Method and device for resisting cooperative type sensing data falsification attack through cognitive wireless network
A technology for cognitive wireless network and data perception, applied in the field of cognitive wireless network anti-cooperative tamper-sensing data attack, it can solve the problems of high probability of misjudgment, trusted user error, sensitive number of malicious users, etc., to improve system detection. probability, reduce the probability of false alarms in the system, and achieve the effect of effective defense
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] In order to make the purpose, technical solution and advantages of the present invention more clear, the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
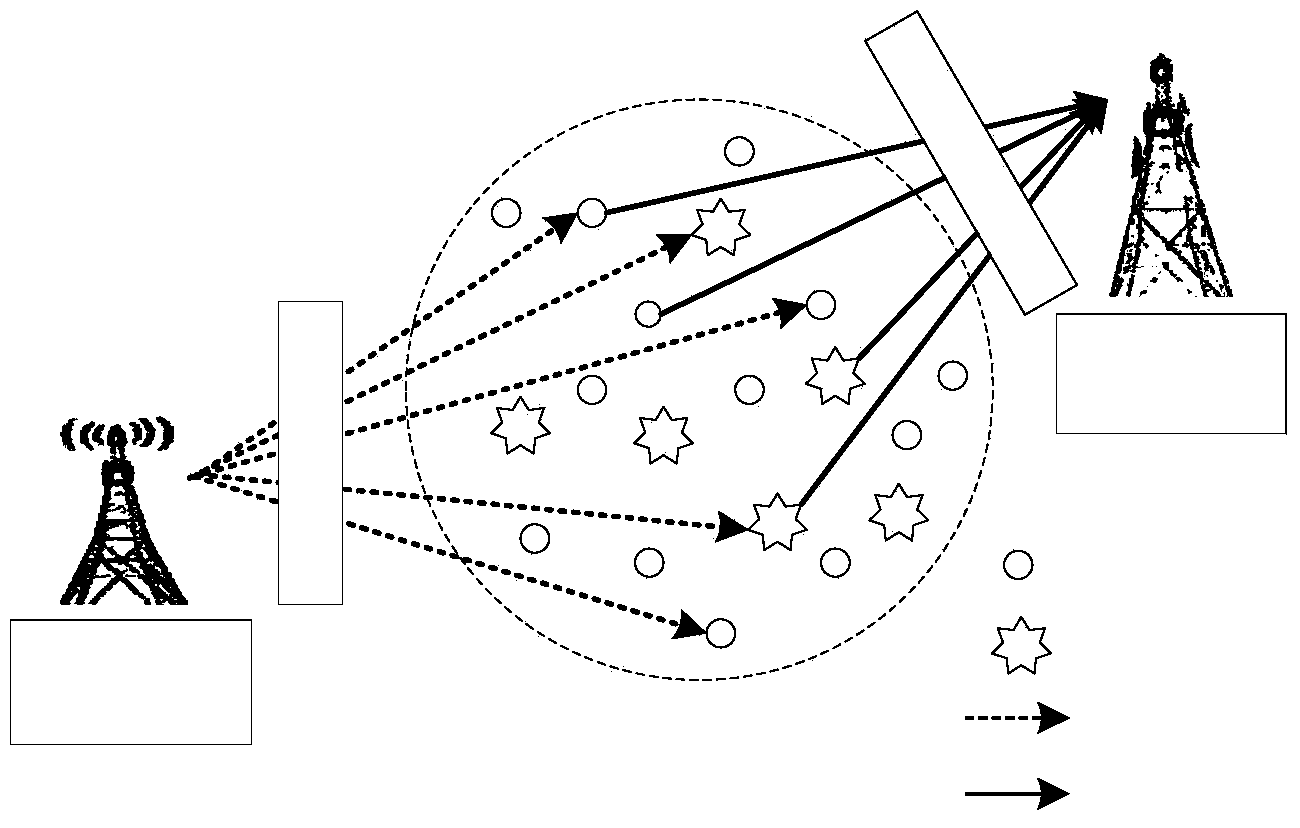
[0028] figure 1 As a typical cognitive wireless network, it has a centralized cooperative spectrum sensing network composed of a single authorized user (also called the main user) and N sensing users (including malicious users and trusted users), among which there are M malicious users who can send to The fusion center launches an SSDF attack. At the end of each sensing moment, each sensing user sends the local sensing results to the fusion center. The perception results of different perception users at different times are independent of each other. After the fusion center makes a judgment based on these results, it notifies each sensing user of the use of the authorized frequency band in the form of broadcast. These information exchanges ar...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com