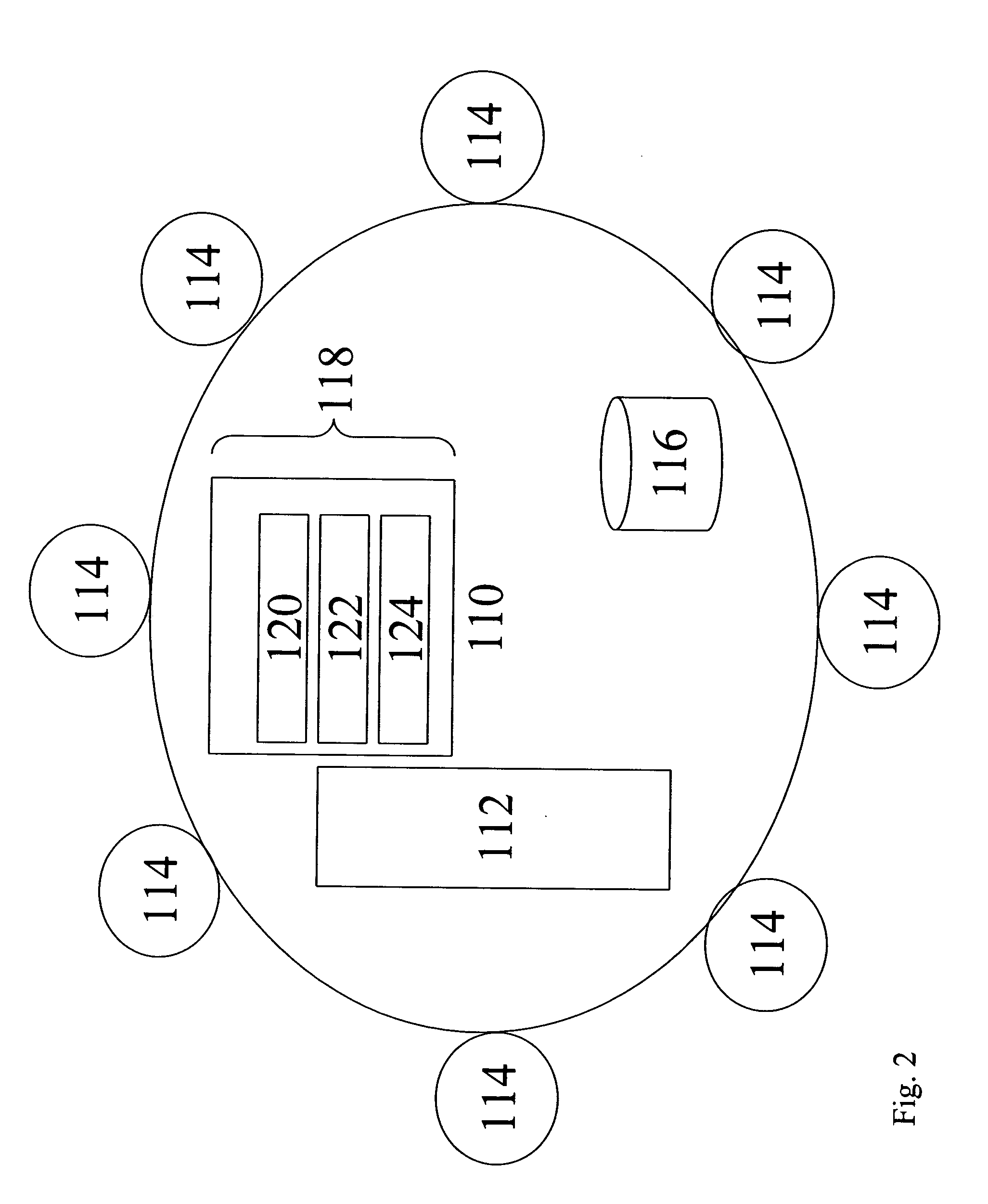
Visibility and synchronization in a multi tier supply chain model
Methods and systems with which manufacturers can review reliable information about supply conditions including multiple supplier tiers, and maintain order collaboration for an extended supply chain. The manufacturer can: view updates to supply chain conditions; aggregate information from multiple products; collect and analyze information regarding supply chain performance of multiple supplier tiers; obtain feedback information for its design process in response to supply chain performance; review and enforce compliance with contract terms between the manufacturer and its suppliers; direct first tier and later tier suppliers to allocate parts in relatively short supply to particular projects within an enterprise in which the manufacturer is included; can define dictionaries of data shared among tiers, such as part numbers; and determine for which parts there is no strong preference in design or manufacture, allowing its first tier and later tier parts suppliers to use any design that meets design specifications.
Owner:E2OPEN
Modeling a supply chain
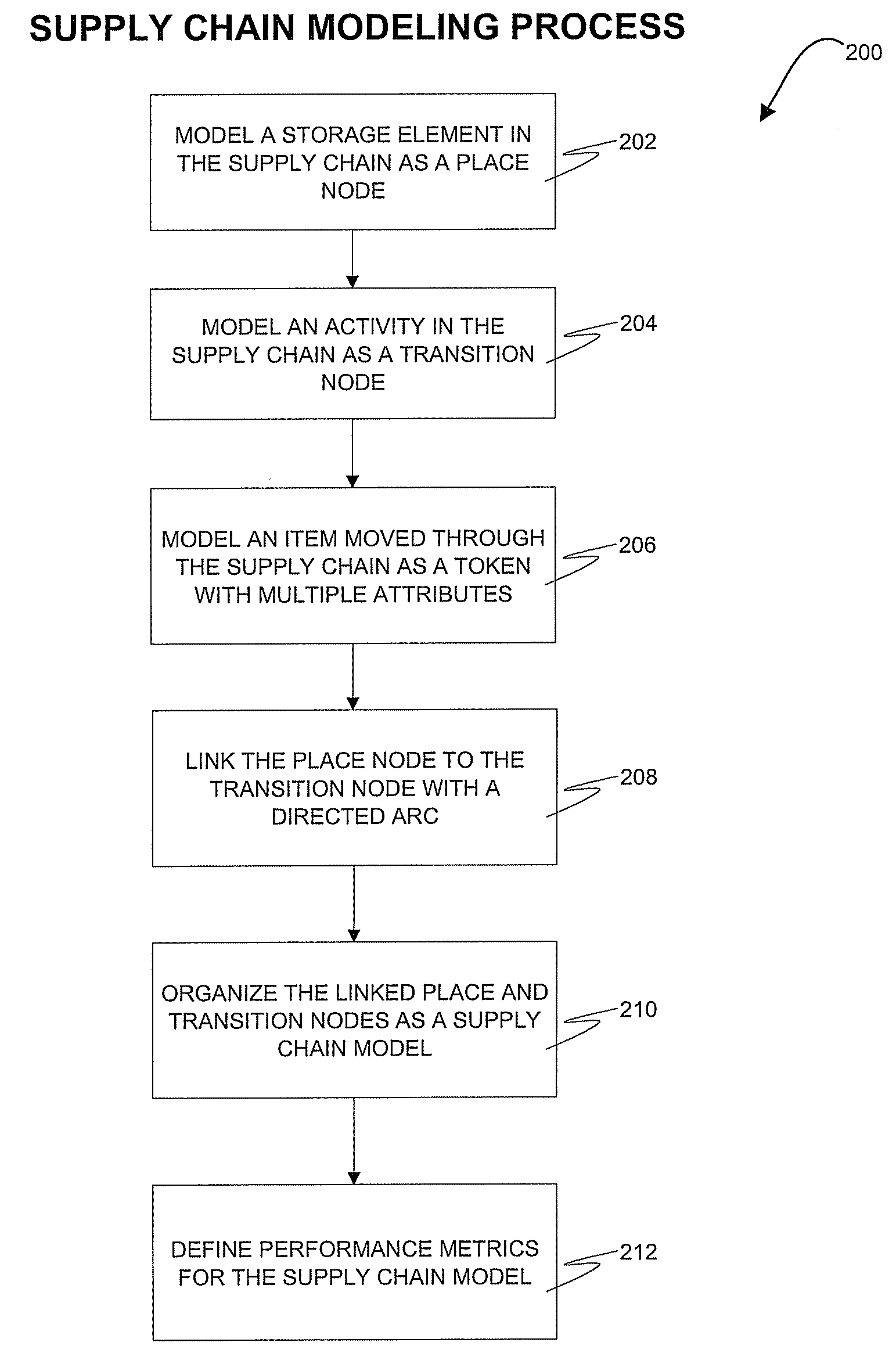
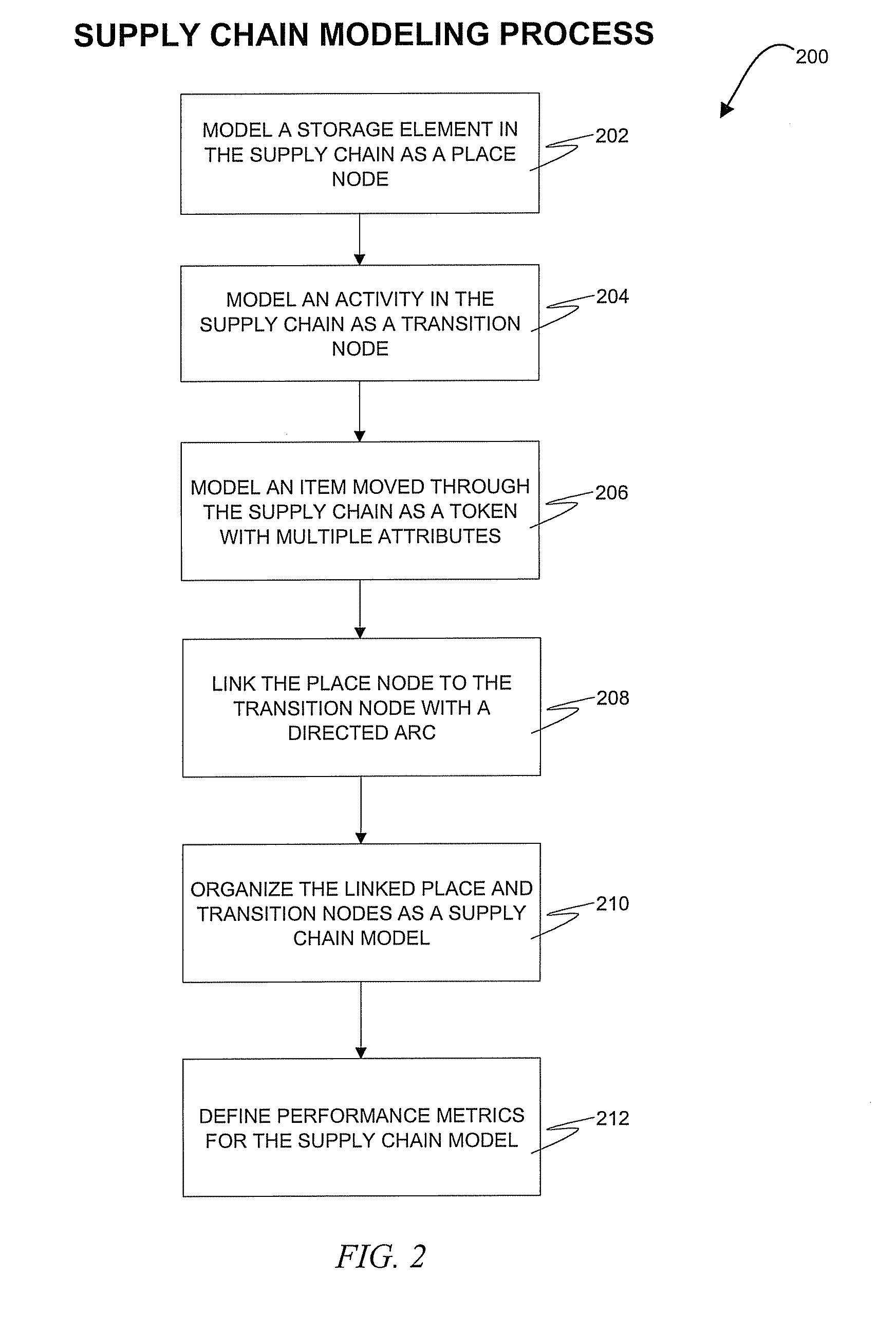
InactiveUS20080306783A1Improve performancePromote modelForecastingLogisticsMultiple attributeChain model
A method, system, and computer program product for modeling a supply chain. The method includes modeling a storage element in the supply chain as a place node and modeling an activity in the supply chain as a transition node. The transition node includes at least one of an immediate transition node, a timed transition node, and a substitution transition node. An item moved through the supply chain is modeled as a token, where the token includes multiple attributes associated with the item. The place node is linked to the transition node with a directed arc, with the directed arc indicating the direction of token movement between the place node and the transition node. The linked place and transition nodes are organized as a supply chain model that represents the flow of items through the supply chain. In addition, performance metrics for the supply chain model are defined.
Owner:GM GLOBAL TECH OPERATIONS LLC
Block chain consensus method based on switching of network topology modes
InactiveCN110138596AOther databases indexingNetworks interconnectionStructure of Management InformationCommunication link
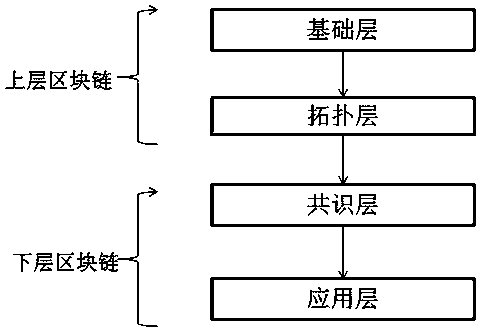
The invention requests to protect a block chain consensus method based on switching of network topology modes. The block chain consensus method is based on a master-slave multi-chain model of the block chains, different consensus mechanisms are adopted for the construction of a main chain and a slave chain, and a basic layer, a topological layer, a consensus layer and an application layer of the block chain are processed in a layered manner, so that the block chain consensus method is more suitable for a transaction-oriented block chain system, and a high-throughput, low-delay, high-efficiencyand energy-saving consensus algorithm is set. In addition, an asynchronous parallel algorithm is achieved in an environment based on the switching of the network topology structure, a single-chip computer which integrates multiple functional blocks, such as a CPU, a memory, a high-speed interconnection communication link, etc., is provided with four pairs of two-way communication links used for linking between processors so as to form a multi-processor system of various topology structures.
Owner:李宝次 +1
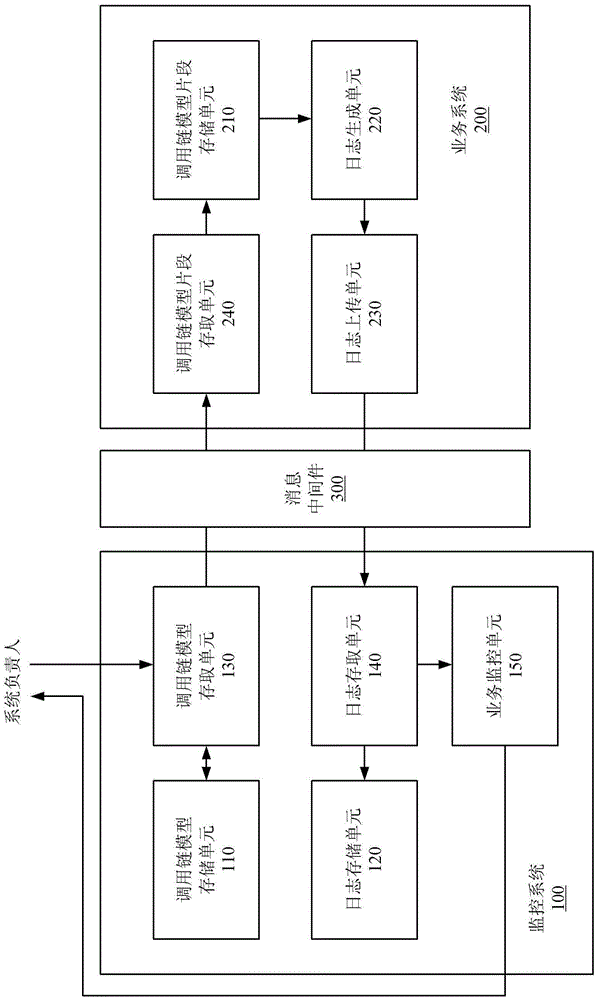
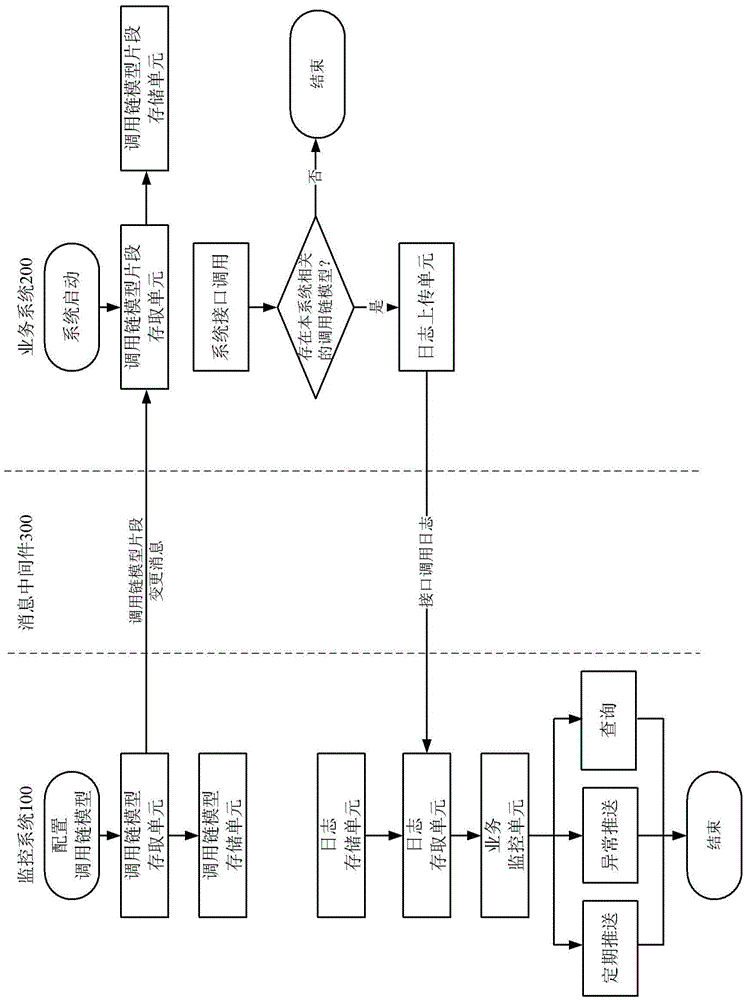
Monitoring system and business system
The invention provides a monitoring system. The monitoring system comprises a call chain model storage unit for storing one or more business call chain models and a log storage unit for storing interface call logs of interfaces in the business call chain models, and each business call chain model records all called interfaces according to an upstream and downstream relationship of the called interfaces in each business system related in a corresponding business process. The invention also provides a business system. The business system comprises a call chain model fragment storage unit for storing one or more business call chain model fragments related to the business system, a log generation unit for generating interface calling logs when the interfaces of the business system are called, and a log uploading unit for uploading the interface calling logs of the interfaces included in the business call chain model fragments to the monitoring system, and each business call chain model fragment records the portion of the called interface of the business system in the corresponding business call chain model.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
Method for quick modeling of Delta robot based on MAPLESIM
ActiveCN104802167AImprove design efficiencyThe solution accuracy is not highProgramme-controlled manipulatorGraphicsAnimation
The invention discloses a method for quick modeling of a Delta robot based on MAPLESIM. The method is characterized by comprising the following steps of 1, according to the multibody mechanical graph theory principle, abstracting a mechanism topology configuration of the actual Delta robot into a linear graph, and expressing in a character and graph type; 2, sequentially selecting the required elements from a built MAPLESIM element base, and setting attributes and parameters; 3, according to the linear graph, connecting the elements and components, and building a single-branch chain physical model of the Delta robot; 4, copying the built single-branch chain model in step 3 into two other branch chains, and connecting the three branch chains in parallel to build a complete basic model of the Delta robot; 5, solving the built single-branch chain model in step 4, and simulating the motion control on the complete model according to the solved explicit inverse solution. The method has the advantage that by operating the MAPLESIM to analyze, the built model is tested according to the three-dimensional cartoons and tracks, so as to obtain the satisfactory property.
Owner:SOUTHEAST UNIV
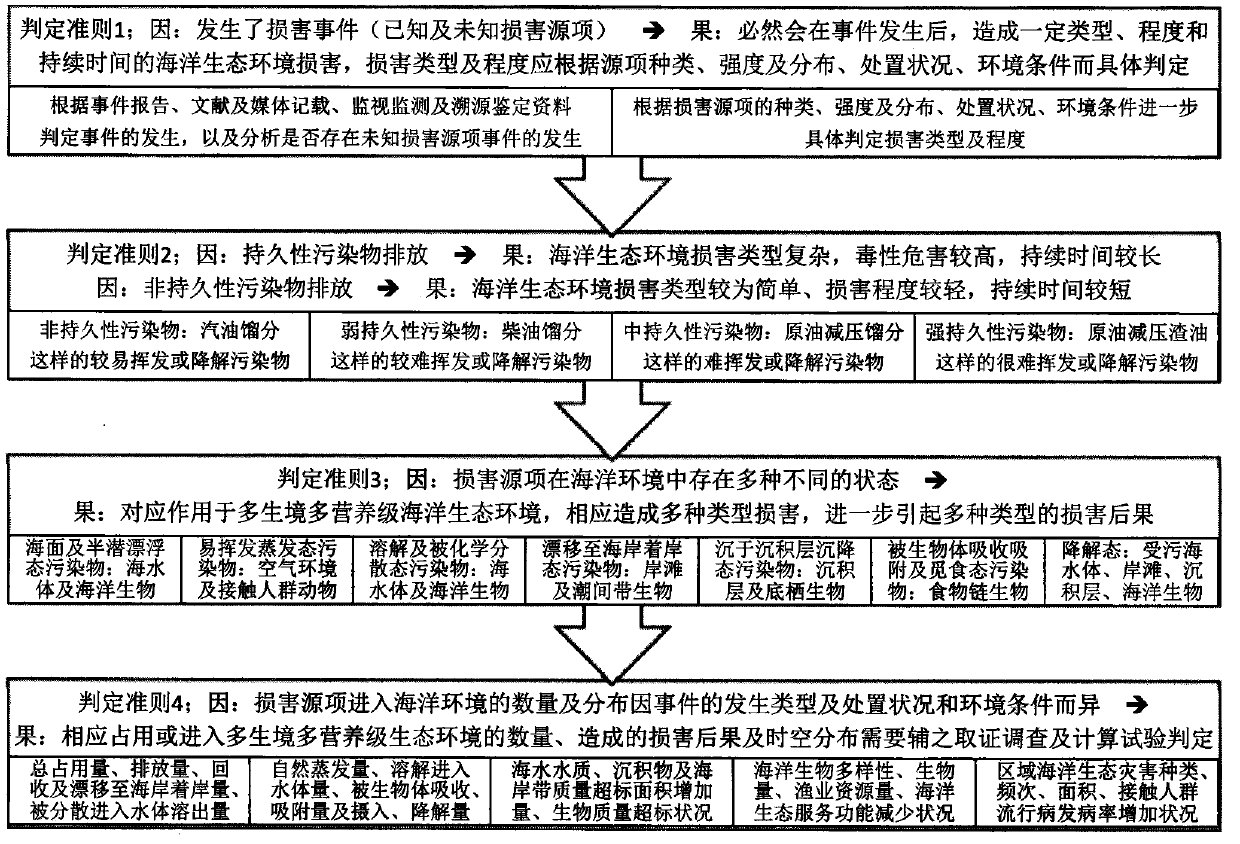
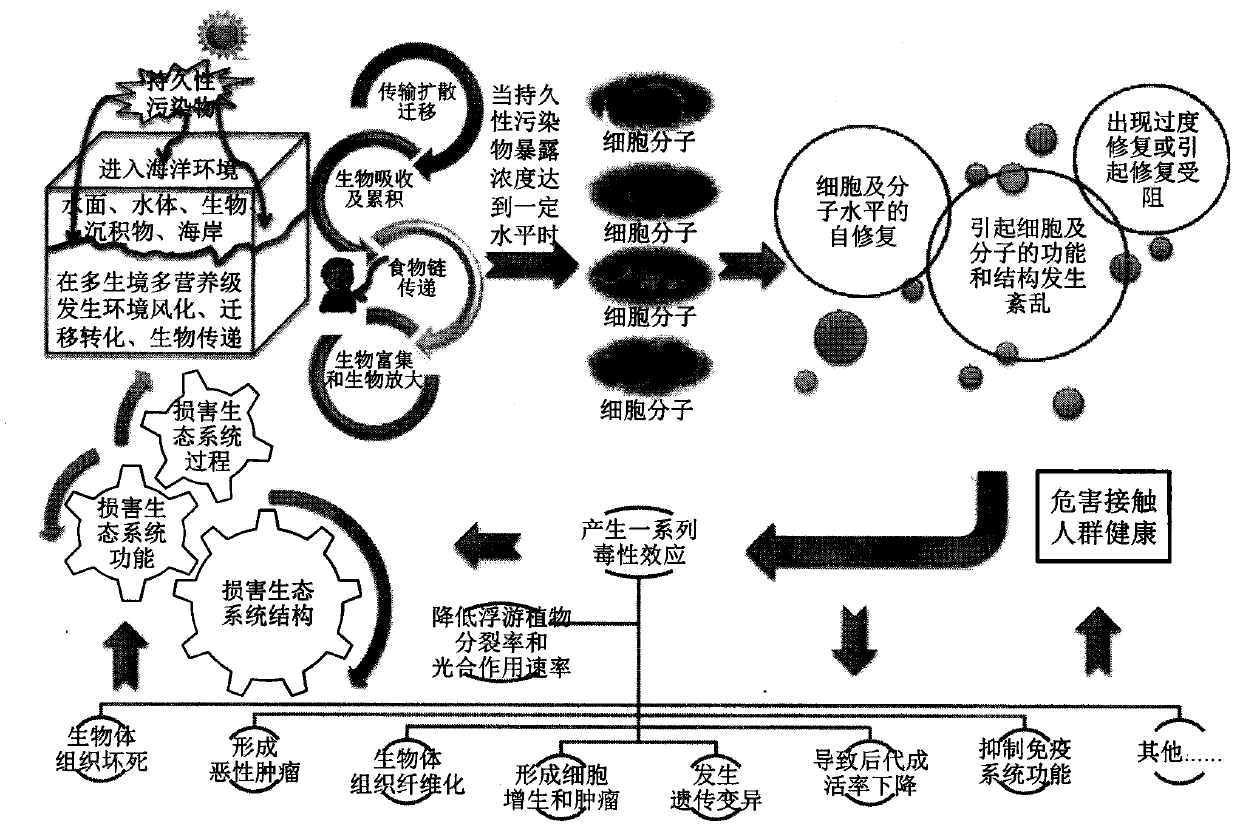
Determination method of marine ecological environment damage causal-relationships
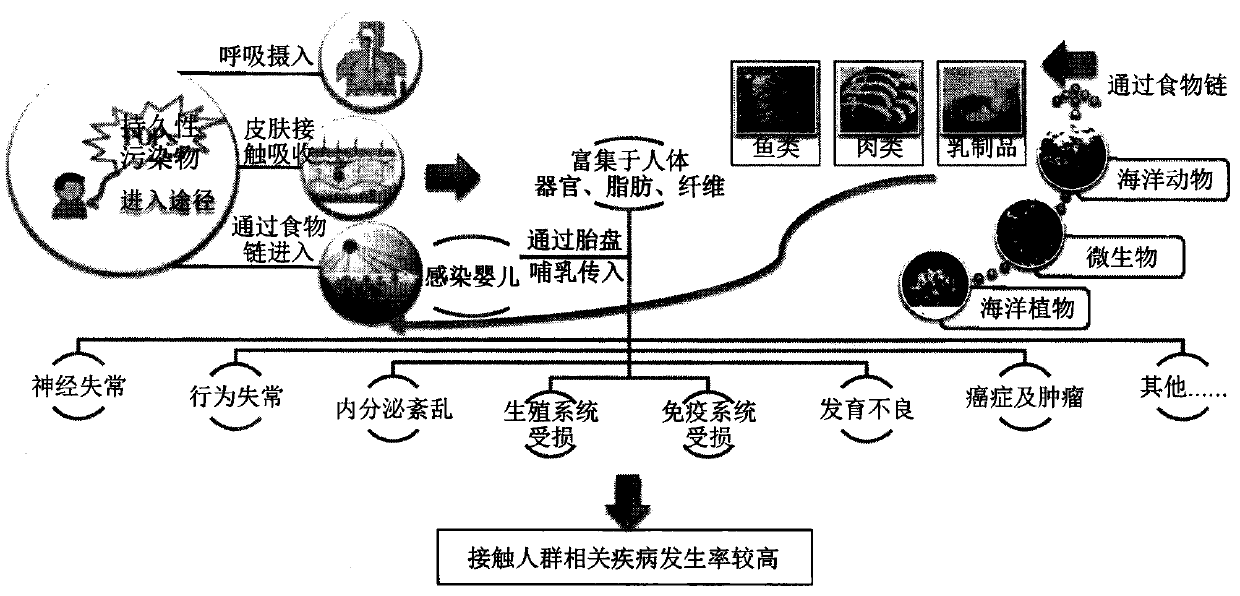
The invention discloses a determination method of marine ecological environment damage causal-relationships, and belongs to the technical fields of marine ecological environment protection and pollution damage identification and evaluation. The method includes 6 marine ecological environment damage causal-relationship chain model, 4 types of causal-relationship determination criteria and indicators with logical progressive relationships, a multi-type auxiliary evaluation model system architecture scheme matching the determination criteria, a marine ecological environment damage environment baseline and damage degree determination criterion and indicator system construction scheme of distinguishing regions, classes, items and levels and a quantitative determination method of damage degreesof the vulnerable factors and contribution of damage source items. A set of clear, simple, fast, systematic and effective causal-relationship determination technology support is provided for scientific determination of damage and consequences caused on marine ecological environments and human body health by sea-related-engineering, production and life pollution emission and suddenly occurring pollution events, identification, evaluation, blaming and compensation of damage and active and effective taking of countermeasures of prevention, preparation and disposal of pollution damage and environment restoration.
Owner:CHINA WATERBORNE TRANSPORT RES INST
A method for modeling rigidity of a transmission chain of a double-screw drive system
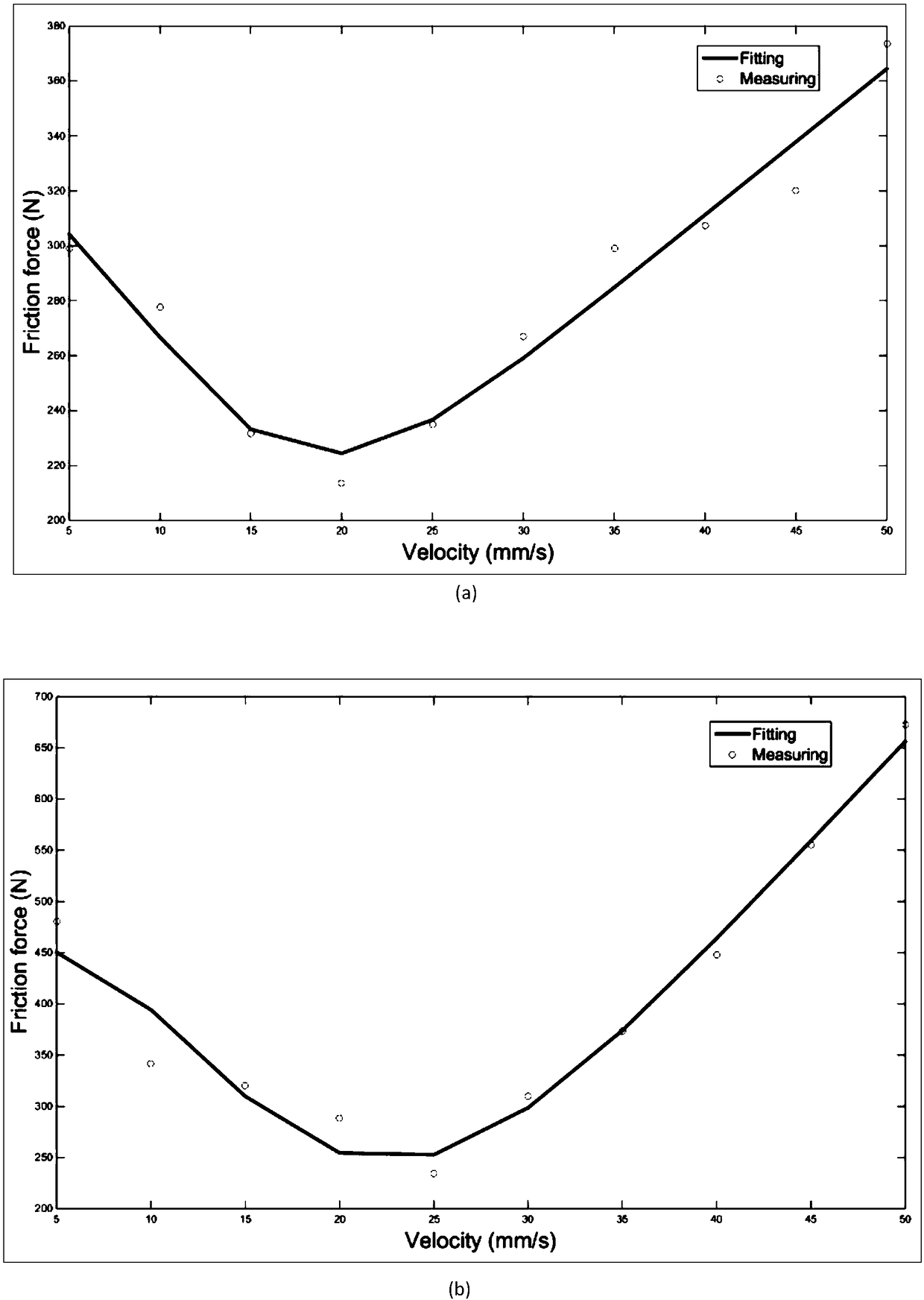
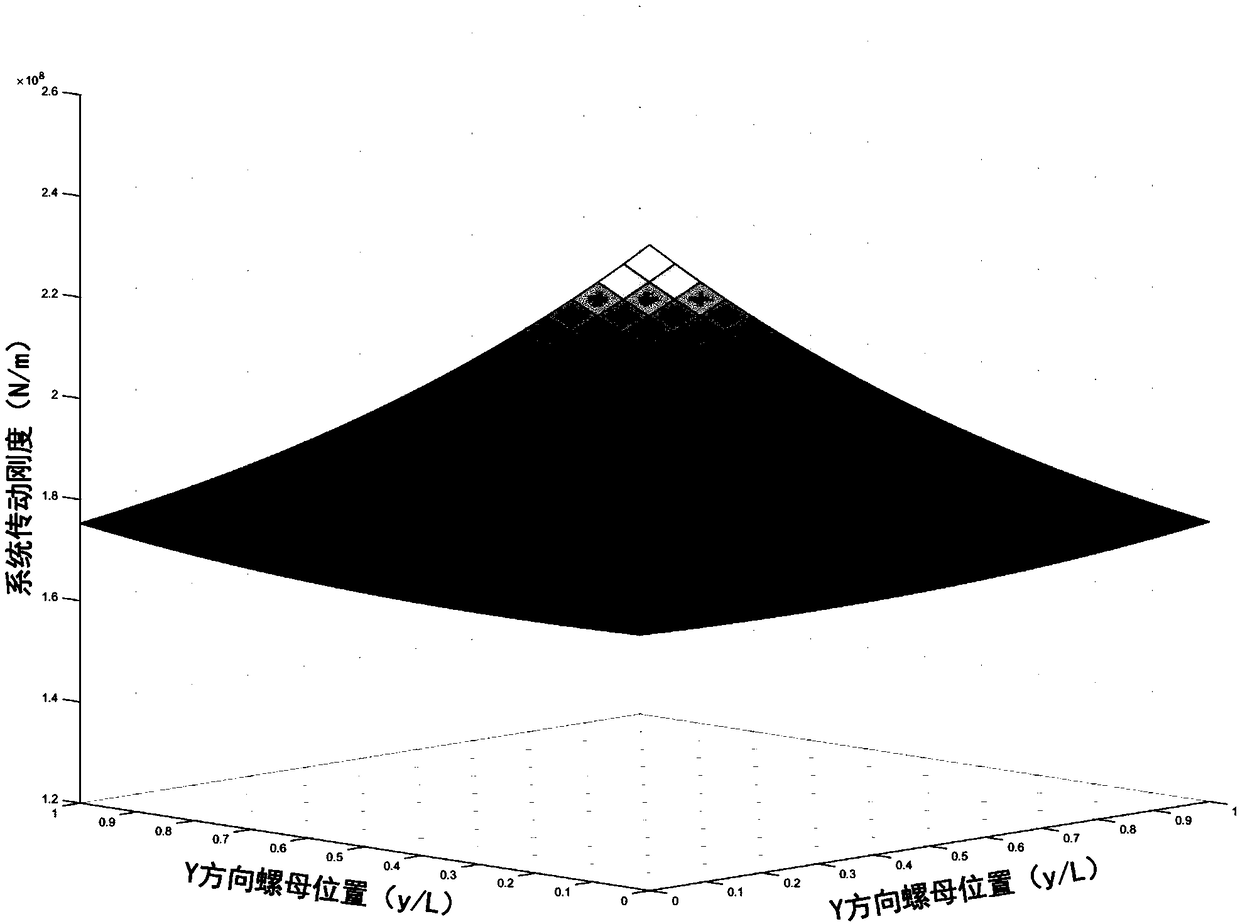
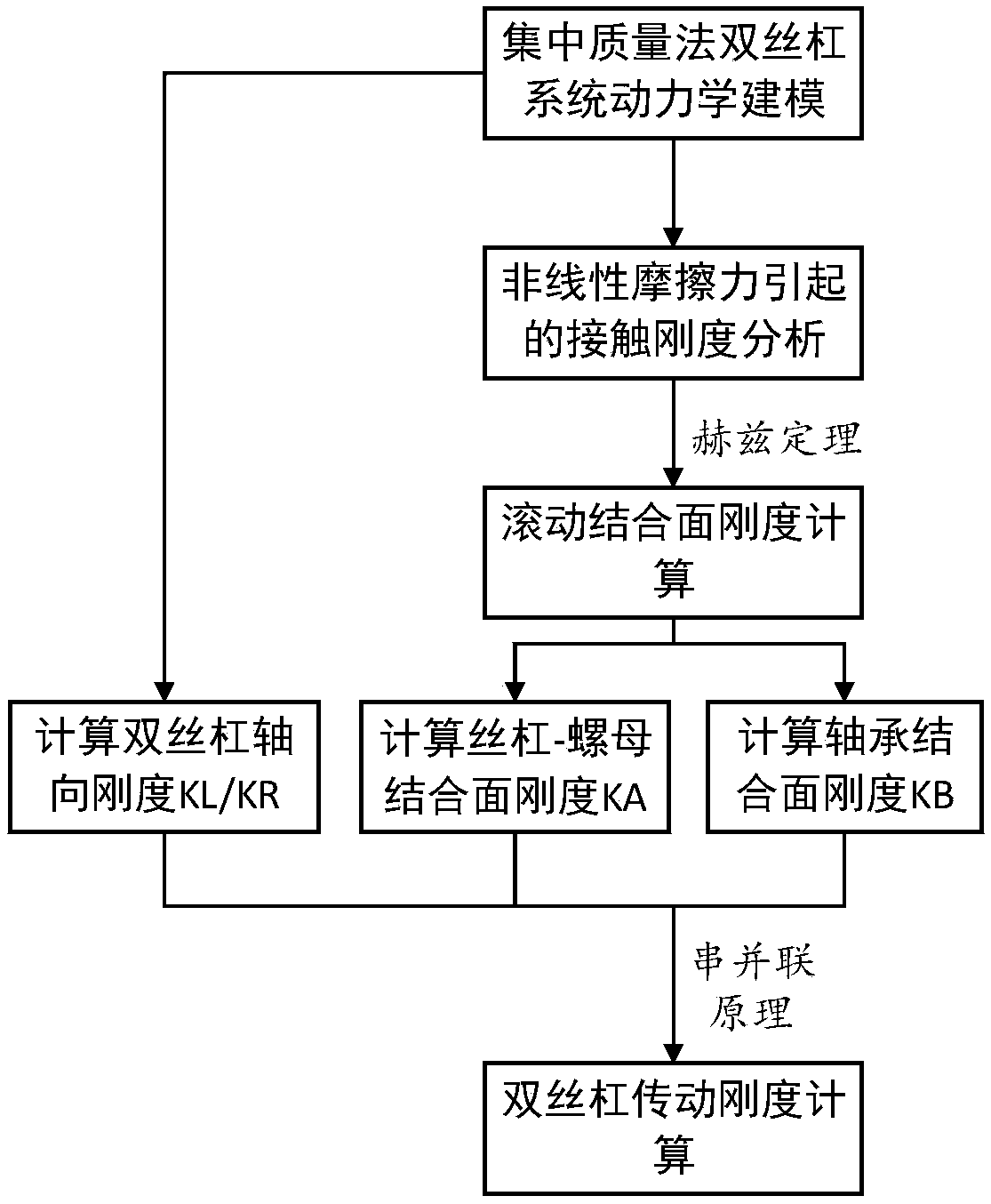
ActiveCN108984831AAccurately Calculated Stiffness ValuesImprove modeling accuracyGeometric CADMachine gearing/transmission testingEngineeringHertz
A method for modeling rigidity of a transmission chain of a double lead screw drive system includes as the steps of calculating the rigidity of a rolling joint surface, analyzing the contact rigiditycause by friction force of lead screw, calculating the rigidity of fixed joint surface, modeling the dynamics of double lead screw, and calculating the rigidity of drive chain of double lead screw, etc, wherein the rolling joint surface comprises a lead screw-nut joint surface and a bearing joint surface, the fixed bonding surface includes a workbench-slide block joint surface, and the contact stiffness of the rolling joint is calculated by using the Hertz contact theory; establishing a friction model and taking into account the stiffness change of the joint surface caused by the friction force of the lead screw; considering the coupling effect of the worktable, establishing an accurate rigidity chain model of the double screw drive system by using the centralized mass method, thereby improving the dynamic modeling accuracy of the double screw drive system and the asynchronous error of the double-drive feed and improving the positioning accuracy of the double-drive machine tool. The method solves the problem that the rigidity of the joint surface is ignored in the dynamics modeling of a conventional double-screw drive system, and the model accuracy is low.
Owner:WUHAN UNIV OF TECH
Method for constructing a three-dimensional digital block chain weight determination system
InactiveCN109064152ARealize traceabilityProtection of legitimate rights and interestsPayment architectureProgram/content distribution protectionTimestampTrusted timestamping
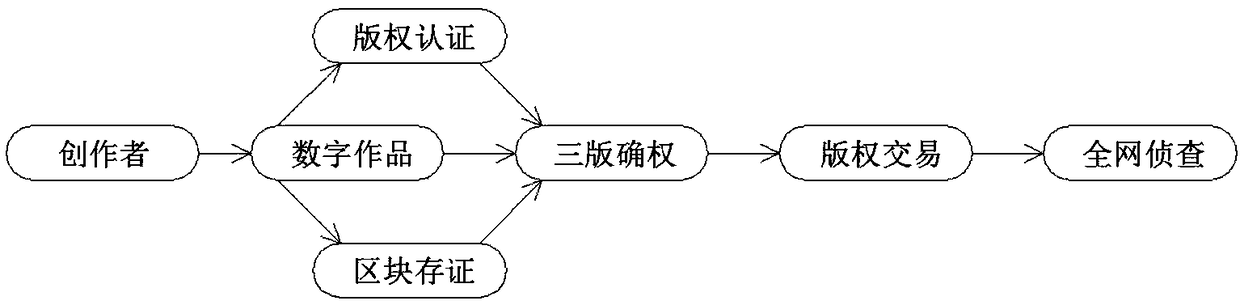
The invention provides a method for constructing a three-dimensional digital block chain confirmation system. The method comprises the following steps of: uploading a work; Copyright Certification; Block Depository; The third edition confirms the right; Copyright trading; Net-wide investigation. The invention adopts a self-developed block chain copyright registration network, Match trusted timestamp, chain stamp double authentication, Generating copyright DNA for each original model can really realize the traceability of three-dimensional model, and the copyright guardian based on the block chain model certification system and the whole network copyright monitoring tool can monitor the network infringement of original works, reconstruct the industry order, make the sovereignty belong to three-dimensional designers, and ensure the legitimate rights and interests of three-dimensional designers.
Owner:十一维度(厦门)网络科技有限公司
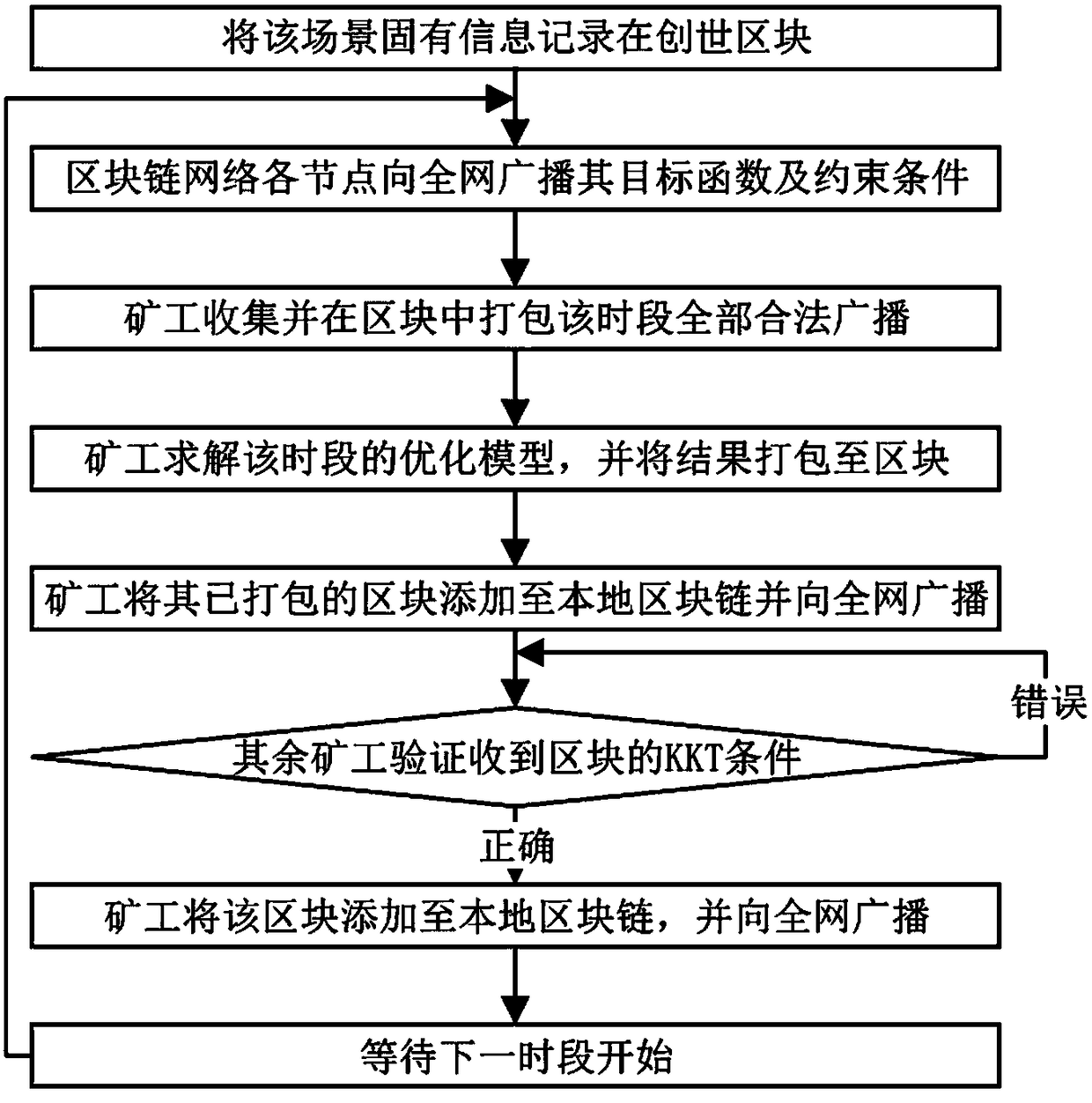
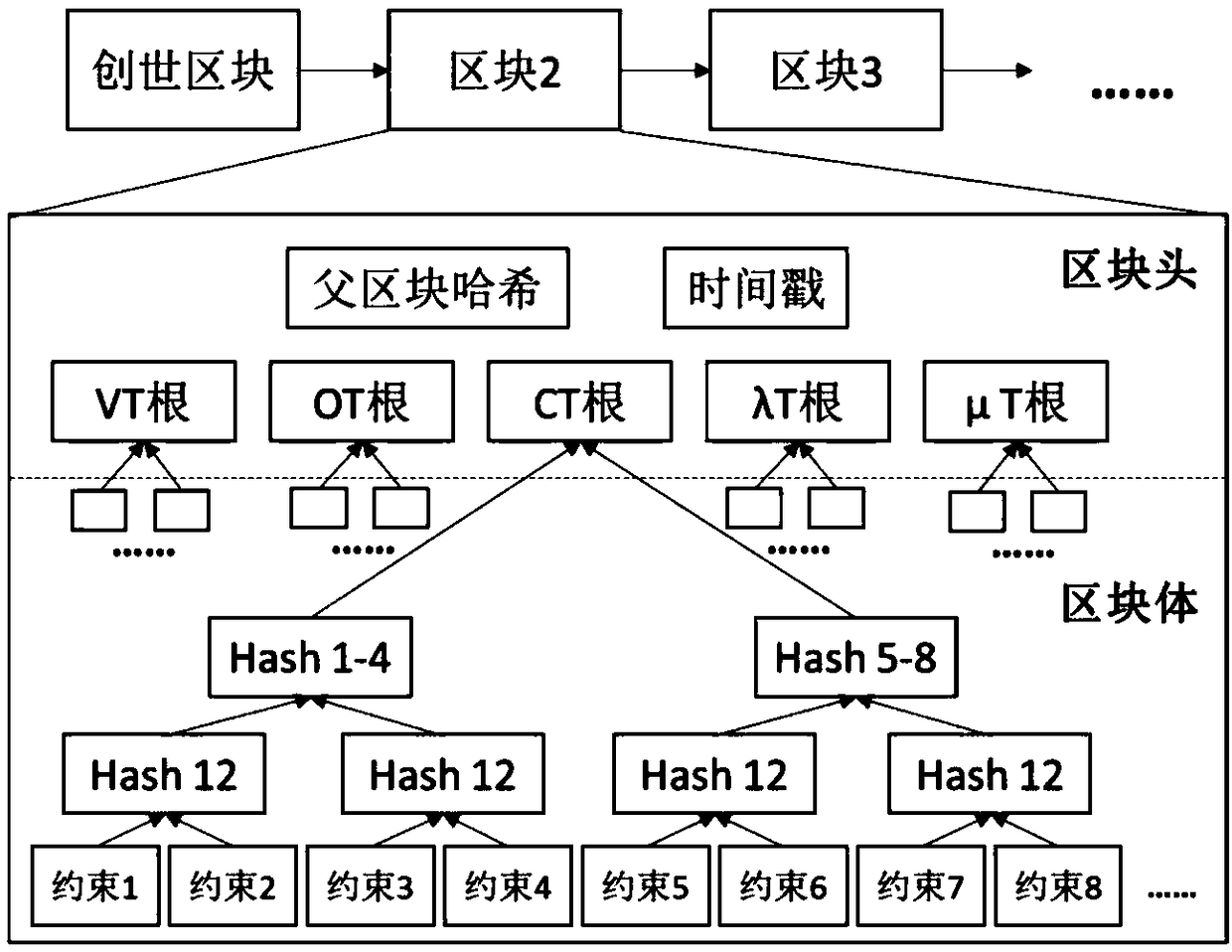
Energy system optimization method based on block chain in complex scenarios
ActiveCN109102120AImprove securityHigh degree of opennessDatabase distribution/replicationForecastingEnergy system optimizationElectric power system
The invention provides a block chain-based energy system optimization method in complex scenarios after initialization. The optimization problem is solved through the nodes of the whole network, the node with the fastest solution obtains the block bookkeeping right and broadcasts it to the whole network, blocks received by other nodes are verified for correctness, the verified block is the globaloptimal solution of the convex optimization model of the power system, and can be confirmed and broadcasted to the whole network. The energy block chain model proposed by the invention can meet the requirements of the security, openness, throughput and the like of the complex optimization scene of the power system, and has the landing and application capability.
Owner:SHANGHAI JIAO TONG UNIV +1
APT attack behavior analysis and detection method and device based on cascade attack chain model
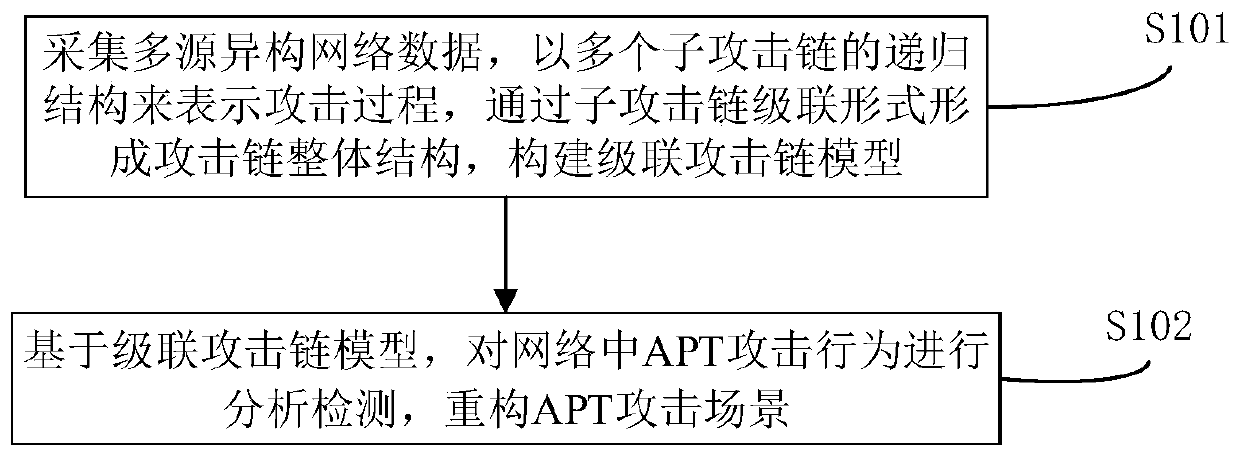
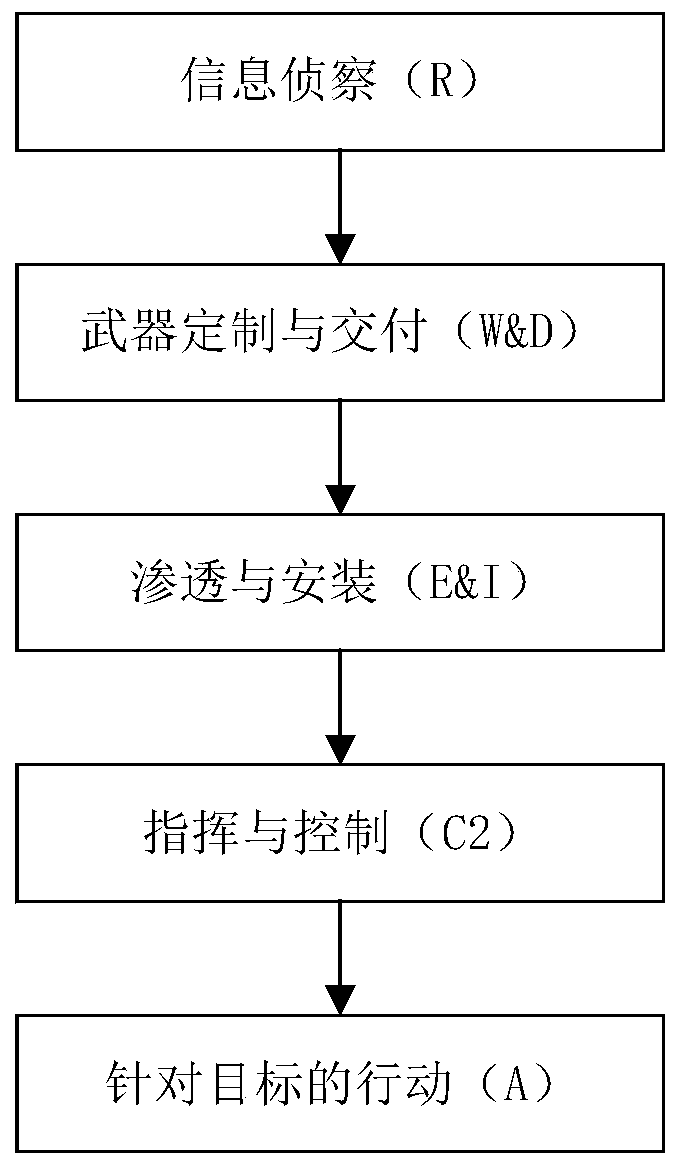
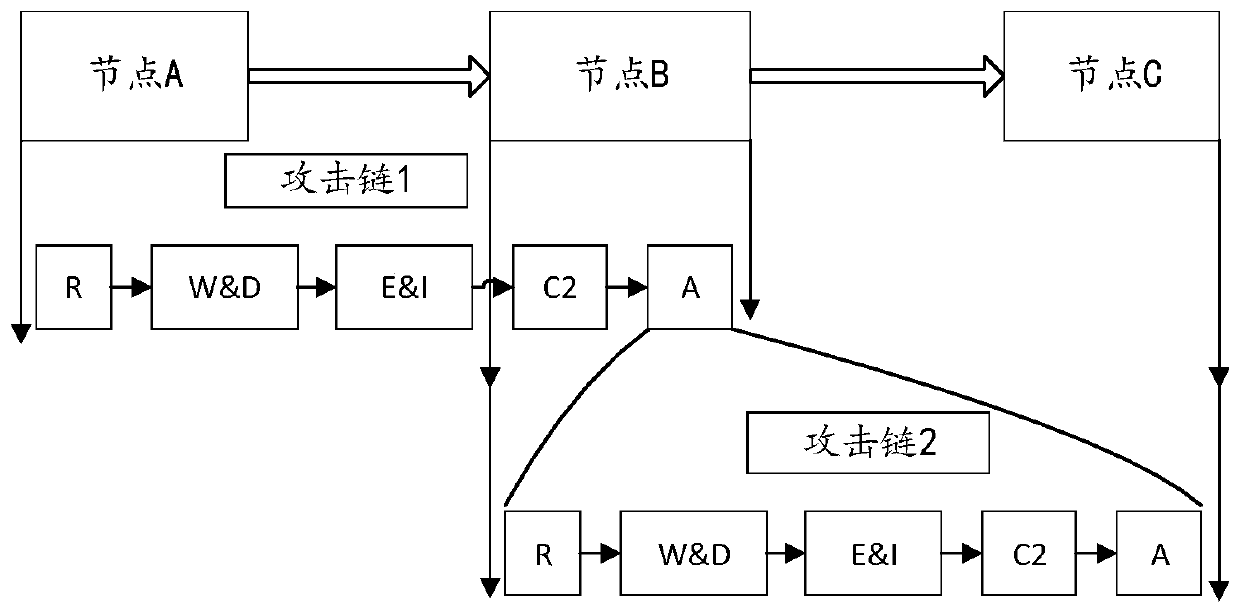
ActiveCN110602042AAdapt to network environment attack behavior detectionLower the threshold for professional knowledge requirementsTransmissionHeterogeneous networkAnalysis method
The invention belongs to the technical field of network security, in particular to an APT attack behavior analysis and detection method and device based on a cascaded attack chain model, and the method comprises the steps: collecting multi-source heterogeneous network data, representing an attack process through the recursive structure of a plurality of sub-attack chains, forming an attack chain overall structure in a sub-attack chain cascading mode, and constructing the cascaded attack chain model; and based on the cascade attack chain model, analyzing and detecting APT attack behaviors in the network, and reconstructing an APT attack scene. According to the method, the limitation of the prior art is overcome, the APT attack behavior is effectively recognized and analyzed, the defect thatan existing analysis method excessively depends on manual analysis is overcome, the accuracy of attack behavior detection is improved, and the method can be conveniently applied to actual analysis.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
Method for dynamically building marine application service chain
InactiveCN102594851AResolve identifiabilitySolve management problemsTransmissionChain modelOperating system
The invention discloses a method for dynamically building and realizing a marine application in a dynamic service chain manner. The method comprises the steps: 1, abstracting atomic service, wherein a normalized atomic service interface is confirmed; 2, abstracting service chain model elements, wherein a visualized representation form of the basic elements of the service chain, as well as a description method, a constraint and the like, is defined; 3, creating a service chain, wherein a service chain model aiming to a specific marine application is formed based on a visualized operation interface; 4, validating the service chain, wherein the validity and logicality of the marine application service chain created by a user are validated; and 5, managing the service chain, wherein monitoring and management are carried out over the forming and implementation sequence of the service chain, and over the state of each atomic service of the service chain. The method provided by the invention is capable of visually and quickly realizing the novel marine application requirement, and has the advantages that what you see is what you get, and flexible and dynamic performances are provided.
Owner:INST OF REMOTE SENSING & DIGITAL EARTH CHINESE ACADEMY OF SCI
Assembly position precision analysis method considering geometric tolerance and deformation influence
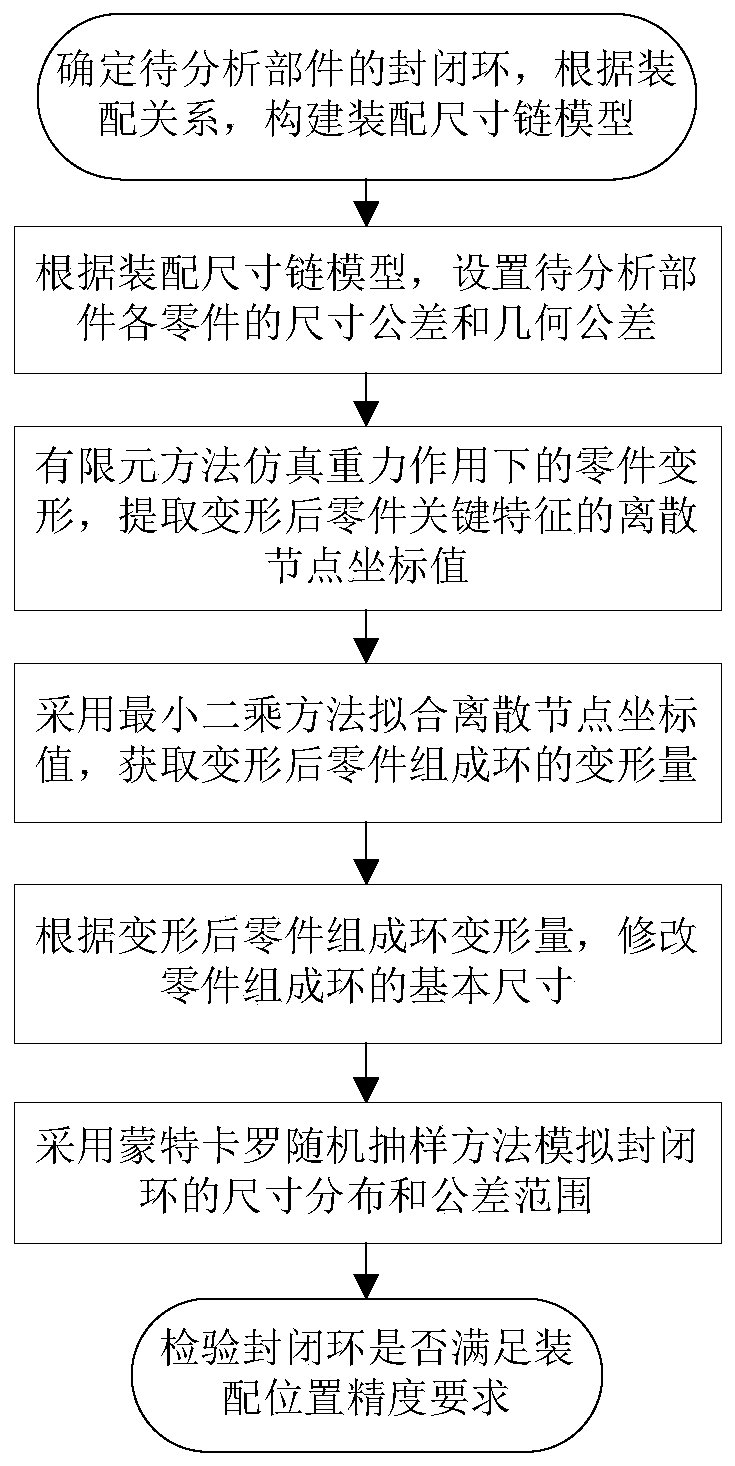
PendingCN110276108ASolving the Problem of Accuracy AnalysisThe analysis result is accurateGeometric CADDesign optimisation/simulationBasic dimensionExtended finite element method
The invention discloses an assembly position precision analysis method considering geometric tolerance and deformation influence. The method comprises the following steps: determining a closed ring of a to-be-analyzed part, and constructing an assembly dimension chain model according to an assembly relationship; according to the assembly dimension chain model, setting the dimension tolerance and the geometric tolerance of each part forming ring of the to-be-analyzed part; simulating part deformation under the action of gravity by a finite element method, and extracting discrete node coordinate values of key characteristics of the deformed part; fitting discrete node coordinate values by adopting a least square method, and obtaining the deformation amount of a ring formed by the deformed part; according to the deformation of the deformed part forming ring, modifying the basic size value of the part forming ring; simulating the size distribution and tolerance range of the closed ring by adopting a Monte Carlo random sampling method; and detecting whether the closed ring meets the crankshaft assembly position precision requirement or not. According to the method, whether the tolerance of each currently arranged part forming ring can meet the assembly position precision can be analyzed.
Owner:NANJING UNIV OF SCI & TECH
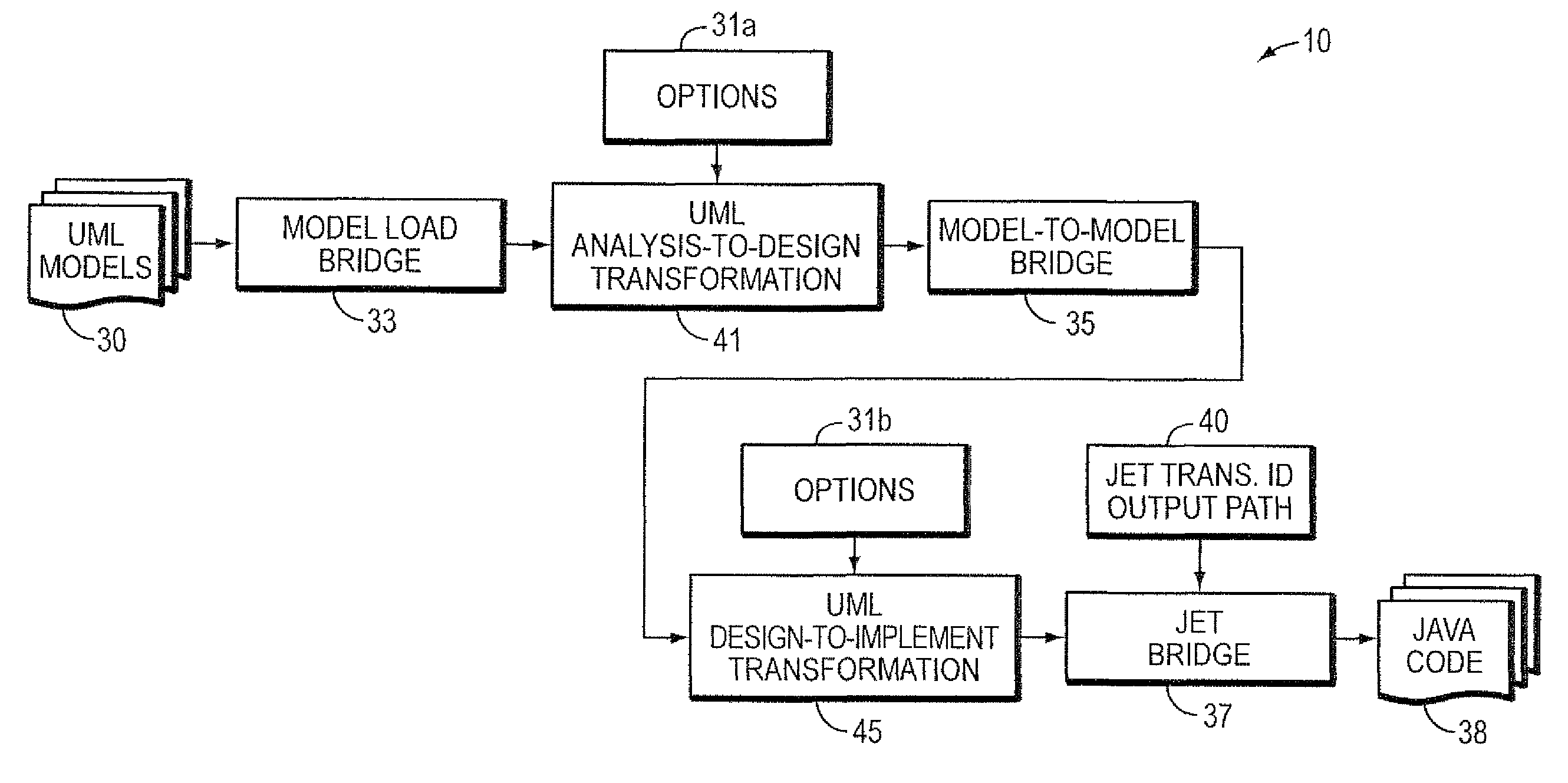
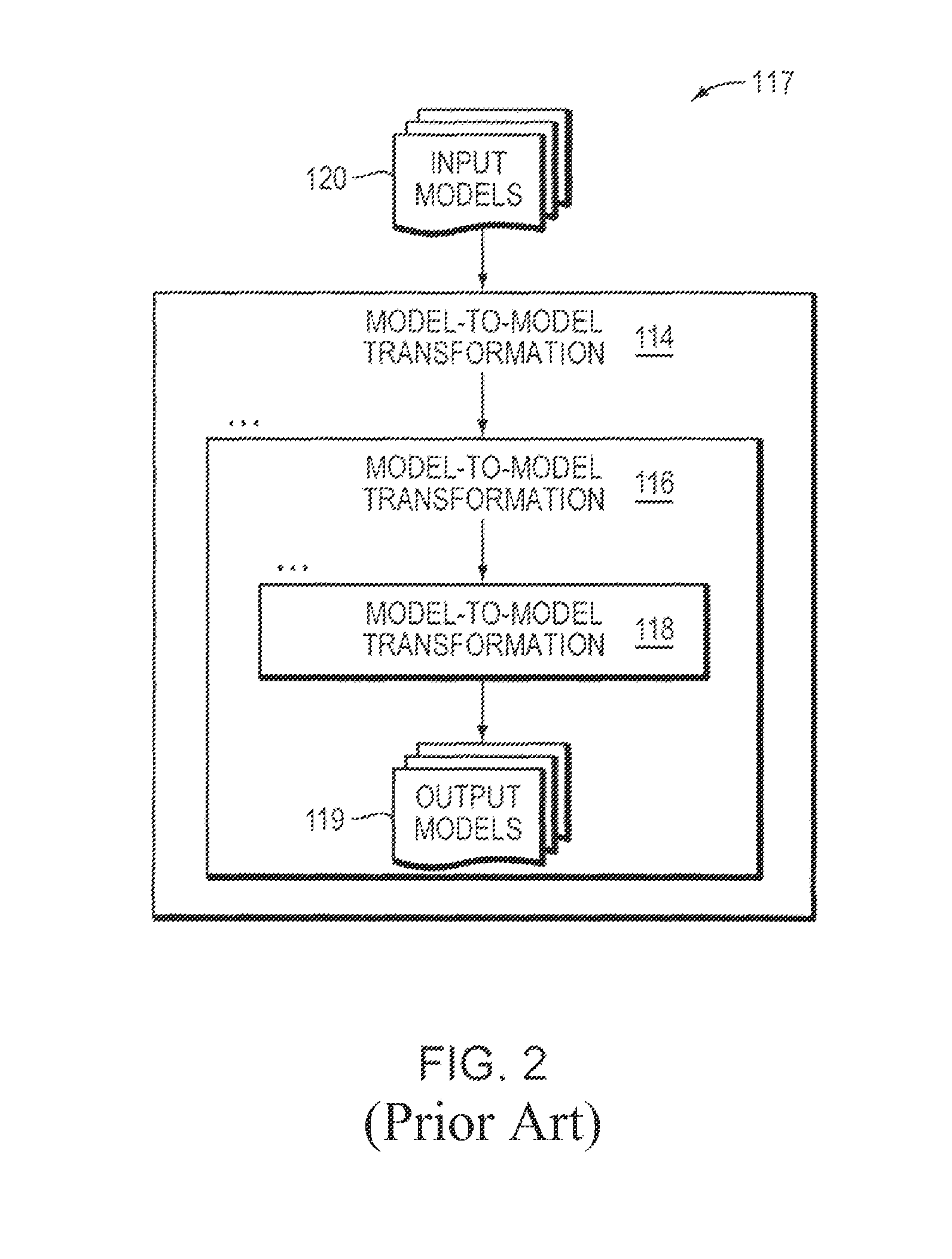
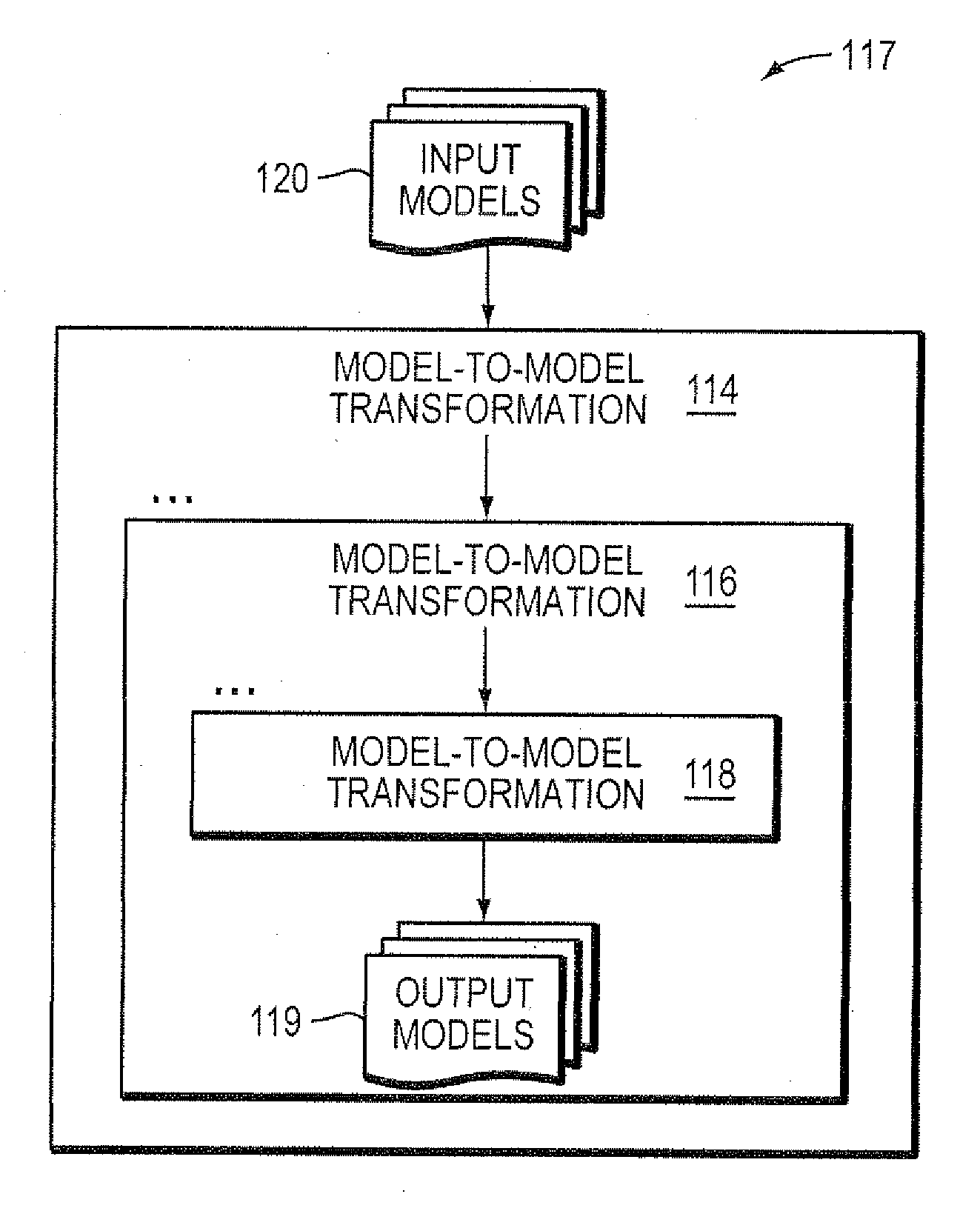
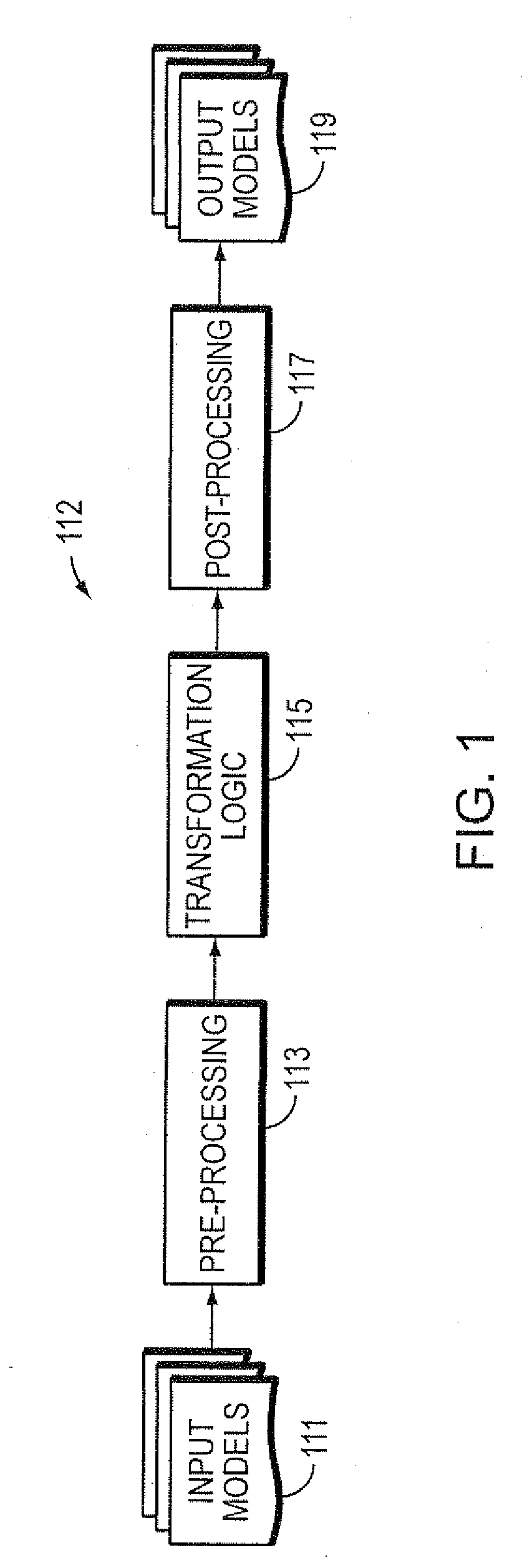
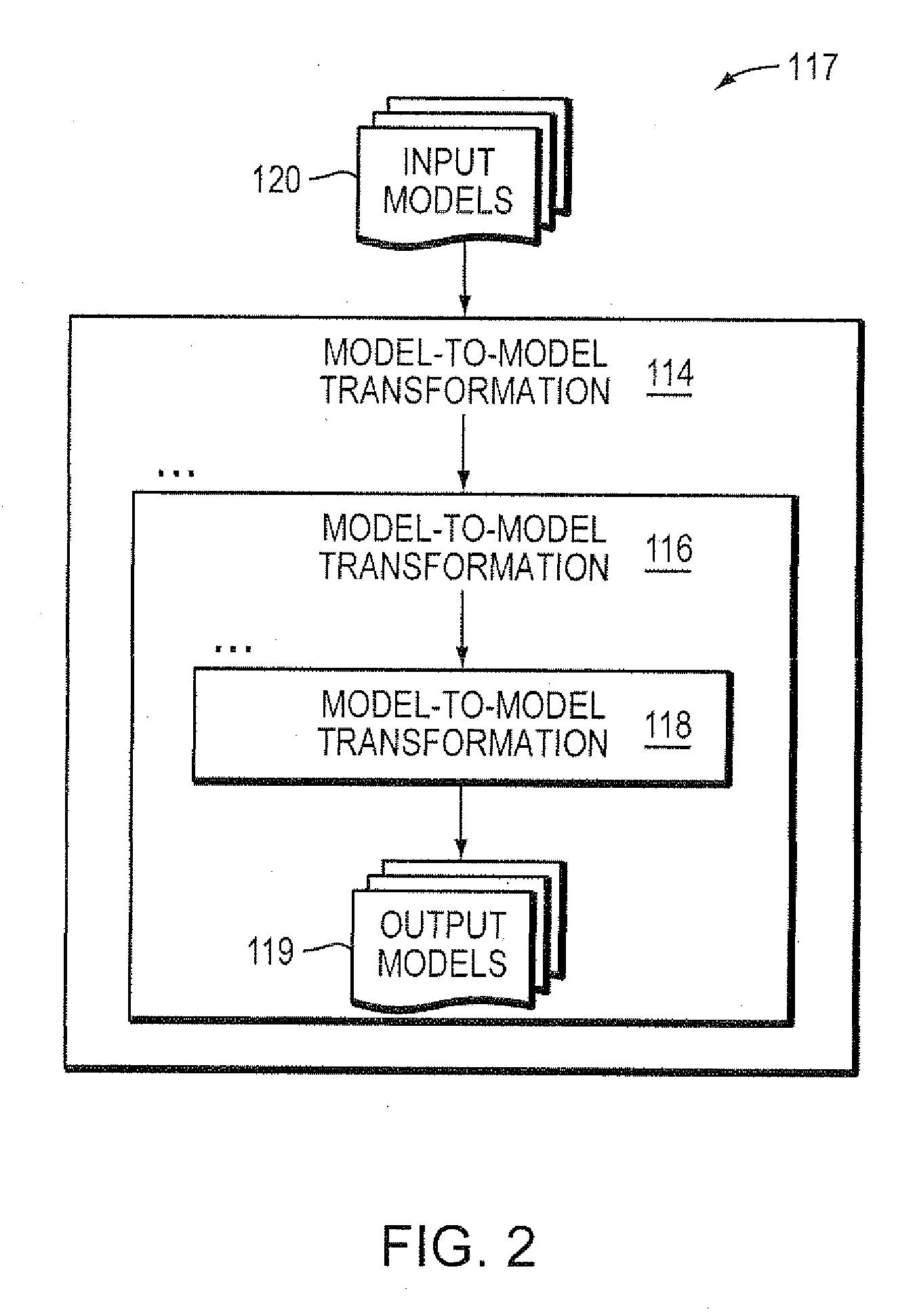
Computer method and apparatus for chaining of model-to-model transformations
InactiveUS8583413B2Precise interfaceEasy to reuseSoftware engineeringComputation using non-denominational number representationLink modelAlgorithm
Computer method, apparatus and system chains model-to-model transformations. In a series of model transformations, there are respective bridges before and after each model transformation. For each pair of consecutive model transformations in the series, the respective bridge (i) receives a model output from a first model transformation of the pair, the received model being in the respective output model format of the first model transformation of the pair, (ii) prepares the received model as input to a second model transformation of the pair, including preparing the received model to be in the respective input model format of the second model transformation of the pair, and (iii) inputs the prepared model to the second model transformation of the pair. The series of model transformations and respective bridges provide chaining of the model-to-model transformations. Each model transformation in the series is able to be separately configured.
Owner:INT BUSINESS MASCH CORP +1
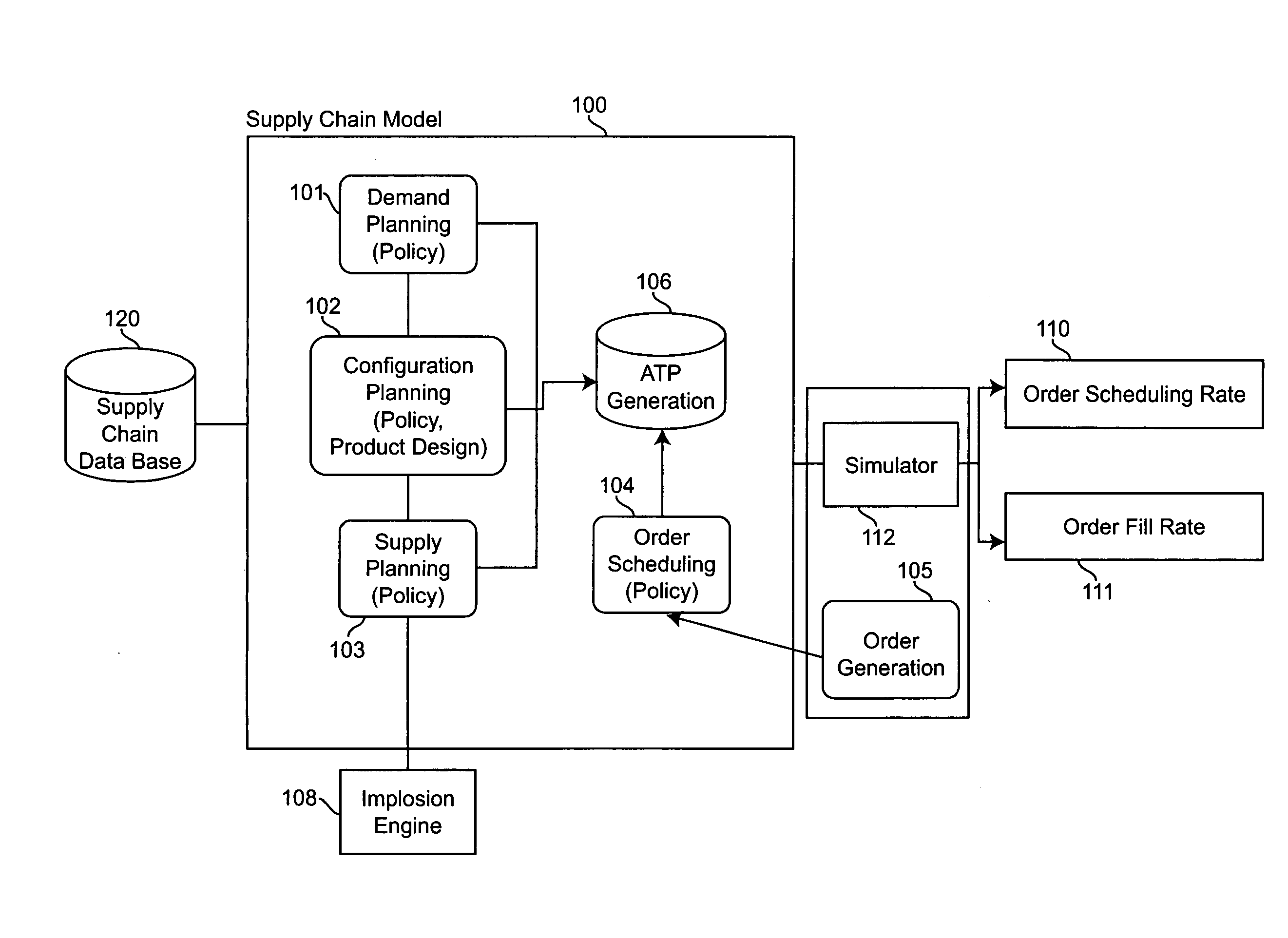
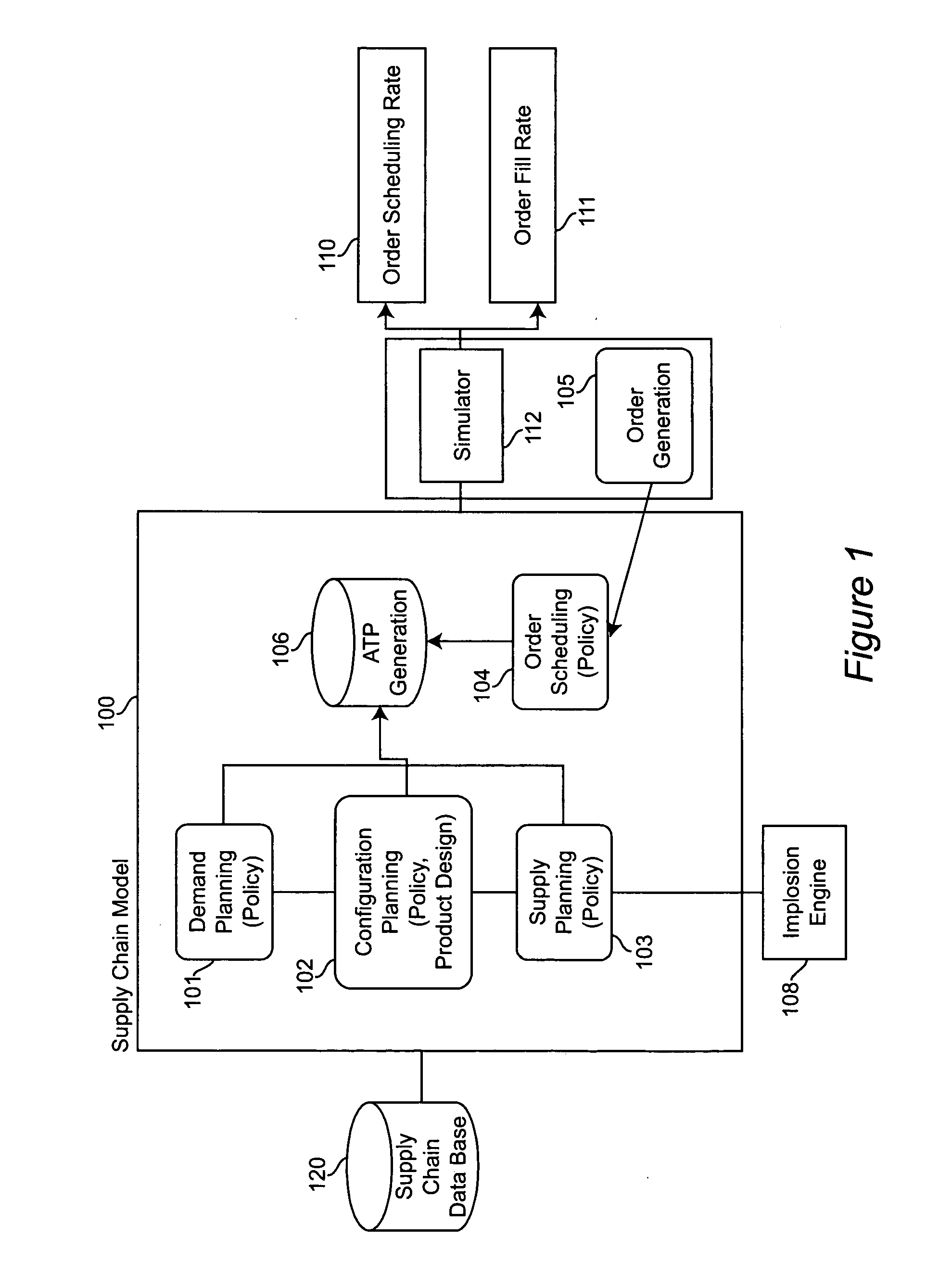
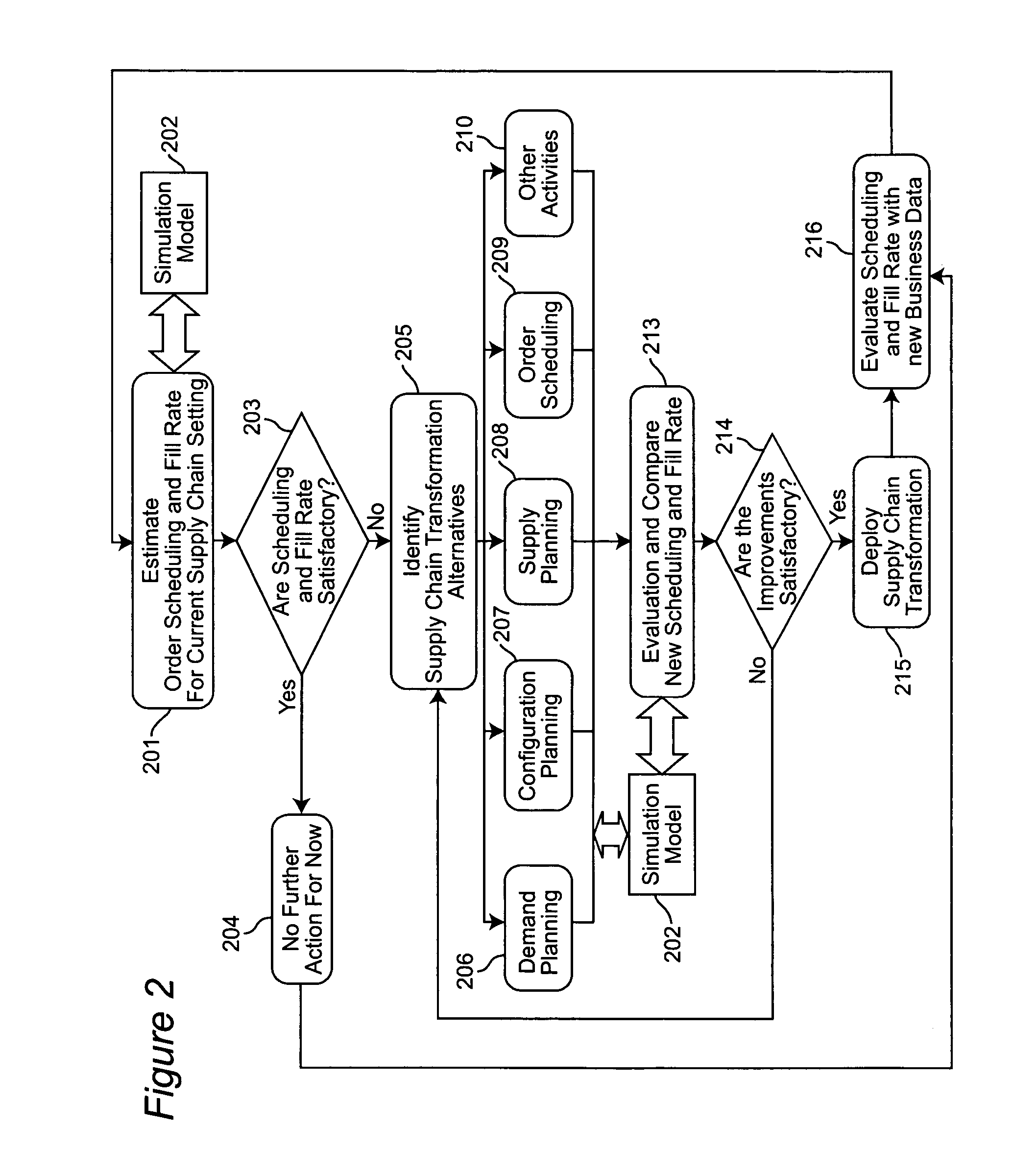
Method and system for estimating order scheduling rate and fill rate for configured-to-order business
InactiveUS20070010904A1Improve performanceTighter capacityResourcesSpecial data processing applicationsFill rateScheduling function
A system and method estimates performance of a supply chain's available-to-promise (ATP) and scheduling functions under various environmental and process assumptions. The supply chain's transformation alternatives are identified using a plurality of modules constituting a supply chain model and including a demand planning module, a configuration planning module, an order scheduling module and a supply planning module, each of said modules being reconfigurable using various policies, which policies, taken together, specify a particular supply chain design that is to be analyzed. A supply chain data base is accessed by the supply chain model to retrieve data elements that dictate appropriate policies within said plurality of modules. The supply chain performance is simulated based on settings of the modules and other environmental factors including demand uncertainty, order configuration uncertainty, supplier flexibility, supply capacity, and demand skew. Based on the simulation, scheduling and fill rate of new business settings are evaluated to determine if improvements to the supply chain are satisfactory.
Owner:IBM CORP
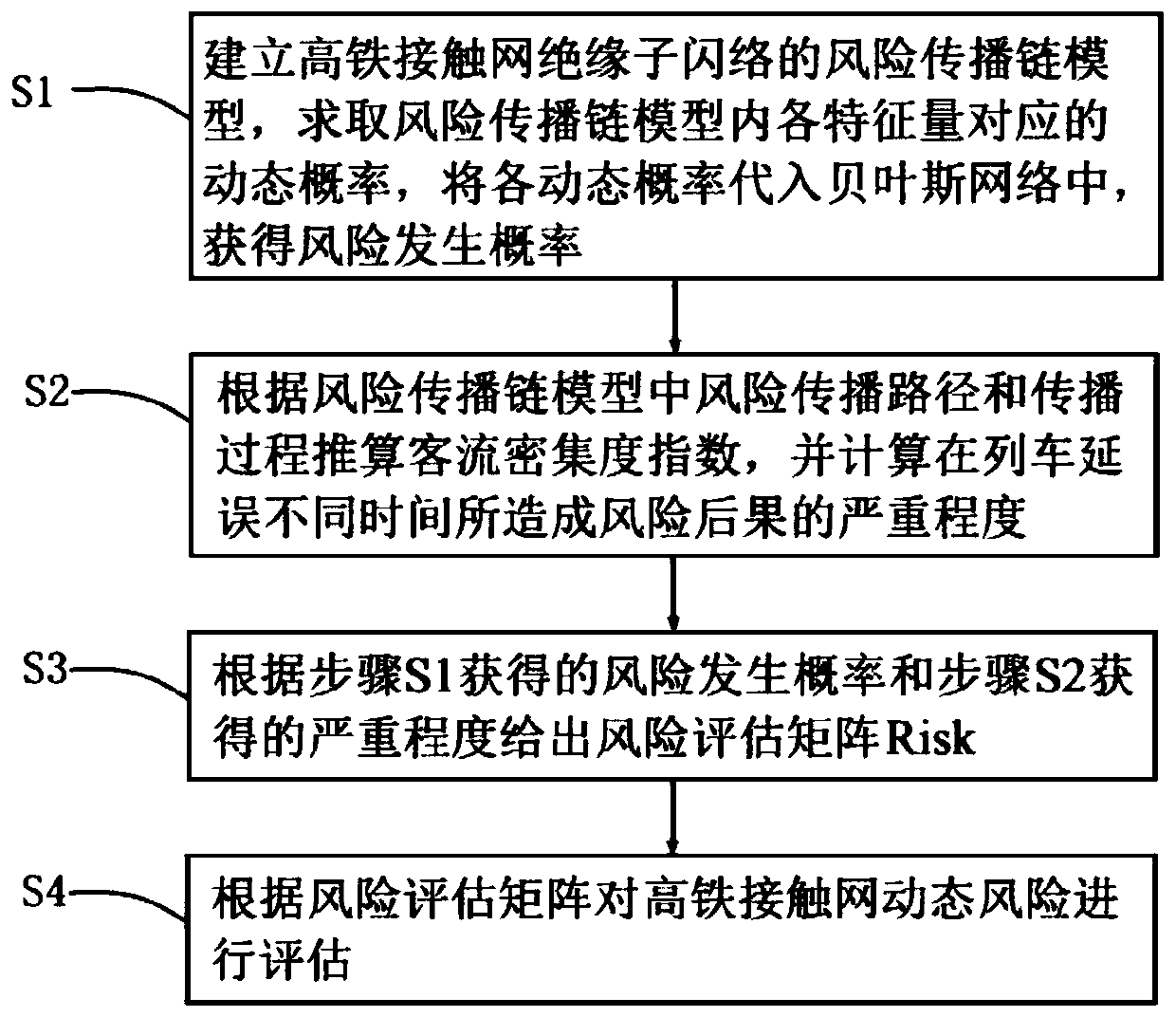
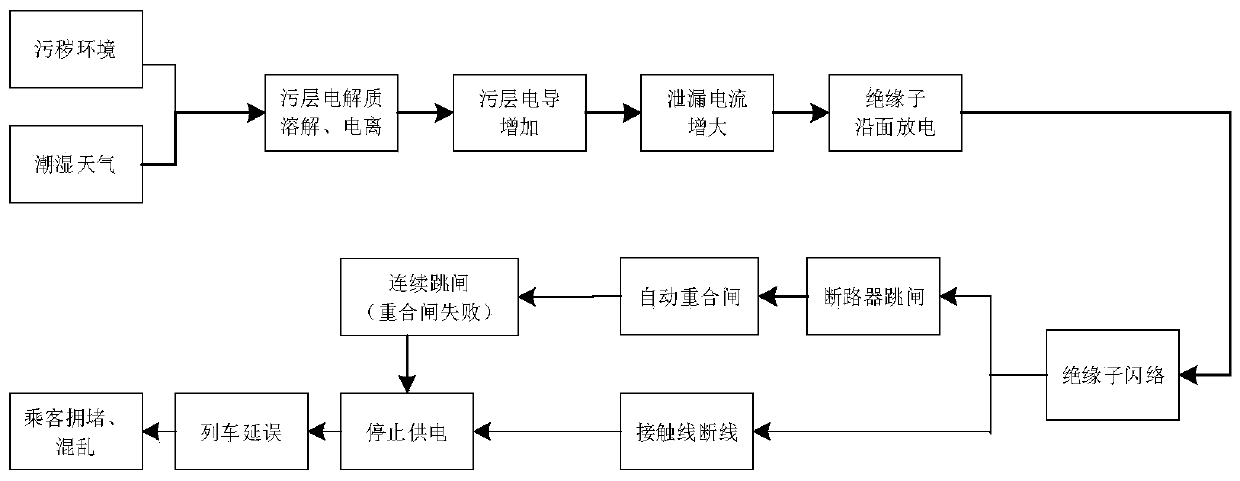
A Bayesian network-based dynamic risk analysis method for a high-speed rail contact network
The invention provides a Bayesian network-based dynamic risk analysis method for a high-speed rail contact network, which comprises the following steps of: establishing a risk propagation chain modelof high-speed rail contact network insulator flashover, carrying out characteristic quantity-dynamic probability dynamic mathematical modeling on the risk chain model, and putting the risk chain modelin a Bayesian network for calculation to obtain a risk occurrence probability; Using the passenger flow intensity index to determine the severity of risk dynamics in both time and space dimensions, taking basic time granularity and stations as basic units for obtaining real-time monitoring data, taking a risk propagation path and a propagation process as a passenger flow density index calculationprinciple, and calculating the severity degree of risk consequences caused by delay of different times of a train; And combining the dynamic probability with the severity, and obtaining the dynamic risk level of the risk chain according to the risk assessment matrix.
Owner:TSINGHUA UNIV
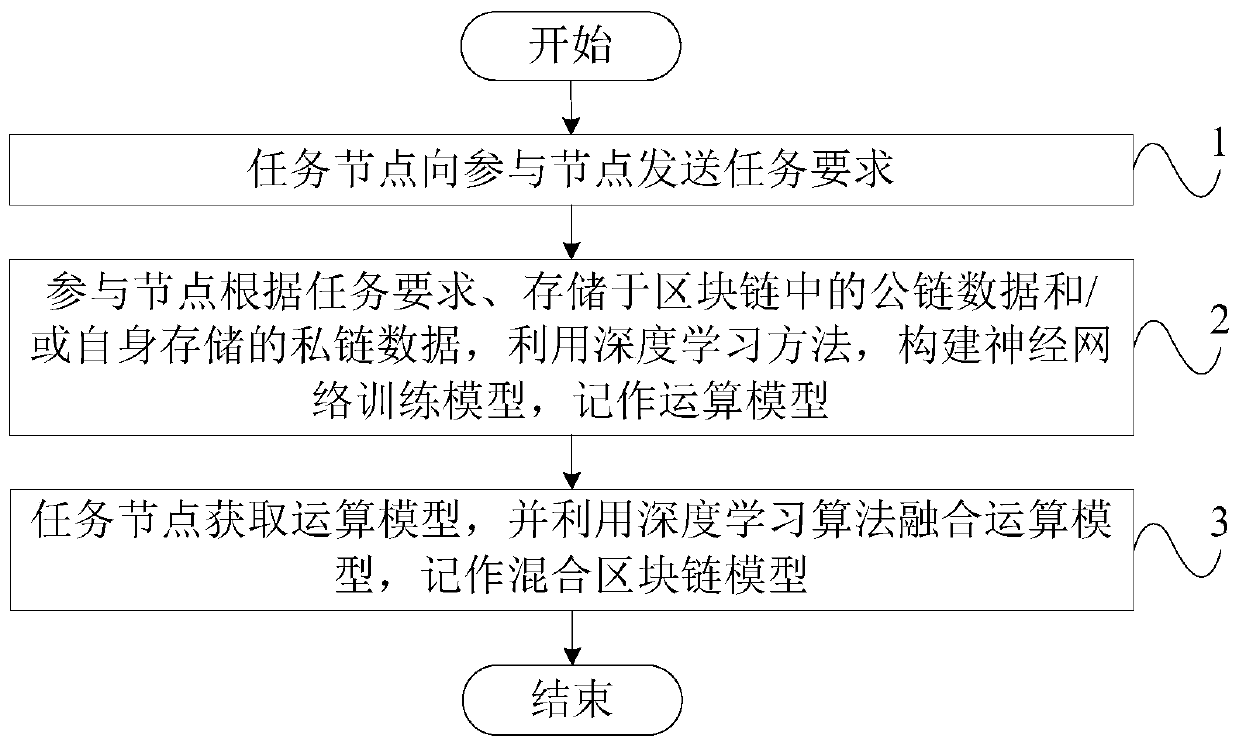
A hybrid block chain model construction method based on deep learning
ActiveCN109710691AReduce the likelihood of a fitImprove accuracyDatabase distribution/replicationOperation modelData storing
The invention discloses a hybrid block chain model construction method based on deep learning, a participation node in the method is used for constructing an operation model according to public chaindata and / or private chain data, a task node is used for constructing a hybrid block chain model according to the operation model, and the method comprises the following steps: the task node sends a task requirement to the participation node; the participation node constructs a neural network training model and records the neural network training model as an operation model by using a deep learningmethod according to task requirements, public chain data stored in a block chain and / or private chain data stored in the participation node; and the task node obtains the operation model, and utilizes a deep learning algorithm to fuse the operation model and record the operation model as a hybrid block chain model. Through the technical scheme provided by the invention, the utilization rate of private chain data in the block chain is favorably improved, and the accuracy in the block chain data processing process is improved.
Owner:TSINGHUA UNIV +1
System and method for simulation of insulator chain wind deflection angle measurement by employing wind tunnel experiment
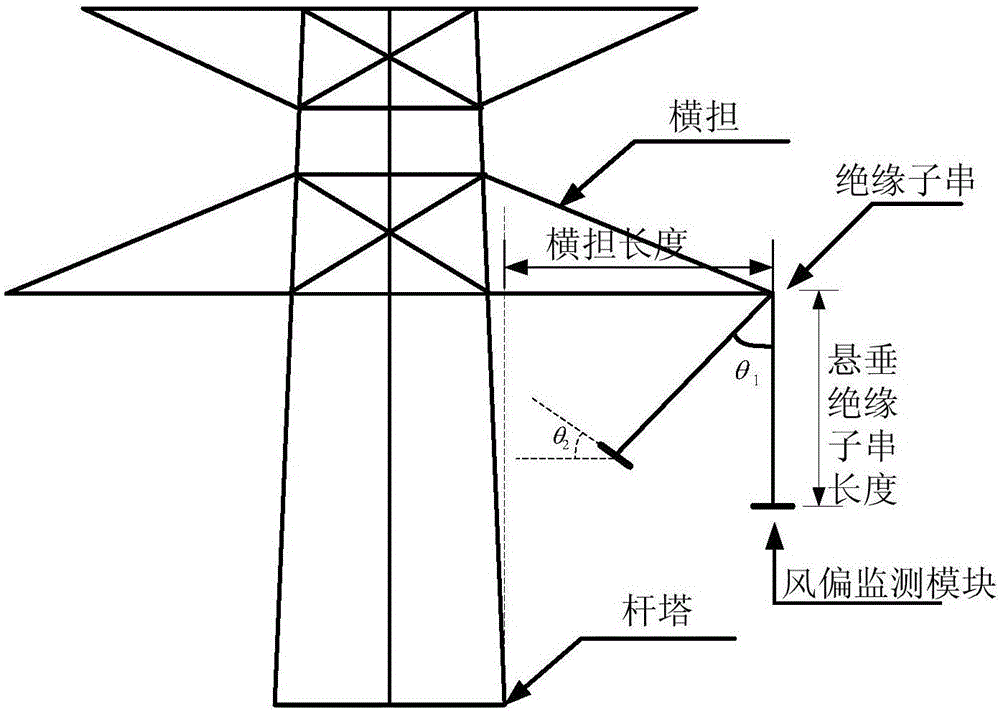
InactiveCN106500586AThe experimental results are accurateEasy to operateTransmission systemsAerodynamic testingWireless transmissionWind field
The present invention discloses a system and method for simulation of insulator chain wind deflection angle measurement by employing a wind tunnel experiment. The system comprises a wind tunnel, a ventilation device, at least three tower insulator chain models, a wind deflection angle monitoring module and a remote monitoring platform. The wind tunnel includes a wind tunnel body which is provided with an inlet, a power section, a transition section, a settling chamber, a contraction section, an experimental section and an expansion section in order; the ventilation device is installed at the power section of the wind tunnel body; the tower insulator chain models are installed at the experimental section of the wind tunnel body; and the wind deflection angle monitoring module is installed on the tower insulator chain models to monitor the insulator chain wind deflection angle data, and the insulator chain wind deflection angle data is transmitted to the remote monitoring platform through the wireless transmission network for processing. The system and method for simulation of insulator chain wind deflection angle measurement by employing the wind tunnel experiment can directly employ the wind tunnel to simulate the wind field for measurement of the wind deflection angle with no need for building a real transmission line tower for experiment, and can ensure that the experiment result is accurately obtained.
Owner:STATE GRID JIANGSU ELECTRIC POWER CO ELECTRIC POWER RES INST +1
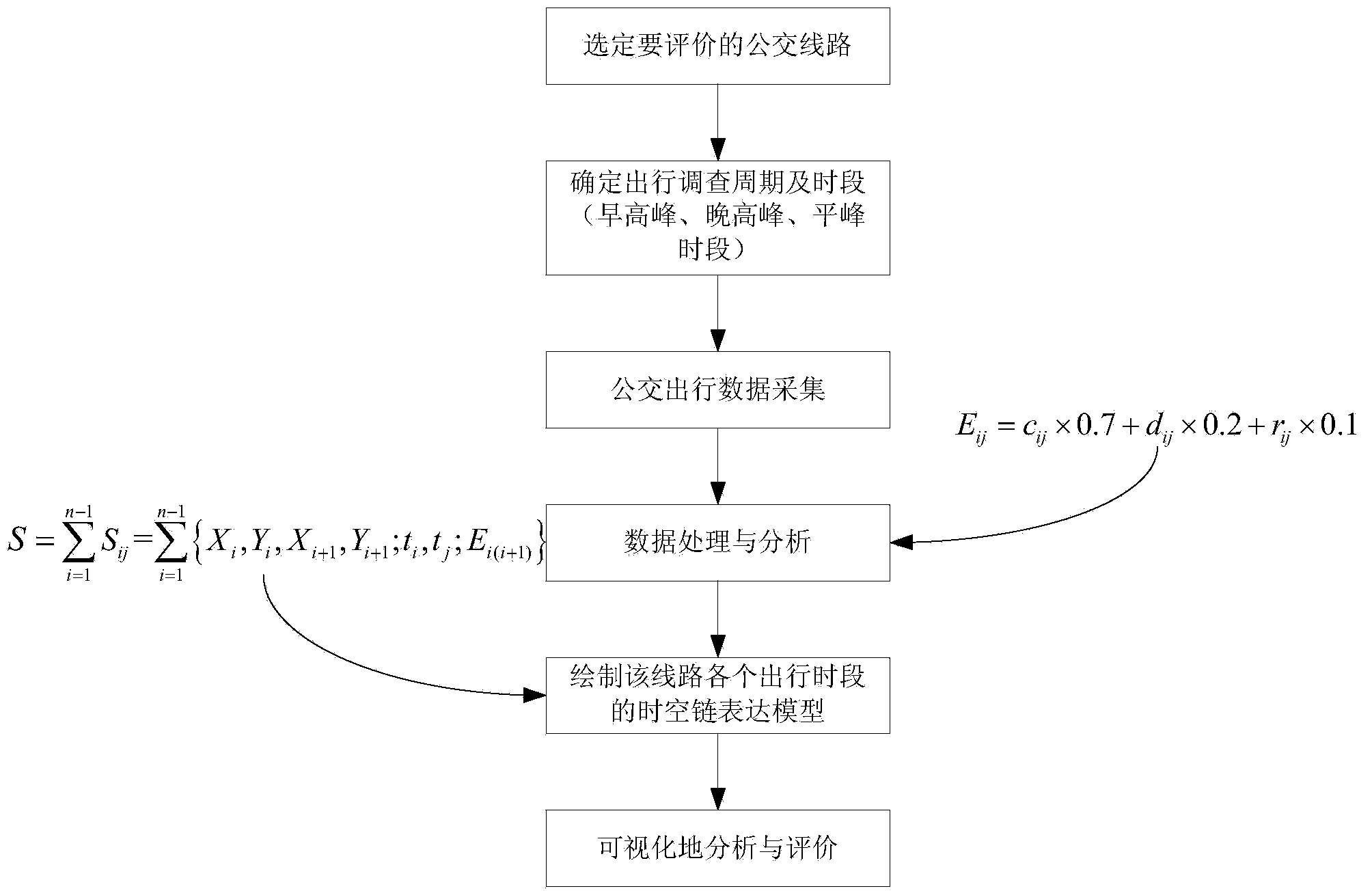
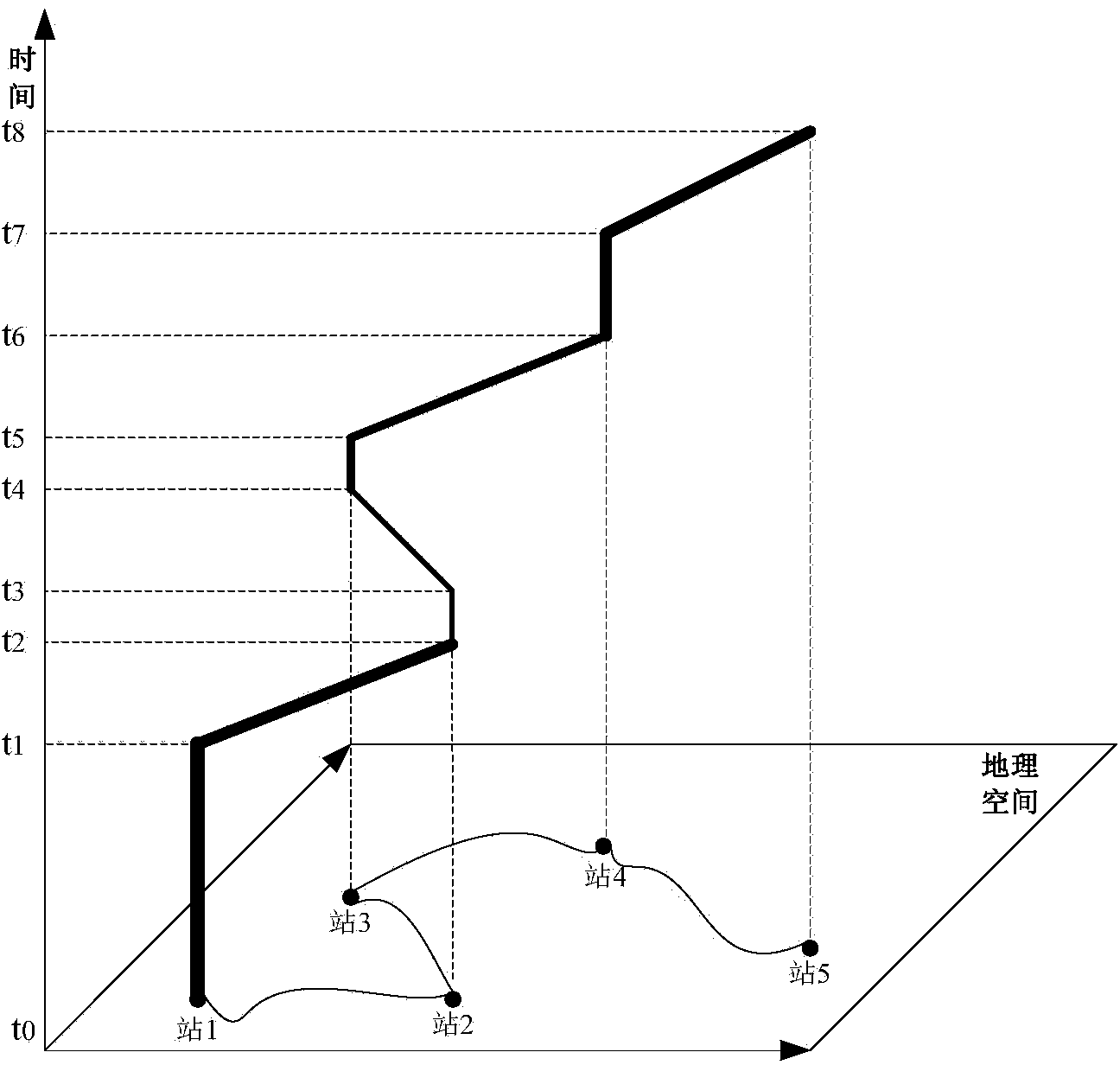
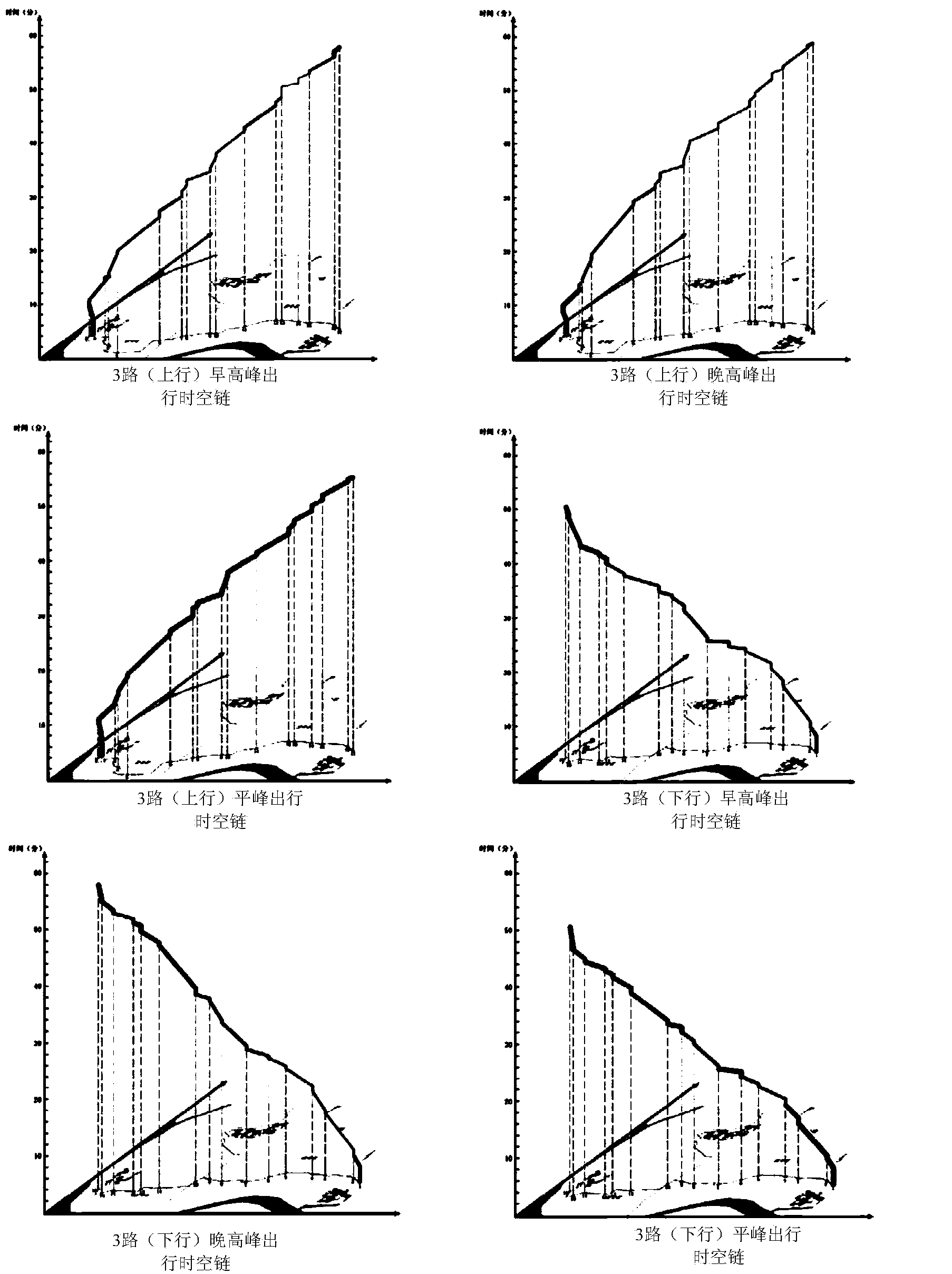
Space-time chain model based bus route evaluation method
The invention discloses a space-time chain model based bus route evaluation method. The method includes the steps: firstly, creating a passenger travel station point set; secondly, acquiring a movement track Sij(t) of a bus between two adjacent bus stations Zi and Zj; thirdly, forming a complete passenger travel space-time path L(t); fourthly, modeling the passenger travel time path L(t) by utilizing the time-space geography theory; fifthly, acquiring a mathematical model S' for evaluation of the complete passenger travel space-time path. The bus route and bus travel behaviors are evaluated and expressed visually, and the method has an important value to scientific evaluation and reasonable setting of the bus route.
Owner:GUANGZHOU INST OF GEOGRAPHY GUANGDONG ACAD OF SCI
SLAM back-end track optimizing method based on pose chain model
InactiveCN107272673ASolve the problem of slow optimization speedMeet online optimization needsPosition/course control in two dimensionsNODALTrajectory optimization
The invention relates to the technical field of a full automatic movement robot, and particularly to an SLAM back-end track optimizing method based on a pose chain model. An SLAM is thought as a key for realizing the full automatic movement robot and is mainly composed of a frontend preprocessing part and a backend optimizing part. The frontend preprocessing part supplies an initial estimated map and position information through analyzing and integrating various kinds of sensor data. The backend optimizing part utilizes a picture model for describing initial estimation and probability restriction and utilizes a most optimized method for optimizing the initial estimation for realizing higher-precision mapping and positioning. According to the method, the pose chain model with a restrict time sequence relation between nodes is introduced; a sparse characteristic of the pose chain model is utilized for settling a problem of online real-time optimization which cannot be realized by common SLAM backend optimization technology; furthermore a requirement for high application precision can be satisfied; and a quick and effective settling method is supplied for settling an SLAM backend optimizing problem.
Owner:SUN YAT SEN UNIV
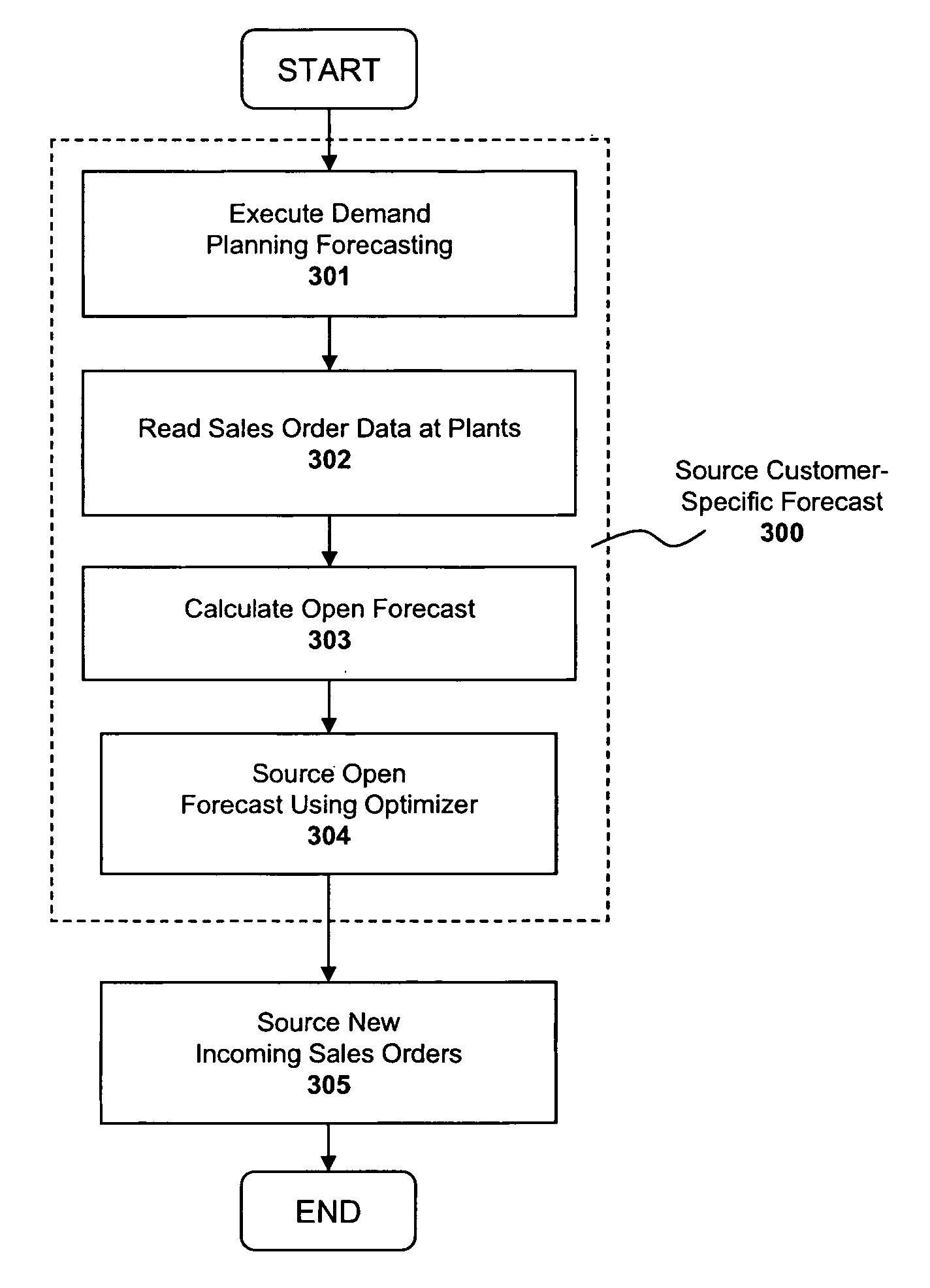
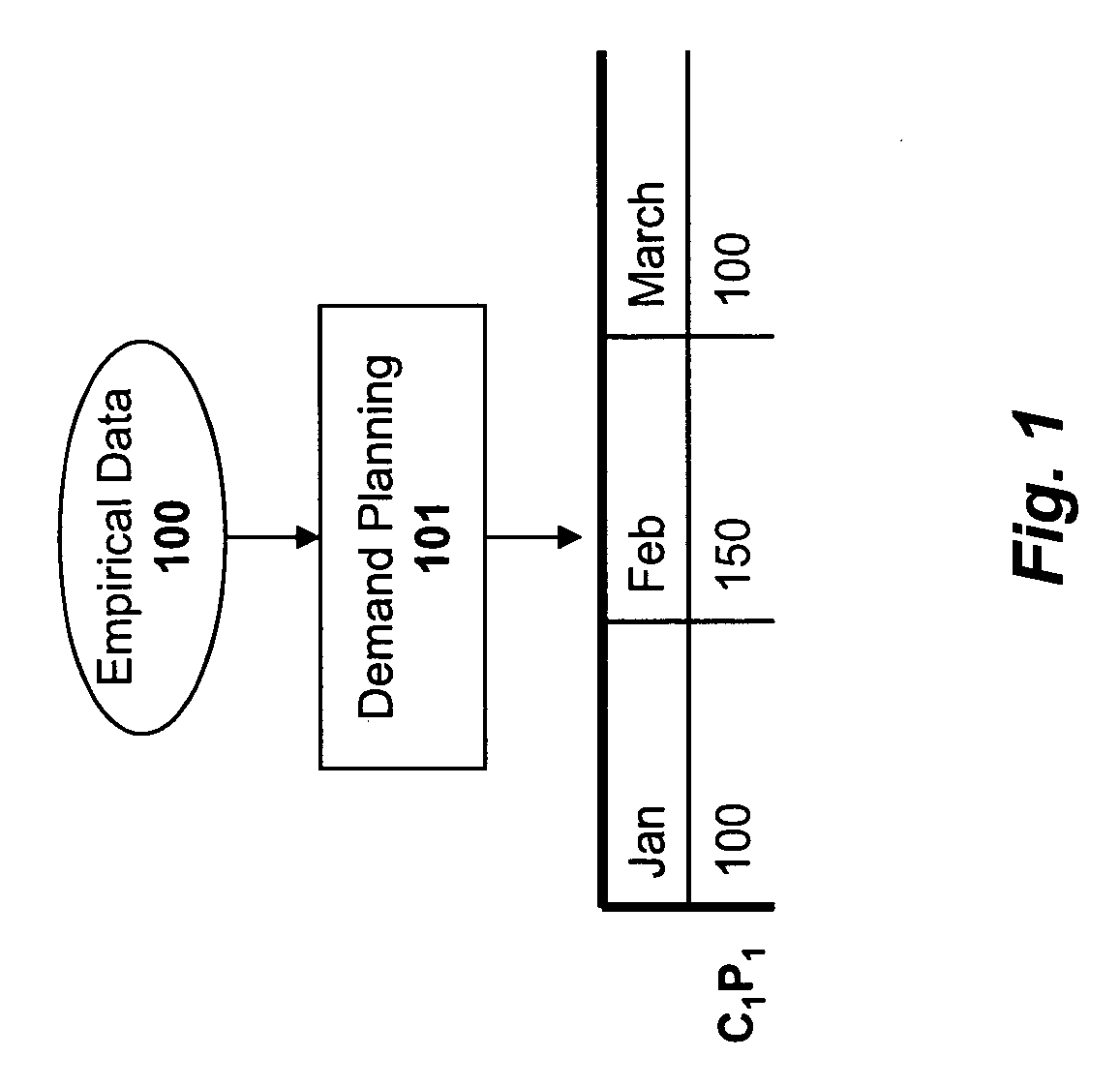
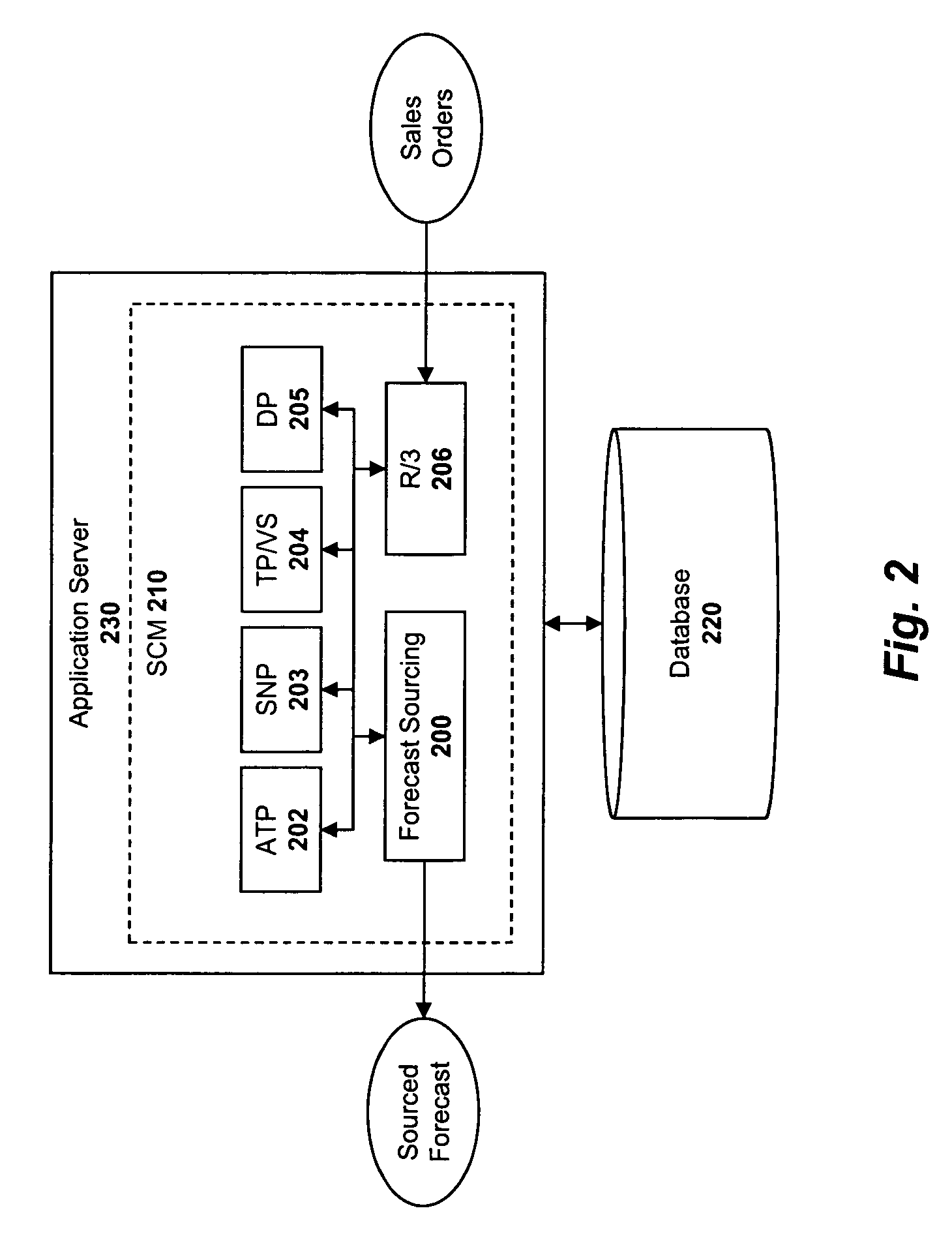
System and method for sourcing a demand forecast within a supply chain management system
A system and method are described for intelligently sourcing demand forecasts within a supply chain management (“SCM”) system based on a constrained supply chain model, in light of material and resource constraints. For example, a computer implemented method according to one embodiment of the invention comprises: calculating a demand forecast identifying anticipated demand for a product over a specified time period; identifying current sales orders for the product with delivery dates scheduled during the specified time period; generating an open forecast for the product based on the current sales orders and the anticipated demand; and sourcing different percentages of the open forecast from different plants, the percentages selected based on supply chain material and / or resource constraints. In addition, after the demand forecast is sourced, one embodiment of the invention employs additional techniques for intelligently sourcing new sales orders entering the SCM system.
Owner:SAP AG
Computer Method and Apparatus for Chaining of Model-To-Model Transformations
InactiveUS20090150125A1Easy to reusePrecise interfaceSoftware engineeringComputation using non-denominational number representationLink modelAlgorithm
Computer method, apparatus and system chains model-to-model transformations. In a series of model transformations, there are respective bridges before and after each model transformation. For each pair of consecutive model transformations in the series, the respective bridge (i) receives a model output from a first model transformation of the pair, the received model being in the respective output model format of the first model transformation of the pair, (ii) prepares the received model as input to a second model transformation of the pair, including preparing the received model to be in the respective input model format of the second model transformation of the pair, and (iii) inputs the prepared model to the second model transformation of the pair. The series of model transformations and respective bridges provide chaining of the model-to-model transformations. Each model transformation in the series is able to be separately configured.
Owner:IBM CORP +1
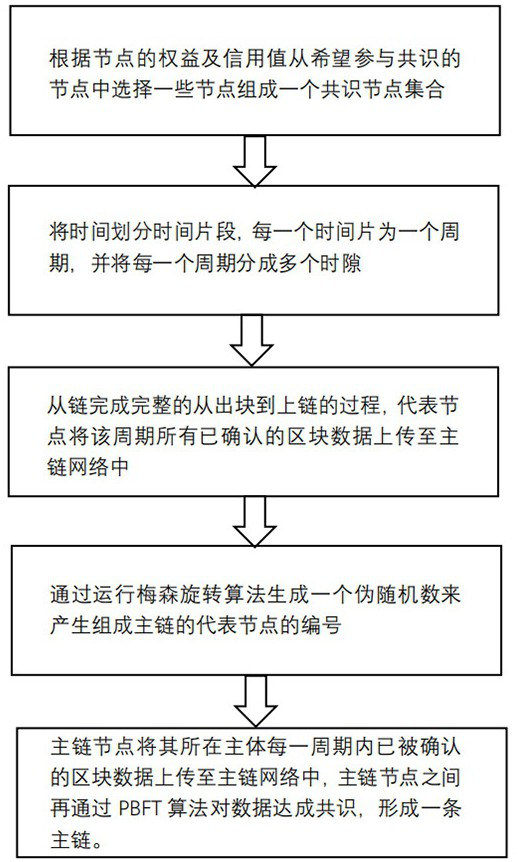
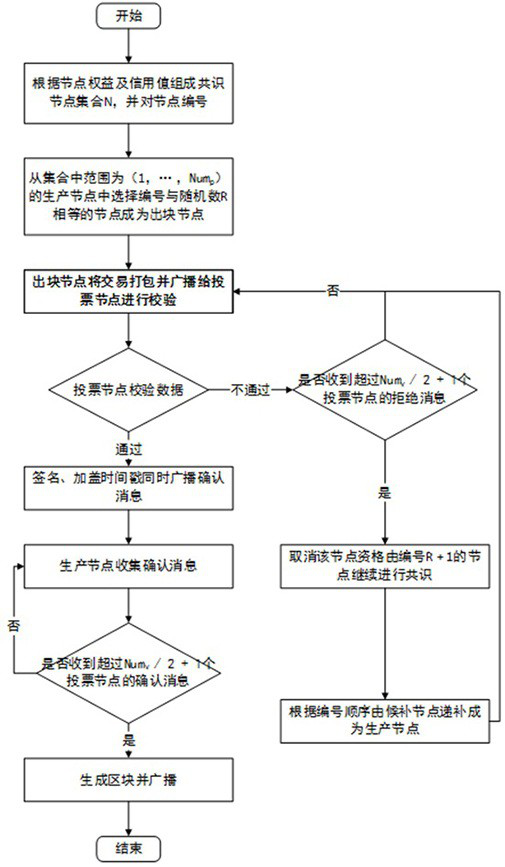
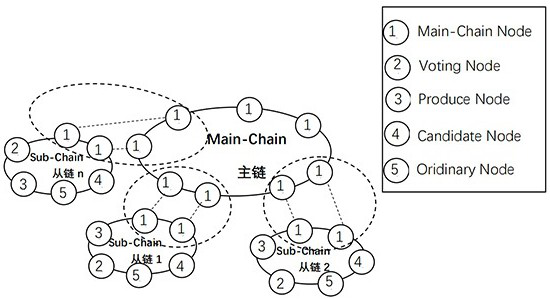
Master-slave multi-chain cross-chain method and system based on voting and credit mechanism
ActiveCN112804101AAvoid computing power competitionGuaranteed reliabilityData switching networksSecuring communicationAttackConsensus
The invention discloses a master-slave multi-chain cross-chain method and system based on a voting and credit mechanism. The ownership of an accounting right is determined by introducing a voting mechanism, so that the computing power competition between nodes is avoided, and all the nodes in the system can obtain the accounting right fairly; the credit value is given to the node, so that the influence of rights and interests on the system is reduced, and meanwhile, the behavior of the node can be better restrained by performing quantitative evaluation on the behavior of the node, so that the node can worry about malicious behaviors; on the basis, a master-slave multi-chain layered cross-chain model with a slave chain based on POVT consensus and a main chain based on PBFT consensus is constructed, experimental analysis is performed on the performance of the master-slave multi-chain layered cross-chain model, and results show that the efficiency of the system is improved; and meanwhile, the system has certain defense capability on attack means such as double-blossom attack, selfish mining and right and interest crushing.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com