A method and system for defending against apt attacks
An attacker and attacked technology, applied in the field of APT attack defense, can solve the problem of difficult detection of attack behavior, and achieve the effect of effective APT attack, effective detection and defense
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
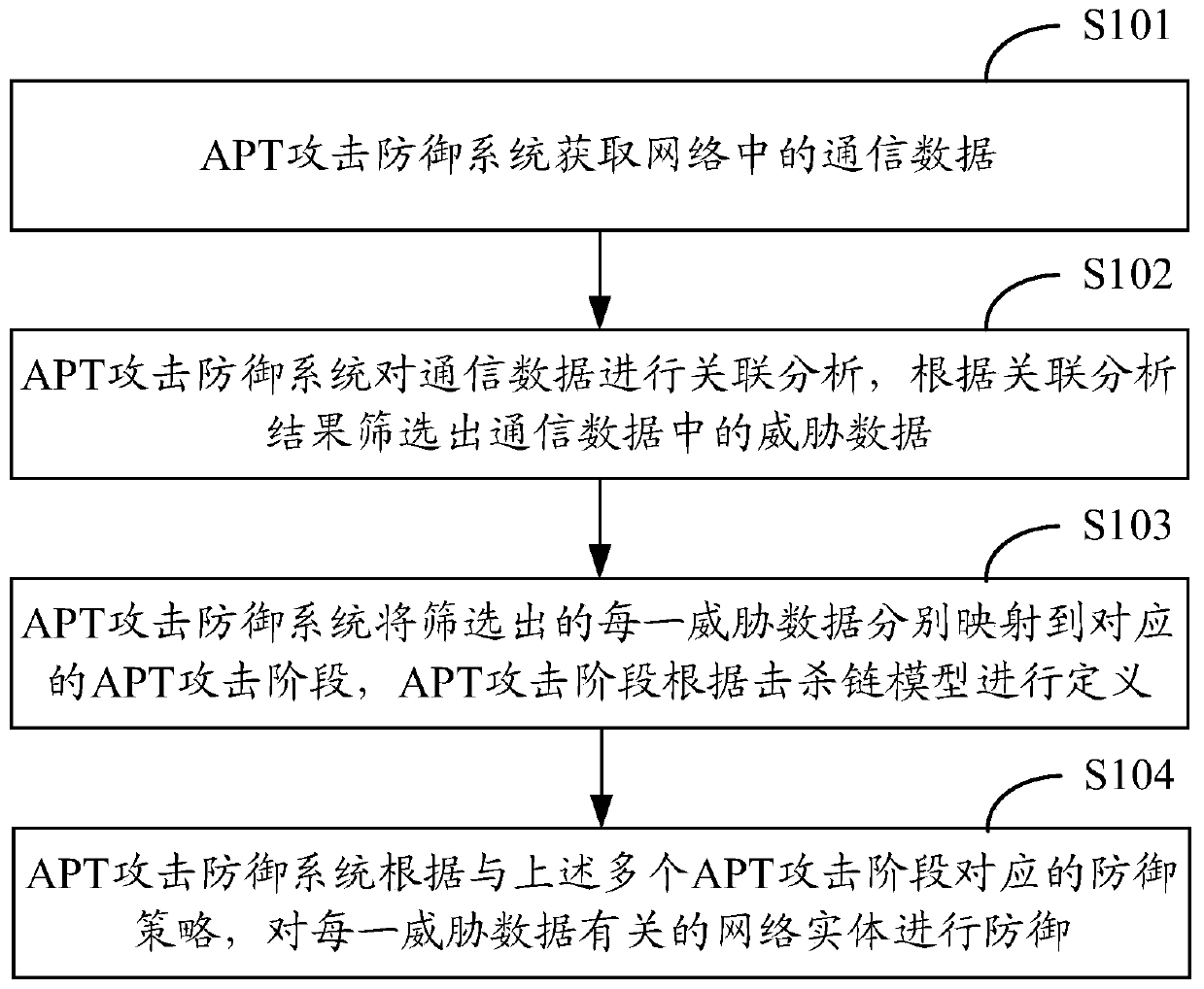
[0027] In order to make the purpose, technical solution and advantages of the present application clearer, the present application will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
[0028] This application mentions the concept of kill chain, which originally came from the military field and refers to the complete process of "discovery-location-tracking-targeting-attack-assessment". From the perspective of the kill chain, an APT attack process can be divided into seven stages:
[0029] Phase 1: Reconnaissance, using social engineering to select and understand the target network, and using scanning technology to perceive the vulnerability of the destination.
[0030] Stage 2: Weaponization mainly refers to the production of targeted attack tools, such as pdf files or office files with malicious codes.
[0031] Stage 3: Delivery, delivering attack tools to the target system. Commonly used methods include email attachments,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com