APT attack scene mining method based on intrusion kill chain and fuzzy clustering
A technology of fuzzy clustering and attack scenarios, applied in electrical components, transmission systems, etc., can solve problems such as incomplete paths and inability to match alarms, and achieve the effects of high correlation, improved accuracy, and improved accuracy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] In order to make the above-mentioned features and advantages of the present invention more comprehensible, the present invention will be further described in detail below in conjunction with specific embodiments and accompanying drawings.
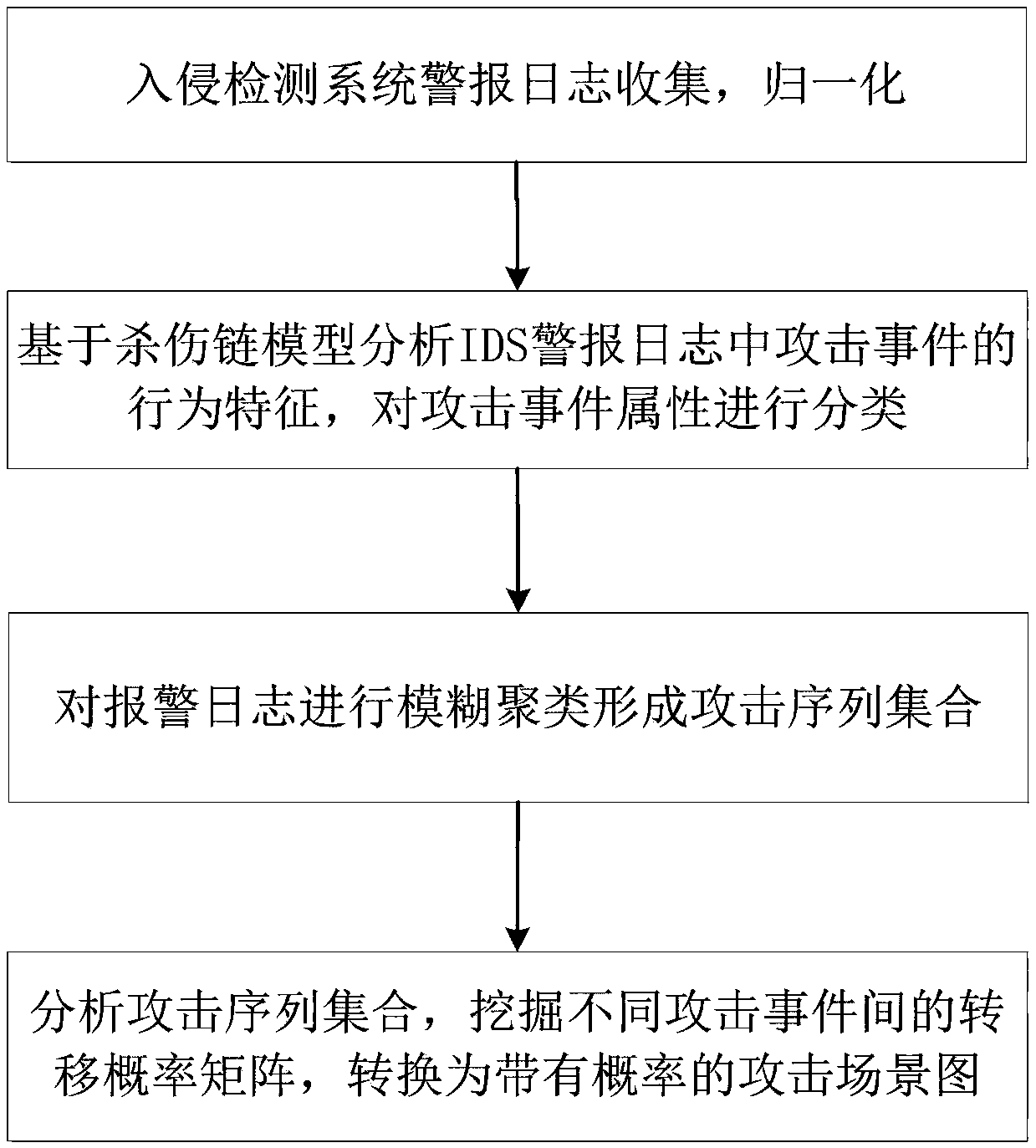
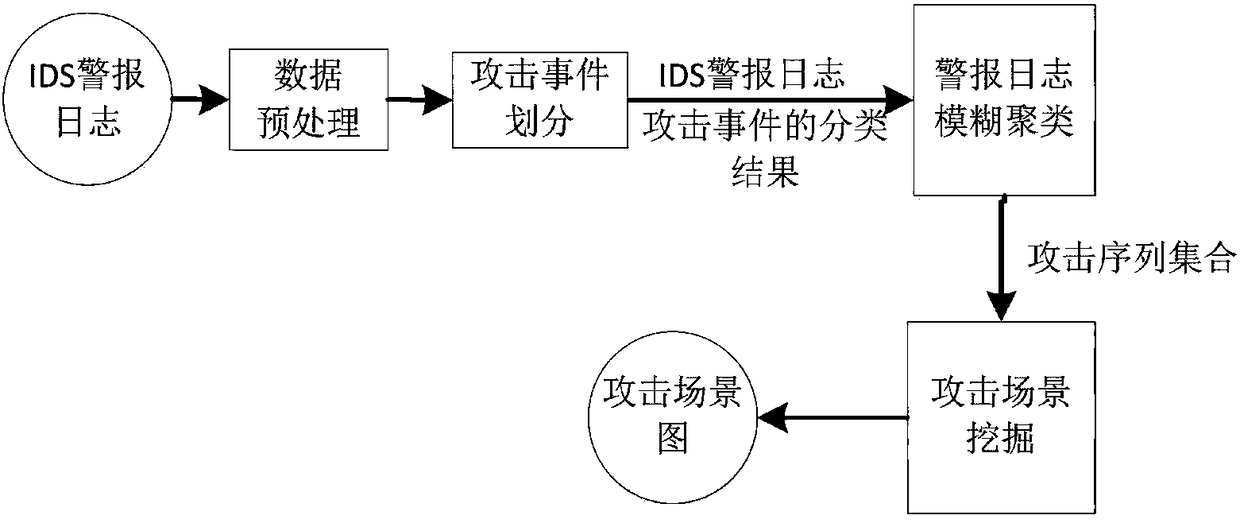
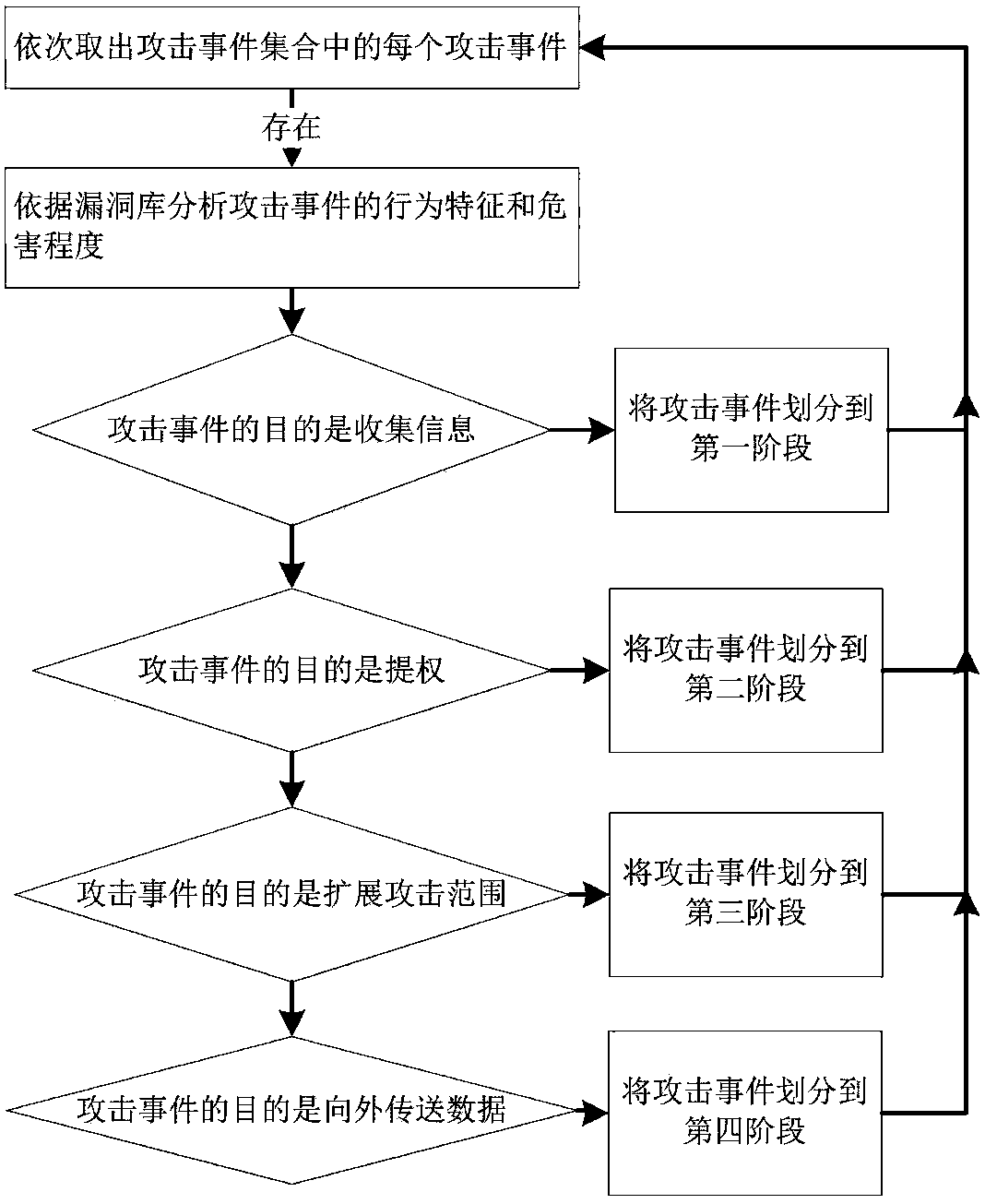
[0038] see figure 2 , which shows a flow chart of an APT attack scenario mining method based on kill chain and fuzzy clustering provided by an embodiment of the present invention. The algorithm forms an attack sequence. In fuzzy clustering, in addition to common attributes such as IP addresses and time stamps, attack event dimensions based on the kill chain model are added to improve the correlation between alarms in an attack sequence, thereby improving APT scene mining. To improve the accuracy of the method, analyze all the attack sequences generated by clustering to dig out the attack scene graph of APT, including the following specific steps:
[0039] step 1:
[0040] The data source of this embodiment is the alarm log data of...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com