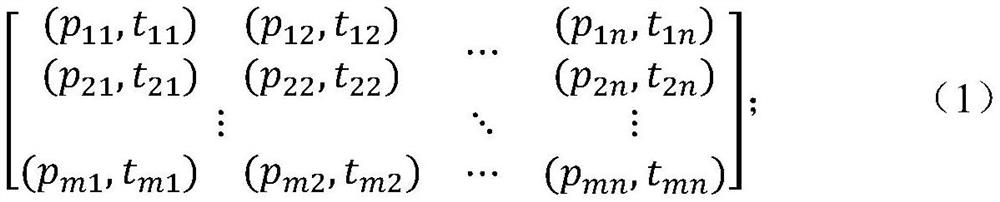Patents
Literature
36 results about "Kill chain" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
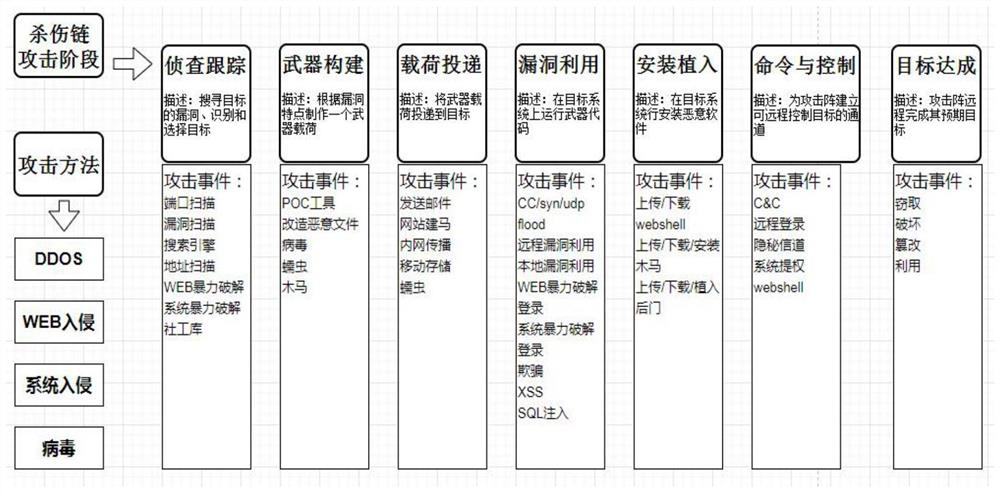
The term kill chain was originally used as a military concept related to the structure of an attack; consisting of target identification, force dispatch to target, decision and order to attack the target, and finally the destruction of the target. Conversely, the idea of "breaking" an opponent's kill chain is a method of defense or preemptive action. More recently, Lockheed Martin adapted this concept to information security, using it as a method for modeling intrusions on a computer network. The cyber kill chain model has seen some adoption in the information security community. However, acceptance is not universal, with critics pointing to what they believe are fundamental flaws in the model.
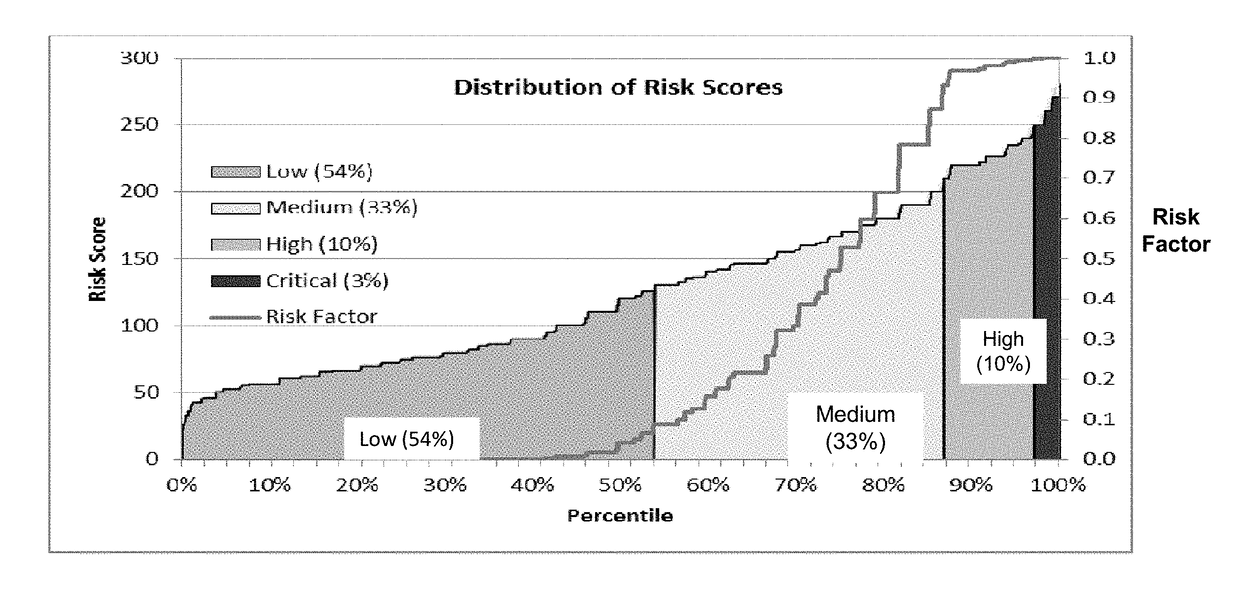
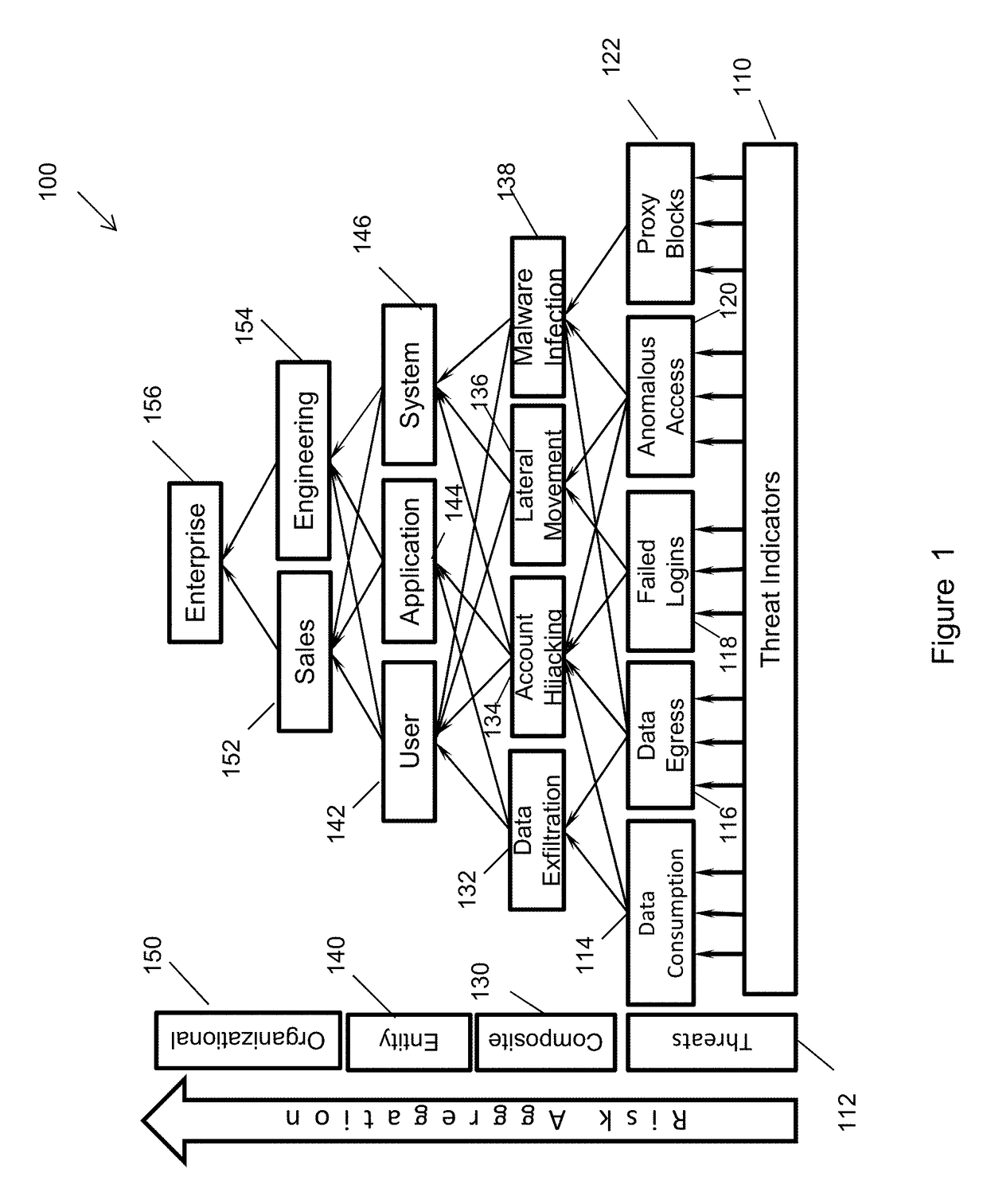
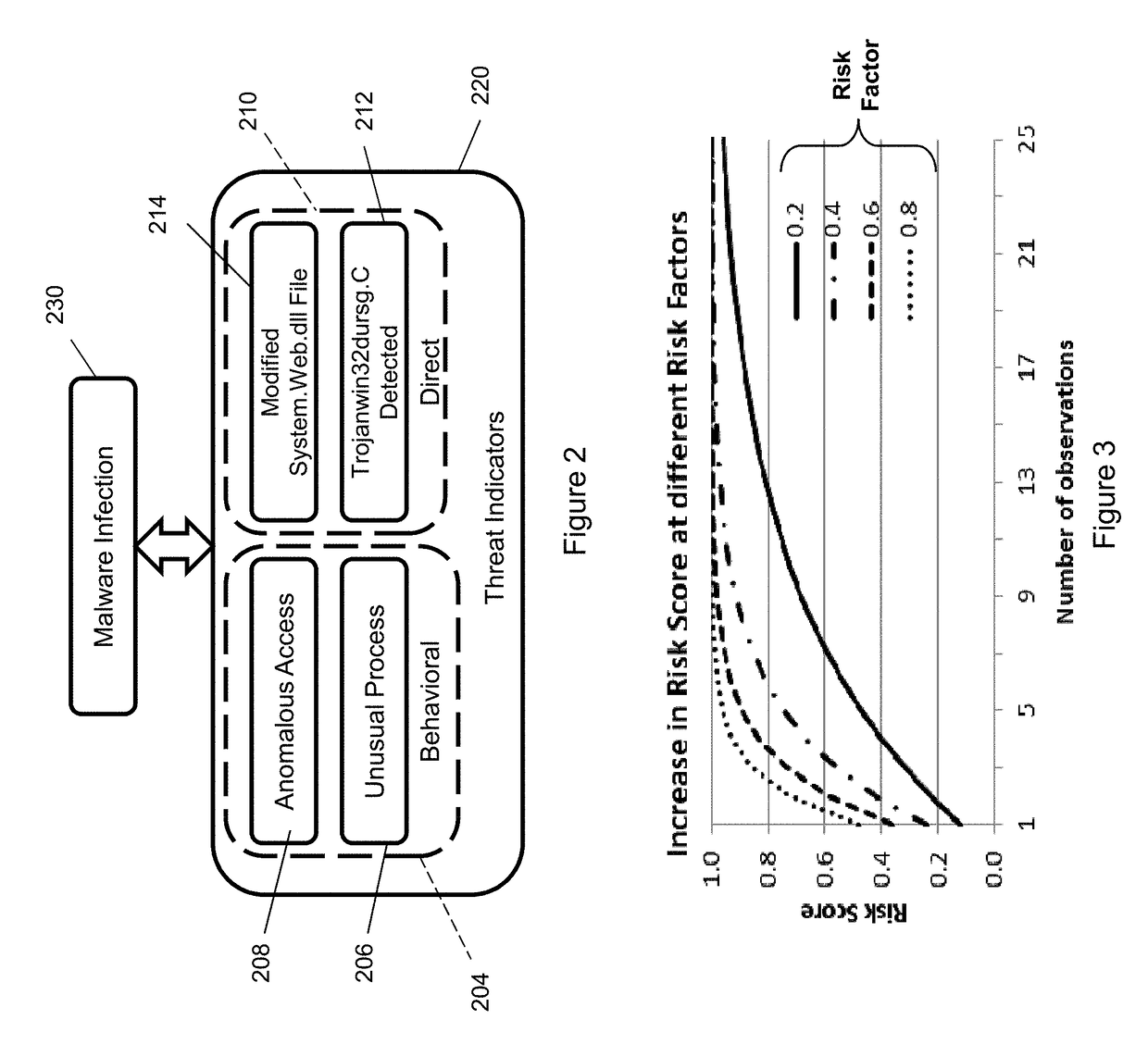
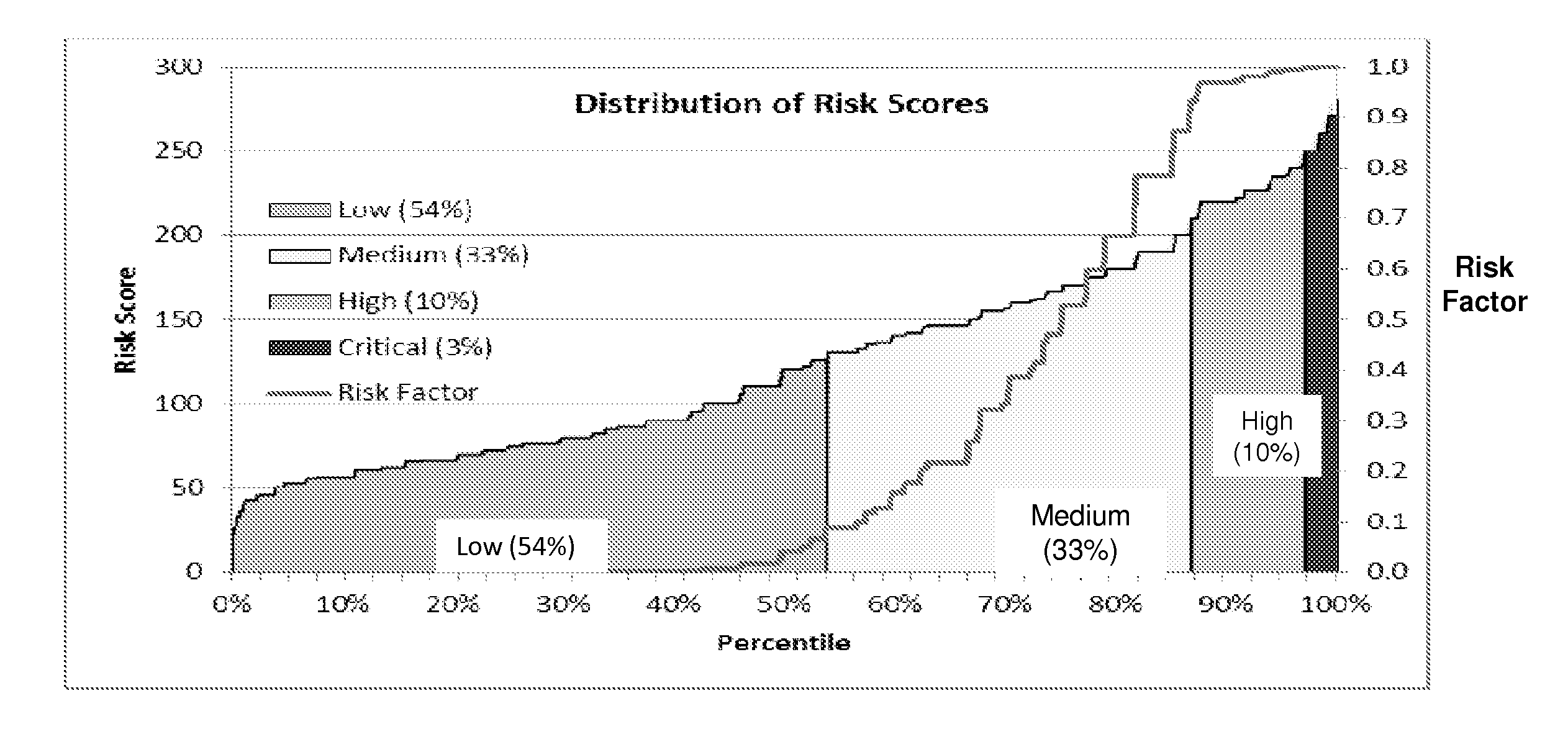
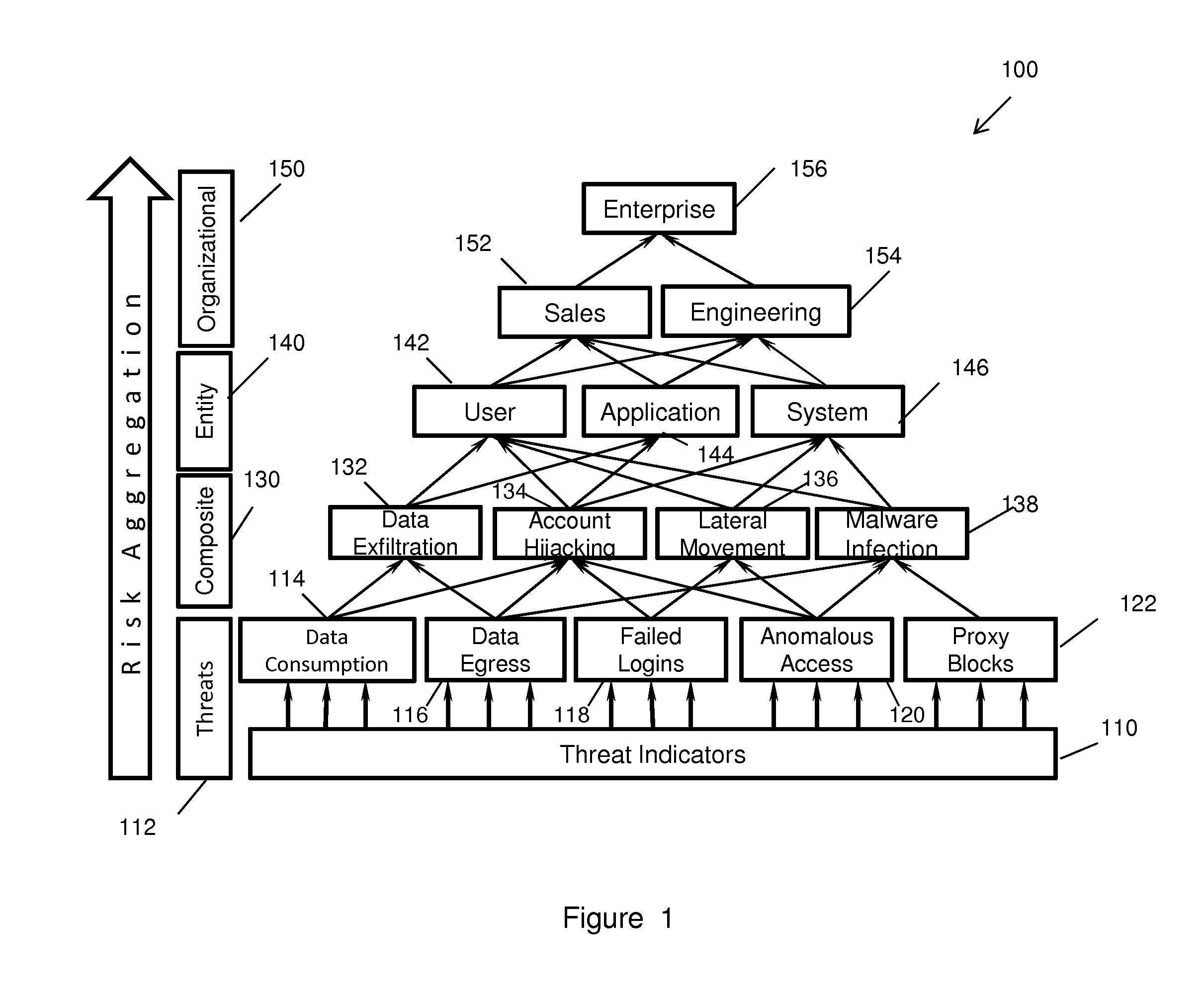
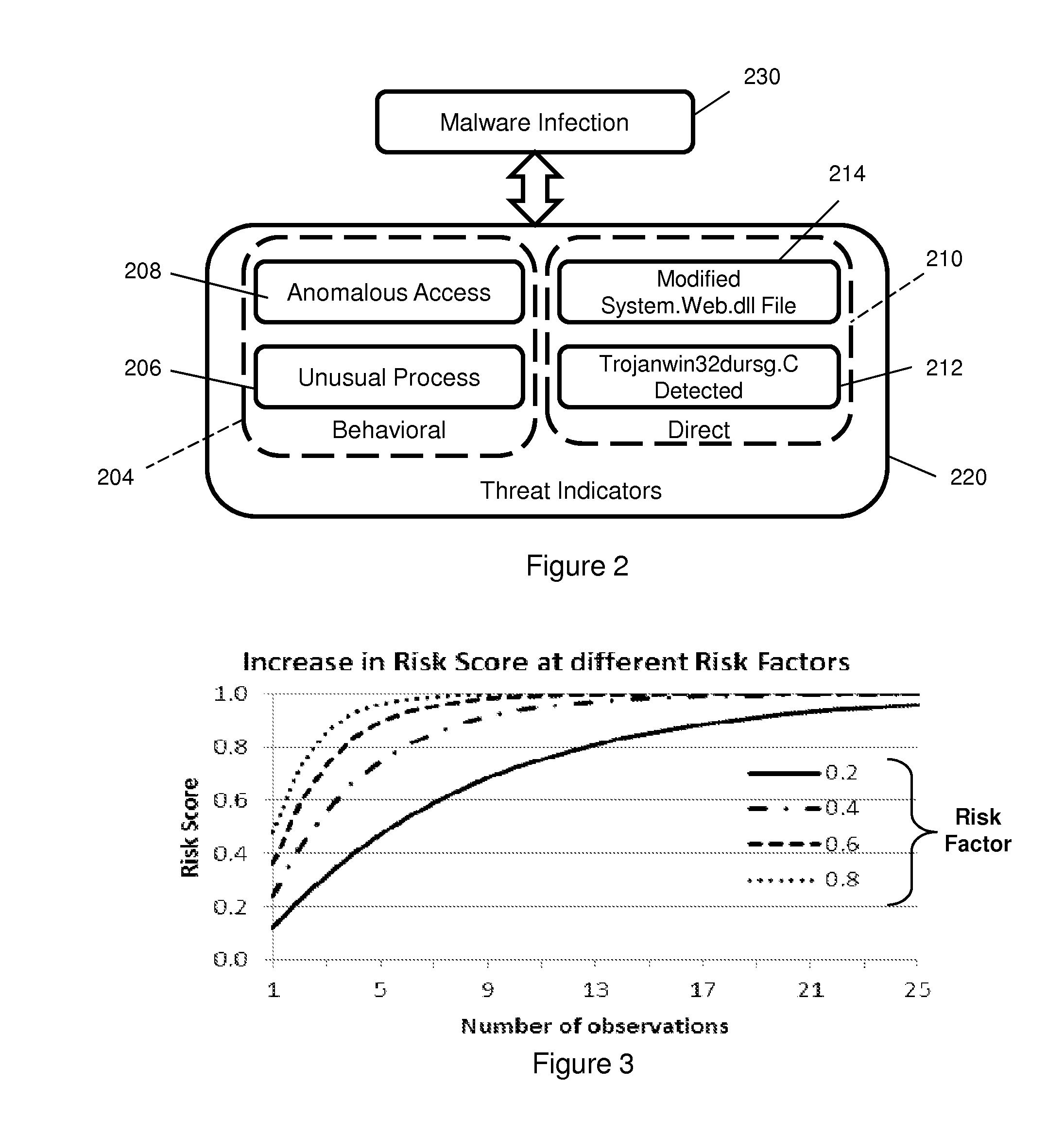
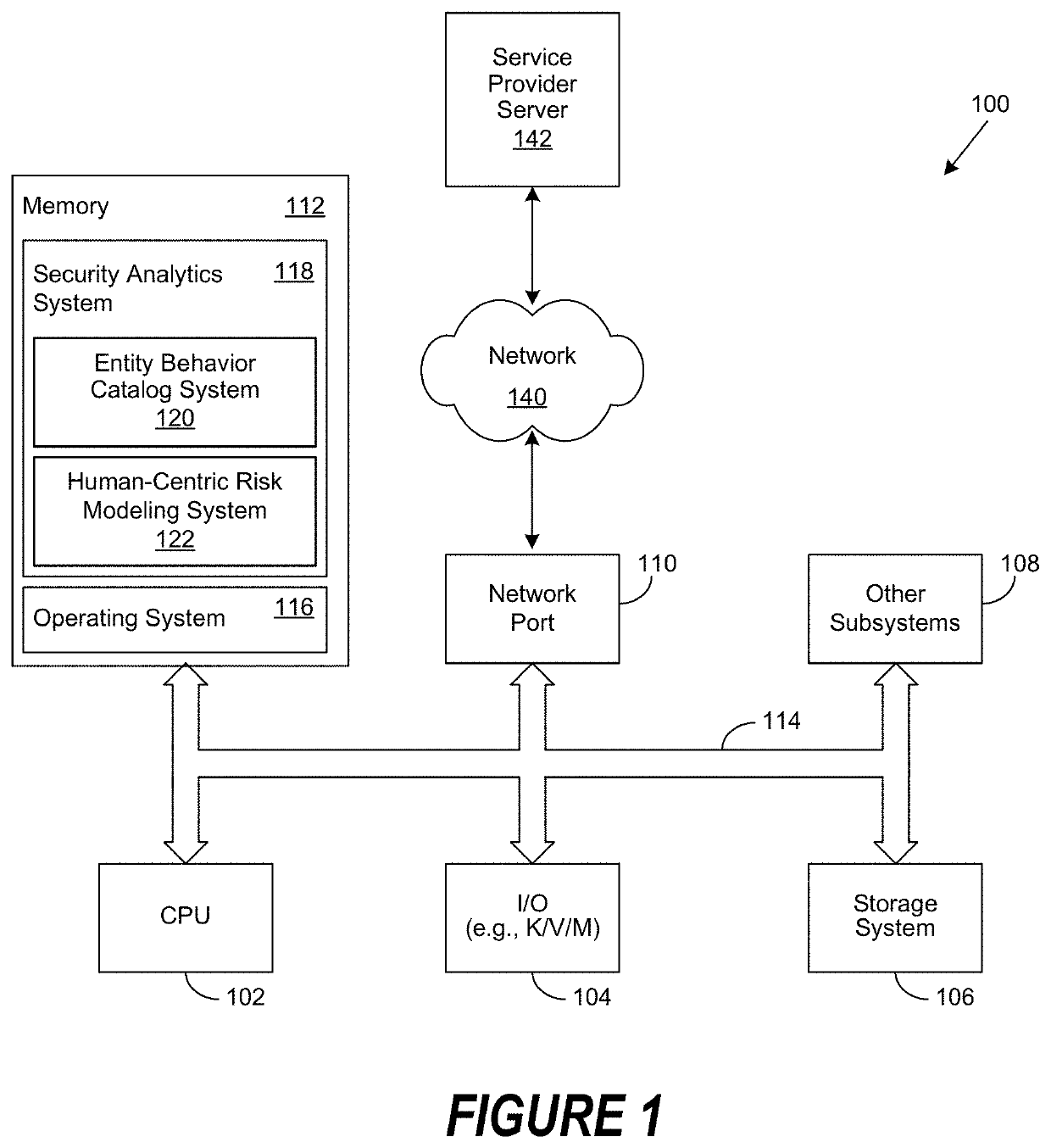
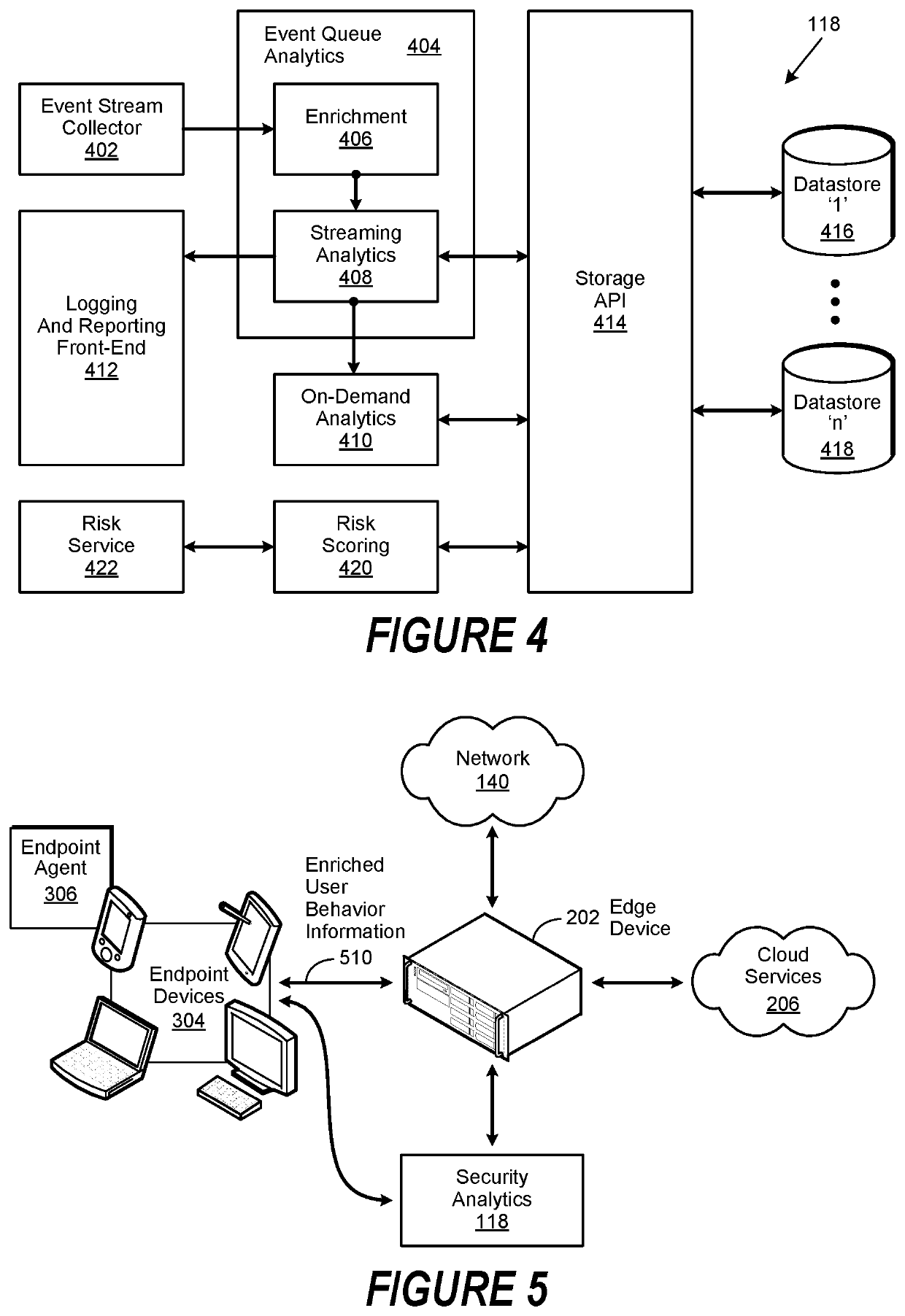
Risk scoring for threat assessment
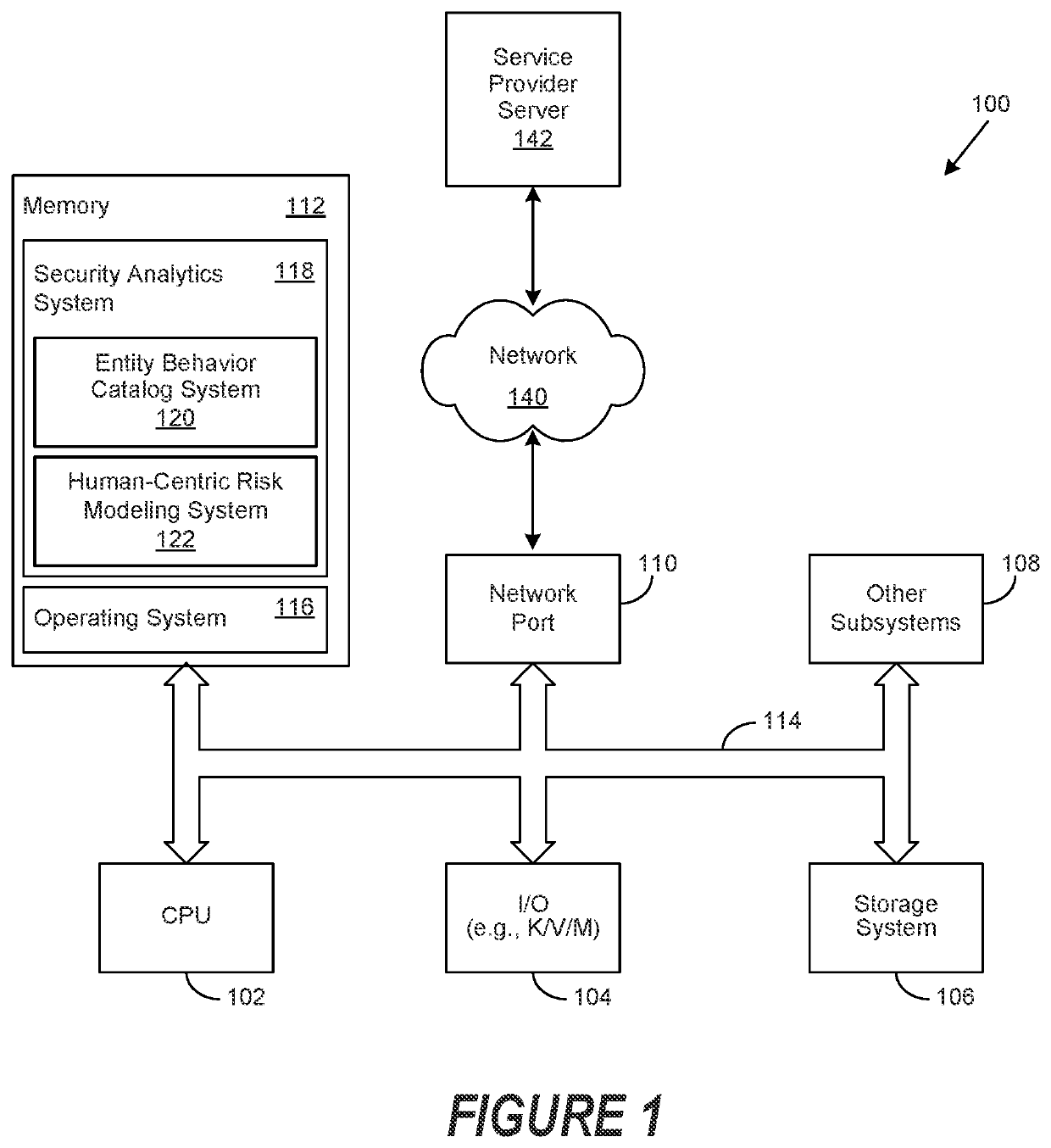
Threat risks to an enterprise are detected and assessed by assembling singular threats identified using both direct and behavioral threat indicators into composite threats to create complex use cases across multiple domains, and to amplify risks along kill chains of known attacks for early detection. Composite threat risk scores are computed from risk scores of singular threats to exponentially increase with the number of events observed along the kill chain. Composite threats are combined with normalized values of static risk and inherent risk for an entity of the enterprise to produce an entity risk score representative of the overall risk to the entity.
Owner:SECURONIX INC
Risk Scoring For Threat Assessment
Threat risks to an enterprise are detected and assessed by assembling singular threats identified using both direct and behavioral threat indicators into composite threats to create complex use cases across multiple domains, and to amplify risks along kill chains of known attacks for early detection. Composite threat risk scores are computed from risk scores of singular threats to exponentially increase with the number of events observed along the kill chain. Composite threats are combined with normalized values of static risk and inherent risk for an entity of the enterprise to produce an entity risk score representative of the overall risk to the entity.
Owner:SECURONIX INC
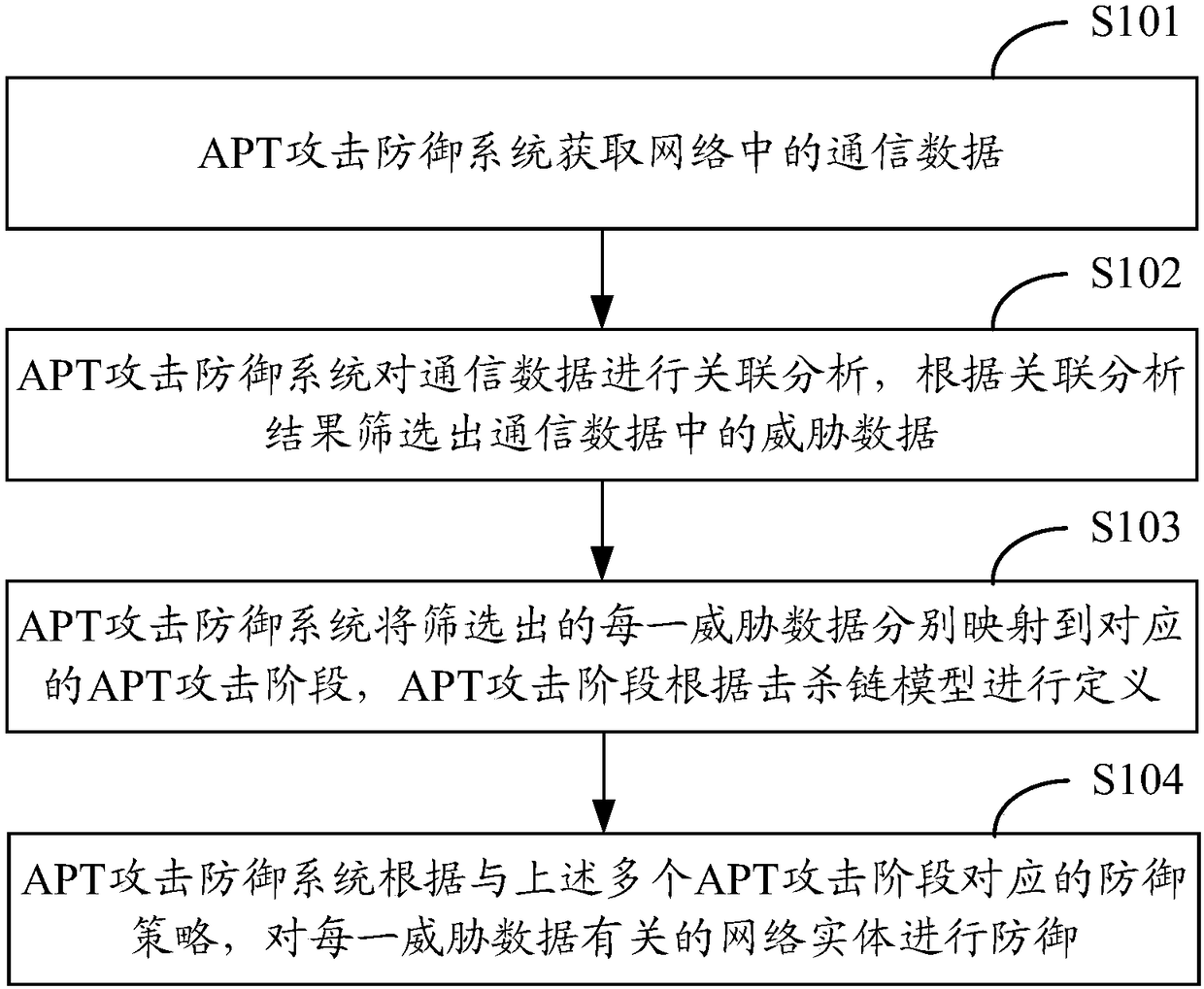
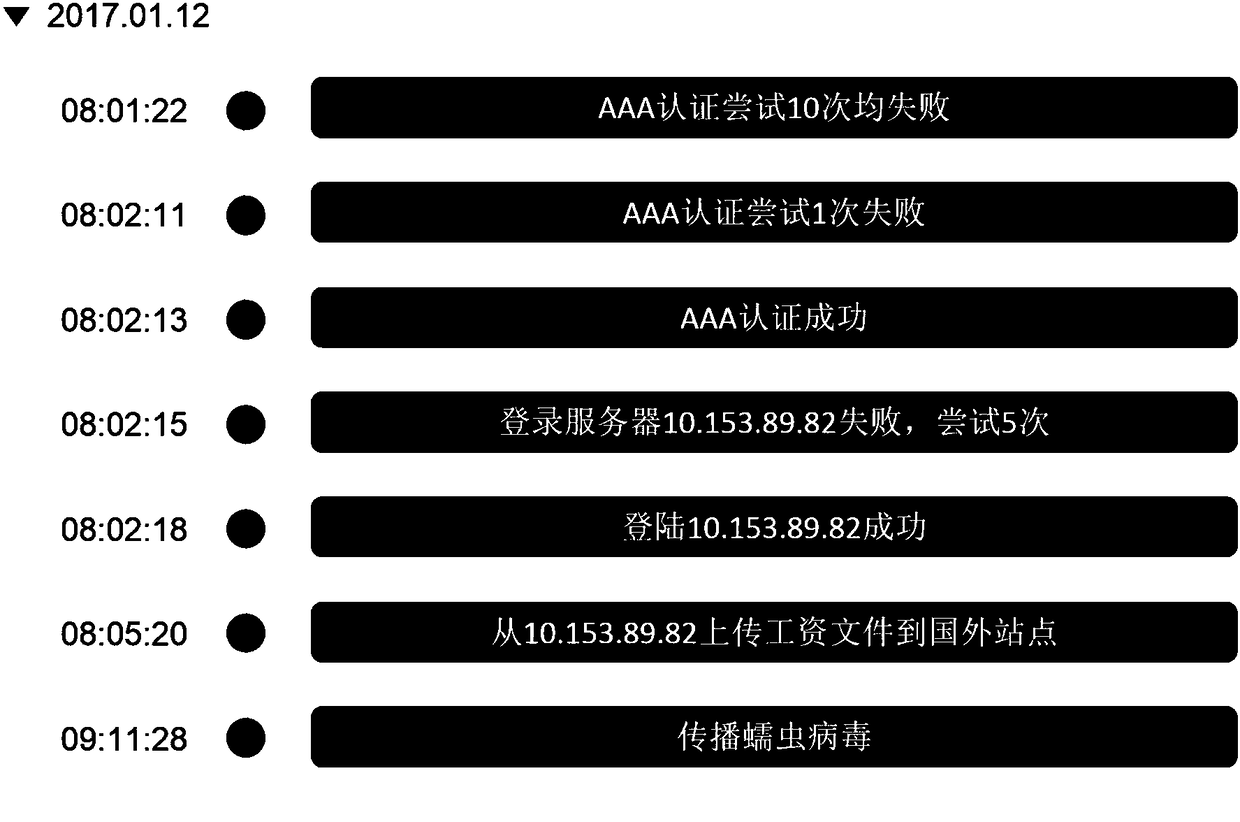
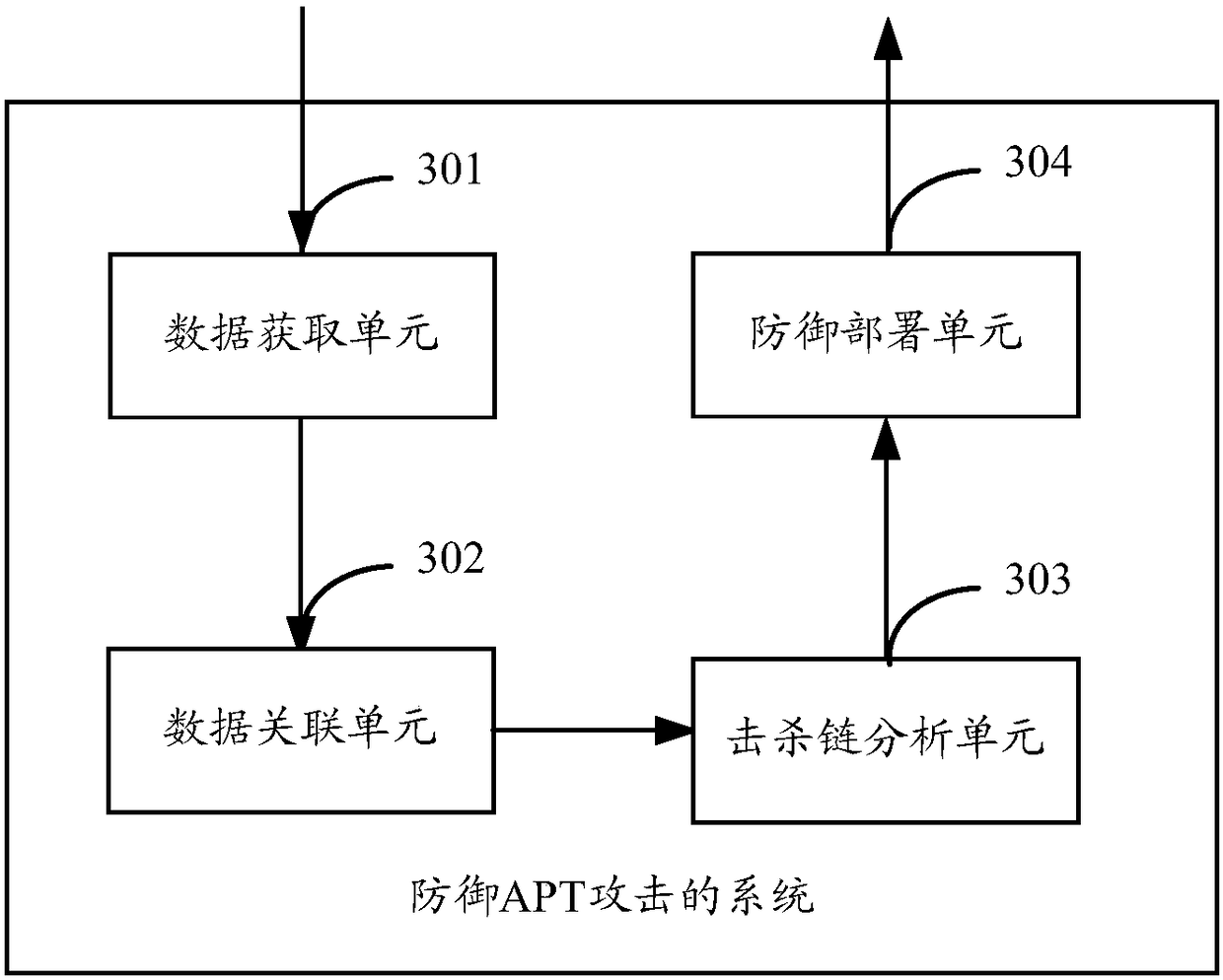
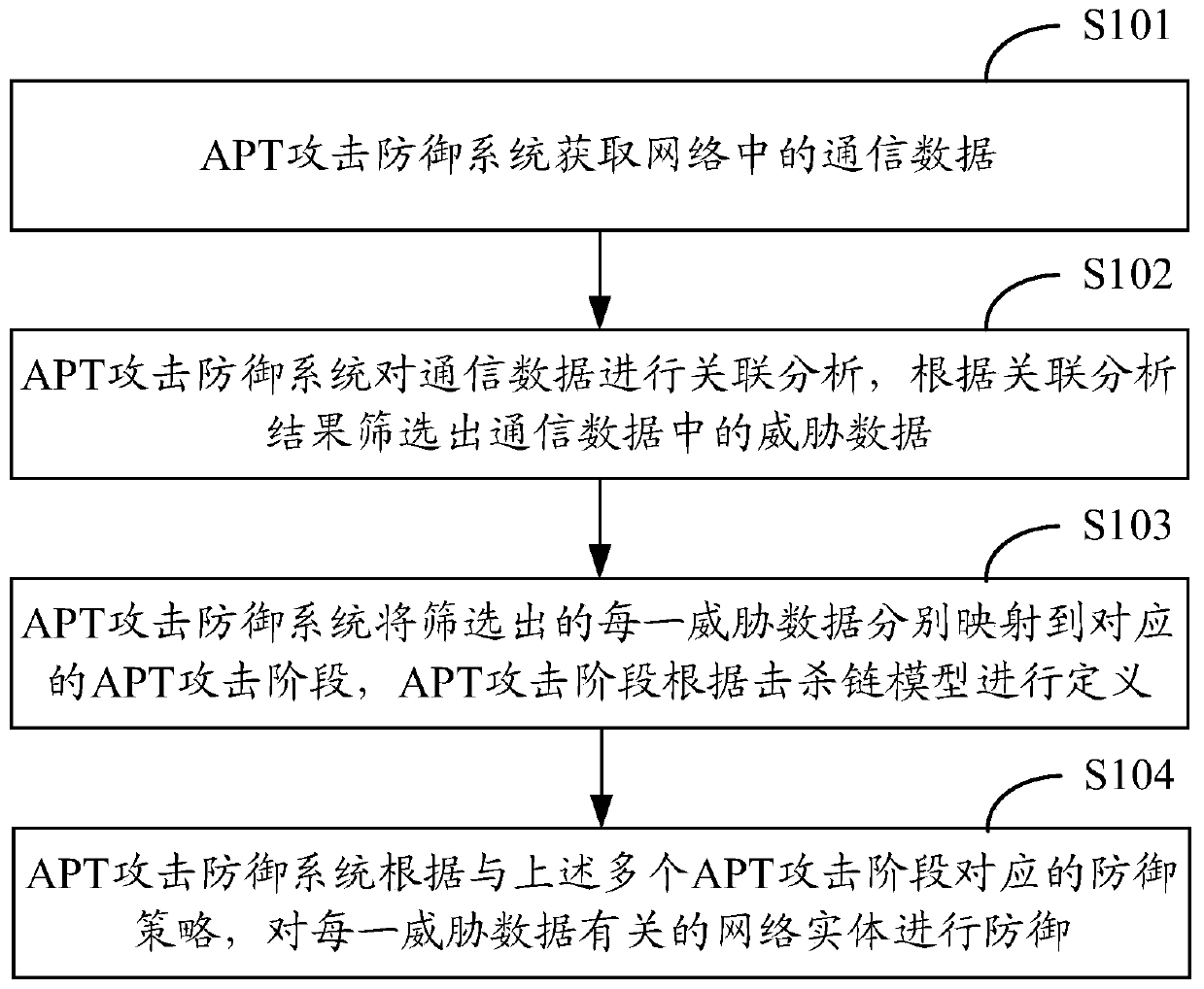
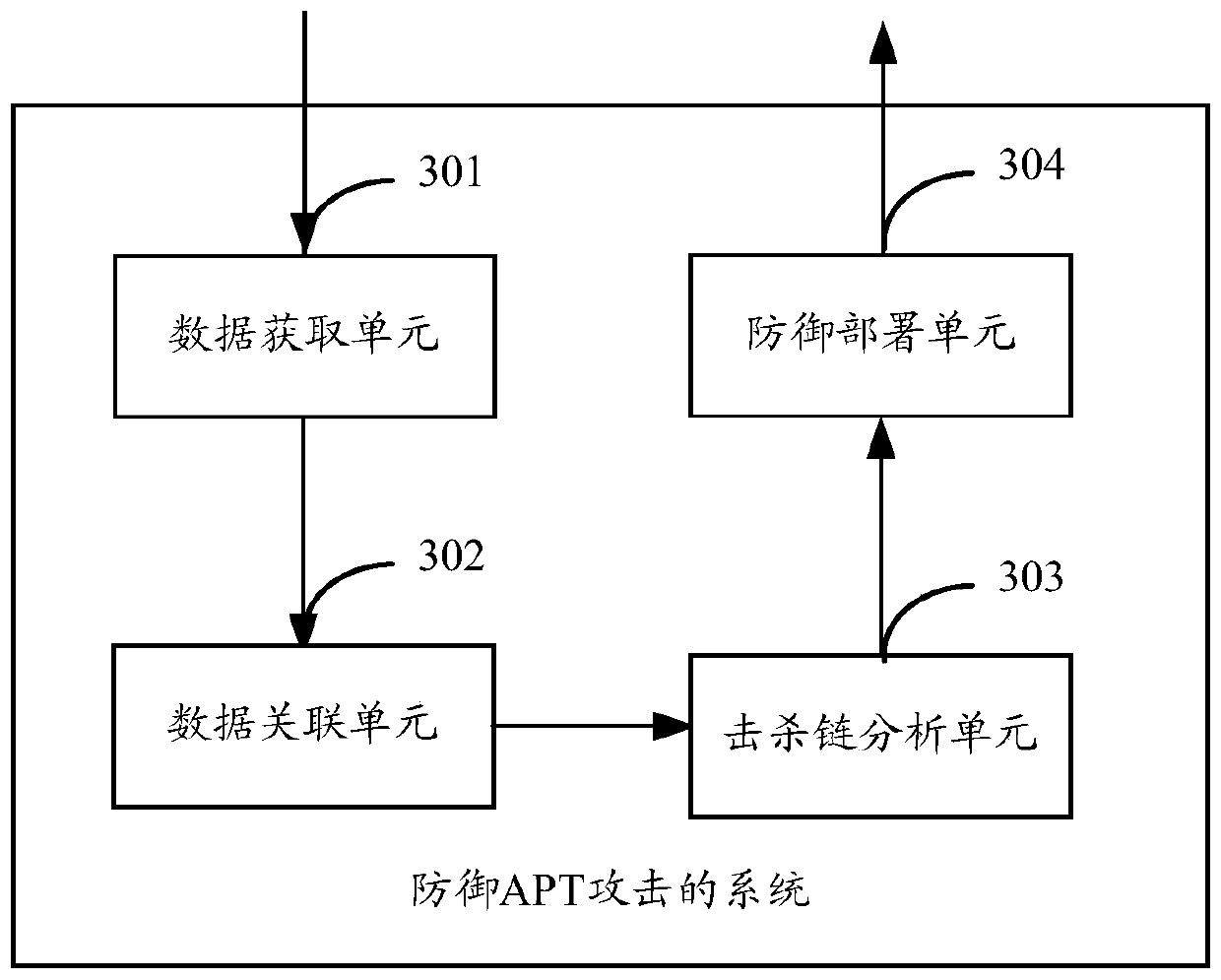
Method and system for defense against APT attacks
ActiveCN108259449AEffective detectionEffective defenseTransmissionAdvanced persistent threatKill chain
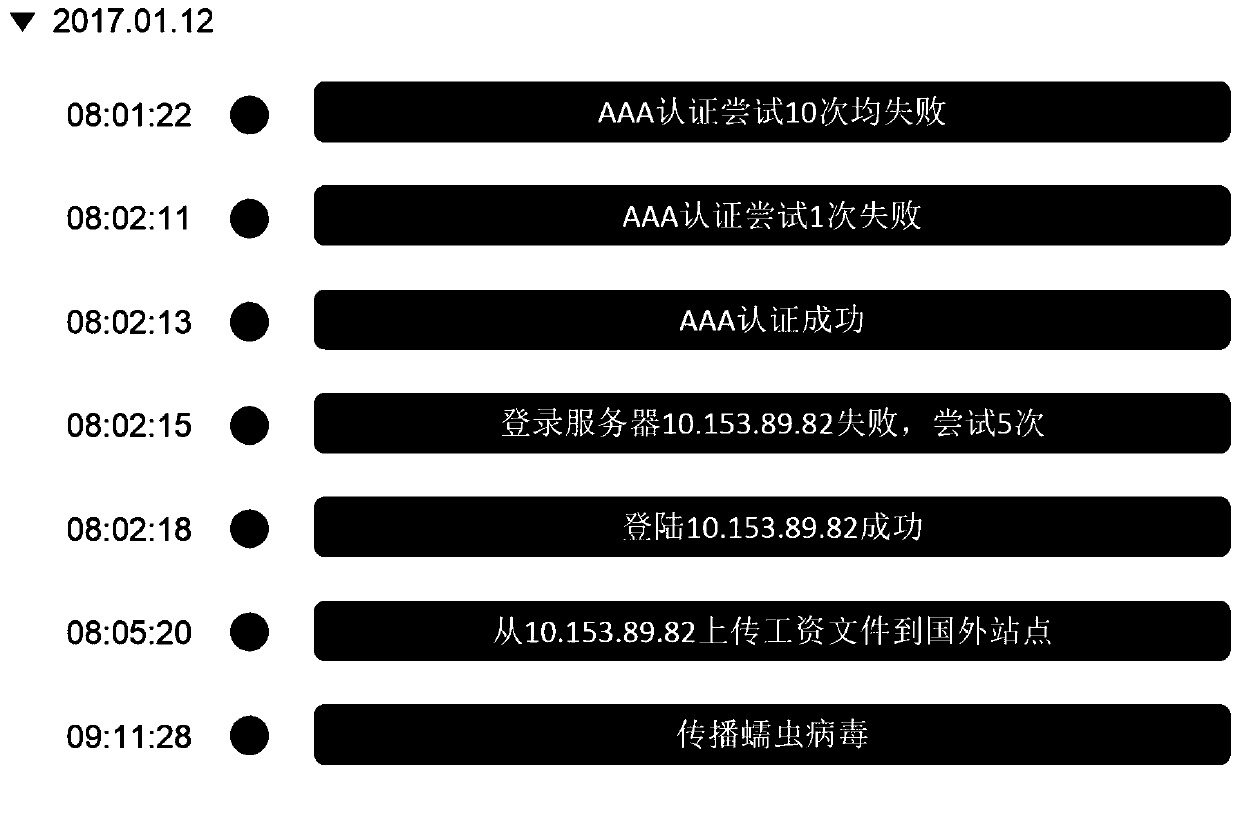
The application provides a method and system for defense against advanced persistent threat APT attacks. The method for defense against the advanced persistent threat APT attacks comprises the following steps: obtaining communication data in a network; performing association analysis on the communication data, and screening out the threat data in the communication data according to the results ofthe association analysis; mapping each piece of threat data to a corresponding APT attack stage separately, wherein the APT attack stage is defined according to the kill chain model; and performing defense on the network entity related to each piece of threat data according to the defense strategy corresponding to the plurality of APT attack stages. According to the method and system for defense against the advanced persistent threat APT attacks, the threat data is mapped to the corresponding APT attack stage, and corresponding defense strategies are taken for different APT attack stages, therefore, the APT attack processing is more targeted, and the APT attacks can be detected and defended more effectively.
Owner:NEW H3C TECH CO LTD
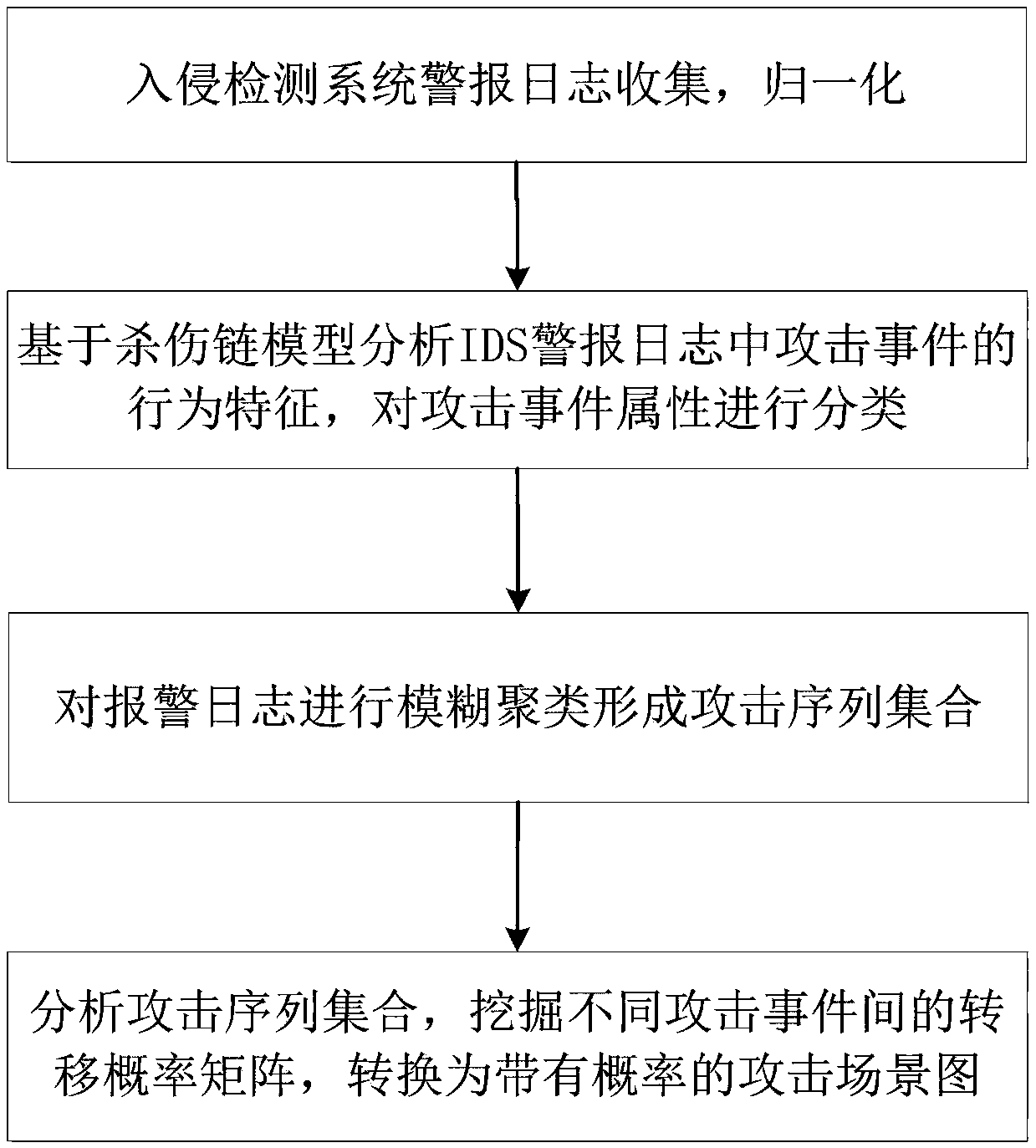
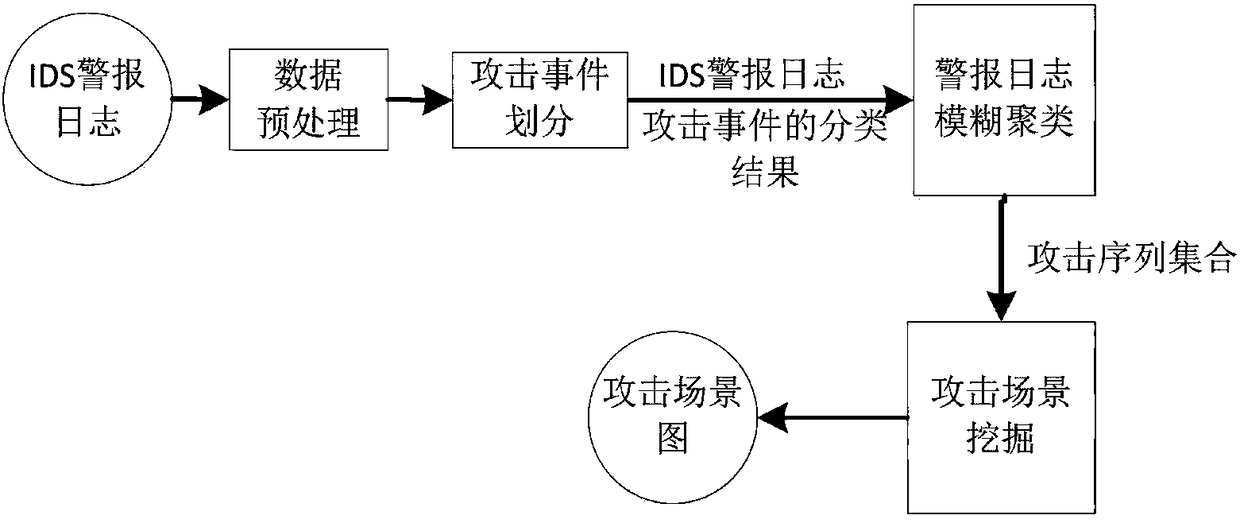
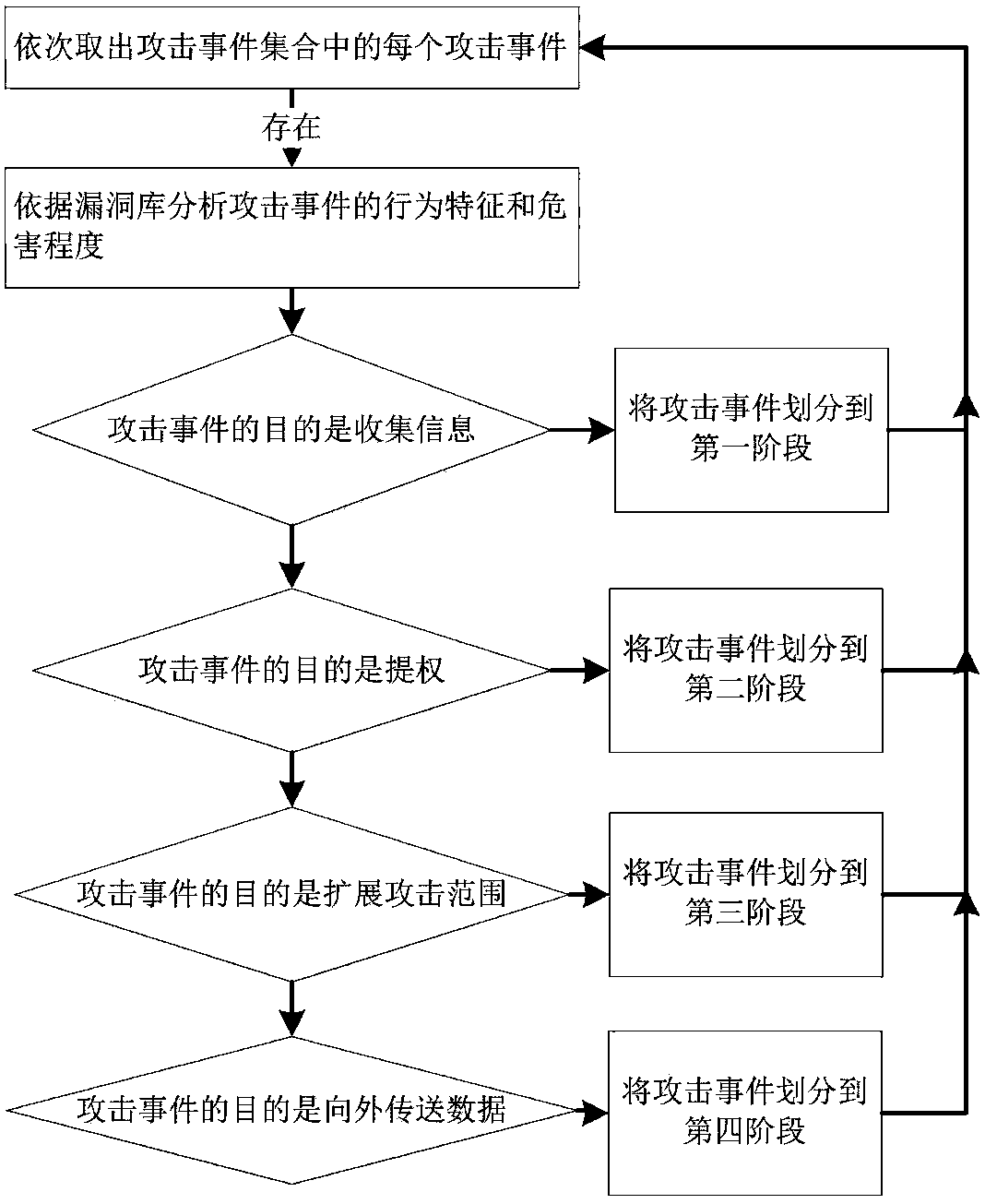
APT attack scene mining method based on intrusion kill chain and fuzzy clustering
ActiveCN108076040AImprove accuracyImprove relevanceTransmissionDirected graphTransition probability matrix
The invention discloses an APT attack scene mining method based on an intrusion kill chain and fuzzy clustering. The method can be used for mining an APT attack scene in an intrusion detection system(IDS) log. The method comprises the steps of collecting and normalizing alert of the intrusion detection system; analyzing behavior characteristics of attack events in alert logs based on an intrusionkill chain model and classifying the attack events; carrying out fuzzy clustering on the alert logs to form an attack sequence set; and analyzing the attack sequence set, deleting incomplete sequences, converting each attack sequence into a directed graph, mining a transition probability matrix among different attack events, and converting the transition probability matrix into an APT attack scene graph with the probability. According to the method, the APT attack graph in true alert can be mined, and the theoretical foundation for APT detection and defense is provided.
Owner:BEIJING UNIV OF POSTS & TELECOMM
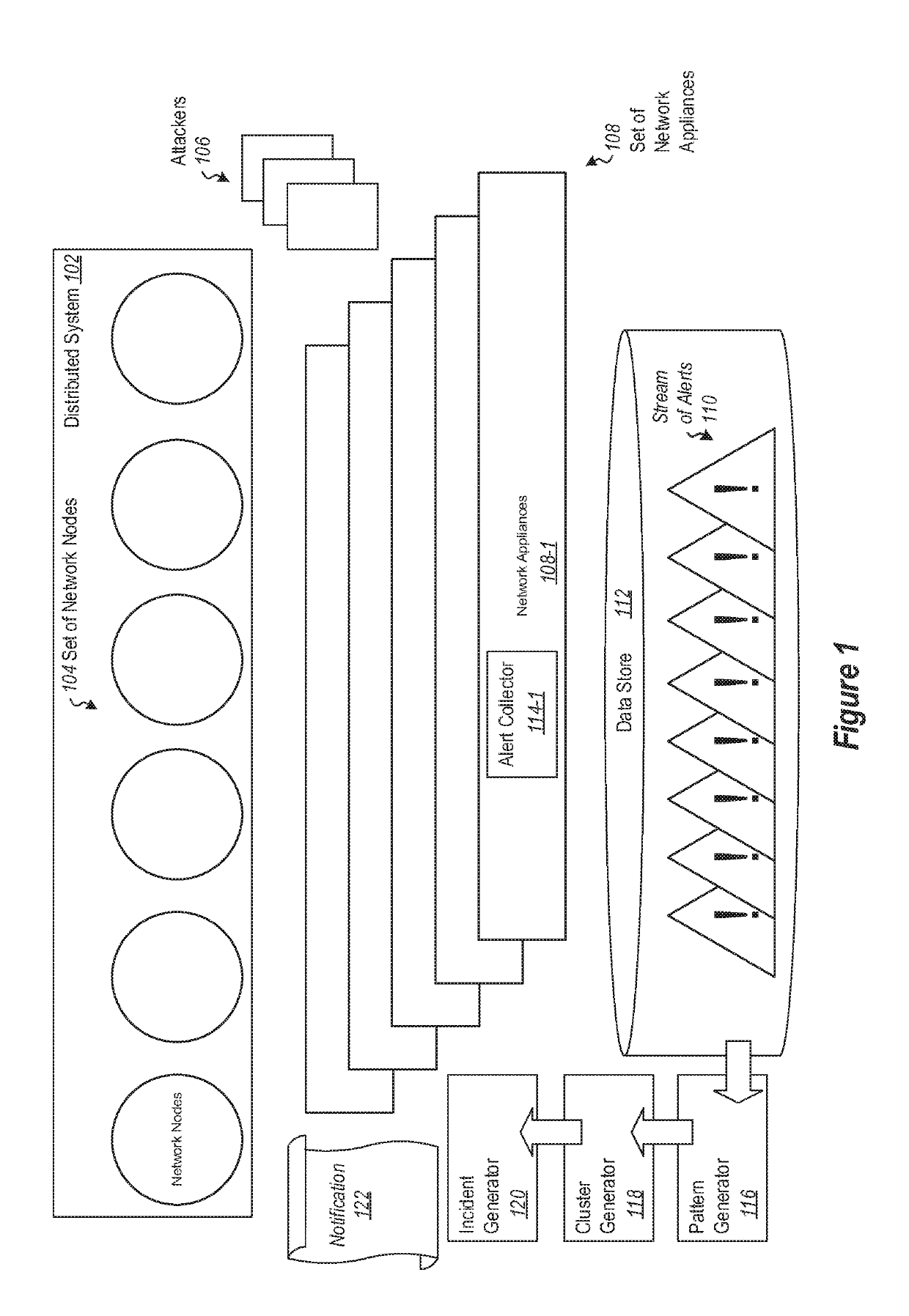
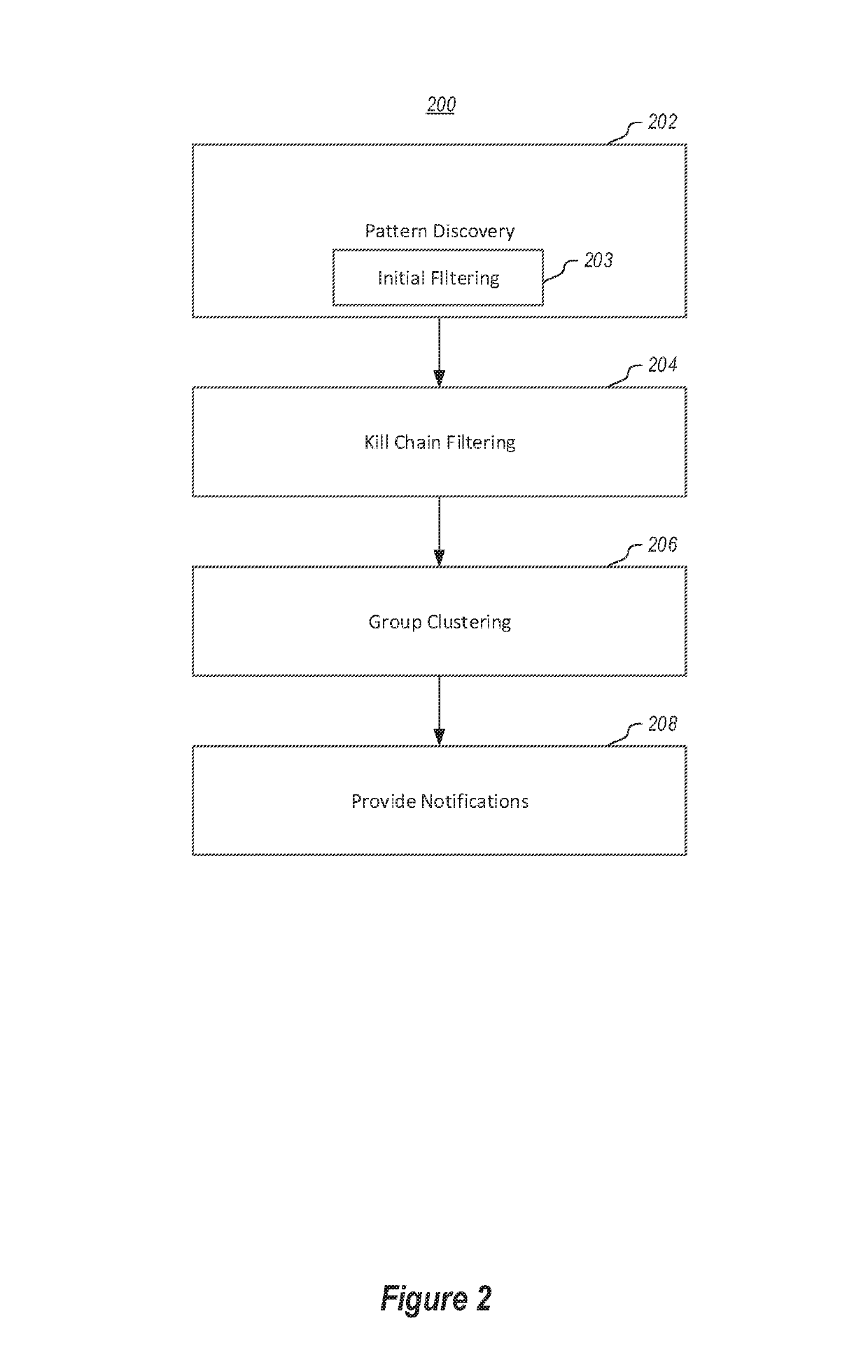
Detecting Cyber Attacks by Correlating Alerts Sequences in a Cluster Environment
ActiveUS20180248893A1Well formedComputer security arrangementsMachine learningCyber-attackHeterogeneous group
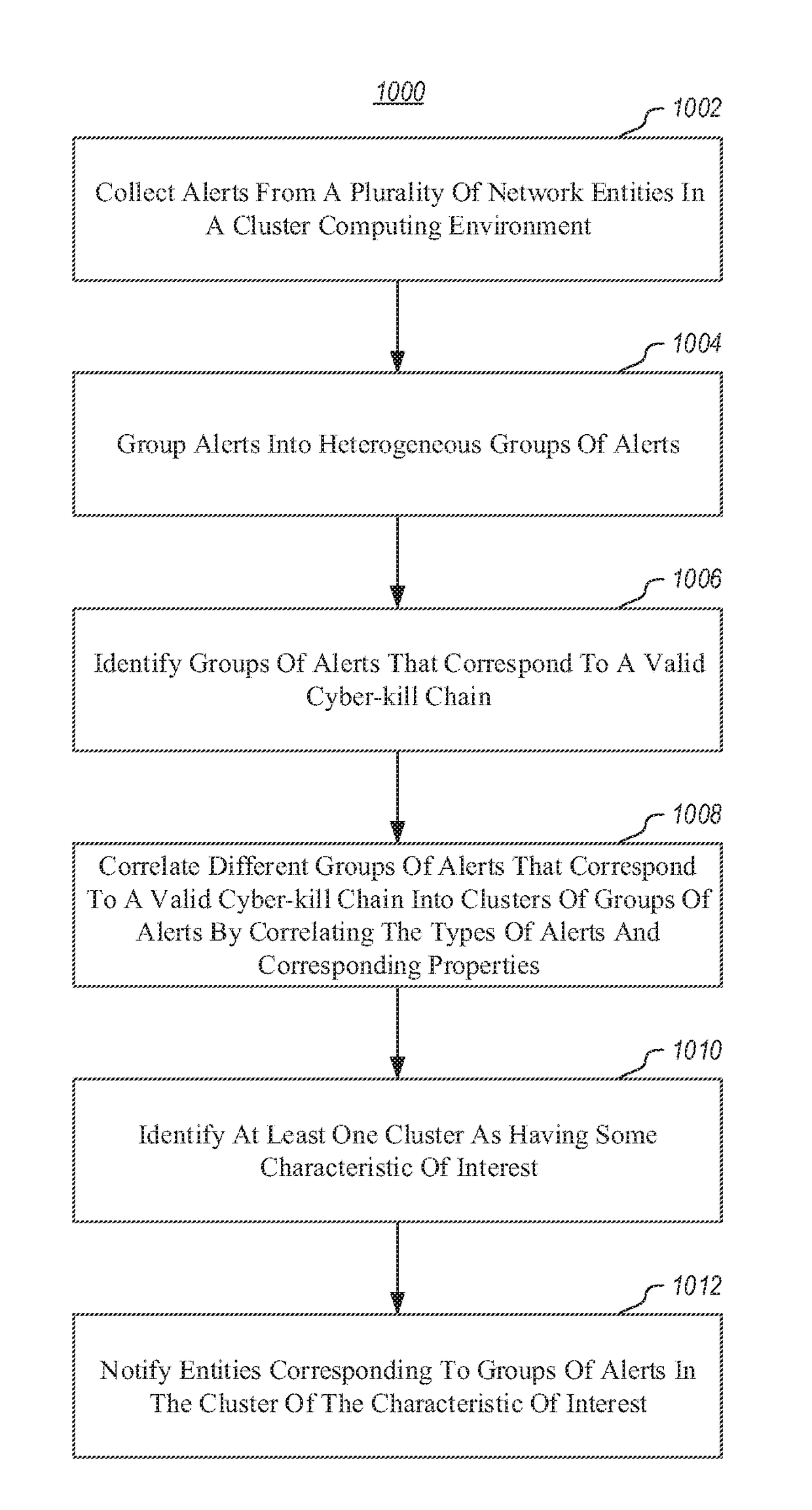
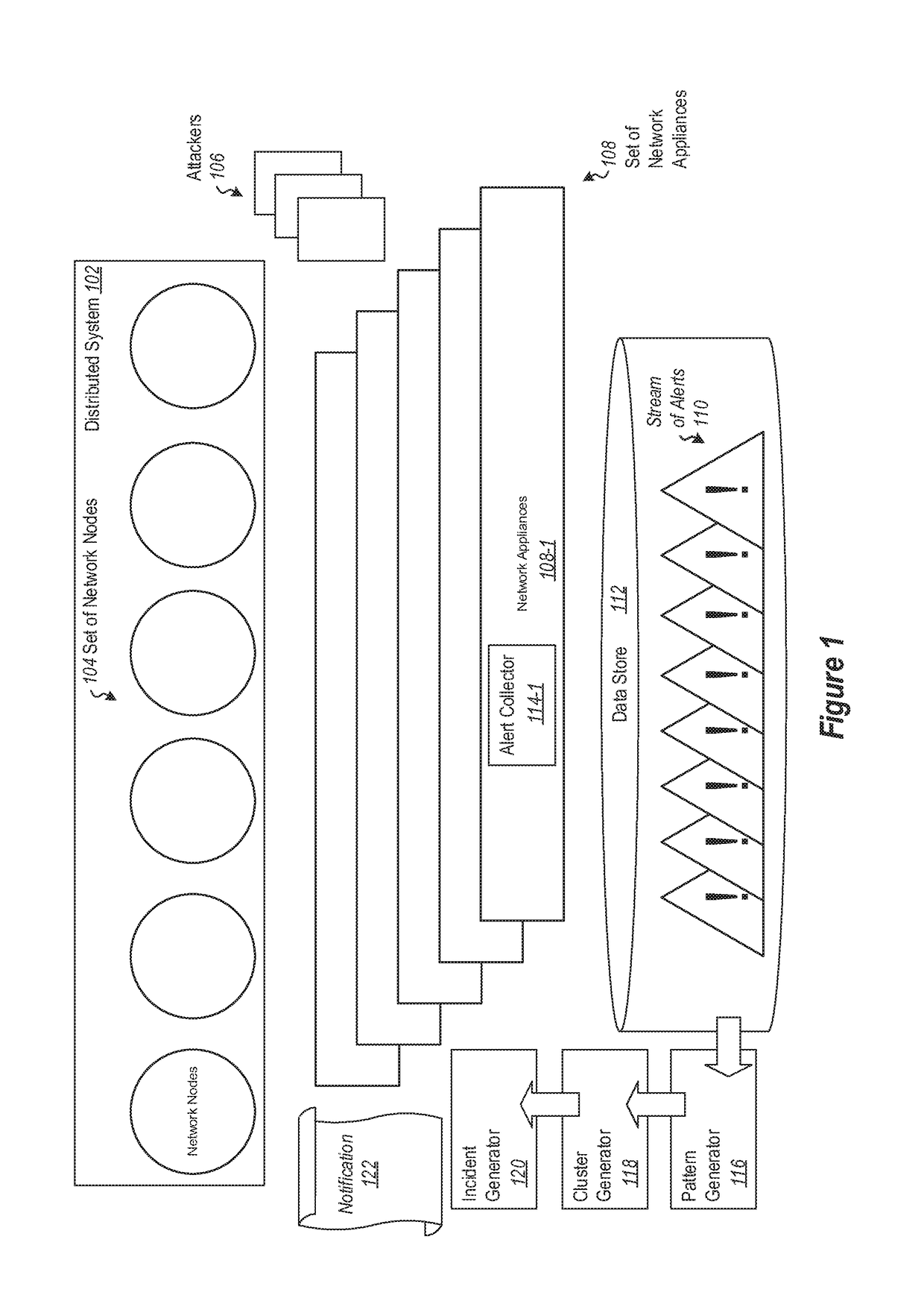
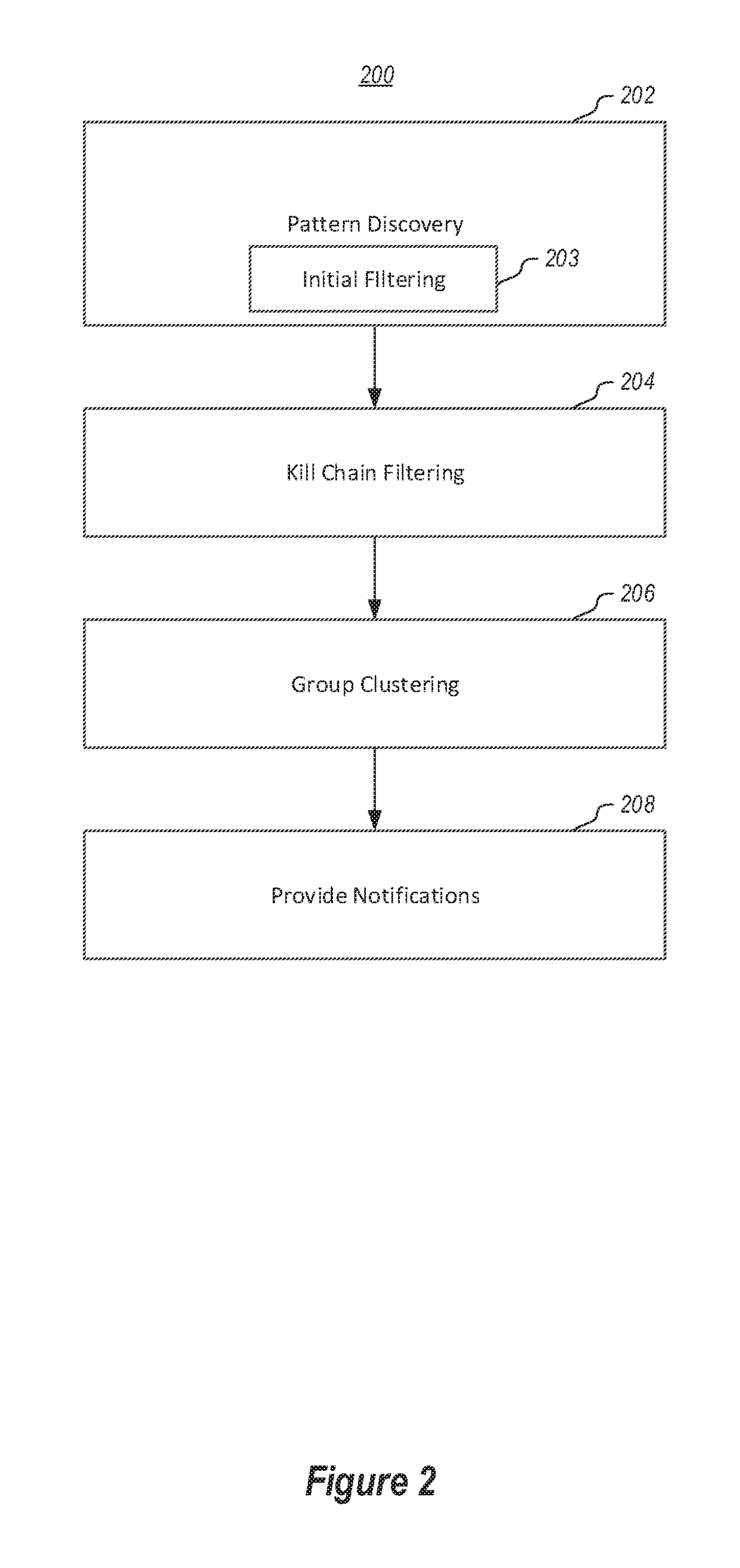
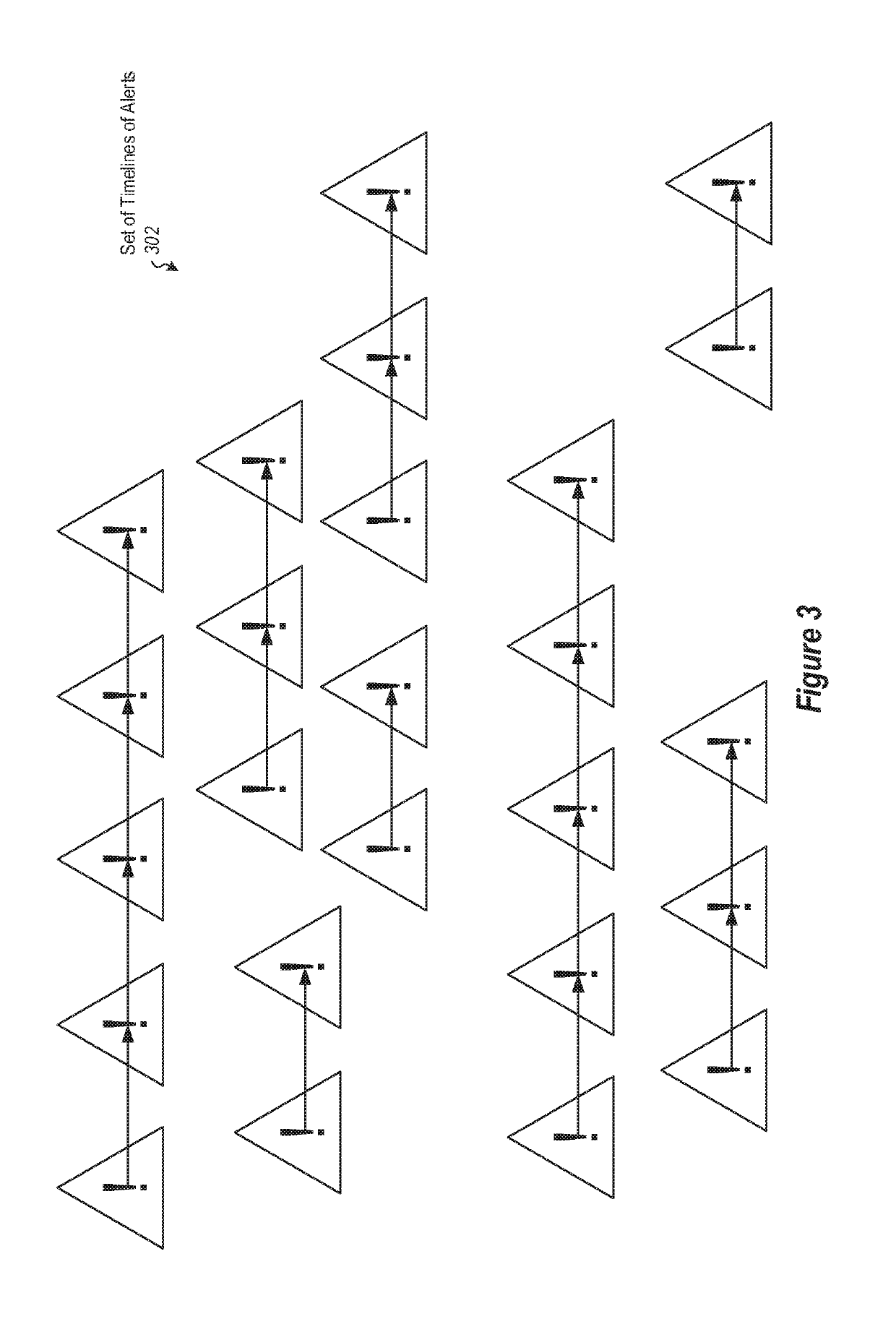
Providing network entities with notifications of attacks on the entities. A method includes collecting alerts from a plurality of network entities in a cluster computing environment. Alerts are grouped into heterogeneous groups of alerts. Each group includes a plurality of different types of alerts. Each alert has corresponding properties, including at least one property identifying the type of alert. Each group of alerts corresponds to a timeline of alerts for a particular entity. Groups of alerts that correspond to a valid cyber-kill chain are identified. Different groups of alerts that correspond to a valid cyber-kill chain are correlated into clusters of groups of alerts by correlating the types of alerts and corresponding properties. At least one cluster is identified as having some characteristic of interest. Entities corresponding to groups of alerts in the cluster are notified of the characteristic of interest.
Owner:MICROSOFT TECH LICENSING LLC
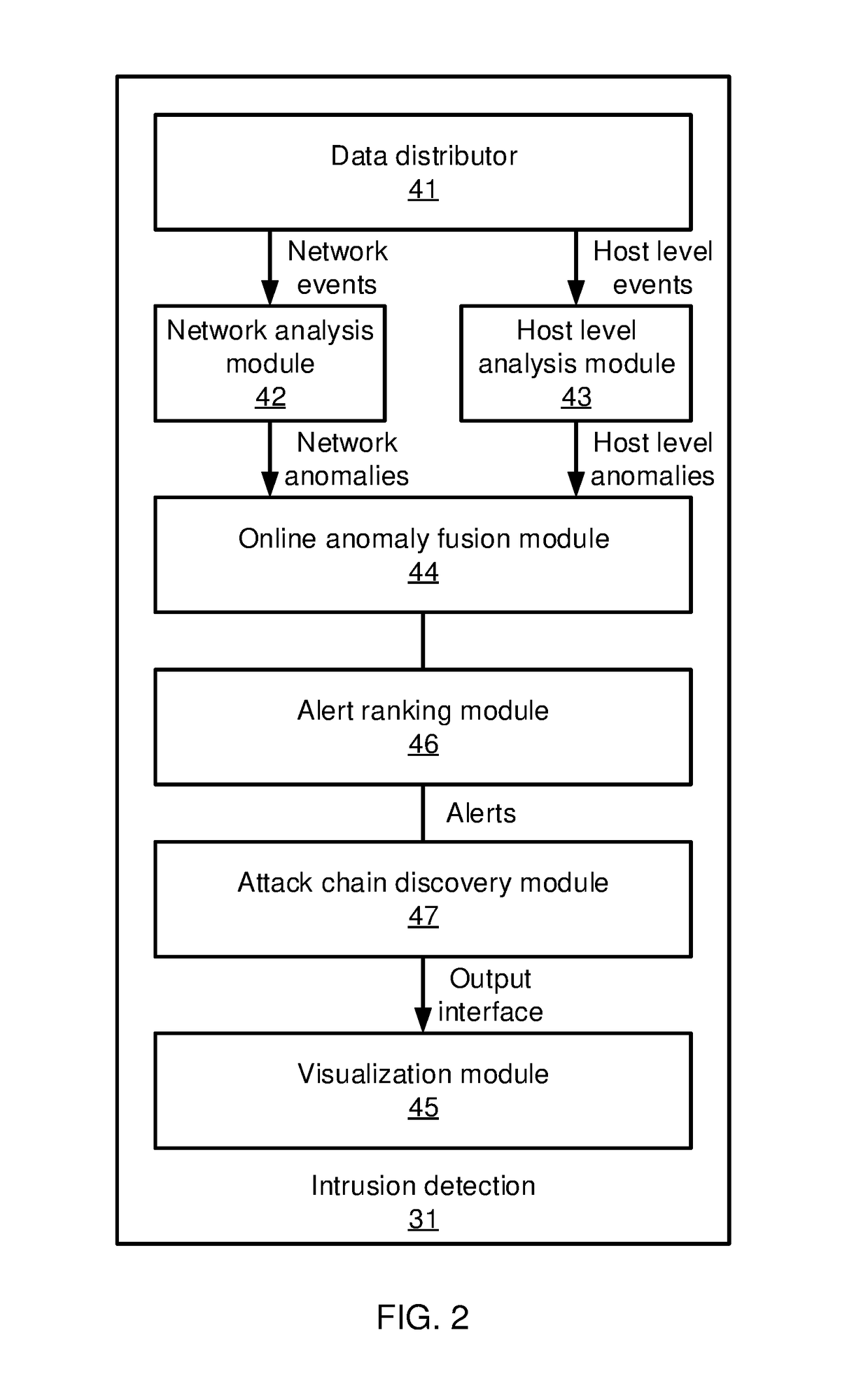
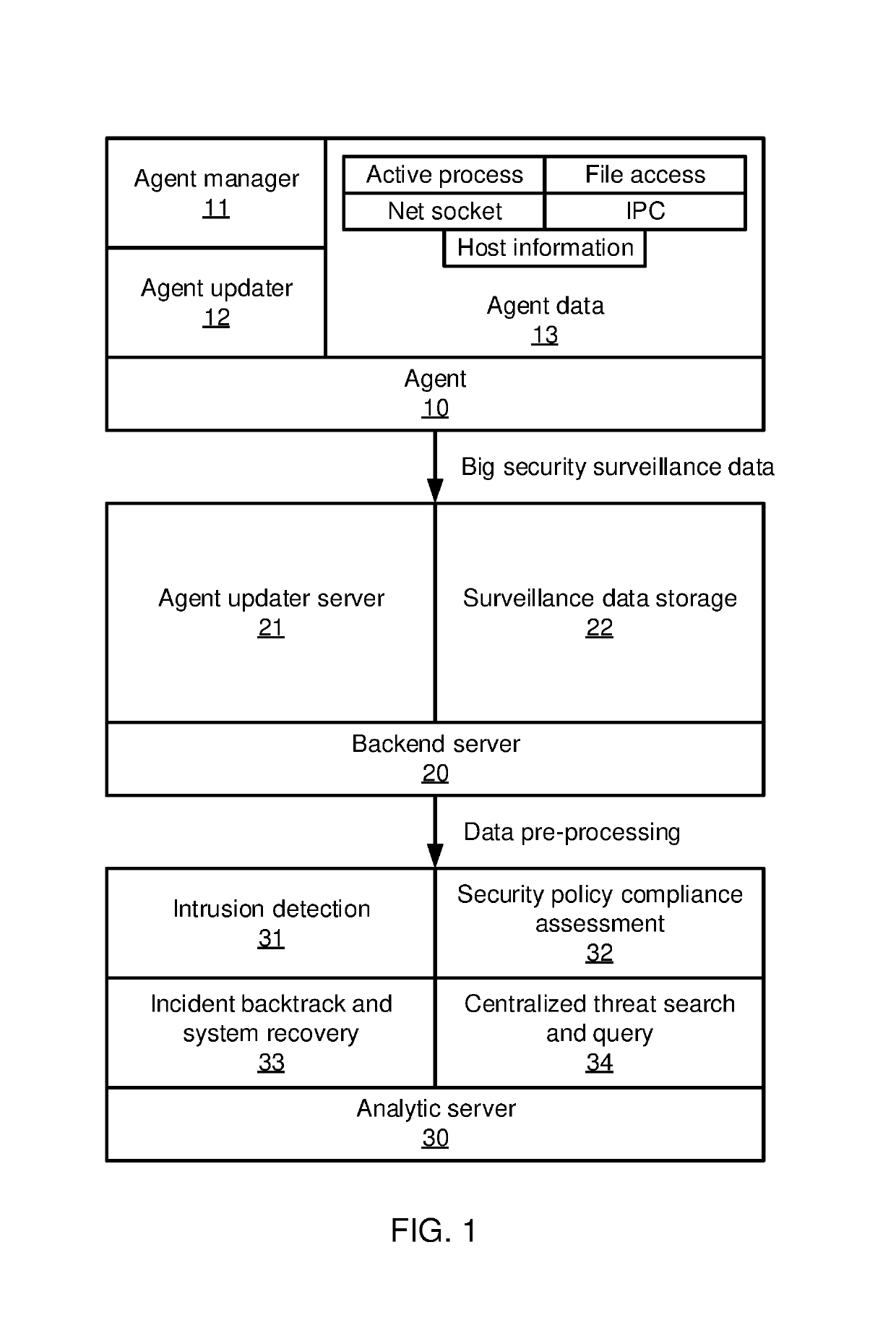
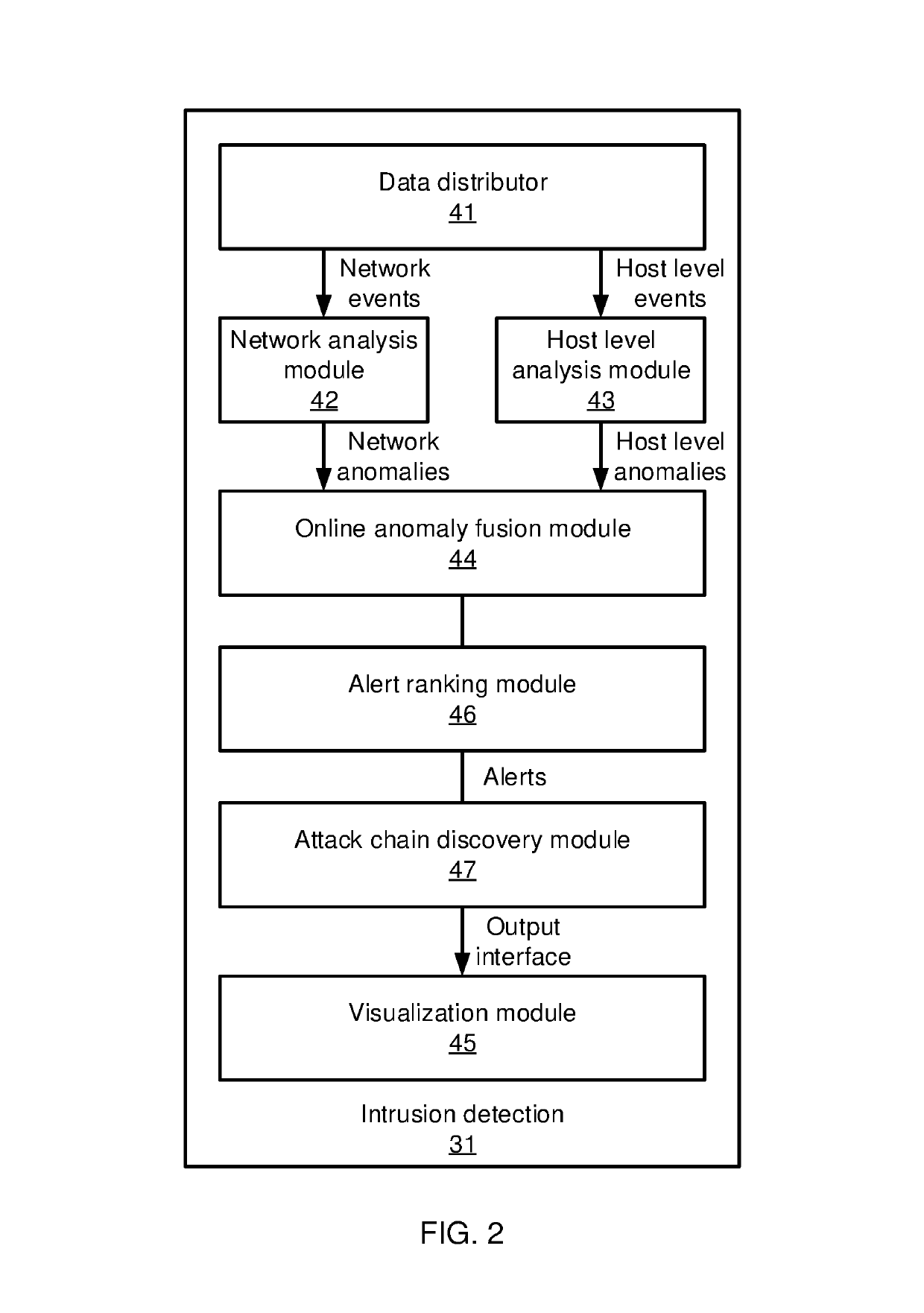
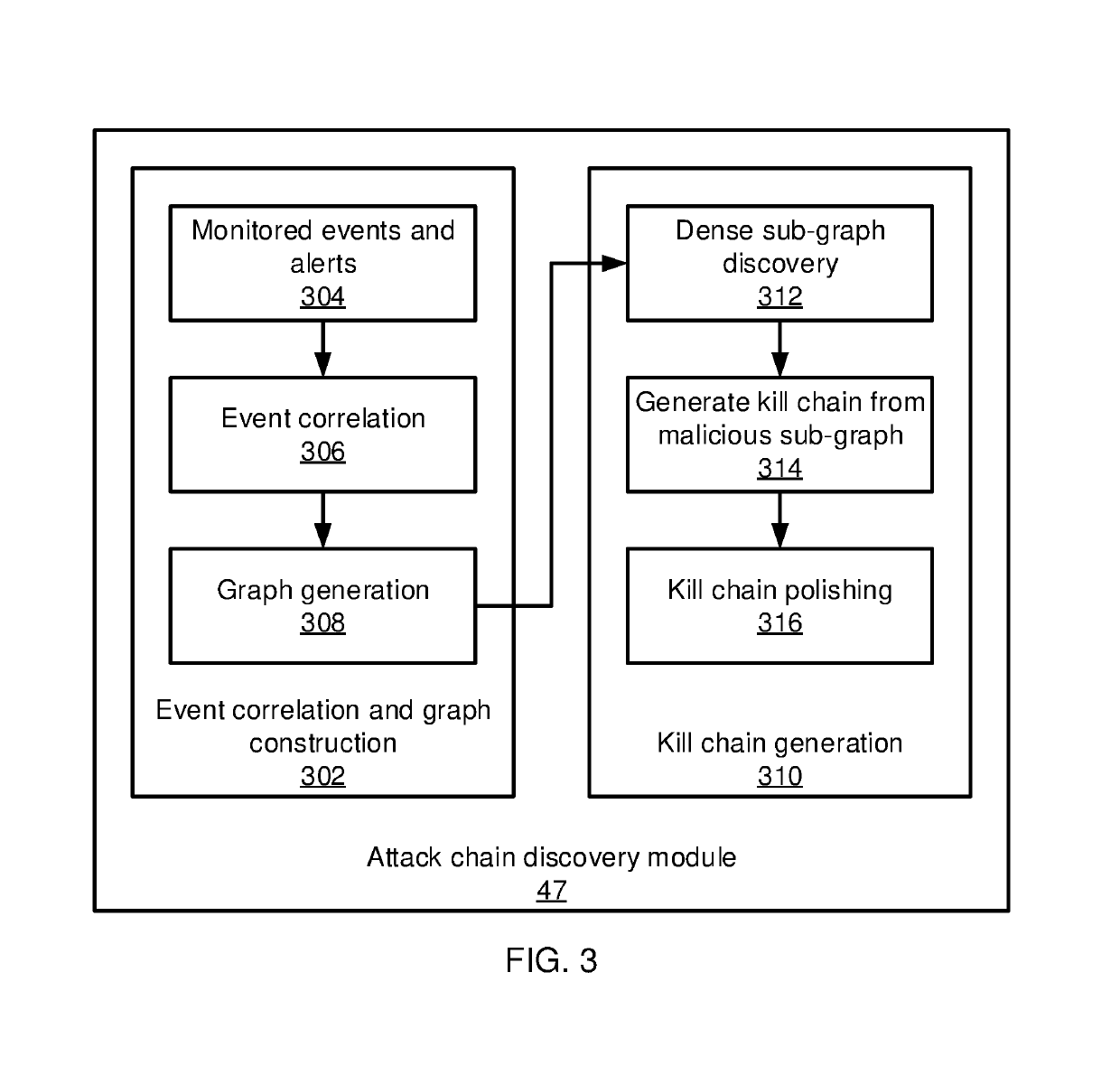
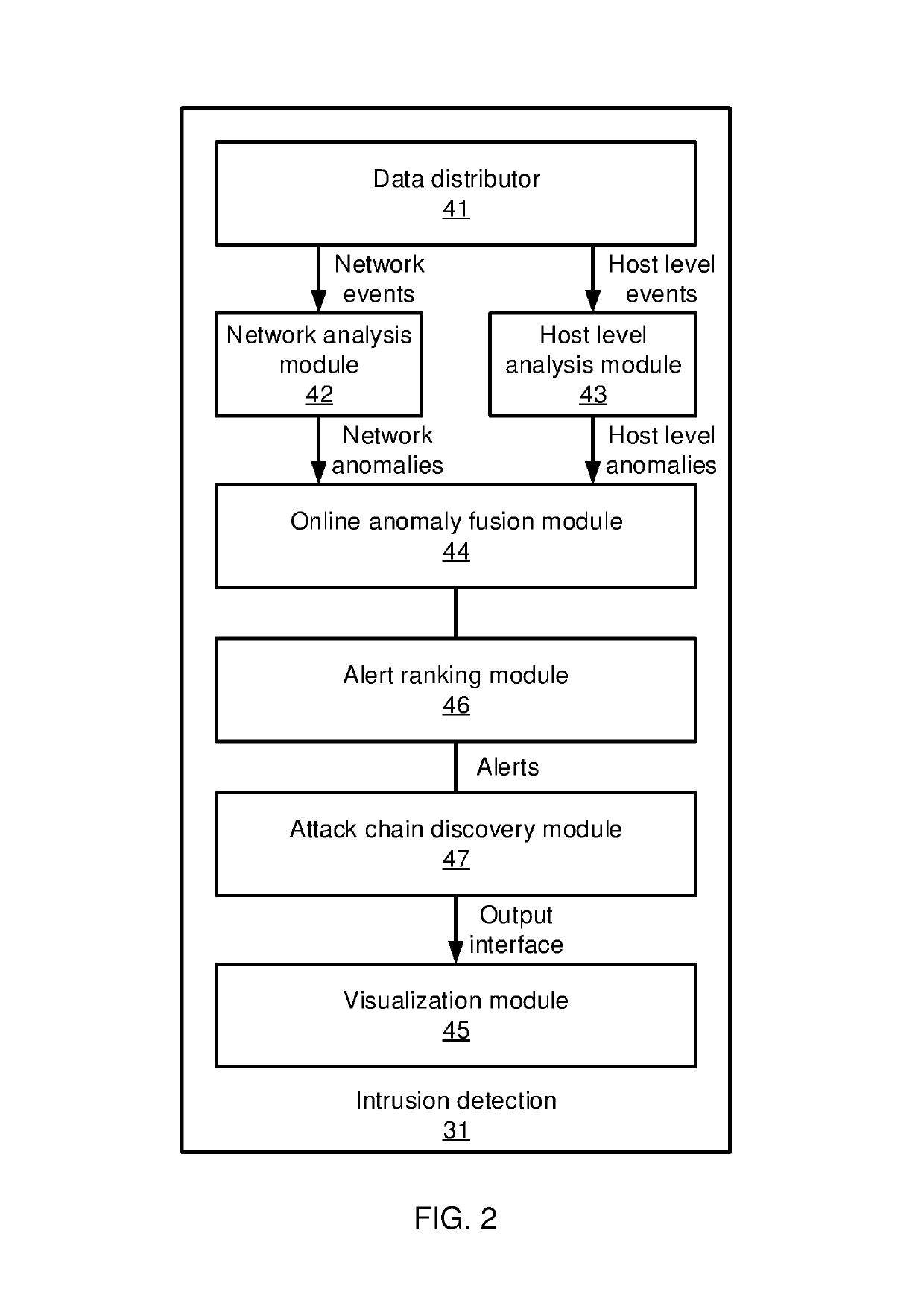
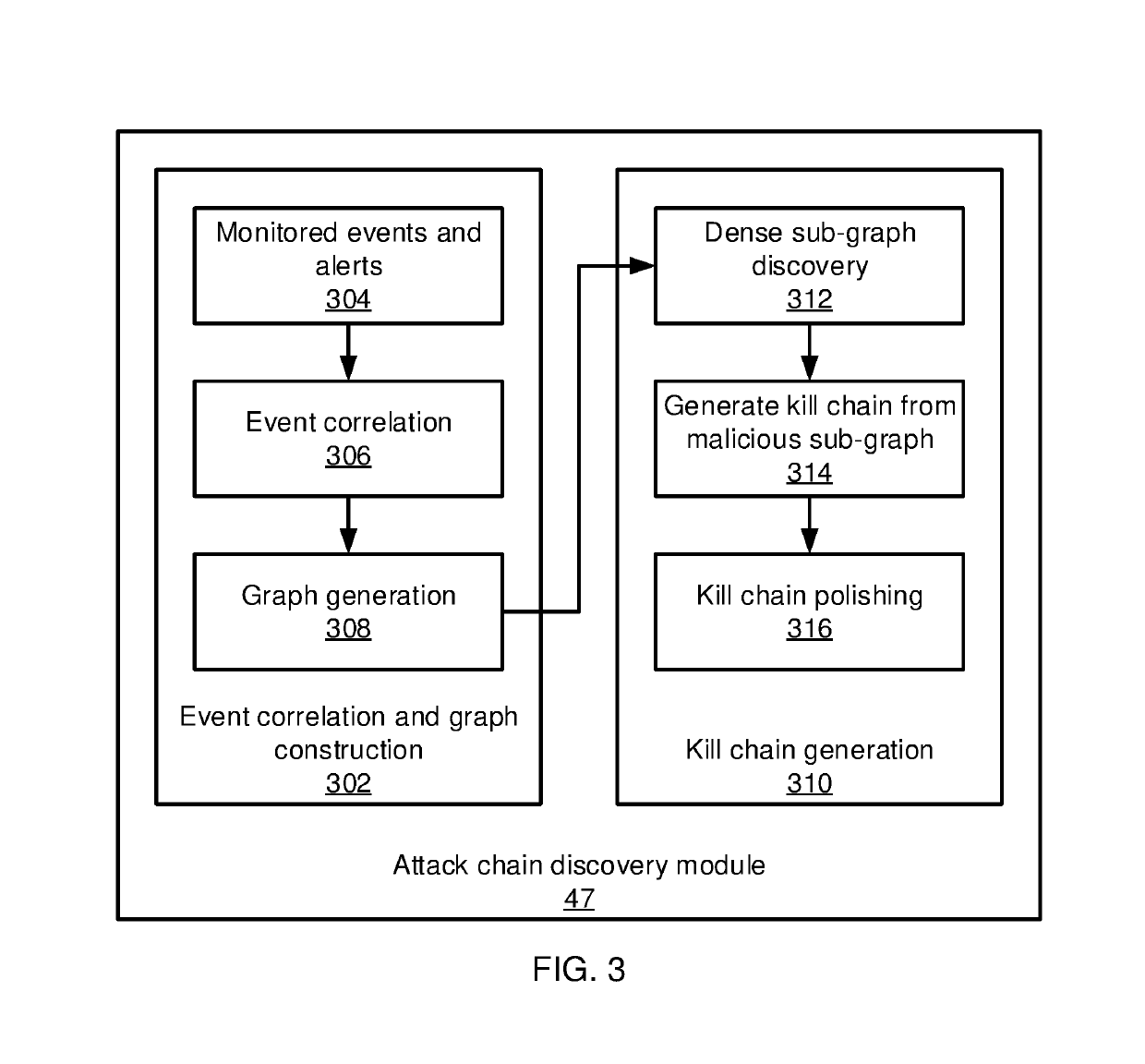
Graph-based attack chain discovery in enterprise security systems
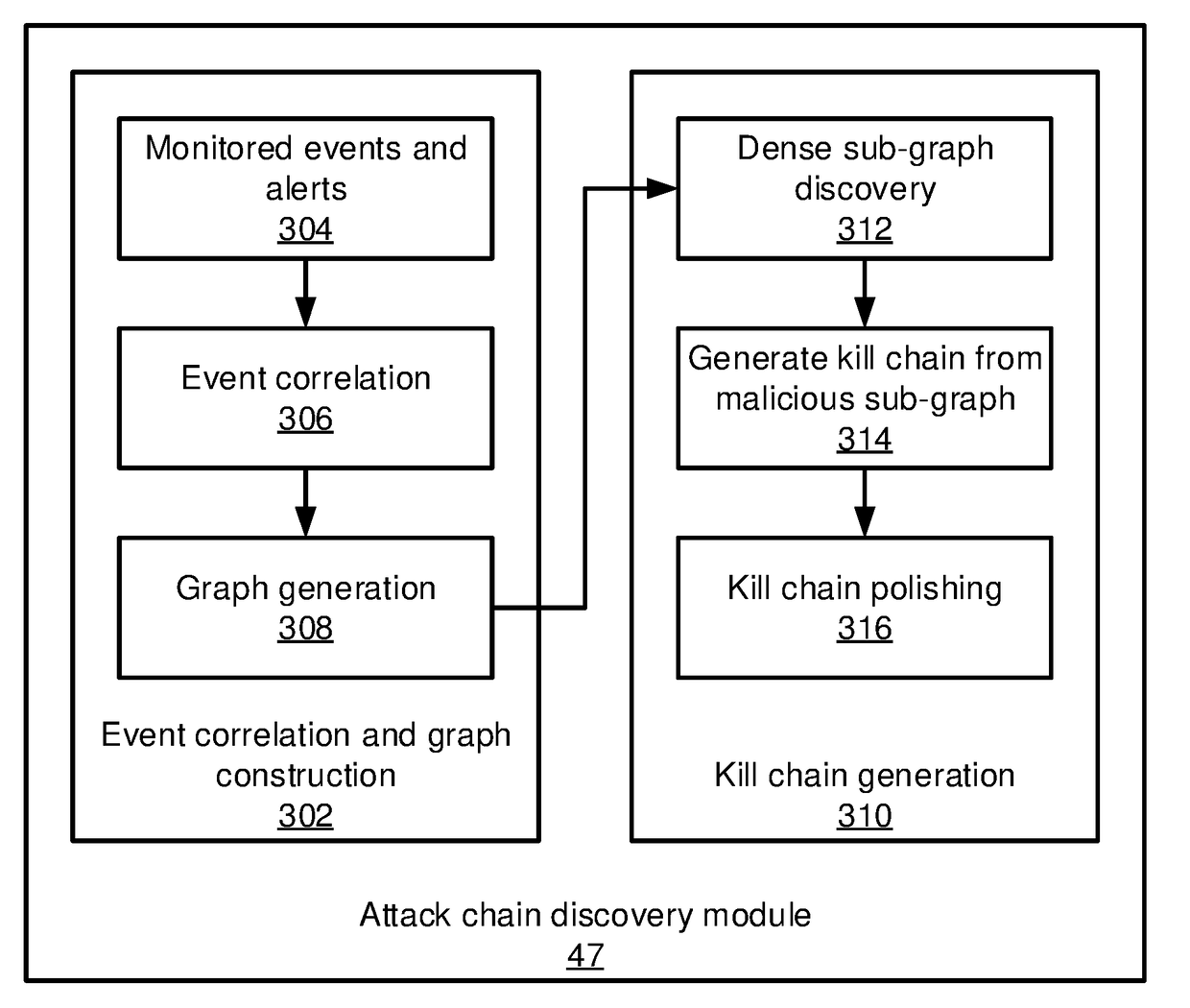
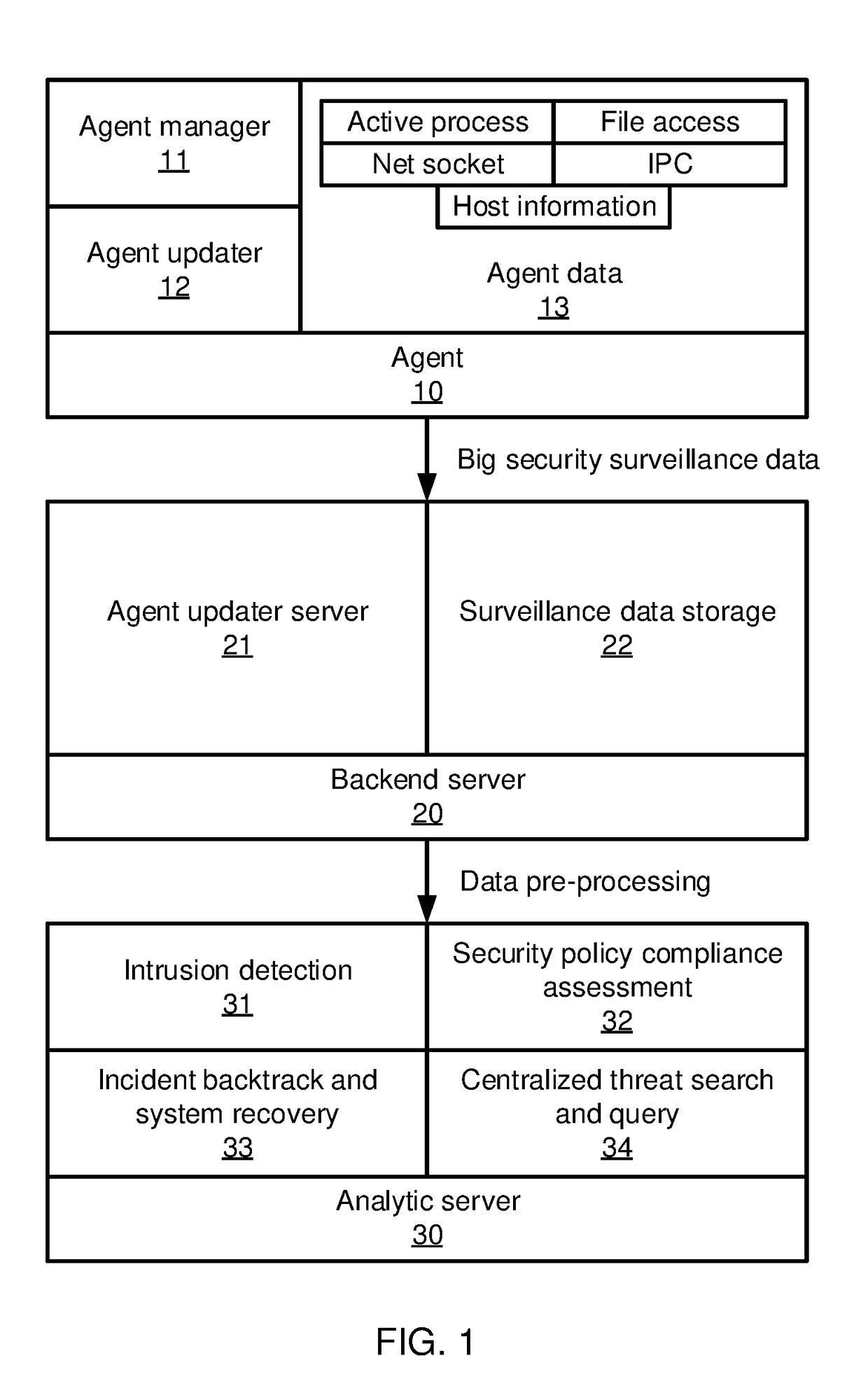
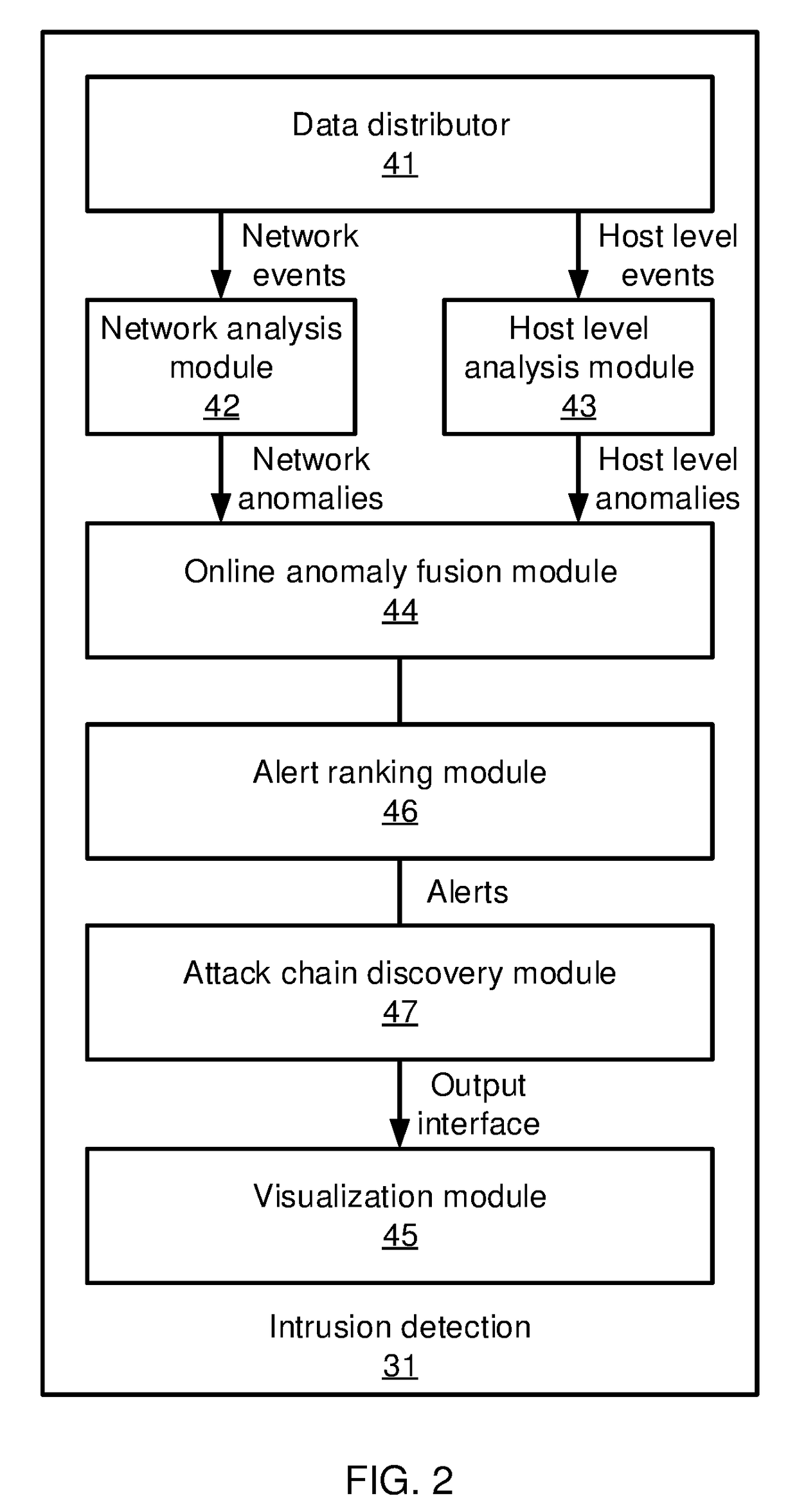
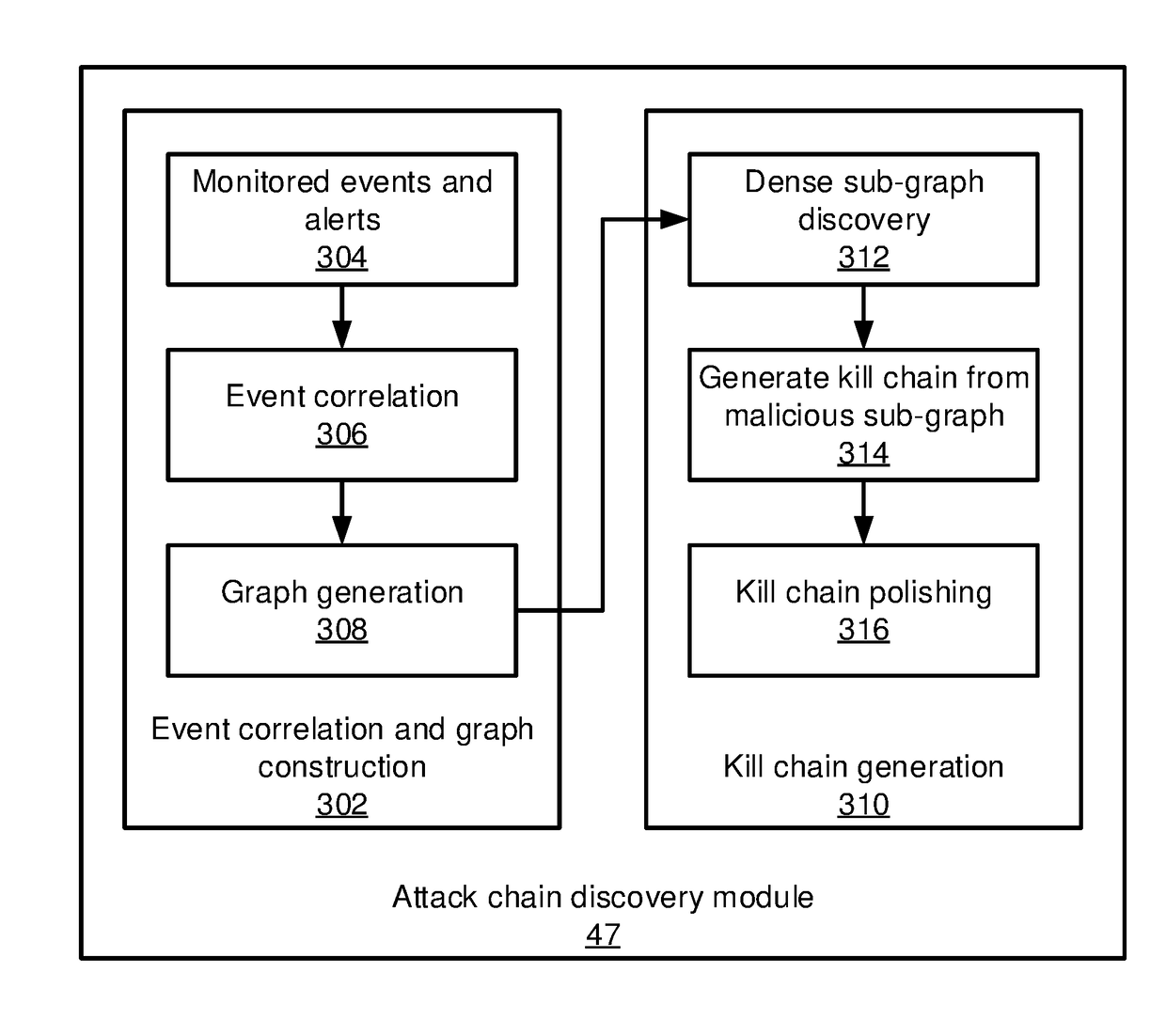
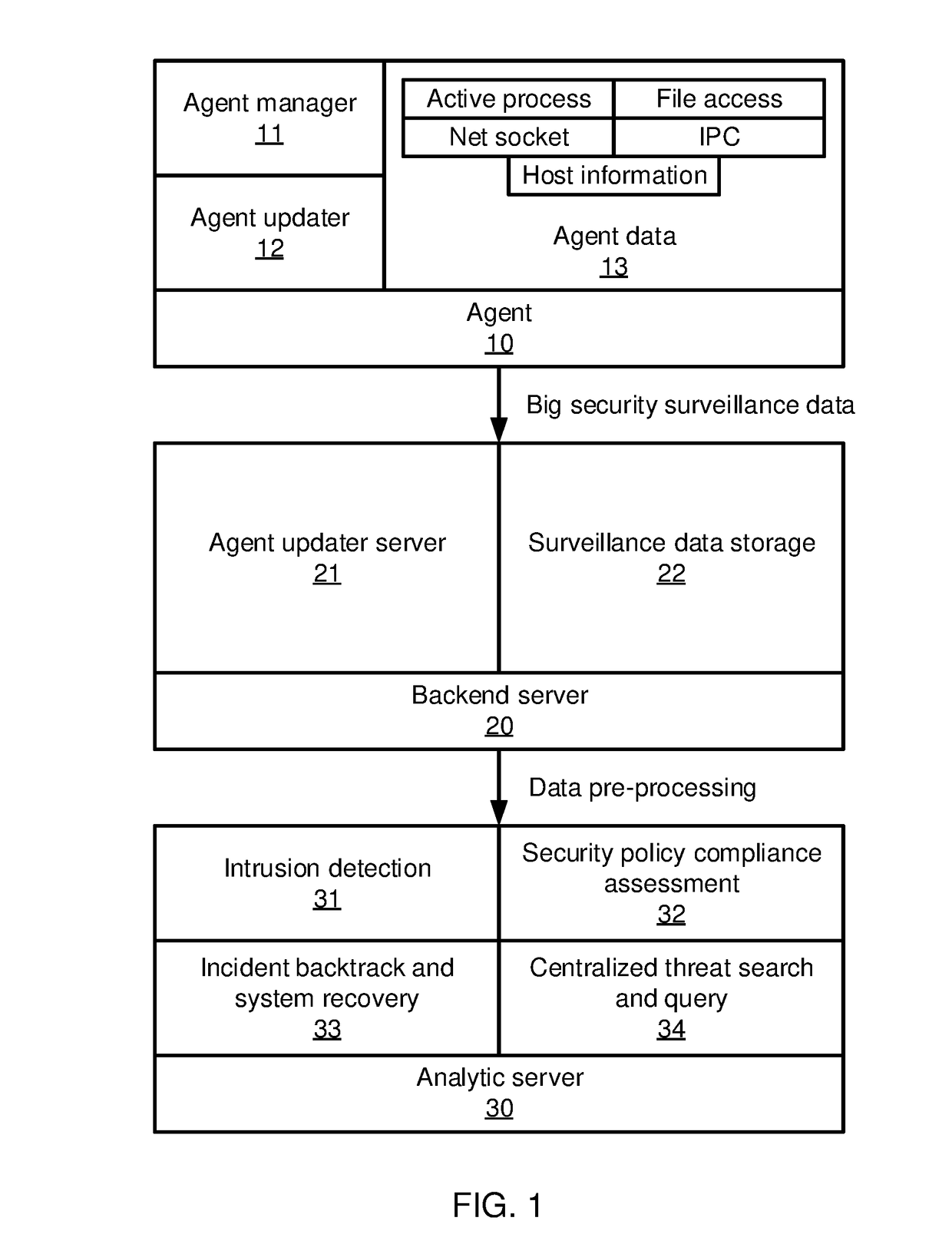
Methods and systems for detecting anomalous events include detecting anomalous events in monitored system data. An event correlation graph is generated based on the monitored system data that characterizes the tendency of processes to access system targets. Kill chains are generated that connect malicious events over a span of time from the event correlation graph that characterize events in an attack path over time by sorting events according to a maliciousness value and determining at least one sub-graph within the event correlation graph with an above-threshold maliciousness rank. A security management action is performed based on the kill chains.
Owner:NEC CORP
Constructing graph models of event correlation in enterprise security systems
ActiveUS20180048667A1Platform integrity maintainanceData switching networksGraph modelSecurity system
Methods and systems for detecting anomalous events include detecting anomalous events in monitored system data. An event correlation graph is generated by determining a tendency for a first process to access a system target, including an innate tendency of the first process to access the system target, an influence of previous events from the first process, and an influence of processes other than the first process. Kill chains are generated from the event correlation graph that characterize events in an attack path over time. A security management action is performed based on the kill chains.
Owner:NEC CORP
Method for analyzing a weapon equipment system based on a kill chain
The invention provides a method for analyzing a weapon equipment system based on a kill chain in view of the limitation of both a battle network model and a battle ring model in the prior art, namely,difficulty in analysis of system effectiveness during battle scene. The method comprises the steps that firstly, the parameters of the evaluation and analysis of the weapon equipment system effectiveness are input to construct a weapon equipment system model based on the kill chain; and then, the analysis of the weapon equipment system based on the kill chain is achieved, the method is based on the battle network model and the battle ring model, the battle rules are introduced to regulate and constraint the modeling process, the problem of violating of military common sense equipment association, such as ''a tank hitting an aircraft'' is avoided, the battle scene can be effectively described, the authenticity of an effectiveness evaluation structure of the equipment system is improved atthe same time, the analysis and evaluation methods of the tactical and technological index of the relevant system effectiveness is increased, and the effectiveness of evaluation results of the equipment system effectiveness is ensured.
Owner:NAT UNIV OF DEFENSE TECH
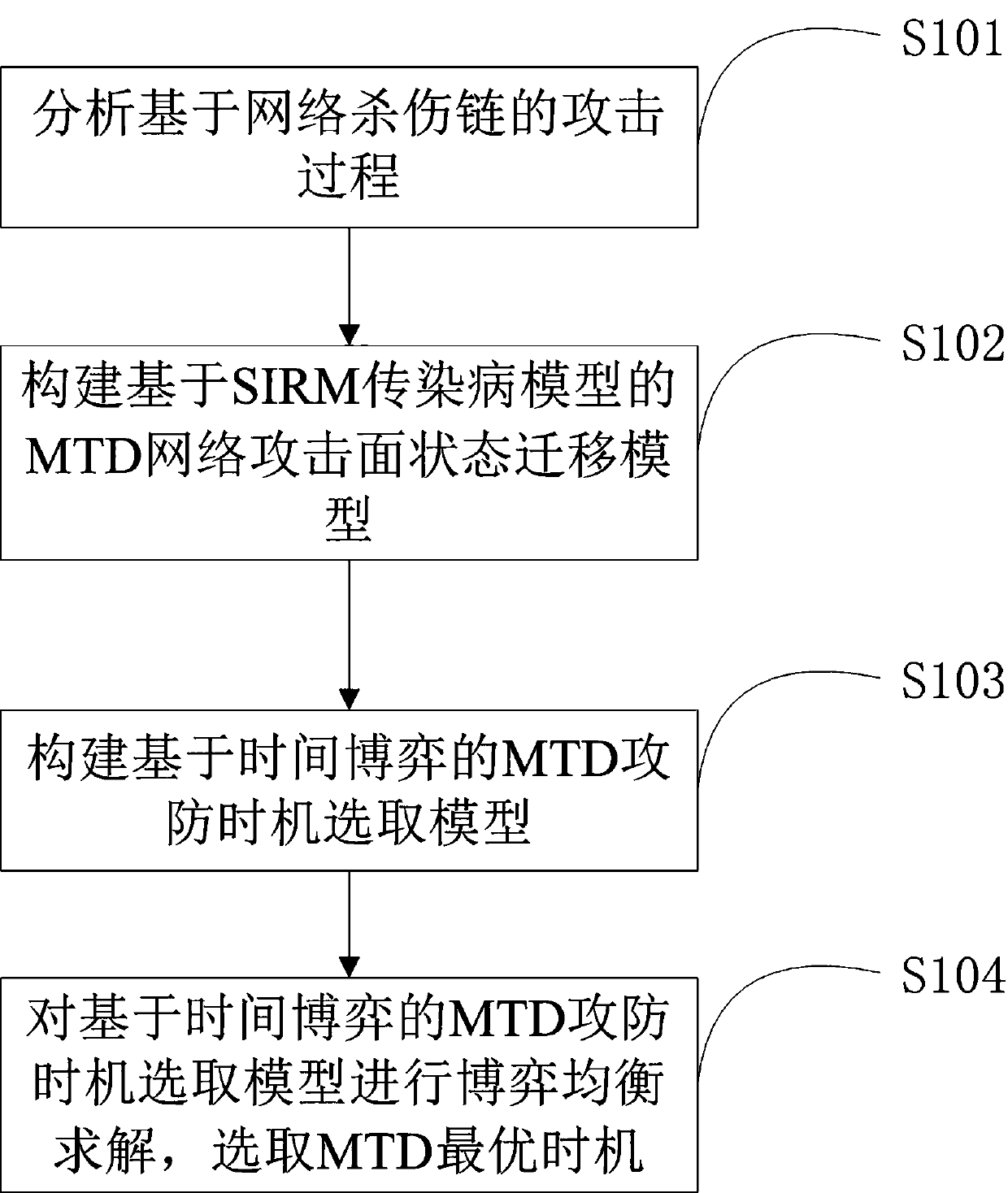
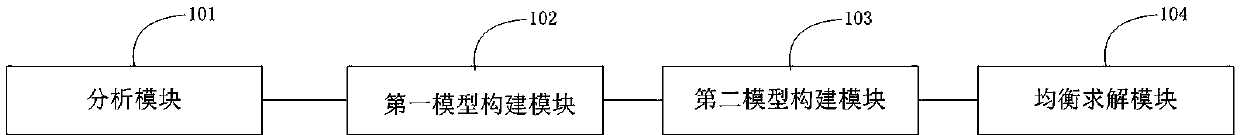
Moving target defense opportunity selection method and device based on covert confrontation
ActiveCN111385288APractical guidance is of good valueGame equilibrium solutionData switching networksQuality of serviceAttack
The invention belongs to the field of network security, and particularly relates to a moving target defense opportunity selection method and a moving target defense opportunity selection device basedon covert confrontation. The moving target defense opportunity selection method comprises the steps of: analyzing an attack process based on a cyber kill chain; constructing an MTD network attack surface state migration model based on a SIRM infectious disease model; constructing an MTD attack and defense opportunity selection model based on time game; and performing game equilibrium solution on the MTD attack and defense opportunity selection model based on the time game, and selecting the optimal opportunity of the MTD. According to the moving target defense opportunity selection method, theoptimal equilibrium point of strategy implementation opportunities of an attacker and a defender is analyzed in a time game theory framework in accordance with a real network attack and defense scene, so that the MTD implementation opportunity is guided for the defender, and the SDN service quality and MTD decision income are balanced.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
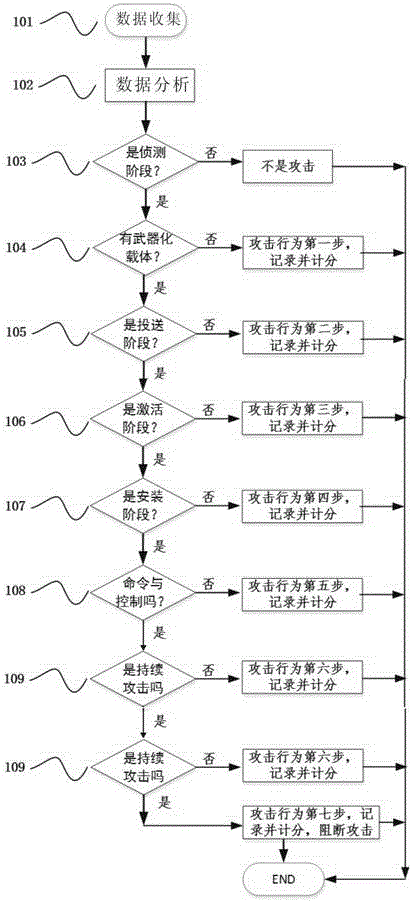
Attack behavior real-time tracking and analysis method for cyber range
The invention discloses an attack behavior real-time tracking and analysis method for a cyber range. The method comprises the following steps: data are collected; the data are analyzed; whether an attack behavior is the first step for an attack kill chain is judged; whether the attack behavior is the second step for the attack kill chain is judged, and recording and scoring are carried out; whether the attack behavior is the third step for the attack kill chain is judged, and recording and scoring are carried out; whether the attack behavior is the fourth step for the attack kill chain is judged, and recording and scoring are carried out; whether the attack behavior is the fifth step for the attack kill chain is judged, and recording and scoring are carried out; whether the attack behavior is the sixth step for the attack kill chain is judged, and recording and scoring are carried out; and whether the attack behavior is the seventh step for the attack kill chain is judged, and recording and scoring are carried out, the attack is blocked or recording and scoring are carried out, and the process is over. Thus, the efficiency for judging whether to be the attack behavior is high, the attack behavior process can be tracked, and the accuracy for judging whether to be the attack behavior is high.
Owner:重庆洞见信息技术有限公司
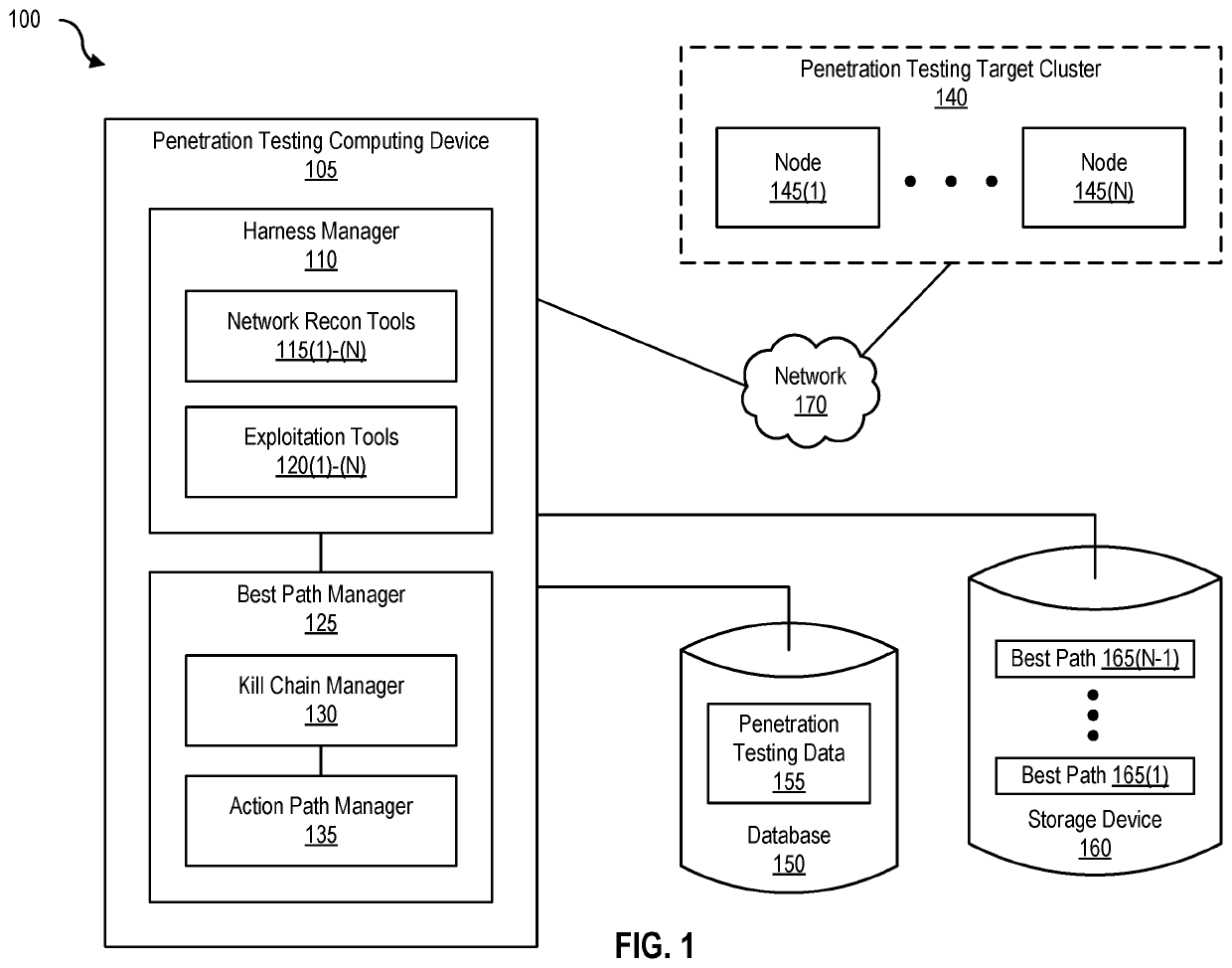
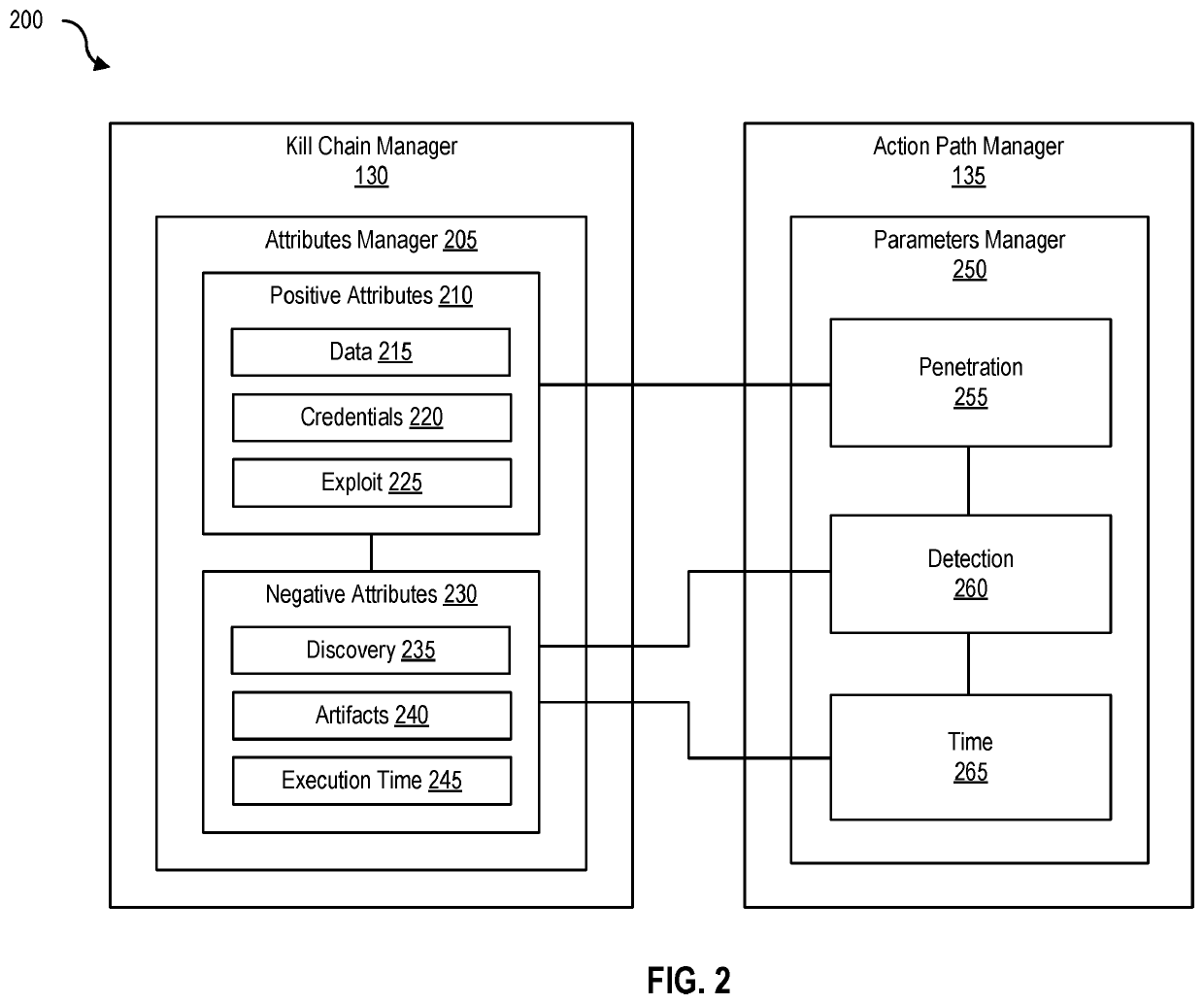
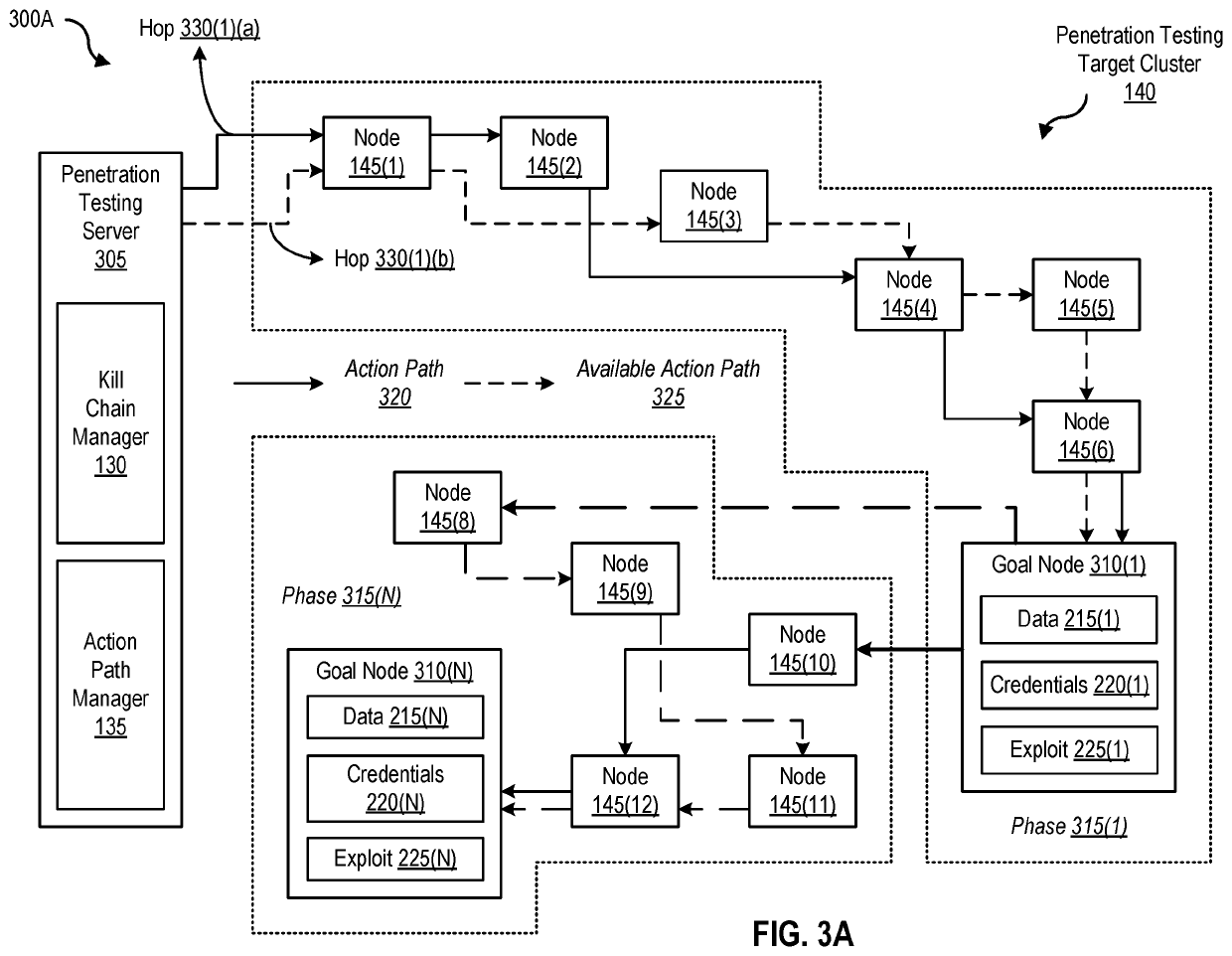
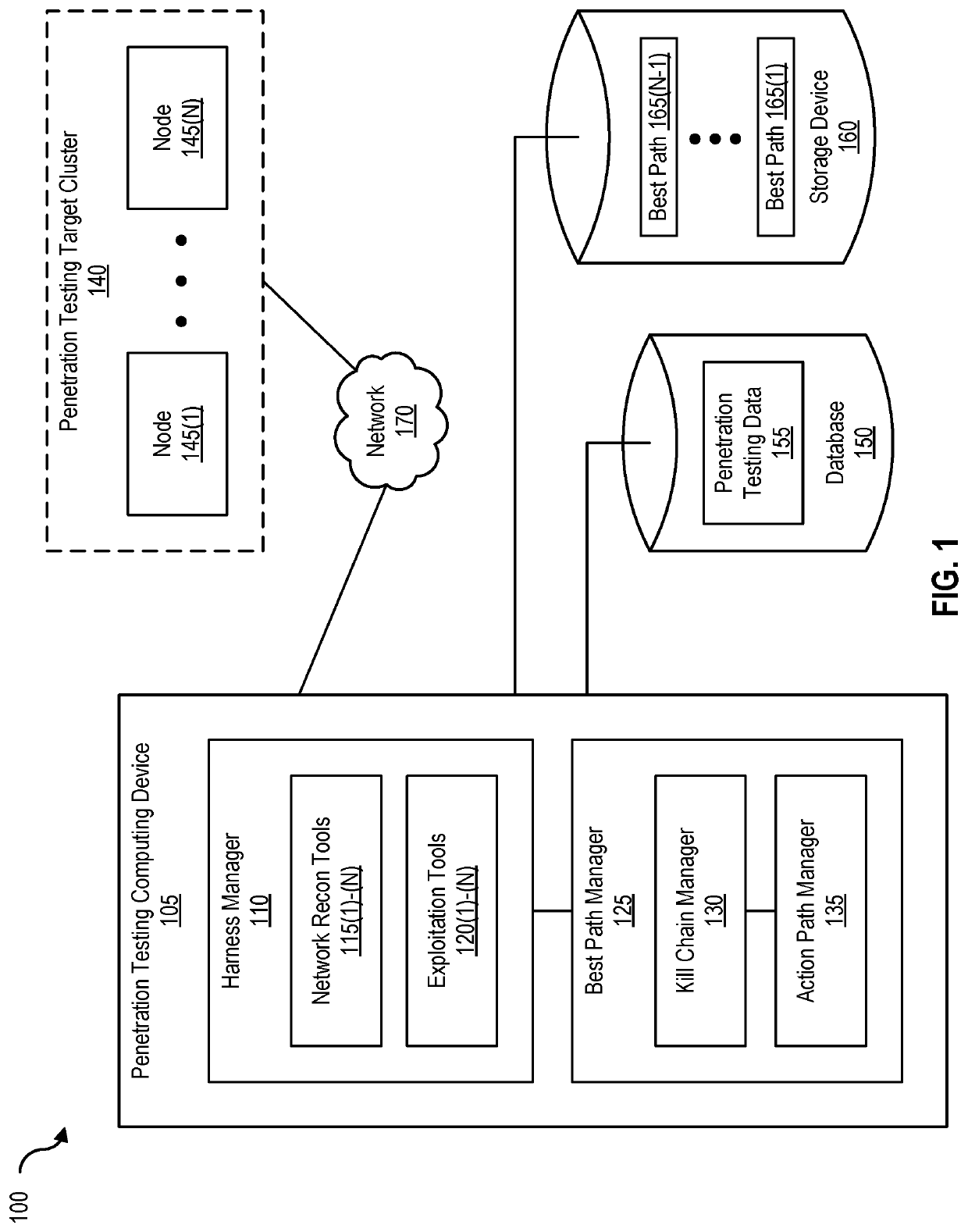
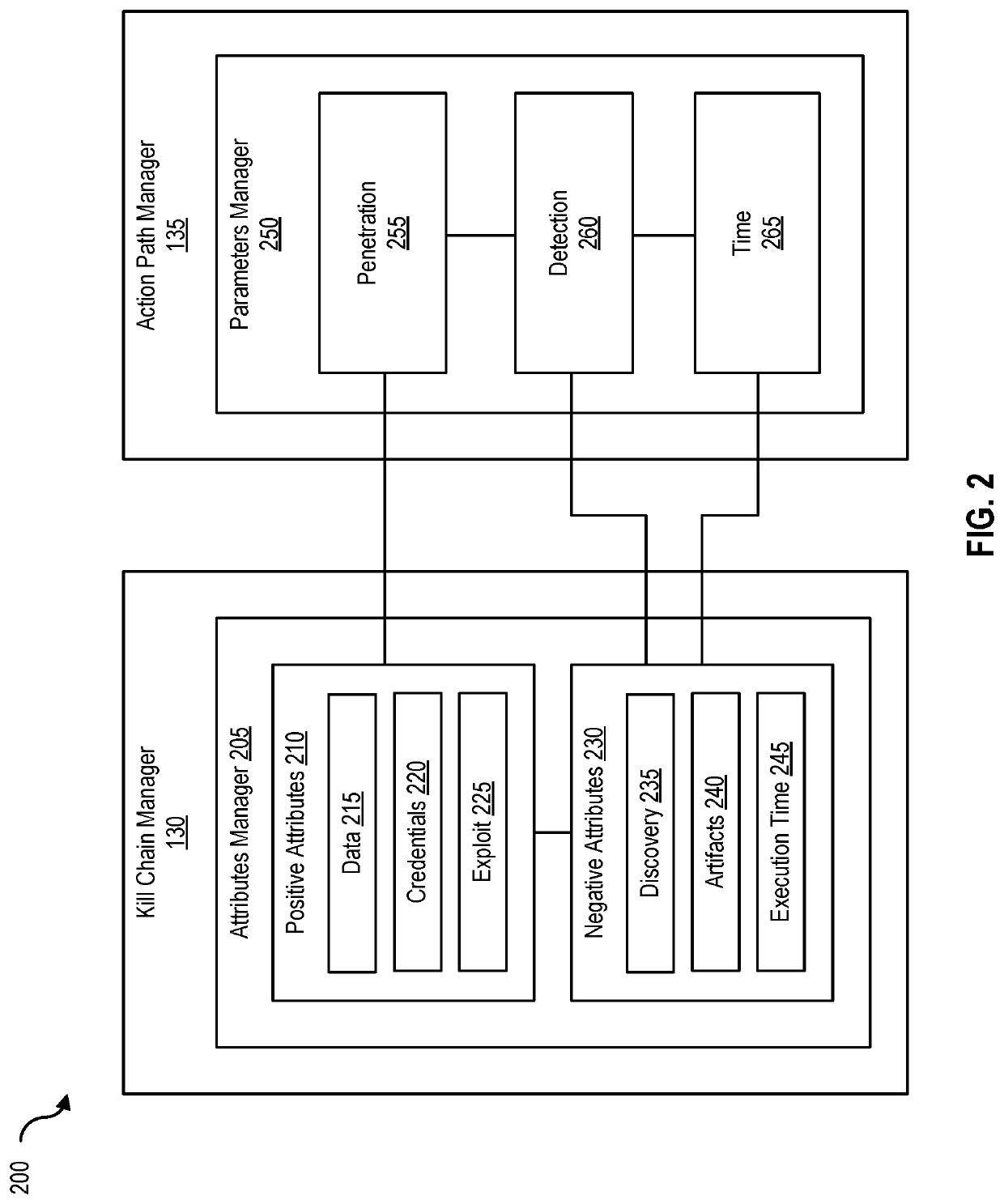
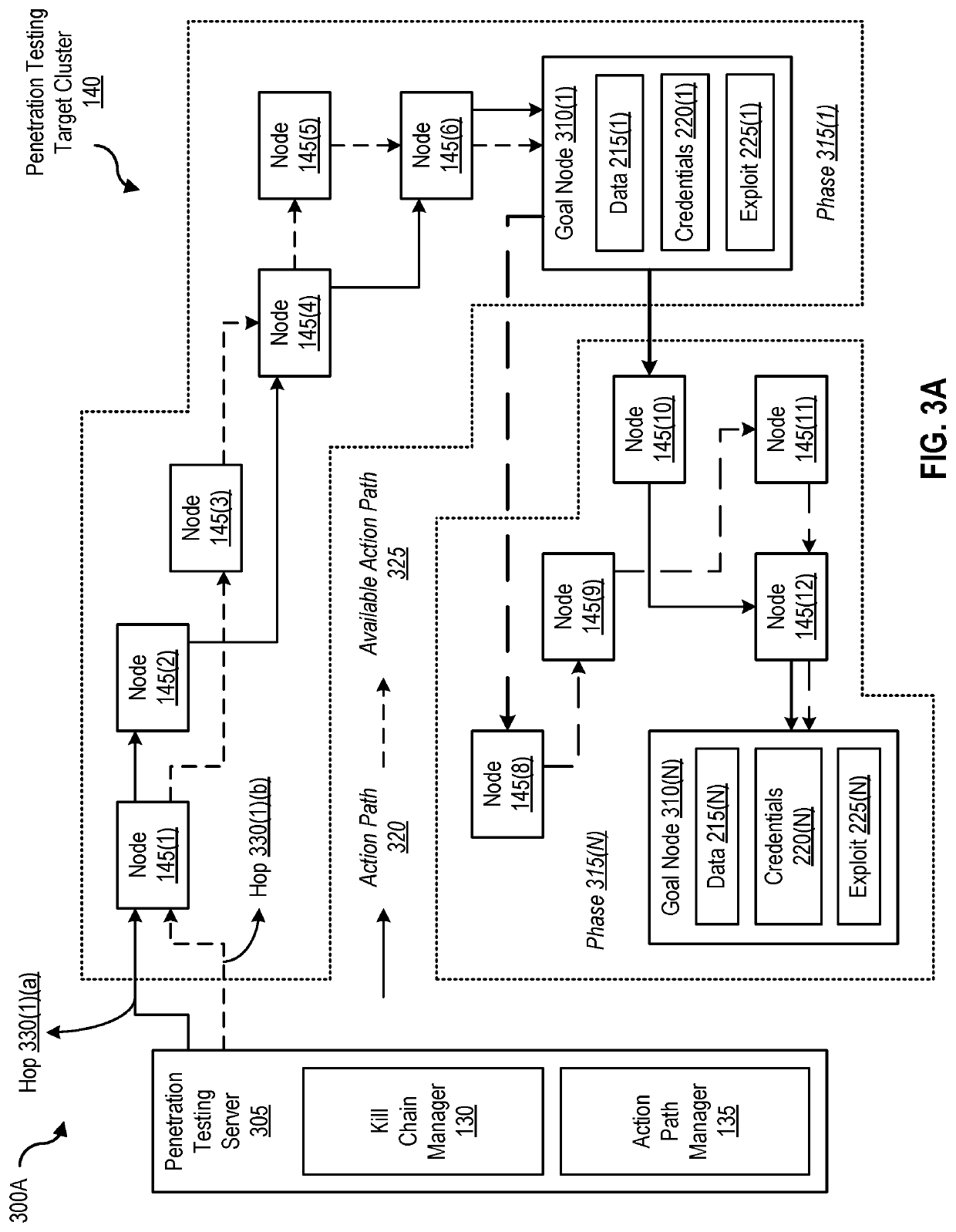
Dynamic best path determination for penetration testing
Disclosed herein are methods, systems, and processes to facilitate and perform dynamic best path determination for penetration testing. An action path that includes a kill chain that involves performance of exploit actions for a phase of a penetration test is generated by identifying the exploit actions based on a penetration parameter, a detection parameter, and / or a time parameter associated with the exploit actions. Performance of the identified exploit actions permits successful completion of the phase of the penetration test and designates the action path for inclusion as part of a best path for the penetration test.
Owner:RAPID7
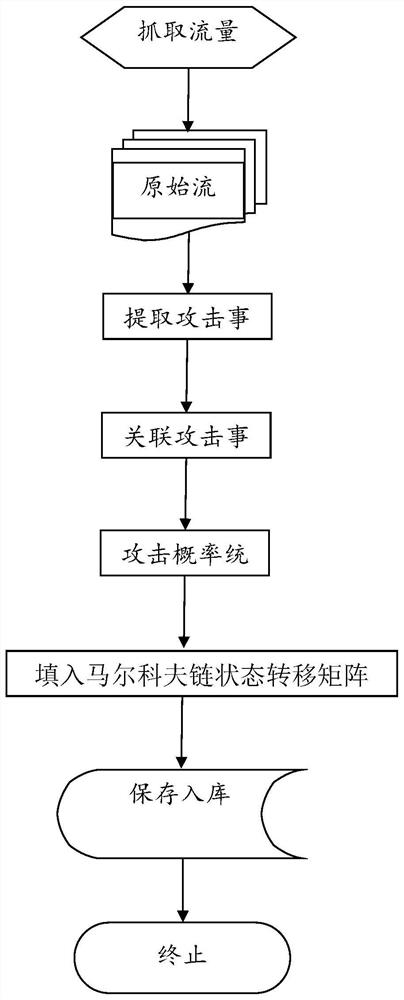
Network attack stage statistics and prediction method based on Markov chain
ActiveCN112769859AImprove accuracyWide adaptabilityMathematical modelsPlatform integrity maintainanceAlgorithmTransition matrices
The invention discloses a network attack stage statistics and prediction method based on a Markov chain, and the method specifically comprises the steps: building a state transition matrix based on the Markov chain, building a state space according to the attack process of a network attack killing chain, and carrying out the probability statistics of the attack state transition of each attack method in the attack process; establishing a Markov chain state transition matrix; correcting the state transition matrix based on the Markov chain, and correcting missing or wrong state data caused by incomplete statistical data in the state transition matrix based on the Markov chain; and predicting an attack stage in the network attack killer chain by using a Markov chain model. According to the method, a network attack chain and a Markov chain which are widely used are combined, so that network attack event statistics is more suitable for being applied to prediction, and the accuracy of an attack prediction model is improved.
Owner:NO 15 INST OF CHINA ELECTRONICS TECH GRP
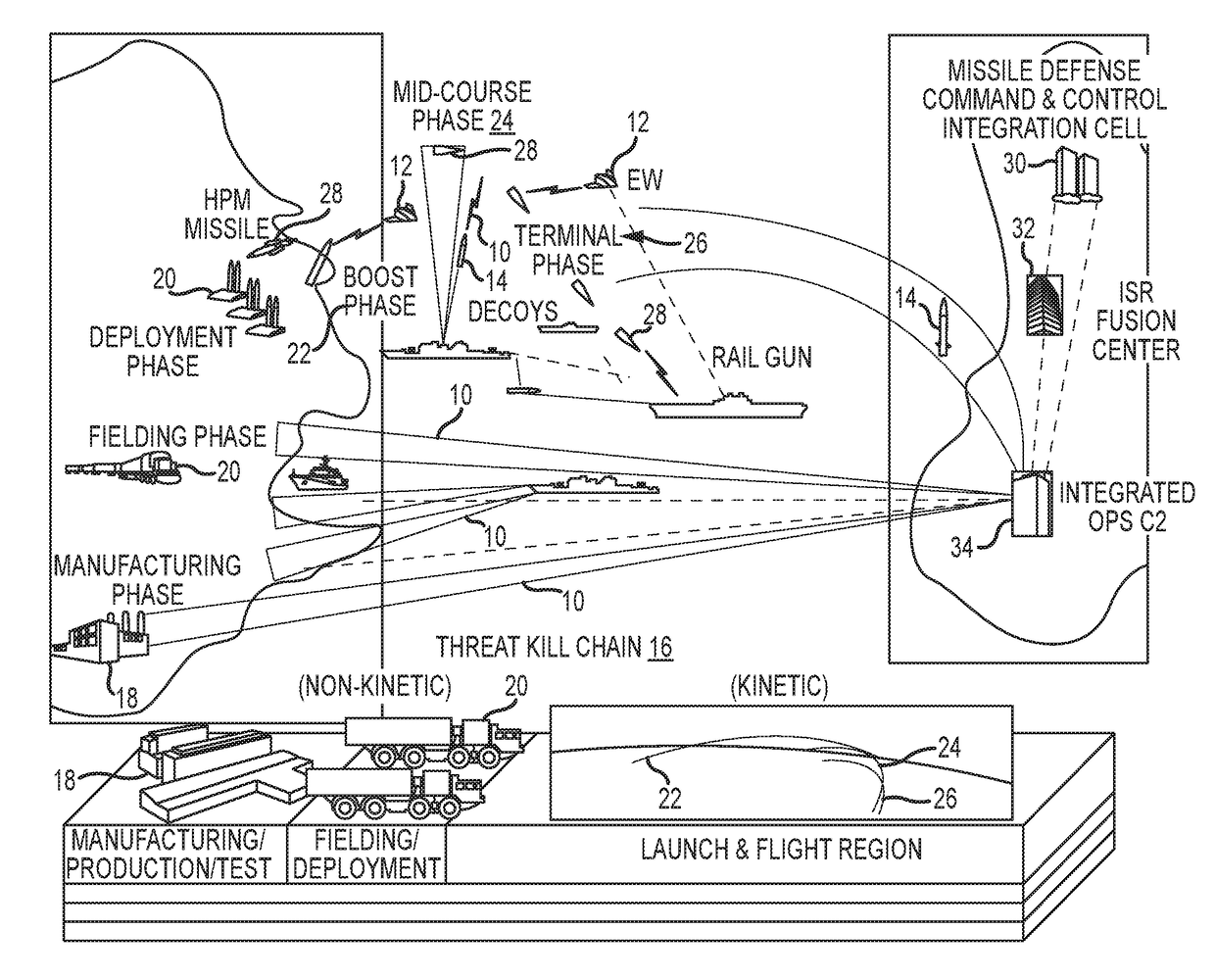
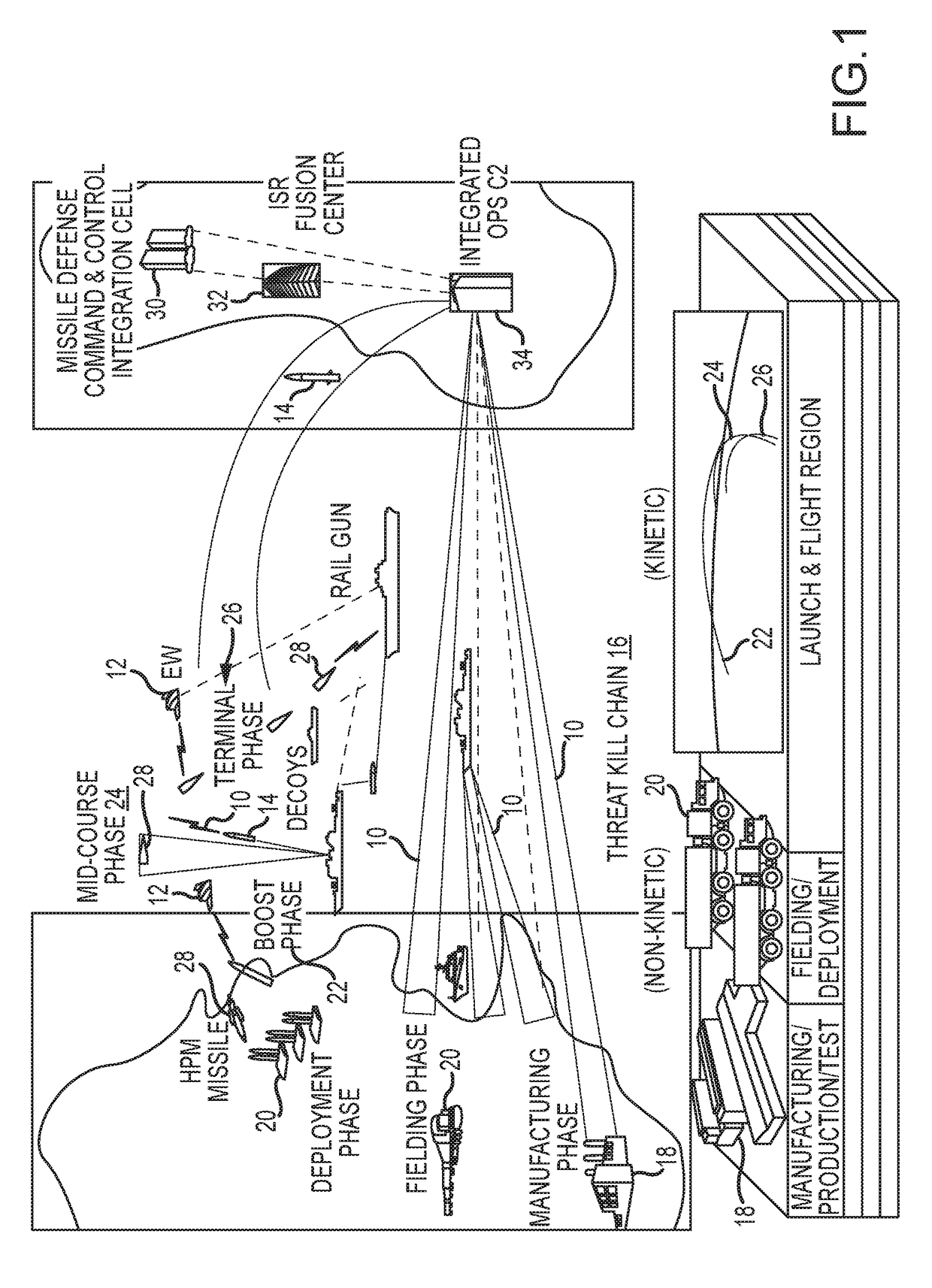
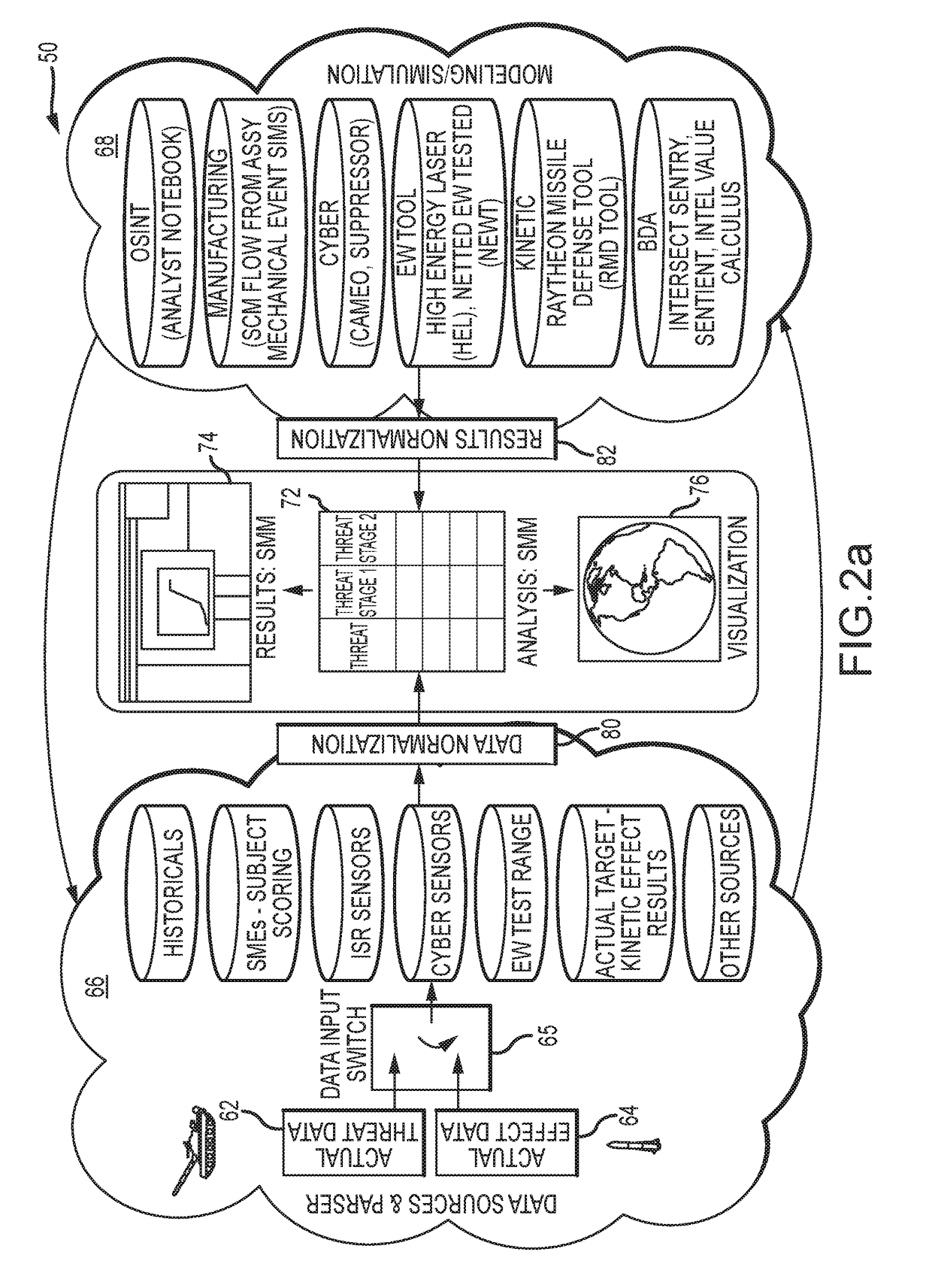
System and method for integrated and synchronized planning and response to defeat disparate threats over the threat kill chain with combined cyber, electronic warfare and kinetic effects
ActiveUS20180038669A1Facilitate user evaluationEasy selectionDefence devicesProbabilistic networksConfidence intervalMathematical model
An automated system and method provides for planning and response to disparate threats with combined kinetic (e.g., missile interceptor) and non-kinetic (e.g., cyber and electronic warfare) effects. The threat and effects inputs and the results of analysis tools that individually apply a single effect type to negate a threat vulnerability are normalized to a form and format ingestible by a Stochastic Math Model (SMM). The normalized inputs reflect the success / failure of the effect versus a threat vulnerability as a score, not a probability. The normalized results decompose a probability of defeat (Pdefeat) for an individual effect as a set of hierarchical parameters represented as probabilities. The SMM and analysis tools are iteratively run on the normalized inputs and results data, including either organically or synthetically injected variability of the data, to compute and visualize a Pdefeat with an associated confidence interval (CI) for each effect and the combined effects at each stage of the threat kill chain.
Owner:RAYTHEON CO
A method for weapon equipment system analysis based on kill chain
The invention provides a method for analyzing a weapon equipment system based on a kill chain in view of the limitation of both a battle network model and a battle ring model in the prior art, namely,difficulty in analysis of system effectiveness during battle scene. The method comprises the steps that firstly, the parameters of the evaluation and analysis of the weapon equipment system effectiveness are input to construct a weapon equipment system model based on the kill chain; and then, the analysis of the weapon equipment system based on the kill chain is achieved, the method is based on the battle network model and the battle ring model, the battle rules are introduced to regulate and constraint the modeling process, the problem of violating of military common sense equipment association, such as ''a tank hitting an aircraft'' is avoided, the battle scene can be effectively described, the authenticity of an effectiveness evaluation structure of the equipment system is improved atthe same time, the analysis and evaluation methods of the tactical and technological index of the relevant system effectiveness is increased, and the effectiveness of evaluation results of the equipment system effectiveness is ensured.
Owner:NAT UNIV OF DEFENSE TECH
Graph-based attack chain discovery in enterprise security systems
ActiveUS10289841B2Platform integrity maintainanceData switching networksMonitoring systemSecurity system
Methods and systems for detecting anomalous events include detecting anomalous events in monitored system data. An event correlation graph is generated based on the monitored system data that characterizes the tendency of processes to access system targets. Kill chains are generated that connect malicious events over a span of time from the event correlation graph that characterize events in an attack path over time by sorting events according to a maliciousness value and determining at least one sub-graph within the event correlation graph with an above-threshold maliciousness rank. A security management action is performed based on the kill chains.
Owner:NEC CORP
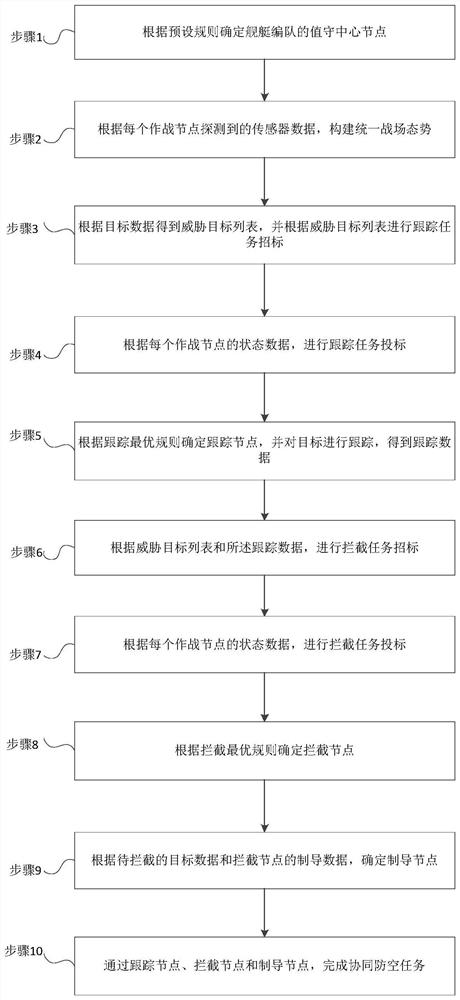
Naval vessel formation networked cooperative air defense task planning method and system
PendingCN114742264AReduce decision-making stressImprove survivabilityForecastingResourcesSimulationReal-time computing
The invention provides a naval vessel formation networked cooperative air defense task planning method and system. The method comprises the following steps: selecting a duty center node; constructing a unified battlefield situation; tracking task bidding; tracking task bidding; determining a tracking node, and tracking the target to obtain tracking data; intercepting task bidding; intercepting task bidding; determining an interception node; determining a guidance node according to the target data to be intercepted and the guidance data of the interception node; and the cooperative air defense task is completed through the tracking node, the interception node and the guidance node. Compared with the prior art, all kinds of combat resources are decoupled locally, networked distributed cooperative combat can be achieved on the aspect of architecture, the survivability of the system is enhanced, meanwhile, under the condition that actual constraint conditions are considered, attack target threats are analyzed and evaluated from the perspective of formation, all kinds of air-defense combat resources in the formation are fully utilized, air-defense task planning is implemented, and the risk of air defense is reduced. A reliable killing chain is generated, and the overall defense efficiency of the formation is improved.
Owner:SHANGHAI INST OF ELECTROMECHANICAL ENG
Network security analysis method and device, computer equipment and storage medium
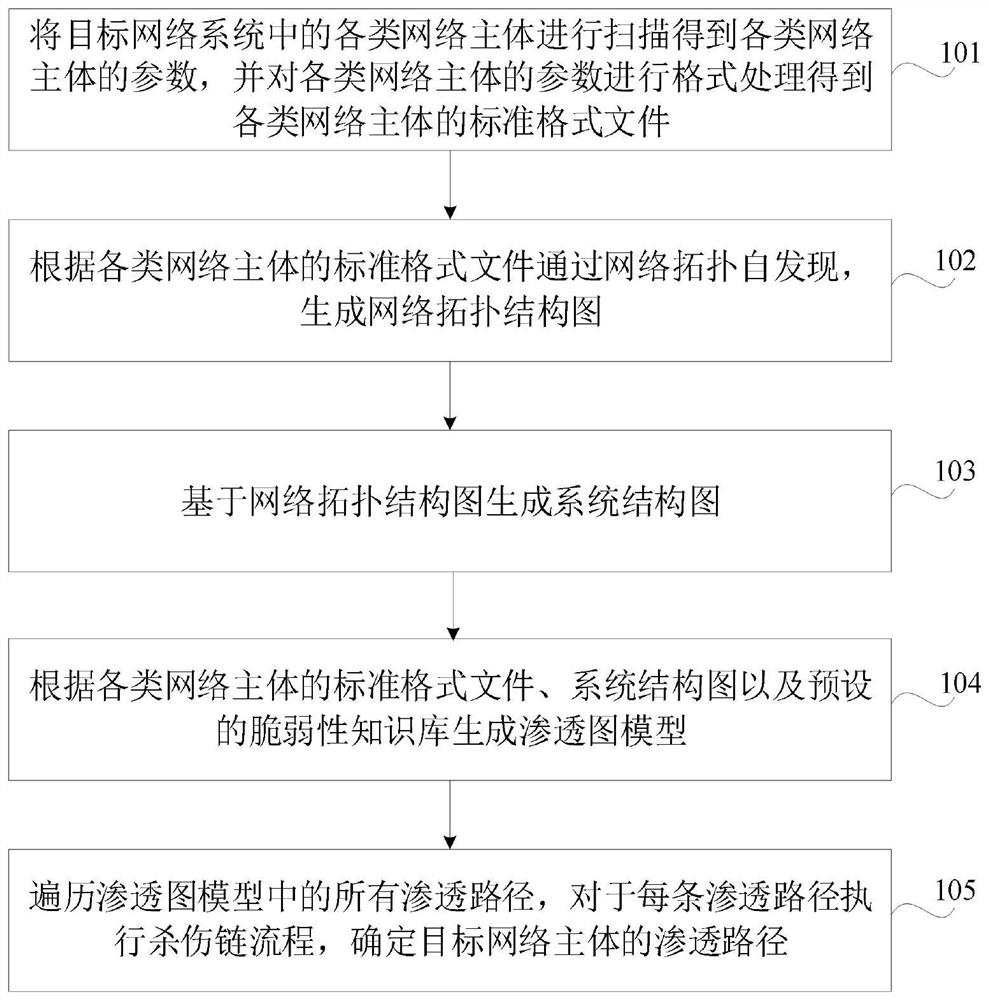
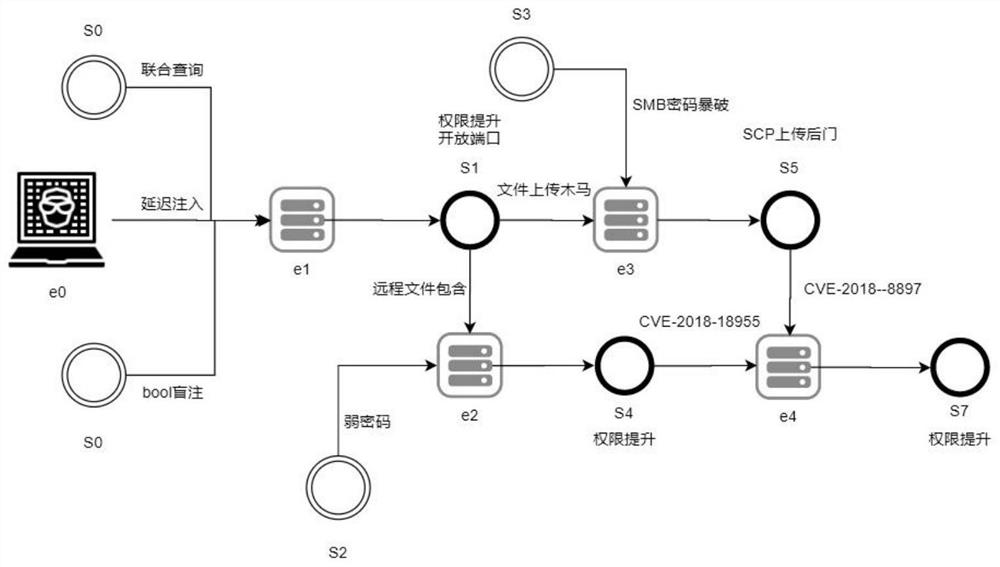
The invention discloses a network security analysis method and device, computer equipment and a storage medium. The method comprises the following steps: scanning various network main bodies in a target network system to obtain parameters, and performing format processing to obtain a standard format file; according to the standard format file, through network topology self-discovery, generating a network topology structure diagram, and then generating a system structure diagram; generating a penetration graph model according to the standard format files of the various network main bodies, the system structure diagrams and a preset vulnerability knowledge base; traversing all the penetration paths in the penetration graph model and executing the killing chain process, and finally determining the penetration path of the target network main body, so the application can not only perform vulnerability verification on the hosts on the whole line from the attacker to the core asset server, but also perform vulnerability verification on the hosts on the whole line from the attacker to the core asset server; hosts on all potential attack paths from the attacker to the core assets are even mined, one-by-one penetration verification is carried out, and based on this, global restoration is carried out, so that the security of the network system is greatly improved.
Owner:北京墨云科技有限公司
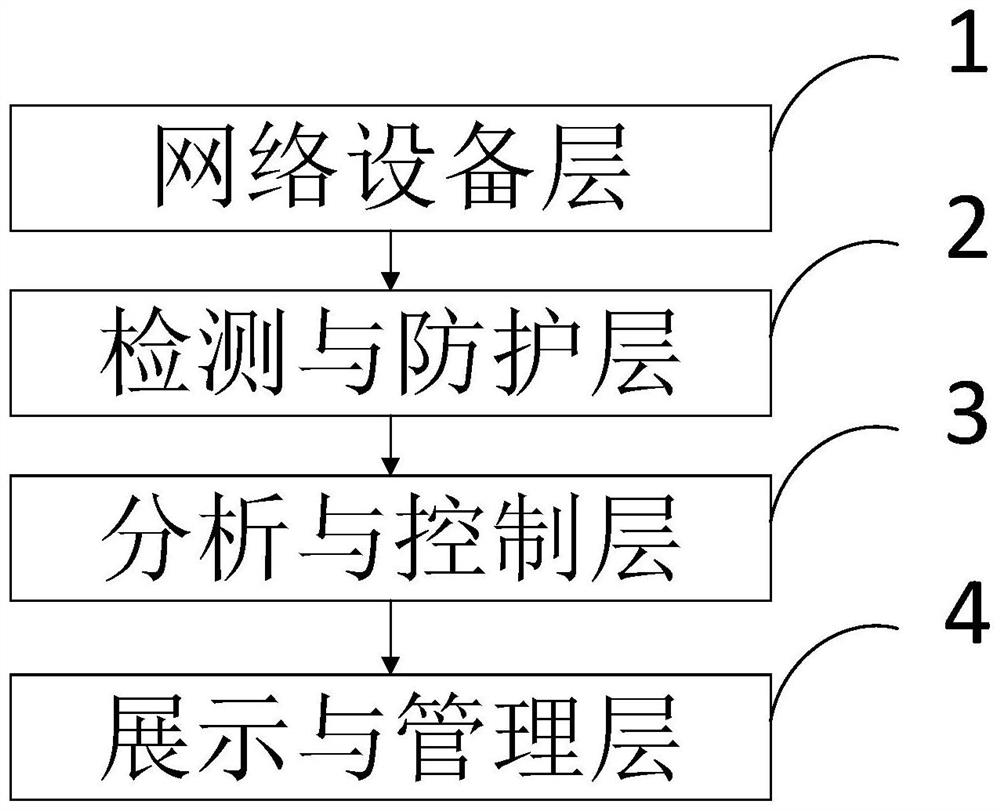
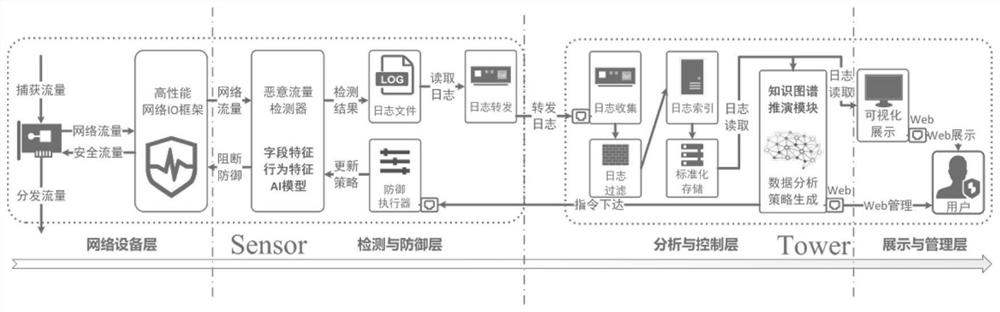
Multi-method mixed distributed APT malicious traffic detection and defense system and method
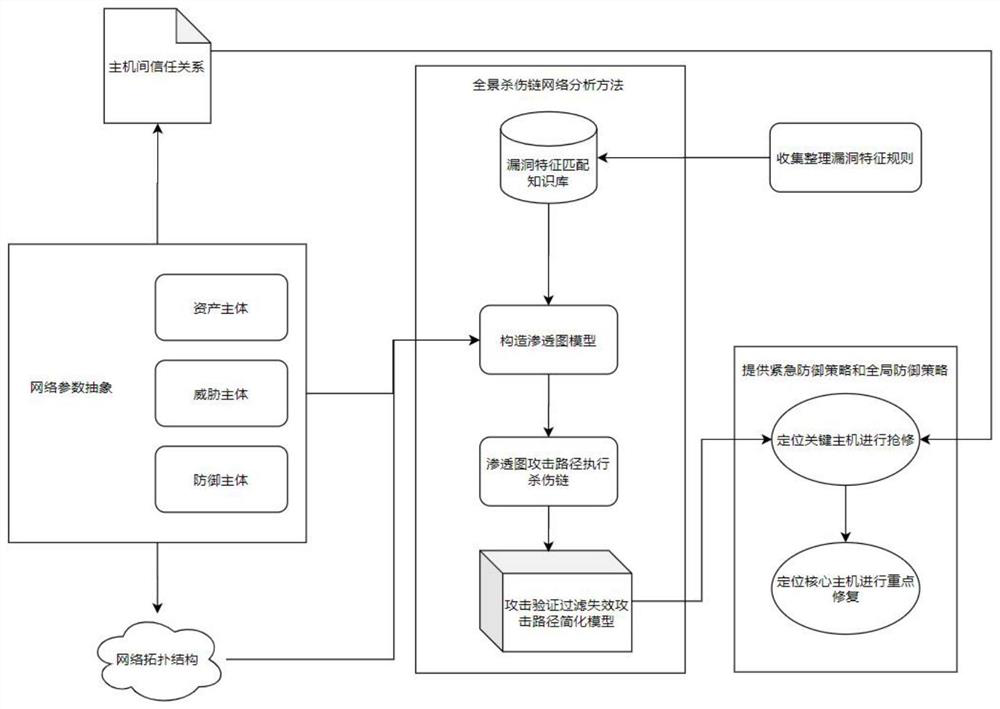
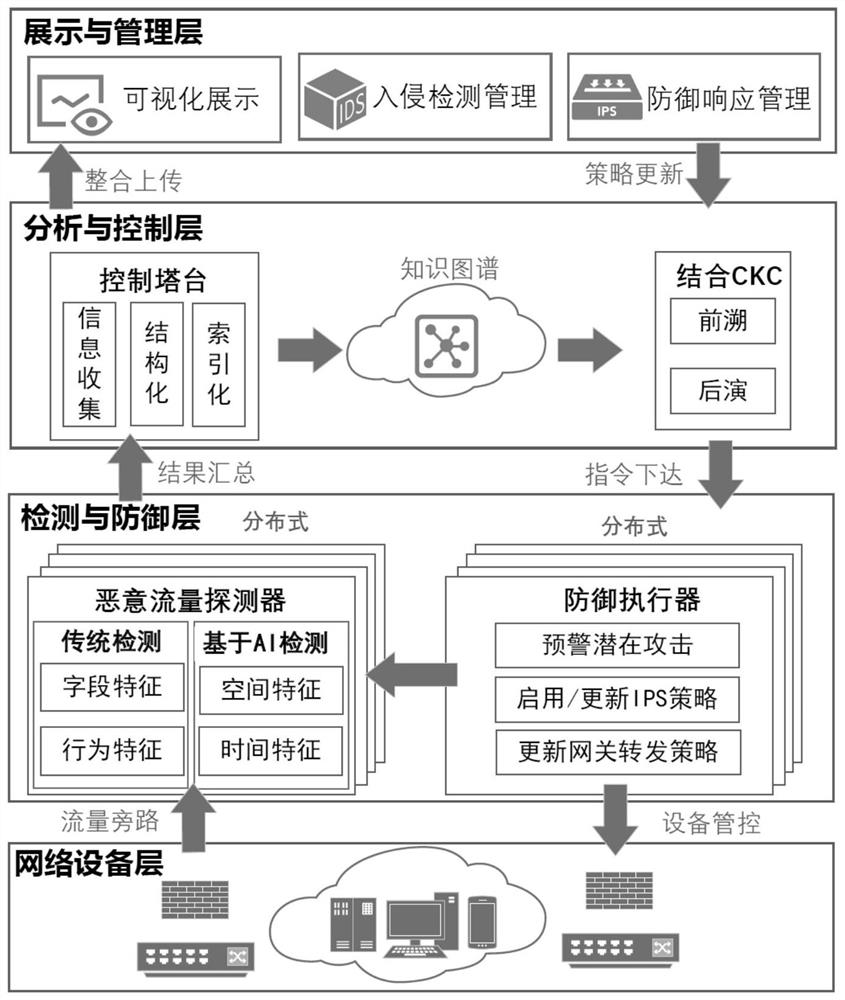
ActiveCN113746832AAccurate and comprehensive threat modelingAccurate detectionTransmissionData displayControl layer
The invention belongs to the technical field of network security, and discloses a multi-method mixed distributed APT malicious traffic detection and defense system and method, and the method comprises the steps that a network equipment layer carries out traffic bypass and equipment management and control, and sends the bypass traffic to a detection and defense layer for detection; the detection and defense layer performs flow detection and instruction execution; the analysis and control layer is used for summarizing and analyzing detection logs and issuing instructions; and a display and management layer performs data display and user interaction. According to the method, the malicious traffic in the network can be accurately detected in an omnibearing and multi-angle manner, so the potential APT attack can be identified. Meanwhile, by using a distributed architecture, accurate and comprehensive threat modeling can be carried out on the intrusion situation of the whole protected network. Meanwhile, a Cyber Kill Chain theoretical model is used, association between alarms in the network under long time and wide space span is fully mined, potential APT attack actions in the network are identified, and corresponding alarms are given.
Owner:HUAZHONG UNIV OF SCI & TECH
Detecting cyber attacks by correlating alerts sequences in a cluster environment
Providing network entities with notifications of attacks on the entities. A method includes collecting alerts from a plurality of network entities in a cluster computing environment. Alerts are grouped into heterogeneous groups of alerts. Each group includes a plurality of different types of alerts. Each alert has corresponding properties, including at least one property identifying the type of alert. Each group of alerts corresponds to a timeline of alerts for a particular entity. Groups of alerts that correspond to a valid cyber-kill chain are identified. Different groups of alerts that correspond to a valid cyber-kill chain are correlated into clusters of groups of alerts by correlating the types of alerts and corresponding properties. At least one cluster is identified as having some characteristic of interest. Entities corresponding to groups of alerts in the cluster are notified of the characteristic of interest.
Owner:MICROSOFT TECH LICENSING LLC
Dynamic best path determination for penetration testing
Disclosed herein are methods, systems, and processes to facilitate and perform dynamic best path determination for penetration testing. An action path that includes a kill chain that involves performance of exploit actions for a phase of a penetration test is generated by identifying the exploit actions based on a penetration parameter, a detection parameter, and / or a time parameter associated with the exploit actions. Performance of the identified exploit actions permits successful completion of the phase of the penetration test and designates the action path for inclusion as part of a best path for the penetration test.
Owner:RAPID7
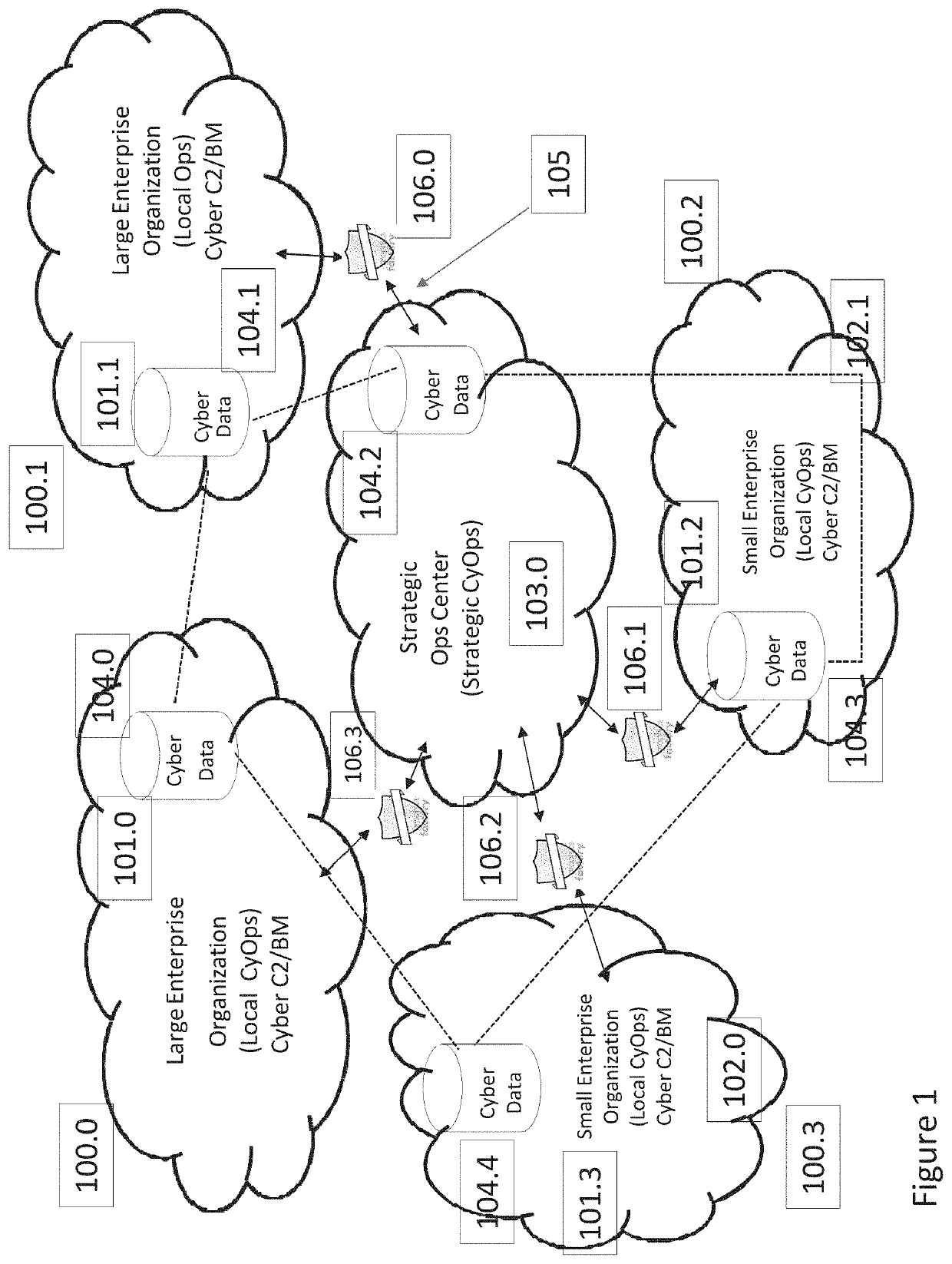
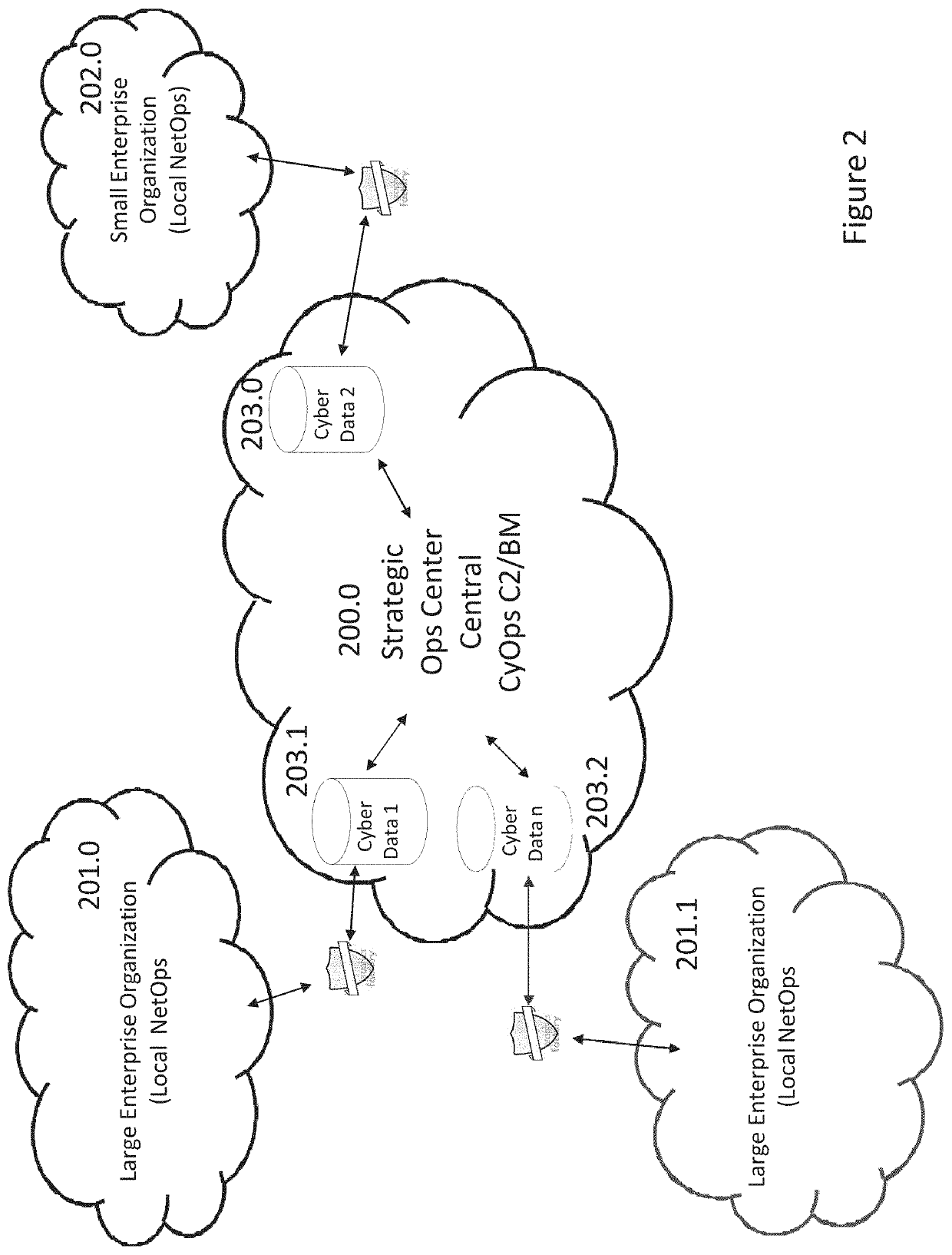
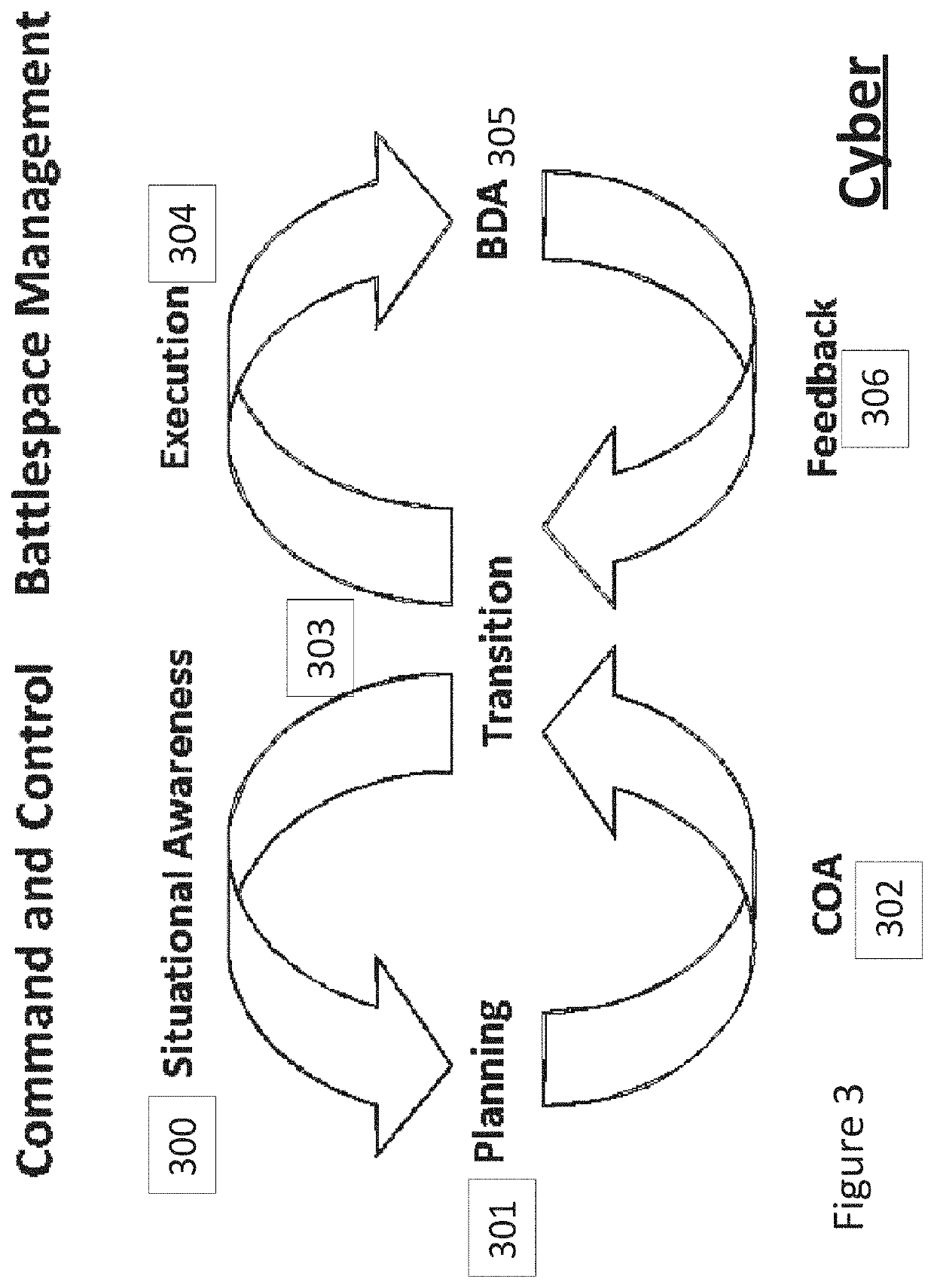
Dynamically-adaptive-resilient measured cyber performance and effects through command and control integration of full spectrum capabilities
System-of-systems architectures and methods for dynamically and adaptively managing and executing a command and control system across a global cyber enterprise are provided. The system-of-systems architecture integrates, synchronizes and executes with kinetic operations employing an adaptive and dynamic mixing and matching of capabilities for optimal effects in near real time so as to measure and maximize effects across the global cyber enterprise. The methods incorporate execution of a Cyber Operations “CyberOps” Chain of interlocking management cycles for the integration with a kinetic “Kill Chain” to optimize cyber / kinetic integration and mission outcomes. An analytical and software framework enables the on-demand formation of mission-specific dynamic cell groups from various cells stretching across the global cyber enterprise in response to ever-changing faces of cyber threats.
Owner:SARKESAIN JOHN F
Constructing graph models of event correlation in enterprise security systems
ActiveUS10298607B2Platform integrity maintainanceNetworks interconnectionMonitoring systemGraph model
Methods and systems for detecting anomalous events include detecting anomalous events in monitored system data. An event correlation graph is generated by determining a tendency for a first process to access a system target, including an innate tendency of the first process to access the system target, an influence of previous events from the first process, and an influence of processes other than the first process. Kill chains are generated from the event correlation graph that characterize events in an attack path over time. A security management action is performed based on the kill chains.
Owner:NEC CORP
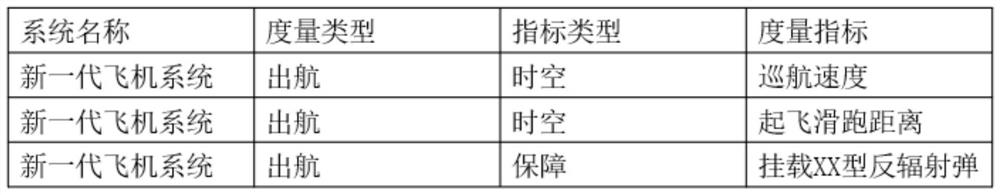
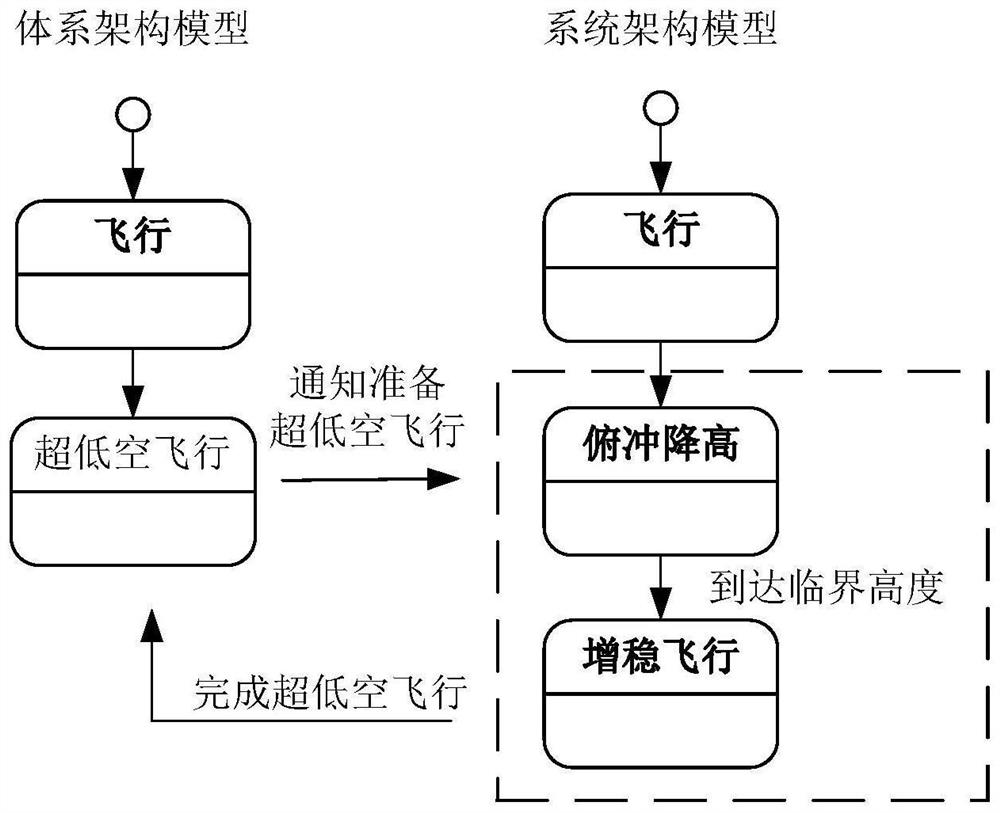
System overall design method output by system architecture model
PendingCN114154322AGuaranteed correctnessIntegrity guaranteedGeometric CADDesign optimisation/simulationSystems designOperating system
The invention relates to the field of system engineering based on a model, in particular to a system overall design method drawn by a system architecture model, which comprises the following steps of: putting a new-generation system into one or more combat tasks (depending on all combat businesses which can be applied by the system), and constructing an activity process of the system combat tasks, a complete combat killing chain based on the system is formed according to an interaction process and operation logic, a guarantee on combat requirements is provided for correctness and integrity of various combat activities and combat factors participated by the system, and input and boundaries of system design are defined according to input of the system architecture, so that completeness of a system design result is guaranteed, and the system design efficiency is improved. And a theoretical basis is provided for research, development and upgrading of a new-generation system.
Owner:上海烜翊科技有限公司
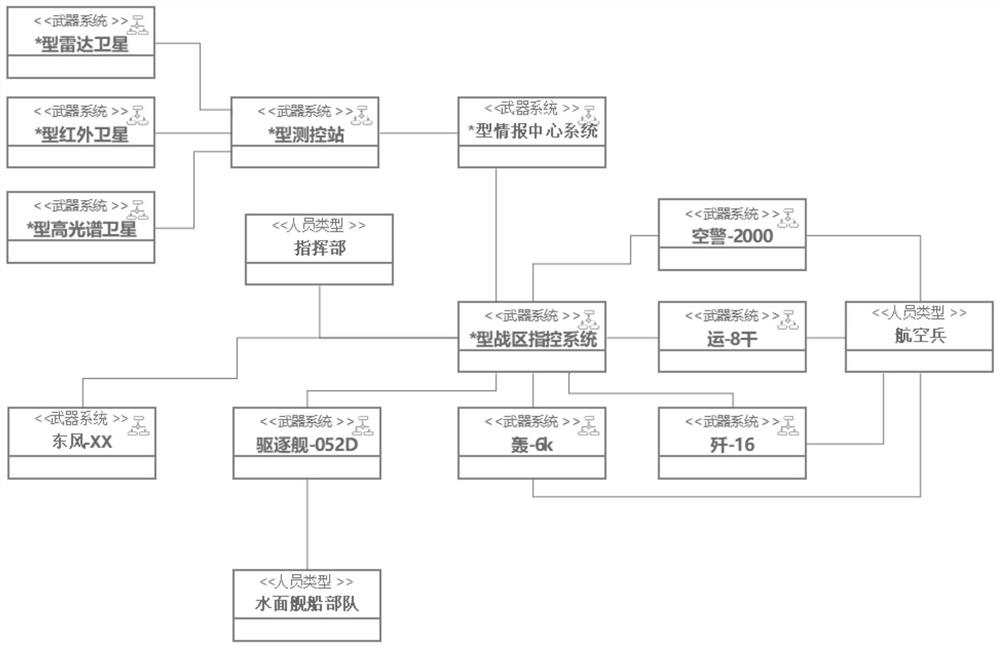
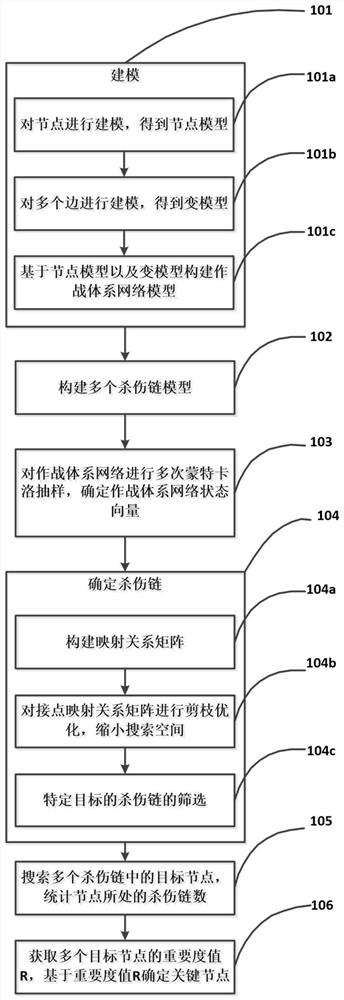
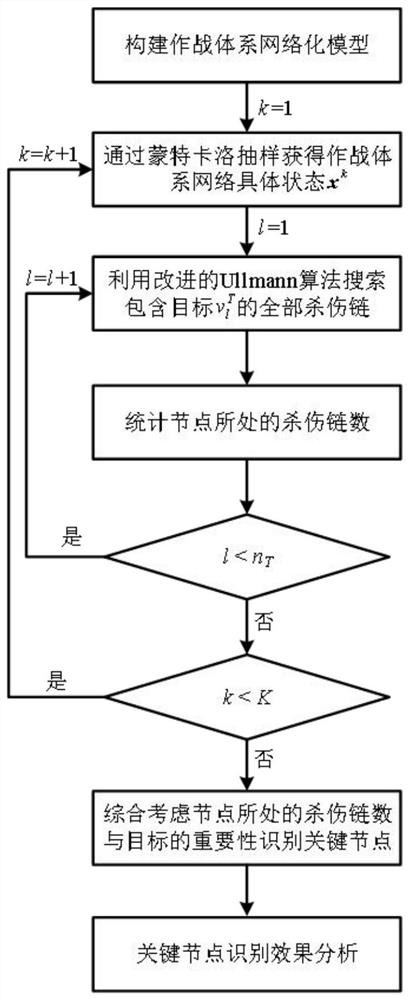
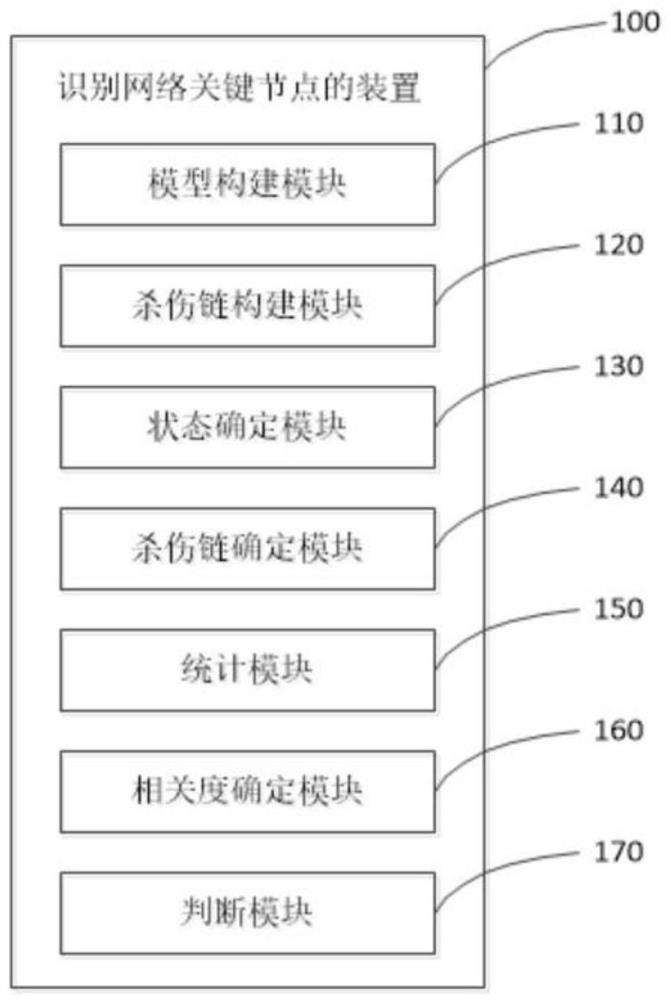
Method and device for identifying key nodes of combat system network
PendingCN114491889AReasonable identificationEfficient identificationGeometric CADData processing applicationsSimulationNetwork key
The invention relates to the field of combat system key node identification, in particular to a combat system network key node identification method based on a killing chain. Modeling the plurality of nodes and the plurality of edges, and constructing a combat system network model based on a node model and an edge model; constructing a plurality of killing chain models based on the target node; performing multiple Monte Carlo sampling on the combat system network to determine a combat system network state vector; based on a Ullmann algorithm, determining a plurality of killing chains containing a specific target in the combat system network; searching a target node in a plurality of killing chains, and counting the number of the killing chains where the node is located; measuring the killing chain to obtain importance values R of a plurality of target nodes, and determining key nodes based on the importance values R; according to the method, the node importance index can reflect the influence of heterogeneous combat factors such as performance differences of different devices and importance of attacking targets, so that reasonable and effective identification of key nodes is realized.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
Anticipating Future Behavior Using Kill Chains
ActiveUS20210226971A1Disruption in performanceComputer security arrangementsTransmissionData sourceSafe operation
A system, method, and computer-readable medium are disclosed for performing a security operation. The security operation includes: monitoring an entity, the monitoring observing at least one electronically-observable data source; deriving an observable based upon the monitoring of the electronically-observable data source; identifying a security related activity of the entity, the security related activity being based upon the observable derived from the electronic data source, the security related activity being of analytic utility; associating the security related activity with a phase of a cyber kill chain; and, performing a security operation on the security related activity via a security system, the security operation disrupting performance of the phase of the cyber kill chain.
Owner:FORCEPOINT LLC
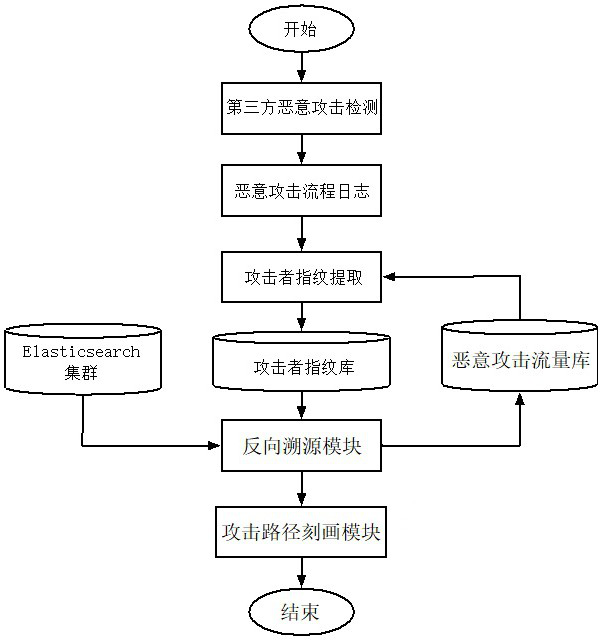
A Flow-Based Tracing Attack Path Method in Network Shooting Range
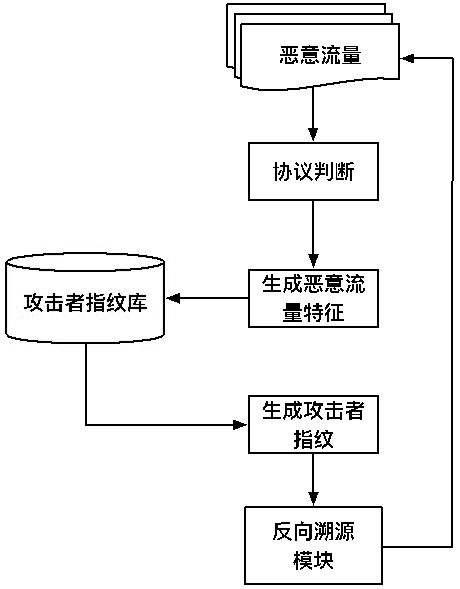
ActiveCN111818103BGuaranteed accuracyEasy to analyzeMachine learningTransmissionPathPingInternet traffic
The invention relates to a flow-based traceability attack path method in a network shooting range, which is designed based on a directional network network attack traceability technology, and through accurate and effective flow monitoring in the network shooting range, from the perspective of reverse traceability, the description of the traceability attack path is realized , which can assist security analysts to better disassemble network attack behaviors. Among them, the reverse source tracing method generates attacker fingerprints through the extraction of attacker behavior characteristics, and directional traces of attacker traffic in historical logs, which is more targeted It can reproduce the attack path in a more comprehensive manner. Aiming at the description of the attack path, the network kill chain model is introduced, and the network traffic of different protocols and time nodes can be reasonably divided by finding the attack time node, which is more conducive to security analysts. Analyze how the attack occurred.
Owner:信联科技(南京)有限公司
Disrupting a Cyber Kill Chain When Performing Security Operations
A system, method, and computer-readable medium are disclosed for performing a security operation. The security operation includes: monitoring an entity, the monitoring observing at least one electronically-observable data source; deriving an observable based upon the monitoring of the electronically-observable data source; identifying a security related activity of the entity, the security related activity being based upon the observable derived from the electronic data source, the security related activity being of analytic utility; associating the security related activity with a component of a cyber kill chain; and, performing a security operation on the security related activity via a security system, the security operation disrupting performance of the component of the cyber kill chain by affecting performance of the security related activity by the entity.
Owner:FORCEPOINT LLC
A method and system for defending against apt attacks
The present application provides a method and system for defending against Advanced Persistent Threat (APT) attacks. The method includes: obtaining communication data in the network; performing correlation analysis on the communication data, and filtering out the threat data in the communication data according to the correlation analysis results; Each threat data screened out is mapped to the corresponding APT attack stage, and the APT attack stage is defined according to the kill chain model; according to the defense strategy corresponding to the multiple APT attack stages, each threat data is related to network entities for defense. This application maps threat data to corresponding APT attack stages, and adopts corresponding defense strategies for different APT attack stages, so that APT attack processing is more targeted, and APT attacks can be detected and defended more effectively.
Owner:NEW H3C TECH CO LTD
Associating a Security Risk Persona with a Phase of a Cyber Kill Chain
A system, method, and computer-readable medium are disclosed for performing a security operation. The security operation includes: monitoring an entity, the monitoring observing an electronically-observable data source; deriving an observable based upon the monitoring of the electronically-observable data source; identifying a security related activity, the security related activity being based upon the observable from the electronic data source; analyzing the security related activity, the analyzing the security related activity using a security risk persona; associating the security risk persona with a phase of a cyber kill chain; and, performing a security operation on the security related activity via a security system, the security operation disrupting performance of the phase of the cyber kill chain.
Owner:FORCEPOINT LLC
Network asset evaluation method and device, electronic equipment and readable storage medium
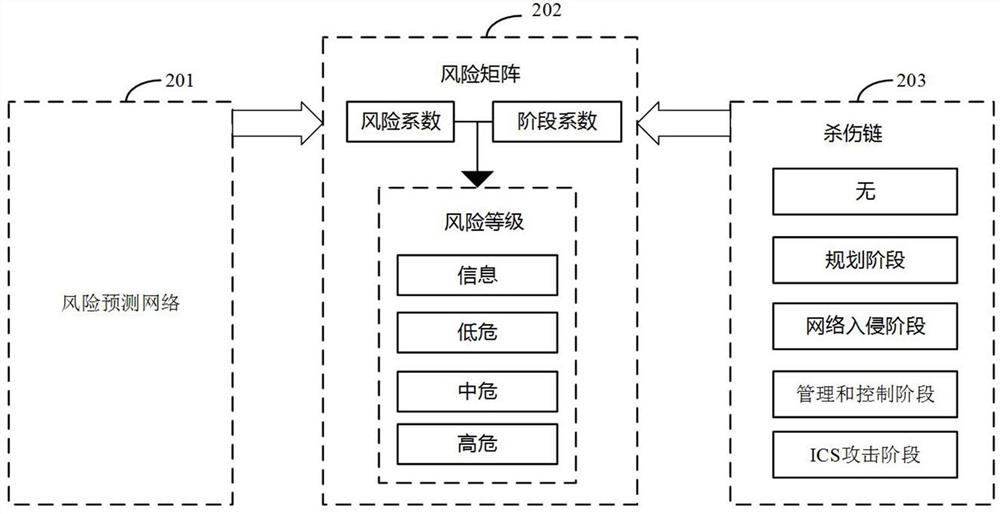
ActiveCN114070650AHigh precisionImprove timelinessResourcesSecuring communicationRisk levelComputer network
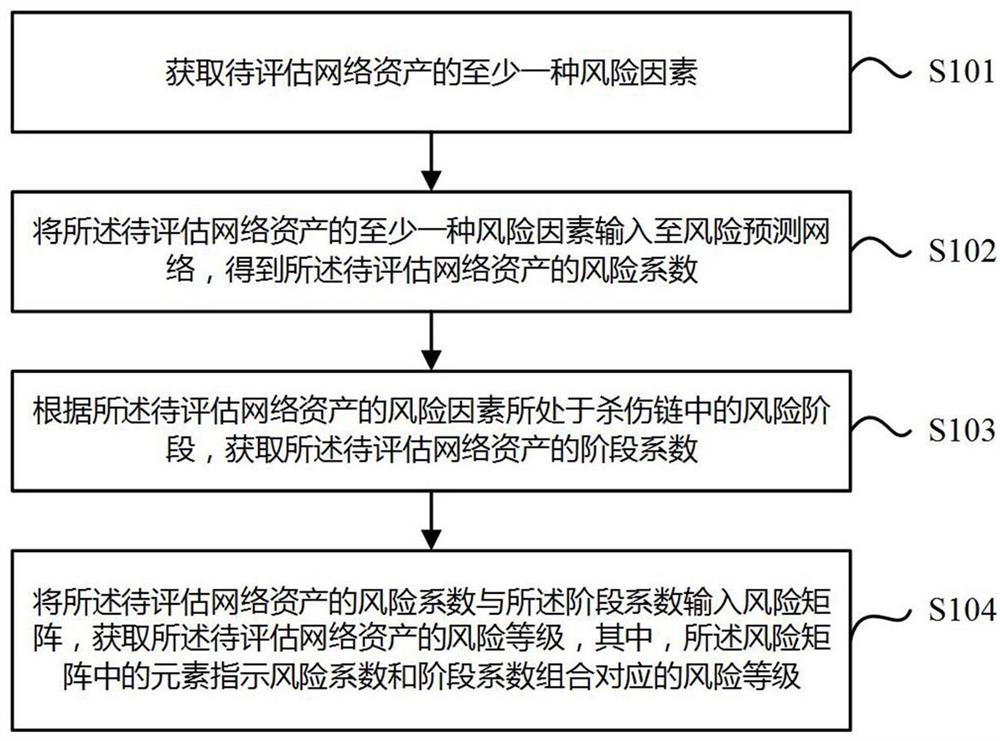
The invention provides a network asset evaluation method and device, electronic equipment and a readable storage medium. The method comprises the following steps: acquiring at least one risk factor of a to-be-evaluated network asset; inputting the at least one risk factor of the to-be-evaluated network asset into a risk prediction network to obtain a risk coefficient of the to-be-evaluated network asset; obtaining a stage coefficient of the to-be-evaluated network asset according to a risk stage of the risk factor of the to-be-evaluated network asset in a killing chain; and inputting the risk coefficient of the to-be-evaluated network asset and the stage coefficient into a risk matrix, and obtaining a risk level of the to-be-evaluated network asset, the element in the risk matrix indicating a risk level corresponding to a combination of the risk coefficient and the stage coefficient. By adopting the method disclosed by the invention, evaluation errors can be effectively avoided, the accuracy and timeliness of evaluating the network assets are improved, and a network asset evaluation result with higher reference value is provided for a user.
Owner:浙江国利网安科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com